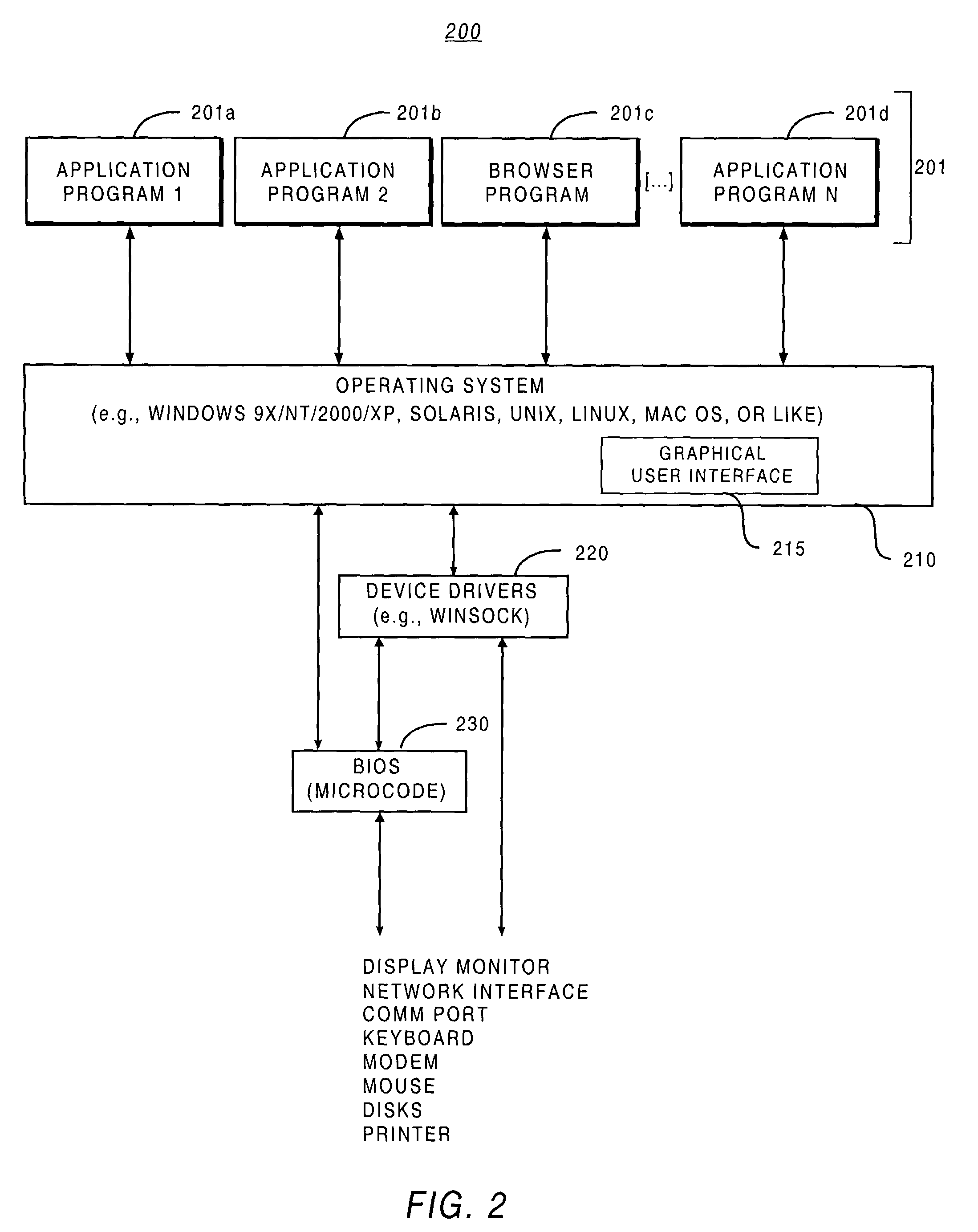
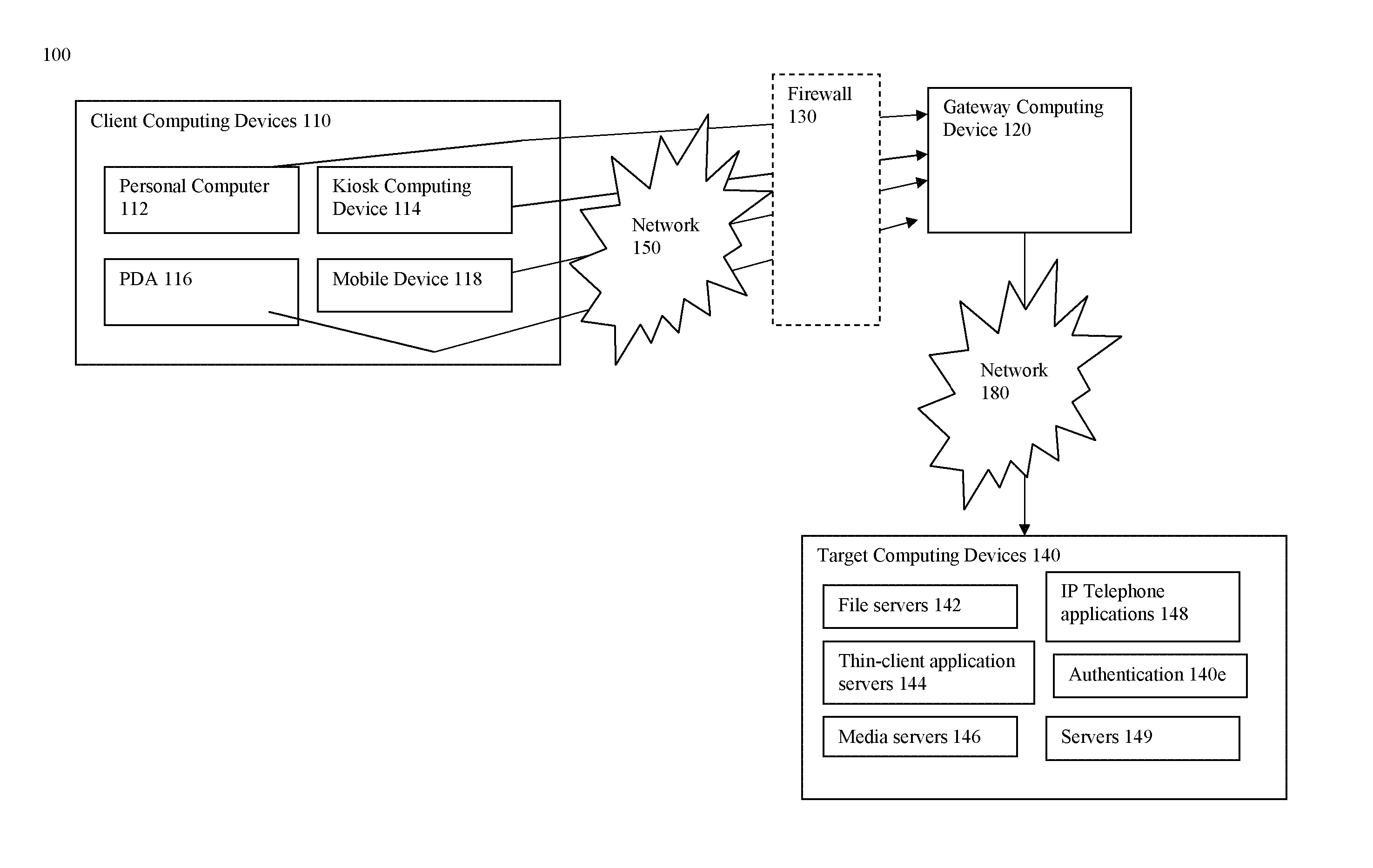
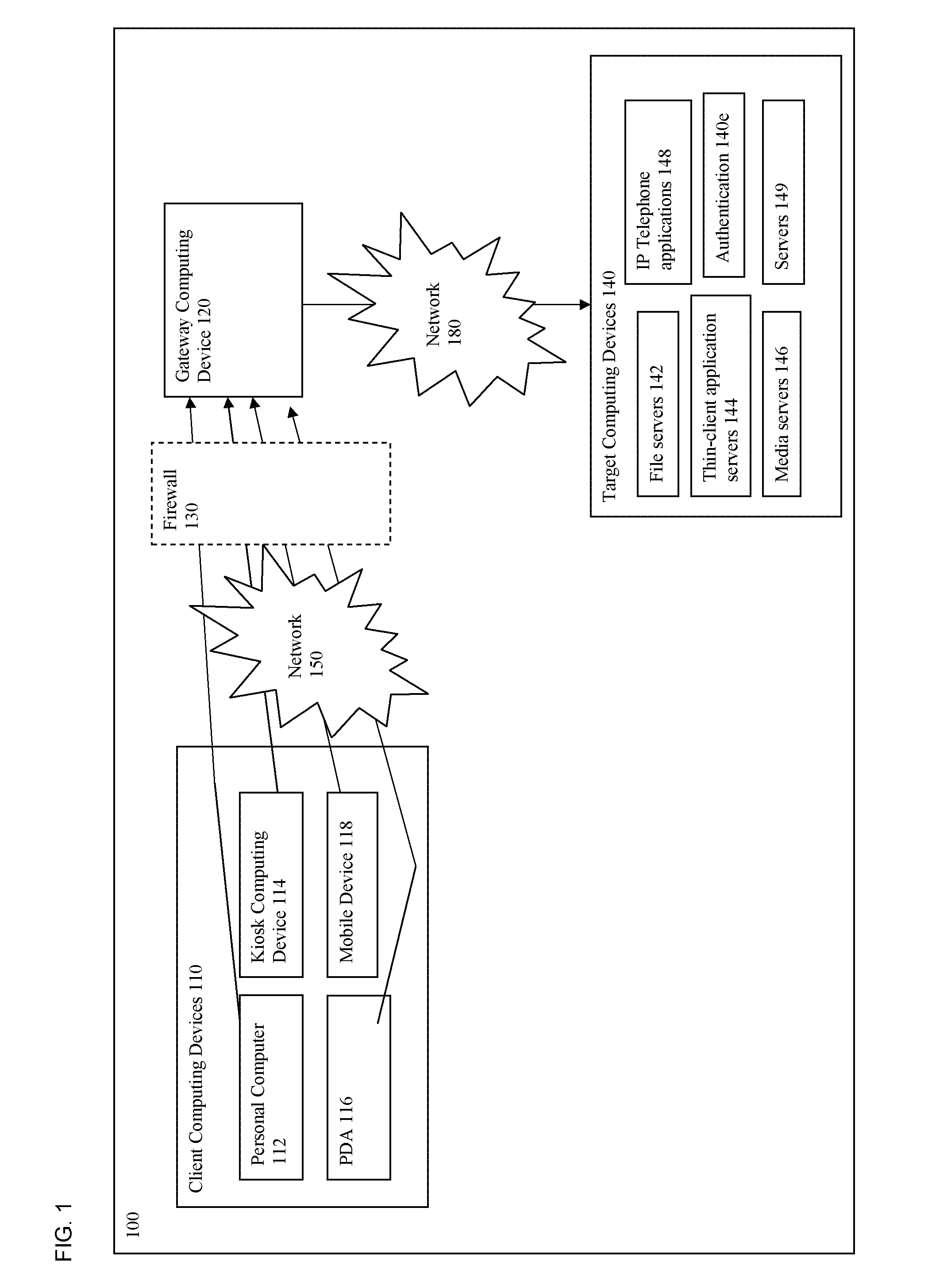
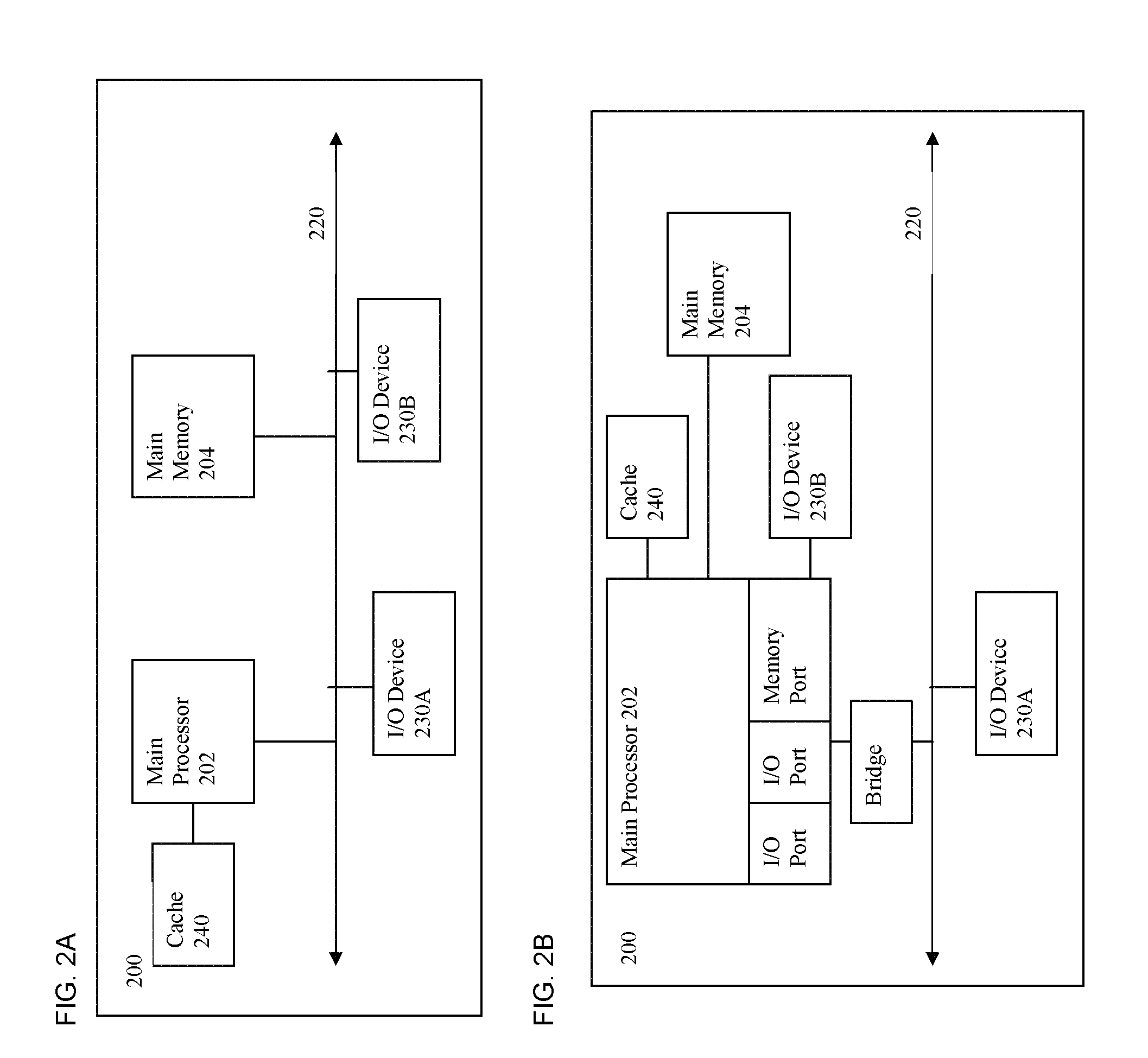
Patents
Literature
2785results about "Wide area networks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System for providing mobile VoIP
ActiveUS20050286466A1Preserve battery lifeLow power capabilityPower managementNetwork topologiesMobile deviceHandover
A system for providing handoff for a mobile devices comprising a mobile phone programmed to automatically handover between differing data bearers and to optimally detect those bearers in a roaming environment keeping power consumption to a minimum. Repeating means for these mobile devices to extend the range of coverage and the protocol for that coverage.
Owner:TRUPHONE
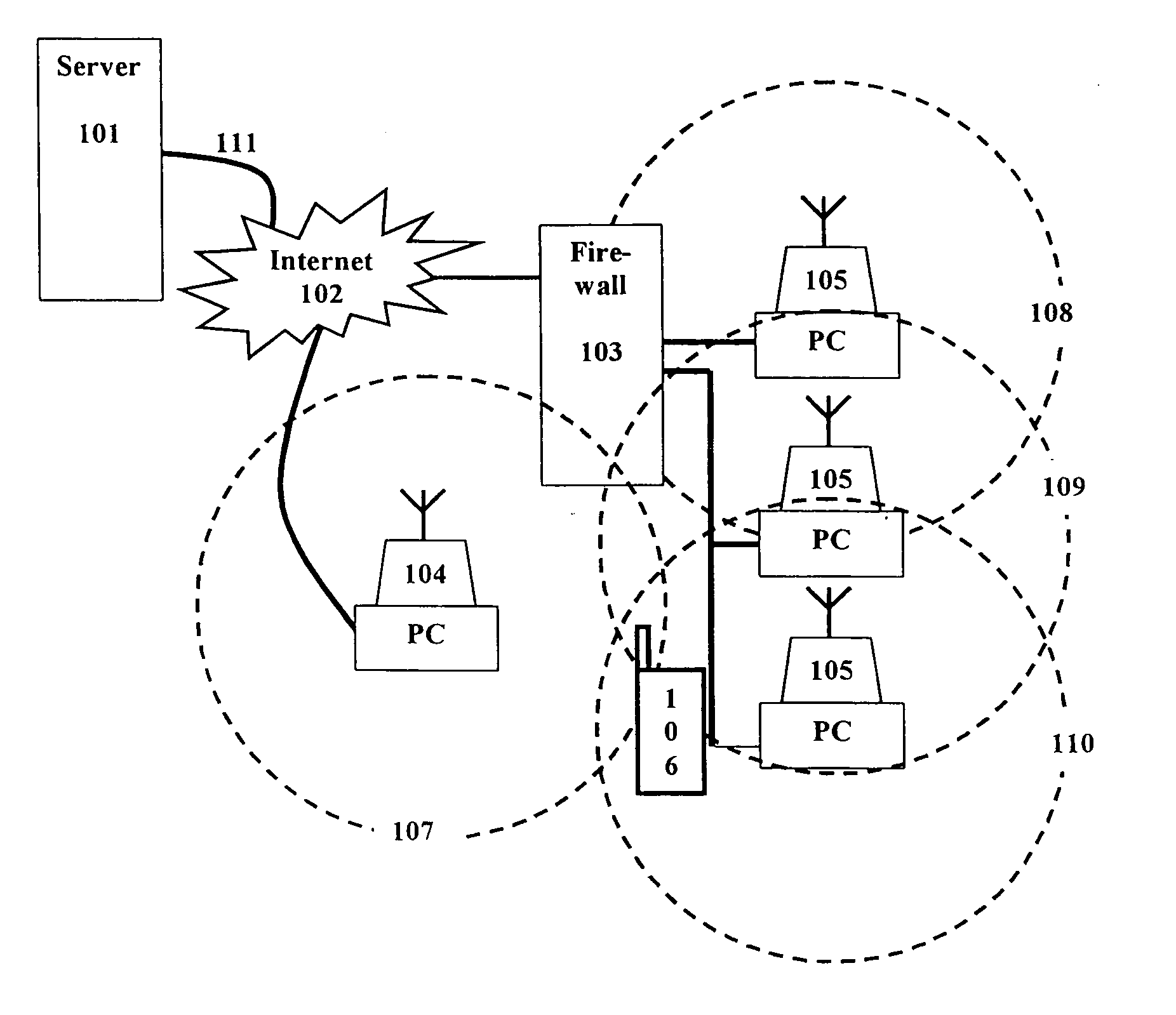
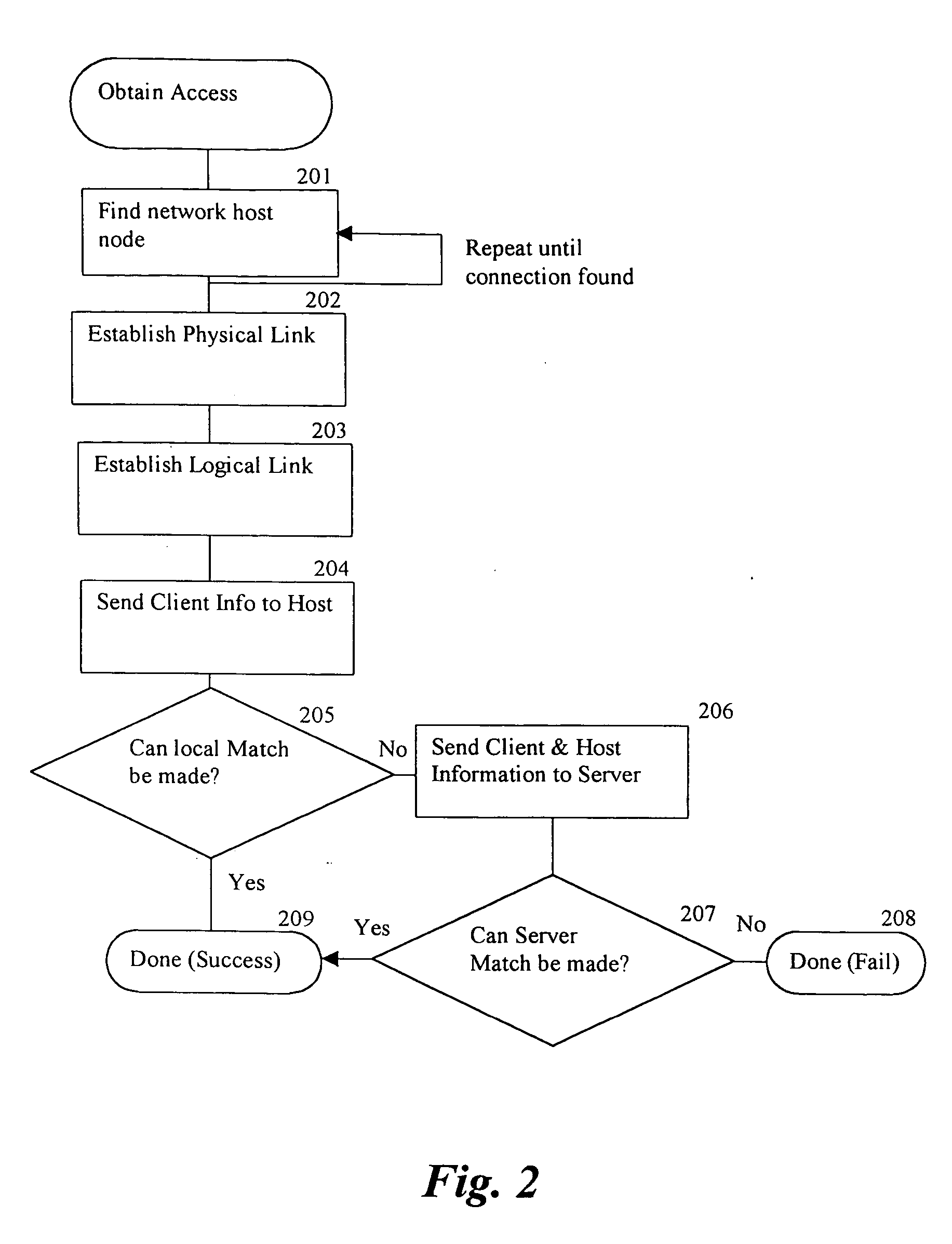
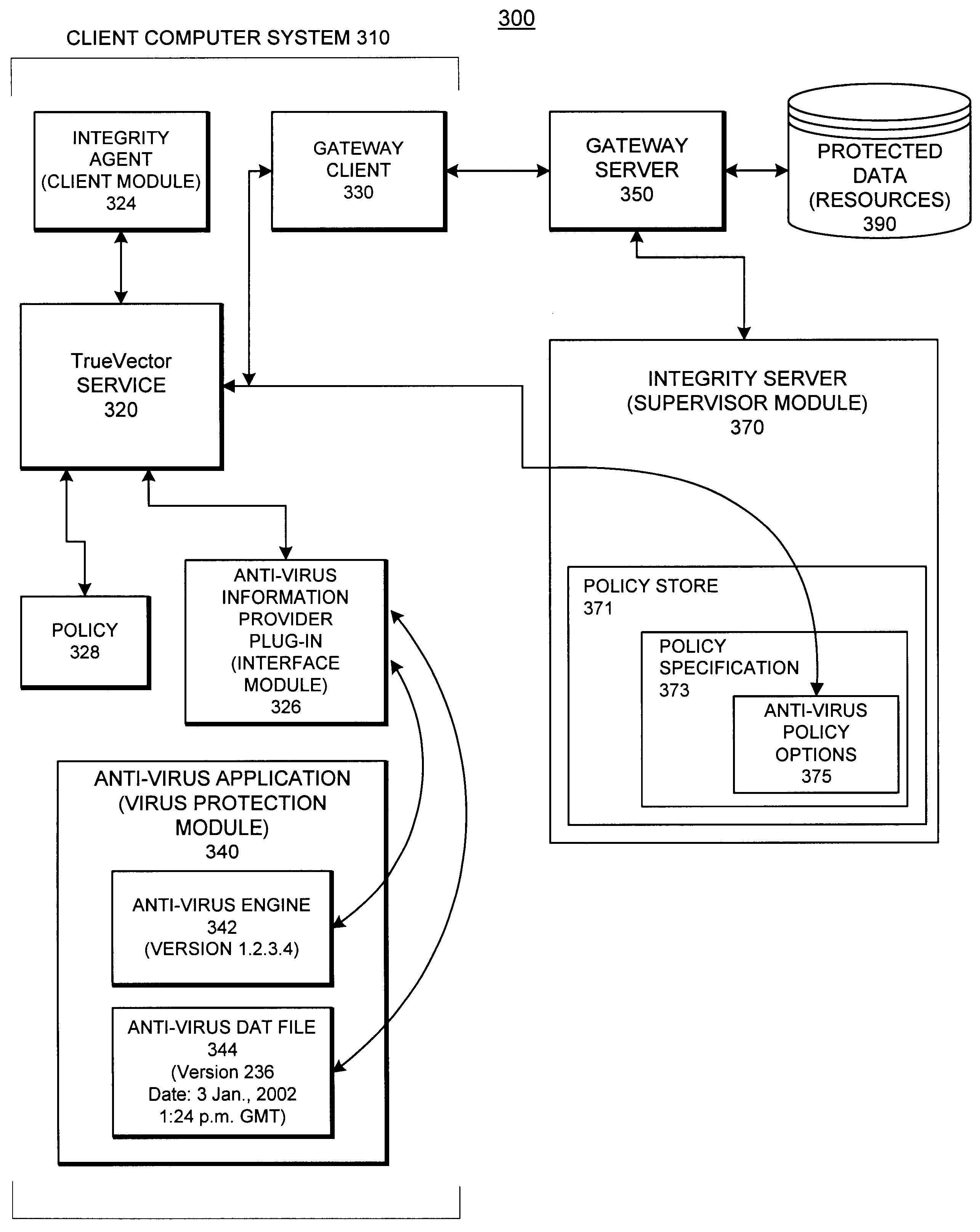
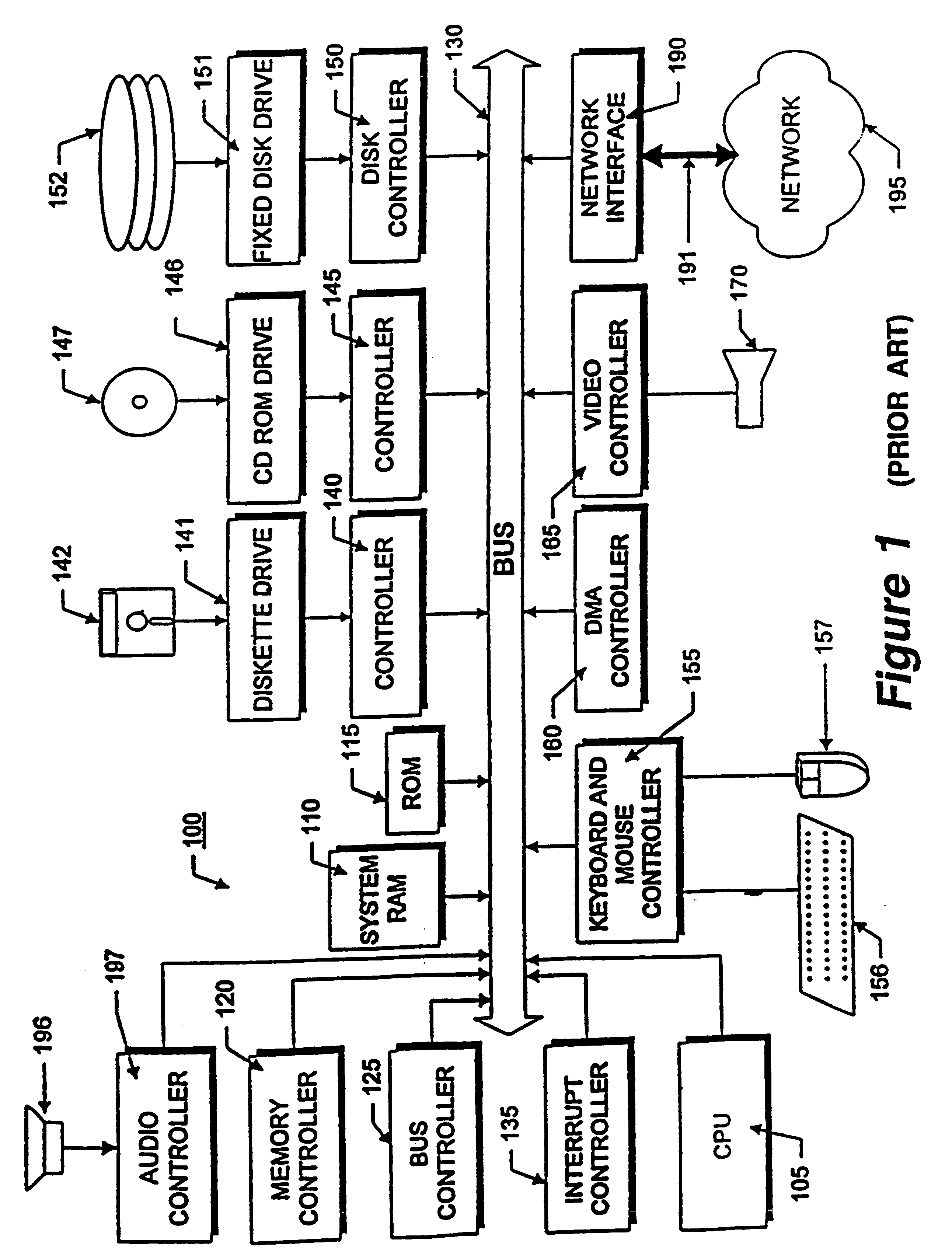
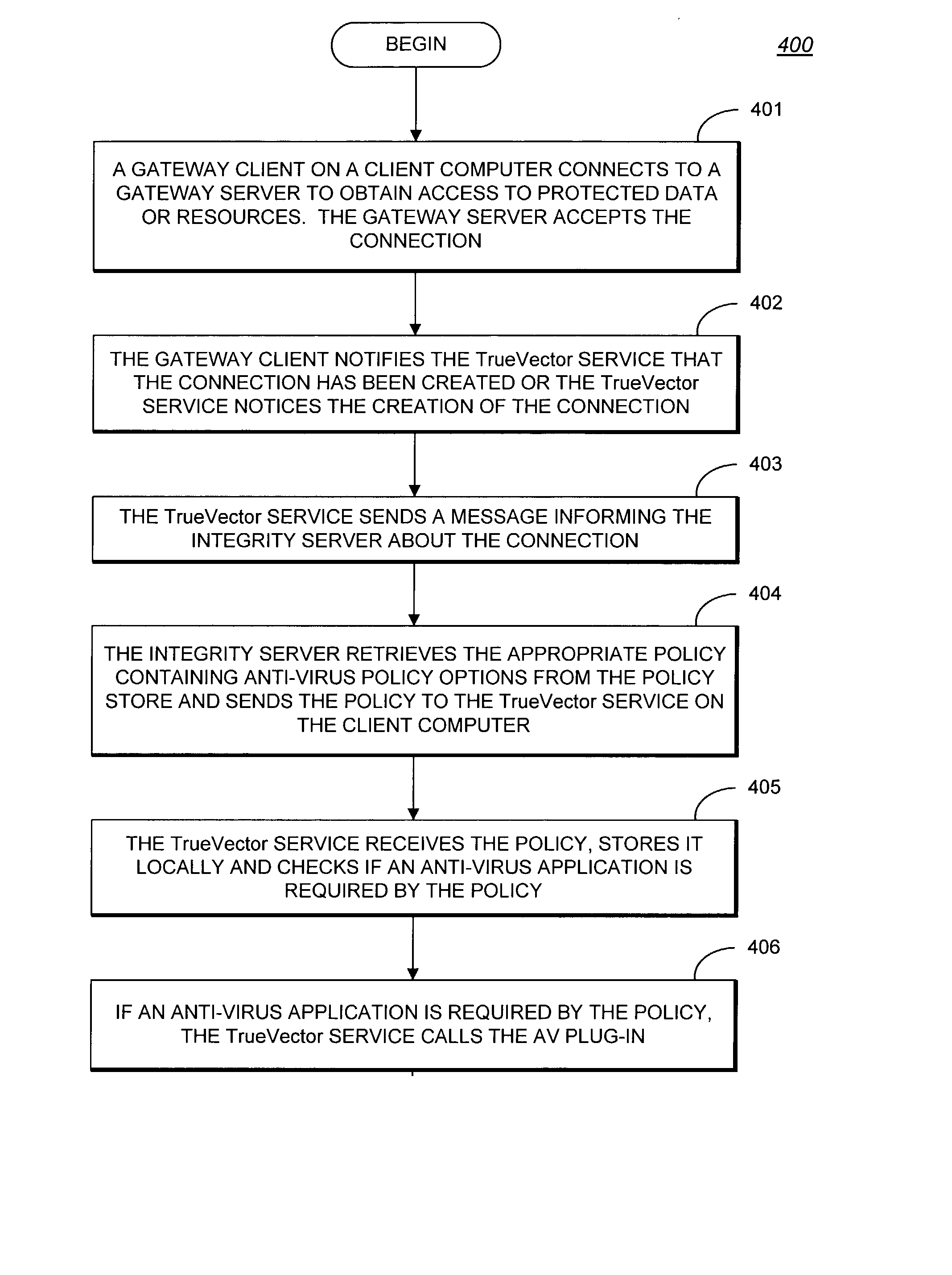
System and methods providing anti-virus cooperative enforcement
InactiveUS6873988B2Data processing applicationsMultiple digital computer combinationsAnti virusComputer network
A system providing methods for anti-virus cooperative enforcement is described. In response to a request from a device for access to protected resources, such as a network or protected data, a determination is made as to whether an anti-virus policy applies to the request for access made by the device. If an anti-virus policy is applicable, information pertaining to virus protection available on the device is collected. The virus protection information that is collected is evaluated to determine whether the device is in compliance with the anti-virus policy. If the device is determined to be in compliance with the anti-virus policy, the device is allowed to access the protected resources.
Owner:CHECK POINT SOFTWARE TECH INC
Dynamic self-configuration for ad hoc peer networking using mark-up language formated description messages
InactiveUS6892230B1CostConnectivity solutionDigital computer detailsNetworks interconnectionAuto-configurationHuman language
A device control model provides an integrated set of addressing, naming, discovery and description processes that enables automatic, dynamic and ad-hoc self-setup by devices to interoperate with other devices on a network. This permits a computing device when introduced into a network to automatically configure so as to connect and interact with other computing devices available on the network, without a user installation experience and without downloading driver software or persisting a configuration setup for connecting and interacting with such other computing devices. Upon completing interaction with such other devices, the computing device automatically releases the setup for such other devices so as to avoid persistent device configurations that might create a configuration maintenance and management burden.
Owner:ROVI TECH CORP
System and methodology for security policy arbitration
ActiveUS20030177389A1Multiple digital computer combinationsProgram controlComputer networkSecurity policy
A system providing methods for a device to apply a security policy required for connection to a network is described. In response to receipt of a request from a device for connection to a particular network, a current policy to apply to said device for governing the connection to this particular network is determined from a plurality of available security policies available to the device. This current policy to apply to said device is generated by merging a plurality of security policies available for governing connections. After said current policy is applied to the device, the connection from the device to this particular network is allowed to proceed.
Owner:CHECK POINT SOFTWARE TECH INC
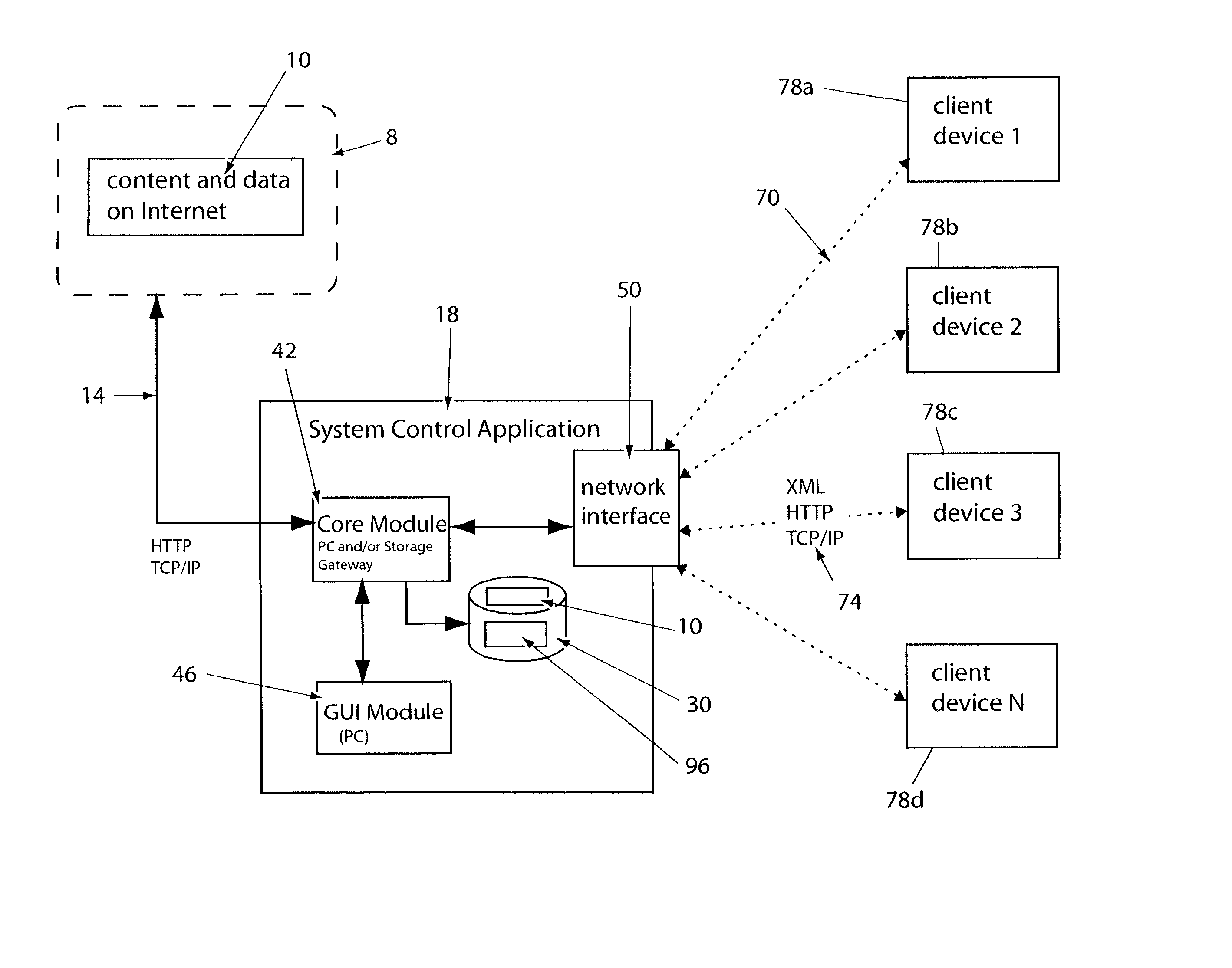
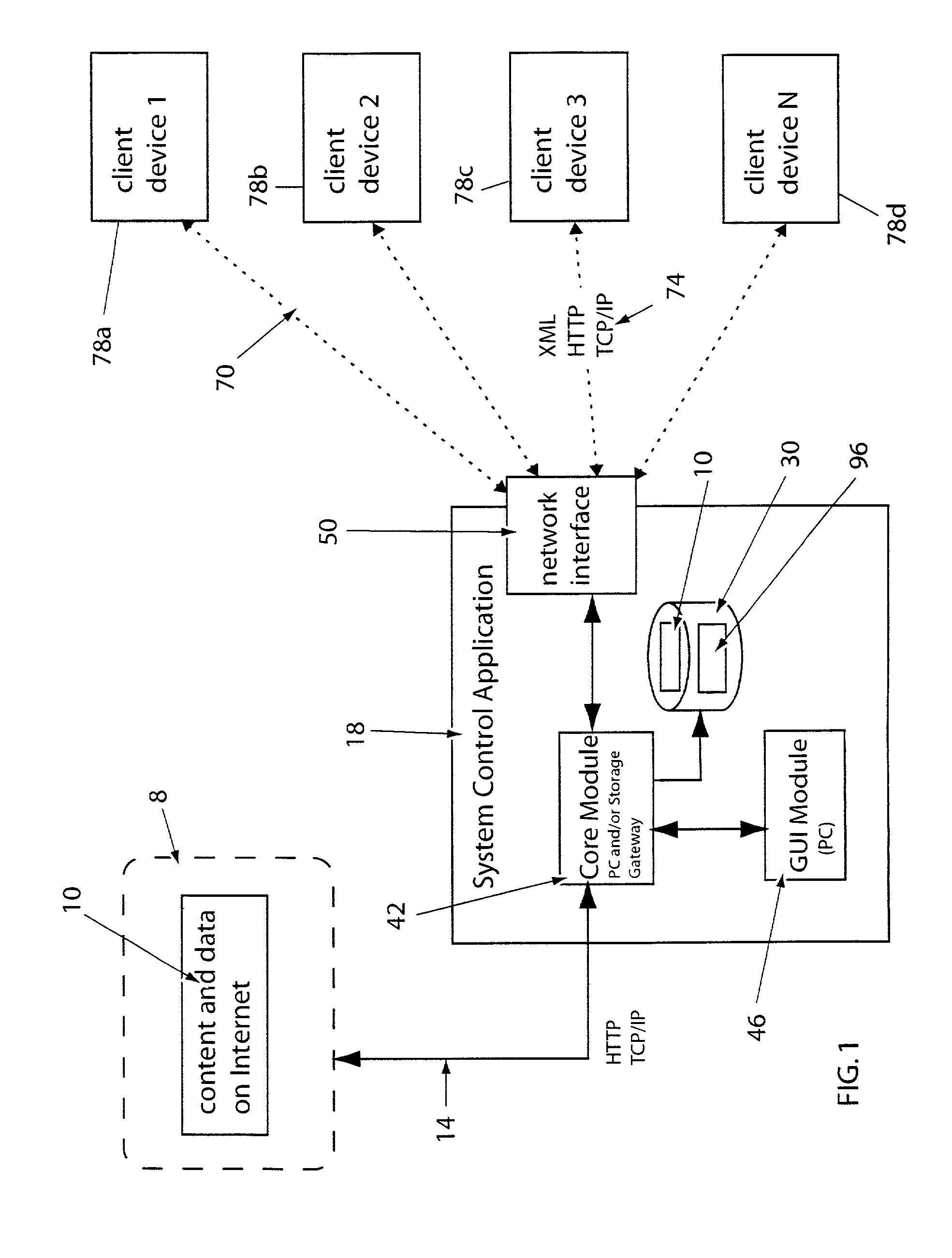
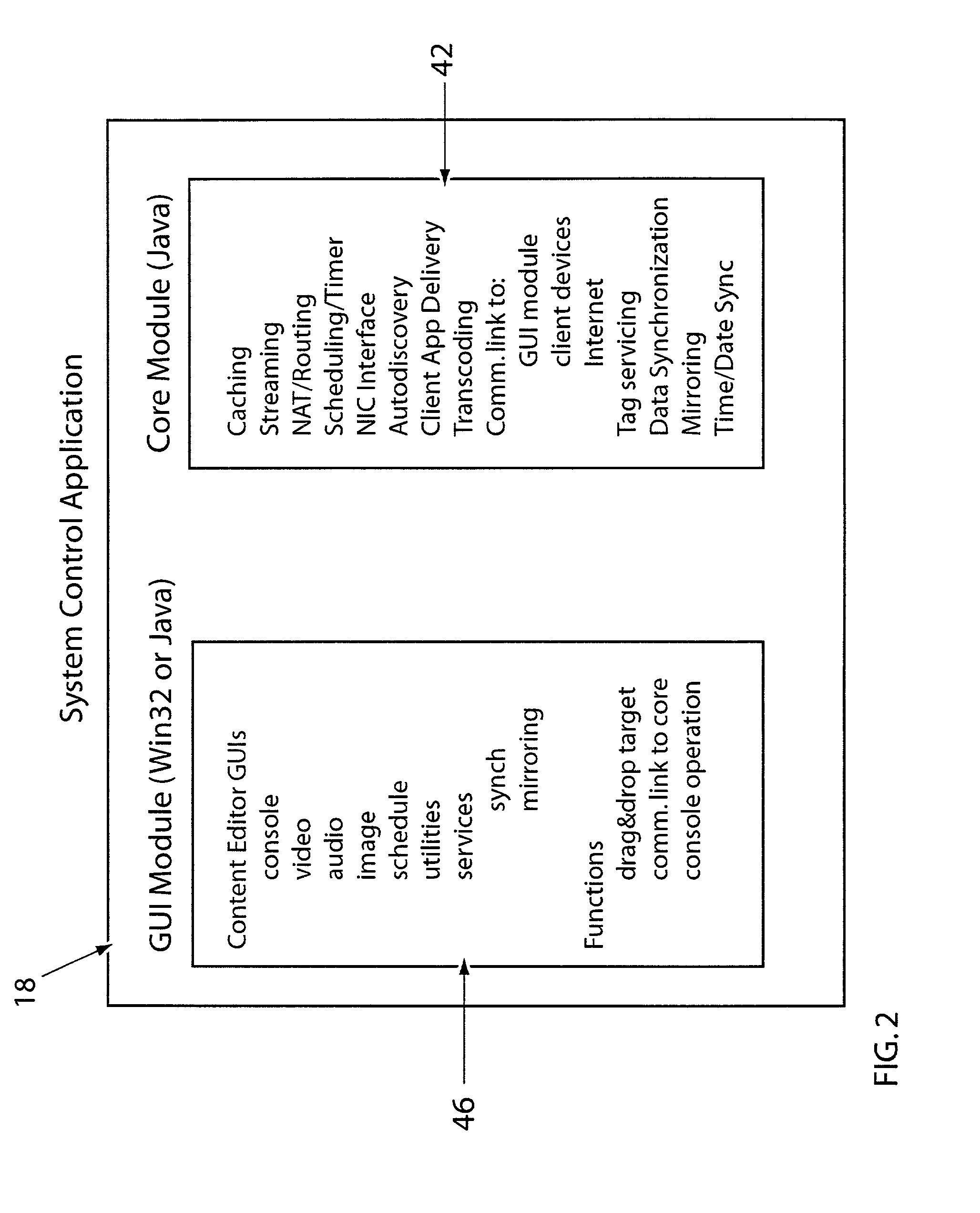
System for providing content, management, and interactivity for thin client devices
InactiveUS20020013852A1Multiple digital computer combinationsSelective content distributionThe InternetProcedural approach
A system is provided for delivering Internet and digital content to a variety of thin client devices. A web portal for accessing and selecting content is used in conjunction with graphical user interfaces on a personal computer for setting up and controlling the content channels. The user interfaces, scheduling, and communication management are controlled by a system control software application running on a local server with an Internet connection. A high speed local area network provides for streaming content from the Internet or local server to thin client devices. A digital audio playback device is connected to the local server via the local area network connection and decodes streamed audio files, and converts them into analog audio signals for input into a conventional stereo. Digital content is streamed automatically from the local server to another Internet playback device, based on end user content preferences and schedule selections.
Owner:VIVIANA RES +2
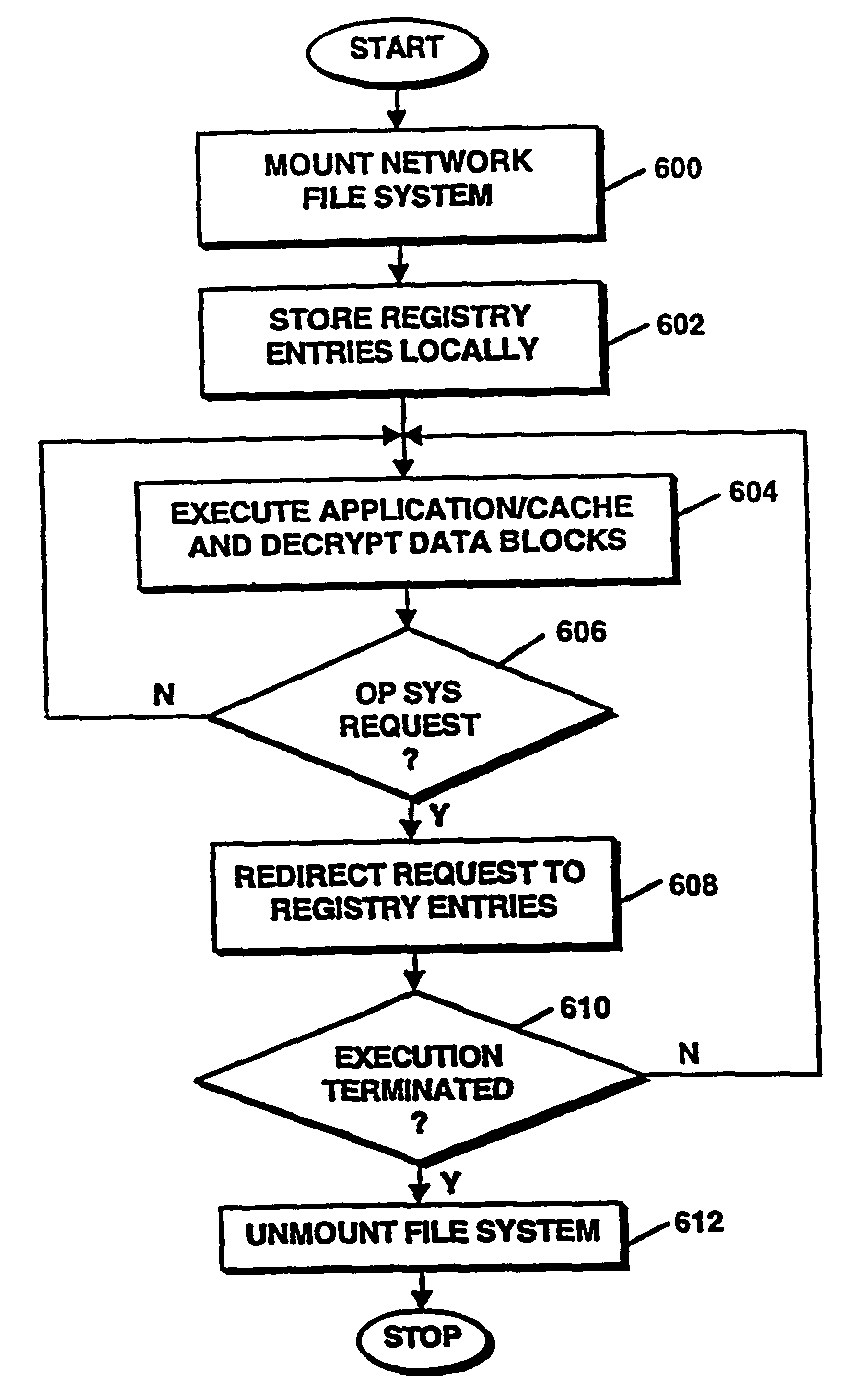
Method and apparatus for installation abstraction in a secure content delivery system
InactiveUS6374402B1Expand accessAvoid leverageTelevision system detailsBroadband local area networksOperational systemNetwork addressing
A system for secure delivery of on-demand content over broadband access networks includes a client application executing on a user's local computer system. The client application interacts with a content server on which a plurality of selectable titles are stored and further interacts with an access server which provides the network address of a title and keying data necessary for to the client process access and execute the title. The client process utilizes an installation abstraction which enables a title to be executed on the local computer system without ever being installed. The abstraction is achieved by mounting a network file system and storing a set of registry entries related to the title on the local computer system. Portions of the title are retrieved from the content server and executed by the local operating system. During title execution, requests from the local operating system are intercepted and redirected to the set of registry entries, as applicable. The times at which the client process may retrieve the title data from the content server are defined by the access server through use of an activator and token.
Owner:MICROSOFT TECH LICENSING LLC
System and methods providing anti-virus cooperative enforcement
InactiveUS20030055994A1Data processing applicationsMultiple digital computer combinationsAnti virusComputer network
A system providing methods for anti-virus cooperative enforcement is described. In response to a request from a device for access to protected resources, such as a network or protected data, a determination is made as to whether an anti-virus policy applies to the request for access made by the device. If an anti-virus policy is applicable, information pertaining to virus protection available on the device is collected. The virus protection information that is collected is evaluated to determine whether the device is in compliance with the anti-virus policy. If the device is determined to be in compliance with the anti-virus policy, the device is allowed to access the protected resources.
Owner:CHECK POINT SOFTWARE TECH INC
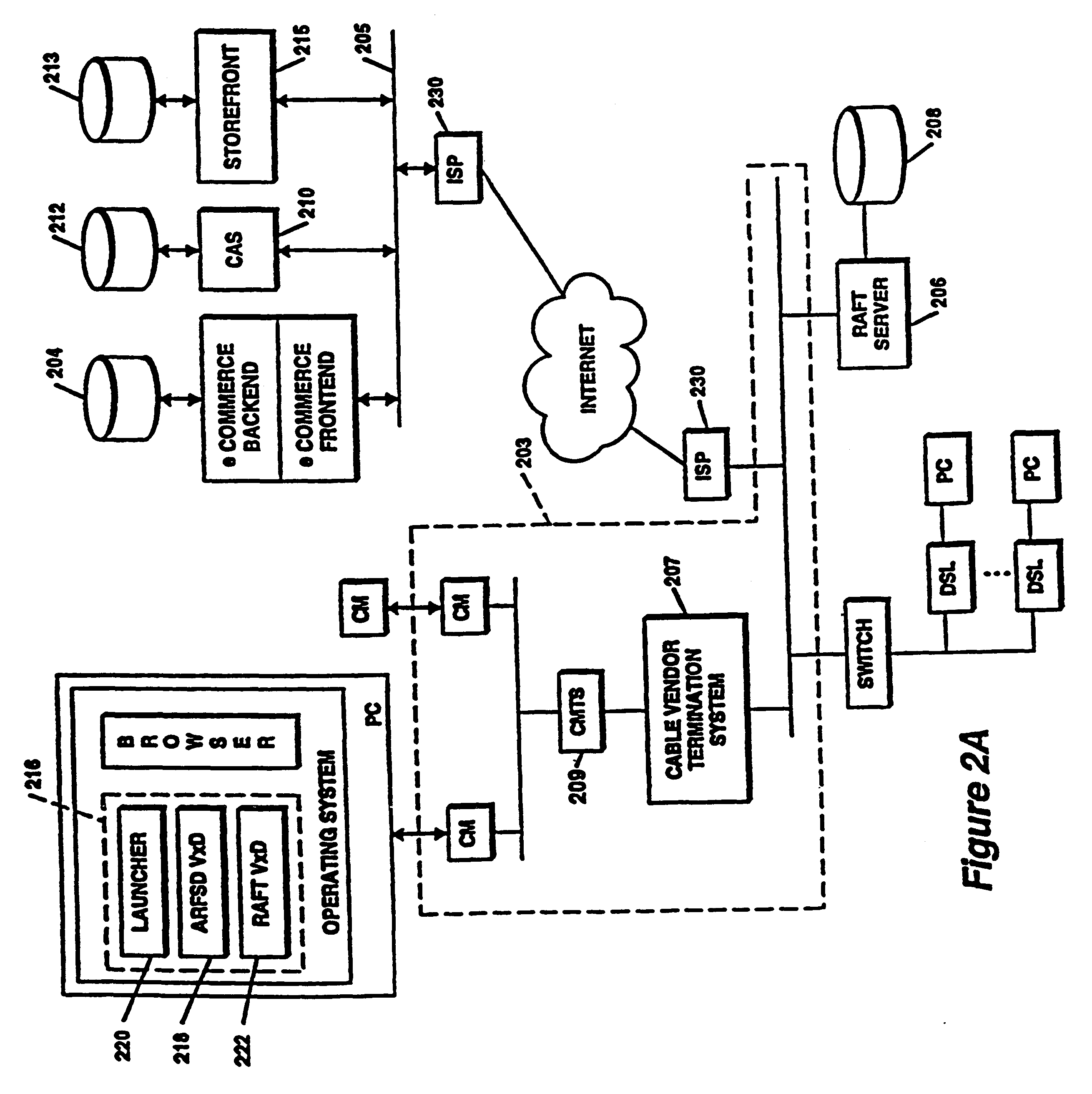
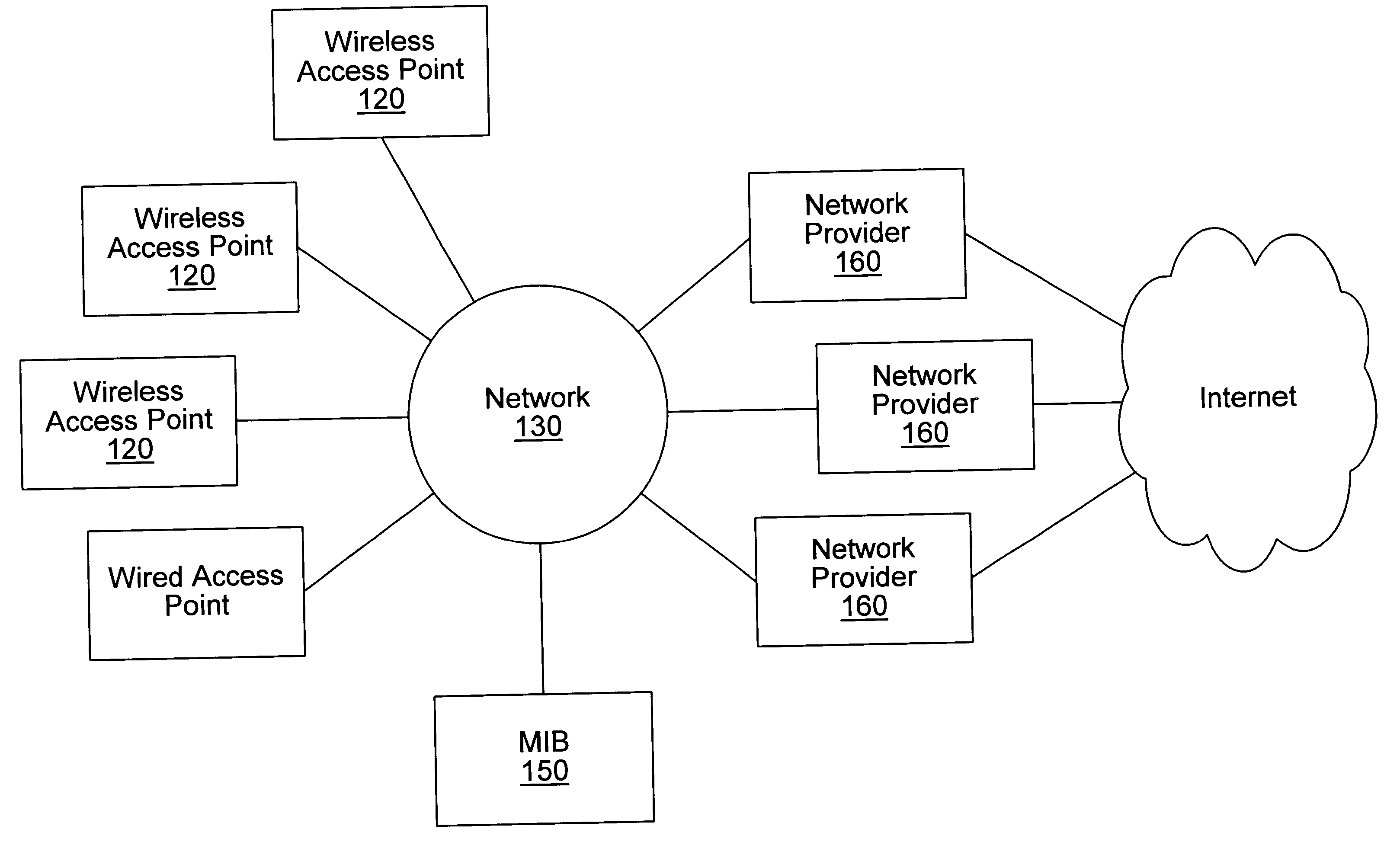
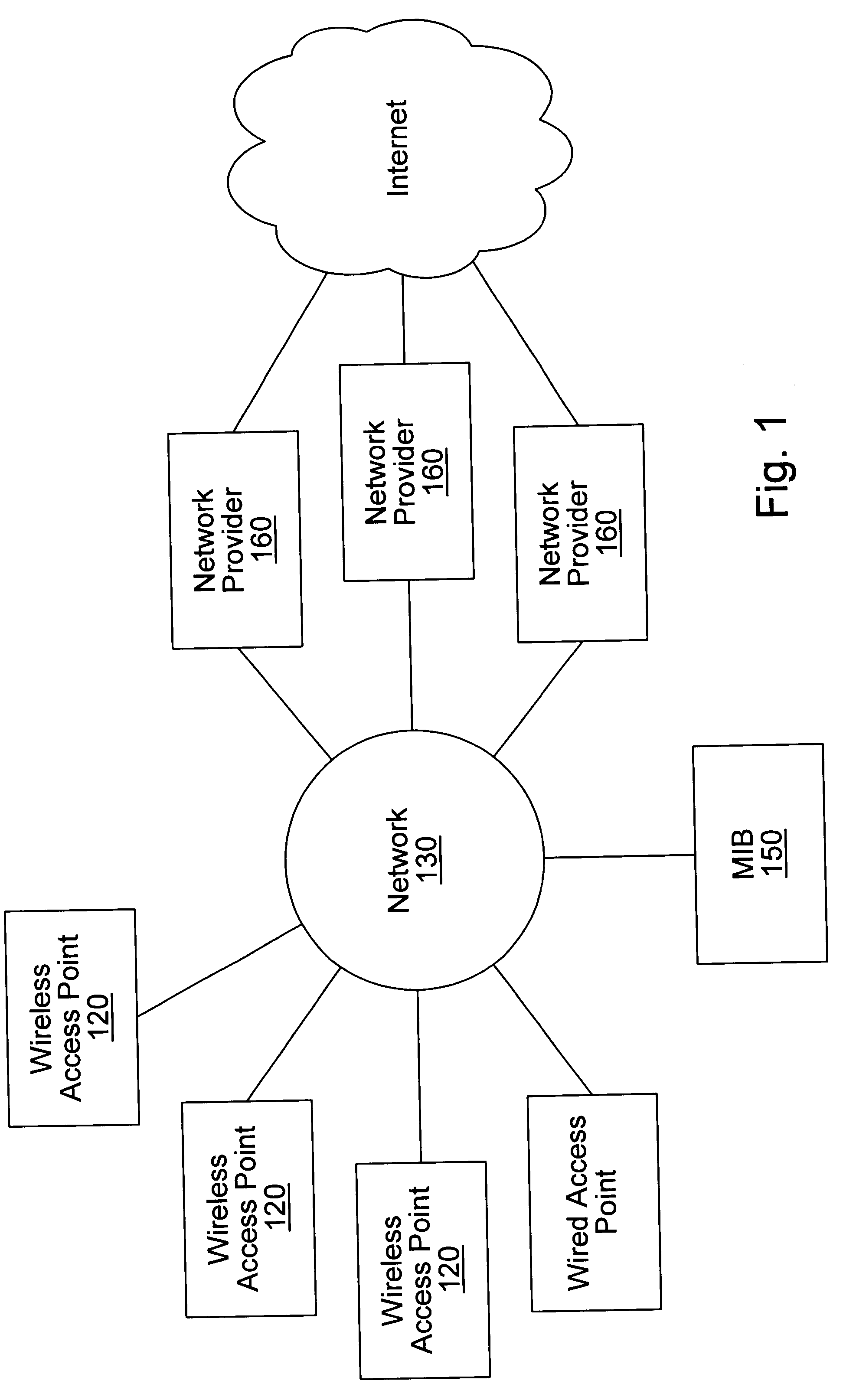
Distributed network communication system which enables multiple network providers to use a common distributed network infrastructure
InactiveUS6732176B1Metering/charging/biilling arrangementsMultiple digital computer combinationsCommunications systemNetworked system
A system and method for providing access and / or roaming features on a network system. The network system includes a plurality of wireless and / or wired access points coupled to a network. A portable computing device (PCD) of a user may store identification information which uniquely indicates a network provider of a plurality of possible network providers. The identification information may also or instead indicate an access or privilege level of the user. When the access point receives the identification information from a PCD of a user, the access point may determine the appropriate network provider for the portable computing device using the identification information. Network access may then be provided to the portable computing device through the determined network provider.
Owner:CISCO TECH INC
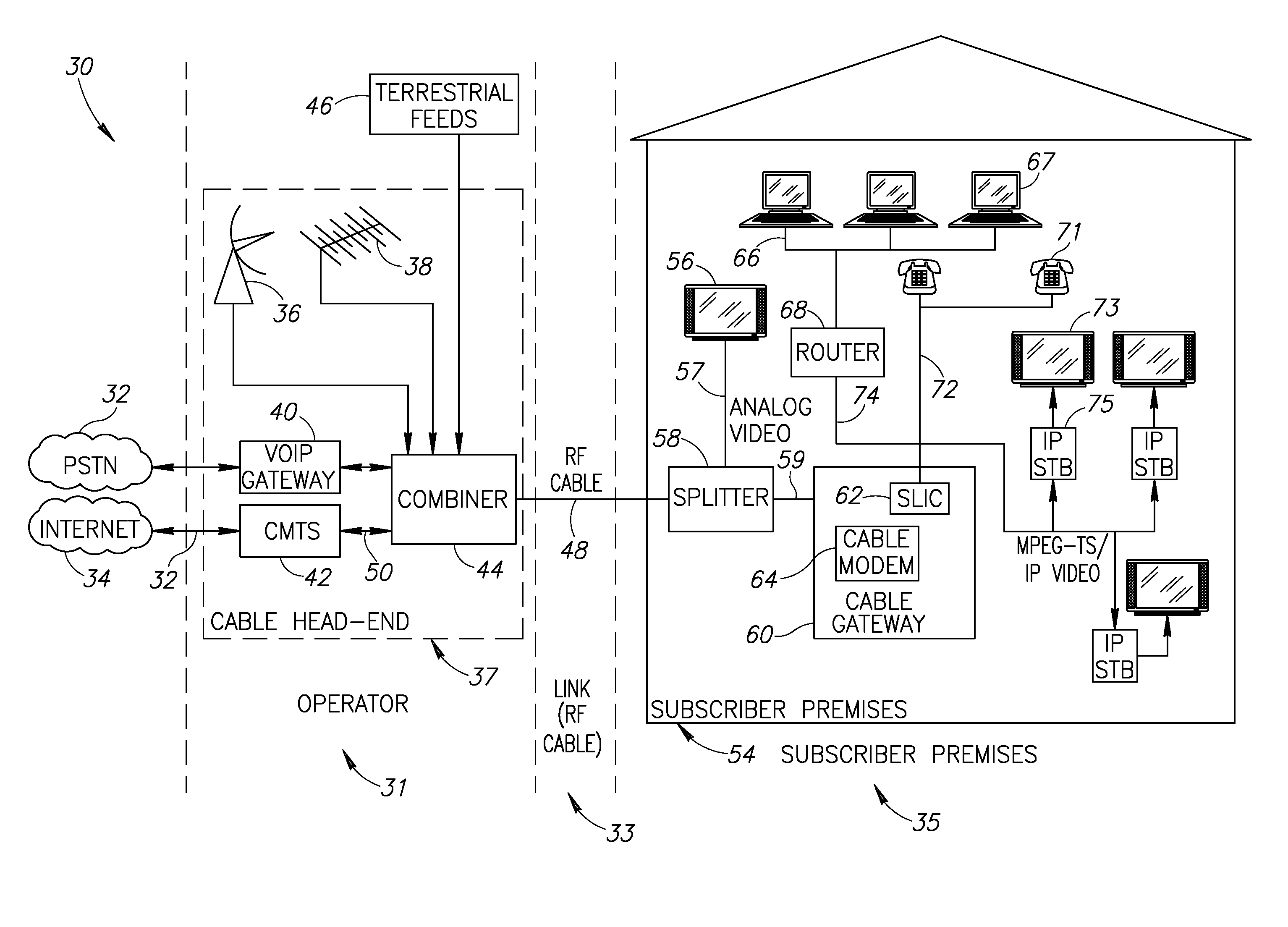
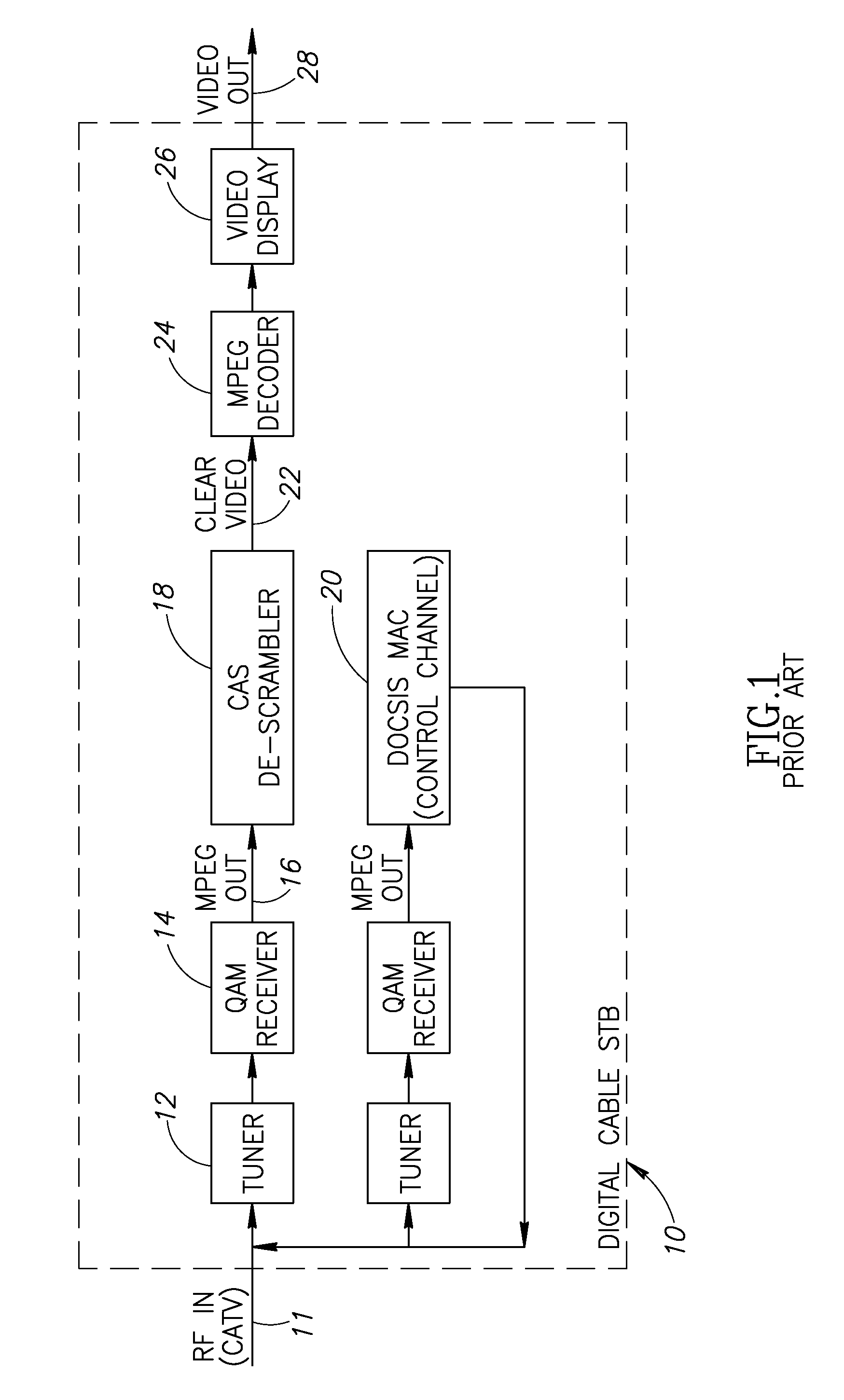
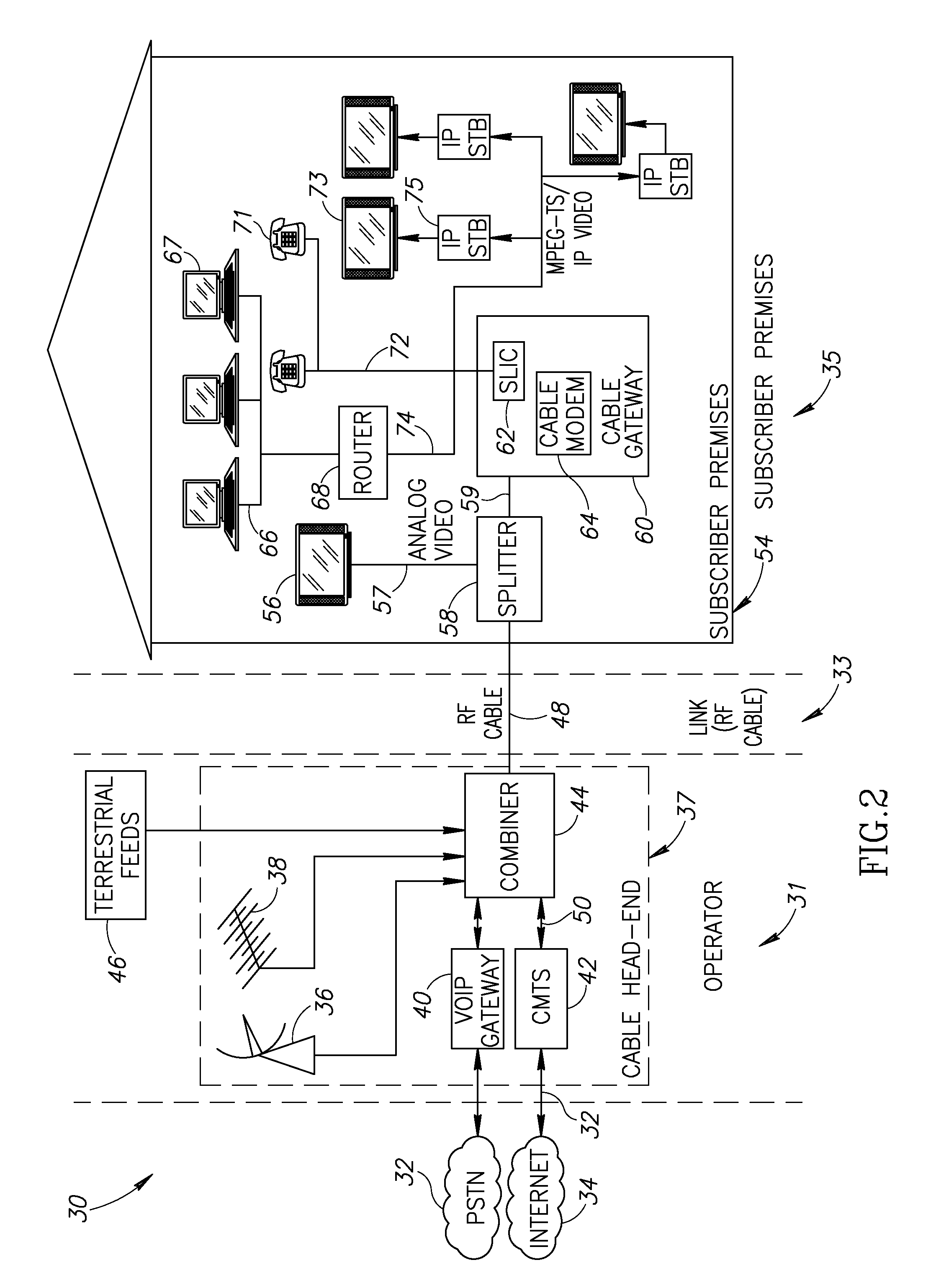
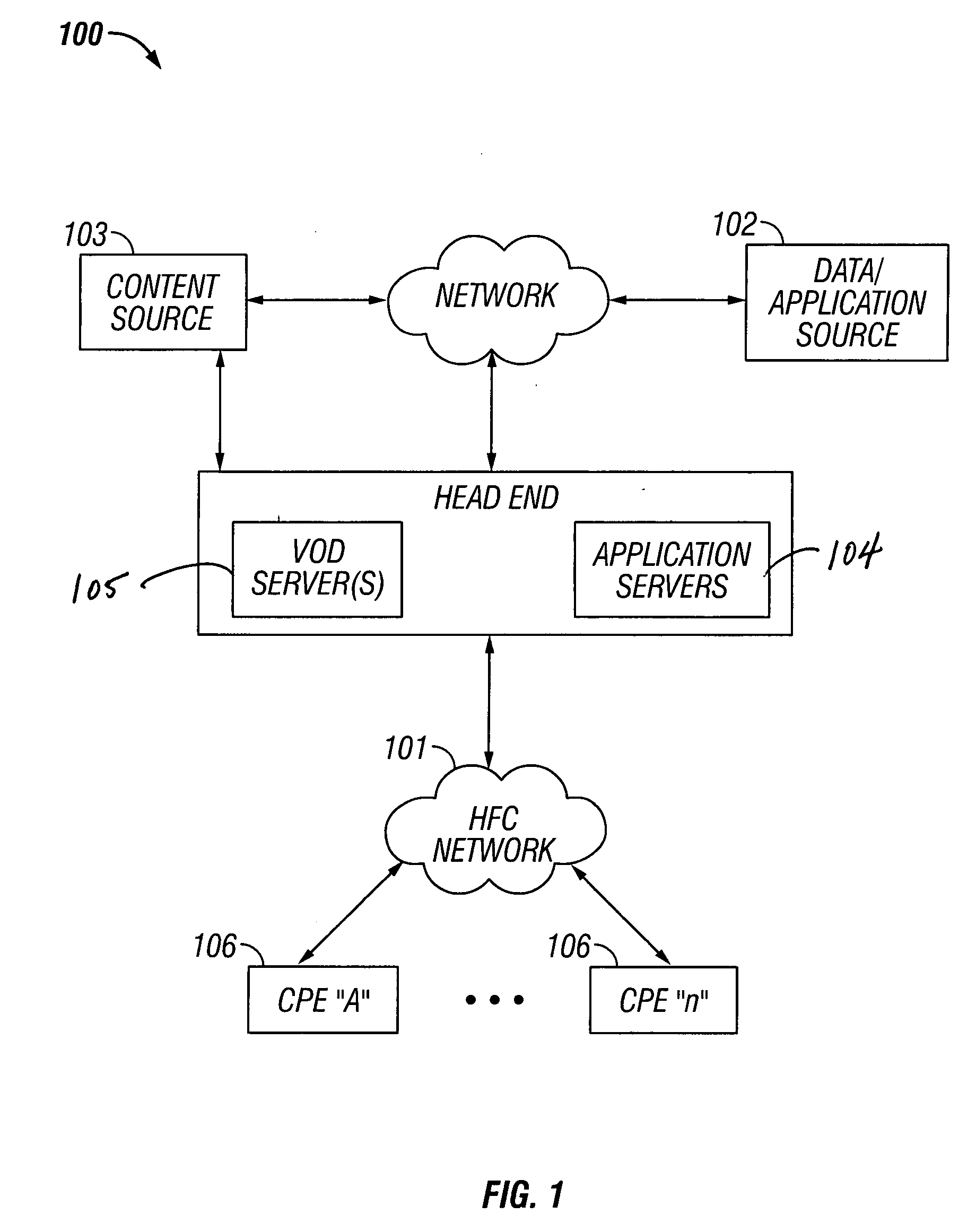
Hybrid mpeg/ip digital cable gateway device and architecture associated therewith
A novel cable gateway system and architecture incorporating a hybrid digital video transceiver. The digital cable system architecture combines reception of legacy video such as MPEG-TS based DVB-C streams with that of original IP video over DOCSIS channels. The system comprises a hybrid DVB / IP cable gateway STB capable of receiving both legacy DVB-C video and original IP video streams. The cable gateway device performs the front-end functionality (including QAM receiver, tuner and broadband connection) while the back-end functionality of video decoding and display is performed by one or more standard IP-STBs connected to the cable gateway device over a network (e.g., home LAN). Legacy MPEG-TS based DVB-C video is captured and encapsulated into packets for distribution over the network to the IP-STBs. The cable gateway distributes the original IP video received over the CATV source and the encapsulated legacy video as video over IP packets over the network.
Owner:INTEL CORP
Premises gateway apparatus and methods for use in a content-based network
ActiveUS20080313691A1Satisfies needColor television signals processingNetwork topologiesDigital videoComputer network
Apparatus and methods for premises gateway functions that integrate or unify functions typically distributed across multiple devices within a content-based network. In one embodiment, the out-of-band (OOB) signaling functionality normally provided in each of a set-top-box (STB) and digital video recorder (DVR) are unified into a common OOB (e.g., DOCSIS) capable premises gateway device, thereby obviating OOB tuners and related components from each device. In another variant, the premises gateway is adapted for all-IP operation, such as for use with IP-based computers and IP set-top boxes, etc. Fully unified variants are also disclosed, wherein the DVR and / or STB functions are physically integrated within the premises gateway.
Owner:TIME WARNER CABLE ENTERPRISES LLC
System and methodology for security policy arbitration
ActiveUS7546629B2Multiple digital computer combinationsSecret communicationComputer networkSecurity policy
A system providing methods for a device to apply a security policy required for connection to a network is described. In response to receipt of a request from a device for connection to a particular network, a current policy to apply to said device for governing the connection to this particular network is determined from a plurality of available security policies available to the device. This current policy to apply to said device is generated by merging a plurality of security policies available for governing connections. After said current policy is applied to the device, the connection from the device to this particular network is allowed to proceed.
Owner:CHECK POINT SOFTWARE TECH INC
A method and systems for securing remote access to private networks
ActiveUS20060037071A1Reduce the burden onImprove experienceMultiple digital computer combinationsProgram controlPrivate networkNetwork address translation
A method for securing remote access to private networks includes a receiver intercepting from a data link layer a packet in a first plurality of packets destined for a first system on a private network. A filter intercepts from the data link layer a packet in a second plurality of packets transmitted from a second system on the private network, destined for an system on a second network. A transmitter in communication with the receiver and the filter performing a network address translation on at least one intercepted packet and transmitting the at least one intercepted packet to a destination.
Owner:CITRIX SYST INC
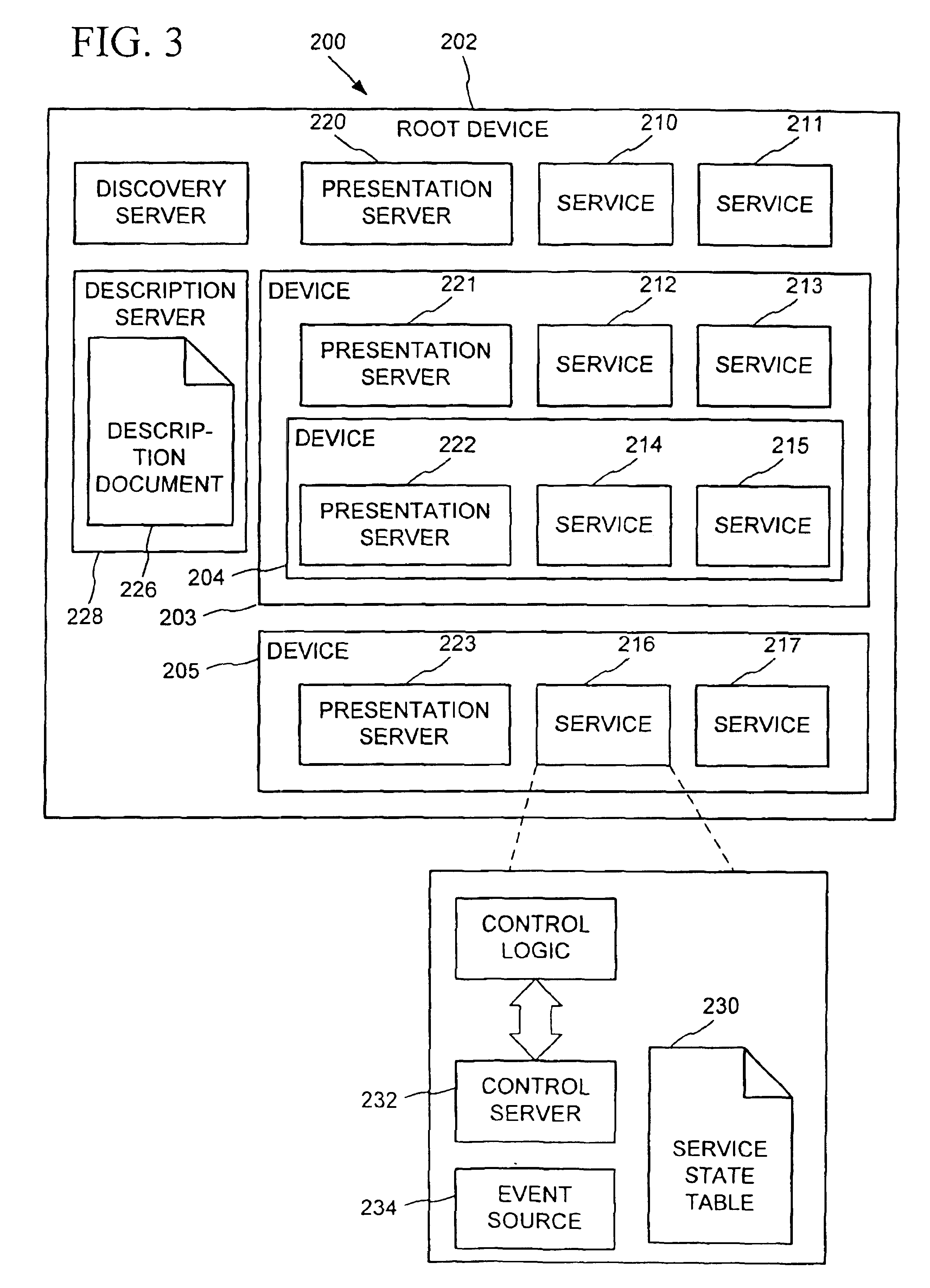
XML-based template language for devices and services
InactiveUS6910068B2CostConnectivity solutionMultiple digital computer combinationsNetworks interconnectionWeb siteProgramming language
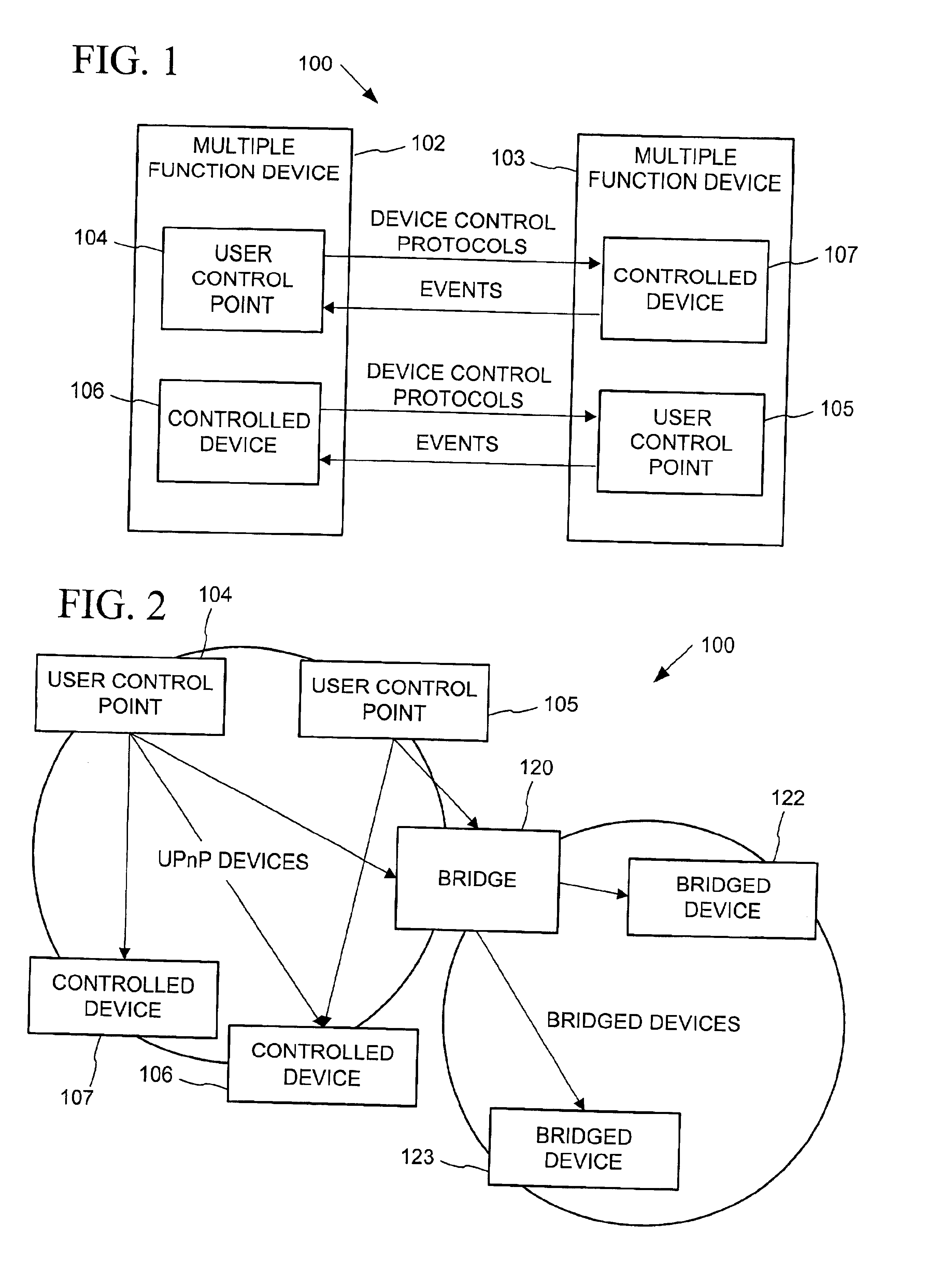
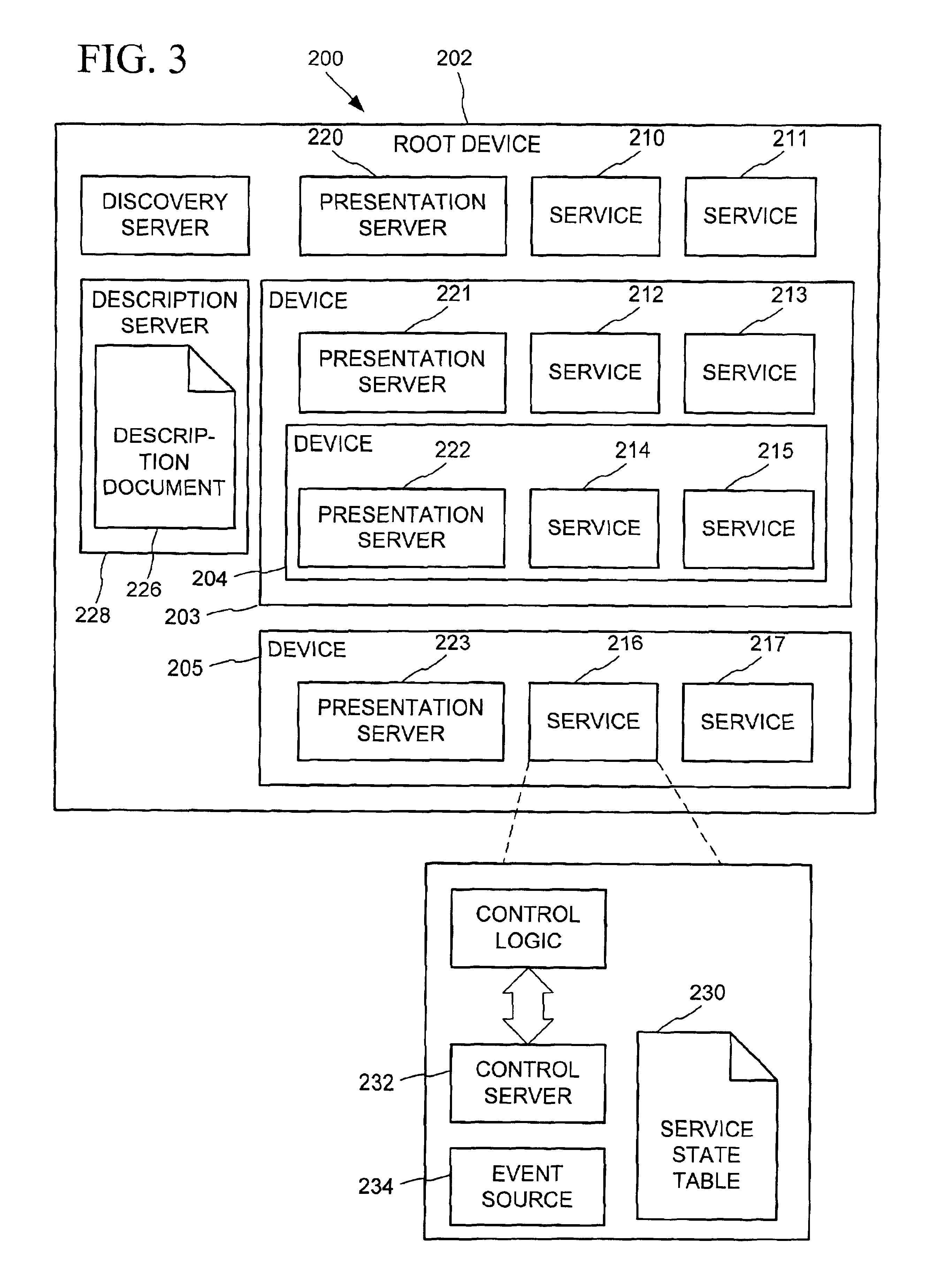
A universal plug and play (UPnP) device makes itself known through a set of processes-discovery, description, control, eventing, and presentation. Following discovery of a UPnP device, an entity can learn more about the device and its capabilities by retrieving the device's description. The description includes vendor-specific manufacturer information like the model name and number, serial number, manufacturer name, URLs to vendor-specific Web sites, etc. The description also includes a list of any embedded devices or services, as well as URLs for control, eventing, and presentation. The description is written by a vendor, and is usually based on a device template produced by a UPnP forum working committee. The template is derived from a template language that is used to define elements to describe the device and any services supported by the device. The template language is written using an XML-based syntax that organizes and structures the elements.
Owner:ROVI TECH CORP
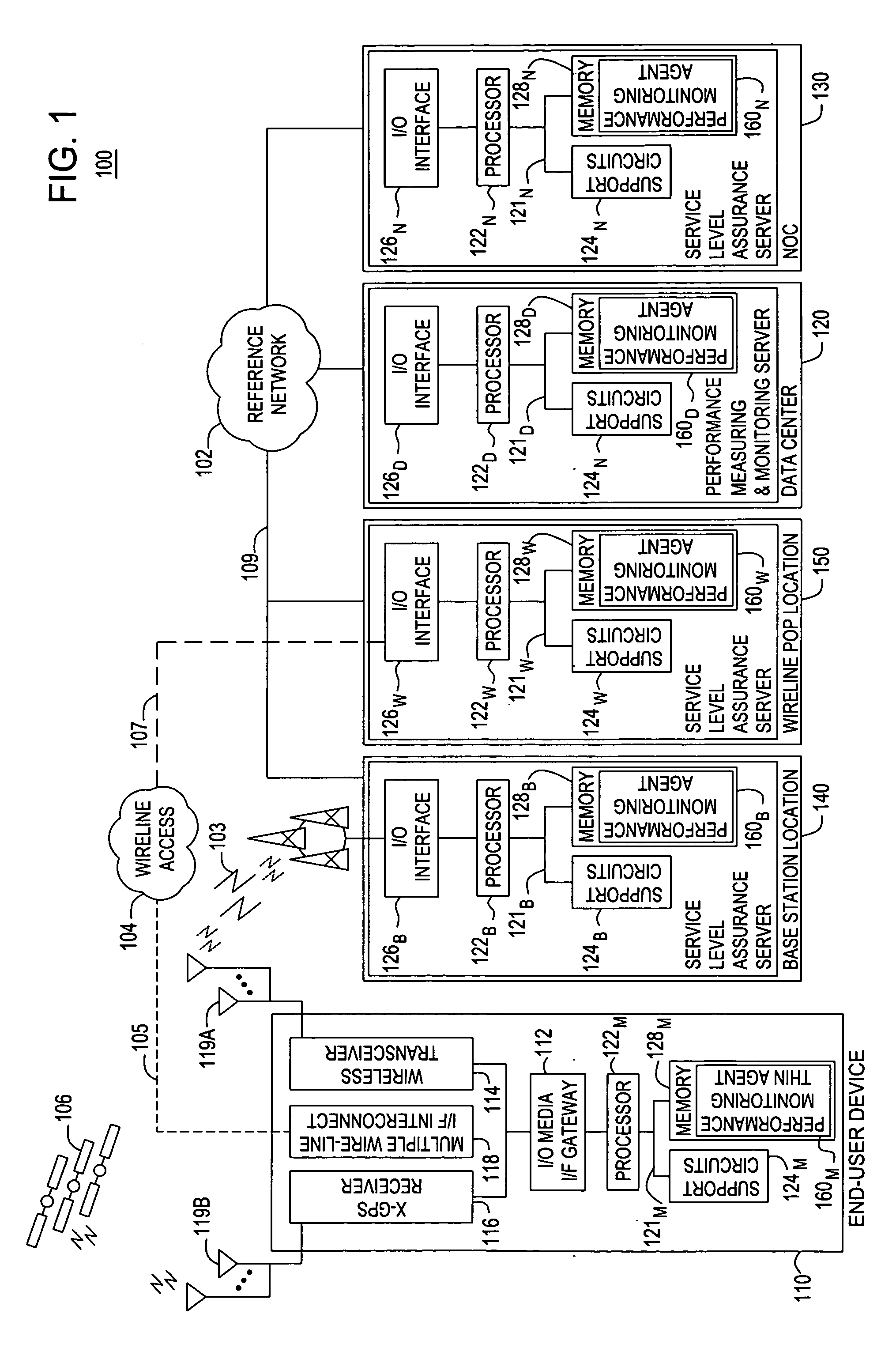
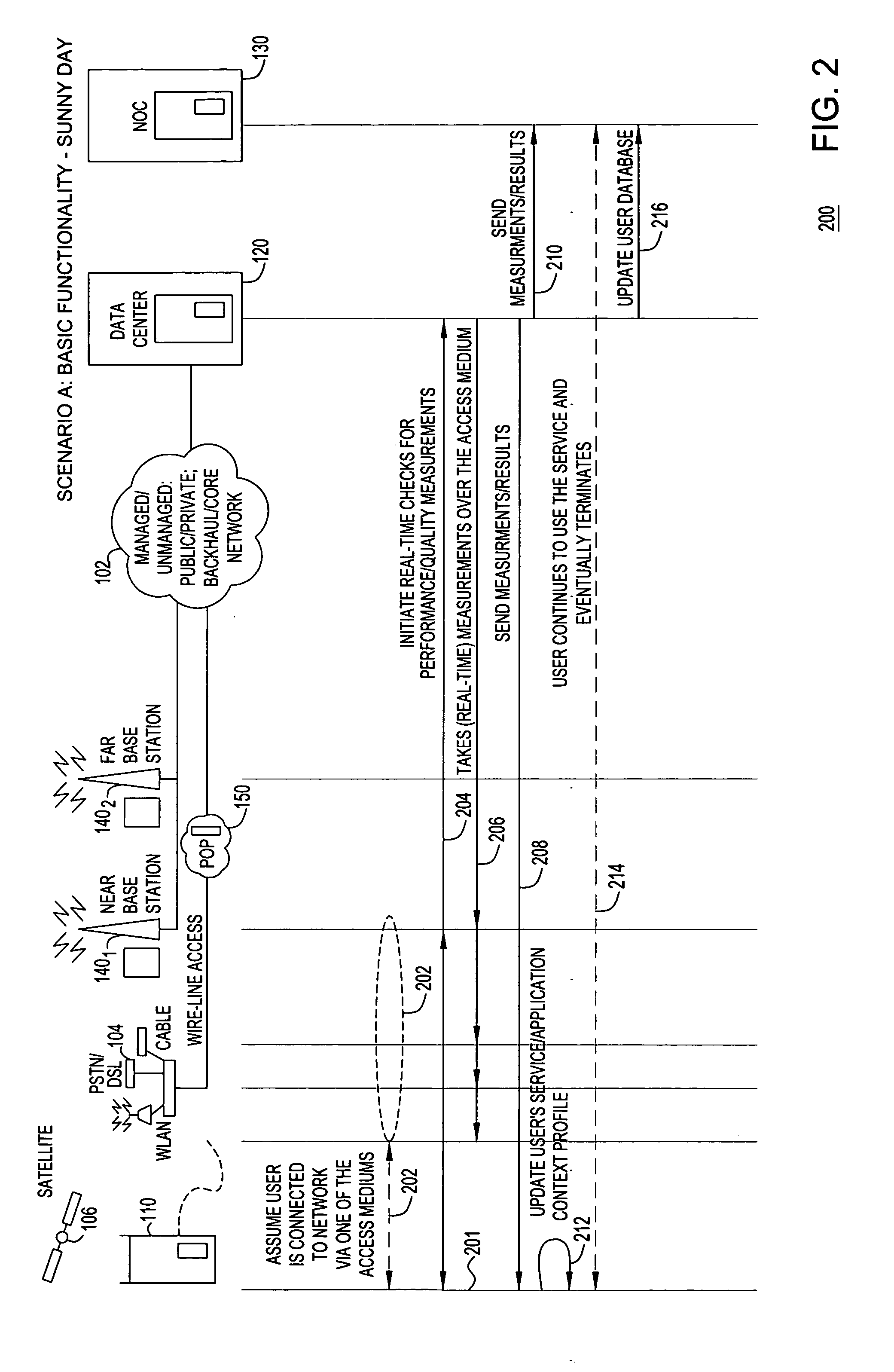
Method and apparatus for providing end-to-end high quality services based on performance characterizations of network conditions
ActiveUS20060285489A1Improve service qualityError preventionFrequency-division multiplex detailsQuality of serviceNetwork conditions
A method and apparatus enforcing and improving end-to-end service quality, based on end-to-end service performance characterization of network conditions, for a convergence enabled end-user device during a user session for service.
Owner:ALCATEL LUCENT SAS
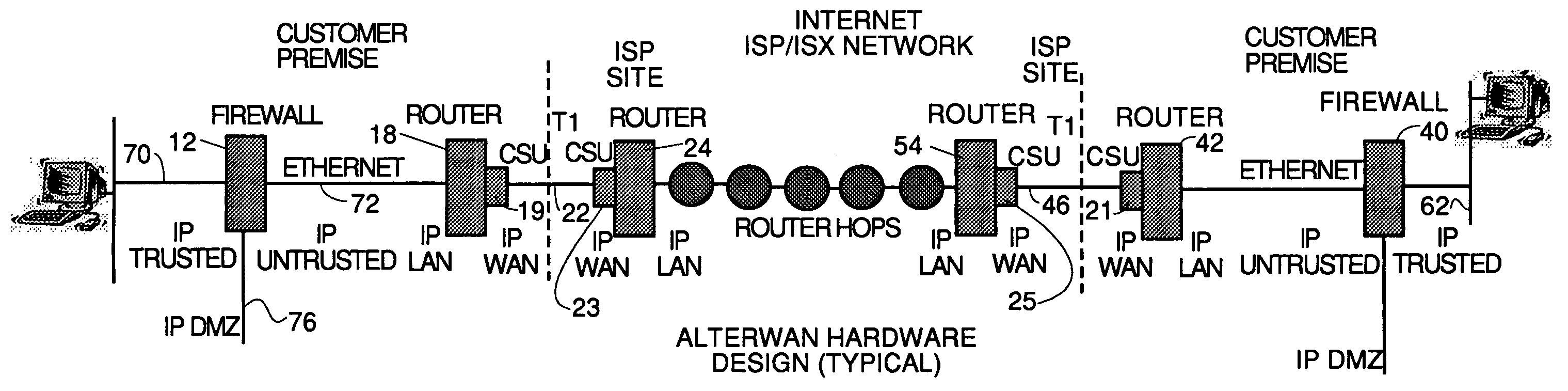
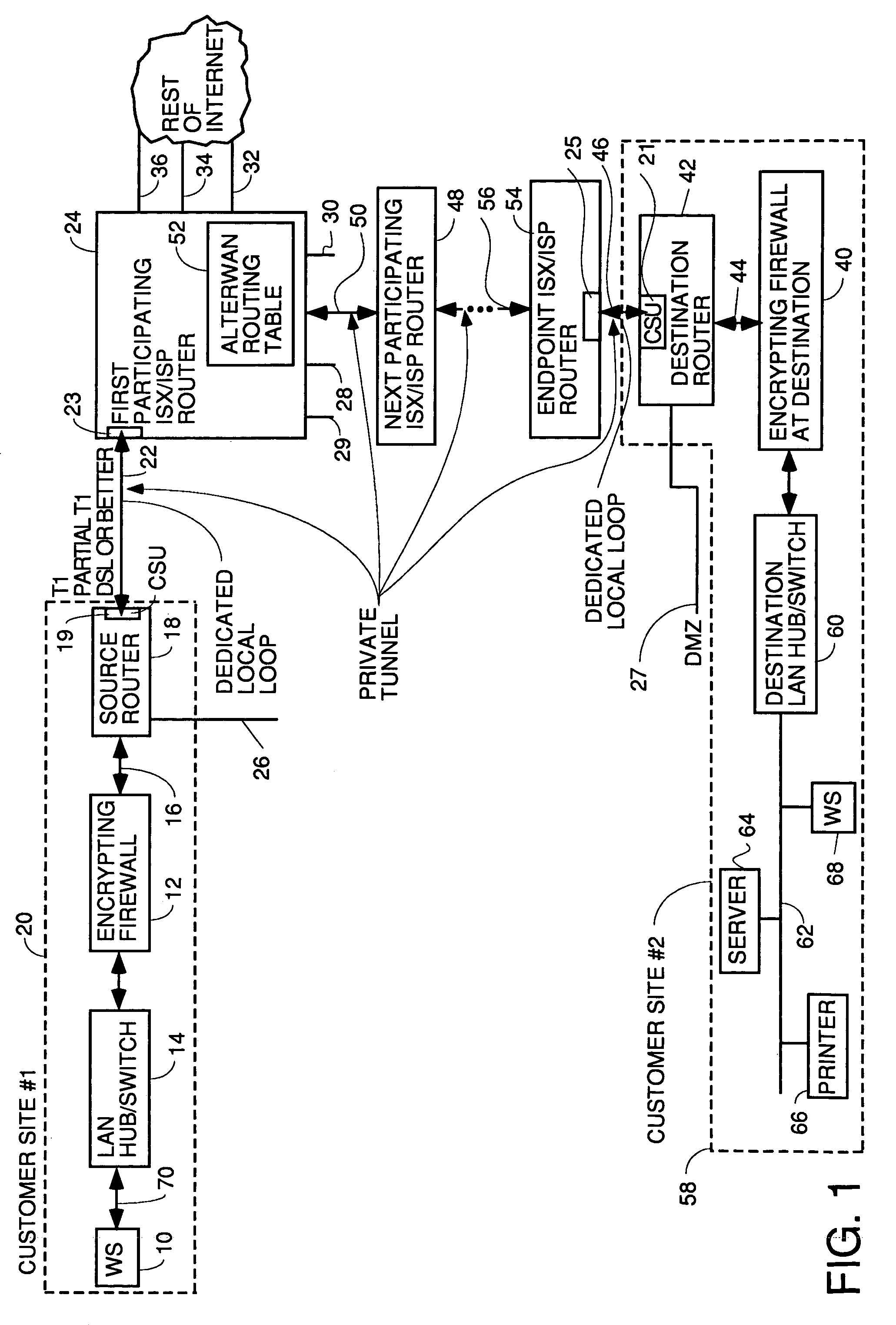
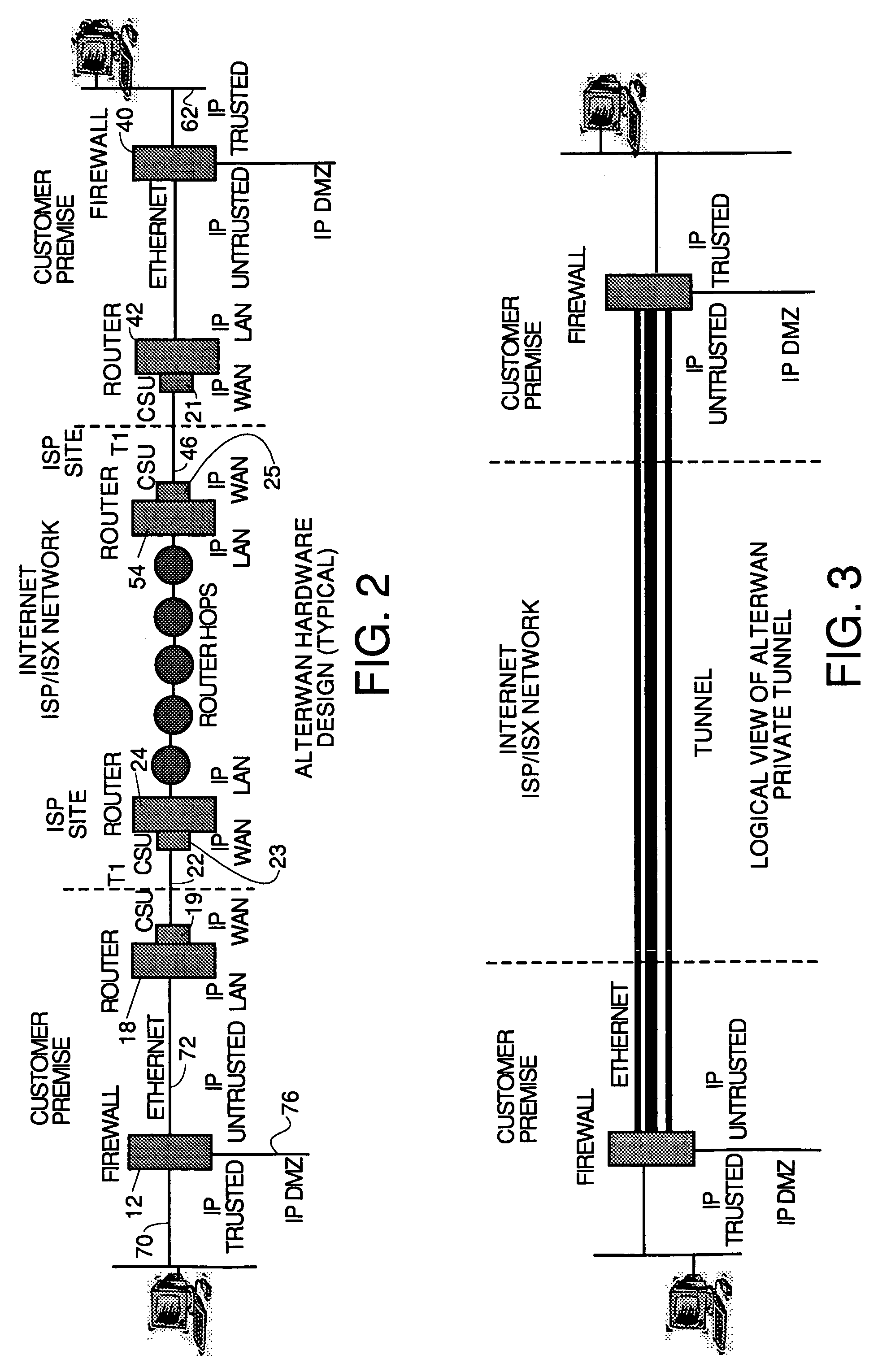
Wide area network using internet with quality of service
InactiveUS7111163B1Reduces monthly costQuality improvementDigital data processing detailsMultiple digital computer combinationsQuality of serviceTTEthernet
A wide area network using the internet as a backbone utilizing specially selected ISX / ISP providers whose routers route AlterWAN packets of said wide area network along private tunnels through the internet comprised of high bandwidth, low hop-count data paths. Firewalls are provided at each end of each private tunnel which recognize IP packets addressed to devices at the other end of the tunnel and encapsulate these packets in other IP packets which have a header which includes as the destination address, the IP address of the untrusted side of the firewall at the other end of the tunnel. The payload sections of these packets are the original IP packets and are encrypted and decrypted at both ends of the private tunnel using the same encryption algorithm using the same key or keys.
Owner:ALTERWAN
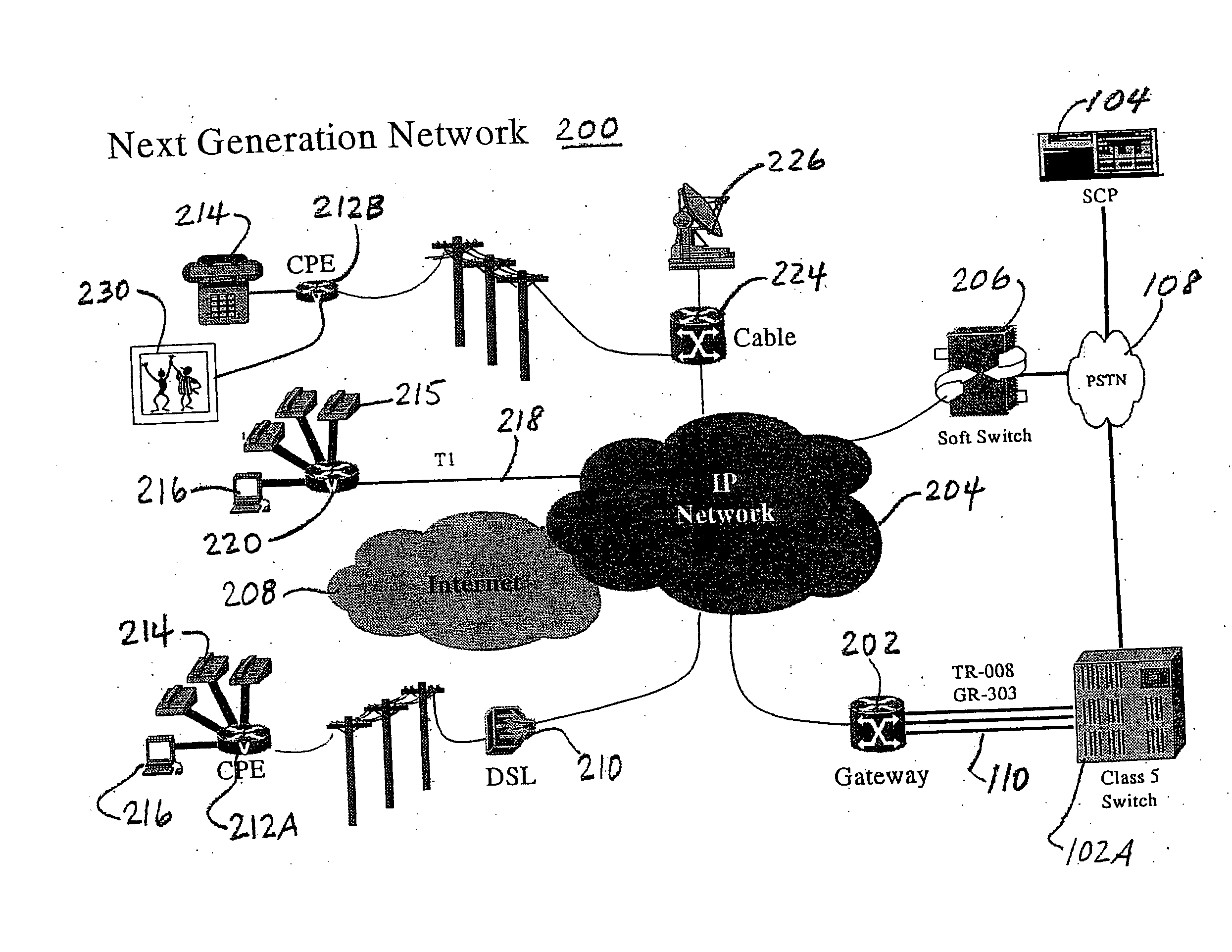
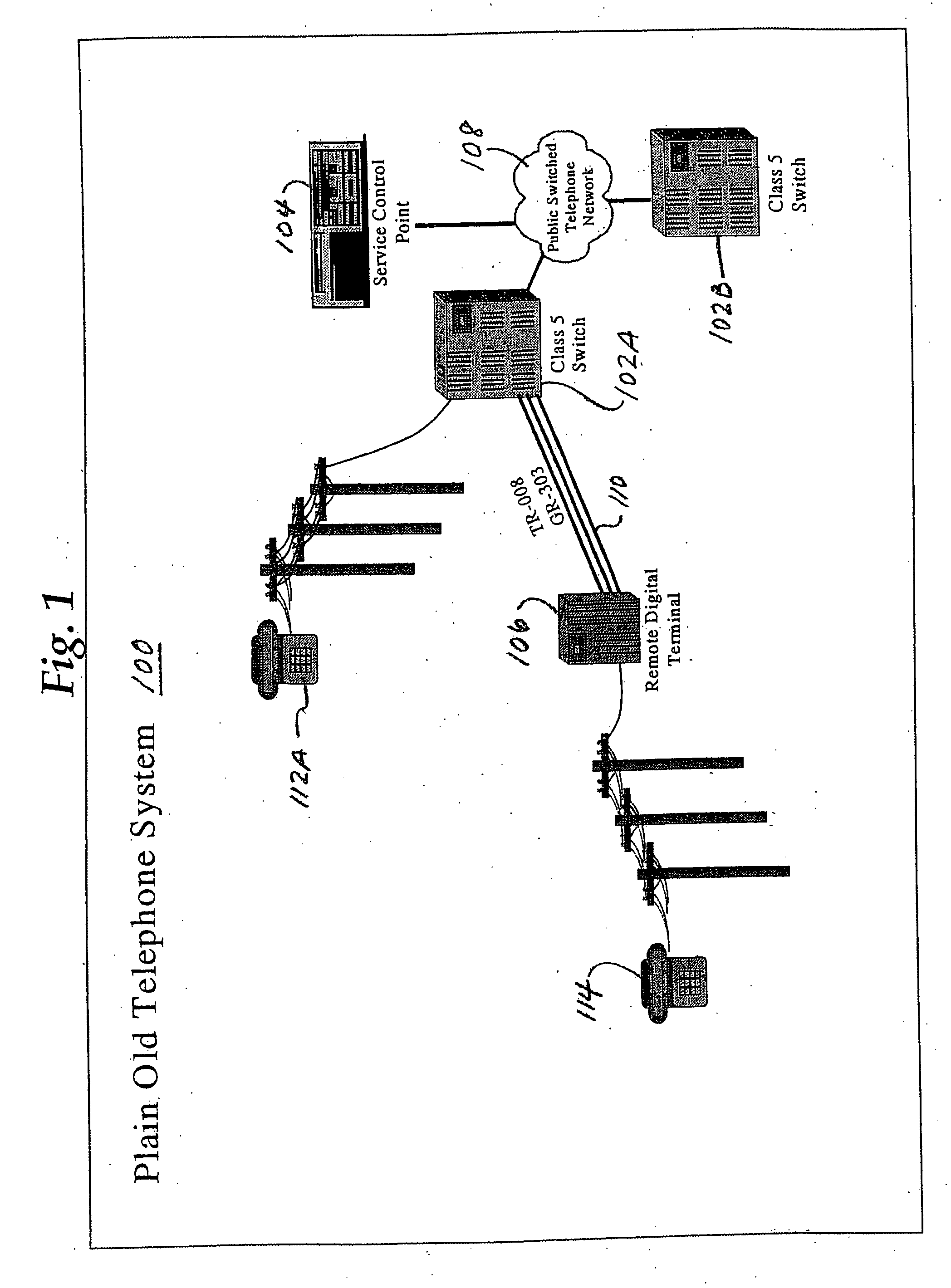
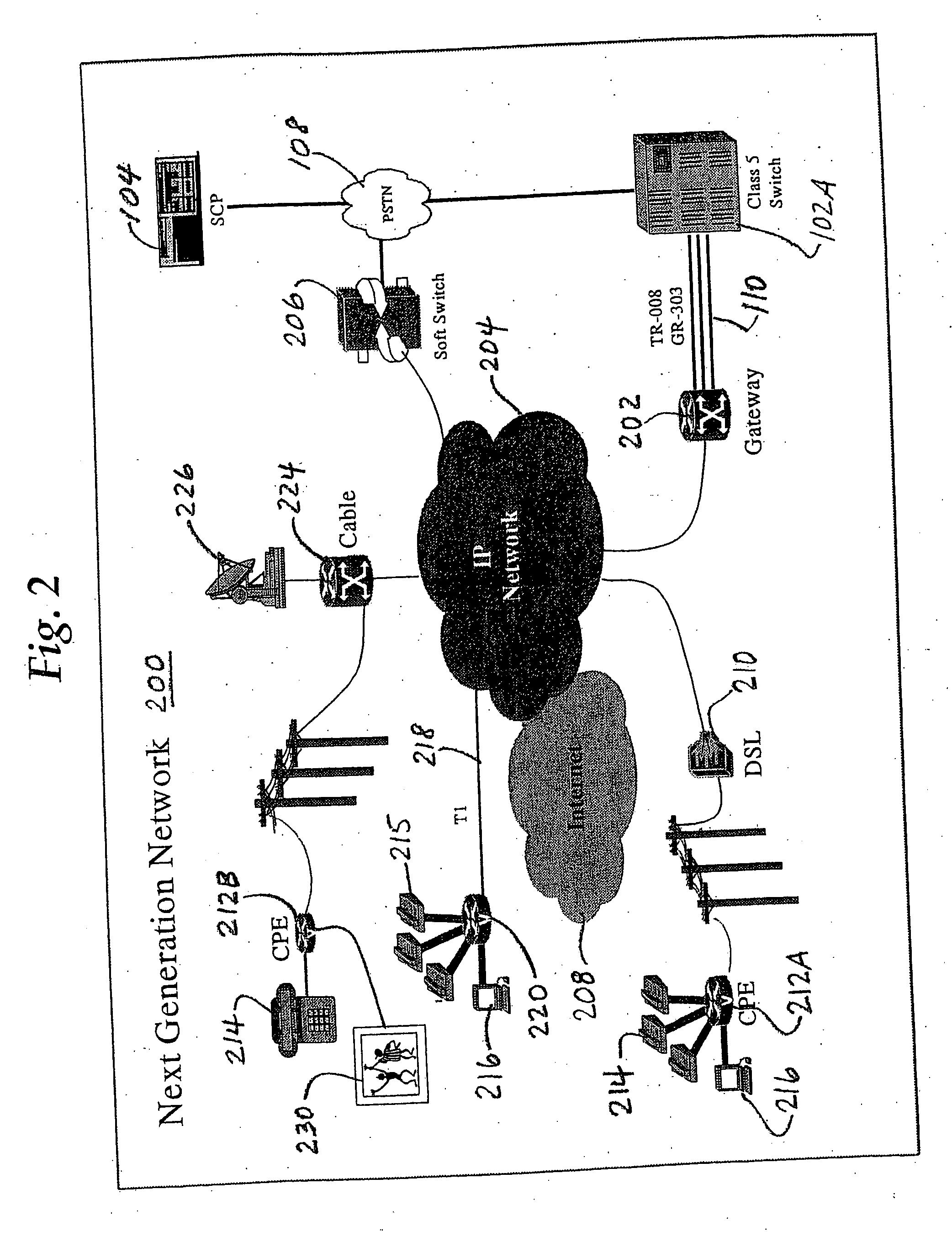
Automation of customer premises equipment provisioning in a telecommunications network
InactiveUS20060050862A1Multiplex system selection arrangementsInterconnection arrangementsTelecommunications networkDecomposition
A method to systematically analyze a next generation telecommunications network to result in creating a provisioning plan for provisioning the network to provide services for one or more subscribers. In one specific embodiment, the method involves creating and storing information that represents a logical decomposition of the next generation network into a plurality of discrete functional areas. The information representing the functional areas is analyzed to identify one or more provisioning requirements for each of the functional areas. One or more provisioning procedures are determined, and one or more required provisioning tools are identified for each of the functional areas, based on the provisioning requirements. A sequence of execution of the procedures and tools is created and stored as a provisioning plan.
Owner:CISCO TECH INC
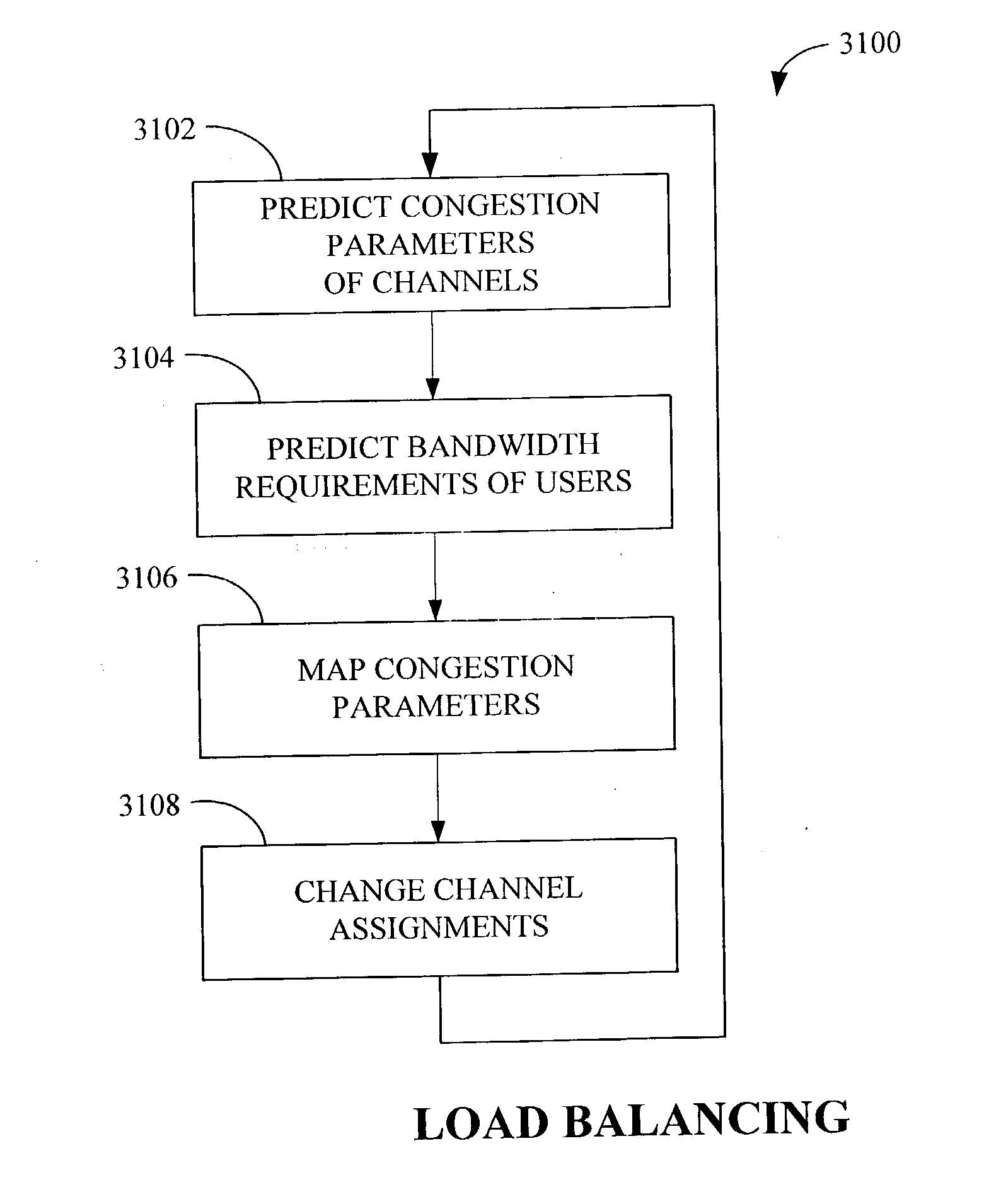
Apparatus and methods for incorporating bandwidth forecasting and dynamic bandwidth allocation into a broadband communication system
InactiveUS20060120282A1Energy efficient ICTError preventionDynamic bandwidth allocationComputer network
A method for providing network access to a shared access communications medium for a plurality of users includes the steps of conducting predictive admission control by arbitrating user requests for access to the shared medium based on predicted aggregate demands, conducting lookahead scheduling for use in making user channel assignments by forecasting schedule transmission opportunities one or more channels of the shared medium, and balancing load by making channel assignments such that a plurality users are each assigned a respective channel of the shared medium based upon a predicted need. Congestion parameters can predicted for each channel of the shared medium and mapped to a congestion measure using a mathematical function that takes into account packet loss rate, packet delay, packet delay jitter, and available capacity.
Owner:CISCO TECH INC
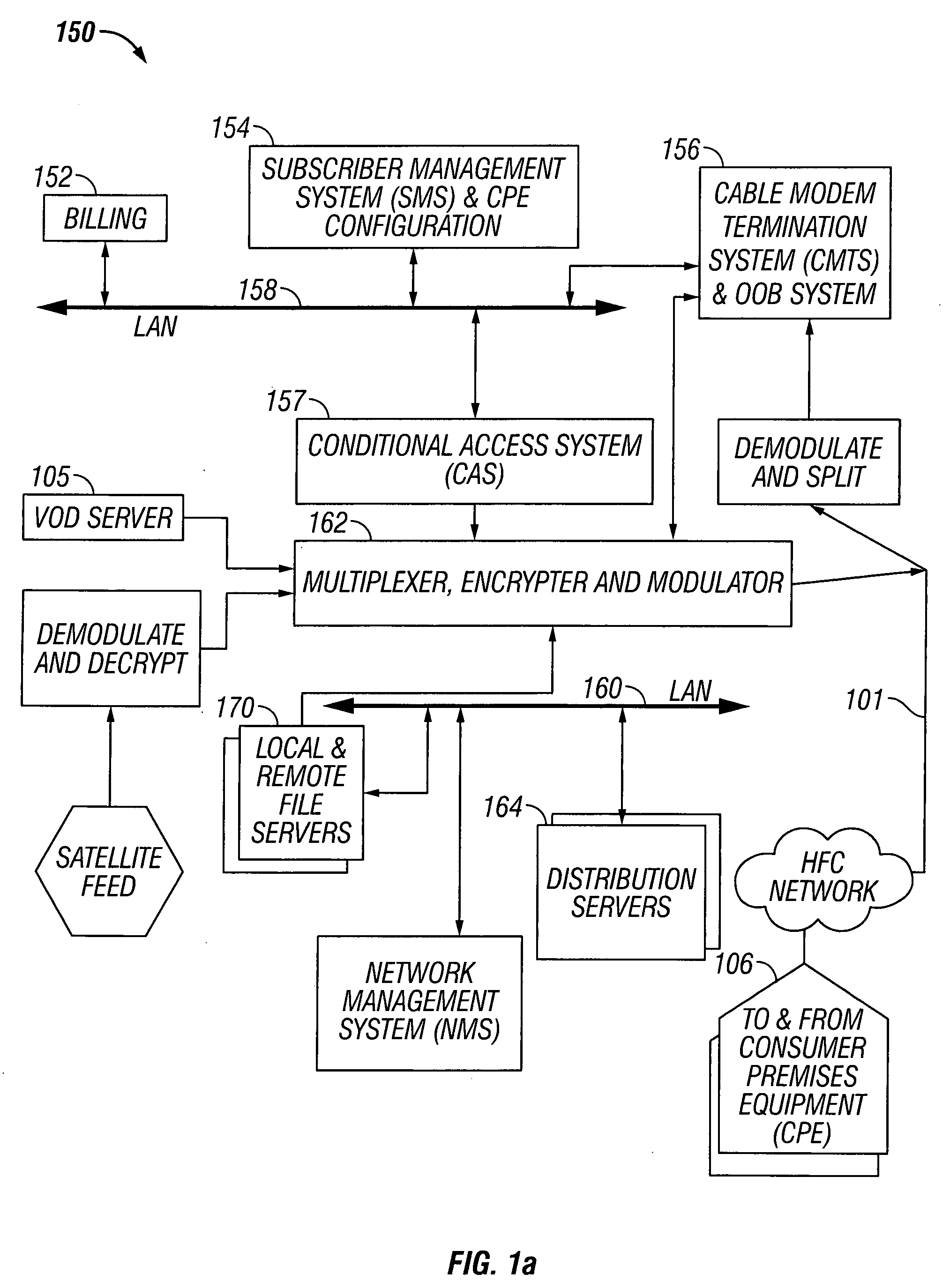
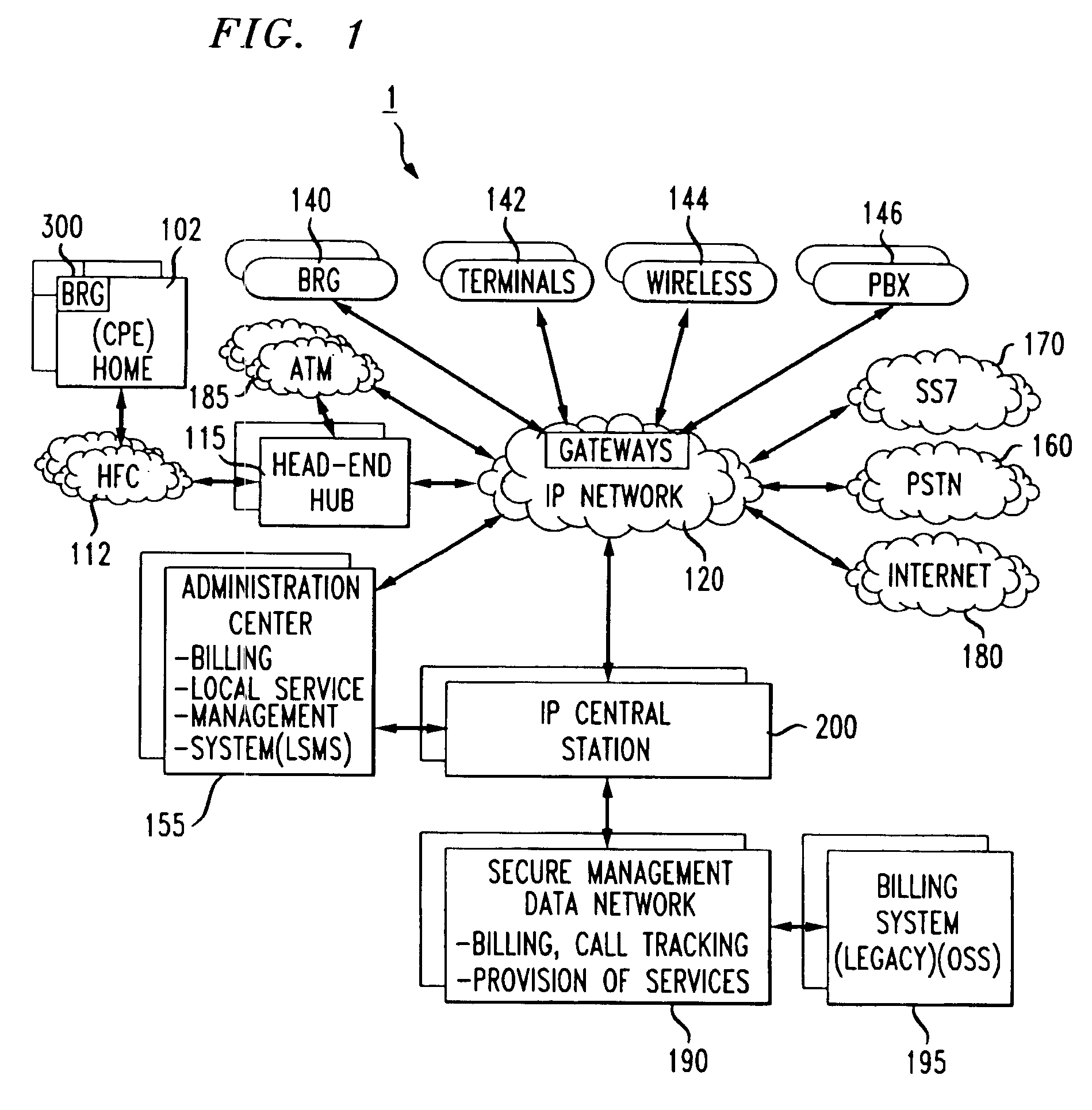
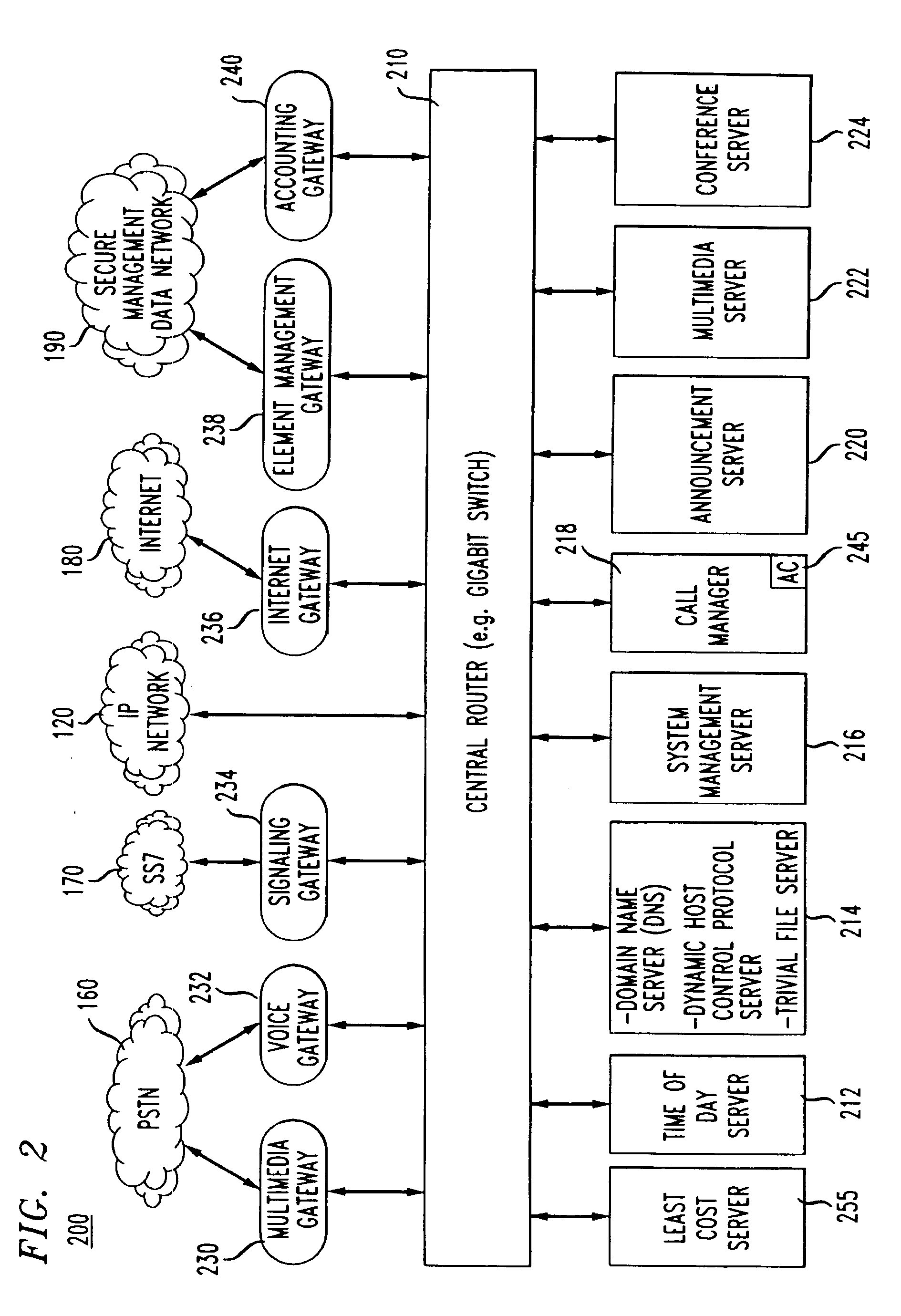
Broadband cable telephony network architecture IP ITN network architecture reference model
InactiveUS7120139B1Easy to deployMinimal costTelephone data network interconnectionsBroadband local area networksVoice communicationNetwork architecture
The present invention provides a system and method for a reliable, low-cost, secure Internet Protocol (IP) based network that provides broadband-based voice communications as well as video and data communications. The IP network is arranged to function with the infrastructure of the Public Switched Telephone Network (PSTN), to control telephone calls in SS7 type networks and to provide the features, applications, and services of the typical SS7 networks in a voice over IP network. The present invention supports large effective call volumes, allows accommodation of a wide range of broadband-based service platforms, provides flexibility to support current and future calling feature services, and provides high quality voice transmission.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
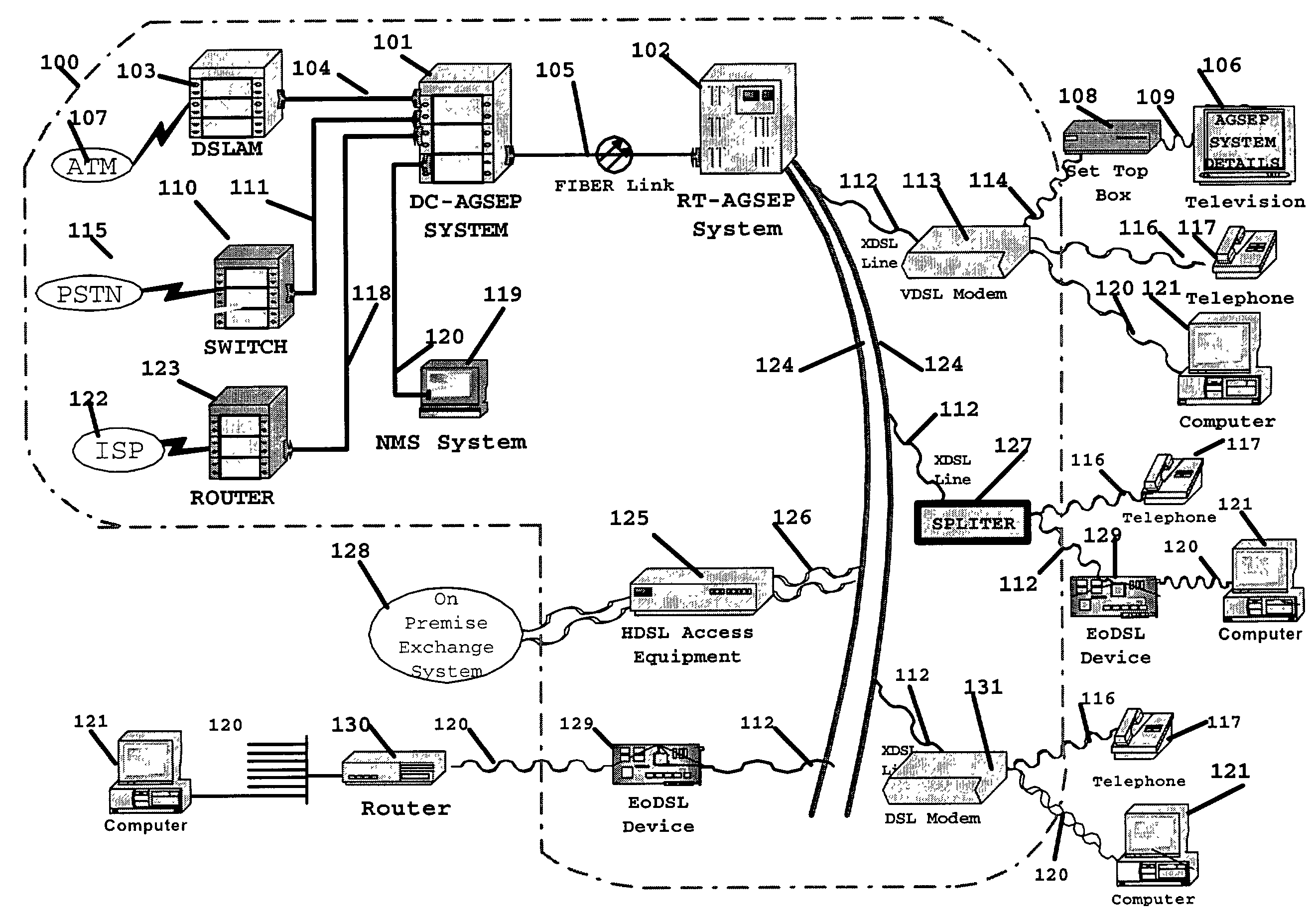
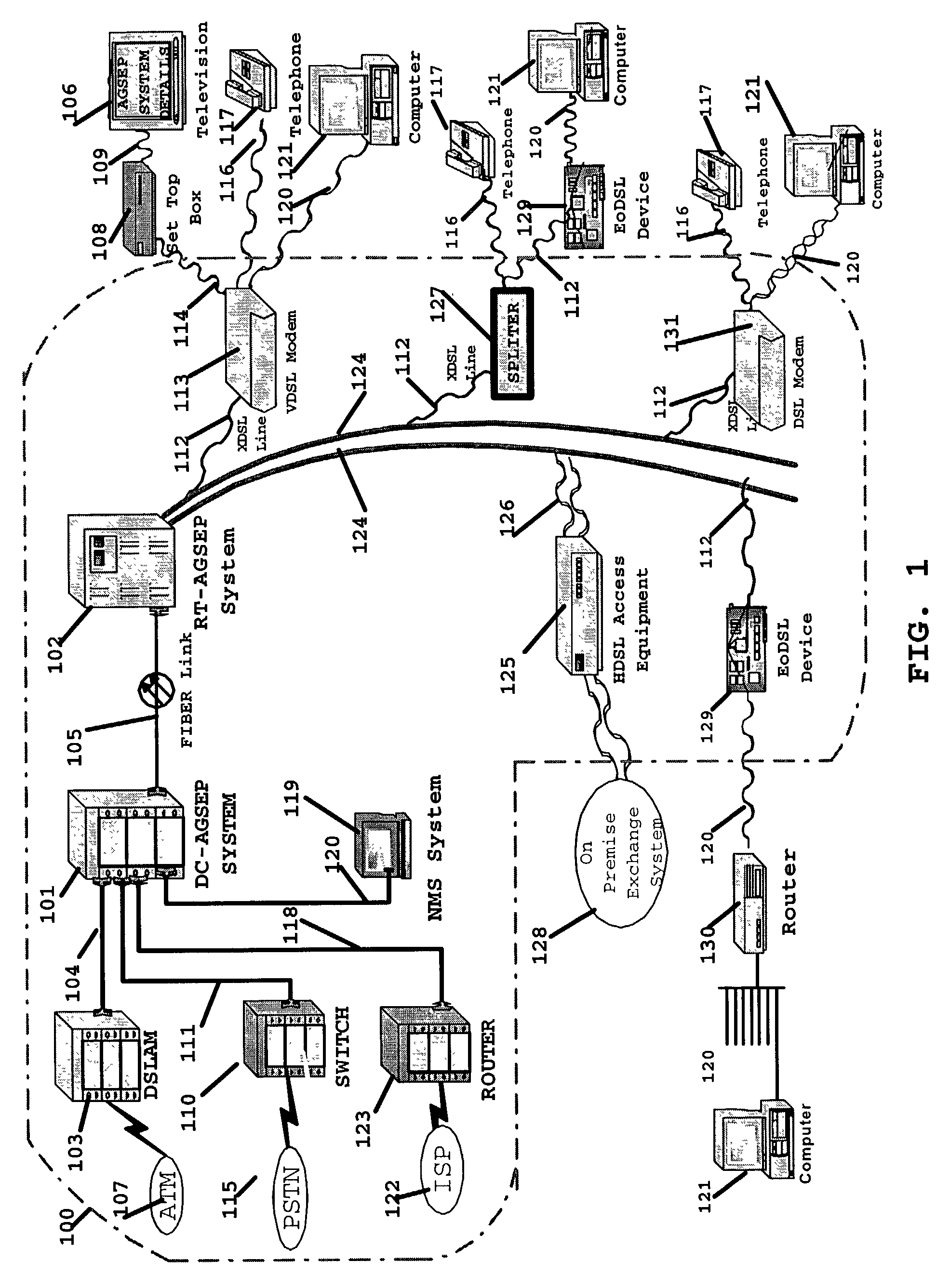
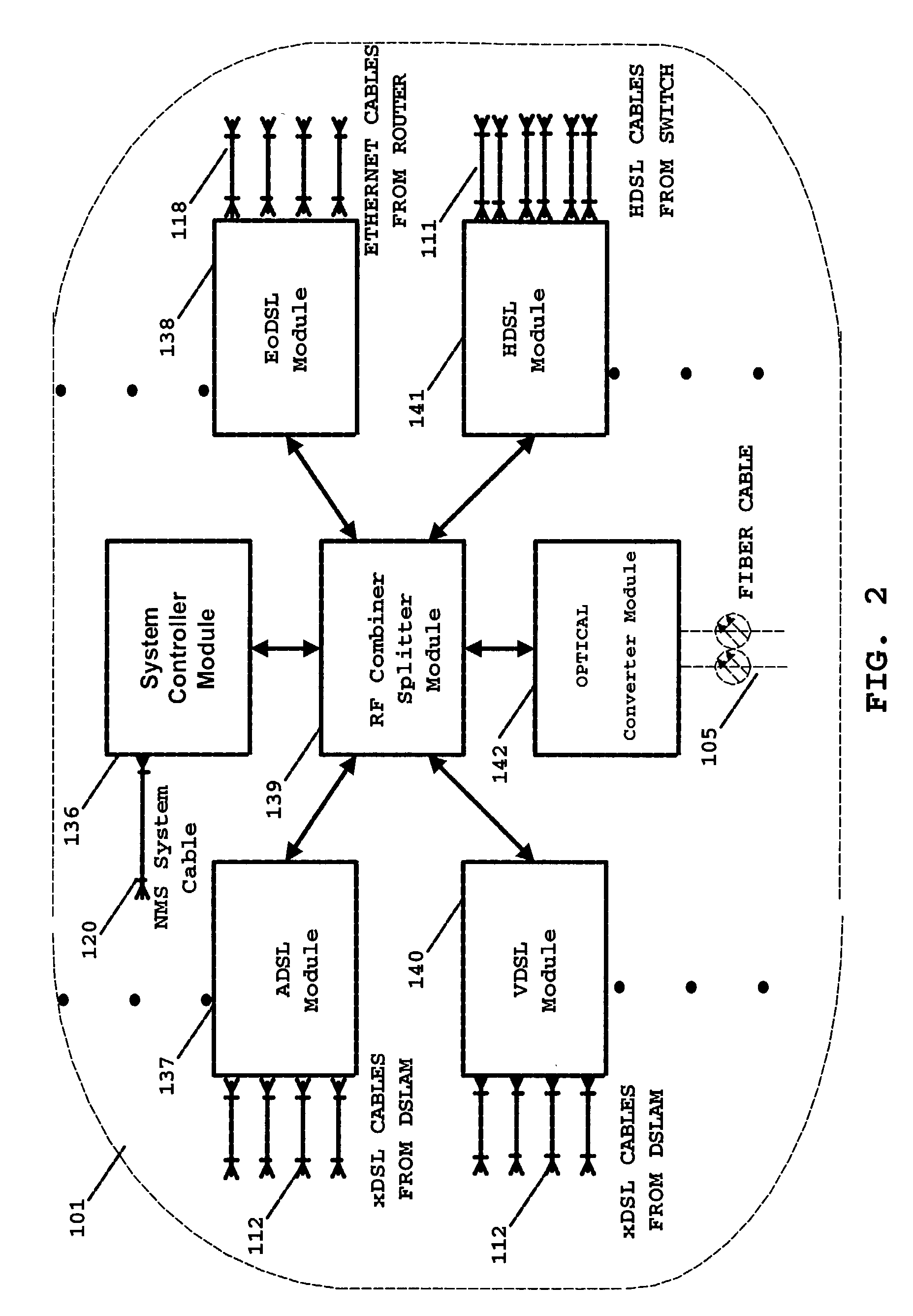
Network architecture and system for delivering bi-directional xDSL based services
InactiveUS7136397B2Good serviceEnergy efficient ICTFrequency-division multiplex detailsTelecommunicationsNetwork architecture
A simple network comprises of: xDSL service equipment located at a distribution center coupled to an Aggregator Separator (AGSEP) System located at a DC; AGSEP system at the DC is coupled, using a high-speed link, to another AGSEP system located at a remote site, which is coupled to subscriber equipment using drop cables. The AGSEP systems aggregate the xDSL signals originating at either DC xDSL equipment or subscriber equipment, are carried over the high-speed link. The AGSEP systems and separate the aggregated signals at either end to distribute the separated signal to the respective equipment.
Owner:RPX CORP
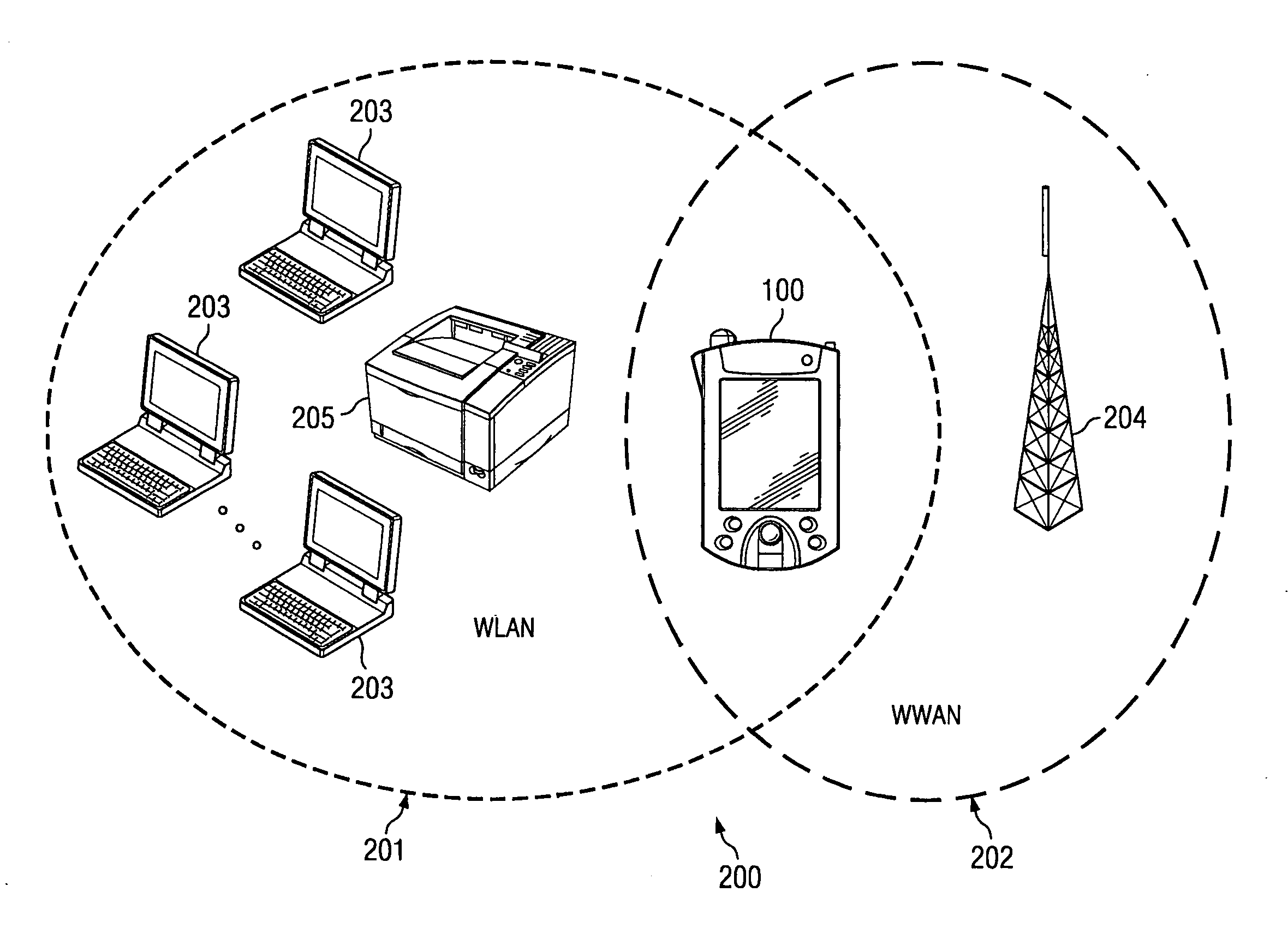
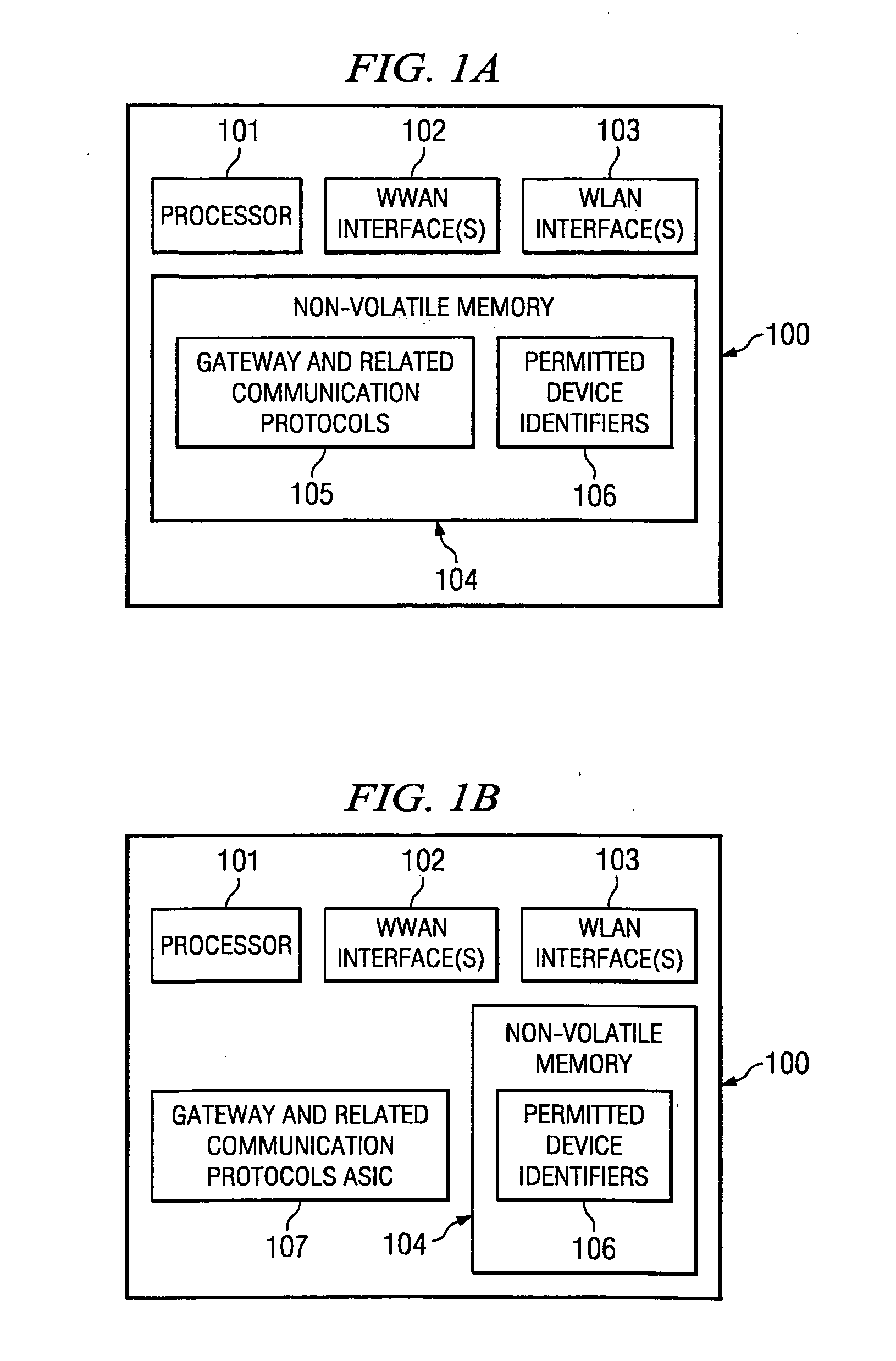
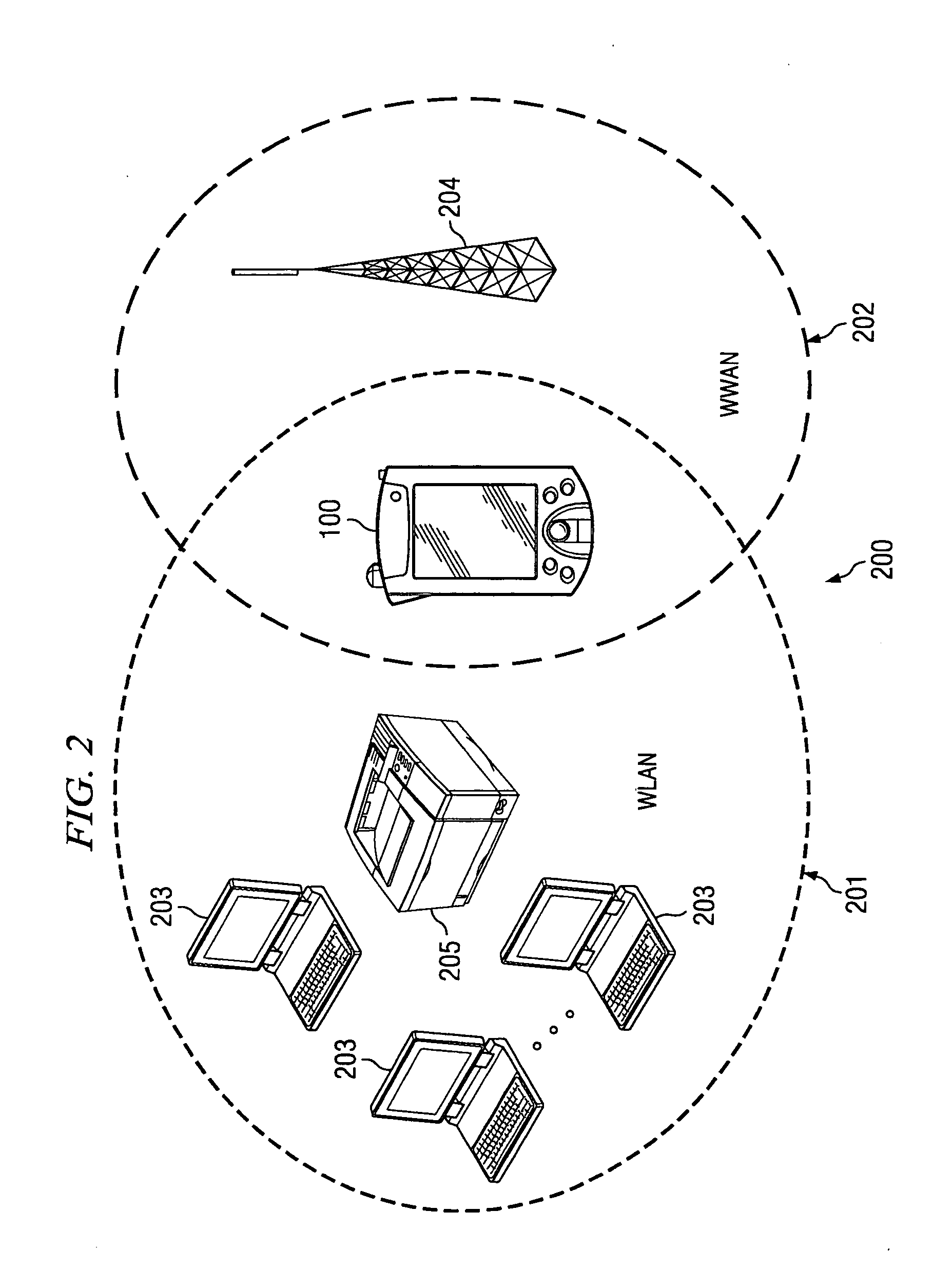
Portable computing device for wireless communications and method of operation
In one embodiment of the present invention, a portable computing device for wireless communications comprises a first network interface for communicating with a public wireless wide area network (WWAN), a second network interface for communicating with a private wireless local area network (WLAN), and a processor executing under control of software instructions, the software instructions defining a gateway protocol, the gateway protocol establishing the portable computing device as an access point within the private WLAN after the wireless presence on the public WWAN is established.
Owner:HEWLETT PACKARD DEV CO LP
Method for service provisioning a broadband modem
A method for automatically provisioning a broadband communication service to a subscriber having a broadband modem. The method includes the step of transmitting a service request from the broadband modem to a central office, which is associated with a network service provider. The network is configured for service in response to the service request. The method further includes automatically configuring the broadband modem by transmitting a configuration signal from the central office to the subscriber. The configuration signal may be transmitted to the broadband modem over a POTS subchannel. Alternatively, the configuration signal may be transmitted to the broadband modem over a subchannel in a broadband service, such as a DMT subchannel for ADSL service.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
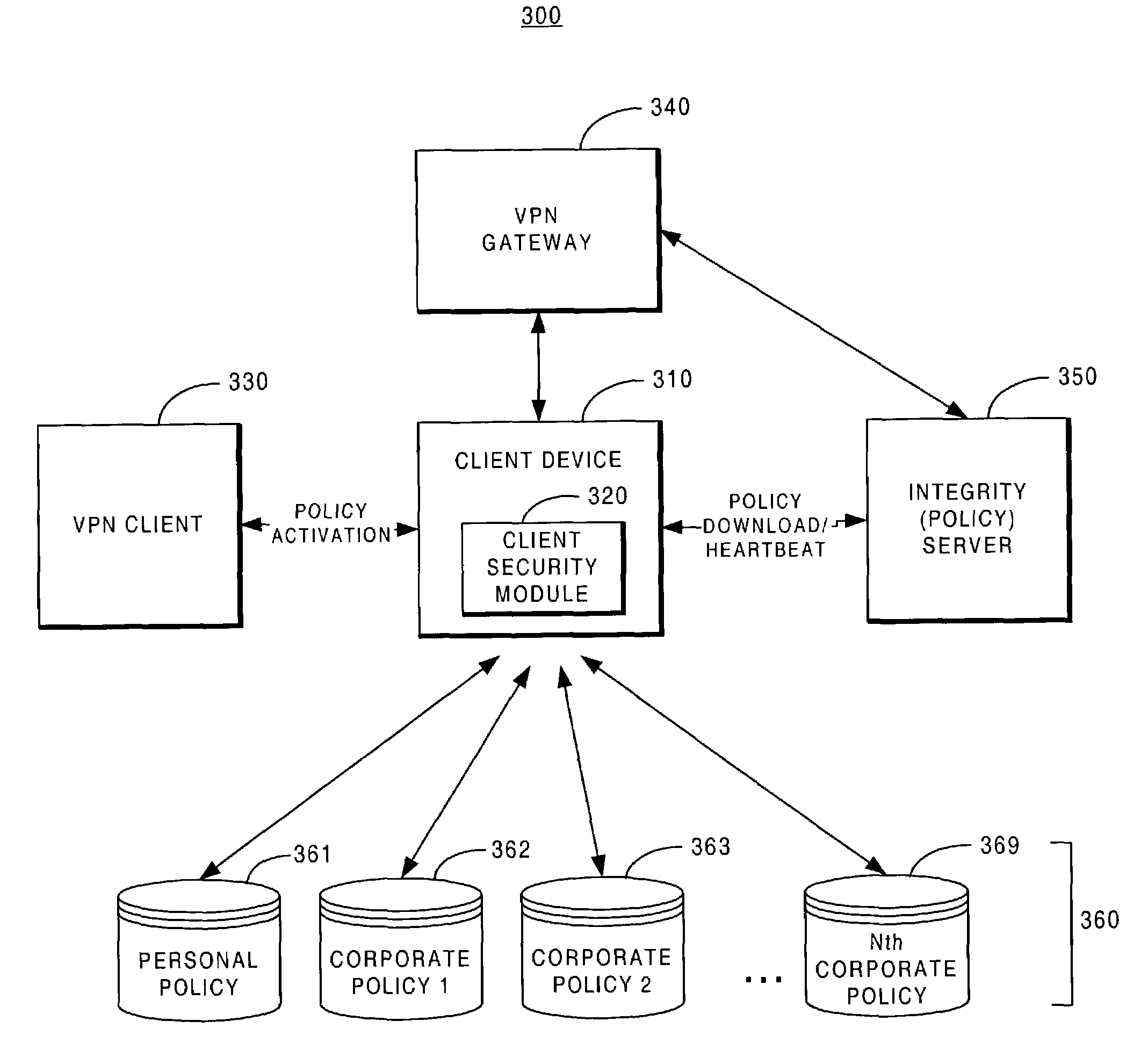
Methods and systems for securing access to private networks using encryption and authentication technology built in to peripheral devices
A method for routing packets from a peripheral device to a Virtual Private Network (VPN) gateway includes the step of implementing, by a peripheral device, a change to a routing table. The peripheral device receives an outbound packet. The peripheral device transmits information about the outbound packet to a VPN client application. The peripheral device modifies address information on the outbound packet with address information associated with the VPN client application. The peripheral device transmits the modified outbound packet to the VPN client application.
Owner:CITRIX SYST INC
System and method for providing peer-oriented control of telecommunication services
InactiveUS20050027870A1Supporting development and deploymentHybrid switching systemsSupervisory/monitoring/testing arrangementsTelecommunications networkEngineering
In a telecommunications network environment including non-participating elements and participating elements, a method for providing a telecommunications service between a first peer element connected to the telecommunications network environment and a second peer element connected to the telecommunications network. At a first peer element, an indication of the type of telecommunications service to be provided between the first peer element and the second peer element is received. A telecommunications service template in association with the indicated telecommunications service is determined, the telecommunications service template including instructions for configuring the non-participating elements of the telecommunications network environment to provide the indicated telecommunications service and instructions for configuring the participating elements of the telecommunications network environment. Upon establishing a communication channel between the first peer element and the second peer element, the service template is transferred to the second peer element. The second peer element then executes the instructions to configure the participating elements and non-participating elements of the telecommunications network environment to provide the telecommunications service.
Owner:TREBES HAROLD HERMAN JR
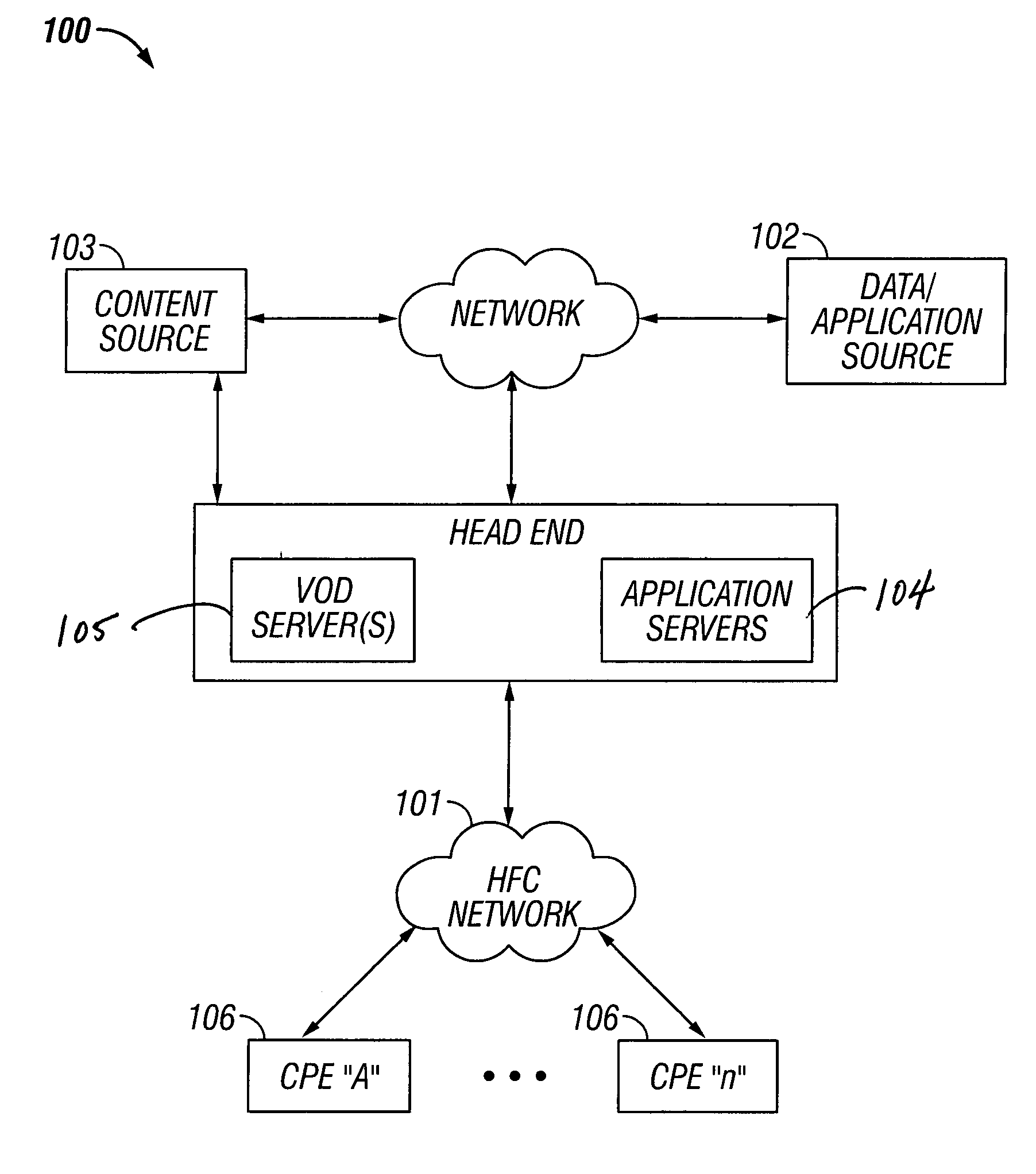
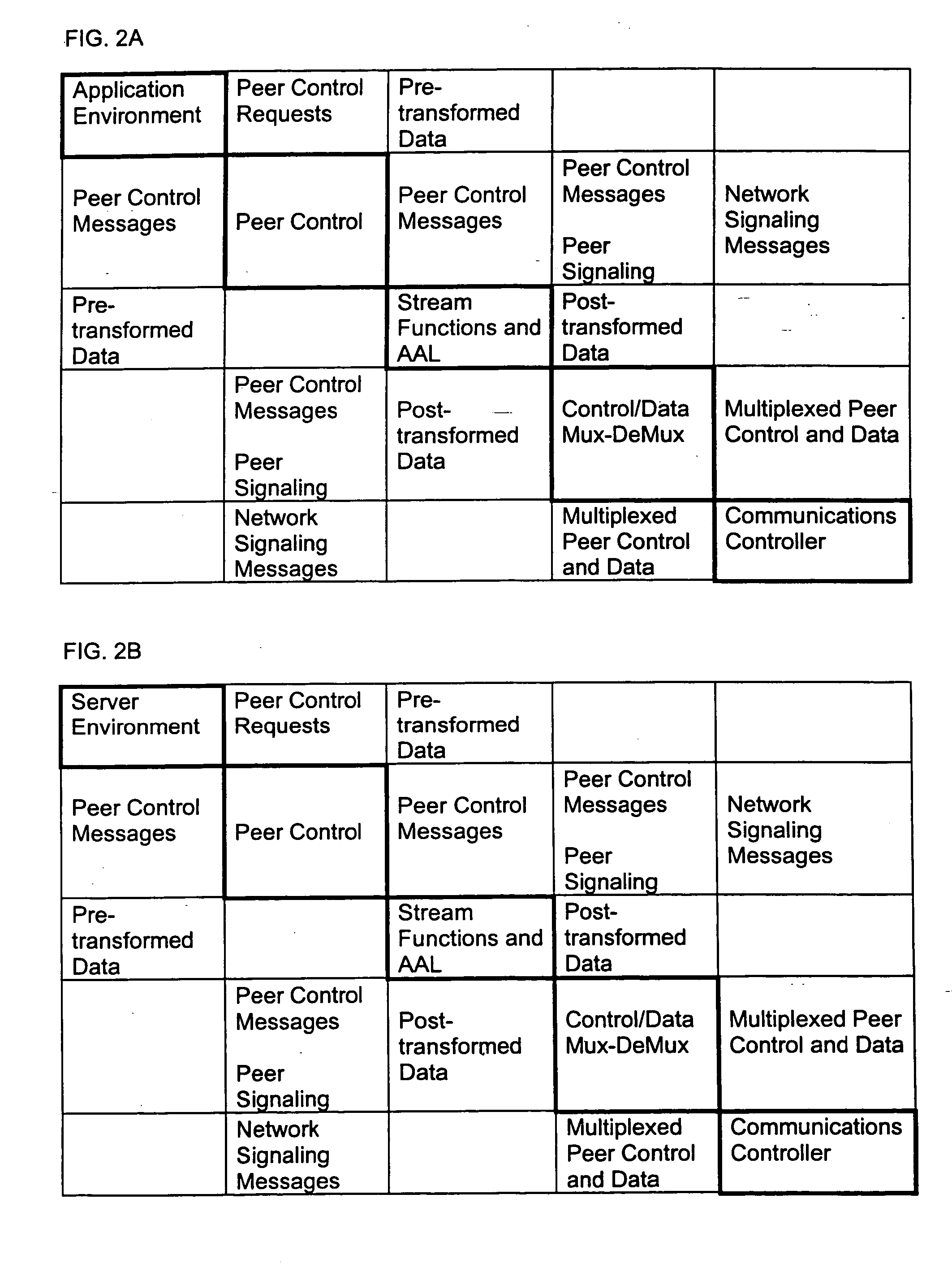
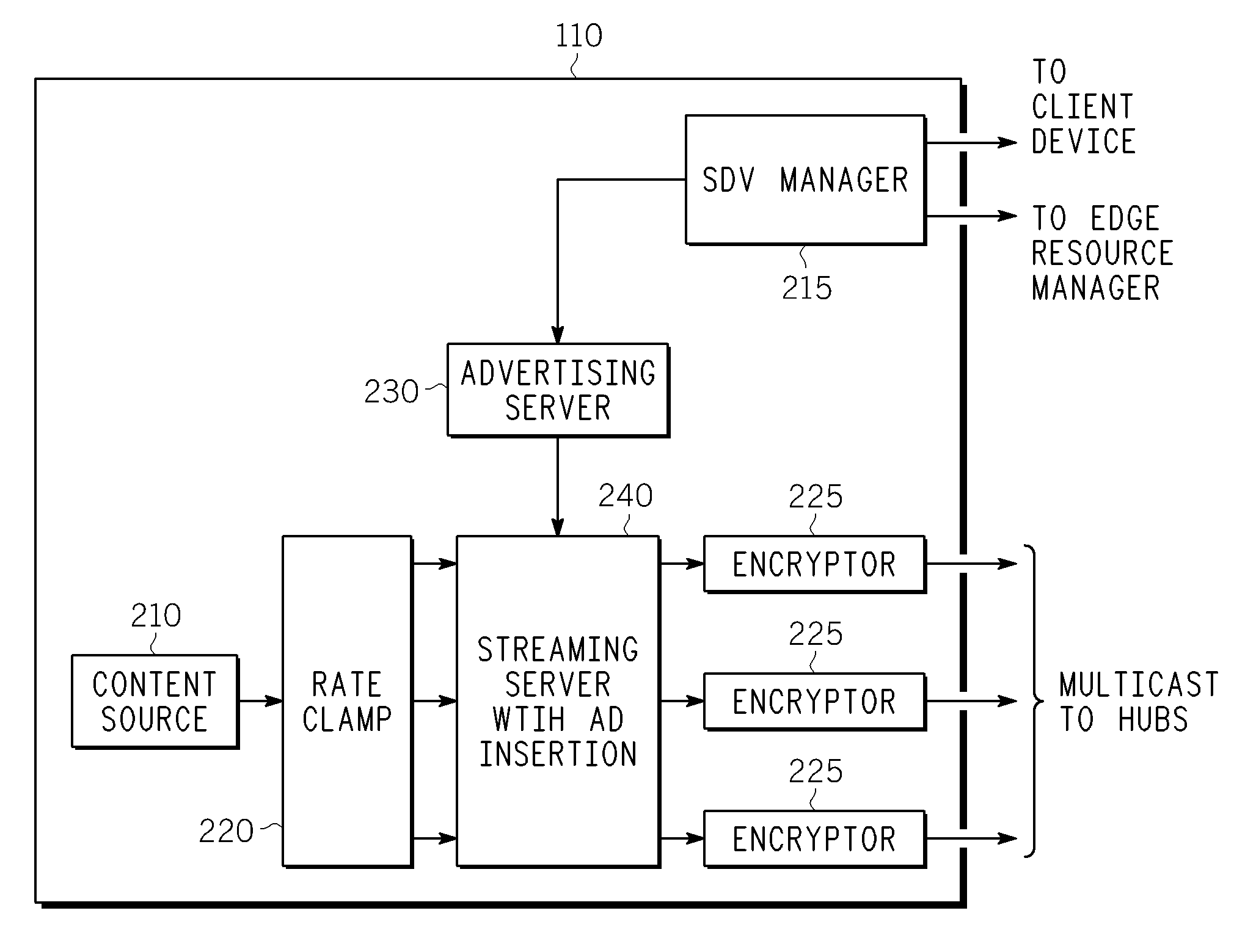
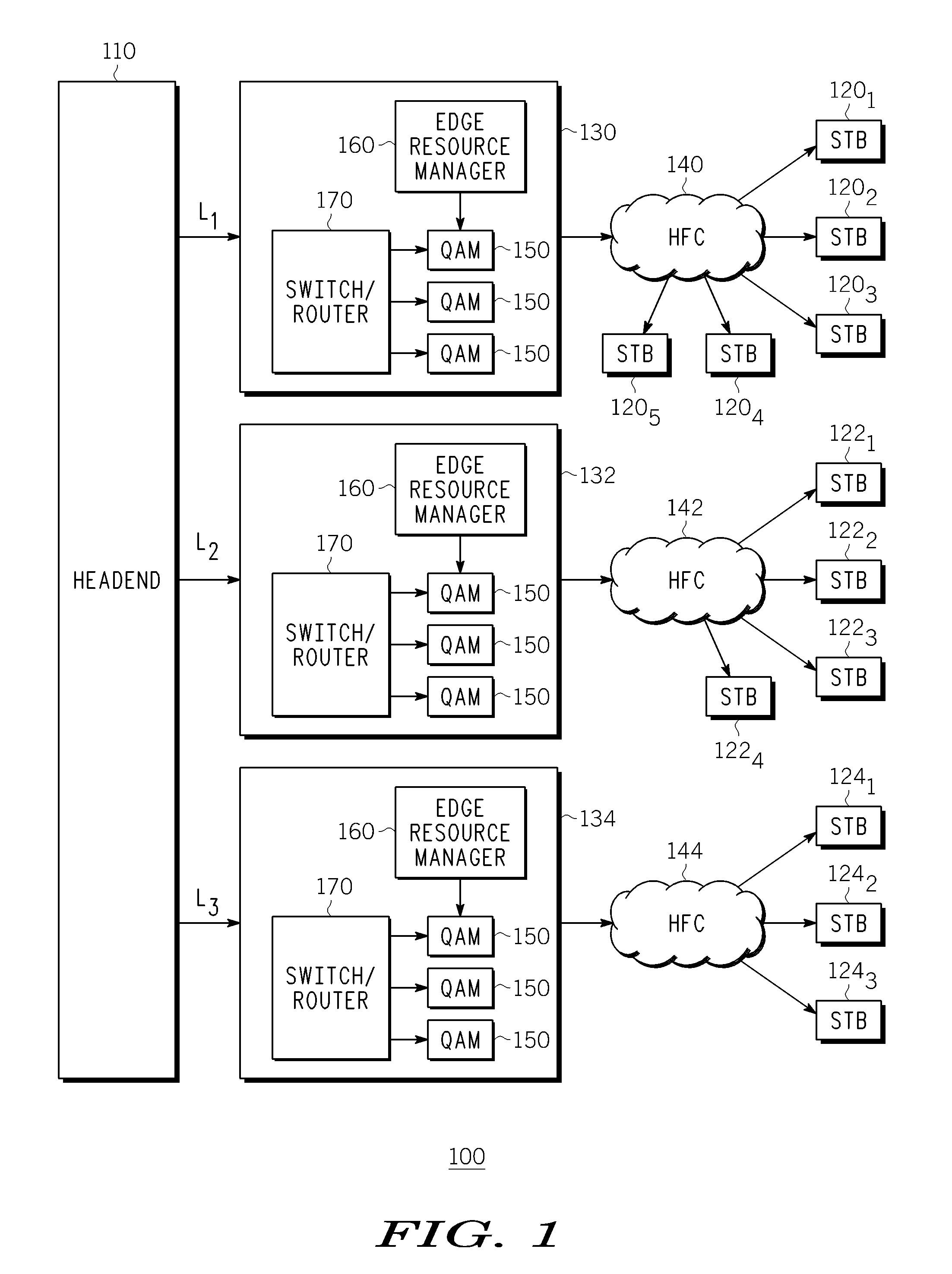
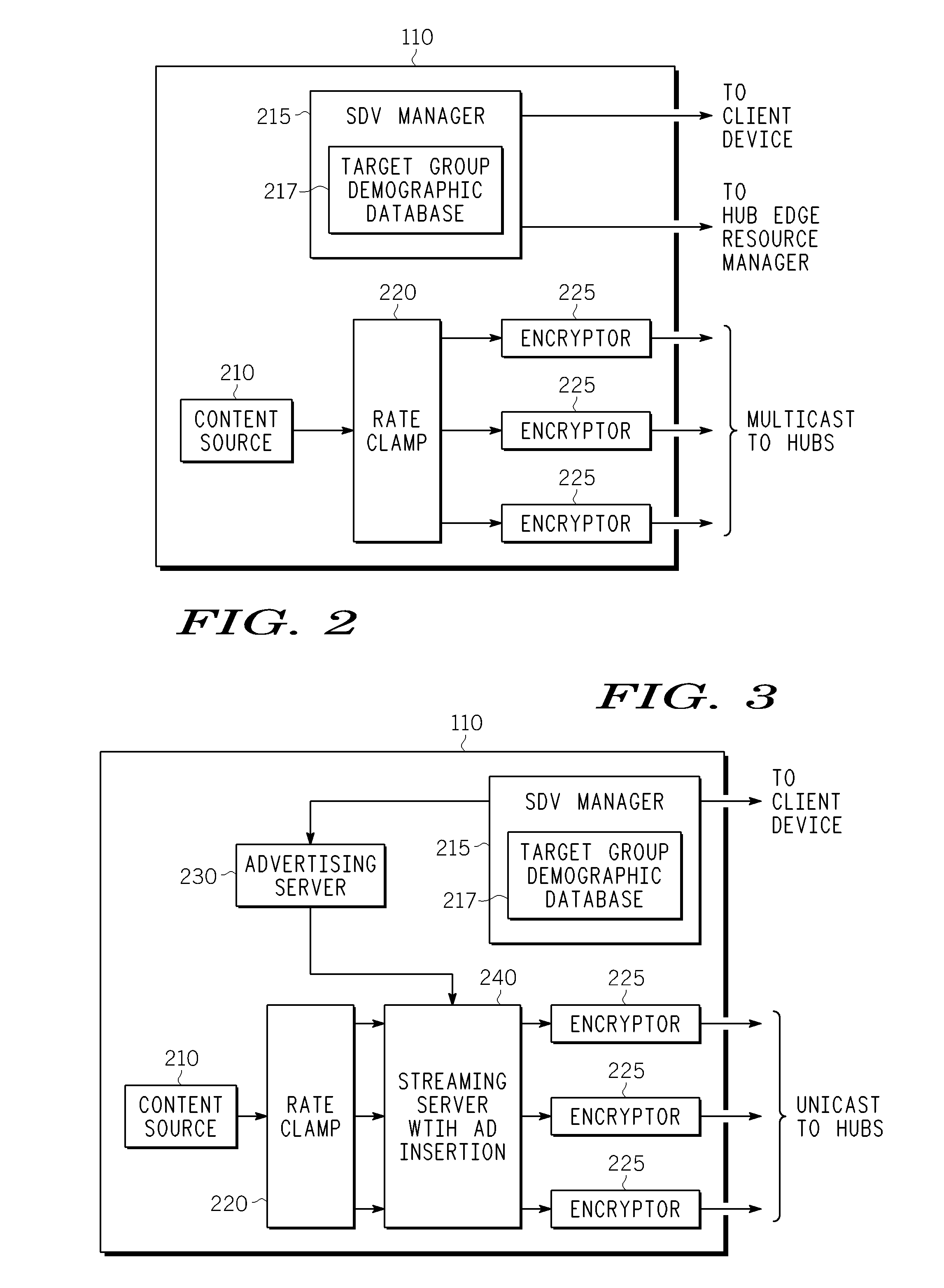
Method And Apparatus For Delivering SDV Programming With Targeted Advertising To Selected Groups Of Subscribers
InactiveUS20090150926A1Broadband local area networksTwo-way working systemsAccess networkDigital video
A switched digital video (SDV) system includes an SDV manager for coordinating a SDV session requested by a subscriber terminal and a storage medium on which resides content to be transmitted during the SDV session. The system also includes a plurality of edge devices for receiving a transport stream that includes content provided by the storage medium and transmitting the transport stream over an access network to the subscriber terminal on one of a plurality of SDV channels. The SDV manager is configured to cause different renditions of an SDV program to be provided by the edge devices to subscriber terminals associated with different target groups. The target groups each include a plurality of subscriber terminals that is less than a number of subscriber terminals serviced by a distinct edge device or devices.
Owner:GOOGLE TECH HLDG LLC
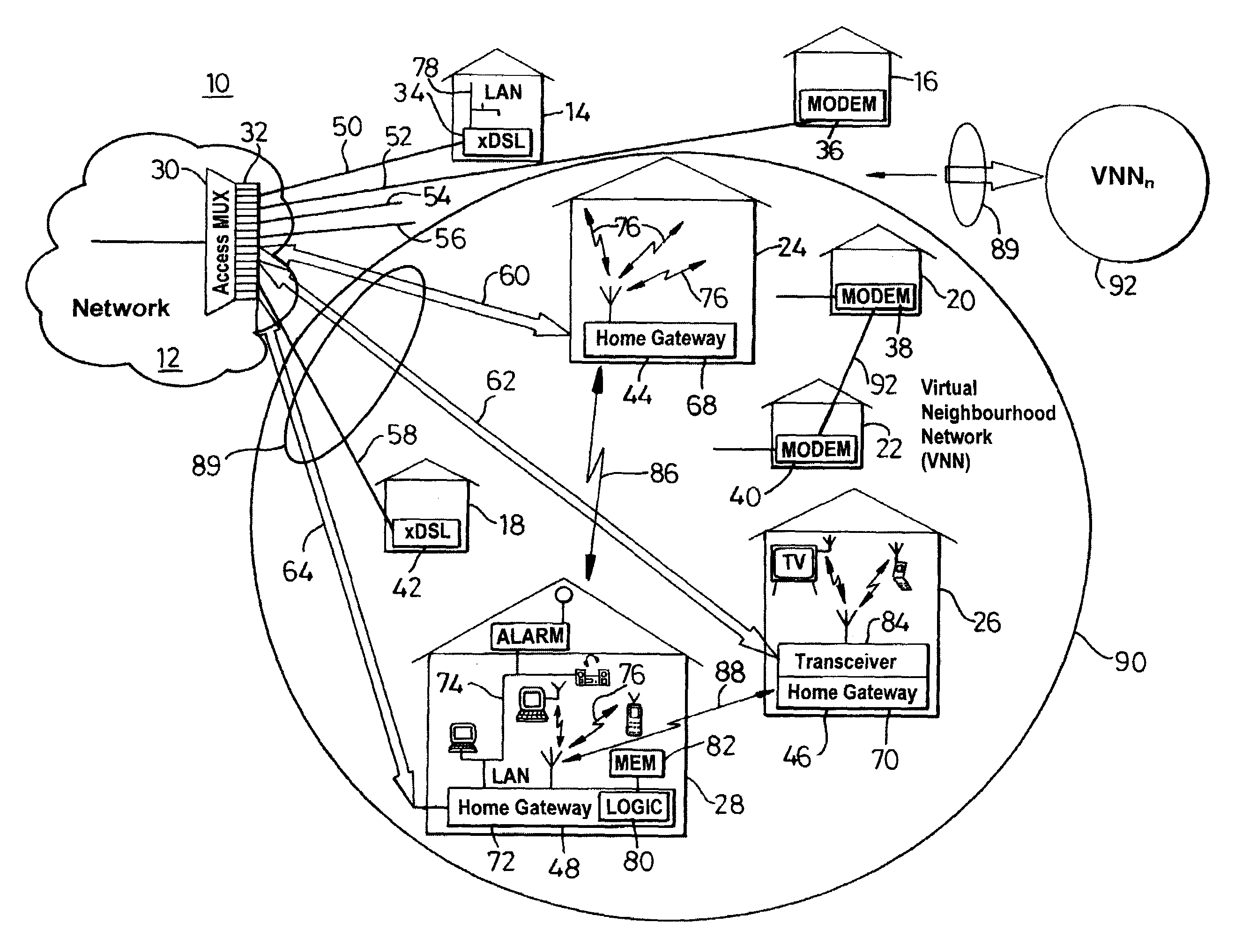
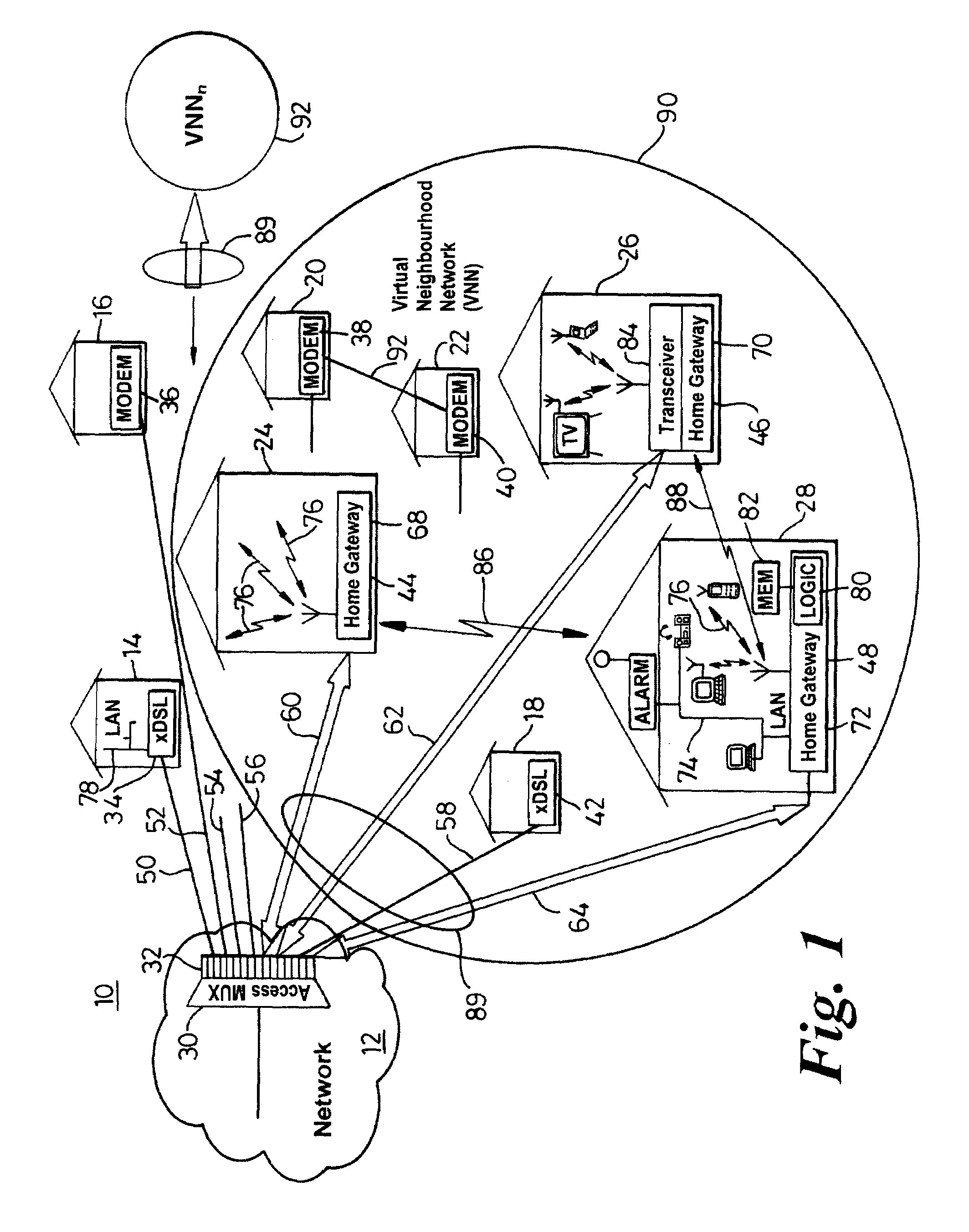
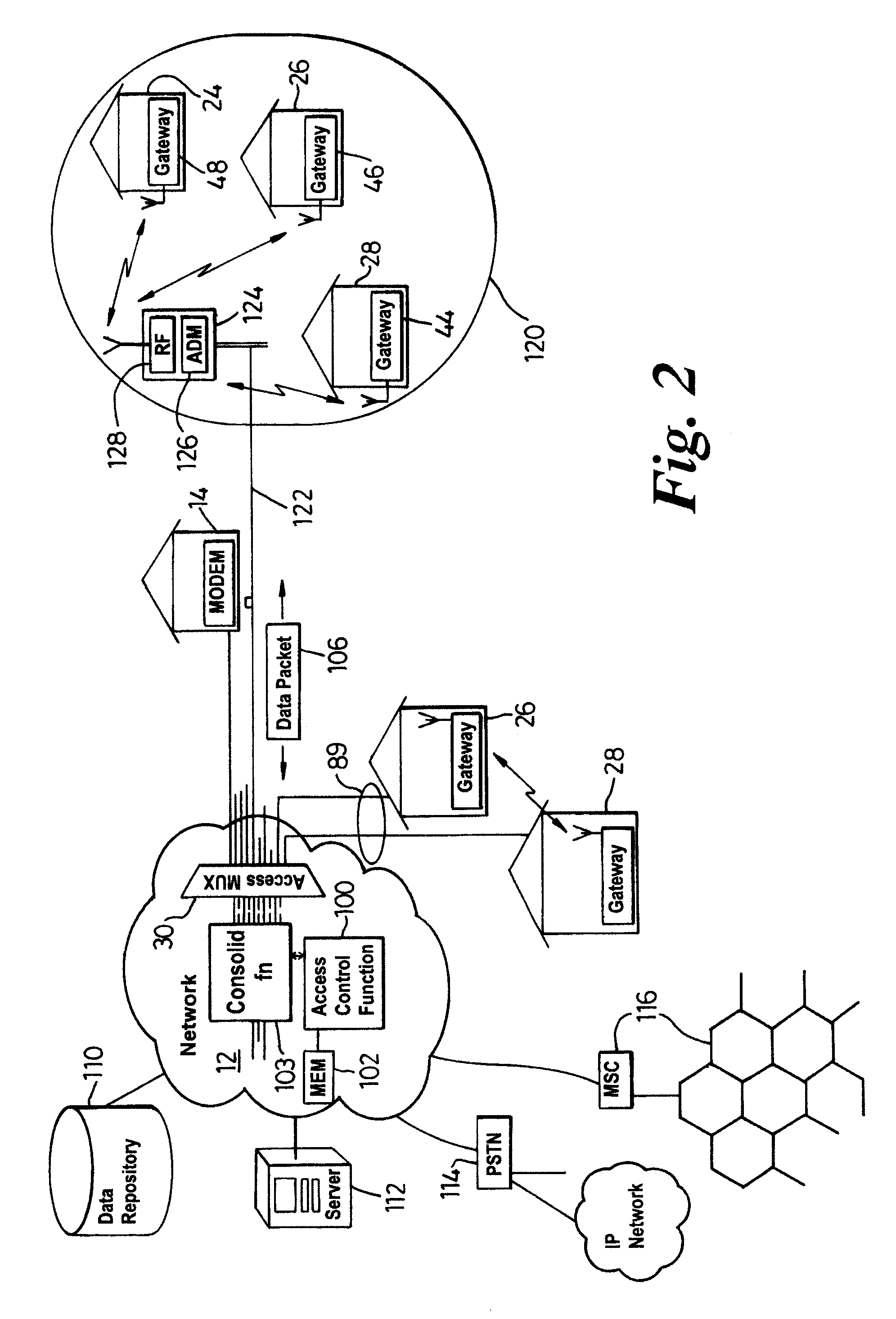
Communication system architecture and operating methodology providing a virtual neighborhood network
InactiveUS7142503B1Overcome bandwidth limitationIncreased peak bandwidth capacityError preventionFrequency-division multiplex detailsEnd-to-end encryptionTransceiver
A communication system (10) supports the provision of a plurality of dedicated communication resources (50–64), such as copper drops, RF links and optical fibers, to dedicated home-gateway devices (44–48) or distribution points (124). The communication resources (50–64) support broadband interconnection (104) between the dedicated home-gateway devices (44–48) or distribution points (124) and an access multiplexor (30) in a network (12). Each gateway device (44–48) or distribution point (124) generally includes a local RF transceiver (84) and associated control logic (80–82) that allows local communication (86) between gateway devices (44–48) and hence statistically multiplexed access (60–64, 89) to multiple communication resources, thereby providing increased bandwidth in uplink and / or downlink directions. With the control logic (80) operable to provide a routing and prioritisation / arbitration function, each gateway (44–48) is able to selectively engage use of supplemental, non-reserved communication resources usually associated with a dedicated ono-to-one connection between the access network (12) and at least one secondary gateway. Physical layer access to information routed via a secondary gateway within a virtual neighborhood network (90–92) comprising several gateways is restricted through an end-to-end encryption algorithm between an originating gateway and, at least, the access multilpexor (30).
Owner:RPX CLEARINGHOUSE
Fixed-mobile communications with mid-session mode switching
ActiveUS20060072542A1Connection managementWireless network protocolsTerminal equipmentMultiple modes
A method for performing mode-agile communications during a communications session is disclosed. A communications terminal device supporting multiple modes of access is configured to determine when, during a session involving a first mode of access communications, a second mode of access is available and is to be used for subsequent communications for the session. The communications terminal device initiates or controls switchover from one mode of access to another.
Owner:VERIZON PATENT & LICENSING INC
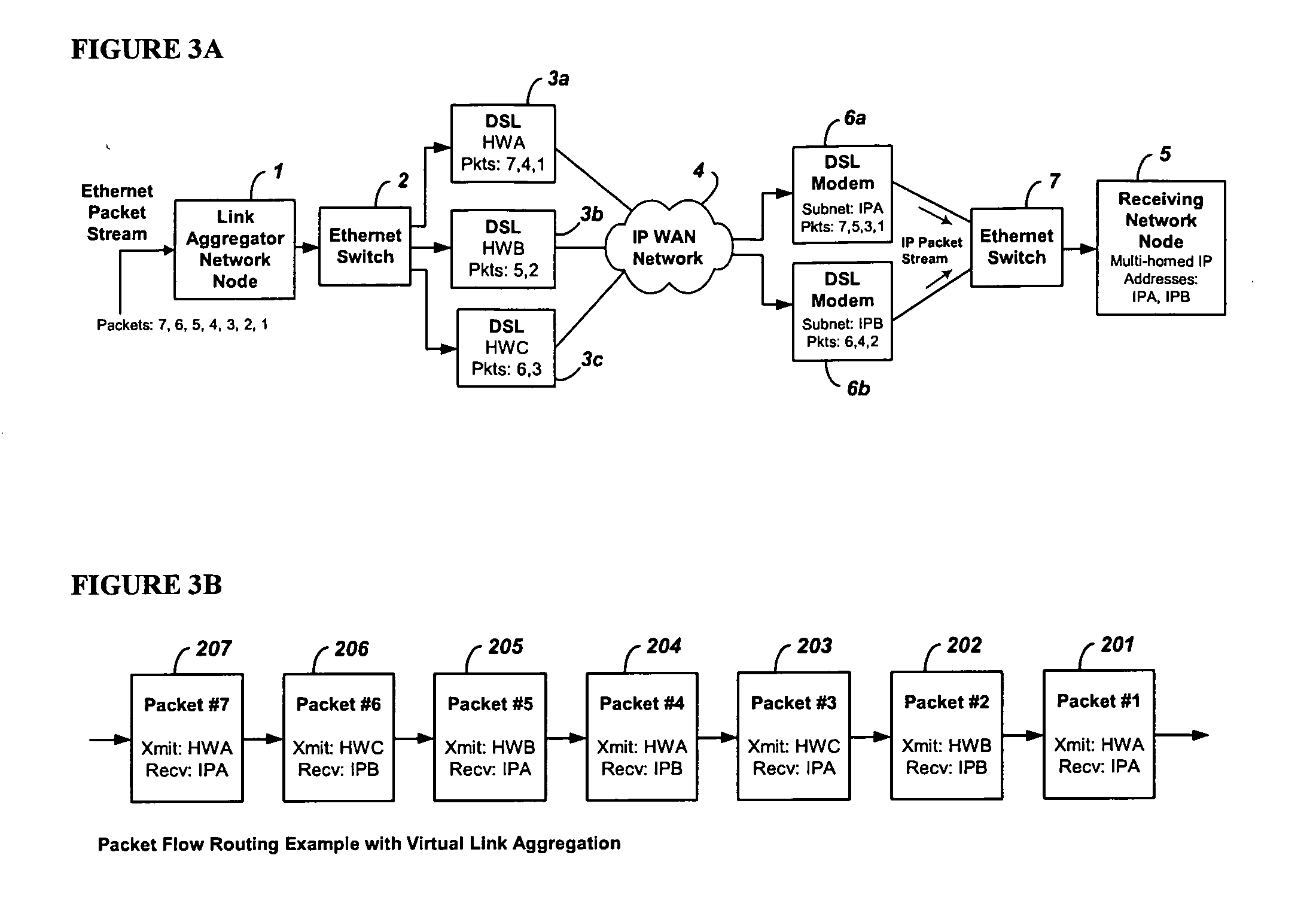
System and method for the virtual aggregation of network links
InactiveUS20060098573A1Improve throughputImprove reliabilityEnergy efficient ICTError preventionNetwork linkRewriting
A system and method for virtual link aggregation for combining network links of various types and speeds to increase throughput and reliability for packetized transport. In contrast with physical port trunking, the system does not require direct control over ports or network interfaces. Instead, the system rewrites packet addresses and works through existing networking equipment, without requiring any new or special protocols, processing, or equipment within the network. The system works through low-level rerouting by rewriting hardware addresses and / or high-level routing by rewriting logical addresses. Thus packets are redirected through multiple routes to a common destination via alternate gateways and links. Different algorithms may be employed to balance the load on each link and determine an optimal route for each packet. Embodiments may also employ packet flow or stream identification and thereby only provide link aggregation for a specified set of packet flows.
Owner:QVIDIUM TECH
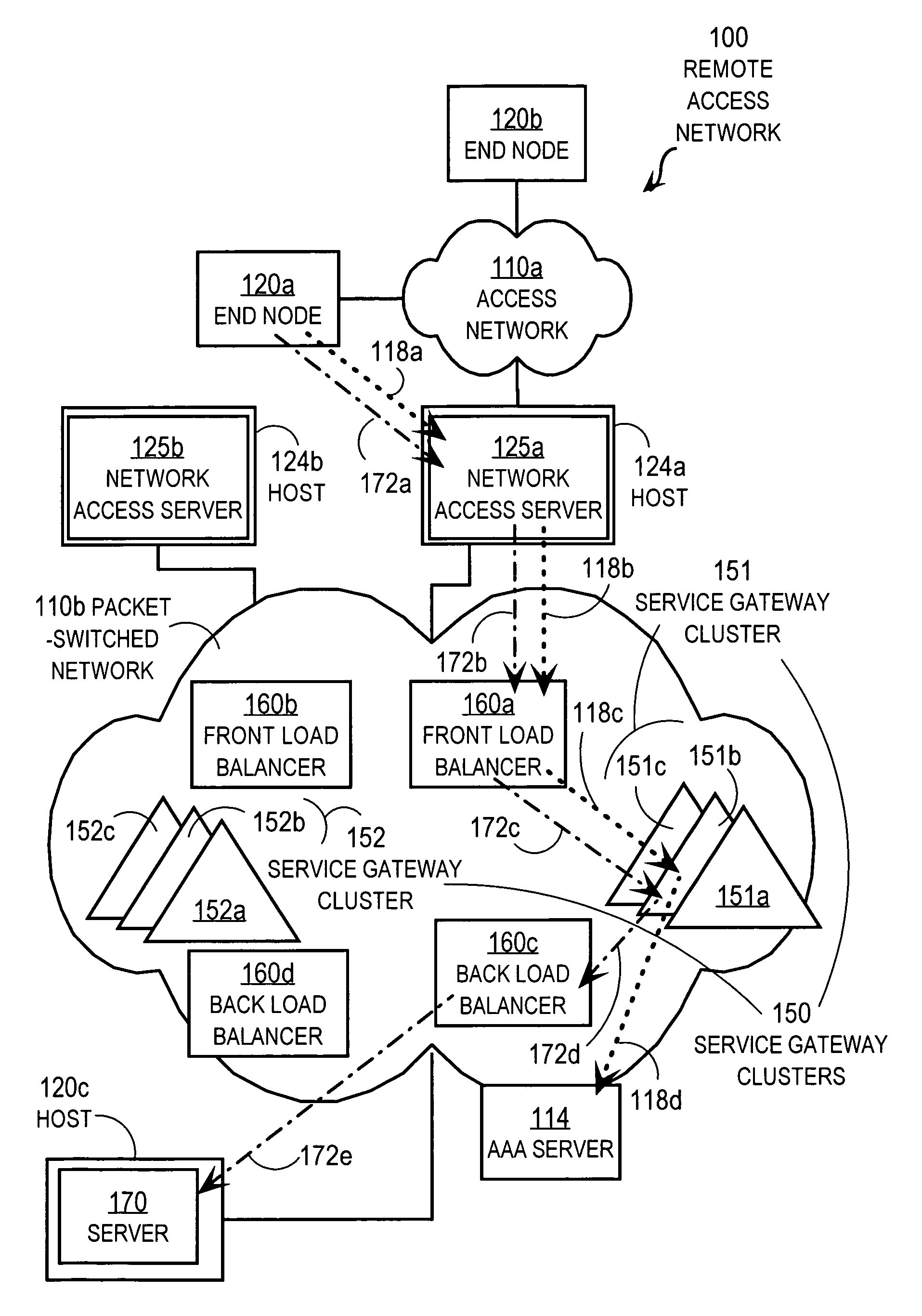
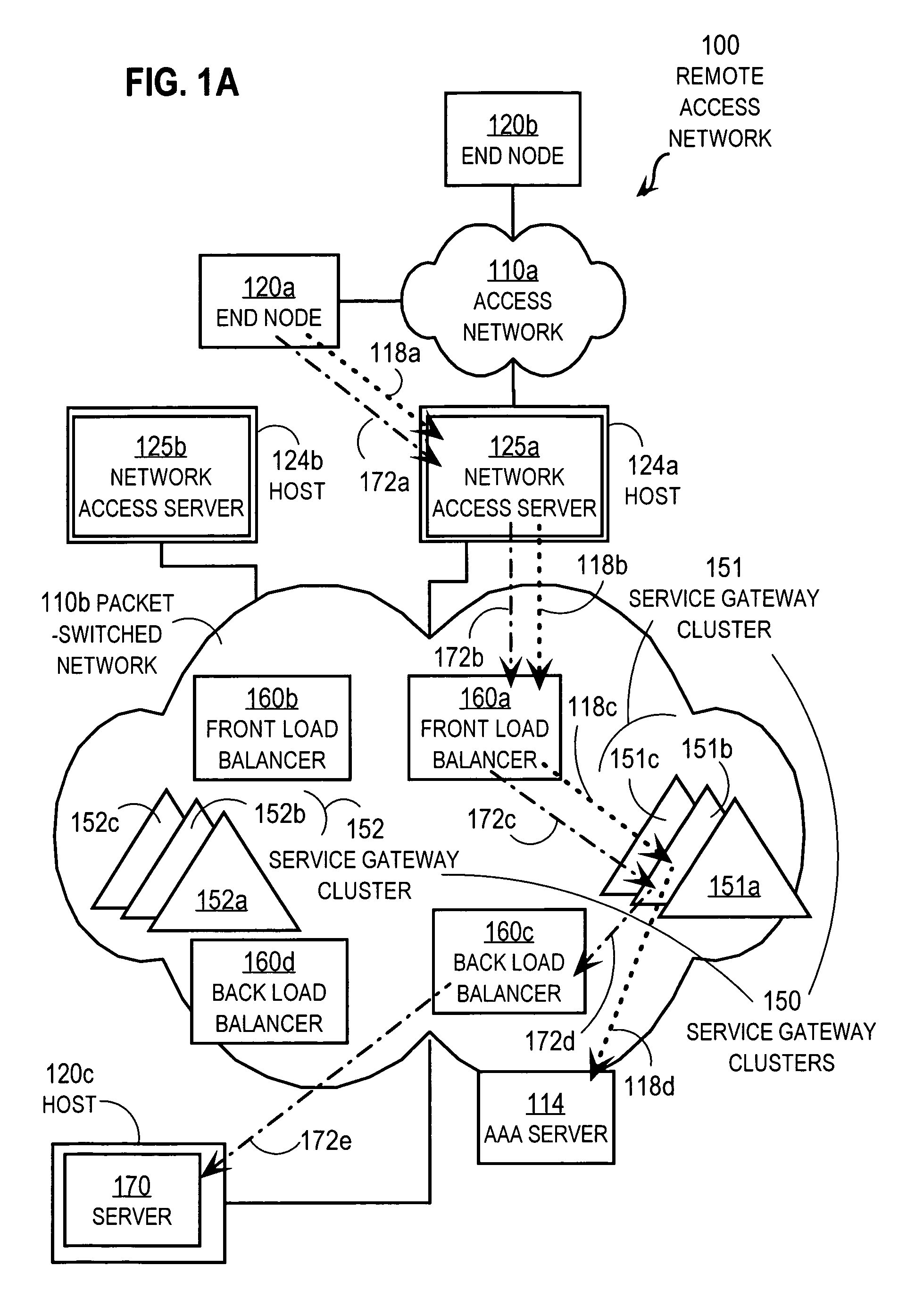
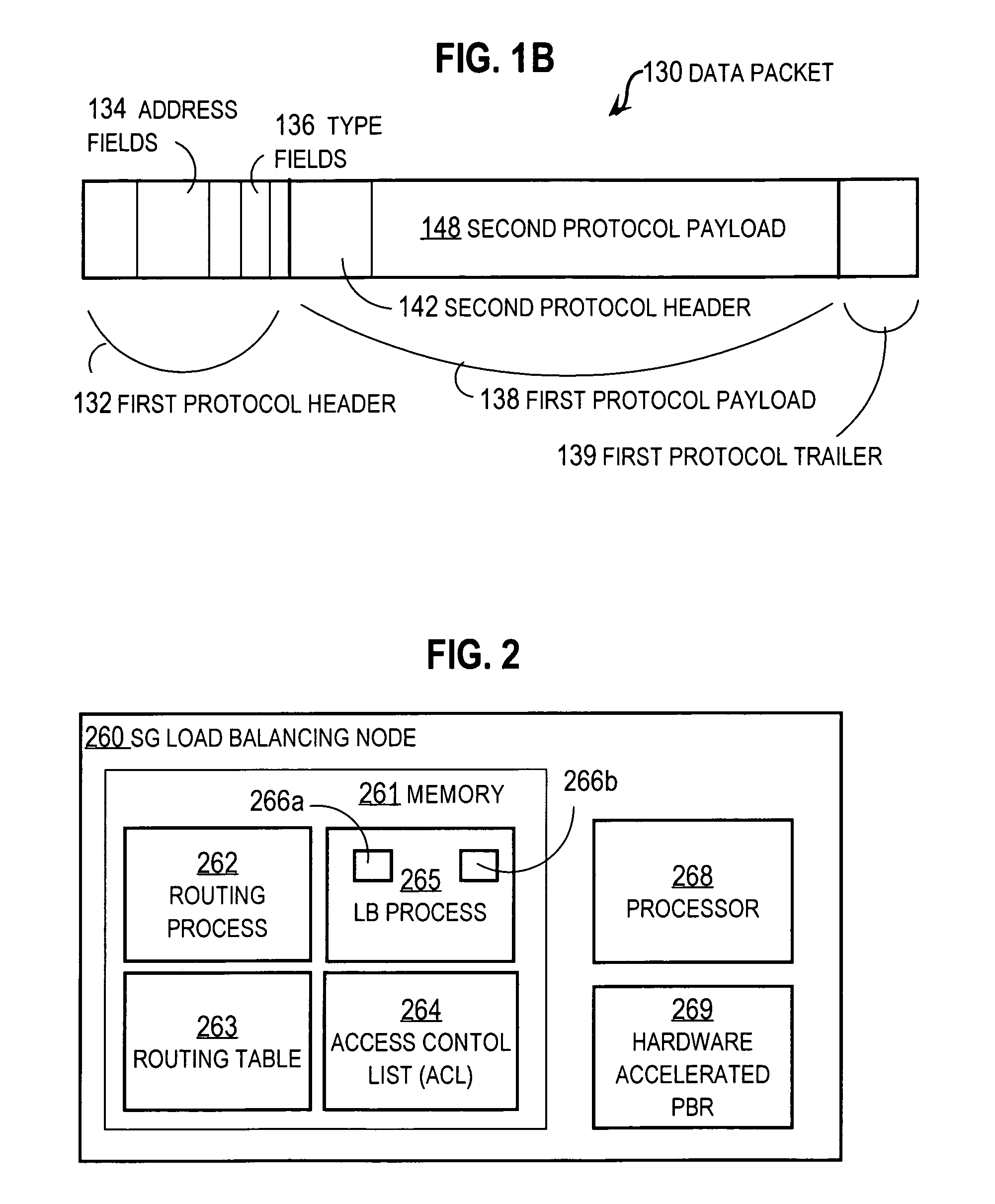
Techniques for load balancing over a cluster of subscriber-aware application servers
InactiveUS20070165622A1Digital computer detailsNetwork connectionsApplication serverDistributed computing
Techniques for distributing control plane traffic, from an end node in a packet switched network to a cluster of service gateway nodes that host subscriber-aware application servers, include receiving a control plane message for supporting data plane traffic from a particular subscriber. A particular service gateway node is determined among the cluster of service gateway nodes based on policy-based routing (PBR) for the data plane traffic from the particular subscriber. A message based on the control plane message is sent to a control plane process on the particular service gateway node. Thereby, data plane traffic and control plane traffic from the same subscriber are directed to the same gateway node, or otherwise related gateway nodes, of the cluster of service gateway nodes. This approach allows currently-available, hardware-accelerated PBR to be used with clusters of subscriber-aware service gateways that must also monitor control plane traffic from the same subscriber.
Owner:CISCO TECH INC
Authentication mechanisms for call control message integrity and origin verification
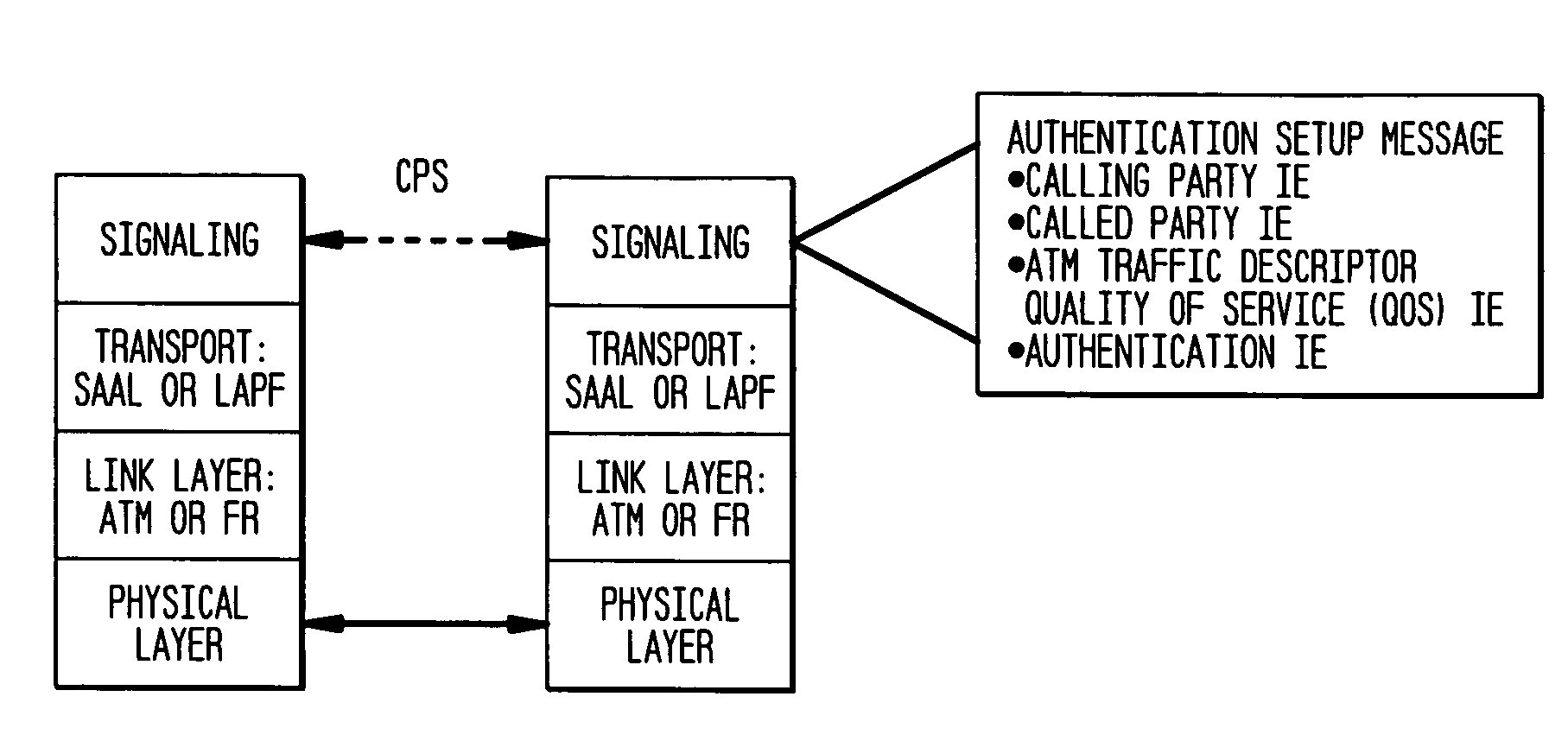
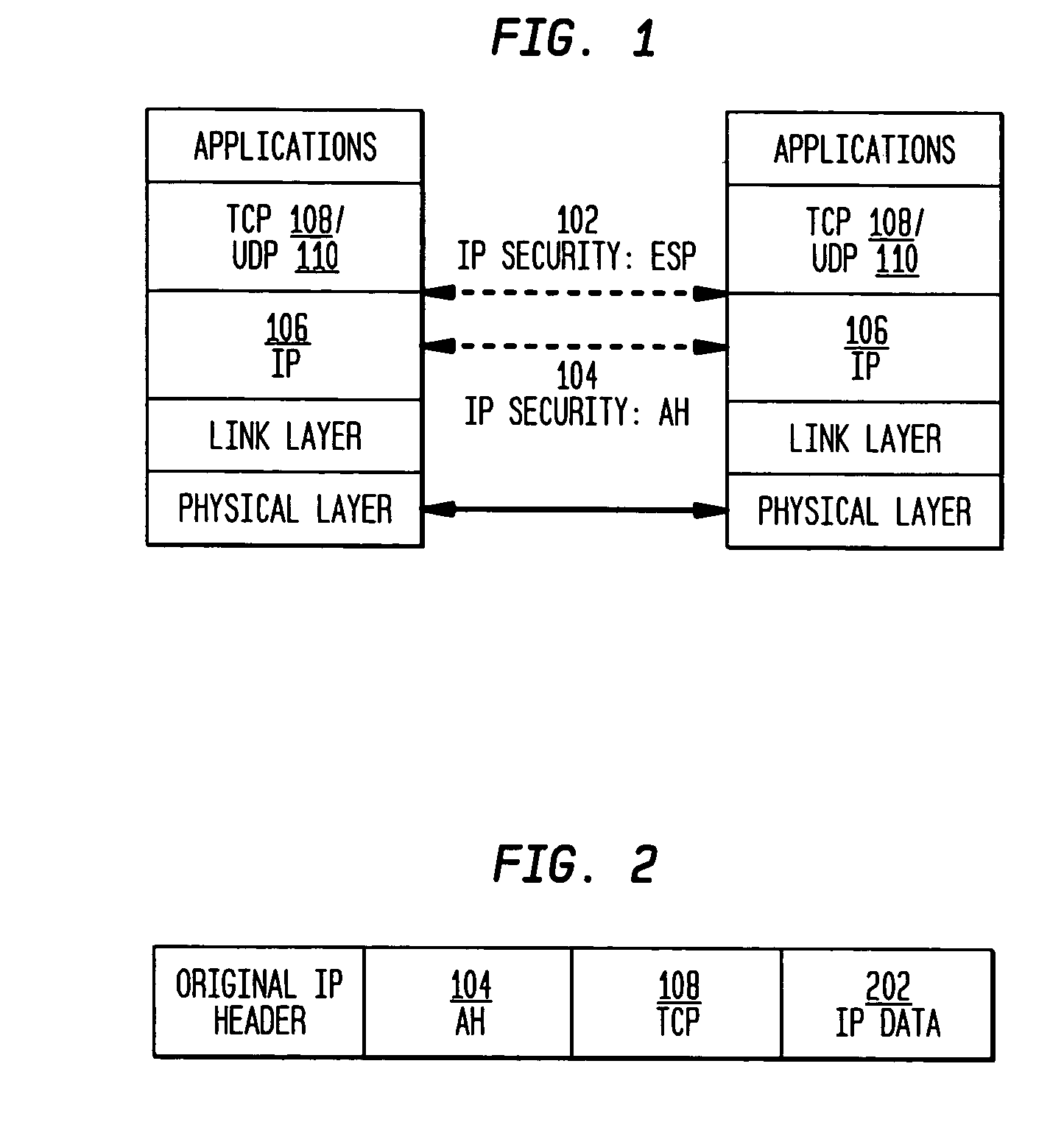
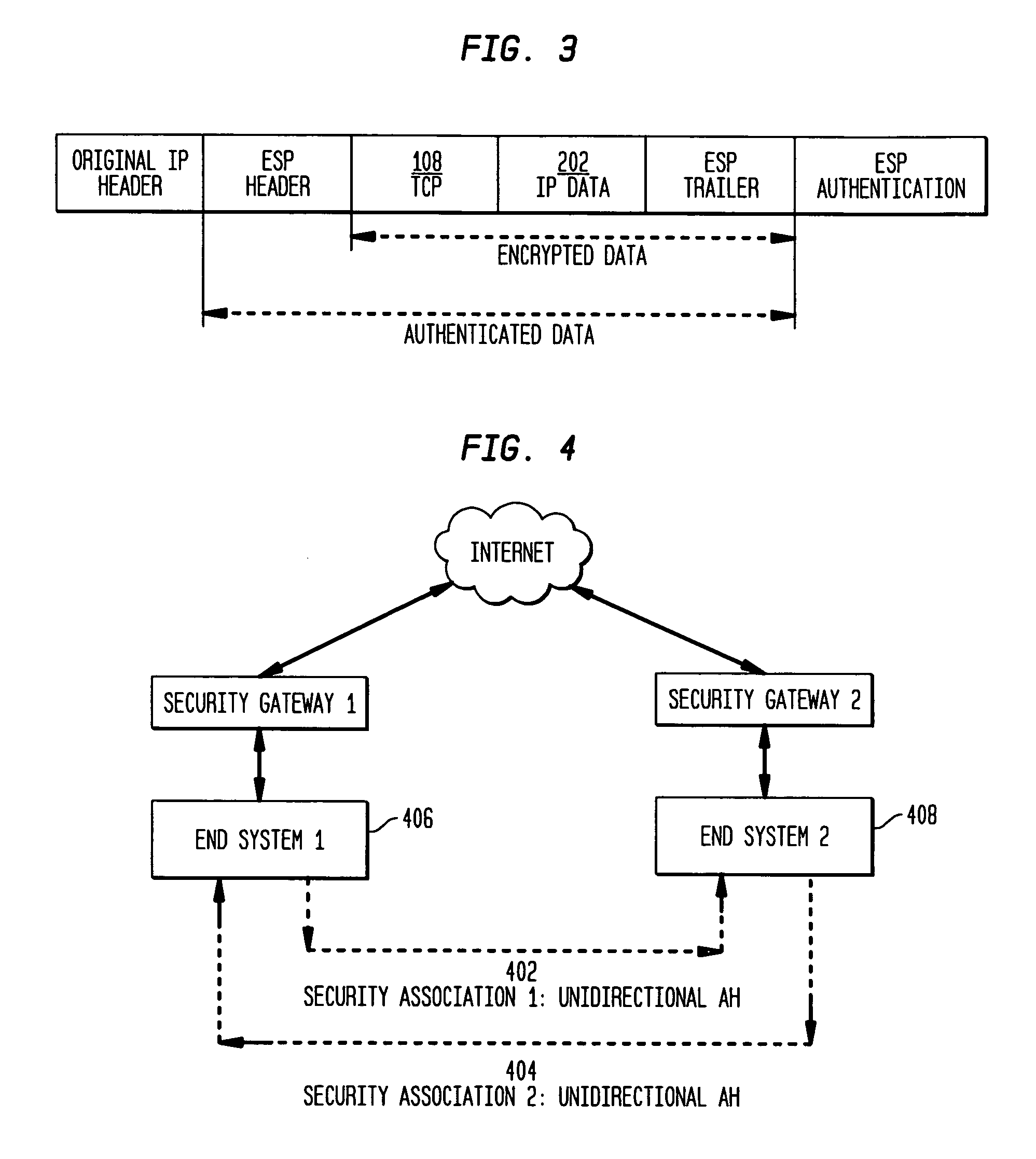
The present invention incorporates methodologies developed in the Internet Engineering Task Force (IETF) Internet Protocol Security (IPSEC) Working Group into asynchronous transfer mode (ATM) and frame relay (FR) signaling to provide message integrity and origin authentication. In one implementation the invention provides a virtual private network (VPN) infrastructure with call control message integrity, origin verification, and transit network filtering. The invention utilizes a set of control plane messages based on the IPSEC authentication header (AH) methodology to provide these security mechanisms for ATM and FR network switching equipment and signaling protocols. This abstract itself is not intended to limit the scope of this patent. The scope of the present invention is pointed out in the appending claims.
Owner:ALCATEL-LUCENT USA INC
Method and device for audience monitoring on multicast capable networks
InactiveUS20060294259A1Eliminates need of cooperationCost effectiveSpecial service provision for substationBroadcast-related systemsData packUser equipment
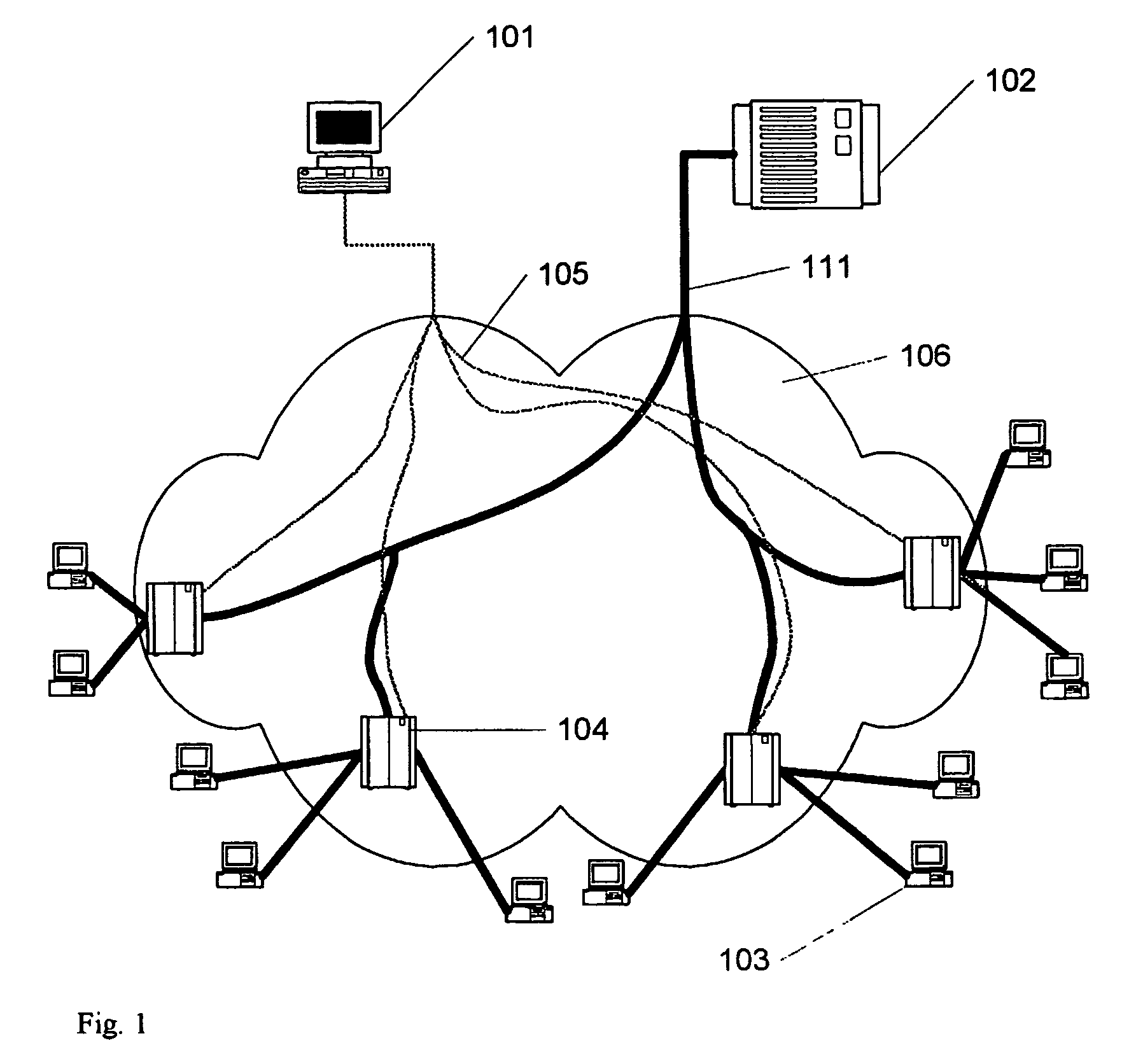
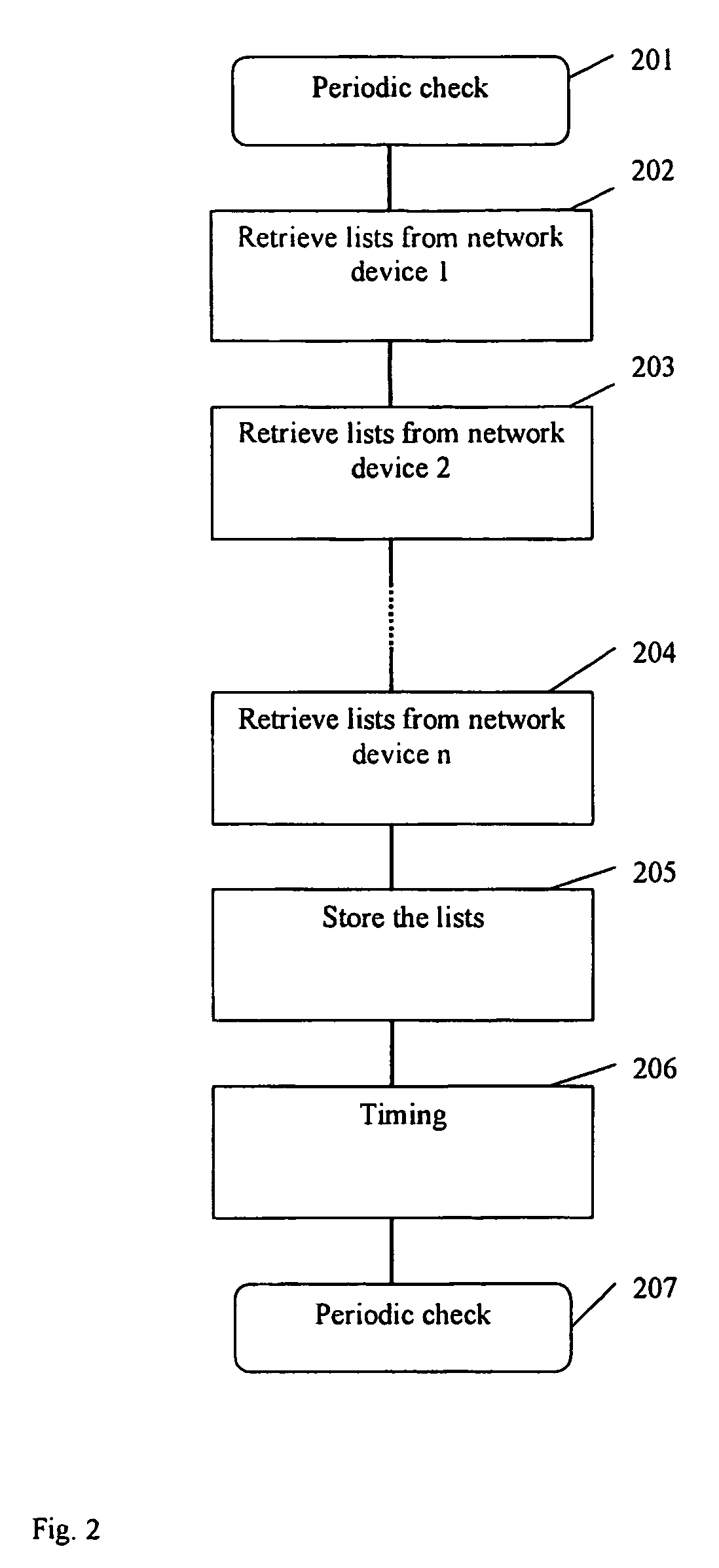
The presented idea is a cheap solution for audience monitoring in multicast capable networks e.g. Ethernet, IP or UMTS. There is no need for user equipment in order to monitor the viewers' watching behavior. The measurement is done in the operator's network; therefore, there is no need to contact the end user. The idea can be applied in systems comprising multicast capable network contention server, network devices and user equipment. The content is carried in data packets to the end user. The network devices are remote manageable. The user can choose between several contents. The aim is to measure the user statistics regarding the chosen content. According to the invention it is enough to place a measurement host with our proposed software block in the network, which collects data from the network devices in the edge of the network periodically in order to make a content access survey.
Owner:TELEFON AB LM ERICSSON (PUBL)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com