Credential vault encryption
a vault encryption and credential technology, applied in the field of credential vault encryption, can solve problems such as potential problems in web applications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
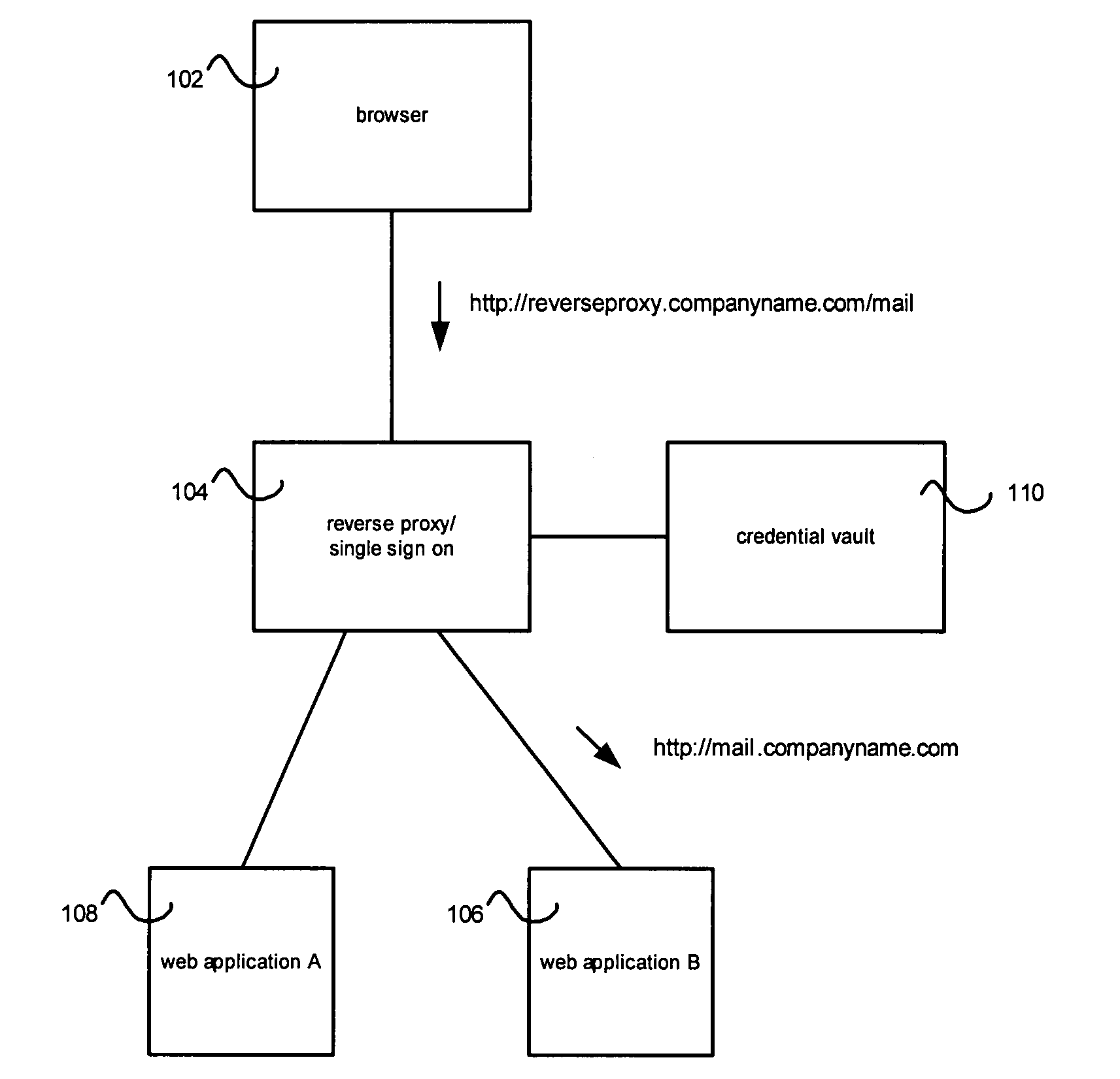
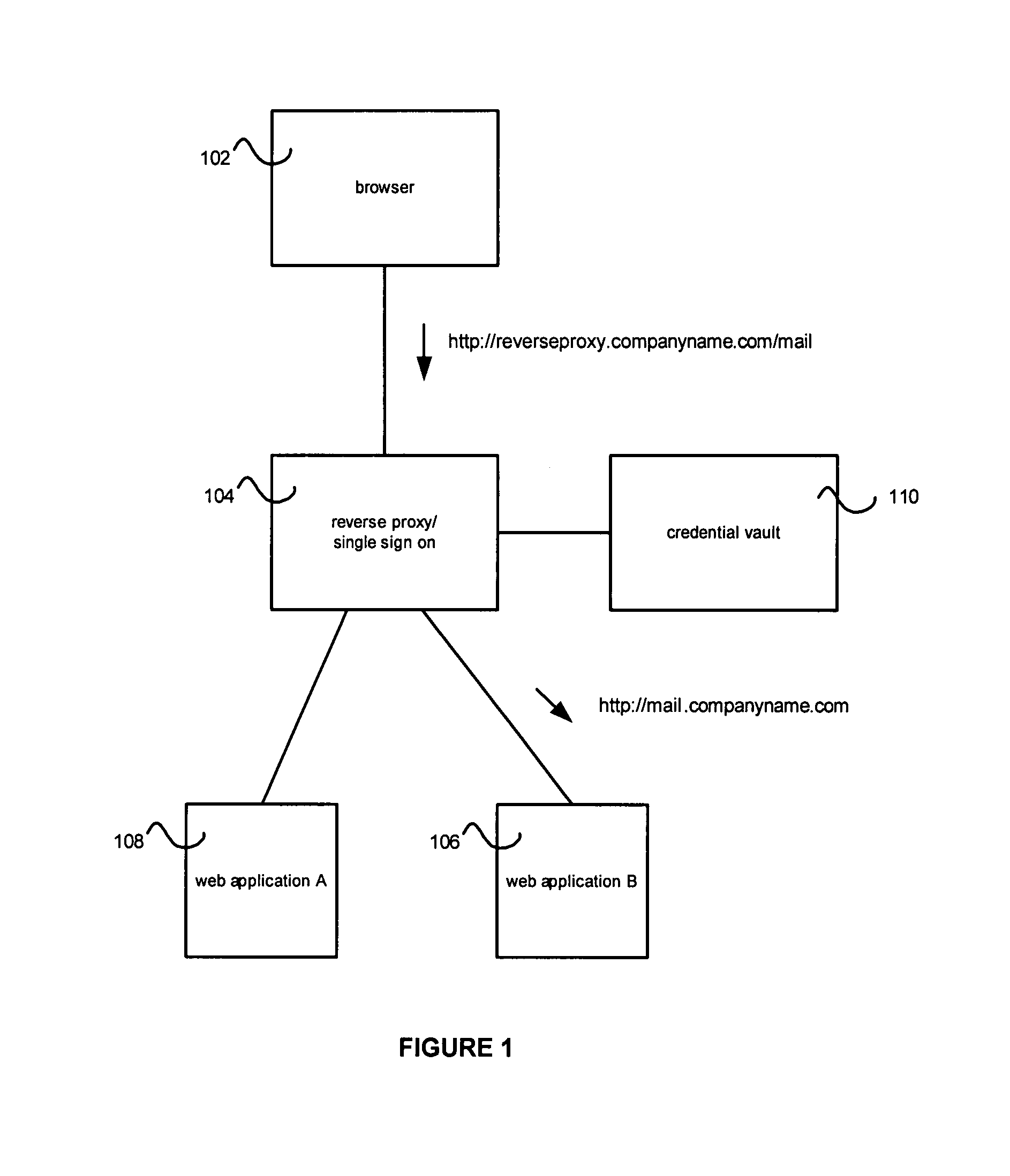
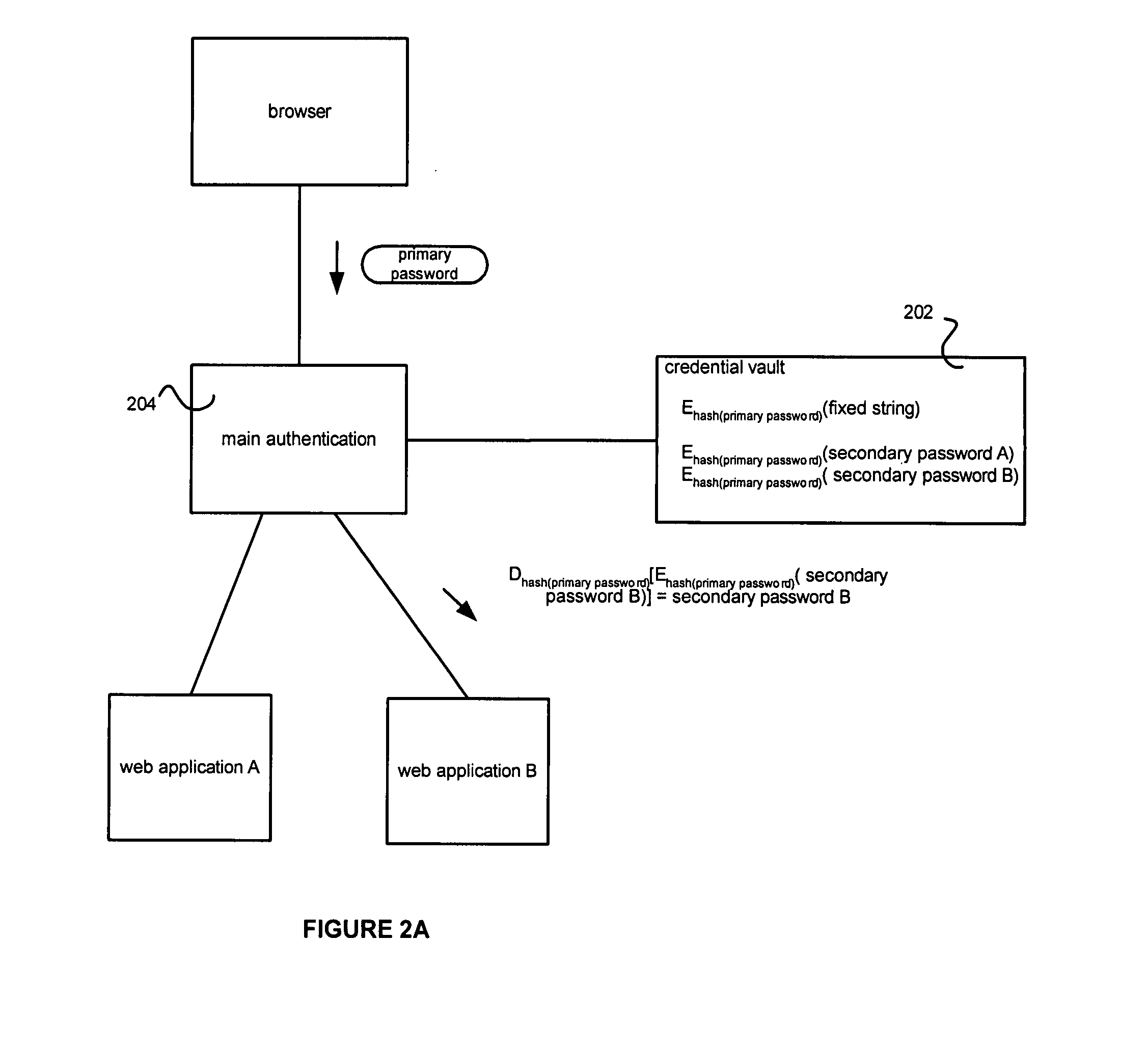
[0020]Some embodiments of the present invention may be useful in reverse proxy and Single Sign On (SSO) environments.
[0021]FIG. 1 shows an exemplary reverse proxy, single-sign-on environment. A user browser 102 can access functionality through the reverse proxy 104. In the example of FIG. 1, a request for “http: / / reverseproxy.companyname.com / mail” is sent to the reverse proxy 104 and mapped to a resource 106 at “http: / / mail.companyname.com”. In one embodiment, the reverse proxy 104 can be set up to access the web application instances 106 and 108.
[0022]For purposes of this application a reverse proxy can be any system that can do such a reverse mapping. In one embodiment, a reverse proxy is a server that proxies content from a remote web application to an end-user and may or may not modify that content.
[0023]No additional or supplemental functionality, such as SSO, should be imputed to the meaning of the term “Reverse Proxy” or “Proxy”.
[0024]Supplemental functionalities can include ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com