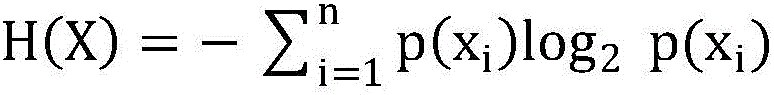Information entropy variance analysis-based abnormal traffic detection method
A technology of variance analysis and abnormal traffic, applied in the information field, can solve problems such as difficult to distinguish between sudden and normal traffic, traditional detection methods are difficult to work, and cannot bear the load, so as to save computing resource consumption, improve real-time detection efficiency, and improve accuracy Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
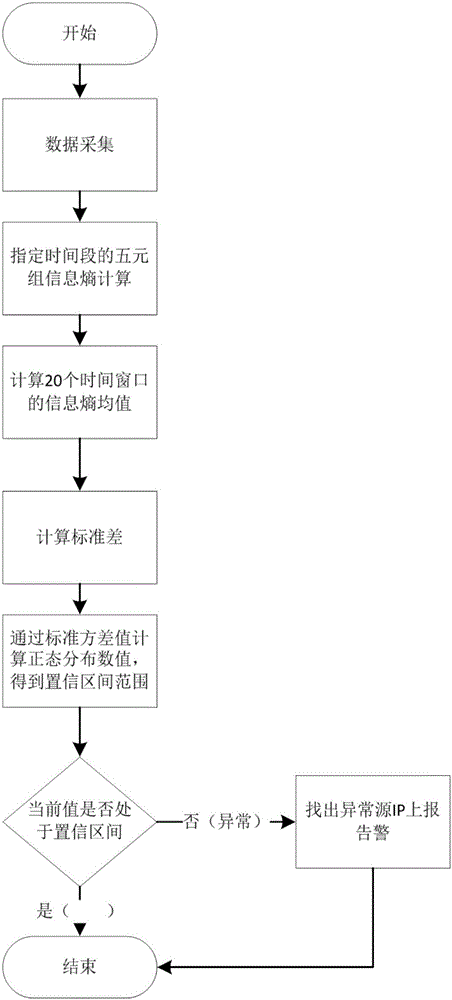
[0044] The specific steps of the abnormal traffic detection method based on the variance analysis of information entropy are as follows: figure 1 shown.
[0045] The backbone network abnormal traffic detection and abnormal flow identification method based on traffic behavior characteristics includes four steps: traffic behavior feature extraction, abnormal time point determination, abnormal destination IP determination, abnormal flow extraction and attack determination. The specific process is as follows:
[0046] (1). Obtain raw data from network equipment and extract traffic behavior characteristics from it;
[0047] (2). Process the coarse-grained traffic behavior characteristic parameters to determine the time point when the abnormal behavior occurs;
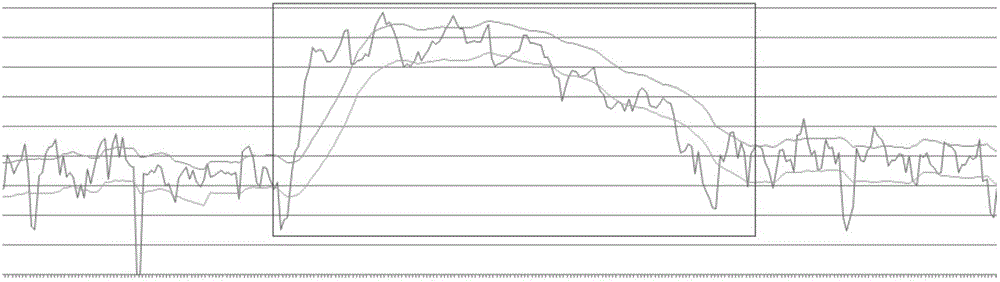
[0048] (3). Analyze the fine-grained traffic parameters of the sub-flows composed of the N destination IPs with the largest traffic at the time point when the abnormal behavior occurs in the historical time window, and det...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com