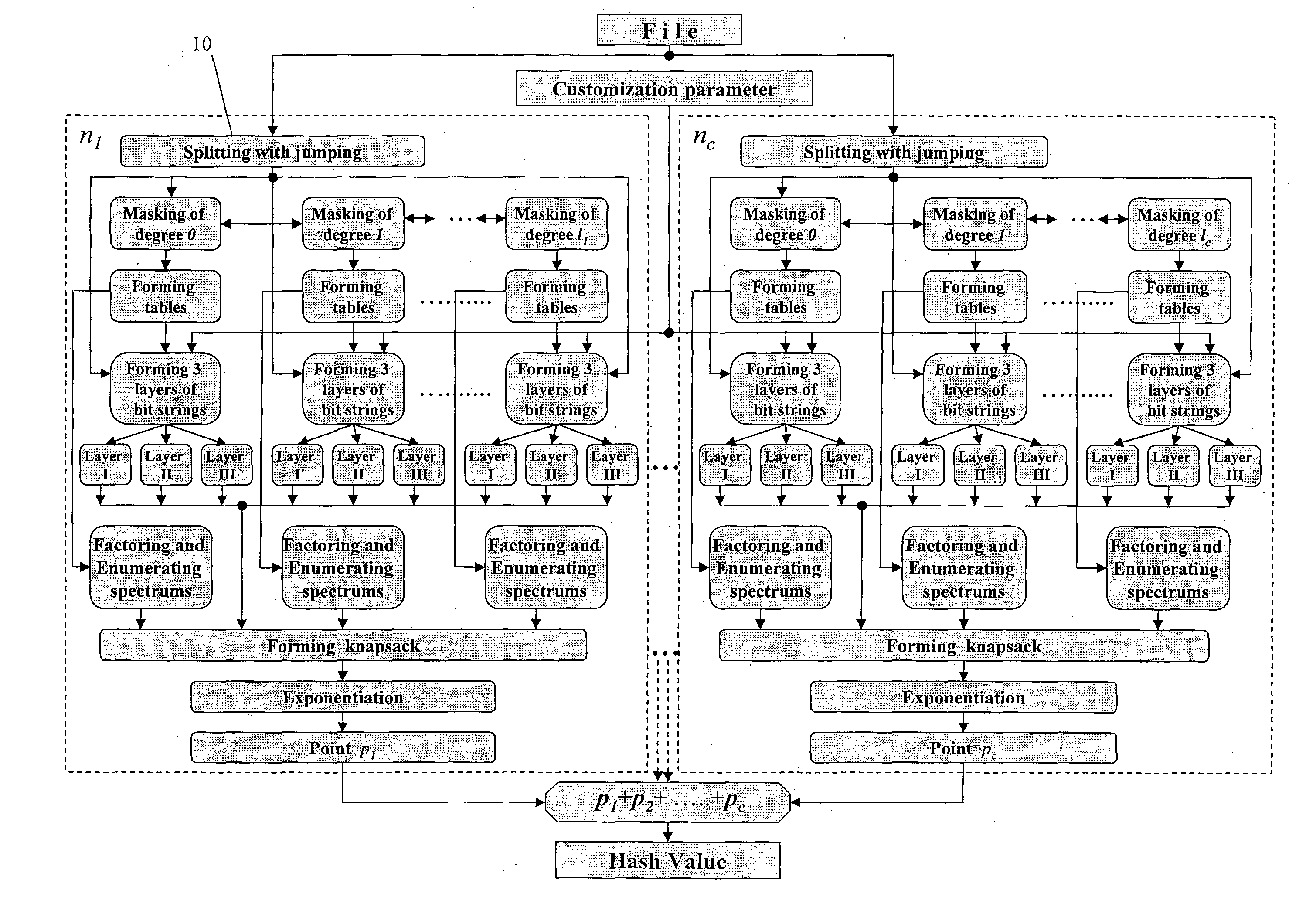
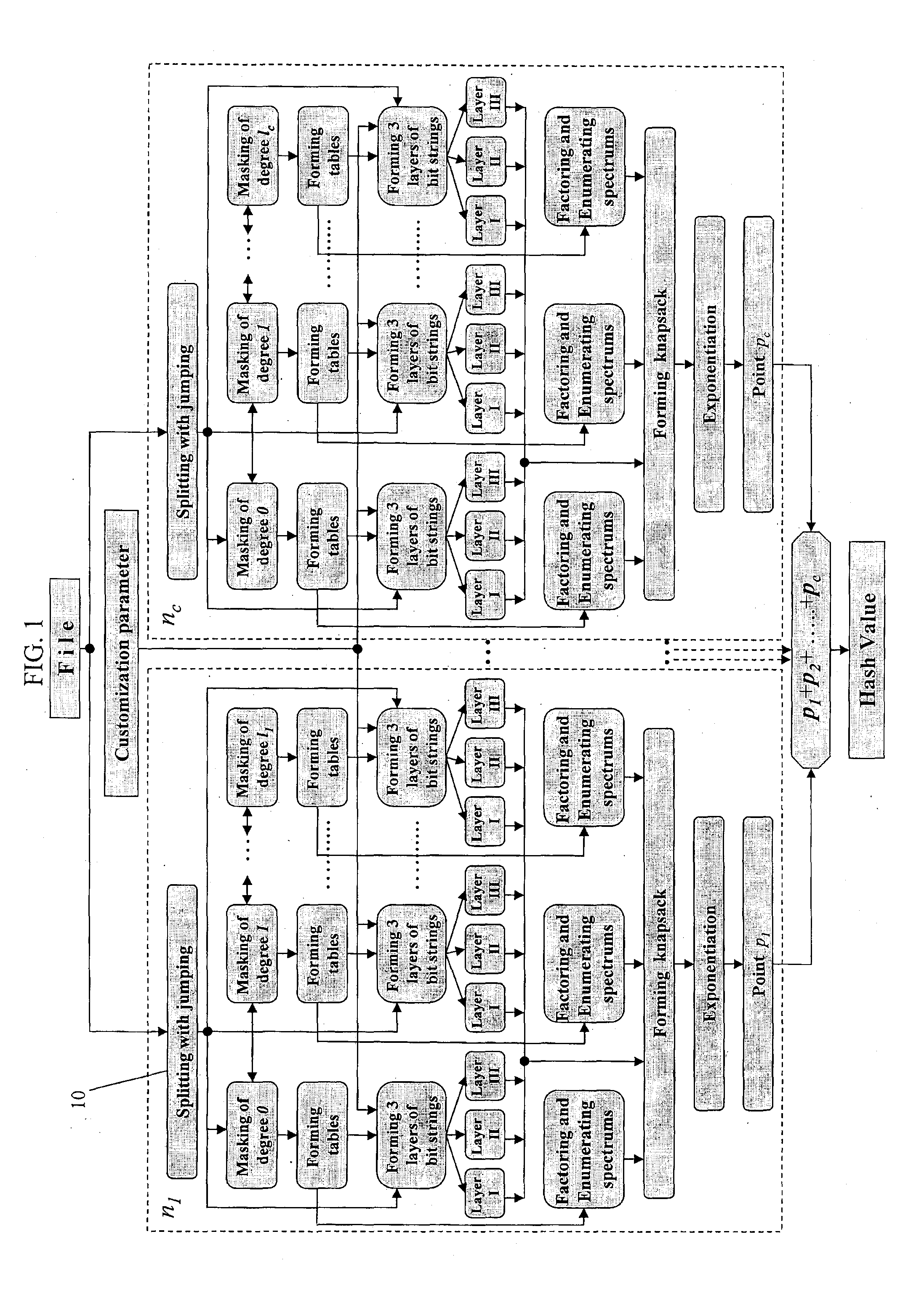
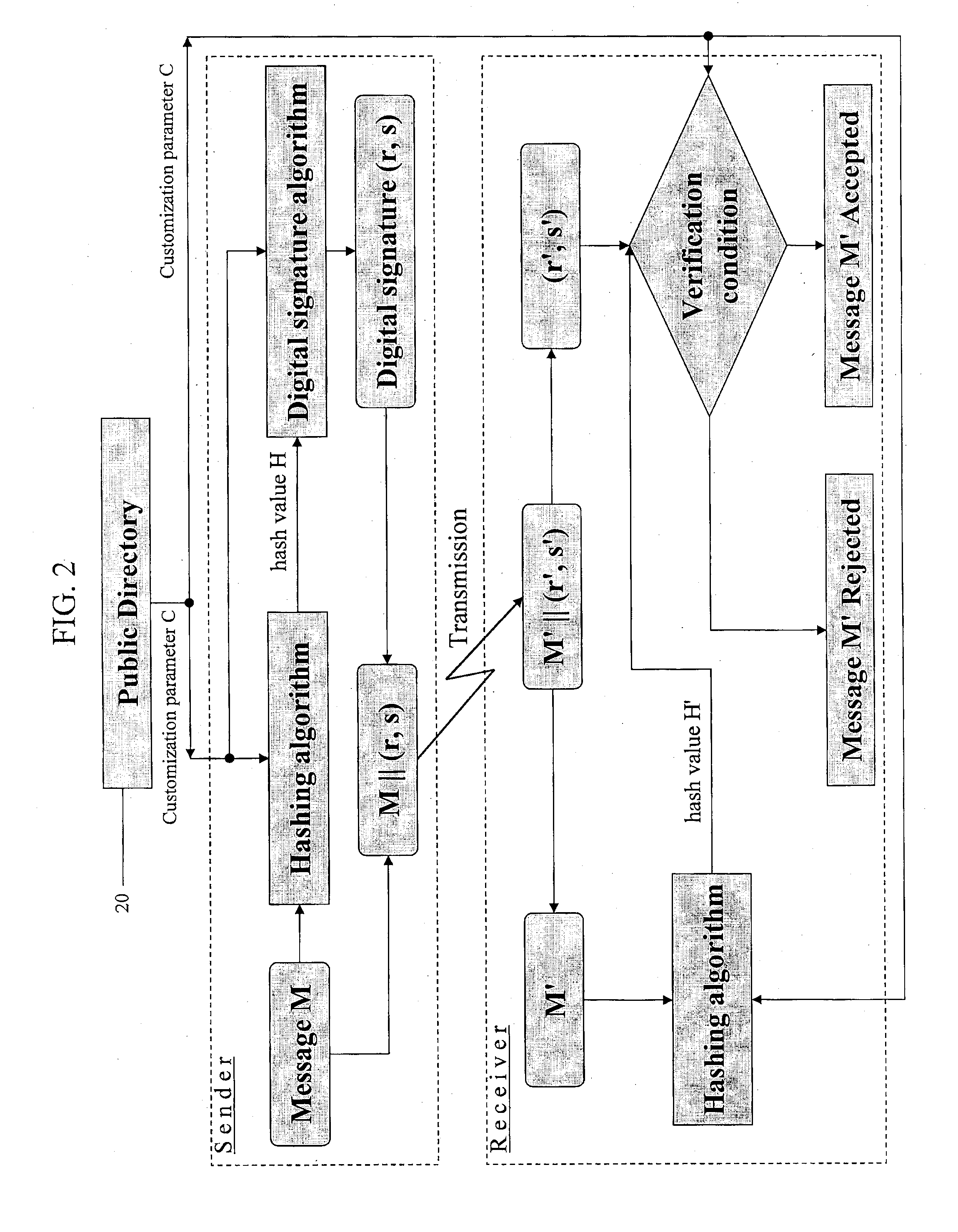
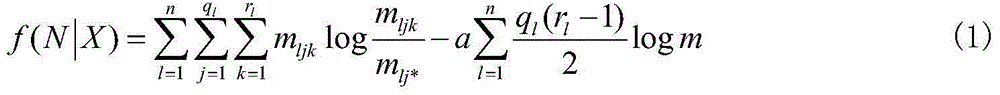Patents
Literature
190 results about "Initial sequence" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
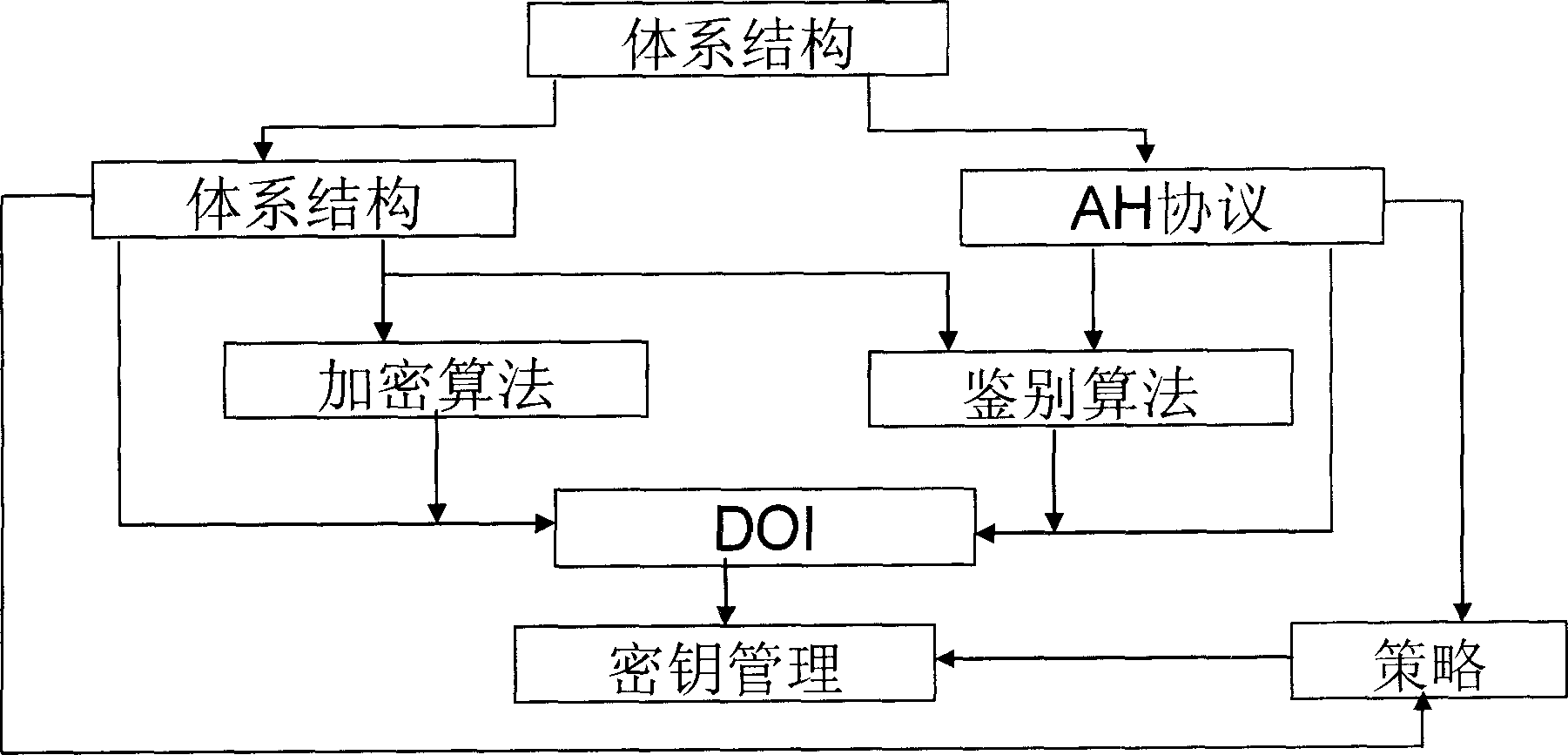
Initial sequence numbers (ISN) refers to the unique 32-bit sequence number assigned to each new connection on a Transmission Control Protocol (TCP)-based data communication.
Method and system for orthogonal modulation of power signals
ActiveCN105067880AImprove accuracyImprove anti-harmonicCurrent/voltage measurementVoltage-current phase angleLower limitFrequency vector
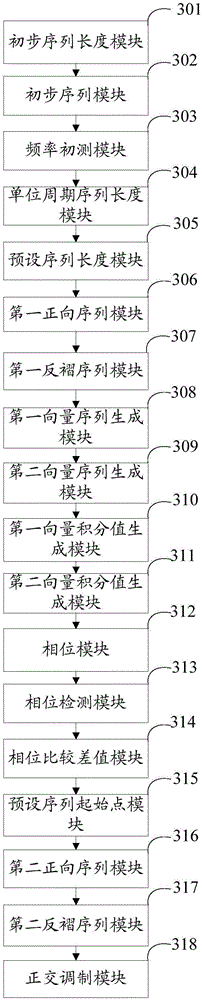
The invention discloses a method and a system for orthogonal modulation of power signals. The method comprises the following steps: acquiring an initial sequence length and an initial sequence according to a frequency lower limit, a preset sampling frequency and an initially set integer signal cycle number of a power signal; acquiring a reference frequency according to the initial sequence, and further acquiring a unit cycle sequence length and a preset sequence length; acquiring first forward and reverse sequences according to a preset sequence starting point and the preset sequence length; generating first real-frequency and imaginary-frequency vector sequences and second real-frequency and imaginary-frequency vector sequences according to the first forward and reverse sequences; converting obtained first and second phases into a first forward sequence average initial phase; obtaining a new preset sequence starting point according to the average initial phase; and obtaining a cosine function modulation sequence and a sine function modulation sequence according to second forward and reverse sequences obtained from the initial sequence. By adopting the method and the system of the invention, an orthogonal modulation sequence with consistent amplitude height can be obtained, and the accuracy and anti-jamming performance of sinusoidal parameter calculation are improved.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID
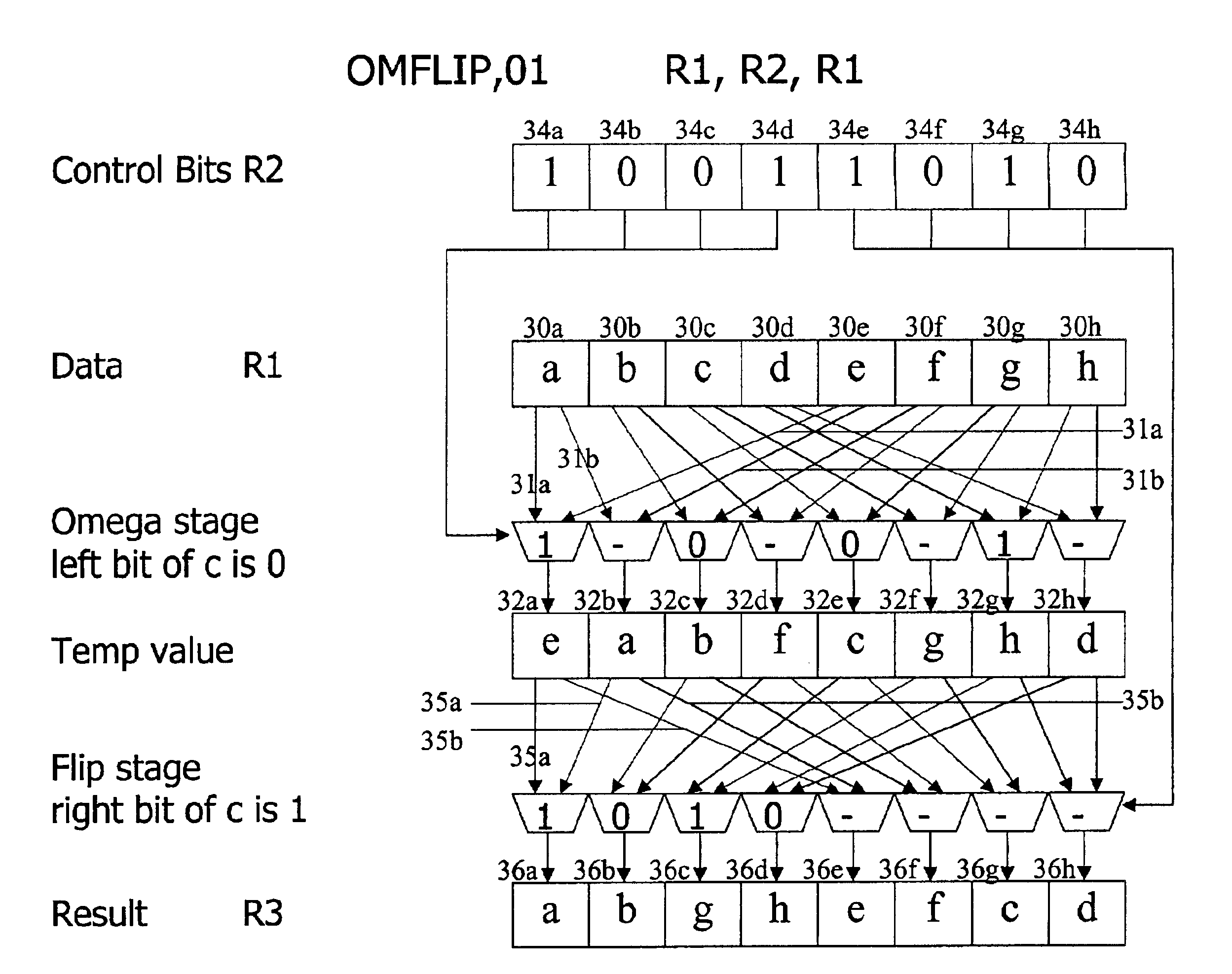
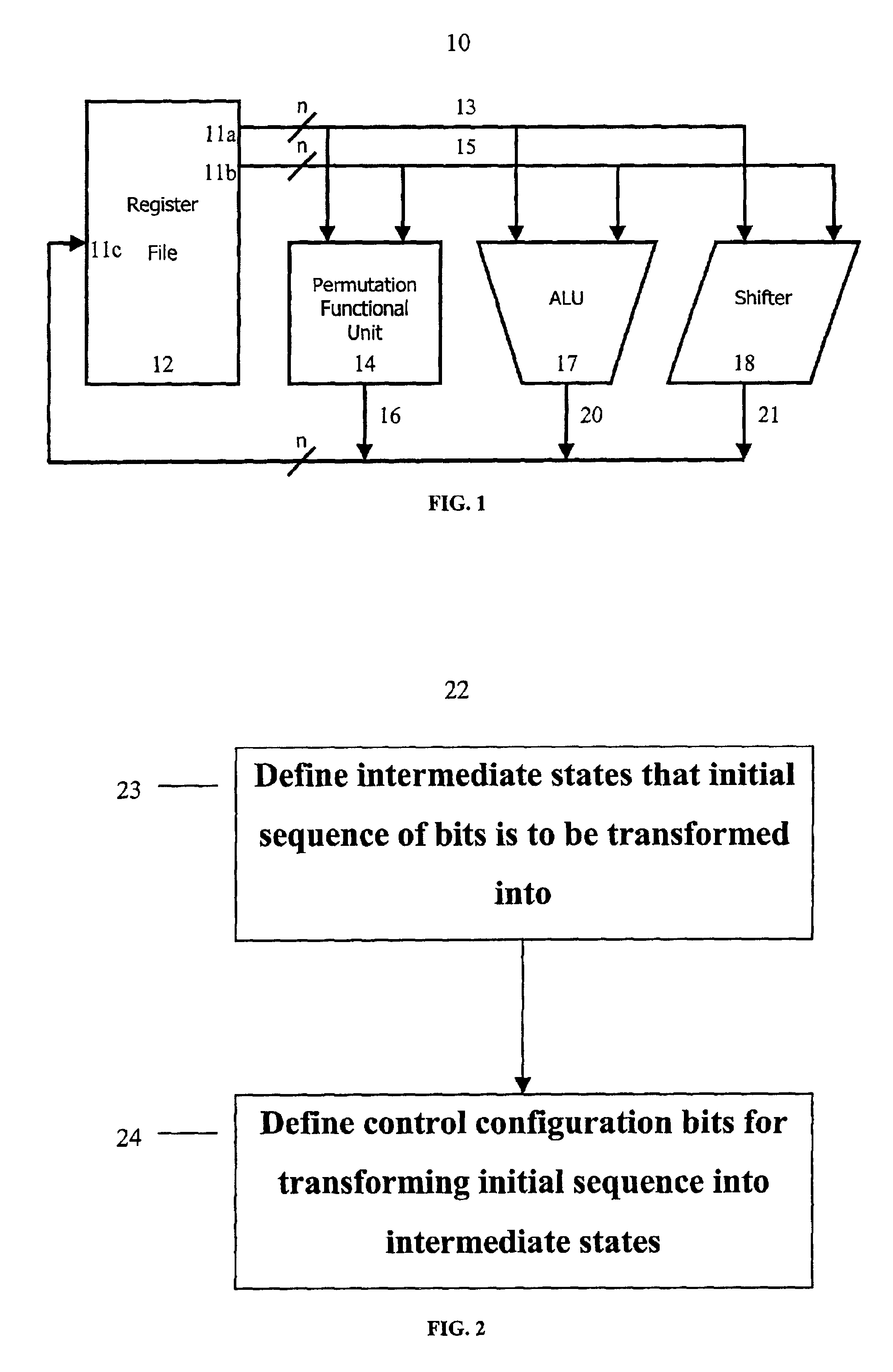
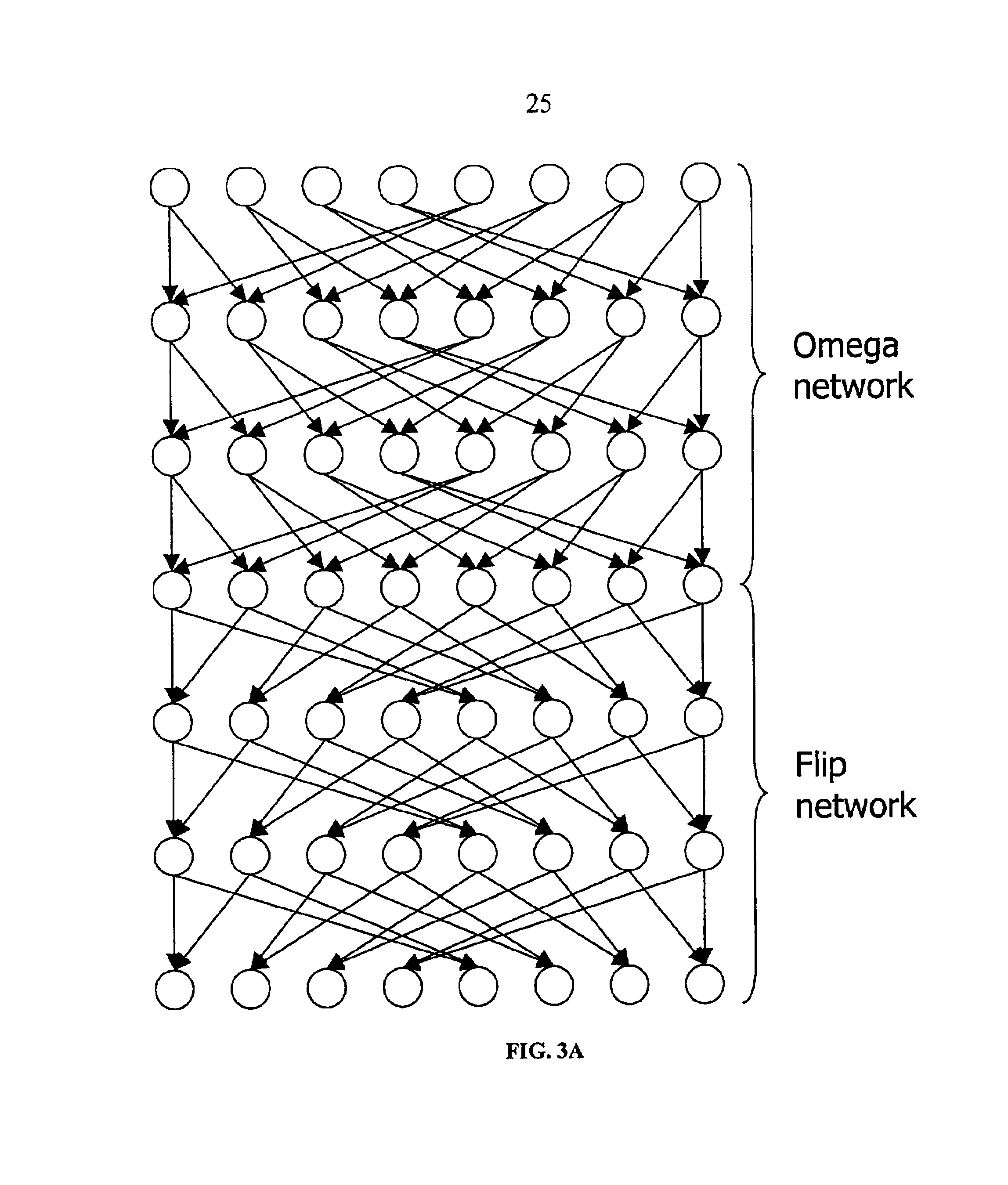
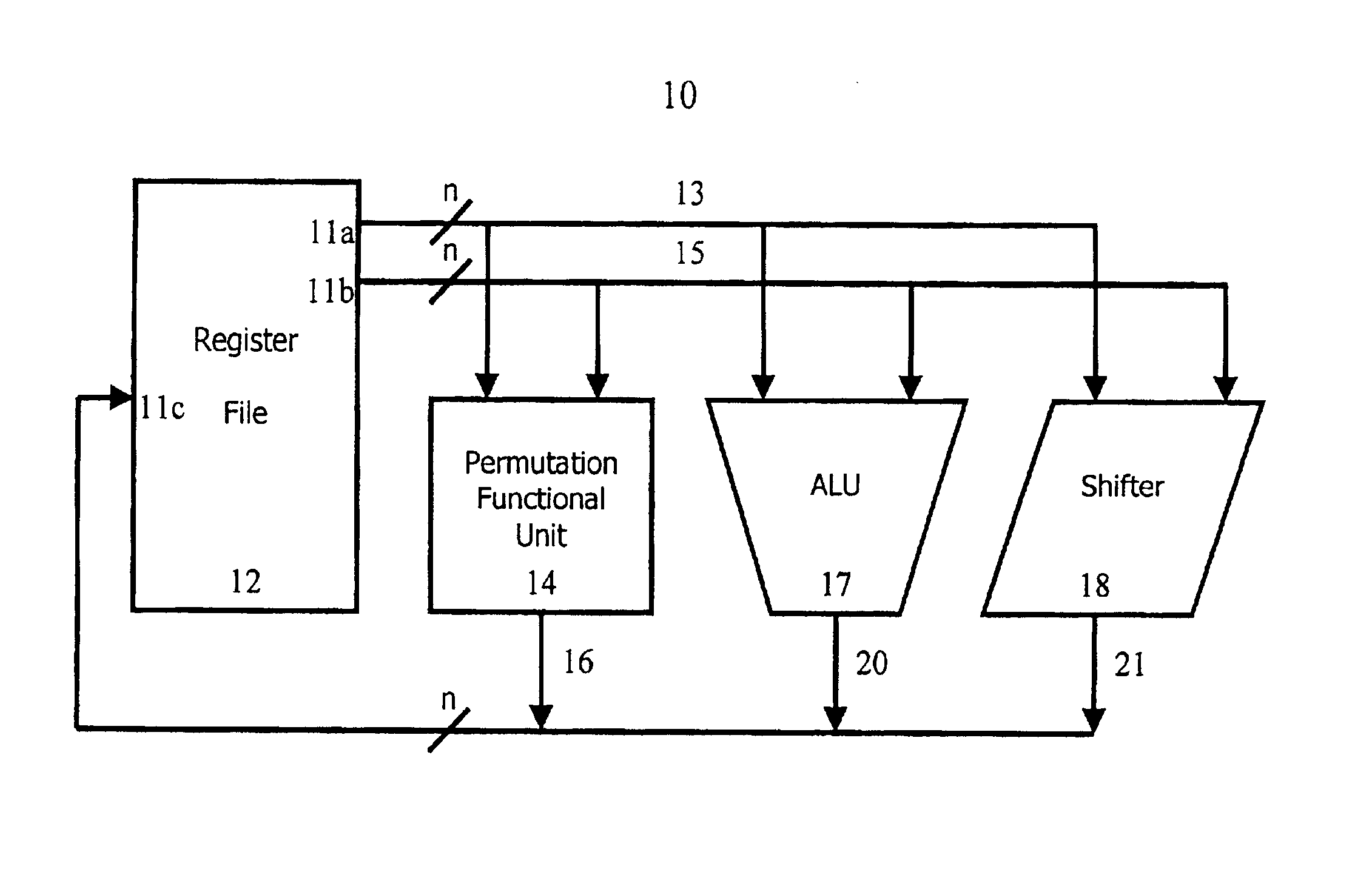
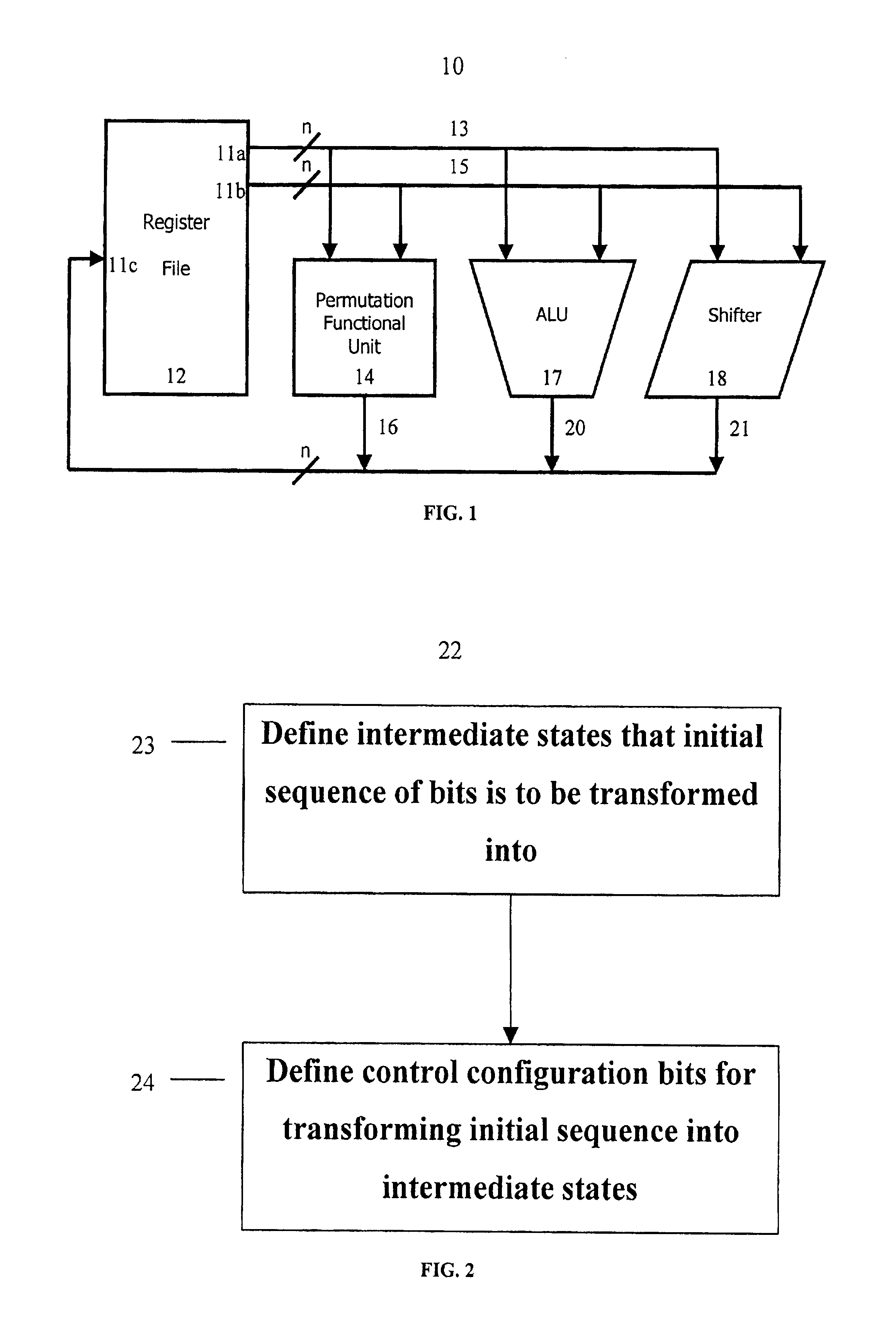
Method and system for performing permutations using permutation instructions based on modified omega and flip stages
InactiveUS6952478B2Digital computer detailsHandling data according to predetermined rulesComputer architectureOmega network
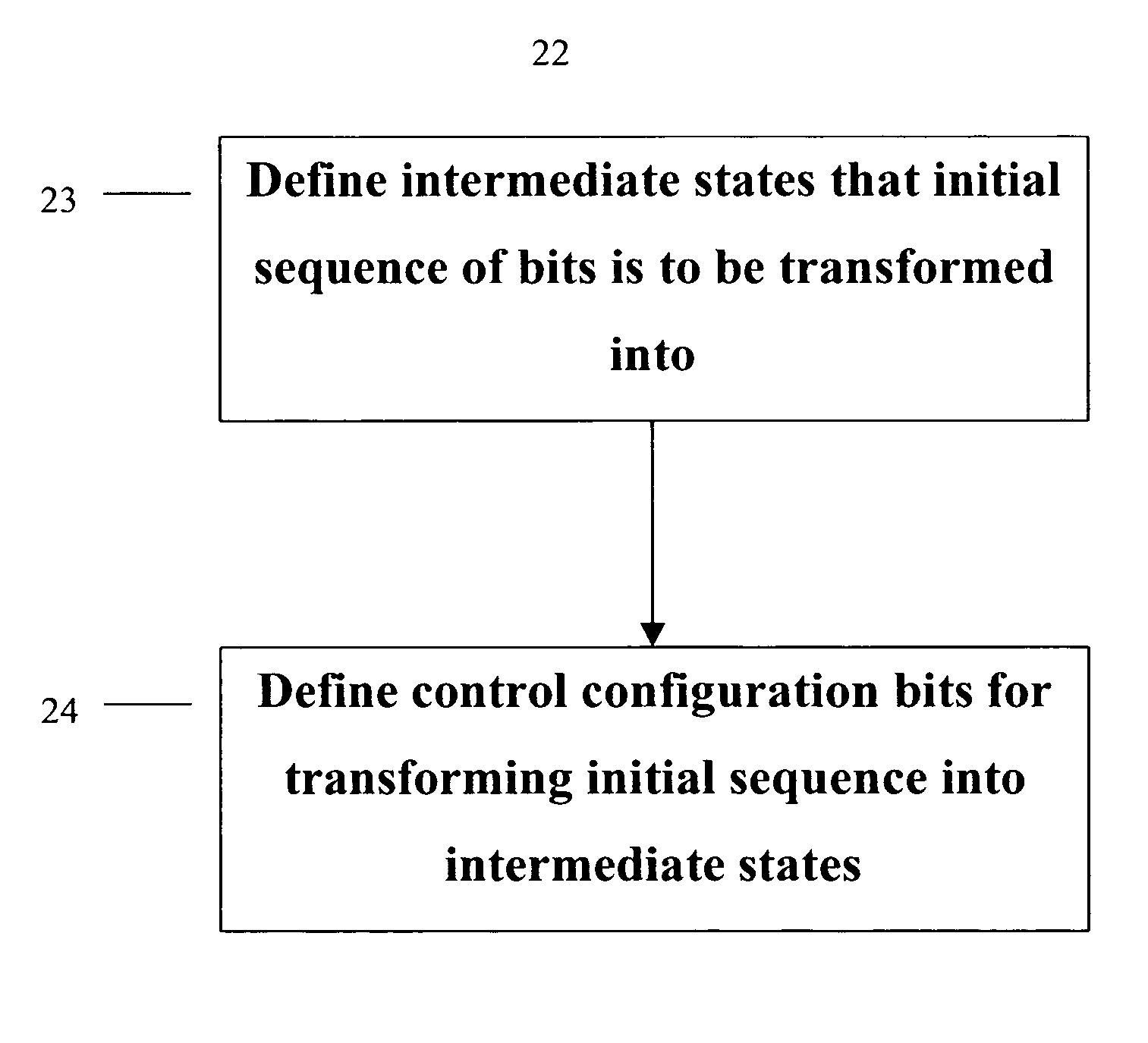
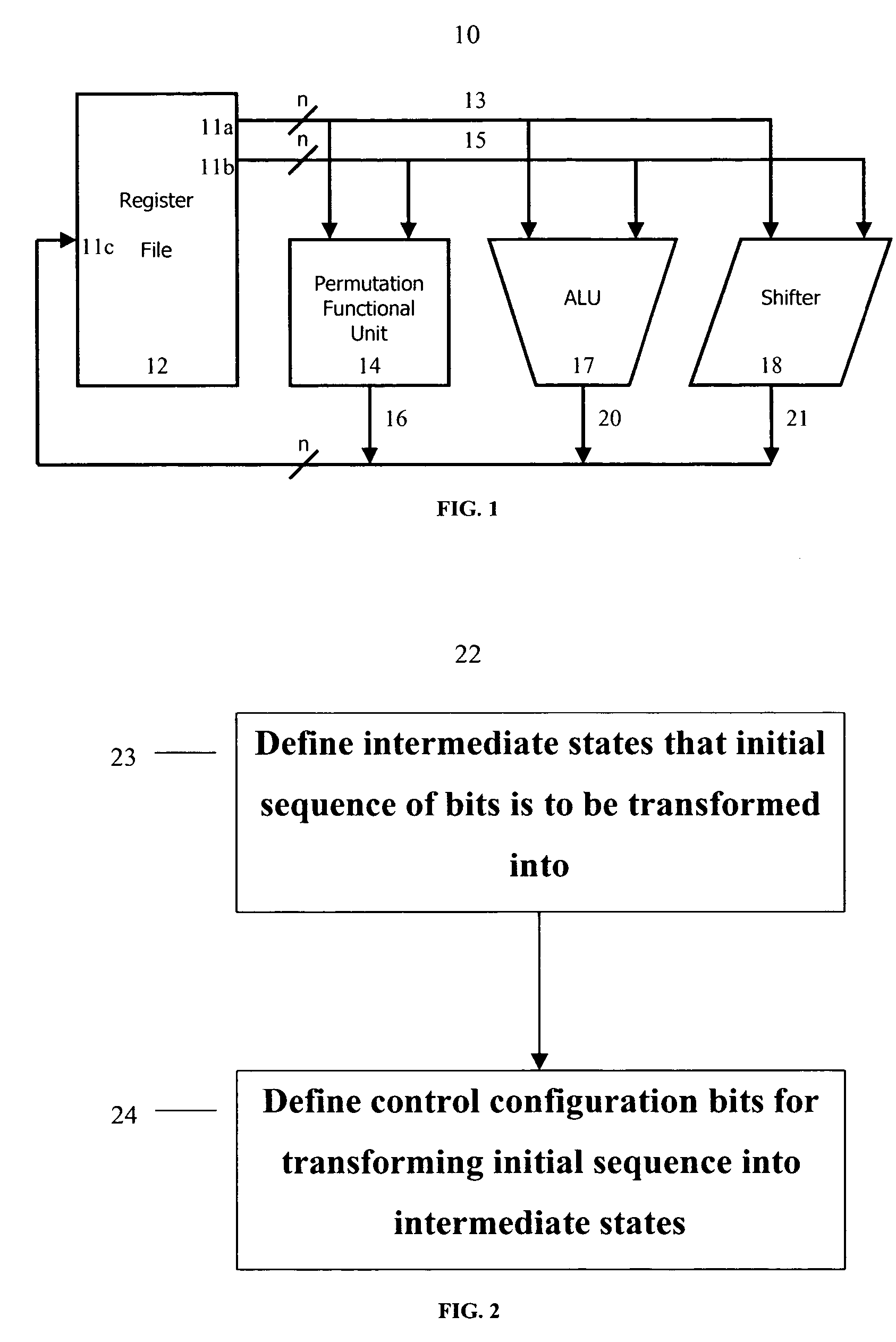
The present invention provides permutation instructions which can be used in software executed in a programmable processor for solving permutation problems in cryptography, multimedia and other applications. The permute instructions are based on an omega-flip network comprising at least two stages in which each stage can perform the function of either an omega network stage or a flip network stage. Intermediate sequences of bits are defined that an initial sequence of bits from a source register are transformed into. Each intermediate sequence of bits is used as input to a subsequent permutation instruction. Permutation instructions are determined for permuting the initial source sequence of bits into one or more intermediate sequence of bits until a desired sequence is obtained. The intermediate sequences of bits are determined by configuration bits. The permutation instructions form a permutation instruction sequence, of at least one instruction. At most 21 gr / m permutation instructions are used in the permutation instruction sequence, where r is the number of k-bit subwords to be permuted, and m is the number of network stages executed in one instruction. The permutation instructions can be used to permute k-bit subwords packed into an n-bit word, where k can be 1, 2, . . . , or n bits, and k*r=n.
Owner:TELEPUTERS
Method for safety packaging network message
ActiveCN1859291ANo friendliness issuesPrevent replay attacksSecuring communicationMessage lengthNetwork address translation
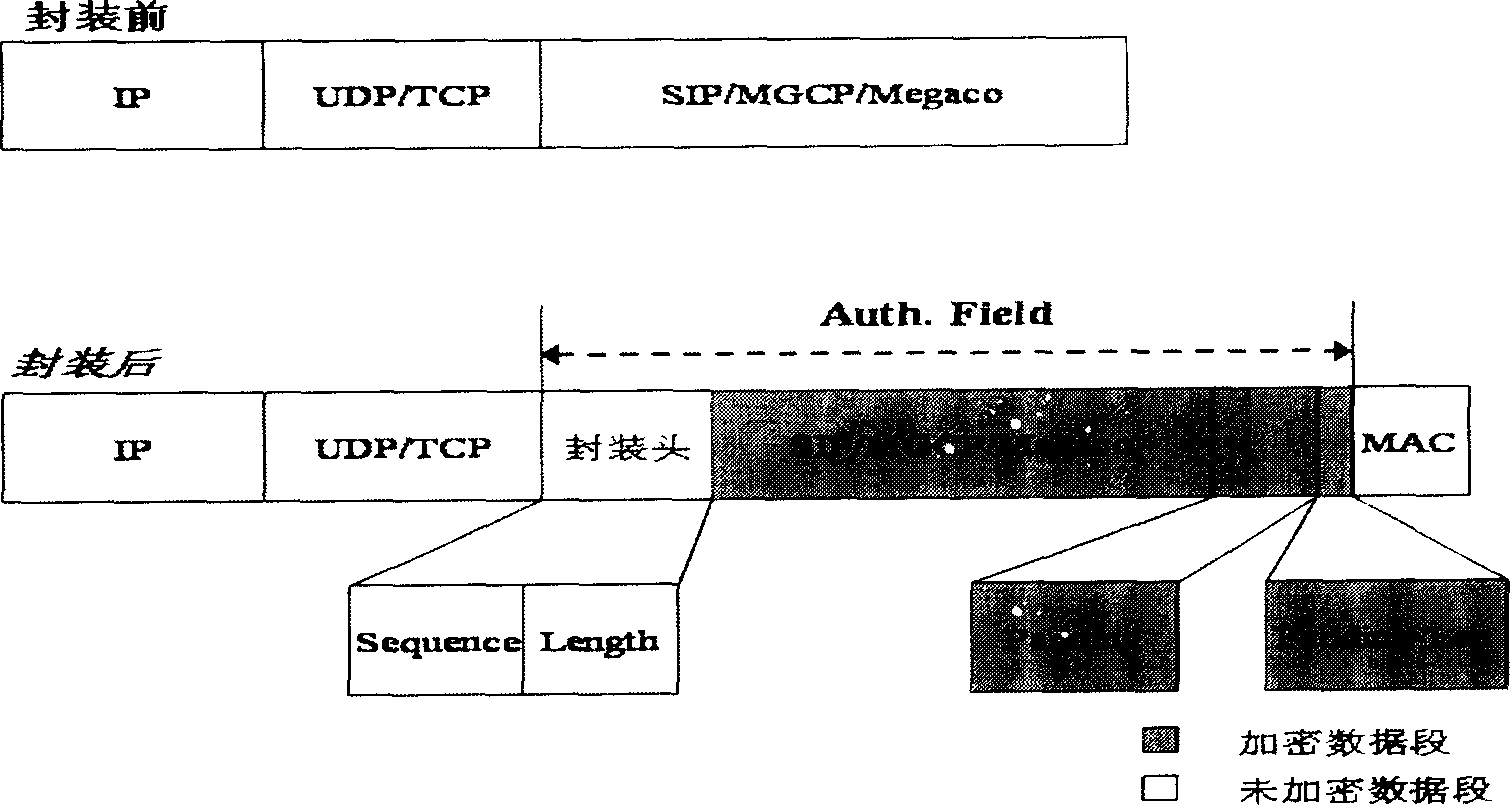
The present invention discloses a network message security package method. It contains generating application layer message; package head generating one random numbers as initial sequence number, serial number added 1 in transmitting one message, using serial number and message length bytes as package head added to message top; load filling its finally bytes meaning filling length; ciphering message; message authentication code message authenticating code calculation; transmitting security packaged signaling message package IP / UDP or TCP head. The present invented method adopts application layer package mode therefore being not related to network address translation equipment NAT, enhancing security.
Owner:HUAWEI TECH CO LTD
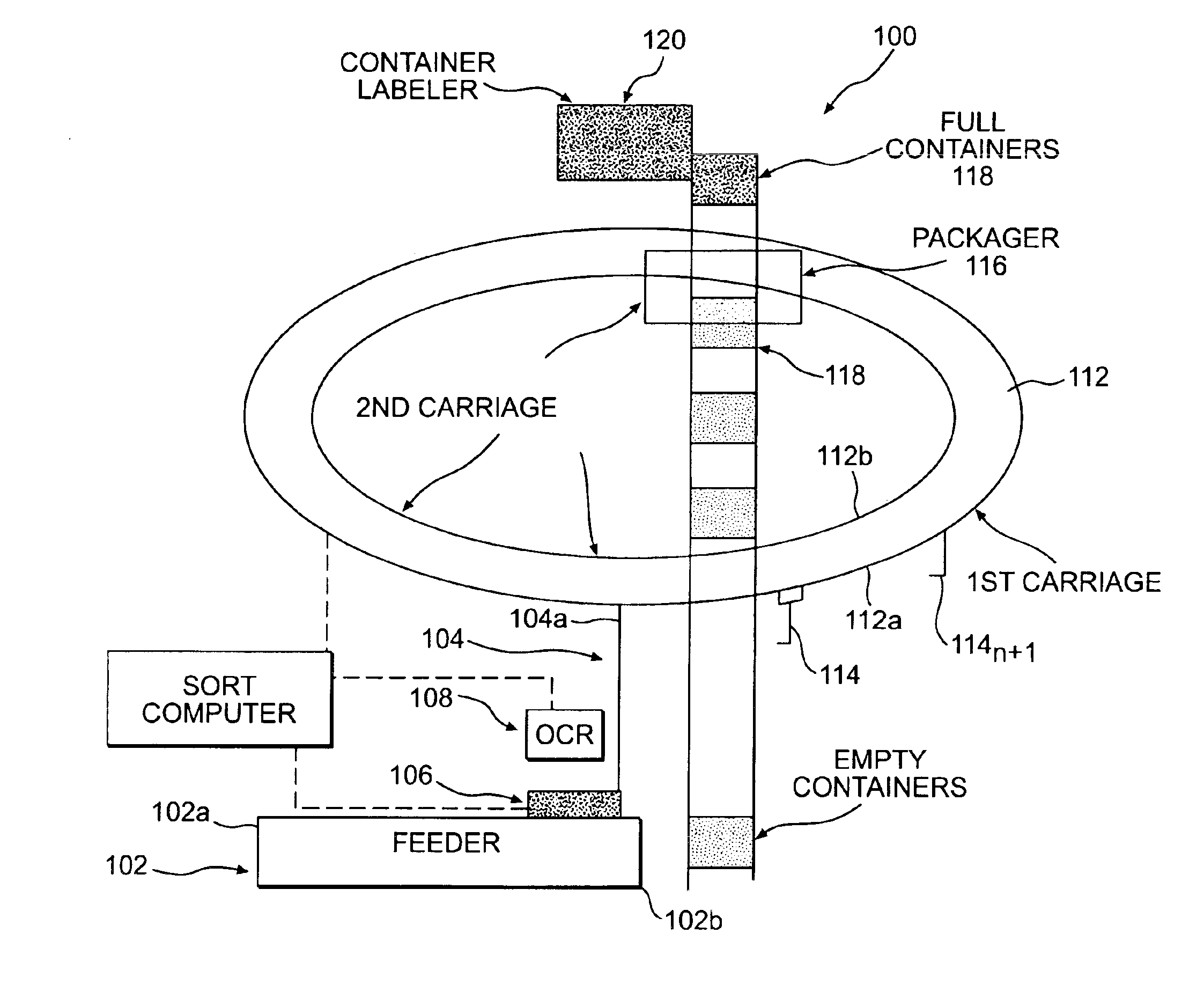
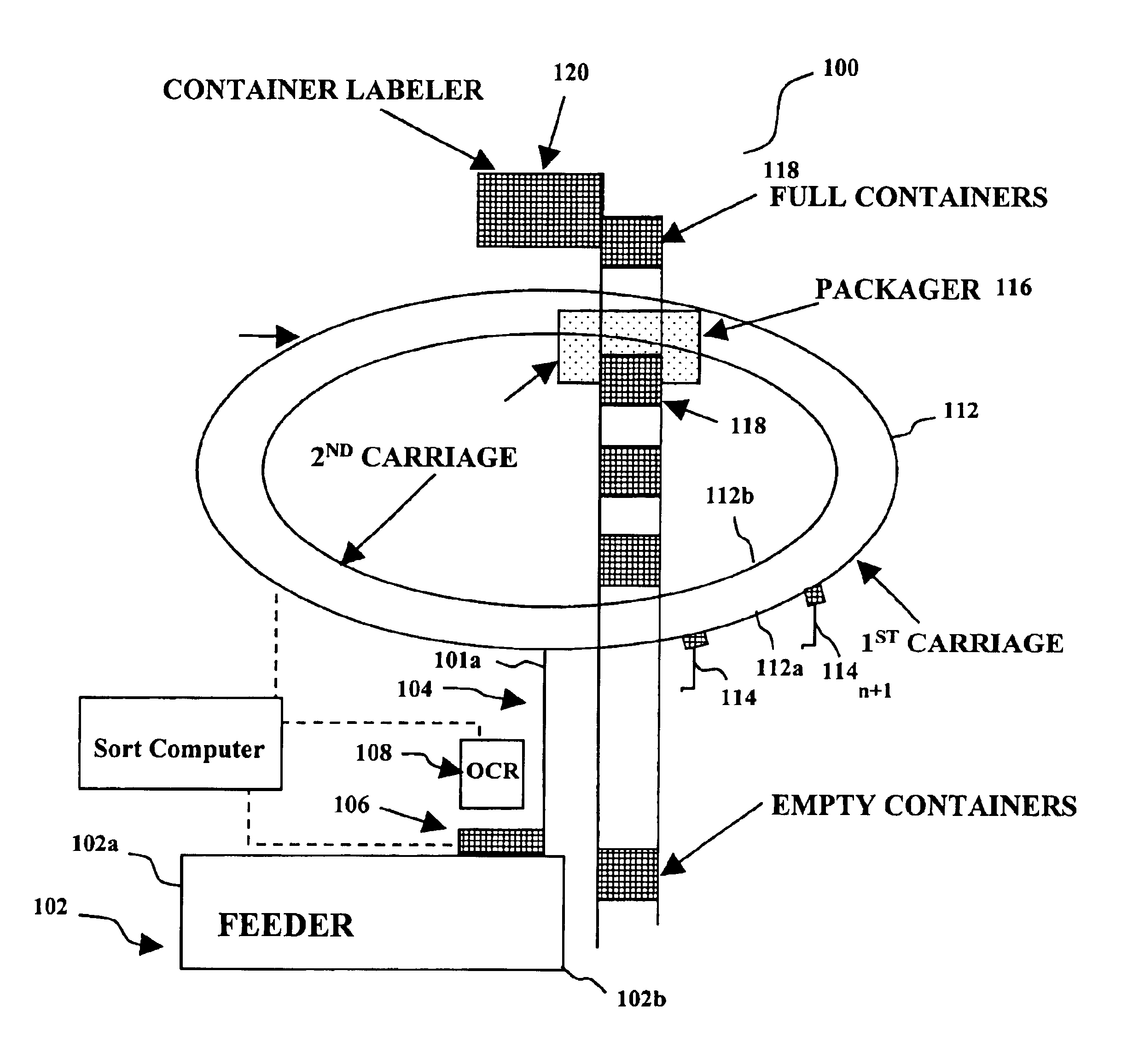
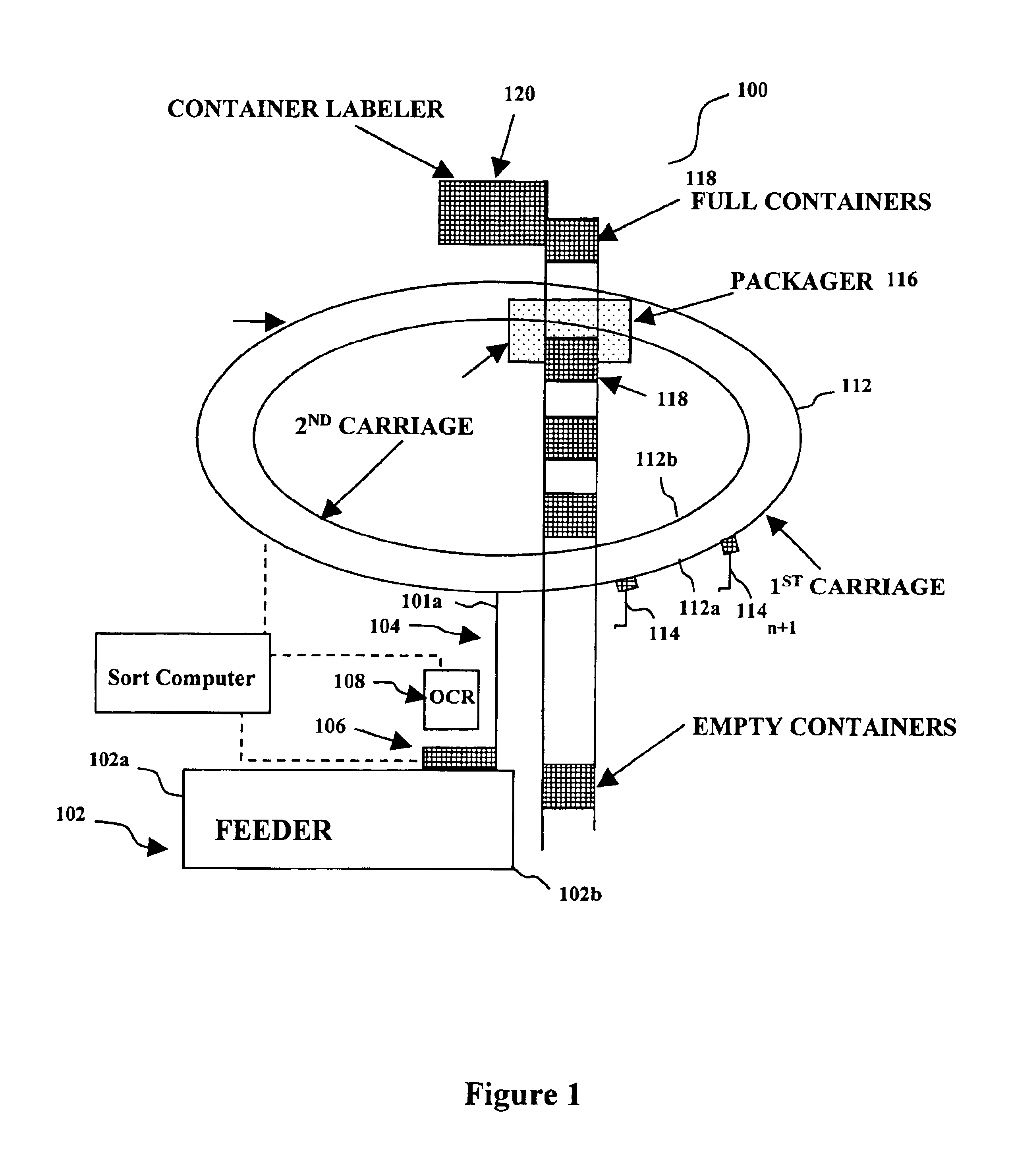
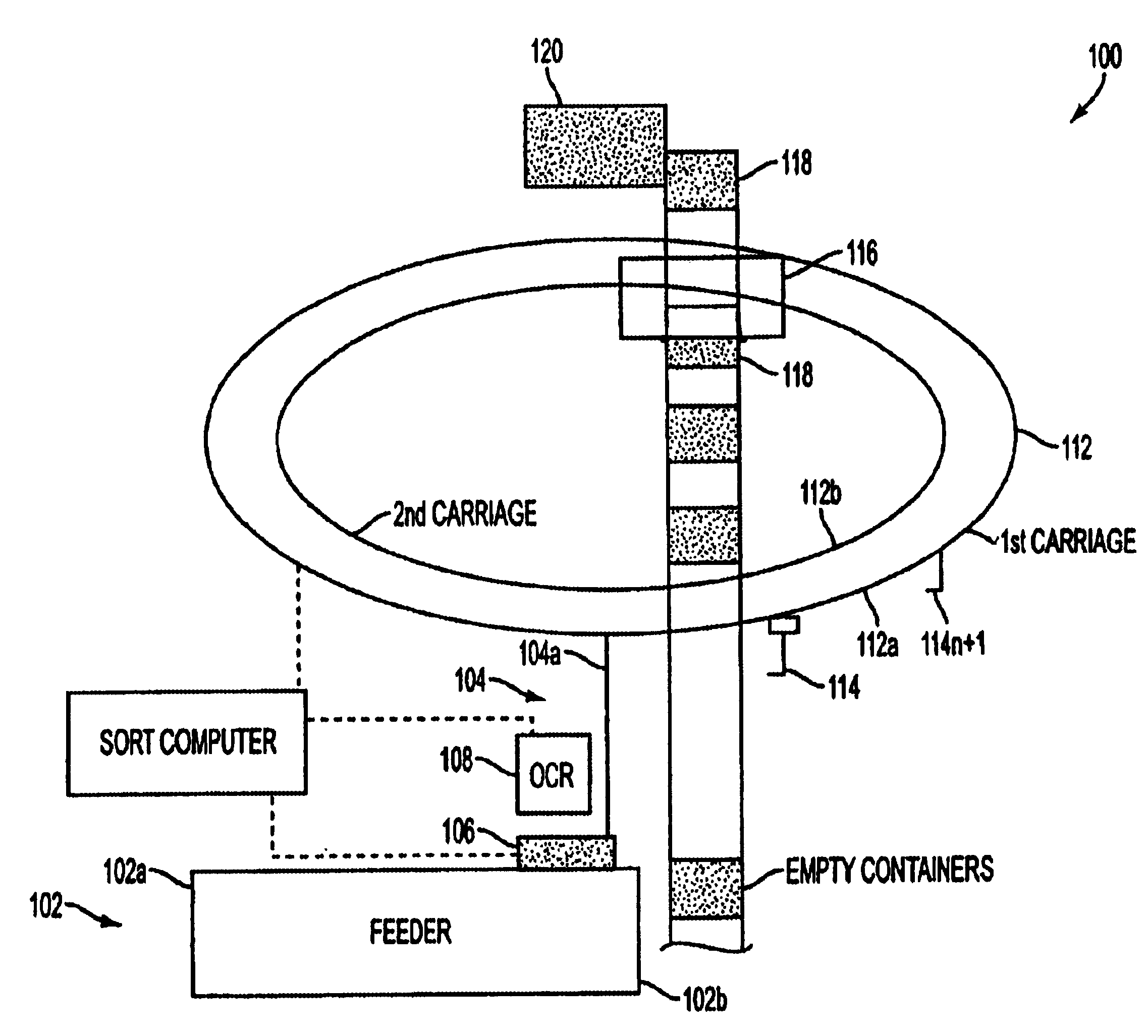
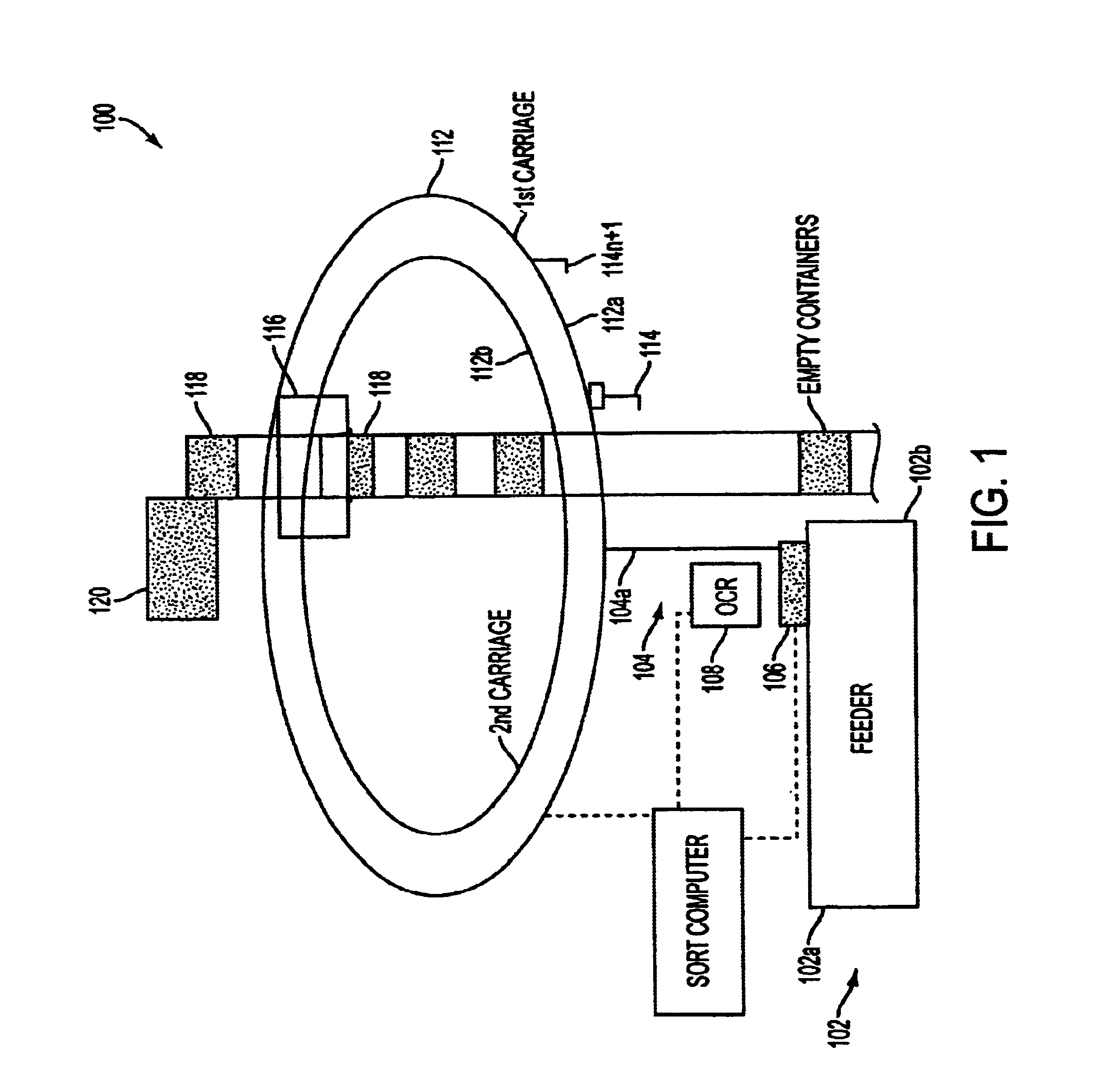
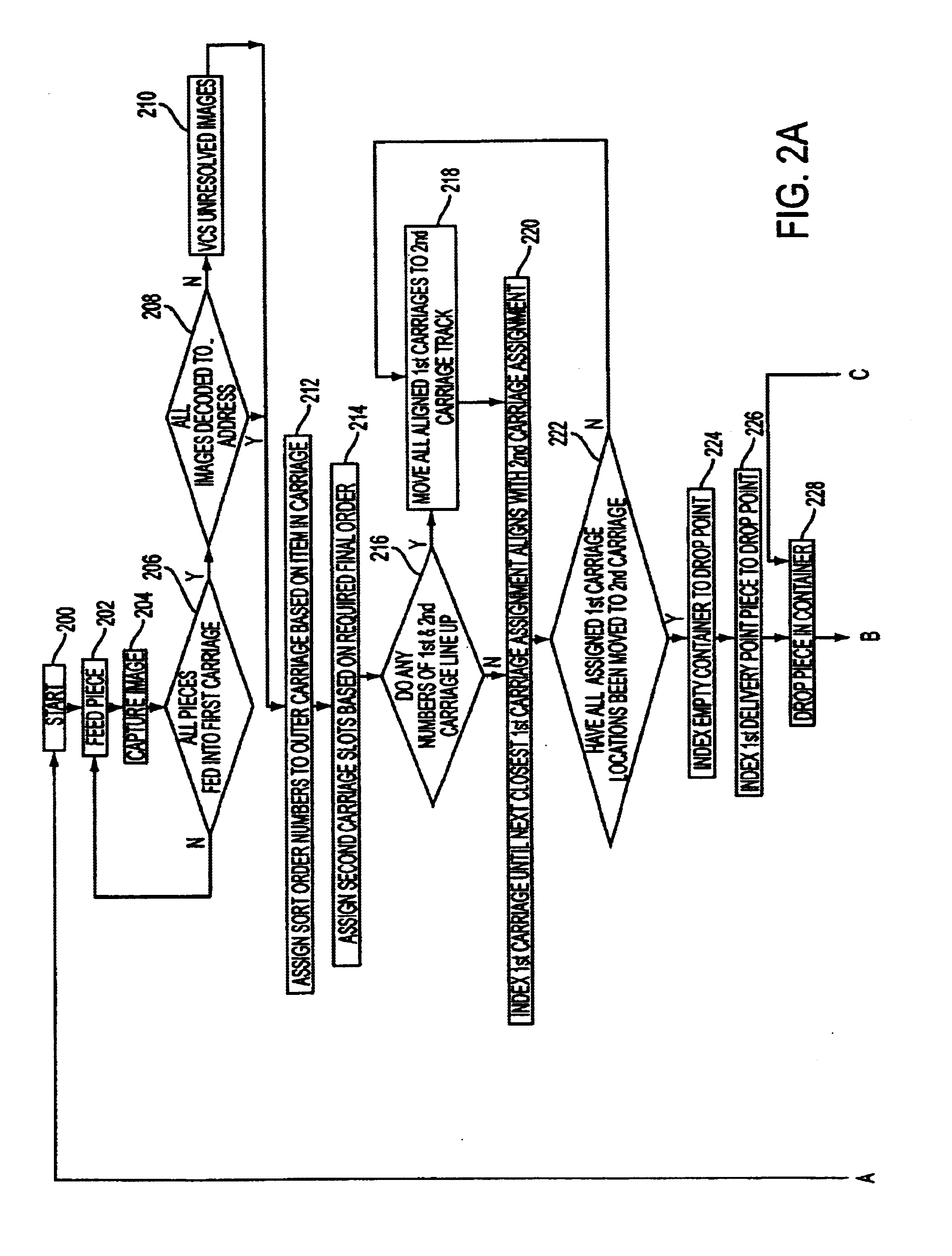
Single pass sequencer
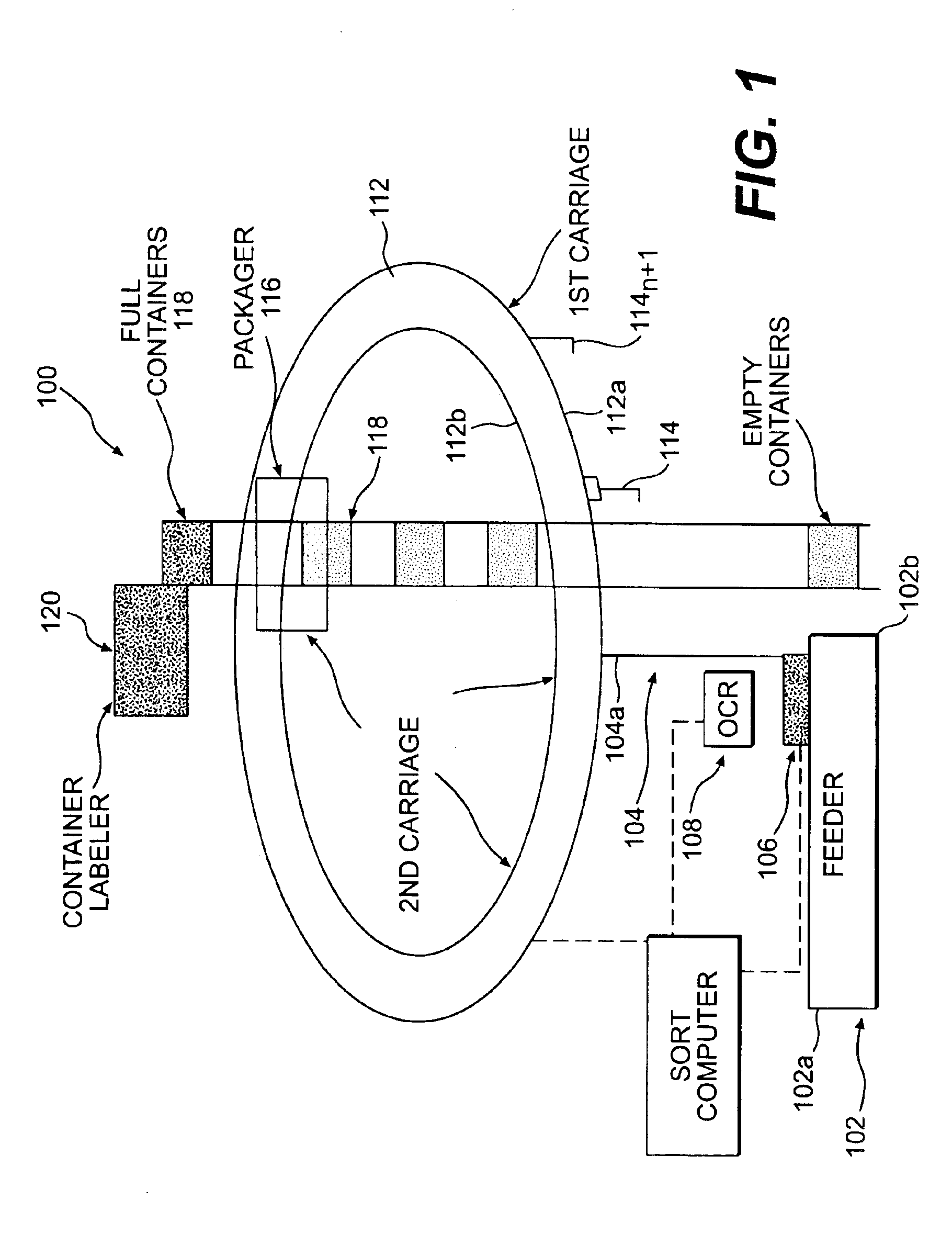
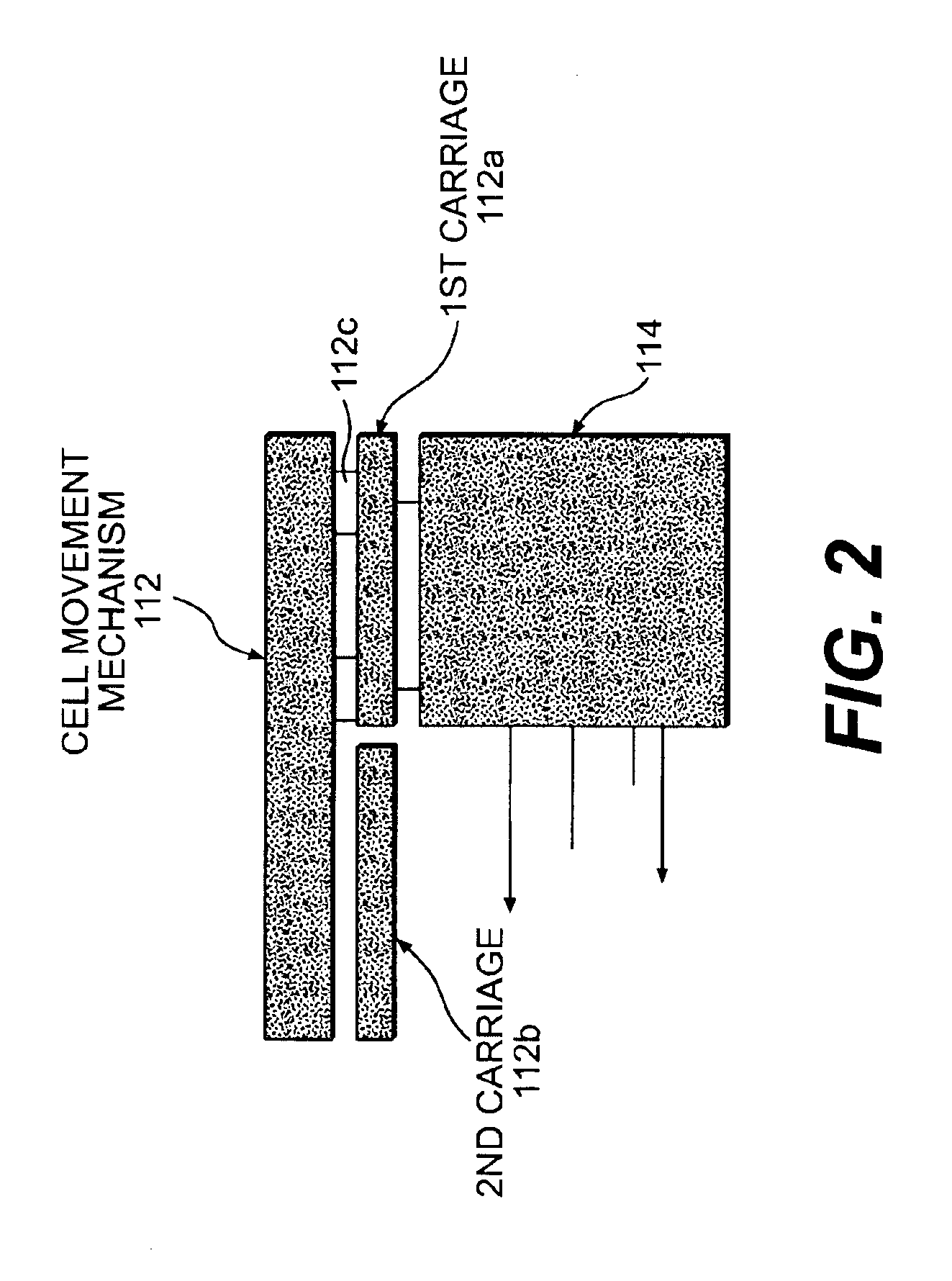
A single pass sequencer having a transport system for transporting the mail pieces and a character recognition system proximate to the transport system for reading destination information associated with the mail pieces. The system includes a first carriage system and a second carriage system with a a plurality of holders slidable between the first carriage system and the second carriage system. Each of the plurality of holders holding a mail piece of the mail pieces received from the transport system. A sorting device stores information from the mail pieces and assigns a code to: (i) the mail pieces based on the destination information, (ii) the plurality of holders on the first carriage based on an initial sequence of each of the plurality of holders on the first carriage, and (iii) a position on the second carriage which corresponds to the initial sequence and a destination sequence of the mail pieces. The sorting device instructs movement of the plurality of holders from the first carriage to the second carriage based on the code assigned to the mail pieces, the plurality of holders on the first carriage and the position on the second carriage such that when the mail pieces are moved to the second carriage they are in sequential order of delivery destination.
Owner:LOCKHEED MARTIN CORP
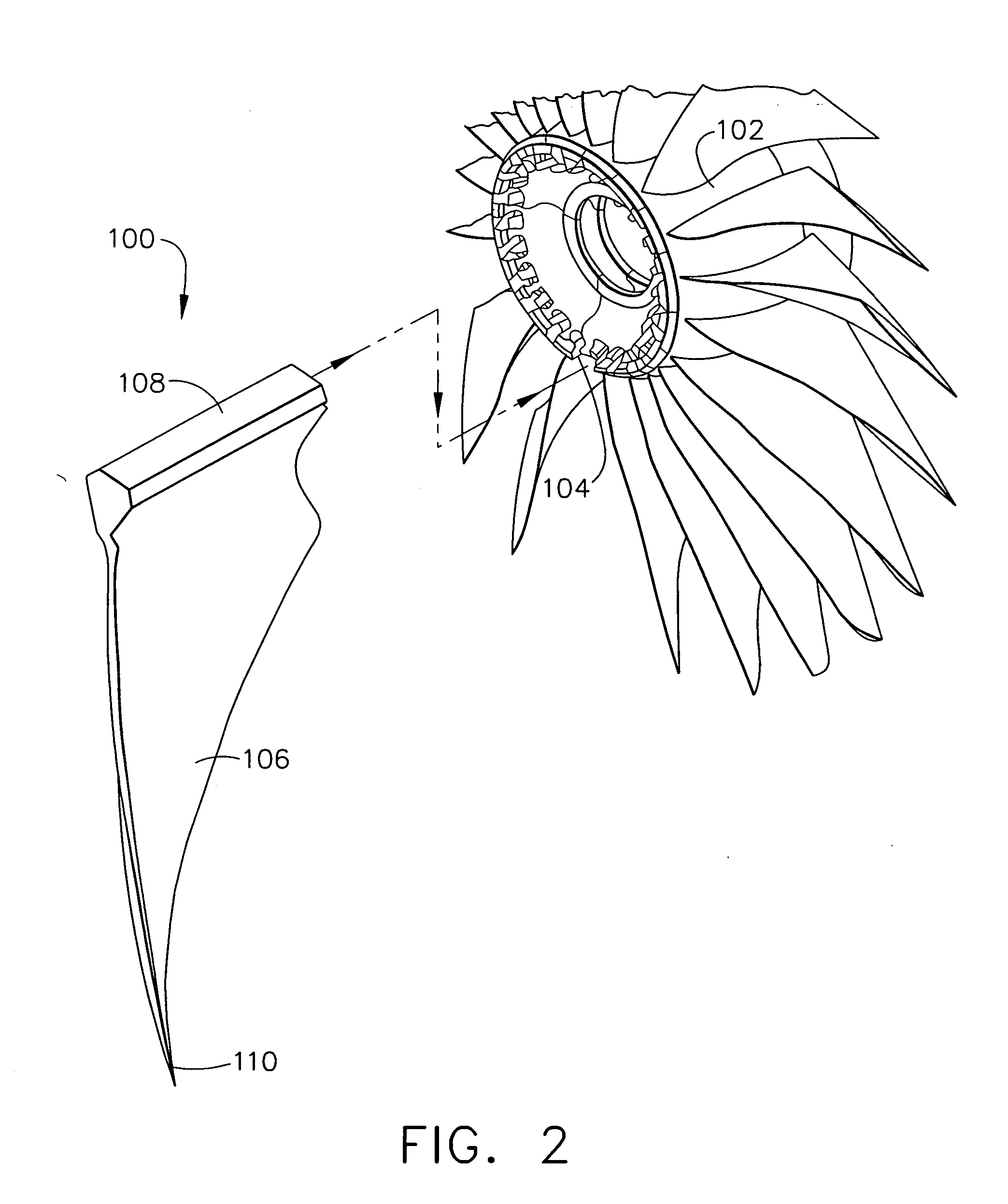
Methods and apparatus for assembling rotatable machines
ActiveUS20060010686A1MiniaturizationWeight optimizationPump componentsMetal-working apparatusEngineeringInitial sequence
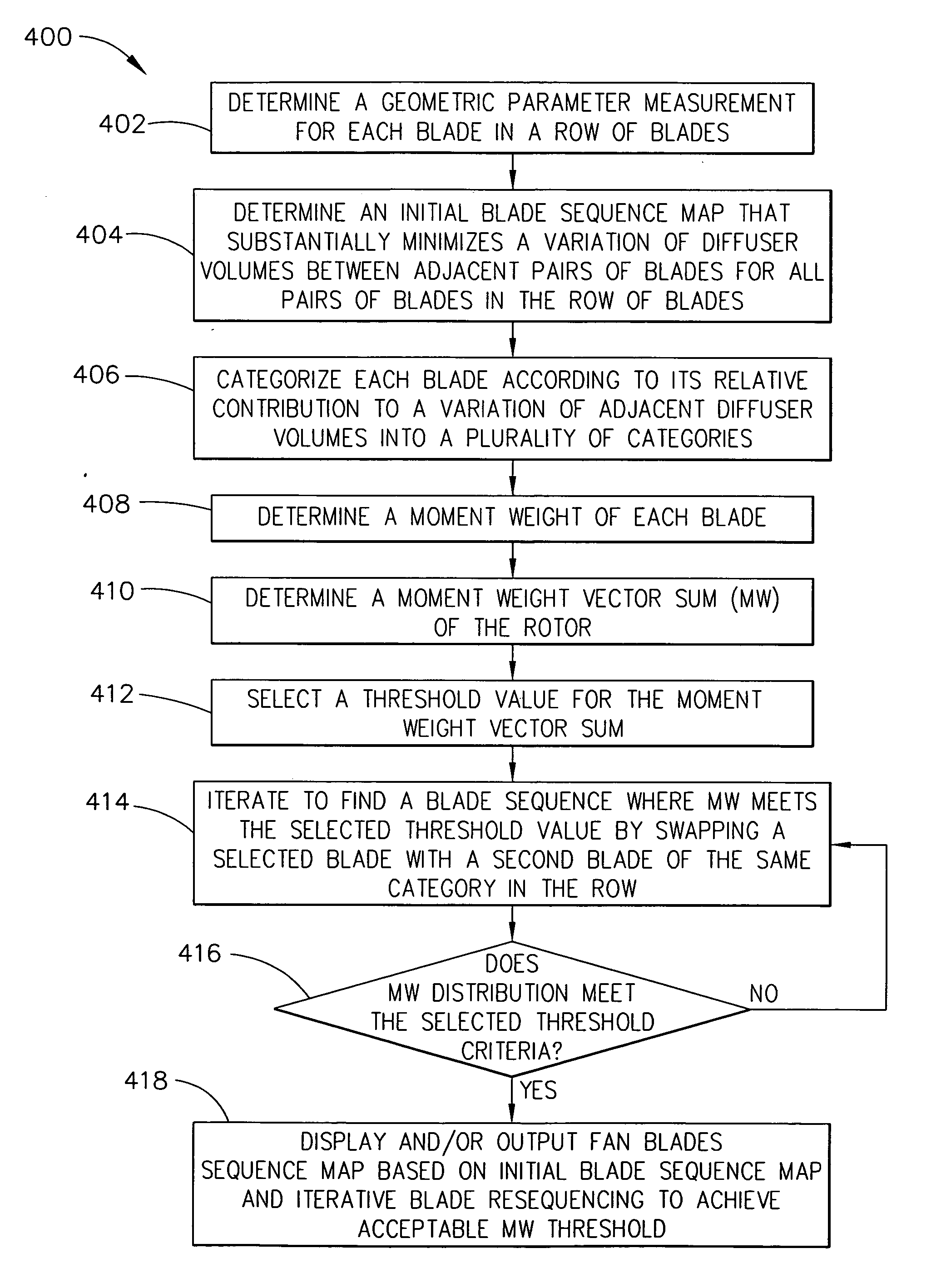
A processor-implemented method of assembling a rotatable machine is provided. The machine includes a plurality of blades that extend radially outwardly from a rotor. The method includes determining a geometric parameter for each blade in a row of blades that is relative to a ratio, R of an inlet area and an outlet area of a predetermined volume defined between each pair of blades, determining an initial sequence map for the row of blades that facilitates minimizing a difference of R between circumferentially adjacent pairs of blades, and iteratively remapping the sequence of the blades to facilitate reducing a moment weight vector sum of the rotor to a value that is less than a predetermined value.
Owner:GENERAL ELECTRIC CO
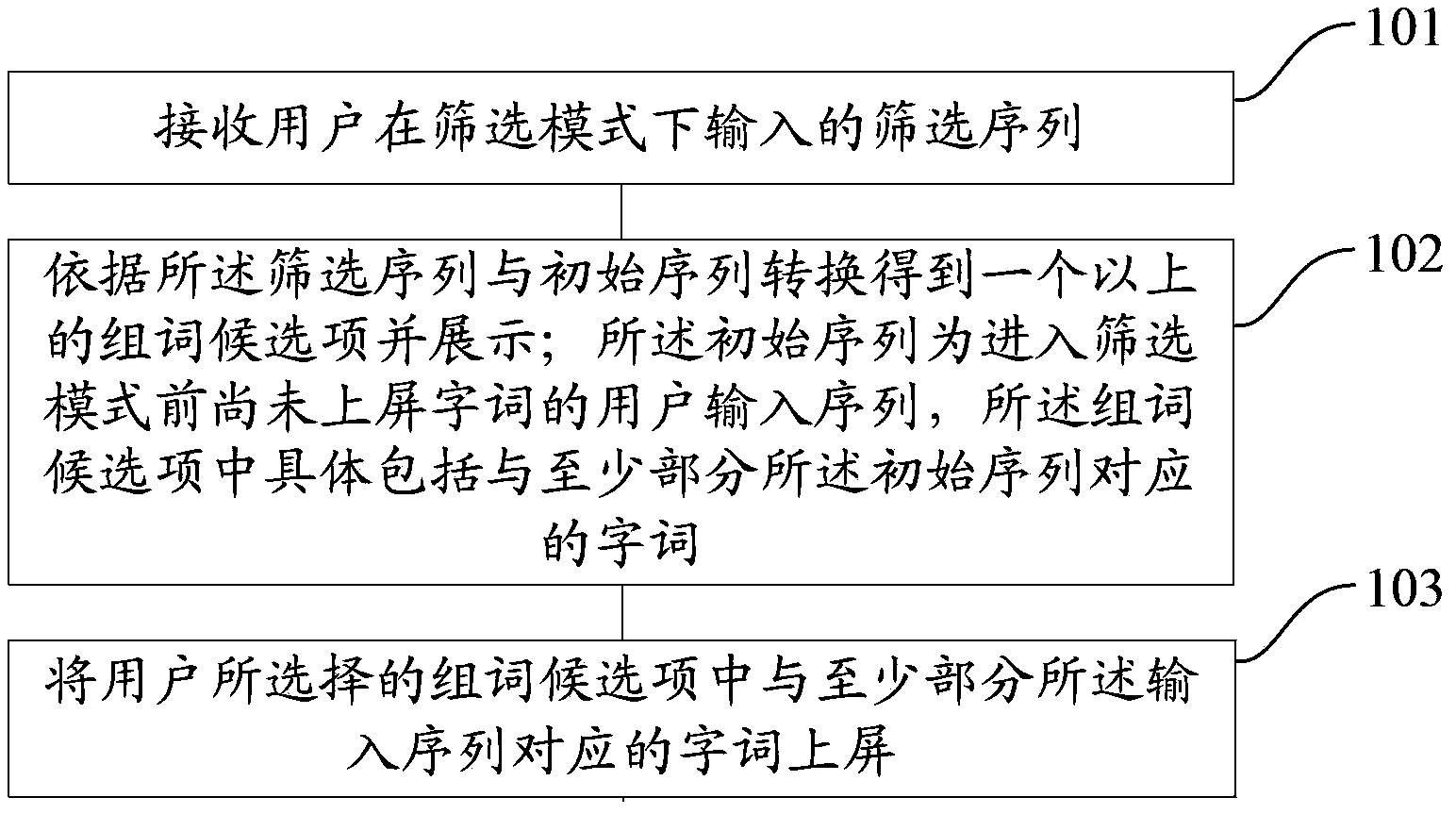
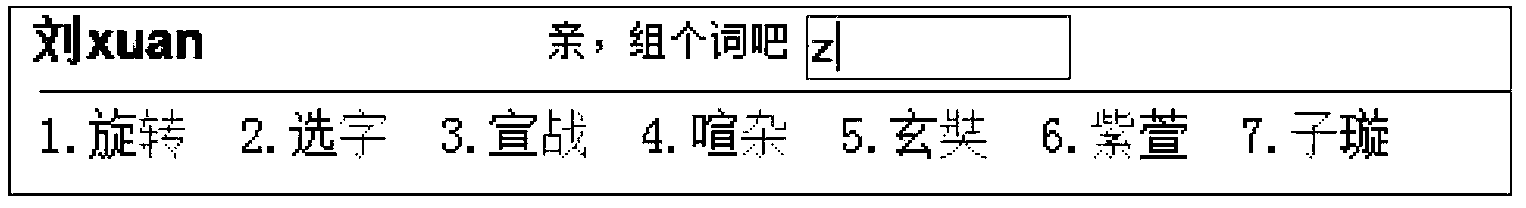
Method and device for screening candidate items in character input
ActiveCN103631385AHigh screening accuracyImprove efficiencySpecial data processing applicationsInput/output processes for data processingUser inputInitial sequence
The invention provides a method and device for screening candidate items in character input. The method comprises the steps that a screening sequence input by a user in a screening mode is received; according to conversion of the screening sequence and an initial sequence, more than one word group candidate item is obtained and displayed; the initial sequence is the sequence which is the words not displayed on a screen and is input by the user before the screening mode, and the word group candidate items comprise words corresponding to at least one part of the initial sequence; the words, which correspond to at least one part of the initial sequence and are selected by the user, of the word group candidate items are displayed on the screen. The method and device for screening the candidate items in character input can reduce the number of candidate items for selection, and improve the efficiency when the user selects the candidate items and the input efficiency of the user.
Owner:BEIJING SOGOU TECHNOLOGY DEVELOPMENT CO LTD
Scrambling code sequence generation method, device and system for scrambling or descrambling
ActiveCN101925056AReduce build timeOvercoming scramblingSecurity arrangementGeneration processCommunications system
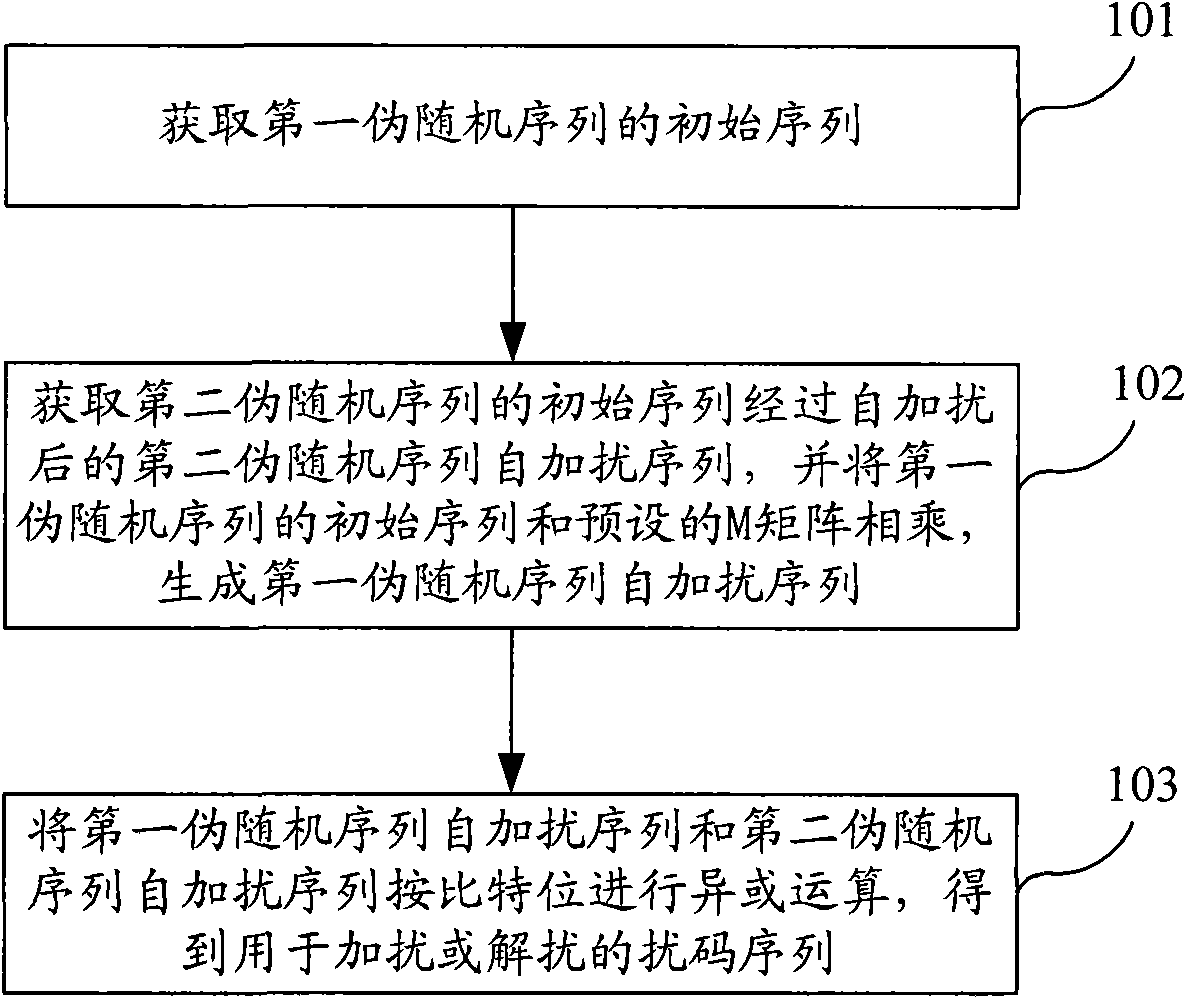
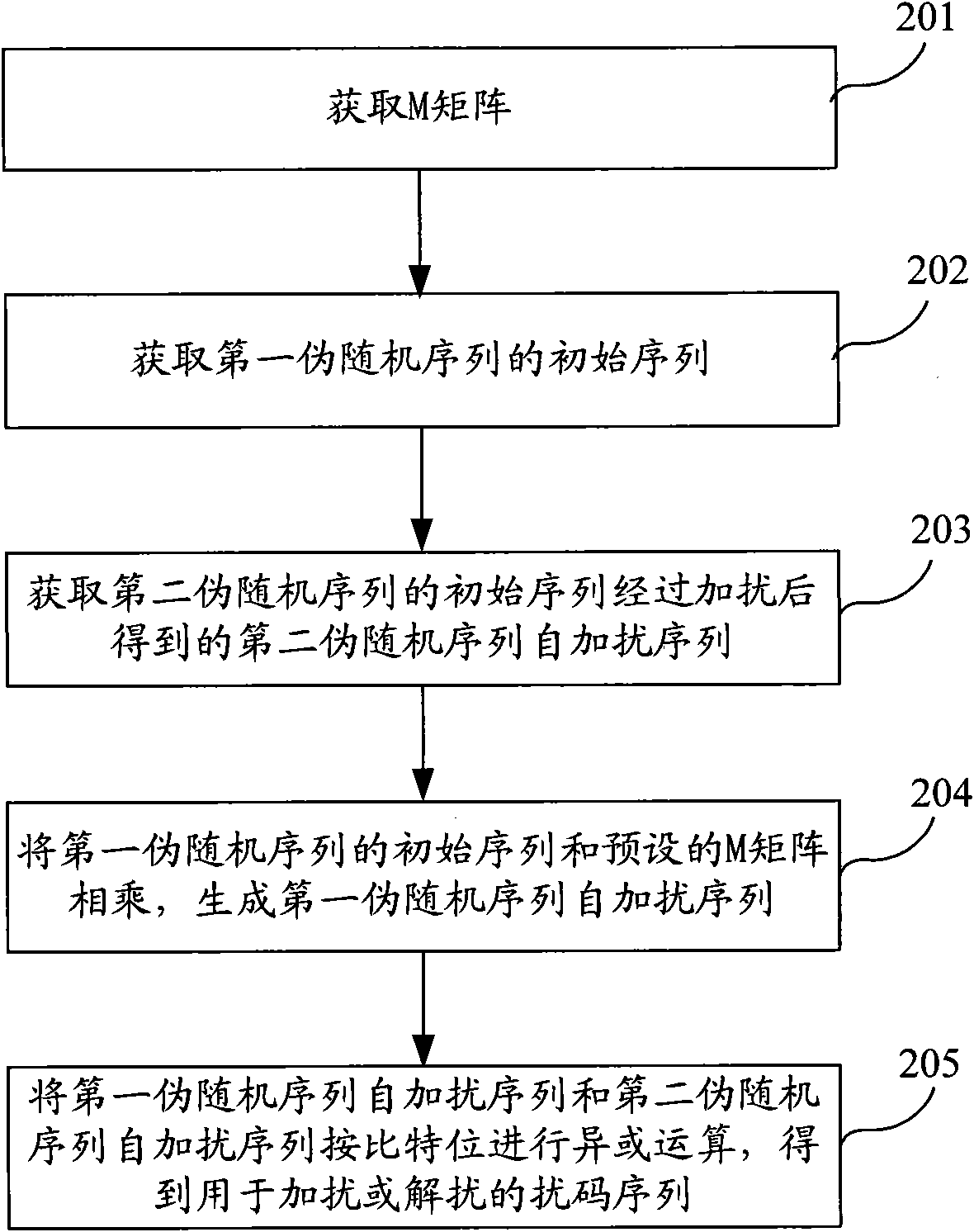
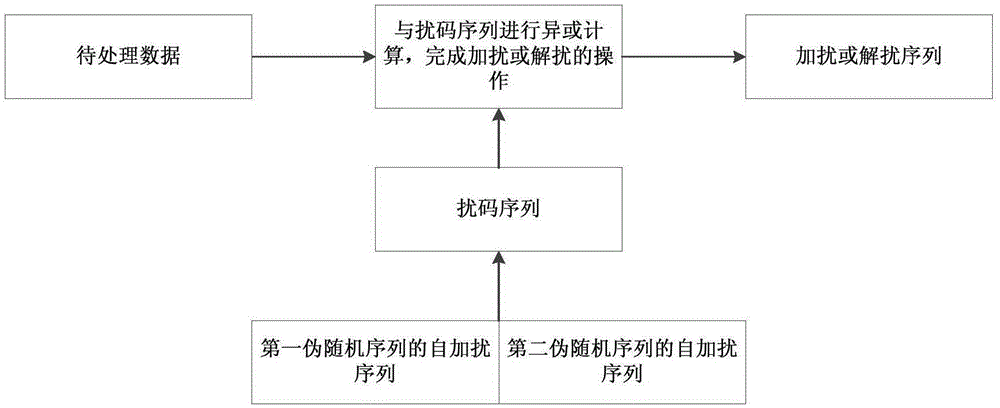
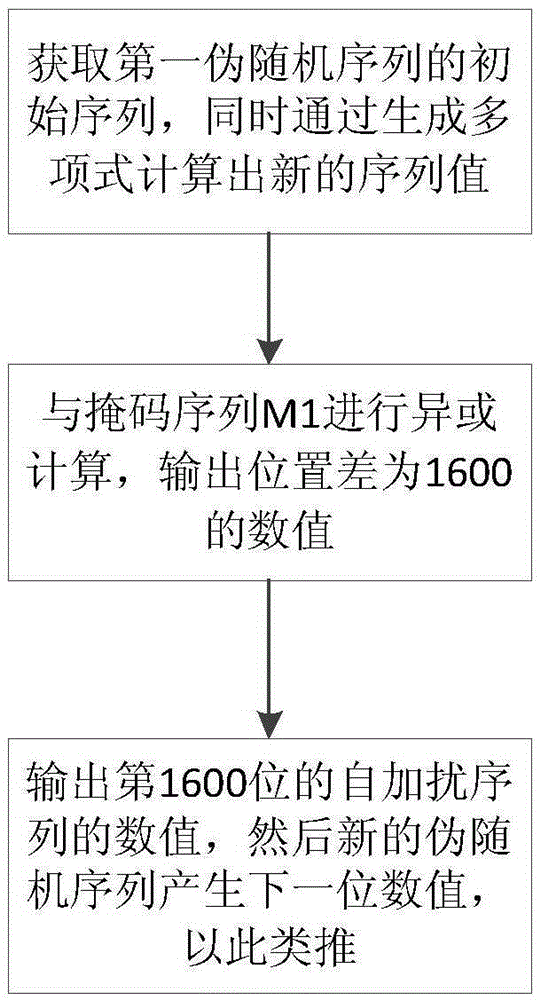
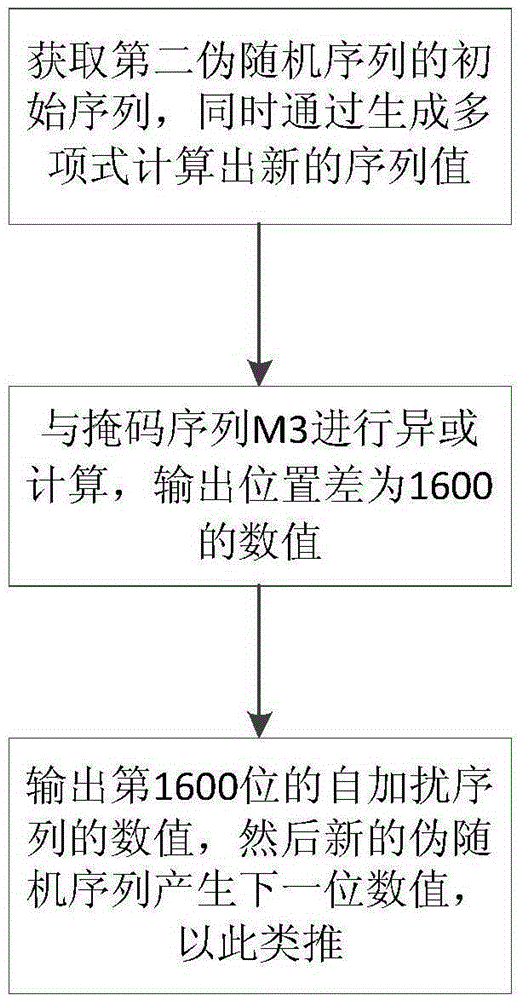
The embodiment of the invention provides a scrambling code sequence generation method, a device and a system for scrambling or descrambling. The method comprises the following steps: obtaining the initial sequence of a first pseudo-random sequence; obtaining a self-scrambled sequence of a second pseudo-random sequence after self-scrambling the initial sequence of the second pseudo-random sequence, multiplying the initial sequence of the first pseudo-random sequence with a preset M matrix, and generating the self-scrambled sequence of the first pseudo-random sequence; and carrying out XOR operation on the self-scrambled sequence of the first pseudo-random sequence and the self-scrambled sequence of the second pseudo-random sequence according to bits and obtaining a scrambling code sequencefor scrambling or descrambling. The embodiment can simplify the generation process of the scrambling code sequence, shorten the generation time of the scrambling code sequence, further shorten the time for scrambling or descrambling transmitted data, accelerate the scrambling or descrambling processing speed of a wireless communication system and save system resources.
Owner:HUAWEI TECH CO LTD
Trusted communications between untrusting parties
InactiveUS20050221889A1Reduce the possibilityDigital data processing detailsComputer security arrangementsThe InternetInitial sequence
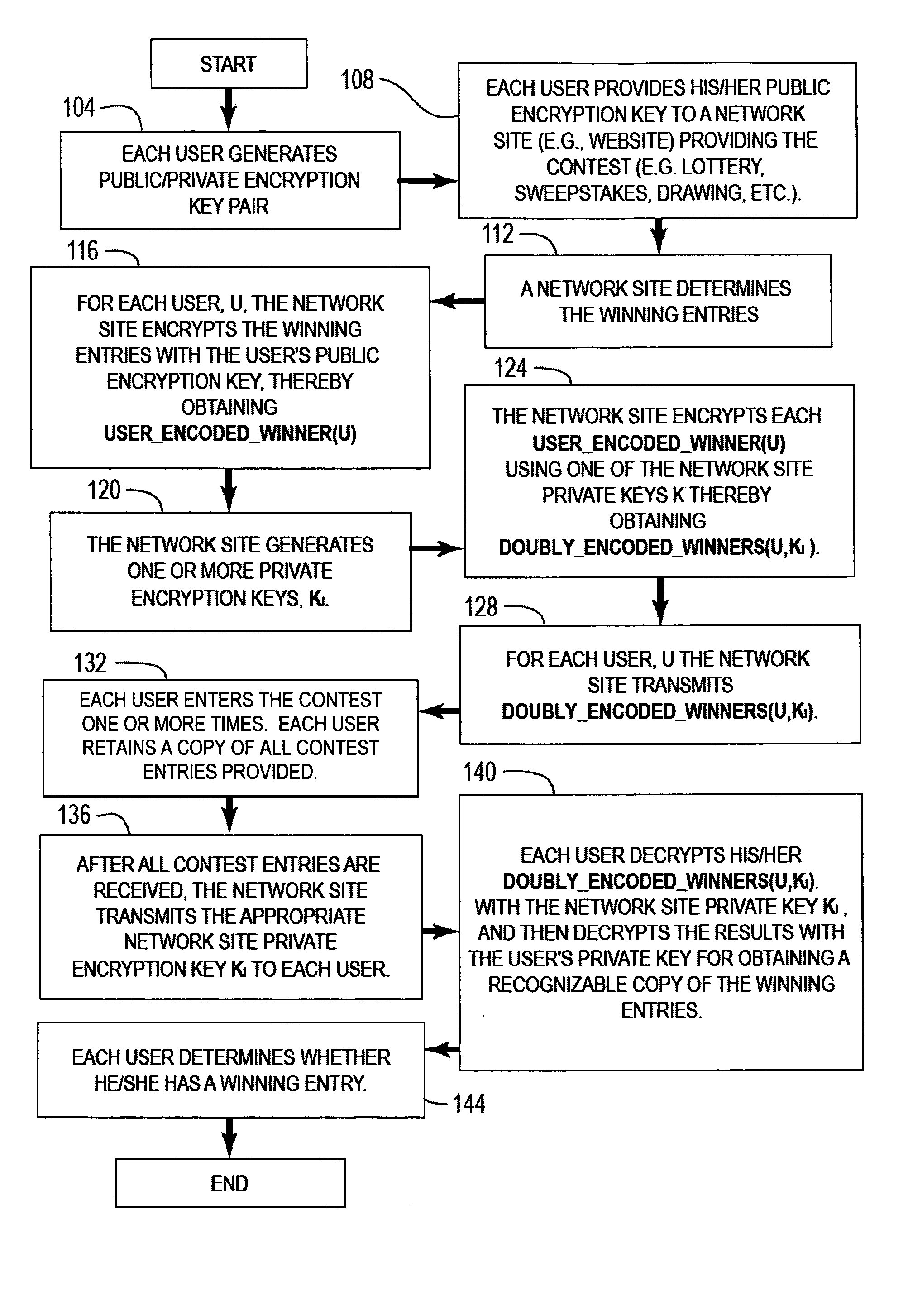
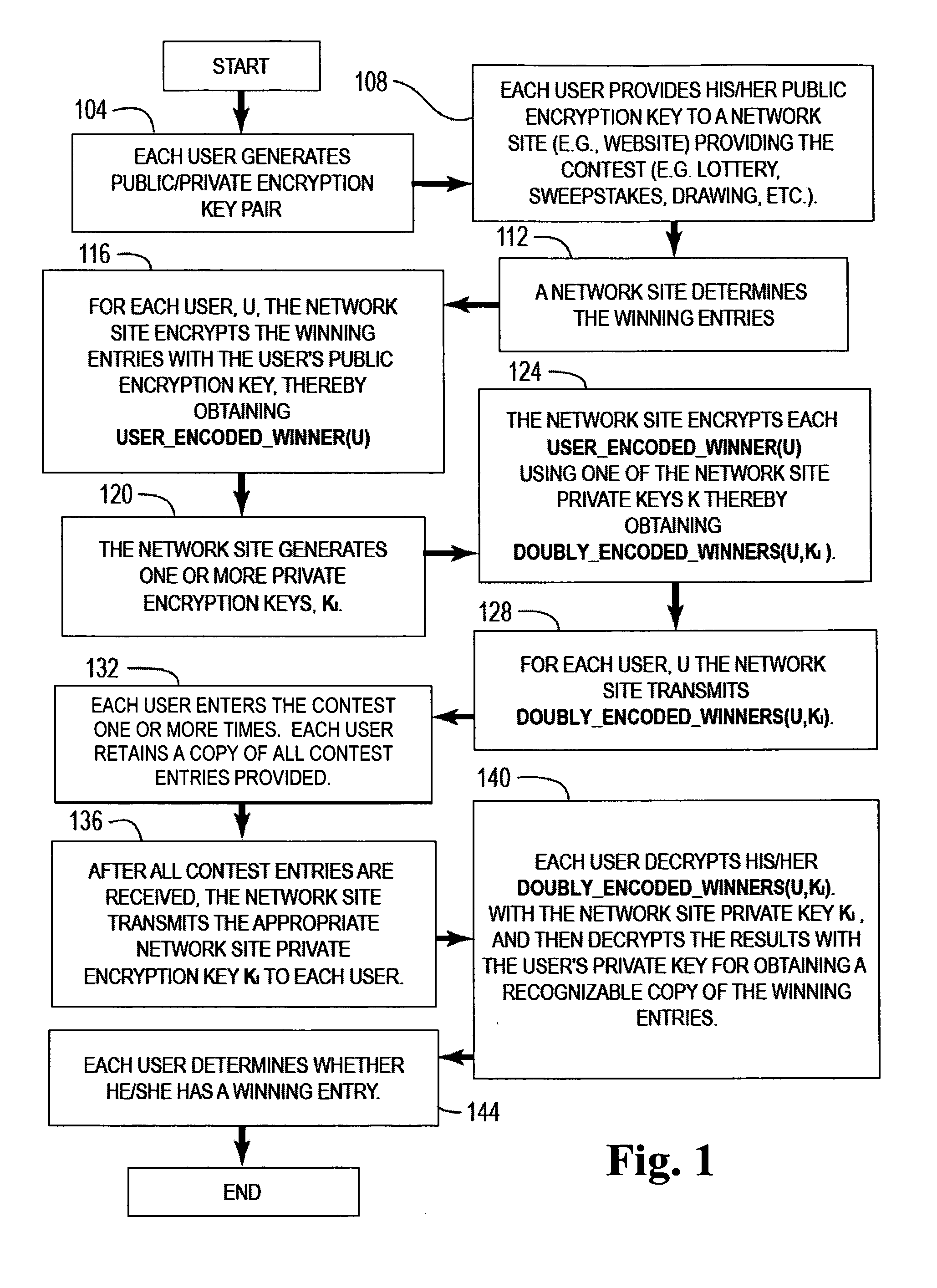
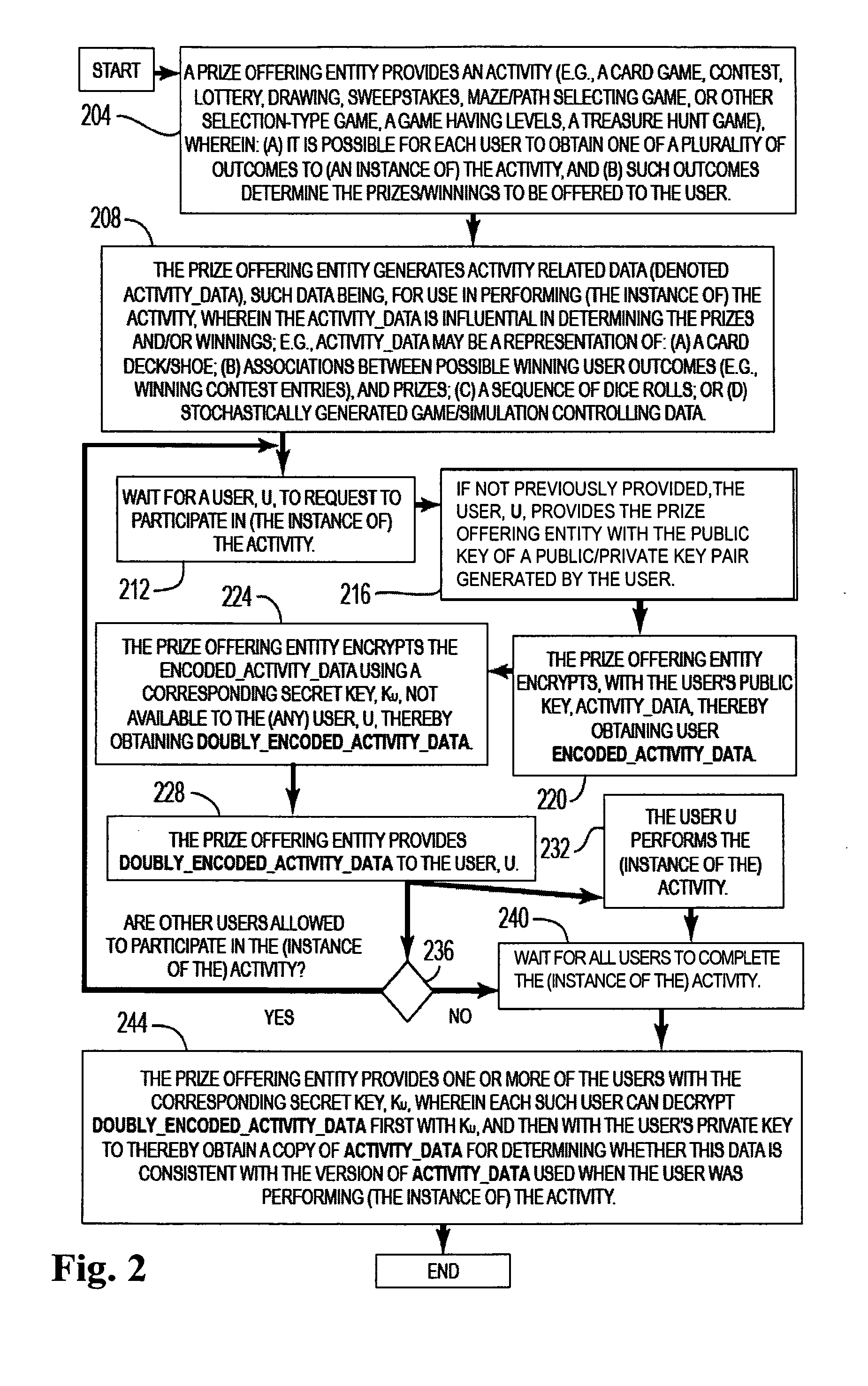
A system and method is disclosed for assuring that networked communications between parties playing a game on a network (e.g., the Internet) are not tampered with by either of the parties for illicitly gaining an advantage over the other party. An initial sequence of tokens (e.g., card representations) for playing the game are doubly encrypted using an encryption key from each of the parties. Accordingly, during play of the game neither party can modify the initial sequence of game tokens during the game. At termination of the game, at least one of the parties can fully decrypt the initial sequence of tokens, and thereby, if desired, compare the played token sequence with the corresponding the initial token sequence.
Owner:DUPRAY DENNIS J +1
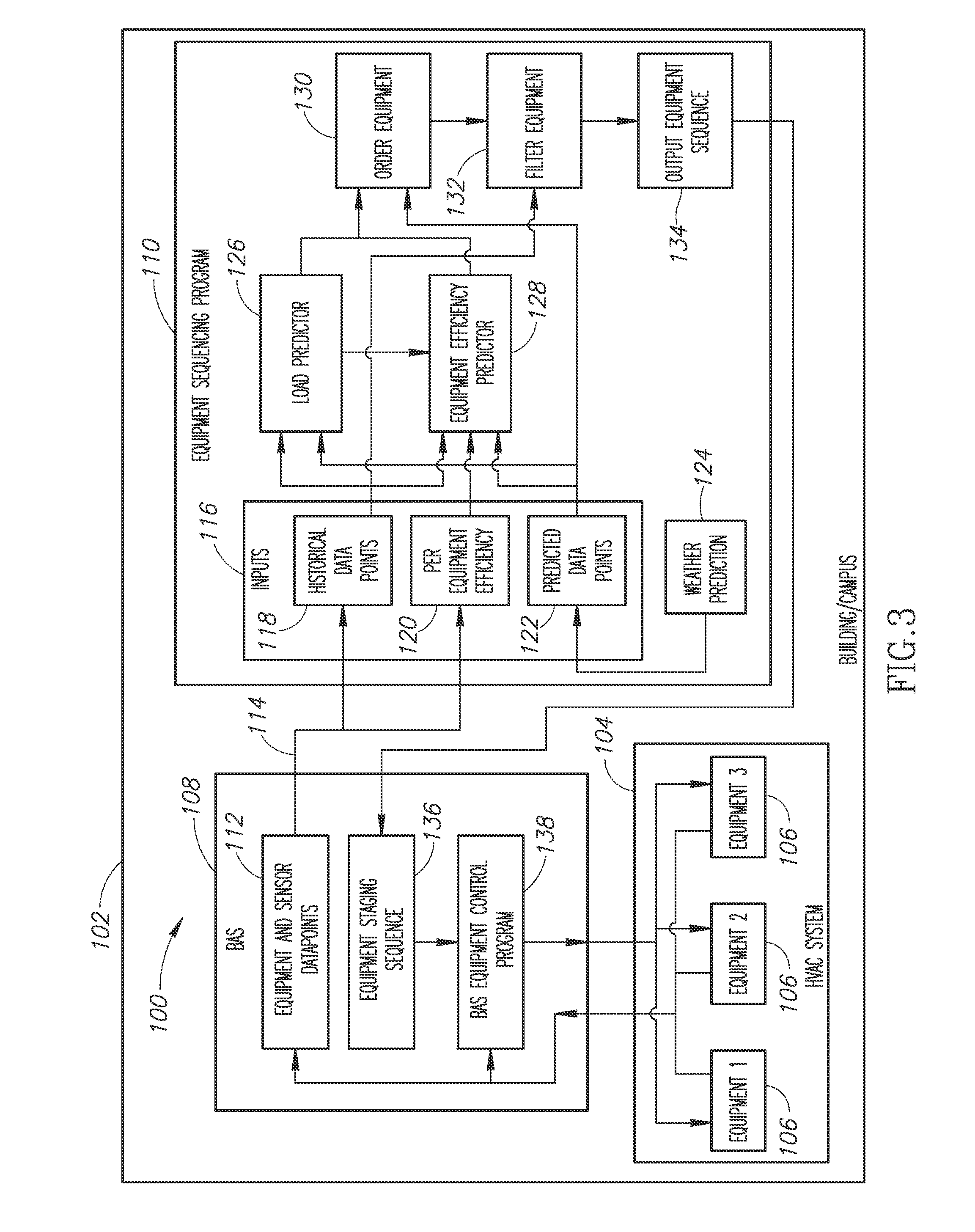
Intelligent equipment sequencing
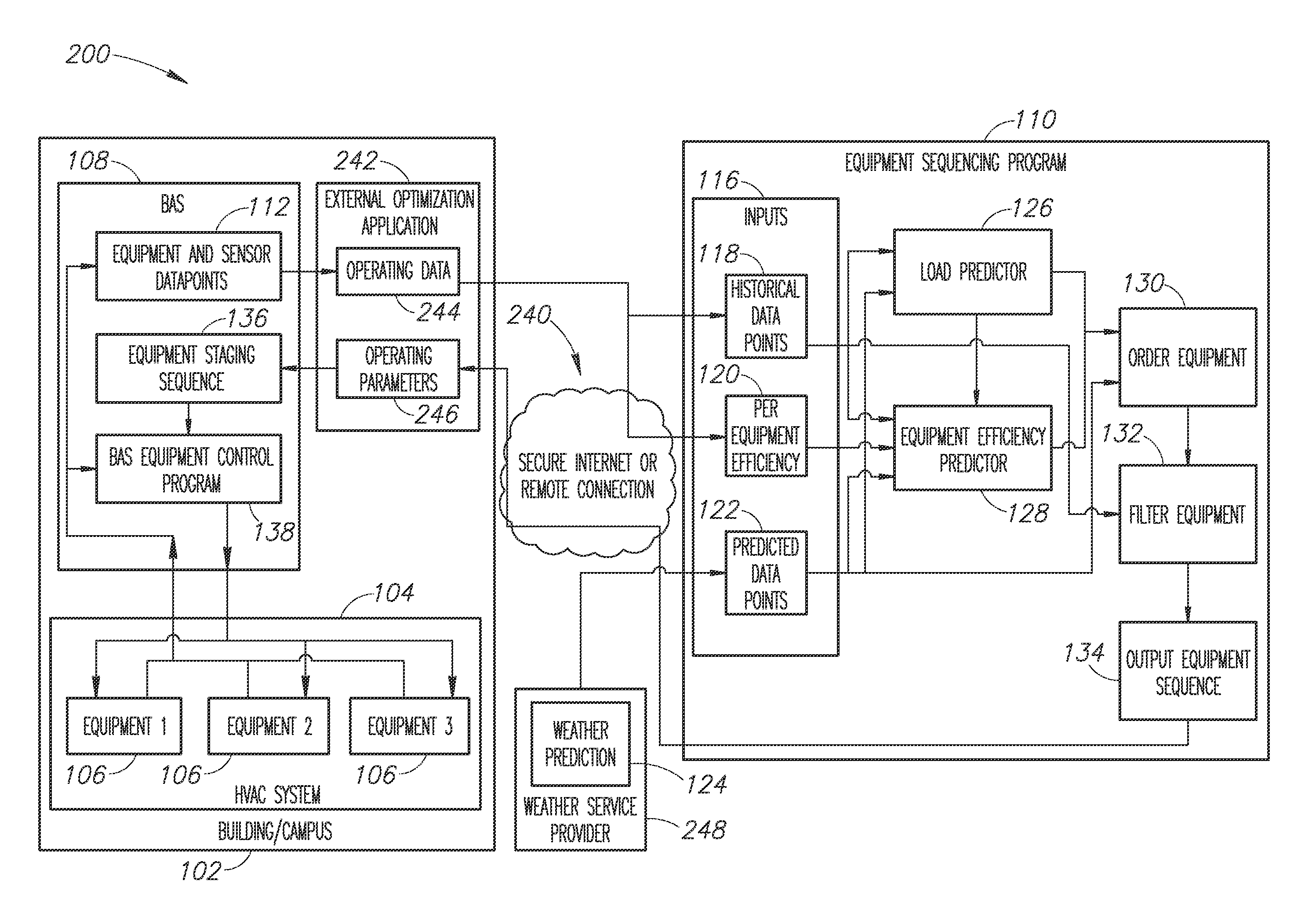
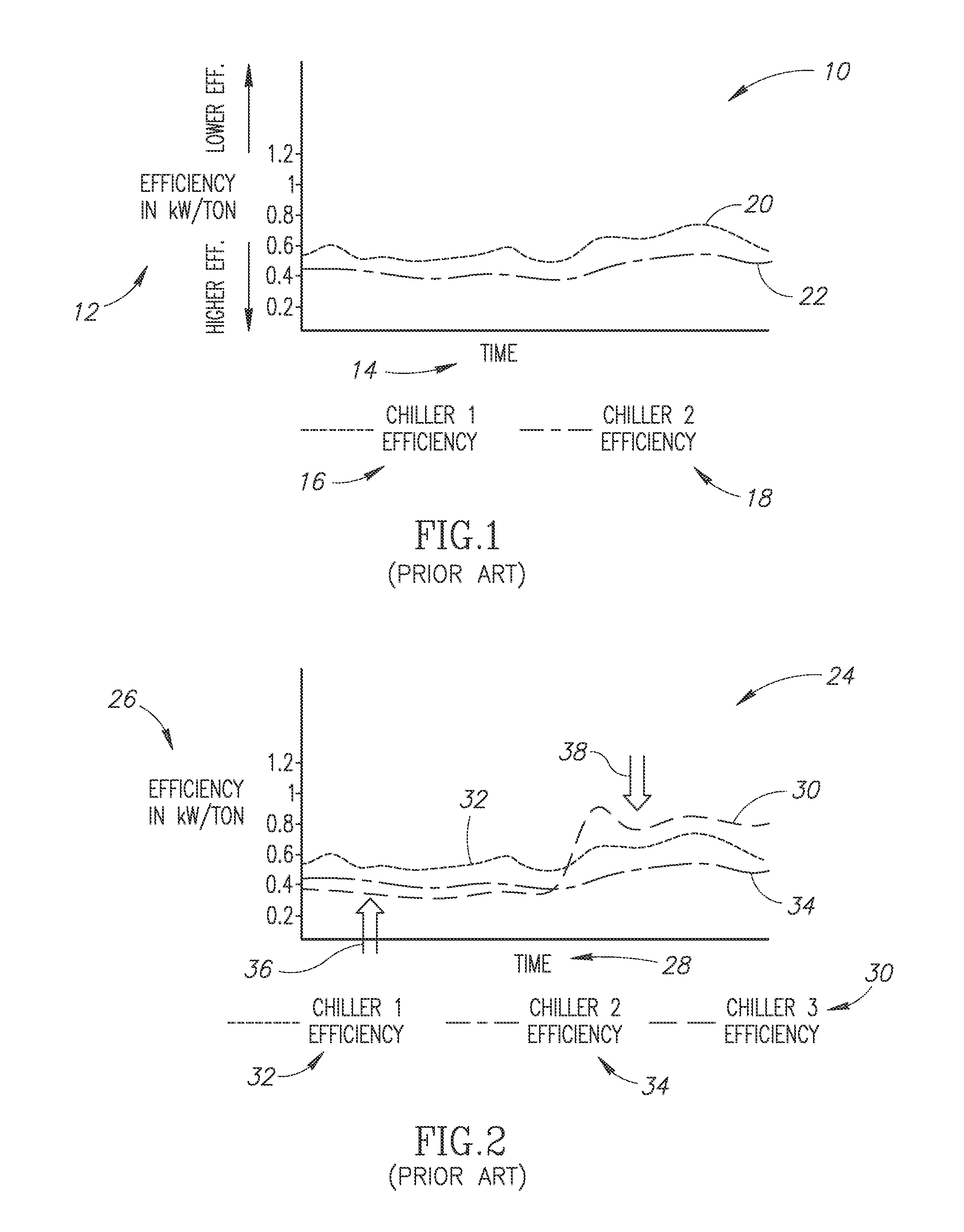
ActiveUS20160187896A1Improved and optimized overall energy efficiencyImprove energy efficiencySampled-variable control systemsMechanical apparatusComputational modelInitial sequence
Systems and methods for sequencing HVAC equipment of an HVAC system using data recorded in situ to build a model capable of making predictions about equipment efficiency and using that information, in combination with predictions about building load, to produce an operational sequence for the HVAC equipment that promotes an improved or optimized overall energy efficiency for the HVAC system. In one embodiment, the process is automated and utilizes Bayesian computational models or algorithms to generate are initial sequence. The process reduces engineering hours and may advantageously provide a means to predict potential sequencing problems for similar types of HVAC equipment.
Owner:OPTIMUM ENERGY
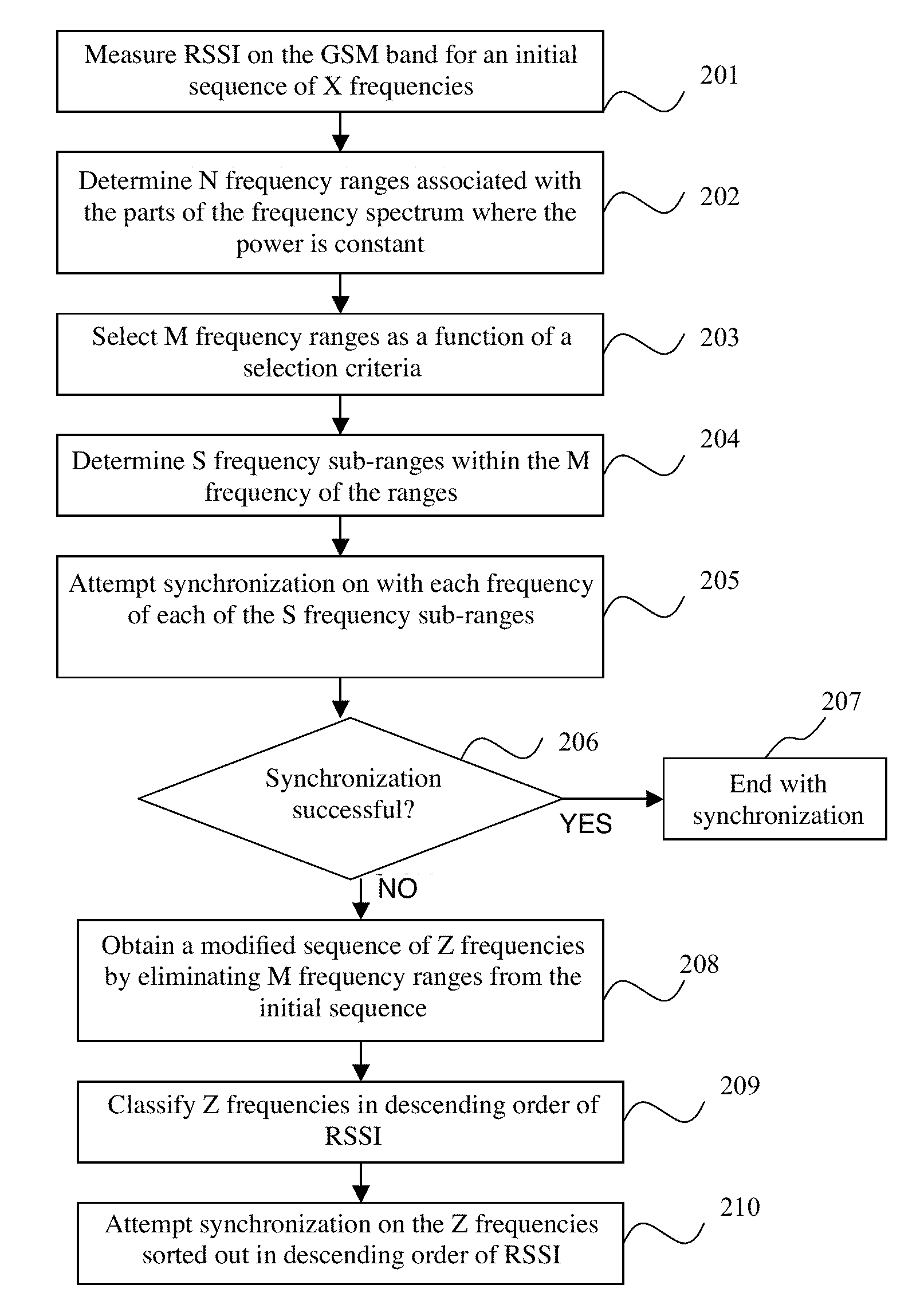
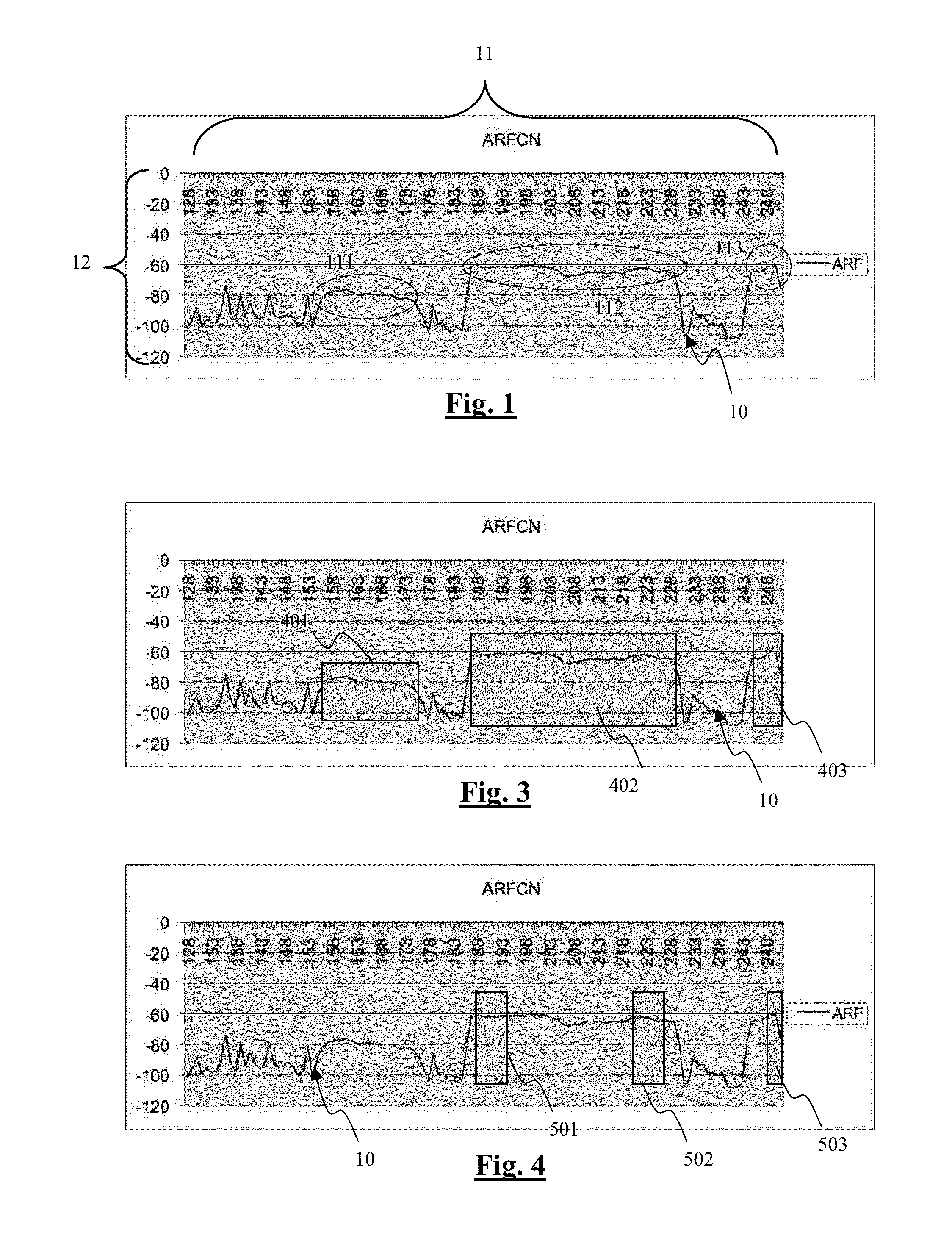
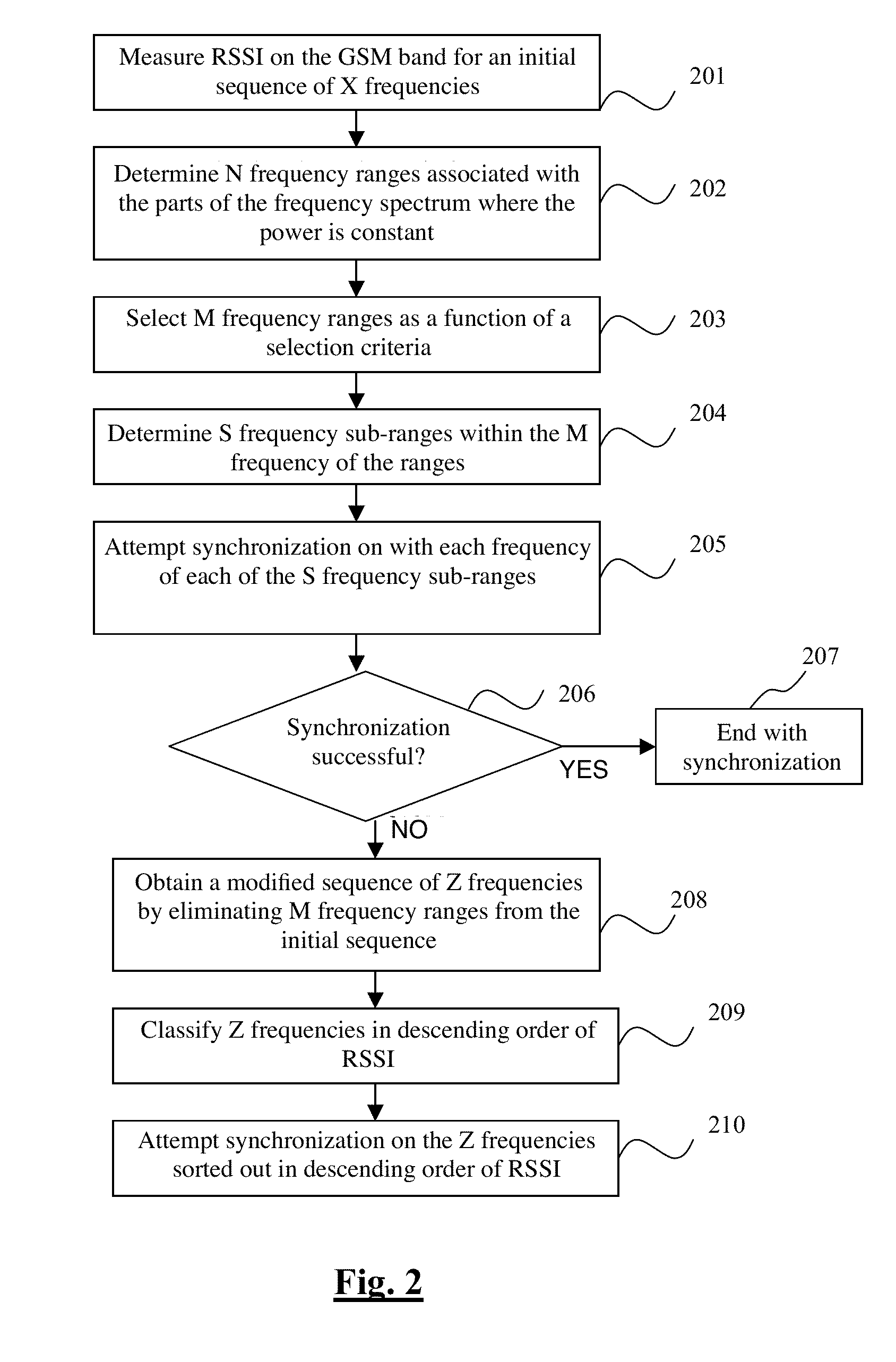
Method for synchronizing a terminal with a frequency of a radio-communications network, corresponding computer software product, storage means and terminal
InactiveUS20110292786A1Reduce energy consumptionSynchronisation arrangementError preventionComputer terminalInitial sequence
A method and apparatus are provided for synchronizing a terminal with a frequency from an ordered initial sequence of frequencies of a radio-communications network. An available power spectrum associates to each frequency of the initial sequence a power value representing the power with which the frequency is received by the terminal. At least one first range of consecutive frequencies is determined within the initial sequence, having a power variation below a first predetermined threshold. The terminal attempts at least one first synchronization with a frequency of the first range. If each first synchronization fails, the terminal obtains a modified sequence by modifying the position of the frequency or frequencies of the at least one first range of the initial sequence or by eliminating the at least one first range. The terminal then attempts a second synchronization with at least one of the frequencies of the modified sequence.
Owner:SIERRA WIRELESS
Pseudorandom sequence generating method
InactiveCN101132383APromote generationGenerate efficientlyRandom number generatorsPhase-modulated carrier systemsTime domainInitial sequence
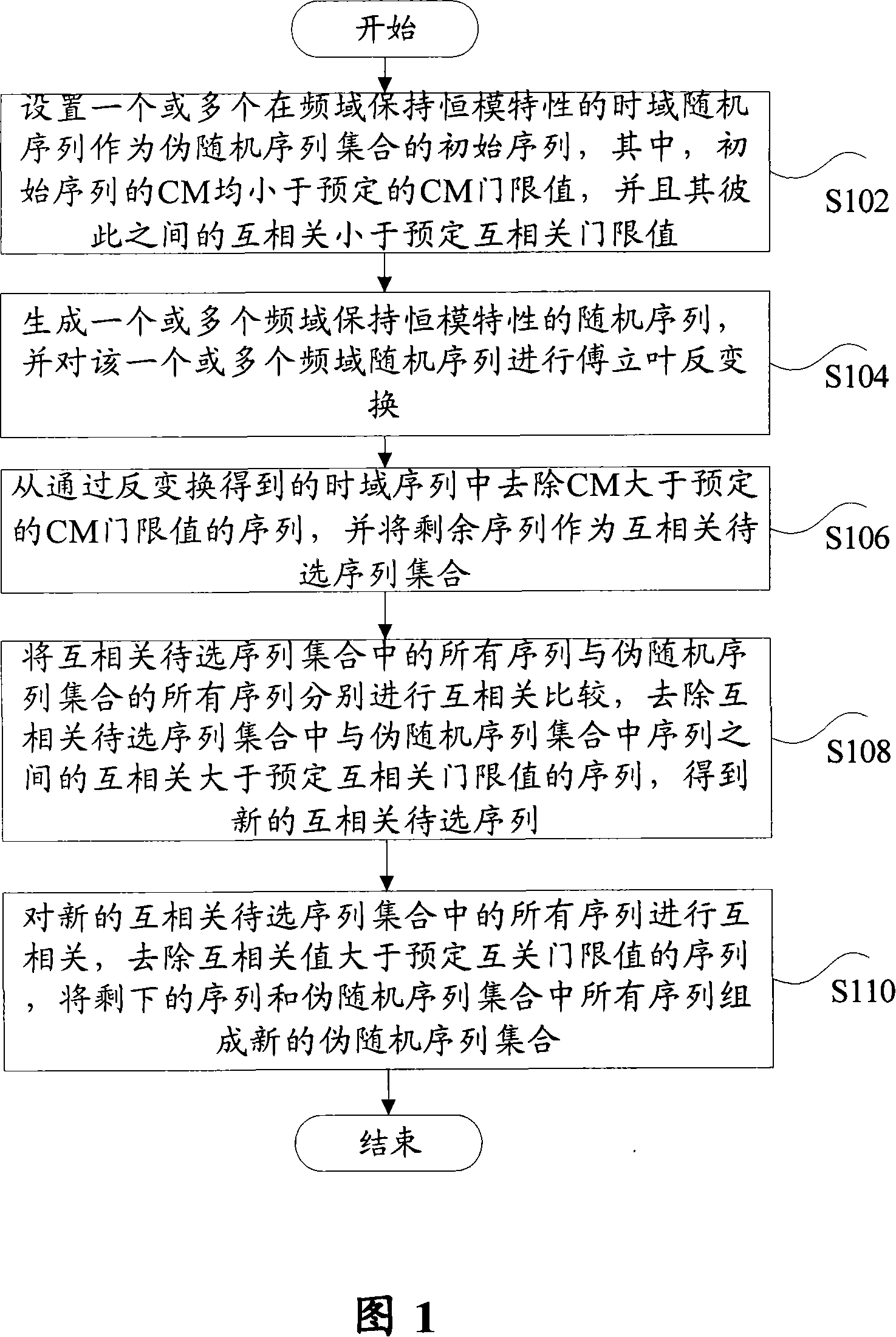
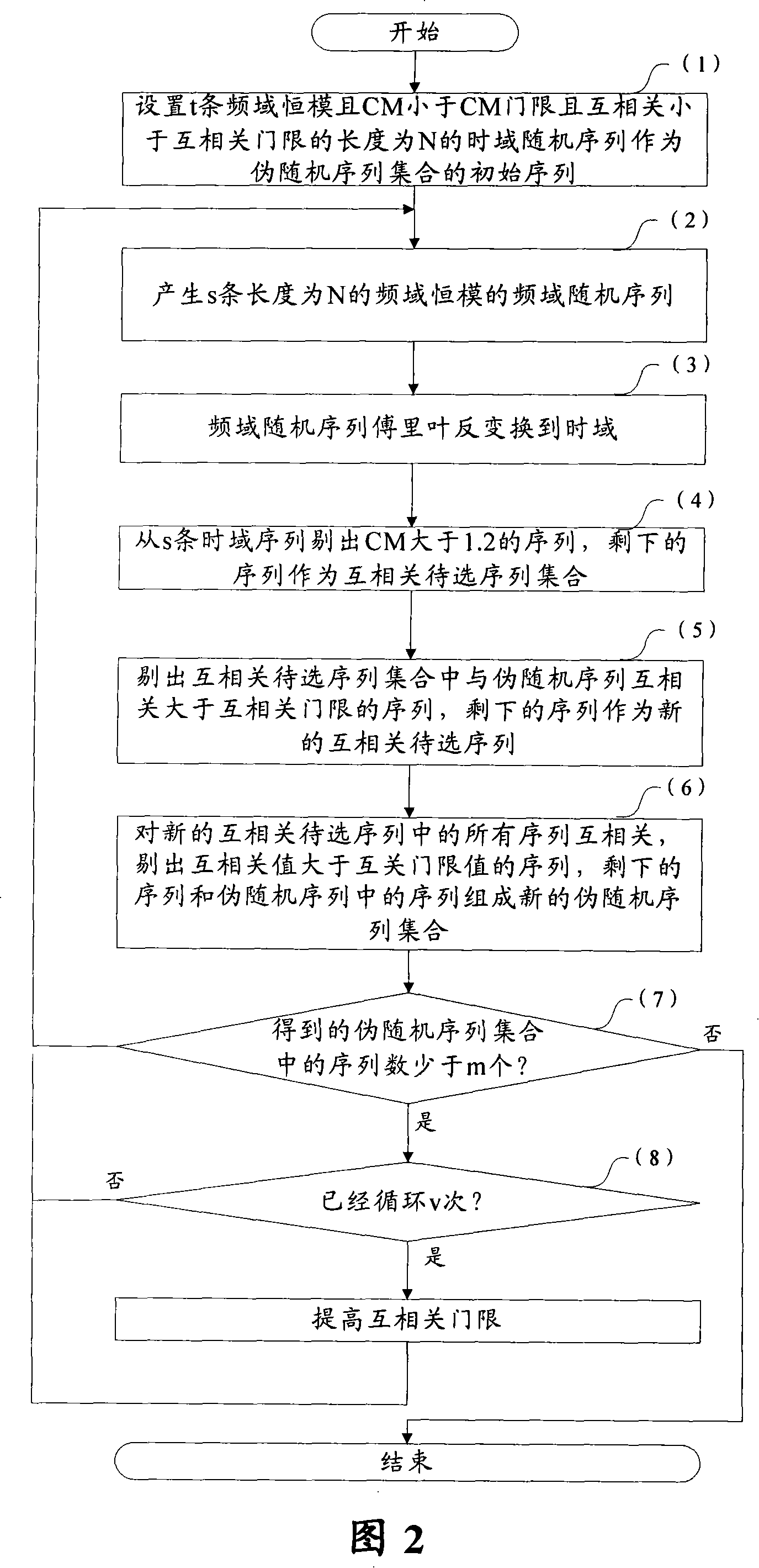
This invention relates to a method for generating false random sequences including: setting one or multiple time domain random sequences keeping constant mode property in the time domain as the intial sequences of a false random sequence set, generating one or multiple frequency domain random sequences of constant mode and making Fourier inversion to them, eliminating sequences with CM greater than a predesigned CM threshold value from the time domain sequences got by the inversion and taking the rest as the mutuallity set being selected and comparing them to eliminate sequences with the mutuality greater than a preset threshold value of mutuality among sequences from the being selected and the false random sequence set to get a new mutuality sequence to be selected to be corss correlated and eliminated sequences with the value greater than the preset threshold value of mutuality to form the rest sequences and those in the false random sequence set to a new false random sequence set.
Owner:ZTE CORP
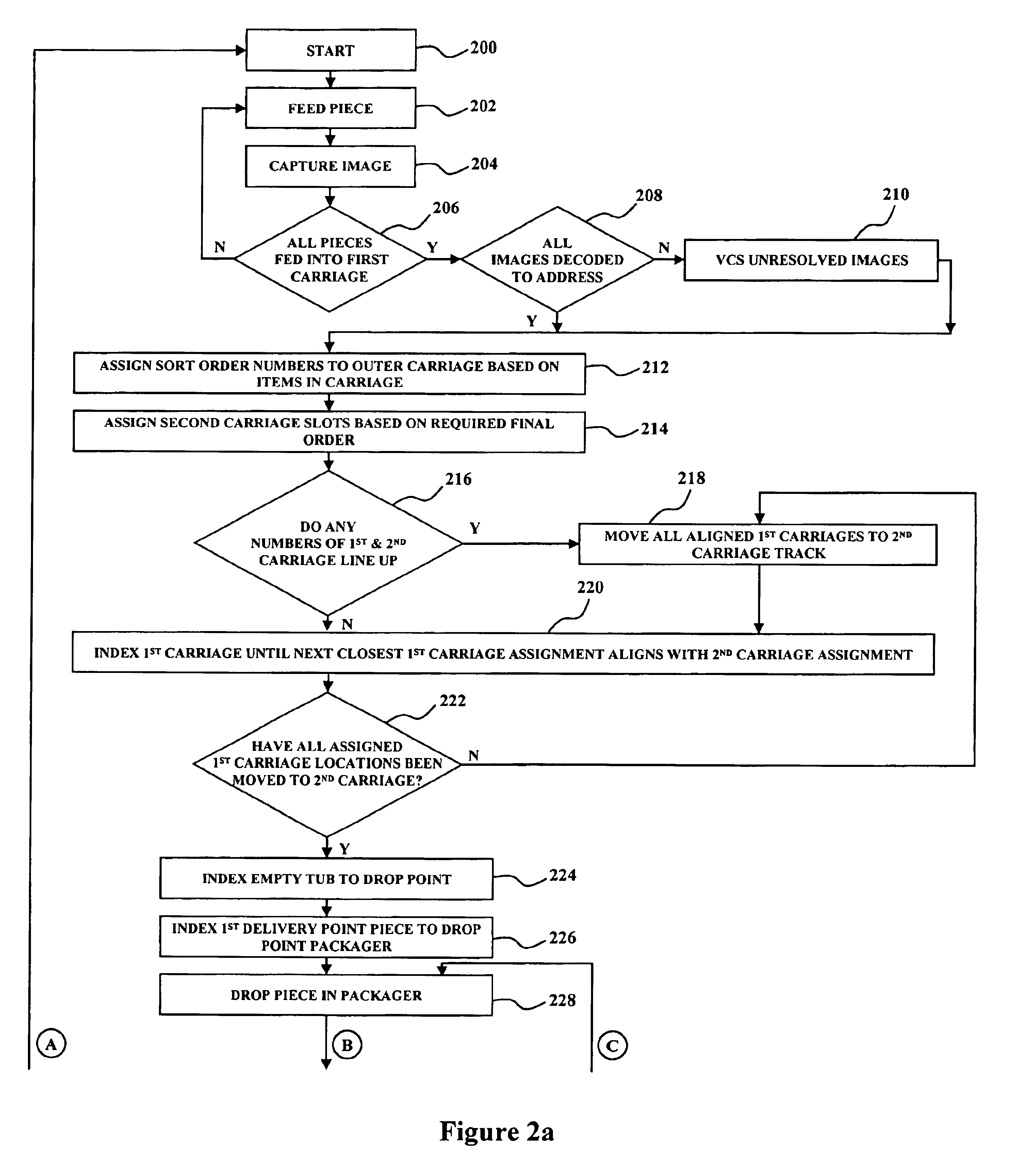
Method for sequentially ordering objects using a single pass delivery point process
A method using a single pass sequencer having a transport system for transporting the mail pieces to a transport system having a first carriage system and a second carriage system with a plurality of holders slidable between the first carriage system and the second carriage system with packaged output. Each of the plurality of holders holding a mail piece of the mail pieces received from the transport system. The method includes assigning a code to: (i) the mail pieces based on the destination information, (ii) the plurality of holders on the first carriage, and (iii) a position on the second carriage which corresponds to the initial sequence and a destination sequence of the mail pieces. The method instructs movement of the plurality of holders from the first carriage to the second carriage based on the code assigned to the mail pieces, the plurality of holders on the first carriage and the position on the second carriage such that when the mail pieces are moved to the second carriage they are in sequential order of delivery destination, ready to be packaged.
Owner:LOCKHEED MARTIN CORP
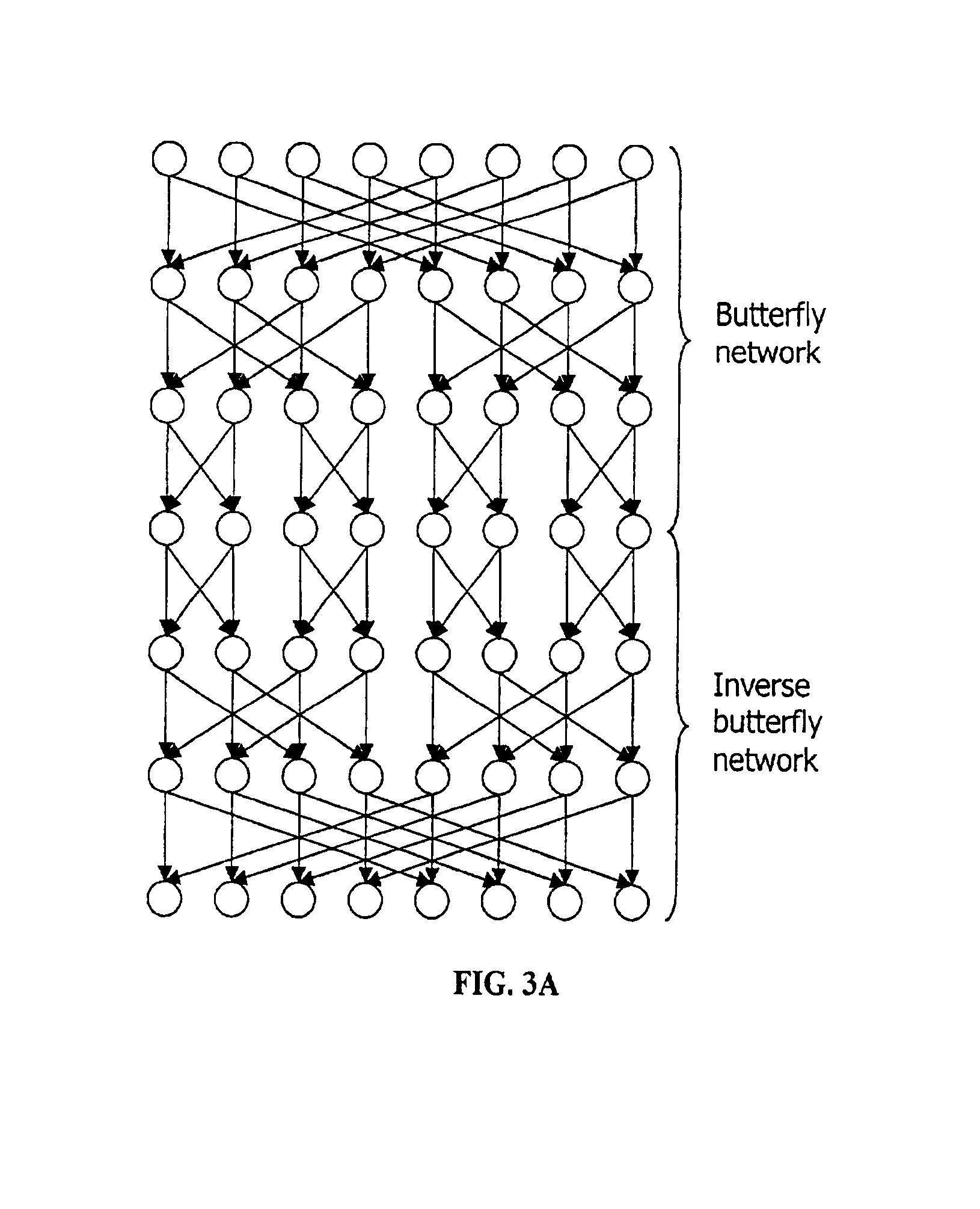
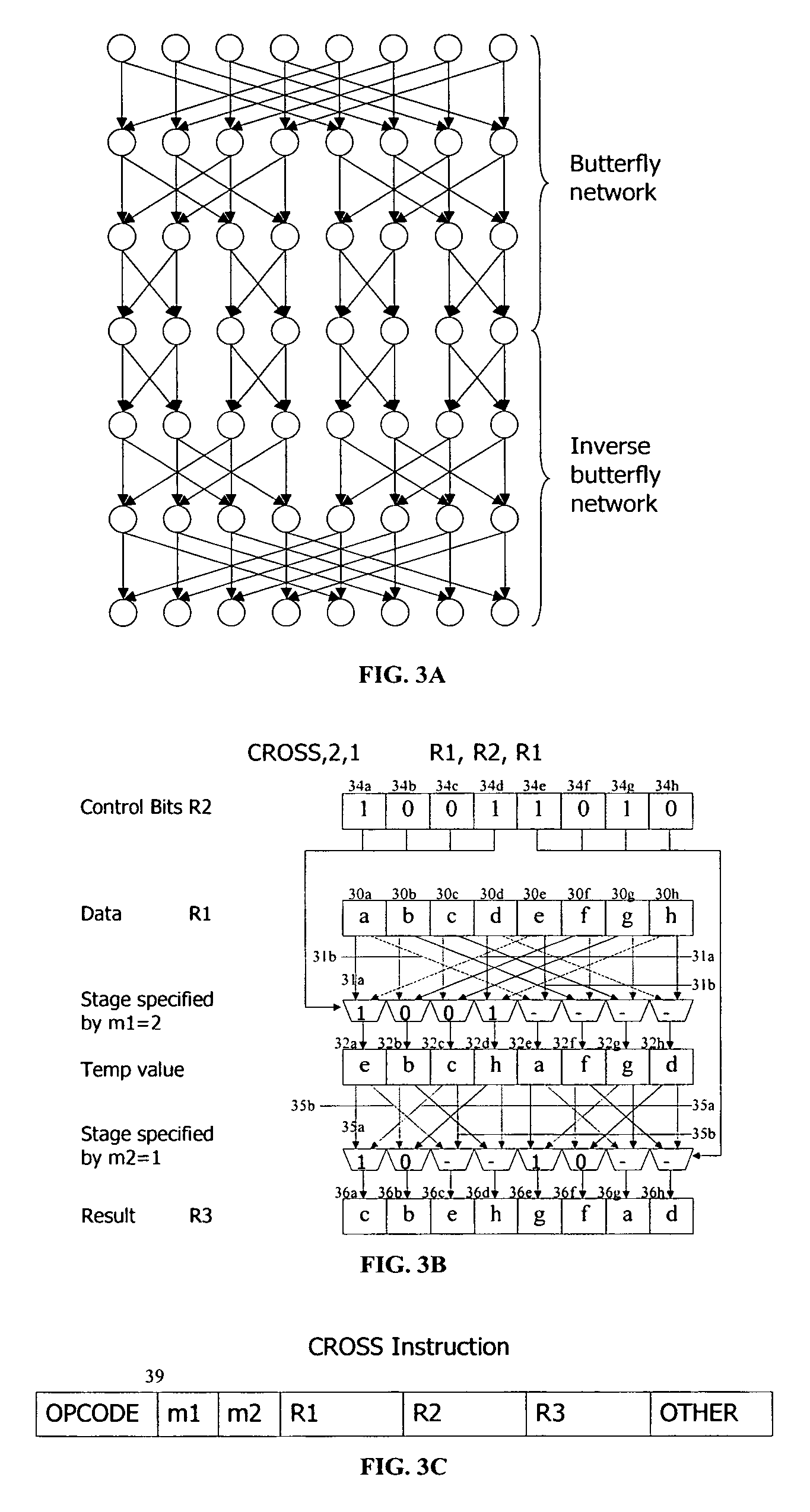
Method and system for performing permutations using permutation instructions based on butterfly networks
ActiveUS6922472B2Telegraphic message interchanged in timeSecret communicationComputer architectureInitial sequence
The present invention provides permutation instructions which can be used in software executed in a programmable processor for solving permutation problems in cryptography, multimedia and other applications. The permute instructions are based on a Benes network comprising two butterfly networks of the same size connected back-to-back. Intermediate sequences of bits are defined that an initial sequence of bits from a source register are transformed into. Each intermediate sequence of bits is used as input to a subsequent permutation instruction. Permutation instructions are determined for permitting the initial source sequence of bits into one or more intermediate sequence of bits until a desired sequence is obtained. The intermediate sequences of bits are determined by configuration bits. The permutation instructions form a permutation instruction sequence of at least one instruction. At most 21 gr / m permutation instructions are used in the permutation instruction sequence, where r is the number of k-bit subwords to be permuted, and m is the number of network stages executed in one instruction. The permutation instructions can be used to permute k-bit subwords packed into an n-bit word, where k can be 1, 2, . . . , or n bits, and k*r=n.
Owner:TELEPUTERS
Method for sequentially ordering objects using a single pass delivery point process
A method using a single pass sequencer having a transport system for transporting the mail pieces to a transport system having a first carriage system and a second carriage system with a plurality of holders slidable between the first carriage system and the second carriage system with packaged output. Each of the plurality of holders holds a mail piece received from the transport system. The method includes assigning a code to: (i) the mail pieces based on the destination information, (ii) the plurality of holders on the first carriage, and (iii) a position on the second carriage which corresponds to the initial sequence and a destination sequence of the mail pieces. The method instructs movement of the plurality of holders from the first carriage to the second carriage so that they are in sequential order of delivery destination, ready to be packaged. Once the mail pieces are in sequential order on the second carriage, they are dropped into a container for a delivery point. A determination is made as to whether the container is full.
Owner:LOCKHEED MARTIN CORP
Order feed message stream integrity
InactiveUS20130060887A1Reduce network trafficEasy to detectError preventionFinanceComputer hardwareMessage flow
Systems, methods, and computer-readable storage media are provided for improving order feed message stream integrity. Certain embodiments provide a method including sending, by a computing device, a first data message; sending a first stop message; clearing a message stream state; and sending a second data message. The first data message includes data related to an order for a tradeable object, a first sequence number with a value of a predefined initial sequence number, and a first phase number. The second data message includes data related to an order, a second sequence number with a value of the predefined initial sequence number, and a second phase number, wherein the second phase number is different than the first phase number. The message stream state is associated with the order.
Owner:TRADING TECH INT INC
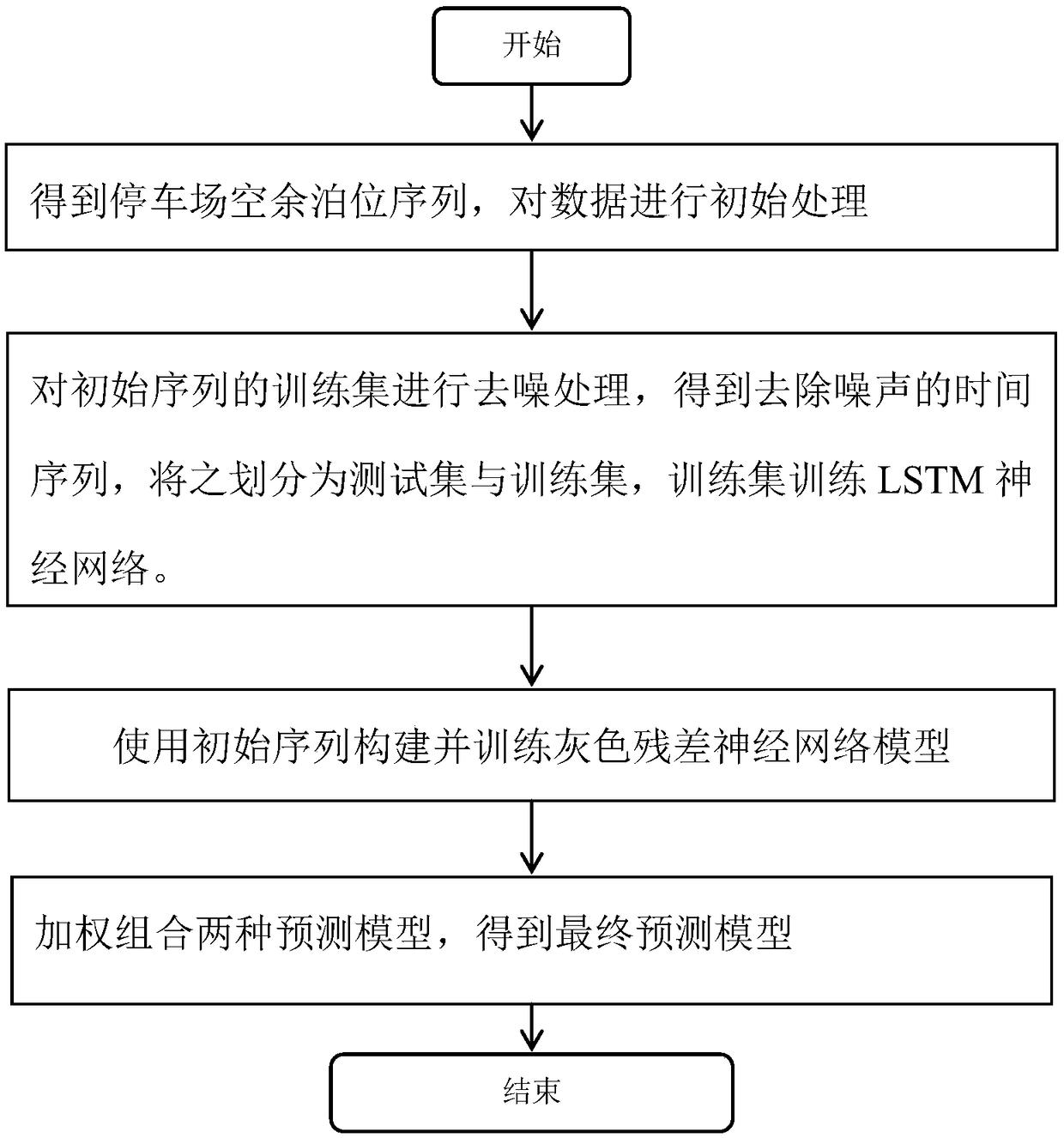
Indoor parking lot remaining parking space prediction method
ActiveCN109492808AImprove accuracyDigital data information retrievalDetection of traffic movementPredictive methodsAlgorithm
An indoor parking lot remaining parking space prediction method comprises the following steps that 1, acquiring a parking lot unoccupied parking space sequence, and carrying out data preprocessing; step 2, performing denoising processing on the training set of the initial sequence to obtain a time sequence with noise removed, recording the time sequence as a smooth sequence, and dividing the smooth sequence into a test set and a training set; Using the smooth sequence training set to train an LSTM neural network; step 3, constructing and training a gray residual neural network model by using the initial sequence; and step 4, weighting and combining the two prediction models to obtain a final prediction model.
Owner:ZHEJIANG UNIVERSITY OF SCIENCE AND TECHNOLOGY
Chip, consumables container and working method of chip
The invention provides a chip, a consumables container and a working method of the chip. The chip comprises a substrate, wherein a communication module and a storage are arranged on the substrate, the storage stores a group of initial sequence number data and at least one group of standby sequence number data and is provided with a bit zone which stores an identification value used for identifying the currently used sequence number; and the storage is also provided with a transformation judging unit used for judging whether the sequence number data transformation condition is met or not and a transforming unit for transforming the identification values. The method comprises the steps of: after electrifying the chip, sending corresponding sequence number data according to the identification values, judging whether the currently used sequence number data is the initial sequence number data according to the identification value, if yes, judging whether the sequence number data transformation condition is met or not by the transformation judging unit, and transforming the identification value by the transforming unit. The invention can effectively avoid the problem that the consumables container can not print because the sequence number stored in the chip is the same with the sequence number stored in a printer, thereby reducing the waste and being beneficial to environment protection.
Owner:ZHUHAI TIANWEI TECH DEV CO LTD
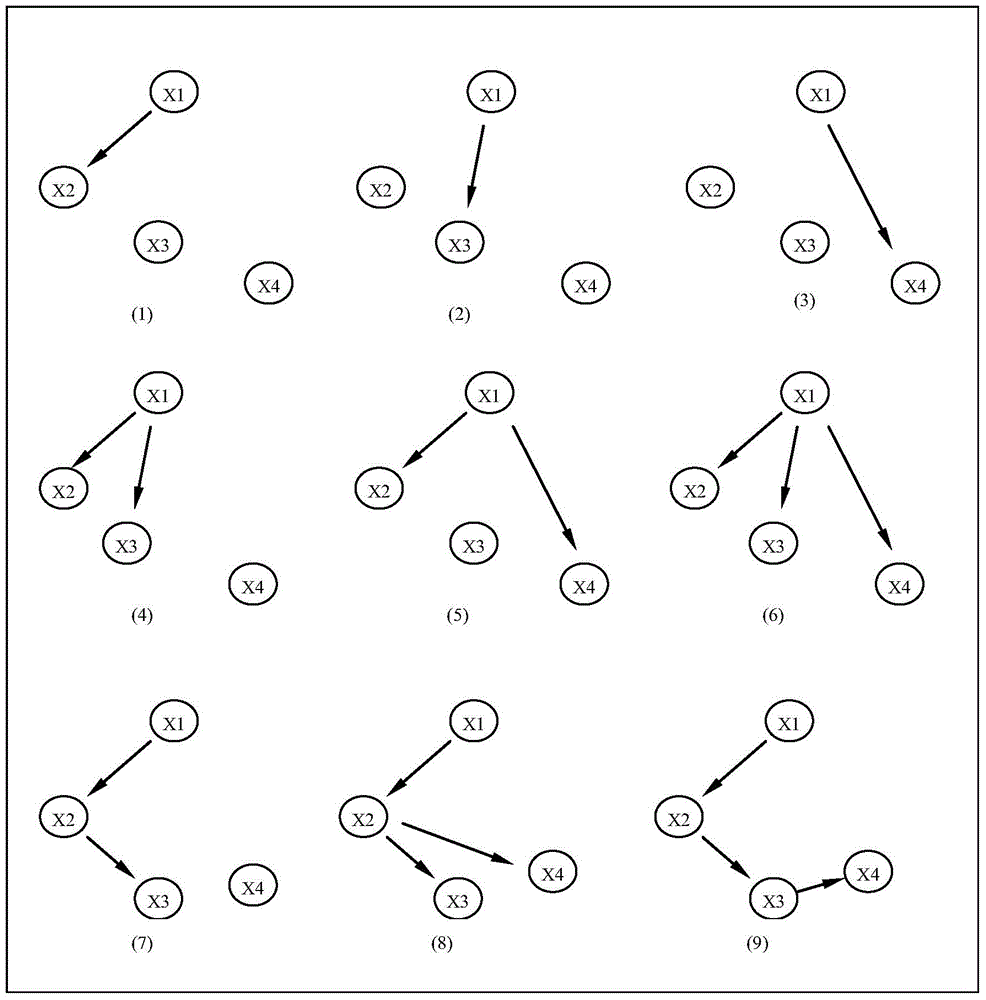
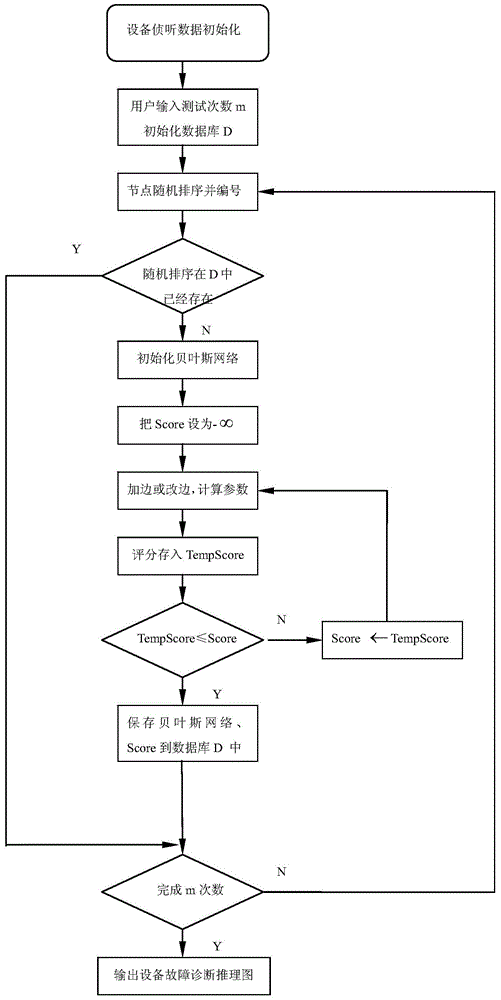
Excavating diagnosis method of failure data based on bayesian network
InactiveCN104462842AAvoid falling intoPrevent overfittingMathematical modelsSpecial data processing applicationsNODALSearch problem
Owner:XIAMEN UNIV
Systems and methods for protecting cluster systems from TCP SYN attack
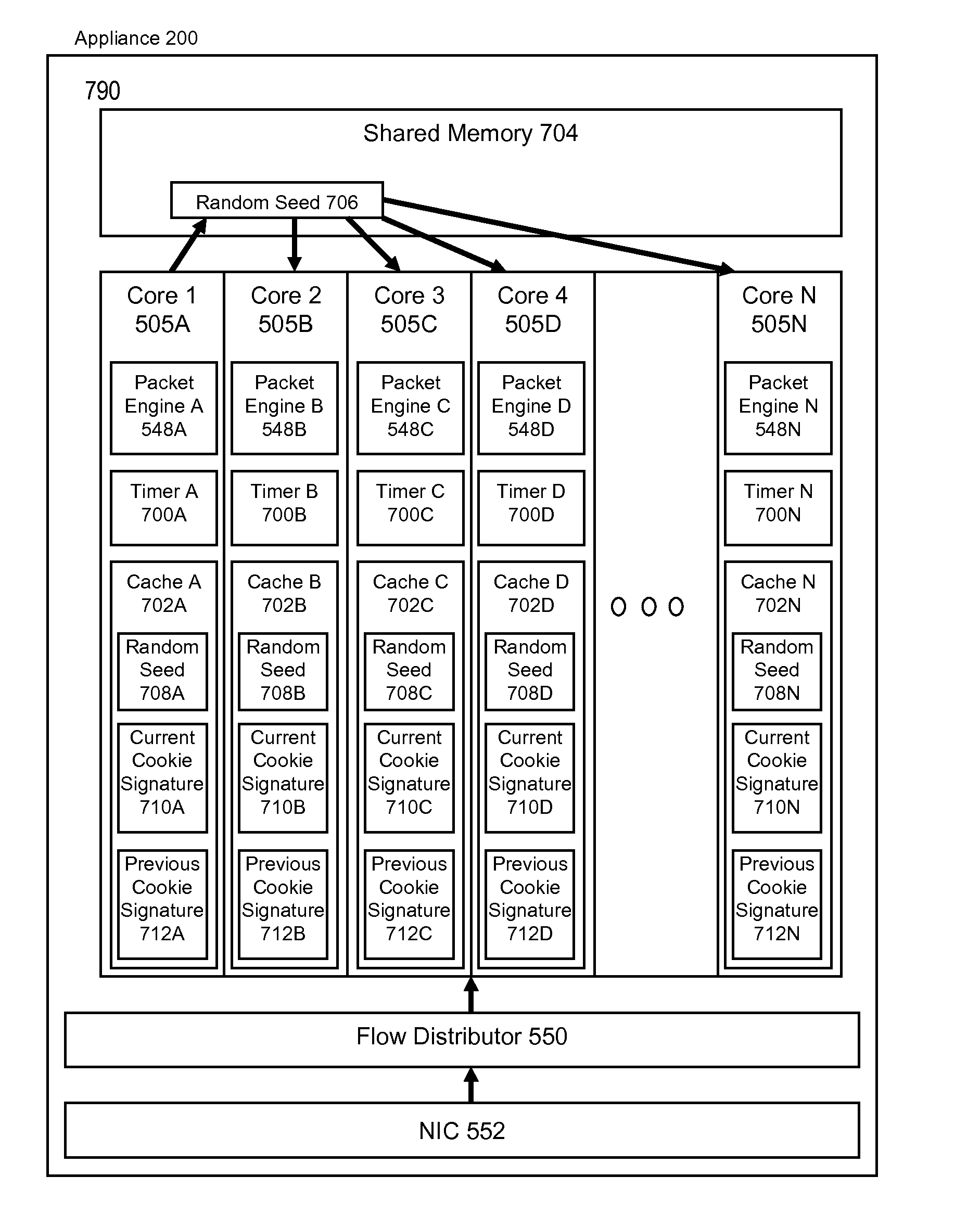
ActiveUS20140304810A1Memory loss protectionError detection/correctionComputer hardwareCluster systems
The present solution is directed to systems and methods for synchronizing a random seed value among a plurality of multi-core nodes in a cluster of nodes for generating a cookie signature. The cookie signature may be used for protection from SYN flood attacks. A cluster of nodes comprises one master node and one or more other nodes. Each node comprises one master core and one or more other cores. A random number is generated at the master core of the master node. The random number is synchronized across every other core. The random number is used to generated a secret key value that is attached in the encoded initial sequence number of a SYN-ACK packet. If the responding ACK packet does not contain the secret key value, then the ACK packet is dropped.
Owner:CITRIX SYST INC
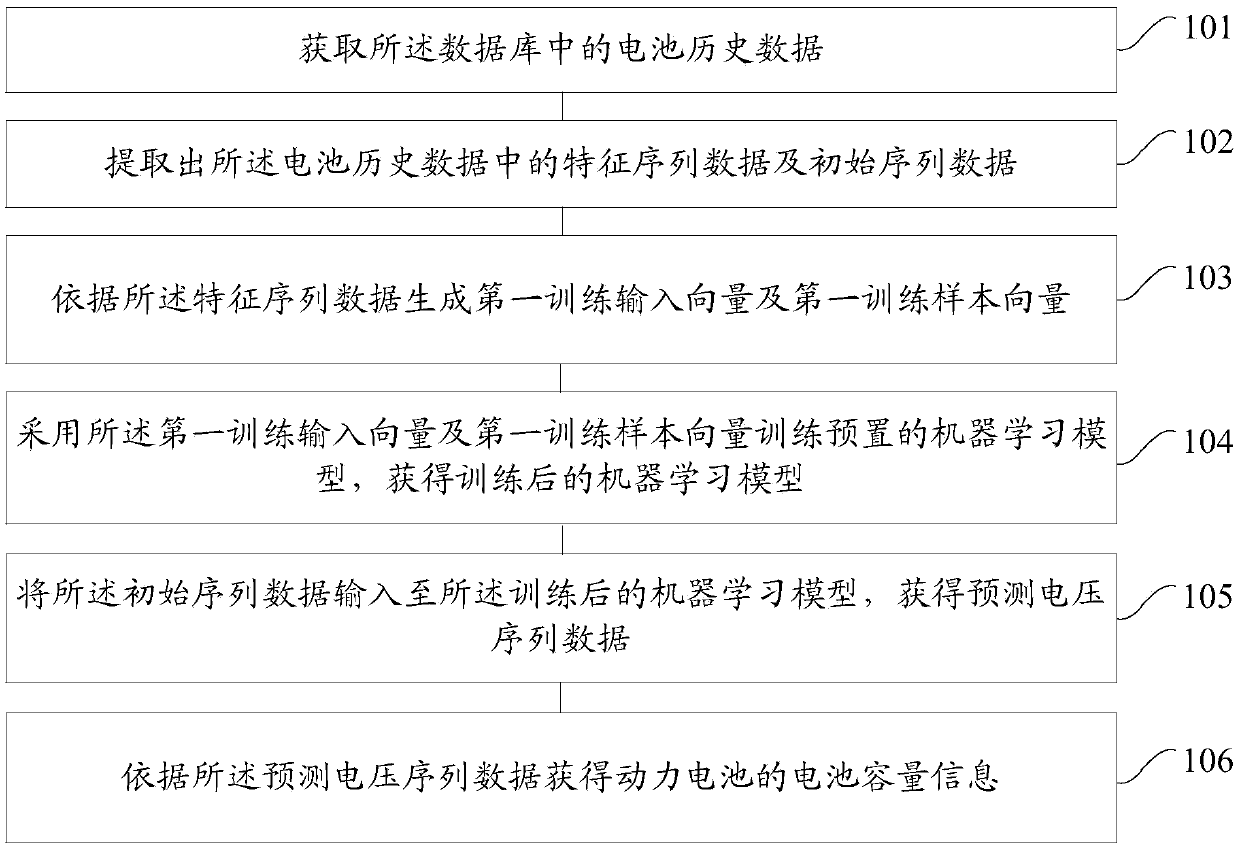
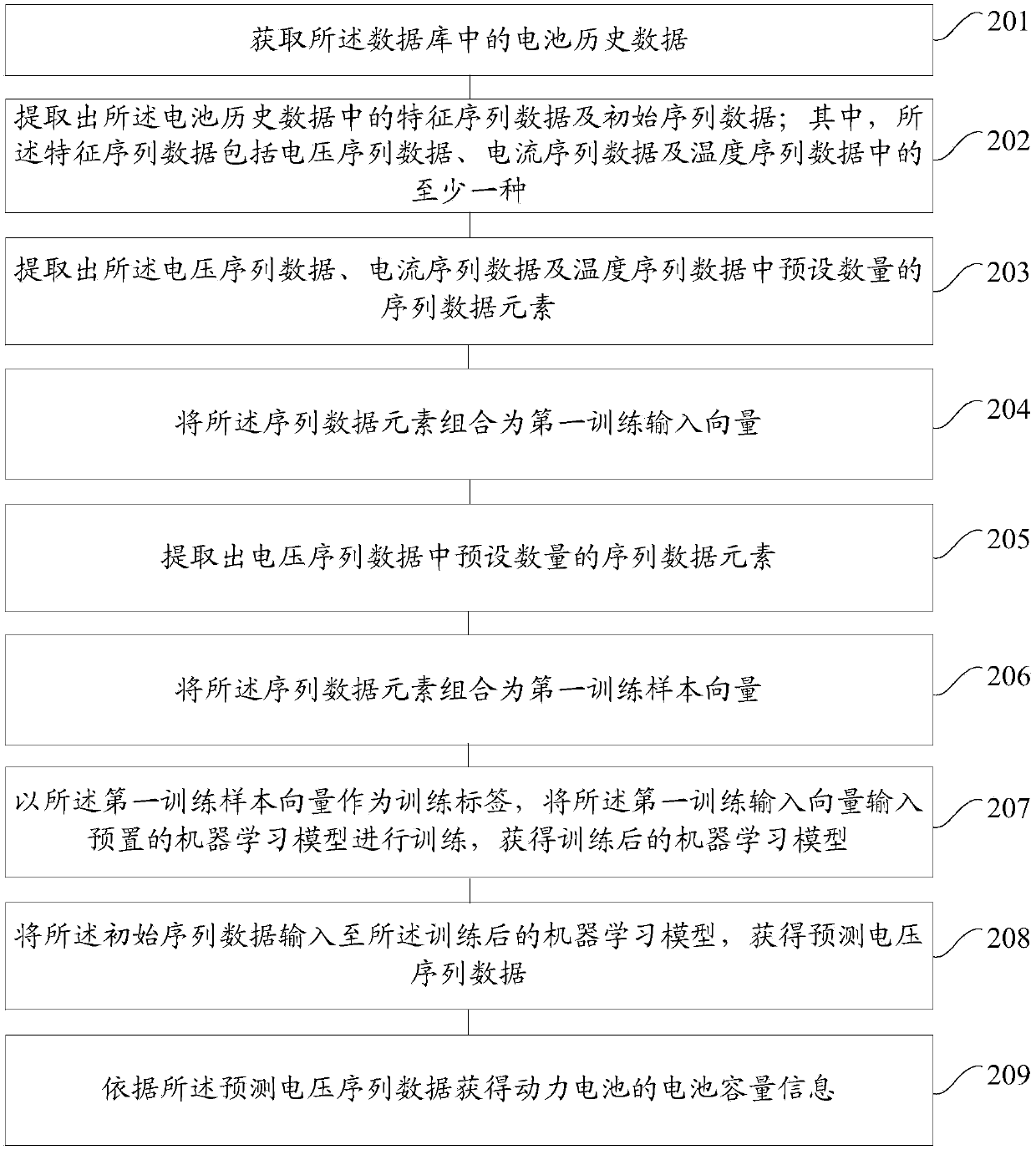
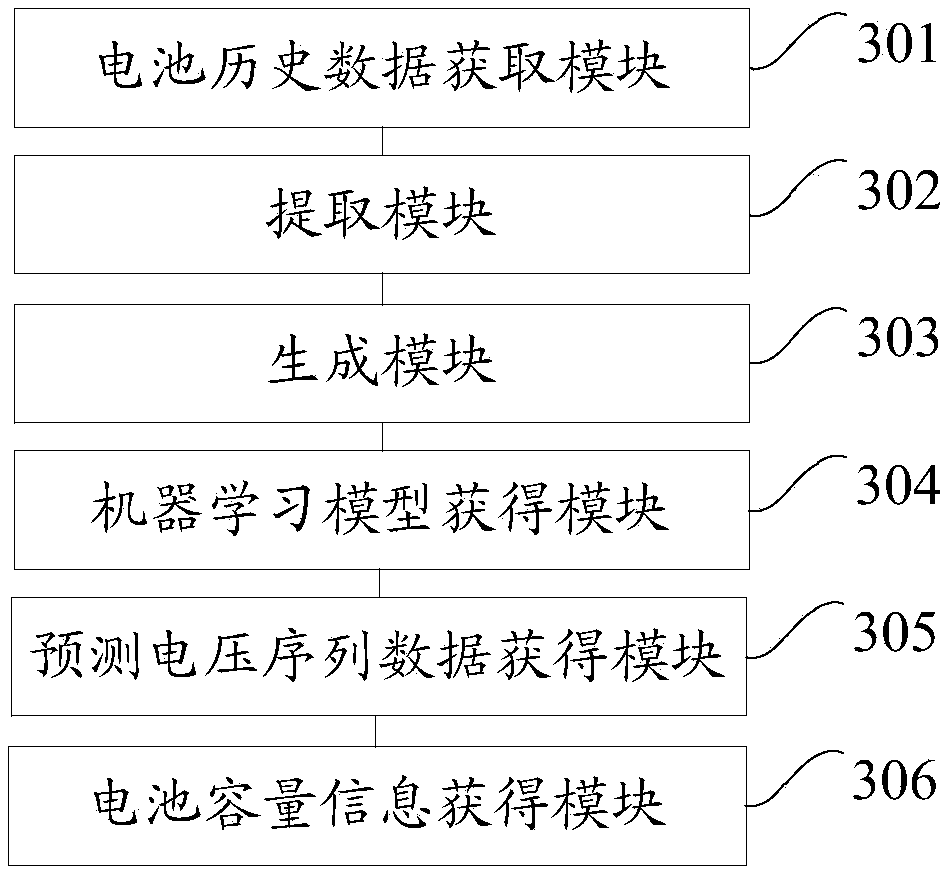
Data processing method for power battery and device
The embodiment of the invention provides a data processing method for a power battery and device, which are applied to a power assembly. A battery management system operates in the power assembly; thebattery management system comprises a database; historical battery data are stored in the database, and the historical battery data in the database are acquired; feature sequence data and initial sequence data in the historical battery data are extracted; according to the feature sequence data, a first training input vector and a first training sample vector are generated; the first training input vector and the first training sample vector are adopted to train a preset machine learning model, and a machine learning model after training is acquired; the initial sequence data are inputted to the machine learning model after training to acquire predicted voltage sequence data; and according to the predicted voltage sequence data, the battery capacity information of the power battery is acquired. The cost is reduced, the time is saved, and the problem of much consumed manpower bright by a capacity estimation experiment can be solved.
Owner:上海科列新能源技术有限公司
Method of generating pseudo-random sequence in LTE system
ActiveCN105391545AExtend build timeImprove performanceEncryption apparatus with shift registers/memoriesCommunications systemComputation complexity
The invention discloses a method of generating a pseudo-random sequence in an LTE system. The method comprises the steps of obtaining an initial sequence of a first pseudo-random sequence according to communication information of the LTE system; obtaining an initial sequence of a second pseudo-random sequence; performing phase mask sequence operation of the first pseudo-random sequence to obtain a self-scrambling sequence; performing phase mask sequence operation of the second pseudo-random sequence to obtain a self-scrambling sequence; and performing XOR operation of the two self-scrambling sequences to finally obtain a scrambling sequence for scrambling or descrambling. The invention can effectively improve the generation time of a scramble code without increasing the computational complexity, and the overall performance of a communication system is improved.
Owner:SOUTHEAST UNIV
Method and system for performing permutations using permutation instructions based on butterfly networks
InactiveUS20060039555A1Telegraphic message interchanged in timeSecret communicationComputer architectureBack-to-back connection
The present invention provides permutation instructions which can be used in software executed in a programmable processor for solving permutation problems in cryptography, multimedia and other applications. The permute instructions are based on a Benes network comprising two butterfly networks of the same size connected back-to-back. Intermediate sequences of bits are defined that an initial sequence of bits from a source register are transformed into. Each intermediate sequence of bits is used as input to a subsequent permutation instruction. Permutation instructions are determined for permitting the initial source sequence of bits into one or more intermediate sequence of bits until a desired sequence is obtained. The intermediate sequences of bits are determined by configuration bits. The permutation instructions form a permutation instruction sequence of at least one instruction. At most 21gr / m permutation instructions are used in the permutation instruction sequence, where r is the number of k-bit subwords to be permuted, and m is the number of network stages executed in one instruction. The permutation instructions can be used to permute k-bit subwords packed into an n-bit word, where k can be 1, 2, . . . , or n bits, and k*r=n.
Owner:LEE RUBY B +2
Method, apparatus and article for determining an initial hand in a playing card game, such as blackjack or baccarat
Methods and apparatus determine a value of an initial hand of playing cards, such as determining whether a dealer has the value of twenty-one, and / or outcome of a game at some point before the dealer receives a second card. The initial sequence may be read, optically, magnetically or wireless from identifiers on the playing cards, before the playing cards are loaded in a card shoe, while the playing cards reside in the card shoe, or as playing cards are removed from the card shoe. Alternatively, the initial sequence may correspond to a computationally generated sequence, such as a computationally pseudo-random sequence.
Owner:BALLY GAMING INT
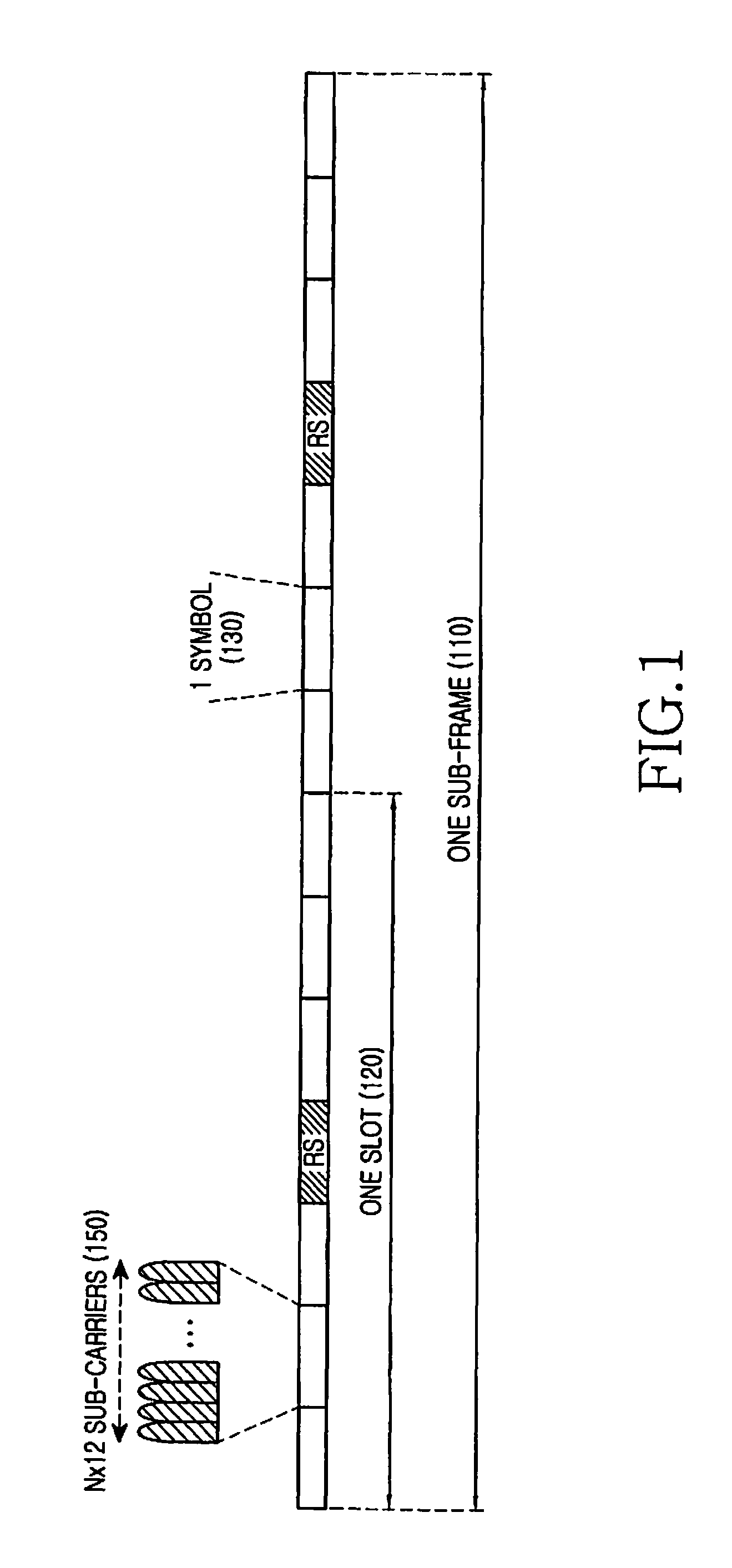
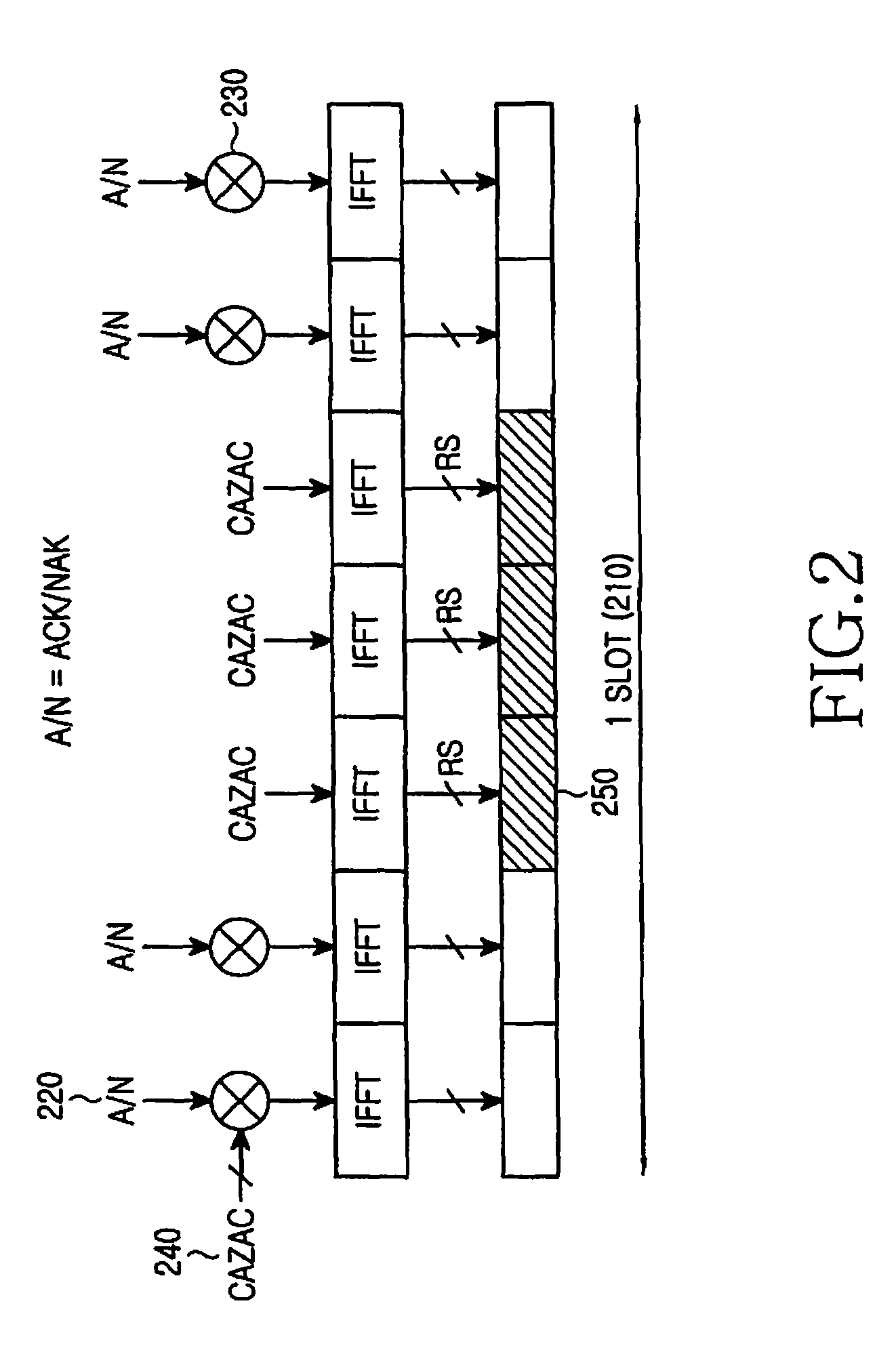
Methods and apparatus for sequence hopping in single-carrier frequency division multiple access (SC-FDMA) communication systems
ActiveUS8441991B2Minimal complexityNetwork traffic/resource managementModulated-carrier systemsCommunications systemCarrier signal
Owner:SAMSUNG ELECTRONICS CO LTD
Method and apparatus for aligning screw caps of hollow bodies, especially bottles
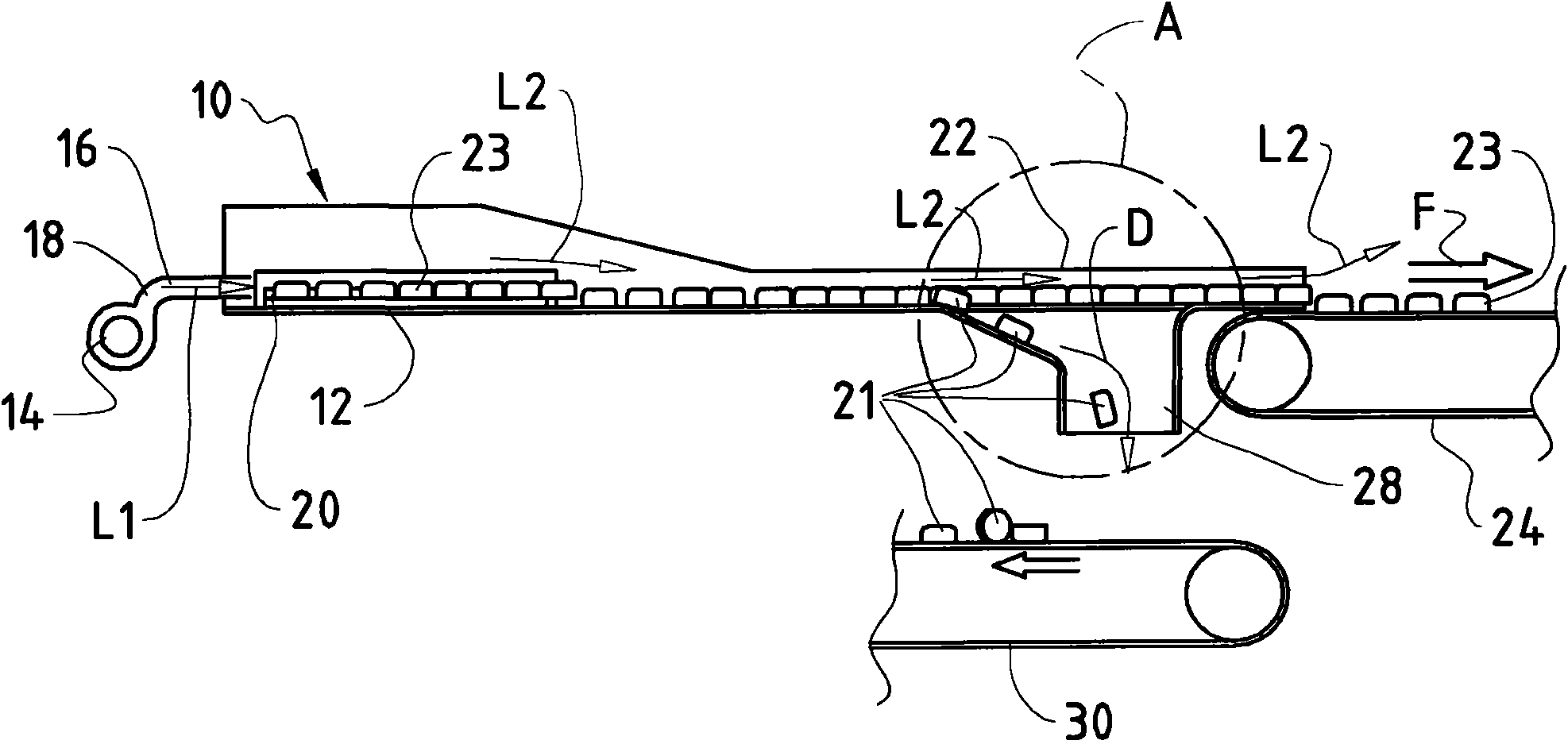
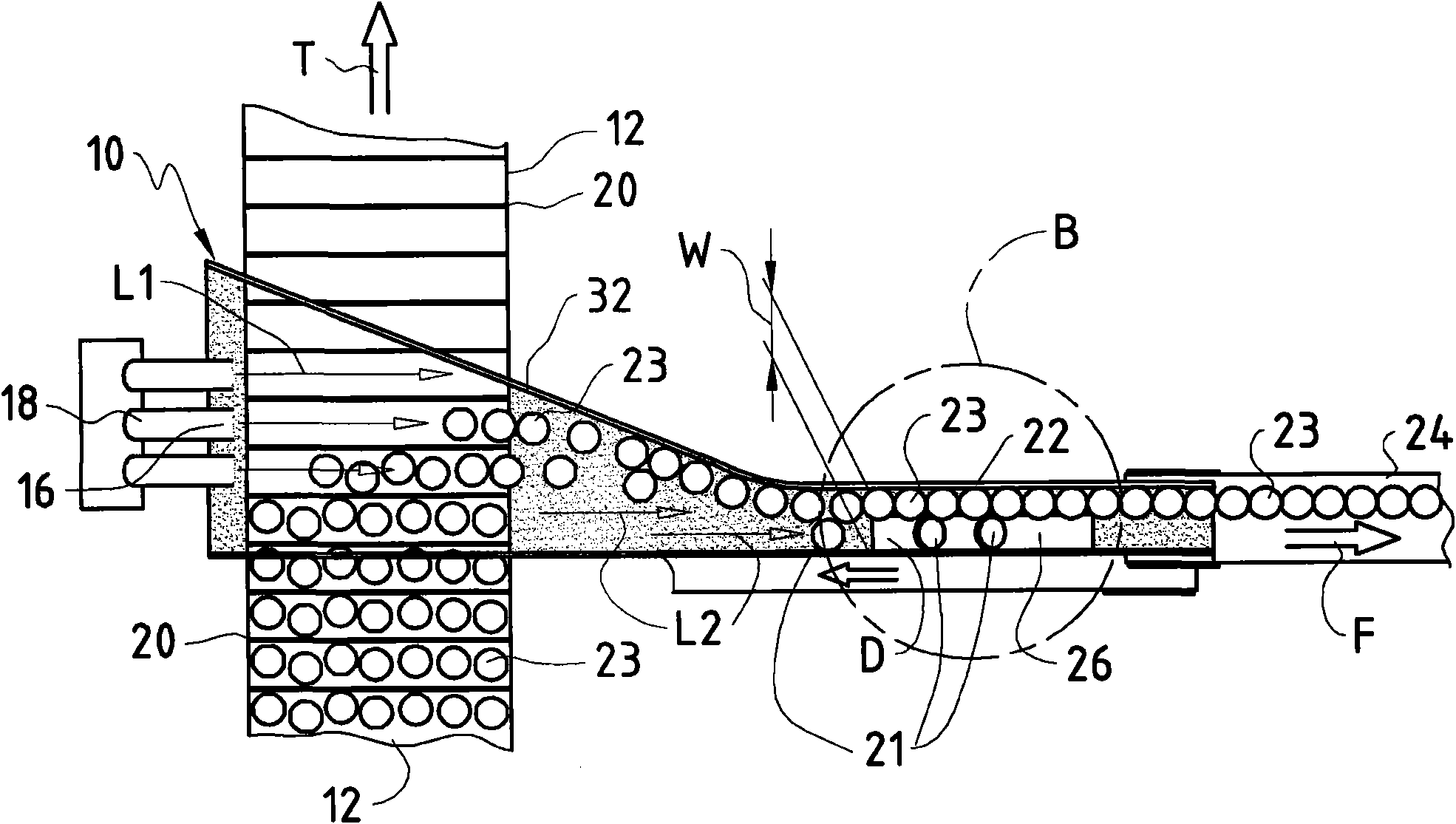
The invention discloses a method for continuously separating and aligning a plurality of cylindrical hollow bodies (23), wherein one sides of the hollow bodies are closed.The hollow bodies (23) are placed in order in a treatment room (10).The hollow bodies arranged in an initial sequence in the treatment room are in linear contact with each other by the action of an air flow.The hollow bodies placed in order move toward the output (22) of the treatment room (10) by the air flow.The hollow bodies (23) are pressed against a guide rail (32) by the air.The hollow bodies (23), which are not within the linear range, are ejected through an opening (28).The invention also discloses an apparatus adopting the above method.
Owner:FINATEC HLDG
Android intelligent device anti-getroot system and calibration method thereof
InactiveCN104123505AImprove the performance of the anti brush machineProtection of rights and interestsDigital data protectionPlatform integrity maintainanceOperational systemApplication software
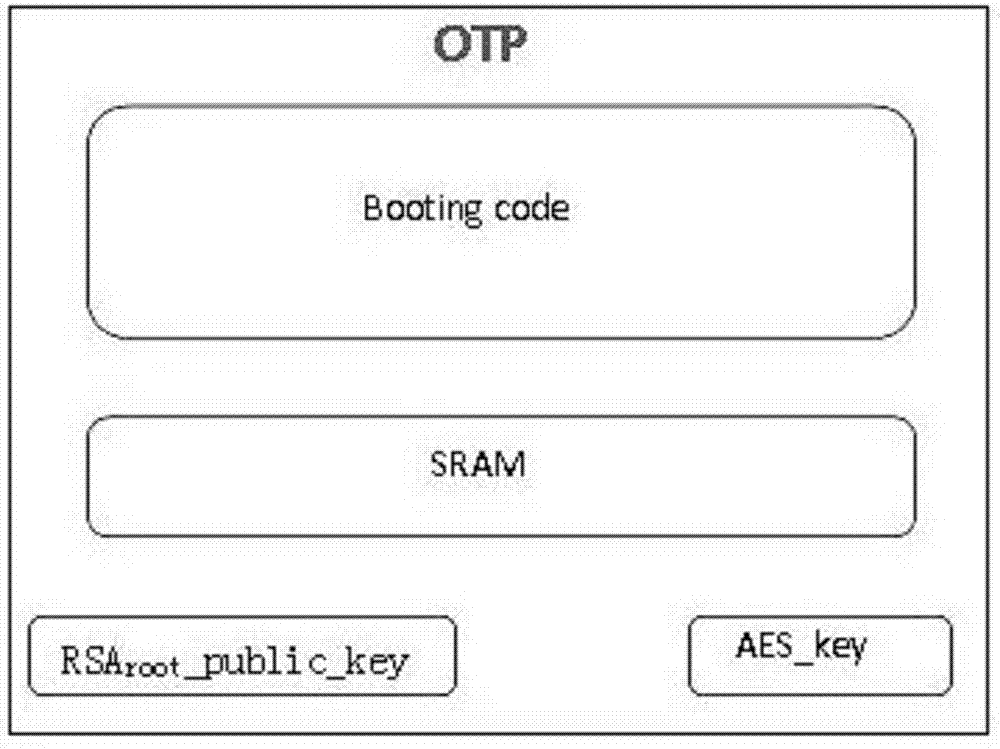
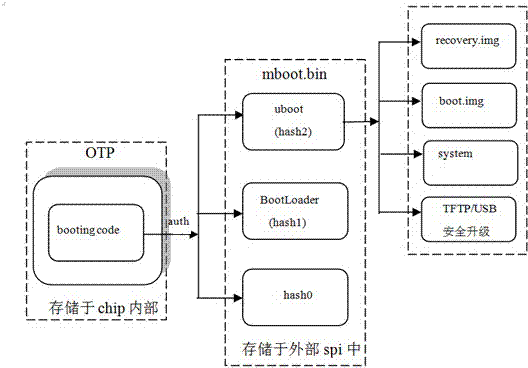
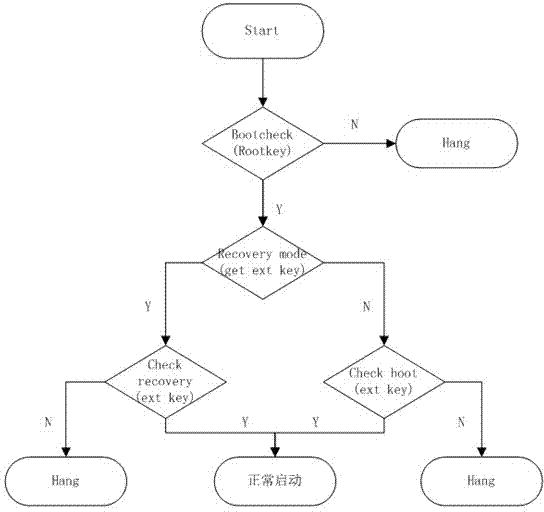
The invention discloses an Android intelligent device anti-getroot system and a calibration method of the Android intelligent device anti-getroot system. The method includes the steps that a dynamic password module is set in a central processor of an intelligent device and comprises programs solidified in the central processor, data to which users and codes of a common domain cannot have direct access are stored, a security algorithm is supported, dynamic password data needed by applications are stored and guaranteed, a security guiding process is executed, a basic security guarantee is provided for an operating system and application software, the system operates in the central processor, and a storage space independent of an external bus is used for operating a security processing program and storing a middle result. Key data mainly comprise symmetrical cryptographic algorithm secret keys and asymmetric cryptographic algorithm public keys and are used for basic initial sequences of an authenticated one-way hash algorithm, the purpose of protecting safety of the system at the hardware level is achieved, the anti-getroot performance of the Android intelligent device is improved, and the safety performance of the whole system is improved.
Owner:丹阳市广播电视台
System and method for the calculation of a polynomial-based hash function and the erindale-plus hashing algorithm
ActiveUS20110211697A1User identity/authority verificationSecret communicationHash functionSpeed of processing
Owner:VOLKOVS NIKOLAJS
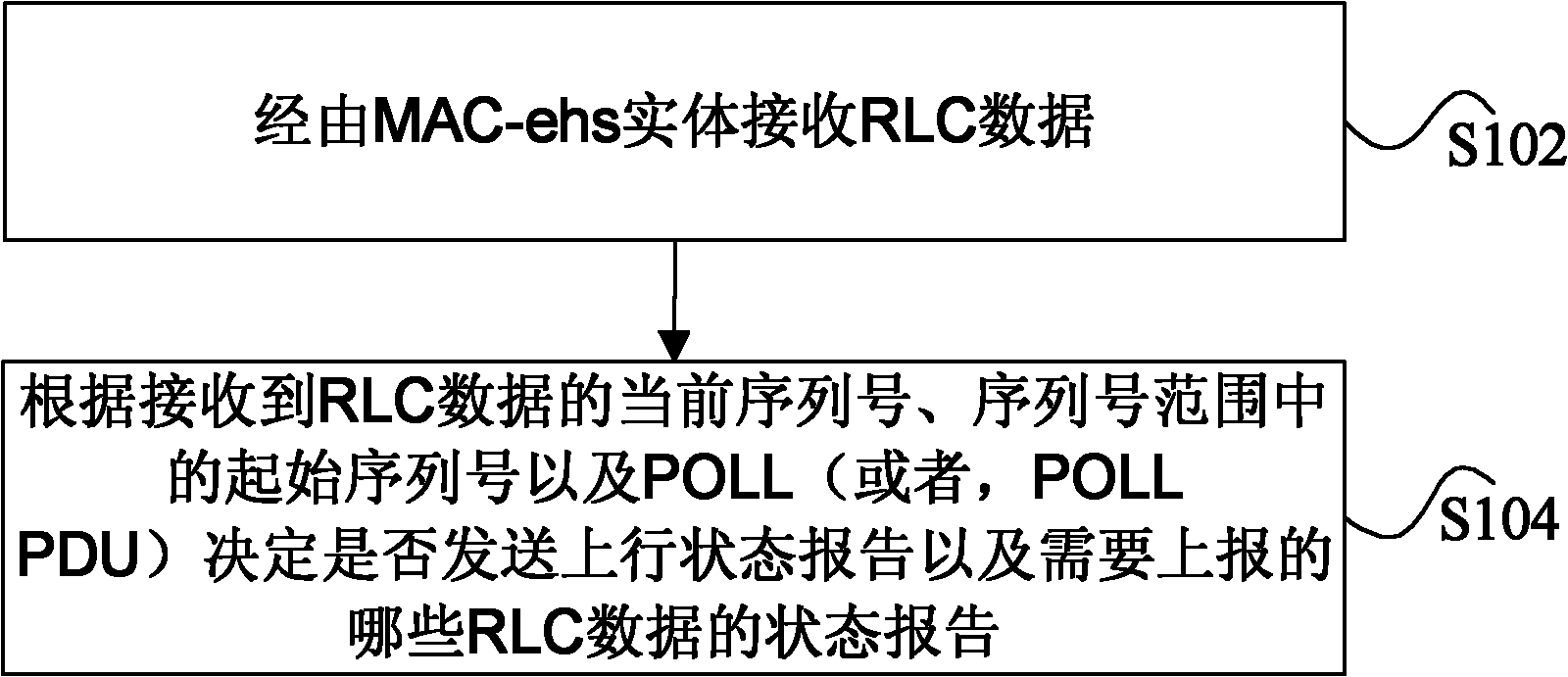
Uplink status report reporting method, radio link control data transmitting method and device
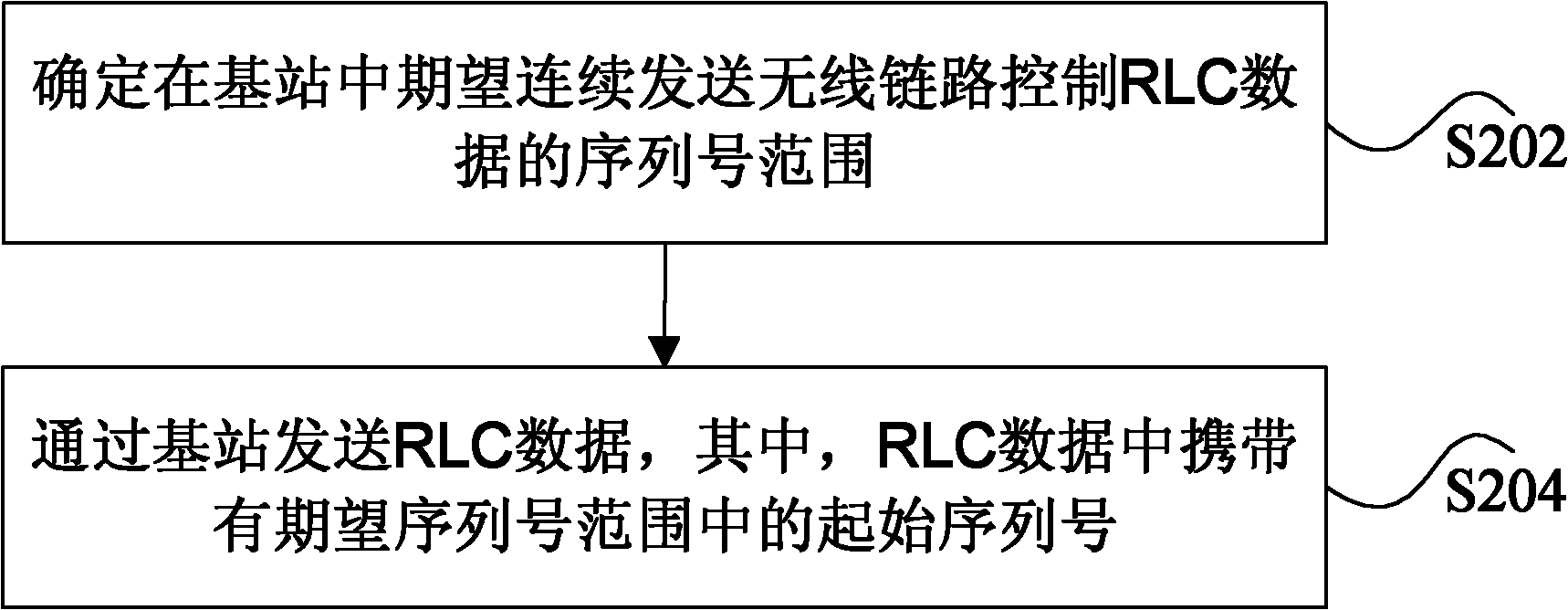
ActiveCN102740353ASolve the problem that it is impossible to judge whether the RLC data is lost normallyIs it normal to lose correctlyError prevention/detection by using return channelNetwork traffic/resource managementControl dataInitial sequence
The invention discloses an uplink status report reporting method, a radio link control data transmitting method and a device. The uplink status report reporting method includes the following steps that: the radio link control (RLC) data are received by an evolution high-speed downlink packet access media access control (MAC-ehs) entity, wherein the RLC data carry an initial sequence number of an expected-sequence number range of the RLC data that are expected to be transmitted continuously through the MAC-ehs entity; and it is determined whether to transmit the uplink status report or a status report of the RLC data which needs to be reported according to a current sequence number and the initial sequence number of the expected-sequence number range of the RLC data as well as received poll information (POLL) or a poll protocol data unit (POLL PDU). The uplink status report reporting method, the radio link control data transmitting method and the device in the invention enable an acceptor to correctly judge whether the RLC data are lost or not.
Owner:广州瀚信通信科技股份有限公司
Method and device for processing data
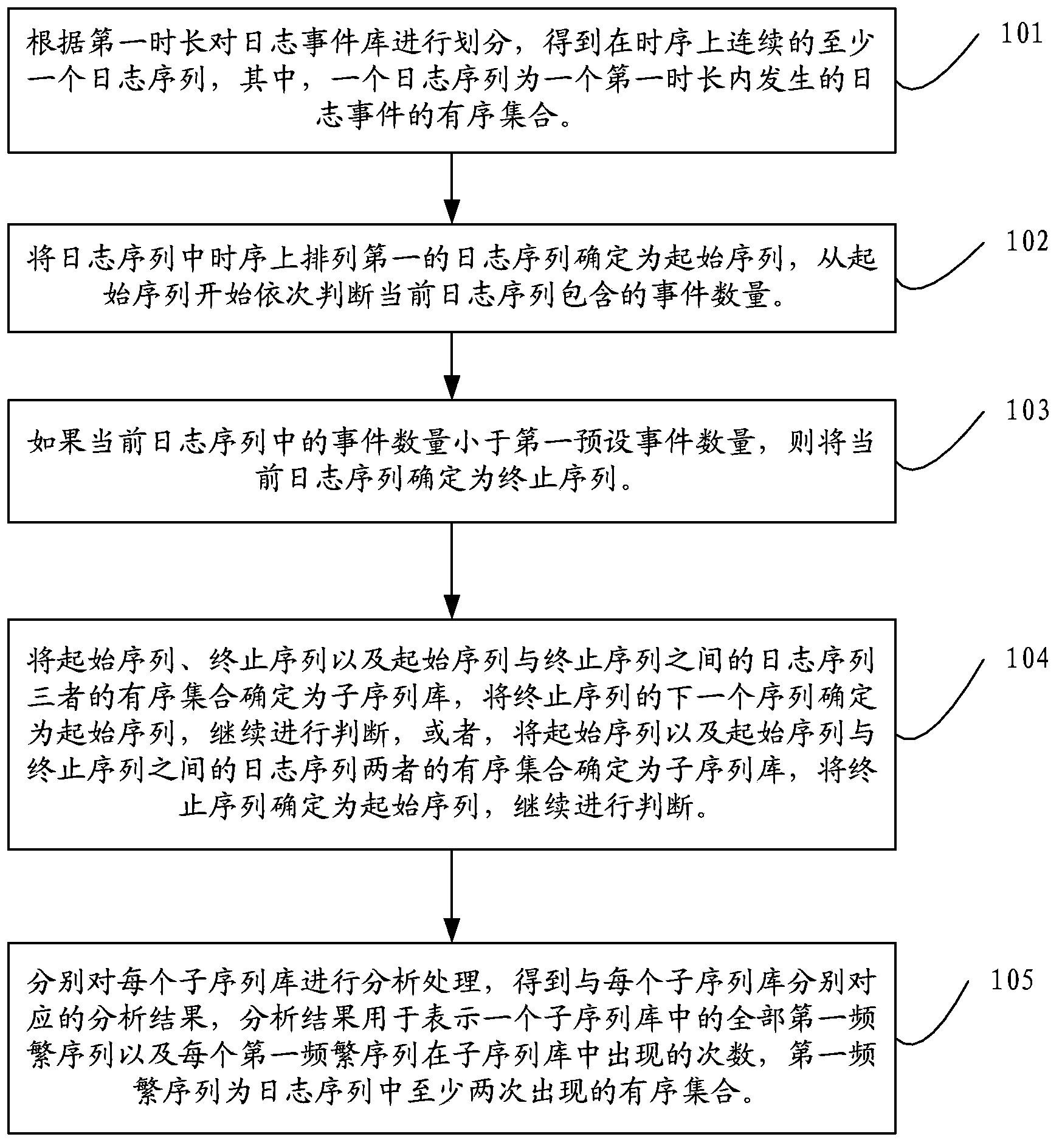
ActiveCN104252406AImprove processing efficiencyDigging efficiency is reducedHardware monitoringNon-redundant fault processingInitial sequenceData mining
The invention discloses a method and a device for processing data and relates to the technical field of data processing. The complex mode integration required after a log event base is divided according to a fixed time length and is dug can be avoided. The method comprises the following steps of according to a first time length, dividing the log event base to obtain at least one log sequence which is continuous in time sequence; determining the first log sequence sequenced on the log sequence as an initial sequence, and sequentially judging the number of events contained in the current log sequence from the initial sequence; if the number of the events contained in the current log sequence is smaller than a preset first event number, determining sub sequence bases; respectively analyzing each sub sequence base to obtain an analysis result corresponding to each sub sequence base. The method and the device are mainly applied in a data processing process.
Owner:HUAWEI TECH CO LTD +1
Magnetic resonance imaging system protecting method and device, and automatic shutoff testing method
ActiveCN103705237AEnsure safetyWon't hurtDiagnostic recording/measuringSensorsComputer moduleInitial sequence
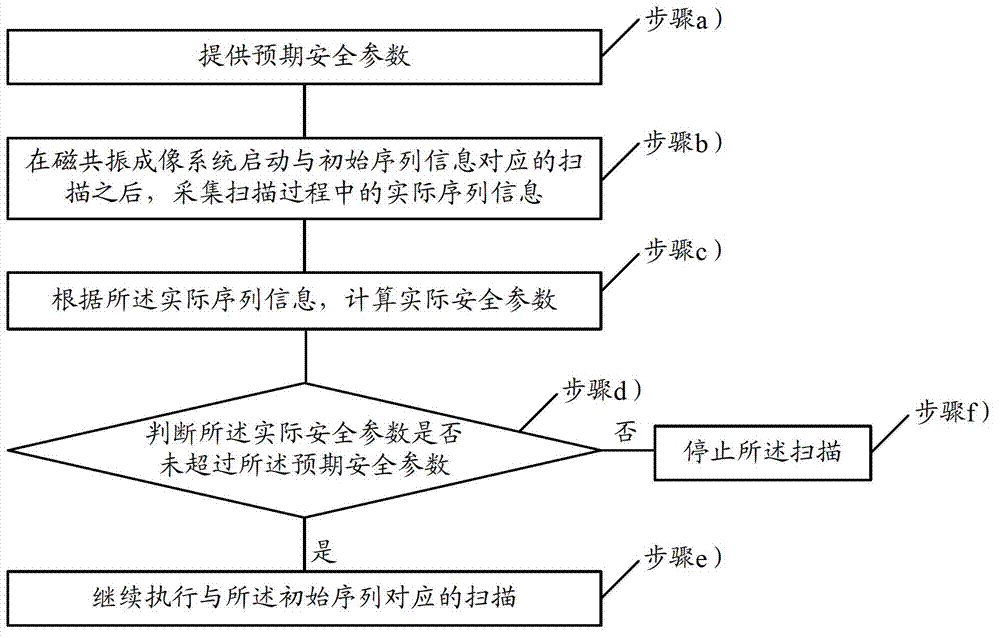
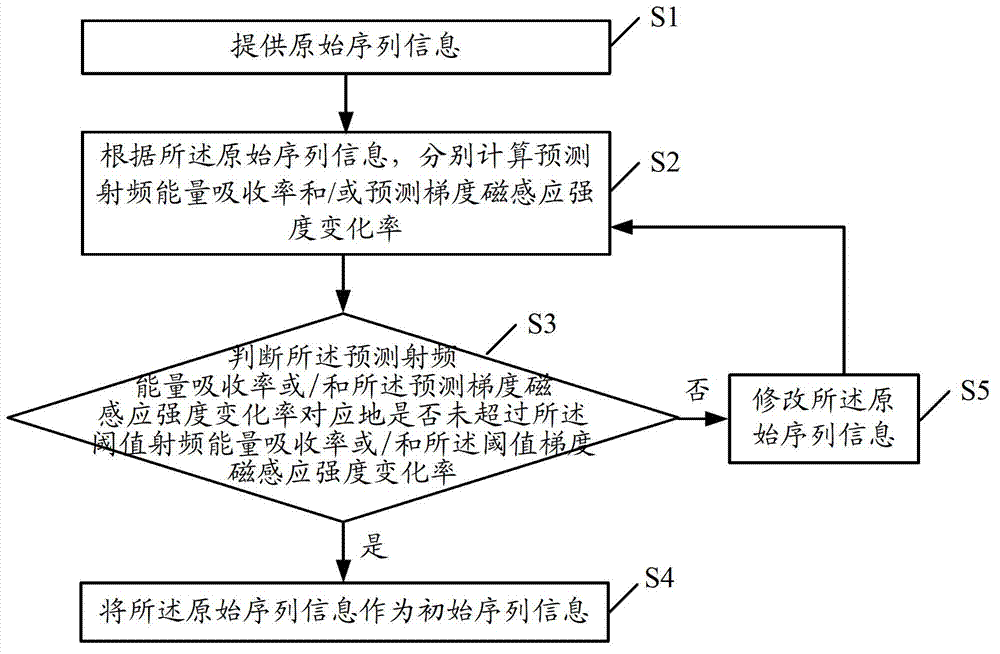
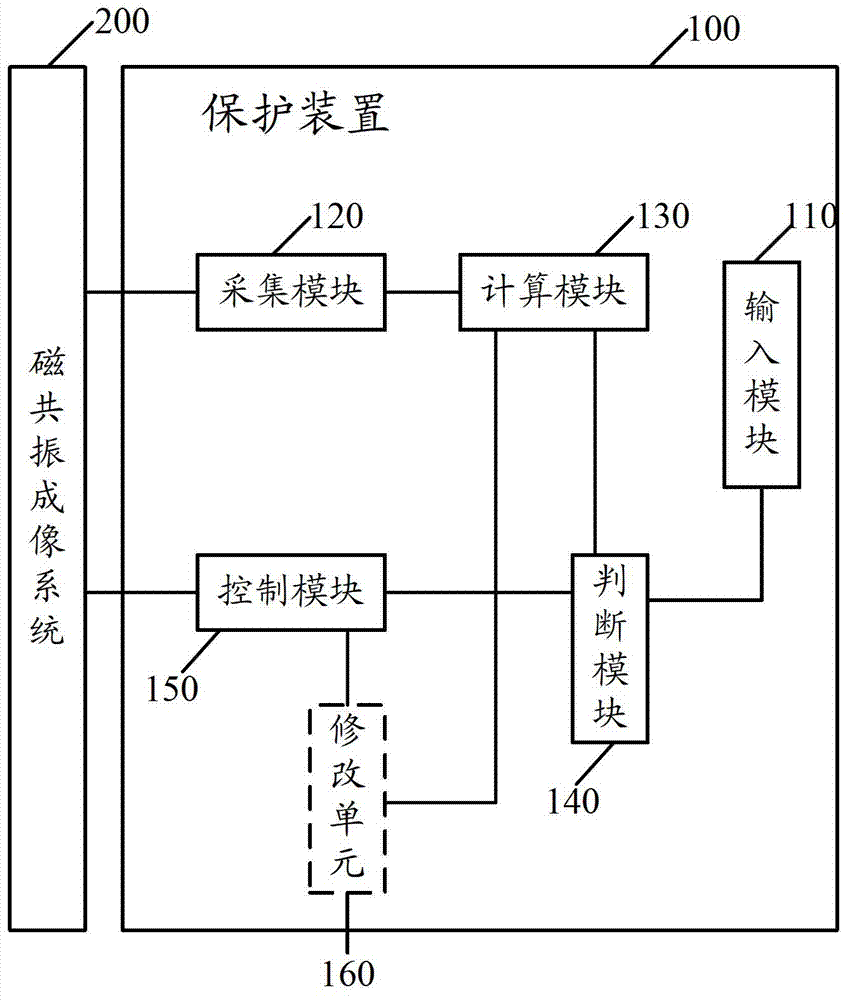
Disclosed are a magnetic resonance imaging system protecting method and device, and an automatic shutoff testing method. The protecting method includes a), providing expected safety parameters; b), after the magnetic resonance imaging system starts scanning corresponding to initial sequence information, collecting actual sequence information in the process of scanning; c), according to the actual sequence information, calculating actual safety parameters; d), judging whether the actual safety parameters do not exceed the expected safety parameters or not; e), if yes, continuing to execute scanning corresponding to an initial sequence; f), if not, stopping scanning. The device comprises an input module used for inputting the expected safety parameters, a collection module used for collecting the actual sequence information, a calculation module used for calculating the actual safety parameters according to the actual sequence information, a judgment module used for judging whether all of the actual safety parameters do not exceed the expected safety parameters or not, and the control module is used for controlling to continue to execute scanning if yes and to stop scanning if not. By the protecting method and the protecting device, safety of a scanning object in the actual process of scanning can be effectively guaranteed.
Owner:SHANGHAI UNITED IMAGING HEALTHCARE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com