Patents
Literature
597 results about "Heuristic" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A heuristic technique (/hjʊəˈrɪstɪk/; Ancient Greek: εὑρίσκω, "find" or "discover"), often called simply a heuristic, is any approach to problem solving or self-discovery that employs a practical method that is not guaranteed to be optimal, perfect or rational, but instead sufficient for reaching an immediate goal. Where finding an optimal solution is impossible or impractical, heuristic methods can be used to speed up the process of finding a satisfactory solution. Heuristics can be mental shortcuts that ease the cognitive load of making a decision. Examples that employ heuristics include using trial and error, a rule of thumb, an educated guess, an intuitive judgment, a guesstimate, profiling, or common sense.
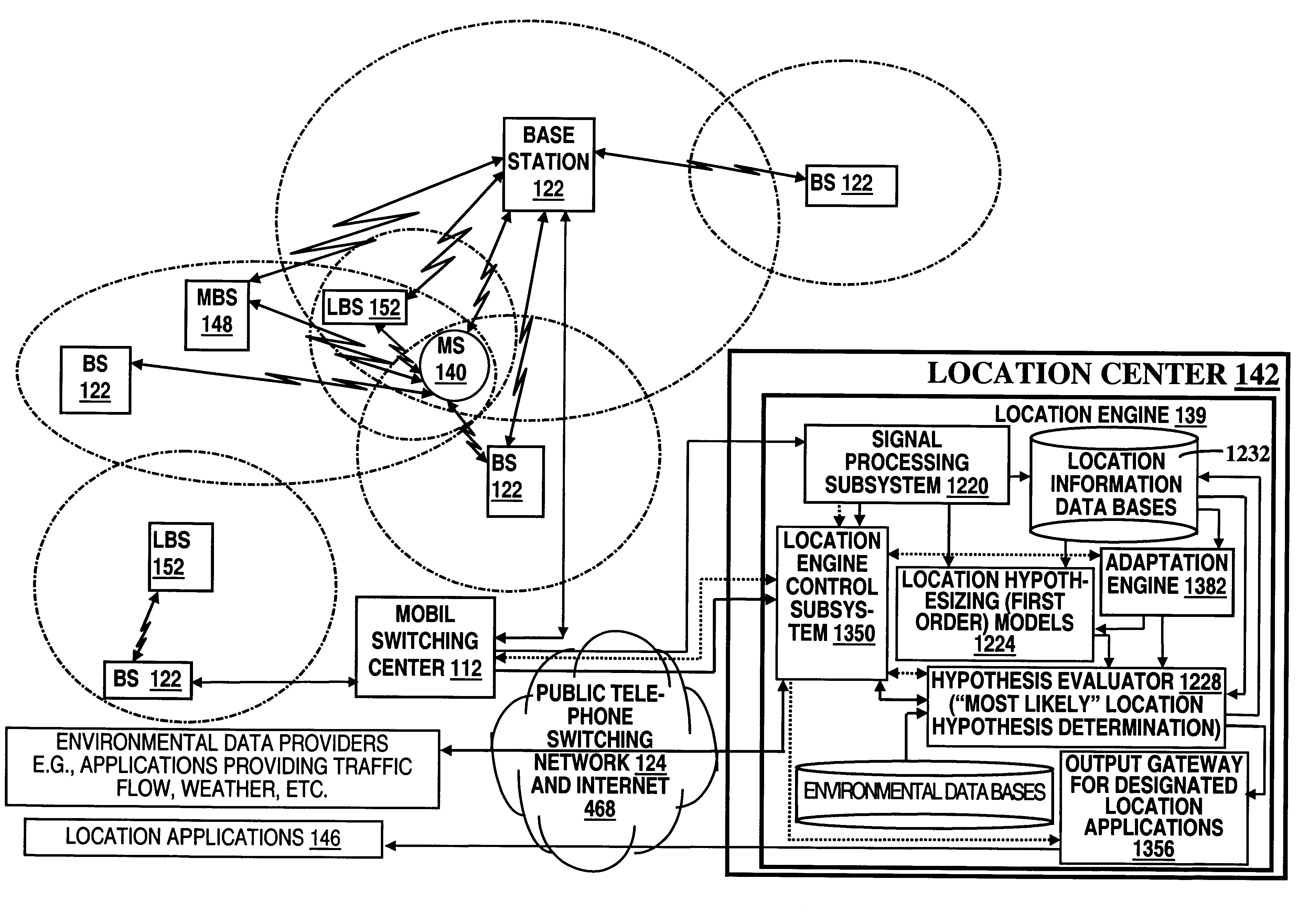
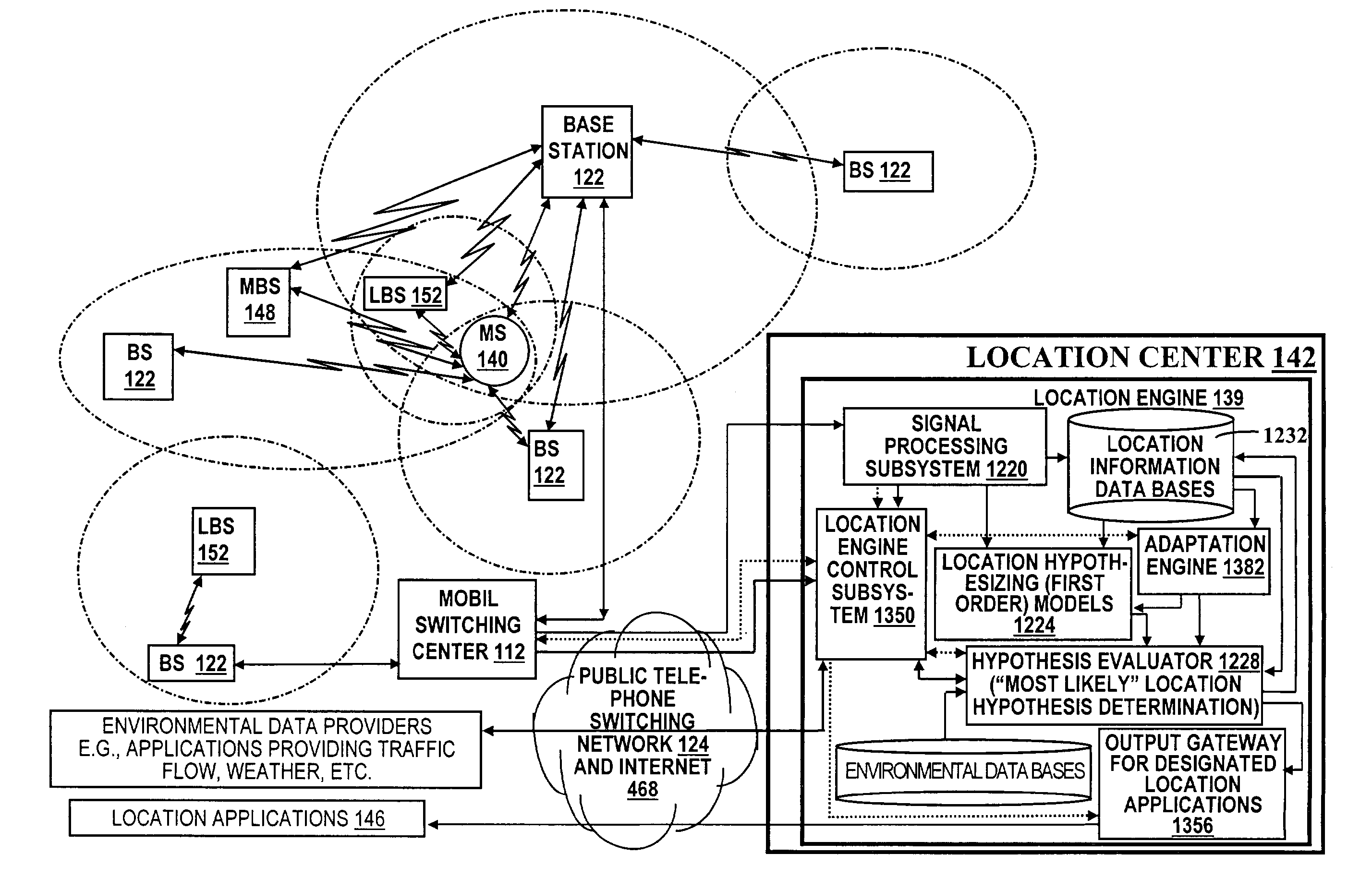
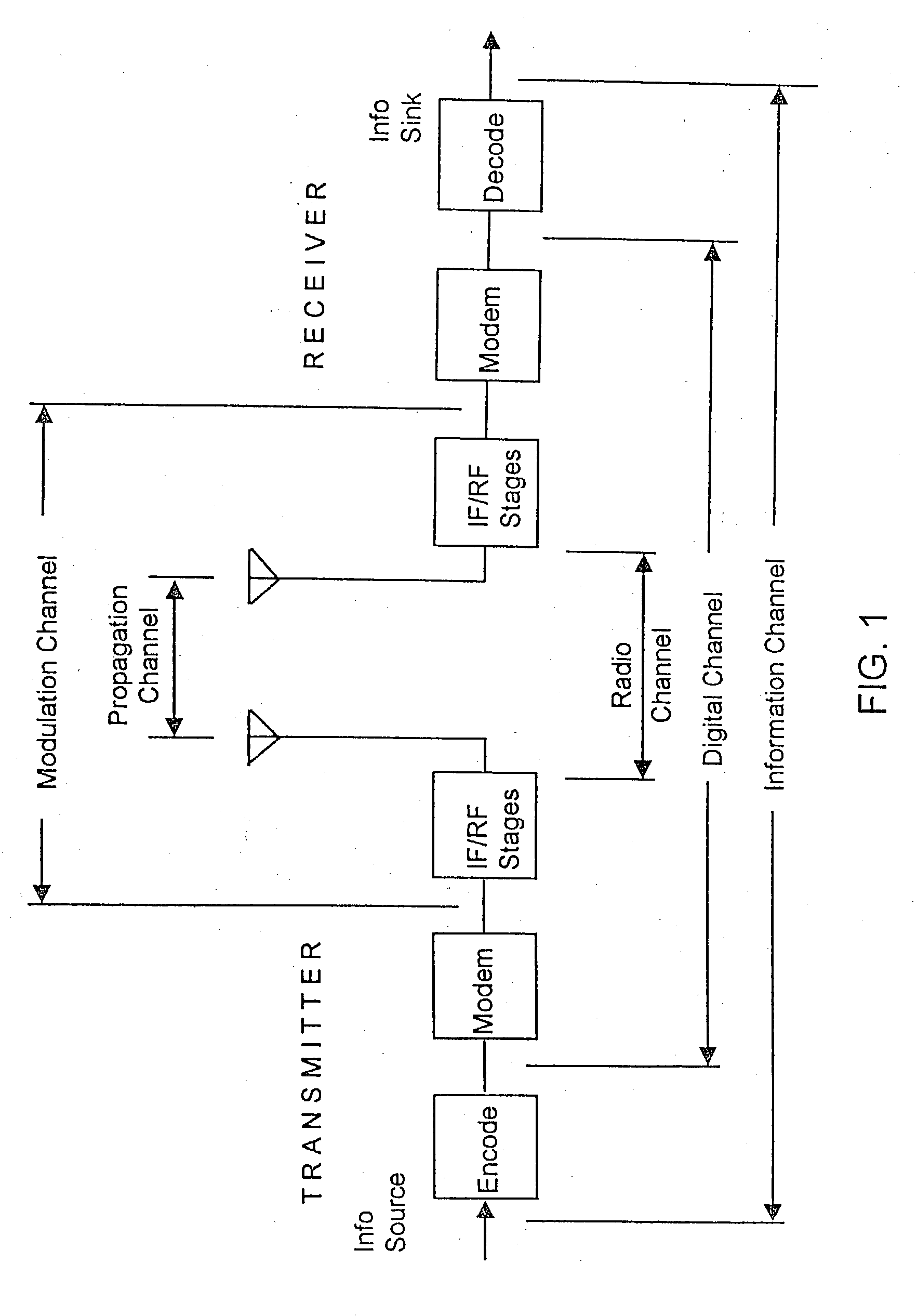
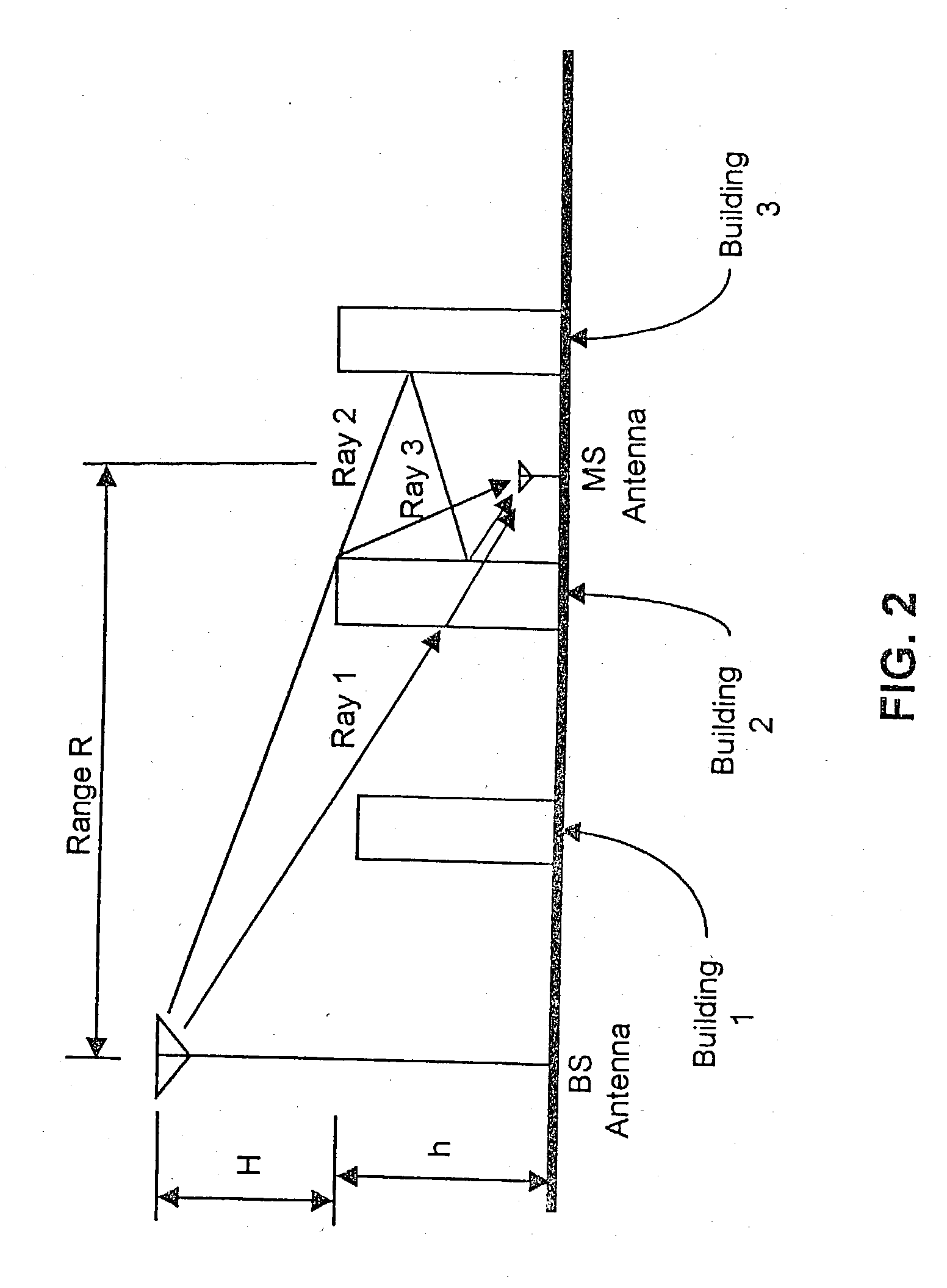
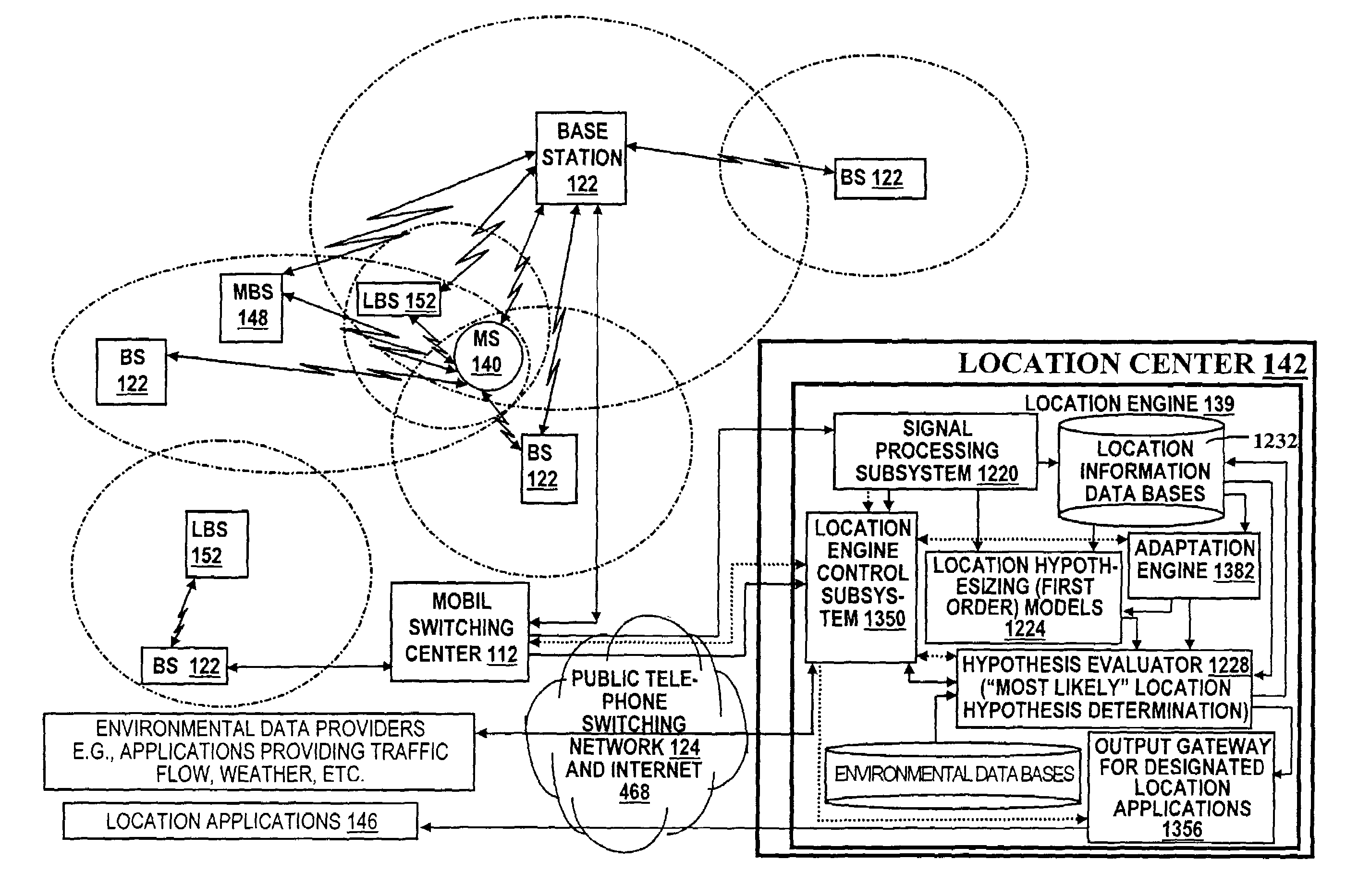
Wireless location using multiple location estimators
InactiveUS6249252B1Effectively and straightforwardly resolvedAmbiguity and conflictDirection finders using radio wavesBeacon systems using radio wavesTerrainHeuristic
A location system is disclosed for commercial wireless telecommunication infrastructures. The system is an end-to-end solution having one or more location centers for outputting requested locations of commercially available handsets or mobile stations (MS) based on, e.g., CDMA, AMPS, NAMPS or TDMA communication standards, for processing both local MS location requests and more global MS location requests via, e.g., Internet communication between a distributed network of location centers. The system uses a plurality of MS locating technologies including those based on: (1) two-way TOA and TDOA; (2) pattern recognition; (3) distributed antenna provisioning; (5) GPS signals, (6) angle of arrival, (7) super resolution enhancements, and (8) supplemental information from various types of very low cost non-infrastructure base stations for communicating via a typical commercial wireless base station infrastructure or a public telephone switching network. Accordingly, the traditional MS location difficulties, such as multipath, poor location accuracy and poor coverage are alleviated via such technologies in combination with strategies for: (a) automatically adapting and calibrating system performance according to environmental and geographical changes; (b) automatically capturing location signal data for continual enhancement of a self-maintaining historical data base retaining predictive location signal data; (c) evaluating MS locations according to both heuristics and constraints related to, e.g., terrain, MS velocity and MS path extrapolation from tracking and (d) adjusting likely MS locations adaptively and statistically so that the system becomes progressively more comprehensive and accurate. Further, the system can be modularly configured for use in location signing environments ranging from urban, dense urban, suburban, rural, mountain to low traffic or isolated roadways. Accordingly, the system is useful for 911 emergency calls, tracking, routing, people and animal location including applications for confinement to and exclusion from certain areas.
Owner:TRACBEAM
Applications for a wireless location gateway
InactiveUS20040198386A1Easy to implementEffectively and straightforwardly resolvedPosition fixationRadio/inductive link selection arrangementsTerrainInternet communication
A location system is disclosed for commercial wireless telecommunication infrastructures. The system is an end-to-end solution having one or more location centers for outputting requested locations of commercially available handsets or mobile stations (MS) based on, e.g., CDMA, AMPS, NAMPS or TDMA communication standards, for processing both local MS location requests and more global MS location requests via, e.g., Internet communication between a distributed network of location centers. The system uses a plurality of MS locating technologies including those based on: (1) two-way TOA and TDOA; (2) pattern recognition; (3) distributed antenna provisioning; (5) GPS signals, (6) angle of arrival, (7) super resolution enhancements, and (8) supplemental information from various types of very low cost non-infrastructure base stations for communicating via a typical commercial wireless base station infrastructure or a public telephone switching network. Accordingly, the traditional MS location difficulties, such as multipath, poor location accuracy and poor coverage are alleviated via such technologies in combination with strategies for: (a) automatically adapting and calibrating system performance according to environmental and geographical changes; (b) automatically capturing location signal data for continual enhancement of a self-maintaining historical data base retaining predictive location signal data; (c) evaluating MS locations according to both heuristics and constraints related to, e.g., terrain, MS velocity and MS path extrapolation from tracking and (d) adjusting likely MS locations adaptively and statistically so that the system becomes progressively more comprehensive and accurate. Further, the system can be modularly configured for use in location signaling environments ranging from urban, dense urban, suburban, rural, mountain to low traffic or isolated roadways. Accordingly, the system is useful for 911 emergency calls, tracking, routing, people and animal location including applications for confinement to and exclusion from certain areas.
Owner:DUPRAY DENNIS J
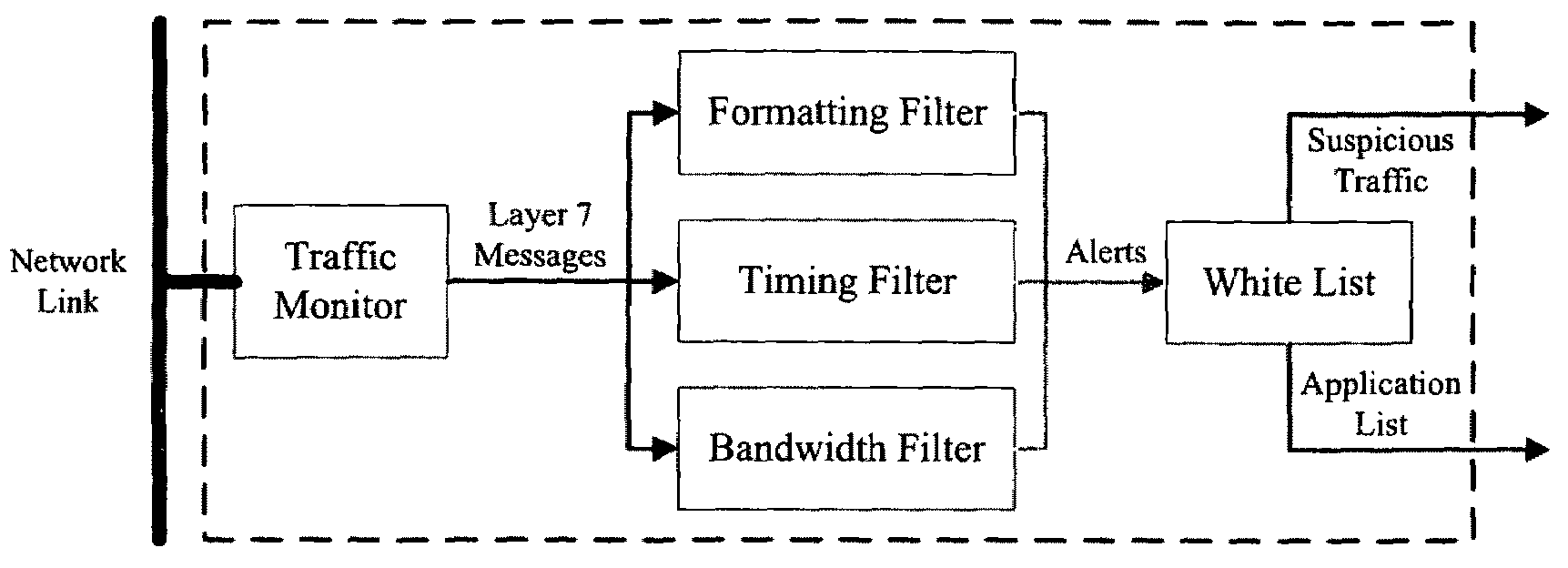
Method, system and computer program product for detecting at least one of security threats and undesirable computer files
Method, system and computer program product for detecting at least one of security threats and undesirable computer files are provided. A first method includes receiving a data stream which represents outbound, application layer messages from a first computer process to at least one second computer process. The computer processes are implemented on one or more computers. The method further includes monitoring the data stream to detect a security threat based on a whitelist having entries which contain metadata. The whitelist describes legitimate application layer messages based on a set of heuristics. The method still further includes generating a signal if a security threat is detected. A second method includes comparing a set of computer files with a whitelist which characterizes all legitimate computer files. The whitelist contains one or more entries. Each of the entries describe a plurality of legitimate computer files.
Owner:SYROWIK DAVID R
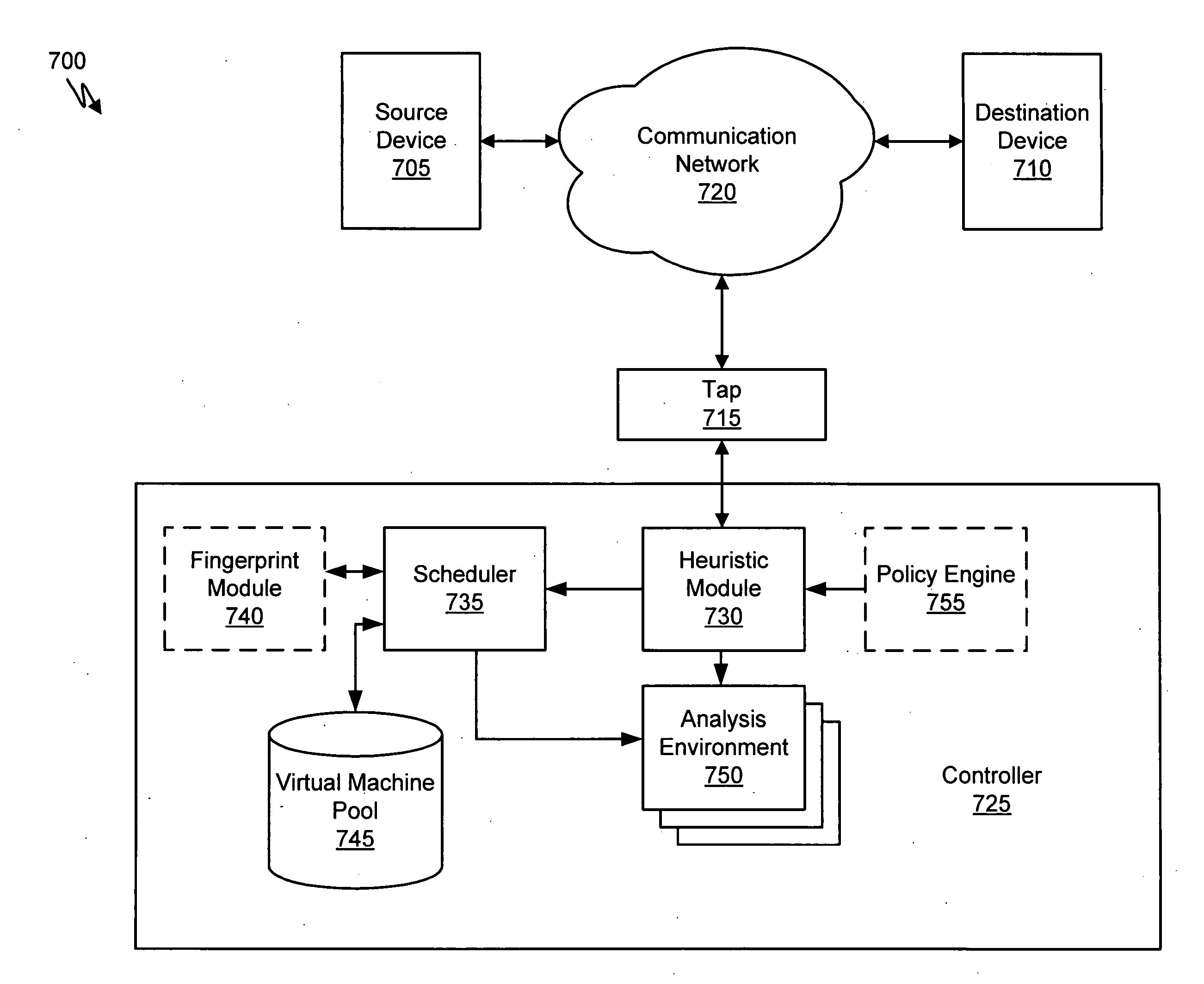
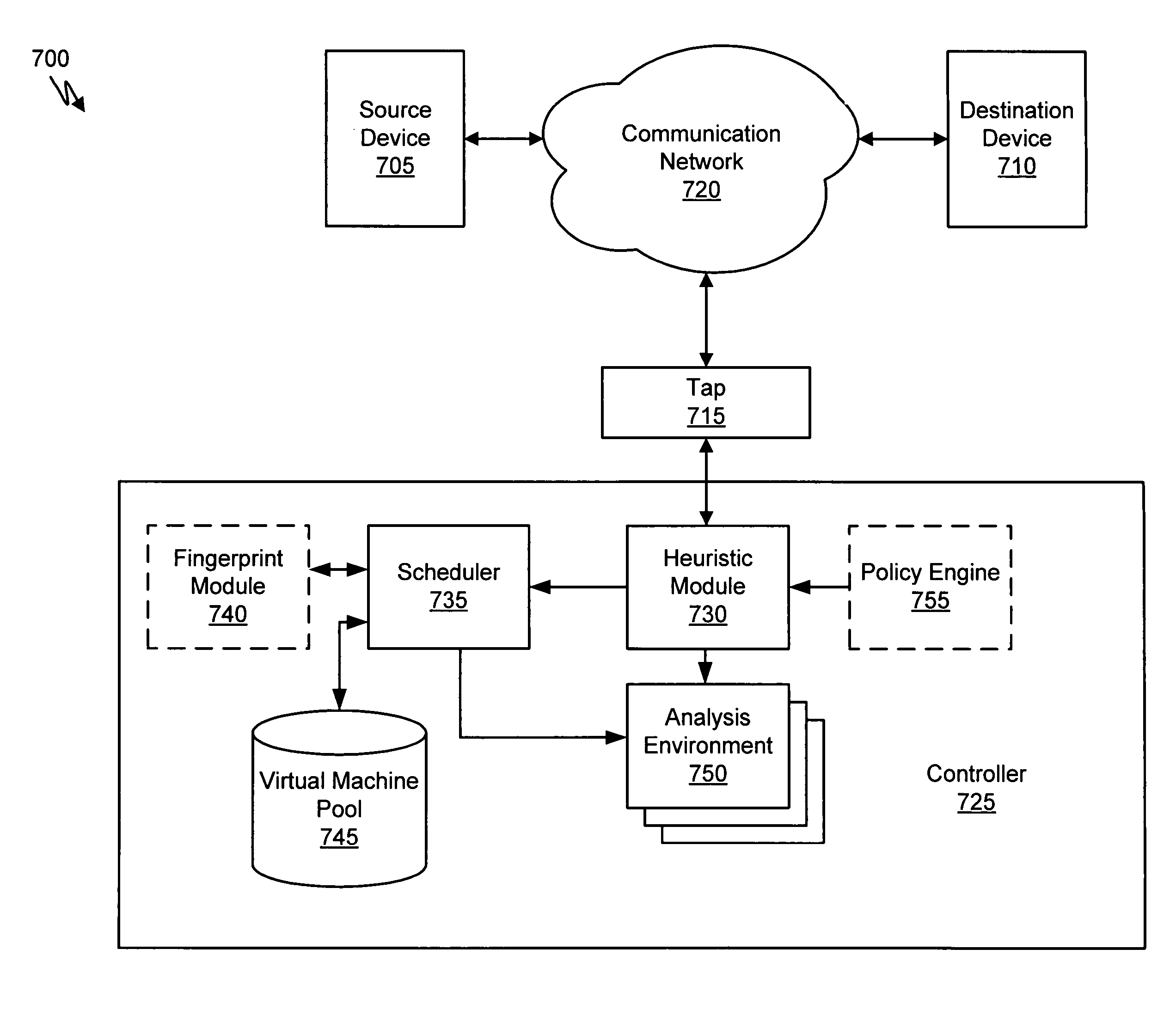
Heuristic based capture with replay to virtual machine
A suspicious activity capture system can comprise a tap configured to copy network data from a communication network, and a controller coupled to the tap. The controller is coupled to the tap and is configured to receive the copy of the network data from the tap, analyze the copy of the network data with a heuristic to flag the network data as suspicious, and simulate transmission of the network data to a destination device.
Owner:FIREEYE SECURITY HLDG US LLC
Geographic location using multiple location estimators
InactiveUS7298327B2Overcome inaccurate recognitionThe result is accurate and reliableDirection finders using radio wavesBeacon systems using radio wavesTerrainHeuristic
A location system is disclosed for commercial wireless telecommunication infrastructures. The system is an end-to-end solution having one or more location centers for outputting requested locations of commercially available handsets or mobile stations (MS) based on, e.g., CDMA, AMPS, NAMPS or TDMA communication standards, for processing both local MS location requests and more global MS location requests via, e.g., Internet communication between a distributed network of location centers. The system uses a plurality of MS locating technologies including those based on: (1) two-way TOA and TDOA; (2) pattern recognition; (3) distributed antenna provisioning; and (4) supplemental information from various types of very low cost non-infrastructure base stations for communicating via a typical commercial wireless base station infrastructure or a public telephone switching network. Accordingly, the traditional MS location difficulties, such as multipath, poor location accuracy and poor coverage are alleviated via such technologies in combination with strategies for: (a) automatically adapting and calibrating system performance according to environmental and geographical changes; (b) automatically capturing location signal data for continual enhancement of a self-maintaining historical data base retaining predictive location signal data; (c) evaluating MS locations according to both heuristics and constraints related to, e.g., terrain, MS velocity and MS path extrapolation from tracking and (d) adjusting likely MS locations adaptively and statistically so that the system becomes progressively more comprehensive and accurate. Further, the system can be modularly configured for use in location signaling environments ranging from urban, dense urban, suburban, rural, mountain to low traffic or isolated roadways. Accordingly, the system is useful for 911 emergency calls, tracking, routing, people and animal location including applications for confinement to and exclusion from certain areas.
Owner:TRACBEAM
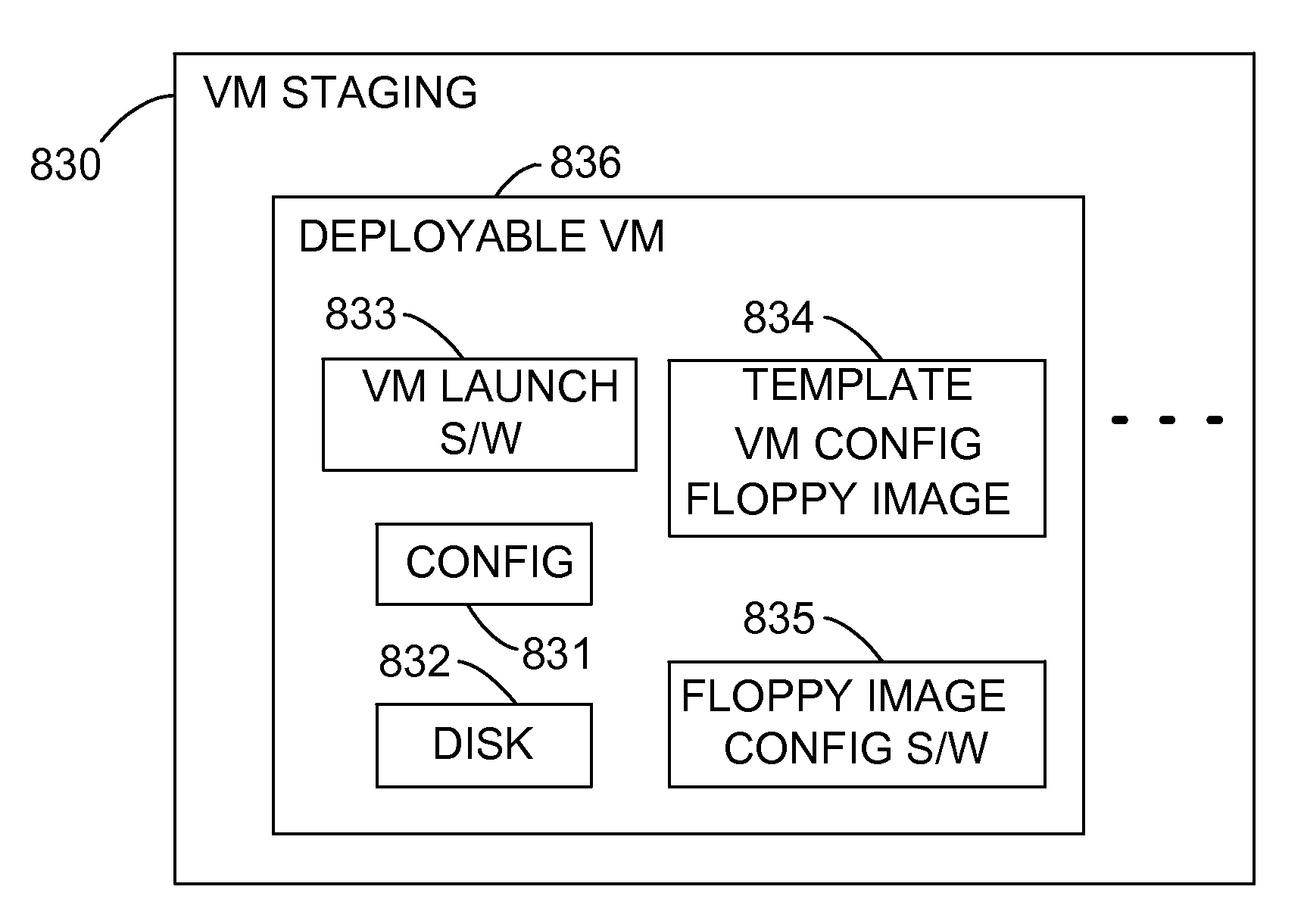
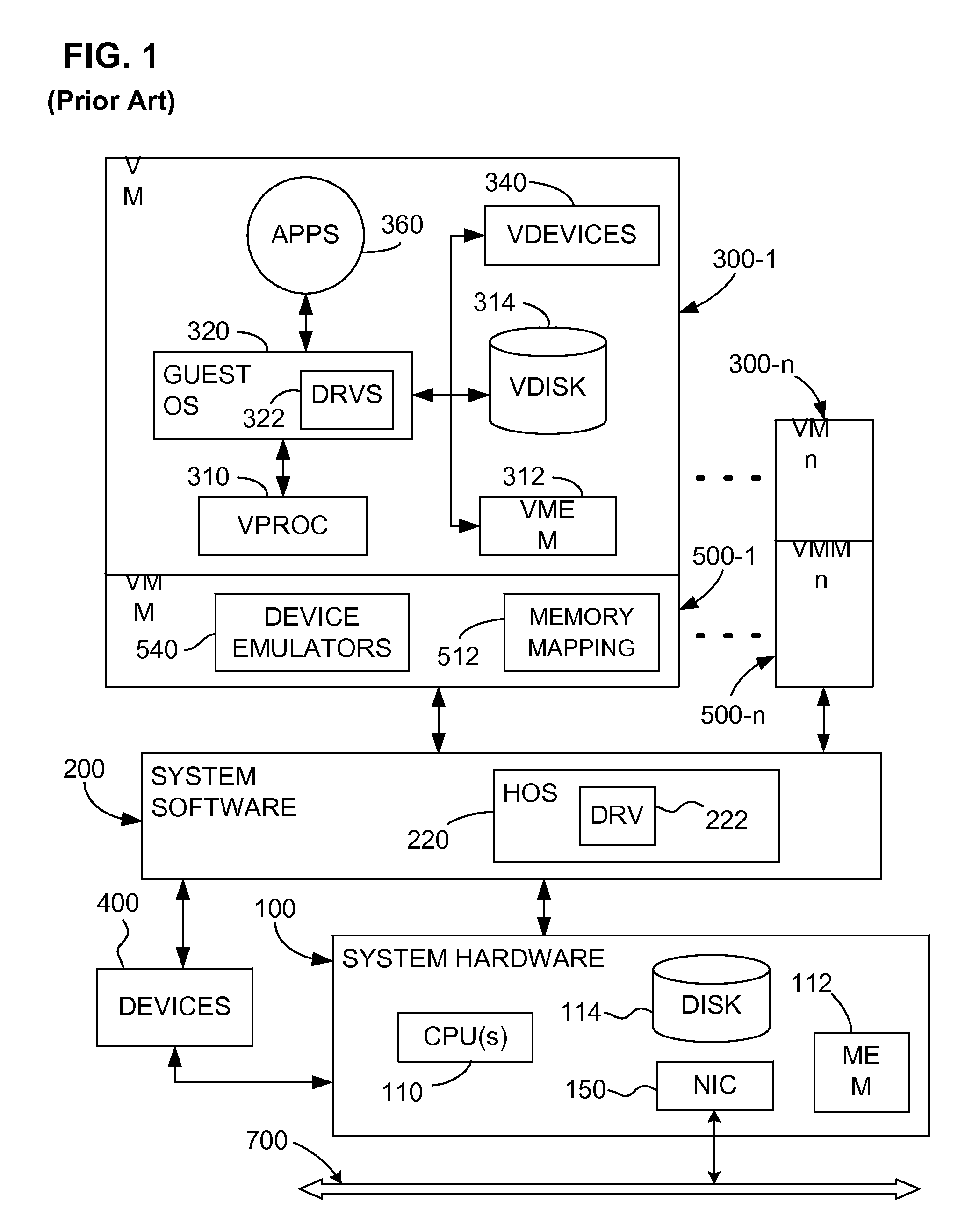
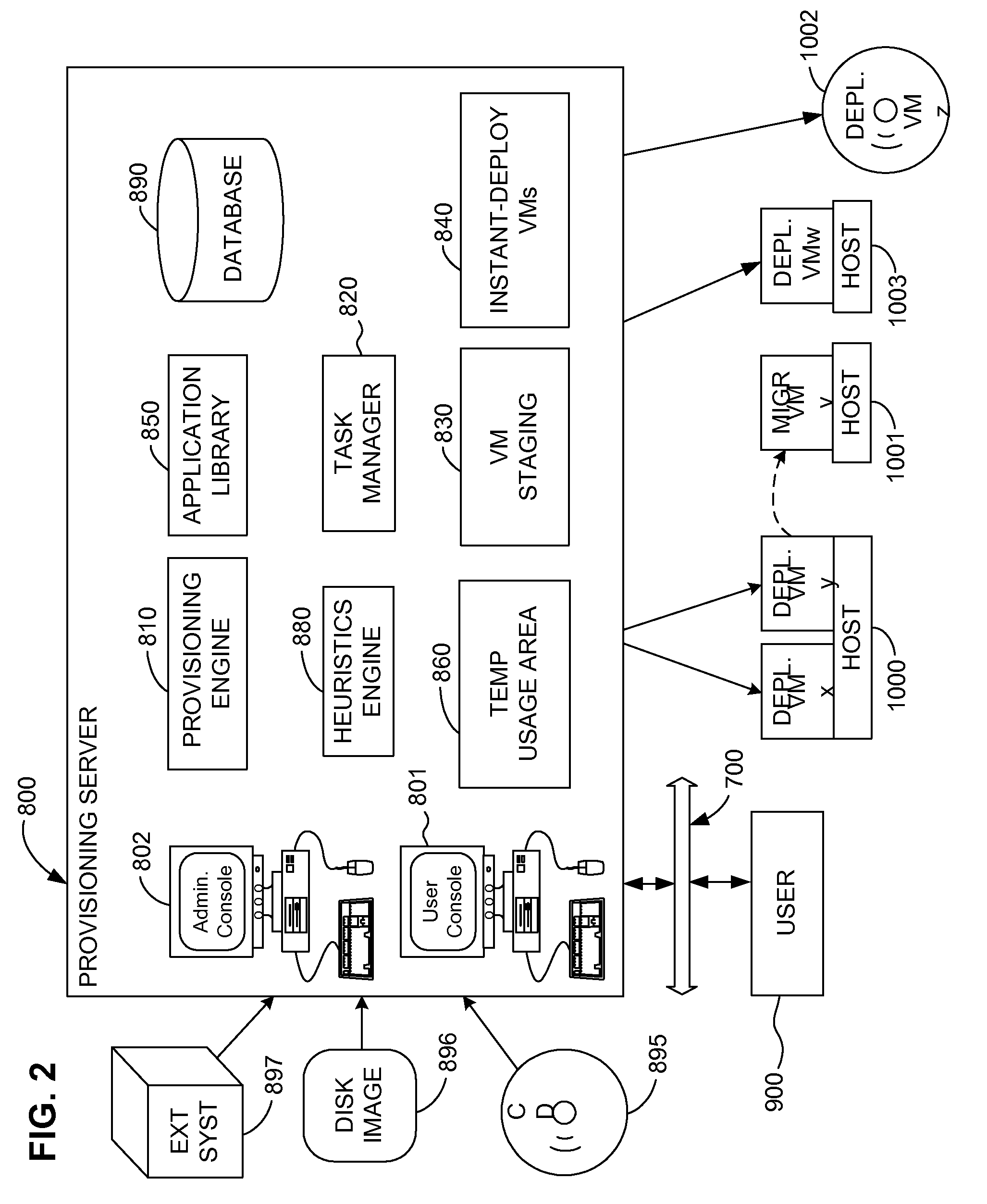
Provisioning of Computer Systems Using Virtual Machines
InactiveUS20090282404A1Multiple digital computer combinationsSoftware simulation/interpretation/emulationOperational systemAuto-configuration
Owner:VMWARE INC
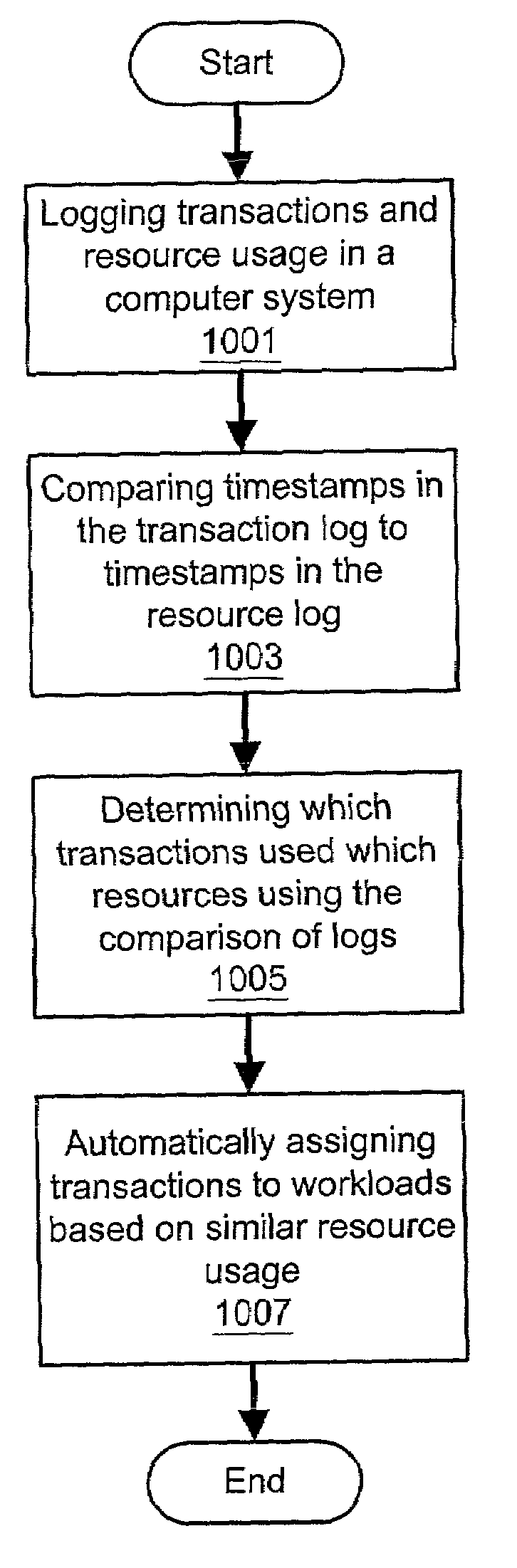
System and method for automatic workload characterization
ActiveUS7028301B2Good precisionEasy accessResource allocationMemory systemsTimestampResource consumption
A system and method for automatic workload characterization are provided. Transactions performed in a computer system may be logged. The log of transactions comprises a timestamp for each transaction. Resource usage in the computer system may be logged. The log of resource usage comprises one or more periods of time during which each of a plurality of resources is used, and the log of resource usage comprises a plurality of system performance metrics which reflect resource consumption by one or more processes that performed the transactions. The timestamps in the log of transactions may be compared to the periods of time in the log of resource usage. It may be determined which transactions used which resources as a result of the comparing the timestamps in the log of transactions to the periods of time in the log of resource usage. One or more workloads may be determined using the determining which transactions used which resources. Heuristics may be used to group processes into workloads.
Owner:BMC SOFTWARE
Automatic organization of browsing histories
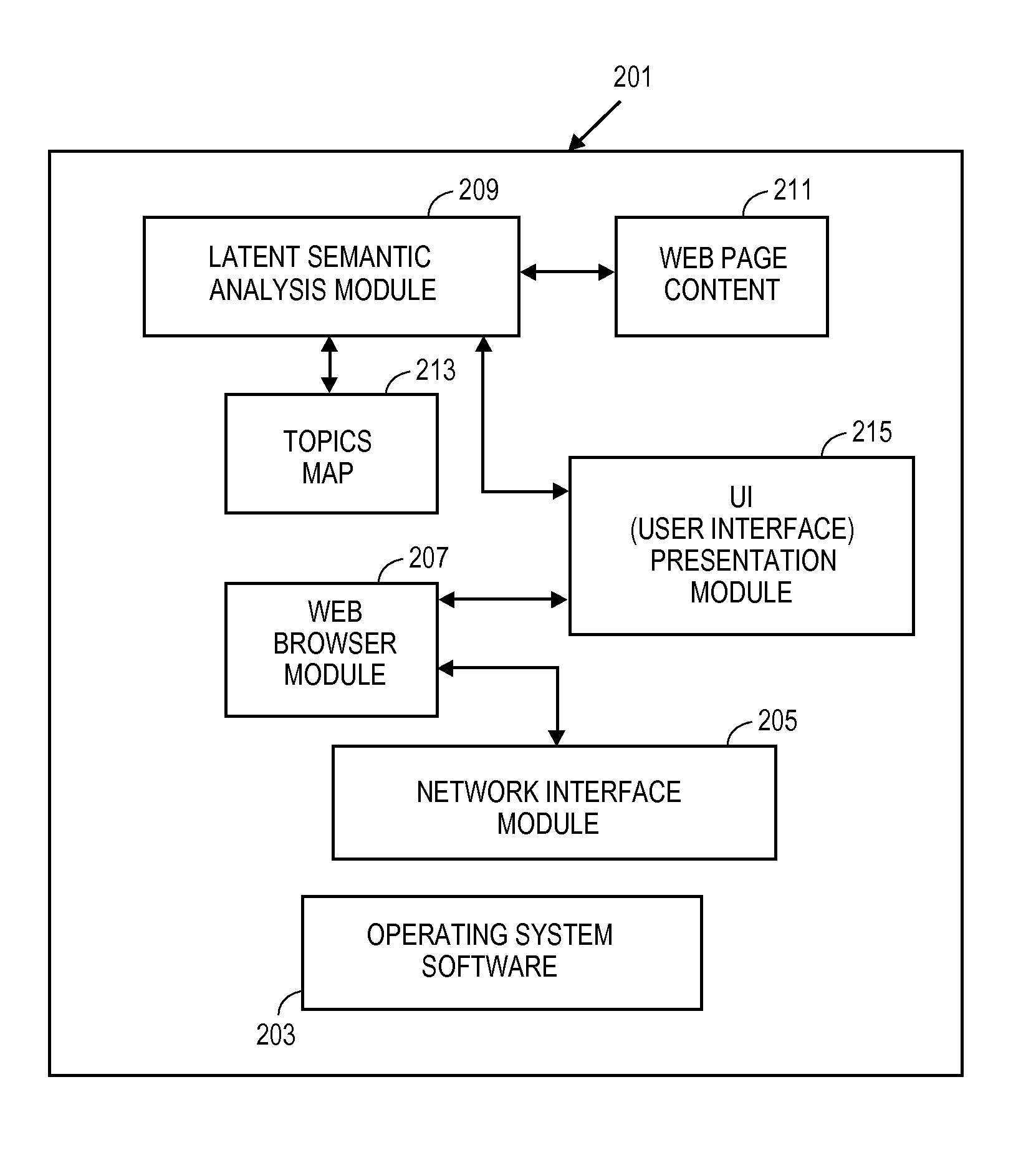
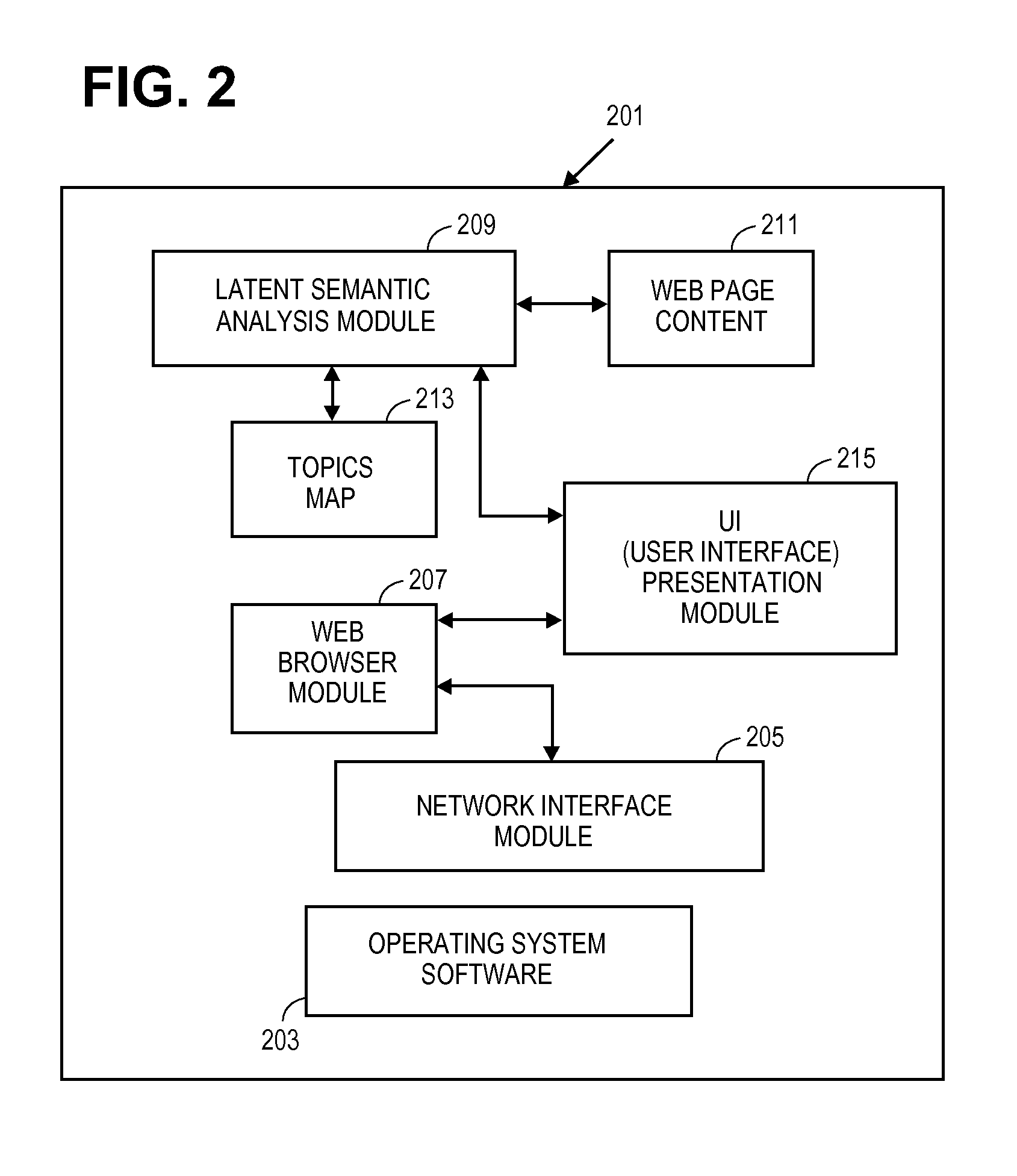
An automatic organization into topics for a browsing history. In one embodiment, a system identifies groups of browsing actions as related, and clusters the browsing history (e.g. a web browsing history) into sessions based on heuristics used to determine relationships. Latent semantic analysis can be used to determine the relationships which can be considered topics. User interfaces for displaying or otherwise presenting these sessions can include icons representative of topics, and these icons can have different sizes depending on a frequency of web page visits within a topic. The topics can be displayed in time ranges or in a cover flow view or both time ranges and cover flow view.
Owner:APPLE INC
Heuristic based capture with replay to virtual machine
Owner:FIREEYE SECURITY HLDG US LLC
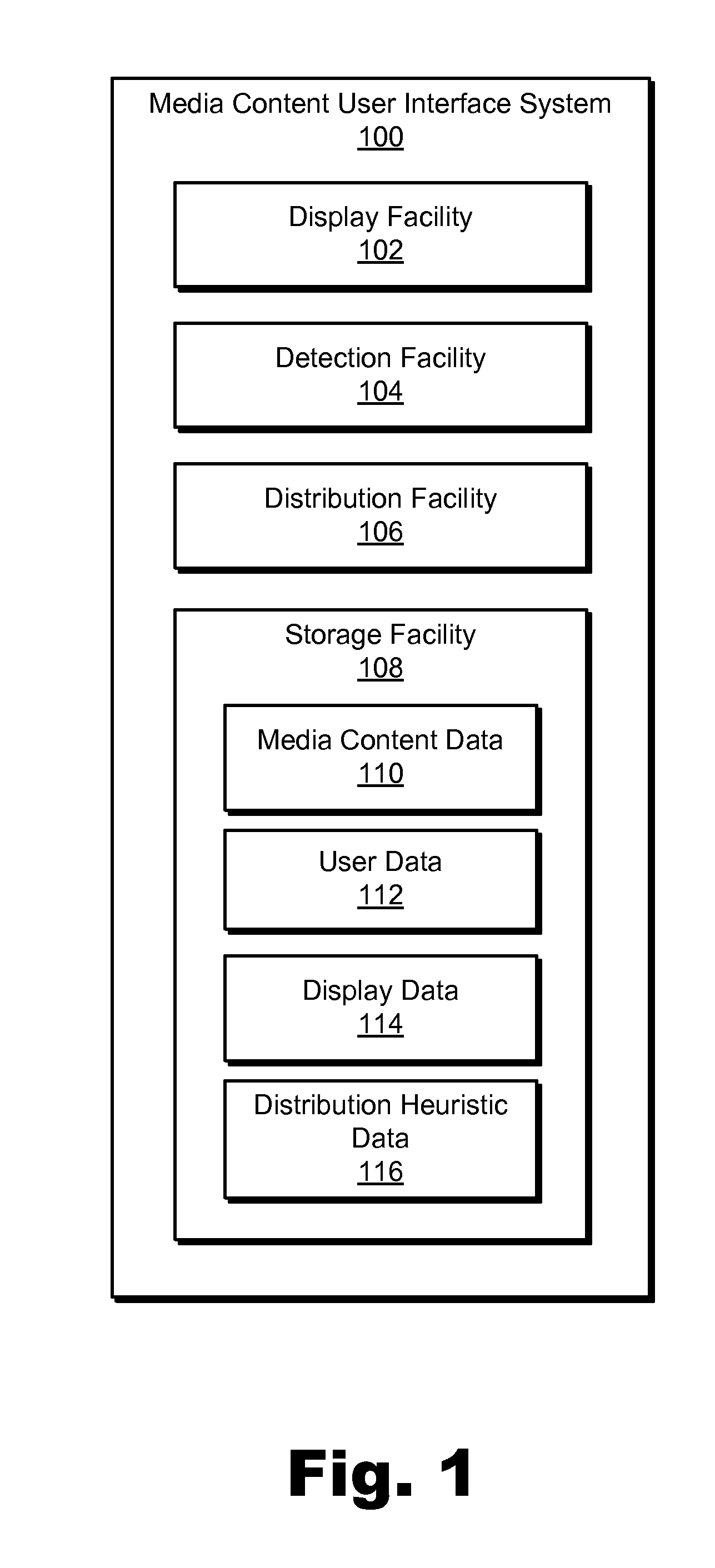
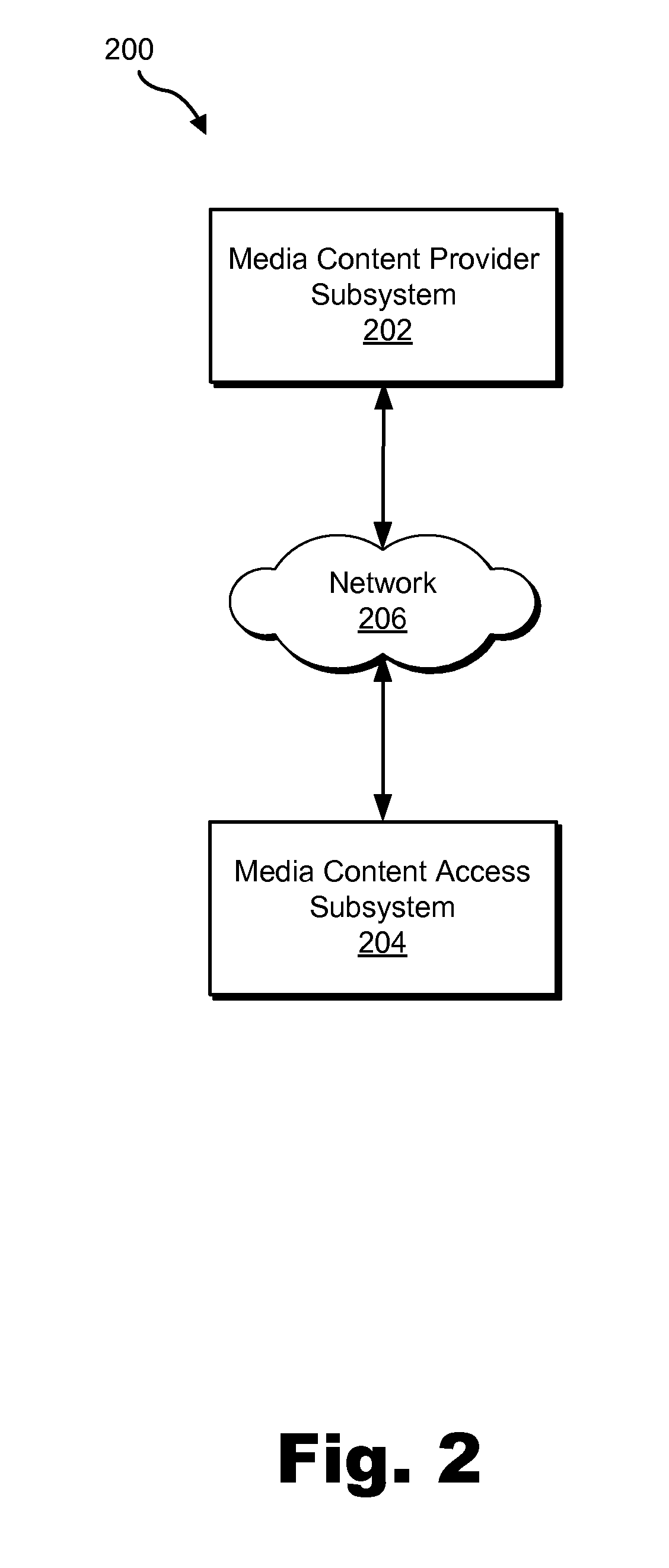
Media Content User Interface Systems and Methods
Exemplary media content user interface systems and methods are disclosed herein. An exemplary method includes a media content access subsystem displaying a plurality of display elements topographically distributed throughout a graphical representation of a virtual world in accordance with one or more distribution heuristics, detecting a user interaction, and dynamically adjusting the topographical distribution of the one or more display elements in accordance with the user interaction. Corresponding systems and methods are also disclosed.
Owner:VERIZON PATENT & LICENSING INC
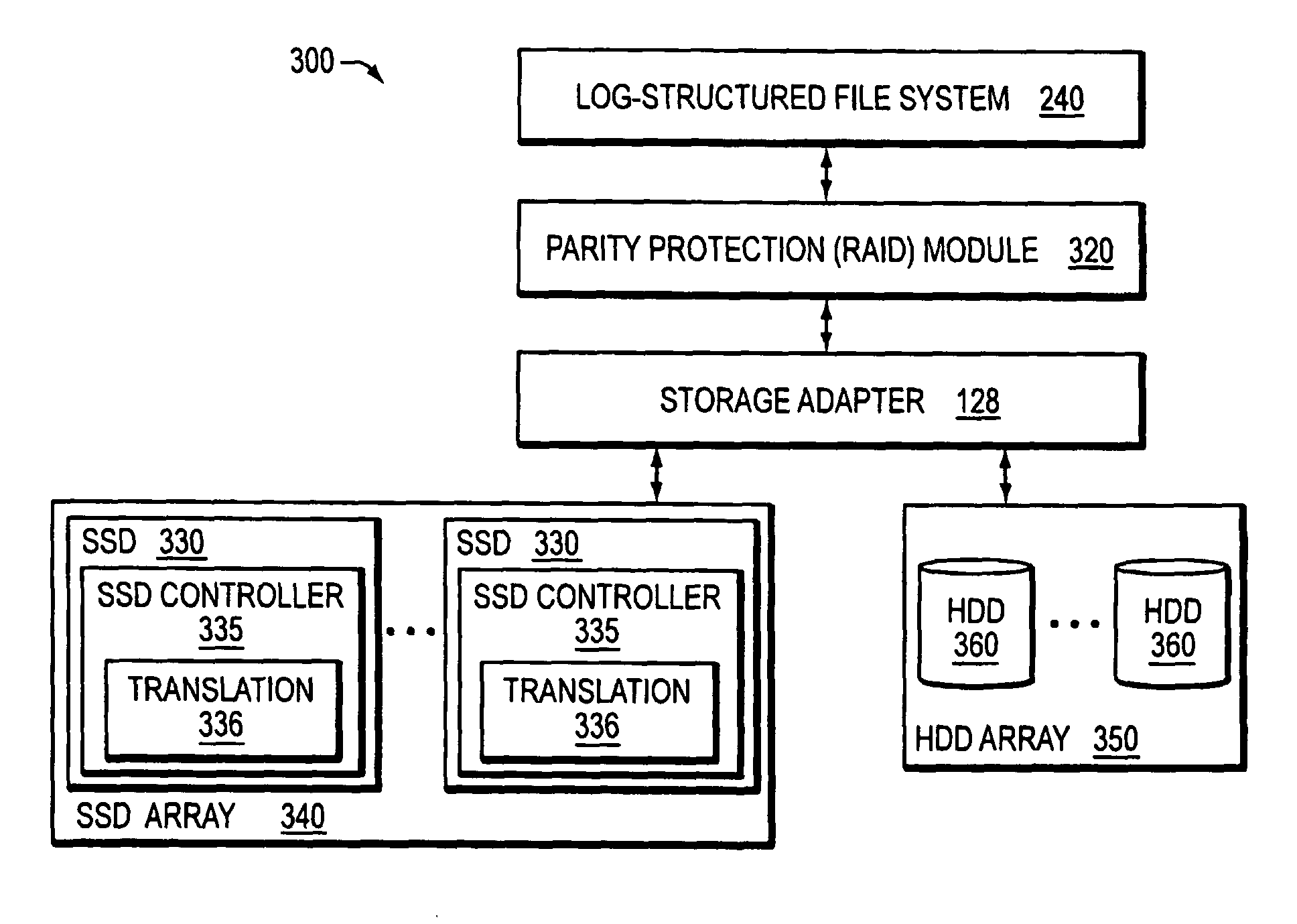
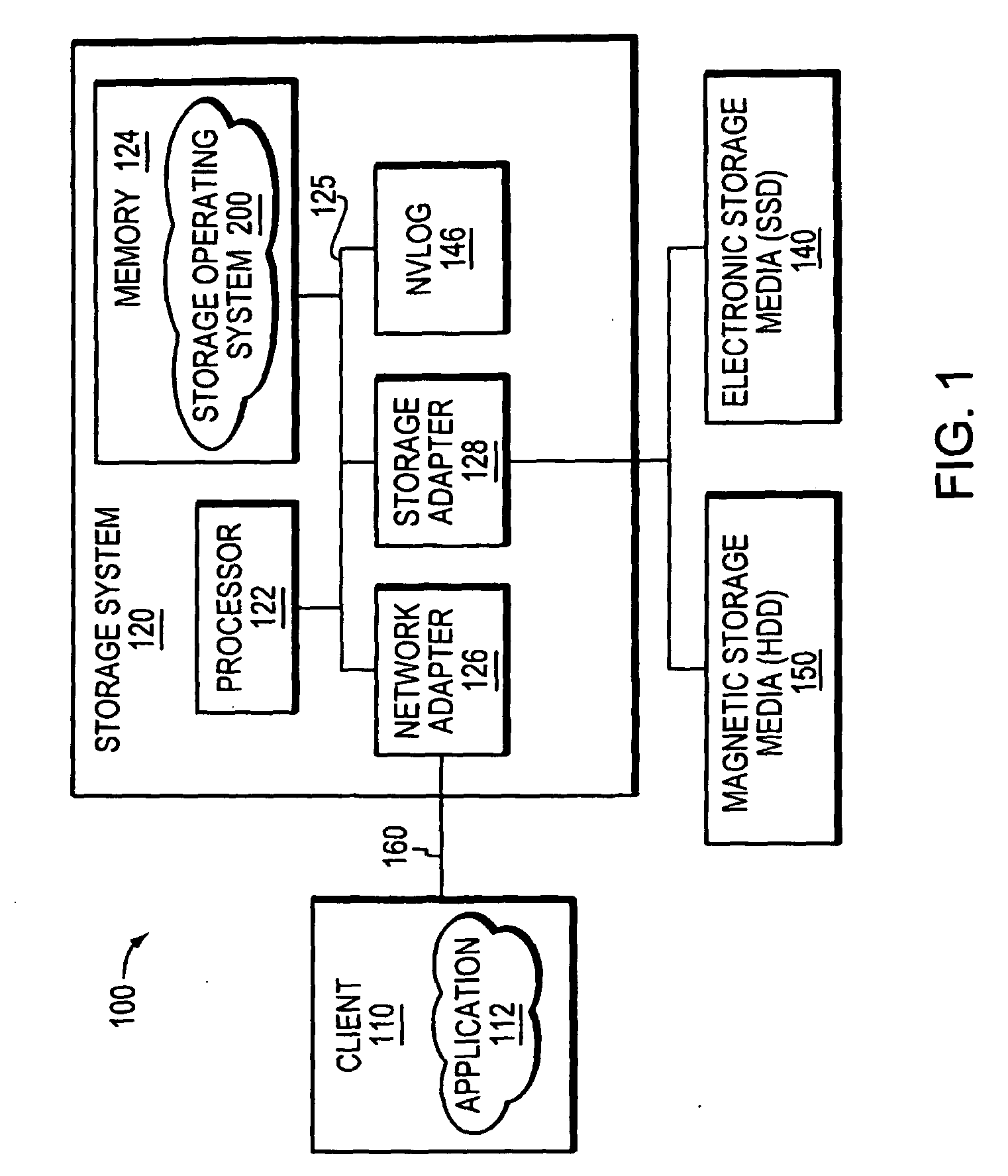
Hybrid media storage system architecture
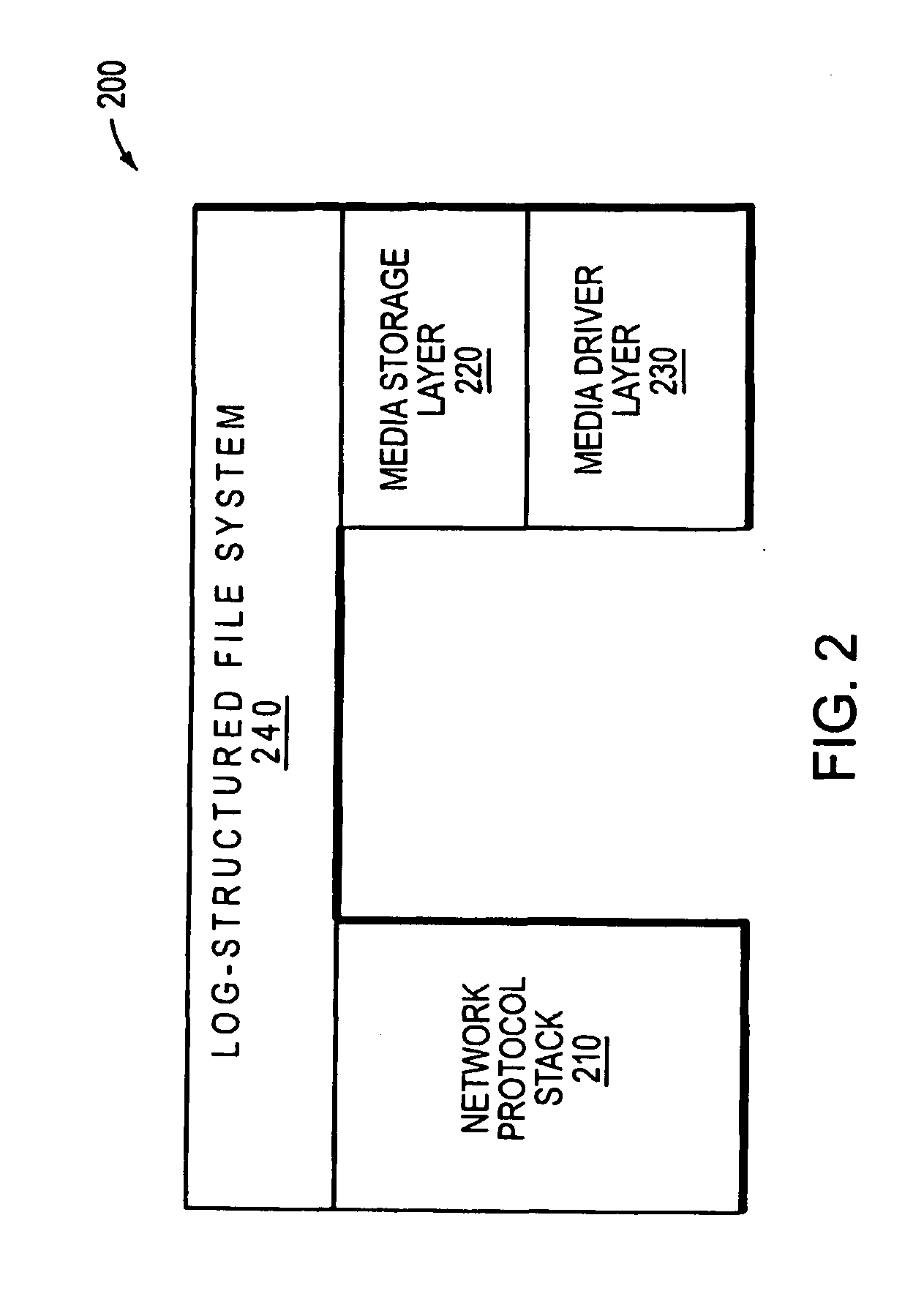
ActiveUS20110035548A1Improved performance characteristicsOvercome disadvantagesDigital data information retrievalError detection/correctionFile systemGranularity
Owner:NETWORK APPLIANCE INC
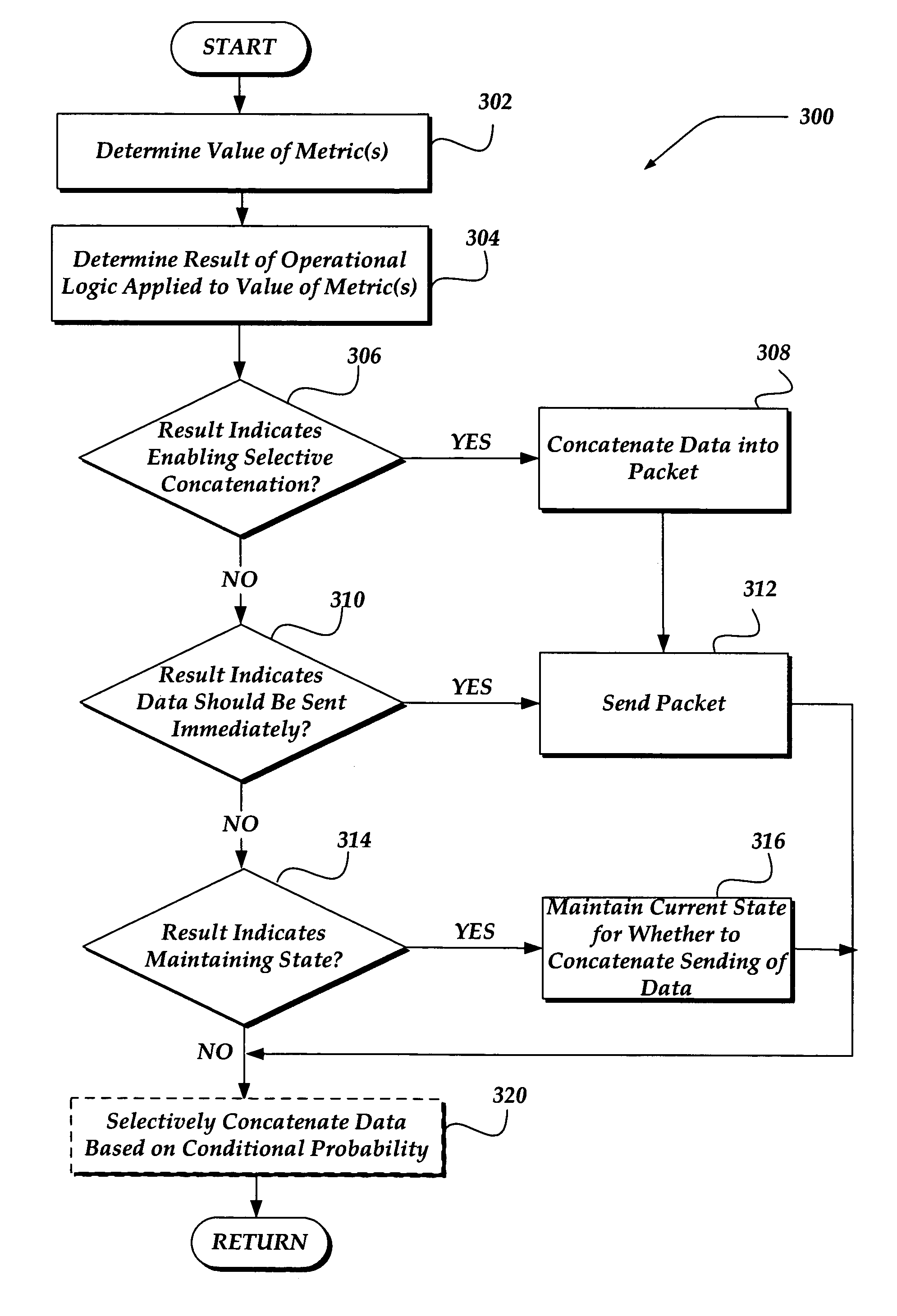
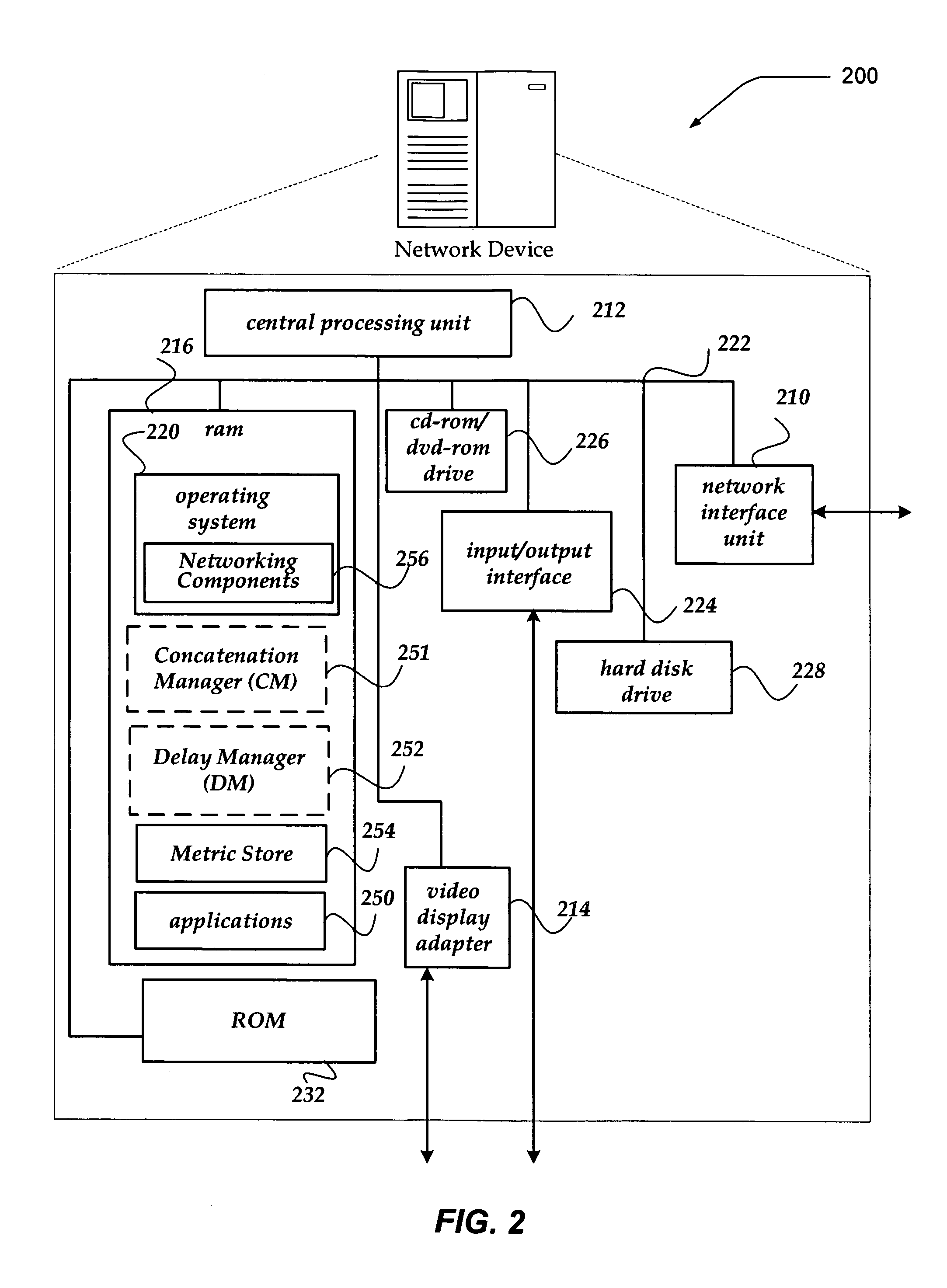
Selectively enabling network packet concatenation based on metrics
InactiveUS7873065B1Data switching by path configurationStore-and-forward switching systemsData connectionNetwork packet
A method, system, and apparatus are directed towards selectively concatenating data into a packet to modify a number of packets transmitted over a network based on a combination of network and / or send-queue metrics. In one embodiment, Nagle's algorithm is used for concatenating data into a packet. The concatenation may be selectively enabled based on heuristics applied to the combination of metrics. In one embodiment, the result may indicate that there should be a concatenation, or that data should be sent immediately, or that a current state for whether to concatenate or not should be maintained. The heuristics may include an expert system, decision tree, truth table, function, or the like. The heuristics may be provided by a user, or another computing device. In another embodiment, the concatenation may be enabled based on a conditional probability determined from the combination of metrics.
Owner:F5 NETWORKS INC
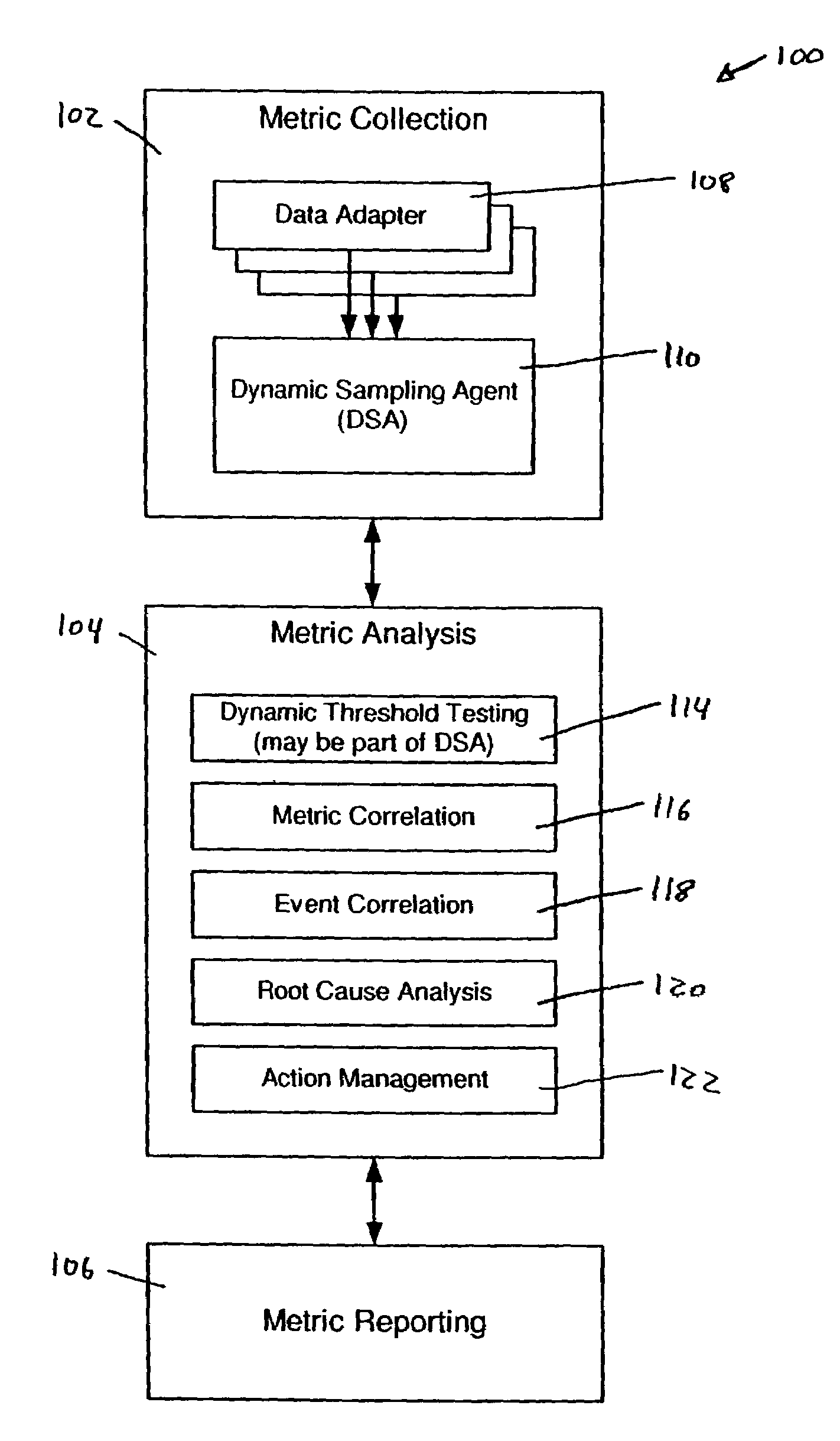
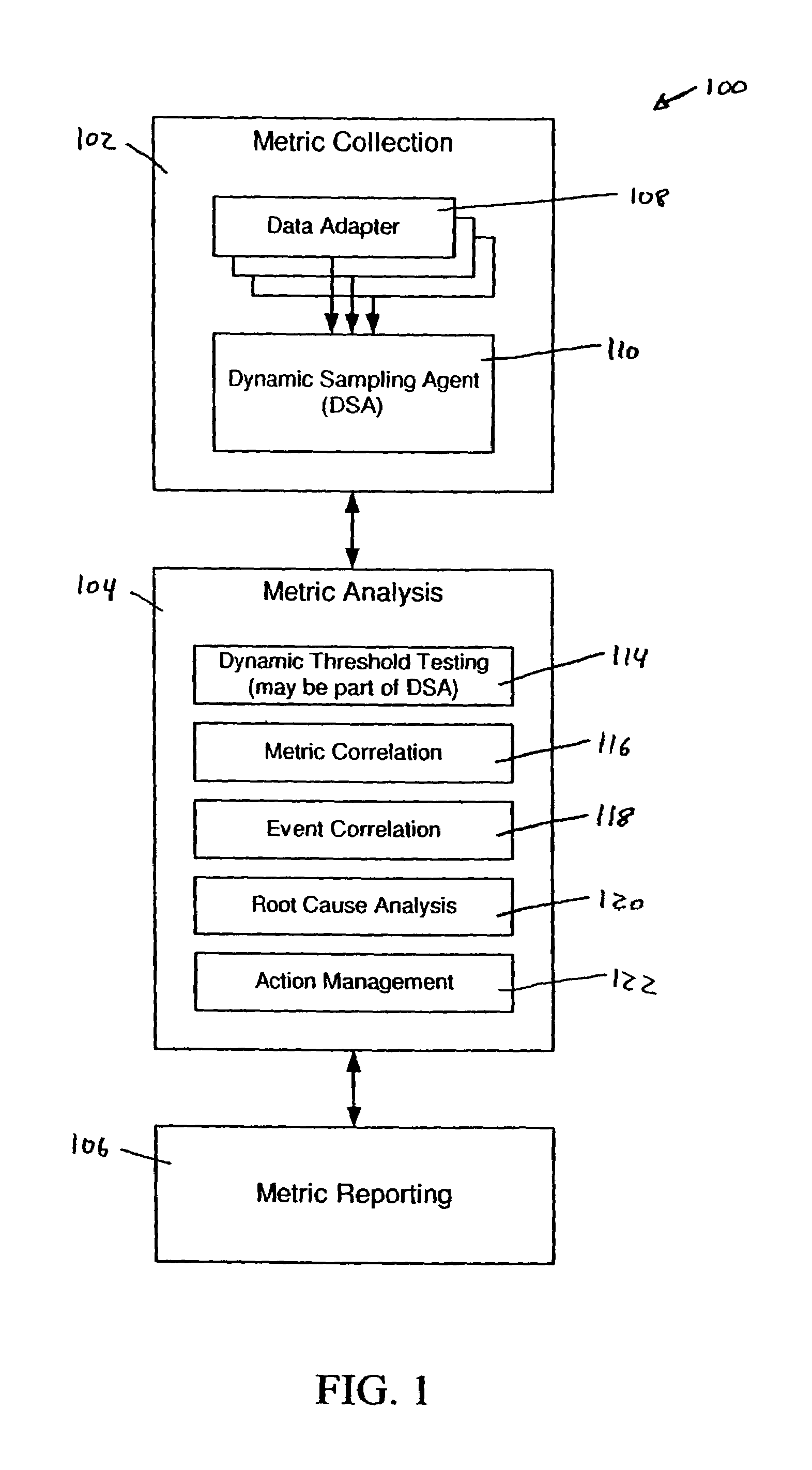
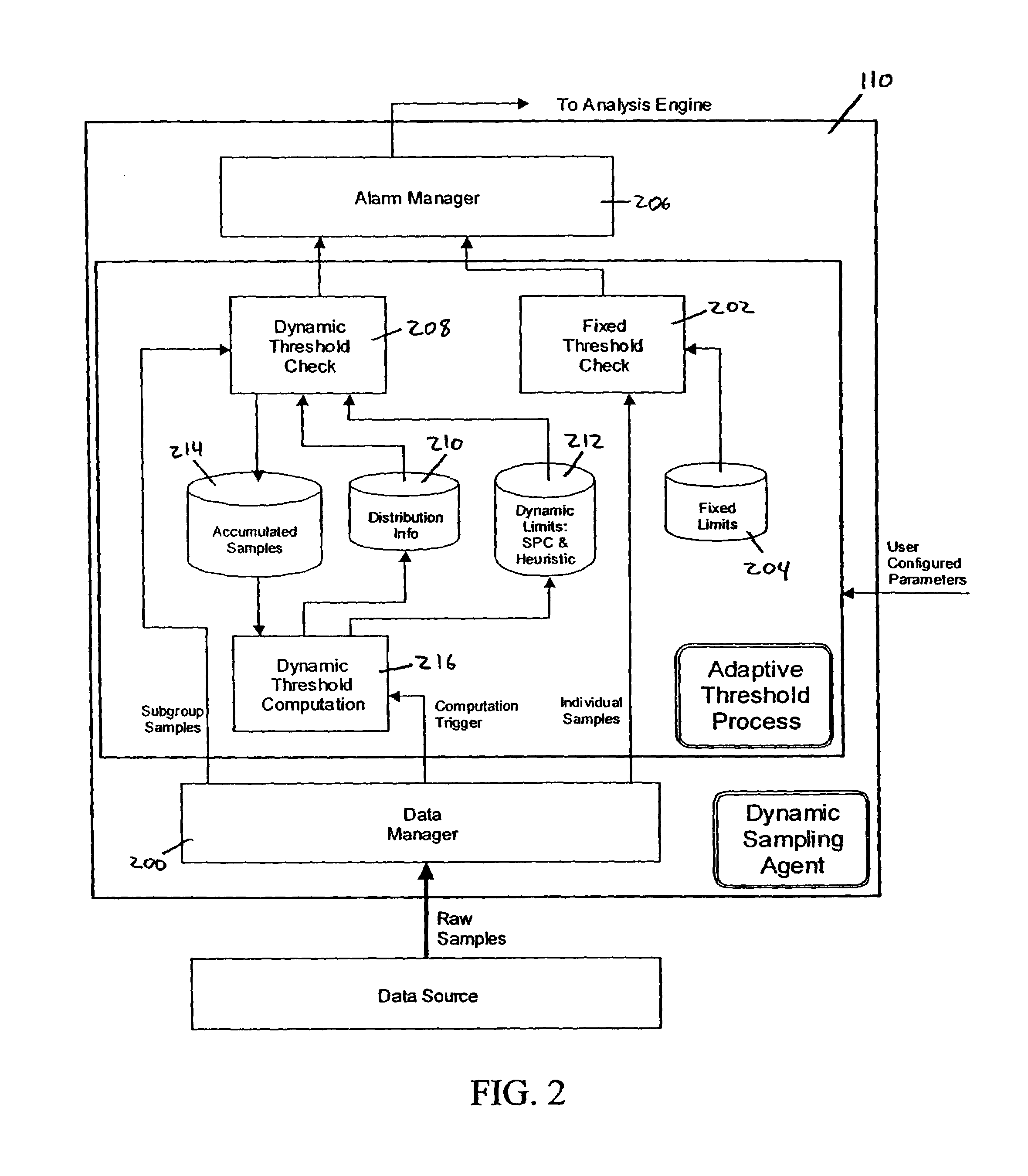
System and methods for adaptive threshold determination for performance metrics
A system and method for dynamically generating alarm thresholds for performance metrics, and for applying those thresholds to generate alarms is described. Statistical methods are used to generate one or more thresholds for metrics that may not fit a Gaussian or normal distribution, or that may exhibit cyclic behavior or persistent shifts in the values of the metrics. The statistical methods used to generate the thresholds may include statistical process control (SPC) methods, normalization methods, and heuristics.
Owner:ATERNITY LLC
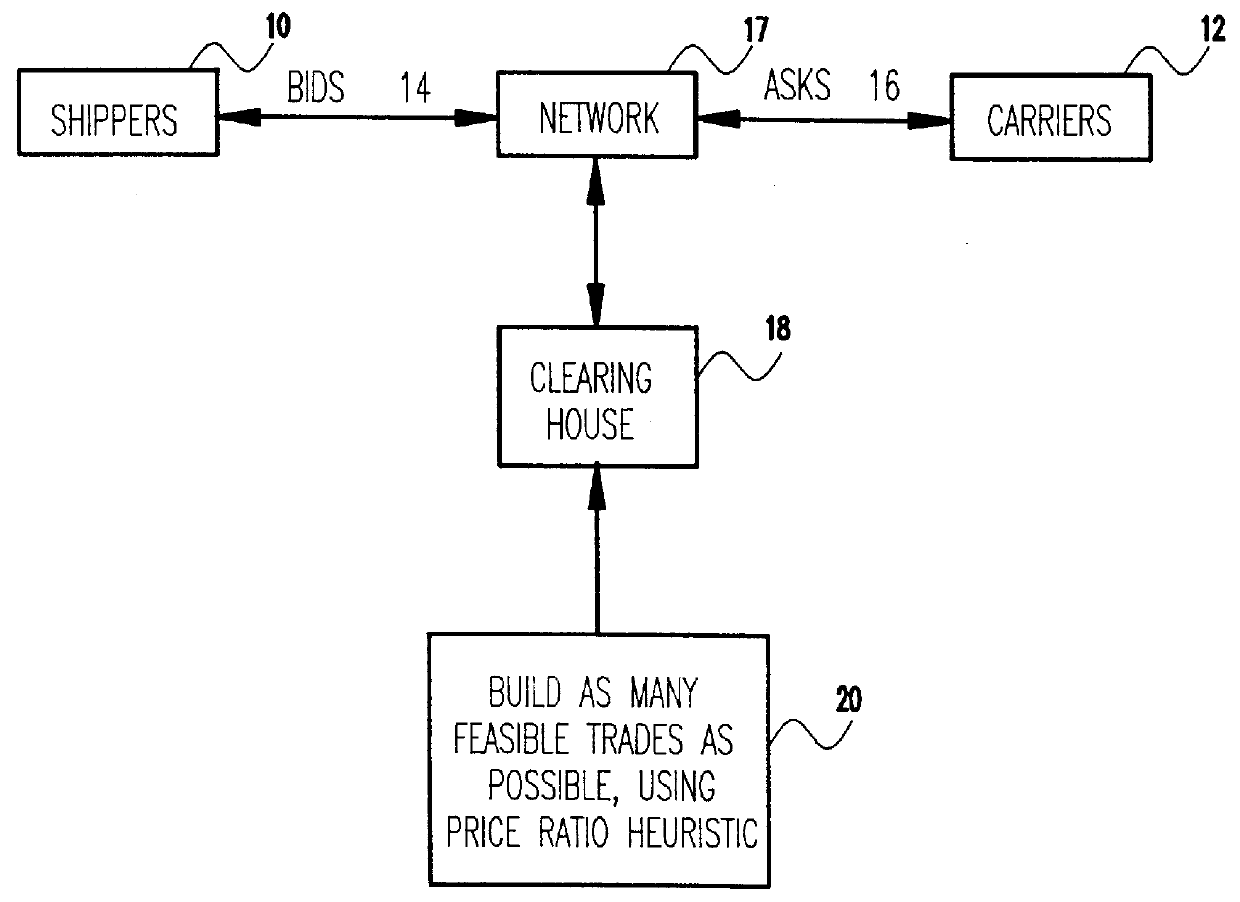
Method and apparatus for electronic trading of carrier cargo capacity
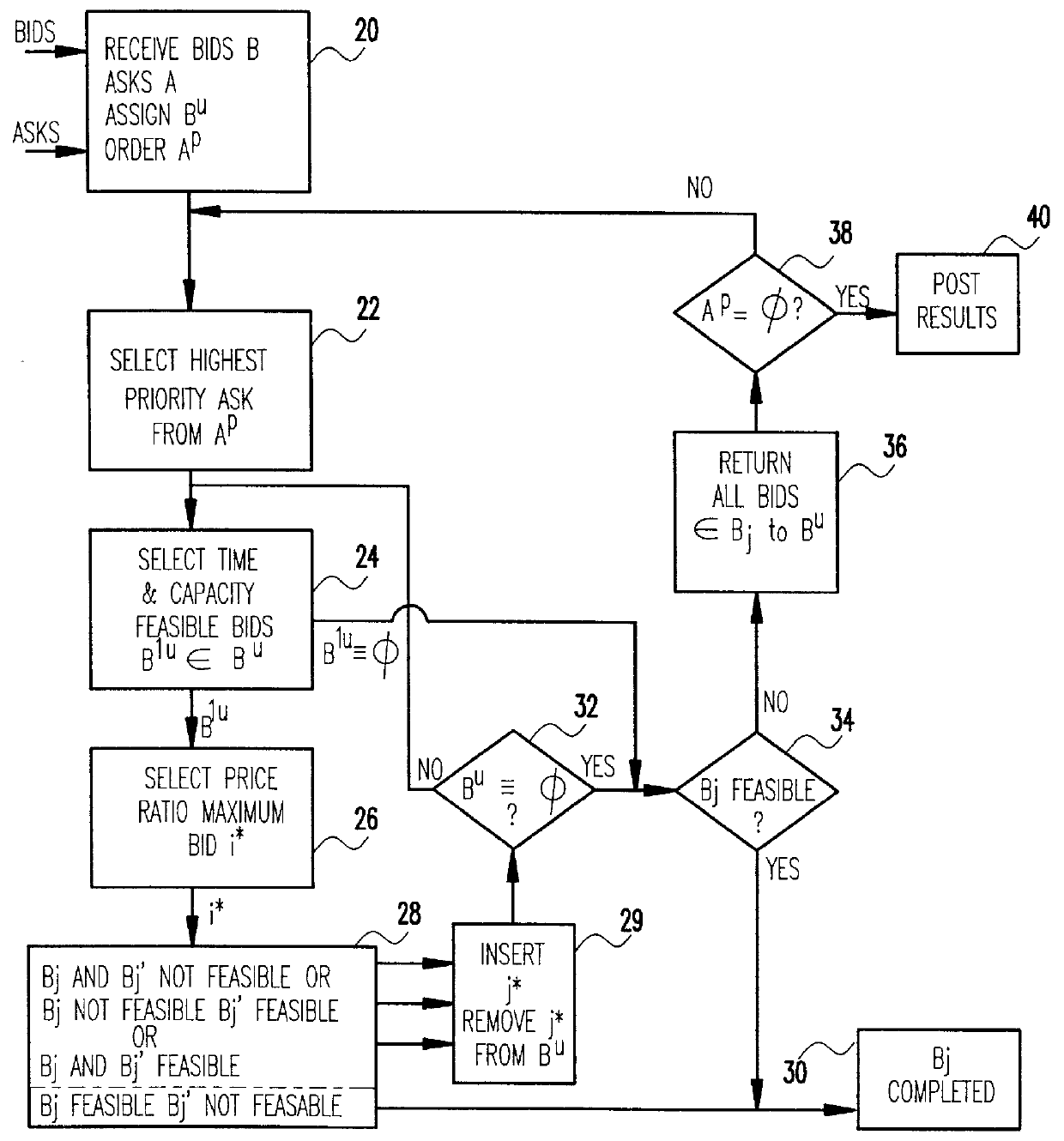
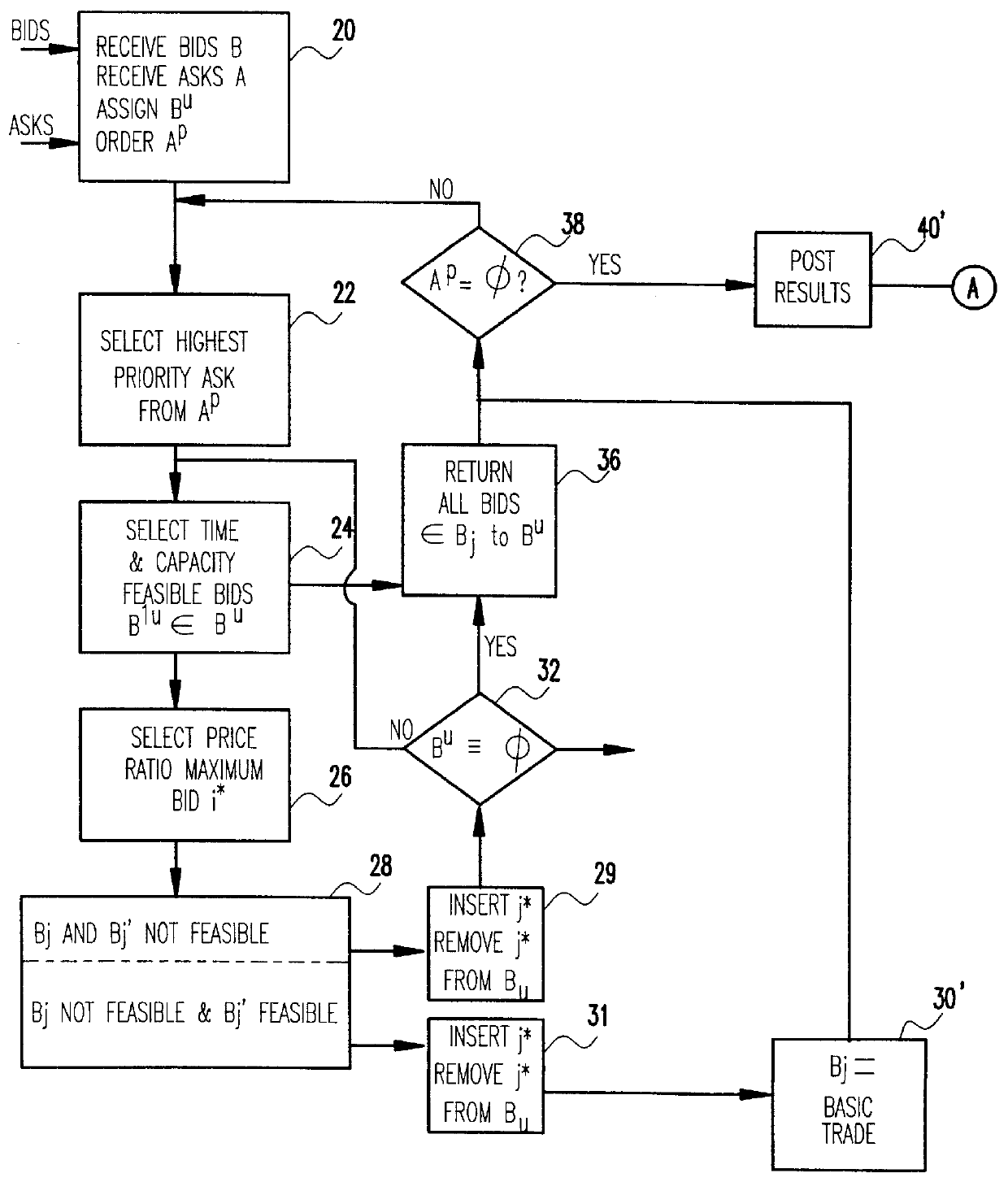
A computer-implemented method for double auction trade-building by matching, based on feasibility and price / cost heuristics, a plurality of electronically posted bid with a plurality of electronically posted ask records. A one-pass sequential trade building method selects ask records one at a time and sequentially inserts, in one pass, as many of the bid records as possible while maintaining feasibility criteria. A two pass sequential trade building method inserts the bid records in two stages, the first terminating when the trade becomes feasible and the second when no further bids can be inserted.
Owner:IBM CORP
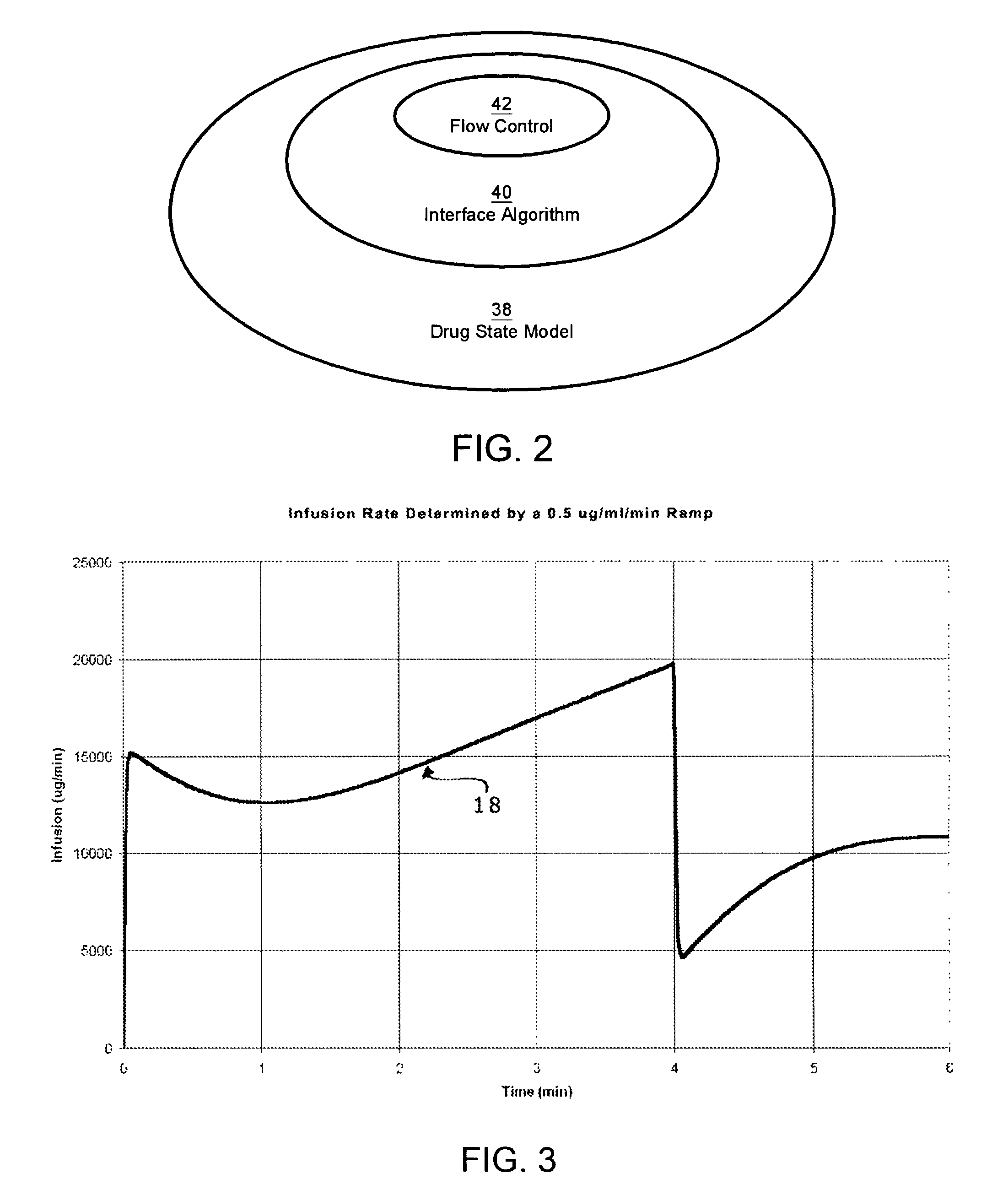
Apparatuses and methods for titrating drug delivery
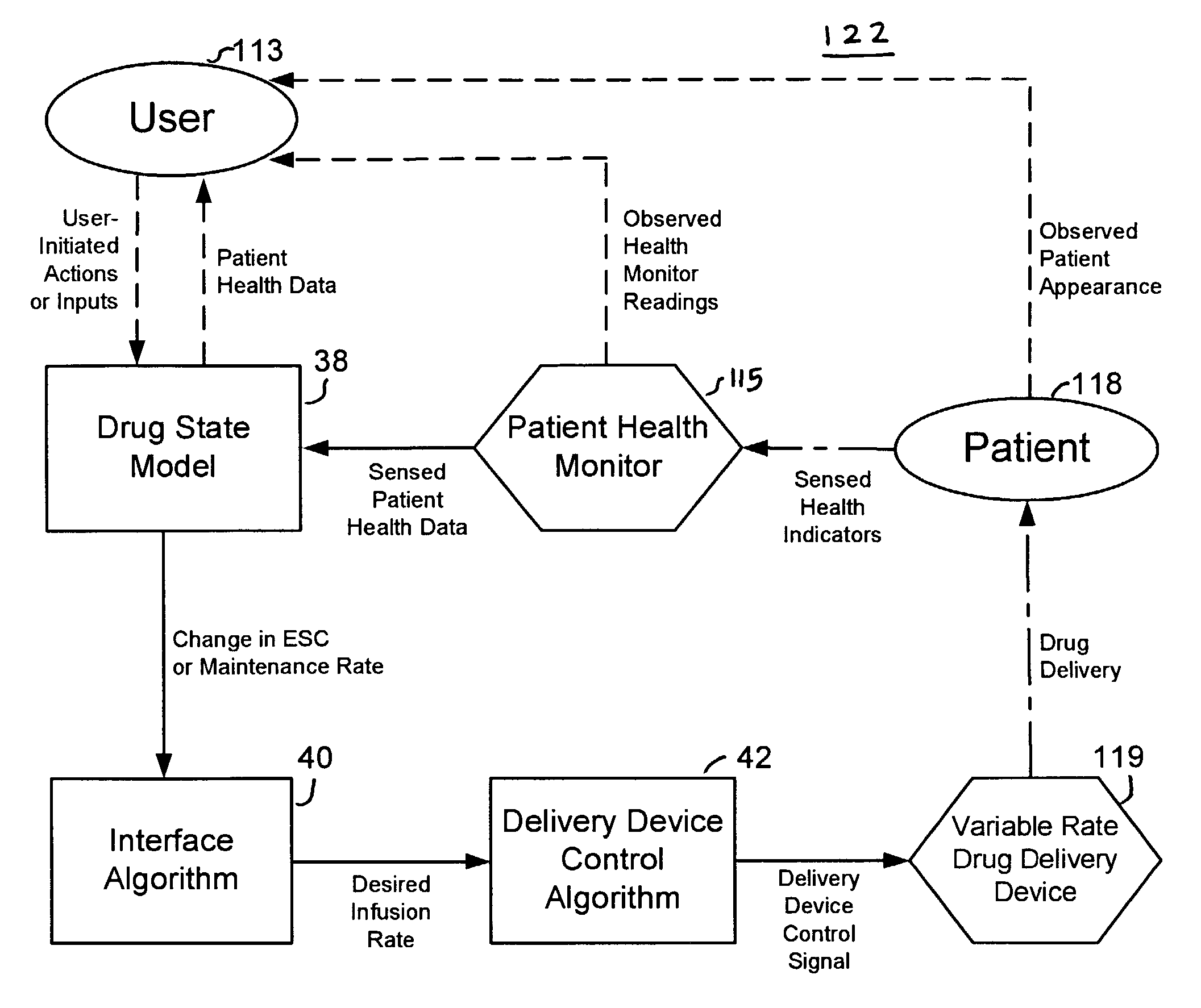
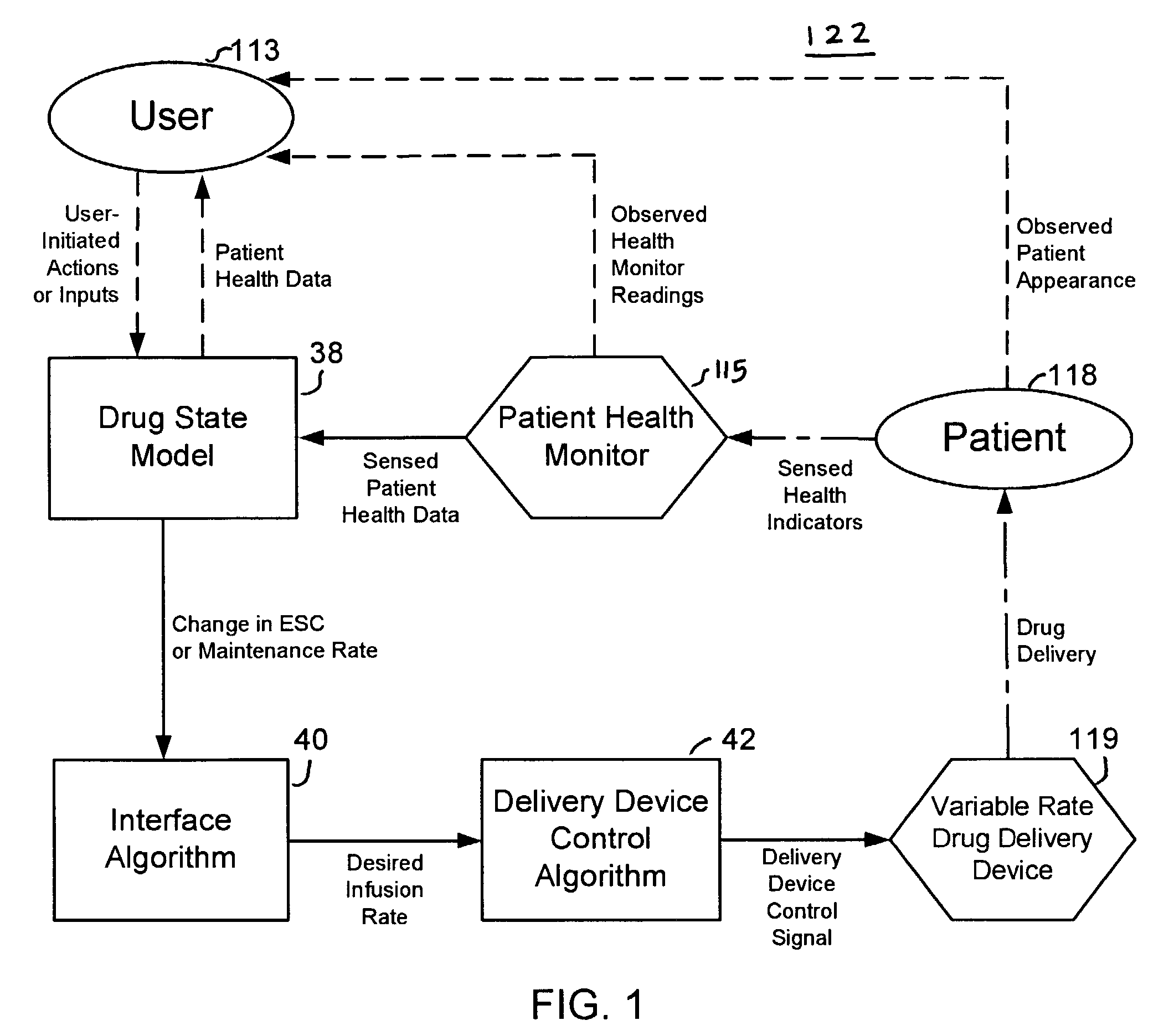
InactiveUS7229430B2Reduce clinical useSafety managementMedical simulationDrug and medicationsState modelTime profile
A method and apparatus for reducing the workload of titrating drug to effect while leaving clinician users in control of a related procedure is described. A drug delivery device is controlled to achieve a target drug concentration at a selected site in the patient or a predetermined infusion rate waveform. The time profile of the target drug concentration or a predetermined infusion rate waveform is controlled by a drug state model that uses clinical heuristics to implement safe, pre-defined changes in the target drug concentration or infusion rate and user-commanded changes in target drug concentration or infusion rate. The invention allows time to assess the response of the patient to changes in drug level by making small incremental and conservative changes in drug level over time.
Owner:SCOTT LAB
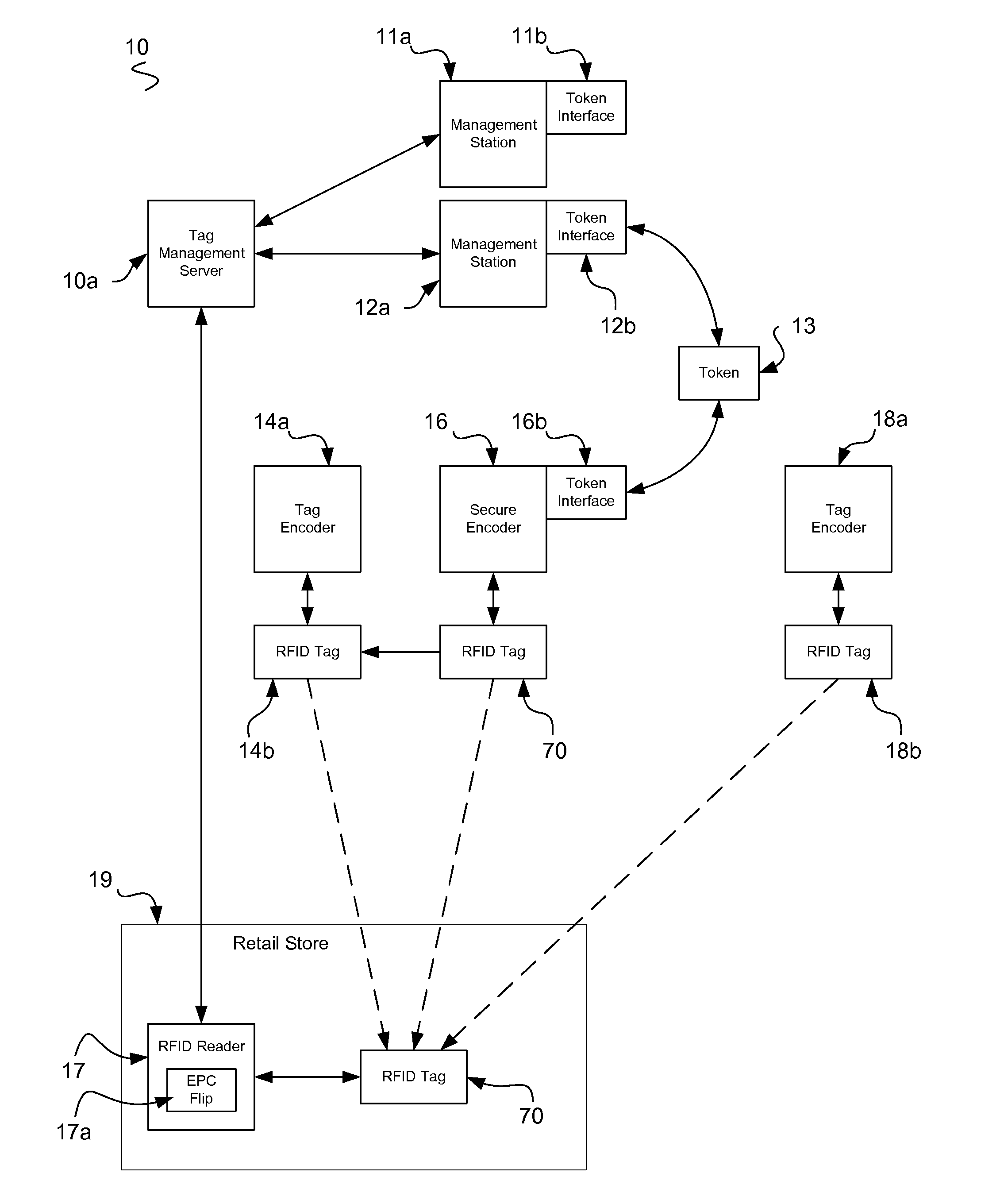
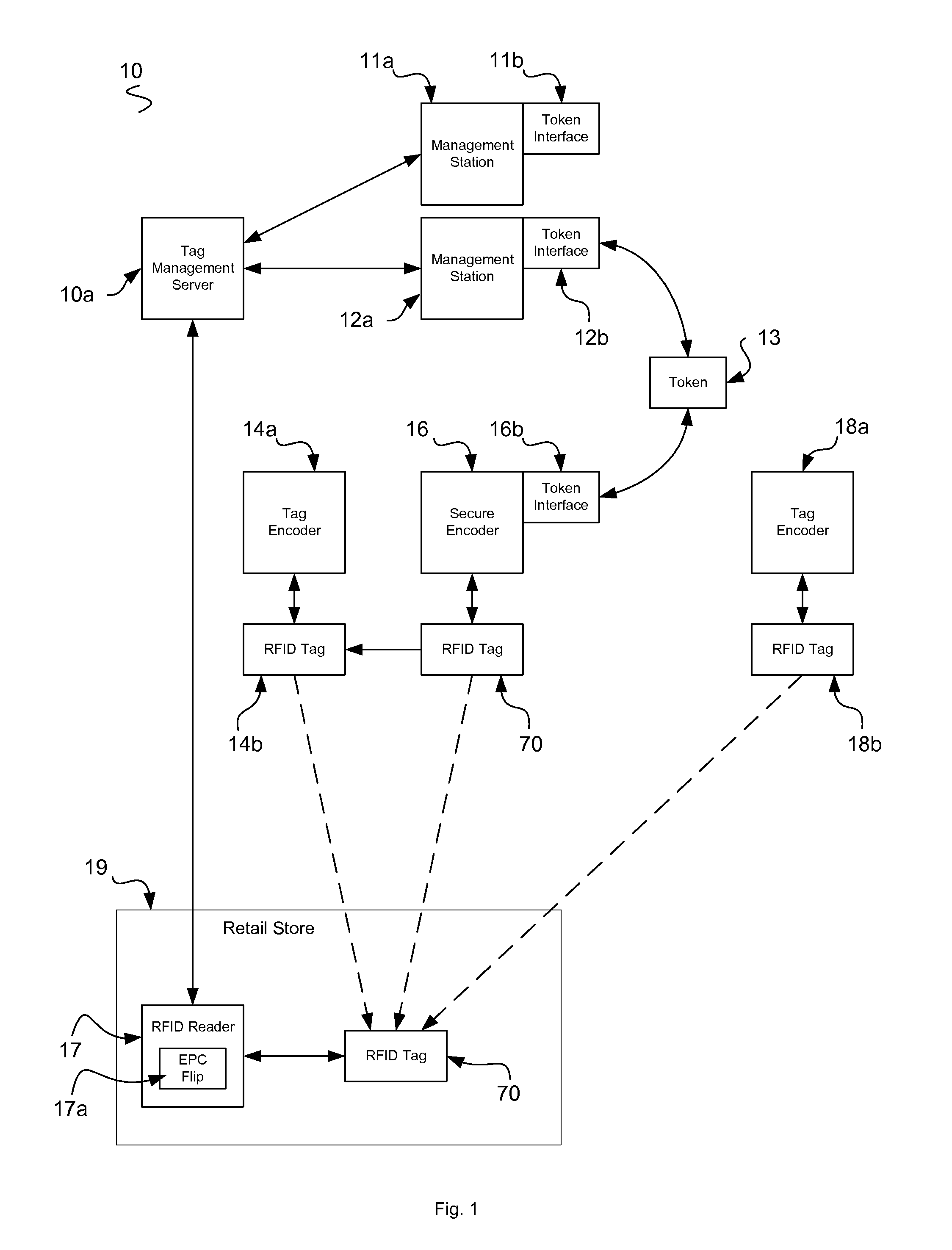
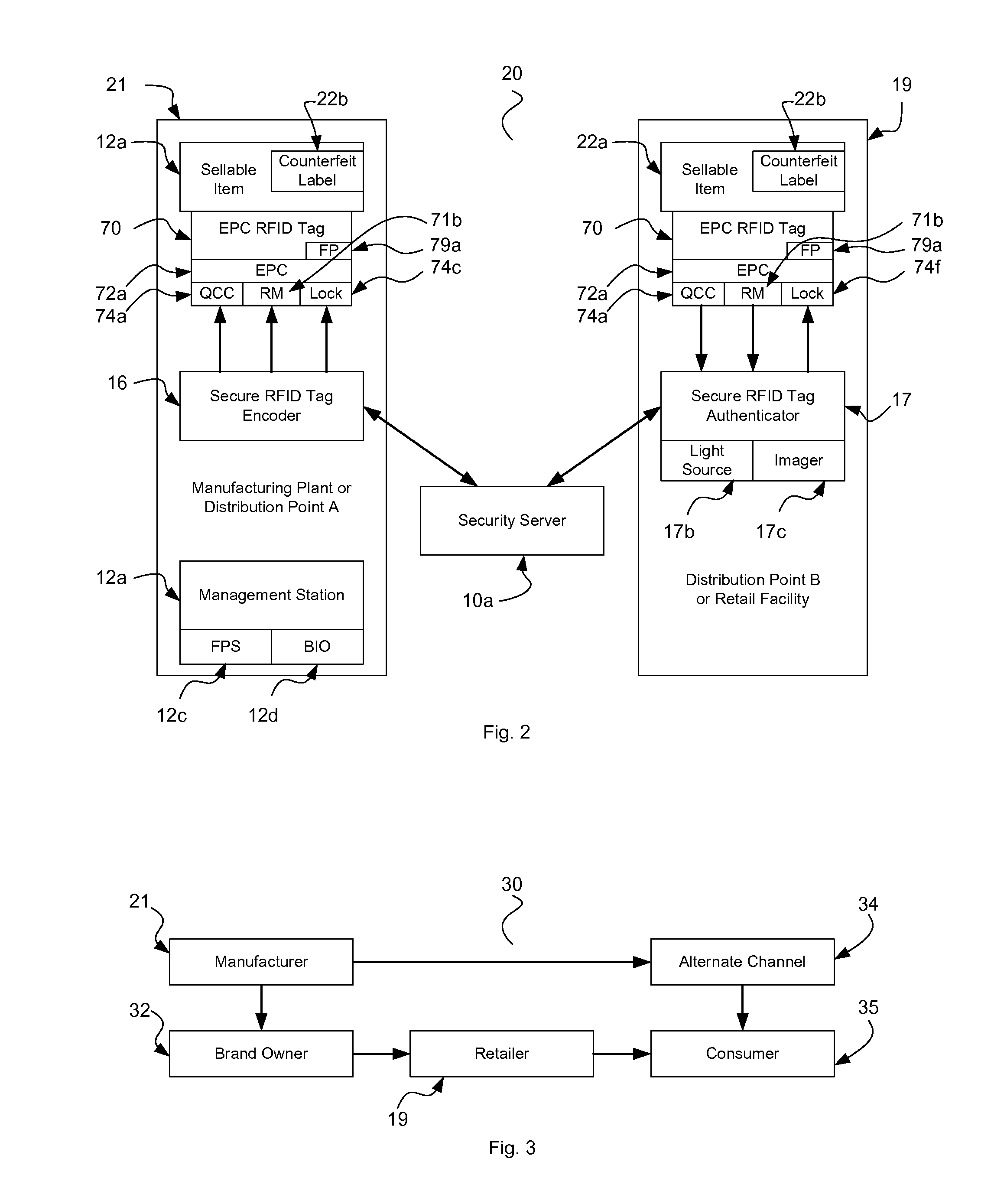
Fully Secure Item-Level Tagging
InactiveUS20100289627A1Efficient and secure and flexibleRobust radio linkDigital data authenticationSubscribers indirect connectionNanolithographyPassword
The present invention provides value to brand owners, retailers, and consumers through the use of radio frequency identification, stenography, nanolithography, fingerprints, novel heuristic threat evaluation, indication, and detection model. Additionally, using cryptography, tag passwords are formulated and identities are reversibly flipped, thus allowing item identities to remain secret to unauthorized observers. This unique combination of heuristics and authentication technologies provides an efficient means of finding and stopping the flow of counterfeit products throughout global supply chains. The present invention includes radio frequency identification (RFID) tags, encoders, servers, identity changers, and authenticity verifiers to make this task a viable and adaptive weapon against the elusive counterfeiters. The present end-to-end RFID system offers unprecedented security for retailers and consumers, while remaining efficient and scalable.
Owner:MCALLISTER CLARKE WILLIAM +1
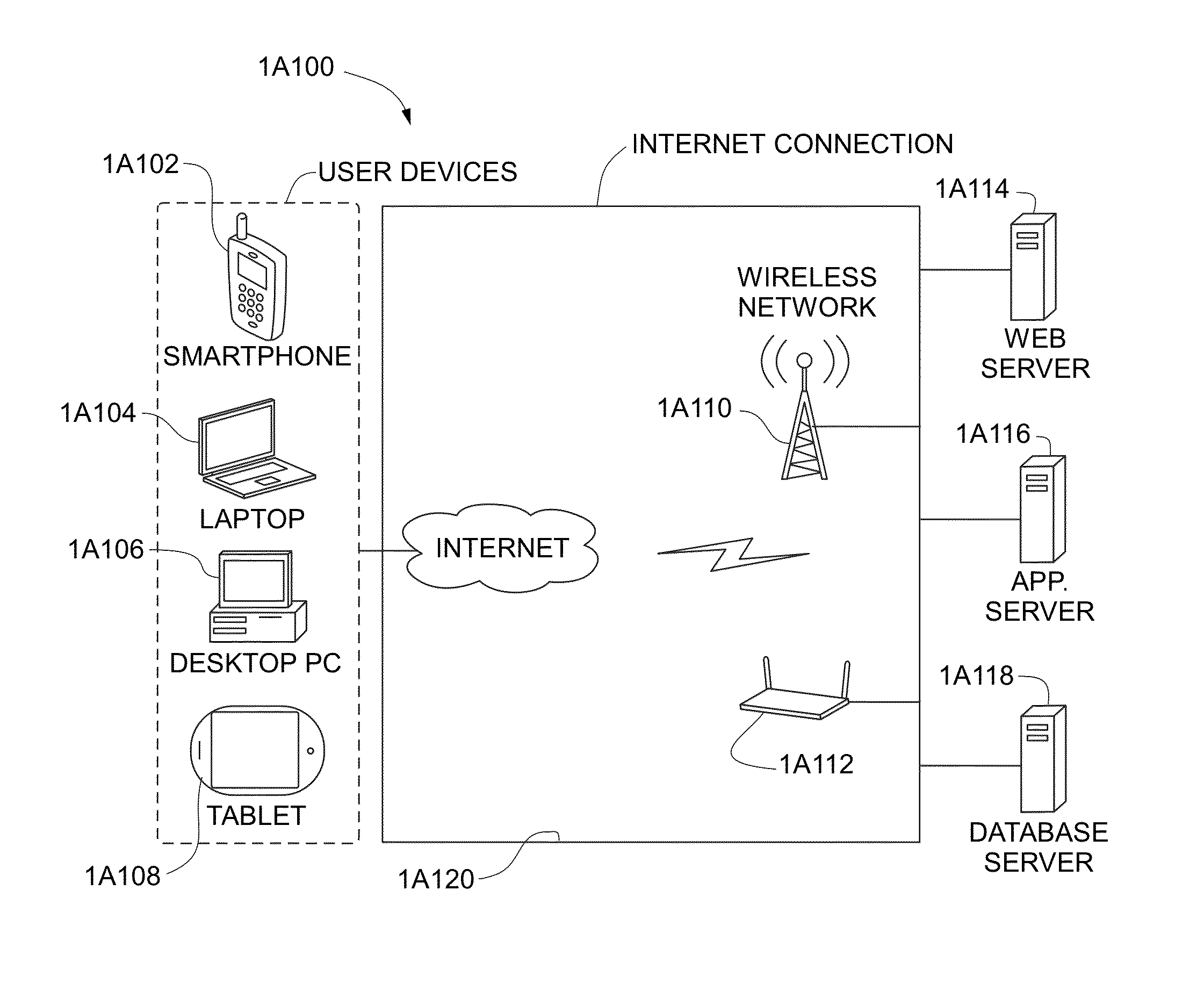
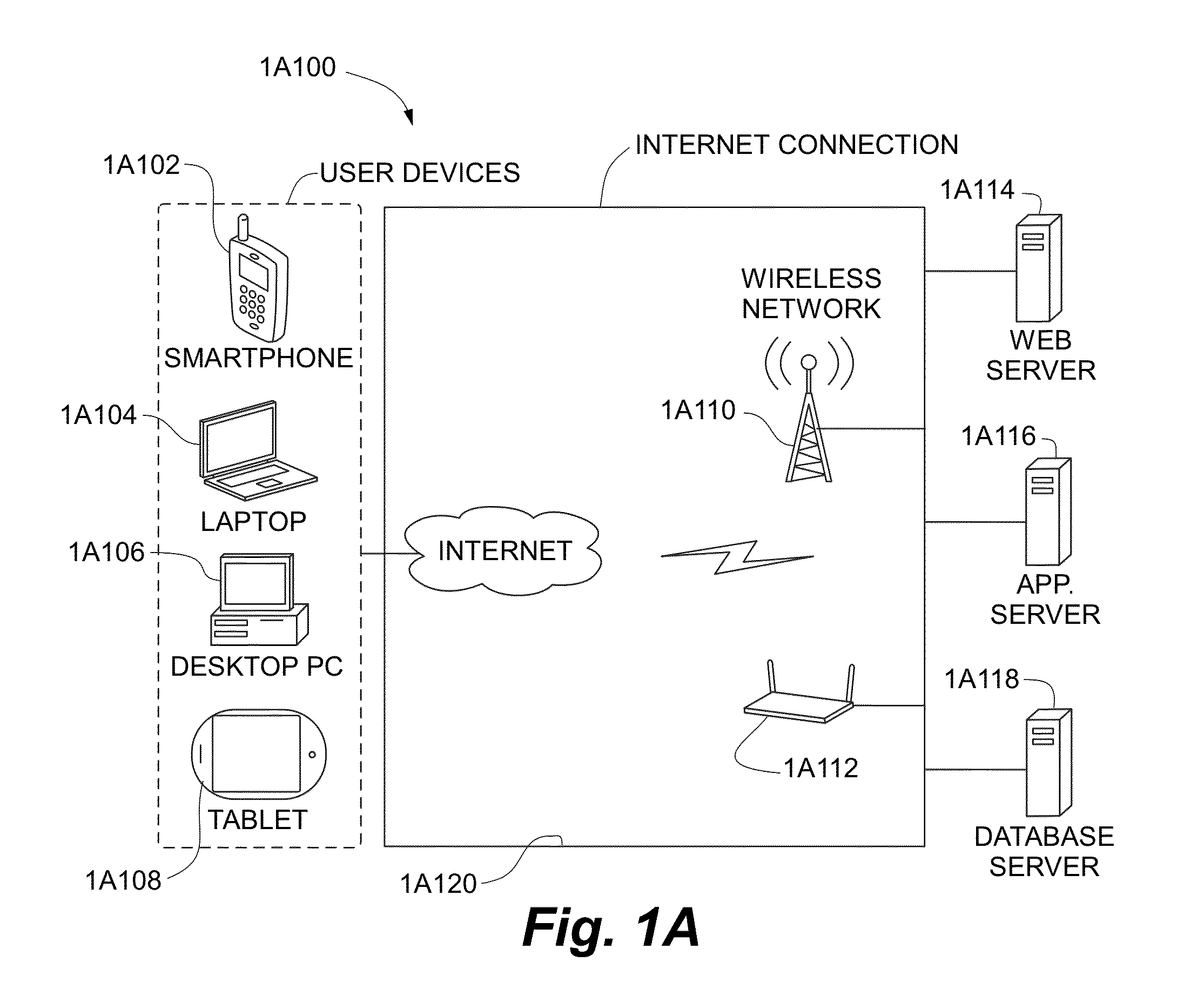
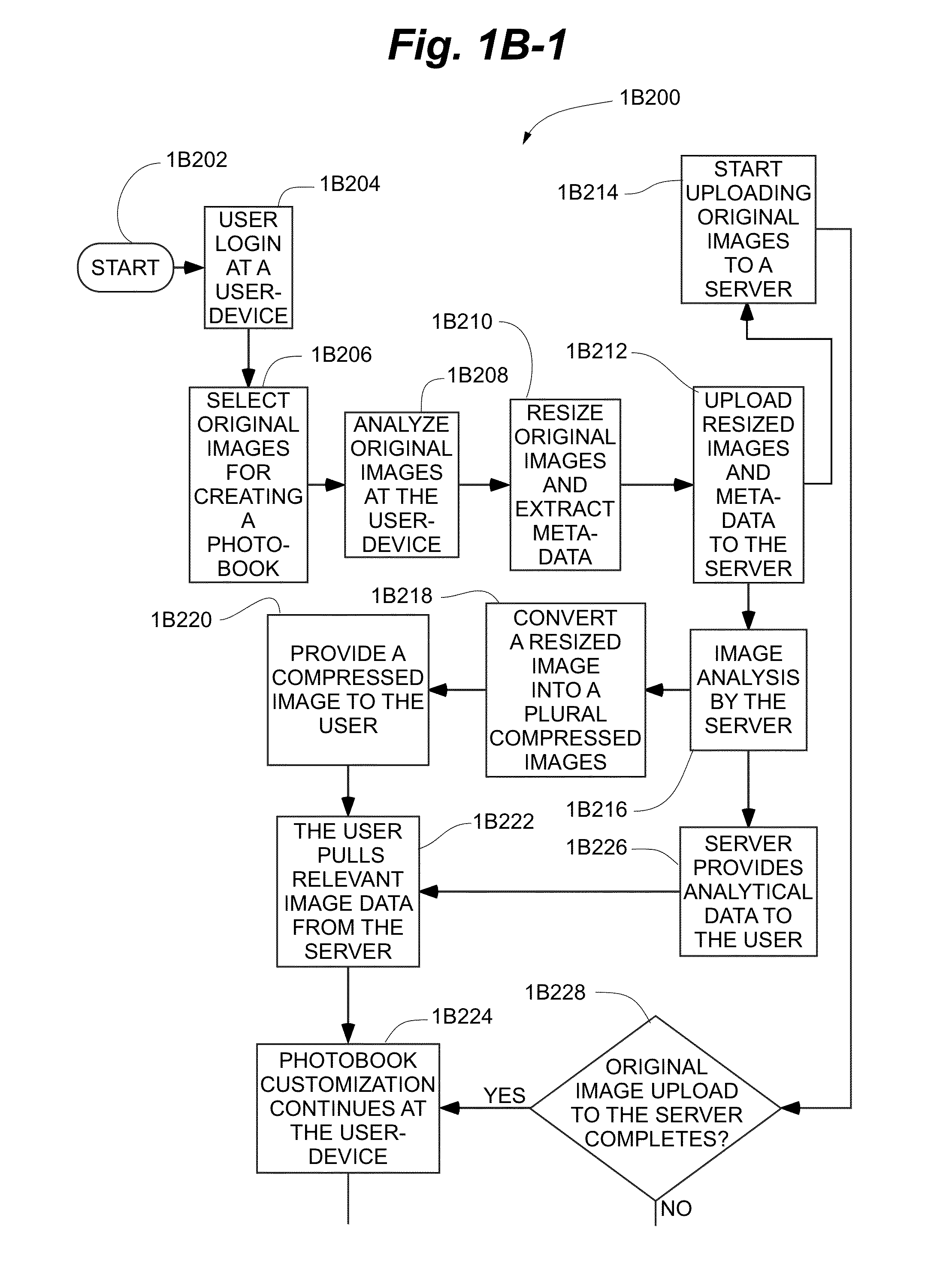
Systems and methods for generating autoflow of content based on image and user analysis as well as use case data for a media-based printable product
ActiveUS20140193047A1Closer to purchaseText processingCharacter and pattern recognitionPattern recognitionComputer graphics (images)
In some embodiments, a server for creating photo-based projects is disclosed. The server executes a method for establishing a client-server connection between the server and a user-operated computer connected to the network, receiving images from the computer and storing the images in the a data repository, receiving a use-case identifier, performing photo analysis on the images, comprising: identifying similar images, identifying faces in the images, identifying objects in the images, identifying undesirable images and identifying relevant portions of the images, performing use-case specific heuristics on the images, comprising: grouping similar images, grouping images having identical faces, grouping images having identical objects, removing undesirable images, and cropping images to highlight relevant portions of said images, and, generating an ordered project subsequent to execution of the use-case specific heuristics, wherein the ordered project comprises the images placed in a particular order and pre-processed for printing in book form.
Owner:INTERACTIVE MEMORIES
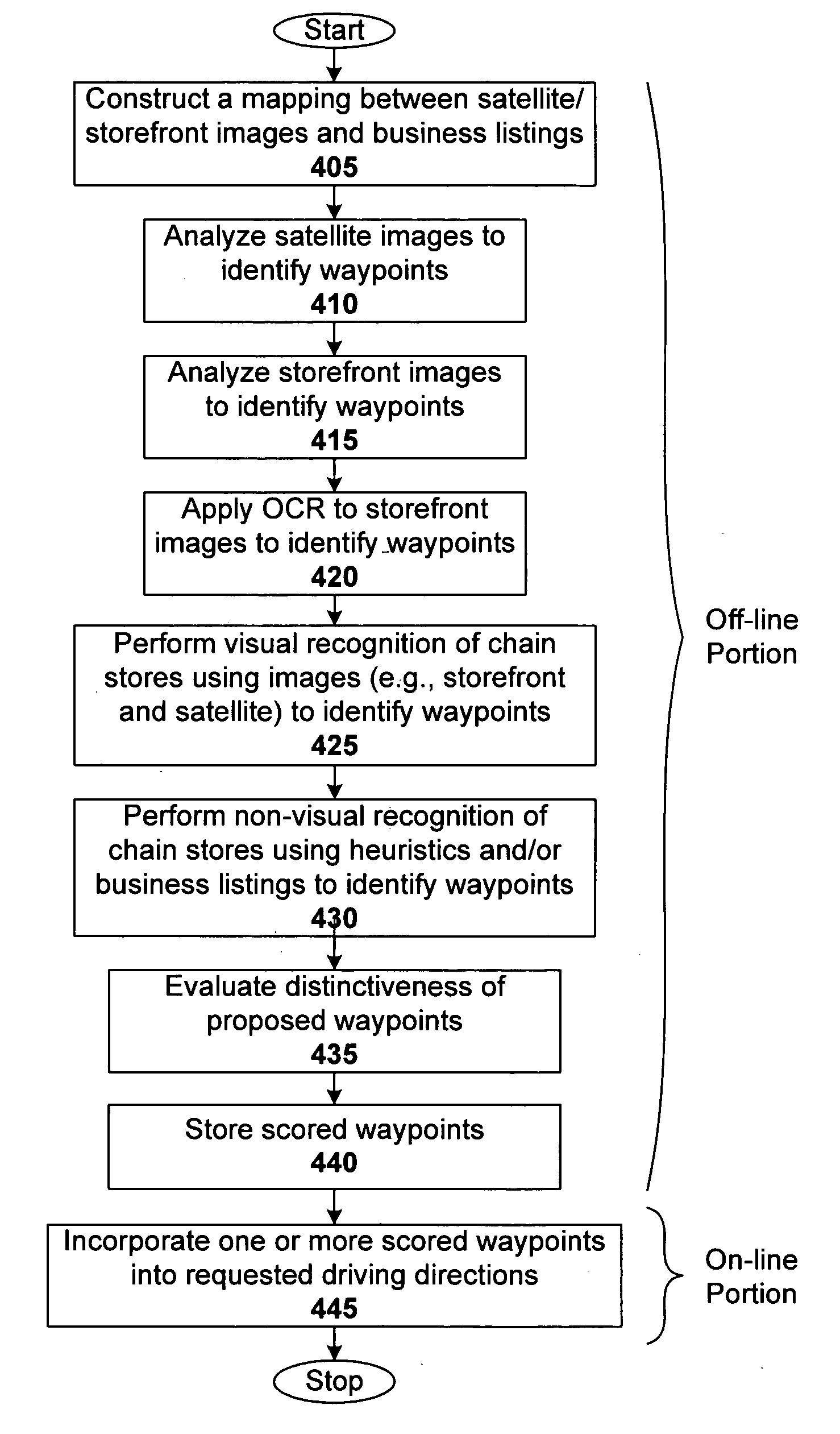
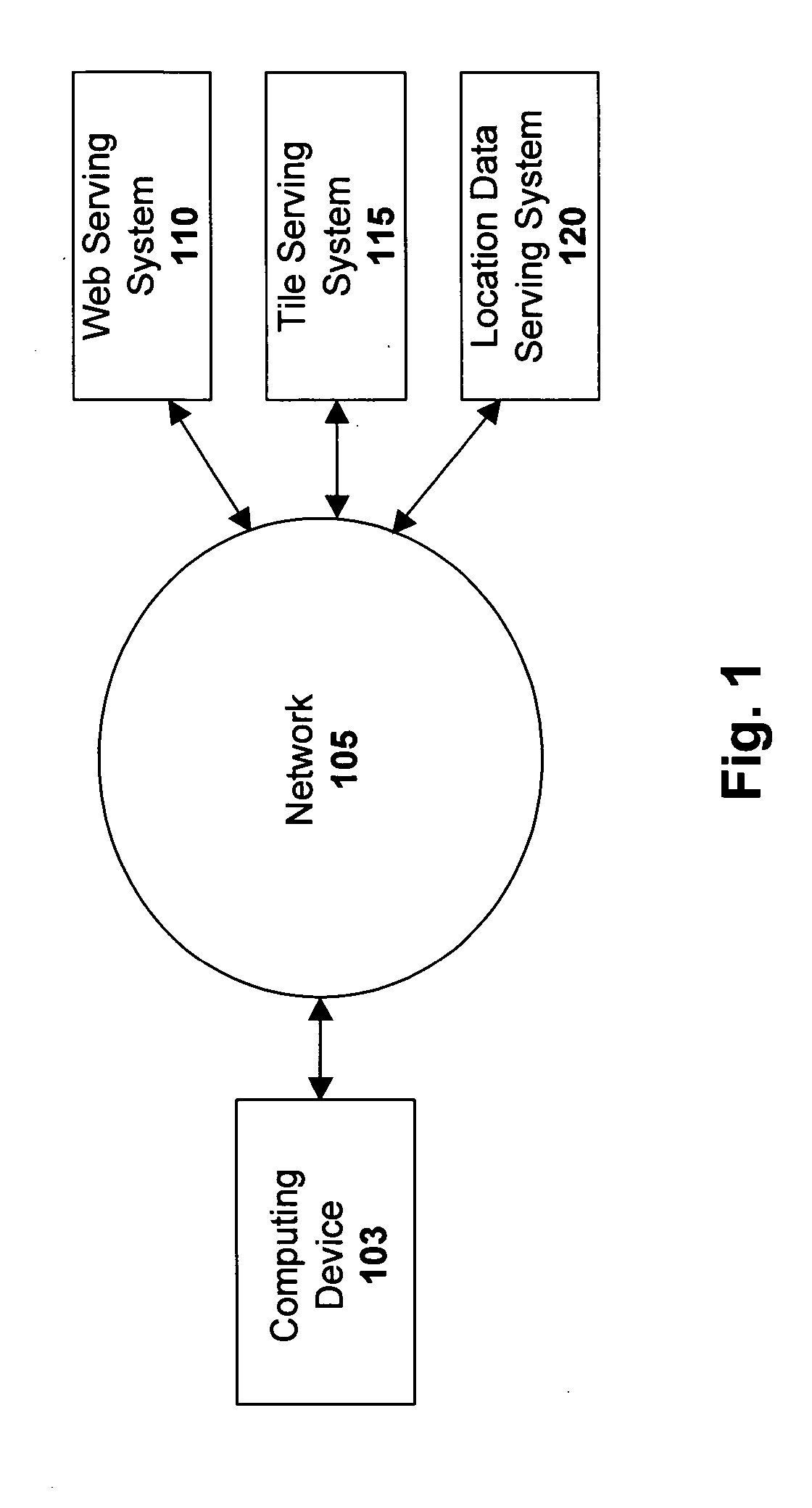
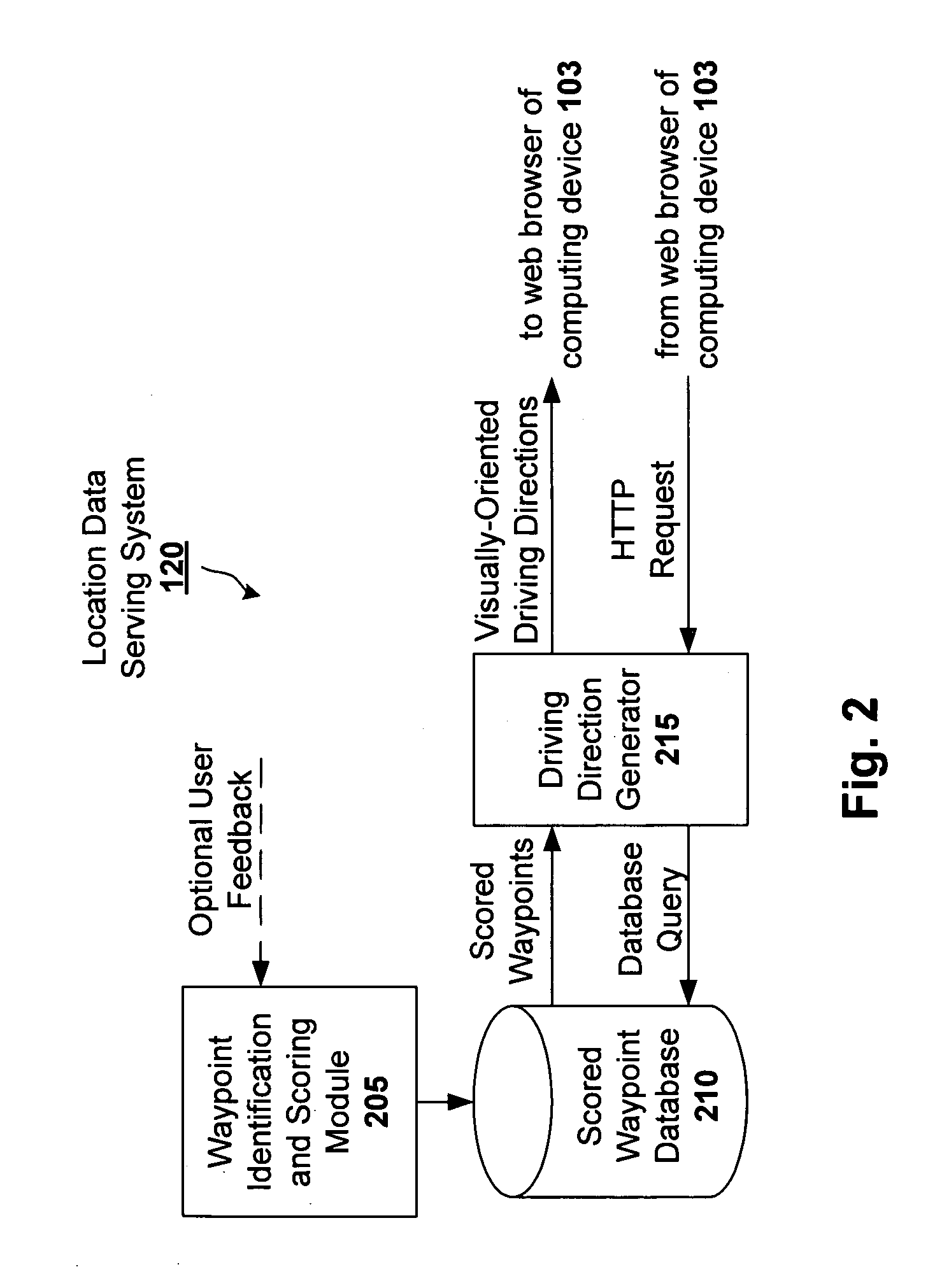
Visually-oriented driving directions in digital mapping system
ActiveUS20050288859A1Instruments for road network navigationRoad vehicles traffic controlSatellite imageHeuristic
Digital mapping techniques are disclosed that provide visually-oriented information to the user, such as driving directions that include visual data points along the way of the driving route, thereby improving the user experience. The user may preview the route associated with the driving directions, where the preview is based on, for example, at least one of satellite images, storefront images, and heuristics and / or business listings.
Owner:GOOGLE LLC
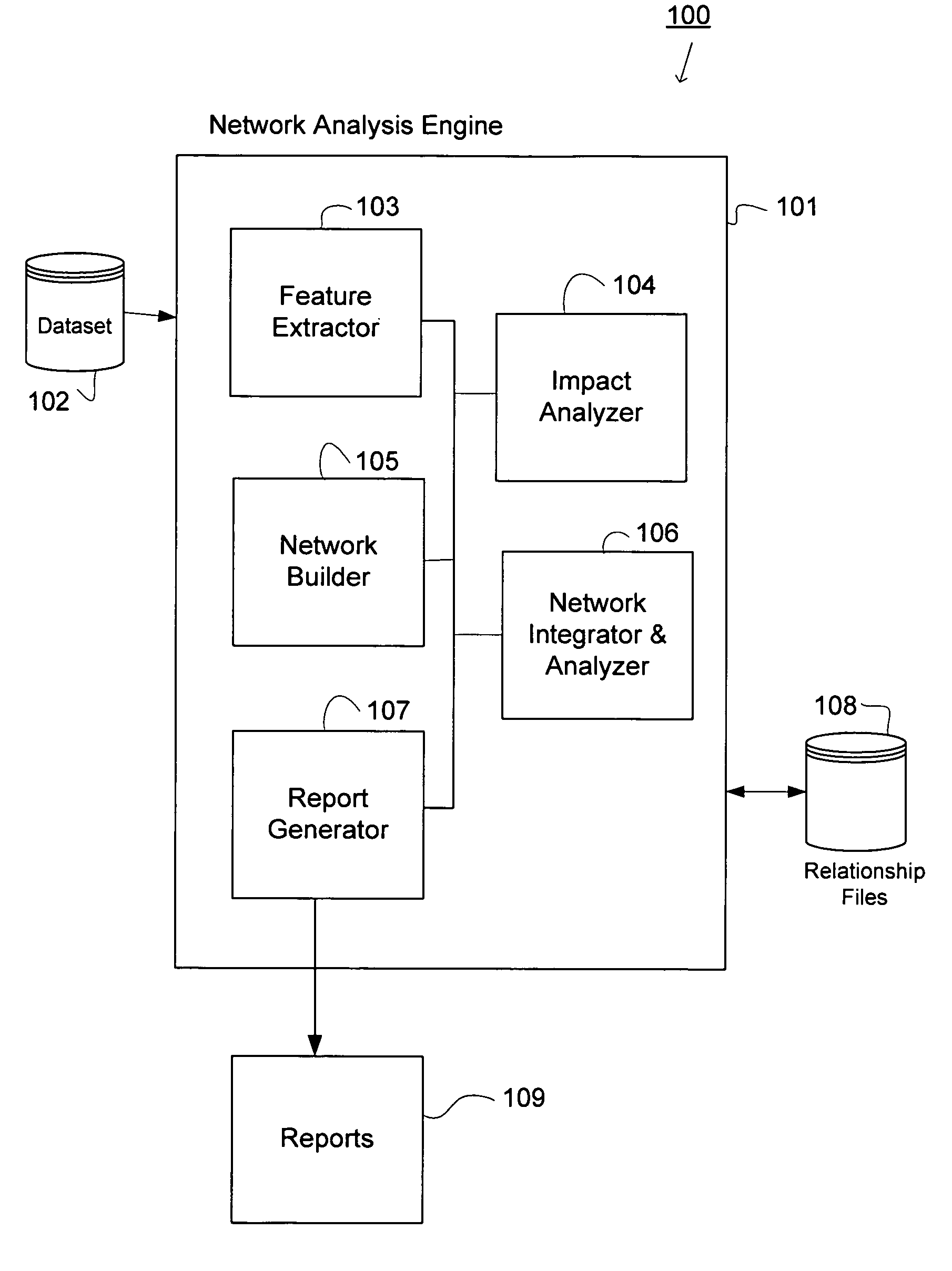
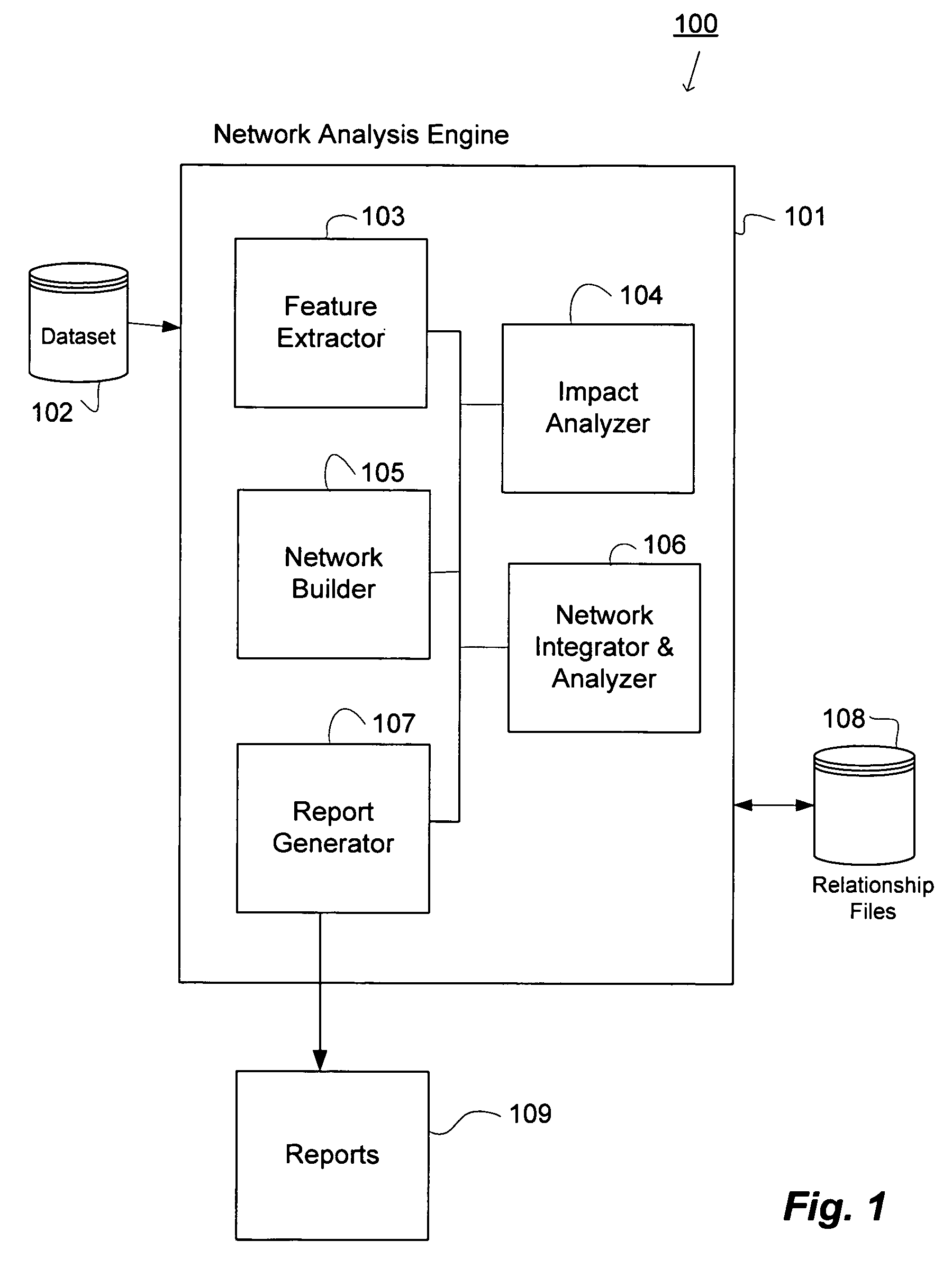
System and methods for data analysis and trend prediction
InactiveUS20060112111A1Digital data information retrievalSpecial data processing applicationsStatistical analysisHeuristic
Systems and methods for data analysis and trend prediction. Multiple networks are combined for analysis to improve the accuracy of the evaluation by broadening the type of criteria considered. Relevant features are extracted from a dataset and at least one network is formed representing various relationships identified among the items contained in the dataset according to heuristics. Statistical analyses are applied to the relationships and the results output to a user via one or more reports to permit a user to evaluate each of the items in the dataset relative to each other. The trend of the relationships may be predicted based on the results of statistical analysis applied to the features over successive discrete time periods.
Owner:NEC LAB AMERICA
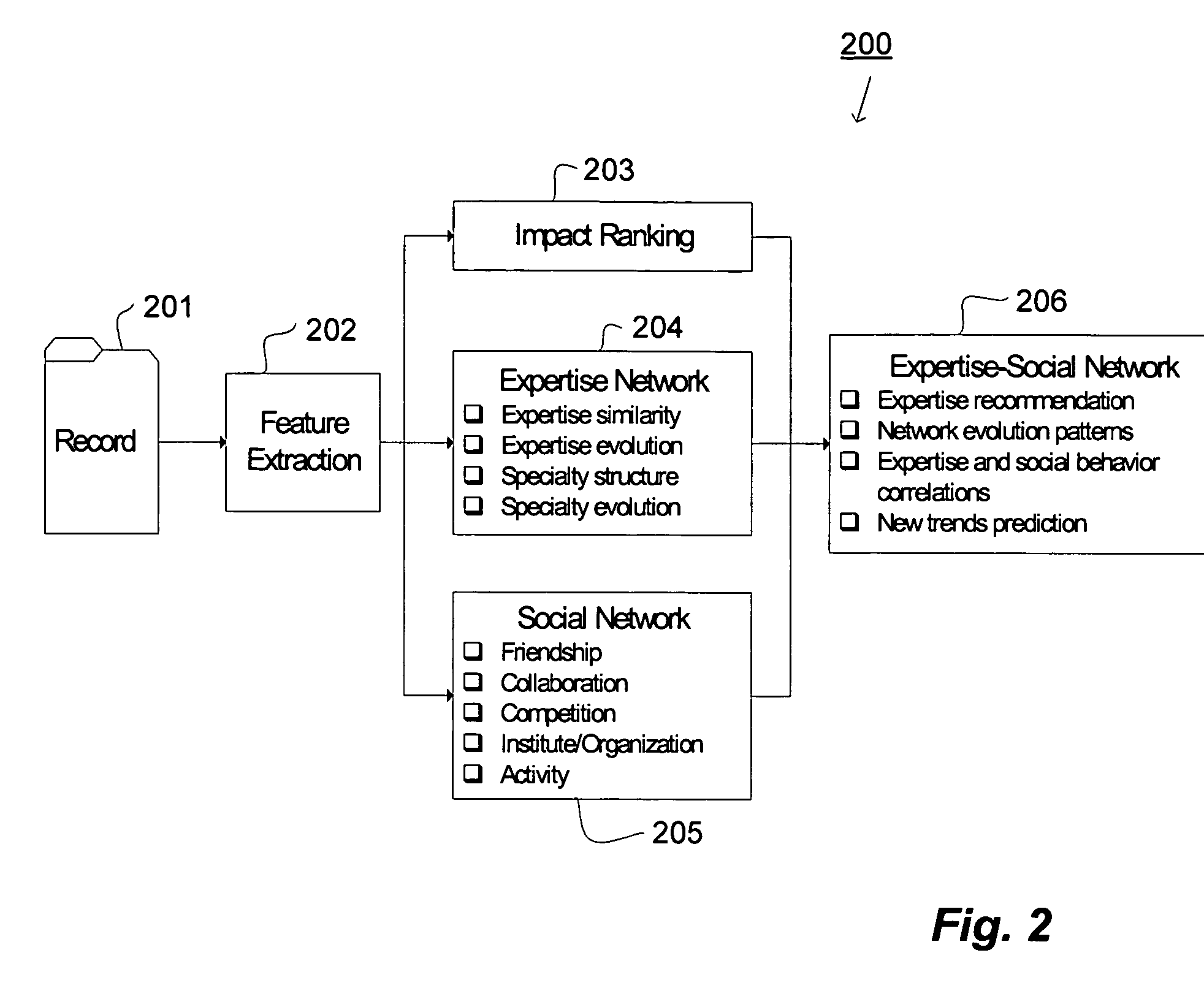
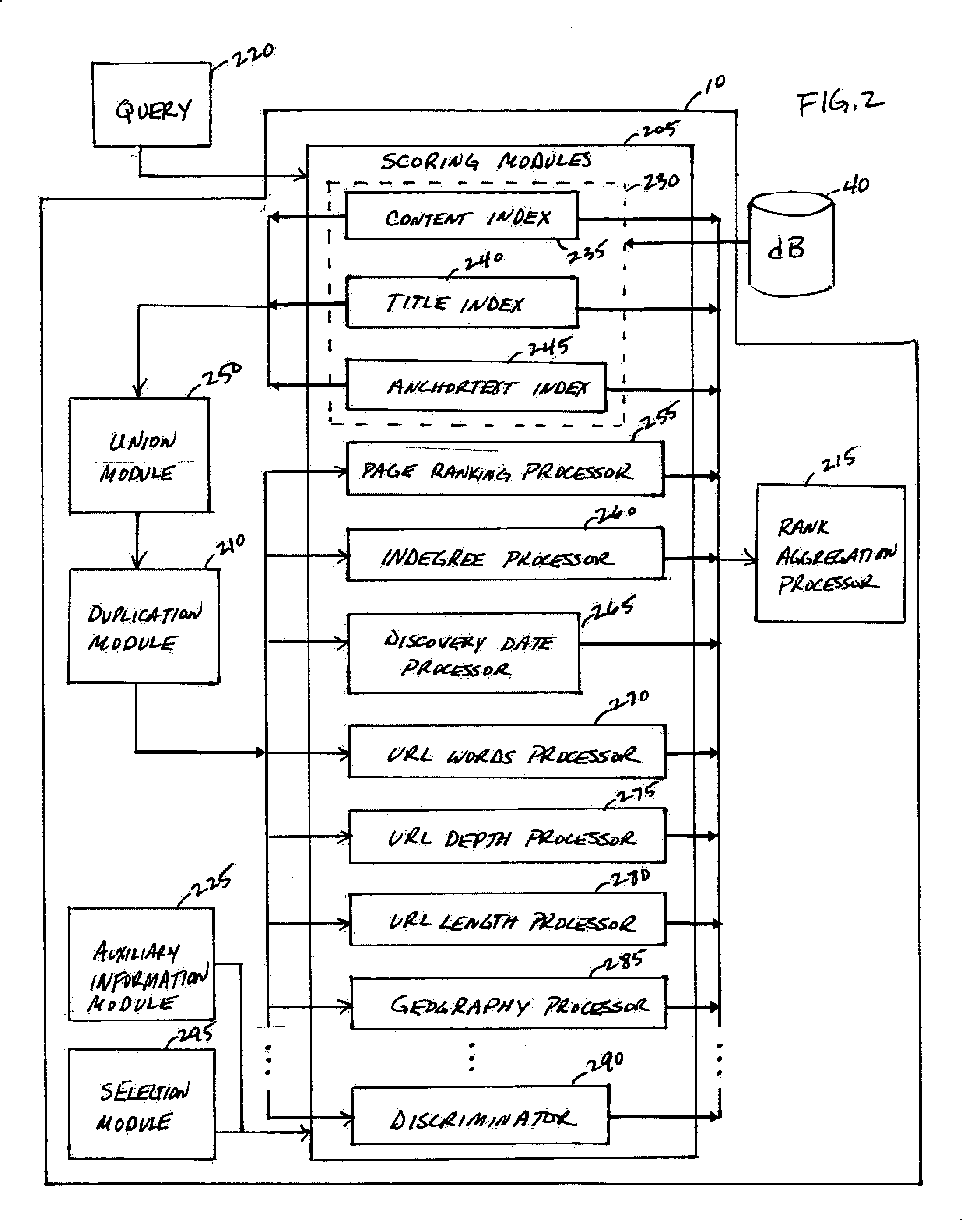
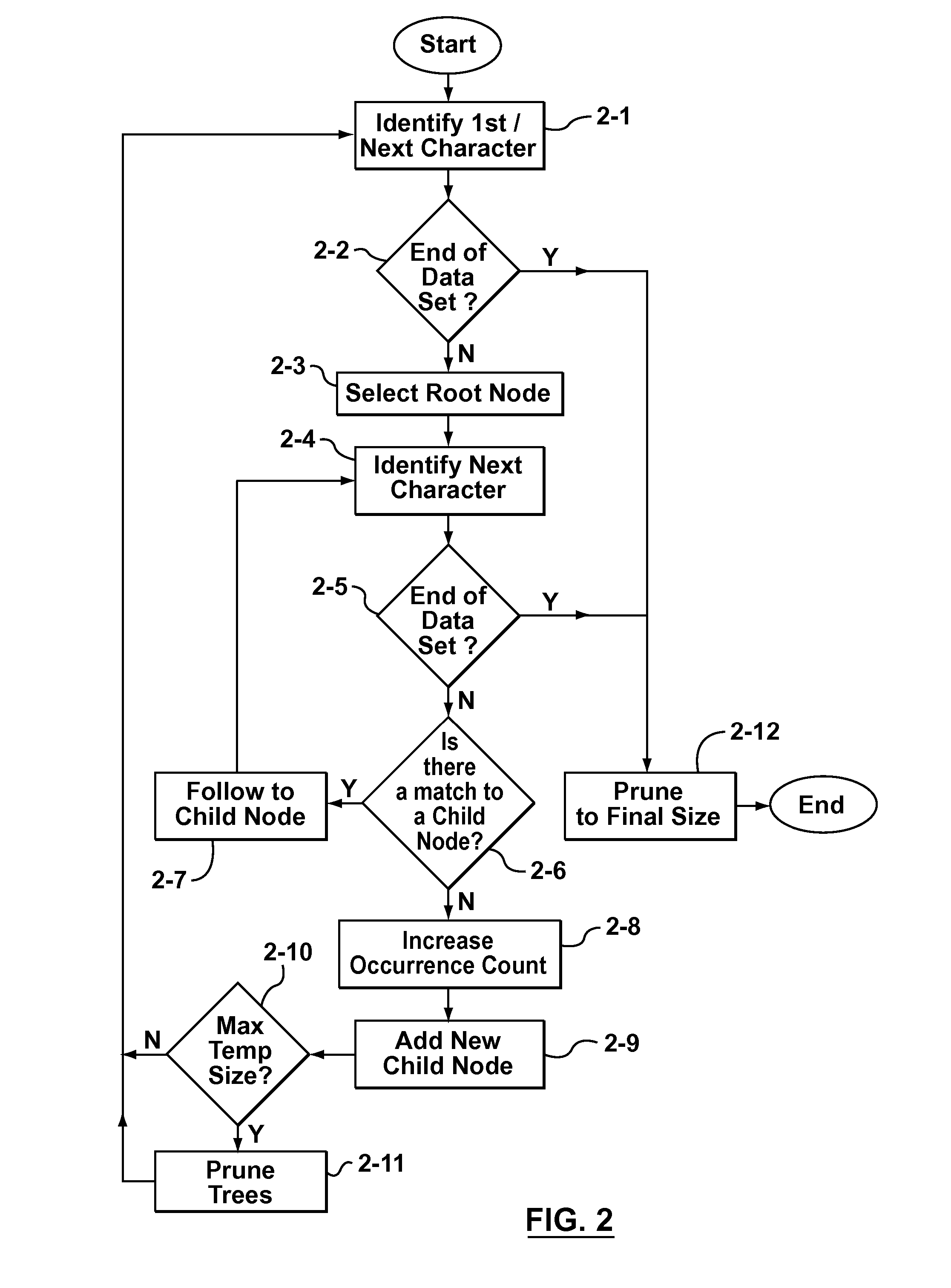
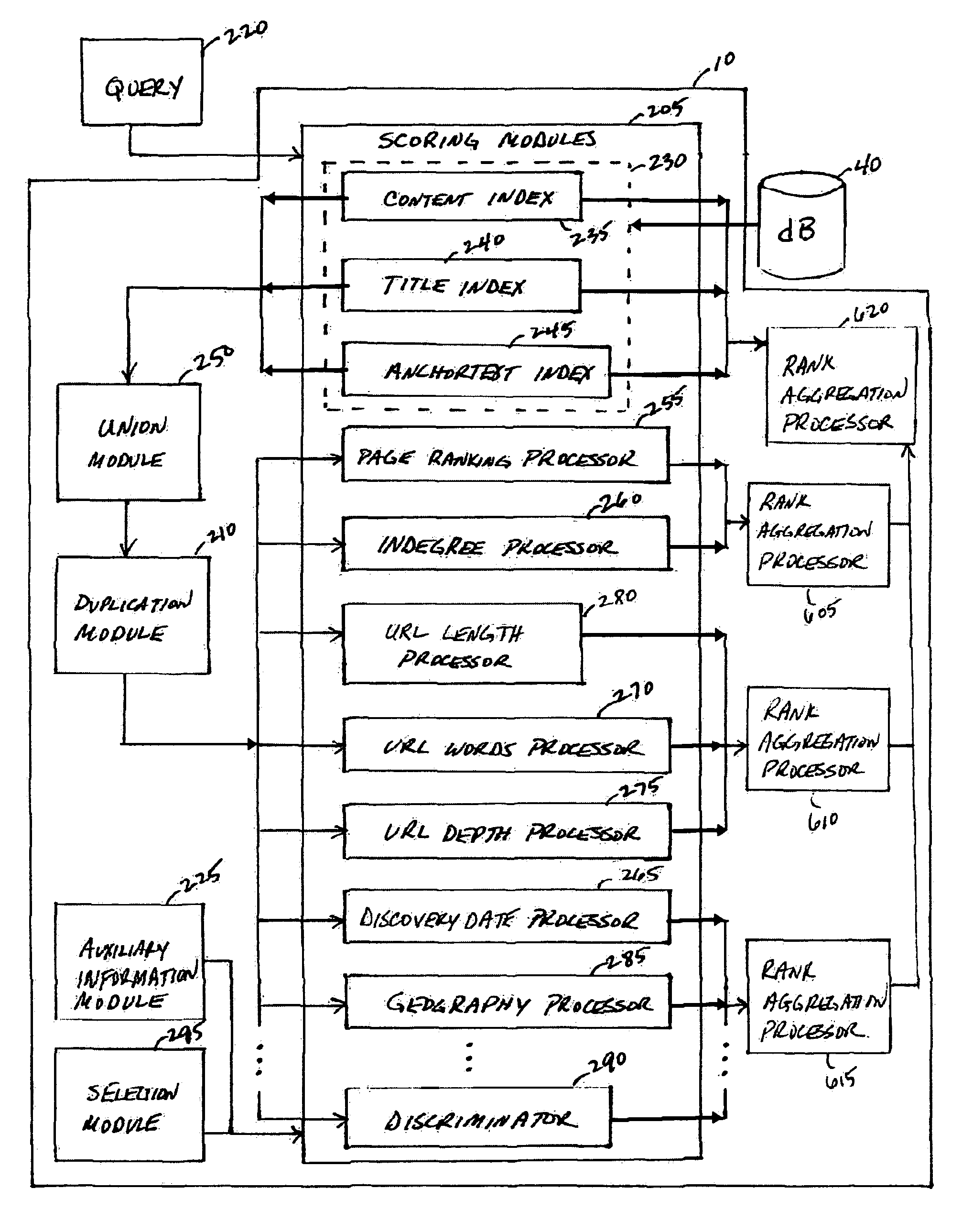
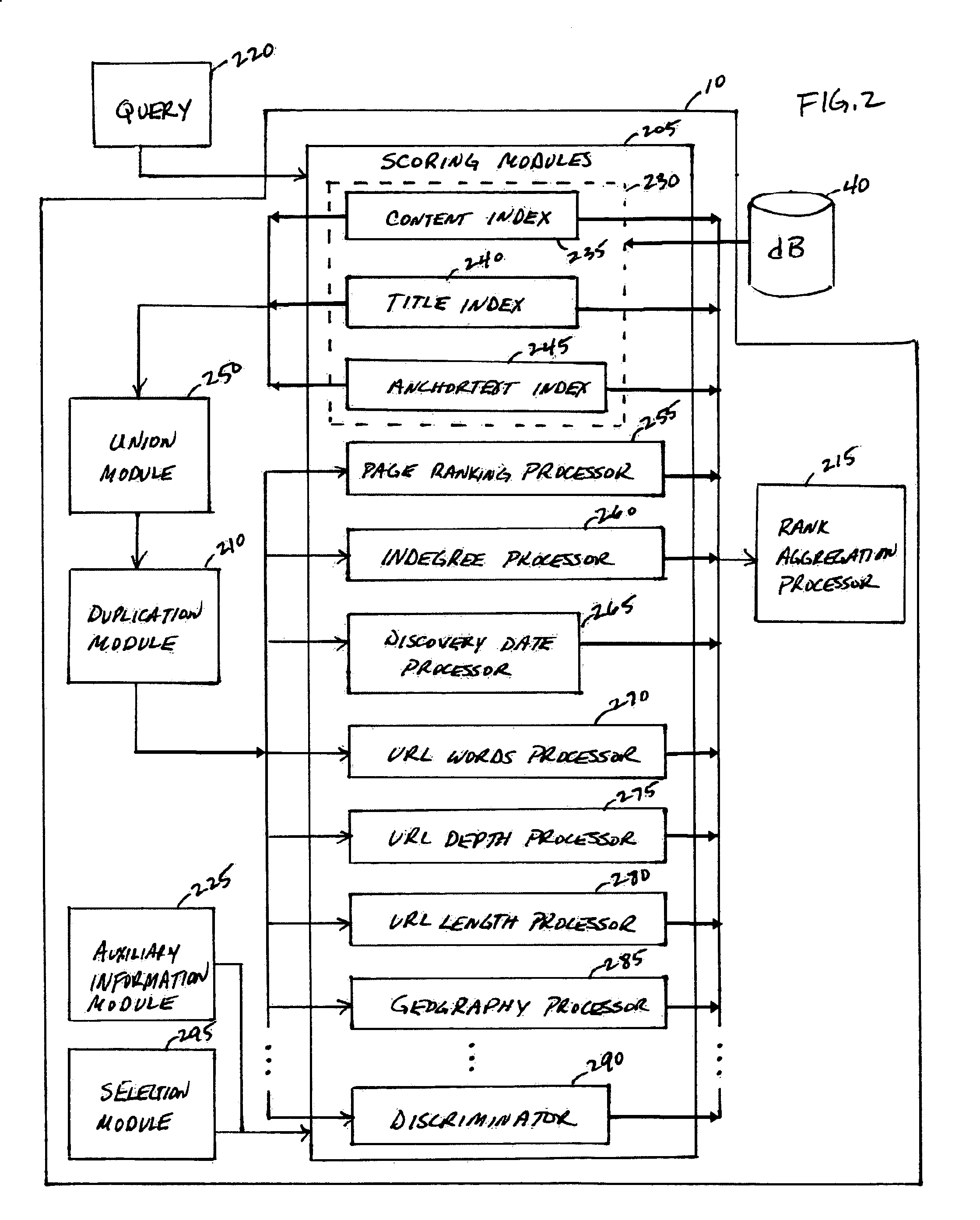
System, method and service for ranking search results using a modular scoring system
ActiveUS20050262050A1Easy to customizeHigh-quality resultData processing applicationsWeb data indexingHeuristicPaper document
A modular scoring system using rank aggregation merges search results into an ordered list of results using many different features of documents. The ranking functions of the present system can easily be customized to the needs of a particular corpus or collection of users such as an intranet. Rank aggregation is independent of the underlying score distributions between the different factors, and can be applied to merge any set of ranking functions. Rank aggregation holds the advantage of combining the influence of many different heuristic factors in a robust way to produce high-quality results for queries. The modular scoring system combines factors such as indegree, page ranking, URL length, proximity to the root server of an intranet, etc, to form a single ordering on web pages that closely obeys the individual orderings, but also mediates between the collective wisdom of individual heuristics.
Owner:GOOGLE LLC
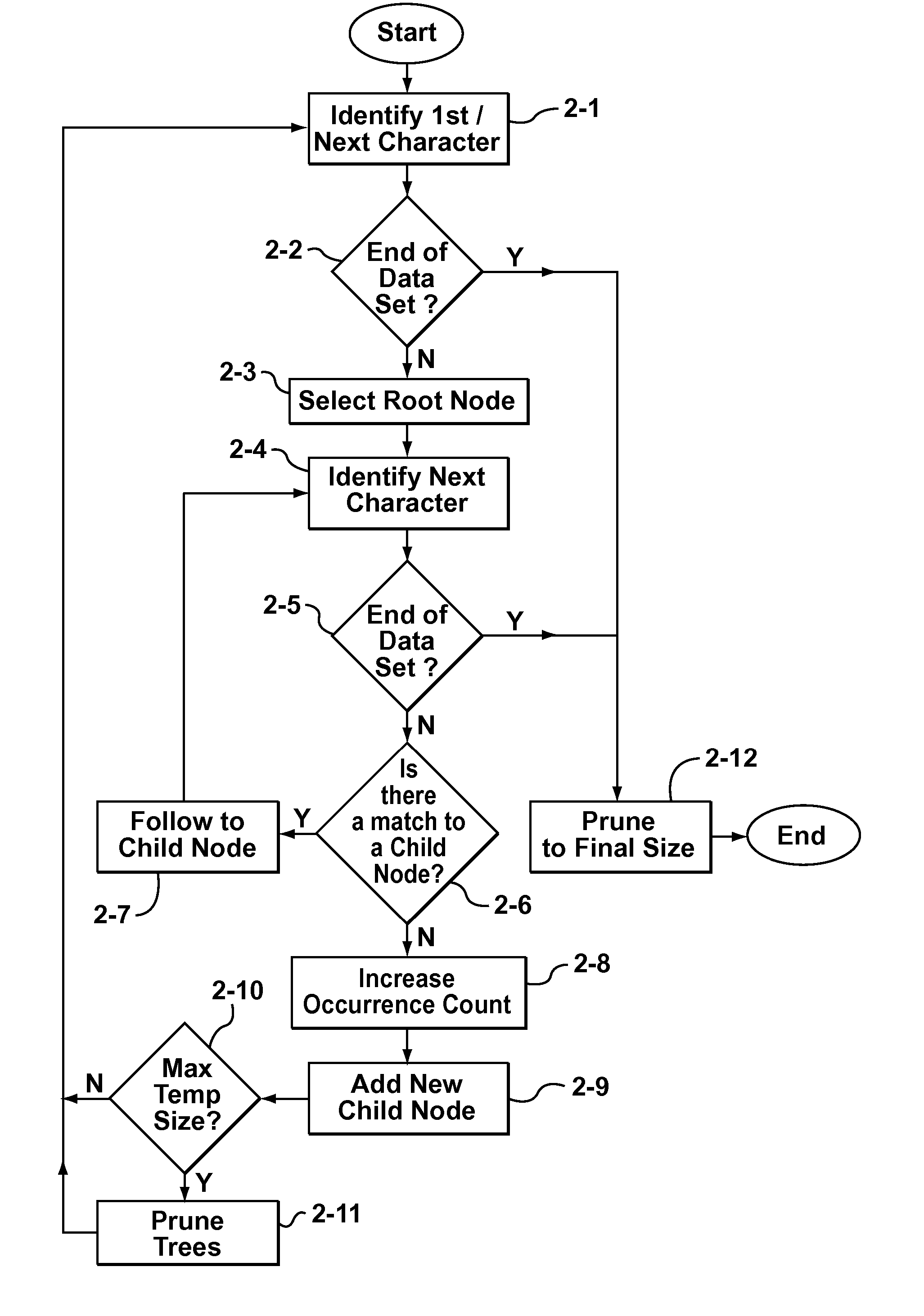
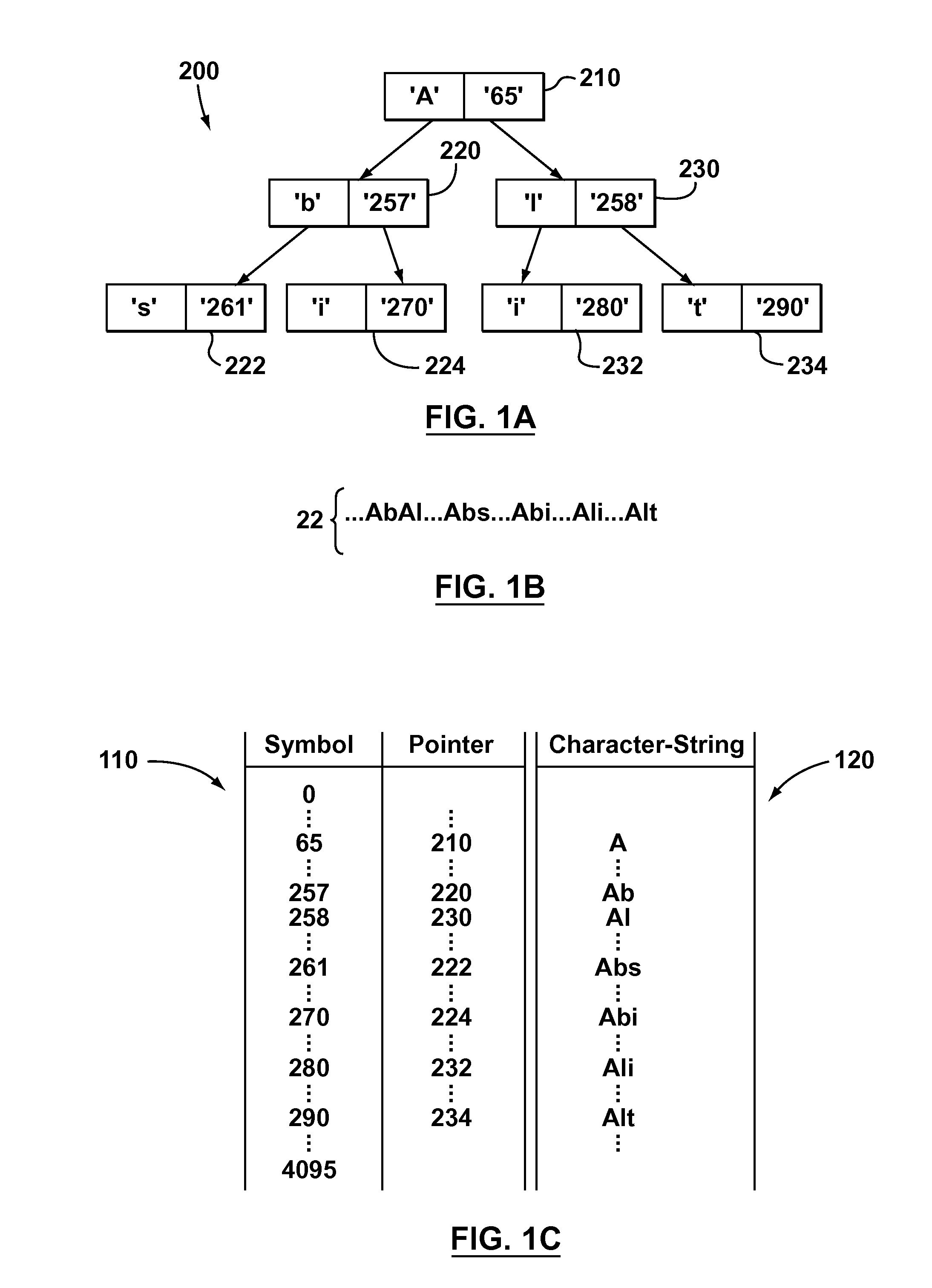
Methods of creating a dictionary for data compression
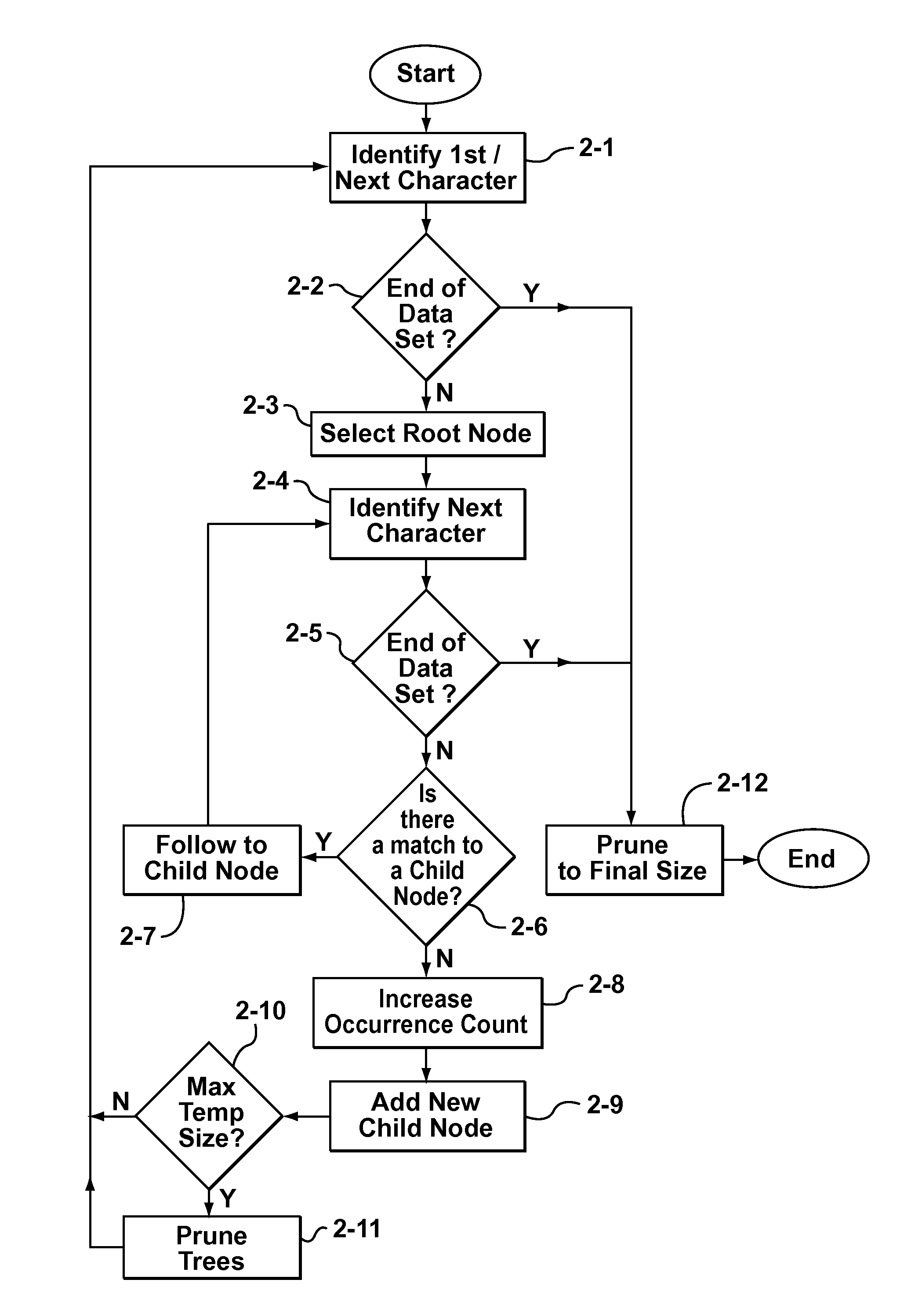
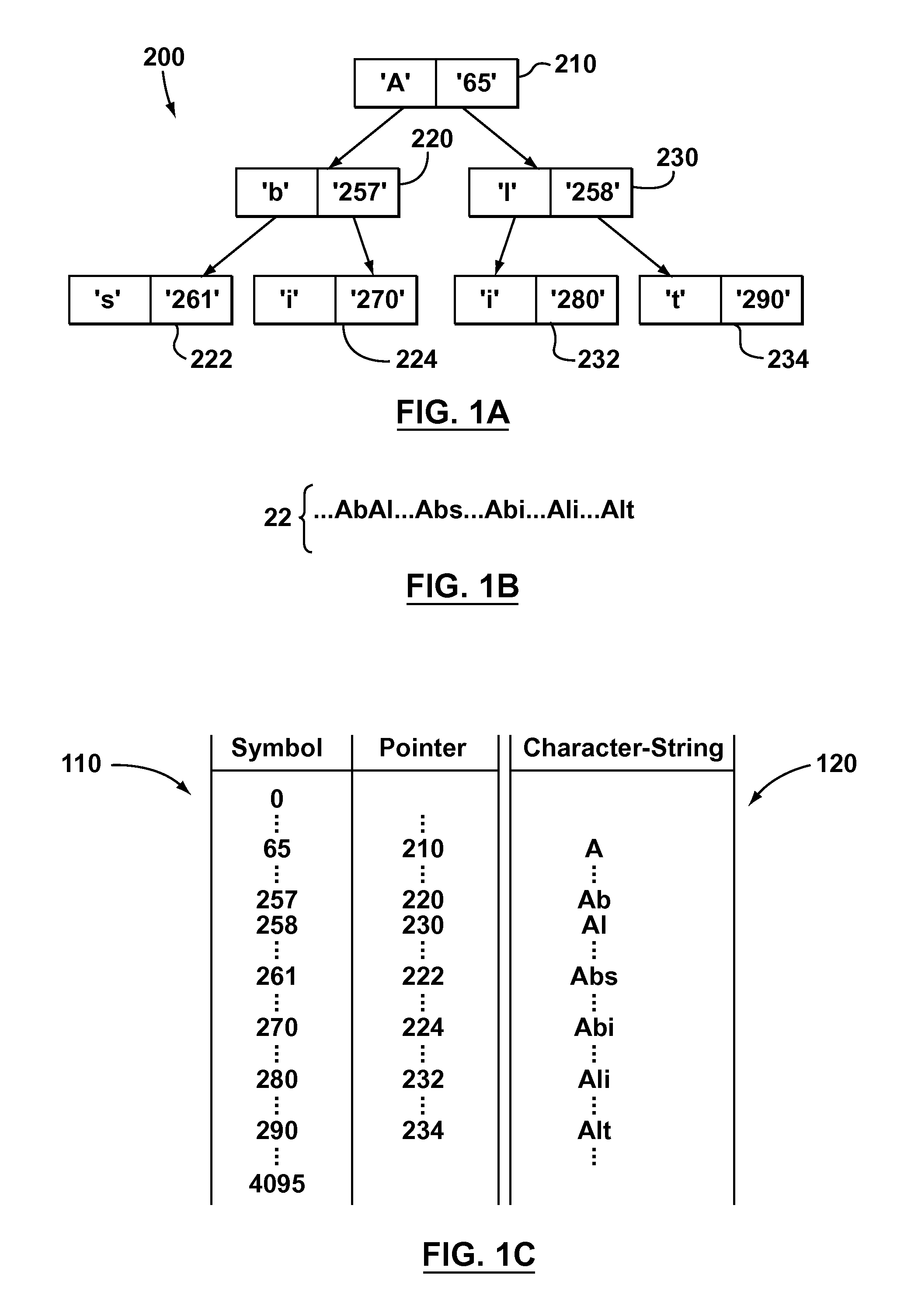
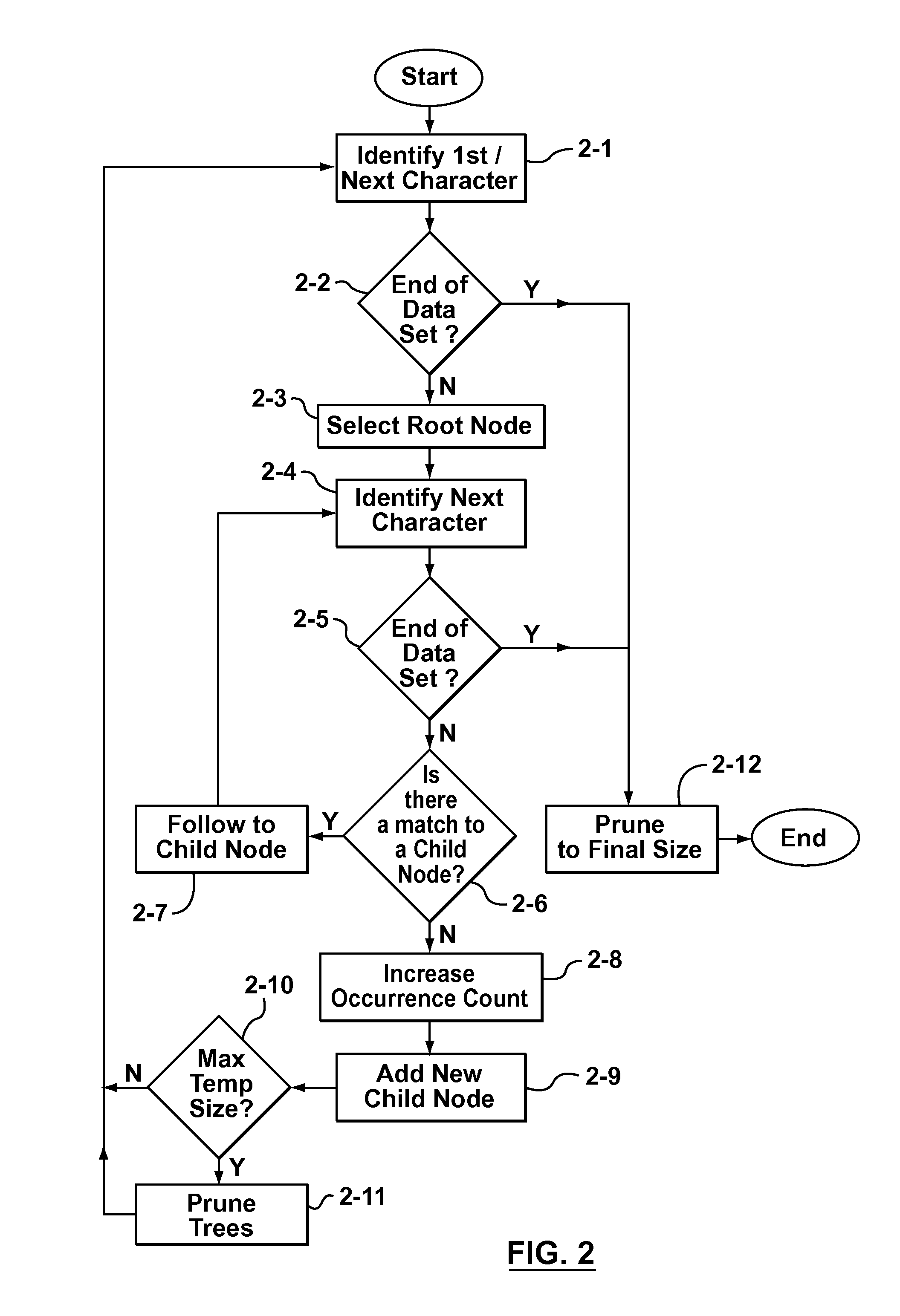
Some aspects of the invention provide methods, systems, and computer program products for creating a static dictionary in which longer byte-strings are preferred. To that end, in accordance with aspects of the present invention, a new heuristic is defined to replace the aforementioned frequency count metric used to record the number of times a particular node in a data tree is visited. The new heuristic is based on counting the number of times an end-node of a particular byte-string is visited, while not incrementing a count for nodes storing characters in the middle of the byte-string as often as each time such nodes are visited. The result is an occurrence count metric that favours longer byte-strings, by being biased towards not incrementing the respective occurrence count values for nodes storing characters in the middle of a byte-string.
Owner:GLOBALFOUNDRIES INC
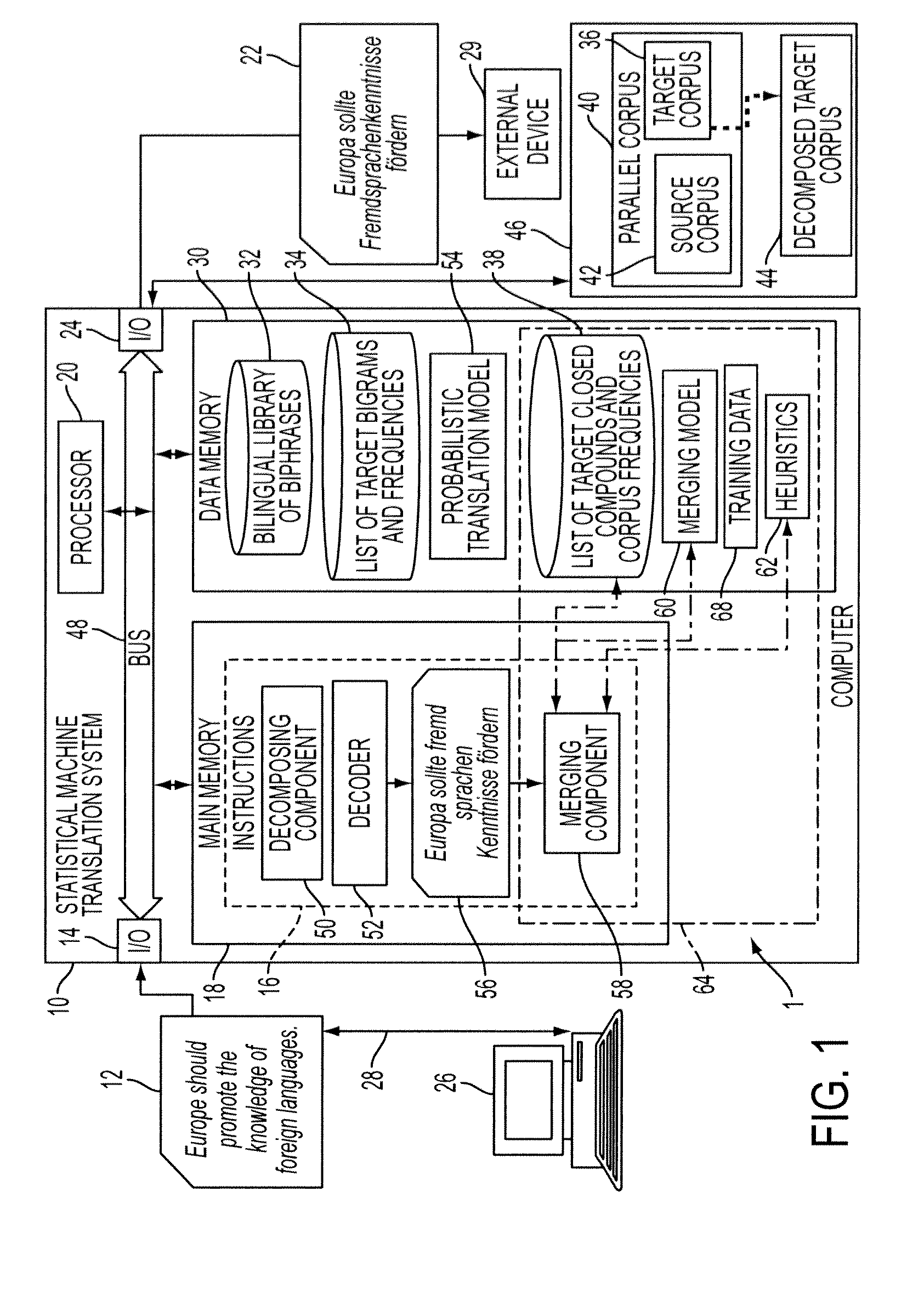
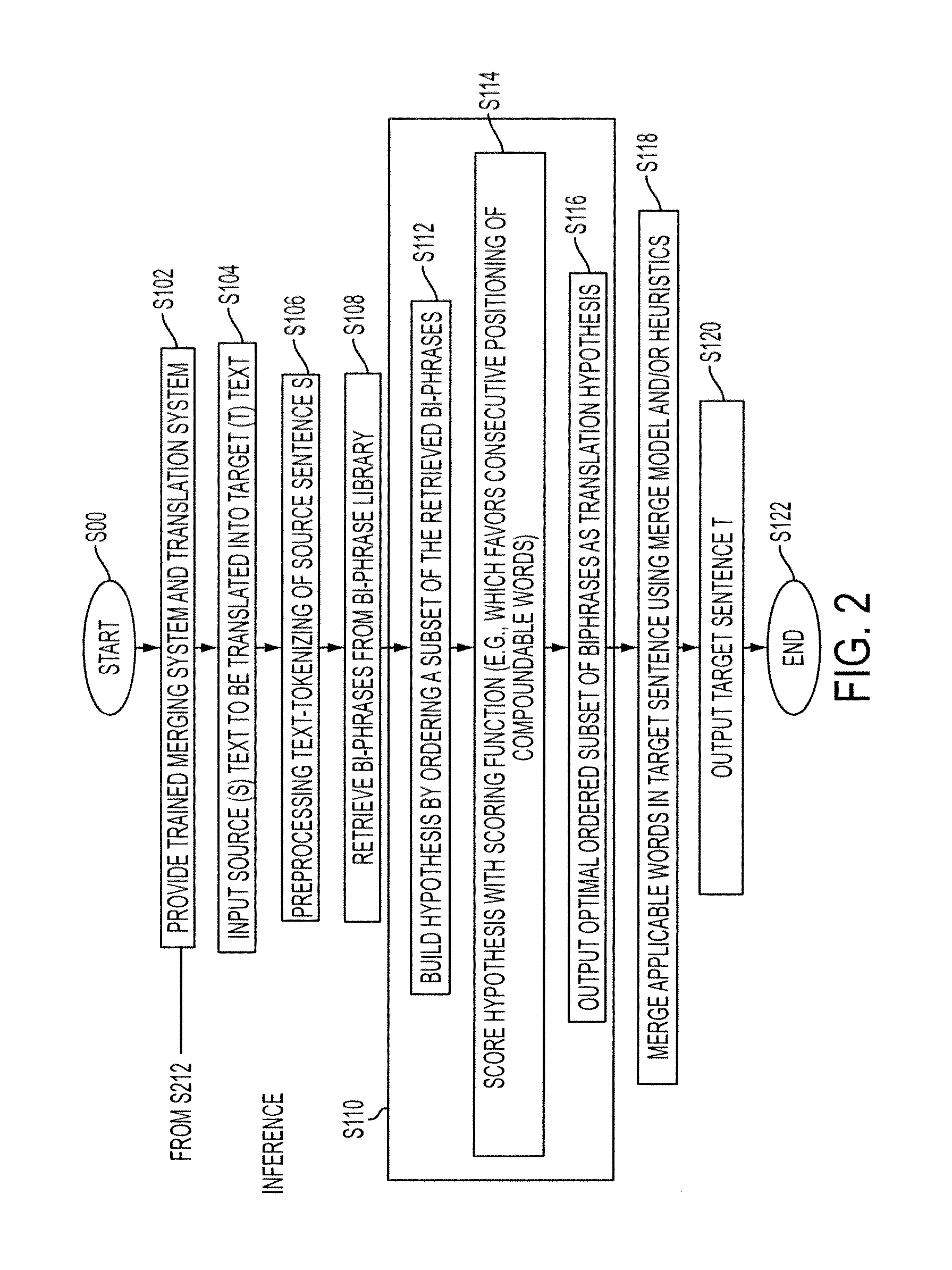
System and method for productive generation of compound words in statistical machine translation
InactiveUS20130030787A1Natural language translationSpecial data processing applicationsAlgorithmTheoretical computer science
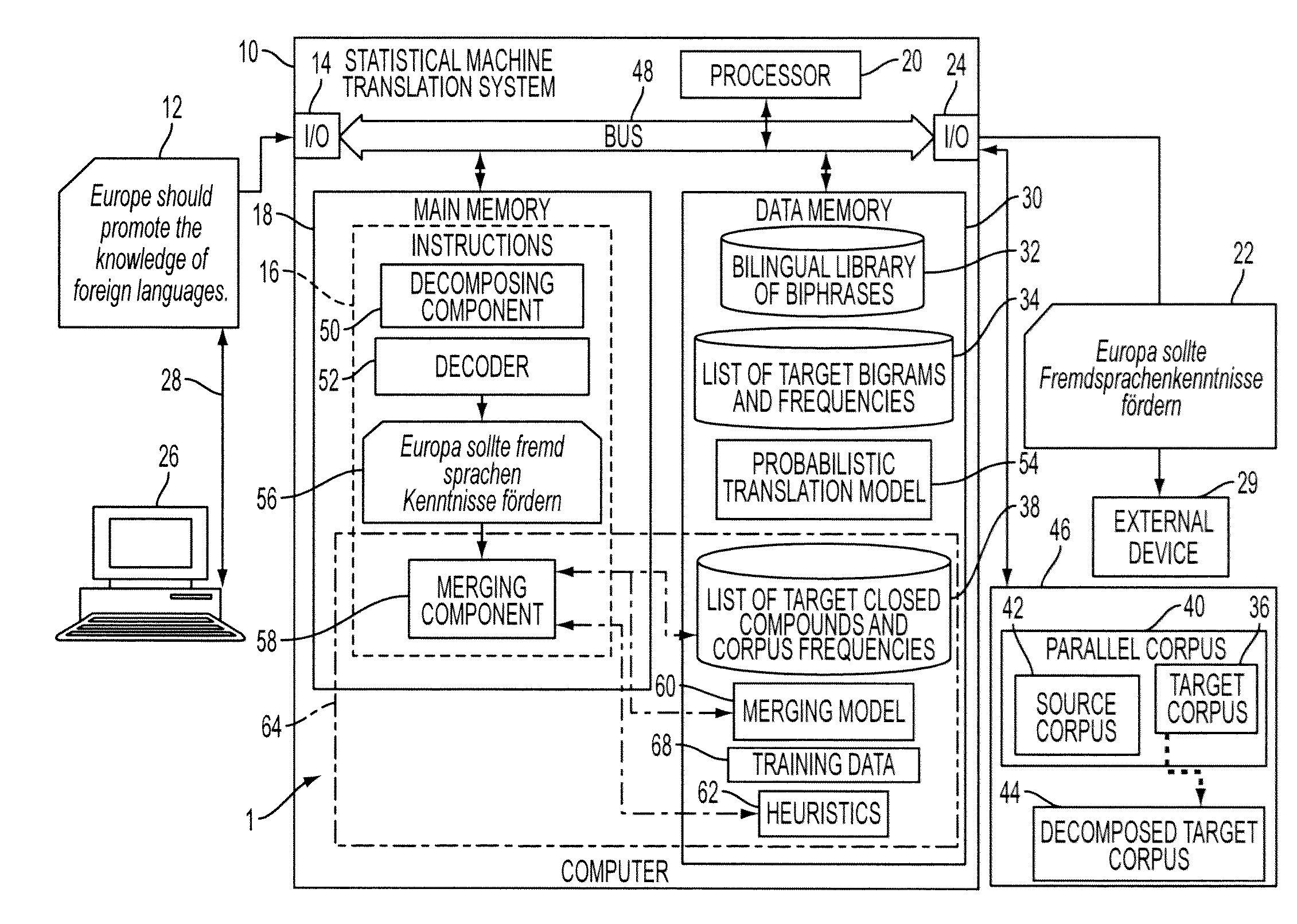
A method and a system for making merging decisions for a translation are disclosed which are suited to use where the target language is a productive compounding one. The method includes outputting decisions on merging of pairs of words in a translated text string with a merging system. The merging system can include a set of stored heuristics and / or a merging model. In the case of heuristics, these can include a heuristic by which two consecutive words in the string are considered for merging if the first word of the two consecutive words is recognized as a compound modifier and their observed frequency f1 as a closed compound word is larger than an observed frequency f2 of the two consecutive words as a bigram. In the case of a merging model, it can be one that is trained on features associated with pairs of consecutive tokens of text strings in a training set and predetermined merging decisions for the pairs. A translation in the target language is output, based on the merging decisions for the translated text string.
Owner:XEROX CORP
Methods of creating a dictionary for data compression
Some aspects of the invention provide methods, systems, and computer program products for creating a static dictionary in which longer byte-strings are preferred. To that end, in accordance with aspects of the present invention, a new heuristic is defined to replace the aforementioned frequency count metric used to record the number of times a particular node in a data tree is visited. The new heuristic is based on counting the number of times an end-node of a particular byte-string is visited, while not incrementing a count for nodes storing characters in the middle of the byte-string as often as each time such nodes are visited. The result is an occurrence count metric that favours longer byte-strings, by being biased towards not incrementing the respective occurrence count values for nodes storing characters in the middle of a byte-string.
Owner:GLOBALFOUNDRIES INC
System, method and service for ranking search results using a modular scoring system
ActiveUS7257577B2Easy to customizeHigh-quality resultData processing applicationsWeb data indexingHeuristicModularity
A modular scoring system using rank aggregation merges search results into an ordered list of results using many different features of documents. The ranking functions of the present system can easily be customized to the needs of a particular corpus or collection of users such as an intranet. Rank aggregation is independent of the underlying score distributions between the different factors, and can be applied to merge any set of ranking functions. Rank aggregation holds the advantage of combining the influence of many different heuristic factors in a robust way to produce high-quality results for queries. The modular scoring system combines factors such as indegree, page ranking, URL length, proximity to the root server of an intranet, etc, to form a single ordering on web pages that closely obeys the individual orderings, but also mediates between the collective wisdom of individual heuristics.
Owner:GOOGLE LLC
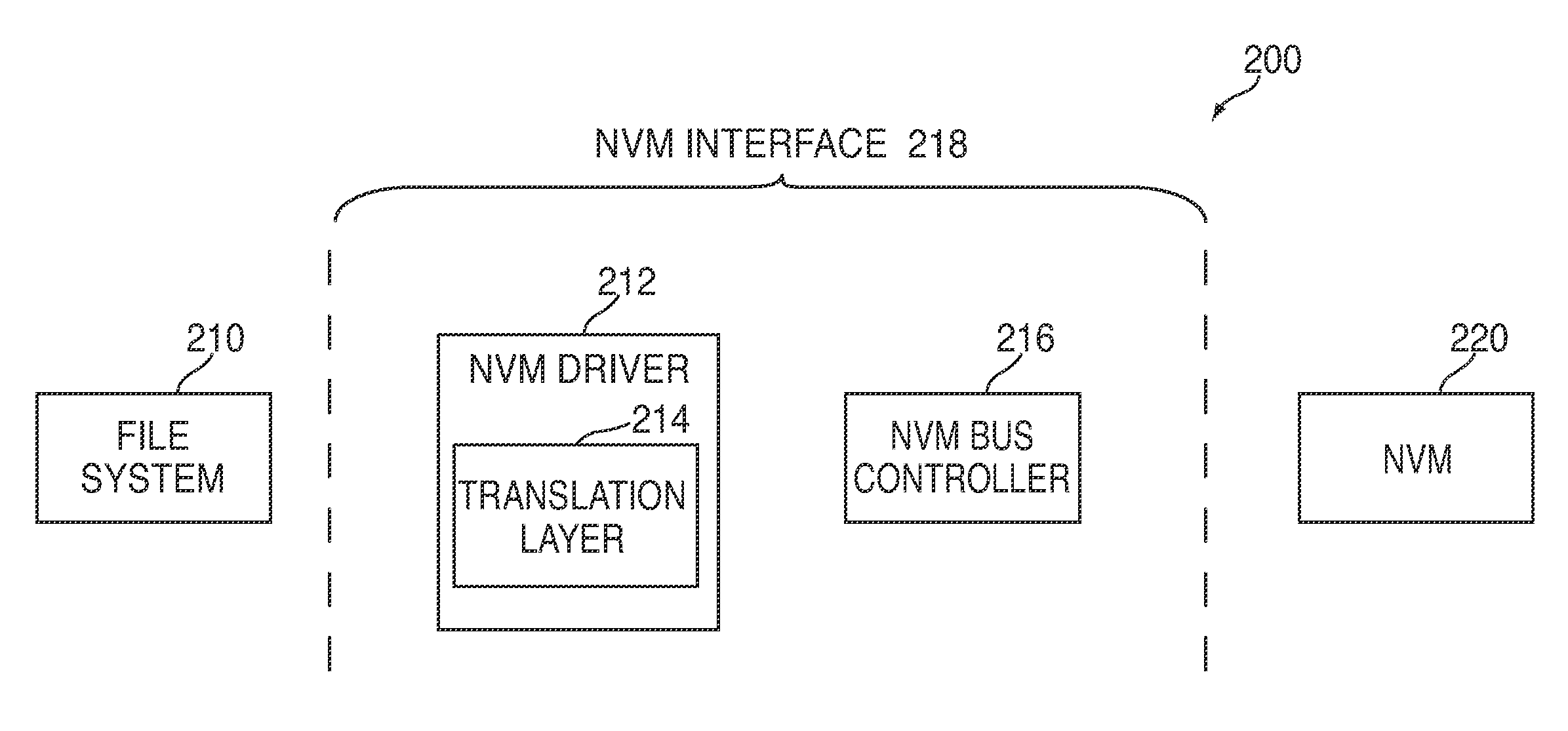
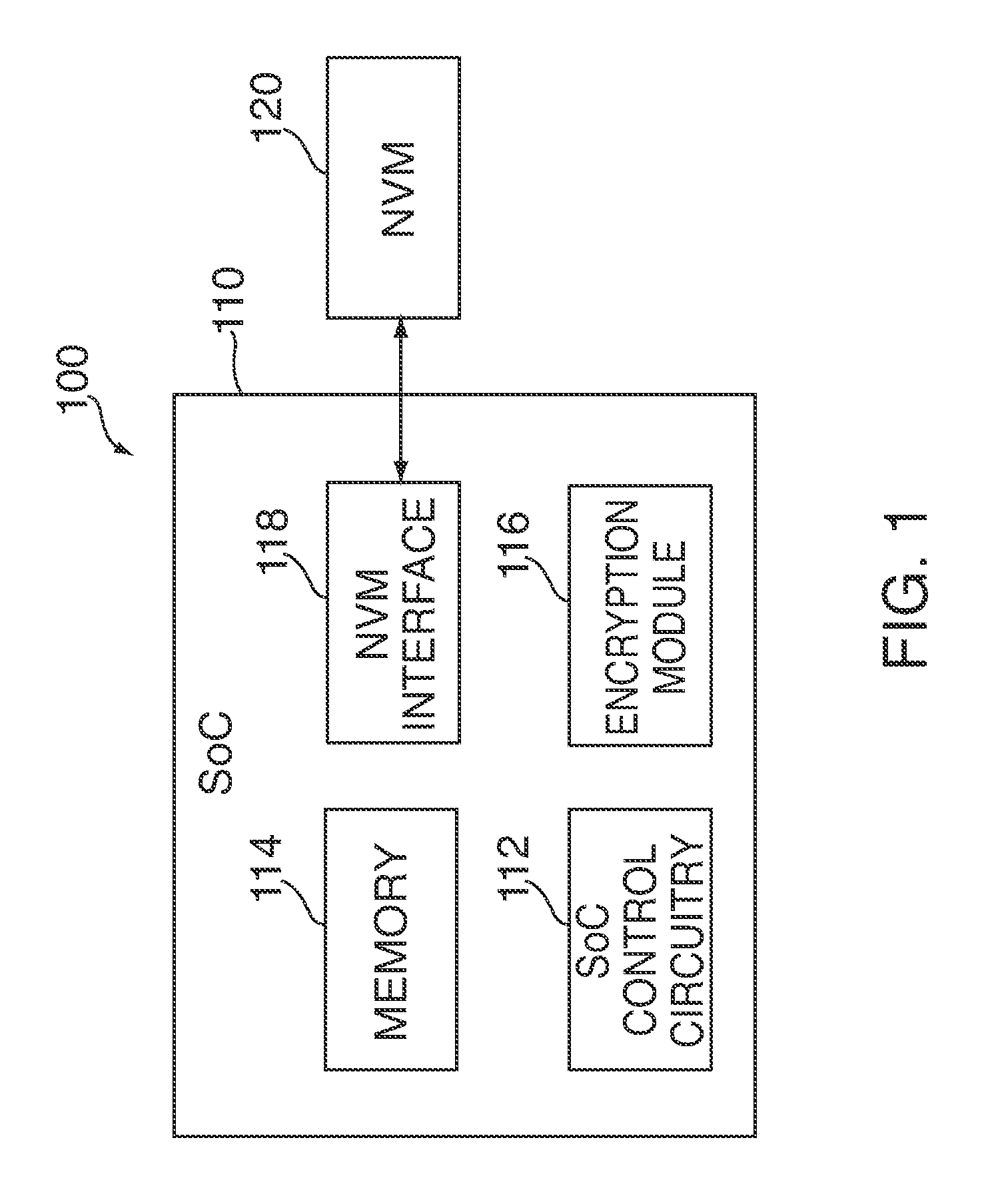
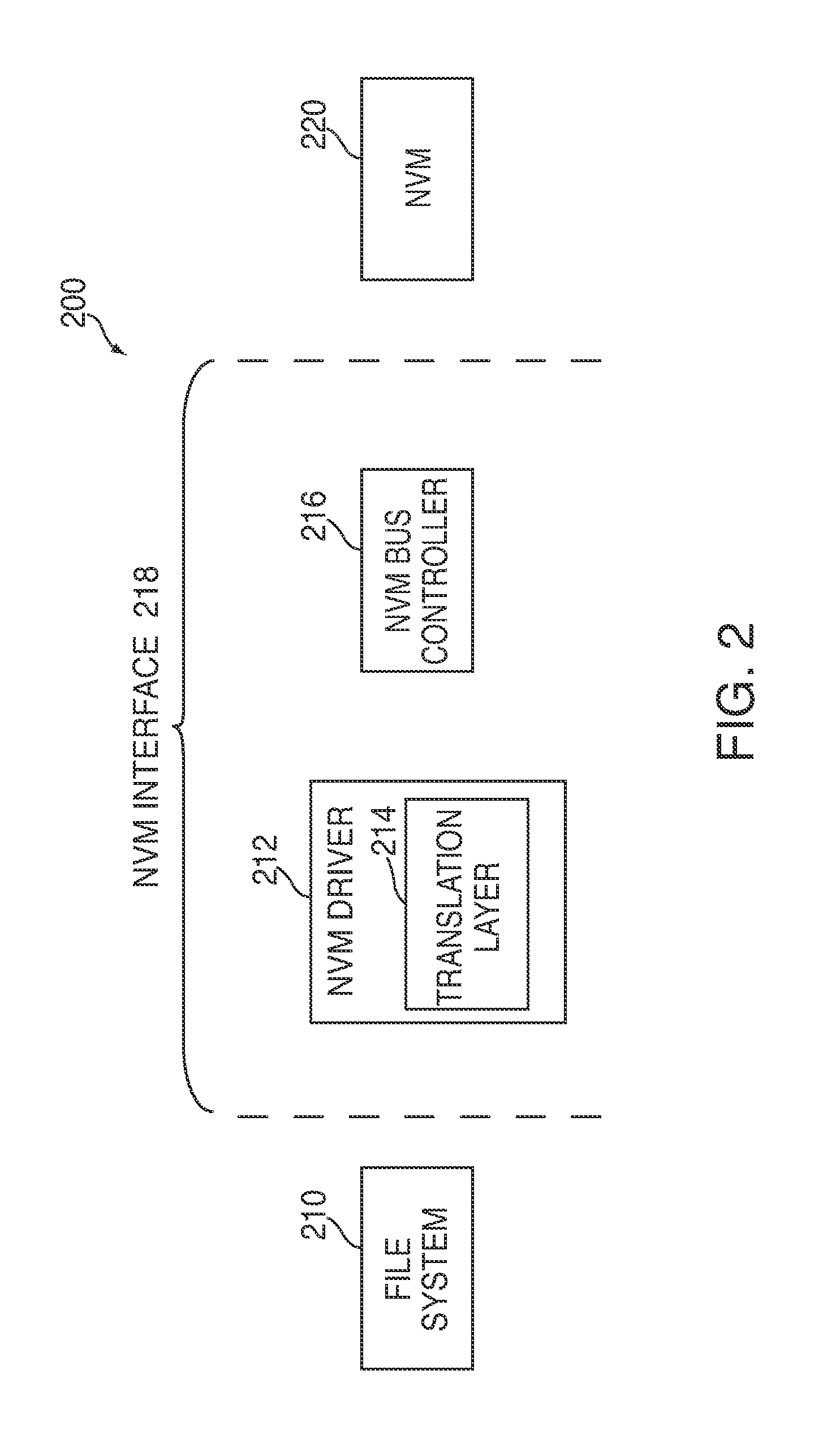
Efficient buffering for a system having non-volatile memory
InactiveUS20120221767A1Effective bufferImprove system performanceMemory architecture accessing/allocationEnergy efficient ICTFile systemHeuristic
Systems and methods are disclosed for efficient buffering for a system having non-volatile memory (“NVM”). In some embodiments, a control circuitry of a system can use heuristics to determine whether to perform buffering of one or more write commands received from a file system. In other embodiments, the control circuitry can minimize read energy and buffering overhead by efficiently re-ordering write commands in a queue along page-aligned boundaries of a buffer. In further embodiments, the control circuitry can optimally combine write commands from a buffer with write commands from a queue. After combining the commands, the control circuitry can dispatch the commands in a single transaction.
Owner:APPLE INC
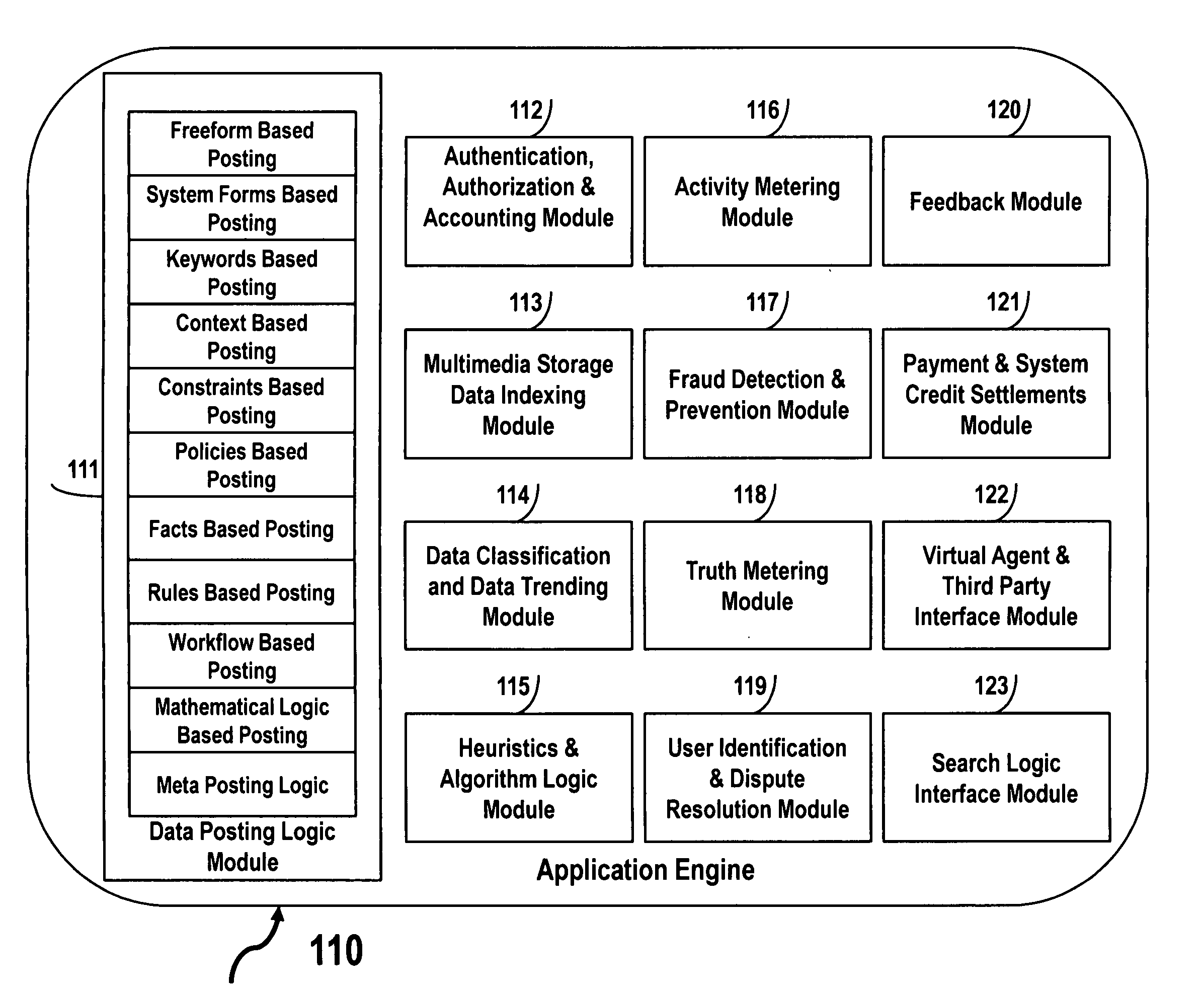
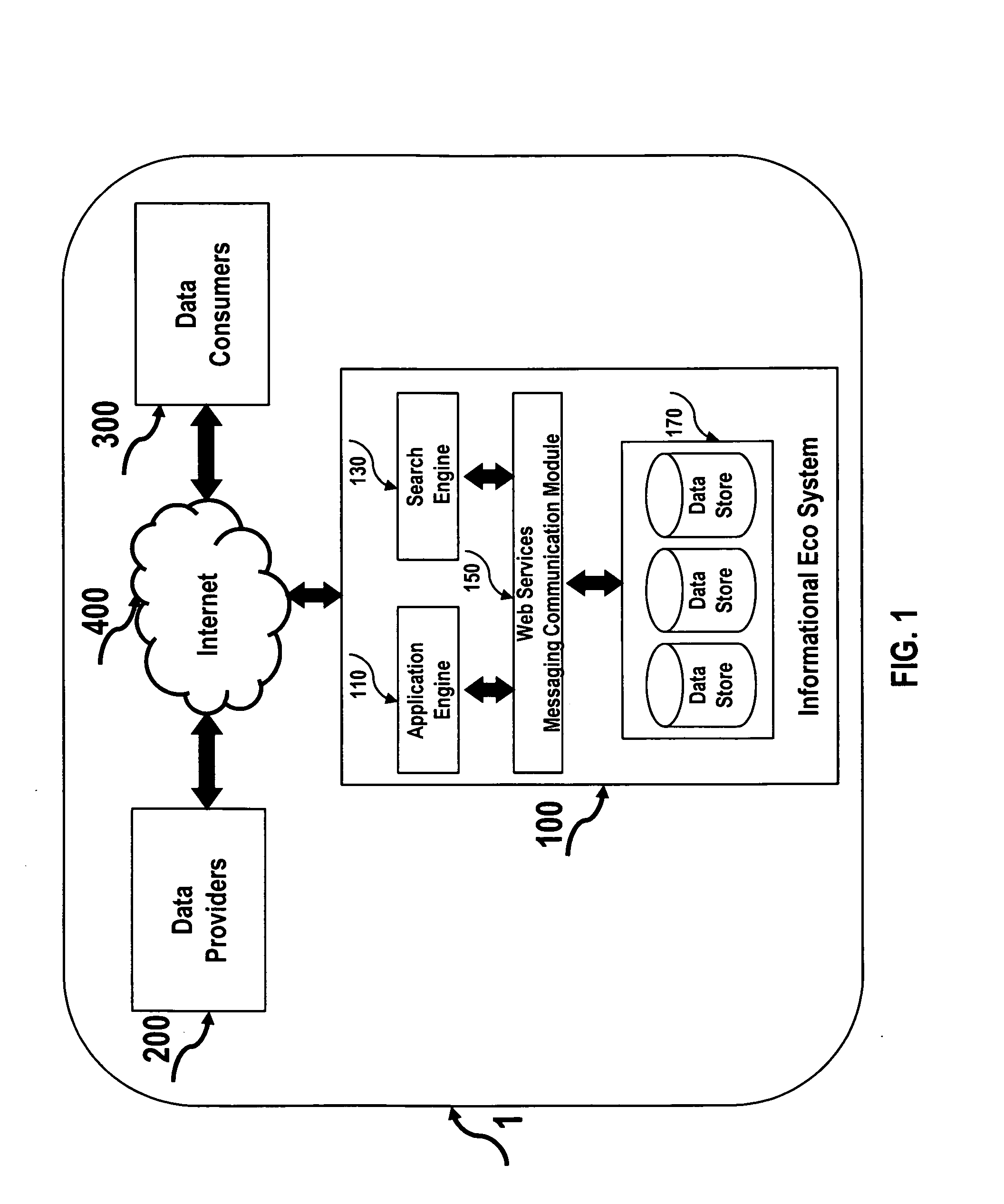
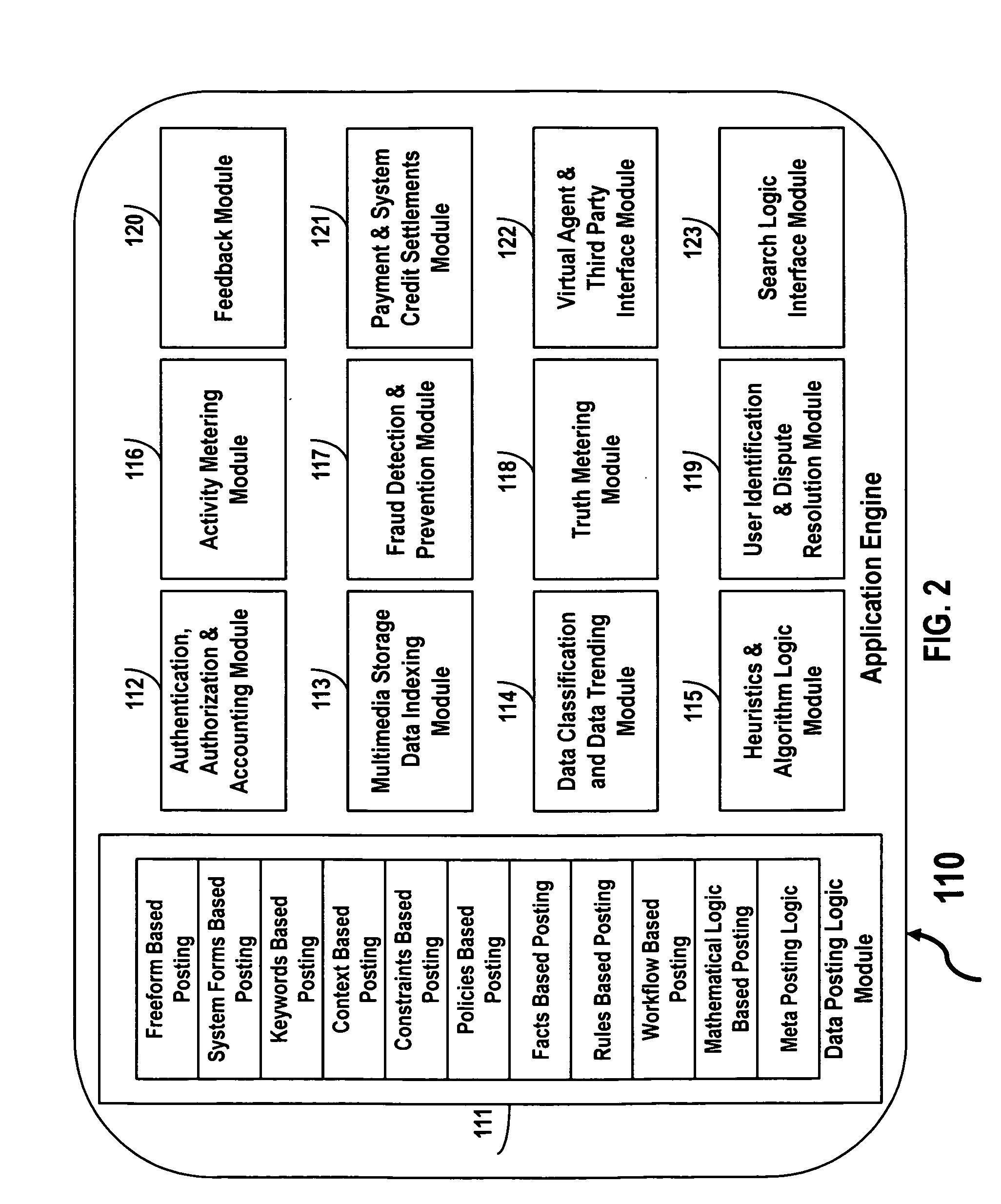
Internet eco system for transacting information and transactional data for compensation
In one embodiment, an Internet eco system includes a data posting platform securely accessible over the Internet to post personal, confidential and business data for conducting informational and transactional transactions for compensation. In another embodiment, the Internet eco system enables data providers to earn monetary compensation, system credits compensation or barter based compensation. In another embodiment, the Internet eco system enables data posting based upon freeform, system forms, keywords, mathematical logic, constraints, policies, facts, rules, workflow, or context logic; such data can be searched and retrieved based upon keywords, mathematical logic, constraints, policies, facts, rules, workflow, or context based search criteria. In yet another embodiment, the Internet eco system provides methods for authentication, authorization, accounting, data indexing, data classification, heuristics, activity metering, fraud detection and prevention, user identification, verification and dispute resolution, providing feedback, payments and systems credit settlement, providing virtual agent capabilities and third party interfacing capabilities and for providing interfaces to search logic. In yet another embodiment of the Internet eco system provides methods for data providers and data consumers to engage in and to consummate social networking based transactions.
Owner:HADI ALTAF
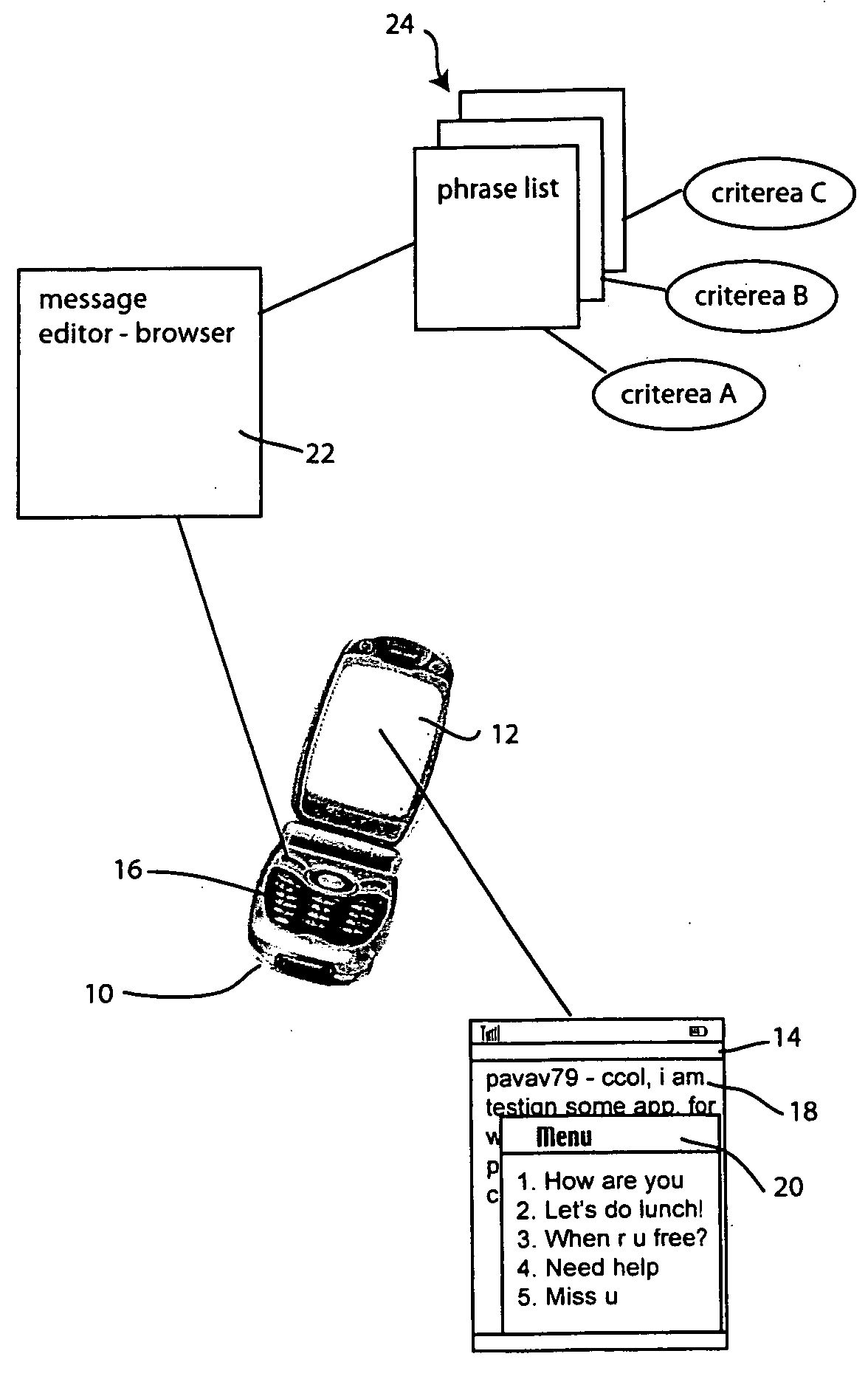
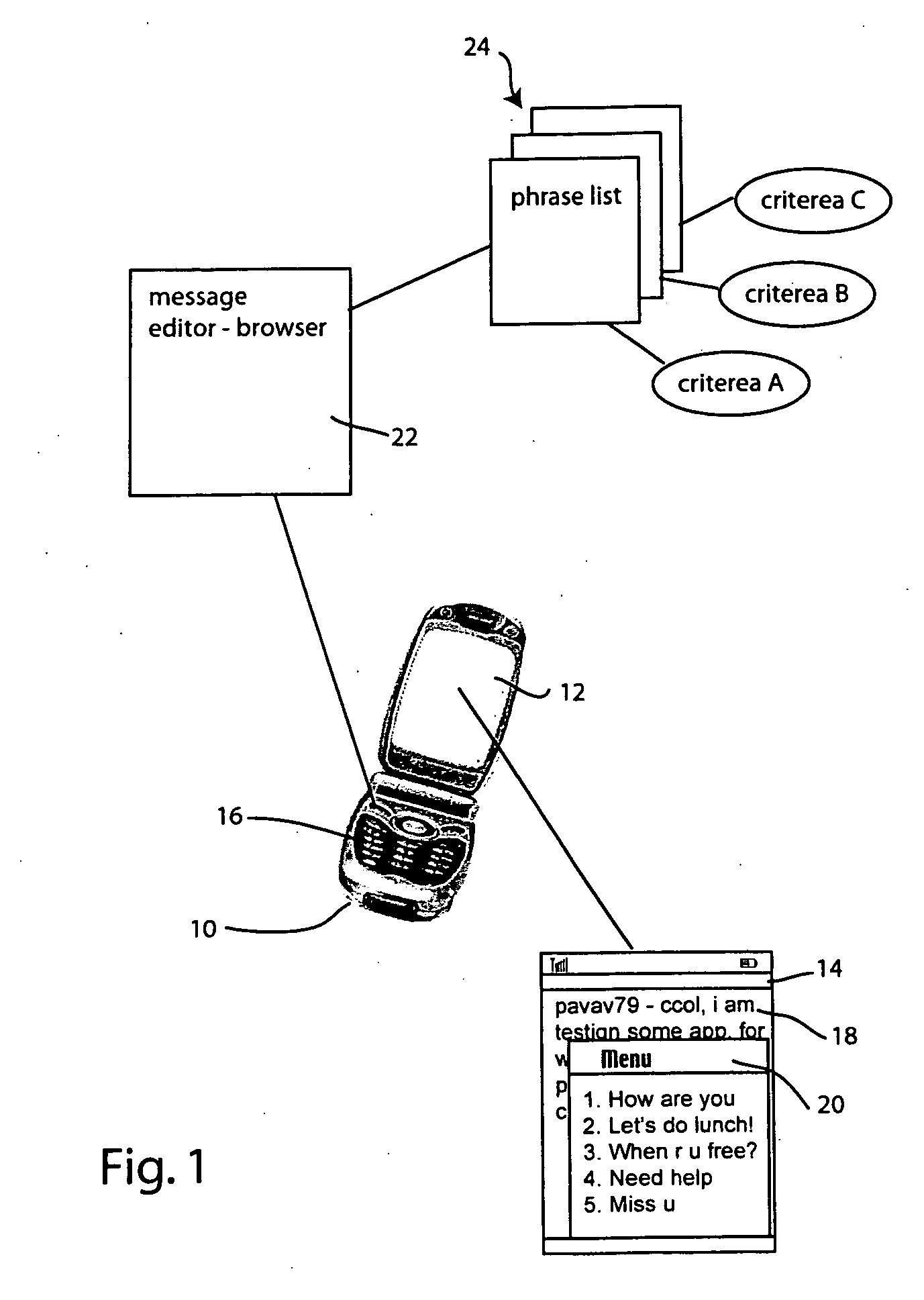
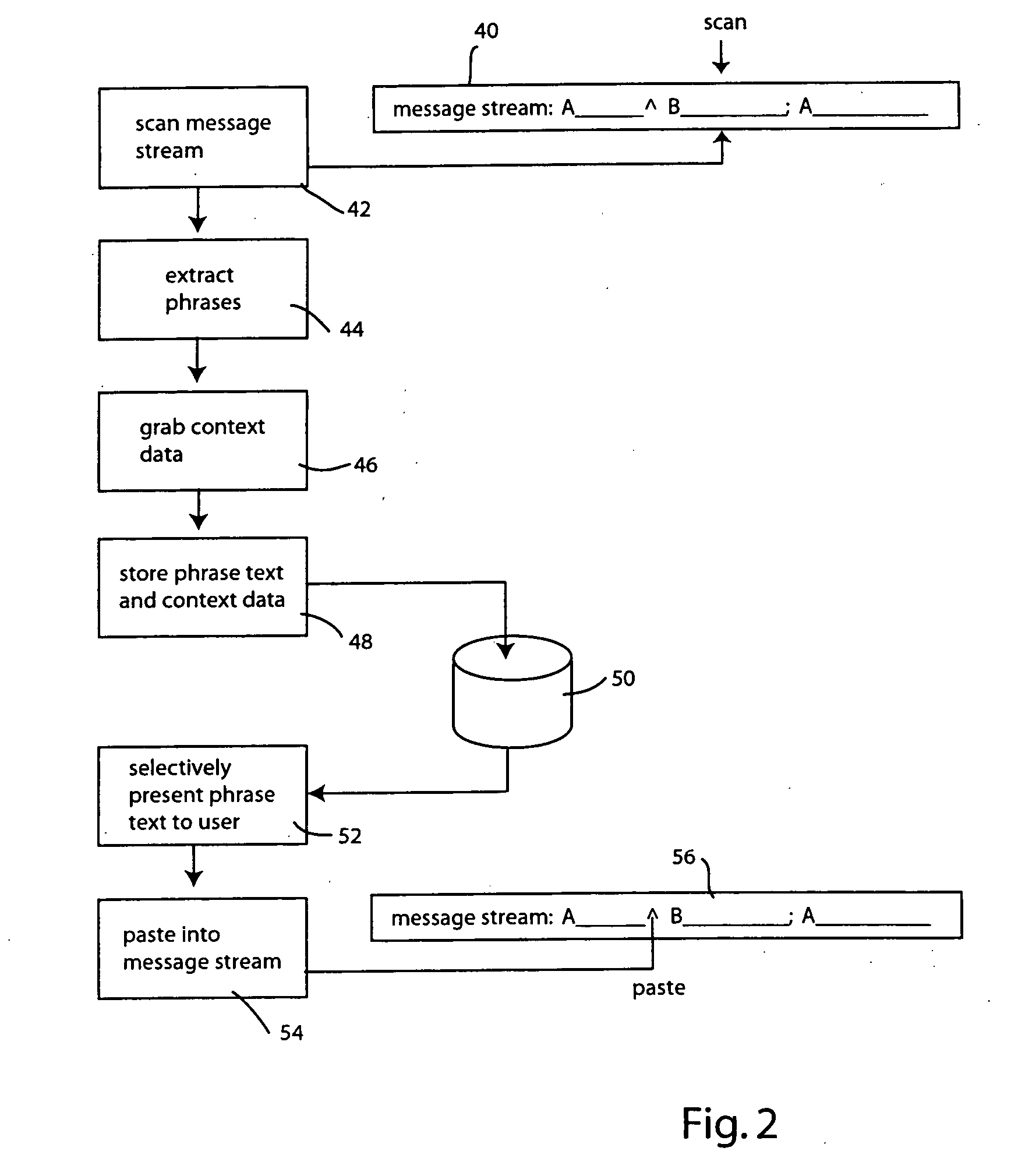
Method for creating and using phrase history for accelerating instant messaging input on mobile devices
Rapid instant messaging input is enabled through a system that displays frequently used or useful message phrases in a pop-up window from which the user may select a desired phrase to be inserted into the message stream. The system allows multiple phrase lists to be utilized and individual phrase messages are tagged with context information, allowing them to be selectively retrieved to provide only the most useful messages for a given context or scenario. The system automatically generates phrase lists by scanning the message stream data within instant messaging log files and the scanned information is then processed to select phrases for inclusion in the phrase list based on predefined heuristics.
Owner:PANASONIC CORP
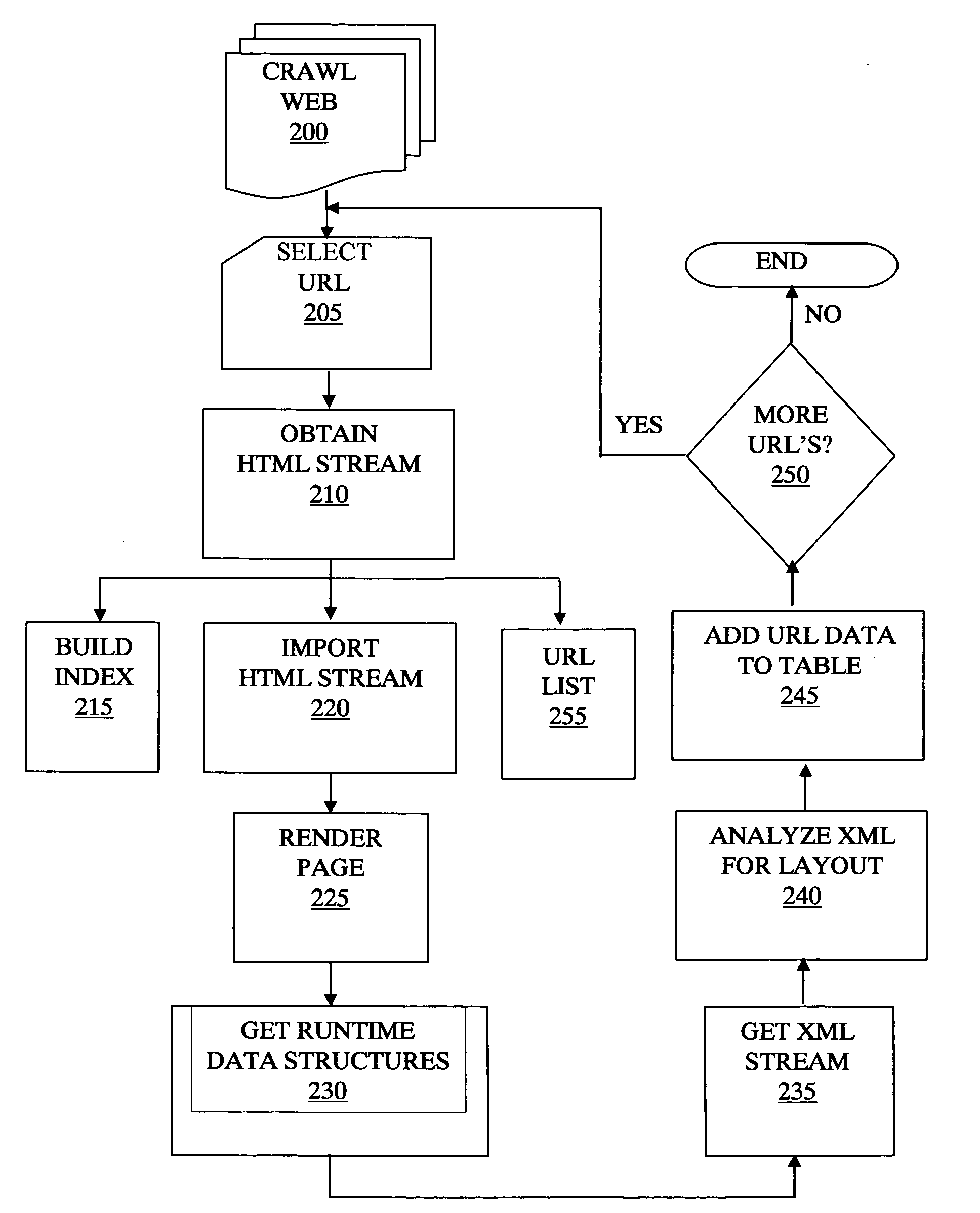
Method and system for extracting information from web pages
InactiveUS20080098300A1Reduce download bandwidthAccurate identificationWeb data indexingDigital data processing detailsHeuristicUniform resource locator
A crawler collects webpage data and obtains a list of URL's of interest used to construct a searchable index. The HTML stream is received for each relevant URL and each HTML stream is imported onto a browser or rendering engine so as to render the page. From the browser, the run-time data structure for each page is obtained. From the run-time data structure, layout information of the webpage is obtained. The layout information can include location and size of images, text, video clips, banners, etc. Using various heuristics, selected items of interest are identified as relevant according to their associated layout information. Then, when a query is received and a match is found in the index, only the information identified as relevant is fetched and presented to the user.
Owner:BRILLIANT SHOPPER
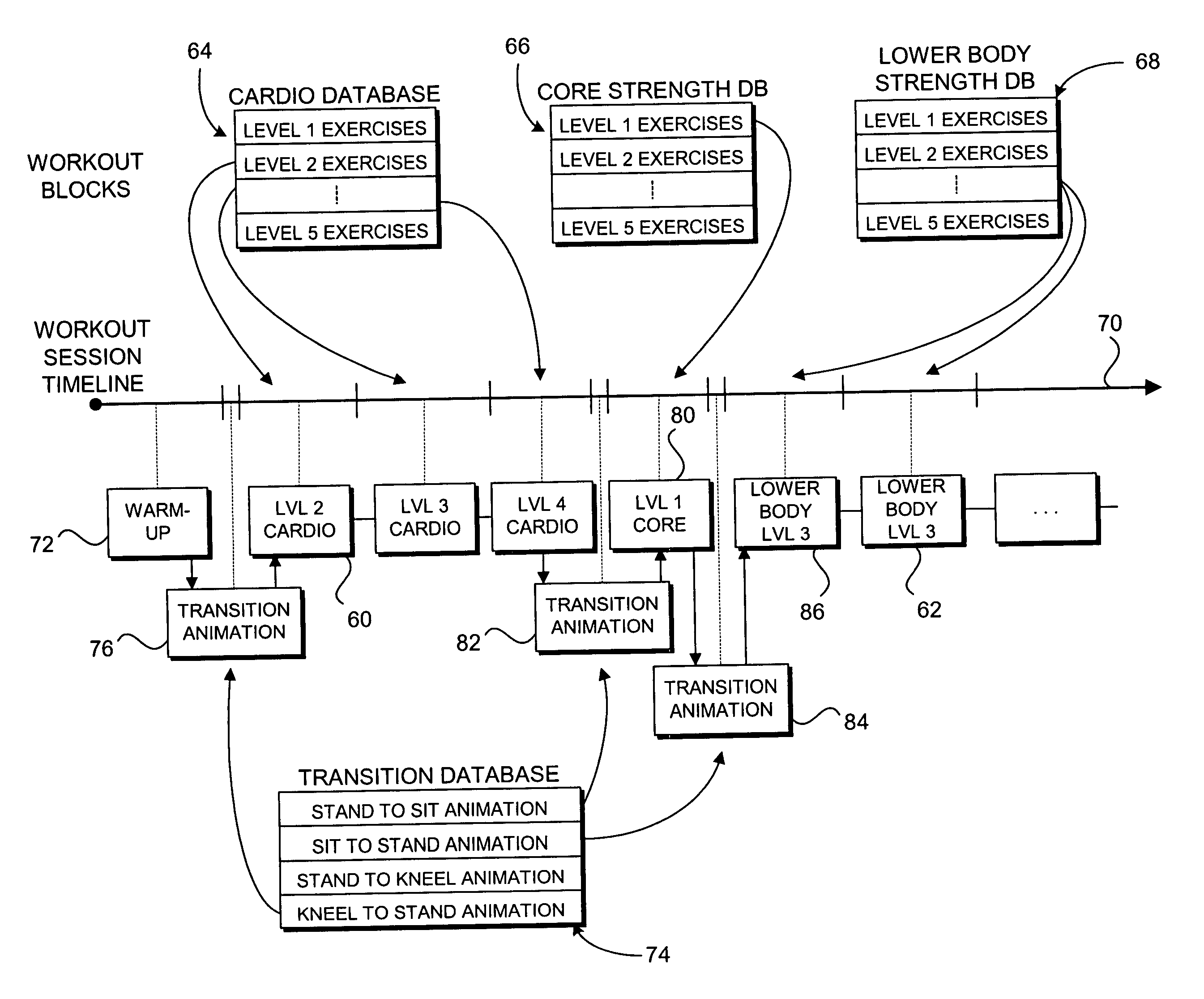
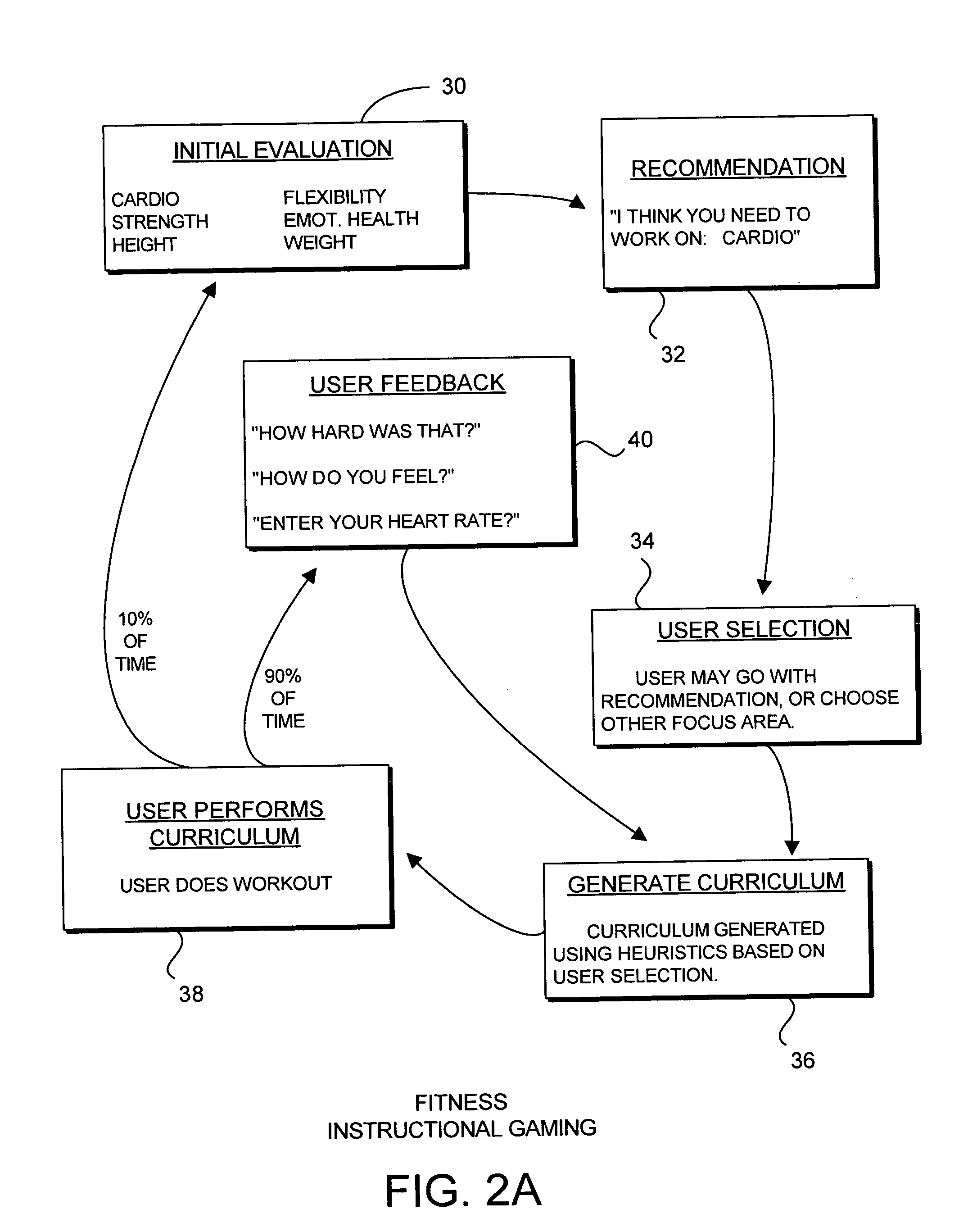
Instructional gaming methods and apparatus
InactiveUS20050181347A1Expectations can be loweredIncreases noElectrical appliancesTeaching apparatusHeuristicSubject matter
An instructional gaming apparatus and method implements adaptive instructional gaming from a start point along a trajectory to a final goal. The system comprises a receiver for electronically receiving data from a user. The system further includes an electronic subject matter database with a clearly defined set of discrete heuristics combined with an electronic processor for the creation of an electronic instructional gaming curriculum unique to the individual user and their goals to enable proficiency in the given subject matter. Performance is periodically tested. And electronic means allows the information from the user performance database to be incorporated into the discrete heuristic utilized by the electronic processor for the creation of future electronic instructional gaming curriculums and / or individual instructional gaming lessons for the specific user in the given subject.
Owner:RESPONDESIGN
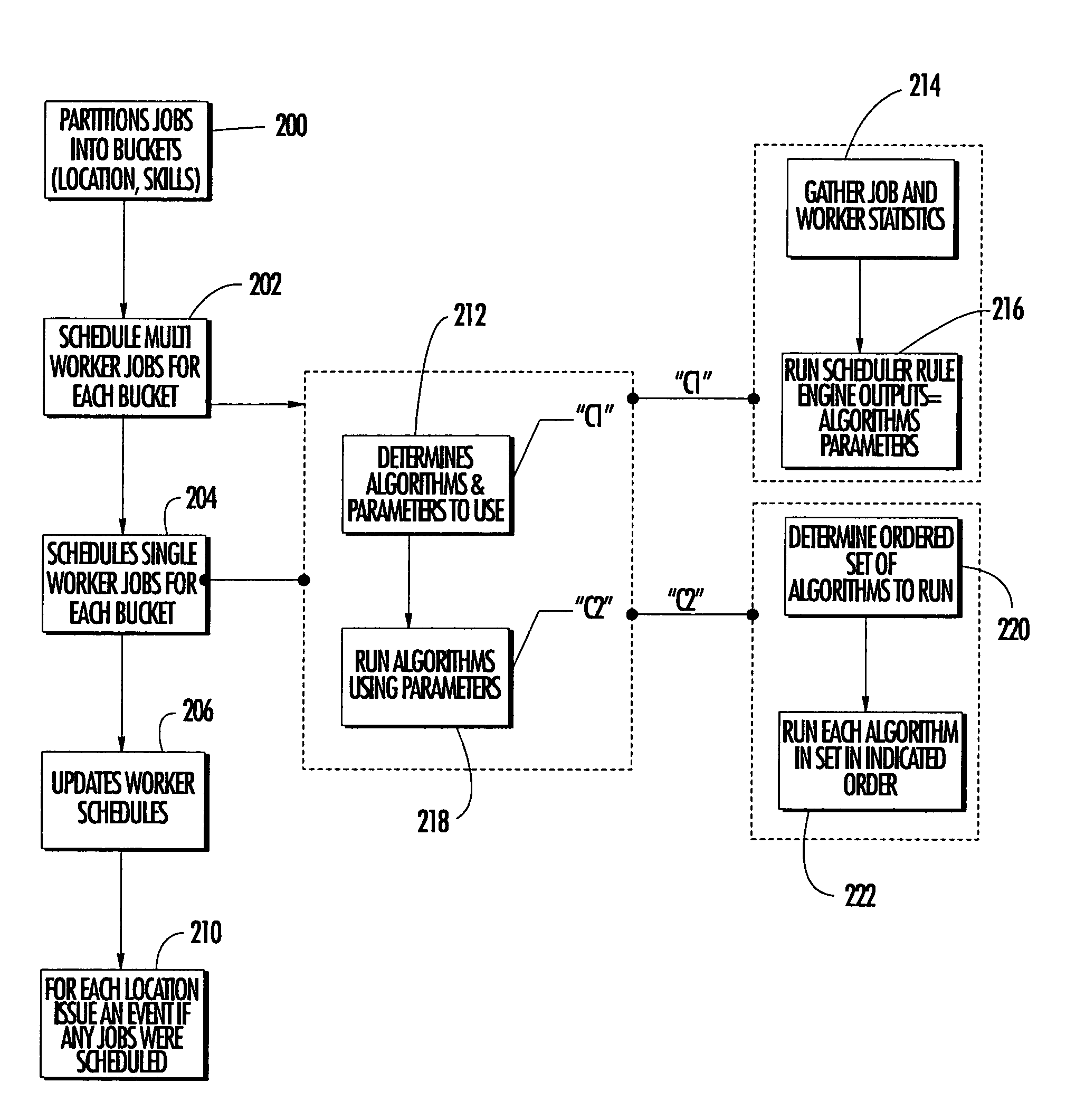
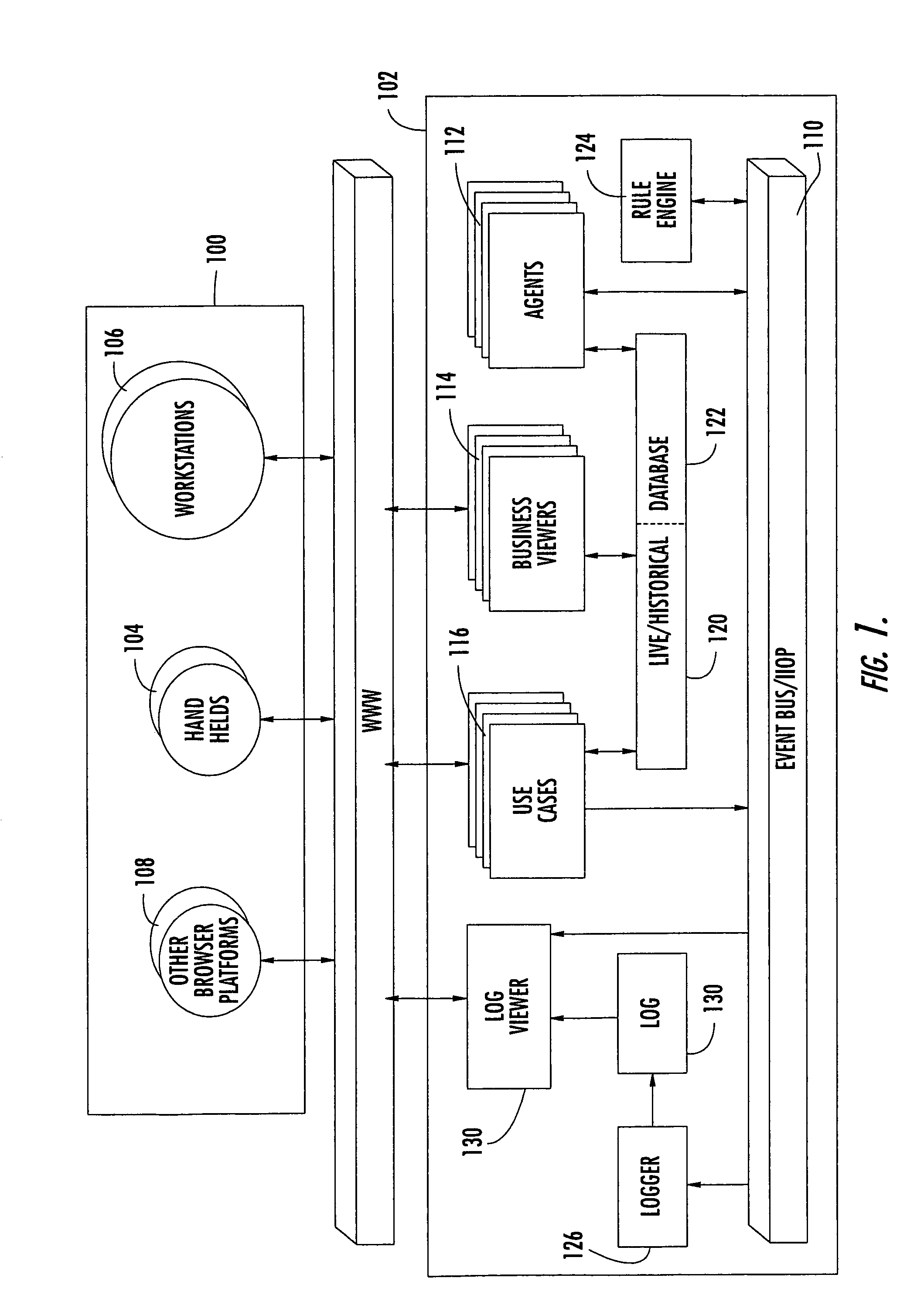
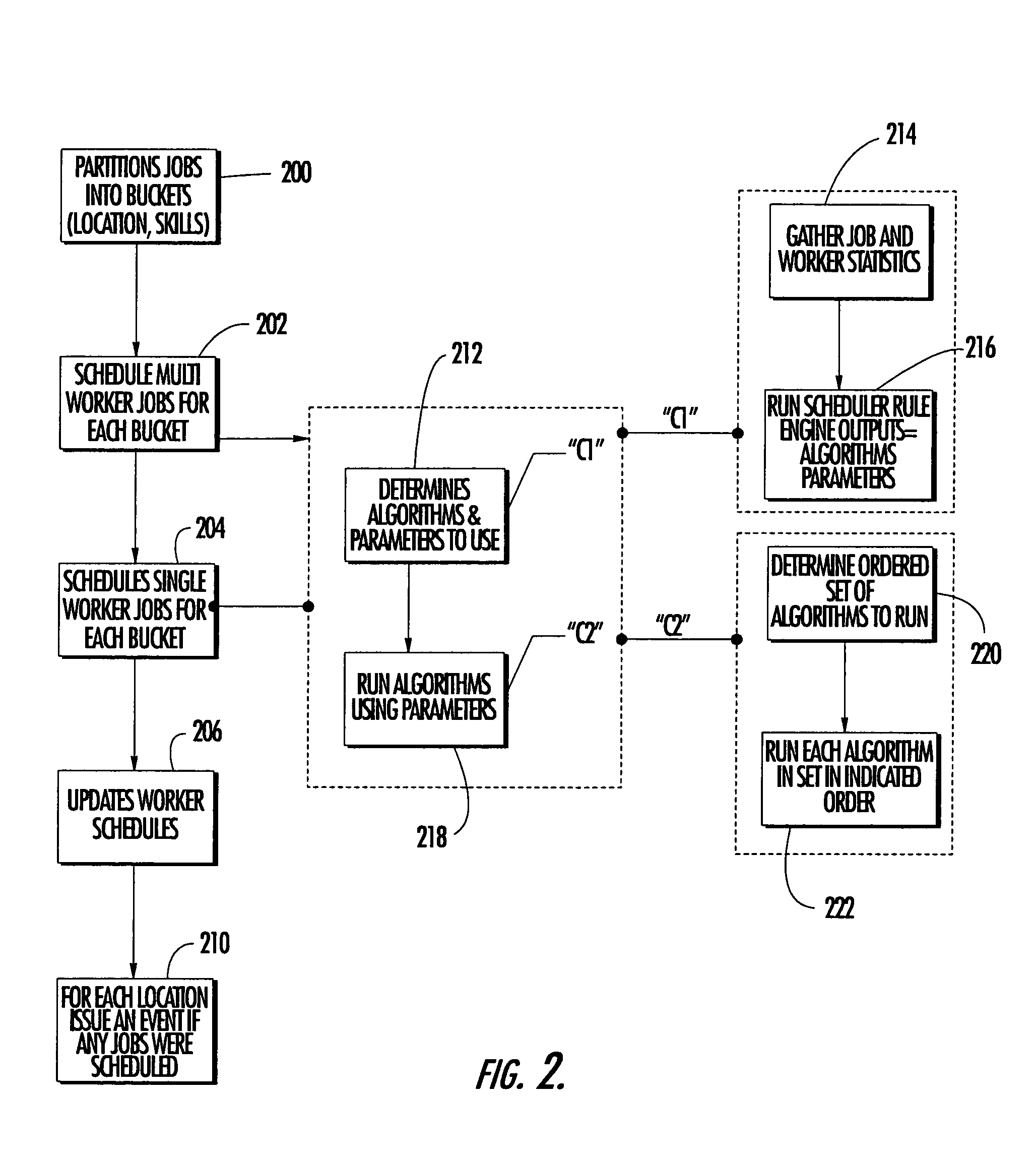
System and method for managing mobile workers
A computer implemented system and method for managing mobile workers in an object oriented programming environment is disclosed. A plurality of target objects that correspond to facilities assets to be worked on by a mobile worker are classified within a database of the computer. The attributes of each target object are defined, including a task to be performed on each target object. Mobile workers are scheduled for the tasks to be performed on target objects by running a rule engine to determine the algorithms and heuristics to be used to schedule mobile workers for the tasks to be performed. The scheduled jobs are then output to the mobile workers.
Owner:MASTERLINK CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com