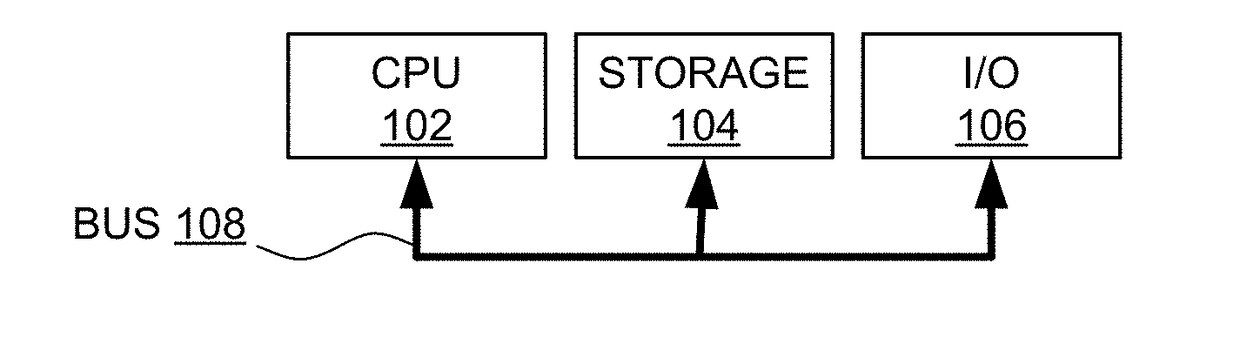
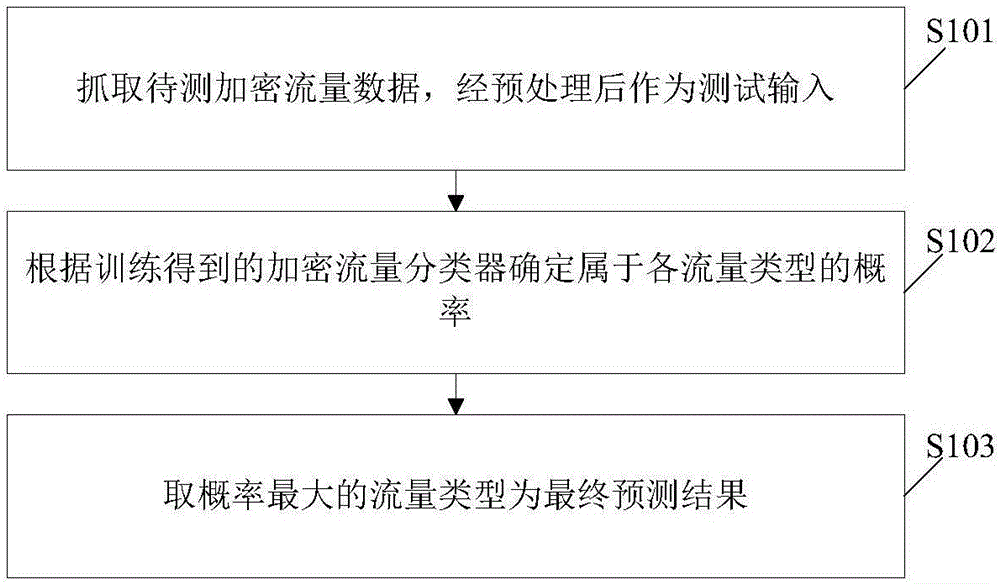
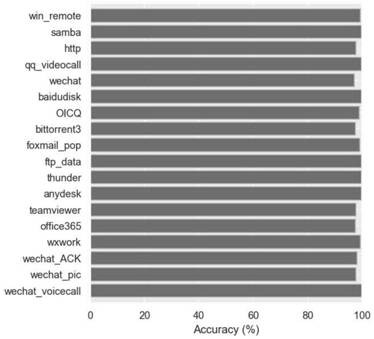
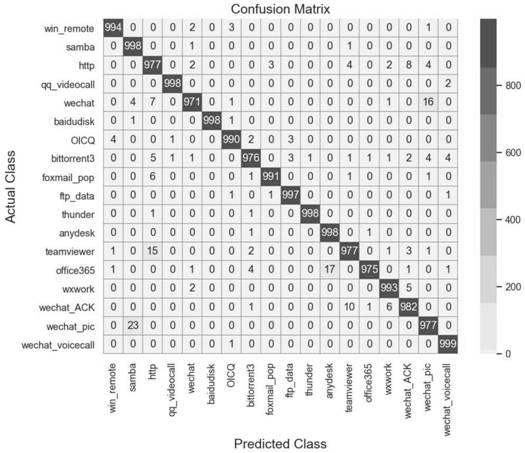
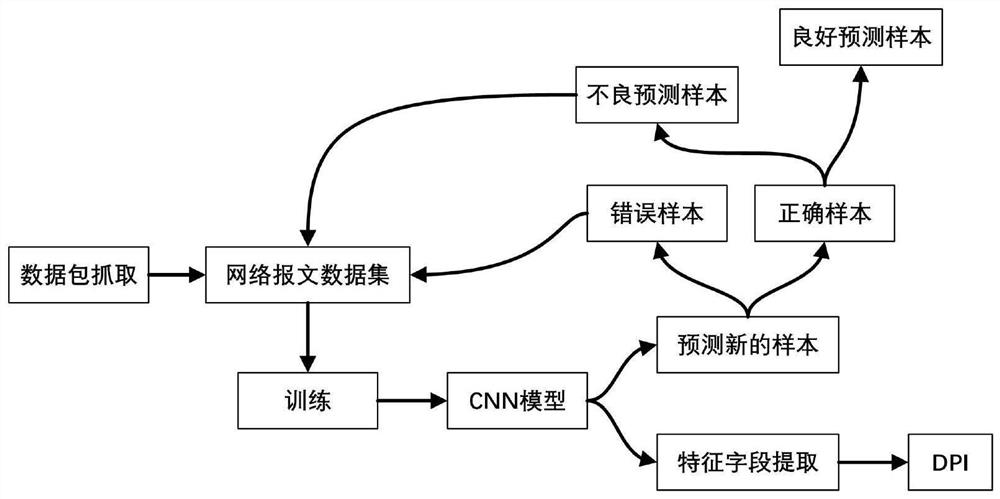
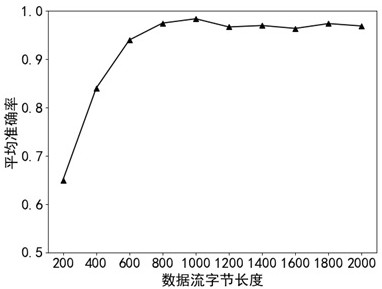
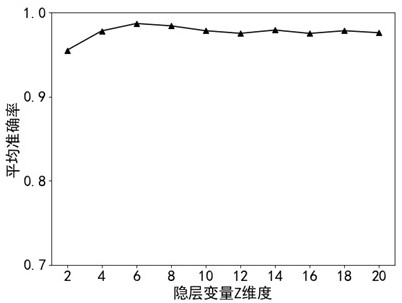
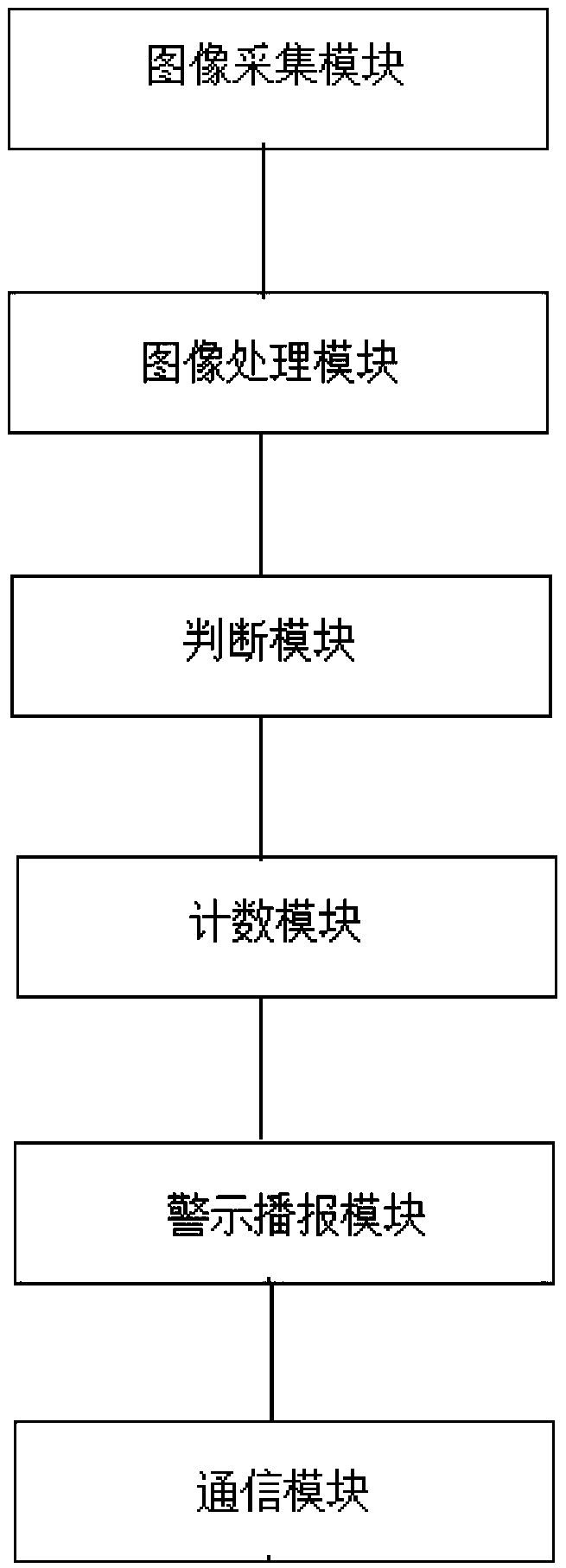
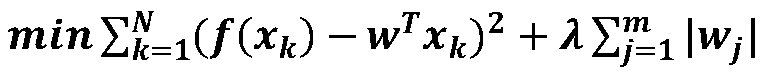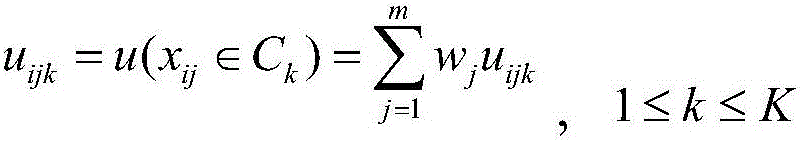Patents
Literature
408 results about "Traffic identification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
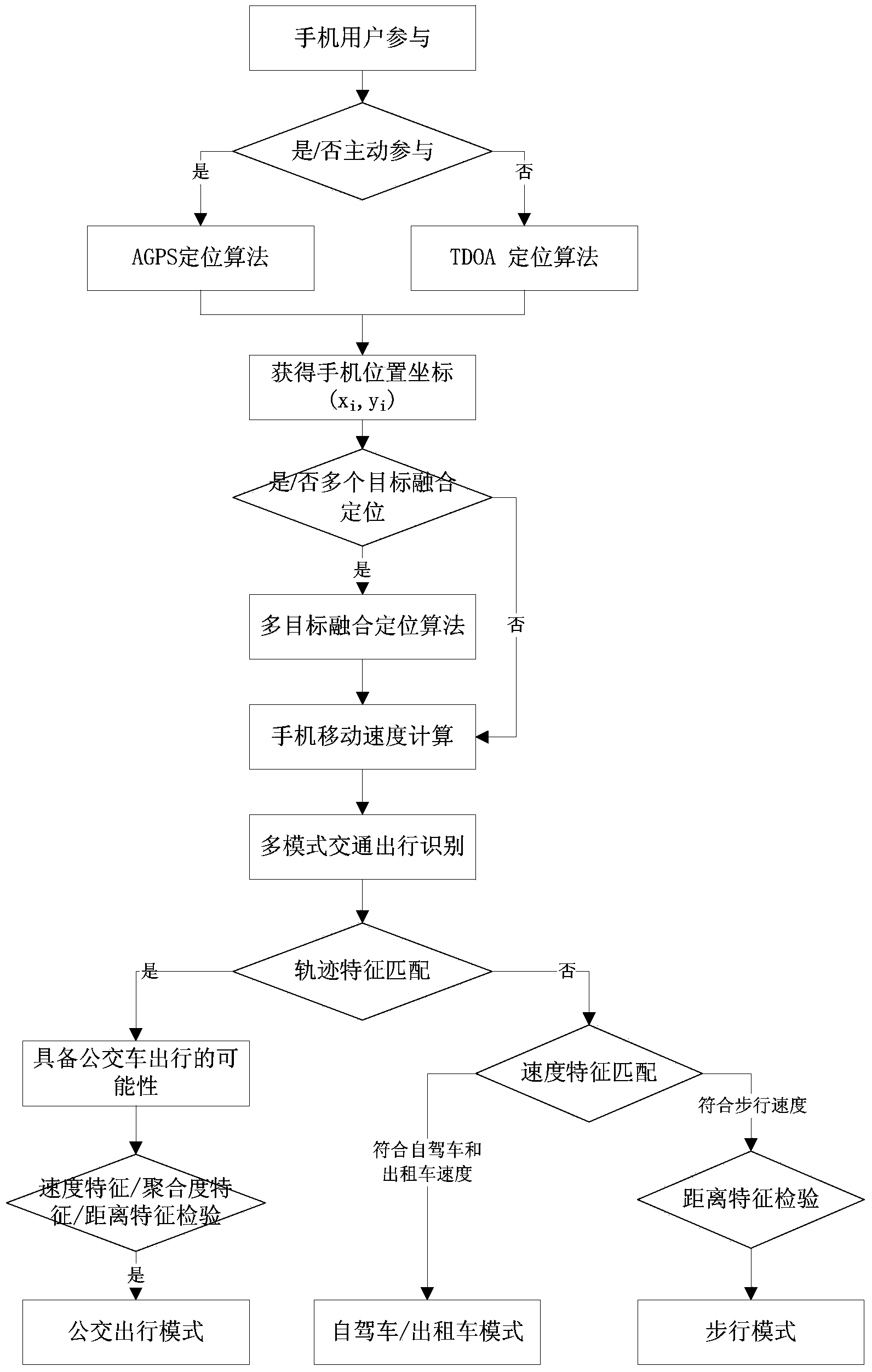
Mobile phone location based traffic mode identification method
ActiveCN103810851AConducive to scientific decision-makingImprove accuracyDetection of traffic movementTravel modeSelf driving
The invention discloses a mobile phone location based transportation mode identification method. The mobile phone location based transportation mode identification method includes the following steps of step one, acquiring a mobile phone position coordinate through a mobile phone location algorithm; step two, determining a travel route according to the mobile phone position coordinate, and calculating a mobile phone positioning movement speed; step three, applying a multi-feature matching method to multi-mode traffic identification. According to the mobile phone location based transportation mode identification method, the multi-feature matching method for traffic mode identification is established to perform collection, analysis and spatial-temporal feature matching on mobile phone location information, so that three typical travel modes of bus travel, self-driving (or taxi) travel or walking travel can be accurately identified. By means of popularization and application of the mobile phone location based transportation mode identification method, a data support can be provided for urban traffic planning, construction and operation management, and scientific decision-making by a traffic management department is facilitated.
Owner:GUANGZHOU INST OF GEOGRAPHY GUANGDONG ACAD OF SCI
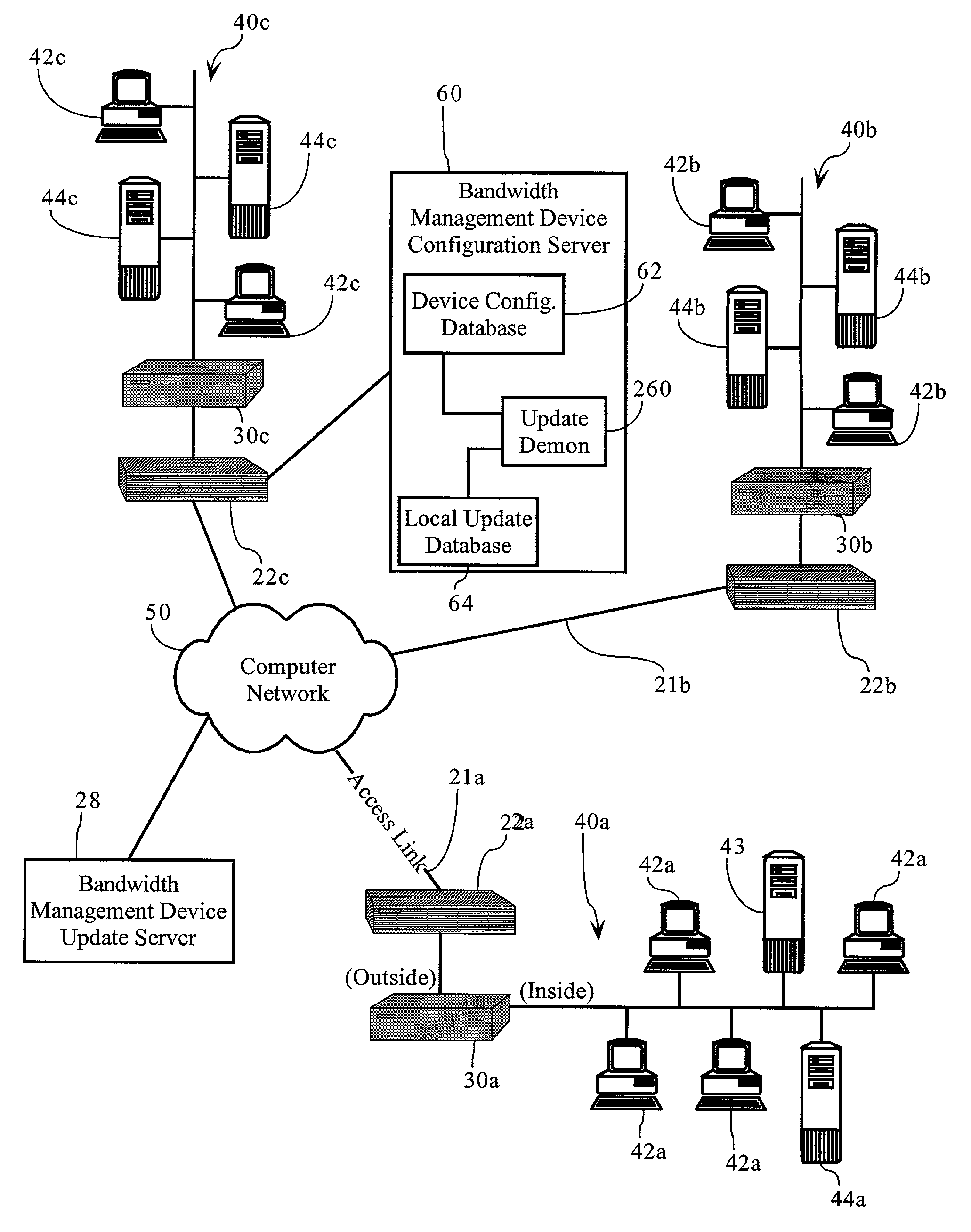
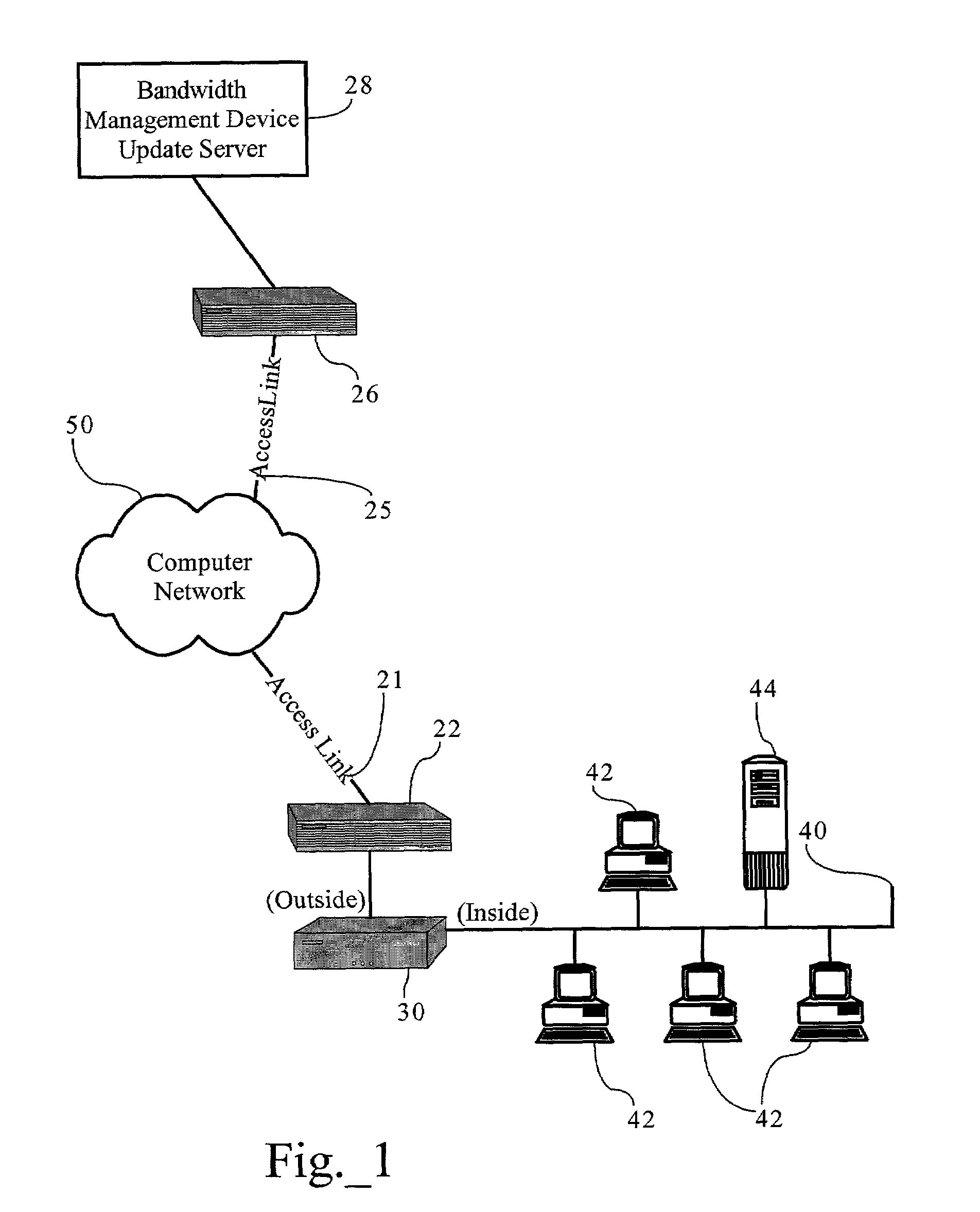
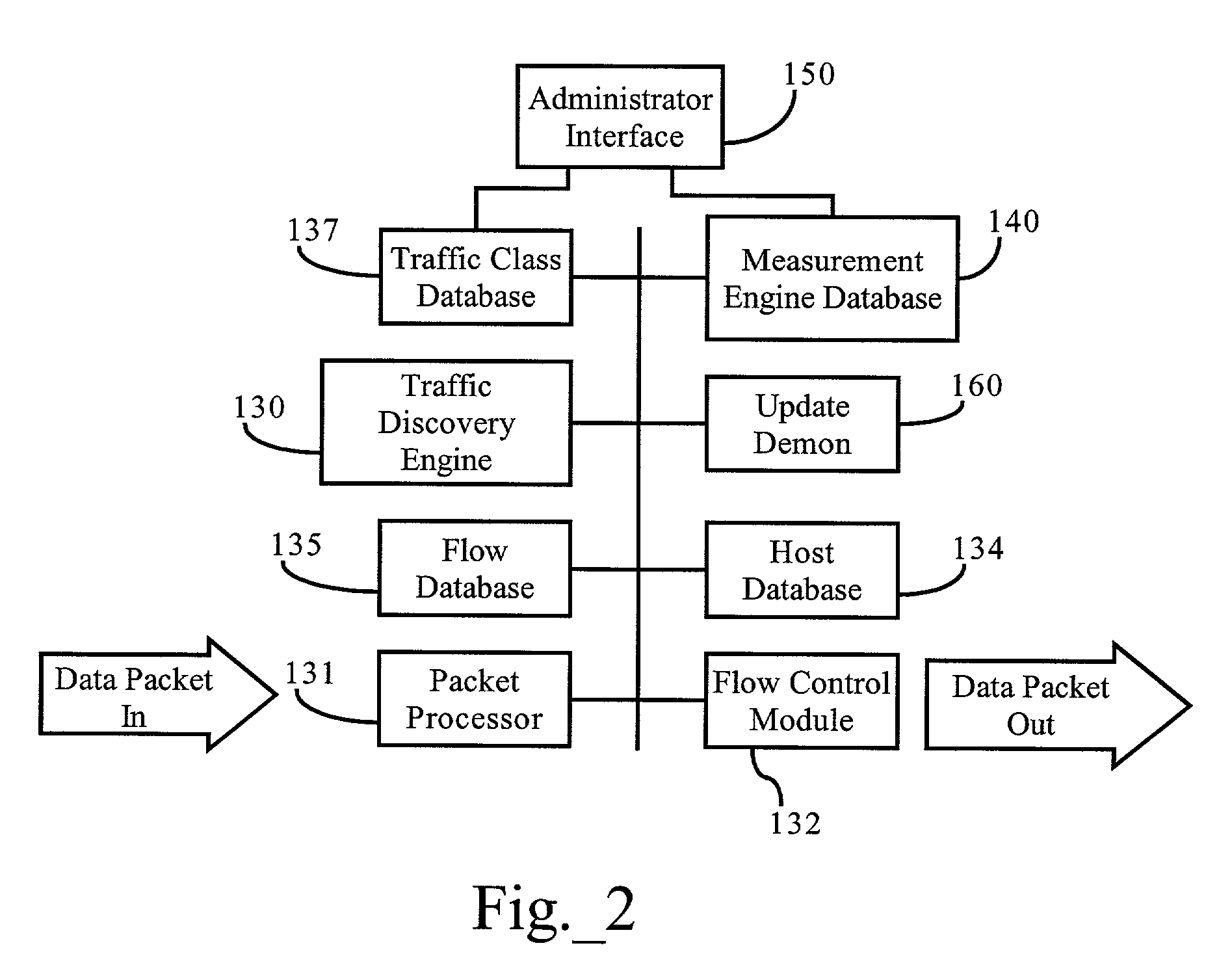
Methods, apparatuses and systems facilitating distribution of updated traffic identification functionality to bandwidth management devices
ActiveUS7155502B1Optimize allocationEasy to manageData switching by path configurationMultiple digital computer combinationsBandwidth managementDistributed computing
Methods, apparatuses and systems facilitating the distribution of updated traffic identification functionality to bandwidth management devices. The present invention, in one embodiment, allows for automatic updates to the traffic identification functionality implemented by bandwidth management devices eliminating the cumbersome upgrade processes required by prior art methods and systems. The present invention, in one embodiment, also provides a system facilitating management of upgrades for multiple bandwidth management devices.
Owner:CA TECH INC
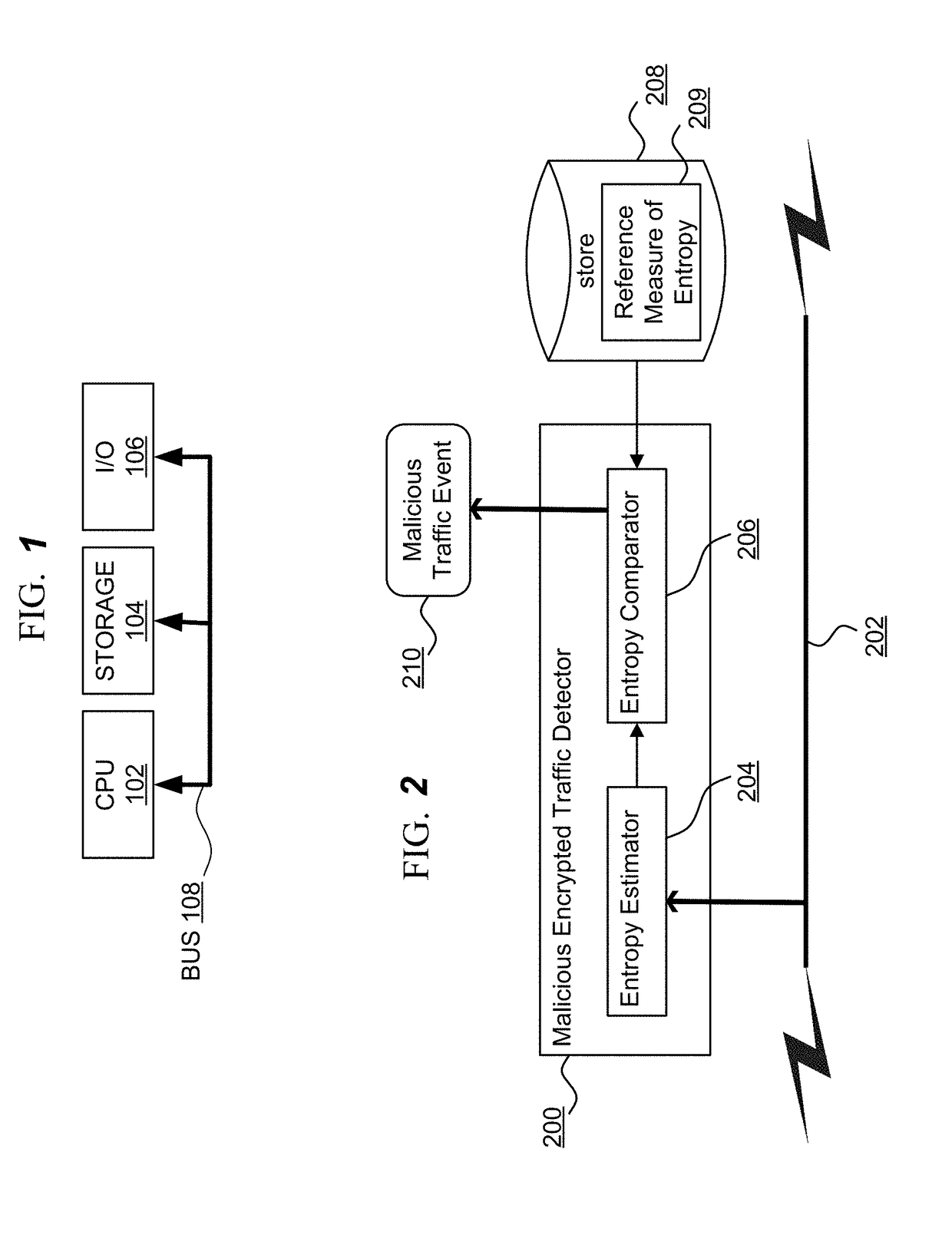
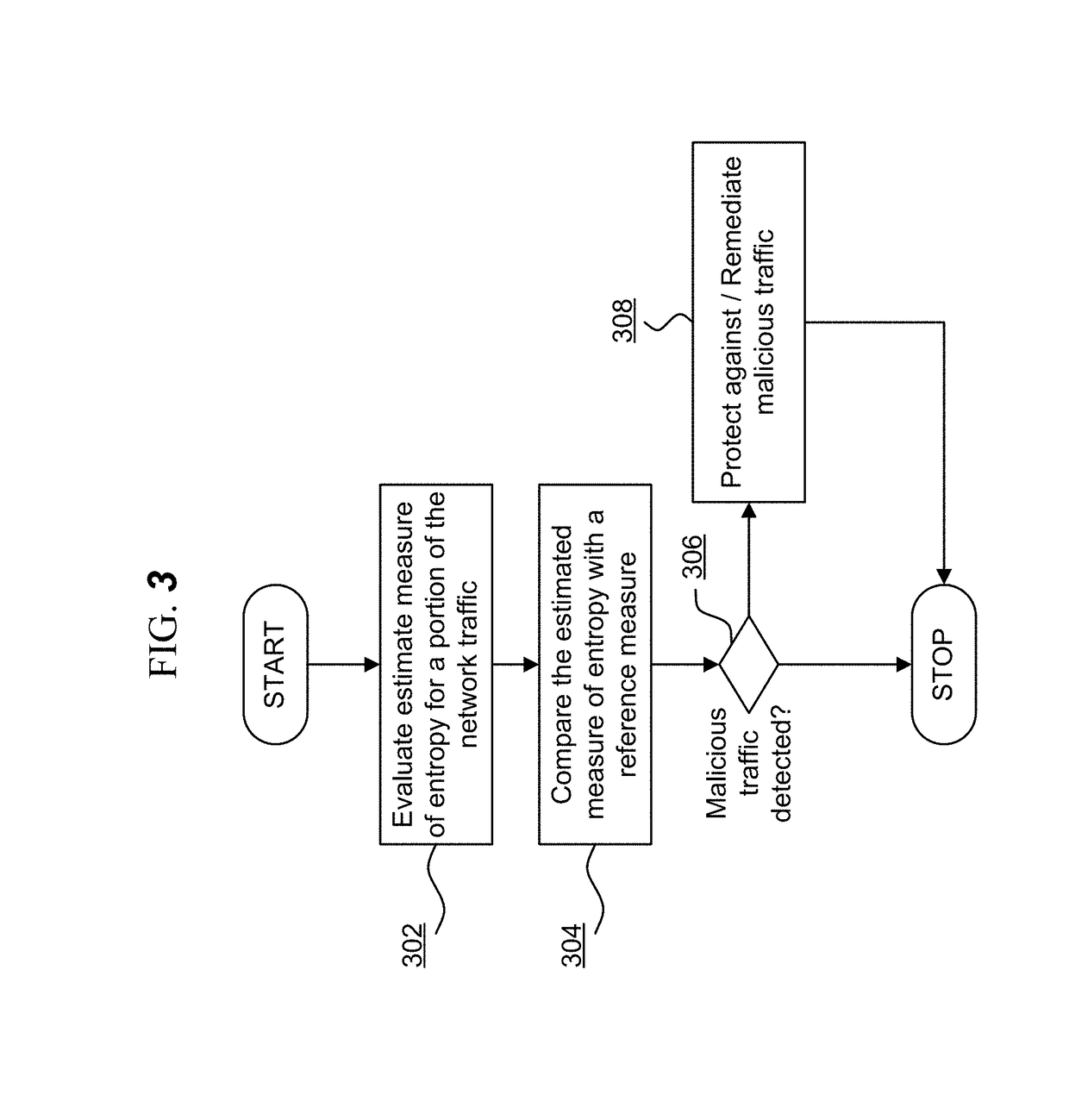
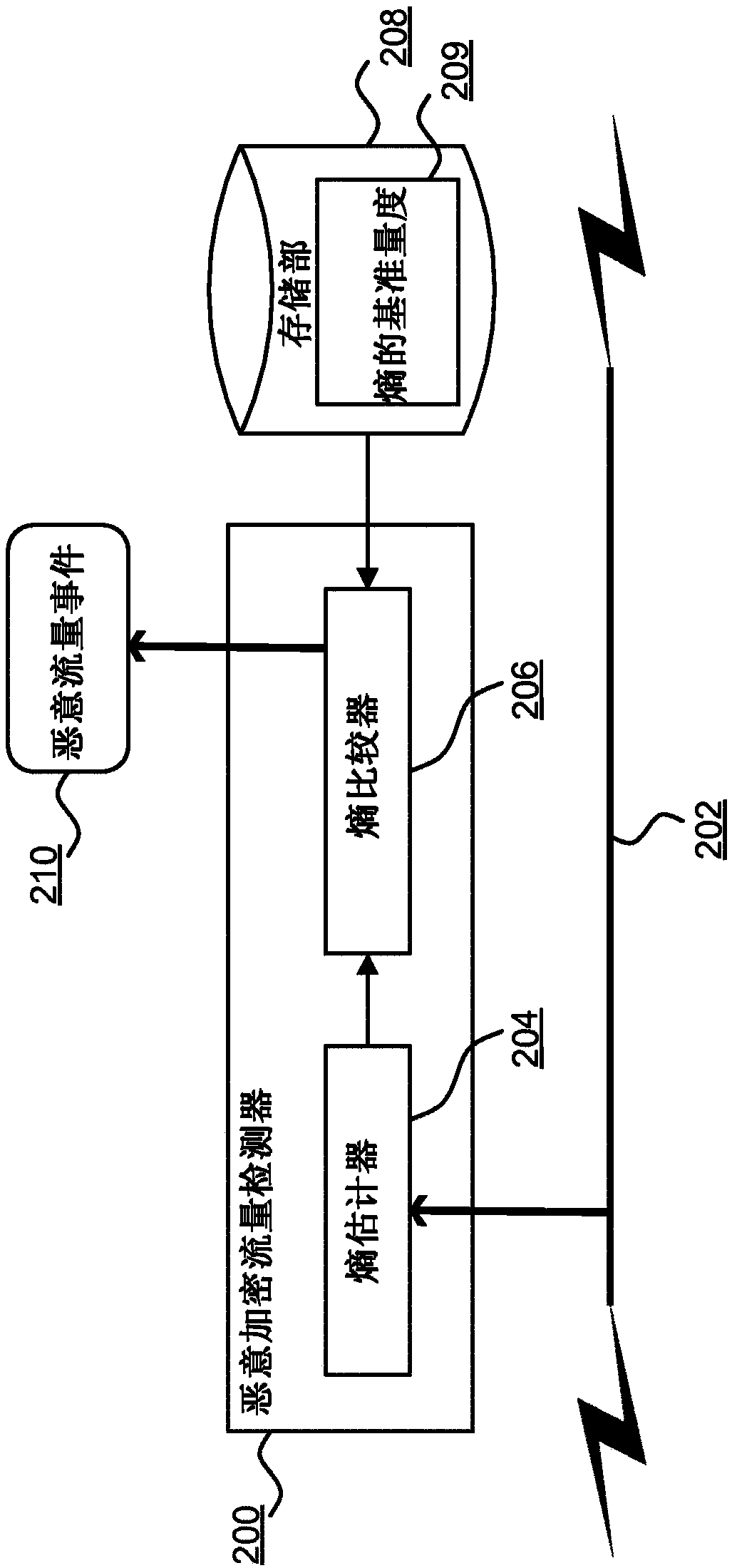
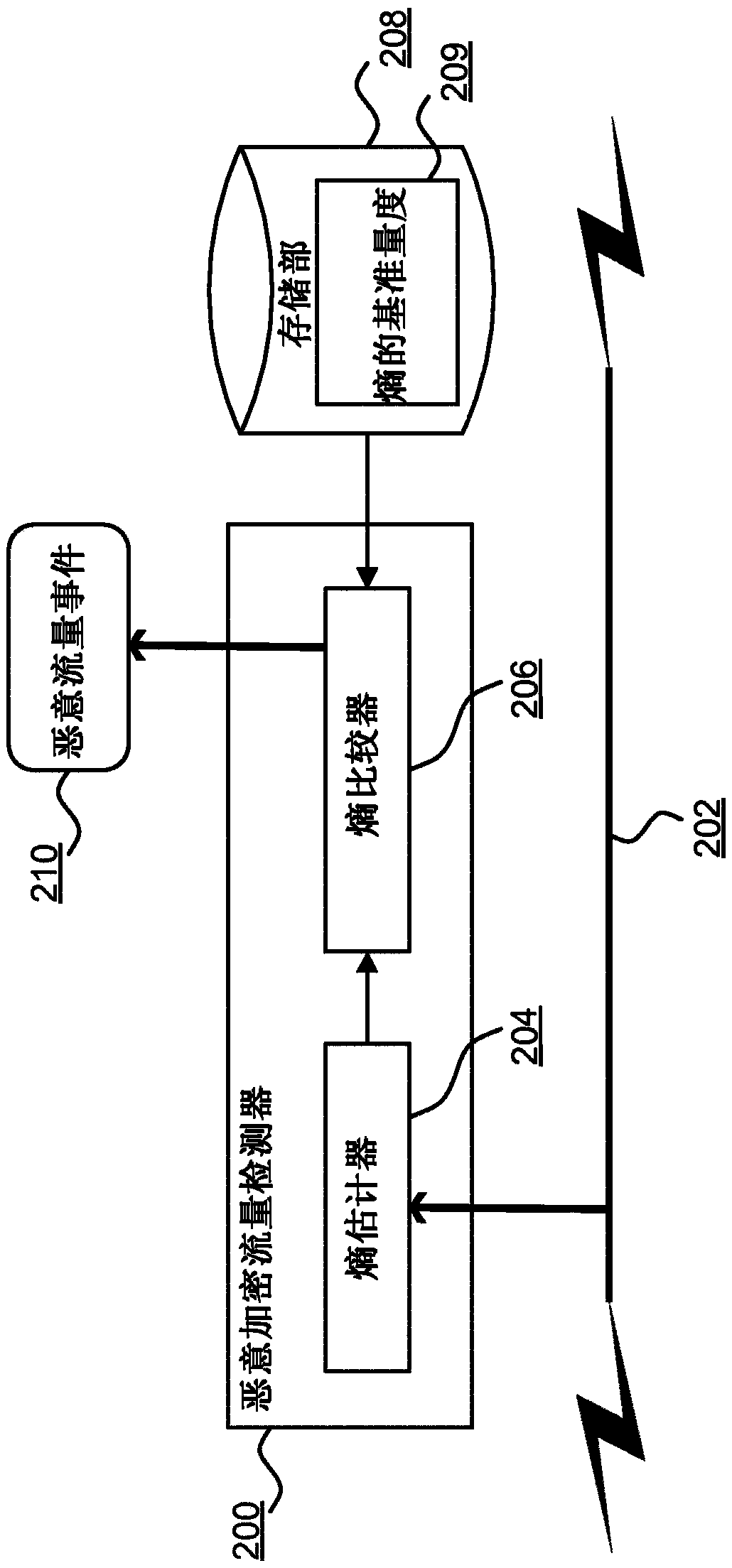
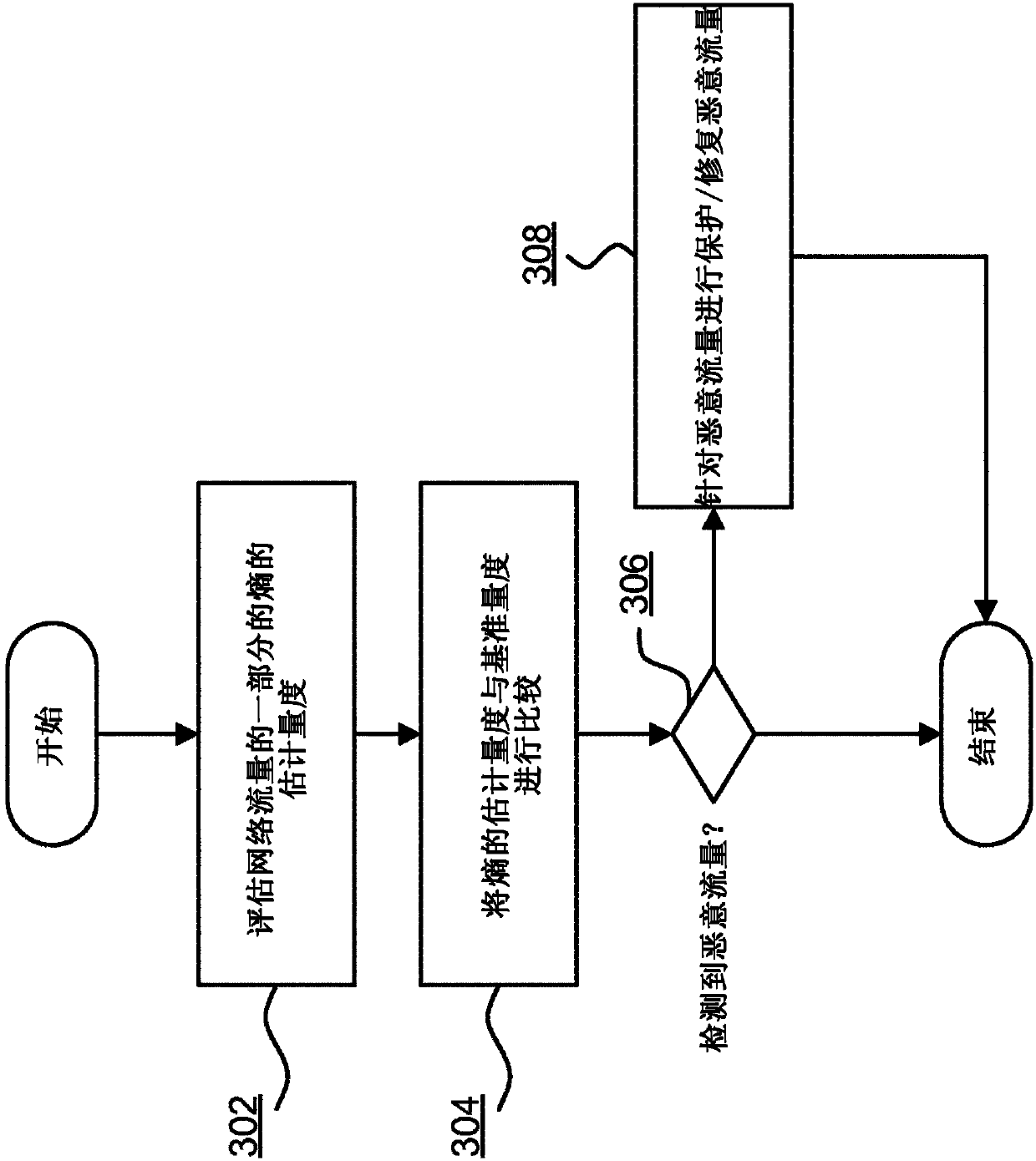
Learned profiles for malicious encrypted network traffic identification
A method for identifying malicious encrypted network traffic associated with a malware software component communicating via a network, the method including: defining, for the malware, a portion of network traffic including a plurality of contiguous bytes occurring at a predefined offset in a network communication of the malware; extracting the defined portion of network traffic for each of a plurality of disparate network connections for the malware; evaluating a metric for each byte in each extracted portion; representing each extracted portion in a matrix data structure as an image of pixels wherein each pixel corresponds to a byte of the extracted portion; training a neural network based on the images for the extracted portions such that subsequent network traffic can be classified by the neural network to identify malicious network traffic associated with the malware based on an image generated to represent the defined portion of the subsequent network traffic.
Owner:BRITISH TELECOMM PLC
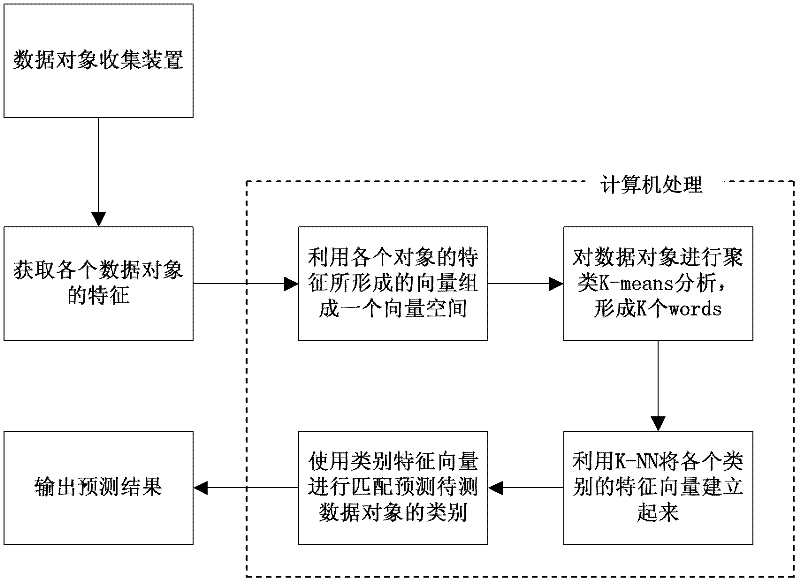
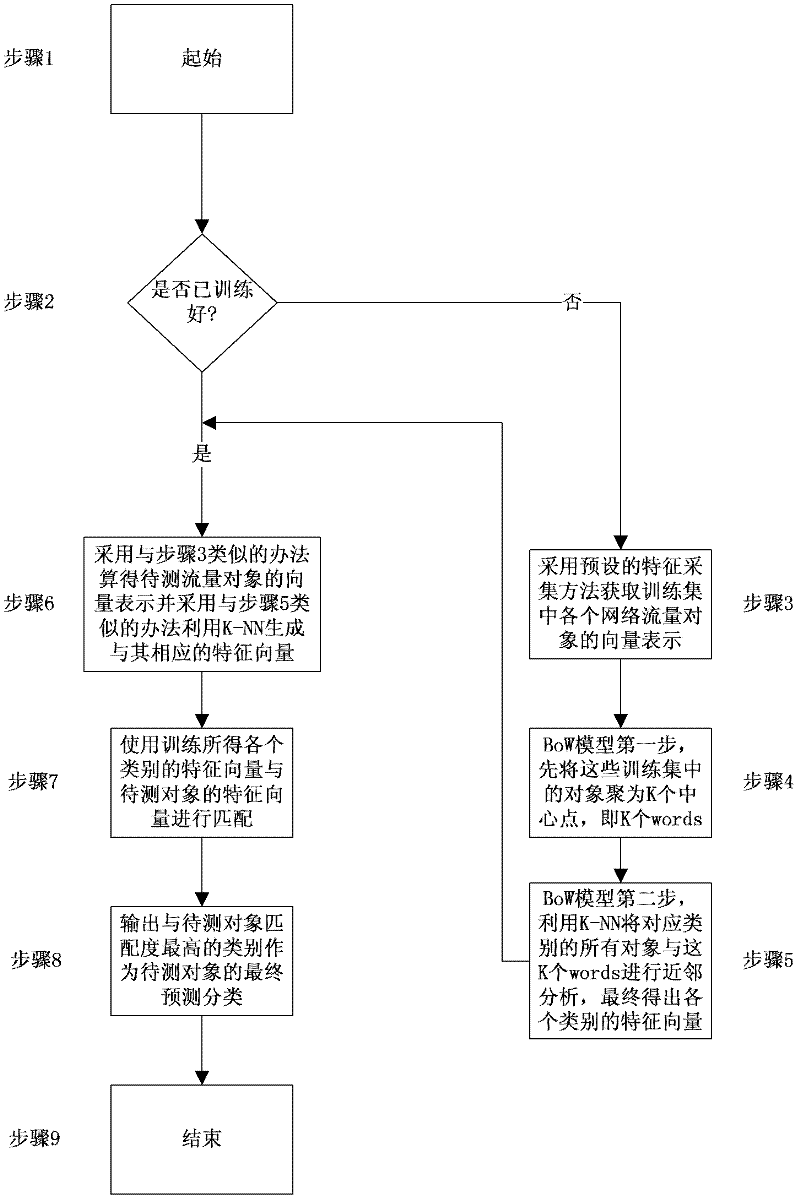
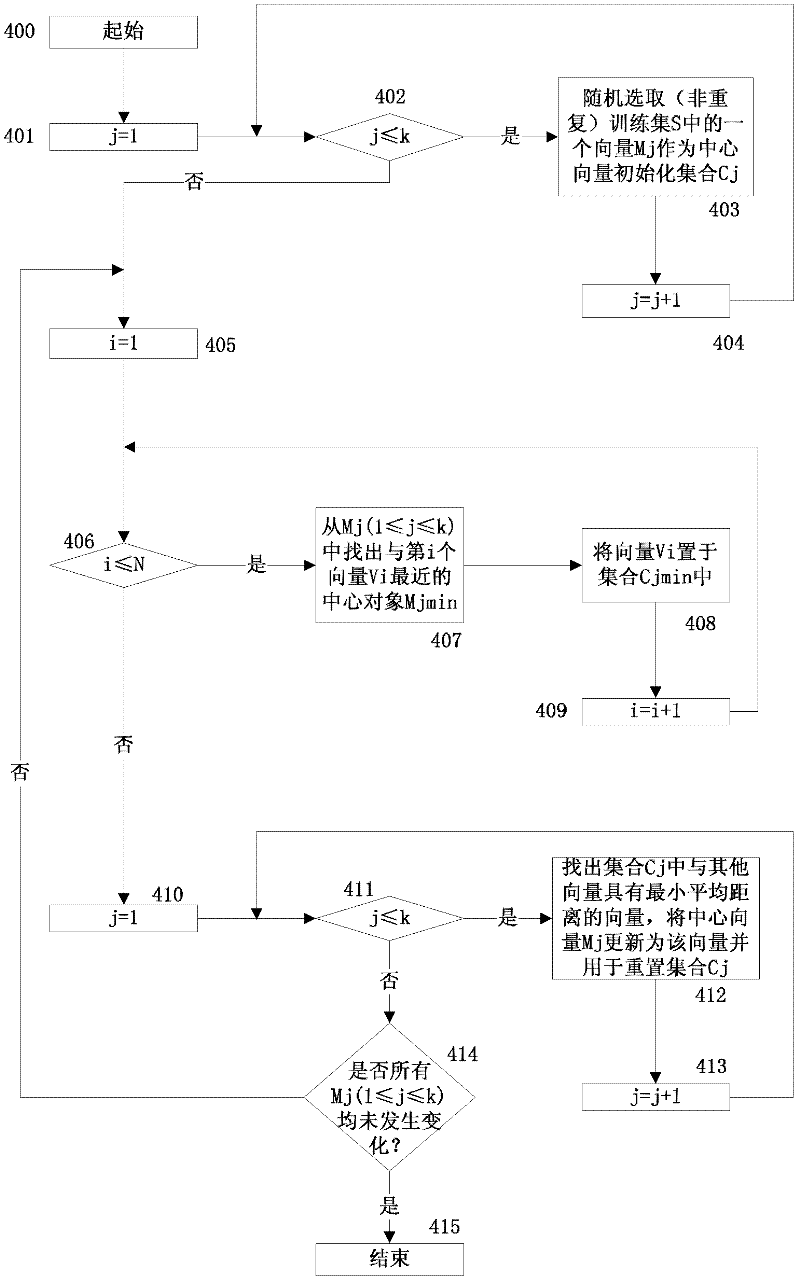
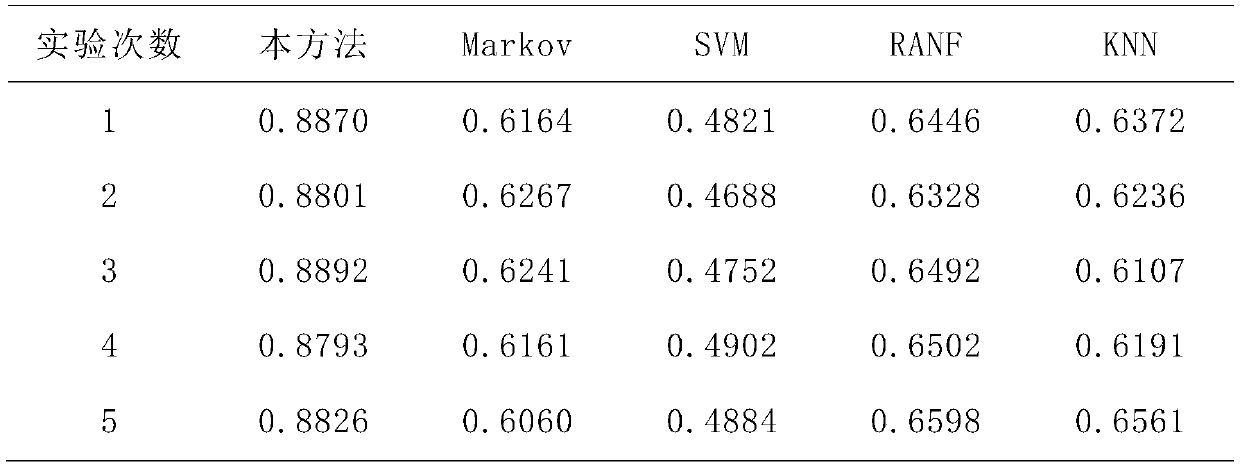
Traffic identification method based on bag of word (BOW) model and statistic features
ActiveCN102571486AQuick identificationAccurate identificationData switching networksFeature vectorFeature extraction
The invention discloses a traffic identification method based on a bag of word (BOW) model and statistic features. The method adopts the BOW model matched with a feature extraction method, trains collected network traffic features, and thus obtains a feature vector corresponding to each network category. For new network traffic, similarly, by extracting traffic features, utilizing the BOW module to obtain a corresponding feature vector, and then sequentially comparing with a feature vector of each network category which is previously established, the category corresponding to the feature vector with highest matching degree serves as a category tag of the new network traffic. The BOW method combines with an unsupervised k-means clustering method and a supervised k-nearest neighbor method, thereby being more suitable for multi-category classification. Due to the fact that the BOW model is not sensitive to space position, during feature extraction, arrangement according to time series of features is not required, and processing is convenient.
Owner:上海深杳智能科技有限公司 +1
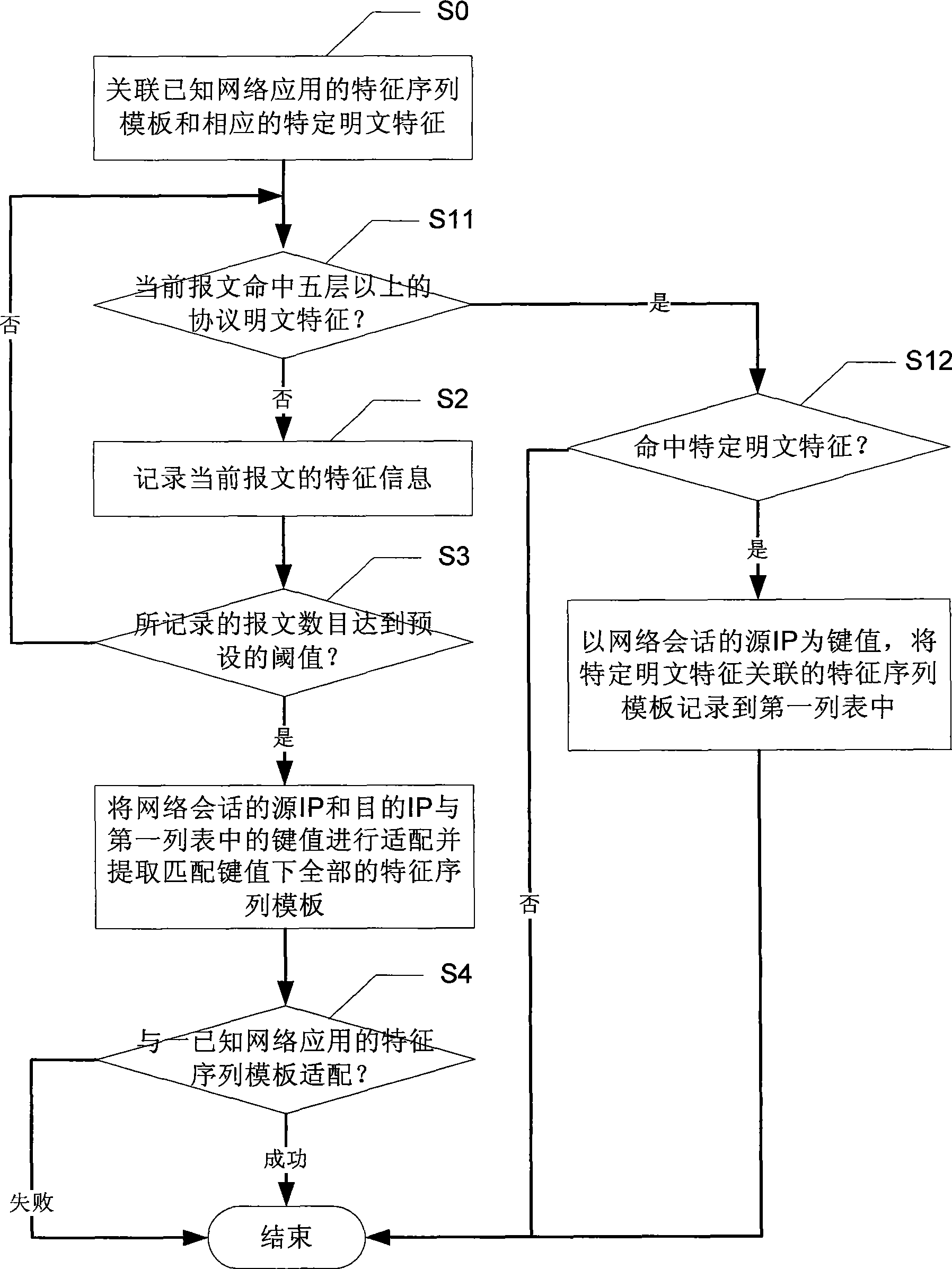
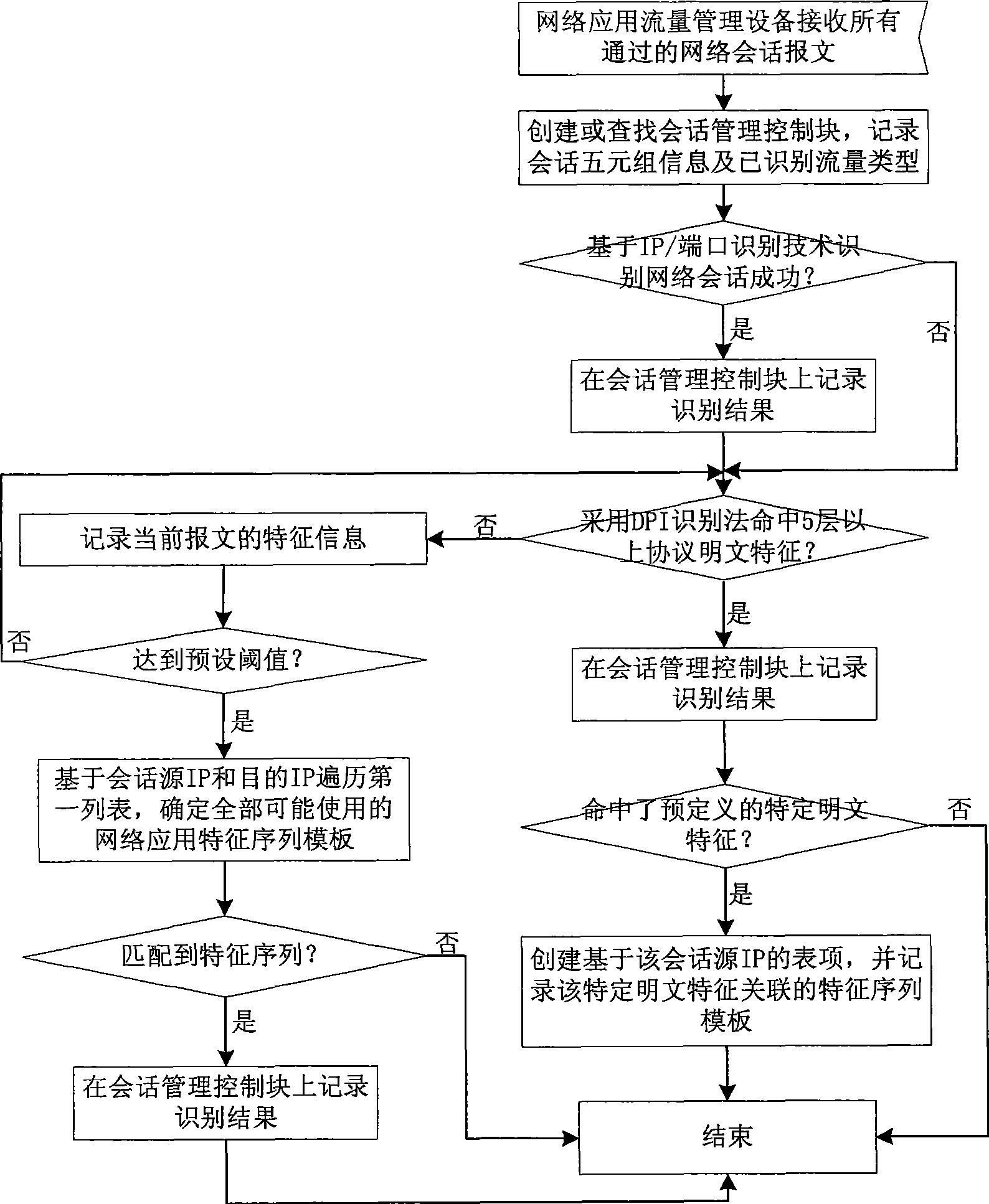
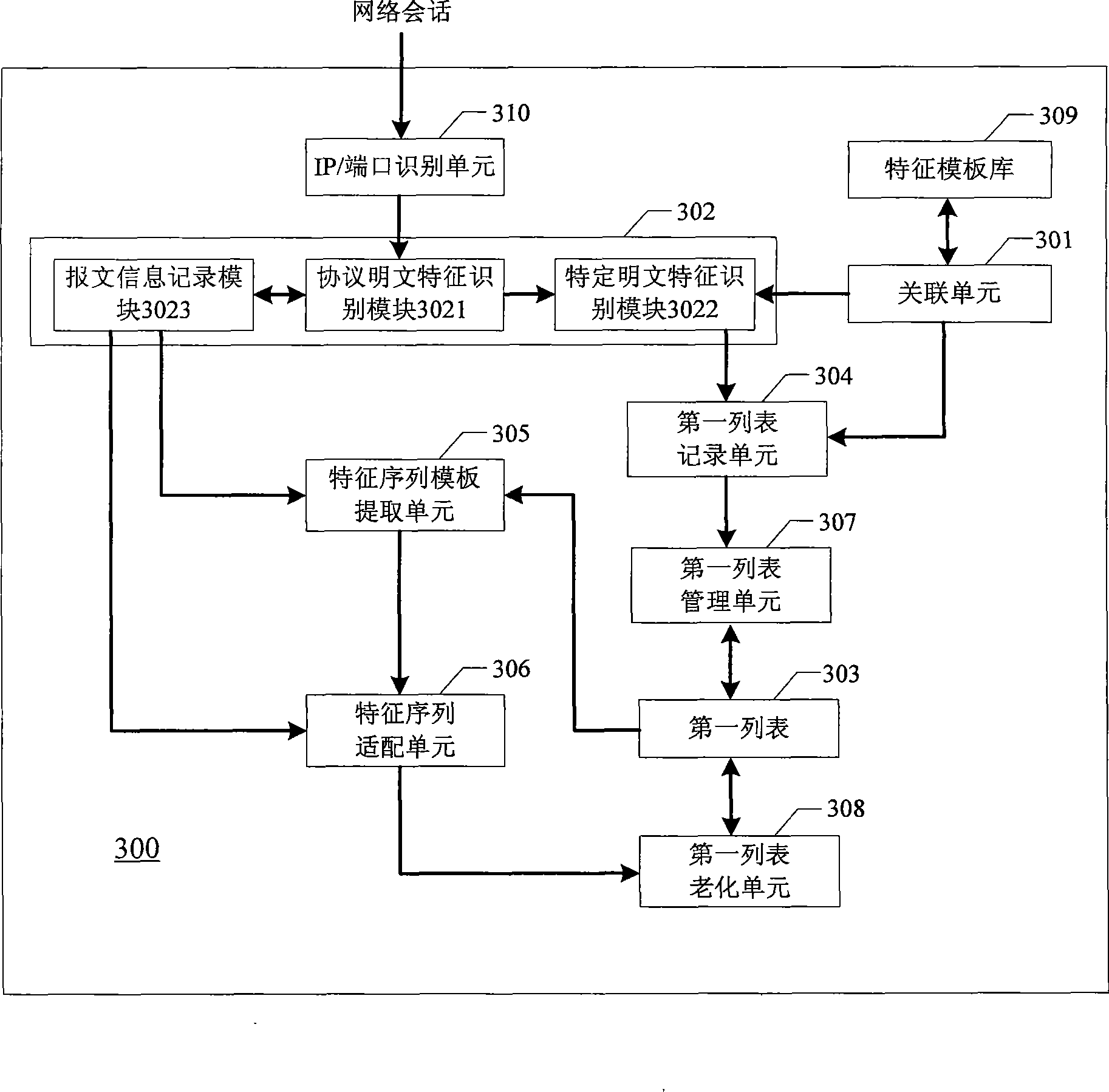
Network application flow recognition method and apparatus and network application flow management apparatus
InactiveCN101505276ALimit application trafficImprove recognition efficiencyData switching networksReporting rateFlow management
The invention discloses a network application traffic identification method, a network application traffic identification device and network application traffic management equipment. The method comprises the following steps of: associating a characteristic sequence template of known network application and corresponding specific plaintext characteristics; taking a source IP of network session as a key value to record the characteristic sequence template which is identified by DPI and is associated with the specific plaintext characteristics into a first list; and for network session which fails to be identified by the prior art, recording characteristic information of a current message, and adapting the characteristic information to the entire characteristic sequence templates under a corresponding key value when a preset threshold is reached to obtain a network application traffic identification result. The network application traffic identification method and the network application traffic identification device can identify network application traffic which fails to be identified by a DPI identification method, improve identification efficiency at the same time, reduce identification cost, and reduce the false report rate of the identification.
Owner:NEW H3C TECH CO LTD
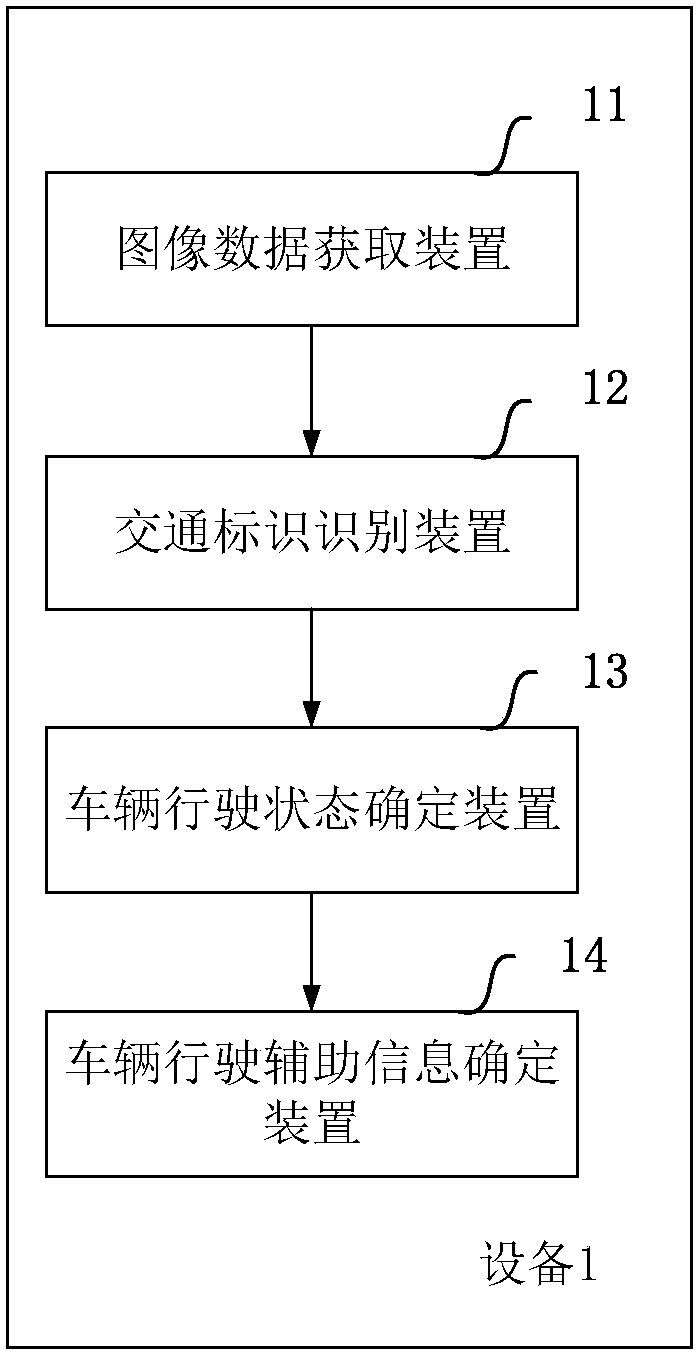
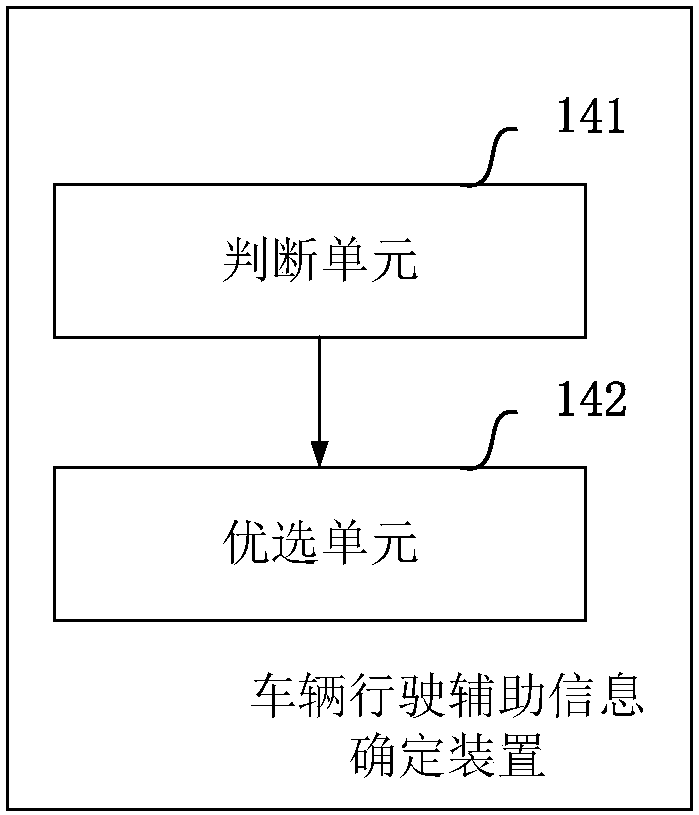
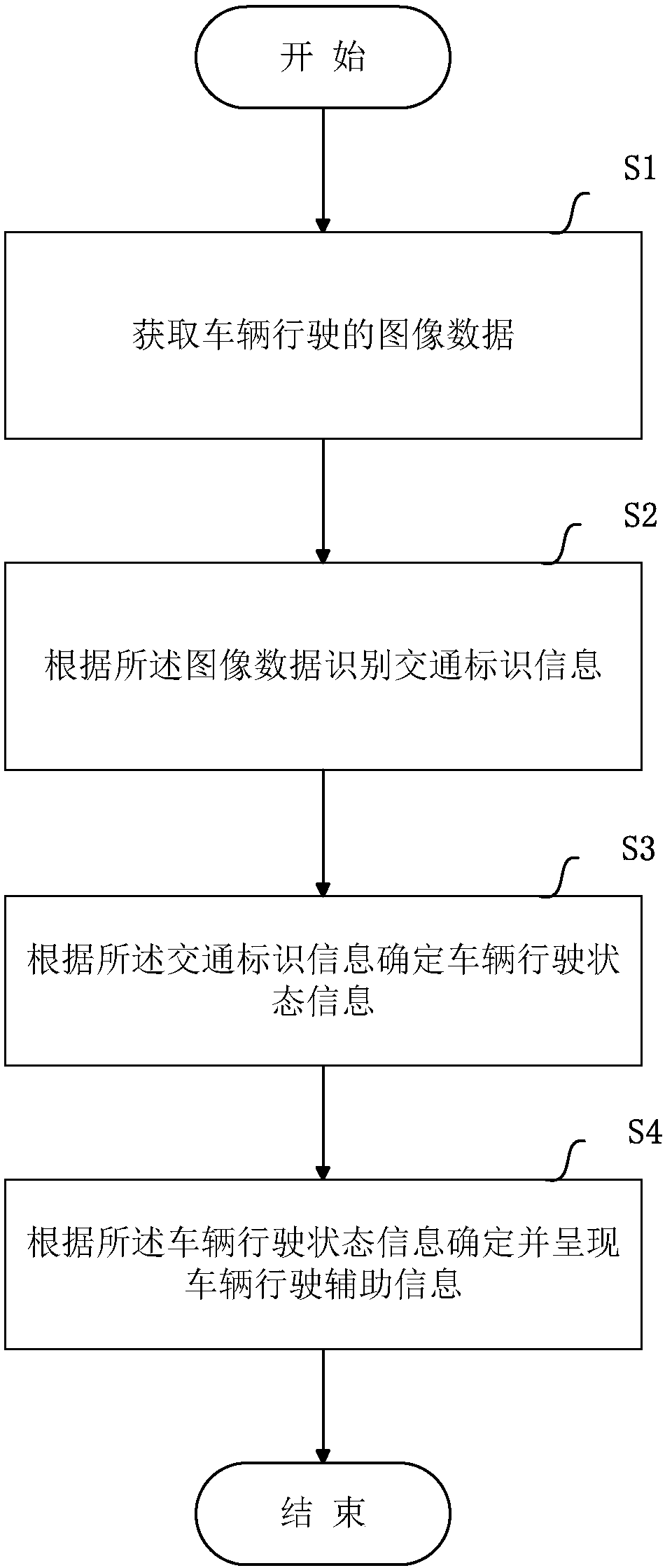
Driving-image-based navigation method and driving-image-based navigation equipment
InactiveCN107560622AReduce the cost of precision navigationAvoid navigation errorsInstruments for road network navigationCharacter and pattern recognitionImage based navigationVehicle driving
A purpose of the present invention is to provide a driving-image-based navigation method and driving-image-based navigation equipment. The driving-image-based navigation method specifically comprises:obtaining vehicle driving image data; identifying traffic identification information according to the image data; determining vehicle driving state information according to the traffic identificationinformation; and determining and presenting vehicle driving auxiliary information according to the vehicle driving state information. Compared to the method in the prior art, the method of the present invention has the following advantage that the traffic identification in the photographed driving environment is identified through the obtained vehicle driving image data, such that the current driving position and the optional route of the vehicle can be determined so as to select the feasible vehicle driving auxiliary information to navigate, and the lane-level navigation can be achieved without the high-precision map or the positioning chip so as to reduce the precision navigation cost.
Owner:70MAI CO LTD
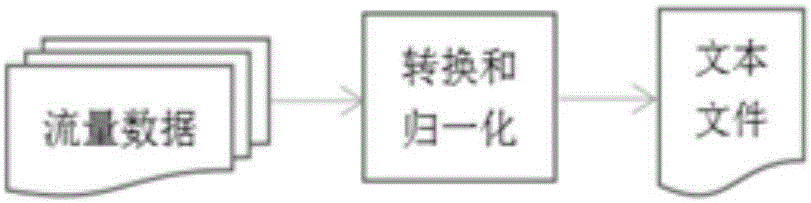
Encrypted traffic identification method and device based on characteristic self-learning
ActiveCN106790019AEfficient identificationWith characteristicsData switching networksTraffic capacityTest input
The invention discloses an encrypted traffic identification method and device based on characteristic self-learning and is used for improving an identification rate of encrypted traffic in the prior art. The method comprises the steps of converting obtained current network traffic data packets into normalized numerical values or normalized gray values; storing the normalized numerical values corresponding to the current network traffic data packets in a text file; or generating a gray image according to the normalized gray values corresponding to the current network traffic data packets and storing the gray image in an image file; taking the text file or the image file as pre-trained test input of an encrypted traffic classifier; and identifying a traffic type of the current network traffic data packets through the encrypted traffic classifier.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
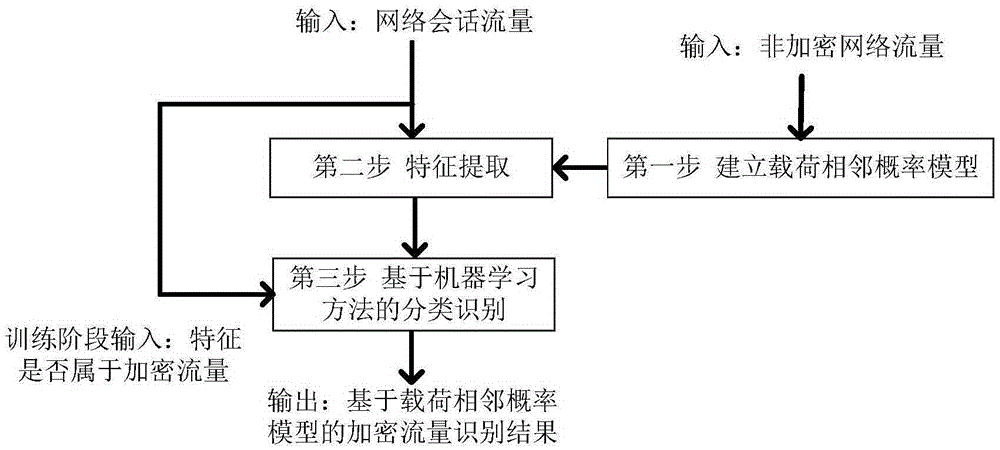
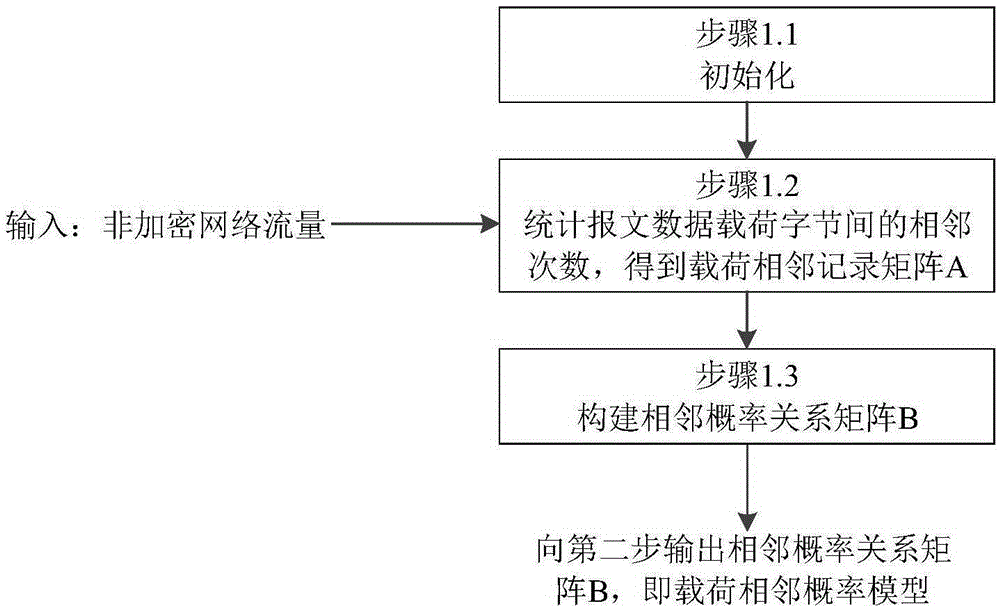
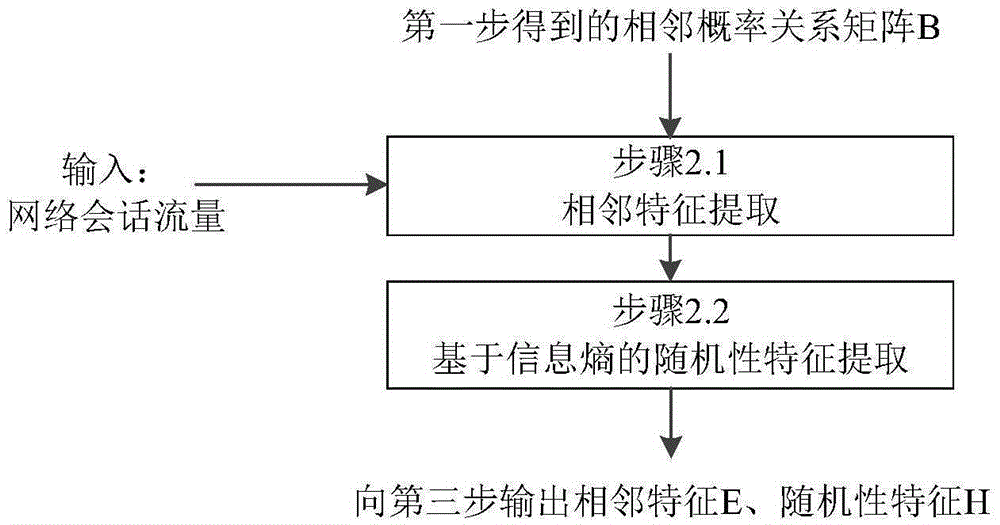
Encrypted traffic identification method based on load adjacent probability model
The invention discloses an encrypted traffic identification method based on a load adjacent probability model, and aims to provide a high-accuracy universal encrypted traffic identification method which utilizes a non-encrypted flow characteristic. The encrypted traffic identification method is technologically characterized by comprising the steps of first step, inputting a non-encrypted network traffic, counting a number of times in which message data load bytes are adjacent, selecting number points for differentiating a high-probability adjacent relationship and a low-probability adjacent relationship, and constructing an adjacent probability relationship model; a second step, inputting a network session traffic, extracting an adjacent characteristic and a random characteristic, and simultaneously acquiring a data random characteristic based on an information entropy; and a third step, transmitting the adjacent characteristics and the random characteristics of the non-encrypted traffic and the encrypted traffic as an input into a classification engine based on machine learning, and furthermore performing encrypted traffic identification based on the adjacent characteristic and the random characteristic of an unknown traffic. Compared with an existing principal encrypted traffic identification method, the encrypted traffic identification method has advantages of realizing universal identification on unknown encrypted protocol traffic and effectively improving identification accuracy.
Owner:NAT UNIV OF DEFENSE TECH
Highway tunnel traffic identification method
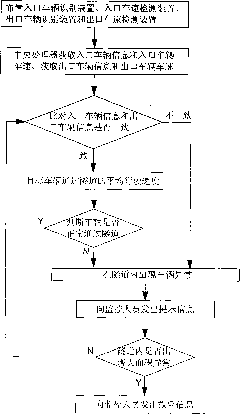
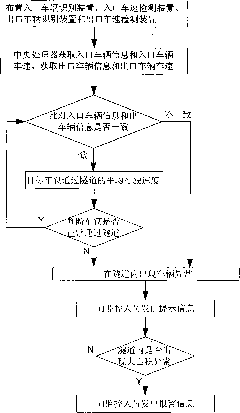
InactiveCN101799985AEasy to layEasy to implementRoad vehicles traffic controlIdentification deviceEngineering
The invention discloses a highway tunnel traffic identification method, which is characterized in that 1. an inlet vehicle identification device and an inlet vehicle speed detection device, an outlet vehicle identification device and an outlet vehicle speed detection device are arranged; 2. a central processing unit obtains the information and speed of the inlet vehicles and the information and speed of the outlet vehicles, and the entering and exiting times of the vehicles are recorded; 3. practical traveling time is calculated; 4. the threshold value range of the traveling time of the vehicles normally and safely passing through the tunnel is determined; 5. abnormal vehicles are determined; 6. abnormal conditions occurring in the tunnel are determined; and 7. the number of the vehicles besieged in the tunnel and average queuing length are calculated and a traffic abnormal event alarming is sent. The invention has the obvious effect that the line laying is simple, implement is easy, cost is low, and real-time monitoring is carried out aiming to the highway tunnel traffic conditions so as to facilitate statistic data; and whether the abnormal conditions occur or not can be obtained in time, and the conditions in the tunnel after the abnormal conditions occur can be predicted.
Owner:CHINA MERCHANTS CHONGQING COMM RES & DESIGN INST
Method for recognizing flux based on characteristic library
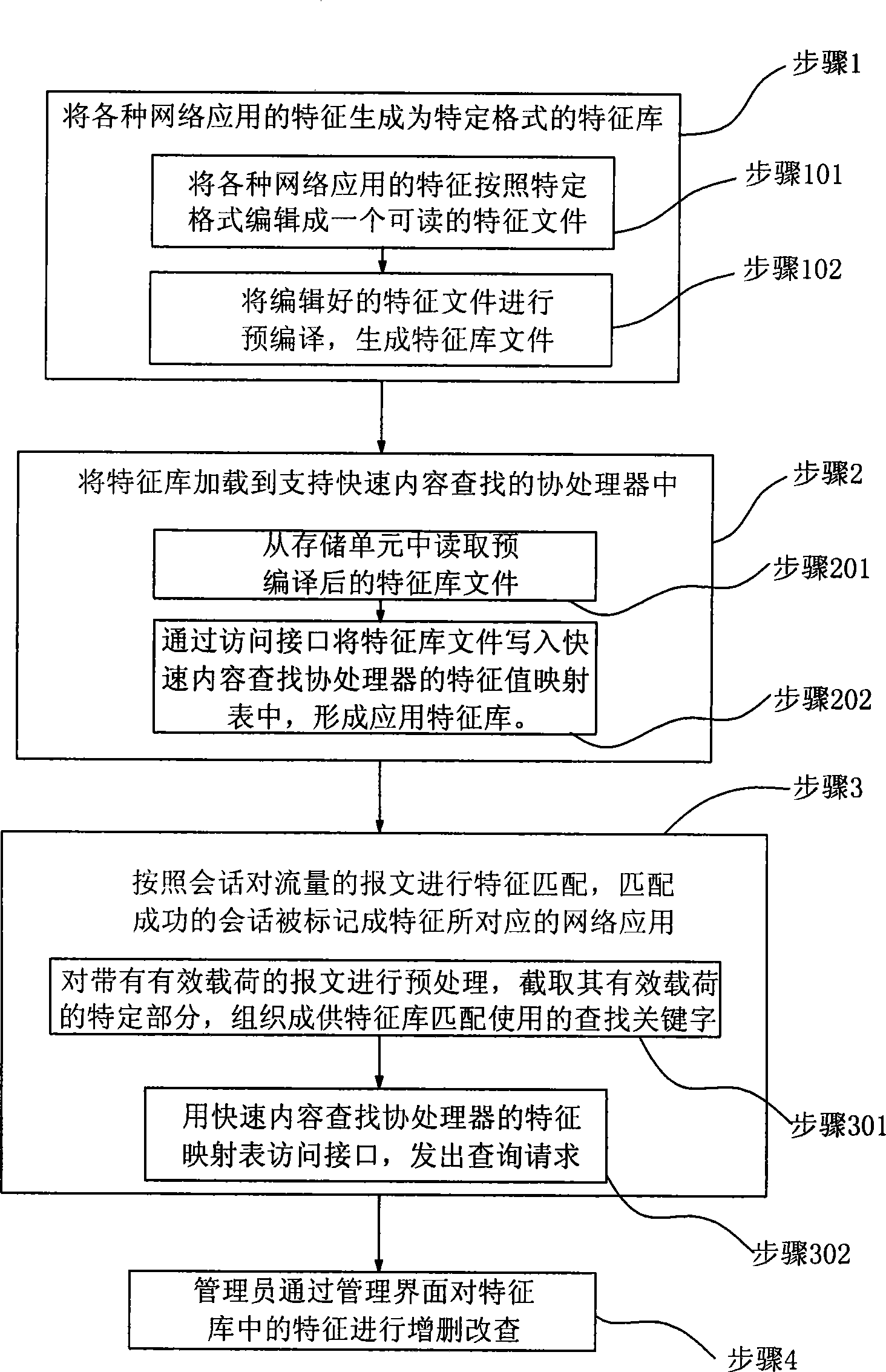
InactiveCN101442489AImprove accuracyImprove performanceData switching networksSpecial data processing applicationsCoprocessorNetwork application
The invention discloses a traffic identification method based on a feature library, which comprises the following steps: the generation of the feature library, the loading of the initialized feature library, traffic identification of the feature library, and on-line maintenance of the feature library. A network application protocol can configure a plurality of feature value descriptions, and features can be concurrently matched in a coprocessor which supports quick content lookup, so the traffic identification method based on the feature library not only effectively improves the accuracy of the traffic identification, but also improves the performance of the traffic identification. A manager can browse each application in the feature library, modify the name of each application, and add or delete each application through a management interface through management interface; for each application in the feature library, the manager can edit any existing feature string and can add or delete the feature string; and all the modification to the feature library can be loaded to the coprocessor which supports the quick content lookup in a real-time mode after the manager confirms, thereby obtaining effective improvement on the expansibility of the traffic identification.
Owner:合肥昊特信息科技有限公司
A traffic state recognition method at intersections based on floating car data
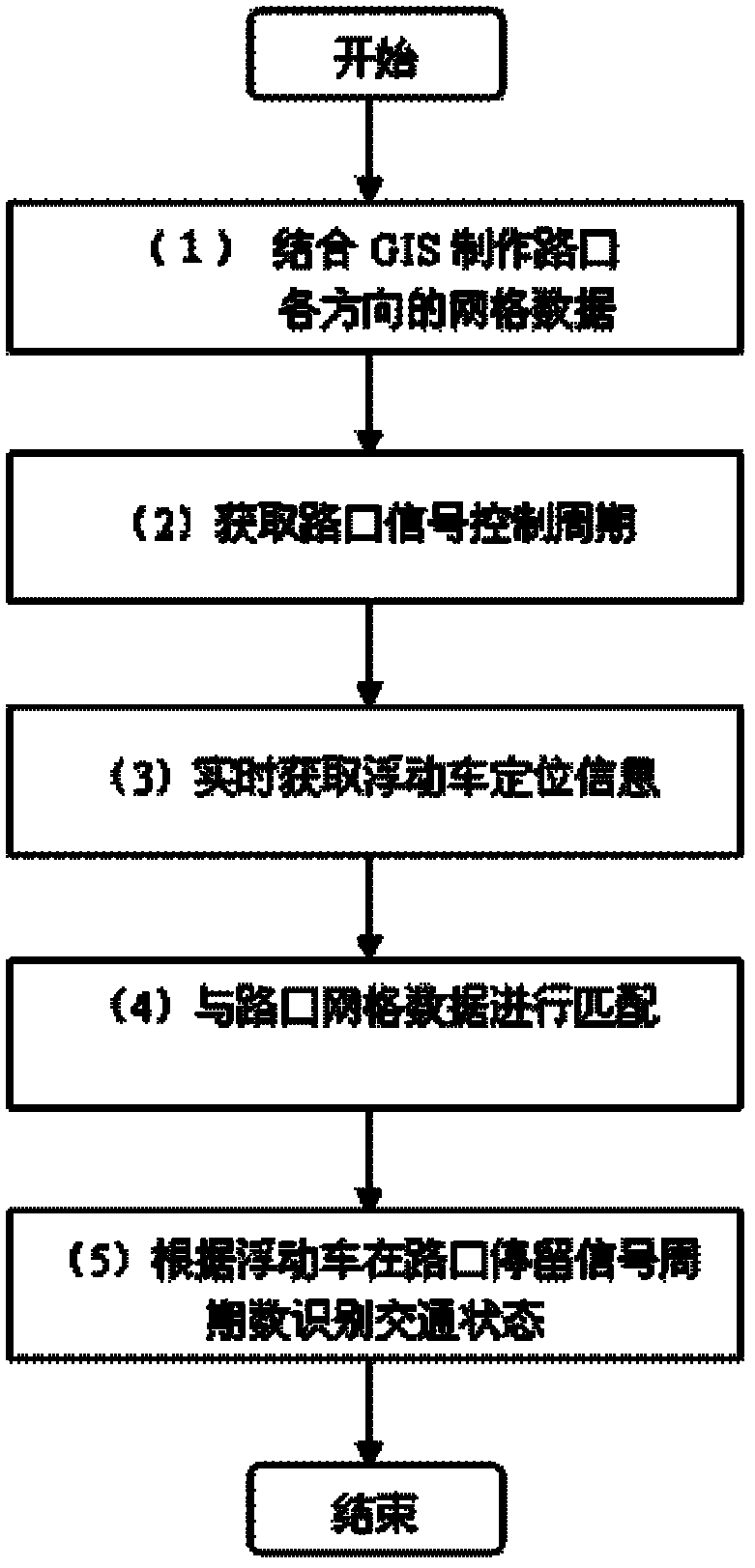
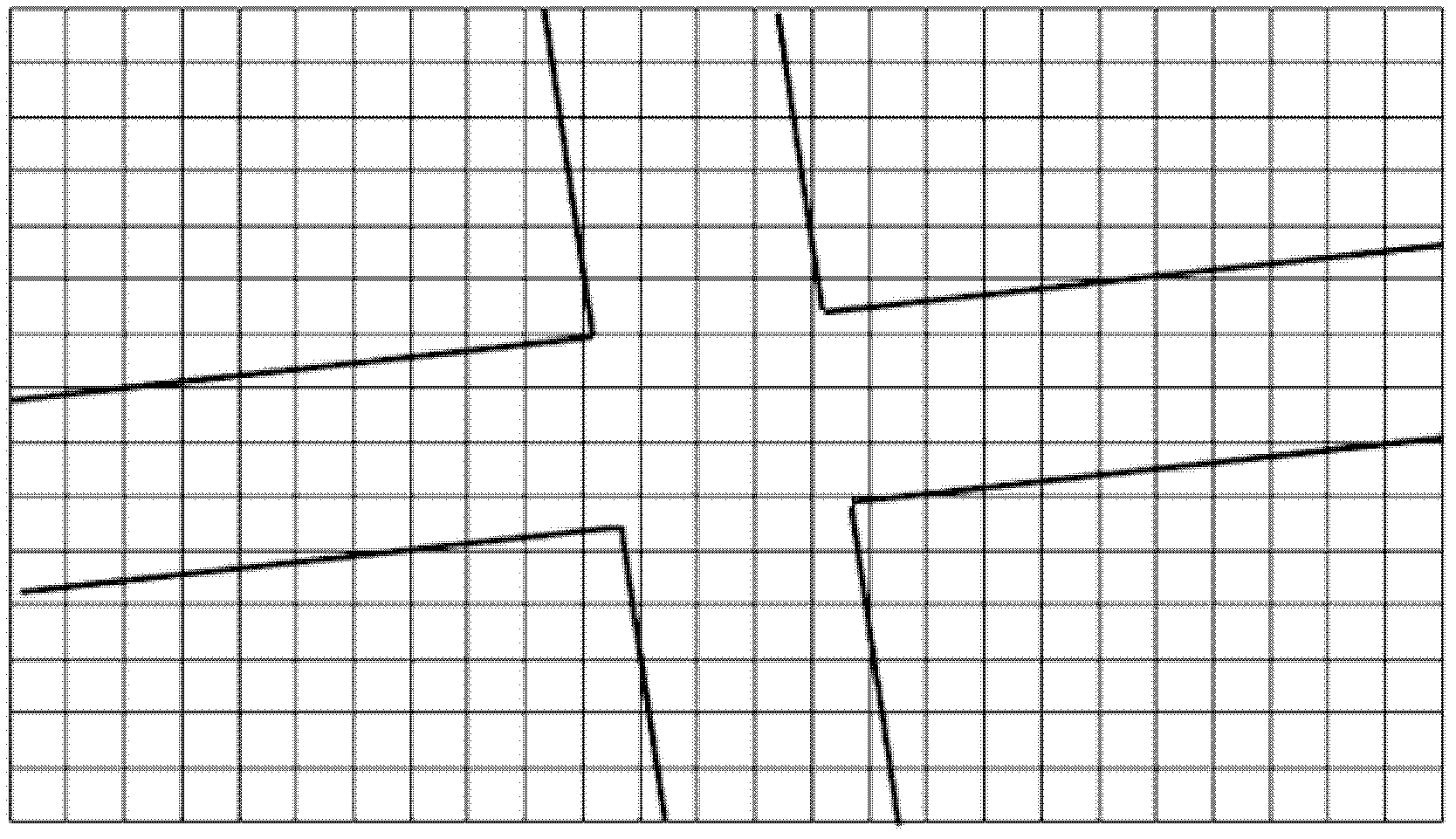
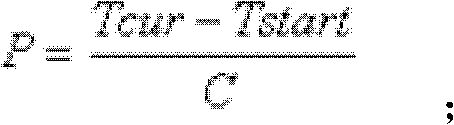
ActiveCN102280031AReal-time perception of traffic statusNo delayDetection of traffic movementTraffic signalSimulation
The present invention discloses a crossing traffic state recognition method based on floating car data. By introducing the duration of the control period of a crossing traffic signal, the factor that the floating car data is affected by a crossing signal lamp is considered when a traffic recognition is carried out; fast match of a detected area is realized by utilizing a GIS grid, and the crossing traffic state is sensed realtimely. Therefore, the crossing traffic state recognition method based on floating car data can realtimely sensor the traffic state, with no delay, and the recognition accuracy is high.
Owner:NANJING LES INFORMATION TECH
Encrypted network traffic identification method based on deep neural network
ActiveCN110247930AEasy extractionGood multi-category recognition accuracyNeural architecturesTransmissionTraffic capacityData set
The invention relates to an encrypted network traffic identification method based on a deep neural network, and belongs to the technical field of deep learning, network service security and traffic identification. The encrypted network traffic identification method based on the deep neural network comprises the steps of 1, obtaining an offline data set based on capture, deployment and extraction operations, and generating a training set and a test set; 2, building a deep neural network model; 3, performing data reading, model training and parameter optimization: inputting the offline data set into a deep neural network model for training and iteration until the accuracy reaches the standard, and then stopping training; 4, establishing and deploying an online network flow capture platform, and capturing an online data set; and 5, performing online network flow identification to obtain an identification result. According to the method, high-dimensional features of the flow data can be better extracted; compared with an existing deep neural network, the method has the advantages of better multi-classification recognition accuracy, lower false positive rate and lower false alarm rate, and ensures the high efficiency of encrypted data flow on-line recognition.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
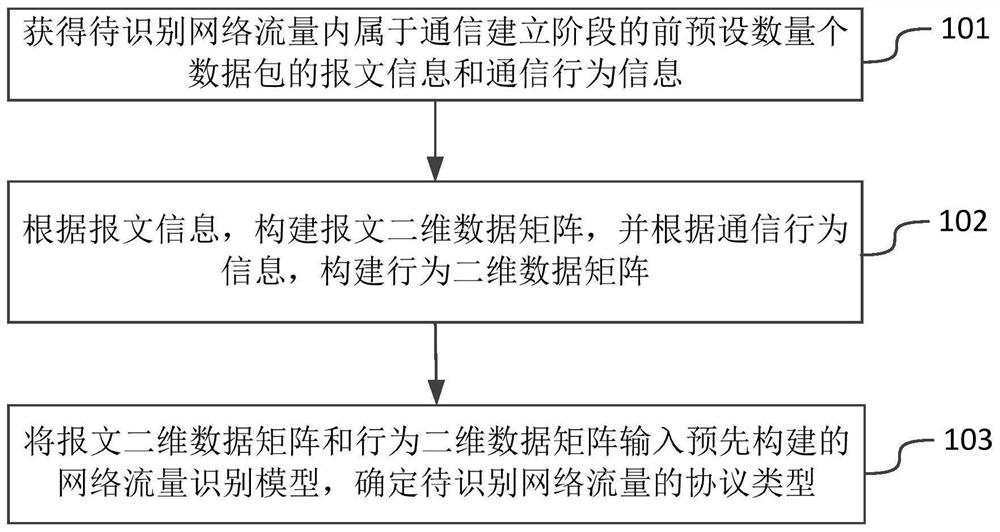
Network encrypted traffic identification method and device based on deep learning
ActiveCN112003870AAdapt to the structural formOvercoming manual extraction of packetsNeural architecturesTransmissionData packInternet traffic
The embodiment of the invention provides a network encrypted traffic identification method and device based on deep learning, relates to the technical field of network security, and can improve the accuracy and efficiency of network encrypted traffic identification. The method comprises the steps of obtaining message information and communication behavior information of a preset number of data packets belonging to a communication establishment stage in to-be-identified network traffic; constructing a message two-dimensional data matrix according to the message information, and constructing a behavior two-dimensional data matrix according to the communication behavior information; and inputting the message two-dimensional data matrix and the behavior two-dimensional data matrix into a network traffic identification model, and determining the protocol type of the to-be-identified network traffic, wherein the network flow identification model is a sample two-dimensional data matrix passing through the sample network flow and a protocol type label corresponding to the sample network flow; and training the deep learning network to obtain a model, wherein the sample two-dimensional datamatrix comprises a sample message two-dimensional data matrix and a sample behavior two-dimensional data matrix corresponding to the sample network flow.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
Learned profiles for malicious encrypted network traffic identification
A method for identifying malicious encrypted network traffic associated with a malware software component communicating via a network, the method comprising: defining, for the malware, a portion of network traffic including a plurality of contiguous bytes occurring at a predefined offset in a network communication of the malware; extracting the defined portion of network traffic for each of a plurality of disparate network connections for the malware; evaluating a metric for each byte in each extracted portion; representing each extracted portion in a matrix data structure as an image of pixels wherein each pixel corresponds to a byte of the extracted portion; training a neural network based on the images for the extracted portions such that subsequent network traffic can be classified bythe neural network to identify malicious network traffic associated with the malware based on an image generated to represent the defined portion of the subsequent network traffic.
Owner:BRITISH TELECOMM PLC
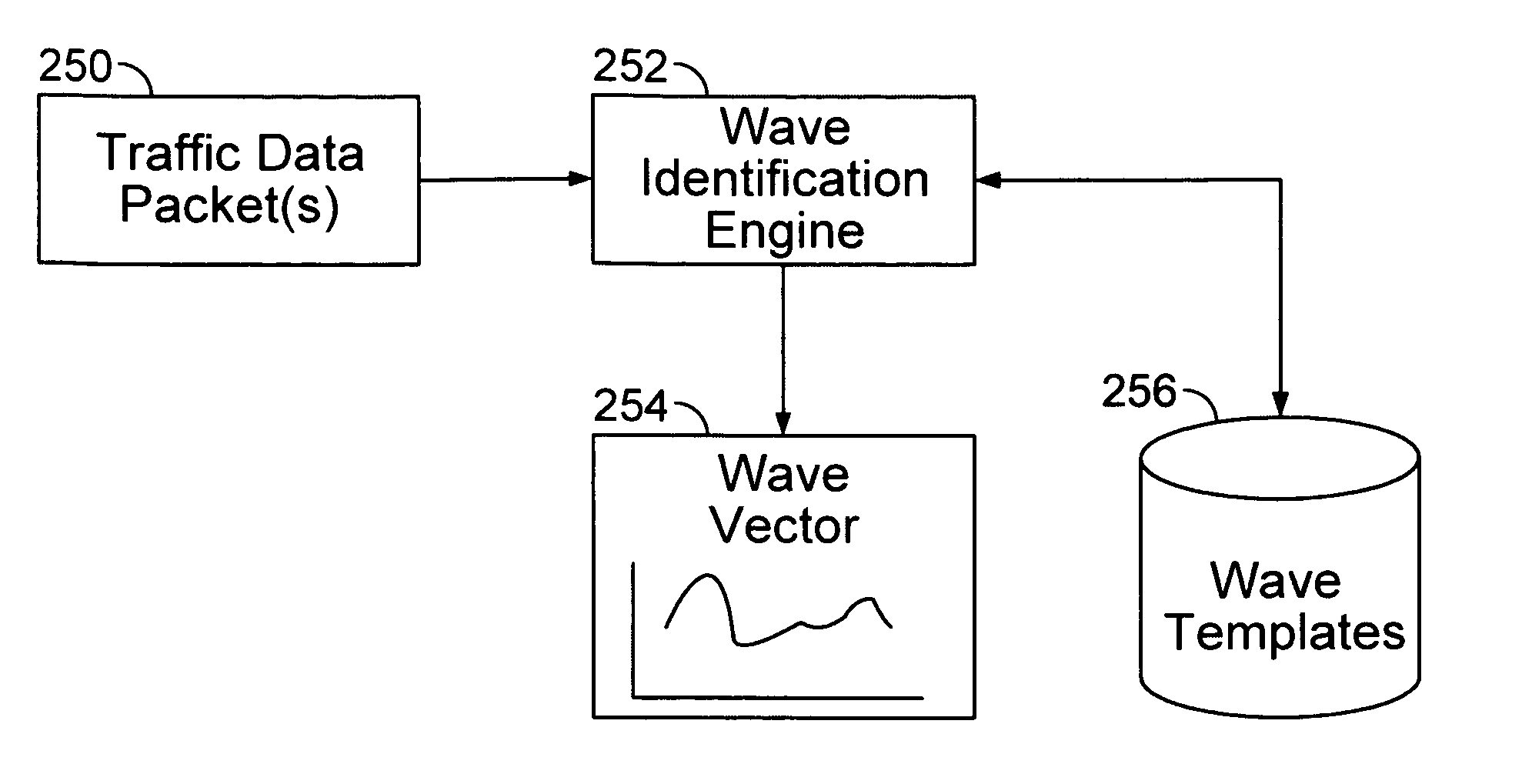
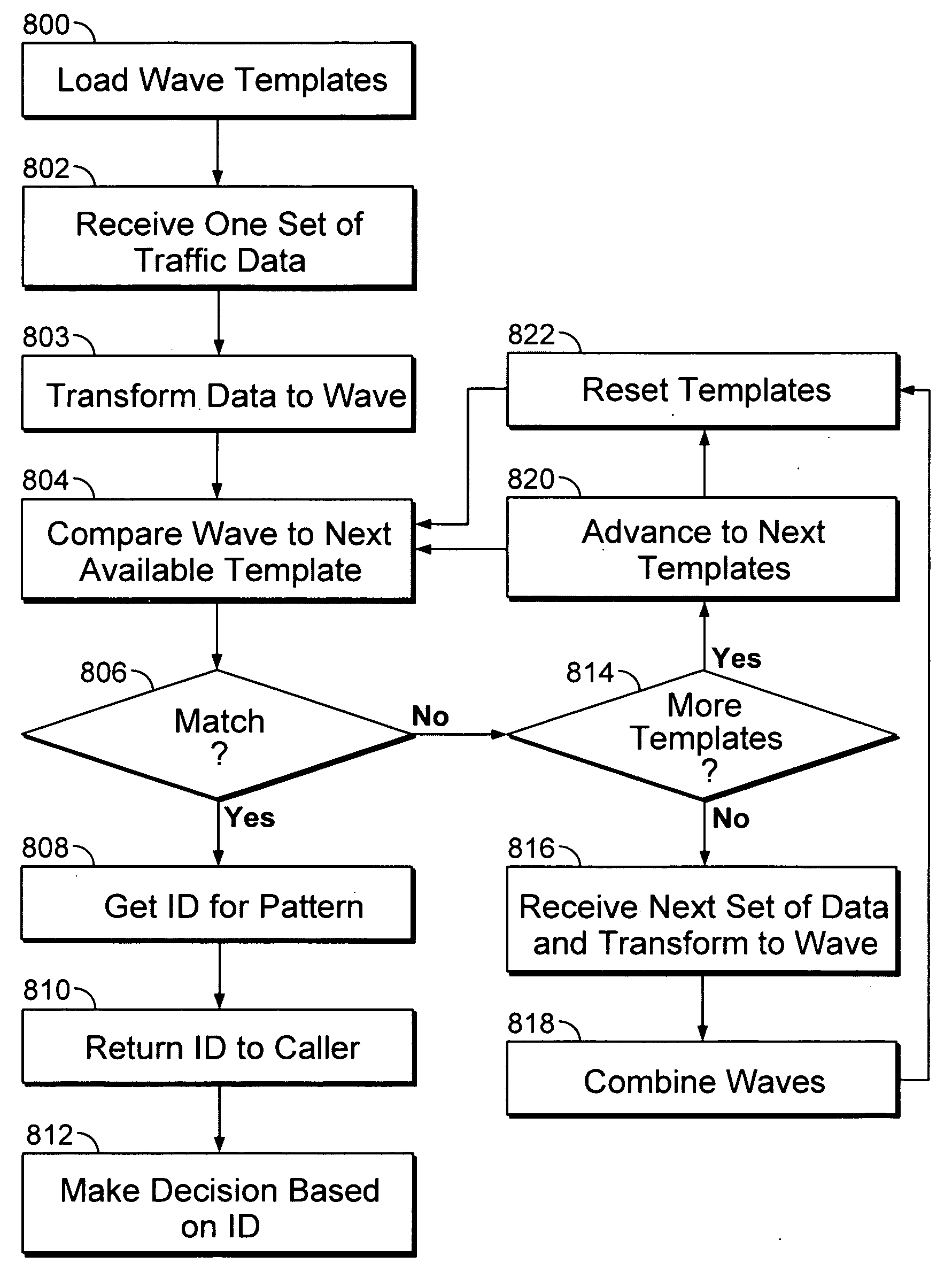
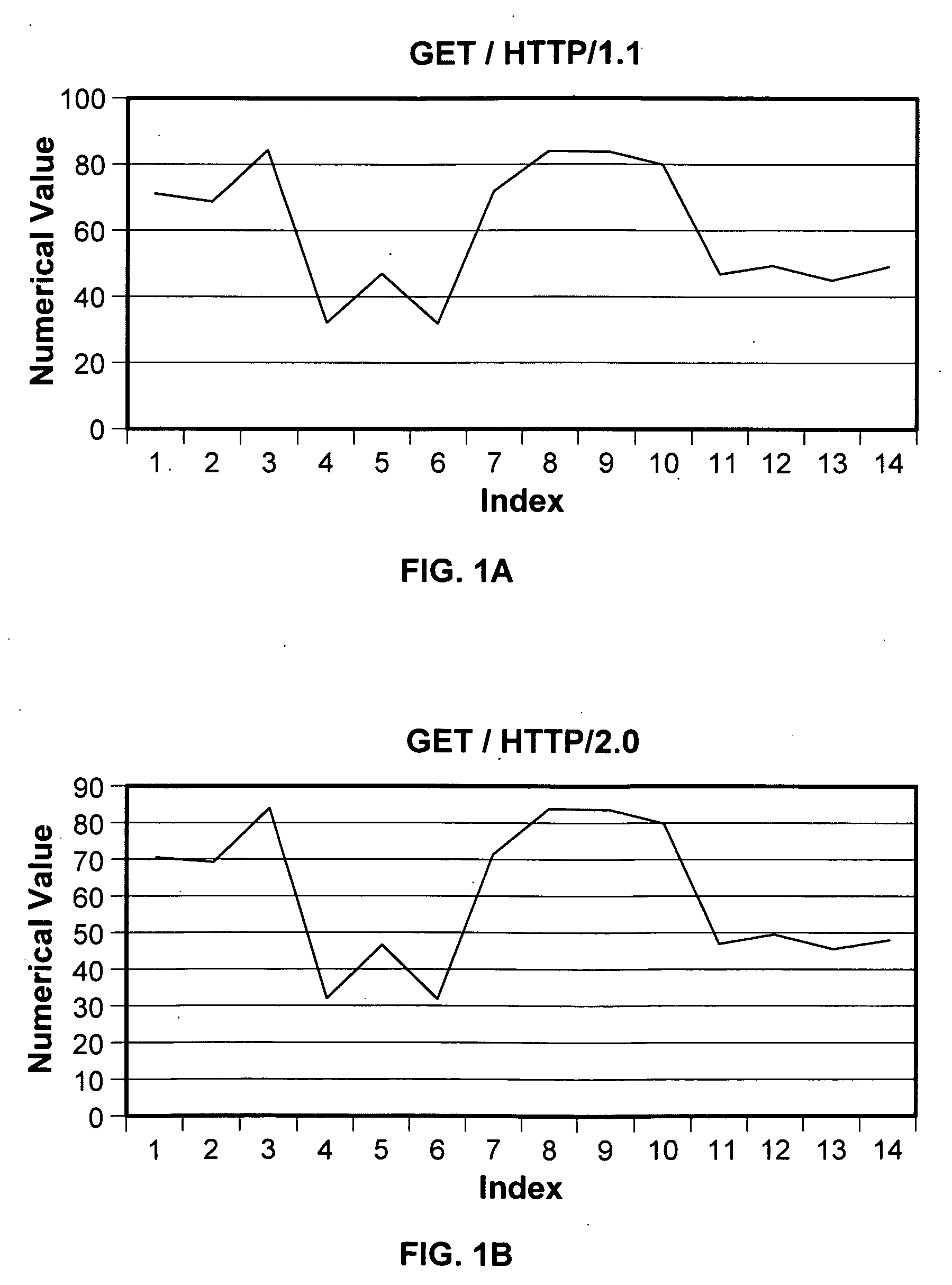
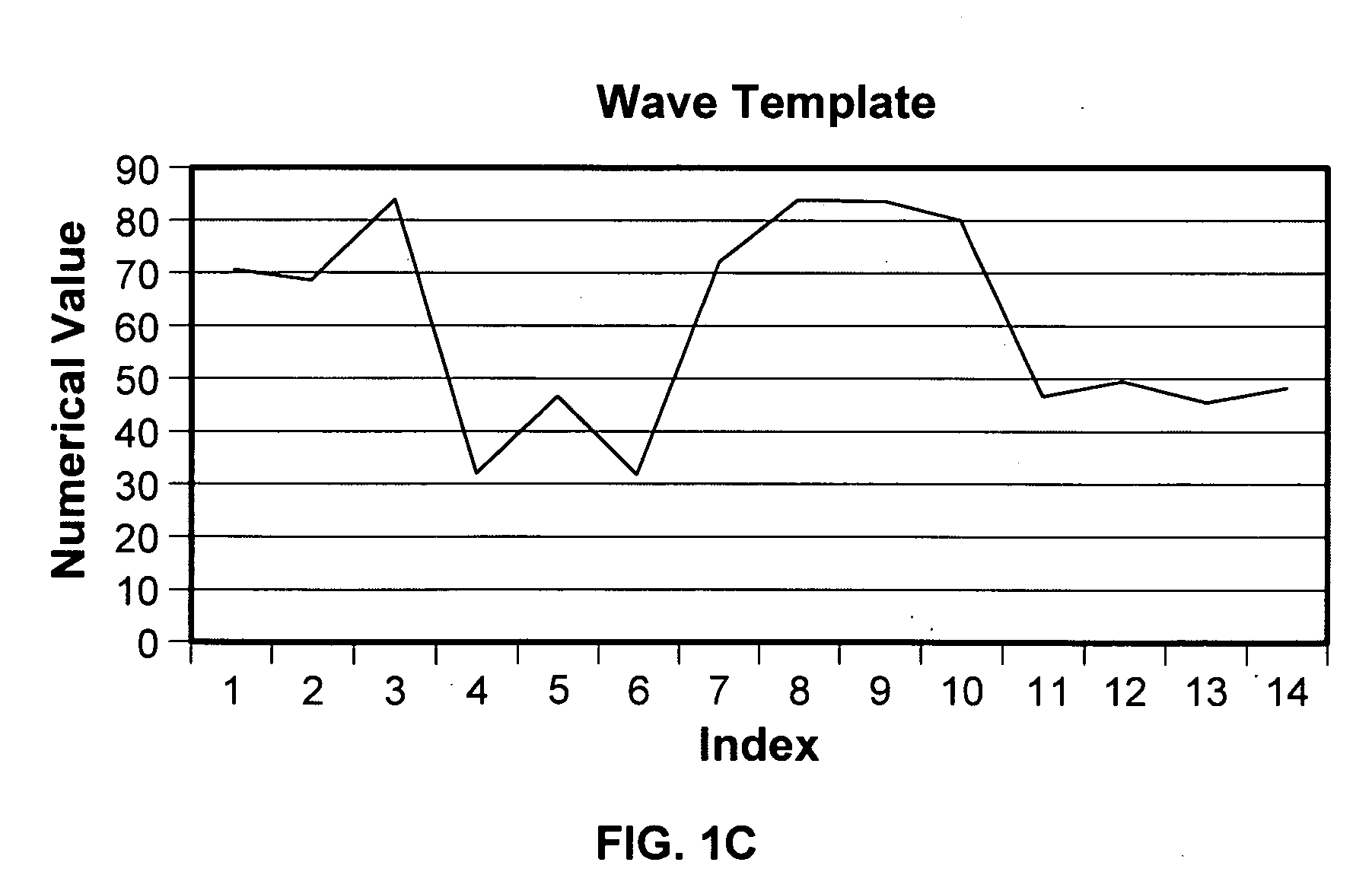
Network traffic identification by waveform analysis
A technique is disclosed for identifying network traffic. The traffic data is converted into a wave vector. The wave vector is compared with a wave template. It is then determined whether the wave vector is substantially similar to the wave template.
Owner:CA TECH INC
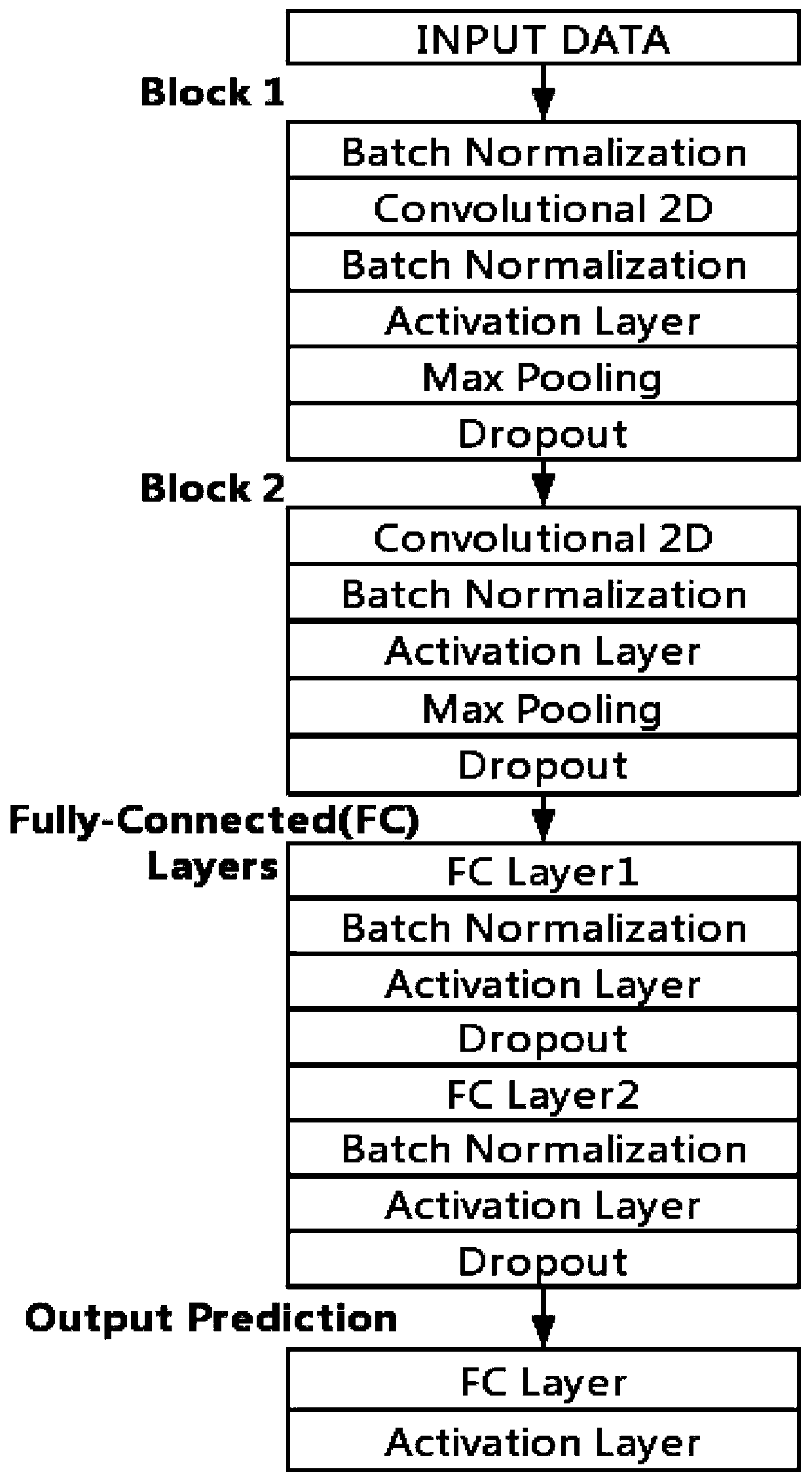
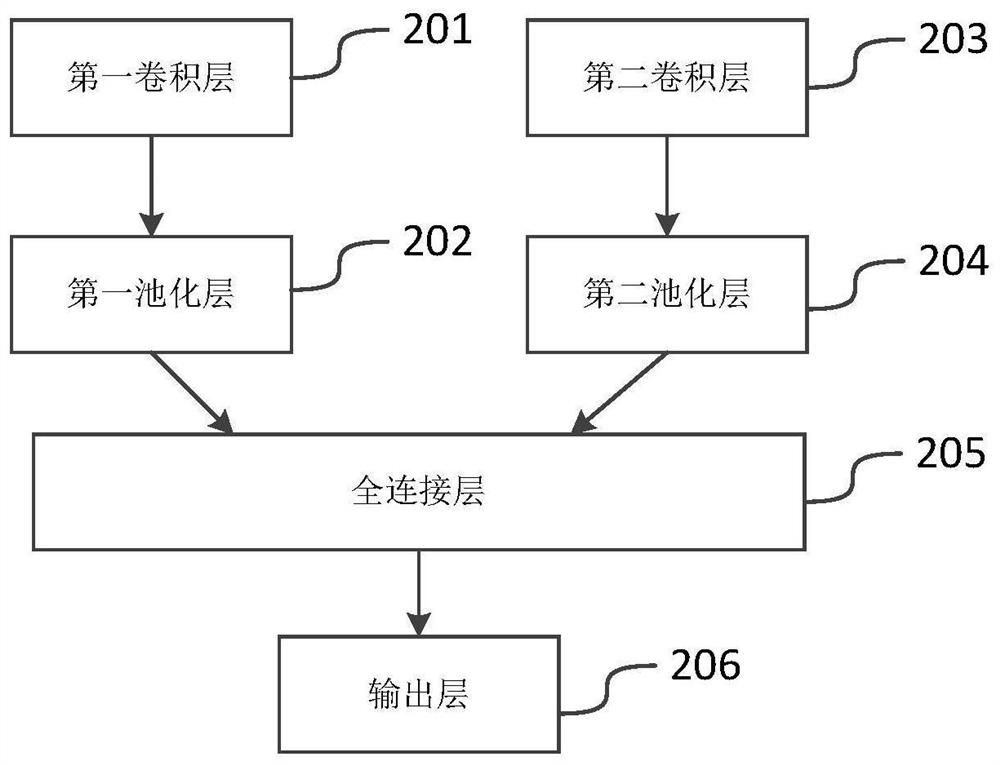
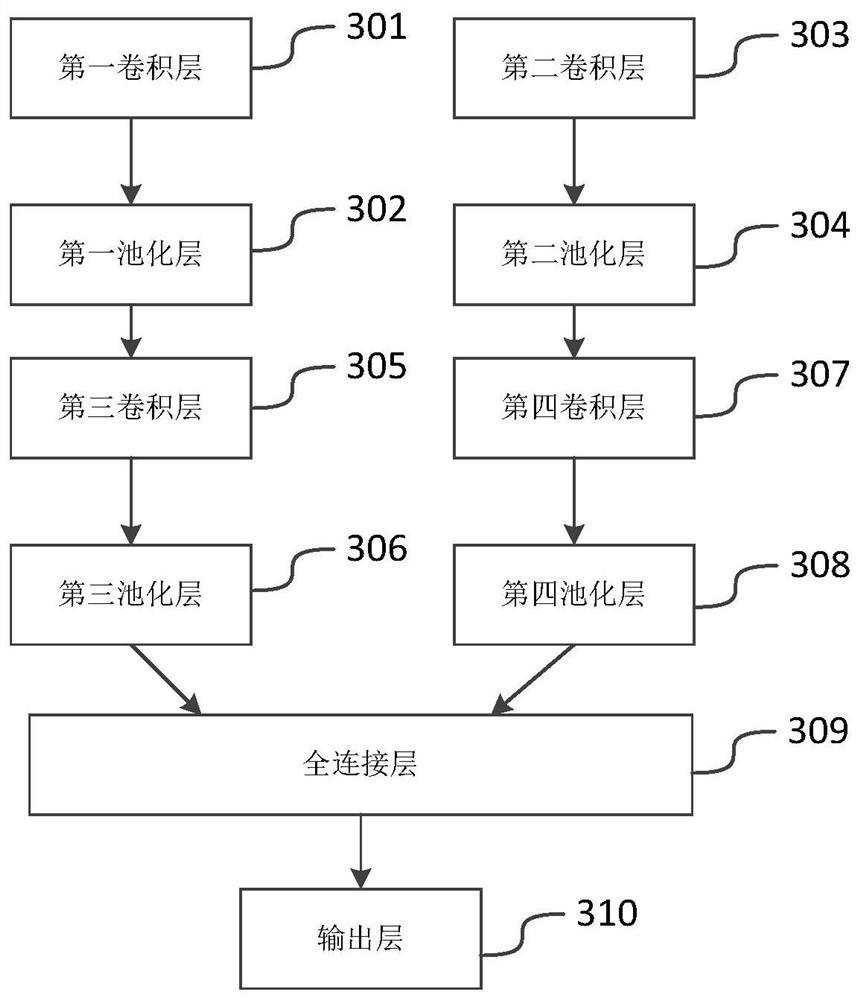
Traffic identification and feature extraction method based on deep learning
PendingCN111860628ARealize self-optimizationWeb data indexingCharacter and pattern recognitionData packData set
The invention discloses a traffic identification and feature extraction method based on deep learning. The method comprises the steps of data packet capture, data set establishment, convolutional neural network establishment, model training, model self-study and optimization, and network data packet feature extraction. According to the method, the good performance of the convolutional neural network in data processing application is fully utilized, and the convolutional neural network which is rapid and accurate and is suitable for network message processing is designed; and flow classification prediction is carried out by utilizing the trained model, data packets with insufficient probabilities of prediction errors and classification under a correct type in a result are selected out and re-fused into a training set training model, thereby realizing autonomous optimization of the model. According to the method, a class activation mapping method is utilized to carry out feature extraction on the traffic, extracted feature fields can enable people to know the features of data packets of specific types, and the feature fields not only can be used for a traditional DPI technology, butalso are suitable for application scenarios where DPI traffic classification has been deployed.
Owner:上海乘安科技集团有限公司
Malicious encrypted network traffic identification using fourier transform
ActiveCN107646190ATransmissionSpecial data processing applicationsTraffic capacityFast Fourier transform
A method for identifying malicious encrypted network traffic communicated via a network between a first and second computer system, the method comprising: monitoring network traffic over the network to detect a network connection as a new network connection; identifying characteristics of the network connection to determine a protocol of the network connection; retrieving a definition of a portionof network traffic for a network connection based on the determined protocol; evaluating Fourier transform coefficient values for each of a plurality of bytes in a portion of network traffic of the new network connection based on the retrieved definition; and comparing the evaluated coefficient values with a dictionary of one or more reference sets of coefficients, each of the one or more reference sets of coefficients being associated with a portion of network traffic of a malicious encrypted network connection, so as to determine if malicious encrypted network traffic is communicated over the network connection.
Owner:BRITISH TELECOMM PLC
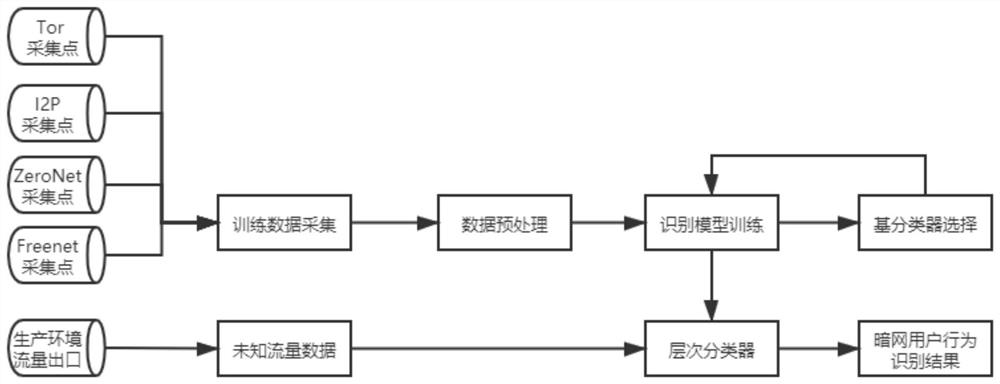
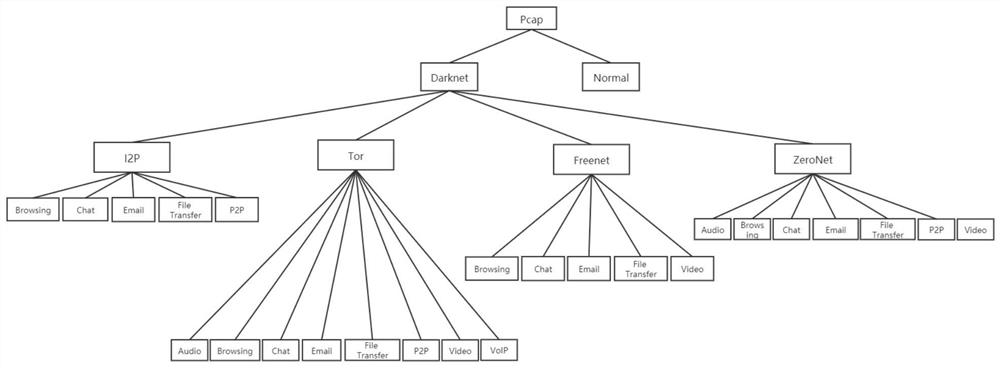
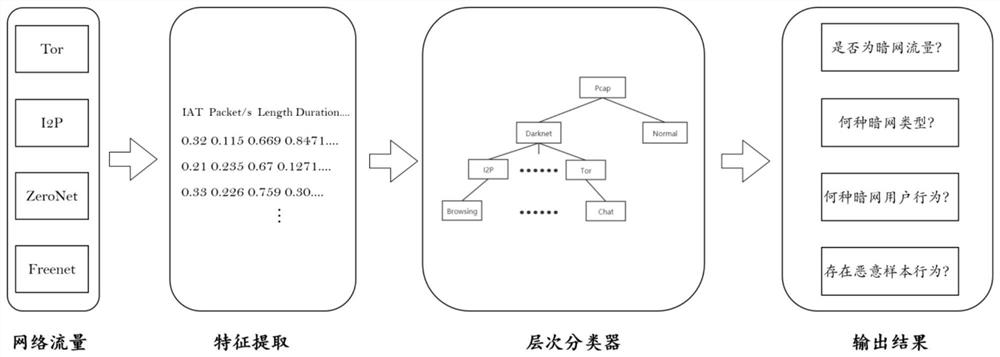
Dark network user behavior detection method and system based on network traffic
The invention discloses a dark network user behavior detection method and system based on network traffic, and relates to the field of computer network security. Analysis and research are carried outon user behaviors in four mainstream dark networks of Tor, I2P, ZeroNet and Freenet. User behaviors are divided into eight classes, and a hierarchical classification model is trained by establishing adark network data collection environment, collecting real dark network flow data, extracting flow characteristics in the data. According to the method, model training is carried out by adopting a hierarchical classification method, and the method is good in performance in dark network traffic identification scenes of four dark network types and 25 user behaviors and has relatively high accuracy.Meanwhile, the base classifiers in the hierarchical classifiers are independent of each other and do not interfere with each other, so that the method and the system have good expandability and can adapt to dark network environments with different ages. The system can be deployed at a flow outlet of an actual production environment and linked with an IDS and a firewall, and a solution is providedfor control and traceability of a dark network.
Owner:SHANGHAI JIAO TONG UNIV
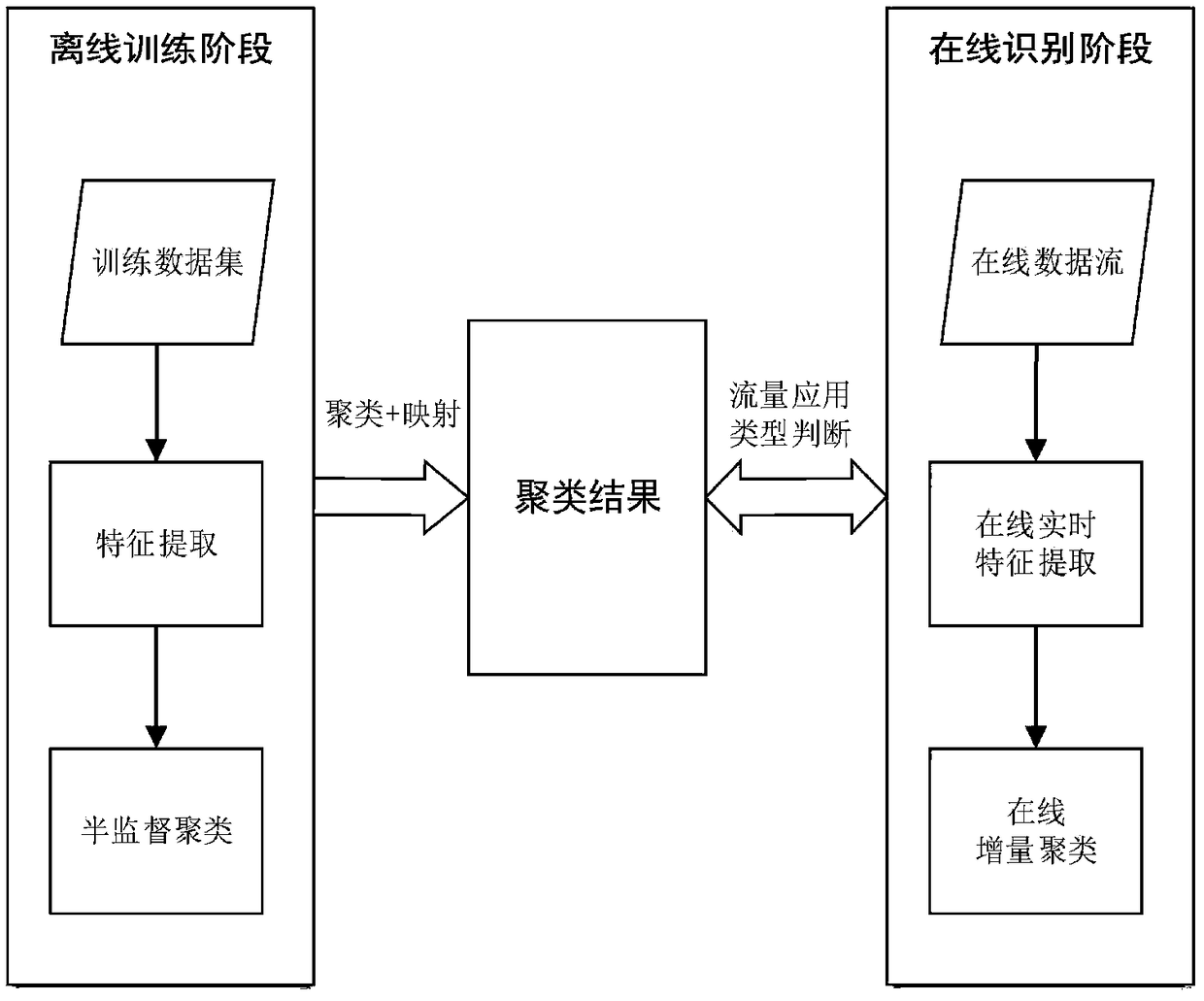
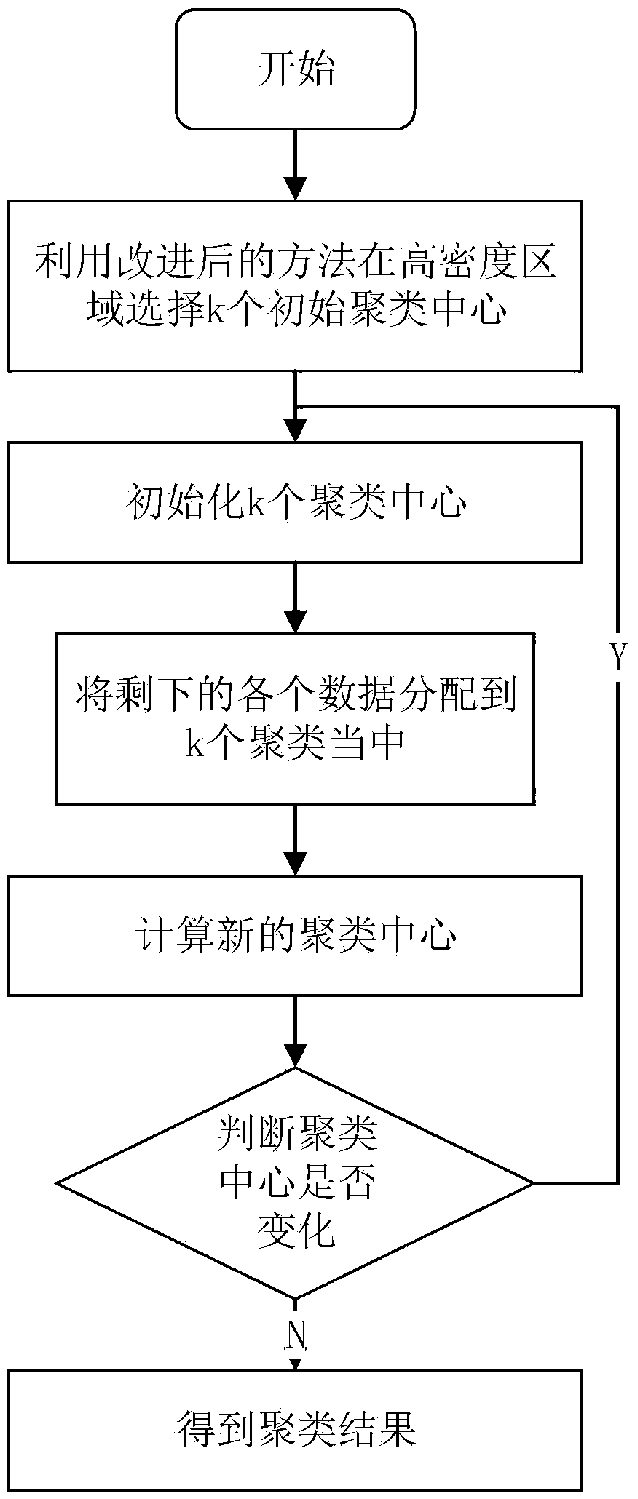
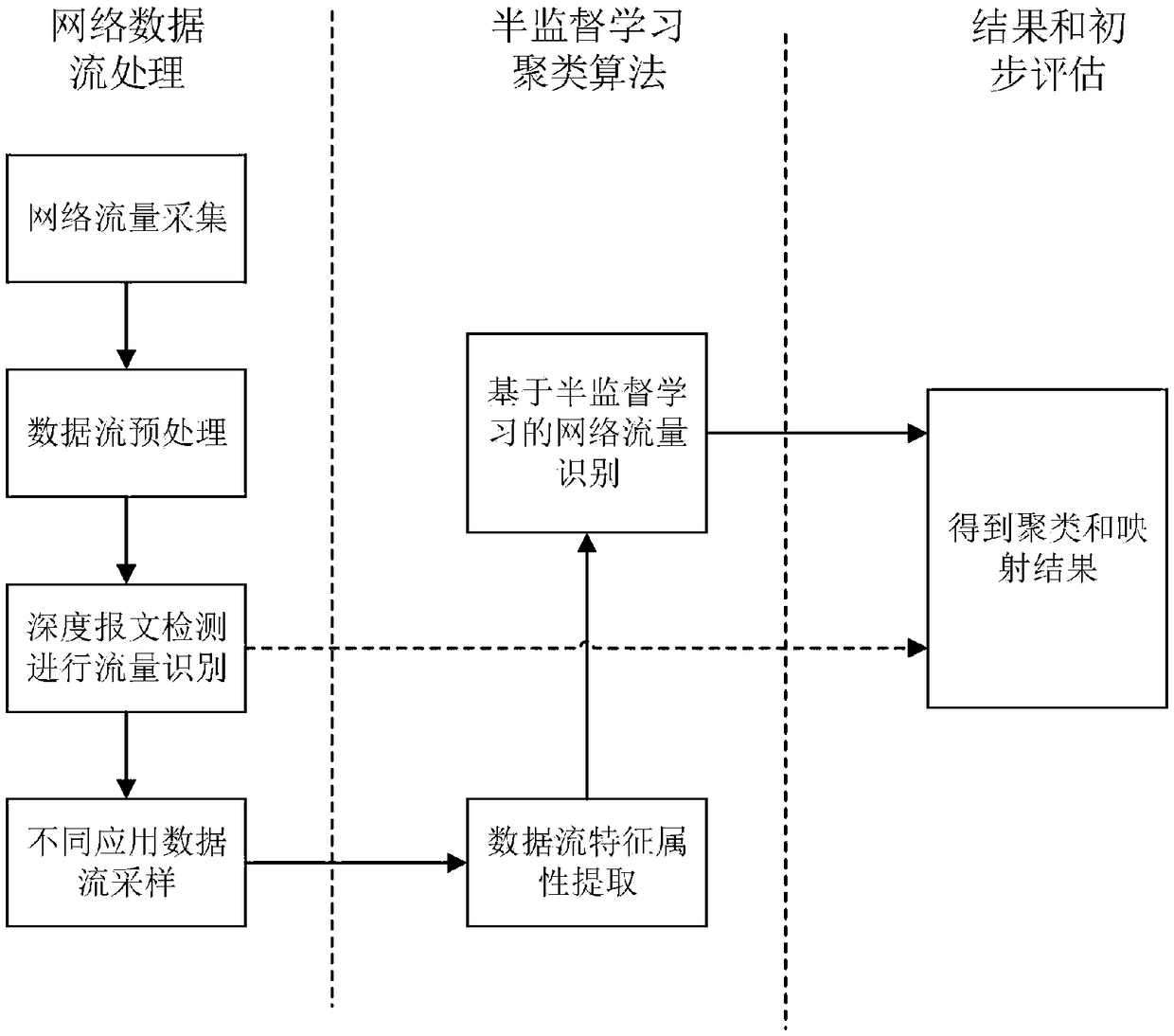
An online traffic identification method based on incremental clustering algorithm
InactiveCN109067612ARealize online identificationImprove real-time performanceCharacter and pattern recognitionData switching networksCluster algorithmData stream
The invention belongs to the network technical field, in particular to an online traffic identification method based on an incremental clustering algorithm. The method includes: an offline recognitionstage and an online recognition stage, wherein in the offline recognition stage,a semi-supervised learning flow algorithm based on an improved K-means algorithm is used to perform preliminary clustering and mapping work on the prepared training data sets, and the data sets which are preliminarily classifiedare obtained; in the online recognition stage,based on the completed clustering and mappingdata sets formed in the offline identification phase, incremental clustering is used to determine the network application type of the newly added data streams online, so as to achieve the purpose oftraffic identification. According to the method,based on machine learning technology, by constructing a suitable recognition model to learn the prepared data, the online traffic can be incrementally clustered in real time, and the preliminary semi-supervised classification can be carried out by combining the prepared training set, which can realize the online recognition of network traffic, and has good real-time performance and high recognition rate.
Owner:HARBIN ENG UNIV
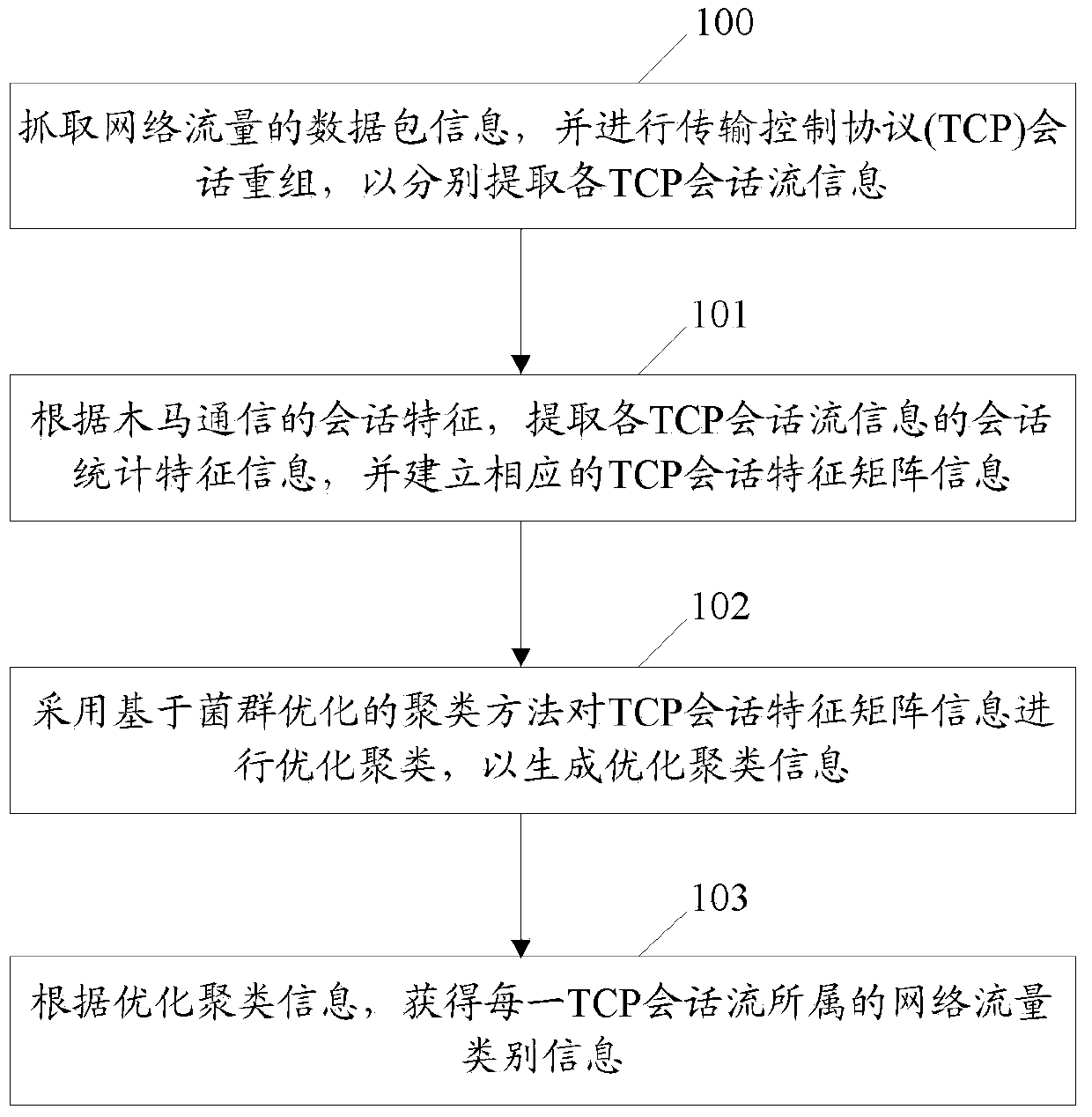
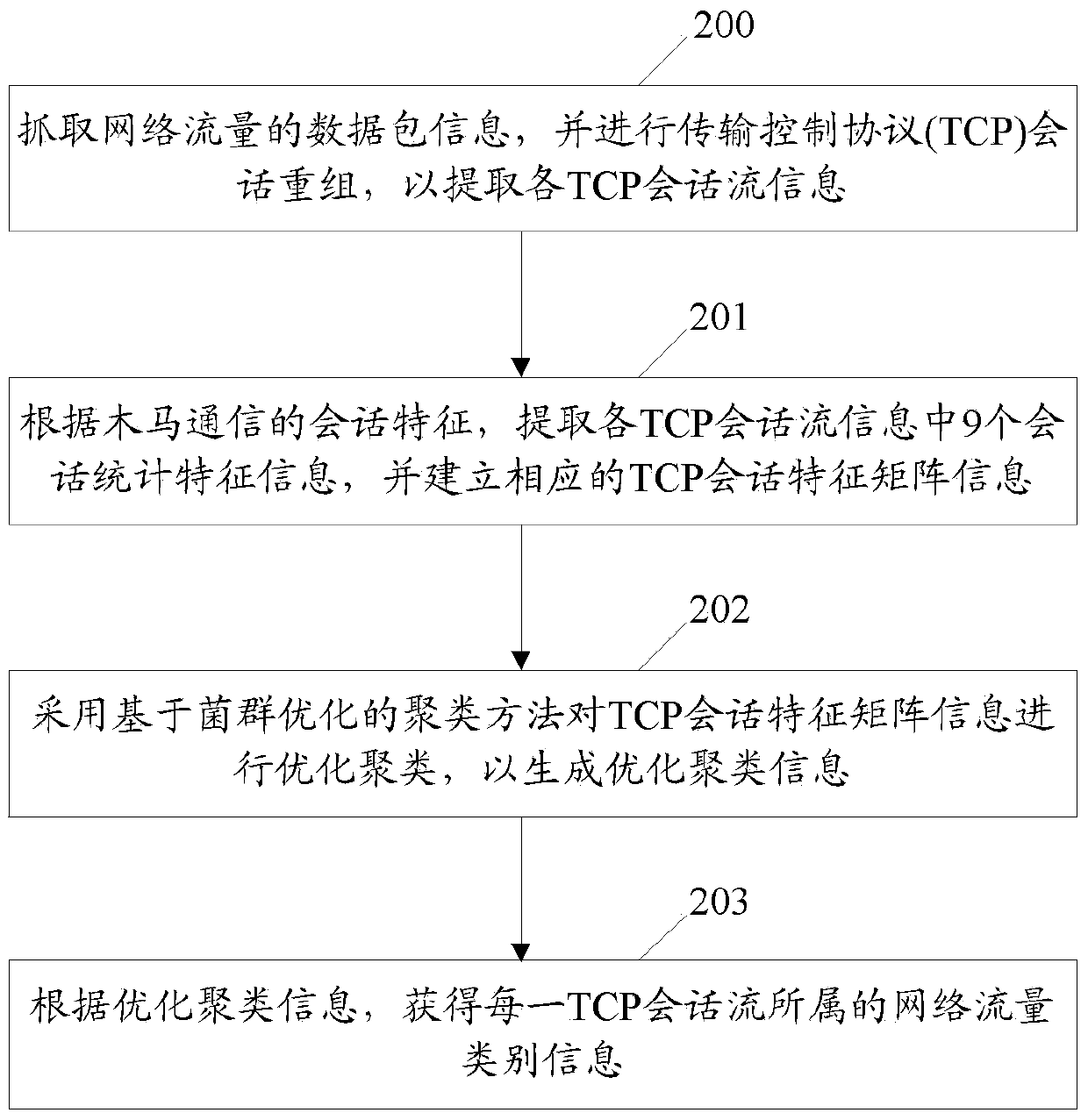
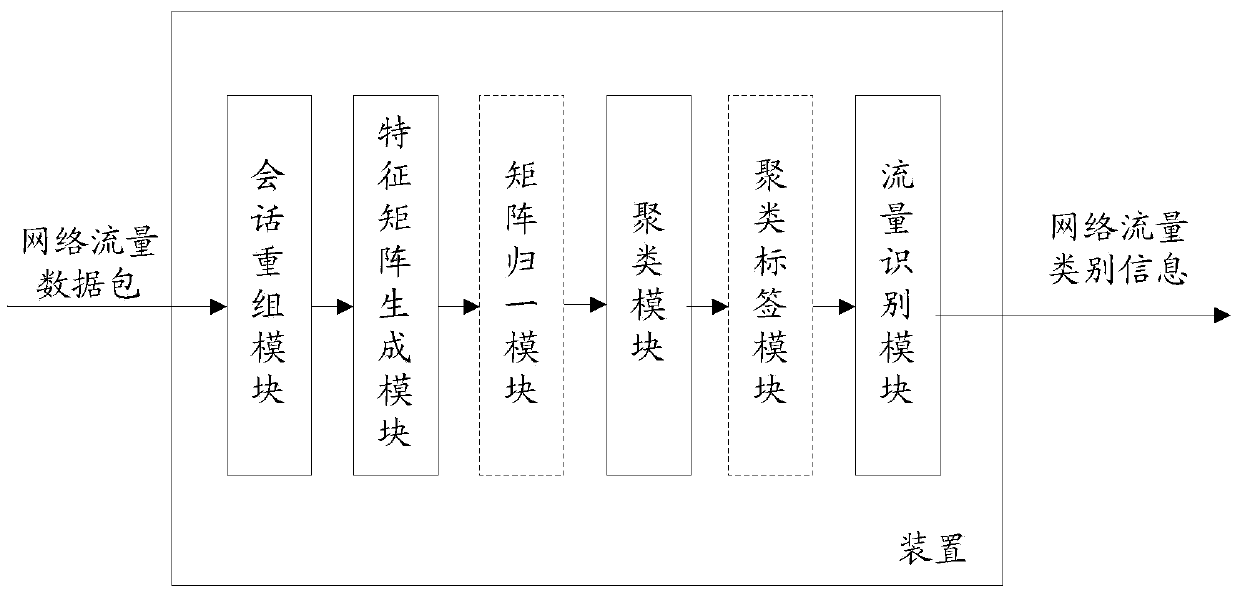
Behavior-detection-based network traffic identification method and device
InactiveCN103701814AData switching networksTraffic capacityProtocol for Carrying Authentication for Network Access
The invention discloses a behavior-detection-based network traffic identification method and a behavior-detection-based network traffic identification device. The method comprises the following steps of capturing data packet information of network traffic, and performing TCP (transmission control protocol) session recombination to extract information of each TCP session stream respectively; extracting information about session statistical characteristics of the information of each TCP session stream according to session characteristics of Trojan communication, and establishing corresponding TCP session characteristic matrix information; optimally clustering the TCP session characteristic matrix information to generate optimally-clustered information by adopting a bacterial foraging optimization-based clustering method; obtaining information about the network traffic type of each TCP session stream according to the optimally-clustered information. According to the method and the device, the TCP session streams are extracted to a data packet of the network traffic, the information about the TCP session statistical characteristics is obtained according to the session characteristics of Trojan communication to generate the TCP session characteristic matrix information, and the bacterial foraging optimization-based clustering method is used for optimally clustering the TCP session characteristic matrix information to obtain the information about the network traffic types of the TCP session streams.
Owner:BEIJING VENUS INFORMATION TECH +1
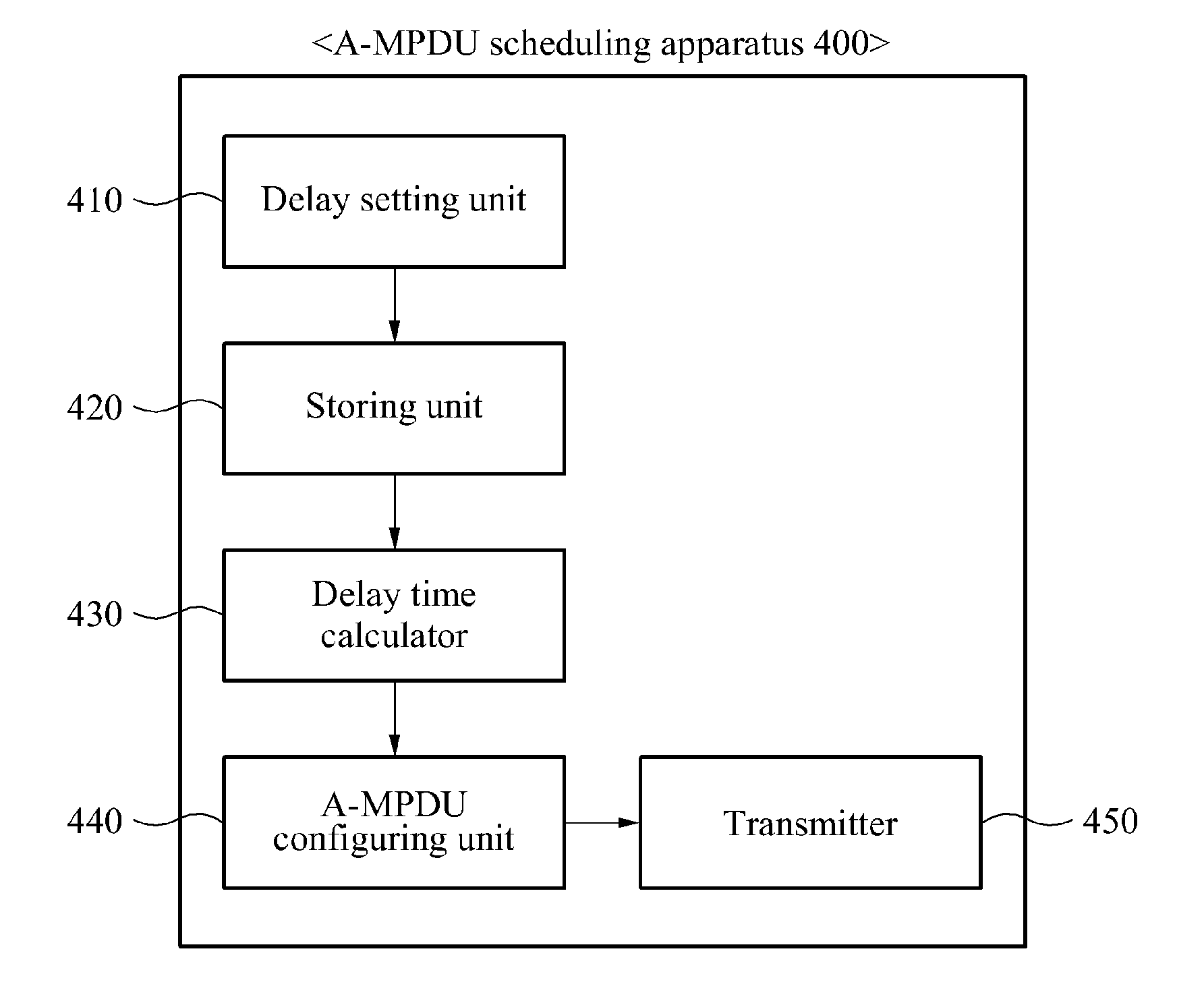
Method and apparatus for efficient aggregation scheduling in wireless local area network (WLAN) system
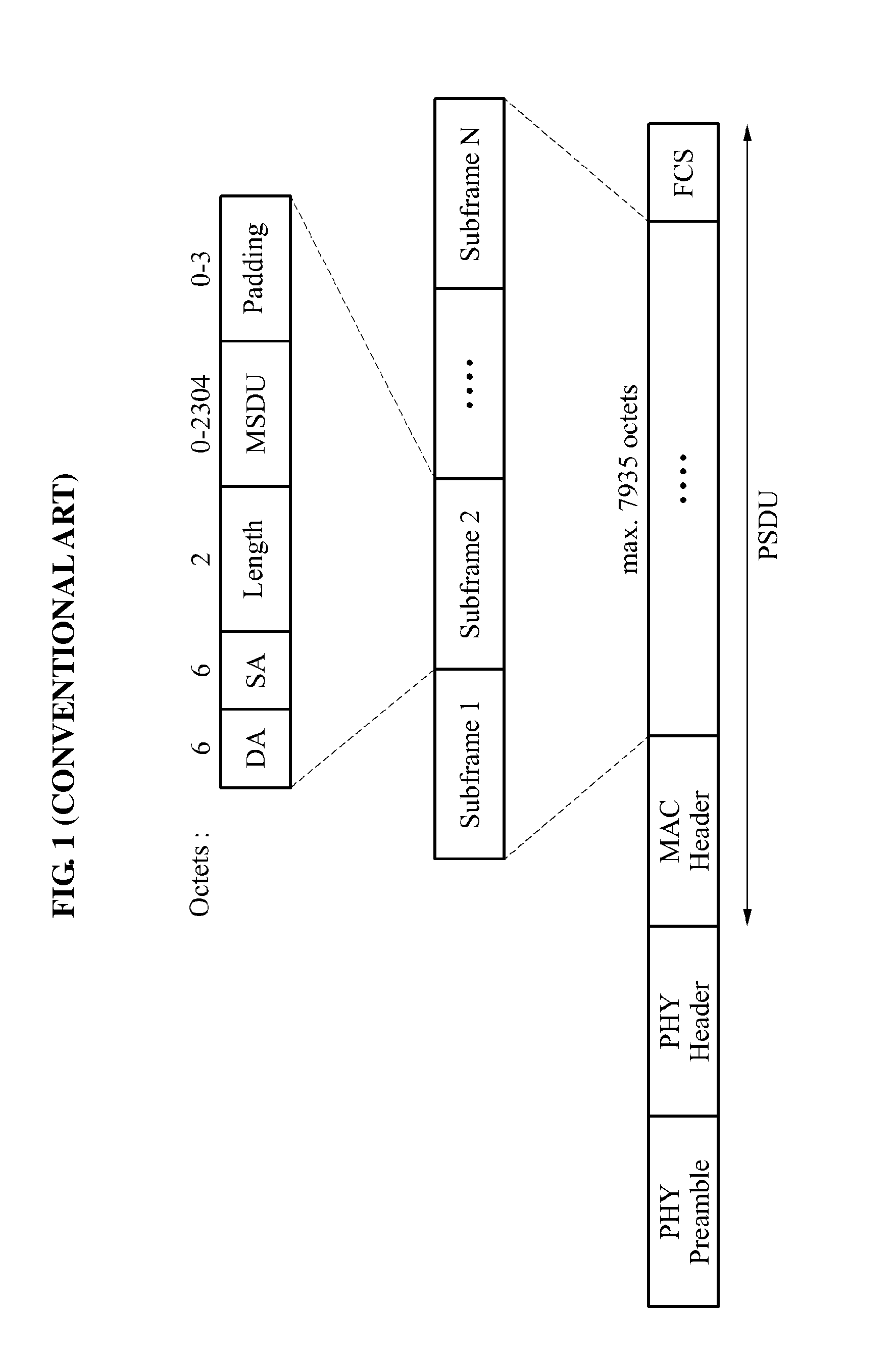
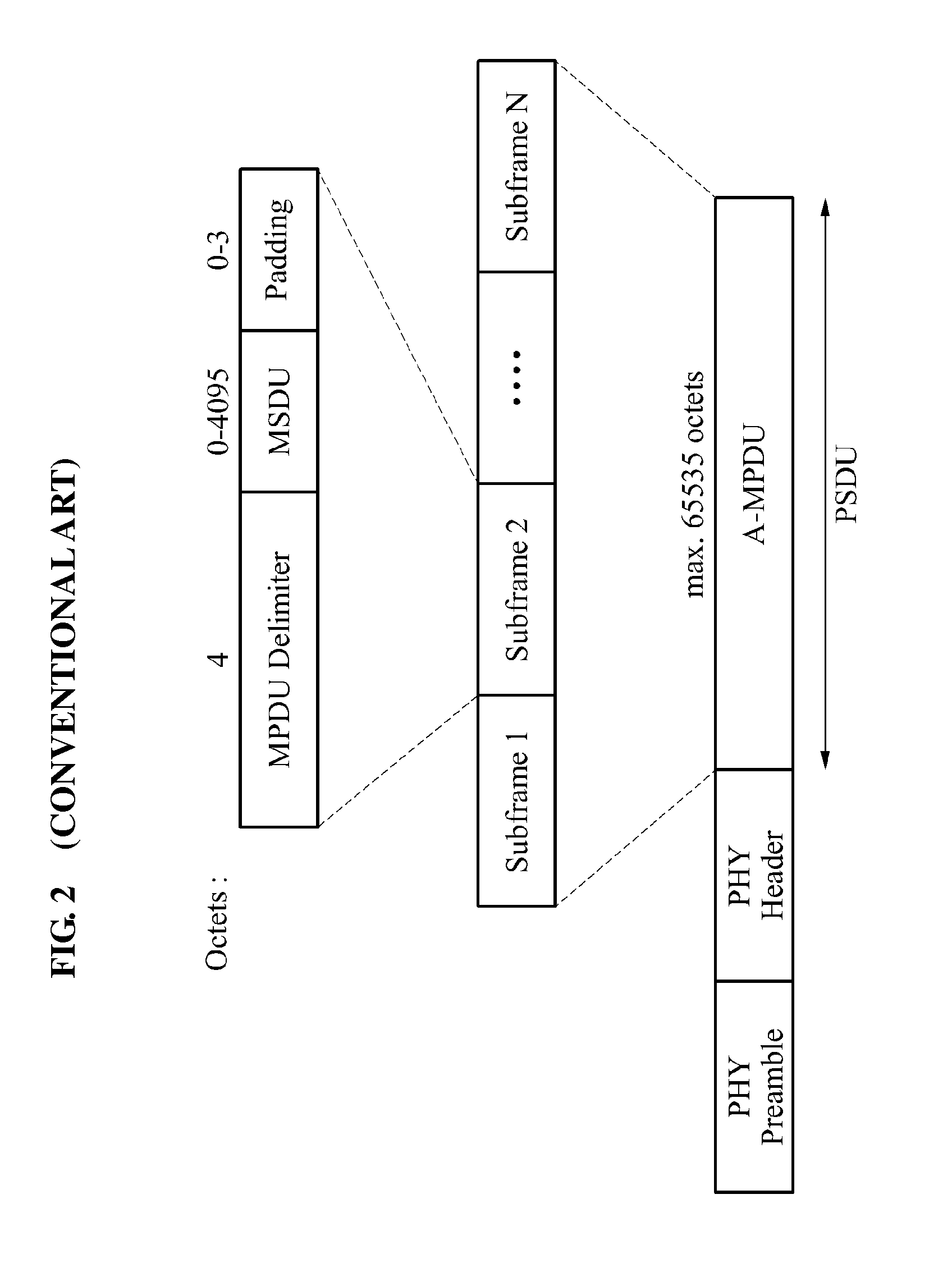
Provided is a method and apparatus for efficient aggregation scheduling in a wireless local area network (WLAN) system, the apparatus including a delay setting unit to set a required delay time for each access category (AC), a storing unit to store a traffic identification (TID) of a packet in a queue of a corresponding AC when the packet arrives, a delay time calculator to calculate a maximum delay time predicted when the packet arriving at the queue is configured to be an A-MPDU and the configured A-MPDU is transmitted, and an A-MPDU configuring unit to compare the calculated maximum delay time and the required delay time, and configure a corresponding A-MPDU when the calculated maximum delay time is greater than the required delay time.
Owner:ELECTRONICS & TELECOMM RES INST
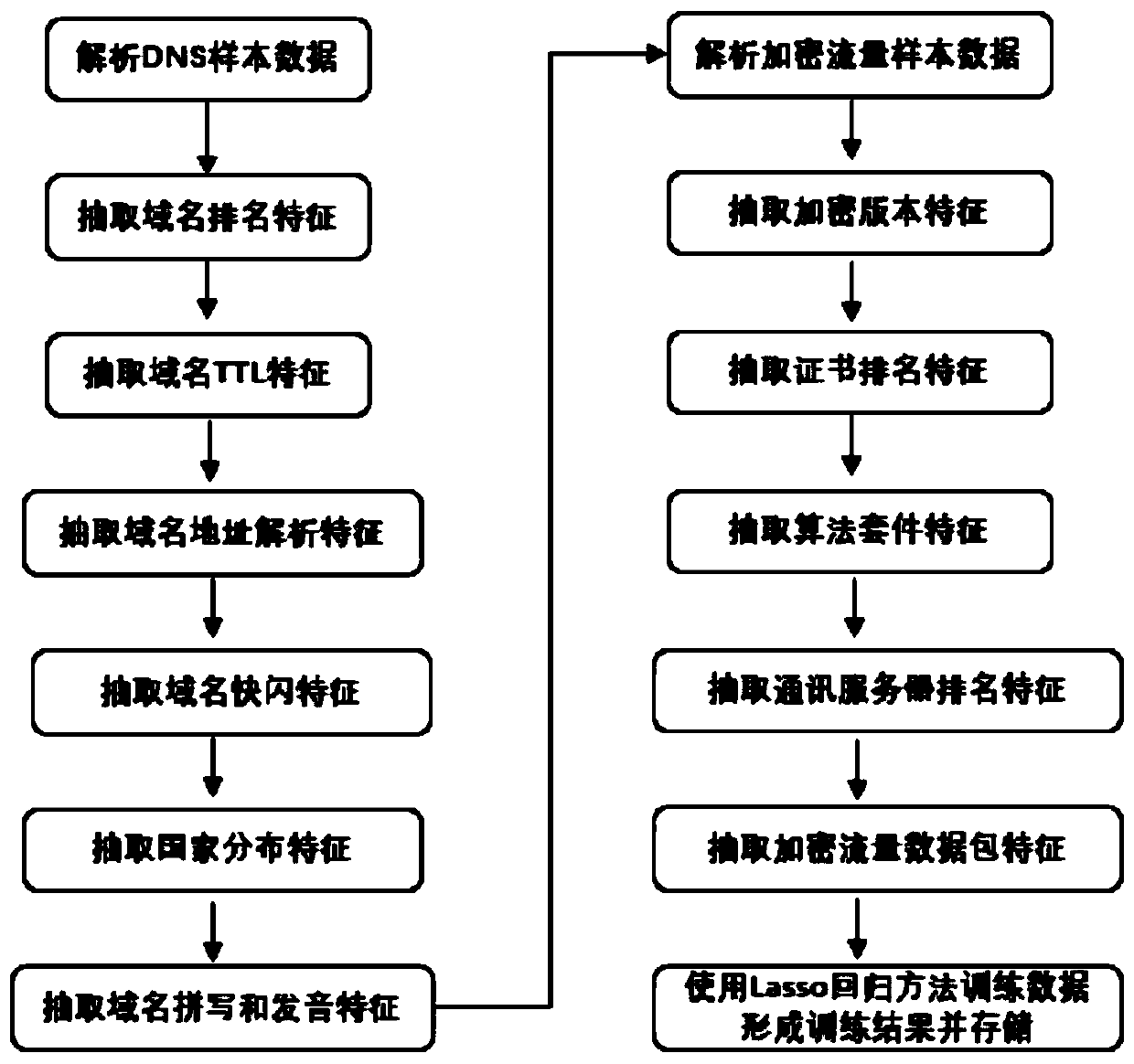
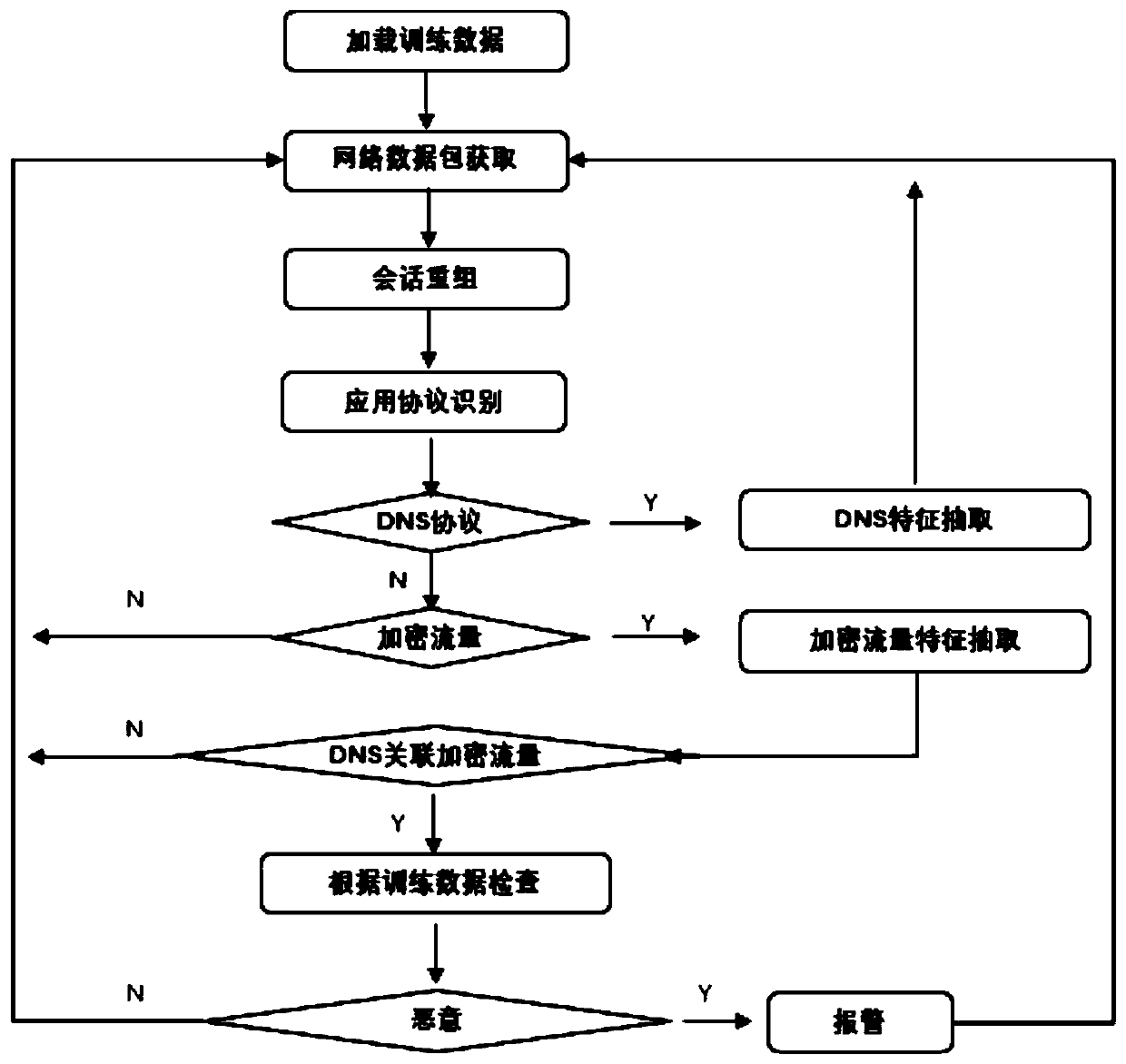
Multi-feature DNS (Domain Name System) and HTTPS (Hyper Text Transfer Protocol Security) combined malicious encrypted traffic identification method
ActiveCN110493208AImprove abilitiesTransmissionFeature extractionHypertext Transfer Protocol over Secure Socket Layer
The invention relates to a multi-feature DNS (Domain Name System) and HTTPS (Hyper Text Transfer Protocol Security) combined malicious encrypted traffic identification method. The method comprises thefollowing steps: 1, extracting all sample DNS communication protocols in a learning network, analyzing a DNS communication protocol; 2, extracting all malicious / non-malicious HTTPS communication protocol handshake parts (non-encrypted contents) in the learning network, analyzing a handshake part of the HTTPS communication protocol; 3, extracting session related feature information of a malicious / non-malicious HTTPS protocol session, 4, correlating the DNS protocol with the HTTPS protocol related content; 5, extracting normal encrypted communication data features through data learning of normal encrypted traffic, 6, carrying out classification processing on the data by using a regression method, and 7, storing weight data to a persistent medium through a training result for subsequent use;8, performing feature extraction and substitution solution on the related encrypted traffic data in the current network by using the solution result.
Owner:南京聚铭网络科技有限公司
Method and device for network traffic identification
InactiveCN104486161AAccurately determineComprehensive recognition resultsData switching networksTraffic capacityNetworking protocol
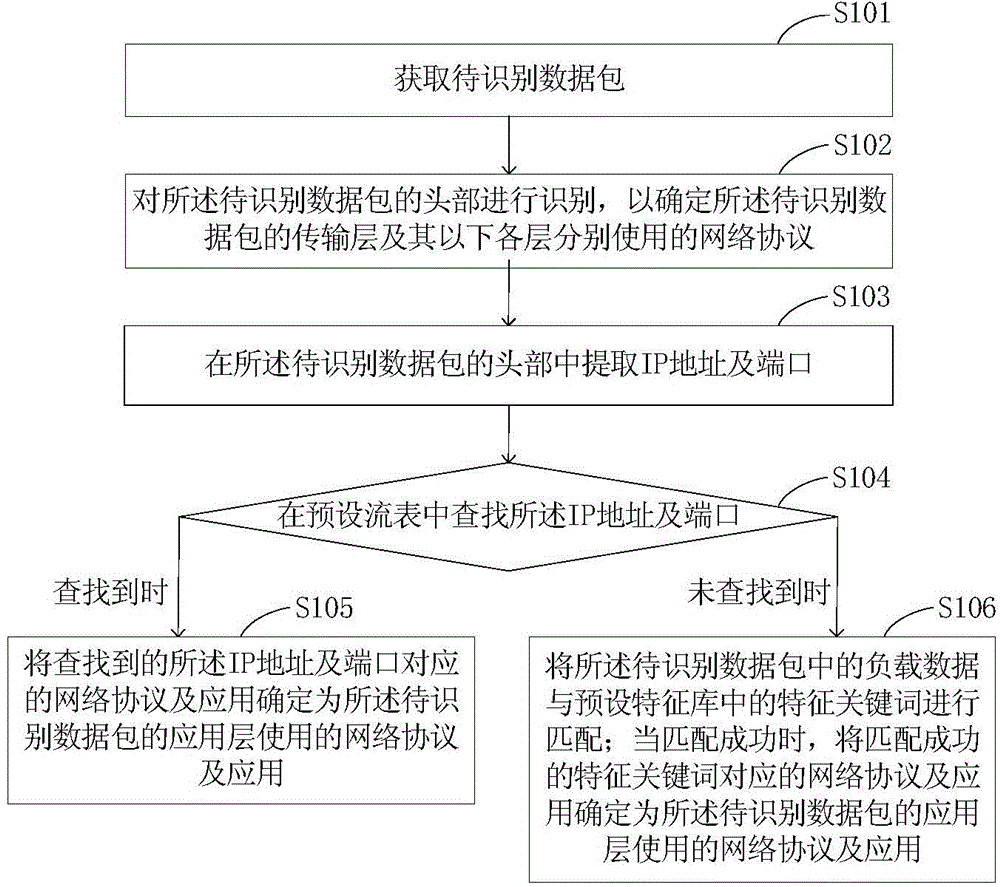
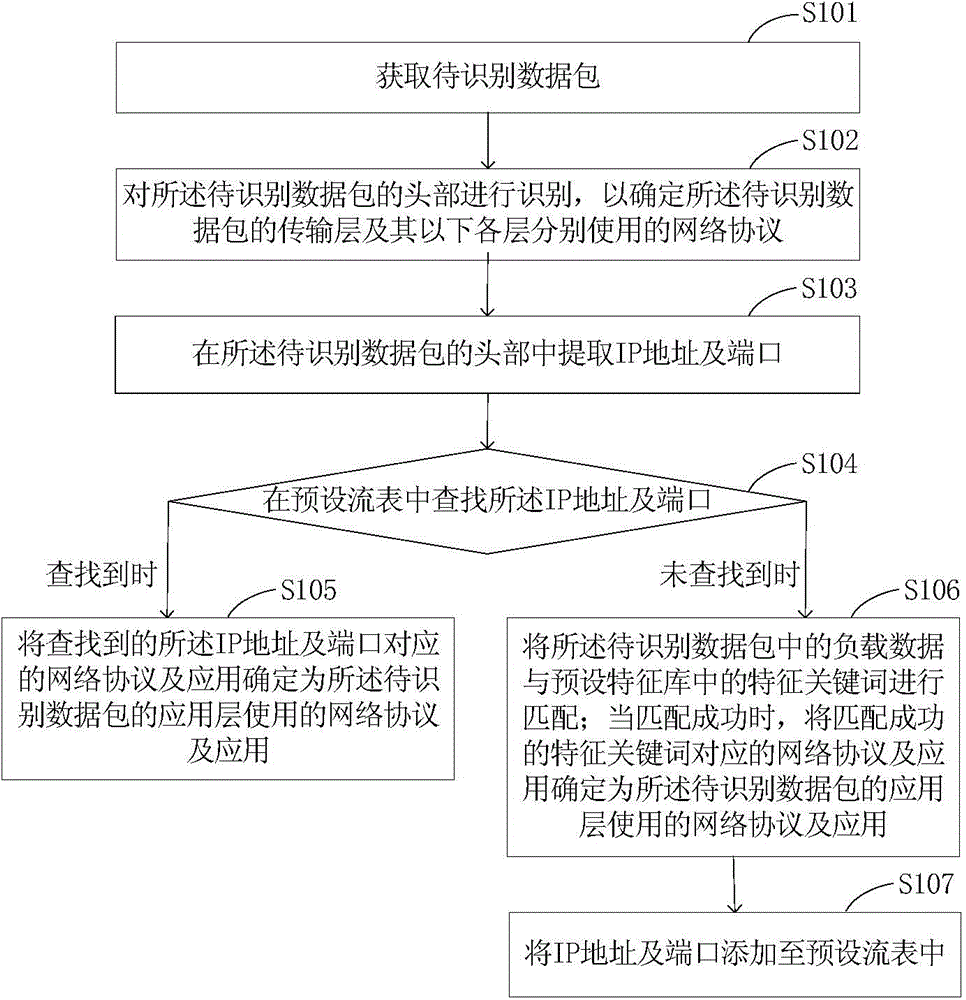
The application provides a method and a device for network traffic identification. The method comprises the following steps: identifying the head of an obtained data packet to be identified, determining network protocols respectively used by a transmission layer and all layers below the transmission layer, extracting an IP address and a port from the head of the data packet to be identified, searching the IP address and the port in a preset flow table, if the IP address and the port are searched, determining that a network protocol and an application which correspond to the IP address and the port are the network protocol and the application which are used by an application layer, if the IP address and the port are not searched, matching load data in the data packet to be identified with feature keywords in a preset feature library, and if matching is successfully carried out, determining that a network protocol and an application which correspond to the feature keywords are the network protocol and the application which are used by the application layer. Compared with the prior art, the application has the advantages that not only can the protocol of the application layer be accurately identified through the flow table and the feature library which are previously set, the application type can also be determined according to corresponding relationships record in the flow table and the feature library; the recognizing results are more comprehensive.
Owner:COLASOFT
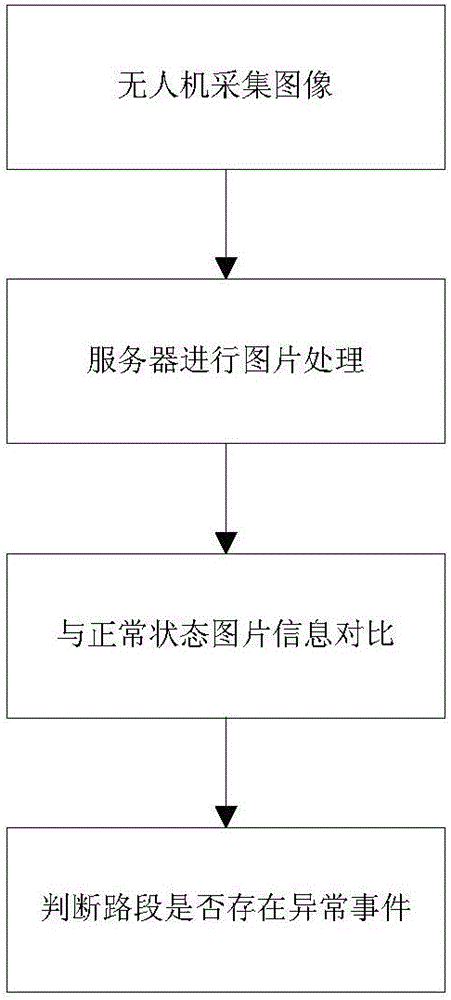
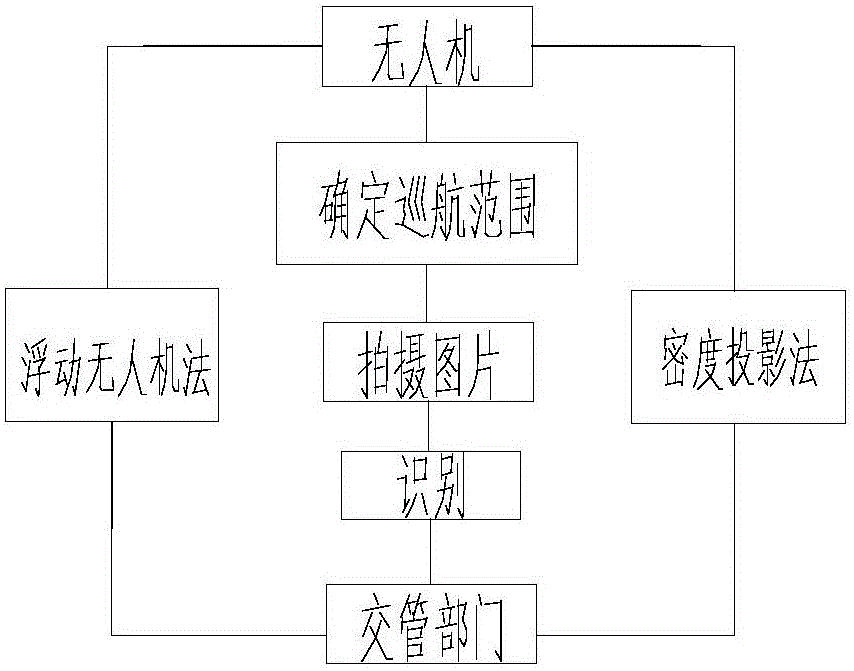
Unmanned aerial vehicle-based abnormal traffic identification method
InactiveCN105788269AEfficient identificationAccurate identificationDetection of traffic movementTime conditionControl system
The invention relates to an unmanned aerial vehicle-based abnormal traffic identification method. The method includes the following steps that: an unmanned aerial vehicle acquires traffic image information in a cruise range and outputs the traffic image information to a server; the traffic image information is processed; current processed traffic image information is compared with preset normal state traffic image information; and whether a anomaly exists in a current road section can be judged. According to the unmanned aerial vehicle-based abnormal traffic identification method of the invention adopted; real-time traffic is photographed by the unmanned aerial vehicle, and pictures are automatically processed; picture information worthy of being distributed is selected and is uploaded to a traffic control system; based on a floating car method principle and an intensity projection method, the unmanned aerial vehicle is utilized to detect the volume of traffic of the road; and the traffic control system can perform operation such as traffic state detection, traffic safety early warning and traffic control induction according to traffic real-time condition and traffic flow in the pictures and perform picture receiving, processing and instruction distribution according to a cloud service platform.
Owner:CHINA MERCHANTS CHONGQING COMM RES & DESIGN INST
Encrypted traffic identification method oriented to category imbalance
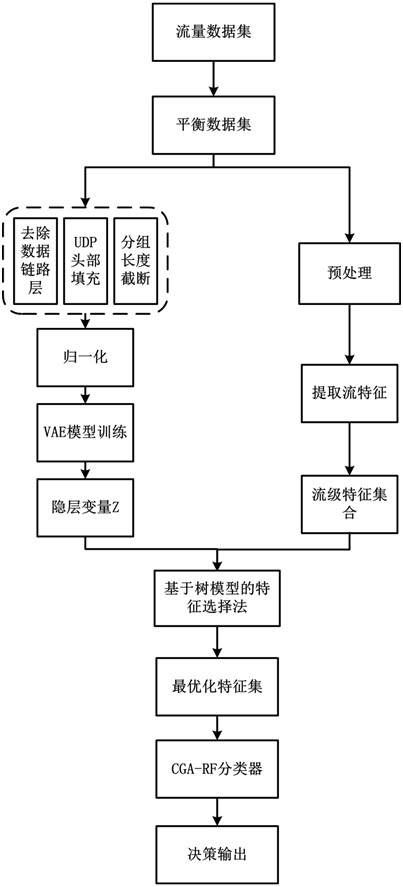
ActiveCN111817982ASolve overfittingAvoid the problem of low identification efficiencyCharacter and pattern recognitionData switching networksData setData stream
The invention discloses an encrypted traffic identification method oriented to category imbalance. The method comprises the following steps: S1, acquiring a data set; S2, balancing the data set: processing the original experimental data set by adopting an improved SMOTE algorithm based on density estimation; S3, data preprocessing: reading a data stream, cutting off data, and carrying out normalization processing; S4, optimizing the feature set: automatically extracting features through a variational automatic encoder model, identifying features commonly used in the field through network traffic, and obtaining the optimal feature set by using a feature selection method based on a tree model; S5, identifying flow: inputting the optimal feature set into a random forest CGA-RF classifier algorithm improved based on a genetic algorithm, and identifying target encrypted flow; and S6, analyzing the obtained index result, and optimizing an encrypted traffic identification method. The method is high in recognition rate and low in false alarm rate, and is suitable for encrypted traffic recognition of data set category imbalance and difficult feature extraction.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
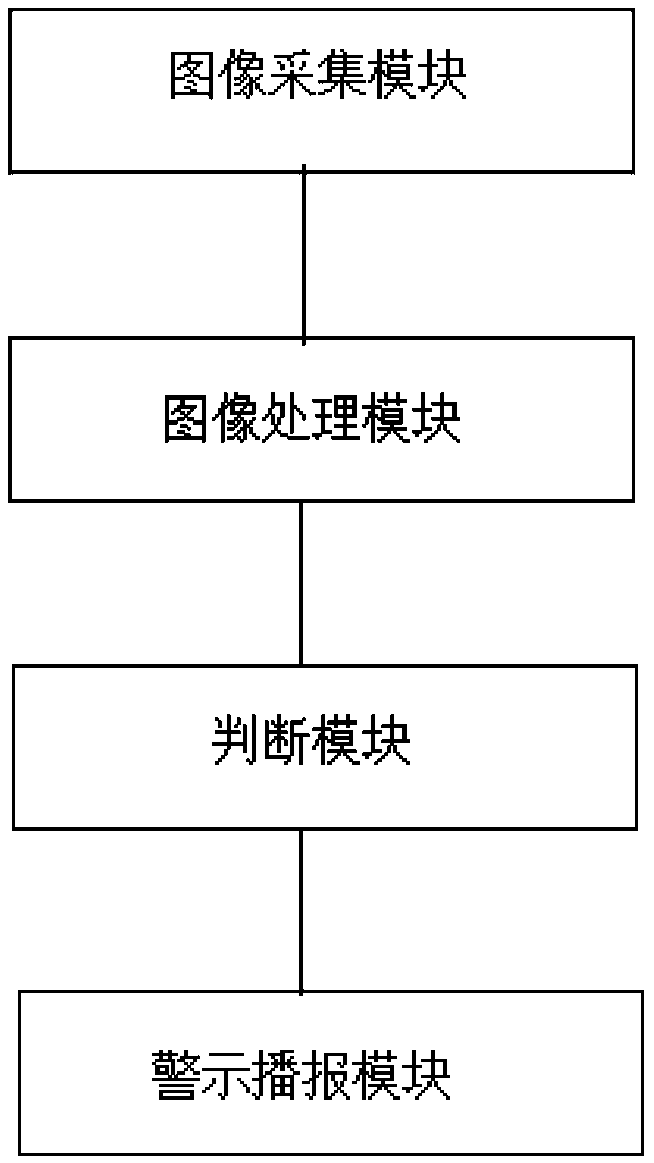
A system and method for monitoring driving misconduct
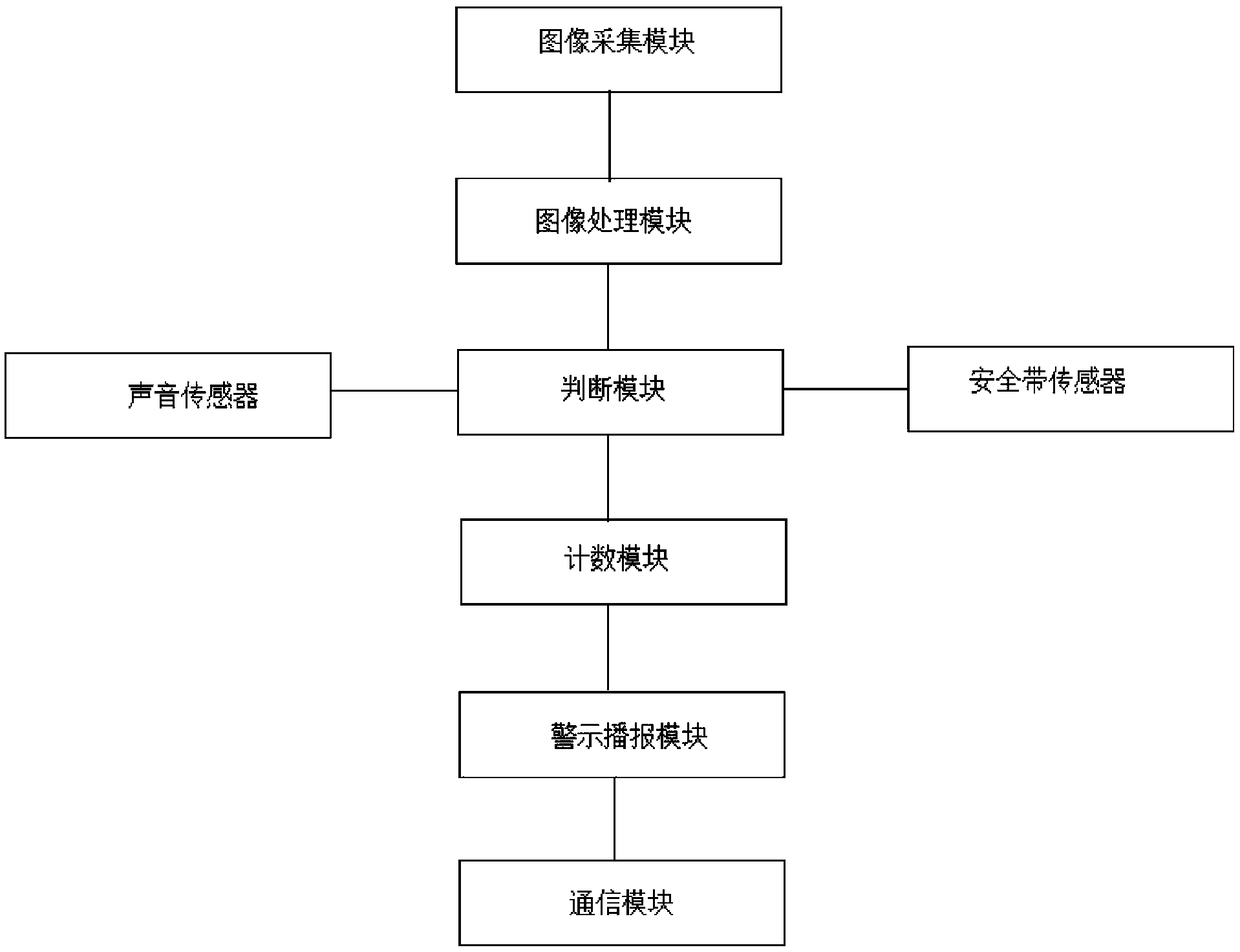
InactiveCN109263647AGet rid of bad driving habitsReduce the risk of traffic accidentsBelt control systemsImaging processingTraffic accident
The invention provides a system and method for monitoring driving misconduct. The system comprises an image acquisition module, an image processing module, a judgment module and a warning broadcast module. The image acquisition module is used for real-time collecting vehicle driving road condition images. The image processing module is used for processing a vehicle driving road condition image toobtain driving road condition target information, wherein the driving road condition target information comprises lane information and traffic identification information; the judging module is used for judging whether the vehicle has bad driving behavior according to the driving road condition target information, and the bad driving behavior includes compaction line behavior, whistle sounding behavior, parking behavior, overtaking behavior and lane changing behavior. The warning broadcast module is used for warning and reporting when the bad driving behavior meets the preset conditions. The driving behavior monitoring system and the driving behavior monitoring method of the invention can prompt the driver in time and reduce the risk of traffic accidents.
Owner:ZHEJIANG GEELY HLDG GRP CO LTD
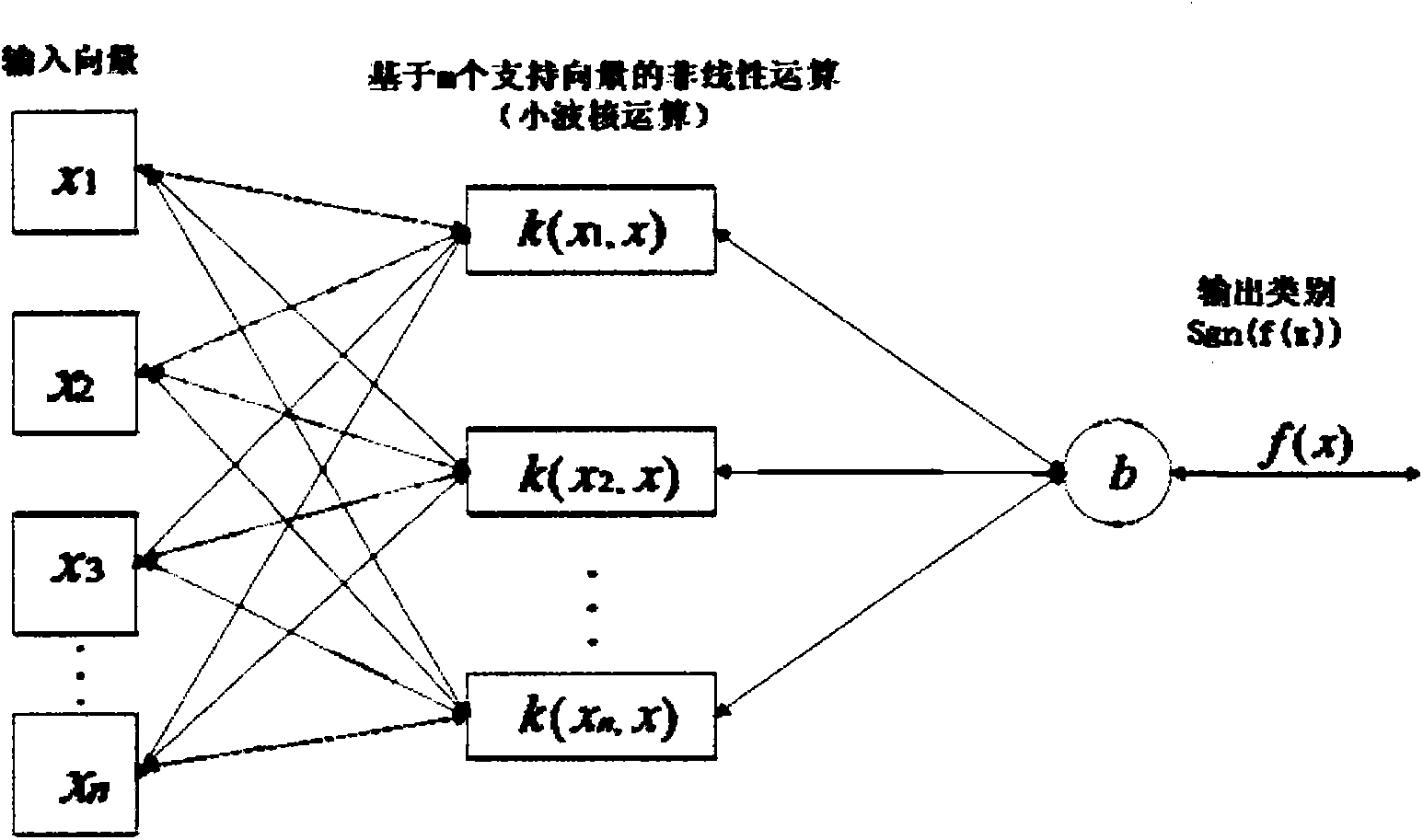
Peer-to-peer network traffic identification method of inseparable-wavelet support vector machine
InactiveCN103780501AEfficient identificationEffective controlData switching networksIp addressSize change
The invention relates to a peer-to-peer (P2P) network traffic identification method of an inseparable-wavelet support vector machine. The method includes the following steps: (1): selecting feature vectors: adopting the following three-dimensional feature vectors: Vector=<v1, v2, v3>, wherein v1 represents a mean-square value of data packet size change, v2 represents the ratio of an uplink speed and a downlink speed at a node and v3 represents a ratio of the number of IP addresses and the number of ports; (2): selecting an appropriate kernel function; (3) selecting a increment training algorithm; (4) performing a Boosting algorithm for P2P traffic identification of wavelet SVM: at last, obtaining a strong classifier H(x) through adoption of a voting method with a weight for identification of the P2P traffic identification. The peer-to-peer network traffic identification method of the inseparable-wavelet support vector machine is capable of identifying the P2P network traffic efficiently and adopting a countermeasure timely to controlling effectively the P2P network traffic.
Owner:PUYANG VOCATIONAL & TECHN COLLEGE +6
Network traffic identification by waveform analysis
A technique is disclosed for identifying network traffic. The traffic data is converted into a wave vector. The wave vector is compared with a wave template. It is determined whether the wave vector is substantially similar to the wave template. If it is determined that the wave vector is substantially similar to the wave template, the traffic data is identified as being associated with a protocol with which the wave template is associated.
Owner:CA TECH INC
Encrypted malicious traffic identification method, equipment and device
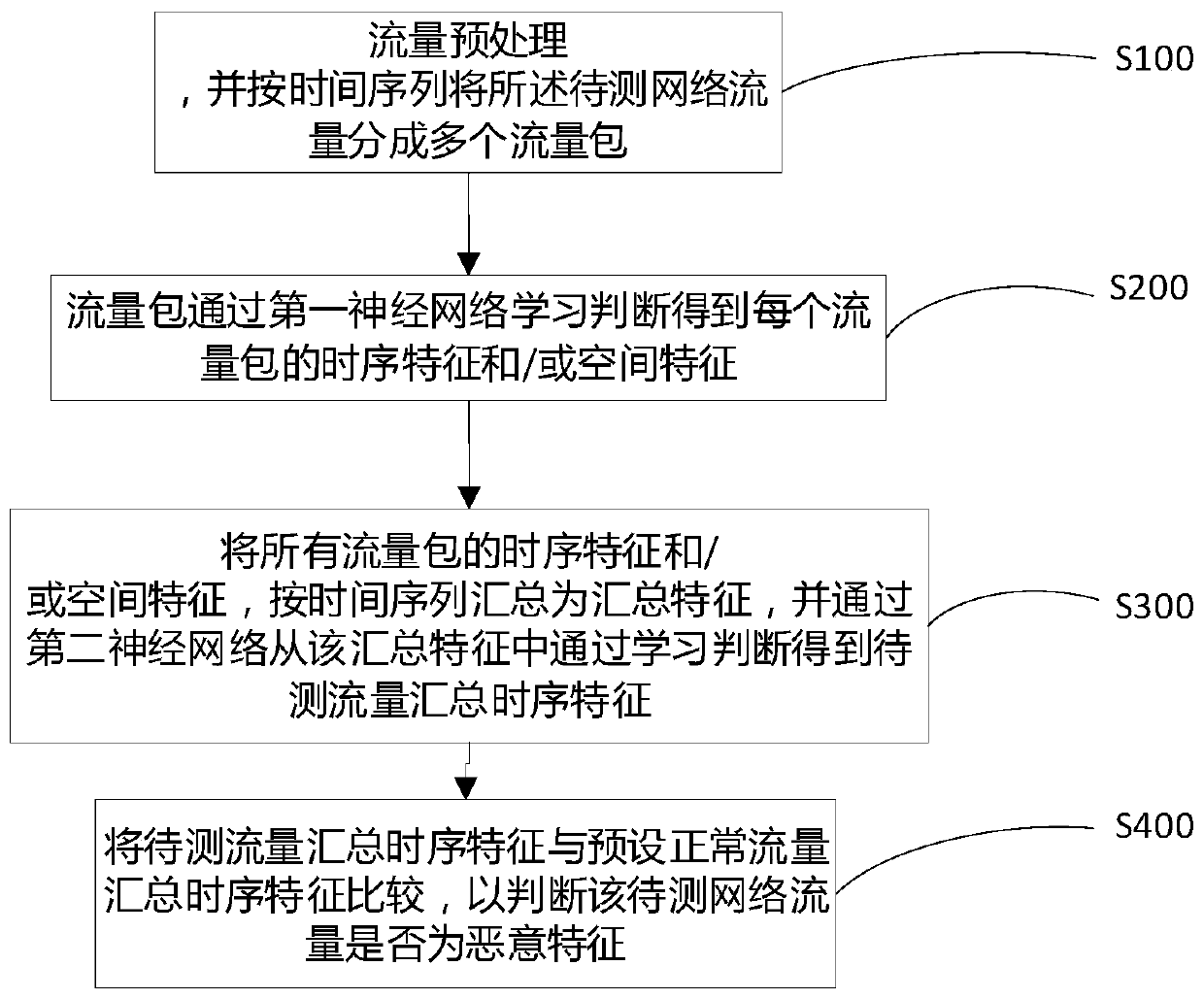
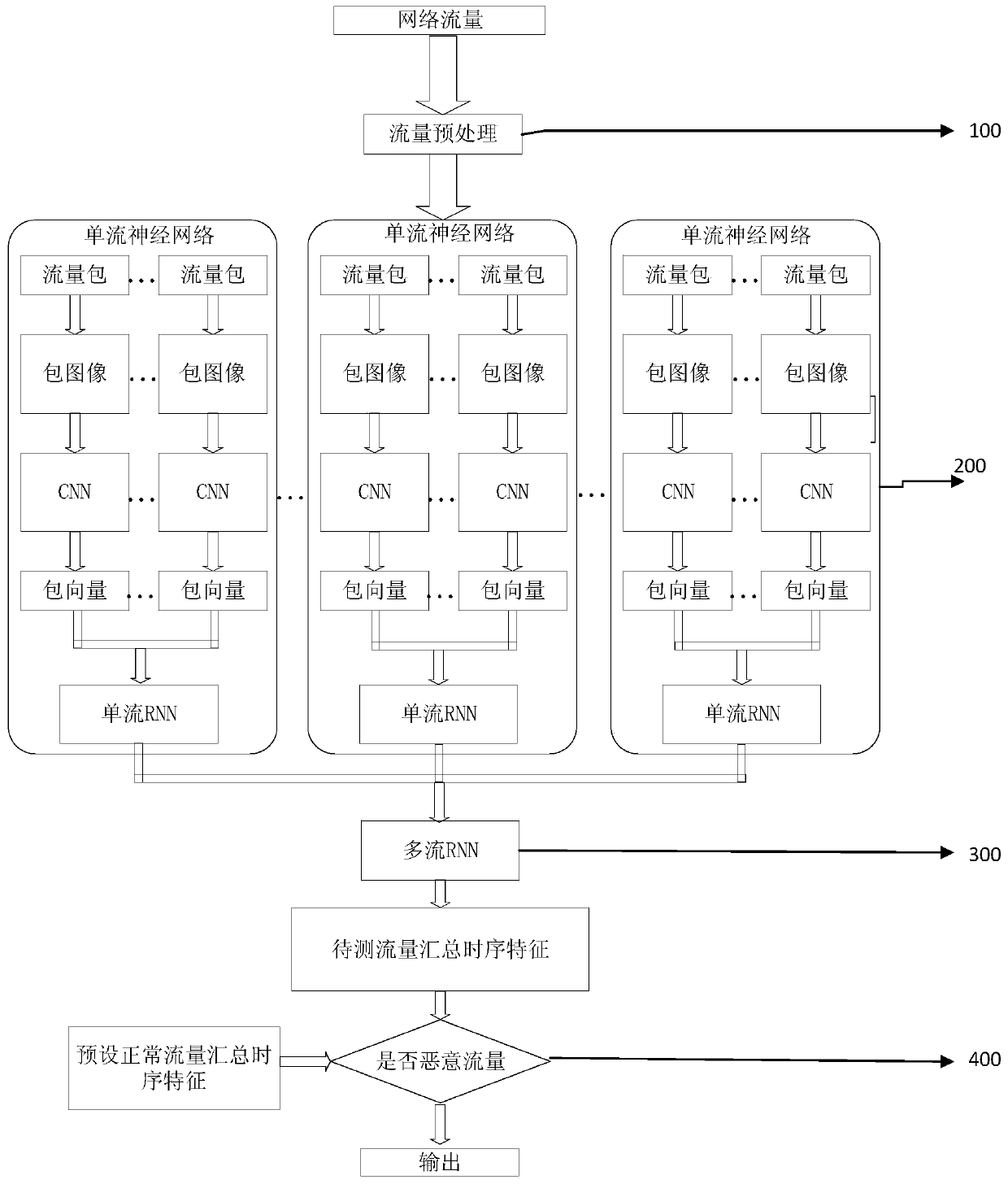
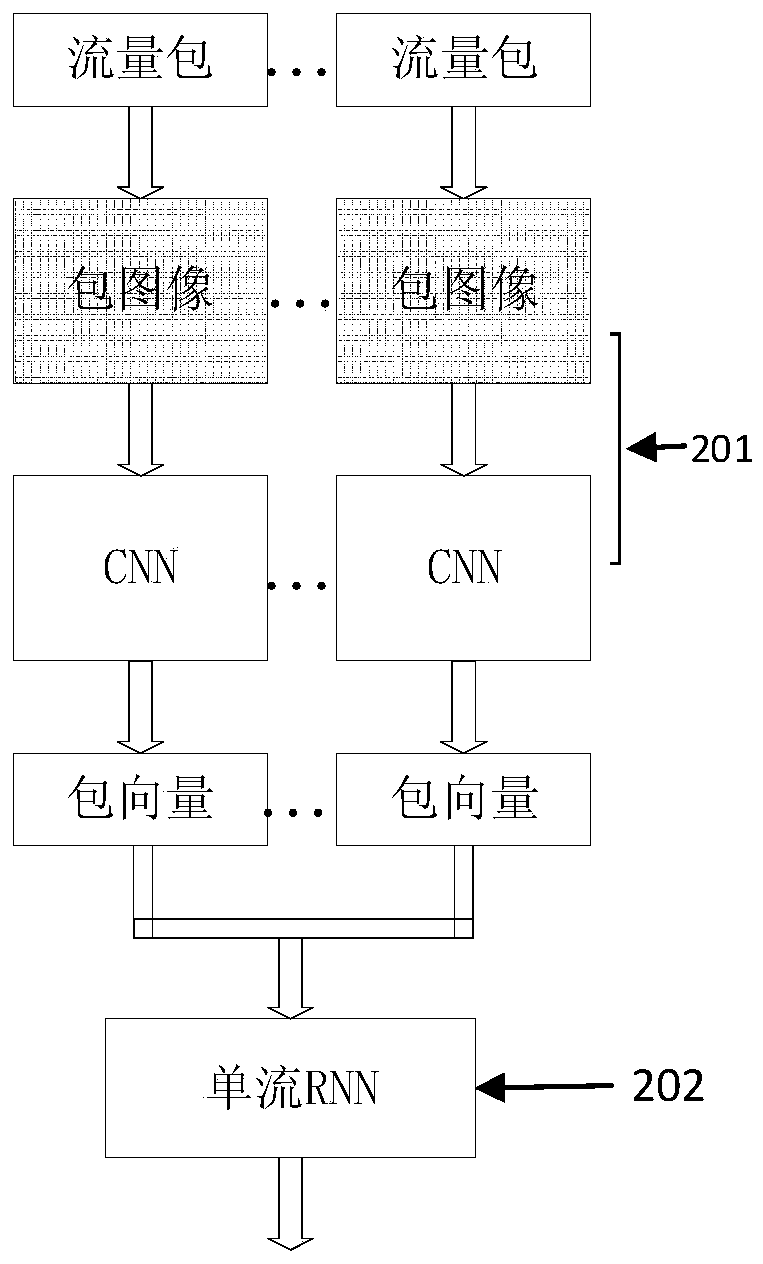
InactiveCN111447190AAccurate and objective representationImprove accuracyCharacter and pattern recognitionNeural architecturesNeural network learningInternet traffic
The invention discloses an encrypted malicious traffic identification method, equipment and device, and the method comprises the steps: separating encrypted to-be-detected network traffic from networktraffic, and dividing the to-be-detected network traffic into a plurality of traffic packets according to a time sequence, wherein the traffic packets are learned and judged through a first neural network to obtain time sequence features and / or space features of each flow packet; summarizing the time sequence features and / or the space features of all the flow packets into summarized features according to a time sequence, and obtaining the summarized time sequence features of the flow to be detected from the summarized features through learning judgment by a second neural network; and comparing the to-be-detected traffic summary time sequence feature with a preset normal traffic summary time sequence feature to judge whether the to-be-detected network traffic is a malicious feature or not.According to the method, the space and time characteristics of the flow are learned by adopting the neural network, a multi-flow network flow processing mode is introduced, behavior characteristics between flows are fully considered, and the accuracy of malicious flow identification can be more accurate.
Owner:北京观成科技有限公司 +1
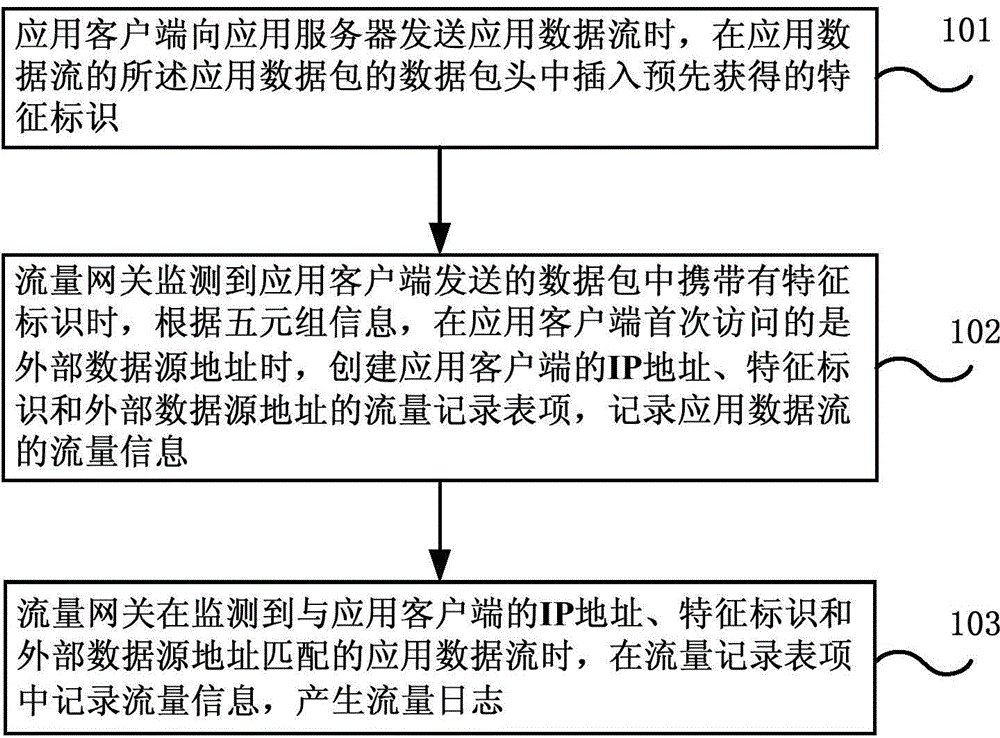
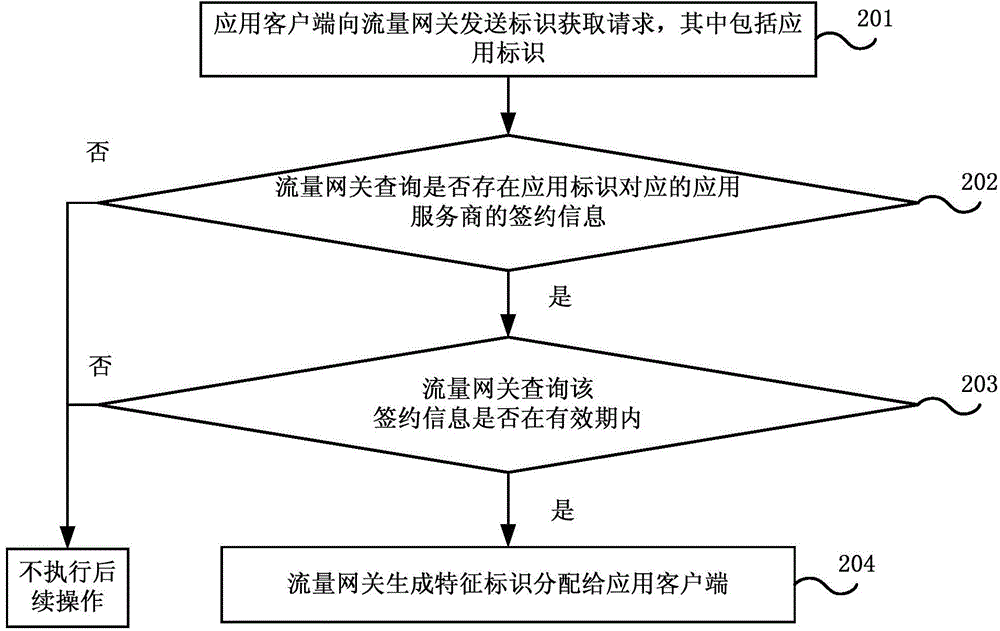
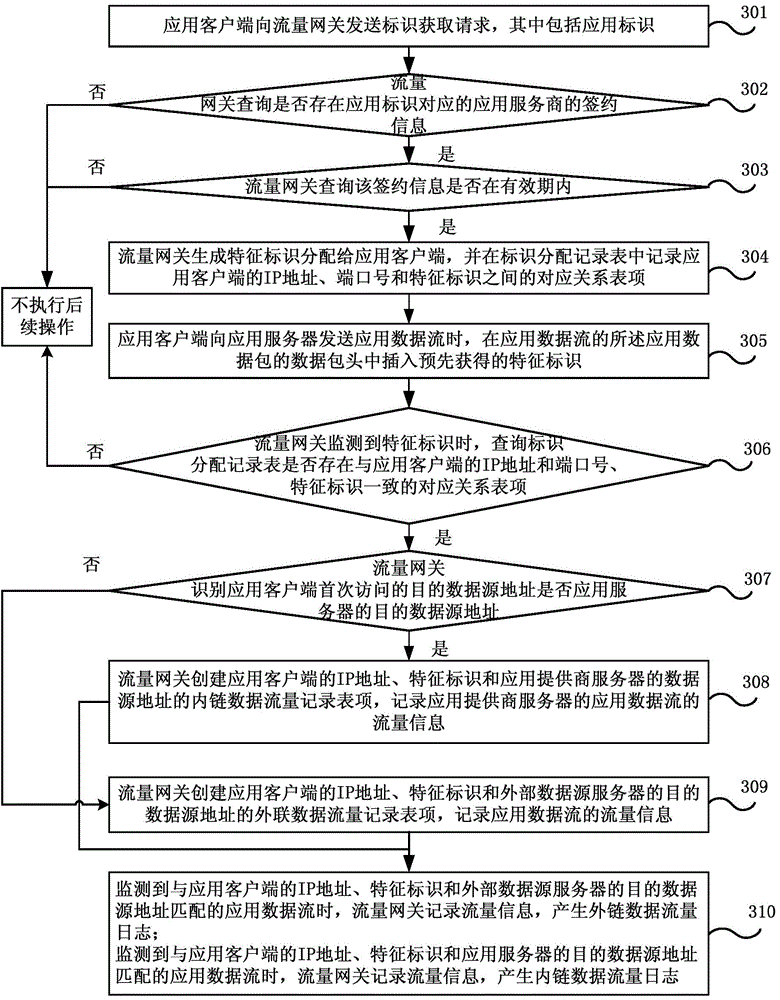
Traffic identification method and system and traffic gateway
The embodiment of the invention discloses a traffic identification method and system and a traffic gateway. The method comprises the steps of when an application client sends application data stream, inserting a feature identifier obtained from the traffic gateway in advance in a data packet header of the application data stream, when the traffic gateway monitors the feature identifier, and when a destination data source address accessed by the application client for the first time is an external data source server, creating an traffic recording table entries of an application client IP address, the feature identifier and an external data source address; when the application data stream matched with the application client IP address, the feature identifier and the external data source address is monitored, identifying the application data stream as external link traffic embedded in the application client, and recording the traffic information in the traffic recording table entries by the traffic gateway. Accurate charging of external link traffic is realized.
Owner:CHINA TELECOM CORP LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com