Malicious encrypted flow feature analysis method
A traffic feature analysis and traffic feature technology, applied in the intersection of network security and machine learning, can solve problems such as difficulty in effectively extracting malicious encrypted traffic, and achieve good interpretability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
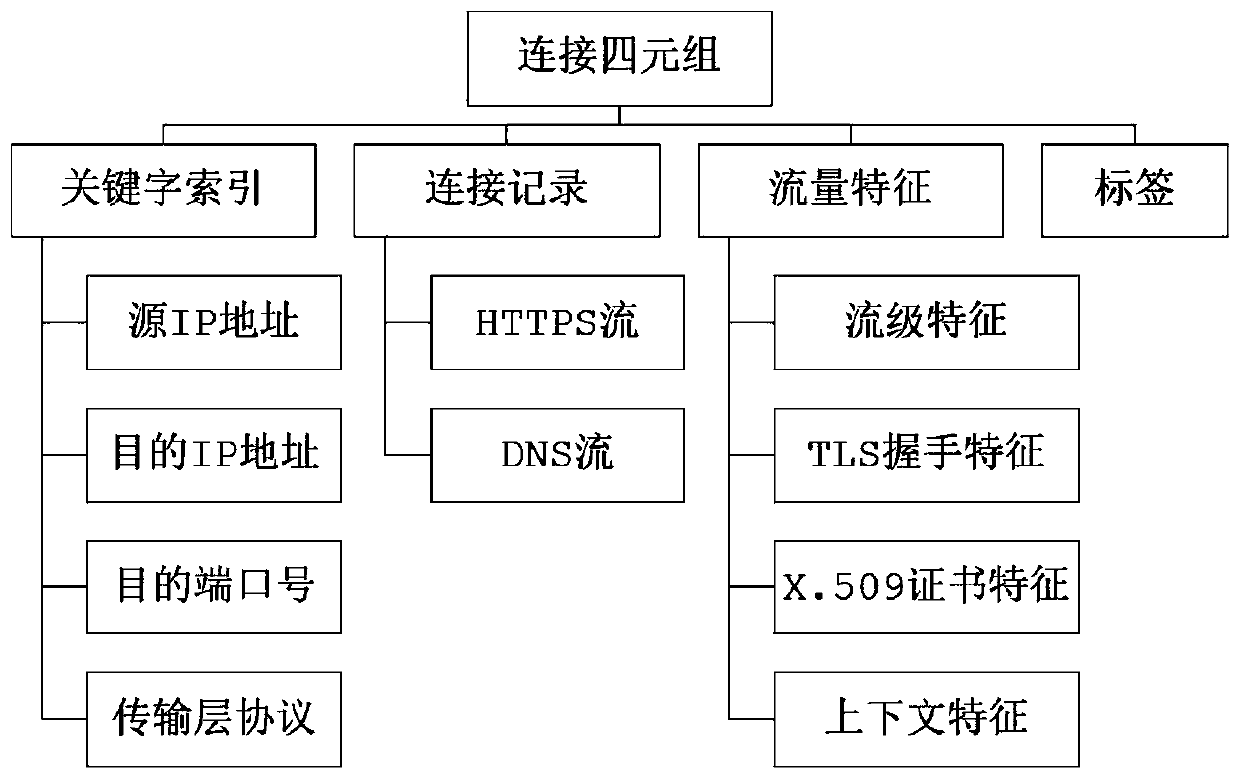
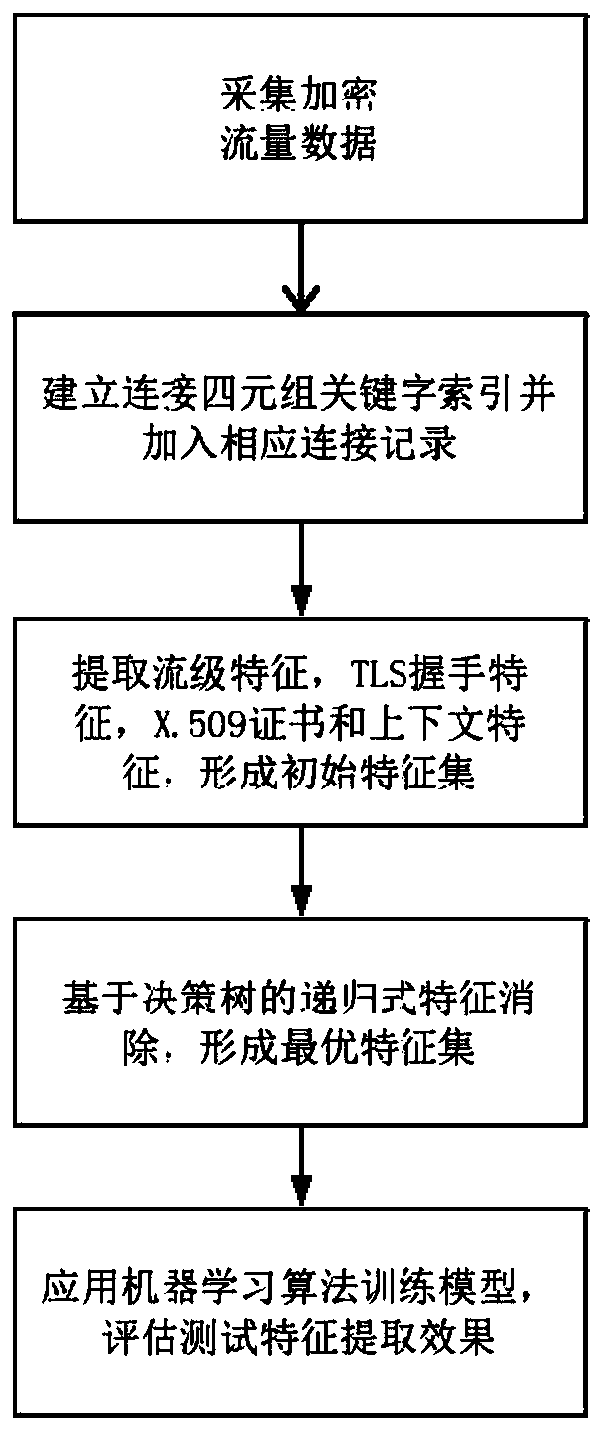
[0020] The present invention uses a traffic analysis and detection tool to clean the collected traffic data files, filters out encrypted traffic, and marks the traffic according to the existing traffic label files in the data set, and the marks are divided into malicious traffic, normal traffic and background traffic. Filter background traffic, preprocess the filtered traffic data in units of connection quadruples, add the HTTPS flow with the same source IP address, destination IP address, destination port number and transport layer protocol, and the corresponding context traffic DNS flow in the corresponding connection quadruple structure.
Embodiment 2
[0022] The invention analyzes the flow by taking the connection quadruple as a unit, and extracts the corresponding flow level feature, TLS handshake feature, certificate feature and context feature. The characteristics of the four types of traffic are as follows:
[0023] (1) Stream-level features
[0024] The average value, maximum value, and standard deviation of the inter-arrival time of the flow, the average value, maximum value, and standard deviation of the connection duration, the average value of the data packet size, the average value of the number of data packets, and the ratio of the size of the sent and received data packets , the ratio of the number of data packets sent and received, the number of lost packets, and the ratio of normal connection status.
[0025] (2) TLS handshake characteristics
[0026] TLS / SSL protocol version, encryption components and extensions provided by the client during the TLS handshake phase, encryption components and extensions sele...
Embodiment 3
[0033] The present invention uses a decision tree-based recursive feature elimination method to perform feature selection on the above-mentioned initial feature set. The recursive feature elimination method sorts the importance of the initial feature set during model training, and removes the least important features after each round of training to form a new feature set, and then trains on the new feature set, repeating the above Process until the size of the remaining feature sets reaches the threshold, and generate the optimal feature set. The optimal feature set and sample labels form training samples.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com