Method for recognizing P2P application encipher flux
An identification method and flow technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problems of inability to identify encrypted peer-to-peer network traffic and low identification accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
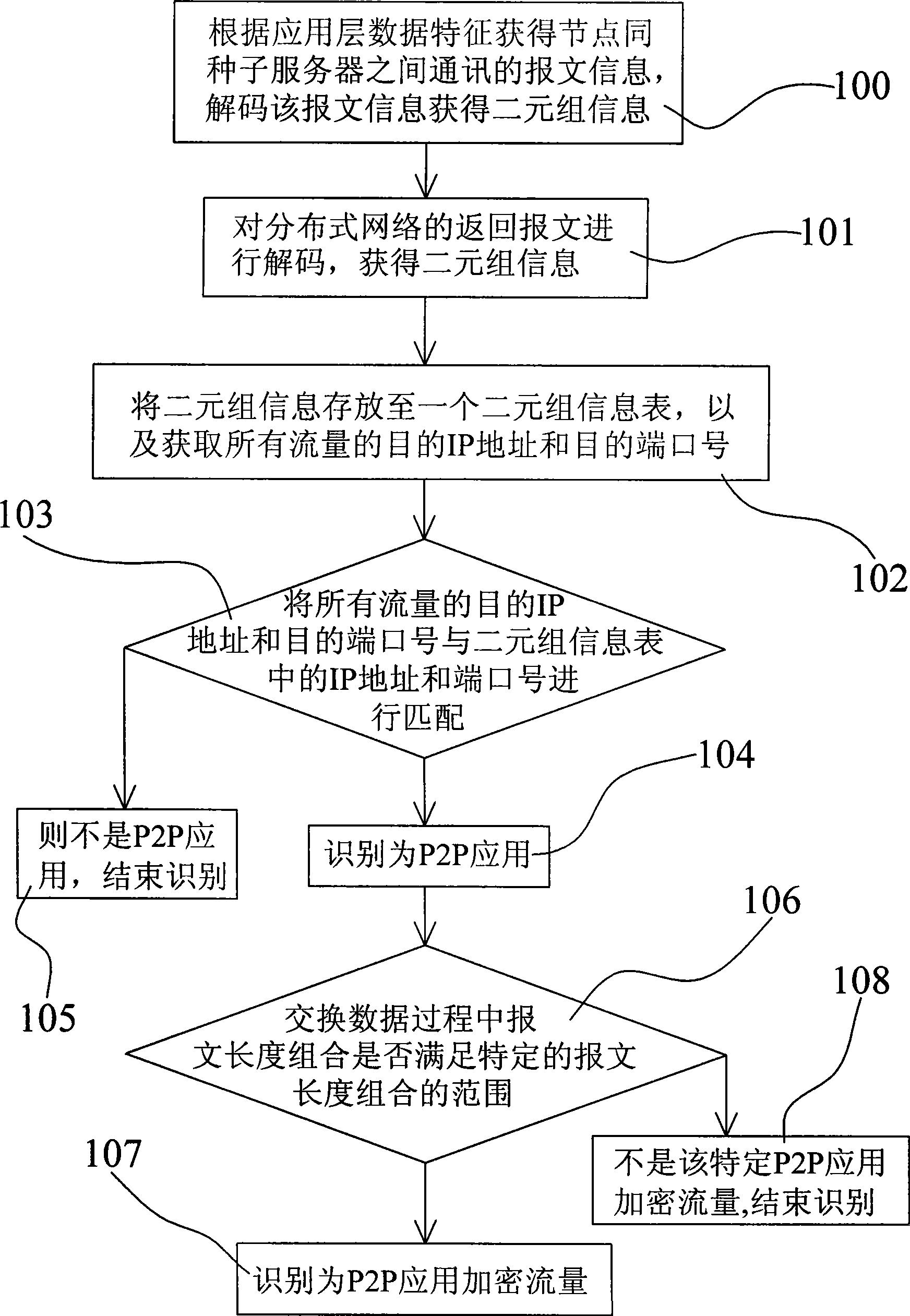
[0017] The identification method of the P2P encryption application of the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0018] The identification method of P2P application encrypted traffic in the present invention flexibly utilizes the characteristics of the P2P protocol information exchange process, and dynamically tracks and analyzes the node traffic in the P2P application network in real time, and accurately locates the session based on the packet length filter (session) traffic identification, and the introduction of the concept of a two-tuple composed of IP and port has completely changed the hysteresis of traffic identification.
[0019] In addition, since a typical P2P network is composed of many nodes, and each node is not only a server, but also a client, it not only uses TCP connection to download data, but also uses UDP distributed hash table information. Information data transmission.
[0020] The fol...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com