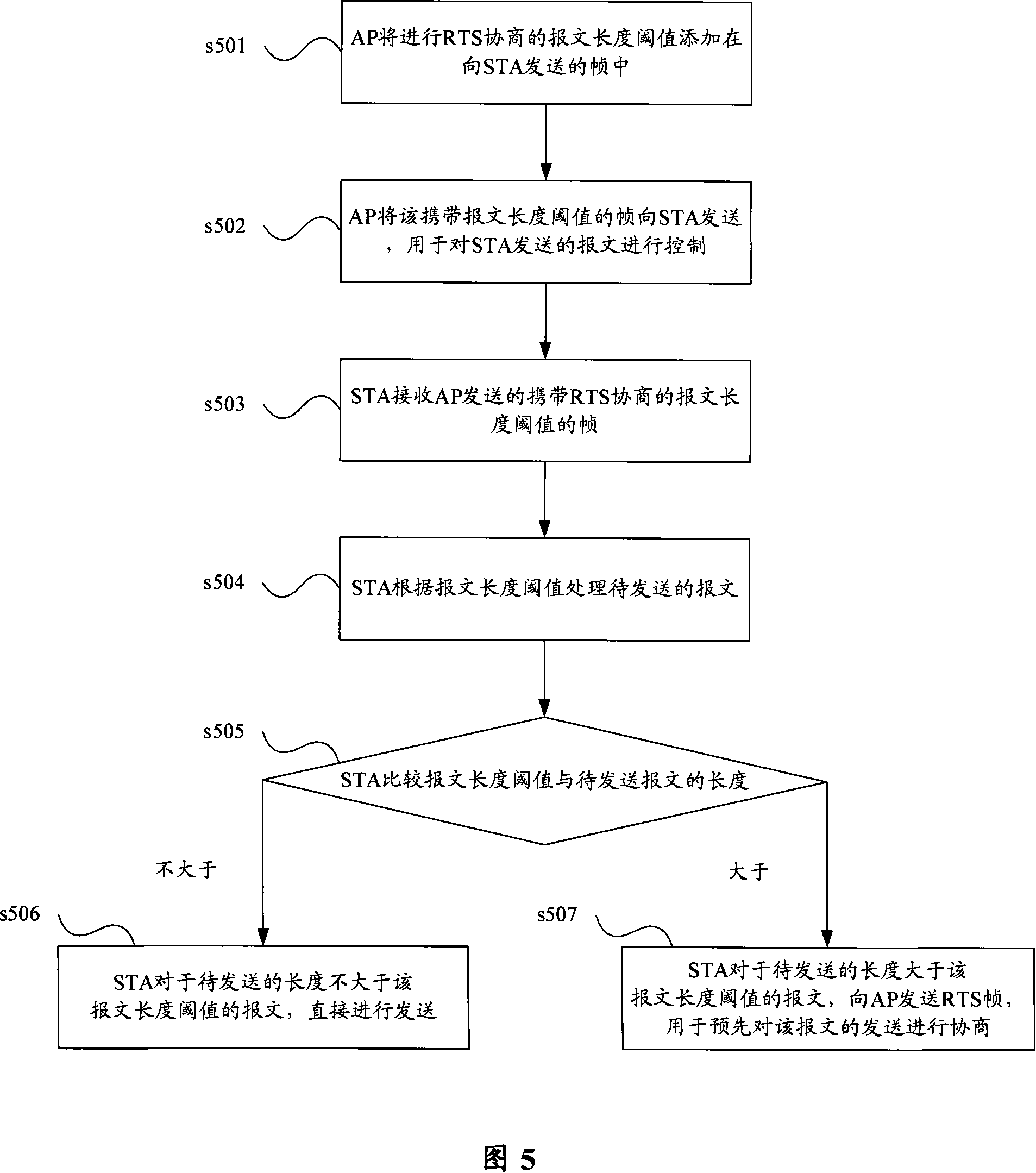
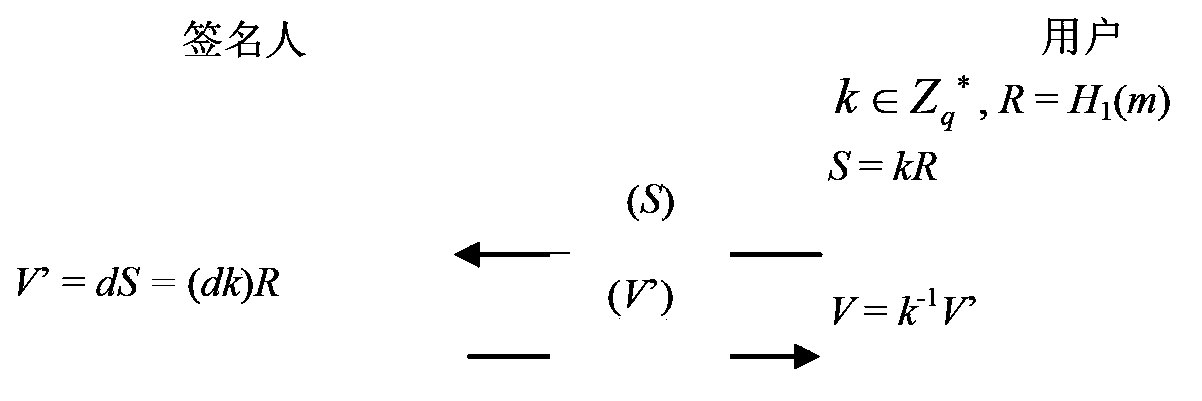Patents
Literature
389 results about "Message length" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
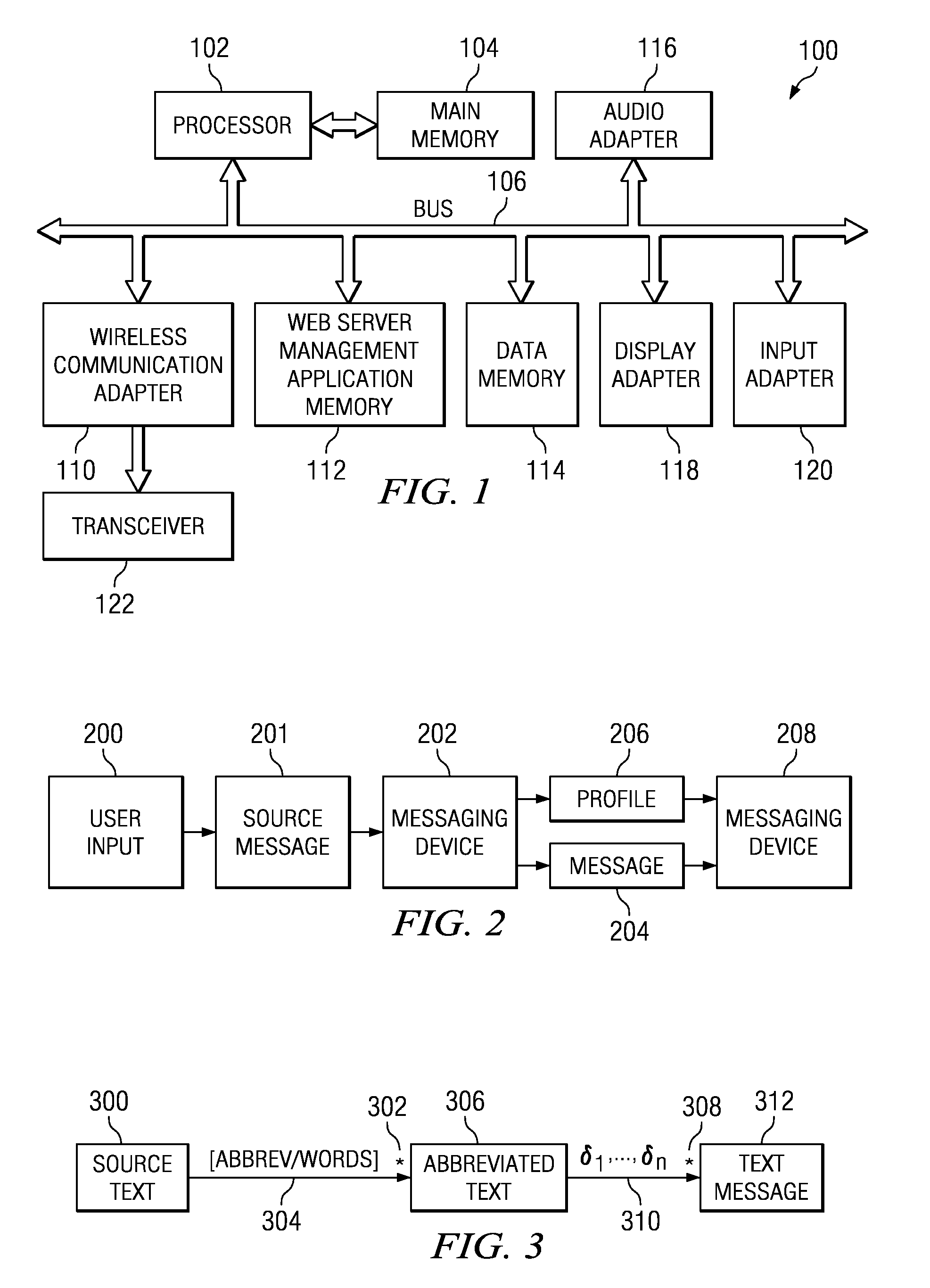
Message is a way to communicate with your friends and relatives anywhere in the world. The message text length is maximum 160 characters. One message length is 160 characters. After 160 characters your message you can continuing your message but its count as a two messages.
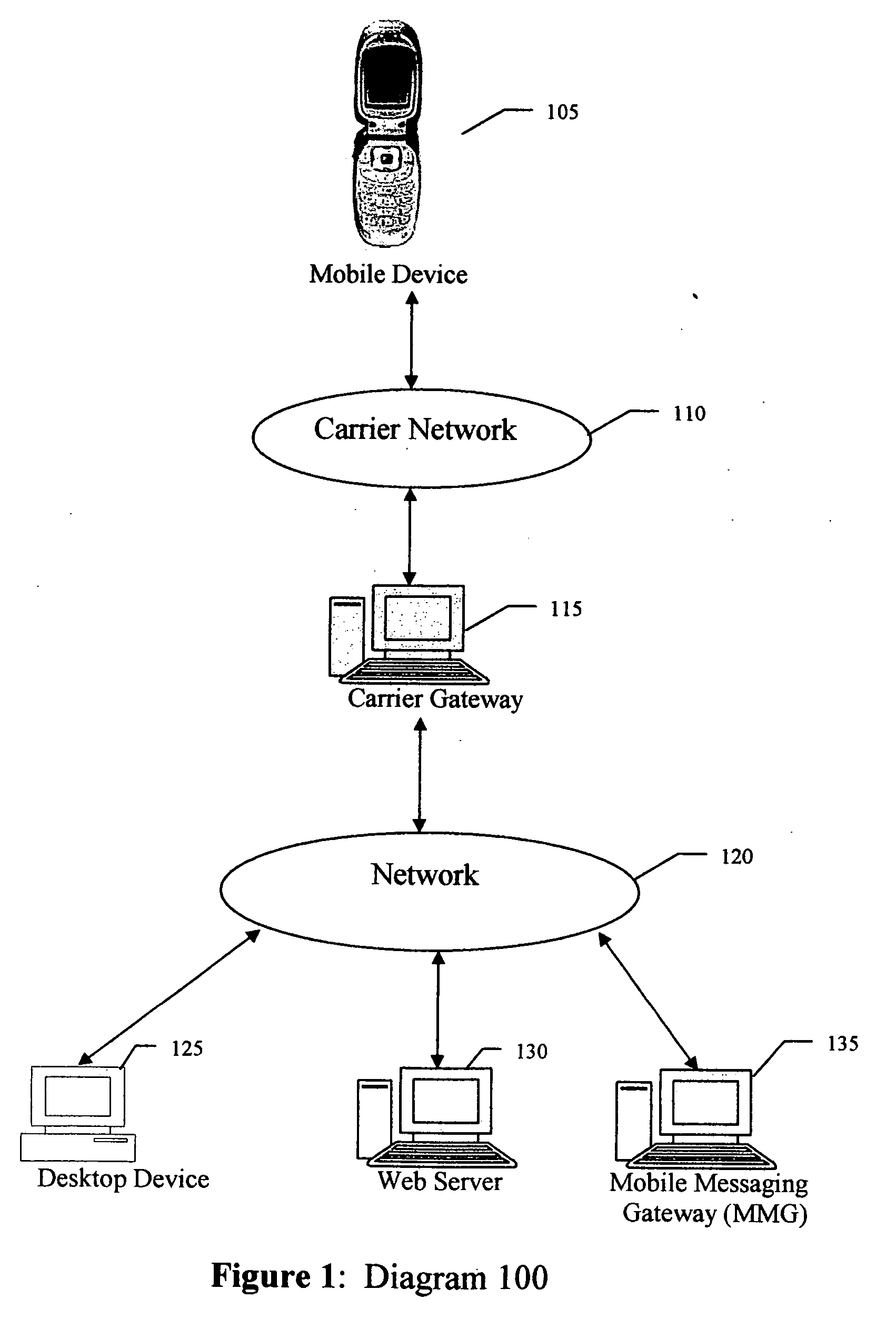
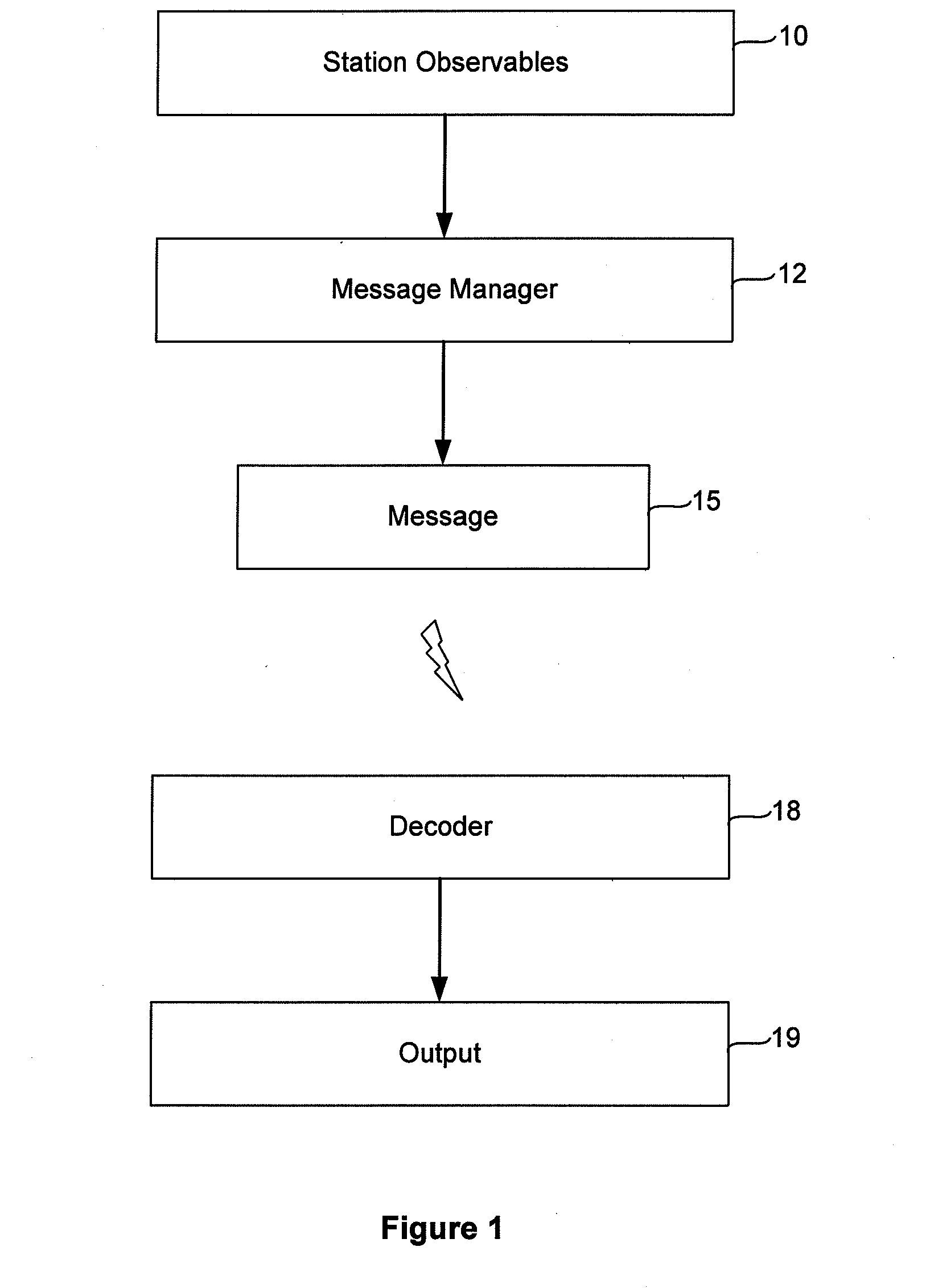
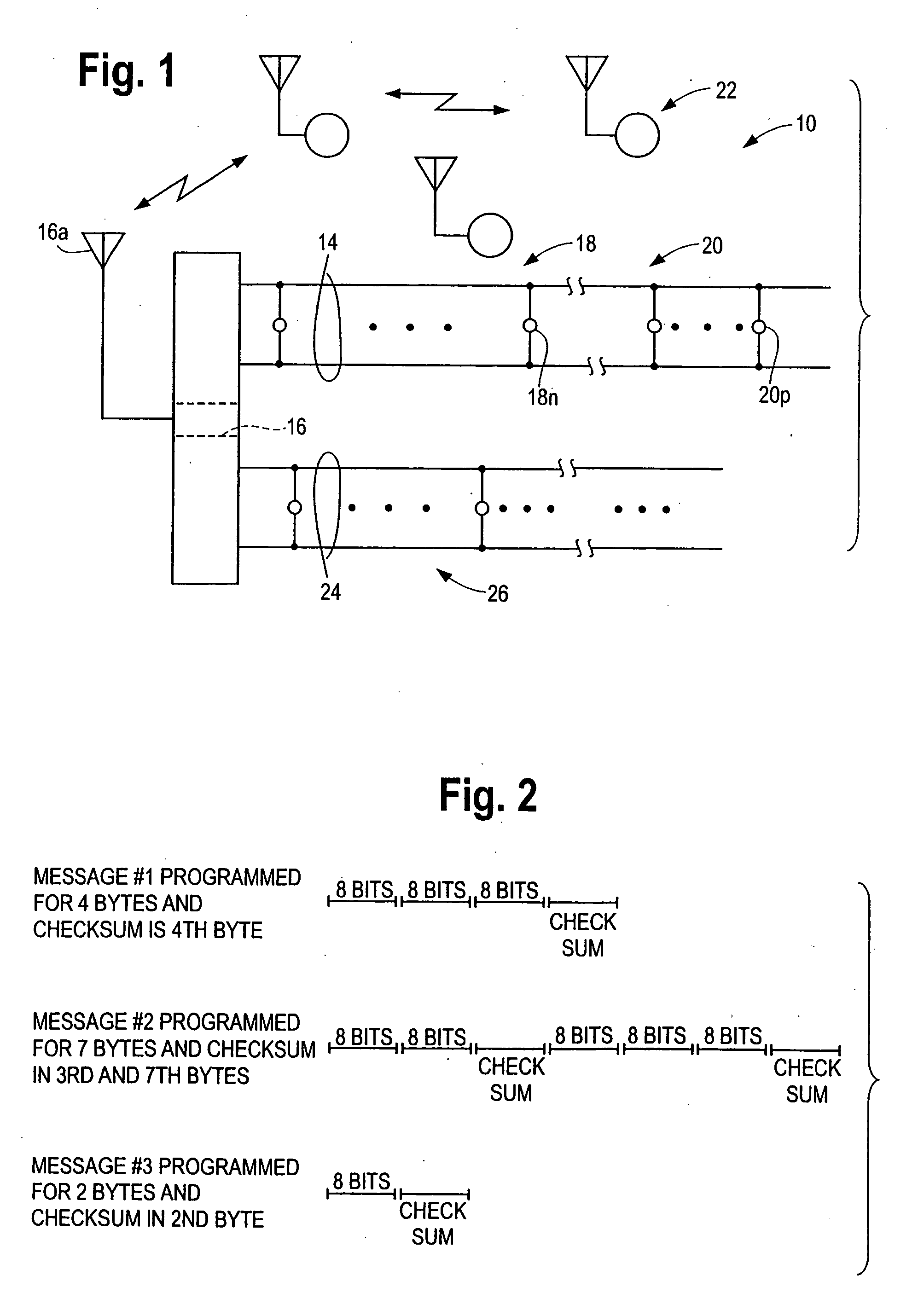
Scheme of sending email to mobile devices
InactiveUS20060218234A1Multiple digital computer combinationsMessaging/mailboxes/announcementsMessage lengthRouting table
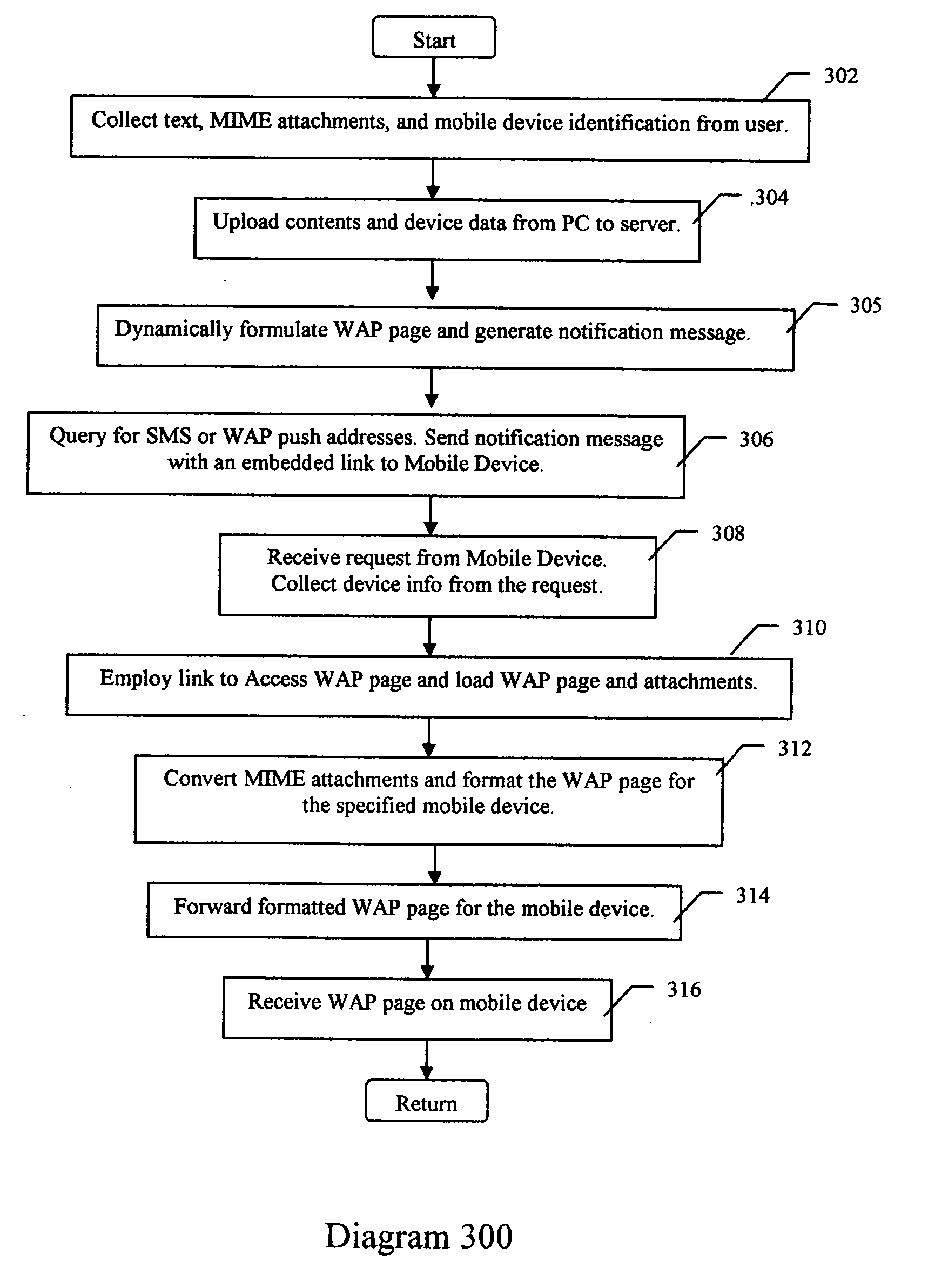
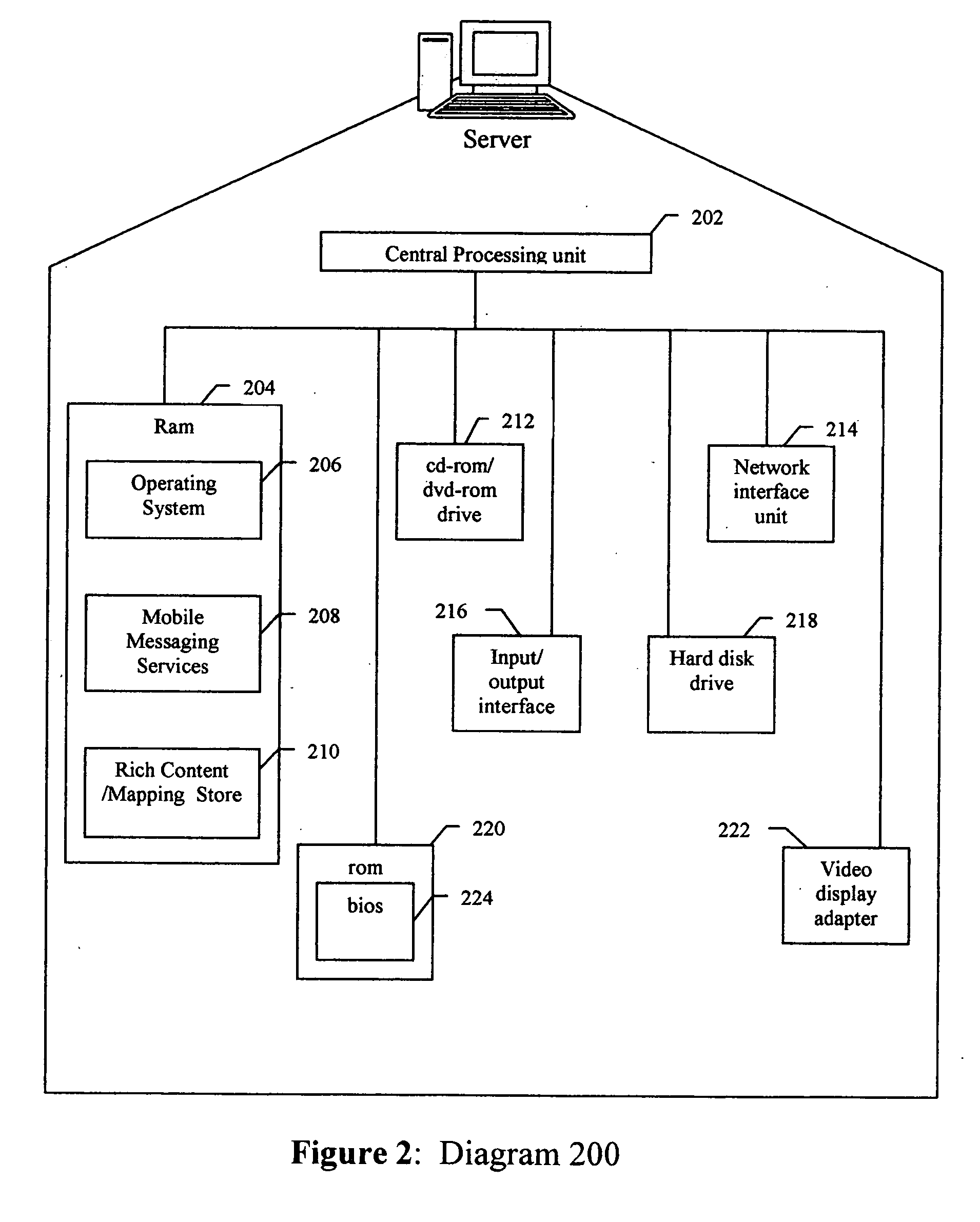
A method, apparatus, client and server are directed at providing a simplified scheme to deliver email messages that include text message body, and / or MIME attachments from desktop computing devices to messaging (such as SMS) and wireless internet capable phones. A web form is provided for users to compose messages and / or adding MIME attachments from their PC. Also provided in the form are input fields for users to enter device numbers for recipients. Upon submitting the form, message body and MIME attachments are uploaded and stored on the server. An email WAP page that contains the message body and the links to all the MIME attachments is created dynamically and stored on the server. The server then queries a service database and looks up a domain routing table to build the email like messaging addresses for recipients. The server sends a notification message with an embedded link to the email like messaging addresses. The link, such as a URL, a script, an executable, a program, and the like, pointing to the email WAP page, can be invoked from mobile devices. When the link is invoked on the mobile device, it sends a request to the server for the email WAP page. Upon receiving the request from the mobile device, the server collects the information about the mobile device; queries a device database for formats, display and capabilities; locates and loads the email WAP page; converts the MIME attachments to the formats supported by the mobile device; formats the email WAP page for display on the mobile device; delivers the formatted email WAP page to the mobile device. The email WAP page can be viewed, downloaded, and played on the mobile device. The scheme of the present invention supports a device number based authentication. The scheme of the present invention can also be implemented to deliver email messages to multiple mobile devices. The scheme of the present invention can expand the PC to SMS capabilities by enabling text messaging with arbitrary message length.
Owner:DENG LI +1
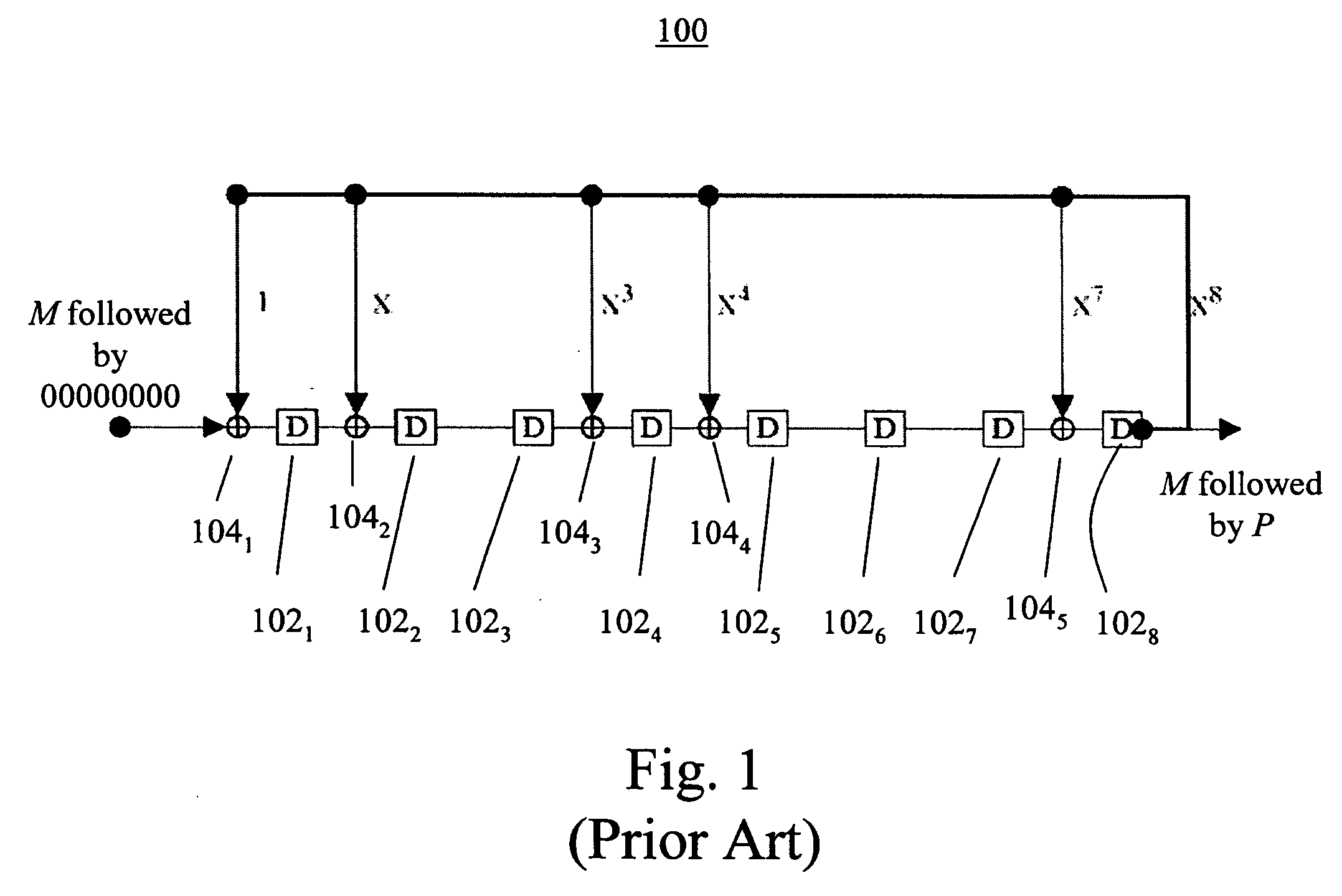
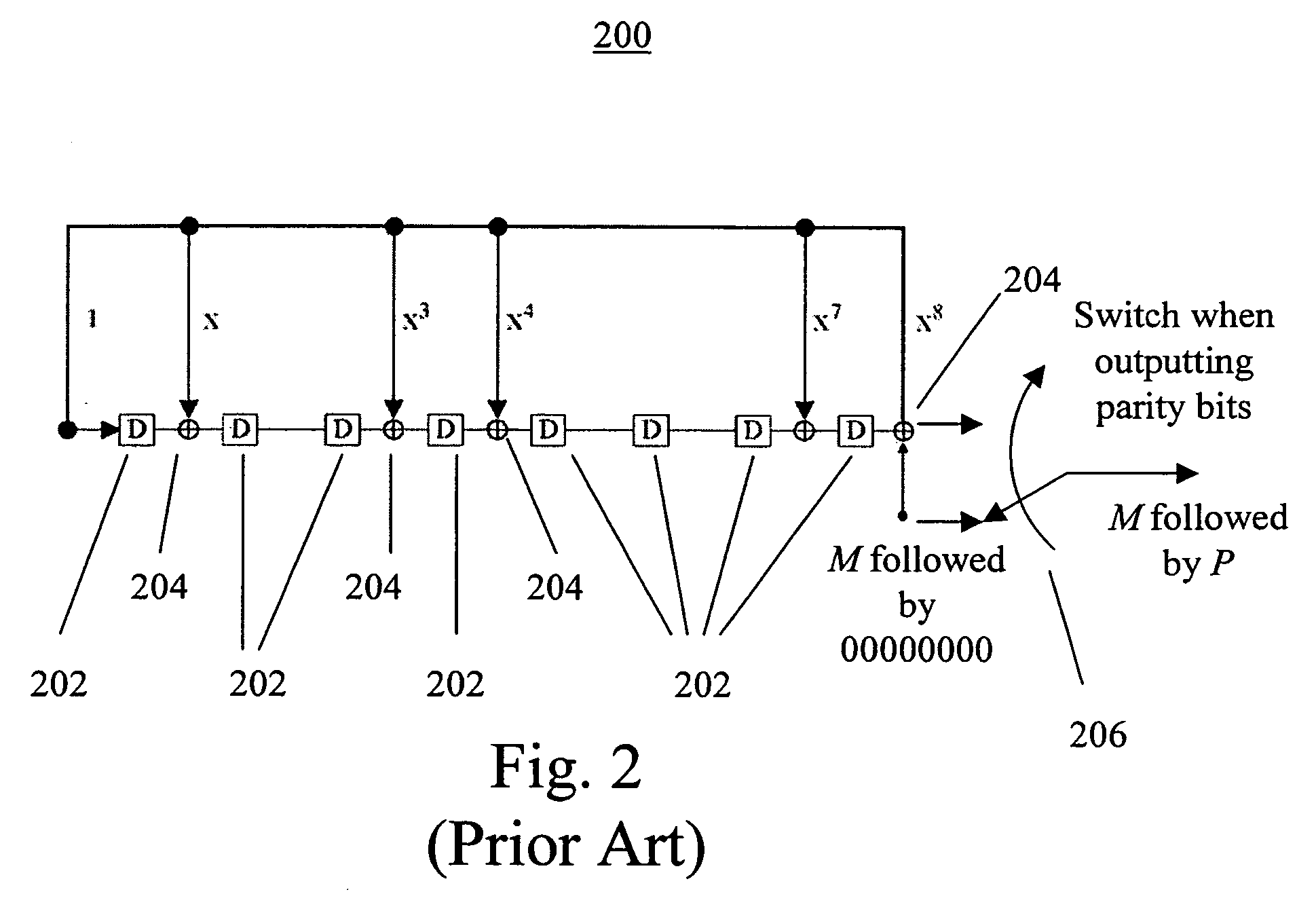
Cyclic redundancy check modification for message length detection and error detection
ActiveUS20050257118A1Reduce probabilityCode conversionError detection onlyMessage lengthCommunications system
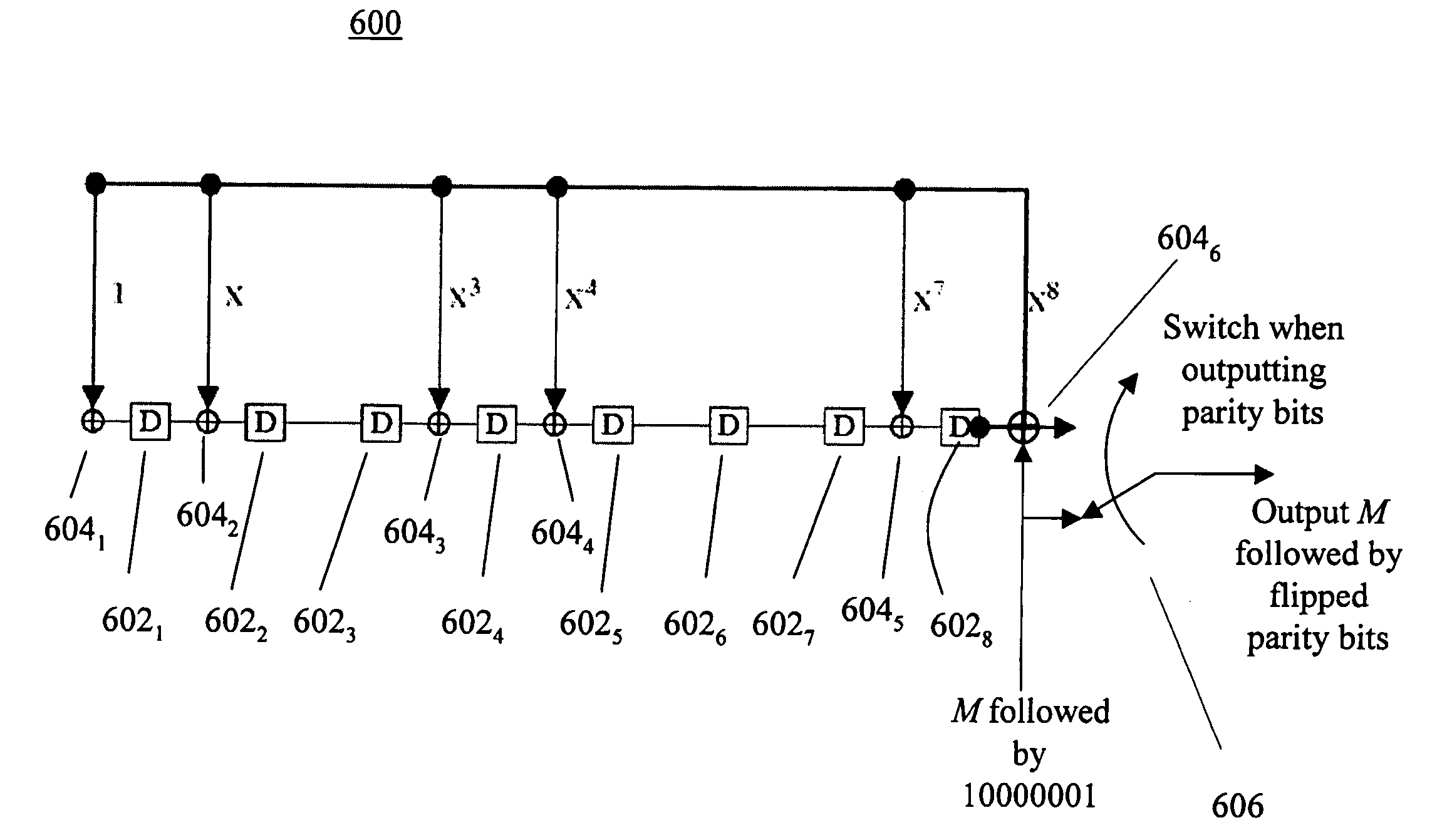
In a method for a variable-length communications system including encoding a message and decoding a data bit stream, the message includes a plurality of message blocks. A message block of the message is encoded by generating a parity check bit stream, flipping the parity check bit stream, and appending the flipped parity check bit stream to the end of the message block. When a data bit stream is received, a guessed message block and a guessed flipped parity check bit stream are extracted based on a guessed message block length. A parity check bit stream is generated for the guessed message block and then flipped. If the flipped parity check bit stream is the same as the guessed flipped parity check bit stream, the message block has been identified. Otherwise, the guessed message block length is increased by 1 and the above step is repeated.
Owner:NAT CHIAO TUNG UNIV +1
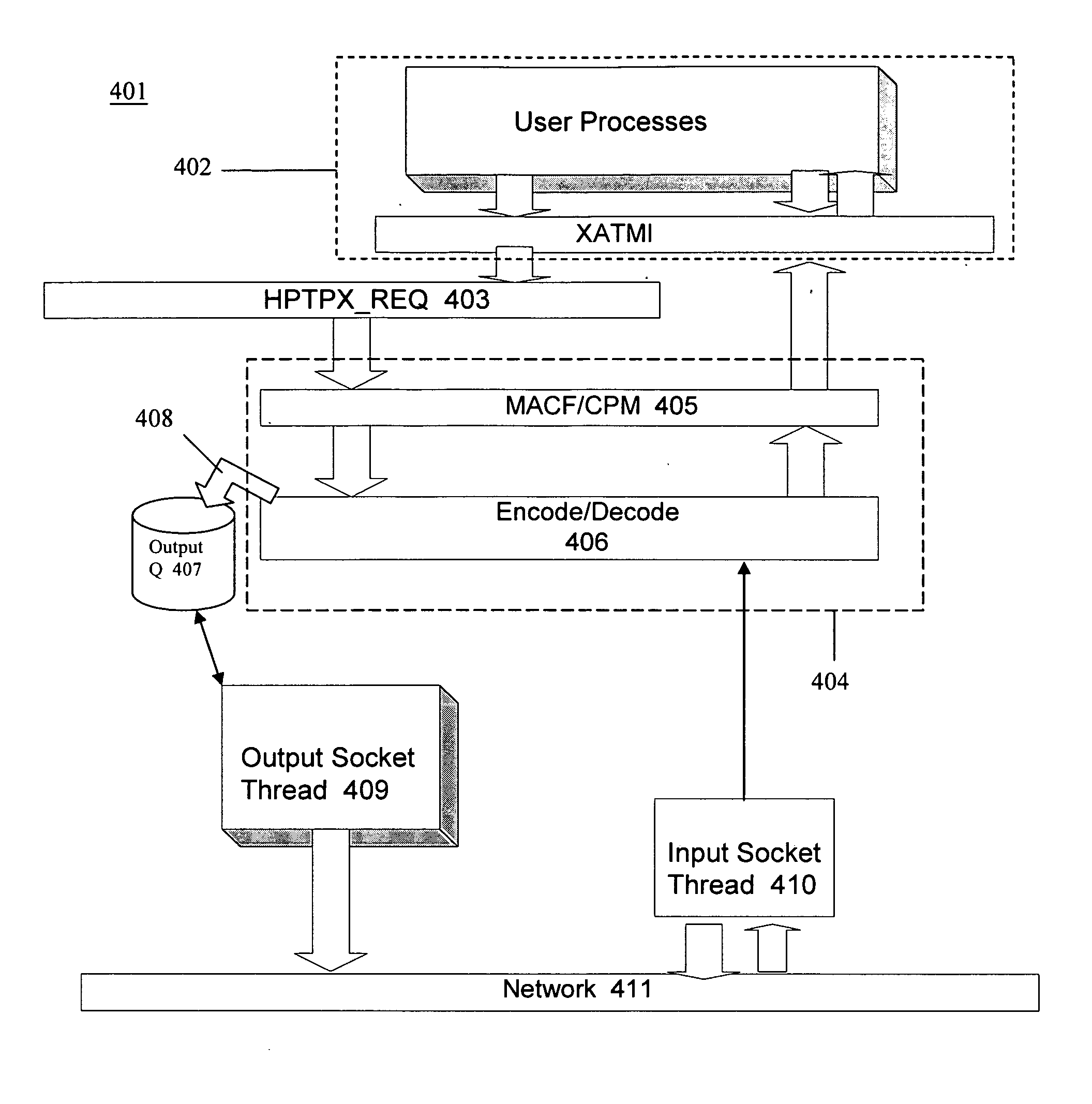
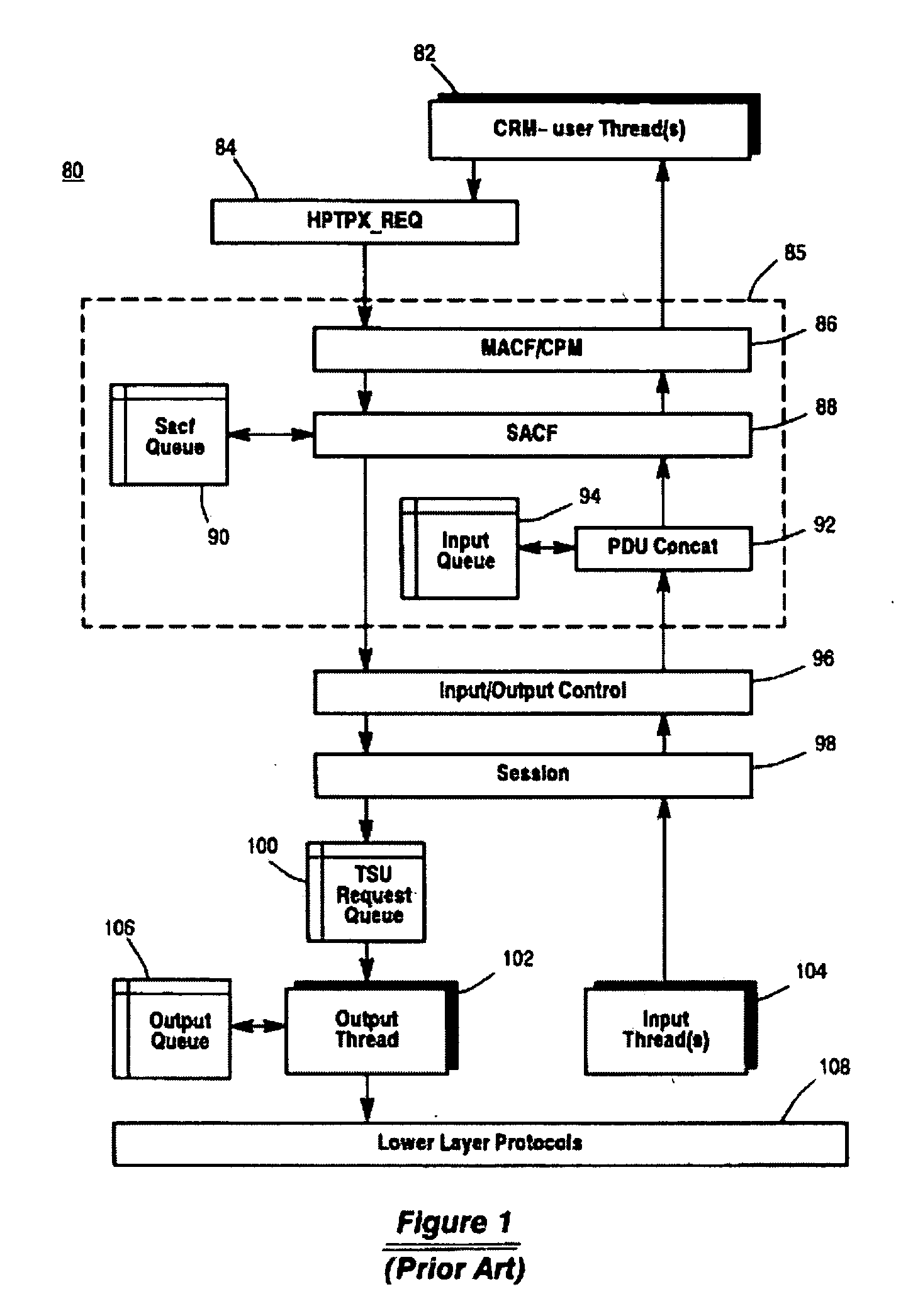
Message transfer using multiplexed connections in an open system interconnection transaction processing environment
InactiveUS20050193056A1Less complexSimpler connection creationMultiple digital computer combinationsSecuring communicationMessage lengthMultiplexing
Novel message formats for use in a distributed transaction environment are disclosed. Each message includes a message type field, a message length field, and a data field, typically in the foregoing order, and each field in the message has a fixed number of bytes. The message type and data length fields may be comprised of a single header. The data field may include novel groups of OSI TP PDUs where each grouping characterizes the content of the data in the PDU. A novel apparatus for use in a distributed transaction environment also is disclosed. The apparatus may include a peer processing machine and a multiplexed TCP / IP connection for exchanging messages with other peer processing machines in the distributed transaction environment.
Owner:UNISYS CORP
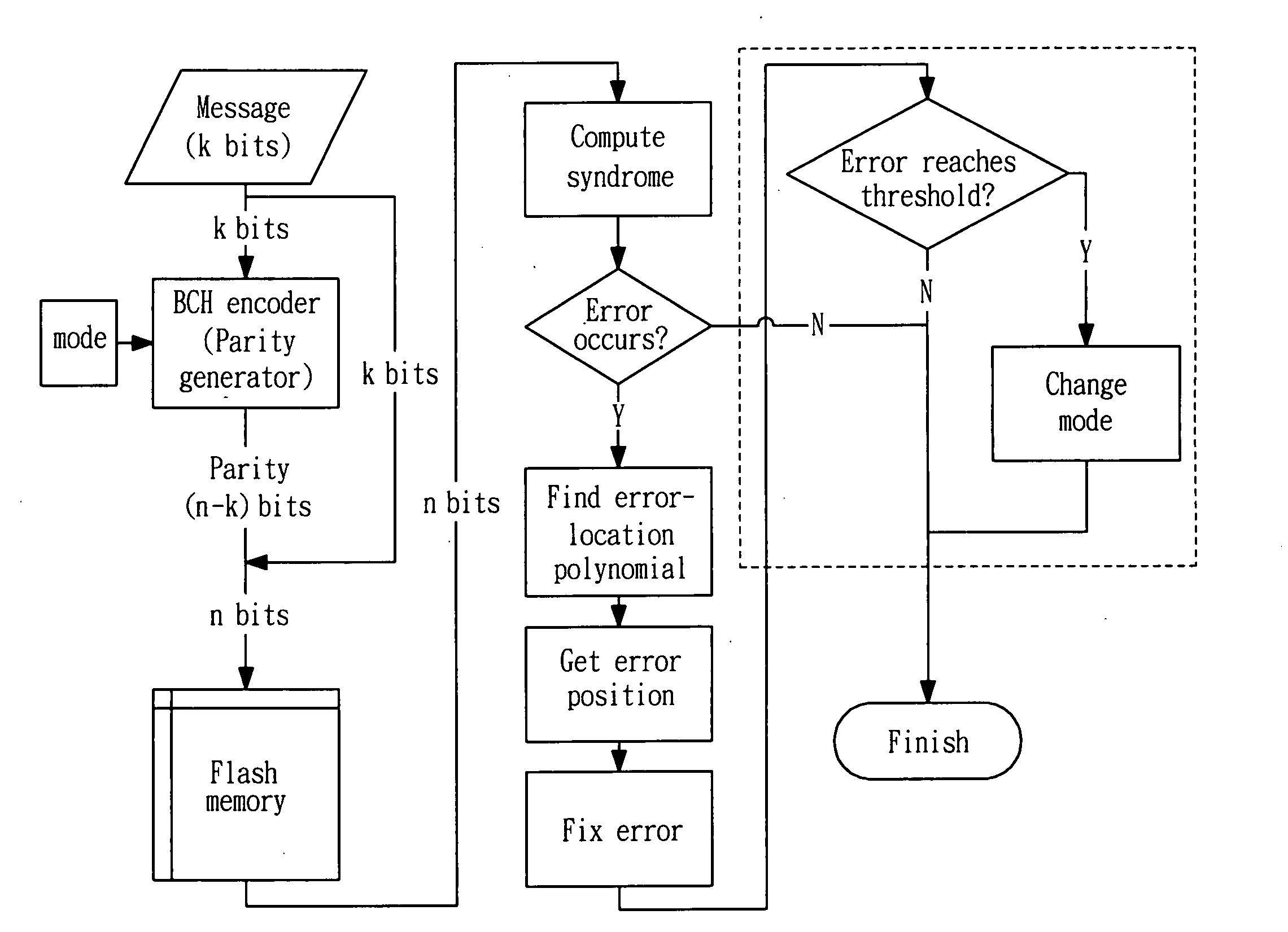
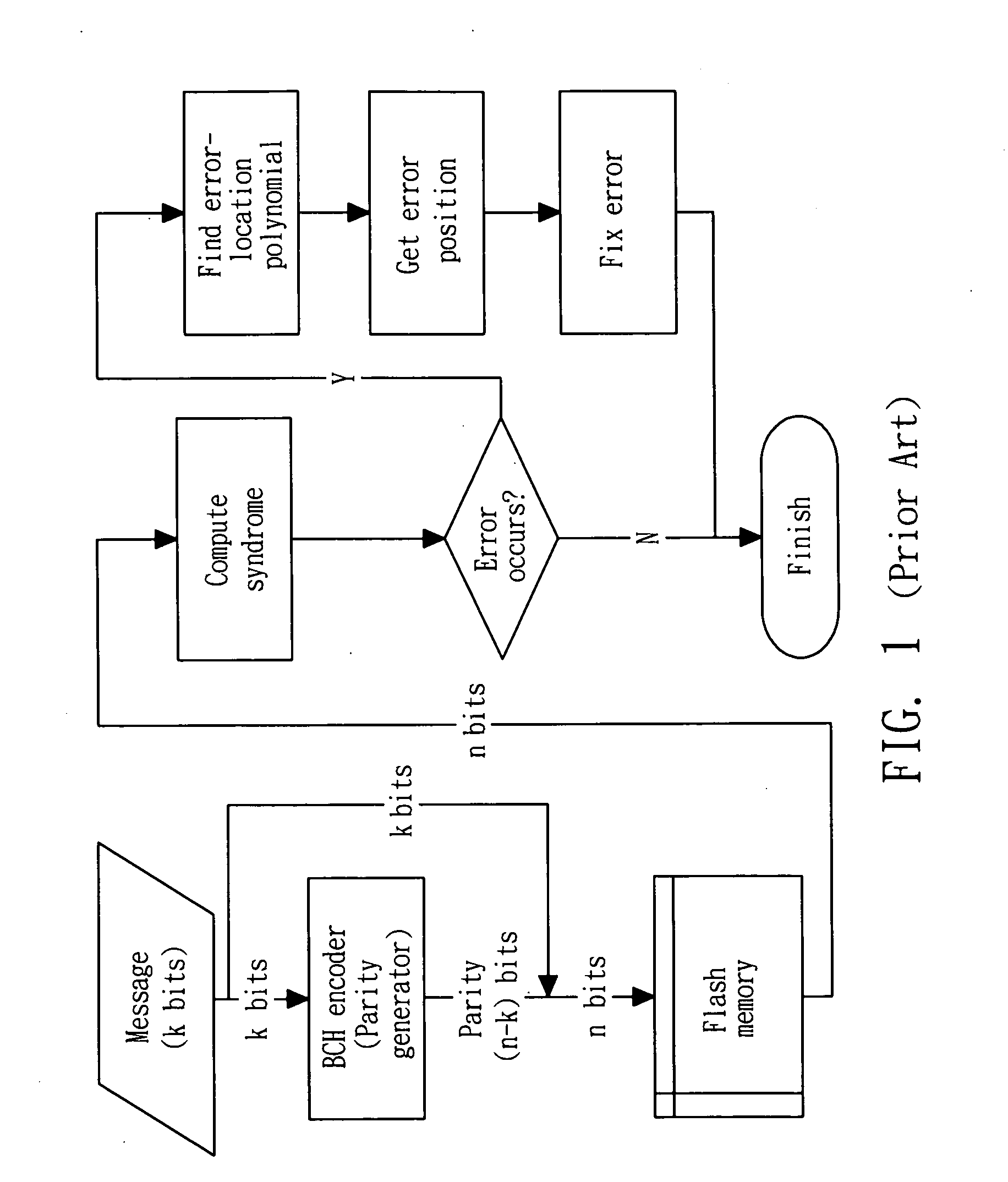
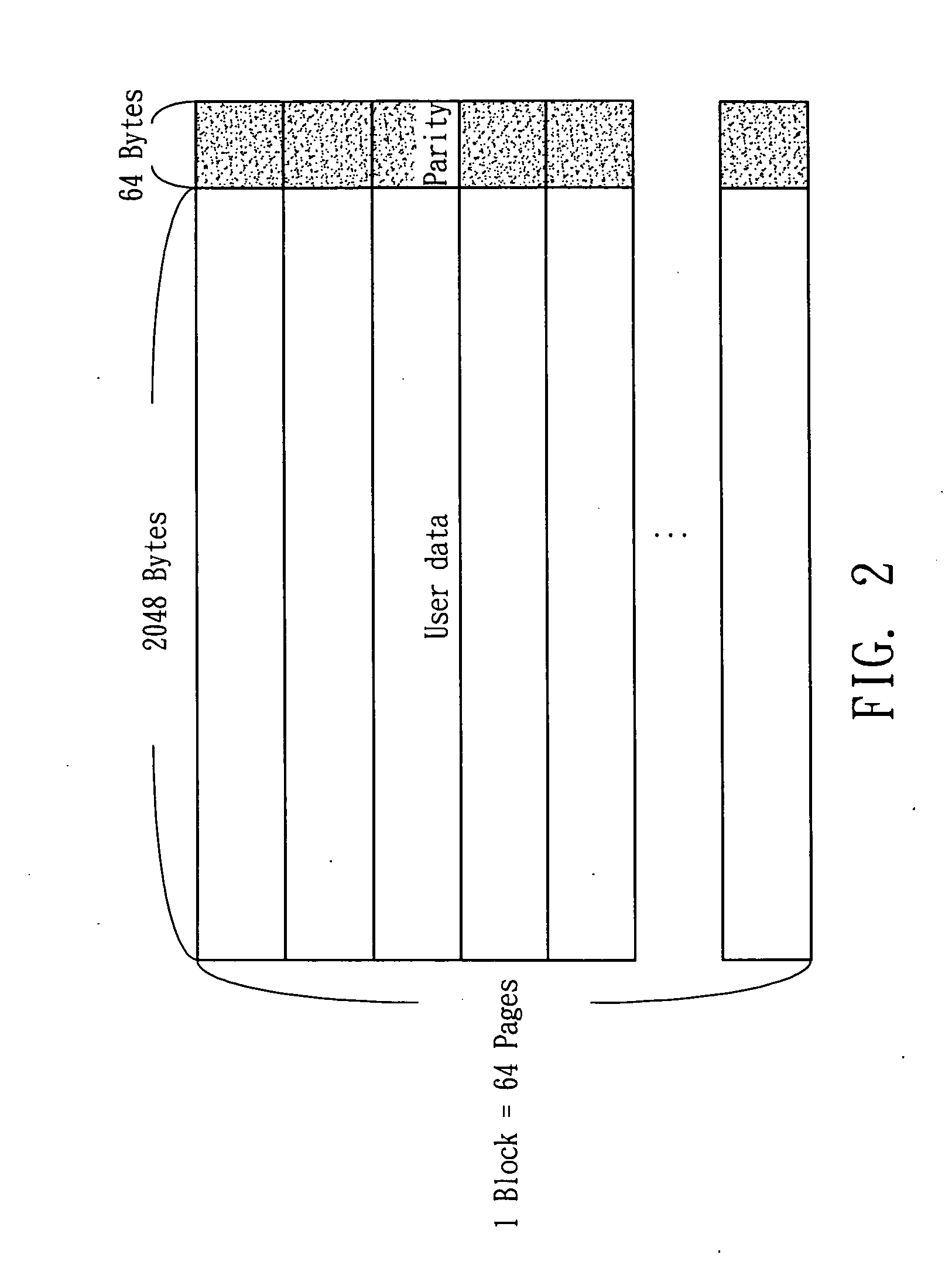
Non-volatile memory management method
ActiveUS20100281341A1Extended service lifeError preventionTransmission systemsMessage lengthNon-volatile memory
A management method for a non-volatile memory comprises the steps of providing the non-volatile memory with at least one block having a plurality of pages to store user data and parity data; dividing at least one of the pages into a plurality of partitions each including the user data and parity data; determining codeword length of each of the partitions, the codeword length comprising message length with sufficient storage to store the user data and parity length storing the parity data; and storing extra parity data in the partition with the codeword length. When storing extra parity data in the codeword length, the parity length is increased and the message length is decreased.
Owner:NATIONAL TSING HUA UNIVERSITY
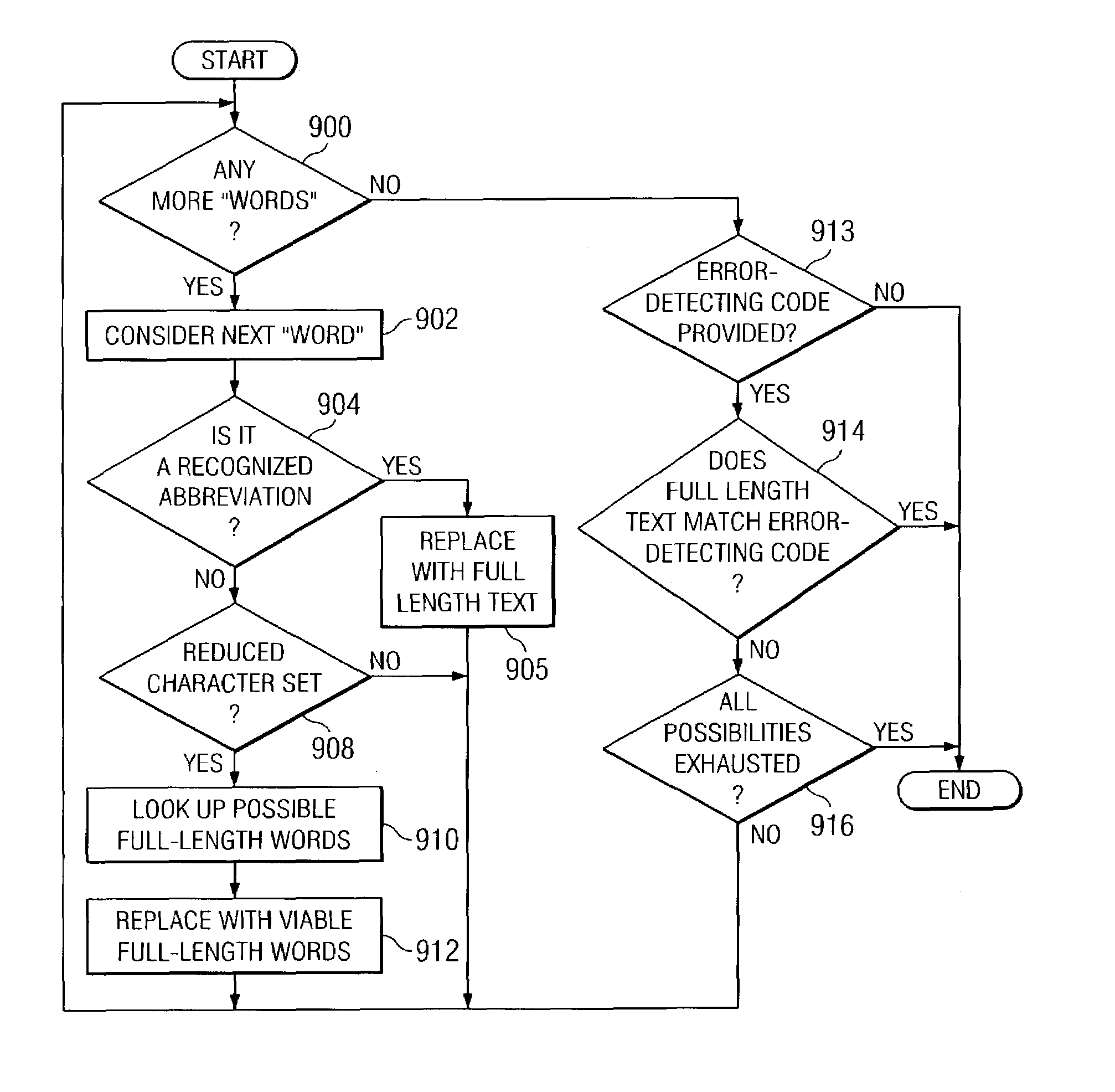
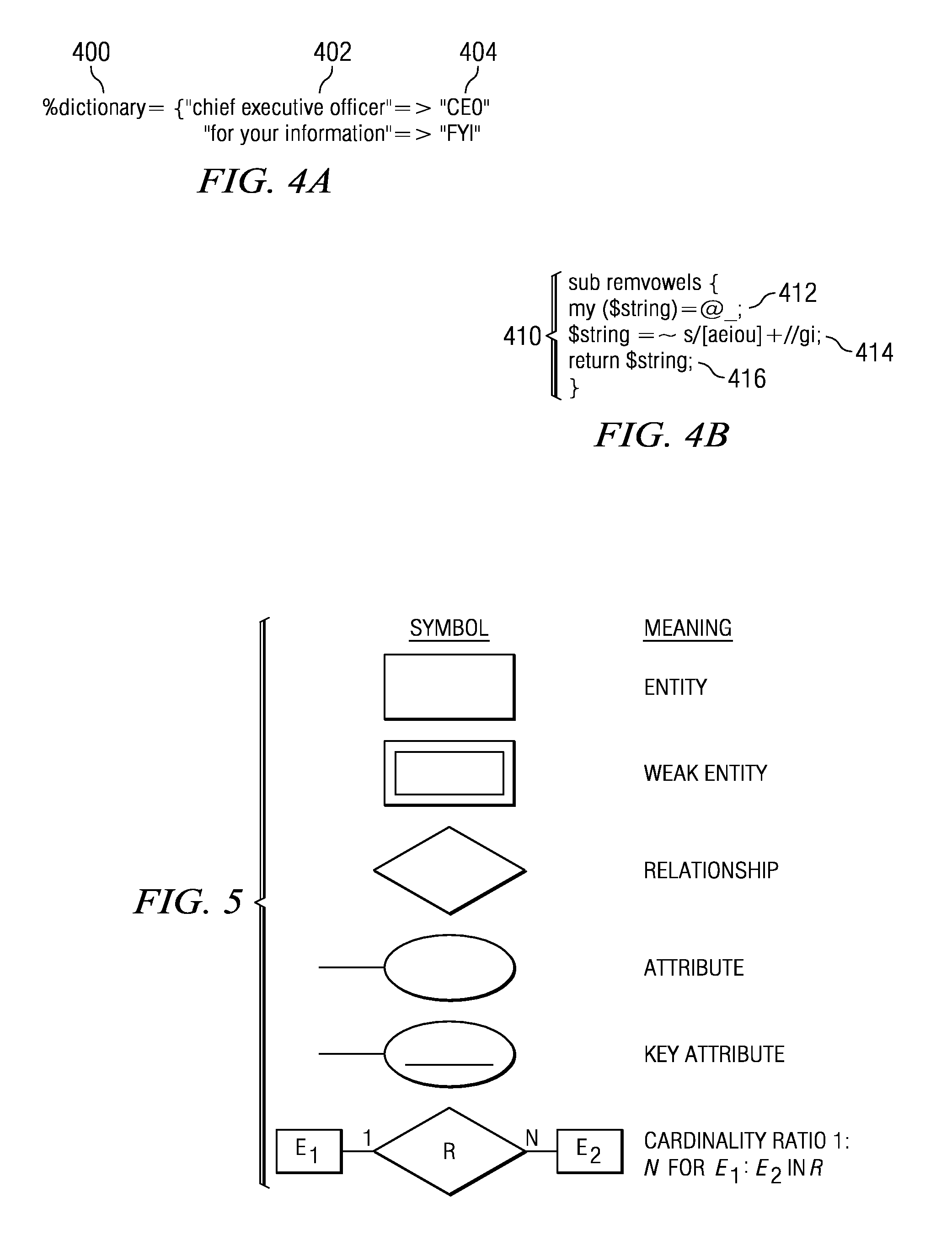
Compression and abbreviation for fixed length messaging
InactiveUS7315902B2Data processing applicationsNatural language data processingMessage lengthData treatment
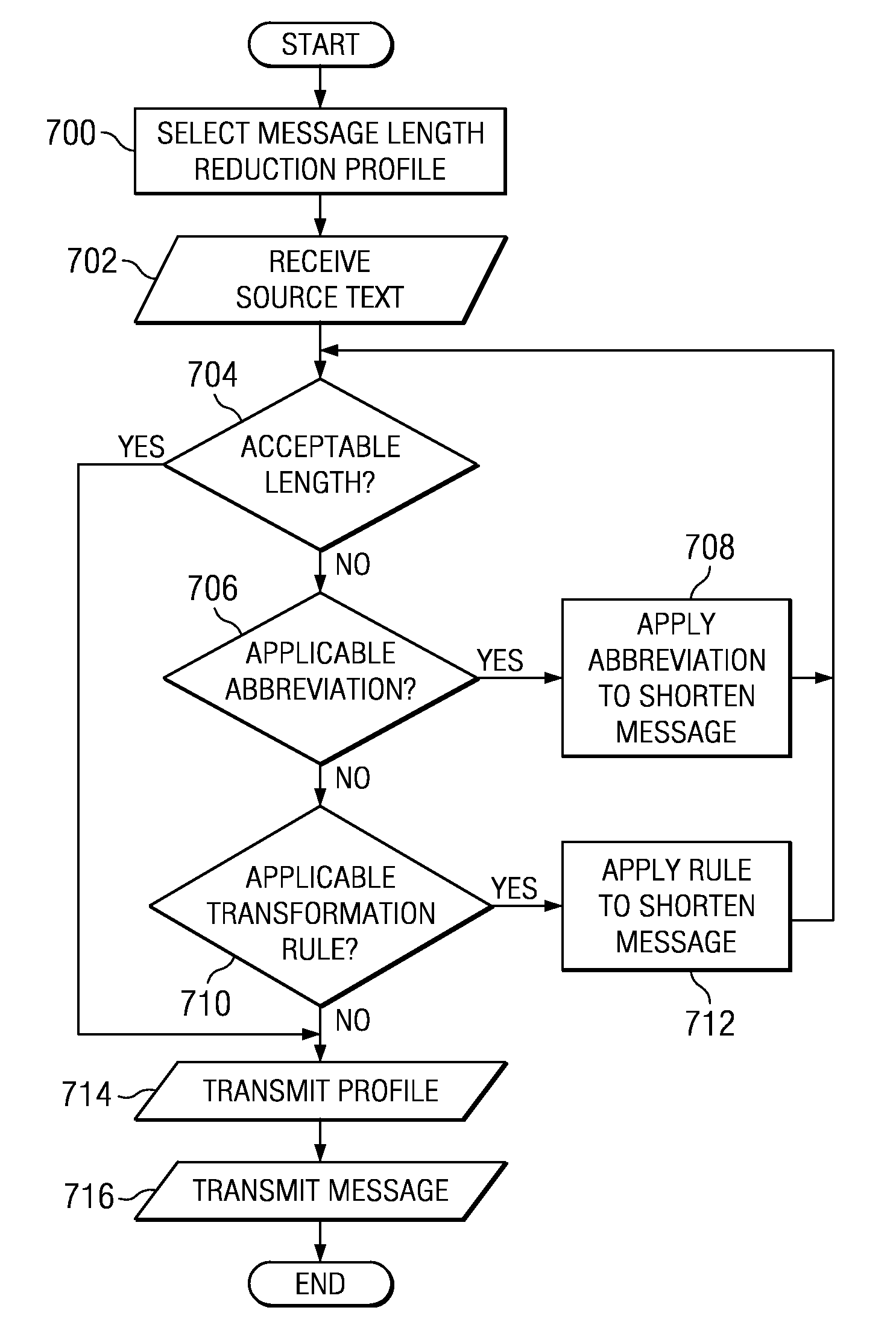
A method, computer program product, and data processing system for compressing and abbreviating text messages at a first text messaging device for transport and subsequent interpretation at a second text messaging device is disclosed. A user-defined message length reduction profile for producing human-readable compressed text is associated with a source text message at a first text messaging device. The source text message is then shortened using abbreviations and transformation rules in the profile. The shortened text message can then be transmitted to a second text messaging device. In addition, the compression provided by the present invention, although intended to be human-readable, can be complemented with decompression software to expand the compressed and abbreviated text to its full length and verifying, using a checksum or other error detecting code, that the expanded version corresponds to the original text.
Owner:IBM CORP
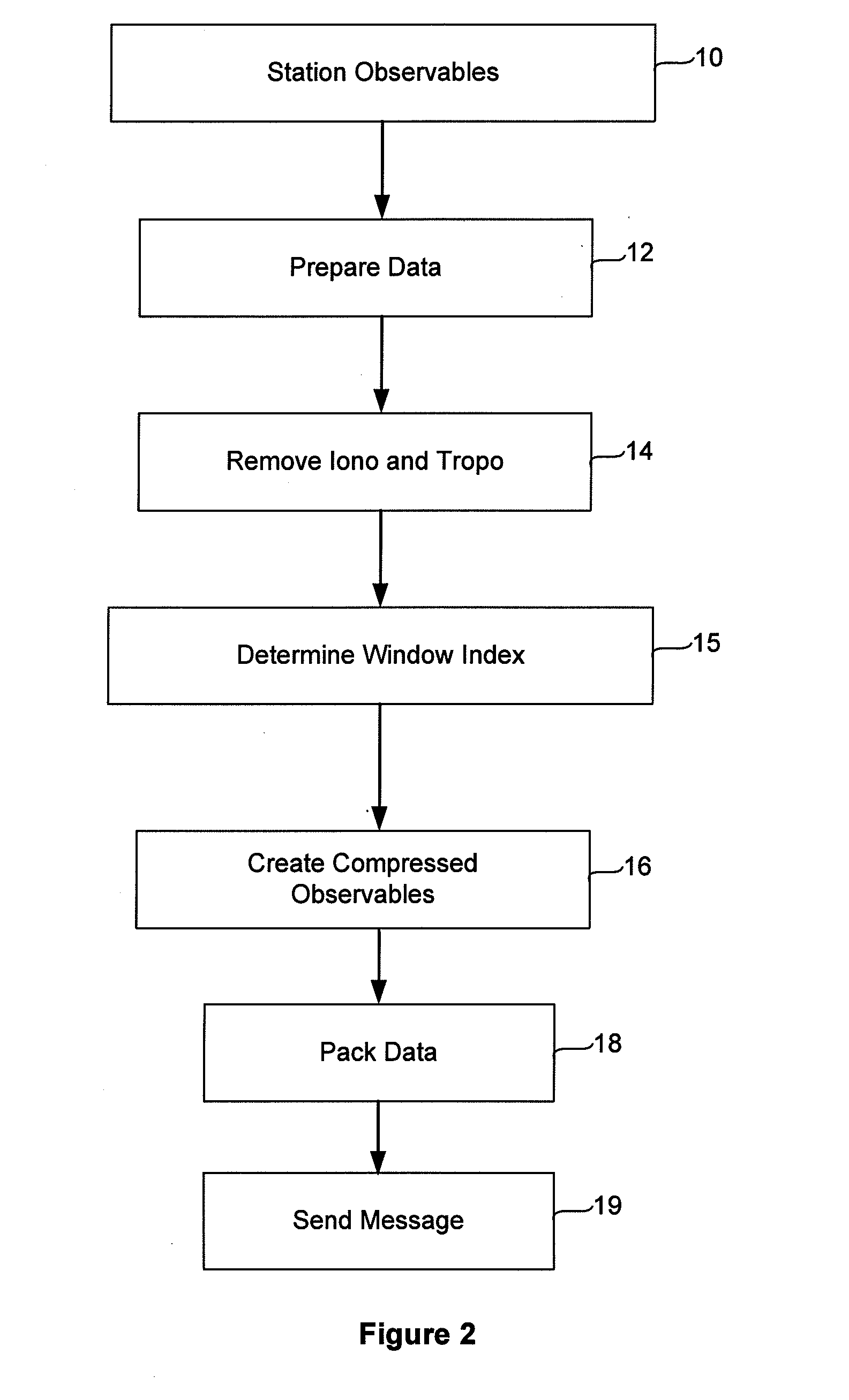
Compact Transmission of GPS Information Using Compressed Measurement Record Format
ActiveUS20100085249A1Smooth bandwidth utilizationGuaranteed usageCode conversionTime-division multiplexMessage lengthObservation data
A format for providing messages among GNSS apparatus includes providing a message identification block and a message body. The message identification block includes information specifying a message length and a message type block specifying a message type. Rather than sending all data from one apparatus to another, ambiguous observation data is sent to conserve bandwidth. At the sender a deconstruction of GNSS code and carrier observations using knowledge of the signal structure and constellation geometry, together with simplifications of atmospheric models, allows removal from the observation data of that information which can be implicitly understood or recreated by the recipient. This enables only the necessary information to be packed for transmission to the recipient.
Owner:TRIMBLE NAVIGATION LTD
A STA management method and device in BSS network
ActiveCN101150442AImprove stabilityRealize managementData switching by path configurationMessage lengthClient-side
Owner:NEW H3C TECH CO LTD
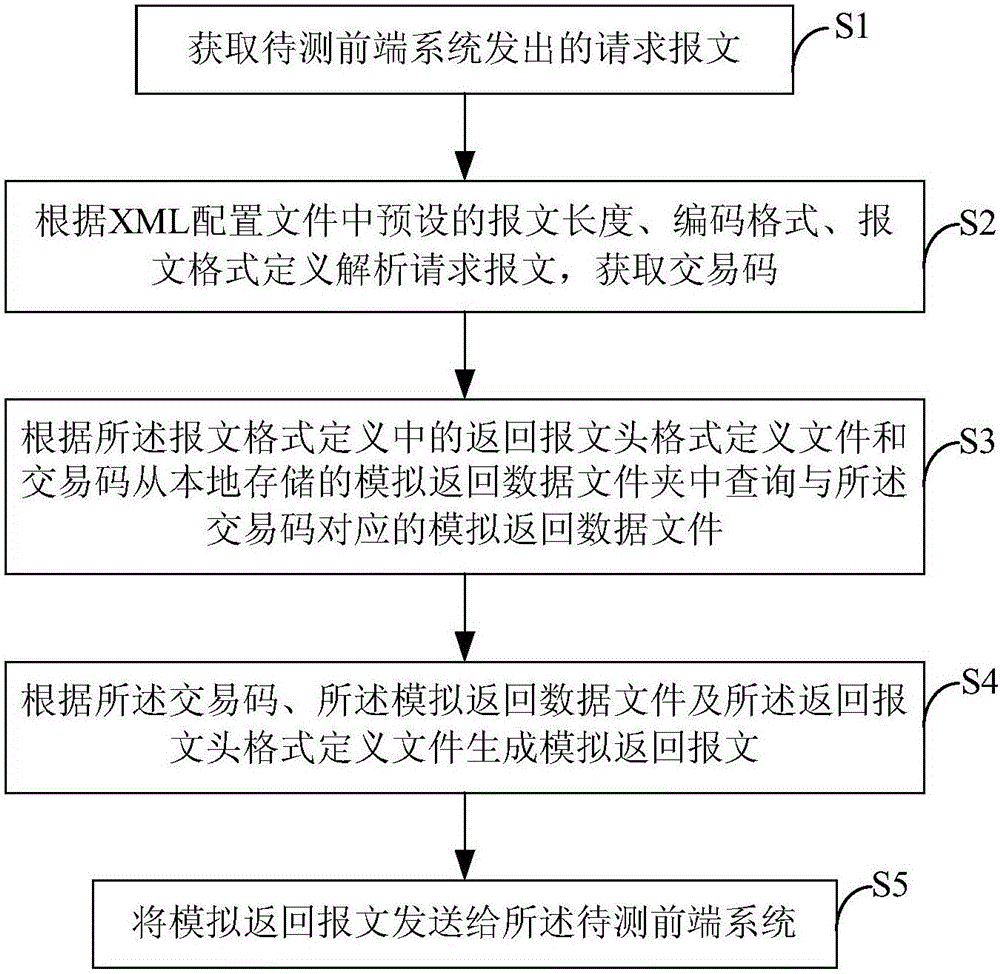
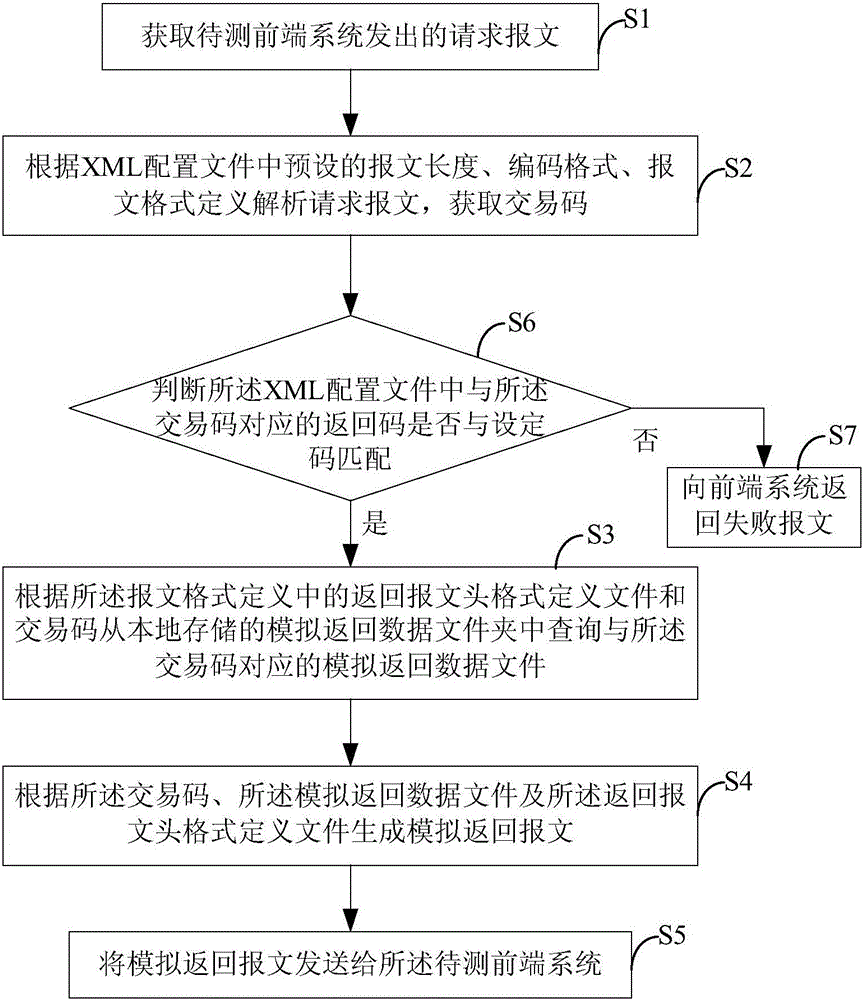
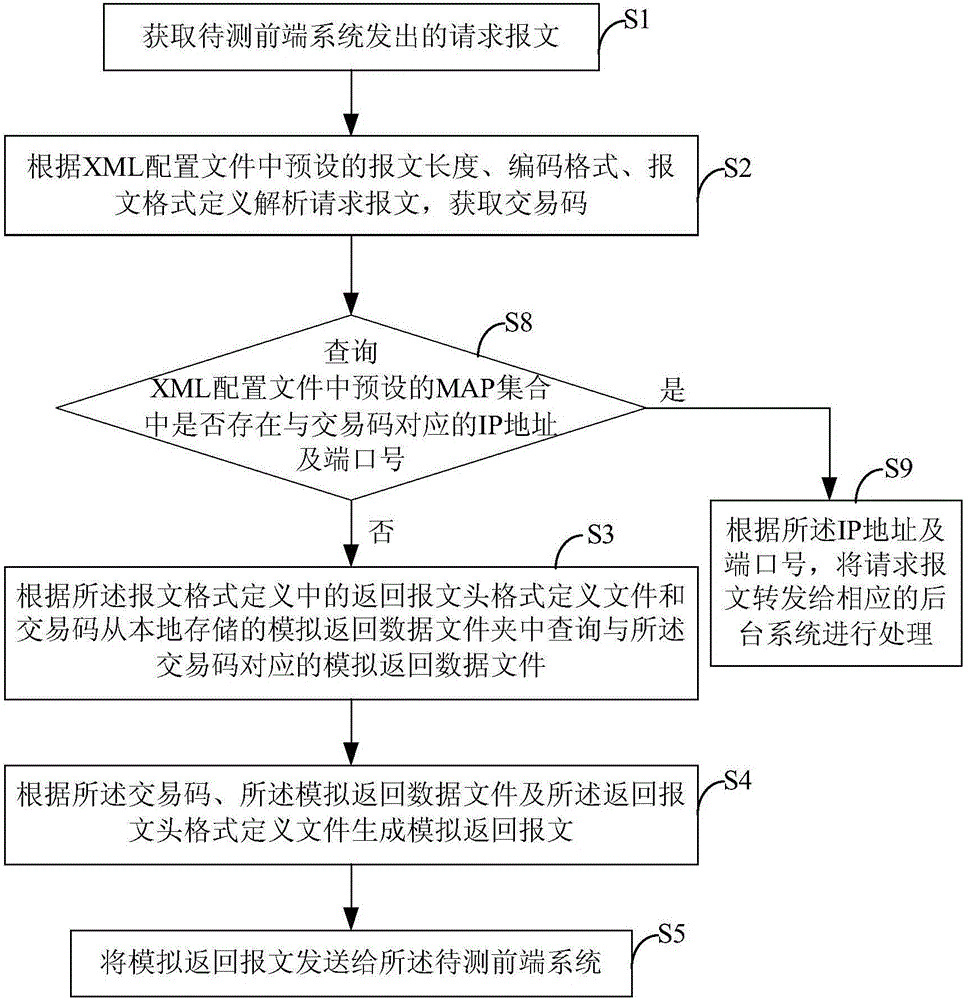
Message testing method for front-end system, and simulation baffle system
ActiveCN106027330AReduce workloadFeature transaction went wellData switching networksComputer hardwareMessage length
The invention provides a message testing method for a front-end system, and a simulation baffle system. The message testing method for the front-end system comprises the following steps of: obtaining a request message sent by the front-end system to be tested; according to the pre-set message length, coding format and message format definition in an XML configuration file, analyzing the request message so as to obtain a transaction code; according to a return message header format definition file in the message format definition and the transaction code, inquiring a simulation return data file corresponding to the transaction code from a locally stored simulation return data folder; according to the transaction code, the simulation return data file and the return message header format definition file, generating a simulation return message; and sending the simulation return message to the front-end system to be tested. By utilizing the message testing method for the front-end system, and the simulation baffle system disclosed by the invention, product systems, such as MCIS / CSPA / IST, directly connected with a network bank system, can be simulated; a message sent by the network bank system is received; interface return message data defined by systems, such as MCIS / CSPA / IST, can be simulated; and thus, functional transaction of a network bank is smoothly carried out, and cannot be restricted by a testing environment.
Owner:BANK OF CHINA
Authentication method and schemes for data integrity protection
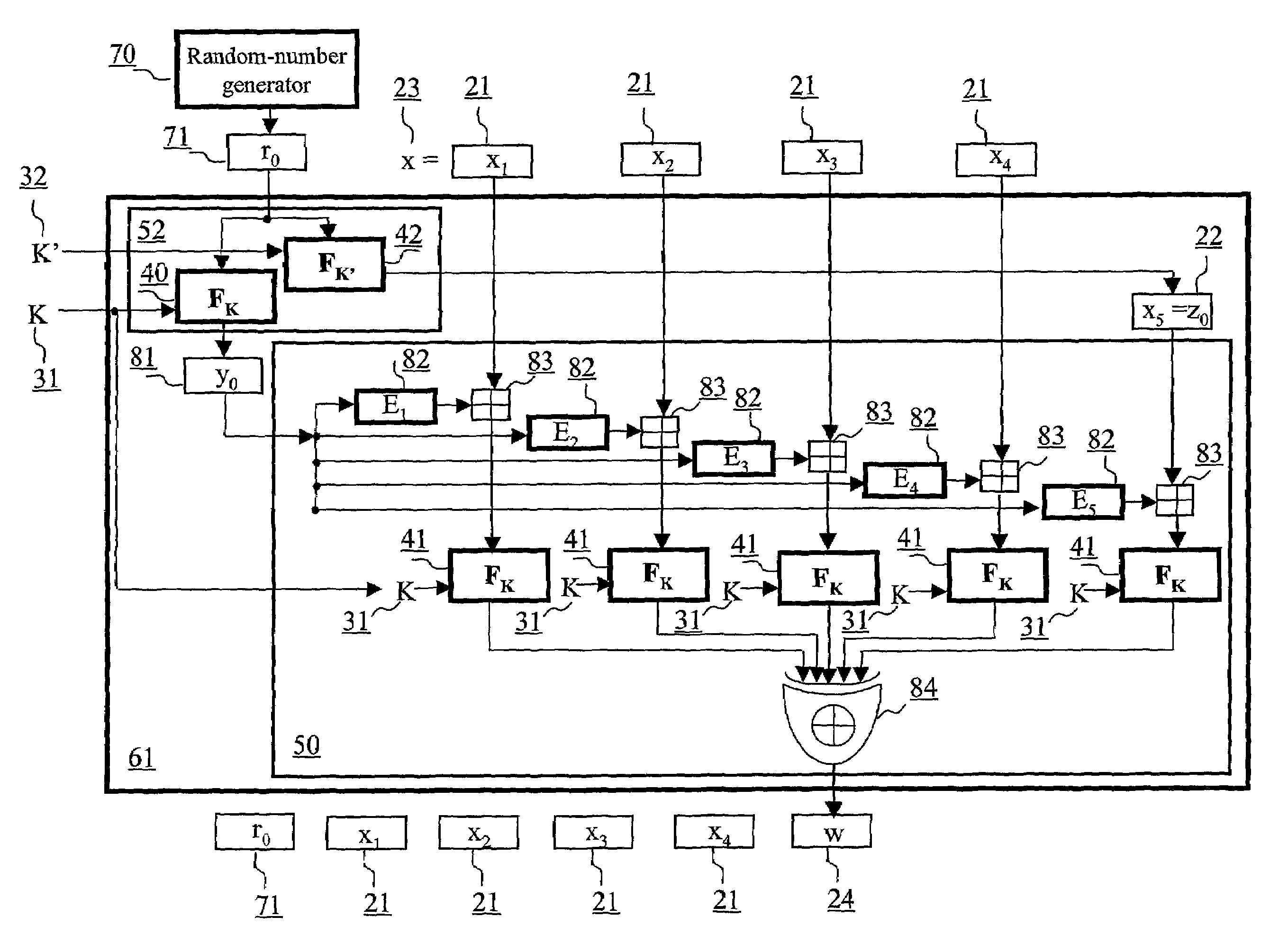
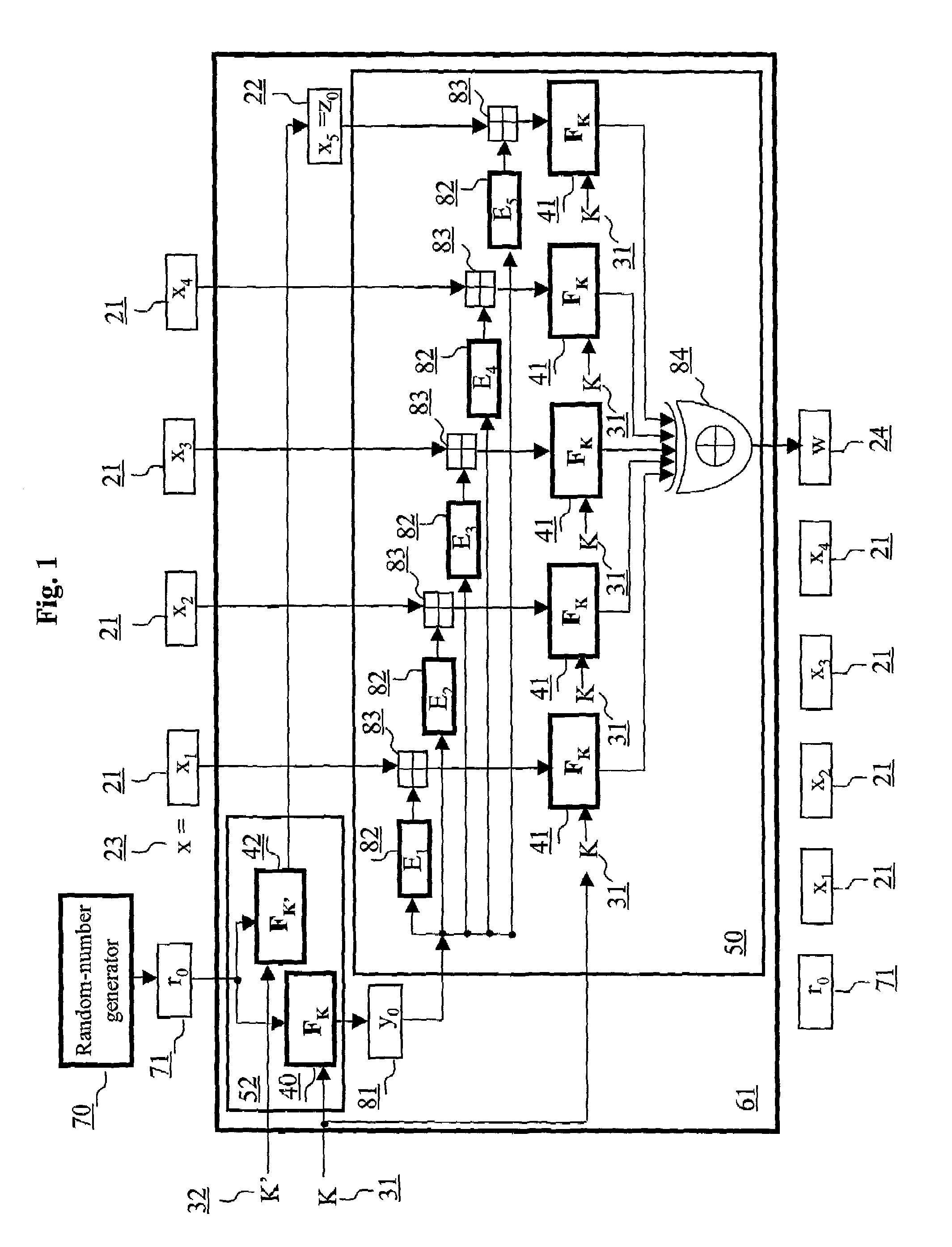
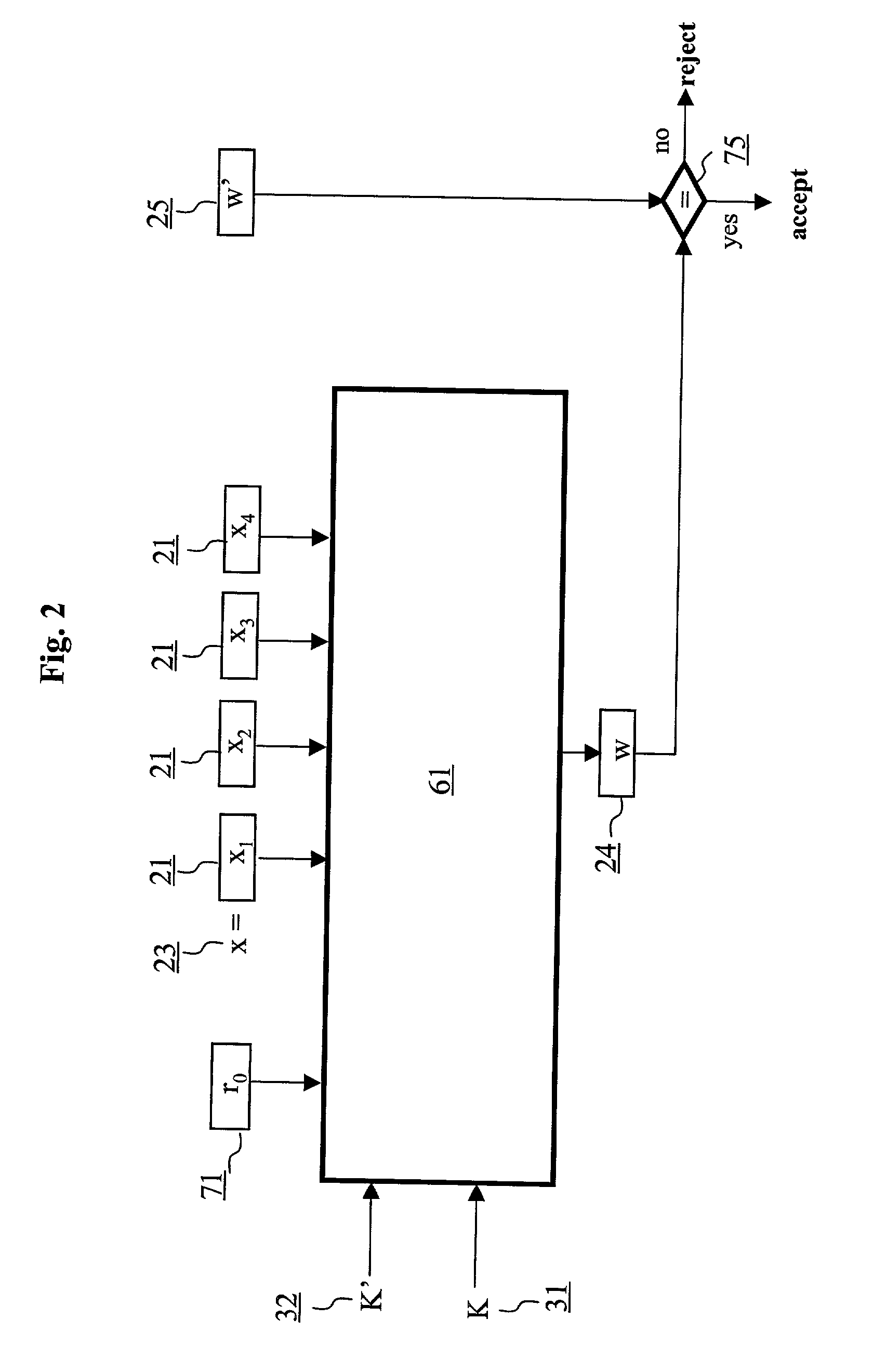
ActiveUS7054445B2Public key for secure communicationUser identity/authority verificationComputer hardwareMessage length
An authentication method and schemes using a block cipher to protect data integrity (authenticity) during communication over insecure channels and during data storage on insecure media. The authentication method and schemes of this invention allow, in a further aspect, message and data signing and verification in parallel or pipelined manners, in addition to sequential operation, without requiring twice as many block enciphering operations as the number of input plaintext blocks. The present invention allows, in a yet further aspect, software and hardware implementations used in high-performance systems and networks where multiple processing units are available for block enciphering operations. In a yet further aspect, the authentication method and schemes of this invention allow incremental updates and out-of-order processing of authentication tags. In a yet further aspect, the authentication method and schemes of this invention are suitable for real-time applications where message length remains unknown until the entire message is received, and commencing message authentication cannot be deferred until the end of the message.
Owner:VDG
Method and system for obtaining path maximum transmission length in channel gateway environment
ActiveCN1716943AThe calculation process is simpleImprove transmission efficiencyTransmissionMessage lengthTelecommunications
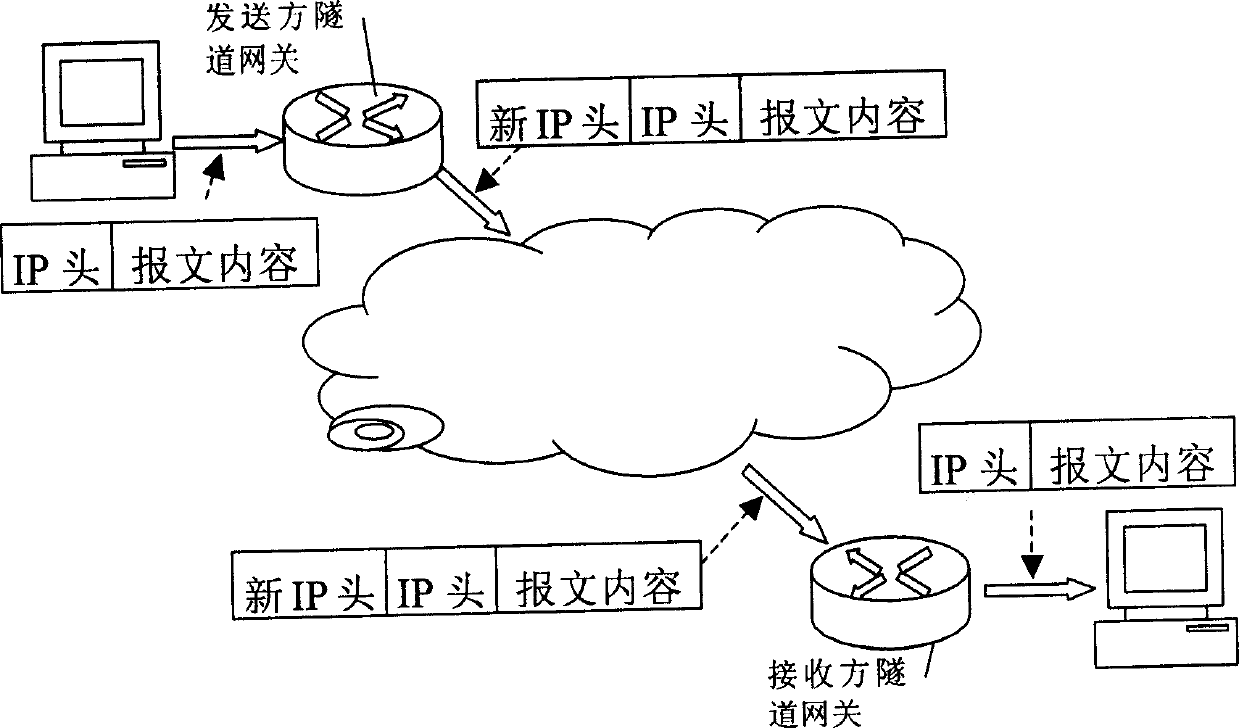
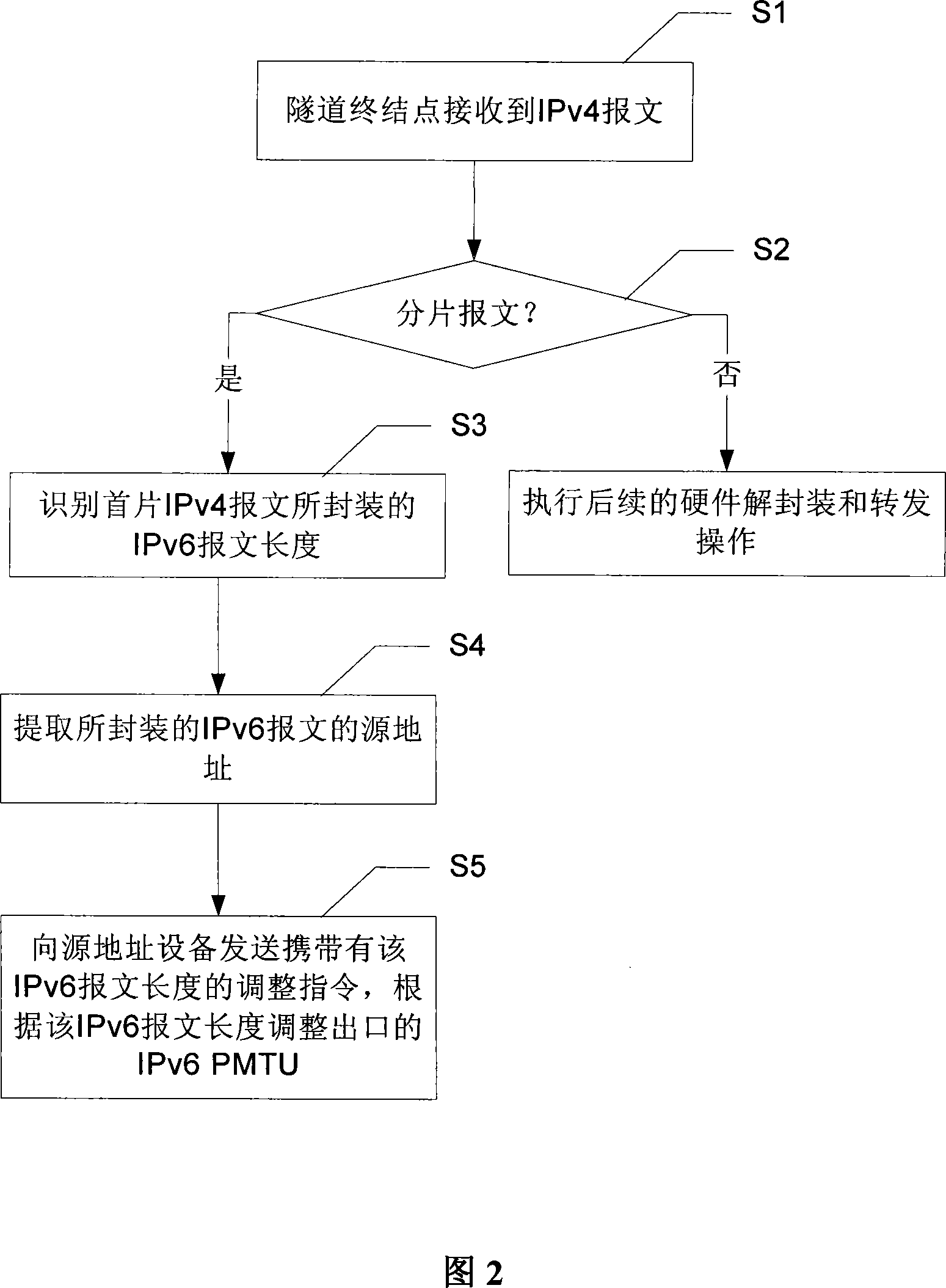
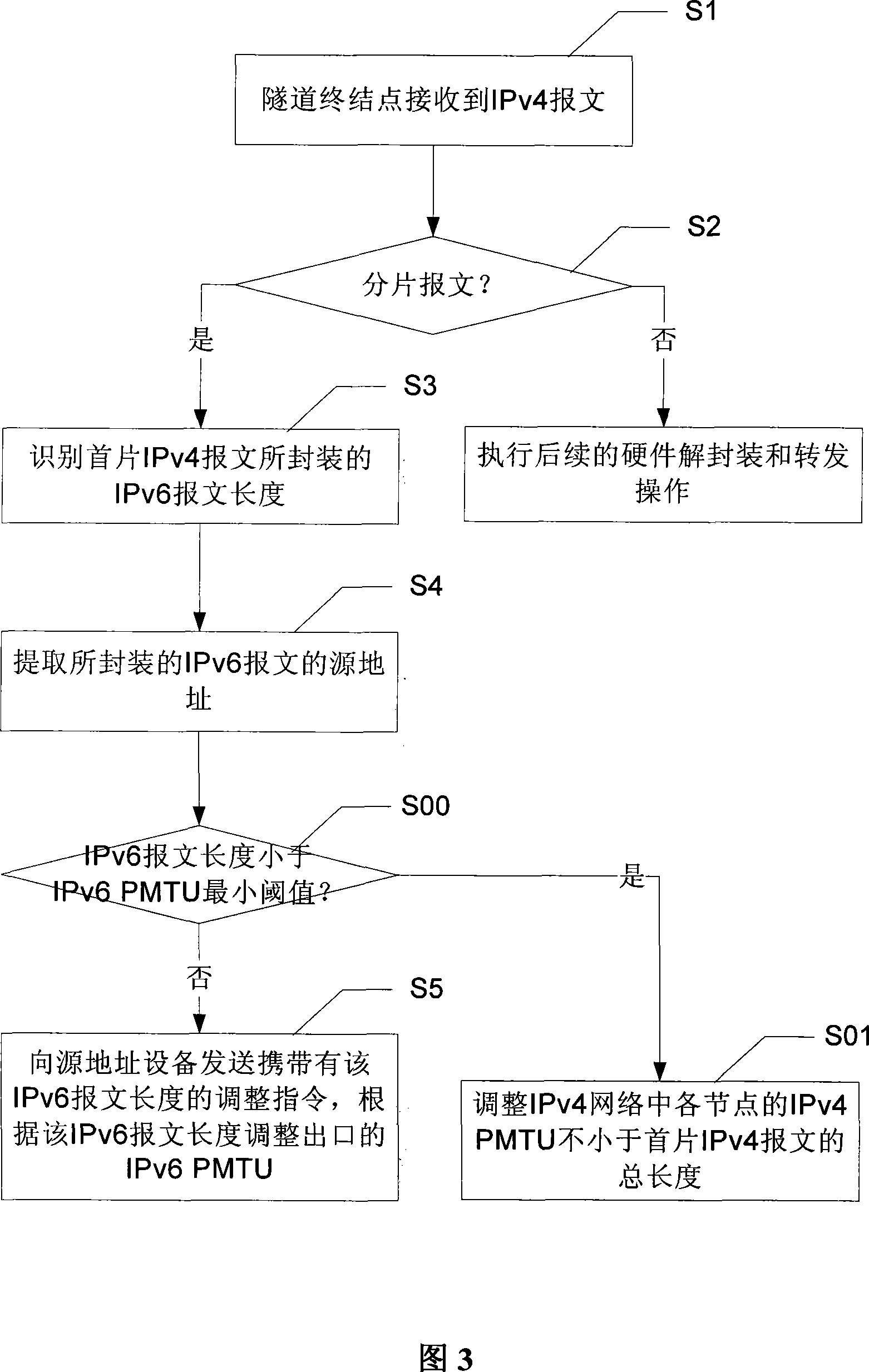
This invention discloses a method and a system for obtaining the largest transmission path length in the tunnel gateway environment. Said system tunnel gateway includes: a tunnel link MTU obtaining device and its assigning device, the tunnel gateway sets up a tunnel link MTU, when a detection message passes through the gateway, it returns back the ICMP control message to the send party according to the tunnel link MTU and the length of the detection message till the send party considers the message will not be segmented. The message length of this time is the path MTU. By this invention, the tunnel gateway can return back ICMP information gateway simply and effectively to un-segmented IP messages or selects the tunnel MTU or link MTU to segment them to segmented IP messages.
Owner:NEW H3C TECH CO LTD
Method for safety packaging network message
ActiveCN1859291ANo friendliness issuesPrevent replay attacksSecuring communicationMessage lengthNetwork address translation
The present invention discloses a network message security package method. It contains generating application layer message; package head generating one random numbers as initial sequence number, serial number added 1 in transmitting one message, using serial number and message length bytes as package head added to message top; load filling its finally bytes meaning filling length; ciphering message; message authentication code message authenticating code calculation; transmitting security packaged signaling message package IP / UDP or TCP head. The present invented method adopts application layer package mode therefore being not related to network address translation equipment NAT, enhancing security.
Owner:HUAWEI TECH CO LTD
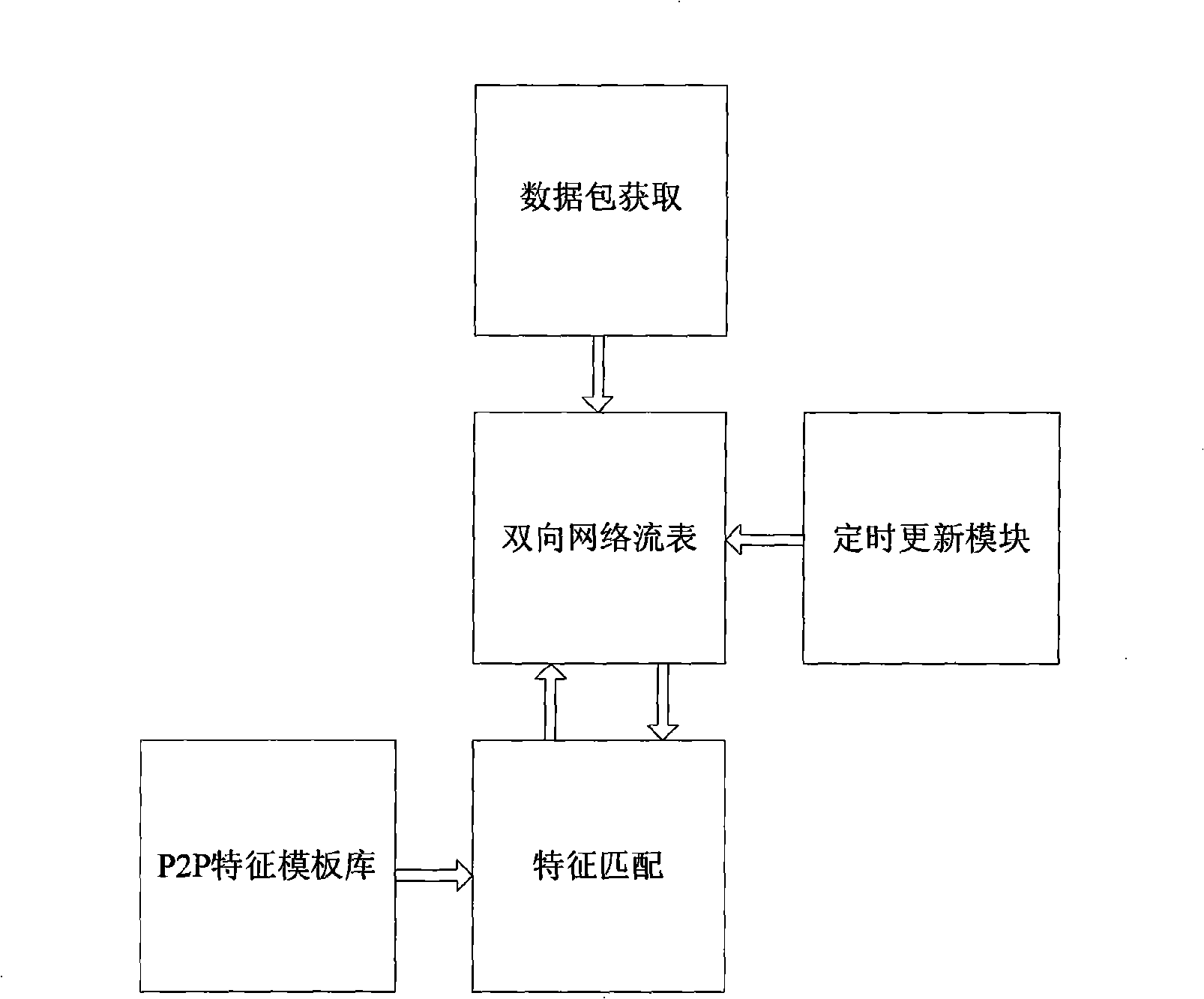
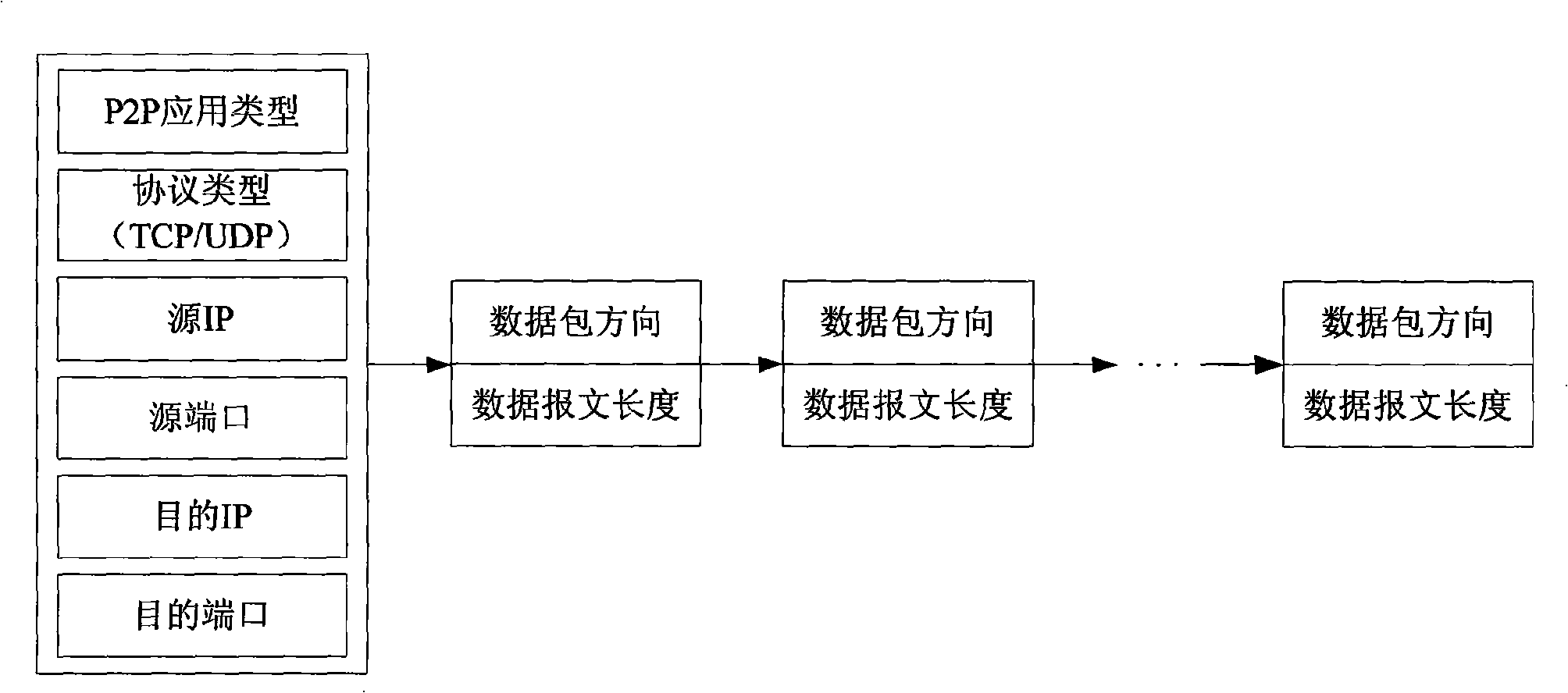
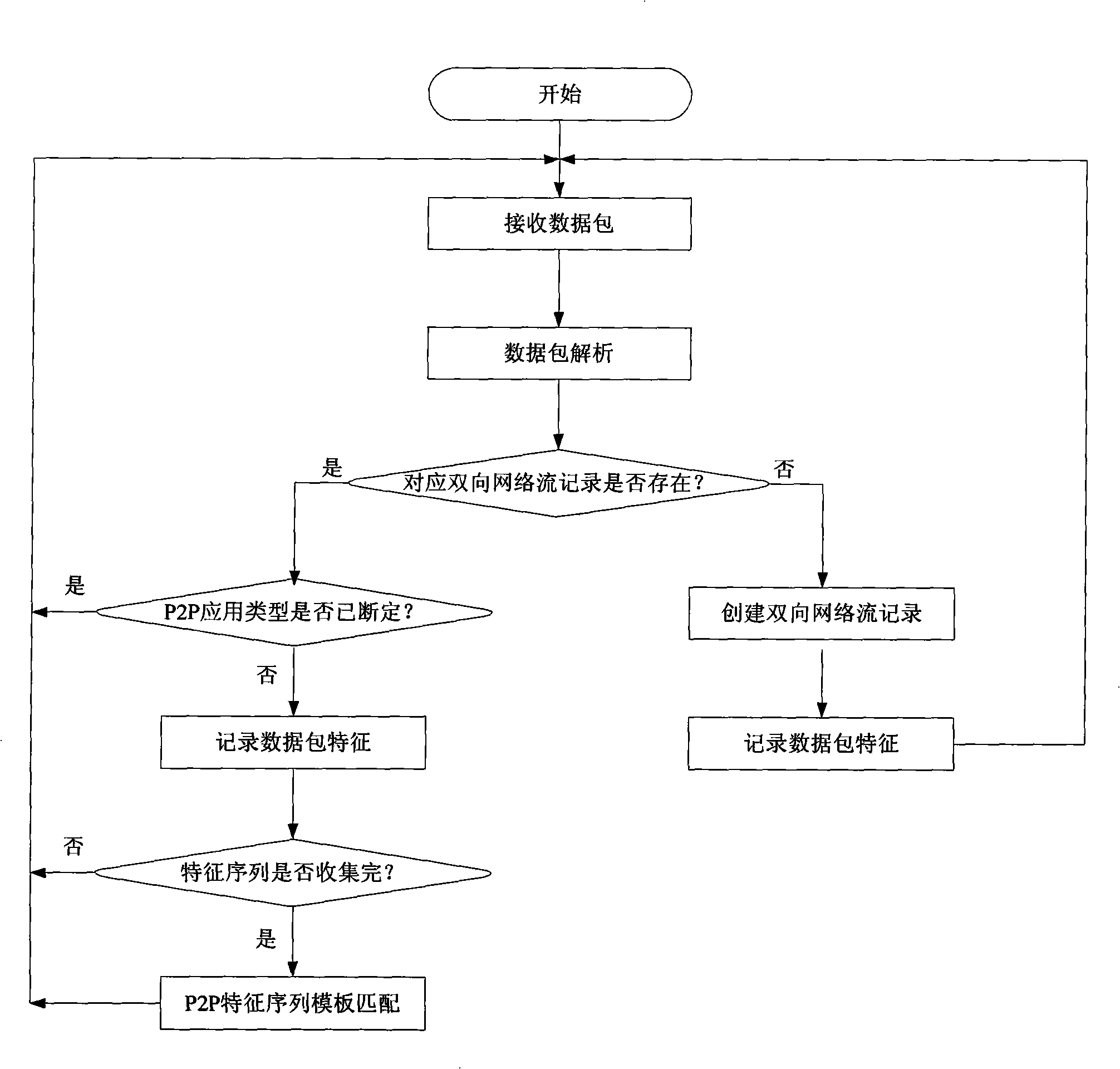
Method for recognizing P2P network flow based on transport layer characteristics
InactiveCN101282331AFast and efficient recognition effectReduce overheadData switching networksMessage lengthTraffic capacity
A P2P network flow identification method based on the character of transport layer extracts the character of P2P application in the transport layer by analyzing the data packet generated by the P2P application, and realizes the P2P application identification according to the character of the transport layer. The method only uses the character information of the several front data packets of the network flow to realize the effective identification of P2P application at network flow establishing initial stage and effectively realize the control of P2P application. Synchronously, the method only uses two characters of data packet direction and data packet message length of eth transport layer; the method is simple and convenient; the method has little system cost without analyzing and detecting the data packet load and realizes the real-time on-line application.
Owner:苏州赛博网垠信息科技发展有限公司
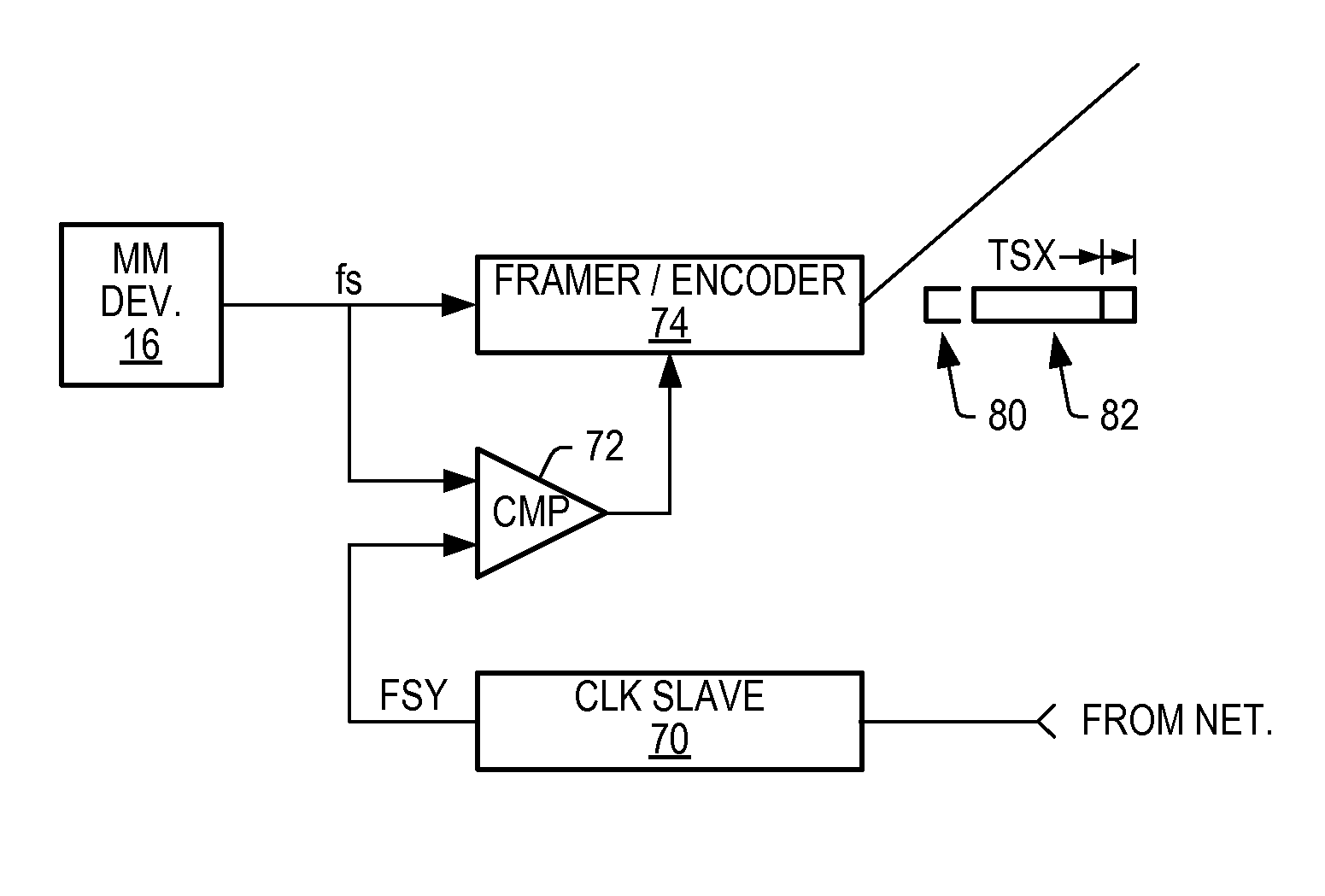
Communication system and method for sending asynchronous data and/or isochronous streaming data across a synchronous network within a frame segment using a coding violation to signify at least the beginning of a data transfer
ActiveUS7283564B2Time-division multiplexMultiple digital computer combinationsMessage lengthData stream
A communication system, network interface, and communication port is provided for interconnecting a network of multimedia devices. The multimedia devices can send streaming and / or non-streaming data across the network. The network accommodates all such types of data and assigns data types to time slots or frame segments within each frame to ensure streaming data maintains its temporal relationship at the receiver consistent with the transmitter. A first coding violation is used to indicate the beginning of asynchronous or isochronous data placed within a segment reserved for such data. A second coding violation within the data stream may also be used to signify the end of the isochronous or asynchronous message or data transfer within that segment. Alternatively, a message length code may be placed within the first coding violation to signify how many valid packets of data will follow in lieu of, for example, using a second coding violation within the data stream sometime after the first coding violation.
Owner:MICROCHIP TECH INC
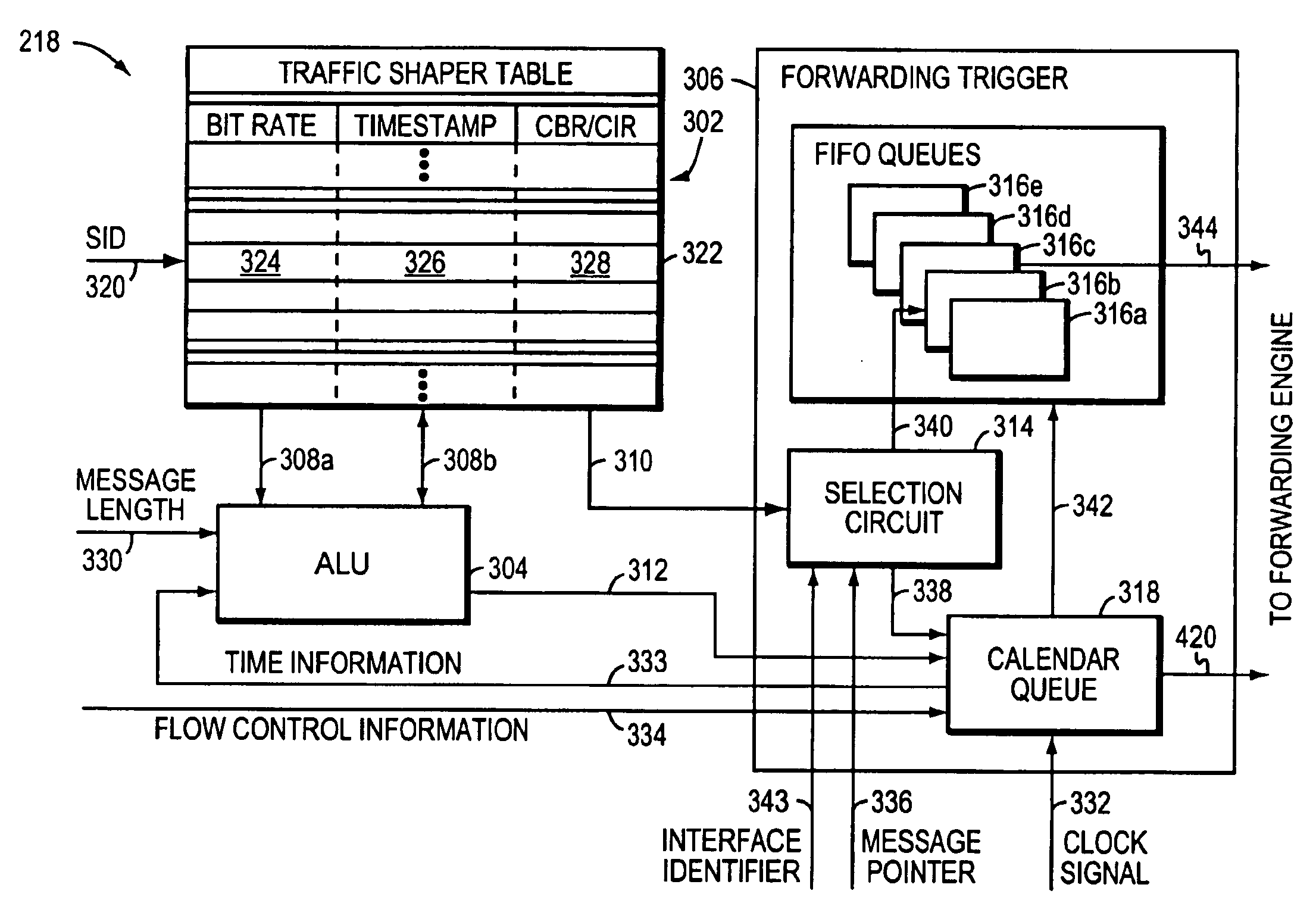
Method and apparatus for performing high-speed traffic shaping
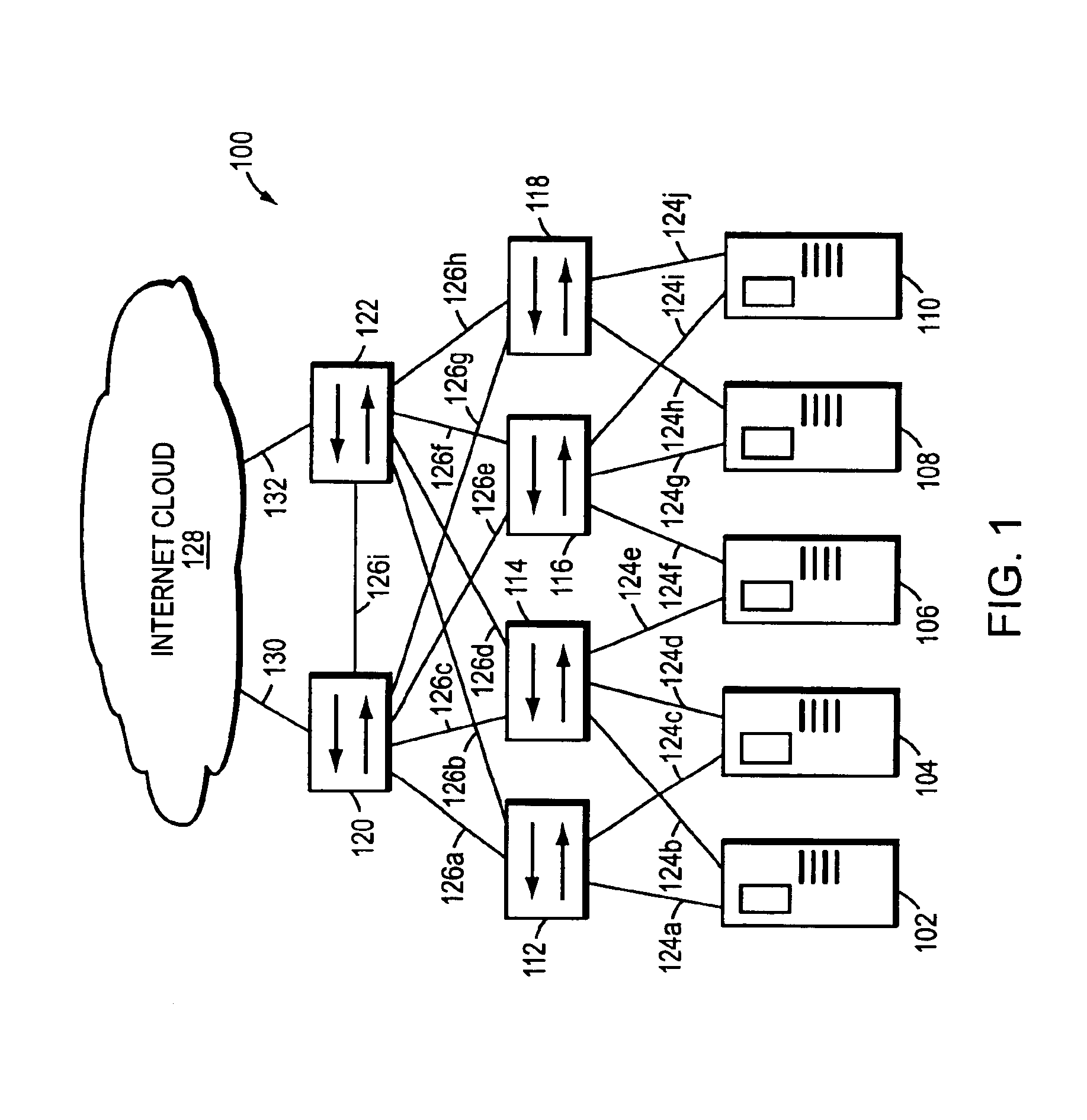
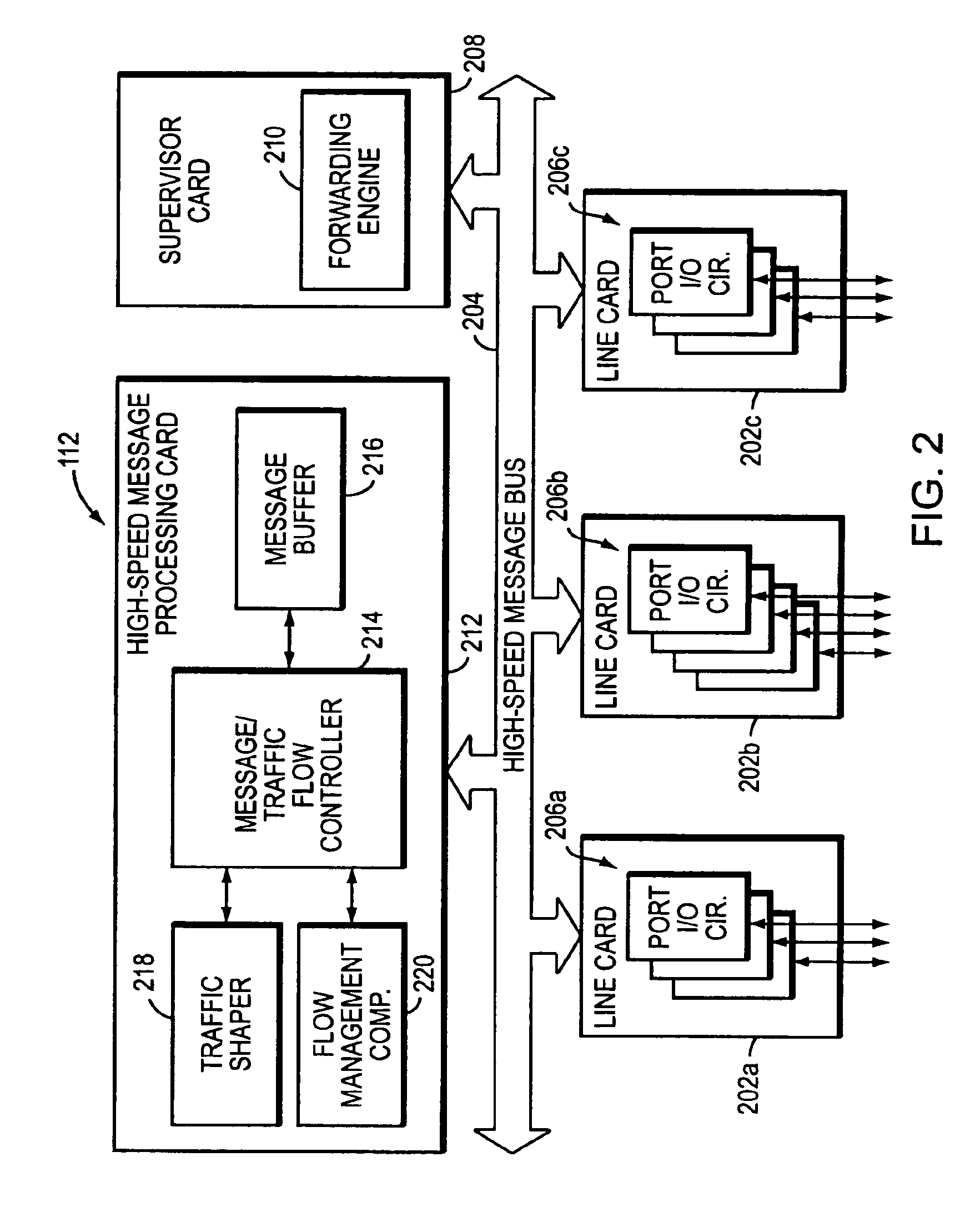
A network traffic shaper includes a traffic shaper table for storing traffic specifiers, such as permissible data transmission rates, an arithmetic logic unit (ALU), and a high-speed forwarding trigger mechanism having at least one time-searchable data structure or queue and a retrieve time generator that substantially tracks, but never exceeds, a system time. As network messages are received, they are stored at a message buffer and certain message parameters, including message length and a corresponding traffic specifier, are provided to the traffic shaper. The traffic shaper determines when the message may be sent in accordance with the associated traffic specifier and stores this transmission start time along with the message's buffer location in the time-searchable queue of the forwarding trigger. The forwarding trigger continuously examines the transmission start times for previously stored messages. When the transmission start time of a given message matches the retrieve time generator, the forwarding trigger mechanism signals that the message may be sent.
Owner:CISCO TECH INC
Cluster communication in heartbeat messages
ActiveUS7330444B1Time-division multiplexTime-division multiplexing usageMessage lengthTelecommunications link
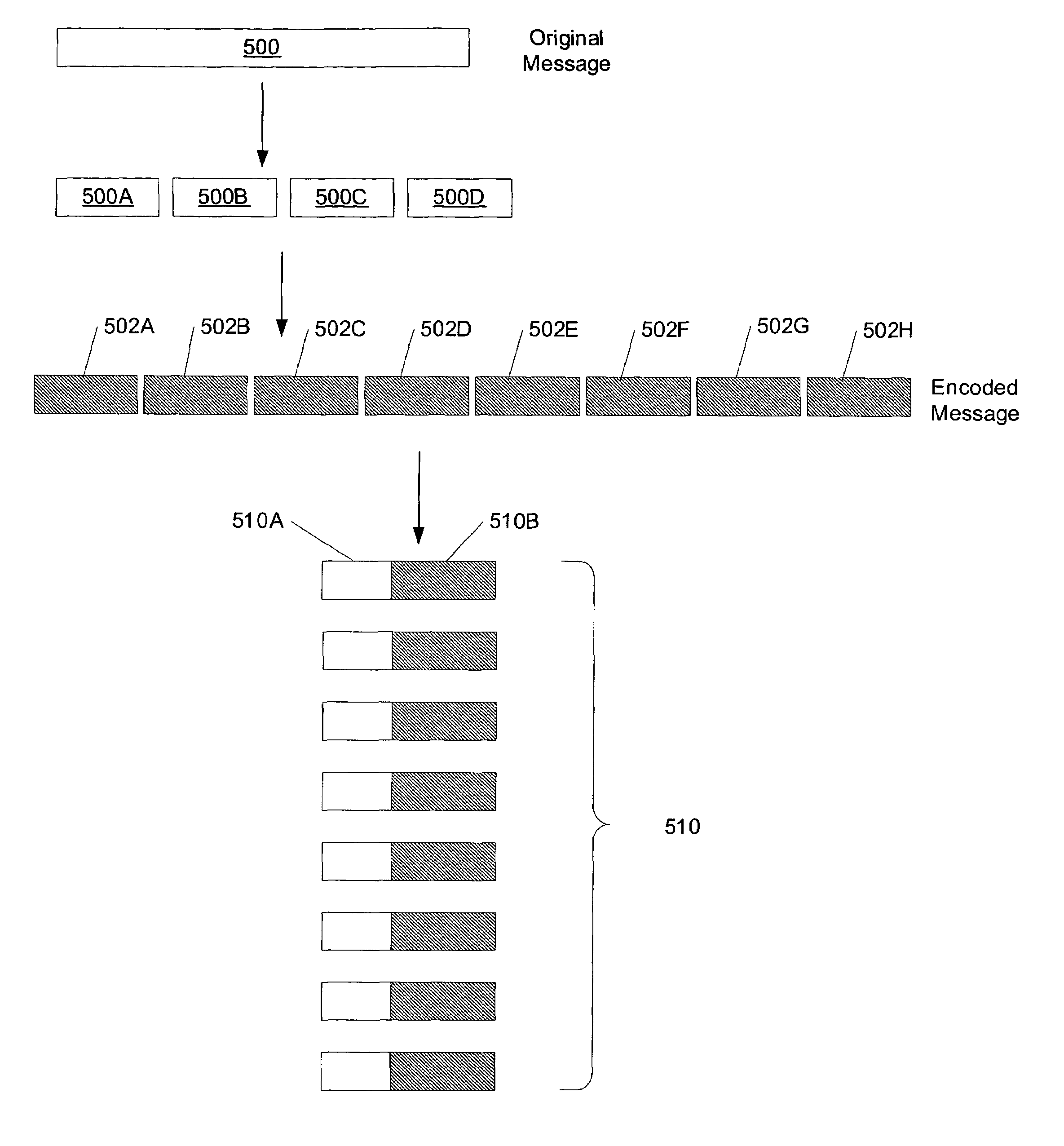
A method and mechanism for inter-node communication. A first node is coupled to a second node via a communication link. The first node is configured to convey a heartbeat or similar data packet to the second node on a periodic or other scheduled basis. A message manager within the first node is configured to detect an inter-node message is available for transmission to the second node. If the detected message exceeds a predetermined size, the message is partitioned into blocks which are less than or equal in size to the predetermined size. The blocks are then encoded pursuant to a forward error correcting algorithm, such as an erasure code algorithm, and stored as payload in the periodically conveyed data packets. Pseudo-header information may also be included with each block to indicate a message type, message identifier, message length, or block sequence number.
Owner:SYMANTEC OPERATING CORP
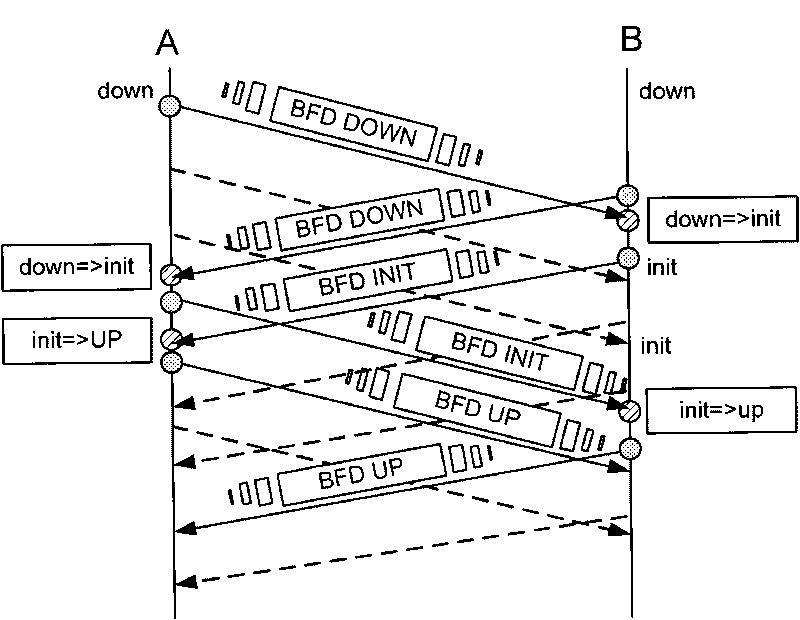
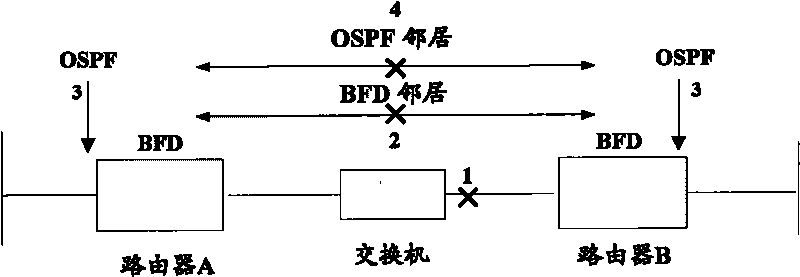
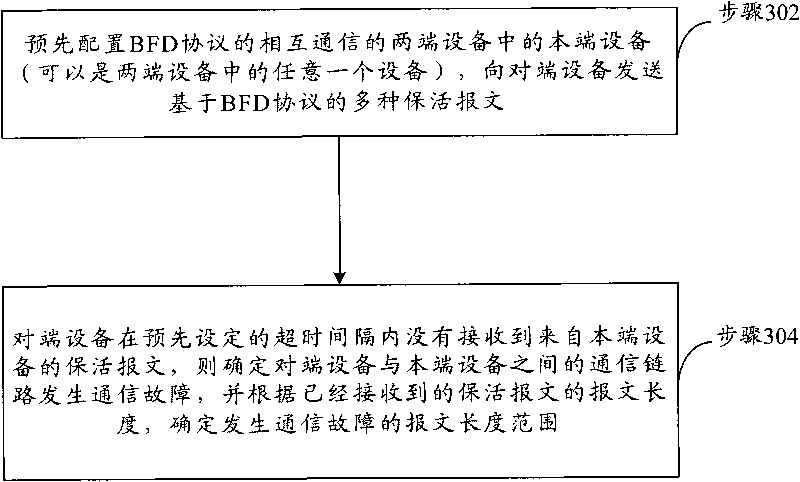
Communication fault detection method and system based on two-way forwarding detection protocol
The invention discloses communication fault detection method and system based on a two-way forwarding detection protocol. In the method, local-end equipment in equipment at both ends of the intercommunication of a BFD protocol is configured in advance, and a plurality of live keeping messages based on the BFD protocol are transmitted to opposite-end equipment, wherein the message lengths of the live keeping messages are different and are within the range of a preset length; if the opposite-end equipment does not receive the live keeping messages from the local-end equipment in the preset overtime, a condition that a communication fault occurs in a communication link between the opposite-end equipment and the local-end equipment is determined, and the length range of the messages in which the communication fault occurs is determined according to the message lengths of the live keeping messages which are already received. According to the technical scheme provided by the invention, the problem that a condition whether the communication fault occurs in flow messages of which the message lengths are different from the lengths of standard BFD live keeping messages in the forwarding process or not can not be detected by a BFD detection mechanism in the prior art is solved.
Owner:ZTE CORP
Message dispatching method and device thereof
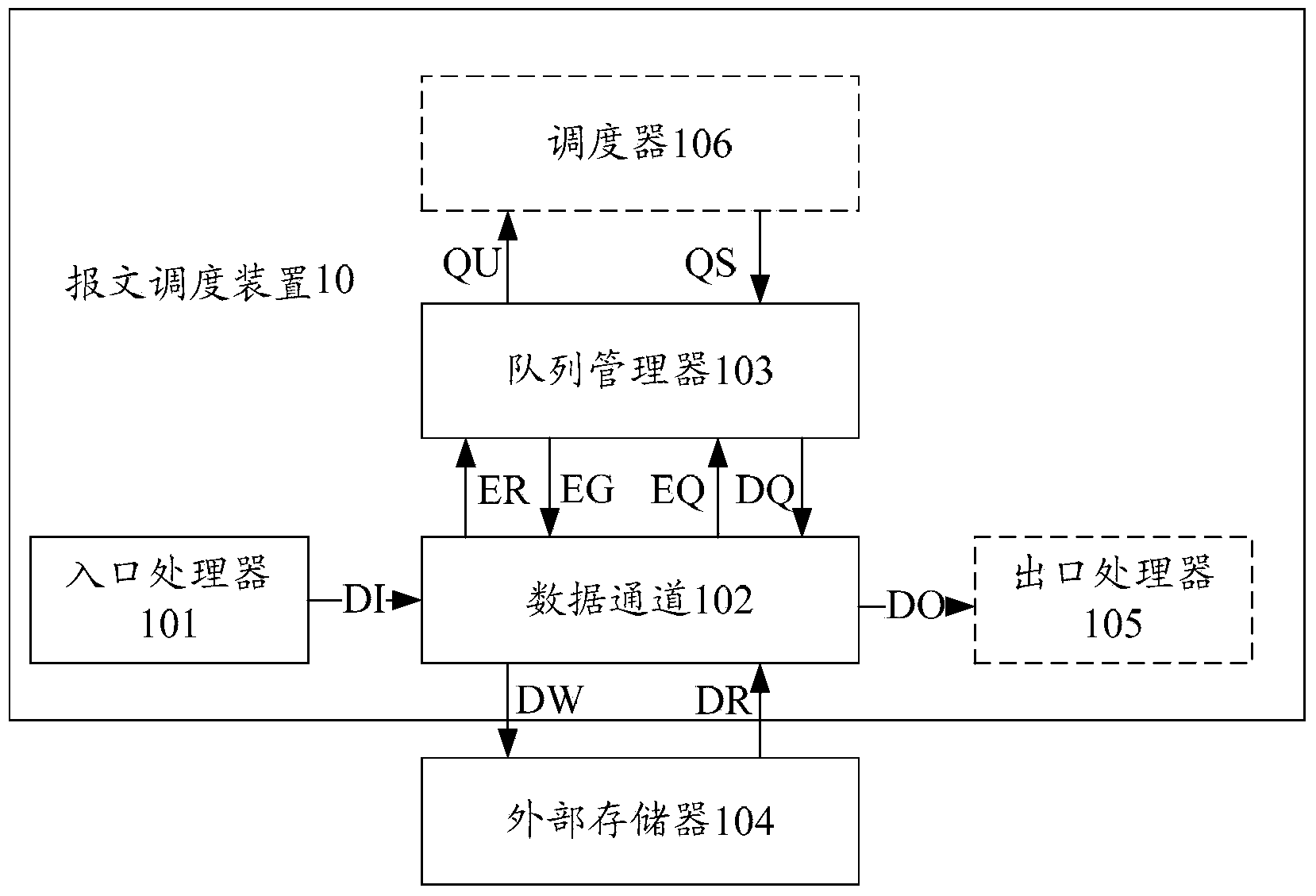
ActiveCN103647726AImprove cache utilizationSave resourcesData switching networksMessage lengthQueue number
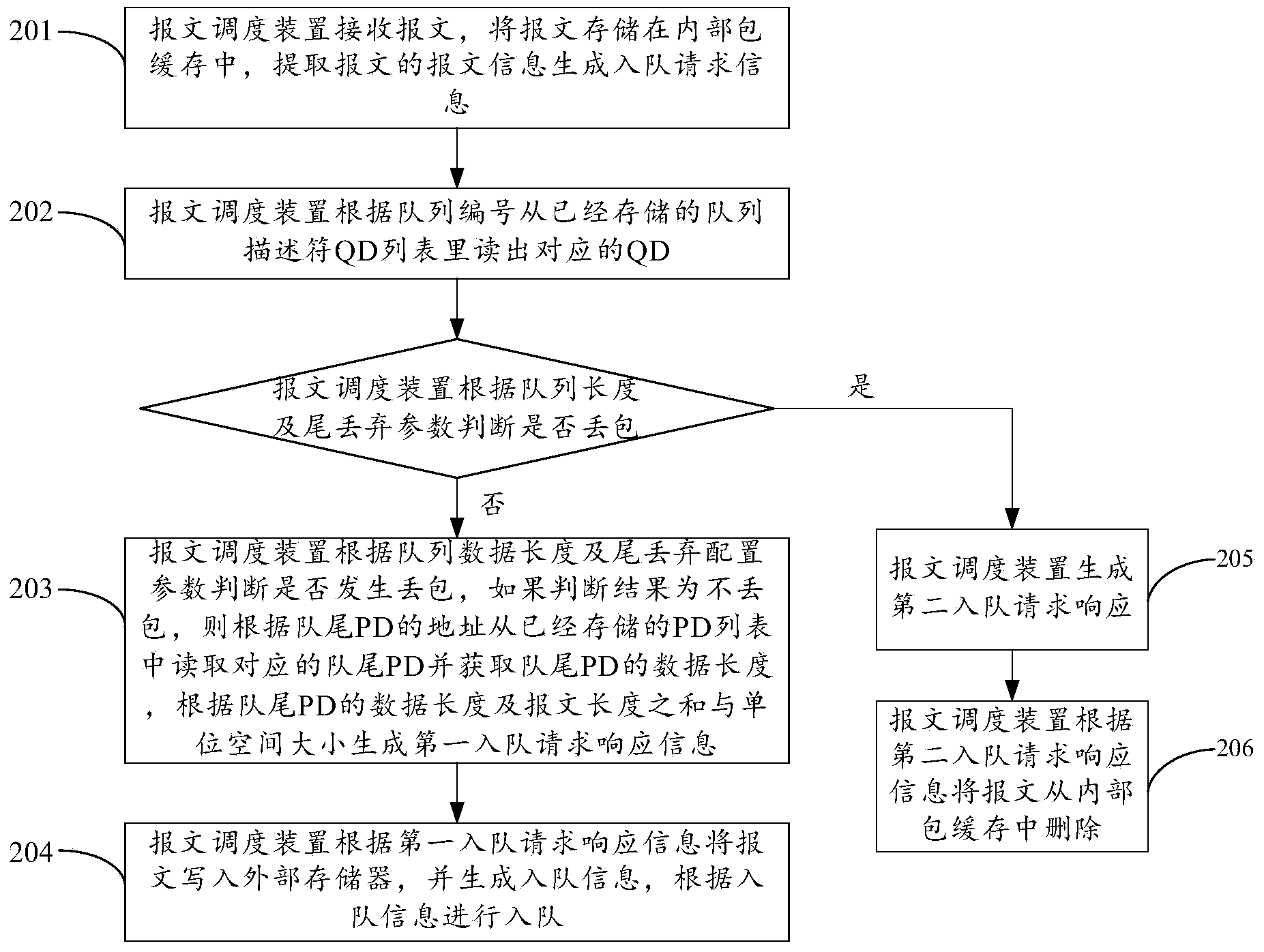
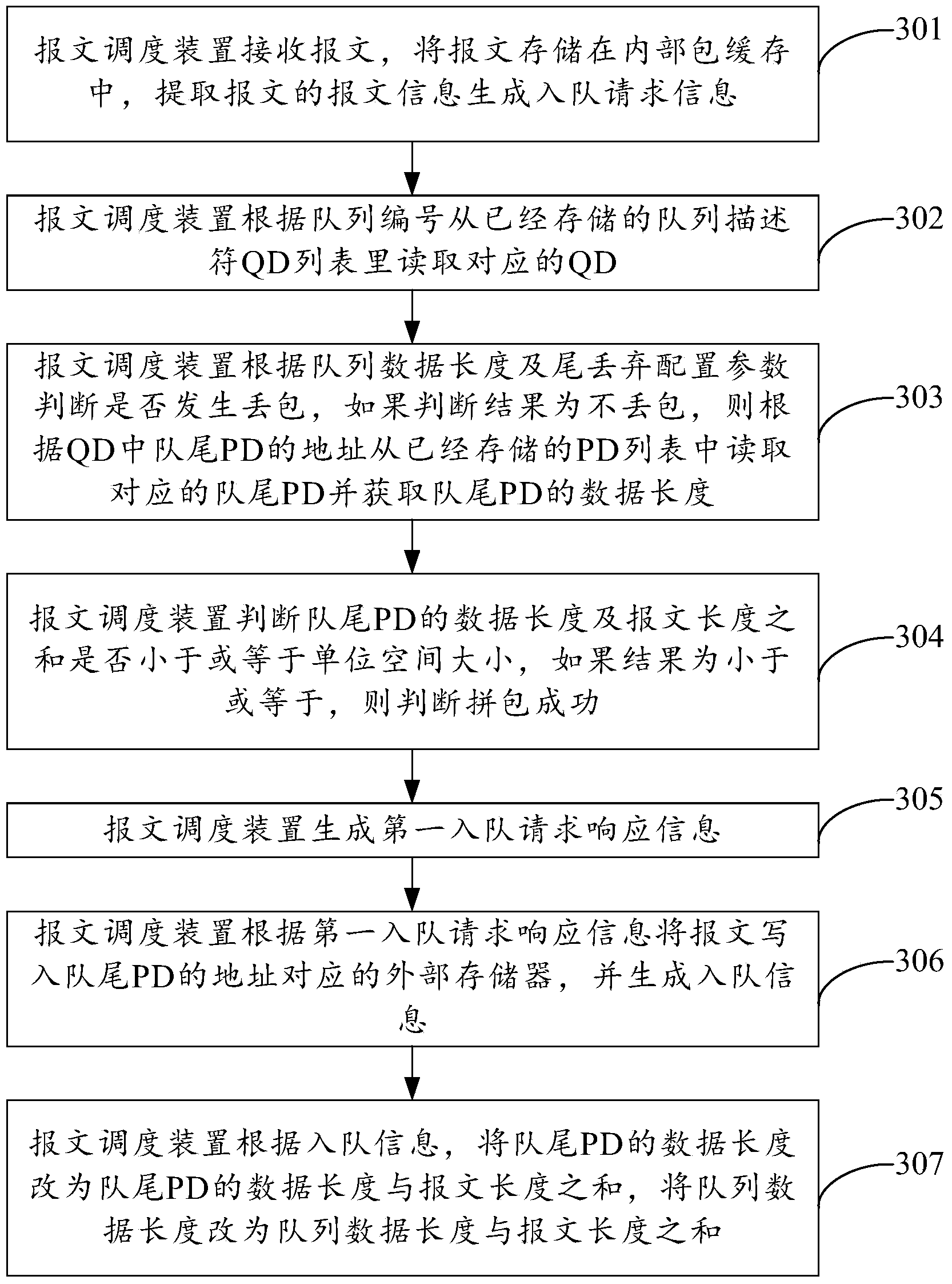
The embodiment of the invention discloses a message dispatching method and a device thereof and relates to the field of communication, the utilization rate of data cache can be raised, and resources are saved. The method comprises the following step: (1) the message dispatching device receives a message and stores the message into internal package cache, the message information is extracted and queue entering request information is generated, and the queue entering request information comprises a queue number and a message length; (2) the corresponding queue descriptor is read from a stored queue descriptor list according to the queue number; (3) whether a packet is lost or not is judged according to the queue descriptor, and if a judgment result is that the packet is lost, first queue entering request response information is generated according to the data length, the message length and the unit space size of a queue tail message descriptor in the queue message descriptor; (4) the message is written into an external memory according to the first queue entering response information, queue entering information is generated, and the message enters the queue according to the queue entering information. The message dispatching method and the device are used for the message dispatching.
Owner:HUAWEI TECH CO LTD
Compression and abbreviation for fixed length messaging
InactiveUS20070299925A1Data processing applicationsNatural language data processingMessage lengthMessage passing
A method, computer program product, and data processing system for compressing and abbreviating text messages at a first text messaging device for transport and subsequent interpretation at a second text messaging device is disclosed. A user-defined message length reduction profile for producing human-readable compressed text is associated with a source text message at a first text messaging device. The source text message is then shortened using abbreviations and transformation rules in the profile. The shortened text message can then be transmitted to a second text messaging device. In addition, the compression provided by the present invention, although intended to be human-readable, can be complemented with decompression software to expand the compressed and abbreviated text to its full length and verifying, using a checksum or other error detecting code, that the expanded version corresponds to the original text.
Owner:IBM CORP
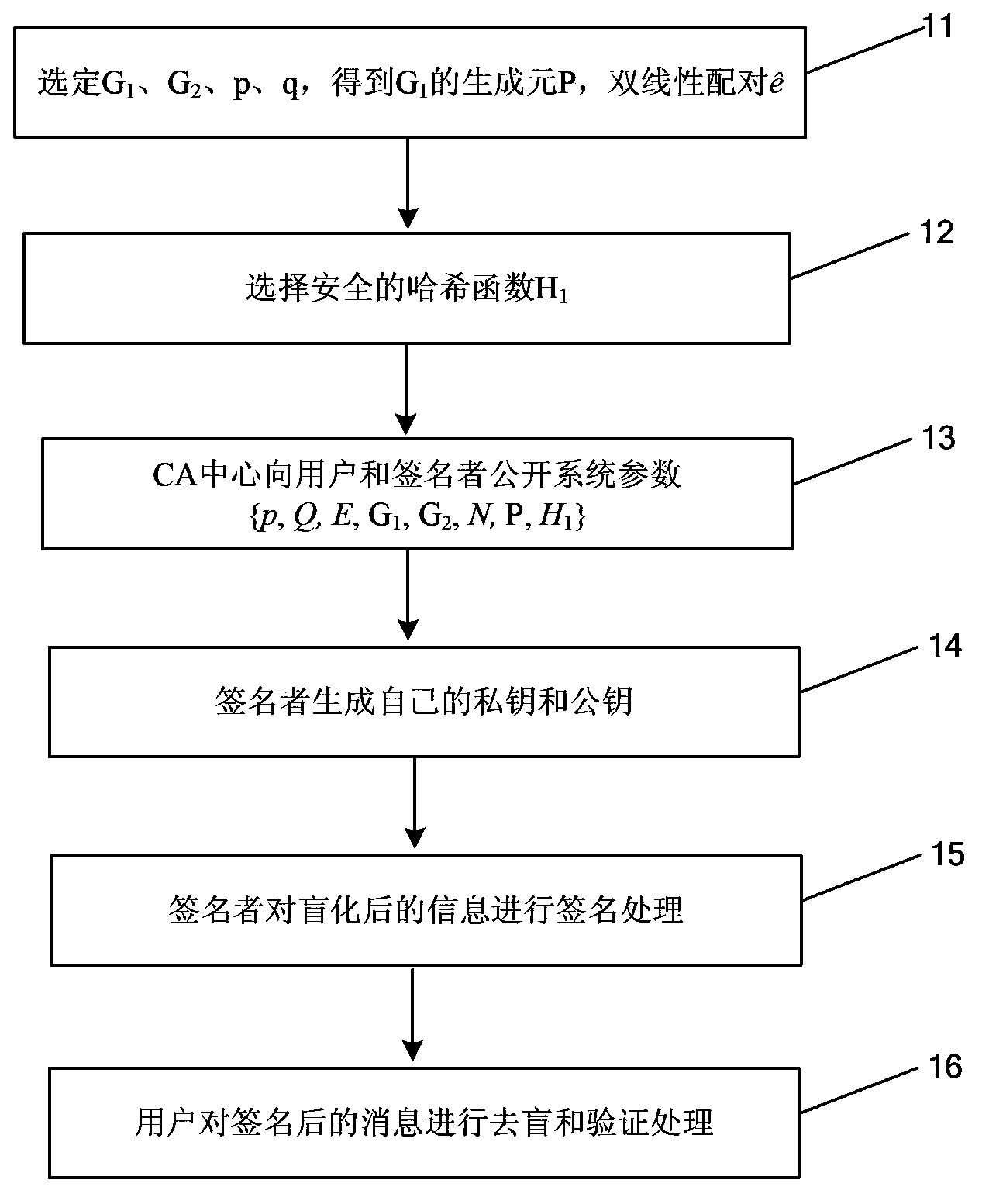
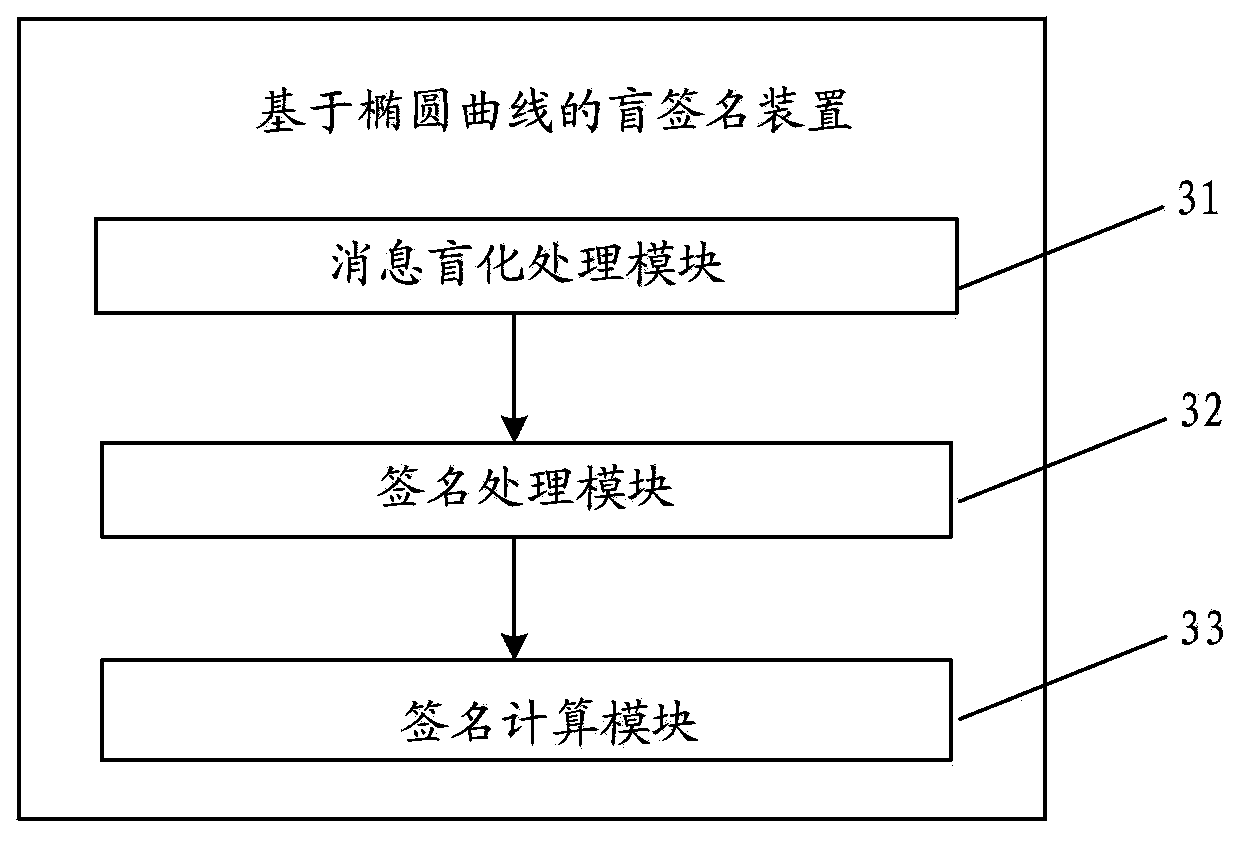
Blind signature method based on elliptic curve and device thereof
ActiveCN103780385AShorten the lengthImprove throughputPublic key for secure communicationUser identity/authority verificationMessage lengthHash function
The invention provides a blind signature method based on an elliptic curve and a device thereof. The method mainly comprises the following steps: (1) a sending user randomly selects a blind factor k belonging to Zq*, formulas R=H1(m) and S=kR are calculated, m is a (0,1) string with any length in information to be signed, S is a blinded message, q is a set large prime number, Zq* represents integers in a range from 1 to (q-1), H1 is a one-way Hash function, Fp is a domain formed by integers from 0 to (p-1), p is a set large prime number, and q is the prime factor of (p+1); (2) a signer uses a private key d of the signer to sign S, a formula V'=dS= (dk)R is calculated, and V' is sent to a receiving user; (3) the receiving user receives V', a formula V=k-1V' is calculated, and the X coordinate of V is the signature of the message m. According to the blind signature method based on the elliptic curve of the embodiment of the invention, the blind signature message length is only the X coordinate of an elliptic curve point, the throughput of system operation is increased, and the method and the device are suitable for a communication environment with a limited bandwidth.
Owner:AEROSPACE INFORMATION
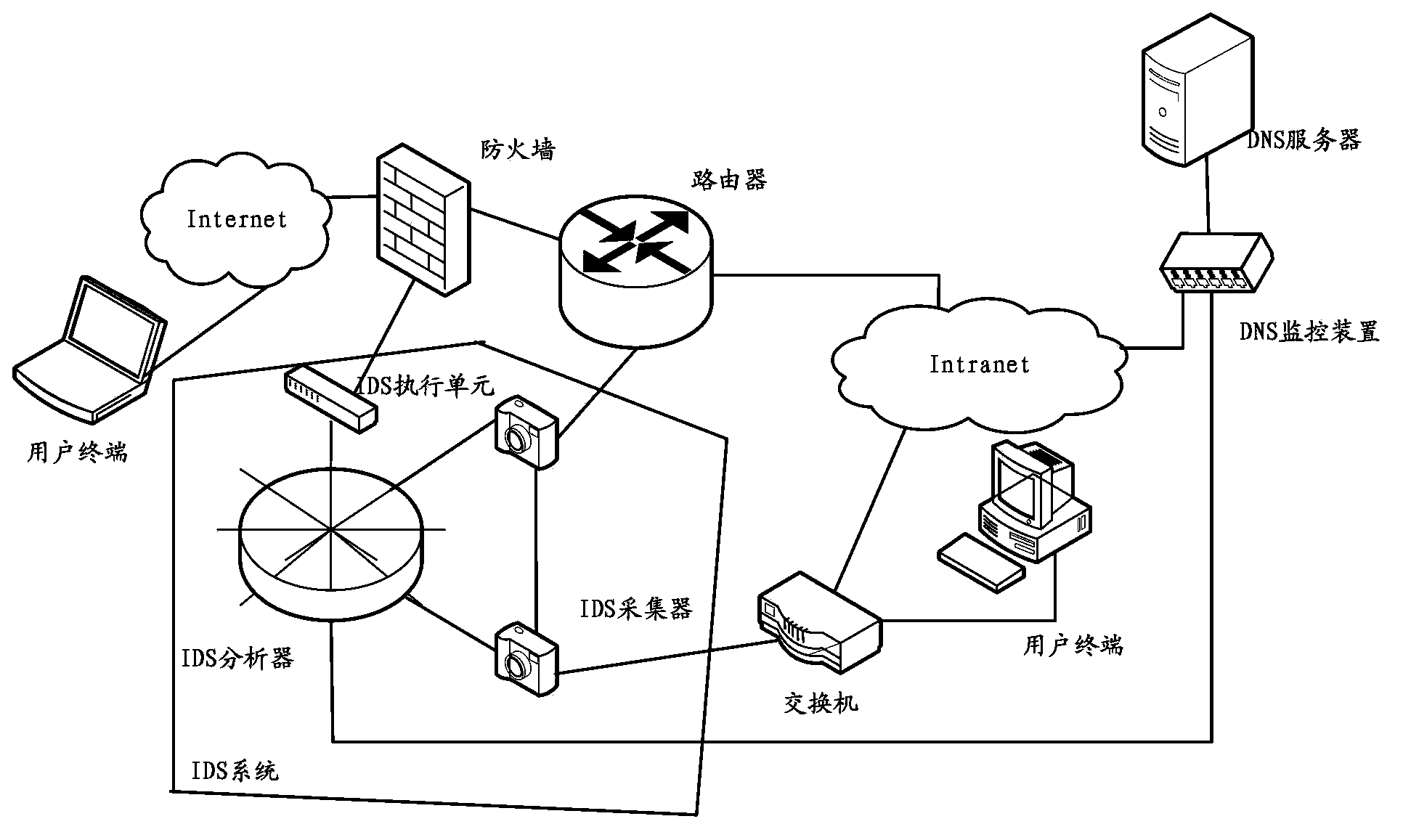
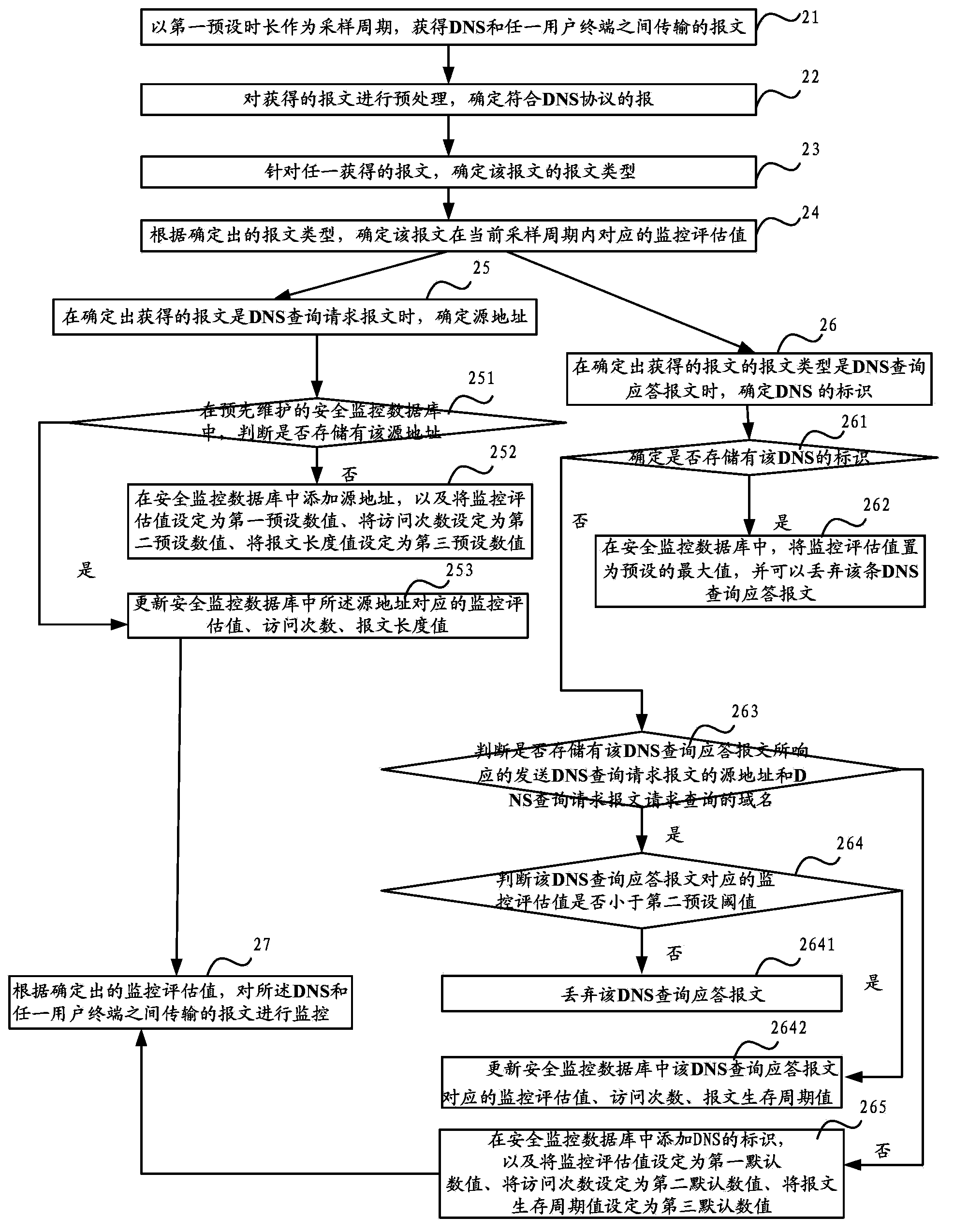
Method, device and system for monitoring messages in domain name resolution service DNS system
The invention discloses a method, device and system for monitoring messages in a domain name resolution service DNS system. The method, the device and the system can provide comprehensive monitoring and protecting abilities for existing special attacks for a DNS, and improve the monitoring accuracy. The method comprises the steps that a first preset length of time is used as a sampling period, and the messages transmitted between the domain name resolution service DNS and any user terminal are obtained; for any obtained messages in the current sampling period, the message types of the messages are determined; according to the determined message types, the message length values and the number of access times of the messages and at least two parameters in a life period are determined; according to the determined message length values, the number of the access times and the two parameters in the life period, monitoring assessment values corresponding to the messages in the current sampling period are determined; according to the determined monitoring assessment values, the messages transmitted between the DNS and any user terminal are monitored.
Owner:CHINA MOBILE COMM GRP CO LTD
Packet scheduling based on message length
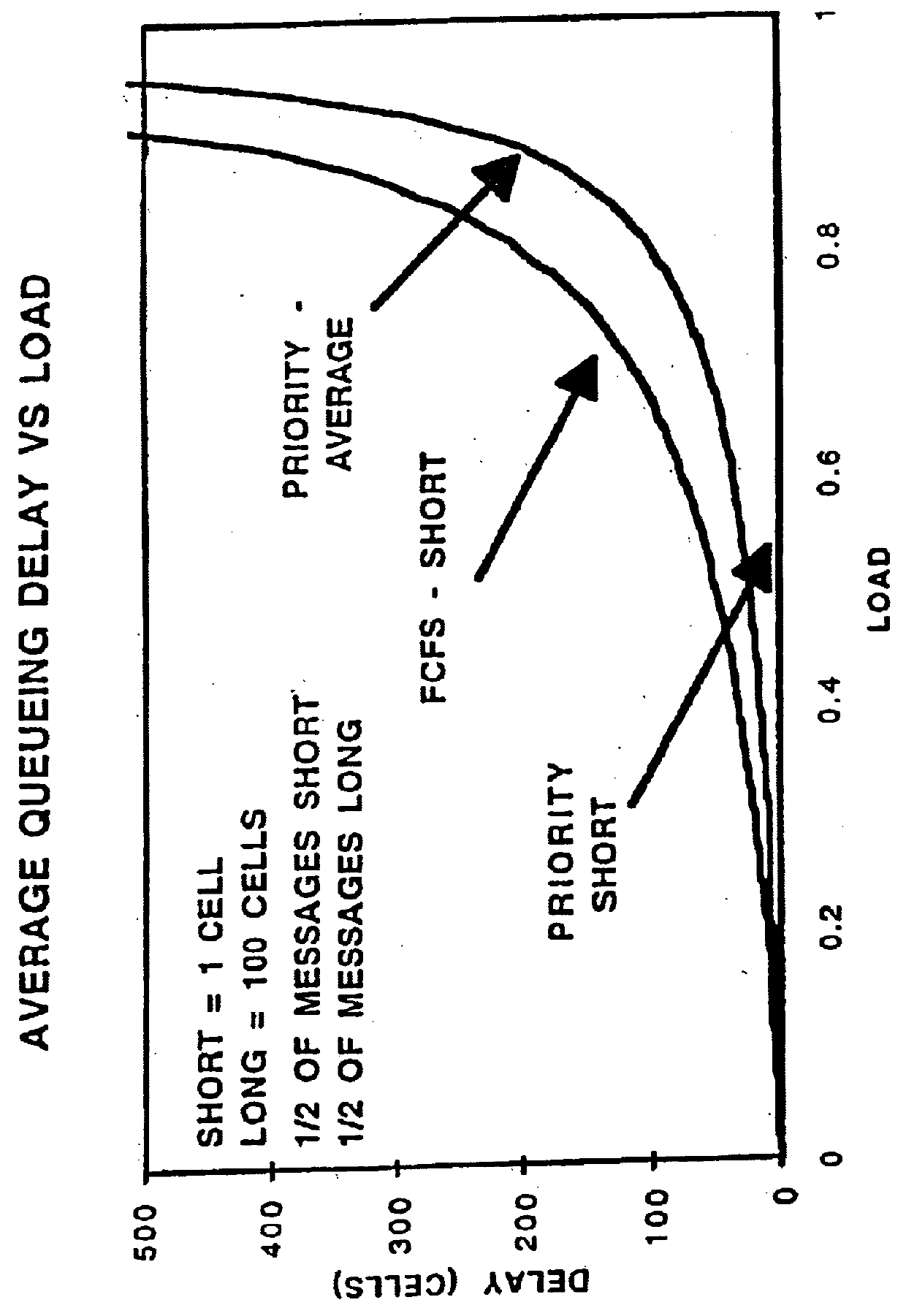
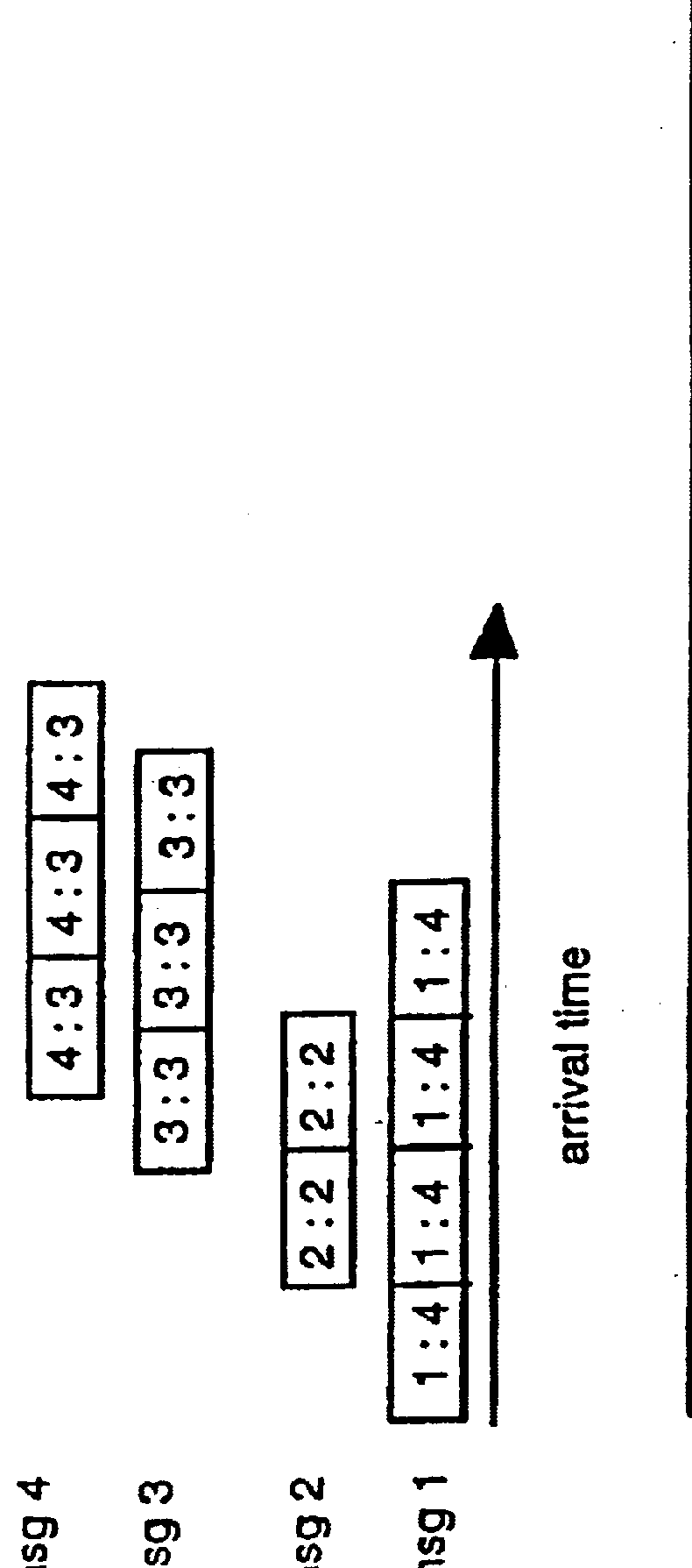
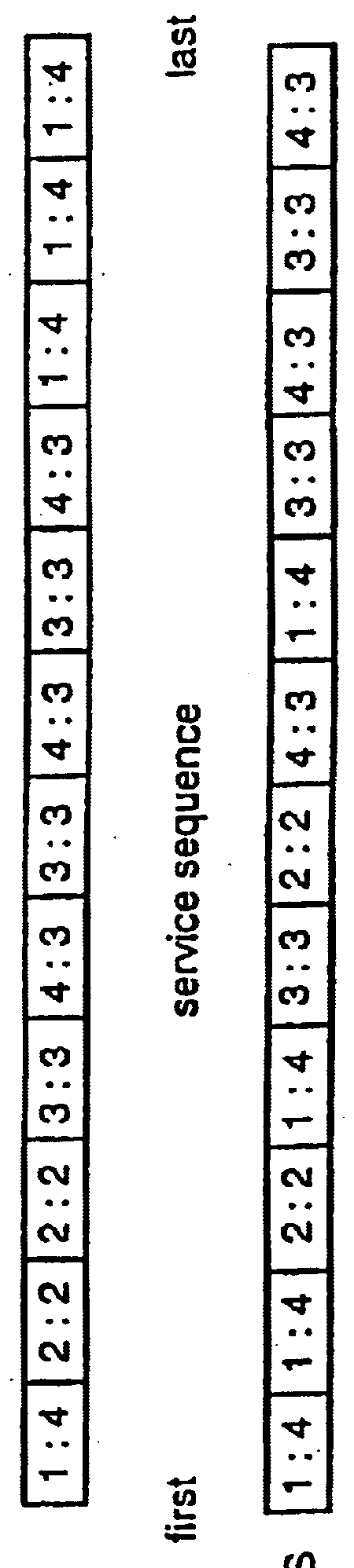
InactiveUSH2103H1Reduce transmission delayReduce delaysError preventionTransmission systemsMessage lengthFirst principle
A system using two algorithms for scheduling packets in a multi-hop network. The objective of the algorithms is to reduce end-to-end message (not packet) transmission delays. Both algorithms schedule packet transmissions based on the length of the original message to which the package belongs. The first algorithm is preemptive and is based on the shortest-message-first principle and the second is based on the shortest-remaining-transmit-time principle. We develop simulation models for analyzing the algorithms. The simulations show that when message sizes vary widely, these algorithms can significantly reduce average end-to-end message delays compared to the First-Come-First-Serve scheduling.
Owner:AIR FORCE UNITED STATES
Robot teaching box with bus communication function and control method thereof
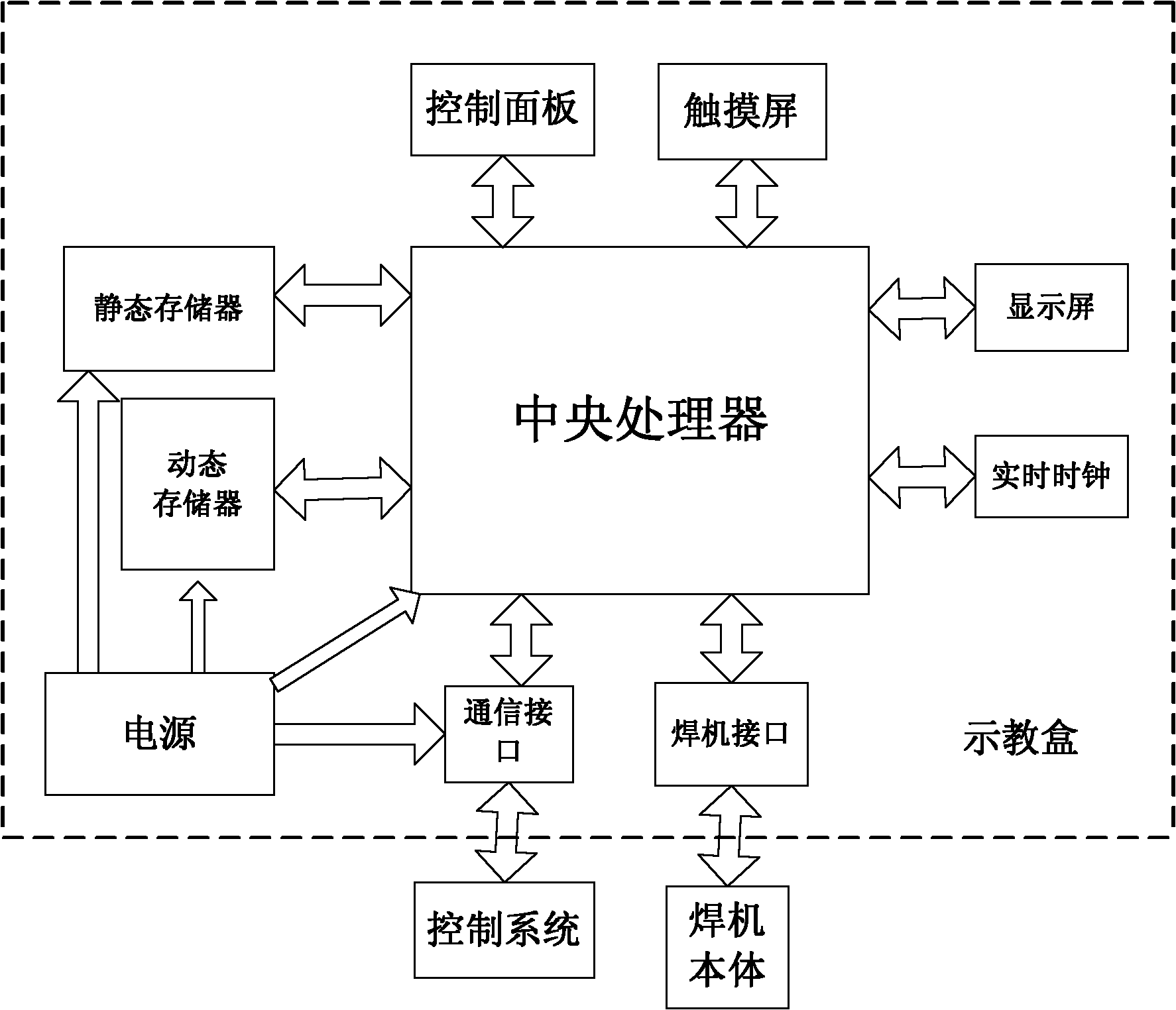
ActiveCN102324206ASimple designEasy to debugEducational modelsMessage lengthStructure of Management Information
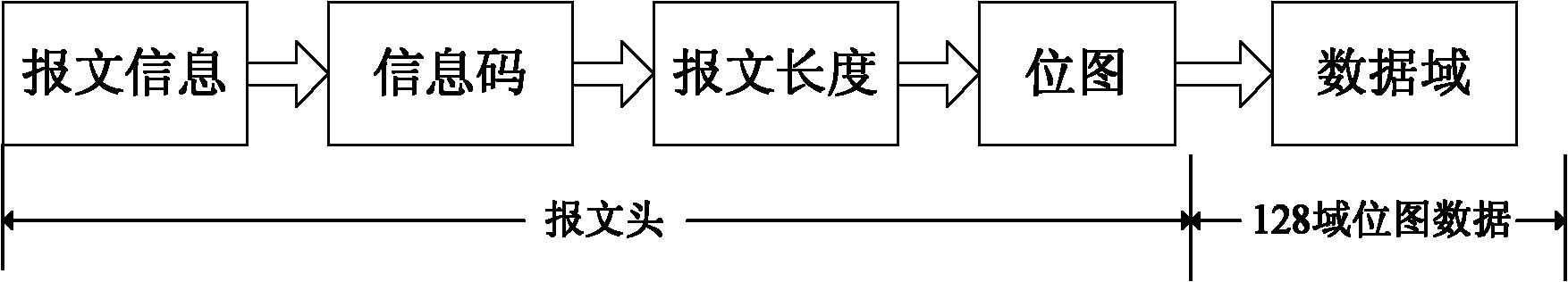
The invention discloses a robot teaching box with a bus communication function and a control method thereof. The teaching box comprises a central processing unit as well as a display screen, a control panel, a storage, a welding machine interface and a commutation interface which are connected with the central processing unit respectively, wherein the communication interface is connected with a robot controller at the lower layer. The robot teaching box is characterized by also comprising a touch screen connected with the central processing unit; the communication interface is based on an NRP (negotiation and resource reservation protocol) communication protocol; the message structure of the NRP communication protocol consists of a message header and field domains, wherein the message header comprises message information, an information code, message length and a bitmap, and the message information comprises a command index, a request code or respond code mark and the number of the field domains. Compared with the traditional teaching box, the teaching box provided by the invention can realize remote operation of a robot and improves the safety of operators; due to the adoption of the NRP communication protocol for data interaction, the loss rate of data is reduced to the minimum and the anti-interference performance of a system is enhanced.
Owner:GSK CNC EQUIP
Method for information transmission by utilizing Wi-Fi (Wireless-Fidelity) message length
The invention discloses a method for information transmission by utilizing a Wi-Fi (Wireless-Fidelity) message length. The method is characterized in that information needing to be transmitted is encoded by adopting the Wi-Fi message length, and a UDP (User Datagram Protocol) is used for constructing a data packet; then a Wi-Fi network is used for carrying out information transmission on data sent by more than one Wi-Fi network external equipment; a receiver is subjected to reverse encoding according to predefinition of a sender to accurately restore transmitted information. Compared with the prior art, the method disclosed by the invention has the advantages that current Wi-Fi network transmission of the data sender is not influenced and sending data can be sent to a plurality of sets of equipment outside the Wi-Fi network; on the basis of not changing a Wi-Fi standard communication protocol, two sets of the Wi-Fi equipment needing to be communicated can carry out the information transmission without establishing a network; the method can be applied to data sending to the equipment outside the network through equipment in other cryptographic wireless networks.
Owner:ALIBABA CLOUD COMPUTING LTD
A self-adapting regulation method, device and system of message tunnel slicing
InactiveCN101217540AEasy to handleReduce tunnel fragmentationData switching networksMessage lengthSelf adaptive
The invention discloses an adaptive adjustment method and a device for message tunnel fragmentation, which are applied in IPv6 in IPv4 tunnel, wherein, the method comprises that: when the terminal point of the tunnel receives an IPv4 fragmentation message, the length of the first IPv6 message sealed by the IPv4 message is identified and the source address of the sealed IPv6 message is extracted; an adjustment instruction carrying the IPv6 message length is sent to the source address device to lead the source address device to adjust the IPv6 PMTU of the outlet according to the IPv6 message length and avoid the subsequent message tunnel fragmentation. The invention further discloses an adaptive adjustment system of message tunnel fragmentation. The invention reduces the tunnel fragmentation of the message in the IPv6 in IPv4 tunnel, and improves the forwarding performance of the tunnel and the processing performance of the start point and the terminal point of the tunnel; meanwhile, the invention has the advantages of real-time performance, simplicity and easy practice.
Owner:NEW H3C TECH CO LTD
Method and system for providing message containing website
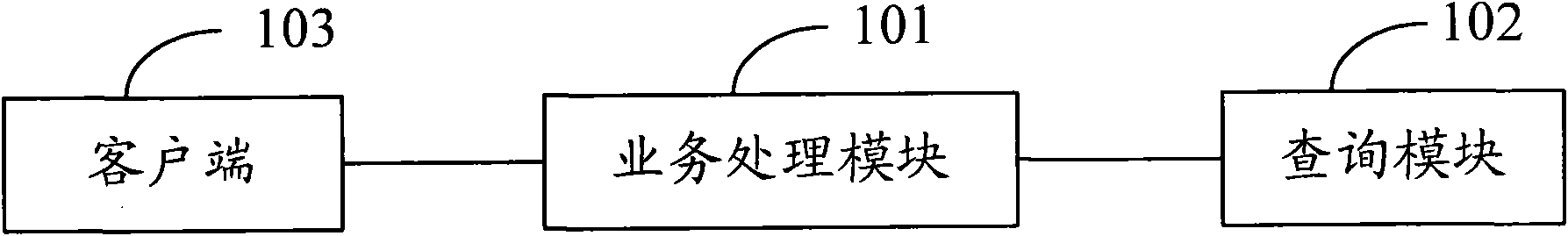
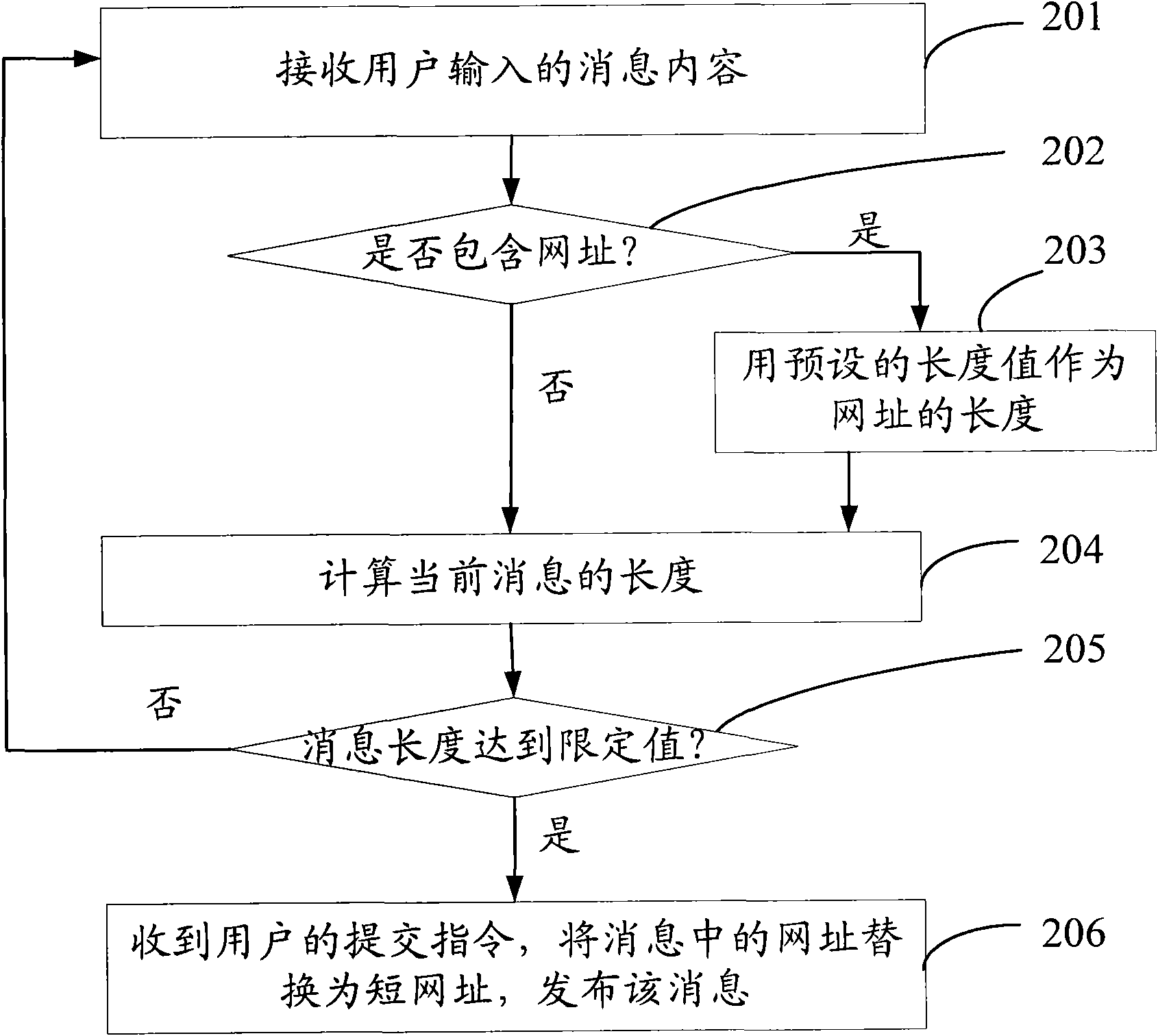
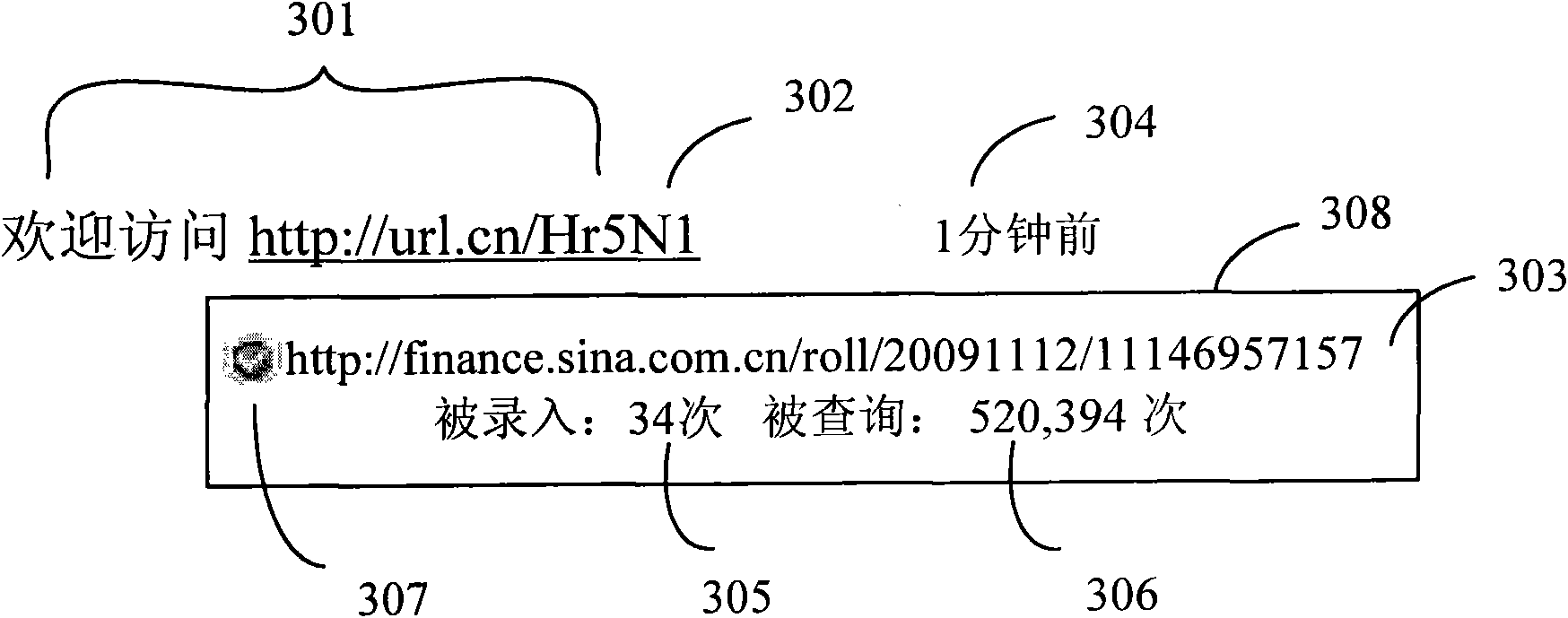
InactiveCN102402558ATake up less lengthIncrease the lengthSpecial data processing applicationsWeb data retrieval using information identifiersMessage lengthWeb page
The invention discloses a method and system for providing a message containing a website. The method comprises the following steps: detecting whether the message content of a message input by a user contains a first website or not, if the message content contains the first website, calculating the message length by utilizing a first length value as the length of the first website; if the message length obtained through calculation is smaller than a preset message length, allowing the user to continue to add the message content; replacing the first website contained in the message by utilizing a second website, and storing the corresponding relation between the first website and the second website; wherein the length of the second website is smaller than or equal to the first length value; and providing the message containing the second website. According to the technical scheme of the invention, the website in the message is replaced by a shorter website, so that the website occupies the length of the message as little as possible, thus overlong message can not be caused when a longer website is inserted into the message.
Owner:TENCENT TECH (SHENZHEN) CO LTD
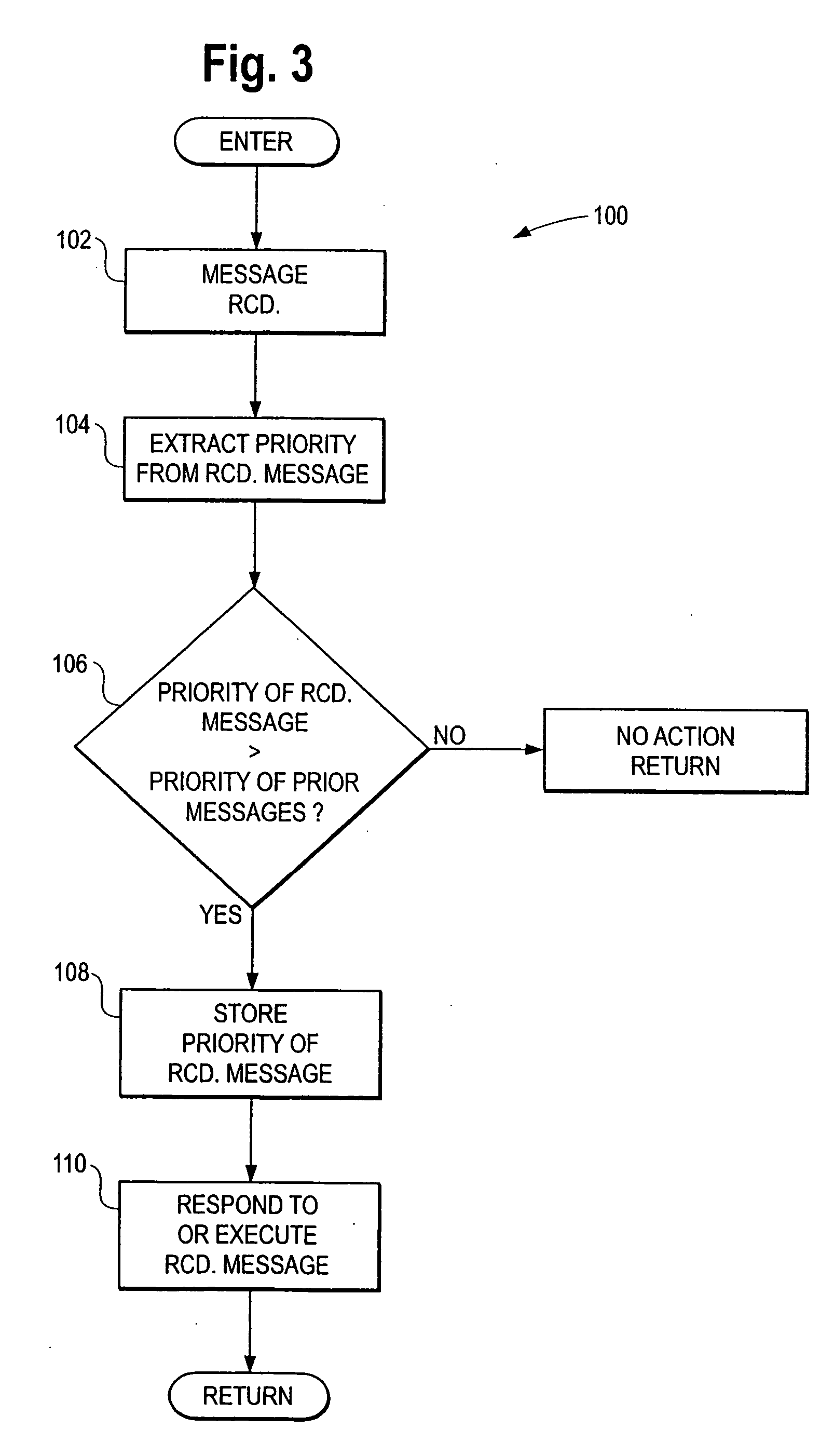
Multi-processor communications system incorporating prioritized messaging
InactiveUS20060271667A1Facilitate communicationIncrease flexibilityDigital computer detailsAlarmsMessage lengthCommunications system
A flexible multi-processor communications system supports variable message lengths and variable groups and application designations at respective processors. The receiving processors determine what action, if any, needs to be taken in response to the combination of group and application information in the messages. The receiving processors can include pluralities of pre-stored groups and applications along with associated priorities and the functions to perform.
Owner:HONEYWELL INT INC
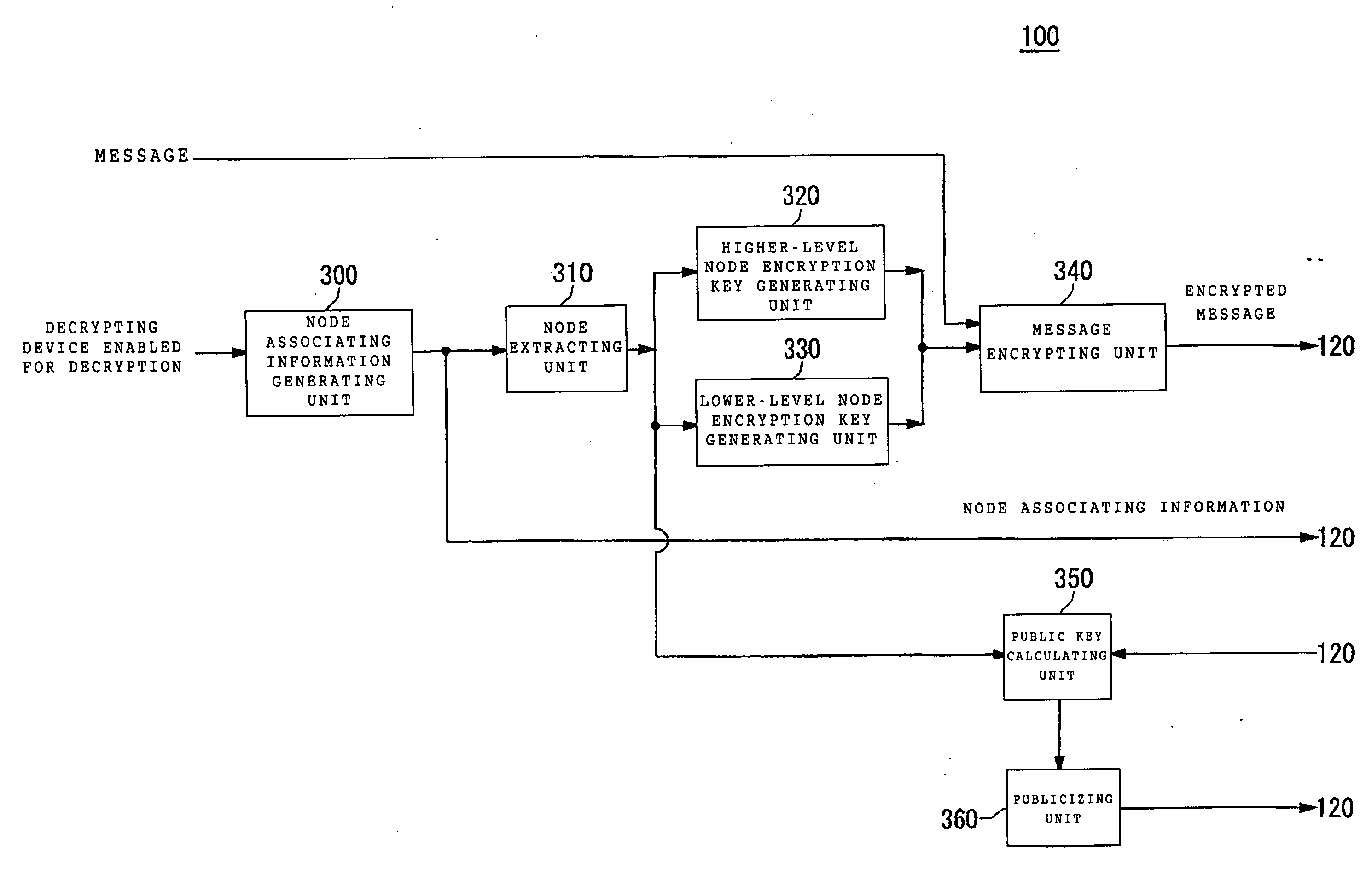
Encrypted communication for selectively delivering a message to multiple decrypting devices
InactiveUS20060062394A1Reduce message lengthKey distribution for secure communicationSecret communicationMessage lengthMessage delivery
Reduces message length of encrypted message to be transmitted selectively to plurality of decrypting devices. An encrypting device includes a generating unit for generating node associating information configured to associate respective terminal nodes in a tree structure with each decrypting device in relation to a group of decrypting devices enabled for decryption, a extracting unit for extracting a decryption enabled node containing decrypting devices in descendant terminal nodes and not containing a decrypting device with decryption disabled in any of the descendant terminal nodes, and a unit for encrypting the message by use of a node encryption key for the decryption enabled node. Decrypting devices include specifying unit for specifying terminal node associated with decrypting device based on node associating information, and a decrypting unit for decrypting encrypted message using a node decryption key for any decryption enabled nodes ranging from terminal node to root node thereof.
Owner:IBM CORP
Method for recognizing P2P application encipher flux
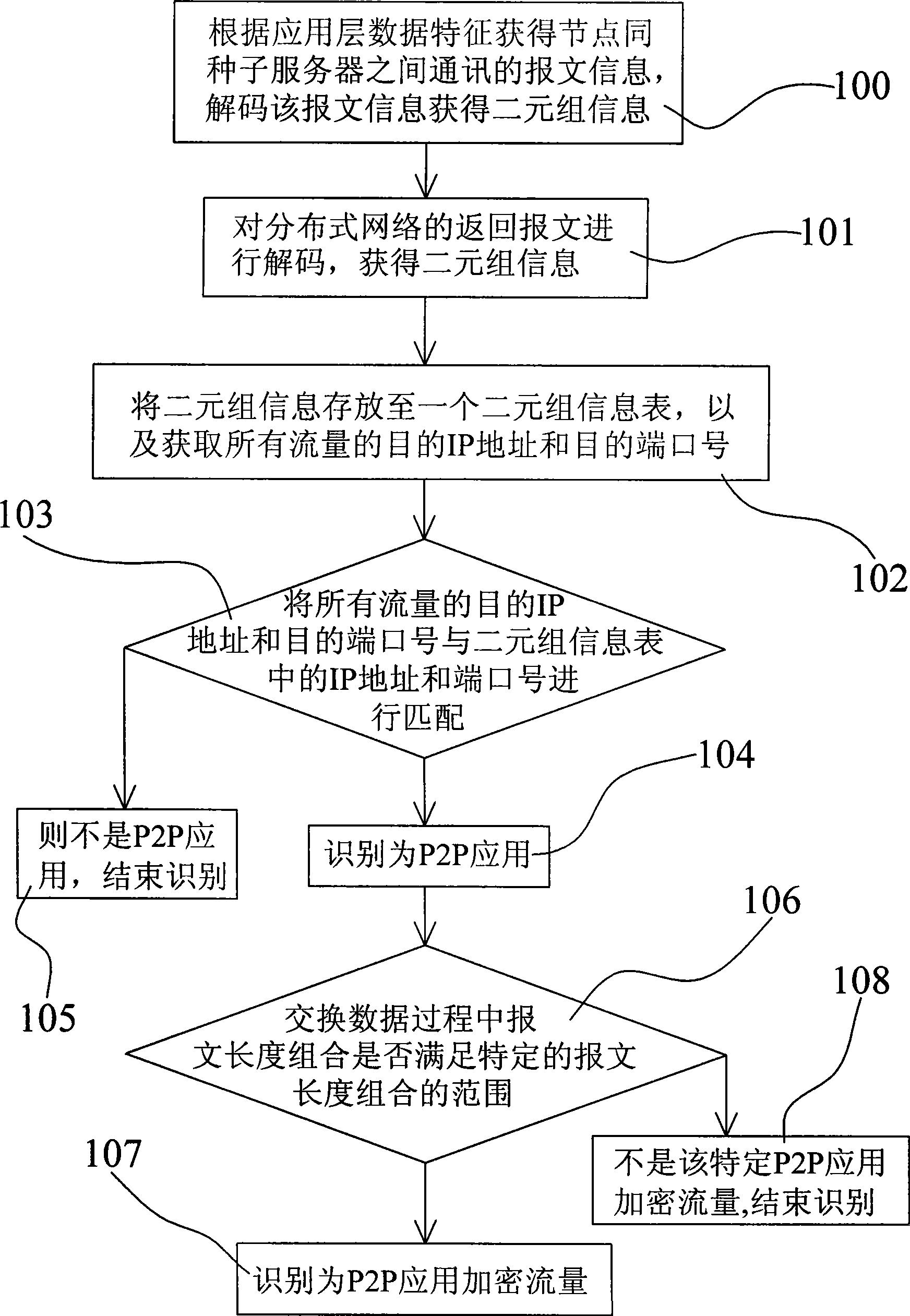
The invention discloses a method for identifying a P2P application encryption flow, which comprises: firstly, acquiring messages communicated between nodes and a seed server according to data characteristics of an application layer, decoding the messages and acquiring binary information; secondly, decoding returned messages of a distributed network and acquiring binary information; thirdly, storing the binary information into a binary information table and simultaneously acquiring destination IP addresses and destination port numbers of all the flows; fourthly, matching the destination IP addresses and the destination port numbers with the binary information table, and labeling the destination IP addresses and the destination port numbers as corresponding P2P application if the destination IP addresses and the destination port numbers are matched with the binary information table; and fifthly, judging message length combination during data exchange according to specified message length combination, and identifying the message length combination as the P2P application encryption flow having the specified message length combination if the message length combination meets the specified message length combination. The method has the advantage of being capable of identifying the P2P application encryption flow and being accurate in identification.
Owner:合肥昊特信息科技有限公司
Message processing method and device, message processing chip and server
InactiveCN107659515AReduce occupancyReduce hardware costsData switching networksMessage queueMessage length
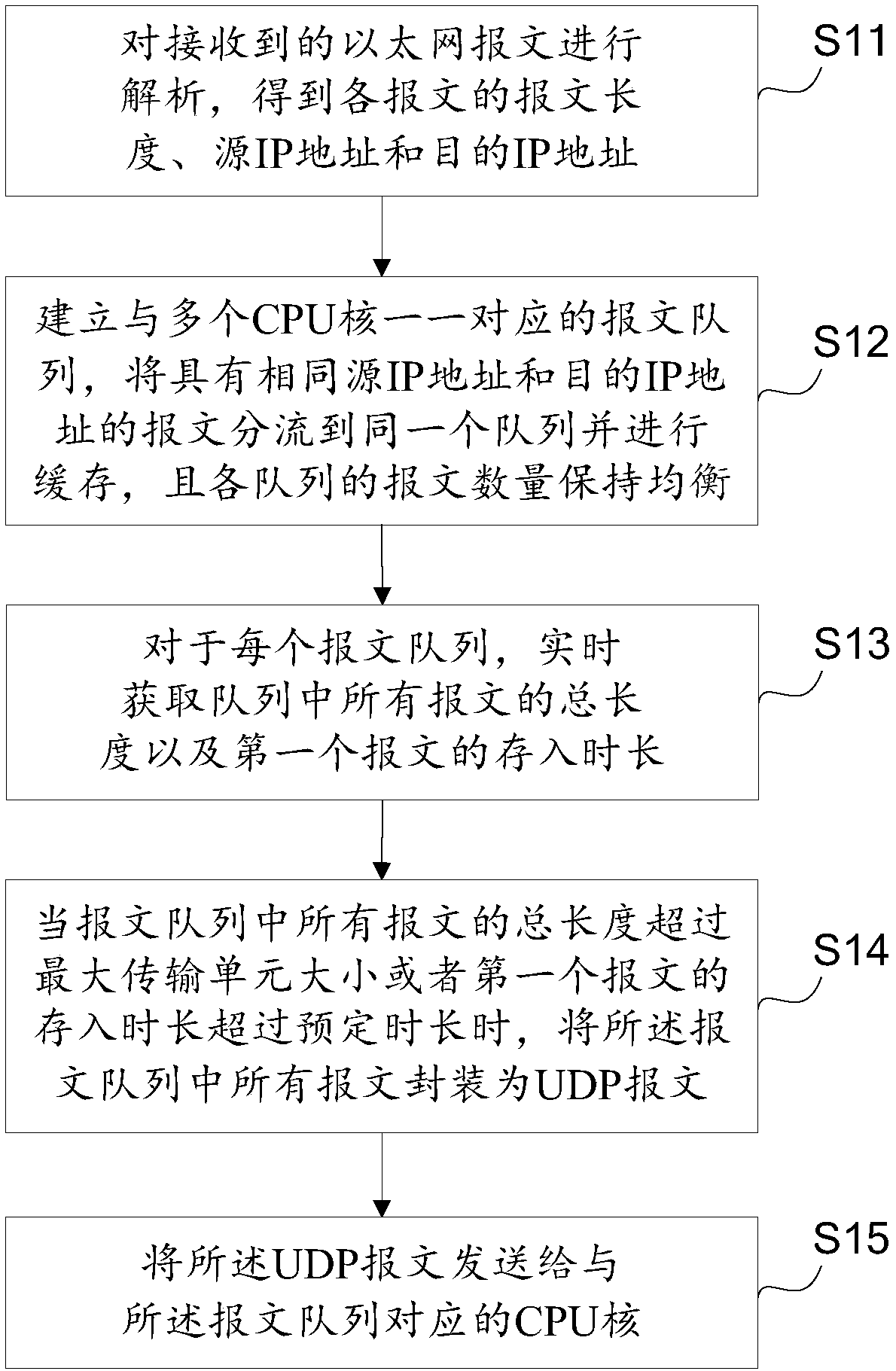
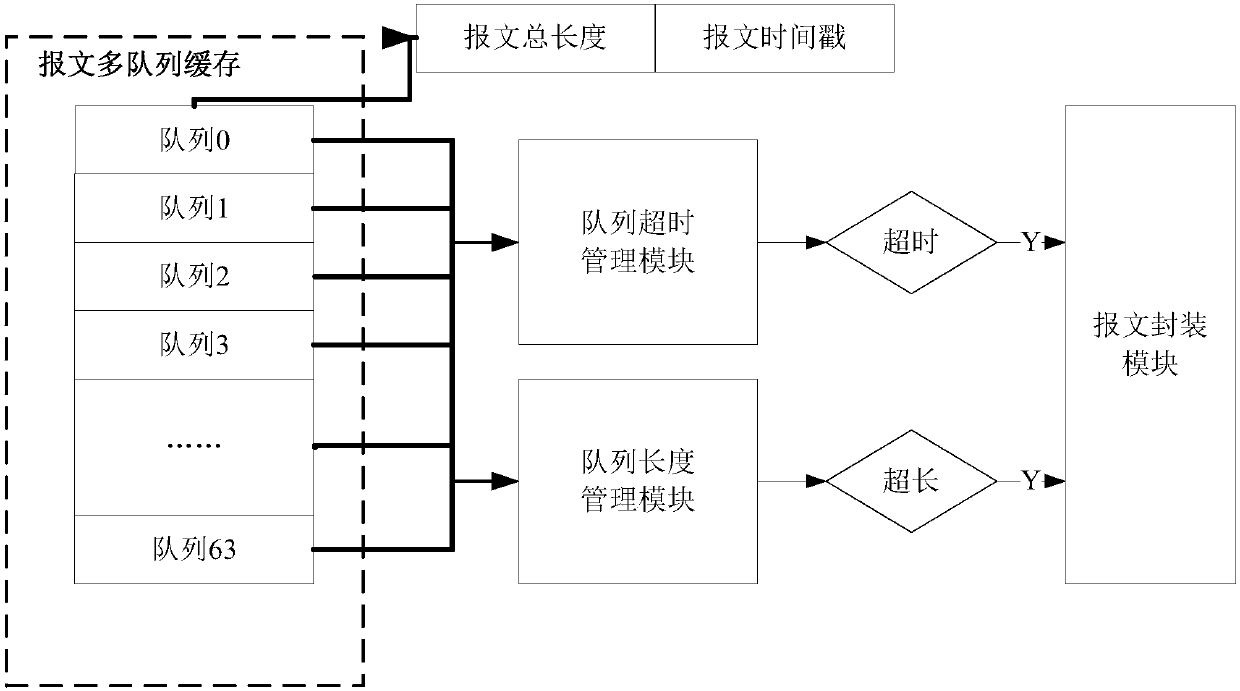
The invention provides a message processing method, a message processing device, a message processing chip and a server. The method comprises the steps of analyzing received Ethernet messages to acquire the message length, source IP address and target IP address of each message; building a message queue corresponding to a plurality of CPU cores one by one, and distributing the messages with the same source IP addresses and target IP addresses into the same queue for caching, wherein the quantities of messages in the queues keep balanced; acquiring an overall length of all the messages in eachmessage queue and storing time of the first message in the queue in real time; when the overall length of all the messages in the message queue exceeds the size of a maximum transmission unit or the storing time of the first message exceeds predetermined time, packaging all the messages in the message queue to be UDP messages; and sending the UDP messages to the CPU core corresponding to the message queue. According to the method provided by the invention, CPU resources occupied by an upper-layer application when the upper-layer application acquires the message are reduced on the basis of notincreasing hardware cost and system complexity.
Owner:DAWNING INFORMATION IND BEIJING
Server and method for collecting performance statistics data of network equipment
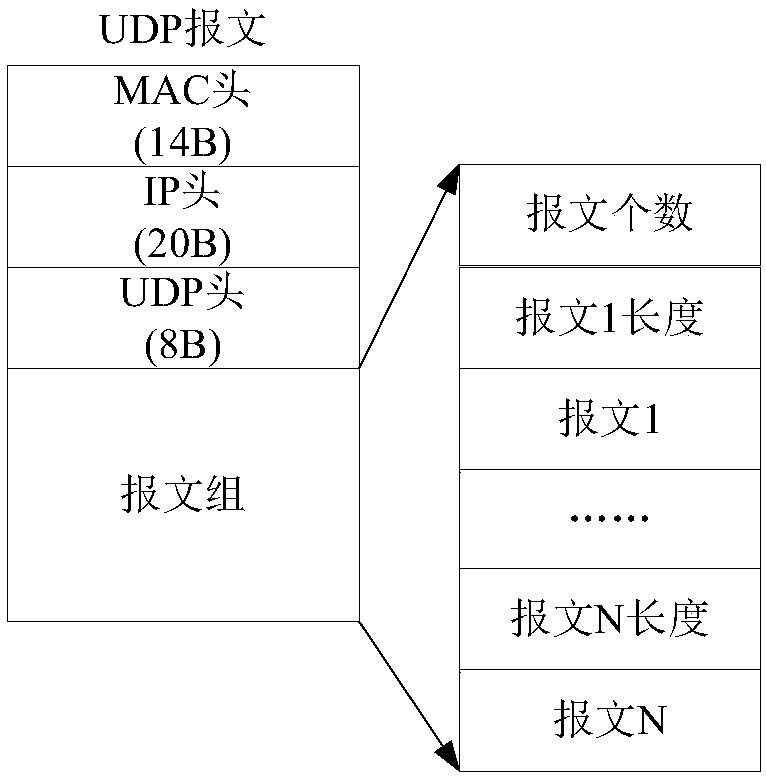
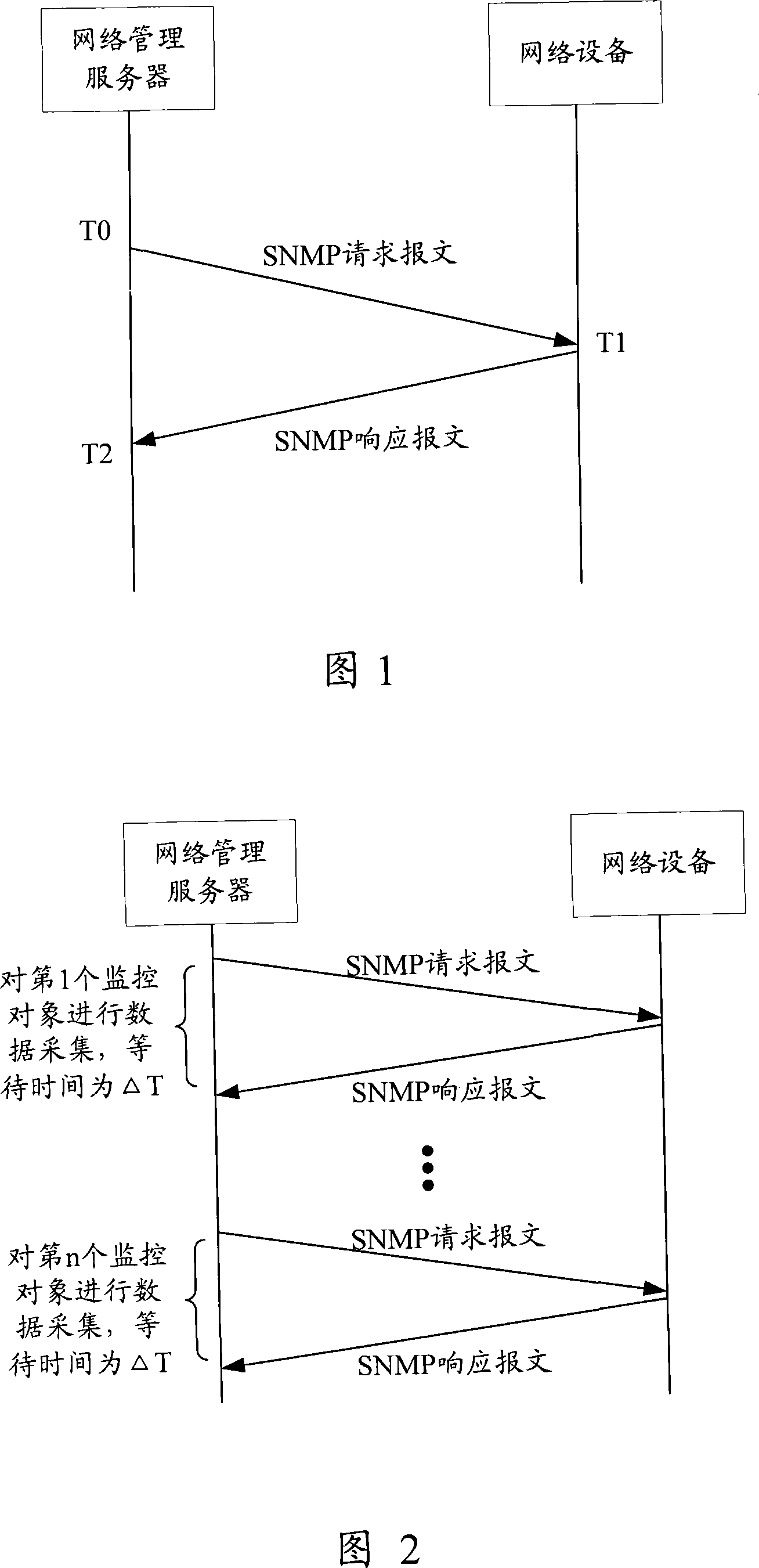
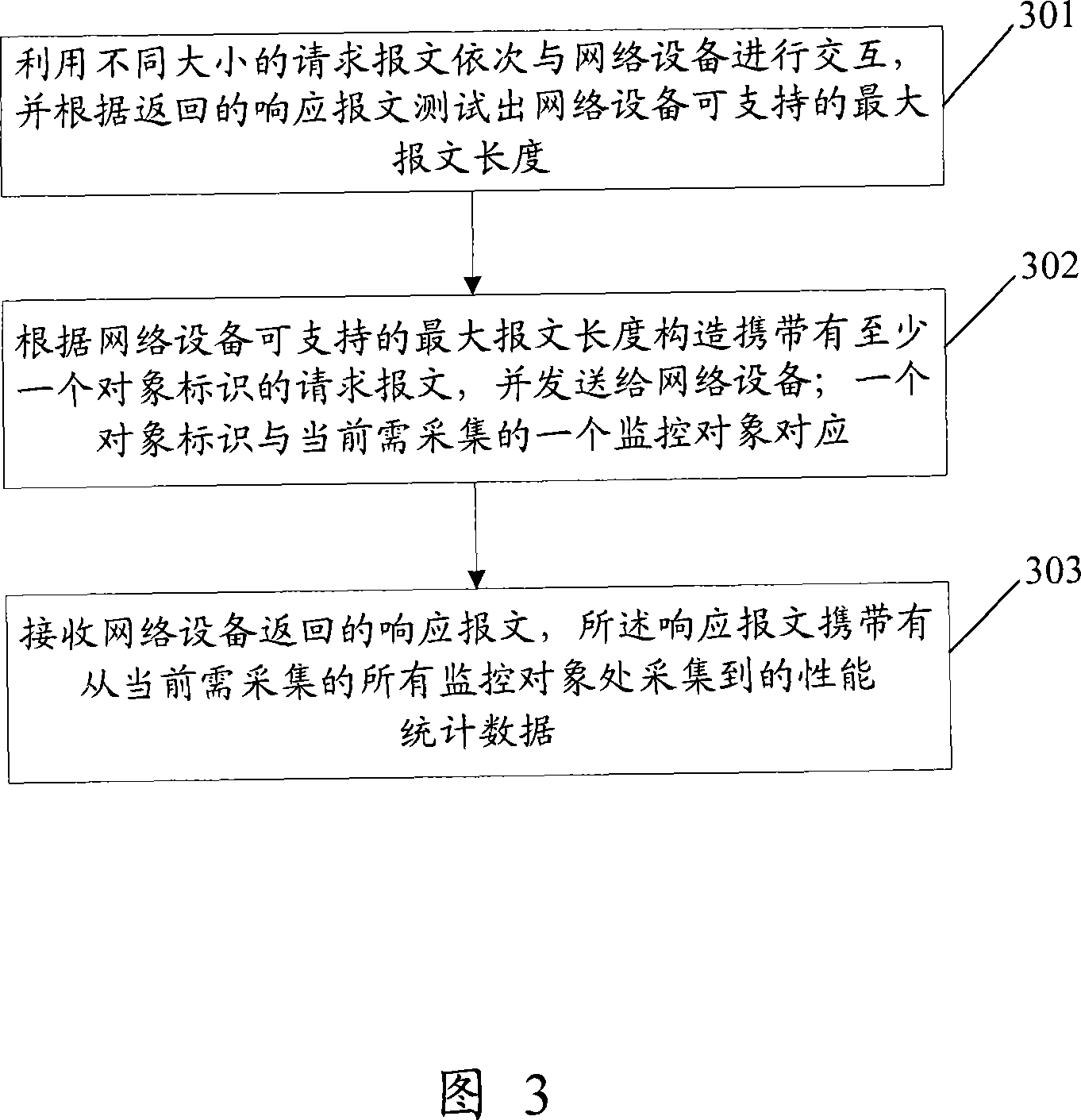
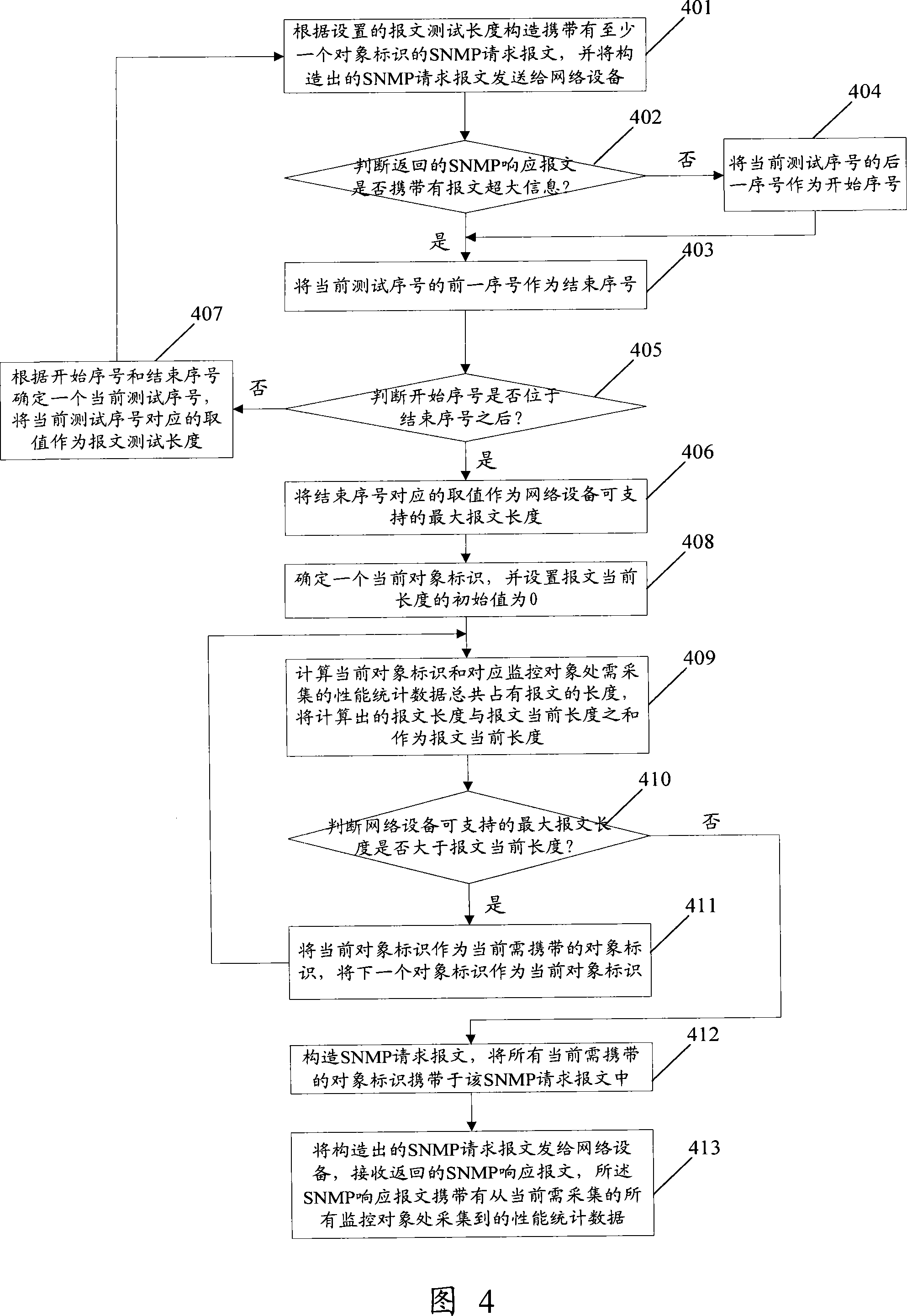
ActiveCN101227348AIncrease the lengthEasy to monitorData switching networksMessage lengthData acquisition
The invention provides a method and equipment for gathering performance statistical data of network equipment, which comprises utilizing request message with different sizes to interact with network equipment in turn, and testing out the maximum message length which can be supported by the network equipment according to response message which returns, constructing request message according to the maximum message length which can be supported by the network equipment and sending to the network equipment, and receiving the response message which is carried with performance statistical data and is returned from the network equipment. In the application of the proposal of the invention, since the maximum request message which can be supported by the network equipment is tested before collecting data, the request message and the response message can not only be guaranteed without exceeding the maximum message length which can be request, but also can carry object marks on the request message as much as possible, and can return performance statistical data on the response message as much as possible. Therefore, the invention can reduce the times of interacting with the network equipment in unit time, and time is completely used to calculate, thereby monitoring monitor objects better.
Owner:NEW H3C TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com