Encrypted network traffic identification method based on deep neural network
A deep neural network and network traffic technology, applied in the field of network service security and traffic identification, deep learning, can solve the problems of poor stability, low recognition accuracy and accuracy rate, high misjudgment and missed judgment rate, and achieve good accuracy rate, Low false positive rate and false positive rate to ensure high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
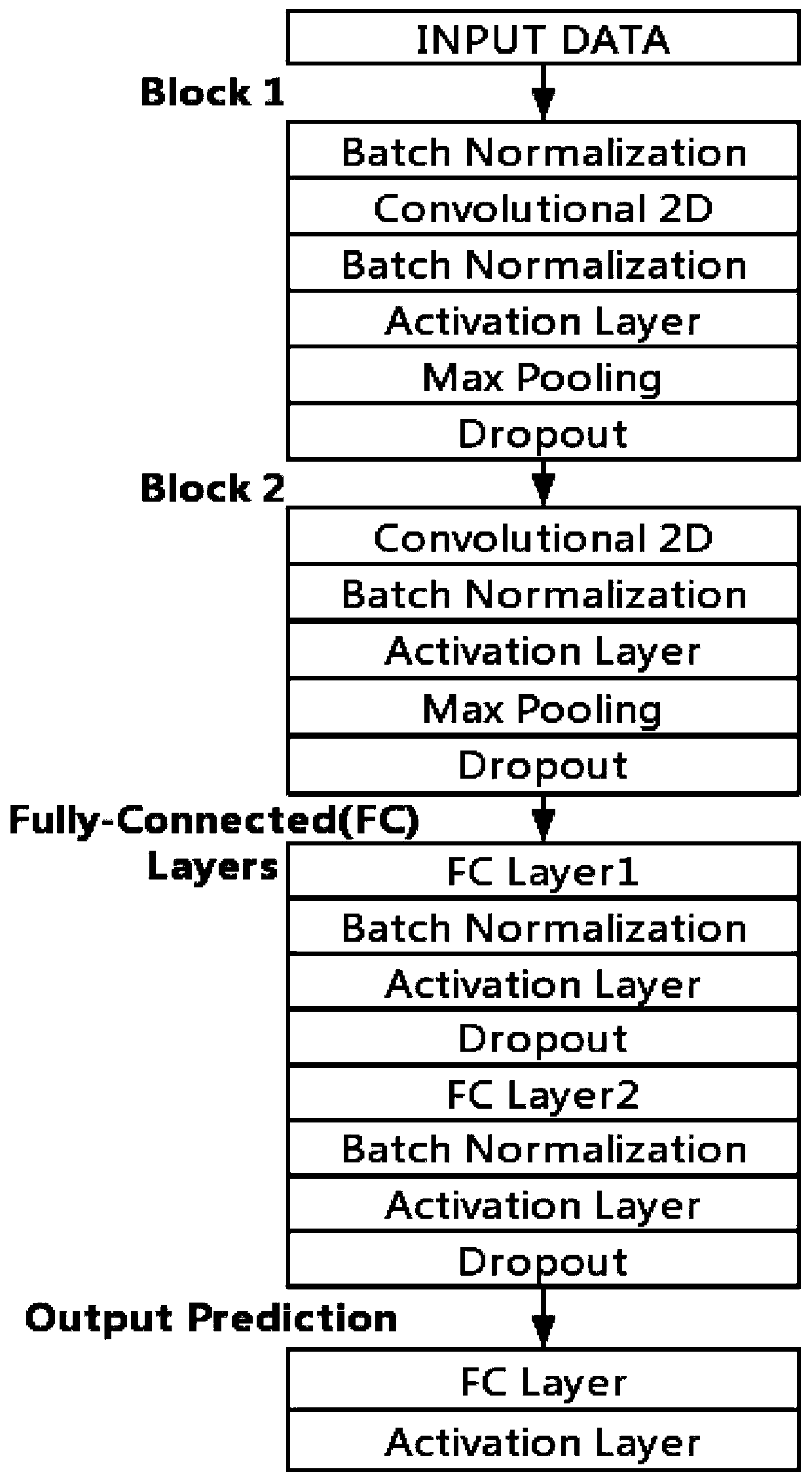
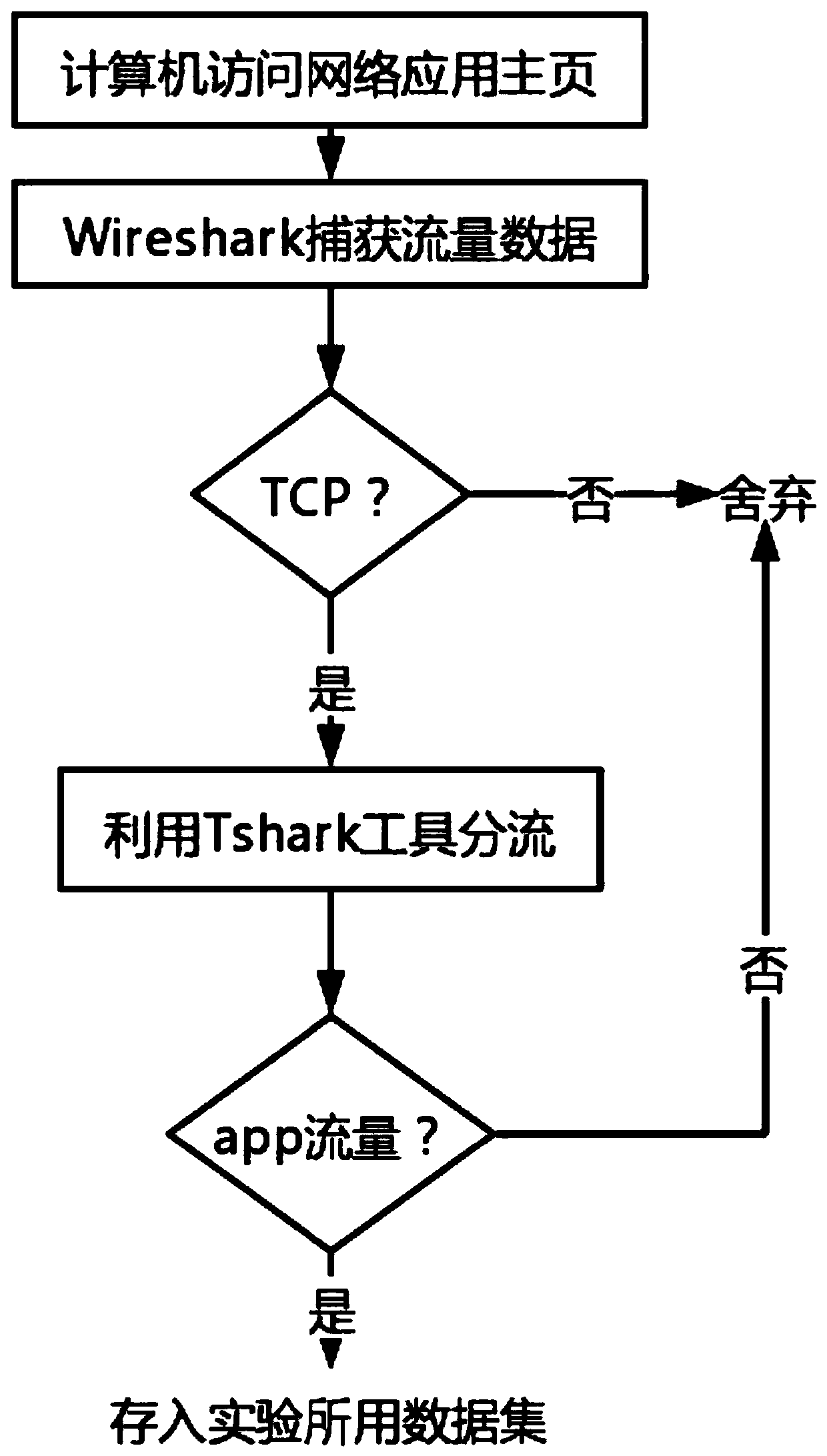
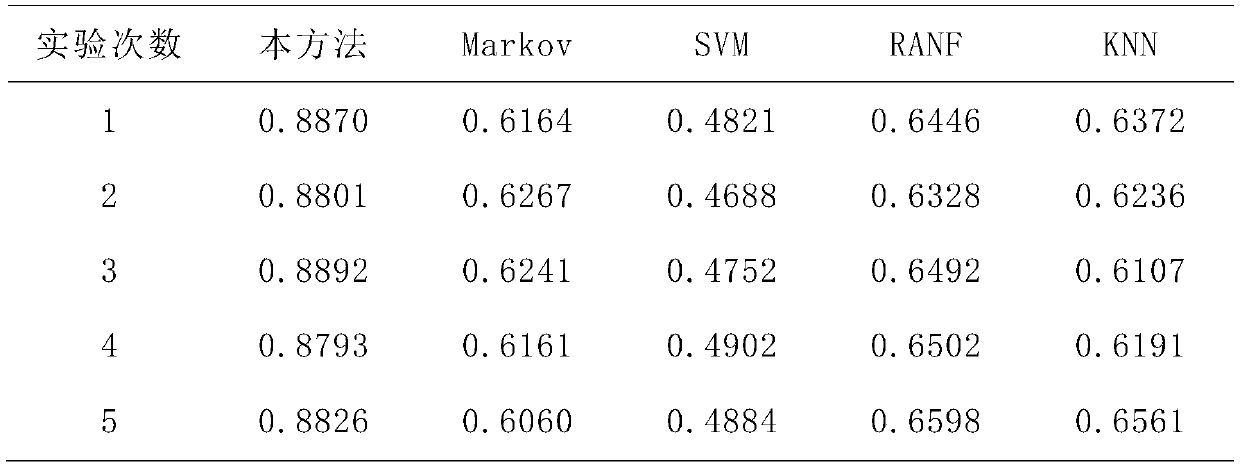
[0068] This embodiment is a complete process based on steps 1 to 5 of the present invention, in which aragon, bancor, canwork, chainy, cryptopepes, eth_town, etheremon, idex, joyso, cryptokitties, lordless, makerdao, matchpool, ono, originprotocol has a total of fifteen Dapps as data sources, covering various fields of games, social networking, and finance in the blockchain platform. The data collection process specifically corresponds to steps 1 and 4 in the content of the invention, and then these collected offline data packets are input into the network training and online recognition.
[0069] When the method for identifying encrypted network traffic based on a deep neural network is specifically implemented, it includes two parts: an offline training phase and an online identification phase;
[0070] Among them, in the offline training phase, corresponding to step 3 in the content of the invention, the system collects the traffic transmitted by 15 Dapps using the encrypti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com