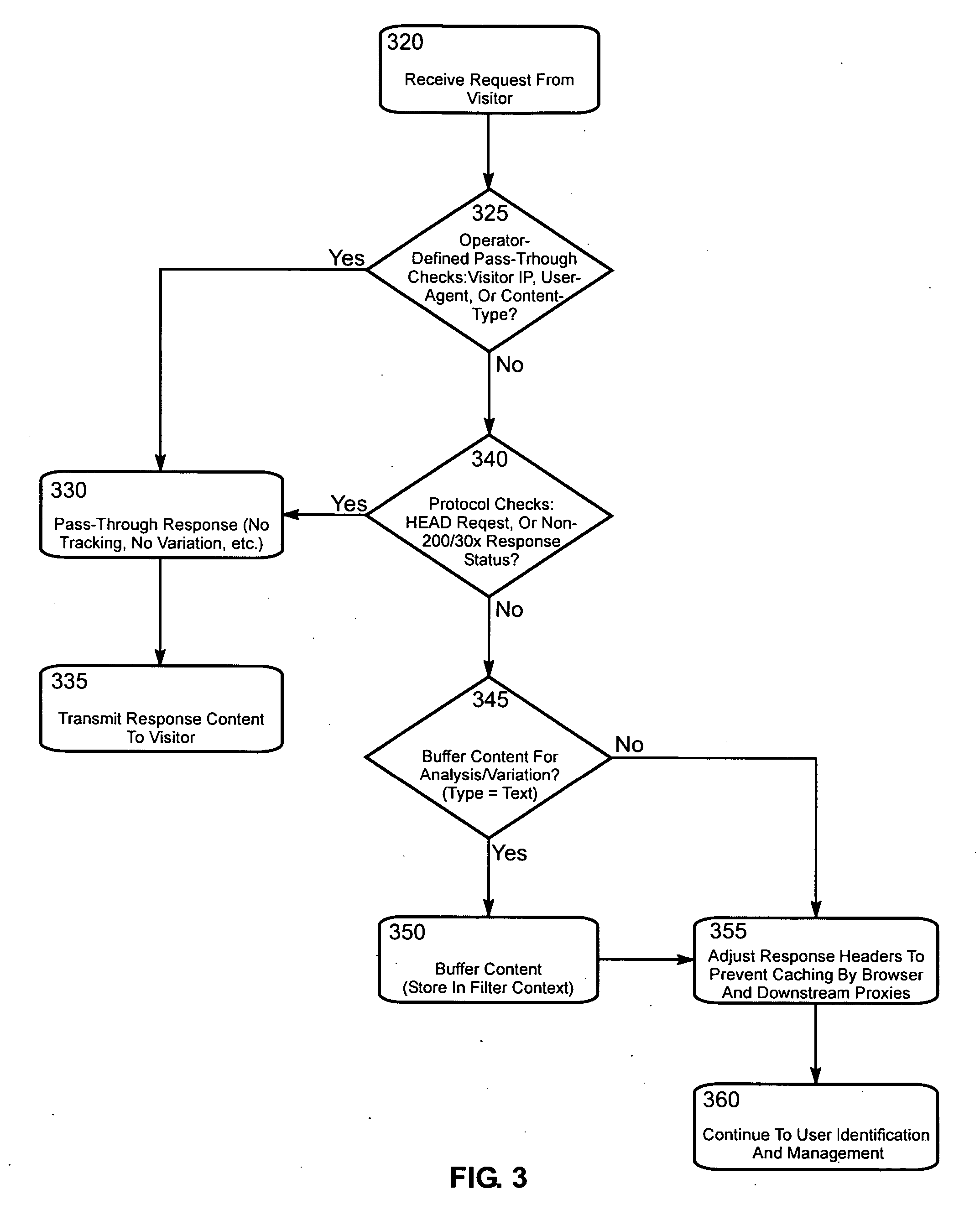
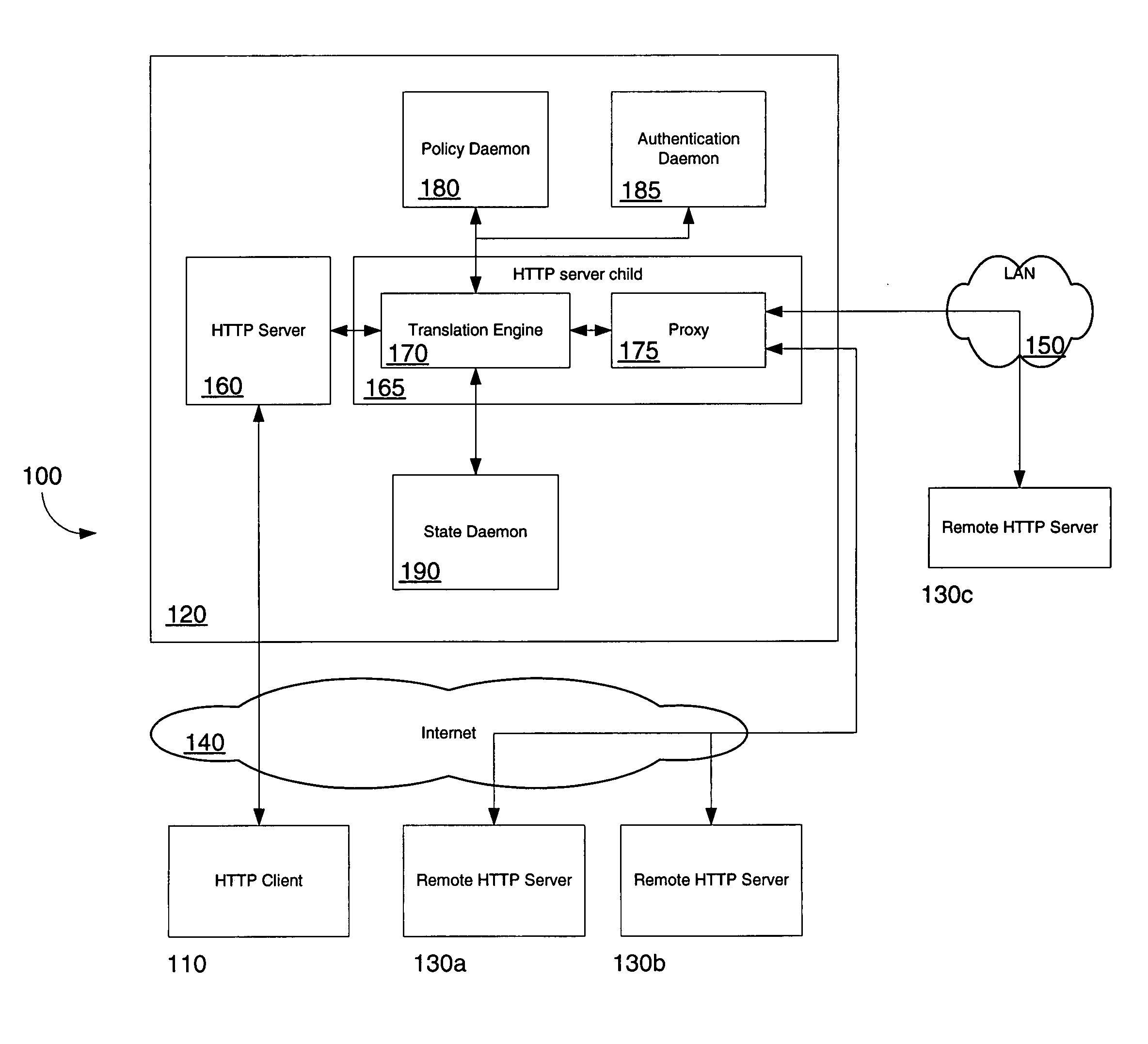
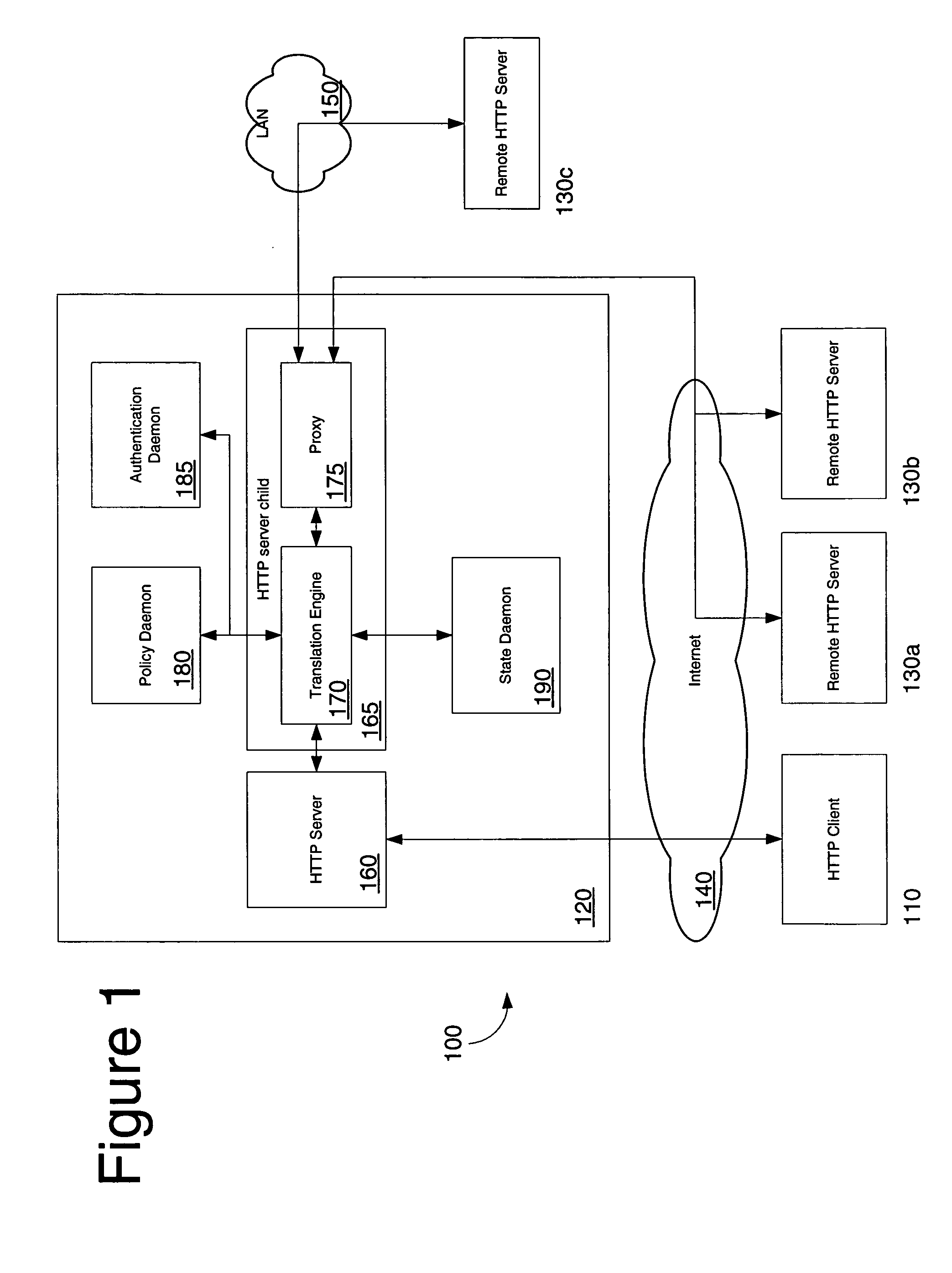
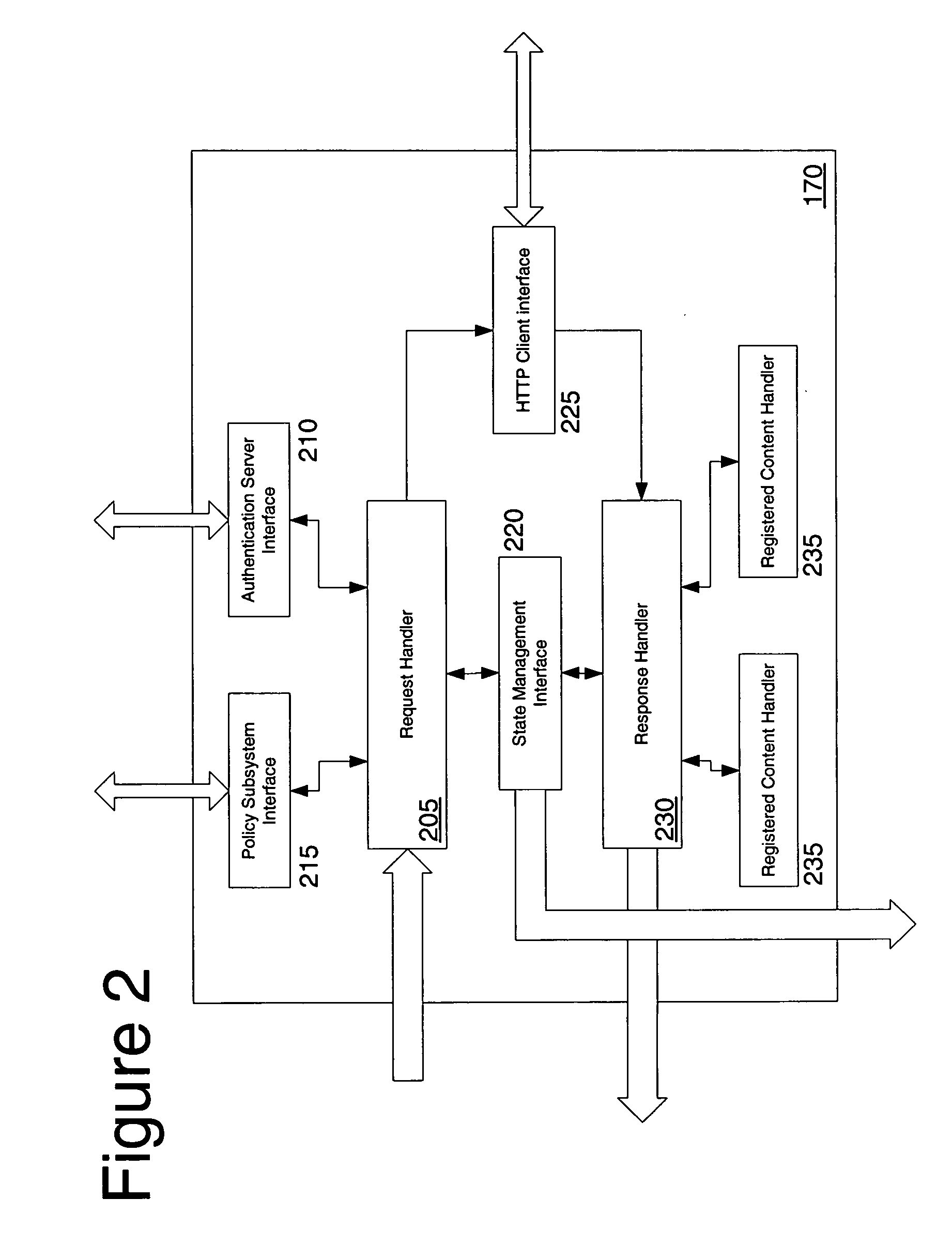
Patents
Literature
616 results about "Reverse proxy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
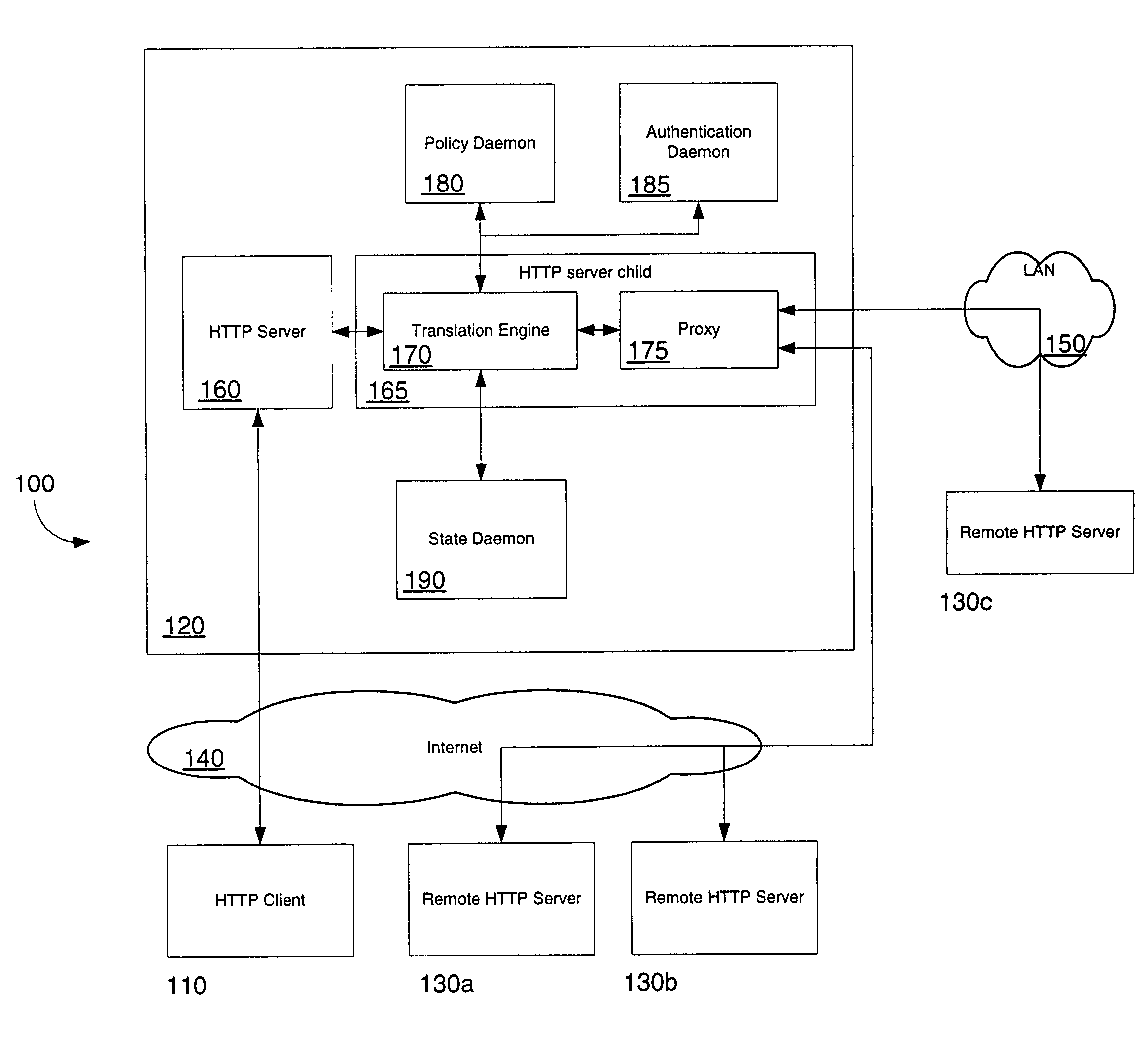
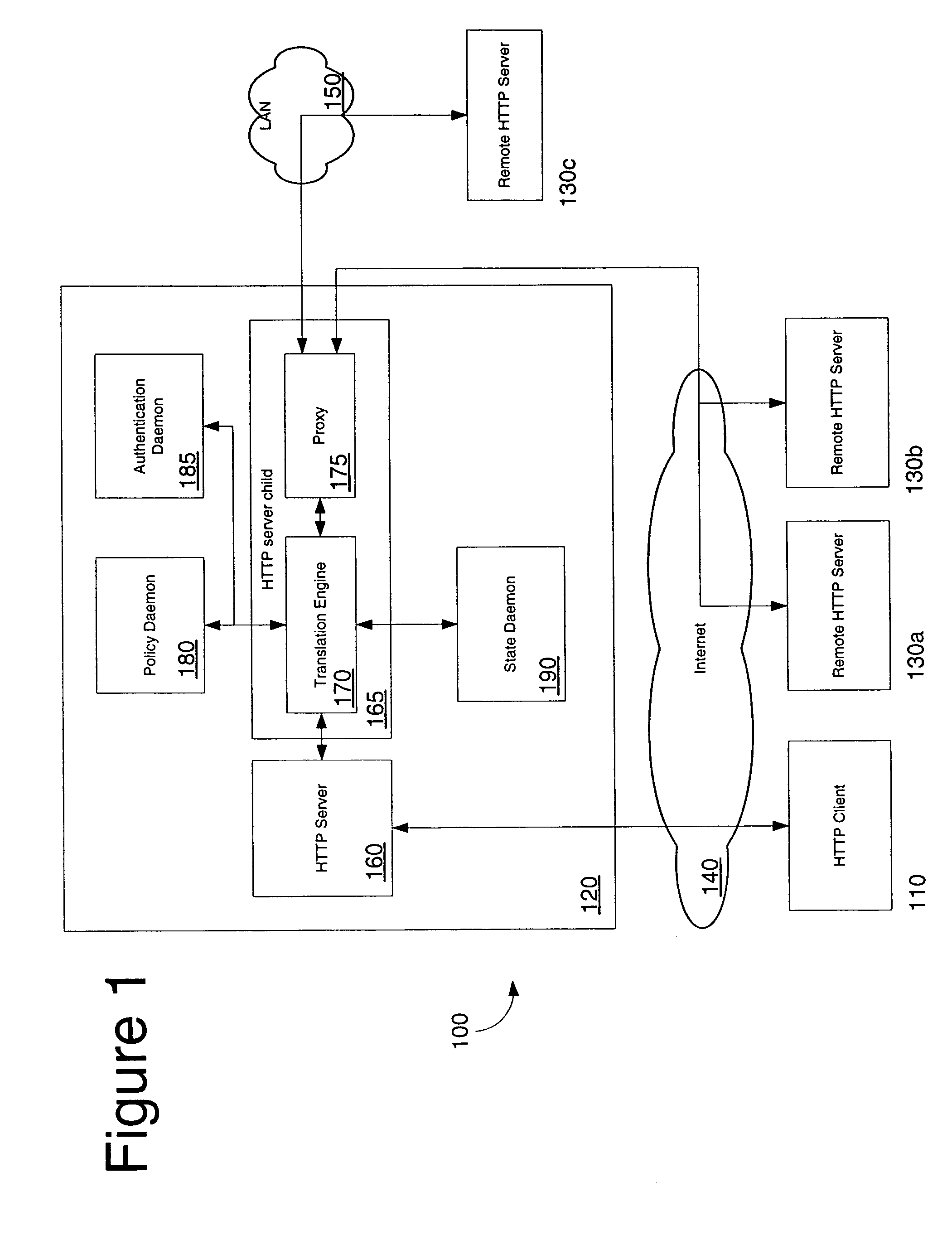
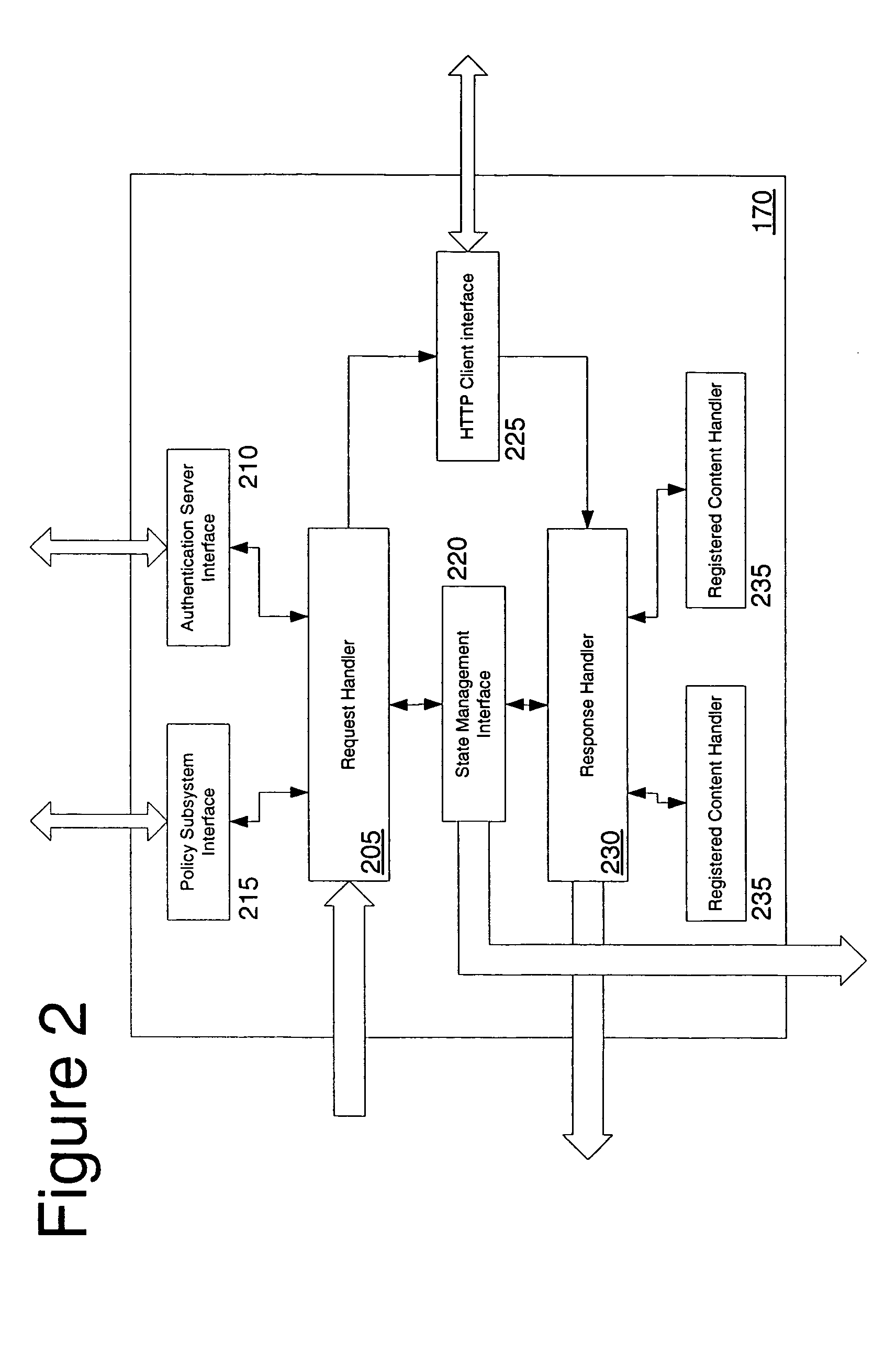
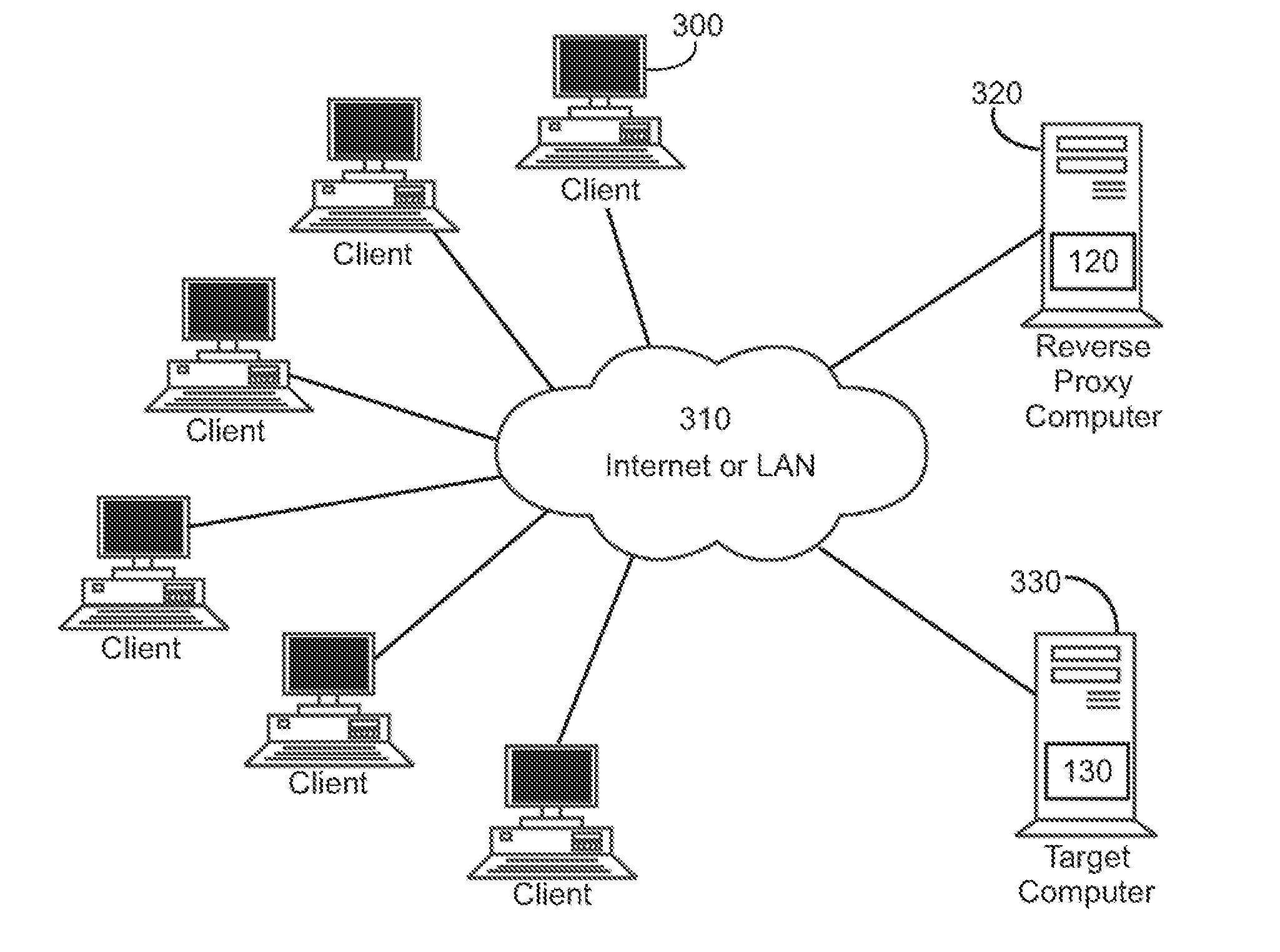
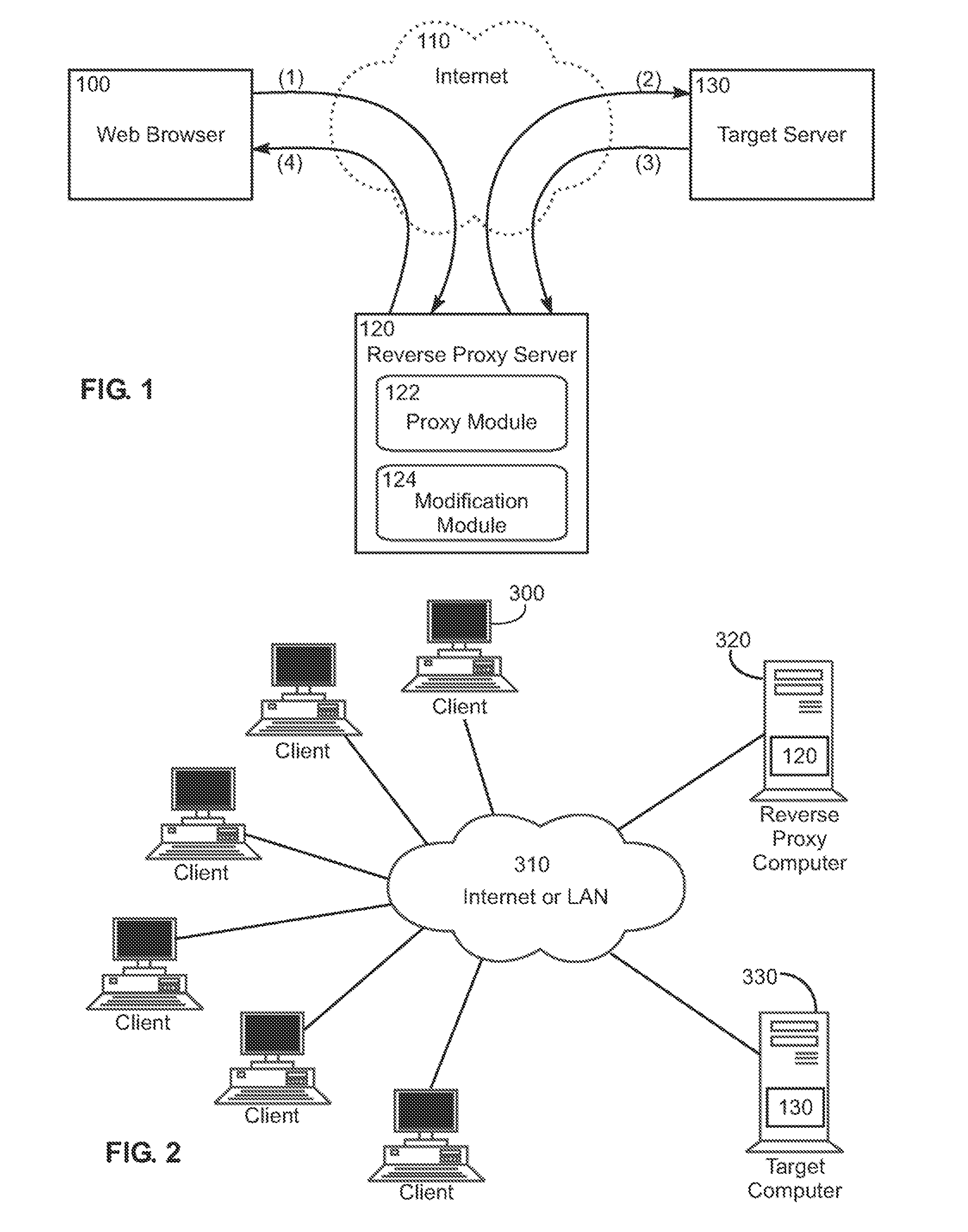
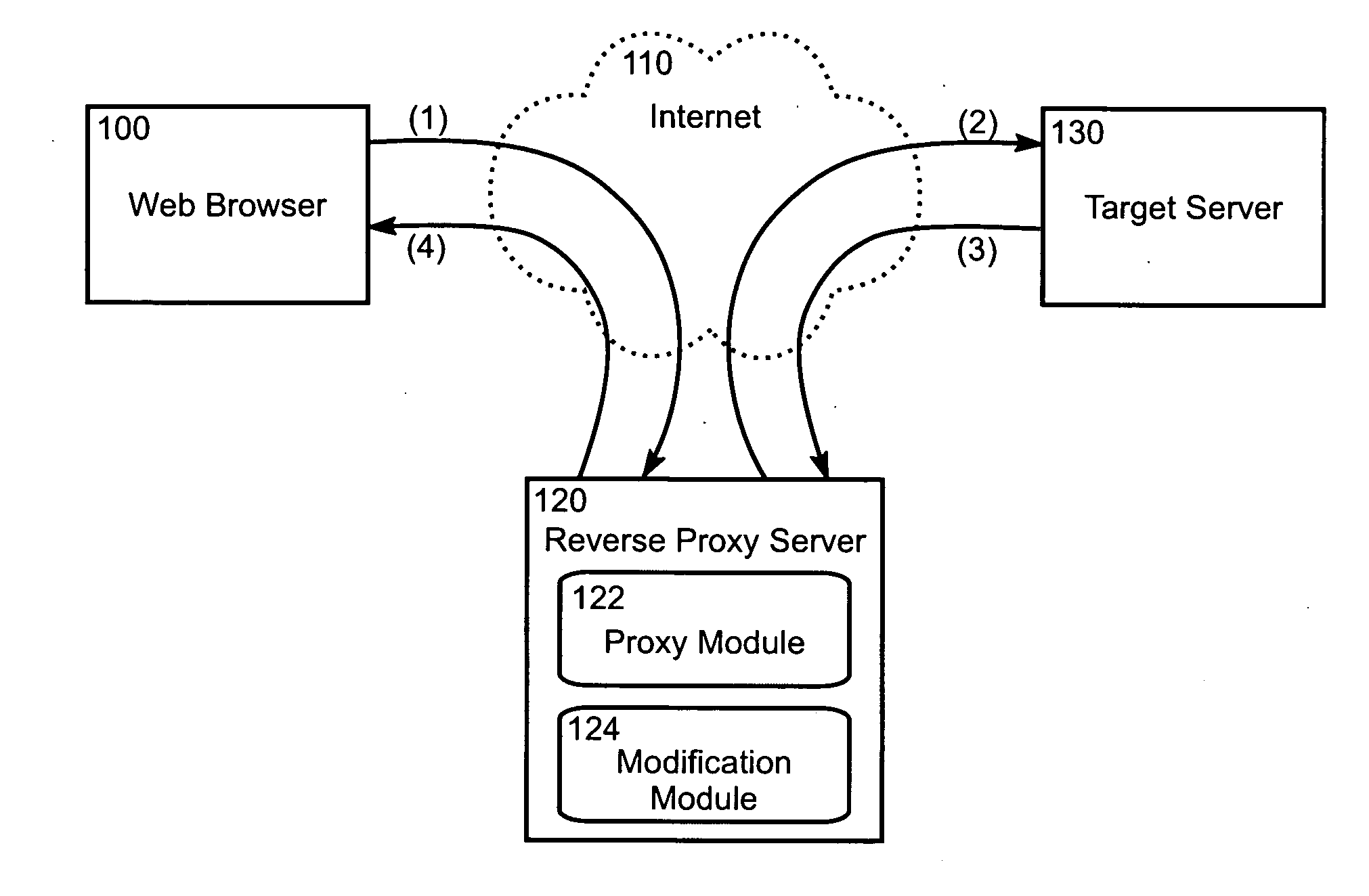
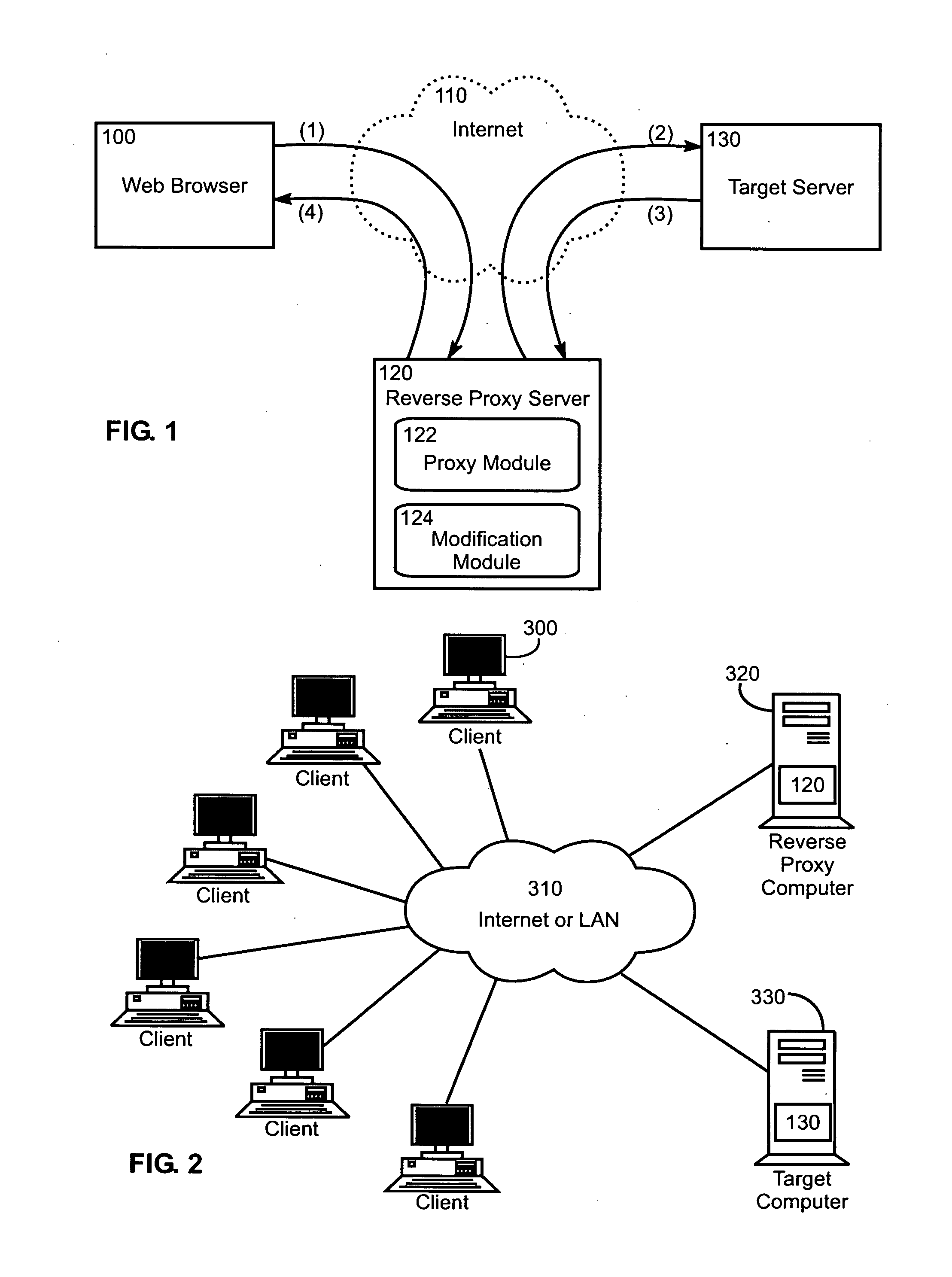
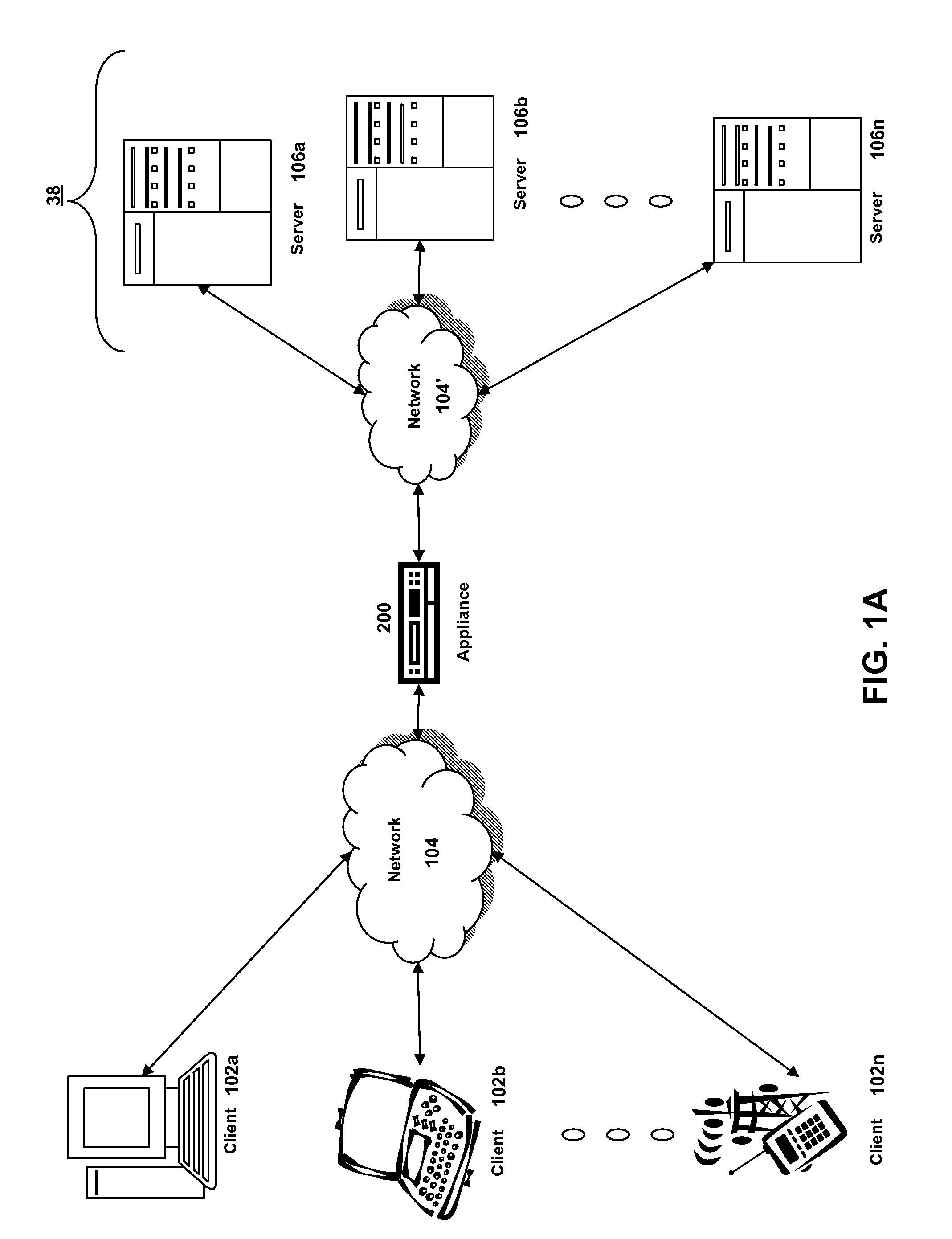
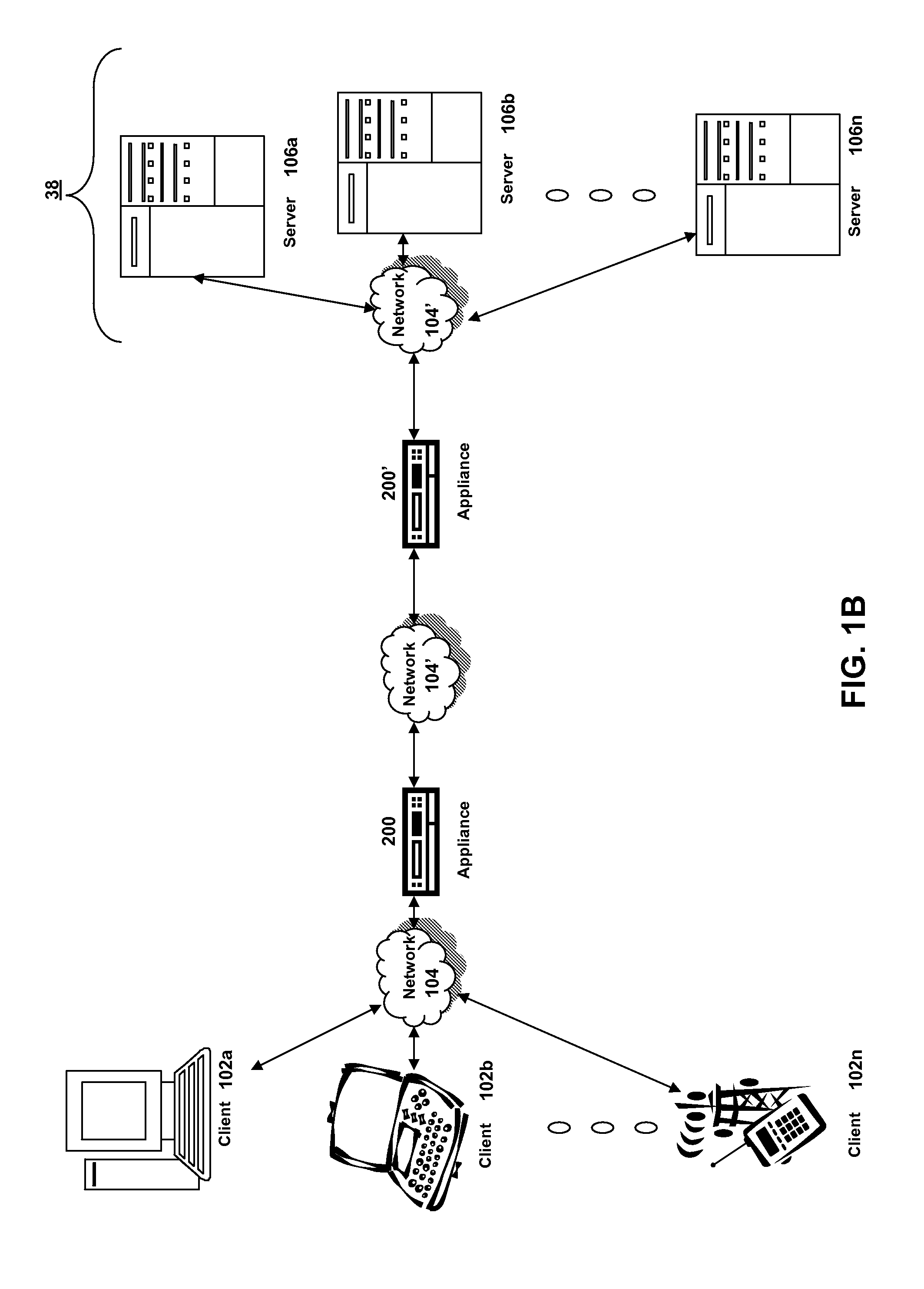
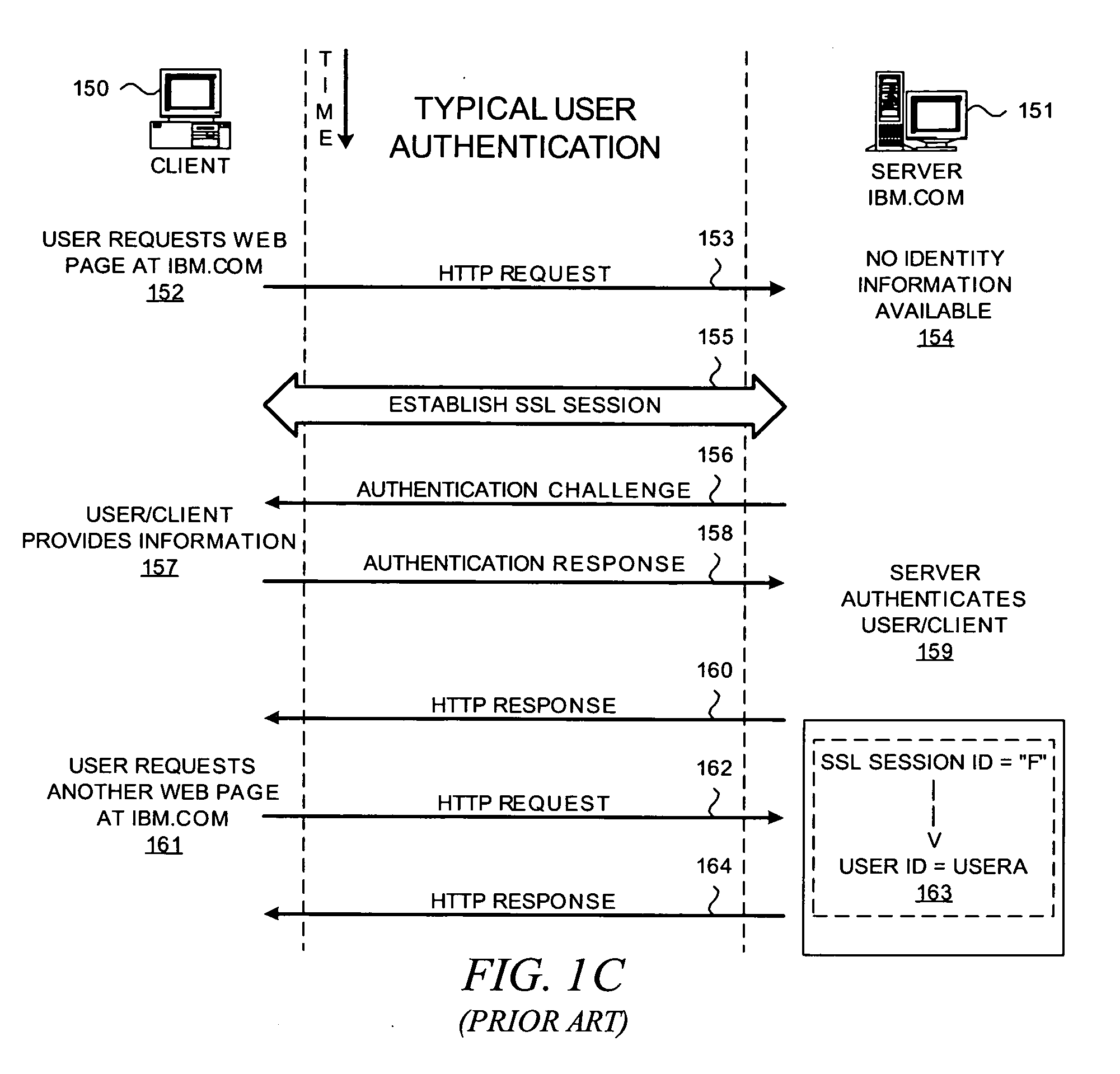
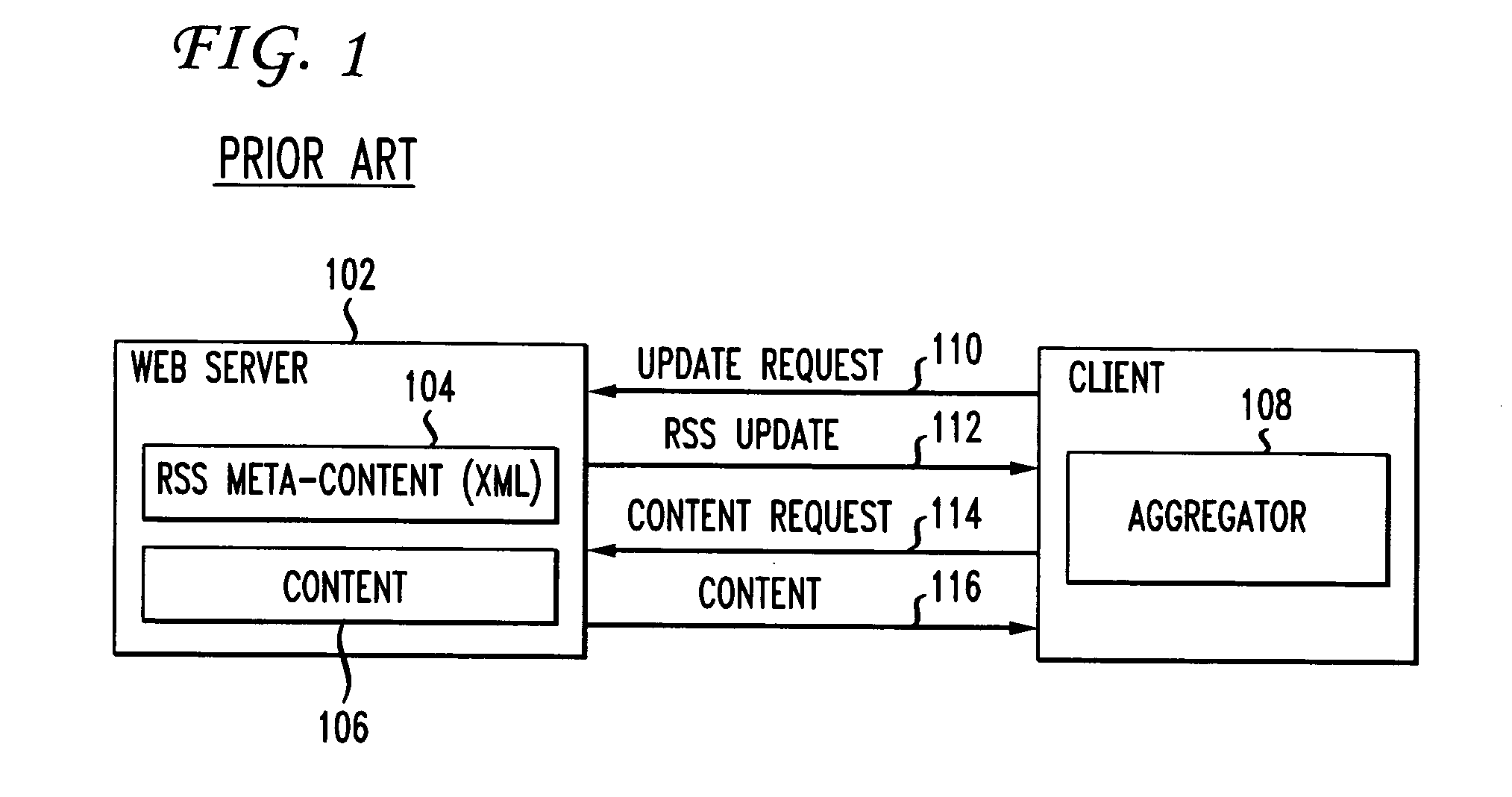
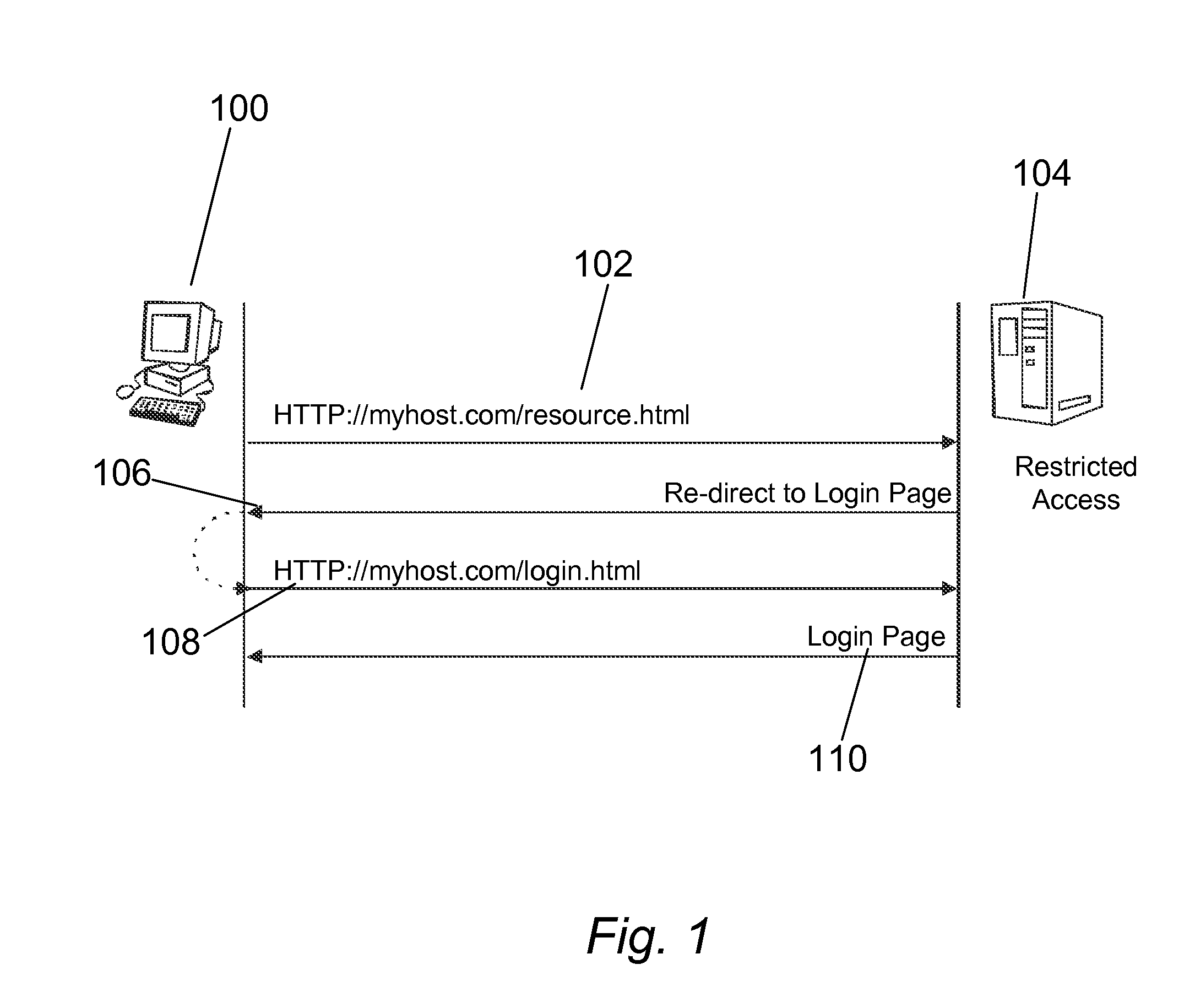
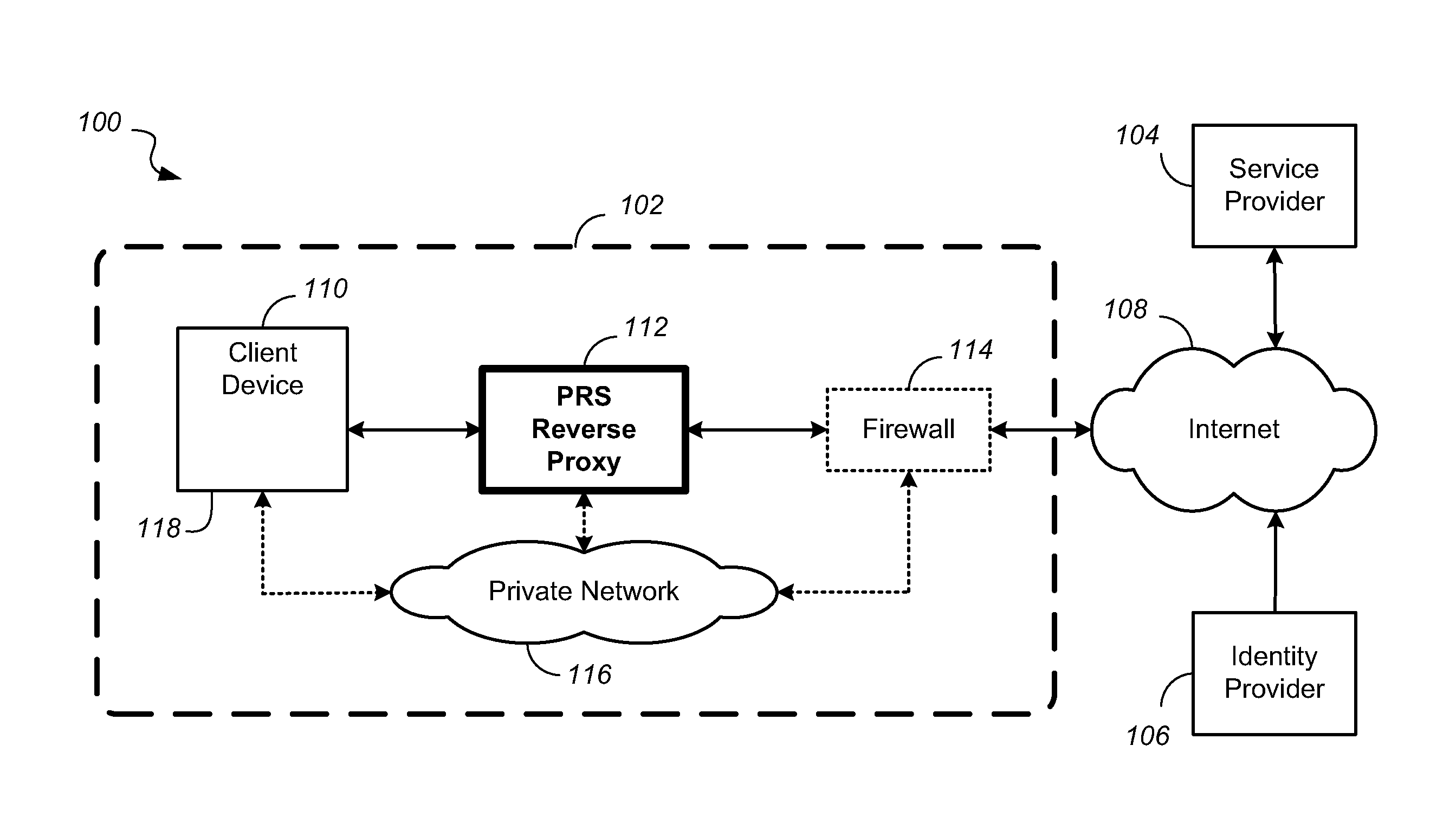
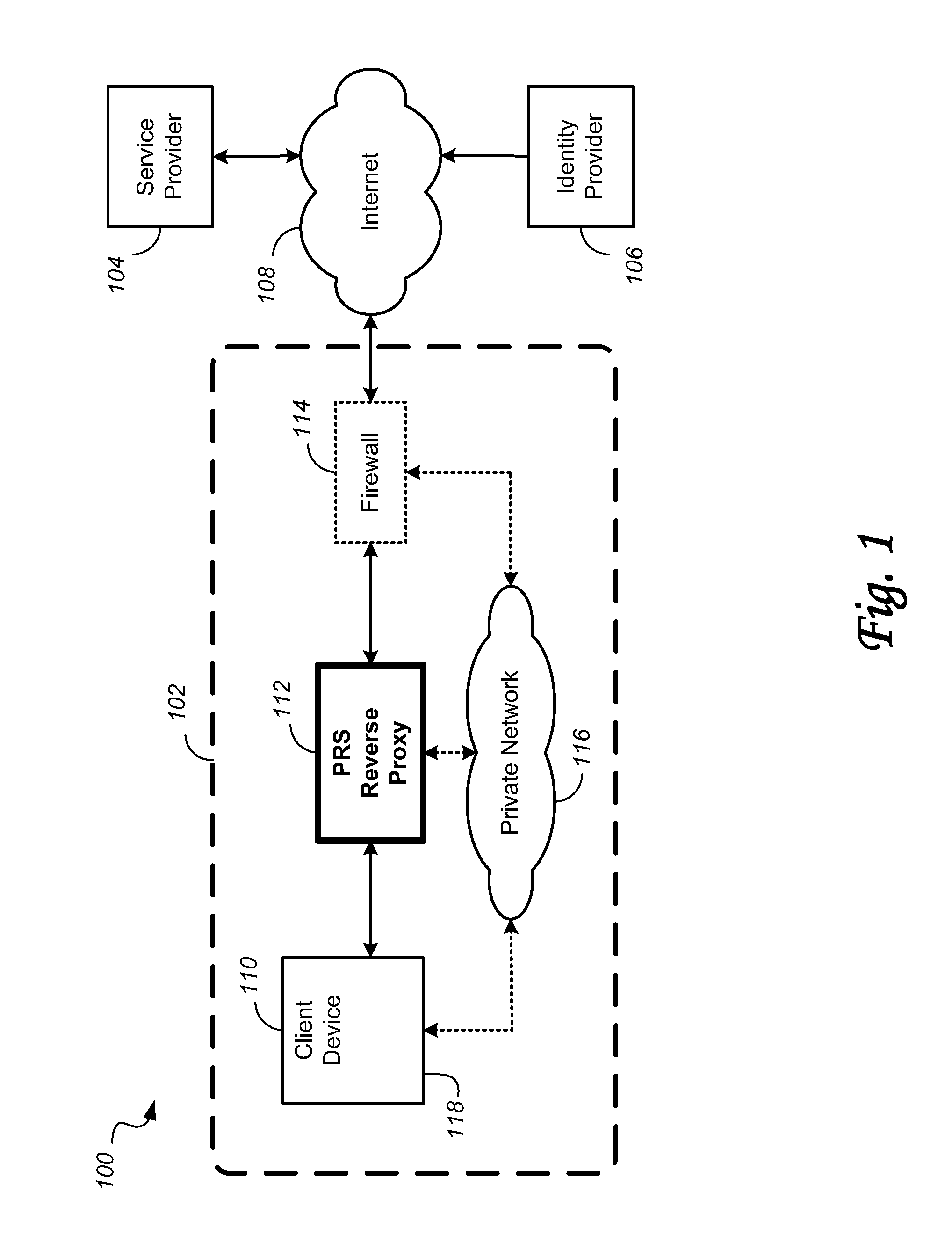
In computer networks, a reverse proxy is a type of proxy server that retrieves resources on behalf of a client from one or more servers. These resources are then returned to the client, appearing as if they originated from the proxy server itself. Unlike a forward proxy, which is an intermediary for its associated clients to contact any server, a reverse proxy is an intermediary for its associated servers to be contacted by any client. In other words, a proxy acts on behalf of the client(s), while a reverse proxy acts on behalf of the server(s).
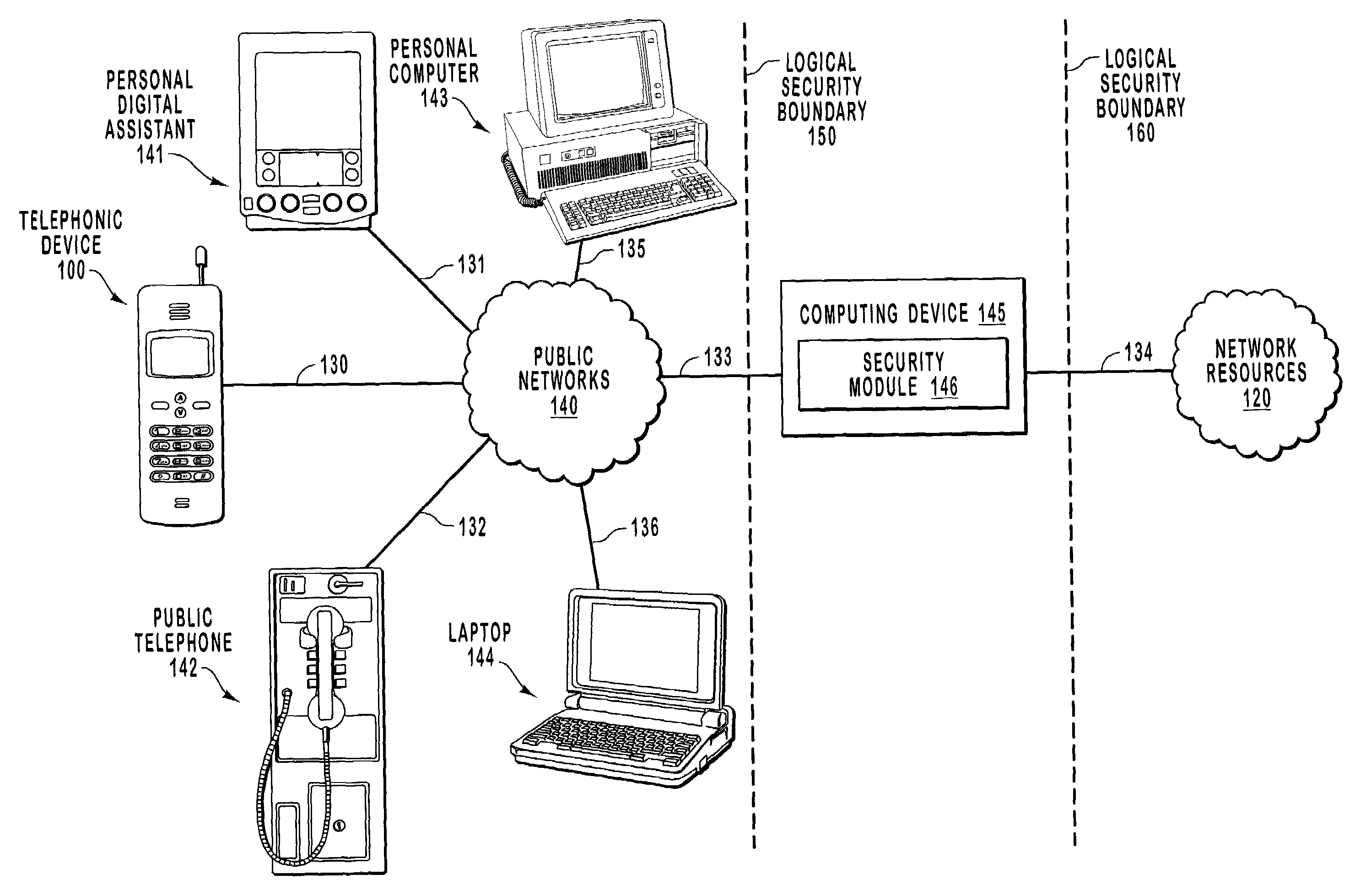
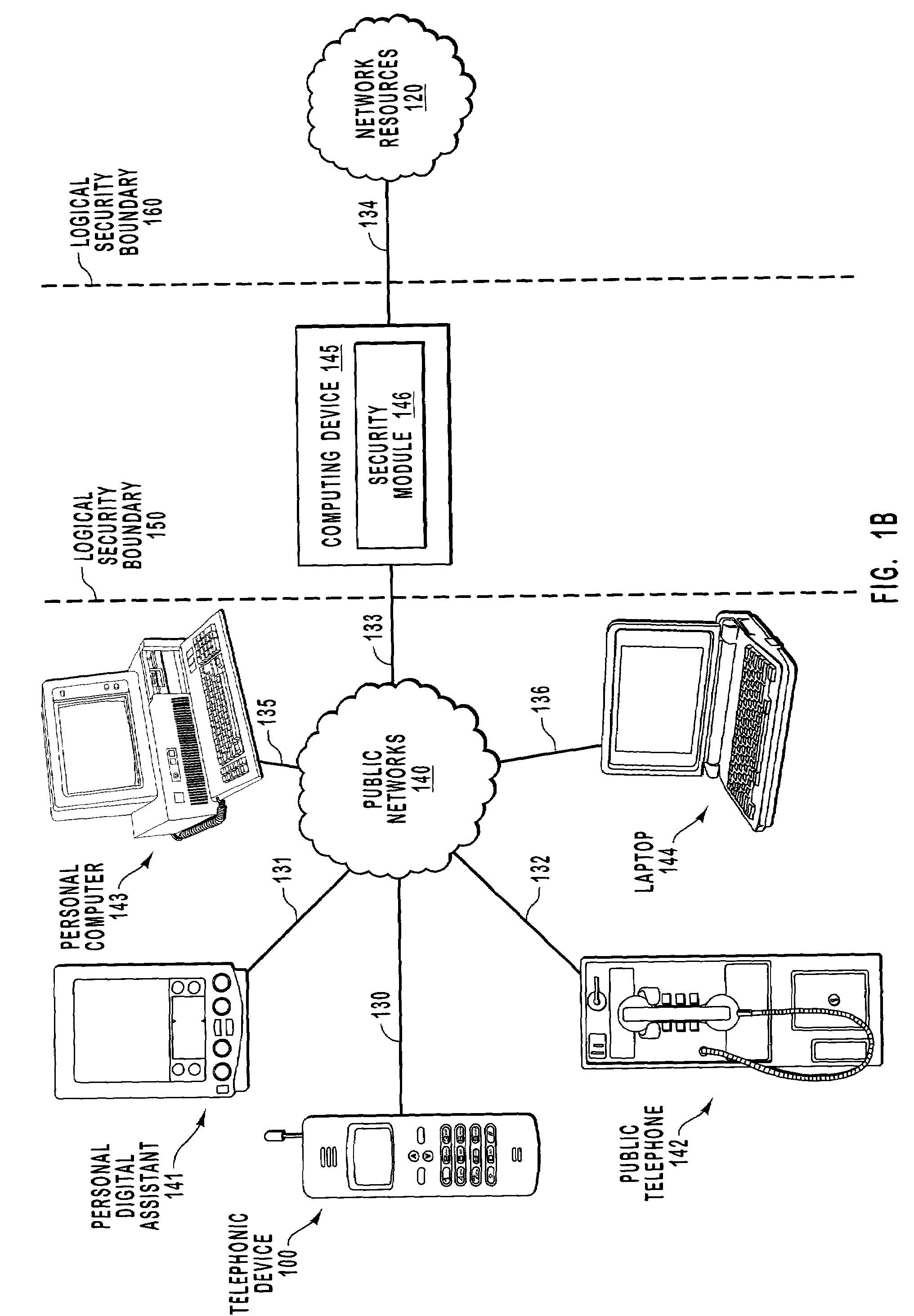
Network access using secure tunnel
InactiveUS20050273849A1Multiple digital computer combinationsProgram controlServer agentSecure communication
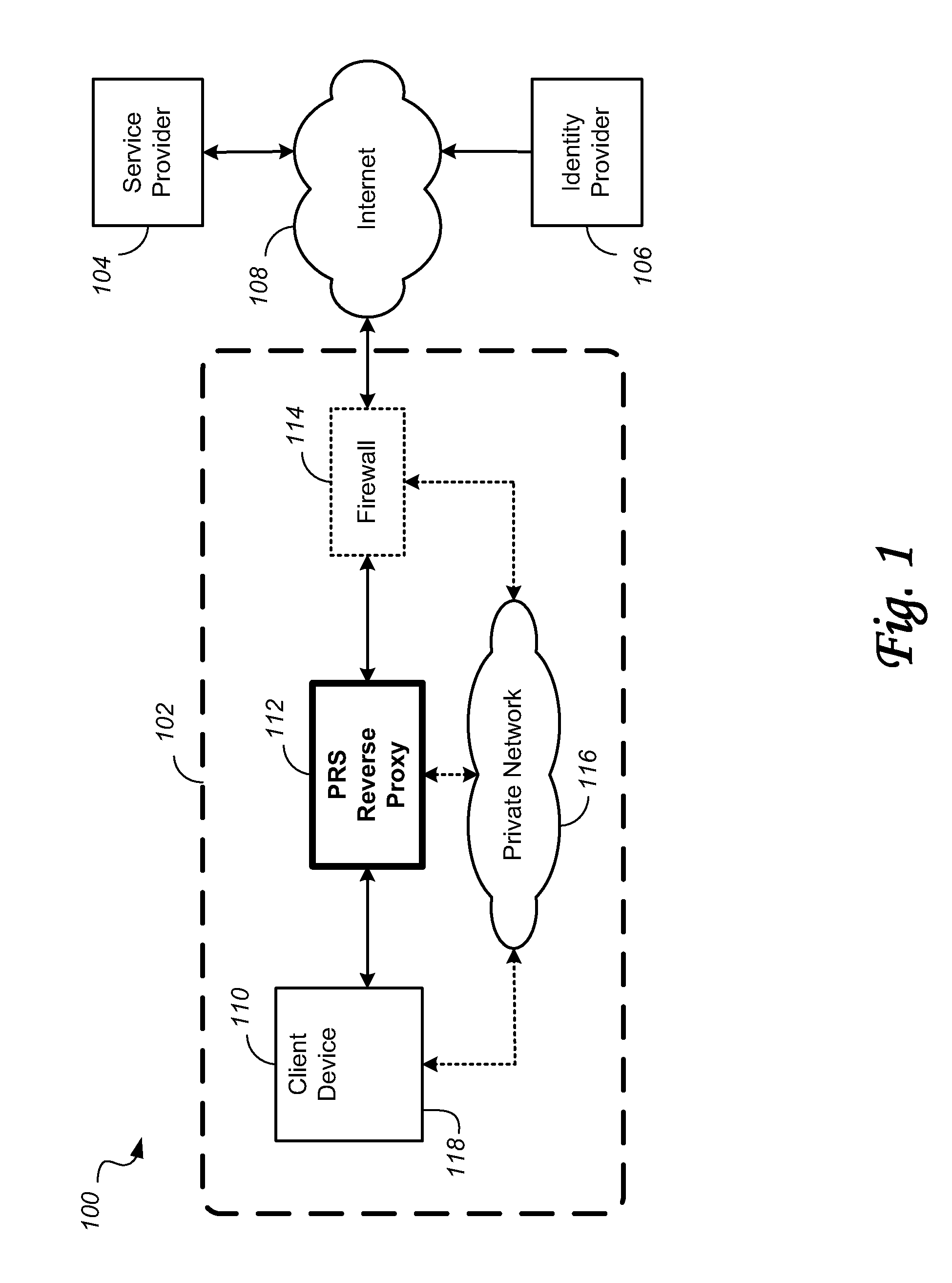
A security platform connected to a private network permits access to the private network from a public network (such as the Internet) through a variety of mechanisms. A reverse proxy system operating as part of the security platform provides access to web-enabled applications from a browser connected to the public network. The reverse proxy rewrites requests and responses so that the browser directs requests to the reverse proxy, from which the requests can be directed to the appropriate server on the public network or the private network. Responses come back to the reverse proxy, and are then forwarded to the browser. An SSL tunneling system permits fat clients to access the private network through an SSL connection. The SSL tunneling system employs a server component operating on the security platform and components downloaded to the client computer from the security platform. The client components include a control component operating in a browser window, a server-proxy component that sets up secure communications with the private network, and an adapter component between the server-proxy and the fat client. The adapter component operates in kernel space. Data is directed from the fat client to the adapter, and then forwarded to the server-proxy; data from the server-proxy is directed to the adapter, and then forwarded to the fat client. Security is provided through the use of multiple authentication realms, each of which provides a set of authentication stages for authenticating users and providing client integrity validation.
Owner:AEP NETWORKS
Method and system for testing variations of website content
ActiveUS20080275980A1Shorten the timeSave effortDigital computer detailsTransmissionThird partyWeb site
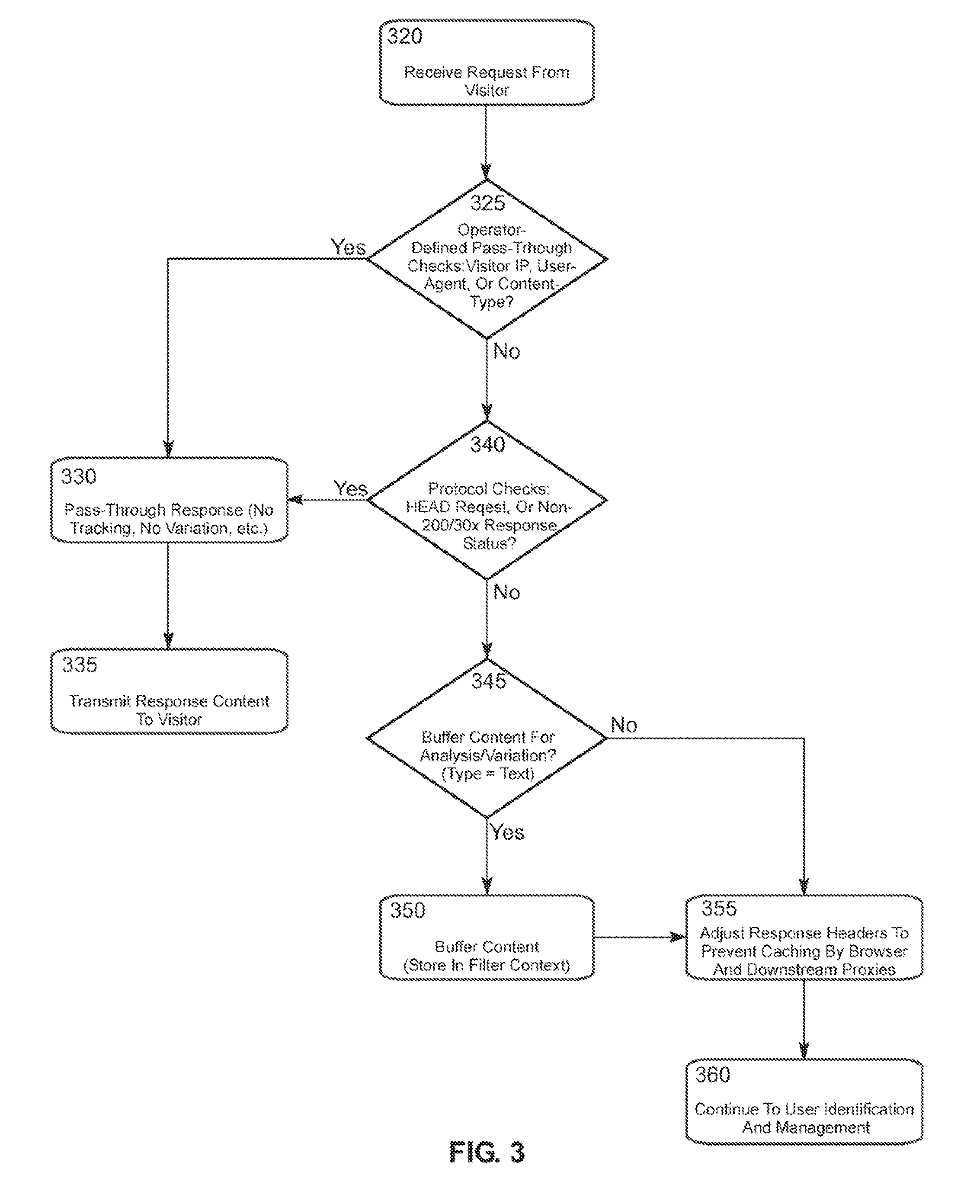
The invention is a method and system for testing variations of website content useful to optimize website visitor conversions. The invention includes integrating test variations of website content with web analytics platforms so that website variations can be tracking and analyzed within web analytics reporting systems. The invention helps website operators create content variations, and then scientifically test and measure the impact of those variations on conversion rates. The invention includes a method of using a reverse proxy server to introduce page variations on existing website content without needing to modify the existing web server. Using the reverse proxy server, the invention automatically injects values, associated with website variations, into web page tags used with web analytics platforms. The invention makes it possible to test any number of website variations and access such data from within web analytics platforms. The invention also provides a method to automatically transform web page tags of a first web analytics platform to web page tags of a second web analytics platform to easily try new third party web analytics solutions.
Owner:SITESPECT
System and method for optimizing website visitor actions
ActiveUS20060271671A1Low costShorten the timeDigital computer detailsTransmissionWeb siteReverse proxy
The invention includes a method and system for optimizing web visitor conversion—the science of measuring, testing, and improving the rate at which website visitors respond to website content. The system helps website operators create content variations, and then scientifically test and measure the impact of those variations on conversion rates. The invention includes a method of using a reverse proxy server to introduce page variations on existing website content without needing to modify the existing target server. The invention makes it possible to test any number of variations—in any combination—on a target server's visitors. Website operators learn how content variations impact visitor behavior and conversion rates.
Owner:SITESPECT
Network access using multiple authentication realms
InactiveUS20050251856A1Multiple digital computer combinationsProgram controlServer agentSecure communication
A security platform connected to a private network permits access to the private network from a public network (such as the Internet) through a variety of mechanisms. A reverse proxy system operating as part of the security platform provides access to web-enabled applications from a browser connected to the public network. The reverse proxy rewrites requests and responses so that the browser directs requests to the reverse proxy, from which the requests can be directed to the appropriate server on the public network or the private network. Responses come back to the reverse proxy, and are then forwarded to the browser. An SSL tunneling system permits fat clients to access the private network through an SSL connection. The SSL tunneling system employs a server component operating on the security platform and components downloaded to the client computer from the security platform. The client components include a control component operating in a browser window, a server-proxy component that sets up secure communications with the private network, and an adapter component between the server-proxy and the fat client. The adapter component operates in kernel space. Data is directed from the fat client to the adapter, and then forwarded to the server-proxy; data from the server-proxy is directed to the adapter, and then forwarded to the fat client. Security is provided through the use of multiple authentication realms, each of which provides a set of authentication stages for authenticating users and providing client integrity validation.
Owner:AEP NETWORKS
Network access using reverse proxy
InactiveUS20050262357A1Computer security arrangementsSecret communicationSecure communicationServer agent
A security platform connected to a private network permits access to the private network from a public network (such as the Internet) through a variety of mechanisms. A reverse proxy system operating as part of the security platform provides access to web-enabled applications from a browser connected to the public network. The reverse proxy rewrites requests and responses so that the browser directs requests to the reverse proxy, from which the requests can be directed to the appropriate server on the public network or the private network. Responses come back to the reverse proxy, and are then forwarded to the browser. An SSL tunneling system permits fat clients to access the private network through an SSL connection. The SSL tunneling system employs a server component operating on the security platform and components downloaded to the client computer from the security platform. The client components include a control component operating in a browser window, a server-proxy component that sets up secure communications with the private network, and an adapter component between the server-proxy and the fat client. The adapter component operates in kernel space. Data is directed from the fat client to the adapter, and then forwarded to the server-proxy; data from the server-proxy is directed to the adapter, and then forwarded to the fat client. Security is provided through the use of multiple authentication realms, each of which provides a set of authentication stages for authenticating users and providing client integrity validation.
Owner:AEP NETWORKS
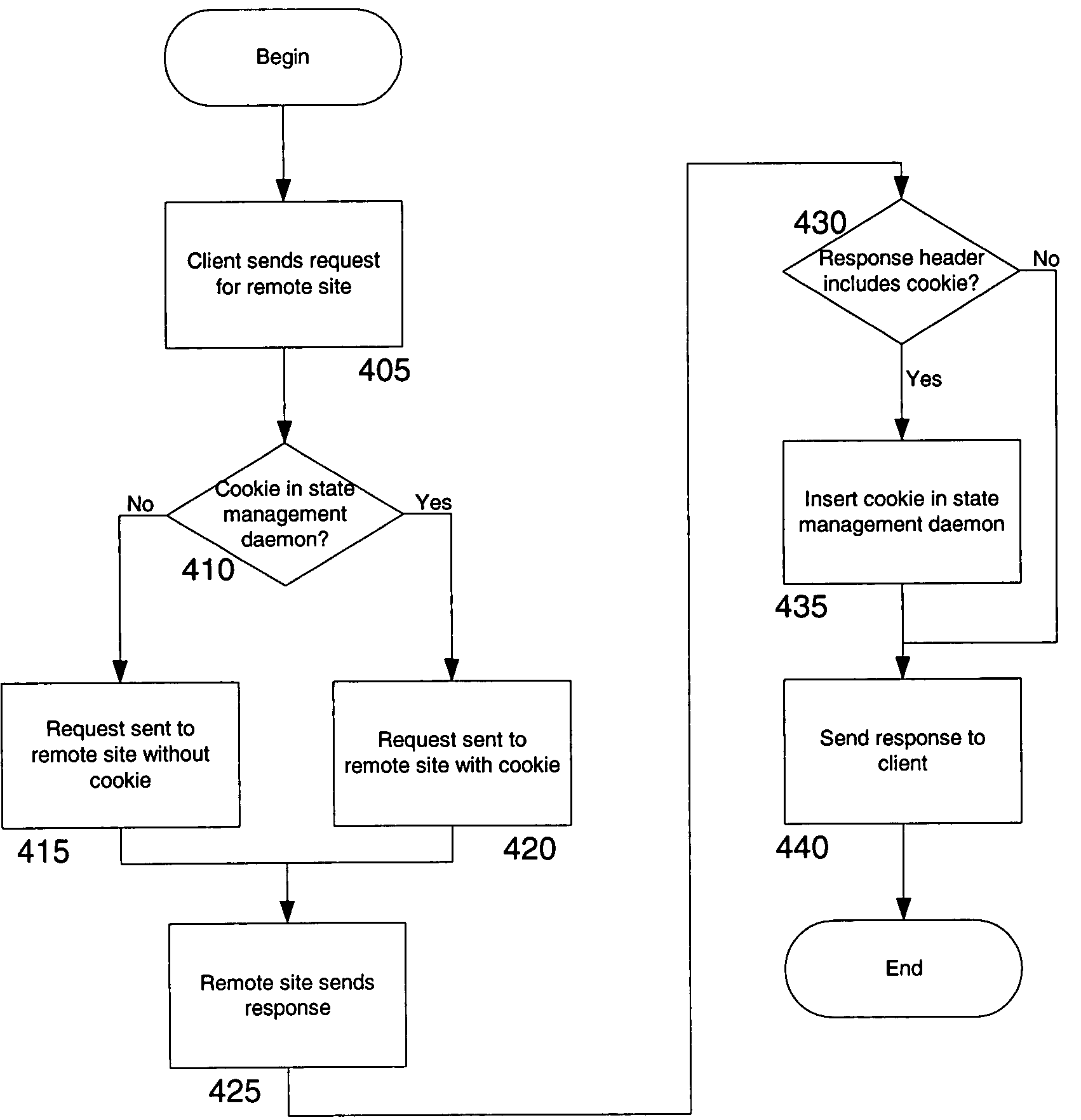
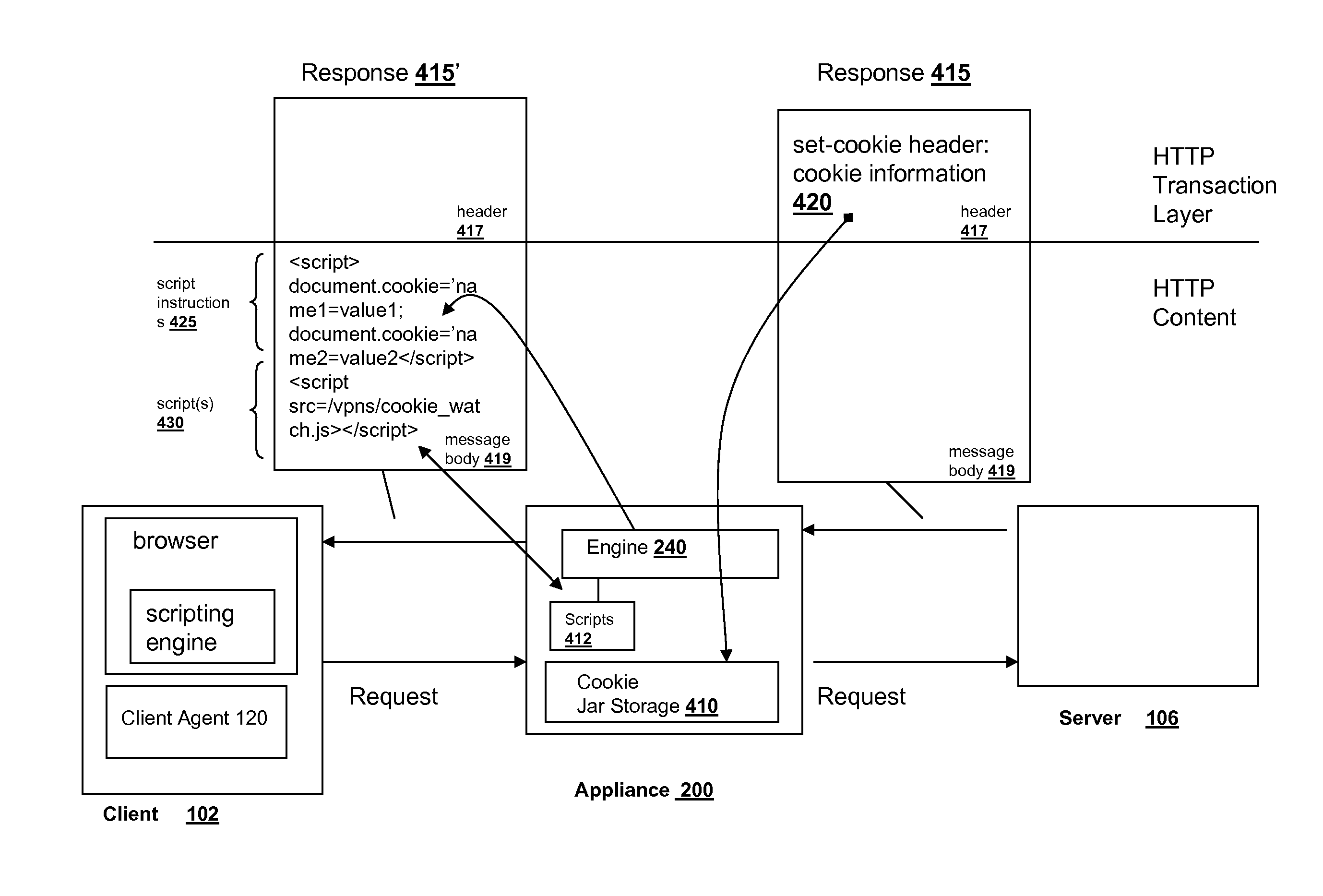
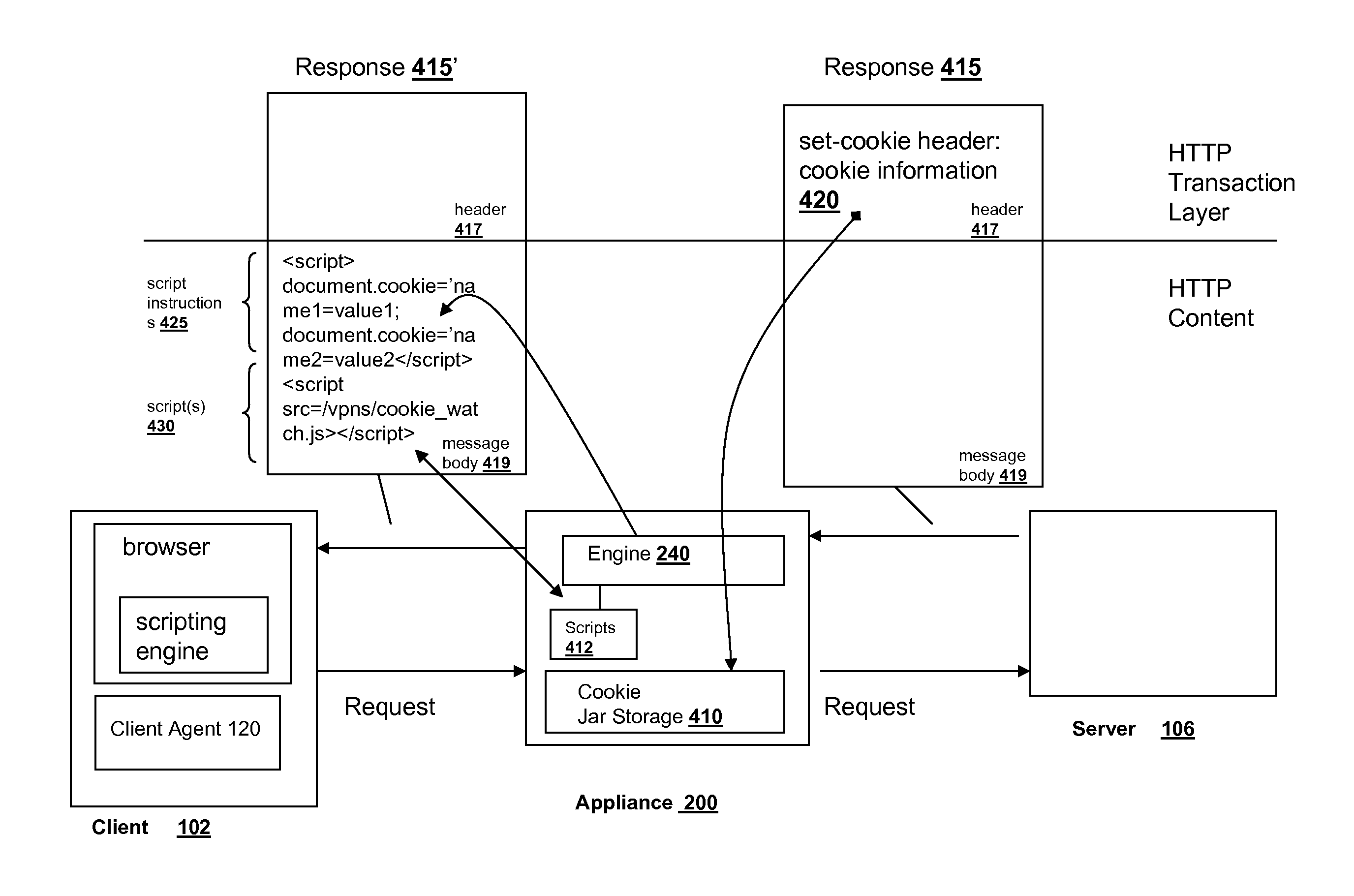
Systems and methods for managing cookies via HTTP content layer
ActiveUS7925694B2Accurate settingMultiple digital computer combinationsTransmissionDomain nameInternet privacy
The cookie management system and methods of the present solution address issues with rewriting cookie headers by handling cookies in the content layer of HTTP instead of the HTTP transaction layer. The present solution maintains cookie information for a browser via an intermediary and installs the correct cookie parameters in the browser via the HTTP content layer. Instead of using the headers of the HTTP transaction layer which may cause issues due to rewriting, the present solution manages the cookies outside of this layer. This avoids the browser managing the cookies incorrectly. Set cookies headers served from a server in response to client HTTP requests are removed by the intermediary. Cookie information from the headers are stored in a cookie jar on the intermediary. The intermediary delivers instructions and scripts via the content layer of the HTTP response to set the cookie in the browser. The scripts detect browser changes to the cookie and communicates the changes to the intermediary to update the cookie jar. With the present solution, the domain and path names of a cookie are set correctly on the browser when delivering content via a reverse proxy.
Owner:CITRIX SYST INC
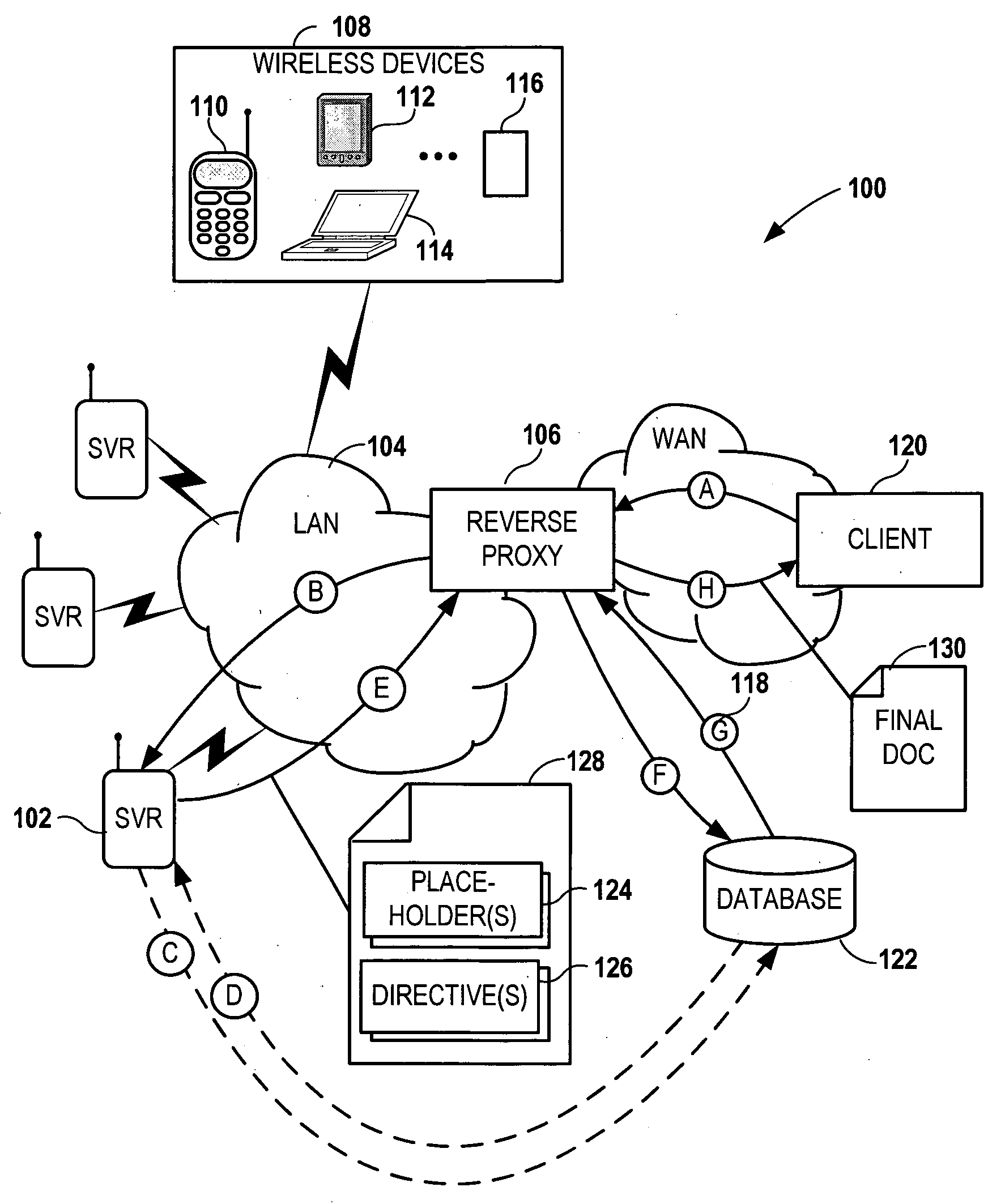
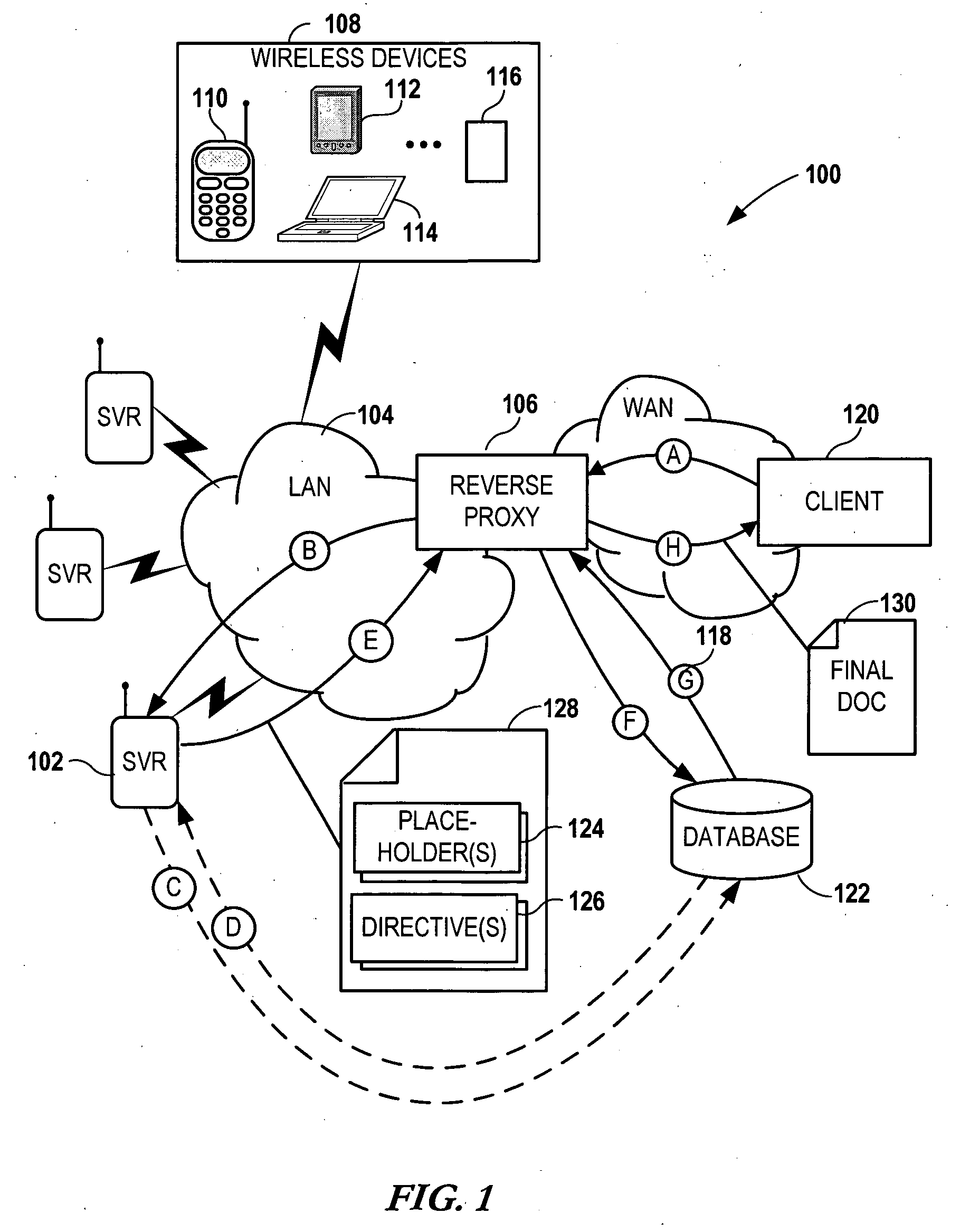
Modifying back-end web server documents at an intermediary server using directives
InactiveUS20060200503A1Digital data information retrievalSpecial data processing applicationsReverse proxyPaper document
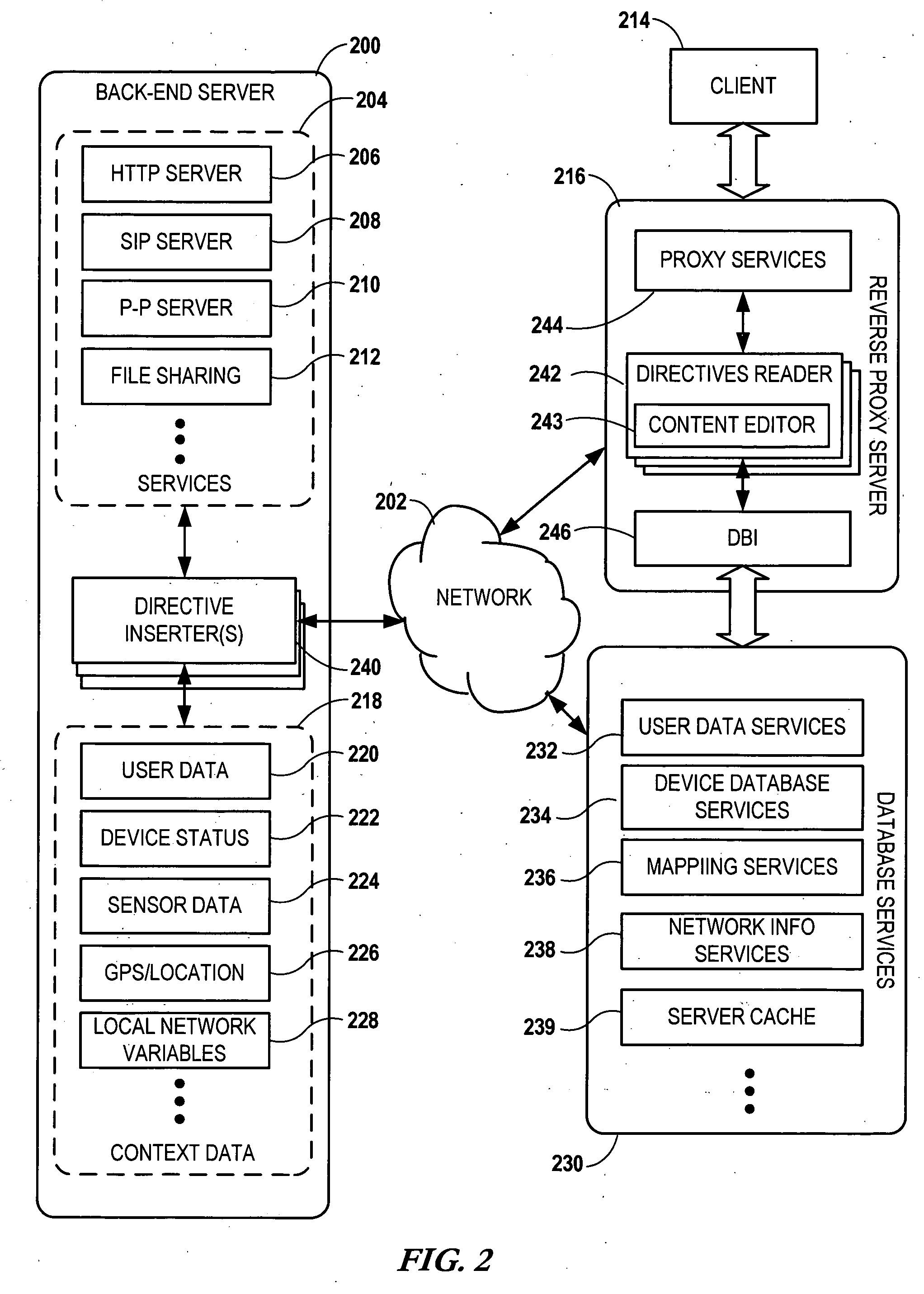
Network services are provided by a network coupled back-end server that is accessed by an intermediary server such as a reverse proxy server. A service request is received at the back-end server via the intermediary server. The back-end server forms a first document in response to the service request. The first document contains a data generation directive targeted for the intermediary server. The first document is sent to the intermediary server. Additional data is generated at the intermediary server using the data generation directive and a second document is formed using the first document and the additional data. The second document is then sent from the intermediary server to an originator of the service request.
Owner:NOKIA CORP
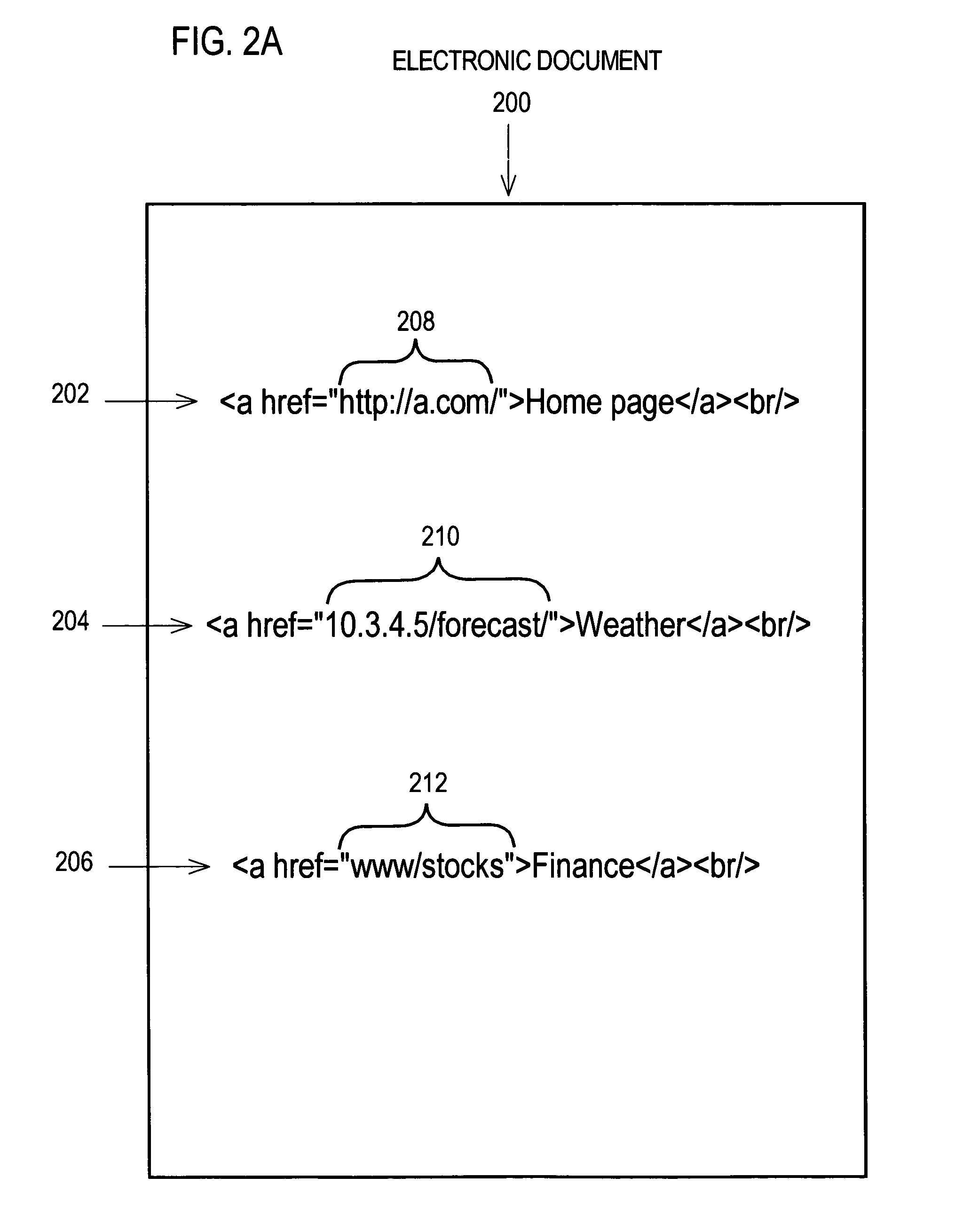
Technique for providing access to data
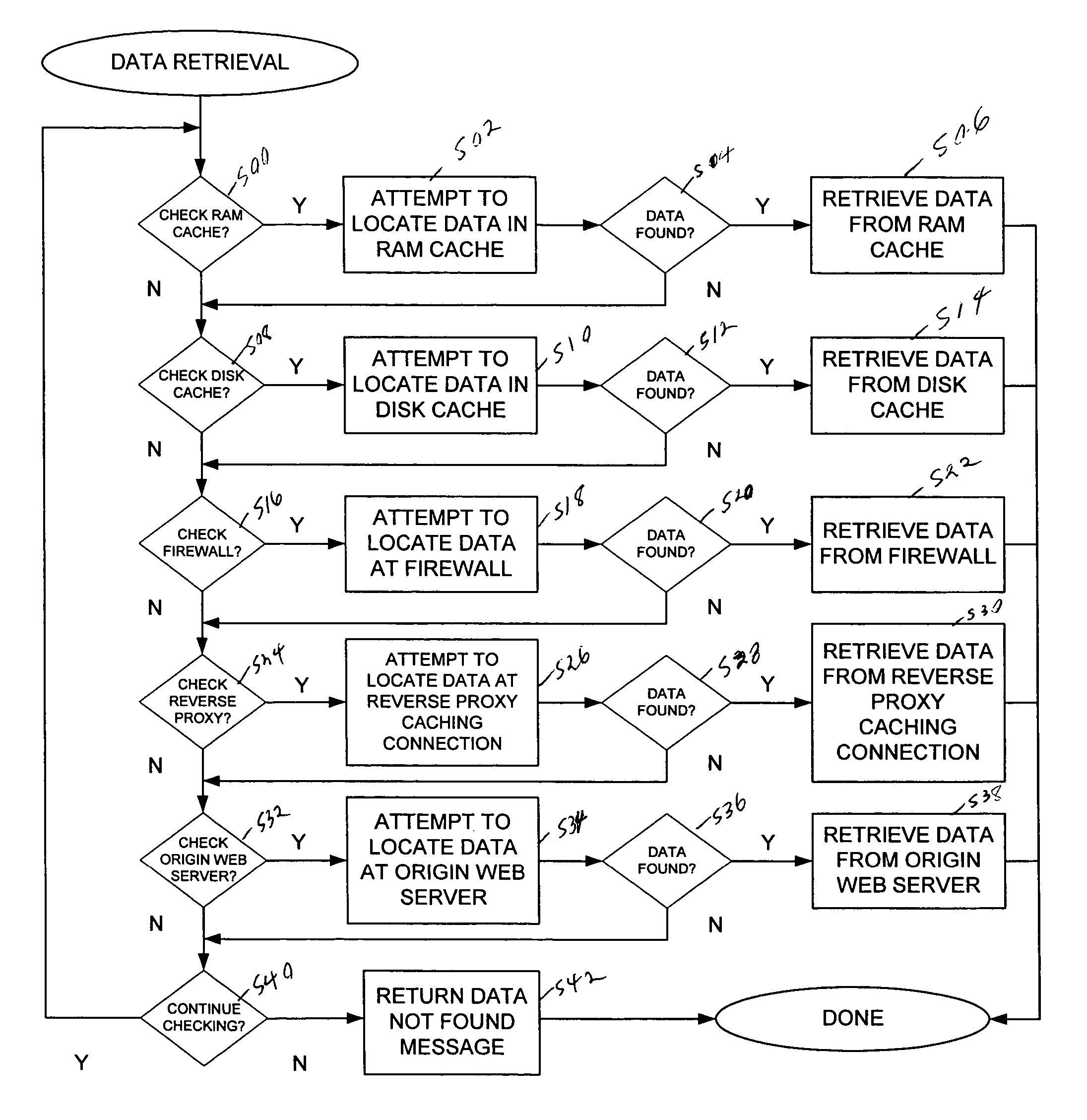
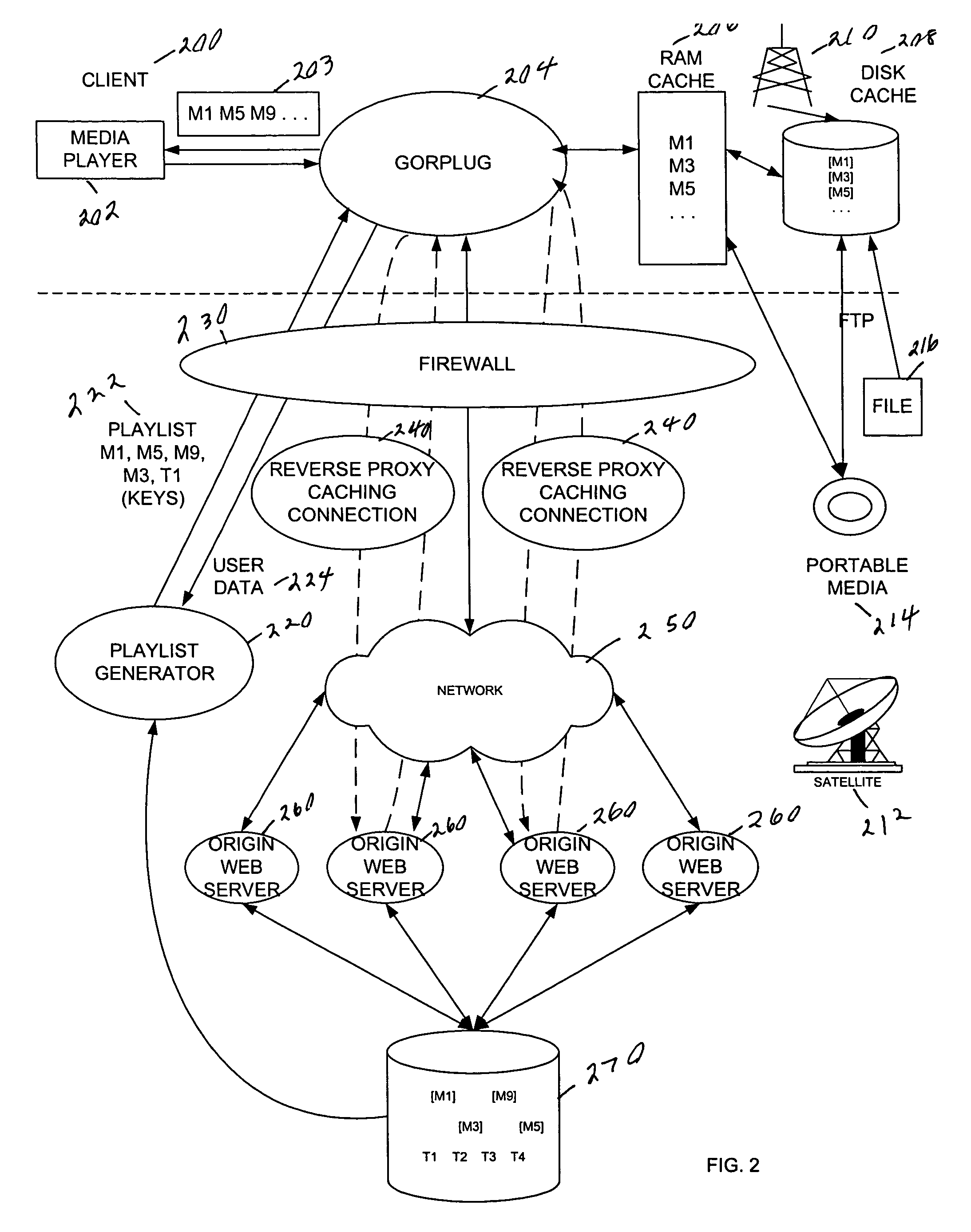
A data retrieval system provides data to a user of a client computer connected to multiple data stores and multiple other computers. A request for data is received at the client computer. The request is forwarded from the client computer to a server computer and intercepted at a reverse proxy caching connection. An attempt is made to locate the data at a data store at the reverse proxy caching connection. If the data is not found the request is forwarded to the server computer. In order to provide data to a user. A user interface is provided. Initially, data elements associated with a grouping of data elements are identified. Then, a subset of the selected data elements are selected based on weights associated with the data elements, without selecting more than a specified number of data elements that are associated with a same sub-category.
Owner:DISNEY ENTERPRISES INC
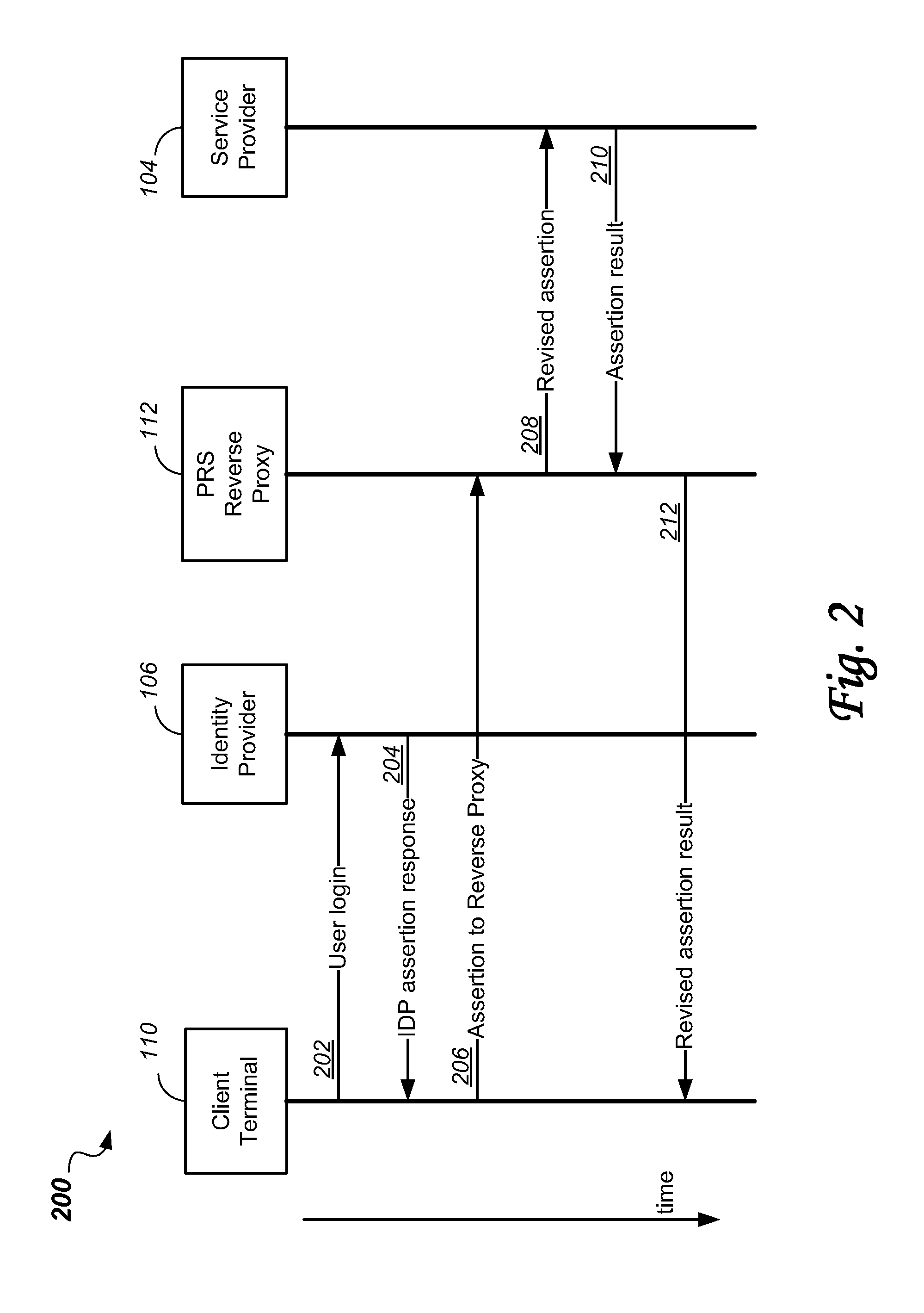
System and method of federated authentication with reverse proxy
InactiveUS20120278872A1Digital data processing detailsMultiple digital computer combinationsReverse proxyApplication software
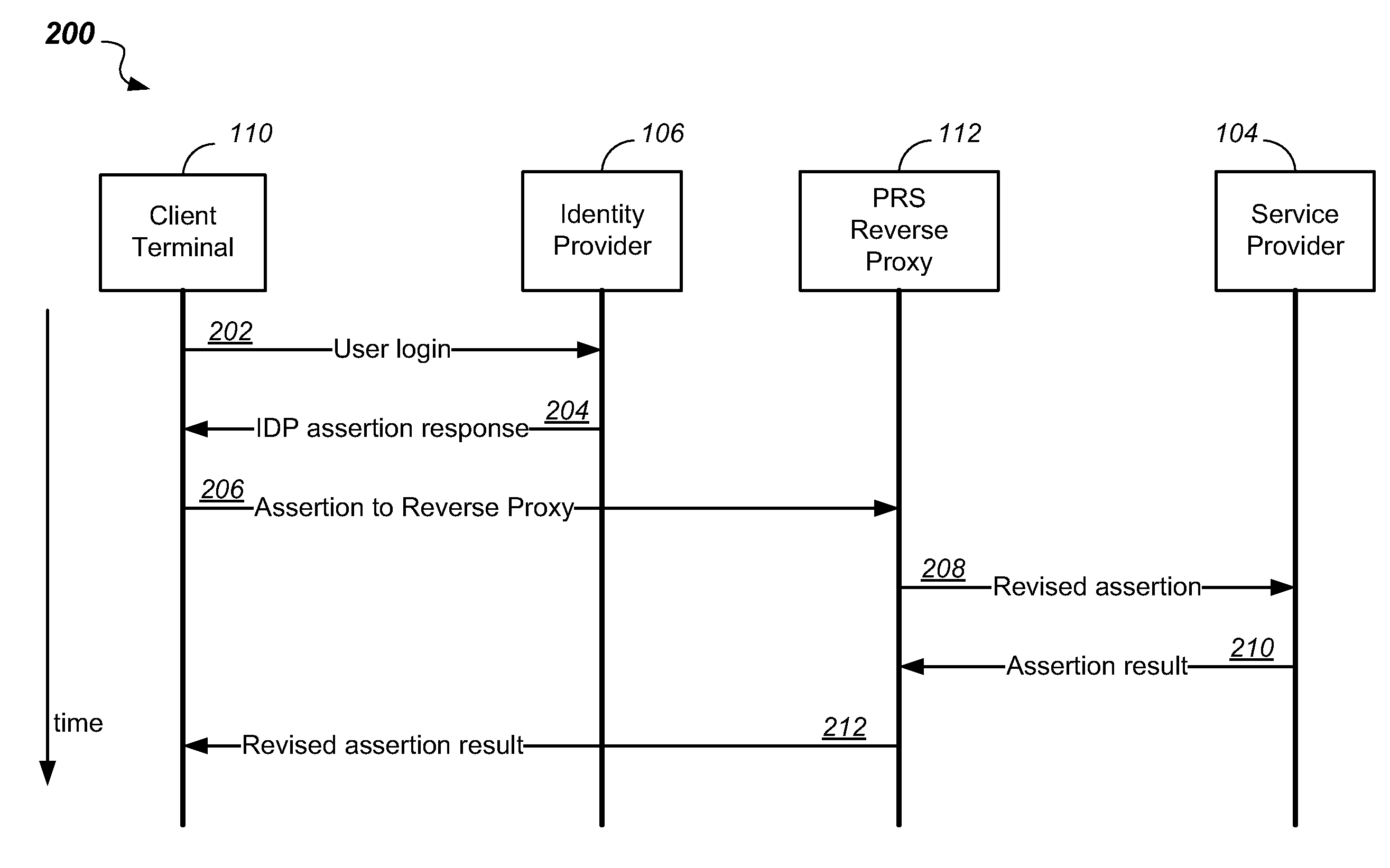
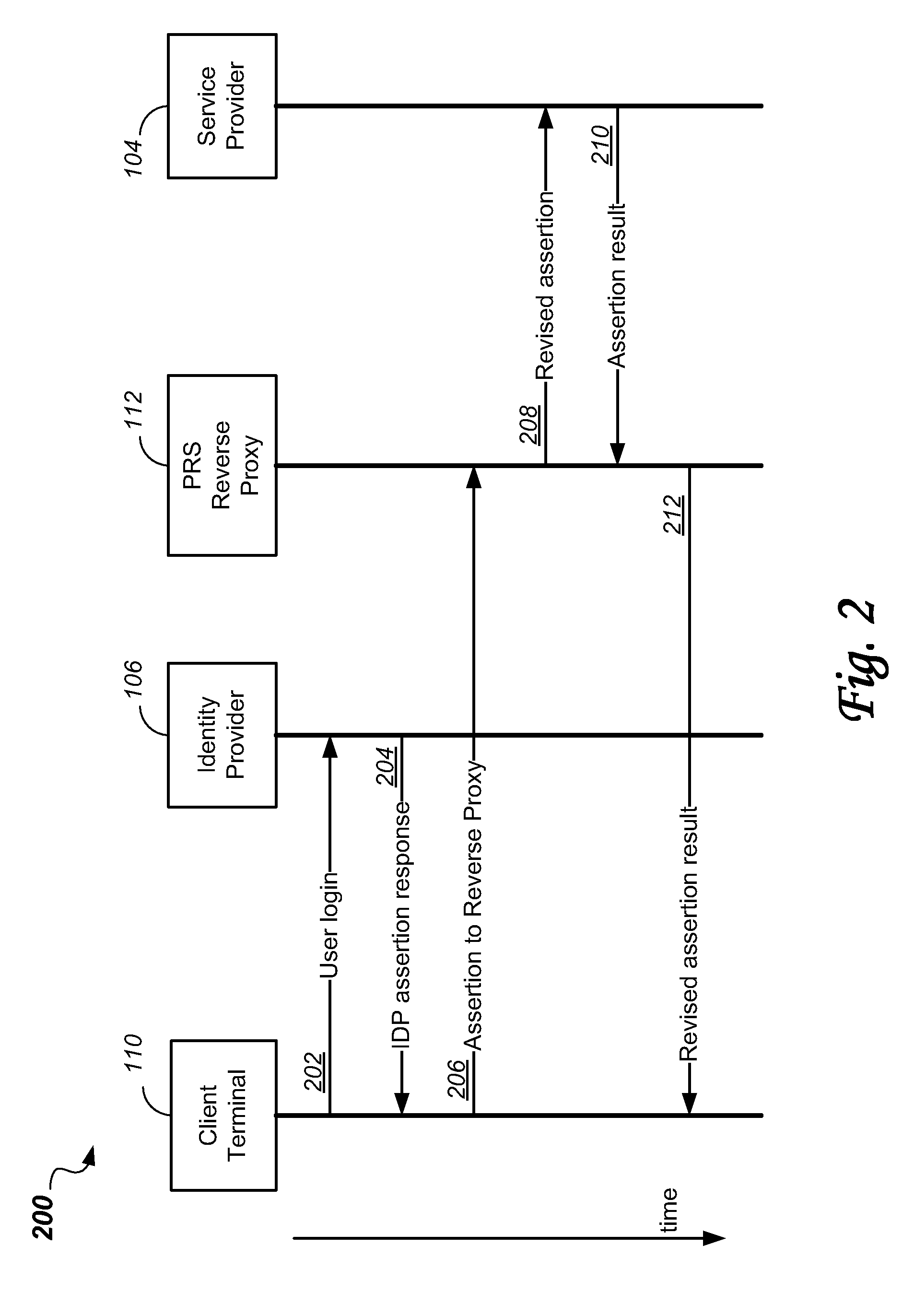
A Security Assertion Markup Language (SAML) conversation is intercepted in an enhanced Reverse Proxy server computer located in the path between a user and a server computer that provide cloud application services to the user. During authentication, the SAML assertion signature is modified in the enhanced Reverse Proxy such that the enhanced Reverse Proxy and the user can share an encryption key. The modified assertion signature permits a common session key to be shared by the enhanced Reverse Proxy and a targeted application in the server, thus enabling the user to be authenticated, and subsequently to communicate via the enhanced Reverse Proxy in a secure session with an application in the server.
Owner:SYMANTEC CORP
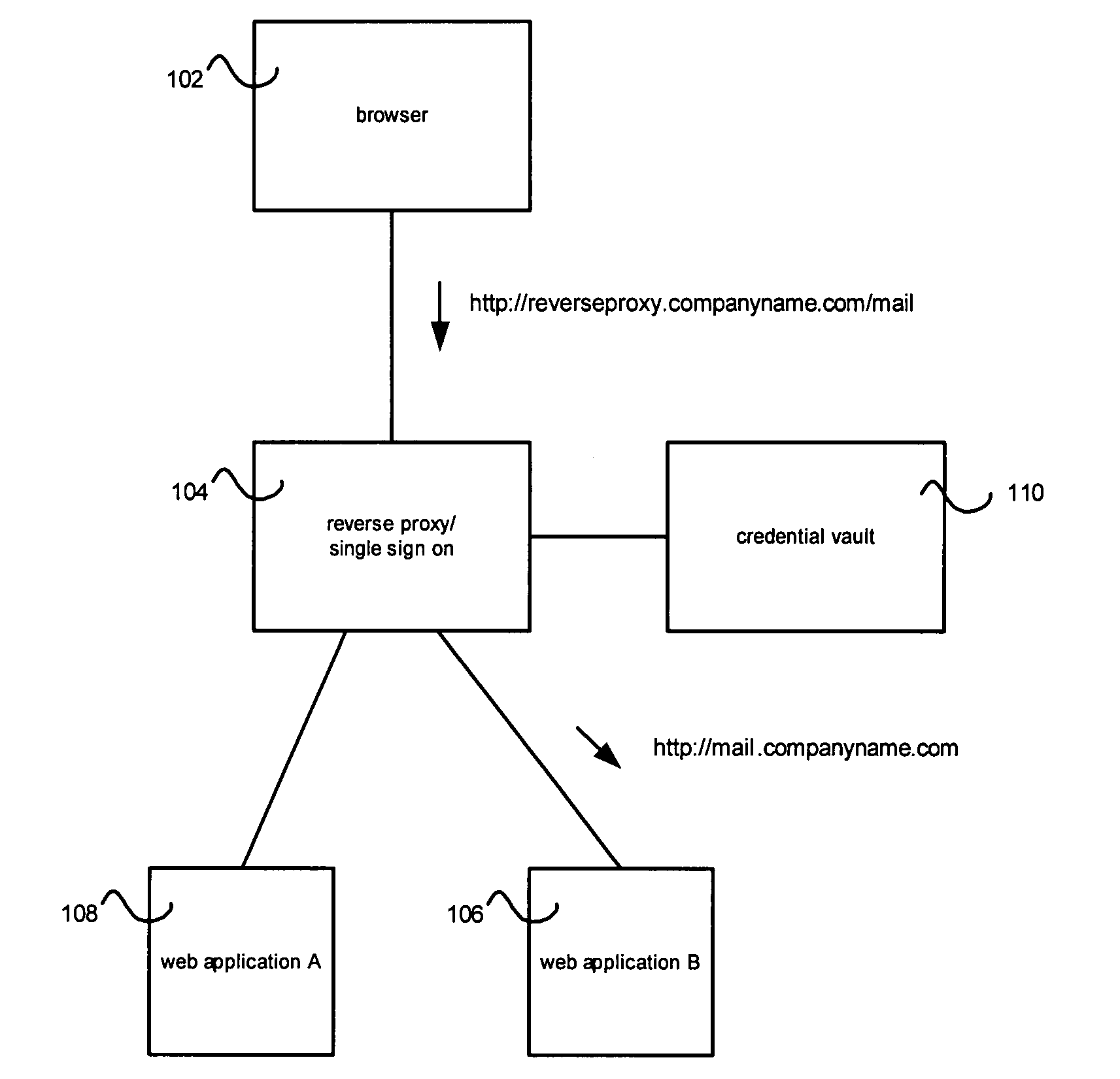
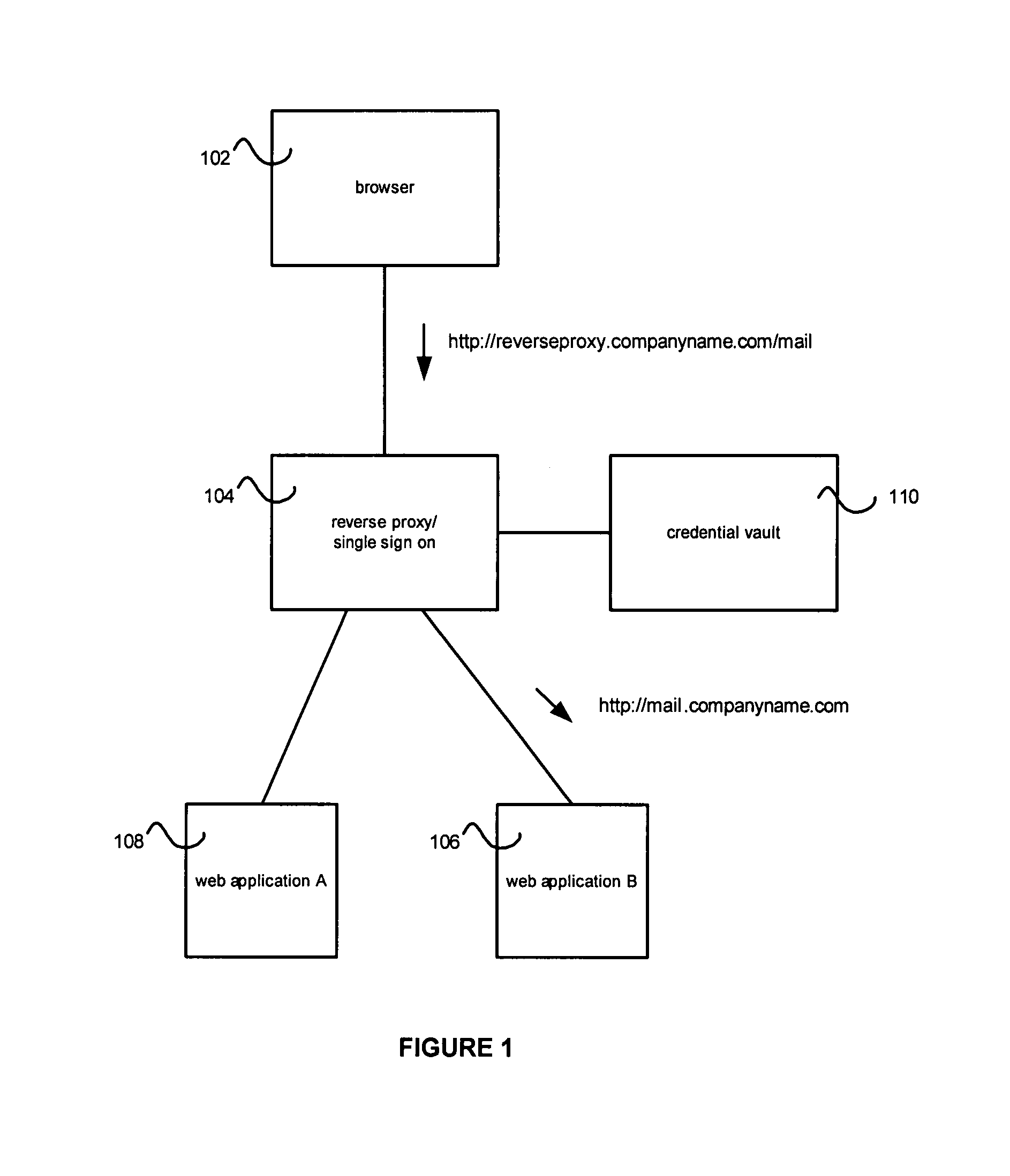
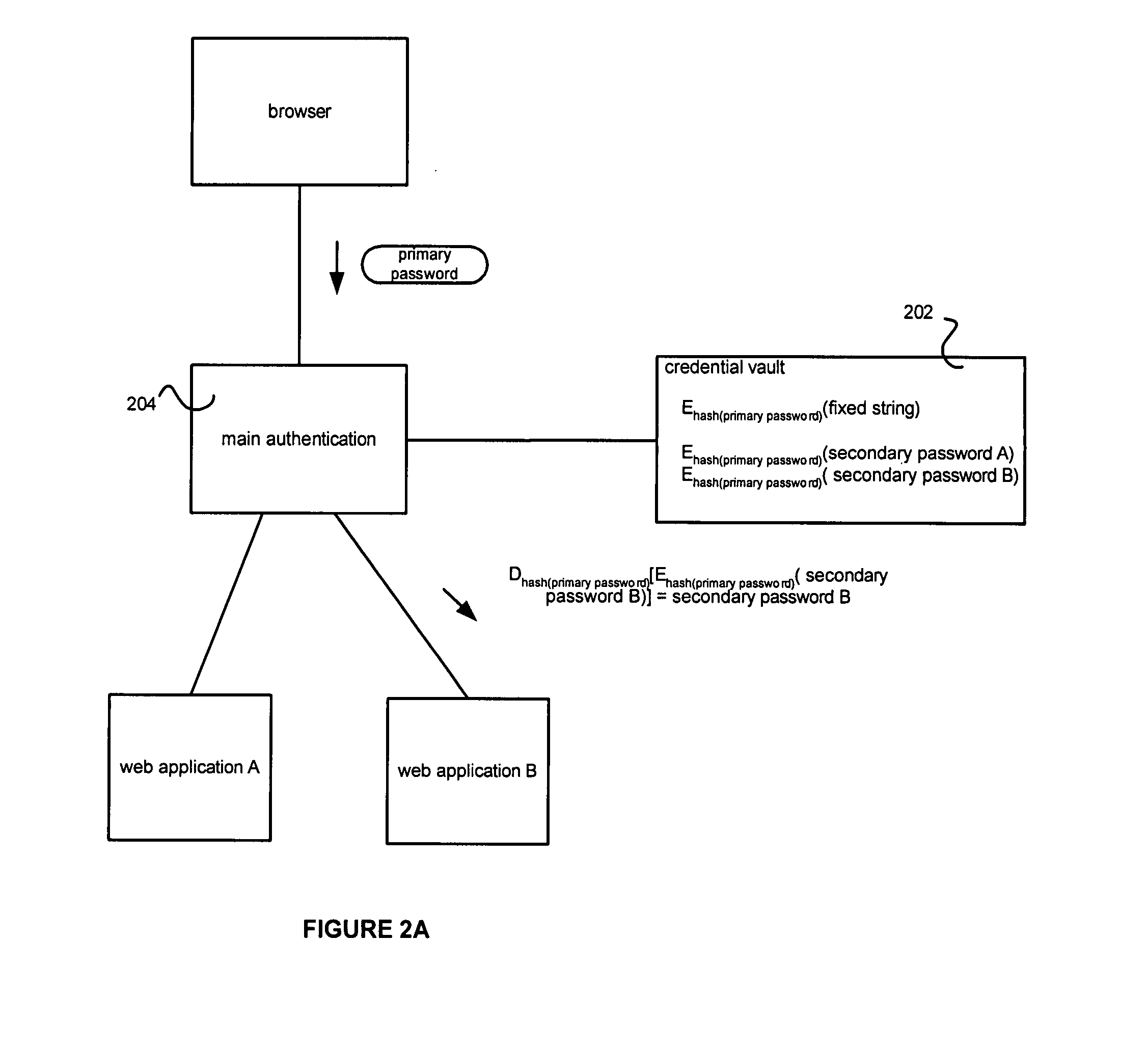
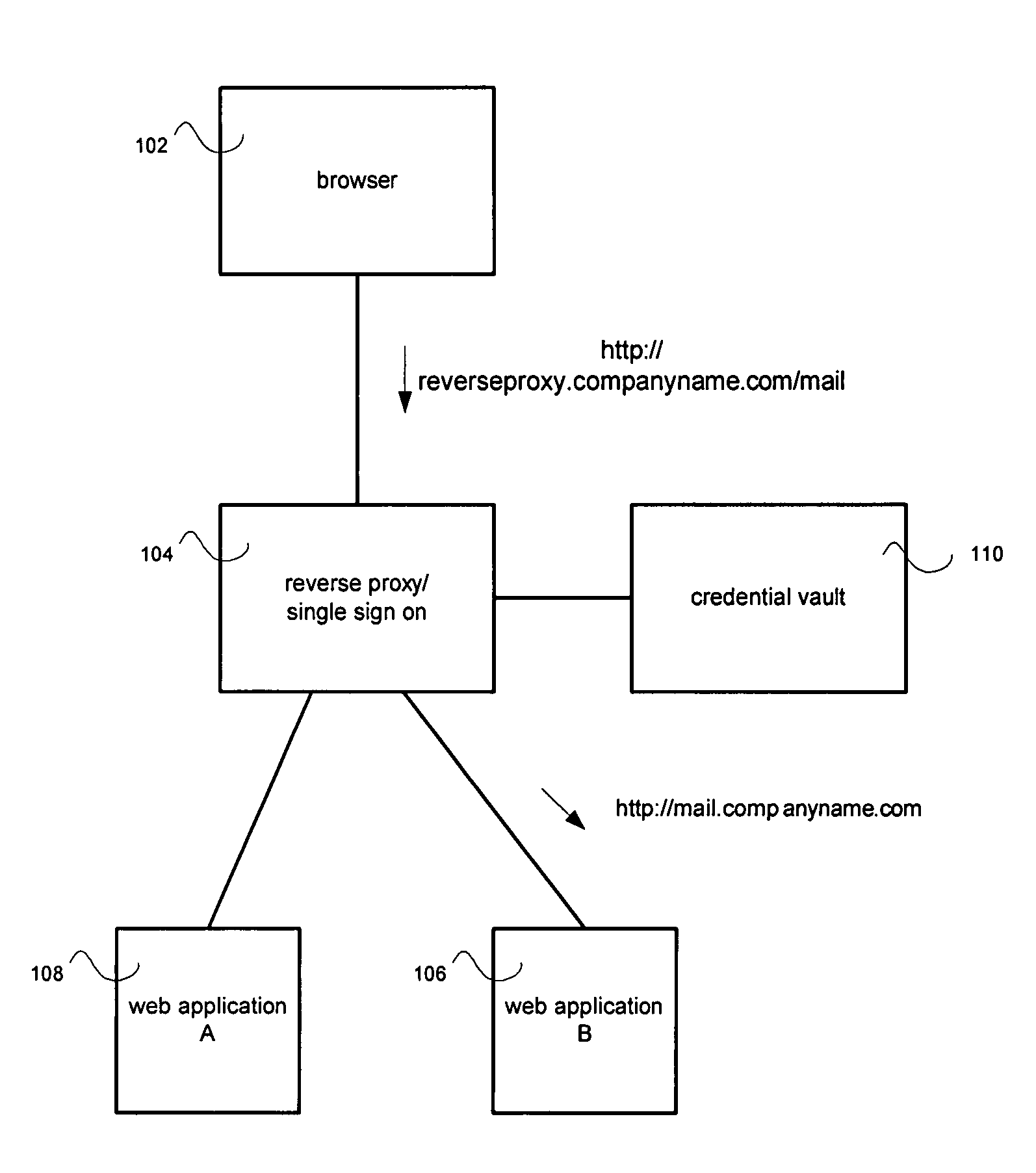
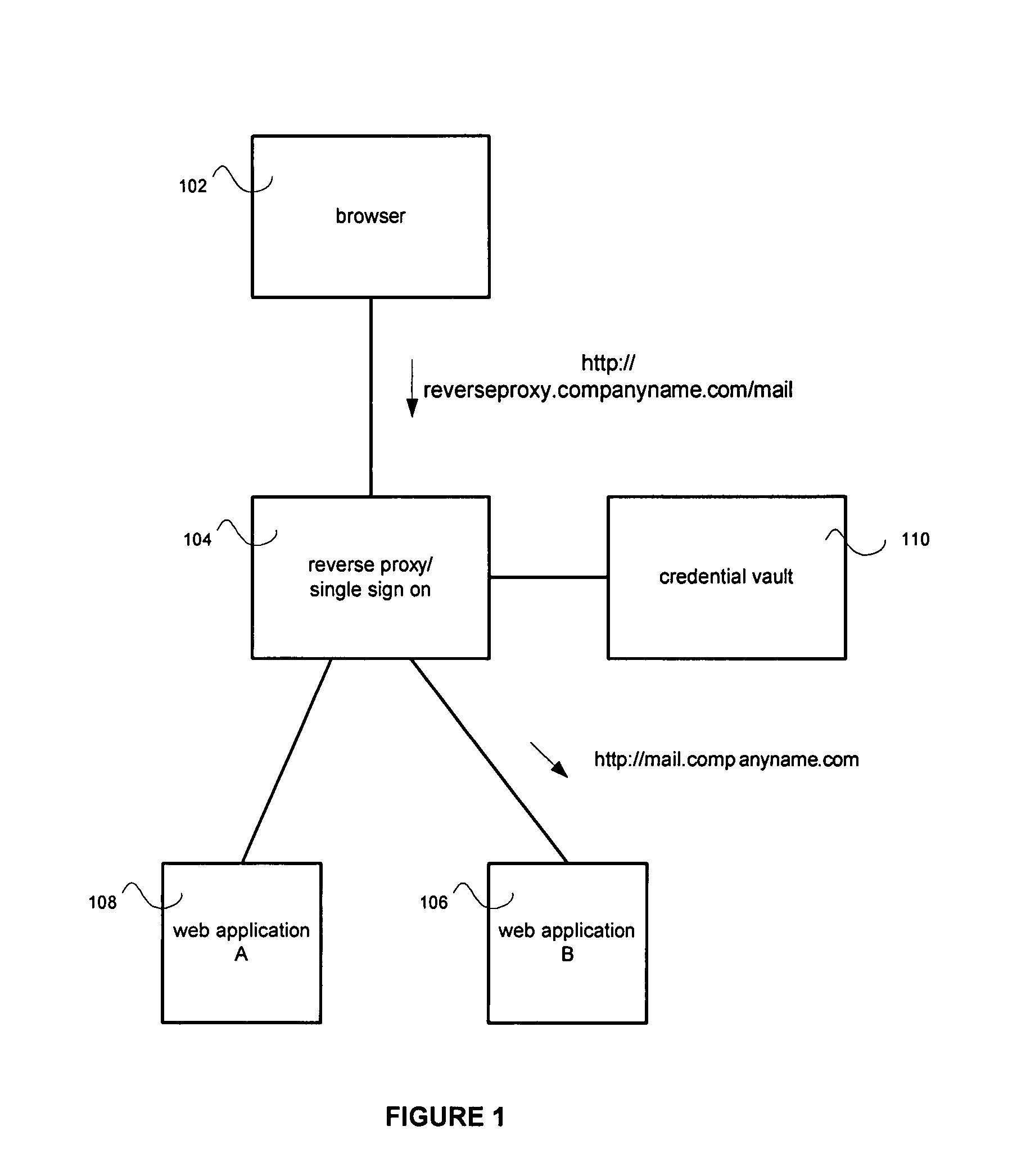
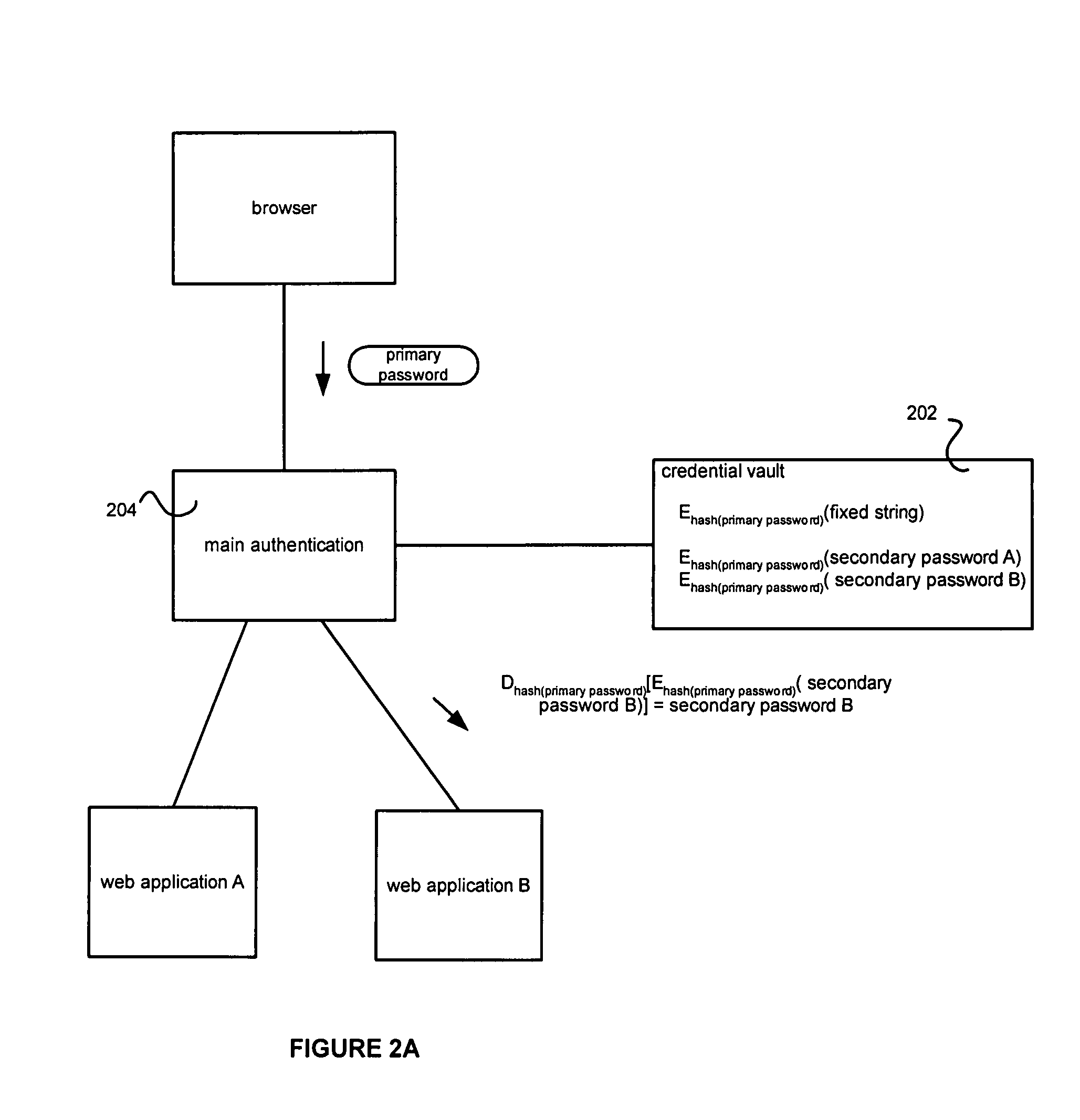
Credential vault encryption
InactiveUS20080077982A1Natural language data processingMultiple digital computer combinationsWeb applicationReverse proxy
Application role mappings can be maintained at a reverse proxy server. When a request for a web application is received at the reverse proxy servers, the proper user role for the web application can be determined at the reverse proxy server. The proper user role can be sent as part of a HTTP header to the web application. The web application can use the user role without doing an independent mapping of the user to a role.
Owner:ORACLE INT CORP
Granular authorization for network user sessions
InactiveUS7076797B2Digital data processing detailsUser identity/authority verificationBiometric dataPassword
Providing access to a mobile user session in a manner that more closely corresponds access to network resources to the trustworthiness of authentication methods and devices associated with the mobile user session. Characteristics of authentication methods associated with a mobile user session are synthesized to generate an authentication bundle. Characteristics may include data associated with passwords, biometric data or devices used to execute an authentication method. By synthesizing characteristics in varied manners, a non-binary sliding scale of access to network resources may be generated. An authentication bundle may be accessed to grant a mobile user session appropriate access to network resources. Granting access may include generating an authorization token that is passed to a filter or reverse proxy. Access to network resources may be dynamically modified as authentication methods associated with a mobile user session change.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for managing cookies via HTTP content layer
ActiveUS20090106349A1Accurate settingMultiple digital computer combinationsTransmissionDomain nameInternet privacy
The cookie management system and methods of the present solution address issues with rewriting cookie headers by handling cookies in the content layer of HTTP instead of the HTTP transaction layer. The present solution maintains cookie information for a browser via an intermediary and installs the correct cookie parameters in the browser via the HTTP content layer. Instead of using the headers of the HTTP transaction layer which may cause issues due to rewriting, the present solution manages the cookies outside of this layer. This avoids the browser managing the cookies incorrectly. Set cookies headers served from a server in response to client HTTP requests are removed by the intermediary. Cookie information from the headers are stored in a cookie jar on the intermediary. The intermediary delivers instructions and scripts via the content layer of the HTTP response to set the cookie in the browser. The scripts detect browser changes to the cookie and communicates the changes to the intermediary to update the cookie jar. With the present solution, the domain and path names of a cookie are set correctly on the browser when delivering content via a reverse proxy.
Owner:CITRIX SYST INC
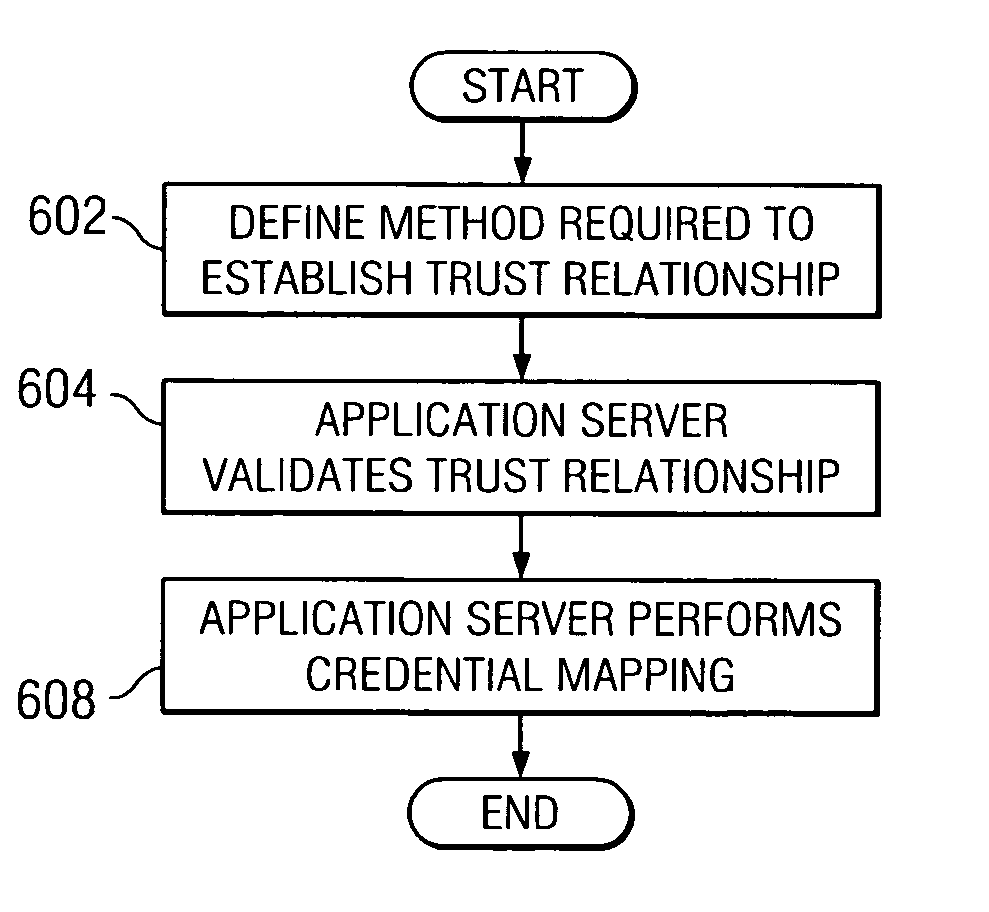
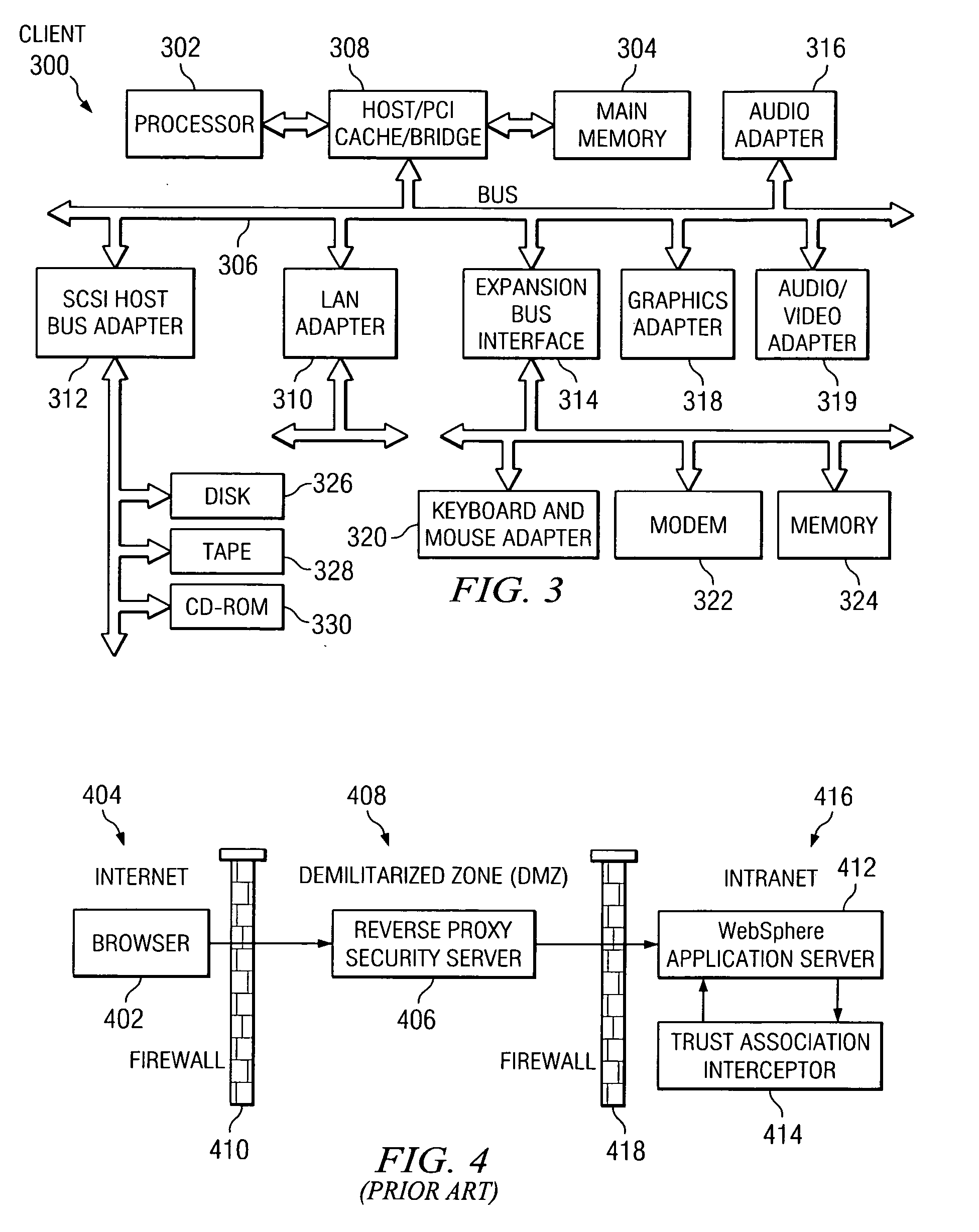
Declarative trust model between reverse proxy server and websphere application server
A method and system for providing a declarative trust association model that formalizes the way trust is established and requires corresponding authentication information to be presented in a standard format. Consequently, the application server may provide a guaranteed level of protection. The mechanism of the present invention provides a framework that allows an application server to enforce a trust evaluation and allows reverse proxy security server to assert a client's security identity, as well as other client security credential information. A known trust association interceptor model is extended to allow the reverse proxy security server to assert the authenticated user's security attributes. Such security attributes include, for example, group information, authentication strength, and location (i.e., where does the user enter the request, intranet vs. internet, IP address, etc.,). The security attributes can be used in making authorization decisions.
Owner:IBM CORP
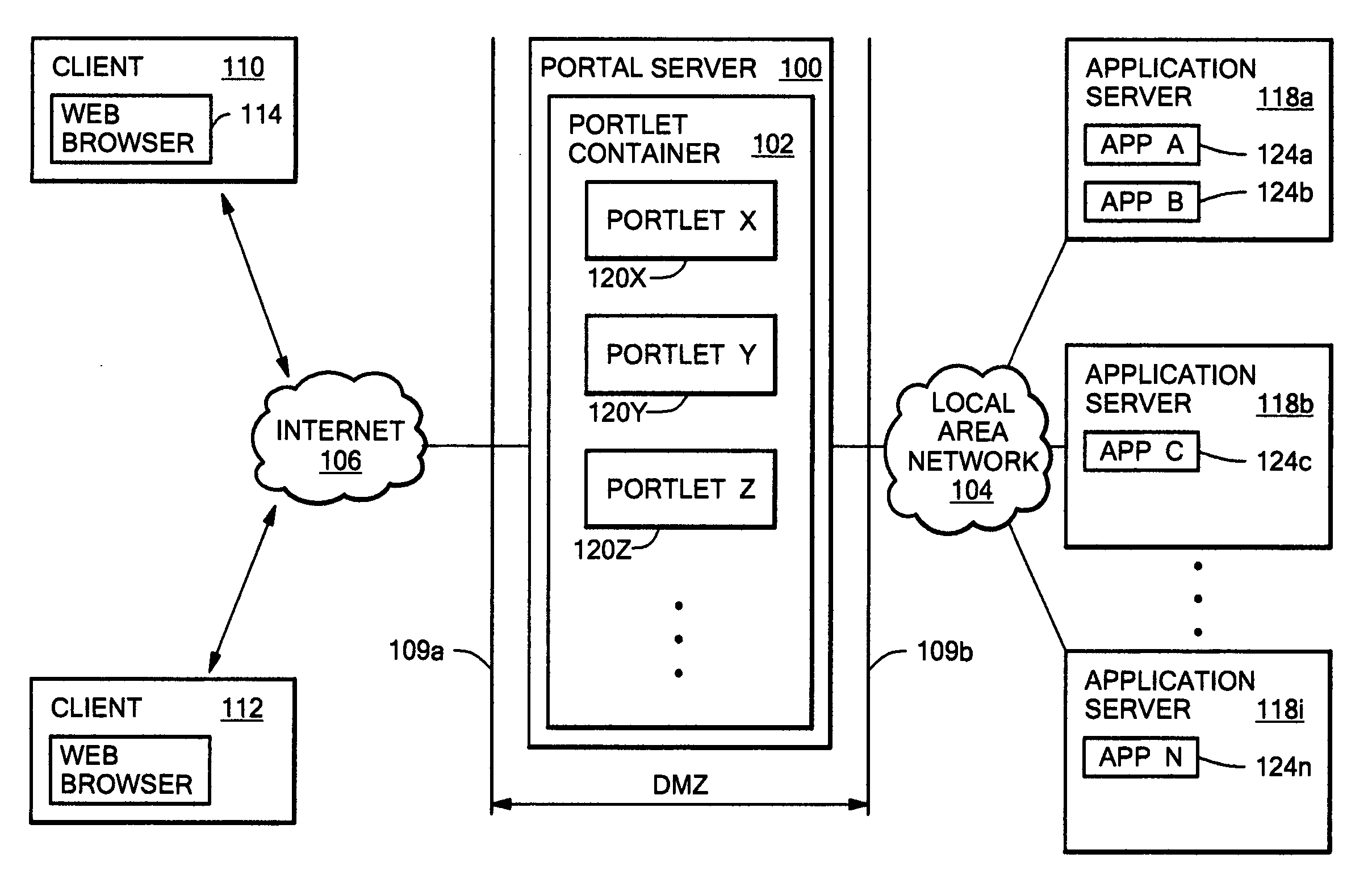
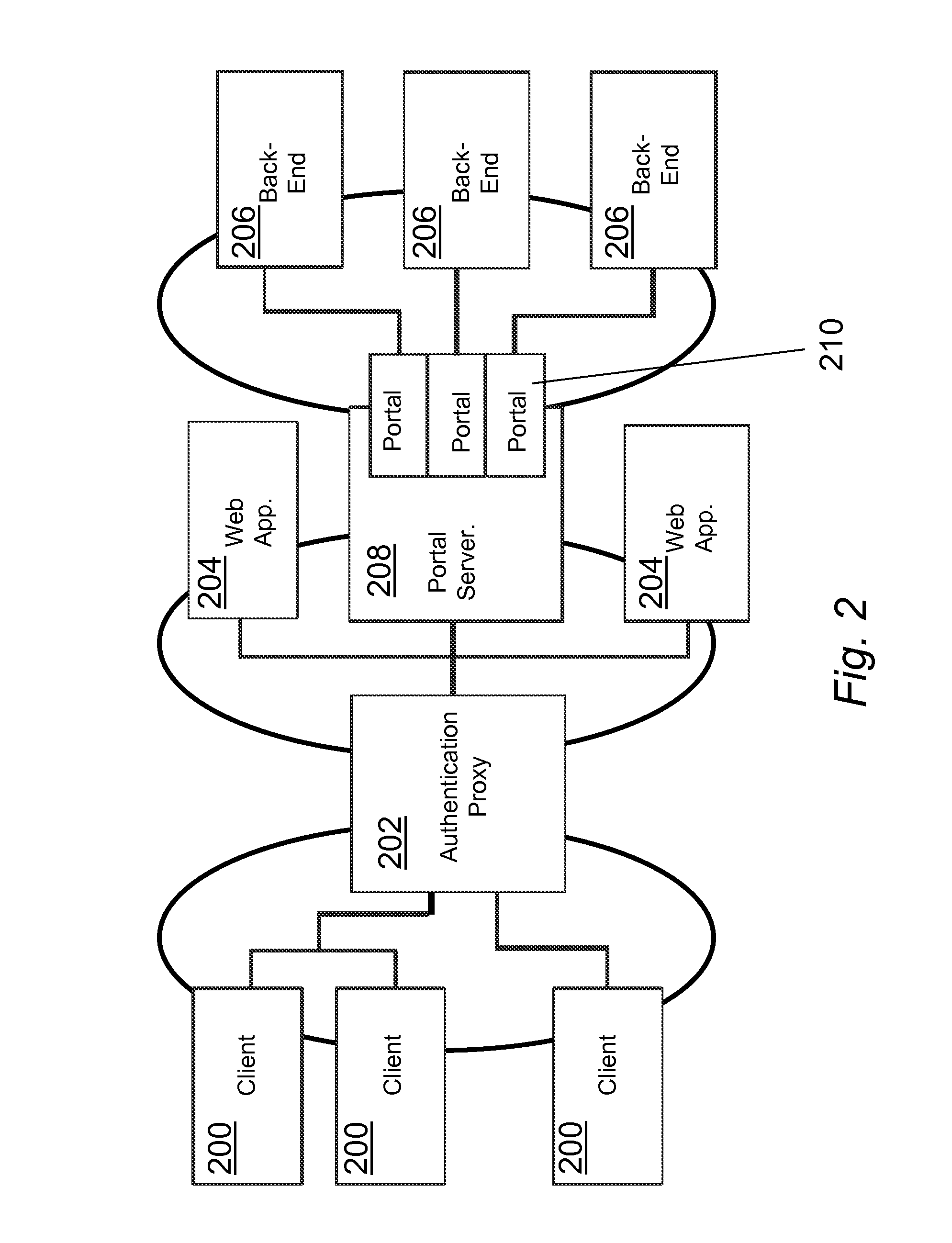
Reverse proxy portlet with rule-based, instance level configuration
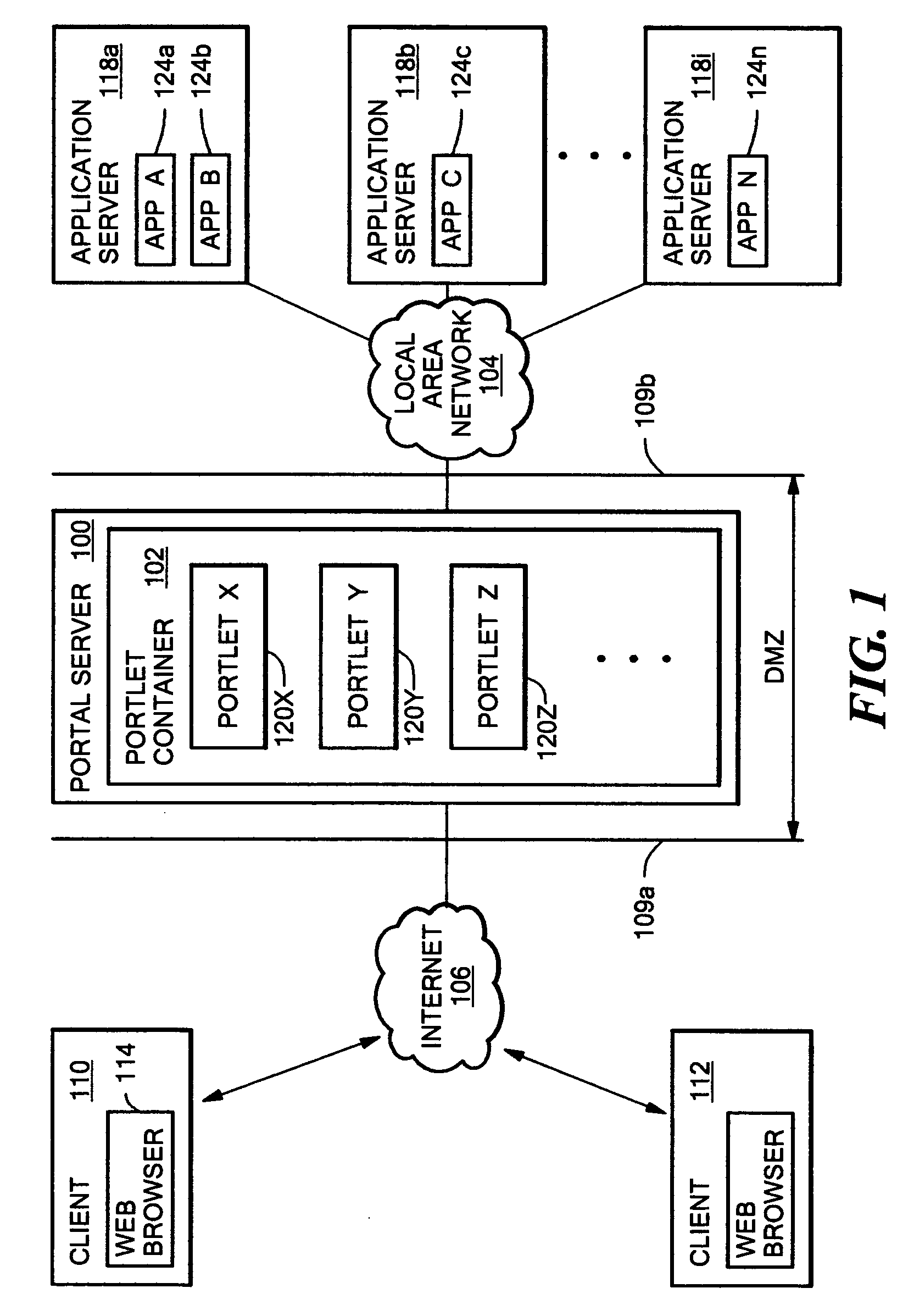
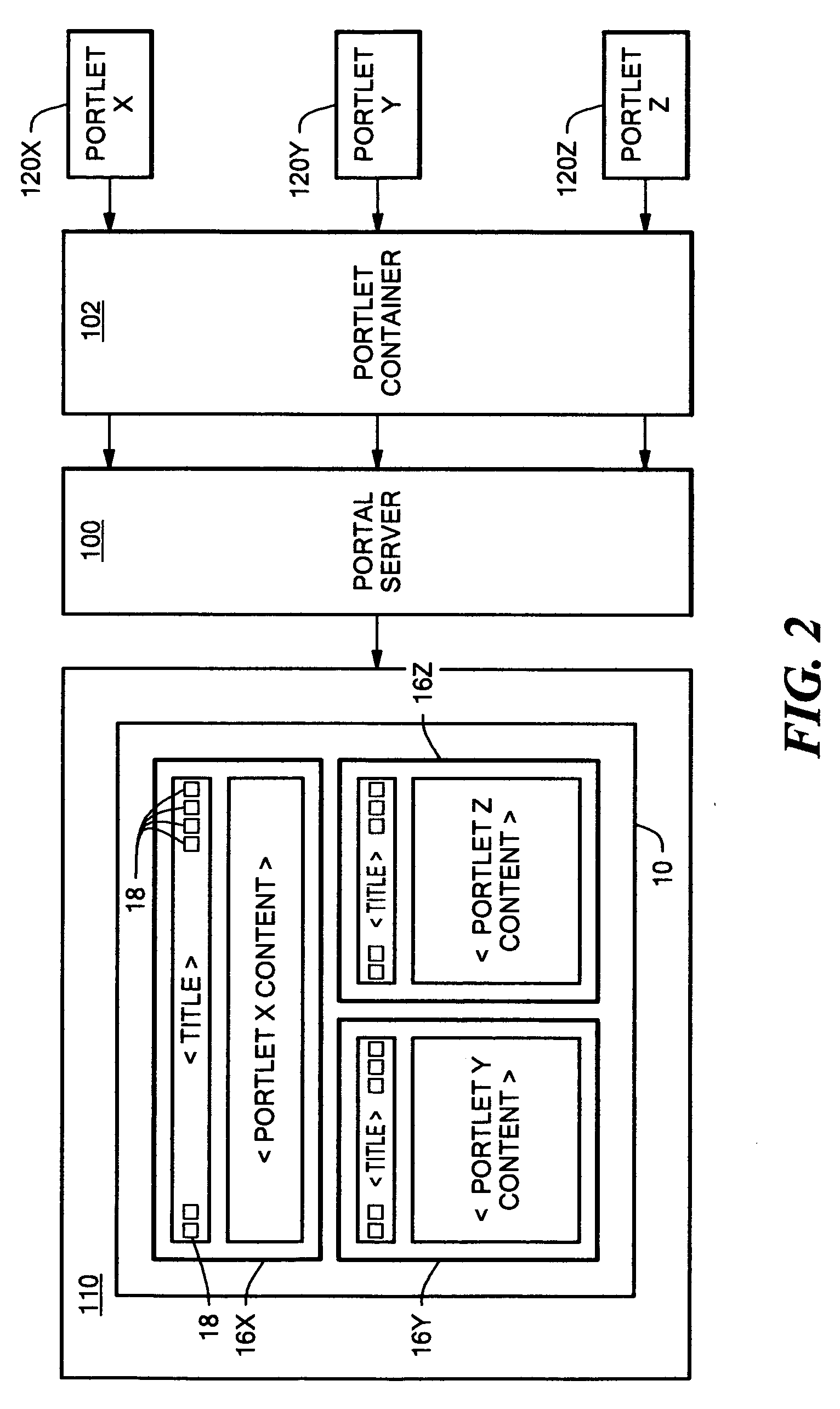
InactiveUS20060041637A1Reduce overheadGood flexibilityMultiple digital computer combinationsProgram controlWeb sitePortlet
A portal server having a reverse proxy mechanism for proxying one or more Web applications on a backend server in response to a request for Web content from a user. The reverse proxy mechanism includes a portlet, a set of configuration rules, and a rewriting mechanism. The rewriting mechanism is configured to forward a user request for Web content to a Web application on the backend server, receive a response from the Web application, and rewrite the received response in accordance with the configuration rules. The portlet is configured to produce a content fragment for a portal page from the rewritten response. The configuration rules include rules for rewriting any resource addresses, such as URLs, appearing in the received response from the Web application to point to the portal server rather than to the backend server. The disclosed system allows the portal server to appear to the client as the real content server. The portal server is arranged such that an external Web application, which is running on a separate backend server, is displayed to the user within the boundary of the portlet window on a portal page. The backend server remains behind a firewall and the reverse proxy function of the portlet allows a user to access the Web application on the portal server, without needing (or allowing) the user to have direct access to the backend server and backend application which provide the actual content.
Owner:LINKEDIN
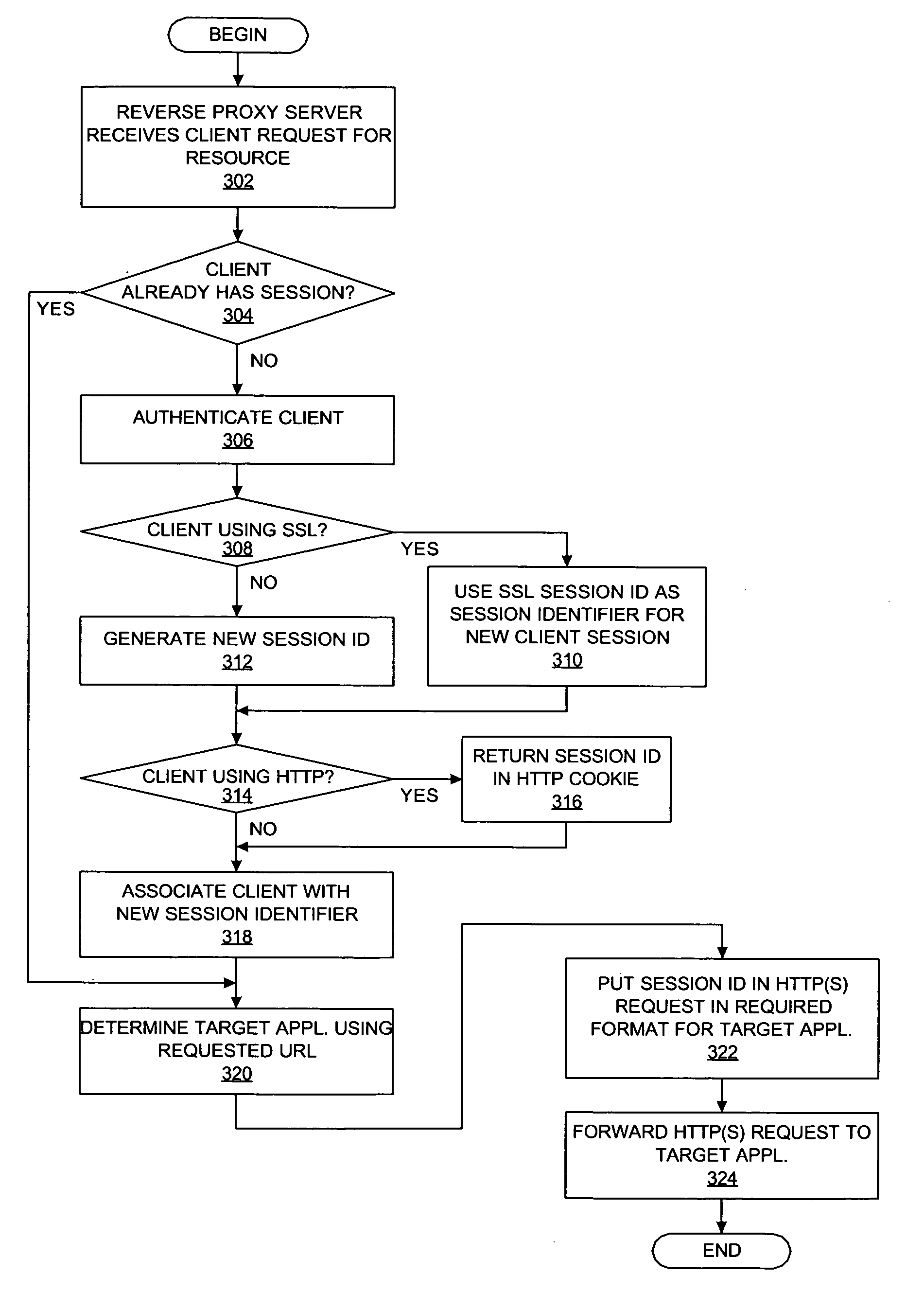
Method and system for externalizing session management using a reverse proxy server
ActiveUS20060031442A1Multiple digital computer combinationsTransmissionSession managementData processing system
A method, system, and computer program product is presented for providing access to a set of resources in a distributed data processing system. A reverse proxy server receives a resource request from a client and determines whether or not it is managing a session identifier that was previously associated with the client by the reverse proxy server; if so, it retrieves the session identifier, otherwise it obtains a session identifier and associates the session identifier with the client using information that is managed by the reverse proxy server. The reverse proxy server then modifies the resource request to include the session identifier and forwards the modified resource request to an application server.
Owner:HULU
Detecting a reverse proxy and establishing a tunneled connection therethrough
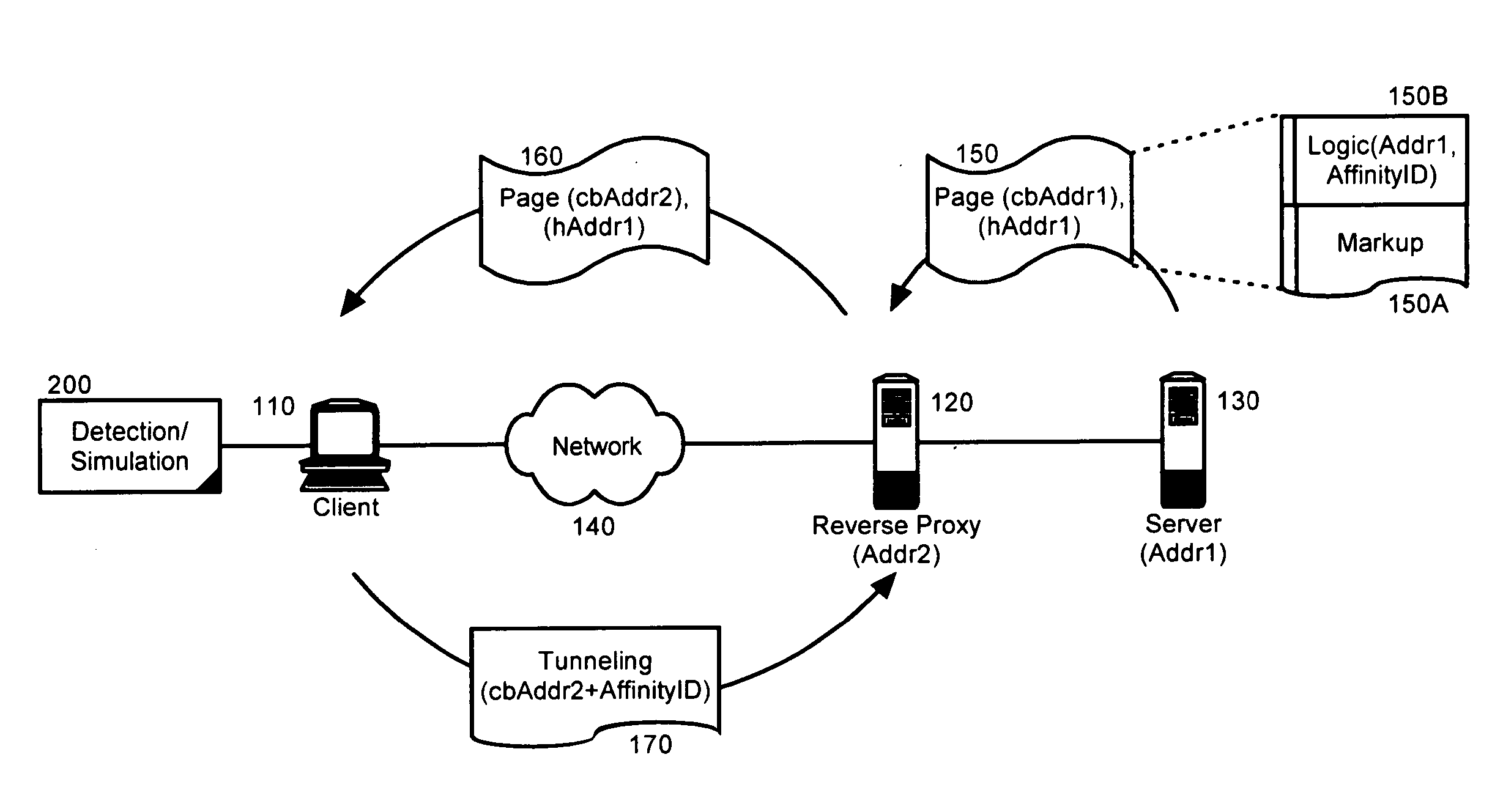
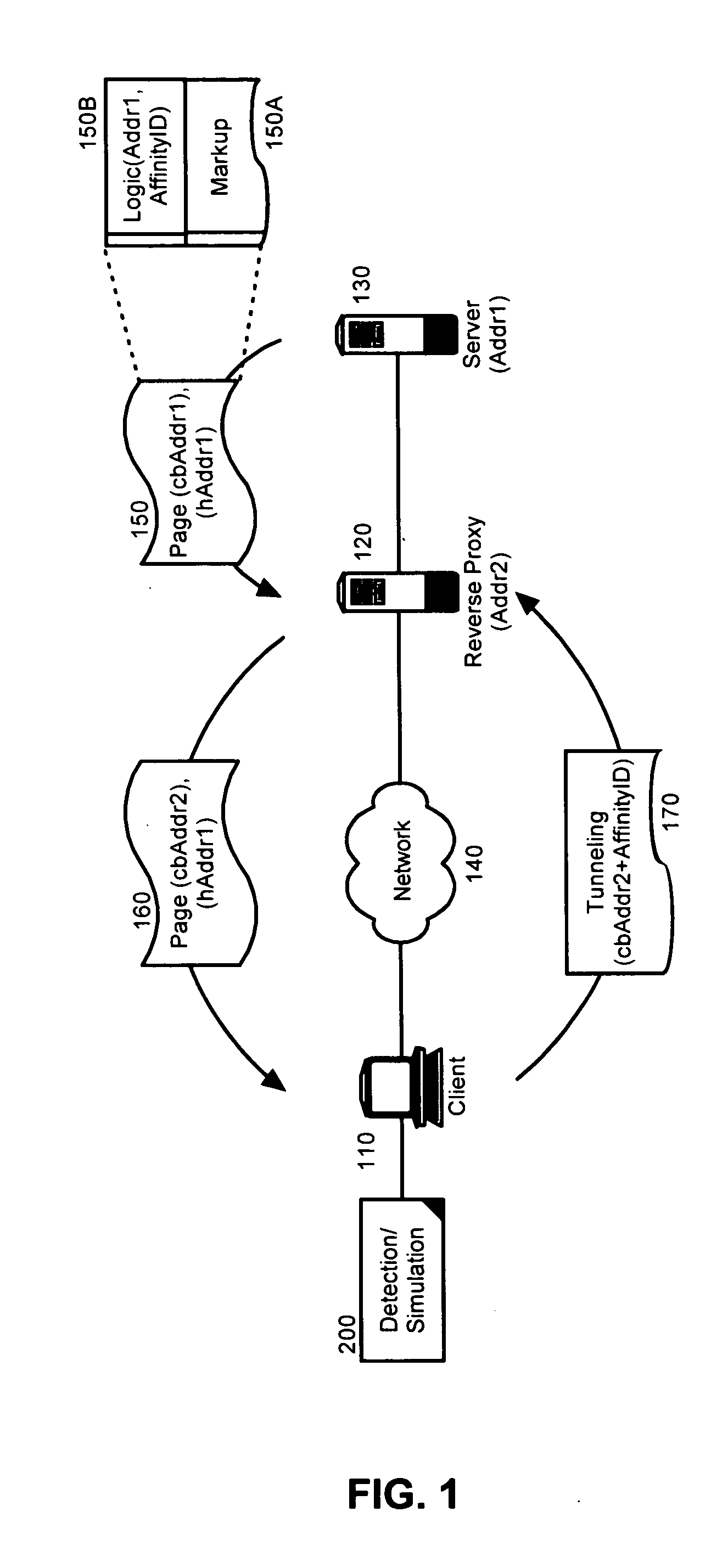
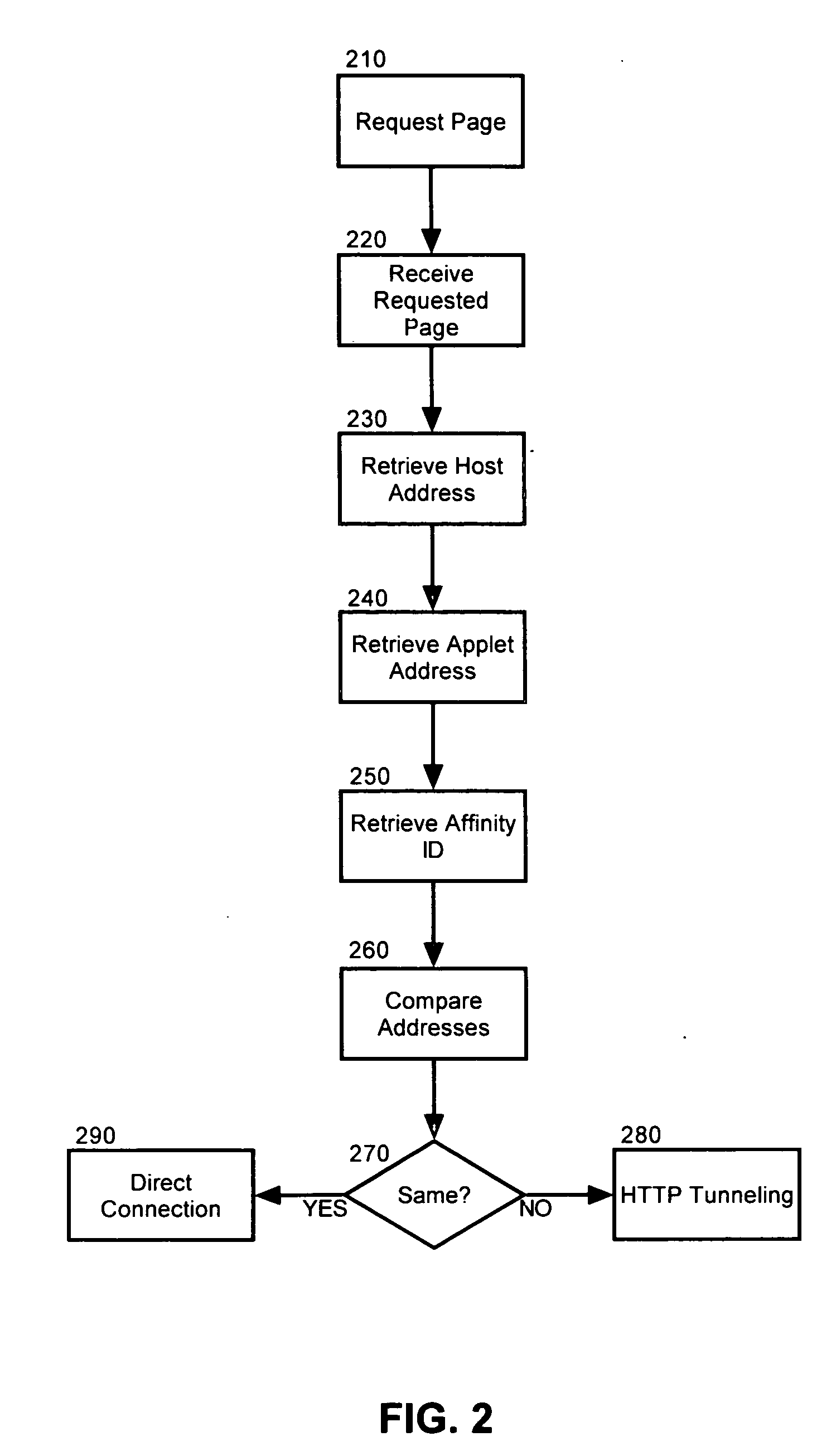
A method, system and apparatus for managing an interposed reverse proxy. The method can include comparing within a markup language document, a host address for the markup language document and a codebase address for a code base supporting logic disposed within the markup language document. If the host address and the codebase address differ, it can be concluded that a reverse proxy has obscured from view a server source of the markup language document. The method of the invention further can include retrieving a server affinity identifier for the server source from the configuration tags for the logic. Responsive to concluding that a reverse proxy has obscured from view a server source of the markup language document, a tunneled connection to the server source can be attempted through the reverse proxy by inserting the server affinity identifier in an address specified in the attempt.
Owner:IBM CORP
Services within reverse proxy servers
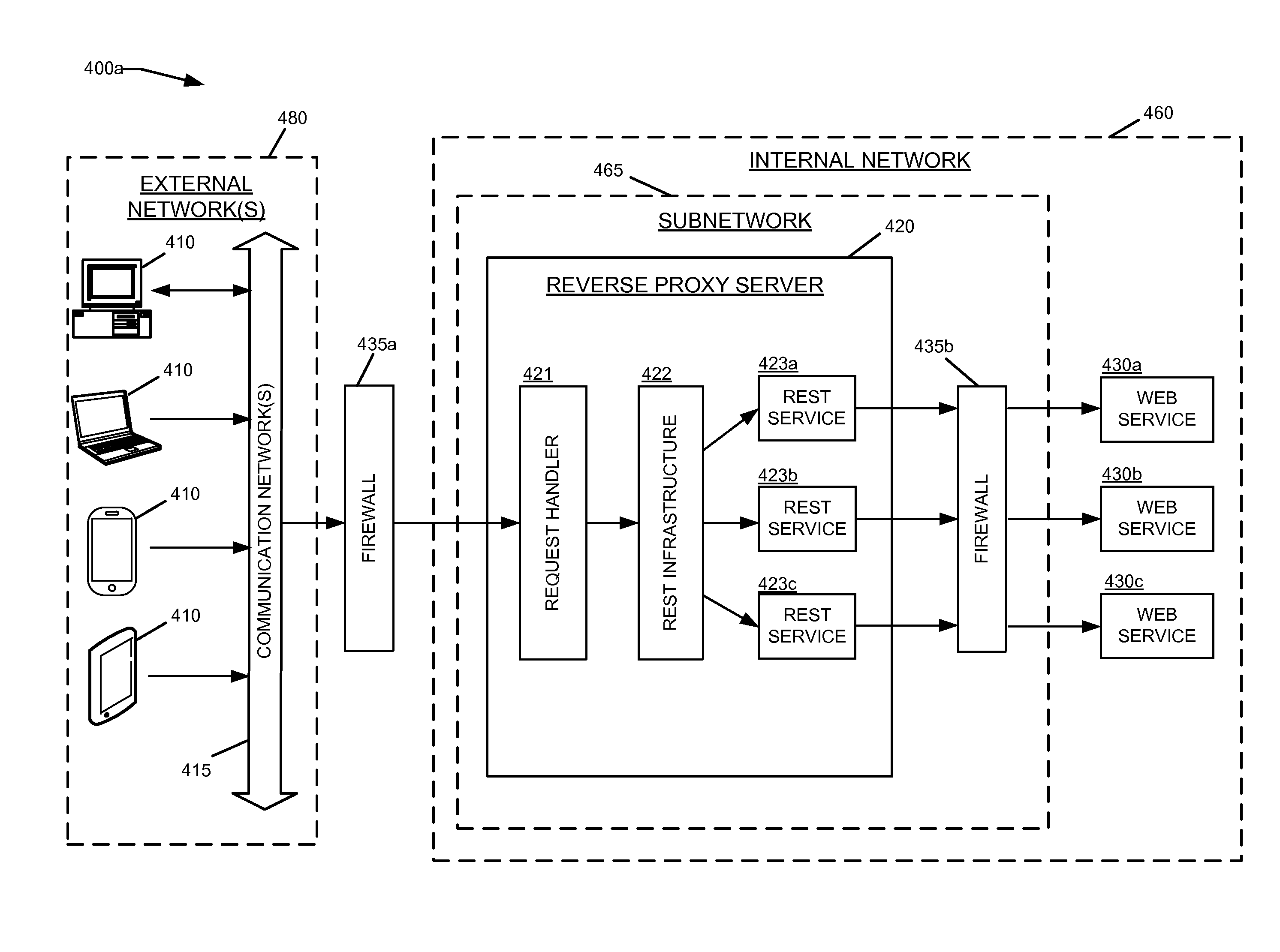
ActiveUS20160088023A1Multiple digital computer combinationsWebsite content managementCommunication endpointRepresentational state transfer
Embodiments of the invention provide techniques for processing messages transmitted between computer networks. Messages, such as requests from client devices for web services and other web content may be transmitted between multiple computer networks. Intermediary devices or applications such as proxy servers may receive, process, and transmit the messages between the communication endpoints. In some embodiments, a reverse proxy server may be configured to dynamically generate Representational State Transfer (REST) services and REST resources within the reverse proxy server. The REST services and REST resources within the reverse proxy server may handle incoming requests from client devices and invoke backend web services, thereby allowing design abstraction and / or enforcement of various security policies on the reverse proxy server.
Owner:ORACLE INT CORP
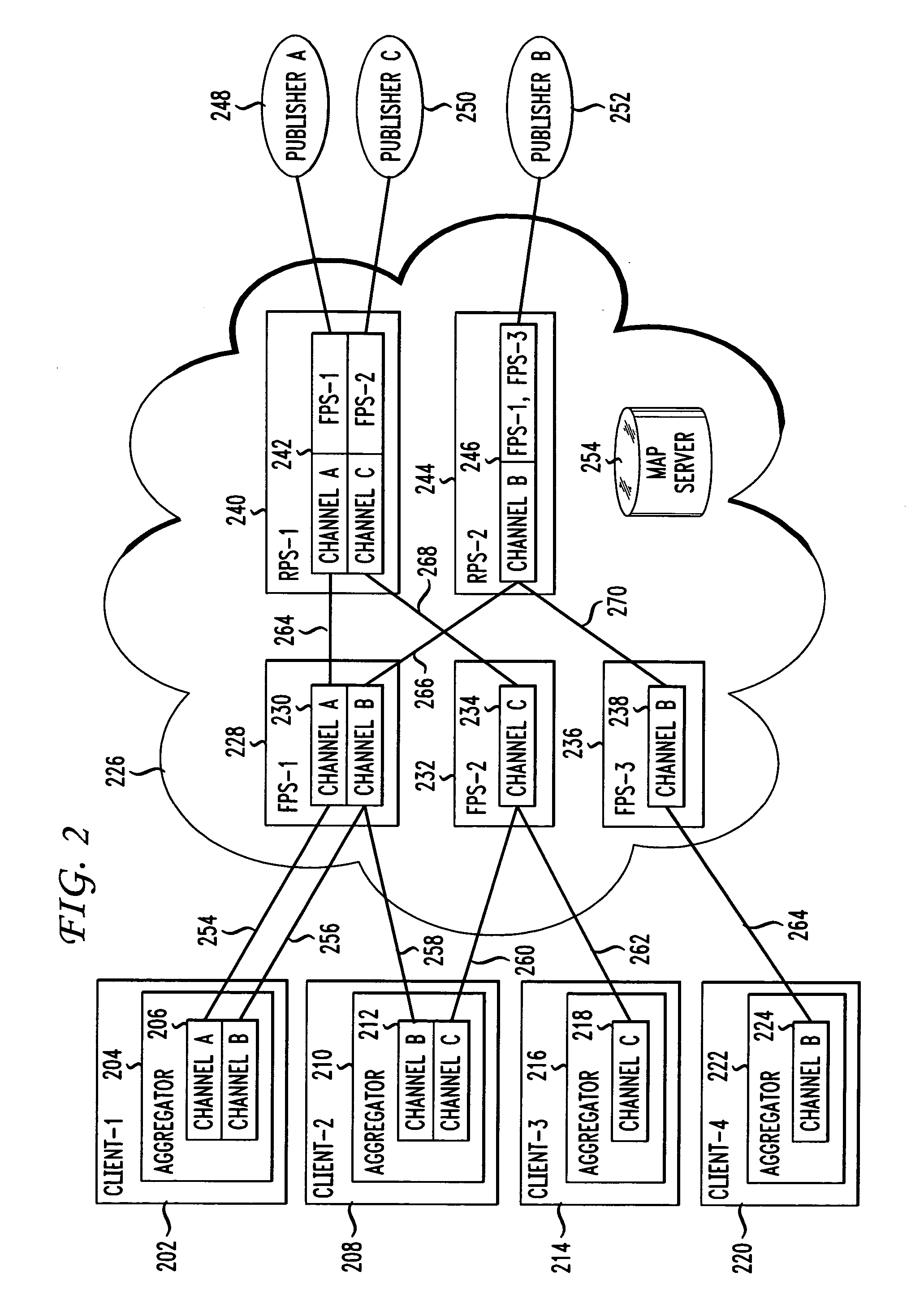
Data network information distribution
Disclosed is a method and apparatus for delivering information of interests from content providers to clients via a data network. A network architecture includes two types of edge servers, referred to as forward proxy servers and reverse proxy servers. The forward proxy servers are assigned to serve particular clients with respect to particular information and the reverse proxy servers are assigned to serve particular forward proxy servers with respect to particular information. Each of the forward proxy servers stores information identifiers associated with information for which the forward proxy server is assigned to serve to at least one client. Each of the reverse proxy servers stores information identifiers and the associated forward proxy servers that the reverse proxy server is assigned to serve with respect to information associated with the information identifiers. Upon receipt of updated content, the reverse proxy servers send the updated content to those forward proxy servers that the reverse proxy server is assigned to serve with respect to the received updated content. The forward proxy servers then provide the updated content to the clients to which they are assigned, either by responding to a request from those clients or by pushing the information to those clients. Network load balancing is provided by a controller network node for controlling the assignments of clients to forward proxy servers and the assignments of forward proxy servers to reverse proxy servers.
Owner:NEC CORP +1
Interstitial pages
ActiveUS20080313728A1Unauthorized memory use protectionHardware monitoringWeb applicationReverse proxy
A reverse proxy server can provide access to web applications. The reverse proxy system can produce interstitial pages not generated with the web application code and optionally block access to the web application until the interstitial pages have been processed.
Owner:ORACLE INT CORP
System and method for integrated recommendations
A recommendation appliance, system and method are provided for generating and deploying additional web page content or functionality (e.g., retail recommendations) to an existing web page server system. For example, the present invention may be embodied as a reverse proxy server that is inserted as an intermediate network node between a web server and the end users accessing the web server. In this position, the recommendation appliance can introduce recommendation messages to web pages generated by the web server without requiring any modification to the code or architecture of the web server. In addition, the appliance may separately track the transaction activities of end users who receive recommendation messages and the transaction activities of end users who do not receive recommendation messages, so that a comparison of the effectiveness of the recommendations may efficiently be demonstrated without requiring any modification to the code or architecture of the web server.
Owner:VERSATA DEV GROUP
Network system, virtual private connection forming method, static NAT forming device, reverse proxy server and virtual connection control device
InactiveUS20120185563A1Multiple digital computer combinationsAutomatic exchangesElectrical conductorReverse proxy
To provide a new network system, a new network connection device and a new reverse proxy device enabling to solve the problems of the conventional VPN and achieve strong security and flexible operability by adding extremely light software and hardware.After a static NAT forming device has performed authentication with a conductor through a control session, if a terminal makes a connection request to a server in a network existing before a reverse proxy server, the static NAT forming device and a stepping node will set a static NAT, and the reverse proxy server will set a reverse proxy, so that a data session will be formed between the terminal and the server. By configuring a network system in such a manner, it is possible to pass through the firewall to achieve a connection from the terminal to the server in a virtual connection state without causing private address collision.
Owner:SPRINGSOFT
Reverse proxy mechanism for retrieving electronic content associated with a local network
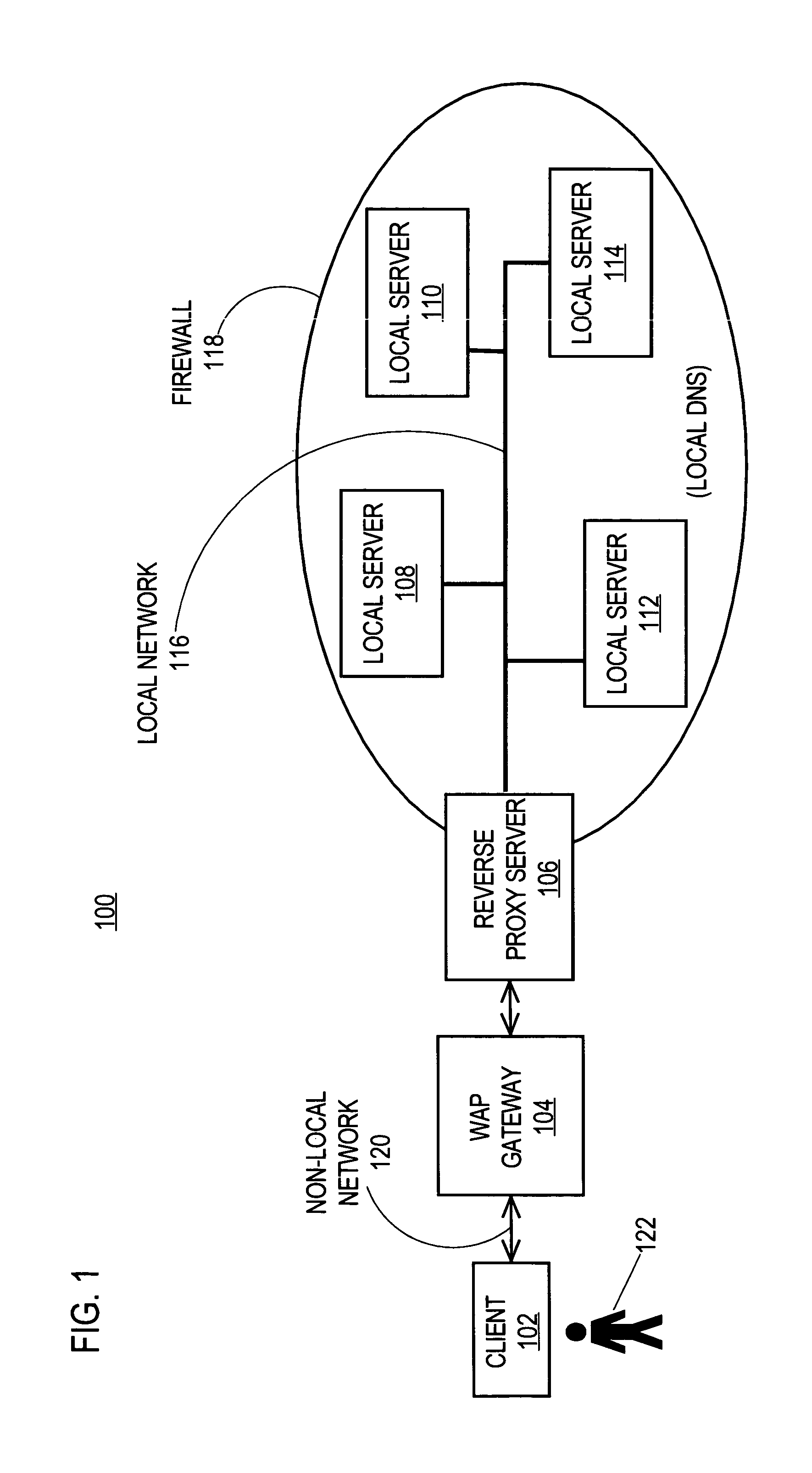
ActiveUS7818435B1Digital data information retrievalDigital data processing detailsReverse proxyClient-side
A method and apparatus for processing requests for delivery of electronic content is provided. According to one aspect of the invention, a request for delivery of first electronic content is received, where (1) the request is for delivery of the first electronic content to a destination client that is not on a local network, and (2) the first electronic content includes one or more links that are only resolvable within the local network. In response to the request, the first electronic content is retrieved, and first updated content is generated by modifying the one or more links associated with the first electronic content to include information identifying a server that can be addressed outside the local network. The first updated content is then delivered to the destination client.
Owner:SYNCHRONOSS TECH
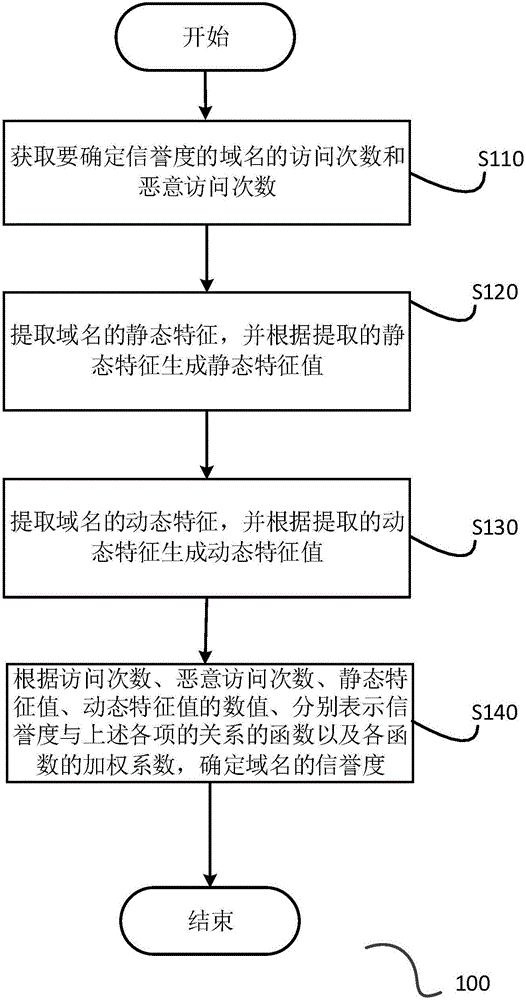
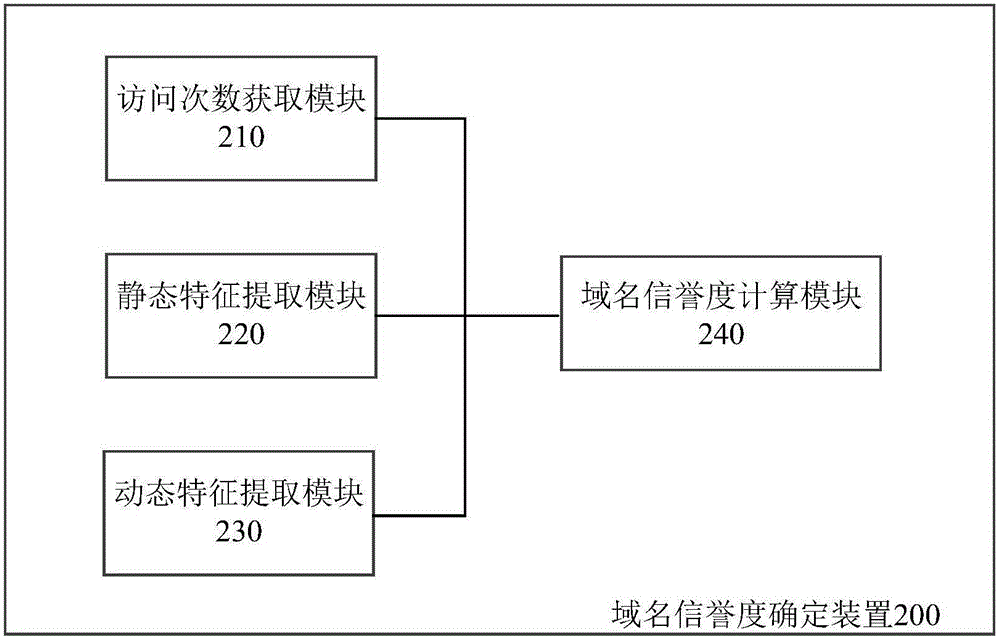
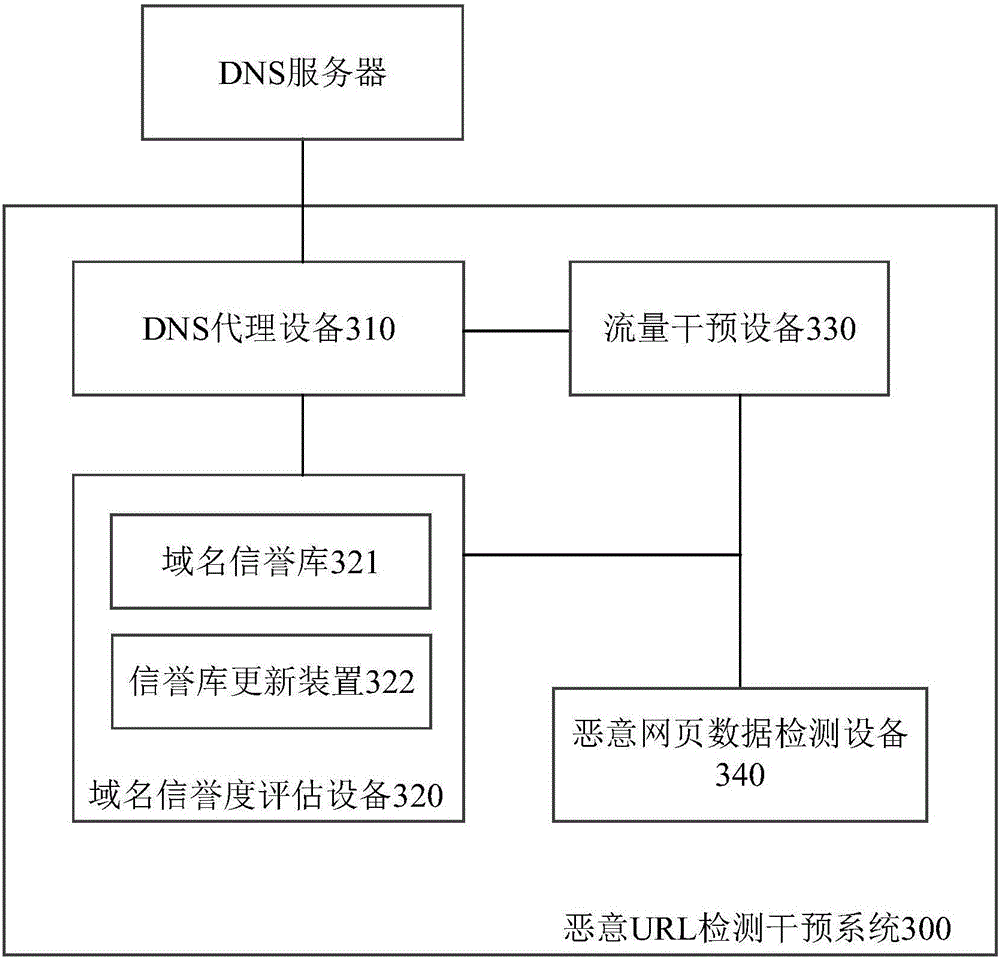
Malicious URL detection intervention method, system and apparatus
ActiveCN106131016AReduce missed detectionReduce false detection rateTransmissionDomain nameIp address
The invention discloses a malicious URL detection intervention system. The system comprises a DNS proxy device, a credit evaluation device and a traffic intervention device, wherein the DNS proxy device is suitable for receiving a domain name resolution request, requesting a domain name credit evaluation device for the credit of a domain name, and returning back an IP address of the traffic intervention device to a user if the credit indicates that the domain name has security risks; the credit evaluation device comprises a domain name credit library, and is suitable for returning back the credit of the domain name in response to the request of the credit of the domain name; and the traffic intervention device is suitable for receiving an access request from the user and performing protocol identification for the access request, and is also suitable for extracting a URL from the access request which is identified as a request of a HTTP or HTTPS protocol, matching the URL with a malicious RUL library, and if matching is failed, being used as a reverse proxy to realize communication of the user and a destination server. The invention also discloses a corresponding domain name credit determining apparatus, a corresponding domain name credit library establishing apparatus and methods.
Owner:BEIJING KNOWNSEC INFORMATION TECH
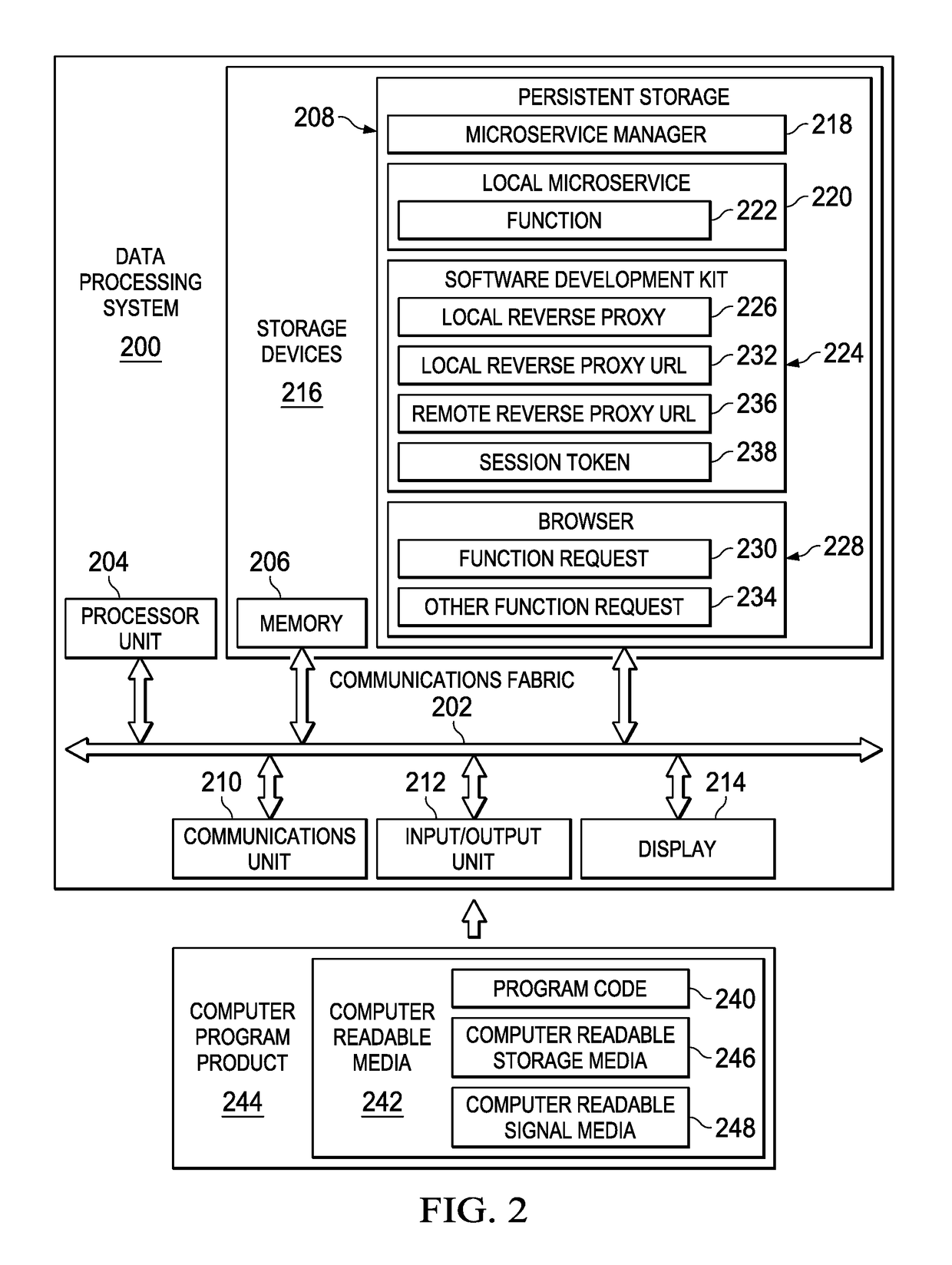
Local Microservice Development for Remote Deployment
Managing microservice function requests is provided. A request originating from a browser of the computer to execute a function corresponding to a microservice locally deployed on the computer is received using a software development kit operating in the computer. The request to execute the function is routed to the microservice using a local reverse proxy running in the software development kit. Other requests originating from the browser of the computer to execute one or more other functions corresponding to one or more microservices in a remotely deployed microservice architecture that interact with the function corresponding to the microservice are received using the software development kit. The other requests to execute the one or more other functions corresponding to the one or more microservices in the remotely deployed microservice architecture are routed, via a single uniform resource locator corresponding to a remote reverse proxy, using the local reverse proxy.
Owner:IBM CORP
Method for realizing WEB reverse proxy
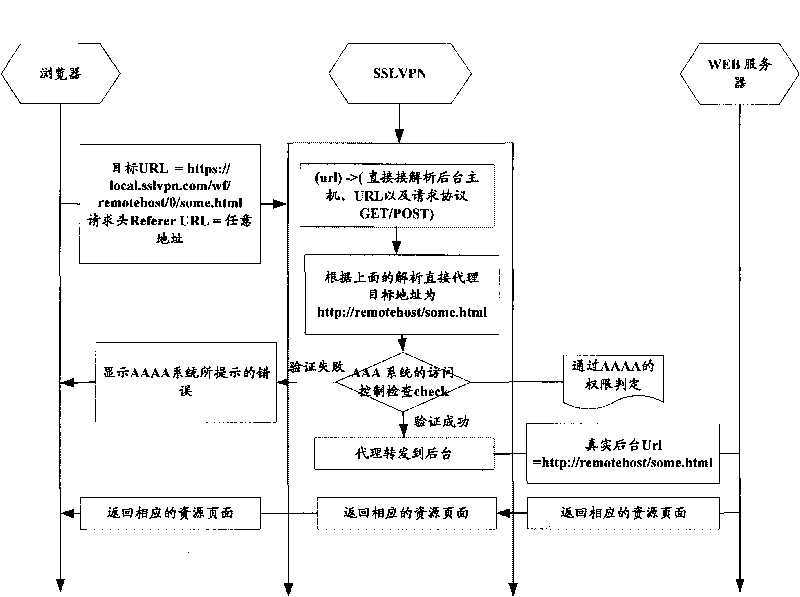
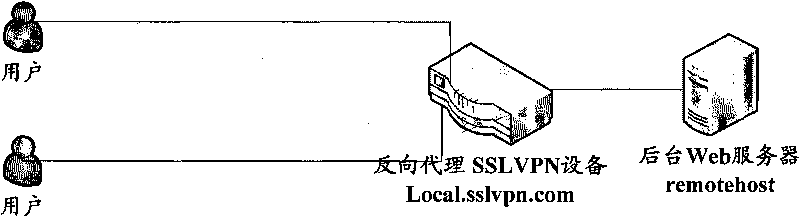
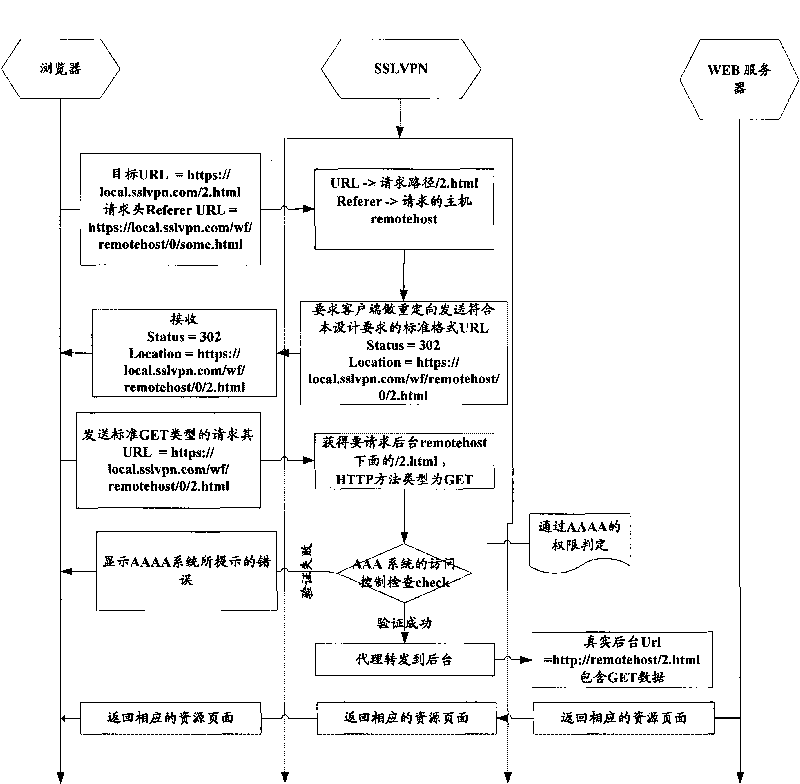
The invention provides a method for realizing WEB reverse proxy. After the user side inputs a first WEB reverse proxy processing request in the bookmark bar or the interface input box of a browser, the method comprises the following steps: the client transmits HTTP (Hyper Text Transport Protocol) / HTTPS request, the Uniform Resource Locator (URL) of the request includes an address of reverse proxy server SSLVPN (Secure Socket Layer Virtual Private Network), an address of an accessed background server and a resource route of the accessed background server; the reverse proxy server SSLNPN extracts the address and the resource route of the accessed background server and forwards the request normally after intercepting the request. In the invention, a response header processes the HTTP request without any replacement in the HTML (Hyper Text Markup Language) page, a relative URL process and an absolute URL format process based on the redirection can be efficiently finished on the Web server by a formative URL.
Owner:BEIJING TOPSEC TECH
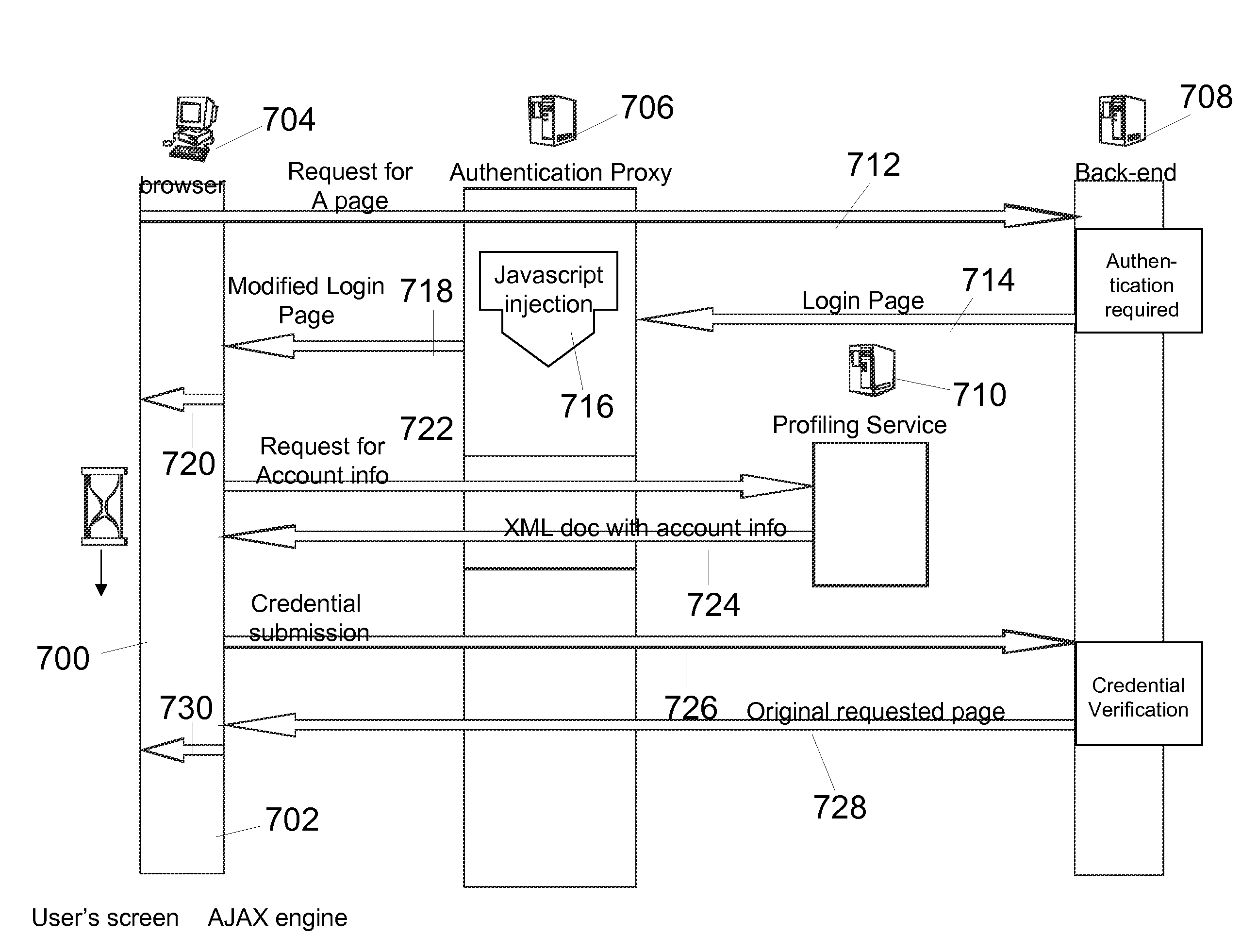
Method and system for establishing and maintaining an improved single sign-on (SSO) facility
ActiveUS20120167193A1Digital data processing detailsMultiple digital computer combinationsReverse proxyBack end server
A method for establishing and maintaining a Single Sign-on between a reverse proxy and a back-end server can include instigating an authentication process through a browser for a user to obtain access to the back-end server, intercepting a login page from the back-end server at the reverse proxy and adding a routine thereto, thereby loading an asynchronous engine on the browser executing a login process with an authentication profiling service, in order to retrieve the login information for the back-end server, and completing the authentication process with the back-end to allow the user access the back-end server through the asynchronous engine.
Owner:IBM CORP
Application idling in a multi-tenant cloud-based application hosting environment
A mechanism for idling an application in a multi-tenant cloud hosting environment is disclosed. A method of the invention includes detecting, by a reverse proxy of a node of a cloud computing architecture, a lack of minimum usage of an application hosted on the node, the application being one of a plurality of applications being hosted on the node and instructing the node to shut down the application in response. The reverse proxy is then; and reconfigured to point to a restarter instead of the application, wherein the restarter restarts the application in response to detecting an access to the application.
Owner:RED HAT
Secure high-throughput data-center network employing routed firewalls
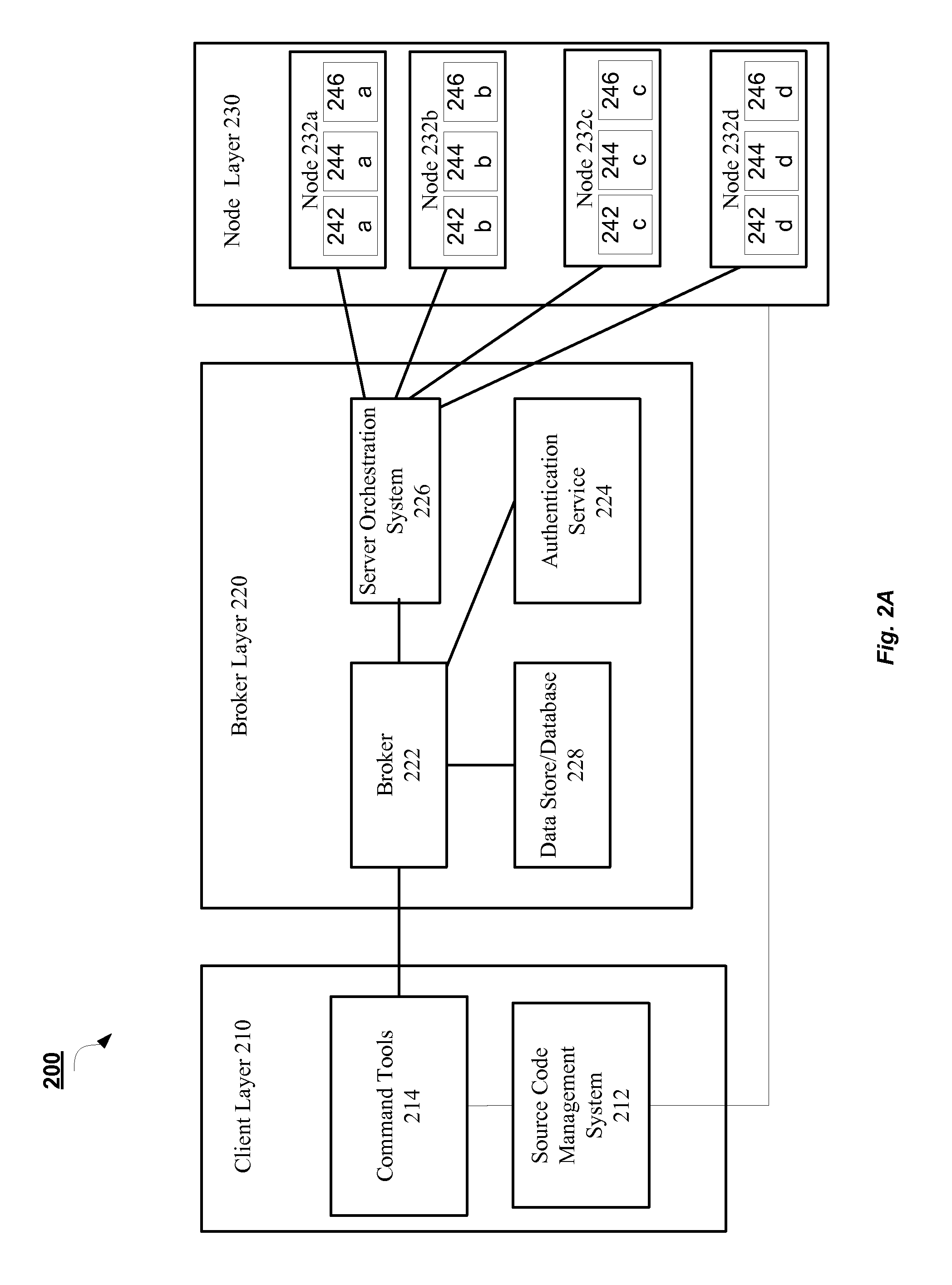
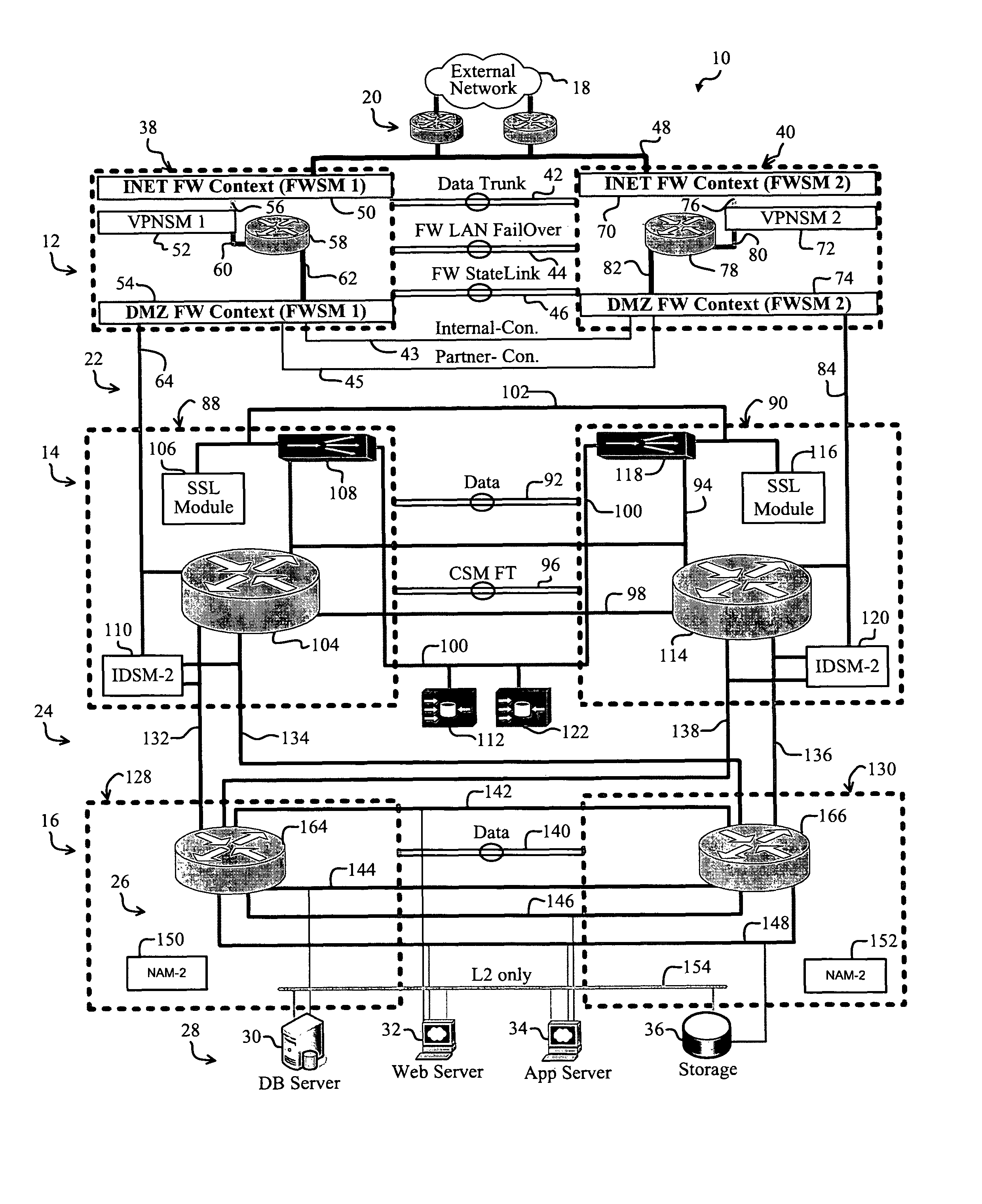
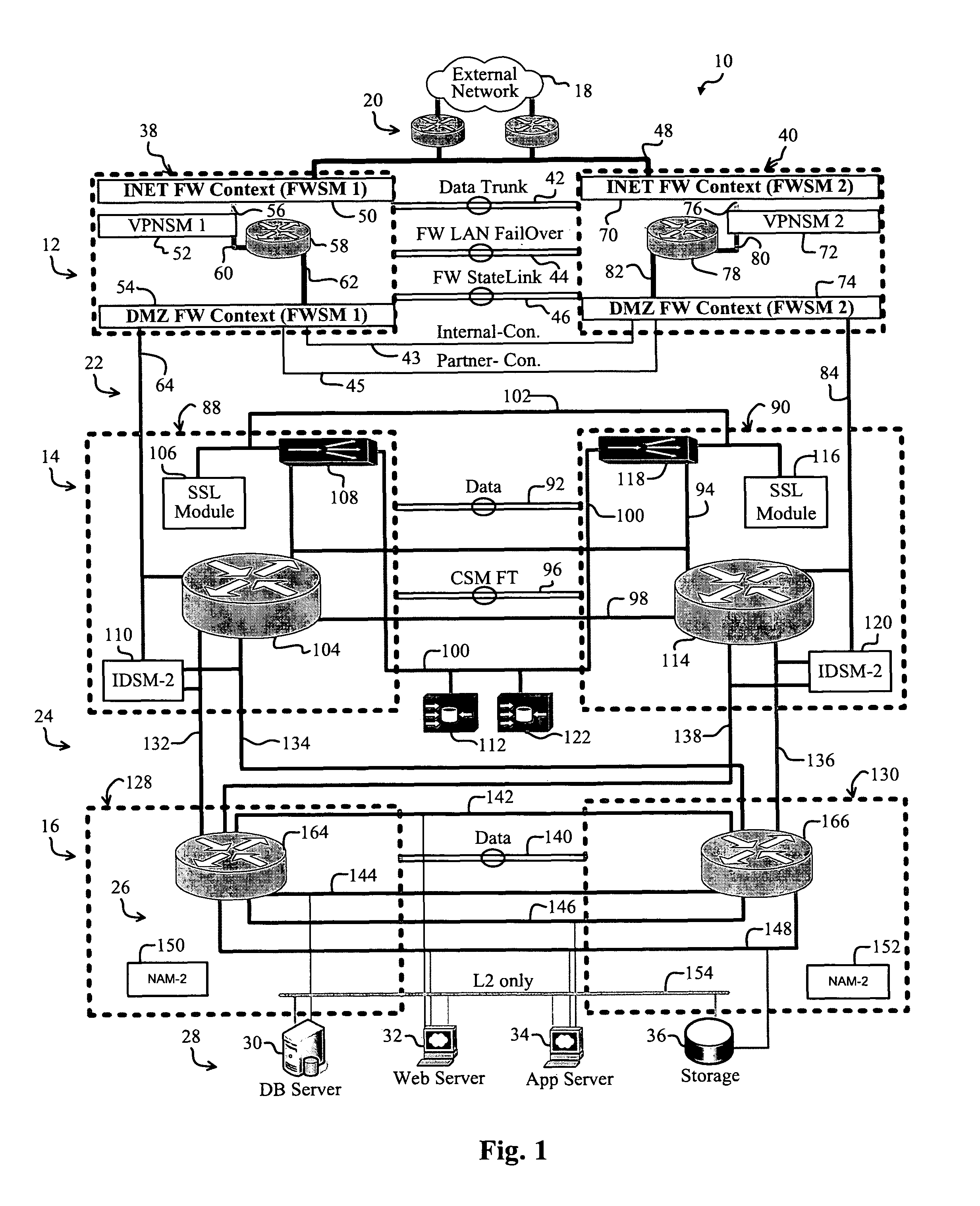
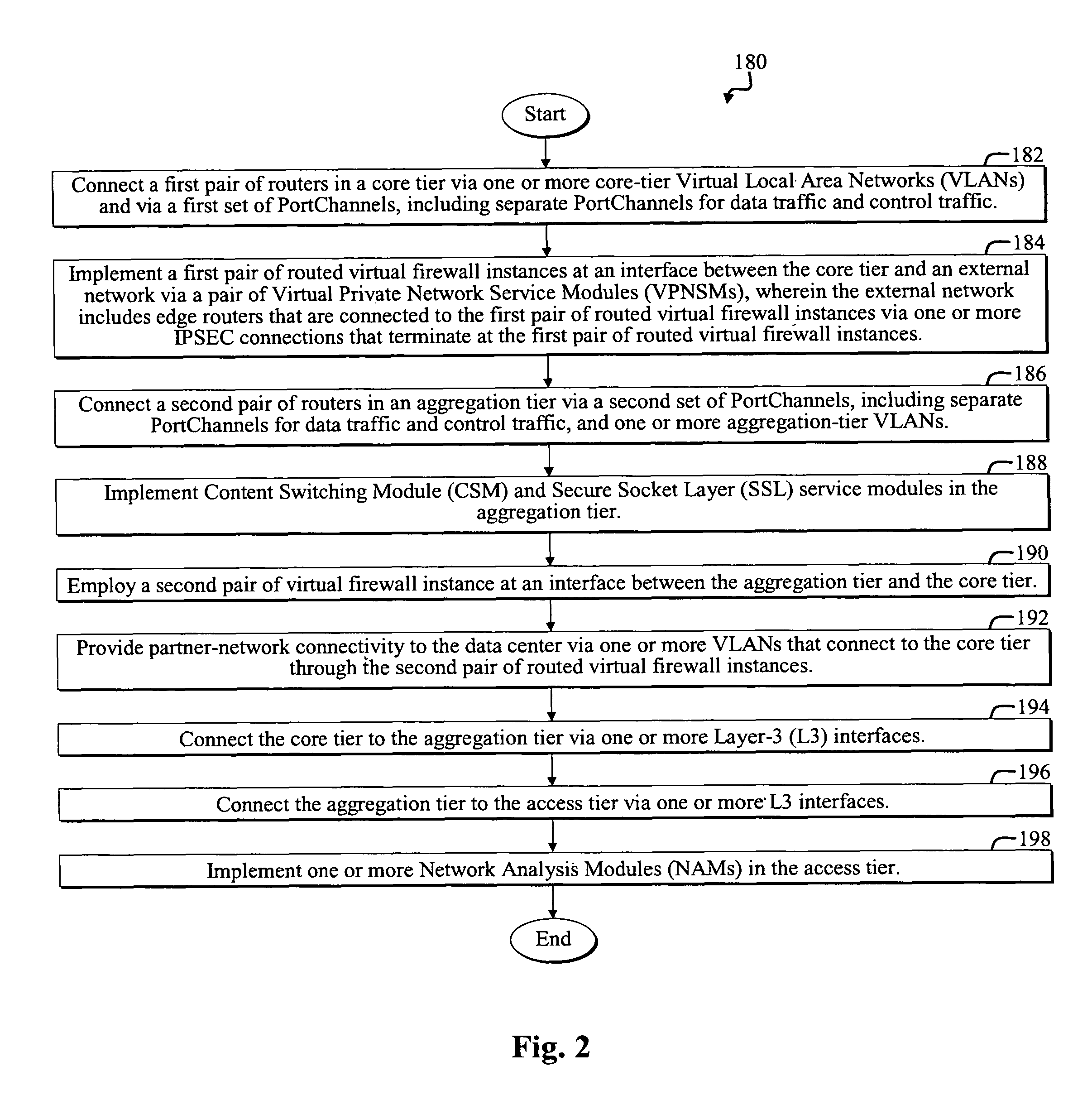
A reliable and secure data-center. The data center includes a first data-center tier that is adapted to connect to an external network and an internal portion of the data center. A first firewall instance interfaces the first tier and the external network. A second firewall instance interfaces the first tier and the internal portion of the data center. In a more specific embodiment, the first firewall instance and the second firewall instance accommodate Internet Protocol SECurity (IPSEC) terminations using one or more VPNSMs. In this embodiment, the first data-center tier implements a core tier that includes one or more core switches that facilitate implementing the first firewall instance and the second firewall instance. The interior portion of the network represents a DeMilitarized Zone (DMZ) that includes a second tier that is connected between the first data-center tier and a third tier. The second tier implements an aggregation tier that includes one or more aggregation switches that facilitate implementing reverse-proxy caching. Overall Layer-3 design methodology is used within each tier and across tiers for optimized packet switching. The aggregation tier includes one or more aggregation-tier service modules for implementing load balancing, Secure Socket Layer (SSL) offloading, and / or the reverse-proxy caching.
Owner:CISCO TECH INC
System and method of handling requests in a multi-homed reverse proxy
Cloud service providers provide resources on a plurality of hosts some of which furthermore reside in different domains. An enhanced Reverse Proxy server is described which is configured to access hosts of multiple domains, handling client requests transparently. A request from a client to any of the supported service provider target hosts is addressed to a path in the domain of the reverse proxy server, and is formatted to include the target host domain coded as a short form name which is inserted in the path component of the request. Arguments in JavaScript calls of the response from the target host to the client are modified to ensure that future JavaScript operations generate similarly formatted requests. The enhanced Reverse Proxy translates Universal Resource Locators (URLs) of traffic between hosts of the service provider and the client in both directions accordingly.
Owner:SYMANTEC CORP
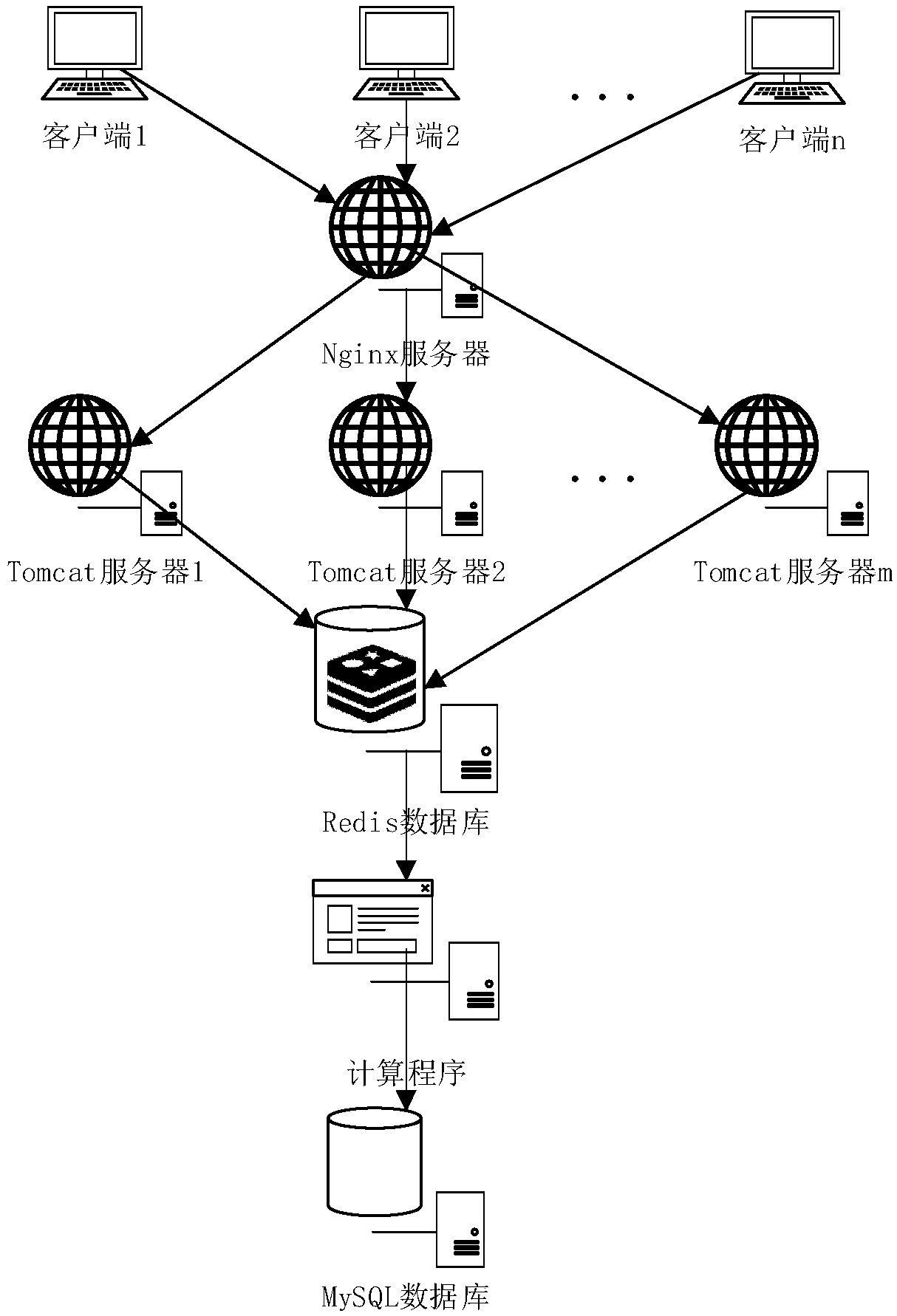
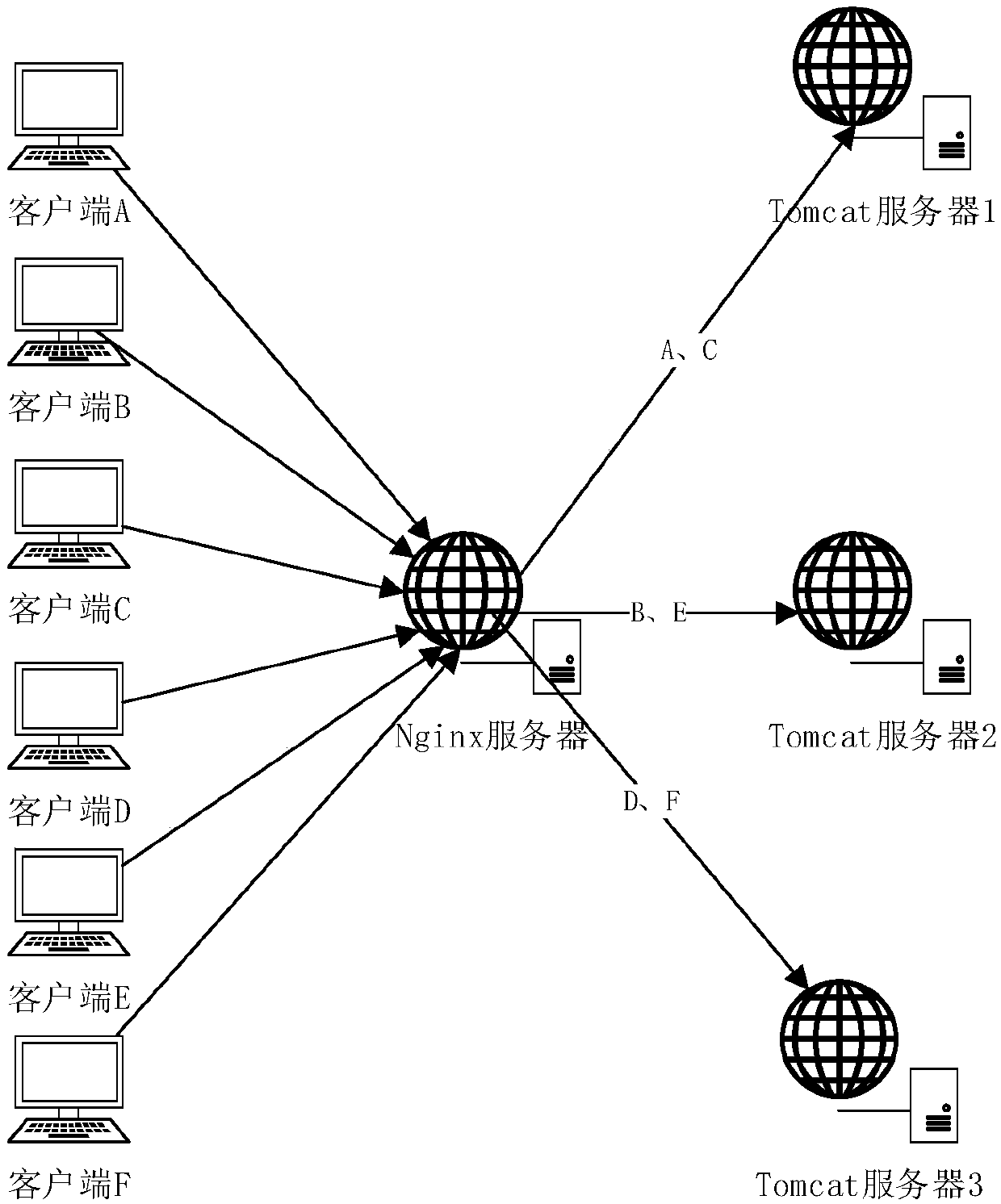
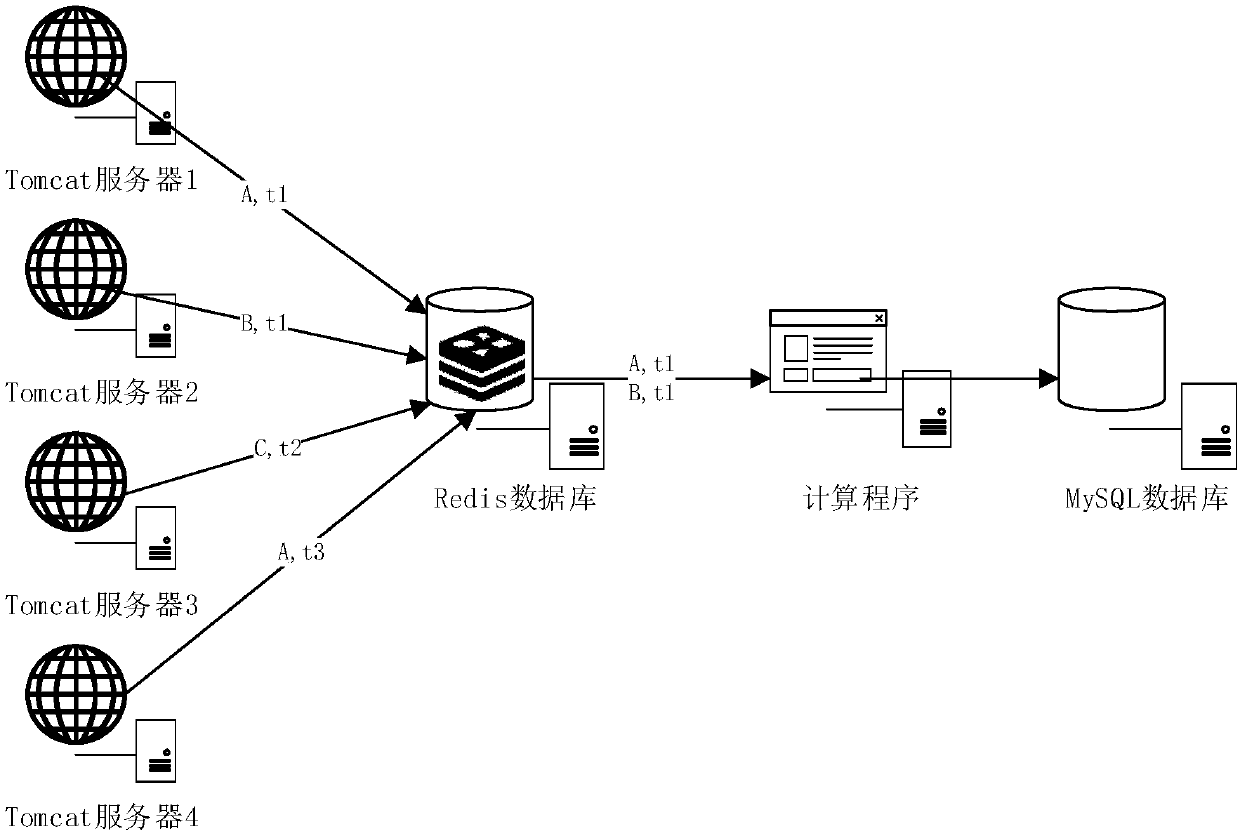
High concurrency load balancing system based on Nginx and Redis
InactiveCN107734004ATroubleshoot performance load issuesMeet operational needsTransmissionReverse proxyTime processing
The invention discloses a high concurrency load balancing system based on Nginx and Redis. The Nginx is taken as a reverse proxy server to conduct reverse proxy on high concurrency requests from multiple clients to distribute the high concurrency requests to different Tomcat servers, the Redis is used as a cache database to be used for saving a real-time calculated cache queue and accelerating thequery efficiency of the database, and MySQL is used as a structuralized database to be used for storing processed data. According to the structure of the system, high concurrency access reverse proxies can be distributed to different servers to achieve the load balancing purpose, and the Redis cache database can meet the real-time processing and storing requirements of high concurrency data, increase the processing speed and reduce the performance influences brought by high concurrency and has the very good practical value.
Owner:HOHAI UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com