Method and device for identifying key nodes of combat system network
A technology of key nodes and identification methods, applied in data processing applications, instruments, geometric CAD, etc., can solve problems such as poor interpretability of results, insufficient reflection of combat process, and failure to reflect the importance of target nodes in mission success rate, and achieve effective identification. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0118] Specific embodiments are given below to further illustrate the technical solution.
[0119] The red and blue sides have a military conflict due to sovereignty issues. The blue team sends an air assault formation composed of 5 fighters of various types to carry out a surprise attack on the red team's targets, and the red team relies on its own combat system composed of 20 pieces of various types of equipment to attack the blue team's assault formation. to intercept. For this typical air interception mission, the key equipment nodes in the red combat system are identified.
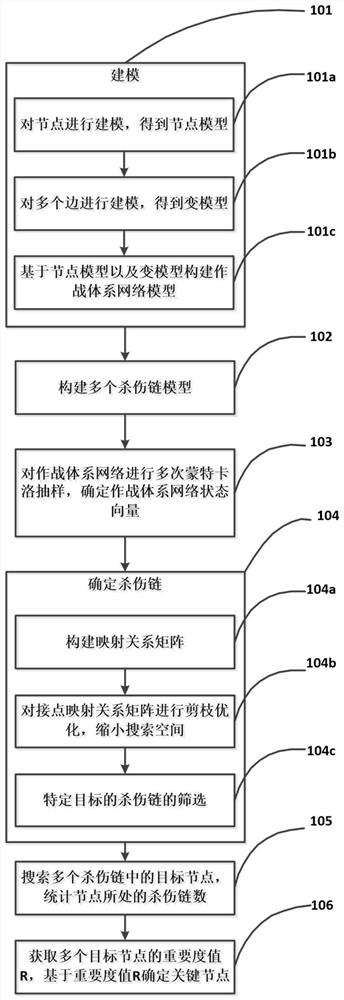
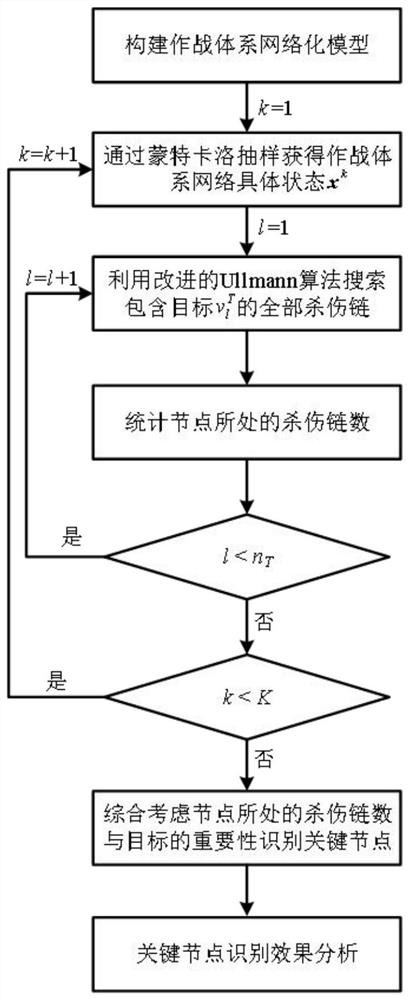
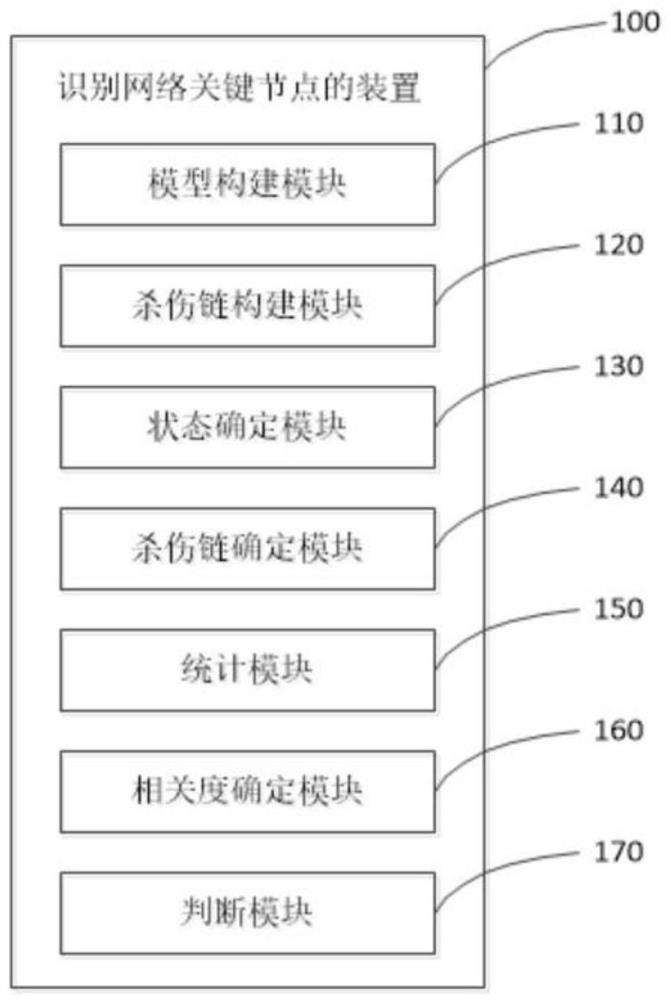
[0120] Step 1: Model the nodes and edges in the combat system network, and build a combat system network model.
[0121] refer to Figure 4 , gives the combat system network diagram. According to the functional characteristics and correlations of various equipment in combat missions, the combat system is mapped to a combat system network. Among them, the target nodes T1-T5 represent the five fight...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com