Transferring a Virtual Machine from a Remote Server Computer for Local Execution by a Client Computer
a client computer and virtual machine technology, applied in the field of transfer of virtual machines from remote server computers to local execution by clients, can solve the problems of increasing complexity and cost of network management, and the inability of client computer systems to join the server computer system's network, so as to increase the security of information in virtual machines
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
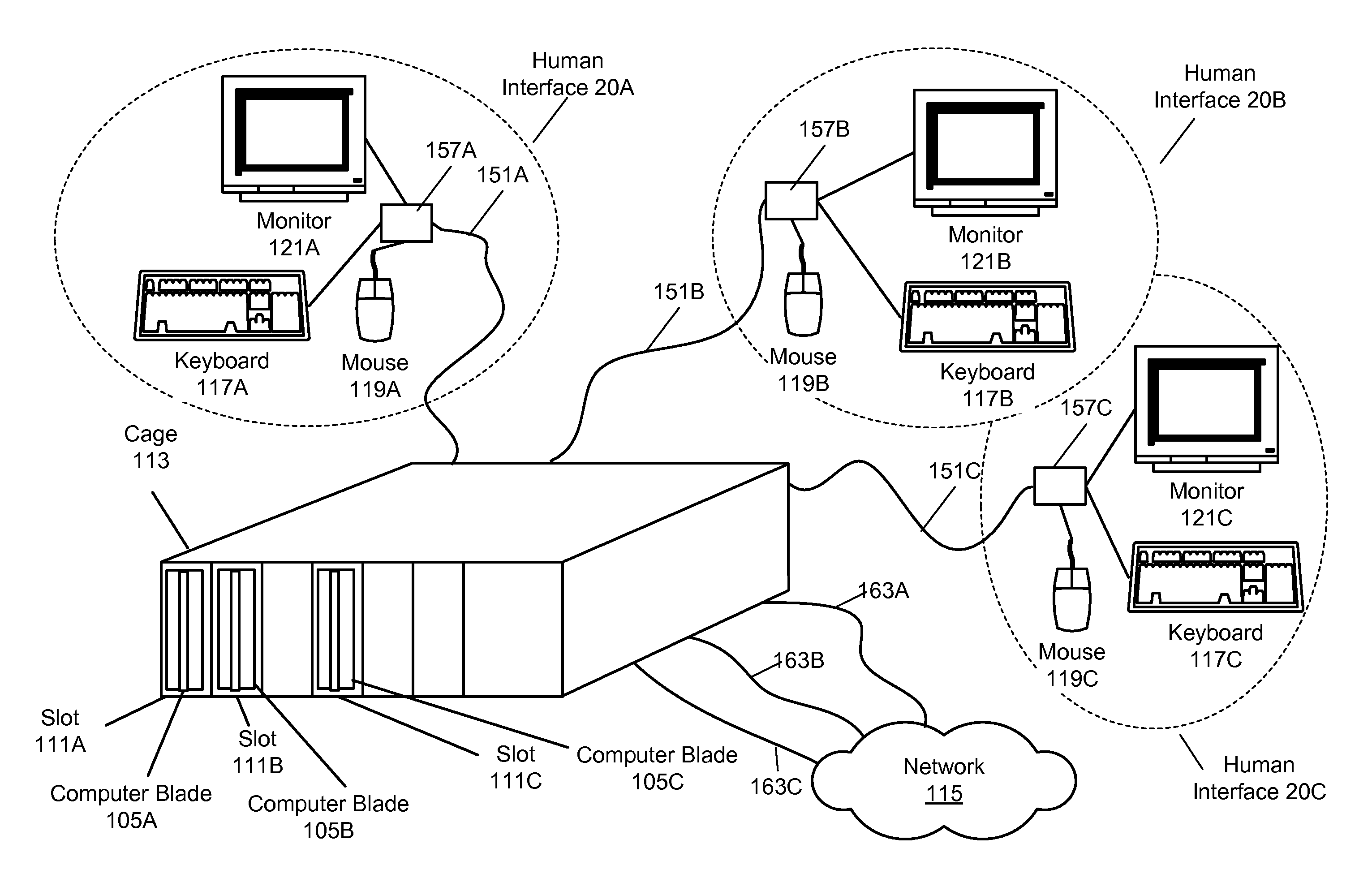
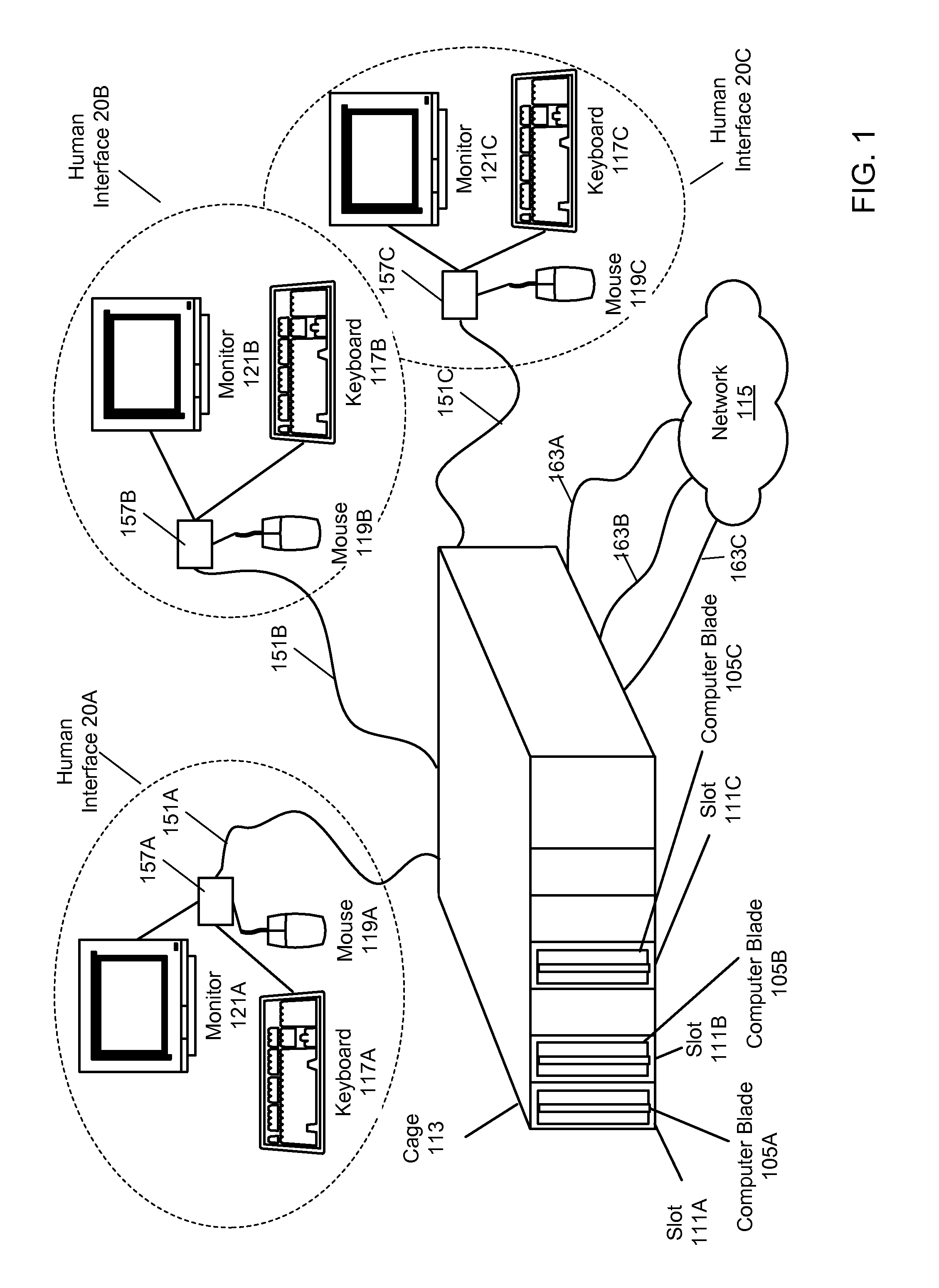
[0044]Various embodiments of a distributed computer system and associated methods are described herein. A plurality of users located at different physical locations may connect through a network to a server computer system including one or more server computers. In some embodiments, upon connecting to the server computer system, each user may be assigned to a virtual machine executing on a server computer in the system. Various methods for assigning users to virtual machines and managing the virtual machines executing on the various server computers are described herein.
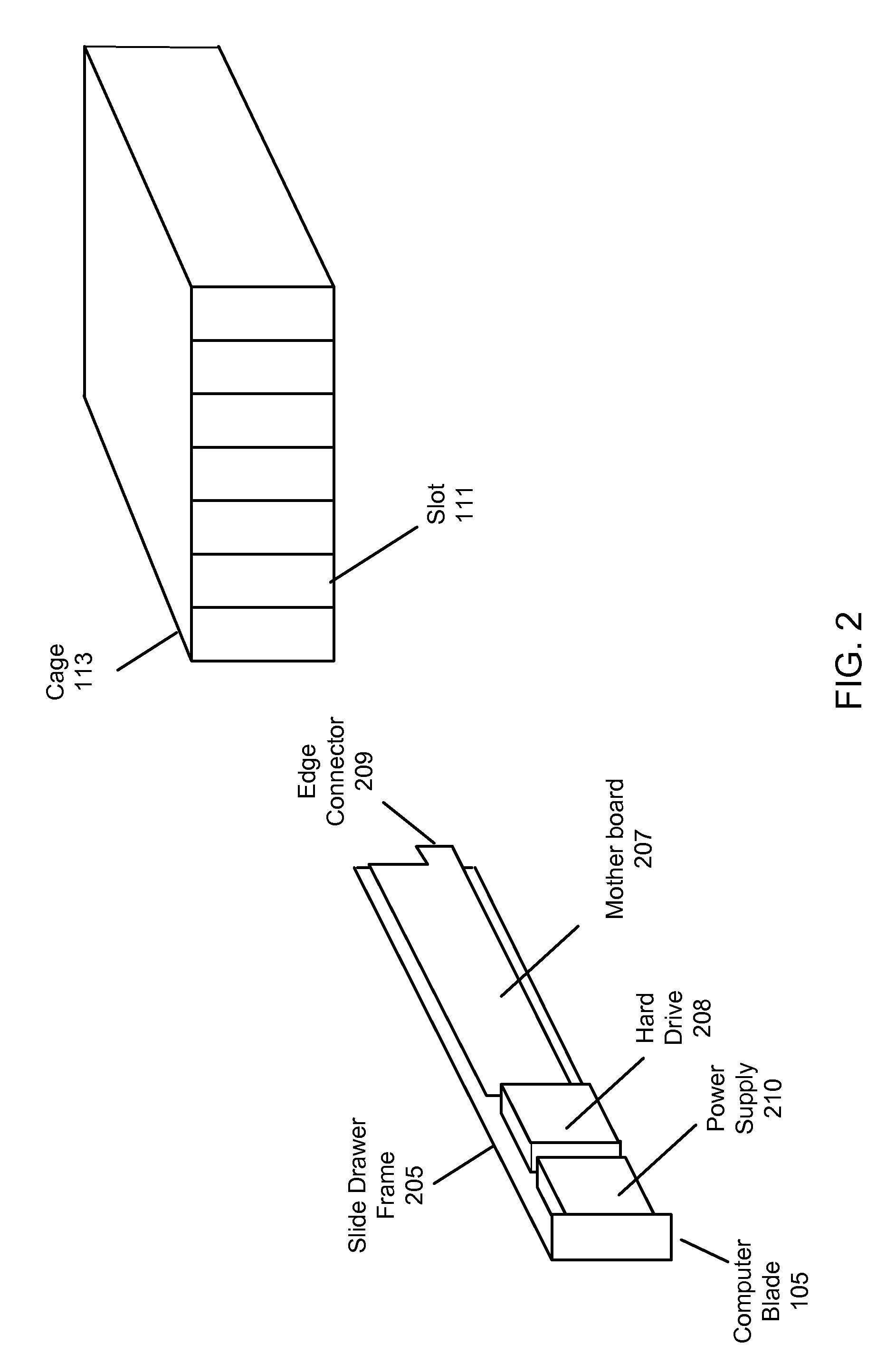
FIGS. 1-4—Blade Computer Systems
[0045]In some embodiments the server computer system may include a blade server computer system, also referred to herein as a blade computer system. In a blade server computer system, multiple physical server computers, e.g., PC's, may be installed into a central frame or cabinet (e.g., physical chassis). Different sets of human interface hardware (e.g., keyboard, display device, mouse...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com