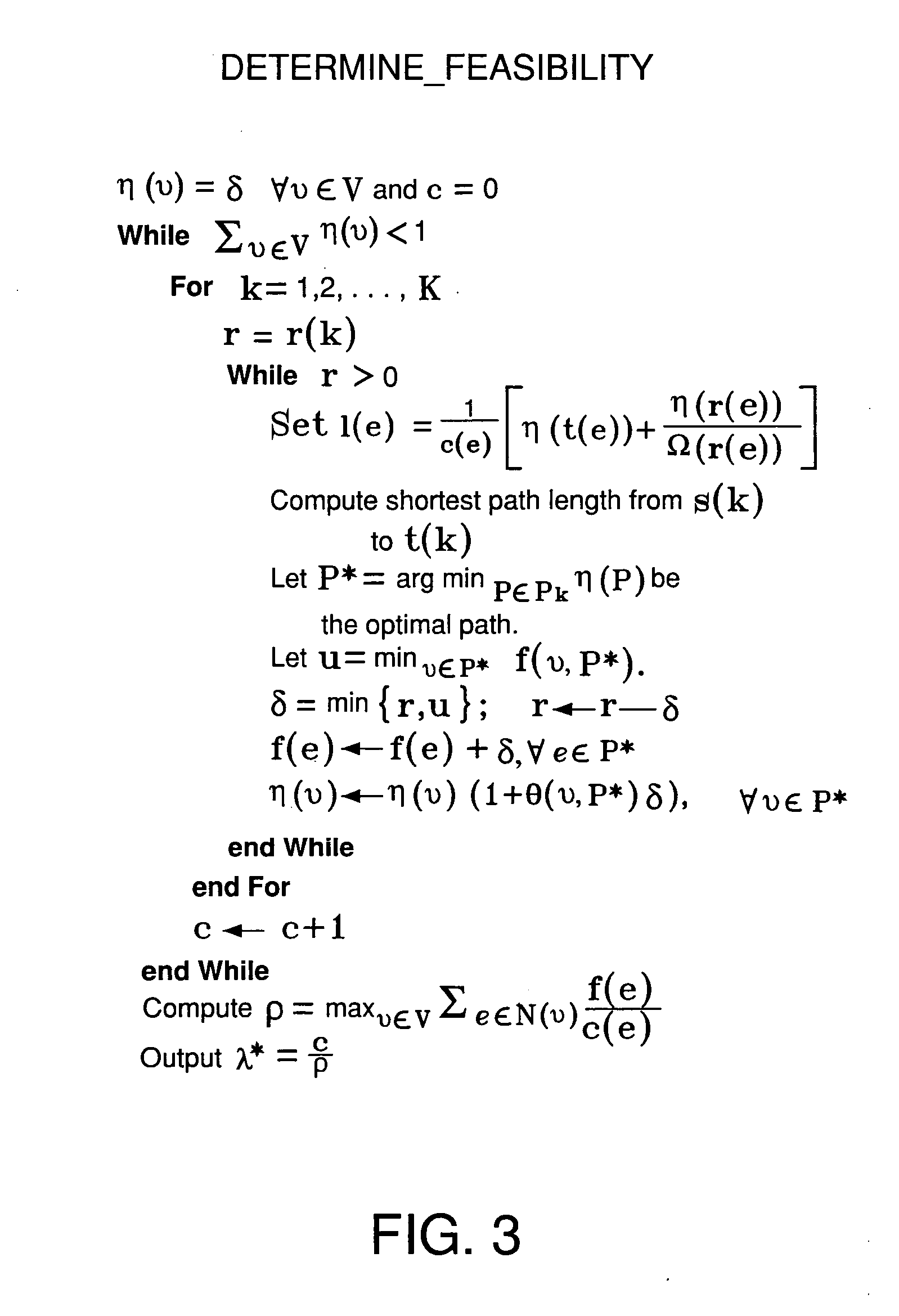Patents
Literature
1446 results about "Goal node" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, a goal node is a node in a graph that meets defined criteria for success or termination. Heuristical artificial intelligence algorithms, like A* and B*, attempt to reach such nodes in optimal time by defining the distance to the goal node. When the goal node is reached, A* defines the distance to the goal node as 0 and all other nodes' distances as positive values.
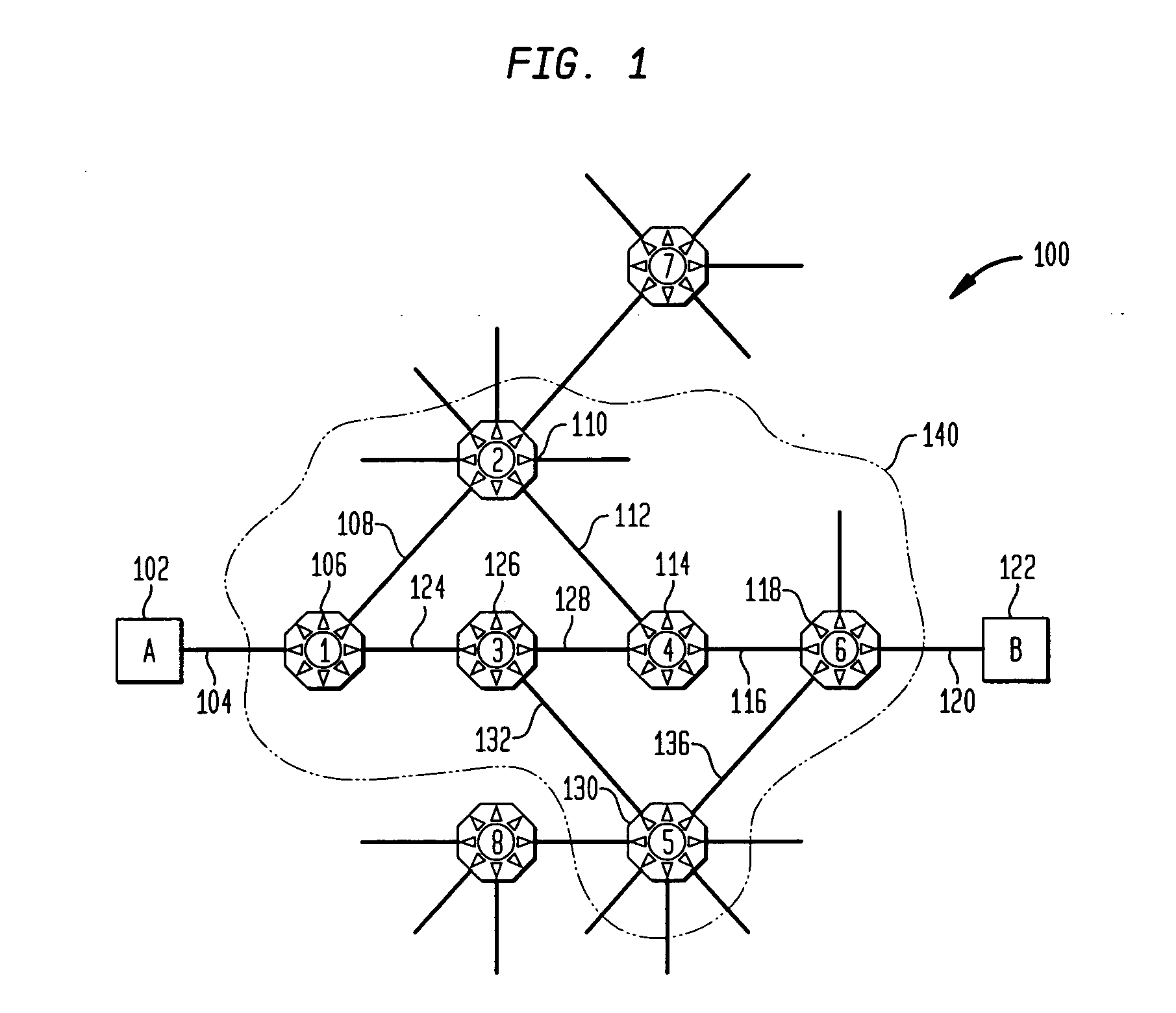
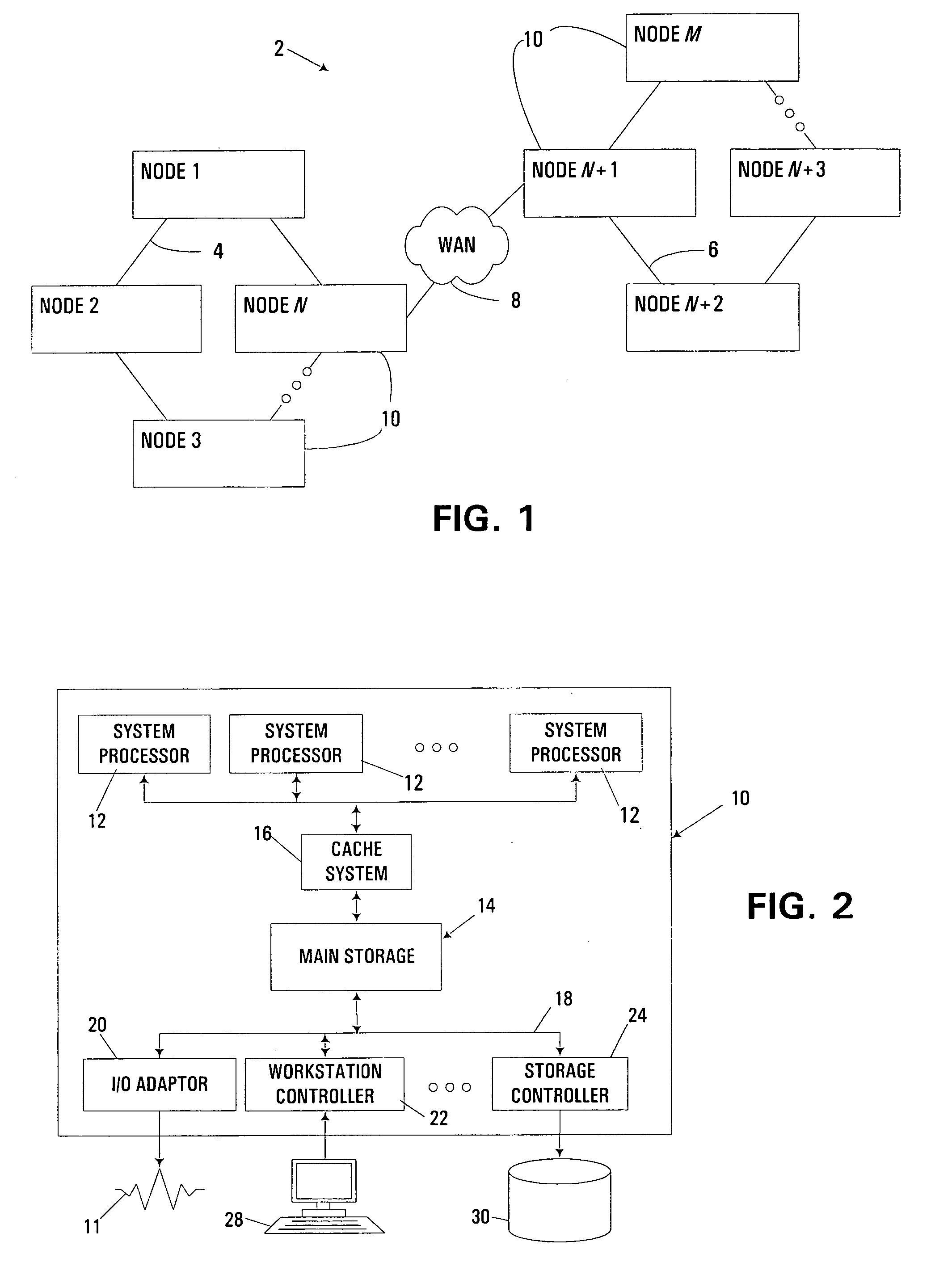
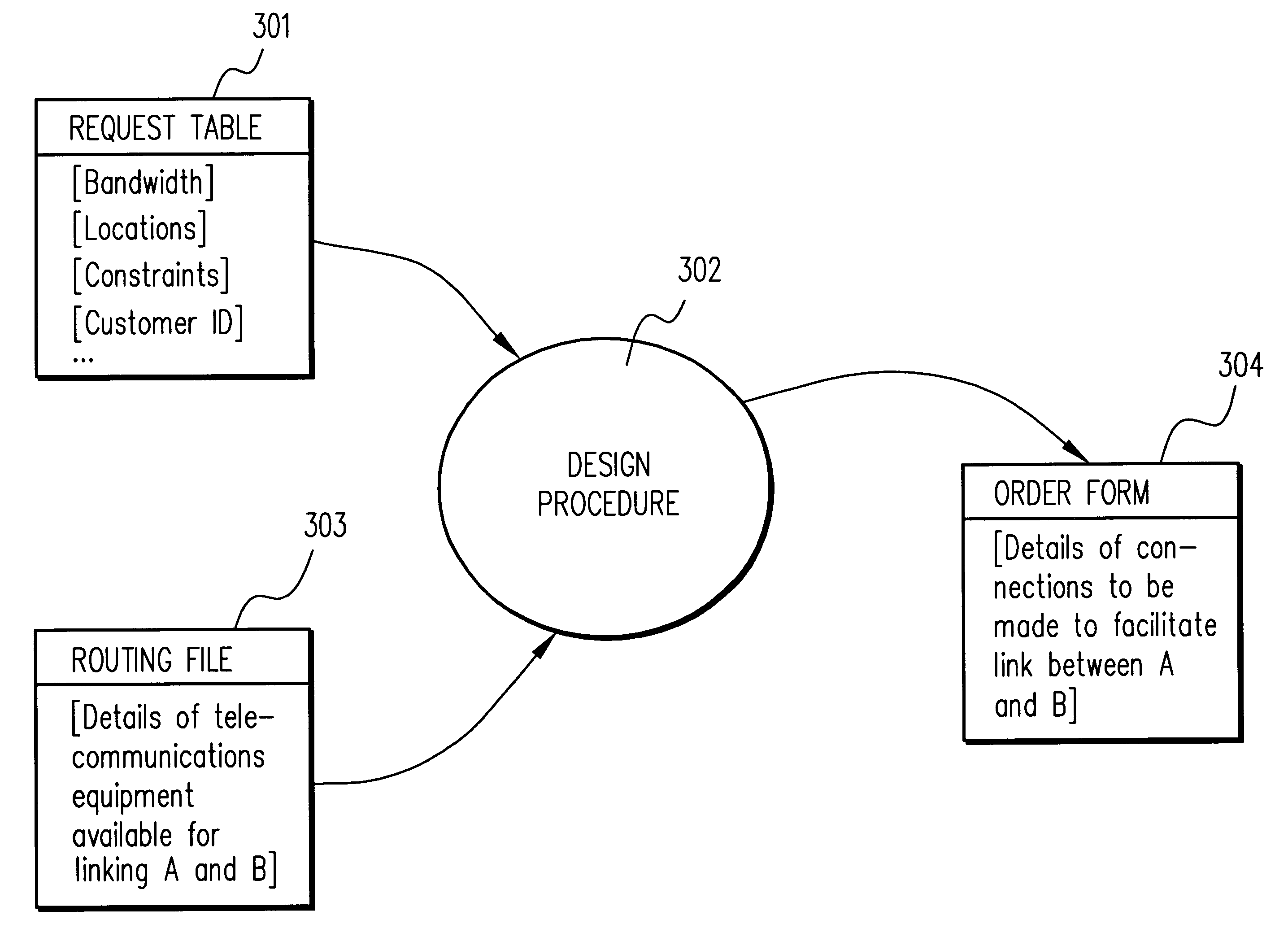
Network routing with path identifiers
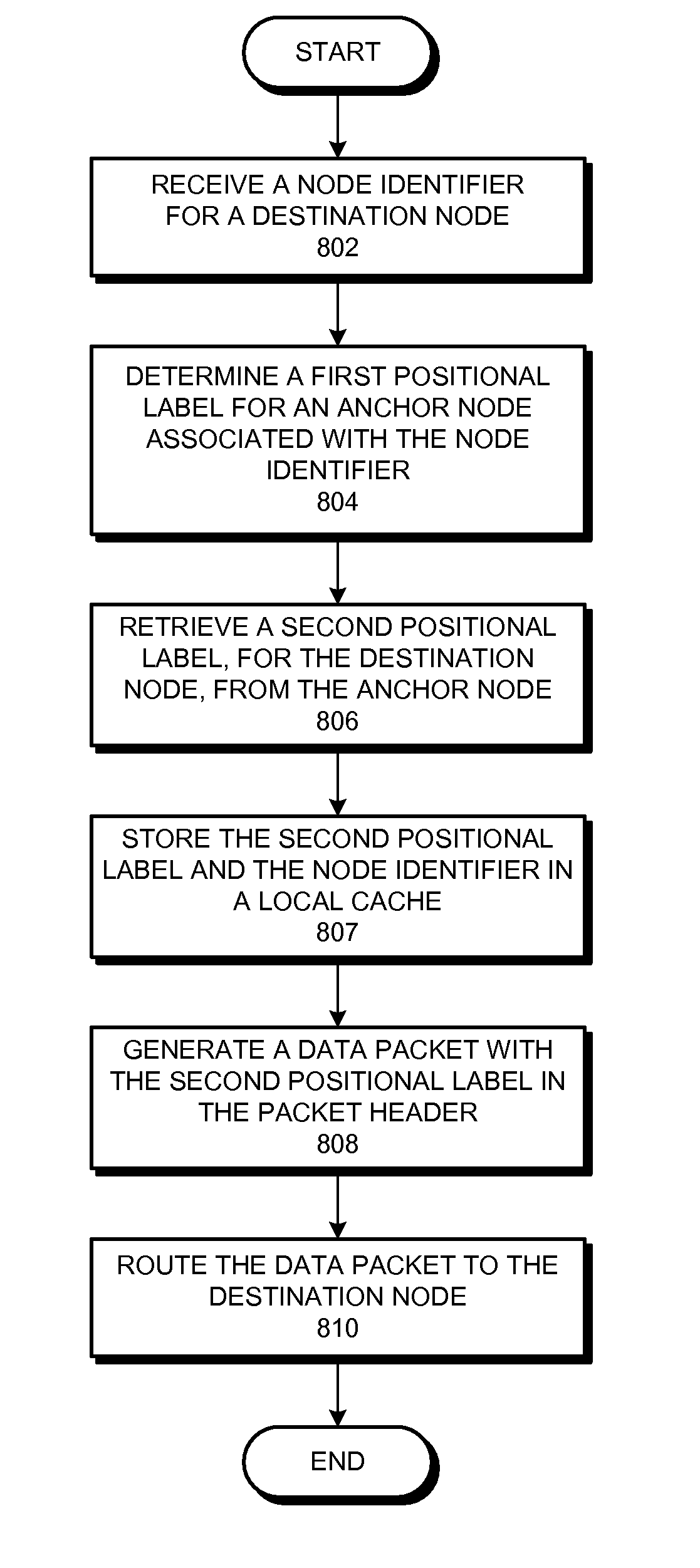
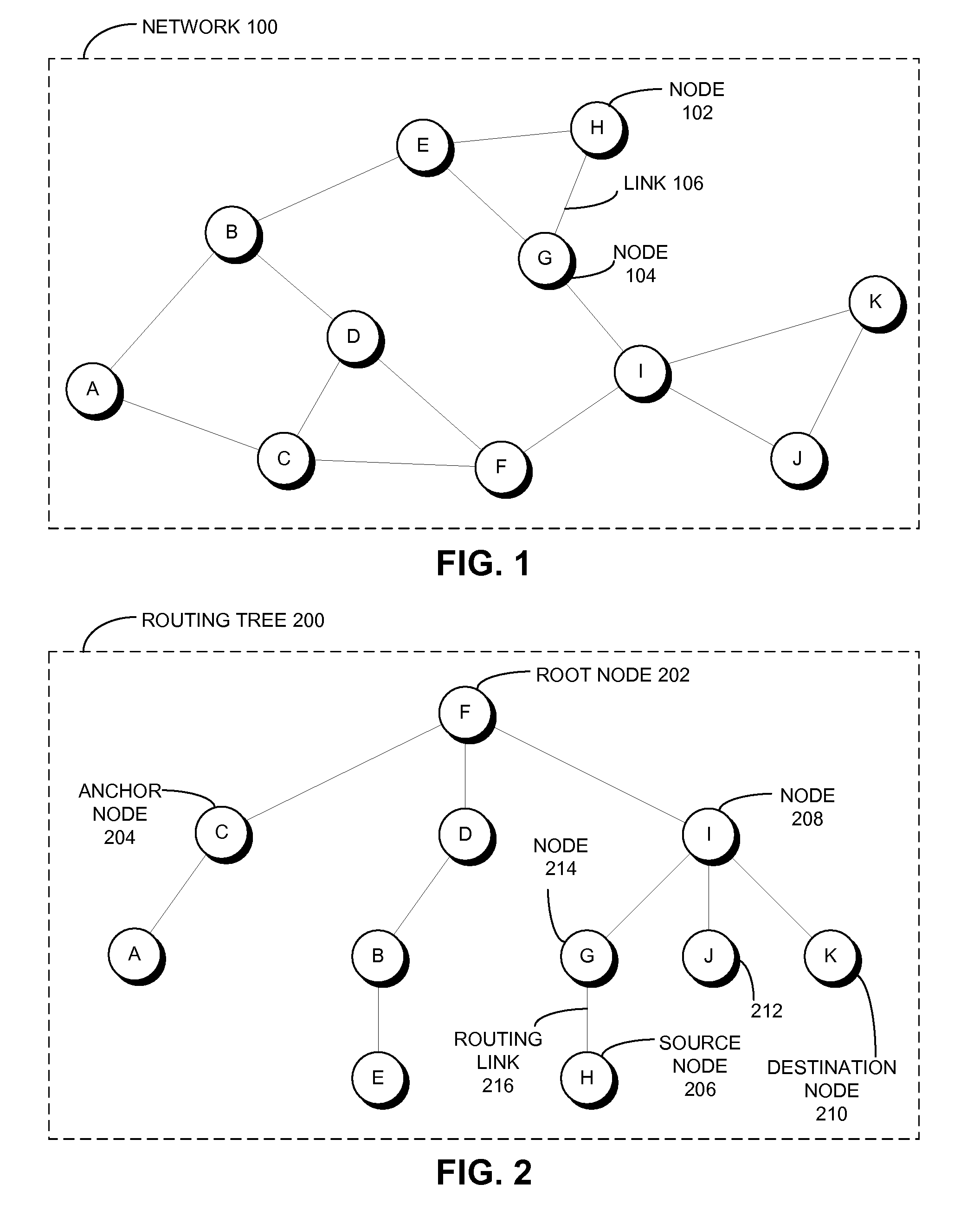
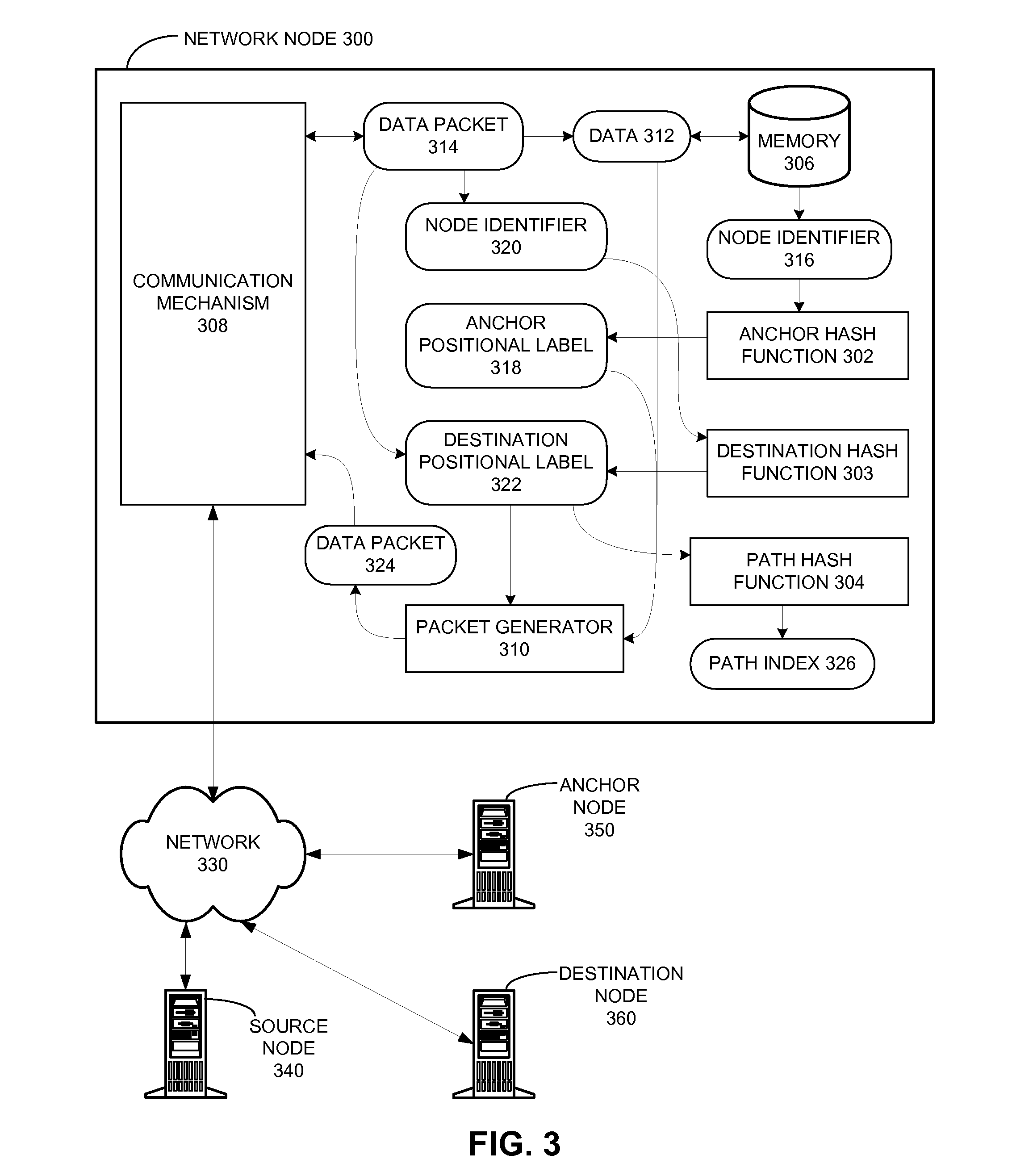
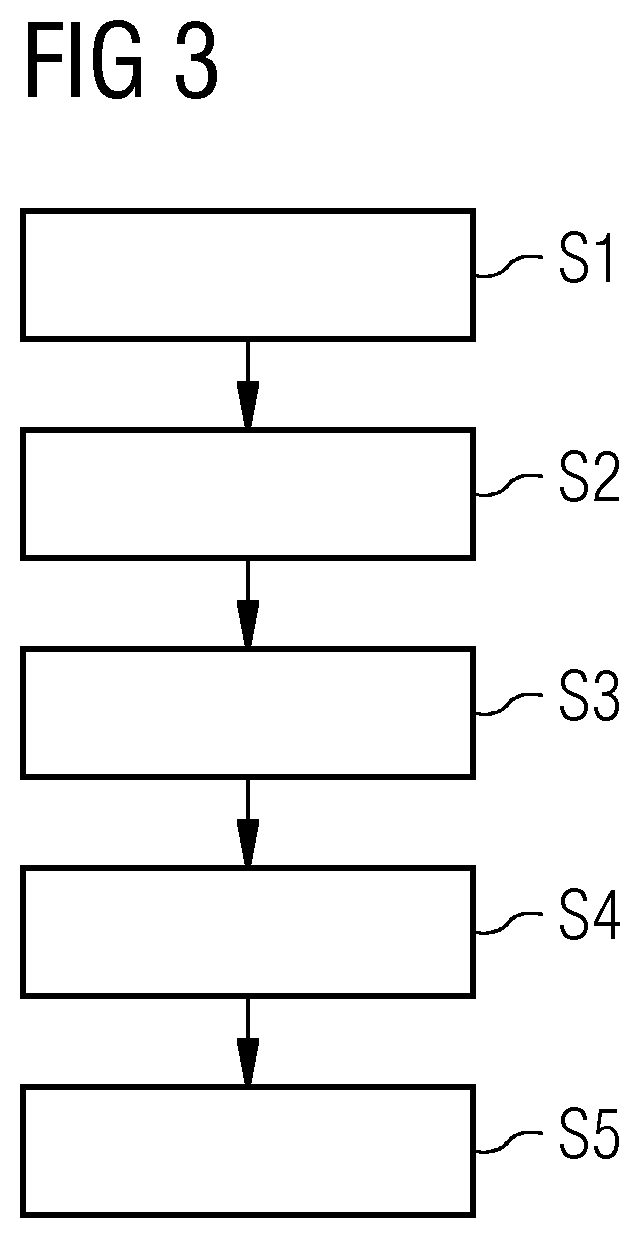
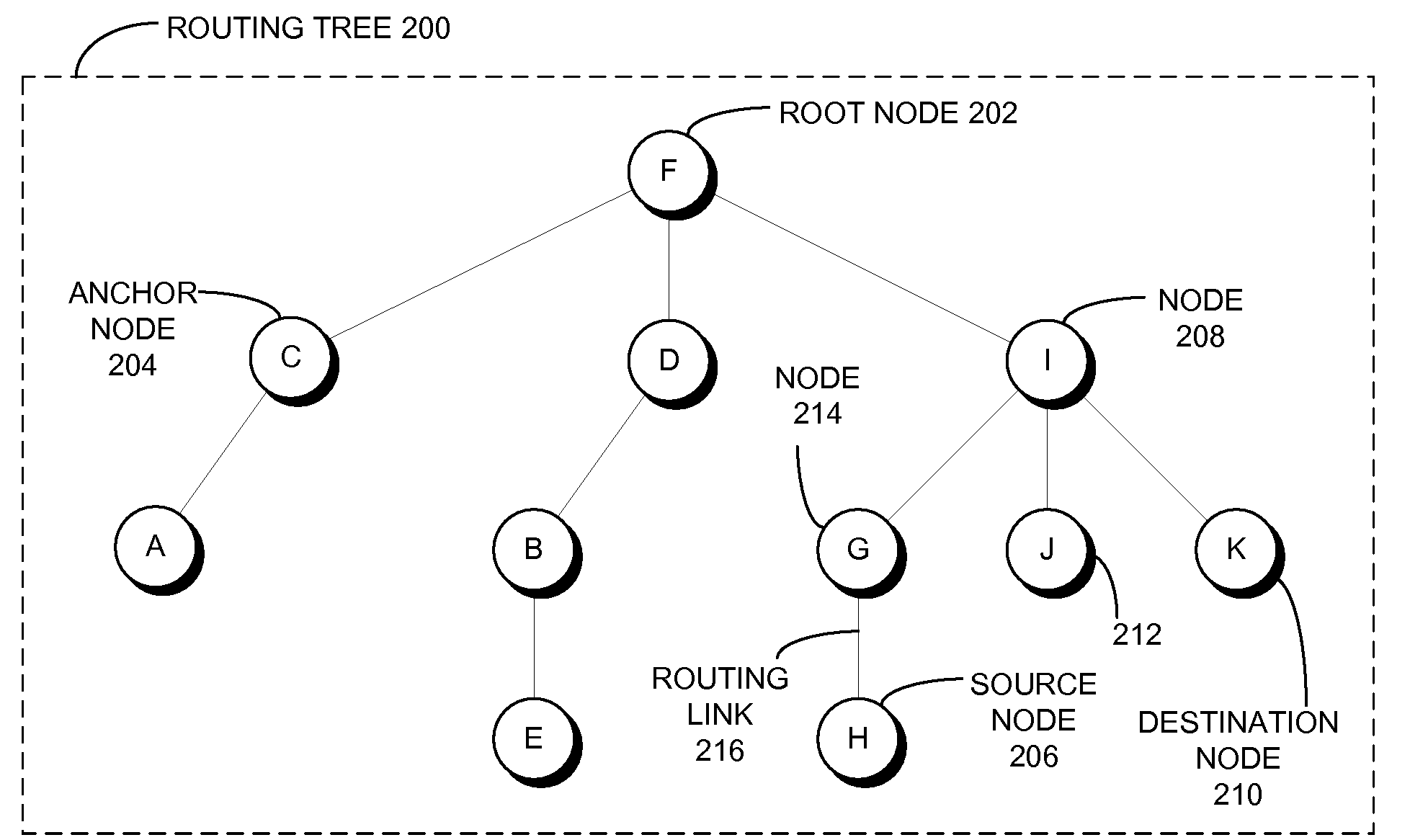
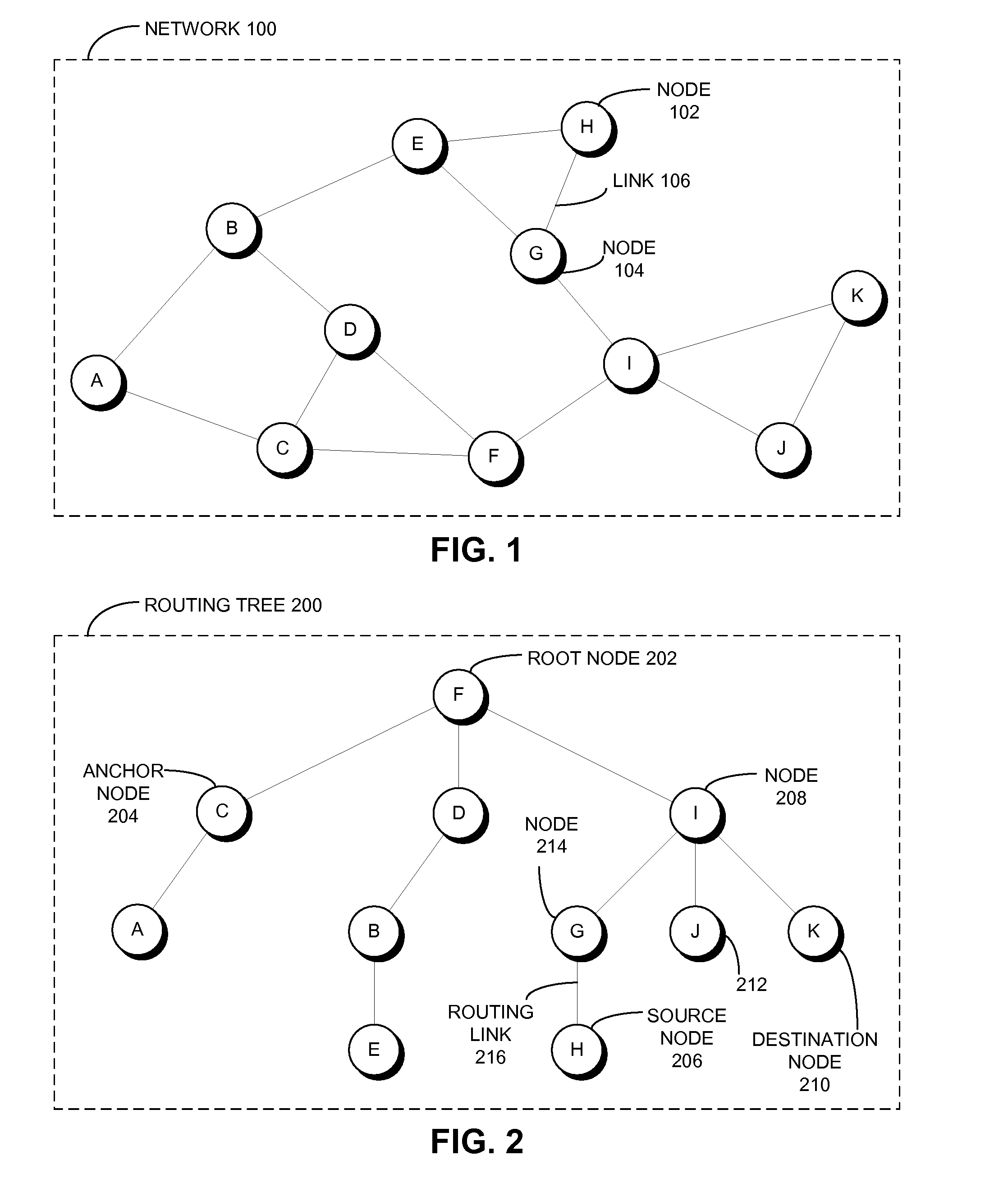
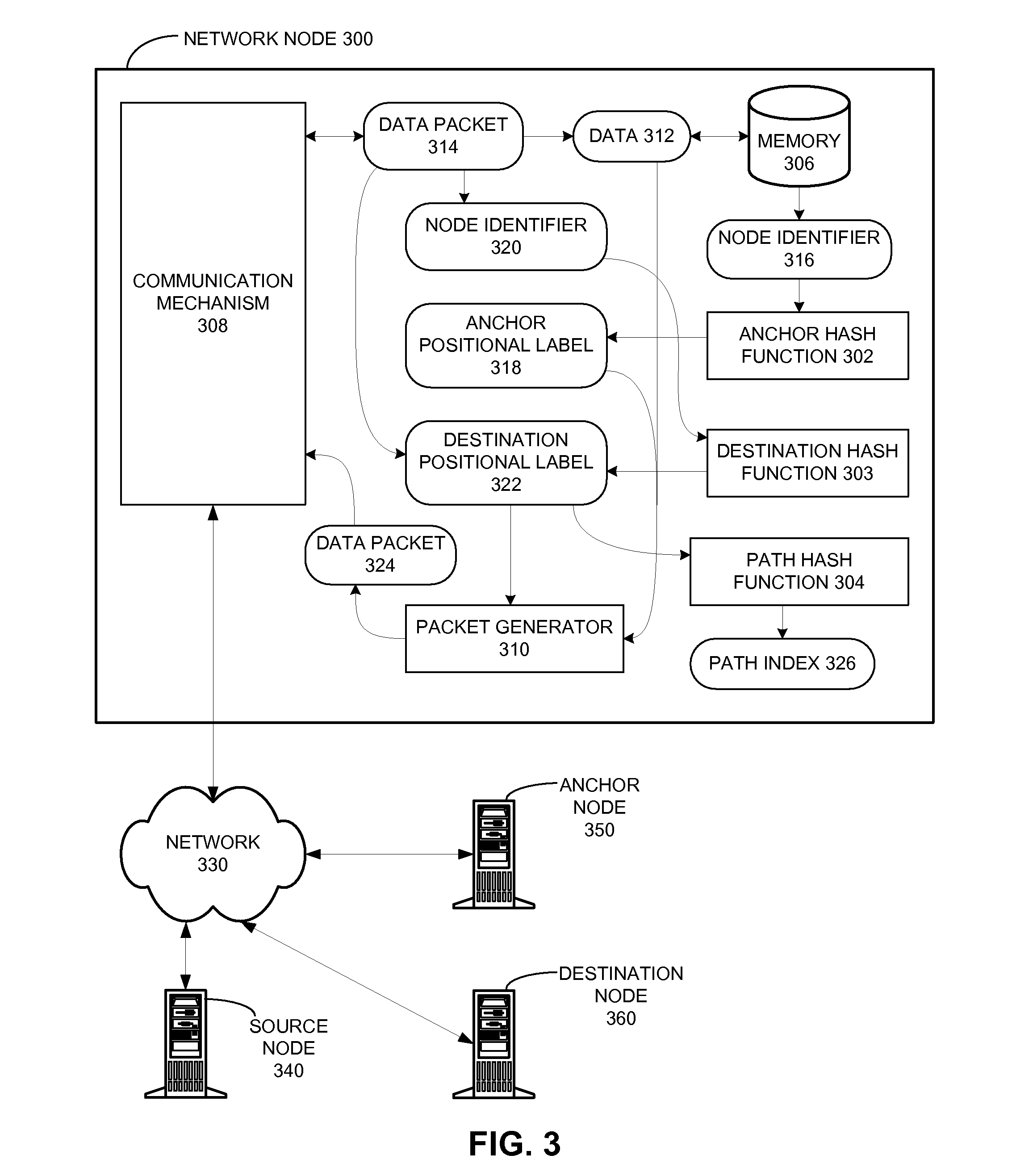
One embodiment of the present invention provides a system that communicates a data packet in a network to a target node. In doing so, the system receives a node identifier for the target node, and determines a first positional label, based in part on the node identifier, for reaching a first anchor node from a root node in the network. The first anchor node stores a second positional label for reaching the target node from the root node in the network, which comprises a number of nodes coupled to the root node in a tree topology. The system then retrieves the second positional label from the first anchor node, and communicates the data packet to the target node based in part on the second positional label.
Owner:CISCO TECH INC
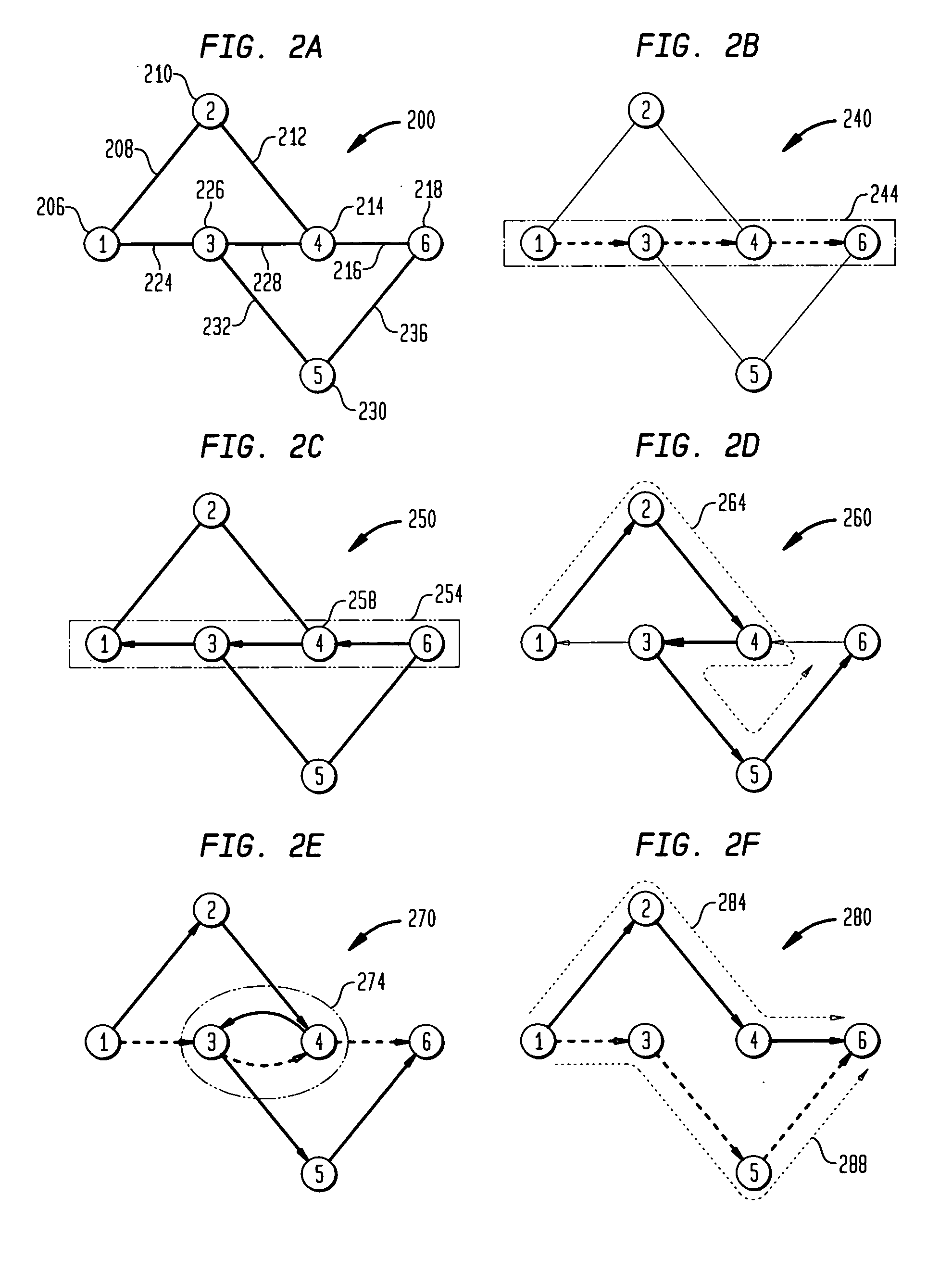
Methods of network routing having improved resistance to faults affecting groups of links subject to common risks
A number of techniques are described for routing methods that improve resistance to faults affecting groups of links subject to common risks. One of these techniques accounts for failure potentials in physical networks by considering shared risk link groups separately from performance and costs metrics in determining a primary routing path and a backup path. A shared risk link group (SRLG) is an attribute attached to a link to identify edges that have physical links in common and can therefore be simultaneously disrupted due to a single fault. Another technique considers node disjointness and provides a solution of two paths that are as node disjoint as possible and minimizes administrative costs. The techniques may further be combined in a priority order thereby providing a solution of at least two paths that are strictly SRLG disjoint, as node-disjoint as possible, and have minimum administrative costs. Due to the priority order of evaluation and typical network physical configurations of links, with the links associated common fault SRLGs, the priority ordering technique is very efficient in determining at least two paths for routing between a source and destination node.
Owner:WSOU INVESTMENTS LLC
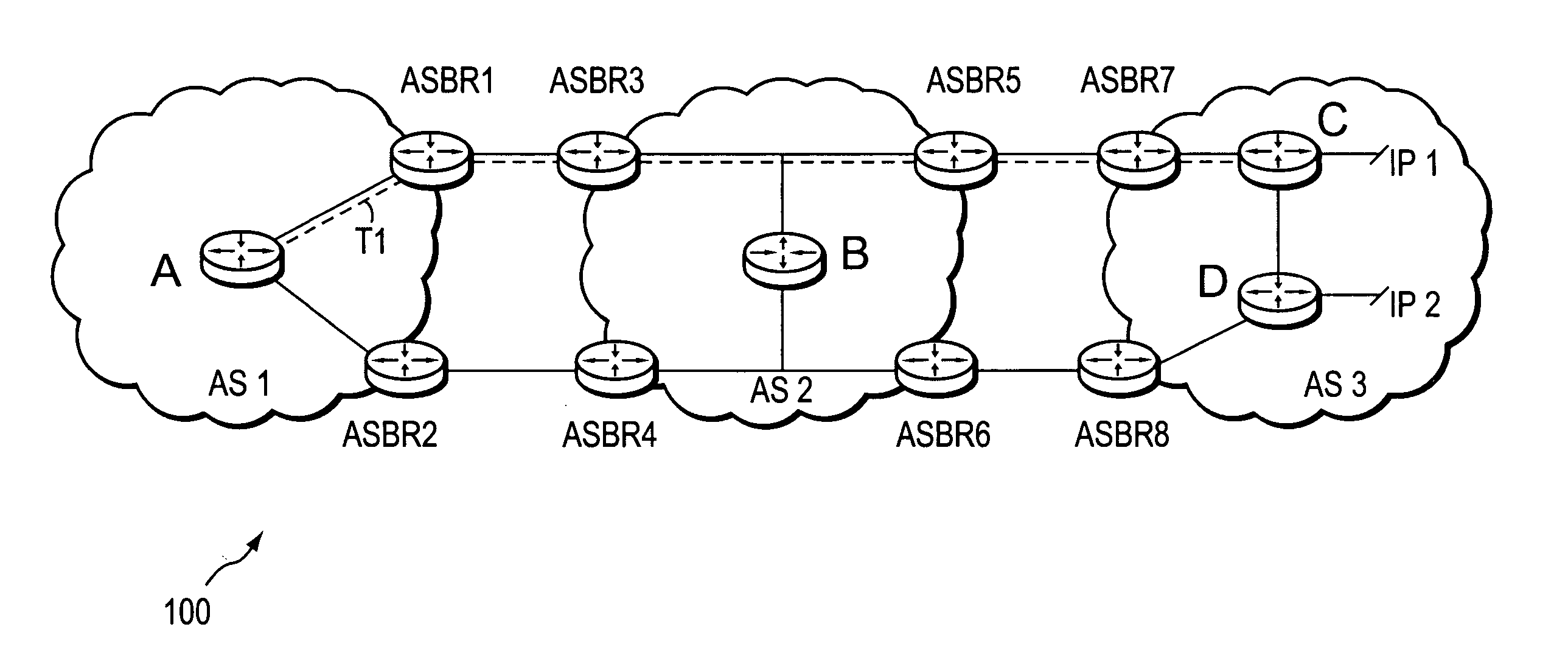
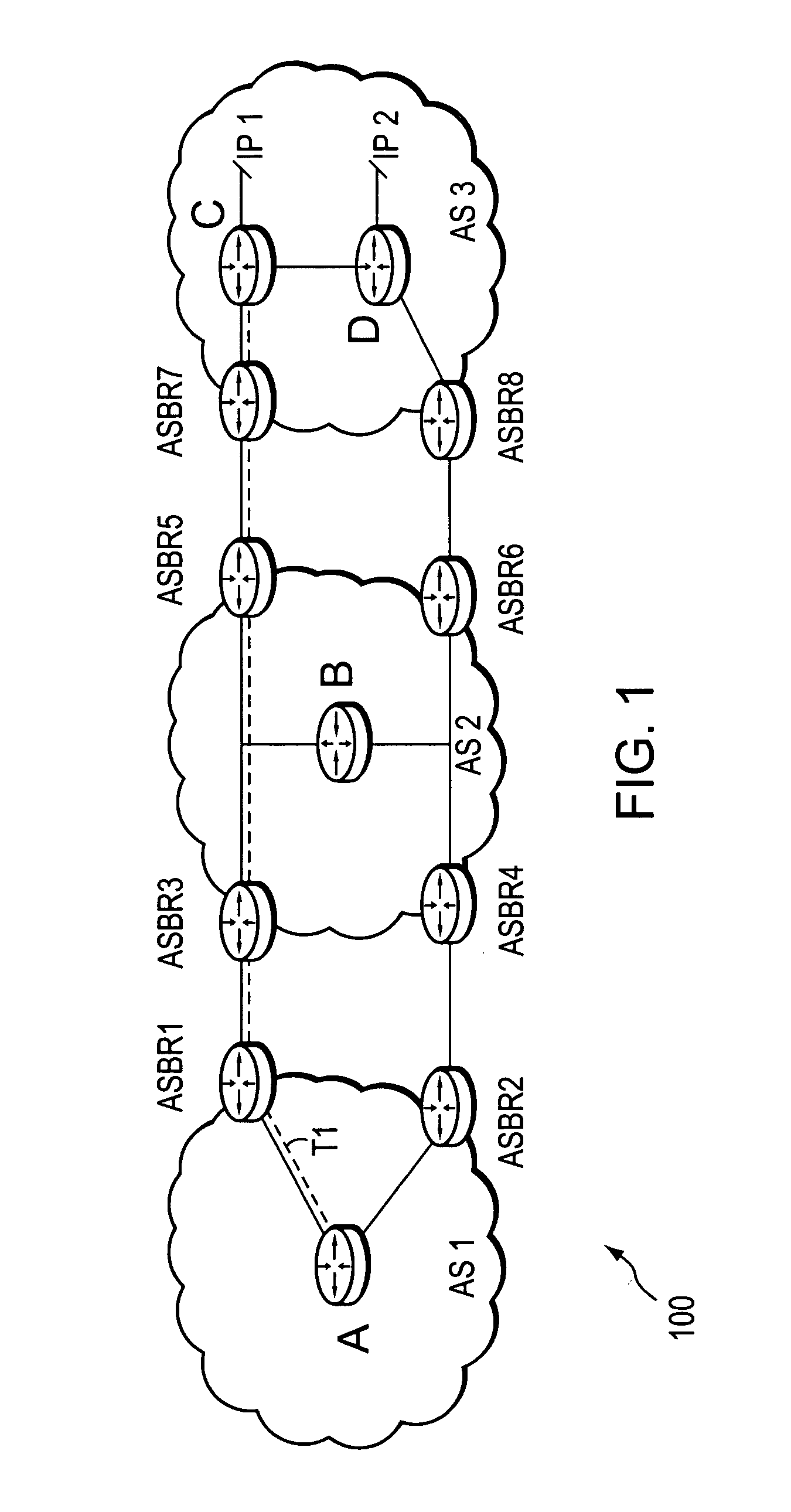
Dynamic retrieval of routing information for inter-AS TE-LSPs
A technique dynamically triggers an exchange of reachability information between a tail-end (remote) domain target node (e.g., a tail-end node) of a traffic engineering (TE) label switched path (LSP) and a local domain head-end node of the TE-LSP in a computer network. The inter-domain information retrieval technique is illustratively based on triggering a Border Gateway Protocol (BGP) session whereby at least a portion of the reachability, i.e., routing, information of the tail-end node is transmitted to the head-end node of the TE-LSP in accordance with BGP. Specifically, once a TE-LSP is established between the head-end node and the tail-end node, the head-end node triggers the tail-end node, e.g., through extensions to a request / response signaling exchange, to establish the BGP session. Establishment of the BGP session enables transmission of the routing information from the tail-end node to the head-end node. The head-end node uses the routing information to calculate routes, i.e., address prefixes and associated attributes, reachable from the tail-end node for insertion into its routing table.
Owner:CISCO TECH INC
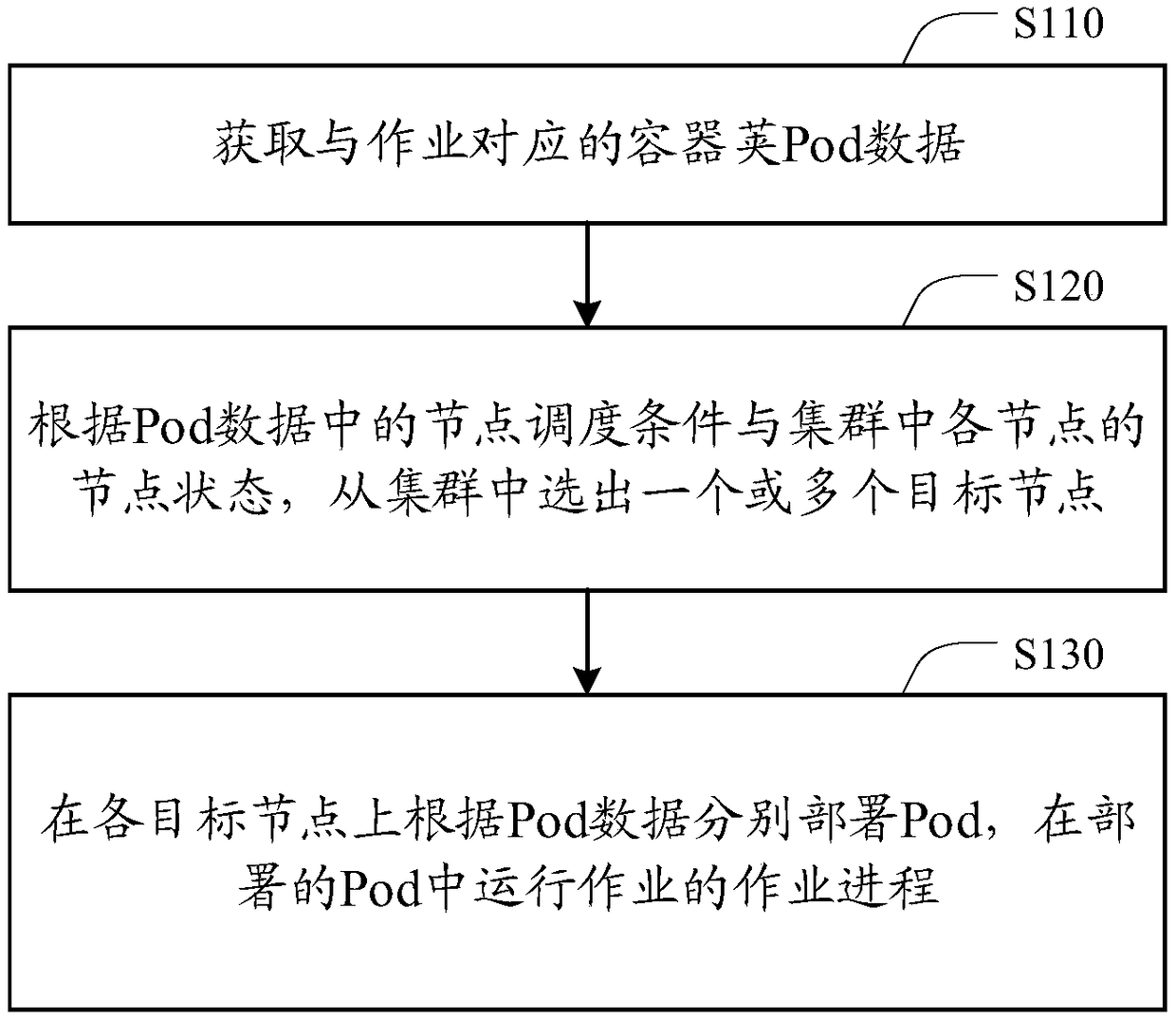
Method, apparatus, device, and storage medium for scheduling jobs in cluster
The invention discloses a method, an apparatus, a device and a storage medium for scheduling jobs in a cluster. The method comprises the following steps of: acquiring pod data corresponding to a job;one or more target nodes are selected from the cluster according to the node scheduling condition in the pod data and the node state of each node in the cluster. A Pod is respectively deployed on eachtarget node according to the Pod data, job processes are run in jobs in eeployed pods. This technical solution deploys job processes in a containerized manner, as the different jobs can be deployed in each corresponding independent contain, the jobs of each application on the cluster can not affect each other, communication can be carried out in the scene needing to be interactive, the effectiveutilization of the cluster resources is realized, and stable job scheduling can be realized for projects requiring multi-application pipelined cooperation such as deep learning and the like.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
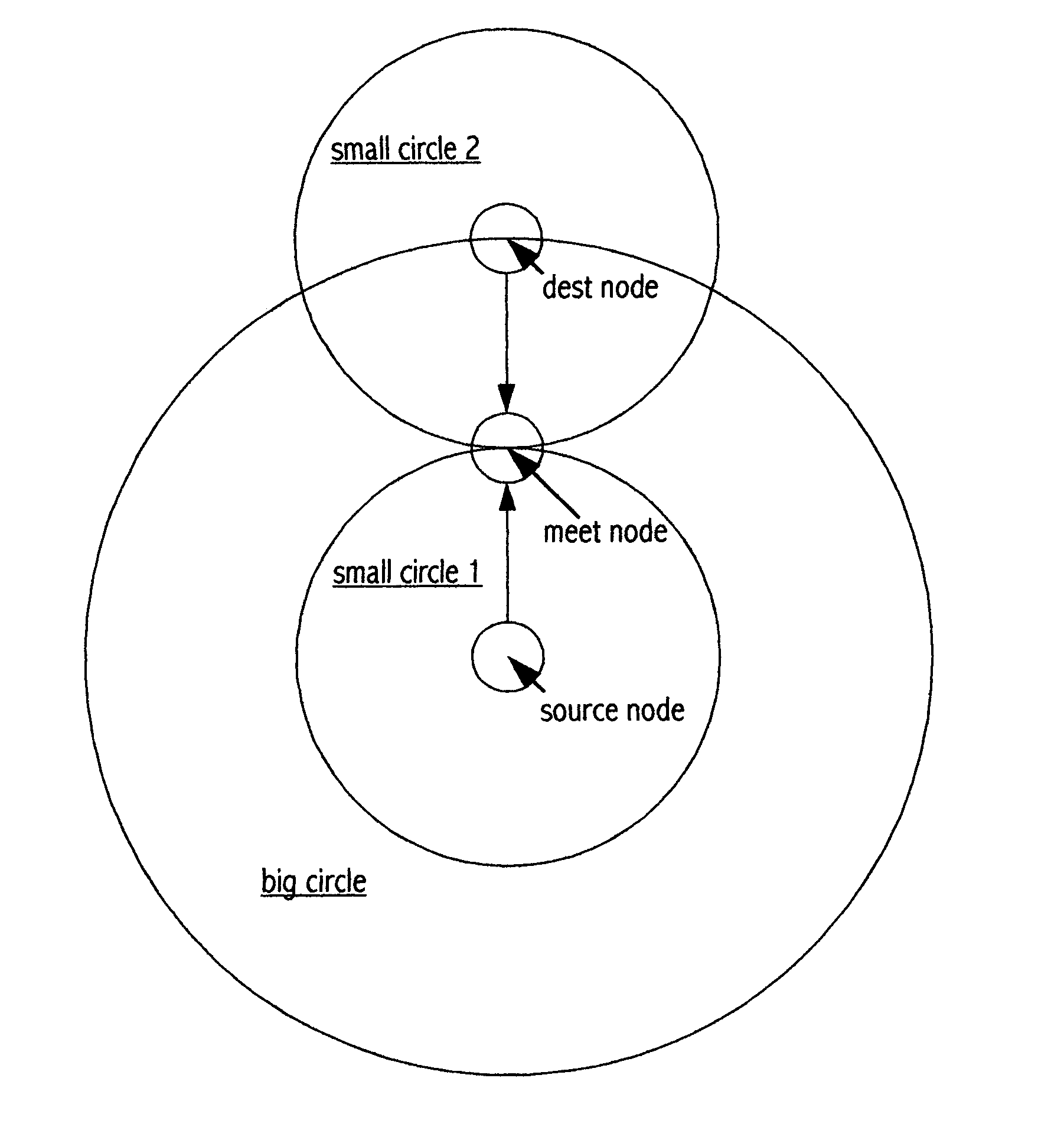
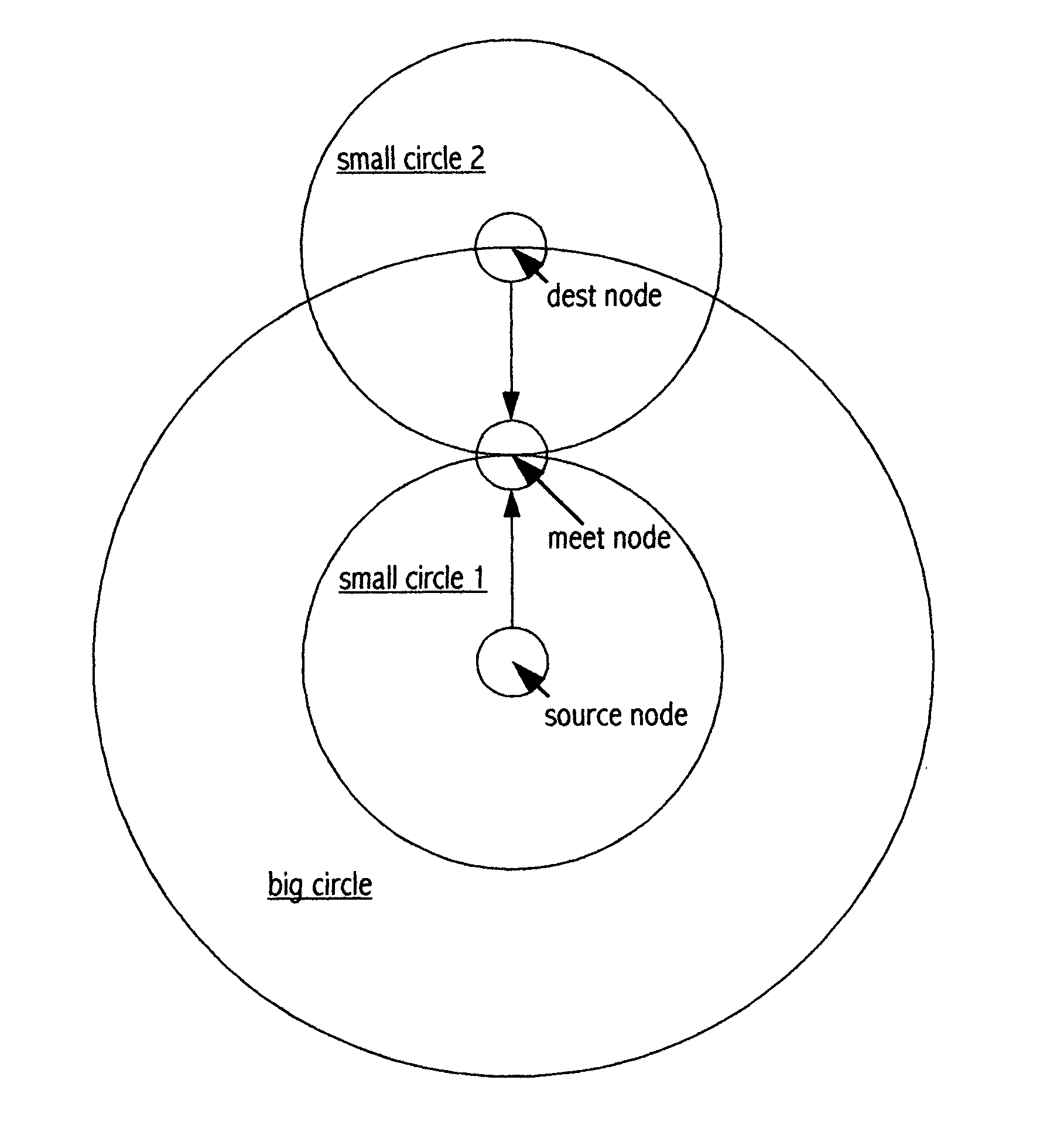
Shortest path search method "Midway"
InactiveUS7280481B2Reduce overheadLess timeError preventionFrequency-division multiplex detailsShort path algorithmShortest path search
A method of searching for a shortest path from a single source node to a single destination node in a two dimensional computer network. The method is similar to Dijkstra shortest path algorithm (“Dijkstra”) in the way it builds a shortest path tree. However, instead of starting from the source node and searching through to the destination node as Dijkstra does, the method runs a shortest path search from both ends (i.e. source and destination) simultaneously or alternatively, until a shortest path tree from one end meets a shortest path tree from the other end at an intermediate node, and the concatenated path (source node intermediate node-destination node) satisfies a condition. Conditions other than those used by Dijkstra determine when the search should terminate, and whether the search has succeeded or failed. It has been verified that the new method requires less overhead and time than Dijkstra.
Owner:RONG GUANGYI DAVID
Characterizing achievable flow rates in multi-hop mesh networks with orthogonal channels
InactiveUS20070025364A1Time-division multiplexData switching by path configurationMultiple edgesEdge coloring
A method of routing data from a source node to a destination node in a multi-hop network of nodes interconnected by links comprises: (a) determining that a link-flow vector satisfies one or more necessary scheduling conditions for achievability, wherein the link-flow vector represents a set of flows to be routed on one or more links from the source node to the destination node; (b) generating a scheduling multi-graph for the network, wherein the scheduling multi-graph comprises a graph having at least one pair of nodes with multiple edges therebetween; (c) deriving one or more sufficient scheduling conditions for achievability of the link-flow vector by edge-coloring the scheduling multi-graph; (d) solving a linear optimization problem over the one or more necessary scheduling conditions to obtain an upper bound on the achievability of the link-flow vector; (e) generating, based on the scheduling multi-graph, a solution comprising a set of routes and an associated schedule for achieving the link-flow vector, the solution being a lower bound on the achievability of the link-flow vector; and (f) implementing a routing method using the set of routes and the associated schedule to route the link-flow vector from the source node to the destination node. At least one node v of the network is adapted to receive transmissions from a specified plurality Ω(v) of other nodes, and at least one of the scheduling conditions depends on Ω(v).
Owner:ALCATEL-LUCENT USA INC +1
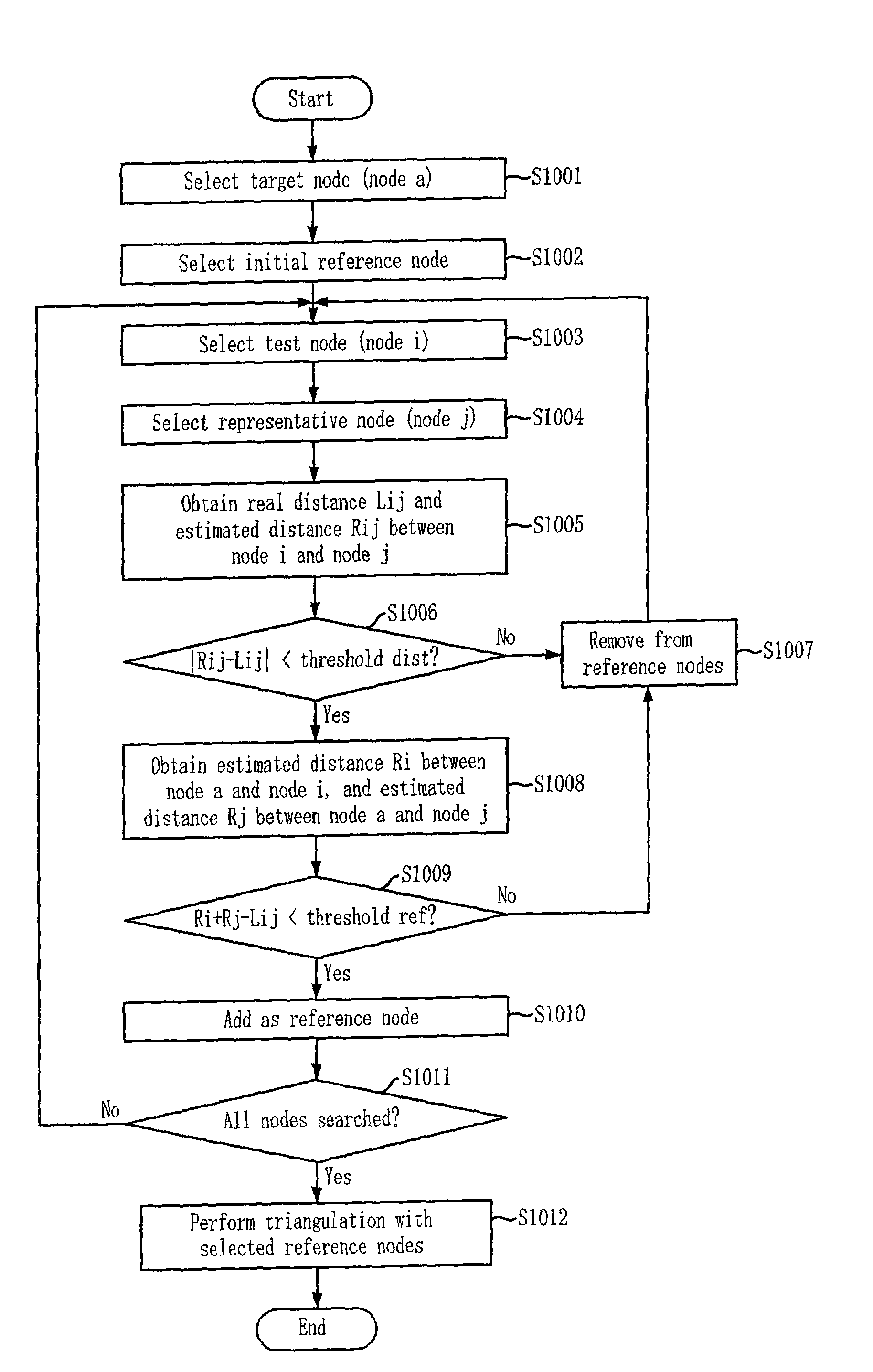
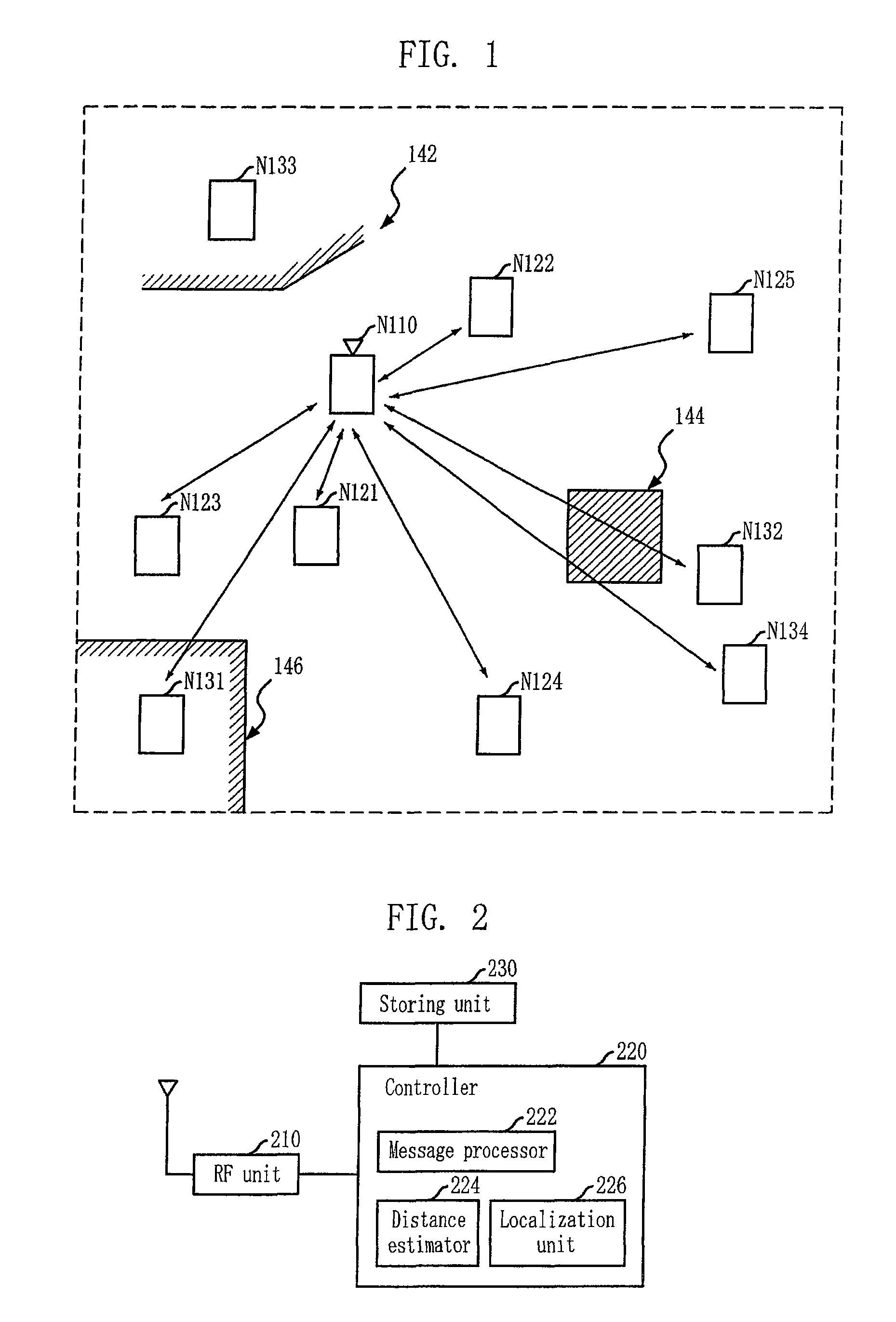
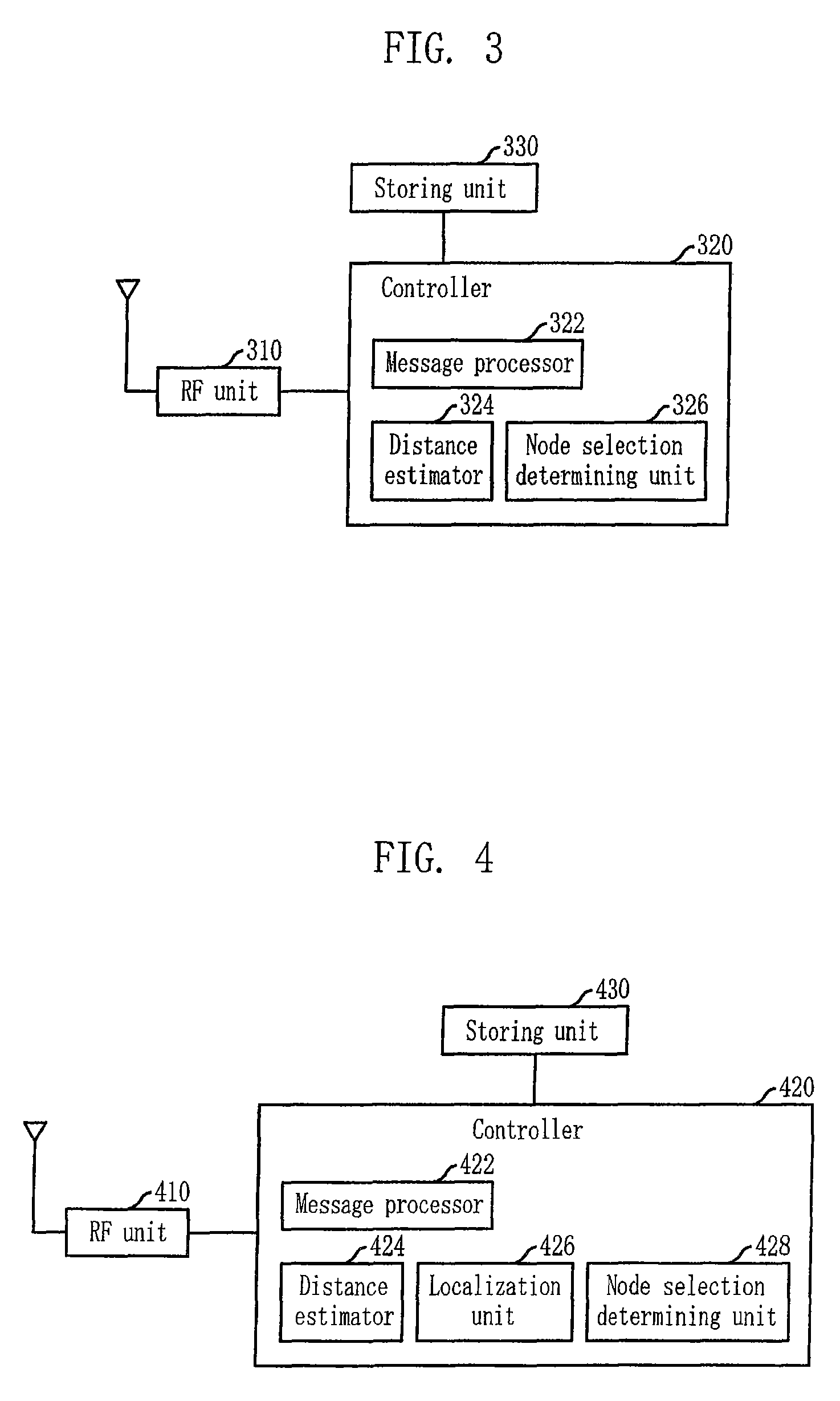
Localization apparatus for recognizing location of node in sensor network and method thereof
InactiveUS7969913B2Accurate detectionAccurate acquisitionNetwork topologiesPosition fixationNODALTriangulation
Owner:ELECTRONICS & TELECOMM RES INST
Method for searching a tree structure
InactiveUS20100082664A1Significant overheadLow scalabilityDigital data information retrievalDigital data processing detailsTheoretical computer scienceTree architecture
A method, apparatus, and computer readable article of manufacture for tracing, on the basis of a key, an index created using a tree structure to access data. The method includes: searching the tree structure to reach a target node that can be associated with the key without acquiring a lock on the root node and on an internal node; setting the target node as a current node when the target node is a leaf node; moving the search to a node at a lower layer when the target node is an internal node by tracing an edge in the tree structure to reach a leaf node and setting the leaf node as the current node; and associating the key with the leaf node specified as the current node by acquiring a lock on the leaf node specified as the current node, thereby accessing the data.
Owner:IBM CORP
Method and device for determining the length of a shortest path in a network
InactiveUS20090040931A1Instruments for road network navigationError preventionDistributed computingPathPing
A computer-implemented method for pre-processing a network, wherein the network comprises nodes and edges, each edge having a length measured according to a given metric, comprises the steps of selecting a source and a target node; determining a transit node for the selection; determining a length of a shortest path between the source node and the transit node; and storing it. A method for determining the length of a shortest path in the network may use the pre-processed network to answer the shortest path query in constant time.
Owner:MAX PLANCK GESELLSCHAFT ZUR FOERDERUNG DER WISSENSCHAFTEN EV
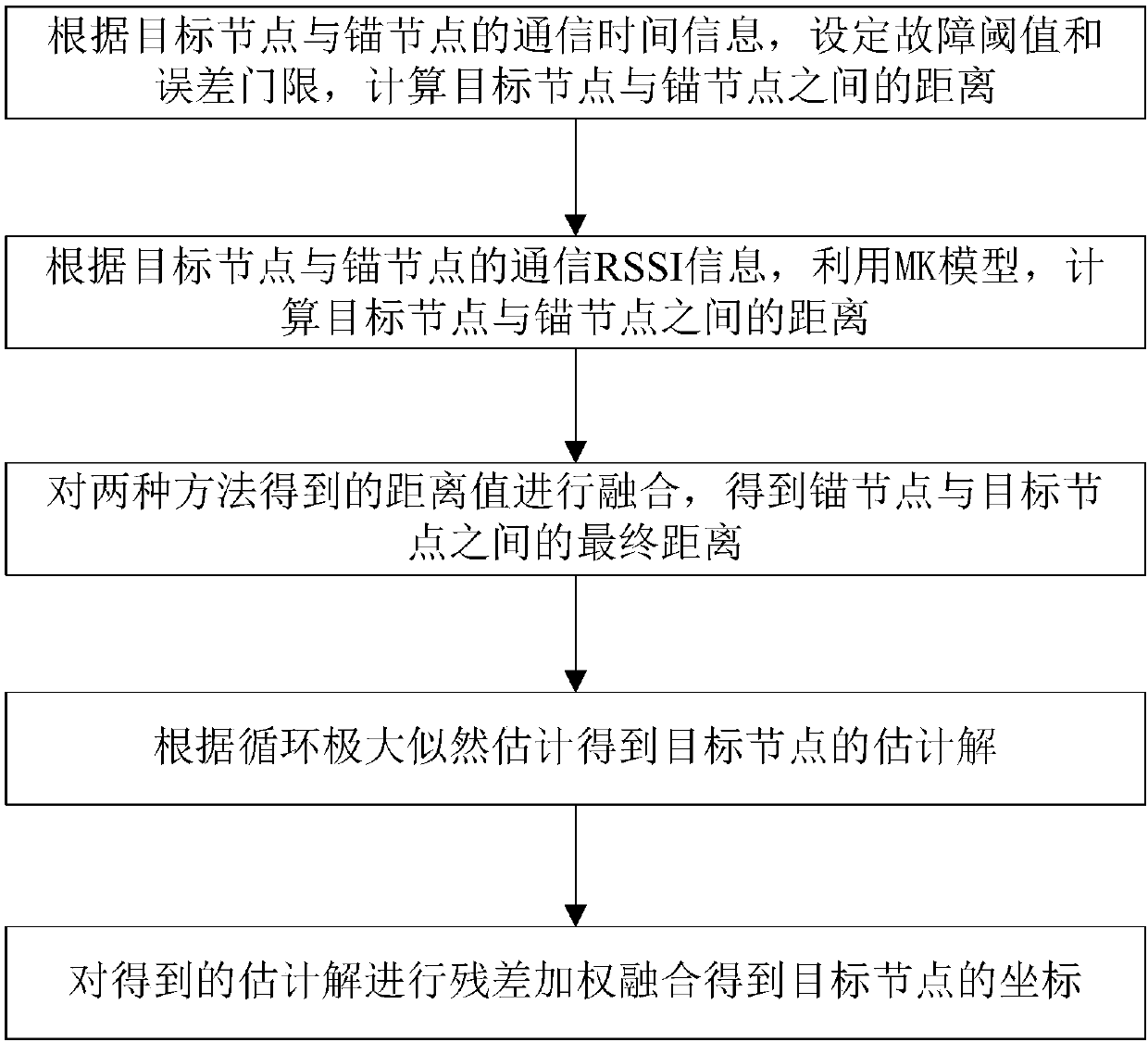
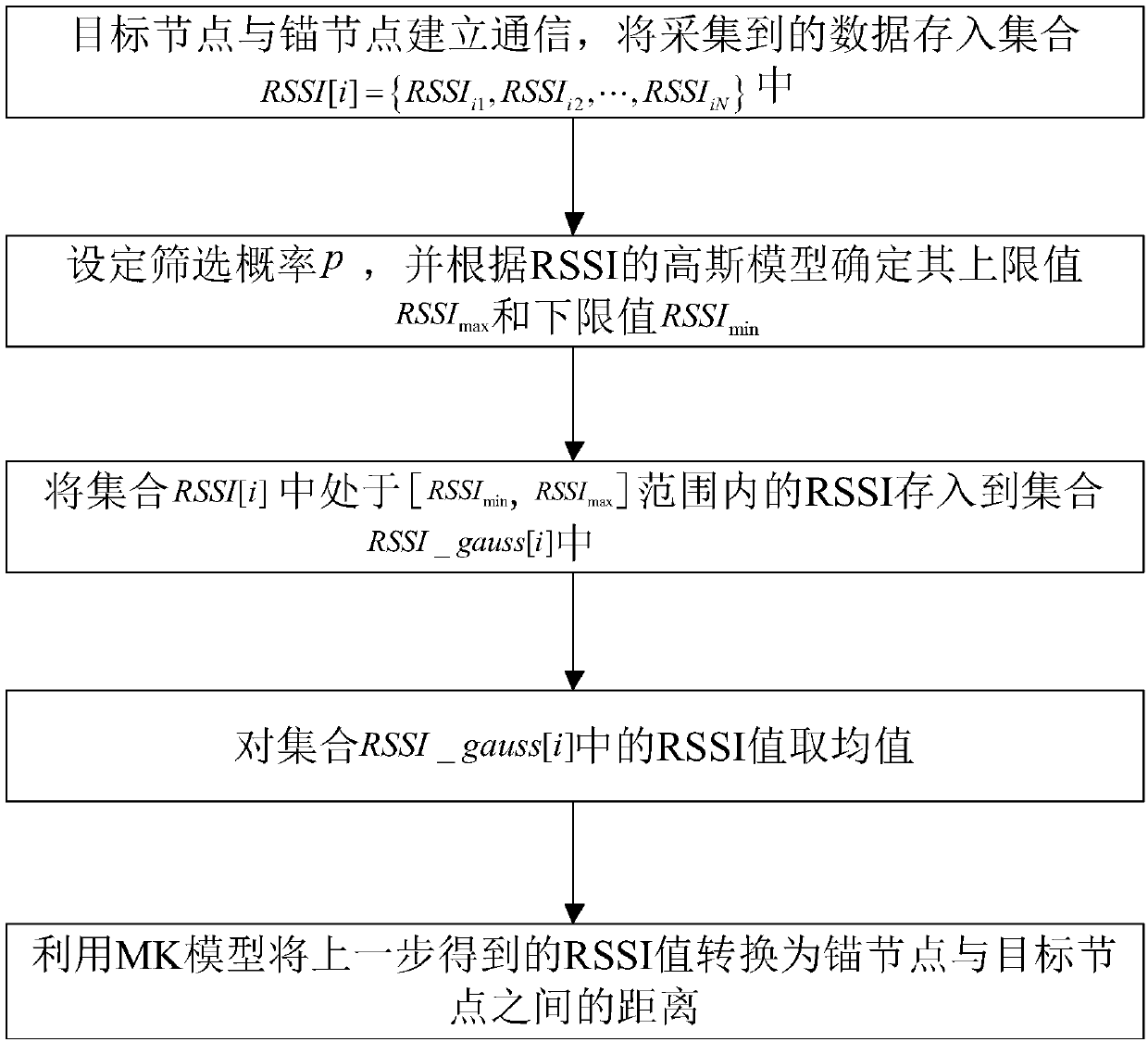
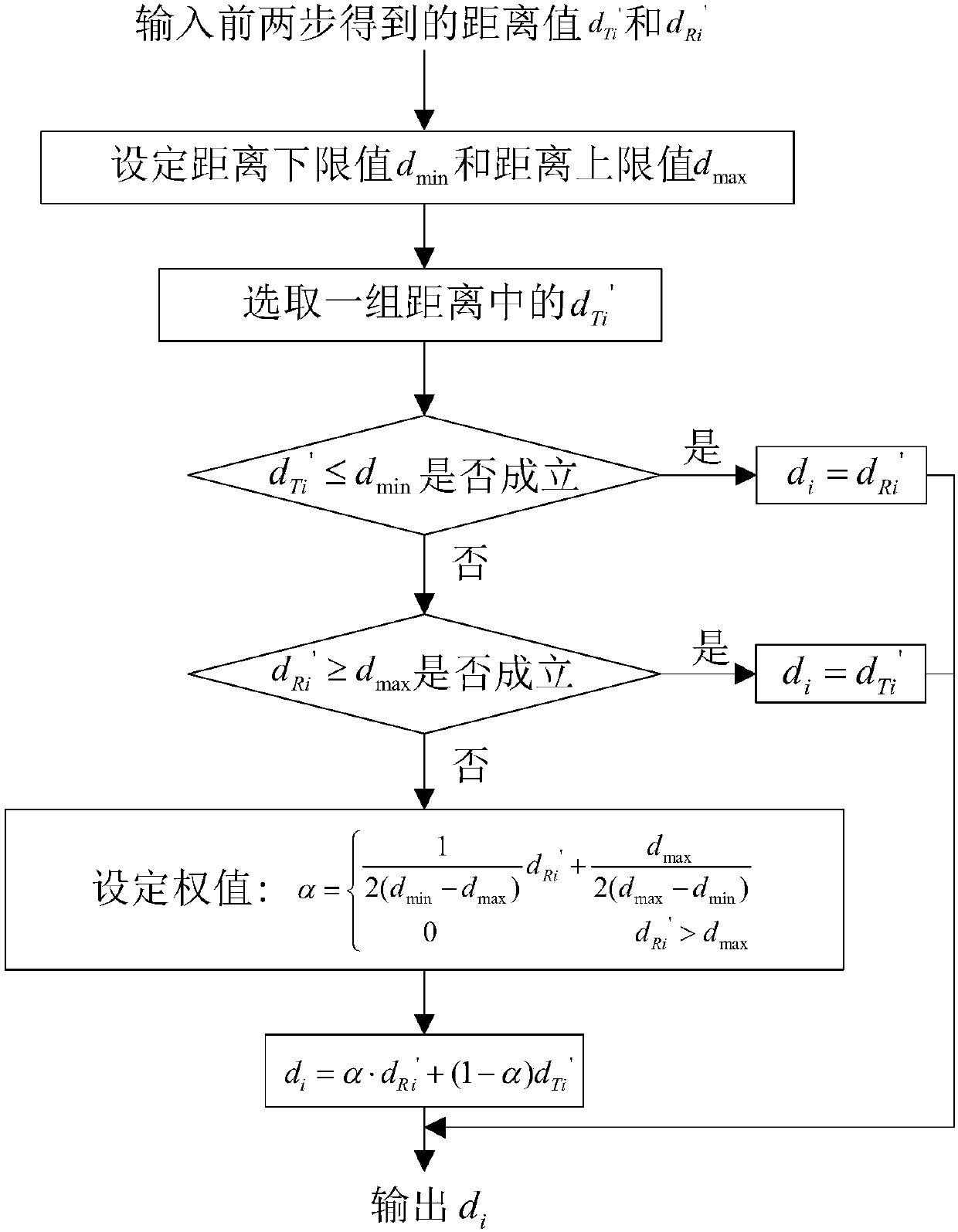
TOF and RSSI information fusion-based indoor wireless positioning method
ActiveCN108535687AHigh precisionImprove ranging accuracyParticular environment based servicesPosition fixationTime informationPositioning technology
The invention discloses a TOF and RSSI information fusion-based indoor wireless positioning method which is mainly used for solving a problem that in conventional indoor positioning technology lacks effective error control and is low in data utilization rate. An implementation solution comprises the following steps: step 1, according to communication time information between a target node and an anchor node, a symmetric bidirectional bilateral distance measuring algorithm is used to calculate distance between the two, and a fault threshold and an error threshold are set to filter the distance;step 2, according to RSSI value information between the target node and the anchor node, an MK model is used for converting the RSSI value information into distance between nodes after a Gaussian model is used for screening operation; step 3, the two types of distance is subjected to weighted fusing operation, and final distance is obtained; step 4, estimated solutions for the target node are obtained via circulation maximum likelihood estimation; step 5, the obtained estimated solutions are subjected to residual error weighted fusing operation, and coordinates of the target node are obtained. Via the method, insufficiency of conventional technologies that are large in positioning calculating errors and low in positioning result reliability, and data utilization rates and positioning andtracking precision are improved.
Owner:XIDIAN UNIV
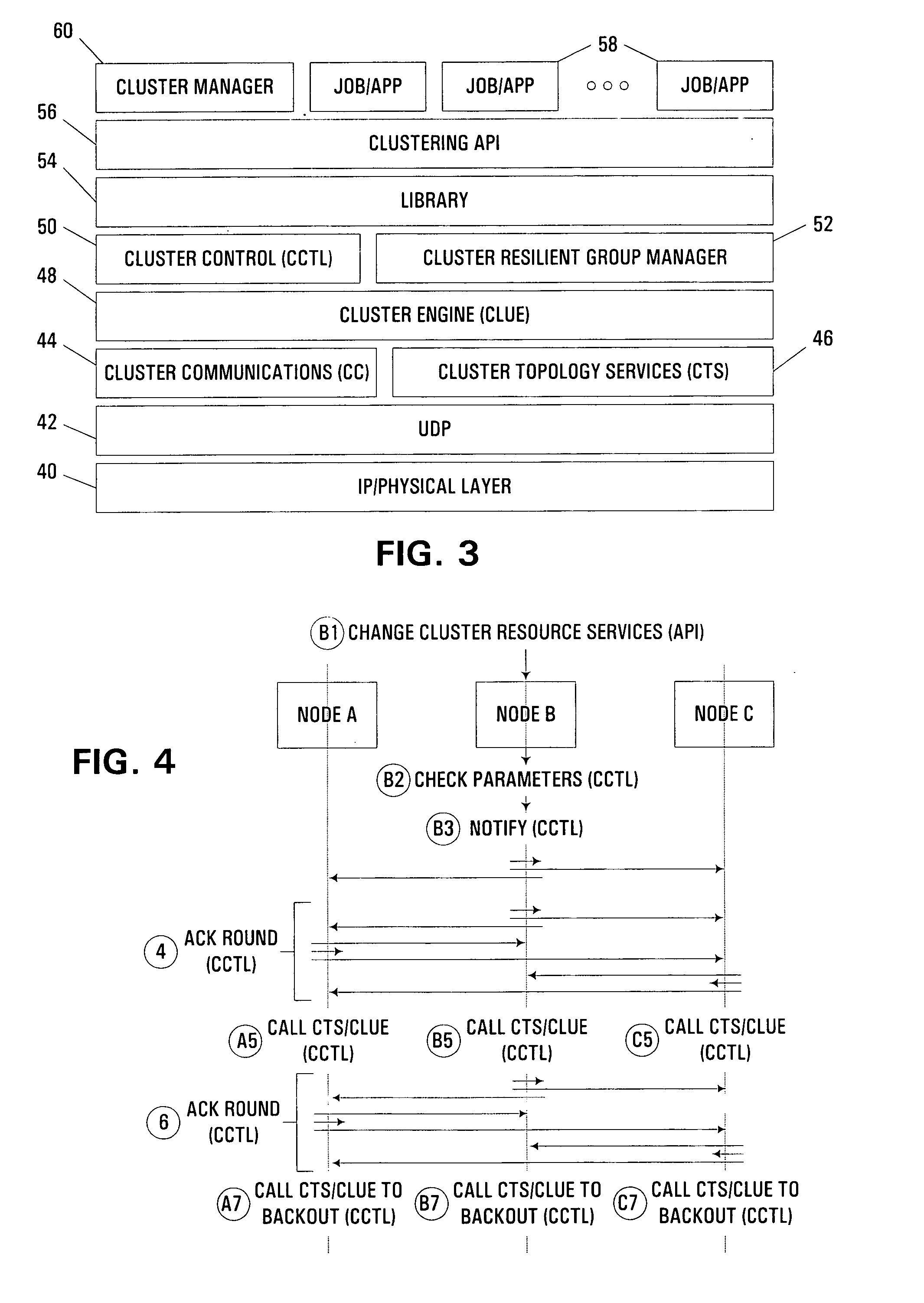
Dynamic modification of fragmentation size cluster communication parameter in clustered computer system
InactiveUS6934768B1Little and no effect on system availabilitySpecial service provision for substationError detection/correctionSize changeDistributed computing
An apparatus, program product and method support the dynamic modification of cluster communication parameters such as a fragmentation size parameter through controllably deferring the processing of a requested fragmentation size change in a source node until after receipt an acknowledgment message for at least one unacknowledged message sent by the source node to a plurality of target nodes. By controllably deferring such processing until it is confirmed that any such previously-unacknowledged messages sent by a source node have been received by any target nodes, synchronization between the source node and the target nodes may be obtained, and a fragmentation size change may occur in a coordinated fashion such that future messages from the source node to the target node will be processed by both the source and the target nodes using the modified fragmentation size parameter.
Owner:IBM CORP
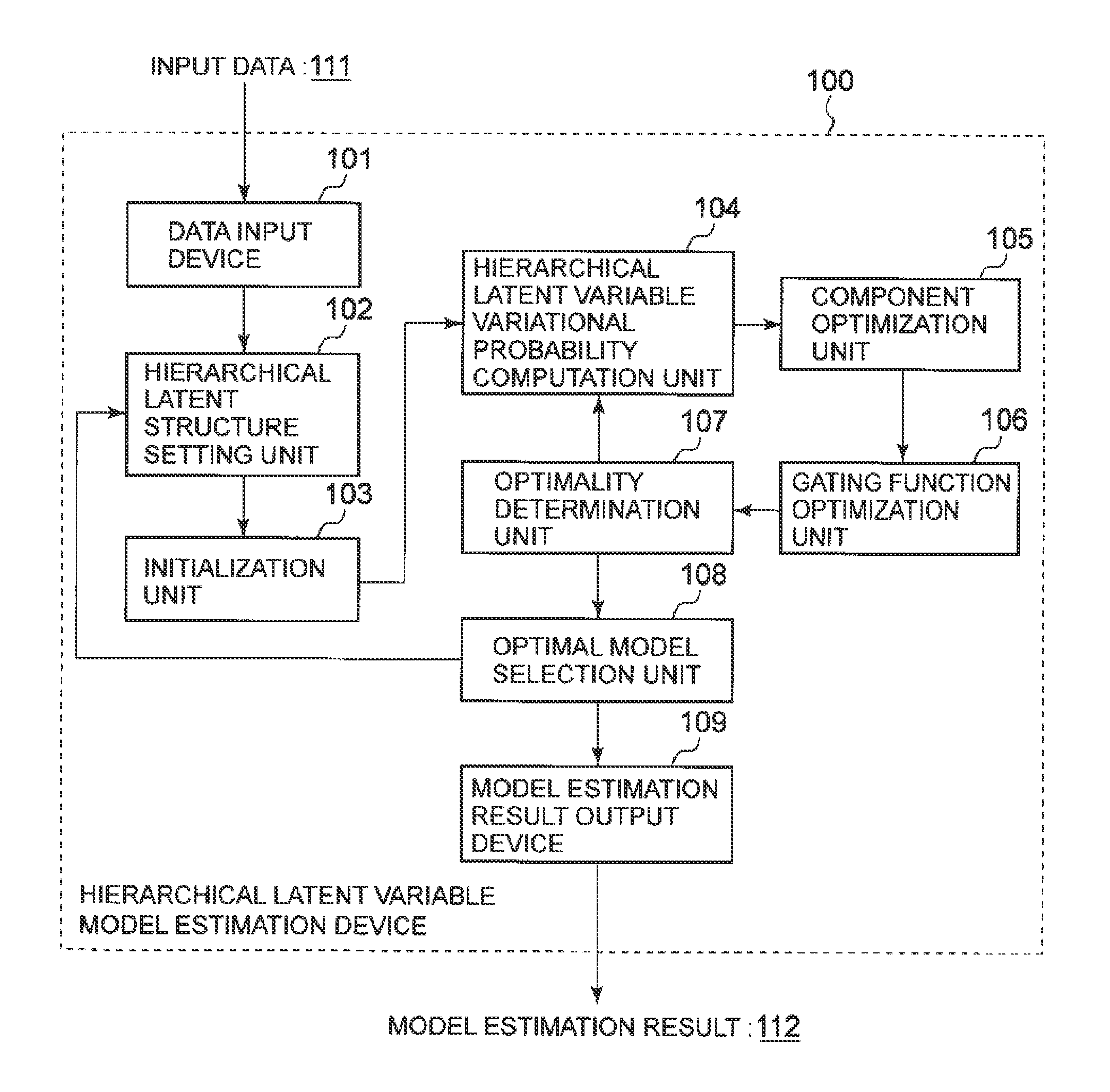
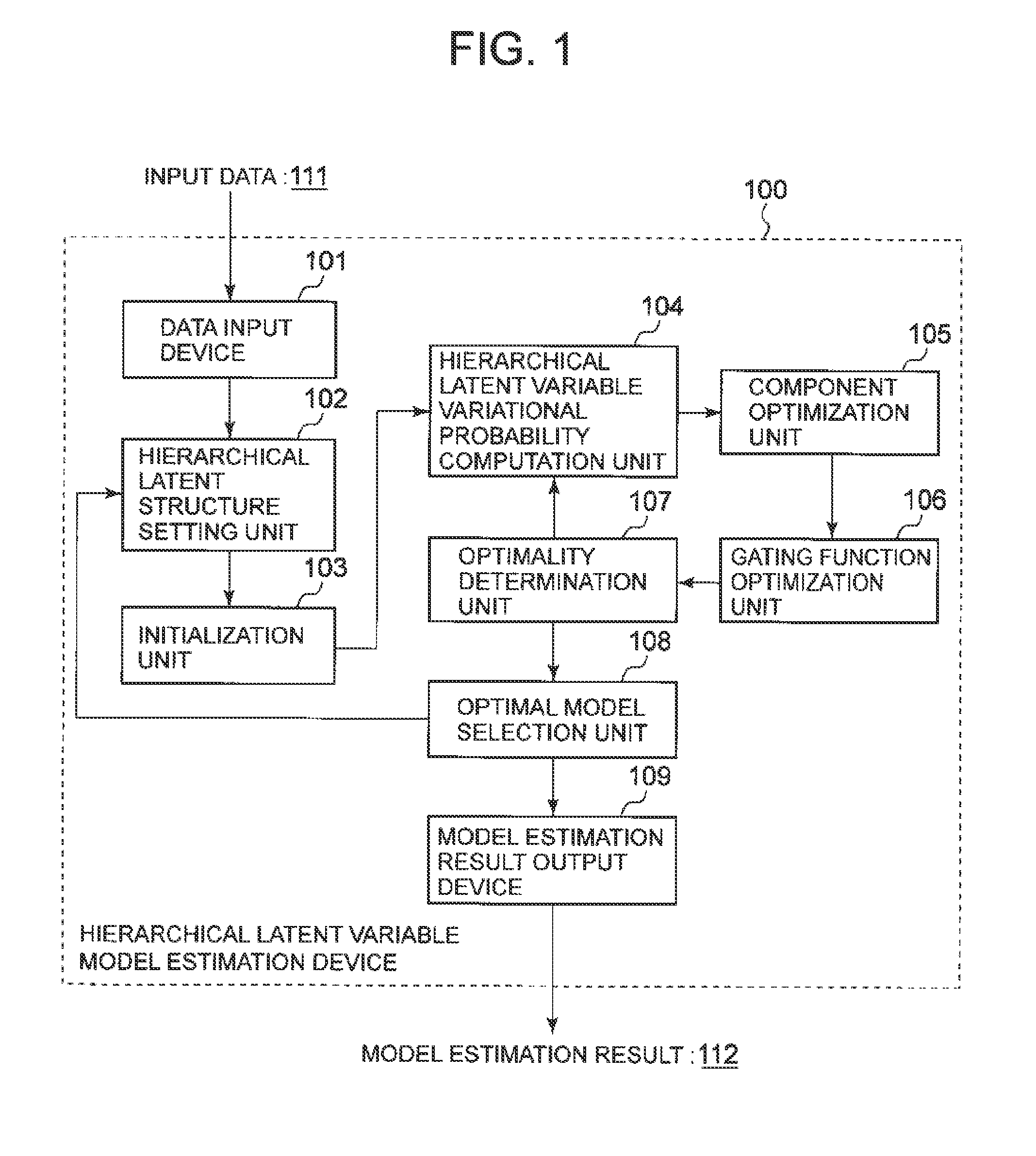
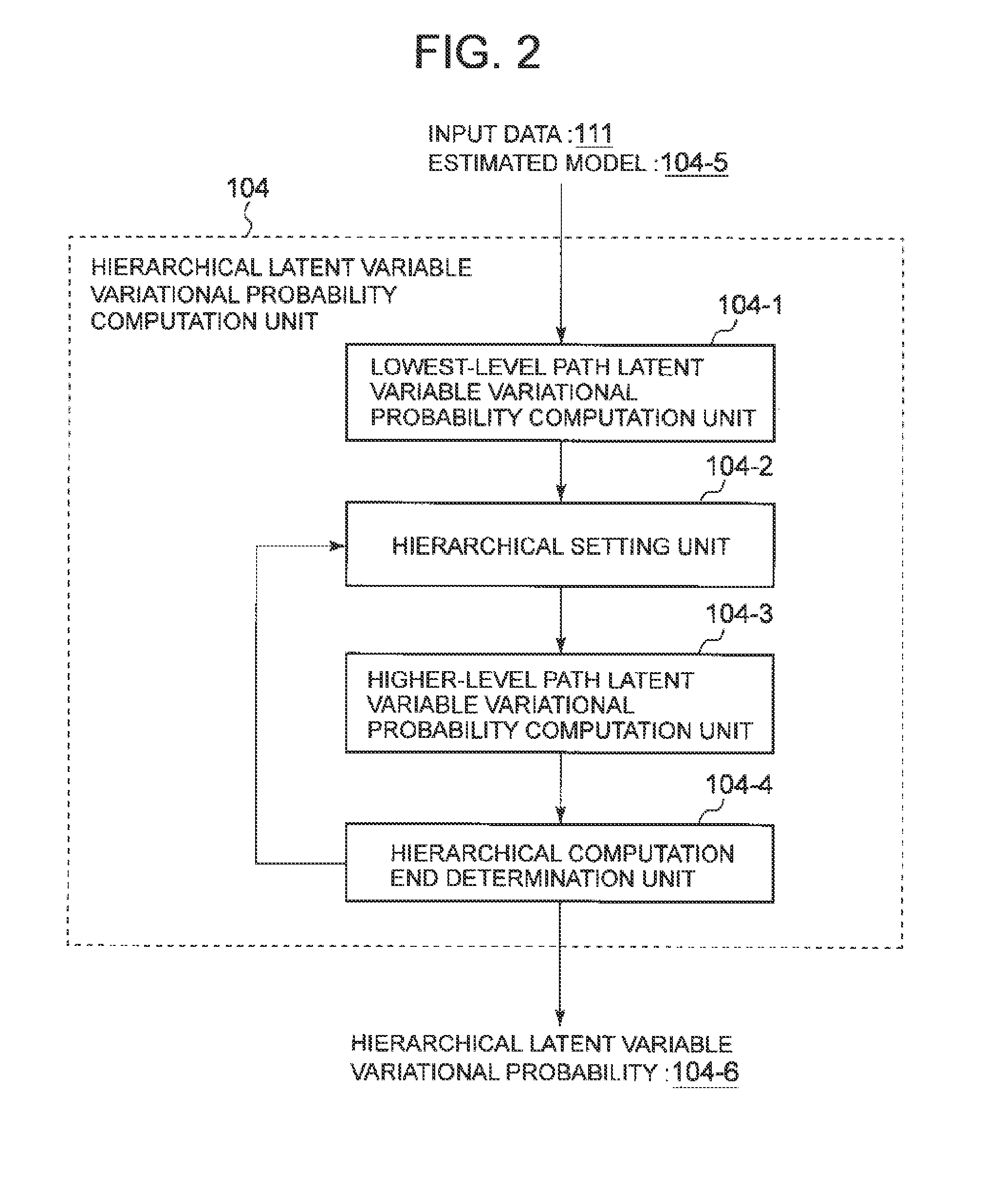
Hierarchical latent variable model estimation device, hierarchical latent variable model estimation method, and recording medium
ActiveUS20140222741A1Losing theoretical justificationProbabilistic networksKnowledge representationProbit modelFunction optimization
A hierarchical latent structure setting unit 81 sets a hierarchical latent structure that is a structure in which latent variables are represented by a tree structure and components representing probability models are located at nodes of a lowest level of the tree structure. A variational probability computation unit 82 computes a variational probability of a path latent variable that is a latent variable included in a path linking a root node to a target node in the hierarchical latent structure. A component optimization unit 83 optimizes each of the components for the computed variational probability. A gating function optimization unit 84 optimizes a gating function model that is a model for determining a branch direction according to the multivariate data in a node of the hierarchical latent structure, on the basis of the variational probability of the latent variable in the node.
Owner:NEC CORP
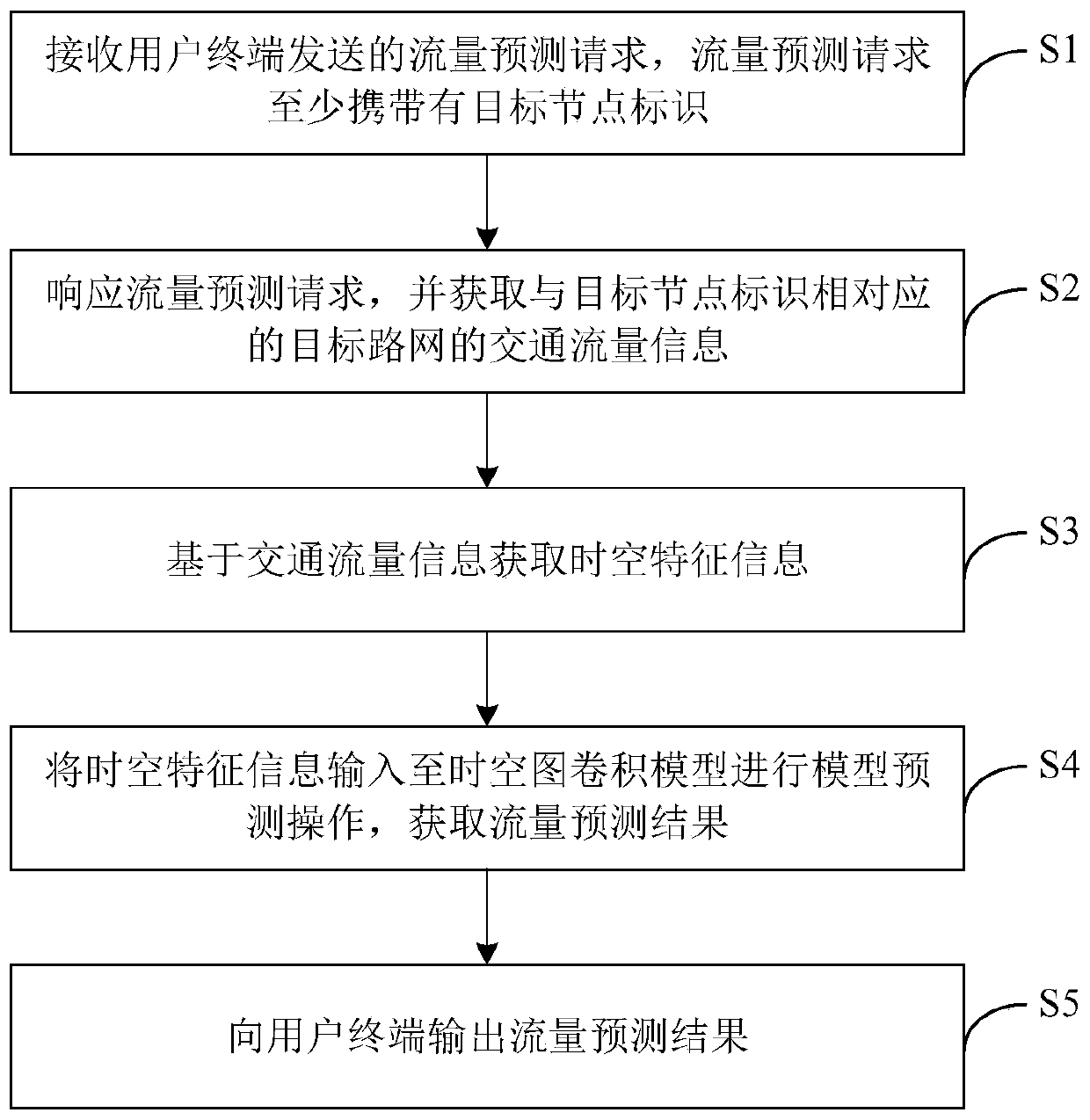
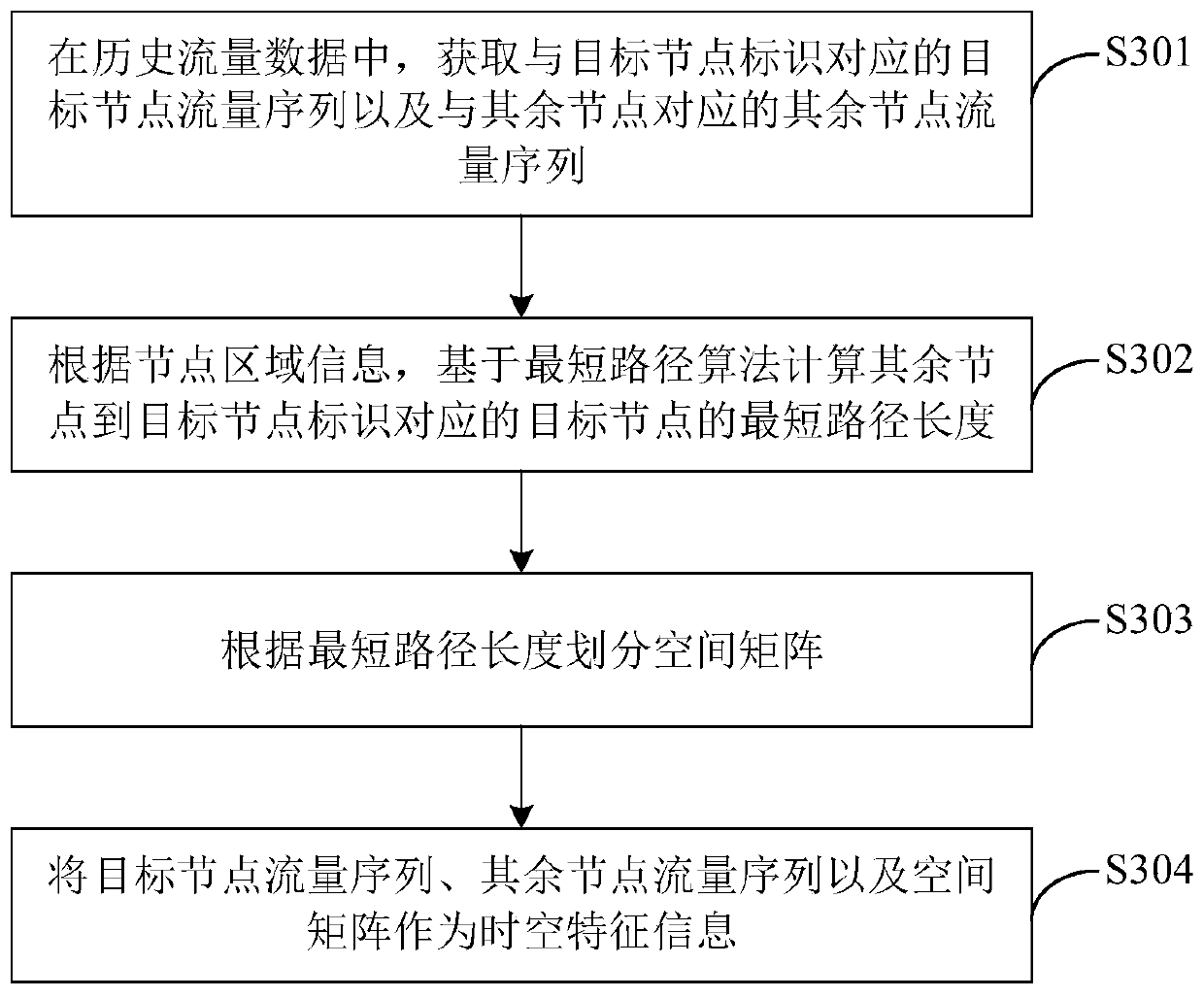
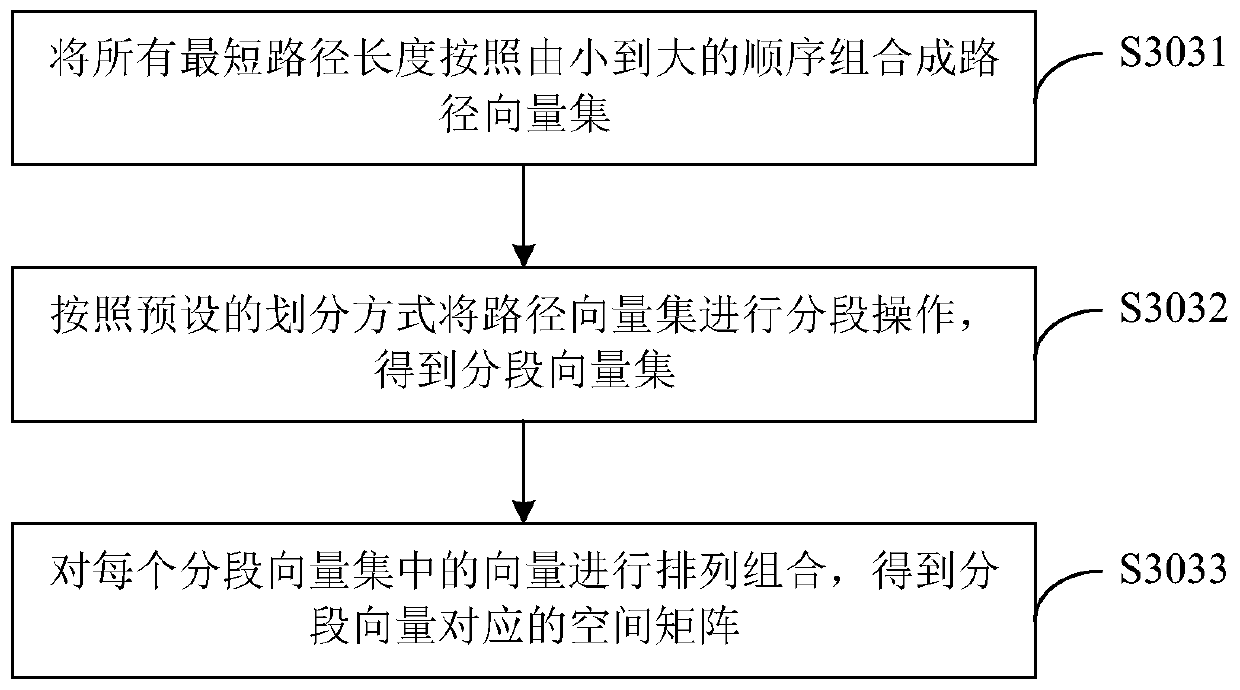
Traffic flow prediction method and device based on deep learning
PendingCN110929962AImprove accuracyDetection of traffic movementForecastingTraffic predictionRoad networks
The invention relates to the field of spatio-temporal data mining or intelligent traffic, in particular to a traffic flow prediction method and device based on deep learning. The traffic flow prediction method comprises the following steps: receiving a flow prediction request sent by a user terminal; then, responding to the flow prediction request, and obtaining traffic flow information of a target road network corresponding to the target node identifier; acquiring spatiotemporal feature information based on the traffic flow information; and inputting the space-time feature information into aspace-time diagram convolution model to perform model prediction operation, and obtaining a flow prediction result, so that the influence of the spatial-temporal characteristics of the traffic flow ofthe whole road network on the traffic flow of the target node can be more comprehensively considered from the perspective of spatial-temporal correlation. The traffic flow prediction method and device based on deep learning can improve the accuracy of predicting the traffic flow of the road network.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
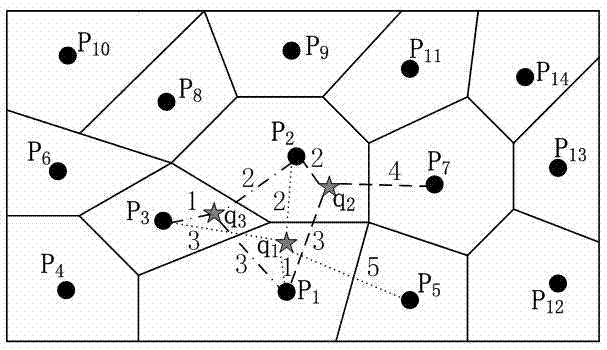
Method for querying road network k aggregation nearest neighboring node based on Voronoi graph
InactiveCN102253961AReduce performanceSpecial data processing applicationsTheoretical computer scienceRoad networks
The invention belongs to the technical field of a spatial database and in particular relates to a method for querying a road network k aggregation nearest neighboring node (k-ANN) based on a Voronoi graph. The method comprises the following steps of: resolving a first nearest neighboring node (1-NN) of each query point through an R tree index; constructing a priority queue to store the 1-NN of all query points, wherein the weight is the current aggregation distance from each query point to a target node; extending a certain query point according to a certain sequence on the basis of a road network Voronoi graph, updating the aggregation distance of the next NN of the query point, inserting or updating and performing other kinds of operation on the priority queue until the target node at the head of the queue is extended by all the query points, then the target node is a first aggregation nearest neighboring node (1-ANN); and after the 1-ANN is deleted from the queue, acquiring a second aggregation nearest neighboring node (2-ANN) which accords with the conditions for the second time, and acquiring the k-ANN according to the characteristics. The method has excellent performance in the aspect of response time and page views of user query.
Owner:FUDAN UNIV
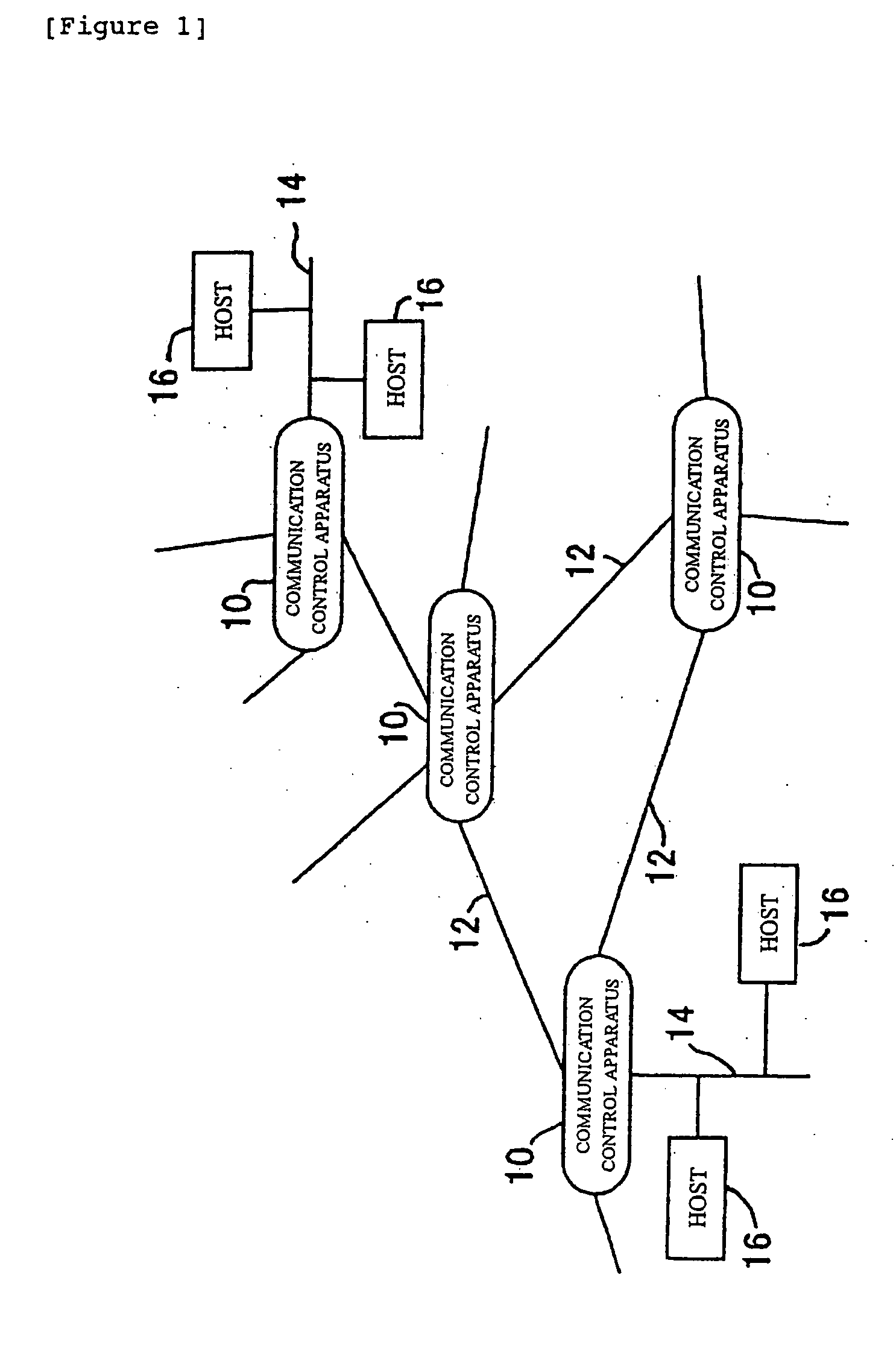
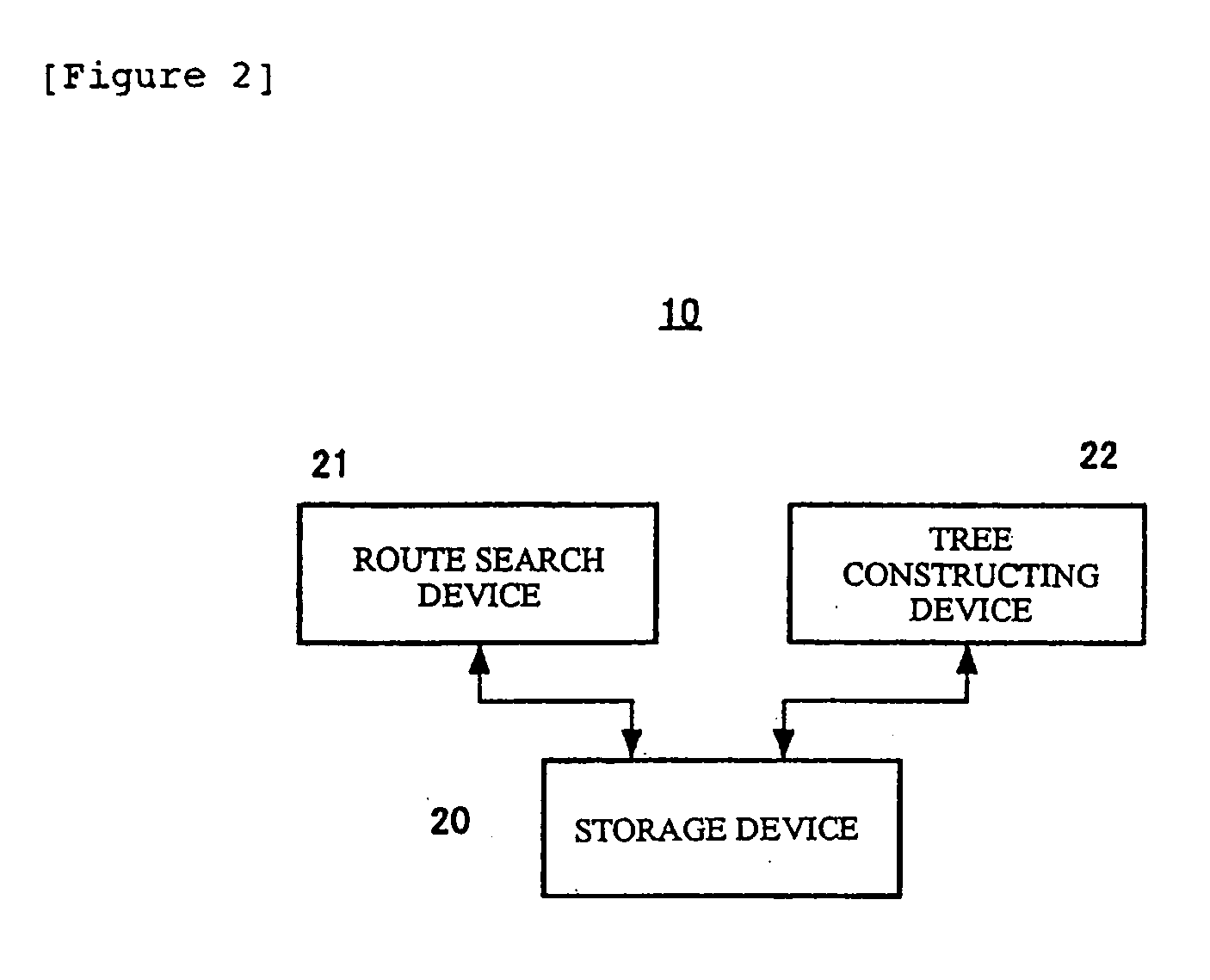
Communication control apparatus and method for searching an internet protocol address
InactiveUS20040215609A1Increase the number ofExtension of timeData switching networksSpecial data processing applicationsPathPingTheoretical computer science
A communication control apparatus and method for improving the search process for determining a transfer route for a packet received based on search information is described. The search information is associated with a tree structure. A mask prefix is associated with at least one entry, each entry including information on the mask length of a mask prefix associated therewith and a sort key. Each entry is assigned to a node in the tree structure according to a sorting order. Each node is linked to a different node at the next lower hierarchy via a branch based on the entry of the node. An extracting means 26 extracts a destination address of the packet received. Search means 27 searches a search target node 28 specified by a search control means 29 for an entry having information on best matched prefix of the extracted address. After completion of the node-by-node search process, a route determining means 30 determines a transfer route for the packet received based on the longest prefix amongst the most appropriate prefixes of all the current search target nodes.
Owner:IBM CORP
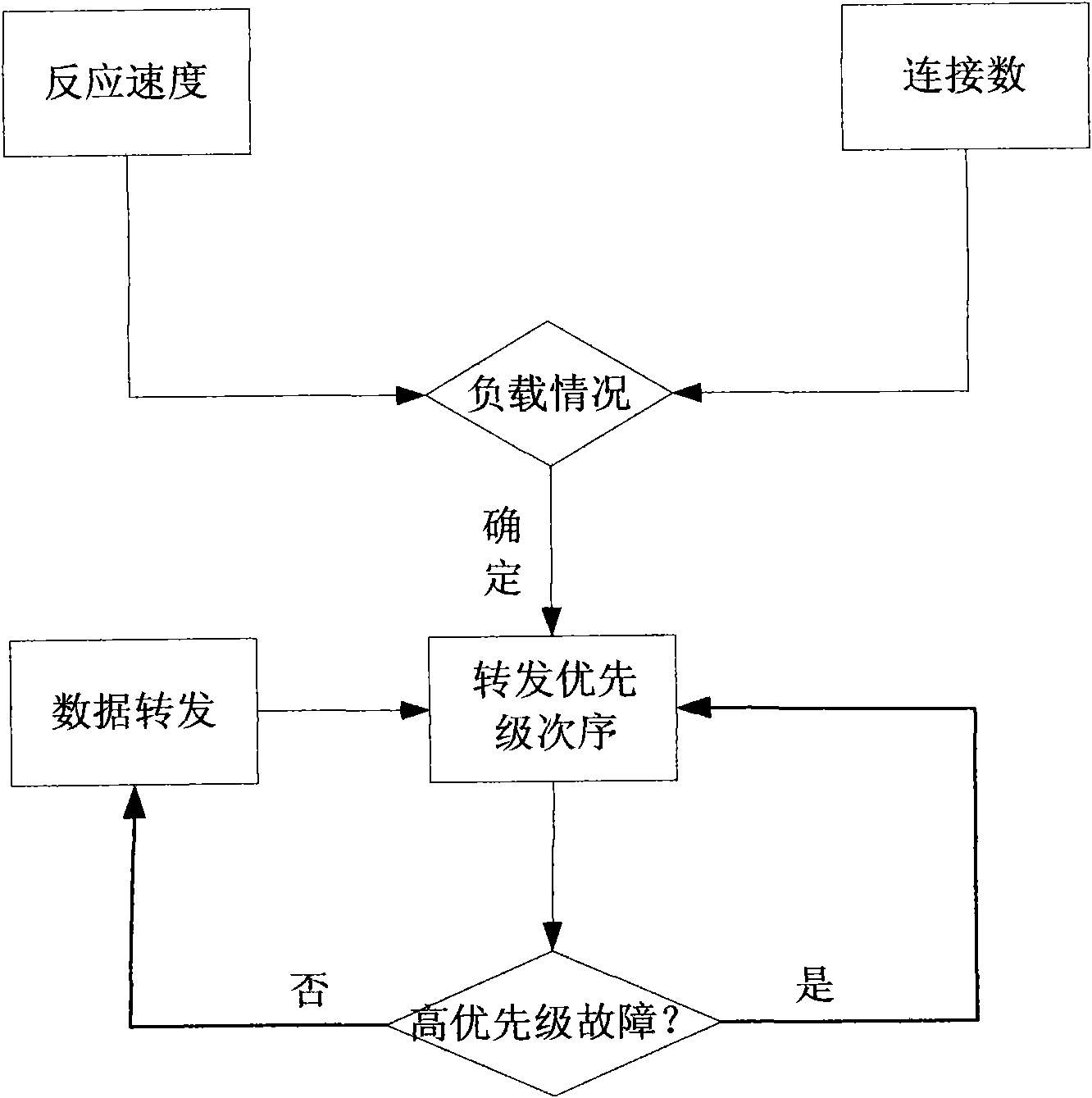
Method for quickly calibrating multi-level forwarding load balance and multi-level forwarding network system
ActiveCN102123087AOvercome the drawbacks of load balancingMeet load balancing requirementsData switching networksResource utilizationNetworked system
The invention relates to a method for quickly calibrating multi-level forwarding load balance of a multi-level forwarding network and a multi-level forwarding network system based on the method. Except the forwarding node of the last level, each forwarding node of each level monitors the load state of each forwarding node of the next level, determines the forwarding priority according to the load weight of the forwarding node of the next level, and preferentially forwards the data which needs to be forwarded to the forwarding node with the lightest load of the next level; if high-priority forwarding fails, the secondary-priority forwarding nodes are sequentially selected to forward the data; the forwarding nodes sending the data form a forwarding source node; and the nodes receiving the data form a forwarding destination node. Through the method and system provided by the invention, the load balance among the forwarding nodes as well as the detection and processing on the link and network system conditions are realized so that the resource utilization of the entire network system is optimized; and the core algorithm of the method can also be used for performing load balance at a server end.
Owner:北京同方艾威康科技有限公司
Routing in a communications network
InactiveUS6314092B1Interconnection arrangementsError preventionTelecommunications networkDistributed computing
A path between a selected first node and a selected second node is identified in a telecommunications network. A system cost is estimated for making a connection between the first node and the second node, a potential first intermediate note interconnectable from the first node is identified and a first set of systems costs are estimated from said first intermediate nodes to said second node. In addition, the second intermediate nodes connectable from the second node are identified and a second set of systems costs are estimated from the second intermediate nodes to the first node. On the basis of a comparison between the first set of systems costs and the second set of systems costs, between the first and second nodes, a starting node and a target node are selected.
Owner:BRITISH TELECOMM PLC
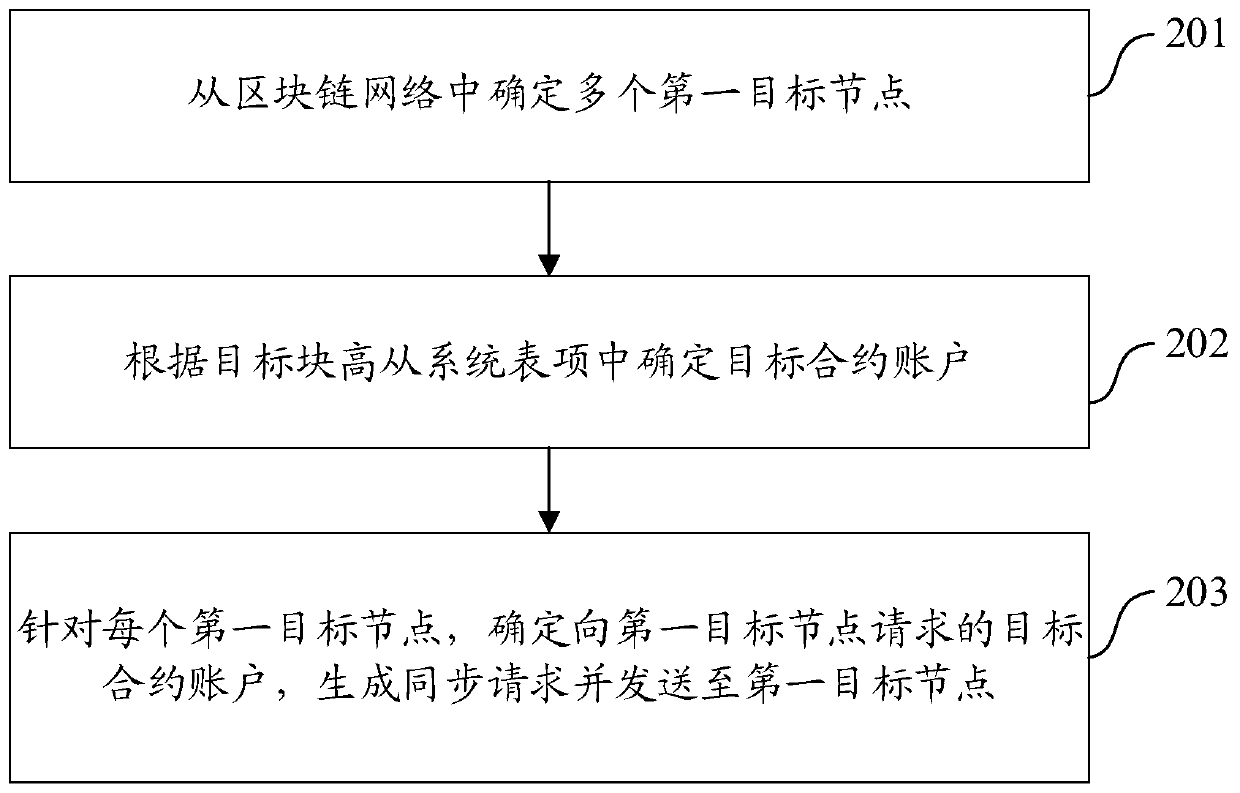
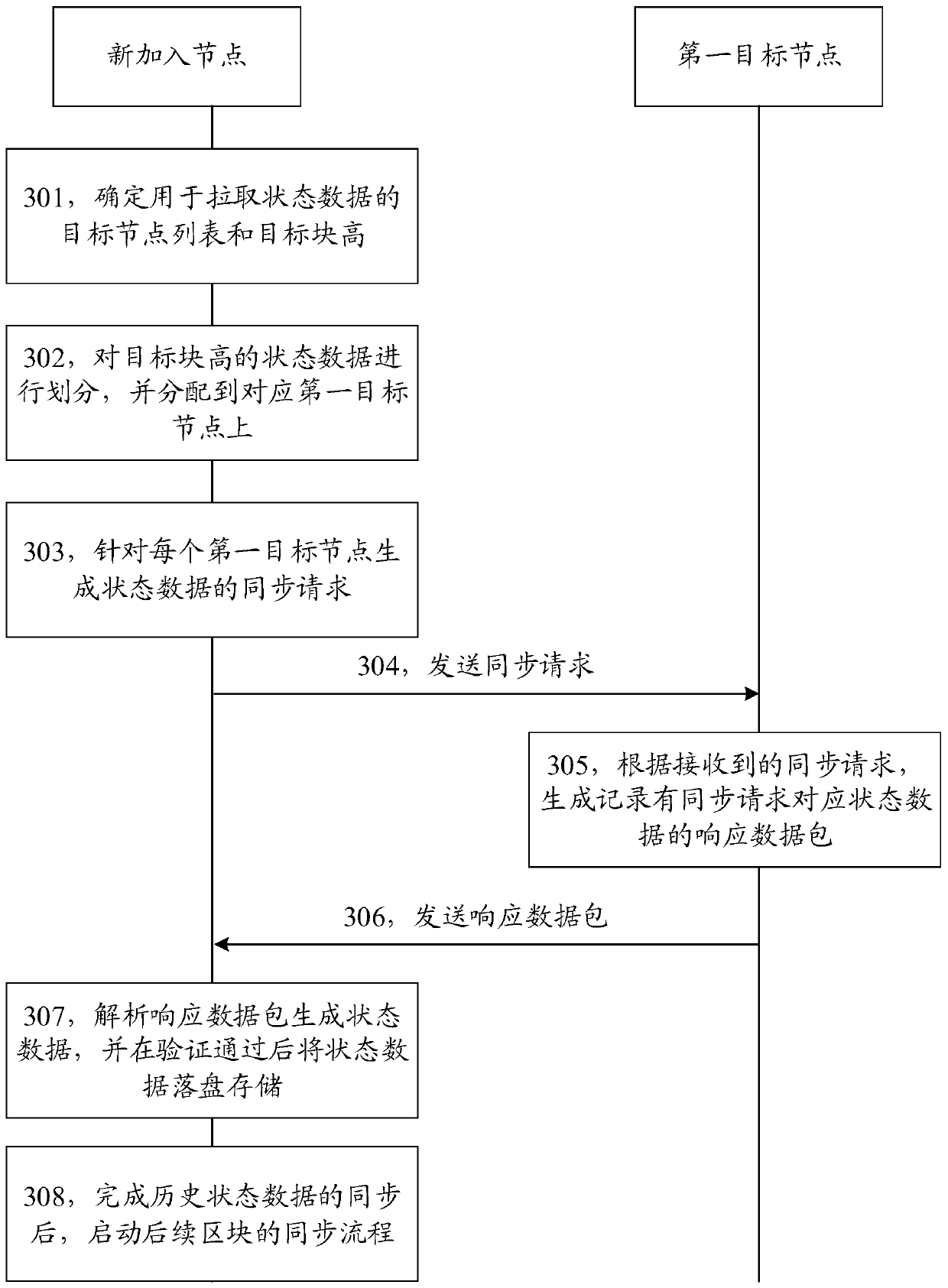
Blockchain node synchronization method and device
The invention discloses a blockchain node synchronization method and a device, and the method comprises the steps: determining a plurality of first target nodes from a blockchain network; determininga target contract account from the system table entry according to the target block height; for each first target node, determining a target contract account requested to the first target node, generating a synchronization request and sending the synchronization request to the first target node; and determining state data of the corresponding target contract account on the target block height andreturning the state data by the first target node. The method and the device are used for improving the block synchronization efficiency.
Owner:WEBANK (CHINA)
Method and system for migration of containers in a container orchestration platform between compute nodes
PendingUS20210042151A1Increase flexibilityReduce the amount requiredProgram initiation/switchingResource allocationGoal nodeDistributed computing
A method for migration of containers in a container orchestration platform, such as Kubernetes or Docker swarm, between compute nodes of a seamless computing platform present in different computing domains is provided. The state of the compute nodes of the seamless computing platform is continuously monitored. On determining a trigger, a container to be moved from a current compute node to a target compute node of a number of compute nodes is identified. A container information of the container to be moved is generated which includes a container context and the current state of the container. The container information is used by the target node to retrieve the current state of the container to be moved which enables restarting the container on the target compute node.
Owner:SIEMENS AG
Network routing with path identifiers
ActiveUS20100215051A1Easy to calculateData switching by path configurationNetwork packetNetwork routing
One embodiment of the present invention provides a system that communicates a data packet in a network to a target node. In doing so, the system receives a node identifier for the target node, and determines a first positional label, based in part on the node identifier, for reaching a first anchor node from a root node in the network. The first anchor node stores a second positional label for reaching the target node from the root node in the network, which comprises a number of nodes coupled to the root node in a tree topology. The system then retrieves the second positional label from the first anchor node, and communicates the data packet to the target node based in part on the second positional label.
Owner:CISCO TECH INC
System and method using collaborative learning of interference environment and network topology for autonomous spectrum sharing
ActiveUS20210258988A1Mathematical modelsEnsemble learningSuccessful transmissionInterference (communication)
Systems and methods of using machine-learning to improve communications across different networks are described. A CIRN node identifies whether it is within range of a source and destination node in a different network using explicit information or a machine-learning classification model. A neural network is trained to avoid interference using rewards associated with reduced interference or retransmission levels in each network or improved throughput at the CIRN node. A machine-learning scheduling algorithm determines a relay mode of the CIRN node for source and destination node transmissions. The scheduling algorithm is based on the probability of successful transmission between the source and destination nodes multiplied by a collaboration score for successful transmission and the probability of unsuccessful transmission of the particular packet multiplied by a collaboration score for unsuccessful transmission.
Owner:INTEL CORP
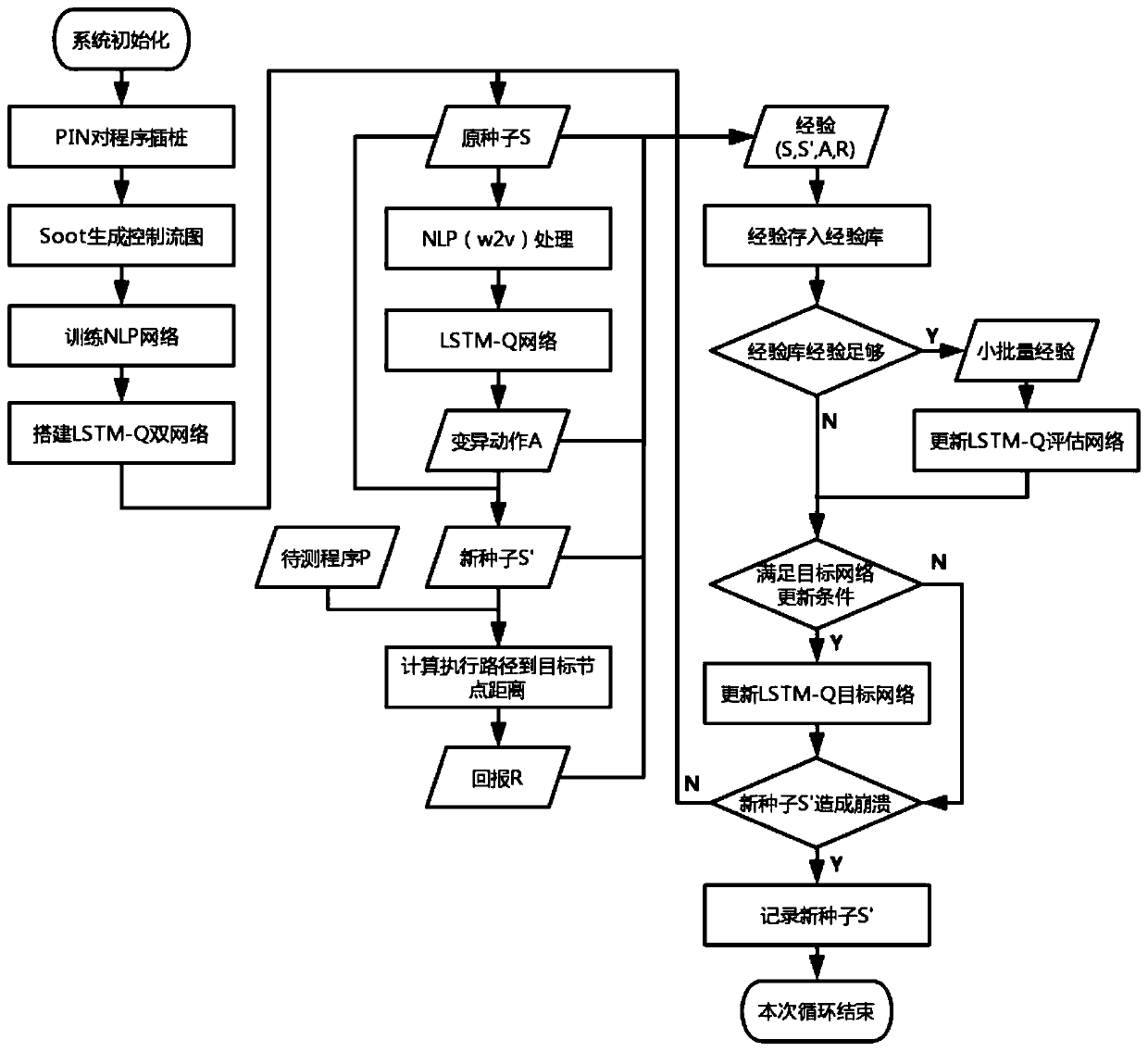
Vulnerability detection method based on deep reinforcement learning and program path instrumentation
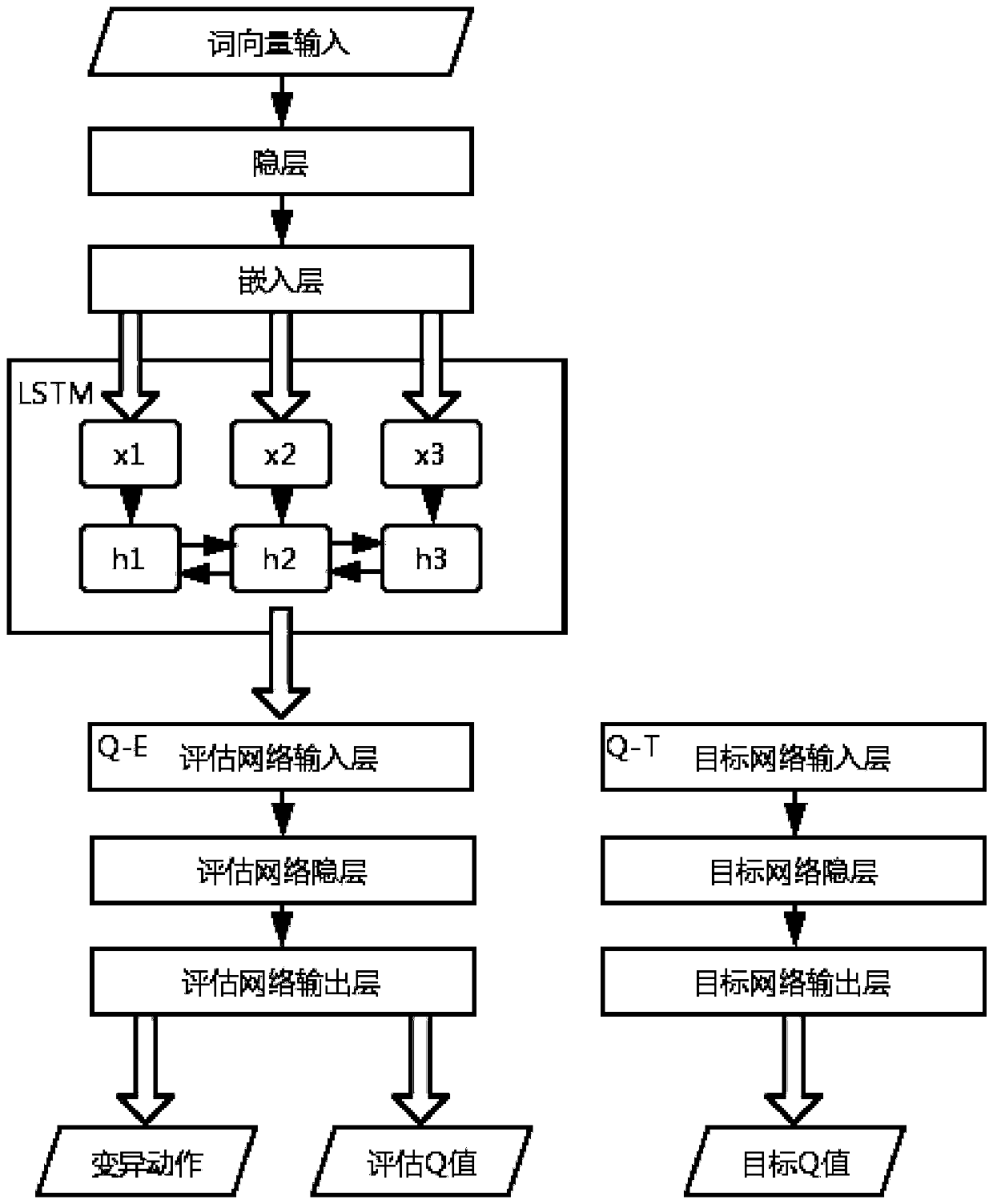
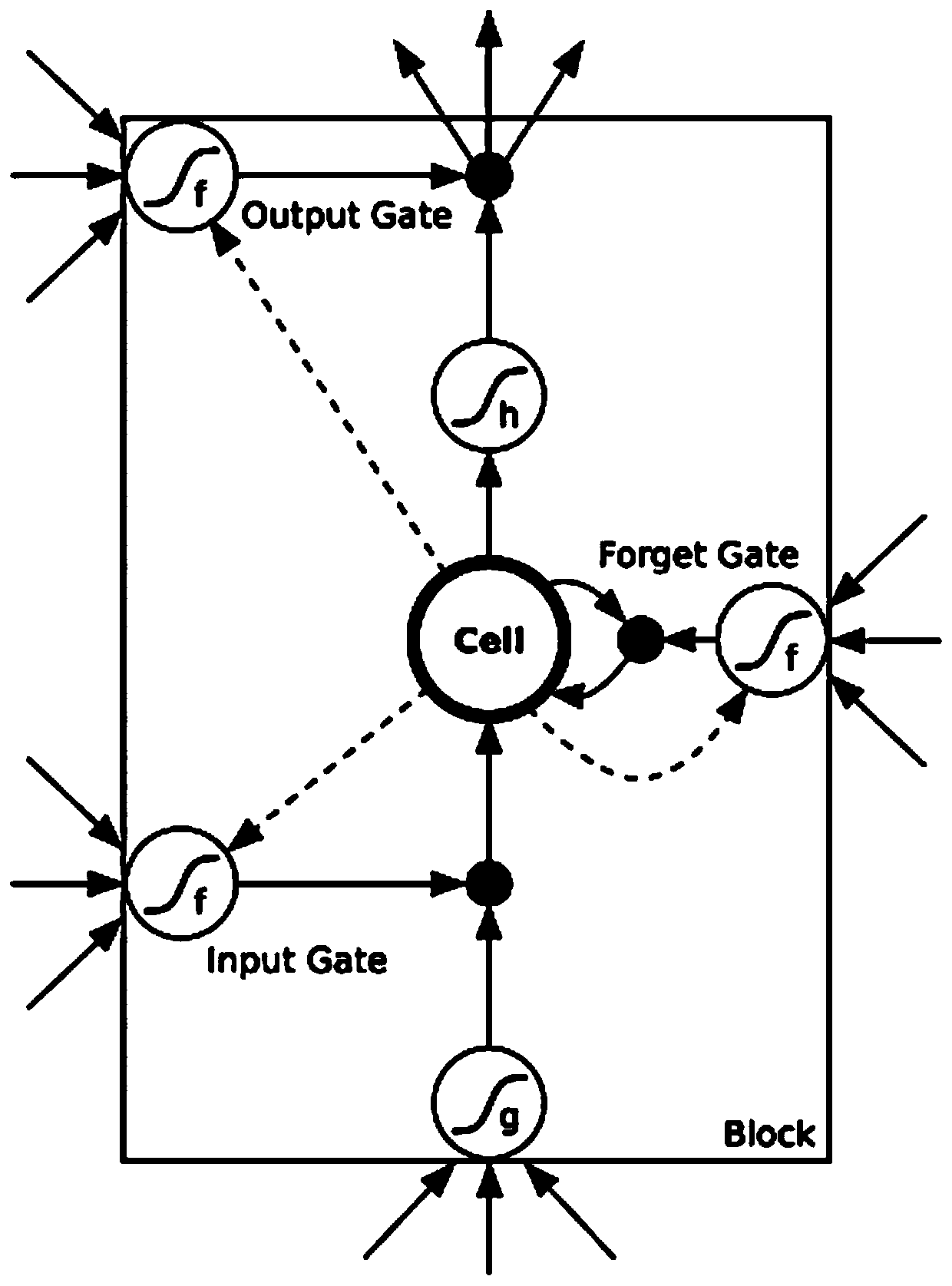
ActiveCN110008710AGood effectGood orientationPlatform integrity maintainanceNeural architecturesNODALCode coverage
The invention discloses a vulnerability detection method combining deep reinforcement learning and a program path instrumentation technology. The method includes: obtaining a path corresponding to input from a control flow diagram of a to-be-tested program in an instrumentation mode; calculating and obtaining a reward value according to the path and a target node in the control flow graph, using the reward value to train a neural network of deep reinforcement learning so as to select a variation action; and performing variation on the input of the to-be-tested program according to the variation action to obtain an updated input and an updated path thereof, calculating an updated reward value, training the neural network again and performing input variation processing, and performing circulating until the to-be-tested program is collapsed to obtain a corresponding input vulnerability. According to the method, the accuracy is higher, the input corresponding to the path where the vulnerability is located can be obtained more efficiently, and compared with a traditional fuzzy test, the method is higher in detection speed and has a certain code coverage amount.
Owner:SHANGHAI JIAO TONG UNIV +1
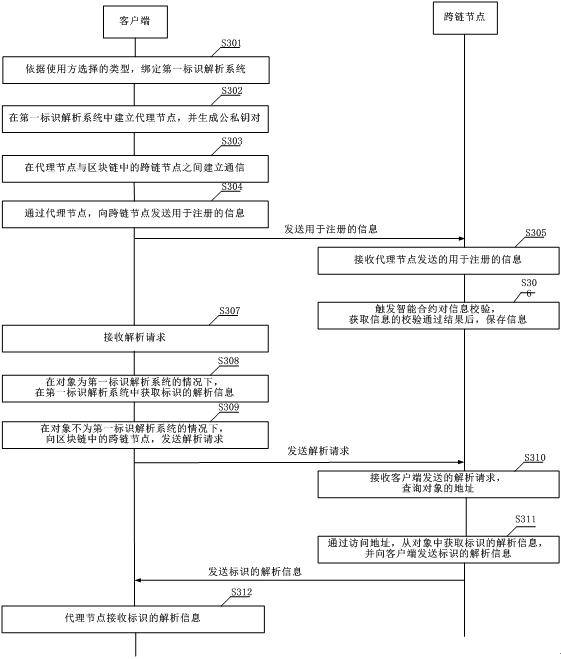
Industrial Internet identifier analysis method and related device
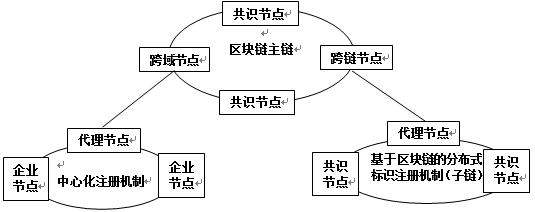
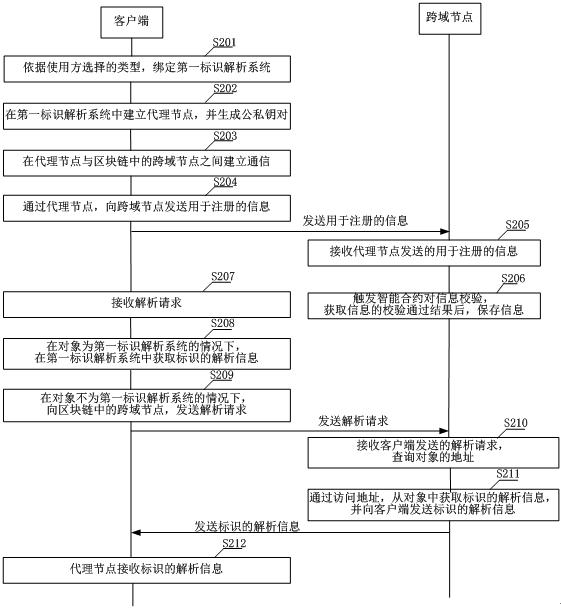
ActiveCN111767484AEnsure safetySpecial data processing applicationsWeb data retrieval using information identifiersComputer networkTheoretical computer science
The embodiment of the invention provides an industrial Internet identifier analysis method, a client and a node of a block chain. According to the method, a client receives a parsing request, whereinthe parsing request comprises a to-be-parsed identifier, the to-be-parsed identifier comprises an identifier prefix and an identifier suffix, and the identifier prefix indicates an object storing theparsing information of the identifier; and the client sends the parsing request to a target node in a blockchain, and the target node obtains the parsing information from the object according to the identifier in the parsing request and sends the parsing information to the client. According to the invention, due to the fact that the identifier prefix indicates the object for storing the analysis information, even if different identifier analysis systems are incompatible or no to-be-queried identifier exists in the system bound with the client, and the analysis information can also be obtainedthrough the identifier prefix, so that mutual access of different analysis systems taking the node in the blockchain as a bridge is realized; and the method is based on the characteristics of the consensus mechanism of the block chain, and the security under the mutual access condition is ensured.
Owner:CHINA ACADEMY OF INFORMATION & COMM
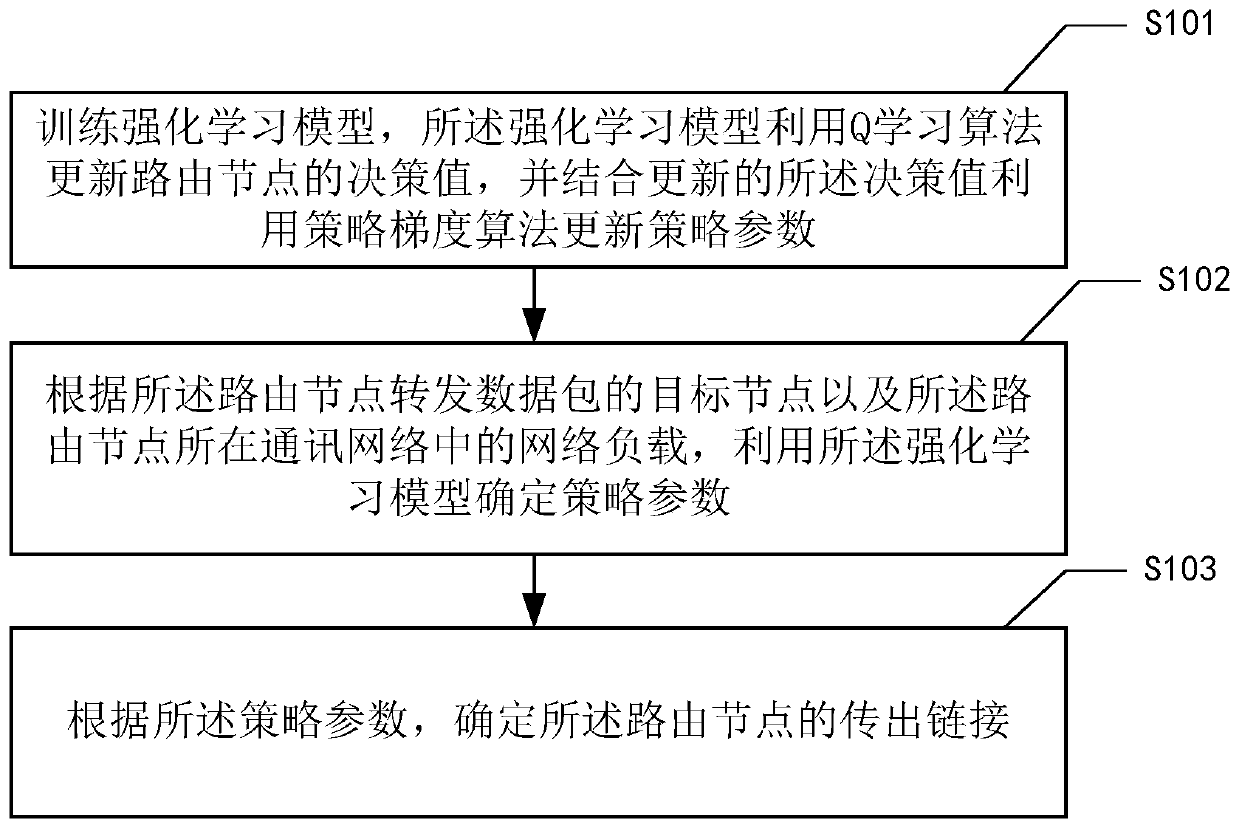
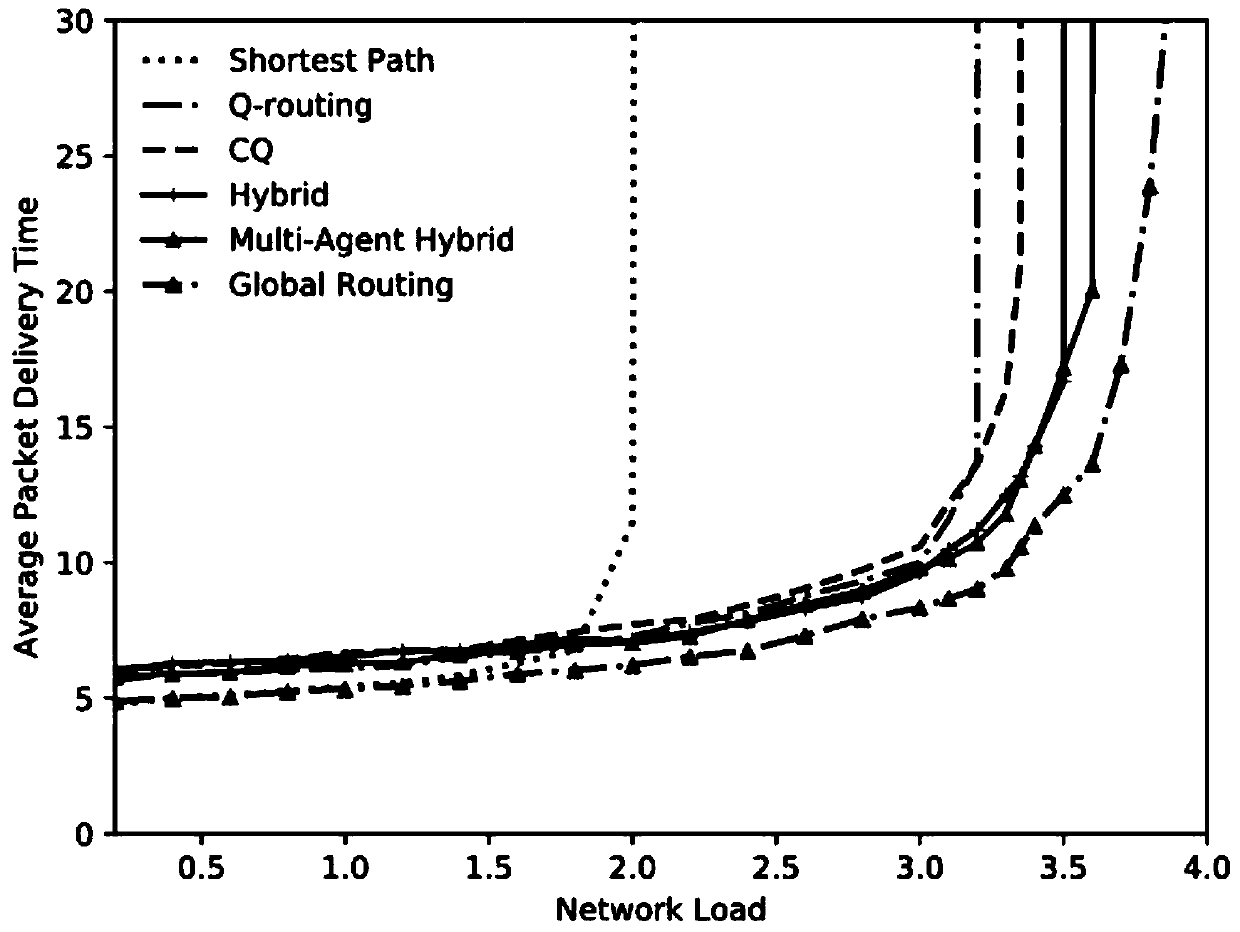
Method for controlling routing actions based on multi-agent reinforcement learning routing strategy
The invention relates to the technical field of information, and discloses a method for controlling routing actions based on a multi-agent reinforcement learning routing strategy. The method comprisesthe following steps: training a reinforcement learning model, updating decision values of routing nodes by the reinforcement learning model by using a Q learning algorithm, and updating strategy parameters by using a strategy gradient algorithm in combination with the updated decision values; determining strategy parameters by using the reinforcement learning model according to the target node towhich the routing nodes forward the data packets and the network load in the communication network where the routing nodes is located; and determining an outgoing link of the routing nodes accordingto the strategy parameter. According to the method, routing strategies can be adjusted in time for dynamically changing network connection modes, network loads and routing nodes; the appropriate shortest path is selected according to the target node of the data packet, and finally the average delivery time of the data packet is greatly shortened.
Owner:SHENZHEN RES INST OF BIG DATA +1
Short video recommendation method based on graph model, intelligent terminal and storage medium
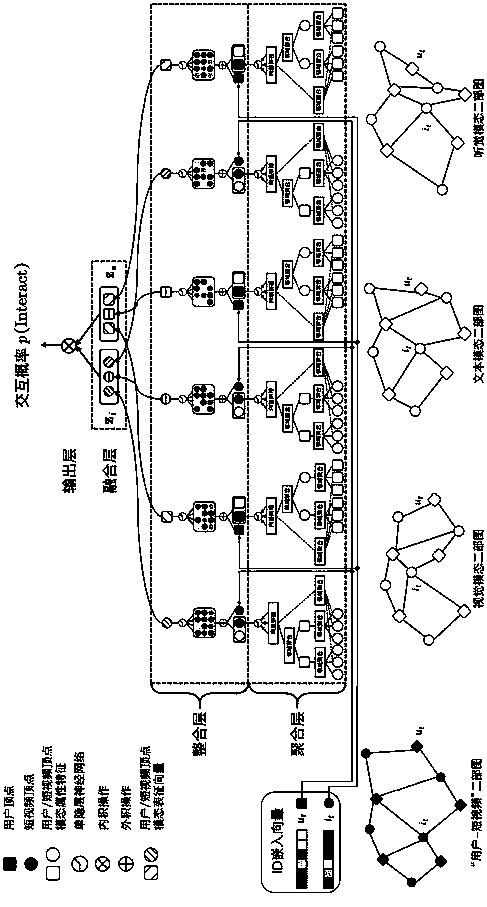
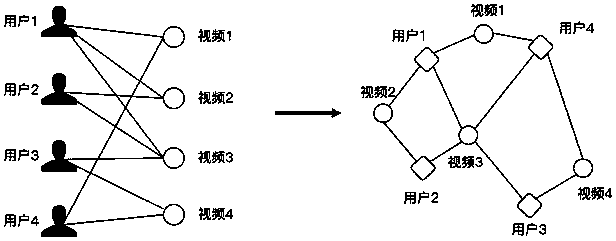
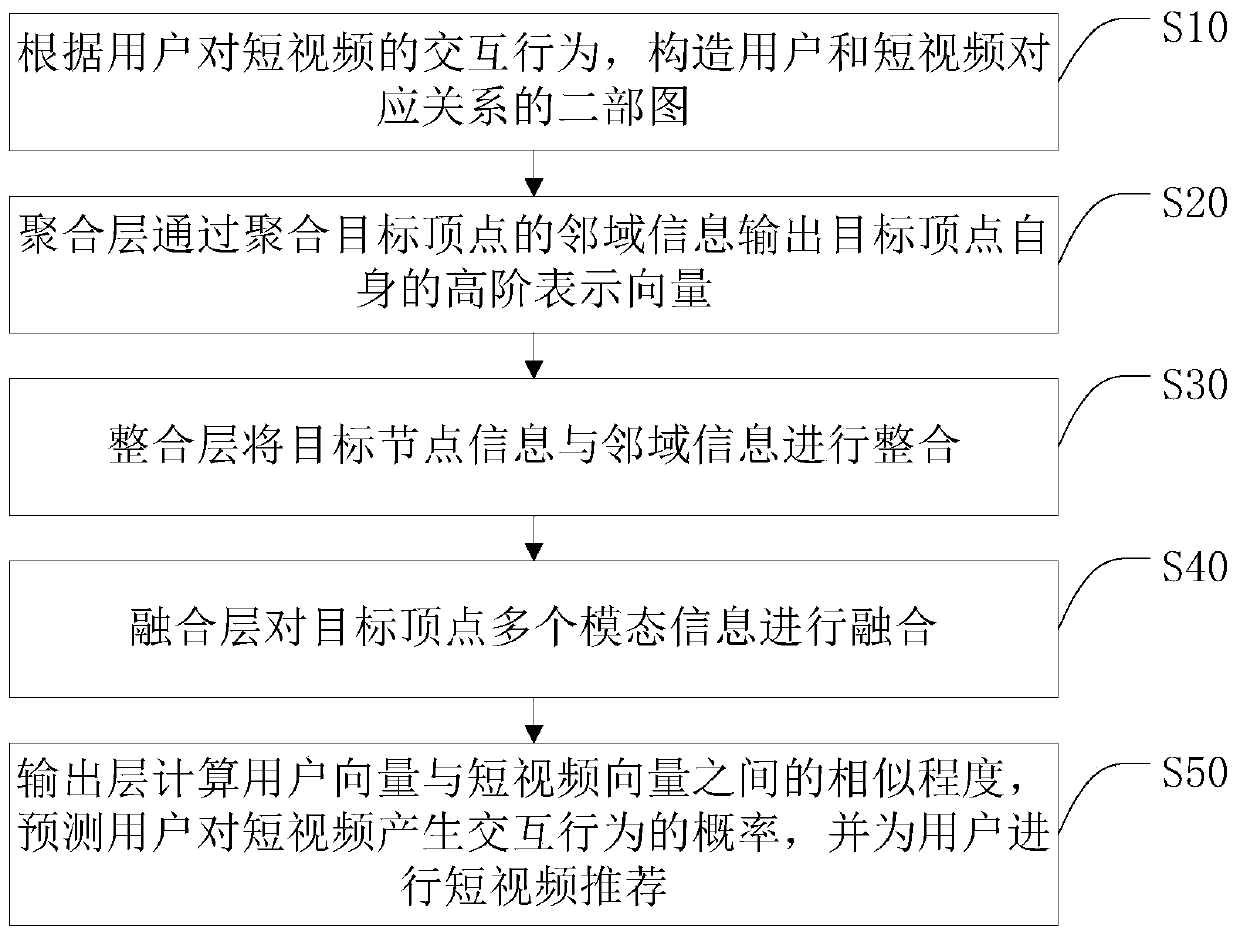
ActiveCN111382309AAchieve the goal of fine-grained personalized recommendationDigital data information retrievalNeural architecturesPersonalizationTheoretical computer science
The invention discloses a short video recommendation method based on a graph model, an intelligent terminal and a storage medium, and the method comprises the steps: constructing a bipartite graph ofa corresponding relation between a user and a short video according to the interaction behavior of the user for the short video; the aggregation layer outputs a high-order representation vector of thetarget vertex by aggregating neighborhood information of the target vertex; the integration layer integrates the target node information and the neighborhood information; the fusion layer fuses the multiple pieces of modal information of the target vertex; and the output layer calculates the similarity between the user vector and the short video vector, predicts the probability that the user interacts with the short video, and recommends the short video to the user. According to the method, the bipartite graph and the corresponding graph convolution network are constructed for different modesof the short video respectively, vector representation of the user and the vertex of the short video in different modes is learned, and the purpose of fine-grained personalized recommendation for theuser is achieved.
Owner:SHENZHEN UNIV
Multicast route method of mobile self-organizing network system
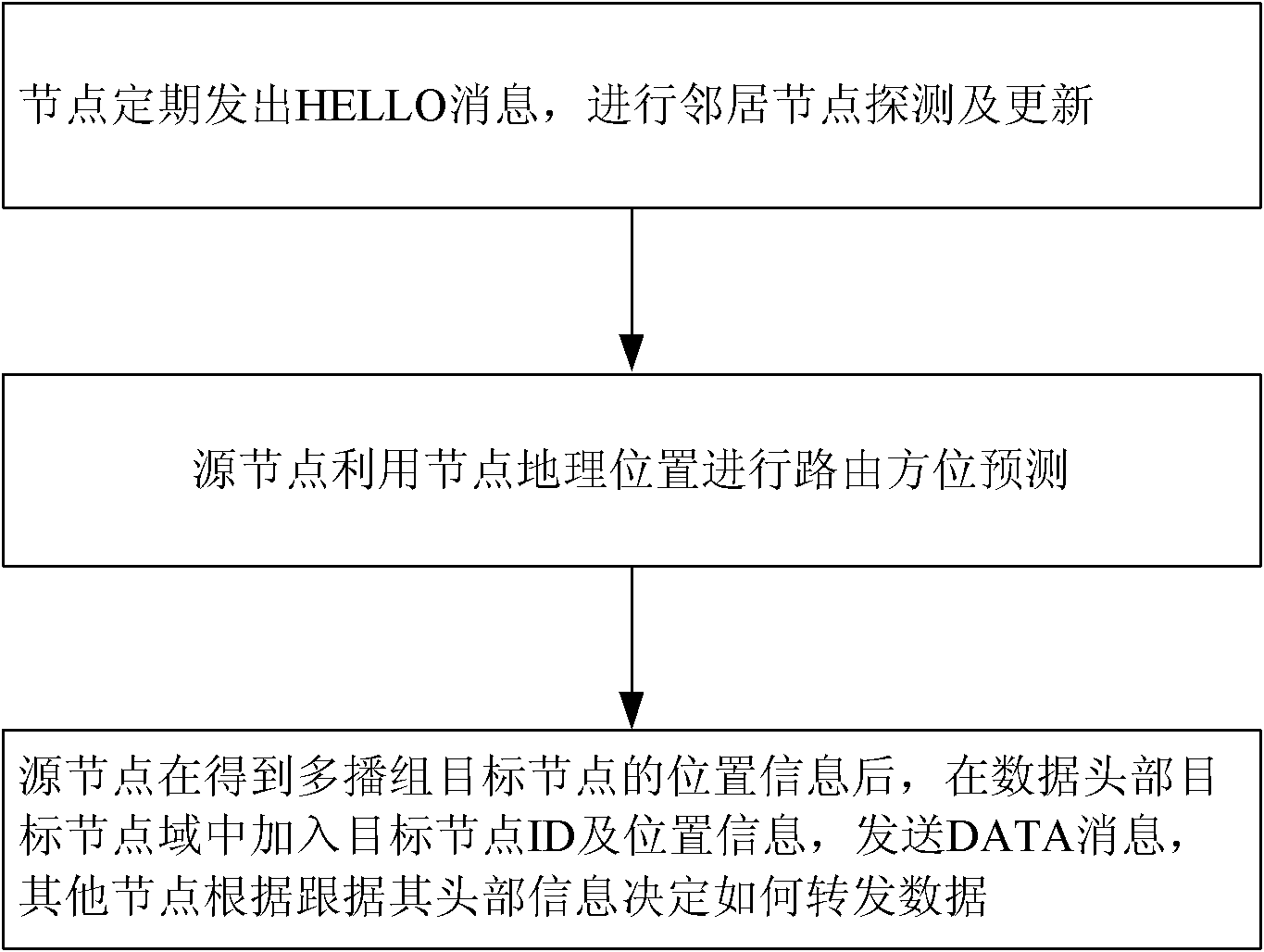
InactiveCN102088666AImprove efficiencyImprove data delivery rateBroadcast service distributionTime delaysNetwork data
The present invention discloses a multicast route method of a mobile self-organizing network system. The method of the present invention is put forward against the prior art that the present multicast route method can not satisfy the self-organizing network with rapidly moving nodes, and the method comprises the steps as follows: a node regularly sends a HELLO message to perform detection and update of a neighbor node; a source node performs a route orientation prediction by using geological position of the node; the source node obtains positional information of a multicast group object node,then adds object node ID and the positional information into a data head object node domain, and sends a DATA message; and other nodes determine how to forward the data according to the head information. The present invention puts forward a data transmission guiding mechanism based on positional information prediction, and applies a delay tolerance technology to the network, therefore in an environment where the nodes move rapidly and topology changes quickly, the method of the present invention can raise use efficiency and data delivery rate of network data transmission with the preconditionthat the requirement of low time delay for the network is satisfied.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
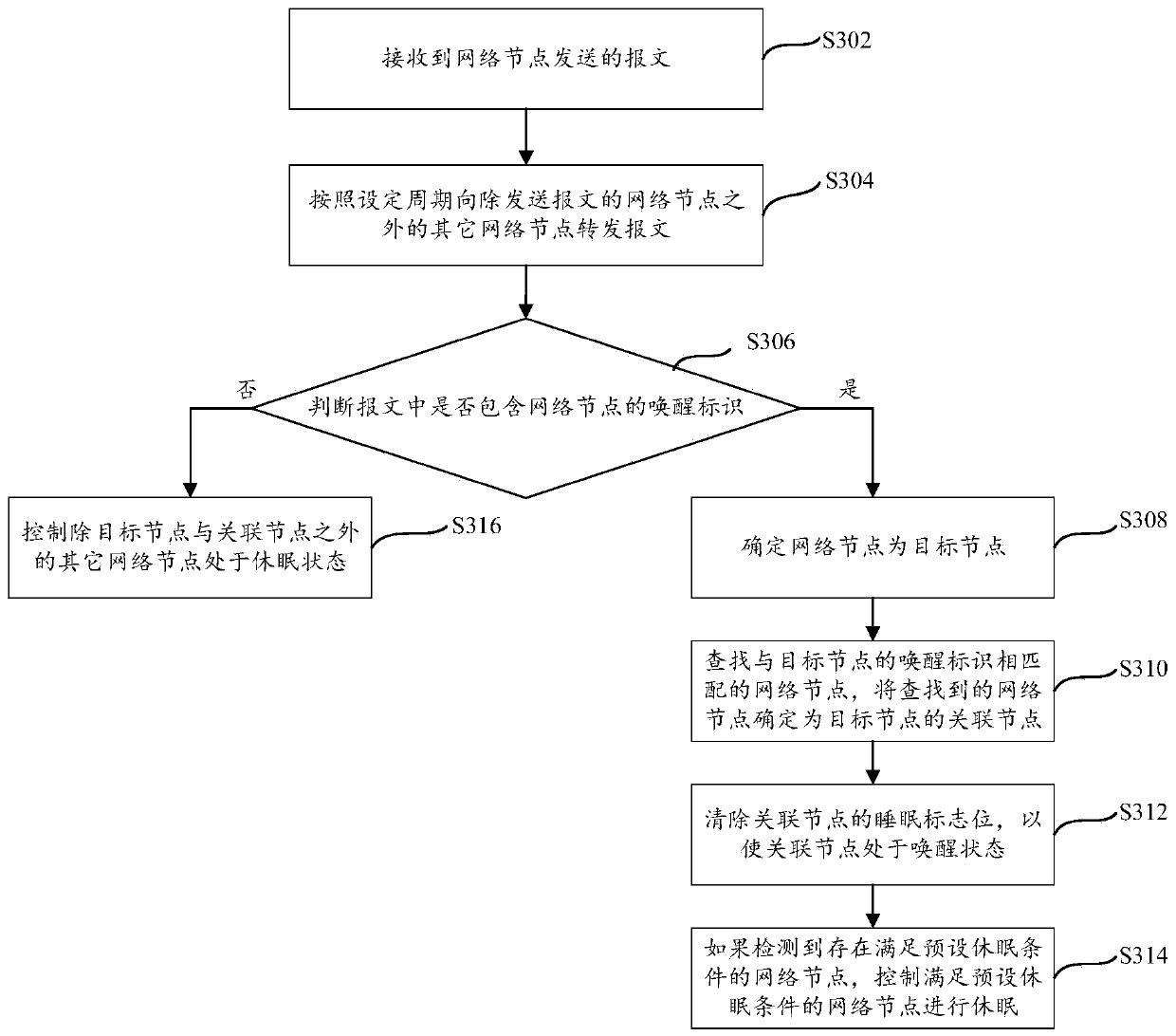
Network node state control method and device and gateway
InactiveCN110830267AImprove experienceReduce power consumptionSubstation remote connection/disconnectionNetwork connectionsComputer networkEngineering
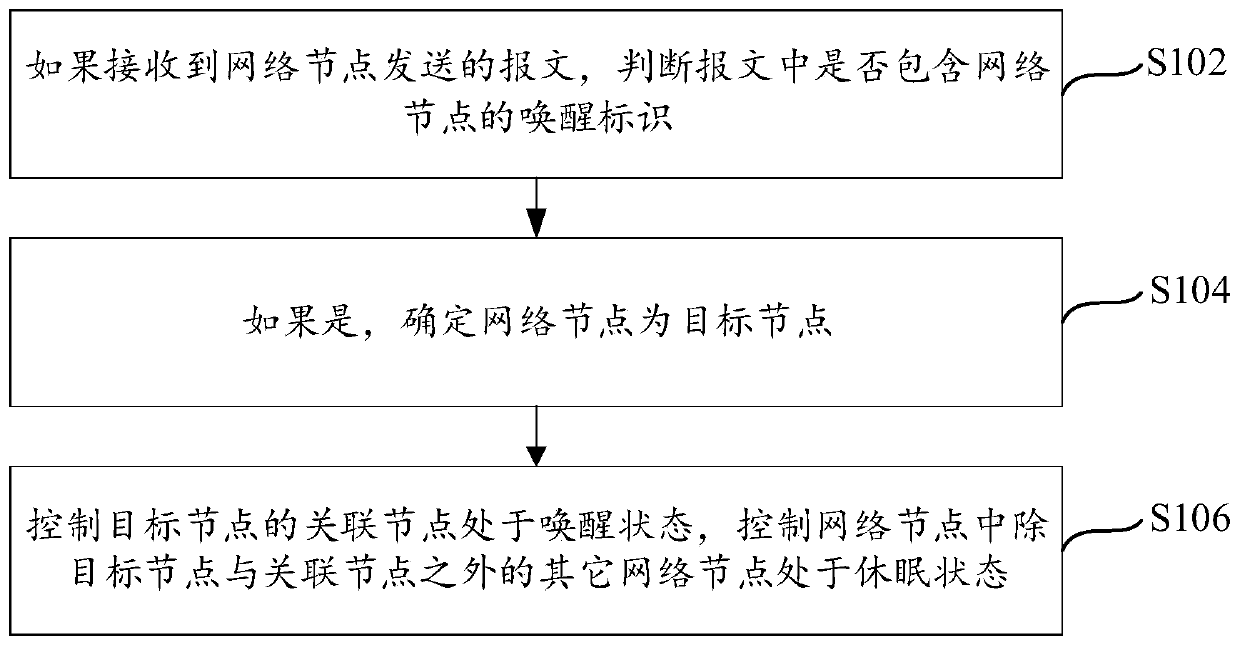
The invention provides a network node state control method and device and a gateway, relating to the technical field of communications, including executing by a gateway, wherein the gateway is connected with a plurality of network nodes; and if the message sent by the network node is received, judging whether the message contains the wake-up identifier of the network node, if so, determining thatthe network node is a target node, controlling an associated node of the target node to be in a wake-up state, and controlling other network nodes except the target node and the associated node in thenetwork node to be in a dormant state. According to the invention, the energy consumption can be effectively reduced, and the user experience is better improved while the energy is saved.
Owner:上海元城汽车技术有限公司
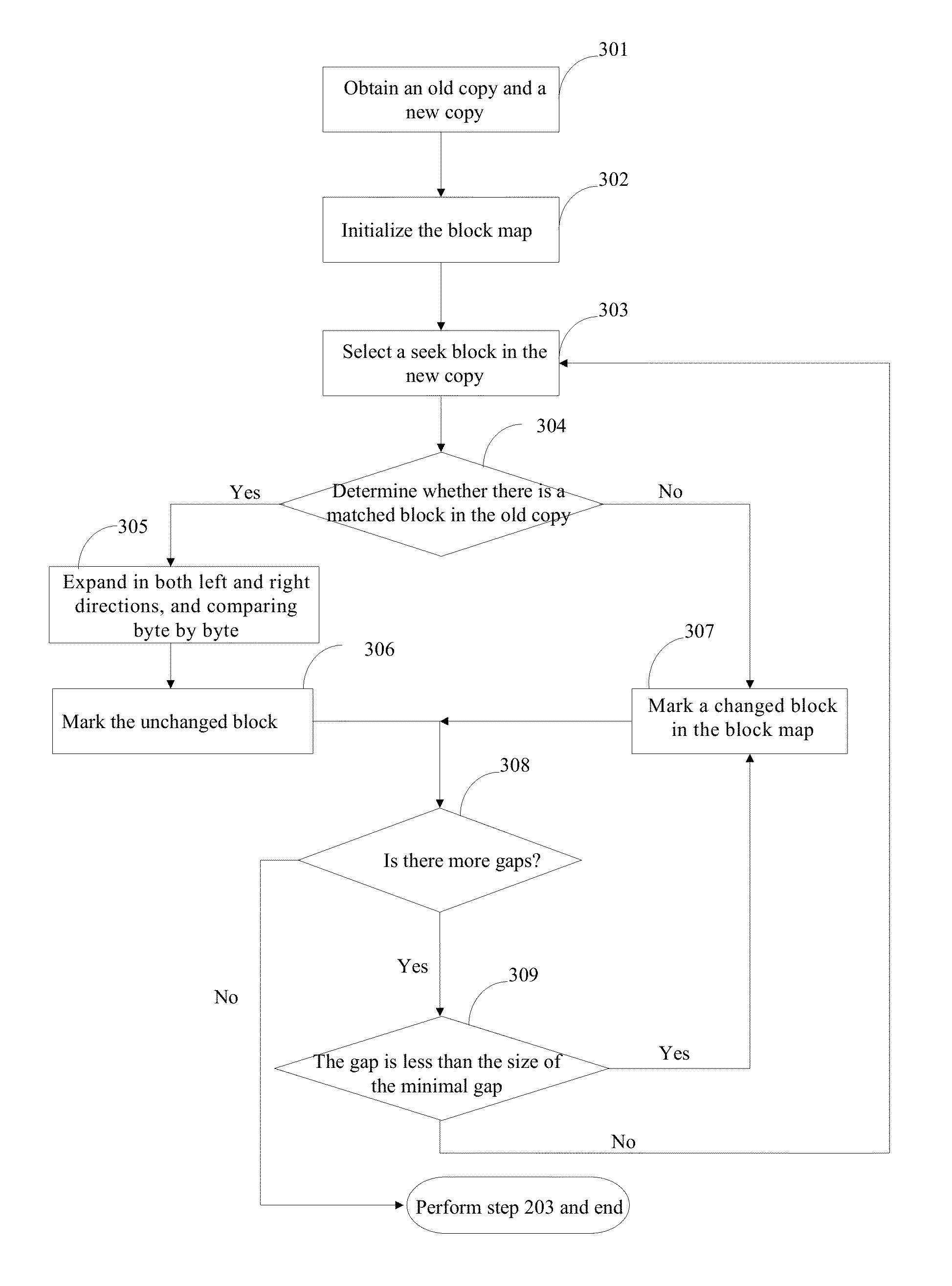
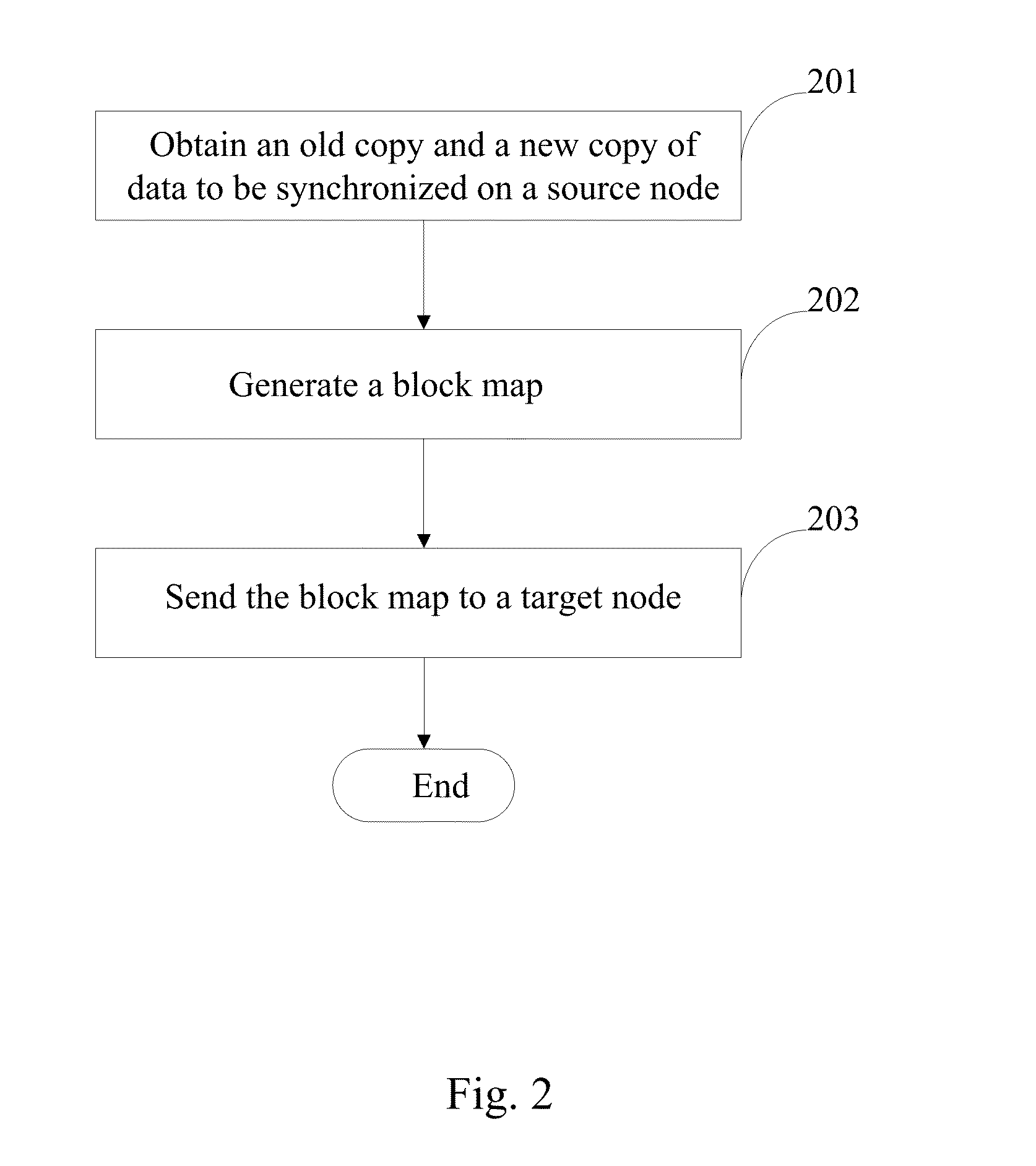
Data synchronization using string matching
InactiveUS20130054522A1Avoid spreadingDigital data processing detailsDatabase distribution/replicationData synchronizationFile synchronization
The present invention relates to the technical field of data or file synchronization. In particular, the present invention relates to a method and system for data synchronization using character string matching. Provided are a method, computer program product, and system for data synchronization between a source node and target node. An old copy and a new copy of data to be synchronized is received. A block map is generated according to the difference determined using character string matching between the old copy and the new copy. The block map, which includes the position information of unchanged blocks and the position information and contents of changed blocks, is transmitted to a target node.
Owner:IBM CORP
Q-learning optical network-on-chip adaptive routing planning method based on Dijkstra algorithm
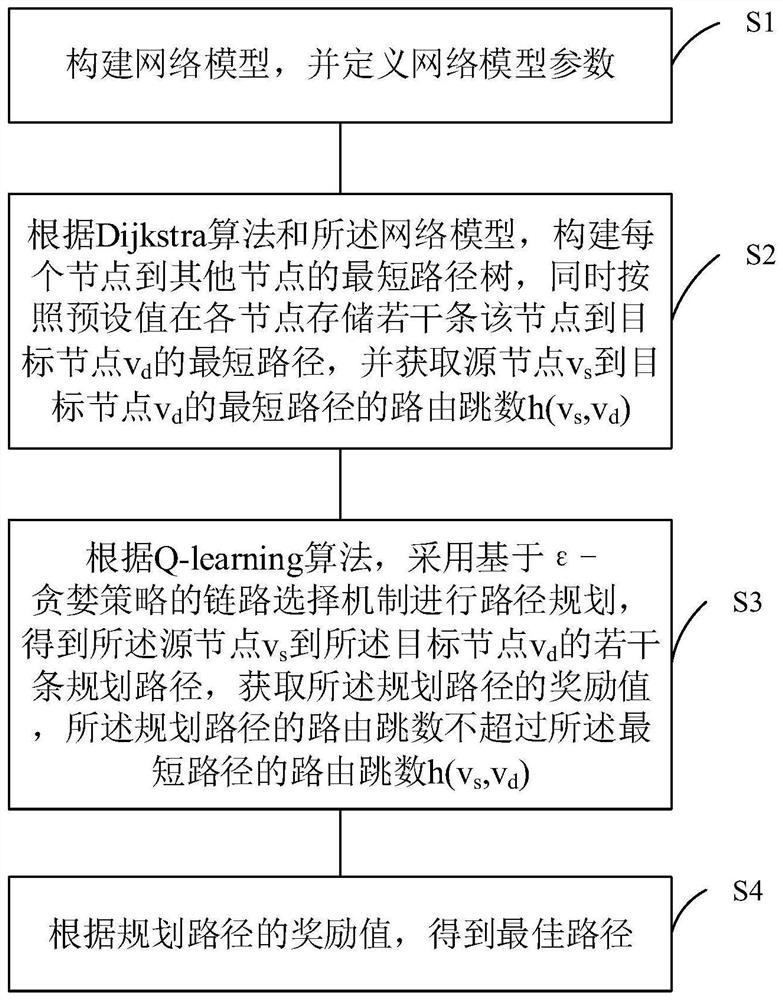
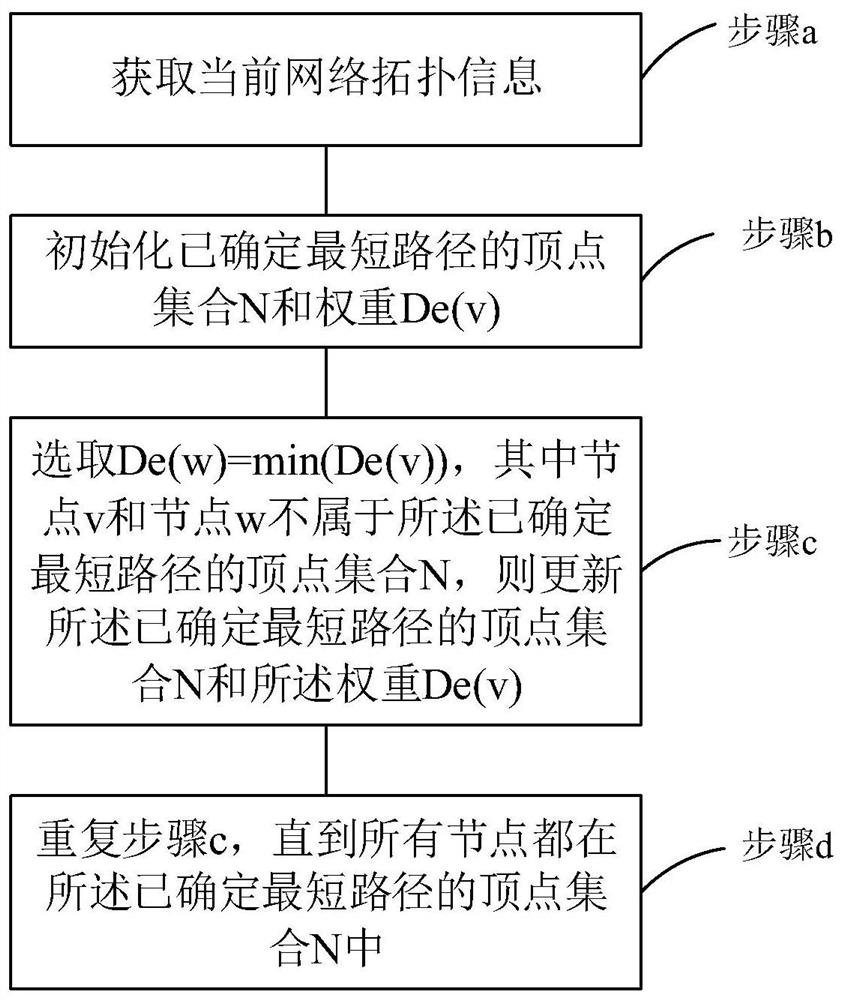
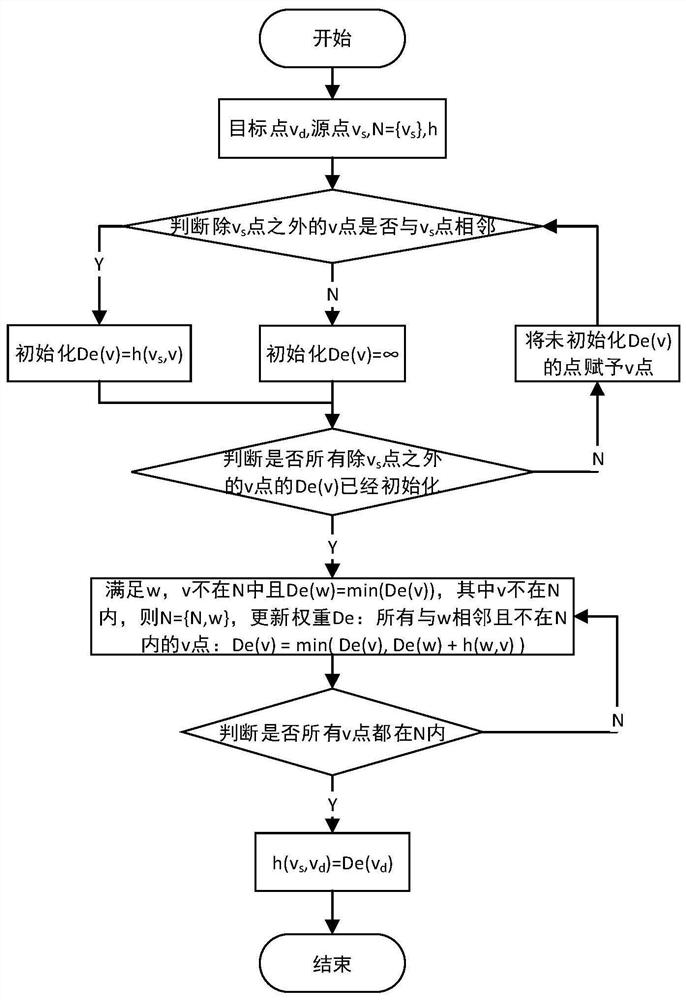
ActiveCN111770019AOvercome the disadvantage of only generating one shortest pathAutomatic planning path controllableMultiplex system selection arrangementsData switching networksPathPingEngineering
The invention relates to a Q-learning optical network-on-chip adaptive routing planning method based on a Dijkstra algorithm, and the method comprises the steps: S1, constructing a network model, anddefining the parameters of the network model; S2, constructing a shortest path tree from each node to other nodes according to a Dijkstra algorithm and a network model, storing a plurality of shortestpaths from the node to a target node vd in each node according to a preset value, and obtaining a routing hop count h (vs, vd) of the shortest path from a source node vs to the target node vd; S3, according to a Q-learning algorithm, performing path planning by adopting a link selection mechanism based on an epsilon-greedy strategy to obtain a plurality of planned paths from the source node vs tothe target node vd, and obtaining reward values of the planned paths, the routing hop count of the planned paths not exceeding the routing hop count h (vs, vd) of the shortest path; and S4, obtainingan optimal path according to the reward value of the planned path. According to the method, the defect that each target point of the Dijkstra algorithm can only generate one shortest path is overcome.
Owner:XIDIAN UNIV
Docker migration method and system for cloud data center
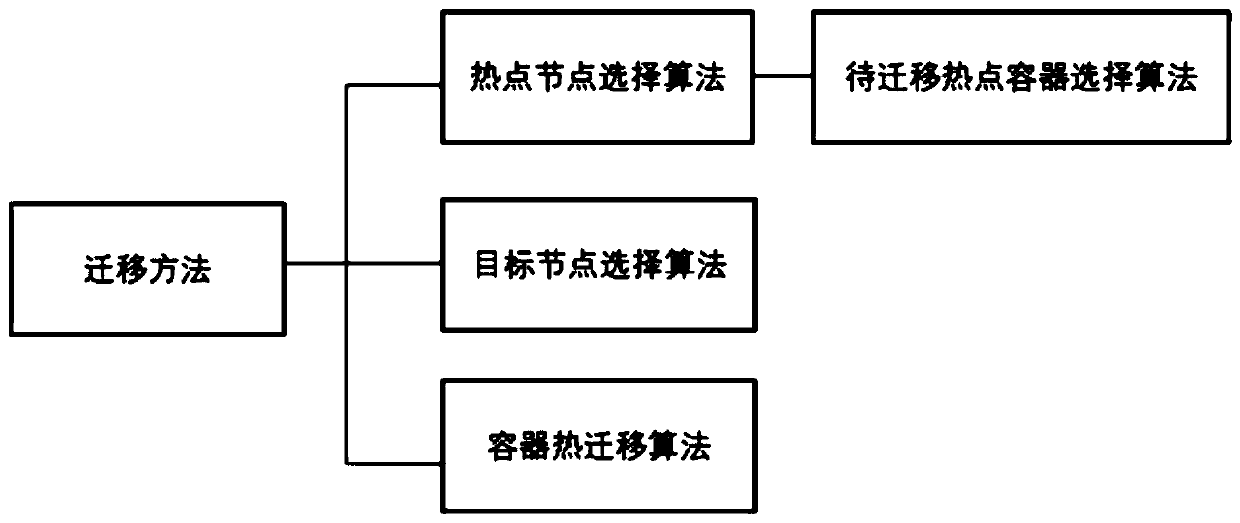
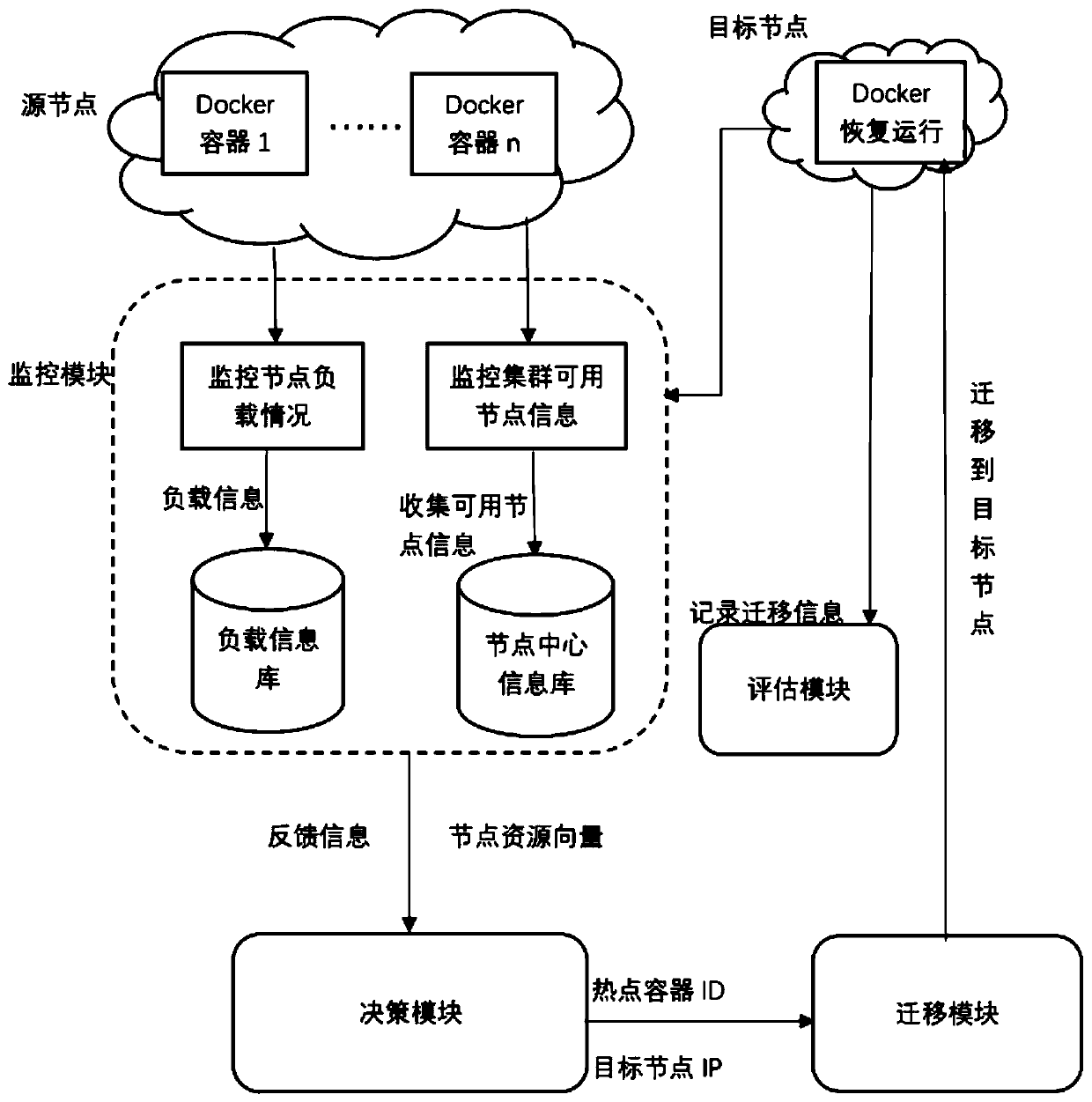
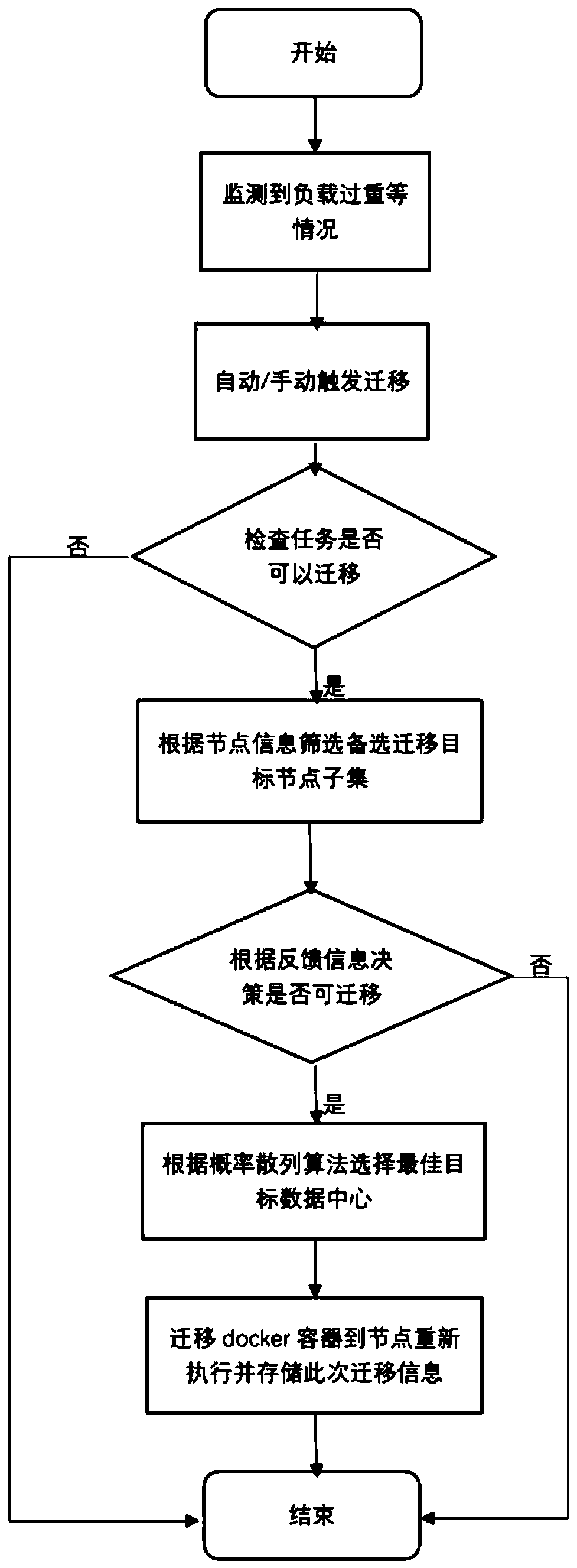
ActiveCN111190688AReduce lossesImprove reliabilityProgram initiation/switchingEnergy efficient computingEngineeringAlgorithm Selection
The invention discloses a Docker migration method and system for a cloud data center. Load information values of all physical nodes in a cluster are collected and quantized; when the condition that the load of a certain node reaches a set threshold value or a container is suspended due to damage is monitored, feedback information is generated, a to-be-migrated container is selected on the overloador no-load node by using a hotspot container selection algorithm, affinity matching is performed according to a resource demand vector of the to-be-migrated container and the residual resource quantity of other nodes, and a target node set is selected. Then, in the target node set, an optimal target node is selected according to a probability selection algorithm, and the to-be-migrated containeris migrated to a target node to recover execution. According to the method, the container migration method is designed by taking the minimum migration amount, the shortest migration time and the lowest energy consumption as principles, so that the loss of the cluster caused by the fault of a certain computing node can be effectively reduced, the reliability and the utilization rate of the existingcluster are improved, the load balance is realized, and higher availability is provided for the cluster.
Owner:XI AN JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com