Patents
Literature
63 results about "Port security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Port security is part of a broader definition concerning maritime security.It refers to the defense, law and treaty enforcement, and counterterrorism activities that fall within the port and maritime domain. It includes the protection of the seaports themselves and the protection and inspection of the cargo moving through the ports. Security risks related to ports often focus on either the physical security of the port, or security risks within the maritime supply chain.
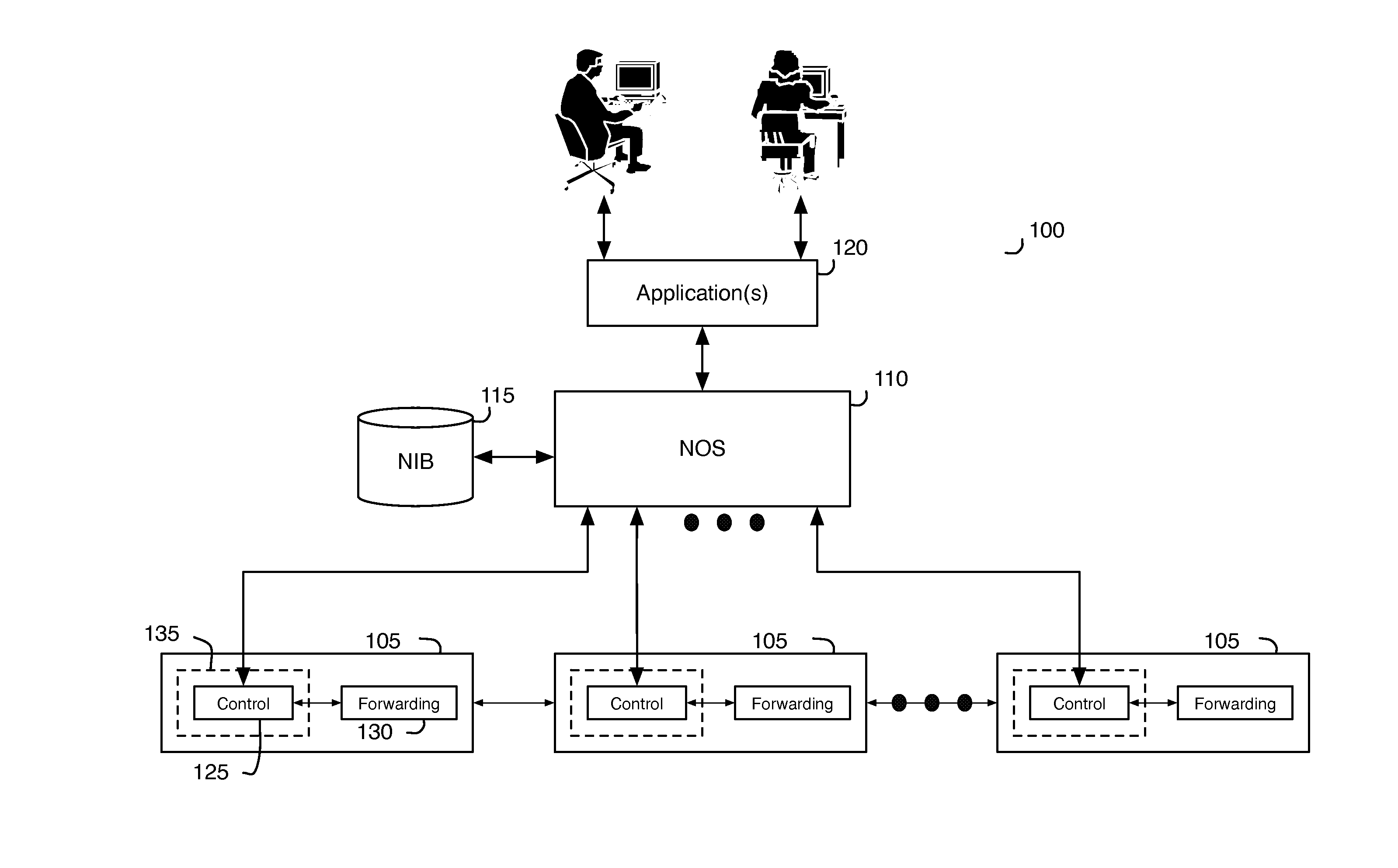
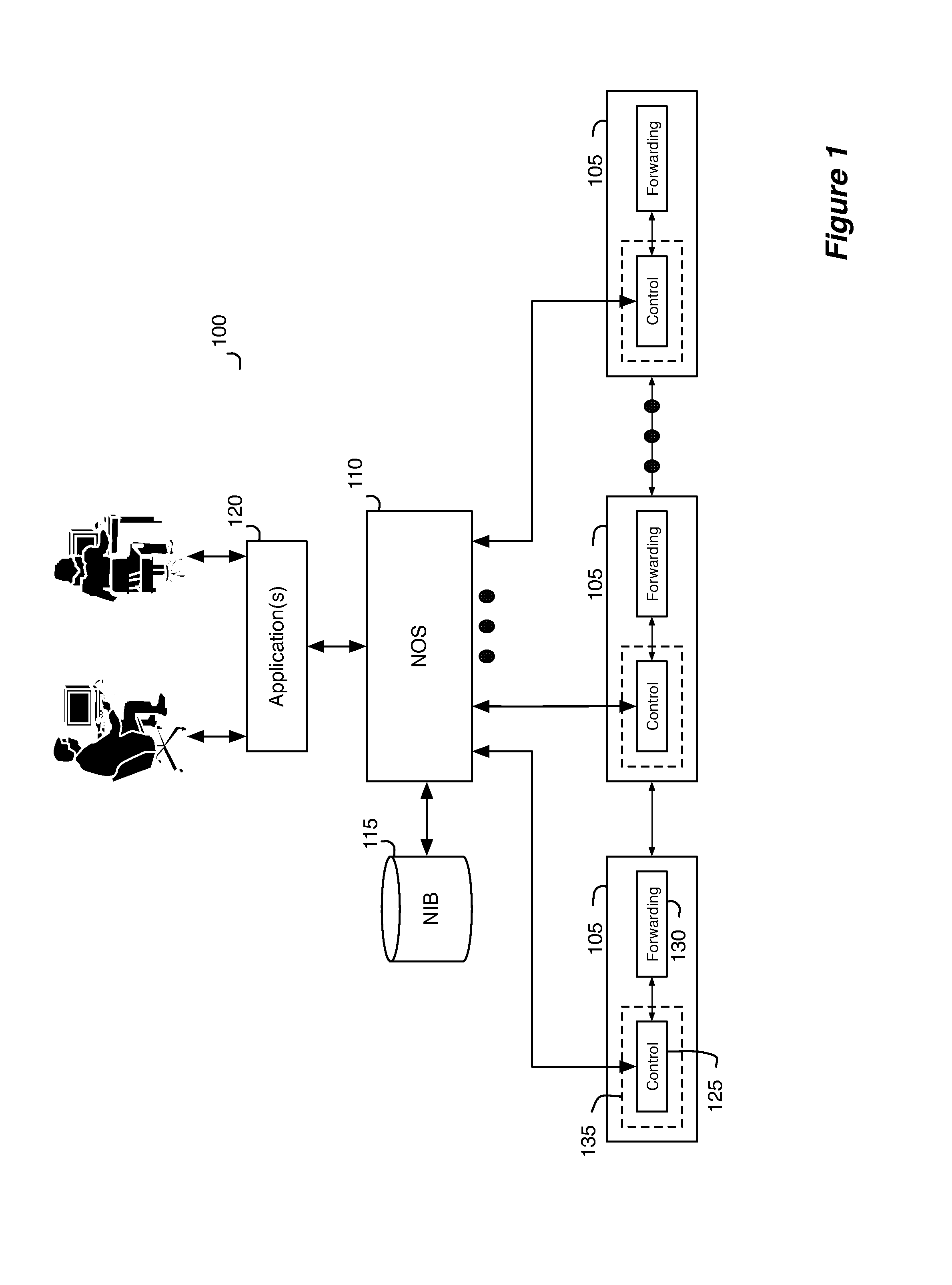
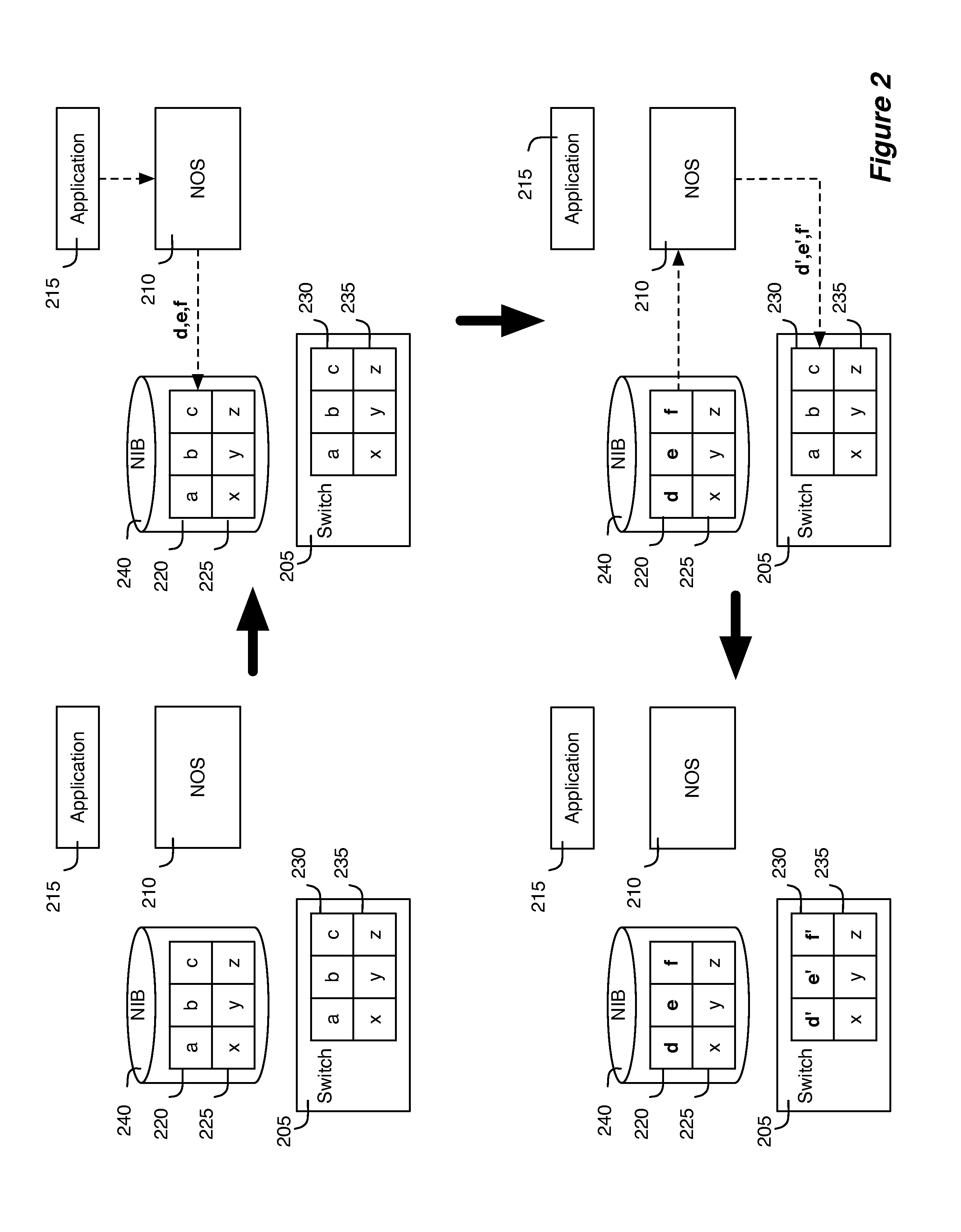
Network control apparatus and method with port security controls
Port security in some embodiments is a technique to apply to a particular port of a logical switching element such that the network data entering and existing the logical switching element through the particular logical port have certain addresses that the switching element has restricted the logical port to use. For instance, a logical switching element may restrict a particular logical port to one or more certain network addresses. To enable a logical port of a logical switch for port security, the control application of some embodiments receives user inputs that designate a particular logical port and a logical switch to which the particular logical port belongs. The control application in some embodiments formats the user inputs into logical control plane data specifying the designation. The control application in some embodiments then converts the logical control plane data into logical forwarding data that specify port security functions.
Owner:NICIRA
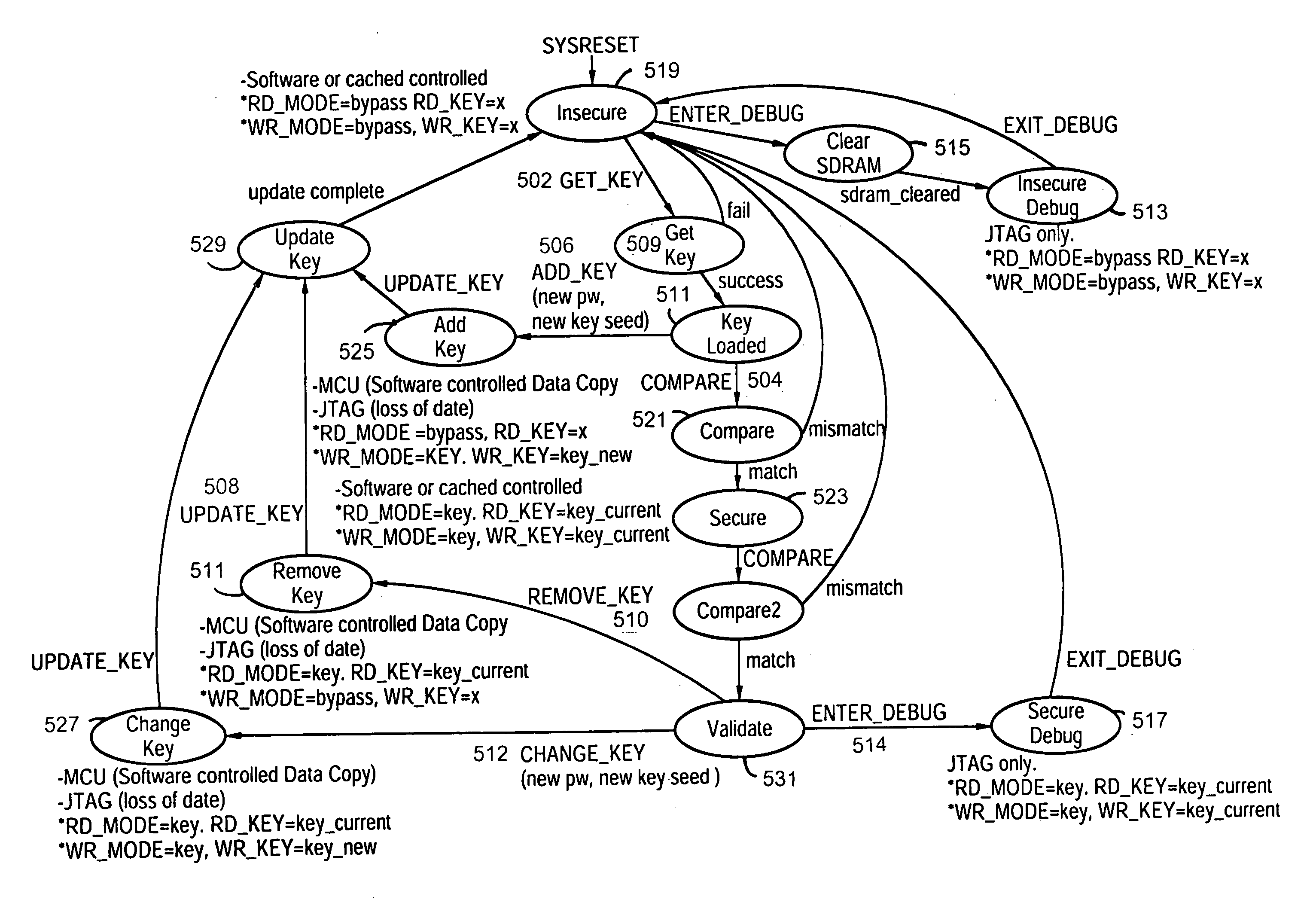
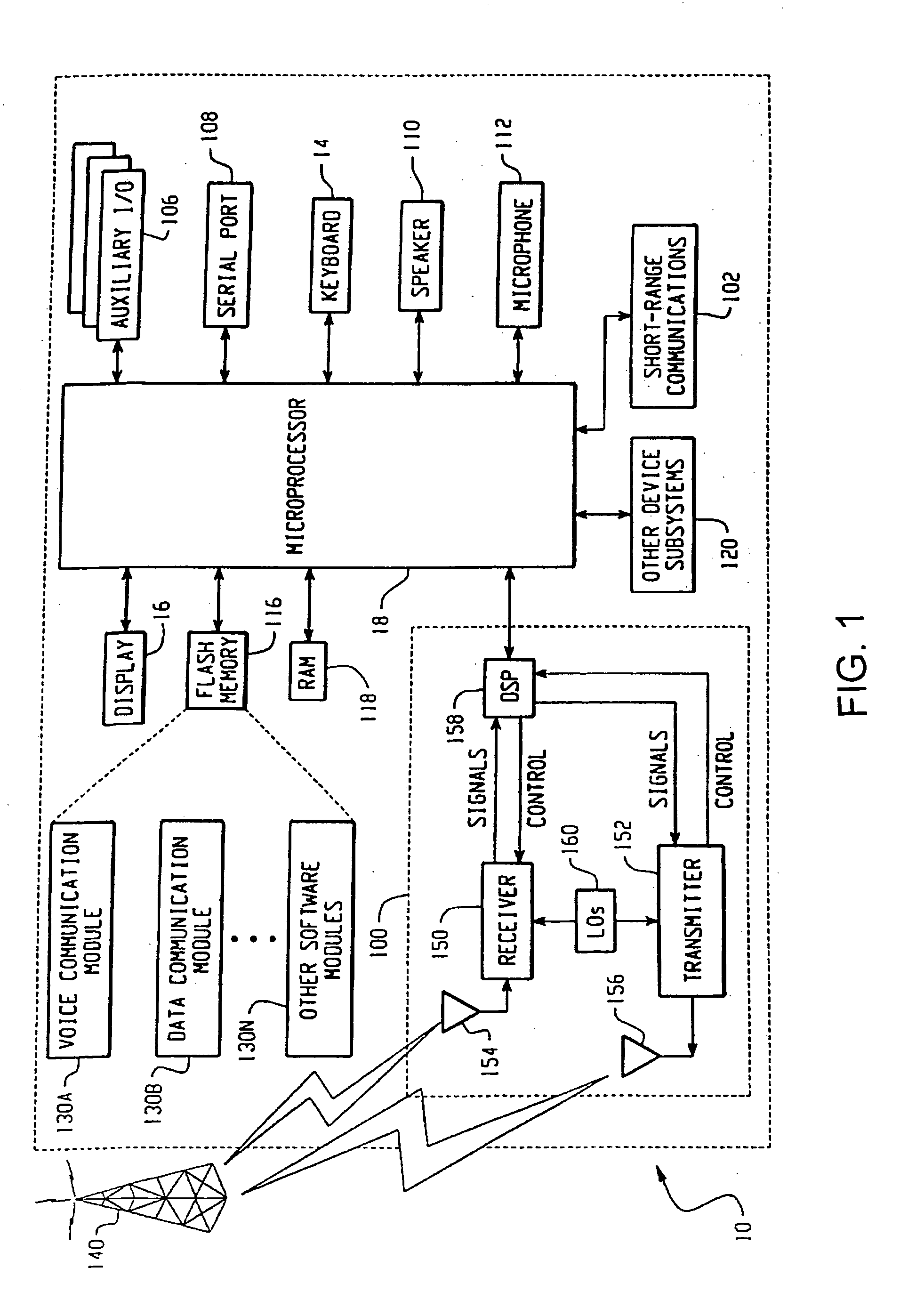
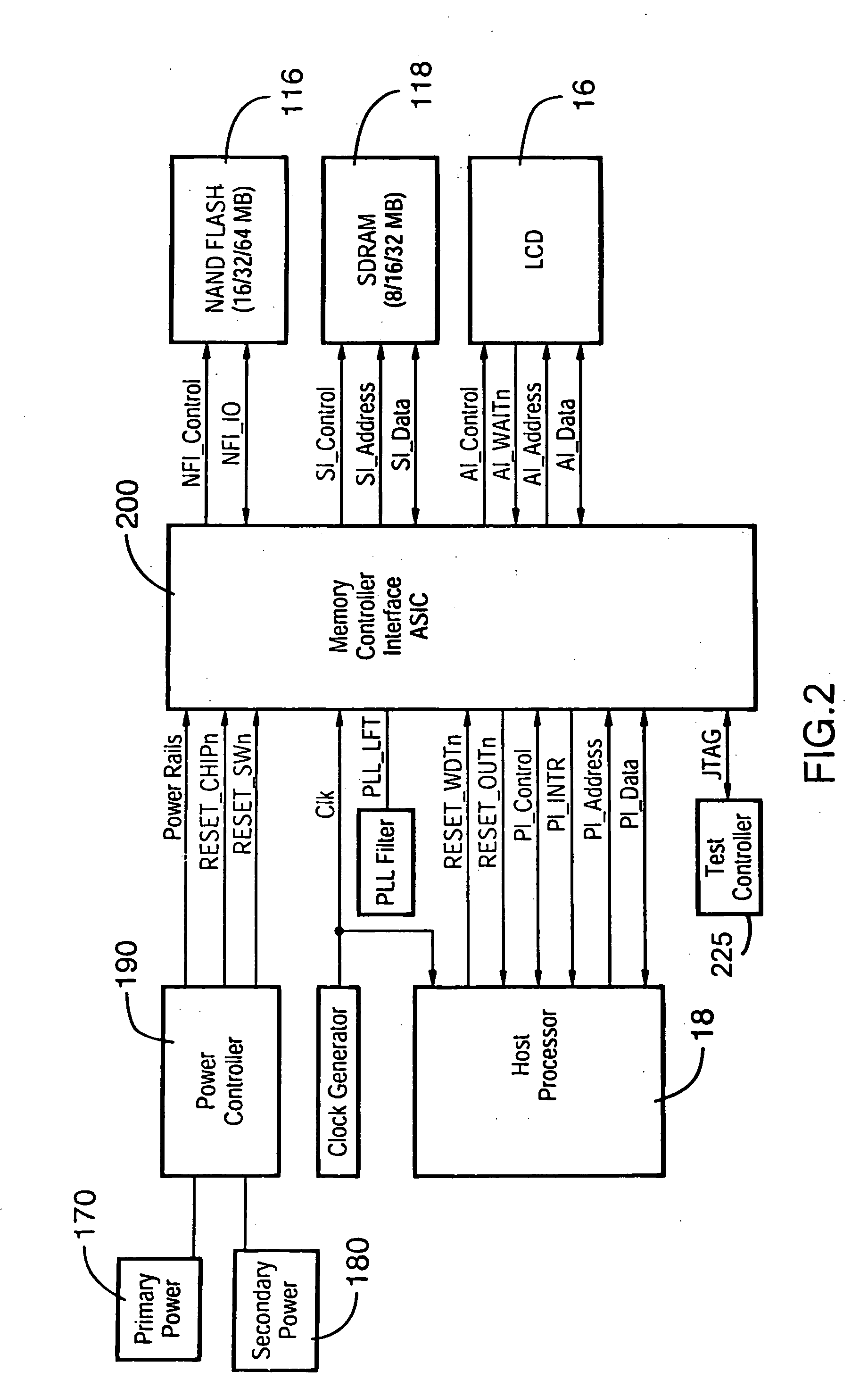
Debugging port security interface
ActiveUS20050193220A1Digital data processing detailsUnauthorized memory use protectionLimited accessJoint Test Action Group
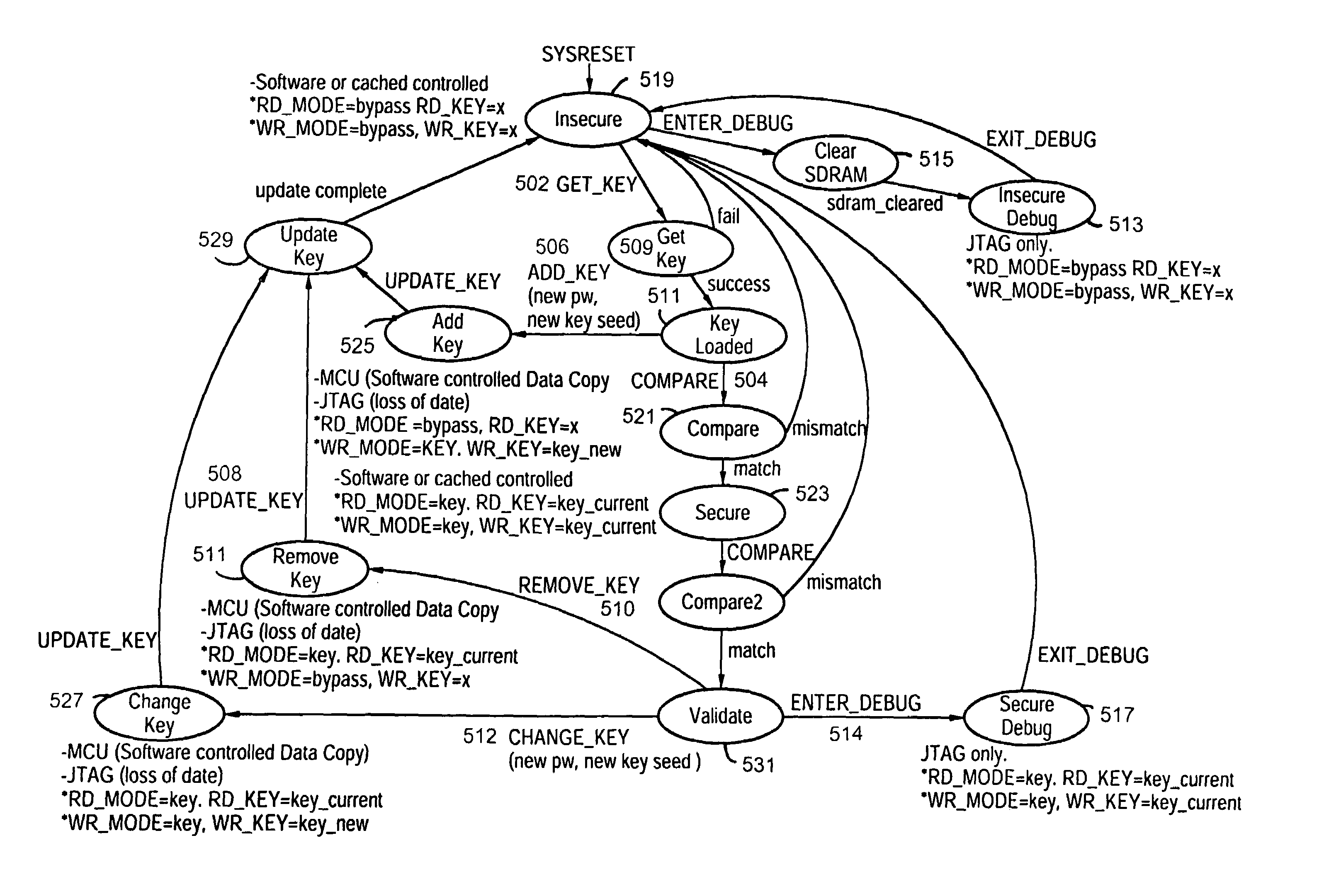
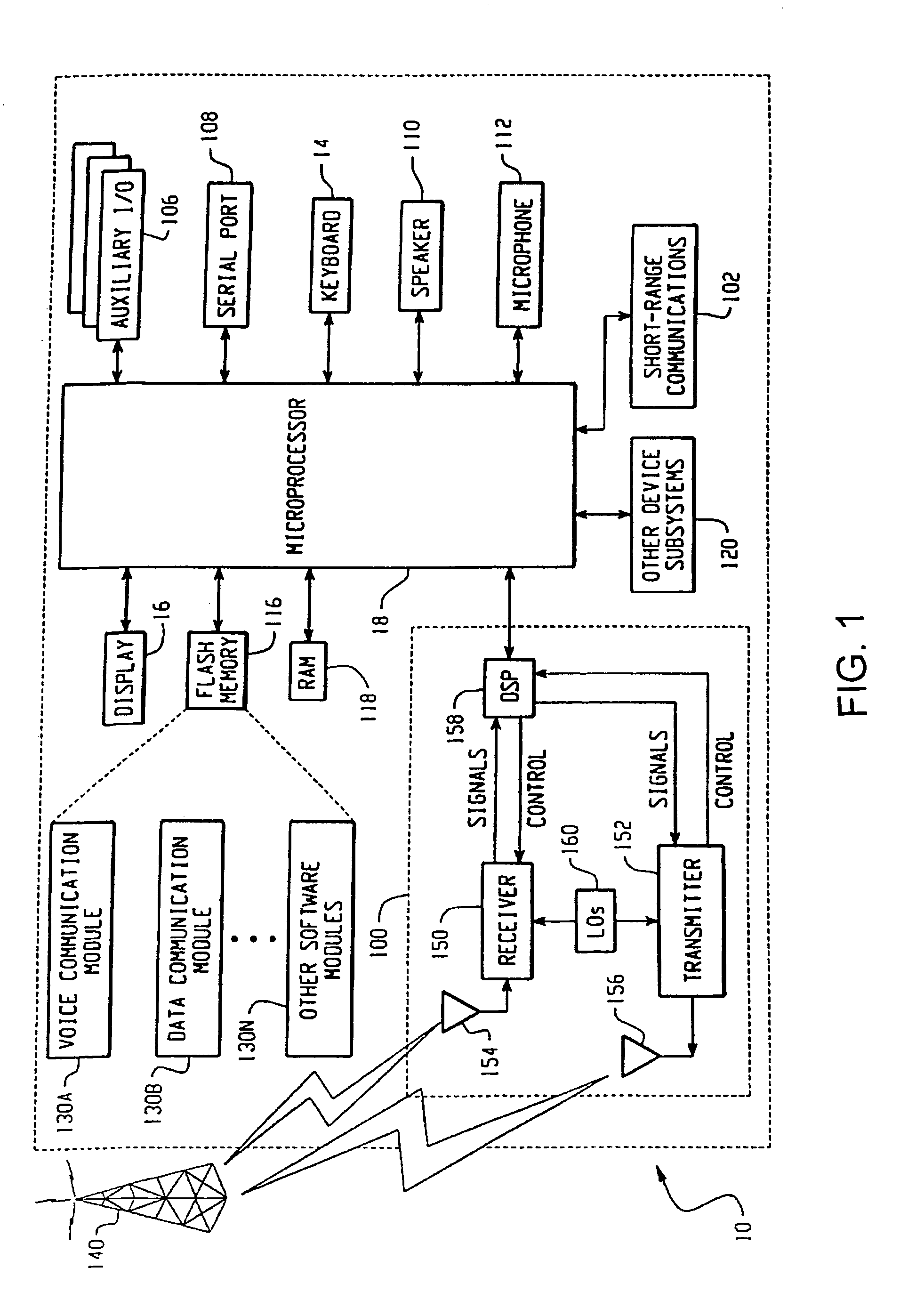
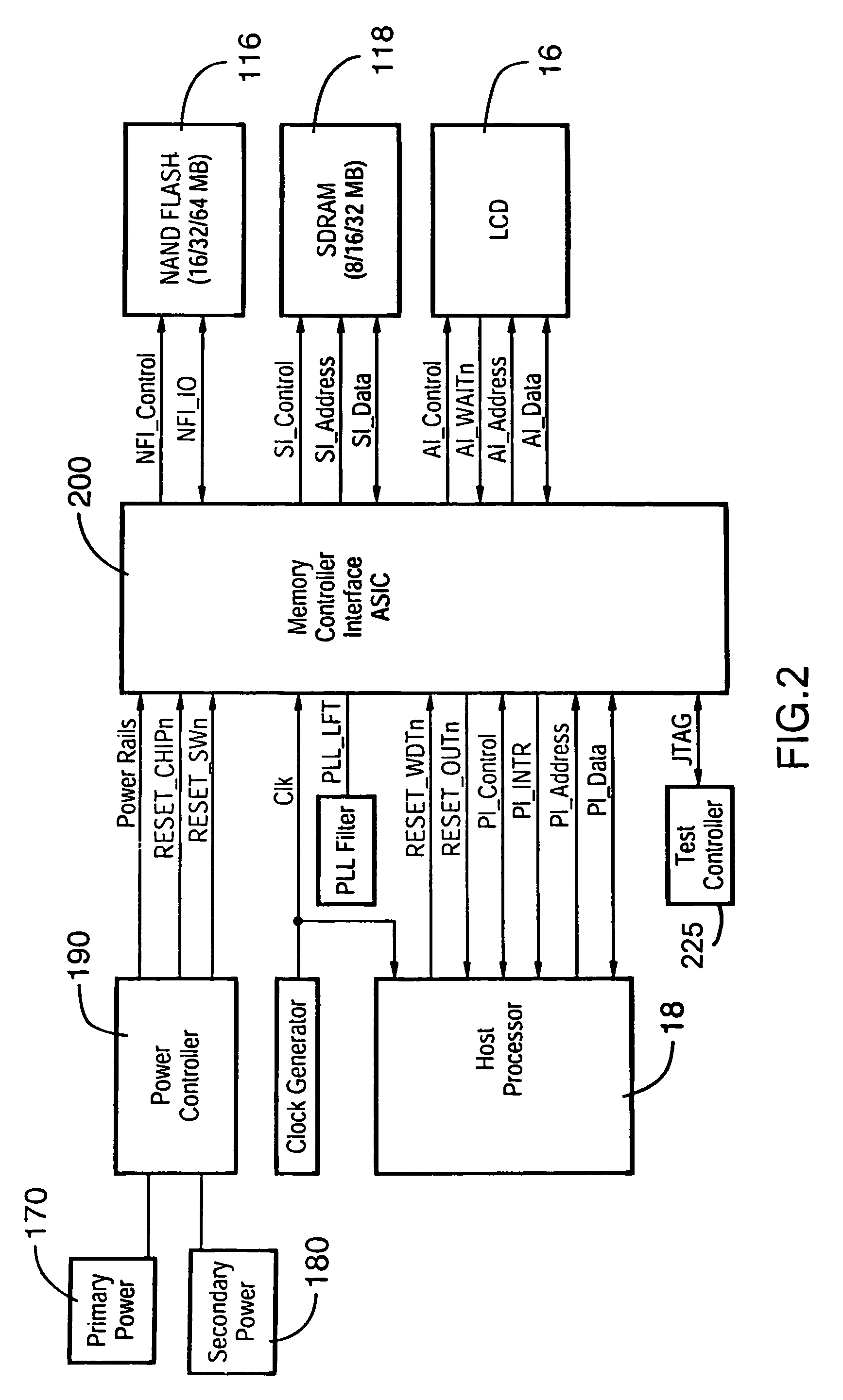
The present invention provides a secure JTAG interface to an application-specific integrated circuit (ASIC). In the preferred embodiment the invention operates through the combined efforts of a Security Module (SM) comprising a state machine that controls the security modes for the ASIC, and a Test Control Module (TCM) which contains the JTAG interface. The TCM operates in either a restricted mode or an unrestricted mode, depending on the state of the SM state machine. In a restricted mode, only limited access to memory content is permitted. In an unrestricted mode, full access to memory content is permitted.
Owner:BLACKBERRY LTD
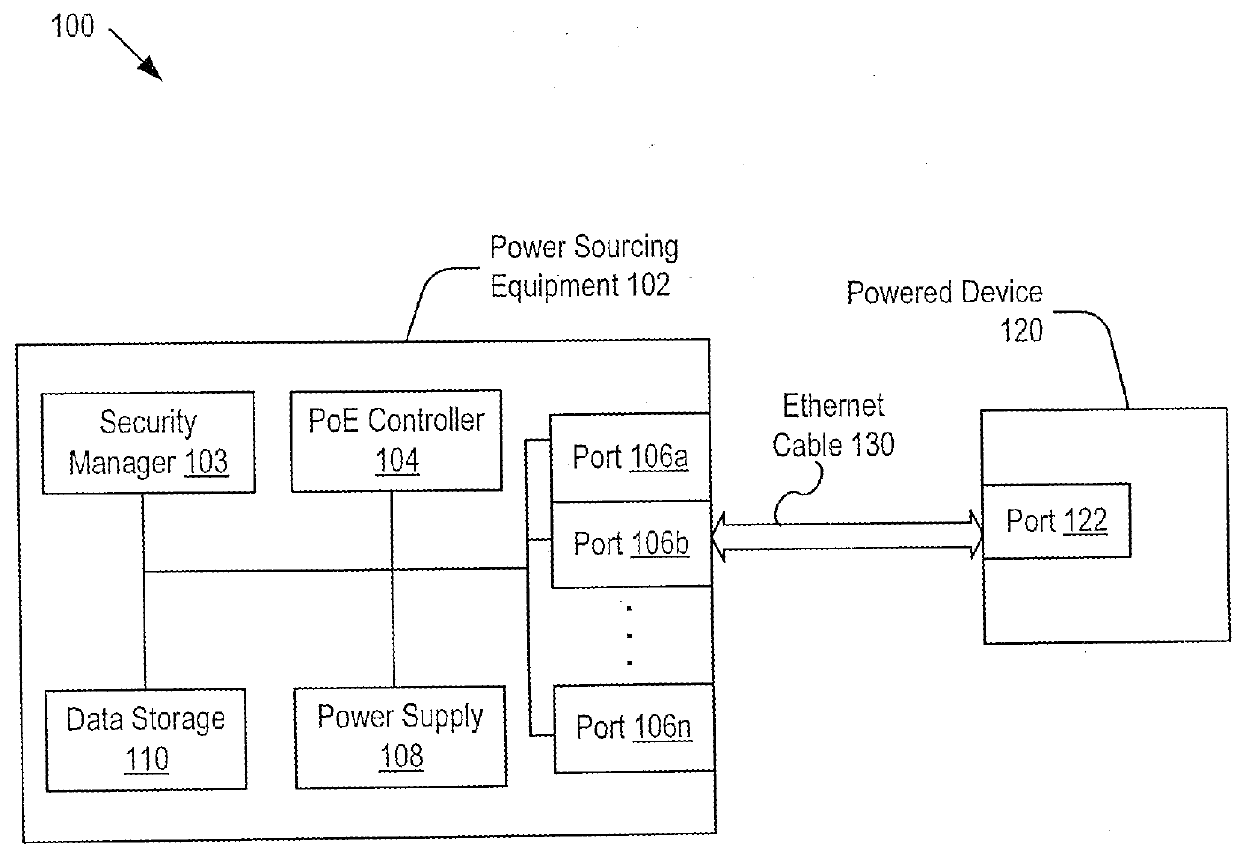
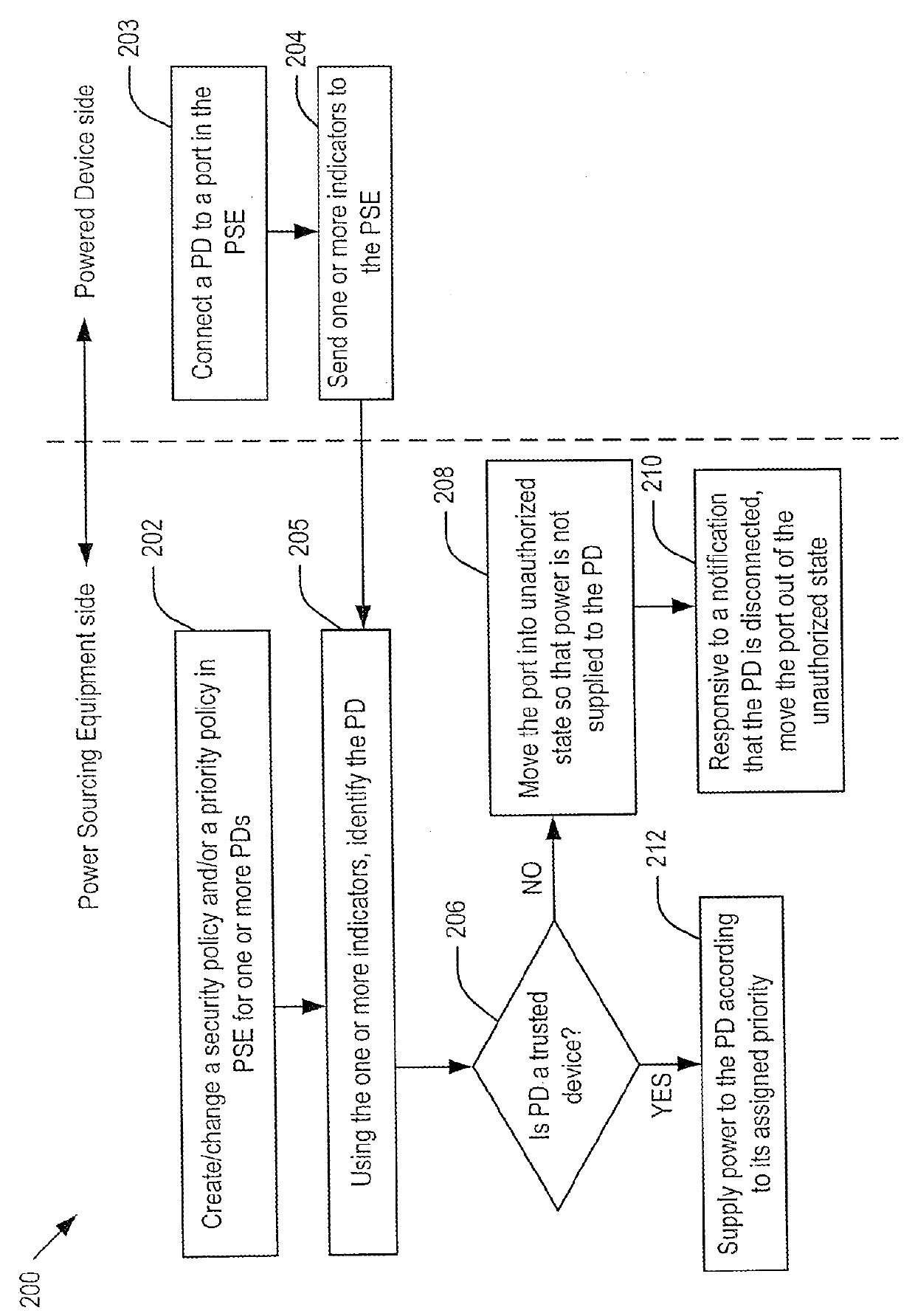
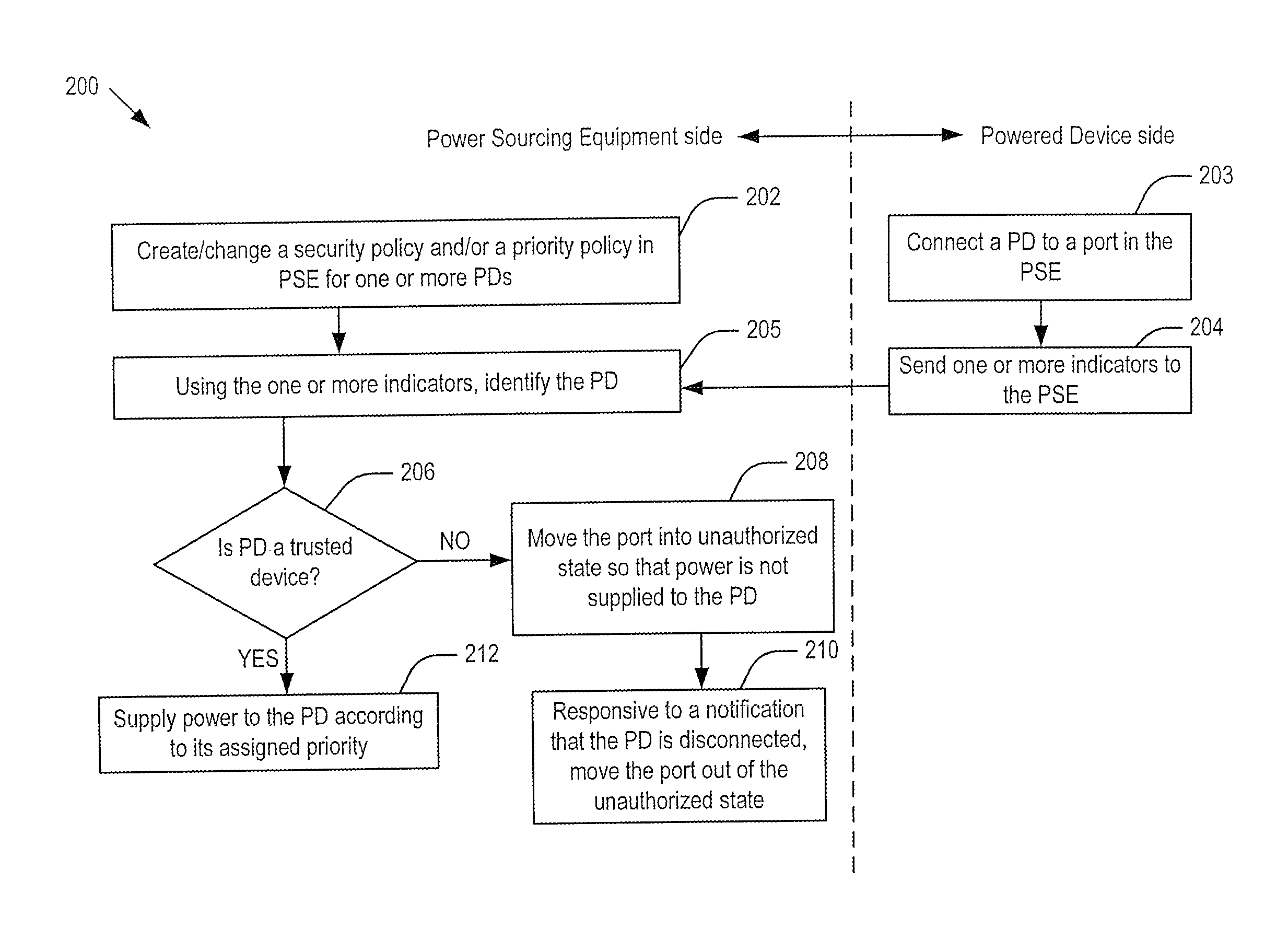
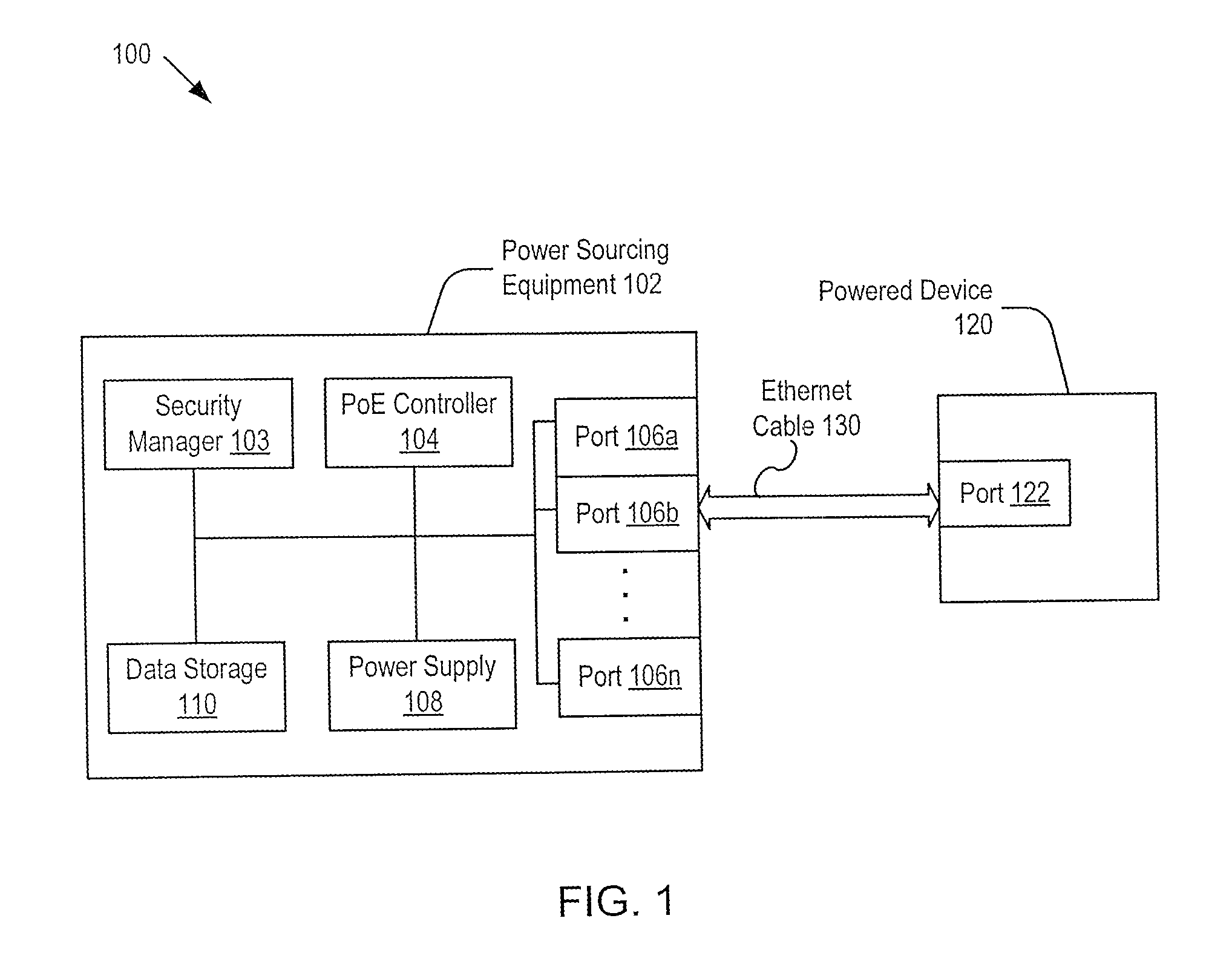
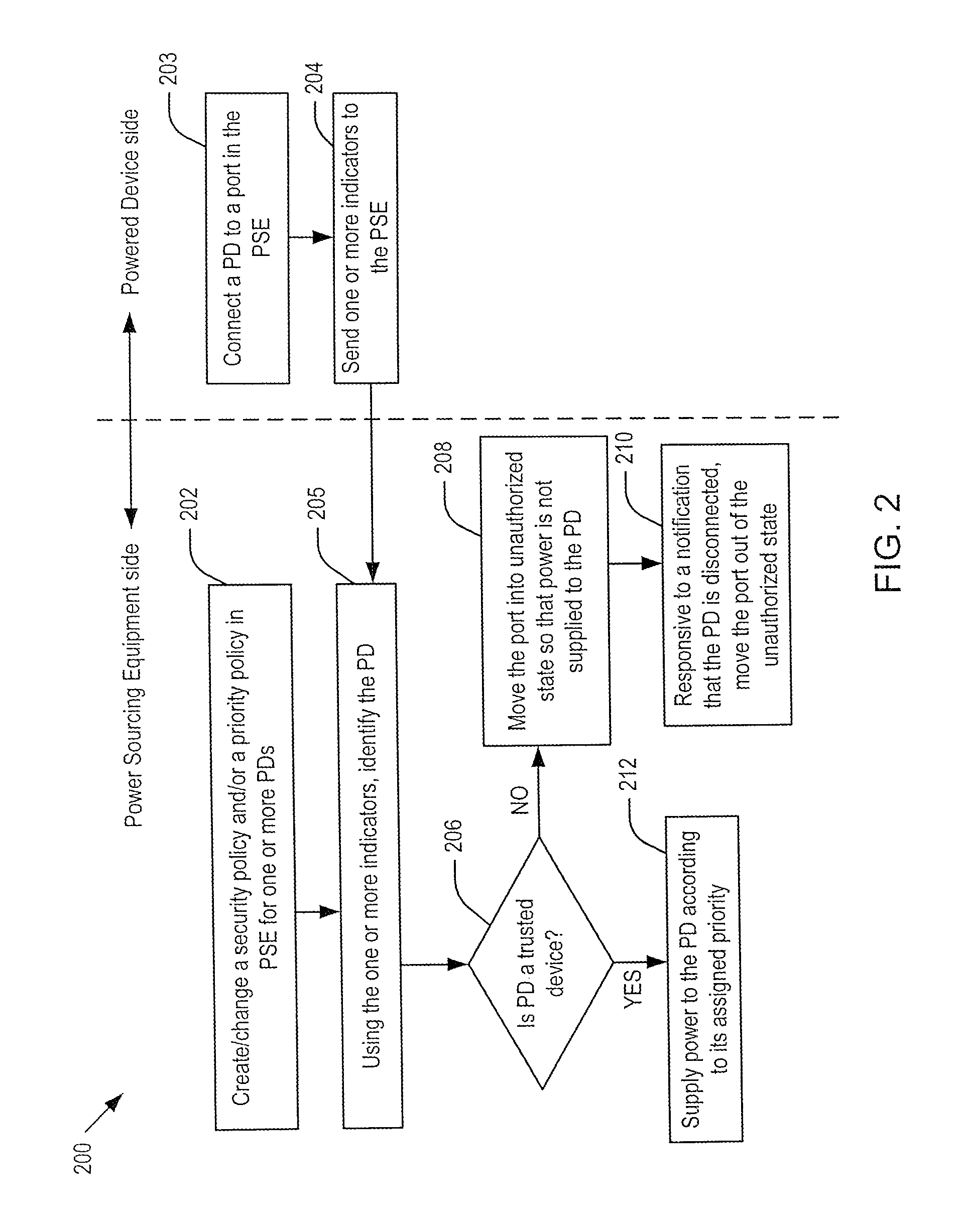
Supporting port security on power-over-ethernet enabled ports
ActiveUS20160055354A1Error detection/correctionVolume/mass flow measurementControl powerElectricity delivery
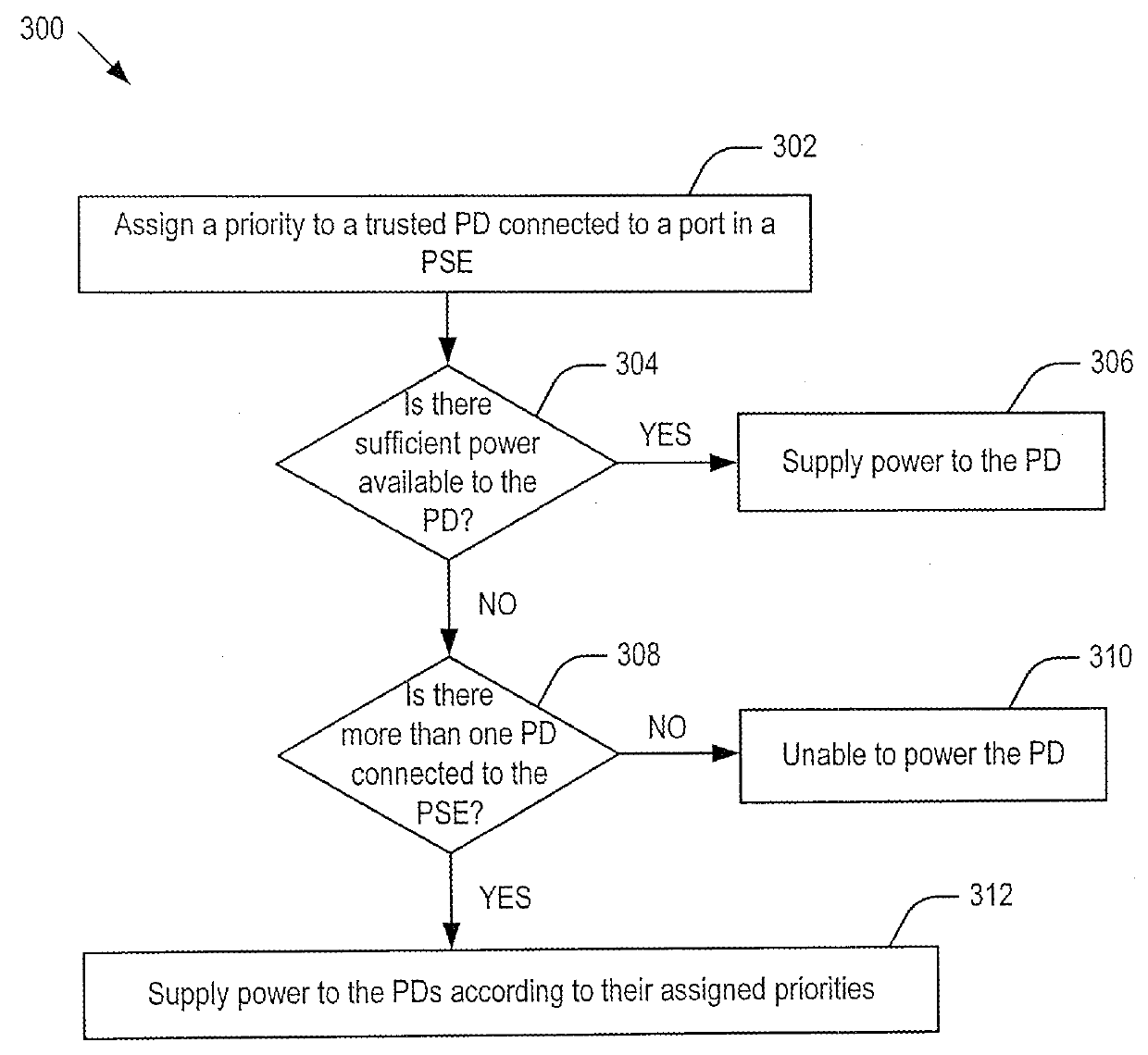
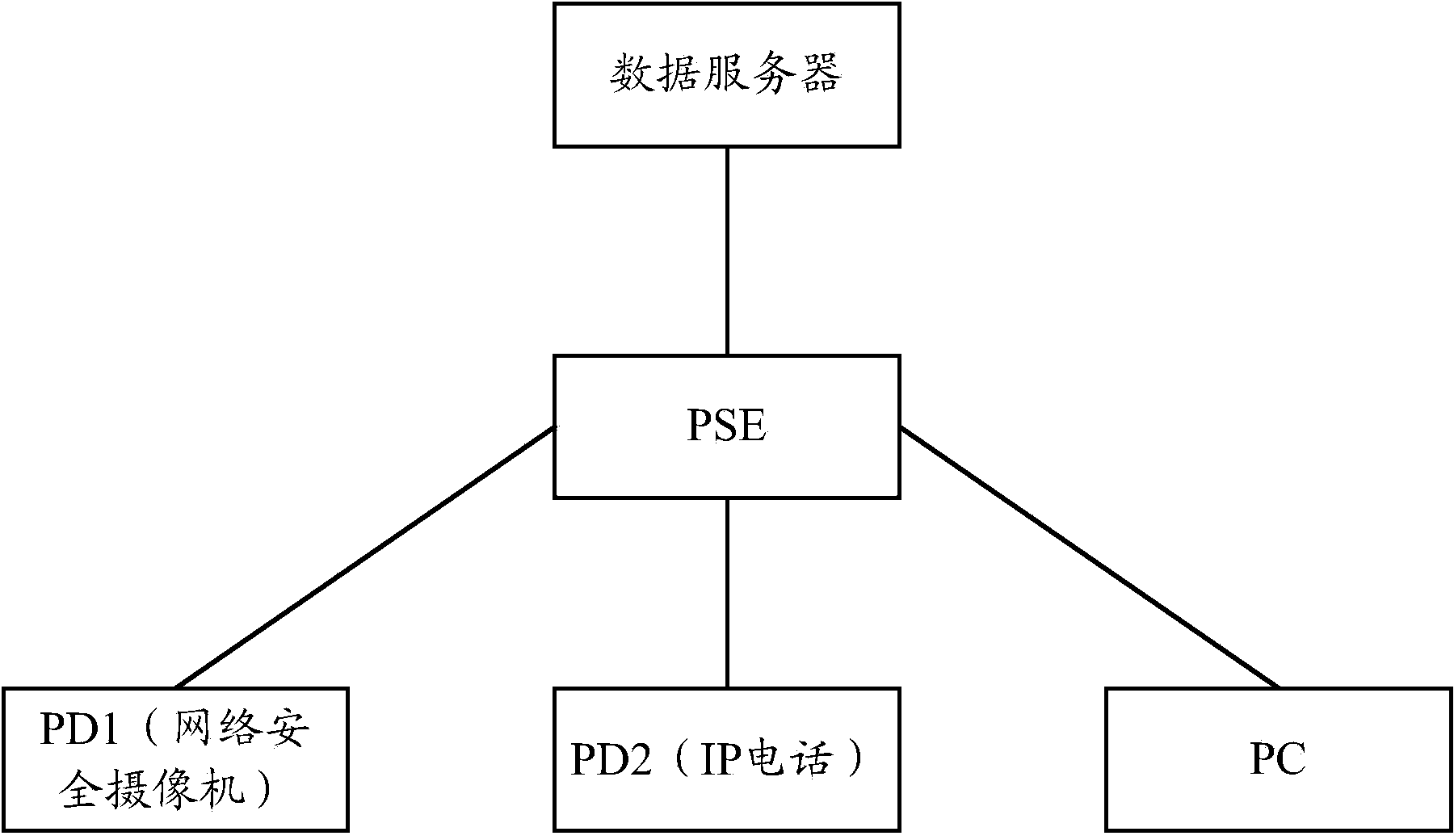
Embodiments of the present invention include systems and methods for controlling power delivery to a port in a power sourcing equipment. The power sourcing equipment receives identity information from a device connected to the port and determines whether the device is a trusted device or a rogue device according to a security policy. If the device is a trusted device, the power sourcing equipment supplies data and electrical power to the port according to a priority policy. If the device is a rogue device, the power source equipment does not supply electrical power to the port.
Owner:DELL PROD LP
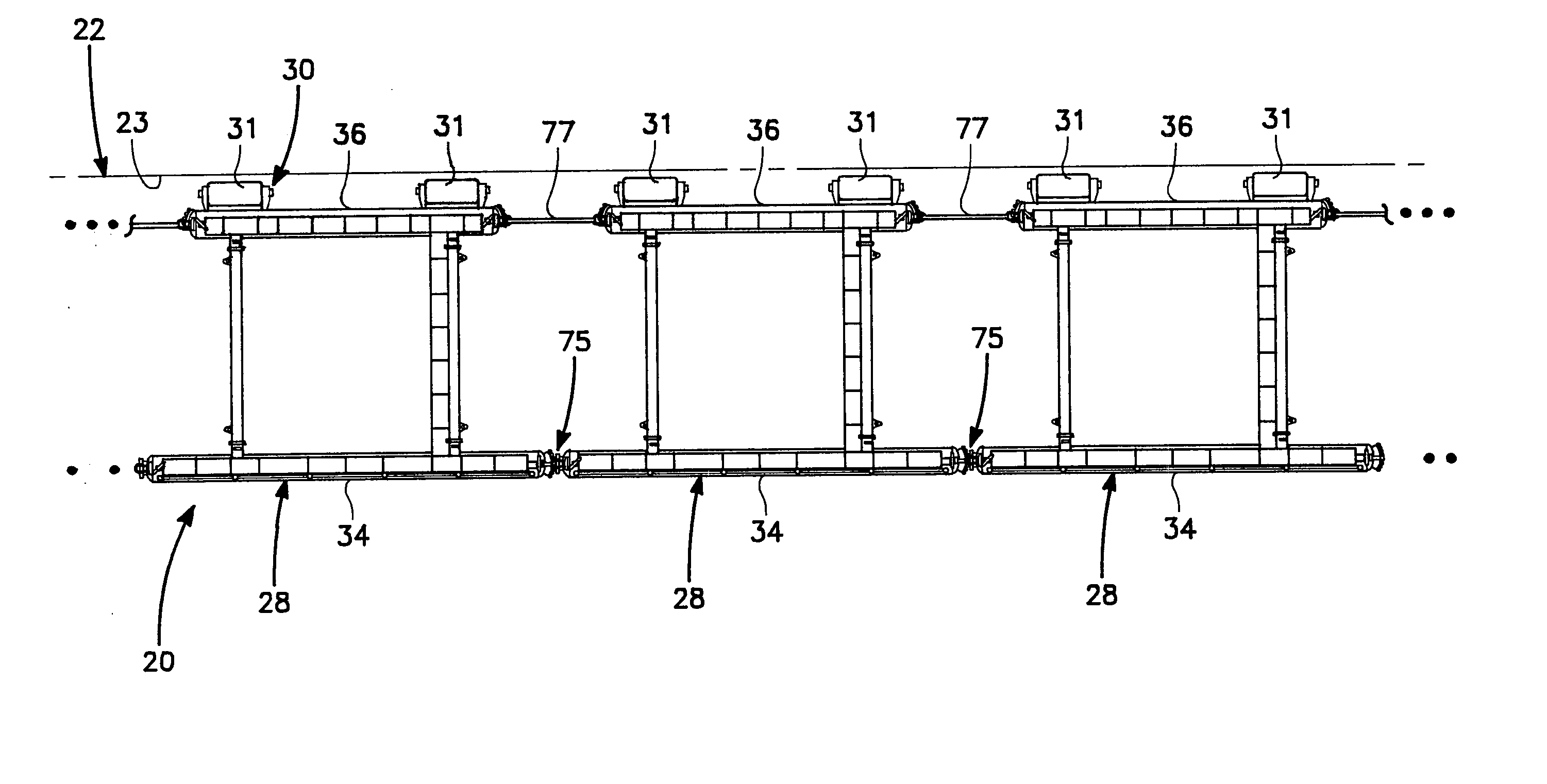
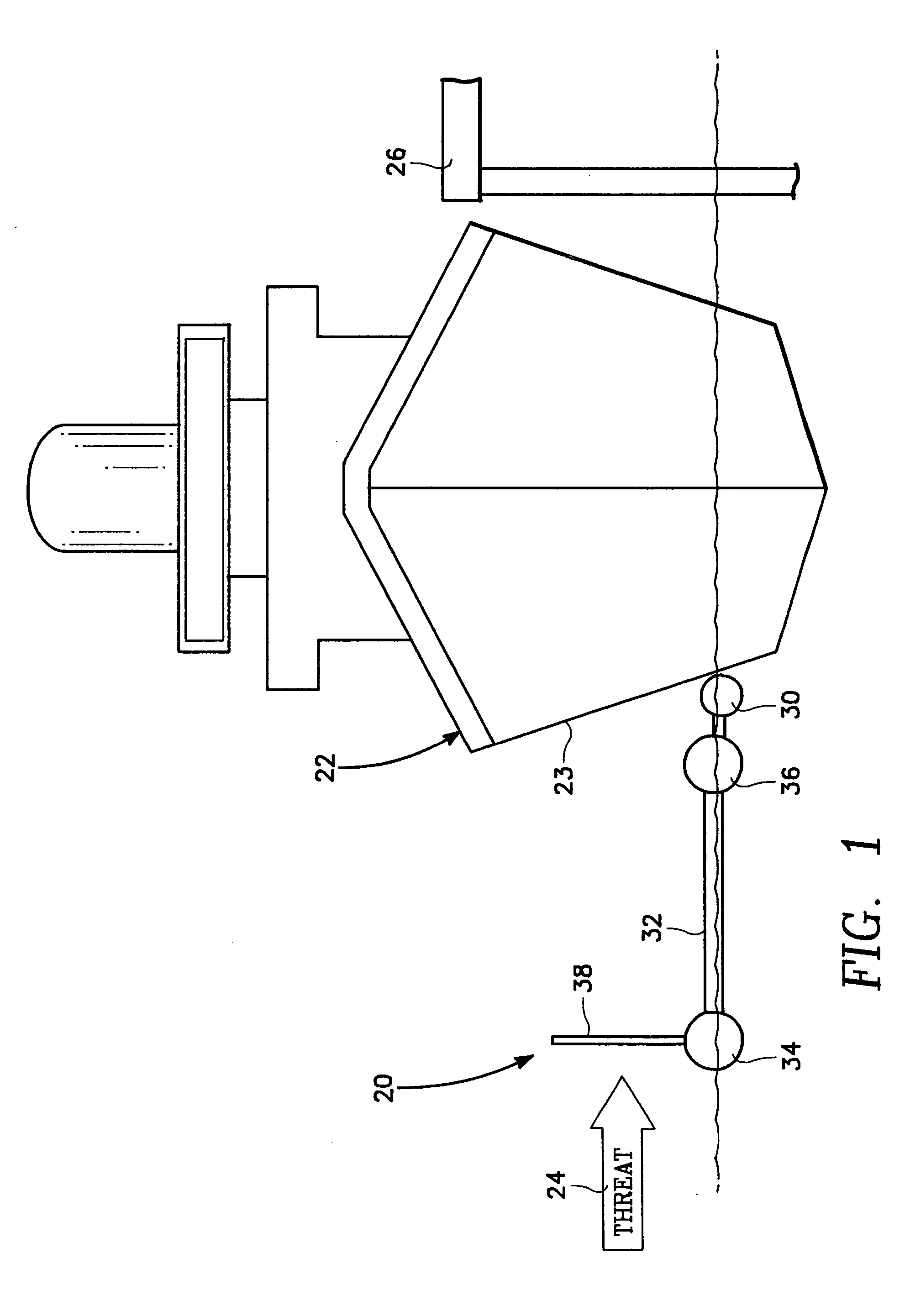
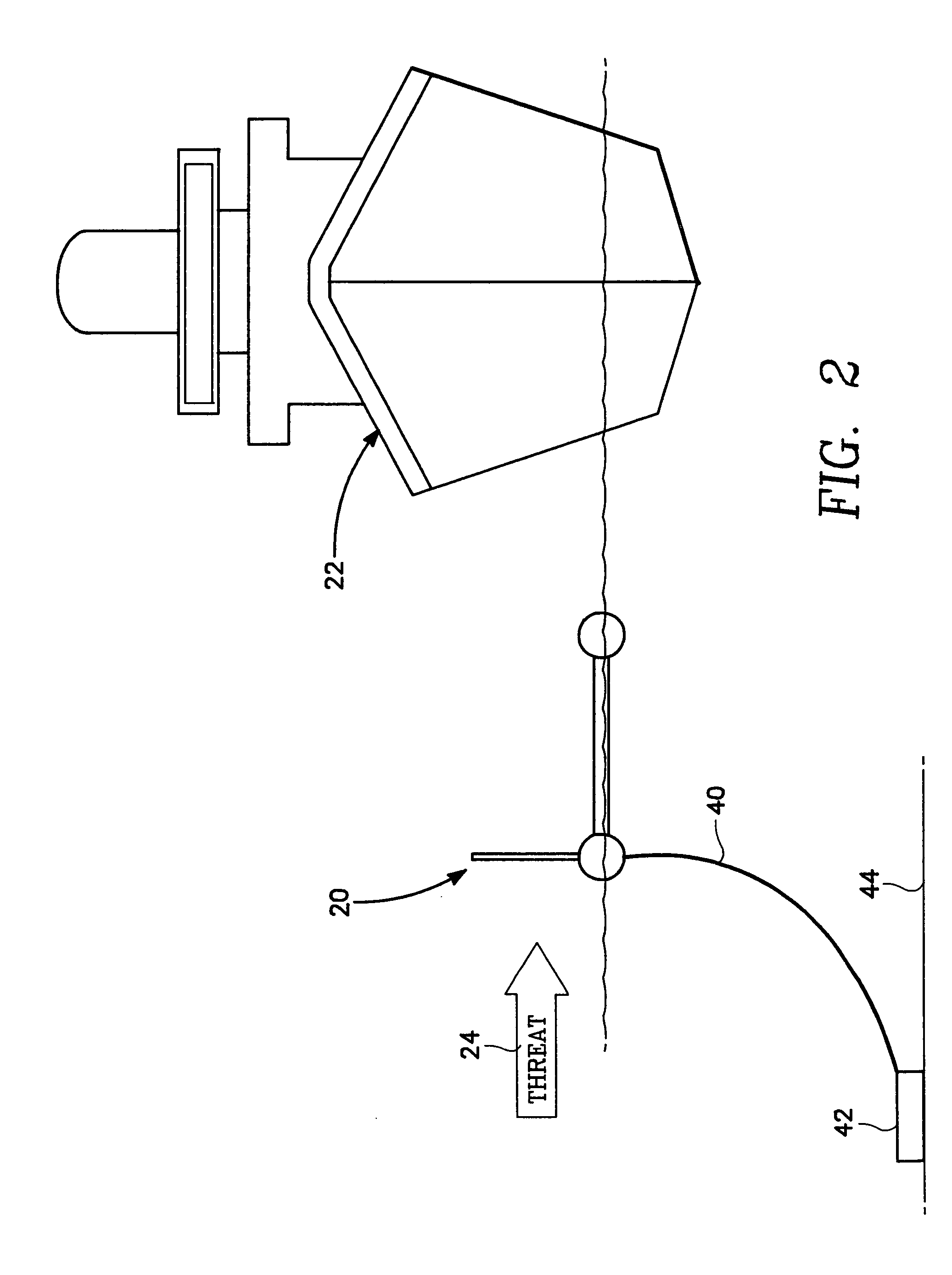
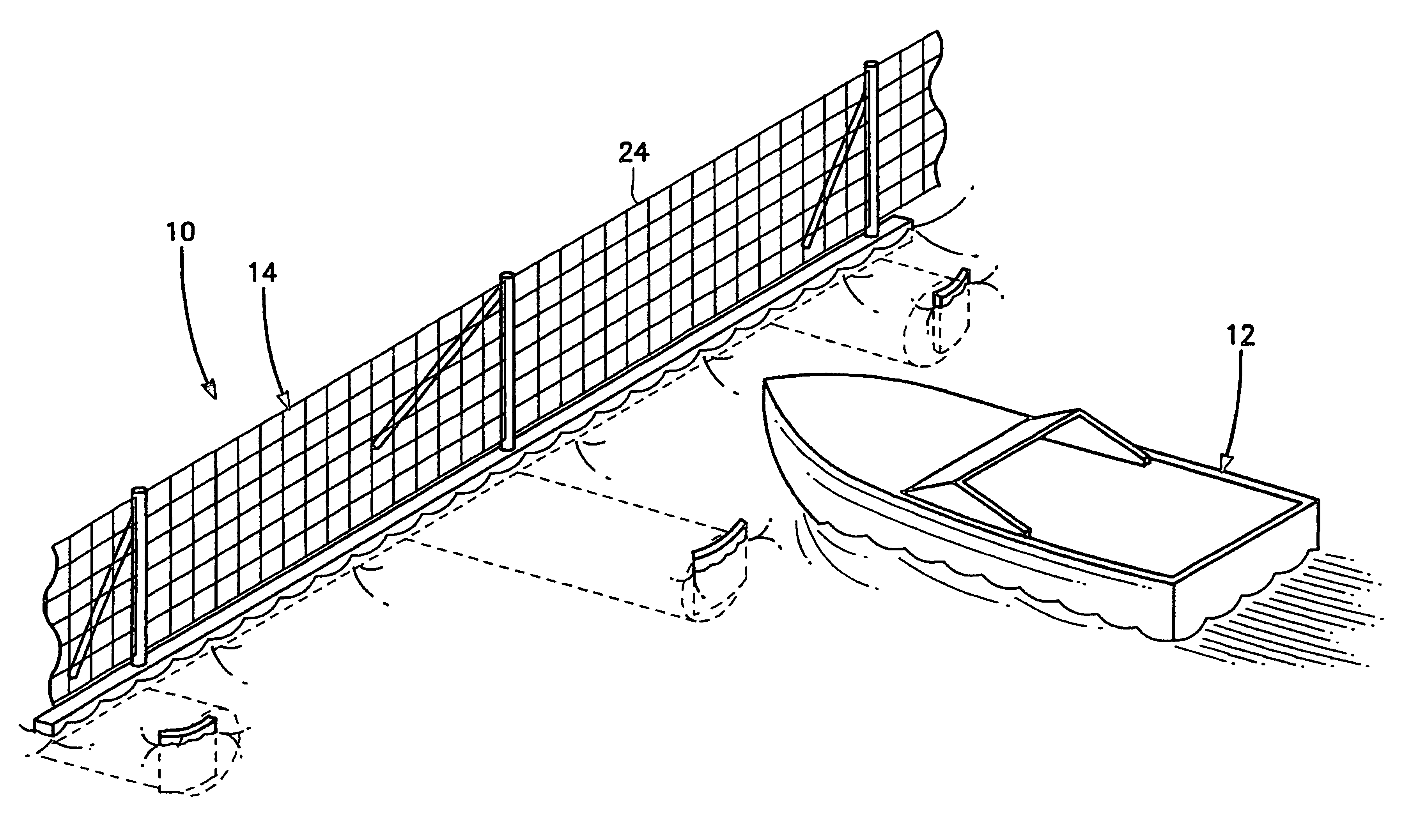
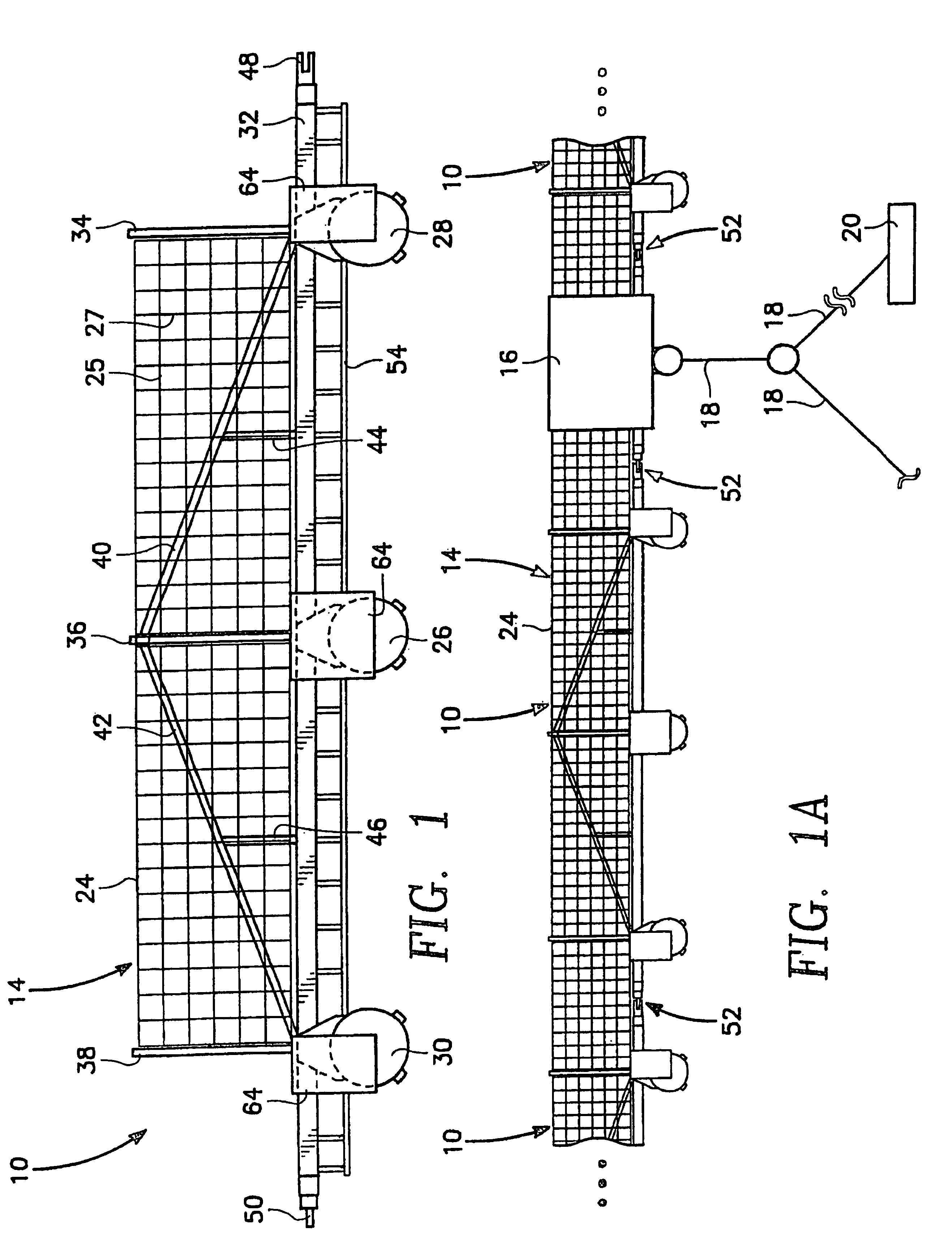
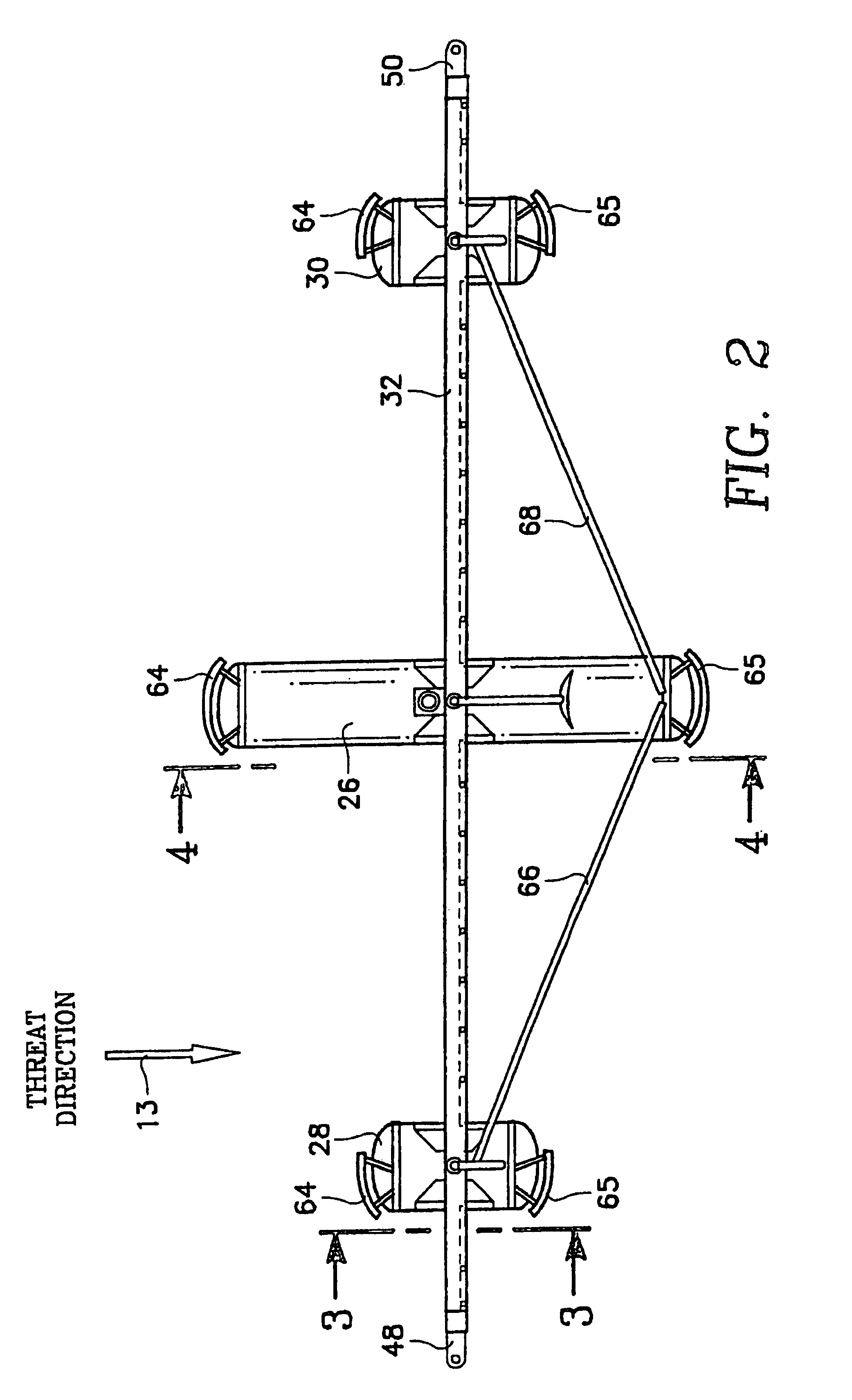
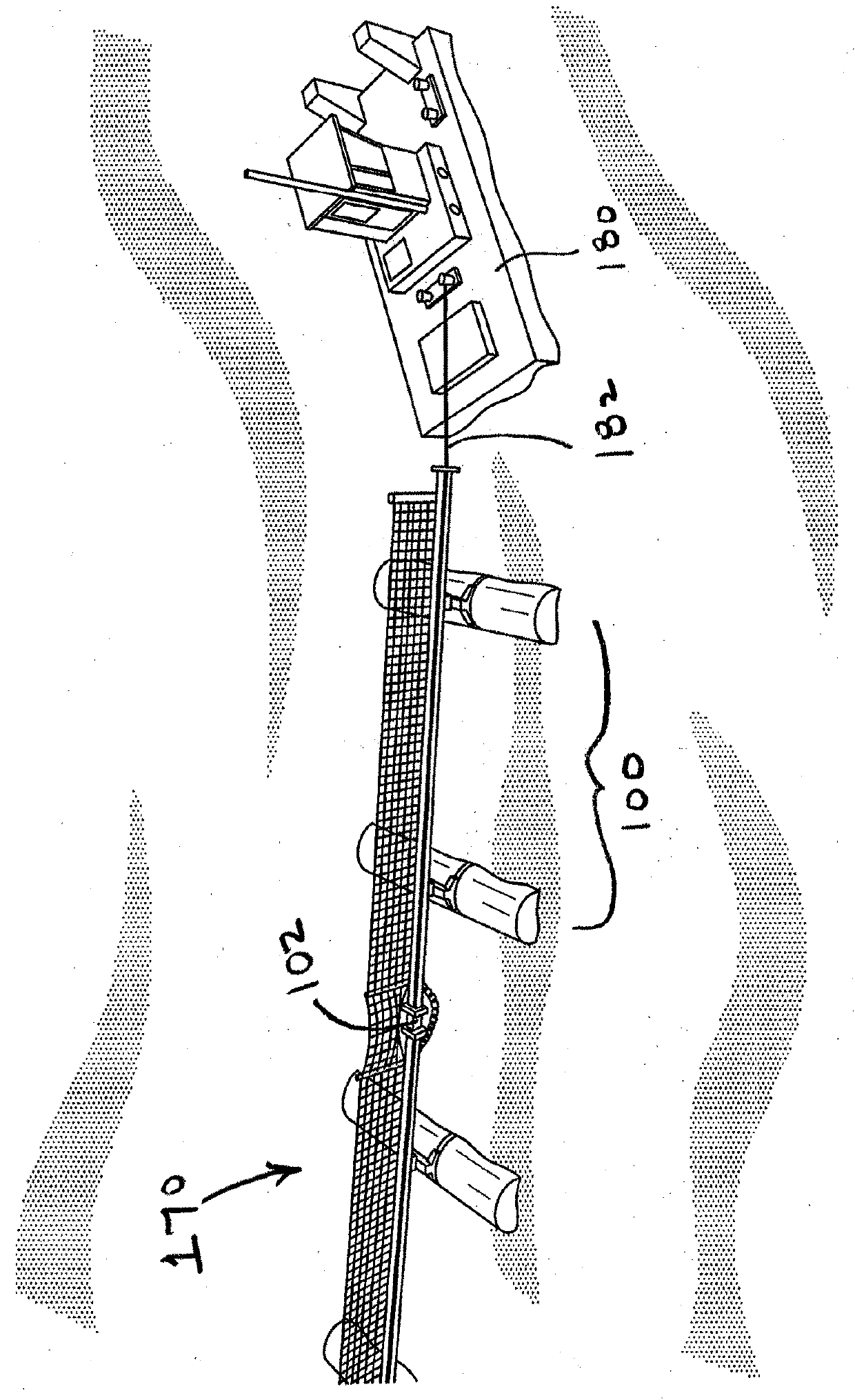
Port security barrier
ActiveUS7401565B2Easy to relocateSimple designDefence devicesDefensive equipmentEmbedded systemPort security
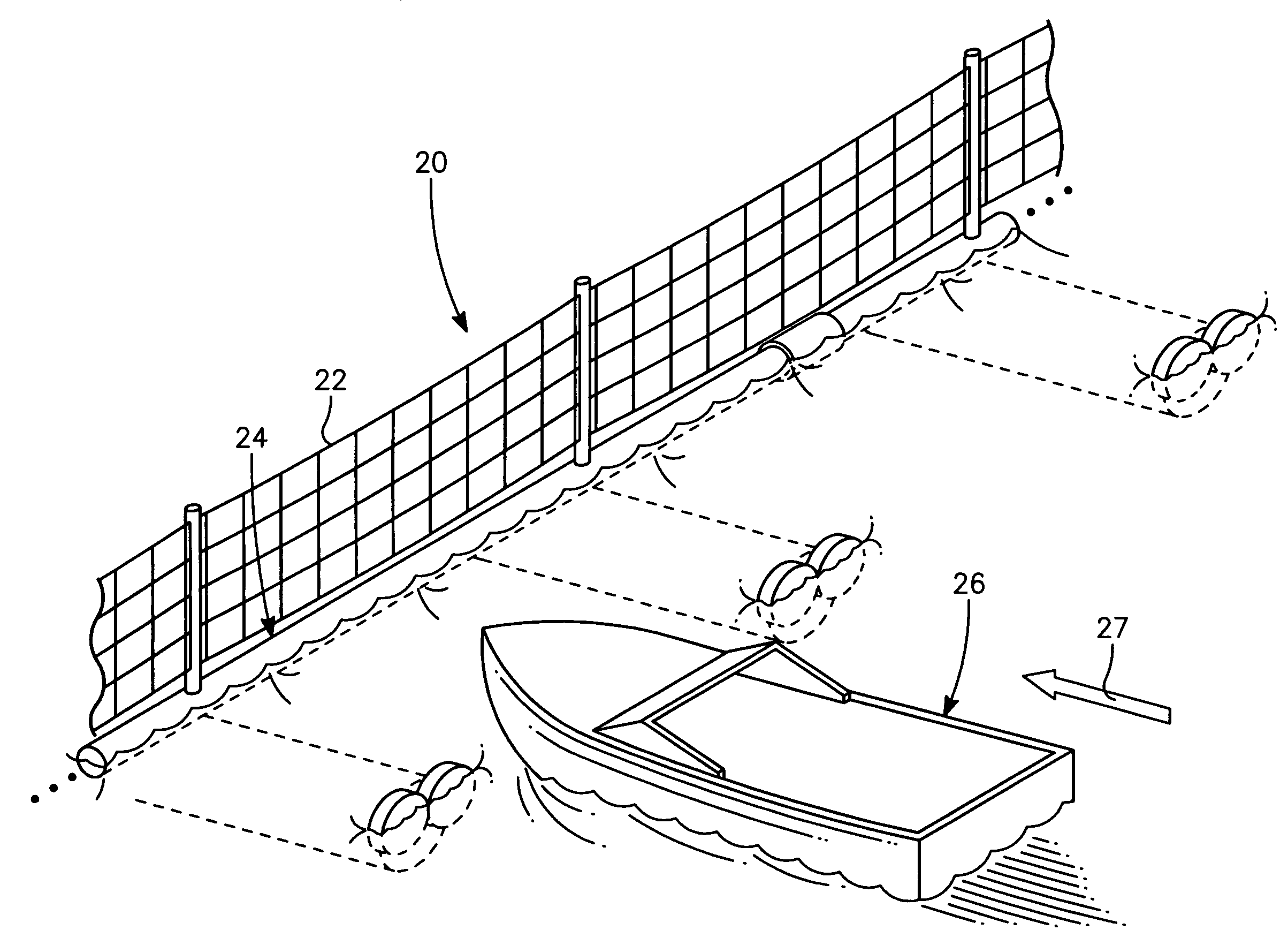
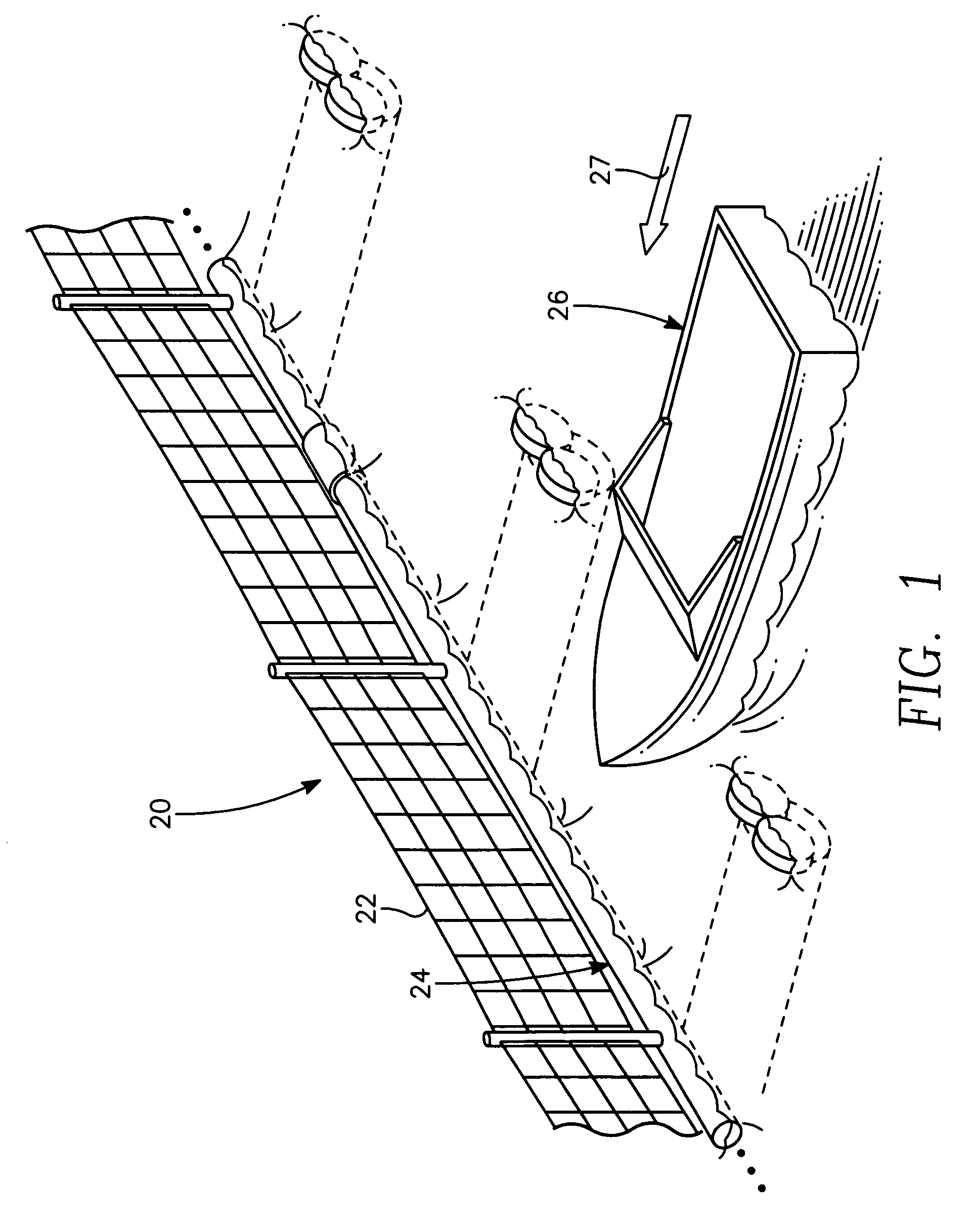
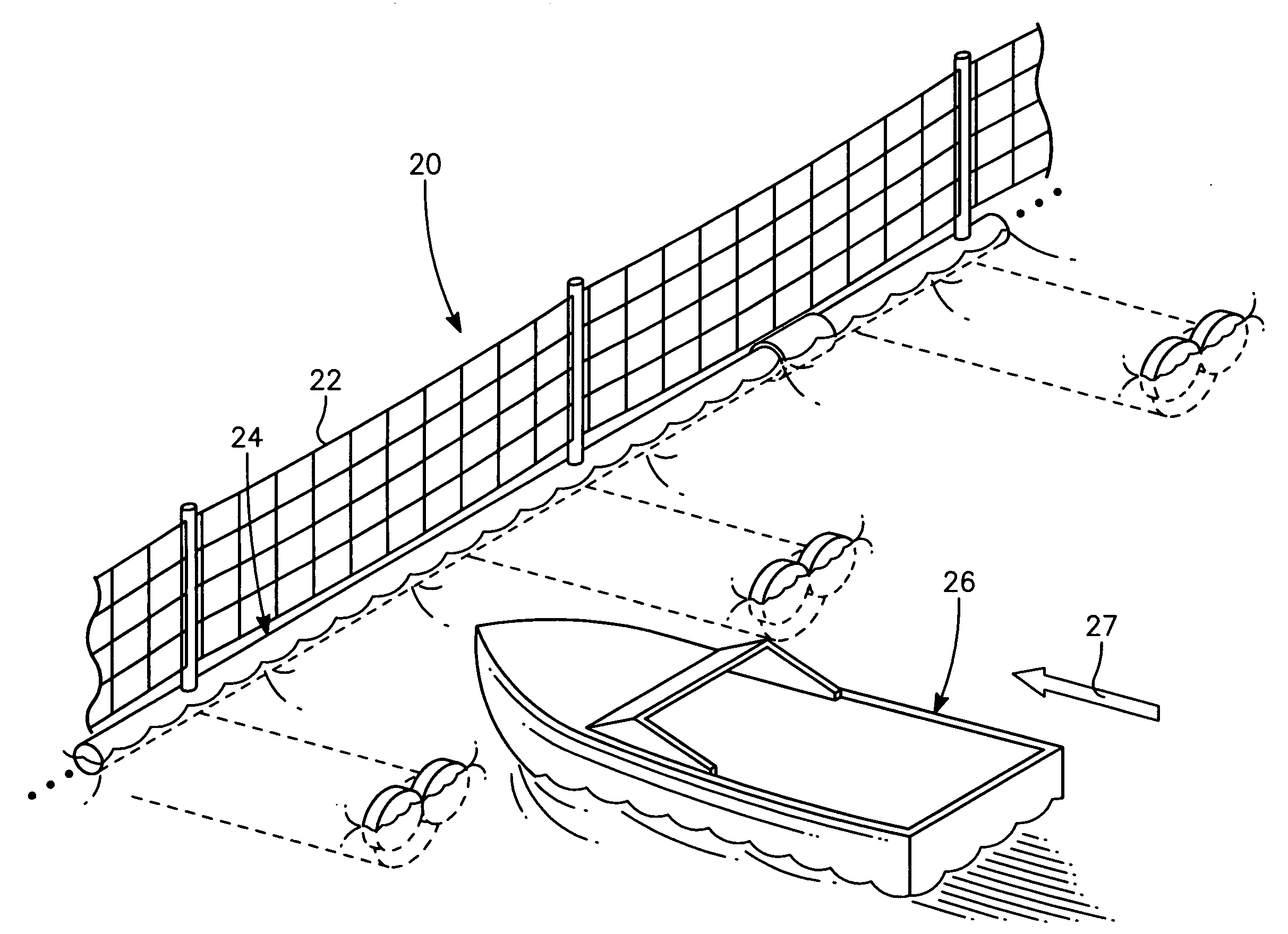
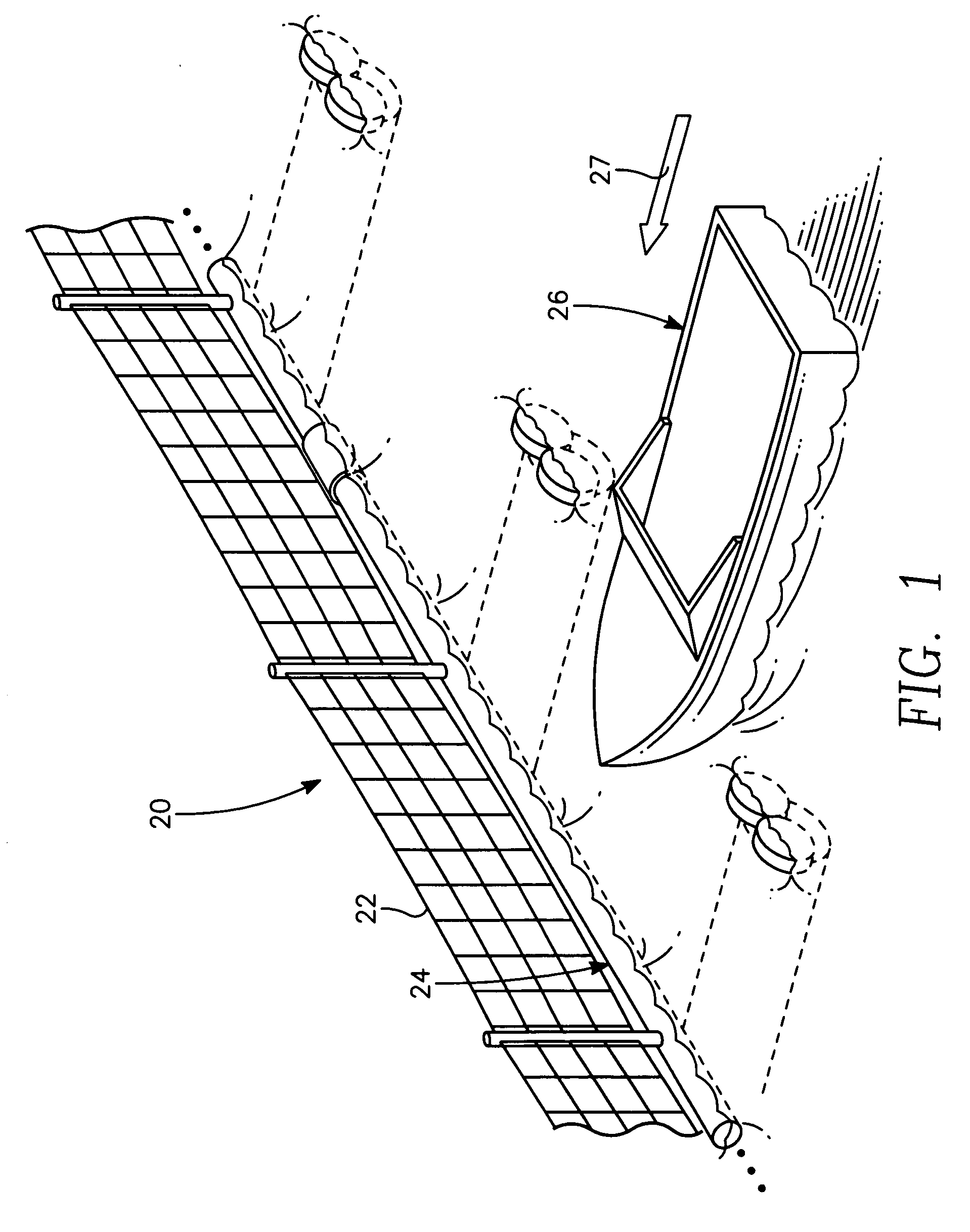
The port security barrier includes multiple barrier float assemblies connected to one another to form a barrier to stop, delay and discourage attacks by high speed boats of sixty five feet or less in length on high valued waterfront assets such as ports and docking facilities. The port security barrier includes multiple barrier floats coupled to one another by flange connectors. Each barrier float assembly also has a capture nylon net which is used to capture the high speeds and prevent an intrusion into restricted waters.
Owner:UNITED STATES OF AMERICA
Port security barrier
ActiveUS20080105184A1Easy to relocateSimple designDefence devicesDefensive equipmentEmbedded systemPort security
The port security barrier includes multiple barrier float assemblies connected to one another to form a barrier to stop, delay and discourage attacks by high speed boats of sixty five feet or less in length on high valued waterfront assets such as ports and docking facilities. The port security barrier includes multiple barrier floats coupled to one another by flange connectors. Each barrier float assembly also has a capture nylon net which is used to capture the high speeds and prevent an intrusion into restricted waters.
Owner:UNITED STATES OF AMERICA
Debugging port security interface
ActiveUS7461407B2Digital data processing detailsUser identity/authority verificationLimited accessComputer module
The present invention provides a secure JTAG interface to an application-specific integrated circuit (ASIC). In the preferred embodiment the invention operates through the combined efforts of a Security Module (SM) comprising a state machine that controls the security modes for the ASIC, and a Test Control Module (TCM) which contains the JTAG interface. The TCM operates in either a restricted mode or an unrestricted mode, depending on the state of the SM state machine. In a restricted mode, only limited access to memory content is permitted. In an unrestricted mode, full access to memory content is permitted.
Owner:MALIKIE INNOVATIONS LTD
Computer information security system
InactiveCN104751036AImprove securityKey distribution for secure communicationDigital data authenticationClassified informationComputer module
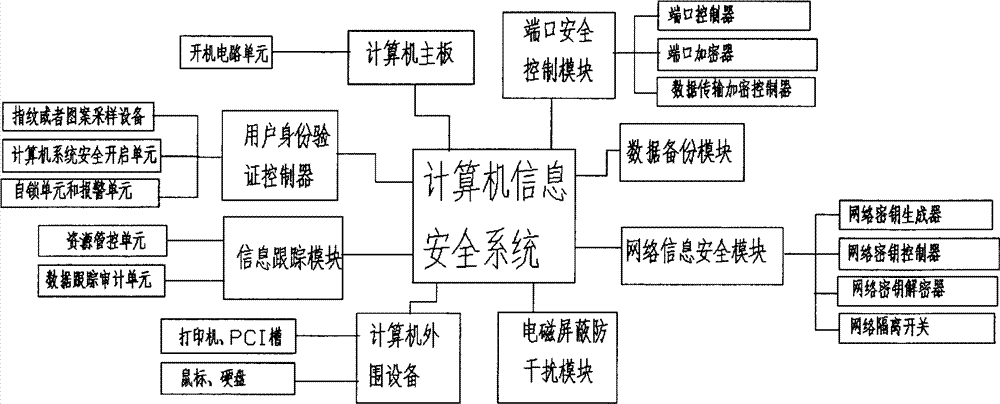
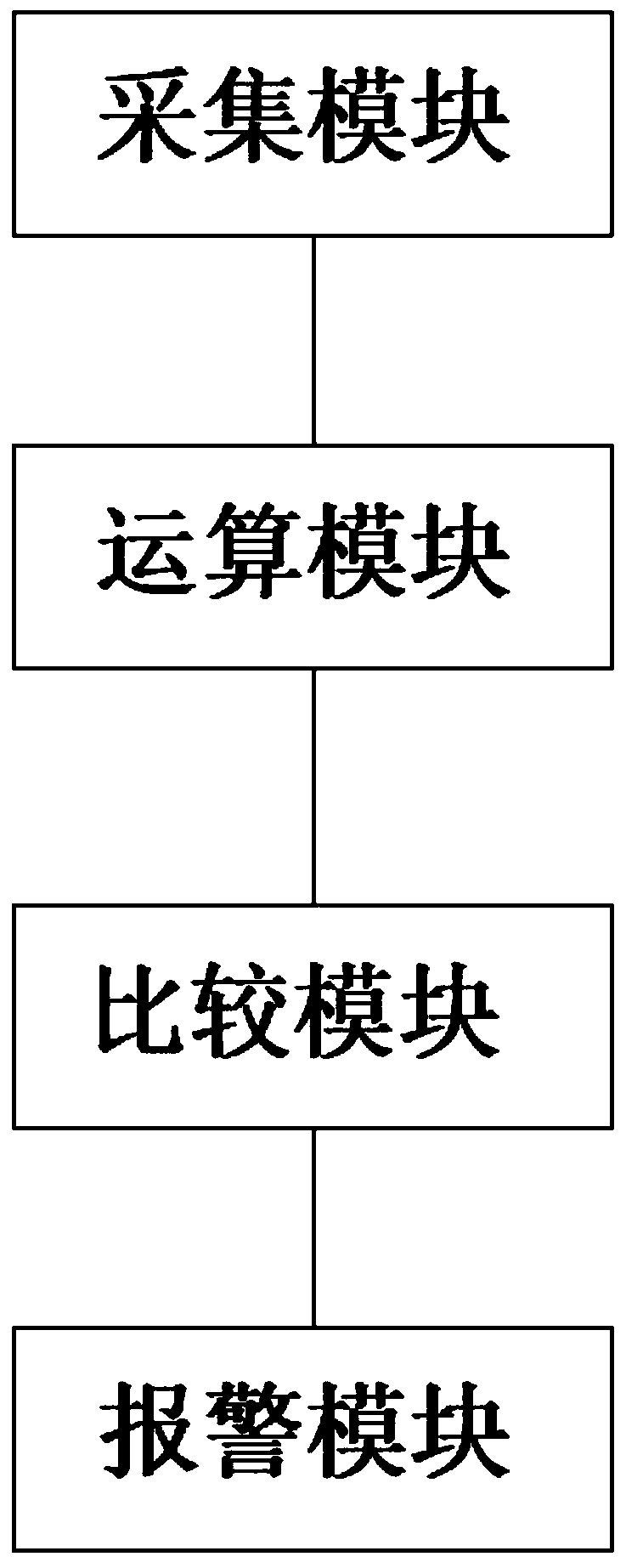
The invention provides a computer information security system. A computer main-board is connected with a computer peripheral, a user authentication controller is used for verifying whether user information has a legal identity, and a network security module is used for identifying and judging whether a network is safe; a port security control module is used for controlling an external interface of a computer system is opened to the outside world, an information tracking module is used for visiting, recording and tracking information visited and downloaded by the computer system, and an electromagnetic shielding anti-interference module is used for preventing electromagnetic leakage to cause classified information leakage. According to the system provided by the invention, the user authentication controller, a network information security module, the port security control module, the information racking module, the electromagnetic shielding anti-interference module and a data back-up module can be arranged to monitor and protect the information of the computer information security system from multiple angles and multiple aspects, therefore the security performances of use and transmission of the computer information security can be improved.
Owner:SHAANXI UNIV OF TECH
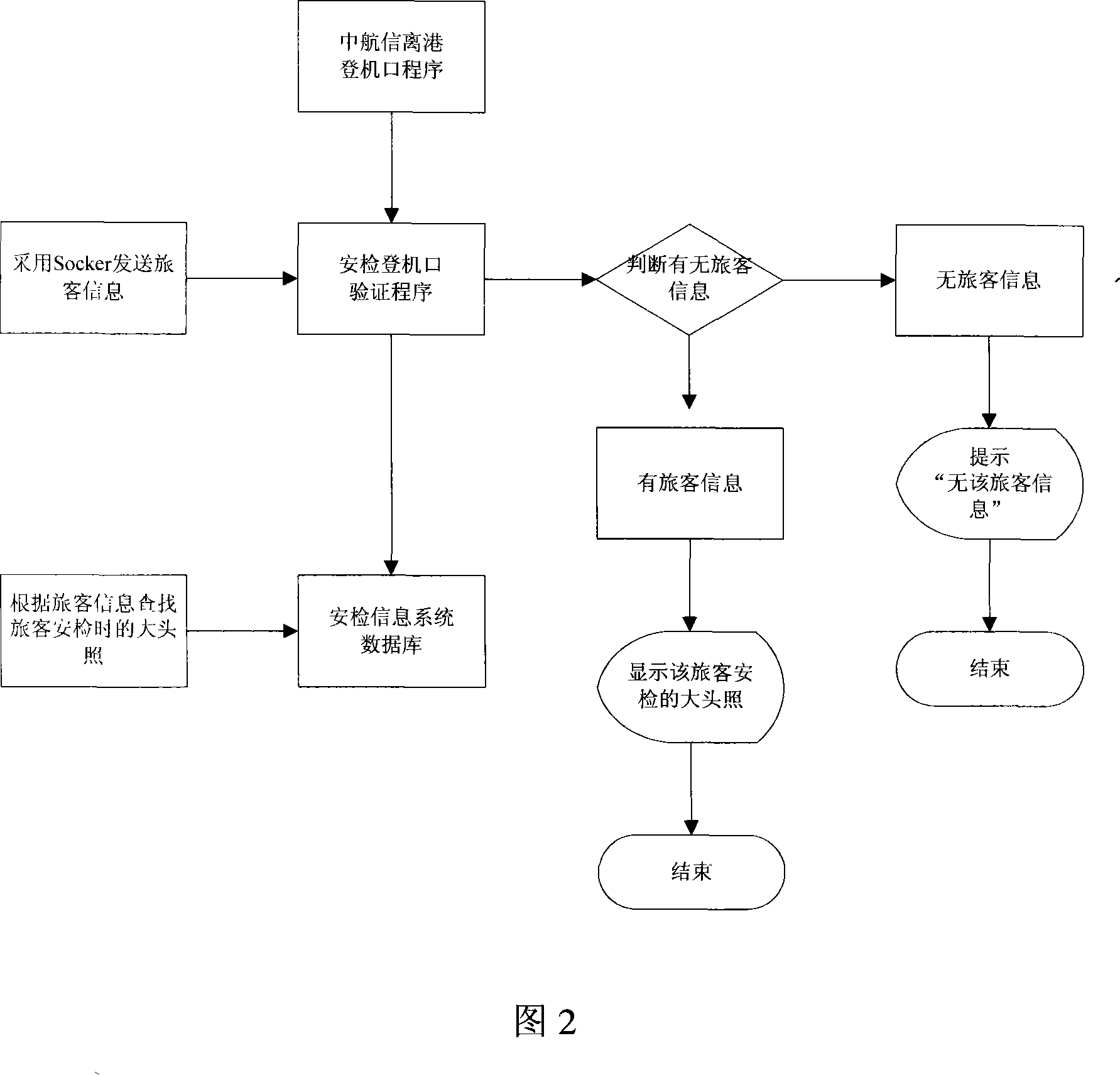
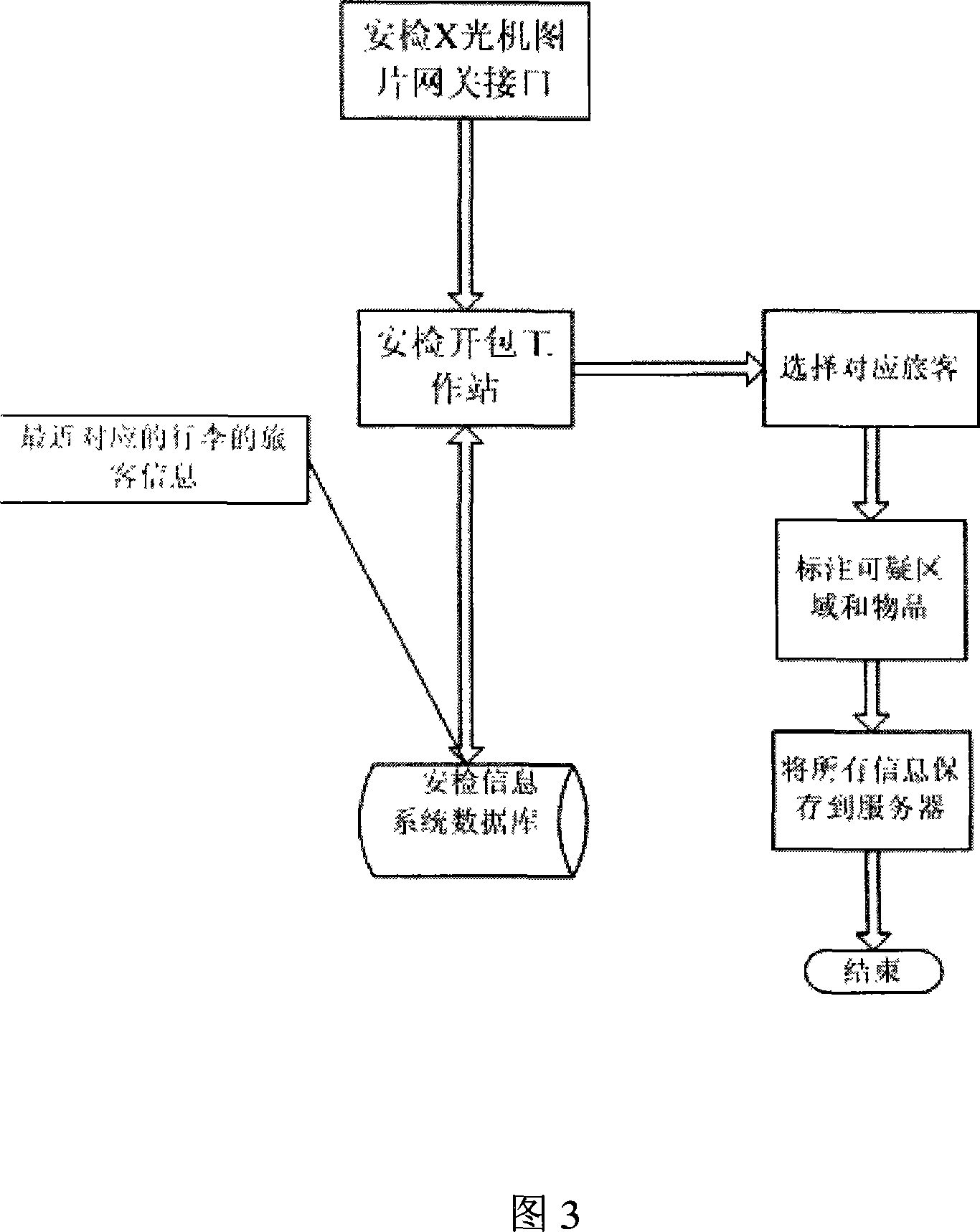
Air station security information system
InactiveCN101221670AGood serviceImprove management levelIndividual entry/exit registersQuality of serviceData sharing
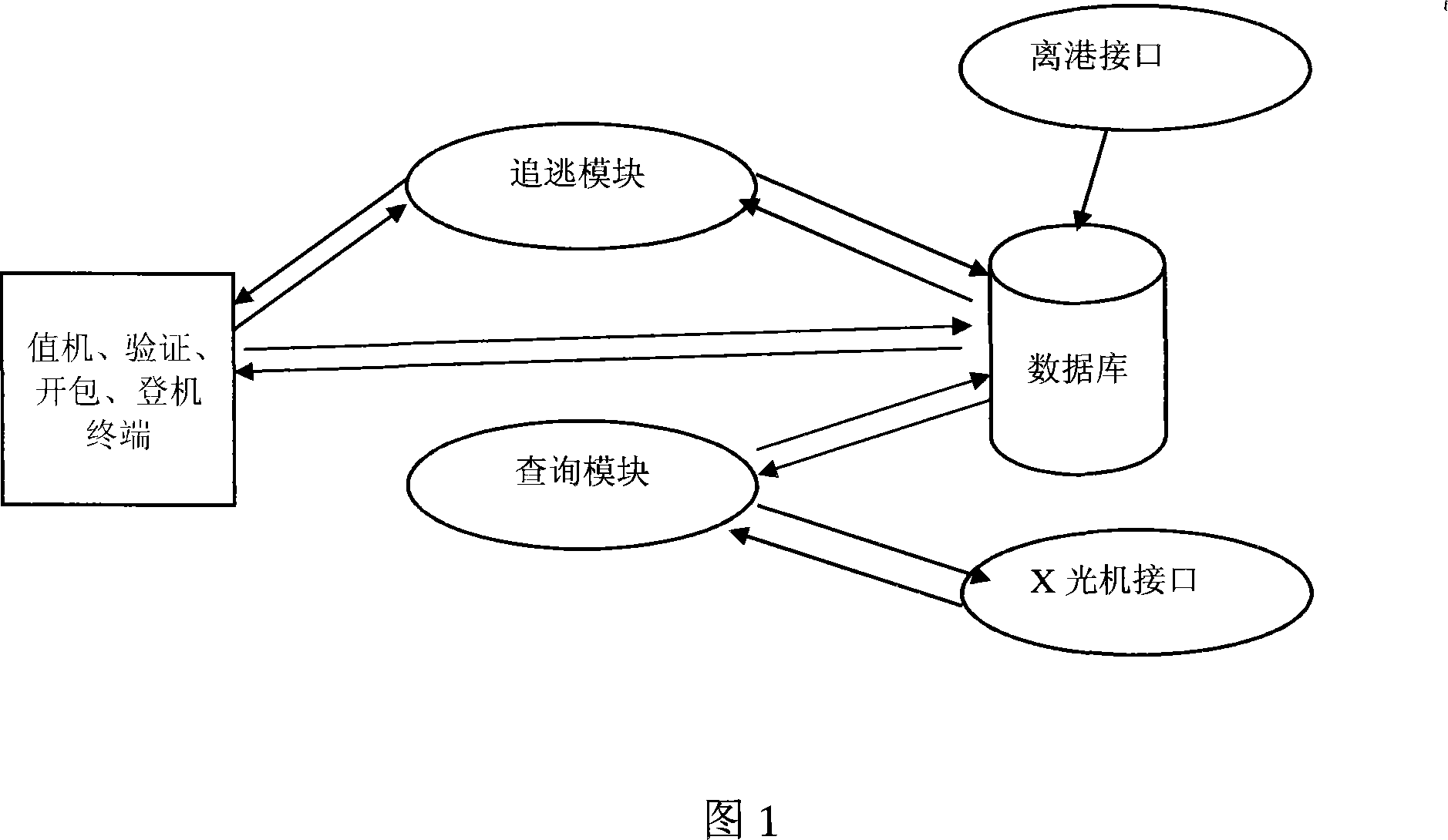
The invention discloses an air port security inspection information system, which comprises the following modules: a local departure module, a security inspection boarding gate verification module, a security inspection unpacking working module, an integral inquiry module, a pursuit information module, a security inspection passage verification desk module and a background management module. The system with simple and reasonable structure can be adapted to the requirements of modernization development, improve the service and management level of the security inspection, provide effective security inspection means for air port, crack down on crimes forcefully, maintain social stability, etc. The invention also provides close and effective security inspection management means to guarantee air defense security, provides a simple, convenient, standardized security inspection process, and improves efficiency as well as service quality. Furthermore, the invention which provides complete reference for security inspection management is closely integrated with other systems (such as the passenger information in the departure system data, etc.), thereby realizing data sharing, saving investment, effectively monitoring security inspection personnel and attendance states and strengthening personnel management.
Owner:成都双流国际机场空港科技有限公司
Near shore port security barrier
InactiveUS20050013668A1Avoid damageEasy to moveDefensive equipmentDefence devicesMarine engineeringShore
A near shore port security barrier for protecting a vessel docked at a port facility from an incoming waterborne craft which is being used to inflict damage on the vessel. The near shore port security barrier consist of a plurality of floating barrier modules connected to one another and placed adjacent the hull of the vessel the near shore port security barrier is designed to protect. A wire mesh barrier fence, which is positioned on the outer perimeter of each floating barrier module is also provided to protect the vessel.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
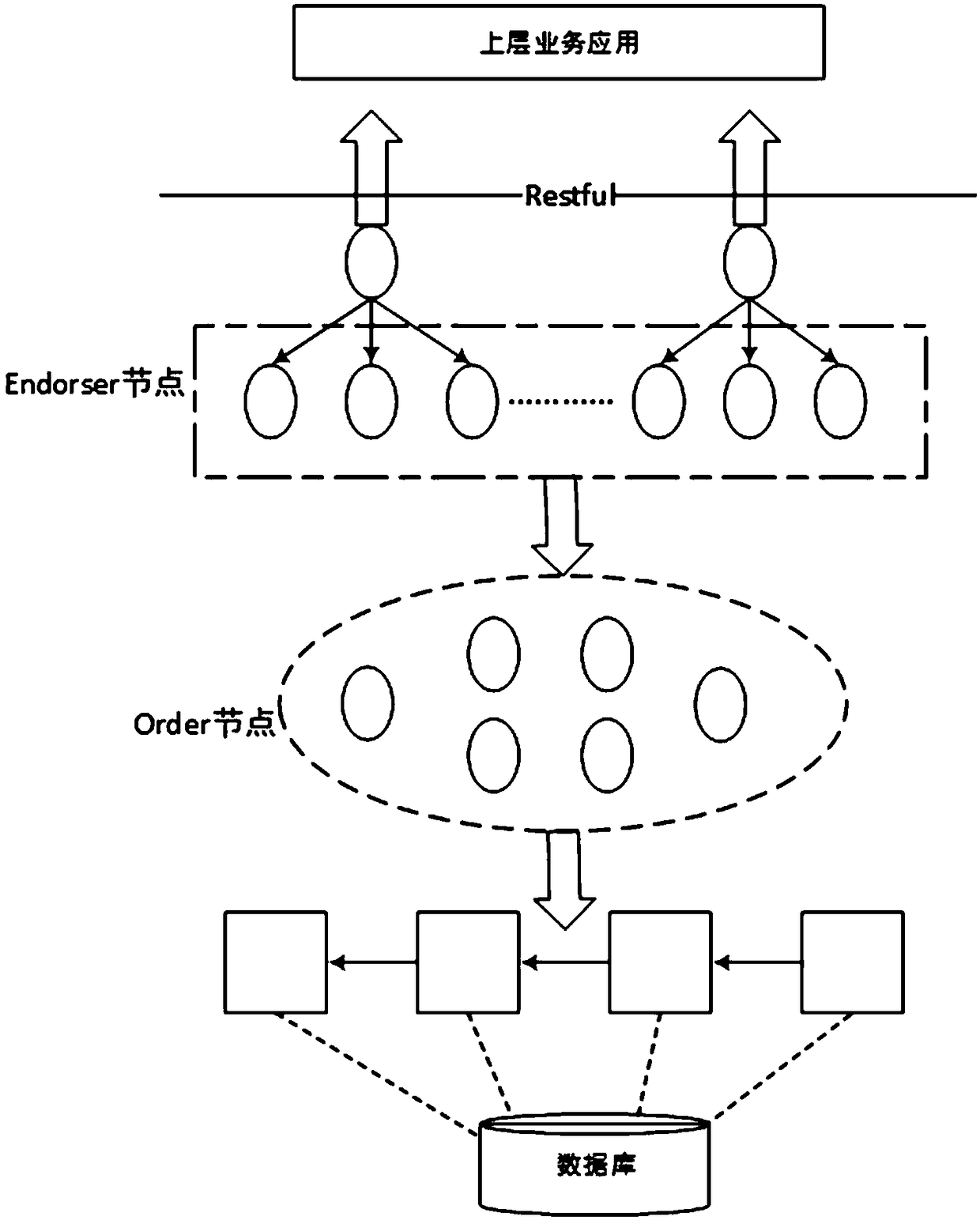
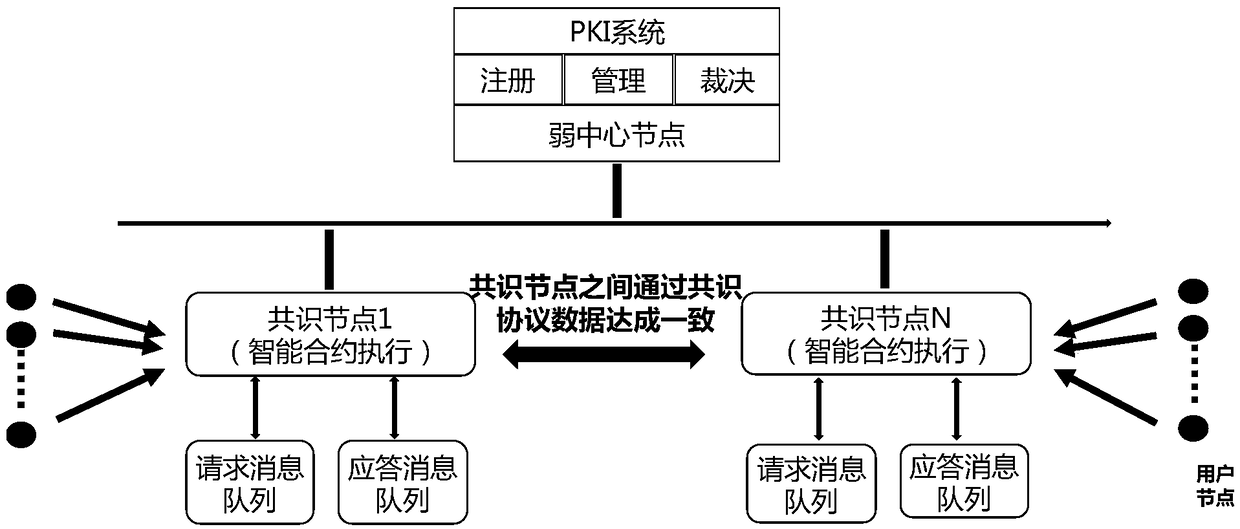
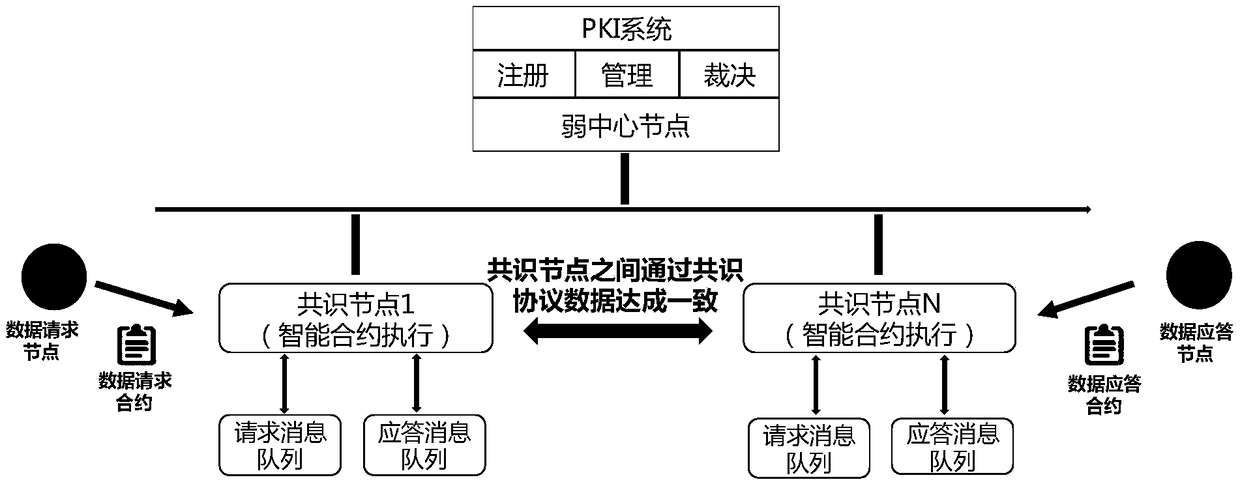
Blockchain-based power data security information system
The invention relates to a blockchain-based power data security information system. The system includes a database, a bottom-layer blockchain subsystem, and an upper-layer service application subsystem which are distributed sequentially from bottom to top; the database is used for storing data corresponding to a blockchain ledger; the bottom-layer blockchain subsystem is used for providing messagequery, message feedback and log query functions to the upper-layer service application subsystem in the form of interfaces, and includes a plurality of peer nodes, a consensus node, and a blockchainledger, wherein the peer nodes generate the blockchain ledger corresponding to the consensus node according to the content of the consensus node; and the upper-layer service application subsystem provides a data access interface by using a Restful-based unified interface mode, and communicates with the peer nodes of the bottom-layer blockchain subsystem through the access interface. Compared withthe prior art, the system of the invention has the advantages of no central data management, non-tampering property, audit fairness, port security shielding and the like.
Owner:SHANGHAI MUNICIPAL ELECTRIC POWER CO +1
Obstacle dodging technical method based on binocular vision
According to the invention, real-time three-dimensional point cloud reconstruction of a scene in an advancing direction of a field tyre-type gantry crane is realized by means of a binocular camera. Through performing projection statistics and non-maximum value suppression on the point cloud data in different dimensions, accurate dividing of noise point cloud, ground point cloud and obstacle pointcloud is realized. Through ground repositioning, effect of vibration of the field tyre-type gantry crane in operation to detecting precision and robustness is effectively suppressed, and detecting precision of the obstacle and an obstacle detecting distance are effectively improved. Through leaning a camera gesture and detecting the number and heights of the point cloud, real-time monitoring to abnormity of the obstacle dodging system is realized, and an important meaning is realized for improving harbor automation and harbor safe production.
Owner:SHANGHAI AWARE INFORMATION TECH +1
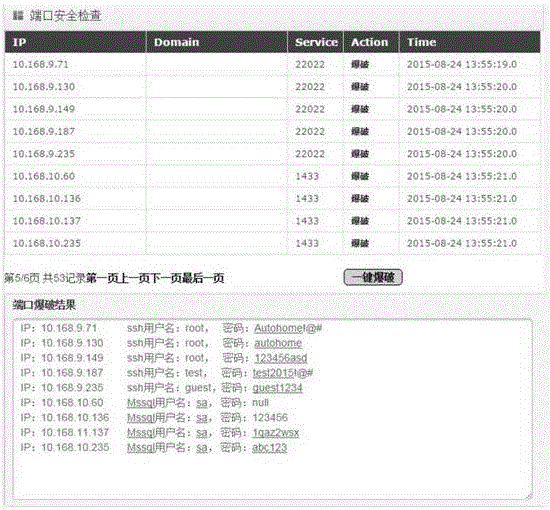
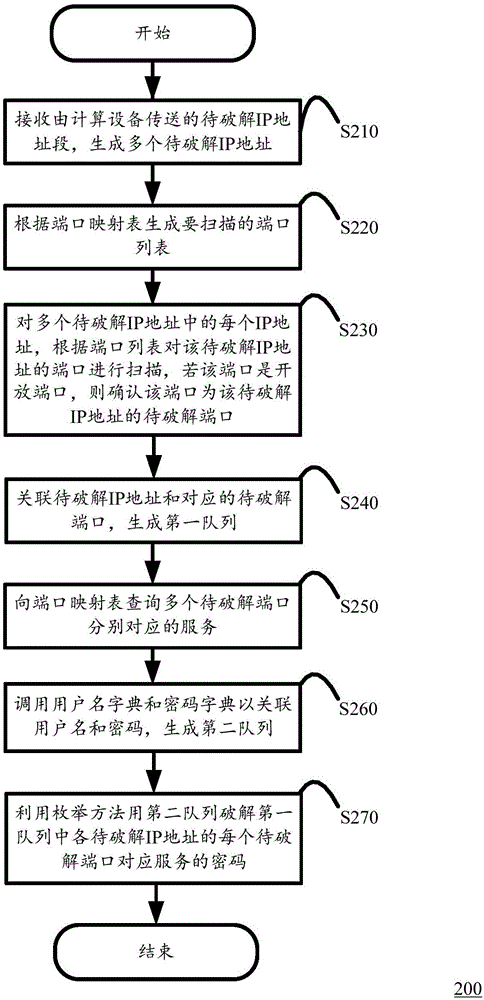
Port security check method, device and system
InactiveCN105721472AImprove security inspection efficiencyImprove cracking efficiencyCryptographic attack countermeasuresOpen portPassword
The invention discloses a port security check method executed in a server. A mapping relationship of ports and services as a port mapping table is stored in the server. The port security check method comprises the following steps of: receiving an IP address segment to be cracked transmitted by calculation equipment to generate a plurality of IP addresses to be cracked; generating a port list to be scanned according to the port mapping table; scanning the port of each IP address in the plurality of IP addresses to be cracked according to the port list, and determining that the port is the port to be cracked of the IP address if the port is an open port; associating the IP address with the corresponding port to be cracked so as to generate a first queue; inquiring services respectively corresponding to the plurality of ports to be cracked from the port mapping table; associating a user name and a password by invoking a user name dictionary and a password dictionary so as to generate a second queue; and cracking passwords of services corresponding to various ports to be cracked of various IP addresses in the first queue by using the second queue through an enumerative method. The invention further provides a corresponding device and system.
Owner:BEIJING CHESHANGHUI SOFTWARE
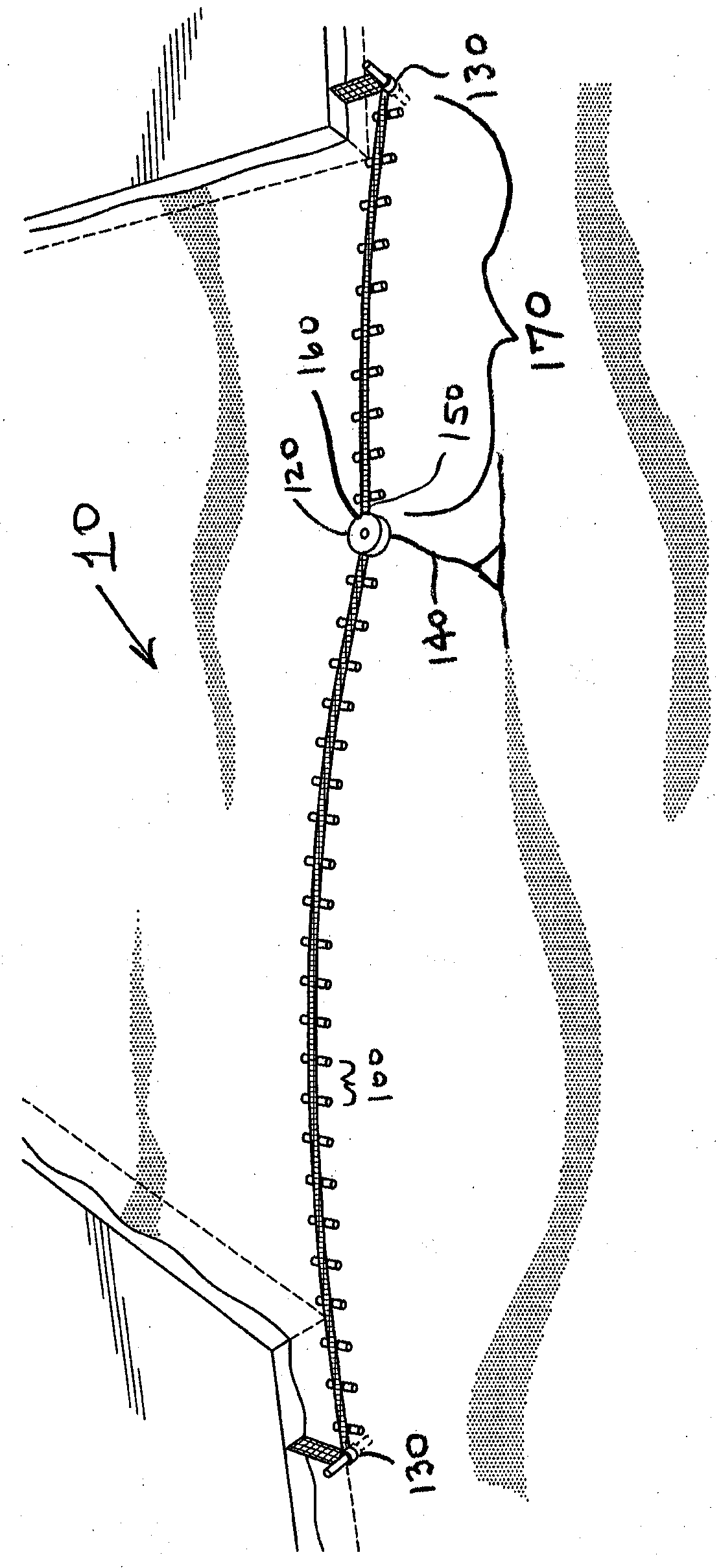
Port security barrier system
InactiveUSRE40616E1Simple designHighly effective port security barrierDefence devicesDefensive equipmentFlight vehicleModularity
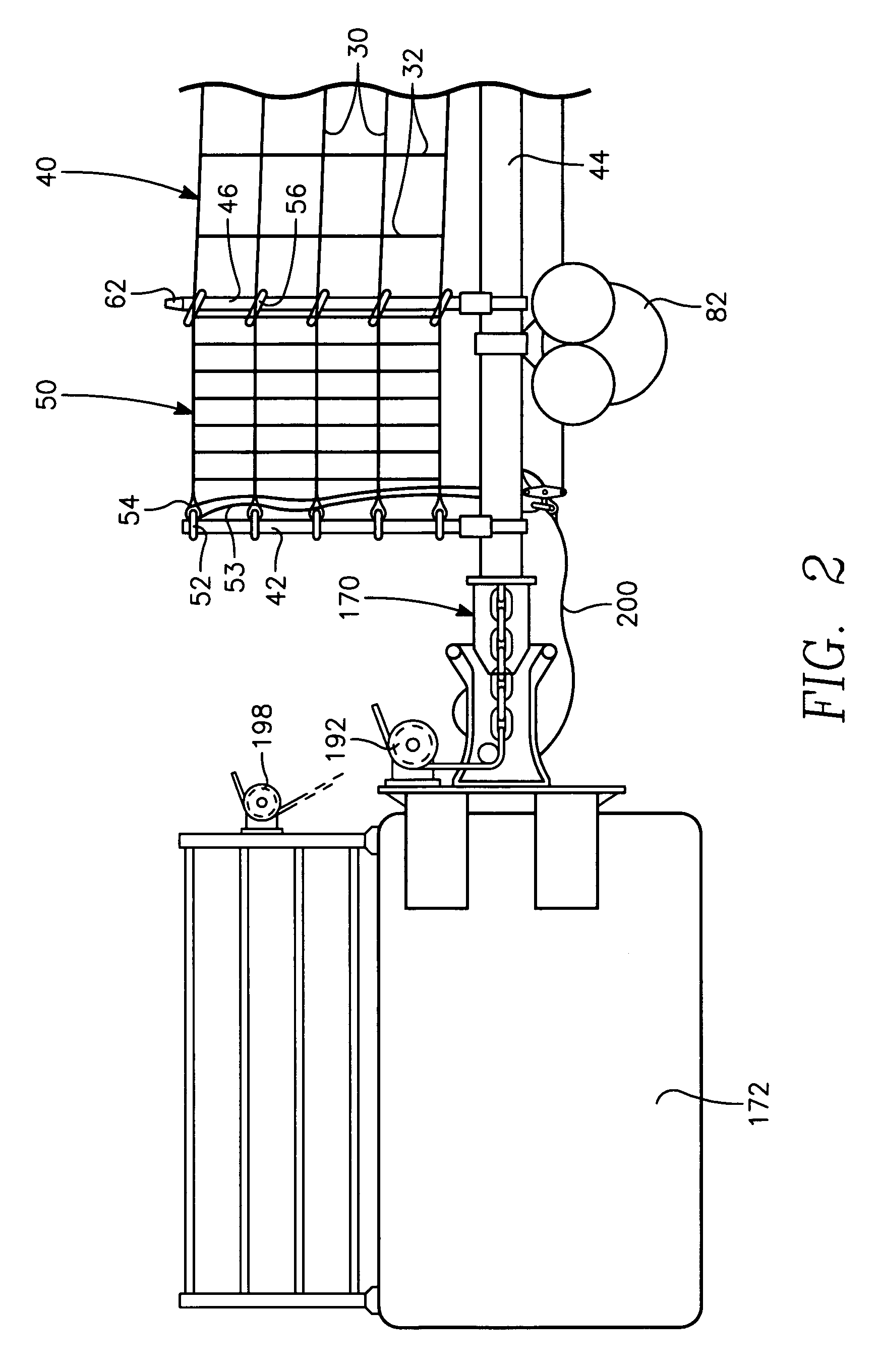
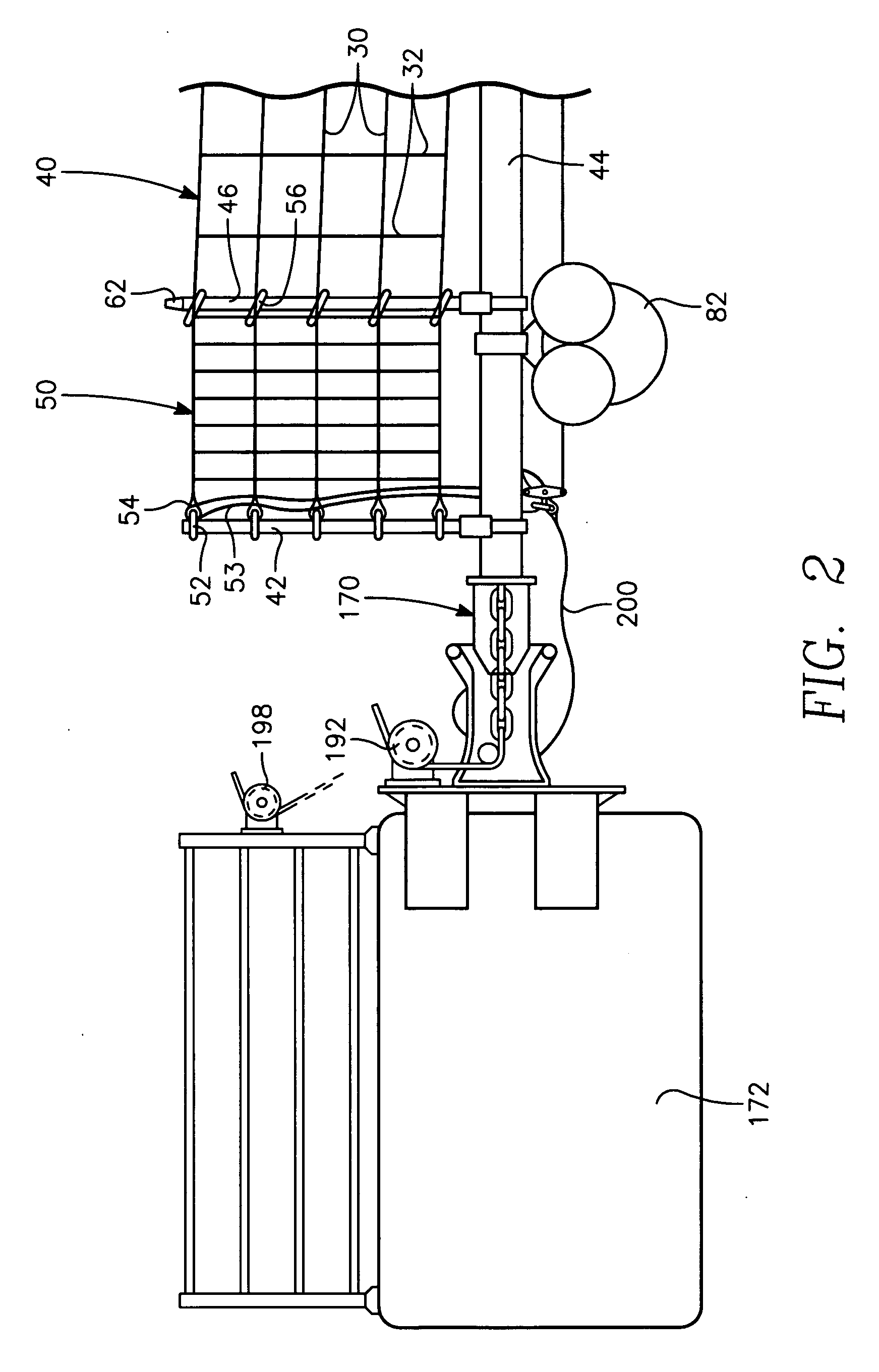
A port security system comprising a continuous modular, floating barrier that is installed in lengths ranging from a few hundred feet to over a mile. The port security system is designed to stop high speed explosive laden waterborne craft traveling at speeds of fifty knots or greater from penetrating a military or commercial port. Each module of the port security system includes a capture net and net support structure which operates to stop the waterborne craft and prevent entry into the port.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
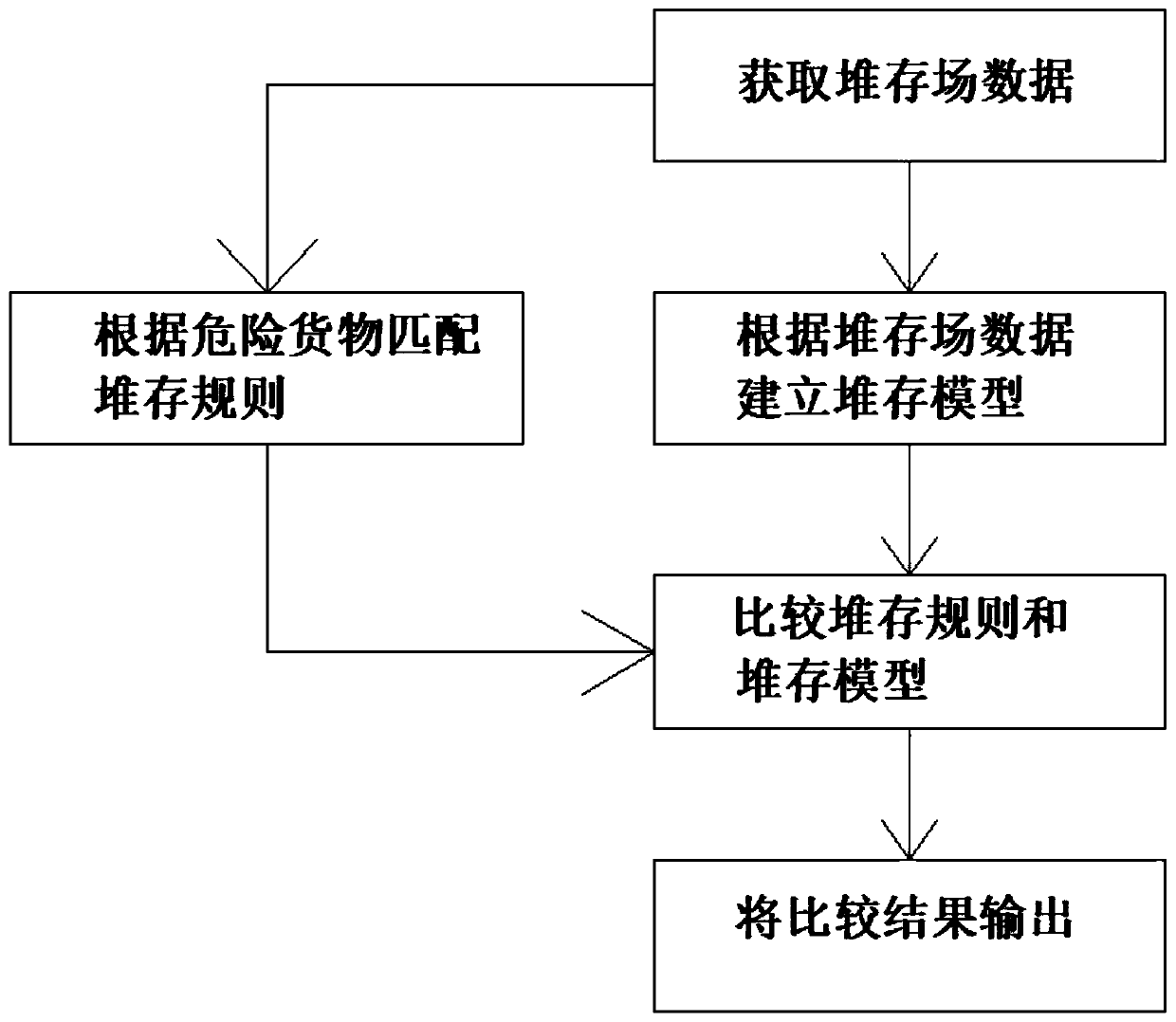
Dangerous cargo container stockpiling early warning method and system
PendingCN110223022ARealize the visualization of the storage yardRealize dynamic storage early warning managementForecastingCo-operative working arrangementsEarly warning systemTime efficient
The invention relates to a dangerous cargo container stockpiling early warning method and system. The method comprises the steps of obtaining stockpiling site data of a container; establishing a stockpiling rule according to the container dangerous cargo stockpiling standard specification; establishing a container stockpiling model according to the stockpiling dangerous goods of the container; matching the stockpiling rules of the containers according to the container stockpiling site; substituting the stockpiling rule into the stockpiling model; and judging whether to send out early warning or not according to the stockpiling rule and the calculation result of the stockpiling model. The invention discloses a real-time analysis and early warning system for port dangerous cargo container stockpiling. Functions of container yard visualization, dynamic stockpiling early warning management, dangerous cargo information integration, information inquiry and the like are realized. Real-time efficient calculation can be achieved, early warning prompt can be conducted on containers which do not meet the stockpiling requirement in the forms of highlight, marks, pop-up windows and the like, apowerful auxiliary tool is provided for port safety management departments and port enterprises to analyze and display the stockpiling condition of the containers, and remarkable effects are achievedin the aspect of guaranteeing the operation safety of port dangerous cargos.
Owner:TIANJIN RES INST FOR WATER TRANSPORT ENG M O T
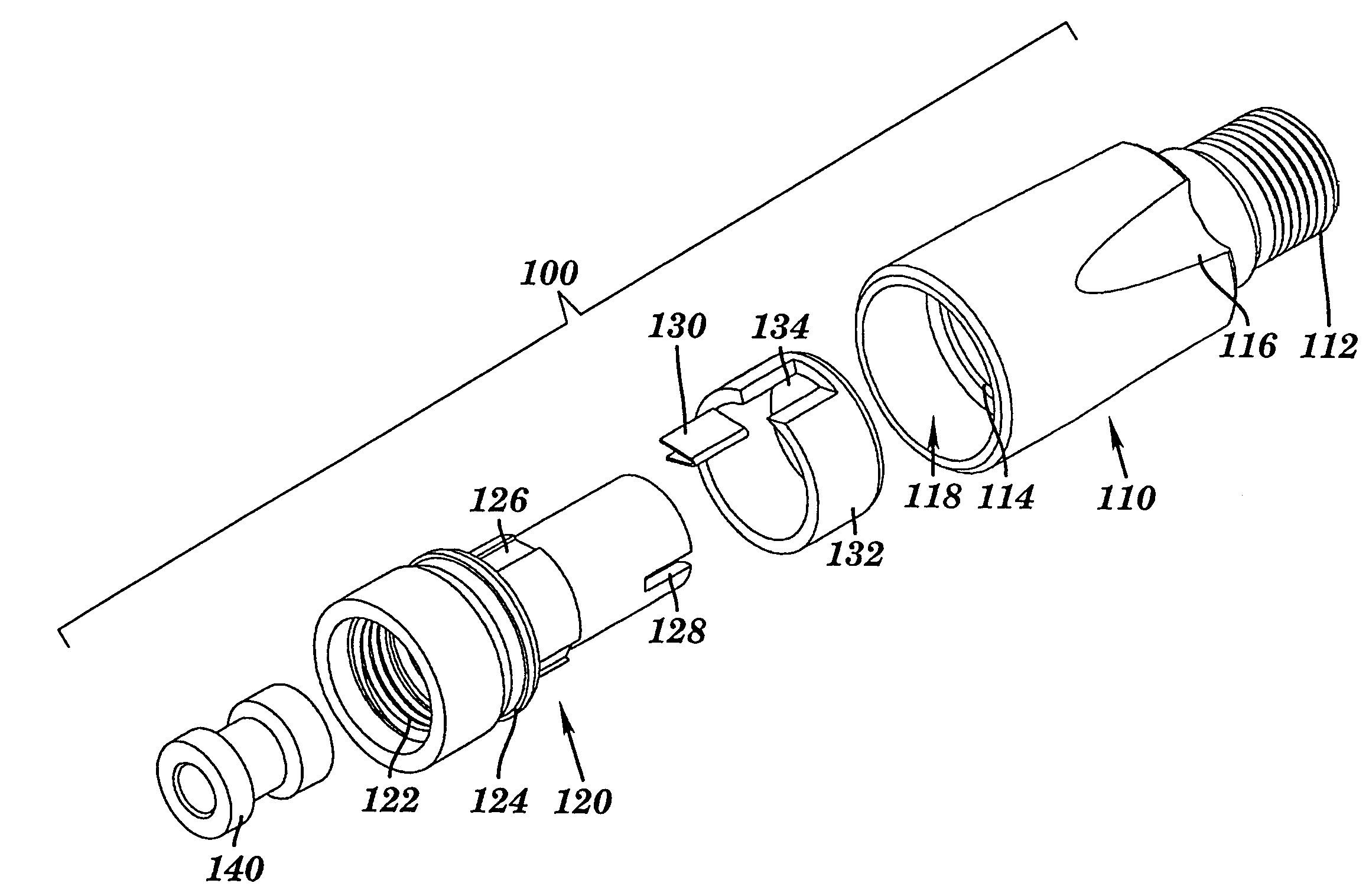
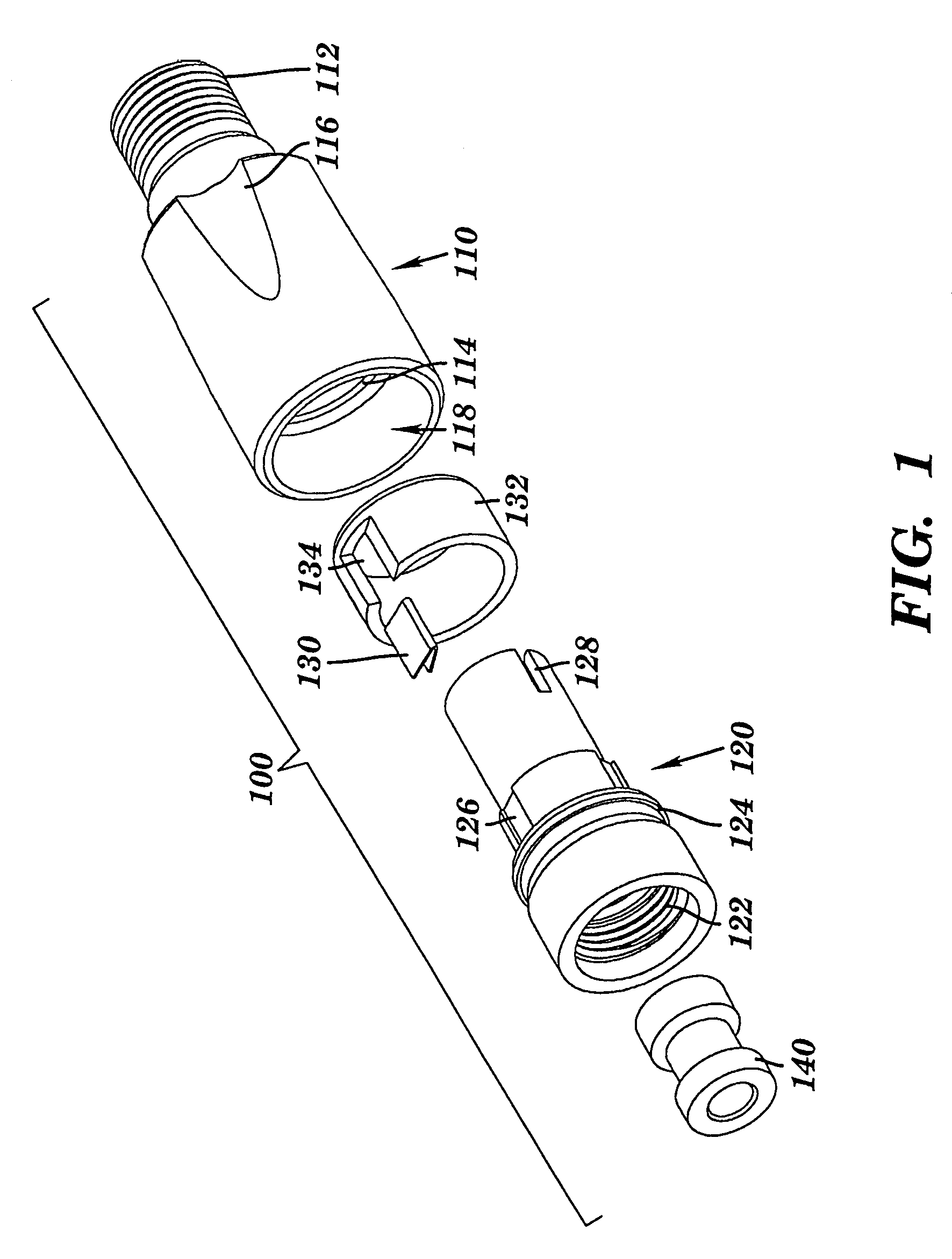
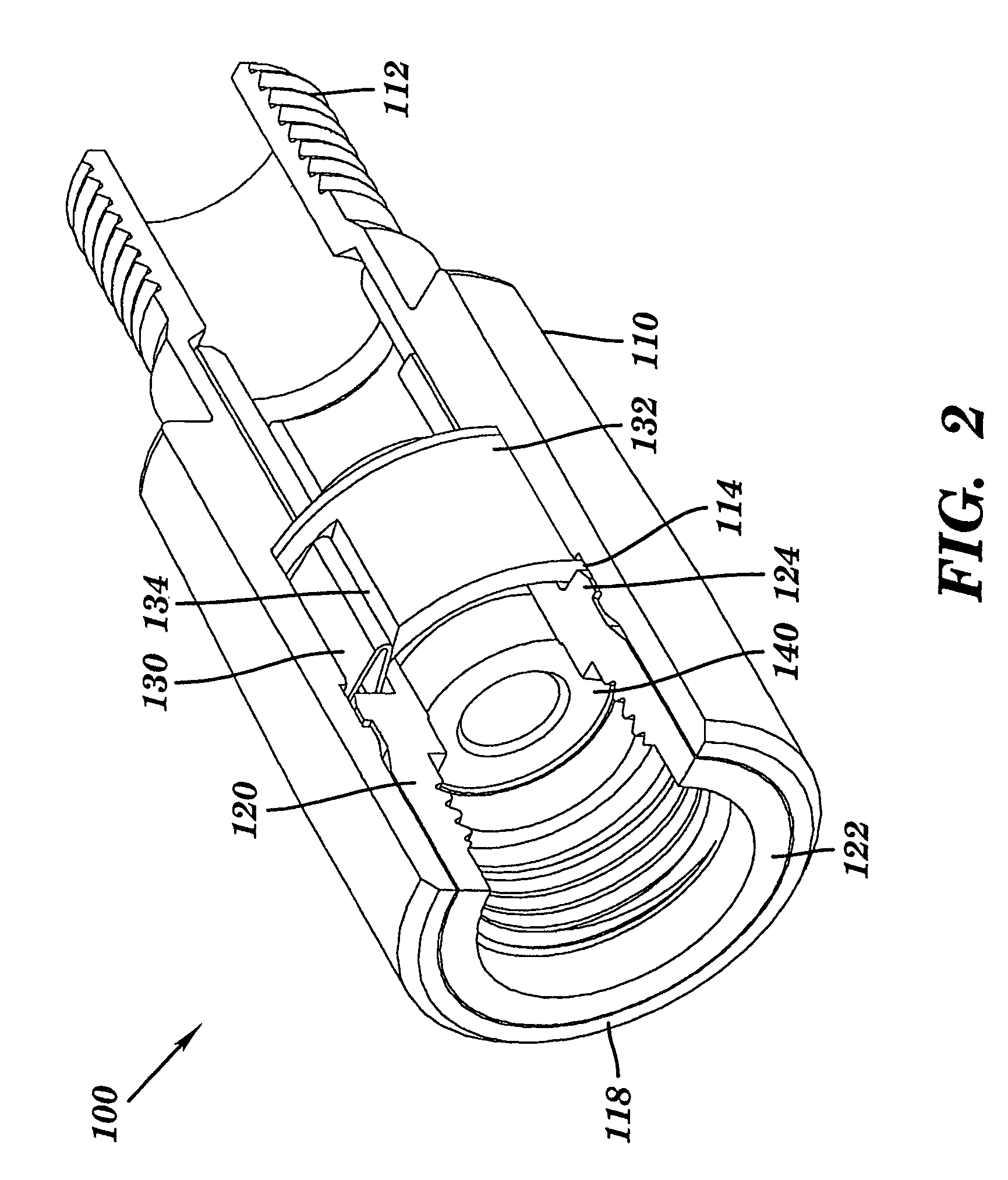
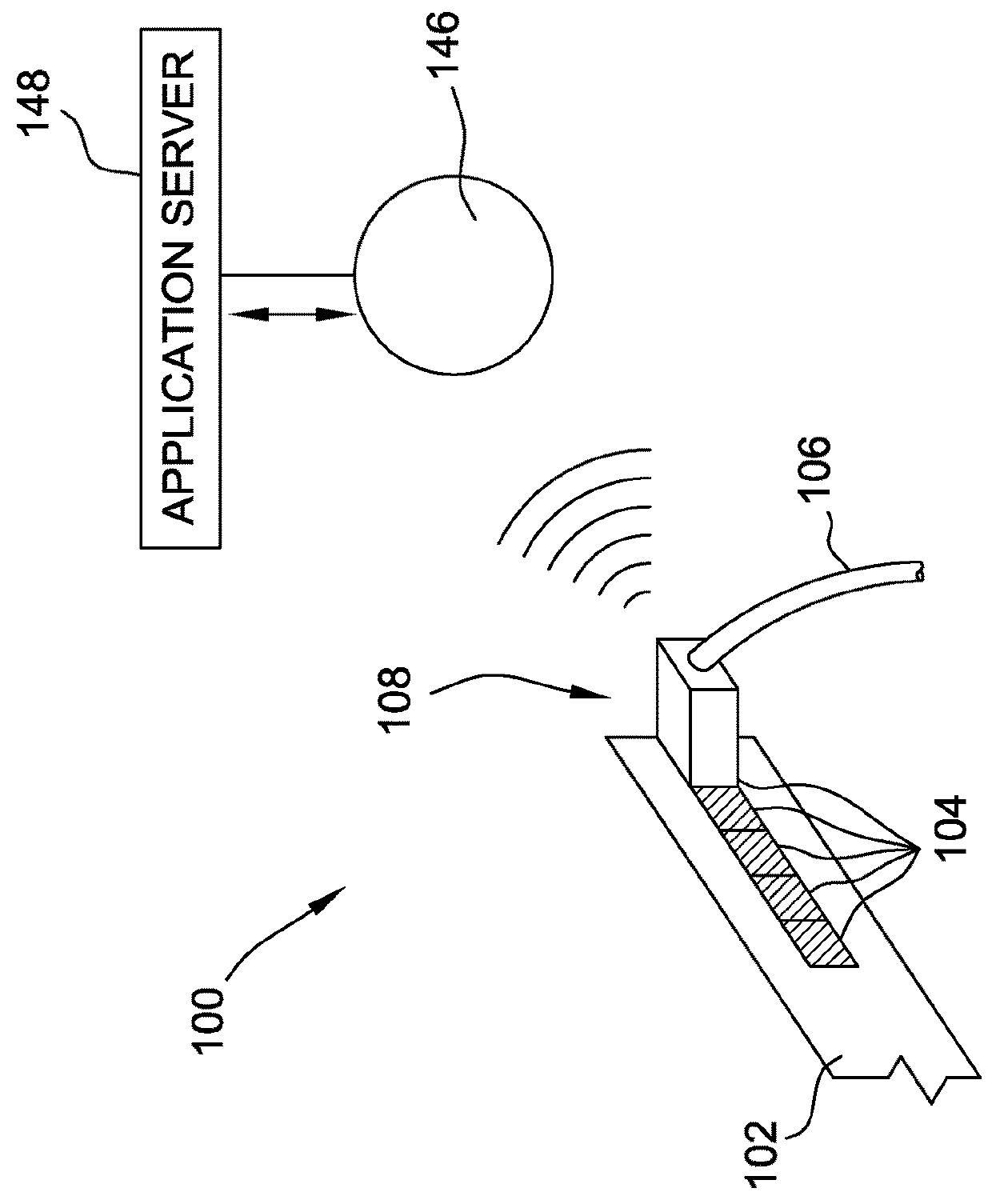
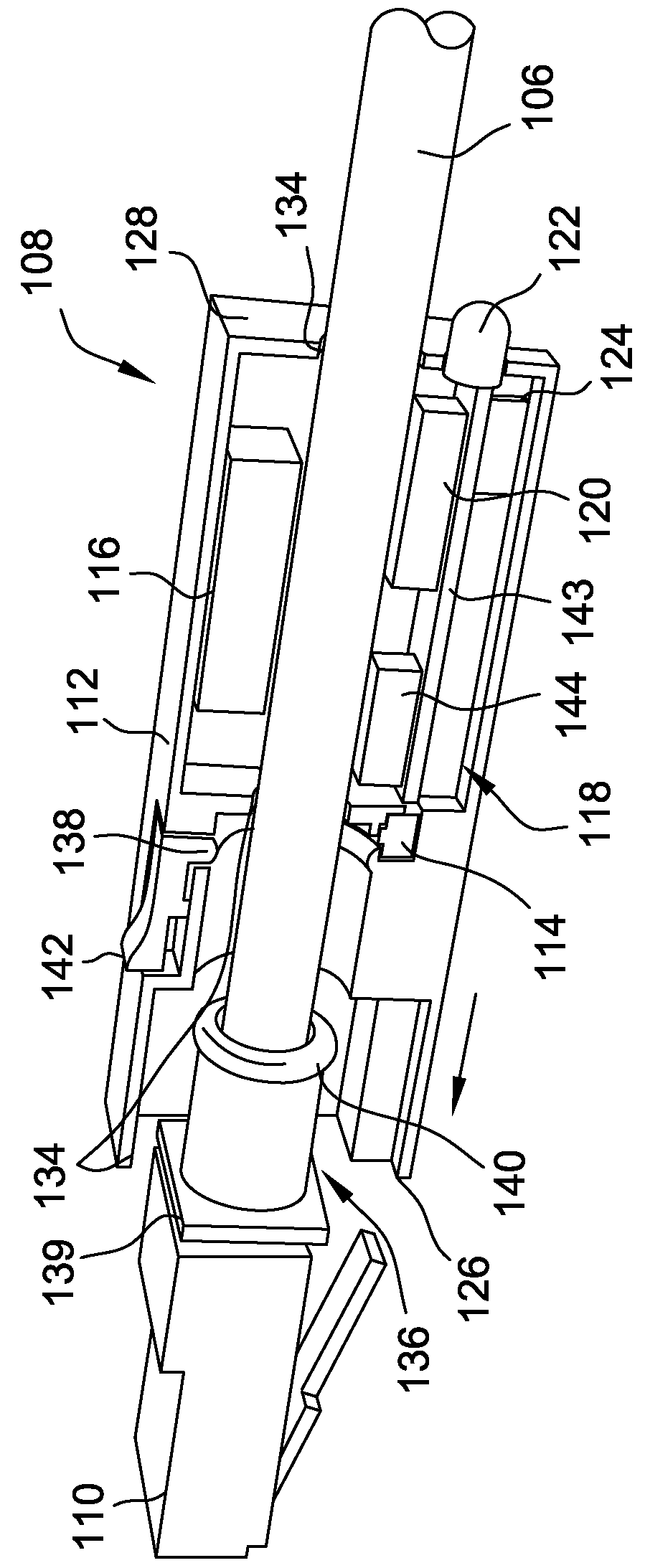
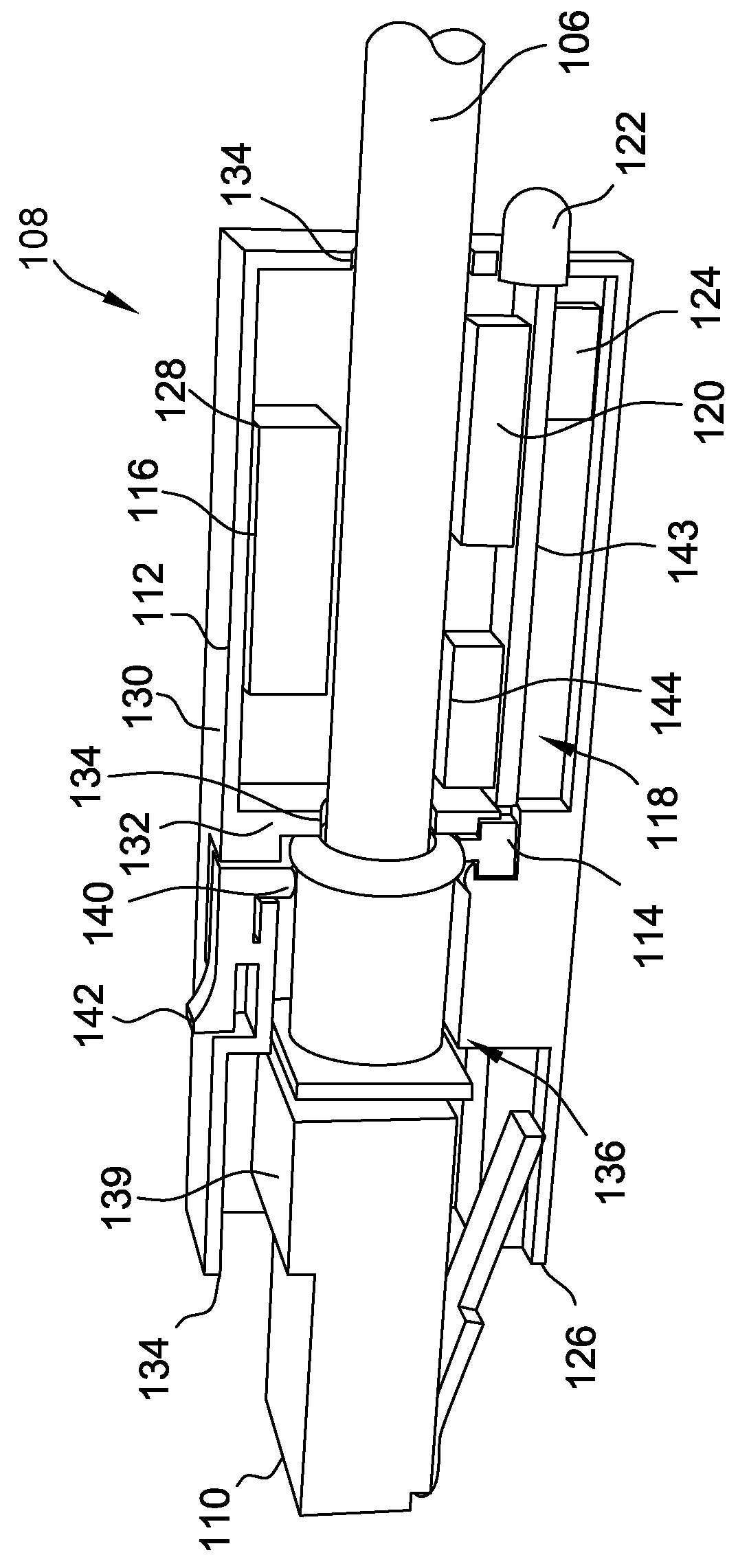
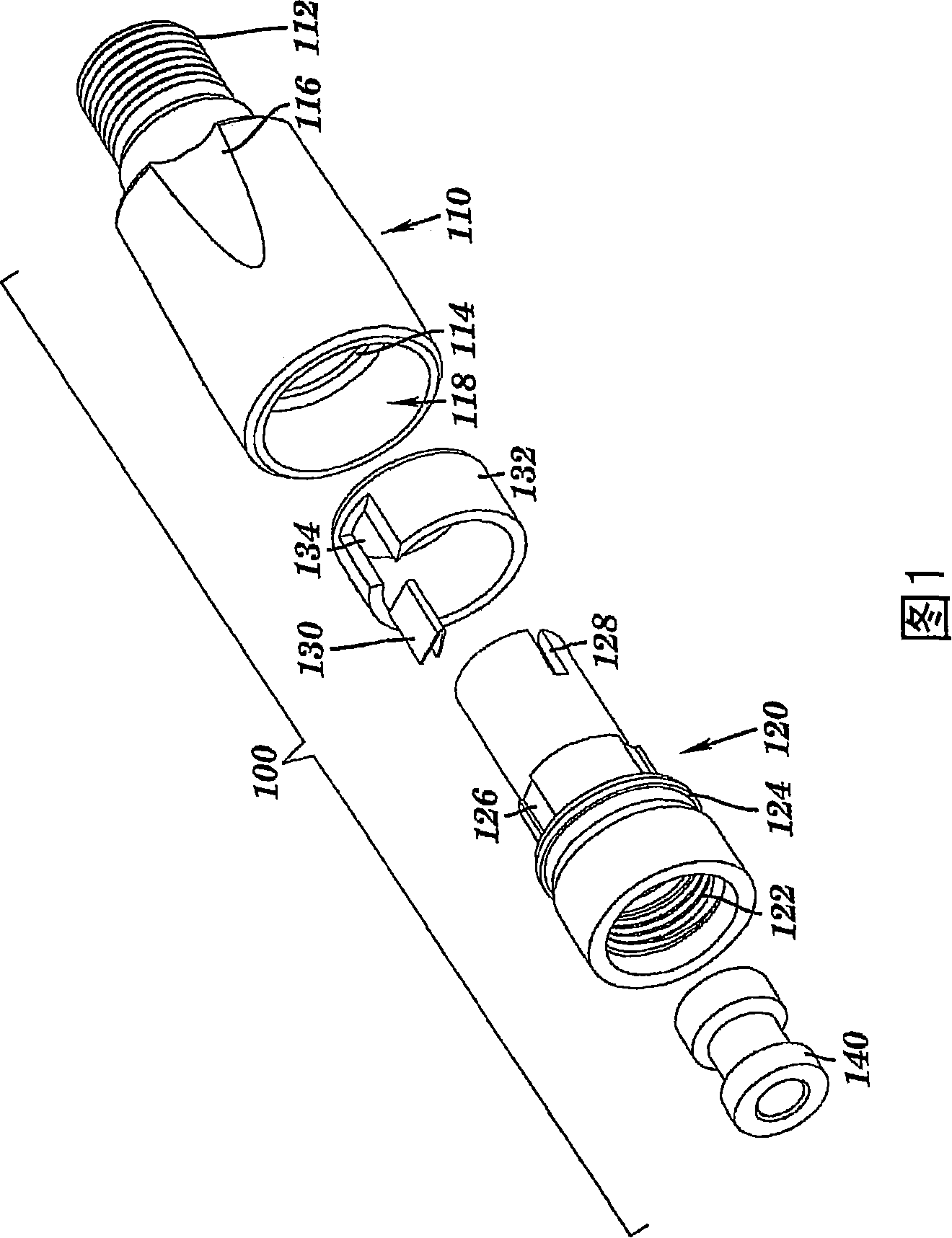
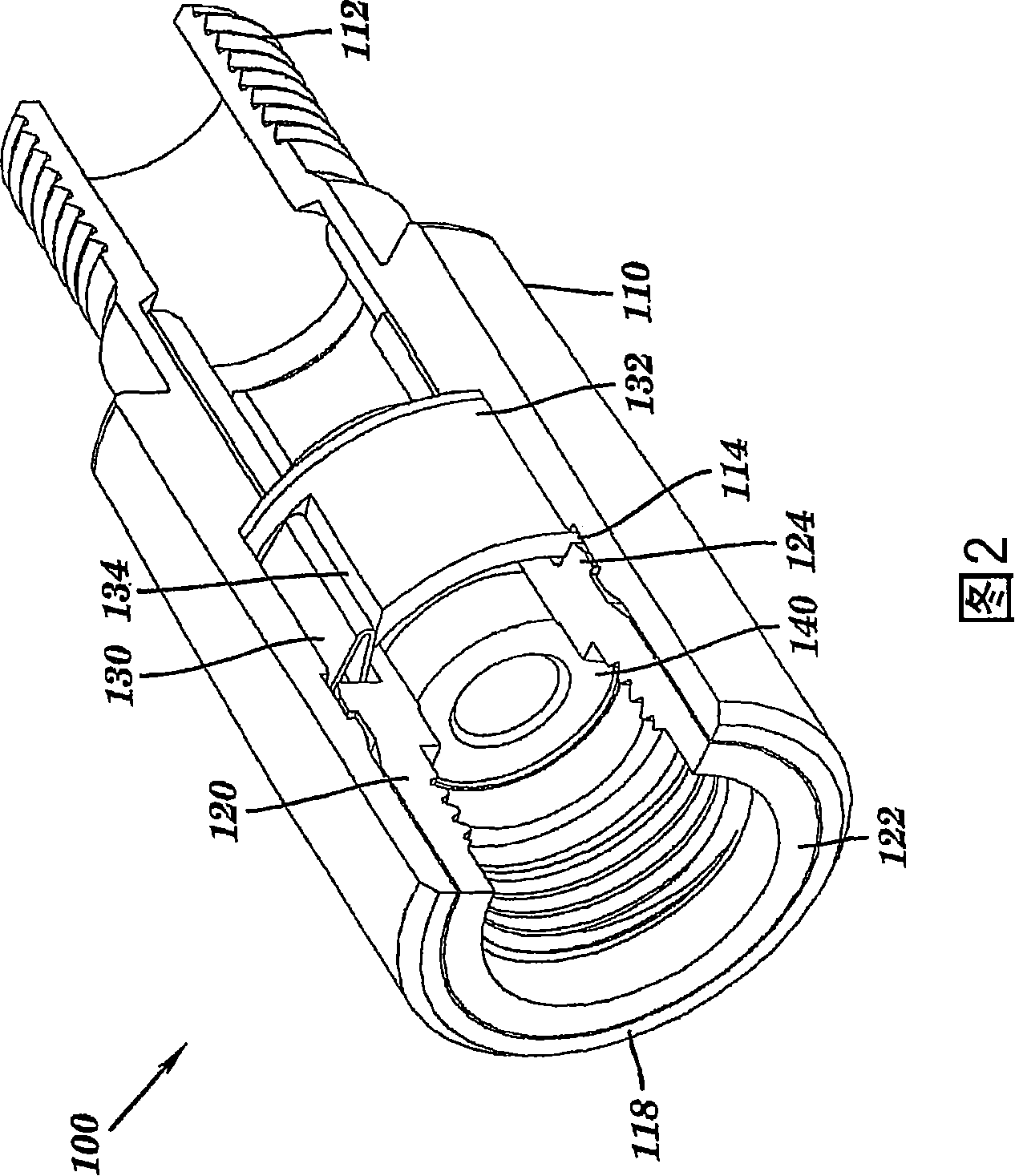
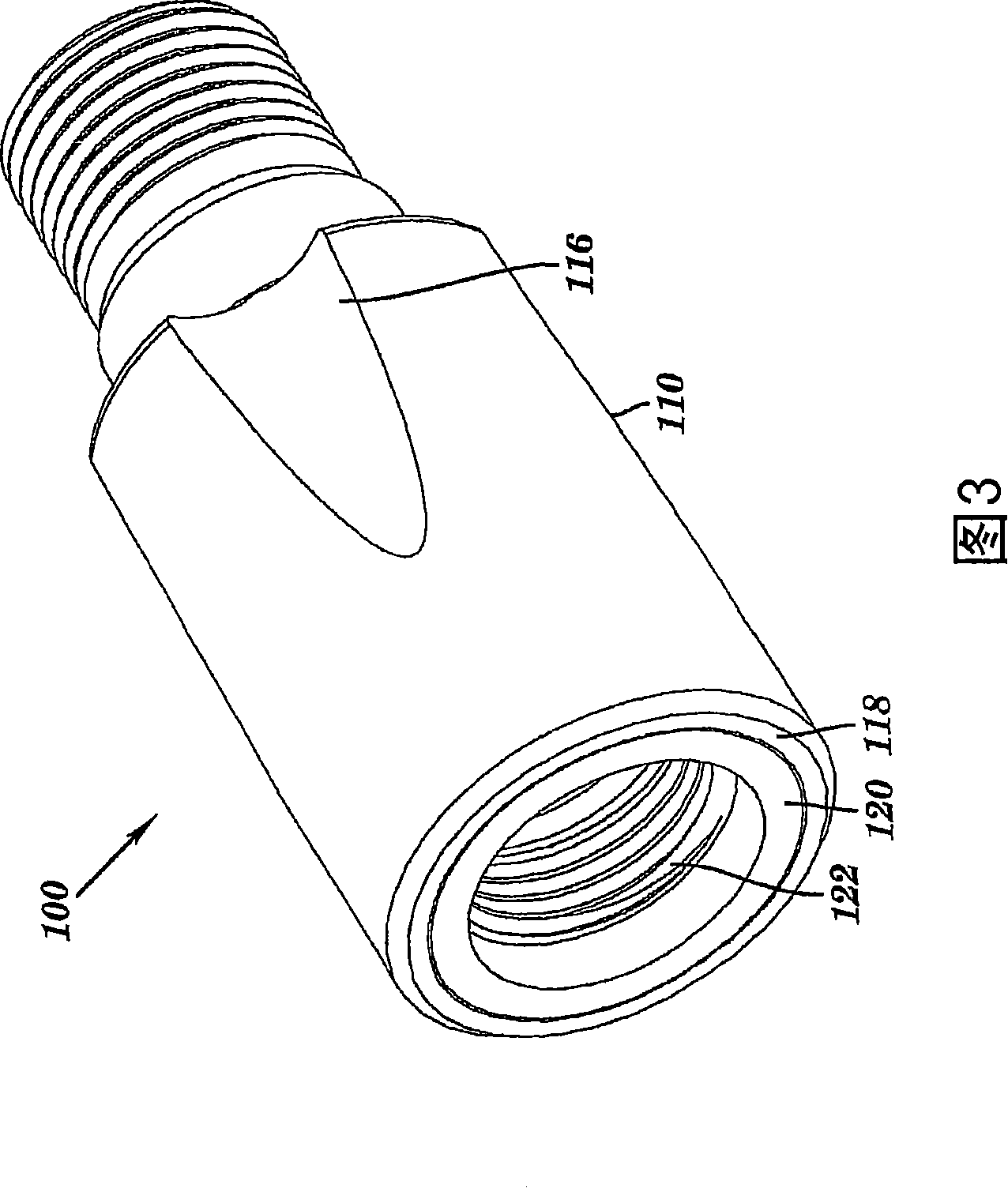
Coaxial cable port security device and method of use thereof
InactiveUS7086876B1Improve reliabilitySmooth rotationEngagement/disengagement of coupling partsElectrically conductive connectionsCoaxial cableEngineering
A coaxial cable port security device is provided, wherein the port security device comprises a one-way clutch mechanism positioned between a first body and a second body and utilized to prevent unauthorized access to a coaxial cable port unless a specific tool is used to negate the operation of the clutch mechanism and remove the port security device, thereby enabling authorized access to the port.
Owner:PPC BROADBAND INC
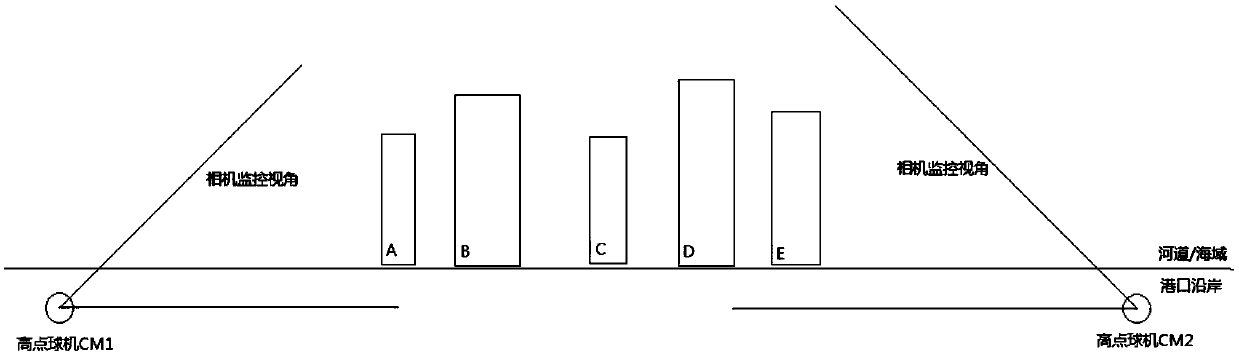
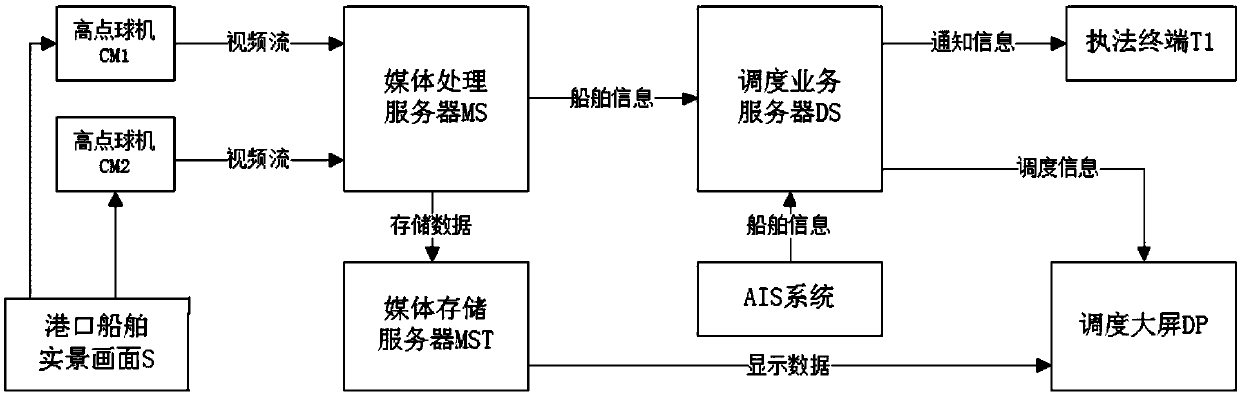
Berth supervision system and method based on satellite positioning and video monitoring technology
ActiveCN109615933ASave manpower and material resourcesTo achieve the purpose of intelligent berthMarine craft traffic controlVideo monitoringWide field
The invention provides a berth supervision system and method based on satellite positioning and video monitoring technology. The berth supervision system based on the satellite positioning and video monitoring technology comprises real scenes of port ships, high-end dome cameras, a media process server, media storage servers, a dispatch service server, an AIS system, a dispatch large screen, and alaw enforcement terminal. The real scenes of port ships refer to the scenes that the high-end dome cameras can monitor, and are the input content of the system. The high-end dome cameras are used forcollecting the real scenes of the berth and ships in the port in real time and sending to the media process server, and have characteristics of high pixel, wide field of view and high stability. Theberth supervision system and the method based on the satellite positioning and video monitoring technology can well liberate the manpower and material resources of the berth supervision, can timely discovery the private, illegal and overtime berth behavior of the port, and notify a port security to reach the purpose of the intelligent berth.
Owner:HANGZHOU XUJIAN SCI & TECH CO LTD
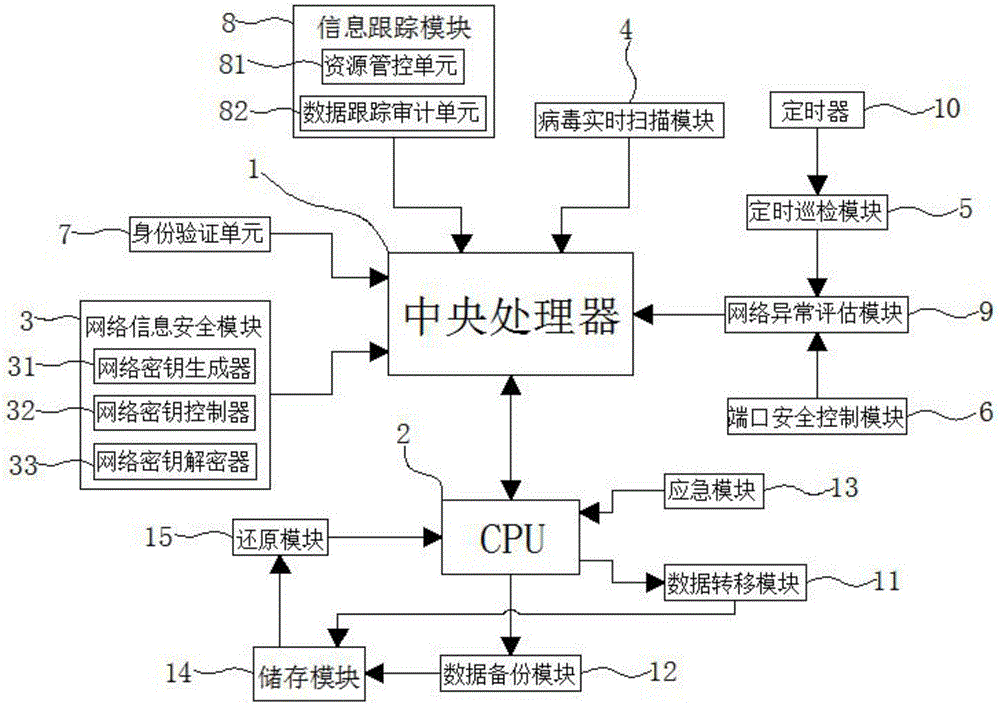
Computer network information security monitoring system
InactiveCN106603517AImprove securityStable operationTransmissionClassified informationMonitoring system
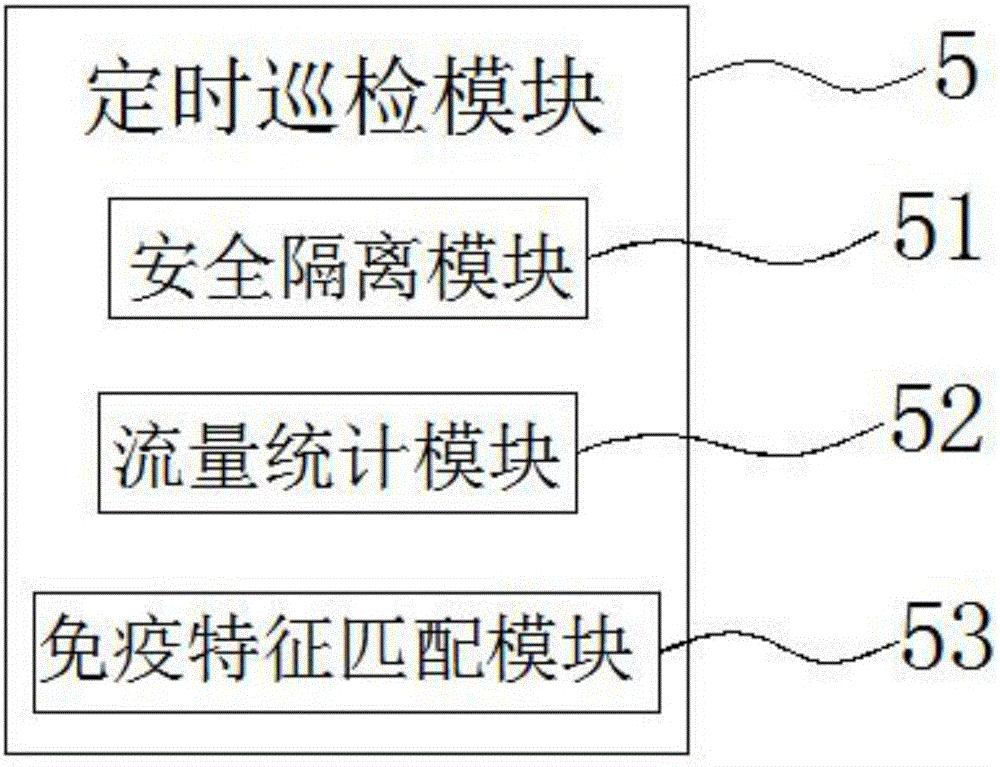
The invention discloses a computer network information security monitoring system comprising a central processing unit, a CPU, a network information security module, a virus real time scanning module, a timed inspection tour module and a port security control module; the central processing unit and the CPU are arranged in a computer; the network information security module, the virus real time scanning module, the timed inspection tour module and the port security control module are used for network information monitoring; an input end of the central processing unit is connected with output ends of the network information security module, an identity verification unit, an information tracking module, the virus real time scanning module and a network abnormity assessment module. Via the computer network information security monitoring system, information of a computer information security system is monitored and protected from a plurality of angles and aspects; security of use and transmission of computer information can be greatly improved; security of classified information of government departments, enterprises and the like can be improved; stable network operation can be maintained, data protection capability can be realized, and information loss can be prevented when a user is away from a computer.
Owner:XINXIANG UNIV
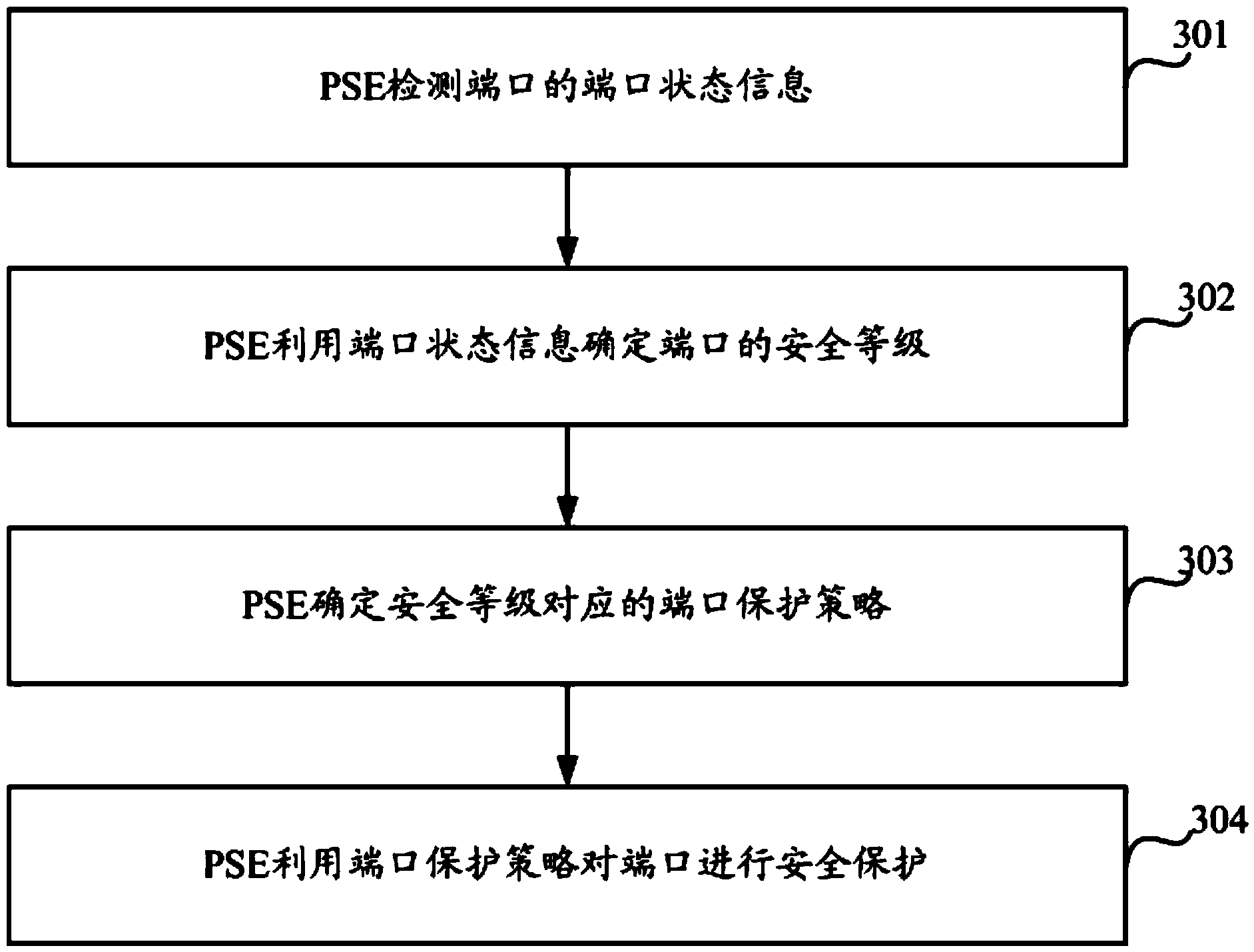
Port protection method of PSE and PSE
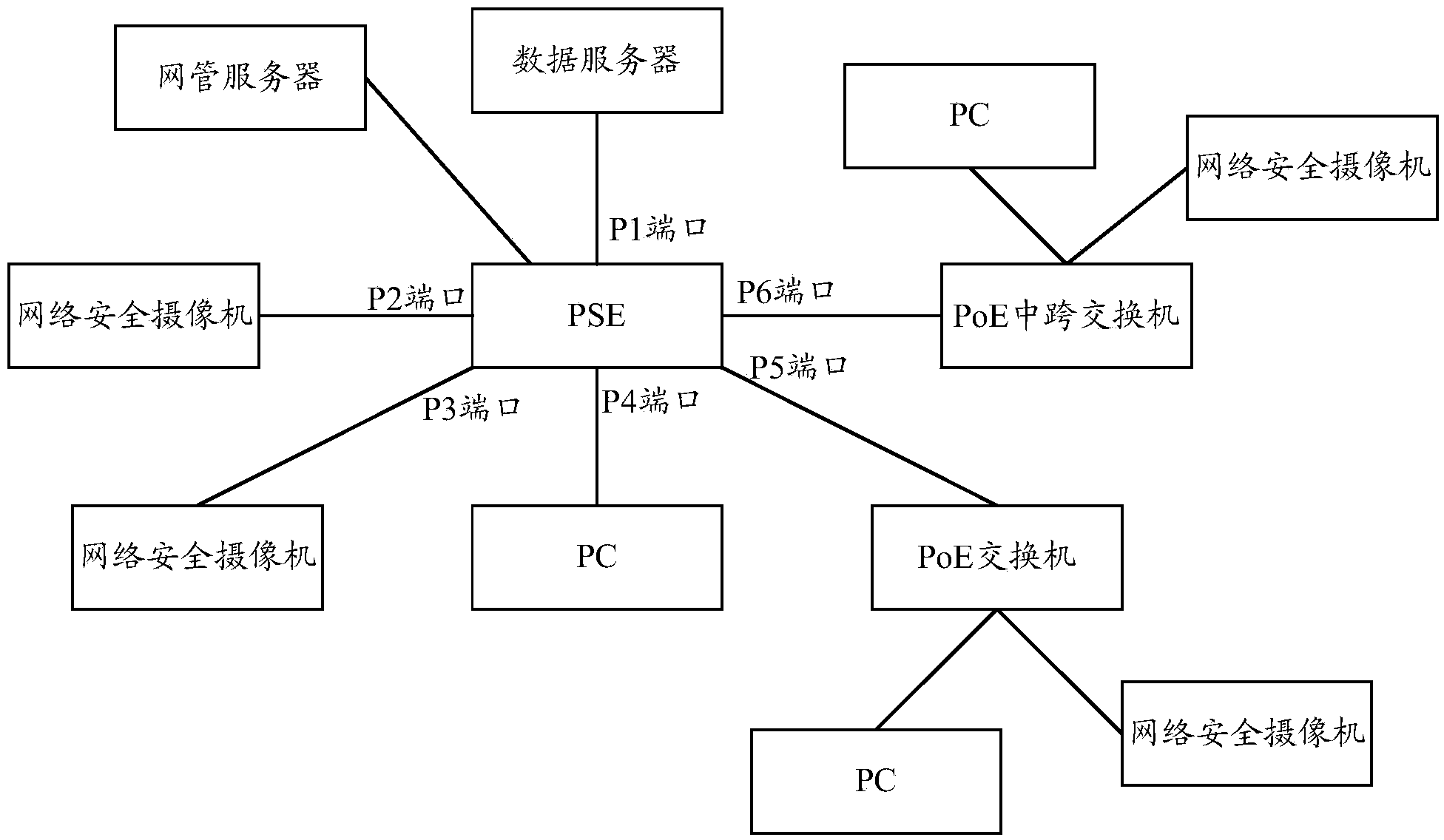
ActiveCN104168121AImprove securityEffective protectionData switching current supplyEngineeringSecurity level
The invention discloses a port protection method of power sourcing equipment (PSE) and a PSE. The method comprises: the PSE detects port state information of a port; the PSE uses the port state information to determine a security level of the port; the PSE determines a port protection strategy corresponding to the security level; and the PSE uses the port protection strategy to carry out security protection on the port. According to the embodiment of the invention, the port data can be effectively protected; the port security is enhanced; and a phenomenon that an illegal user obtains legal powered device (PD) data can be prevented.
Owner:NEW H3C TECH CO LTD
Quantitative evaluation method for post safety competency of port operators
InactiveCN111639864AImprove the status of production safetySolve the optimal matchResourcesIndex systemOptimal matching
Owner:TIANJIN RES INST FOR WATER TRANSPORT ENG M O T
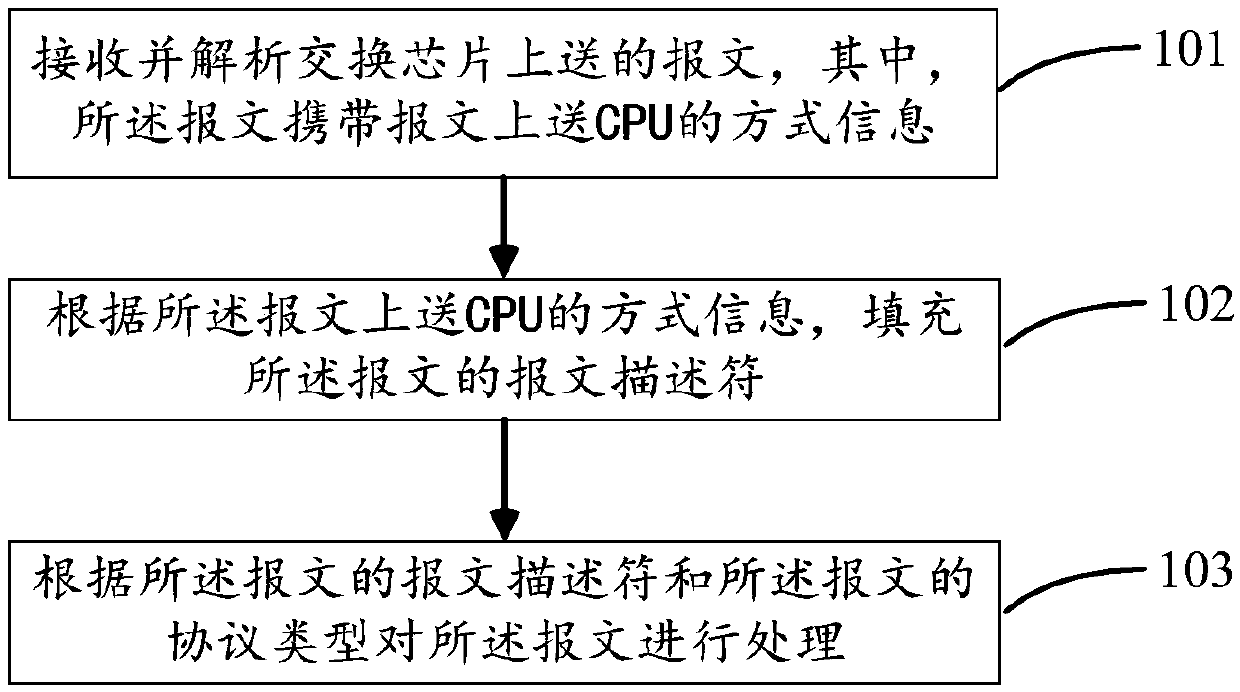
Message processing method, device and equipment
ActiveCN111262782AImprove usabilityAvoid risk of failureData switching networksEngineeringNetwork communication
The embodiment of the invention discloses a message processing method, device and equipment, relates to the field of data communication, and aims to realize the availability of a port security function and improve the reliability of network communication under the condition of not increasing hardware overhead. The method comprises the steps that a message sent by a switch chip is received and analyzed, wherein the message carries mode information of sending the message to a CPU, a message descriptor of the message is filled according to the mode information of uploading the message to the CPU,and the message is processed according to the message descriptor of the message and the protocol type of the message.
Owner:MAIPU COMM TECH CO LTD
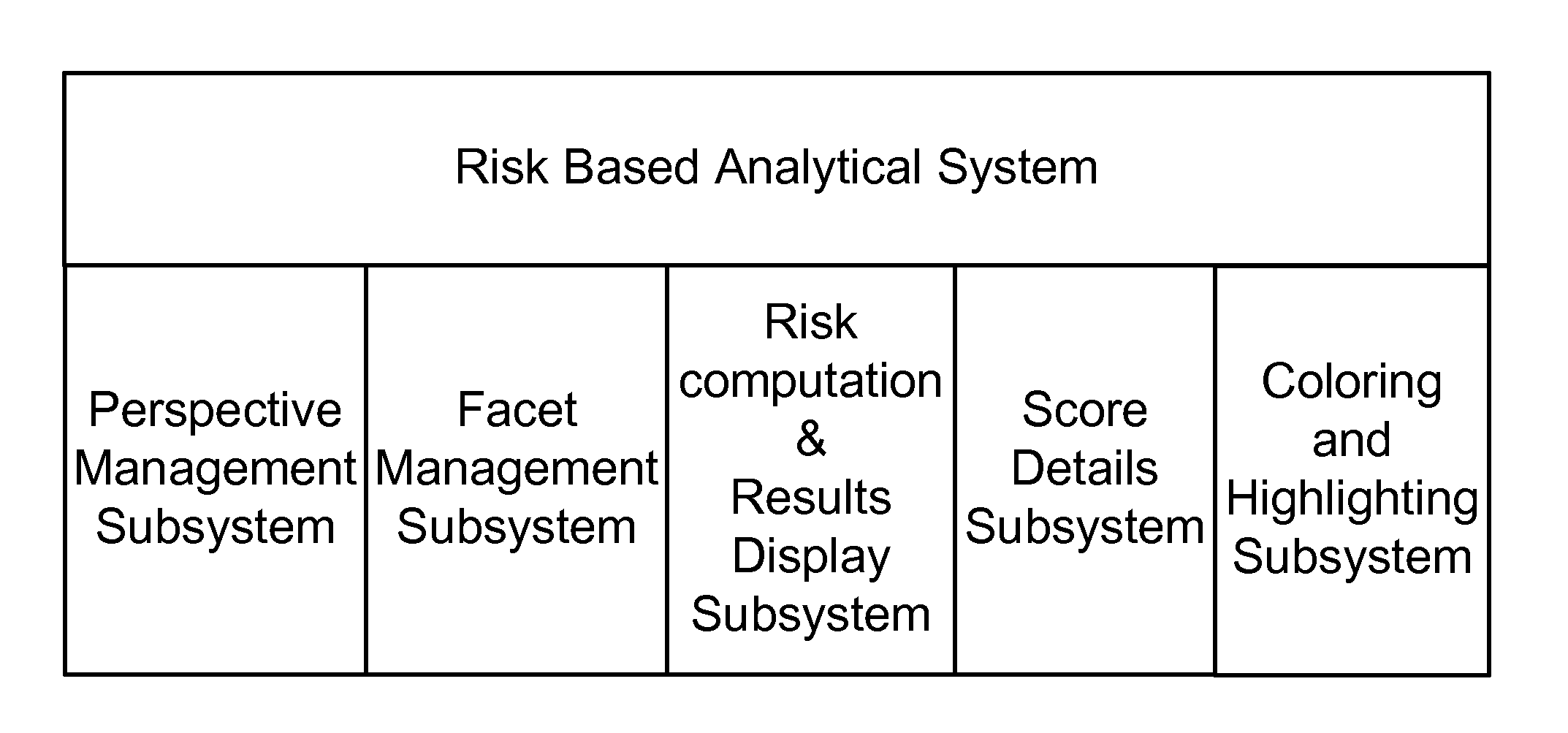
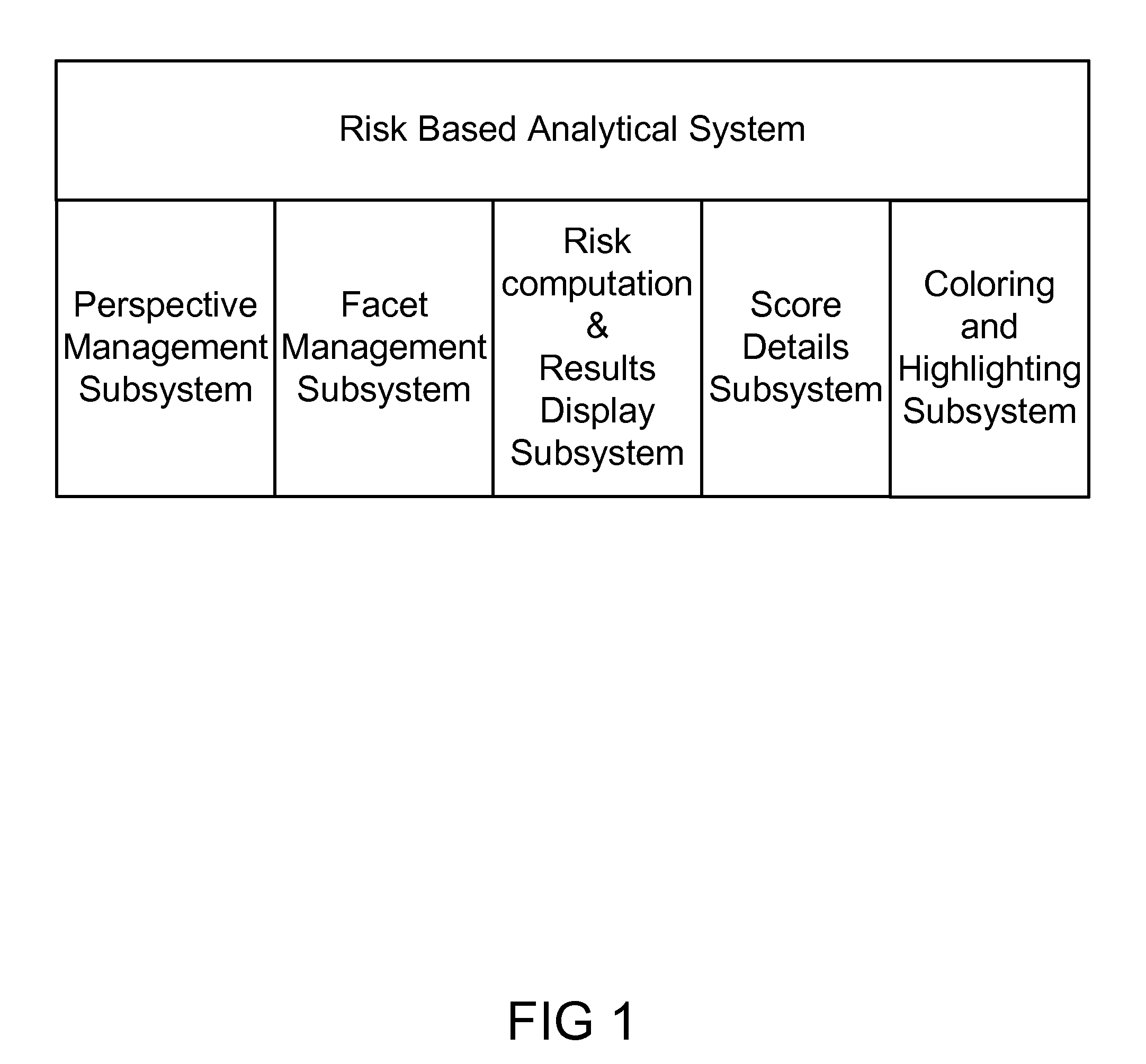
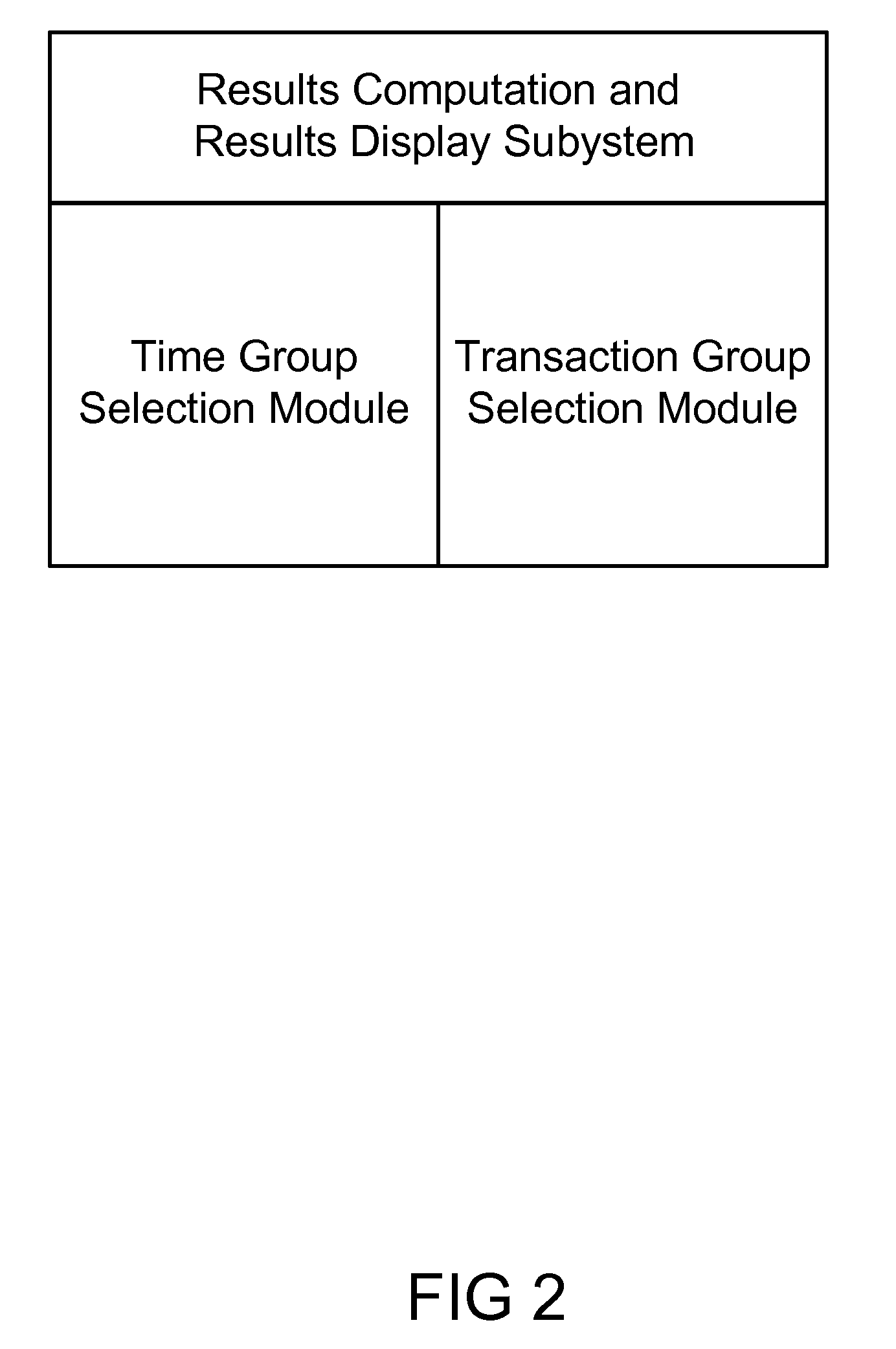
Method, System, and Apparatus for Categorizing and Presenting Risk Based Analytical Results
A system for computing, categorizing and presenting risk based analytical results to a human user for a cargo port security is presented. The system computes analytical results and presents that to the human user in a variety of configurable displays, allowing the user to evaluate the transaction on particular subset of data elements (also called aspect or facet) and a particular viewpoint (also called perspective or intelligence source). The system also enables the human user to compare the transaction to similar transactions (by allowing the user to define “similar”) from relevant past time periods (by allowing the user to define “relevant” periods).
Owner:ARORA AMRINDER S
Port security device for computing devices and methods of operating such
ActiveUS9965655B1Restricted accessInternal/peripheral component protectionTransmissionTransceiverUser interface
A system includes a first computing device and a second computing device. The first computing device includes a port. The second computing device is configured to communicate with the first computing device. The system also includes a port security device configured to restrict access to the port. The port security device includes a transceiver configured to communicate with a third computing device. The third computing device is configured to determine a status of the port security device. At least one of the port security device and the third computing device includes a user interface configured to provide an indication of the status of the port security device.
Owner:ERKIOS SYST INC
Enterprise network security management method
PendingCN113676469AReduce riskImprove securityUser identity/authority verificationWide area networksBusiness enterpriseProtocol for Carrying Authentication for Network Access
The invention discloses an enterprise network security management method, which comprises the following steps of: constructing a DMZ firewall between an enterprise network and an extranet to realize the functions of real IP hiding and access control, and establishing an IPSecVPN between a head office and a branch company to realize security information transmission of intranets in different regions, so that the risk is reduced, and the security is improved. Port security is configured on a two-layer switch, a data packet threshold value through which the port passes is preset, or MAC addresses allowed to be connected to the switch port are recorded through an MAC address table, a specific number or specific MAC addresses are allowed to use the port for communication, illegal equipment is prevented from accessing a network, MAC address table overflow caused by MAC address flooding can also be prevented, and by dividing vlan, the broadcast storm is reduced, and the pressure of the two-layer switch is fully shared; and in addition, link binding aggregation is used, the transmission bandwidth between the switches is increased, bidirectional authentication is carried out by configuring a PPP protocol and adopting chap, connection of illegal users is prevented, and the safety is further improved.
Owner:YANCHENG INST OF TECH
Coaxial cable port security device and method of use thereof
InactiveCN101171722AElectrically conductive connectionsTwo-part coupling devicesCoaxial cableEngineering
A coaxial cable port security device is provided, wherein the port security device comprises a one-way clutch mechanism positioned between a first body and a second body and utilized to prevent unauthorized access to a coaxial cable port unless a specific tool is used to negate the operation of the clutch mechanism and remove the port security device, thereby enabling authorized access to the port.
Owner:JOHN MEZZALINGUA ASSOC INC
Boat Gate
ActiveUS20190212103A1Wide openMaintain positionDefence devicesGates/doorsEngineeringGlobal Positioning System
A boat gate system for controlling vessel access to a port or similar waterbody has a number of connected, floating Port Security Barrier (“PSB”) segments. A remote latching and unlatching mechanism, combined with a powered mover mounted on one or more PSB segments, permits remote unlatching of the PSB segments; moving the PSB segments to a desired location (whether rotating same about a point, or moving a longer section laterally) so as to open the PSB, then moving the PSBs back to a closed position and latching same. Both the unlatching, movement, and latching are remotely controlled. Positional indicators, for example Global Positioning Systems or similar systems, are provided to monitor and assist in controlling PSB segment movement and unlatching, and movement of the PSB segments in a desired direction to a desired location.
Owner:OCEANETICS
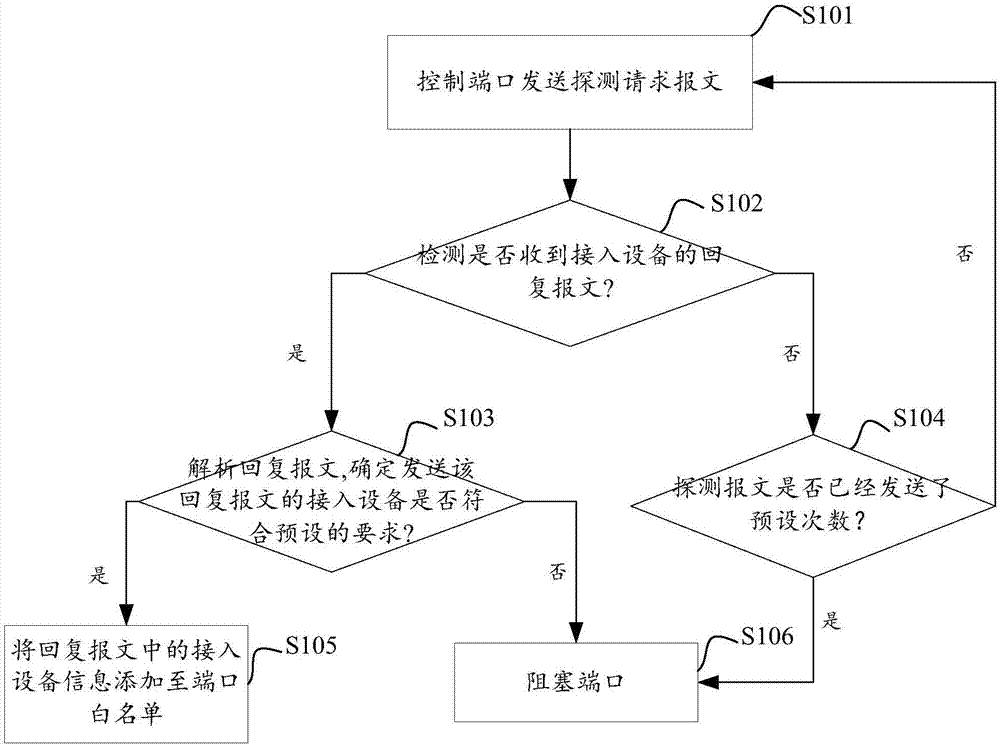
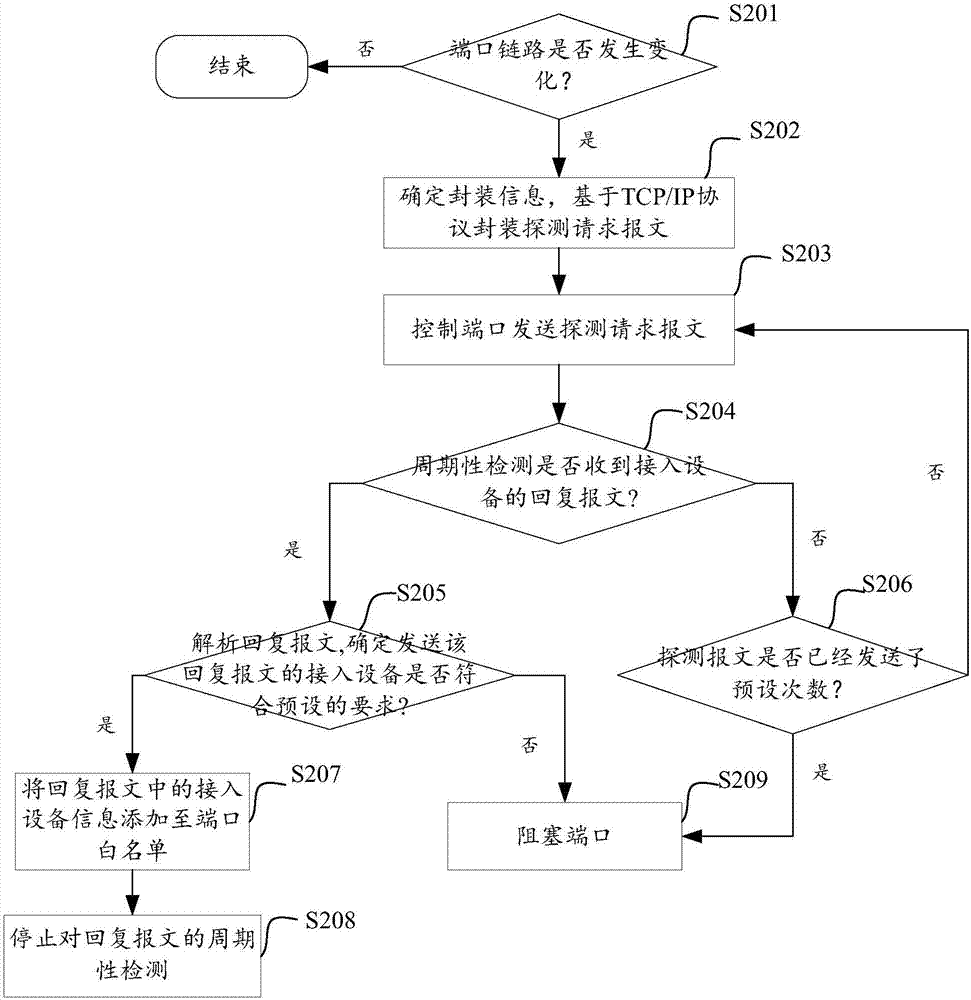
Switch port security protection method and apparatus based on TCP/IP
InactiveCN107483431AReduce labor costsData switching networksProtocol for Carrying Authentication for Network AccessEmbedded system
The invention provides a switch port security protection method and apparatus based on TCP / IP. A detection request message is sent to an access device via a switch physical port based on TCP / IP, the device information of the access device is identified by whether a reply message is received and the contents of the reply message, so that a switch issues blockage, release, white list and a series of strategies. Compared with the prior art, the device of the access device does not need to be manually determined, a switch port white list does not need to be manually set neither, thereby reducing the labor cost.
Owner:HANGZHOU DPTECH TECH
Network communication guarantee device
PendingCN107846312ATimely detection of communication failuresReduce volumeData switching networksAccess networkNetwork communication
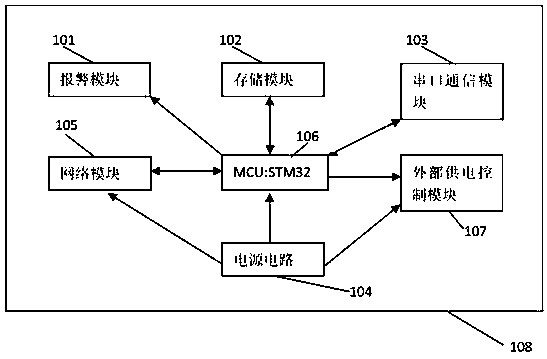
The communication guarantee device relates to a network communication device. The communication guarantee device is installed next to the network device and connected to the network through a network cable, and includes an alarm module, a storage module, a serial port communication module, a power supply circuit, a network module, an MCU part, and The external power supply control module is composed. The network port of the communication guarantee device, the relay output port, and the power input port; the relay output port is connected to the power line of the network device, and the control relay output terminal is connected to the power supply; the IO port of the chip computer is connected to the relay and the power supply. The invention is installed next to the device whose network communication needs to be guaranteed, so that it can discover the communication problem of the network device and control its restart to solve the communication failure of the network device. If it still fails to communicate normally after multiple restarts, it will send out an audible and visual alarm signal and record related events.
Owner:北方智能装备有限公司
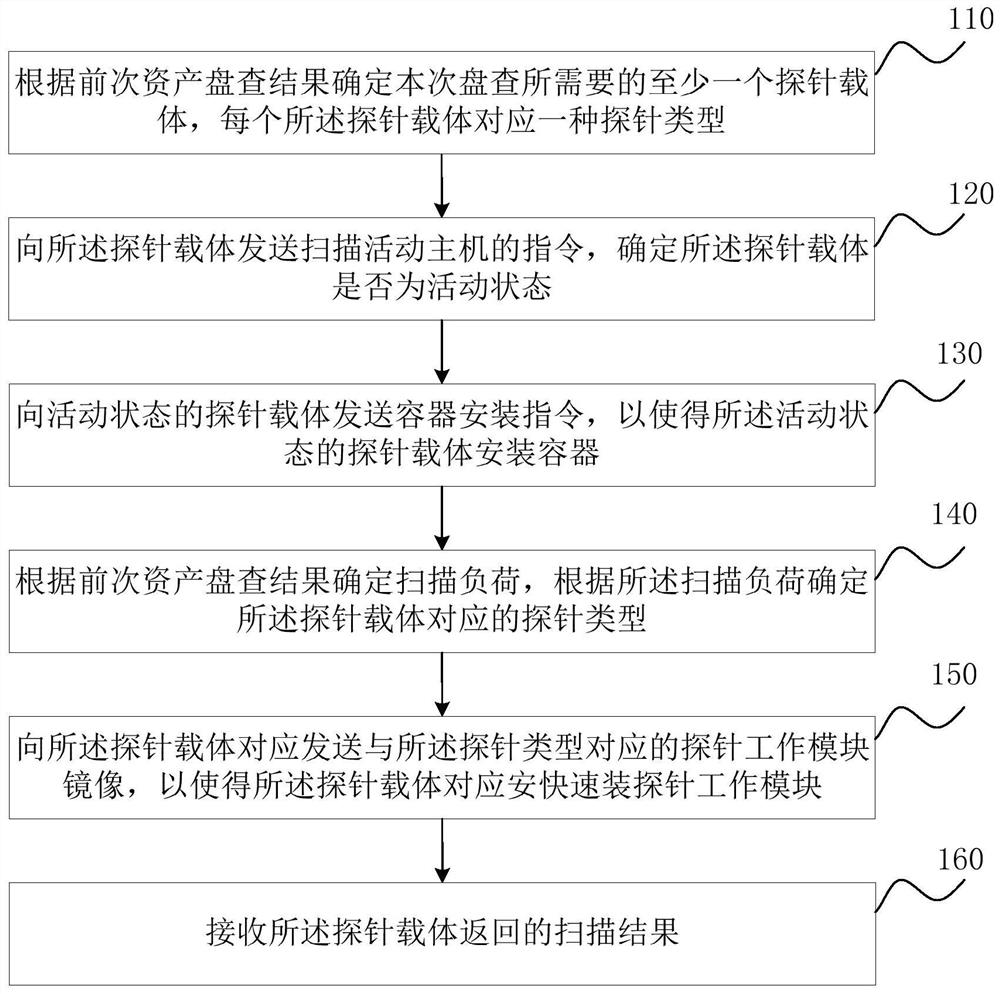
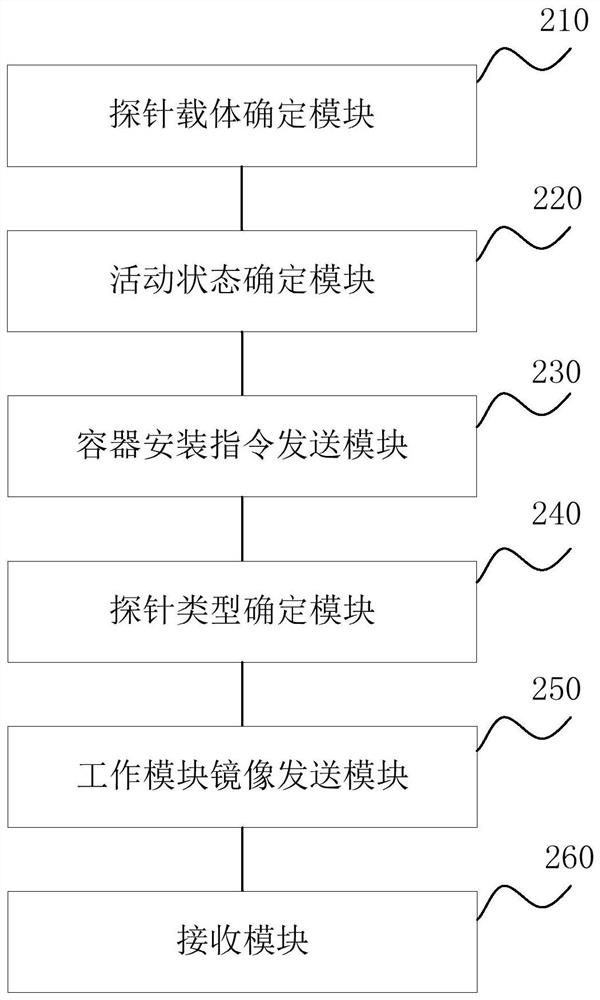
Probe distribution method and device based on network asset interrogation
ActiveCN113067818ARapid deploymentSecurity scans are fast and accurateResource allocationData switching networksProbe typeDistribution method
Owner:CEPO BEIJING INFORMATION TECH CO LTD
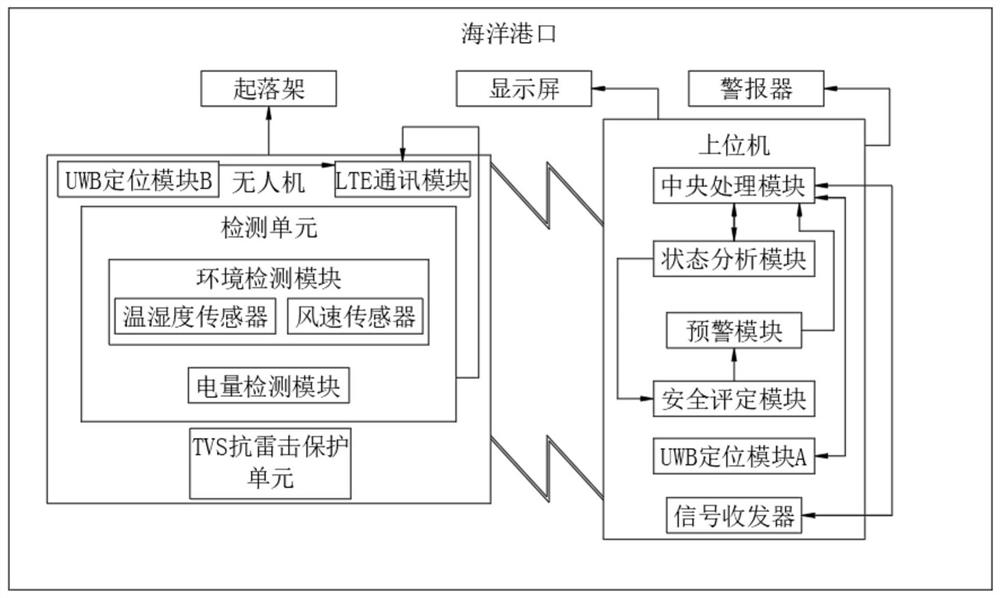
Marine port safety unmanned aerial vehicle detection system
InactiveCN112179401AProtect personal safetyProtect production securityMeasurement devicesTransmission systemsTransceiverMarine engineering
The invention discloses a marine port safety unmanned aerial vehicle detection system. The system comprises an undercarriage arranged at a marine port, a display screen, an alarm, an unmanned aerial vehicle and an upper computer; the unmanned aerial vehicle is in signal connection with the upper computer; the unmanned aerial vehicle comprises an LTE communication module, a UWB positioning module Band a detection unit; the upper computer comprises a central processing module, a state analysis module, an early warning module, a safety evaluation module, a UWB positioning module A and a signal transceiver. The unmanned aerial vehicle is arranged to detect the environment of a marine port, detected data signals are sent to the upper computer through the LTE communication module, the state analysis module in the upper computer analyzes the current state of the marine port, and analyzed data signals are sent to a safety evaluation module; the safety evaluation module evaluates the safety level of the current marine port environment state, gives an alarm to workers in advance, prevents mechanical equipment from being damaged, and protects the personal and production safety.
Owner:TANGSHAN HARBIN SHIP TECH CO LTD +1
Supporting port security on power-over-Ethernet enabled ports
ActiveUS9489543B2Digital data processing detailsInternal/peripheral component protectionControl powerSecurity policy
Embodiments of the present invention include systems and methods for controlling power delivery to a port in a power sourcing equipment. The power sourcing equipment receives identity information from a device connected to the port and determines whether the device is a trusted device or a rogue device according to a security policy. If the device is a trusted device, the power sourcing equipment supplies data and electrical power to the port according to a priority policy. If the device is a rogue device, the power source equipment does not supply electrical power to the port.
Owner:DELL PROD LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com