Static analysis method and static analysis device for Android application program
A static analysis and application technology, applied in computer security devices, instruments, electronic digital data processing, etc., can solve the problem of inability to effectively detect and confirm mobile phone virus attack behaviors, so as to reduce the risk of misjudgment and reduce misjudgment the effect of reducing the probability of misjudgment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
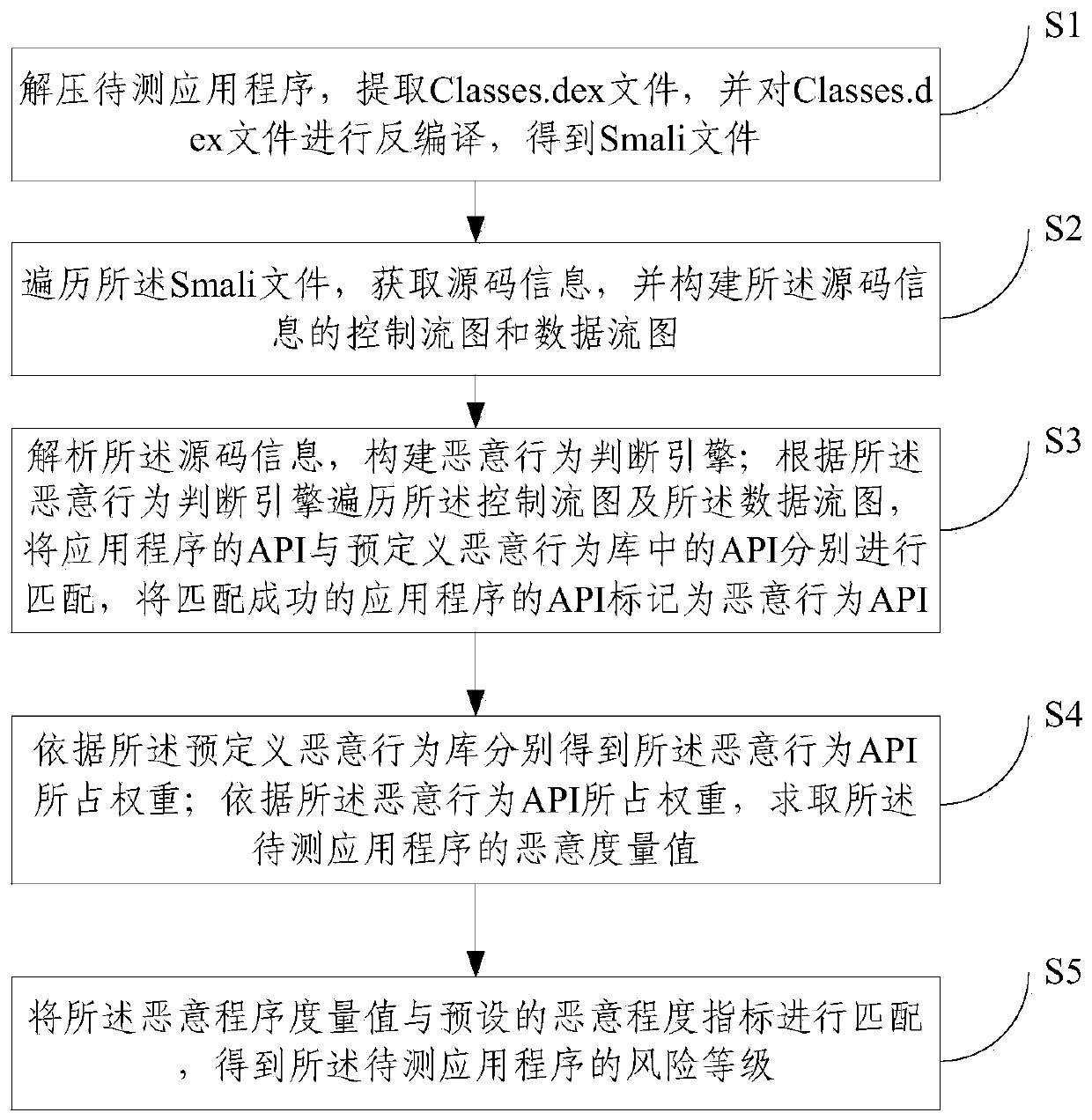
[0044] S1. Decompress the application program to be tested, extract the Classes.dex file, and decompile the Classes.dex file to obtain the Smali file;
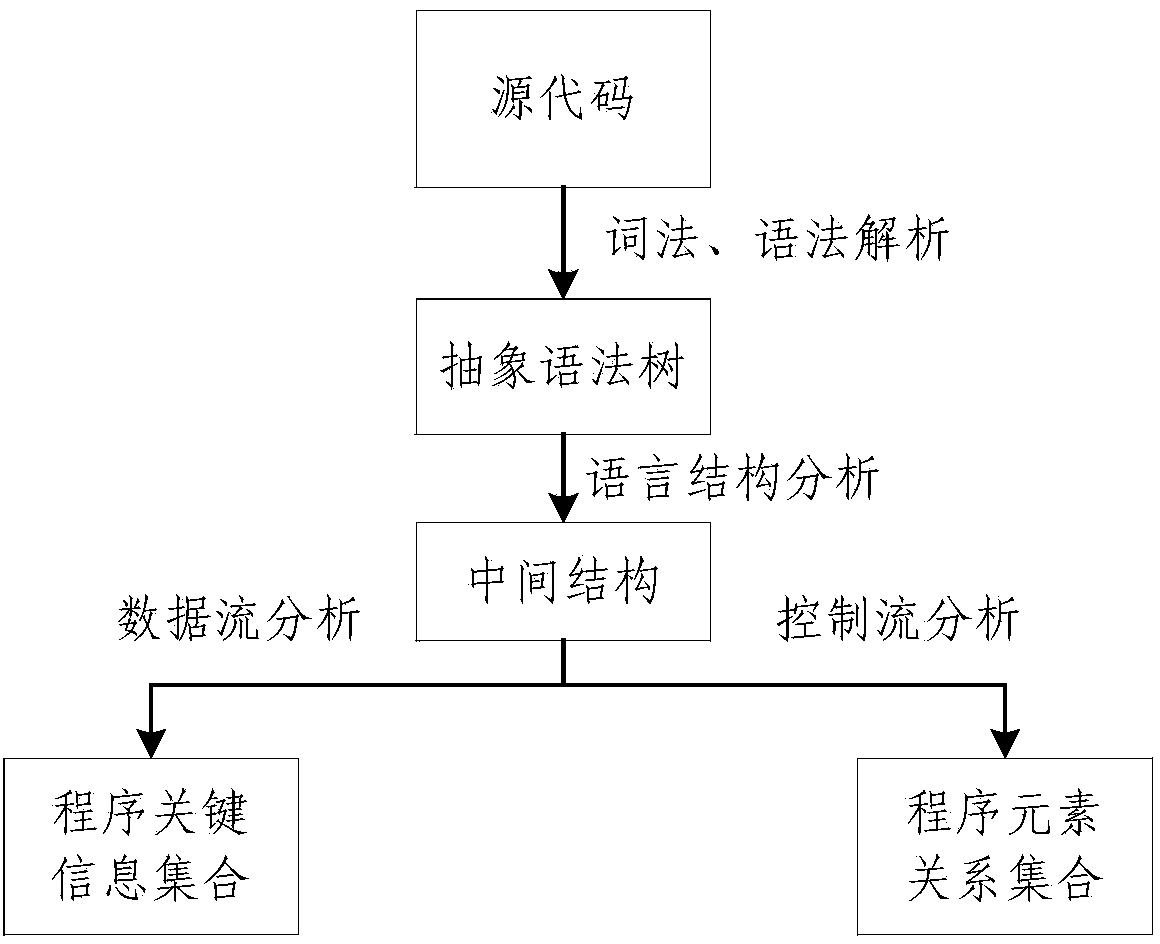
[0045] S2. Traversing the Smali file, obtaining source code information, and constructing a control flow graph and a data flow graph of the source code information;
[0046] S3. Analyzing the source code information, constructing a malicious behavior judgment engine; traversing the control flow graph and the data flow graph according to the user behavior judgment engine, and comparing the API of the application program with the predefined malicious behavior library (as shown in Table 2) shown) to match the APIs respectively, and mark the APIs of the successfully matched applications as malicious behavior APIs;
[0047] S4. Obtain the weights of the malicious behavior APIs according to the predefined malicious behavior library; obtain the malicious measurement value of the application program under test according to the weights o...
Embodiment 2
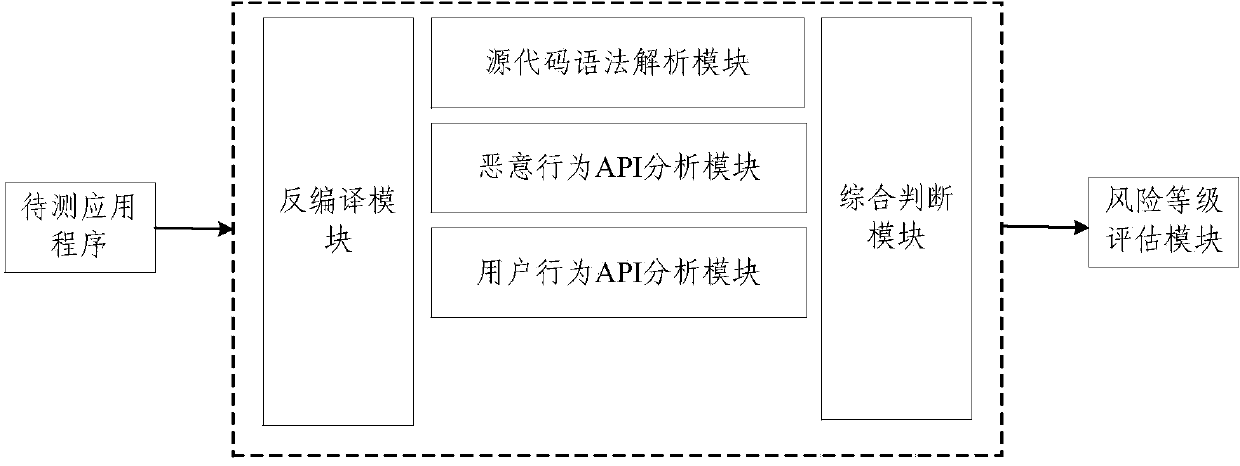
[0071] The decompilation module is used to decompress the application program under test, extract the Classes.dex file, and decompile the Classes.dex file to obtain the Smali file;
[0072] A source code syntax parsing module for traversing the Smali file, obtaining source code information, and constructing a control flow graph and a data flow graph of the source code information;
[0073] The malicious behavior API analysis module is used to analyze the source code information and build a malicious behavior judgment engine; according to the user behavior judgment engine, it traverses the control flow graph and the data flow graph, and compares the API of the application program with the predefined malicious behavior The APIs in the library are matched separately, and the APIs of the successfully matched applications are marked as malicious behavior APIs;
[0074] The comprehensive judgment module obtains the weights of the malicious behavior APIs respectively according to the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com