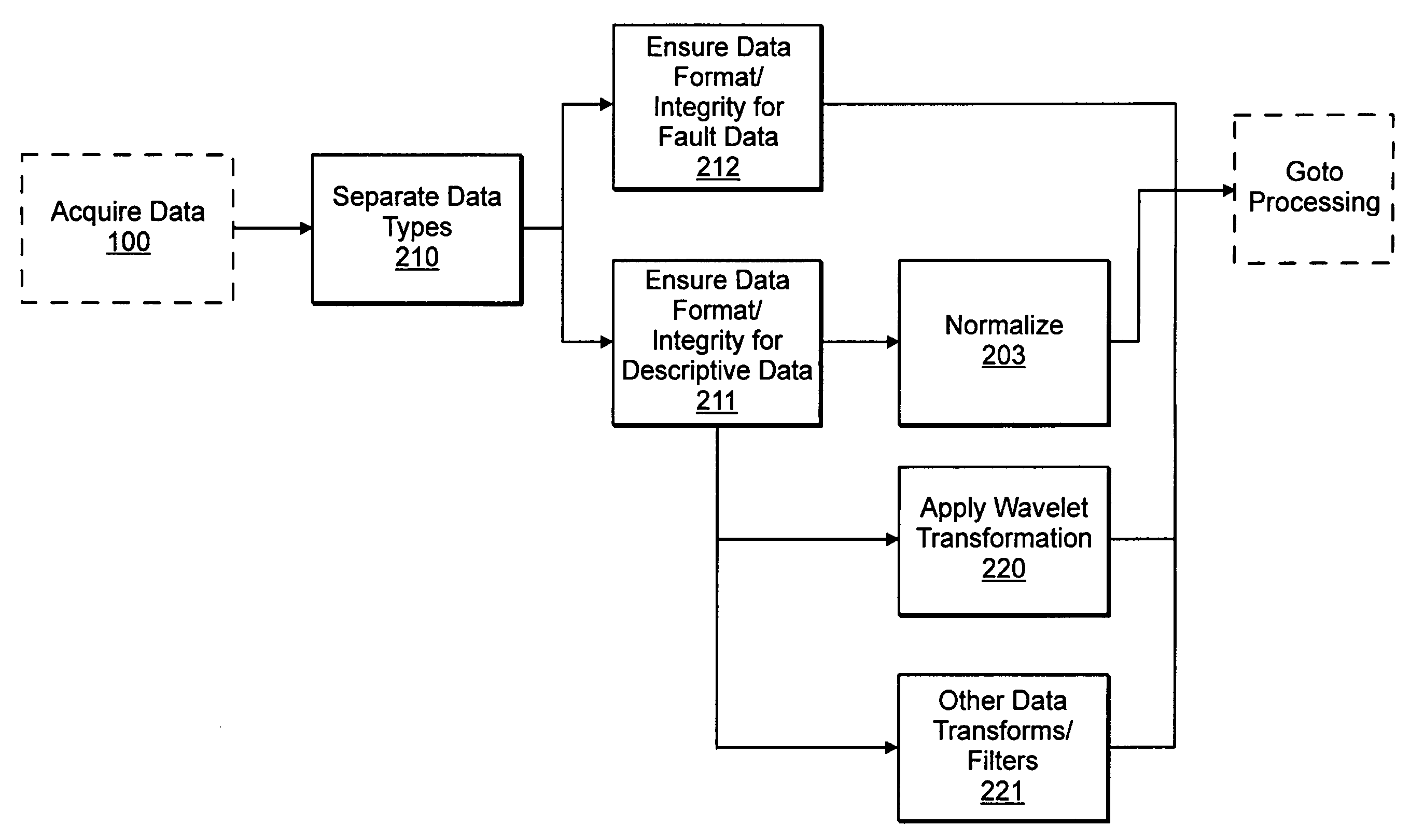
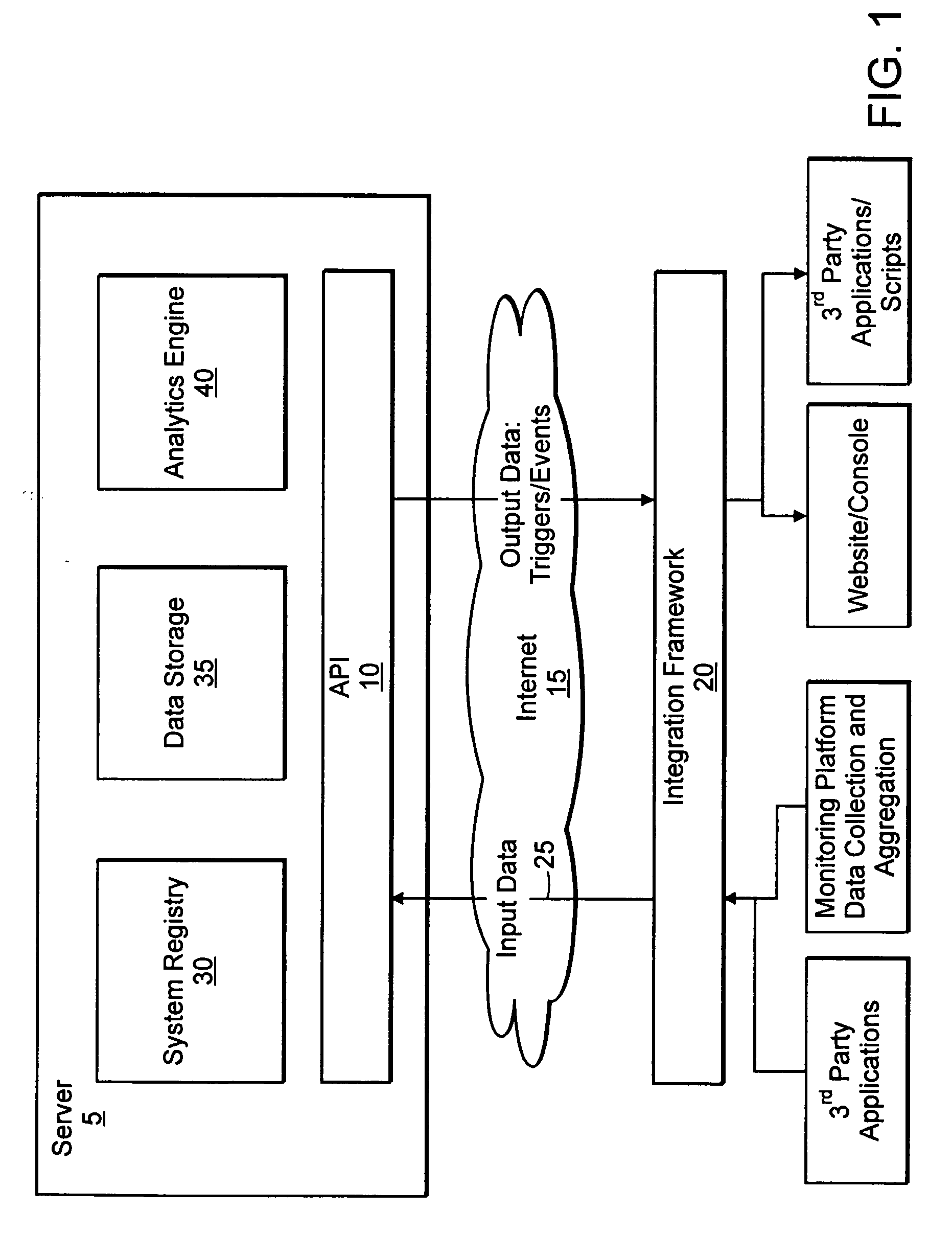
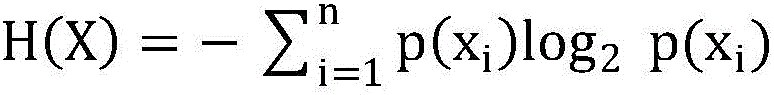Patents
Literature
1683 results about "Statistical analyses" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Statistical analysis is a component of data analytics . In the context of business intelligence ( BI ), statistical analysis involves collecting and scrutinizing every data sample in a set of items from which samples can be drawn. A sample, in statistics, is a representative selection drawn from a total population .
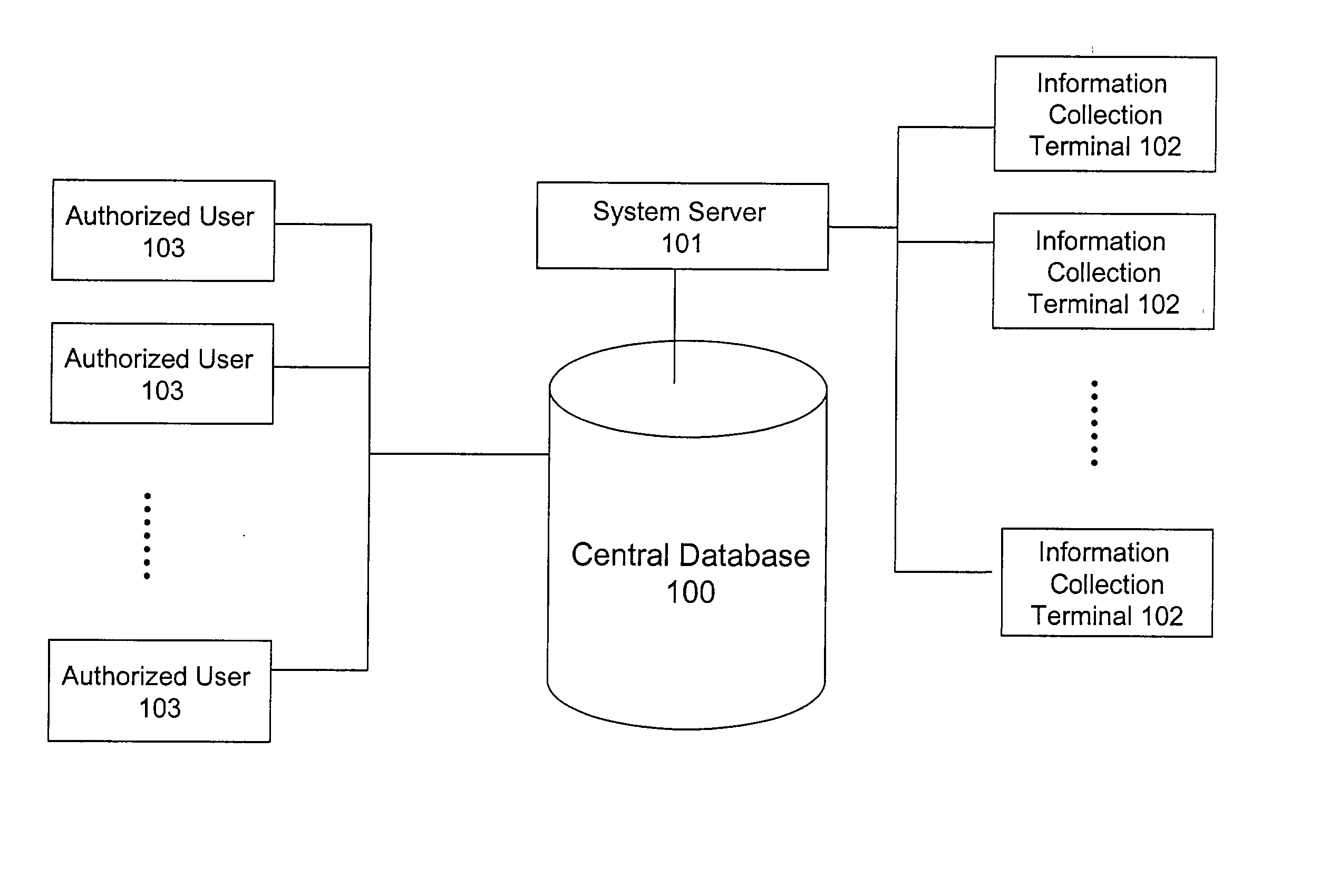
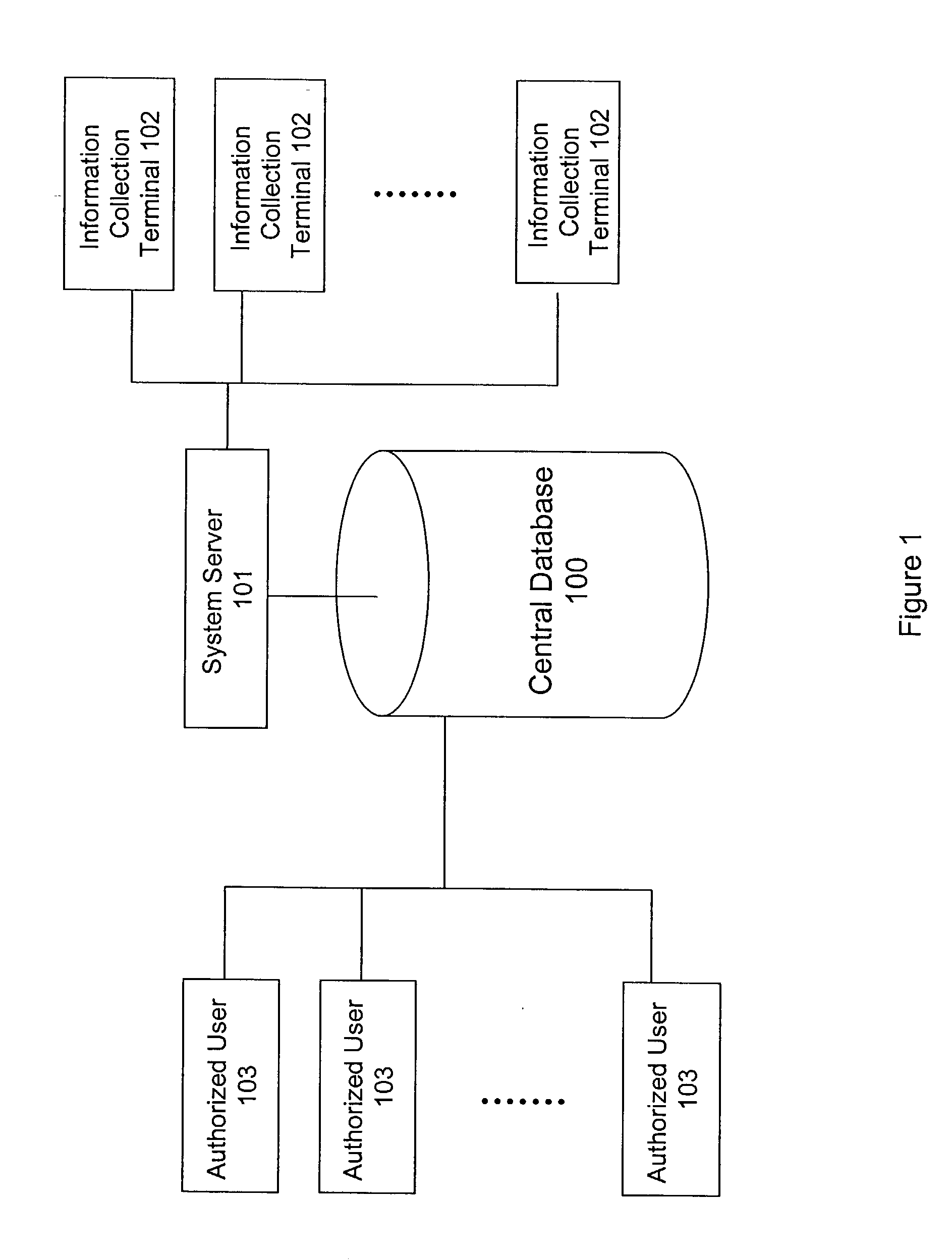
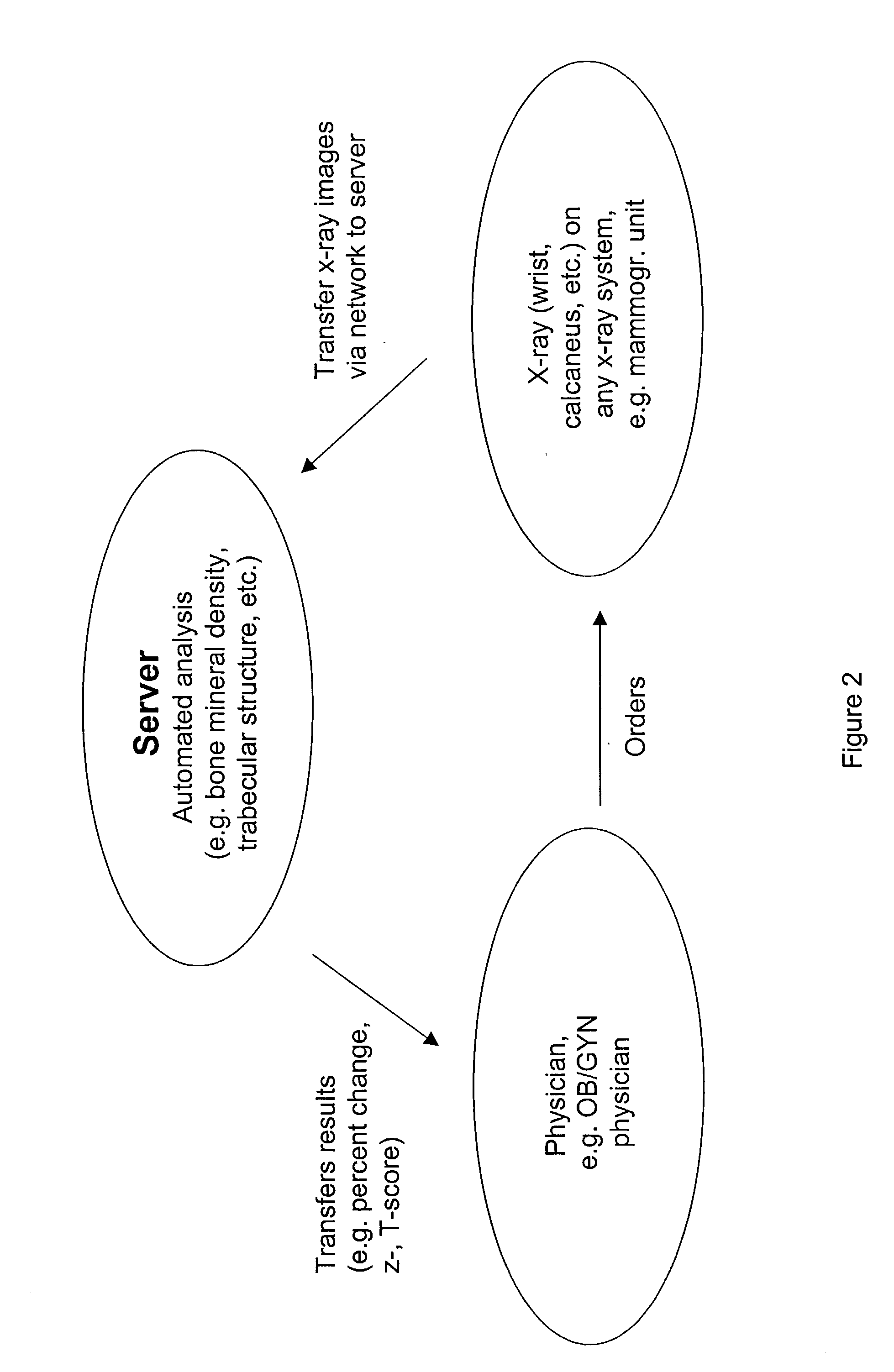
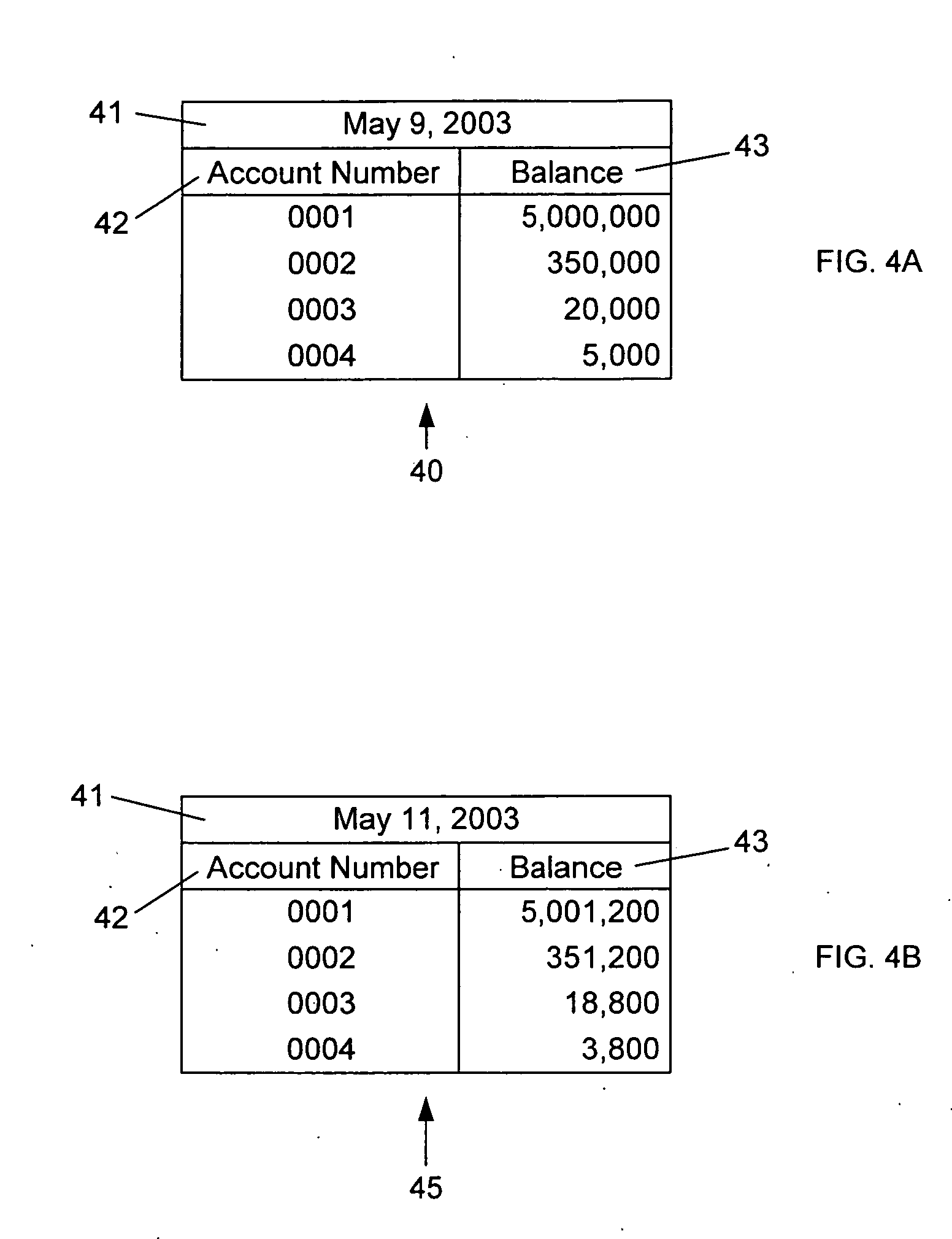
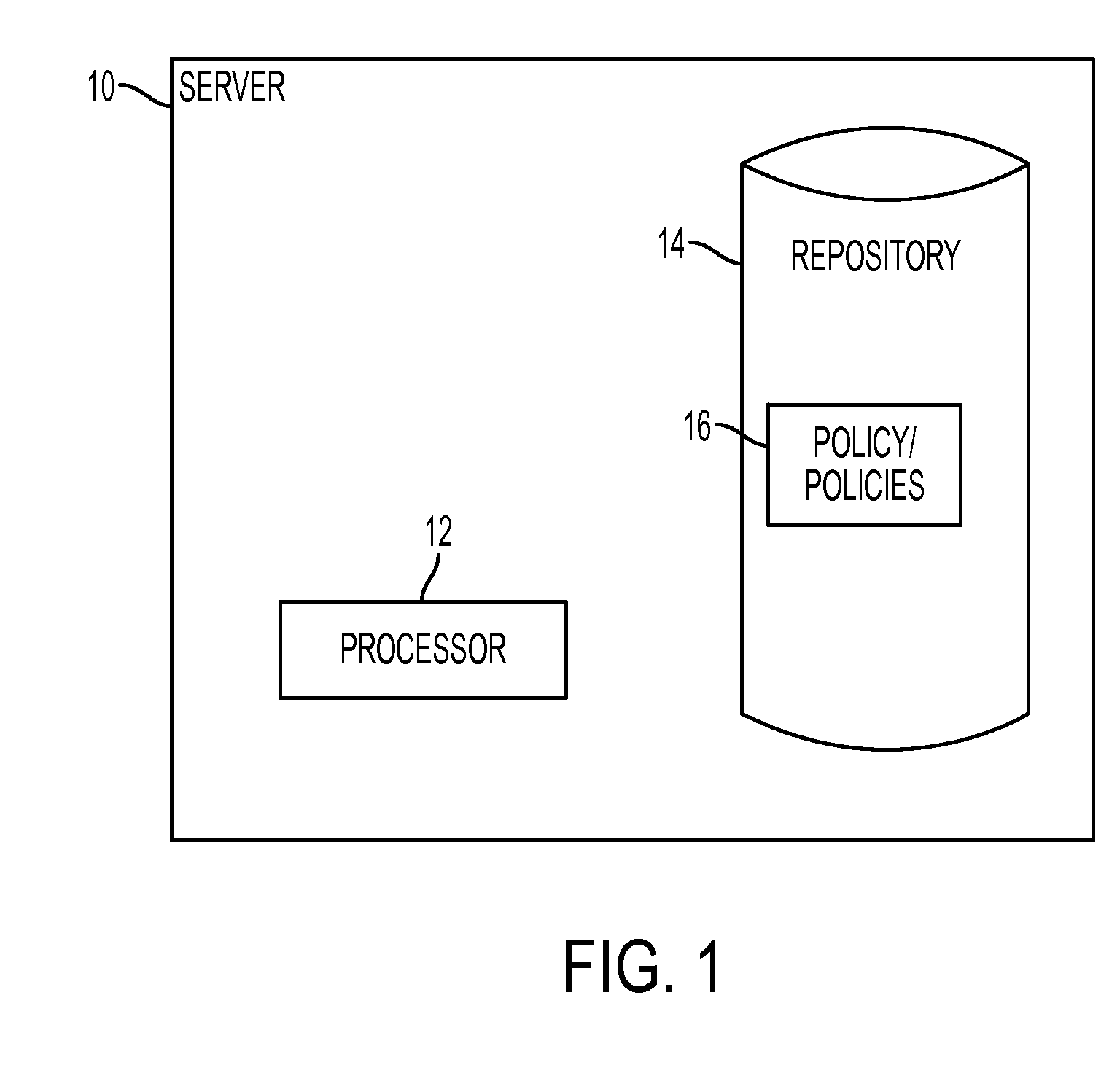
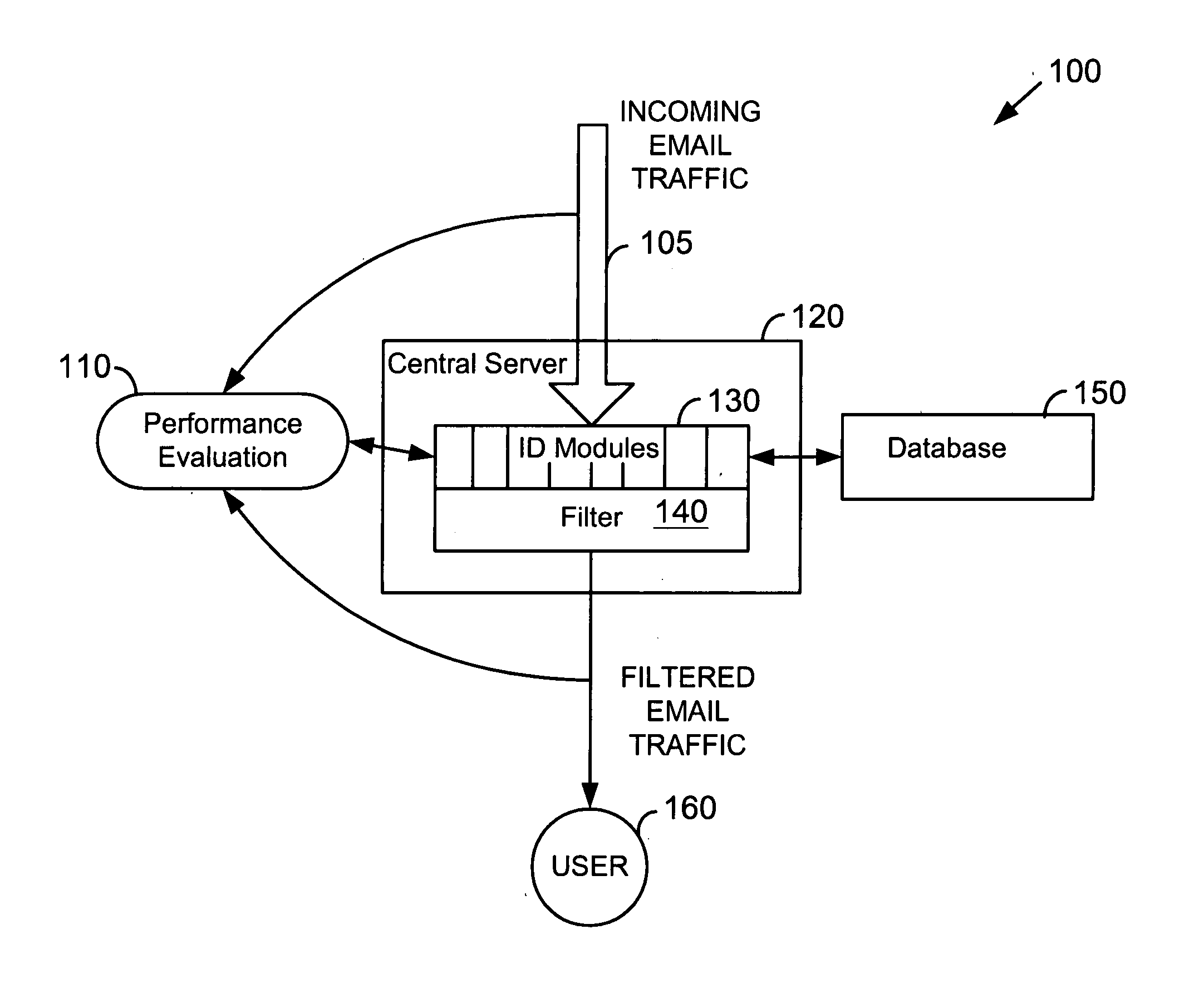
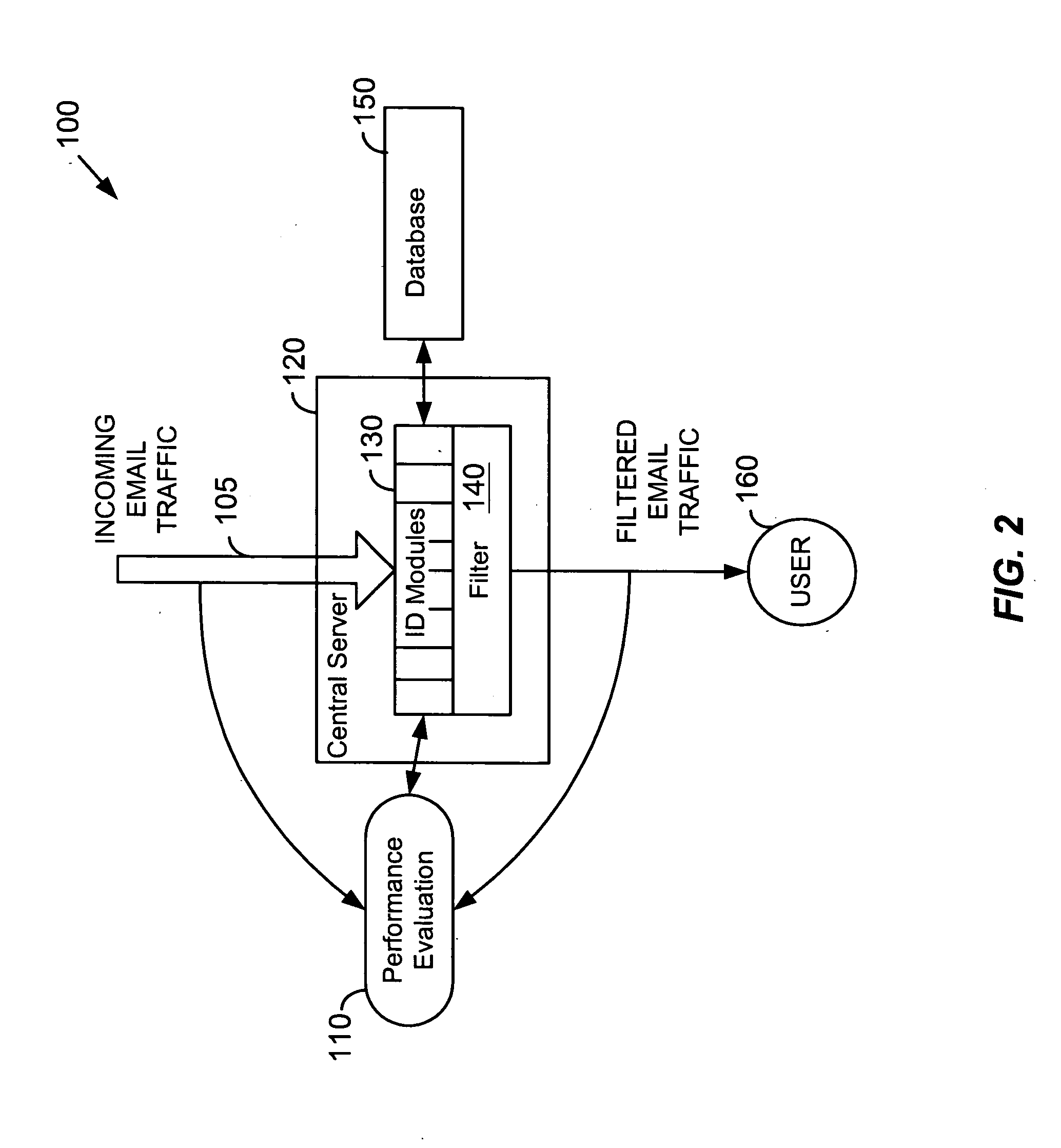
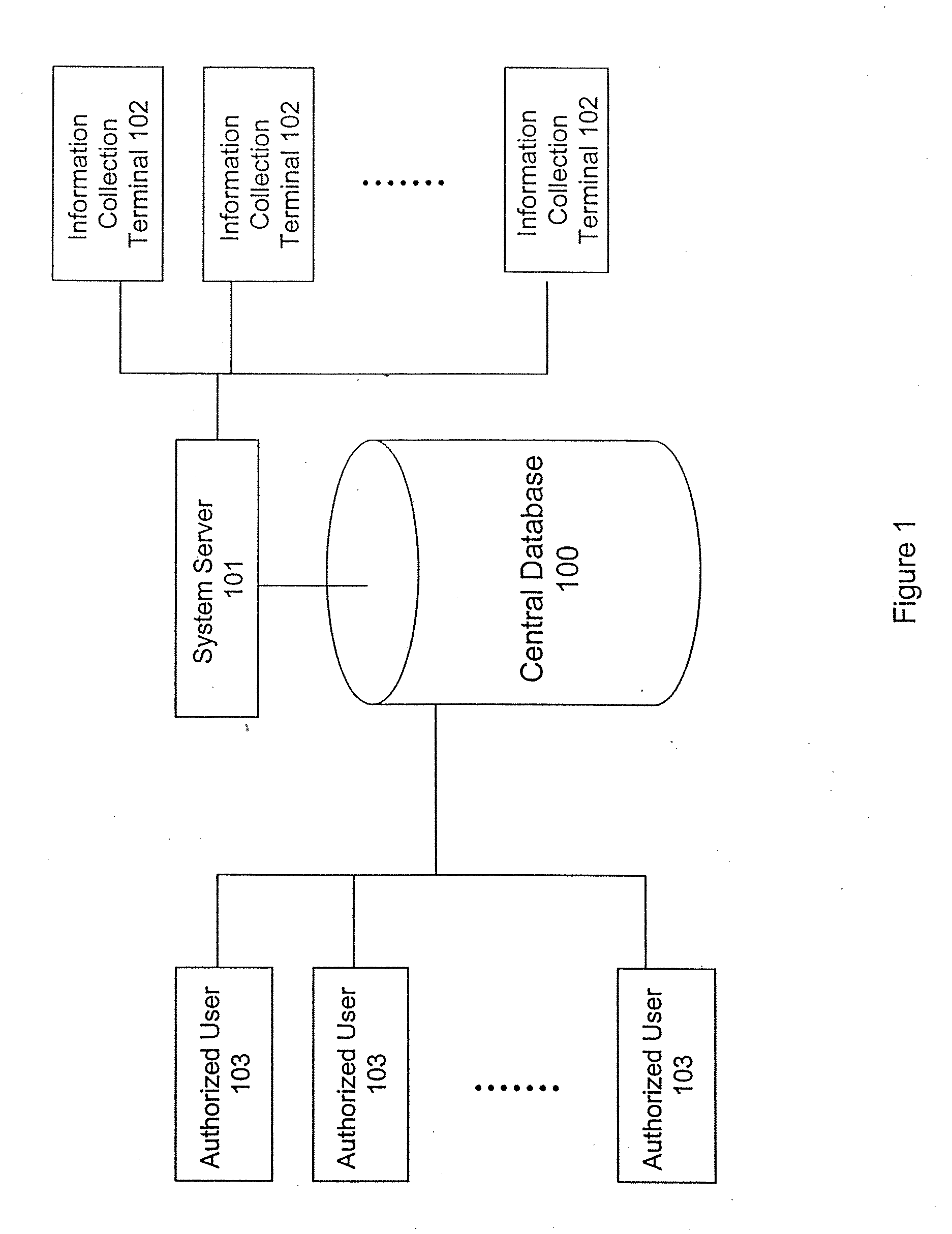
System and method for building and manipulating a centralized measurement value database
InactiveUS20020186818A1Low penetrationEasy to aimImage enhancementImage analysisMarket penetrationEfficacy
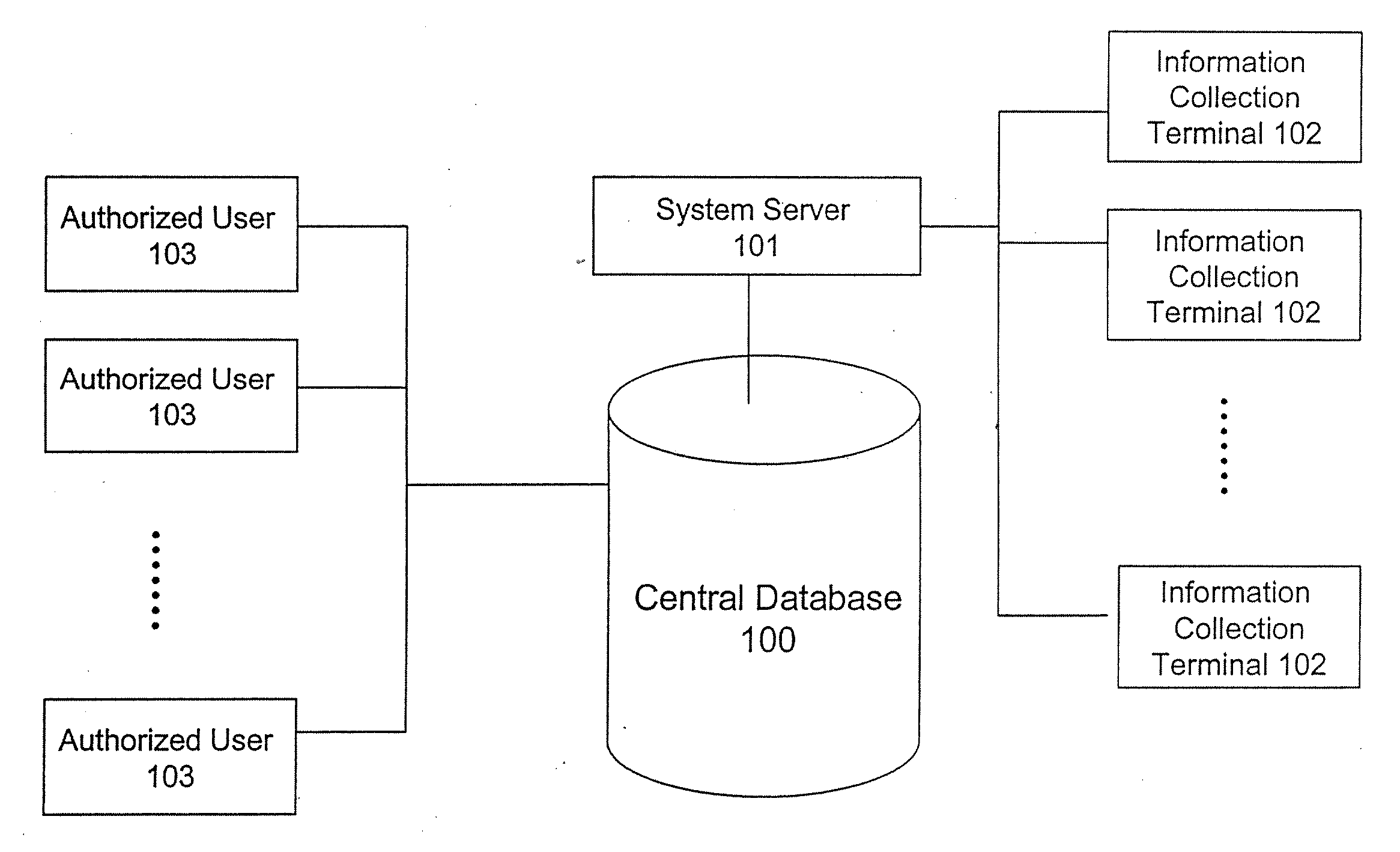
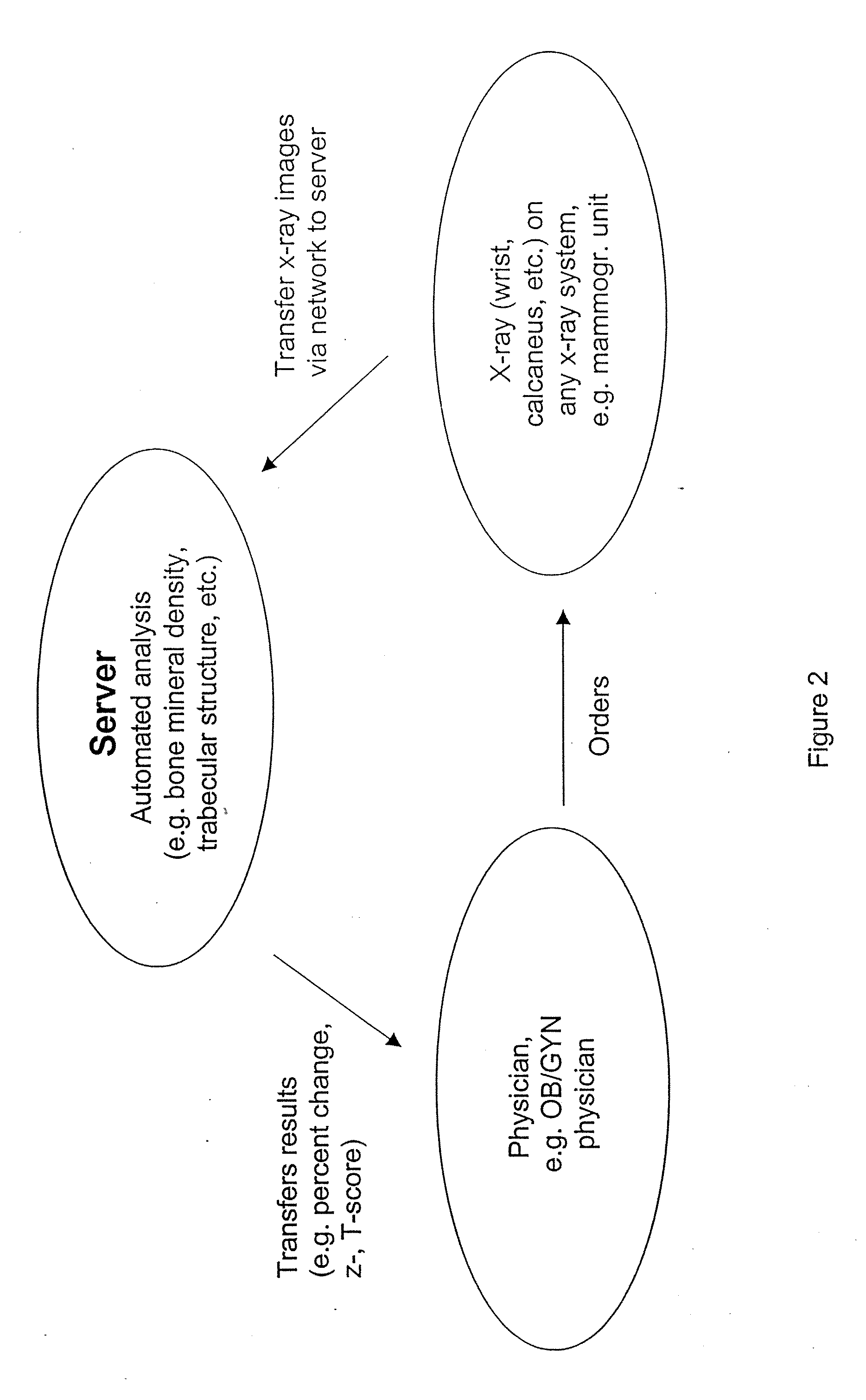
A system and method for building and / or manipulating a centralized medical image quantitative information database aid in diagnosing diseases, identifying prevalence of diseases, and analyzing market penetration data and efficacy of different drugs. In one embodiment, the diseases are bone-related, such as osteoporosis and osteoarthritis. Subjects' medical images, personal and treatment information are obtained at information collection terminals, for example, at medical and / or dental facilities, and are transferred to a central database, either directly or through a system server. Quantitative information is derived from the medical images, and stored in a central database, associated with subjects' personal and treatment information. Authorized users, such as medical officials and / or pharmaceutical companies, can access the database, either directly or through the central server, to diagnose diseases and perform statistical analysis on the stored data. Decisions can be made regarding marketing of drugs for treating the diseases in question, based on analysis of efficacy, market penetration, and performance of competitive drugs.
Owner:IMAGING THERAPEUTICS +1
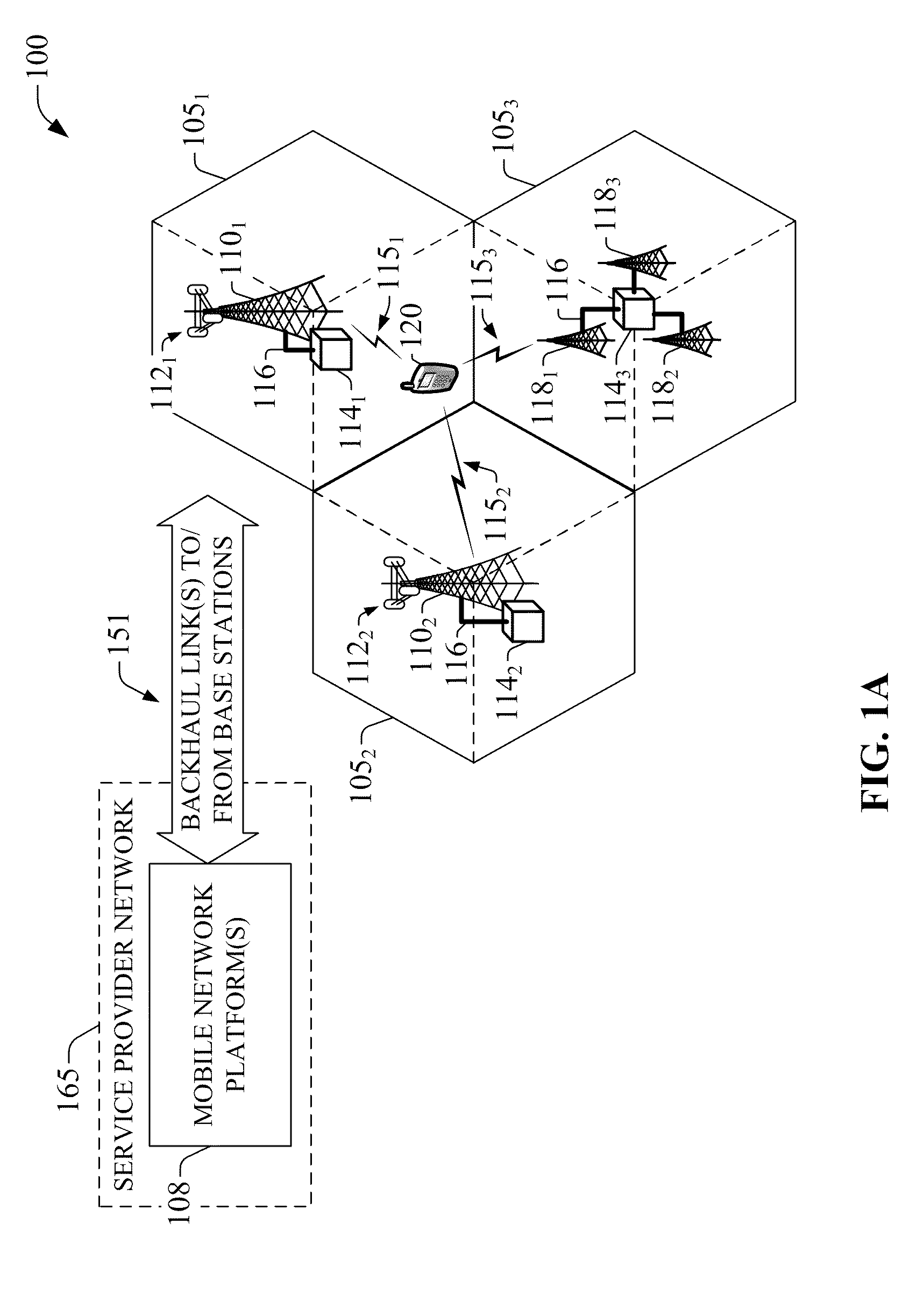
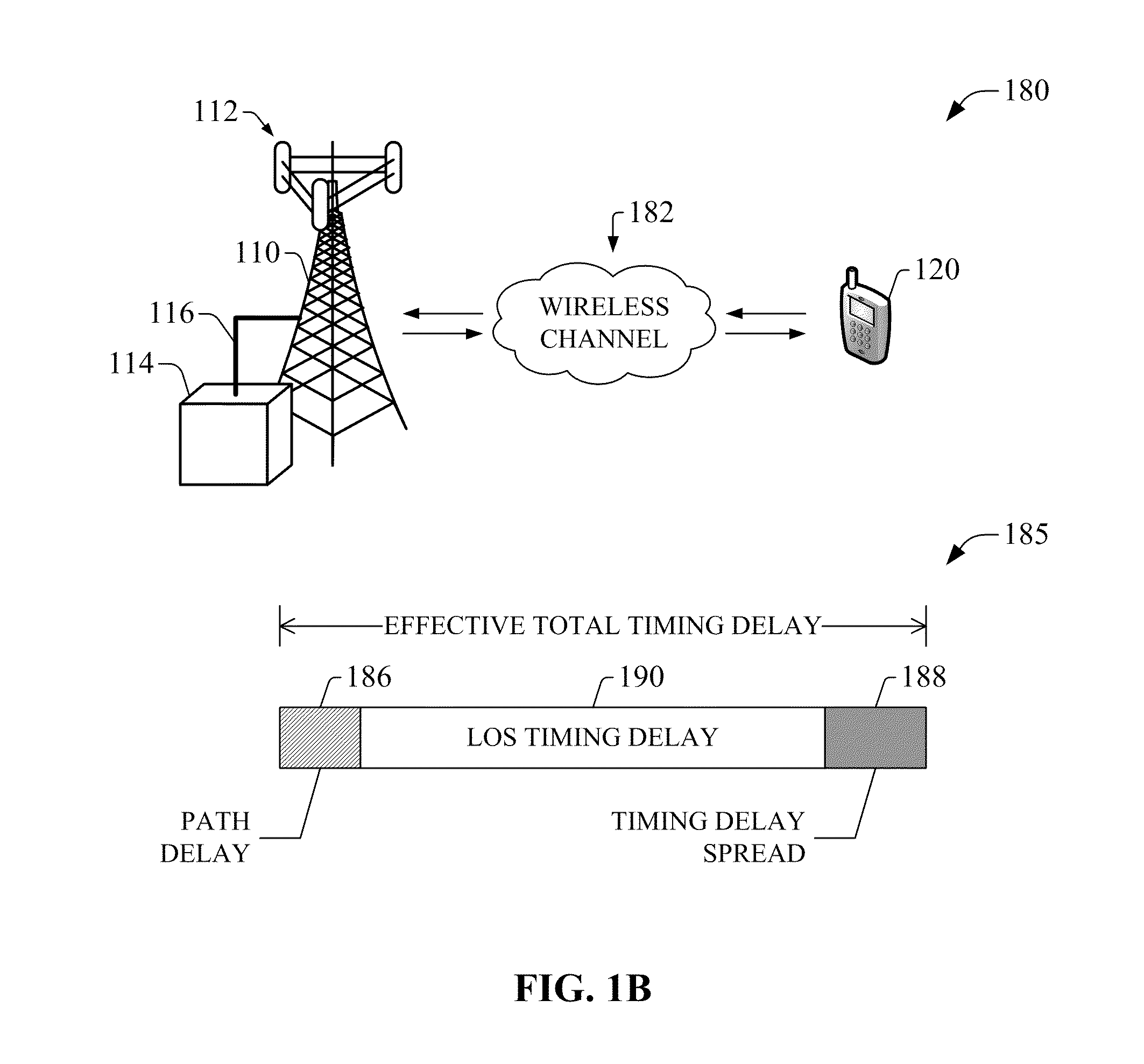
Compensation of propagation delays of wireless signals
ActiveUS20100190509A1Weakening rangeImprove accuracySynchronisation arrangementLocation information based servicePropagation delayRadio networks
System(s) and method(s) for compensation of propagation delay offsets of wireless signals. Compensation is accomplished through determination of an effective wireless signal propagation delay that accounts for signal path delay and propagation delay over the air. Such determination is based at least in part on statistical analysis of accurate location estimates of reference positions throughout a coverage sector or cell, and location estimates of the reference positions generated through time-of-flight (TOF) measurements of wireless signals. Determination of propagation or signal path delay offset also is attained iteratively based at least in part on reference location estimates and TOF location estimates. High-accuracy location estimates such as those obtained through global navigation satellite systems are employed as reference location estimates. Position of probes or wireless beacons, deployed throughout a sector or cell, also are employed as reference locations. Compensation of propagation delay offset improves accuracy of conventional TOF location estimates and radio network performance.
Owner:AT&T MOBILITY II LLC
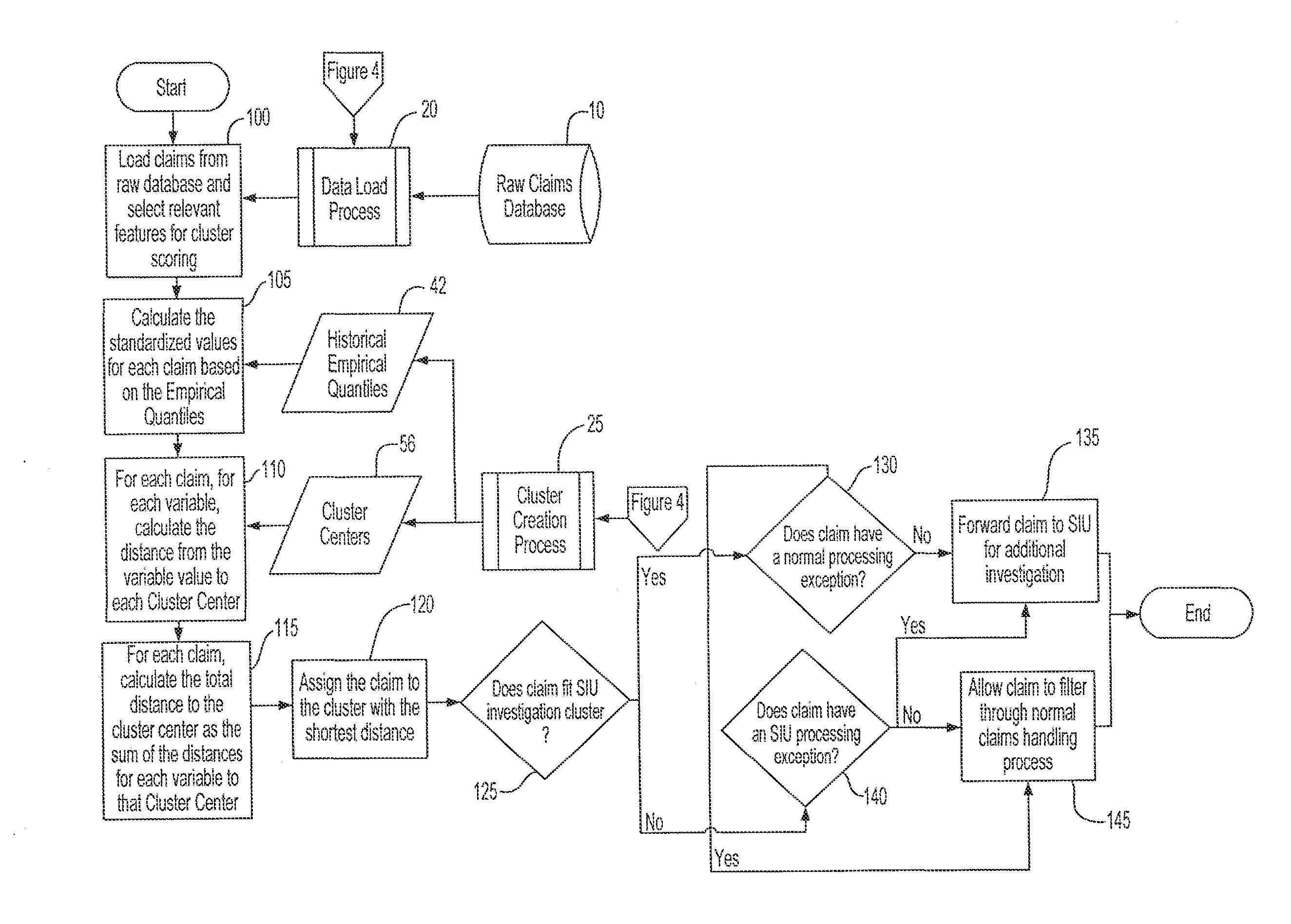
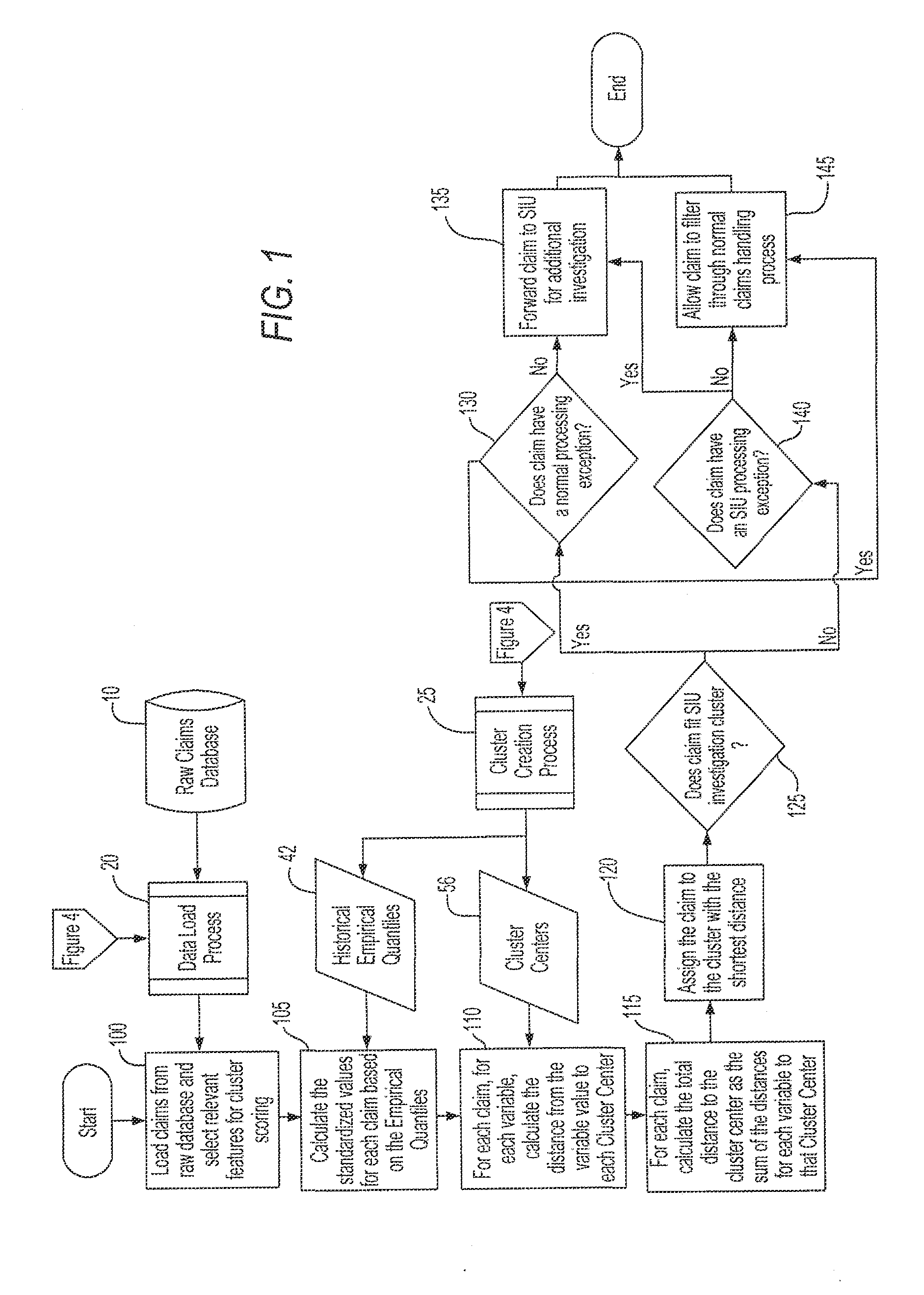
Fraud detection methods and systems
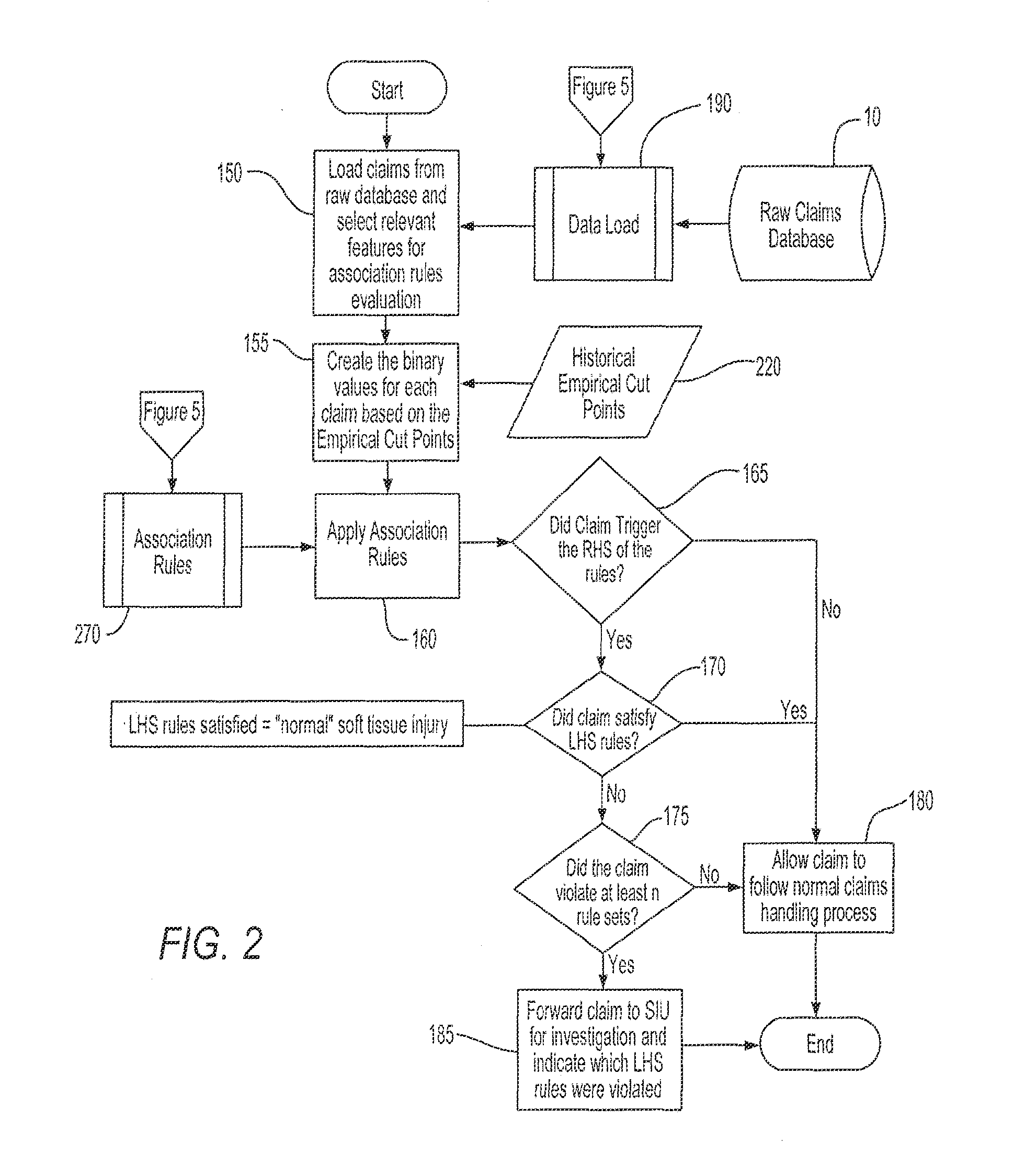
An unsupervised statistical analytics approach to detecting fraud utilizes cluster analysis to identify specific clusters of claims or transactions for additional investigation, or utilizes association rules as tripwires to identify outliers. The clusters or sets of rules define a “normal” profile for the claims or transactions used to filter out normal claims, leaving “not normal” claims for potential investigation. To generate clusters or association rules, data relating to a sample set of claims or transactions may be obtained, and a set of variables used to discover patterns in the data that indicate a normal profile. New claims may be filtered, and not normal claims analyzed further. Alternatively, patterns for both a normal profile and an anomalous profile may be discovered, and a new claim filtered by the normal filter. If the claim is “not normal” it may be further filtered to detect potential fraud.
Owner:DELOITTE DEV
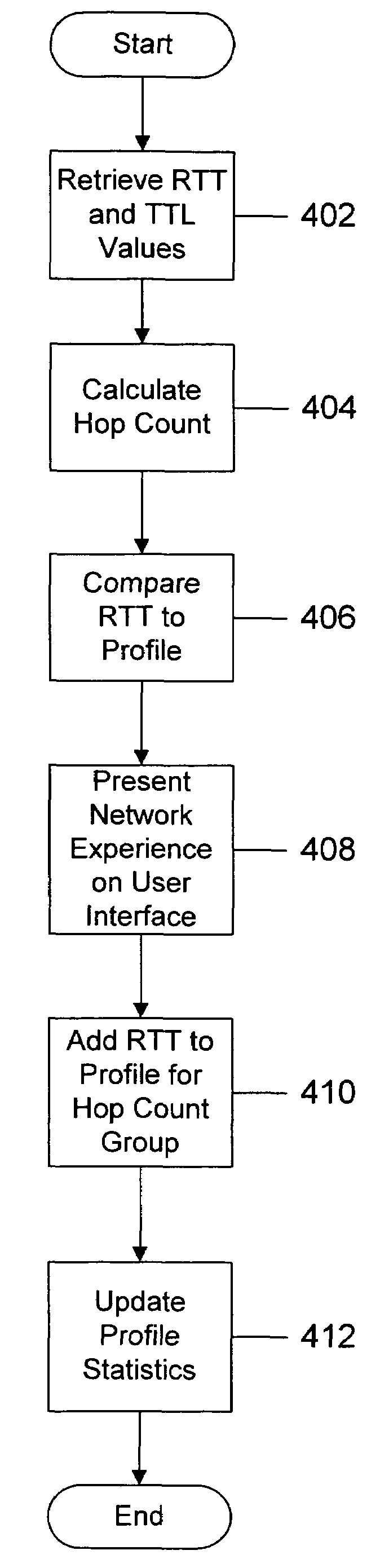
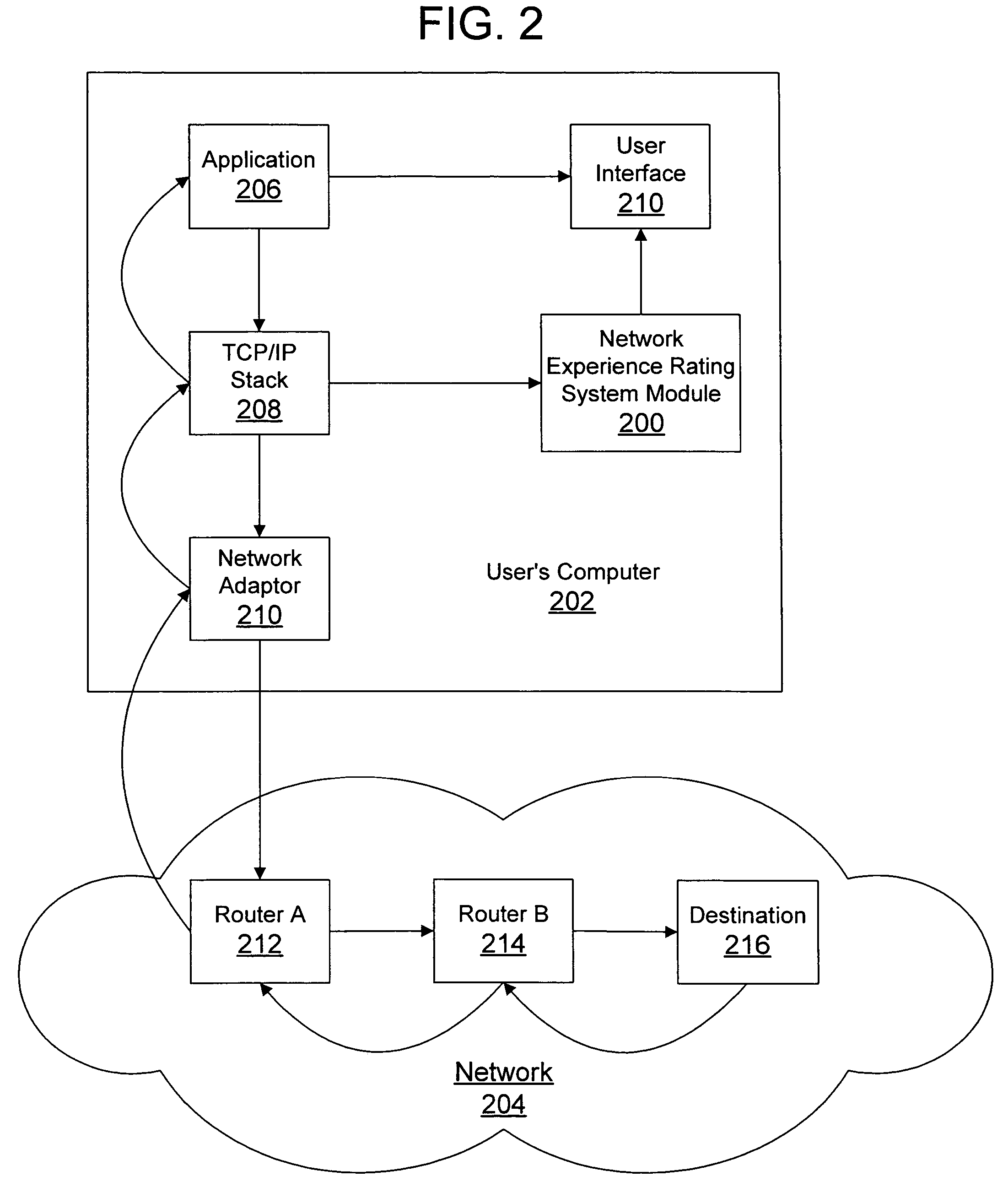
Network experience rating system and method
InactiveUS7506052B2Reliably perceiveMultiple digital computer combinationsTransmissionRating systemPersonalization
A network experience rating system and method determines a network connection quality for a computer by monitoring characteristics of data traffic through a connection with another computer on the network. The network experience rating system statistically analyzes the characteristic data and compares the statistically analyzed data to historical data gathered for the computer. The network experience rating system thus provides a rating that is individualized for a particular computer based on the computer's network usage.
Owner:MICROSOFT TECH LICENSING LLC
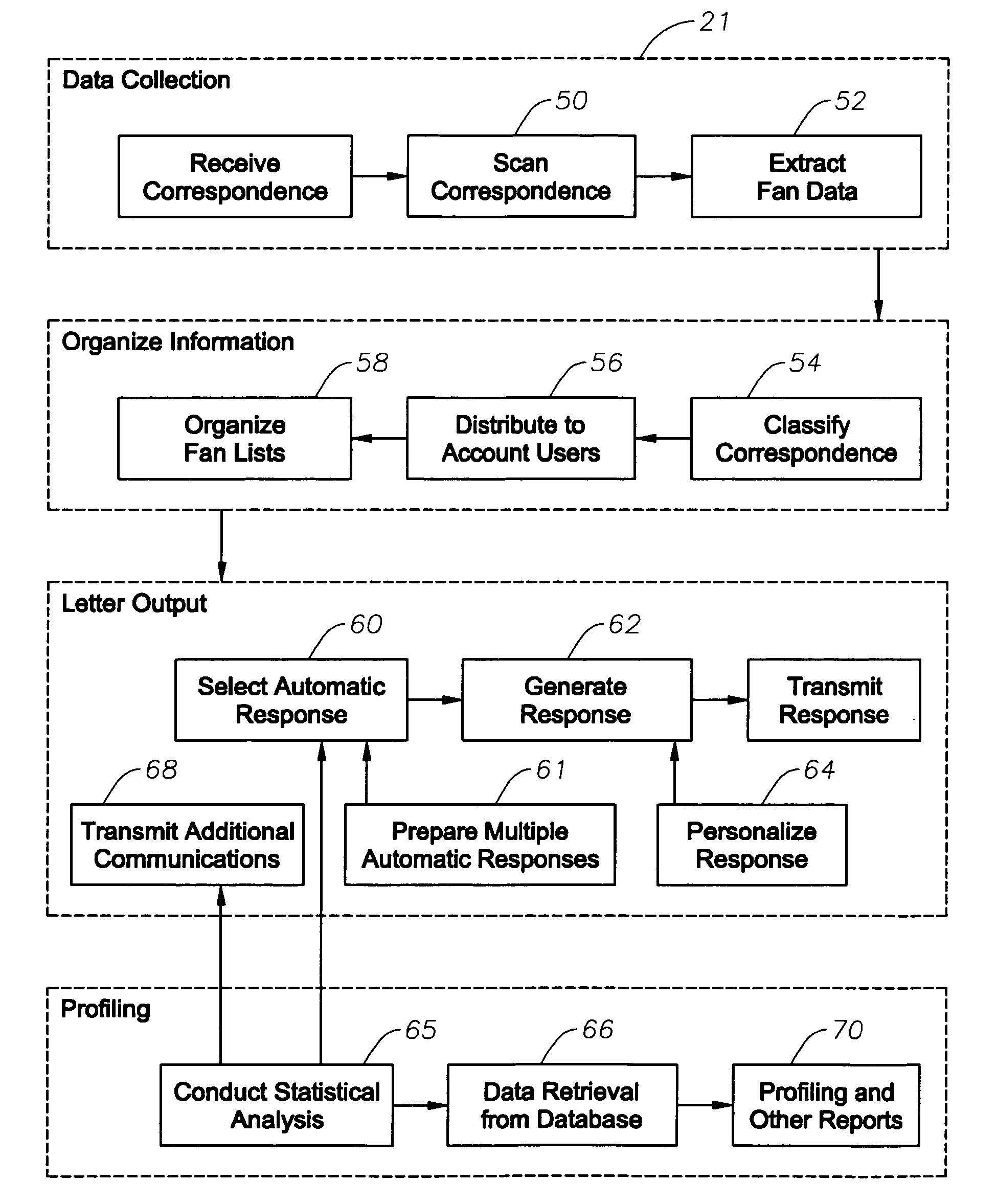
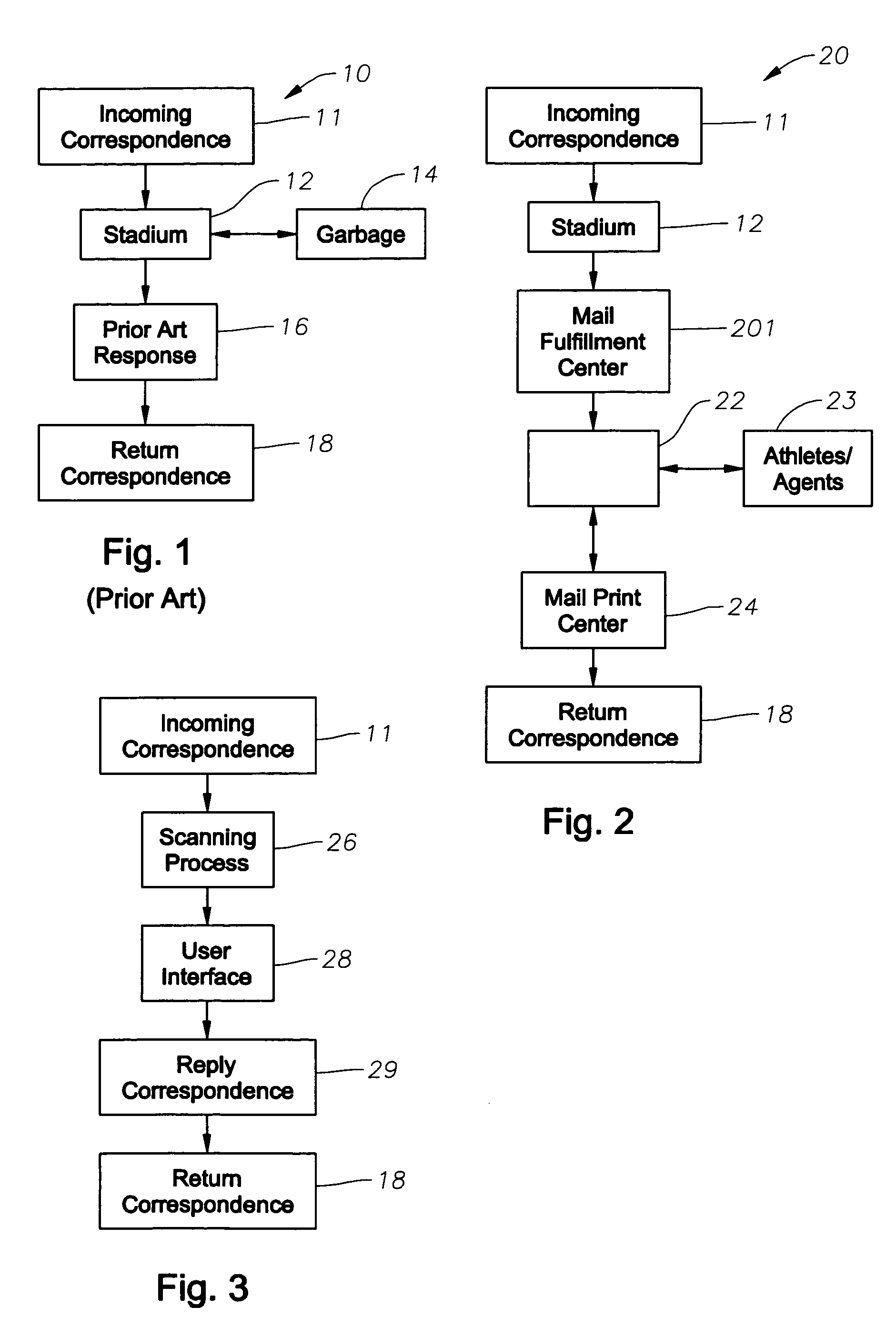
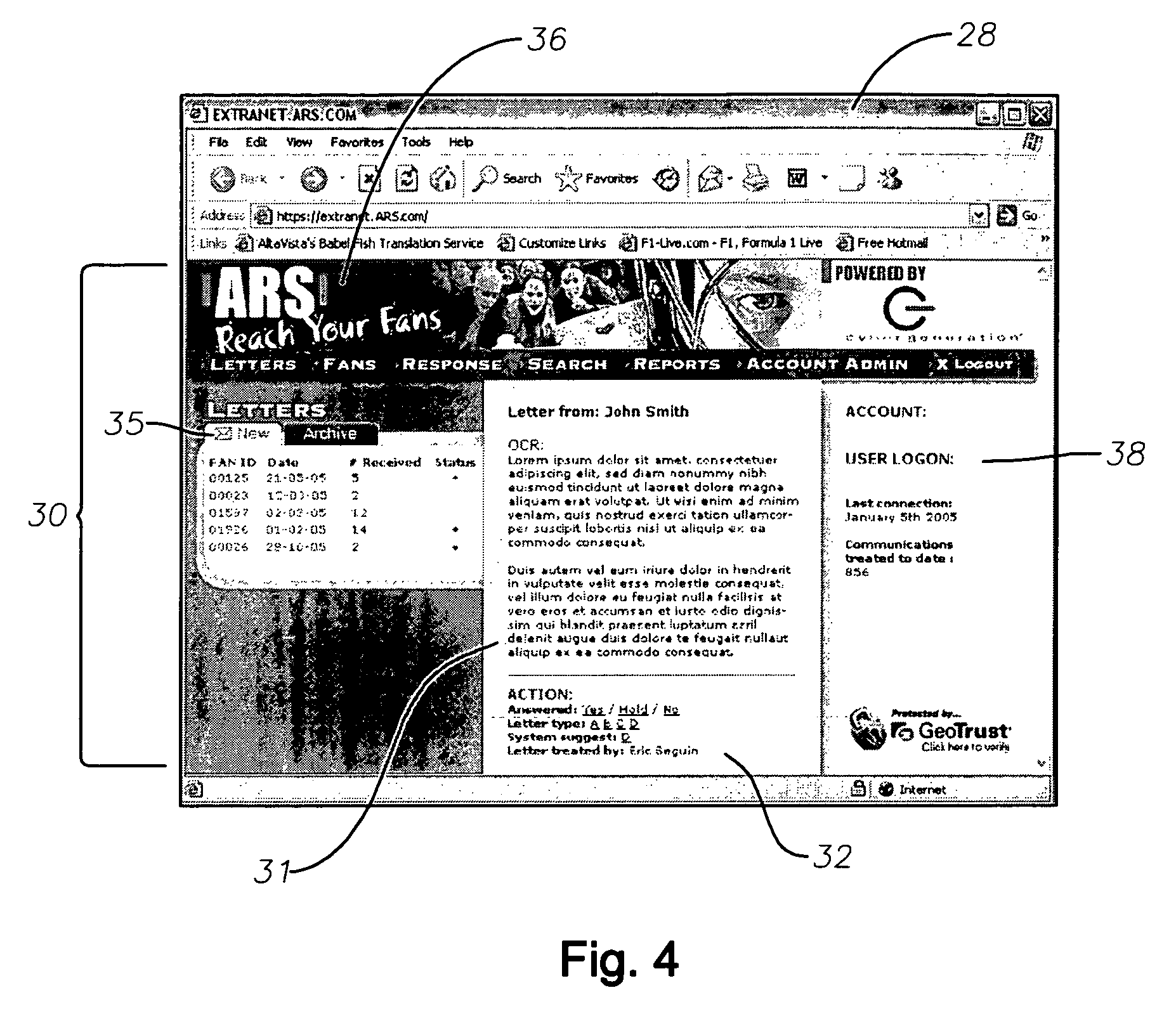
Automated response to solicited and unsolicited communications and automated collection and management of data extracted therefrom
InactiveUS7996372B2Digital data information retrievalDigital data processing detailsSystems analysisData mining
An automated correspondence response system is provide for permitting a receiving entity to generate customized responses based on data extracted from received communications. The system also provides for automated management and manipulation of data extracted from correspondence received by a receiving entity for group profiling and to perform various statistical analysis thereof.The system analyzes content of received correspondence, such as celebrity fan mail, and manages the automation of responses via targeted or “customized” letters, wherein the receiving entity creates content specific fields or terms in order to respond to correspondence in an automated and yet relevant manner. The receiving entity can electronically define what data is extracted from the correspondence. A particular “customized” response to the correspondence may be electronically selected from a plurality of possible responses based on the data extracted from the sender's correspondence so that the receiving entity can effectively respond to the sender. The “customized” automated response can also be “personalized” by including sender specific data in the “customized” automated response.
Owner:MERCURY COMM GROUP
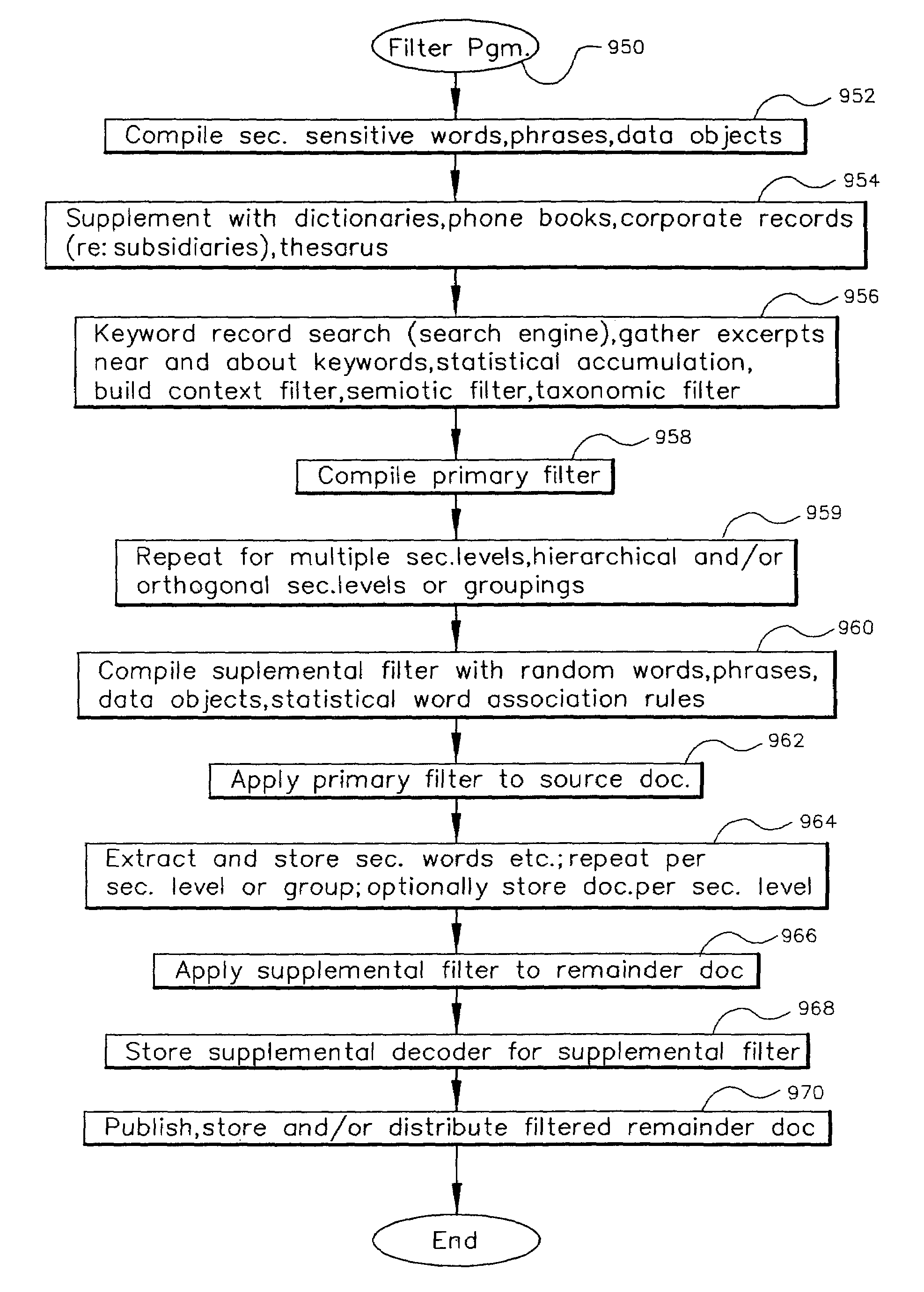
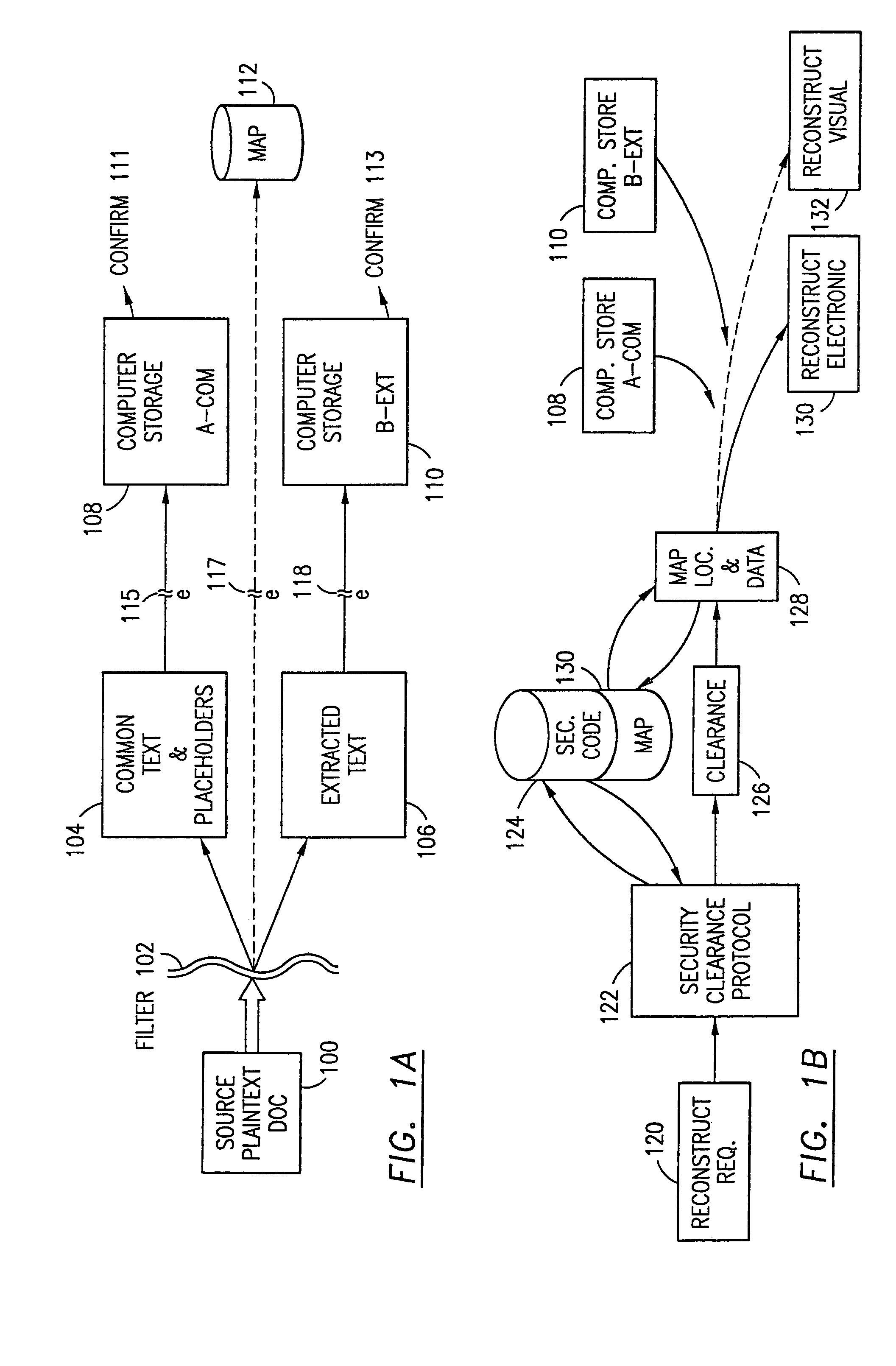
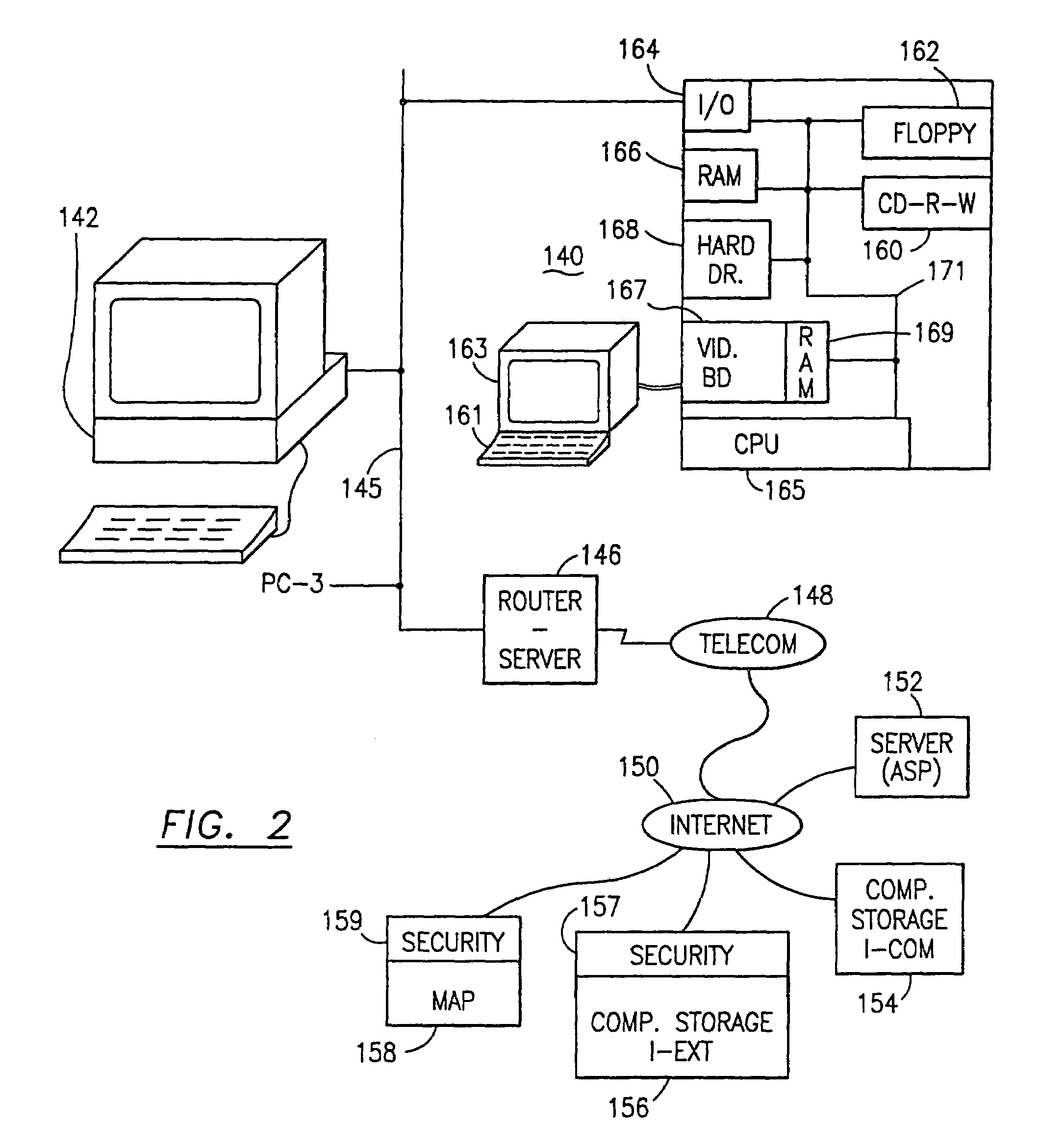
Data security system and method with adaptive filter
ActiveUS7546334B2Digital data information retrievalDigital data processing detailsInformation processingAdaptive filter
A method, program and information processing system filters and secures data (security sensitive words-characters-data objects) in a source document. The adaptive filter uses a compilation of additional data (typically networked) and identifies the sensitive words / objects in the compilation of additional data, and retrieves contextual, semiotic and taxonomic words / objects from the compilation related to the sensitive words / objects. The resulting compiled filter is used to extract sensitive words / objects and retrieved data (words / objects) from the source document to obtain extracted data and remainder data therefrom. Contextual words, related to the security sensitive words / objects, are based upon statistical analysis of the additional data compilation. Semiotic words related words are synonyms, antonyms, and pseudonyms, syntactics relative to the target words and retrieved words, and pragmatics relative to the sensitive words and retrieved words.
Owner:DIGITAL DOORS
Systems and methods for investigation of financial reporting information
Owner:PRICEWATERHOUSECOOPERS
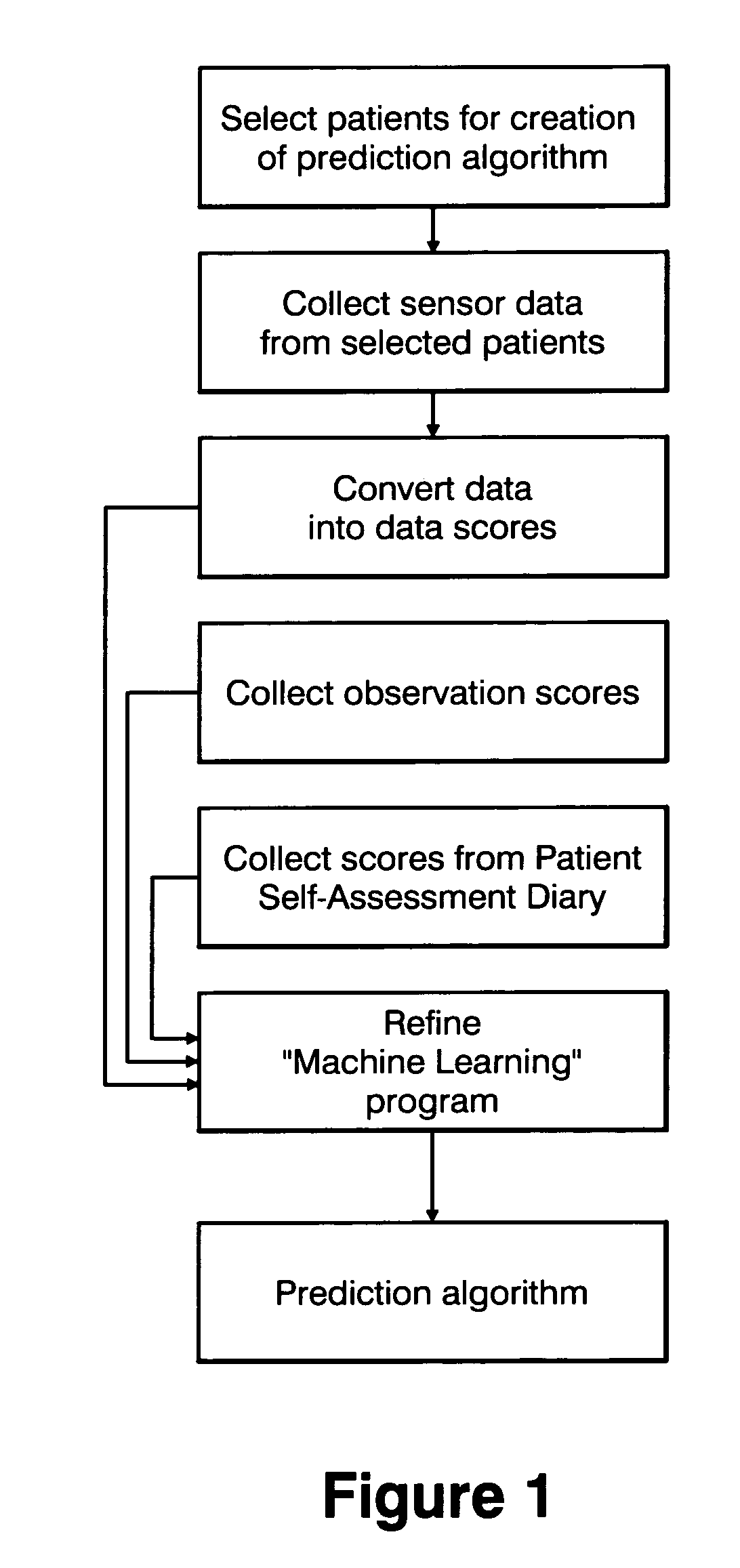
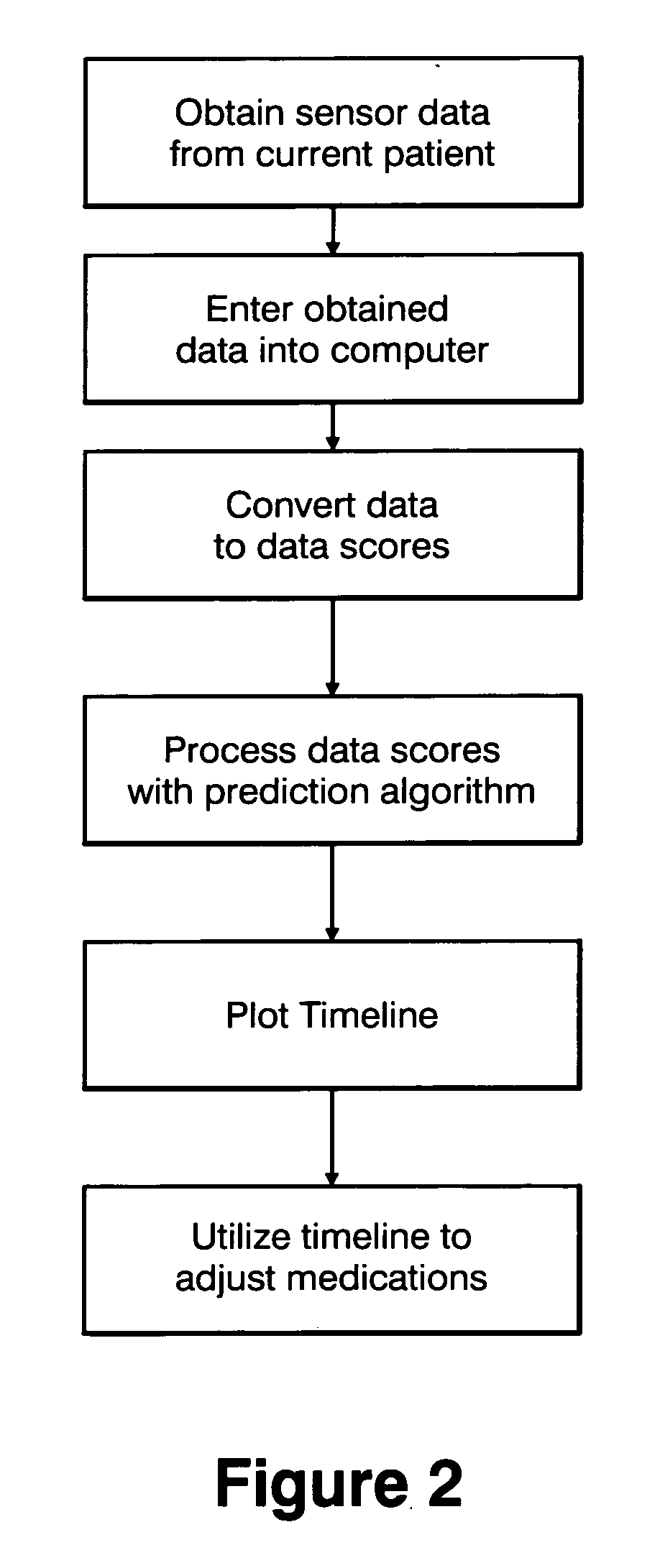
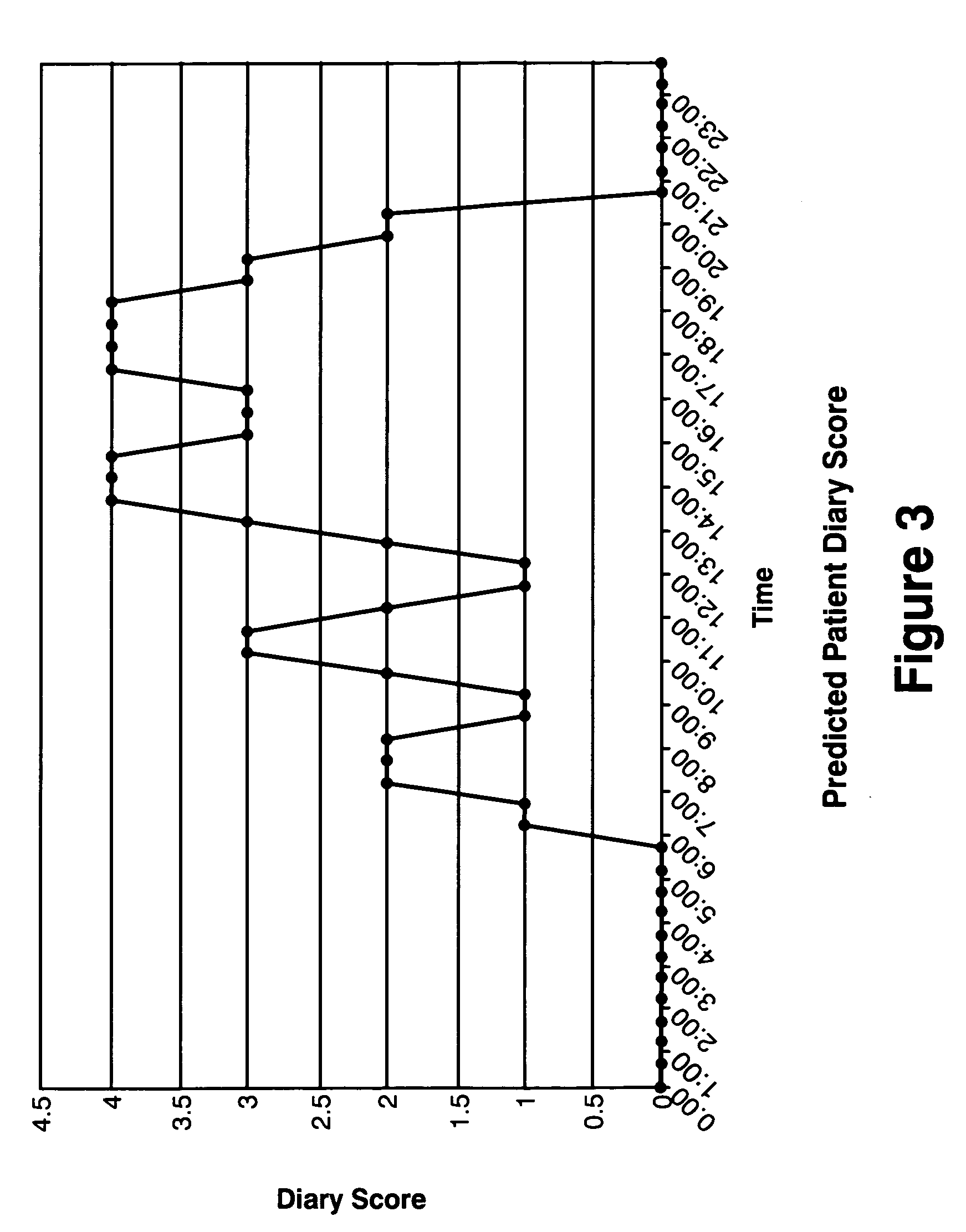
Method and apparatus for classification of movement states in Parkinson's disease
InactiveUS20050234309A1Easy to predictInertial sensorsMedical automated diagnosisAccelerometerClinical psychology
For Parkinson's patients to function at their best, their medications need to be optimally adjusted to the diurnal variation of symptoms. For this to occur, it is important for the managing clinician to have an accurate picture of how the patient's bradykinesia / hypokinesia and dyskinesia and the patient's perception of movement state fluctuate throughout the normal daily activities. The present invention uses wearable accelerometers coupled with computer implemented learning and statistical analysis techniques in order to classify the movement states of Parkinson's patients and to provide a timeline of how the patients fluctuate throughout the day.
Owner:PARK KINESIS INSTR
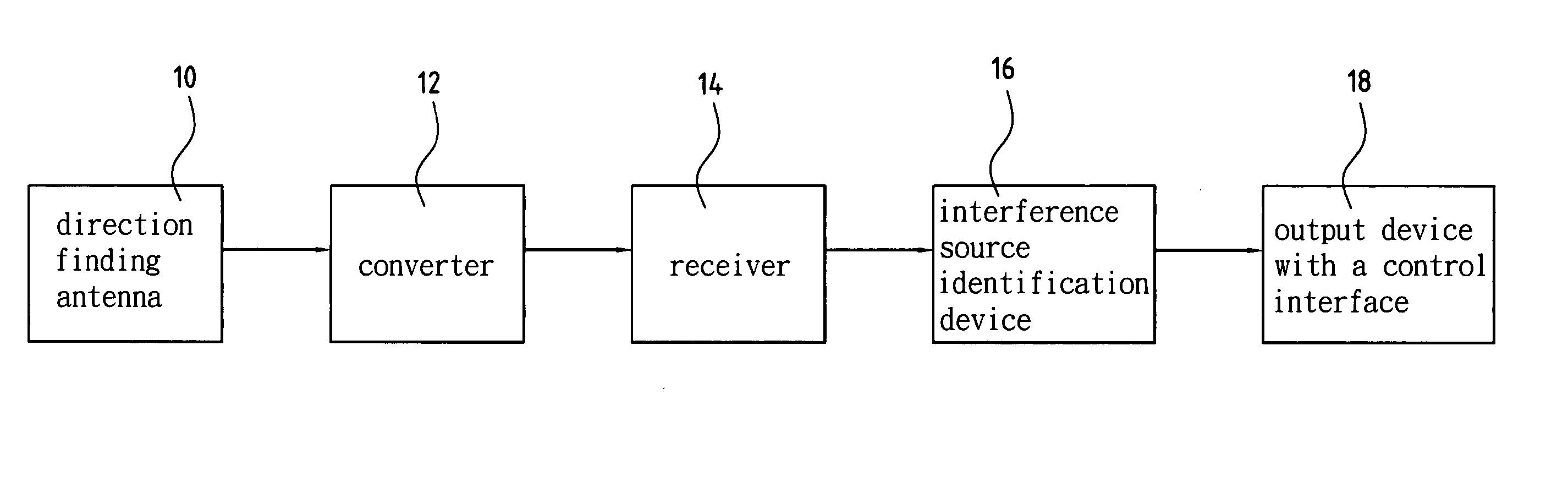
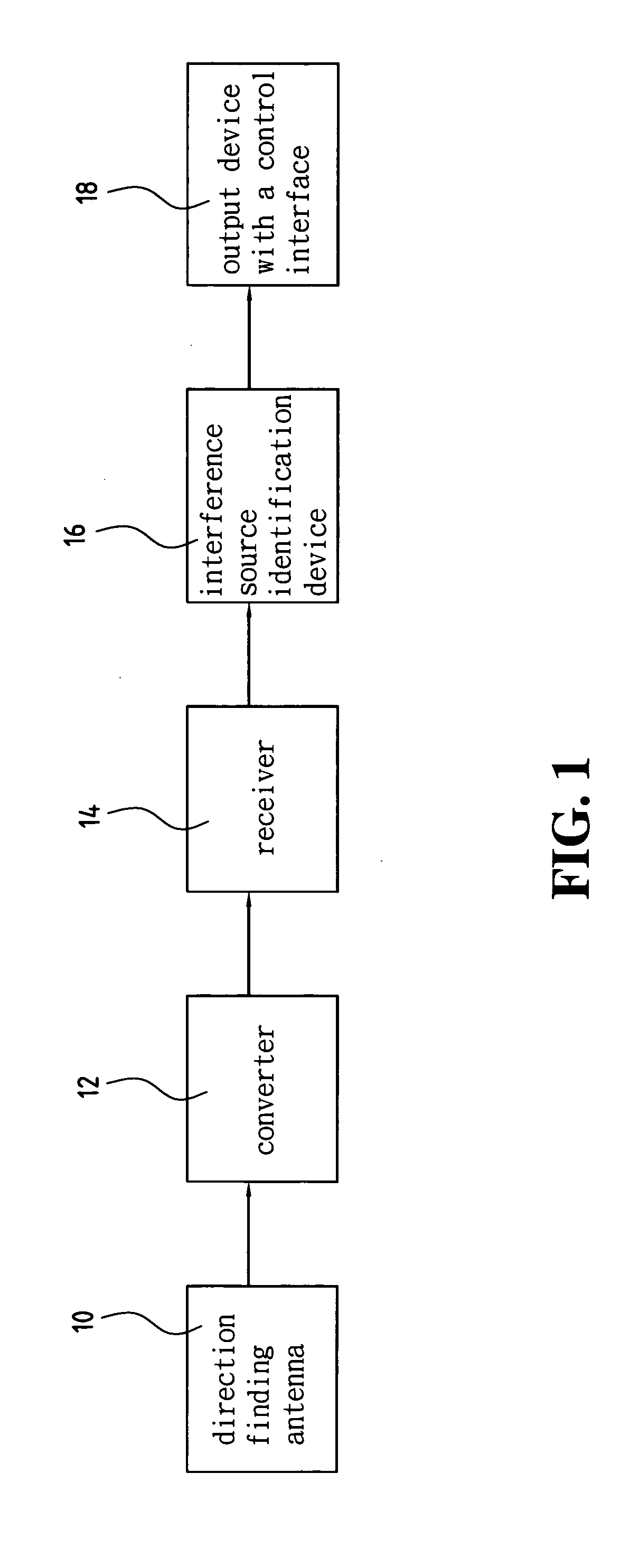
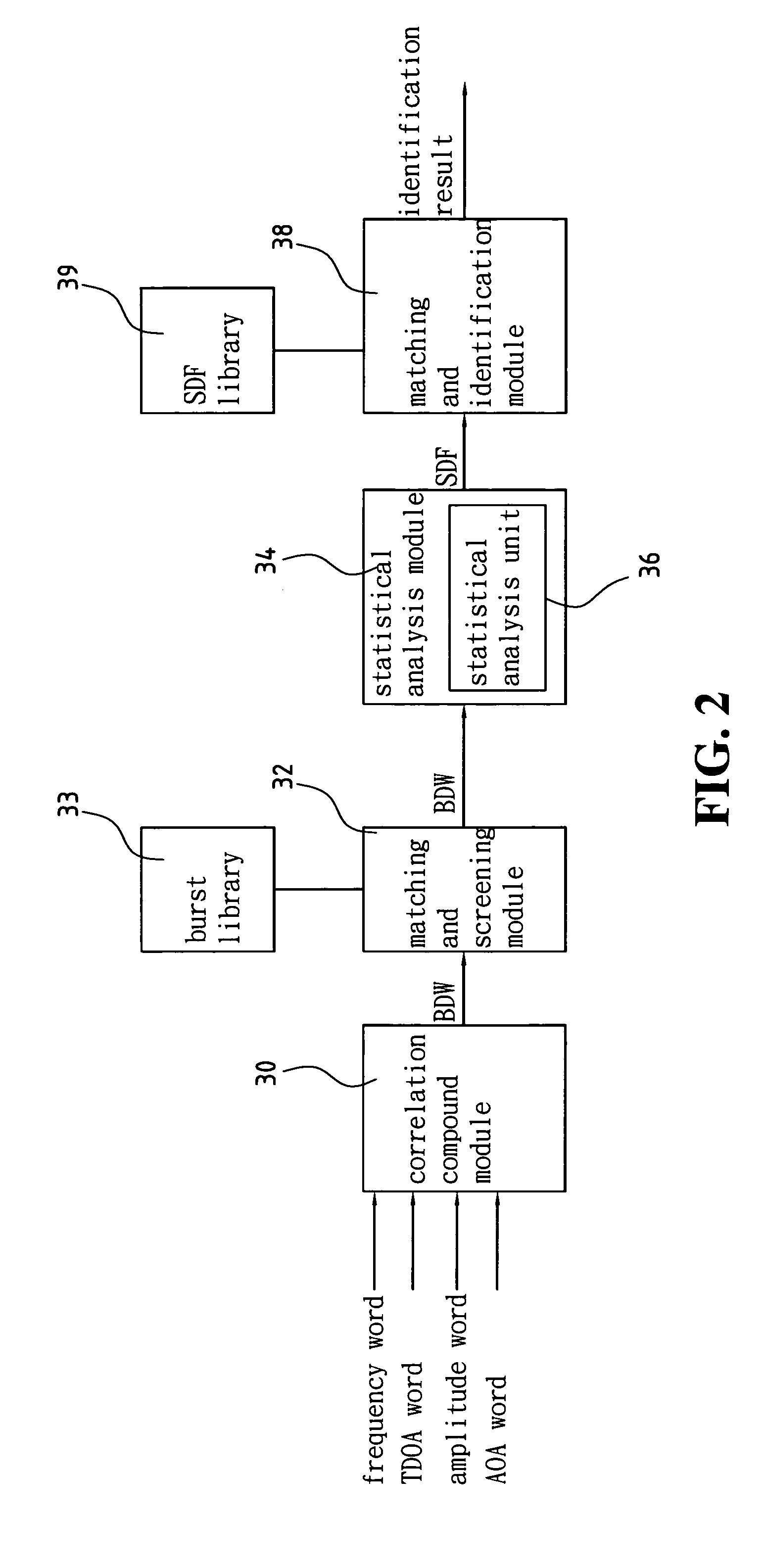
Device and method for identifying interference source in wireless communications
InactiveUS20050117676A1Improve transmission performanceError detection/prevention using signal quality detectorLine-faulsts/interference reductionDiscriminatorMultilateration
A device for identifying interference source in wireless communications is provided, including a correlation compound module, a matching and screening module, a statistical analysis module, and a match identification module. The correlation compound module uses the time of arrival (TOA) of the burst as the synchronization basis to compound the correlated frequency word, time difference of arrival (TDOA) word, amplitude word and angle of arrival (AOA) word to form a burst descriptor word (BDW). The matching and screening module uses the BWD to match the burst library to screen out the non-interference sources. The statistic analysis module uses the screened outcome for statistical analysis, and obtains a source discriminator file (SDF). The matching and identification module uses the SDF to search the interference source library for matching and obtains an identification result.
Owner:ACCTON TECHNOLOGY CORPORATION
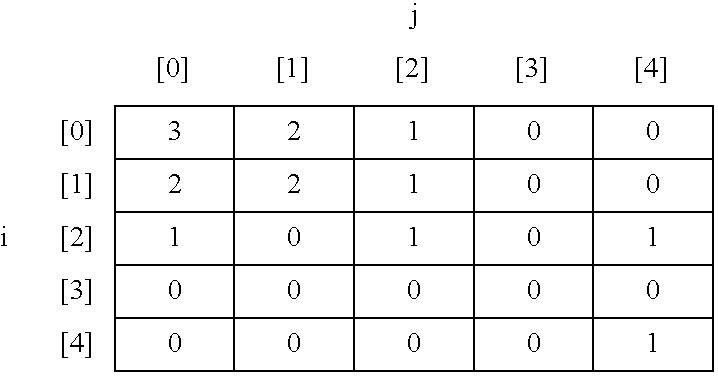
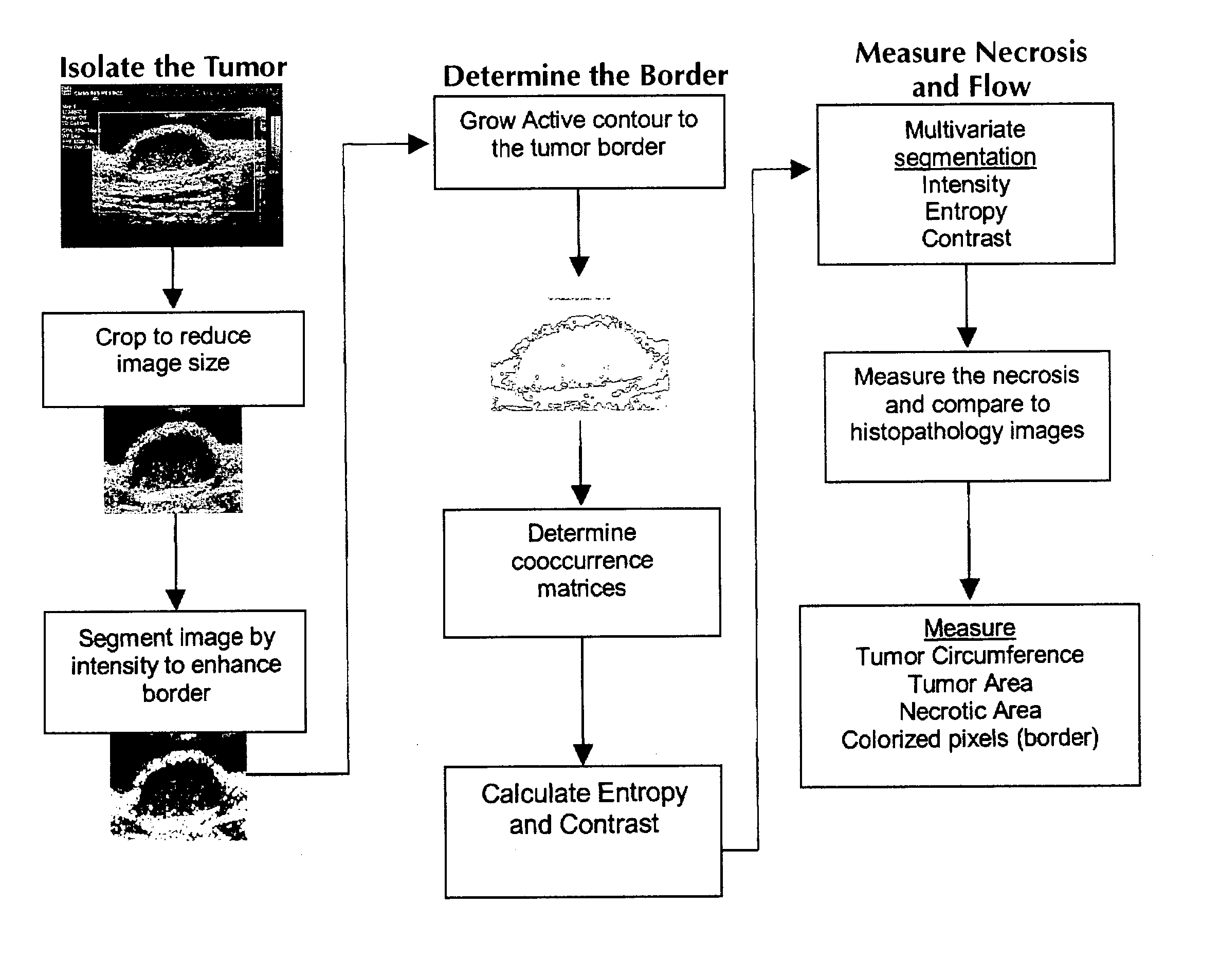
Apparatus and method for statistical image analysis
An apparatus, system, method, and computer readable medium containing computer-executable code for implementing image analysis uses multivariate statistical analysis of sample images, and allows segmentation of the image into different groups or classes, depending on a correlation to one or more sample textures, or sample surface features. In one embodiment, the invention performs multivariate statistical analysis of ultrasound images, wherein a tumor may be characterized by segmenting viable tissue from necrotic tissue, allowing for more detailed in vivo analysis of tumor growth beyond simple dimensional measurements or univariate statistical analysis. Application of the apparatus and method may also be used for characterizing other types of samples having textured features including, for example, tumor angiogenesis biomarkers from Power Doppler.
Owner:PFIZER INC
Adaptive network traffic classification using historical context
Adaptive network traffic classification using historical context. Network traffic may be monitored and classified by considering several attributes using packet filters, regular expressions, context-free grammars, rule sets, and / or protocol dissectors, among other means and by applying a variety of techniques such as signature matching and statistical analysis. Unlike static systems, the classification decisions may be reexamined from time to time or after subsequent processing determines that the traffic does not conform to the protocol specification corresponding to the classification decision. Historical context may be used to adjust the classification strategy for similar or related traffic.
Owner:EXTRAHOP NETWORKS
Power load forecasting method based on big data technology, and research and application system based on method
InactiveCN105678398AImprove horizontal scalabilityImprove fast data access responsivenessForecastingPower gridDecision-making
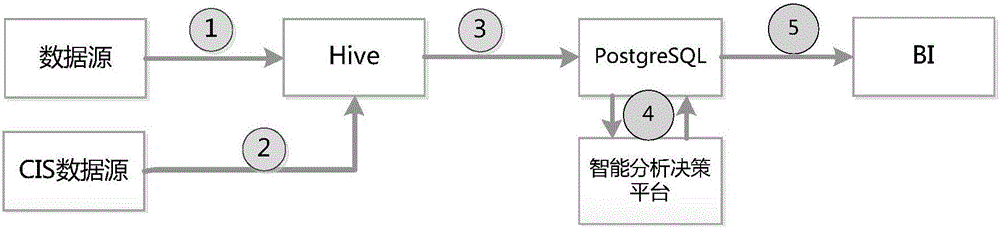
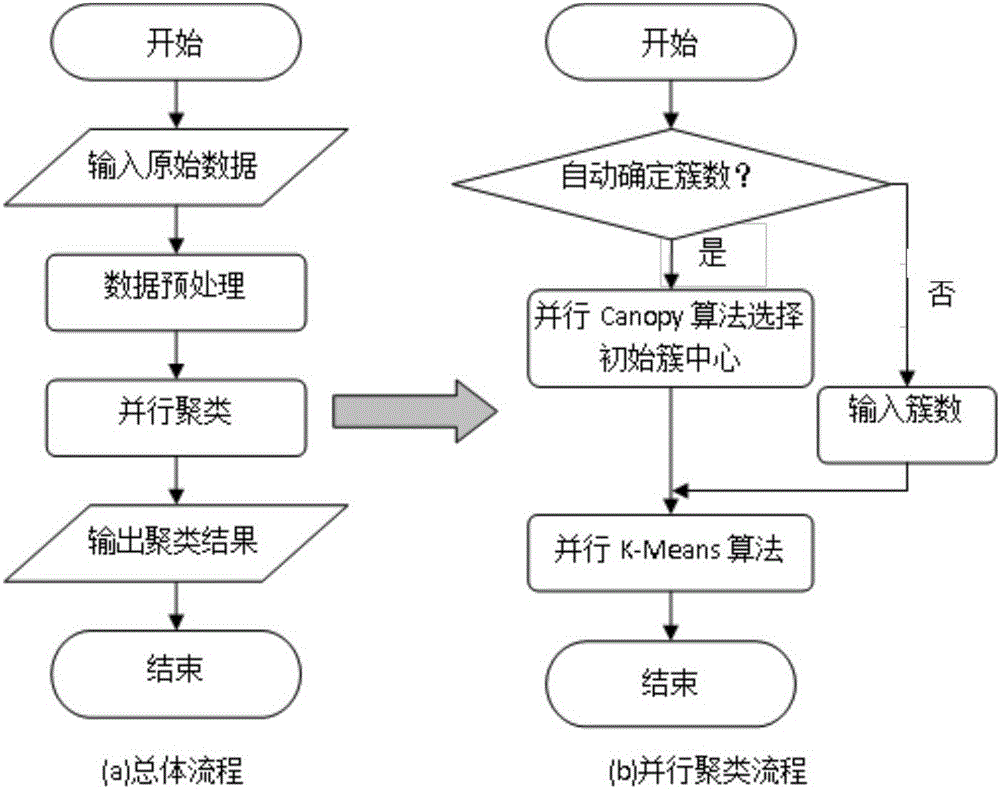
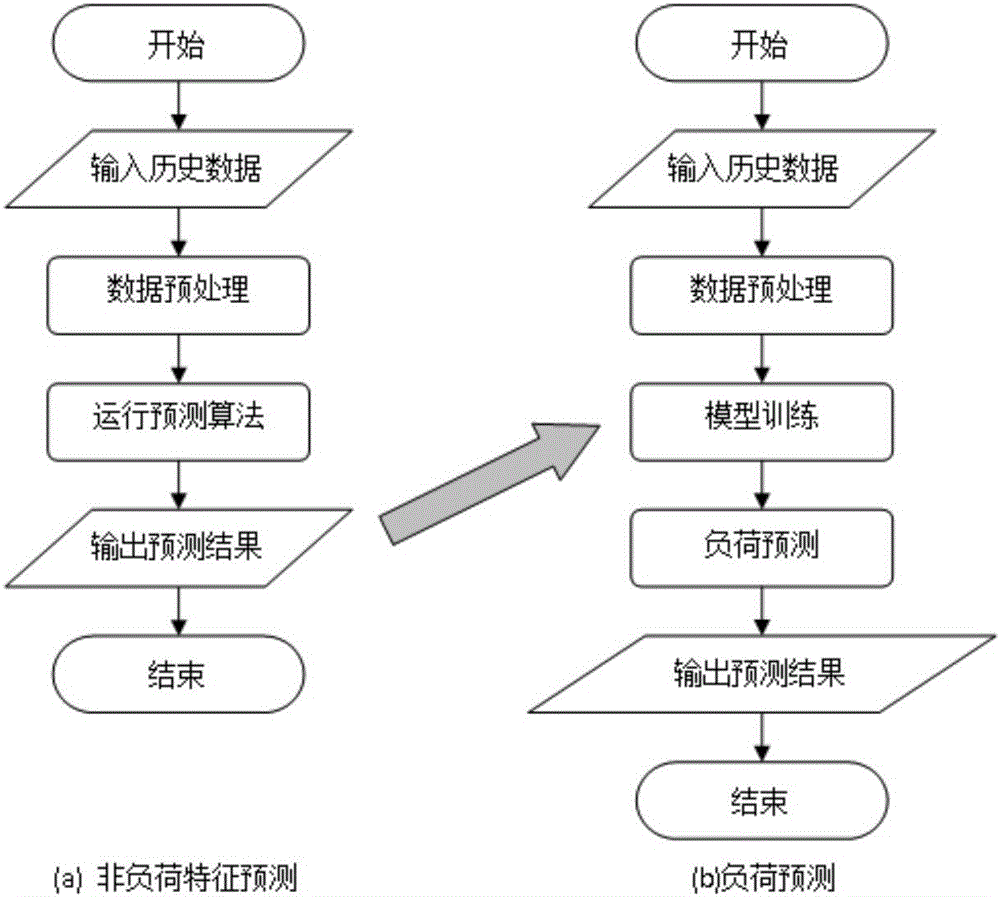
The present invention is a power load forecasting method based on big data technology and a research application system based on the method. With the support of big data technology, a variety of mature open source products are integrated to form a data source, data integration, data storage, Data calculation, data analysis, implementation of electrical load characteristic analysis and electrical load forecast analysis. The invention effectively improves the efficiency of mass data processing, and solves the limitations of traditional statistical analysis assumptions and judgments. It can scientifically and accurately predict the electricity demand of the future power, which is conducive to the peak-shaving and valley-filling and stable operation of the power grid, and provides decision-making support for the company's power grid planning, equipment maintenance, and power deployment.
Owner:STATE GRID CORP OF CHINA +4
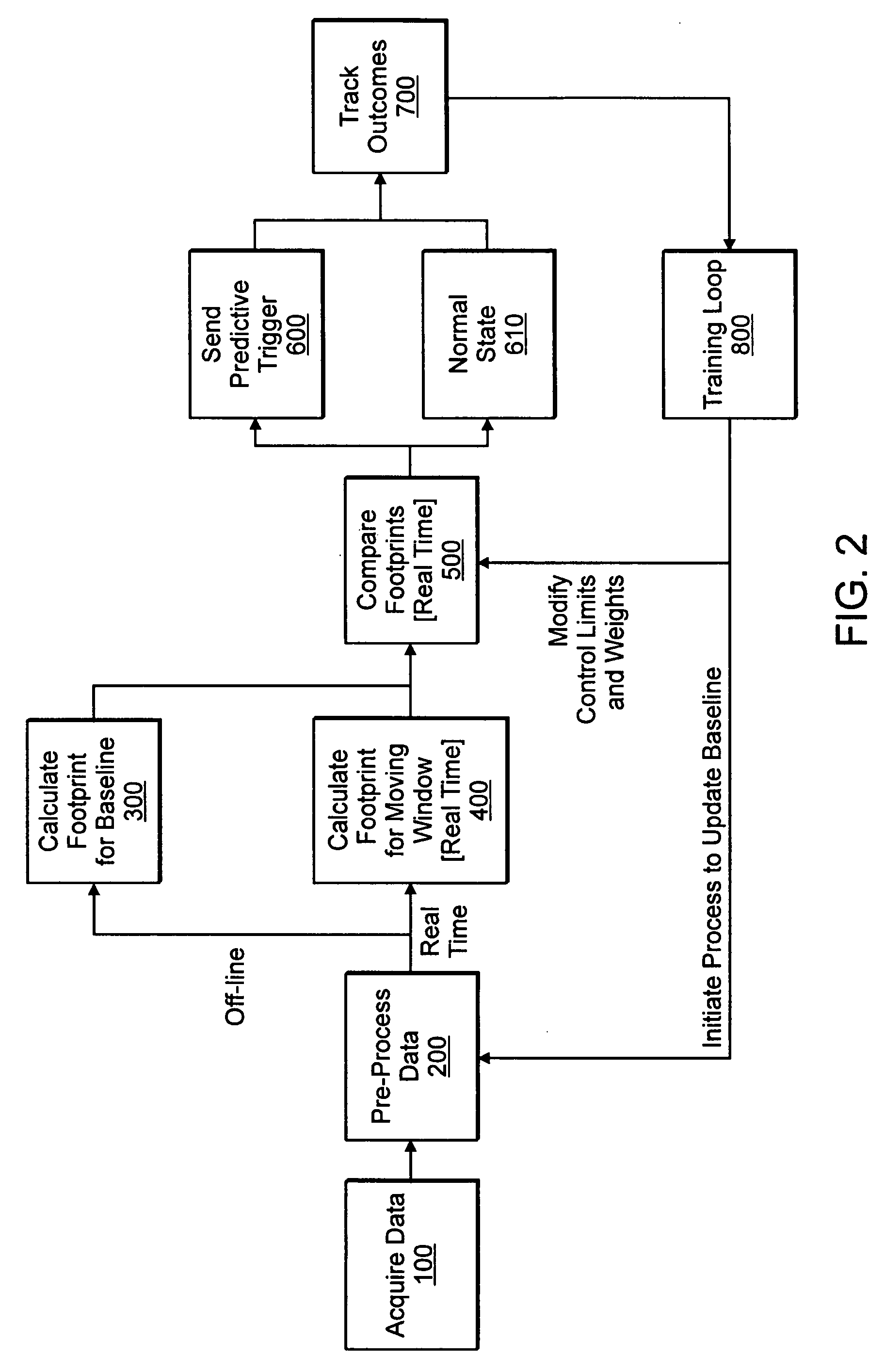
System and method for monitoring performance of groupings of network infrastructure and applications using statistical analysis
InactiveUS20060020924A1Non-redundant fault processingProgram loading/initiatingOperational behaviorUnit group
Systems, methods and computer program products for monitoring performance of groupings of network infrastructure and applications using statistical analysis. A method, system and computer program monitors managed unit groupings of executing software applications and execution infrastructure to detect deviations in performance. Logic acquires time-series data from at least one managed unit grouping of executing software applications and execution infrastructure. Other logic derives a statistical description of expected behavior from an initial set of acquired data. Logic derives a statistical description of operating behavior from acquired data corresponding to a defined moving window of time slots. Logic compares the statistical description of expected behavior with the statistical description of operating behavior; and logic reports predictive triggers, said logic to report being responsive to said logic to compare and said logic to report identifying instances where the statistical description of operating behavior deviates from statistical description of operating behavior to indicates a statistically significant probability that an operating anomaly exists within the at least managed unit grouping corresponding to the acquired time-series data.
Owner:K5 SYST
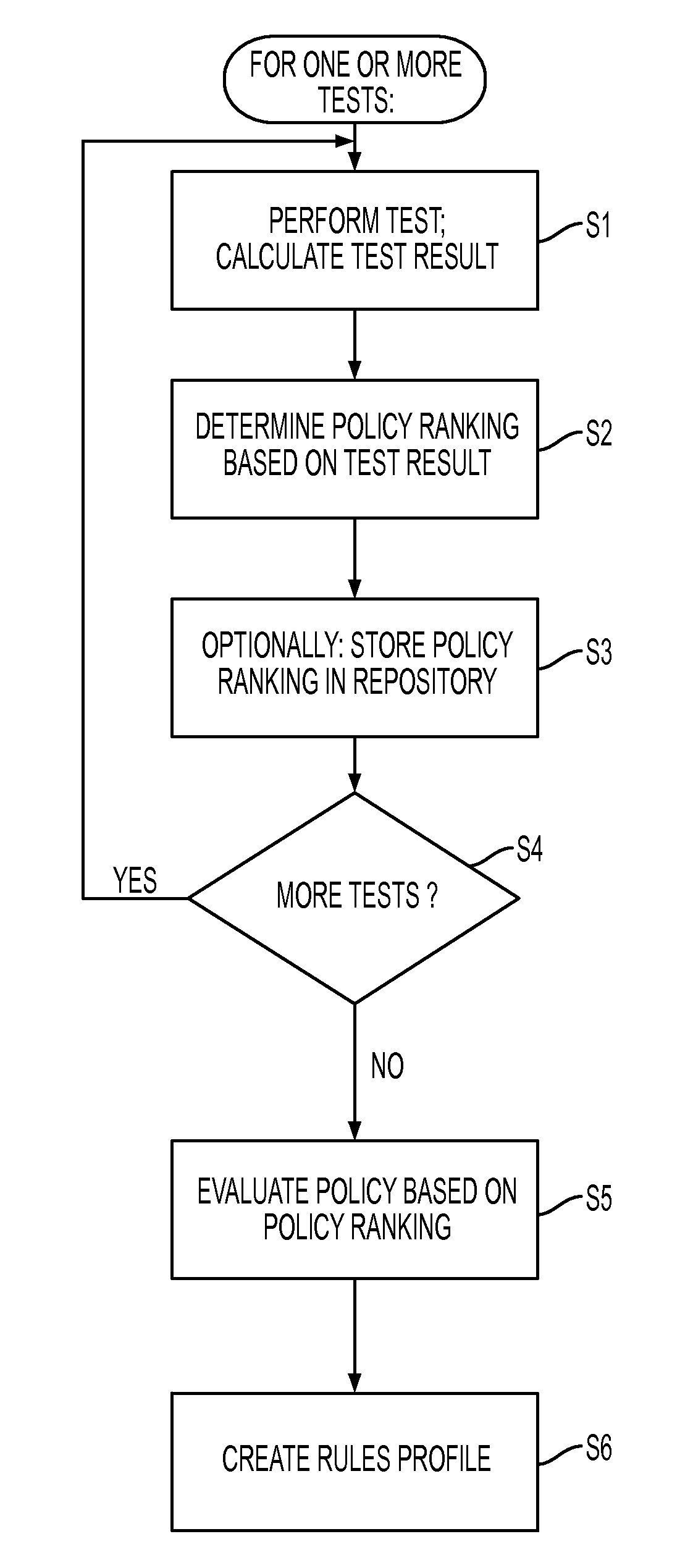
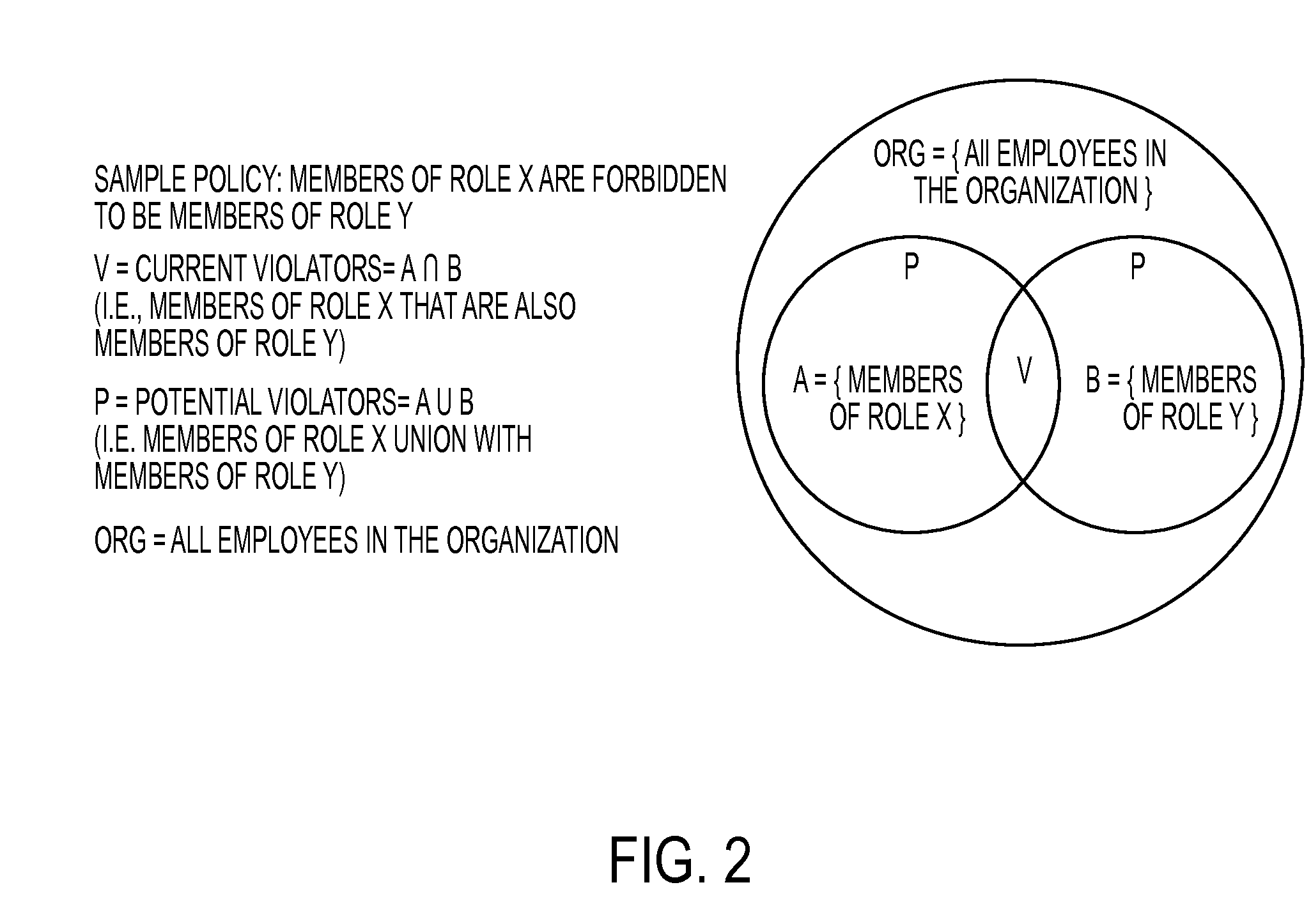
Heuristic policy analysis
A system and method using statistical analysis for the process of analyzing and generating organizational policies is presented. This inventive method comprises, for one or more tests, using a test to calculate a test result for the policy based on current violator entities and potential violator entities, and determining a policy ranking for the policy based on the test result of the test, and evaluating the policy based on the policy rankings determined from the tests. The method can also comprise creating a repository comprising the policy rankings for the plurality of policies. The repository can be used to trend, benchmark, alert and improve the policies. The method can also comprise creating a rule profile for the one policy comprising the one policy, the current violator entities of the policy, the potential violator entities of the policy, the test results and the policy rankings from the tests.
Owner:CA TECH INC
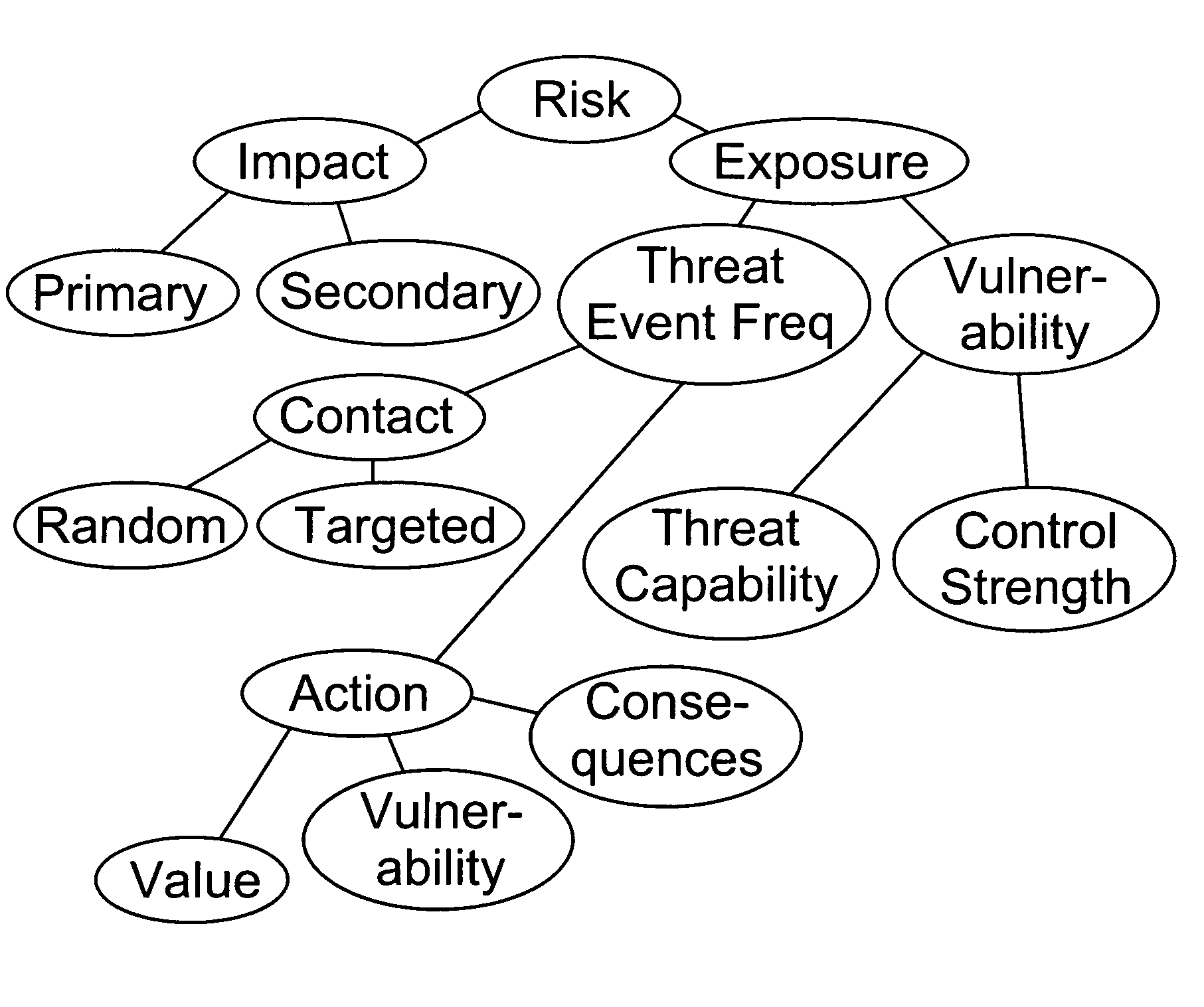
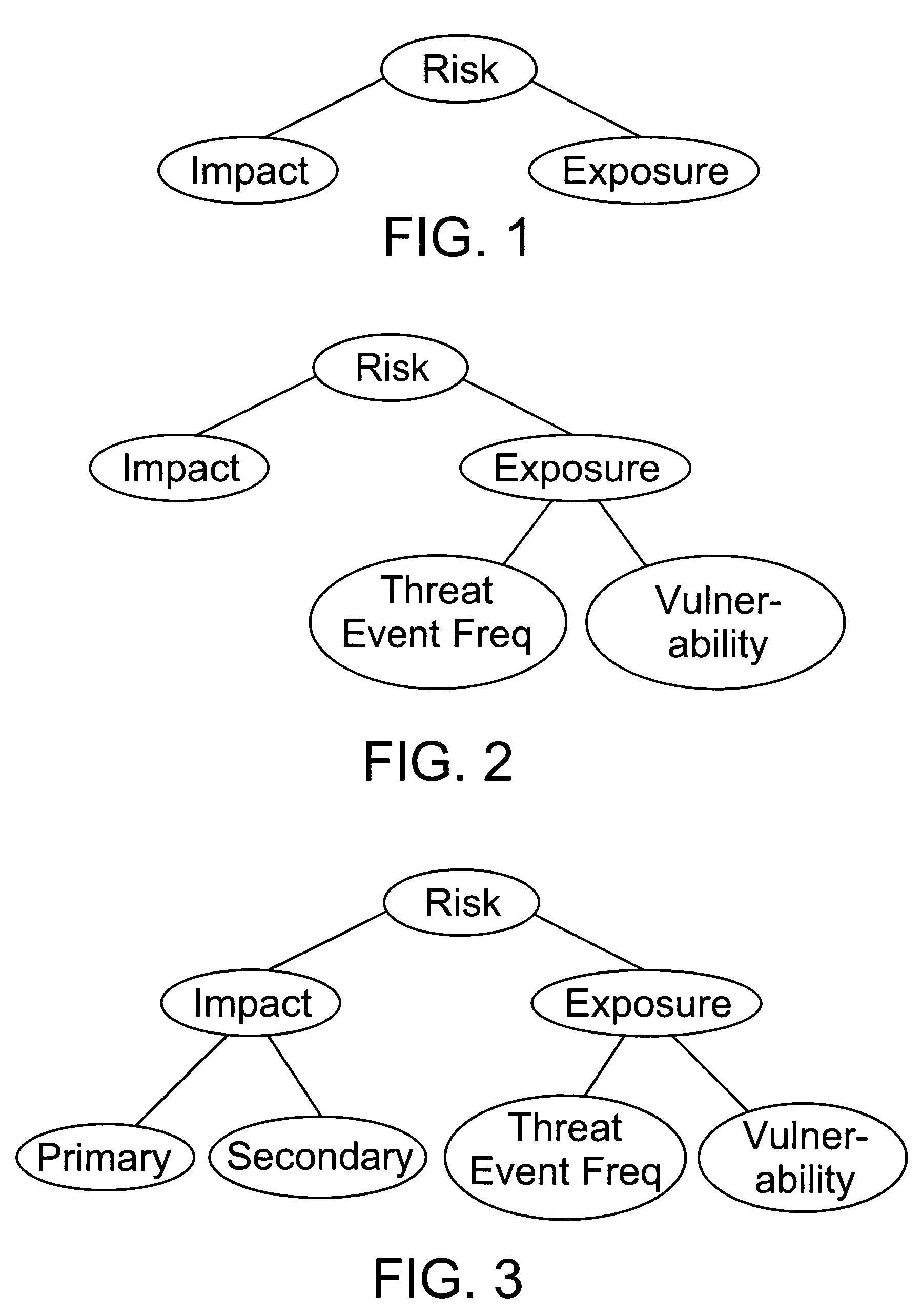
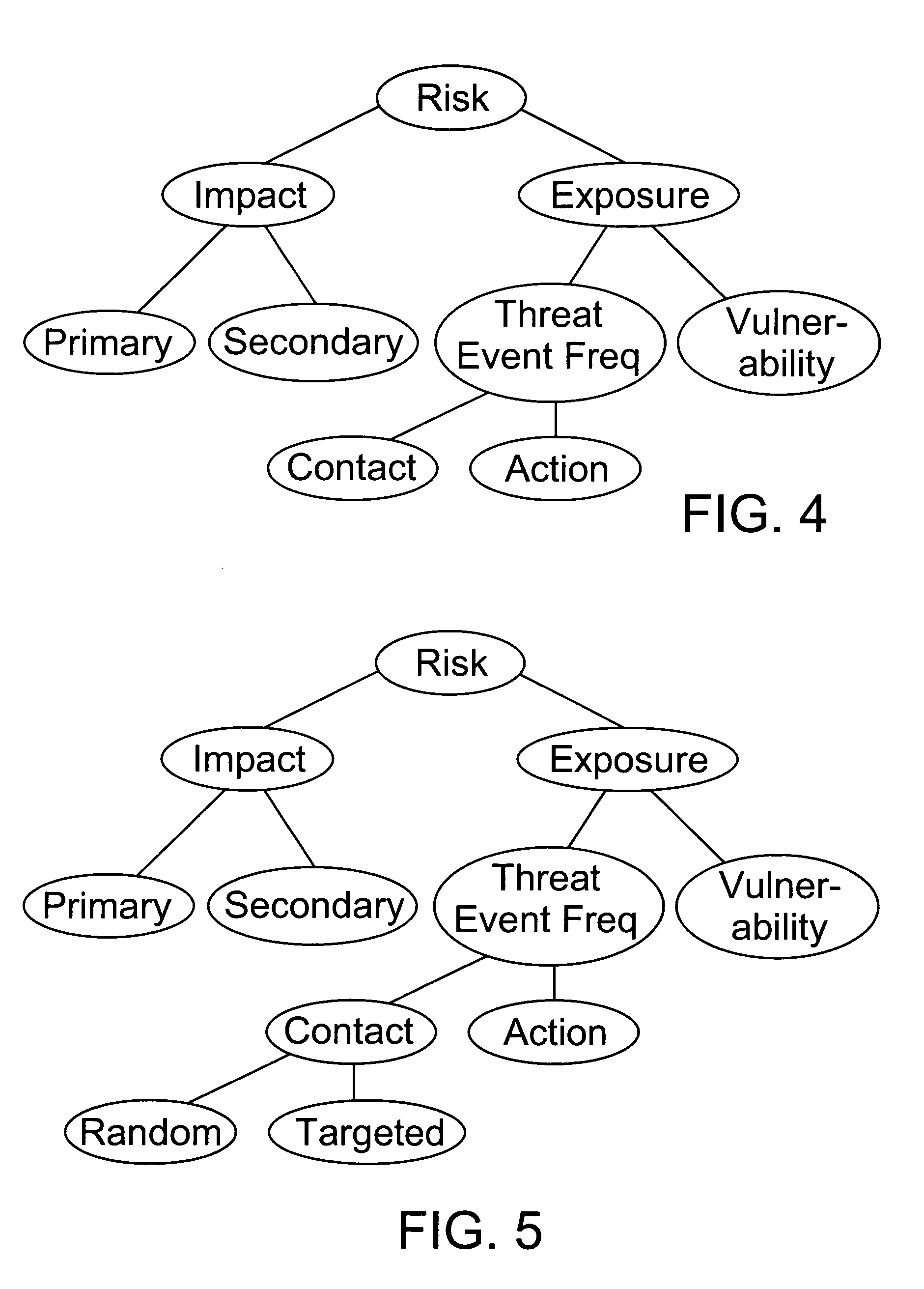
Factor analysis of information risk
InactiveUS20050066195A1Risk management decisions can become more effective and efficientGood return on investmentDigital data processing detailsComputer security arrangementsSalient objectsObject definition
The invention is a method of measuring and representing security risk. The method comprises selecting at least one object within an environment and quantifying the strength of controls of at least one object within that environment. This is done by quantifying authentication controls, quantifying authorization controls, and then quantifying structural integrity. In the preferred method, the next step is setting global variables for the environment, for example, whether the environment is subject to regulatory laws, and then selecting at least one threat community, for example, professional hackers, and then calculating information risk. This calculation is accomplished by performing a statistical analysis using the strengths of controls of said at least one object, the characteristics of at least one threat community, and the global variables of the environment, to compute a value representing information risk. The method identifies the salient objects within a risk environment, defines their characteristics and how they interact with one another, utilizing a means of measuring the characteristics, and a statistically sound mathematical calculation to emulate these interactions and then derives probabilities. The method then represents the security risk, such as the risk to information security, such as by an integer, a distribution or some other means.
Owner:JONES JACK A
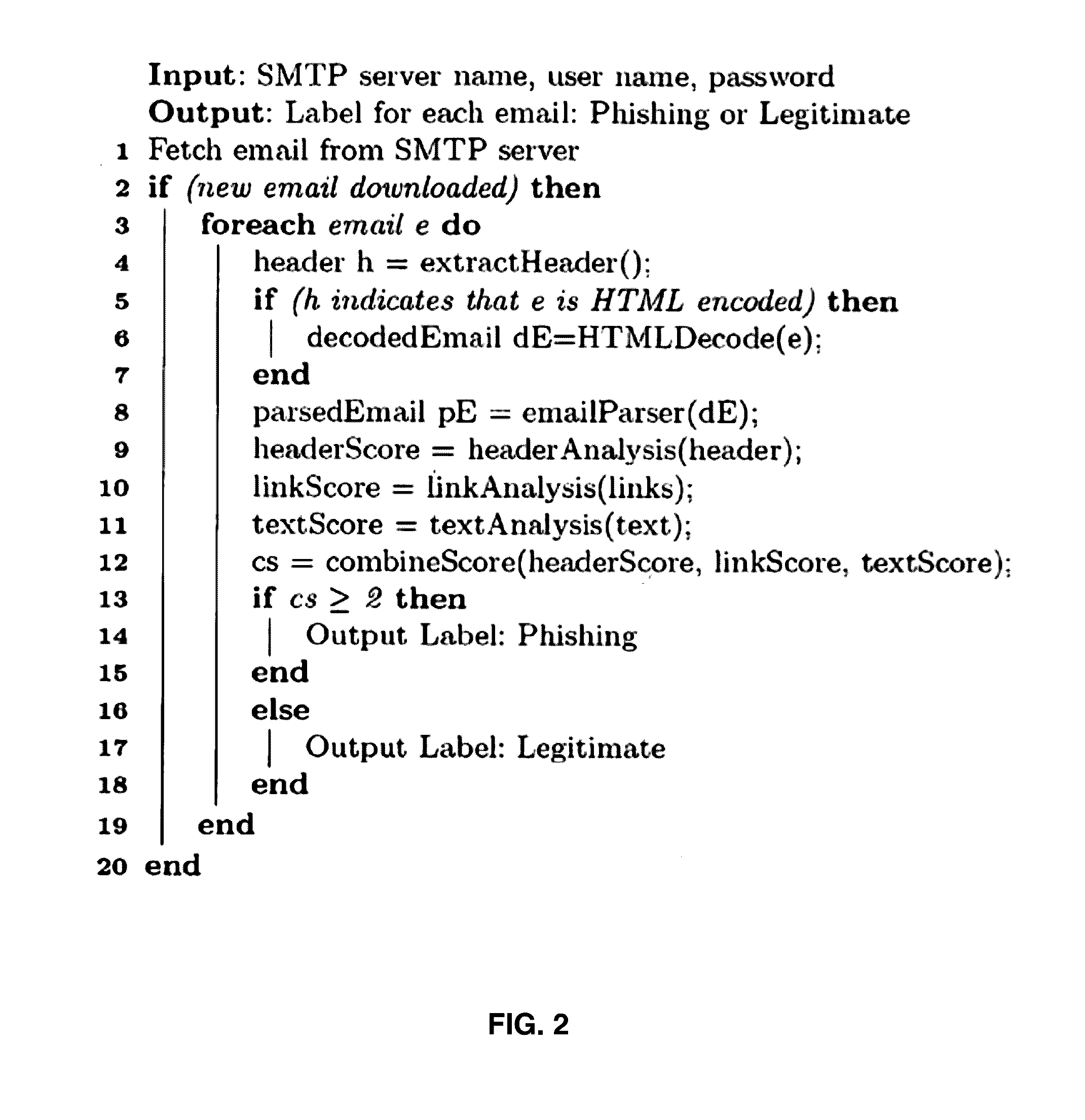
Automatic Phishing Email Detection Based on Natural Language Processing Techniques
ActiveUS20160344770A1Improve performanceMinimize detection timeEnsemble learningData switching networksPhishingLink analysis
A comprehensive scheme to detect phishing emails using features that are invariant and fundamentally characterize phishing. Multiple embodiments are described herein based on combinations of text analysis, header analysis, and link analysis, and these embodiments operate between a user's mail transfer agent (MTA) and mail user agent (MUA). The inventive embodiment, PhishNet-NLP™, utilizes natural language techniques along with all information present in an email, namely the header, links, and text in the body. The inventive embodiment, PhishSnag™, uses information extracted form the embedded links in the email and the email headers to detect phishing. The inventive embodiment, Phish-Sem™ uses natural language processing and statistical analysis on the body of labeled phishing and non-phishing emails to design four variants of an email-body-text only classifier. The inventive scheme is designed to detect phishing at the email level.
Owner:VERMA RAKESH +3
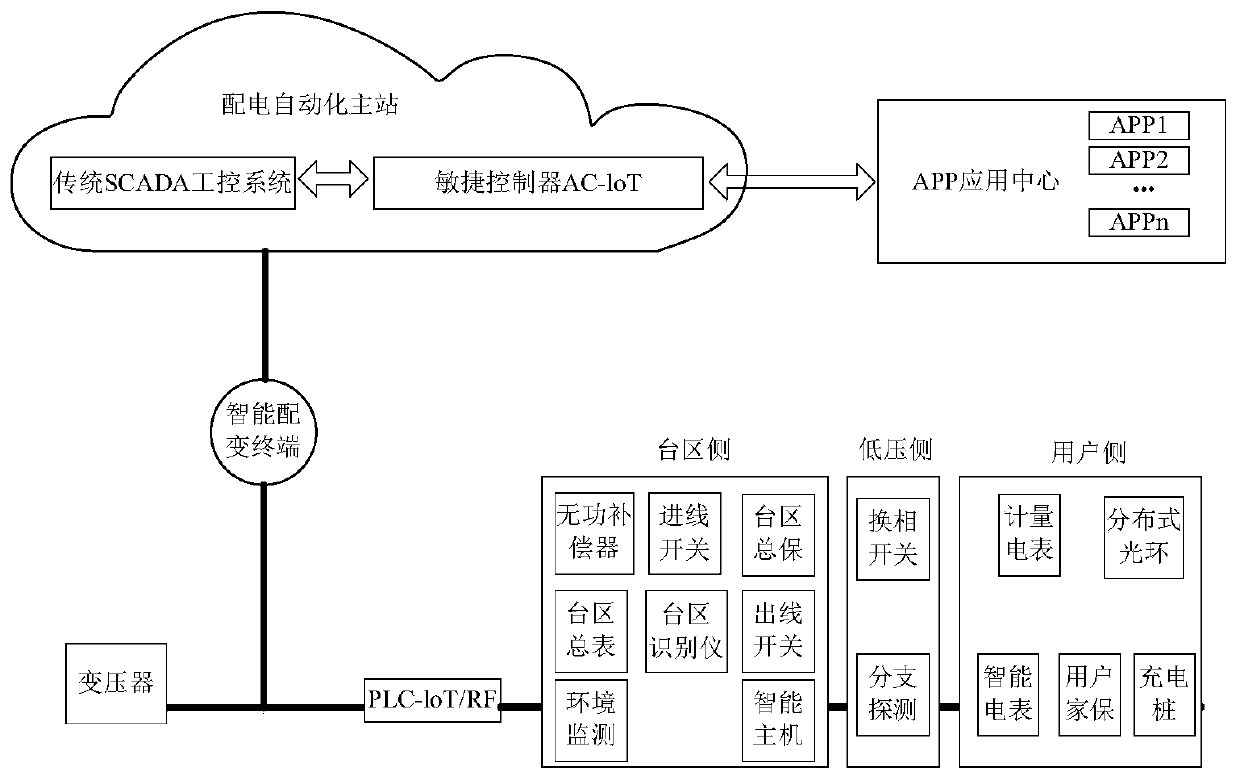
Power grid power supply guarantee and intelligent management and control system based on ubiquitous power Internet of things
InactiveCN110071579ATo achieve the purpose of data sharingCircuit arrangementsInformation technology support systemDecision controlElectric power system
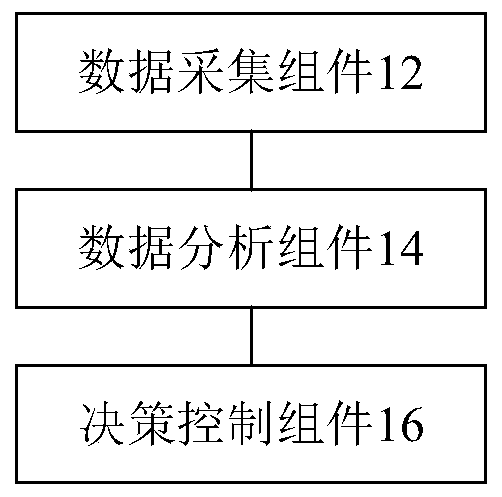
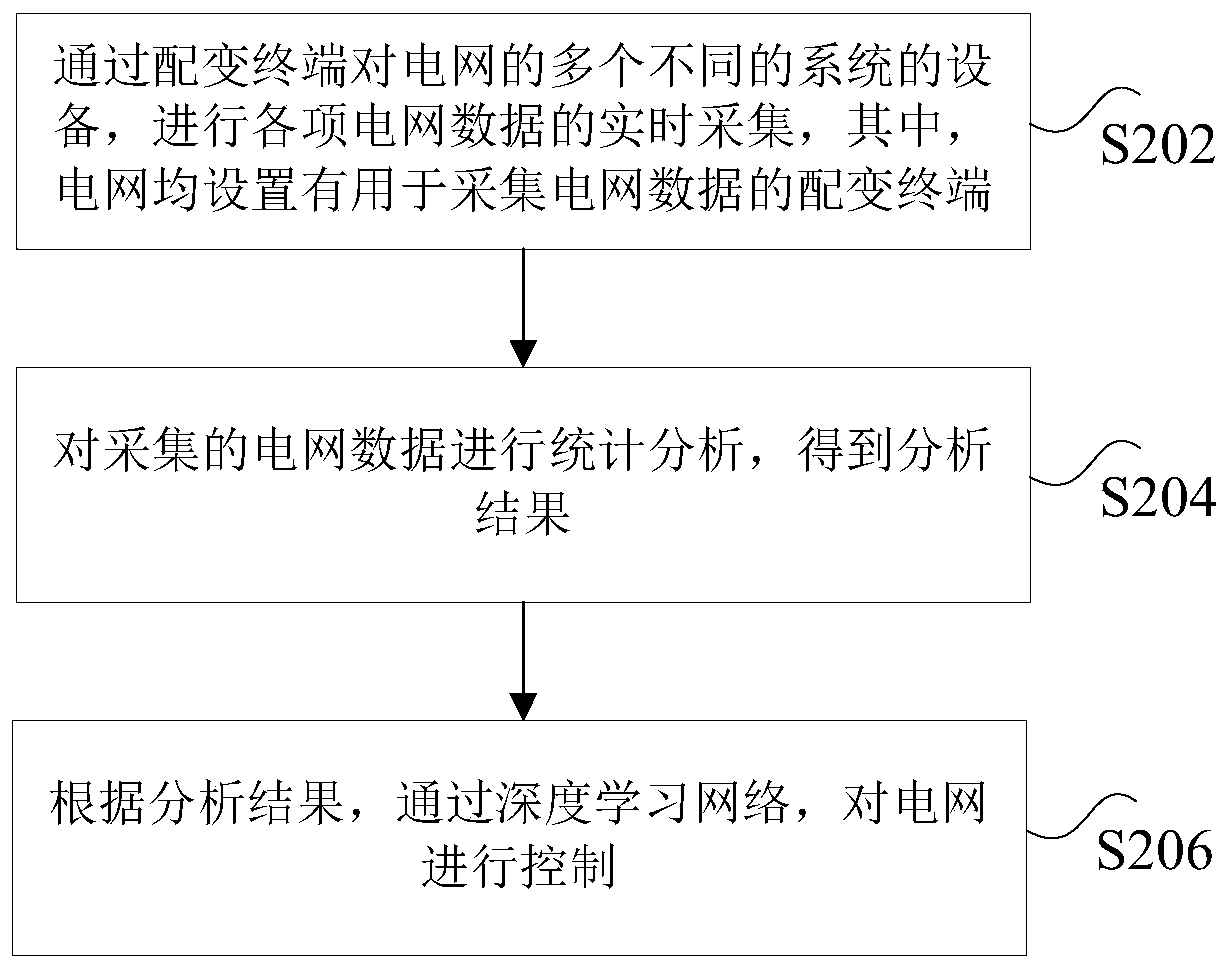
The invention discloses a power grid power supply guarantee and intelligent management and control system based on ubiquitous power Internet of things, wherein, the system comprises a data acquisitioncomponent which is used for acquiring various power grid data of a plurality of different devices of a power grid, wherein the data acquisition component comprises various sensors and the like whichare arranged on the power grid and used for acquiring the power grid data; a data analysis component is used for carrying out statistical analysis on the collected power grid data through the intelligent distribution transformer terminal to obtain an analysis result; and a decision control component is used for controlling the power grid through the deep learning network according to the analysisresult. The power grid power supply guarantee and intelligent management and control system based on ubiquitous power Internet of things solves the technical problems that a plurality of sets of electric systems in the related technology cannot share, the acquired data is less, and real-time feedback cannot be realized.
Owner:STATE GRID BEIJING ELECTRIC POWER +2
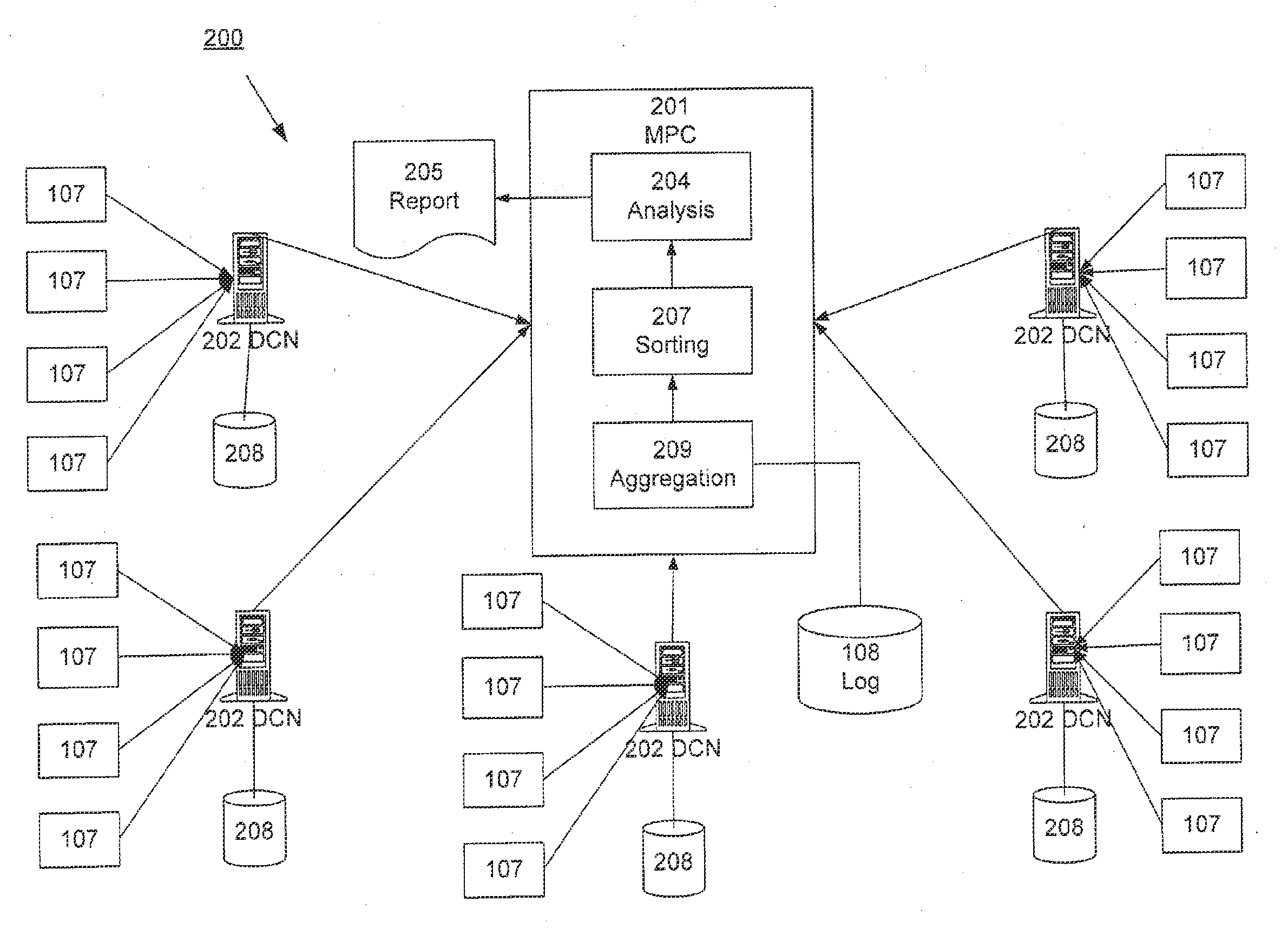
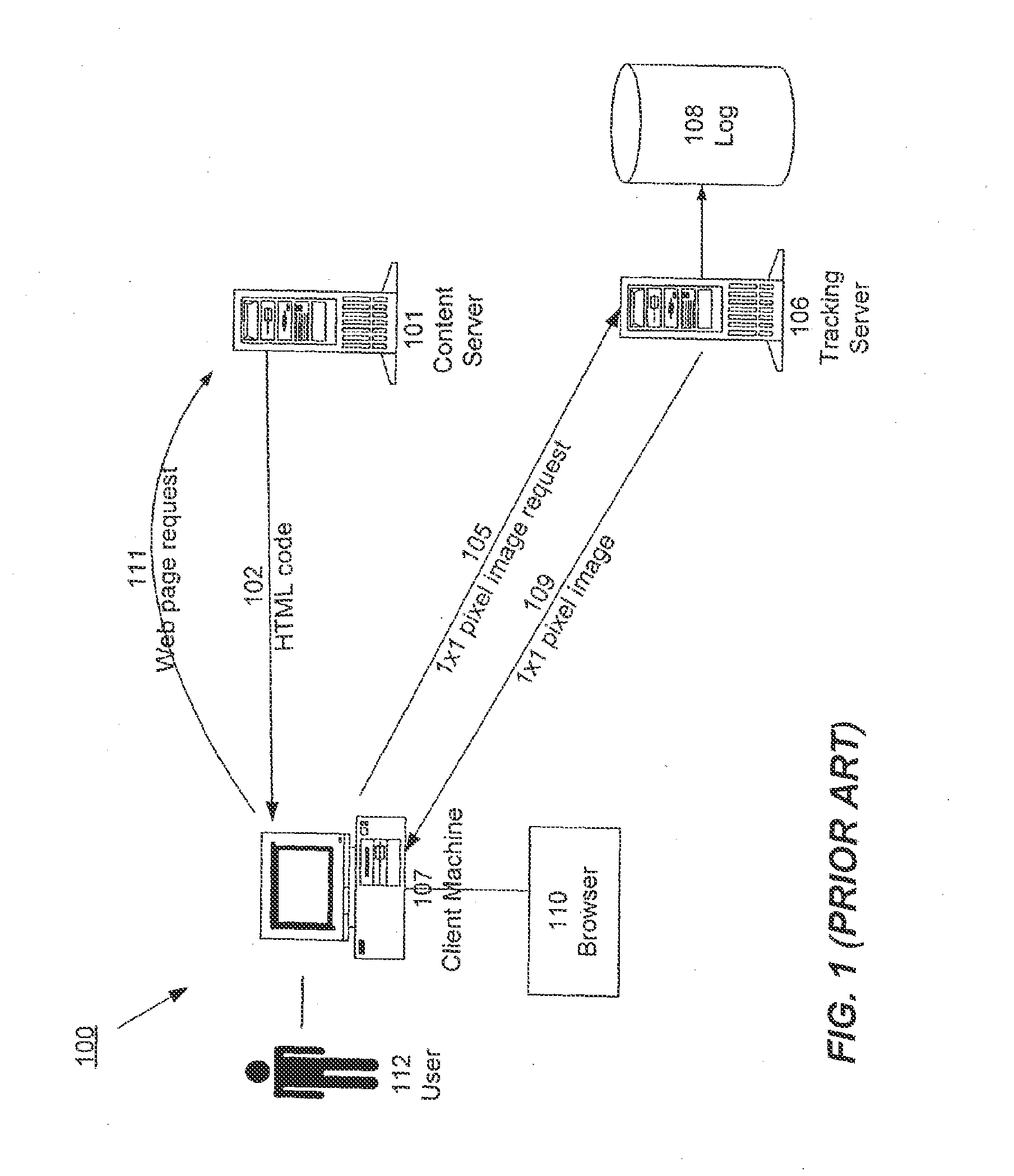
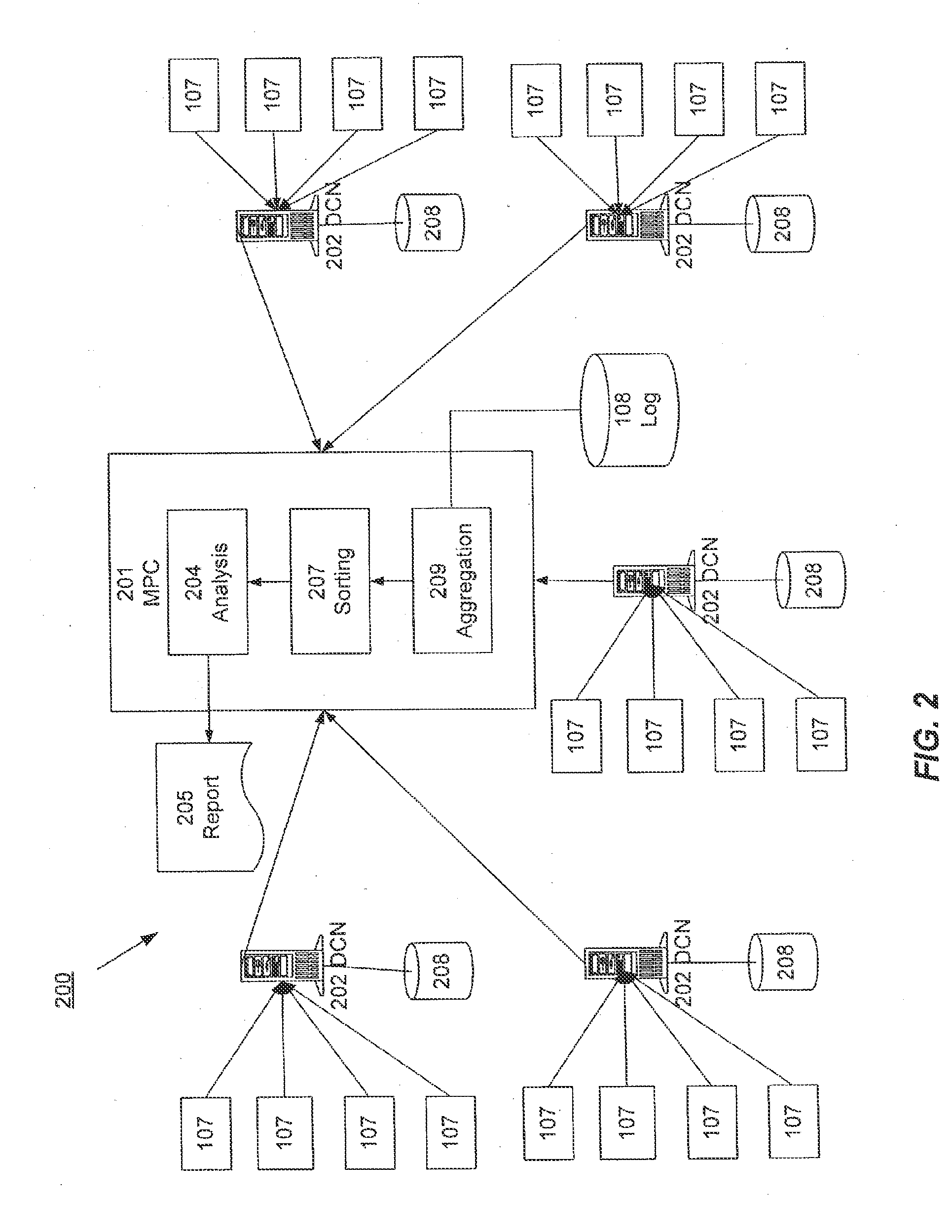
Distributed Data Collection and Aggregation
InactiveUS20120185588A1Efficiently collect informationFacilitates improved reliability in data collectionDigital computer detailsMarketingGeographic siteTimestamp ordering
A distributed, redundant, multi-homed system collects and aggregates website usage information. Two or more data collection nodes, preferably situated in diverse locations, efficiently collect and time-stamp information from users in a wide variety of geographic locations. Data collected by the individual data collection nodes is aggregated at a master processing center, sorted according to time stamps, and subjected to statistical analysis in order to generate complete and accurate reports regarding website traffic.
Owner:ADOBE SYST INC
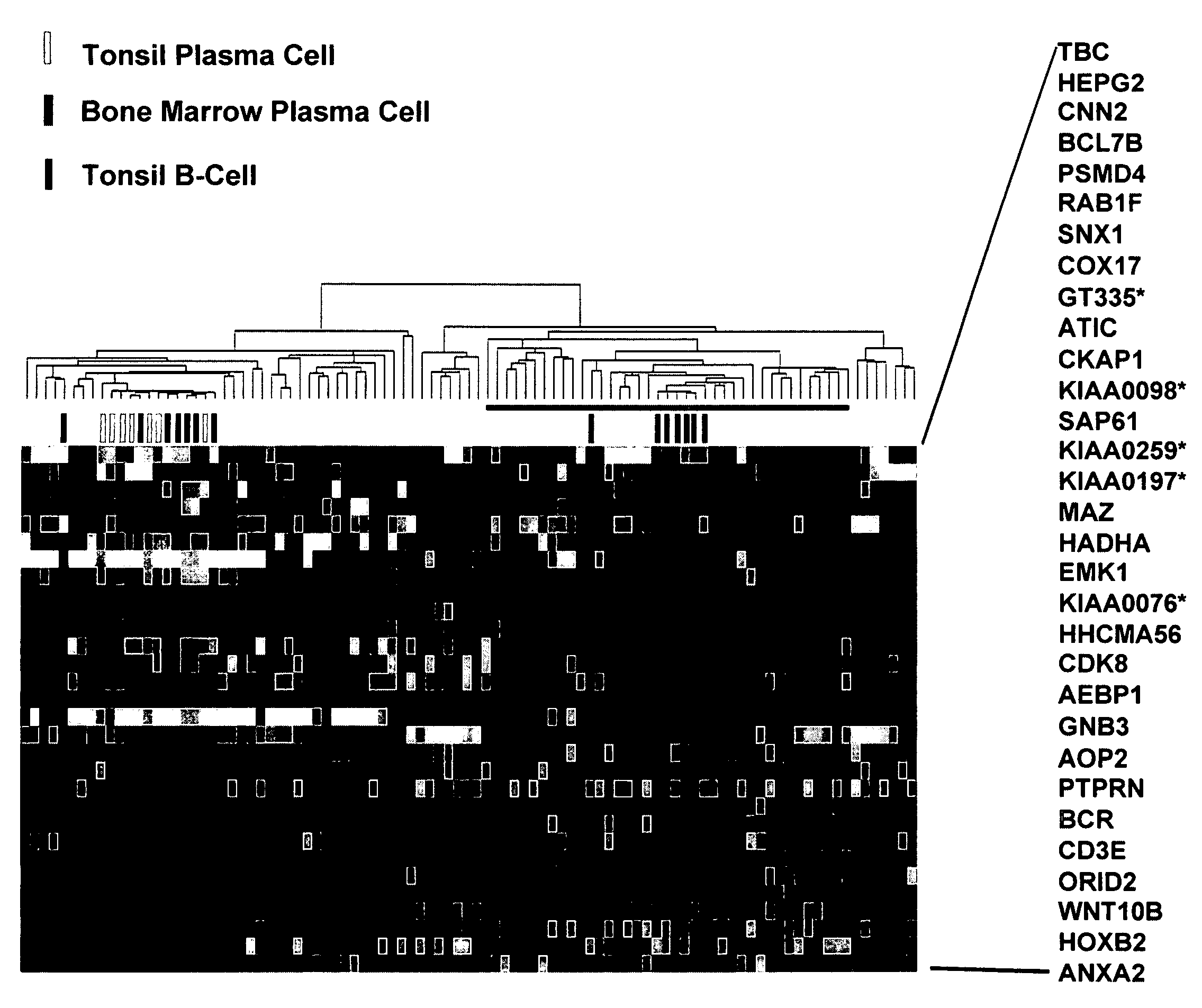
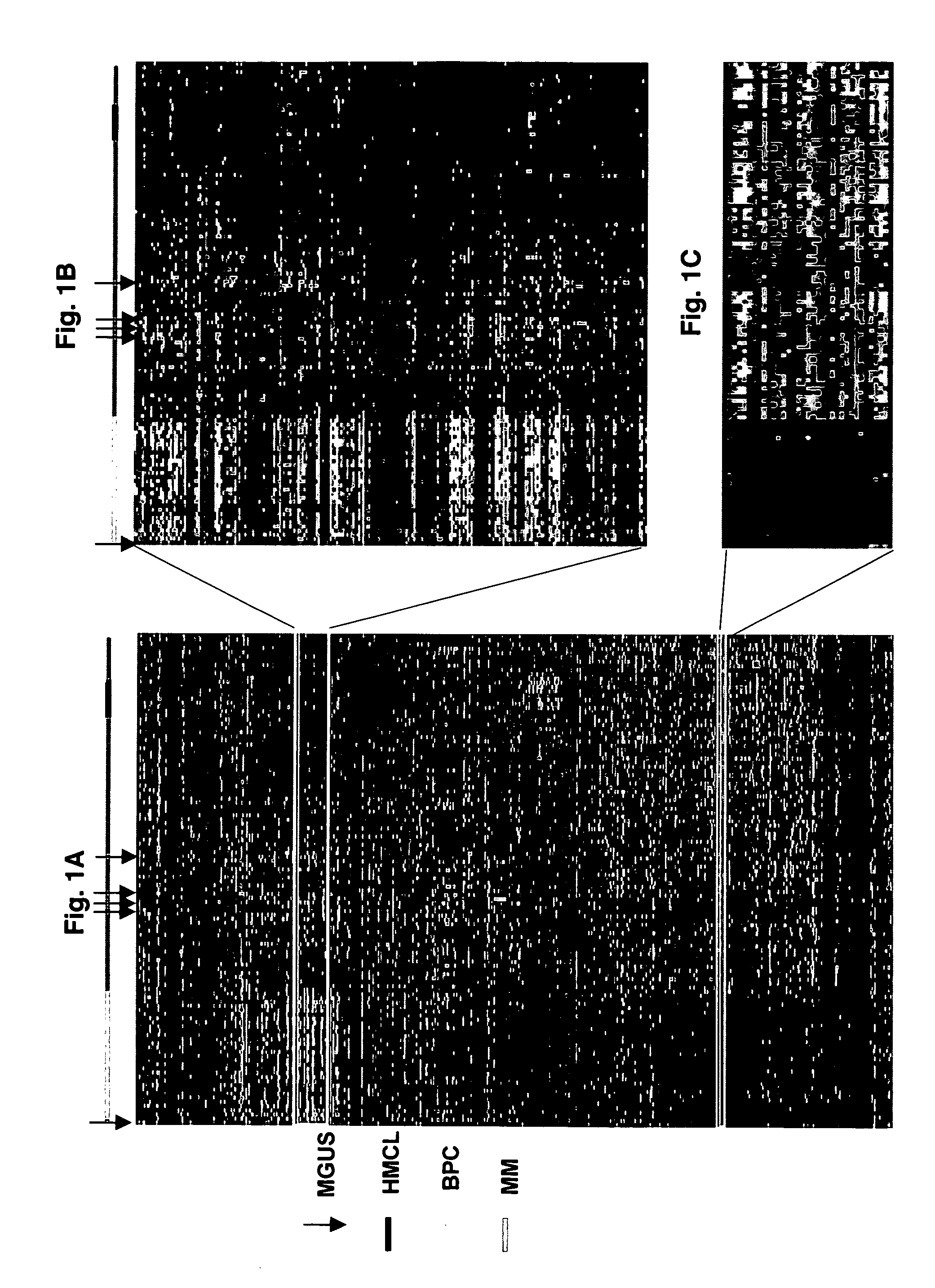
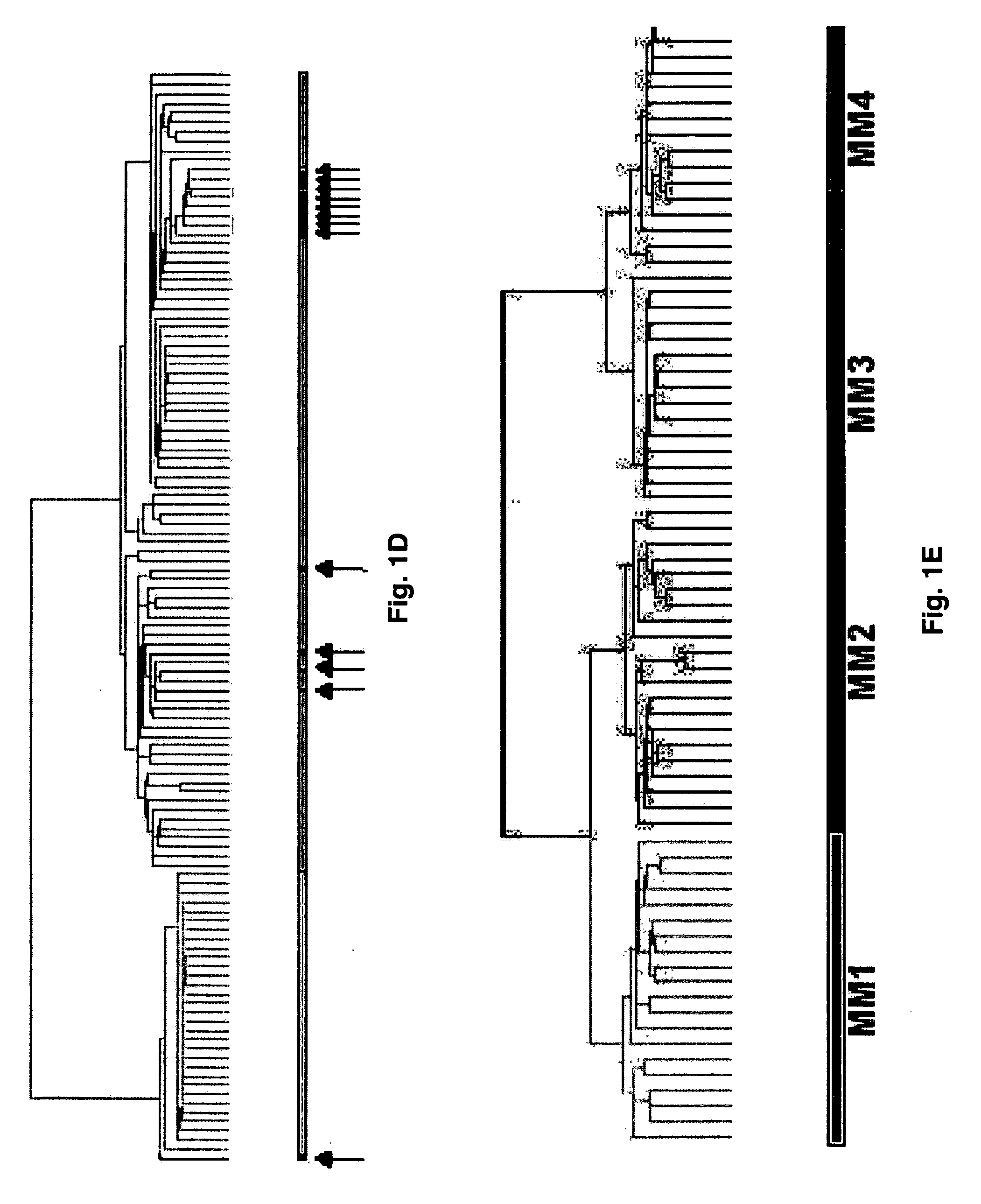
Diagnosis, prognosis and identification of potential therapeutic targets of multiple myeloma based on gene expression profiling
InactiveUS20080234139A1Microbiological testing/measurementLibrary screeningDevelopmental stagePlasma cell
Provided herein are methods for diagnosing and treating multiple myeloma based on statistical analysis of and subsequent increasing / inhibiting expression of subgroups of plasma cells and B cell genes. Also provided are methods for a developmental stage-based classification for multiple myeloma using hierarchical clustering analysis of plasma cell and B cell nucleic acids and for discriminating among normal, hyperplastic and malignant using gene expression array data and statistical analysis thereof. In addition methods for determining the risk of developing bone disease in a test individual by examining expression levels of a WNT signaling antagonist, such as DKK1, are provided. A kit comprising anti-DKK1 antibodies and detection reagents for measuring DKK1 protein levels also is provided.
Owner:BIOVENTURES LLC
Input device to continuously detect biometrics
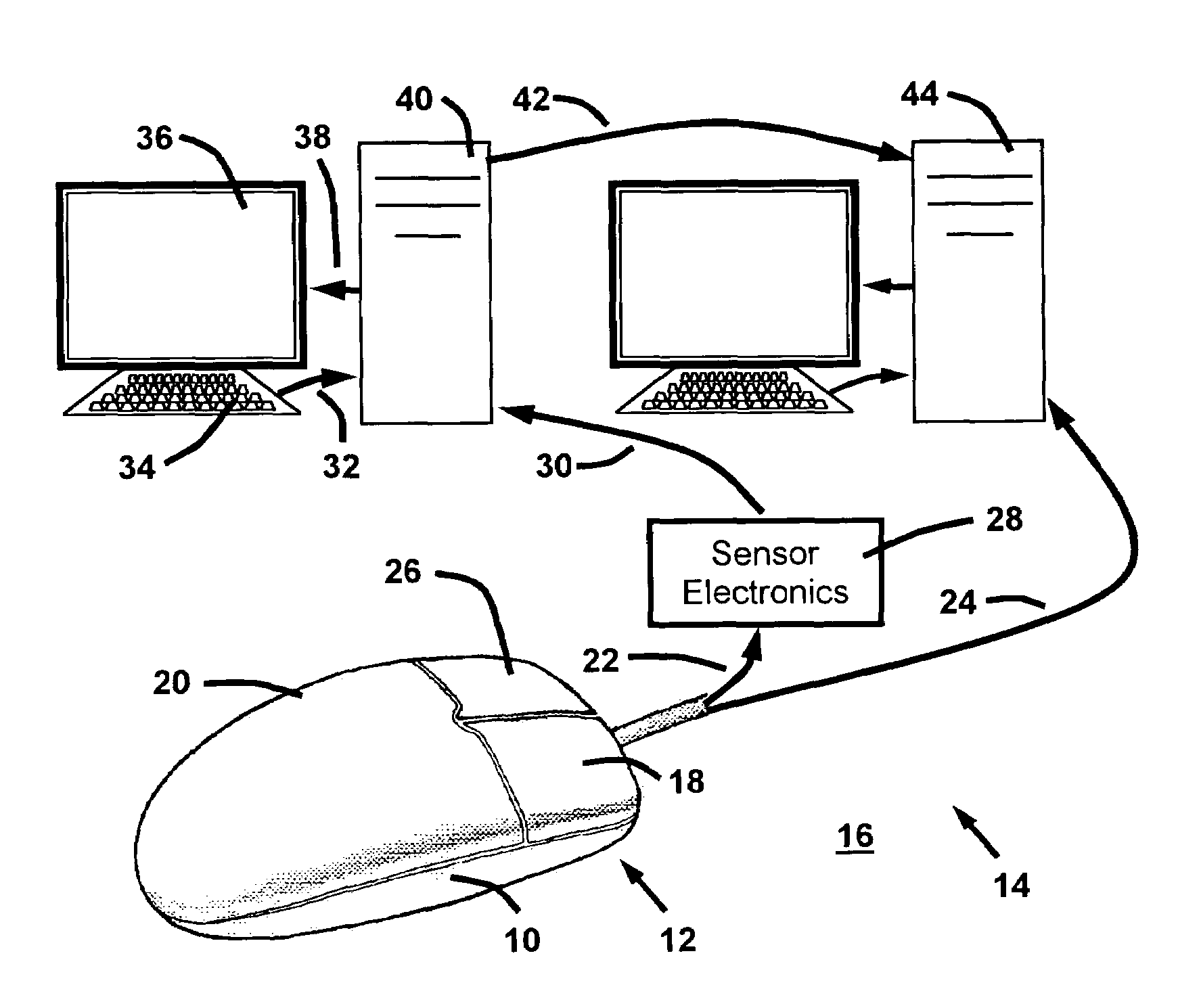
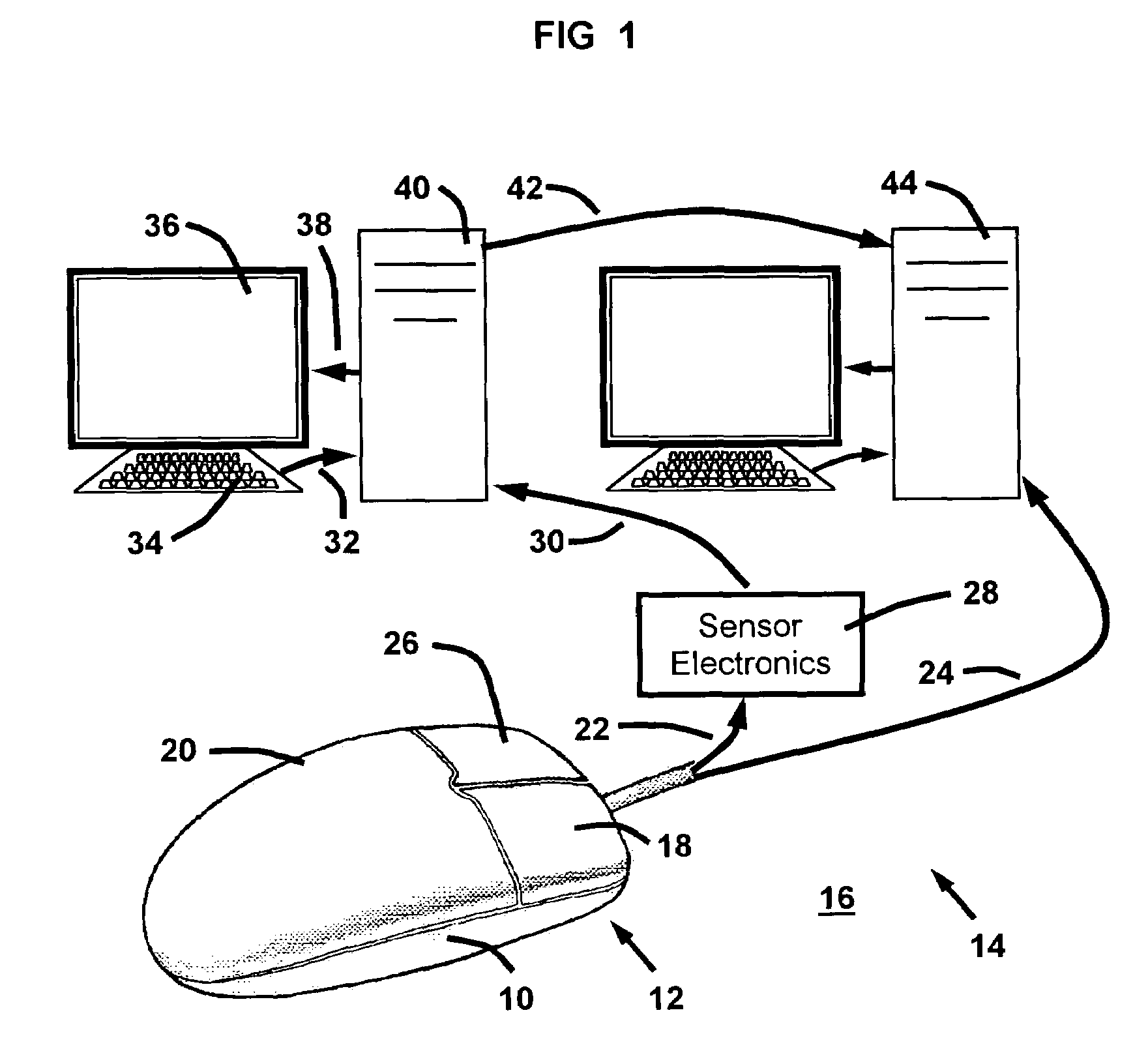
ActiveUS7245218B2Electric signal transmission systemsImage analysisPattern recognitionFinger pressure
A method and system for correlating control surface finger pressures to identifying biometric characteristics of a user from a computer input device, such as a mouse. Pressure sensors attached to a computer mouse sense the biometric characteristics, which are correlated to identifying biometric characteristics using a correlation model. The correlation model is derived from a registration process in which a baseline biometric attribute-to-identity correlation is rendered based on statistical analysis of registration signals generated by users. During routine use, the correlation model is use to continuously authenticate the identity of the user from surface finger pressures on the computer mouse.
Owner:IKEHARA CURTIS SATORU +1
System for determining degrees of similarity in email message information
InactiveUS20050160148A1Improve reliabilityImprove performanceMultiple digital computer combinationsData switching networksSpammingWord count
Similarity of email message characteristics is used to detect bulk and spam email. A determination of “sameness” for purposes of both bulk and spam classifications can use any number and type of evaluation modules. Each module can include one or more rules, tests, processes, algorithms, or other functionality. For example, one type of module may be a word count of email message text. Another module can use a weighting factor based on groups of multiple words and their perceived meanings. In general, any type of module that performs a similarity analysis can be used. A preferred embodiment of the invention uses statistical analysis, such as Bayesian analysis, to measure the performance of different modules against a known standard, such as human manual matching. Modules that are performing worse than other modules can be valued less than modules having better performance. In this manner, a high degree of reliability can be achieved. To improve performance, if a message is determined to be the same as a previous message, the previous computations and results for that previous message can be re-used. Users can be provided with options to customize or regulate bulk and spam classification and subsequent actions on how to handle the classified email messages.
Owner:GOZOOM COM
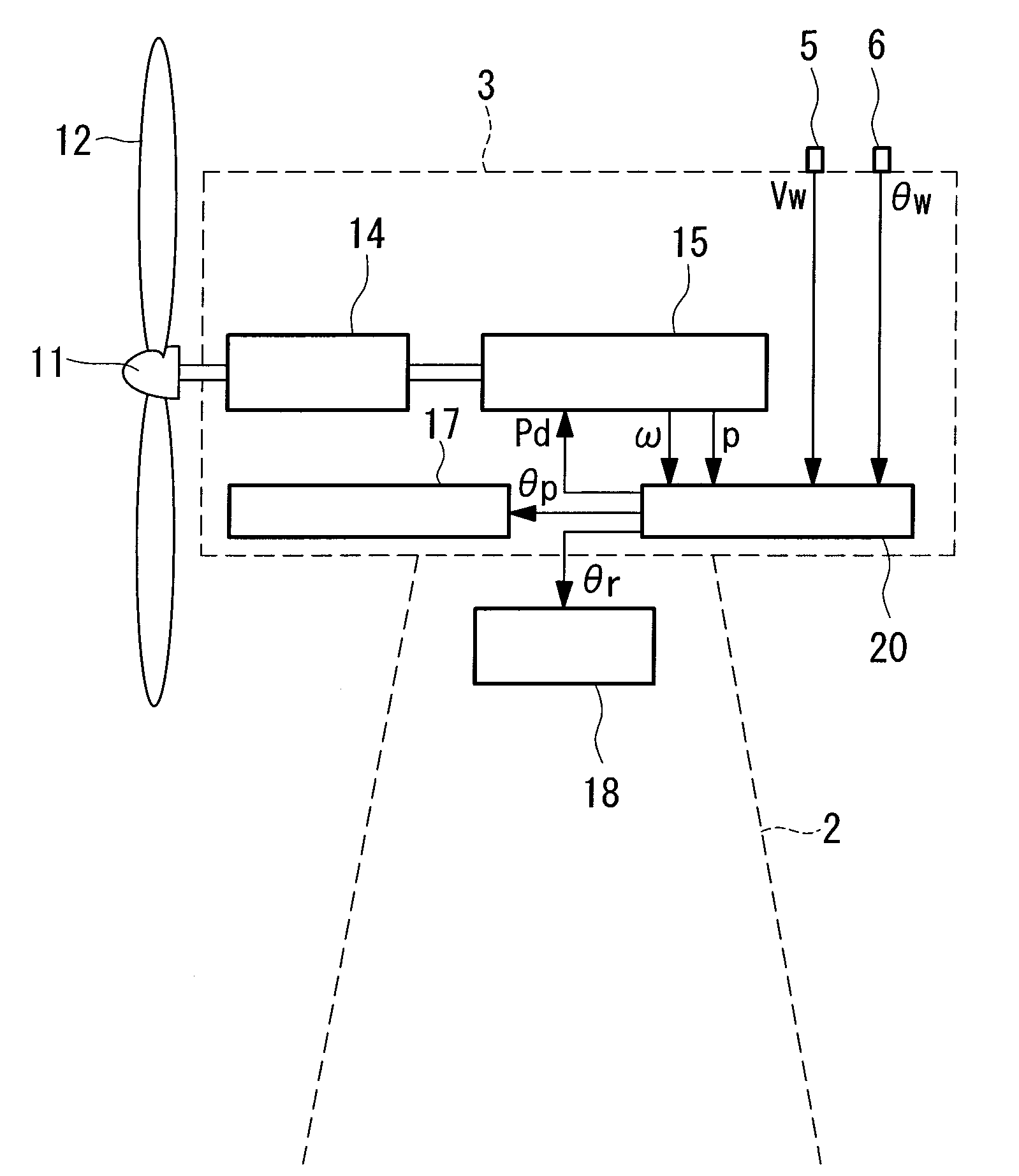
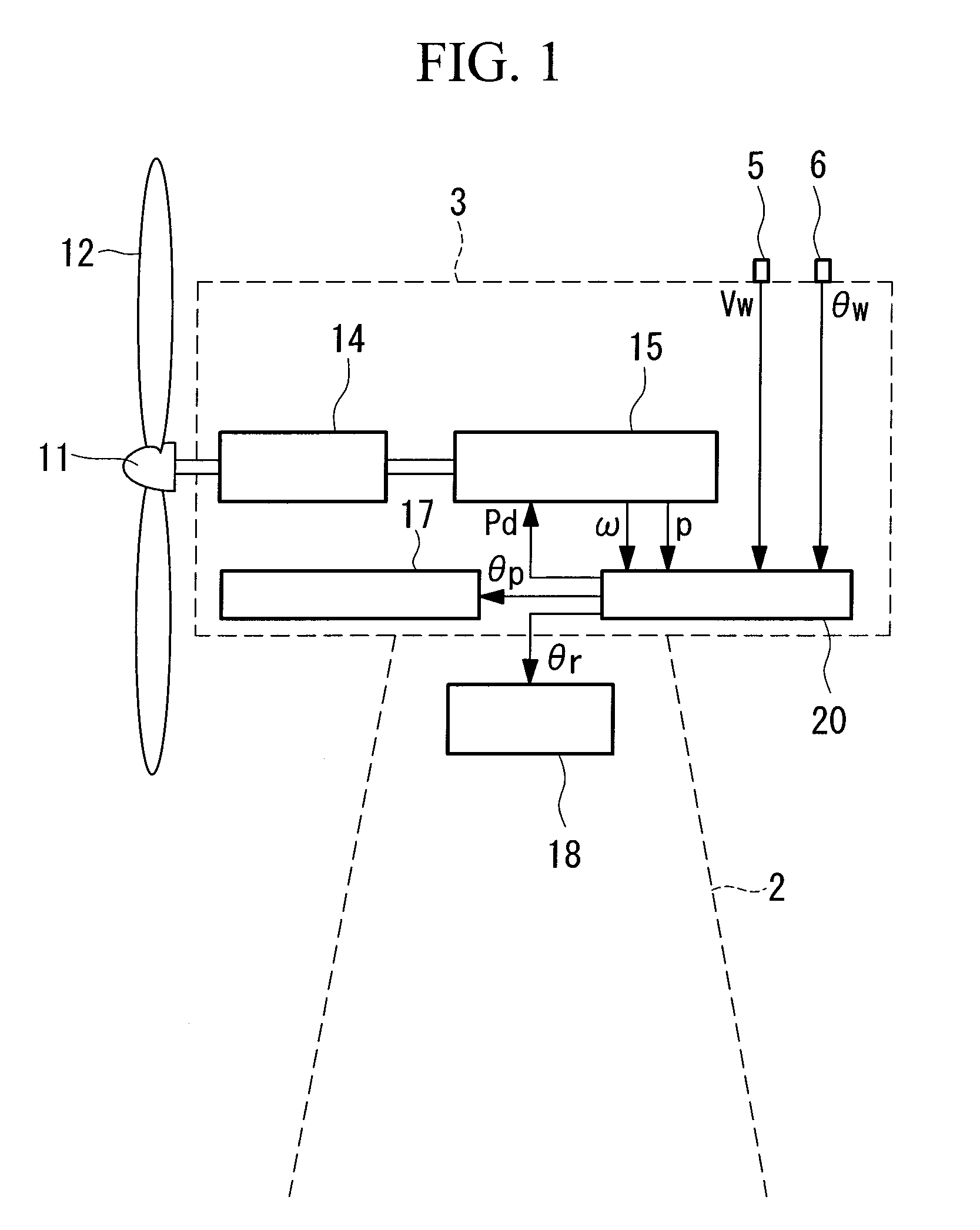
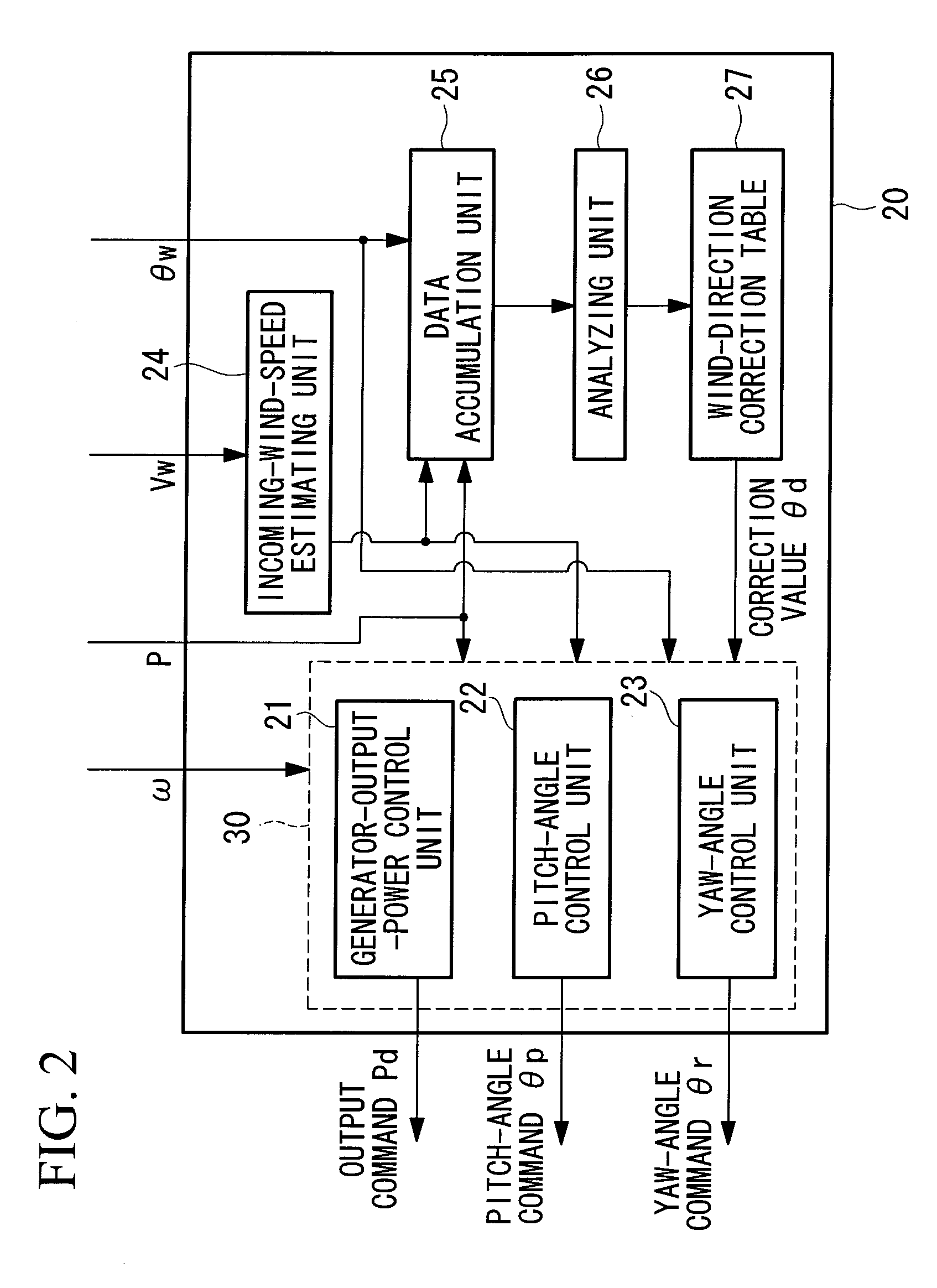
Wind turbine generator, wind turbine generator system, and power generation control method of wind turbine generator
ActiveUS20100066087A1Accurate wind directionIncrease costElectric motor controlWind motor controlNacellePeak value
To provide a wind turbine generator, a wind turbine generator system, and a power-generation control method of a wind turbine generator that are capable of improving the power-generation capability and reducing the fatigue load on the windmill. A data accumulation unit 25 sequentially accumulates data sets of a generated output power P during operation of the wind turbine generator, an incoming wind speed Ws estimated on the basis of a wind speed measured at the anemometer, and a wind direction deviation, which is the difference between a wind direction θw measured at the anemoscope and the orientation of the nacelle; statistical analysis of the data accumulated is carried out by an analyzing unit 26; a distribution curve corresponding to the wind direction deviation of the generated output power at each incoming wind speed is determined; the wind direction deviation corresponding to the peak of the distribution curve is set as a correction value θd of the anemoscope; the correction value of the anemoscope for each incoming wind speed is stored in the wind-direction correction table 27; the wind direction Vw measured at the anemoscope is corrected with the correction value θd of the anemoscope for each incoming wind speed Ws; and power-generation control is carried out using the corrected wind direction as a control parameter.
Owner:MITSUBISHI HEAVY IND LTD
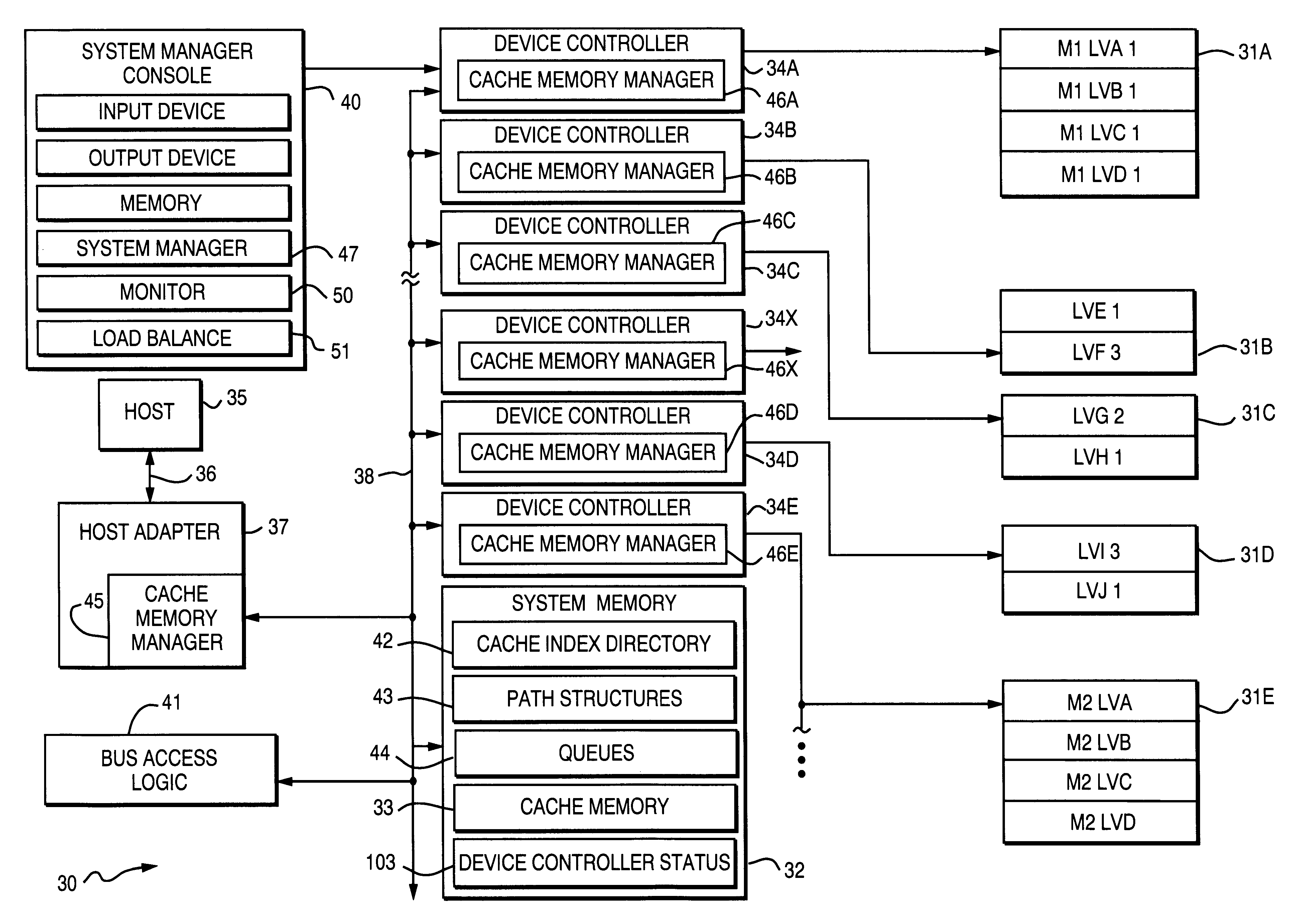
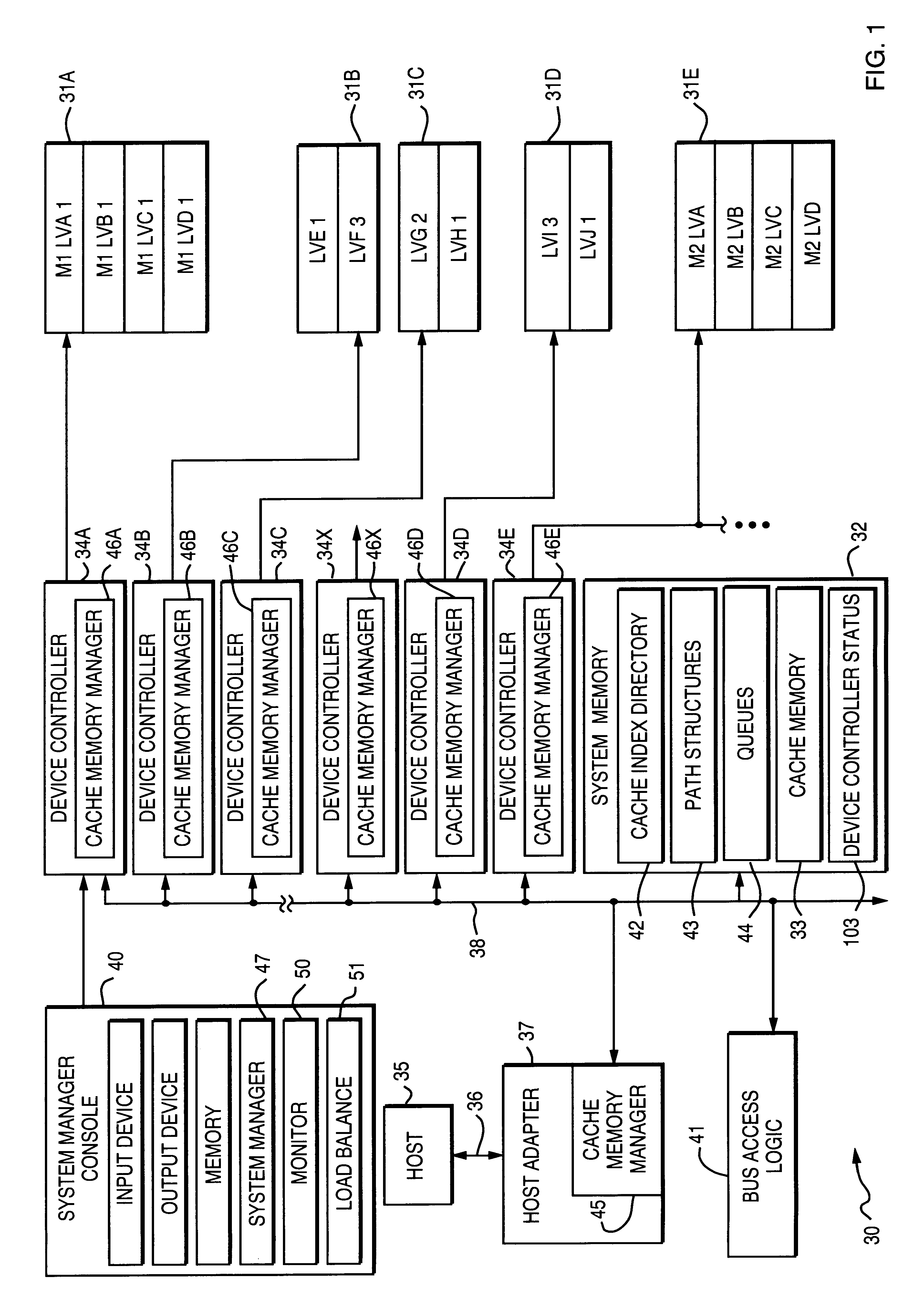
Method for maximizing sequential output in a disk array storage device
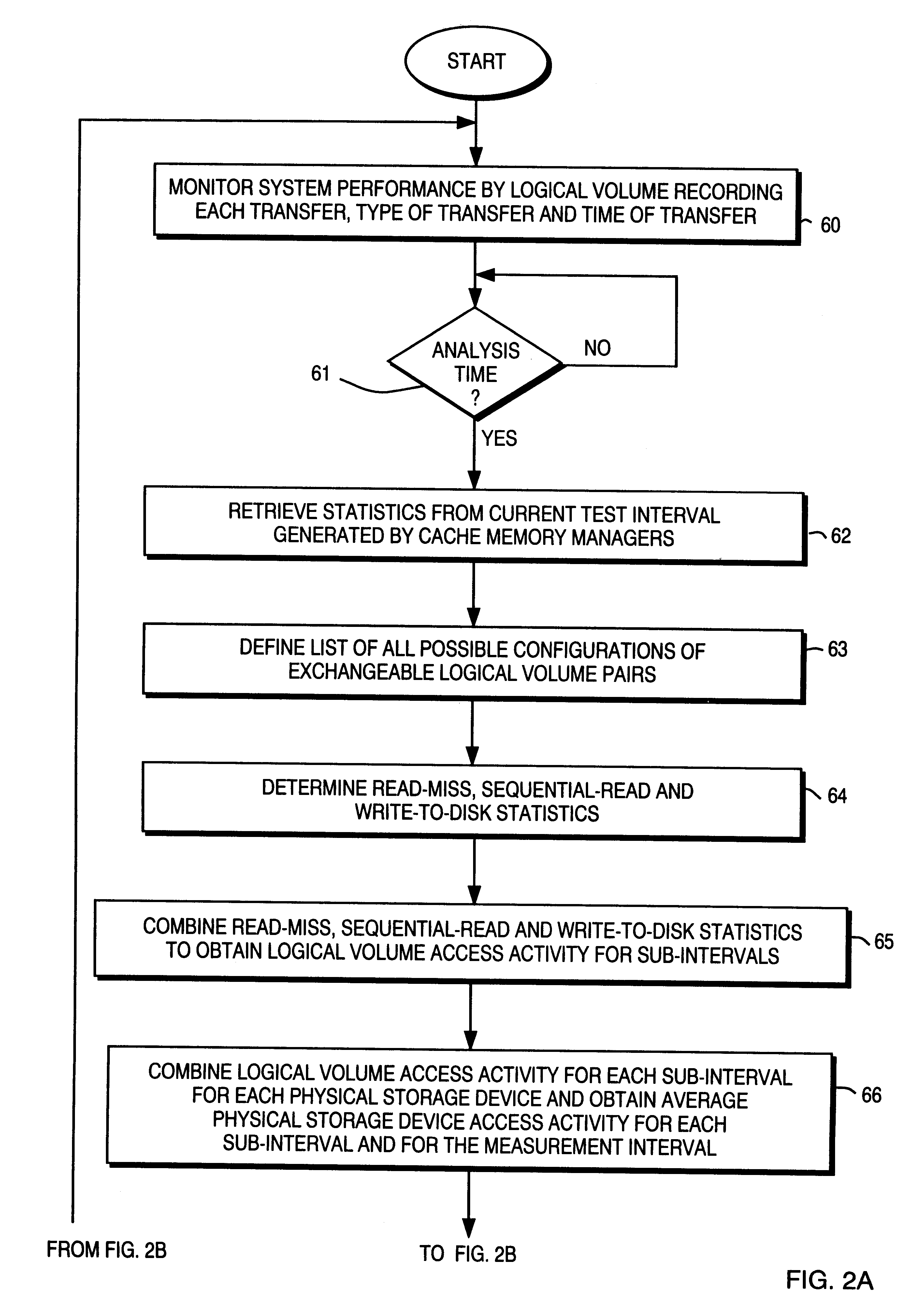
InactiveUS6189071B1Load balancingThe equipment is easy to operateInput/output to record carriersHardware monitoringDisk arrayStatistical analyses
Load balancing of activities on physical disk storage devices is accomplished by monitoring reading and writing operations to blocks of contiguous storage locations on the physical disk storage devices. A list of exchangeable pairs of blocks is developed based on size and function. Statistics accumulated over an interval are then used to obtain access activity values for each block and each physical disk drive. A statistical analysis leads to a selection of one block pair. After testing to determine any adverse effect of making that change, the exchange is made to more evenly distribute the loading on individual physical disk storage devices.
Owner:EMC IP HLDG CO LLC
System and method for musical instruction
InactiveUS20080271591A1Electrophonic musical instrumentsMusicStatistical analysesMusic visualization
The present disclosure relates to music instruction devices and methods. A system is provided which allows a user to more intuitively understand music theory and performance. The system also streamlines composition and arrangement in multi-instrument environments. The user is able to select from a variety of available music visualizations and instrument views, allowing comparison therebetween. The system may comprise a step-by-step instruction method, free-play performance abilities, and recording and playback features. Certain embodiments incorporate statistical analysis of student progress, remote access for teacher consultation, and video games for enhancing student interest.
Owner:MASTER KEY LLC
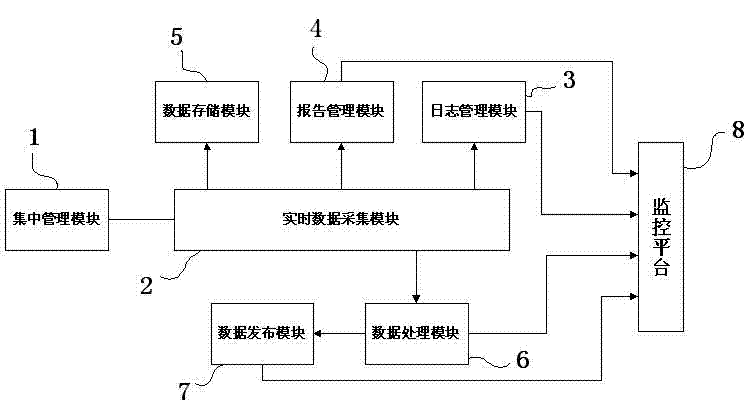
System operation monitoring and controlling visual platform
InactiveCN103491354AMonitor operating conditionsReduce the potential risk of operation and maintenanceClosed circuit television systemsTransmissionTime dataReliability engineering
The invention provides a system operation monitoring and controlling visual platform which comprises a monitoring and controlling platform body (8). The system operation monitoring and controlling visual platform is characterized by comprising a centralized management module (1), a real-time data collecting module (2), a log management module (3), a report management module (4), a data storage module (5), a data processing module (6) and a data releasing module (7). According to the system operation monitoring and controlling visual platform, the operation situations of a power grid dispatching system can be collected, disposed, processed and summarized, information of operation and other aspects of service systems can be reflected in a centralized mode, and the system operation monitoring and controlling visual platform has the functions such as centralized displaying, managing and customizing. On the basis, the statistic analysis can be carried out on operation data of the power grid dispatching system, the variation trend of key data can be predicted, events having a significant effect on the system can be recognized, and a necessary basis is provided for daily maintaining management and an operation decision analysis. The emphasis is laid on founding various alarms and performance abnormalities in time and improving the speed that an operator responds to various events.
Owner:STATE GRID CORP OF CHINA +2
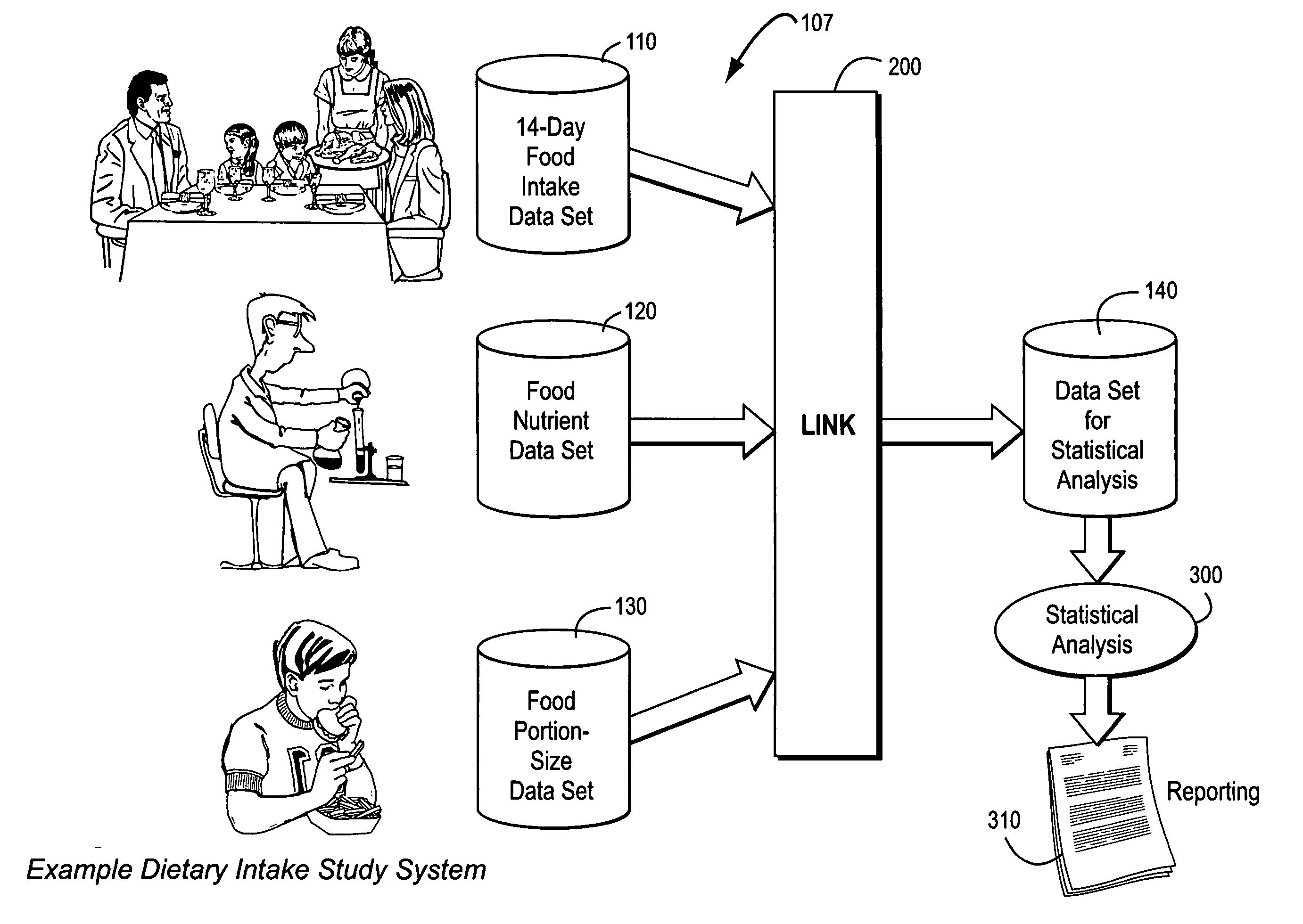
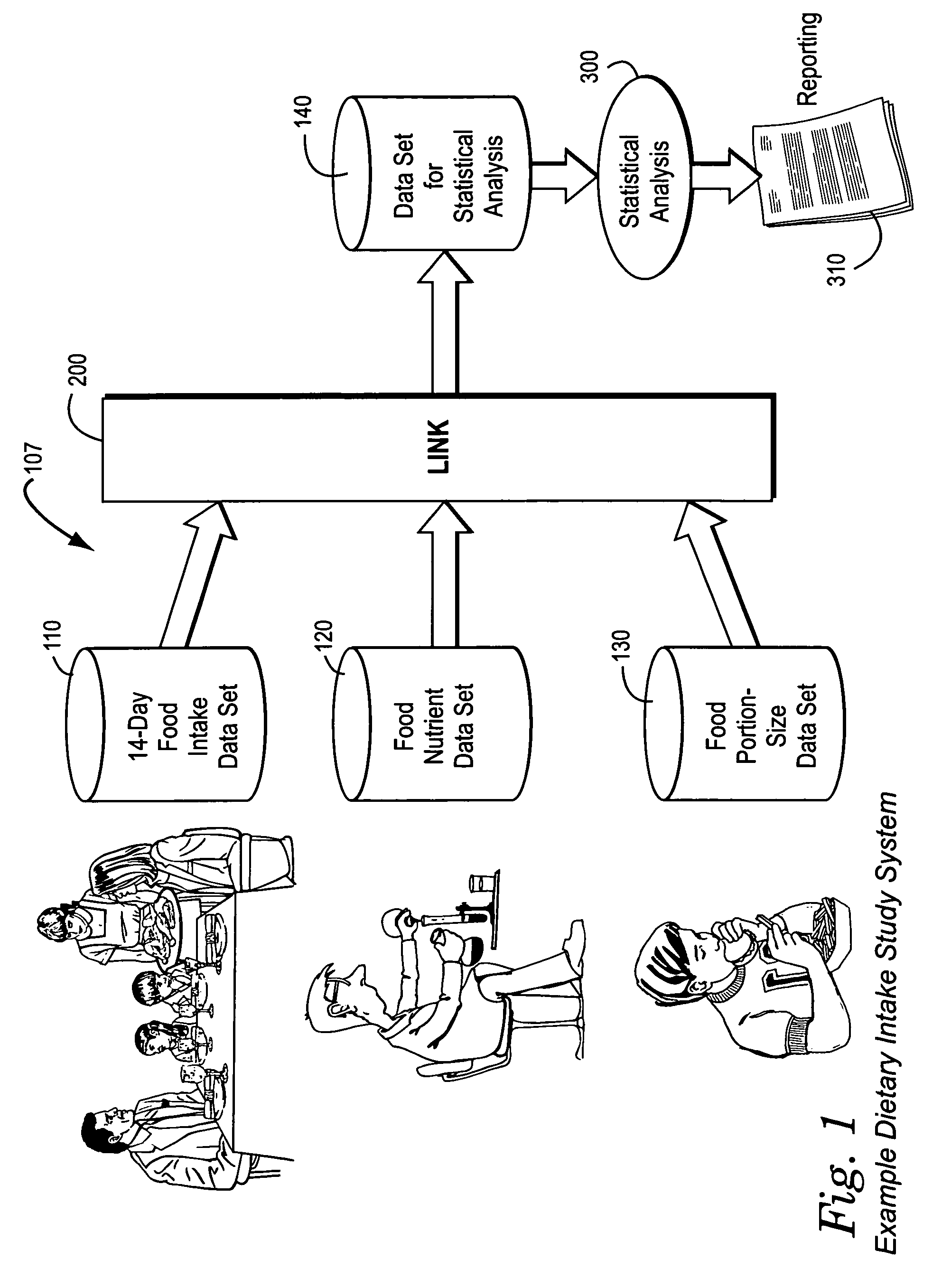
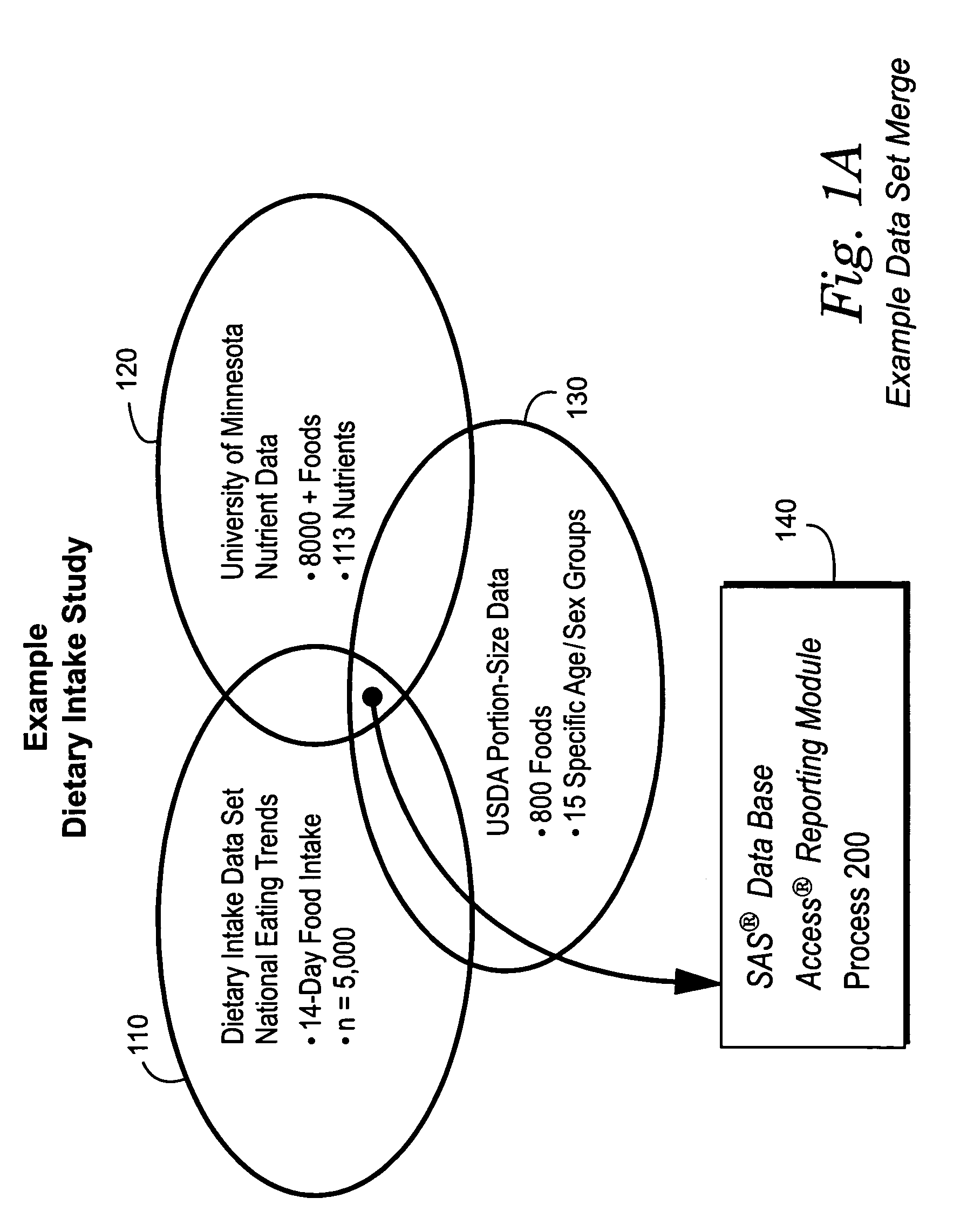
Systems and methods for determining nutrients within dietary intake
The present invention uses market research data to access nutrient intakes of a population. Dietary collection using 24-hour recall generally does not reflect a pattern of “usual” intake behavior for a population group. To determine the impact of food consumption patterns on nutrient intake, a unique methodology using 14-day food diary was developed. The food industry has traditionally used detailed food records to track the consumption of specific branded food items and monitor the growth of food categories, but some of the most valuable databases available concerning longer-term (e.g., 14-day) food intake do not record portion size on an individual consumption basis. Other databases based on shorter-term (24-hour recall) survey periods record portion sizes but are not very representative of eating habits. The preferred exemplary embodiment integrates two such databases with a third data set providing detailed nutrient information for each of a wide variety of foods consumed to provide a combined database for processing nutrient intake reports using statistical analysis. This flexible system allows the user to categorize the population based on “usual” consumption of food categories, specific foods and / or specific brands of foods and determine dietary differences versus their “non-using” counterparts.
Owner:GENERAL MILLS INC
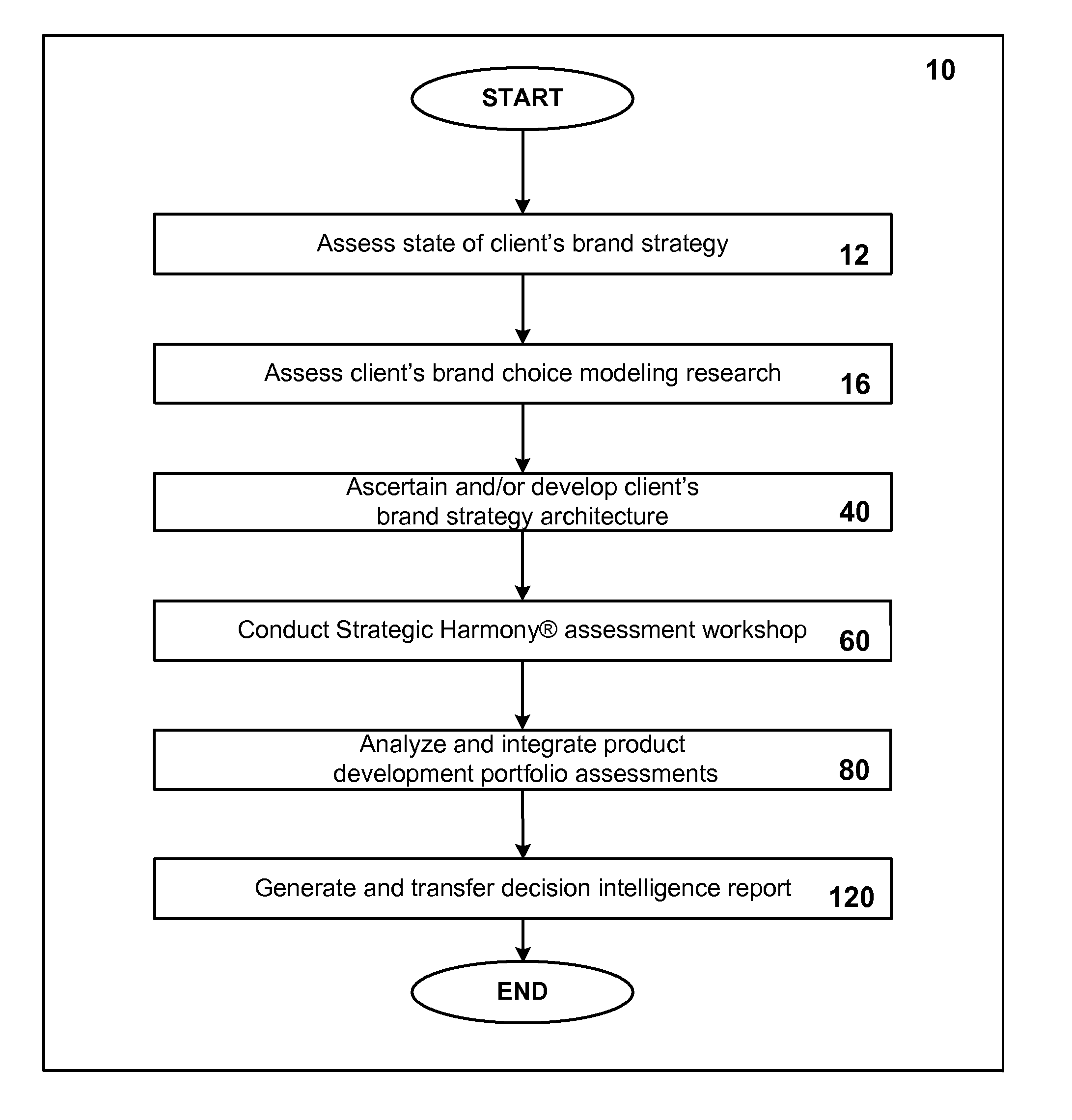
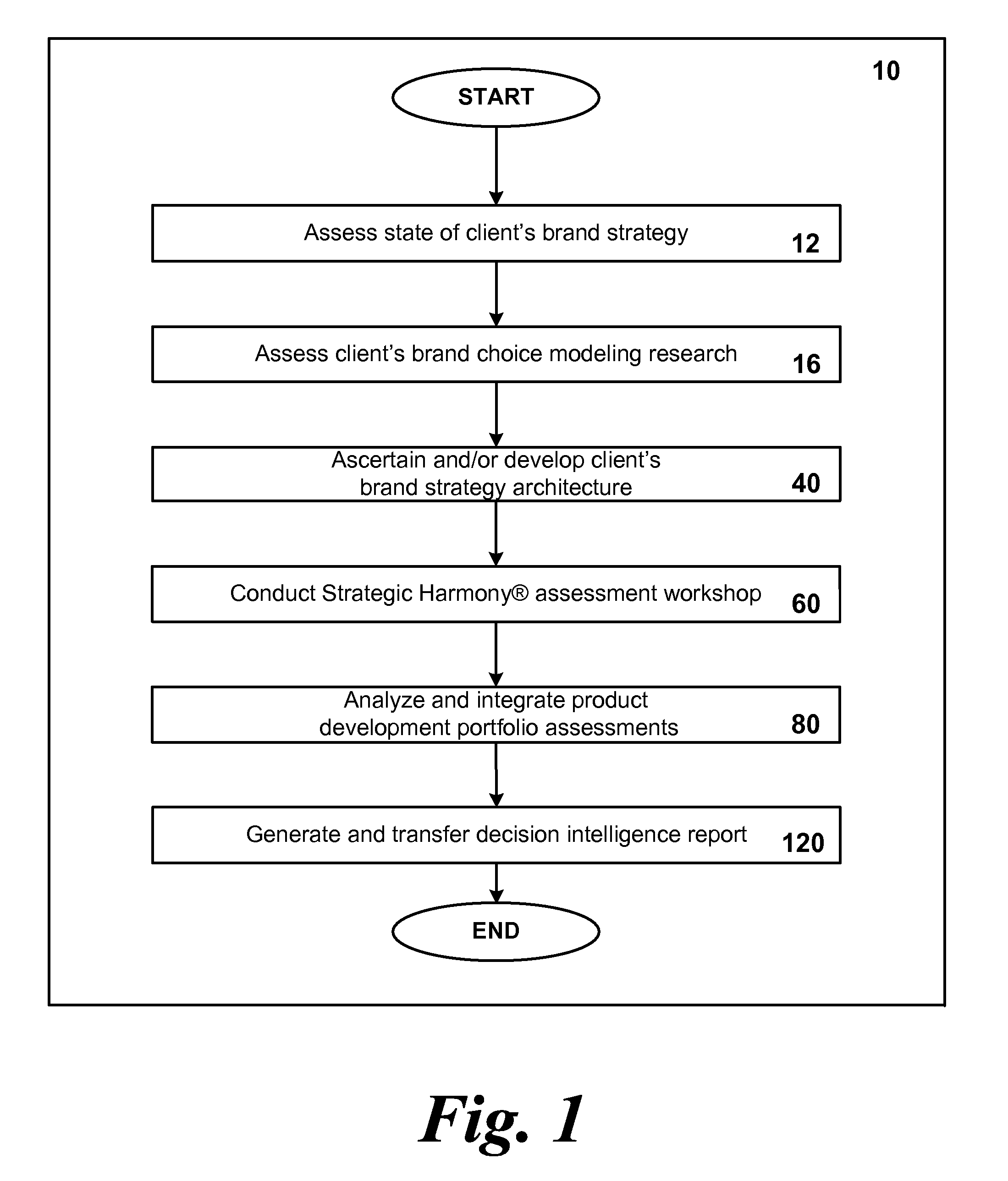
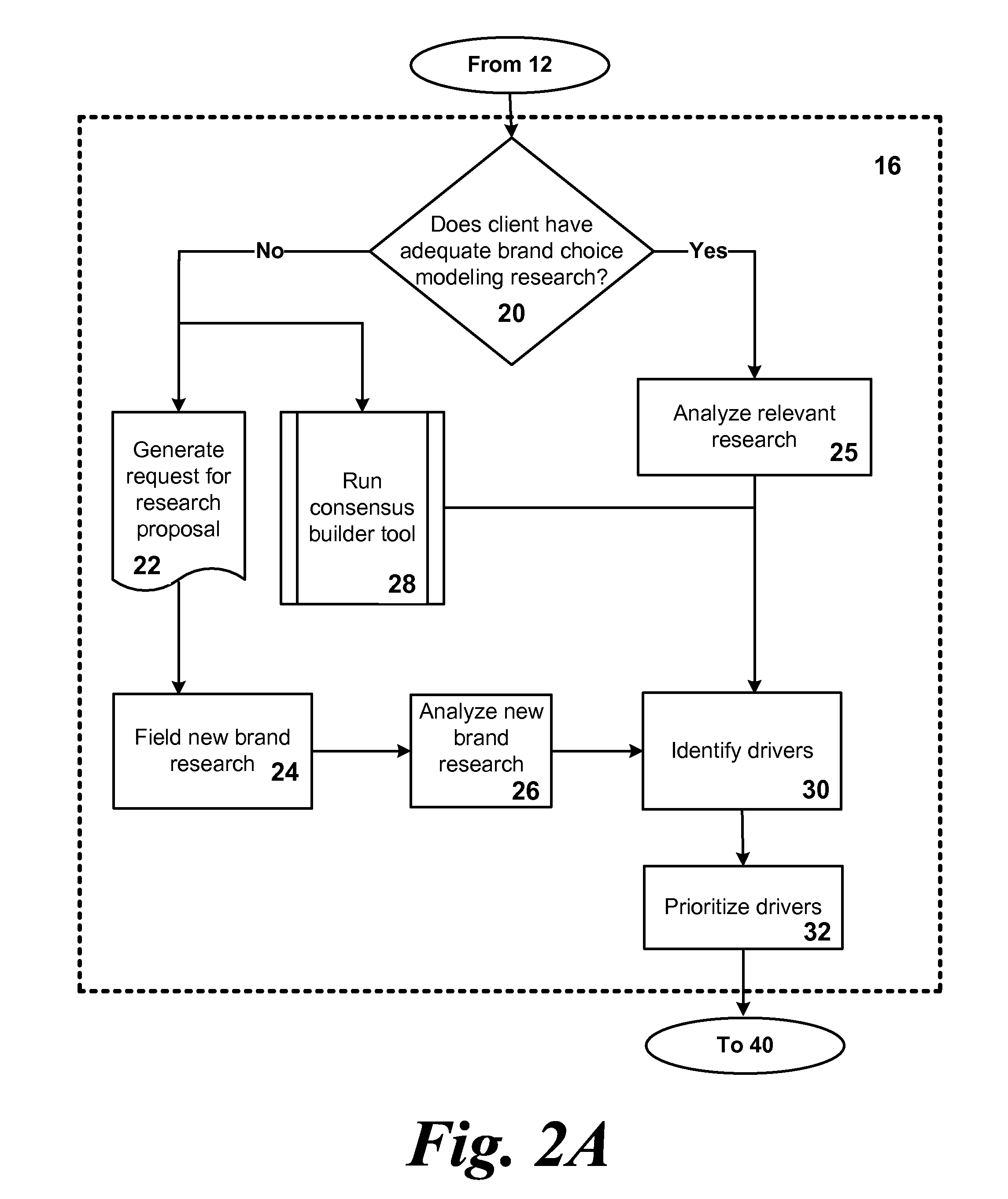
System and method for optimizing product development portfolios and integrating product strategy with brand strategy
InactiveUS20070192170A1Shorten the time to marketImprove business performanceFinanceResourcesTime to marketService composition
A business and software method to cost-effectively optimize product and / or service development portfolios, to reduce time to market, and to better integrate and align product or service strategy with brand strategy. The business and software method includes defining in detail the product and service attributes that characterize the ideal customer experience, categorizing the attributes, assigning a numerical value of importance to the attributes, and applying those values to statistical analysis of each assessed product development initiative in terms of alignment with ideal experience and potential competitive impact relative to the resources and risks required to bring each initiative to market. A prioritization for product development resource allocation is developed based upon these analyses. The prioritization is presented in the form of decision intelligence tools for an organization to use and reach informed judgments concerning resource allocation to develop, maintain, or optimize a given product or service portfolio. The decision intelligence tools serve to improve business performance, increase market impact, and build brand equity for products and services of a given organization by improving alignment between what the organization promises customers and what it actually delivers.
Owner:CRISTOL STEVEN M
System and Method for Building and Manipulating a Centralized Measurement Value Database
Owner:IMATX INC
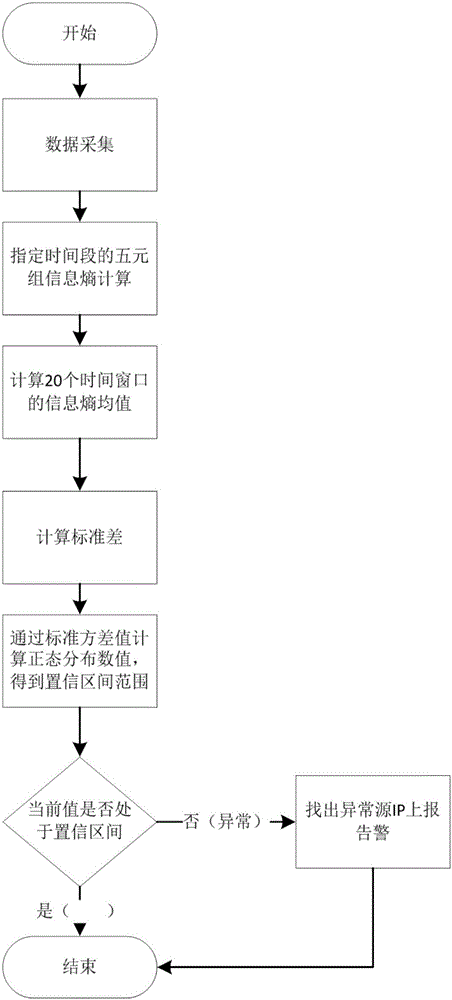
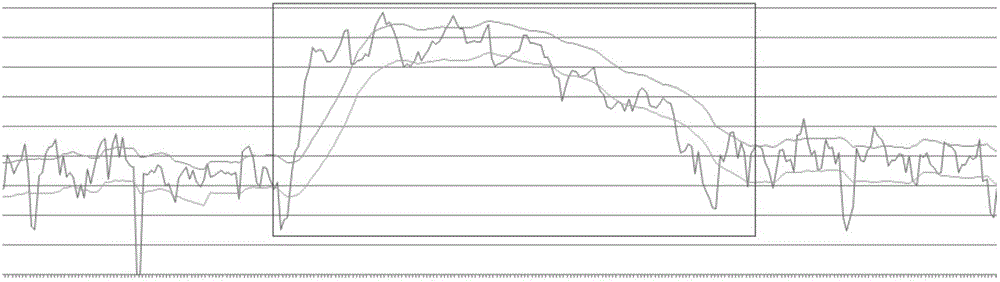
Information entropy variance analysis-based abnormal traffic detection method
The invention discloses an information entropy variance analysis-based abnormal traffic detection method. According to the method, a large quantity of Internet user access logs are obtained, and collected data is processed via a system; attack behaviors or abnormal behaviors can be rapidly identified and recorded via big data mining, association and statistical analysis; invasive attack alarm information data can be formed; a complete attack path can be constructed via relevant invasive attack data analysis, and therefore an object of invasion tracking and positioning can be attained. Via use of the abnormal traffic detection method, behavior after events can be traced and machine learning of user access behaviors can be realized, a false alarm rate of a system can be lowered, a network traffic detectability set is put forward, a baseline for normal network traffic is described, and reference is provided for abnormity detection.
Owner:深圳市傲天科技股份有限公司
Method And Device For Monitoring The Risks For Sudden Infant Death Syndrom And For Positional Plagiocephaly
ActiveUS20120083670A1Easy to useSmall encumbranceHealth-index calculationInertial sensorsCaregiver personSIDS - Sudden infant death syndrome
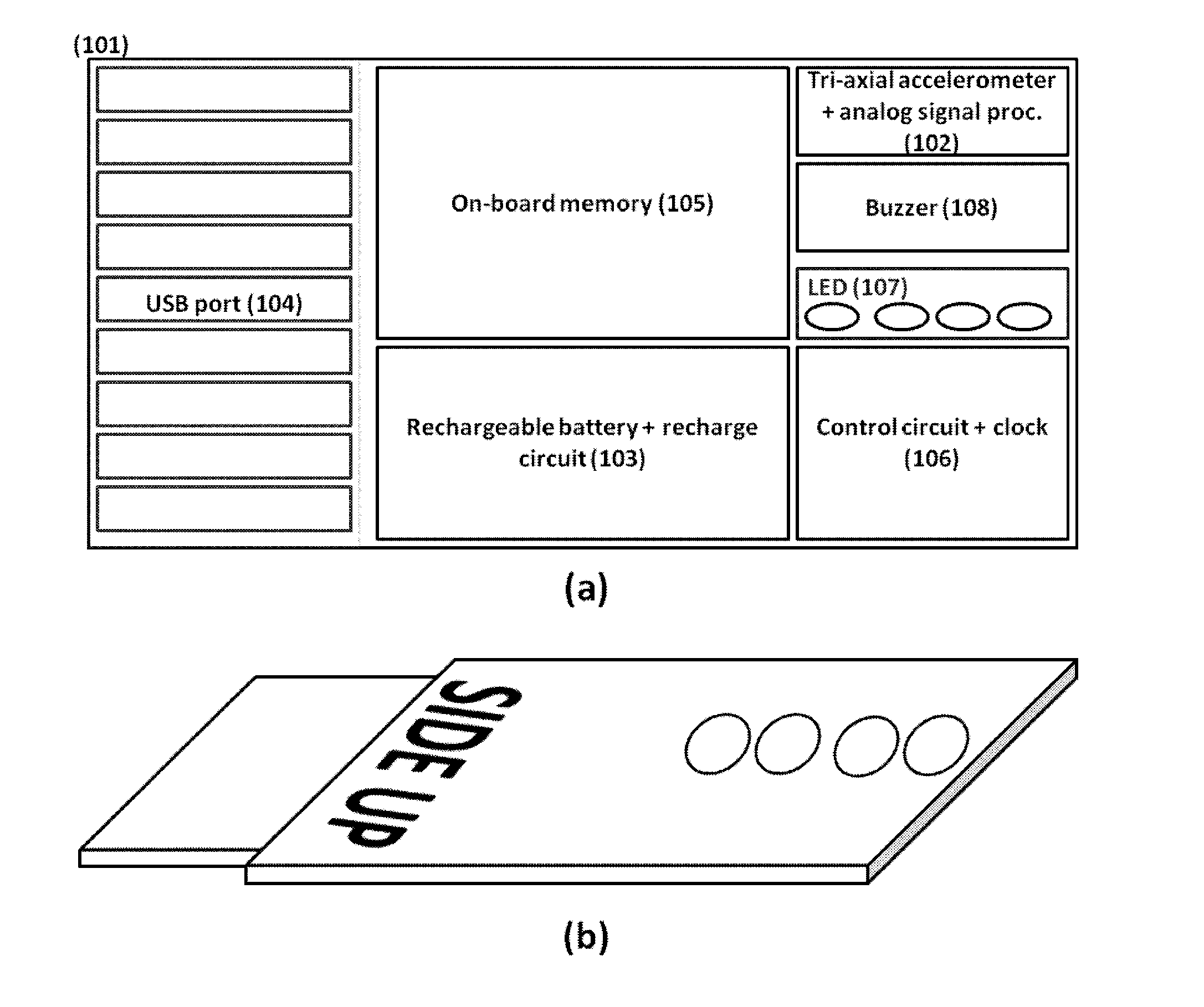
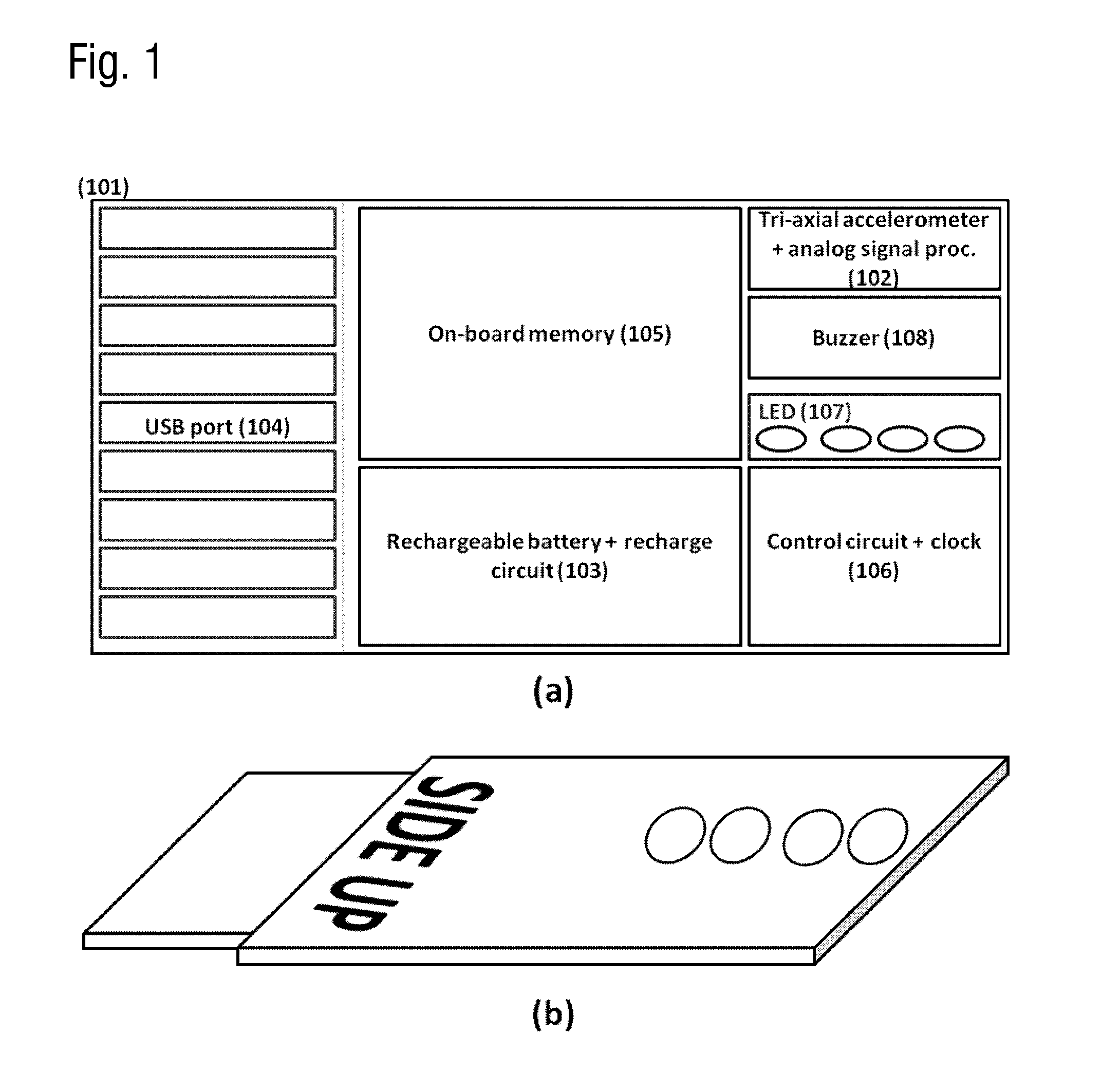
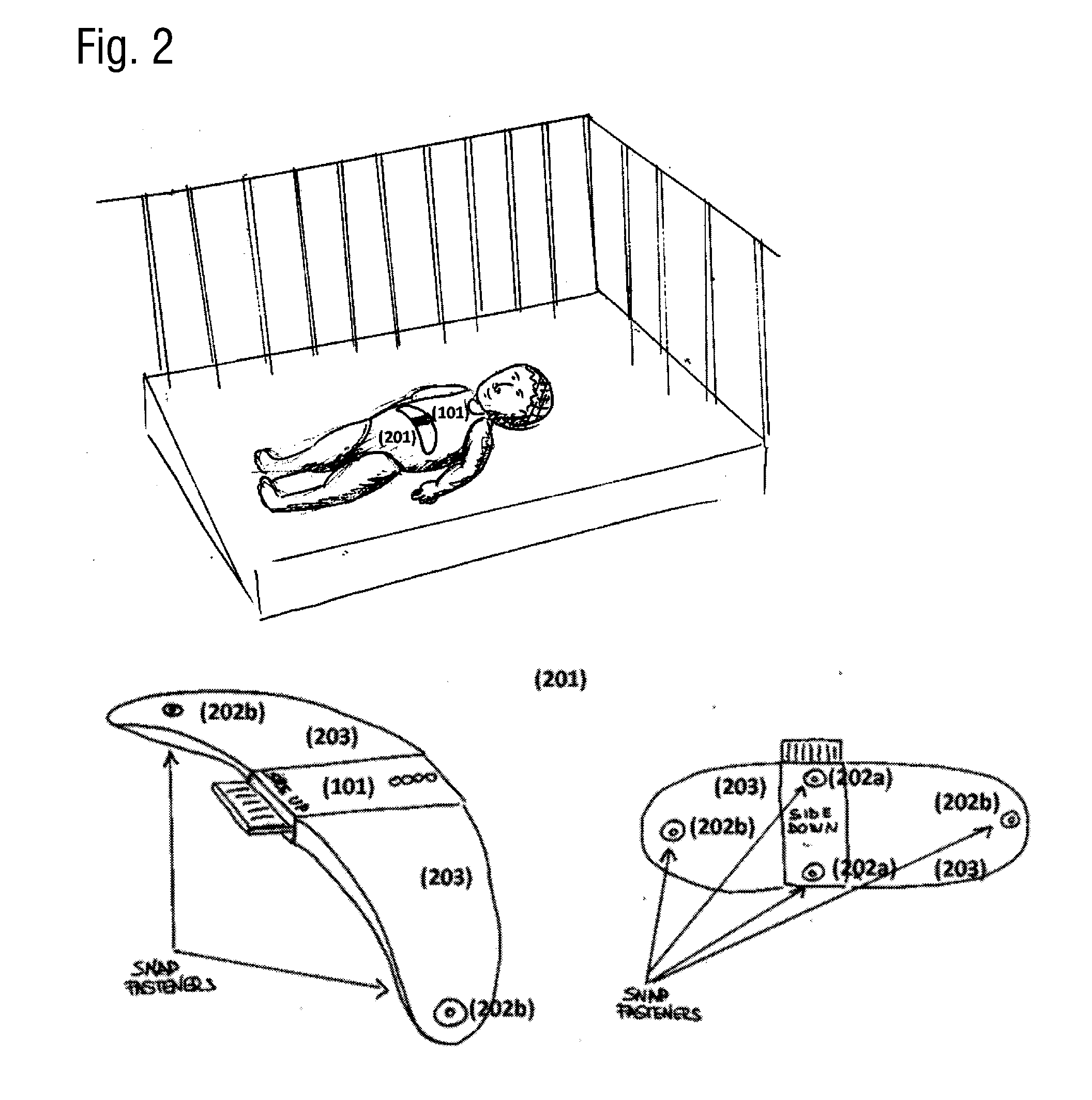
A portable monitoring device for monitoring of the short term, mid term and long term risks of Sudden Infant Death Syndrome (SIDS) and to estimate the risk of onset of positional plagiocephaly. The monitoring device acquires one or more signals associated to the typical breath and positioning patterns of an infant through a tri-axial accelerometer, and registers the data in electronic format, where statistical analysis of the signal and pattern recognition are performed in real time by a processing unit. The device monitors the breath activity of an infant in various conditions, alerting a caregiver when a potentially dangerous situation is detected. The monitoring is attached to the clothes of the infant. Statistical analysis of the registered data is performed for quantifying the long term SIDS risk, the risk of plagiocephaly and for optimizing the functional parameters of the monitoring device.
Owner:MONDEVICES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com