Patents
Literature
57 results about "SYN flood" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
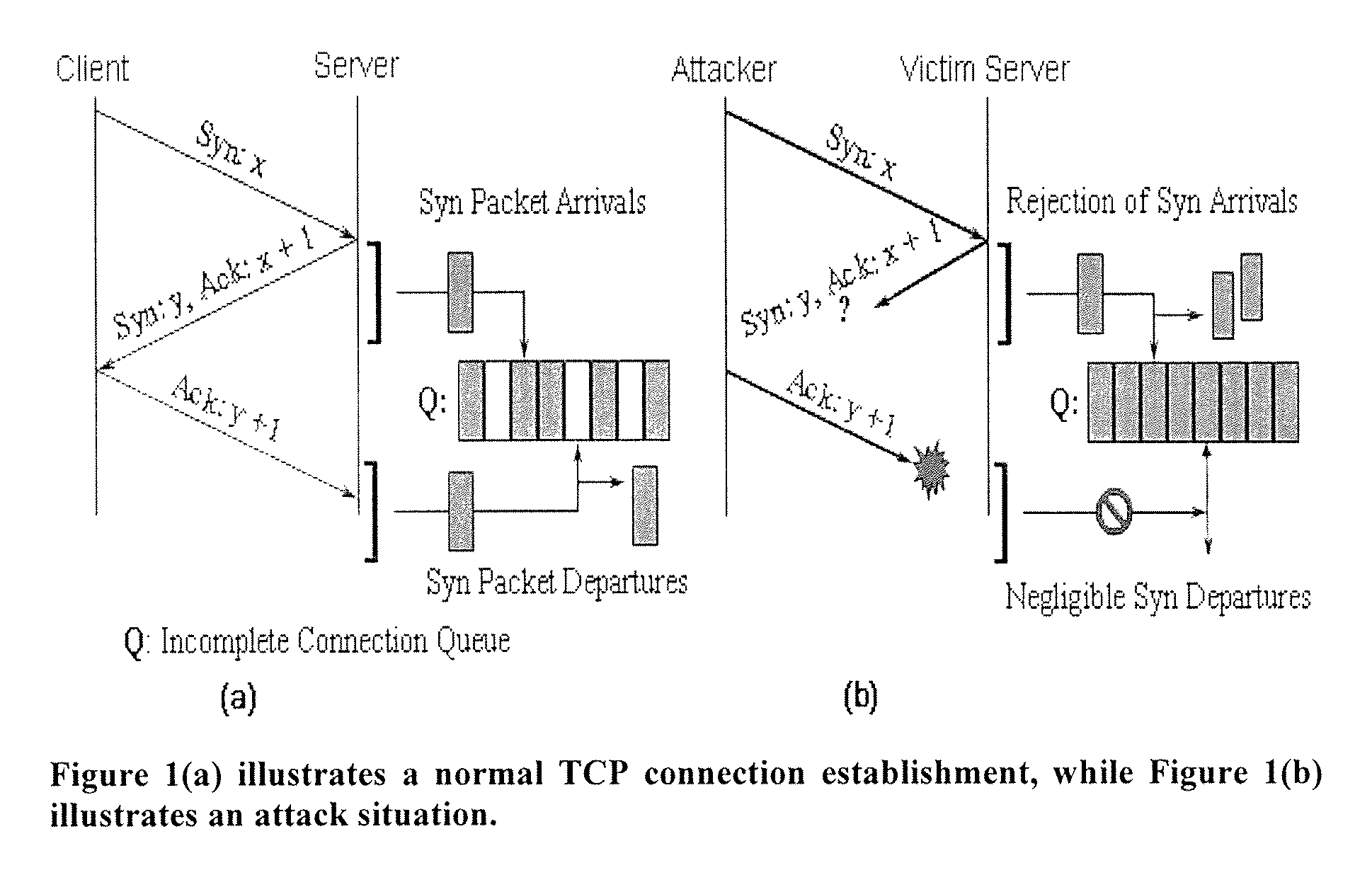
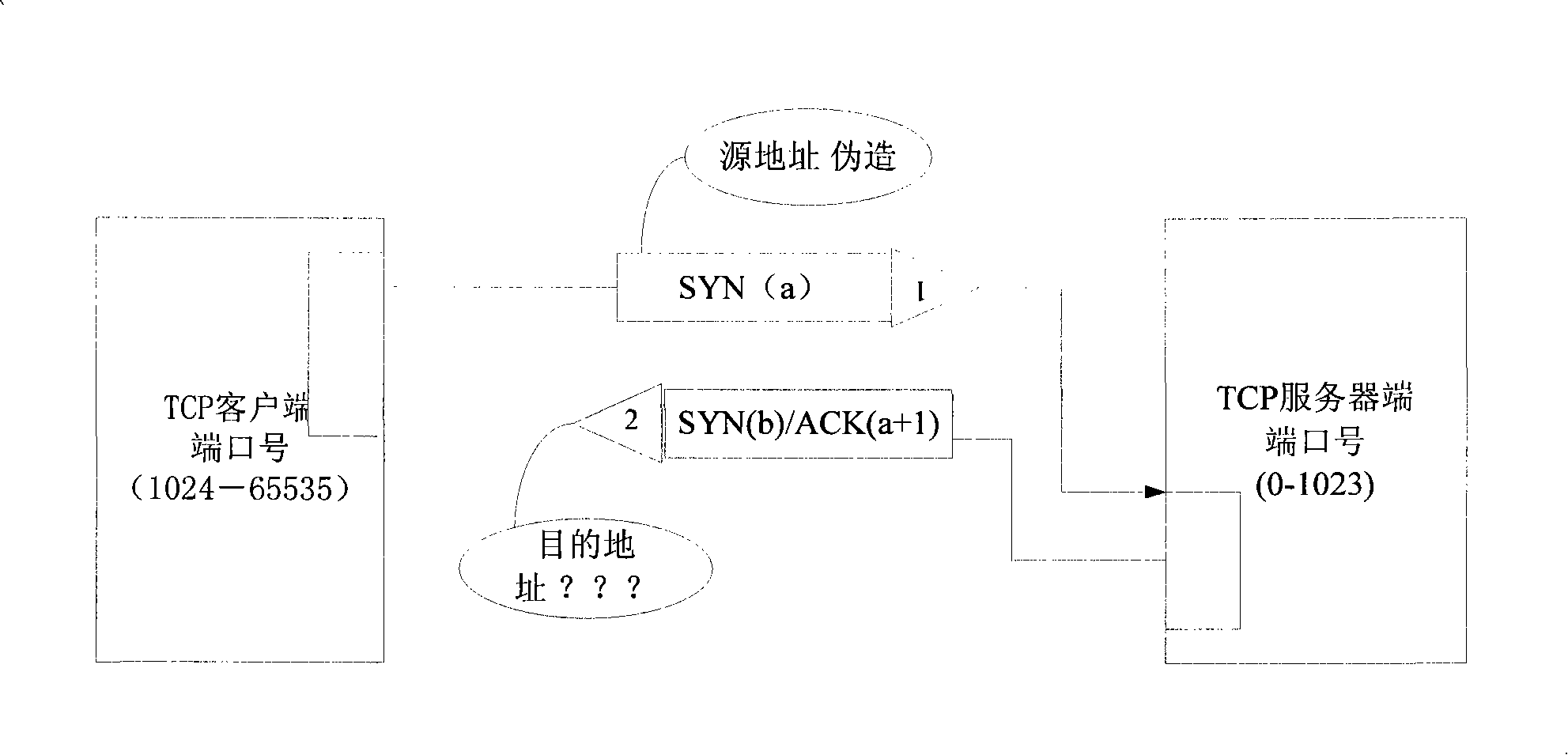
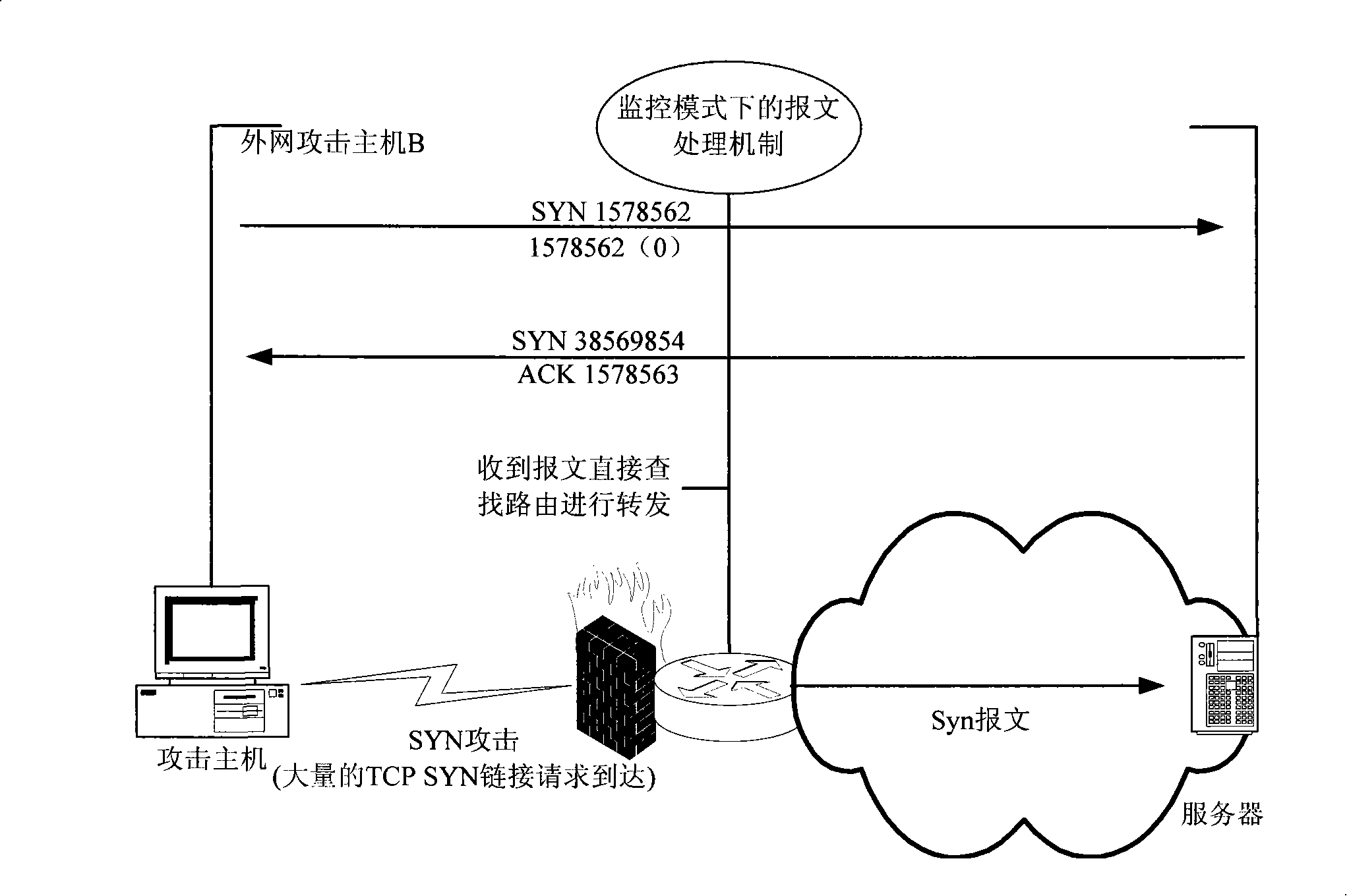
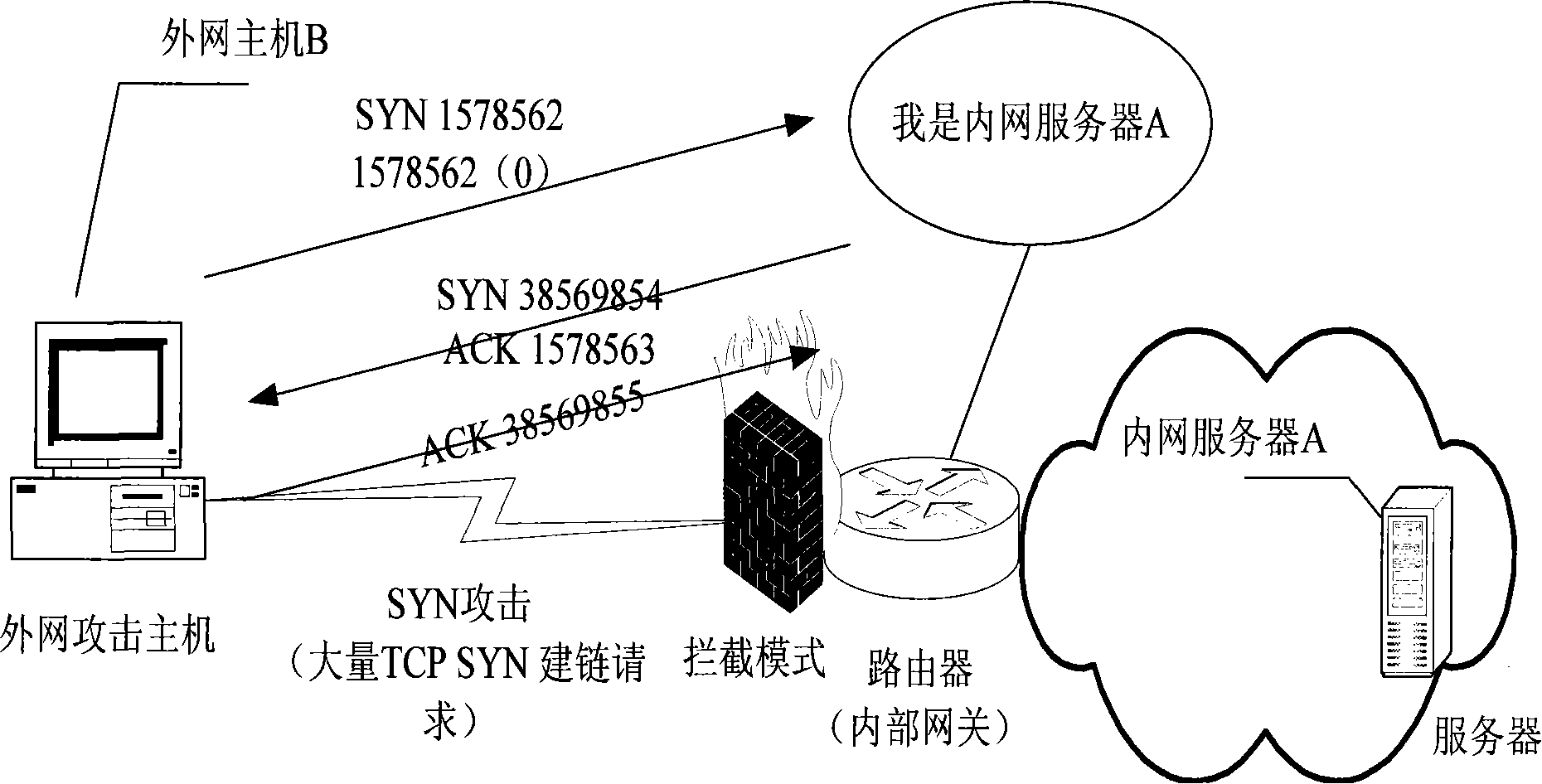
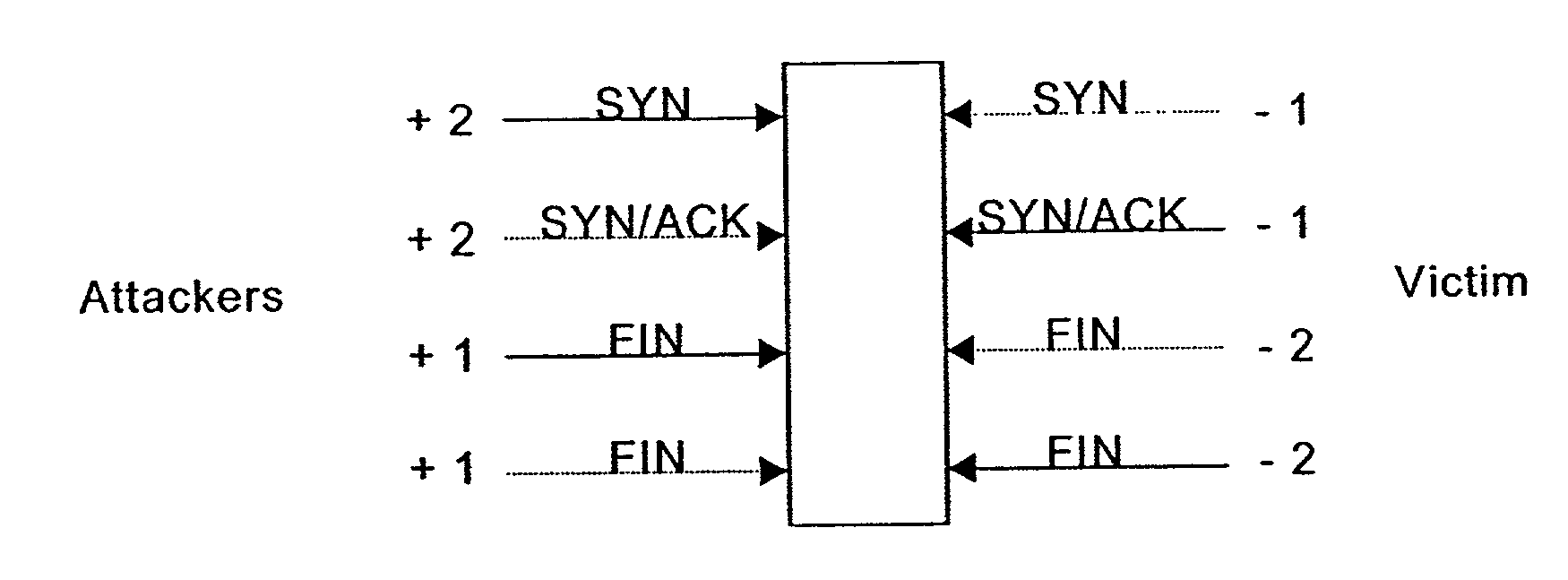
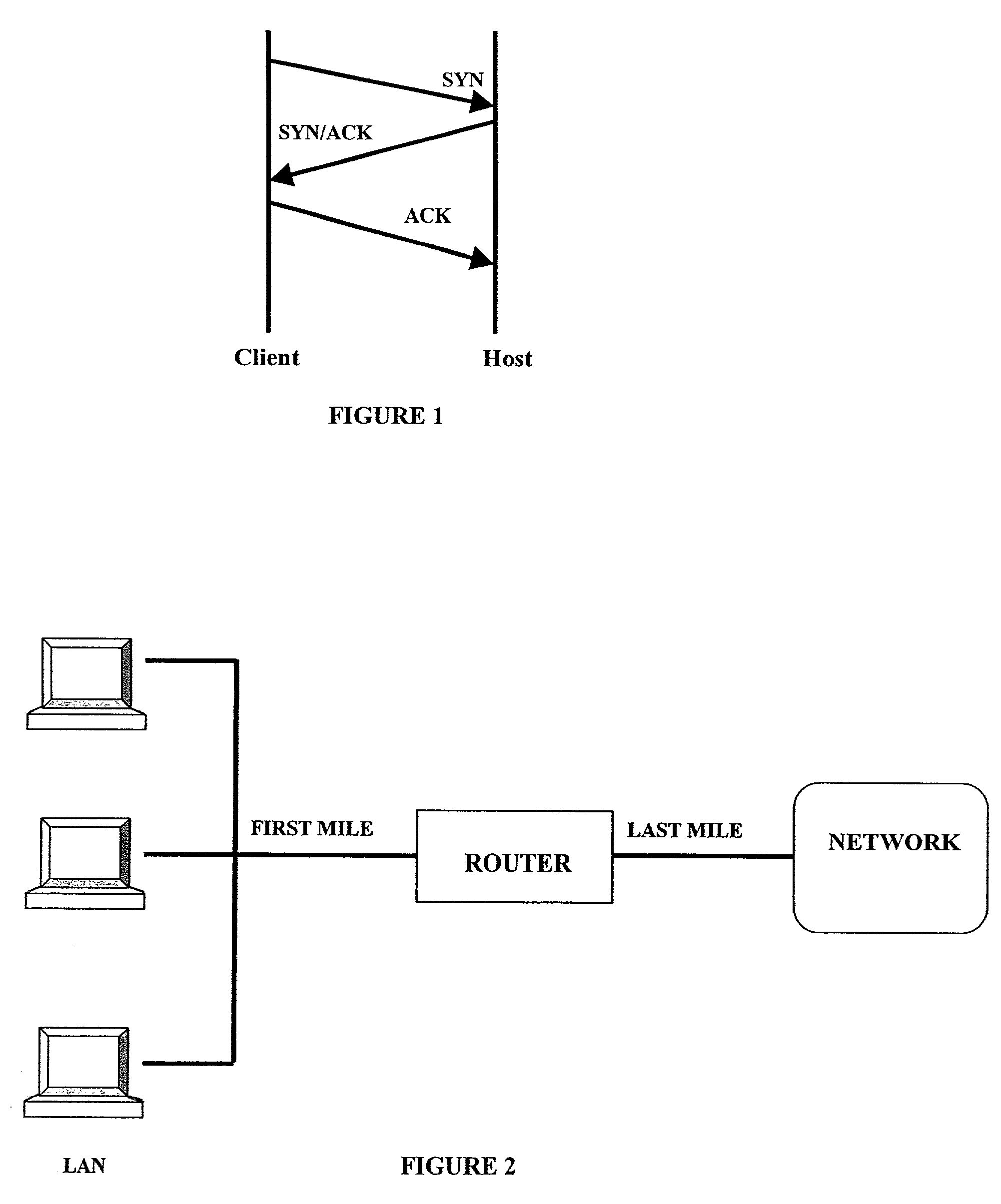
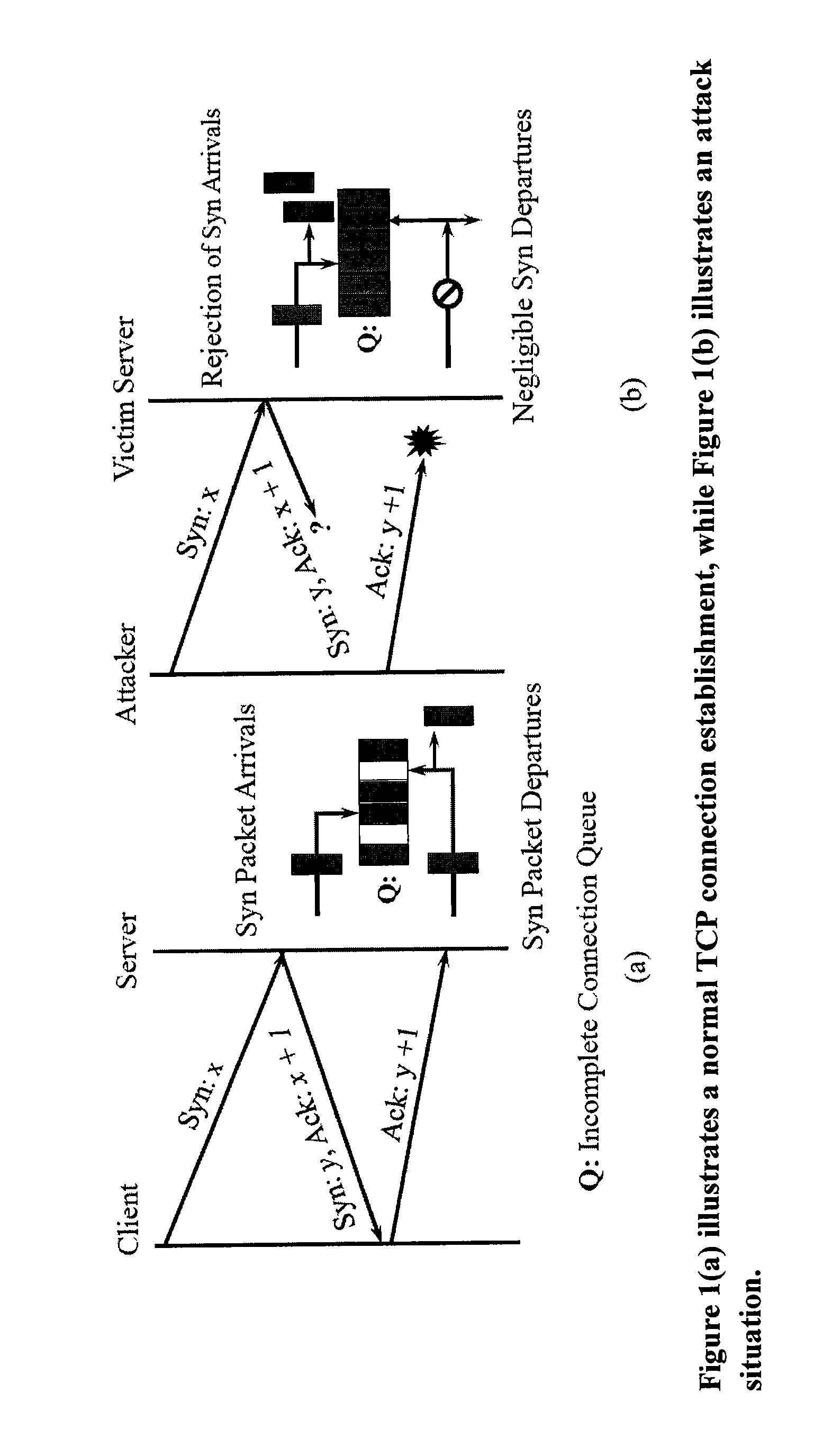
A SYN flood is a form of denial-of-service attack in which an attacker sends a succession of SYN requests to a target's system in an attempt to consume enough server resources to make the system unresponsive to legitimate traffic.
Method and system for protecting a computer system from denial-of-service attacks and other deleterious resource-draining phenomena related to communications
ActiveUS20080256623A1Avoid attackMultiple digital computer combinationsProgram controlRate limitingComputerized system
Embodiments of the present invention include a variety of different integrated, multi-tiered methods and systems for preventing various types of attacks on computer systems, including denial-of-service attacks and SYN-flood attacks. Components of these integrated methods and systems include probabilistic packet droppers, packet-rate throttles, resource controls, automated firewalls, and efficient connection-state-information storage in memory resources and connection-state-information distribution in order to prevent draining of sufficient communications-related resources within a computer system to seriously degrade or disable electronics communications components within the computer system.
Owner:SECURE64 SOFTWARE
Method to detect SYN flood attack
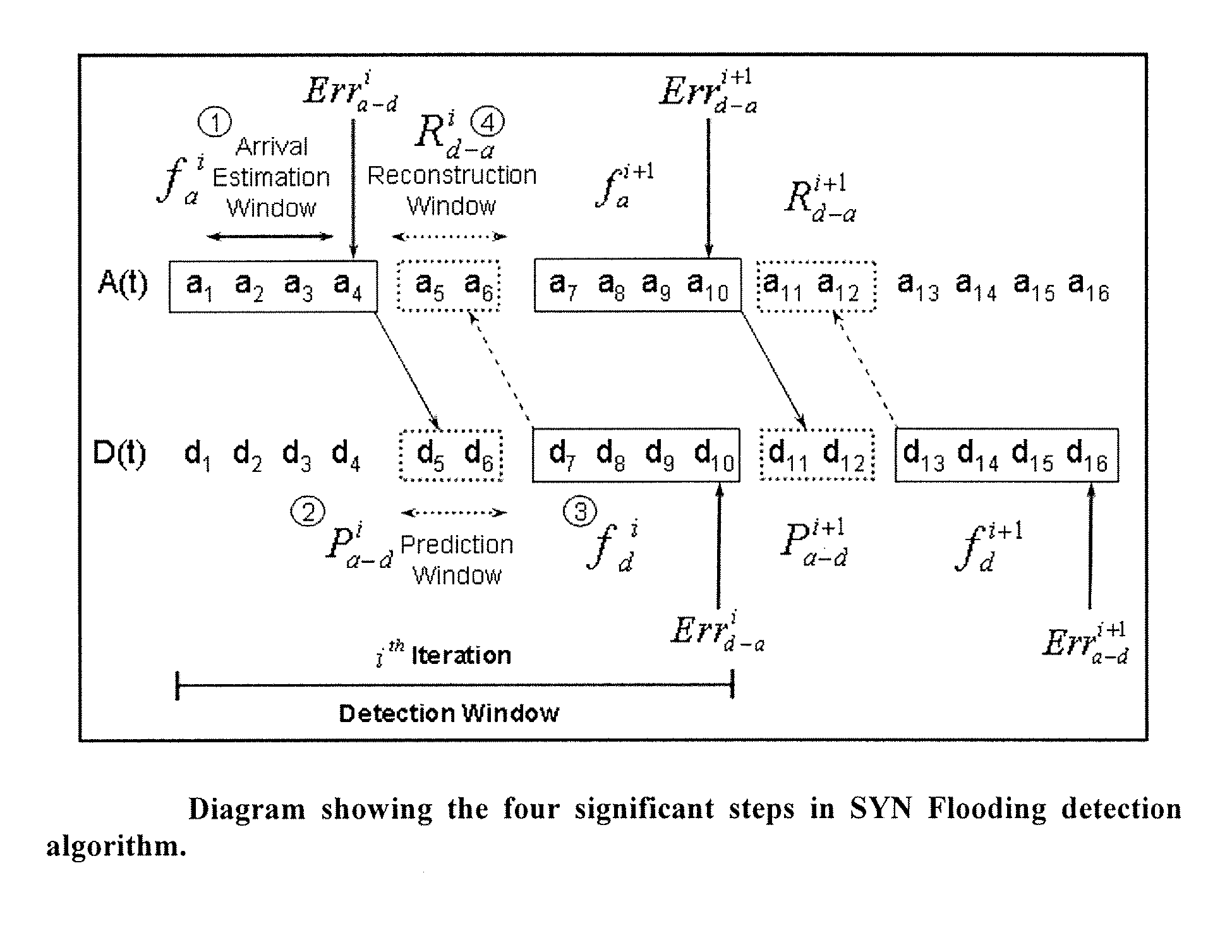
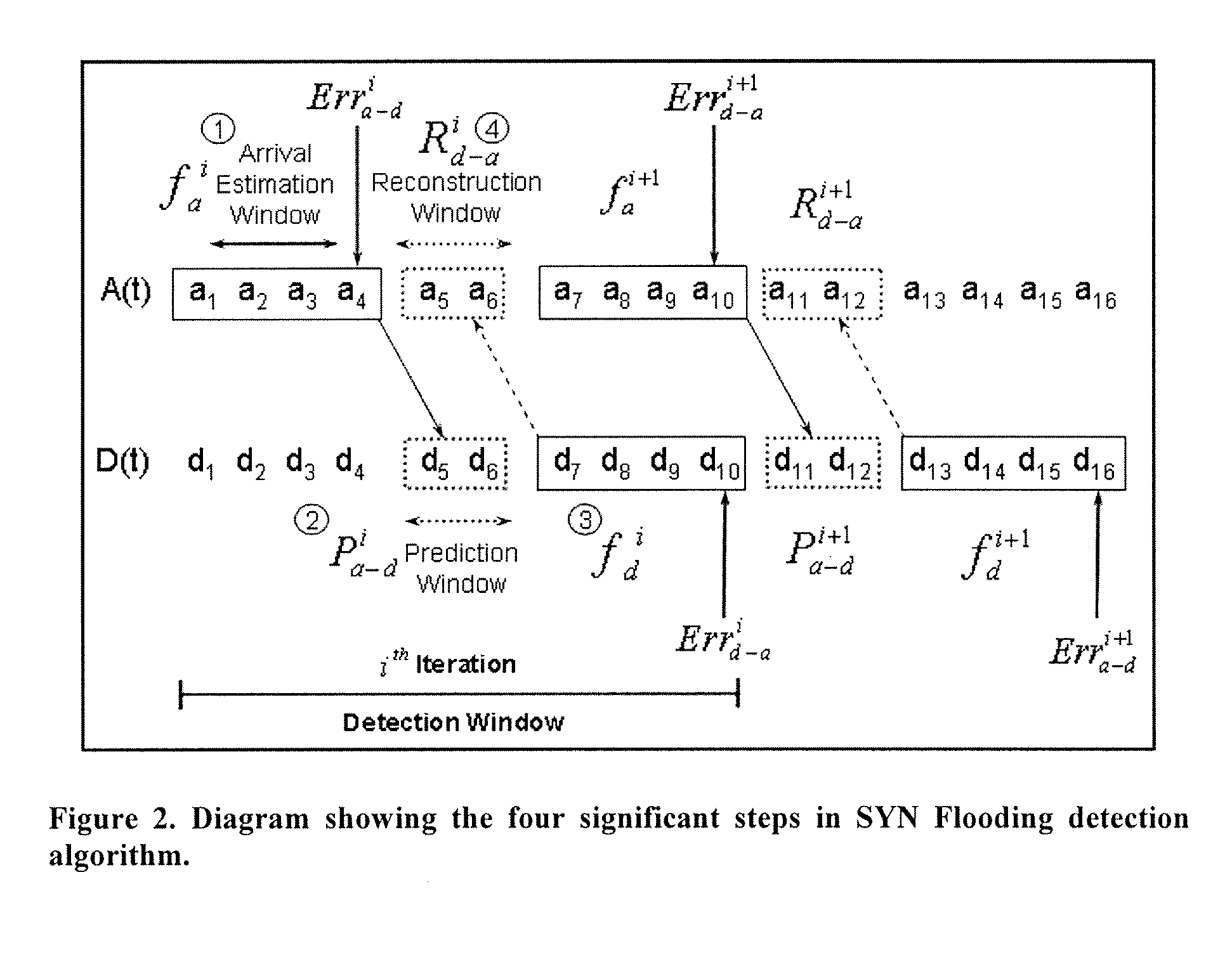
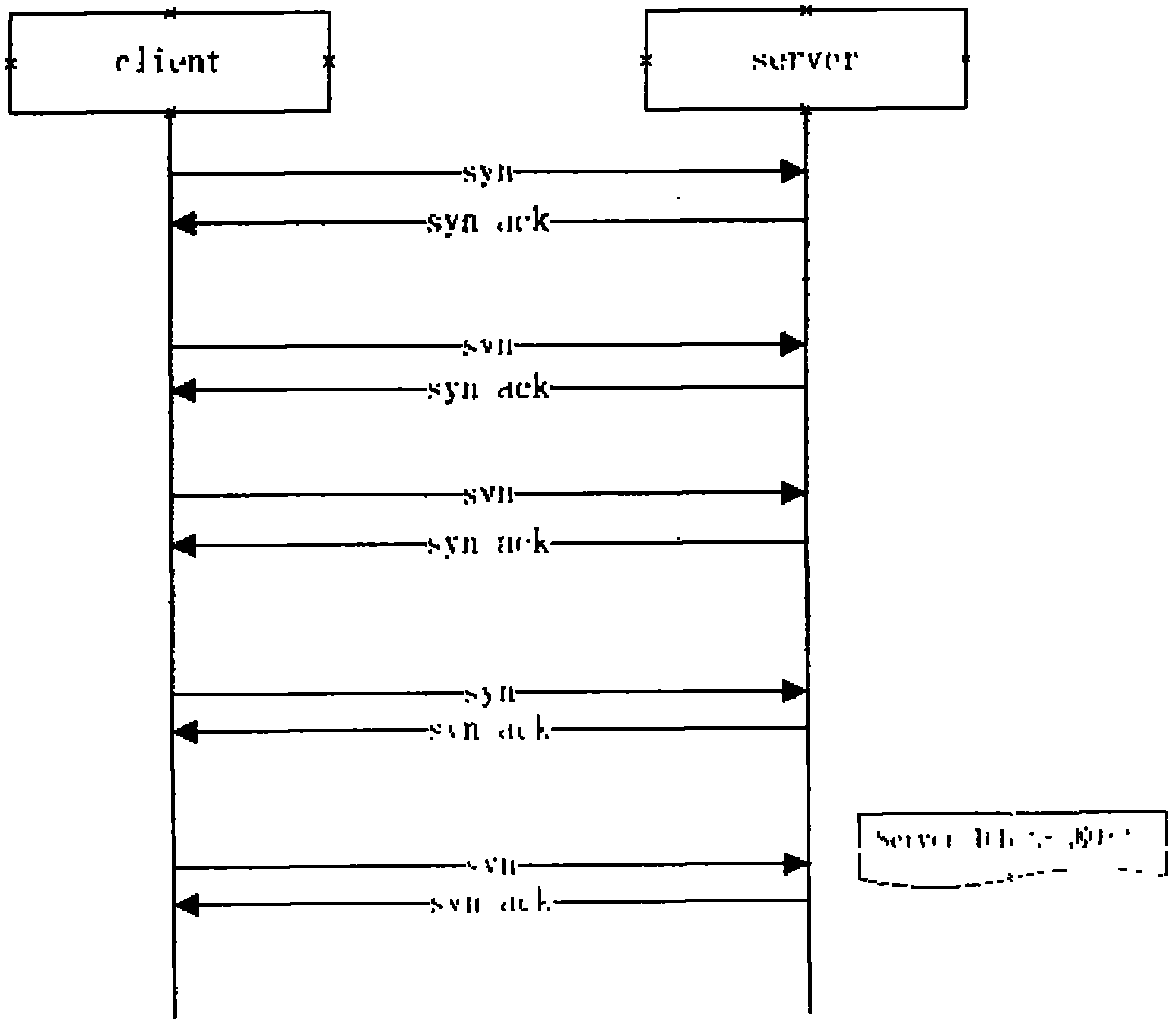
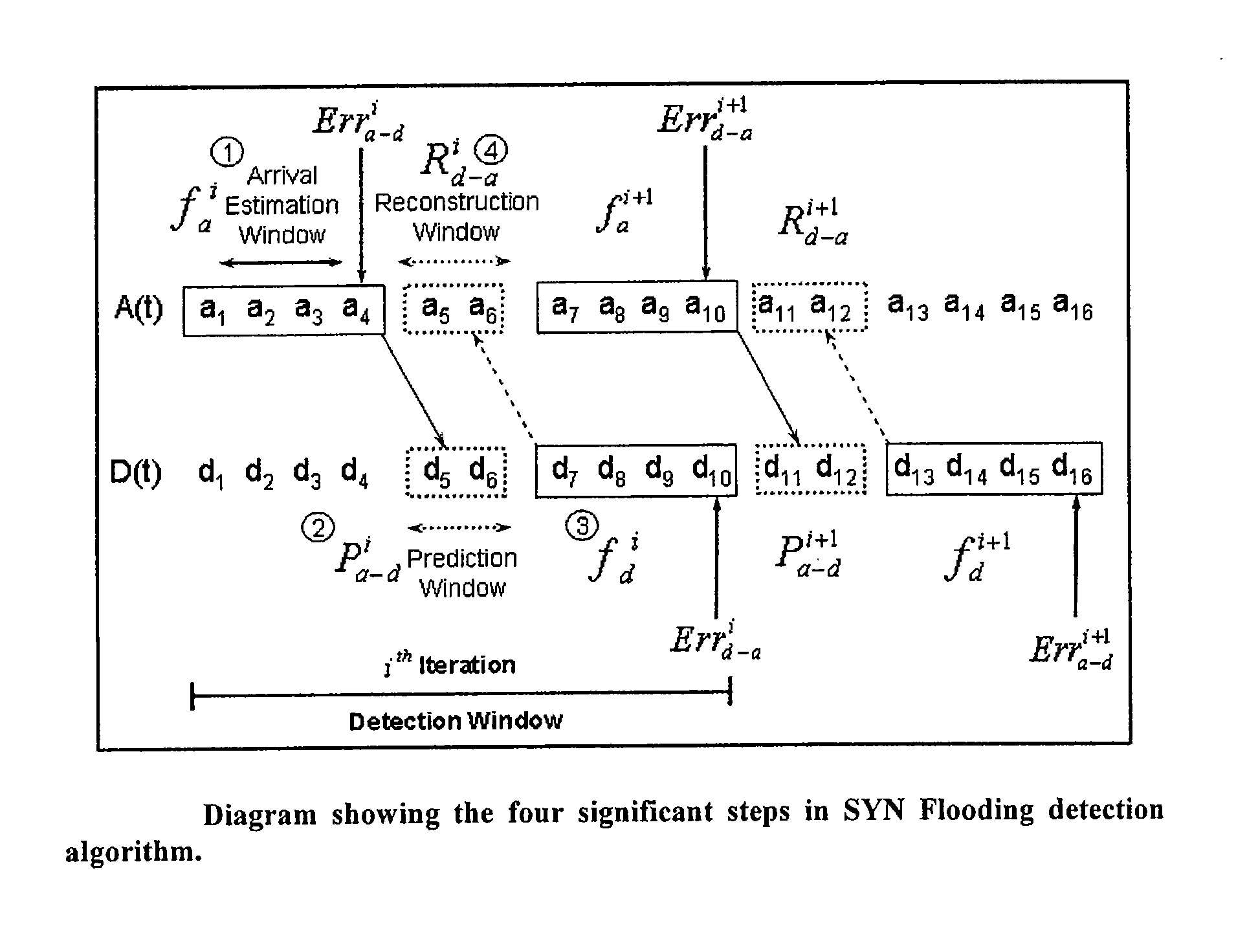
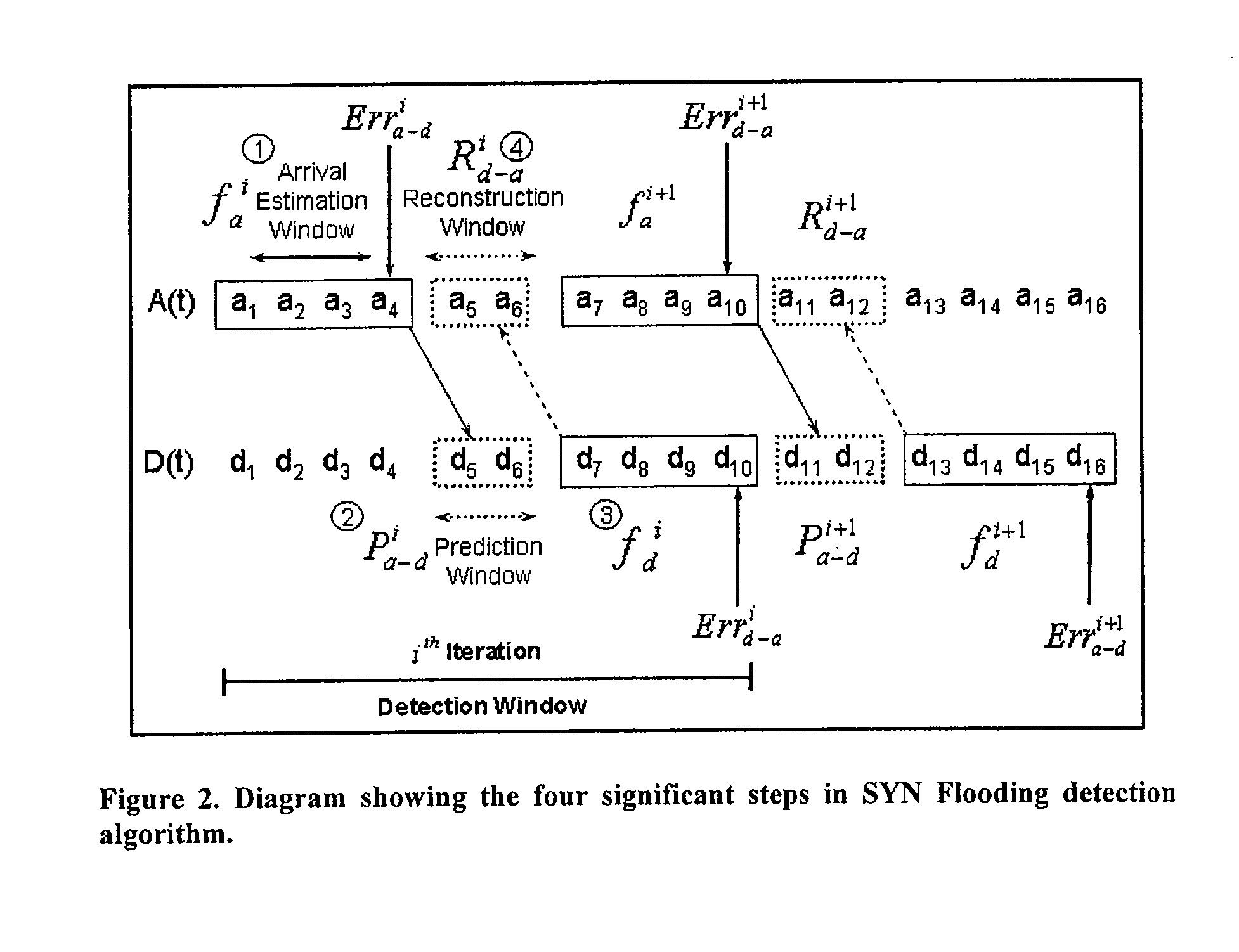
The invention is a method of predicting a SYN flooding attack on a server. The method tracks the number of SYN signals received (or SYN+ACK signals sent) over the communications port of the server in a specified time interval, the arrival estimation window. The invention then predicts the number of anticipated ACK signals to be received over the communication port within a predetermined time length prediction window. The prediction may be made at multiple points within the prediction window. The prediction window is offset in time from the arrival estimation window. The prediction of ACK signals to be received is based upon the number of SYN signals received or SYN+ACK signals sent in the arrival estimation window. In one embodiment, a polynomial is fit to the data in the Arrival estimation window and extrapolated to the prediction window. The predicted number of ACK signals is compared to the actual number received in the prediction window, and if the difference is in excess of a threshold value, and attack is indicated.
Owner:LOUISIANA TECH RES CORP
Method and device for processing TCP connection
InactiveCN101547210AAvoid attackPrevent intrusionData switching networksSYN floodReal-time computing
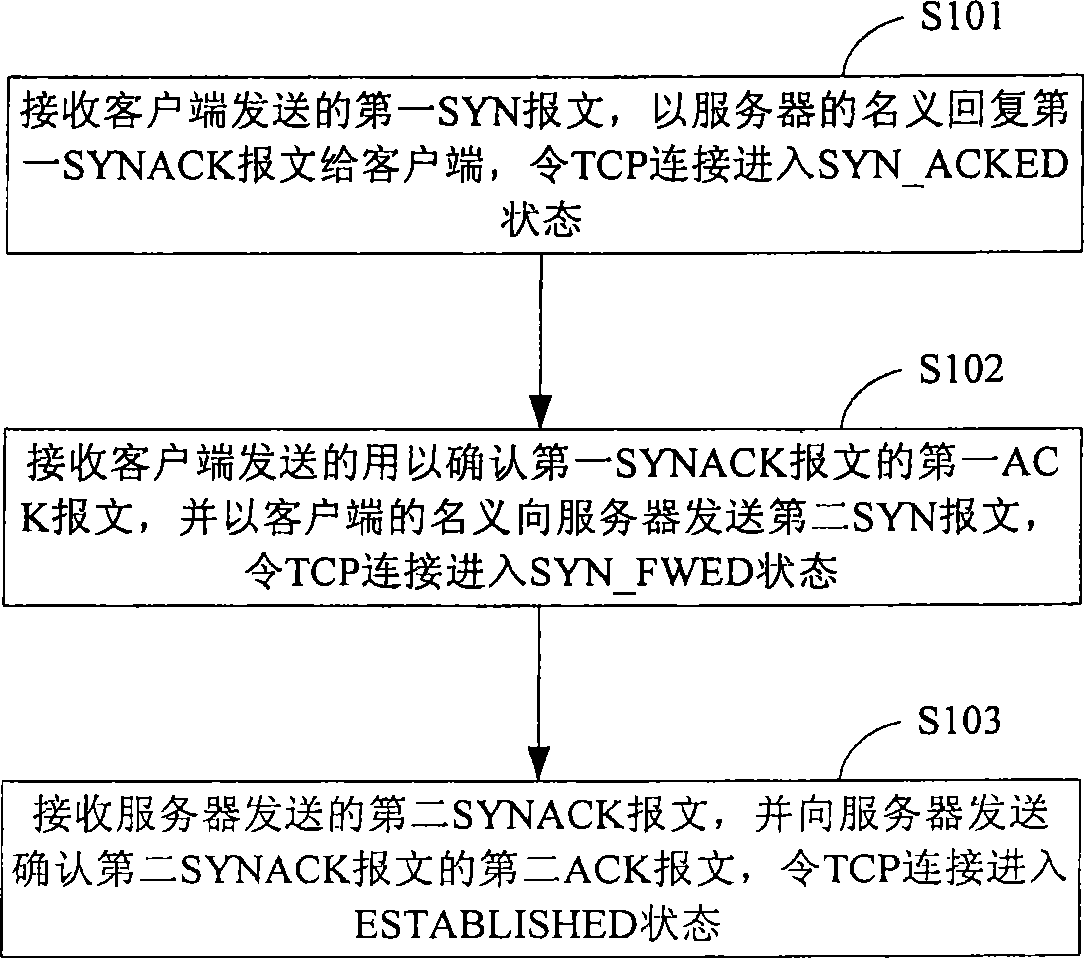
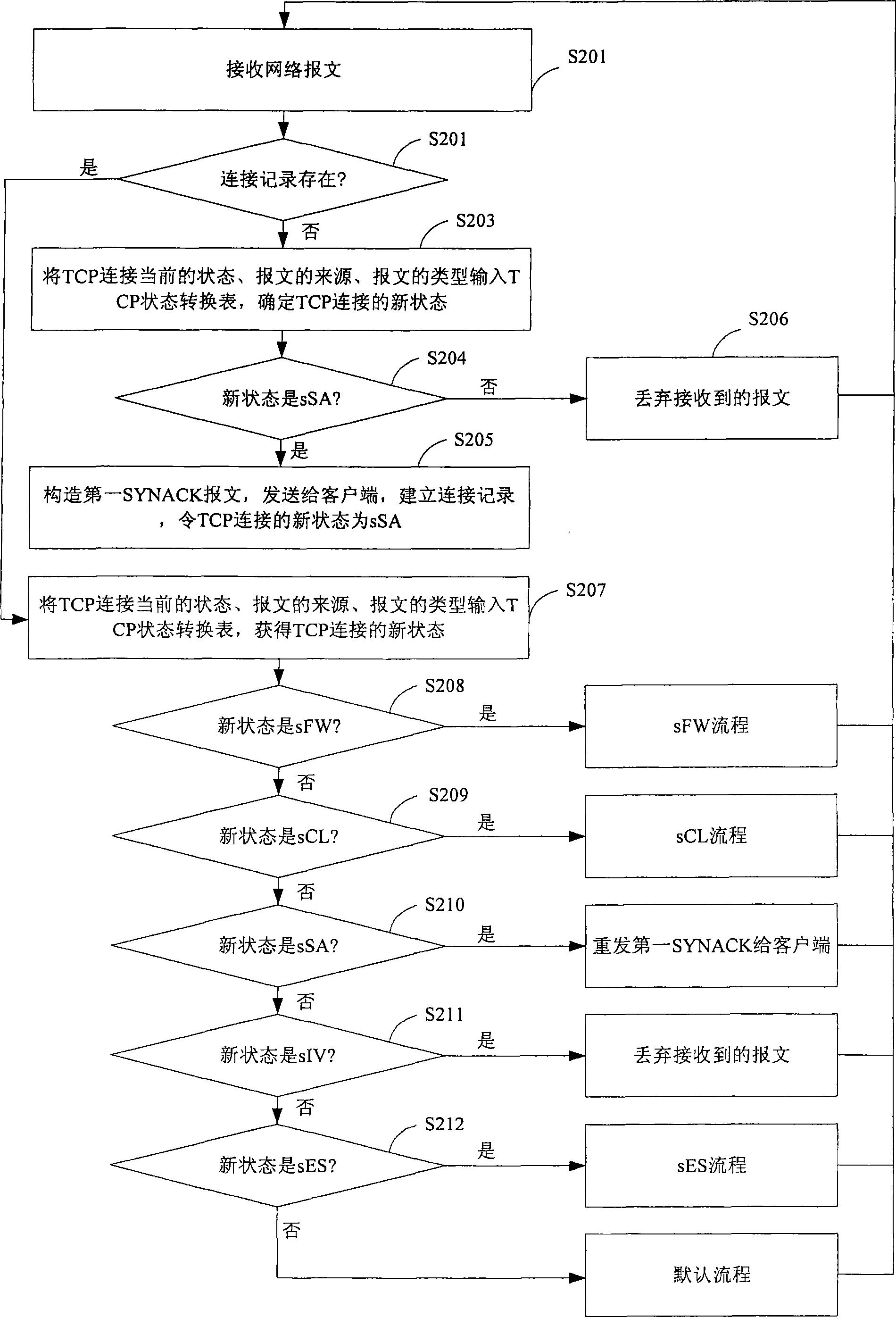
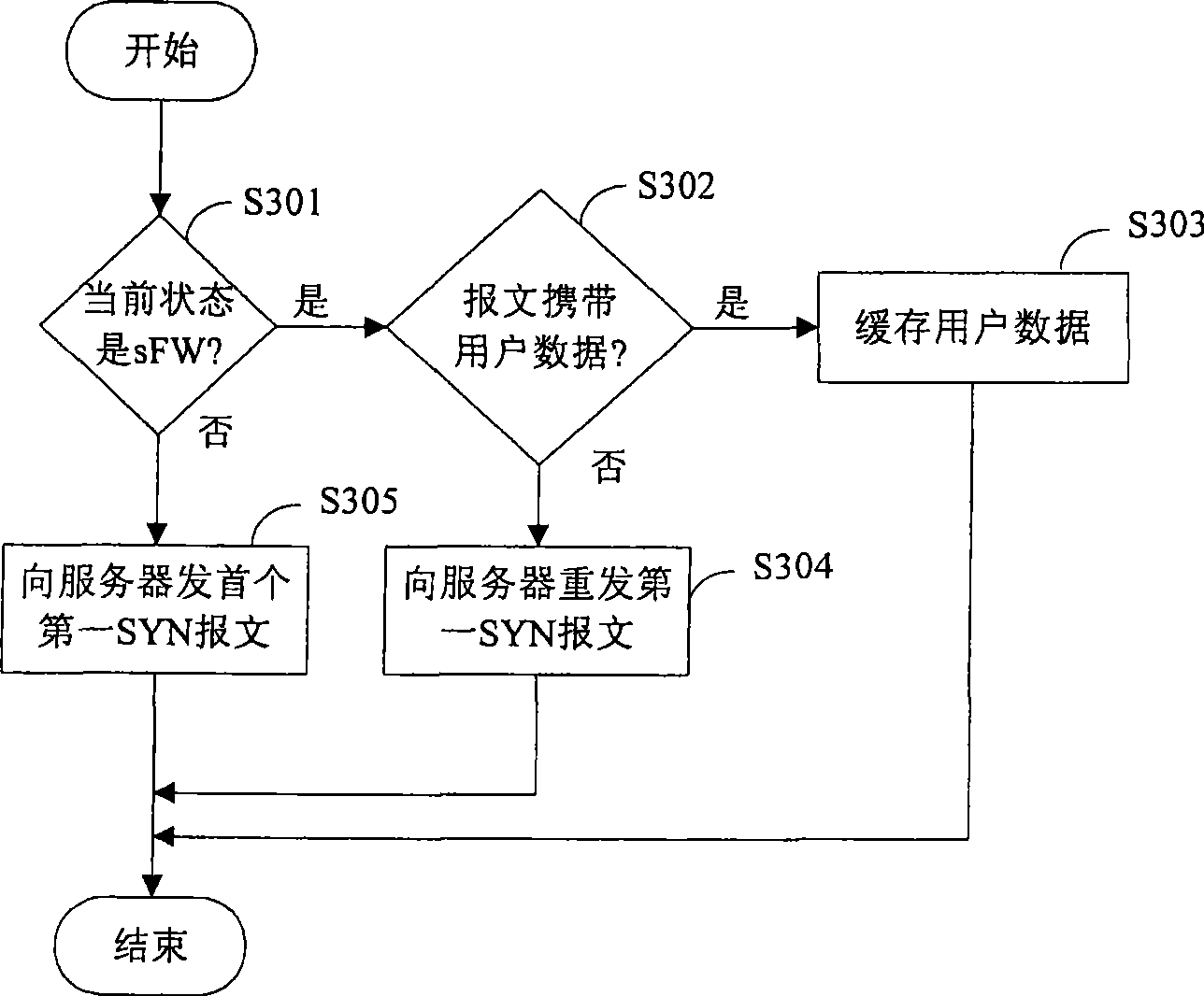
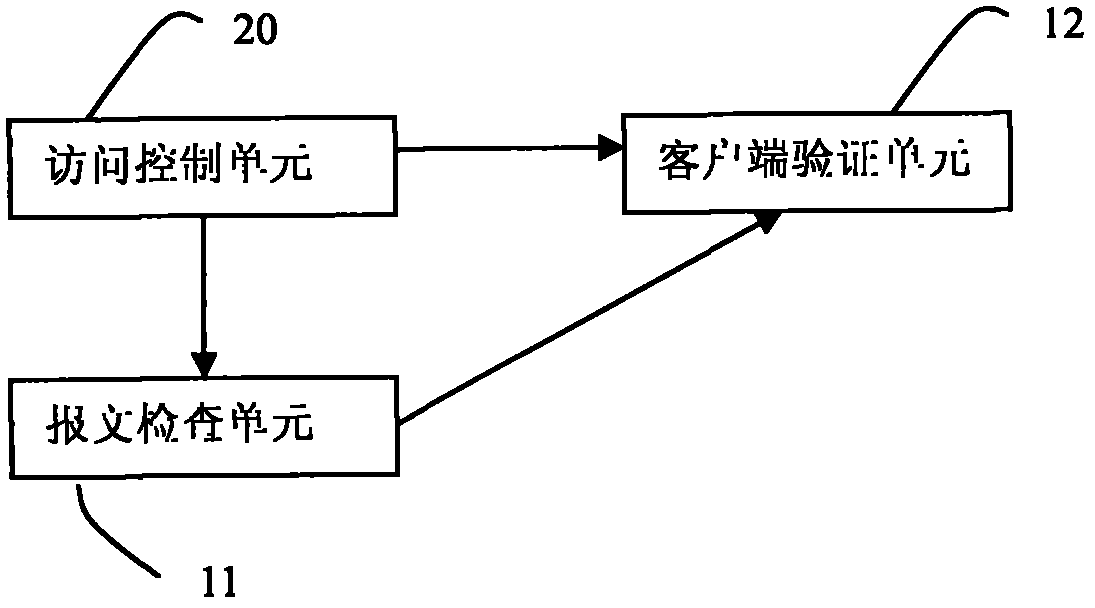
An embodiment of the invention relates to the field of communication technology, and especially to a method and a device for processing TCP connection. The technical scheme provided by the embodiment of the invention adopts an SYN proxy for establishing the TCP connection thereby guaranteeing that the connection to the server is legal connection. The SYN-FLOOD attack can be prevented effectively. Furthermore, when the TCP connection is in each state, whether the received message is legal can be determined according to the legal message which can be received in each preset condition thereby preventing the intrusion that exists properly.
Owner:RUIJIE NETWORKS CO LTD
A method and security agent device for preventing syn flood attack
ActiveCN102291441AStrong randomnessIncrease the difficultyError prevention/detection by using return channelIp addressWhitelist
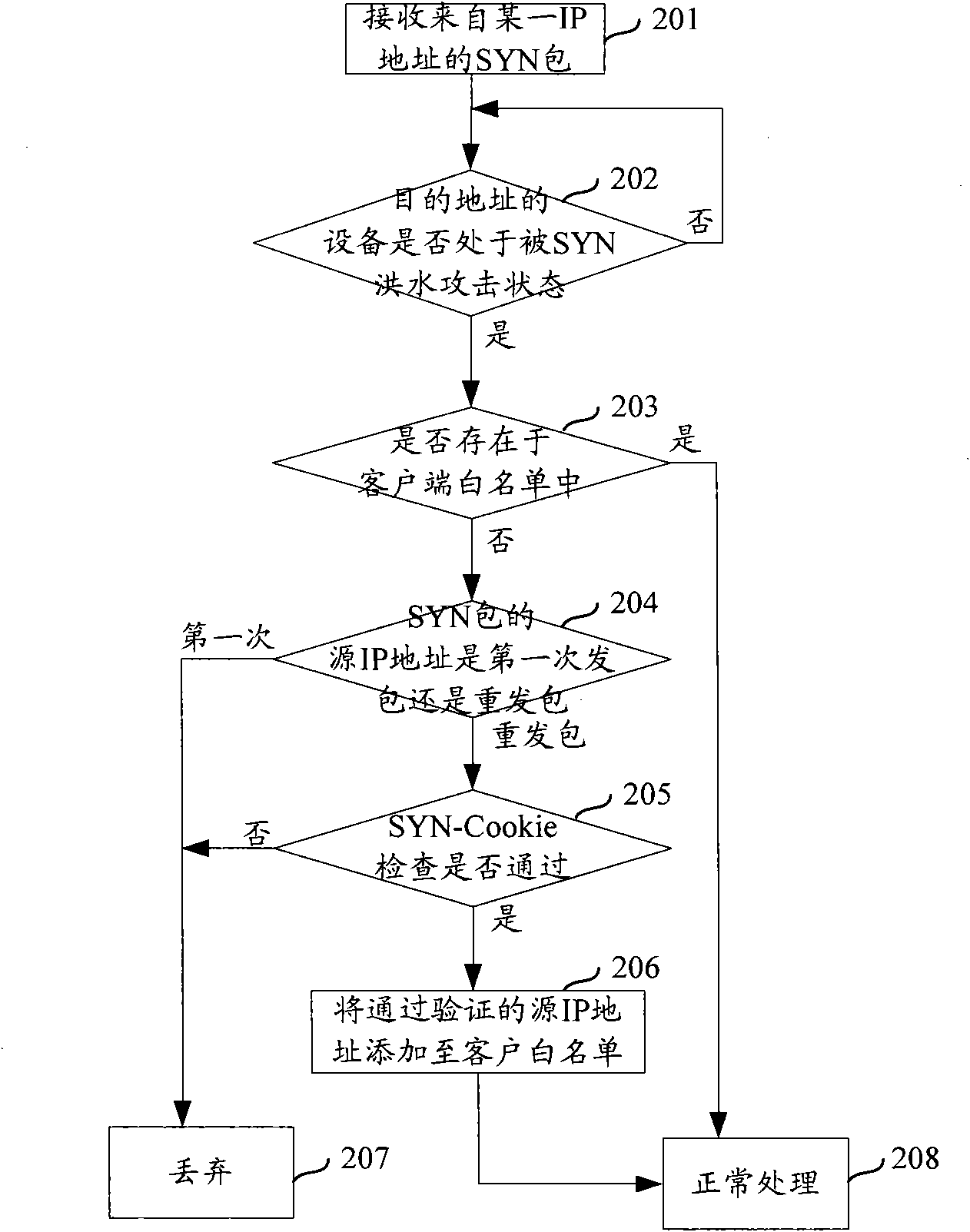
The invention provides a method for protecting against the attack of synchronize (SYN) Flood. The method comprises the following steps of: A, checking whether a client which sends a transmission control protocol (TCP) SYN message is in a white list, if so, allowing the passing of the message and deleting corresponding table entries, otherwise returning to B; and B, sending a verification request to the client and checking whether the client is legal according to a verification response returned by the client, if so, adding the corresponding table entries in the list, otherwise, abandoning a response message. By the method, a table entry deletion mechanism is ingeniously improved, and the problem that an attacker forges an internet protocol (IP) address which can be possibly coincided with the IP address of the client is solved. The method can be matched with signature of the IP address and the design of content of table entries of a source port, and fully utilizes the characteristic that a TCP connection source port has high randomness so as to make undercover passing of the attacker by using a legal IP address in the white list impossible.
Owner:杭州迪普信息技术有限公司
Attack defense method
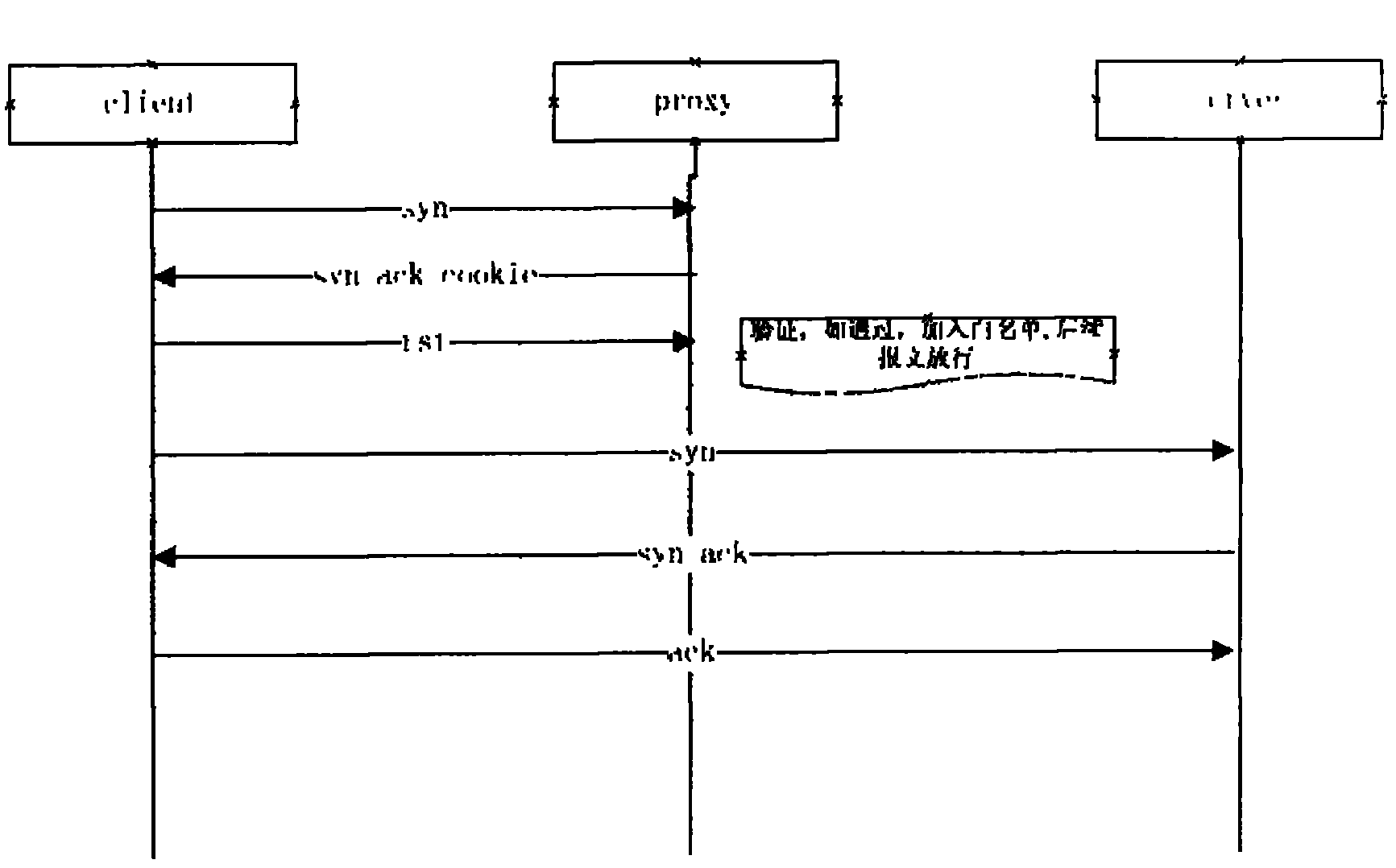
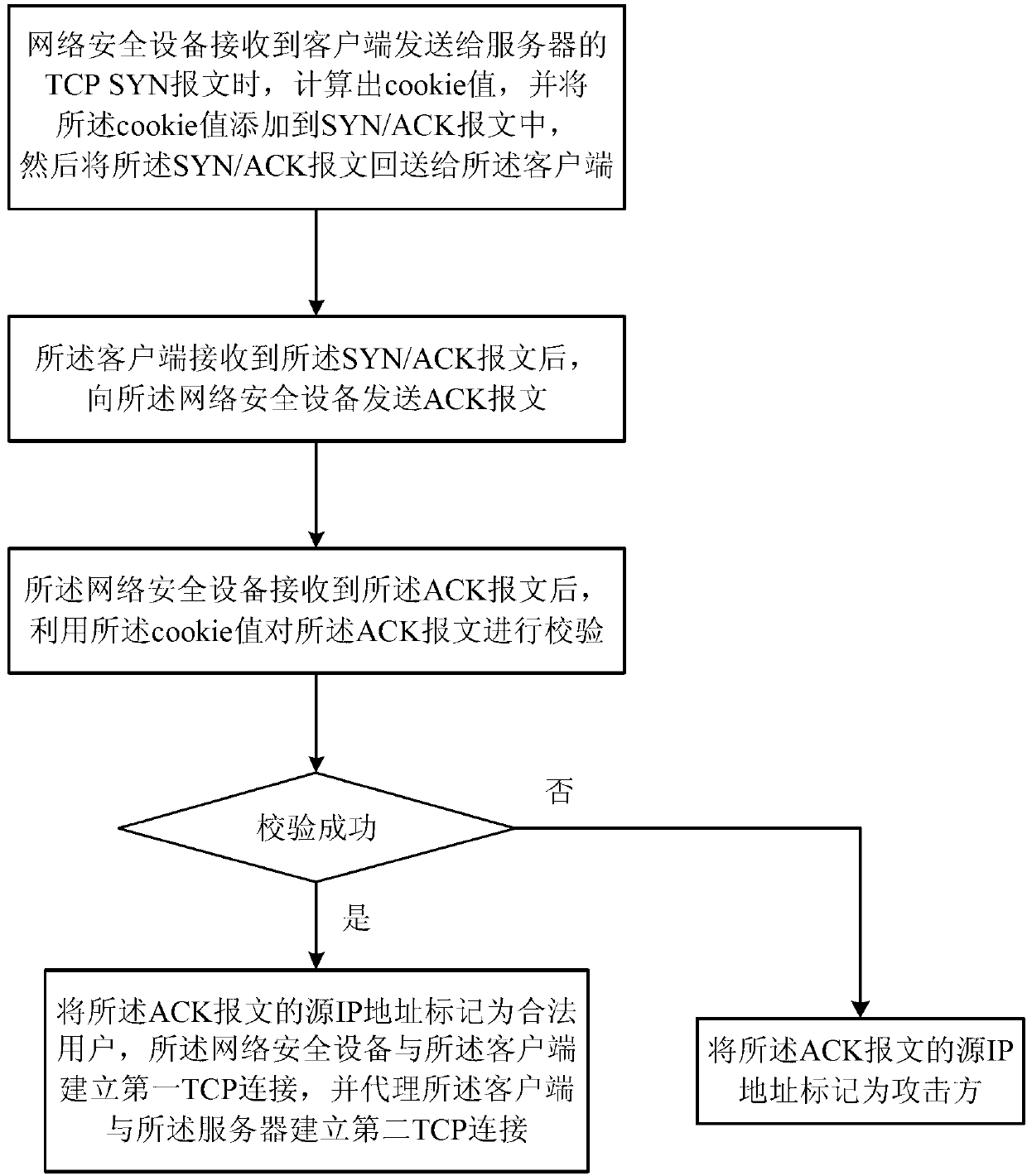
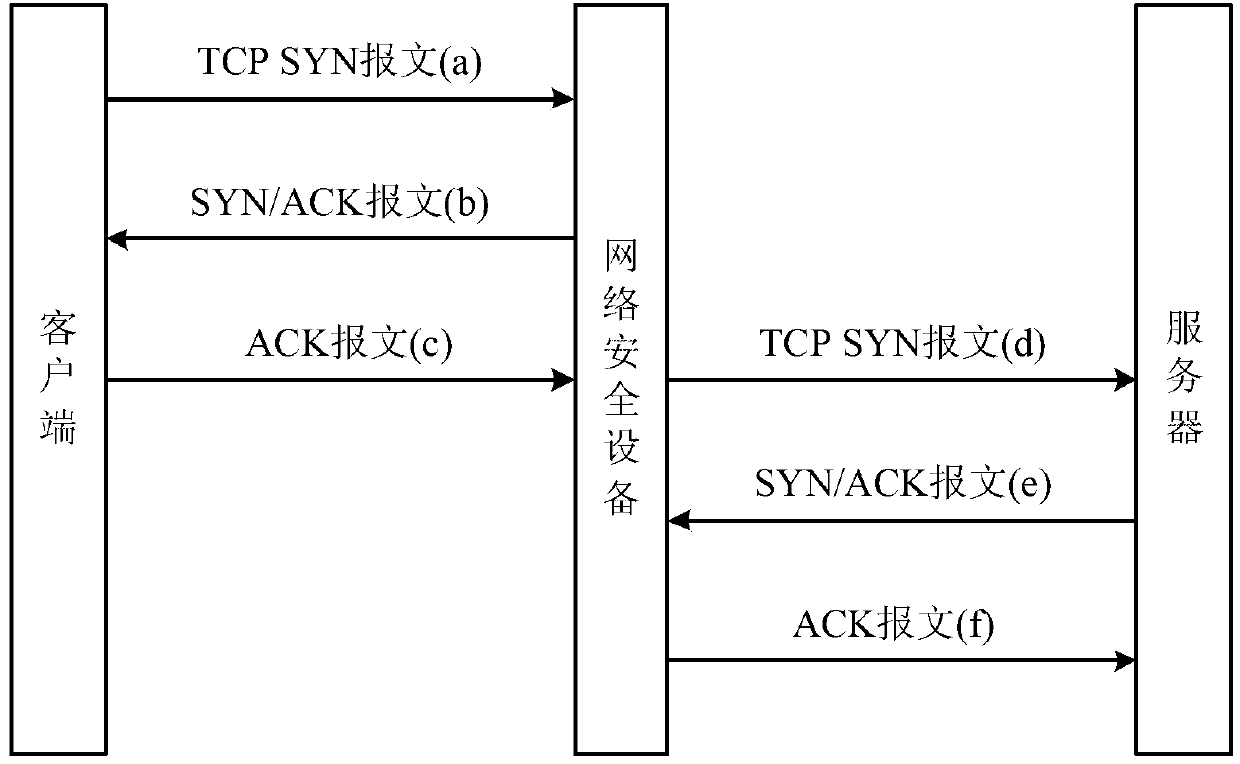
The invention discloses an attack defense method, and relates to the technical field of network security. When a network security device receives TCP SYN messages sent by a client side to a server, an agency function is started, TCP connecting requests are verified based on a cookie verification mechanism, a source IP address is marked to be a valid user if the successful verification is achieved, a first TCP connection is built between a network security device and the client side, a second TCP connection is built between an agency client side and the server, or the source IP address is marked to be an attack party. The network security device conducts judgment on the TCP connecting requests of the client side based on the cookie verification mechanism, and SYN Flood attacks can be effectively identified. After the verification is finished, interaction with all client sides are finished by the network security device in an agency mode, the server cannot be influenced, and therefore the server can be prevented from undergoing the SYN Flood attacks.
Owner:天津汉柏汉安信息技术有限公司
Method and apparatus for preventing reject access aggression
ActiveCN101378395AImprove reliabilityLow costData switching networksCommunications securityIp address
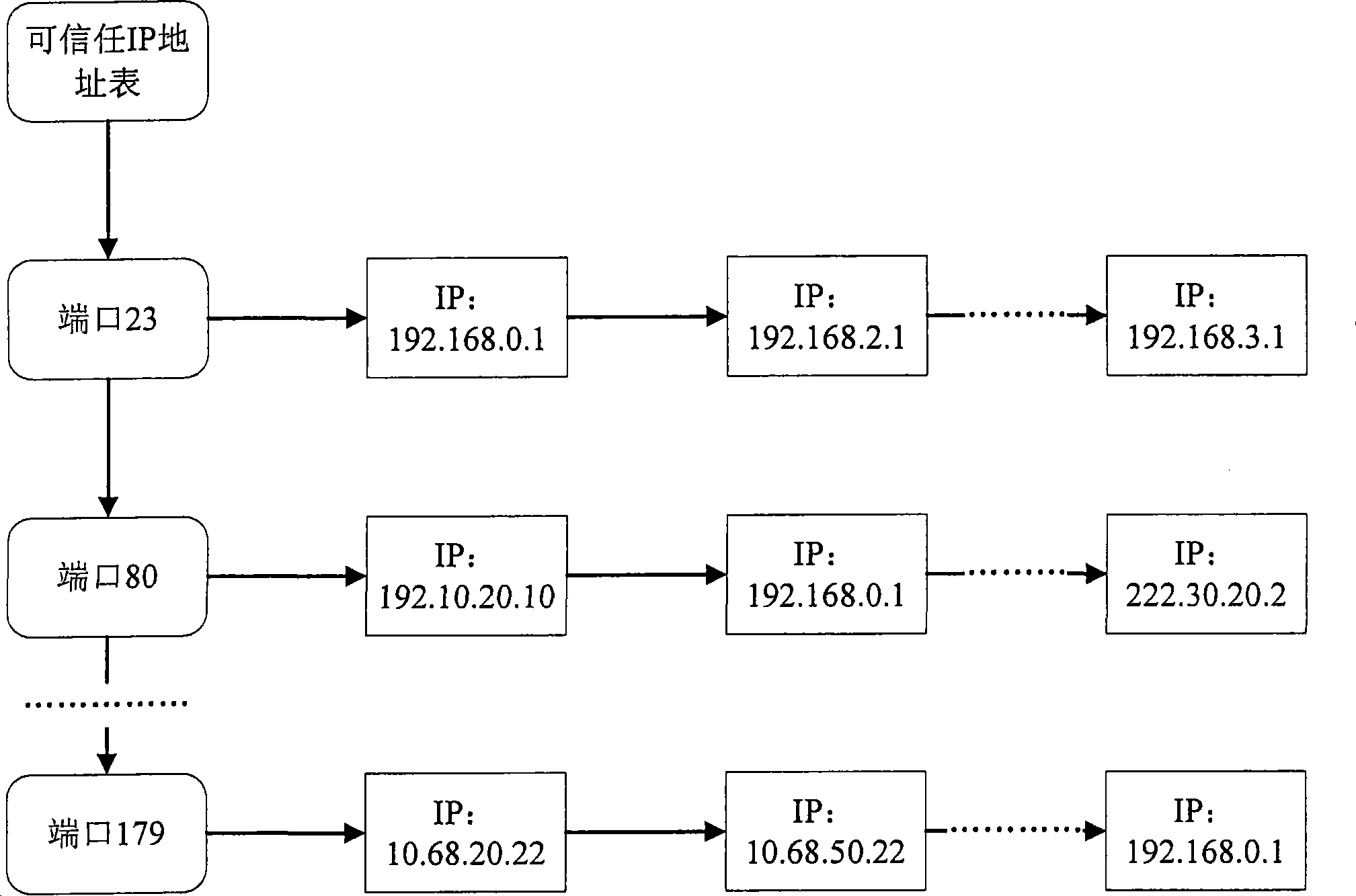
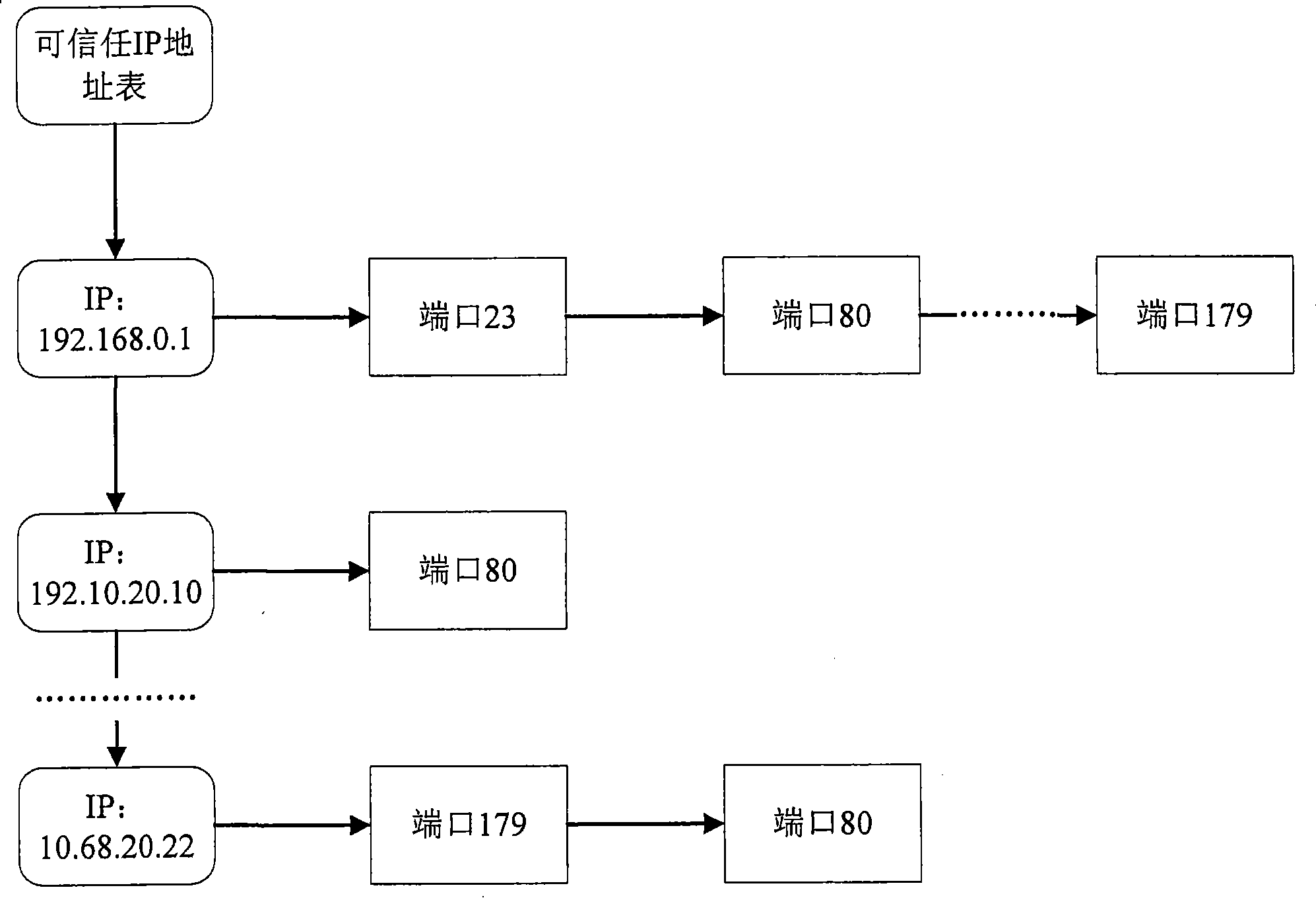
The invention relates to the communication security field and provides a method and a device for preventing refusal access attack, aiming at solving the shortcomings of high cost and low accuracy of preventing SYN flood attack in the prior art. The method comprises the following steps: a believable IP address list is set in network equipment, which stores the believable IP address and a TCP port number; when a user initiates a connection request, the network equipment judges whether the target TCP port and the source IP address of the connection request are matched with the corresponding record in the believable IP address list, if so, the connection is allowed to be established, otherwise, the connection is refused to be established. The invention has the advantages of high reliability, low cost, and not being carried out on firewall, and the network equipment using the method has higher speed of processing connection compared with the method for preventing refusal access attack in the prior art.
Owner:RUIJIE NETWORKS CO LTD
System and method for enhancing a server's ability to withstand a "SYN flood" denial of service attack
InactiveUS20050027872A1Improve robustnessMinimize involvementHardware monitoringMultiple digital computer combinationsEnhanced serviceSYN flood
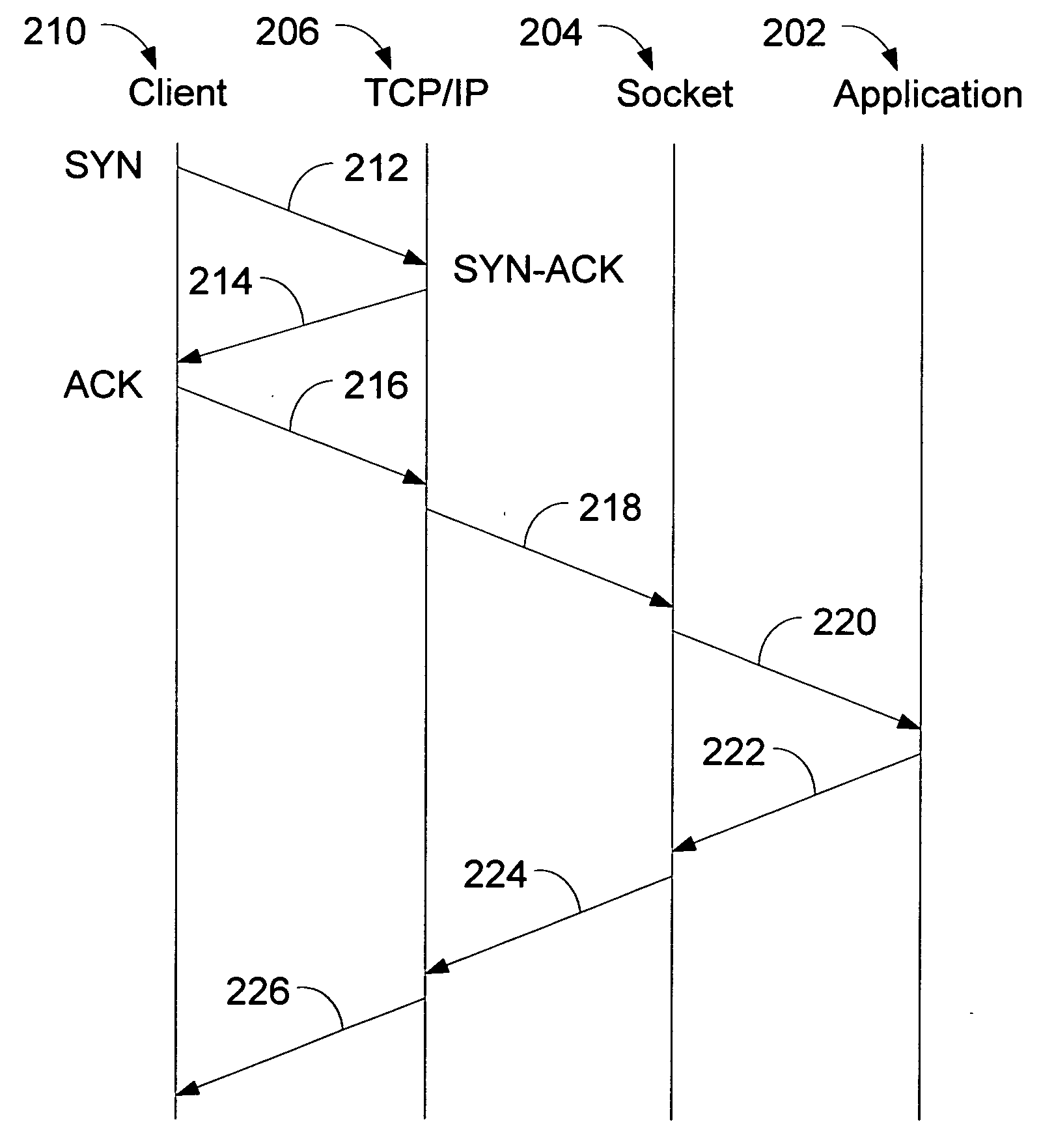
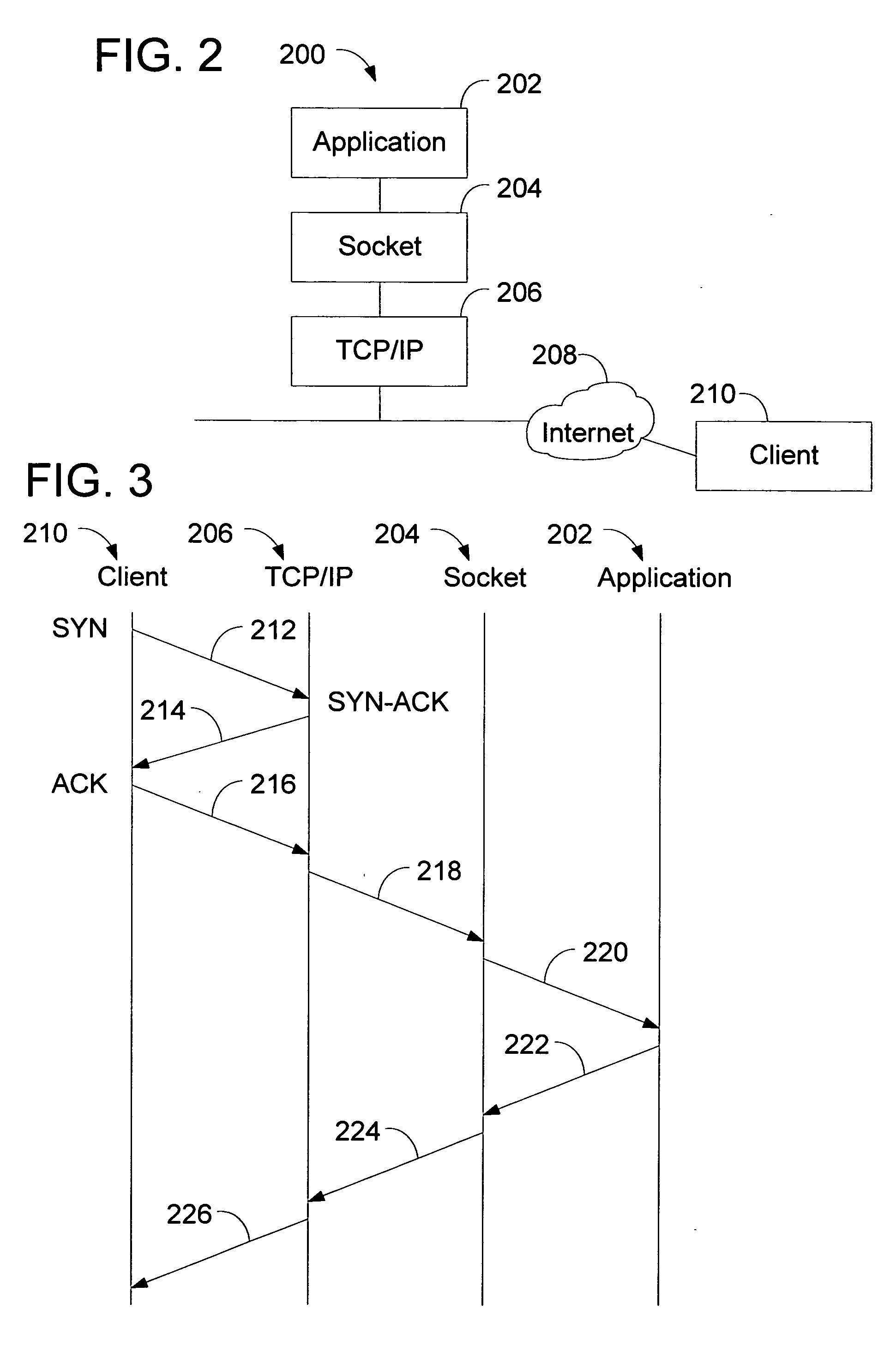
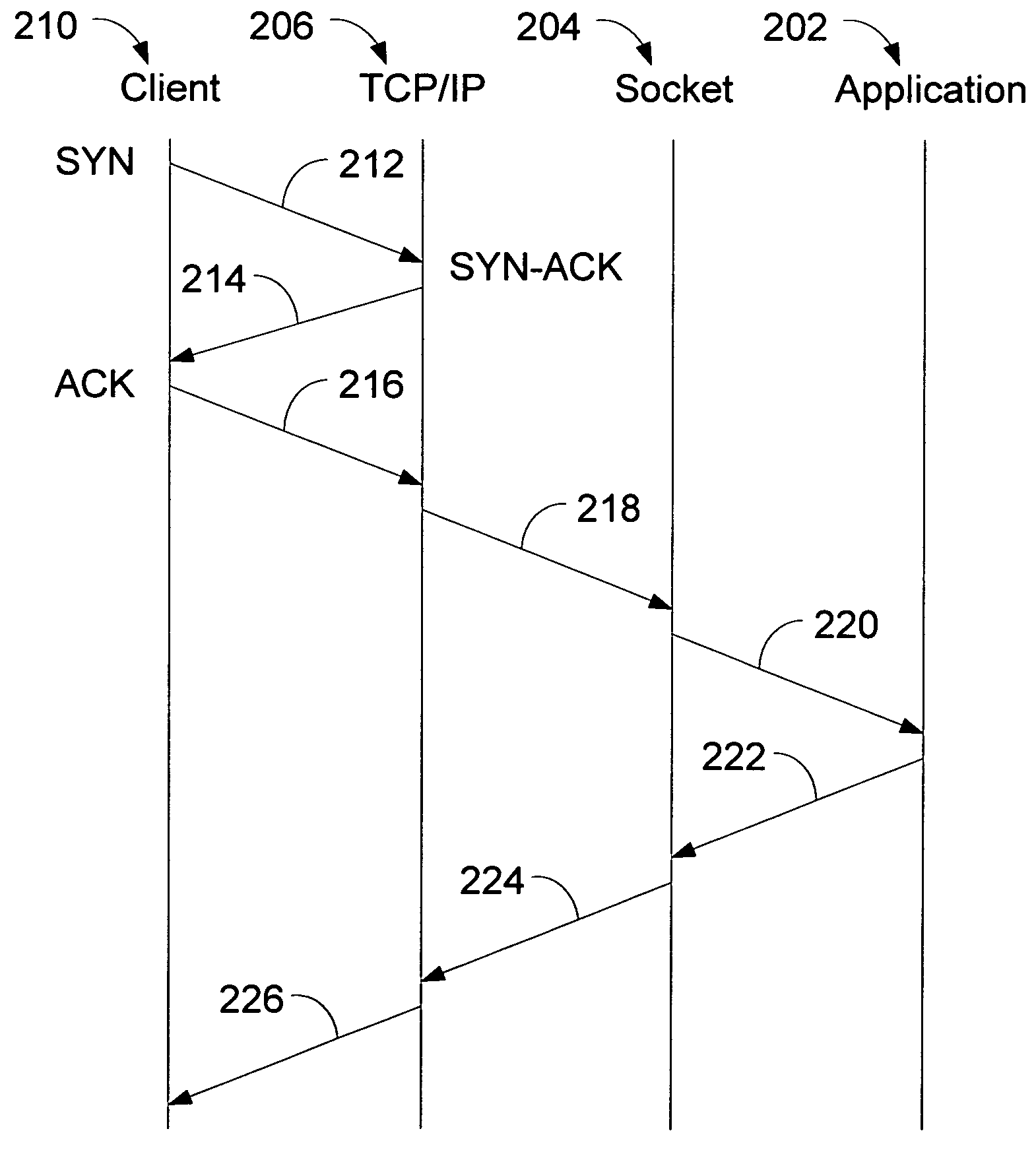
A method of enhancing a server's ability to withstand a SYN flood type denial of service attack is presented. Modifications to the TCP / IP layer of a server reduce the amount of system resources that are allocated, and the amount of CPU overhead that is required to process a connection request until the TCP / IP three-way handshake is completed to verify the presence of a legitimate client. Specifically, the TCP / IP layer allocates a small TCP control block (TCB) of a size sufficient only to service the connect request upon receipt of the SYN packet. A full TCB is not allocated until the connection is completed. Further, the TCP / IP layer delays notification to the socket layer of the receipt of the SYN packet until after the connection is completed. Finally, the route information of the connection is not cached until after the connection is completed.
Owner:MICROSOFT TECH LICENSING LLC
SYN flood defence method and device
ActiveCN101599957AImprove attack defense capabilitiesImprove defenseError prevention/detection by using return channelIp addressOperating system
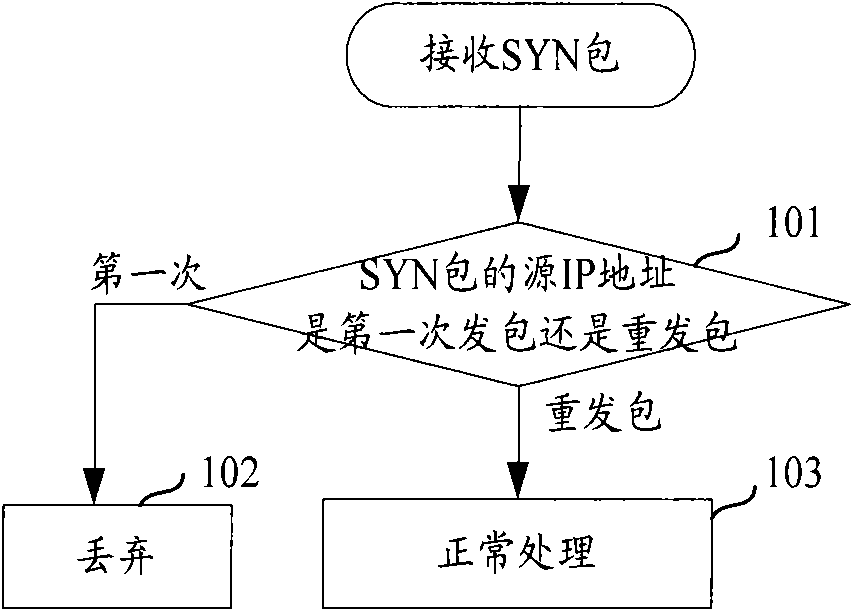
The invention discloses an SYN flood defence method and a device thereof. The method comprises: after a destination address device is determined in the state of SYN flood, the source IP address of a received SYN package is judged to be in contract issuing the first time or not within the first preset time period; if the source IP address is in contract issuing the first time, the SYN package is discarded, but if not, normal follow-up treatment continues to carry out. The invention can effectively defence SYN flood. Experiments prove that the invention can greatly improve SYN flood defence performance; if practically used under operator client environment, the invention has favourable effect in defencing SYN flood.
Owner:NEUSOFT CORP
System and method for enhancing a server's ability to withstand a "SYN flood" denial of service attack
InactiveUS7269654B2Improve robustnessMinimize involvementHardware monitoringMultiple digital computer combinationsEnhanced serviceIp layer
Owner:MICROSOFT TECH LICENSING LLC
Bloom Filter and open-source kernel-based method for defensing SYN Flood attack
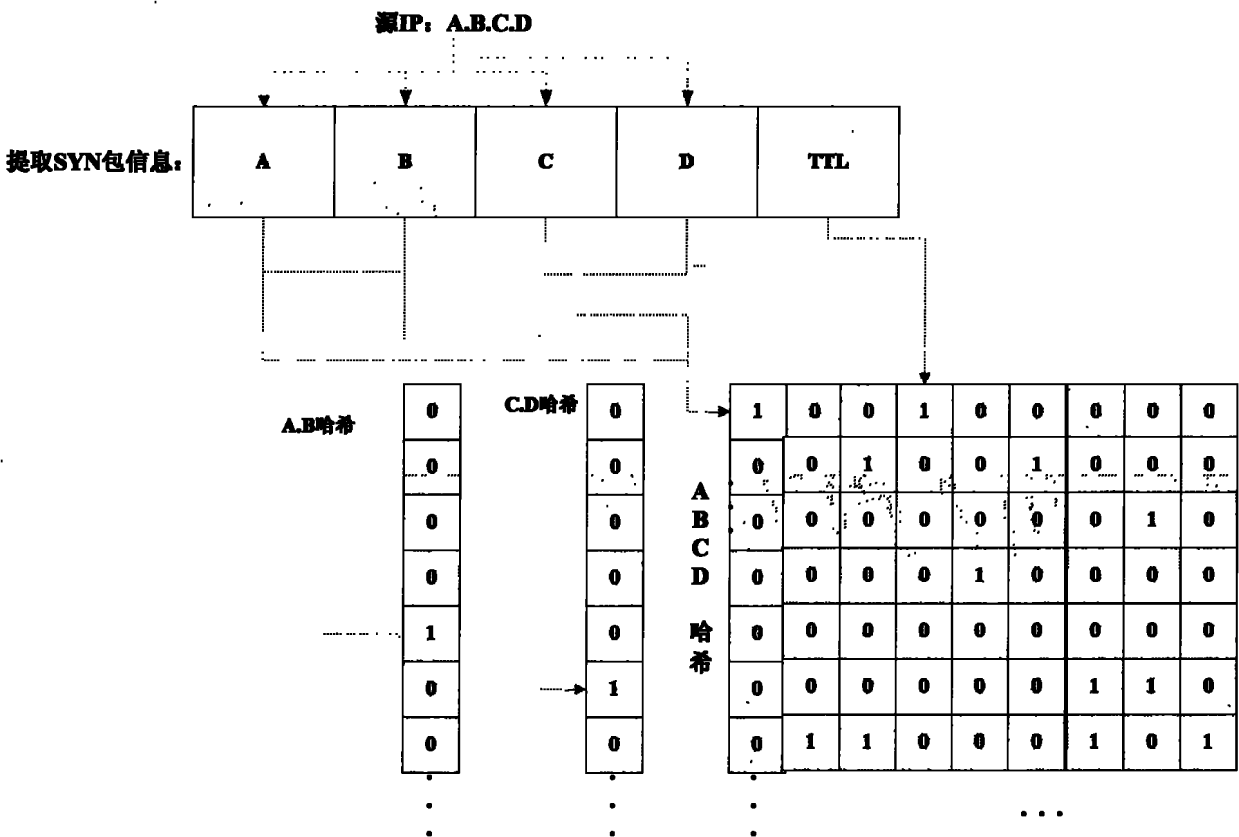
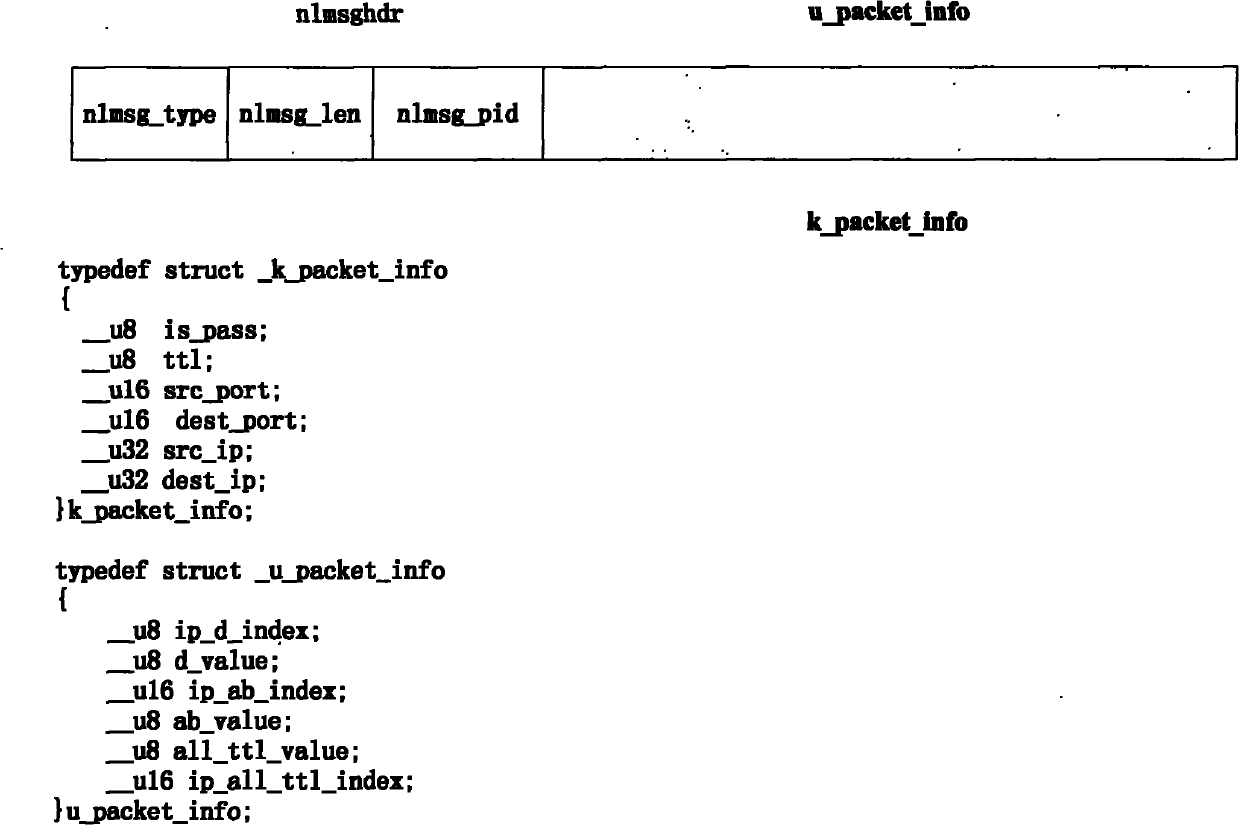
InactiveCN101958883AImprove efficiencyReduce false alarm rateTransmissionHash functionArray data structure
The invention discloses a Bloom Filter and open-source kernel-based method for defensing an SYN Flood attack, which comprises the following steps of: 1, judging whether being subjected to the SYN-Flood attack; 2, establishing a Bloom Filter structure; 3, updating a credible IP address and TTL data of a kernel layer, and starting to filter a data packet of the kernel layer; 4, filtering a TCP SYN data packet according to the credible IP address and the TTL record by using the kernel layer; and 5, stopping filtering the data packet of the kernel layer. The method has the advantages that: 1, by improving an original structure of a Bloom Filter that a single bit array corresponds to a plurality of hash functions, a structure that a hash function corresponds to a bit array is adopted, so that the false alarm rate is effectively reduced, and the efficiency of storing and searching the data packet on the premise of ensuring the accuracy rate is improved; therefore, the method can effectively defense the SYN Flood attack; and 2, the problems that the kernel layer has high efficiency but is not suitable for processing complicated programs and a user layer is not compact with a kernel protocol stack are solved by the cooperative processing of combining the kernel layer and the user layer of an open-source operating system, so that the efficiency of processing the data packet is improved.
Owner:XIANGTAN UNIV
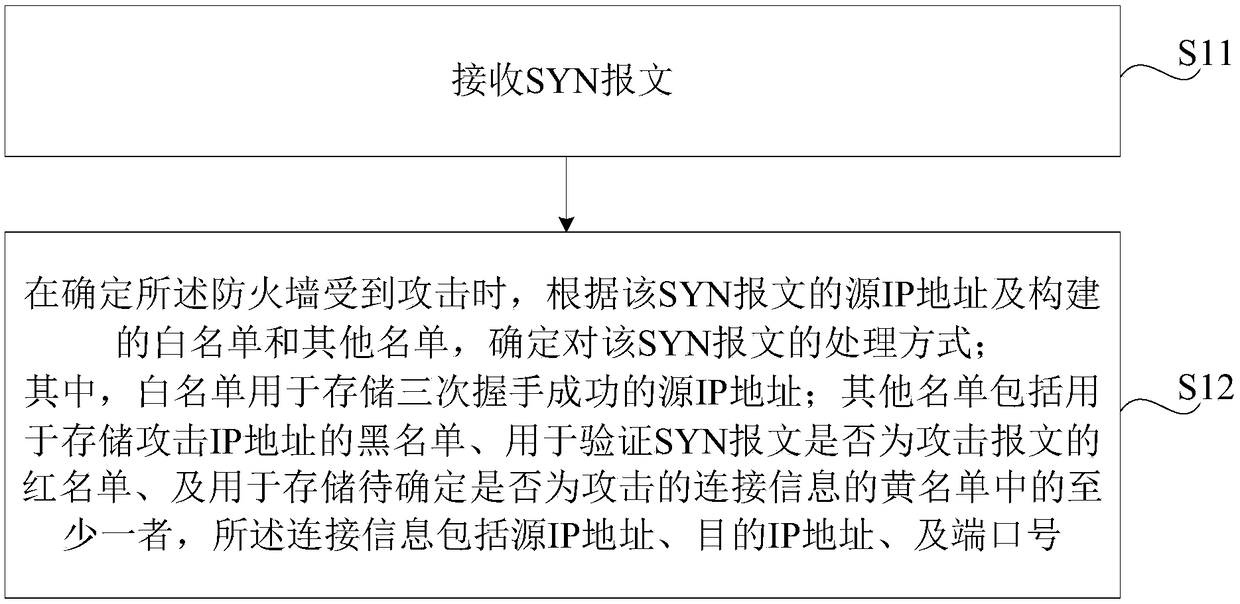
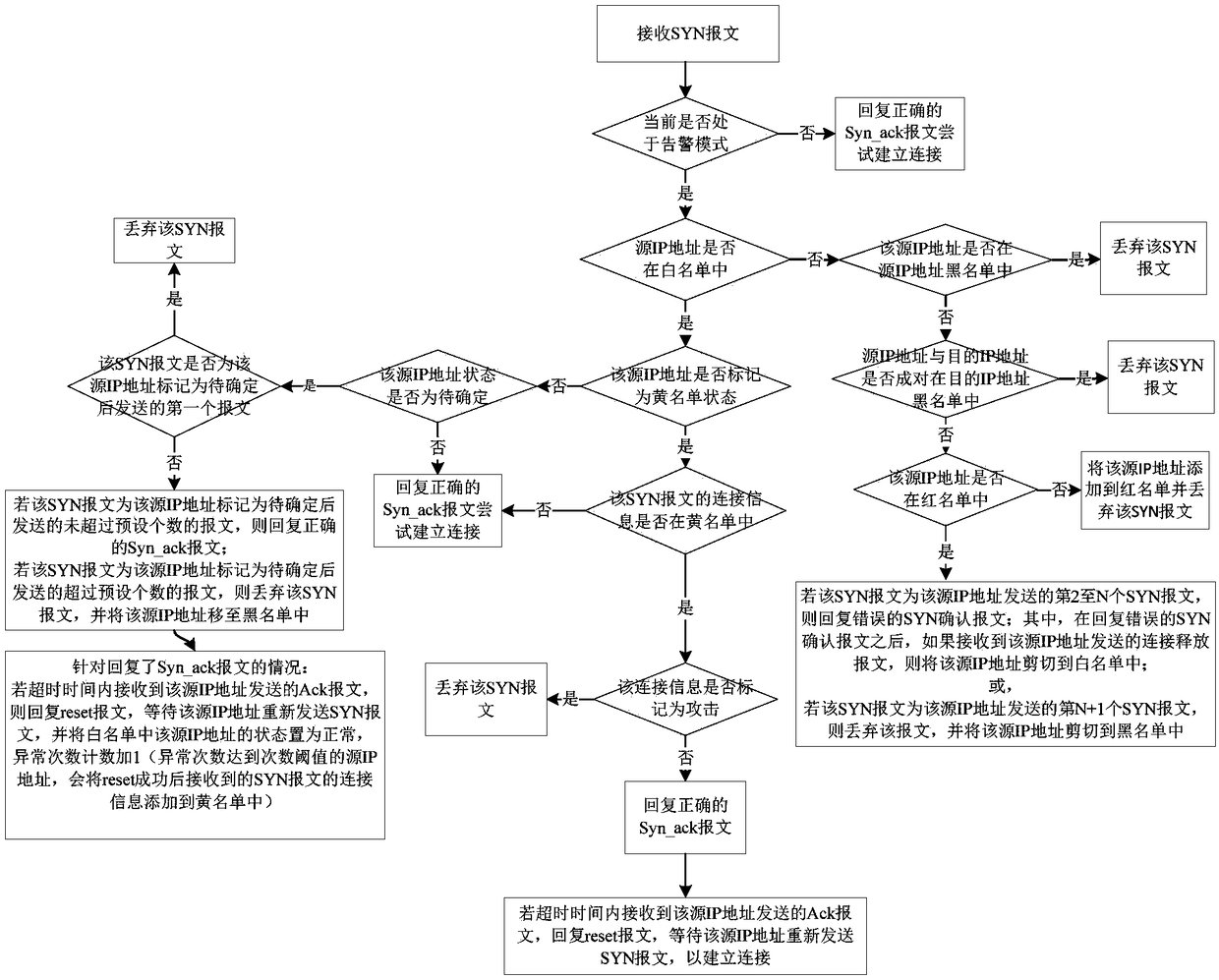
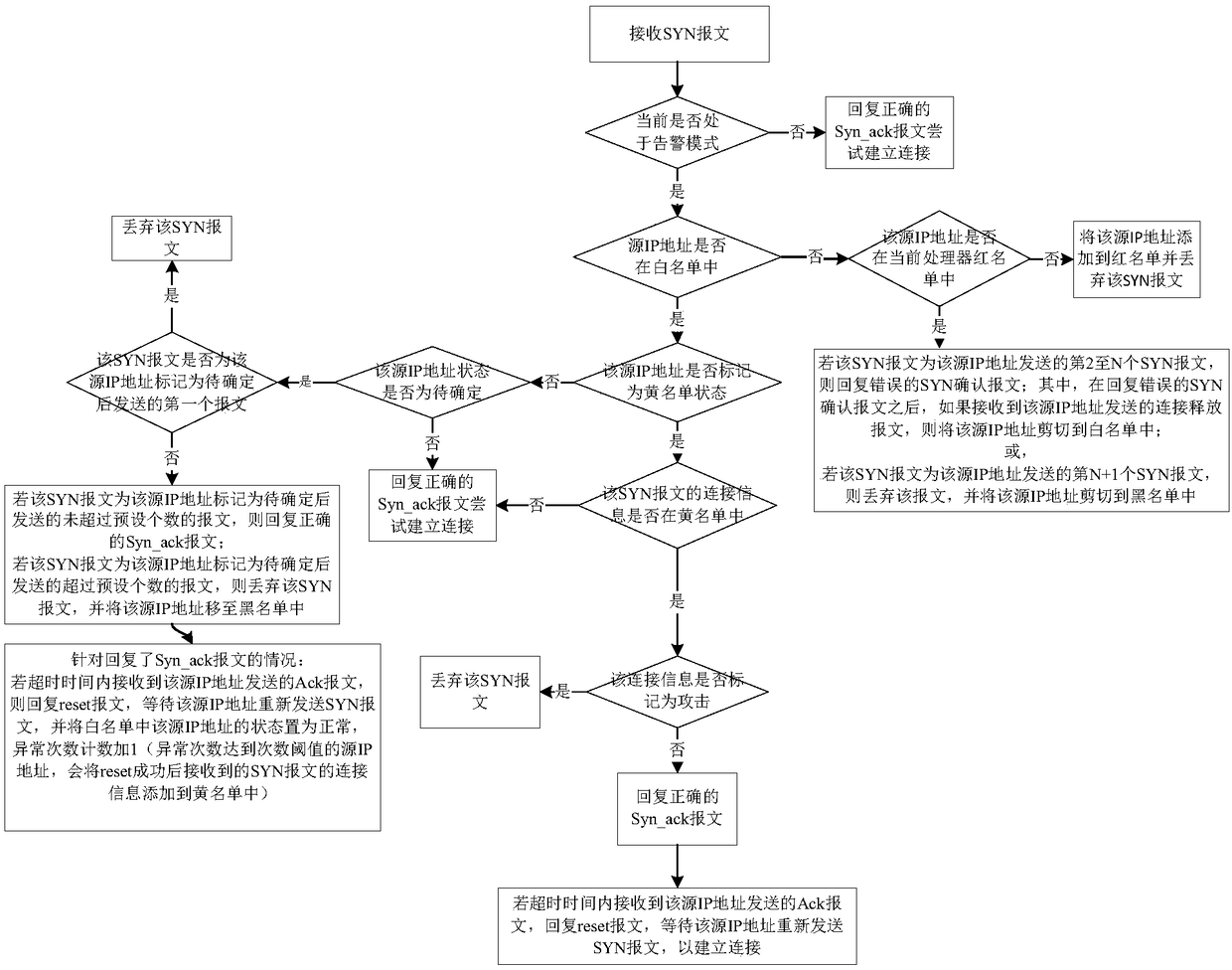
Anti-attack SYN message processing method, device, firewall and storage medium
The invention relates to an anti-attack SYN message processing method and device, firewall and a storage medium, and the performance of resisting the SYN Flood attack by the firewall is improved. Themethod comprises the following steps: receiving a SYN message; determining a processing way on the SYN message according to a source IP address of the SYN message and the constructed white list and other lists when determining the firewall is attacked, wherein the white list is used for storing source IP address of three-time successful handshaking, and the other lists comprises at least one of ablack list for storing the attack IP address, a red list for verifying whether the SYN message is the attack message, and a yellow list for storing the connection information to be determined whetheris the attack; and the connection information comprises the source IP address, the destination IP address and the port number.
Owner:NEUSOFT CORP
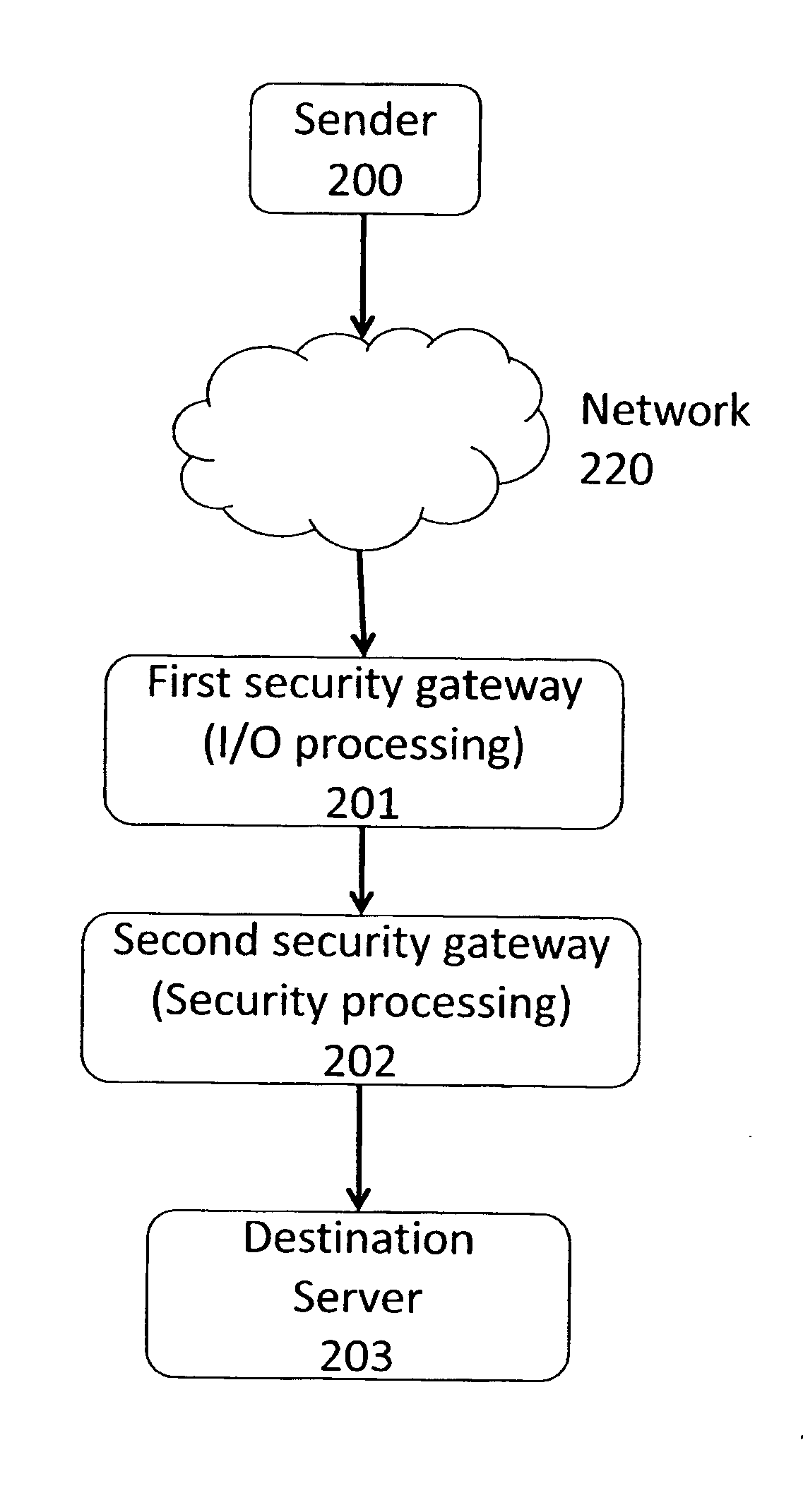
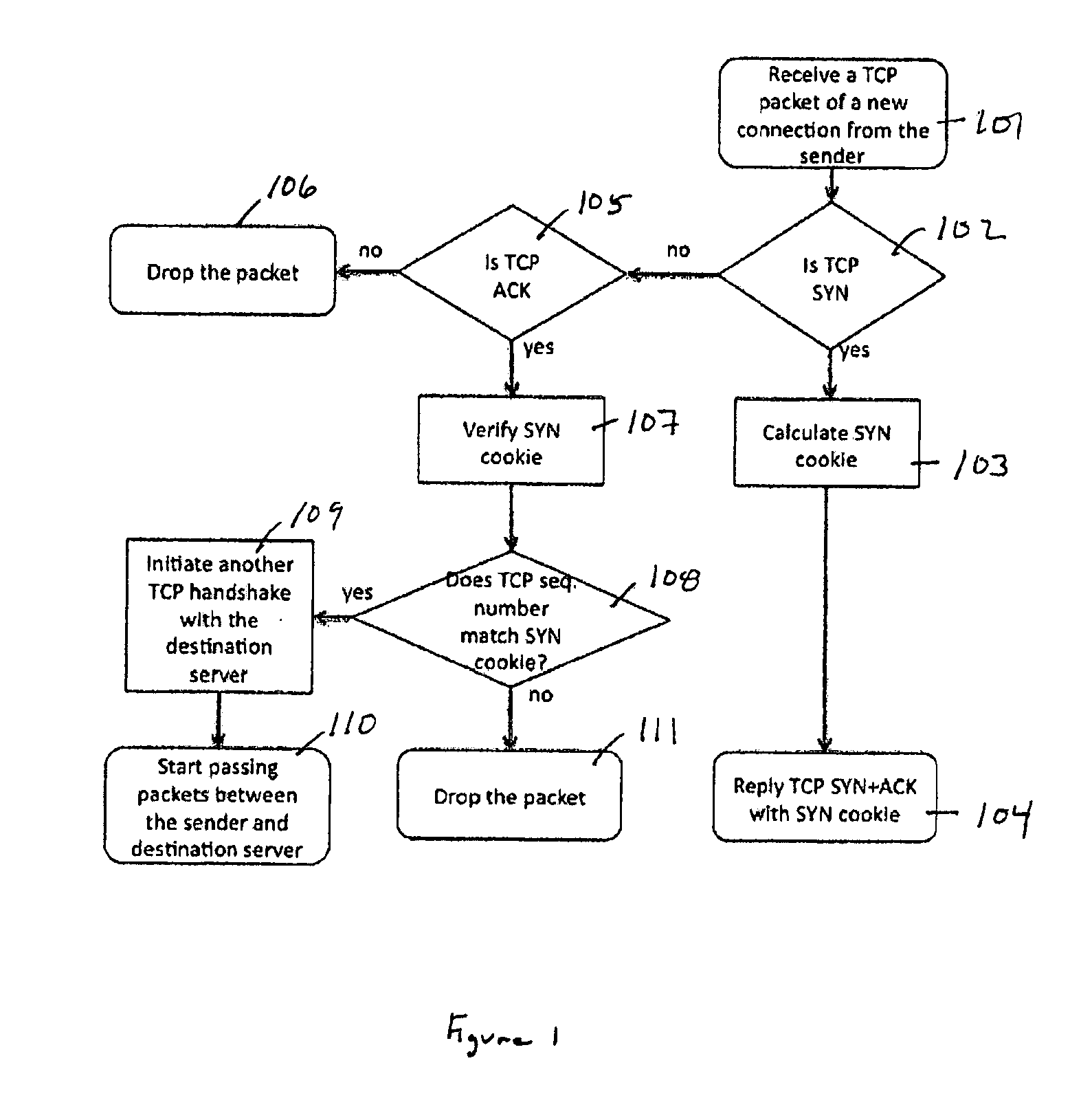
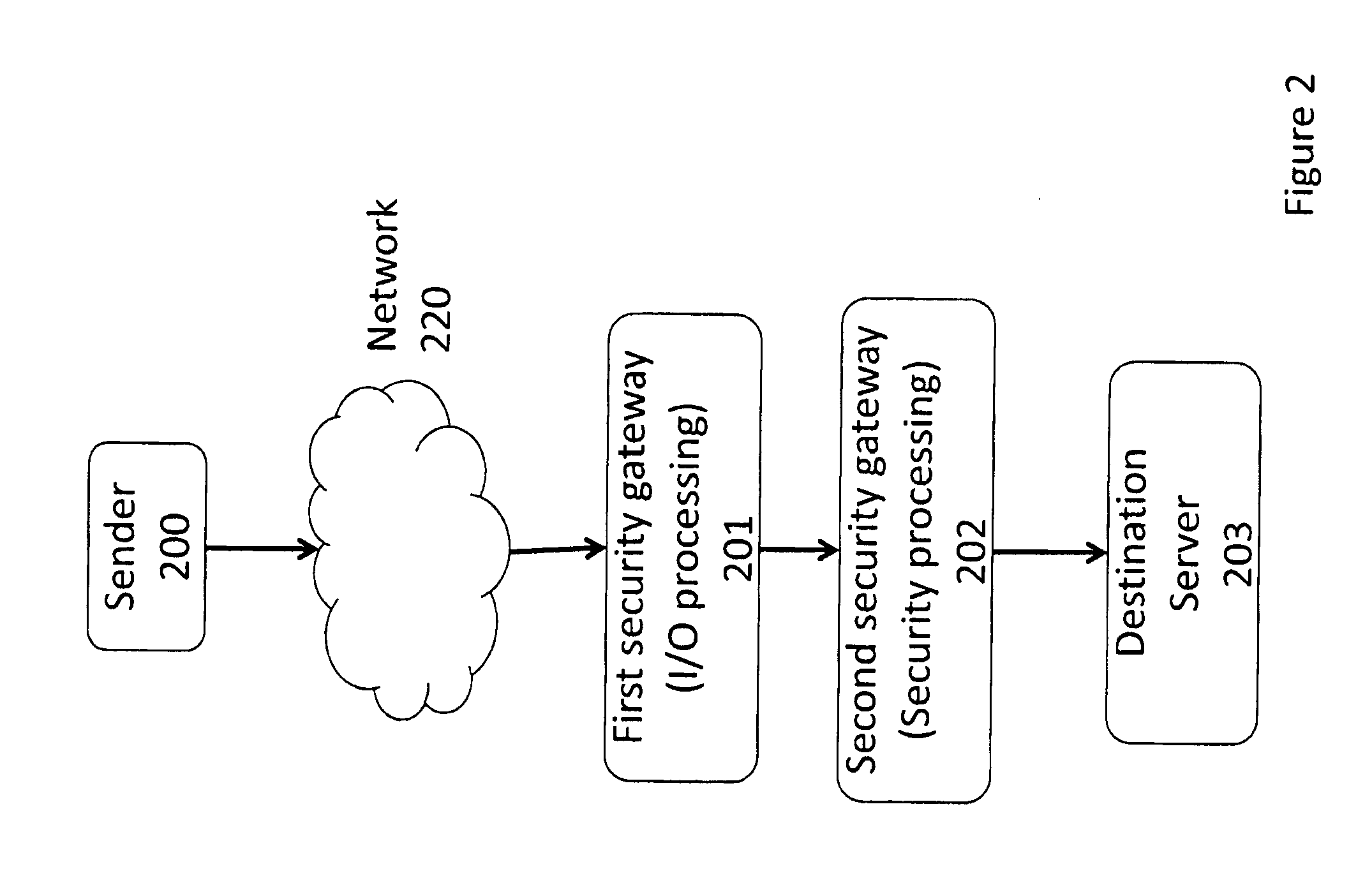
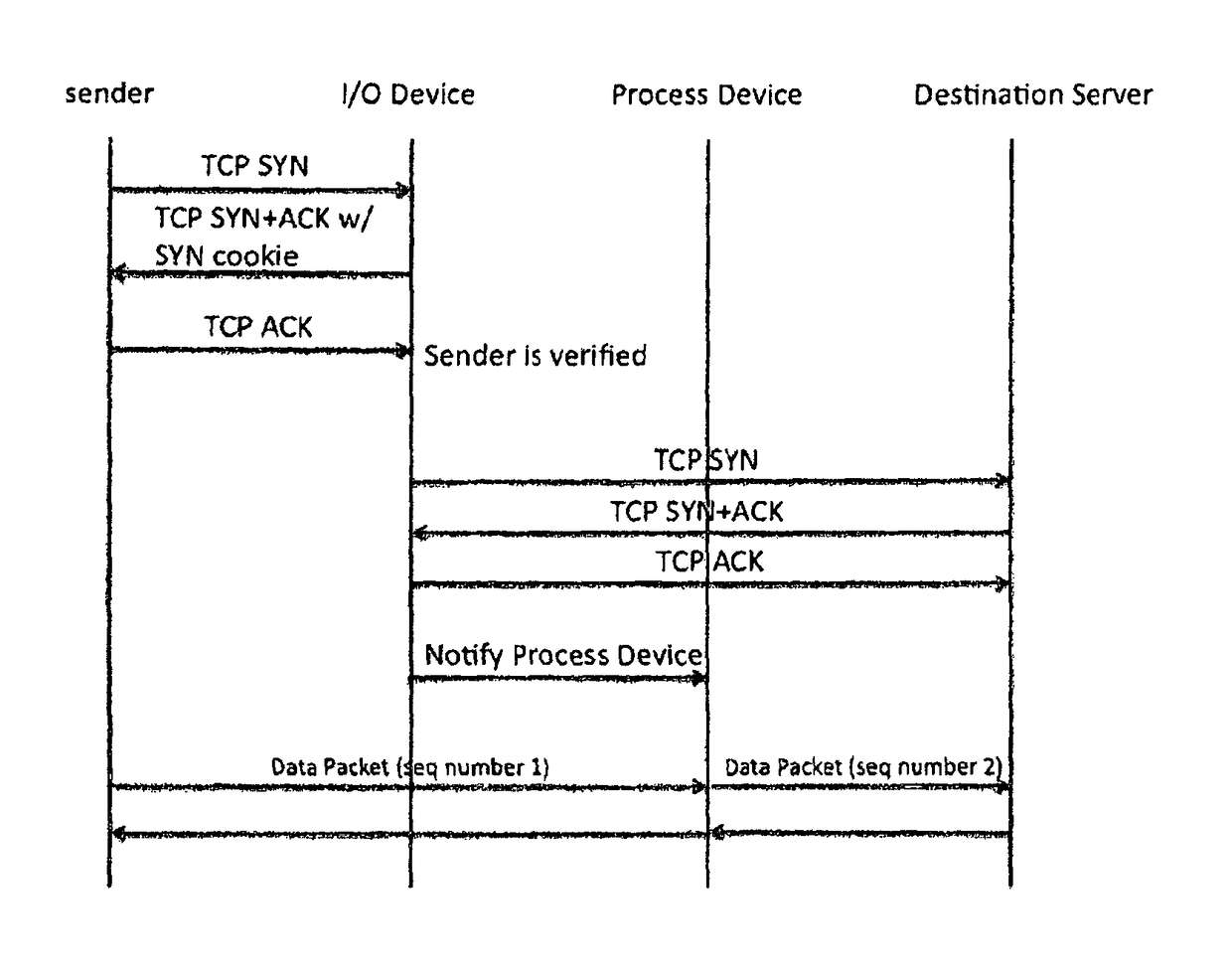
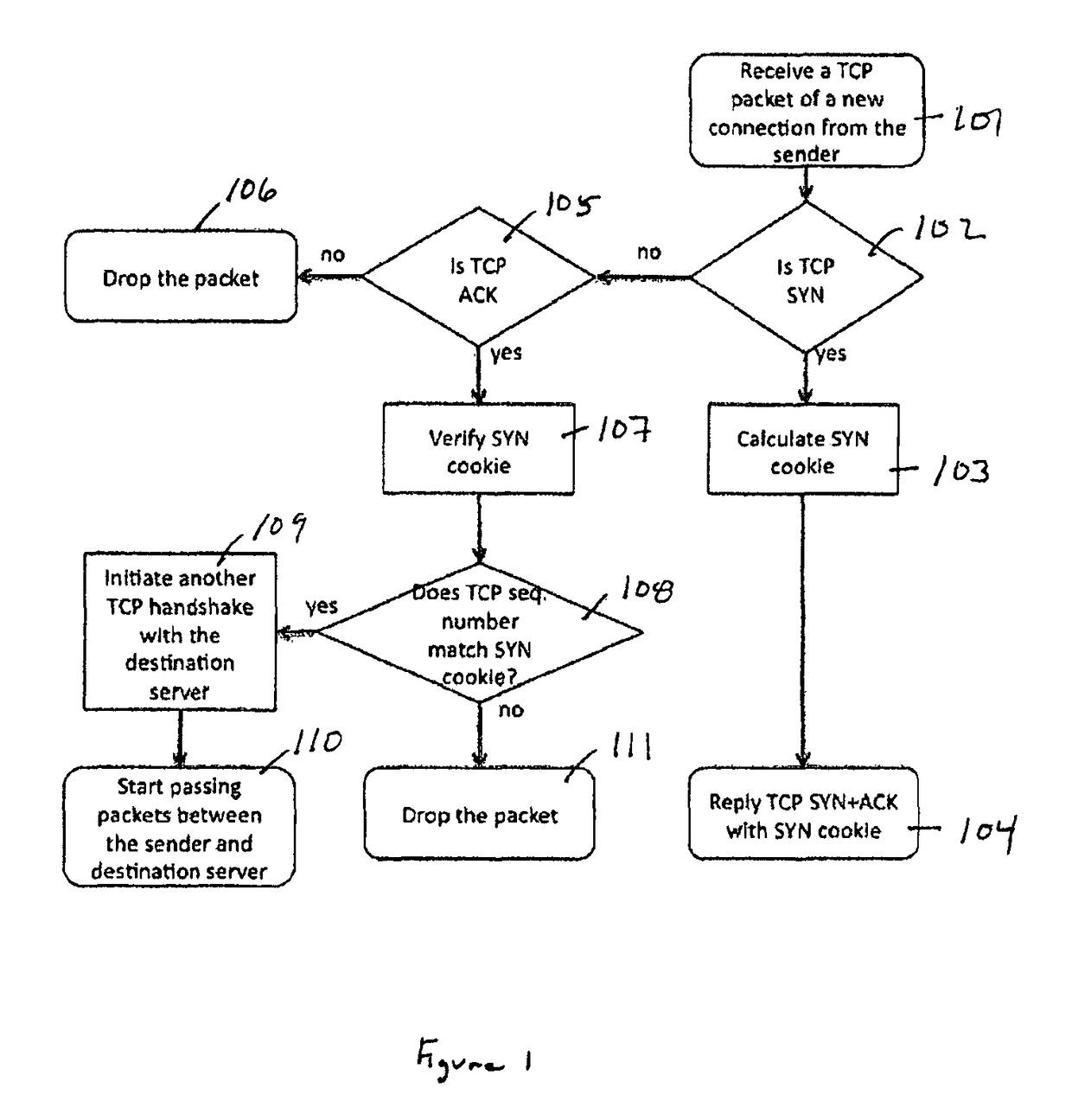
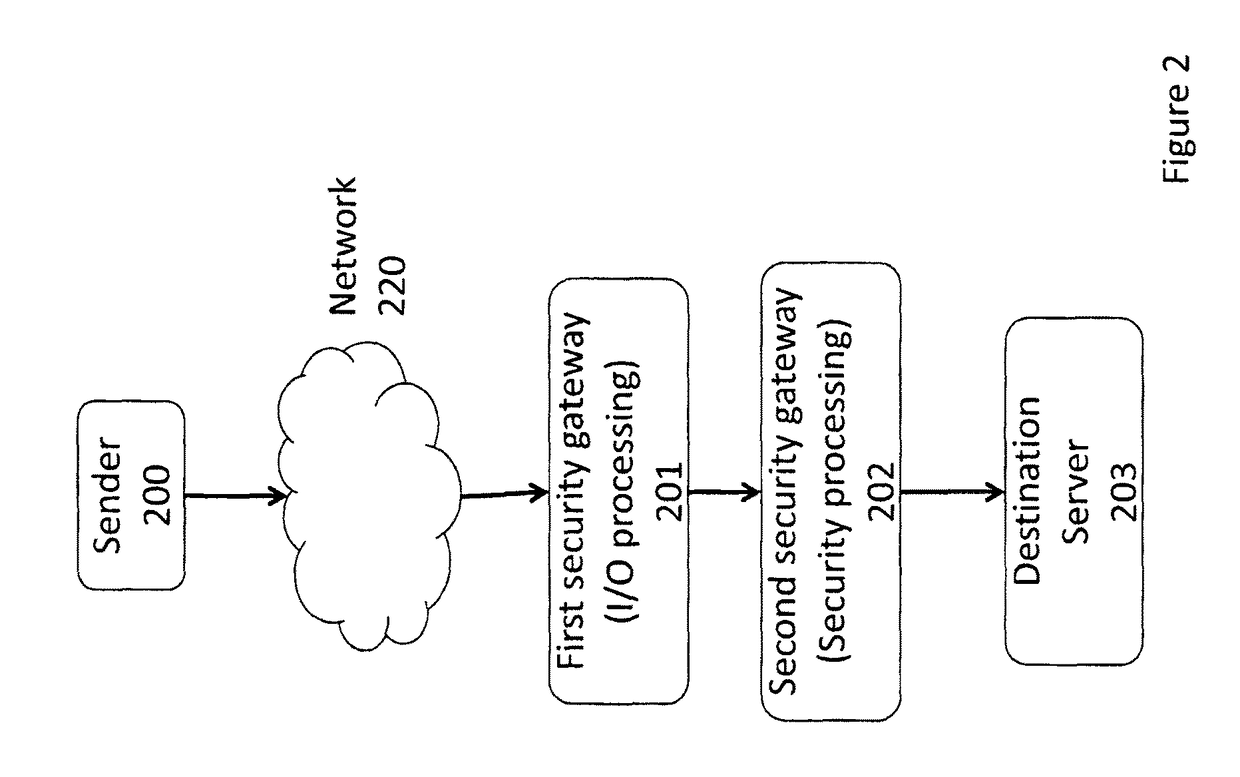
Distributed TCP SYN flood protection
A method and apparatus is disclosed herein for TCP SYN flood protection. In one embodiment, a TCP SYN flood protection arrangement comprises a first device operable to process packet input and output functions, including performing sender verification with respect to a connection initiation from a sender for a first TCP connection between the sender and a destination server and a second device, separate from the first device, to perform one or more security processing operations on packets of the first TCP connection from the sender after the first device verifies the sender is legitimate.
Owner:VARMOR NETWORKS
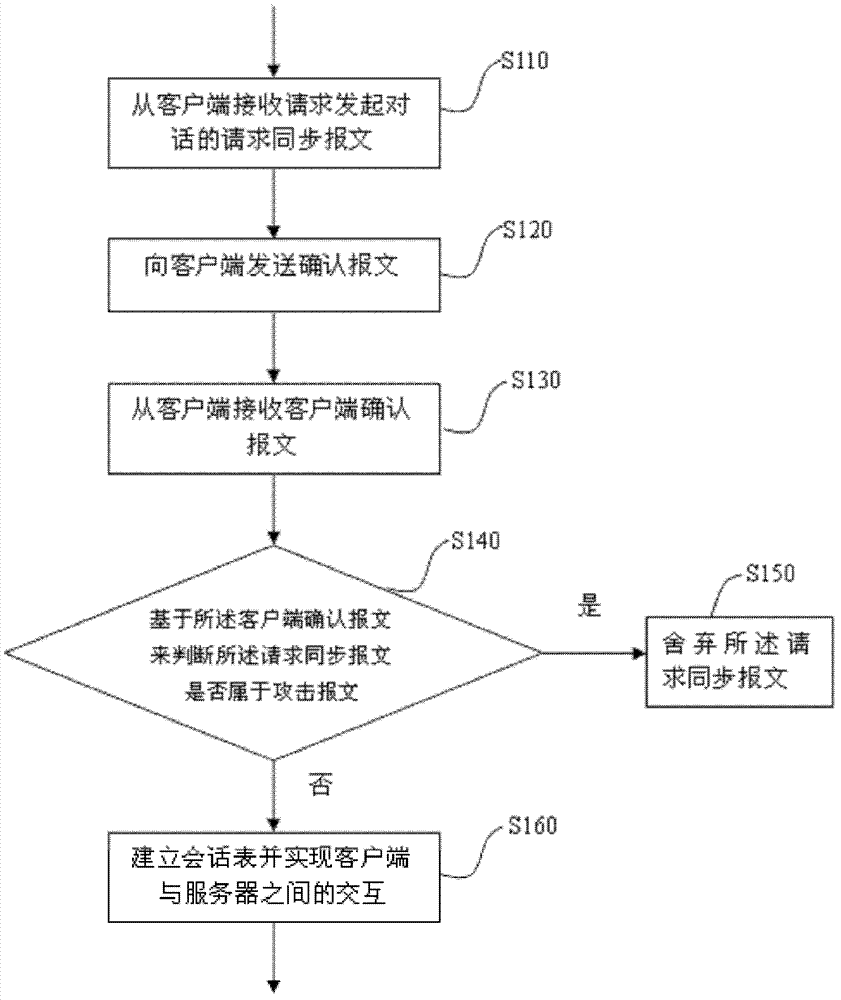
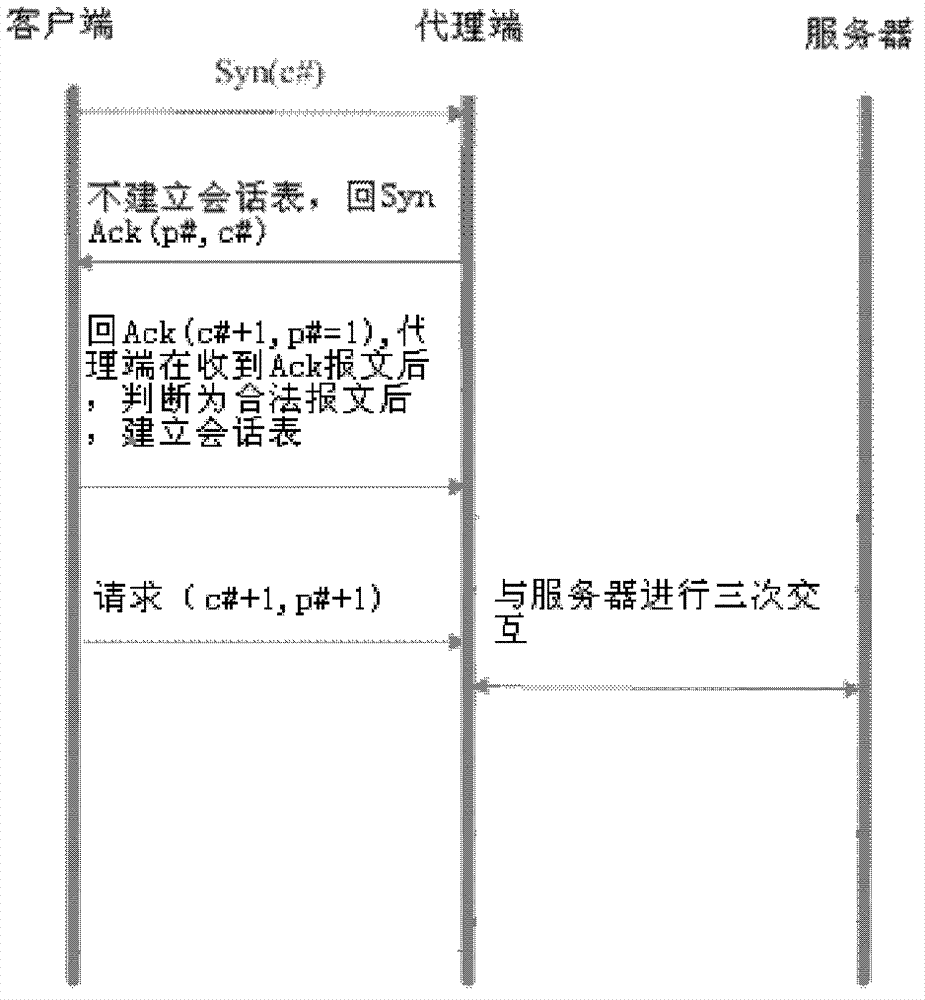
Method and device for preventing attack under transmission control protocol (TCP)
The invention discloses a method and device for preventing an attack under a transmission control protocol (TCP). The method comprises the following steps: receiving a request synchronization message which is sent by a client and requests to establish a session with a sever; sending a first confirmation message to the client; receiving a second confirmation message sent by the client; judging whether the request synchronization message belongs to an attack message based on the second confirmation message; if the request synchronization message is judged to belong to the attack message, abandoning the request synchronization message; and if the request synchronization message is judged to belong to a legal message, establishing a session table between the client and the server. By using the method and device disclosed by the embodiment of the invention, under the condition of a large number of SYN Flood attacks, the attacks can be effectively prevented, and normal connection between a user and the server can be guaranteed; and therefore, the service experience is enhanced.
Owner:XFUSION DIGITAL TECH CO LTD
Firewall attack defense method
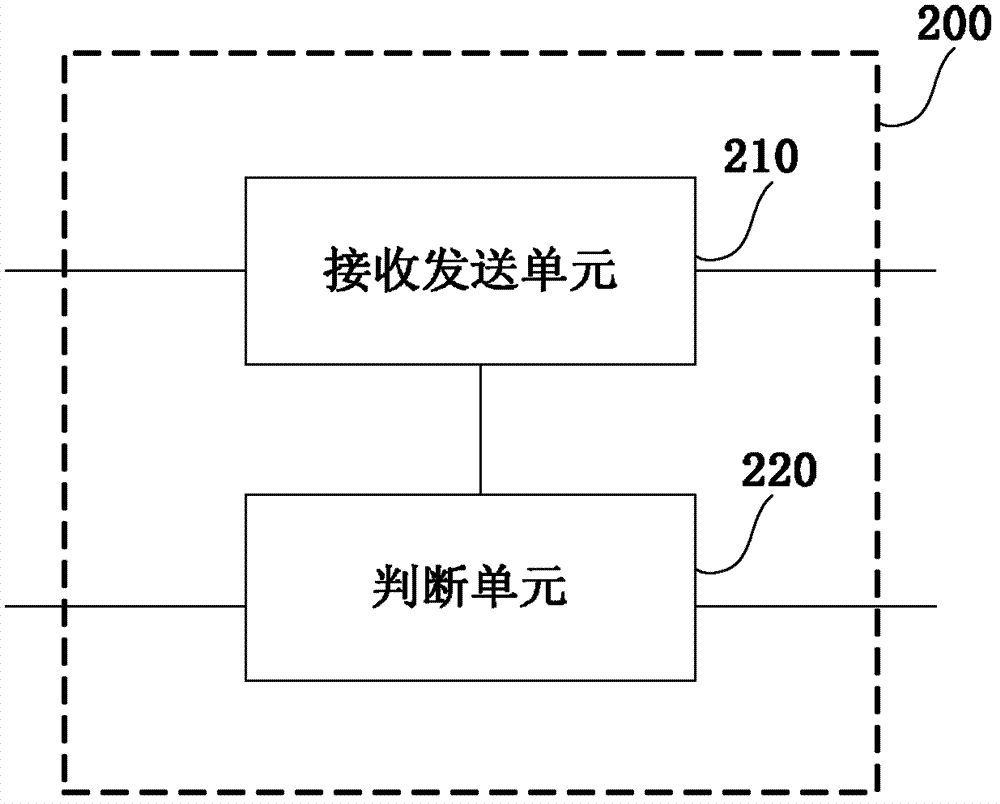
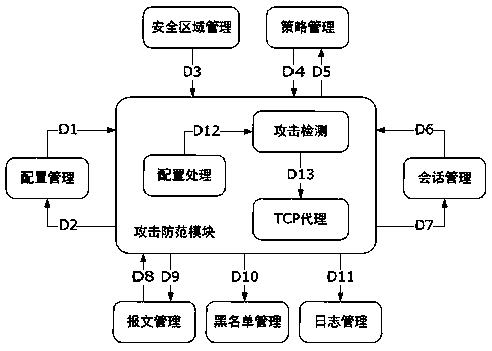
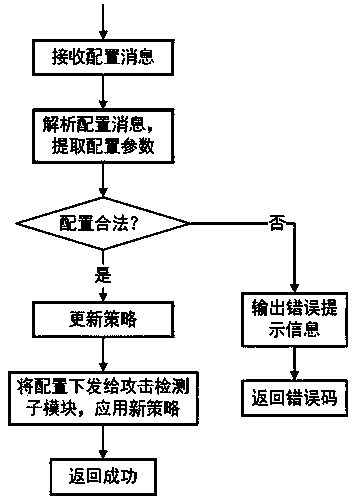
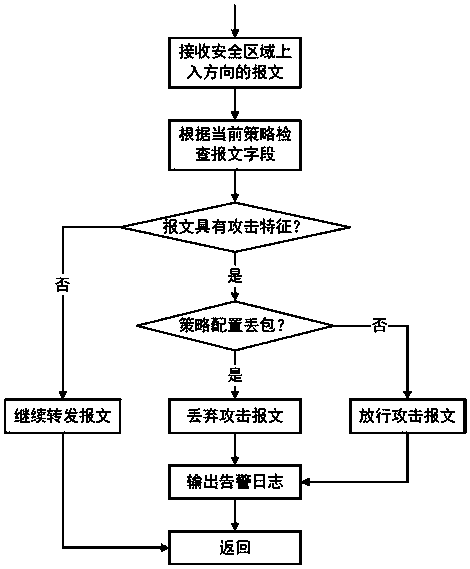
The invention provides a firewall attack defense method which achieves a network attack detection function and can accurately detect a single-packet attack, a scanning attack and a flood attack by applying an attack defense module to a firewall with functions of configuration management, message management, session management and the like based on a security zone. The single-packet attack particularly comprises: an ICMP redirection attack, an ICMP inaccessible attack, an IP source routing option attack, a route record option attack, a Land attack, a Smurf attack, a Fraggle attack and a WinNukeattack. The scanning attack particularly comprises: an address scanning attack and a port scanning attack. The flood attack comprises: a TCP SYN Flood attack, an ICMP Flood attack and a UDPFlood attack. After a network attack is detected out, corresponding defense measures of abandoning a message, adding into a blacklist, outputting an alarm log and the like for example are adopted according to configuration. A Safe Reset technology under a TCP agent linkage mechanism is implemented, and the TCP SYN Flood attack is effectively defended.
Owner:白令海
Method for implementing fire wall chip participation in SYN proxy
ActiveCN101296223AIntegrity guaranteedImprove good performanceSecuring communicationComputer hardwareConnection table
The invention discloses a method for realizing that a firewall chip takes part in SYN agent. The consultation process of the SYN agent is finished by software operating on a general CPU. After the consultation with a server is finished, the software operating on the general CPU registers the difference of TCP sequence numbers in the data structure of a connection table, and then the originally distributed special data structure of the SYN agent is cancelled; for normal communication, the connection of which is established, the firewall chip processes communication messages rapidly on the basis of transforming the TCP sequence numbers. In the method of the invention, complex processing consuming memory resources, such as the maintenance of TCP connection state and the retransmission of data packets, etc. is carried out by the software operating on the general CPU, thereby ensuring the completeness of the function of the SYN agent. When the method of the invention resists the attack of SYN Flood, the lawful and normal communication can still be transmitted rapidly by chips, thereby enhancing the performance of systems.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH
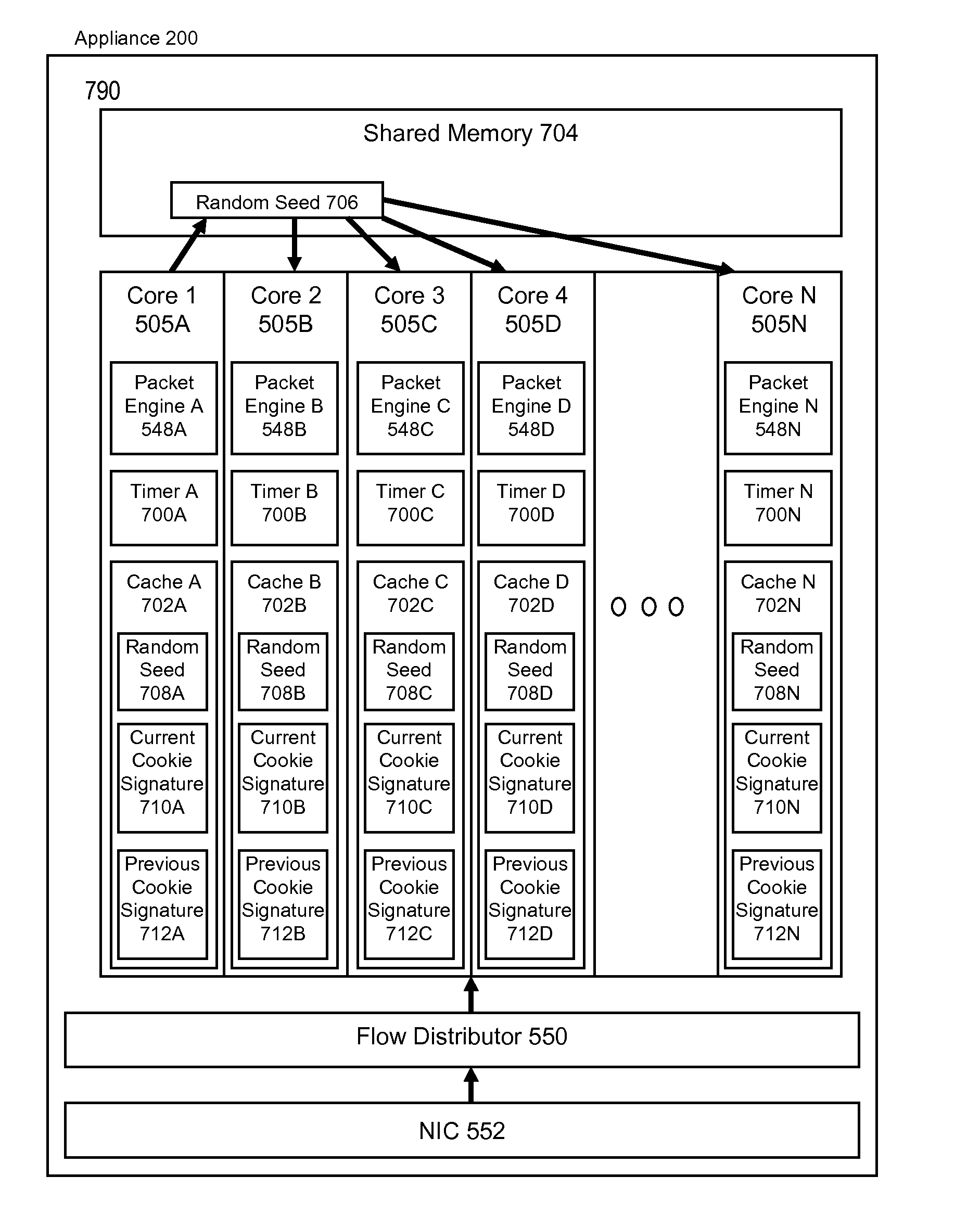
Systems and methods for protecting cluster systems from TCP SYN attack
ActiveUS20140304810A1Memory loss protectionError detection/correctionComputer hardwareCluster systems
The present solution is directed to systems and methods for synchronizing a random seed value among a plurality of multi-core nodes in a cluster of nodes for generating a cookie signature. The cookie signature may be used for protection from SYN flood attacks. A cluster of nodes comprises one master node and one or more other nodes. Each node comprises one master core and one or more other cores. A random number is generated at the master core of the master node. The random number is synchronized across every other core. The random number is used to generated a secret key value that is attached in the encoded initial sequence number of a SYN-ACK packet. If the responding ACK packet does not contain the secret key value, then the ACK packet is dropped.
Owner:CITRIX SYST INC
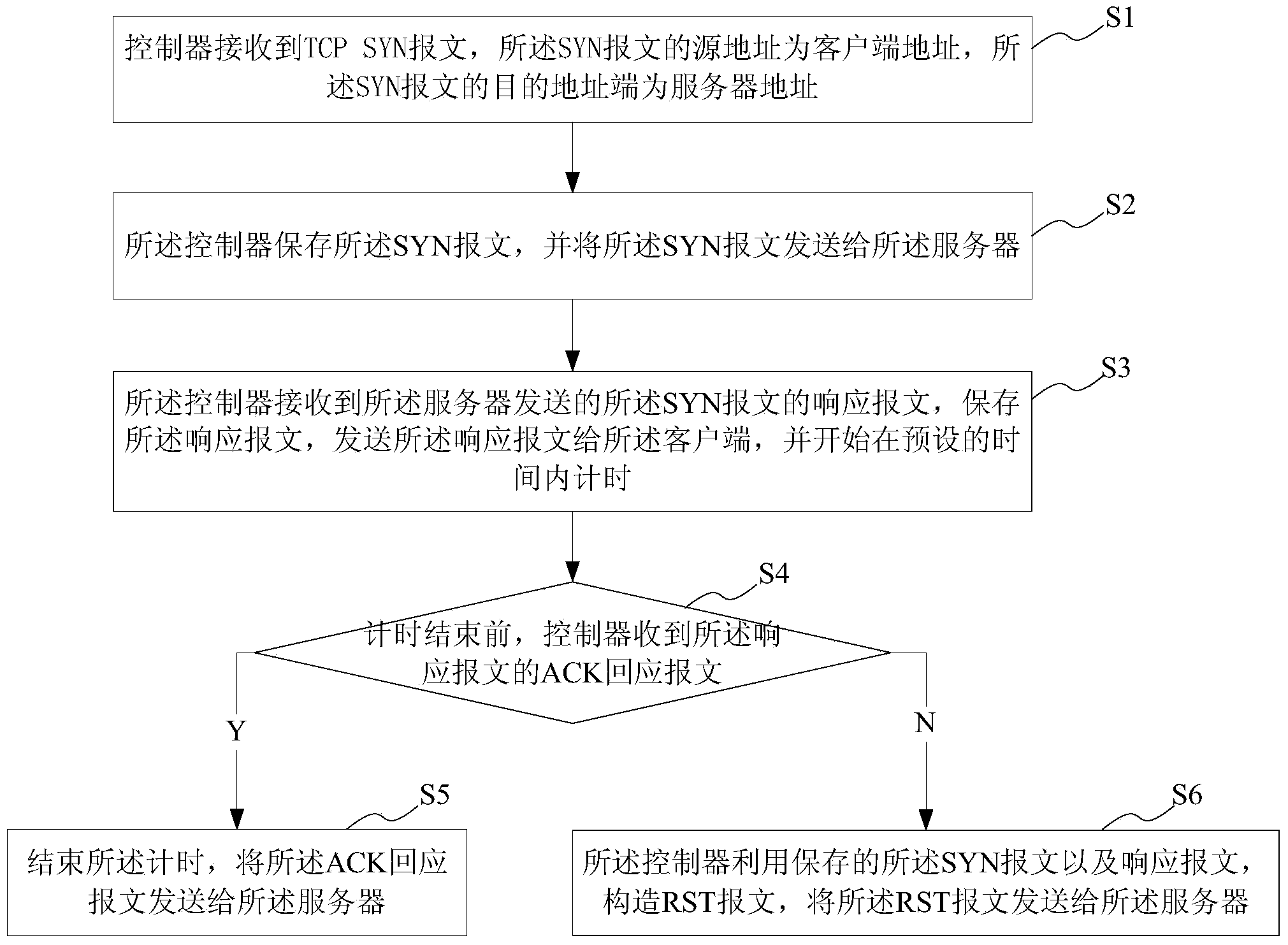
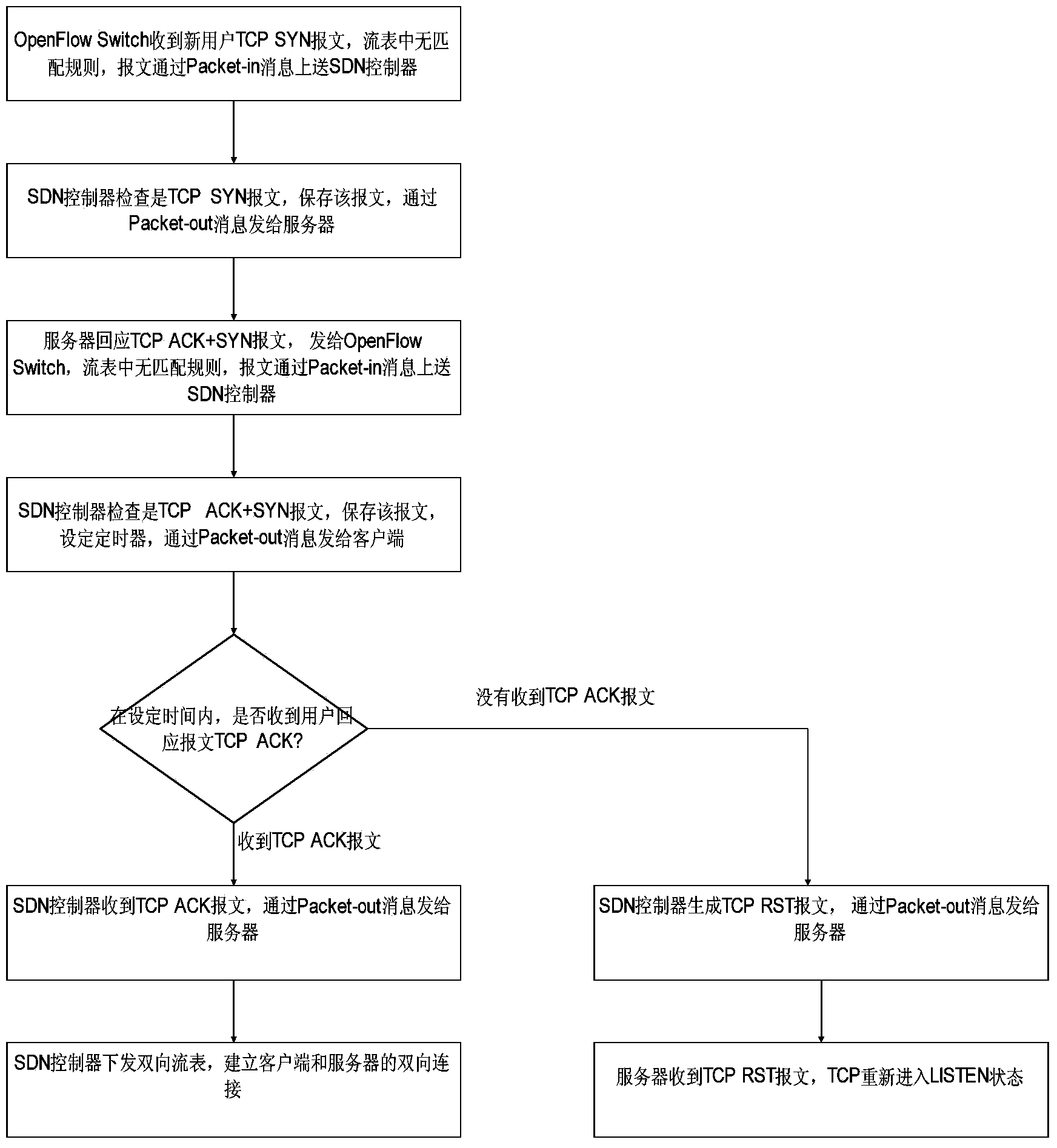
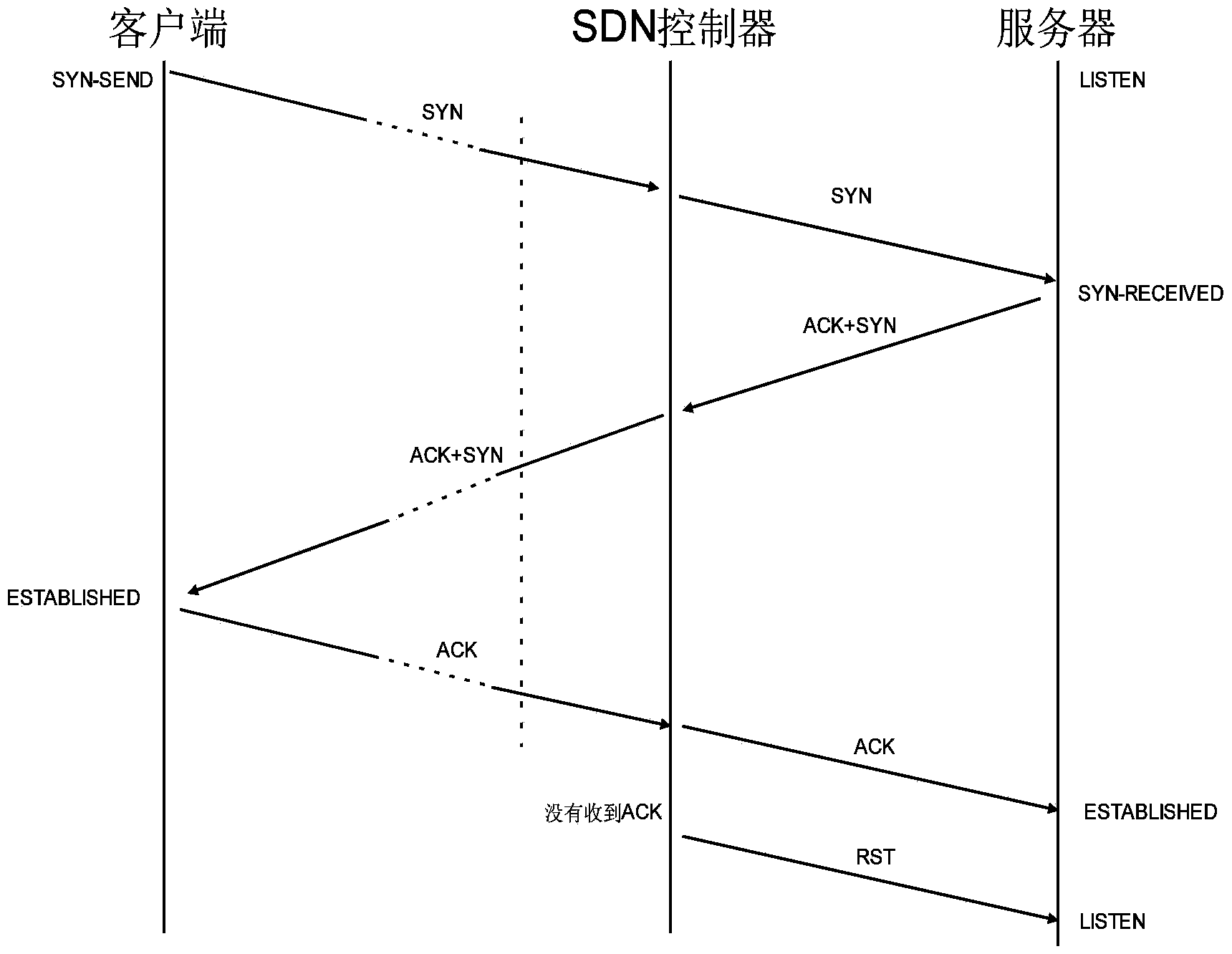
SDN network access method and system
ActiveCN104184749AAvoid wastingAvoid attackError prevention/detection by using return channelAccess methodClient-side
The invention provides an SDN network access method and system. The SDN network access method comprises the steps that a controller receives an SYN message; the controller saves the SYN message and sends the SYN message to a server; the controller receives a response message, sent by the server, of the SYN message, saves the response message, sends the response message to a client side and starts to perform timing within preset time; if the controller receives an ACK response message of the response message before timing is over, timing is ended, and the ACK response message is sent to the server; if the controller does not receive the ACK response message of the response message till timing is over, the controller utilizes the saved message to construct an RST message and sends the RST message to the server. According to the scheme, the SDN network access method and system can defend against an SYN Flood attack.
Owner:东莞市鸣鹿信息科技有限公司
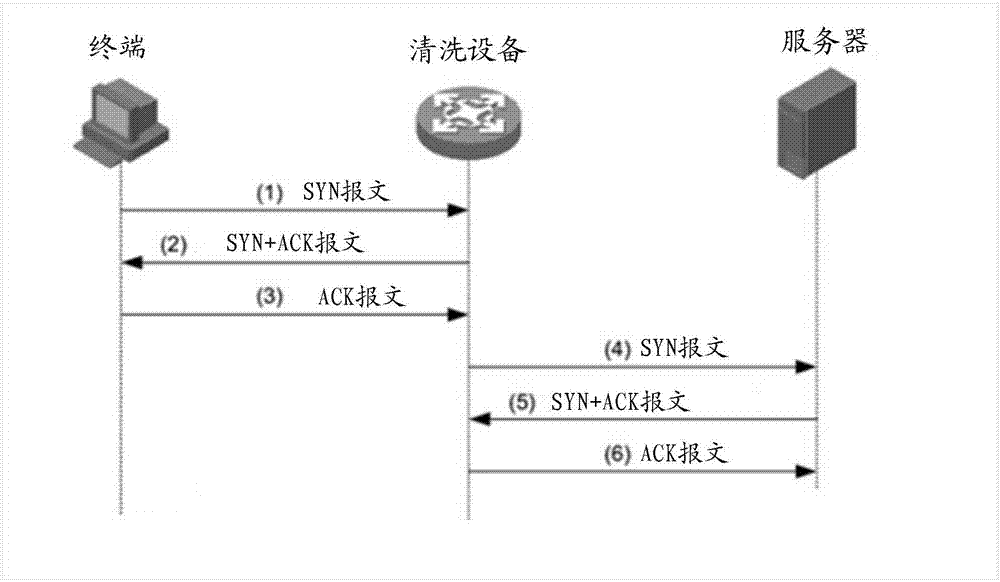
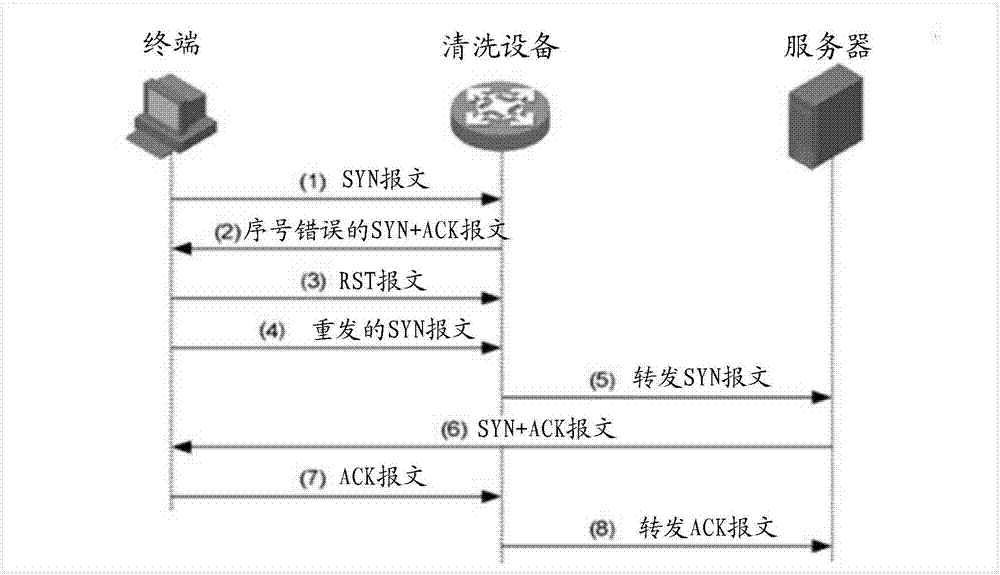
SYN Flood protection method and apparatus, cleaning device and medium
ActiveCN107395632AImprove processing efficiencyNo need to occupy resourcesError prevention/detection by using return channelComputer terminalProtocol for Carrying Authentication for Network Access
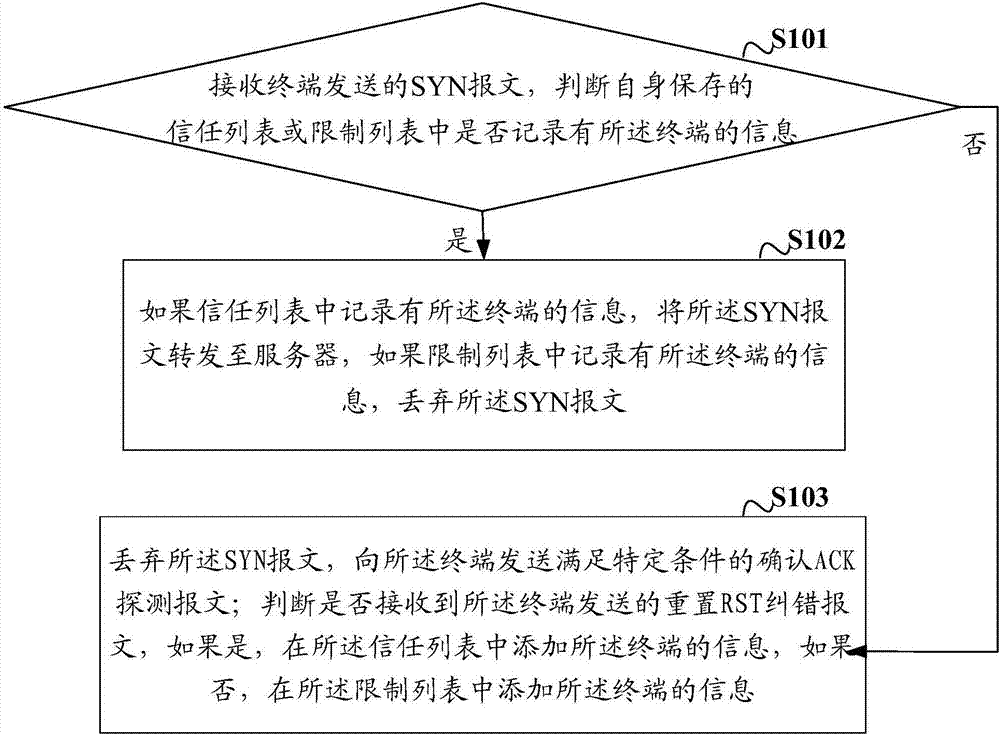
The invention discloses an SYN Flood (synchronize Flood) protection method and apparatus, a cleaning device and a medium. The SYN Flood protection method includes the steps: receiving an SYN message sent from a terminal, and determining whether the information of the terminal is recorded in a trust list or a restriction list; if not, abandoning the SYN message, and sending an ACK (acknowledgement) detection message to the terminal; and determining whether an RST (RESET) message is received, if so, adding the information to the trust list, and if not, adding the information of the terminal to the restriction list. In the SYN Flood protection method and apparatus, the trust list and the restriction list are saved in a cleaning device; if the terminal is not recorded in any one list, the ACK detection message is sent to the terminal, and the ACK detection message does not destroy the TCP (Transmission Control Protocol) protocol connection between the terminal and a server; according to whether the terminal sends the RST message, the SYN Flood protection method and apparatus can determine to add the terminal to which list; and the SYN message is abandoned, the resource is not occupied, so that the processing efficiency of the cleaning device can be improved.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
Transmission control protocol option processing method and apparatus
ActiveCN106685930AImprove experienceImprove efficiencyData switching networksTraffic capacityNetworked Transport of RTCM via Internet Protocol
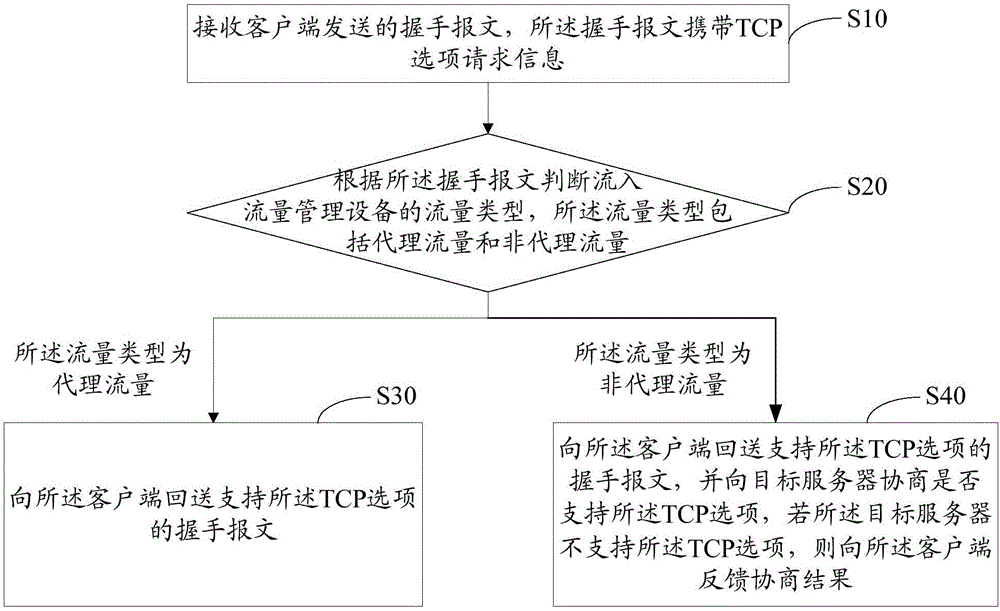
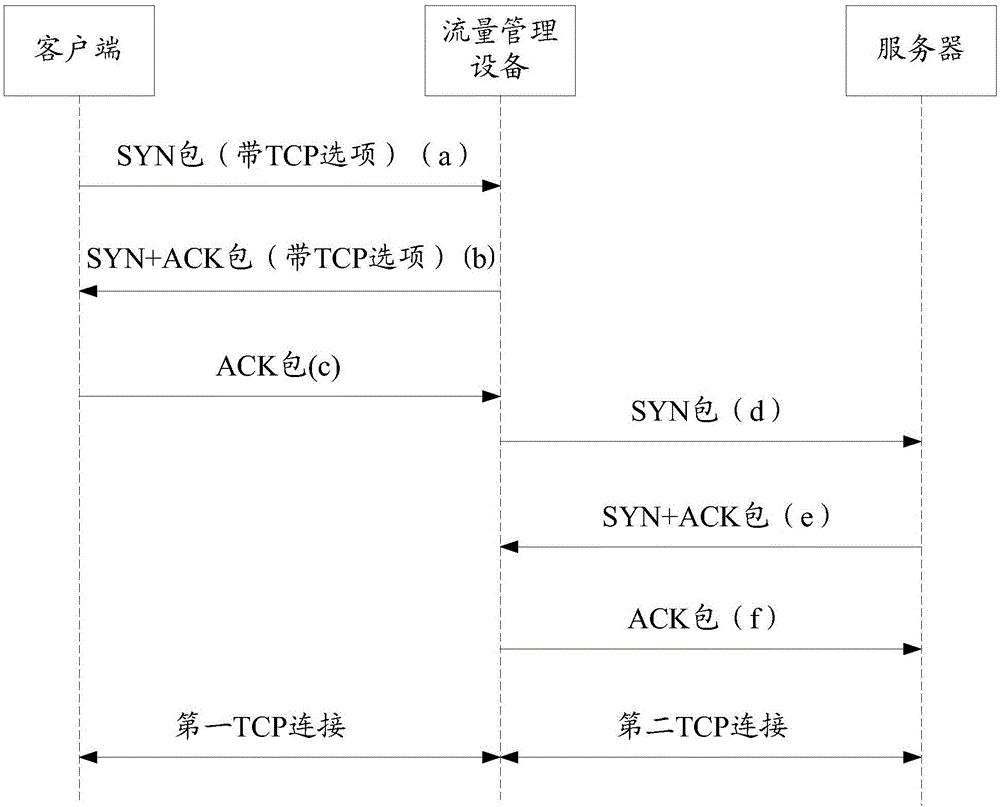
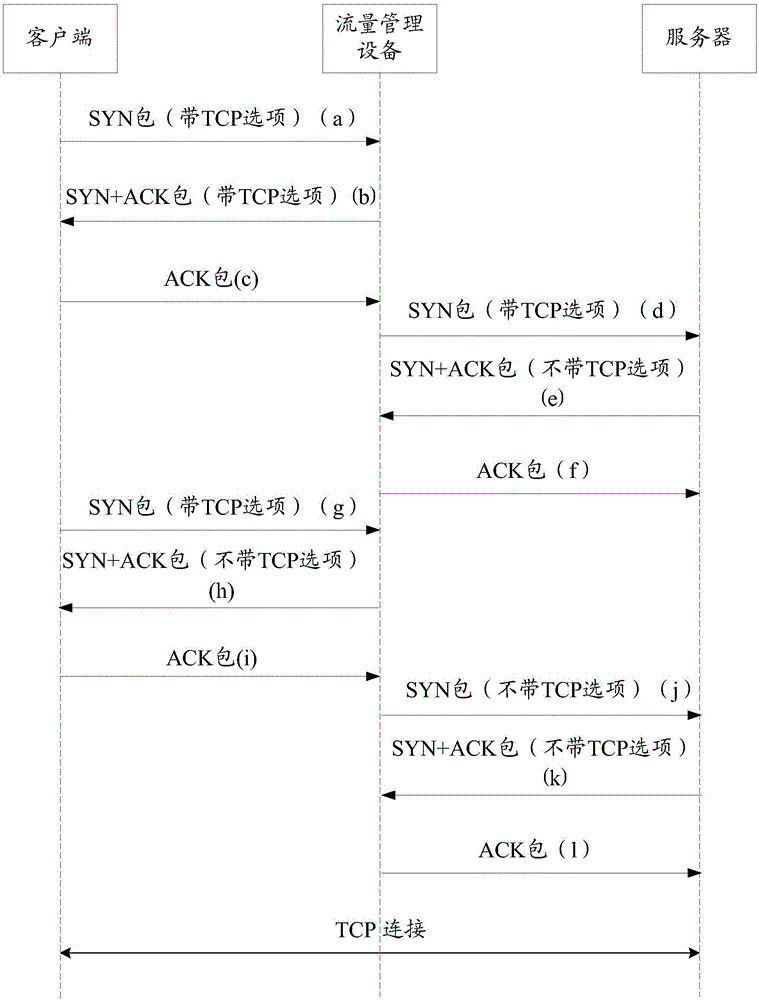
The present invention discloses a transmission control protocol option processing method and apparatus. The method includes the following steps that: a handshake message sent by a client is received, wherein the handshake message carries TCP (transmission control protocol ) option request information; the traffic type of traffic flowing into a traffic management device is determined according to the handshake message, wherein the traffic type can be a proxy traffic type or a non-proxy traffic type; if the traffic type is the proxy traffic type, a handshake message supporting a TCP option is sent back to the client; and if the traffic type is the non-proxy traffic type, a handshake message supporting the TCP option is sent back to the client, and a target server is negotiated with to decide whether to support the TCP option, if the target server does not support the TCP option, a negotiation result is fed back to the client. With the transmission control protocol option processing method and apparatus of the invention adopted, the traffic management device can reasonably process the TCP option in an SYN Flood attack prevention process, and therefore, the efficiency and quality of network transmission can be improved, and user experience can be enhanced.
Owner:SANGFOR TECH INC
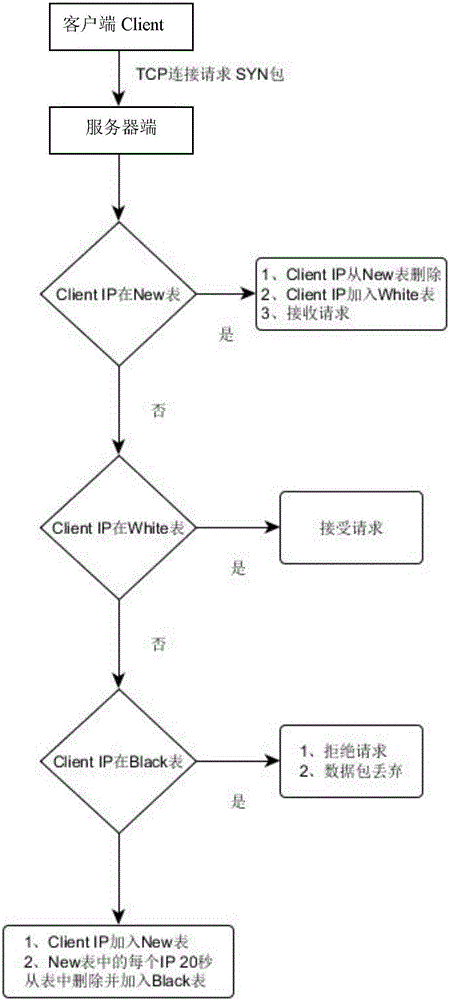
Efficient SYN Flood attack identification and disposal method
InactiveCN106453373AHigh attack accuracy recognition rateImprove recognition accuracyTransmissionBlack listSYN flood
The invention discloses an efficient SYN Flood attack identification and disposal method. The method comprises the steps that: 1, a New table for storing a to-be-classified IP list, a White table for storing an IP white list and a Black table for storing an IP black list are set at a server side; 2, the server side abandons a first SYN data packet on each connection request and records a source address of each SYN data packet into the New table; and 3, the server side acquires the source address of the SYN data packet for the received SYN data packet of each connection request, transfers the source addresses into the White table if the source addresses are positioned in the New table, and directly abandons the SYN data packets if the source addresses are positioned in the Black table. The efficient SYN Flood attack identification and disposal method disclosed by the invention has an identification rate of 98%, and can minimize attack influence.
Owner:北京知道未来信息技术有限公司
Method of preventing syn flood and router equipment
The invention discloses a method and a router device, which are used for keeping away the flood attack of a syn when a TCP link is established. The method comprises that an agent water line and an attack water line is set; when the number of the half link exceeds the agent water line, the establishment of the TCP link is proceeded by the router instead of a server on the router device; after the TCP link is established, the TCP link is initiated to the server by the router instead of a client server; when the number of the half link reaches up to the attack water line, after a syn message is received, the half link with the longest existence time is aged and a time of retransmit-overtime is shortened; until the number of the half link is pushed out of the water line number, a normal work pattern is reentered. The invention realizes the response of the TCP link which is initiated to the client server by an agent server, which greatly saved resource and improves the use ratio of resource. And the effect of improving the security of the equipment is achieved.
Owner:ANHUI WANTONG POSTS & TELECOMM CO LTD
Method and device for processing SYN flood prevention
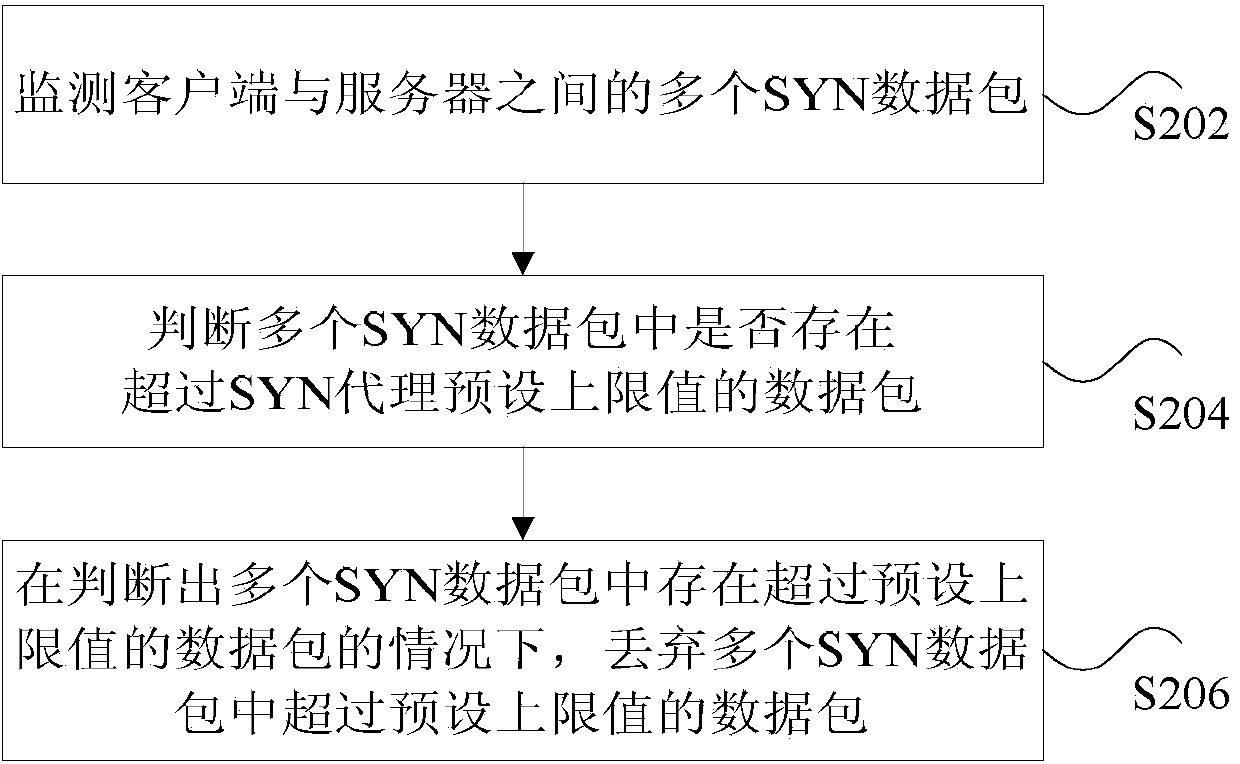
ActiveCN103475657AAvoid the disadvantages of unlimited quantityAvoid consumptionClimate change adaptationTransmissionLimit valueClient-side
The invention discloses a method and device for processing SYN flood prevention. The method for processing SYN flood prevention comprises the steps that multiple SYN data packages between a client-side and a server are monitored; whether the data package exceeding the SYN proxy preset upper limit value exists in the multiple SYN data packages or not is judged; under the condition that the data package exceeding the SYN proxy preset upper limit value exists in the multiple SYN data packages, the package exceeding the SYN proxy preset upper limit value in the multiple SYN data packages is removed. According to the method for processing SYN flood prevention, the problem that a method for processing SYN flood prevention in the prior art is prone to causing system performance degradation so that the effects that the system performance and the system network speed are improved can be achieved.
Owner:QI-ANXIN LEGENDSEC INFORMATION TECH (BEIJING) INC +1
Method and device for rapidly detecting SYN Flood attacks
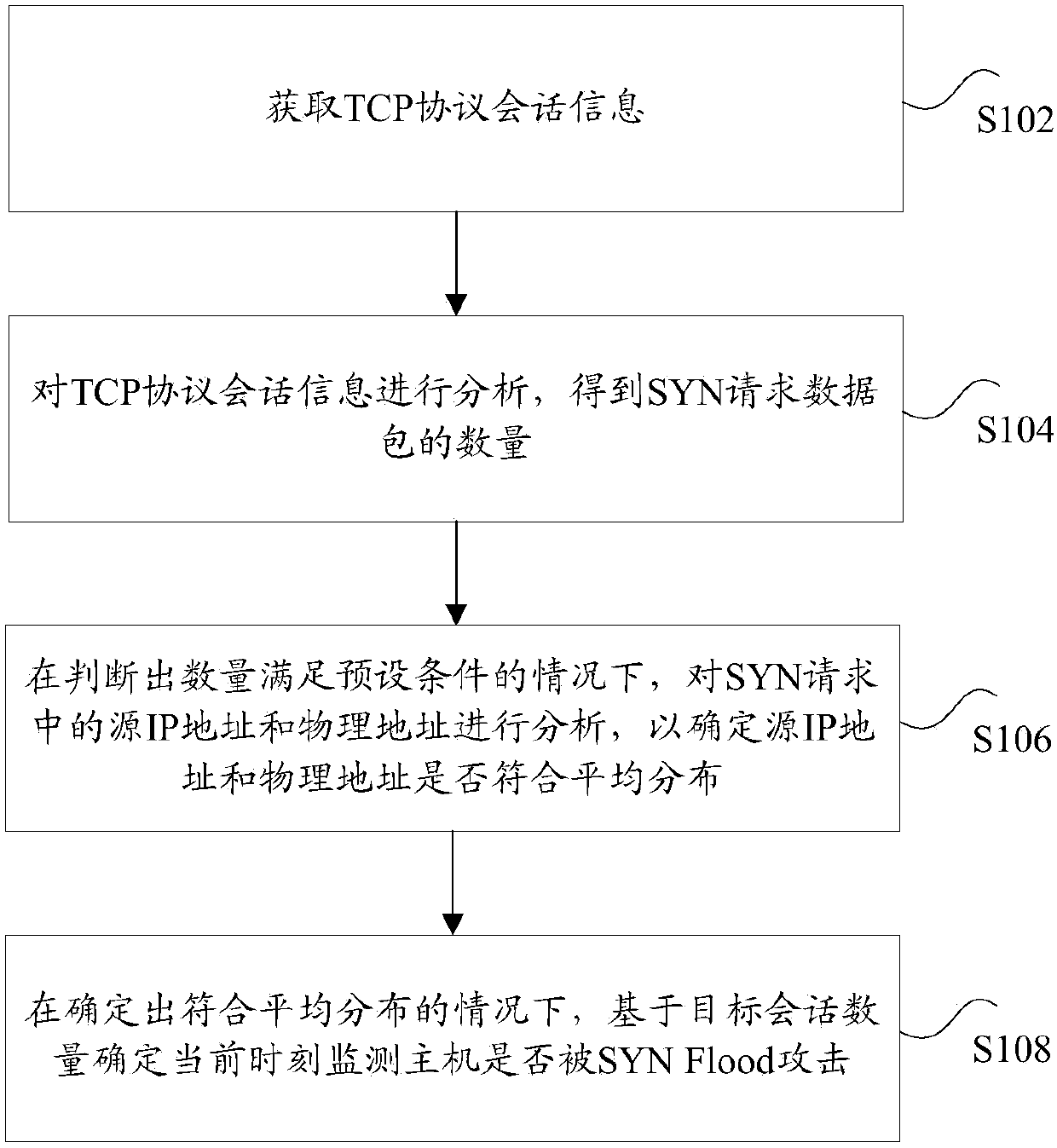
ActiveCN107623685AAcceptable consumptionLow equipment requirementsTransmissionTraffic capacityIp address
The invention provides a method and device for rapidly detecting SYN Flood attacks, relating to the technical field of network information security. The method comprises the following steps: acquiringTCP session information, wherein the TCP session information is at least one piece of session information between a target IP and a monitoring host; analyzing the TCP session information to obtain the number of SYN request data packets; when determining that the number meets preset conditions, analyzing source IP addresses and physical addresses in an SYN request to determine whether the source IP addresses and the physical addresses are in accordance with even distribution; and when determining that the addresses meet the even distribution, determining whether the monitoring host is attackedby SYN Flood at the current time based on the number of target sessions, wherein the number of the target sessions is the number of the sessions with zero application layer traffic in all IP addresssessions in the network traffic at the current time. Thereby, the technical problem that an SYN Flood detection method is higher in cost in the prior art can be alleviated.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
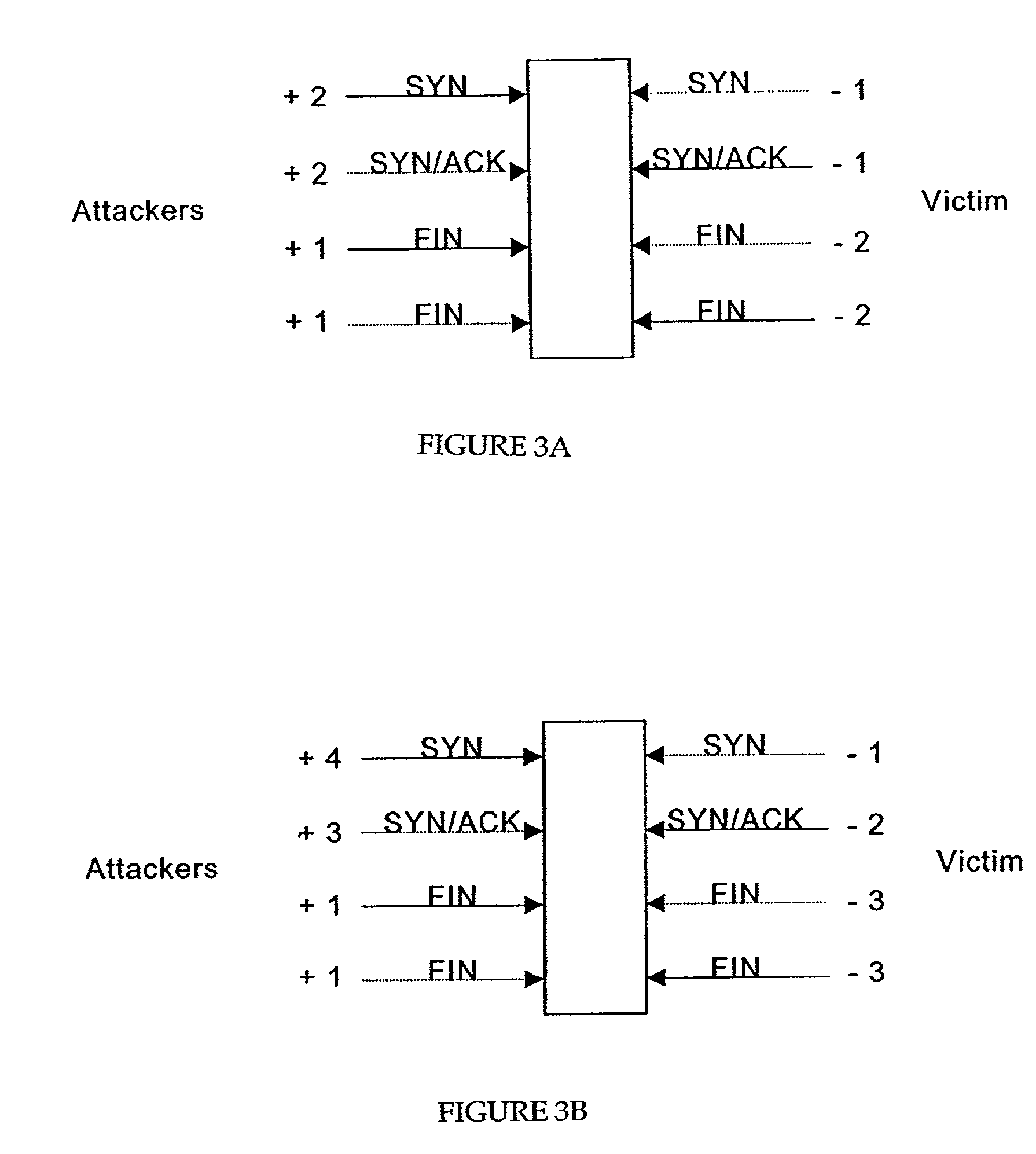
Statistical methods for detecting TCP SYN flood attacks
ActiveUS7114182B2Memory loss protectionDetecting faulty computer hardwareThe InternetAbnormal number
Methods of detecting TCP SYN flooding attacks at a router located between a LAN and a network such as the Internet are described. The methods rely on a counting arrangement in which SYN and Fin packets are counted on both the LAN side and the network or Internet side of the router during a time interval. Weighting factors are applied to each count, the factor for the LAN side count having the opposite polarity to the factor for the network side count. The absolute values of the sums of the weighting factors of like polarity are equal. An abnormal number of unsuccessful connection attempts are determined based on a parameter calculated using the weighting factors in conjunction with the respective counts.
Owner:PIECE FUTURE PTE LTD
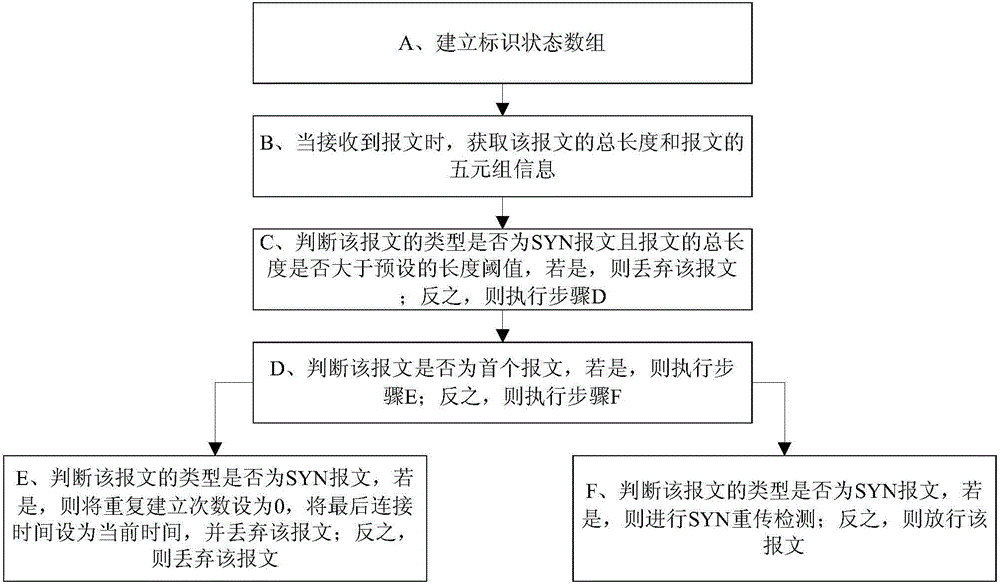
Method and system for cleaning SYN FLOOD attack
The invention discloses a method and a system for cleaning SYN FLOOD attack. The method has the advantages that by filtering an overlong SYN message, the stress during connection establishing and analysis is greatly reduced; then, by analyzing after a connection identification is established, the reloading time of SYN is judged, and the reloading times are limited, so as to prevent an attacker from simulating reloading activity and counterfeiting into legal traffic; the method can be widely applied to SYN attach defense techniques.
Owner:GUANGDONG EFLYCLOUD COMPUTING CO LTD
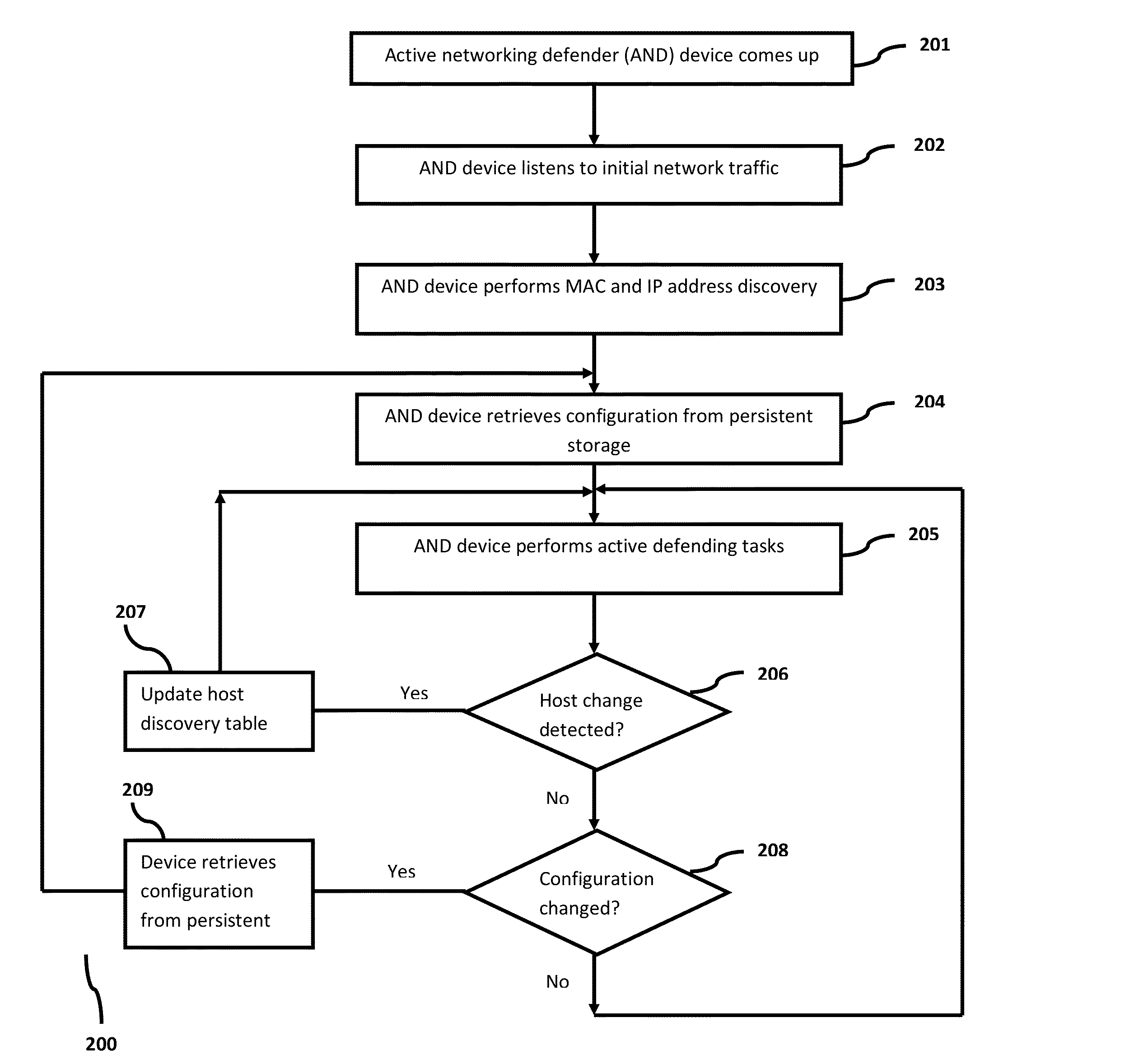
Method and system to actively defend network infrastructure
InactiveUS20160205135A1Low costReduced networkMemory loss protectionError detection/correctionLimited accessClient-side
Disclosed is an invention related to a system and device for actively defending a network infrastructure by implementing certain features that are attributed with lower performance cost and network complexity. The features implemented for protecting the network infrastructure comprises of: protecting the network from hostile scanning, providing a faster authenticated and limited access response to a network traffic request for sage guarding dedicated connections, intervening a TCP connection that is established between one or more clients and servers for terminating unwanted connections, and cleaning up SYN flood attacks to terminate one or more outstanding TCP connection.
Owner:NGUYEN NGUYEN
Method to detect SYN flood attack
Owner:LOUISIANA TECH RES CORP
Improved method for SYN FLOOD protection of traditional DDOS firewall in industrial network
ActiveCN110071939AReduce memory usage timeTo achieve the effect of safety protectionTransmissionIp addressIndustrial equipment
The invention discloses an improved method for SYN FLOOD protection of a traditional DDOS firewall in an industrial network. The invention relates to an improvement method for SYN FLOOD protection ofa traditional DDOS firewall in an industrial network. The method comprises the following steps: step 1, capturing a data packet in an Ethernet; 2, analyzing the SYN message of the TCP protocol, and counting the number of the target IP addresses; and step 3, comparing the threshold value of the preset value with the SYN message statistic number, if the statistic number does not exceed the thresholdvalue, entering the step 4, and if the statistic number exceeds the threshold value, entering the step 8. The method has the beneficial effects that the SYN FLood attack flow which does not exceed the threshold value part is actively released, the memory occupation time of the attacked target is reduced, the attacked target can be quickly recovered to the normal working state without being attacked, and therefore the effect of safety protection on industrial equipment is achieved.
Owner:江苏亨通工控安全研究院有限公司
Distributed TCP SYN flood protection
Owner:VARMOR NETWORKS
Method, device and equipment for protecting SYN Flood attack
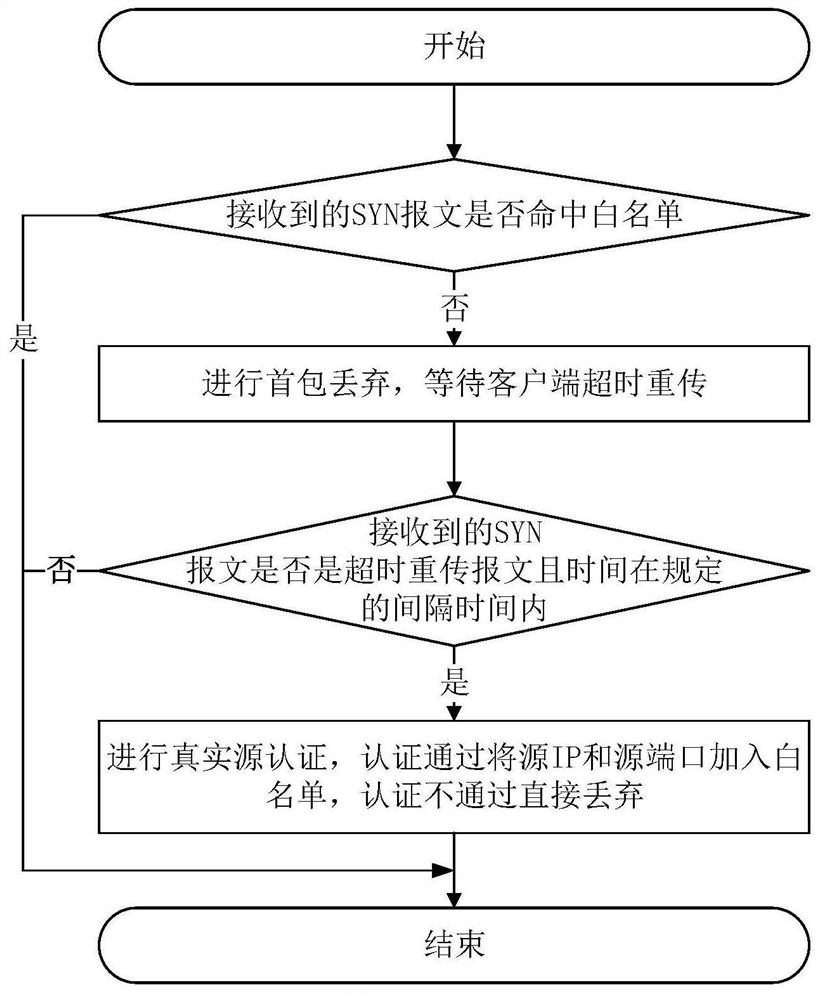
InactiveCN111970308AGuarantee authenticityReduce in quantityData switching networksData packInternet privacy
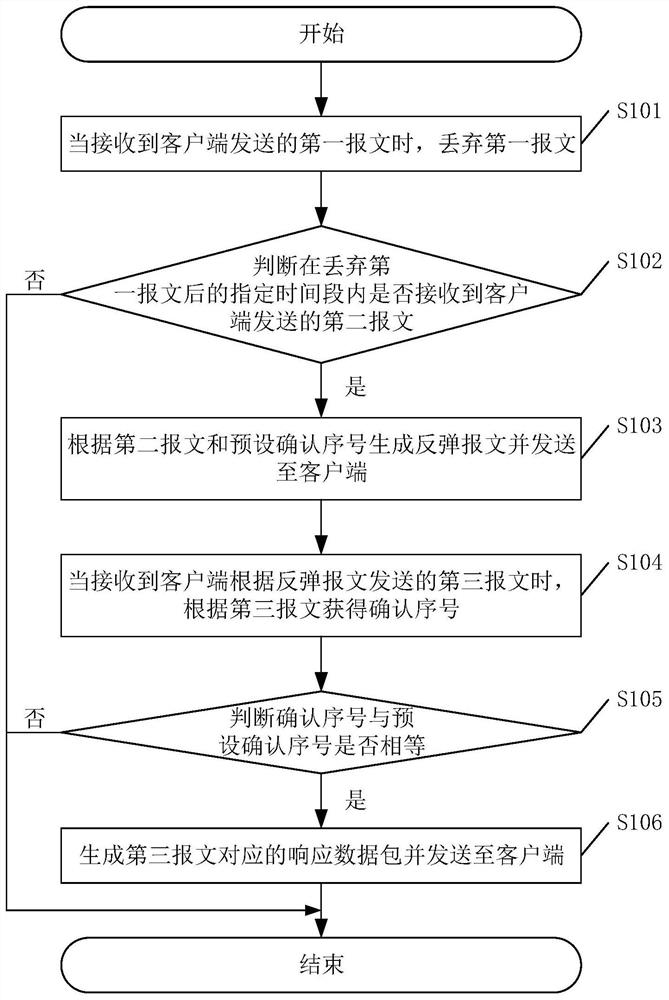
The invention discloses a method for preventing SYN Flood attacks, which comprises the following steps: when a first message sent by a client is received, discarding the first message; judging whethera second message sent by the client is received within a specified time period after the first message is discarded or not; if so, generating a rebound message according to the second message and a preset confirmation serial number and sending the rebound message to the client; when a third message sent by the client according to the rebound message is received, obtaining a confirmation serial number according to the third message; judging whether the confirmation serial number is equal to a preset confirmation serial number; if so, generating a response data packet corresponding to the thirdmessage and sending the response data packet to the client. The method can effectively solve the problem that a hacker carries out SYN Flood attack by using a legal IP, improves the attack protectioncapability of the system, and ensures the normal operation of the system. The invention further discloses a device and a system for protecting the SYN Flood attack and a computer readable storage medium, which all have the above beneficial effects.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com