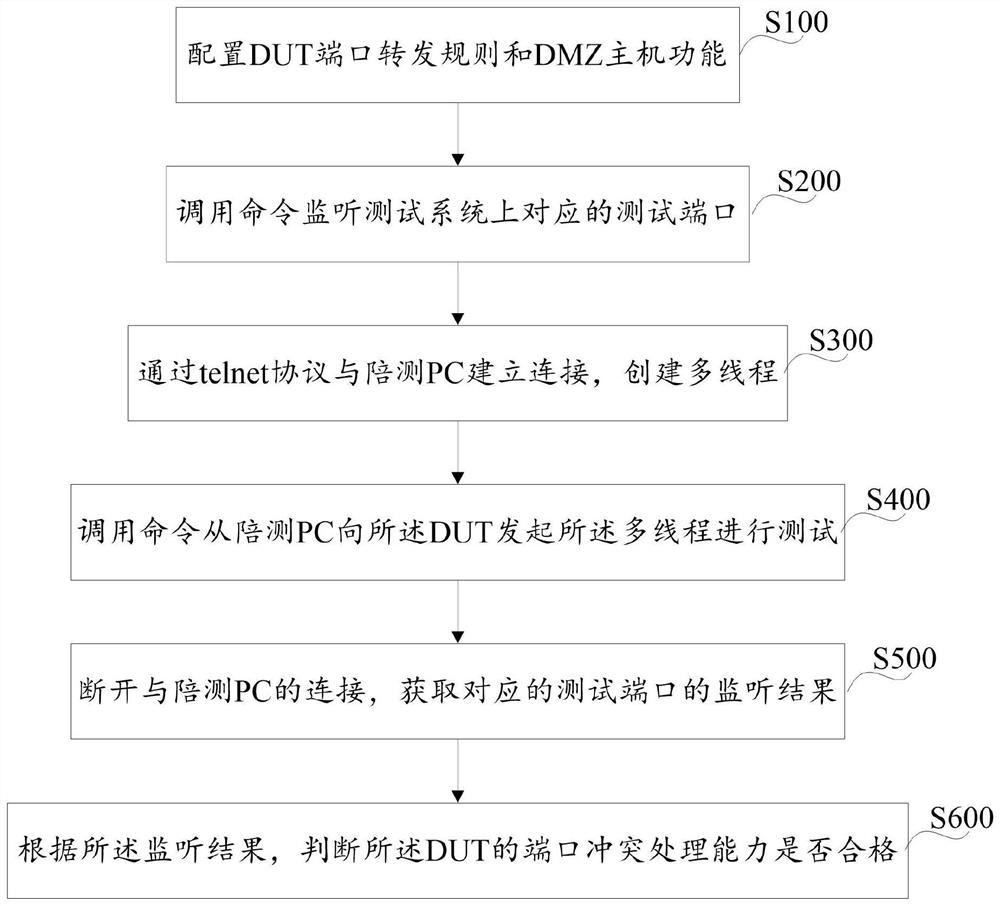
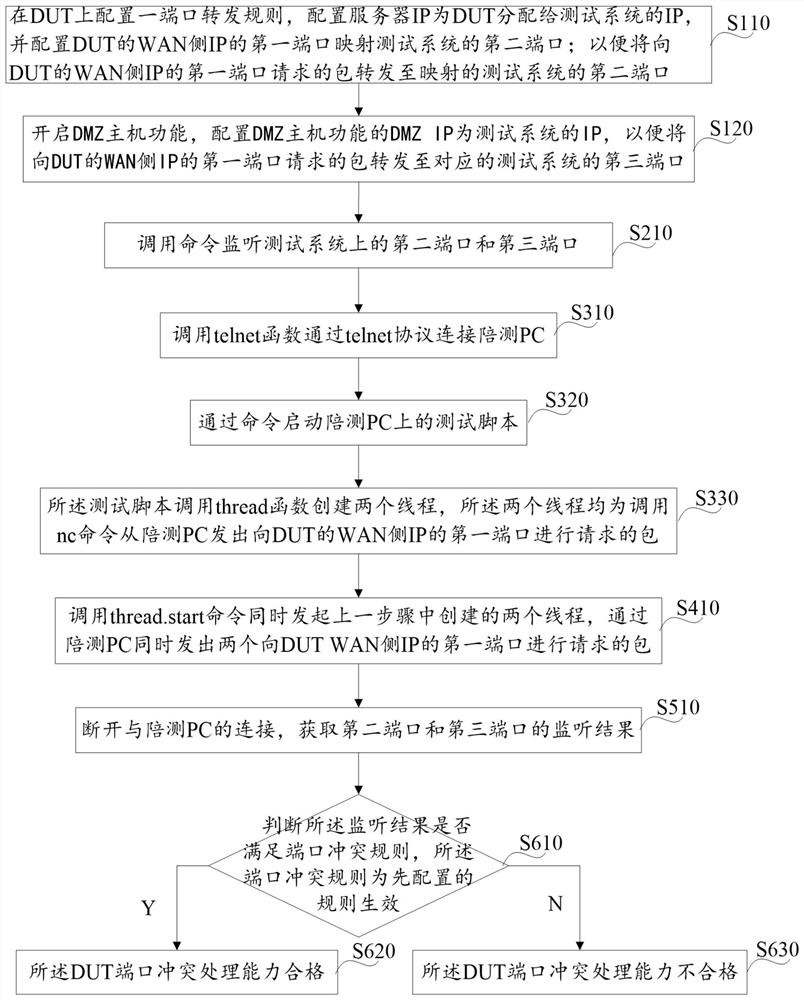
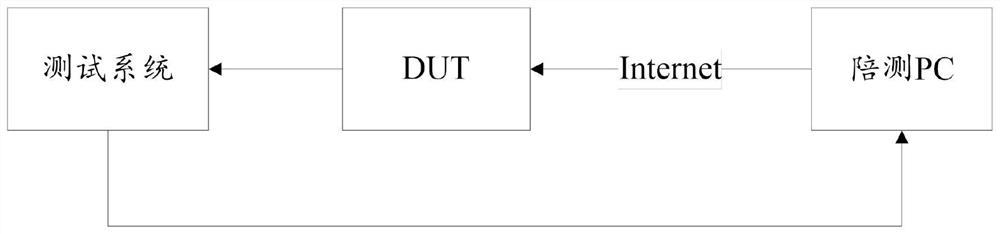
Patents
Literature
36 results about "DMZ" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
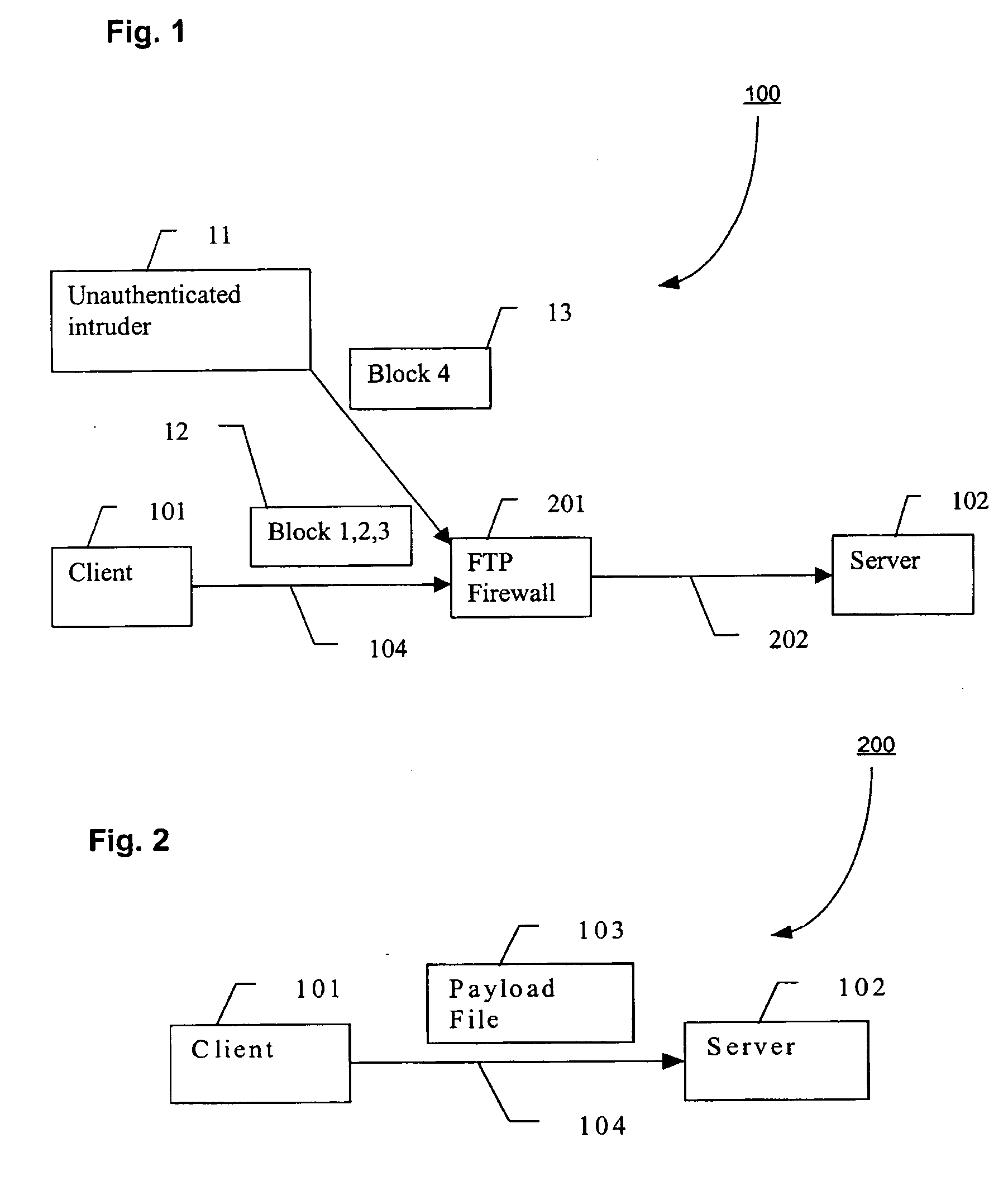
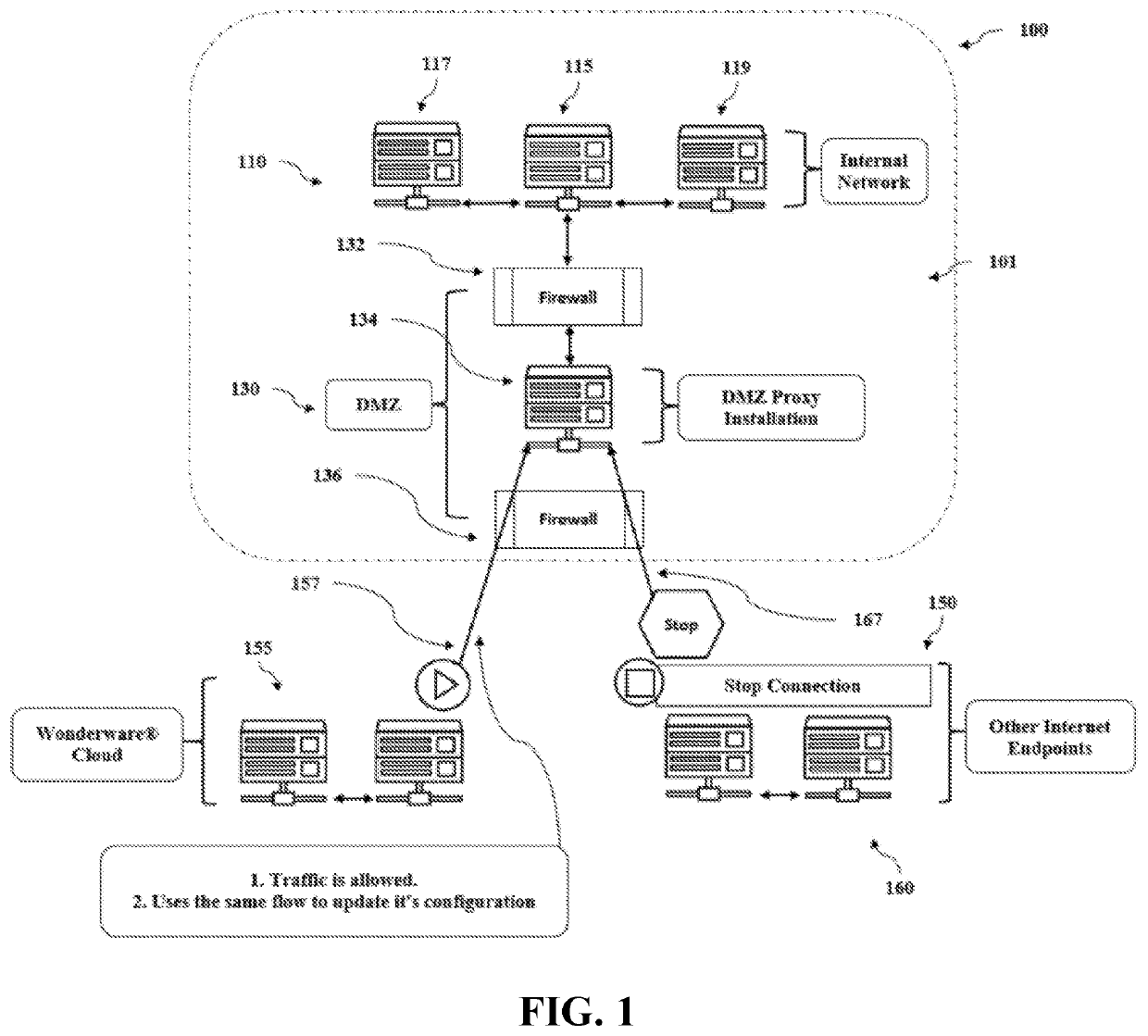
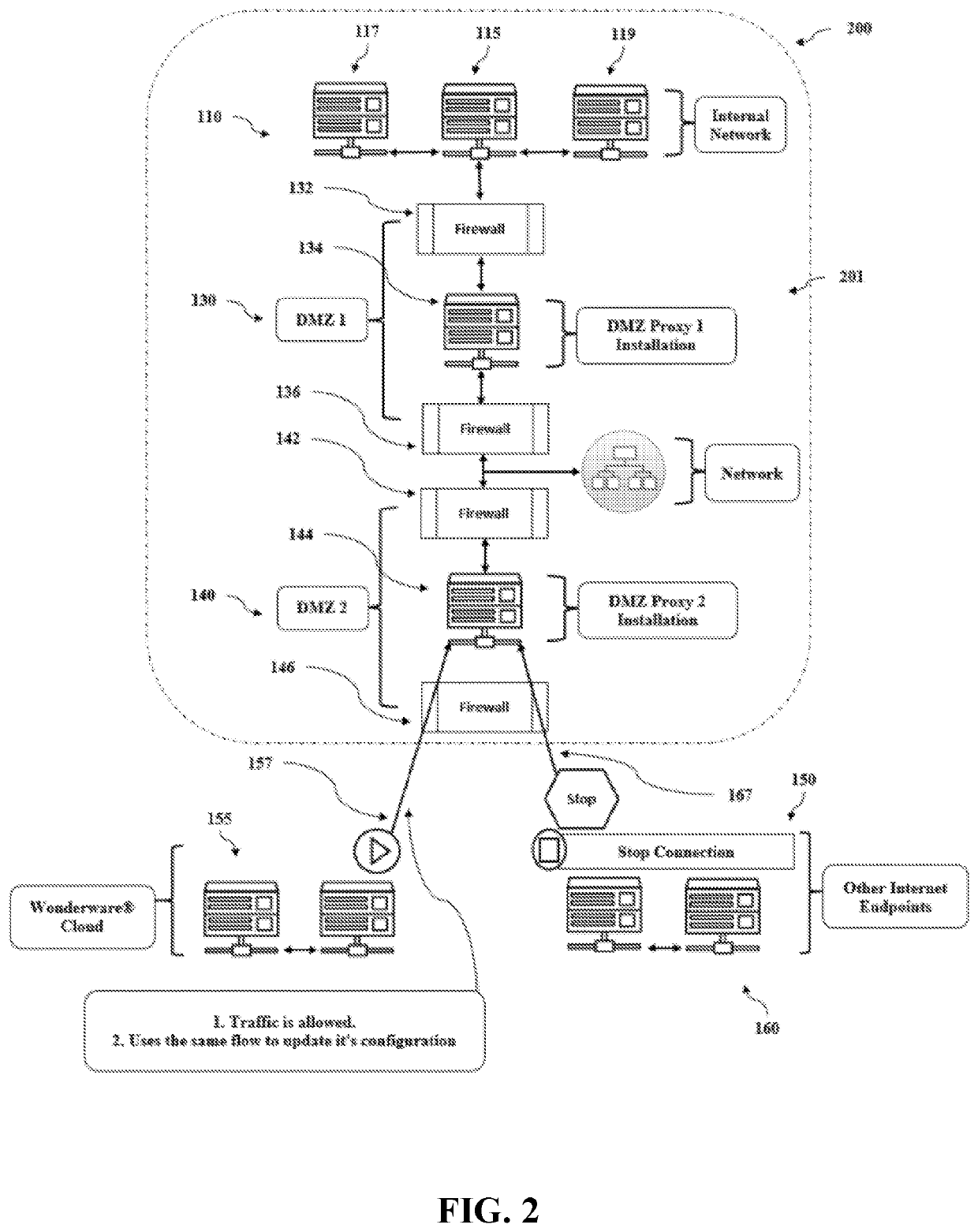
In computer security, a DMZ or demilitarized zone (sometimes referred to as a perimeter network or screened subnet) is a physical or logical subnetwork that contains and exposes an organization's external-facing services to an untrusted network, usually a larger network such as the Internet. The purpose of a DMZ is to add an additional layer of security to an organization's local area network (LAN): an external network node can access only what is exposed in the DMZ, while the rest of the organization's network is firewalled. The DMZ functions as a small, isolated network positioned between the Internet and the private network and, if its design is effective, allows the organization extra time to detect and address breaches before they would further penetrate into the internal networks.
Integrated customer web station for web based call management
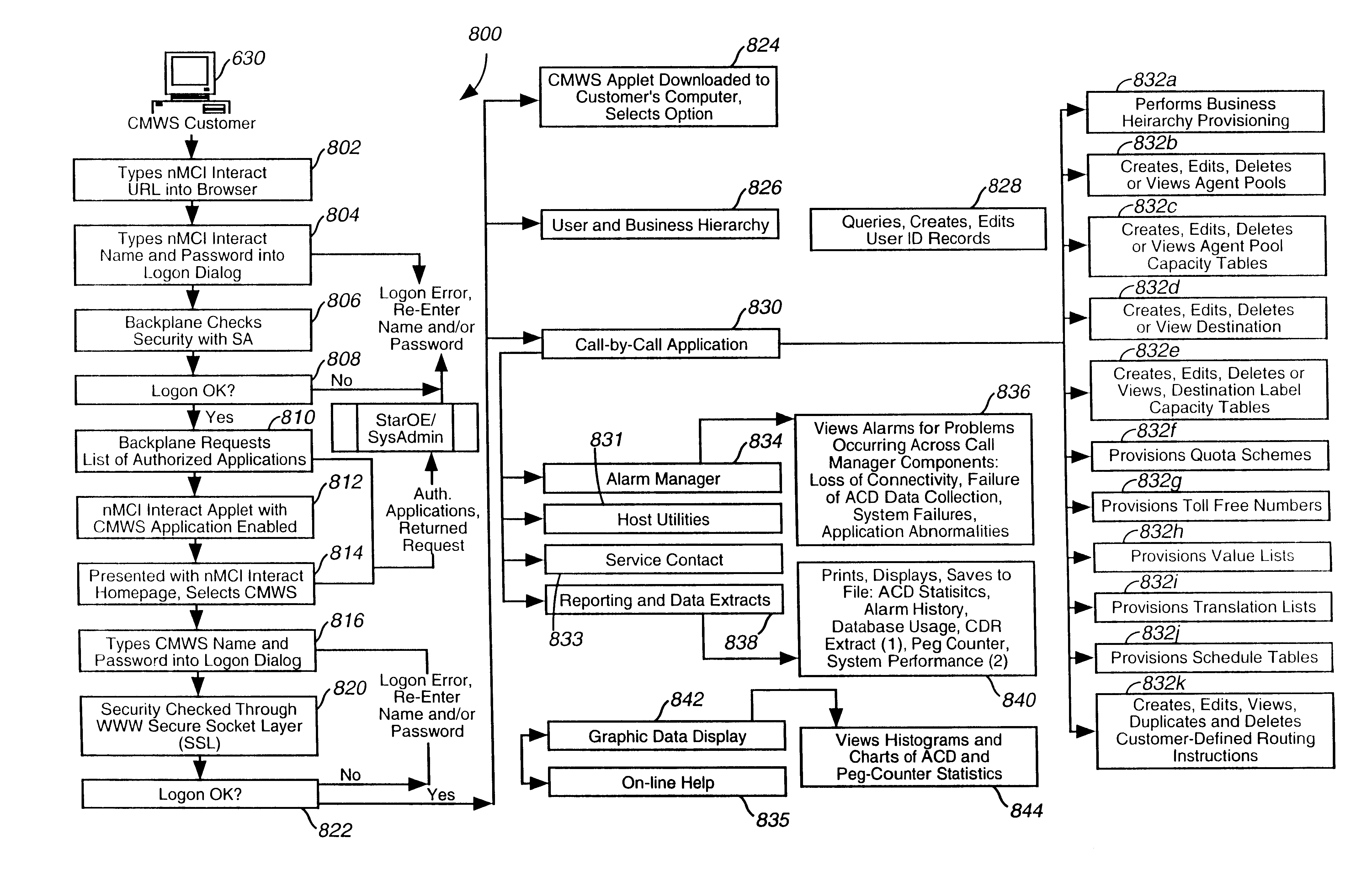
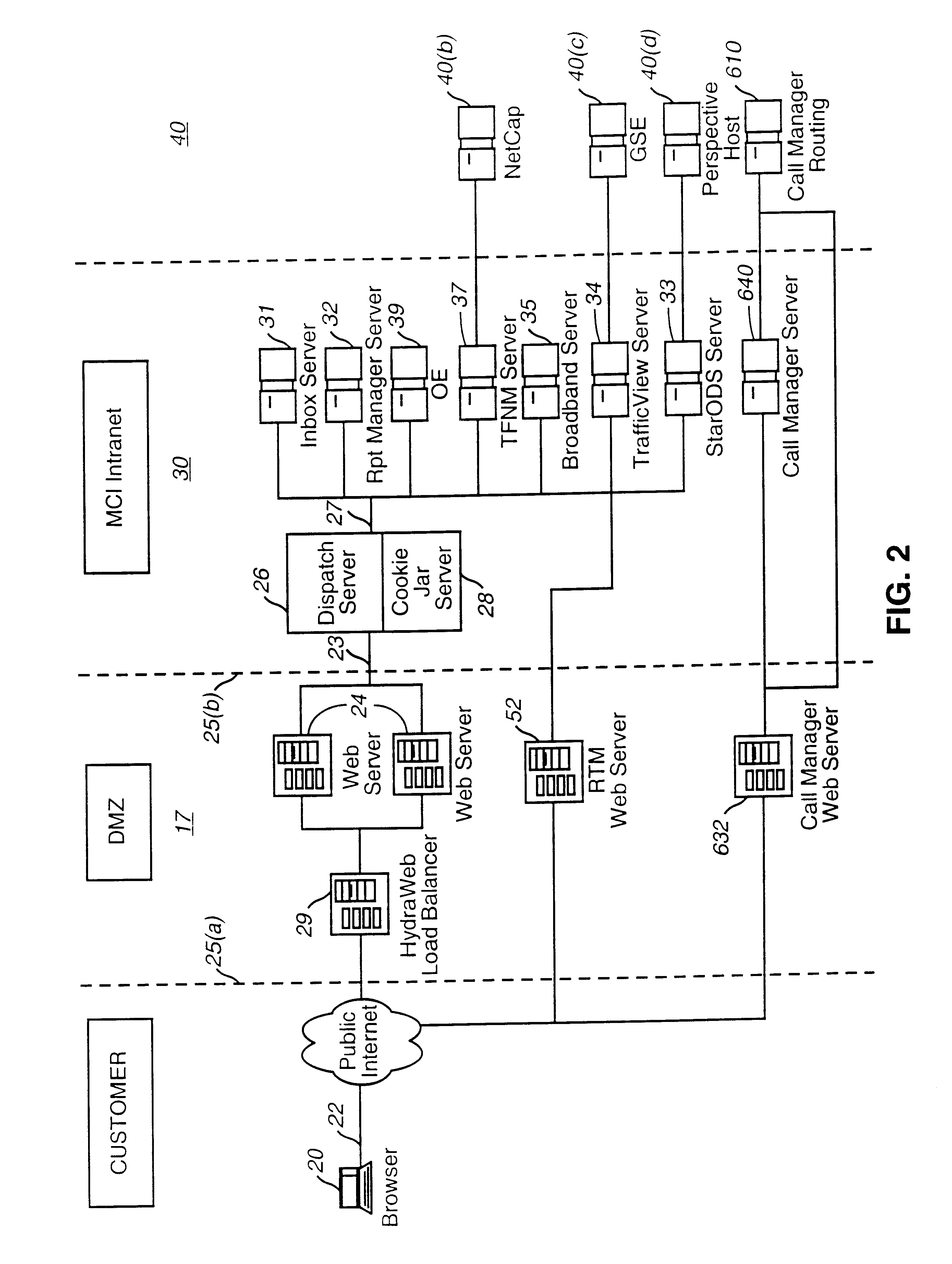
A Web-based call routing management workstation application which allows authorized customers to control toll free routing and monitor call center status. An architecture including one or more web servers located in a firewalled demilitarized zone (DMZ) as communications medium between the customer workstations at the customer sites and the enterprise back-end applications providing the call routing management services, provides a secure infrastructure for accessing the enterprise applications via the otherwise insecure public Internet. The present invention enables creation and management of call by call routing rules by a customer with a workstation having an Internet access and a supported Web browser. The customized rules may be tested and / or debugged via the Web-enabled workstation, using a debugger / tester which runs the routing rules under a simulated environment. In addition, customers may provision hierarchies for their business; create, modify or delete agent pools; manipulate capacity tables; and define quota schemes, value lists and schedule tables, all at the customer site via the Web-enabled workstation. The present invention also enables the customers to view near real-time displays of call center ACD statistics and peg counts based on routing rules, as well as, run provisioning and statistical reports on provisioning and statistical data and also to extract the data for further analysis. Additionally, the present invention supports foreign language and branding features on a graphical user interface. An infrastructure is provided which enables secure initiation, acquisition, and presentation of the call manager functionalities to customers from any computer workstation having a web browser and located anywhere in the world.
Owner:VERIZON PATENT & LICENSING INC
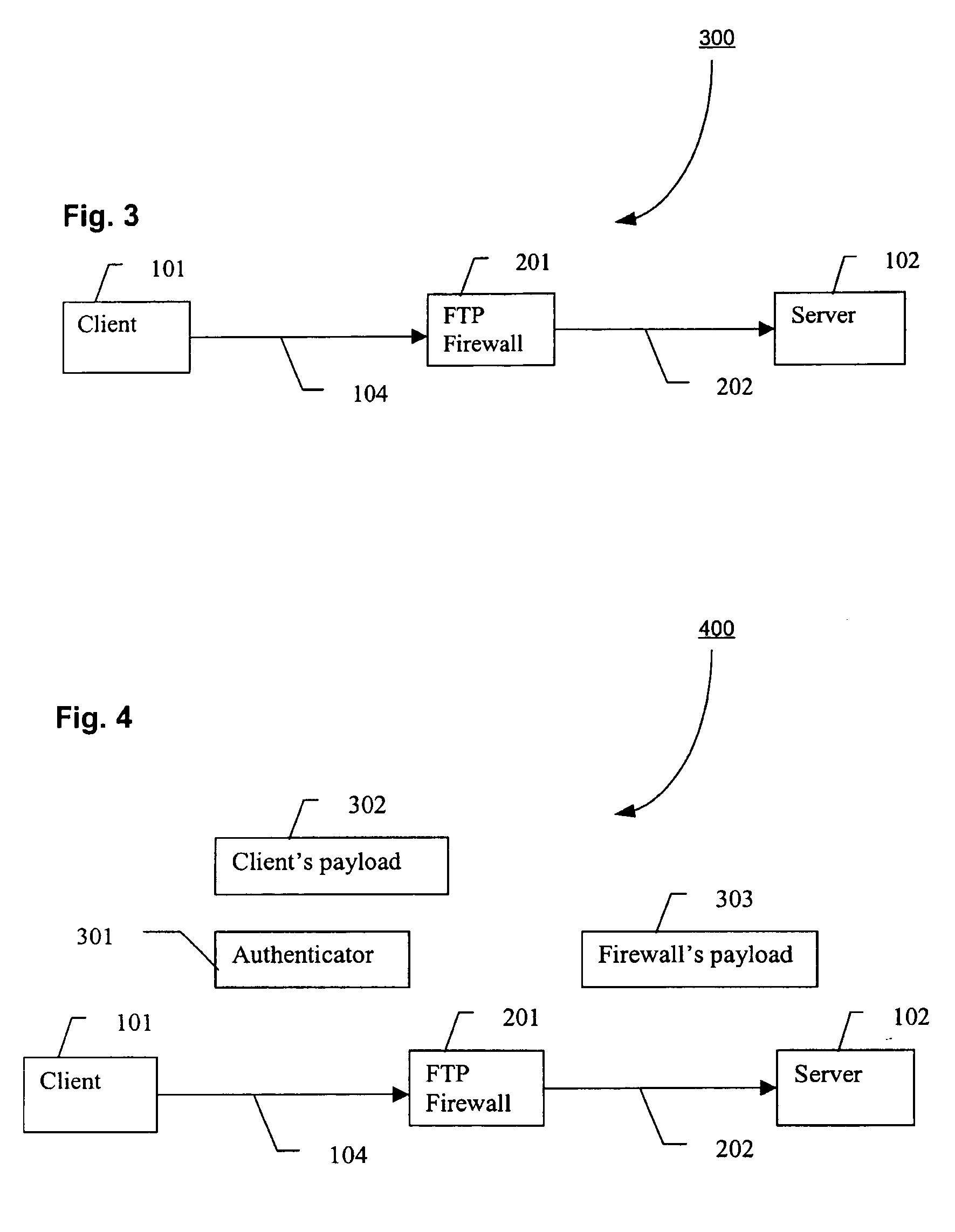
Payload layer security for file transfer
InactiveUS20060190723A1Communication securityEasy to optimizeSecuring communicationTimestampClient-side
A method for providing file transfer security includes receiving an authentication file including a first key and authentication information, extracting the first key from the authentication file, decrypting the authentication information with the first key, and validating the authentication information. The authentication information is encrypted, and may include a nonce, a timestamp, and / or a second key. A system for providing file transfer security includes a DMZ proxy programmed and configured to receive an authentication file from a client including authentication information. The DMZ proxy extracts a first key from the authentication file, decrypts the authentication information with the first key, and validates the authentication information.
Owner:JPMORGAN CHASE BANK NA
Client-server-communication system
InactiveUS20050251855A1Save resourcesImprove securityUser identity/authority verificationUnauthorized memory use protectionCommunications systemClient-side
A client-server-communication comprises at least one internet-based client and at least one intranet-based server located in an intranet system. A demilitarized zone is defined between an outbound firewall system to the internet and an inbound firewall system to the intranet system. A proxy server is located in this demilitarized zone and provides for any communication connection to at least one of the intranet-based servers required from one of the internet-based clients.
Owner:HOB GMBH & CO KG
Method, system and software for maintaining network access and security
InactiveUS20050240994A1Digital data processing detailsMultiple digital computer combinationsSecure communicationMultiplexing
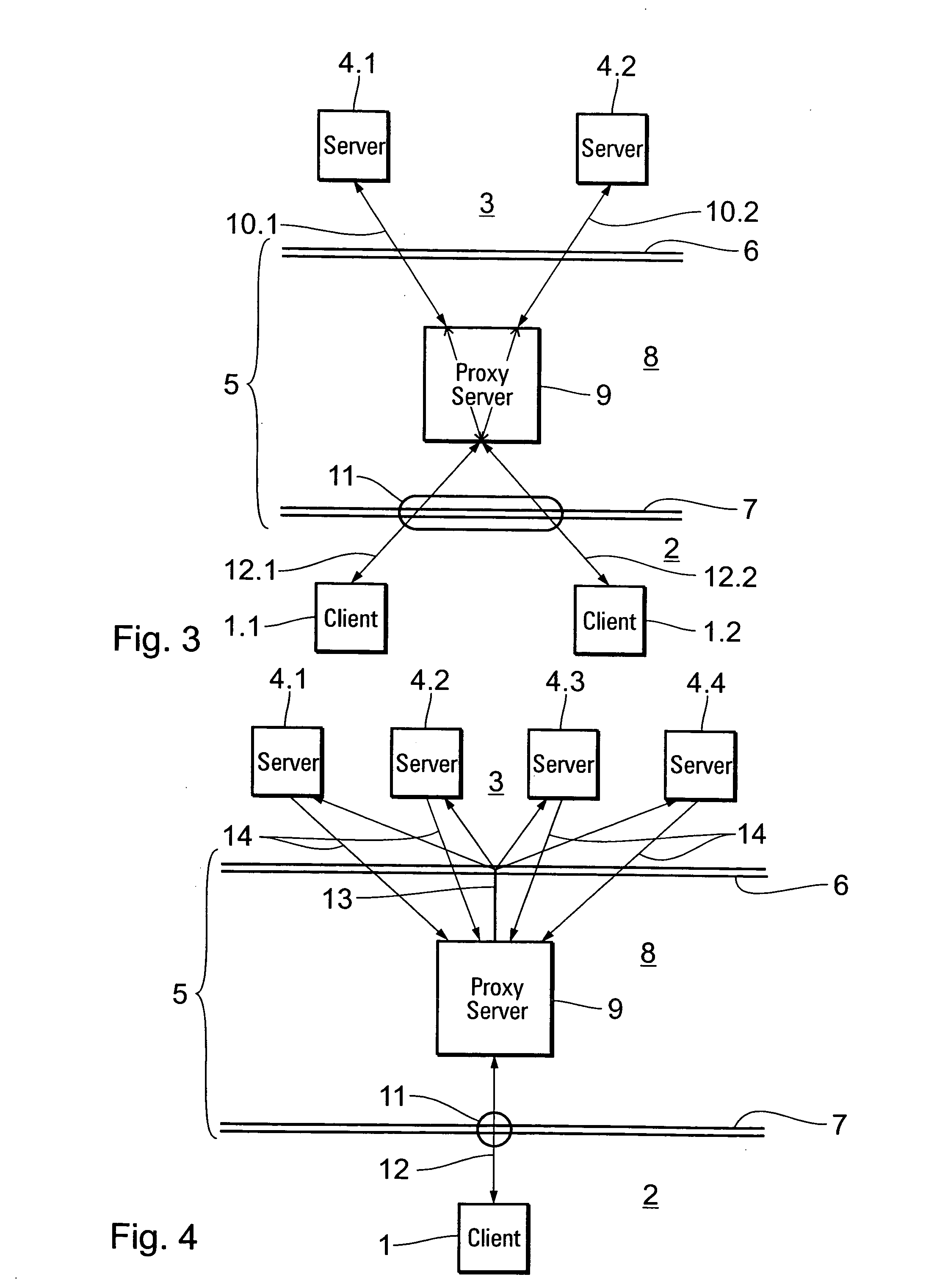
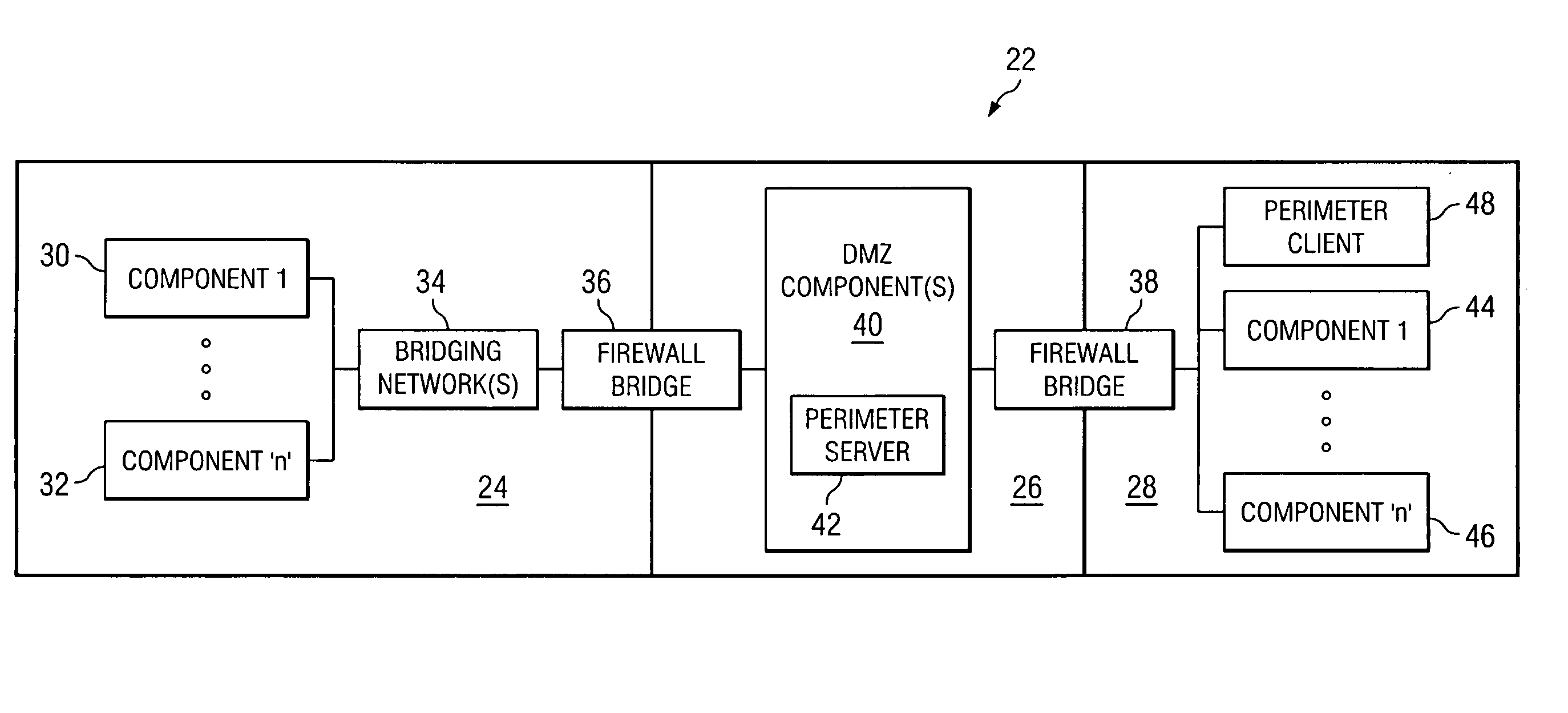
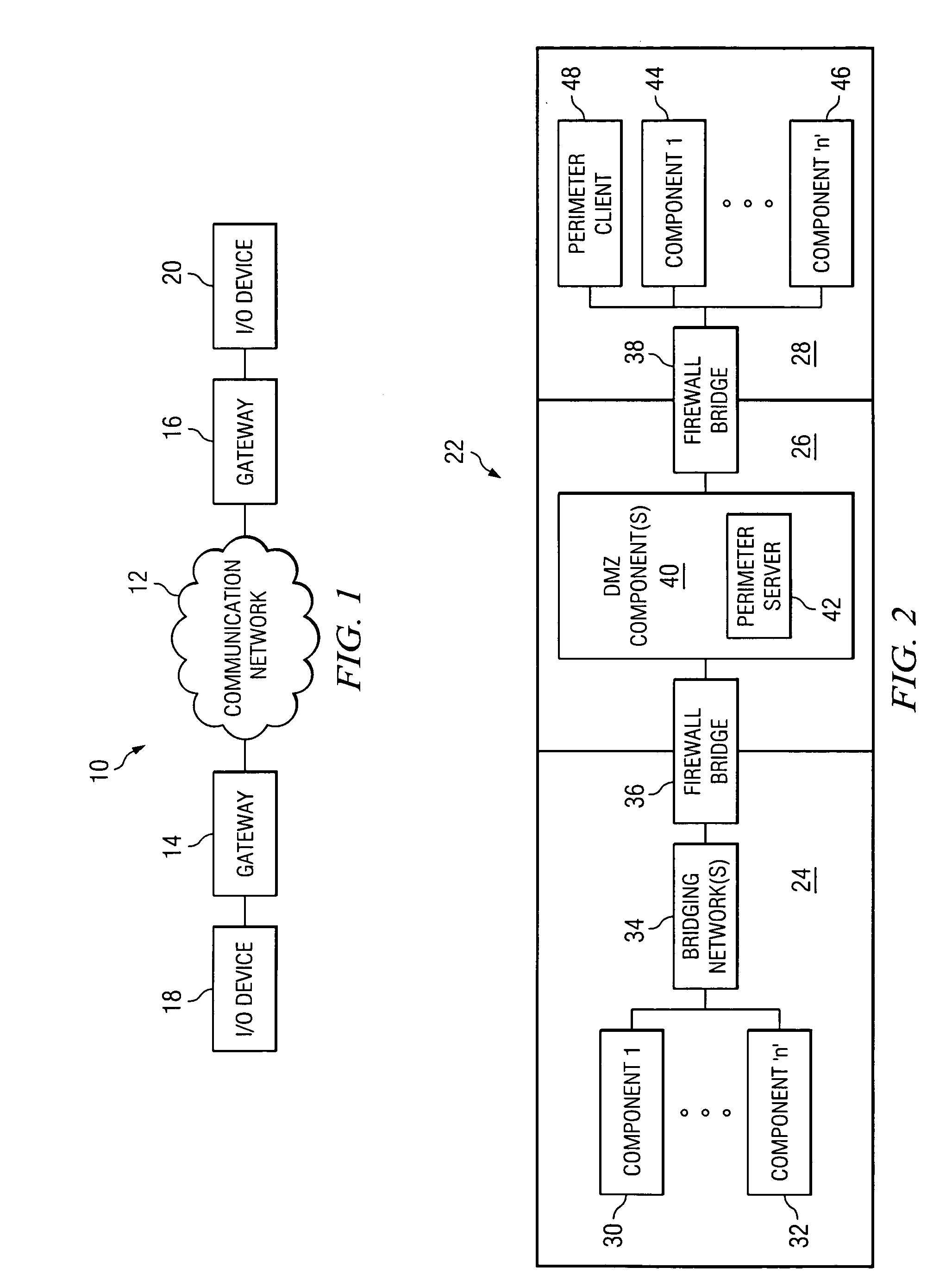
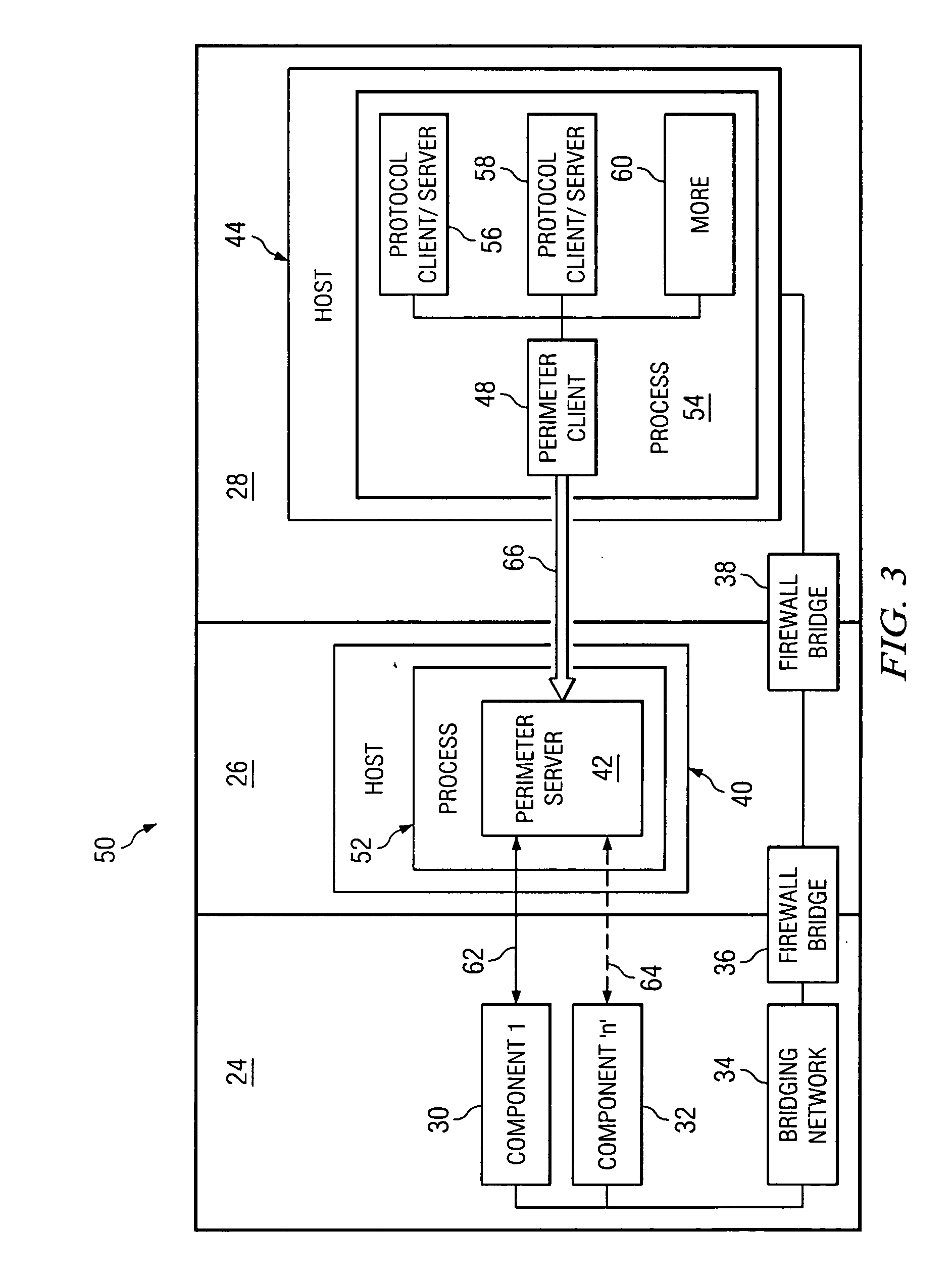
A system, method and apparatus for securing communications between a trusted network and an untrusted network are disclosed. A perimeter client is deployed within the trusted network and communicates over a session multiplexing enabled protocol with a perimeter server deployed within a demilitarized zone network. The perimeter client presents requests to make available and communication initiation requests to the perimeter server which presents corresponding sockets to the untrustred network. The session multiplexing capabilities of the protocol used between the perimeter server and perimeter client permit a single communication session therebetween to support a plurality of communication sessions between the perimeter server and untrusted network. In the event data flows across the communication sessions are encrypted, decryption of the data flows is left to the components at the end points of the communication session, thereby restricting exposure of privileged information to areas within trusted networks.
Owner:SBC KNOWLEDGE VENTURES LP +1
Method for realizing security isolation of virtual machine based on OpenStack
PendingCN112099913AImprove securitySoftware simulation/interpretation/emulationNetwork onEngineering
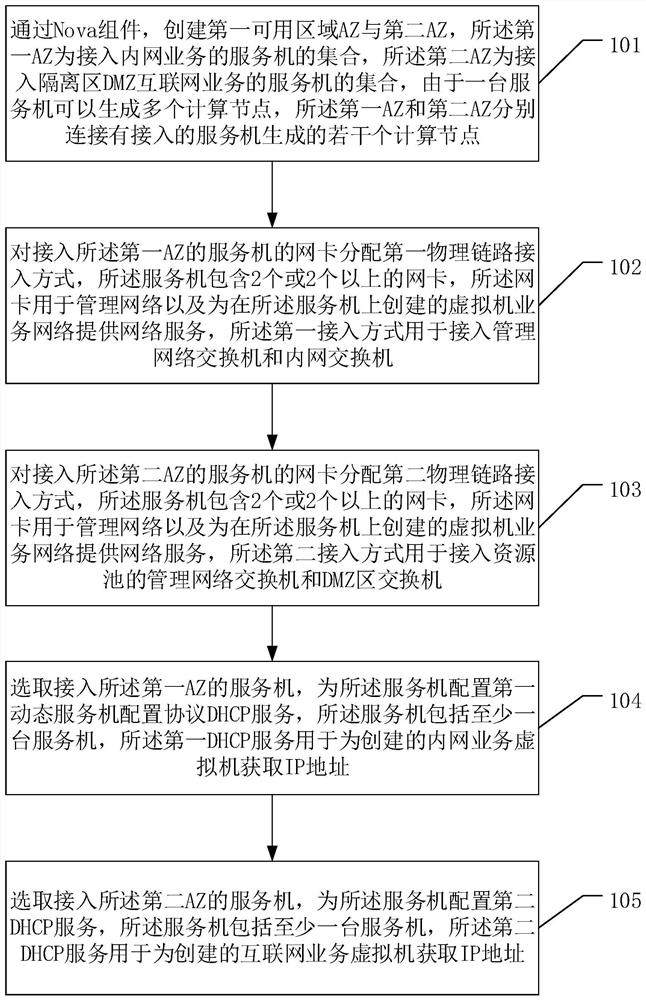
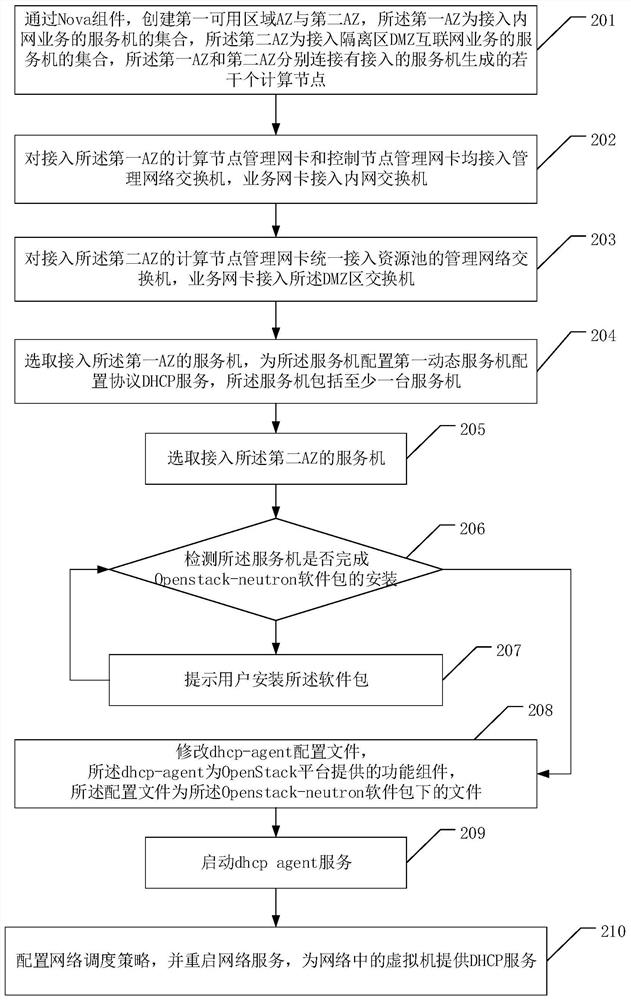
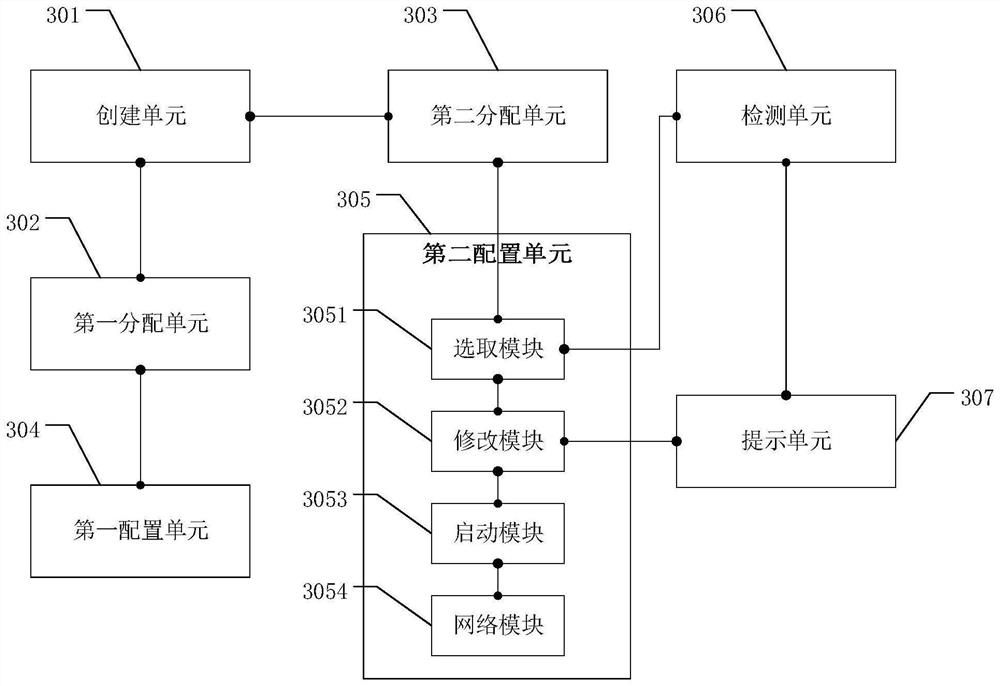
The invention discloses a method for realizing virtual machine security isolation based on OpenStack and a related device, and realizes isolation between a virtual machine accessing an Internet service on an OpenStack platform and an intranet application virtual machine on a network. The method comprises the following steps: creating a first available area AZ and a second available area AZ througha Nova component; allocating a first physical link access mode to network cards of a server accessed to the first AZ, the server comprising two or more than two network cards, and the first physicallink access mode being used for accessing a management network switch and an intranet switch; allocating a second physical link access mode to network cards of a server accessed to the second AZ, theserver comprising two or more than two network cards, and the second physical link access mode being used for accessing the management network switch and a DMZ area switch; selecting the server accessed to the first AZ, and configuring a first dynamic host configuration protocol DHCP service for the server; and selecting the server accessed to the second AZ, and configuring a second DHCP service for the server.
Owner:北京思特奇信息技术股份有限公司
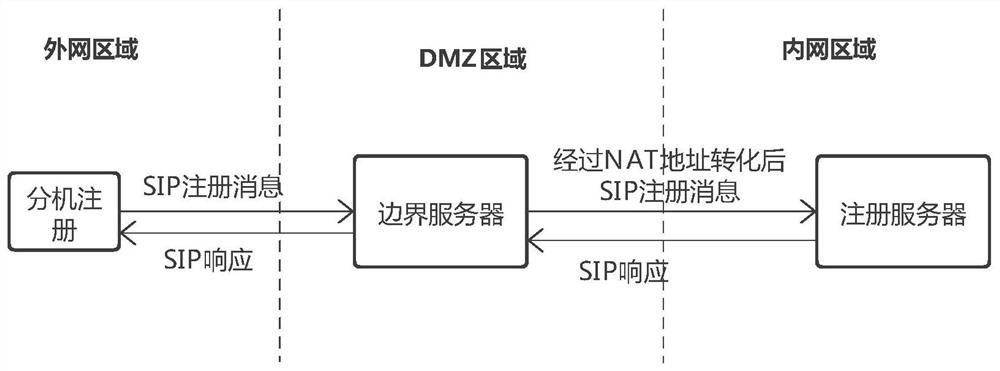
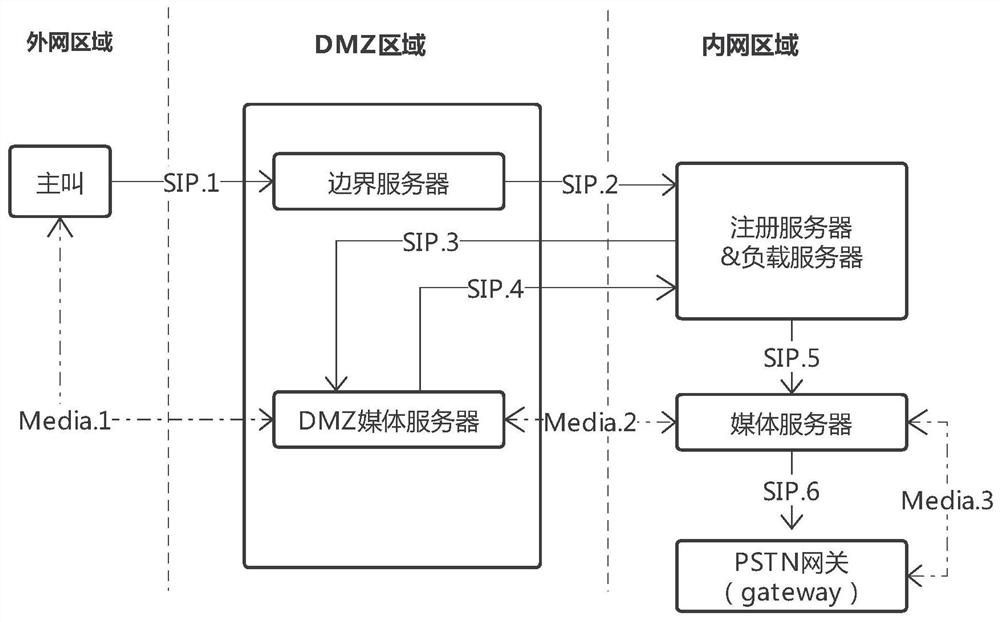
SIP WebRTC gateway system capable of penetrating DMZ network
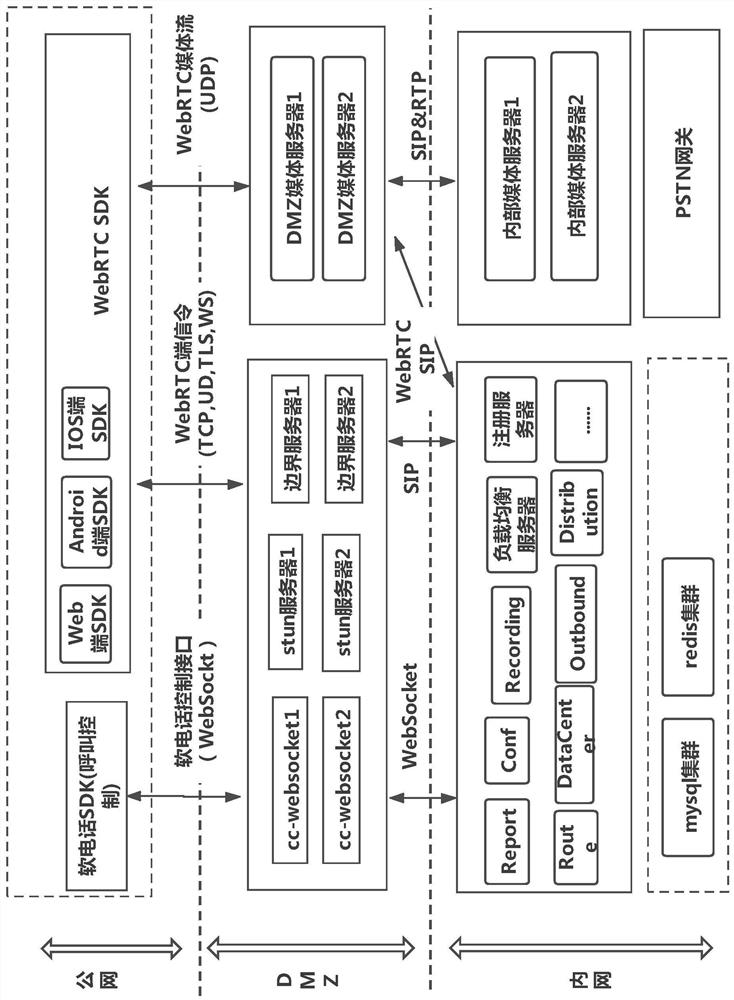
The invention discloses an SIP WebRTC gateway system capable of penetrating through a DMZ network. The system comprises an extranet module, a DMZ network module and an intranet module. The extranet module comprises a softphone SDK and a WebRTC terminal SDK; the DMZ network module comprises an SIP boundary server and a DMZ media server; the intranet module comprises an intranet internal media server and a registration server / load balancing server, wherein the registration server is used for realizing registration, and the load balancing server is used for interacting with the DMZ media server or interacting with the internal media server; and the DMZ media server is used for establishing a media transmission channel with a calling party and establishing a media transmission channel with the intranet media server, or respectively establishing a media transmission channel with the calling party and the called party, and establishing a media transmission channel with the intranet media server. According to the application, through the DMZ network module, the media transmission channel between the intranet media server and the extranet terminal is established, and voice communication between the extranet and the intranet is realized.
Owner:上海井星信息科技有限公司
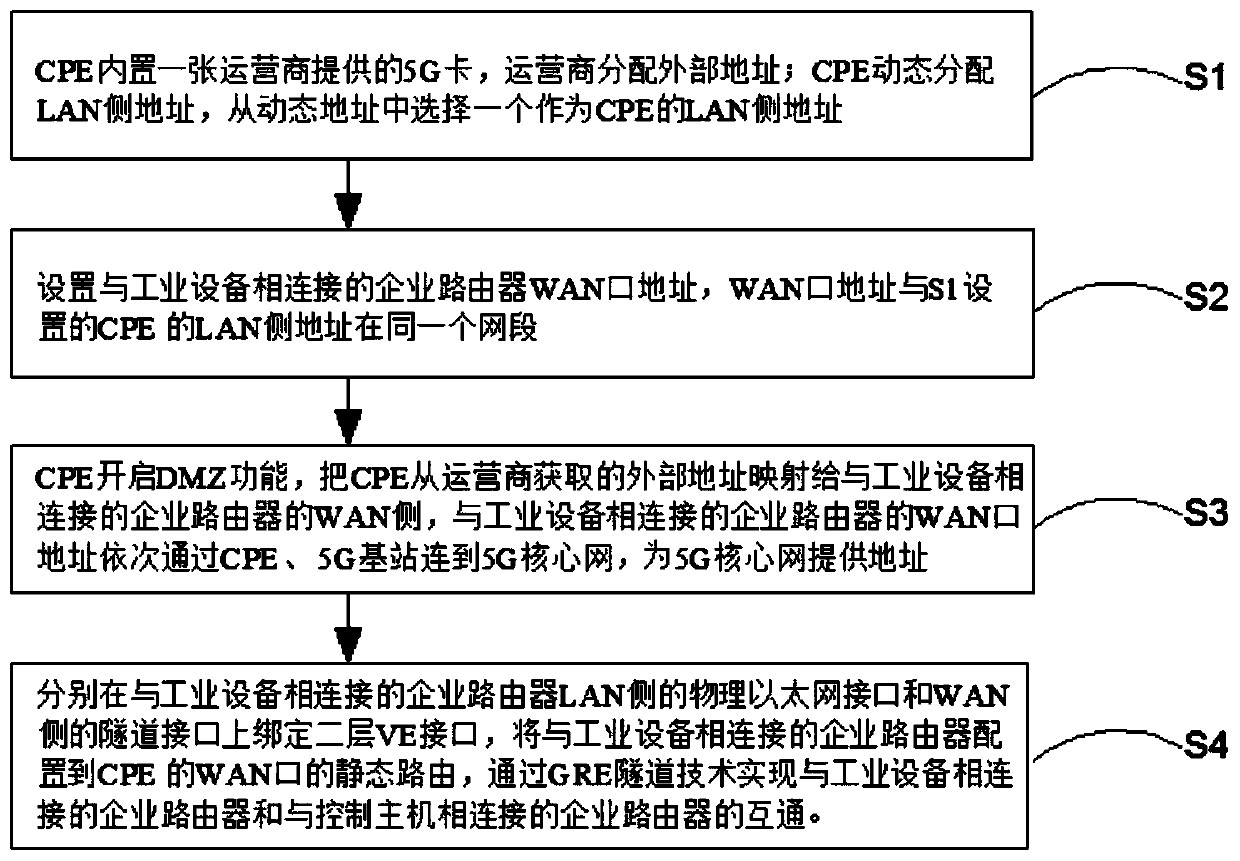
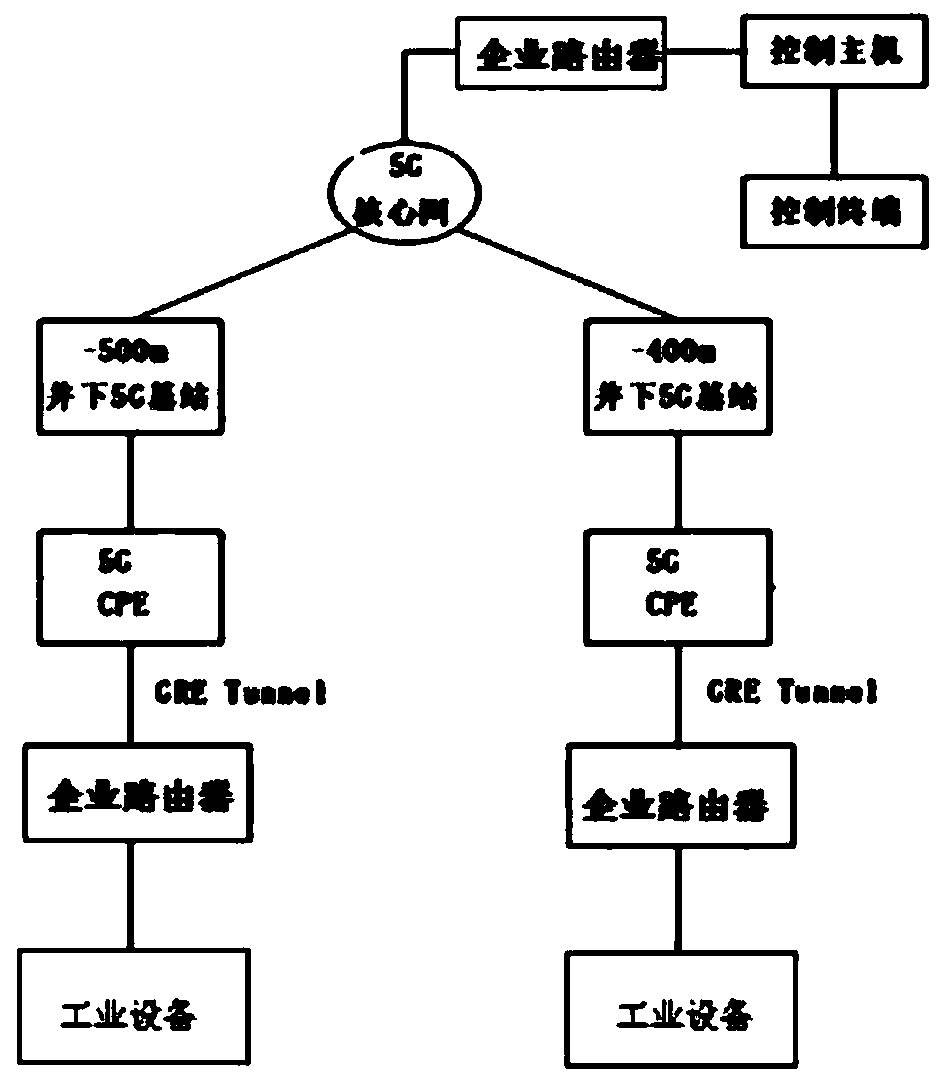
Method and system for realizing two-layer communication between CPE and enterprise router
InactiveCN111465038AReal-time high-precision control responseNetworks interconnectionWireless communicationPrivate networkBusiness enterprise
The invention provides a method and a system for realizing two-layer communication between CPE and an enterprise router. According to the invention, setting is carried out at a WAN port of an enterprise router connected with industrial equipment; services are provided for private network addresses in a DMZ port mapping mode; two layers of VE interfaces are bound to a physical Ethernet interface onthe LAN side and a tunnel interface on the WAN side of an enterprise router connected with industrial equipment respectively; the Ethernet message is transparently transmitted through the GRE tunnel,the tunnel from the enterprise router connected with the industrial equipment to the WAN port of the CPE is opened, the LAN port of the CPE is directly connected with the enterprise router connectedwith the industrial equipment, and the two-layer networks on the two sides are opened through the network. According to the method and the system provided by the invention, data exchange between the industrial detection and execution equipment of the terminal and the industrial control host can be realized, real-time and high-precision control response is realized, and a new path is pointed out for the development of a 5G technology and the upgrading of industrial control equipment.
Owner:SHANDONG GOLD MINING IND LACEY CO LTD
Enterprise network security management method
PendingCN113676469AReduce riskImprove securityUser identity/authority verificationWide area networksBusiness enterpriseProtocol for Carrying Authentication for Network Access
The invention discloses an enterprise network security management method, which comprises the following steps of: constructing a DMZ firewall between an enterprise network and an extranet to realize the functions of real IP hiding and access control, and establishing an IPSecVPN between a head office and a branch company to realize security information transmission of intranets in different regions, so that the risk is reduced, and the security is improved. Port security is configured on a two-layer switch, a data packet threshold value through which the port passes is preset, or MAC addresses allowed to be connected to the switch port are recorded through an MAC address table, a specific number or specific MAC addresses are allowed to use the port for communication, illegal equipment is prevented from accessing a network, MAC address table overflow caused by MAC address flooding can also be prevented, and by dividing vlan, the broadcast storm is reduced, and the pressure of the two-layer switch is fully shared; and in addition, link binding aggregation is used, the transmission bandwidth between the switches is increased, bidirectional authentication is carried out by configuring a PPP protocol and adopting chap, connection of illegal users is prevented, and the safety is further improved.
Owner:YANCHENG INST OF TECH
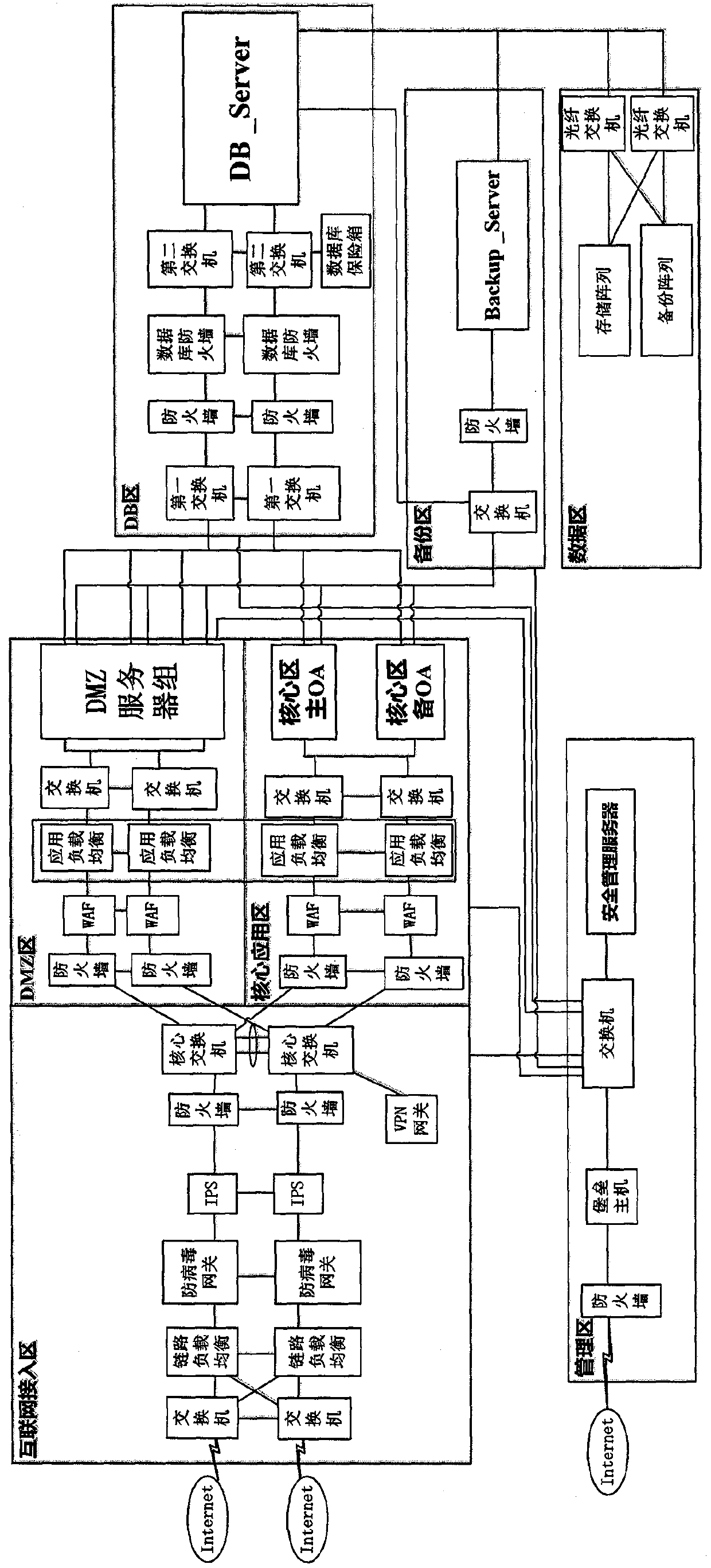
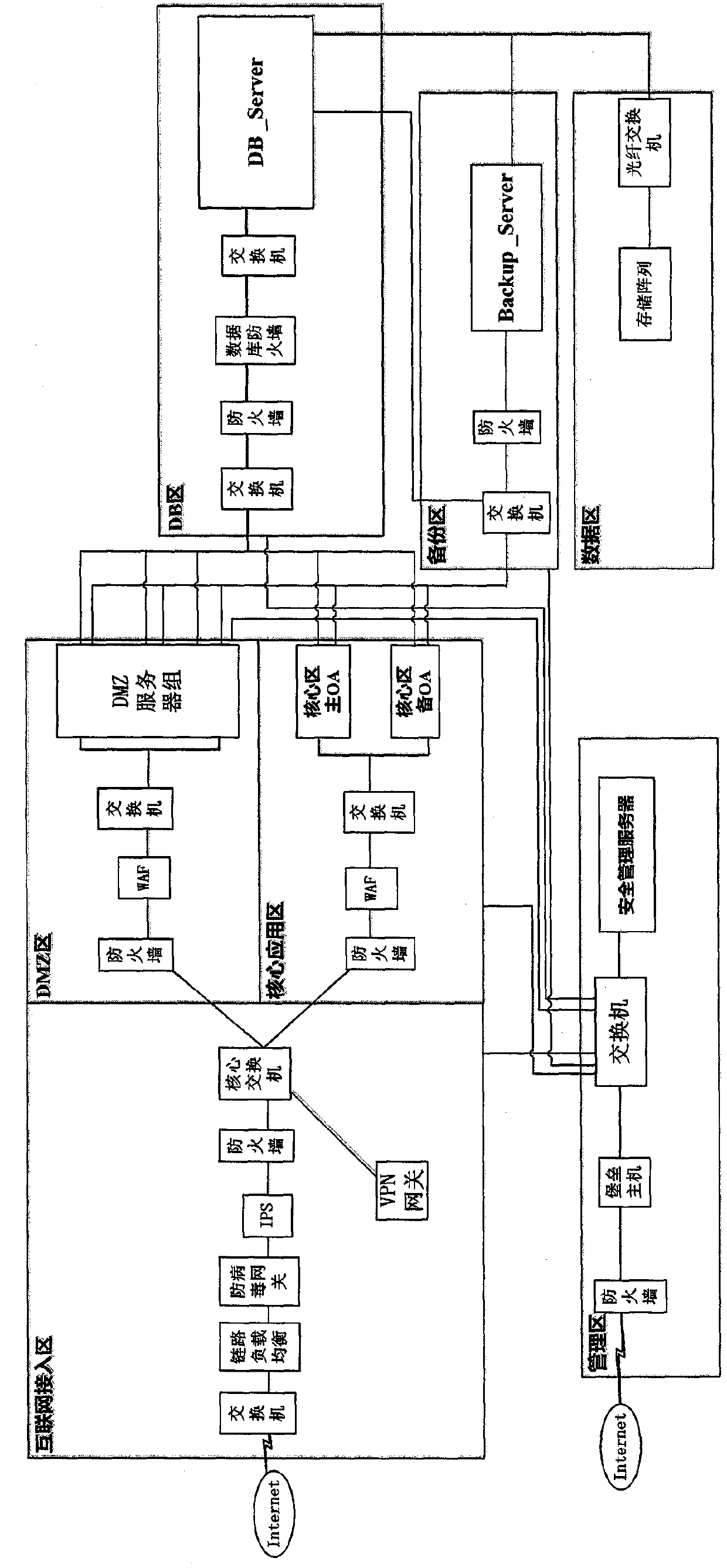
Depth defense system for effectively responding to APT (Advanced Persistent Threat) attacks
ActiveCN107659582AReduce in quantityReduce attack pathsData switching networksHigh level techniquesAttackNetwork structure
The invention relates to a depth defense system for effectively responding to APT (Advanced Persistent Threat) attacks. The depth defense system comprises an Internet access area, a DMZ area, a core application area, a DB area, a data area, and a management area; the DMZ area is connected with the Internet access area; the core application area is connected with the Internet access area; the DB area is respectively connected with the DMZ area and the core application area; and the management area is respectively connected with the Internet access area, the DMZ area, the core application area and the DB area. The depth defense system provided by the invention adopts a deep network structure, which reduces the number of regional firewalls, reduces the equipment cost, shares the load to various hierarchical networks, realizes the function of releasing the pressure of a core switch, and improves the service life of the switch; besides, the division of functional modules is realized, and the controllability of each functional module is improved; and all functional sub-networks are of the closed loop design, and the security of the system is improved.
Owner:李刚
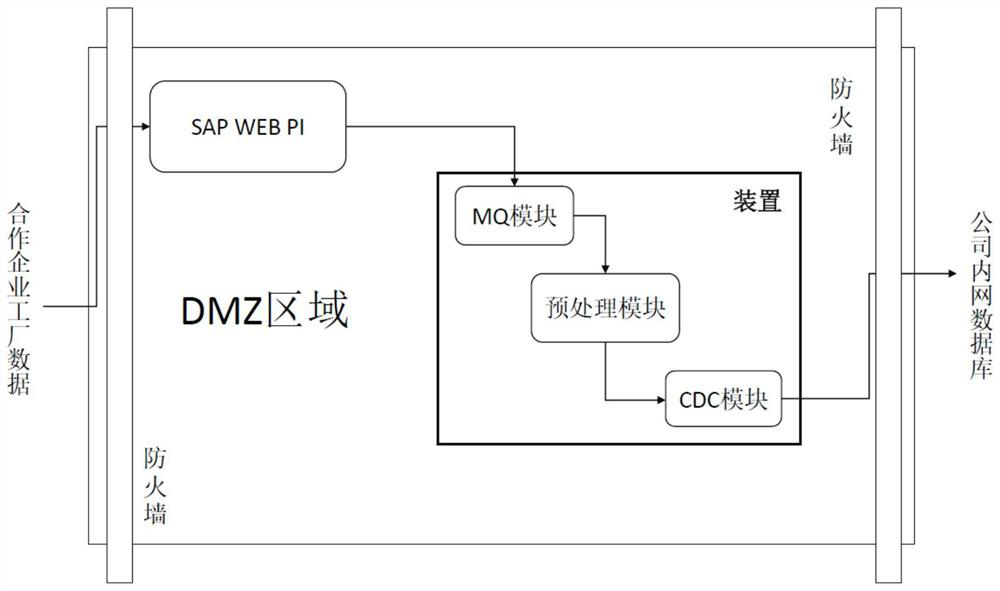
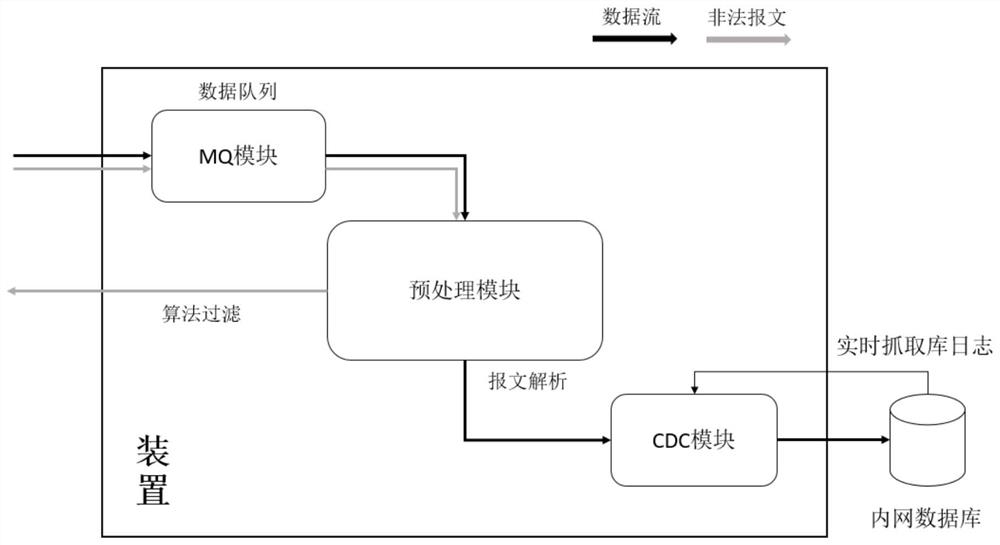
Method and device for improving safety of data interaction between enterprises
PendingCN112241540AEffective protectionImprove efficiencyDigital data protectionData transformationData stream
The invention discloses a method and device for improving safety of data interaction between enterprises. The device is arranged in a DMZ space deployed between an enterprise intranet and an externalnetwork. The device comprises an MQ module used for organizing external incoming data in a message queue mode; a preprocessing module used for sequentially preprocessing the data organized by the message queue, wherein preprocessing comprises data cleaning, data integration and data transformation; and a CDC module used for synchronizing the preprocessed data flow to an enterprise intranet database in real time by adopting a changed data capture mode. According to the device and the method, high security and high stability of data exchange between enterprises are improved.
Owner:CHINA TOBACCO ZHEJIANG IND
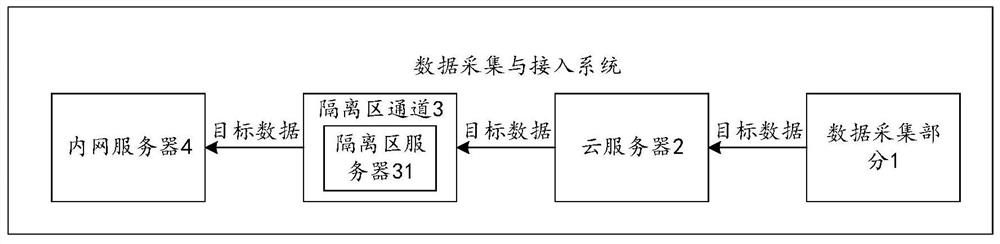
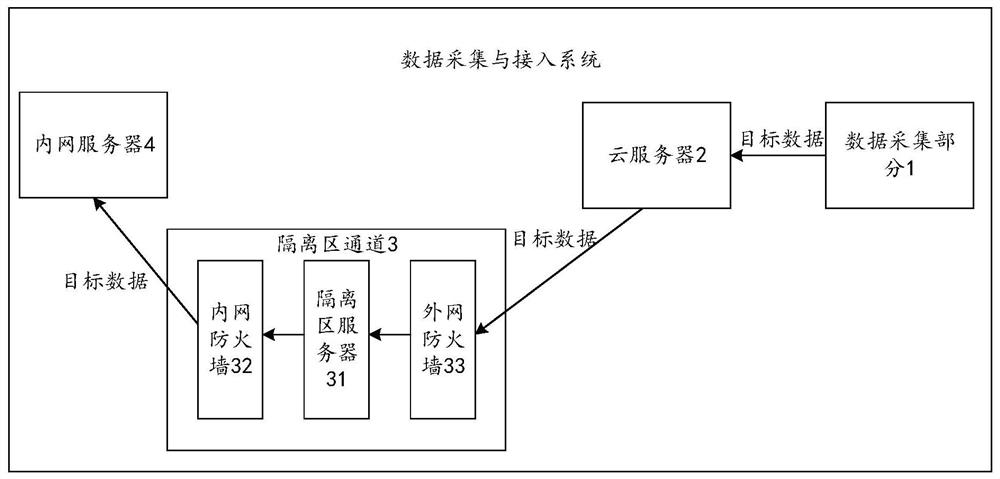
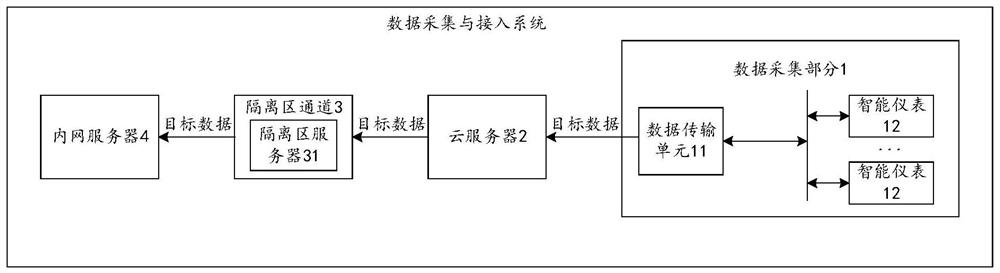
Data acquisition and access system
PendingCN114745398ARealize acquisitionCompliance with safety regulationsParticular environment based servicesTransmissionBusiness enterpriseData acquisition
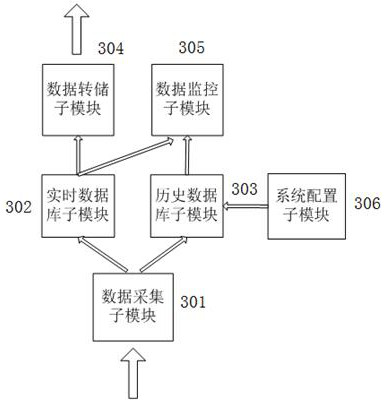
The invention provides a data acquisition and access system, and belongs to the technical field of oil field information. The system comprises a data acquisition part, a cloud server, a DMZ channel and an intranet server, the data acquisition part is located at an acquisition site, the cloud server is located outside an enterprise, the intranet server is located inside the enterprise, and the cloud server is used for sending a data acquisition request to the data acquisition part when data acquisition conditions are met, and receiving the target data sent by the data acquisition part, and sending a first message comprising the target data to the DMZ server through address information of the DMZ server in the DMZ channel. And the DMZ server is used for determining the address information of the intranet server according to the corresponding relationship between the stored address information of the DMZ server and the address information of the intranet server, and sending a second message comprising the target data to the intranet server through the address information of the intranet server. According to the invention, the system for accessing the collected data to the internal network of the oilfield enterprise is provided.
Owner:PETROCHINA CO LTD
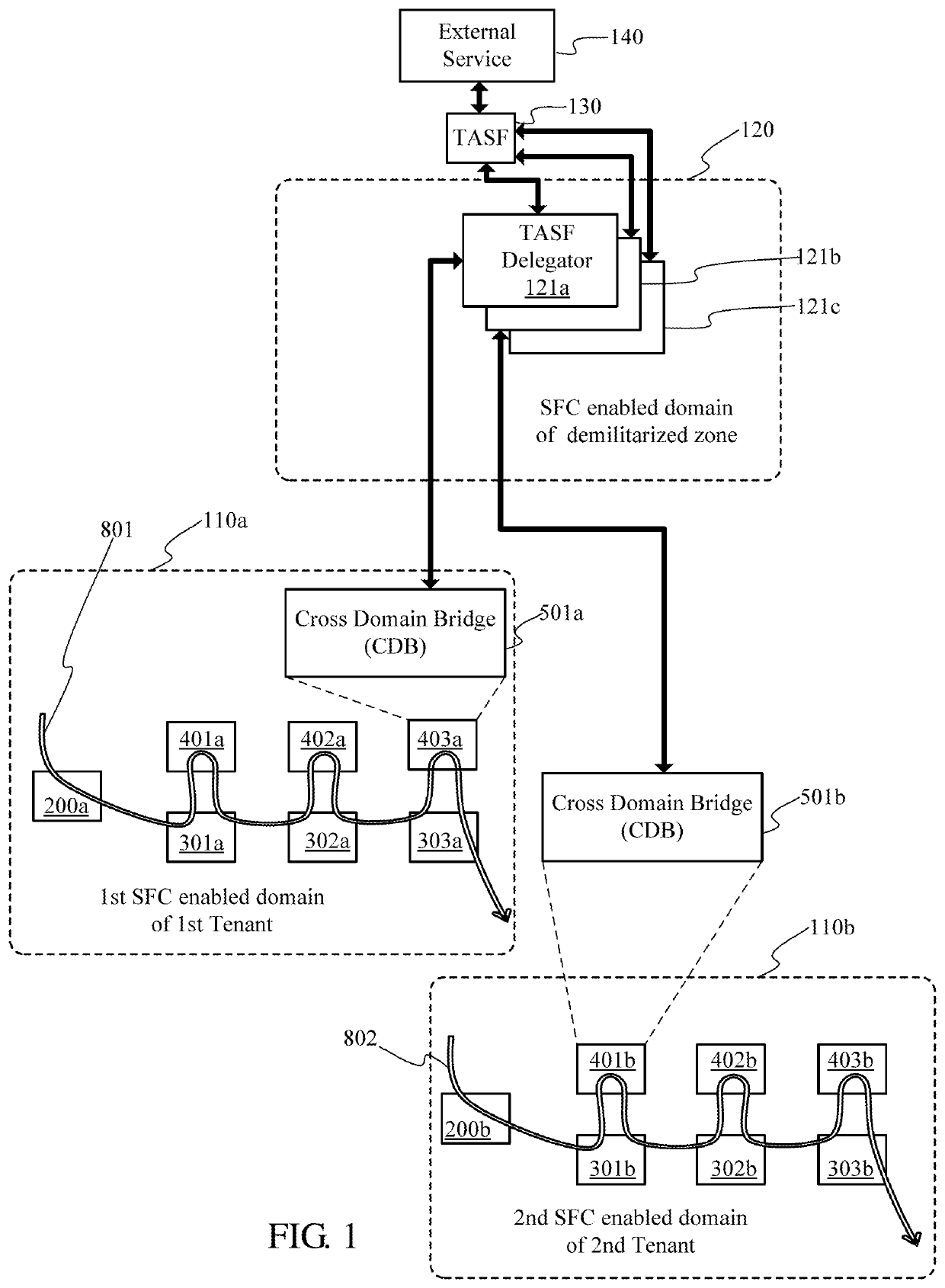
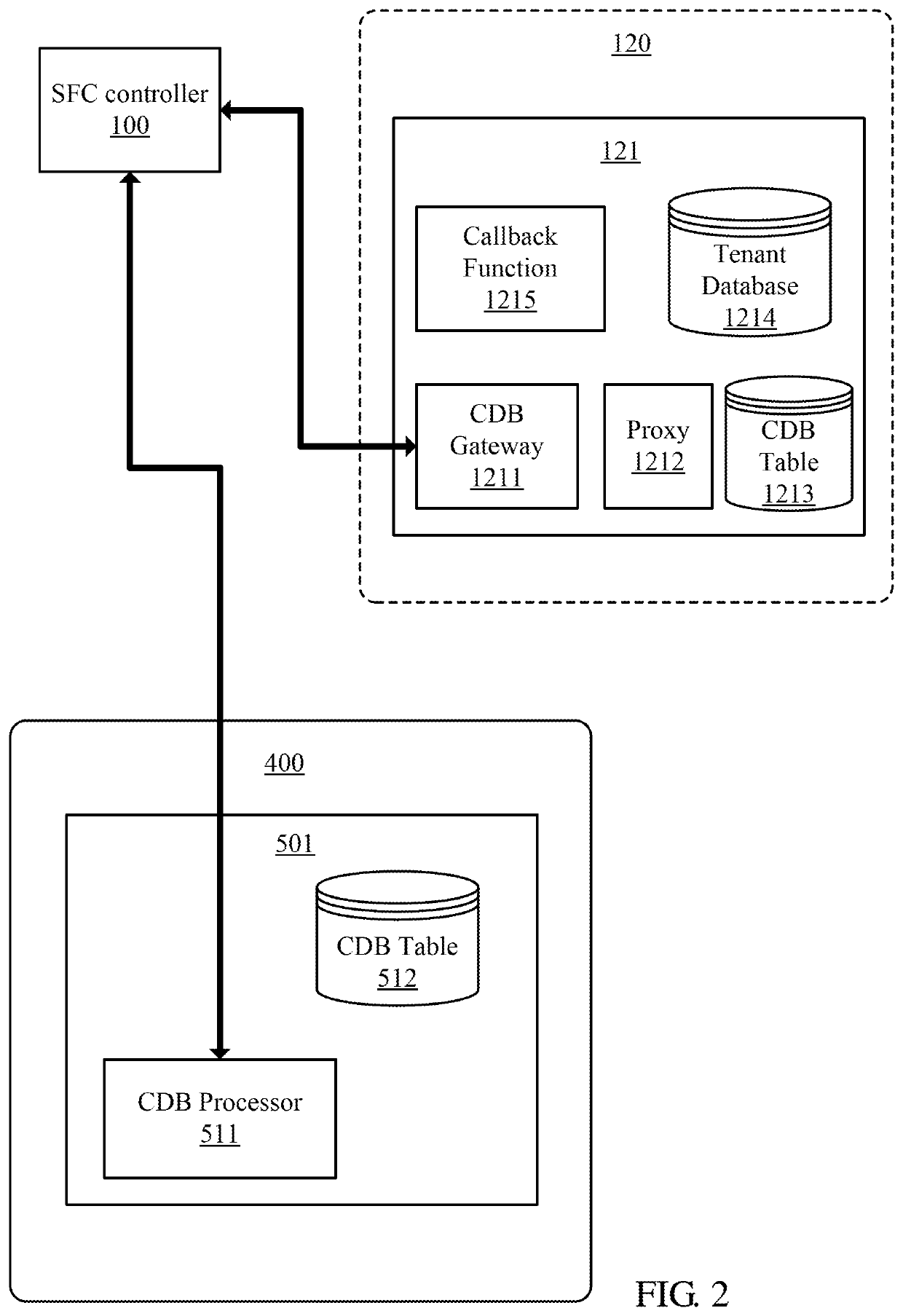
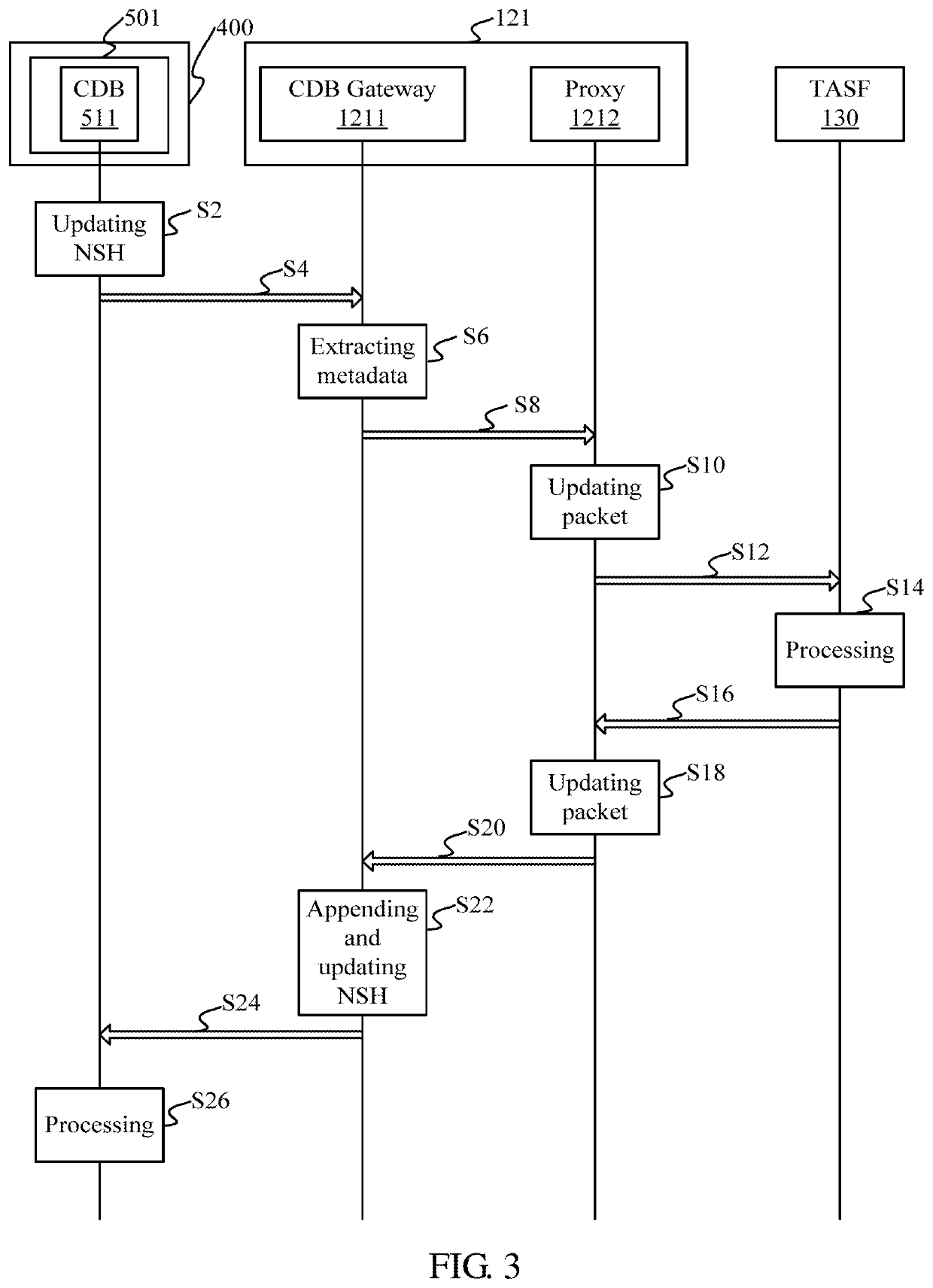
Service function chain (SFC) based multi-tenancy processing method
ActiveUS20200162562A1Networks interconnectionSoftware simulation/interpretation/emulationData packData set
A service function chain (SFC) based multi-tenancy processing method. The disclosed method allows isolation between SFC enabled domains while facilitating aggregation of tenant related data sets from SFC packet flows of various service function paths (SFPs) through cross domain bridges (CDB) in SFC enabled domains, delegators in a demilitarized zone, and a tenant aware service function (TASF). A CDB serves as a service function (SF) in a SFP and also serves as a classifier forwarding SFC packets to the demilitarized zone. A CDB gateway serves as a classifier in a delegator receives the SFC packets from the CDB. The TASF collects information from the SFC packets.
Owner:NANNING FUGUI PRECISION IND CO LTD
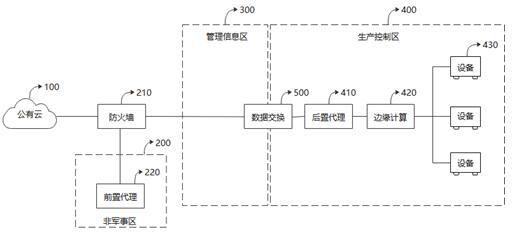
Security system and method based on data exchange between cloud end and edge end
PendingCN113709109AUser identity/authority verificationCharacter and pattern recognitionThe InternetIndustrial Internet
The invention relates to a security system and method based on data exchange between a cloud end and an edge end. The system comprises a data exchange front agent, which is disposed in a non-military area of an enterprise network, is connected with a public cloud network through an enterprise firewall, and carries out the bidirectional identity authentication based on a digital certificate. A security data exchange device is arranged between the management information area and the production control area of the enterprise; a data exchange post agent is arranged in the enterprise production control area; the rear agent exchanges data with the front agent in the non-military area through the security data exchange equipment; and the edge computing node in the enterprise production control area downloads the artificial intelligence model and parameters from the cloud through the rear agent, collects process data from the production equipment, and operates an artificial intelligence algorithm. The method accords with the existing security policy of an industrial enterprise, and solves the security problem of data exchange between the cloud end and the edge end in the industrial internet artificial intelligence application at three levels of a network layer, a transmission layer and an application layer.
Owner:YUNNAN KUNGANG ELECTRONICS INFORMATION TECH CO LTD
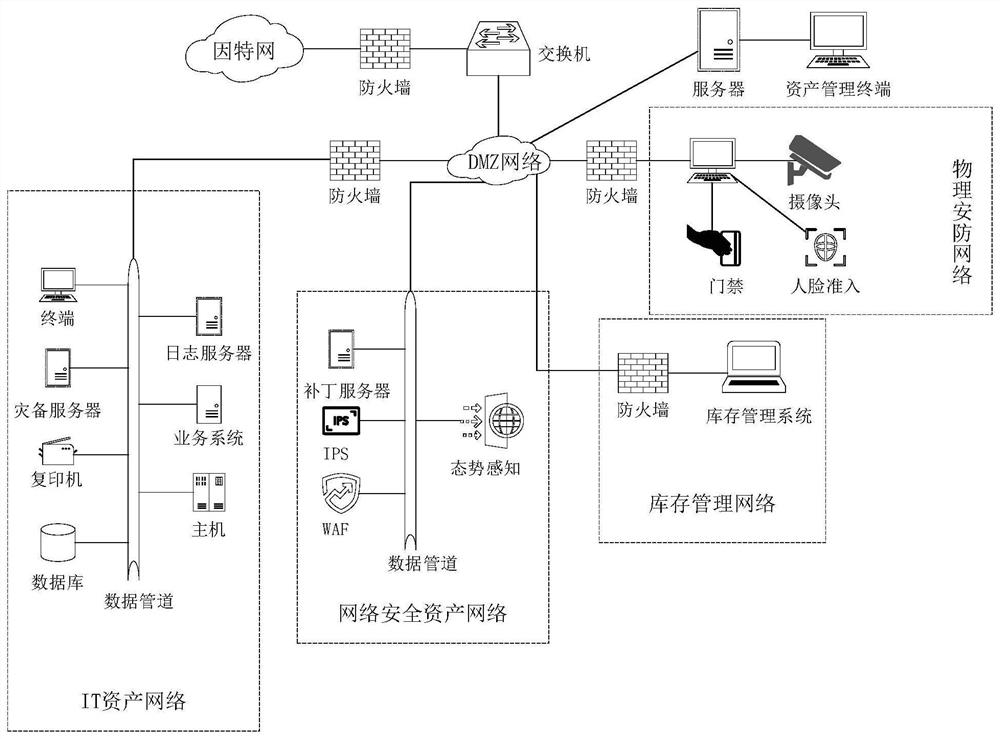
Asset whole-process management system
InactiveCN113570274AImprove comprehensivenessImprove orderHardware monitoringOffice automationPhysical securityOnline and offline
An asset whole-process management system comprises a DMZ network, an inventory management network, a network security asset network, an IT asset network, a physical security network and an asset management platform. The asset management platform is connected with the other four network spaces through a DMZ network, acquires asset data from the other network spaces through an API, and can perform batch online and offline operation on equipment in the network; and when the risk information is found, the risk information is transmitted to the safety equipment through the API to be handled. The system can be compatible with an existing asset management system, can record, track, audit and monitor IT assets, and has the advantages of being good in integration, high in compatibility degree, excellent in performance, comprehensive in management type and good in safety.
Owner:XIAN THERMAL POWER RES INST CO LTD
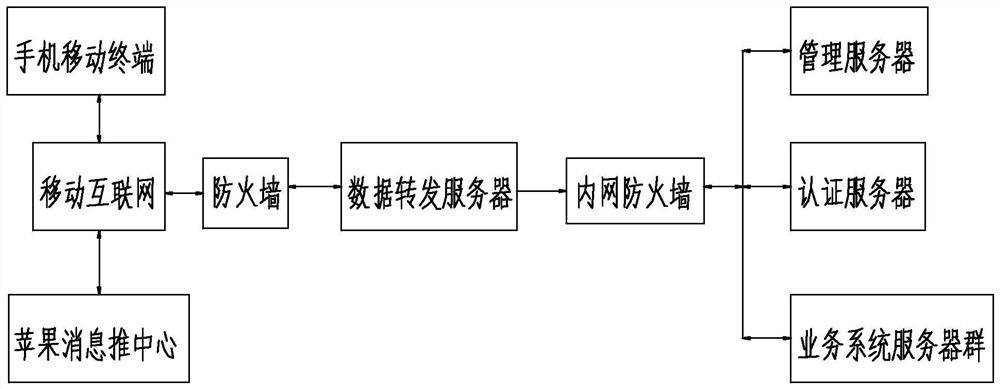
Secure Network Tunnel for Mobile Apps
The invention relates to a mobile application secure network tunnel, mainly comprising mobile Internet data, a mobile secure network SDK software packet, a firewall interface, a data forwarding server, an enterprise network internal firewall and a mobile secure tunnel management server. According to the tunnel, after an SDK software data packet is integrated in a mobile device APP, the mobile Internet data is input and the mobile secure tunnel management server is deployed in a DMZ area of an enterprise internal network, a user can access data of the enterprise internal network through the mobile application secure network tunnel; a network communication type of the tunnel is a TCP type; HTTP and UDP type protocol encryption is compatible; SSL encryption is carried out on a mobile application data forwarding process; the mobile secure tunnel is used for securely transmitting the mobile network data between the enterprise internal network and a public network; and all background server access can be supported only by arranging a port on the firewall.
Owner:深圳安软信创技术有限公司
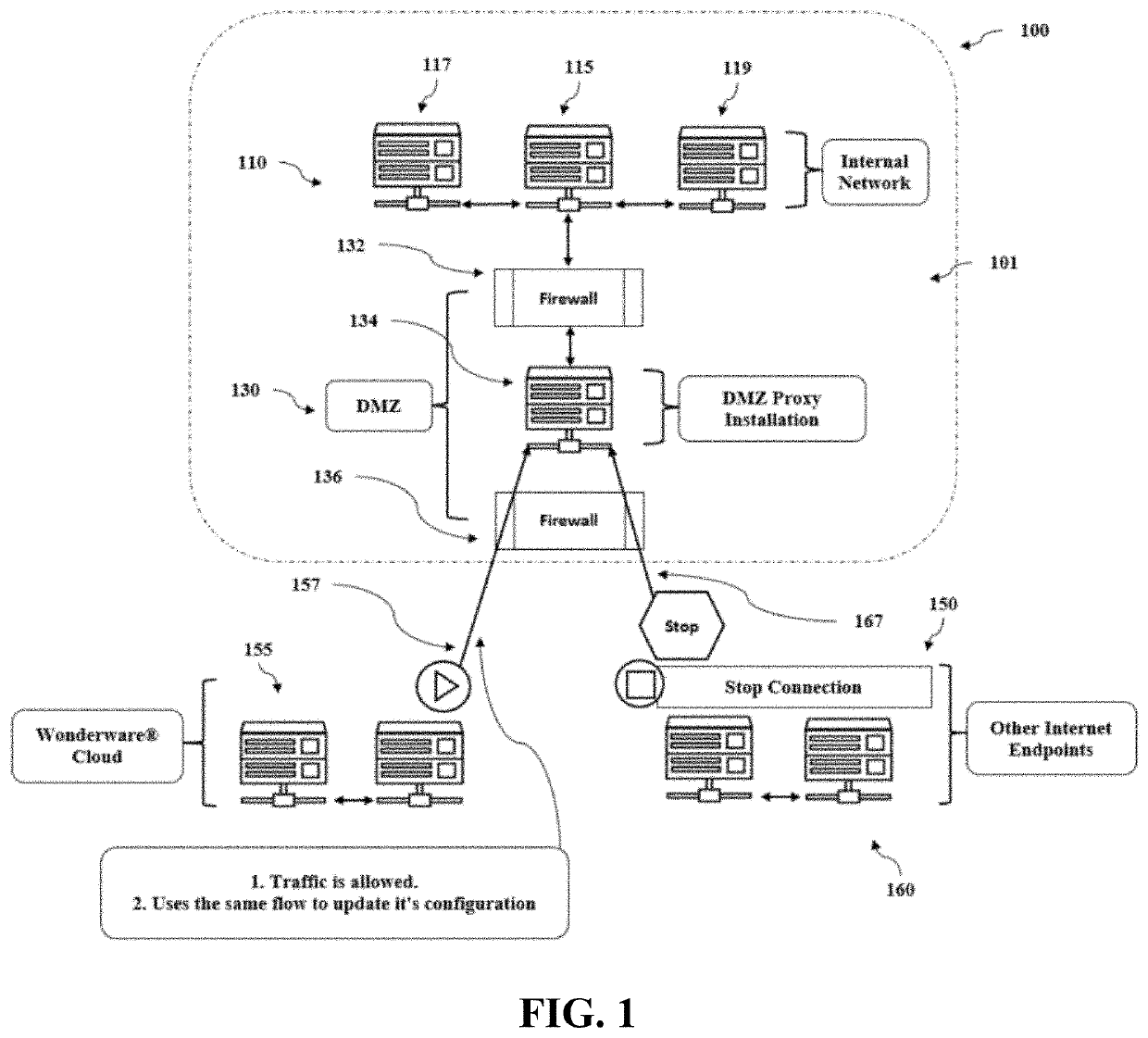
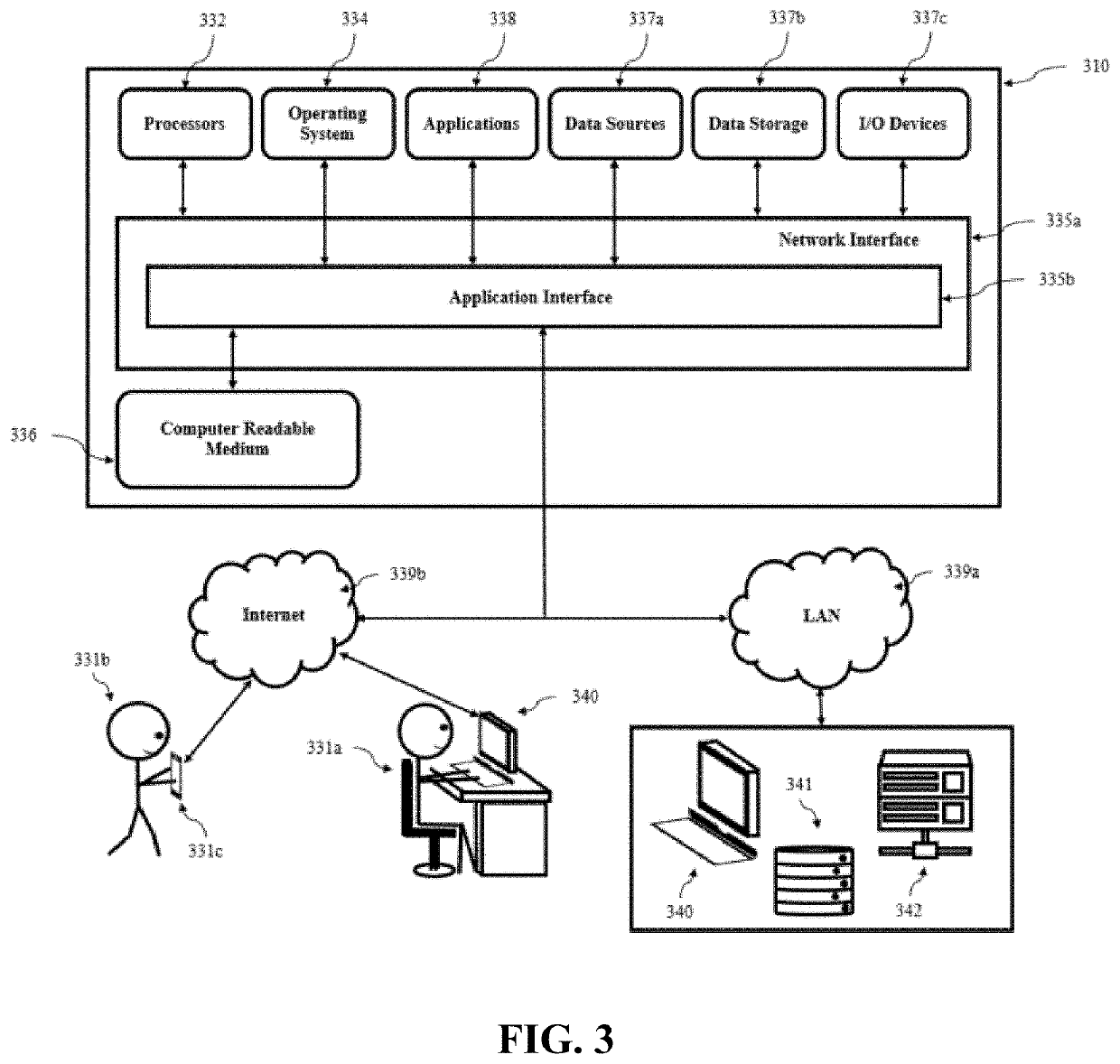
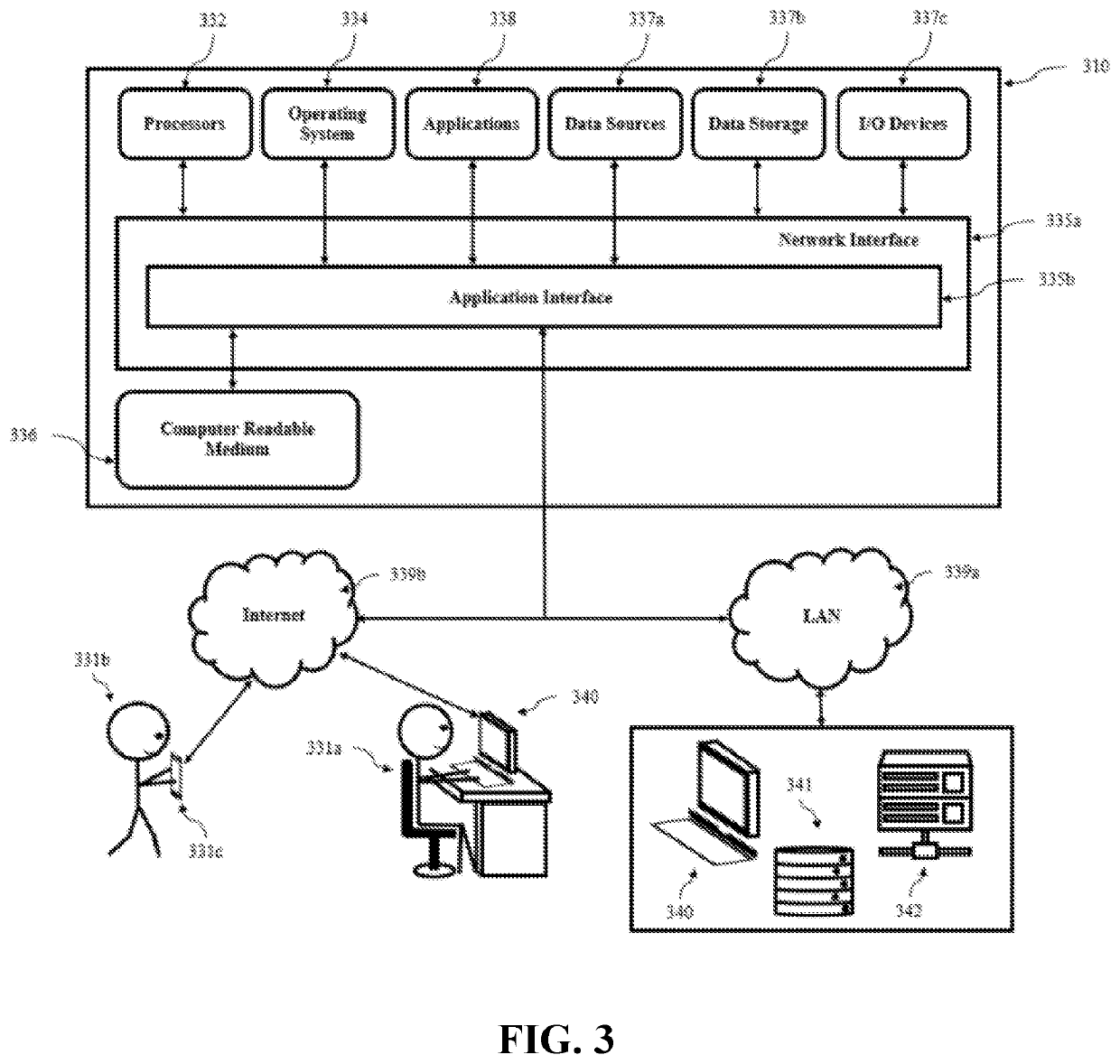
Server and system for secure configuration push for dmz proxy clients
A server system can include an internal computer network including at least one client server configured to establish a data transfer connection to an external computer network, and at least one proxy server system positioned between the internal computer network and the external computer network. The proxy server system can include a proxy server positioned between a first firewall and a second firewall, where the first firewall is positioned between the first proxy server and the internal computer network, and the second firewall is positioned between the proxy server and the external computer network. The server system can develop and maintain a proxy server system that includes a whitelist of sites deemed necessary and / or desirable for system operation. The whitelist can be updated as a user works with and uses the system. Such updates can take place continuously in real or near-real time or periodically as frequently as desired. A single party can be the only entity that can update the whitelist, ensuring the whitelist contains all required sites. Whitelist updates can be automatically delivered to all proxy instances as the whitelist changes over time.
Owner:AVEVA SOFTWARE LLC
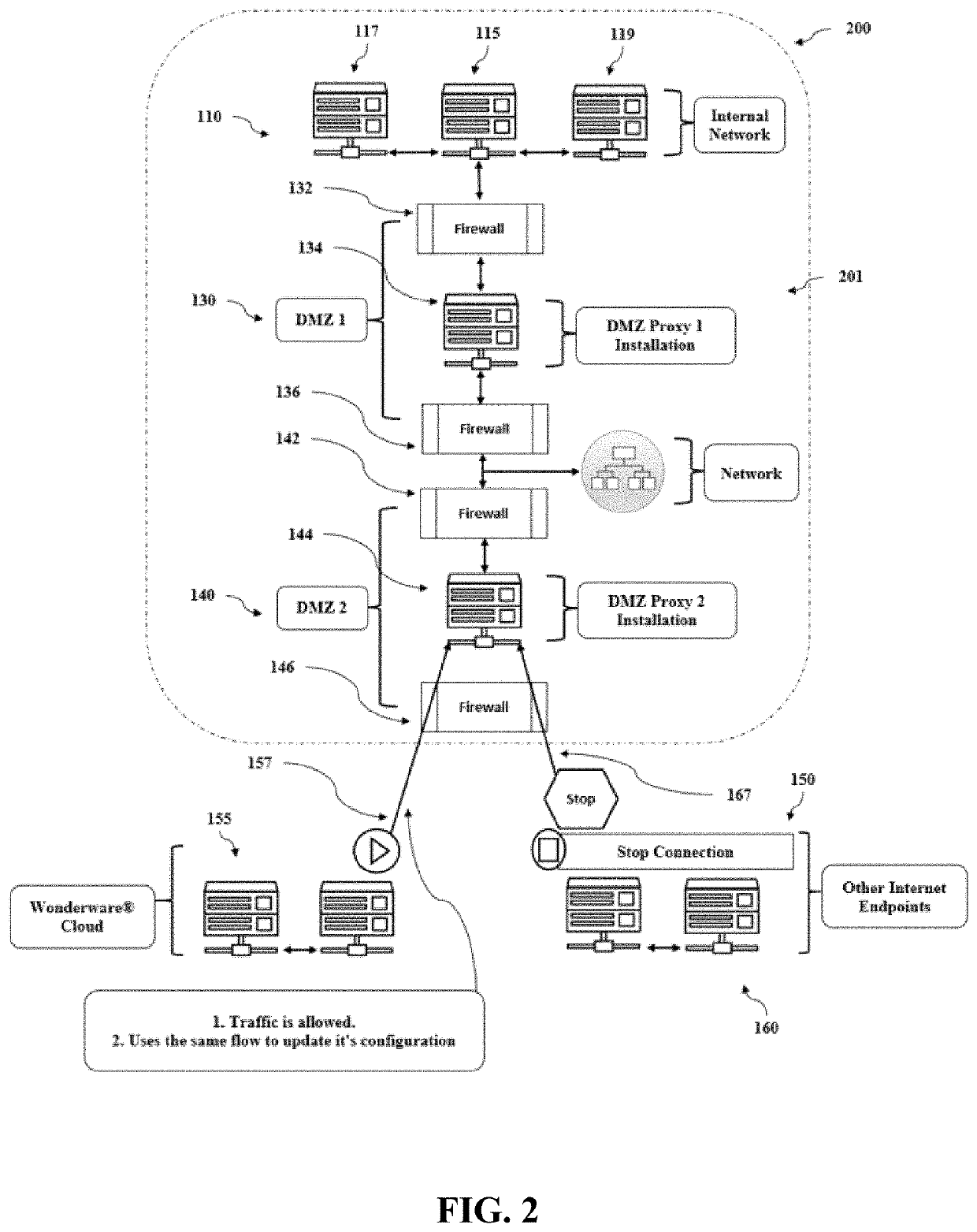
Server and system for secure configuration push for dmz proxy clients
A server system can include an internal computer network including at least one client server configured to establish a data transfer connection to an external computer network, and at least one proxy server system positioned between the internal computer network and the external computer network. The proxy server system can include a proxy server positioned between a first firewall and a second firewall, where the first firewall is positioned between the first proxy server and the internal computer network, and the second firewall is positioned between the proxy server and the external computer network. The server system can develop and maintain a proxy server system that includes a whitelist of sites deemed necessary and / or desirable for system operation. The whitelist can be updated as a user works with and uses the system. Such updates can take place continuously in real or near-real time or periodically as frequently as desired. A single party can be the only entity that can update the whitelist, ensuring the whitelist contains all required sites. Whitelist updates can be automatically delivered to all proxy instances as the whitelist changes over time.
Owner:AVEVA SOFTWARE LLC
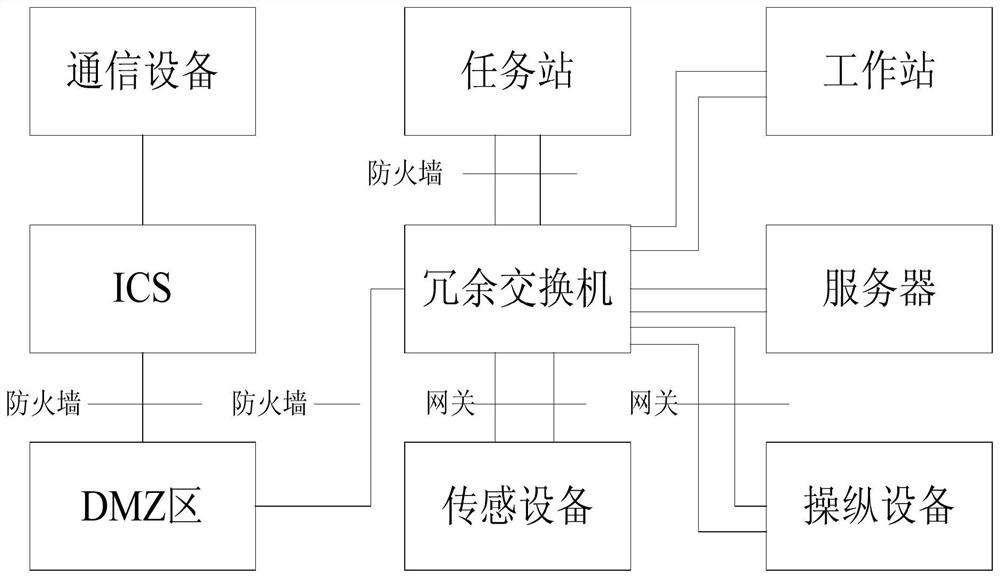
A network architecture of ship-side integrated navigation system based on cloud platform
ActiveCN107959586BRealize information transmissionAchieve interactionData switching networksNetwork architectureEngineering
Owner:CHINA ACAD OF LAUNCH VEHICLE TECH
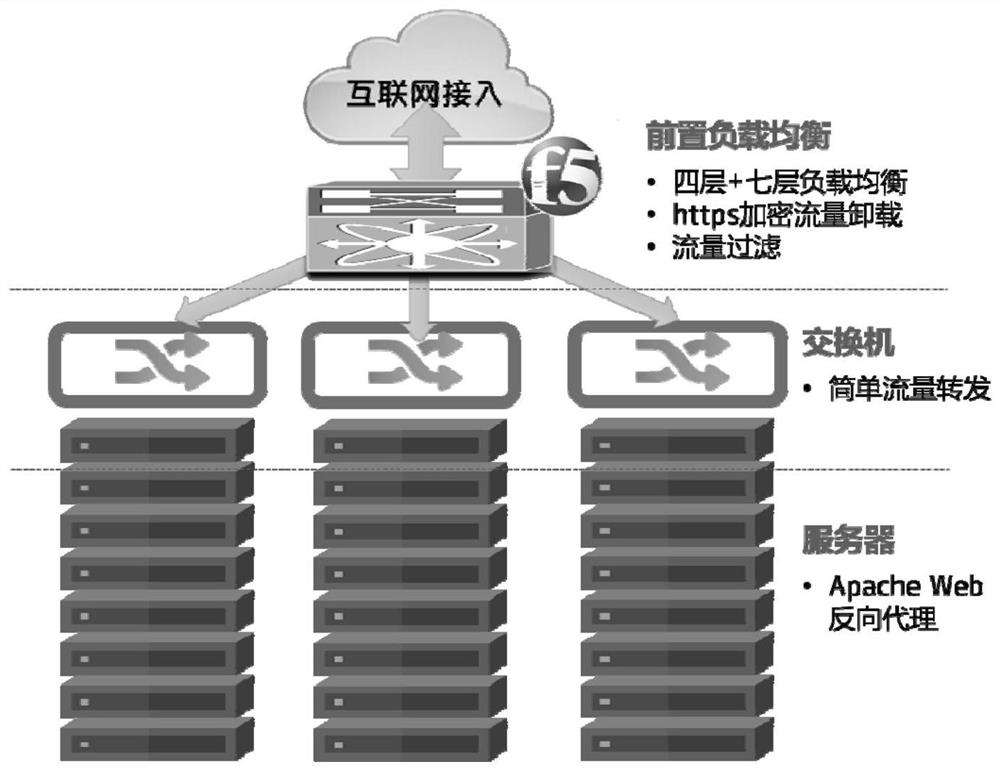
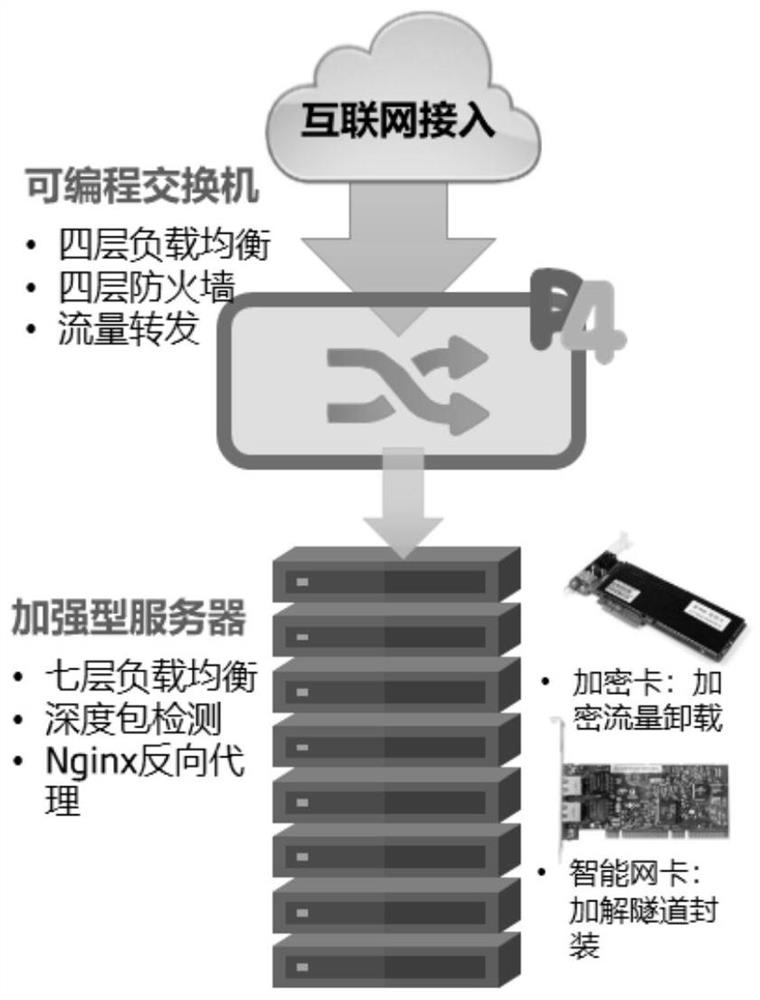
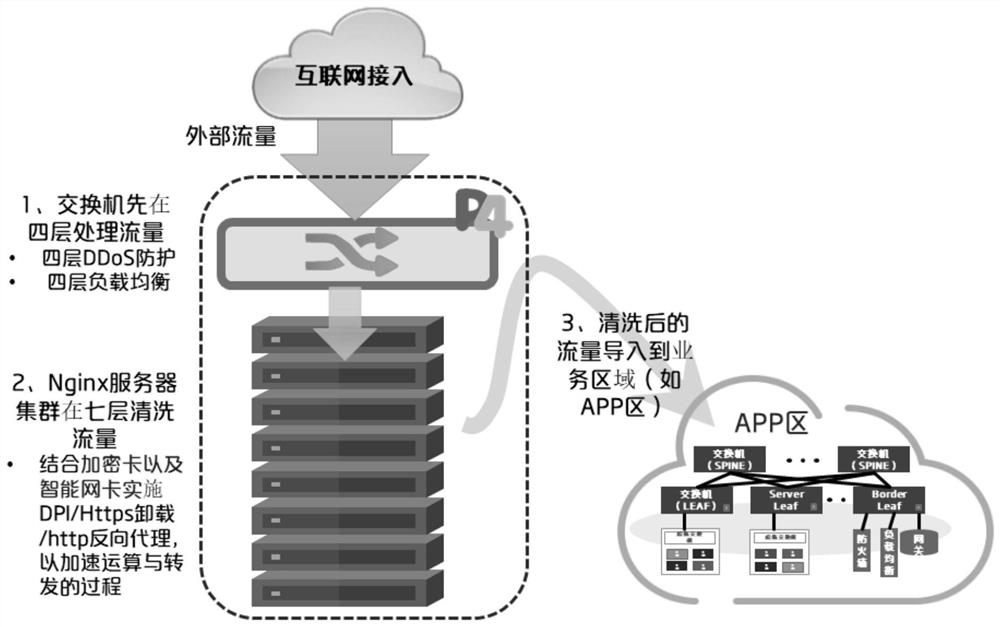
A system and method for composing a DMZ zone
The invention discloses a system for forming a DMZ area, including: a programmable switch, which is used to receive and process traffic from an external network, and forward the processed traffic to a server cluster; a server cluster, which is used to receive and cleaning the processed traffic, and forwarding the cleaned traffic to the programmable switch, wherein the programmable switch is also used to forward the cleaned traffic to a service area.
Owner:CHINA UNIONPAY
An industrial control system security experiment system for penetration testing
ActiveCN108769022BImprove scalabilityEnsure safetyData switching networksData acquisitionPhysical model
Owner:ZHEJIANG UNIV
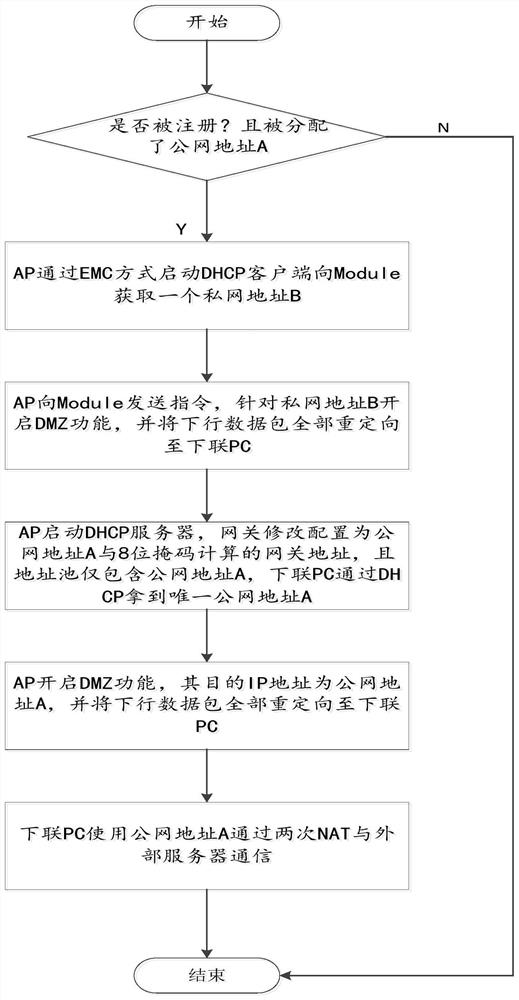
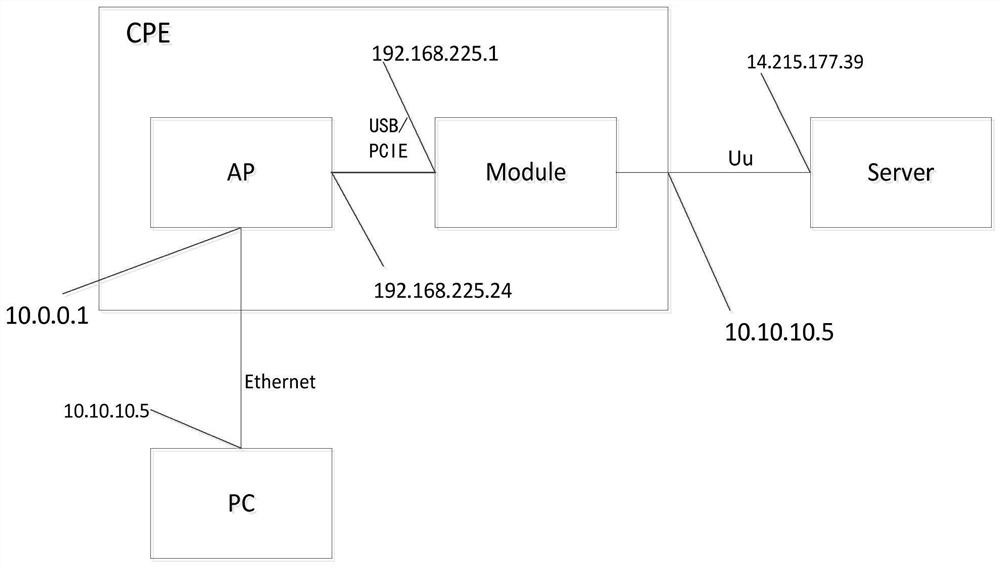
Method for realizing LTE/5G bridge mode and wireless routing equipment
PendingCN113301179AImplement LTE/5G bridge modeNetworks interconnectionWireless communicationTelecommunicationsPrivate network
The invention discloses a method for realizing an LTE / 5G bridge mode and wireless routing equipment, and belongs to the technical field of data communication. The method comprises the steps of judging whether a Module is registered and allocated with a public network address A, if so, continuing, and otherwise, ending; an AP starting a DHCP client in an EMC mode to obtain a private network address B from the Module; the AP sending an instruction to the Module, and a DMZ function is started for the private network address B; the AP starting a DHCP server, a gateway modifies and configuring a gateway address calculated by a public network address A and an 8-bit mask, and an address pool only comprising the public network address A; the AP starting a DMZ function, wherein a destination IP address of the AP is a public network address A; and a downlink PC using the public network address A to communicate with the external server through twice NAT. According to the invention, the downlink equipment is connected with the public network through the bridge mode; and the public server communicates with the downlink equipment through the public network IP address allocated to the equipment.
Owner:武汉大塔技术有限公司
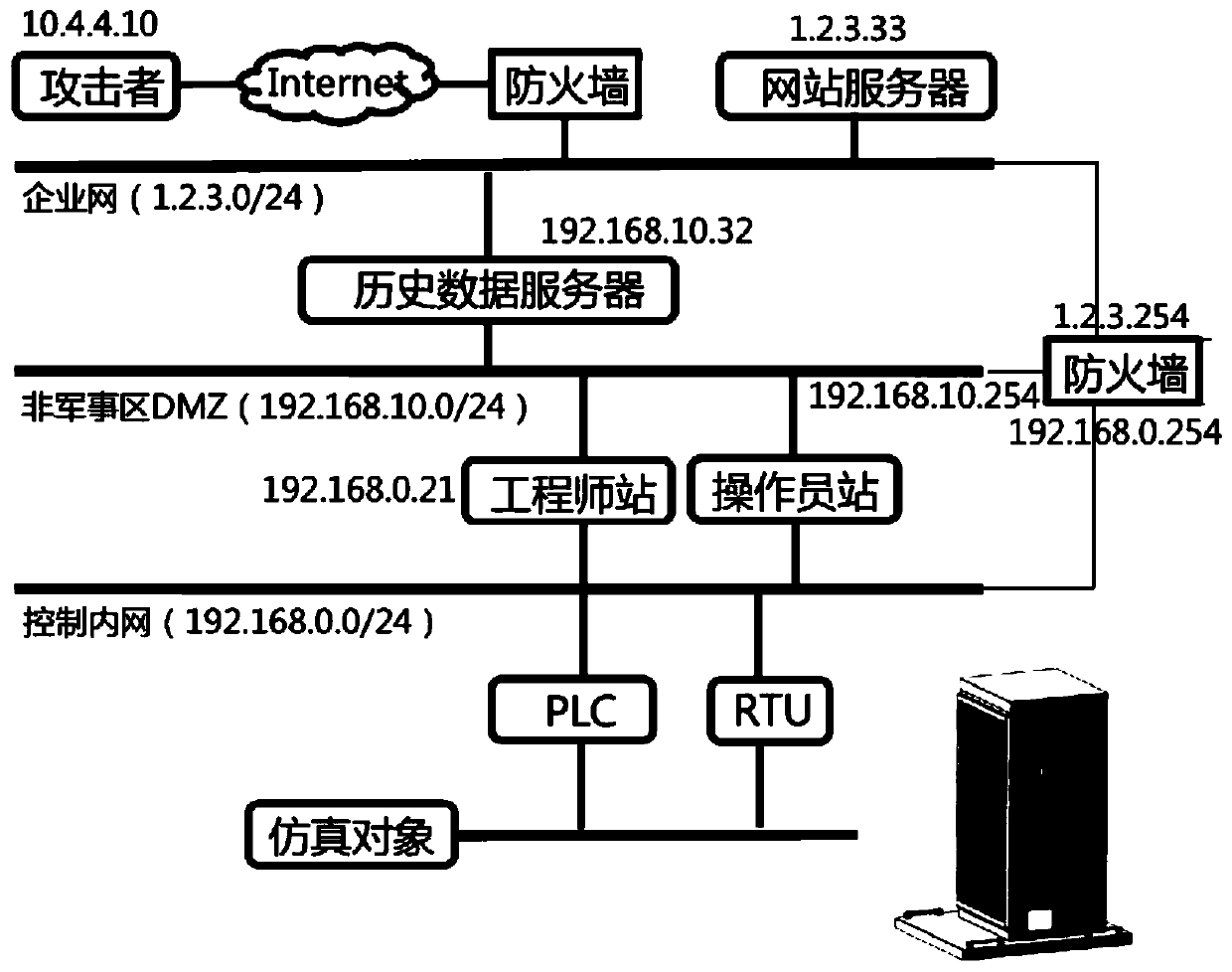
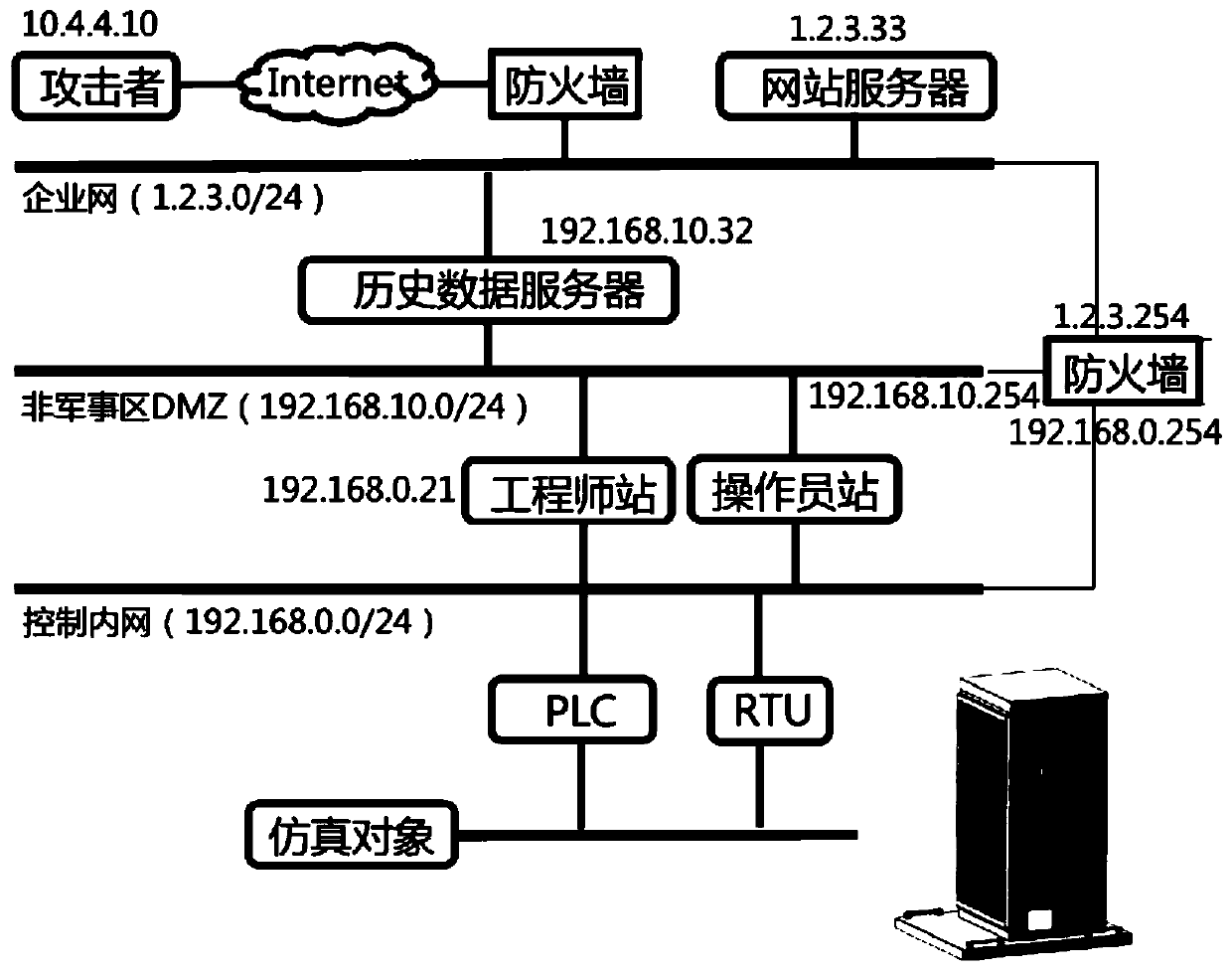
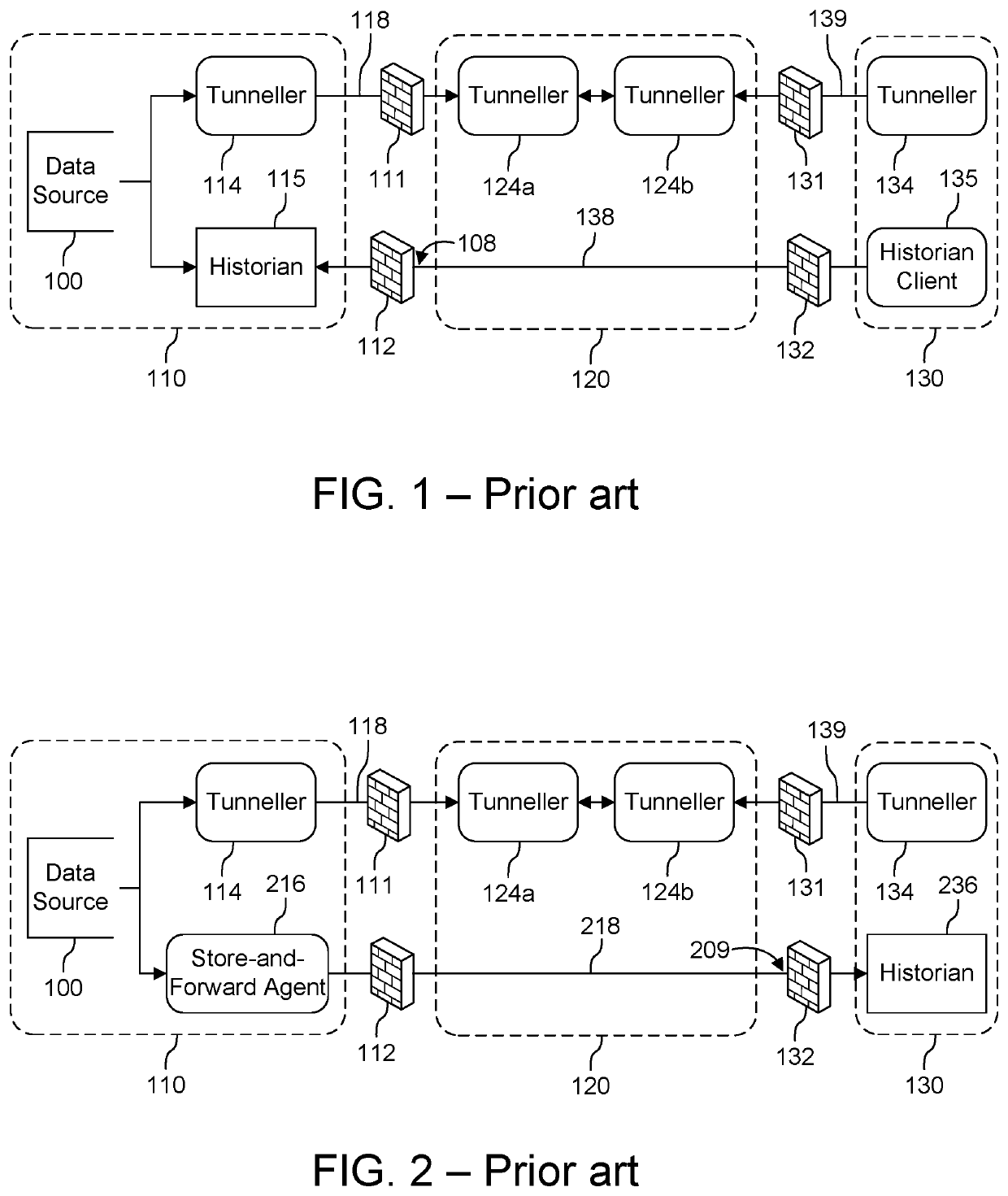
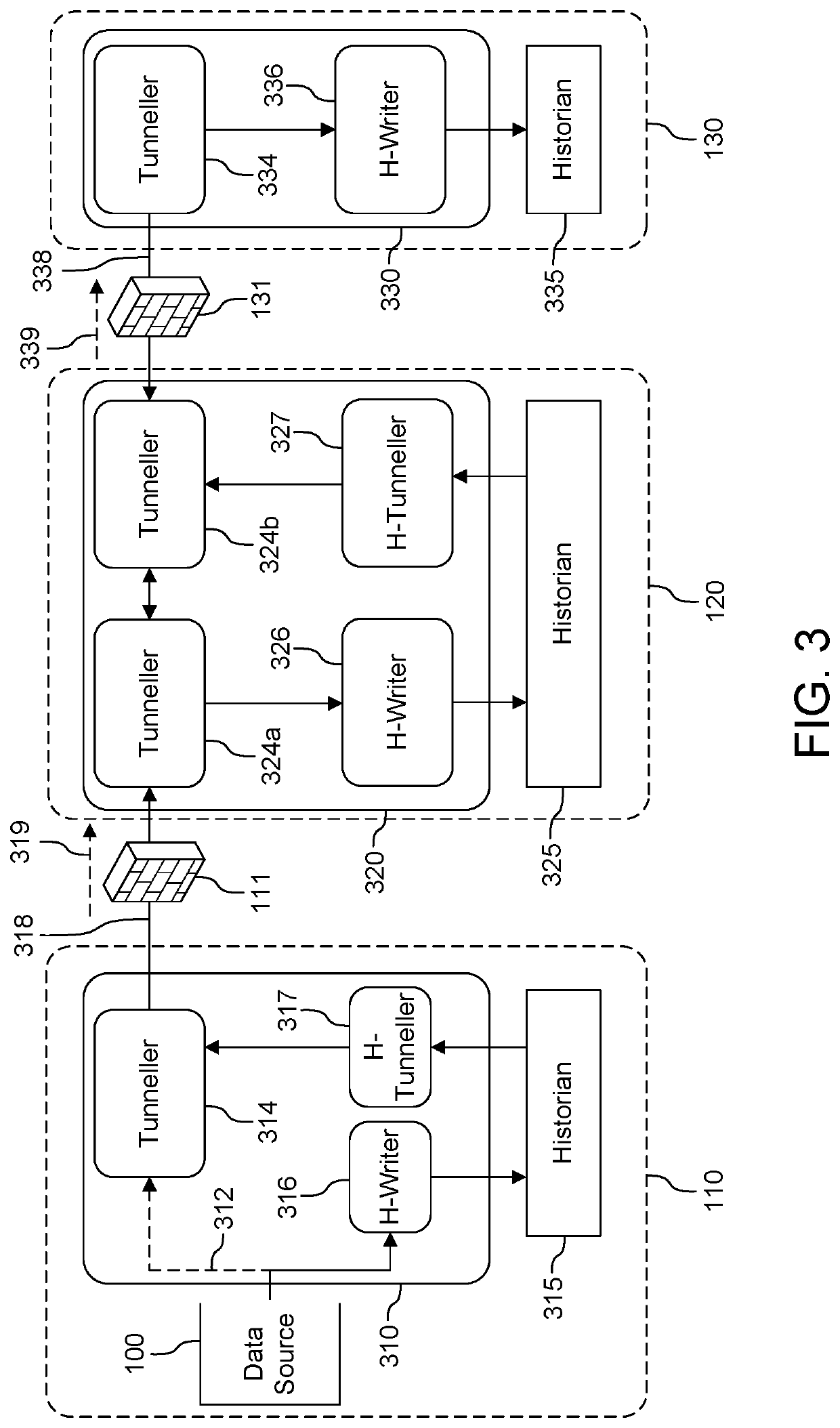
Secure remote access to historical data
ActiveUS20210336927A1Safe and reliableInefficient performanceTransmissionSecure communicationComputer network
Systems and methods for providing access to historical data over a real-time tunnel are disclosed. The method provides a mechanism for secure communication between one or more historians. In an example, attack surfaces on historians in an industrial control system operational technology (OT) network and in an information technology (IT) networks are reduced and possibly entirely eliminated by tunneling through a DMZ (de-militarized zone) or “secured network”.
Owner:REAL INNOVATIONS INT
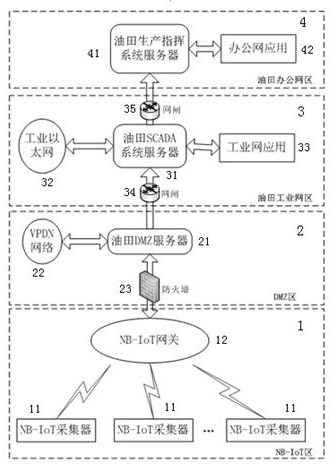
NBIoT technology-based oil and gas internet-of-things data acquisition system
PendingCN113453182AReduce engineering costsReduce the difficulty of on-site constructionParticular environment based servicesTransmissionData acquisitionInformation security
The invention provides an NBIoT technology-based oil and gas internet-of-things data acquisition system, which comprises an NB-IoT area, a DMZ area, an oil field industrial network area and an oil field office network area, and is characterized in that the NB-IoT area acquires and stores real-time data of an oil and gas production site and transmits the real-time data to the DMZ area, the DMZ area acquires and stores data of wireless communication equipment, the field data and the data of the wireless communication equipment are transmitted to the oil field industrial network area, and the oil field industrial network area collects and stores the data of the wired communication equipment and transmits the field data, the data of the wireless communication equipment and the data of the wired communication equipment to the oil field office network area. The oil field office network area receives the data, stores the data and applies the data to oil field production command work. According to the oil and gas internet-of-things data acquisition system based on the NBIoT technology, the engineering cost is greatly reduced, the information safety of an oil field industrial network is ensured, and the production efficiency is improved.
Owner:CHINA PETROLEUM & CHEM CORP +1
DMZ-based oil and gas industry internet data processing system
ActiveCN113448289AGuaranteed privacyGuaranteed high-speed performanceTotal factory controlProgramme total factory controlData acquisitionIndustrial Internet
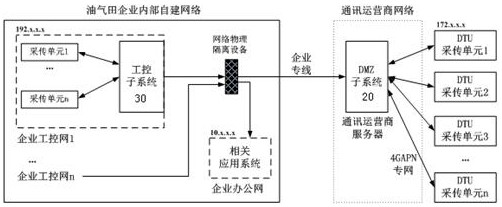
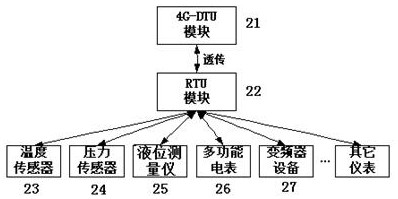
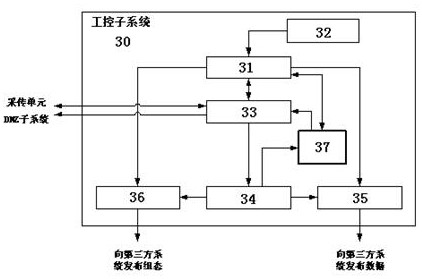
The invention provides a DMZ-based oil and gas industry internet data processing system, which comprises a plurality of DTU acquisition and transmission units, a DMZ subsystem and an industrial control subsystem; the plurality of DTU acquisition and transmission units are used for collecting field data signals of long-distance well stations of oil and gas fields and carrying out data interaction with the DMZ subsystem through a communication operation network; the DMZ subsystem is deployed in an isolation service area of a communication operator, on one hand, the DMZ subsystem communicates with the DTU acquisition and transmission units, on the other hand, the DMZ subsystem respondsto a data acquisition request and a remote control request of an internal network of an oil and gas field enterprise; the industrial control subsystem is deployed in a certain industrial control network of the oil and gas field and communicates with an office network and the DMZ subsystem through a gatekeeper or a firewall so as to collect, monitor and control data of all well stations. According to the system, the network security and the data transmission rate of data processing are fully considered, and the information privacy, the high speed and the industrial control security of remote data acquisition of the oil and gas field are guaranteed.
Owner:CHINA PETROLEUM & CHEM CORP +1
Information network virus intrusion detection system and method
InactiveCN112637840ARealize detectionAchieve isolationSecurity arrangementInformation networksEngineering
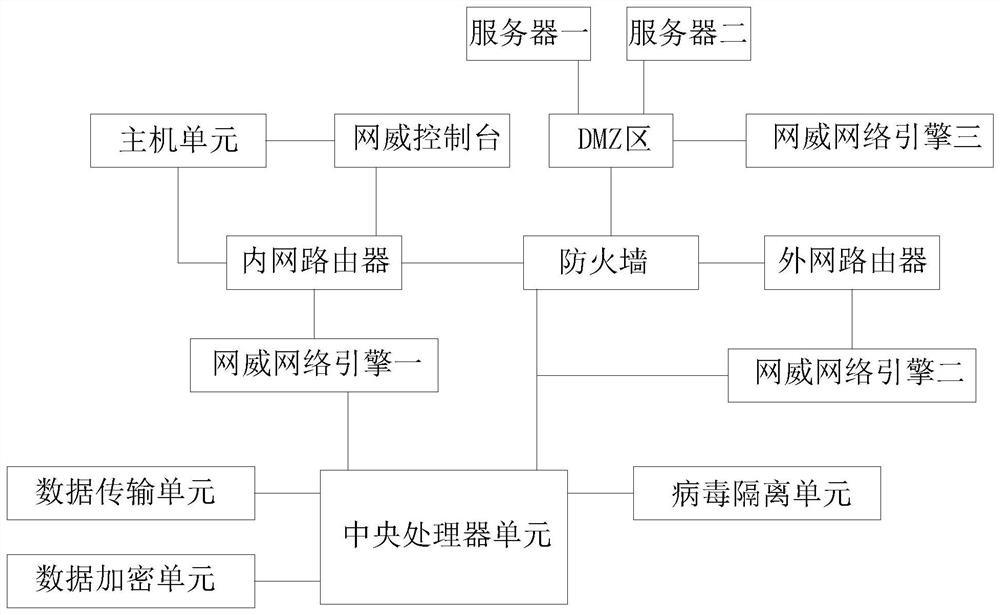
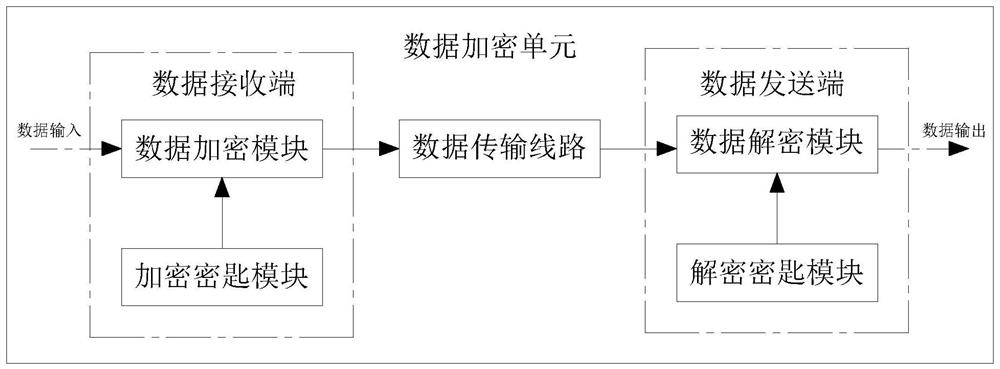
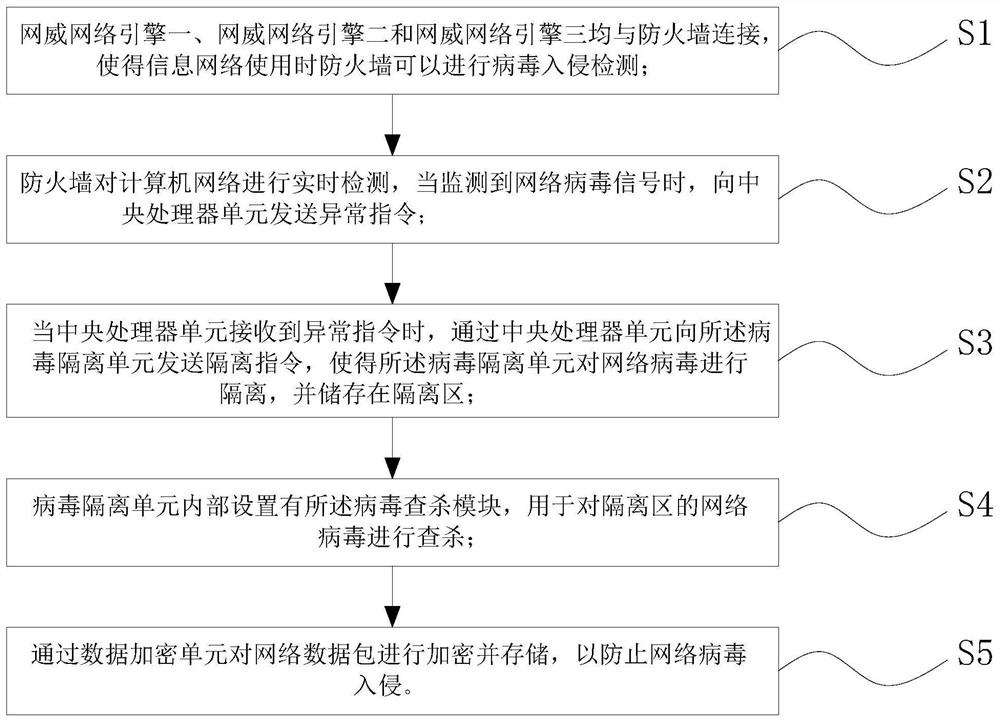
The invention discloses an information network virus intrusion detection system and method, and relates to the technical field of information networks. The host unit is in network connection with a firewall through an intranet router, the firewall is in network connection with an extranet through an extranet router, and the firewall is in bidirectional electrical connection with the central processing unit. The output end of the central processing unit is bidirectionally and electrically connected with the input ends of a data transmission unit, a data encryption unit and a virus isolation unit, the firewall is electrically connected with a DMZ area, and the DMZ area is electrically connected with a network threat engine III, a server I and a server II. The information network virus intrusion detection system and the information network virus intrusion detection method are high in safety, can realize detection, isolation, searching and killing of network viruses, can encrypt network data, can encrypt and transmit the data, effectively prevent data leakage, and further improve the safety performance of information network data transmission.
Owner:GUANGDONG TOPWAY NETWORK
Cross-data-center data dictionary sharing method for financial institution
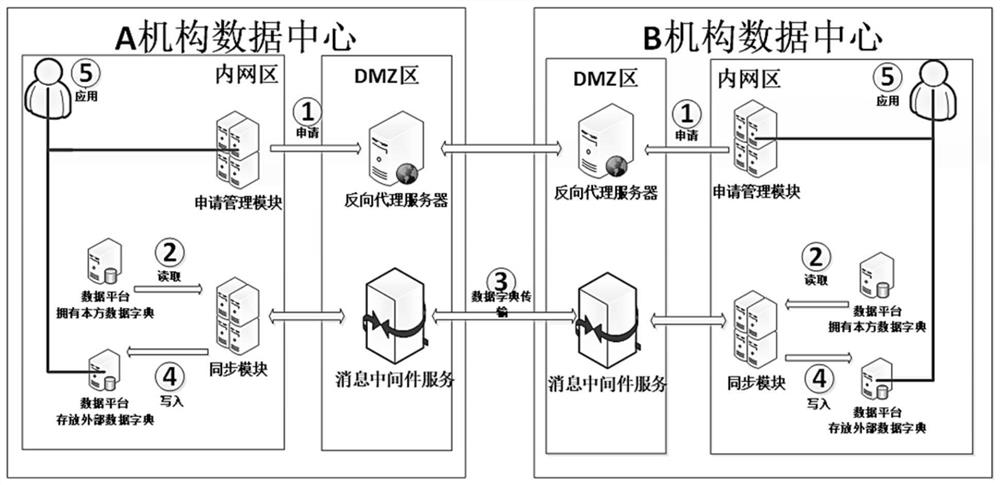
PendingCN114518967AEasy to manageIntelligent managementProgram synchronisationInterprogram communicationMessage queueMiddleware
The invention relates to a cross-data-center data dictionary sharing method for financial institutions, and the method is characterized in that a data dictionary sharing management system is created for the data center of each financial institution; and message queue middleware for creating message channels for transmission of data dictionaries of data centers of financial institutions of all parties is deployed in respective DMZ areas, and the message queue middleware reads and writes the shared data dictionaries through a synchronization module. Compared with the prior art, the method has the advantages that the efficiency of data dictionary sharing application work is effectively improved, and management is more convenient and intelligent.
Owner:中银金融科技有限公司
Application store system and method for developing by using application store system
PendingCN111552902AEasy to useReduce investmentWeb data indexingWebsite content managementSoftware engineeringSoftware development
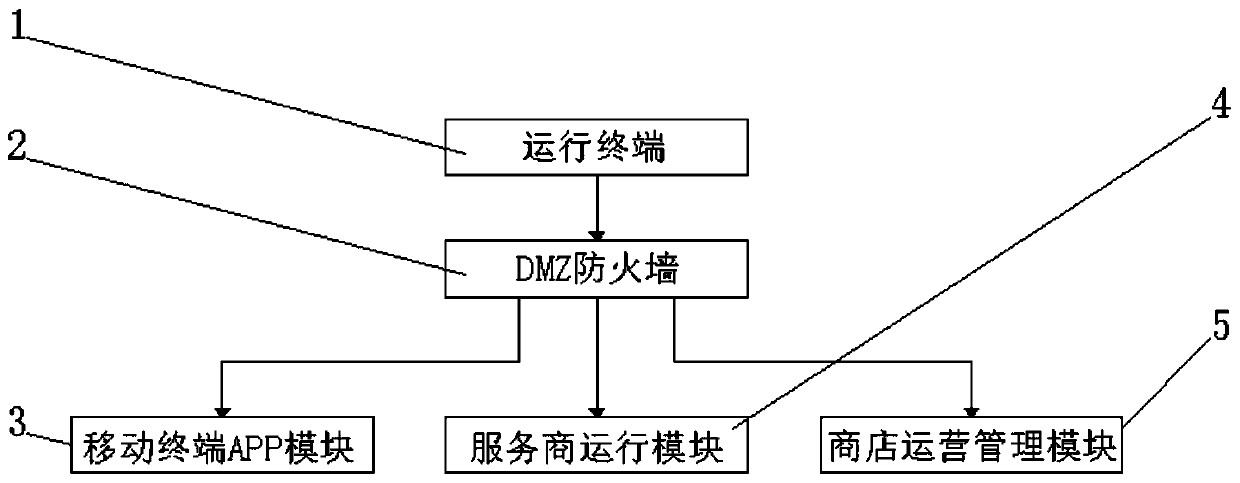
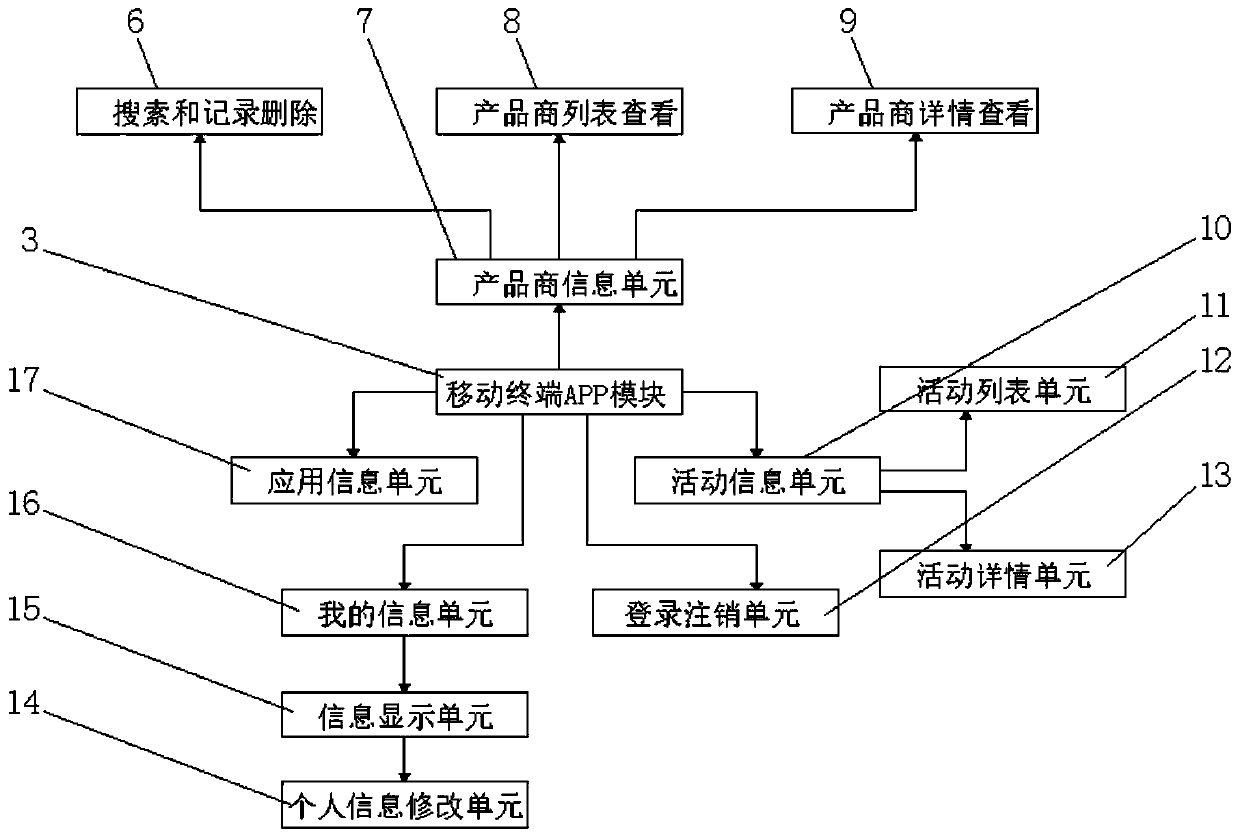
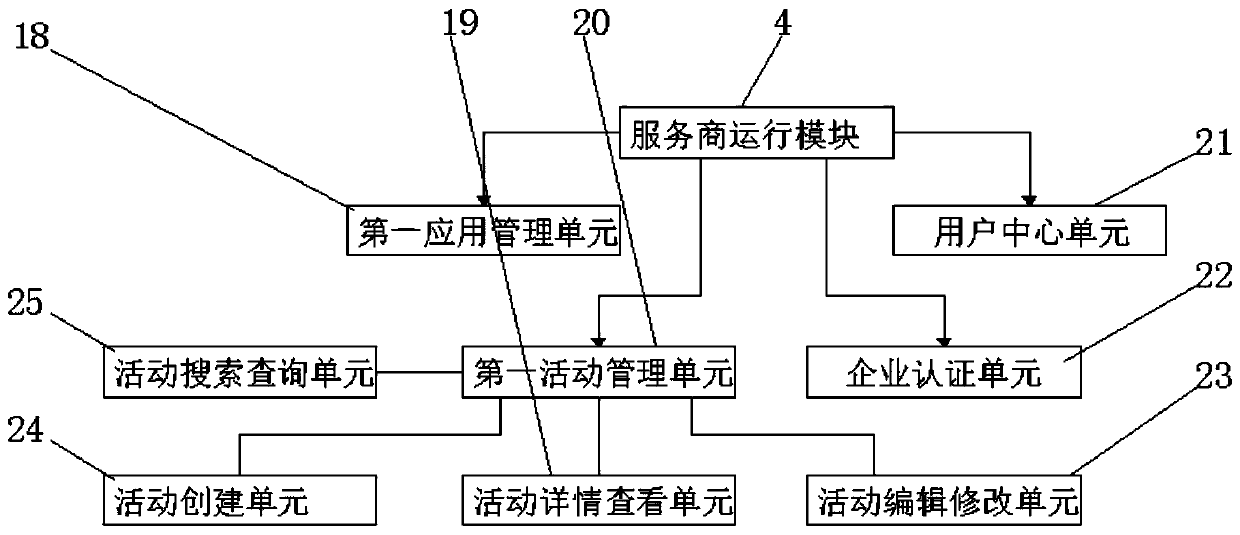
The invention discloses an application store system and a method for developing by using the application store system. The application store system includes an operation terminal, wherein the operation terminal is electrically connected with a DMZ firewall through a wire; the DMZ firewall is electrically connected with a mobile terminal APP module through a wire; the DMZ firewall is electrically connected with a service provider operation module through a wire; the DMZ firewall is electrically connected with a store operation management module through a wire; and the mobile terminal APP moduleis electrically connected with a product provider information unit through a wire. According to the application store system and the method for developing by using the application store system, the B / S has unified browser client software; investment of client software development is saved, and time and energy for maintaining client software, client training and other work are reduced; cross-platform use can be achieved; the workload of developers at the client is reduced; and the developers focus on how to reasonably organize information and provide programming work of a server side of clientservice.
Owner:GUANGZHOU KETENG INFORMATION TECH
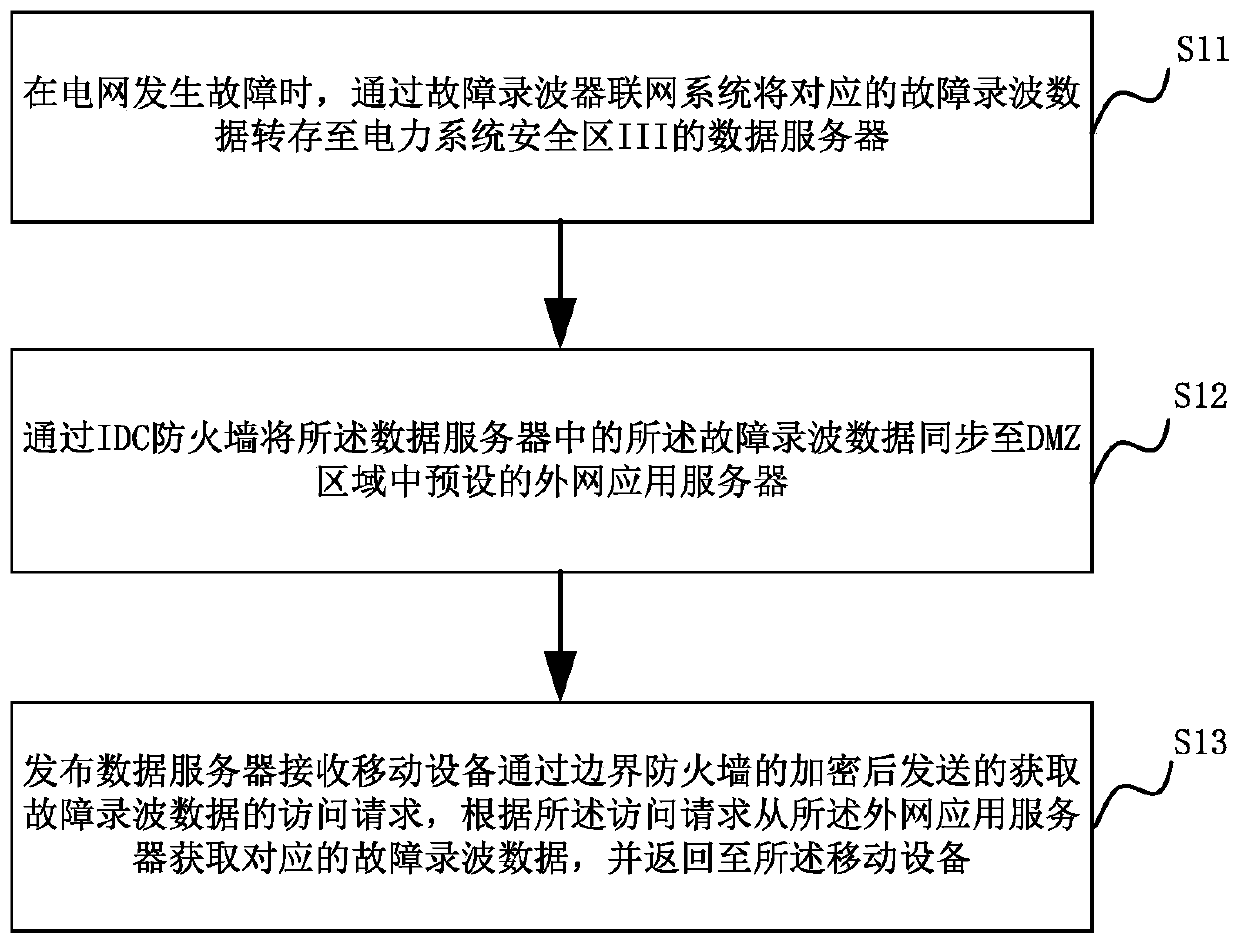
Method and system for acquisition of power grid fault recording data
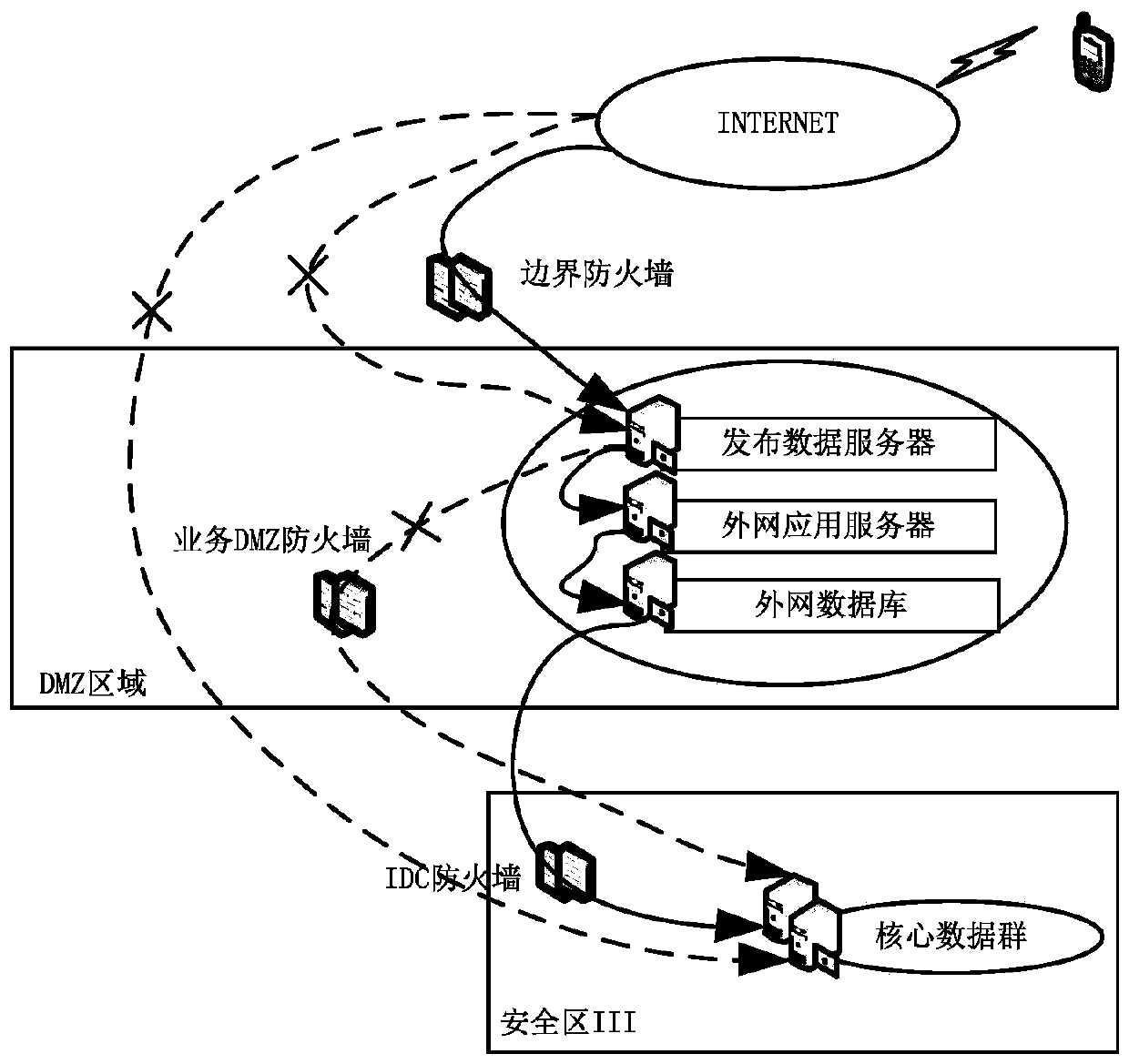
The invention relates to a grid fault recording data acquisition method and a grid fault recoding data acquisition system. The method comprises the following steps: when a power grid has a fault, a fault recorder networking system uploads corresponding fault recording data to a data server in a power system safety zone III; an IDC firewall synchronizes the fault recording data in the data server to an outer-net application server preset in a DMZ zone; a data issuing server is also set in the DMZ zone, and the data issuing server is in communication connection with the outer-net application server; the data issuing server receives an access request of acquiring the fault recording data sent by mobile equipment subjected to encryption by a boundary firewall, acquires corresponding fault recording data from the outer-net application server according to the access request, and returns the fault recording data to the mobile equipment. The method and the system disclosed by the invention can bring convenience for workers to acquire the grid fault recording data in real time, thus being favorable for timely providing professional support for fault analysis.
Owner:GUANGZHOU POWER SUPPLY BUREAU GUANGDONG POWER GRID CO LTD
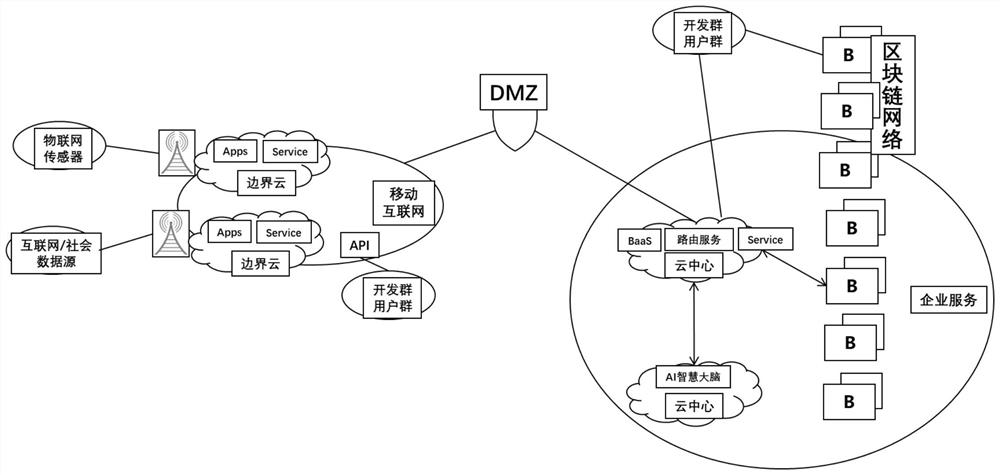
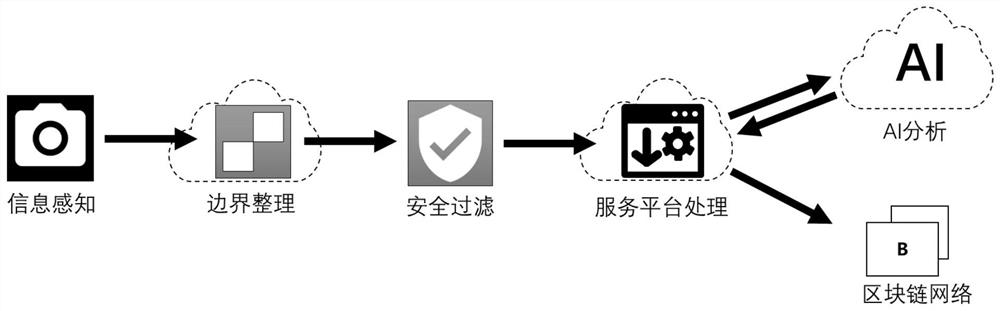
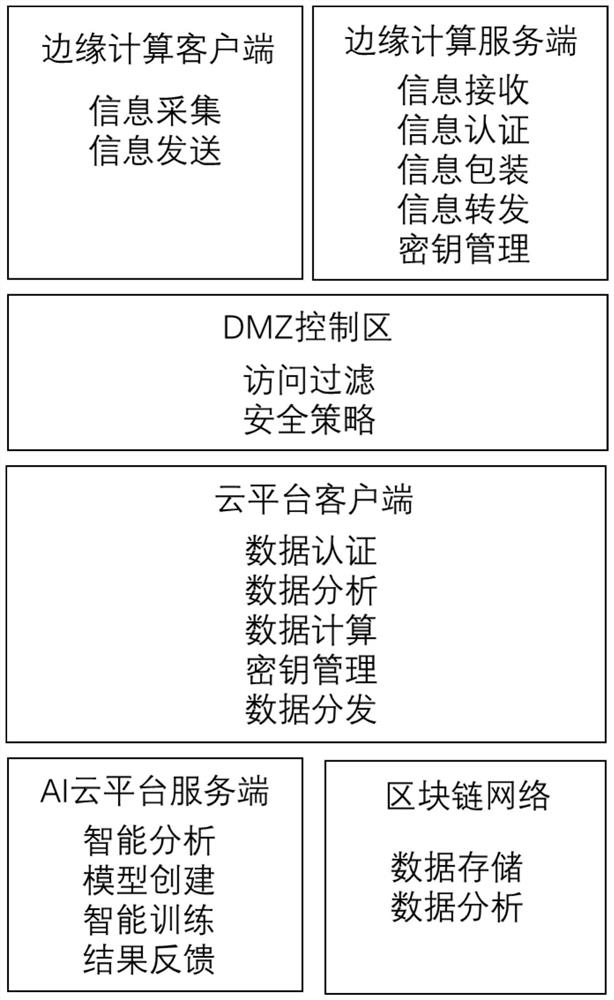
Physical evidence traceability system based on blockchain-based edge computing services
ActiveCN108769031BGuaranteed authentic relevanceData switching networksEdge computingReliability engineering
The present invention provides a physical object deposit traceability system based on block chain edge computing service. The system uses the edge computing client to collect basic data and further sends this data to the edge computing server, which performs preliminary processing on the edge computing server, and is received by the cloud platform client under the network security protection of the DMZ control area , and then the cloud platform client directly submits this data to the blockchain network for deposit (certificate data stored on the chain of physical information), and at the same time, sends it to the AI cloud platform server for judgment, and then passes the cloud platform client Submit to the blockchain network for deposit (off-chain certificate data of physical information), so as to effectively ensure the real correlation between the certificate data circulating on the chain and the physical objects under the chain.
Owner:中化能源科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com