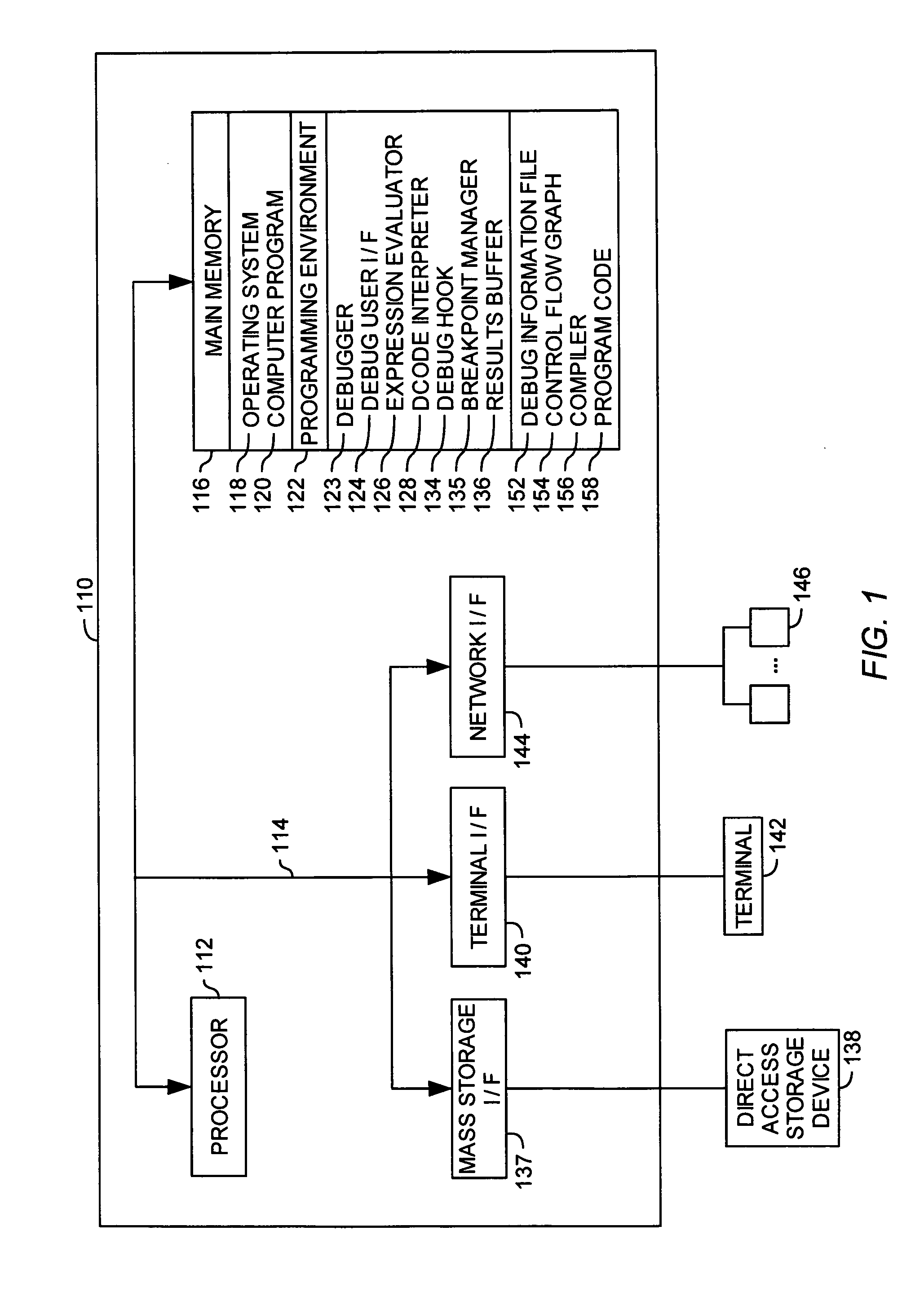
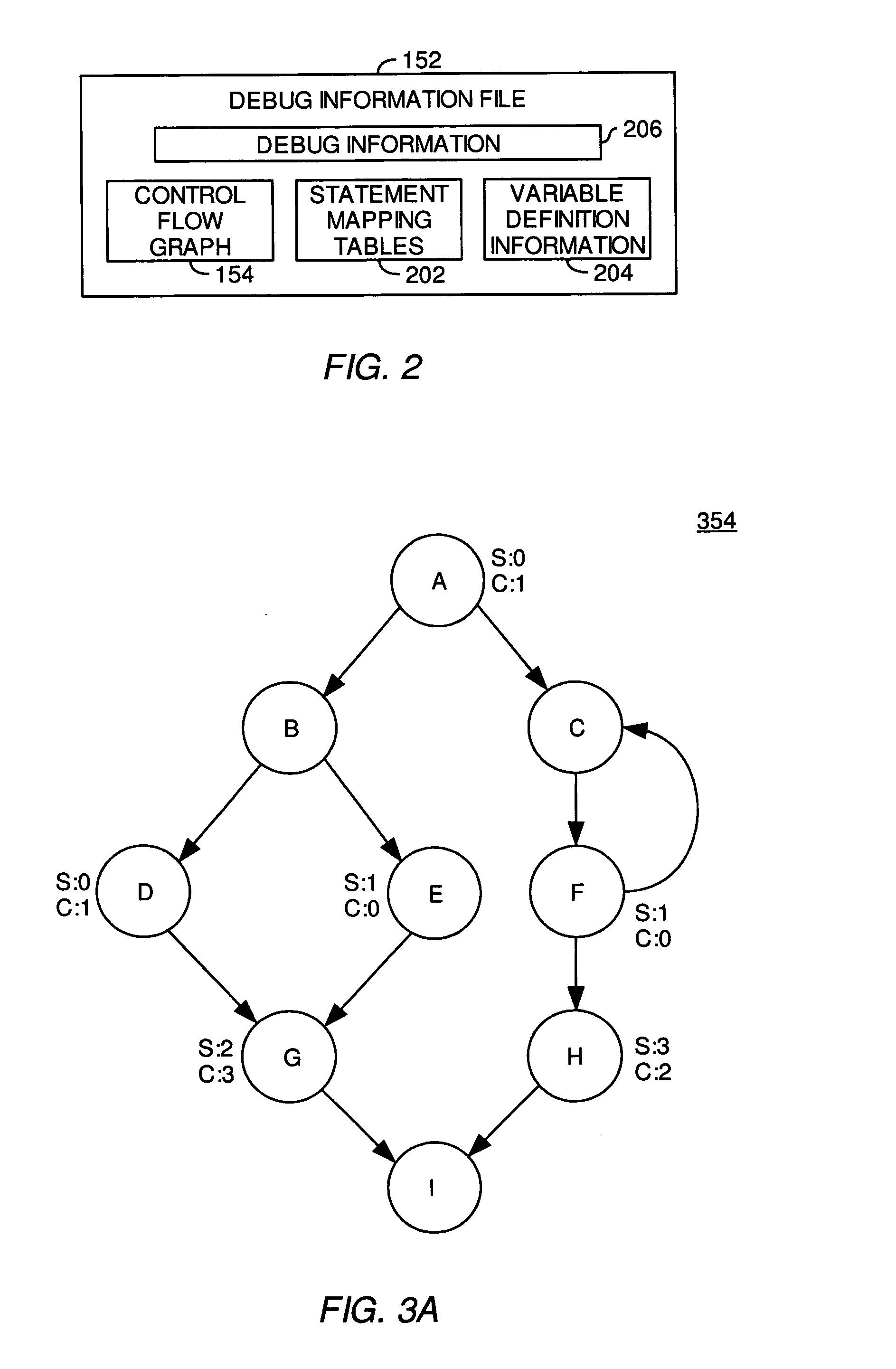
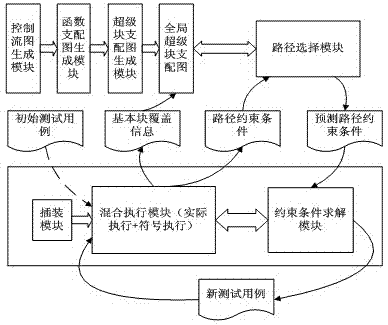
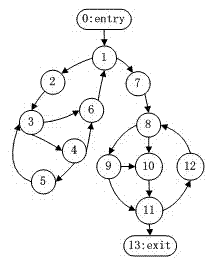
Patents
Literature
187 results about "Control flow diagram" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
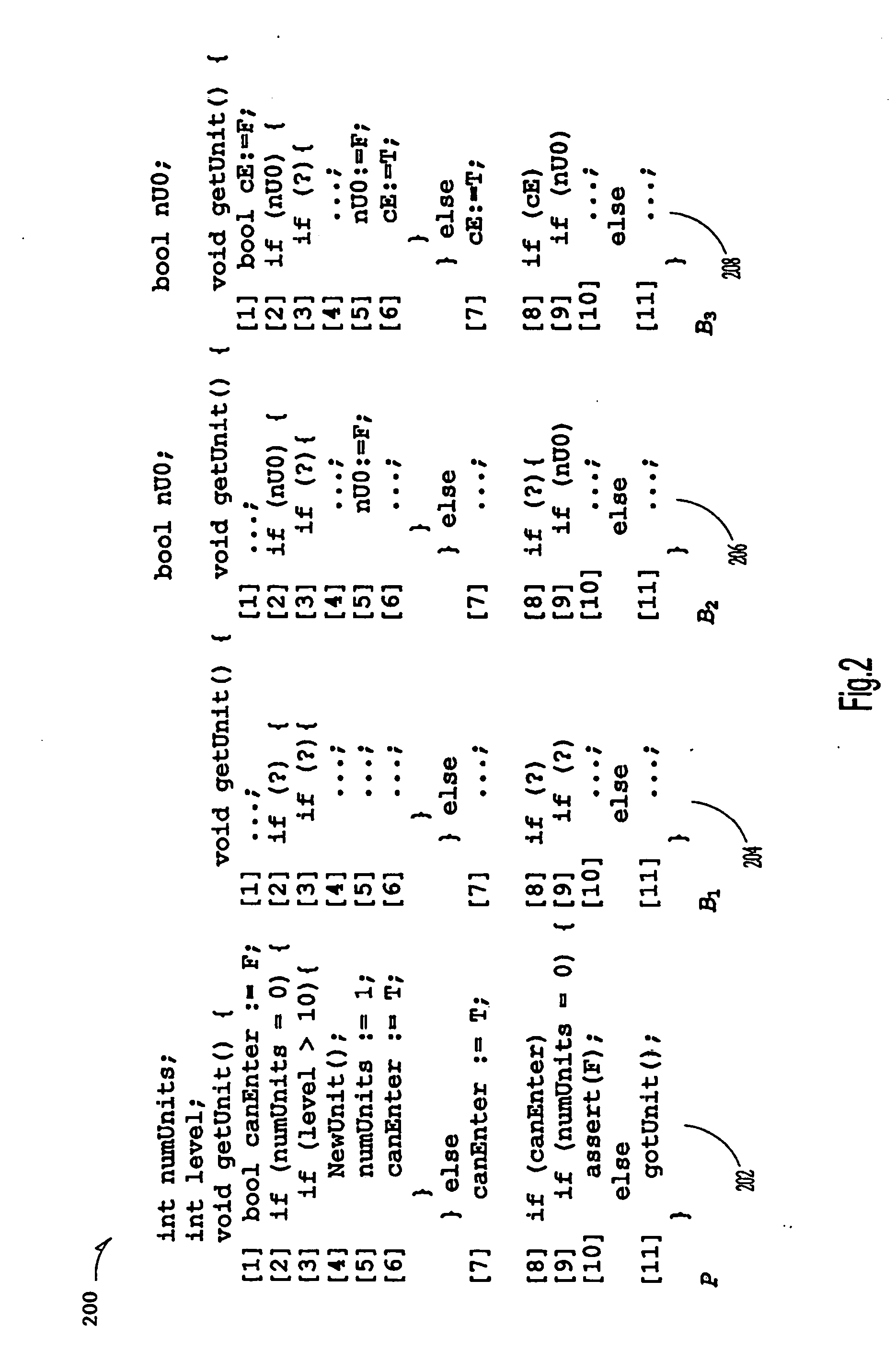
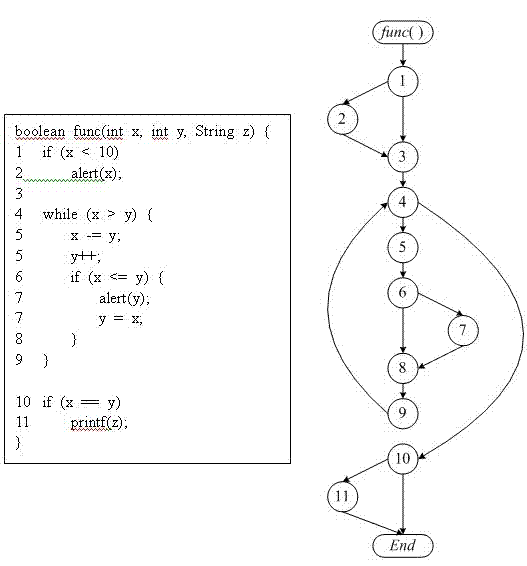
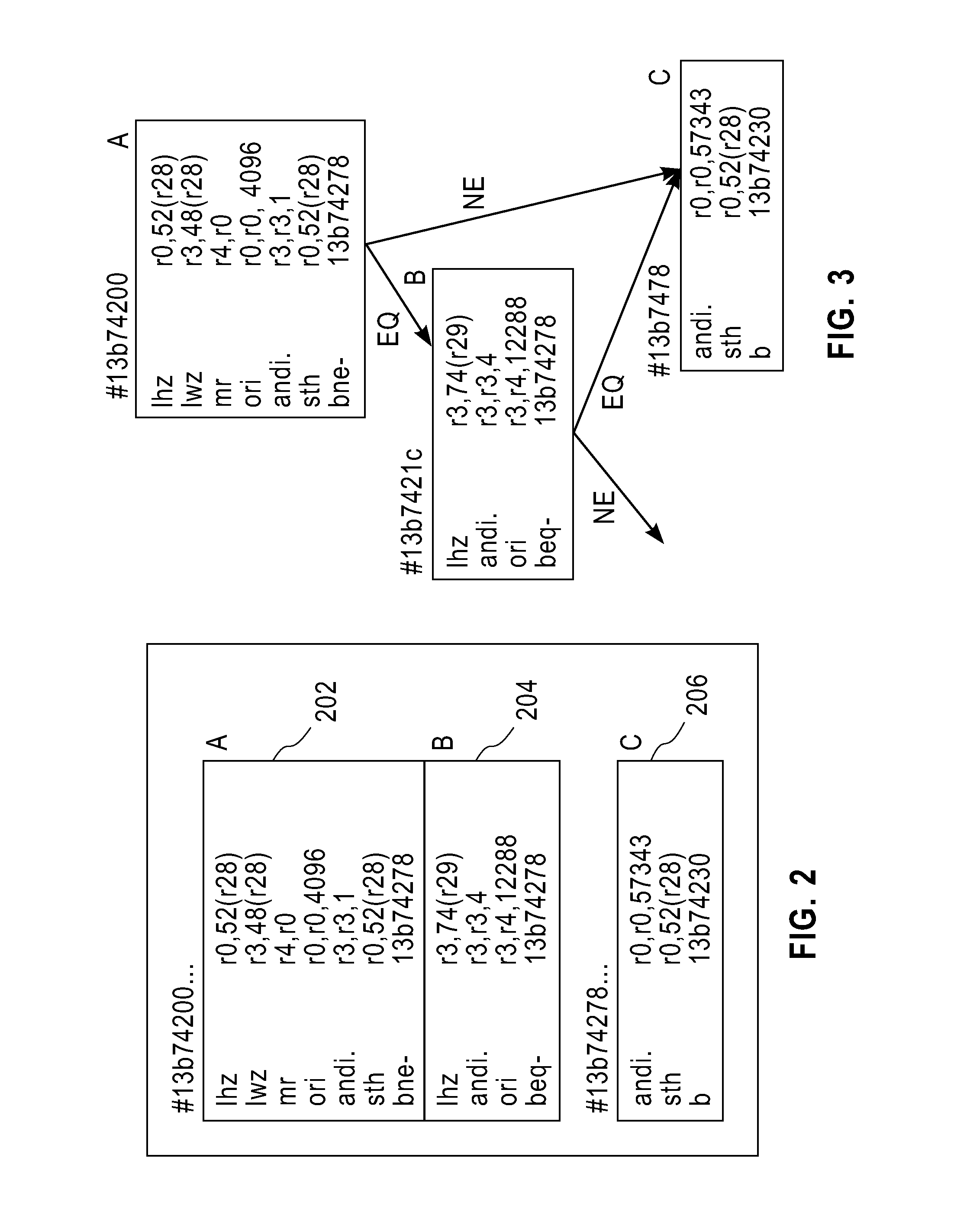
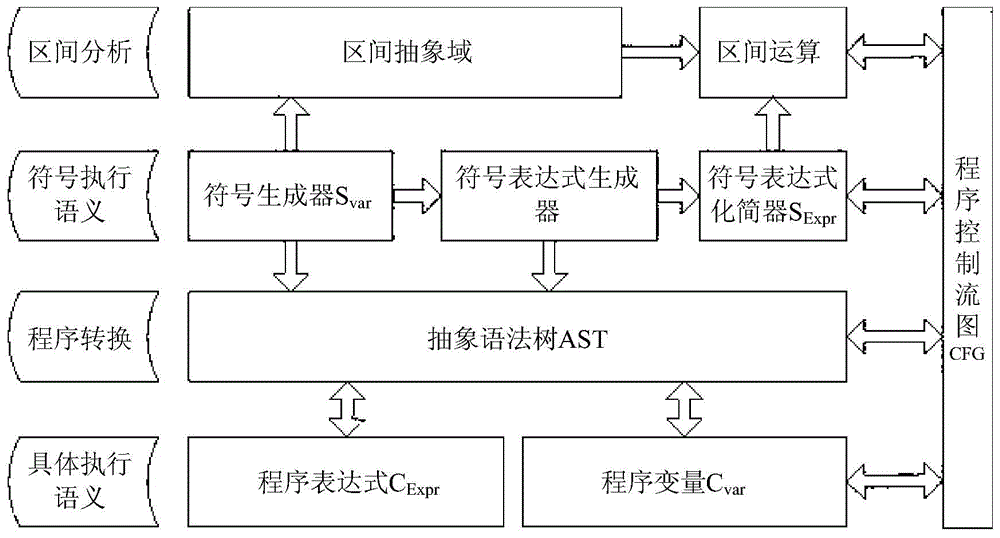
A control-flow diagram (CFD) is a diagram to describe the control flow of a business process, process or review. Control-flow diagrams were developed in the 1950s, and are widely used in multiple engineering disciplines. They are one of the classic business process modeling methodologies, along with flow charts, drakon-charts, data flow diagrams, functional flow block diagram, Gantt charts, PERT diagrams, and IDEF.
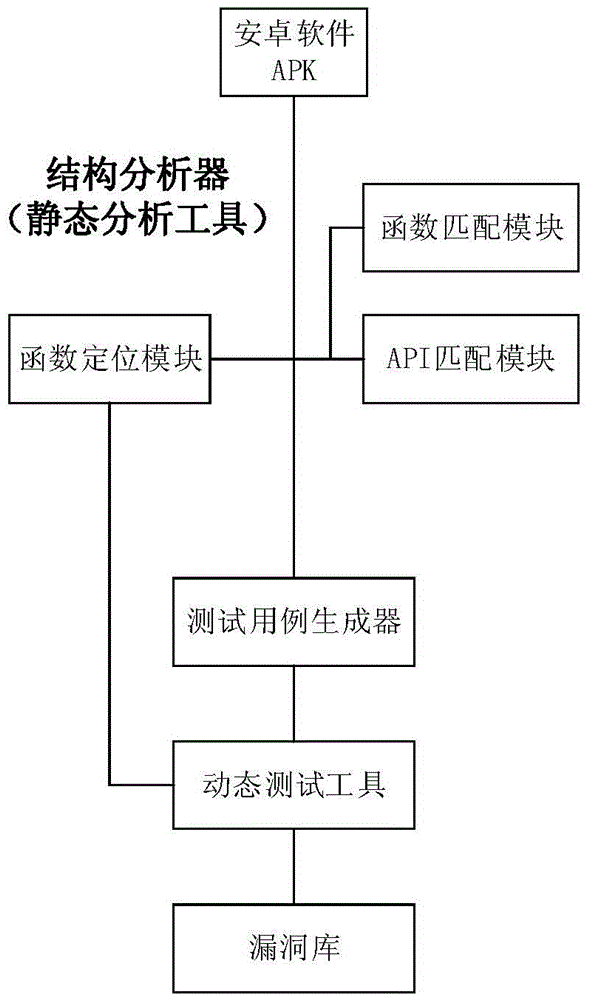
Static analysis method and static analysis device for Android application program
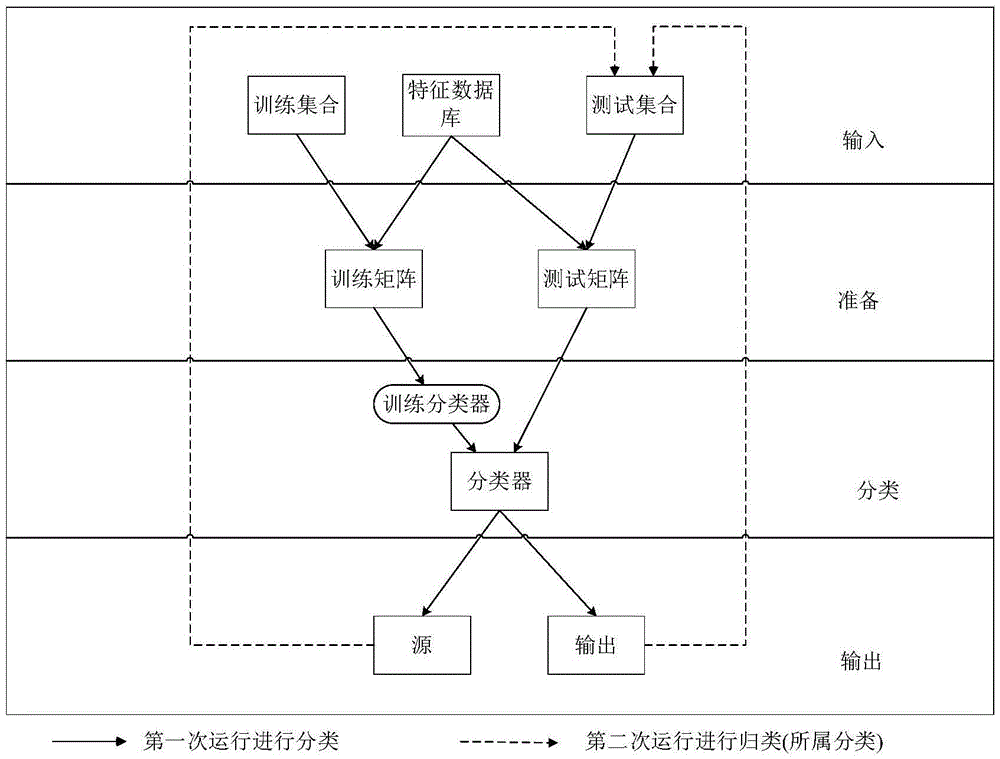
InactiveCN103793650AReduce the risk of miscalculationReduce misjudgmentPlatform integrity maintainanceRisk levelData stream
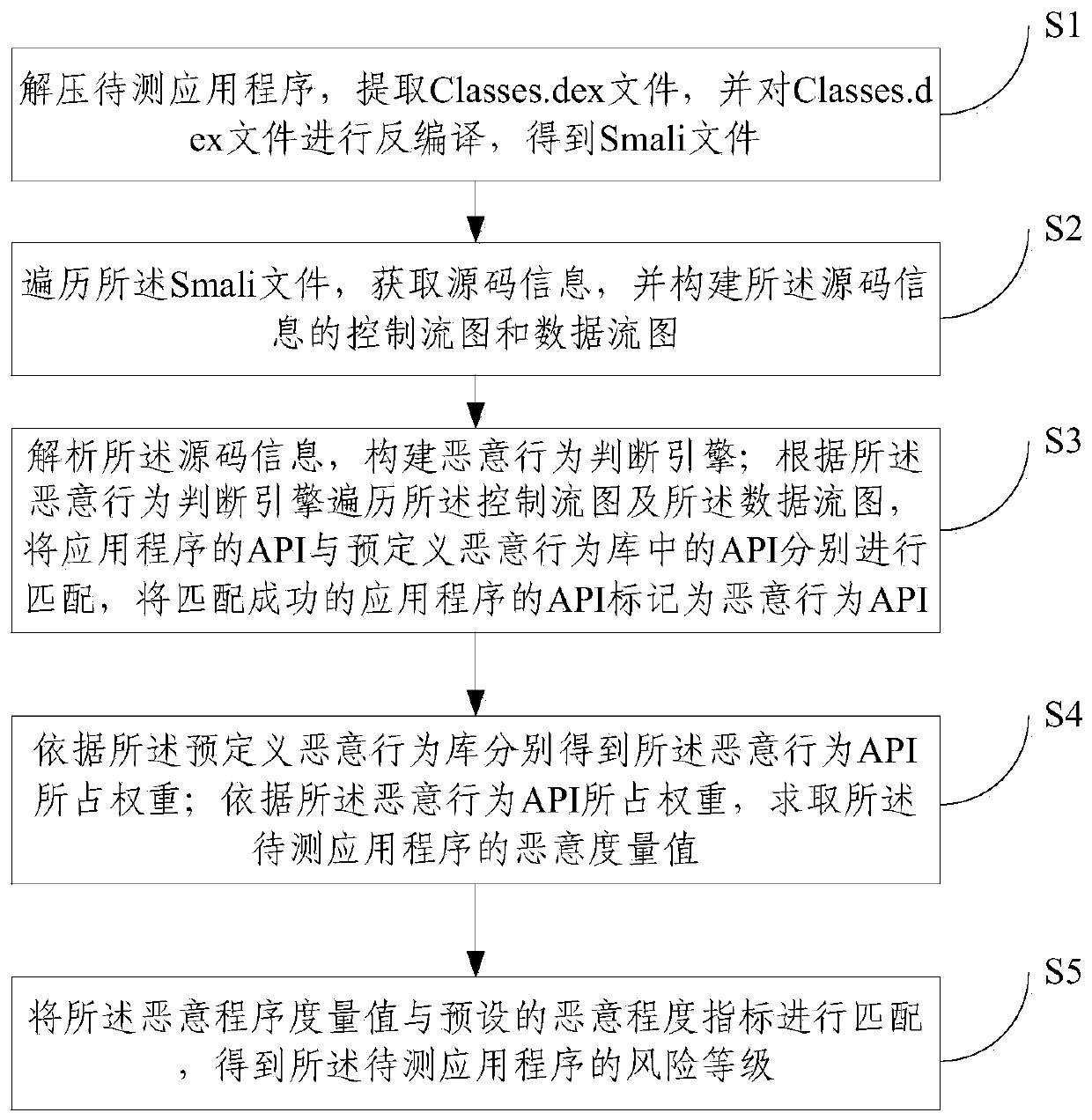
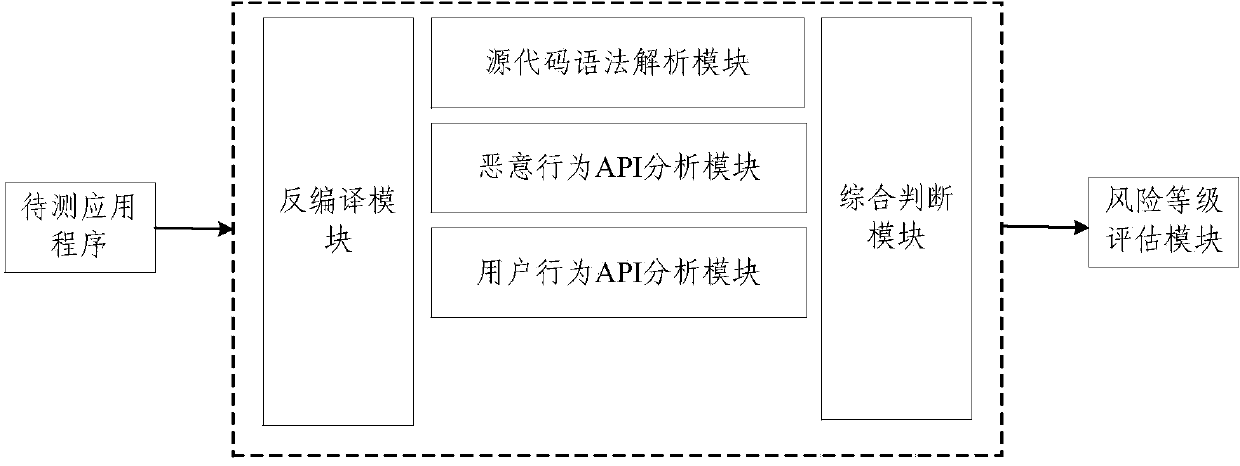
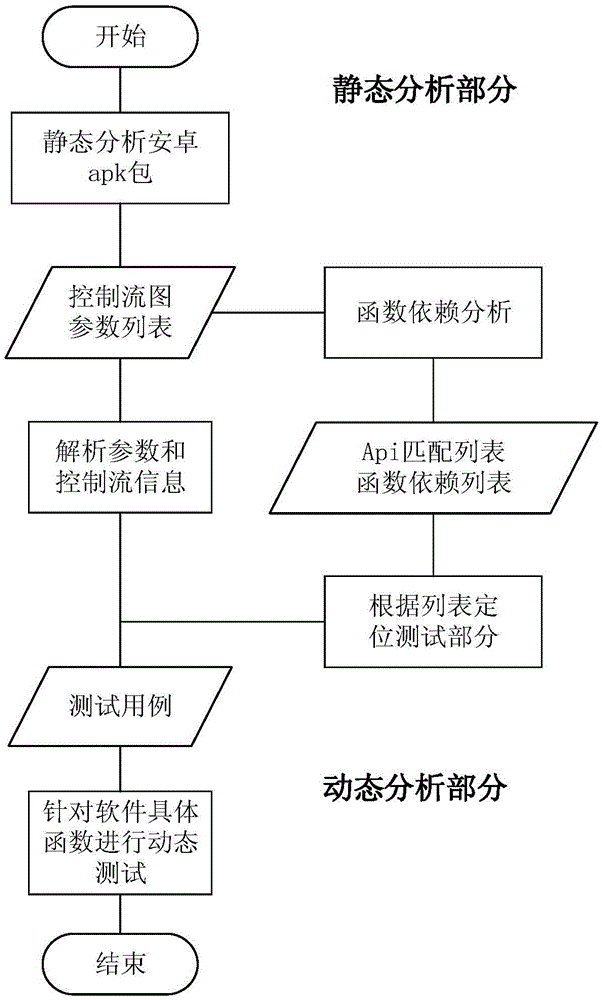
The invention provides a static analysis method and a static analysis device for an Android application program and relates to the technical field of security detection. The static analysis method includes: S1, unzipping an application program to be detected to obtain a Smali file; S2, traversing the Smali file to acquire a source code information and structuring a control flow diagram and a data flow diagram of the source code information; S3, traversing the control flow diagram and the data flow diagram according to a malicious behavior judging engine to respectively match an API (application program interface) of the application program with another API in a predefined malicious behavior library and marking the successfully matched API of the application program as the malicious behavior API; S4, calculating the malicious measuring value of the application program to be detected; S5, matching the malicious measuring value with a predefined malicious degree index to acquire risk level of the application program to be detected. Through behavior analysis and comprehensive judgment of combined rules, misjudgment rate of virus detection upon the Android application program can be reduced.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
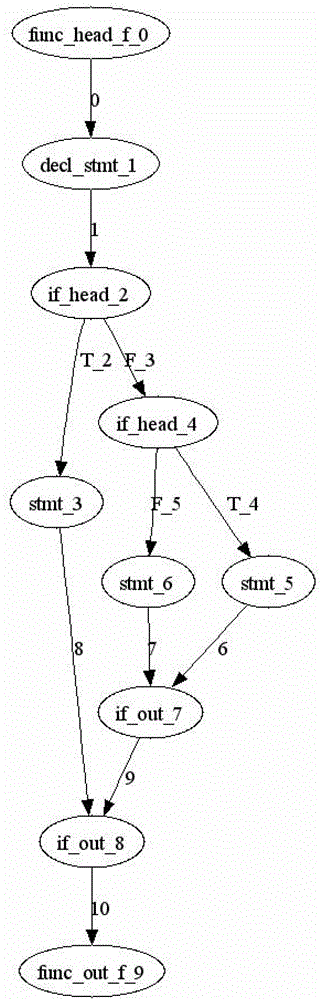
Method for optimizing unit regression test case set based on control flow diagram
InactiveCN102915271AImprove efficiencyImprove effectivenessSoftware testing/debuggingRegression testingAlgorithm
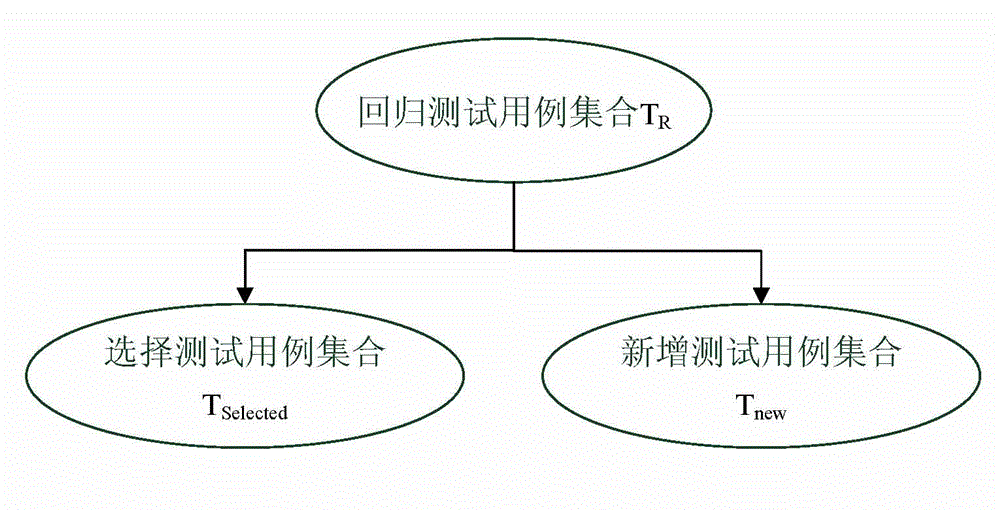
The invention discloses a method for optimizing a unit regression test case set based on a control flow diagram. The method comprises the following steps: A, finding out modified points corresponding to a modified part from the control flow diagram of a tested unit being tested unit before and after; B, screening out test cases, of which the execution paths pass through the modified points, to serve as one part of the regression test case set, namely a selected test case set (Tselected), and running all the test cases in the set; C, calculating all the reachable successor nodes of the modified points and selecting a node subset N which is not covered in the running process of the step B; D, if the N is null, executing the step F, and if the N is not null, executing the step E; E, selecting one node from the N to serve as a coverage target generation test case, adding the coverage target generation test case into a new test case set (Tnew) and then completely running, updating the N, deleting the nodes covered in the running process and returning to the step D; and F, finishing construction of the regression test case set (TR). By application of the method, the efficiency of the regression test can be improved and the effectiveness and the sufficiency of the regression test are guaranteed.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method for enhancing program analysis
InactiveUS20050149904A1Easy to analyzeAvoid explosionSoftware testing/debuggingSpecific program execution arrangementsTheoretical computer scienceFlow sheet
Methods are discussed that enhance program analysis. One aspect of the invention includes a method for checking a model of a program. The method includes a control-flow graph having vertices from the model, applying a transfer function to each vertex to form a set of path edges, and analyzing the set of path edges of a vertex. The set of path edges includes valuations that are implicitly represented so as to inhibit an undesired explosion in the valuations that would hinder the act of analyzing.
Owner:MICROSOFT TECH LICENSING LLC
Memory access abnormity detecting method and memory access abnormity detecting device
ActiveCN104636256AImplement detection operationsRealize the detection operation of memory access out of boundsSoftware testing/debuggingPlatform integrity maintainanceData dependency graphLexical analysis
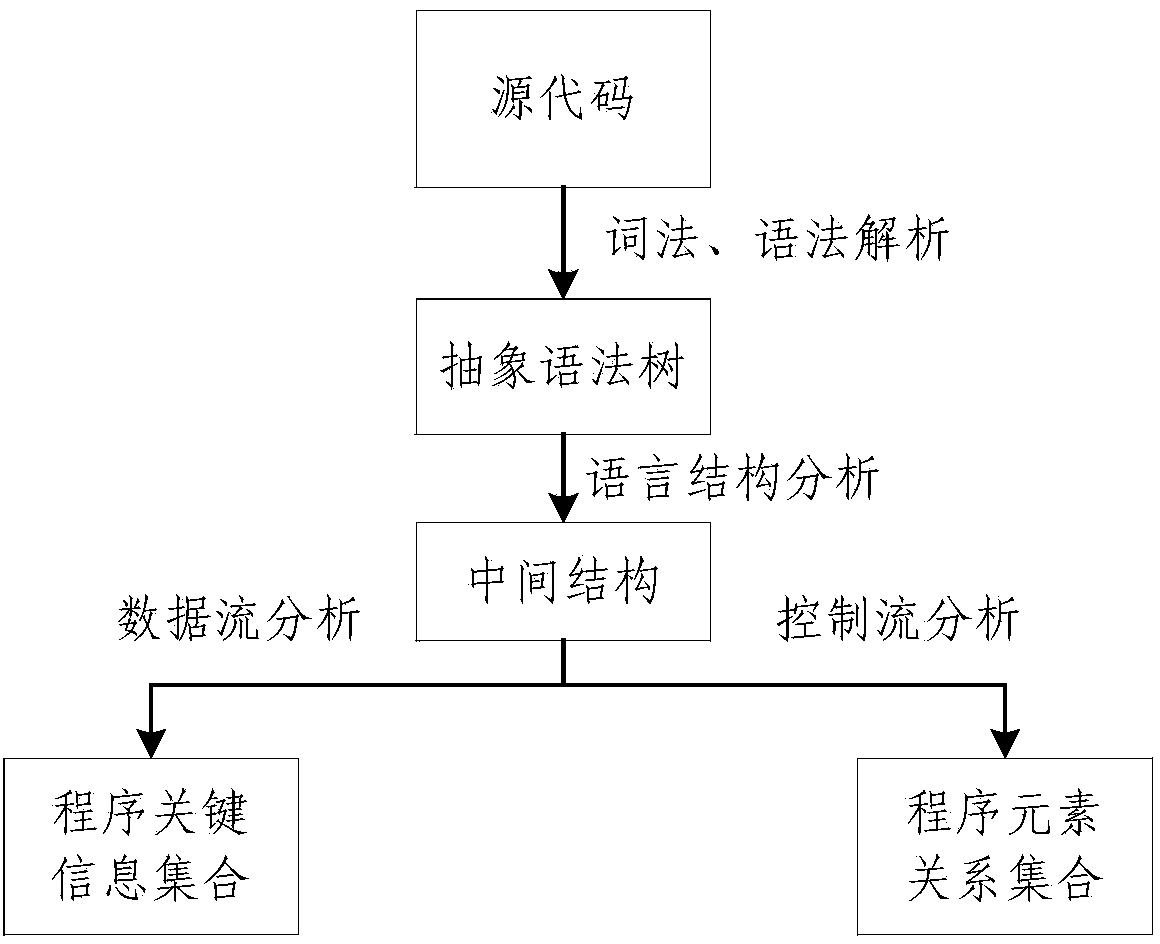
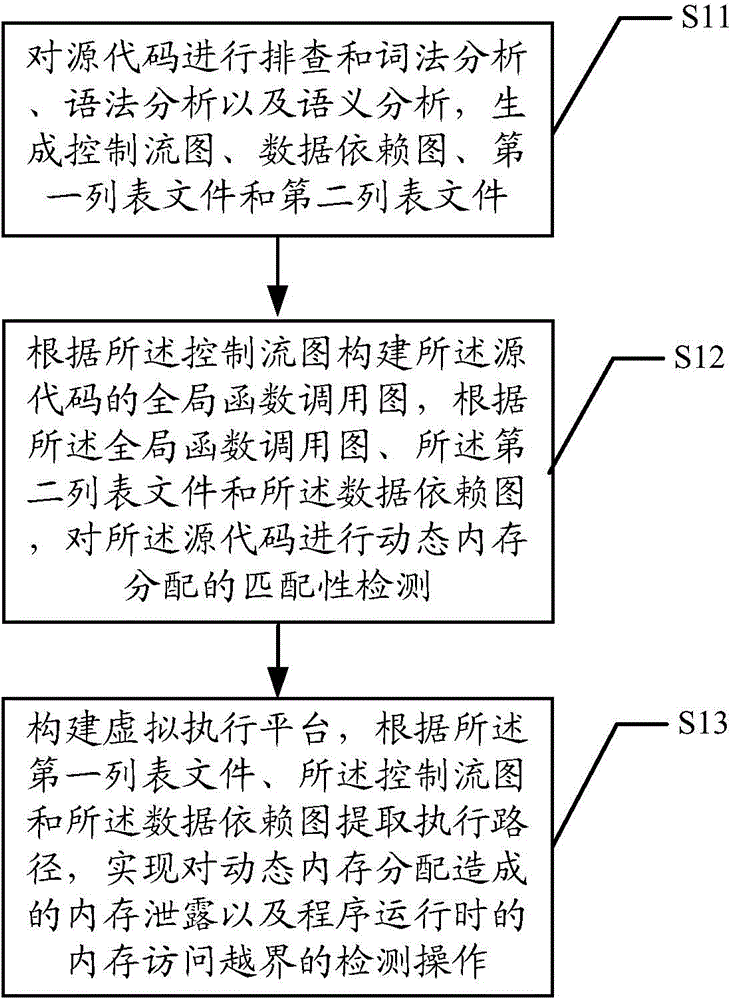
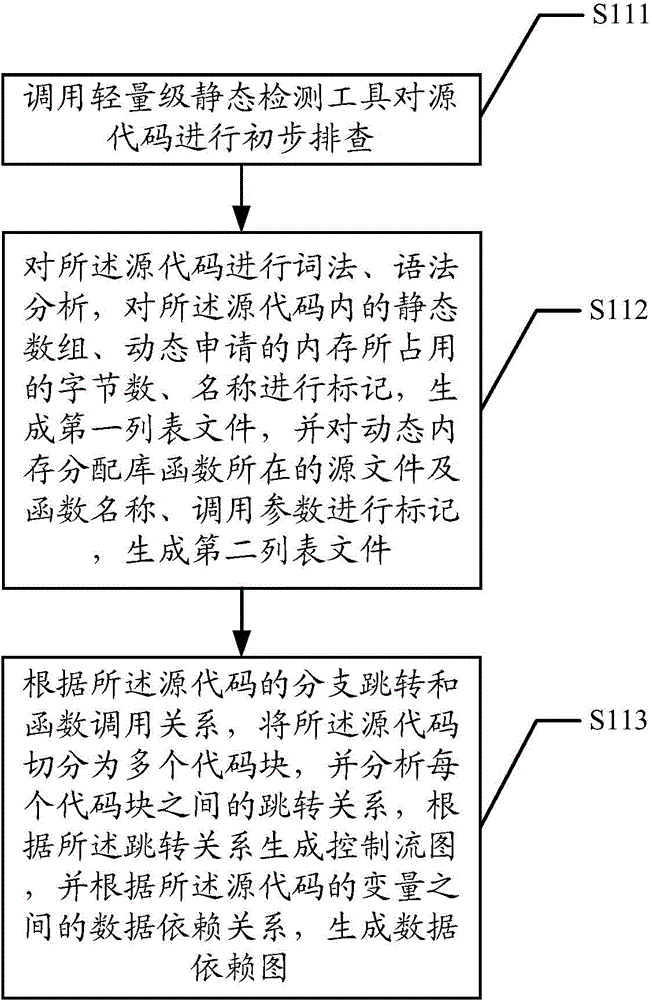
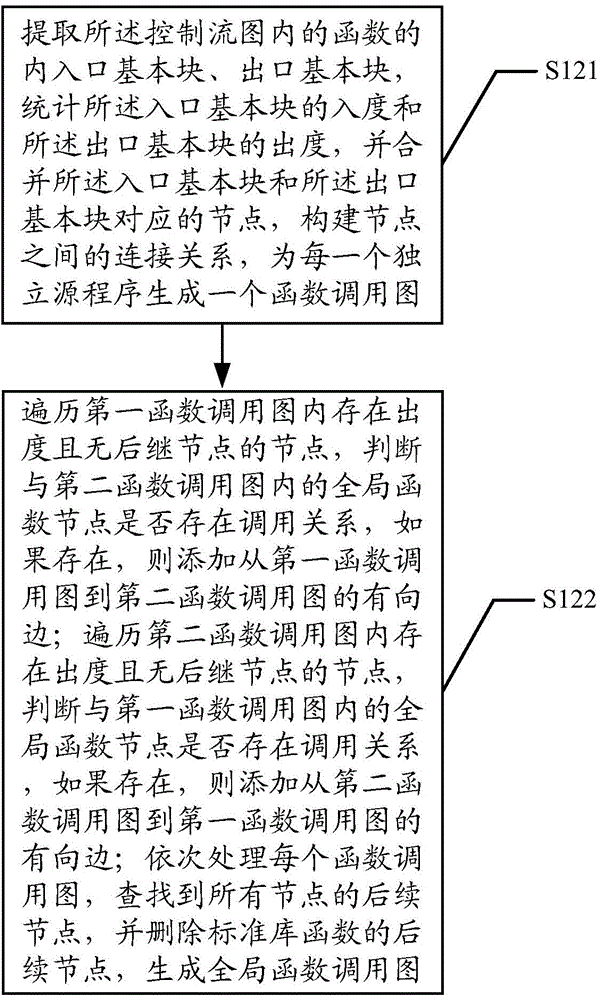
The invention discloses a memory access abnormity detecting method and a memory access abnormity detecting device. The memory access abnormity detecting method comprises the following steps of checking source codes and analyzing the morphology, the grammar and the semanteme of the source codes to generate a control flow diagram, a data dependence diagram, a first list file and a second list file; establishing a global function invocation diagram of the source codes according to the control flow diagram; performing matching detection on dynamic memory allocation of the source codes according to the global function invocation diagram, the second list file and the data dependence diagram; and establishing a virtual executing platform; and extracting an executing path according to the first list file, the control flow diagram and the data dependence diagram so as to detect memory leakage caused by dynamic memory allocation and memory access violation during running of a program. Memory access abnormity in the source codes can be sufficiently dug by analyzing the first list file, the second list file, the control flow diagram, the data dependence diagram and the global function invocation diagram, establishing the virtual executing platform and extracting the executing path, and the memory access abnormity can be detected efficiently.
Owner:AGRICULTURAL BANK OF CHINA
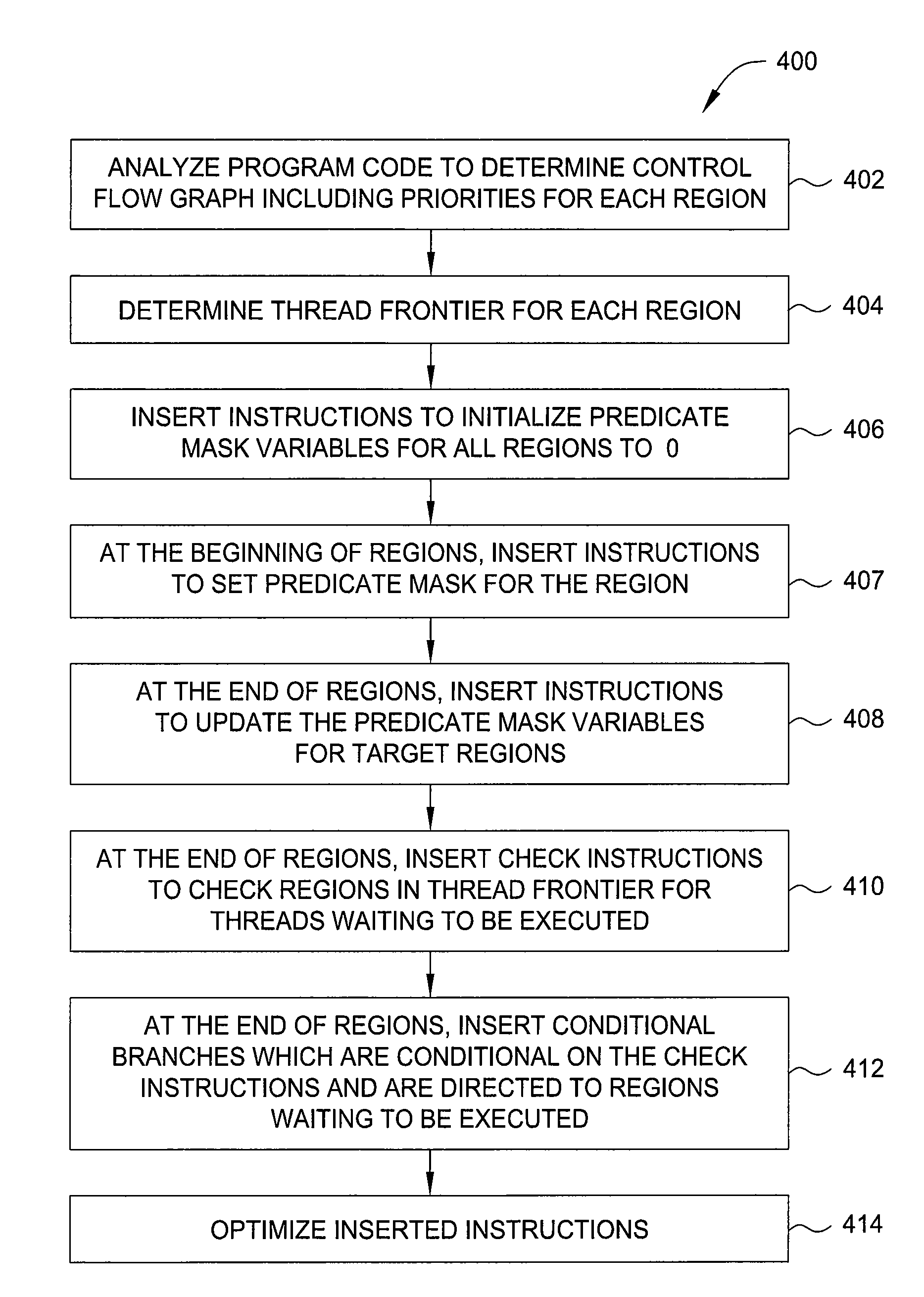
Compiler-controlled region scheduling for simd execution of threads
A compiler-controlled technique for scheduling threads to execute different regions of a program. A compiler analyzes program code to determine a control flow graph for the program code. The control flow graph contains regions and directed edges between regions. The regions have associated execution priorities. The directed edges indicate the direction of program control flow. Each region has a thread frontier which contains one or more regions. The compiler inserts one or more update predicate mask variable instructions at the end of a region. The compiler also inserts one or more conditional branch instructions at the end of the region. The conditional branch instructions are arranged in order of execution priority of the regions in the thread frontier of the region, to enforce execution priority of the regions at runtime.
Owner:NVIDIA CORP
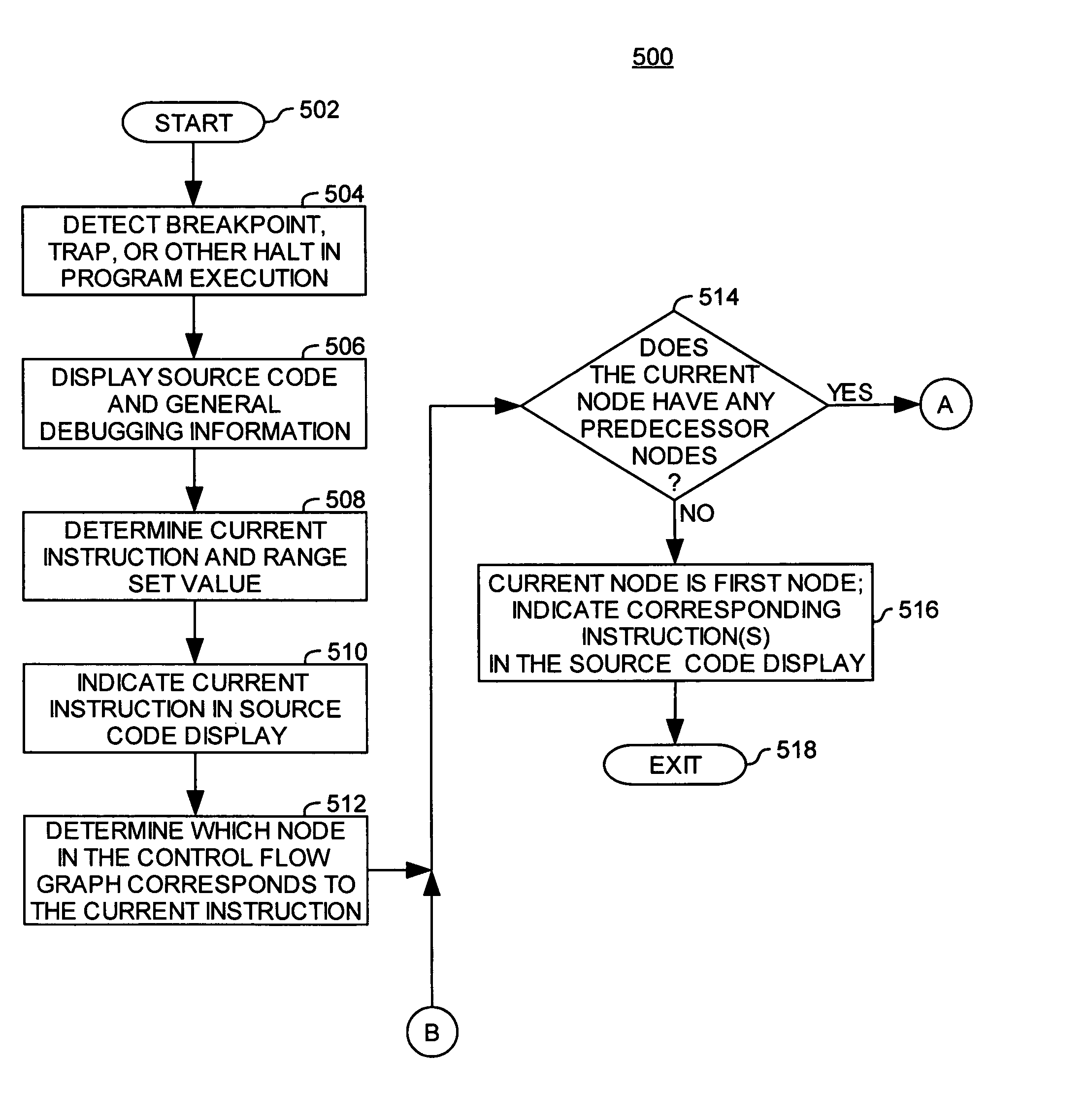
Method of tracing back the execution path in a debugger
InactiveUS20070168992A1Error detection/correctionSpecific program execution arrangementsParallel computingFlow sheet
A method, computer-readable medium, and system for tracing the execution path of a program are provided. In one embodiment, a control flow graph is created for the program. For each node in the control flow graph, a determination is made of whether the node has two or more predecessor nodes. For each node determined to have two or more predecessor nodes, a set instruction is inserted into program code corresponding to the predecessor node which sets a corresponding value of a variable. The corresponding value of the variable indicates that one or more instructions in the predecessor node were executed during an execution of the program.
Owner:IBM CORP
Dynamic symbolic execution method and device thereof based on overall situation super block dominator graph
ActiveCN103116540AImprove execution efficiencyAlleviate the path explosion problemSoftware testing/debuggingAlgorithmTheoretical computer science
The invention provides a dynamic symbolic execution method and a device of the dynamic symbolic execution method based on an overall situation super block dominator graph and belongs to the field of computer software testing and software security. The method is as follows: a control flow diagram of a tested executable program is obtained, and the control flow diagram is transformed to a super block dominator graph according to relevant theories of a dominance relation. Each nodal point in the super block dominator graph is marked with 'weight' which is updated before symbolic execution at each time, and the 'weight' indicates the least number of basic blocks which can be covered when the nodal point is executed. When one dynamic symbolic execution is over, the nodal point with the largest 'weight' value is selected from the super block dominator graph, and corresponding forecasting path constraint conditions are generated, and then a new testing use case is generated by solving of a solver, so that the next execution is driven. Compared with the prior art, the dynamic symbolic execution method and the device of the dynamic symbolic execution method based on the overall situation super block dominator graph are capable of covering code blocks as many as possible with least testing use cases, so that the growth rate of the code coverage rate is effectively accelerated, and the problem of path explosion is relieved. The dynamic symbolic execution method and the device of the dynamic symbolic execution method based on the overall situation super block dominator graph is of great importance for the performance of testing large-scale utility software of the dynamic symbolic execution.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Method and a system for constructing control flows graphs of binary executable programs at post-link time
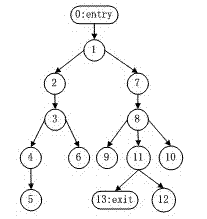
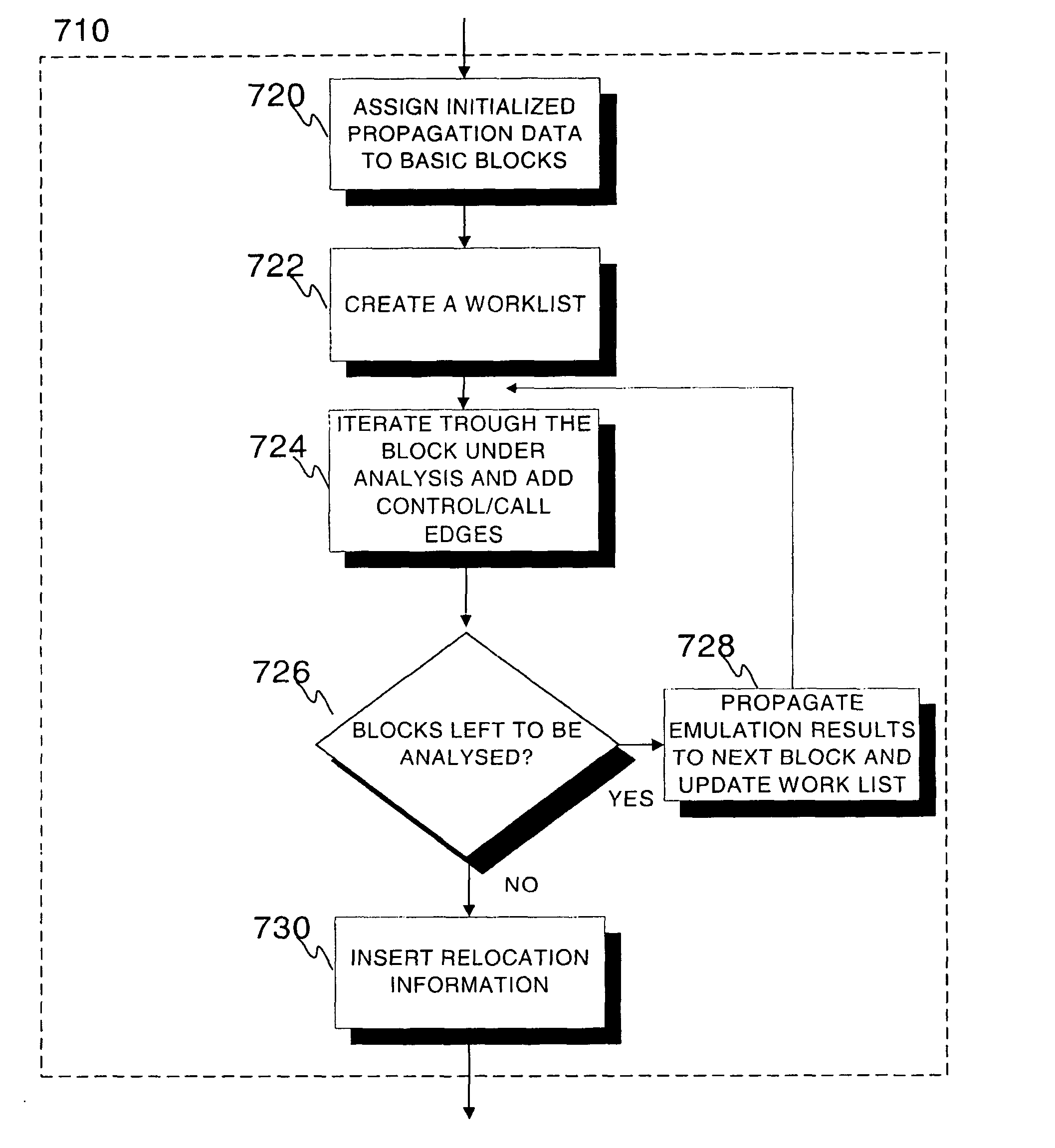
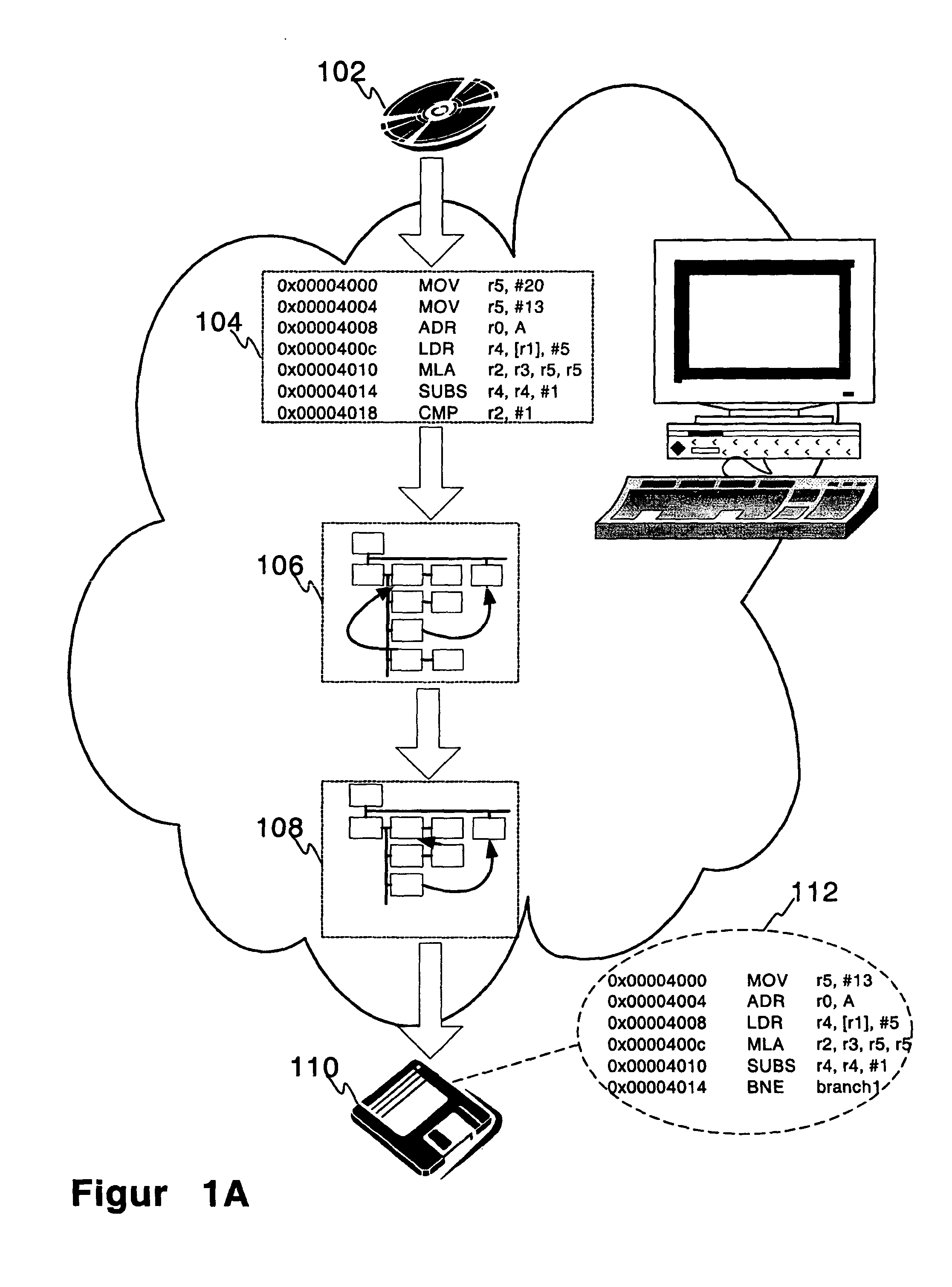
InactiveUS20050060696A1Clarifies overall structureReduce memory usageSoftware engineeringSoftware simulation/interpretation/emulationControl flowBasic block
A method and a system for constructing a control flow graph (CFG, 106) from an executable computer program (104). The solution detects data intermixed with instructions and instruction set changes. The method includes the steps of defining block leader types specifying basic block boundaries in the program (104), building a CFG structure (106) according to the basic blocks found in the program, and adding control flow and addressing information to the CFG (106) by propagating through the basic blocks and internals thereof. The CFG (106) may be then optimised (108) and a compacted executable (112) created as a result.
Owner:NOKIA CORP
Security detection method for android application file
ActiveCN105550594AEasy to operateOvercoming the difficulties of analysisDigital data protectionOperating systemControl flow diagram
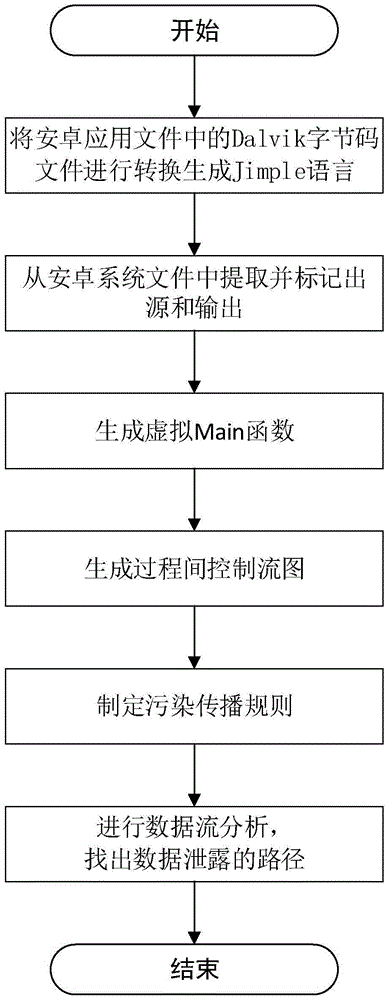
The invention discloses a security detection method for an android application file, and mainly solves the problem of privacy leakage vulnerability detection capability shortage of an existing android application file. The method is implemented by the steps of 1, converting a Dalvik byte code file in the android application file into a Jimple language; 2, extracting input and output functions related to sensitive data by classification from an android system file, classifying the input and output functions, and marking a source and an output; 3, generating a virtual Main function in the Jimple language and generating an interprocedural control flow diagram according to the function; 4, establishing a taint spread rule; 5, generating a taint access path according to the interprocedural control flow diagram; and 6, according to the marked source and output, executing the taint spread rule in the taint access path to find out a data leakage path. According to the method, the missing and false reporting of privacy leakage vulnerabilities is reduced and the security protection performance is improved, so that the method can be used for detecting the android application file.
Owner:XIDIAN UNIV
Attitude and orbit control data analysis method based on decision tree
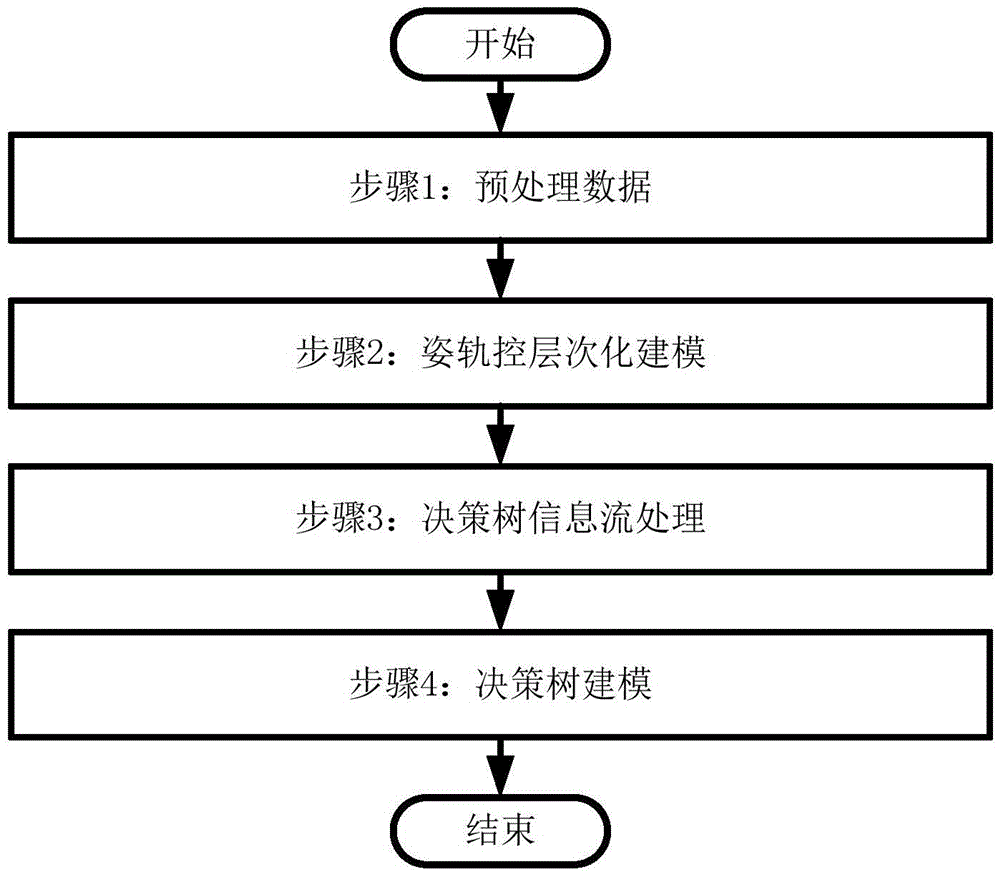
ActiveCN105573329AResolve identifiabilitySolving the Difficulties of Fault InversionCosmonautic vehiclesCosmonautic partsAlgorithmEngineering
The invention provides an attitude and orbit control data analysis method based on a decision tree. The method comprises the following steps: attitude and orbit control data preprocessing, i.e., finishing remote measurement data deduplicating, remote measurement data sequencing, remote measurement data extraction and remote measurement data outlier rejection through the data preprocessing; hierarchical modeling of an attitude and orbit control, i.e., establishing an information and control flow chart of the attitude and orbit control, determining remote measurement variables related to current faults of the attitude and orbit control, and taking the variables as input variables for decision tree analysis; establishing a flow chart of the decision tree analysis; and decision tree modeling, i.e., creating a decision tree C5.0 algorithm model, defining a model name in the model, boosting algorithm test frequency, and trimming attributes and a minimum recording number of each sub branch. The method provided by the invention solves the problem of difficulties in satellite attitude and orbit control complex data analysis and has a certain guidance effect on satellite fault identification, diagnosis and anticipation.
Owner:SHANGHAI SATELLITE ENG INST
Static detection method for privacy information disclosure in mobile applications
ActiveCN103577324AAccurate discoveryImprove detection efficiencySoftware testing/debuggingControl flowOperational system
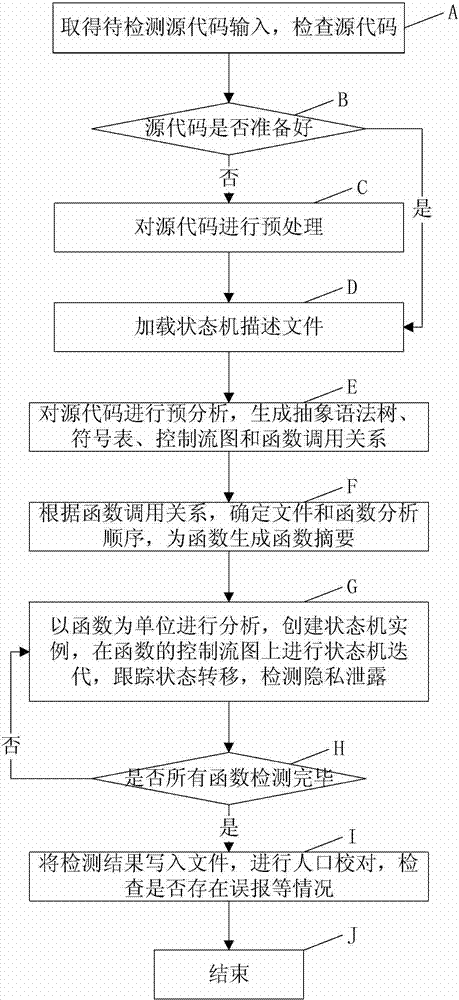
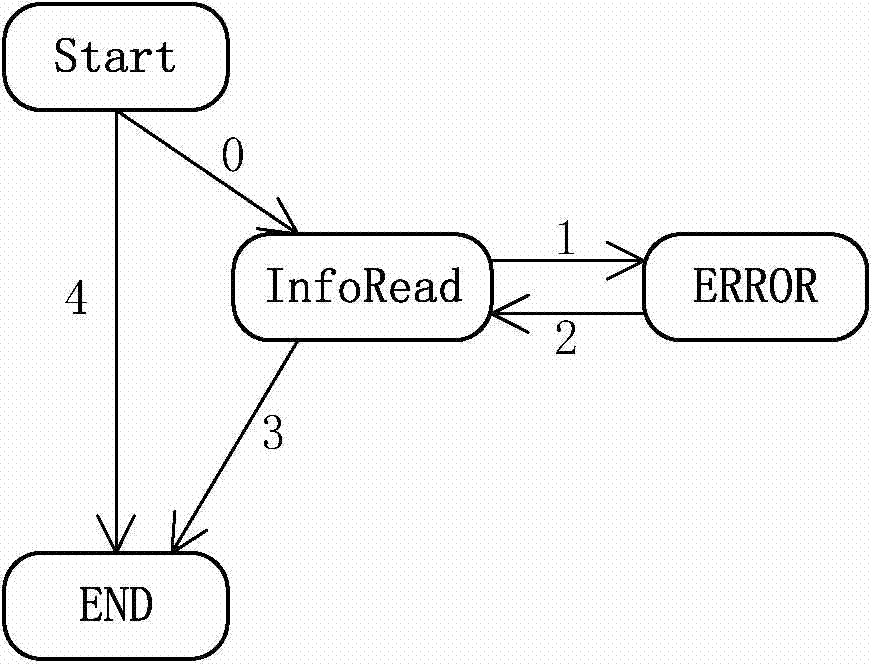
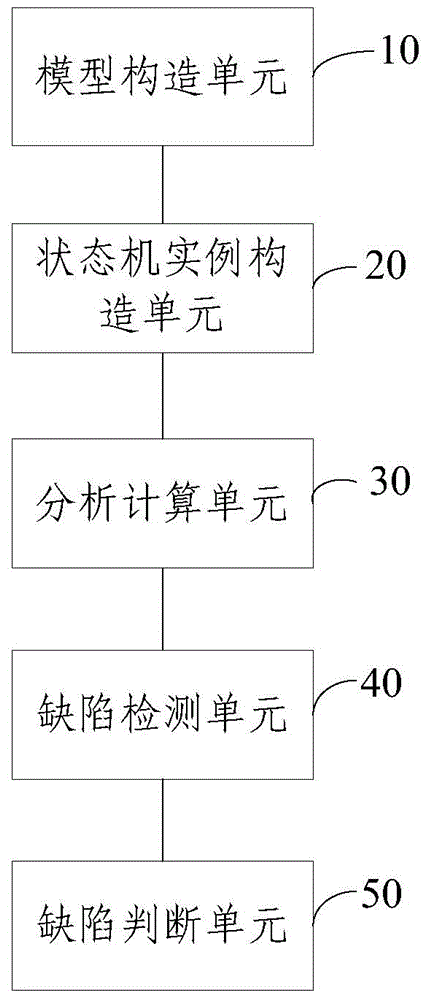
The invention discloses a static detection method for privacy information disclosure in mobile applications. The method comprises the steps as follows: firstly, the completeness of codes is checked, if the codes are incomplete, preparatory work is performed on source codes, state machine description files corresponding to the privacy disclosure are loaded, related state machine information is obtained, the source codes are compiled to obtain detailed information of classes, functions and the like, pre-analysis is performed on the source codes, basic data structures such as abstract syntax trees and the like are generated, and call relations among the functions are obtained; and then detection and analysis is performed in units of the functions, state machine instances are created for all state machines with associated methods in the state machines, state machine instance iteration is performed on control flow diagrams corresponding to the functions, when the state machine instances are in error states, errors are reported, after detection is finished, the detected errors are checked manually, and detection results are confirmed. With the adoption of the method, the privacy disclosure codes existing in application programs of different operating system platforms can be effectively detected, so that the privacy information disclosure of users can be effectively prevented.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method of fully detecting null pointer reference defects
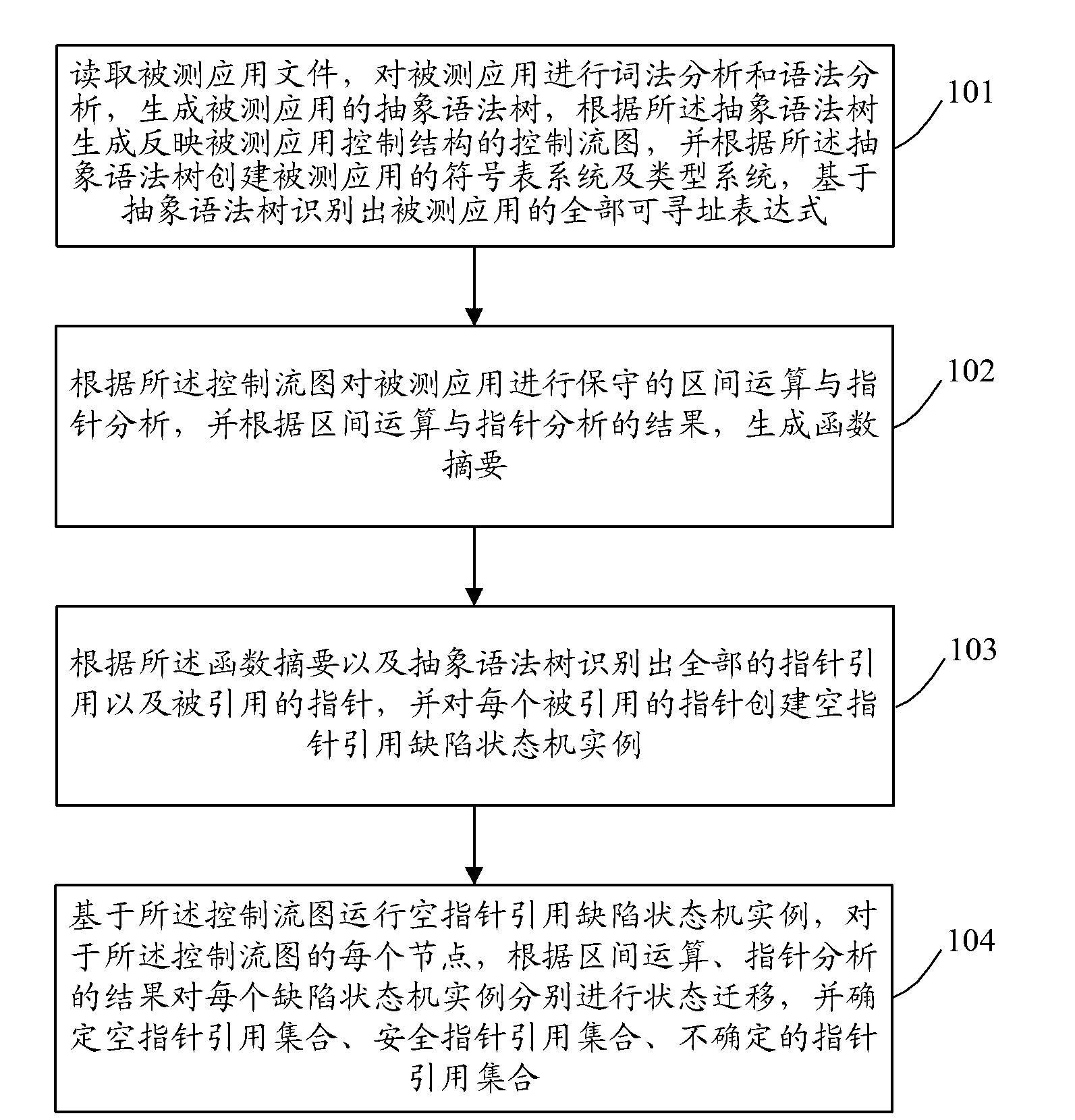
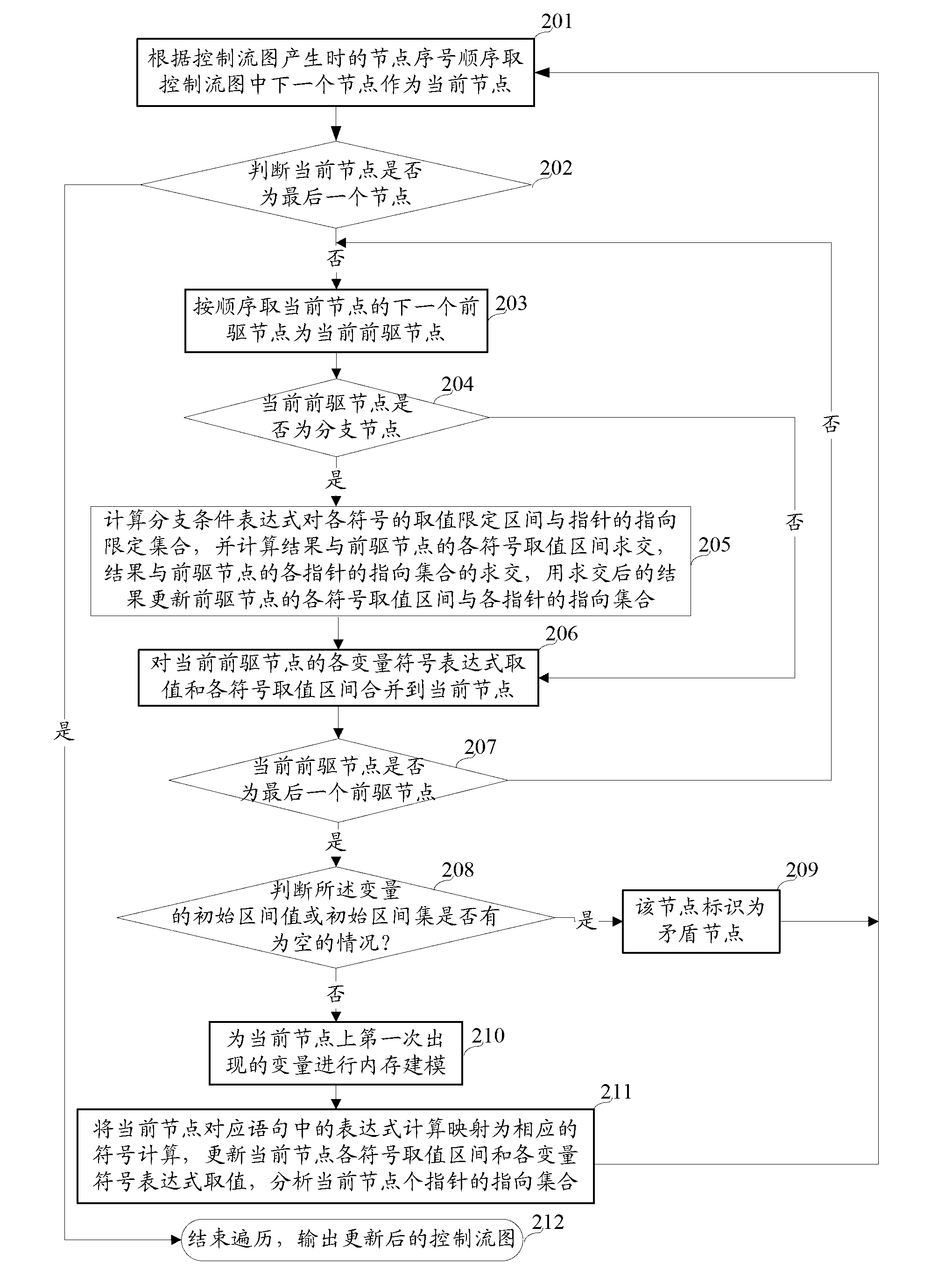
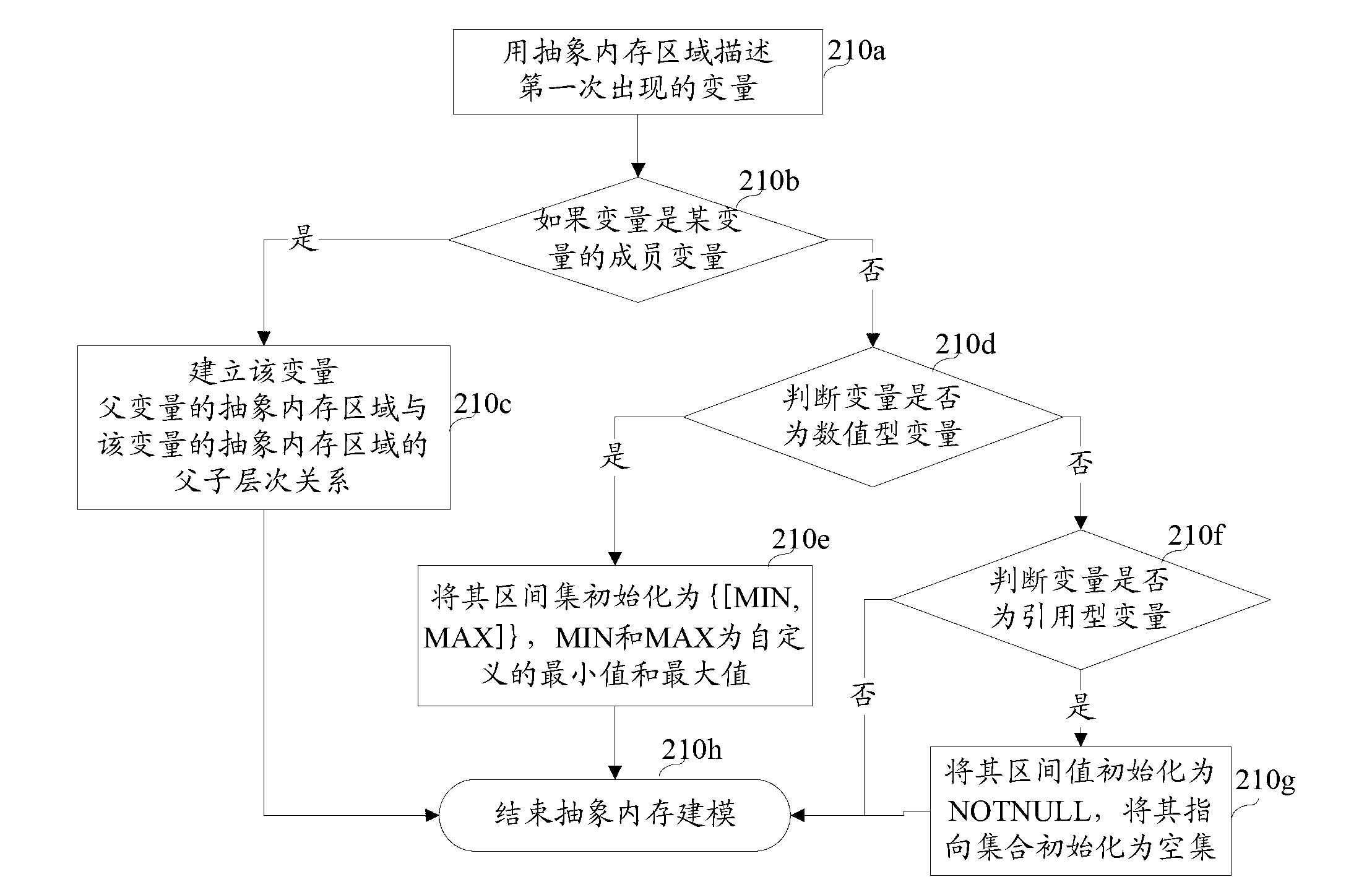
InactiveCN103218296ASolve the problem of false positivesAchieve zero false negativesSoftware testing/debuggingInterval arithmeticTheoretical computer science
The invention discloses a method of fully detecting null pointer reference defects. The method comprises recognizing all addressable expressions of an application to be detected based on an abstract syntax tree; carrying out conservative interval arithmetic and pointer analysis on the application to be detected according to a control flow diagram, and generating a procedural summary according to results of the interval arithmetic and the pointer analysis; recognizing all pointer reference and referred pointers according to the procedural summary and the abstract syntax tree, and creating a null pointer reference defect state machine example on each referred pointer; and running the null pointer reference defect state machine examples based on the control flow diagram, carrying out state transition on each defect state machine example on each node of the control flow diagram according to the results of the interval arithmetic and the pointer analysis, and carrying out null pointer reference detection. By adopting the method of fully detecting the null pointer reference defects, the problem of failing to report the null pointer reference defects can be effectively solved, and zero omission and low misinformation of the null pointer reference defect detection are achieved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
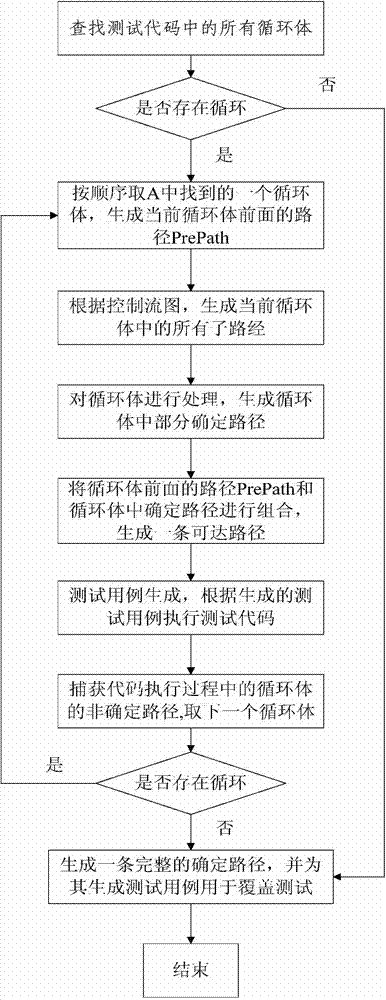
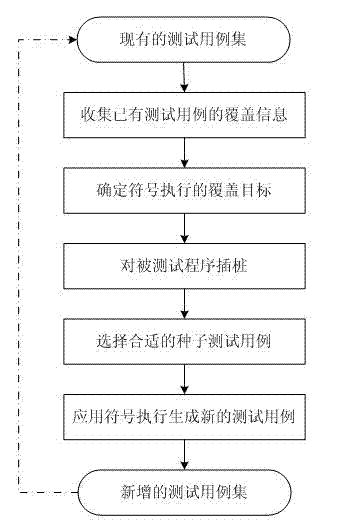
Symbolic-execution-based method for generating test cases with feedback
InactiveCN102736979AReduce problem sizeReduce in quantitySoftware testing/debuggingSoftware development processAutomatic testing
The invention discloses a symbolic-execution-based method for generating test cases with feedback. The method comprises the following steps of: (1) executing the conventional test cases, and collecting information covered by the test cases; (2) determining a symbolic execution covering object according to a control flow diagram of a tested program; (3) instrumenting the tested program, and implanting a symbolic execution control code; (4) selecting a proper seed test case from the conventional test case set; (5) generating a new test case for the covering object by using a symbolic execution method, and supplementing the new test case into the test case set; and (6) repeating the steps until a given test case generation aim is fulfilled. The method can be widely applied to automatic test in a software development process, and is used for automatically generating the test cases, so that the problem of constraint condition explosion of independent symbolic execution is solved, and efficiency is improved; and in addition, other generation methods can be combined, so that the problem that complex data structures cannot be processed by the symbolic execution method can be alleviated.
Owner:NANJING UNIV
Fault confirmation method and system thereof
ActiveCN104360938ASolve the problem of massive false positives in static testingCutting costsSoftware testing/debuggingControl flow diagramReliability engineering
The invention relates to a fault confirmation method and a system thereof. The fault confirmation method comprises the following steps: S1, matching doubt fault points in the static analysis process by using a preset fault mode, screening the doubt fault points, and marking the doubt fault points in a control flow diagram of a tested program; S2, adding fault triggering conditions at the doubt fault points to form fault nodes, establishing a fault route, and adding newly generated fault nodes into the control flow diagram, and marking; S3, calculating the weight of each doubt fault point at each node according to preset route selection strategy; S4, traversing the control flow diagram, selecting a fault route according to the weight of each fault point at a present node, extracting a constraint of each node of the selected route to instruct dynamically executed valuing, and confirming each doubt fault point. According to the method, the route selection strategy and a dynamic symbol execution technique are combined in the execution process, and the program is instructed to efficiently cover fault condition nodes, so that the fault confirmation efficiency is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
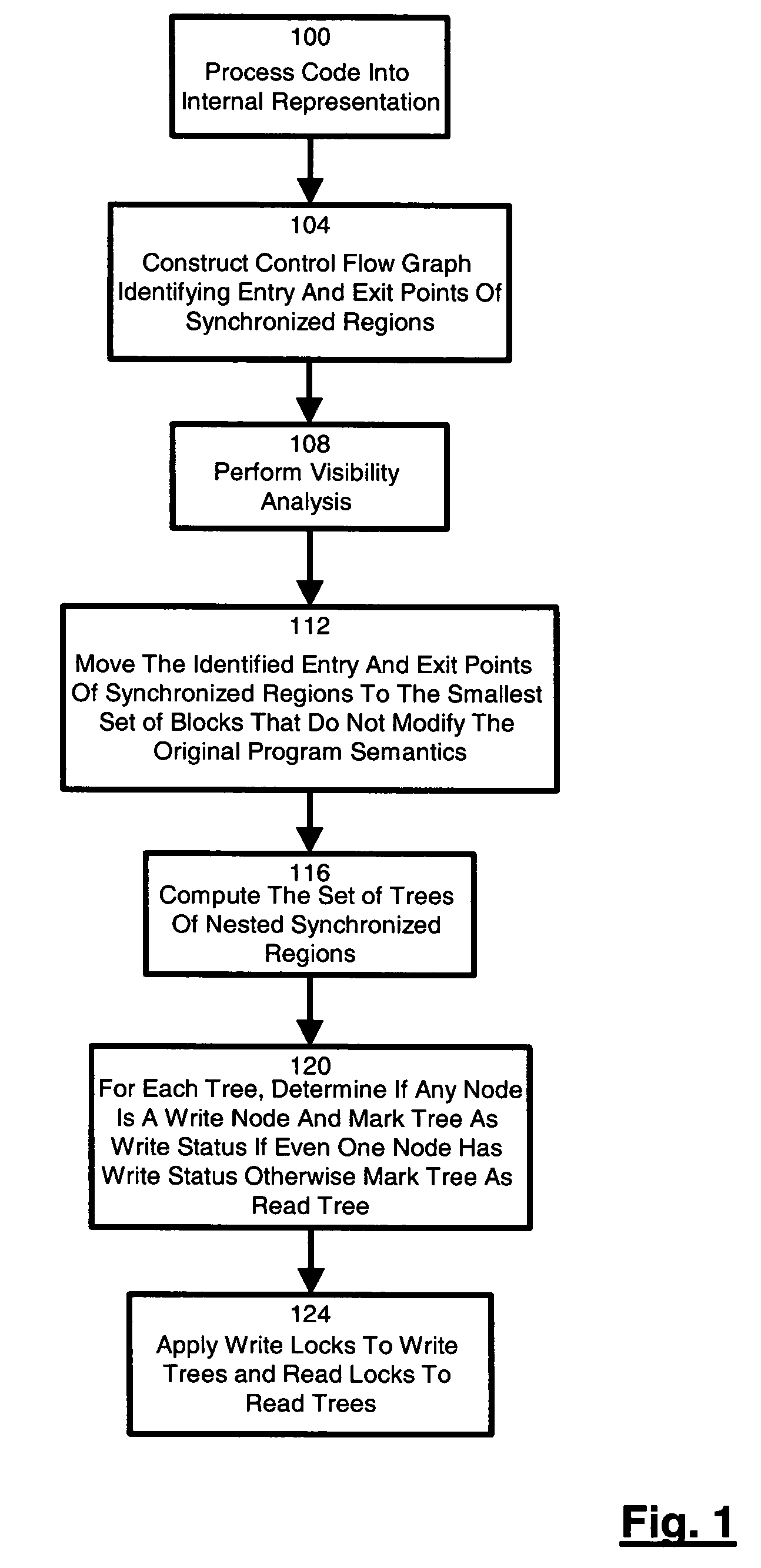
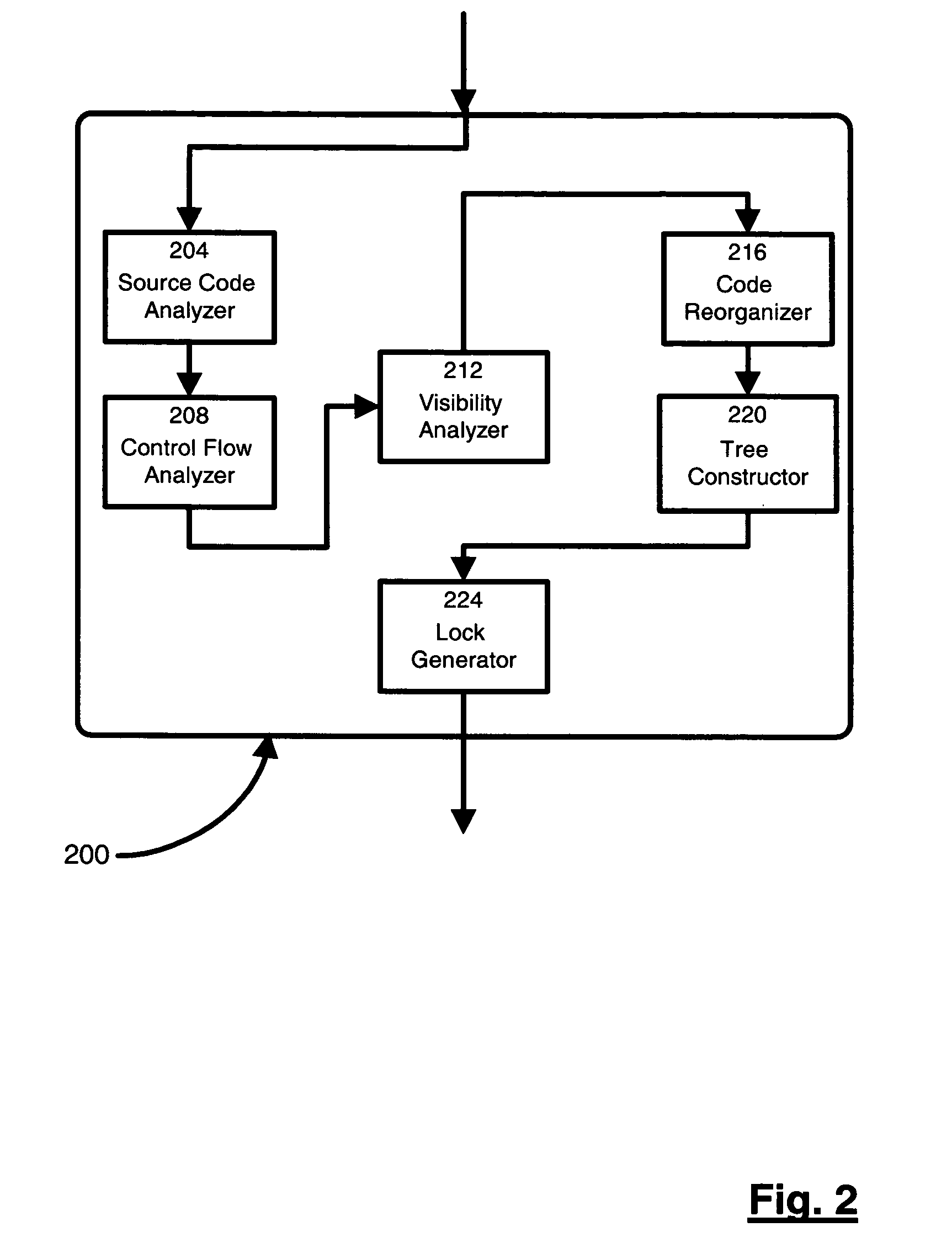
Method, system and product for identifying and executing locked read regions and locked write regions in programming languages that offer synchronization without explicit means to distinguish between such regions
InactiveUS20050198626A1Efficient executionProgram synchronisationConcurrent instruction executionTheoretical computer scienceProgram code
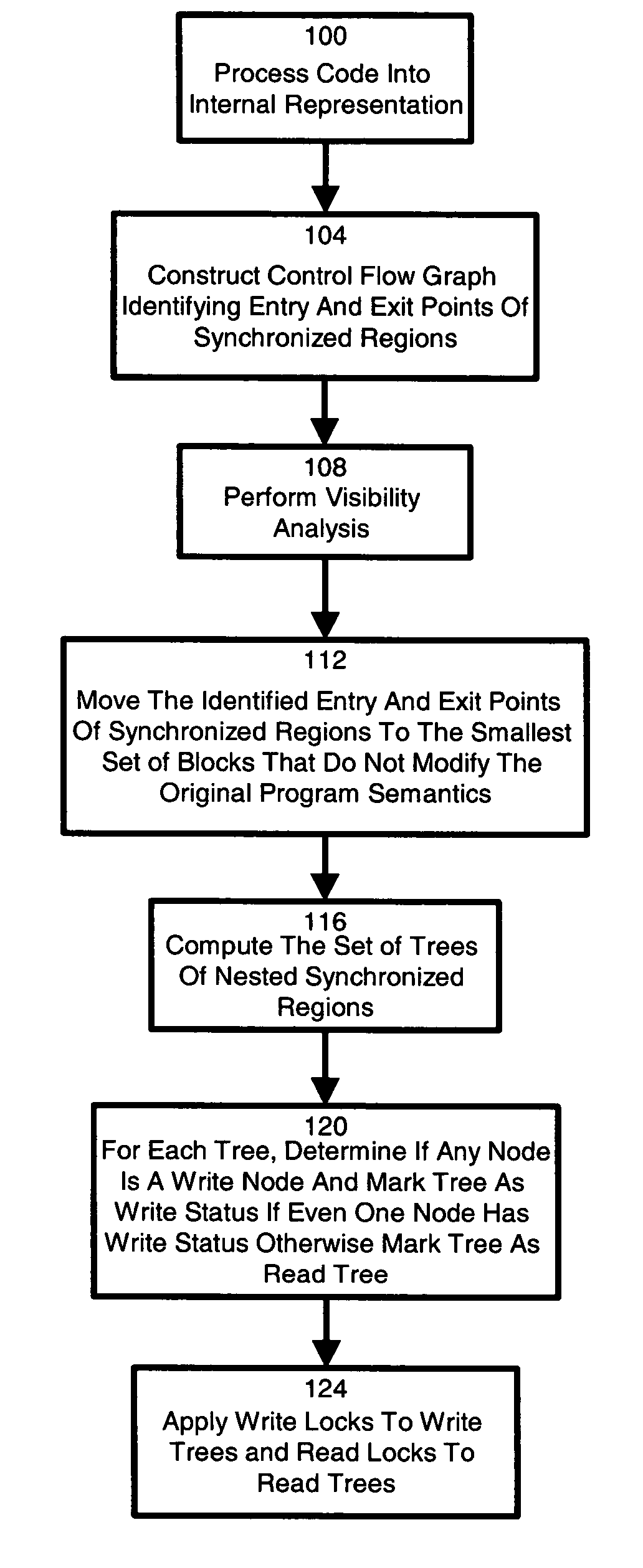
A technique for identifying and executing synchronized read regions and synchronized write regions is provided. The technique processes program code with a software tool to convert the code to an internal representation for the software tool and constructs a control flow graph of code blocks which also identifies the entry and exit points for each region of code subject to a lock. For each code block in the control flow graph, visibility analysis is performed. Each determined entry and exit point is moved to enclose the smallest set of code blocks subject to a lock which can be achieved without altering code semantics. A set of trees is created to represent the manner in which the synchronized regions are nested. If the tree contains at least one block previously identified, then the tree is marked a write. Otherwise, the tree is marked a read tree. A write lock is then created for the region in each tree identified as a write tree and a read lock is created for the regions in each tree identified as a read tree.
Owner:IBM CORP
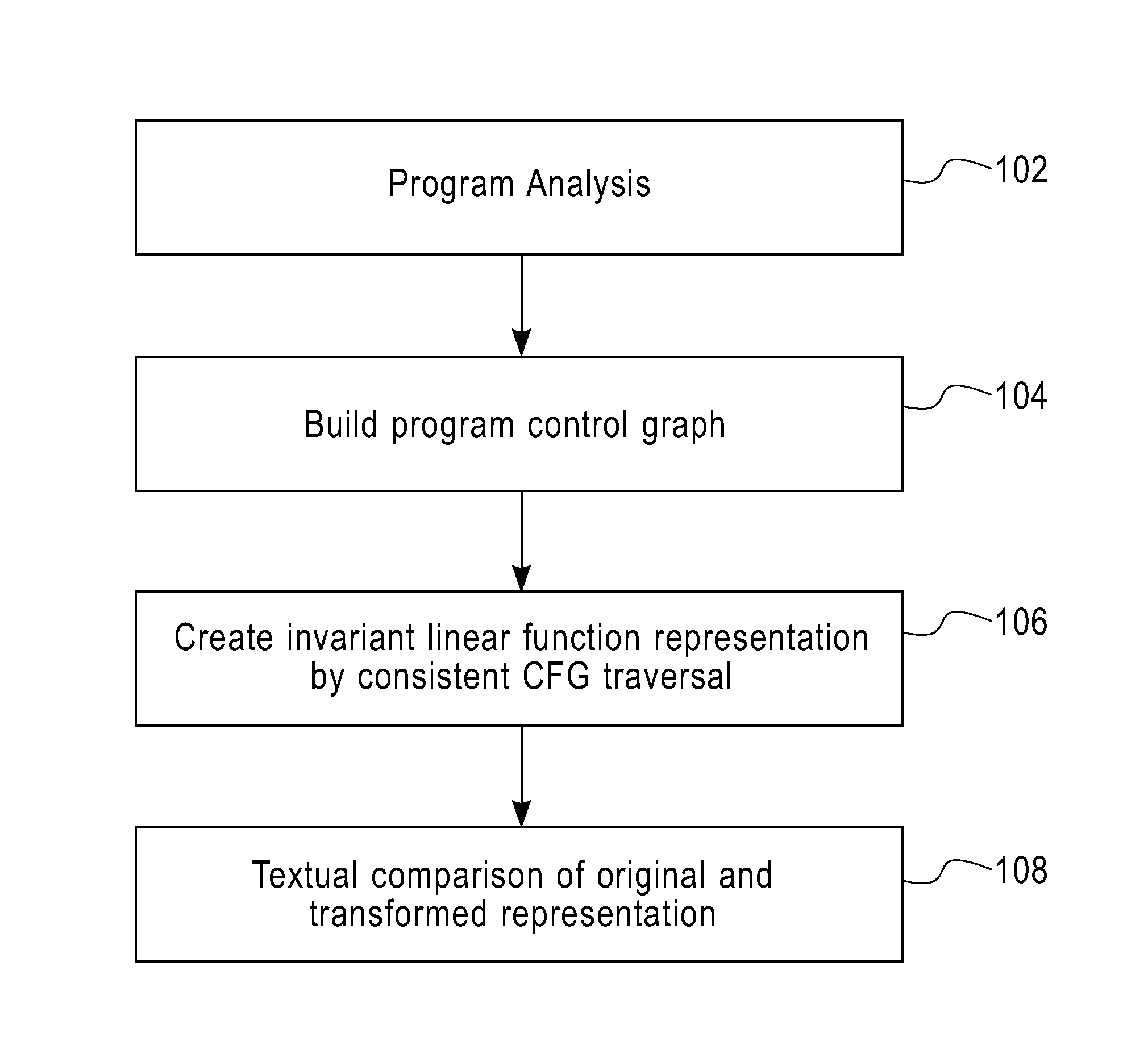
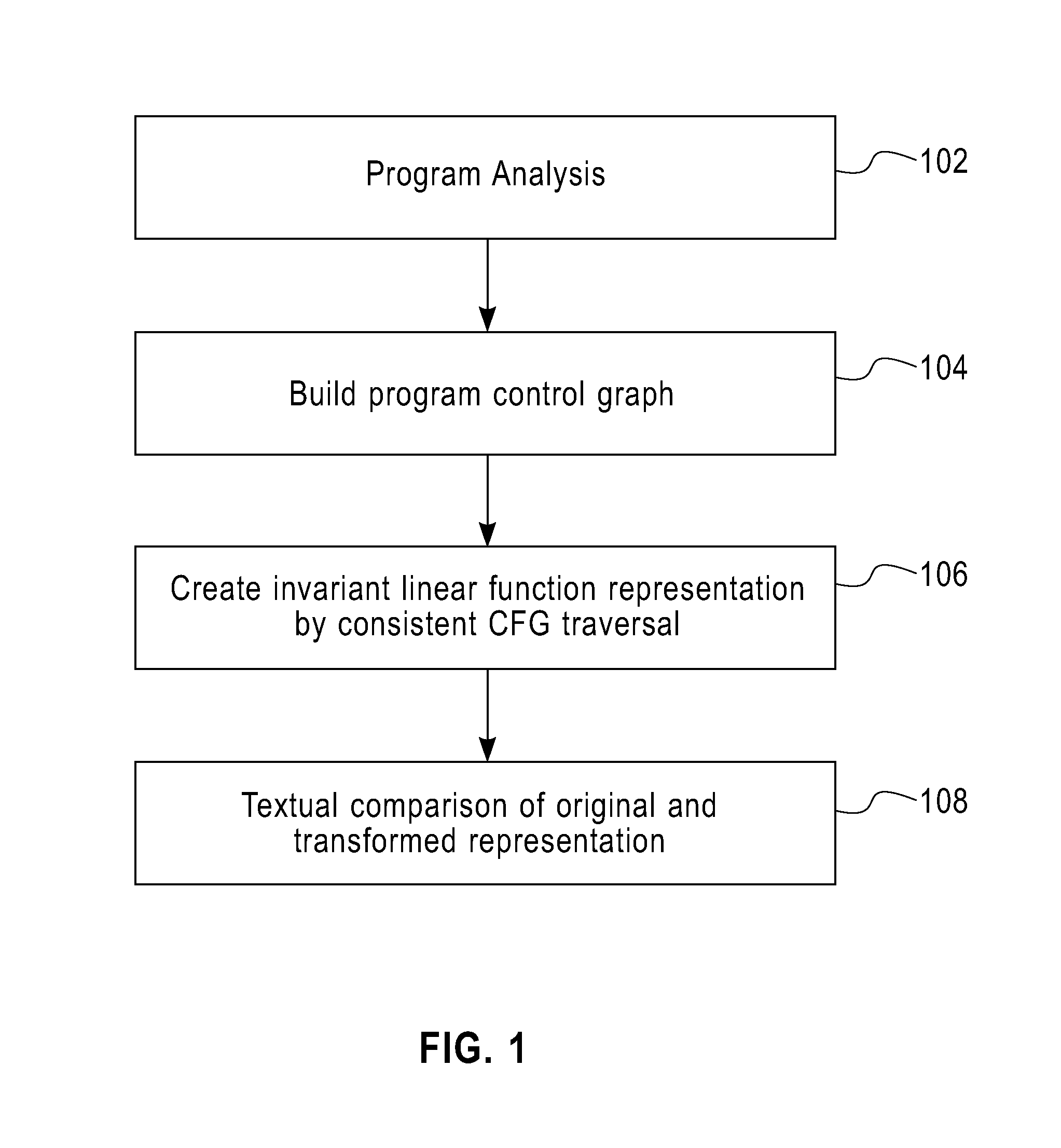
Method for validation of binary code transformations
A method of validating binary code transformation in one aspect includes analyzing original program and transform program. Control flow graphs are generated for both programs. The two graphs are traversed to create respective linear invariant representations. The linear representations are compared to identify incorrect transformations.
Owner:IBM CORP
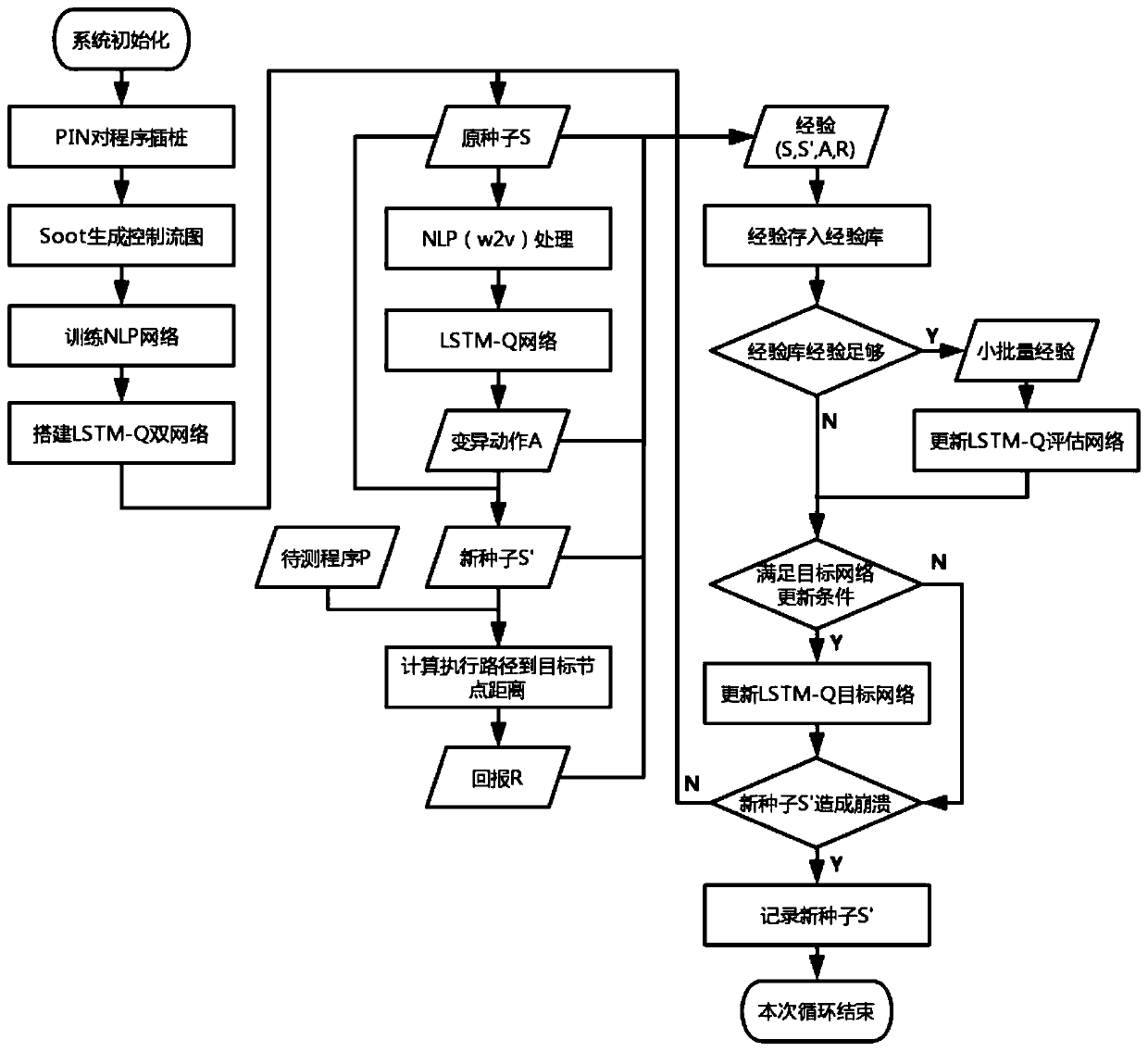
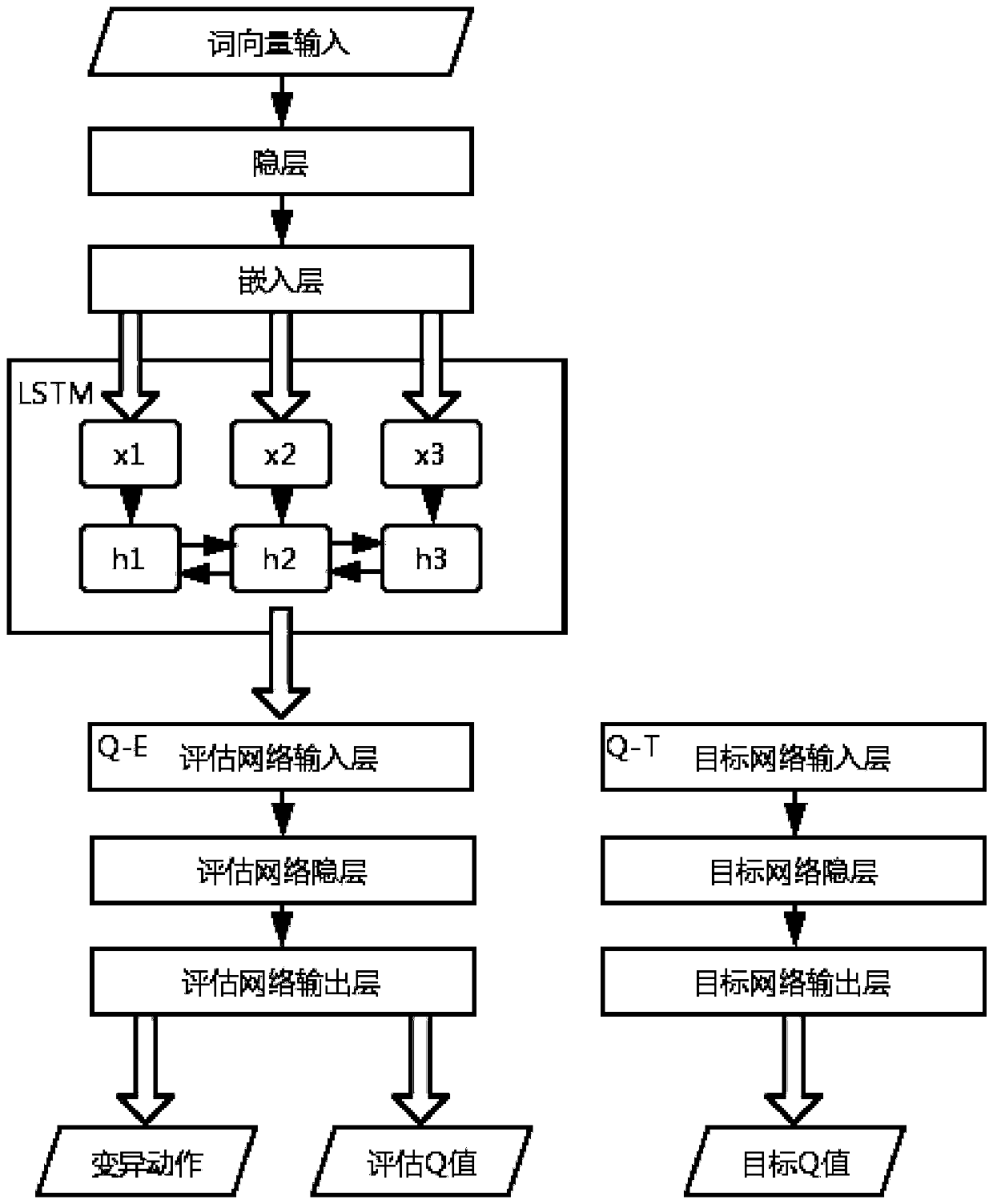
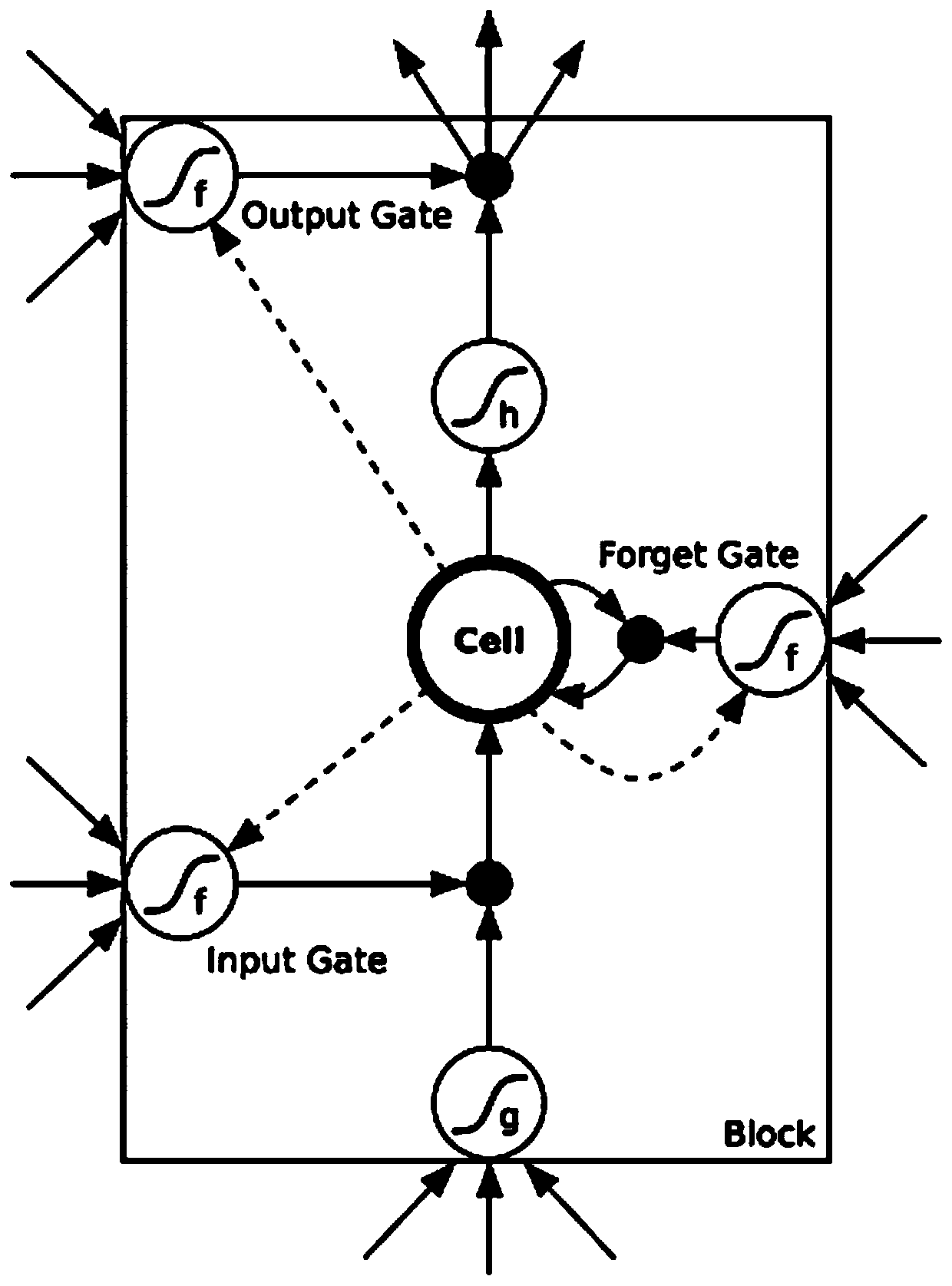
Vulnerability detection method based on deep reinforcement learning and program path instrumentation
ActiveCN110008710AGood effectGood orientationPlatform integrity maintainanceNeural architecturesNODALCode coverage
The invention discloses a vulnerability detection method combining deep reinforcement learning and a program path instrumentation technology. The method includes: obtaining a path corresponding to input from a control flow diagram of a to-be-tested program in an instrumentation mode; calculating and obtaining a reward value according to the path and a target node in the control flow graph, using the reward value to train a neural network of deep reinforcement learning so as to select a variation action; and performing variation on the input of the to-be-tested program according to the variation action to obtain an updated input and an updated path thereof, calculating an updated reward value, training the neural network again and performing input variation processing, and performing circulating until the to-be-tested program is collapsed to obtain a corresponding input vulnerability. According to the method, the accuracy is higher, the input corresponding to the path where the vulnerability is located can be obtained more efficiently, and compared with a traditional fuzzy test, the method is higher in detection speed and has a certain code coverage amount.
Owner:SHANGHAI JIAO TONG UNIV +1
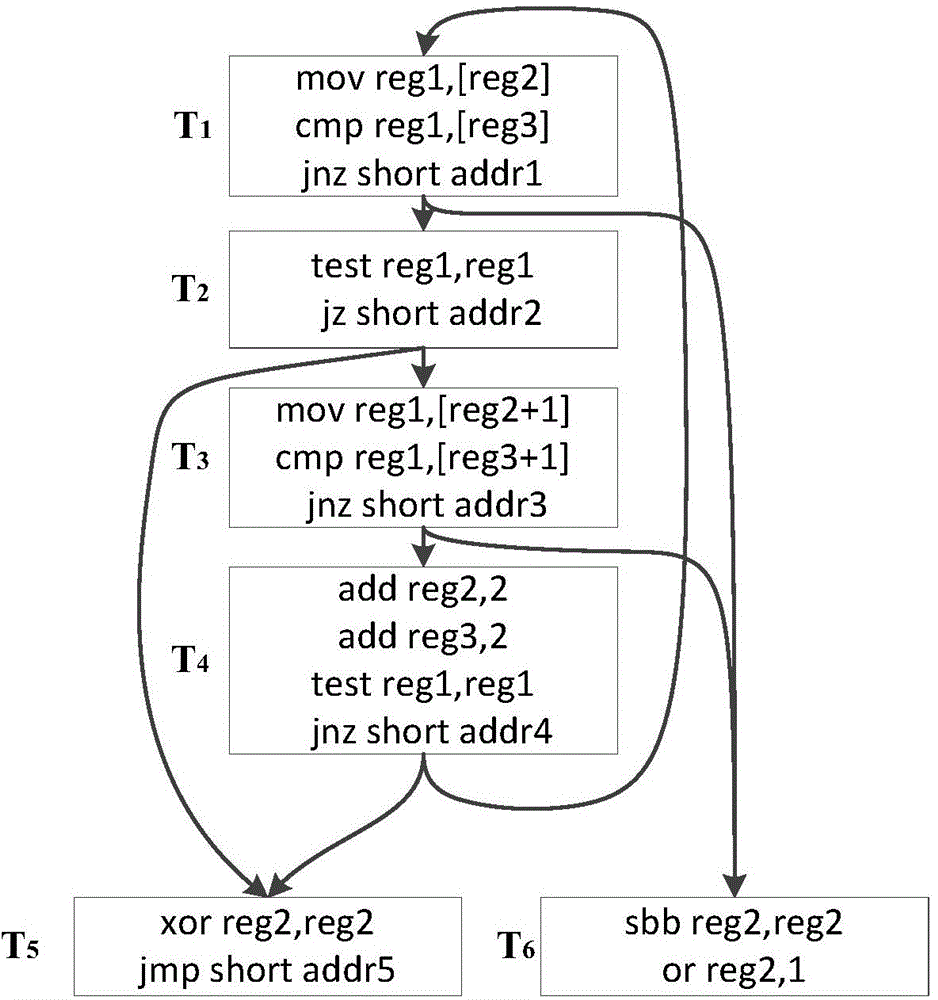
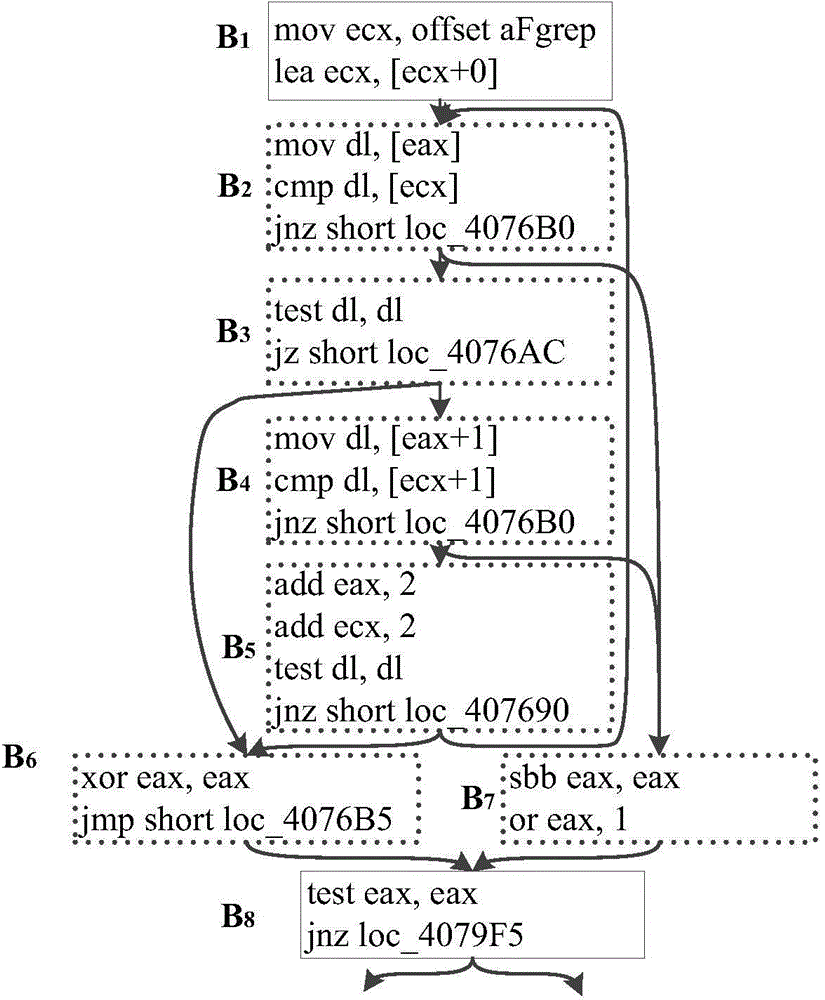
Intrinsic function recognition method based on sub-graph isomorphism matching algorithm in decompilation
InactiveCN104915211ARealize automatic identificationEfficient identificationSpecific program execution arrangementsTheoretical computer scienceInline expansion
The invention discloses an intrinsic function recognition method based on a sub-graph isomorphism matching algorithm in decompilation, and belongs to the technical field of decompilation. According to the method, an intrinsic function template library is established, sub-graph isomorphism matching is conducted on intrinsic function templates and target assembling files generated through decompilation on the basis of a control flow diagram, and intrinsic functions which are subjected to compiler optimization and inline expansion in target programs of the target assembling files are positioned. According to the intrinsic function recognition method, inline intrinsic functions in the decomplation process can be recognized automatically, meanwhile, the templates and prototypes of the intrinsic functions are analyzed, the function names, returned values, returned value types and function parameters of the intrinsic functions are recovered, and thus the purpose of promoting the semantics of the inline intrinsic functions is achieved. More type information is provided for type analysis in decompilation through the promoted inline intrinsic functions, the complexity of data flow analysis and control flow analysis is lowered, the level of abstraction of intermediate codes is improved, and the readability of decompilation results is enhanced.
Owner:XI AN JIAOTONG UNIV
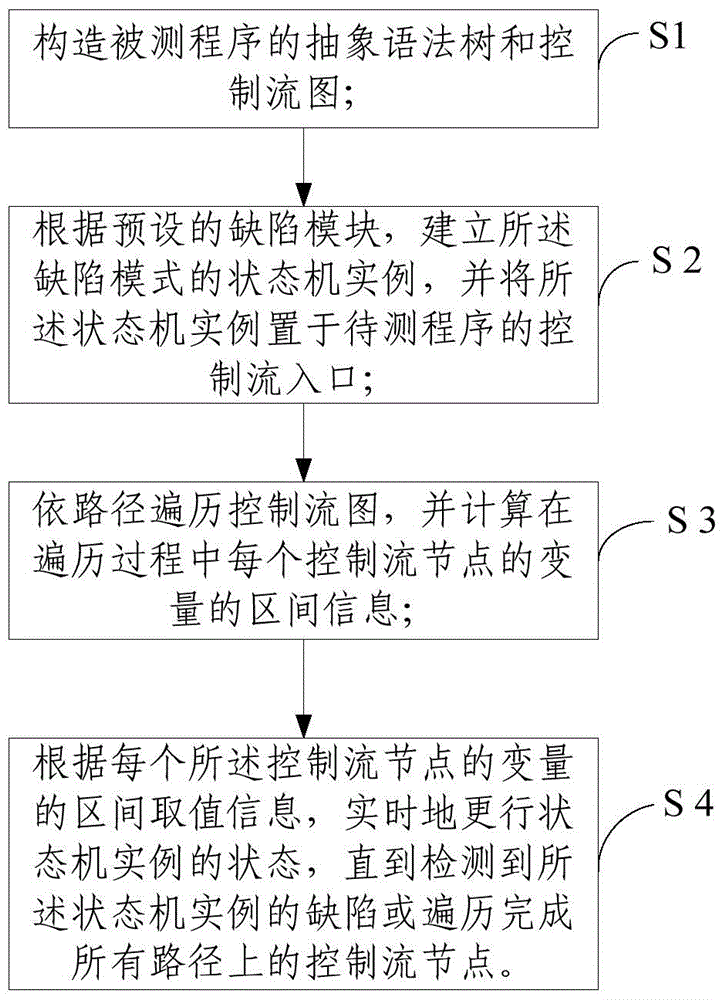
Static defect detecting method and system thereof
ActiveCN104536883AHigh precisionEliminate false positivesSoftware testing/debuggingControl flowTheoretical computer science
The invention relates to static defect detecting method and system thereof. The method comprises the steps of S1, creating an abstract syntax tree and a control flow diagram of a program to be detected; S2, building a state machine instance of a defect mode according to the preset defect mode, and placing the state machine instance to a control flow inlet of the program to be detected; S3, traversing the control flow diagram according to the path, and calculating the block information of variable of each control flow joint during the traversing process; S4, updating the state of the state machine instance on real time according to the block value taking information of the variable of each control flow node until detecting the defect of the state machine instance or traversing the control flow nodes on all paths. The method is on the basis of symbolic block analyzing technology, and the infeasible path in the program can be comprehensively determined by the conflict variable value taking determining and conditional constraint verification method, so as to improve the defect detecting accuracy.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Android application vulnerability detection method and system based on function control flow
ActiveCN105677574ASolve stressSolve the speed problemSoftware testing/debuggingPlatform integrity maintainanceData streamDynamic testing
The invention discloses an android application vulnerability detection method and system based on function control flow. The method includes the steps that on the basis of an existing static analysis method, an existing dynamic analysis method and a dynamic-static combination method, a function control flow diagram is obtained through once code analysis operation; an accurate dynamic analysis testing case is made according to the function control flow diagram, and dynamic testing is automatically conducted. In this way, the defect of high loads, caused when running of data flow is simulated multiple times in an existing analysis method, of a system is overcome. According to the android application vulnerability detection method and system, the testing cast is generated through the function control flow diagram, a testing system framework suitable for the method is provided, the defect that an existing analysis technology is low in analysis speed is overcome accordingly, and testing efficiency is improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method and apparatus for obtaining profile data for use in optimizing computer programming code
InactiveUS7386838B2Reduce scopeEasy constructionSoftware engineeringSpecific program execution arrangementsComputer programmingCollections data
Program execution profile data is collected by direct measurement of some code paths, and by inferring data for unmeasured paths. The data collection process may cause errors, which are propagated by the inferencing process. The profile data thus constructed is further enhanced by detecting certain data mismatches, and adjusting inferred data to reduce the scope of errors propagated during the inferencing process. Preferably, a control flow graph of the program being measured is constructed. Mismatches in the total weights of input arcs versus output arcs are detected. For certain specific types of mismatches, it can be known or guessed which count is incorrect, and this count is accordingly corrected. Correction of arc counts proceeds recursively until it is no longer possible to correct mismatches. Additionally, certain other conditions are adjusted as presumed inaccuracies.
Owner:IBM CORP
Unit test method which is automatically generated based on a path coverage test case
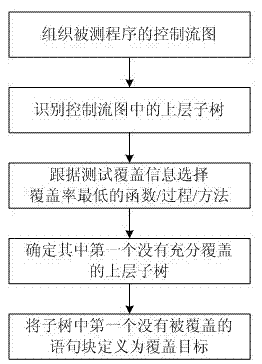
ActiveCN108710575AImprove test efficiencyEasy to completeSoftware testing/debuggingControl flowLexical analysis
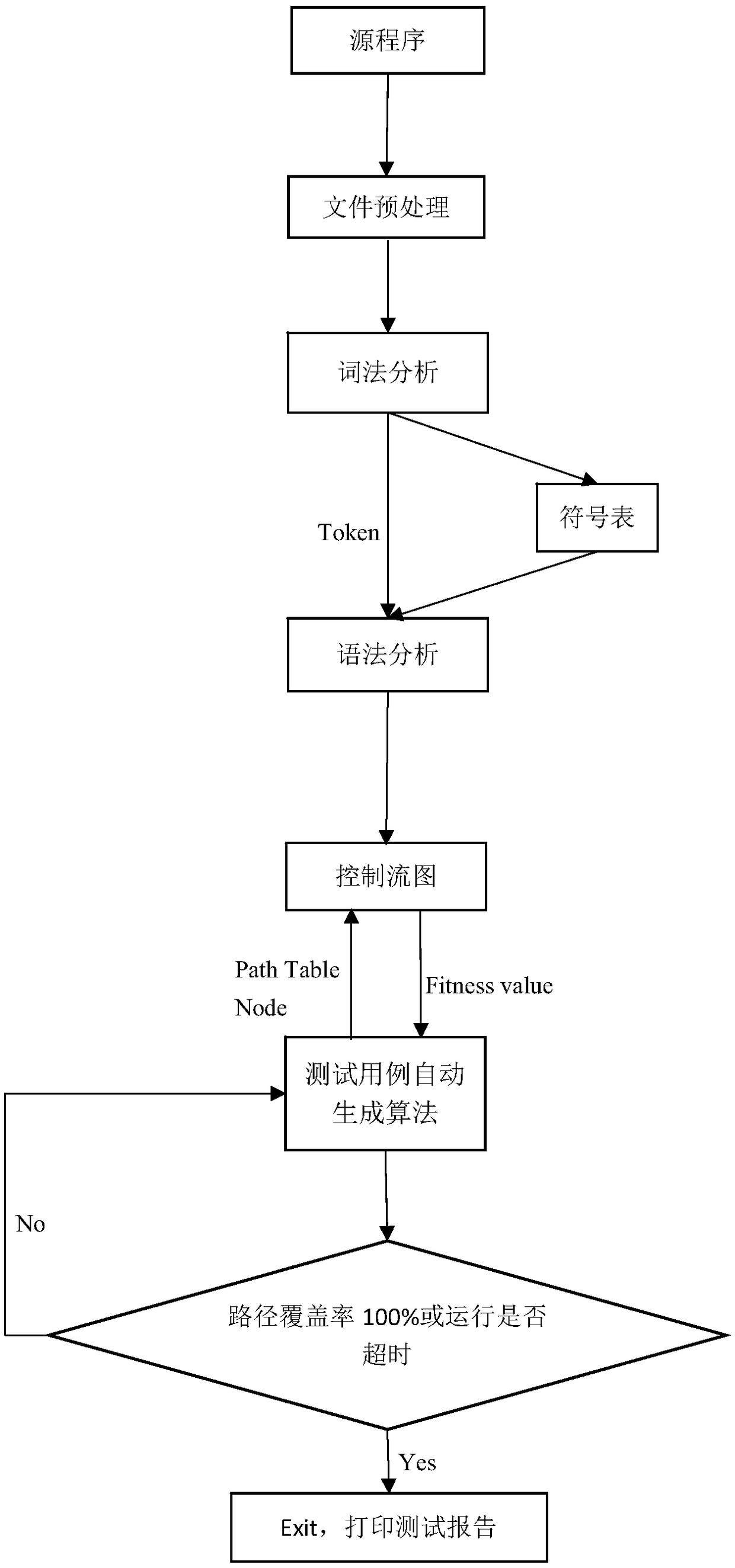
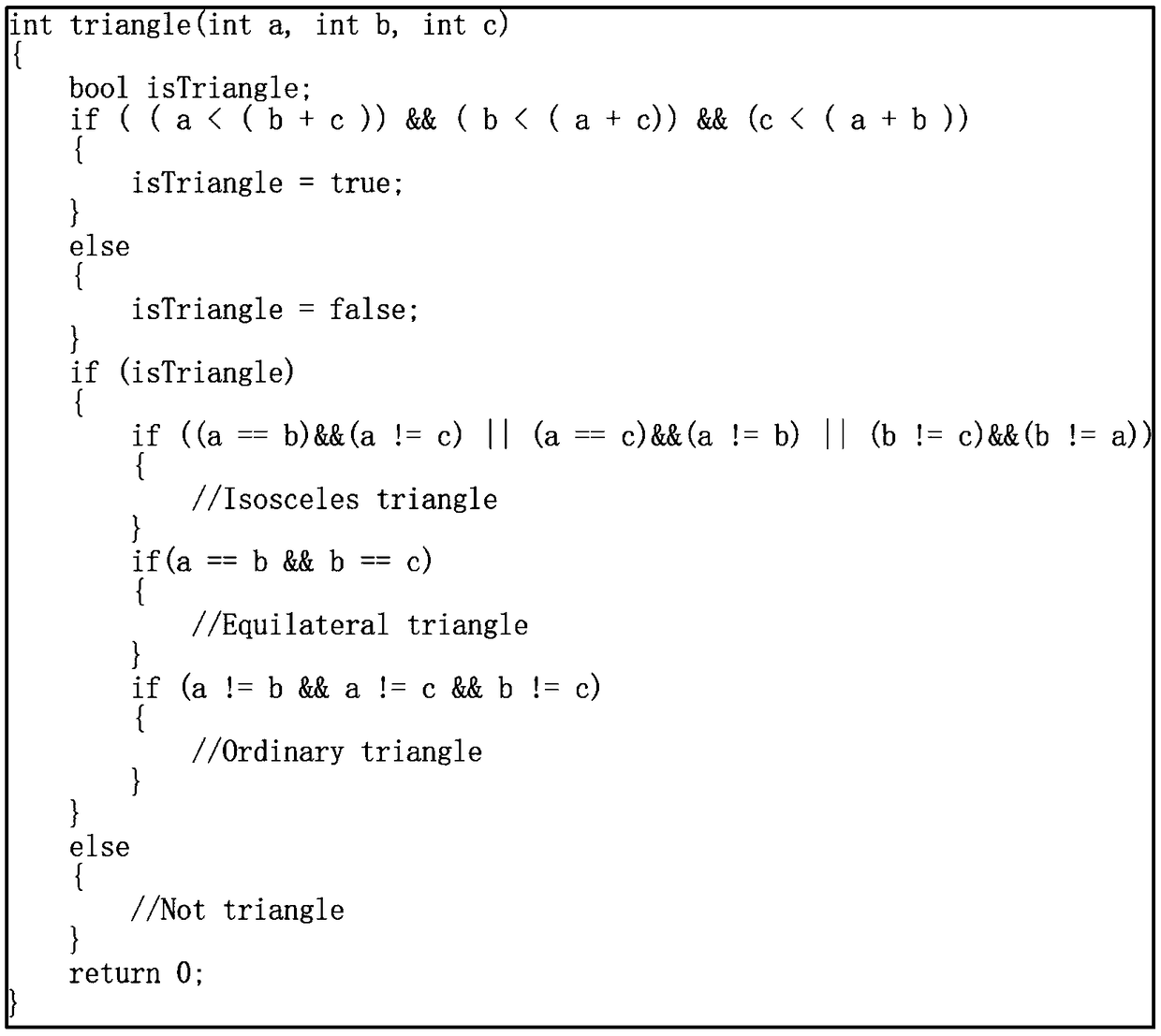
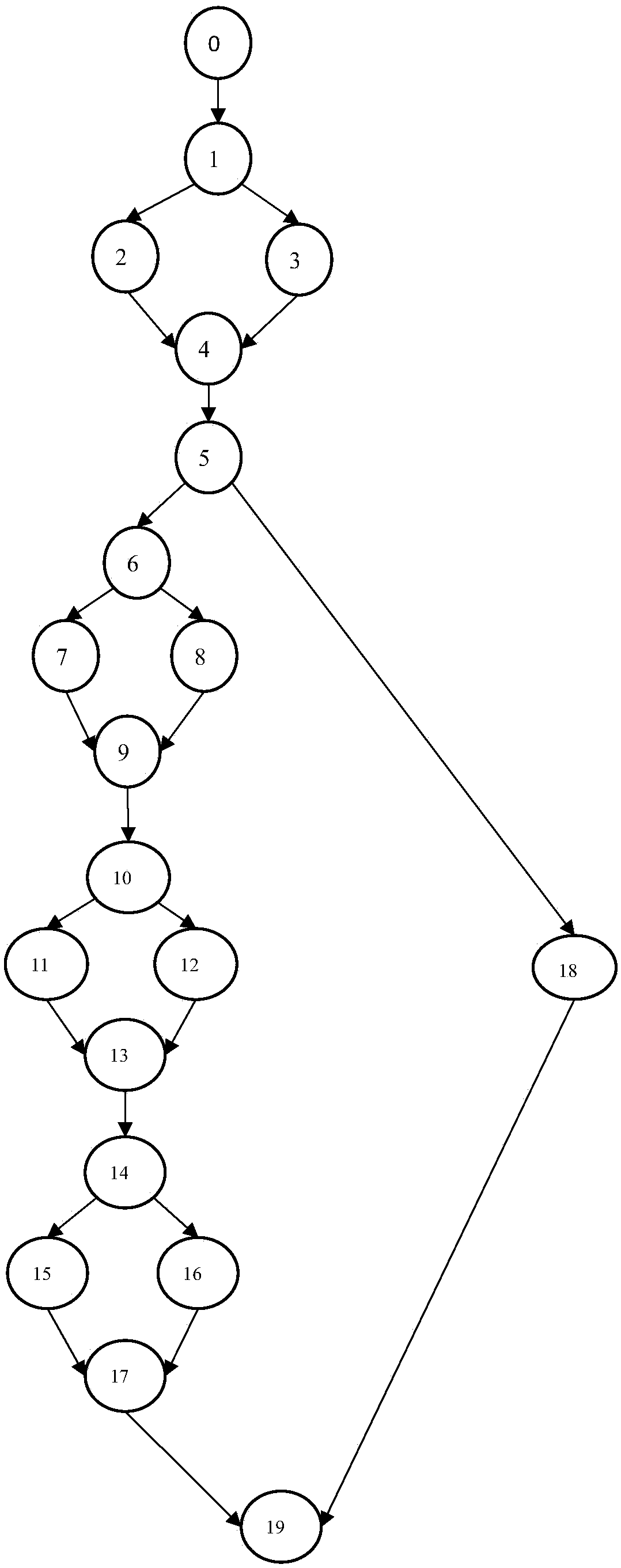
The invention provides a unit test method which is automatically generated based on a path coverage test case. Firstly, a lexical analysis and a syntax analysis are carried out on a code of a programto be tested, and then a control flow diagram of the program is obtained. After obtaining the control flow graph, the node table is generated according to the known number of nodes. Based on the automatically generated test cases, the execution of executable codes in the nodes is driven in the generated control flow diagram, at the same time, according to the execution result of executable codes,the fitness value is calculated and obtained, and the child nodes are selected to continue to repeat the process until the termination node in the graph is found, and finally, the path marker and thefitness value corresponding to the path marker are generated. Then the automatic test case generation algorithm is run, which automatically generates test cases according to the fitness value returneduntil the path is completely covered or exits when the set run time expires. The invention is suitable for software testing, and can be applied to actual software testing working environment throughexperimental verification.
Owner:SOUTH CHINA UNIV OF TECH +1
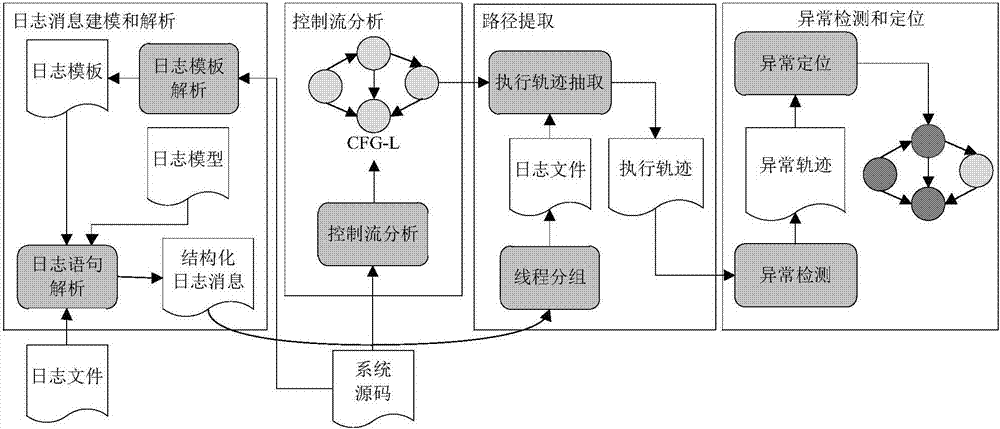
Log-based complex software system abnormal behavior detection method
ActiveCN107391353AAccurately obtain reachable relationsOperational logical relationship is clearHardware monitoringSoftware testing/debuggingCluster algorithmSoftware system
The invention discloses a log-based complex software system abnormal behavior detection method. The problems that an existing method can only analyze log sentences when the system is abnormal, and tracking cannot be performed according to abnormal log sentences are solved. The method comprises the steps of collecting a system source code, converting the source code into a control flow diagram adopting a function as a unit, extracting a log template, and obtaining the reachable relation among log printing languages; adopting the operation logic relation among the log sentences for log message analysis; on the basis of structured log messages and the source code control flow diagram, performing log execution track extraction and processing filtering, and achieving relatively accurate and complete abnormal detection and positioning. The log template is obtained by analyzing the source code, an experiment result is more accurate, and the defect of instability of a clustering algorithm is overcome. Log tracks are extracted, on the basis of abnormal sentence tracking, root causes resulting in system abnormity can be obtained conveniently and then the abnormal problem is solved. The method is used for operating and maintaining a distributed complex software system.
Owner:河钢数字技术股份有限公司
Application permission divulgence detection method and system based on reverse symbolic execution
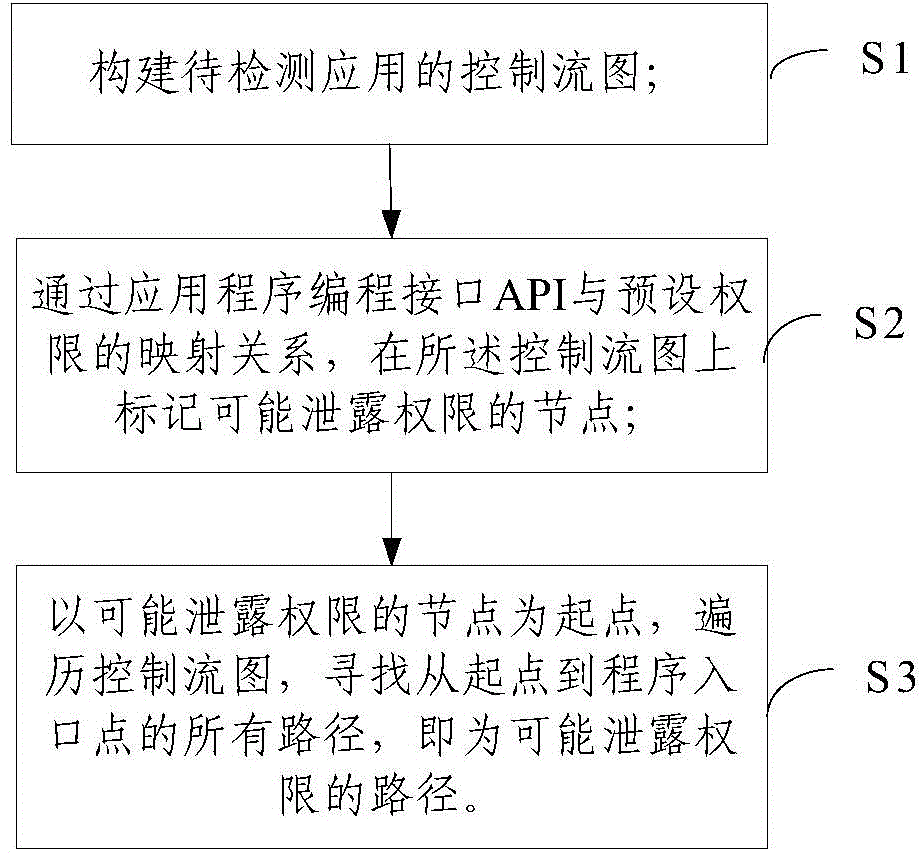
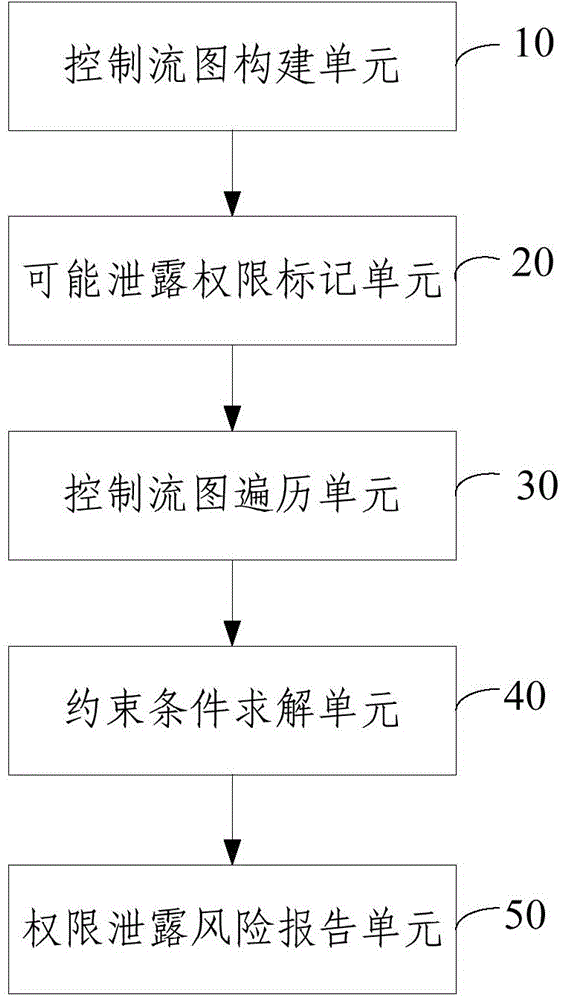
ActiveCN104462984AAvoid overheadImprove detection efficiencyPlatform integrity maintainanceControl flowEntry point
The invention relates to an application permission divulgence detection method and system based on reverse symbolic execution. The method comprises the steps of S1, establishing a control flow diagram of an application to be detected; S2, according to the mapping relation between an API and a preset permission, marking a node possibly divulging the permission on the control flow diagram; S3, with the node possibly divulging the permission as a starting point, searching for all paths between the starting point and a program entry point by traversing the control flow diagram through reverse symbolic execution, wherein all the paths between the starting point and the program entry point are paths possibly divulging the permission. By adopting the reverse symbolic execution mode, it is only needed to traverse all the possible paths between a calling point of the sensitive API and the program entry point, it is avoided that paths unrelated to permission divulgence are traversed, and therefore detection efficiency is improved.
Owner:BEIHANG UNIV
Function call path extracting method and device based on control flow diagram
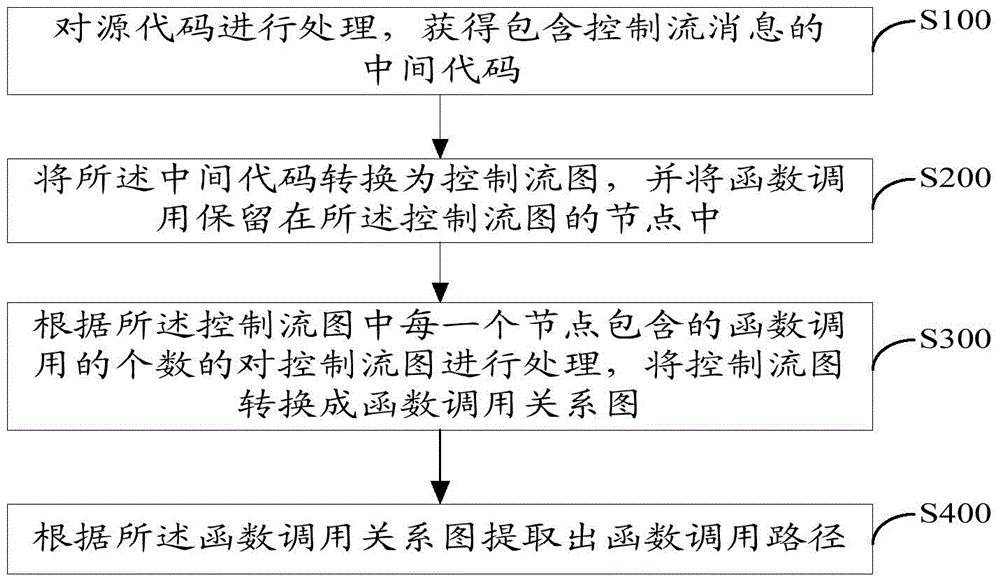
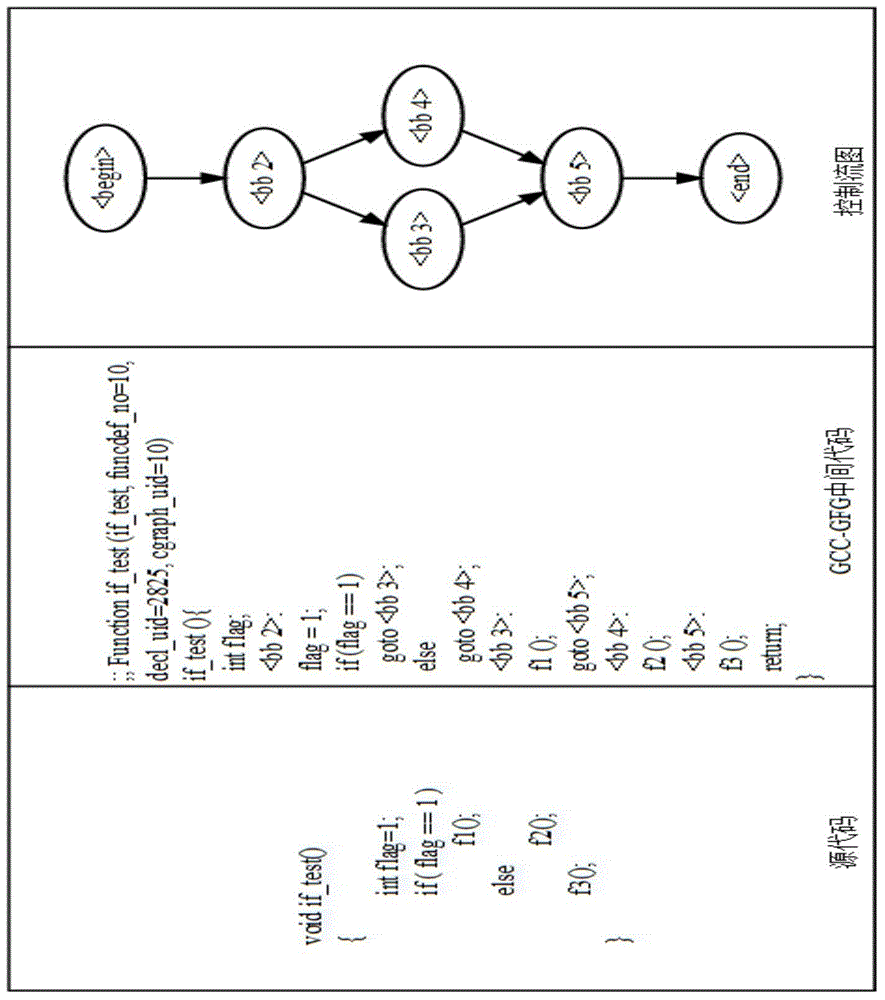
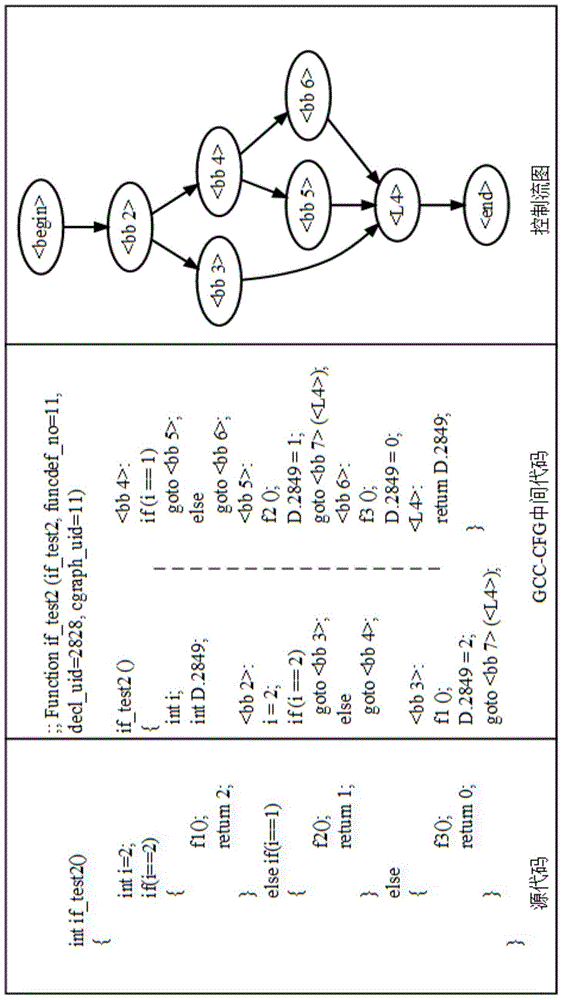
InactiveCN105138335ASimplify the analysis processSpecific program execution arrangementsControl flowSource code
Owner:牟永敏 +1
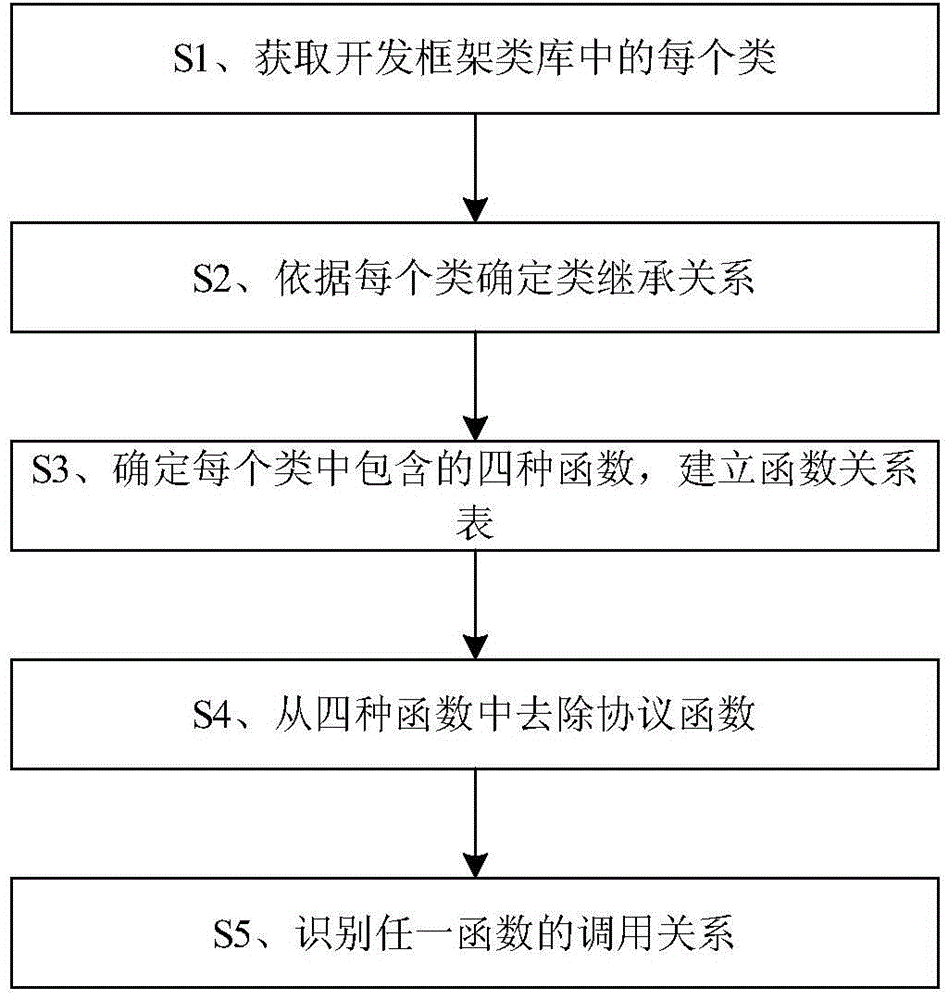
Identification method and device for function call relationships
ActiveCN105677311AAccurate analysis and judgmentSpecific program execution arrangementsSoftware engineeringControl flow diagram
The invention discloses an identification method and device for function call relationships. The method comprises following steps: S1, acquiring each category of a development framework class library; S2, determining class inheritance relations of each category; S3, determining four functions of each category based on inheritance relations and setting up a function relation table, wherein four functions are respectively a self-defining function, a protocol function, an embodiment function and a classification function; S4, removing the protocol function out of the four functions; and S5, identifying a call relation of any function. The identification method and device for function call relationships have following beneficial effects: by setting up and extracting an integral model of inheritance relations in a public category from an iOS development framework and corresponding relations between the public category and other categories of member functions, integral call relations of all functions in an iOS application can be calculated by static analysis; an application code control flow diagram and a function call path are generated so that privacy data analysis is more accurately determined.
Owner:卓望数码技术(深圳)有限公司
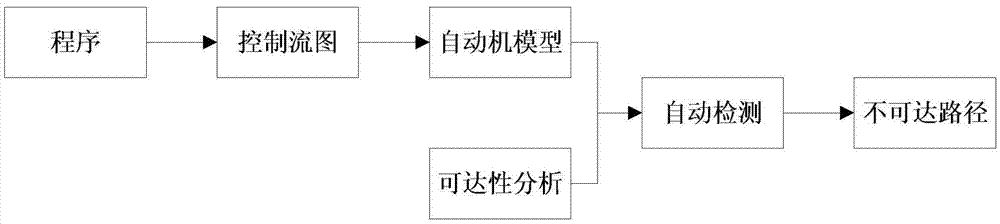
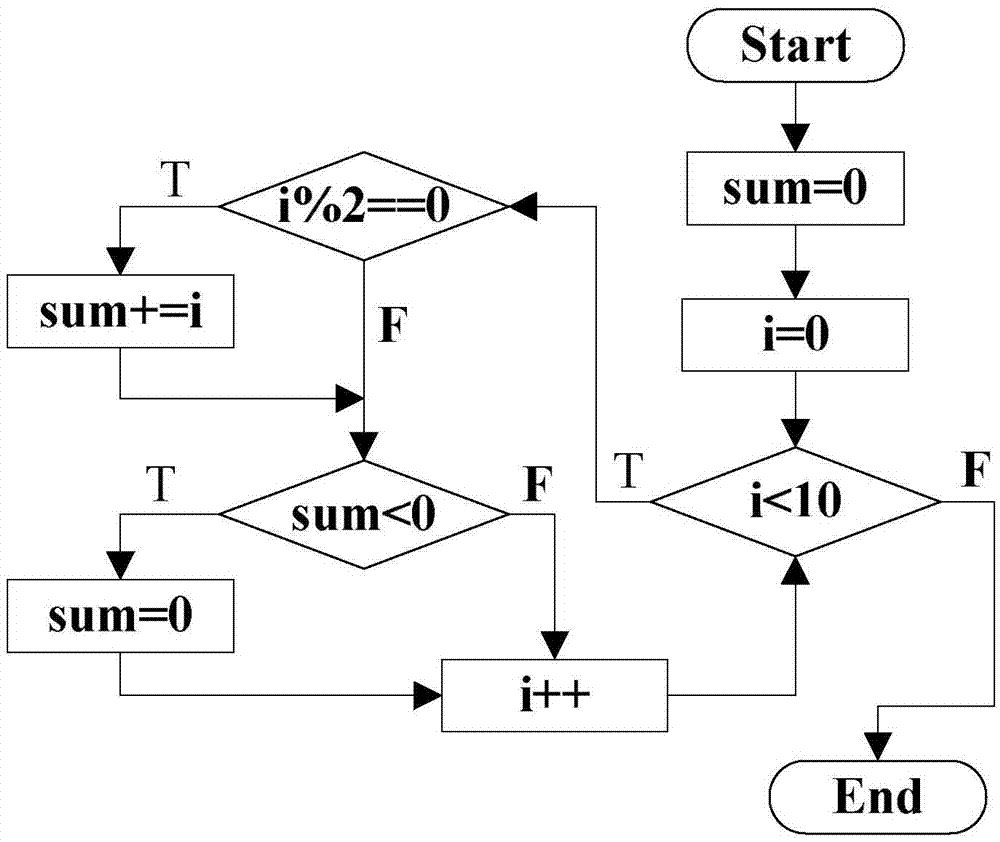
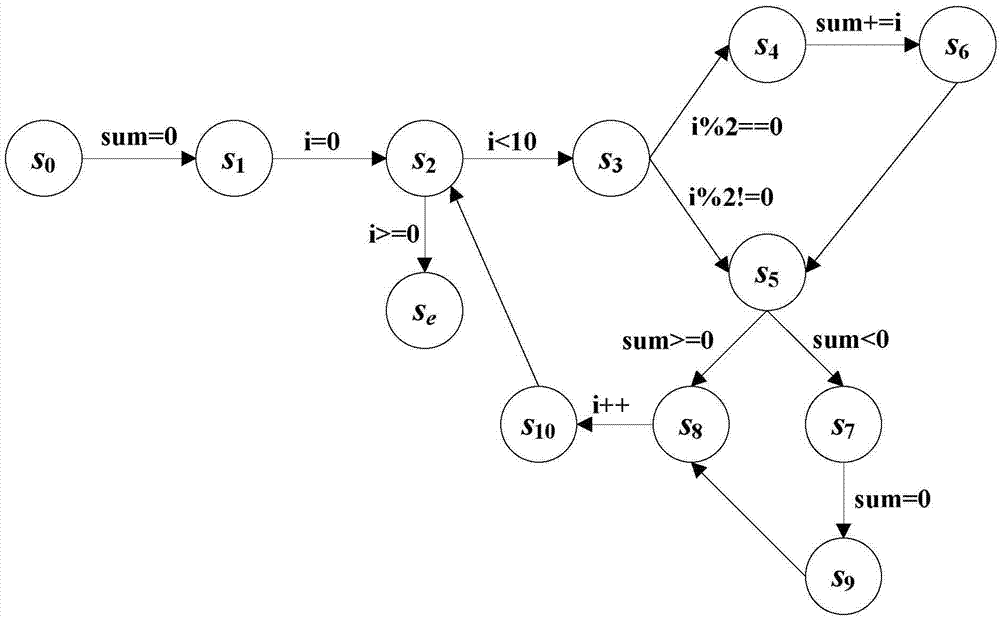
Automatic detection method for program unaccessible paths
InactiveCN105446881ASimple principleSimple processSoftware testing/debuggingReachabilityAccessibility
The present invention discloses an automatic detection method for program unaccessible paths. The method comprises the steps of: converting a to-be-detected computer program into a control flow diagram; and converting the control flow diagram into a program model, performing accessibility analysis to obtain unaccessible states, automatically detecting the unaccessible states to obtain an unaccessible state set, and then obtaining an unaccessible path set according to the unaccessible state set. The automatic detection method for the program unaccessible paths is based on a state searching technology being simple in theory, and effectively lowers the technology application and promotion difficult when being compared with the prior art usually based on complex mathematical technology; the detection method for the program unaccessible paths is complete and has high automatization degree; the problem of accessibility detection of the control flow diagram is solved; problems of difficulties and low efficiency of a static analysis technology in processing of complex programs are solved; and the problem that the static analysis technology has difficult in expressing compound data in processing a multi-branch procedure is solved.
Owner:FUJIAN UNIV OF TECH
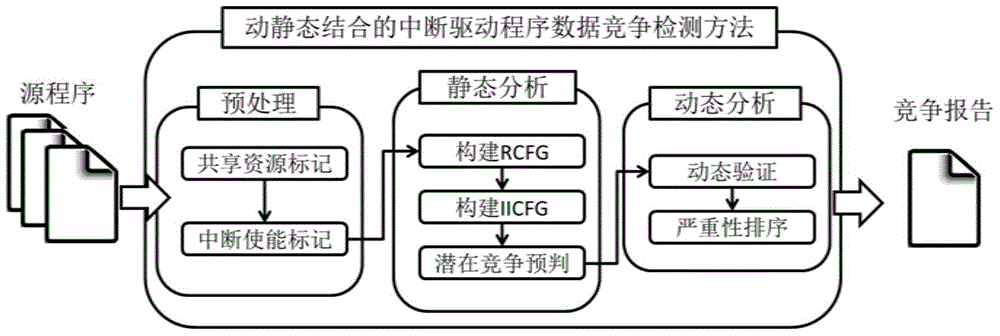
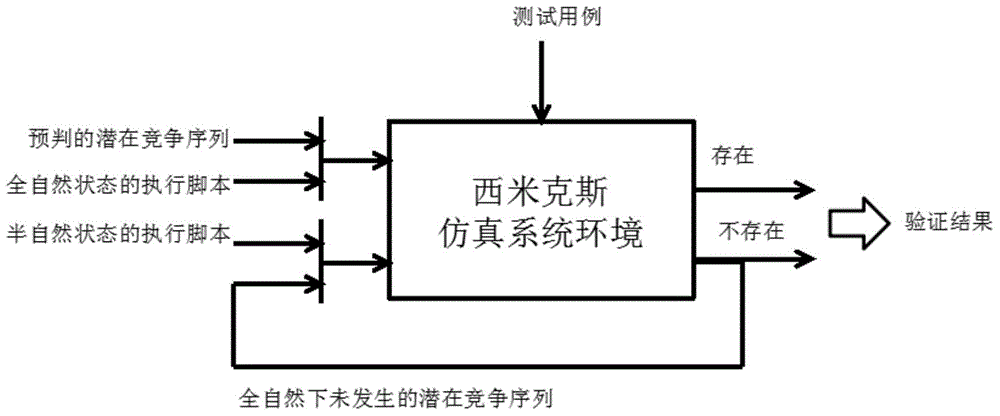
Dynamic and static combined interrupt drive program data race detection method
ActiveCN104090798AReal competitionEfficiently detect competitionProgram loading/initiatingData streamDependability
The invention relates to a dynamic and static combined interrupt drive program data race detection method. According to the method, through a detection technology of a shared source, a control flow diagram generation technology, a data flow analysis technology and a simulator operational control technology, static analysis is carried out on a source program with a static method so that a potential data race sequence can be obtained, dynamic execution is carried out on the result of static analysis to verify authenticity of potential races, sorting is carried out according to severity of the potential races, and a test result report is obtained. An implemented tool of the method is used for testing an interrupt drive program, the real competitive relation related to interruption can be effectively detected, a series of potential competitive relations are provided for guidance according to the severity, working efficiency of a tester can be greatly improved, data race detection of an interrupt drive is achieved, safety and stability of an embedded system are ensured, and the reliability guarantee can be provided for the key safety fields with the requirement for highly stable embedded programs such as the spaceflight field and the medical field.
Owner:NANJING UNIV
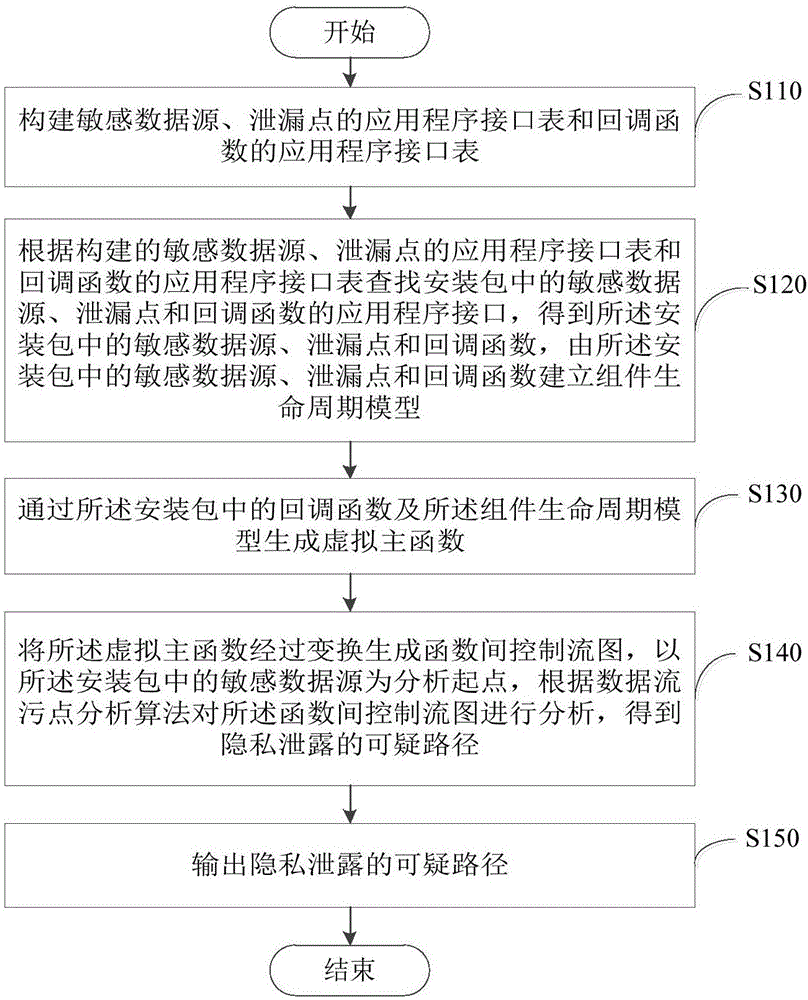
Method and system for privacy disclosure detection
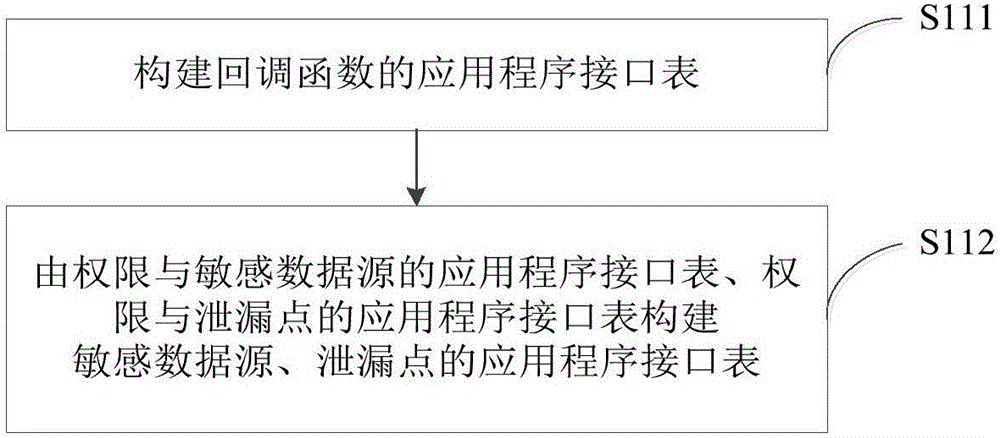
ActiveCN106778254AAvoid Privacy LeakageSoftware testing/debuggingPlatform integrity maintainanceData sourceApplication software
The embodiment of the invention provides a method and system for privacy disclosure detection. The method comprises the steps of searching a sensitive data source, a disclosure point and an application program interface of a callback function in an installation package according to a constructed sensitive data source, an application program interface table of disclosure points and an application program interface table of callback functions, and obtaining the sensitive data source, the disclosure point and the callback function in the installation package, and establishing an assembly life cycle model through the sensitive data source, the disclosure point and the callback function in the installation package; generating a virtual main function through the callback function in the installation package and the assembly life cycle model; causing the virtual main function to generate an inter-function control flow diagram through conversion, taking the sensitive data source in the installation package as an analysis starting point, analyzing the inter-function control flow diagram according to a data flow taint analysis algorithm, and obtaining a suspicious path of privacy disclosure; and outputting the suspicious path of privacy disclosure. Privacy disclosure behaviors in an application program assembly can be effectively found.
Owner:四川无声信息技术有限公司
Parallel symbolic execution method based on path cluster reductions
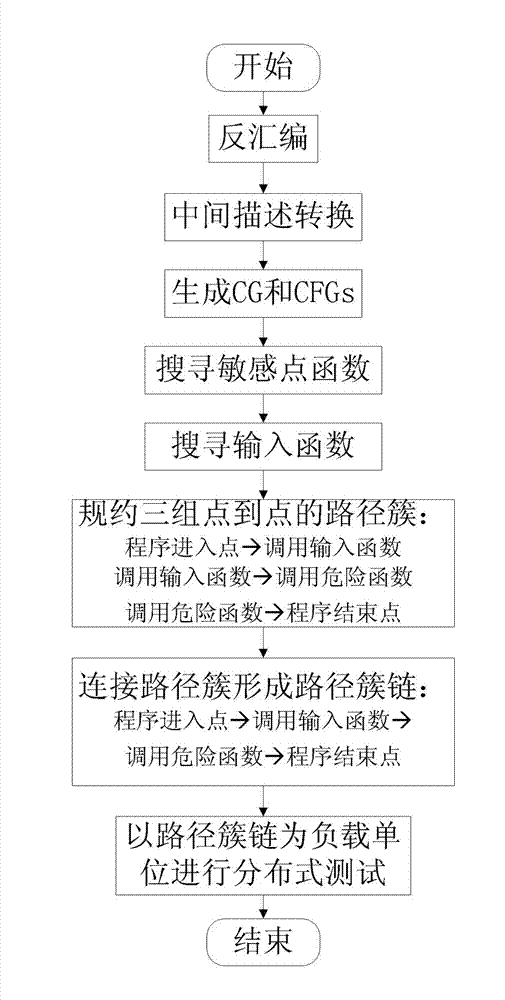
ActiveCN103049377AReduce time overheadImprove abilitiesSoftware testing/debuggingCall graphEntry point
The invention relates to a computer software safety testing method based on program symbolic execution path cluster partitions. The parallel symbolic execution method based on path cluster reductions includes the steps of: (1) disassembling an tested executable program, (2) obtaining assembly codes of the tested executable program and transferring into uniform intermediate assembly language forms, (3) generating a function call graph and a control flow diagram of the tested executable program according to intermediate assembly language forms, (4) finding a dangerous function and an input function according to a static analysis of the function call graph; (5) respectively creating a path between a program entry point and a call input function, between the call input function and a call dangerous function, and between the call dangerous function and a program end point and reducing into path cluster, (6) subjecting the obtained paths to point-to-point connection to form an integral path cluster chain assembly from program entry point to program end point, and (7) generating corresponding test cases to perform actual program safety tests with an integral path cluster chain from program entry point to program end point formed in step (6) serving as a load unit.
Owner:CHINA INFORMATION TECH SECURITY EVALUATION CENT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com