Vulnerability detection method based on deep reinforcement learning and program path instrumentation
A technology of reinforcement learning and vulnerability detection, applied in the field of information security, it can solve the problem of attackers accessing and modifying computers without permission, and achieves obvious effects, high orientation and efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
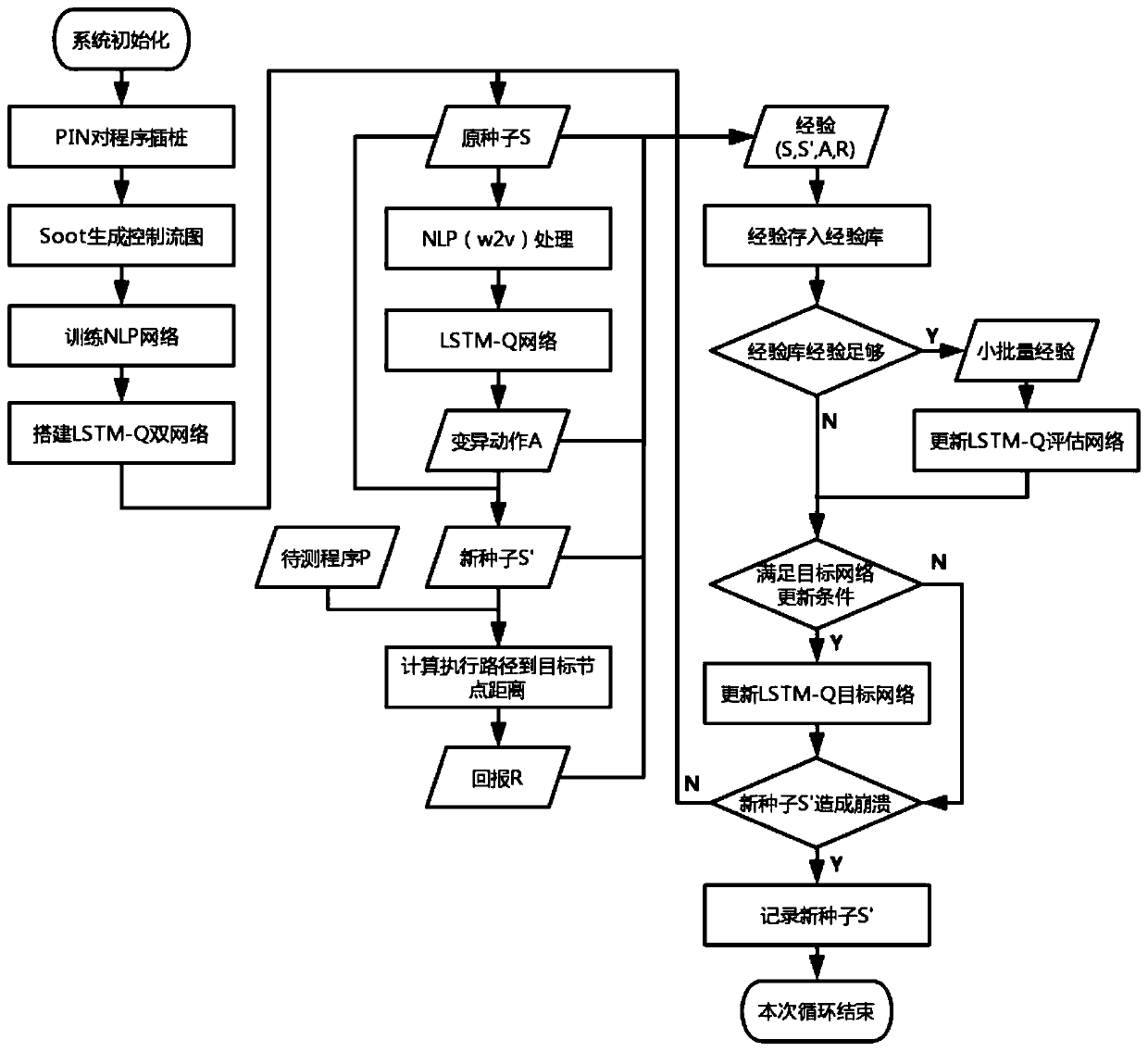
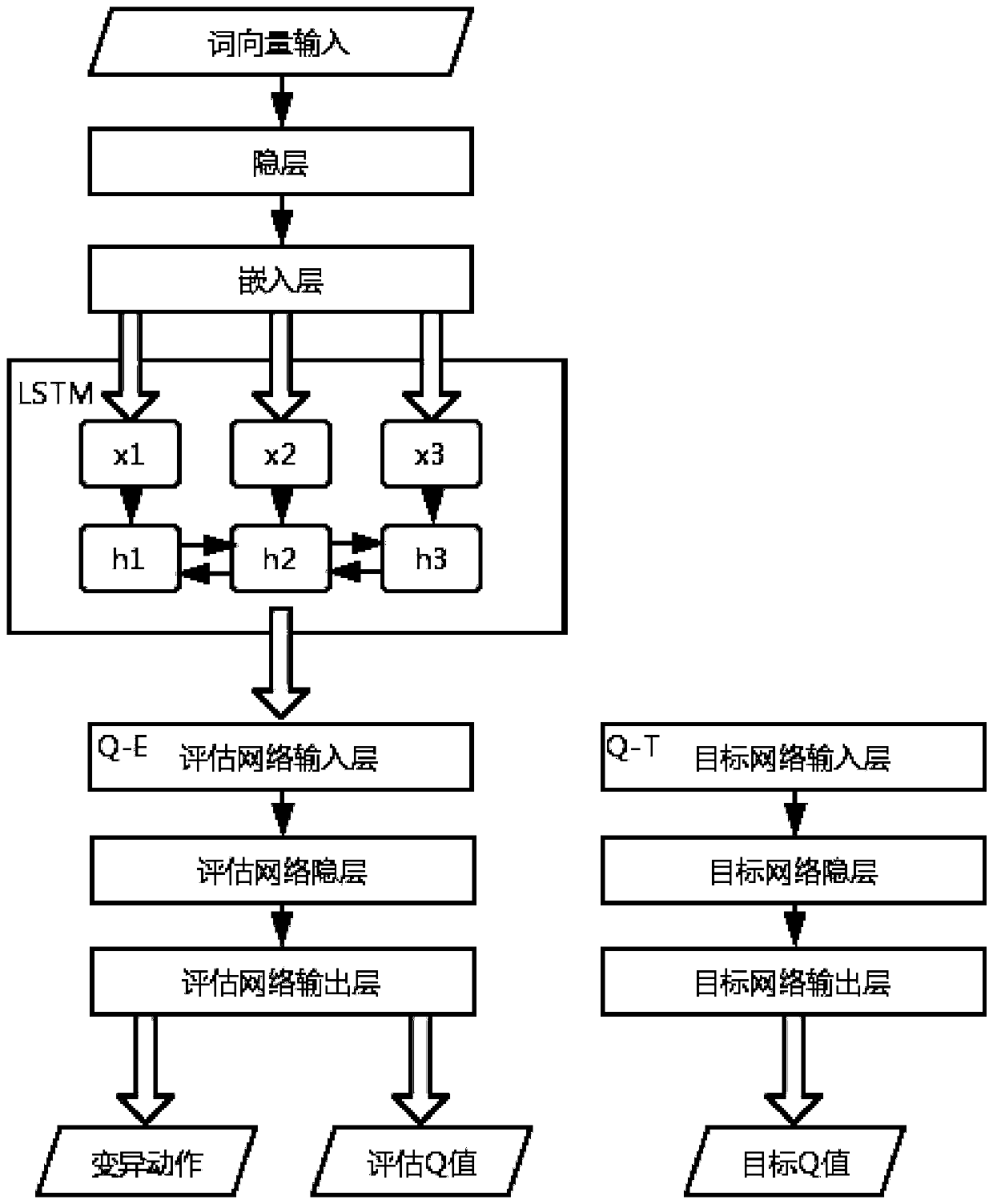
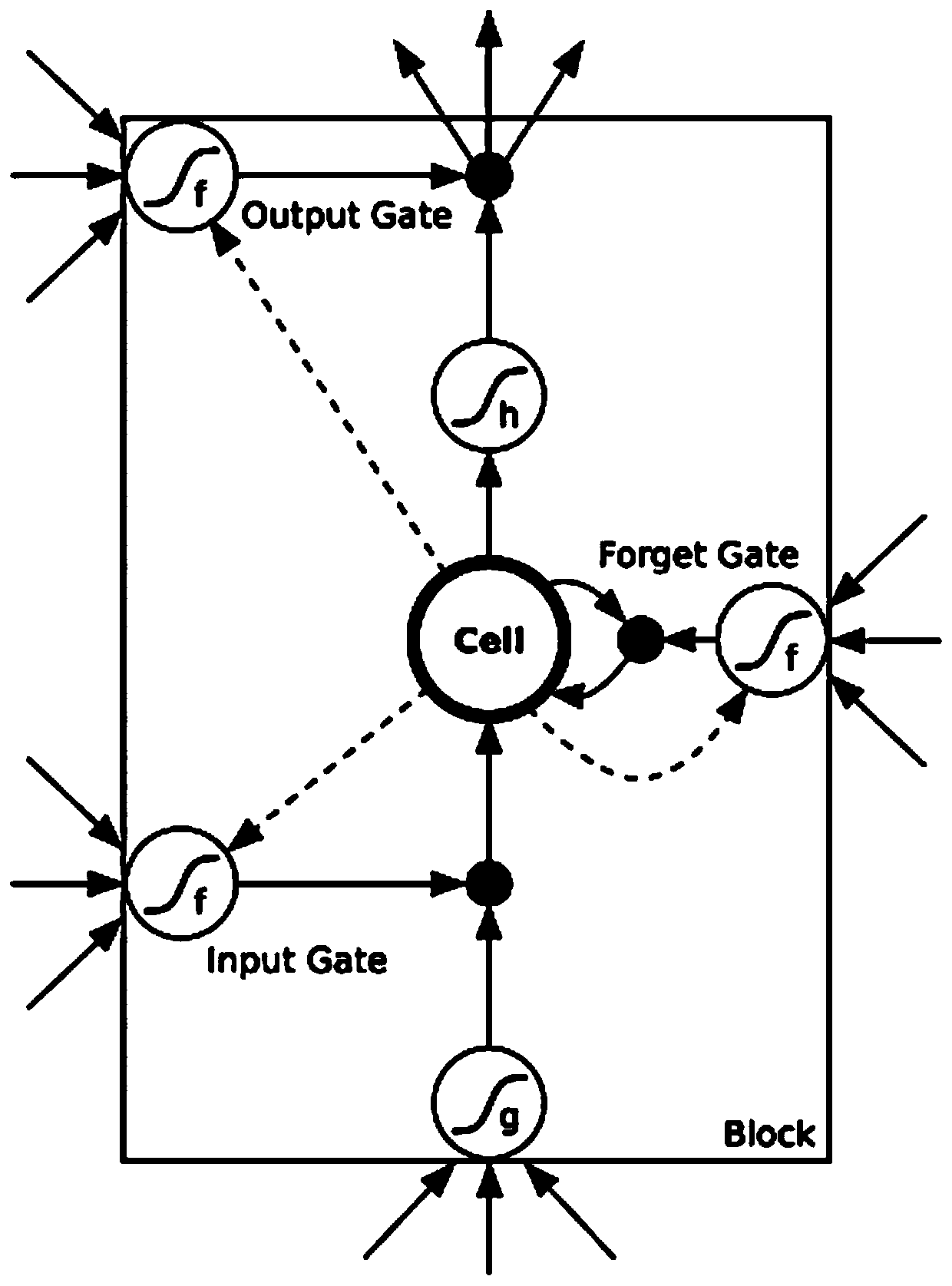
[0029] The vulnerability code targeted by this embodiment can be a cross-platform language, and the main applicable language is C / C++. Such as figure 1 As shown, it is a vulnerability detection system based on deep reinforcement learning (DQN) and program path instrumentation involved in this embodiment, including: a preprocessing module, a mutation module, a reward module and a training module, wherein: the preprocessing module is based on fuzzy The test seeds generate a set of features, and the features are mutated through the neural network to obtain mutation actions. The mutation module generates new seeds according to the action mutation seeds. The reward module combines the control flow graph of the program to be tested, the program execution path and the target node to calculate the reward value. The training module trains the Deep Q-Learning (DQN) model according to the reward value fed back by the reward module.
[0030] The vulnerability code base is the buffer over...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com