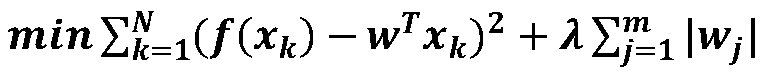Multi-feature DNS (Domain Name System) and HTTPS (Hyper Text Transfer Protocol Security) combined malicious encrypted traffic identification method
A traffic identification and multi-feature technology, applied to electrical components, transmission systems, etc., can solve problems such as missing important information, high proportion, undetectable traffic, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
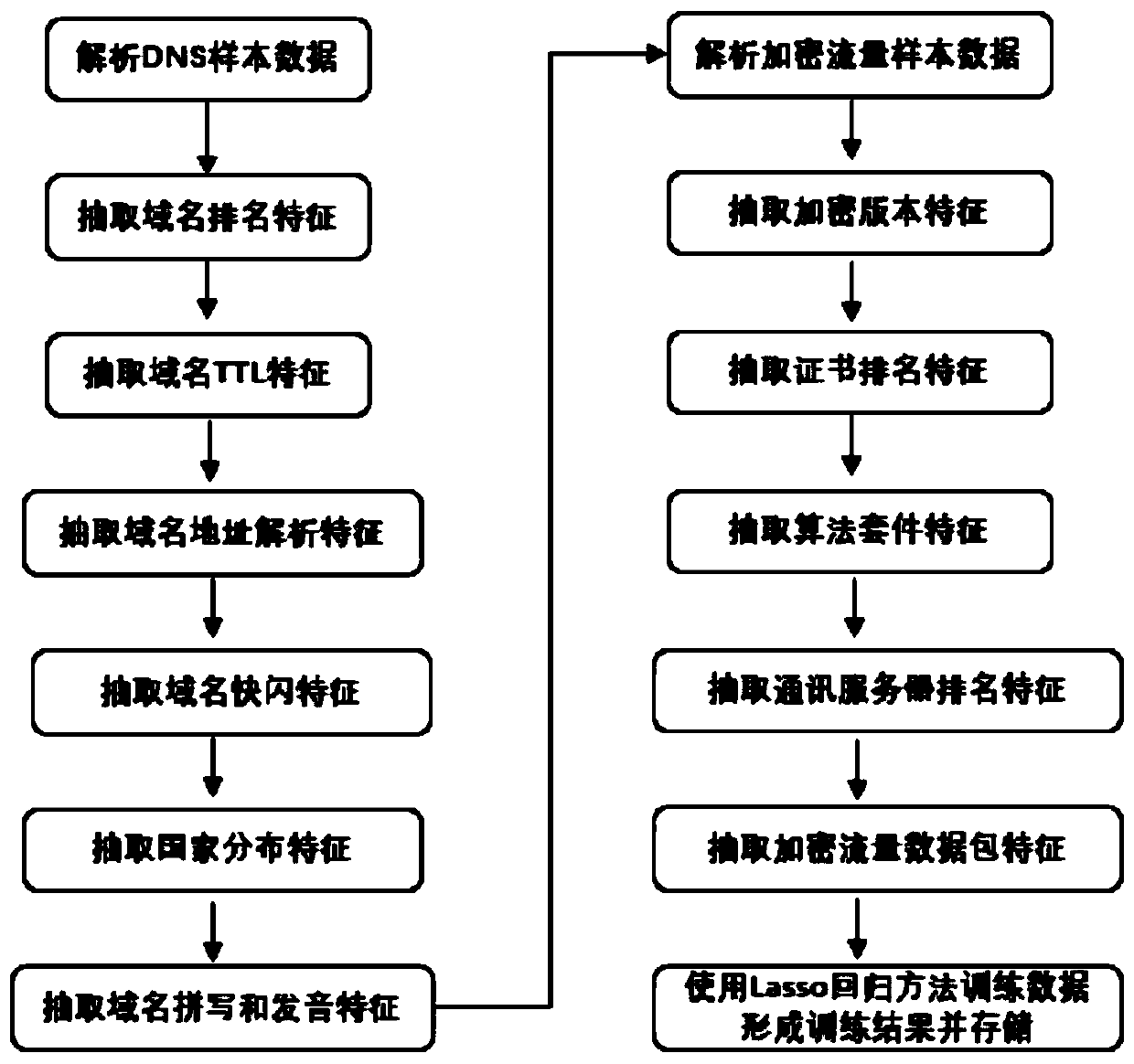
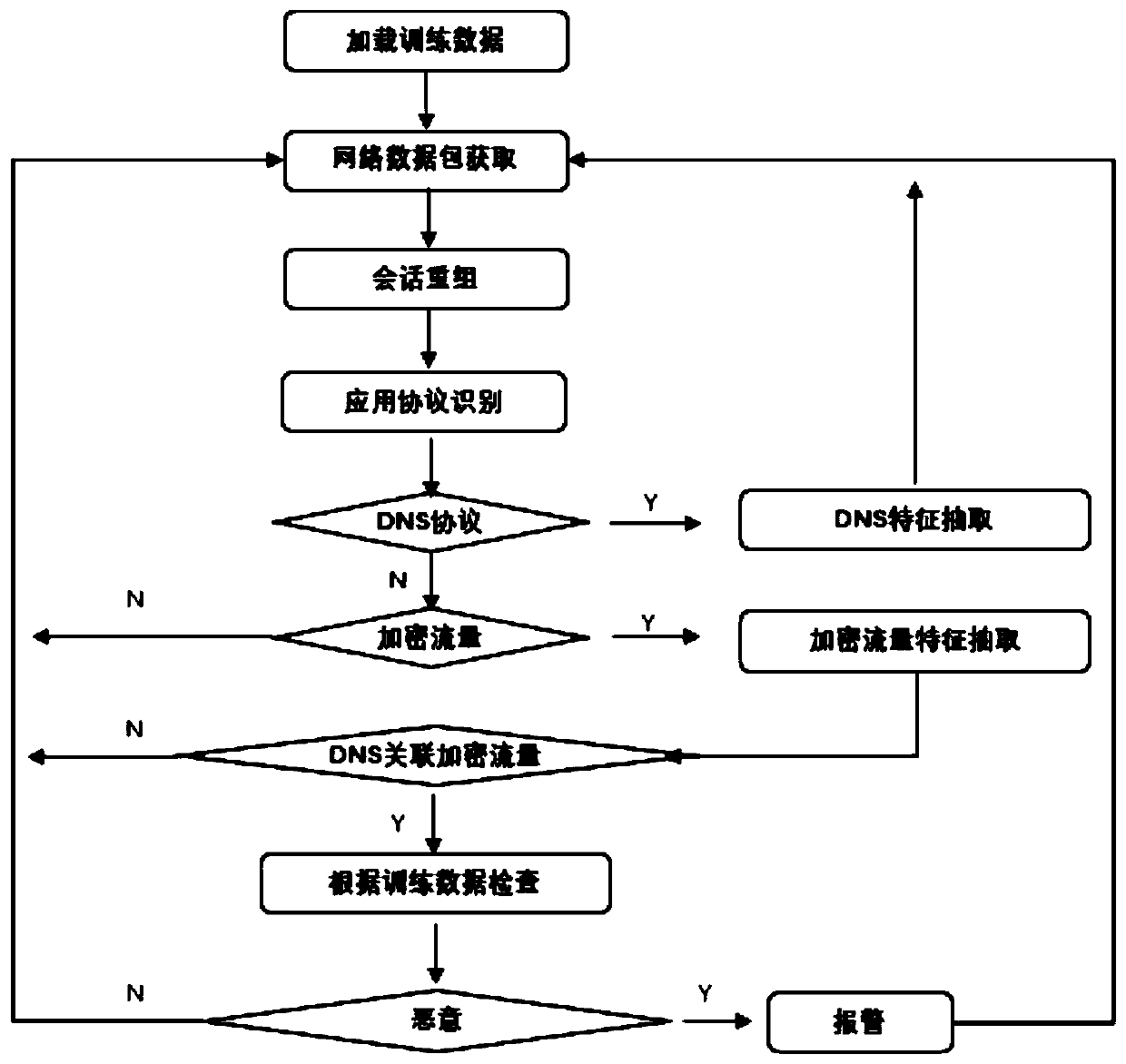
[0074] Embodiment 1: see figure 1 , a multi-featured DNS combined with HTTPS malicious encryption traffic identification method, the method may further comprise the steps:
[0075] Step 1: Extract all sample DNS communication protocols in the learning network, and analyze the DNS communication protocols:
[0076] Step 2: Extract all malicious / non-malicious HTTPS communication protocol handshake parts (non-encrypted content) in the learning network, and analyze the HTTPS communication protocol handshake part:
[0077] Step 3: Extract session-related characteristic information of malicious / non-malicious HTTPS protocol sessions, which include the following main aspects:
[0078] Step 4: Associate the DNS protocol with the relevant content of the HTTPS protocol. The basis for the association is the query IP address returned by the DNS and the destination address connected in the HTTPS protocol;
[0079] Step 5: Through the data learning of normal encrypted traffic, extract the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com