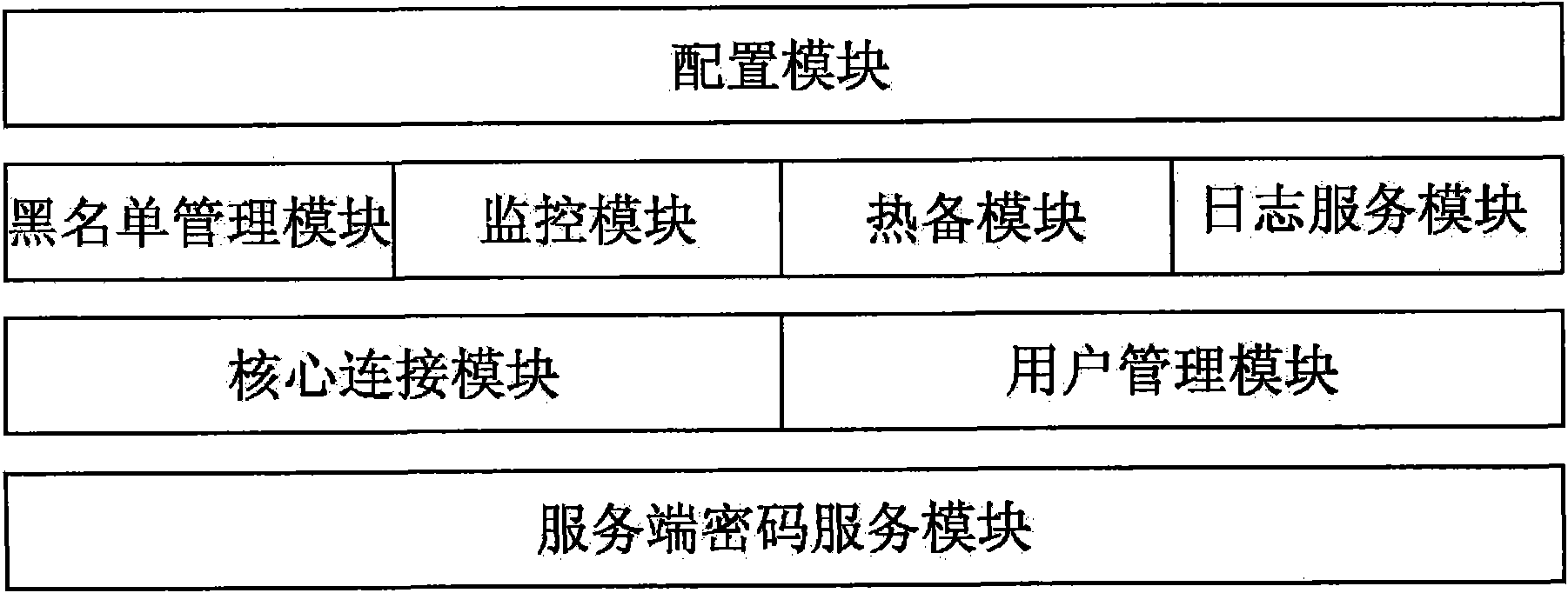
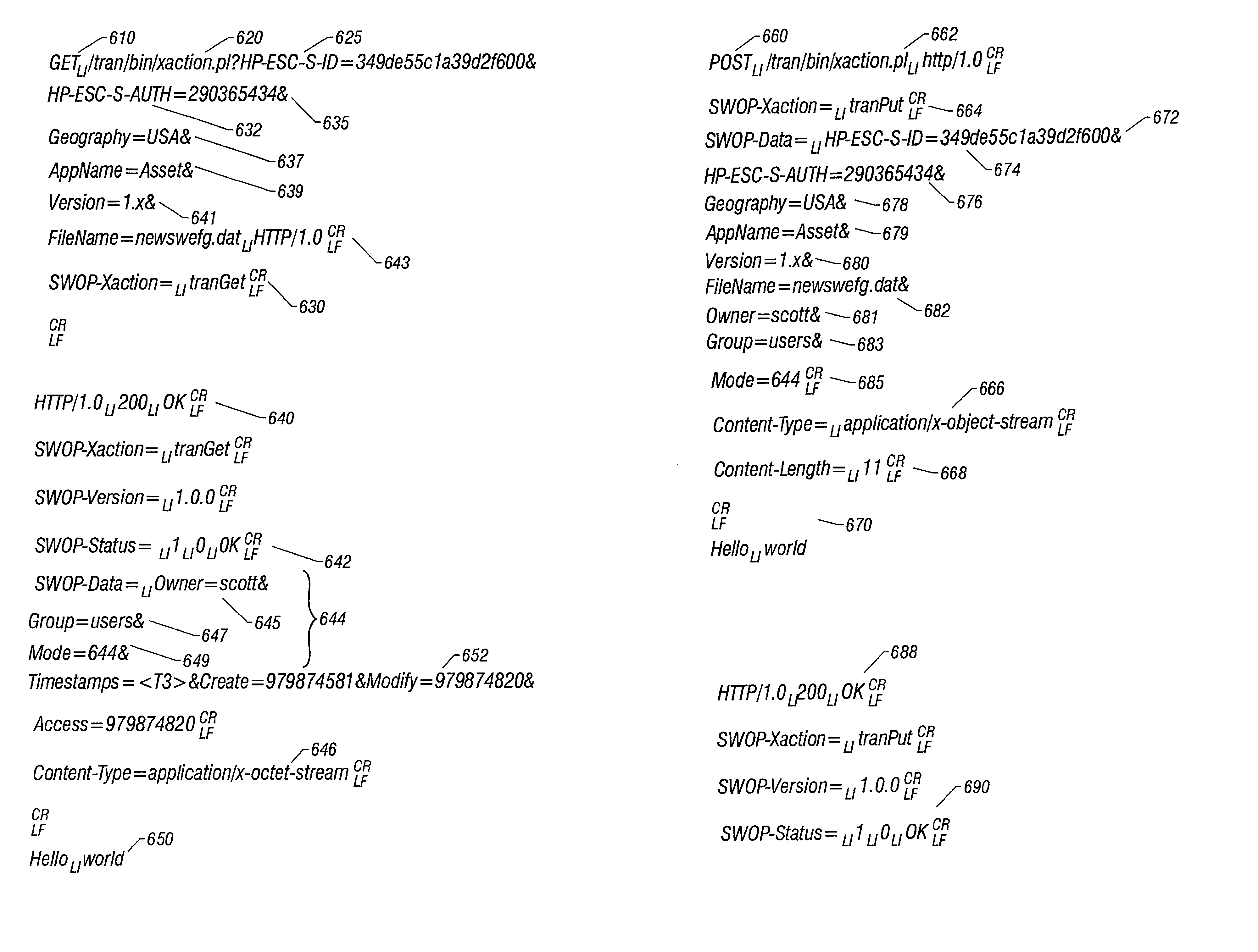Patents
Literature
303 results about "Hypertext Transfer Protocol over Secure Socket Layer" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Hypertext Transfer Protocol Secure (HTTPS) is an extension of the Hypertext Transfer Protocol (HTTP). It is used for secure communication over a computer network, and is widely used on the Internet. In HTTPS, the communication protocol is encrypted using Transport Layer Security (TLS), or, formerly, its predecessor, Secure Sockets Layer (SSL). The protocol is therefore also often referred to as HTTP over TLS, or HTTP over SSL.
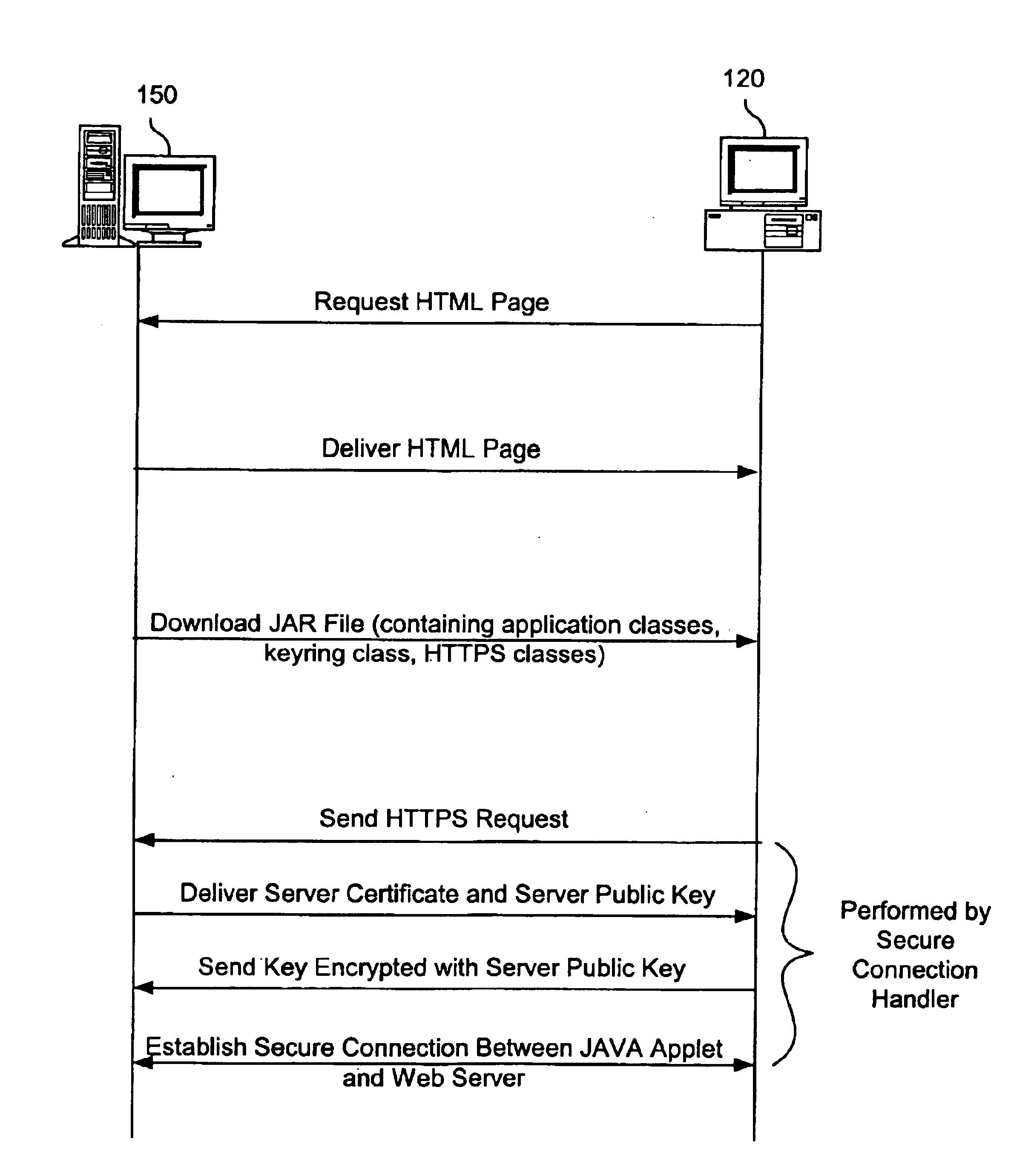
Method and apparatus for establishing a secure communication connection between a java application and secure server
InactiveUS6874084B1Improve portabilityIncrease flexibilityDigital computer detailsSecuring communicationSecure communicationWeb service
A method and apparatus for establishing a secure communication connection between a Java application or applet and a secure server is provided. An HTTPS handler is provided that may be used by Java applications or applets to establish secure communication connections with secure Web servers.
Owner:IBM CORP
Transferring a Virtual Machine from a Remote Server Computer for Local Execution by a Client Computer
InactiveUS20080201414A1Improve securityReduce the amount requiredError detection/correctionMultiple digital computer combinationsComputerized systemHypertext Transfer Protocol over Secure Socket Layer
Various embodiments of a system and method for transferring a virtual machine stored on a server computer system to a client computer system in order to execute the virtual machine locally on the client computer system are disclosed. The system and method may also be operable to transfer the virtual machine back from the client computer system to the server computer system. File differencing techniques may be used in both directions so that only changed data in the virtual machine image file is transferred across the network. The client computer system may be operable to download the virtual machine image file from the server computer system using common communication protocols such as HTTP, HTTPS, or FTP so that the virtual machine can be transferred to the client computer system without needing to be able to access files on the server computer system through a VPN.
Owner:CITRIX SYST INC
Method and apparatus for implementing secure and adaptive proxies
InactiveUS20100107222A1Digital data processing detailsComputer security arrangementsGraphicsThe Internet
Methods and apparatus for implementing common authentication and security policies across applications served over a data transmission network, such as the internet, http or https, are disclosed. The common authentication and security policies are implemented without mandating specific changes to be applied to the applications themselves. An authentication process can be dynamically performed based on different needed security levels. Applications can be graphical (e.g., web) or voice in nature and can use any applicable and available security method.
Owner:AVERY GLASSER
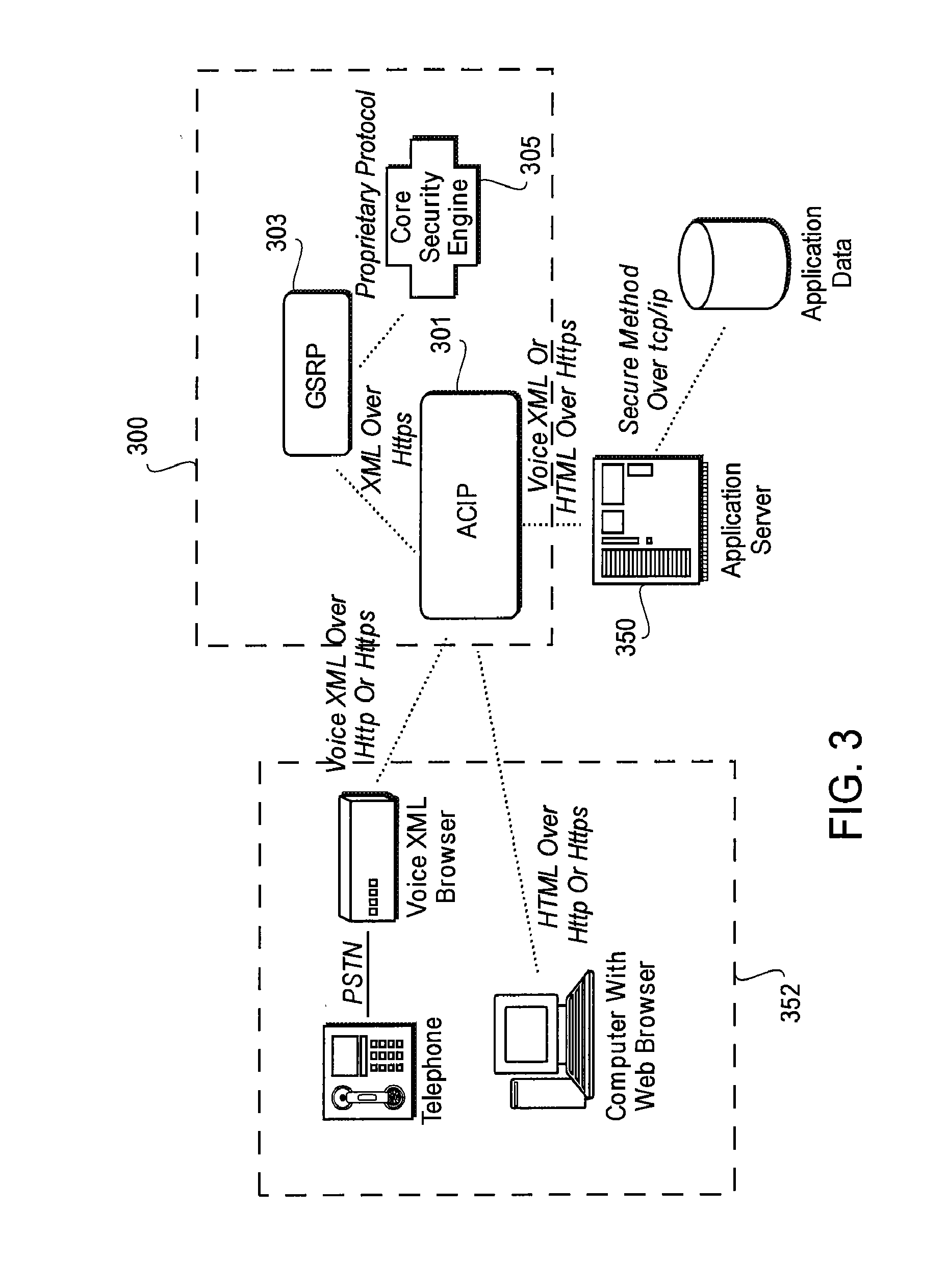
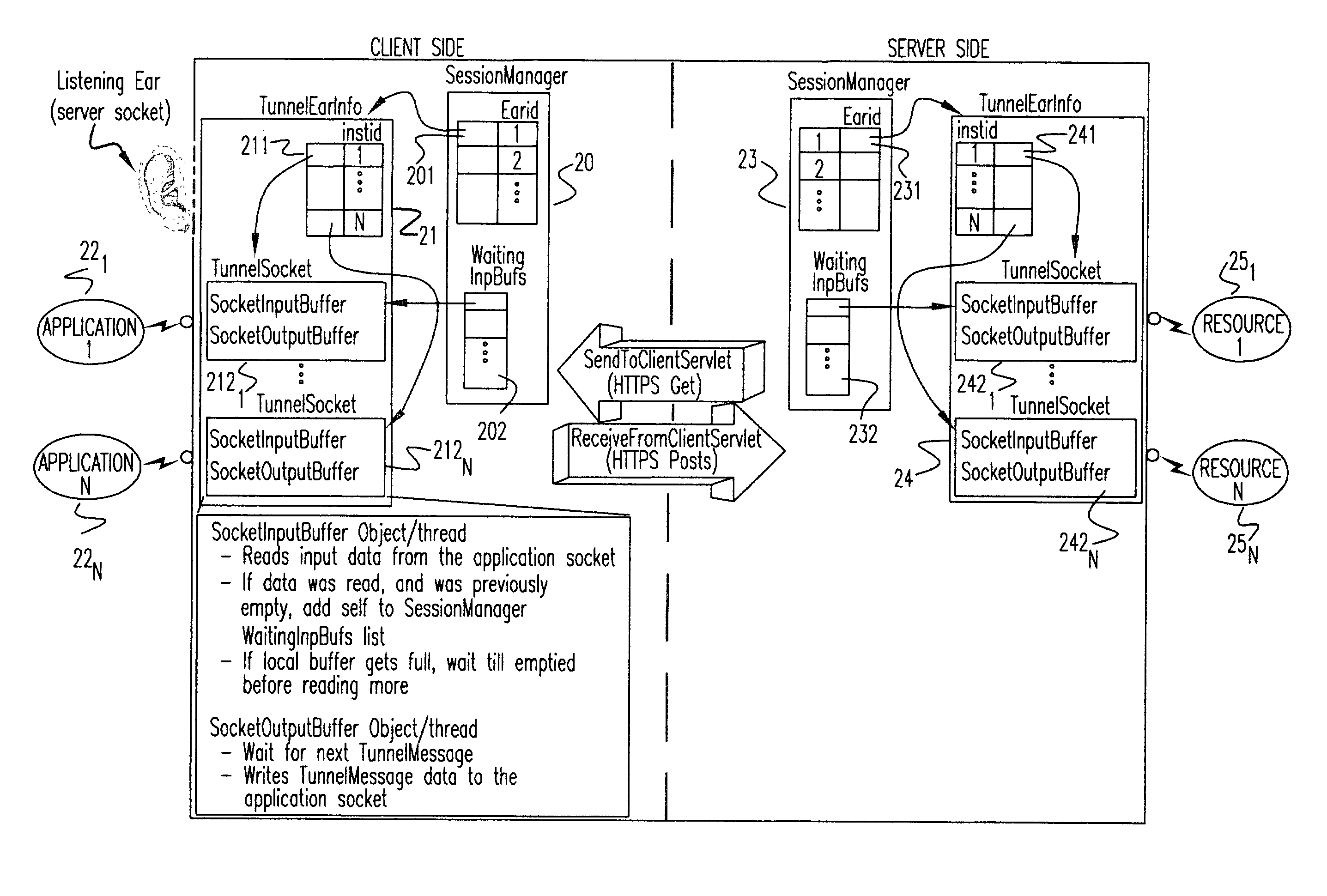
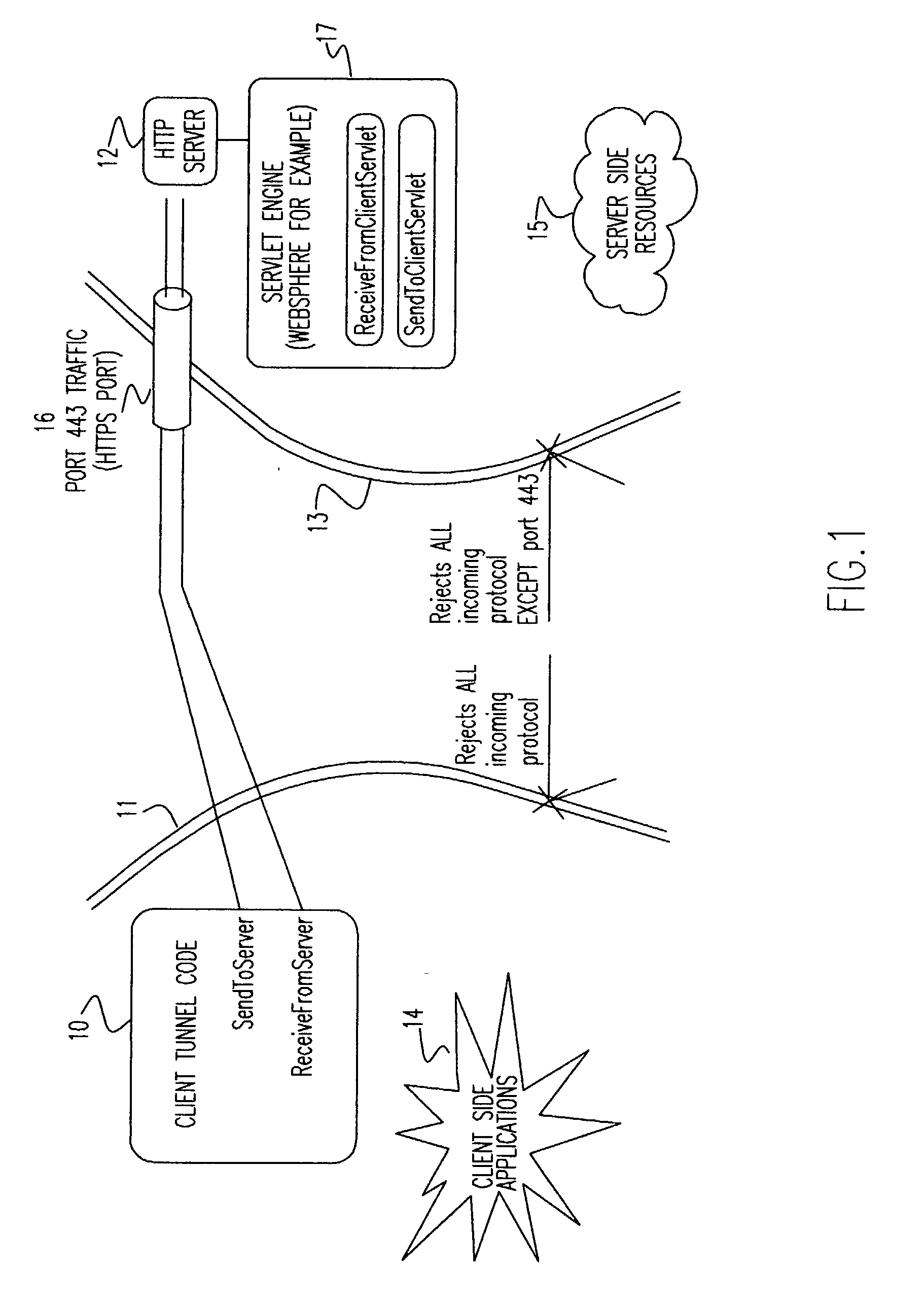
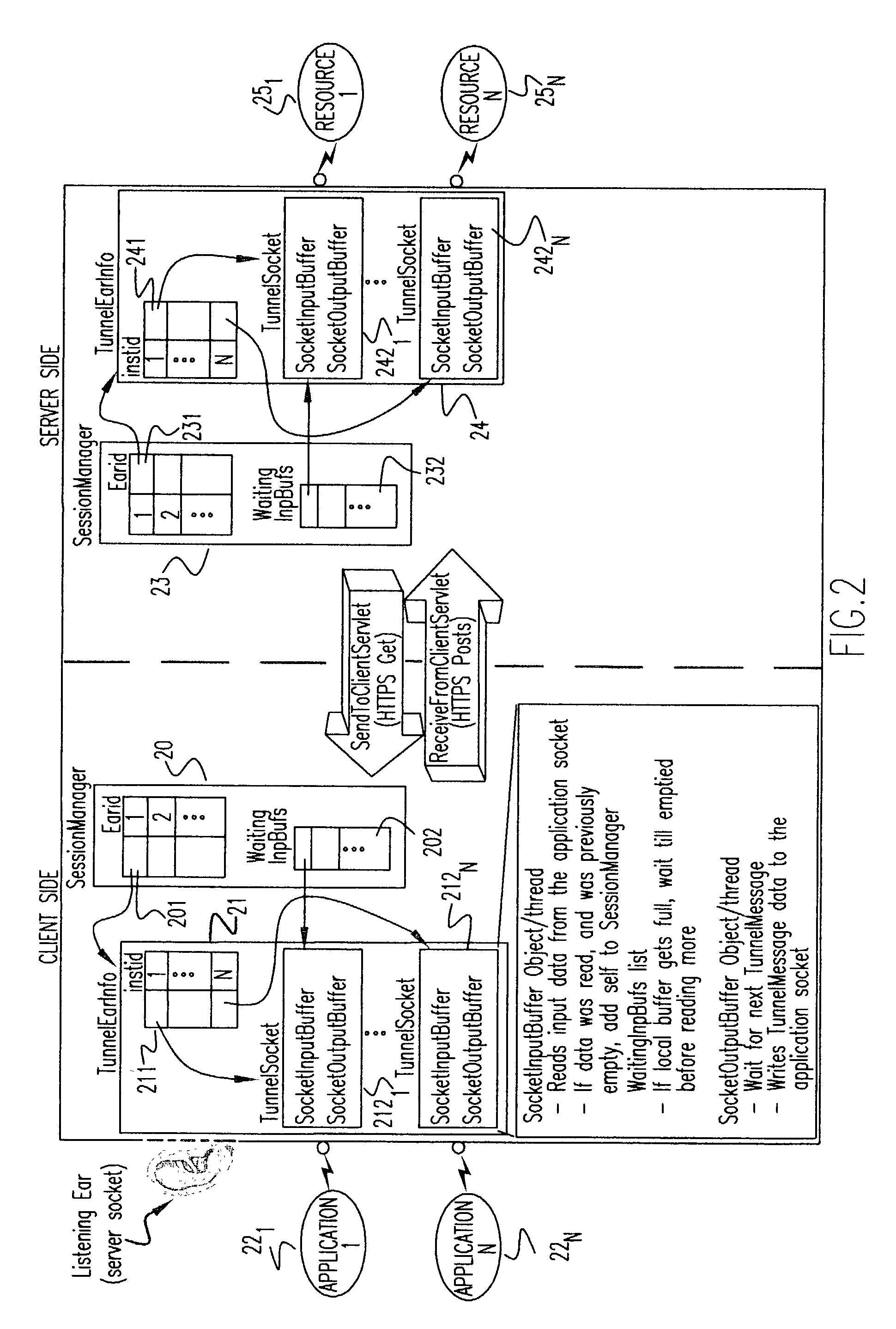
Method and apparatus for tunneling TCP/IP over HTTP and HTTPS
InactiveUS20030217149A1Multiple digital computer combinationsTransmissionHypertext Transfer Protocol over Secure Socket LayerUniform resource locator
A tunneling infrastructure provides TCP port forwarding from a client running on a client network to a server running on a server network, where the client and servers can be behind separate firewalls. To tunnel TCP, a "server socket" capability is provided, allowing the client to establish a connection to the server across the tunnel. A direct, port forwarding scheme is implemented. The client side is the driver for the tunnel operation. The client maintains multiple URL (Universal Resource Locator) connections to the server side tunnel allowing data to flow in both directions. The client's SendToServer connection(s) use the HTTP POST method to send data from the client side to the server side. The client's ReceiveFromServer connection(s) use the HTTP GET method, and allow data to be sent from the server side to the client side.
Owner:IBM CORP
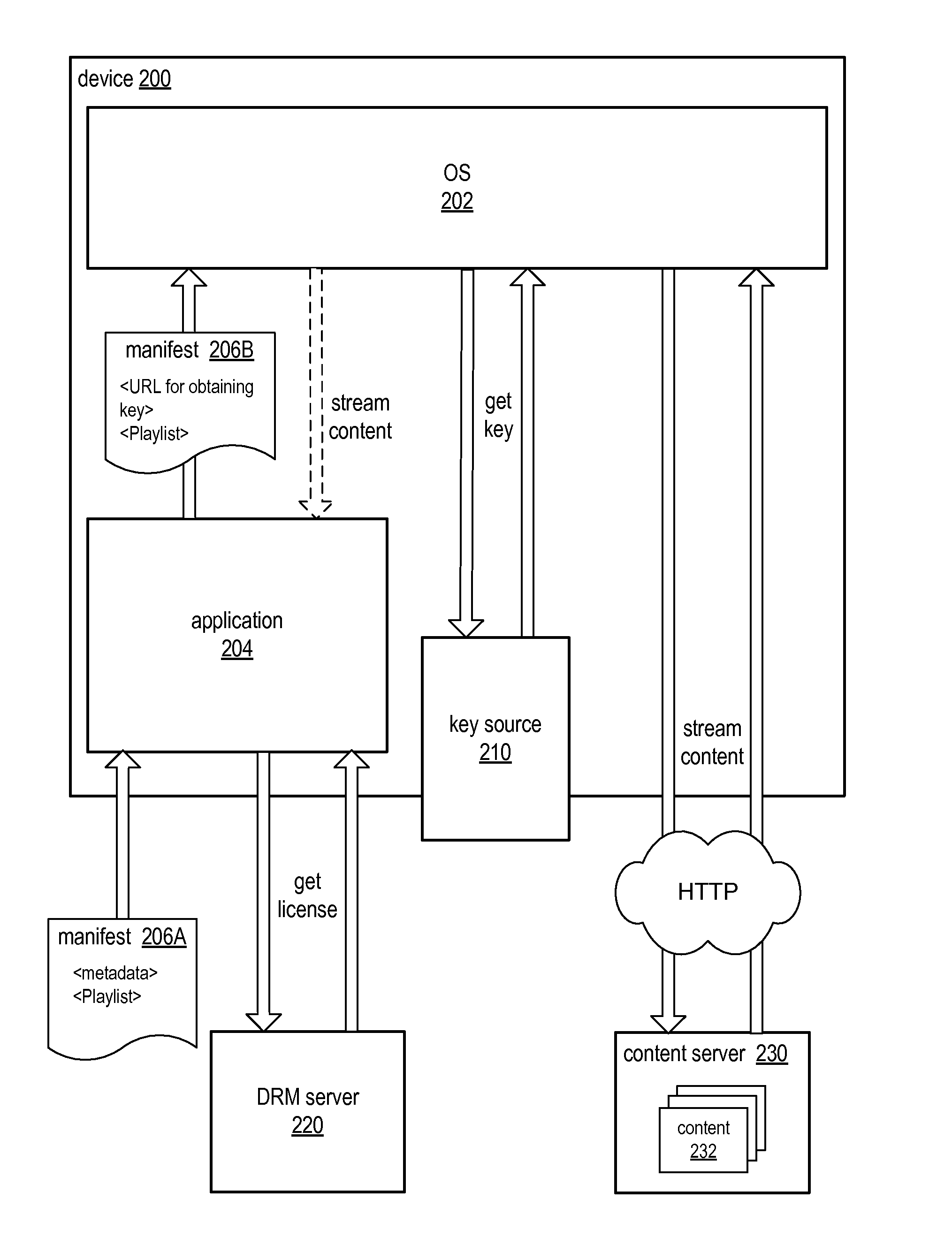
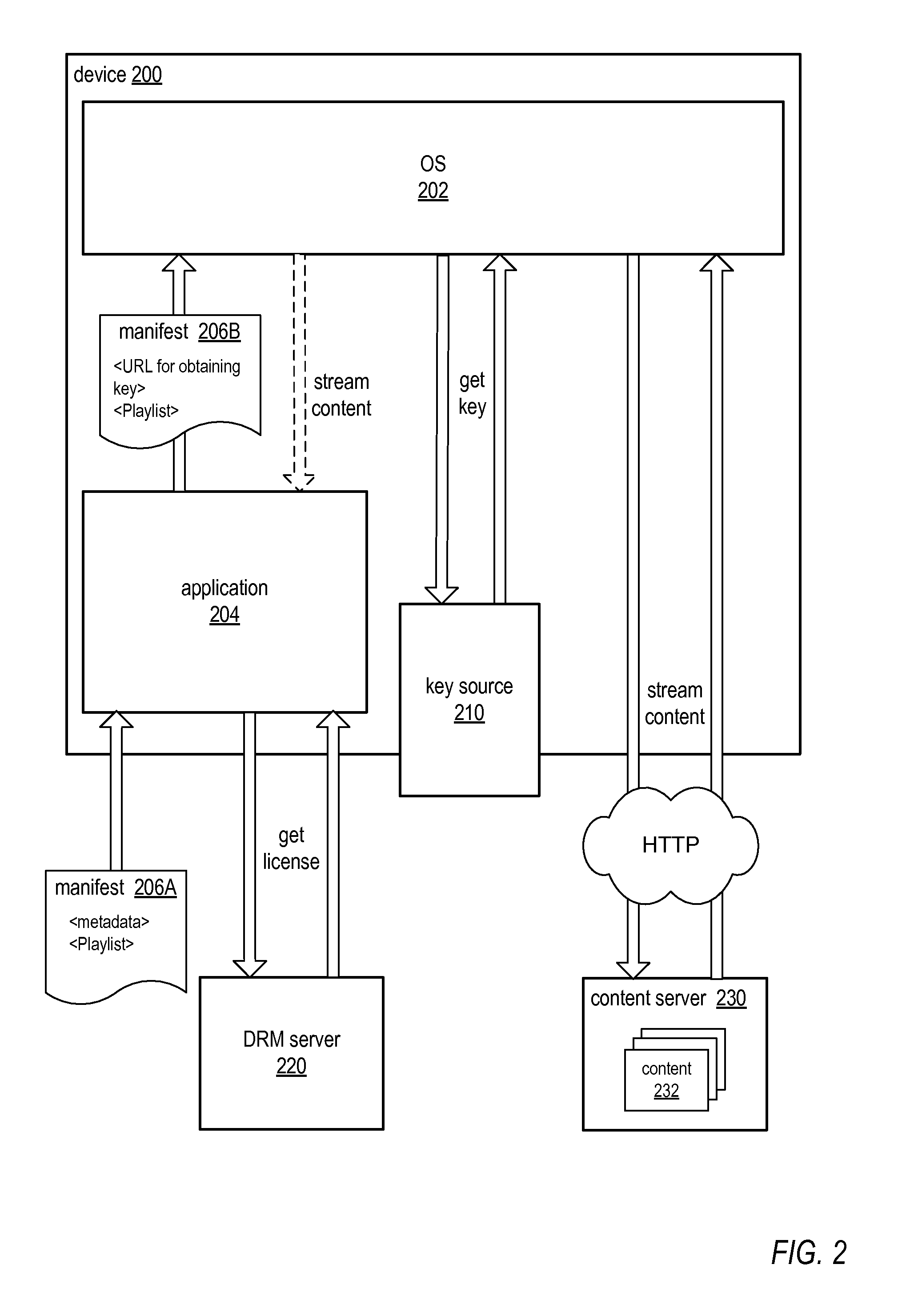
Methods and Apparatus for Key Delivery in HTTP Live Streaming
ActiveUS20130163758A1Reduce deliveryImprove scalabilityKey distribution for secure communicationPublic key for secure communicationOperational systemHttp live streaming
A key delivery mechanism that delivers keys to an OS platform (e.g., iOS platform) devices for decrypting encrypted HTTP live streaming data. An HTTPS URL for a stateless HTTPS service is included in the manifest for an encrypted HTTP live stream obtained by an application (e.g., a browser) on an OS platform device. The URL includes an encrypted key, for example as a query parameter value. The application passes the manifest to the OS. The OS contacts the HTTPS service to obtain the key using the URL indicated in the manifest. Since the encrypted key is a parameter of the URL, the encrypted key is provided to the HTTPS service along with information identifying the content. The HTTPS service decrypts the encrypted key and returns the decrypted key to the OS over HTTPS, thus eliminating the need for a database lookup at the HTTPS service.
Owner:ADOBE INC
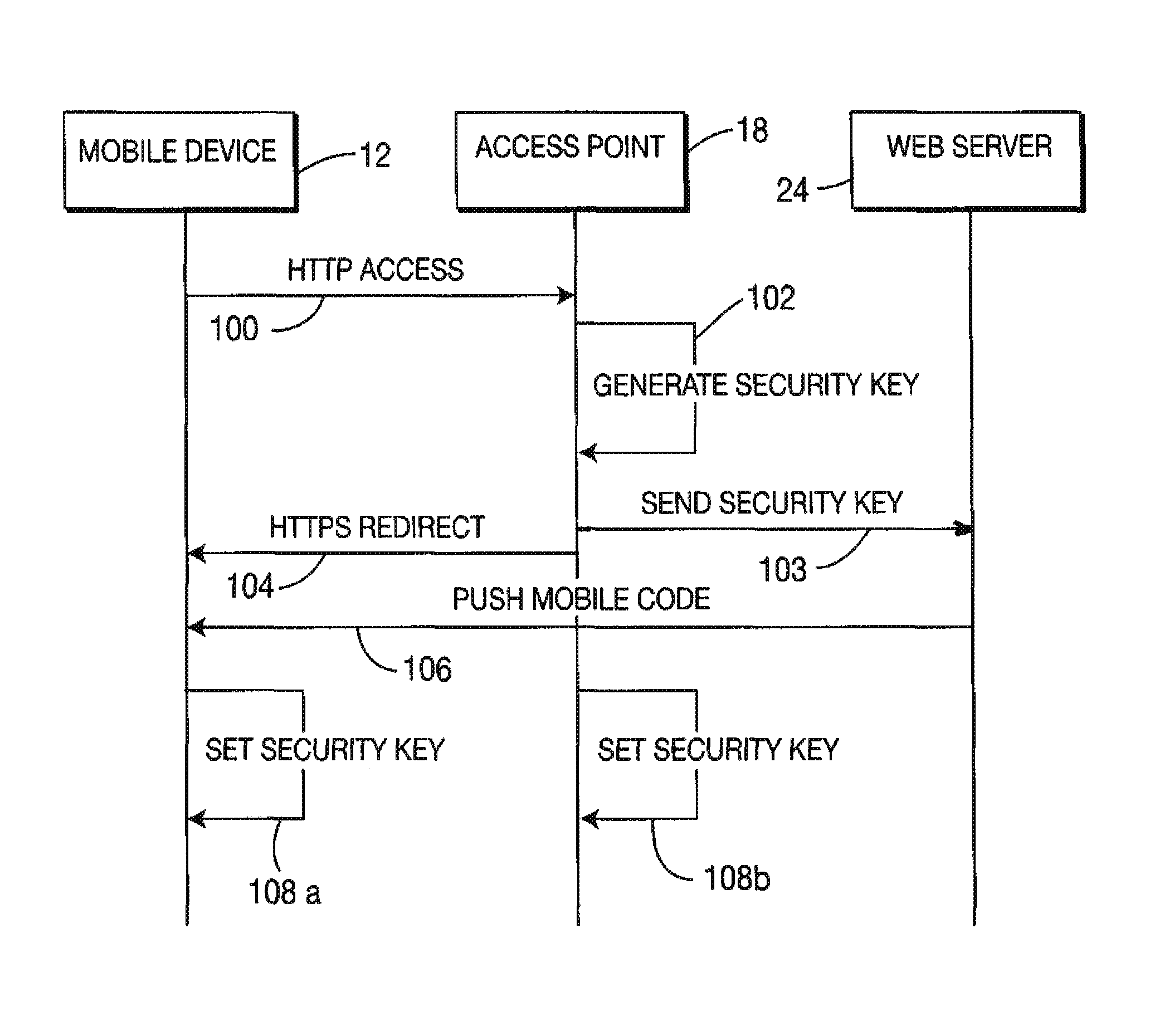
Method and apparatuses for secure, anonymous wireless LAN (WLAN) access
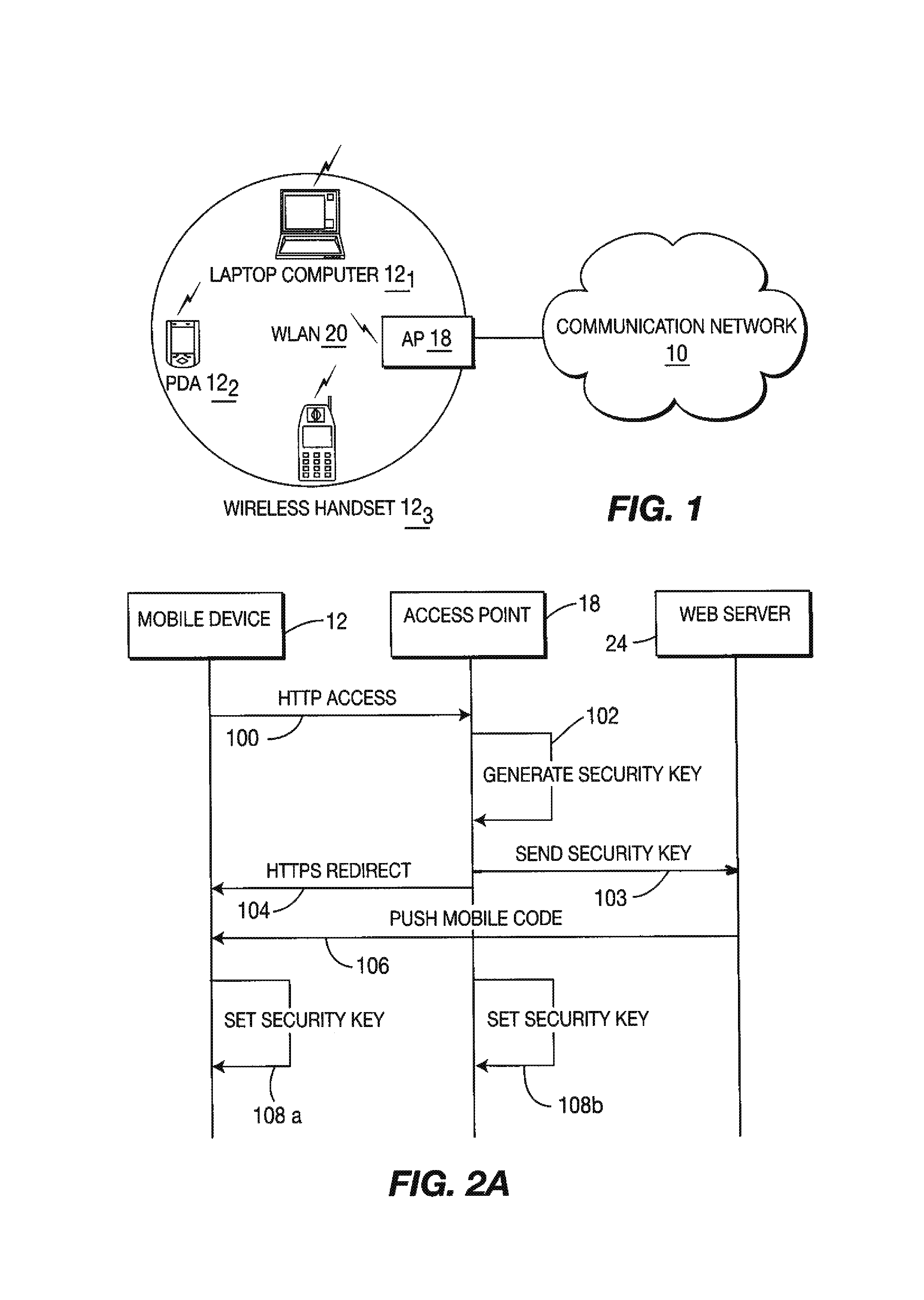
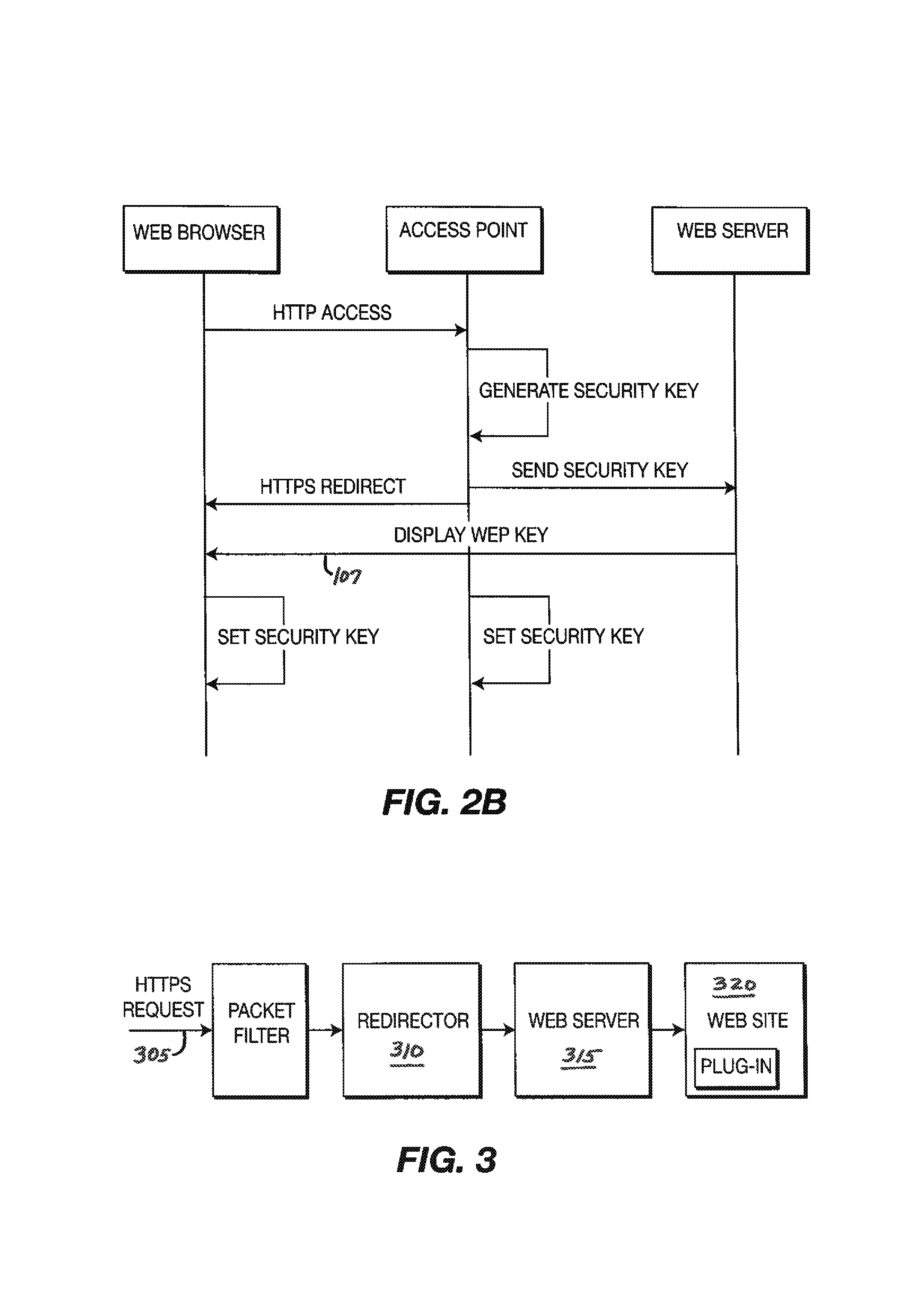
ActiveUS8285992B2Digital data processing detailsUser identity/authority verificationWeb browserWeb service
A method and system for providing secure, anonymous access to a wireless local area network, including configuring an access point to drop packets except packets exhibiting an URL access protocol like HTTP and HTTPS, intercepting a URL access request by an access point from a mobile device via a web browser, re-directing the URL access request to a web server by the access point generating a security key by one of the access points and the web server, communicating the generated security key to the said web server securely by the access point or vice versa and setting the security key by the access point is described. A mobile device including means for forwarding a request for secure access to a wireless local area network via a URL access request, means for receiving a mobile code or a signal for displaying a security key and means for setting the security key is also described.
Owner:THOMSON LICENSING SA
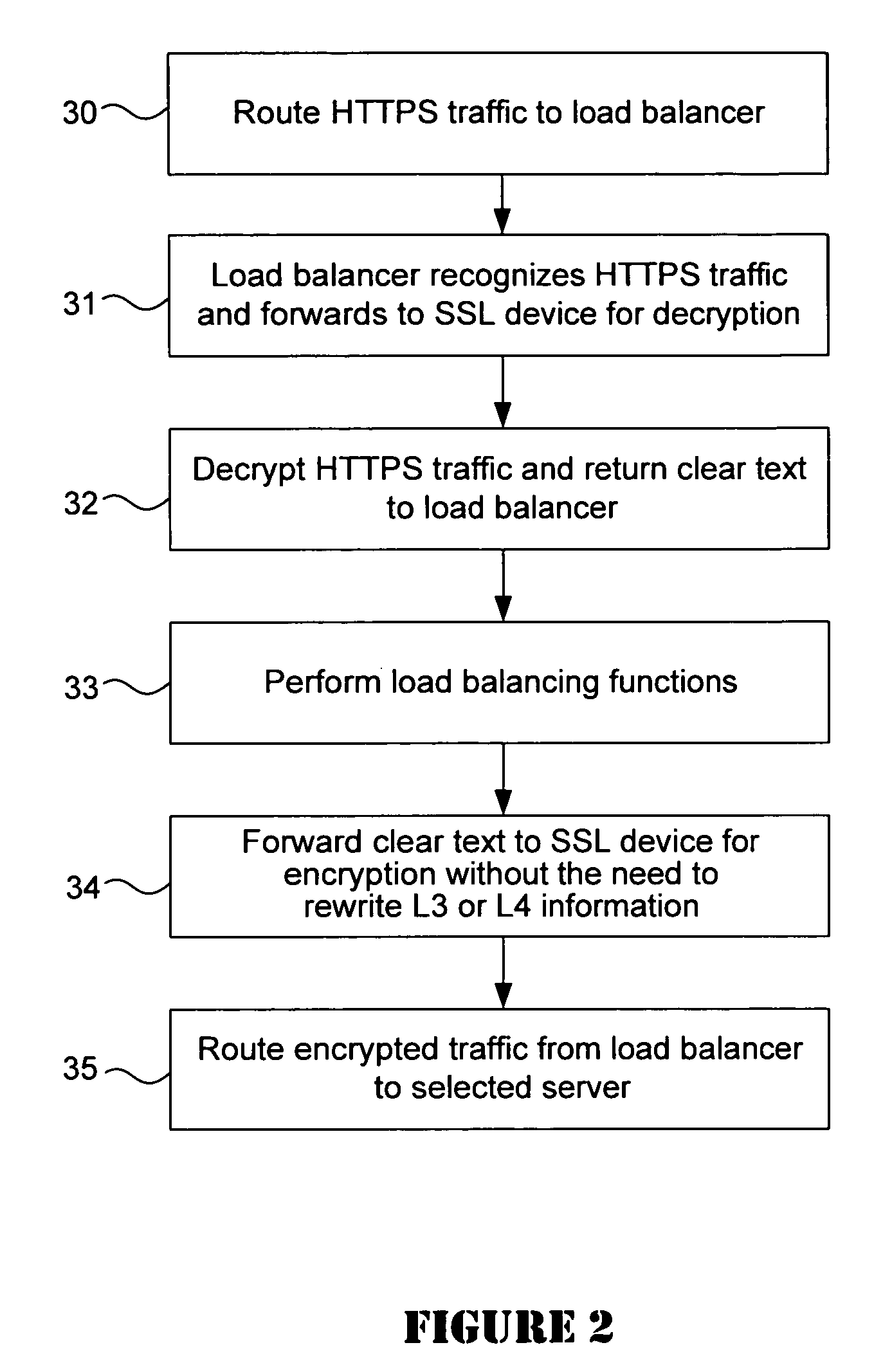
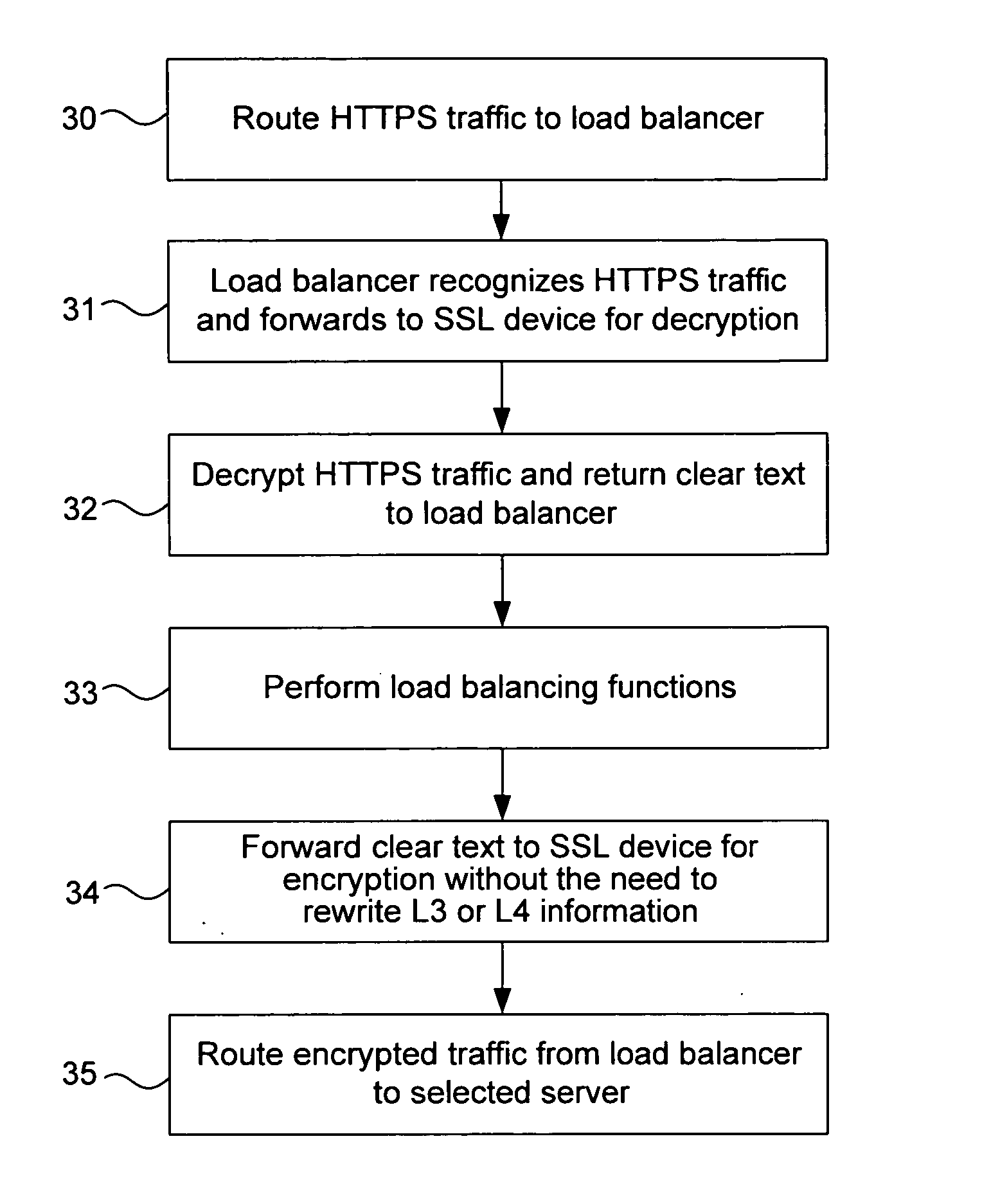
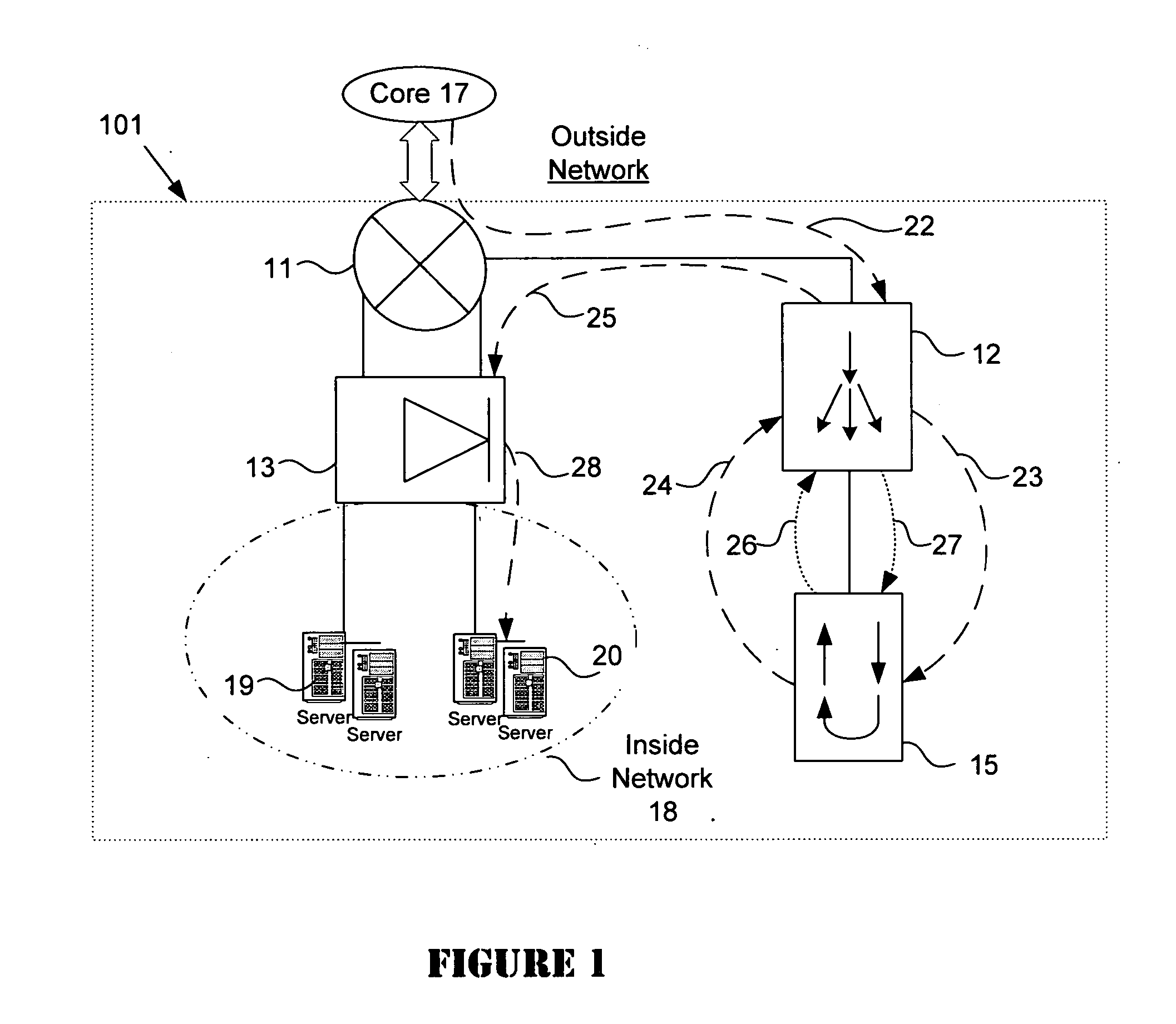
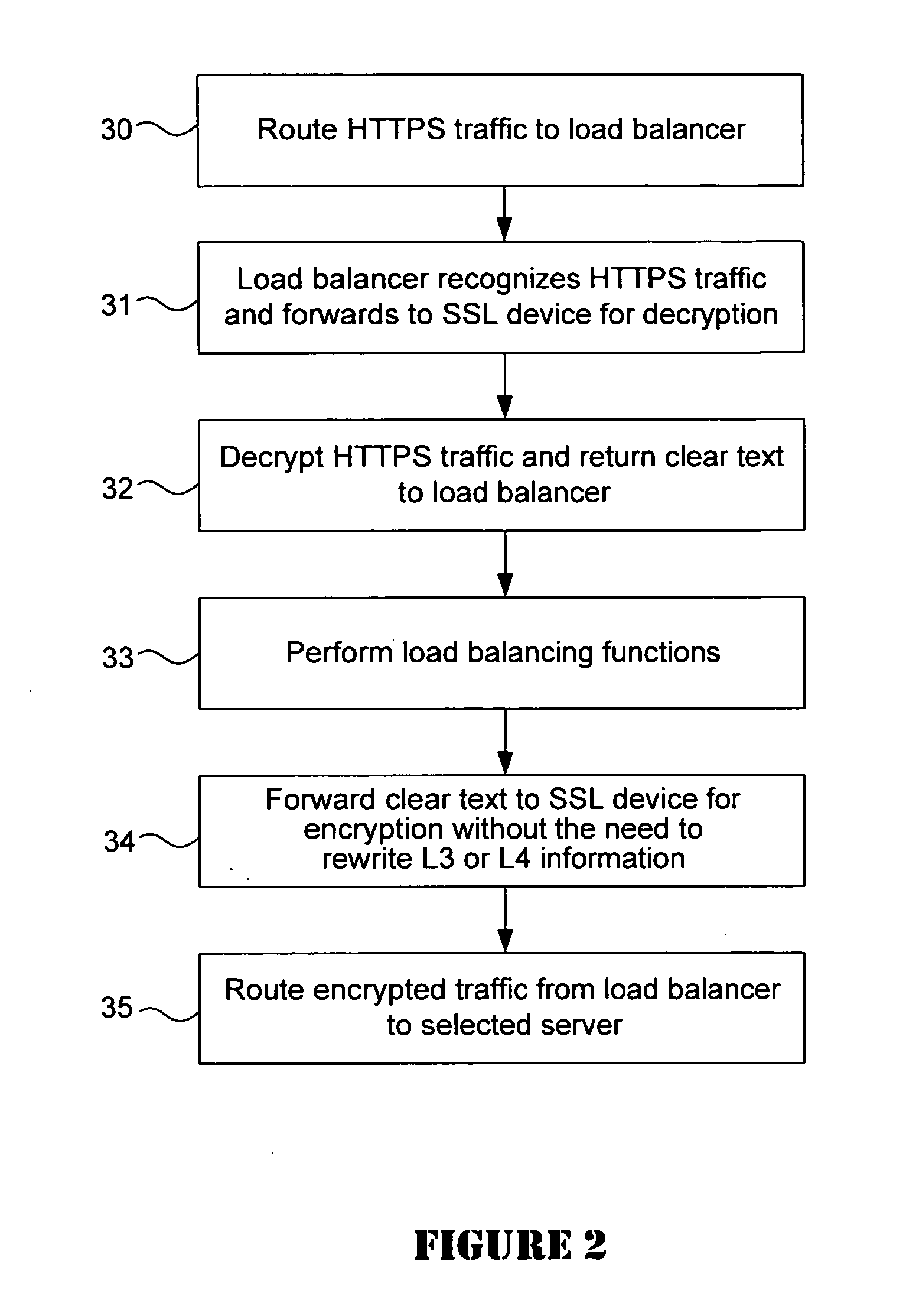
System for SSL re-encryption after load balance
A data center provides secure handling of HTTPS traffic using backend SSL decryption and encryption in combination with a load balancer such as a content switch. The load balancer detects HTTPS traffic and redirects it to an SSL offloading device for decryption and return to the load balancer. The load balancer then uses the clear text traffic for load balancing purposes before it redirects the traffic back to the SSL offloading device for re-encryption. Thereafter, the re-encrypted traffic is sent to the destination servers in the data center. In one embodiment, the combination with the back-end SSL with an intrusion detection system improves security by performing intrusion detection on the decrypted HTTPS traffic.
Owner:CISCO TECH INC
Apparatus for detecting and filtering application layer ddos attack of web service
InactiveUS20110099622A1Minimum arithmetic complexityMemory loss protectionError detection/correctionData packIp address
Owner:KOREA INTERNET & SECURITY AGENCY
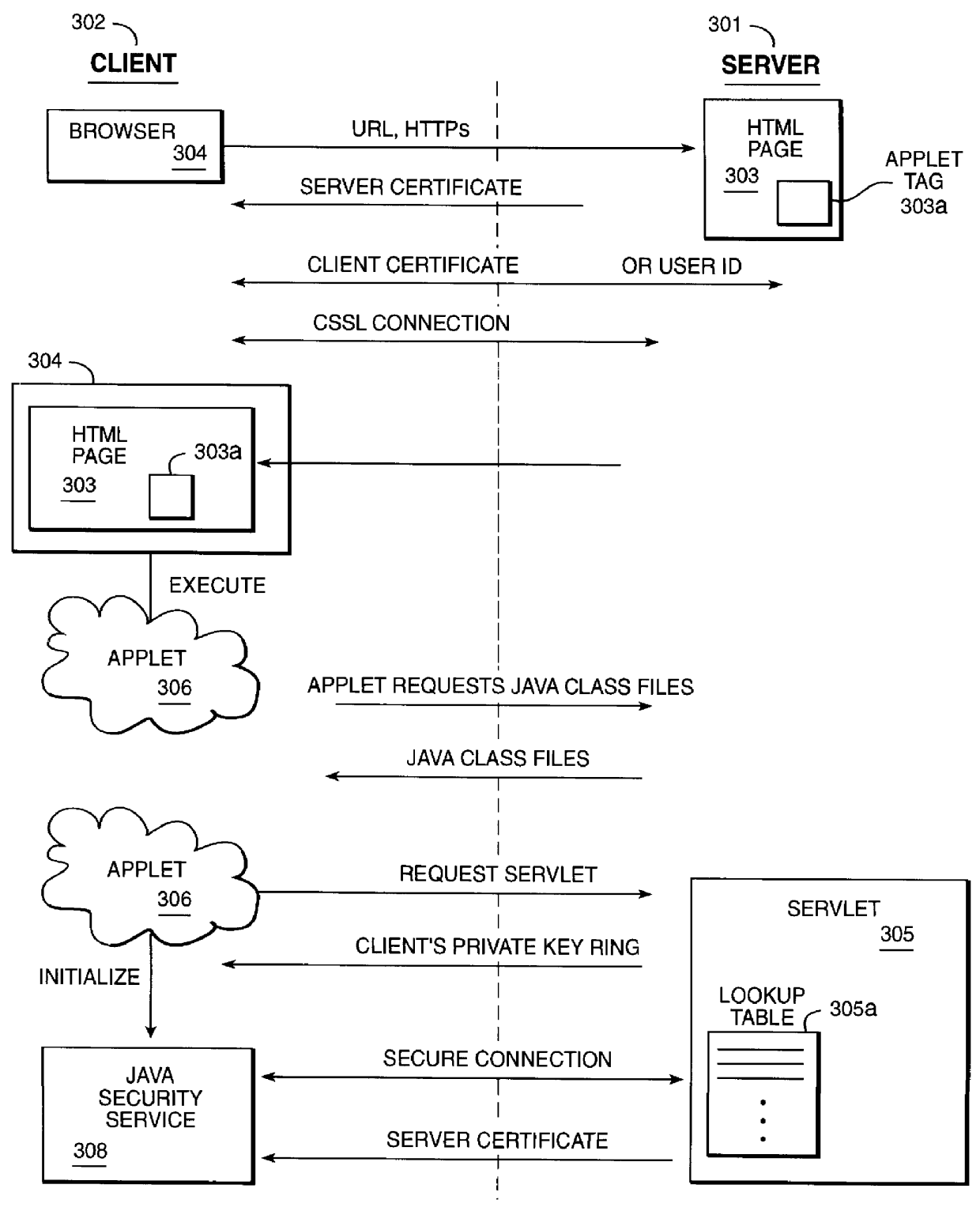
Method and apparatus for providing security certificate management for Java Applets
InactiveUS6023764ADigital data processing detailsUnauthorized memory use protectionWeb browserWeb service
The present invention defines a means for establishing a secure connection between a Java Applet and a secure web server for protocols other than Https via the use of a Java Security Service. More specifically, the present invention uses the web browser's installed certificates to setup and establish an encrypted session between the Java Applet and the secure web server. The secure connection is then used to retrieve the certificates required by the Java security service.
Owner:IBM CORP
System for SSL re-encryption after load balance
A data center provides secure handling of HTTPS traffic using backend SSL decryption and encryption in combination with a load balancer such as a content switch. The load balancer detects HTTPS traffic and redirects it to an SSL offloading device for decryption and return to the load balancer. The load balancer then uses the clear text traffic for load balancing purposes before it redirects the traffic back to the SSL offloading device for re-encryption. Thereafter, the re-encrypted traffic is sent to the destination servers in the data center. In one embodiment, the combination with the back-end SSL with an intrusion detection system improves security by performing intrusion detection on the decrypted HTTPS traffic.
Owner:CISCO TECH INC
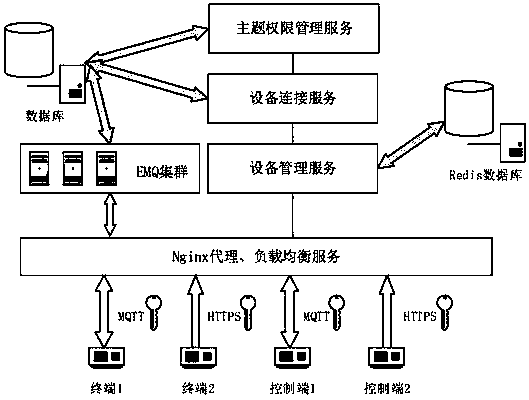
Public protocol Internet of things platform and device access method
ActiveCN109587228AImplement two-way authenticationRealize associationTransmissionAccess methodTransmission channel
The invention discloses a public protocol Internet of things platform and a device access method. The public protocol Internet of things platform uses eMQTT message-oriented middleware based on an MQTT communication protocol, the EMQTT message-oriented middleware is deployed on server nodes in a cluster mode, and message synchronization is maintained among the server nodes. A database, a Redis database and an HTTPS protocol message access interface are also included. The HTTPS protocol message access interface adapts an HTTPS request to an MQTT protocol. The server nodes are deployed with a load balancing service, a device access service, a device management service, and a theme authority management service. Each service carries out communication through an RESTful API interface. By usingthe public protocol Internet of things platform and the device access method, the bidirectional authentication between a device end and a server side is realized, and the association between a certificate user and the theme authority of publishing subscription is also realized. At the same time, adaption to the MQTT protocol is implemented, and the controllability of a device access authority anda data transmission authority, and the safety of a data encryption transmission channel are ensured.
Owner:SHANDONG INSPUR SCI RES INST CO LTD
Data interaction method, client and server
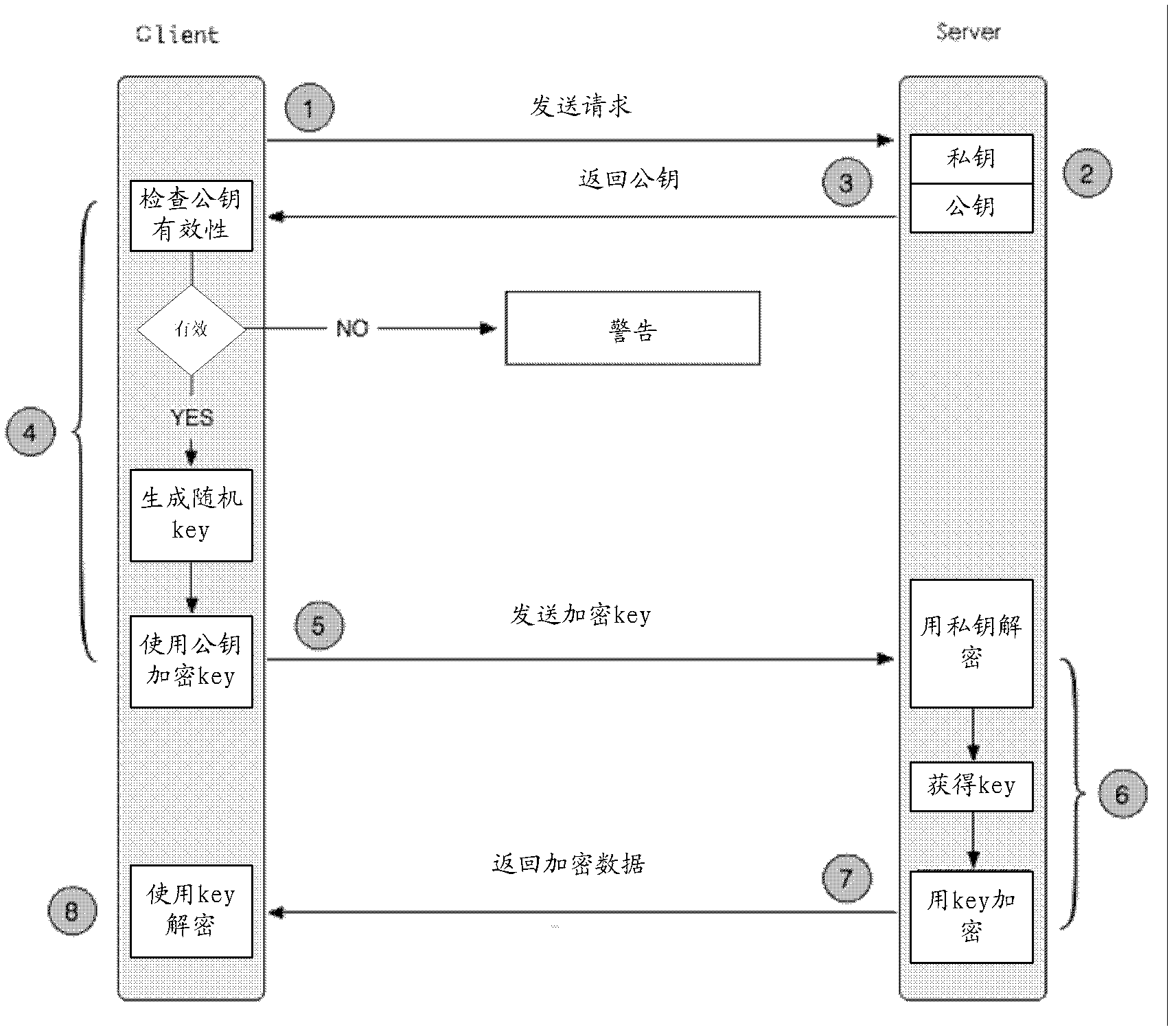
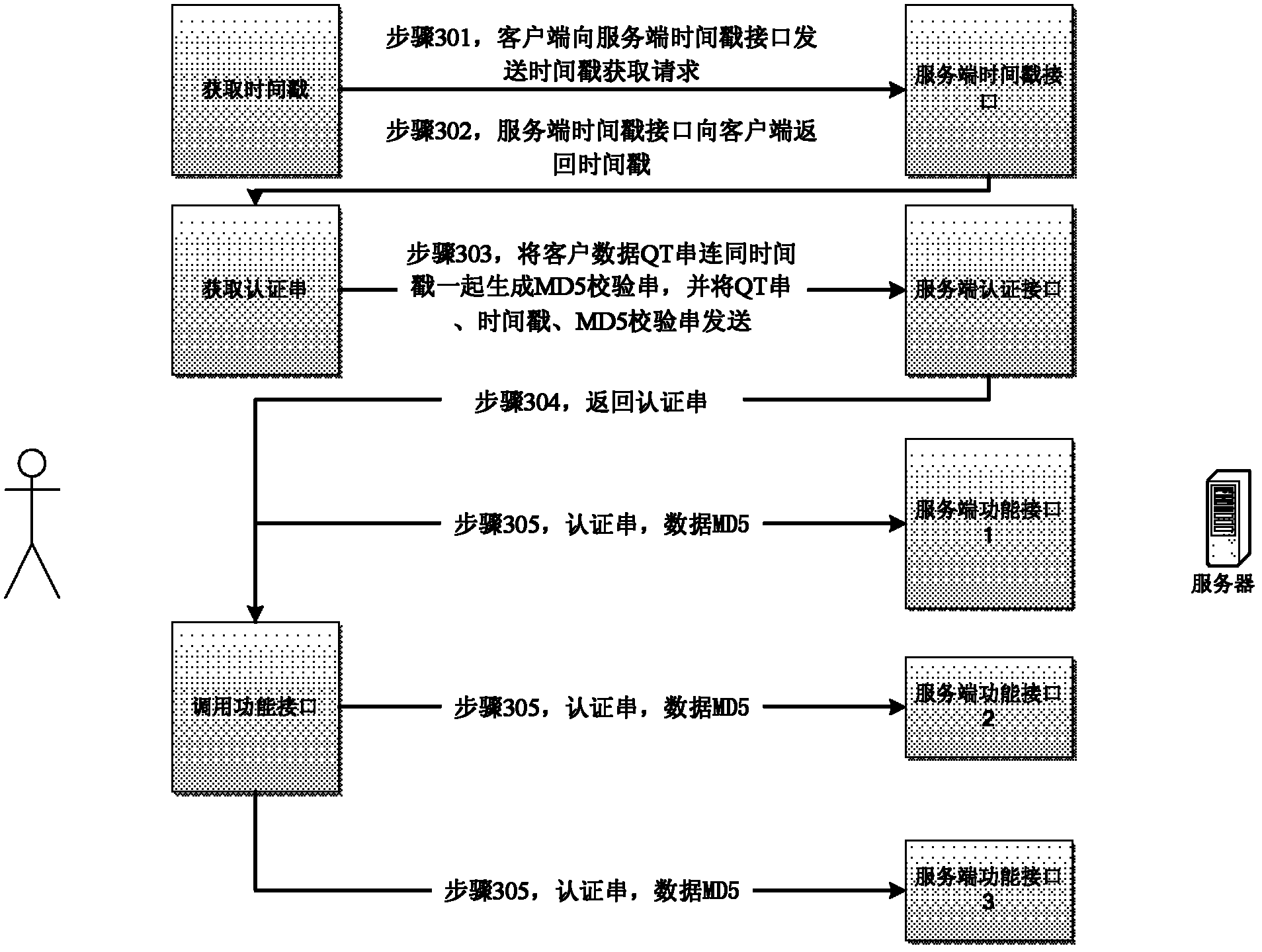
ActiveCN102624740APrevent tamperingAvoid the danger of vandalismUser identity/authority verificationTimestampHypertext Transfer Protocol over Secure Socket Layer
The invention provides a data interaction method, a client and a server, so as to solve the problems of requested replaying and client computer safety that cannot be solved by adopting HTTPS (Hyper Text Transfer Protocol Secure) technique. The method comprises the following steps: obtaining a timestamp from a service terminal; sending the first identifying information of a user, the timestamp and verifying data generated according to the first identifying information of the user and the timestamp to the service terminal; obtaining certified data encrypted by the service terminal, wherein the certified data comprises the encrypted data generated for the timestamp and second identifying information of the user; and using the certified data to access the service terminal. According to the method provided by the invention, HTTPS encryption and improved MD5 are used together while the encryptions at the client and service terminal are adopted, so that the possibility of distorting and falsifying data at 'end' and 'path' is efficiently avoided. Besides, the timeliness control is performed on interface calling by using effective time through the timestamp, so that the data damage risk caused by recording and largely replaying a user request is efficiently avoided.
Owner:BEIJING QIHOO TECH CO LTD
Systems and methods for intelligent transport layer security
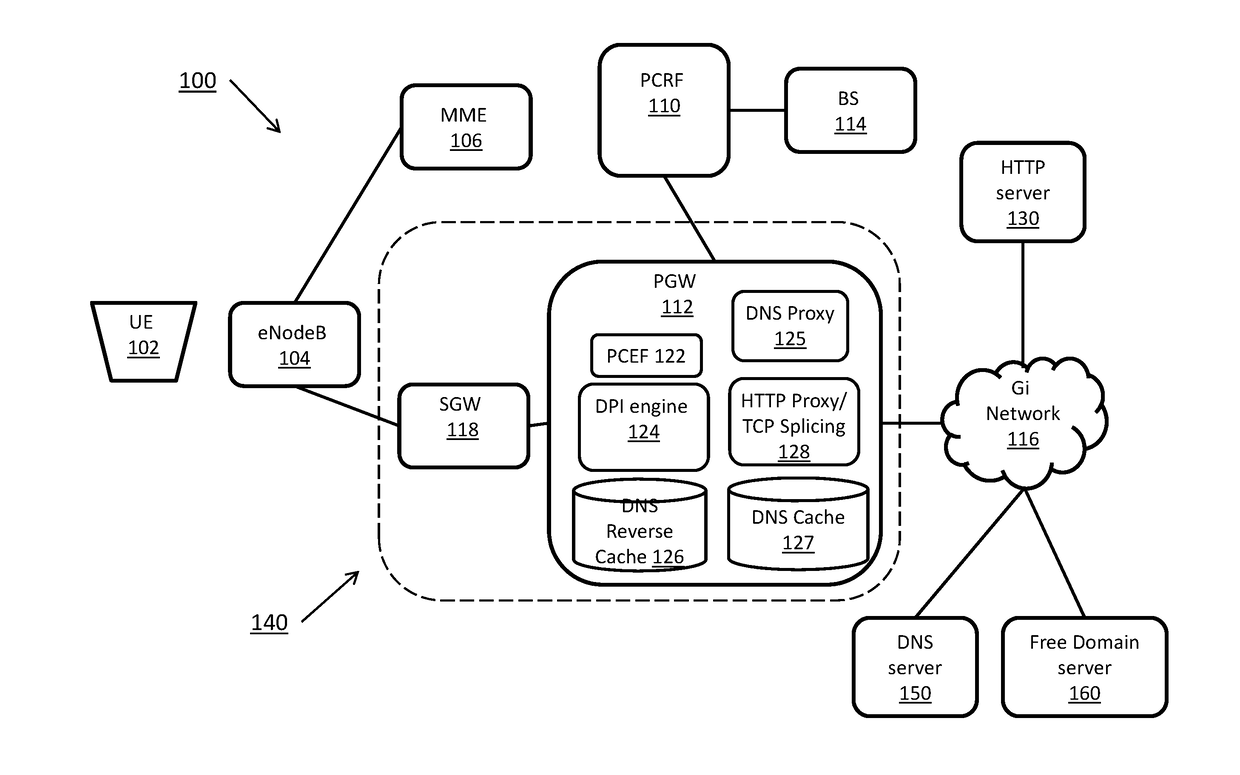
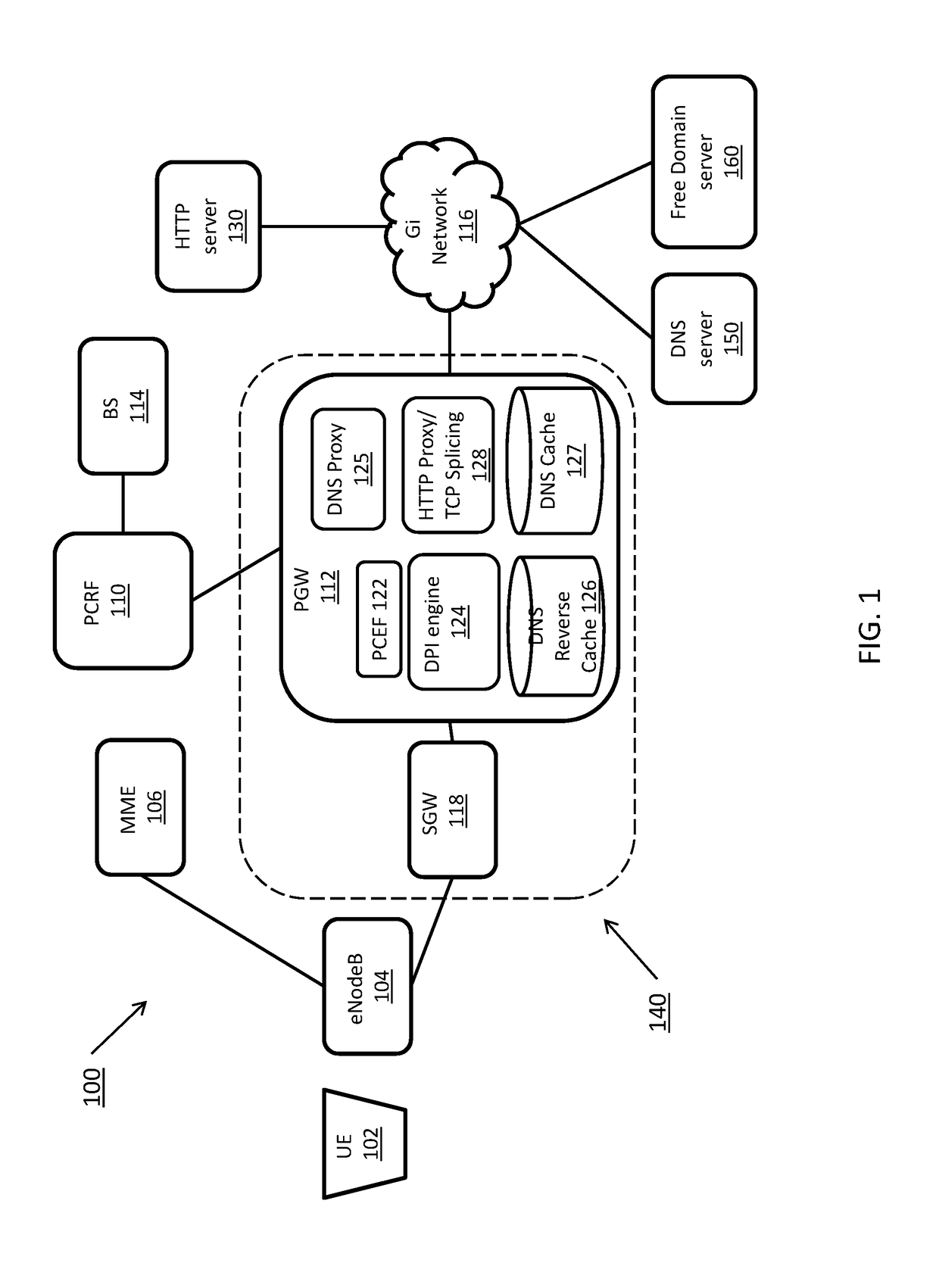
InactiveUS20170272470A1Accounting/billing servicesTelephonic communicationDomain nameComputer network
Systems and methods for detecting a domain name in a mobile network session for use in applying mobile policy and enforcement functions based on the domain name. A computing device receives a packet associated with a request from a user equipment to access a domain at a server. The computing device determines a traffic type associated with the packet, the traffic type including one of Hypertext Transfer Protocol (HTTP) traffic, Hypertext Transfer Protocol Secure (HTTPS) traffic, and non HTTP or HTTPS traffic. The computing device determines a domain name based on the traffic type and determines a service to apply to the packet based on the domain name.
Owner:MICROSOFT TECH LICENSING LLC
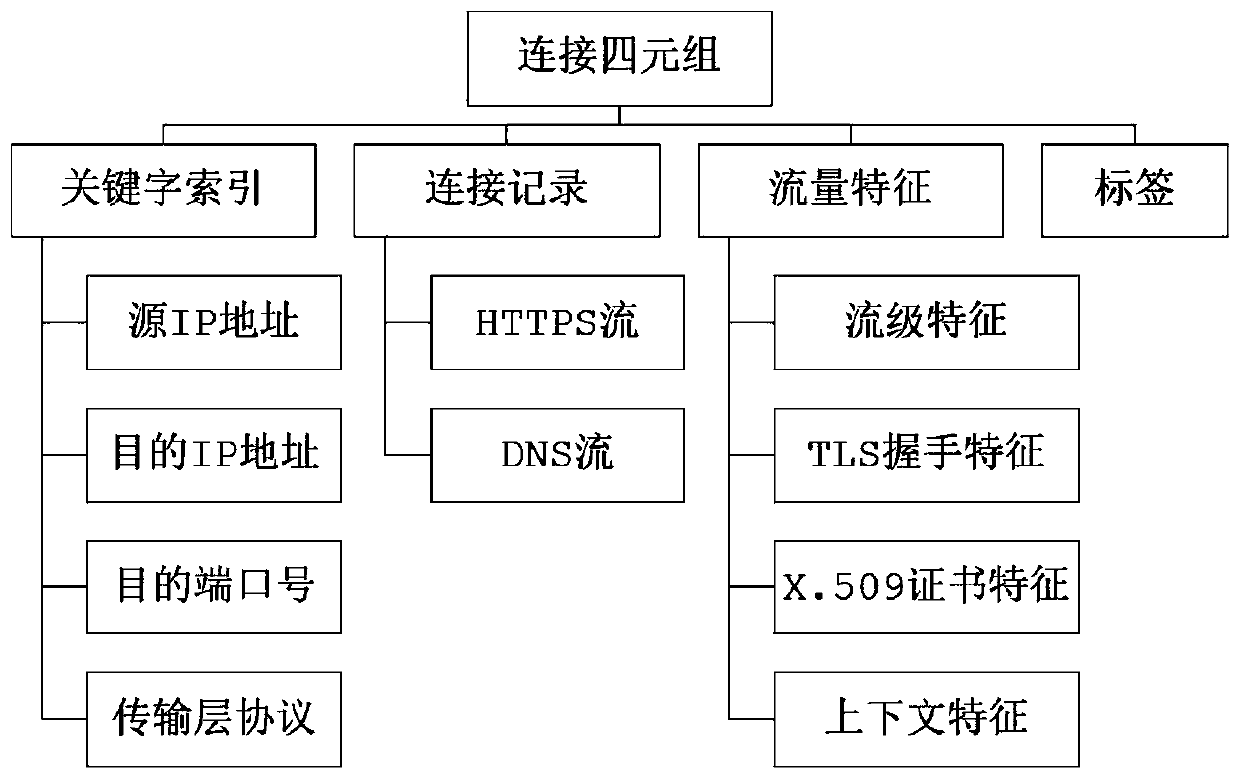
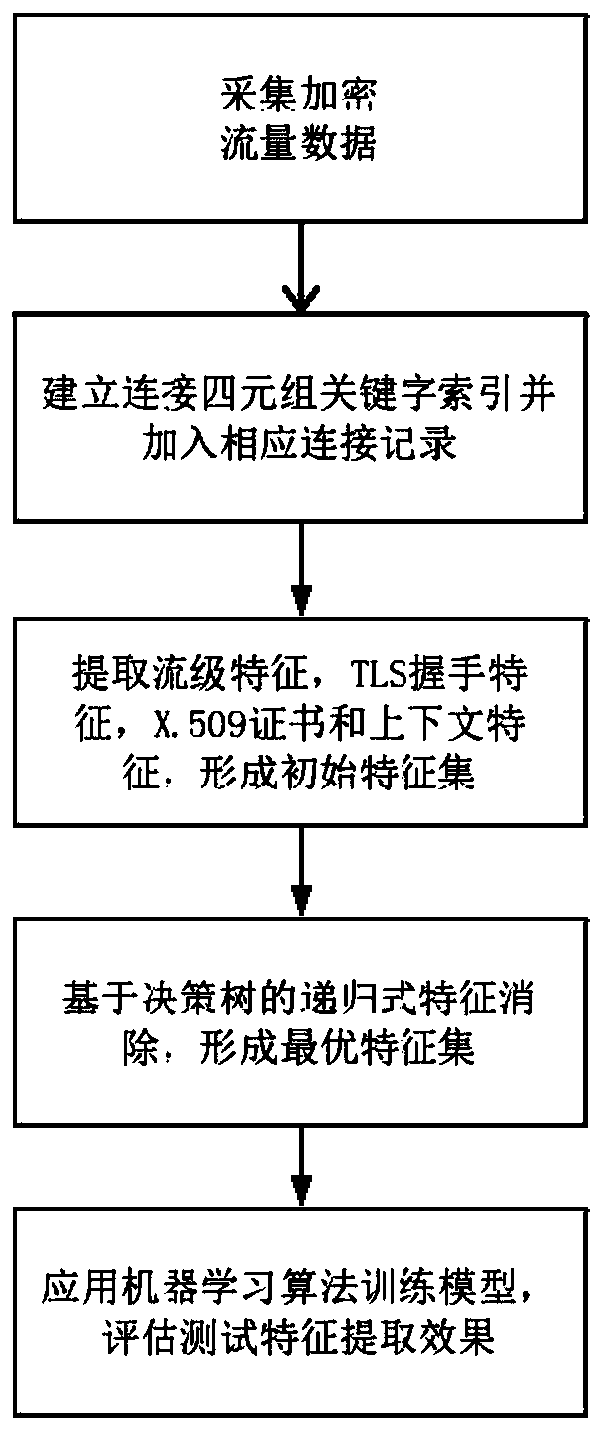
Malicious encrypted flow feature analysis method
The invention discloses a malicious encrypted flow feature analysis method, which belongs to the crossing field of network security and machine learning, and is used for analyzing the HTTPS flow and detecting the malicious threats in the HTTPS flow. The method comprises the following steps of modeling the flow data by taking a connection quaternion as a data structure, analyzing the encrypted flowfrom four levels by taking the connection quaternion as a unit, and extracting the flow-level features, TLS handshake features, X.509 certificate features and context features of the connection quaternion to obtain an initial feature set, adopting a recursive feature elimination method based on a decision tree to screen the initial feature set to obtain an optimal feature set used for the machinelearning model training to thereby obtain a malicious encrypted flow detection model.
Owner:BEIJING UNIV OF TECH
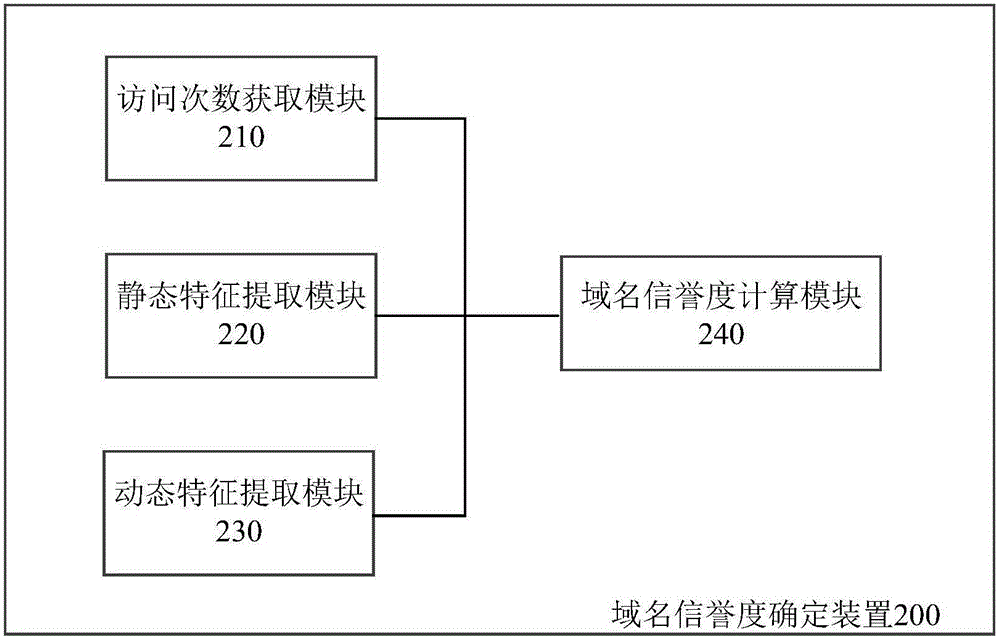
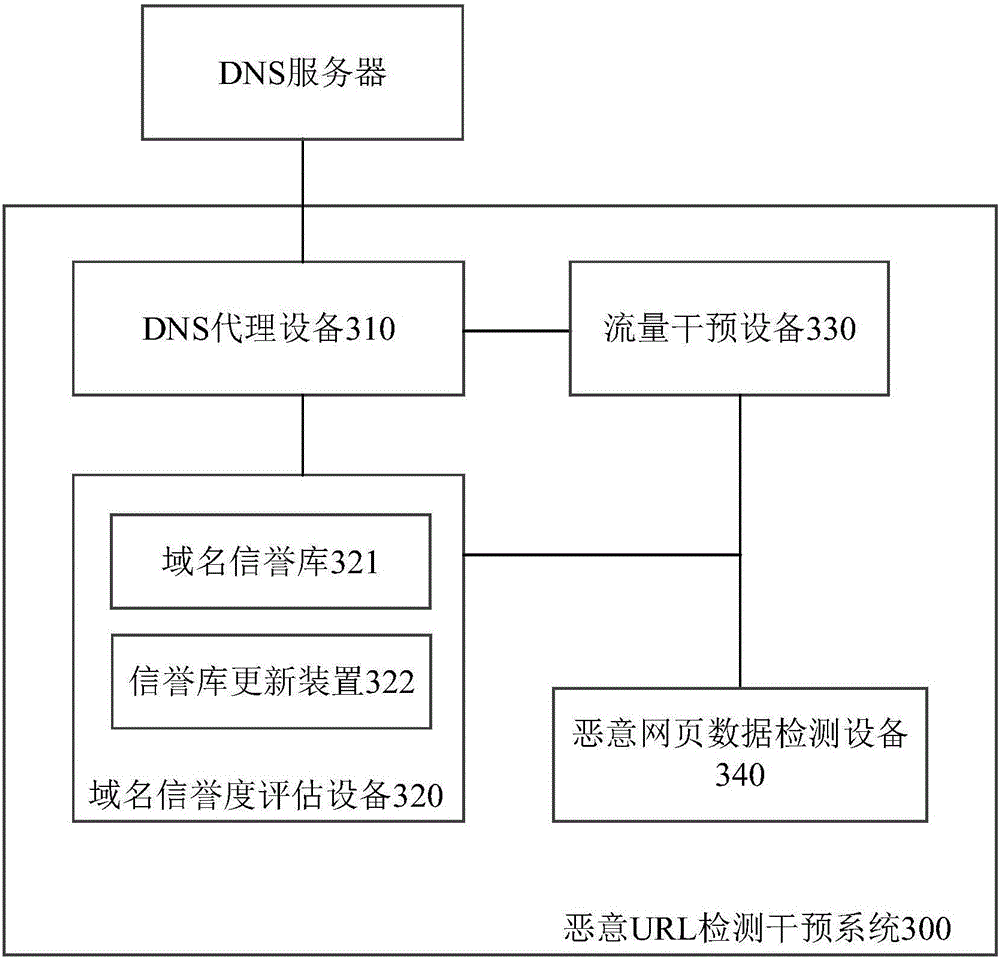
Malicious URL detection intervention method, system and apparatus
ActiveCN106131016AReduce missed detectionReduce false detection rateTransmissionDomain nameIp address
The invention discloses a malicious URL detection intervention system. The system comprises a DNS proxy device, a credit evaluation device and a traffic intervention device, wherein the DNS proxy device is suitable for receiving a domain name resolution request, requesting a domain name credit evaluation device for the credit of a domain name, and returning back an IP address of the traffic intervention device to a user if the credit indicates that the domain name has security risks; the credit evaluation device comprises a domain name credit library, and is suitable for returning back the credit of the domain name in response to the request of the credit of the domain name; and the traffic intervention device is suitable for receiving an access request from the user and performing protocol identification for the access request, and is also suitable for extracting a URL from the access request which is identified as a request of a HTTP or HTTPS protocol, matching the URL with a malicious RUL library, and if matching is failed, being used as a reverse proxy to realize communication of the user and a destination server. The invention also discloses a corresponding domain name credit determining apparatus, a corresponding domain name credit library establishing apparatus and methods.
Owner:BEIJING KNOWNSEC INFORMATION TECH
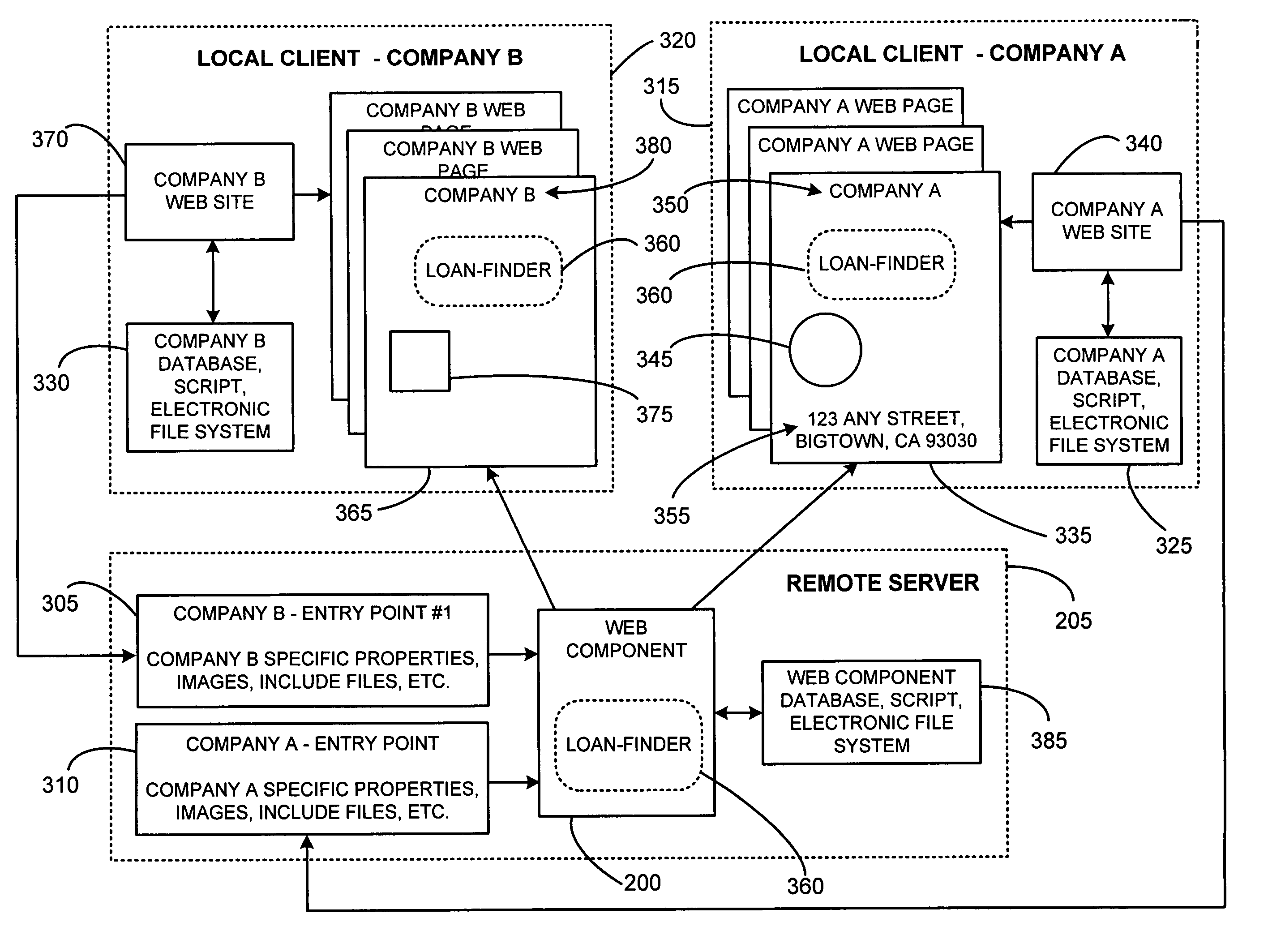
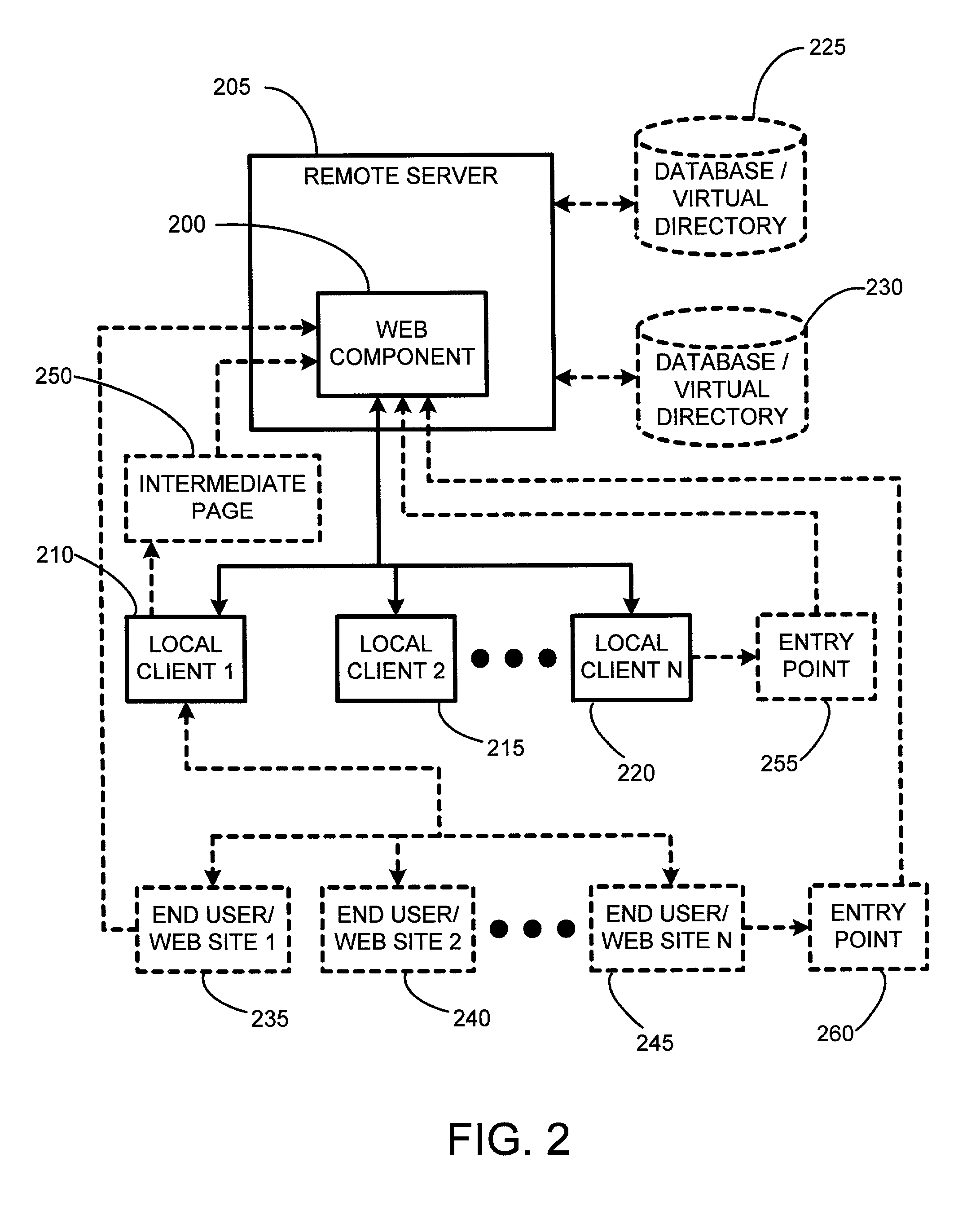
System and method for using dynamic web components to remotely control the security state of web pages
ActiveUS7000107B2Reduce test costsFaster time-to-marketDigital data processing detailsUser identity/authority verificationAutomatic controlWeb browser
The present invention involves a new system and process for automatically controlling whether a displayed web page and associated frames displayed within a window of a web browser are secure or non-secure. For example, whether the displayed web page and associated frames are provided via a secure socket layer (SSL), i.e. a web page from an HTTPS address (secure), or simply via an HTTP address (non-secure), respectively. Specifically, the present invention uses a dynamic “Web Component” to remotely control web page security states. Further, the Web Component according to the present invention uses the same script and HTML for all implementations or instantiations of the Web Component, regardless of which, or how many, unique local clients make use of the Web Component. This code reuse is accomplished by using entry web pages, or “entry points,” as described in further detail below, to set the value of function properties or parameters of the Web Component for dynamically and controlling the security state of a web page having at least two frames. The script and / or HTML source code of the Web Component pages does not change based on each new implementation or instantiation. Consequently, little setup work is required for each implementation, and only a basic verification test pass is needed for each unique automatically customized Internet web page.
Owner:MICROSOFT TECH LICENSING LLC
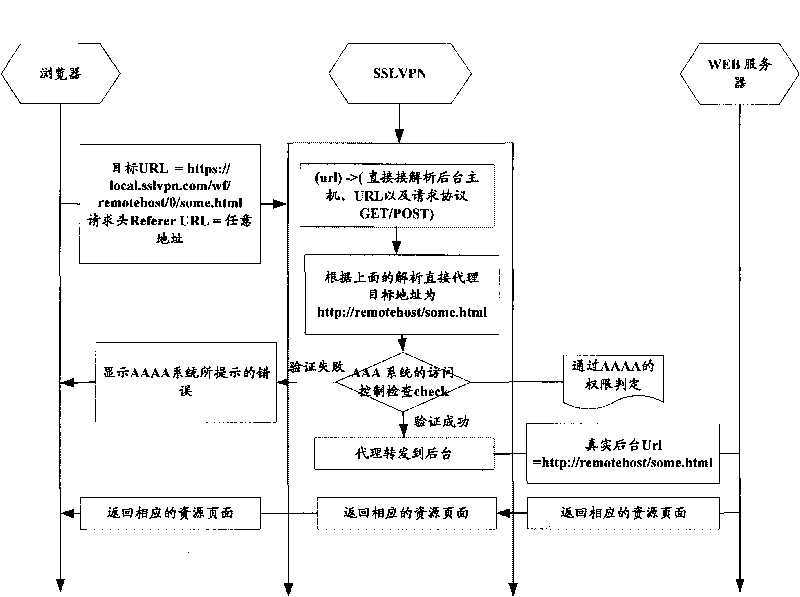
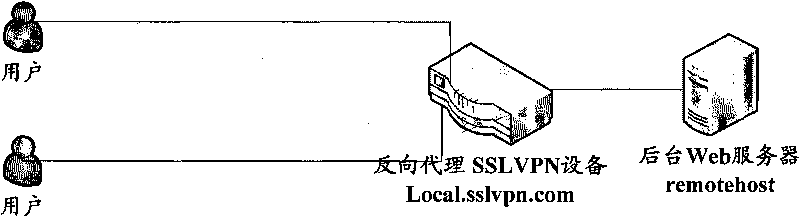
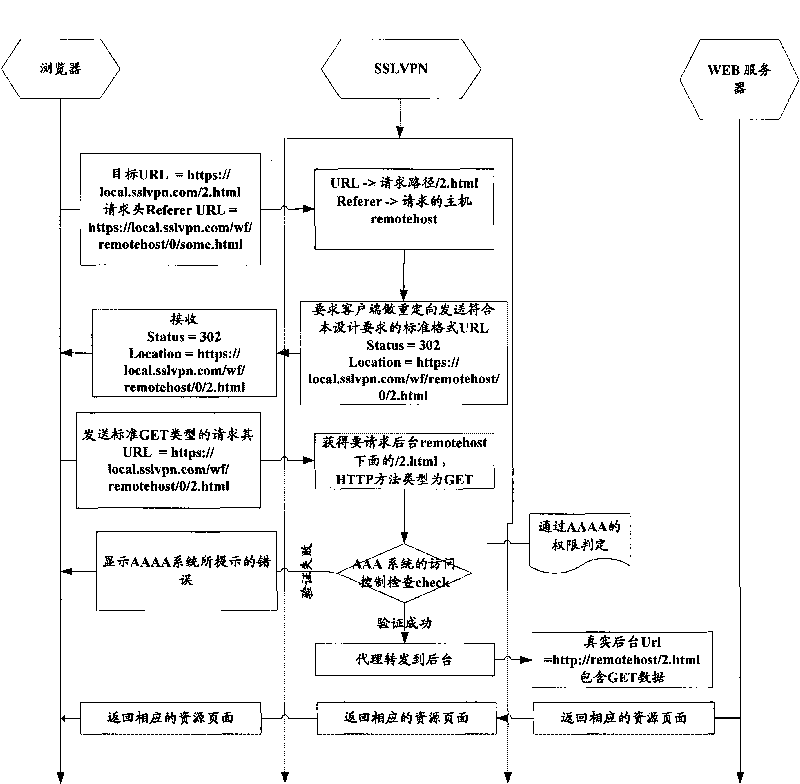
Method for realizing WEB reverse proxy
The invention provides a method for realizing WEB reverse proxy. After the user side inputs a first WEB reverse proxy processing request in the bookmark bar or the interface input box of a browser, the method comprises the following steps: the client transmits HTTP (Hyper Text Transport Protocol) / HTTPS request, the Uniform Resource Locator (URL) of the request includes an address of reverse proxy server SSLVPN (Secure Socket Layer Virtual Private Network), an address of an accessed background server and a resource route of the accessed background server; the reverse proxy server SSLNPN extracts the address and the resource route of the accessed background server and forwards the request normally after intercepting the request. In the invention, a response header processes the HTTP request without any replacement in the HTML (Hyper Text Markup Language) page, a relative URL process and an absolute URL format process based on the redirection can be efficiently finished on the Web server by a formative URL.
Owner:BEIJING TOPSEC TECH
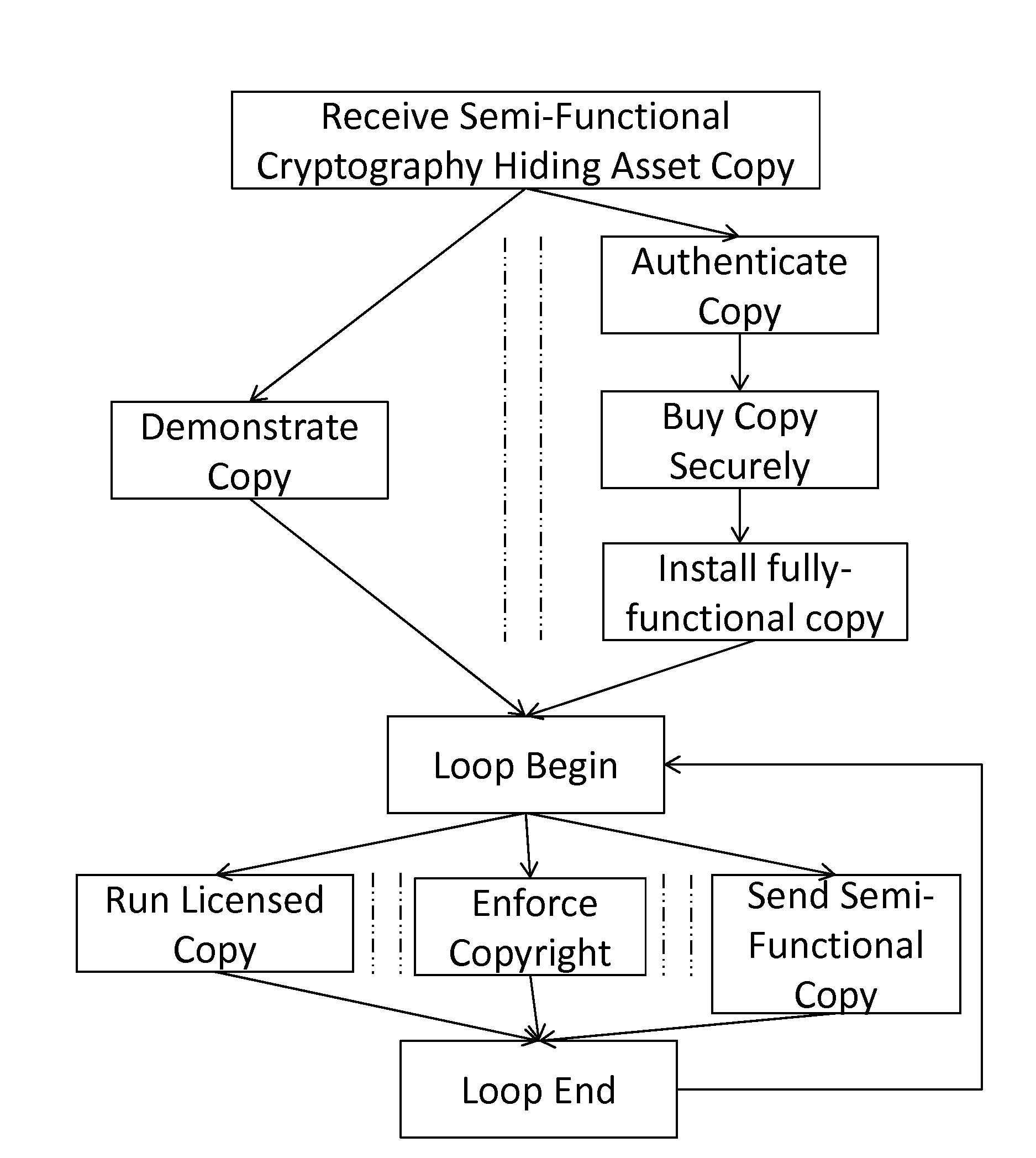
Potentate: A Cryptography-Obfuscating, Self-Policing, Pervasive Distribution System For Digital Content
InactiveUS20160364707A1Cryptography processingDigital data protectionSource transformationViral marketing
A system and method for self-policed, authenticated, offline / online, viral marketing and distribution of content such as software, text, and multimedia with effective copyright and license enforcement and secure selling. The system is based on key and cryptography hiding techniques, using source-to-source transformation for efficient, holistic steganography that systematically inflates and hides critical code by: computation interleaving; flattening procedure calls and obfuscating stack by de-stacking arguments; obfuscating memory management; and encoding scalars as pointers to managed structures that may be distributed and migrated all over the heap using garbage collection. Multimedia / text content may be partitioned and sold with expiry dates for protection and updates for long life. Authenticity of software installed on a machine may be monitored and ensured, supporting even authentic software deployment in an unknown environment. The system can be implemented with commonplace networking or browser software, commonplace hardware and content provision over a secure website (https standard).
Owner:VARMA PRADEEP
Secure routable file upload/download across the internet
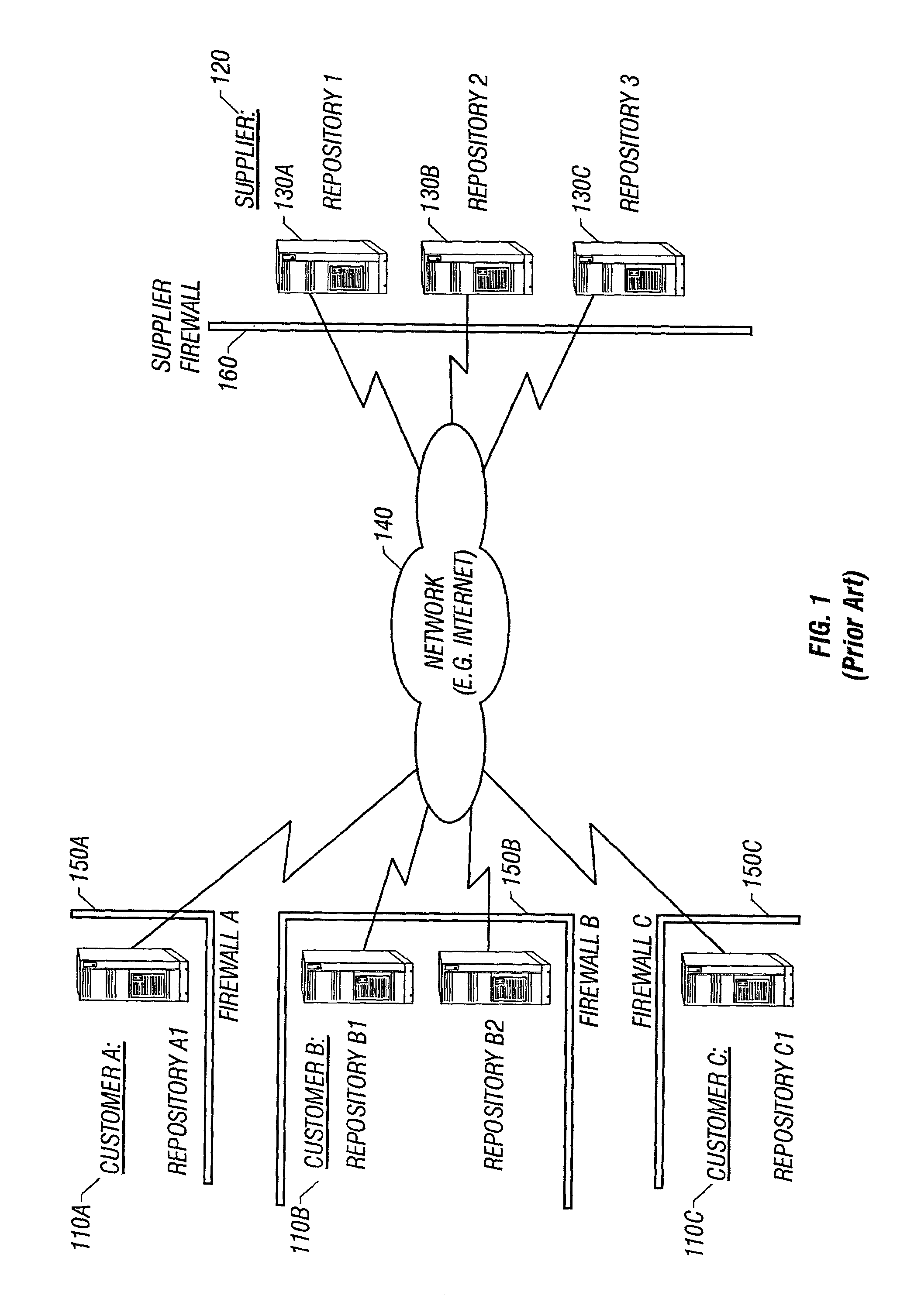
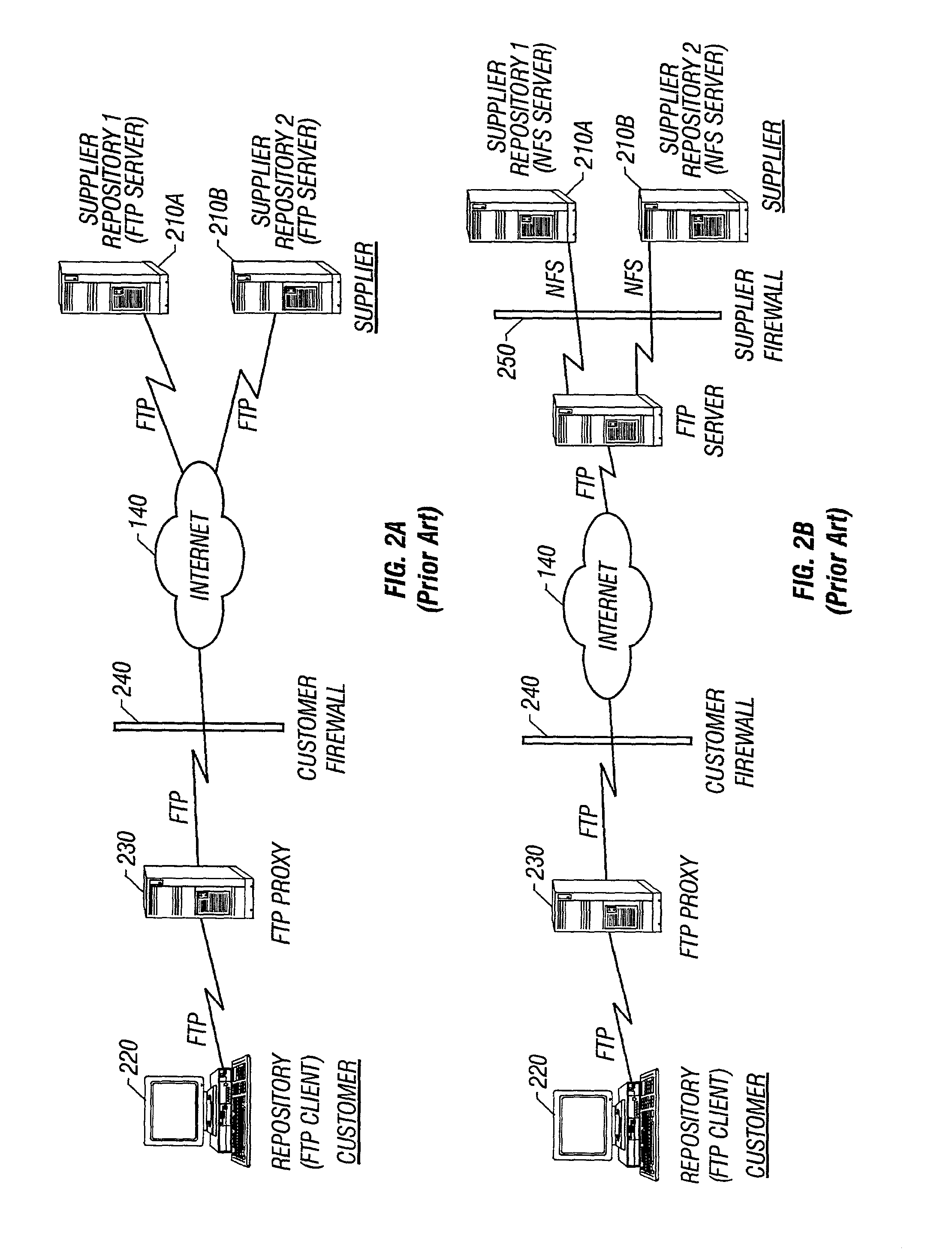
InactiveUS7003799B2Computer security arrangementsMultiple digital computer combinationsClient agentThe Internet
A system and method are provided for performing file transfers using an HTTP- or HTTPS-based Supplier Transport Gateway to connect Customer and Supplier Repositories located behind their respective firewalls. In some embodiments, the Transport Gateway is placed outside the Supplier firewall, and a Supplier Transport Proxy inside the firewall connects the Transport Gateway to the internal Supplier Repositories. In other embodiments, the Transport Gateway and Transport Proxy are reversed, the Proxy residing outside the Supplier firewall and relaying Customer HTTP / HTTPS traffic to the Transport Gateway inside the firewall, which then connects to the internal Supplier Repositories. In either case, the HTTP- or HTTPS-based Customer Repository connects through a Customer Proxy to the Supplier's Transport Gateway to request file upload / download operations. In turn, the Transport Gateway implements the Supplier's request validation policy, and Supplier Repository routing rules that abstract the Supplier Repository topology to the Customer. The Transport Gateway then performs a corresponding upload / download operation against the selected Supplier Repository using HTTP, HTTPS, FTP, or a similar protocol.
Owner:VALTRUS INNOVATIONS LTD
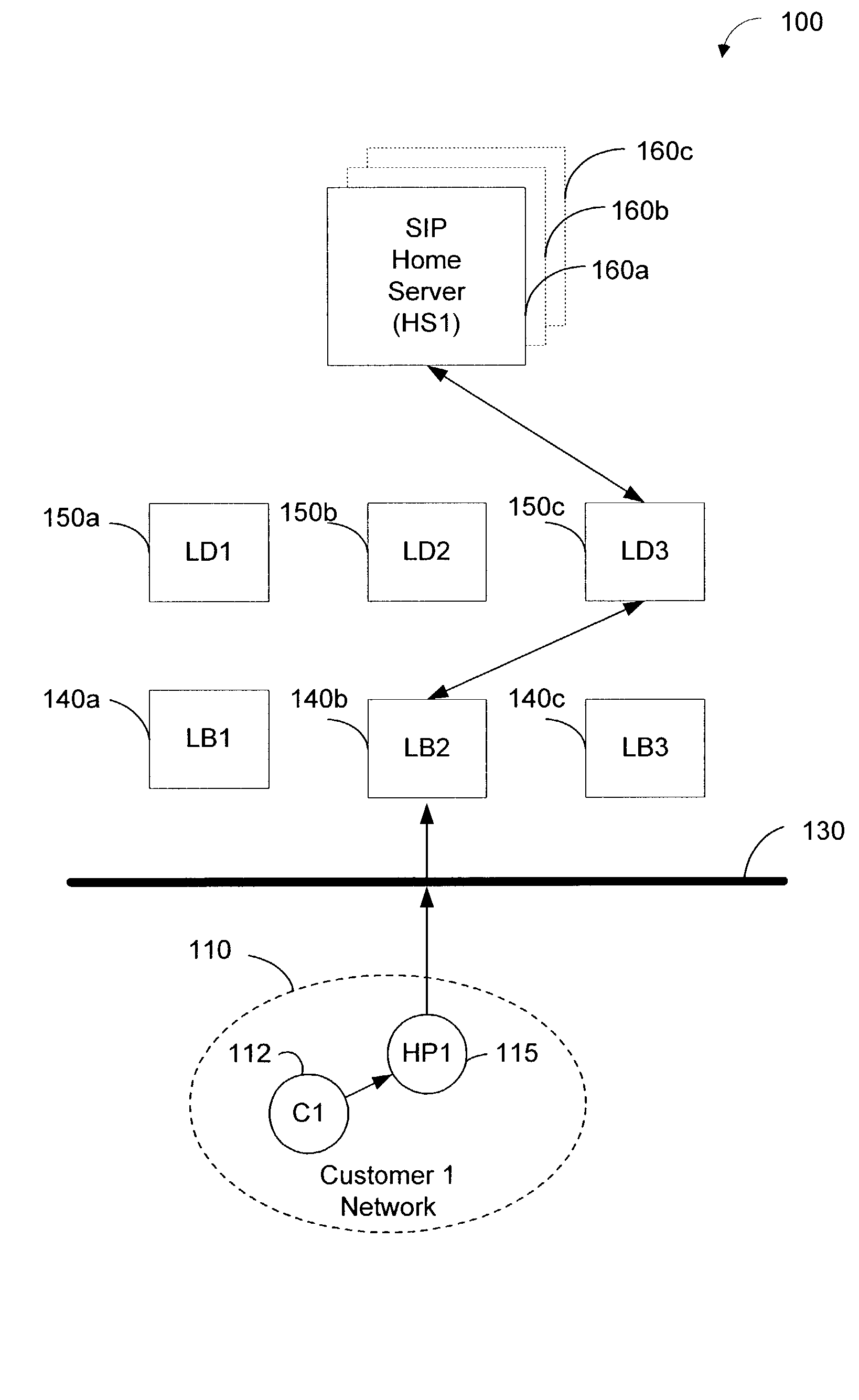
End-point identifiers in SIP
ActiveUS7412521B2Improved connection managementImproved management security associationMultiple digital computer combinationsTransmissionIp addressSecurity association
A system and method for uniquely identifying an SIP device extends the SIP communications protocol with an end point identifier, carried for example in the header of an SIP transmission. The end point identifier is useful for routing, registration, subscription, and authentication. The end point (device) of a given user epid can be uniquely identified by creating a key from an epid and a user's address-of-record (URI). This in turn enables improved connection management and security association management when the connections / IP addresses are transient, such as when HTTPS tunneling is used.
Owner:MICROSOFT TECH LICENSING LLC
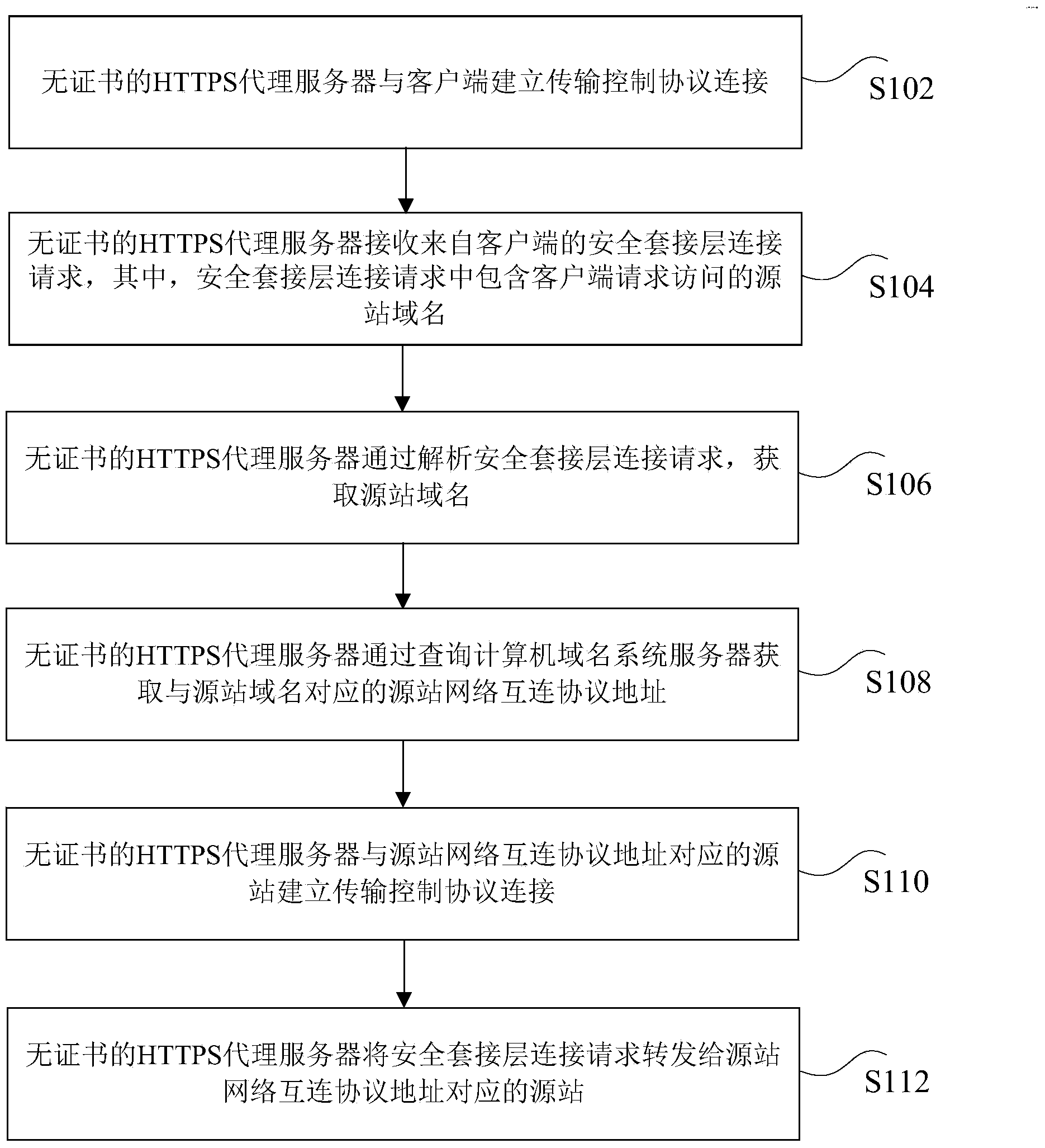
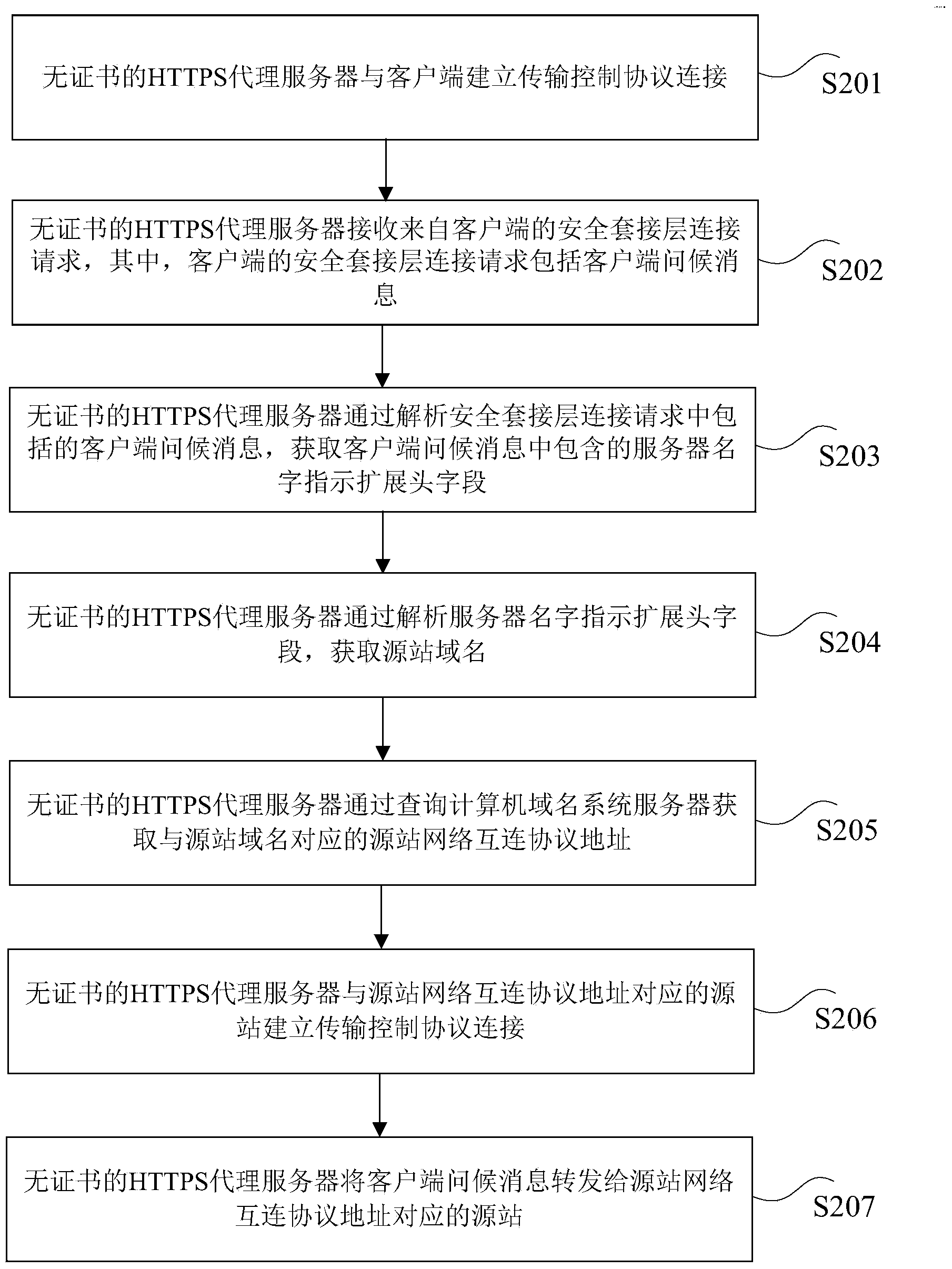
HTTPS proxy forwarding method and device based on transmission control protocol
ActiveCN104270379ASolve wasteRealize proxy forwarding functionTransmissionDomain nameInterconnection
The invention discloses an HTTPS proxy forwarding method and device based on a transmission control protocol. The method comprises the steps that transmission control protocol connection is set up between a certificateless HTTPS proxy server and a client side; the certificateless HTTPS proxy server receives a security socket layer connection request from the client side; the certificateless HTTPS proxy server obtains a source station domain name by analyzing the security socket layer connection request; the certificateless HTTPS proxy server obtains a source station network interconnection protocol address corresponding to the source station domain name by inquiring a computer domain name system server; transmission control protocol connection is set up between the certificateless HTTPS proxy server and a source station corresponding to the source station network interconnection protocol address, and the certificateless HTTPS proxy server forwards the security socket layer connection request to a source station corresponding to the source station network interconnection protocol address. Through the HTTPS proxy forwarding method and device based on the transmission control protocol, a general HTTPS proxy forwarding function is achieved, and meanwhile the effect of saving IP sources is achieved.
Owner:CHINACACHE INT HLDG
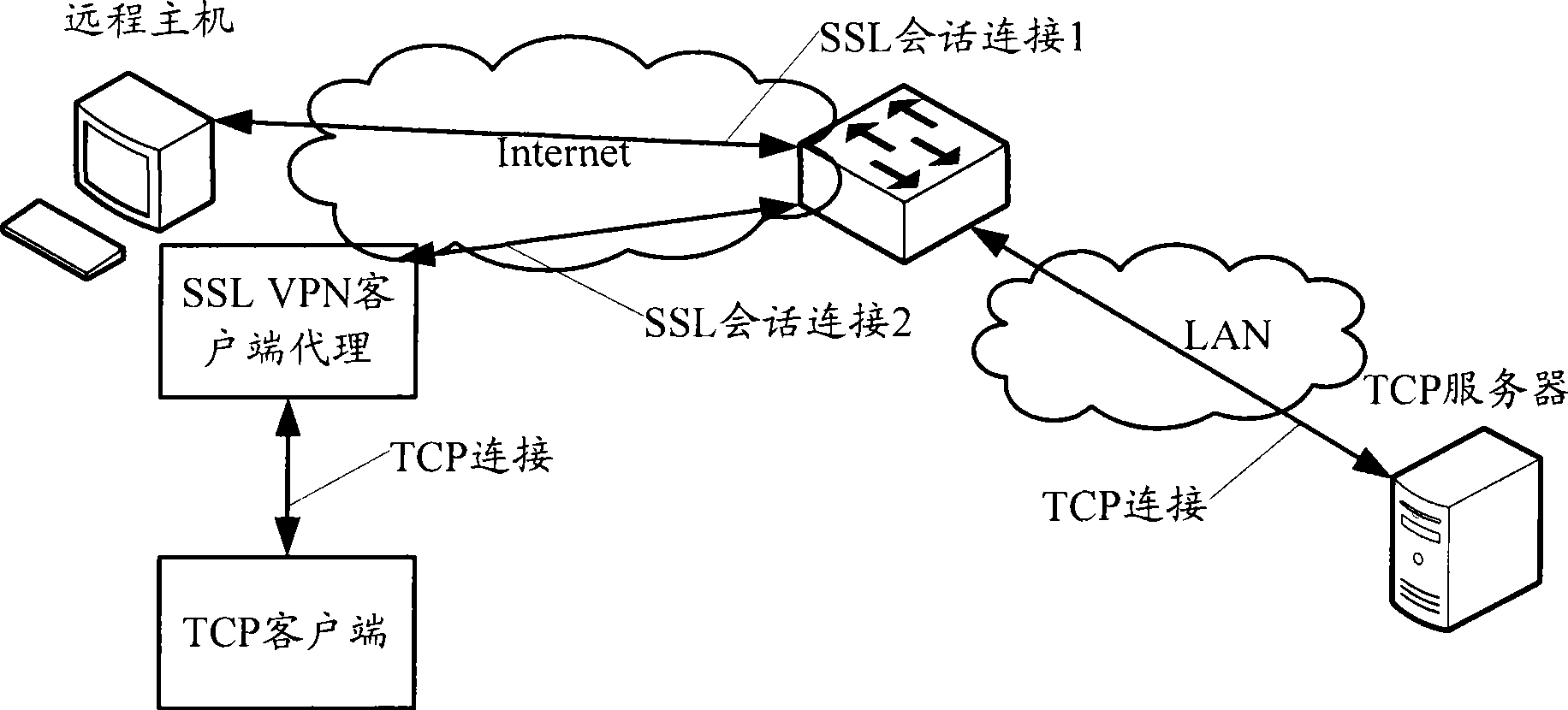
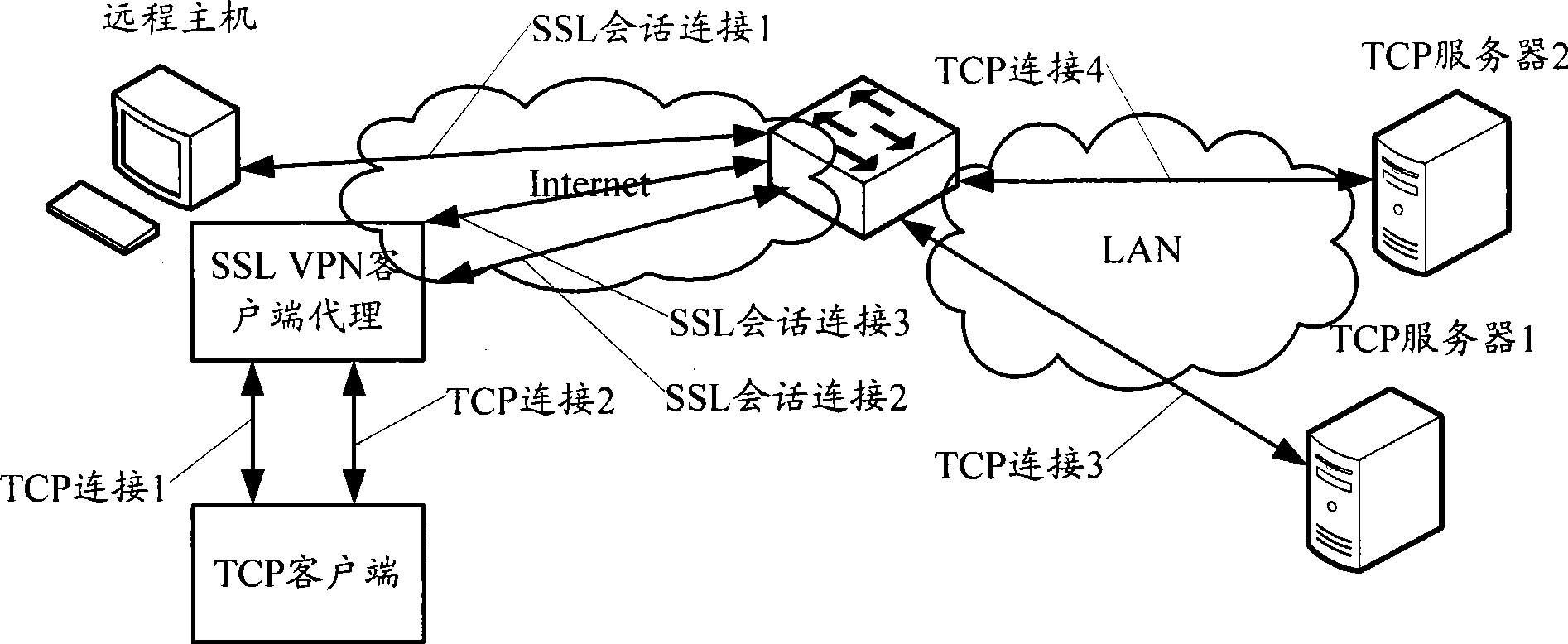
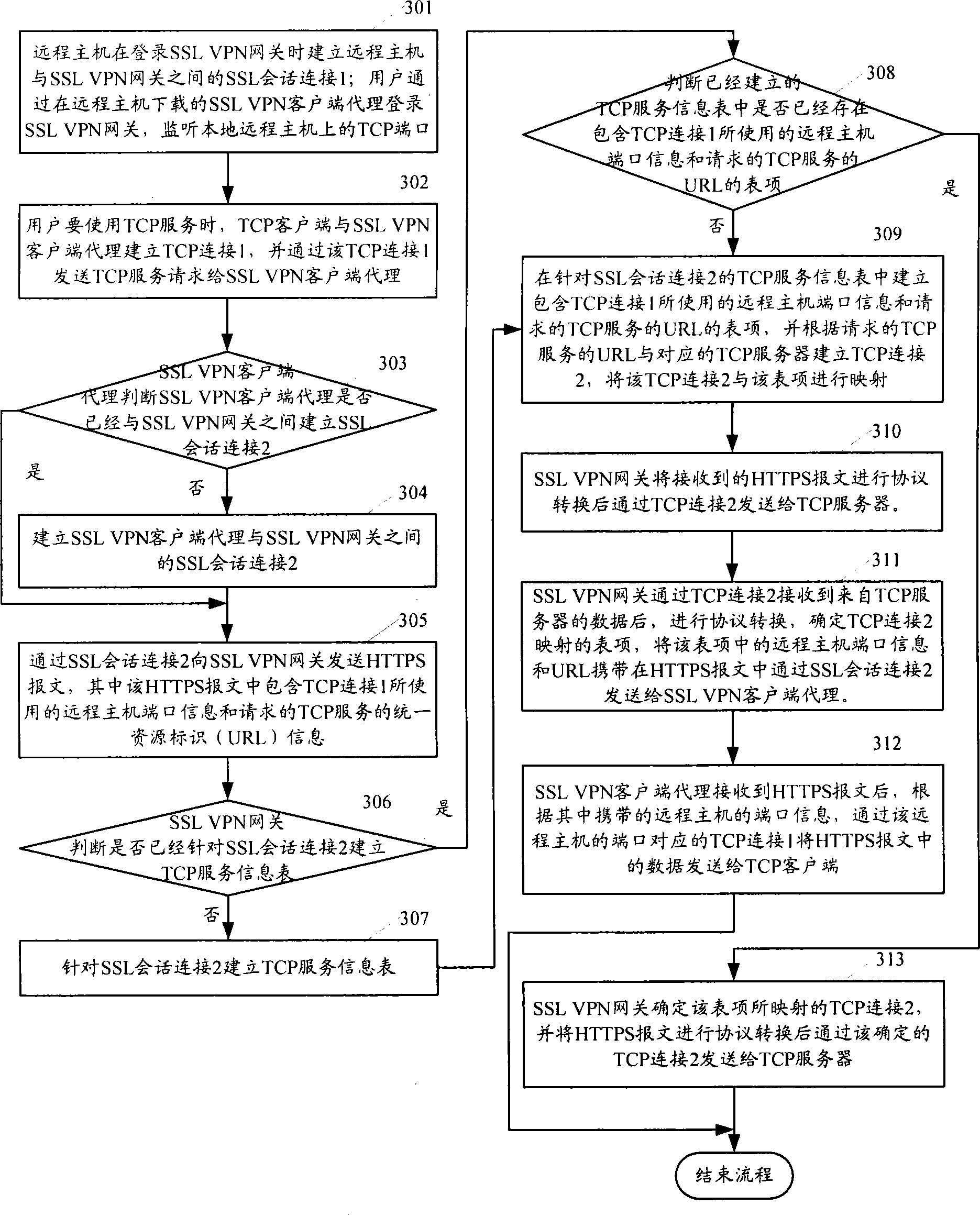
Method for providing TCP service, system and relevant device thereof
ActiveCN101534302AImprove performanceReduce occupancyNetwork connectionsClient agentHypertext Transfer Protocol over Secure Socket Layer
The invention relates to a method for providing transmission control protocol (TCP), a system and a relevant device thereof; wherein, the method comprises: an SSL VPN client agent receives TCP request through a first TCP connection, HTTPS message of the TCP service information containing the first TCP connection information and request by the sole SSL VPN conversation connection between the SSL VPN client agent and the SSL VPN gateway; the SSL VPN gateway memorizes the list item of the TCP service information containing the first TCP connection information and request in a TCP service information table for the SSL conversation, and after establishing a second TCP connection with the TCP server providing the requested TCP service, the message relay between the SSL VPN client agent and the TCP server is carried out according to the TCP service information table.
Owner:NEW H3C TECH CO LTD
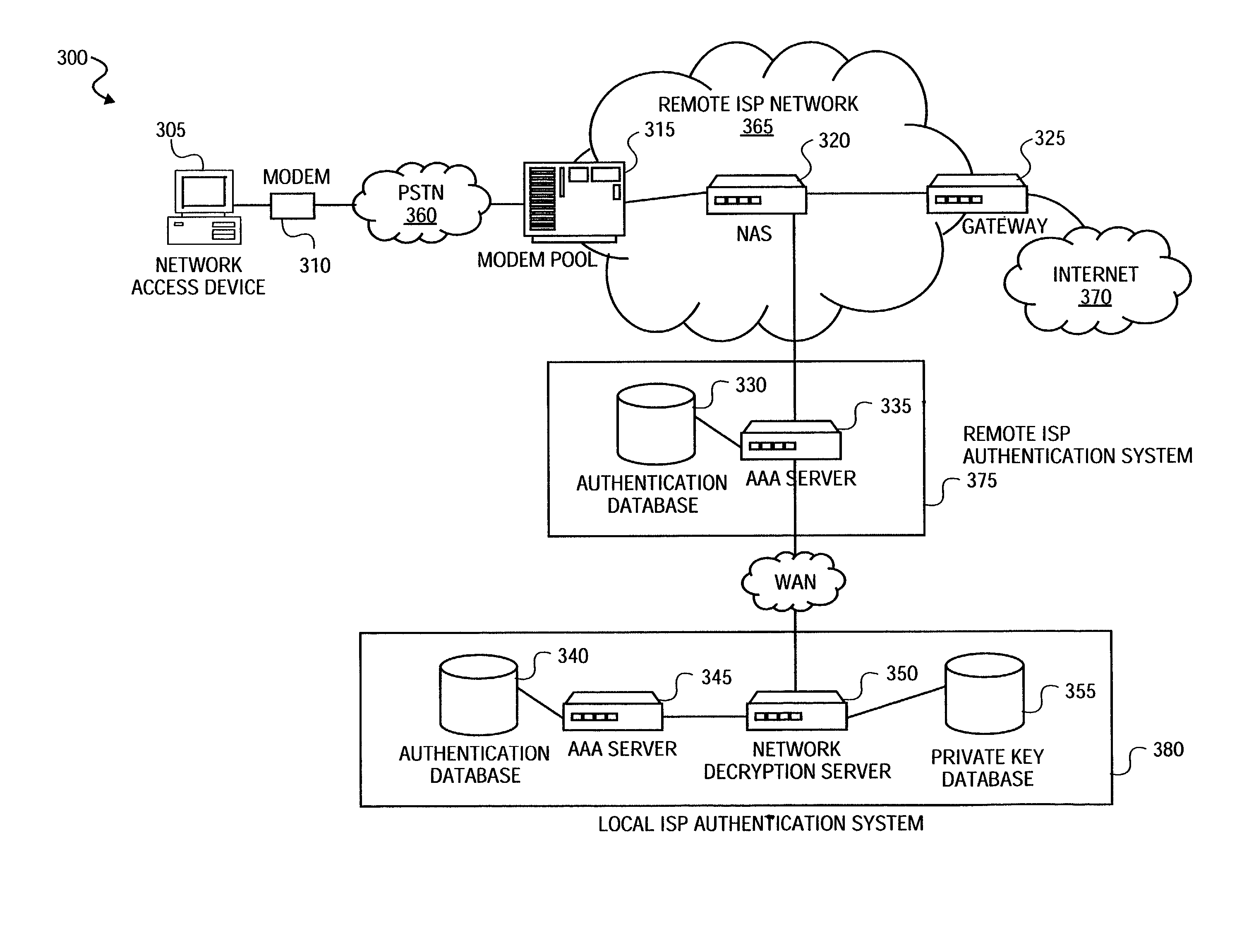
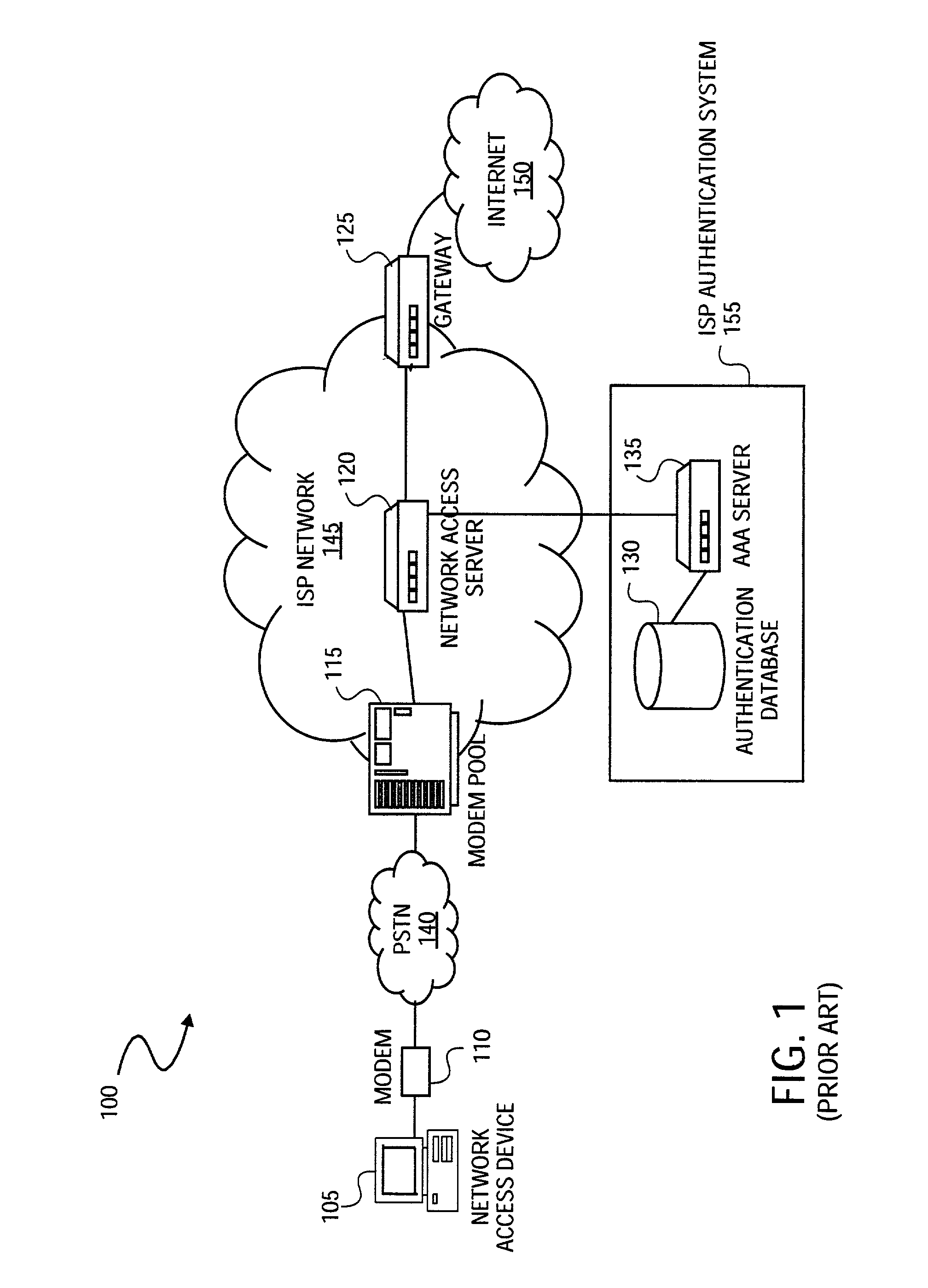
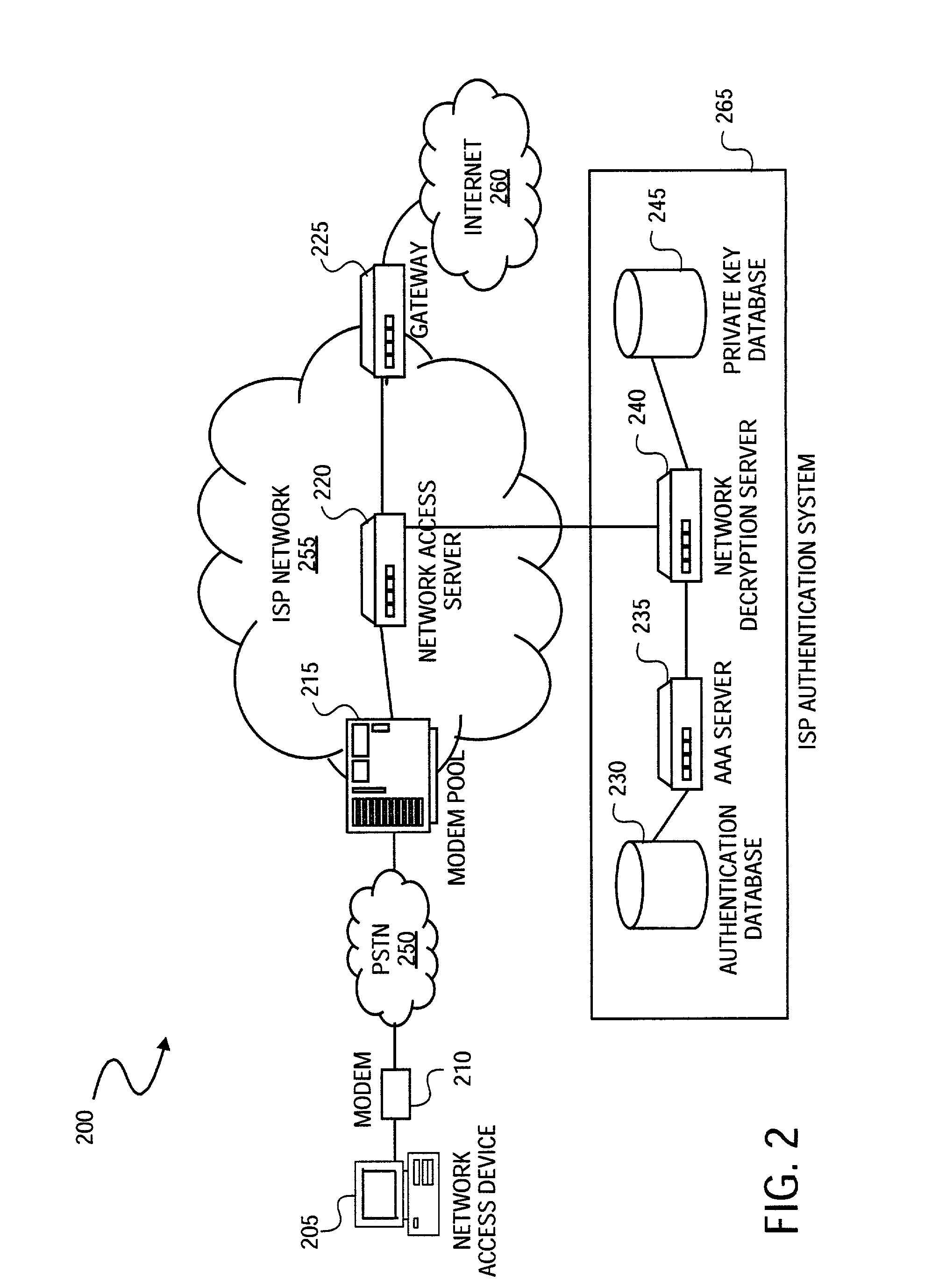
Method and system for securely authenticating network access credentials for users
InactiveUS7921290B2Digital data processing detailsUser identity/authority verificationHypertext Transfer Protocol over Secure Socket LayerDirectory Access Protocol
A method is provided to securely authenticate user credentials. The method includes encrypting a user credential with a public key at an access device wherein the public key is part of a public / private key pair suitable for use with an encryption algorithm. The encrypted network user credential is transmitted from the access device to a decryption server where it is decrypted with a private key, the private key being part of the public / private key pair suitable for use with the encryption algorithm. The decrypted user credential is then transmitted from the decryption server to an authentication server for verification. The decryption server typically forms part of a multi-party service access environment including a plurality of access providers, the method including decrypting the user credential of a user proximate an access provider associated with the user credential. The method can be used in legacy protocols such as Point-to-Point protocol (PPP), Password Authentication Protocol (PAP), Challenge-Handshake Authentication Protocol (CHAP), Remote Authentication Dial In User Service (RADIUS) protocol, Terminal Access Controller Access Control System (TACACS) protocol, Lightweight Directory Access Protocol (LDAP), NT Domain authentication protocol, Unix password authentication protocol, HyperText Transfer Protocol (HTTP), HyperText Transfer Protocol over Secure sockets layer (HTTPS), Extended Authentication Protocol (EAP), Transport Layer Security (TLS) protocol, Token Ring protocol and / or Secure Remote Password protocol (SRP).
Owner:CHANNEL IP BV
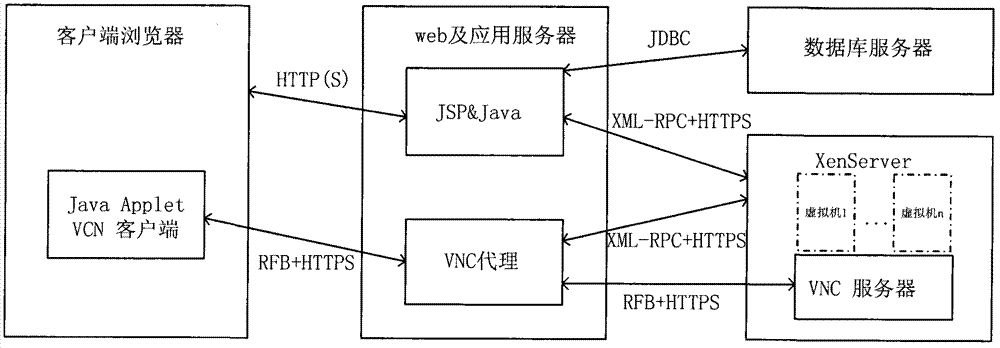
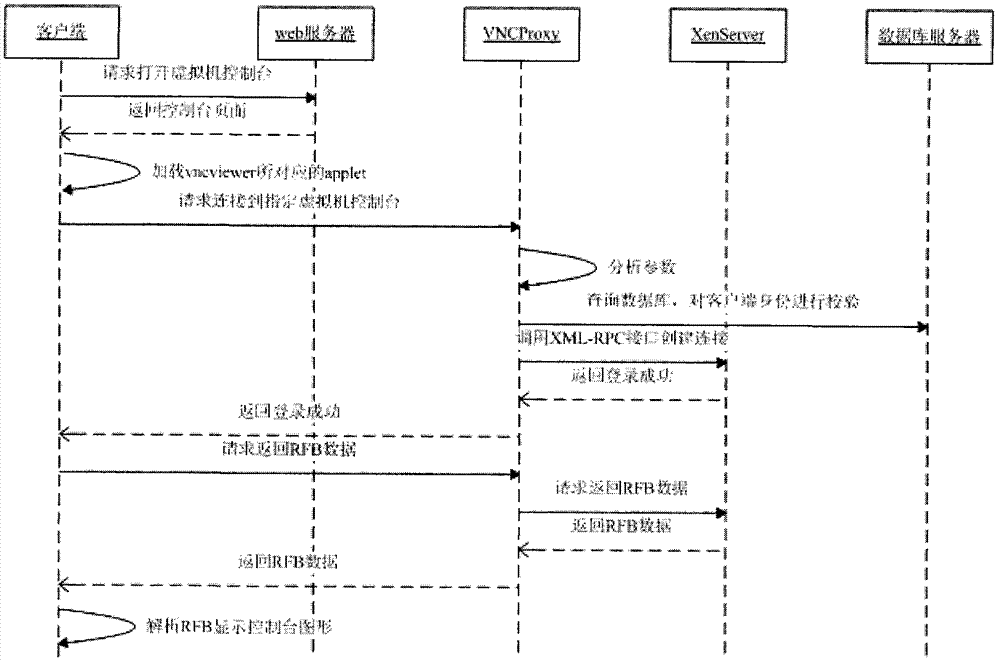
Method achieving XenServer virtual machine remote control on https
InactiveCN103200215ARealize the proxy functionSolve the problem that the XenServer virtual machine console cannot be accessed directlyNetworks interconnectionApplication serverRemote control
The invention discloses a method achieving XenServer virtual machine remote control on https. The method comprises a VNC client capable of operating on a browser and a VNC agent server used for identity verification and RFB data transmission, wherein the VNC client is based on a Java Applet technology, transmits VNC remote control data through the https, deploys on a web and a Java application server and can operate on the browser provided with JVM. Because the https is adopted to transmit the data, the VNC client can solve the problem that a firewall limits outer network access well. The VNC agent server is used for solving the problem of Applet safe limit when the VNC client accesses a VNC service end of an XenServer, and at the same time achieves safe verification to client identity through an XML-RPC interface of the XenServer. The method enables any browser of the client to achieve the remote control and access of an XenServer virtual machine.
Owner:PCI TECH GRP CO LTD
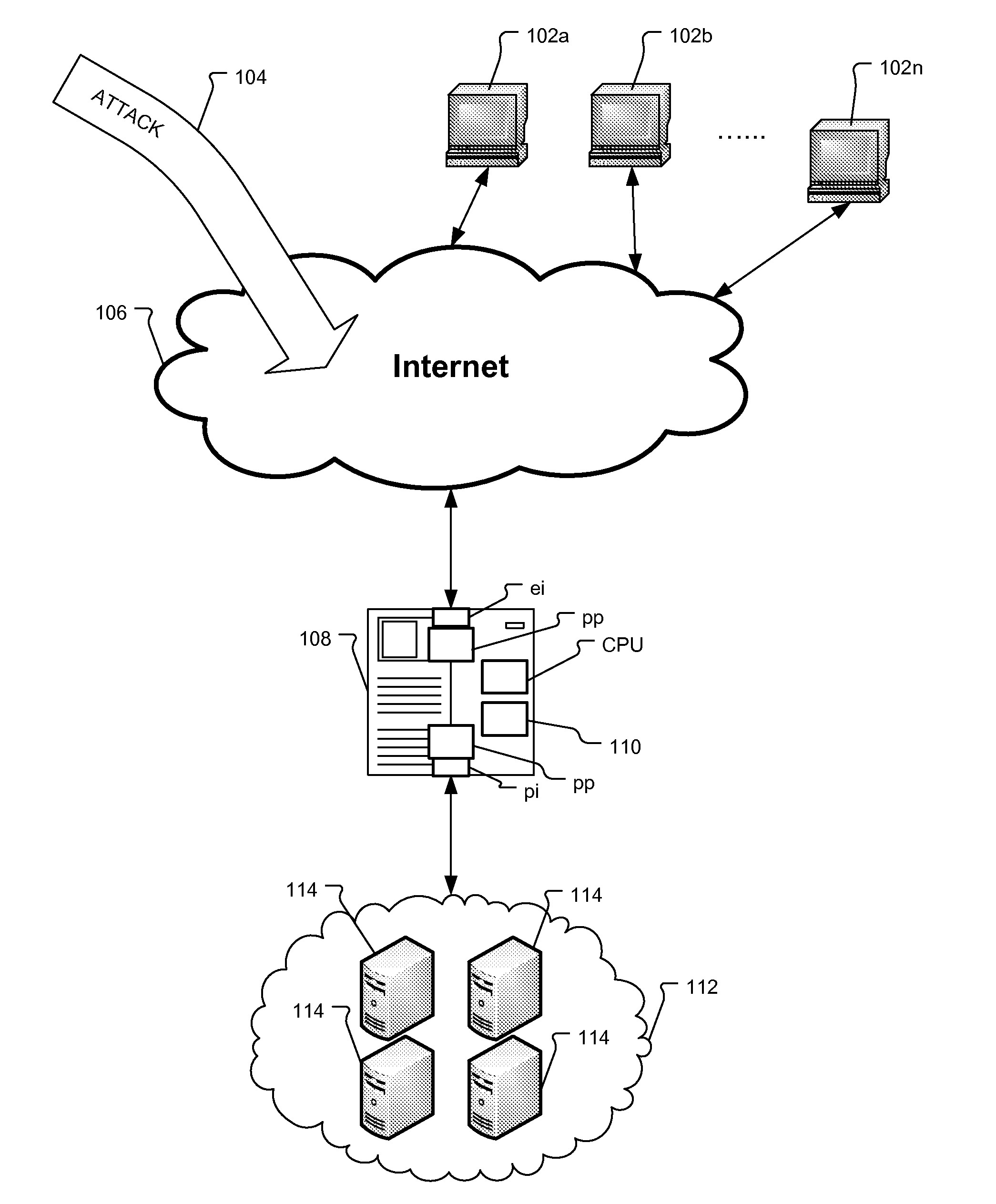
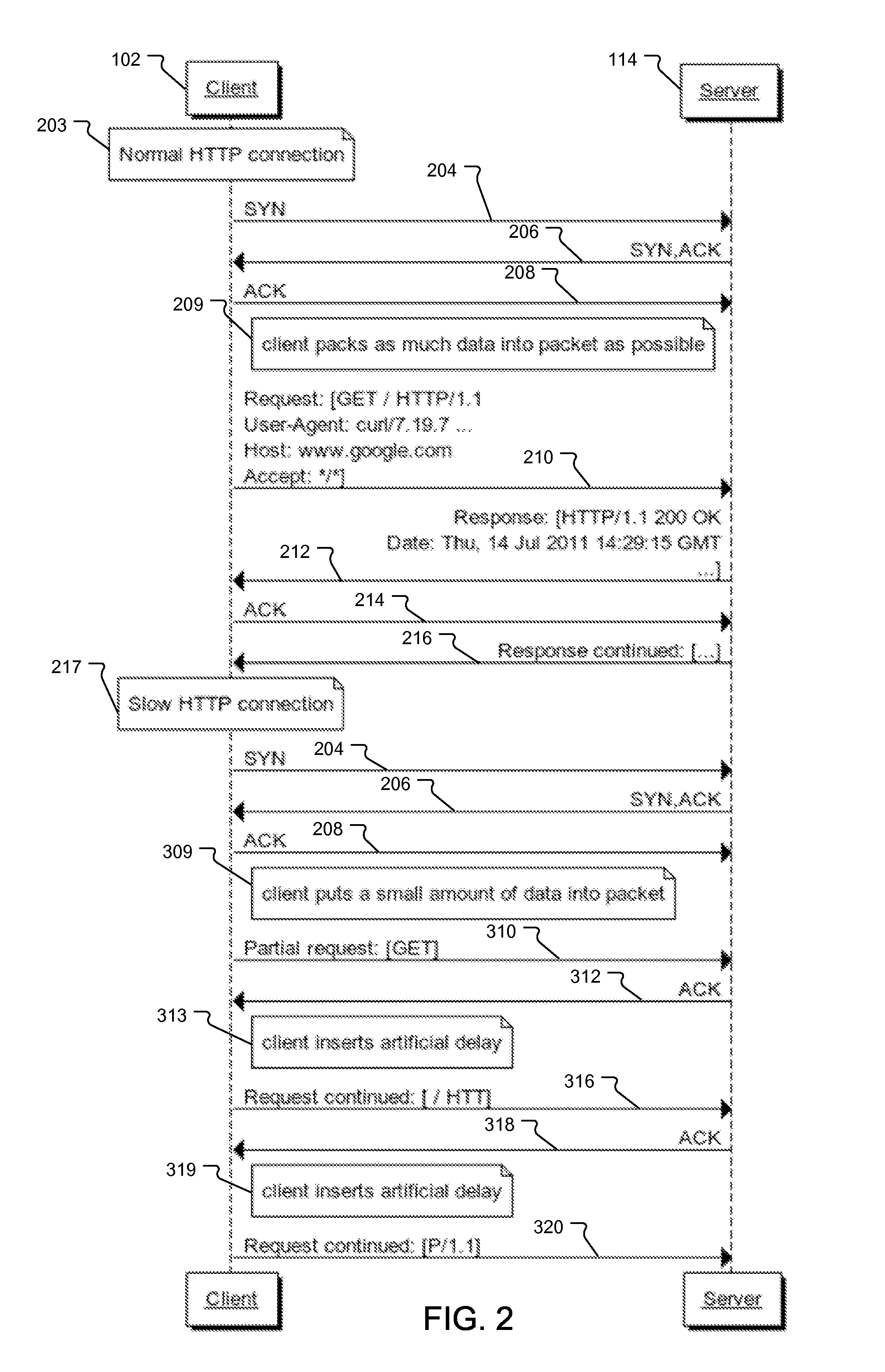
Method and Protection System for Mitigating Slow HTTP Attacks Using Rate and Time Monitoring
ActiveUS20130055375A1Computer security arrangementsMultiple digital computer combinationsMinimum timeHypertext Transfer Protocol over Secure Socket Layer
A system and methods for mitigation slow HTTP, SSL / HTTPS, SMTP, and / or SIP attacks. A protection system monitors each TCP connection between a client and a server. The protection system monitors the header request time and minimum transfer rate for each client and TCP connection. If the client has not completed the data transfer in the minimum time or the data are not transferred at the minimum transfer rate, the protection system determines the connections are potentially a slow attack and resets the connections for the protected devices.
Owner:ARBOR NETWORKS
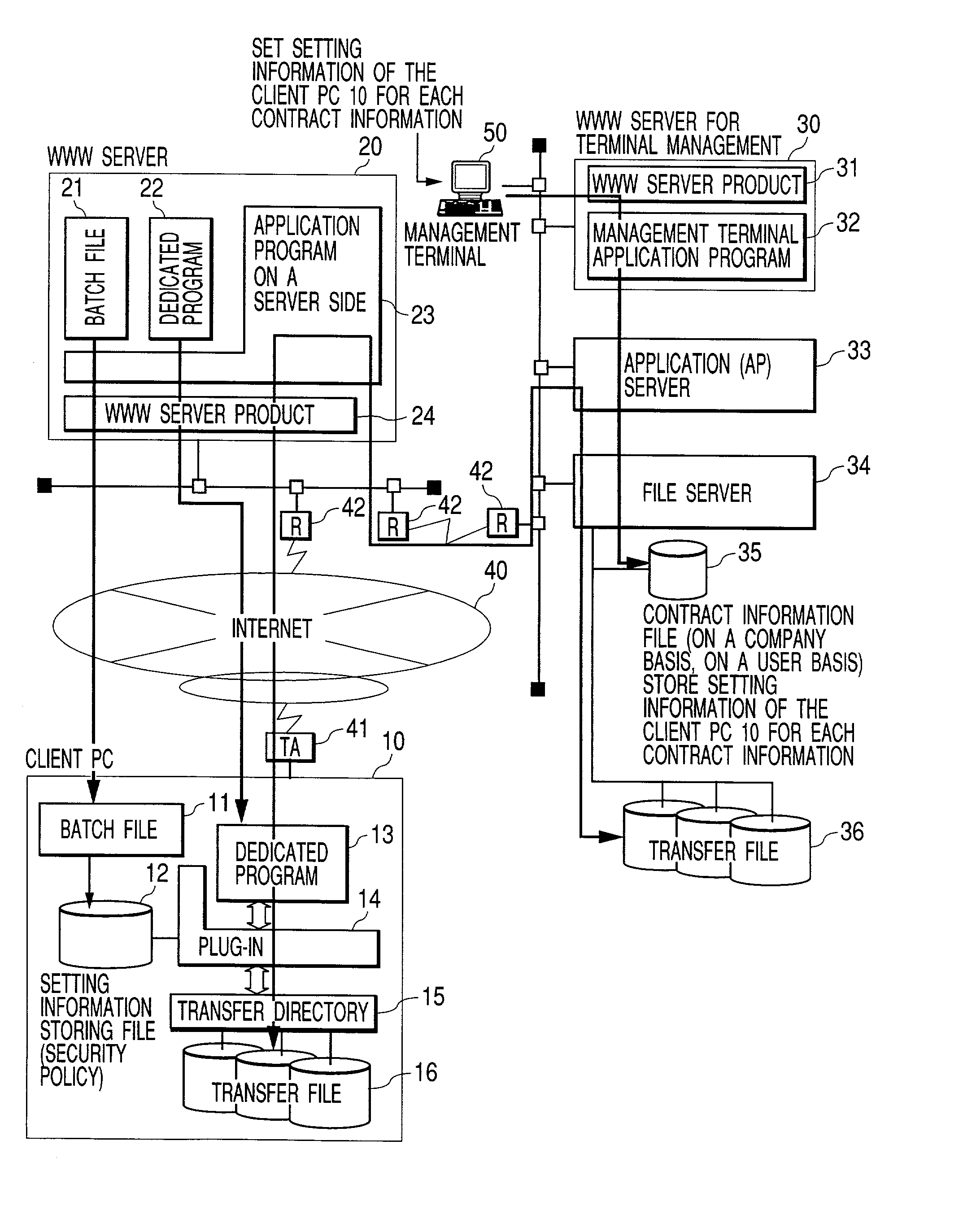
File transmitting method and system
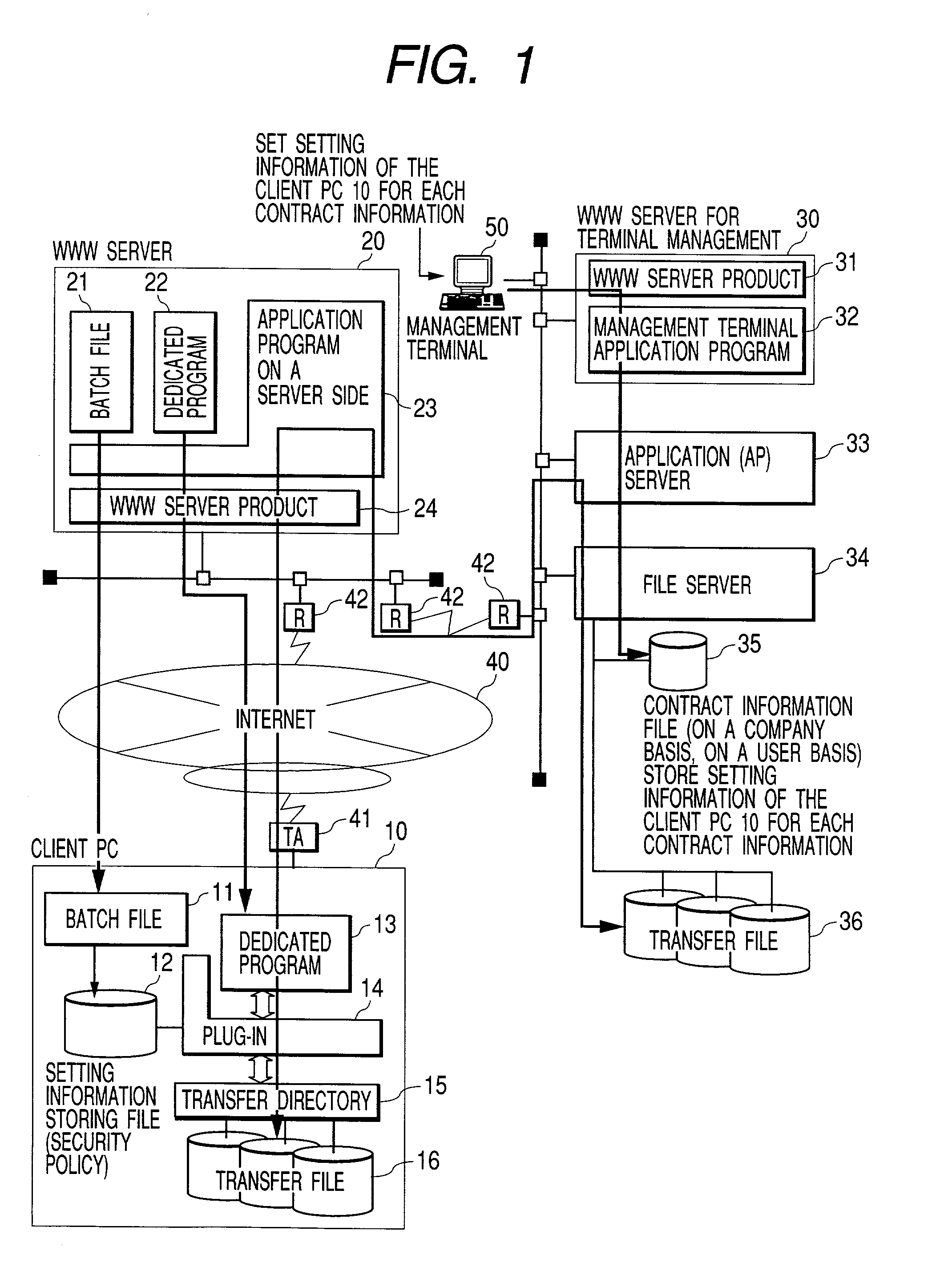
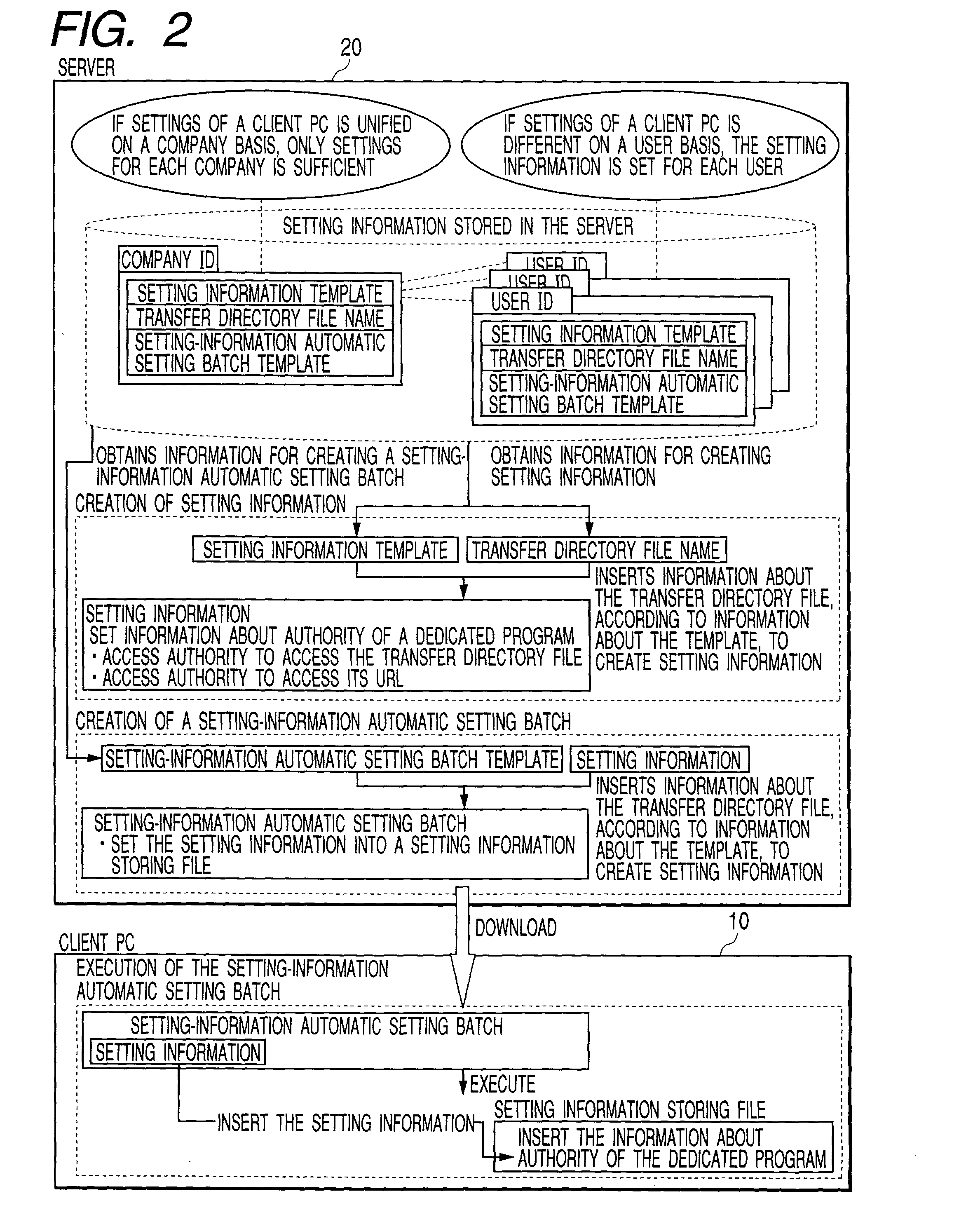
InactiveUS20030046415A1Improve reliabilityLarge fileMultiple digital computer combinationsSecuring communicationTerminal serverMulti platform
An object of the present invention is to transmit and receive a very large file with high reliability and with efficiency using the Internet, which is apt to be unstable, without special operation in a client PC. A file transmitting system according to the present invention is configured as a system in which a client PC 10 is connected via Internet 40 to a processing system comprising a WWW server 20, a management terminal server 30, an AP server 33, and a file server 34. Transmission of file data between a PC and a transfer file 36 of the file server is performed using HTTPS (HyperText Transfer Protocol Secure) that uses a dedicated program. The file data is divided into data having a fixed size, each of which is compressed for transmission. In addition, in preparation for occurrence of a failure, a checkpoint for retransmission is provided for each divided data. The dedicated program is devised so that multi-platform is supported. In addition to it, the dedicated program can be used by downloading it from the server as part of PC operation.
Owner:HITACHI LTD
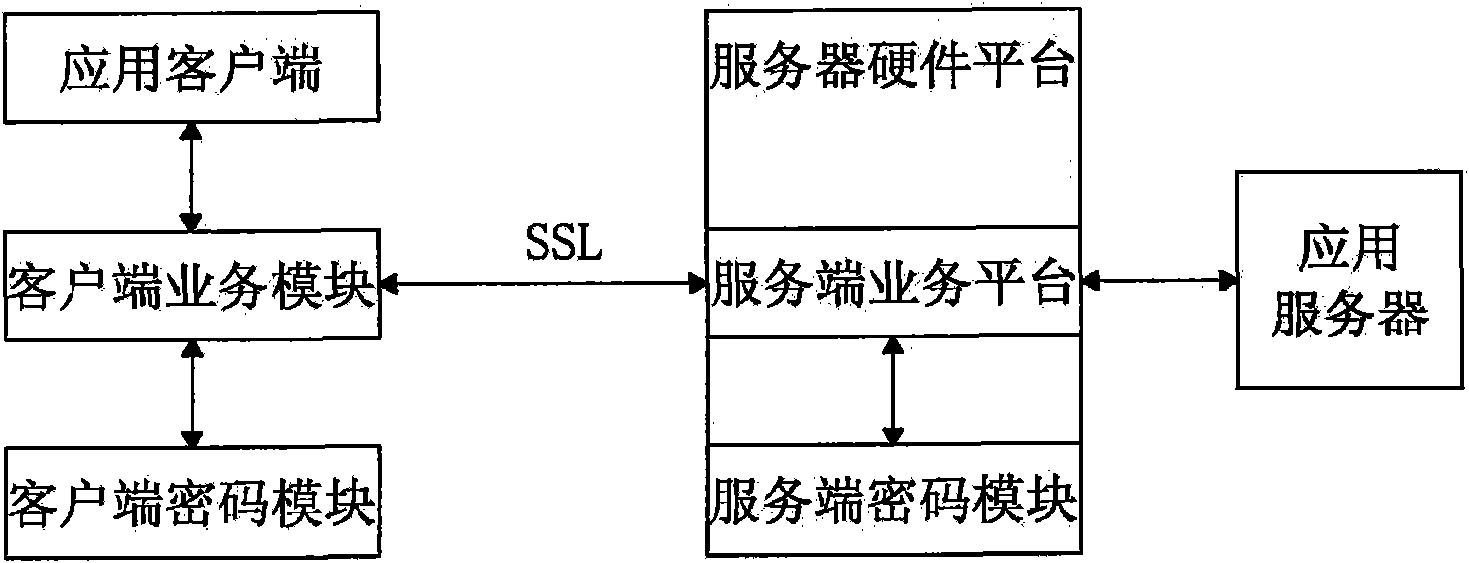
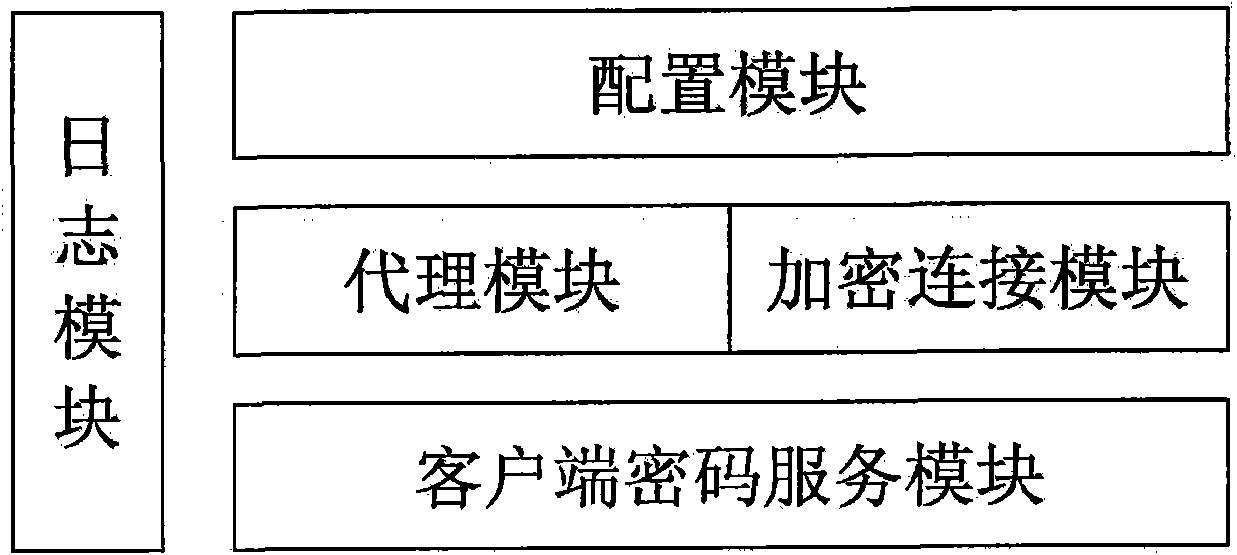
Security certificate gateway
InactiveCN102111349ARealize data transmission securityAchieving Valid AuthenticationNetwork connectionsInternet Authentication ServiceRemote desktop
The invention discloses a security certificate gateway, comprising a client crypto module, a client business module, a service business module and a service crypto module, wherein the client business module is used as an agent of an application client and used for calling the client crypto module and the service business module interactively to build an encrypted connection; and the service business module is used for calling the service crypto module and the service business module to build a secure encrypted channel. Based on the high-strength identity authentication service, the high-strength data link encryption service and the digital signature and authentication service of a digital certificate, the gateway provided by the invention effectively protects secure access of network resources, and supports B / S applications of a hypertext transport protocol (HTTP) and hypertext transfer protocol secure (HTTPS) as well as common C / S applications of a file transfer protocol (FTP), a remote desktop and the like.
Owner:KOAL SOFTWARE CO LTD
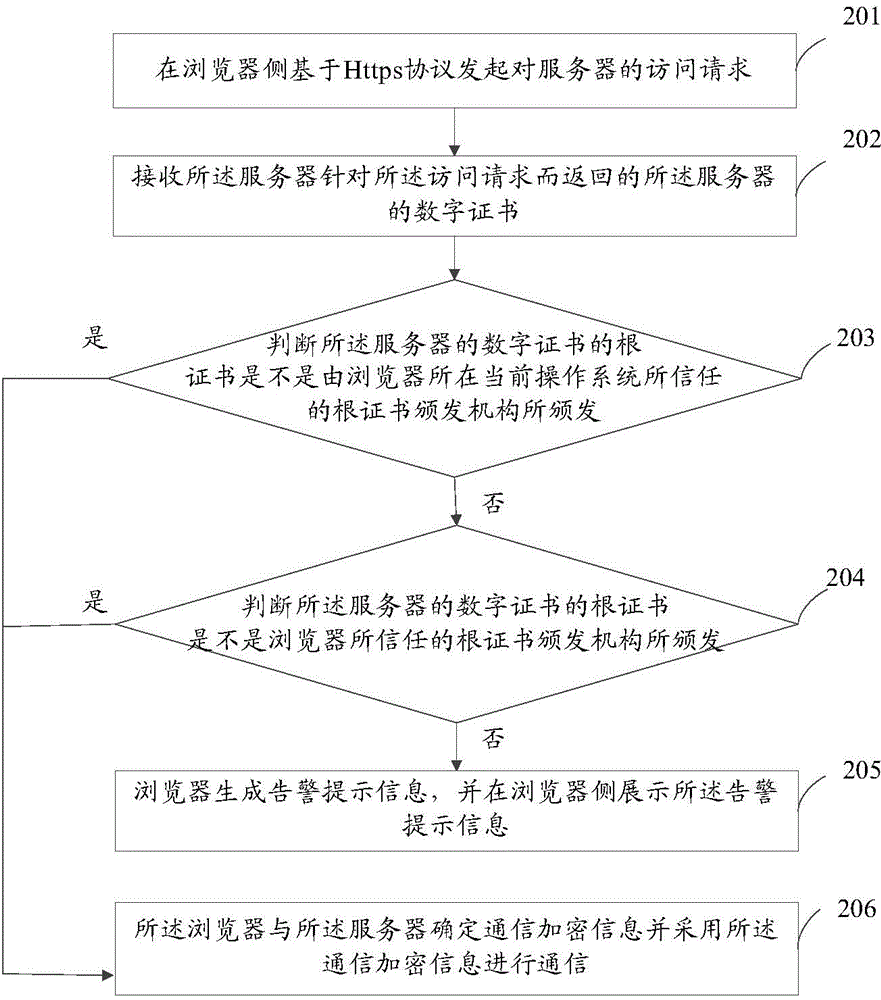
Data communication method and device based on https (hypertext transfer protocol over secure socket layer)
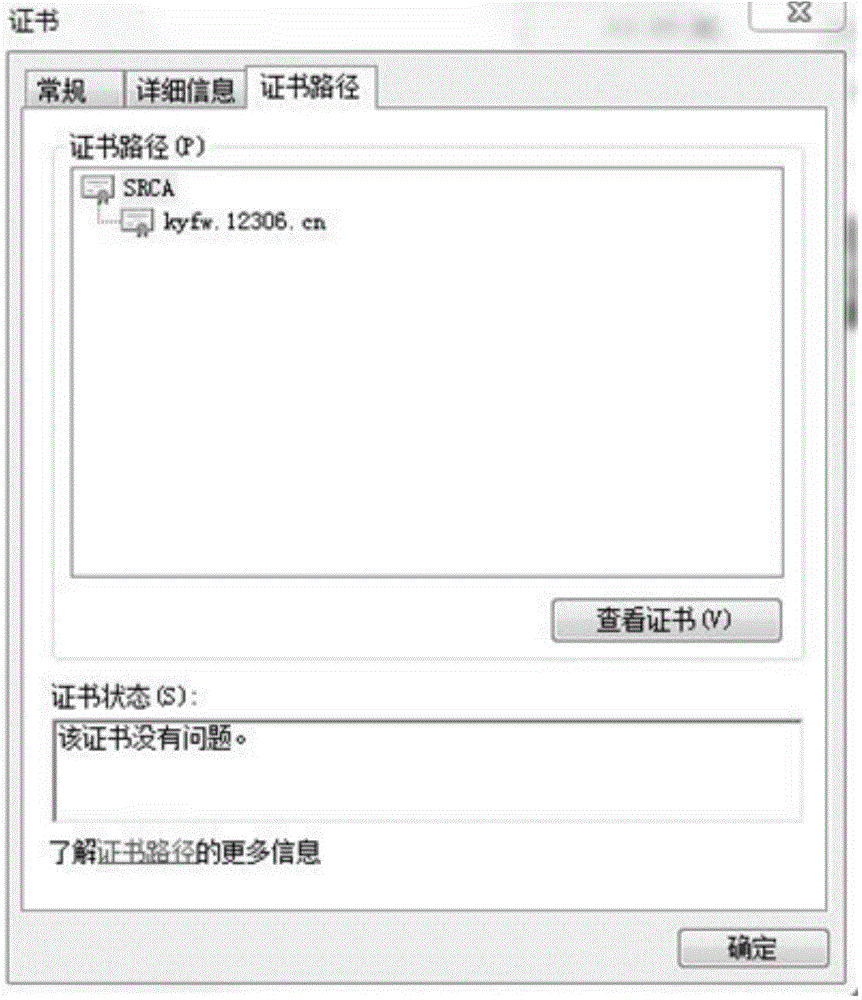
The invention discloses a data communication method and device based on the https (hypertext transfer protocol over secure socket layer). The method comprises steps as follows: an access request for a server is initiated on a browser side on the basis of the Https; a digital certificate, returned by the server, of the server for the access request is received; whether a root certificate of the digital certificate of the server is issued by a root certificate authority trusted by a current operating system where a browser is located or not is judged; if no, whether the root certificate of the digital certificate of the server is issued by the root certificate authority trusted by the browser or not is judged; if yes, the browser and the server determine an encrypted communication message and communicate with each other through the encrypted communication message. With the adoption of the data communication method and device, authentication modes of the digital certificates are enriched, and the authentication passing probability of the digital certificates of the server is increased.
Owner:BEIJING QIHOO TECH CO LTD
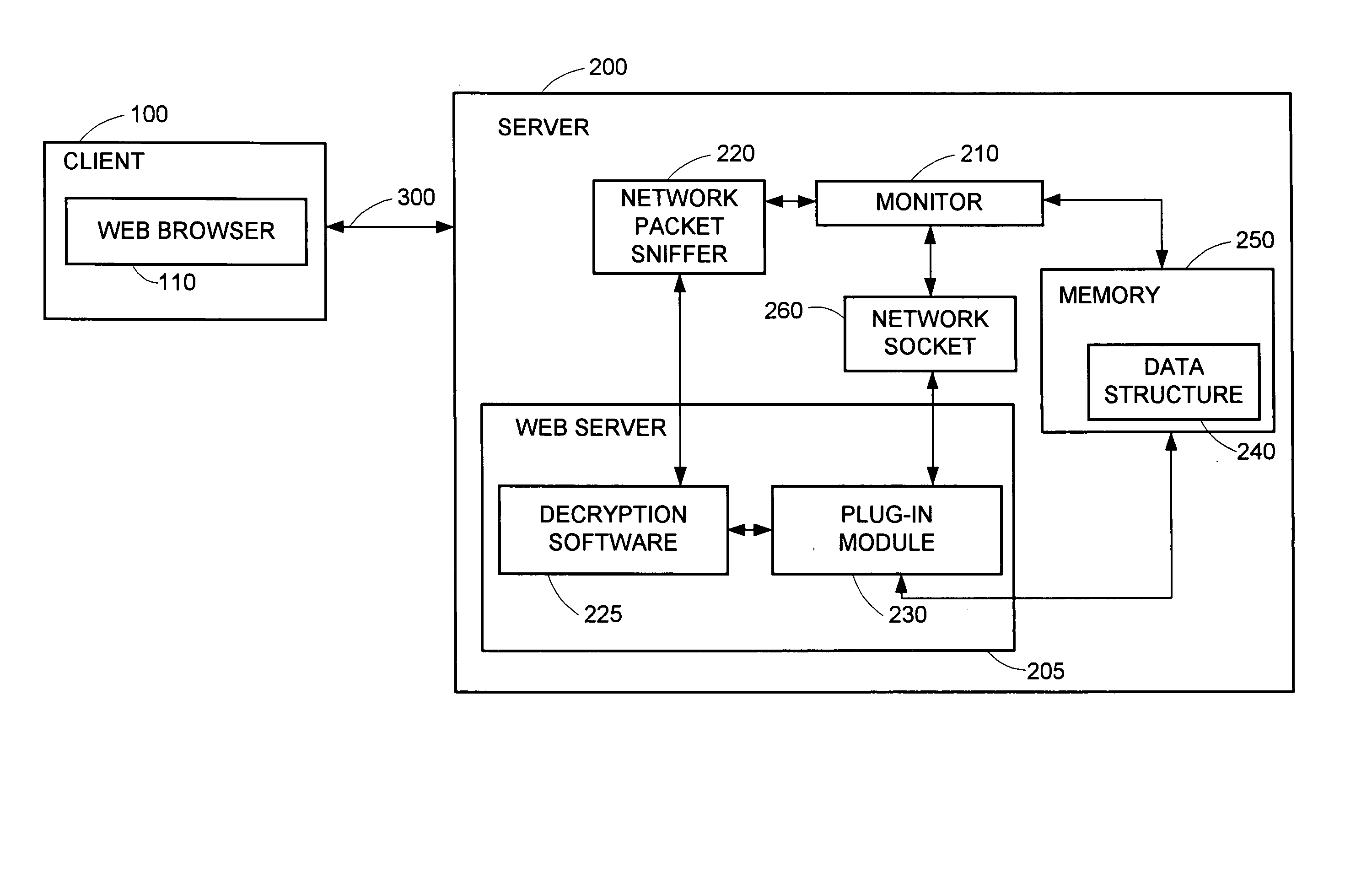
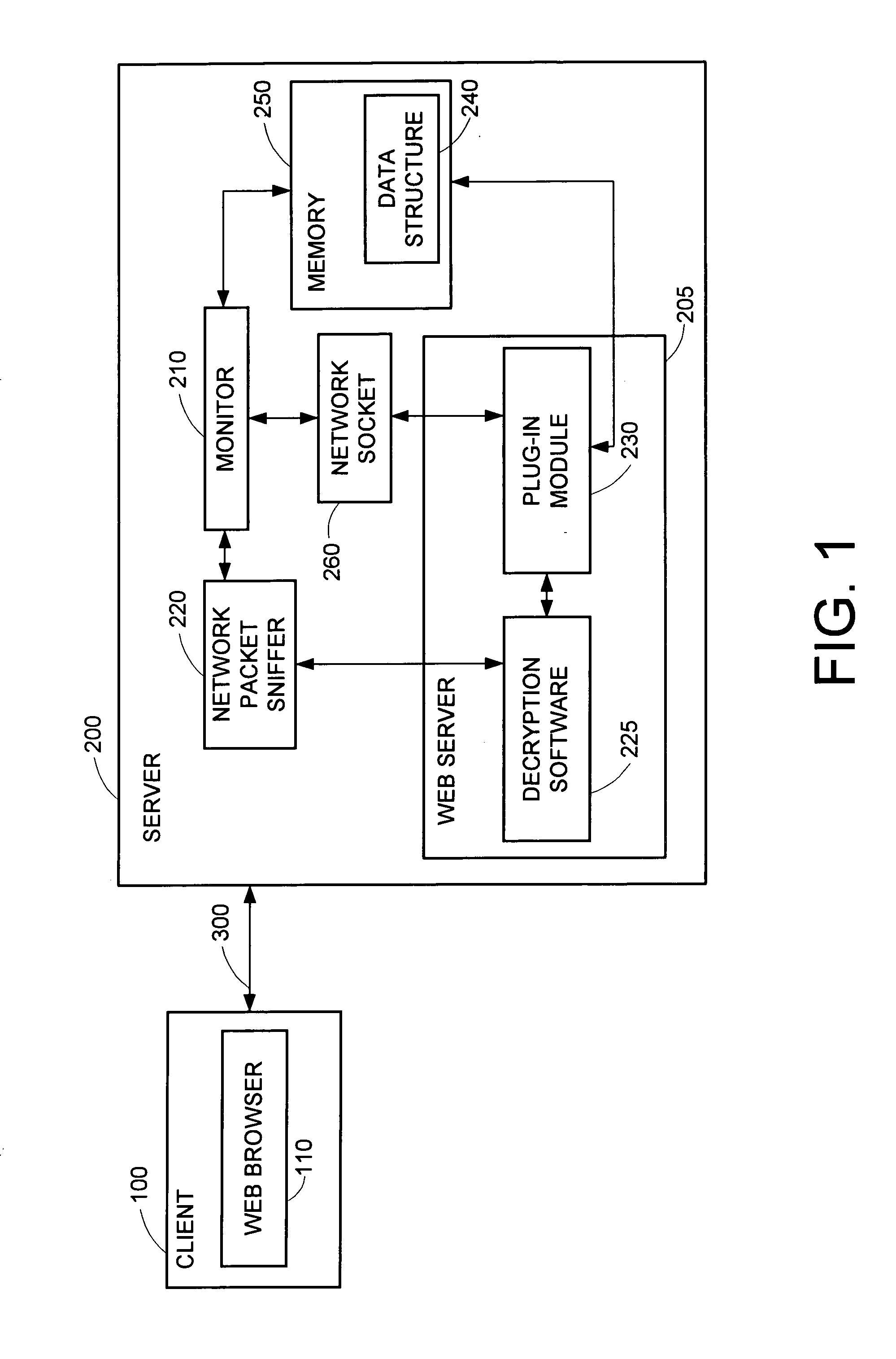
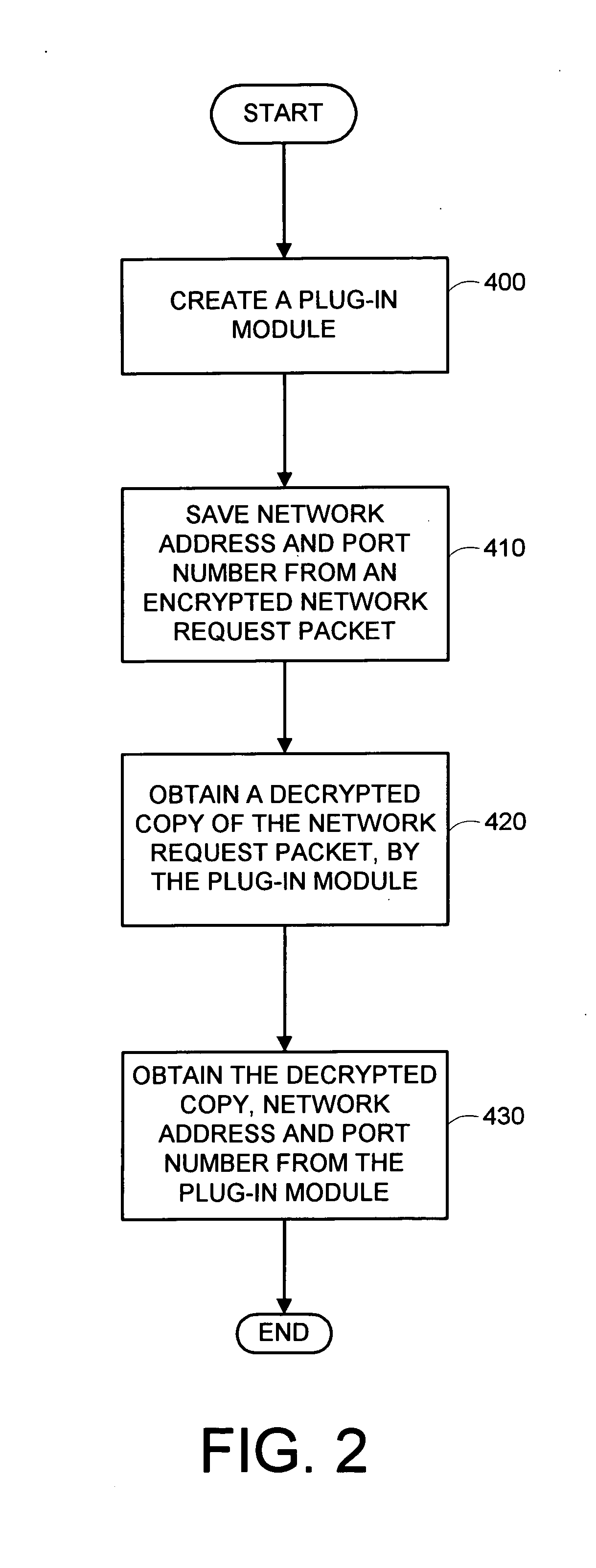
System and method for mapping an encrypted HTTPS network packet to a specific URL name and other data without decryption outside of a secure web server
A computer-based system and method of mapping an encrypted network request packet to its decrypted copy in a secure computer network web server. Method creates a plug-in module on a secure web server and saves at least one network address and port number from a captured encrypted network request packet. Plug-in module obtains a decrypted copy of the network request packet from the secure web server decryption module and returns it with the network address and port number.
Owner:IBM CORP
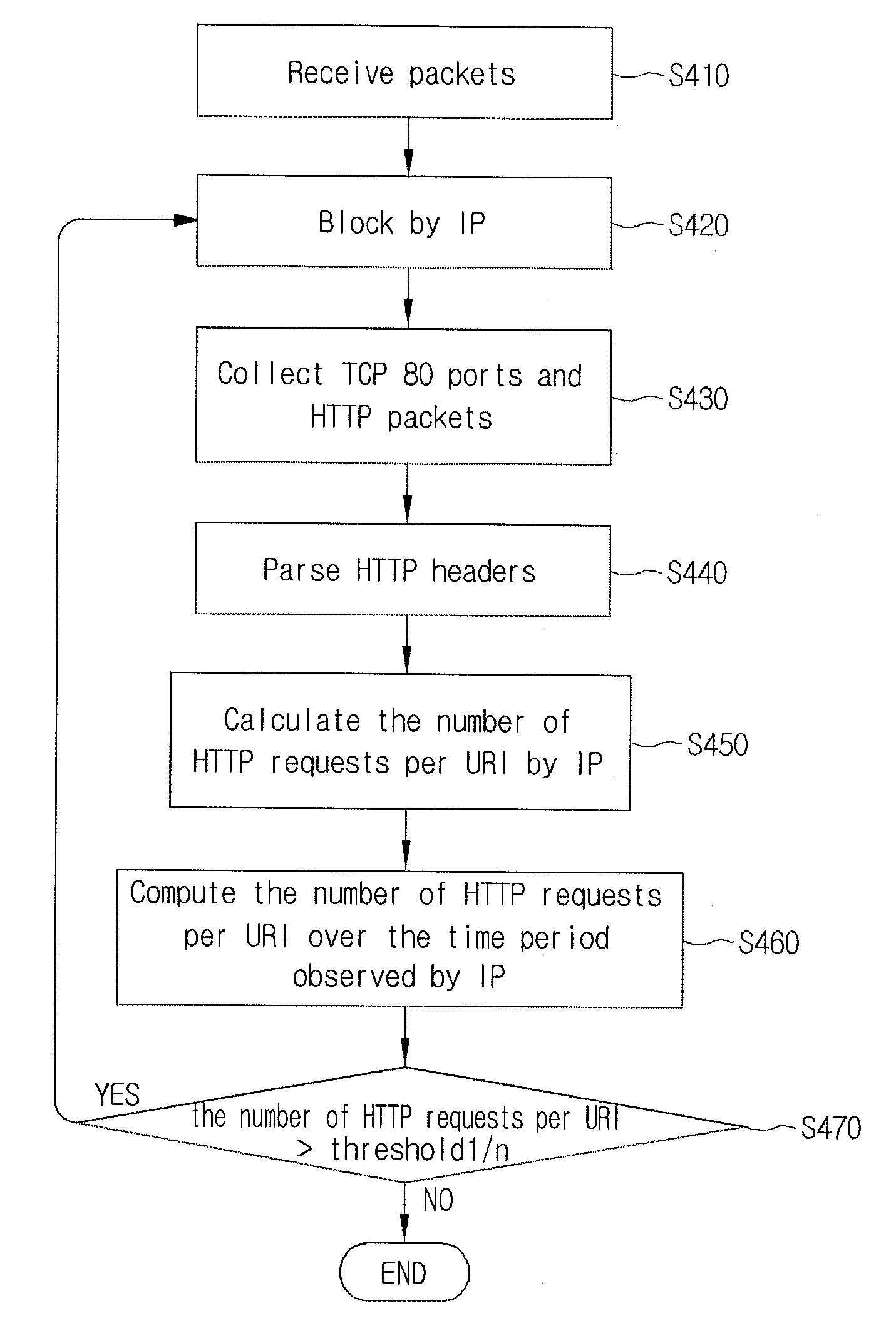
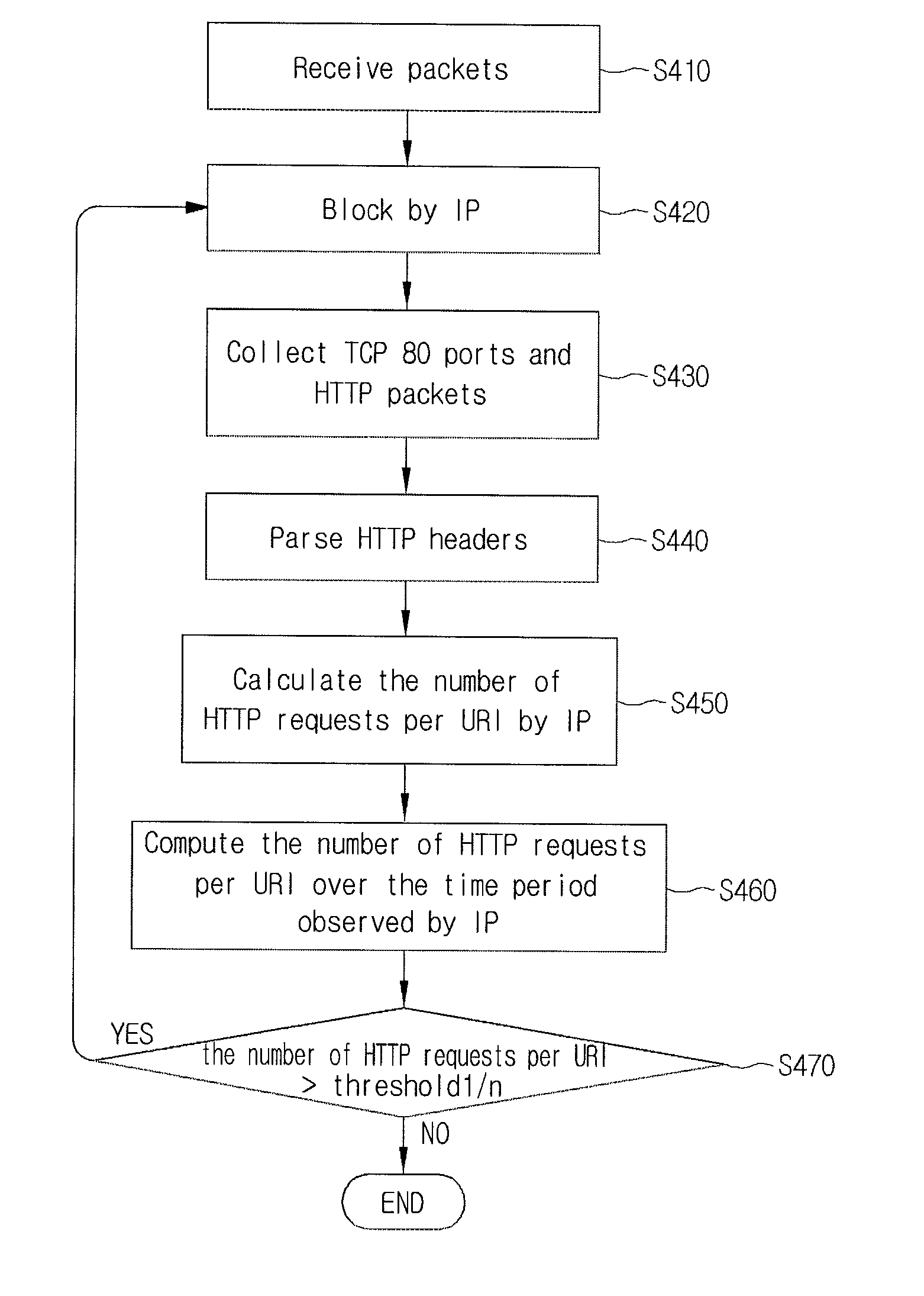
Apparatus for detecting and filtering application layer DDoS attack of web service
InactiveUS8438639B2Minimum arithmetic complexityMemory loss protectionError detection/correctionWeb serviceIp address
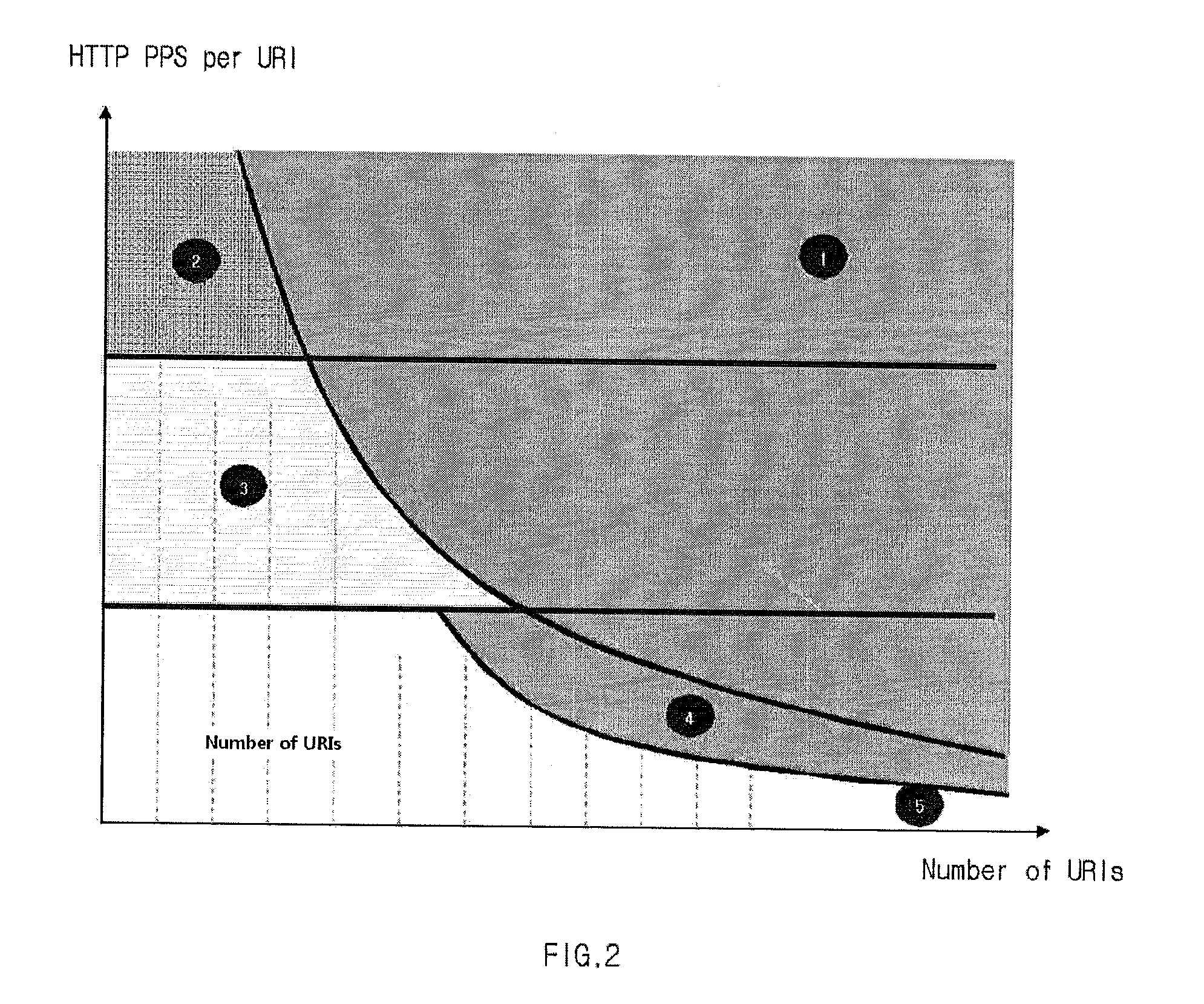
Disclosed is a DDoS attack detection and response apparatus. The DDoS attack detection and response apparatus comprises: a receiver unit receiving HTTP requests from a client terminal which is characterized as an IP address; a data measuring unit computing the number of HTTP requests by IP and the number of URIs per HTTP over a certain time period; a DDoS discrimination unit comparing the number of HTTPs per URI with a threshold value and defining an access of the client terminal having the IP address as a DDoS attack when the number of HTTPs per URI is larger than the threshold value; and a blocking unit blocking packets from the IP address when the DDoS discrimination unit detects a DDoS attack.
Owner:KOREA INTERNET & SECURITY AGENCY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com