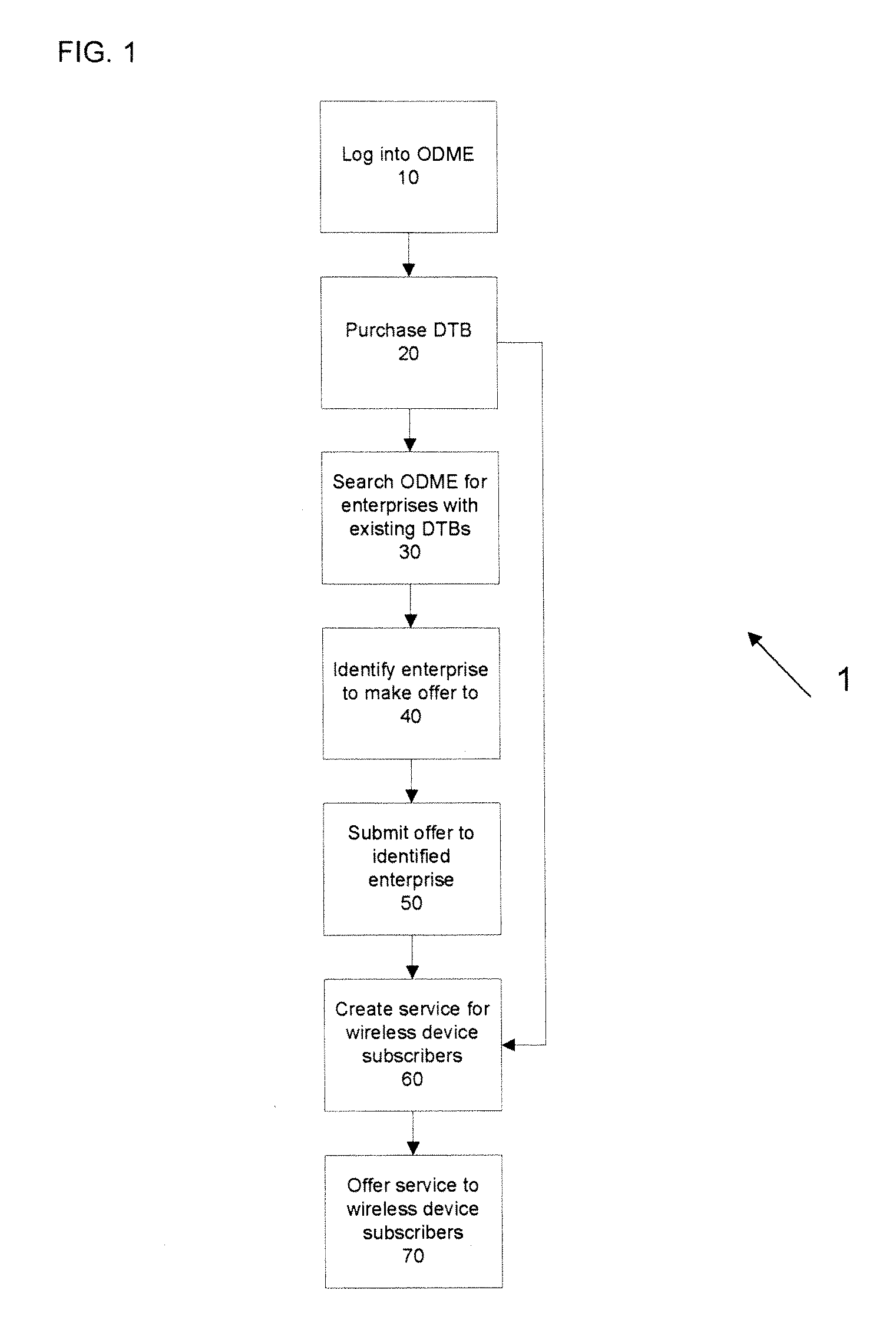
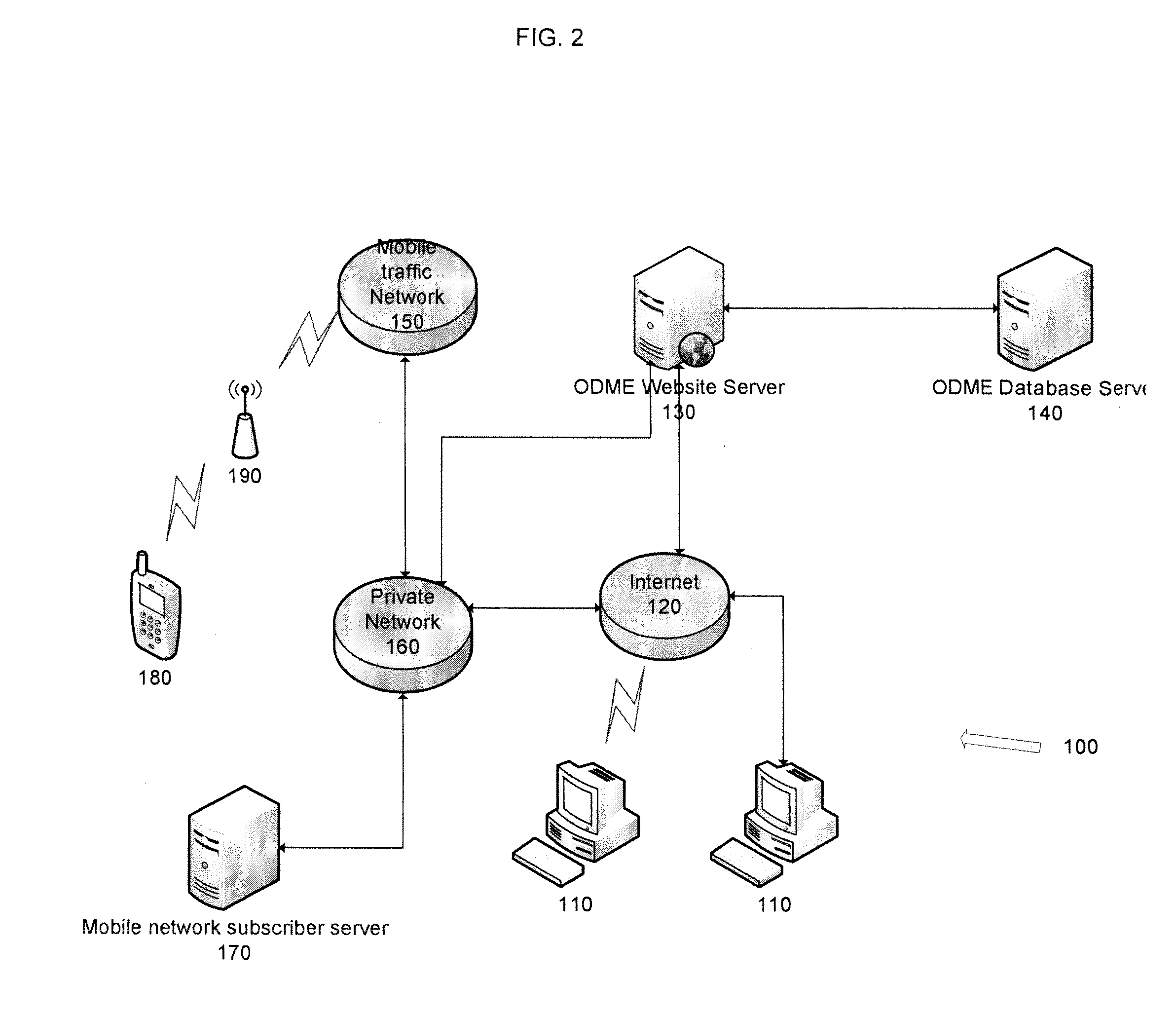
Patents
Literature
374 results about "Network providers" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
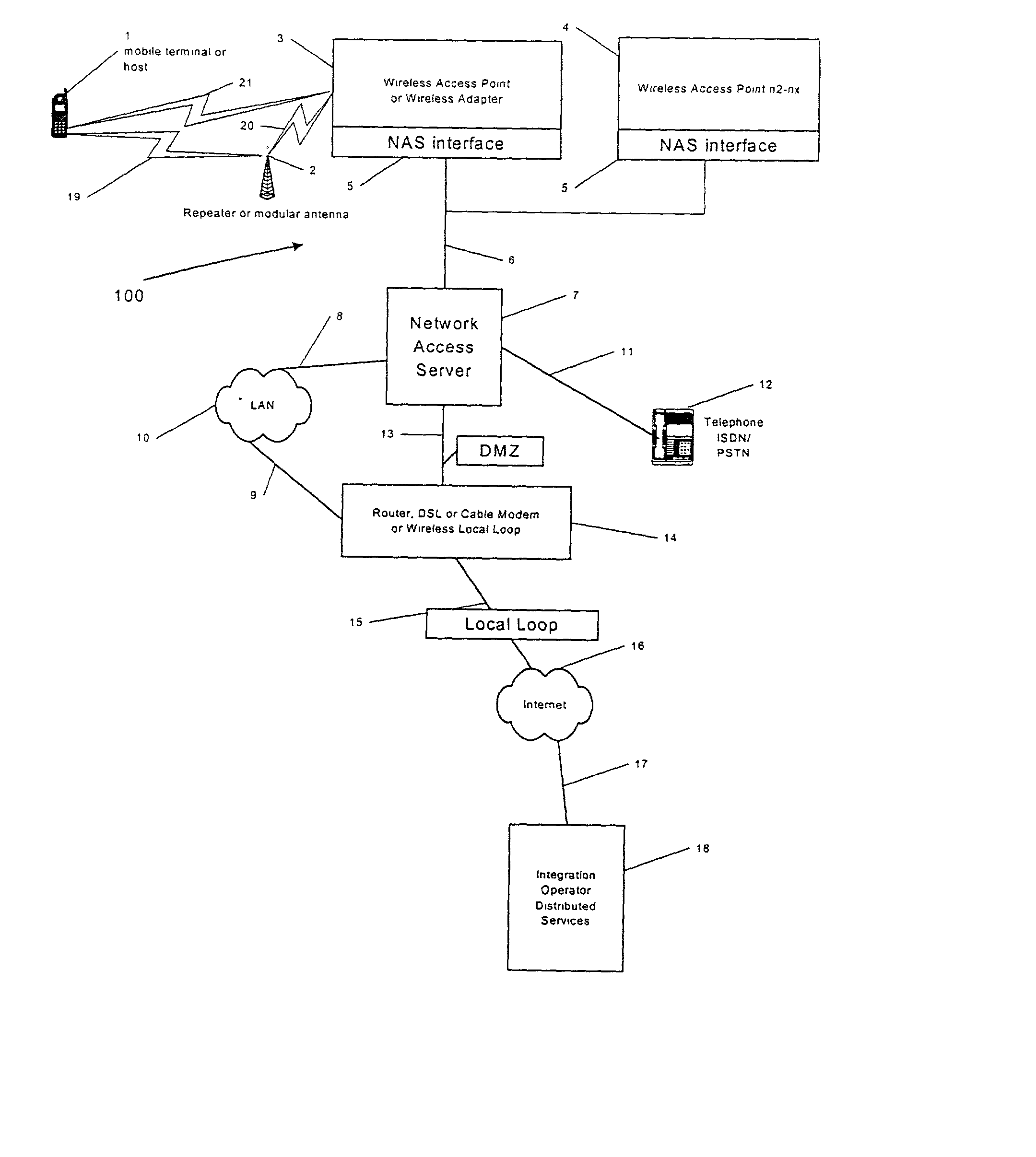
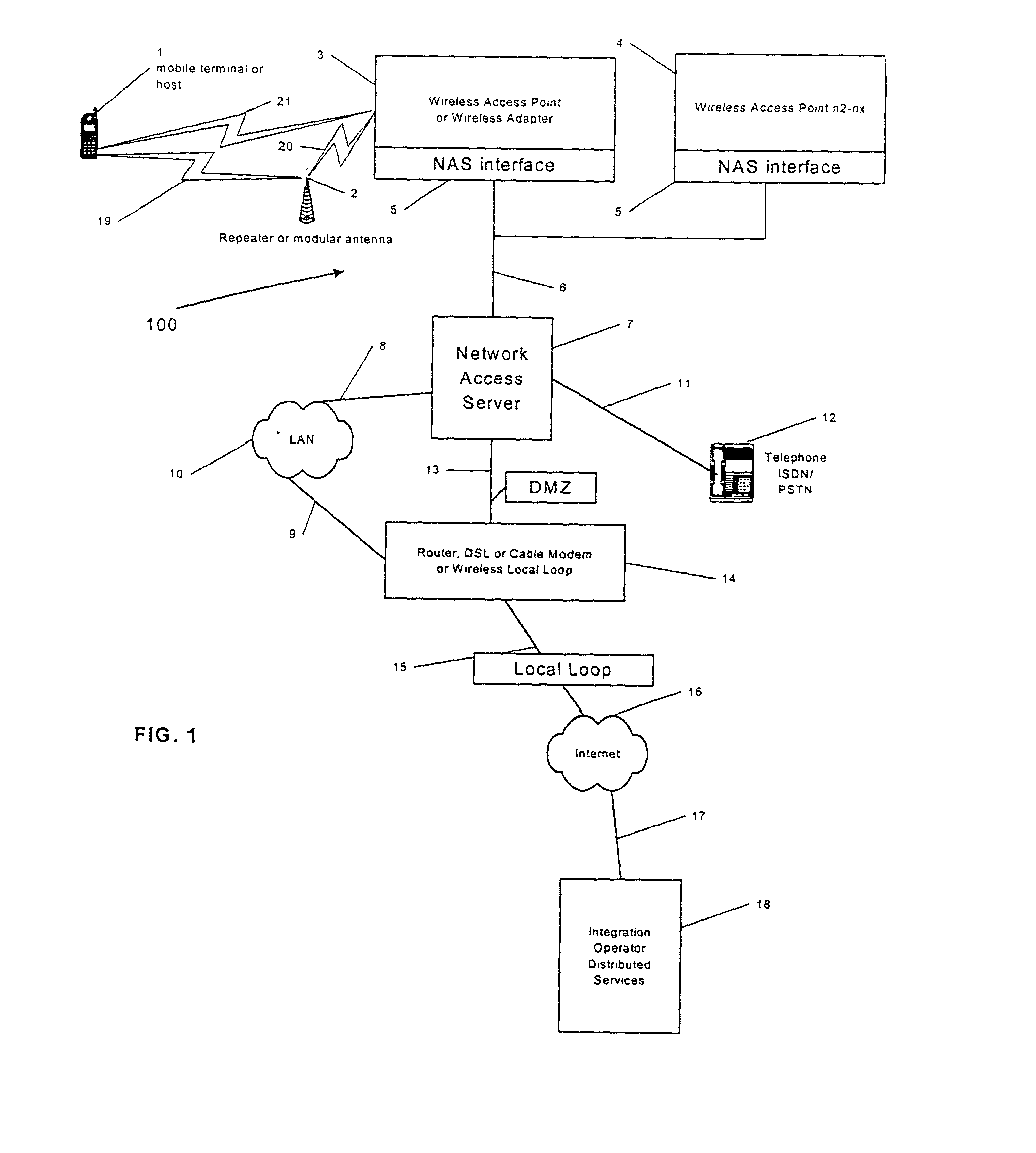
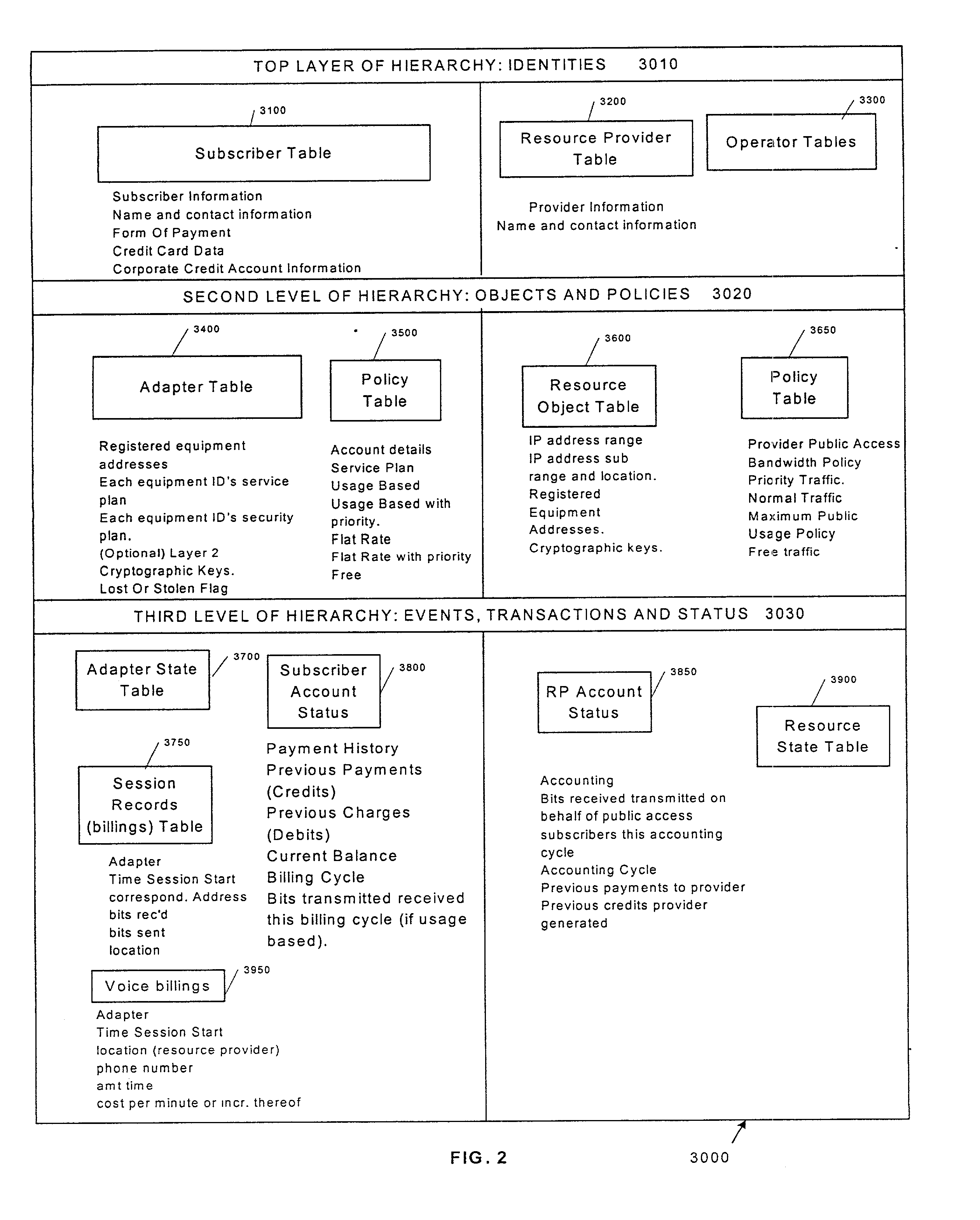
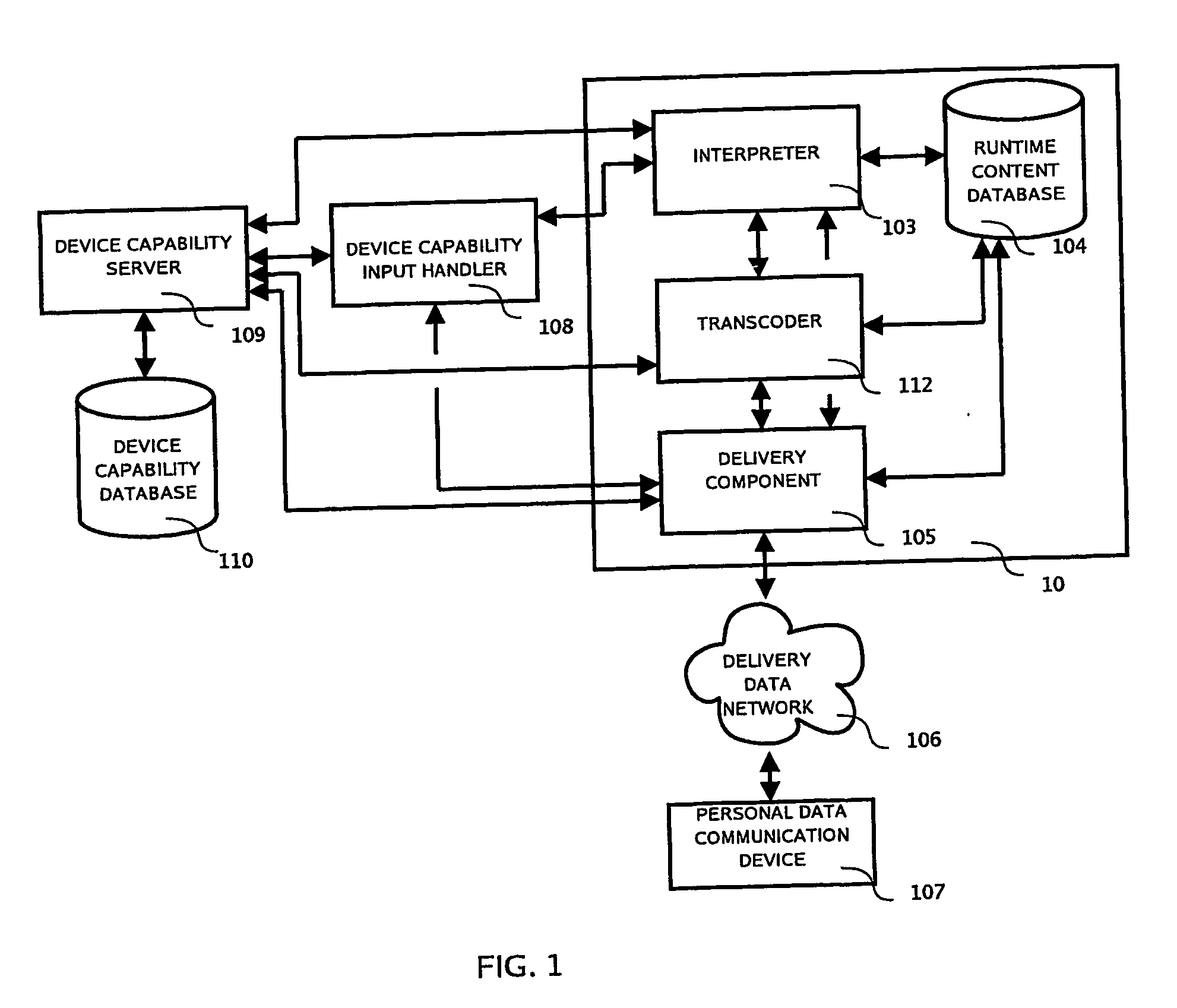
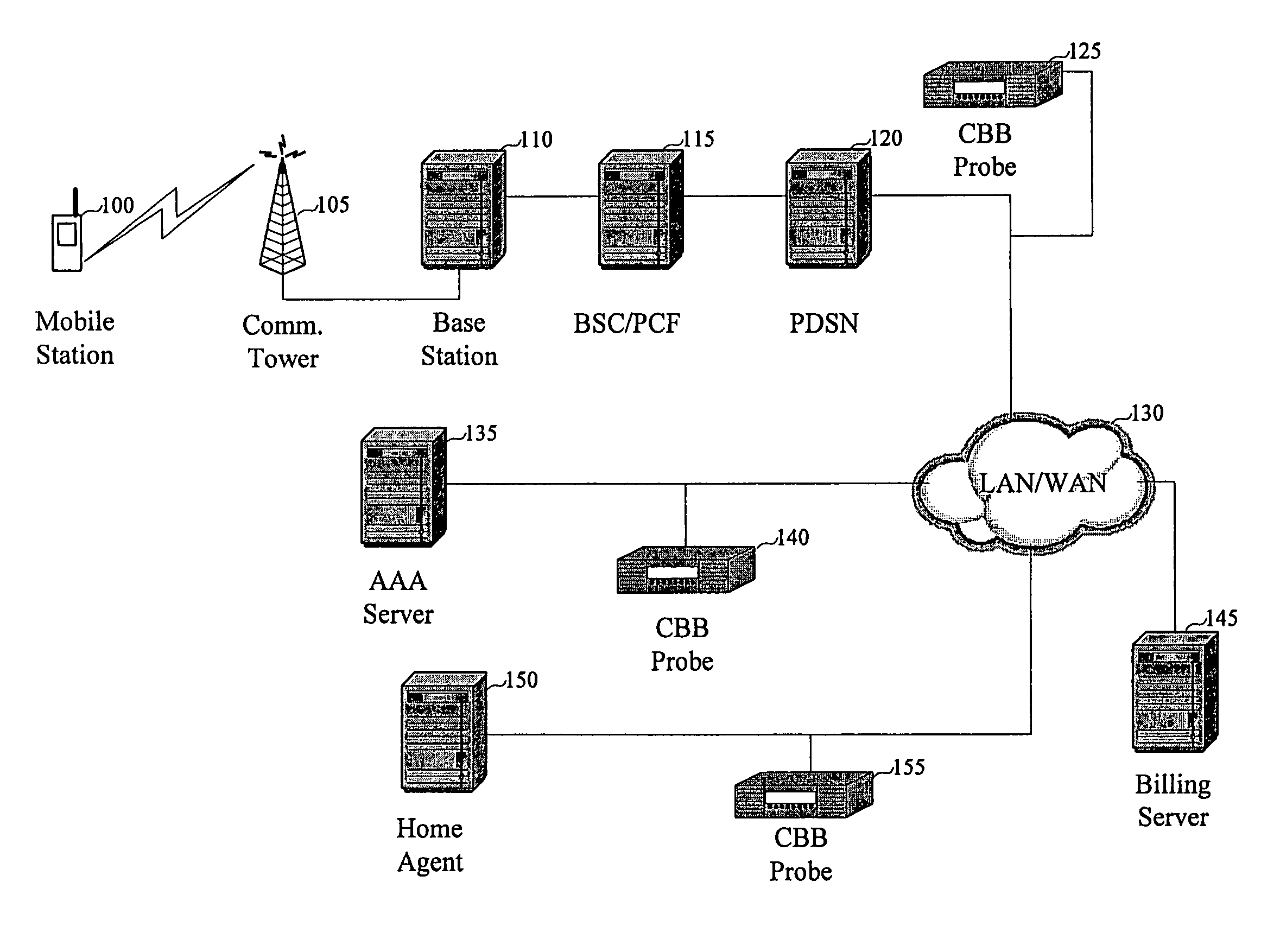
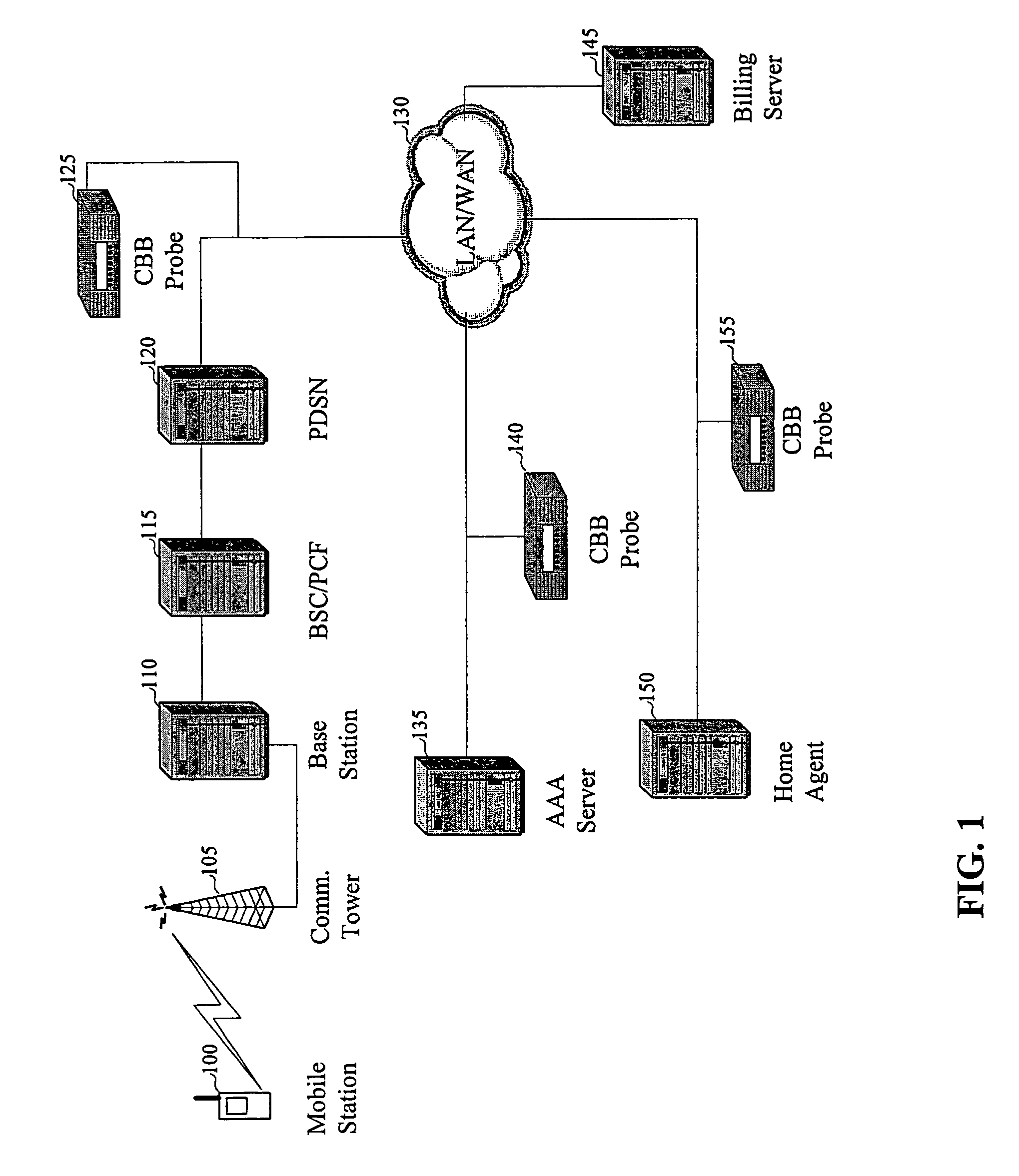
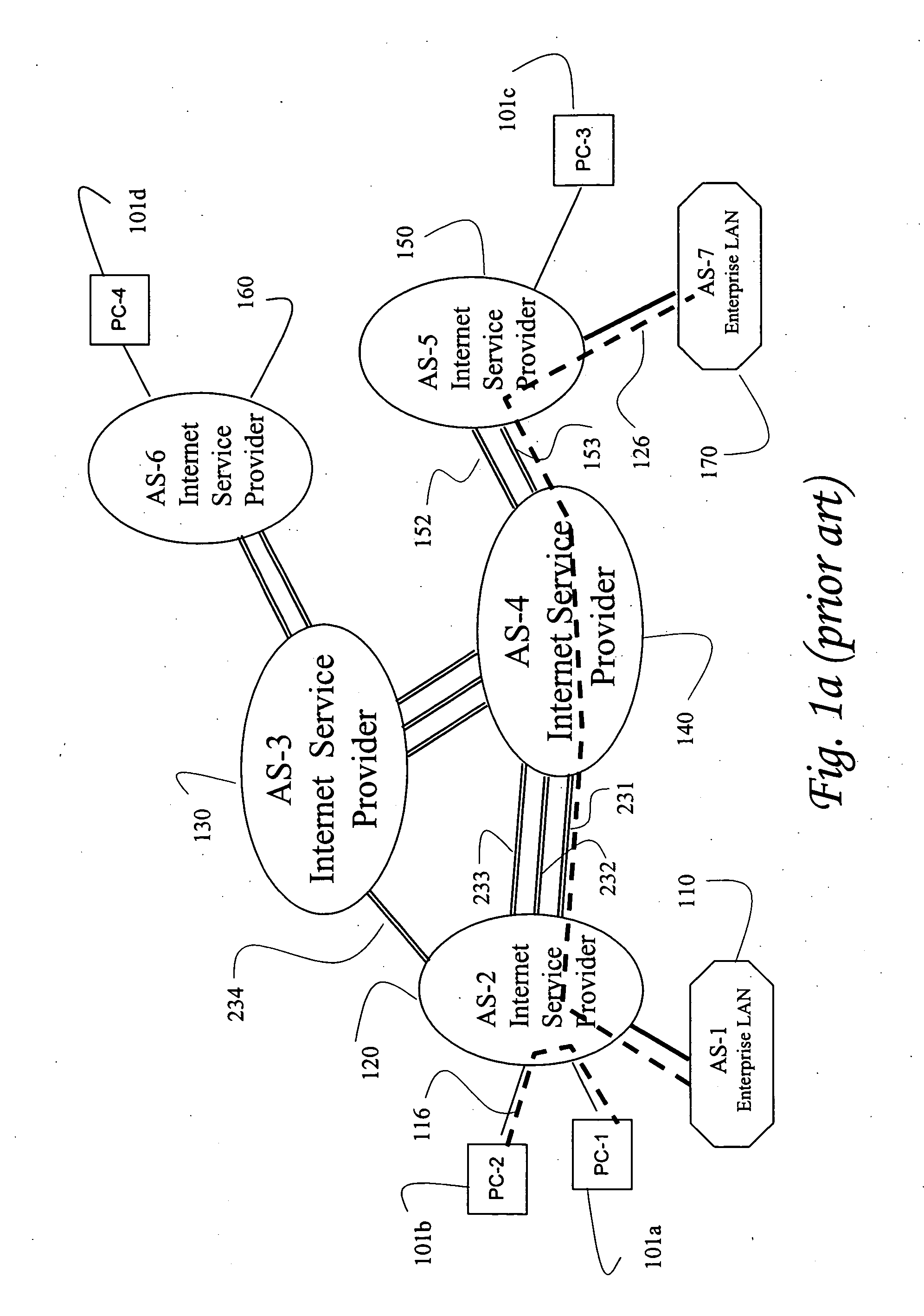
Integrating public and private network resources for optimized broadband wireless access and method
InactiveUS20020075844A1Network traffic/resource managementNetwork topologiesNetwork access serverPrivate network
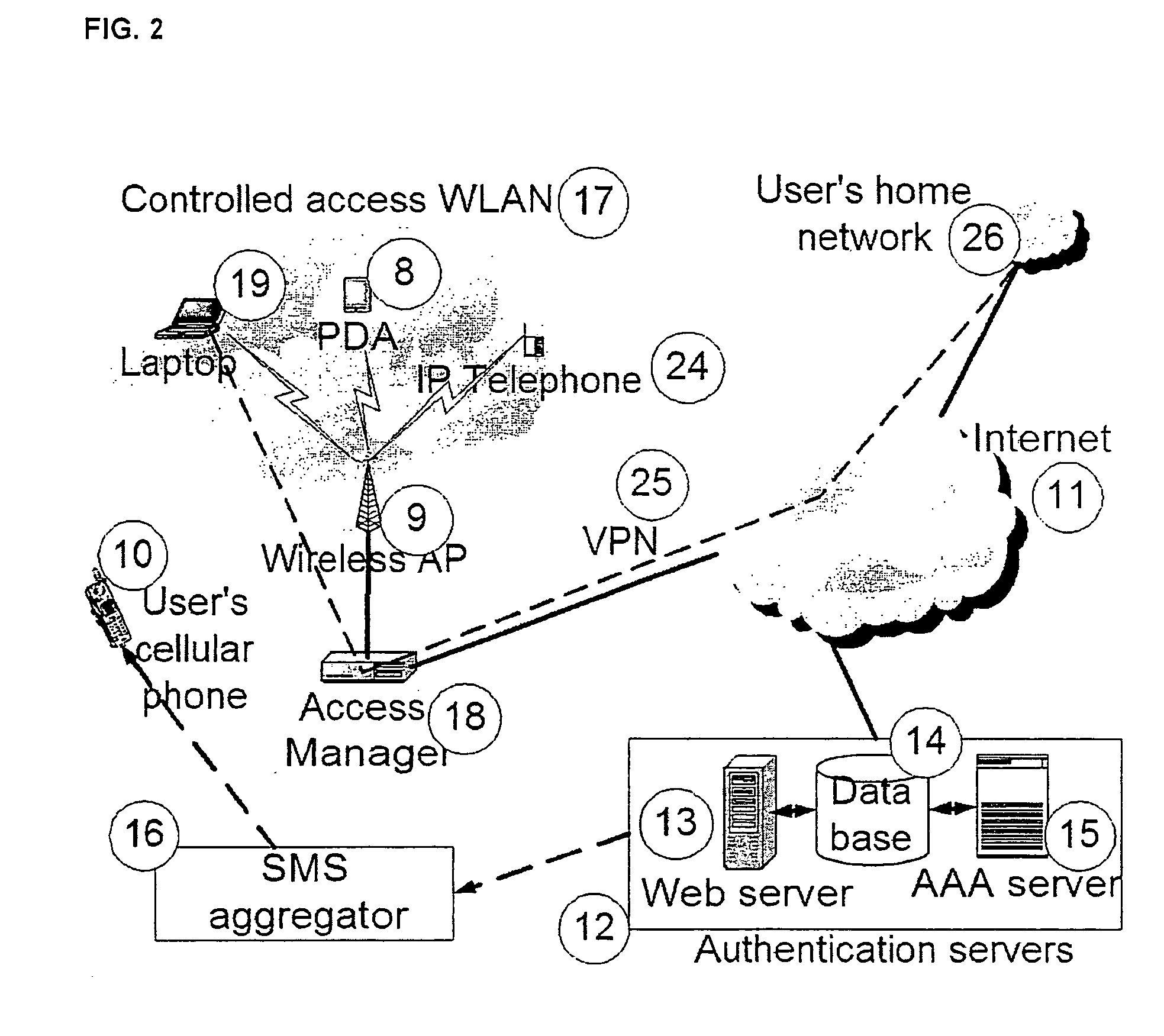
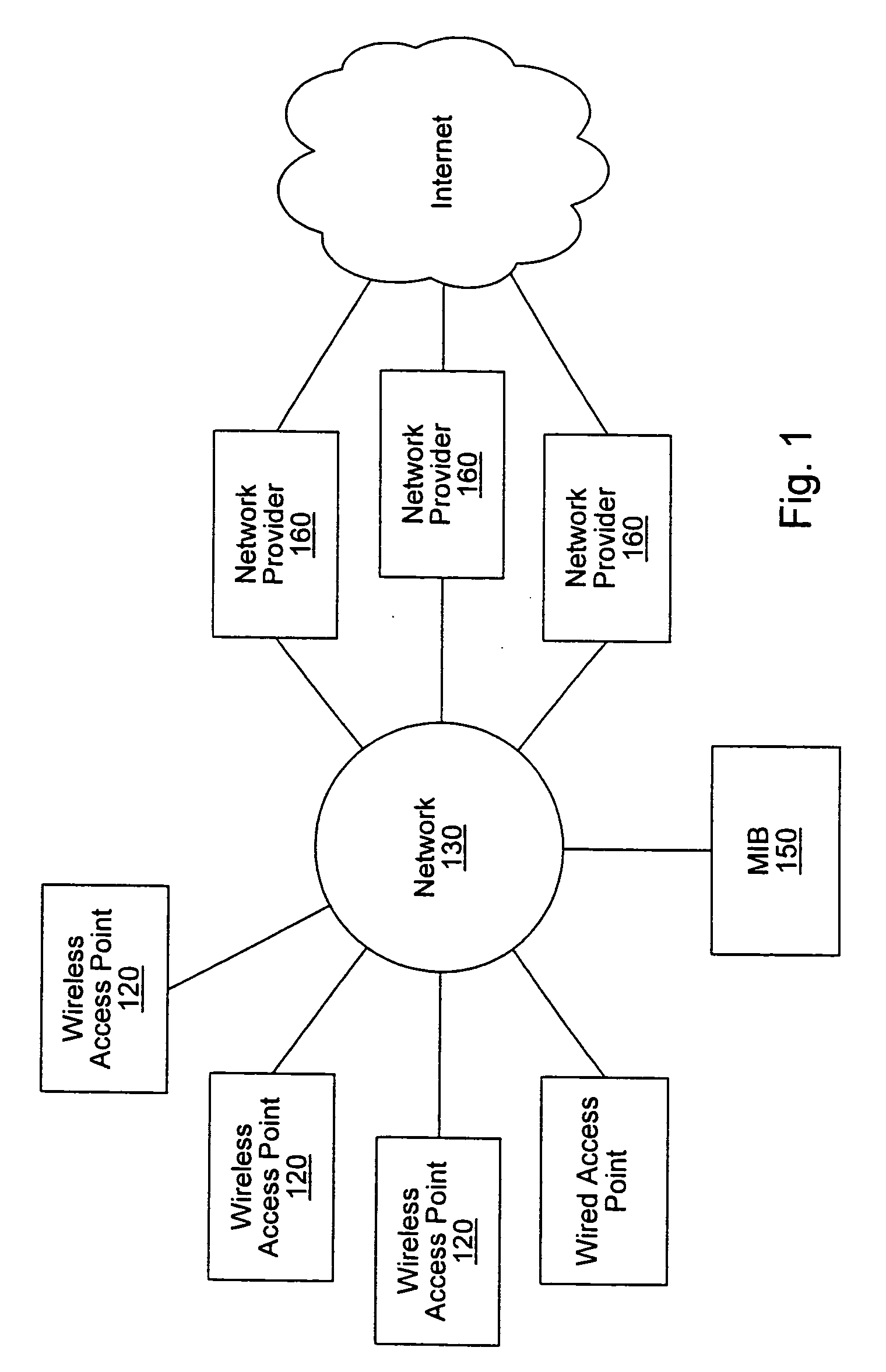
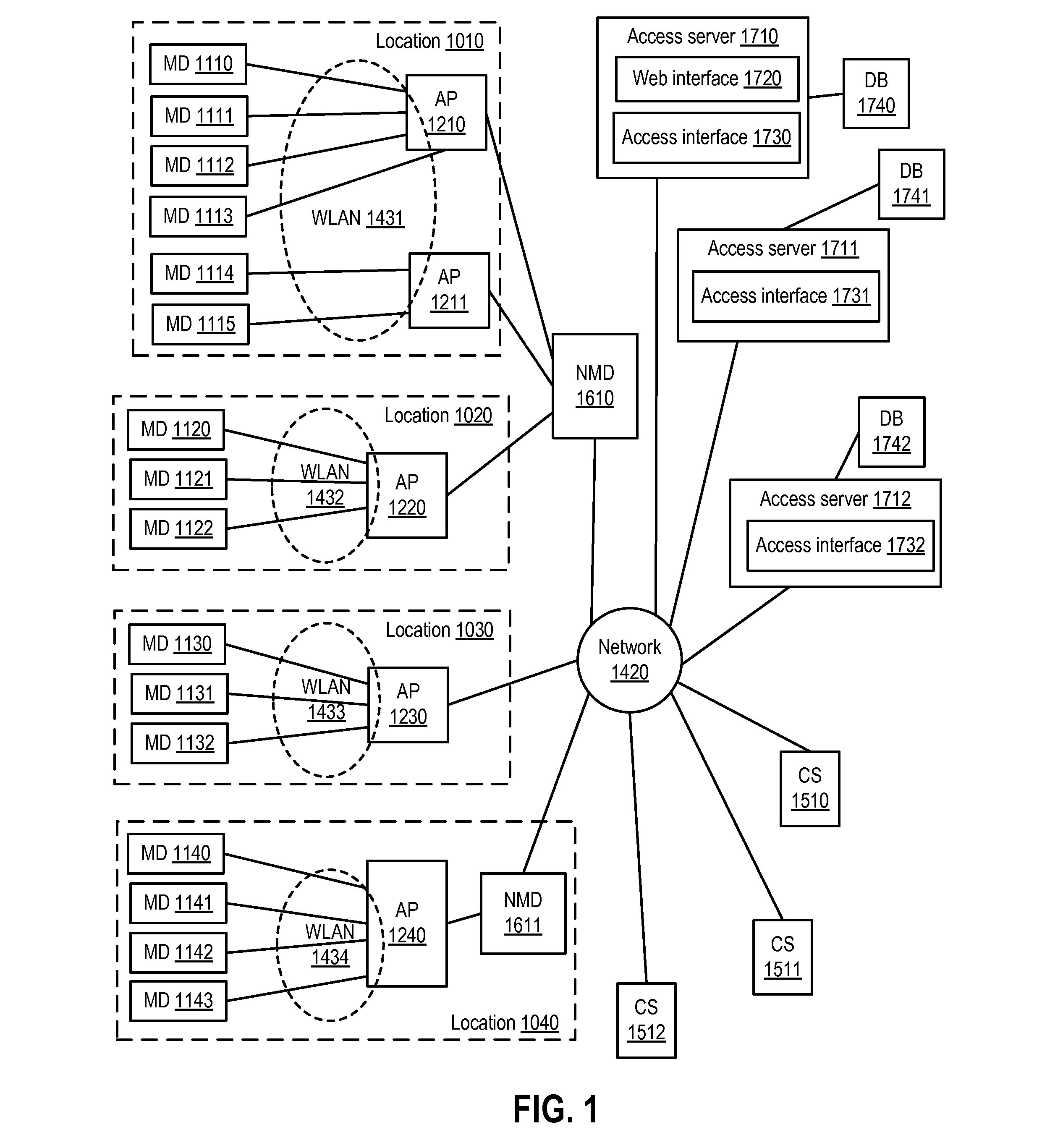
A system and method are disclosed for providing ubiquitous public network access to wireless, mobile terminals using private networks having private network access points and connections with the public network. The wireless, mobile terminals are permitted to use wireless, radio frequency communication devices comprising private network access points. A network access server (NAS) is associated with each wireless, radio frequency communication device and provides an interface between the wireless, mobile terminals and the private network. The NAS controls registration of wireless, mobile terminals as subscribers, and provides public network access to the mobile terminals through the private network's access point and public network connection. The NAS also restricts access by the mobile terminals to the private network, meters network useage by the mobile terminals, and controls use of bandwidth by the mobile terminals. The NAS also interfaces with integration operator distributed services over the public network. The integration operator services include databases and servers for storing and providing subscriber and network provider information for subscriber registration, network access and useage control, and accounting purposes. The NAS may be provided as a standalone element embodied in a computer, or may be integrated with the wireless radio frequency device and / or a network adaptor device for the private network.
Owner:NTT DOCOMO DCMR COMM LAB USA
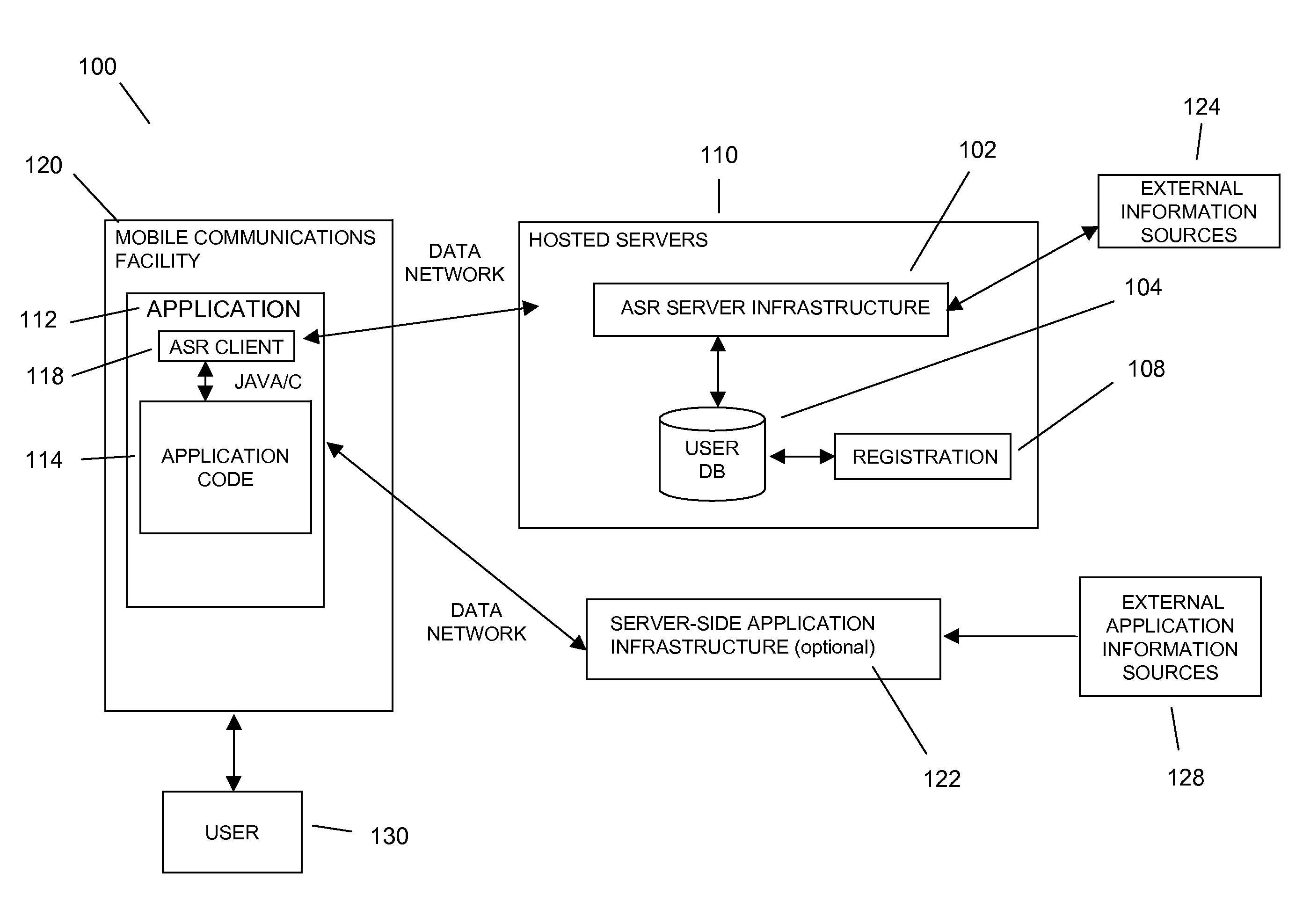
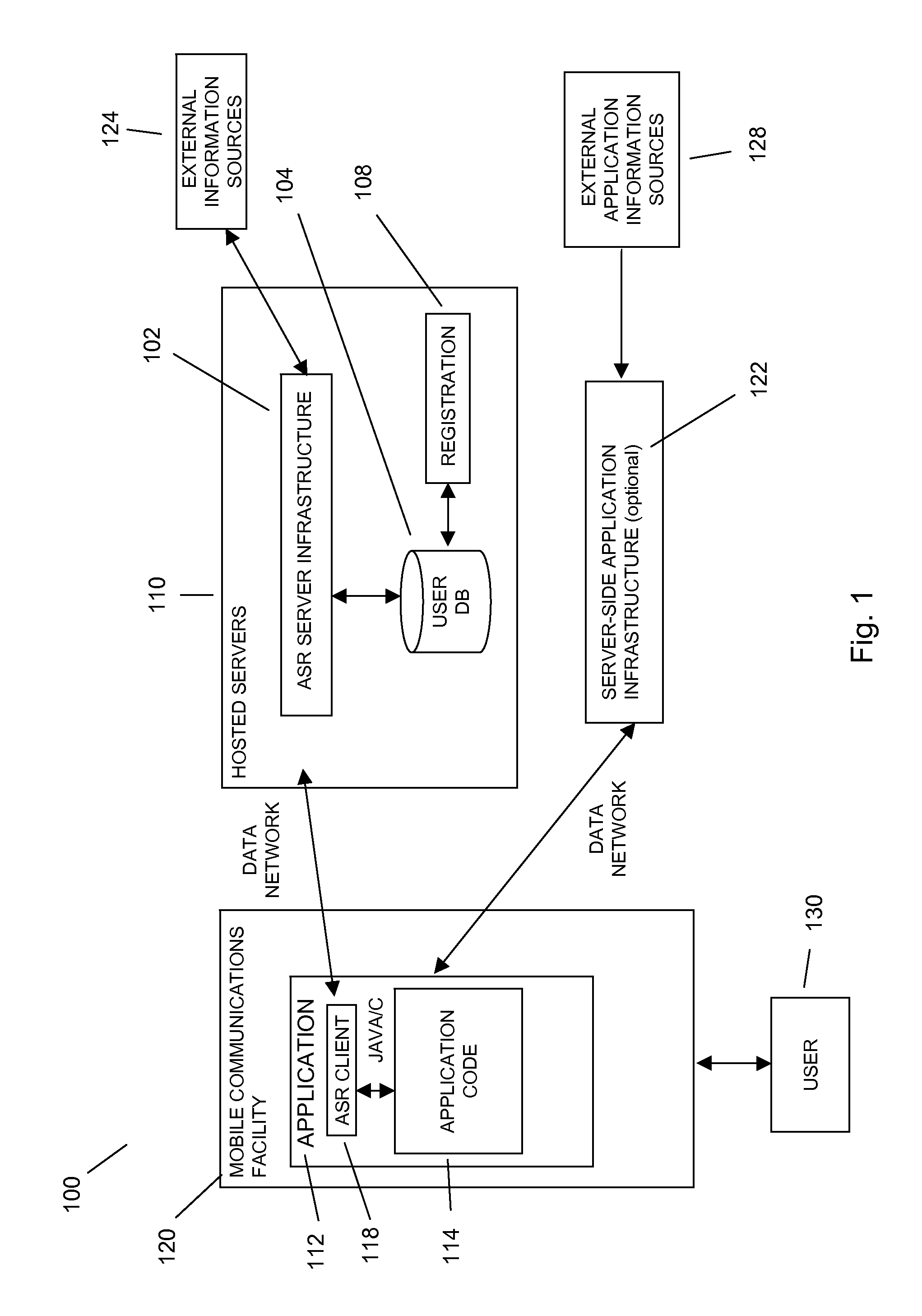
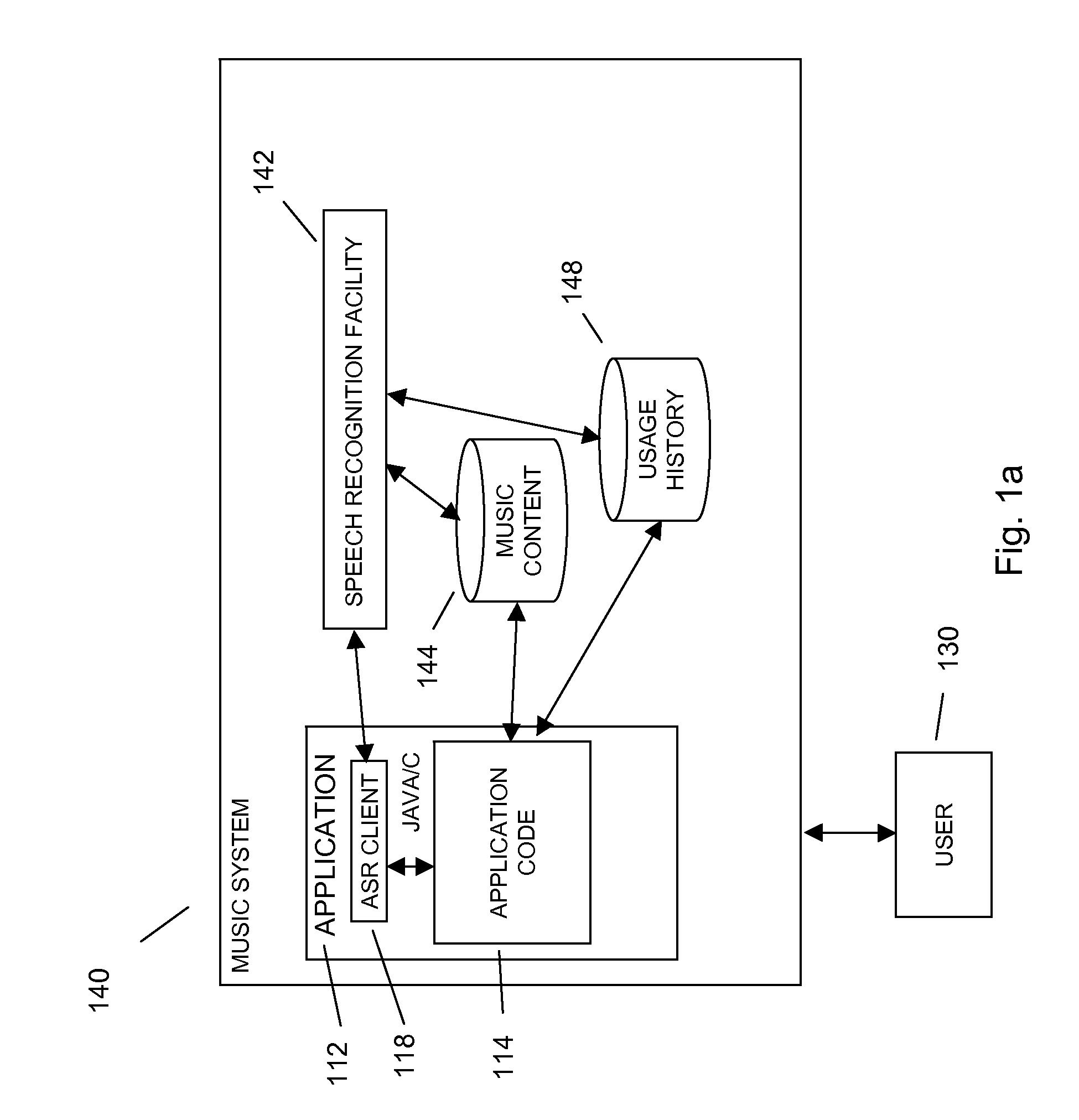
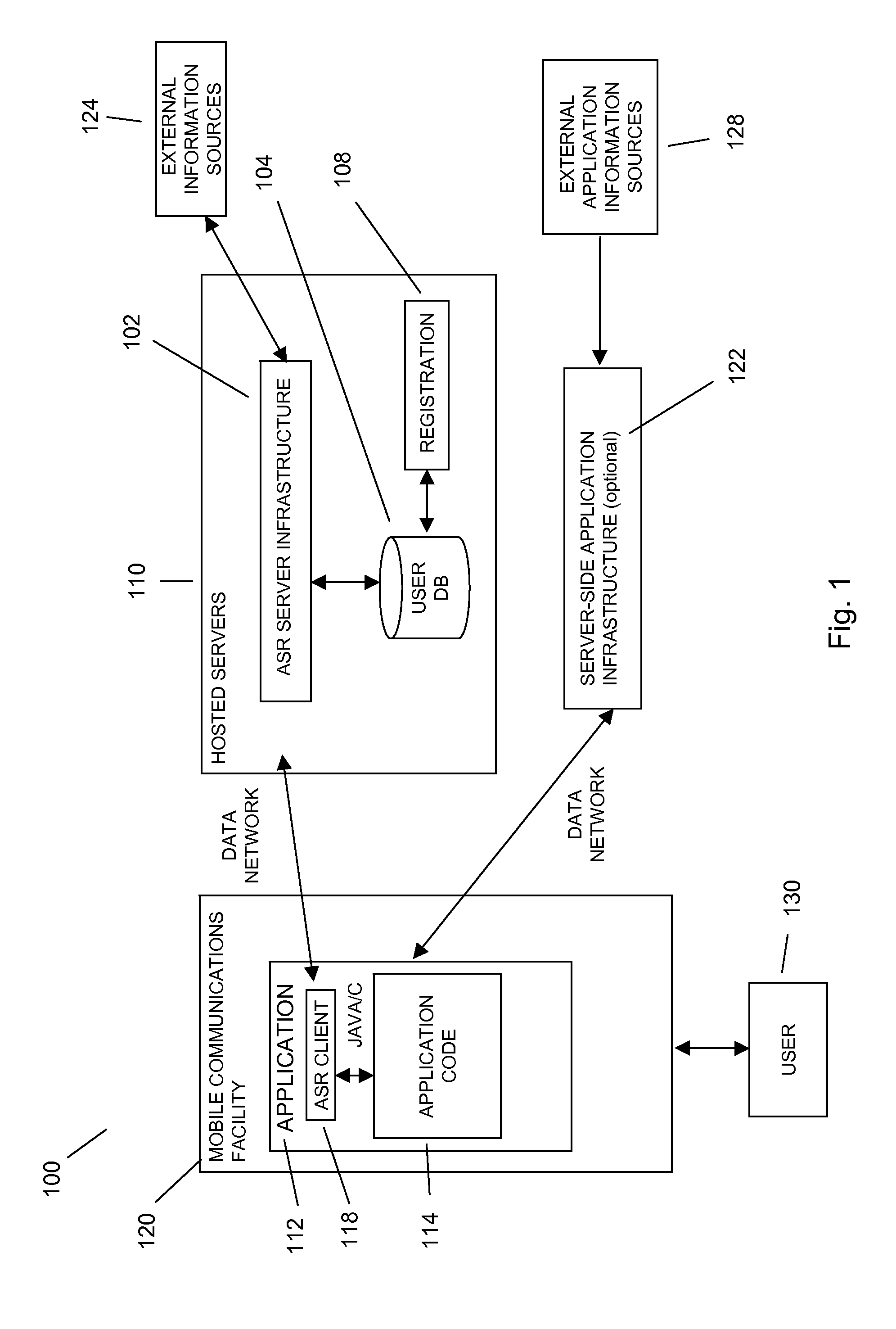
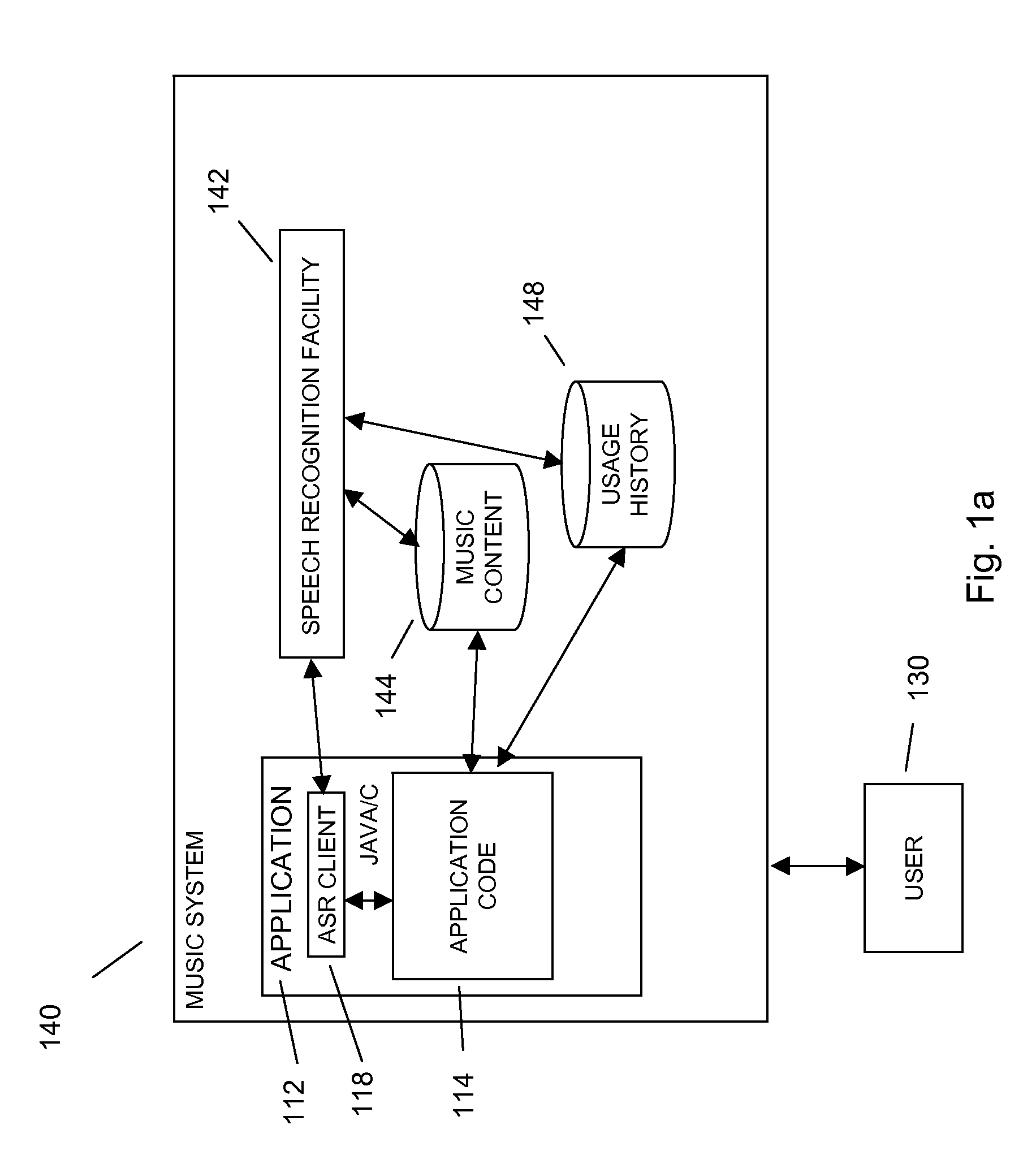
Command and control utilizing ancillary information in a mobile voice-to-speech application
In embodiments of the present invention improved capabilities are described for controlling a mobile communication facility utilizing ancillary information comprising accepting speech presented by a user using a resident capture facility on the mobile communication facility while the user engages an interface that enables a command mode for the mobile communications facility; processing the speech using a resident speech recognition facility to recognize command elements and content elements; transmitting at least a portion of the speech through a wireless communication facility to a remote speech recognition facility; transmitting information from the mobile communication facility to the remote speech recognition facility, wherein the information includes information about a command recognizable by the resident speech recognition facility and at least one of language, location, display type, model, identifier, network provider, and phone number associated with the mobile communication facility; generating speech-to-text results utilizing the remote speech recognition facility based at least in part on the speech and on the information related to the mobile communication facility; and transmitting the text results for use on the mobile communications facility.
Owner:VLINGO CORP
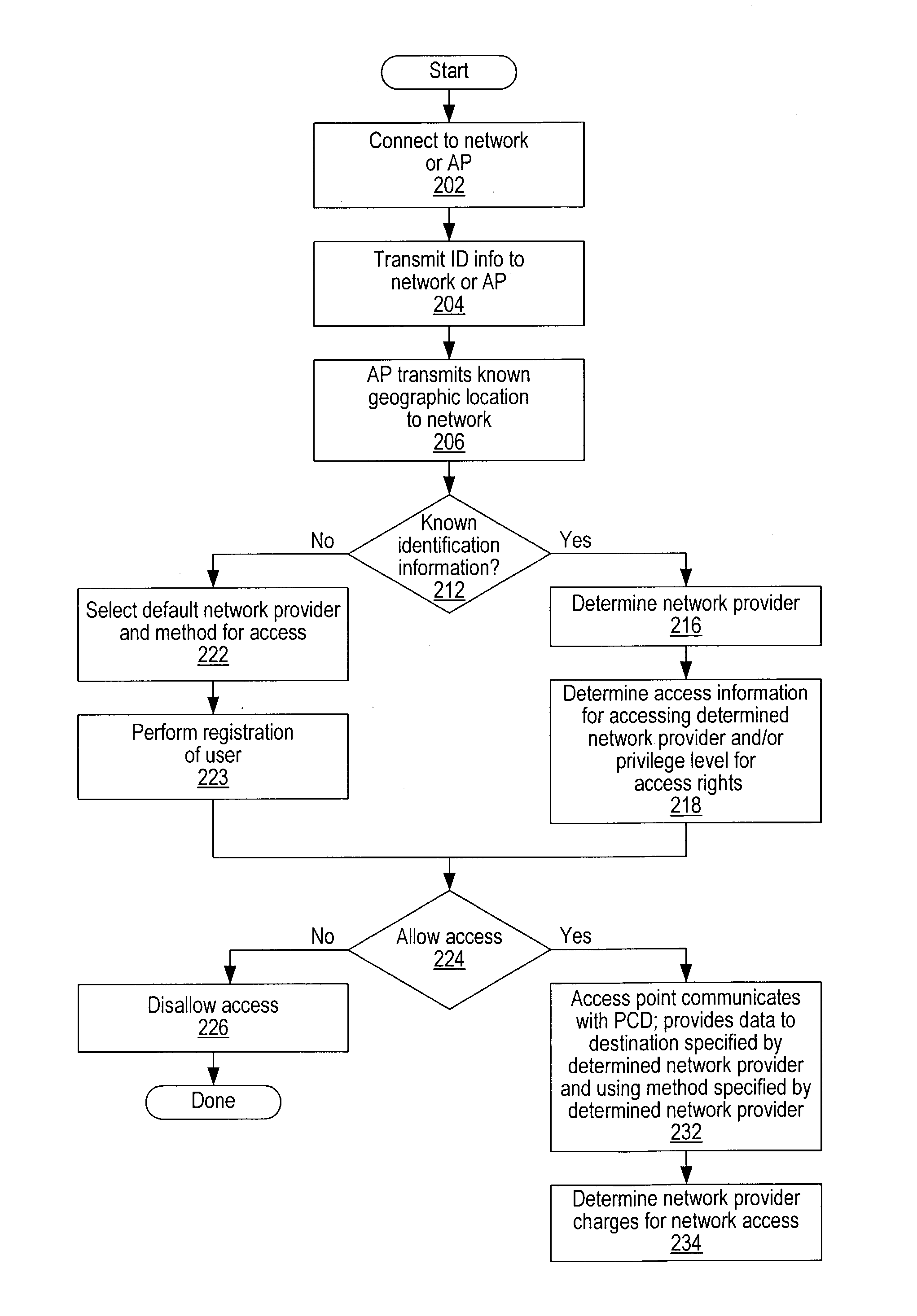
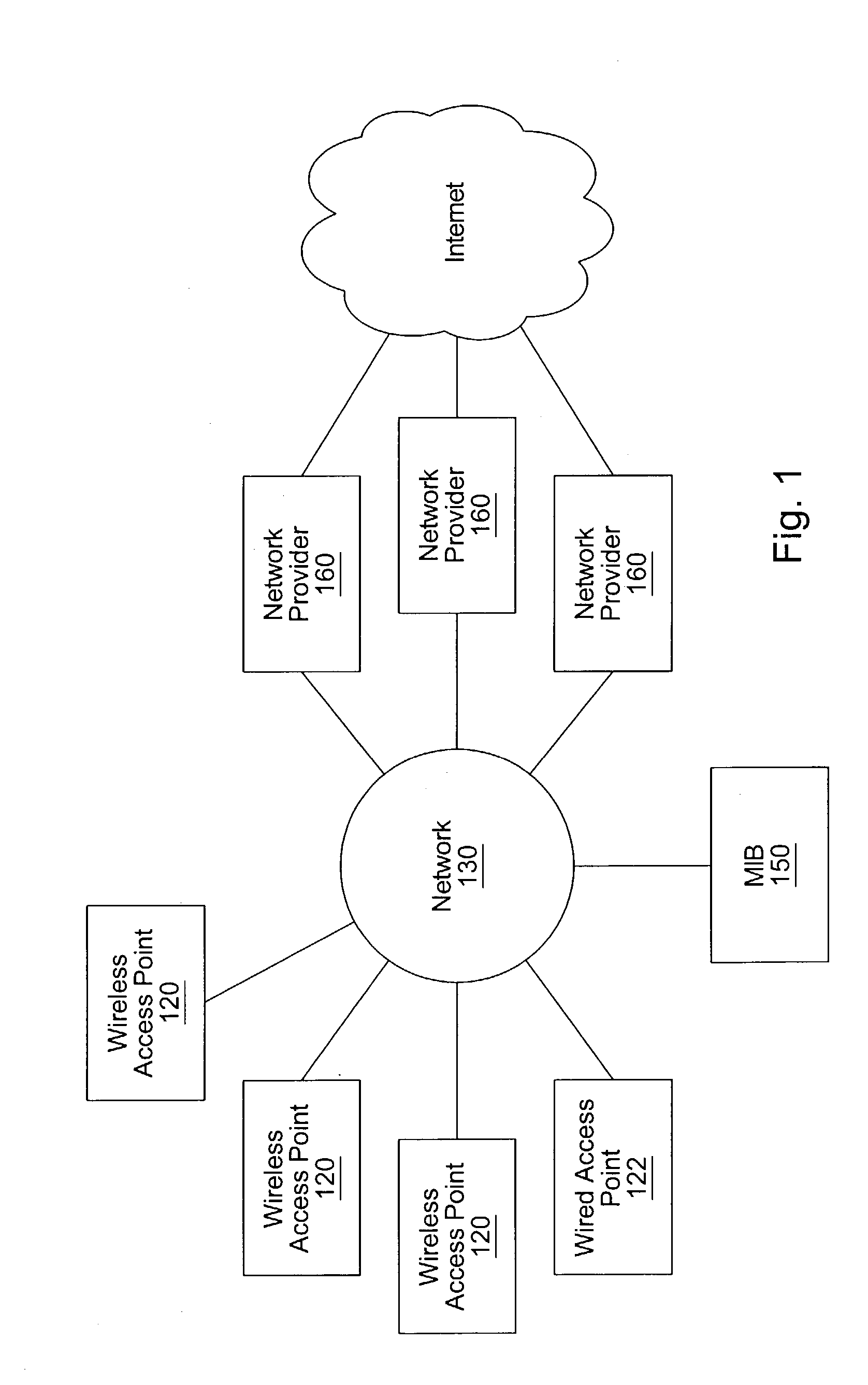
Distributed network communication system which enables multiple network providers to use a common distributed network infrastructure
InactiveUS6732176B1Metering/charging/biilling arrangementsMultiple digital computer combinationsCommunications systemNetworked system
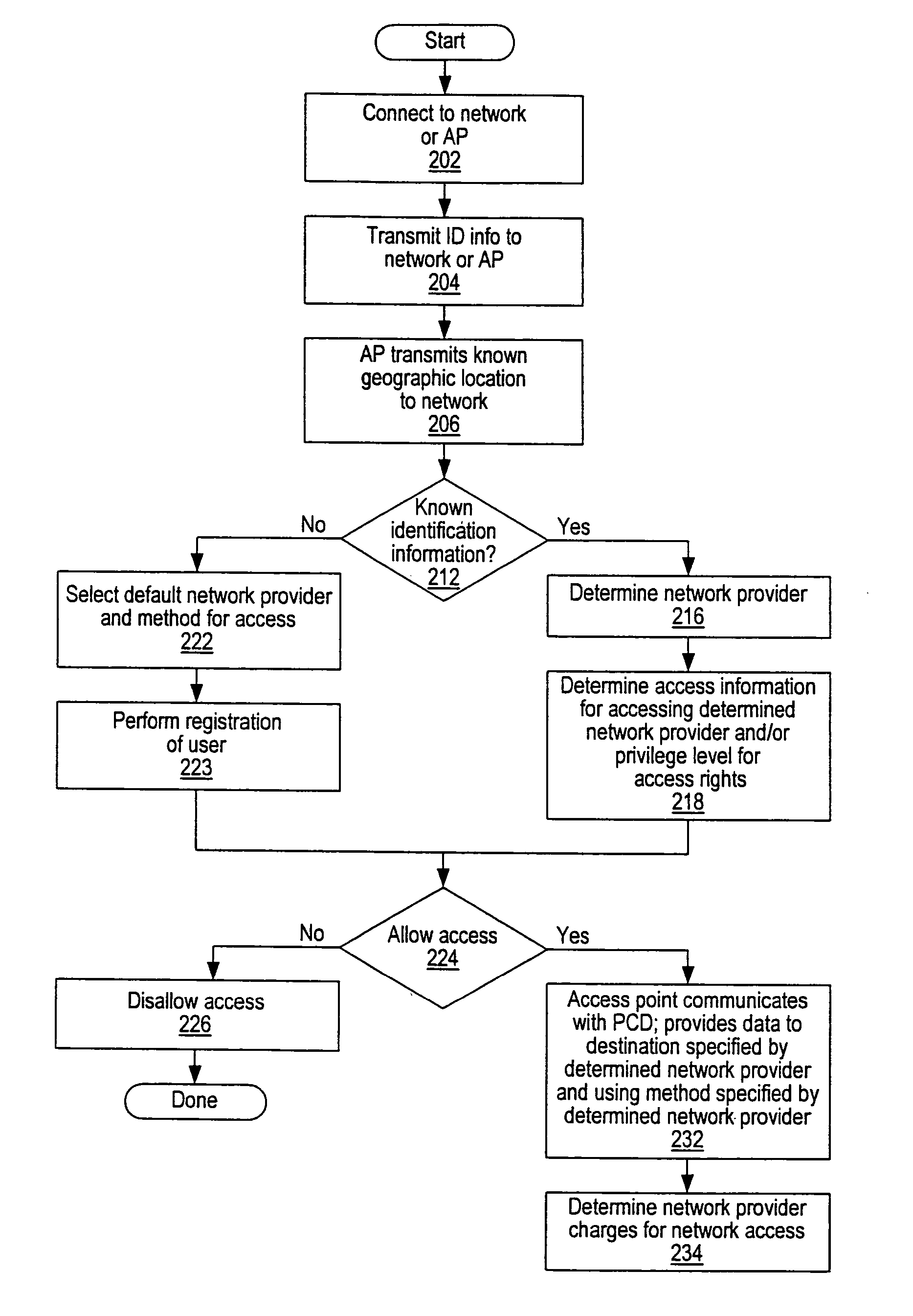
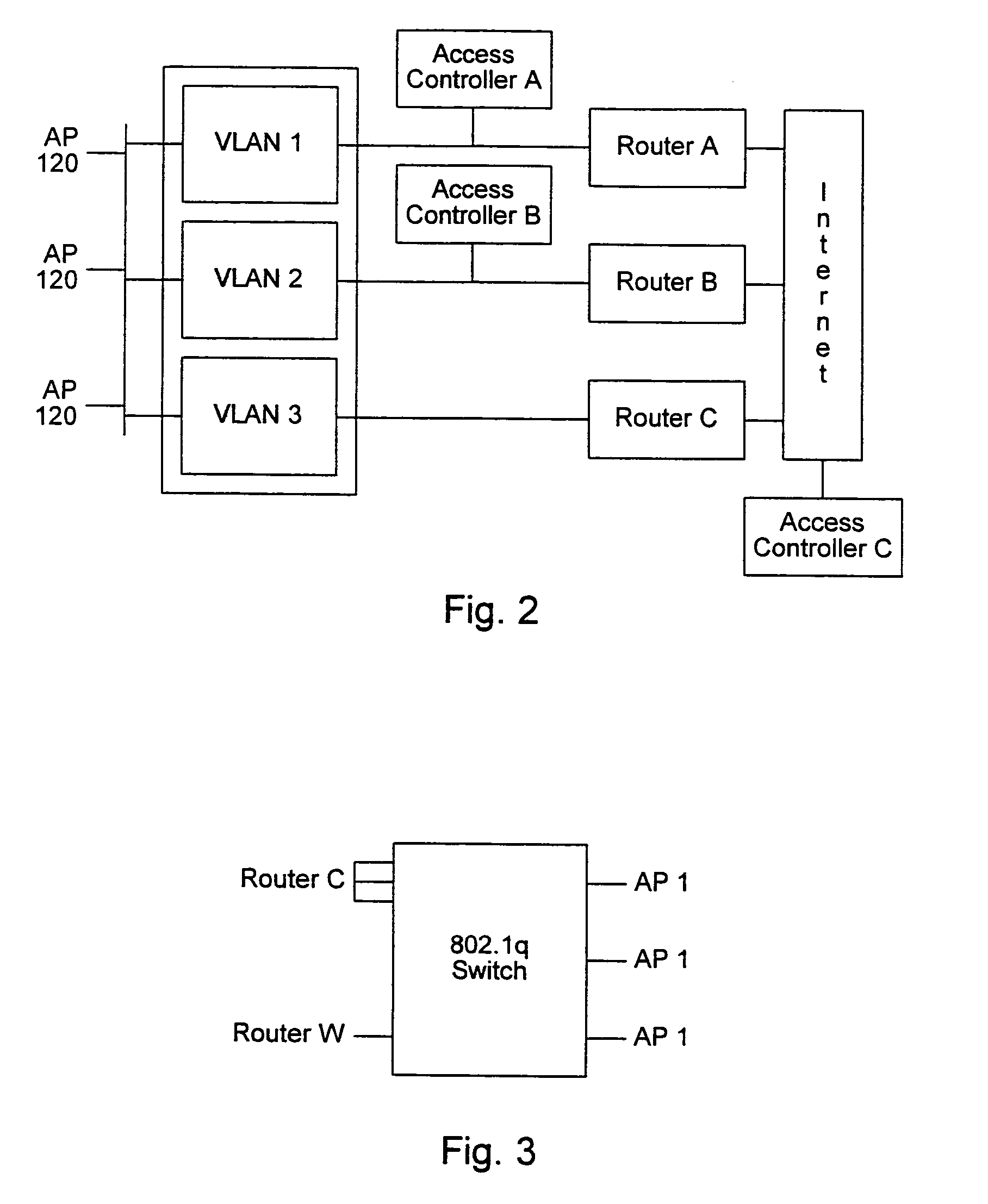
A system and method for providing access and / or roaming features on a network system. The network system includes a plurality of wireless and / or wired access points coupled to a network. A portable computing device (PCD) of a user may store identification information which uniquely indicates a network provider of a plurality of possible network providers. The identification information may also or instead indicate an access or privilege level of the user. When the access point receives the identification information from a PCD of a user, the access point may determine the appropriate network provider for the portable computing device using the identification information. Network access may then be provided to the portable computing device through the determined network provider.
Owner:CISCO TECH INC
System and method for user access to a distributed network communication system using persistent identification of subscribers
InactiveUS20030233332A1Market predictionsMetering/charging/biilling arrangementsDevice registerCommunications system
A system and method for providing network access are disclosed. After connecting to a network at an access point, a user of a computing device registers for network access with a network provider. In response to the registration, the network provider sends a completion page to the computing device. The completion page includes a link to an embedded file such as a small, transparent GIF image. When the computing device retrieves the embedded file, the embedded file is associated with a header than includes an instruction to generate a network system identifier (e.g., a cookie). The network system identifier may be stored by the computing device and later used to identify the computing device as a registrant for network access with the network provider. The embedded file may also be sent at other times, such as after authentication of the user for network access.
Owner:WAYPORT
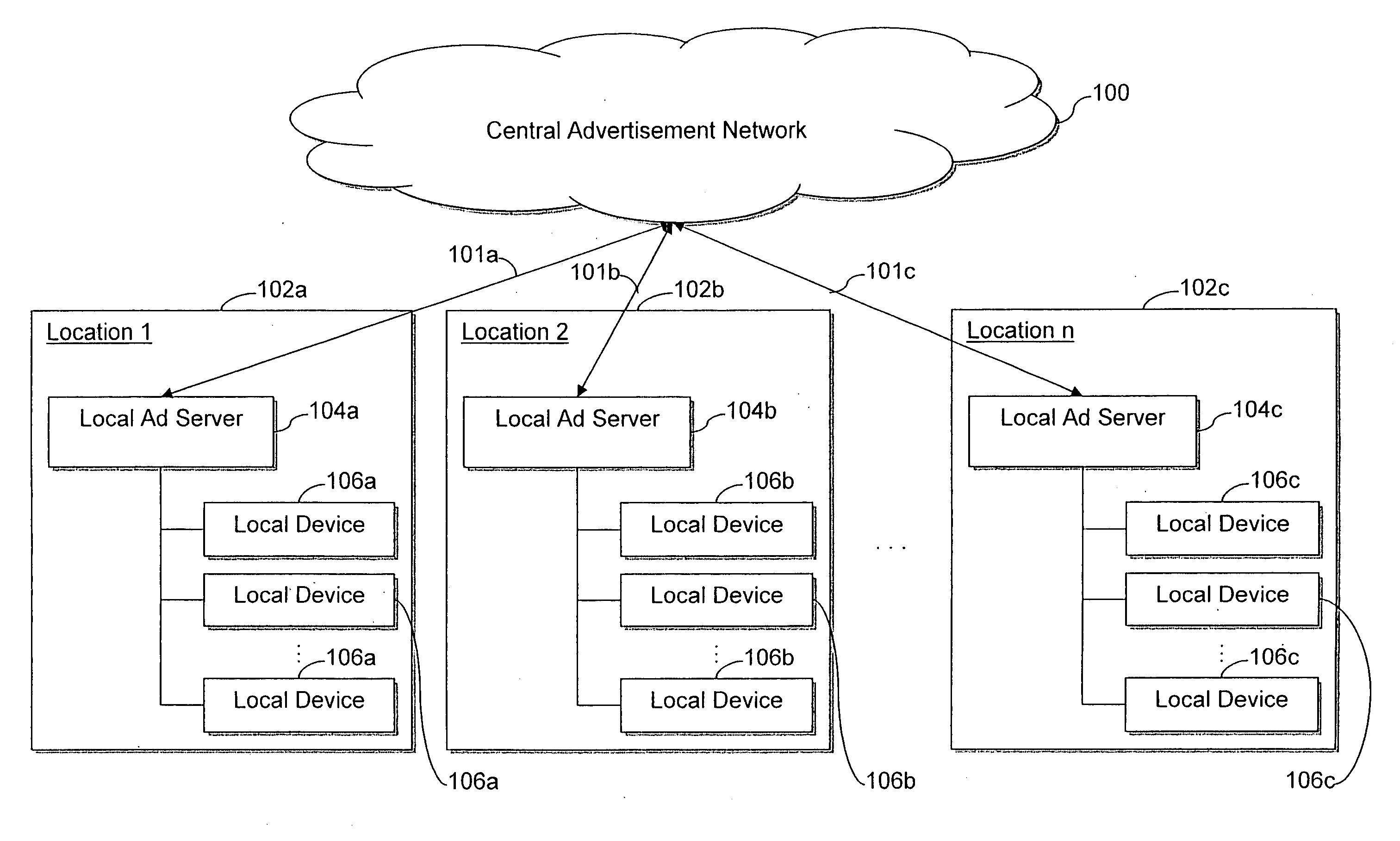
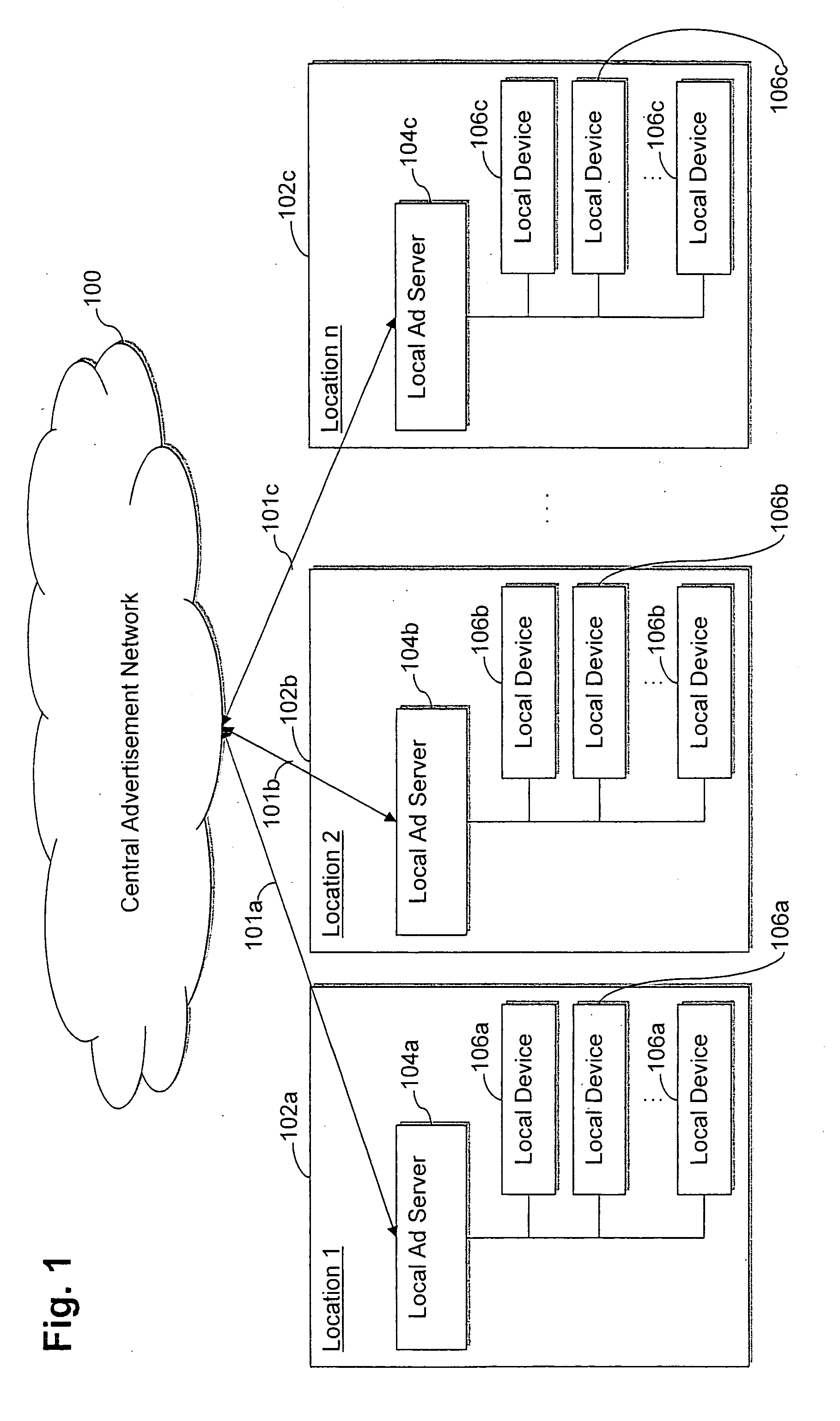
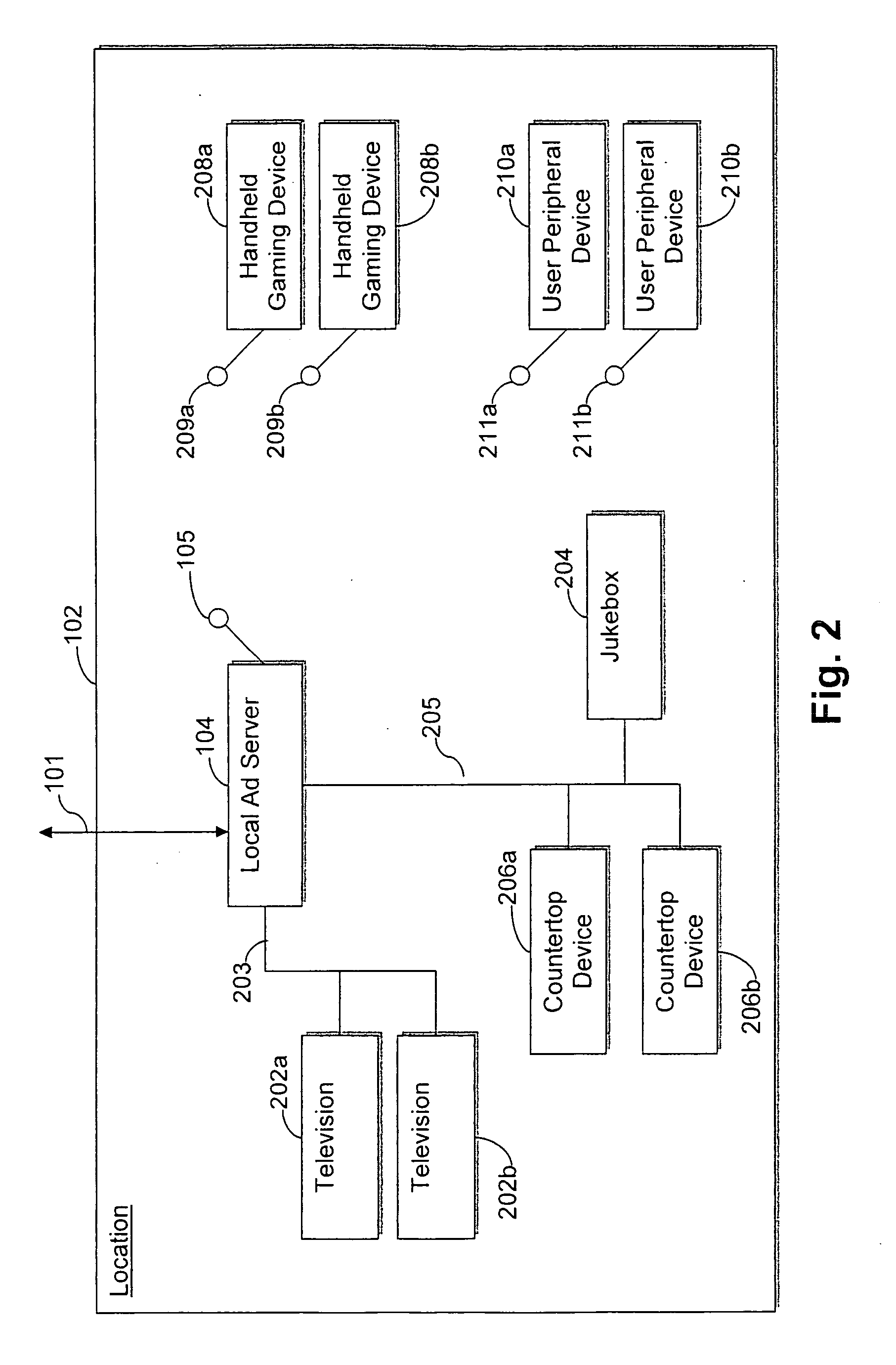
System and/or methods for distributing advertisements from a central advertisement network to a peripheral device via a local advertisement server
ActiveUS20090265734A1Selective content distributionElectrical cable transmission adaptationDevice typeWorld Wide Web
Certain exemplary embodiments disclosed herein relate to systems and / or methods for distributing advertisements from a central advertisement network to one or more peripheral devices at a location via a local advertisement server. In certain exemplary embodiments, the local advertisement server within a location receives advertisements from the central advertisement network and rebroadcasts them to peripheral devices within that location. Advertising information may be tracked and reported, e.g., for accounting, revenue-sharing, and / or other purposes in certain exemplary embodiments. Thus, in certain exemplary embodiments, the distribution of advertisements is provided to peripherals via a non-web- and non-PC-dependent network. Moreover, in certain exemplary embodiments, reporting and advertising related communications are substantially bi-directional regardless of device type. Certain exemplary embodiments provide revenue sharing among some or all of the central advertising network provider, the proprietors of locations, operators tasked with maintaining the local ad server and / or the peripheral devices, etc.
Owner:TOUCHTUNES MUSIC CO LLC
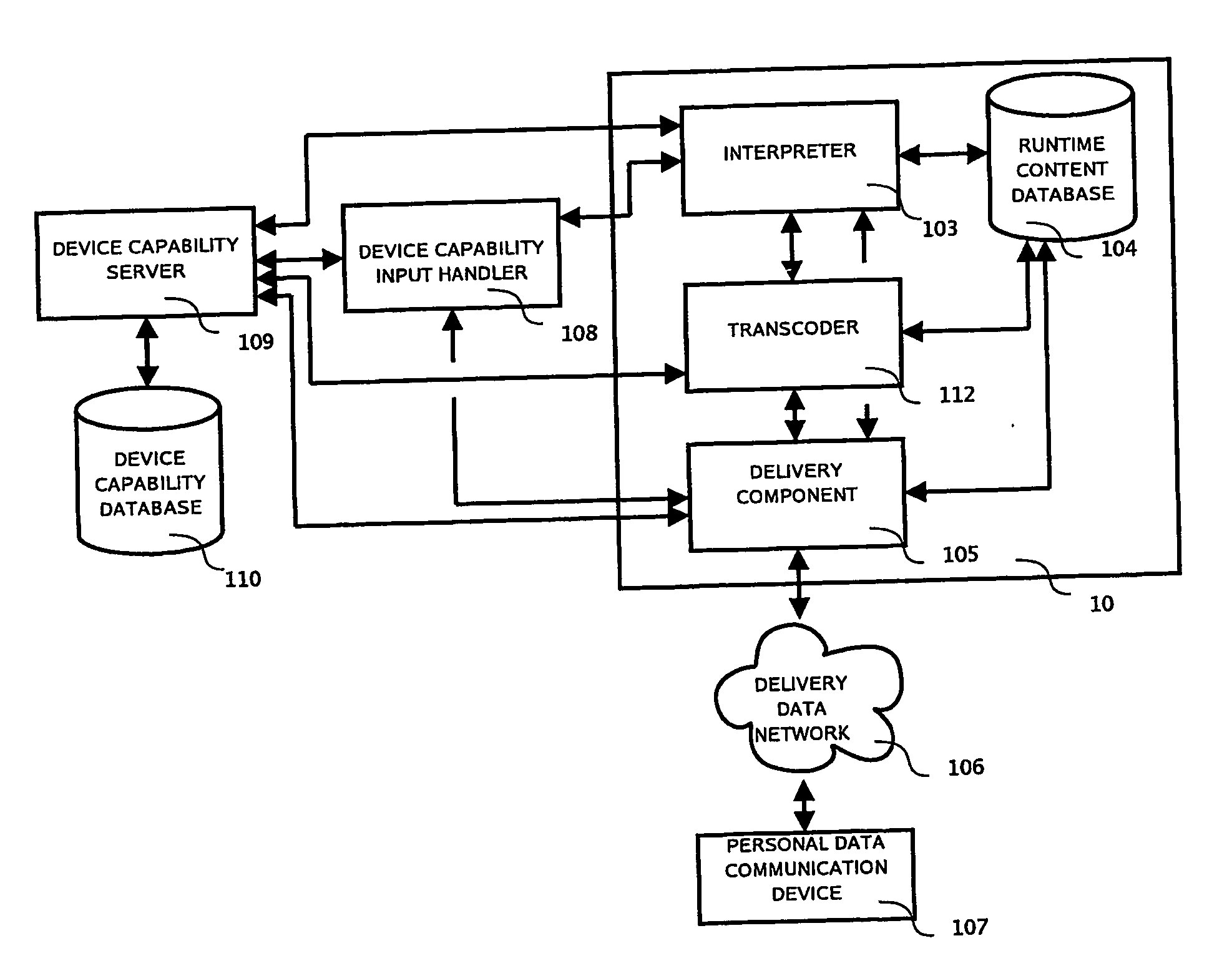
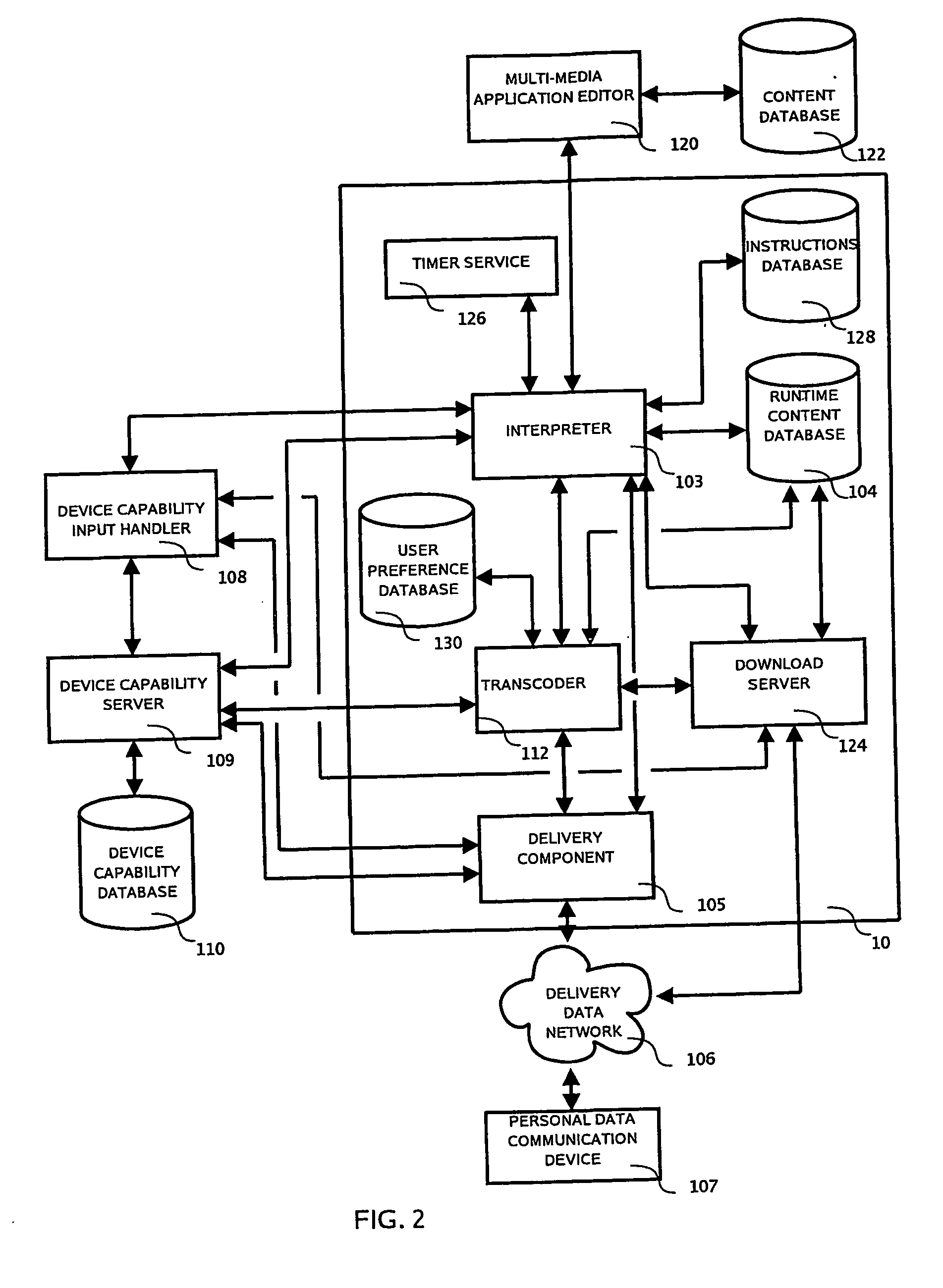
System and method for determining and delivering appropriate multimedia content to data communication devices
InactiveUS20100041380A1Improve developmentInformation formatContent conversionApplication serverAnimation
Owner:MOBILE MESSENGER GLOBAL INC
Authorization and authentication of user access to a distributed network communication system with roaming features
InactiveUS20030233580A1Market predictionsMetering/charging/biilling arrangementsNetwork communicationNetwork management
A system and method for providing roaming access on a network are disclosed. The network includes a plurality of wireless and / or wired access points. A user may access the network by using client software on a client computer (e.g., a portable computing device) to initiate an access procedure. In response, a network management device operated by a network provider may return an activation response message to the client. The client may send the user's username and password to the network provider. The network provider may rely on a roaming partner, another network provider with whom the user subscribes for internet access, for authentication of the user. Industry-standard methods such as RADIUS, CHAP, or EAP may be used for authentication. The providers may exchange pricing and service information and account information for the authentication session. A customer may select a pricing and service option from a list of available options.
Owner:WAYPORT
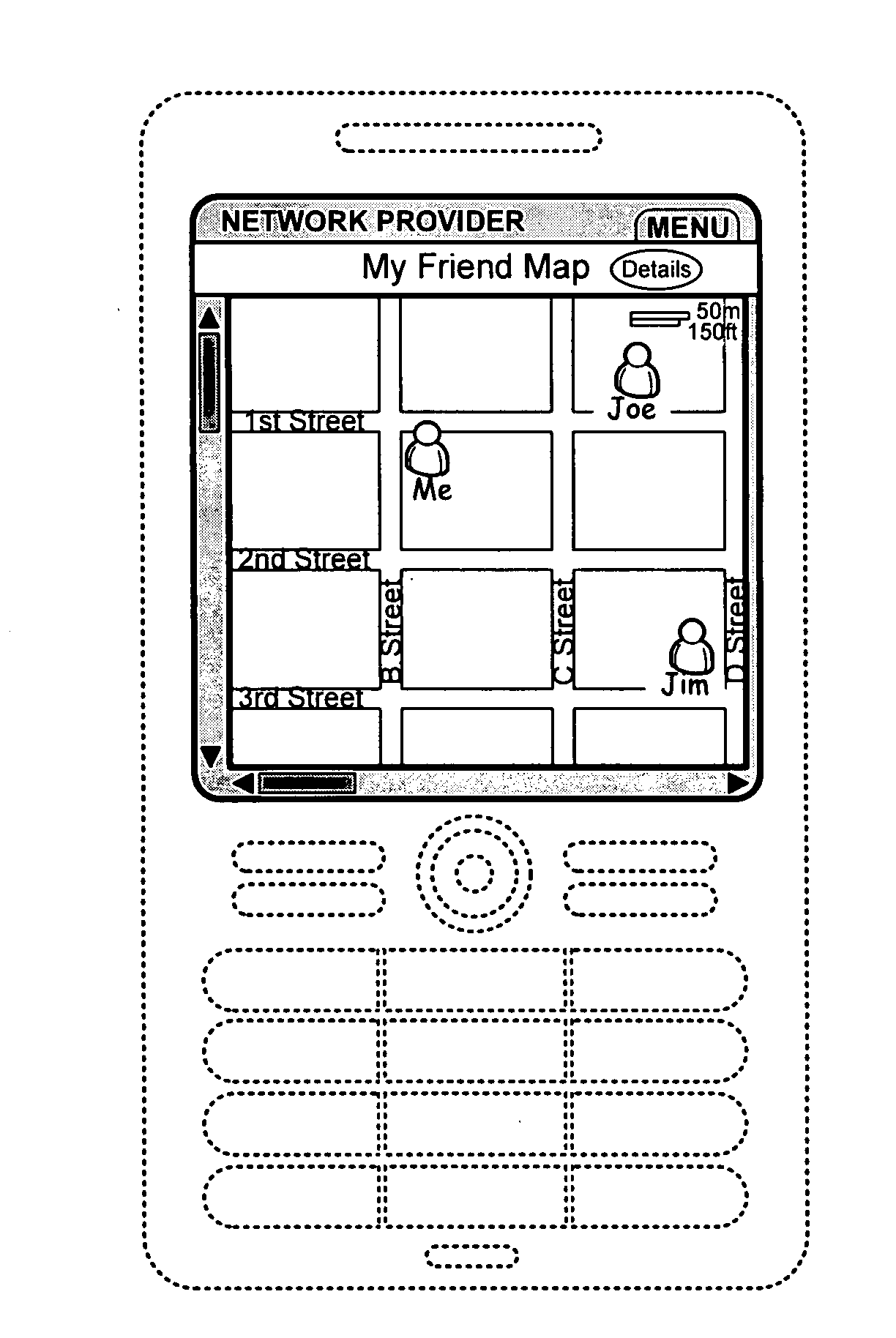
Location-aware instant messaging
InactiveUS20090319616A1Services signallingMultiple digital computer combinationsMobile deviceComputer science
A method includes receiving, at a carrier network provider, a request from a requestor's mobile device to locate an instant messaging (IM) friend from the requestor's IM friends list; authenticating the request for use of location-based services on the carrier network; receiving geographic location coordinates from the requestor's mobile device; adding random error to the geographic location coordinates; sending the request to locate an IM friend and the geographic location coordinates with random error to an IM portal; receiving a list of the requestor's IM friends within a particular region near the geographic location coordinates with random error; and sending to the requestor's mobile device the list of IM friends within the particular region near the geographic location coordinates with random error.
Owner:VERIZON PATENT & LICENSING INC
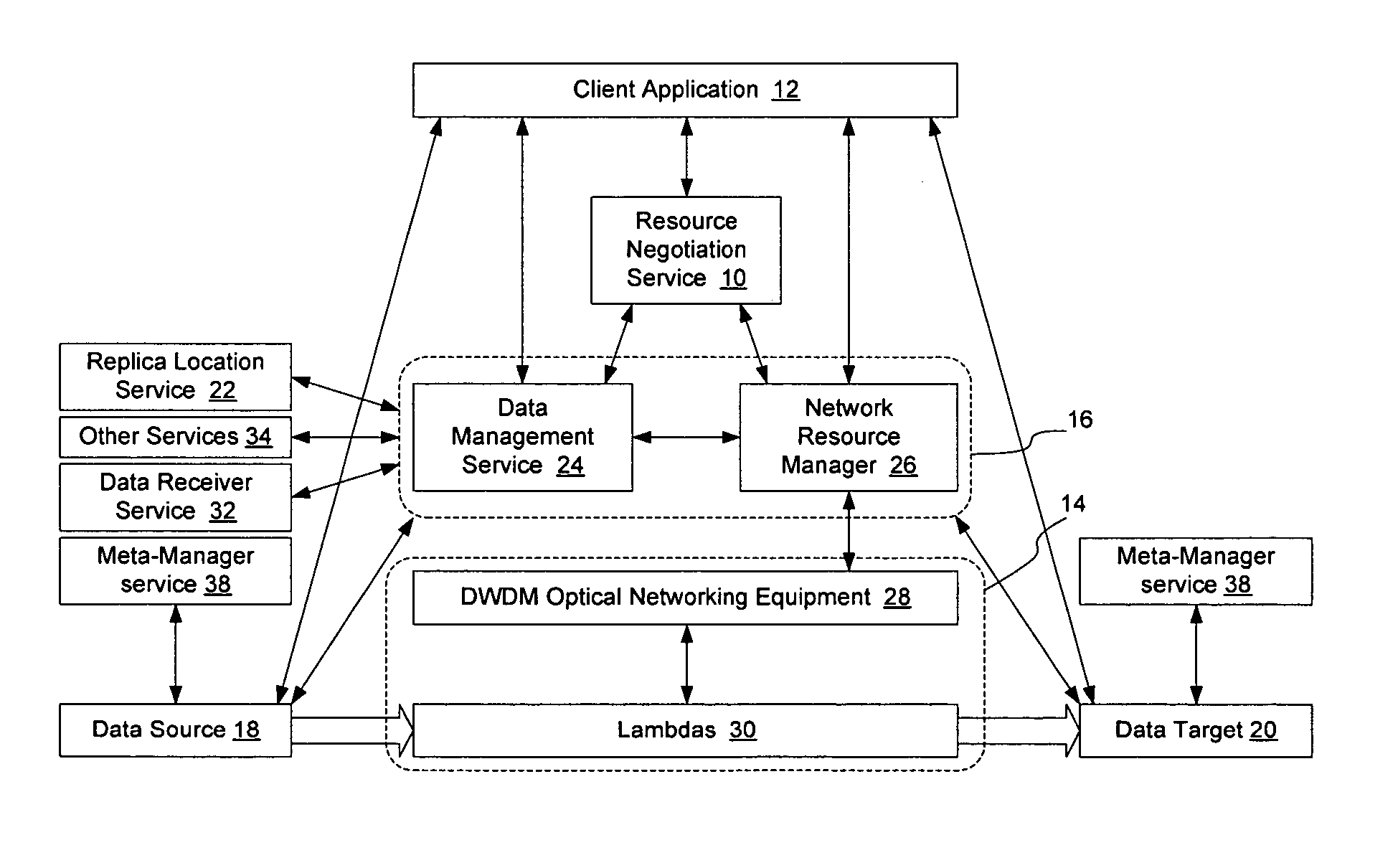
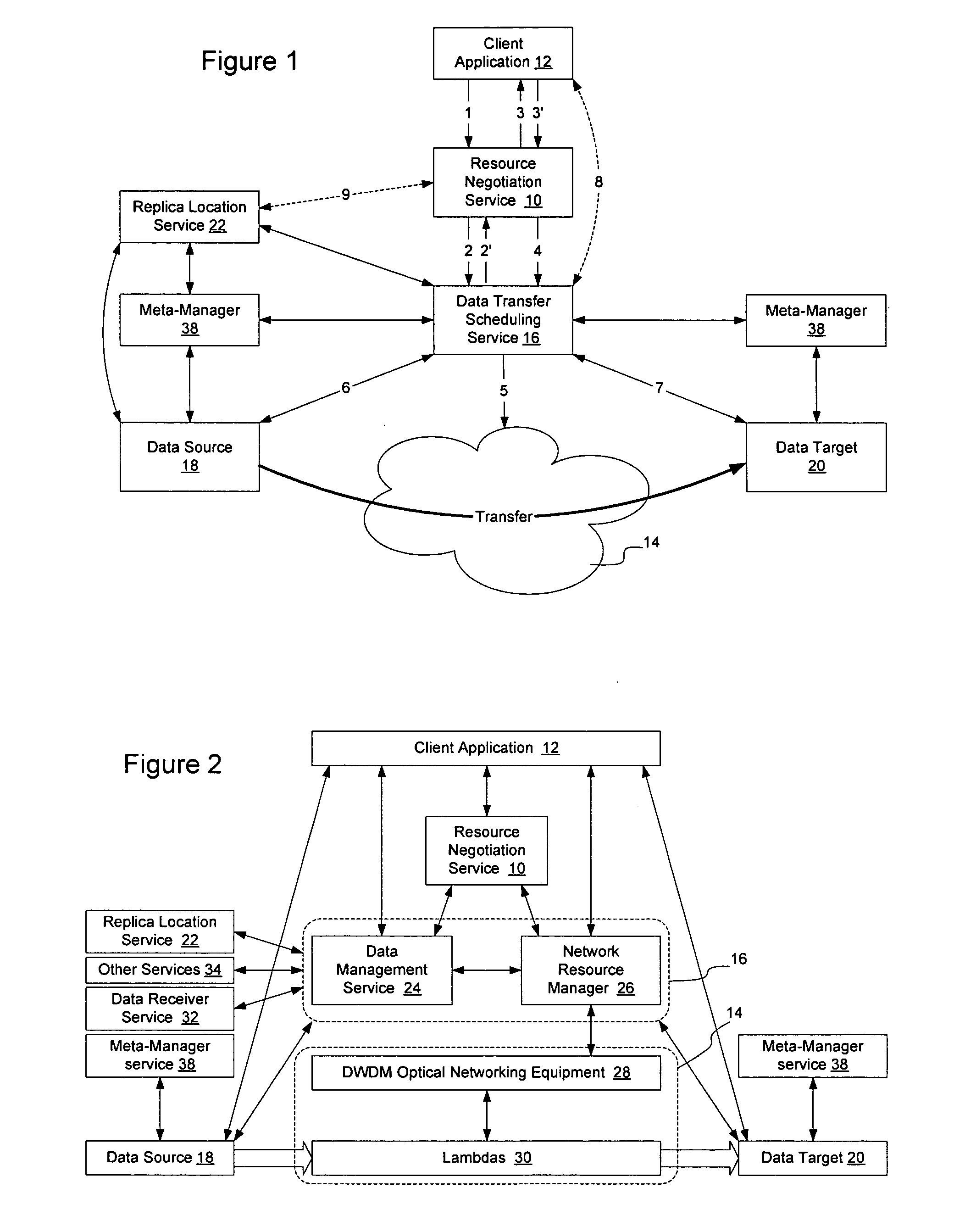
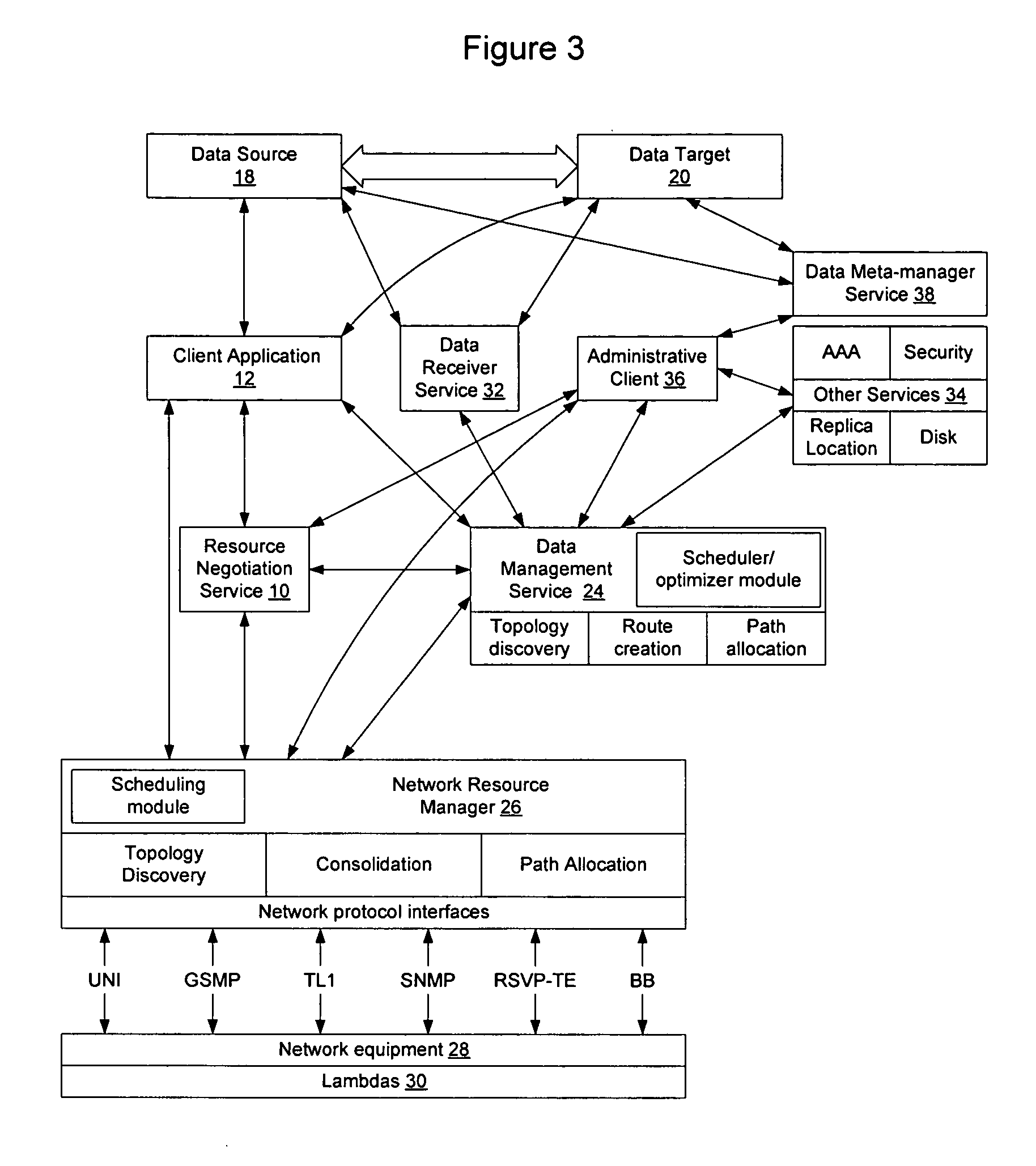
Method and apparatus for automated negotiation for resources on a switched underlay network
A resource negotiation service is provided to enable business logic decisions to be made when obtaining switched underlay network resources, to interface business logic with network conditions and schedules. The resource negotiation service may be implemented as a web service or other network service to enable business logic to be used in the selection of available network resources. This may allow policy to be used on both the subscriber side and the network provider side to optimize network resource allocations for a proposed transfer. The policy may include subscriber policy, network policy, and other factors such as current and expected network conditions. The resource negotiation service may include an interface to enable existing subscribers and new customers to obtain switched underlay resources.
Owner:NORTEL NETWORKS LTD
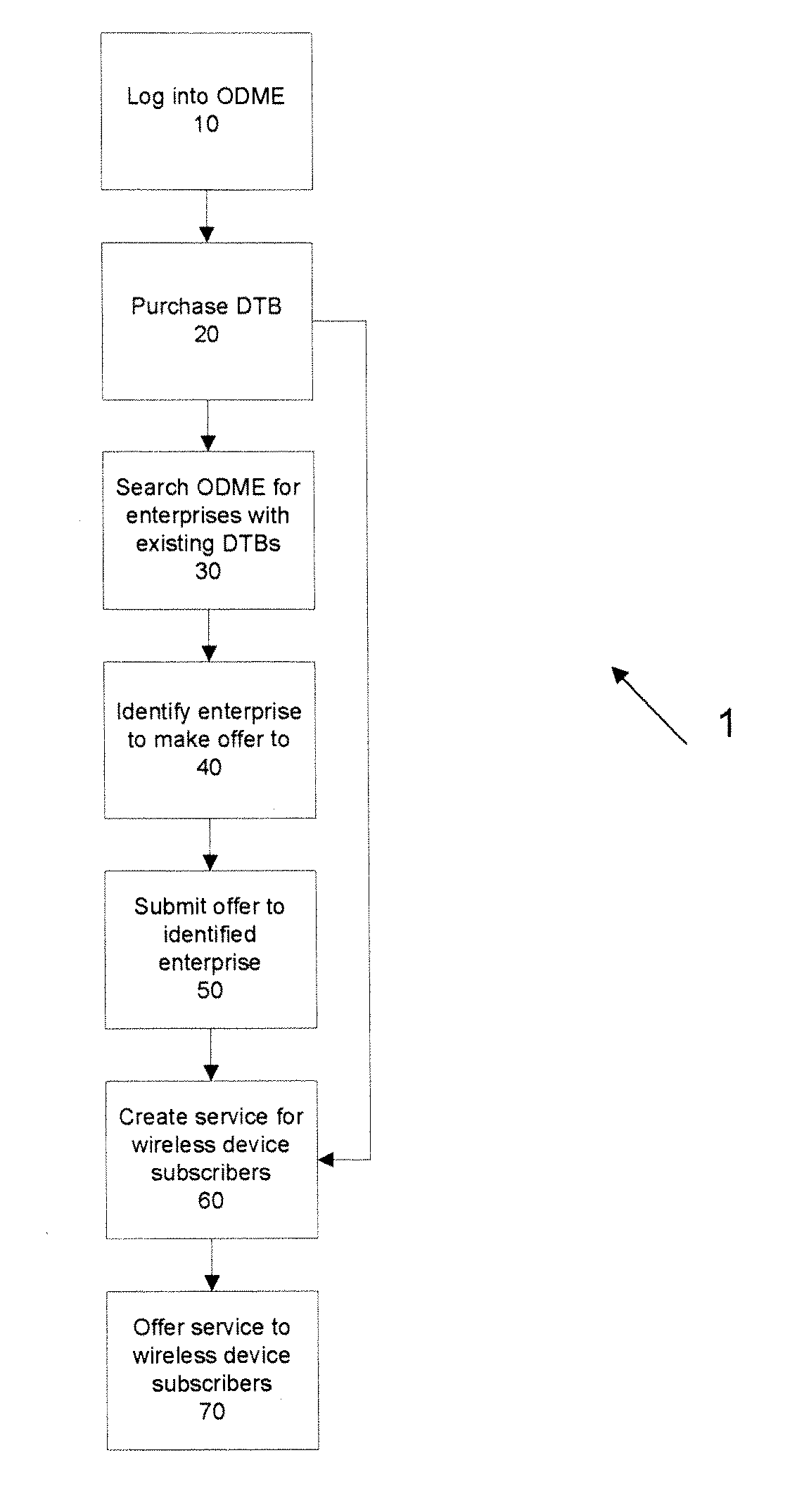
Alternative data plans
A method is presented that enables the creation of an alternative data plan by third party enterprises for mobile network end users. The method includes purchasing data transport bundles from one or more network service providers through an exchange, and either alone or with other enterprises, developing the alternative data plan for offer to end-users to consume data transport from the data transport bundle or bundles. The alternative data plan may be offered to the end user for free or the end user may be charged for use of the ADP based on the number of transactions, file type. The ADP may be billed to the user by the network provider or the ADP may be pre-purchased from the creator of the ADP.
Owner:CELLCO PARTNERSHIP INC
Numeric/voice name Internet access architecture and methodology
InactiveUS20050125723A1Easily access InternetMultiple digital computer combinationsSubstation equipmentDomain nameDisplay device
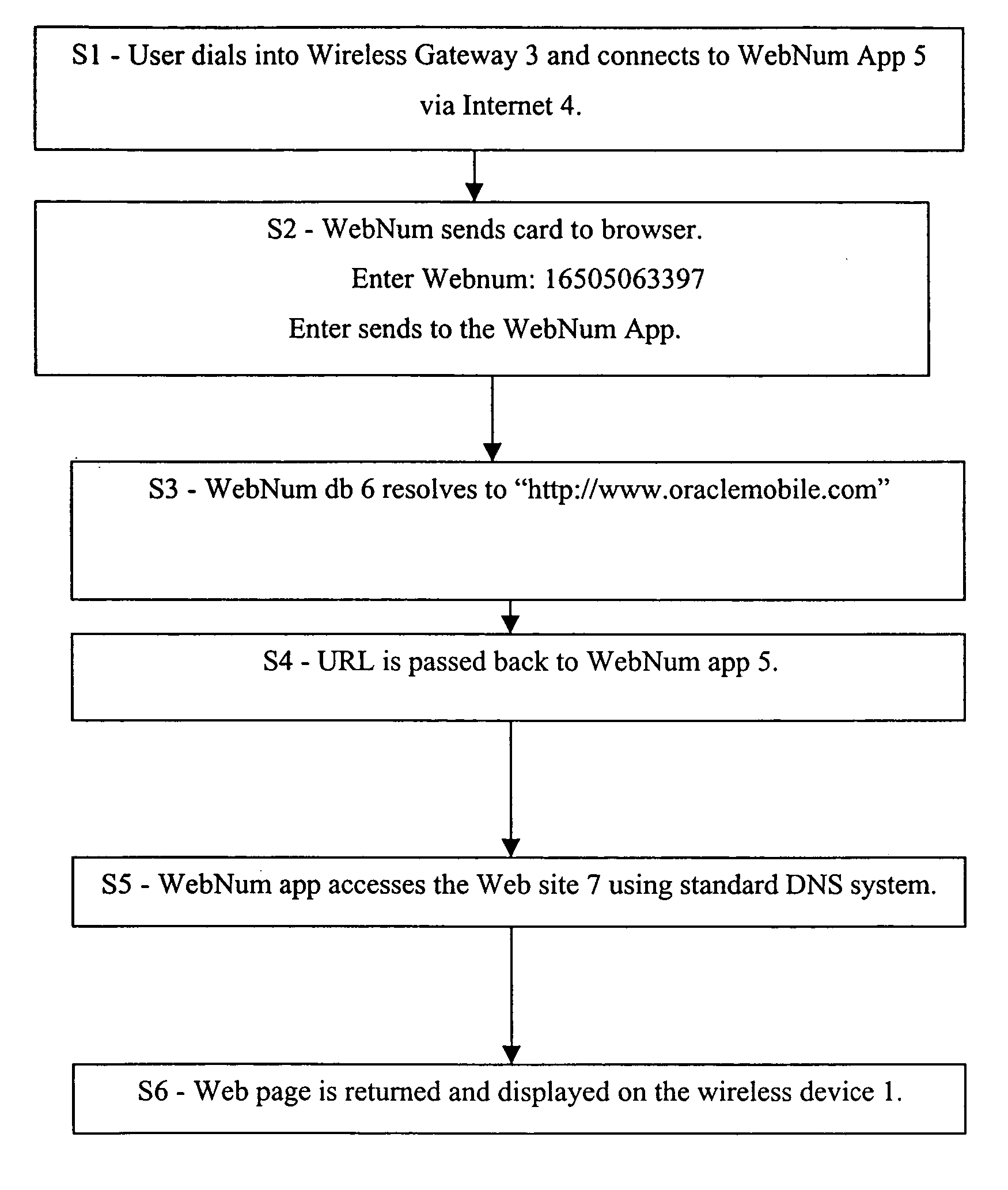
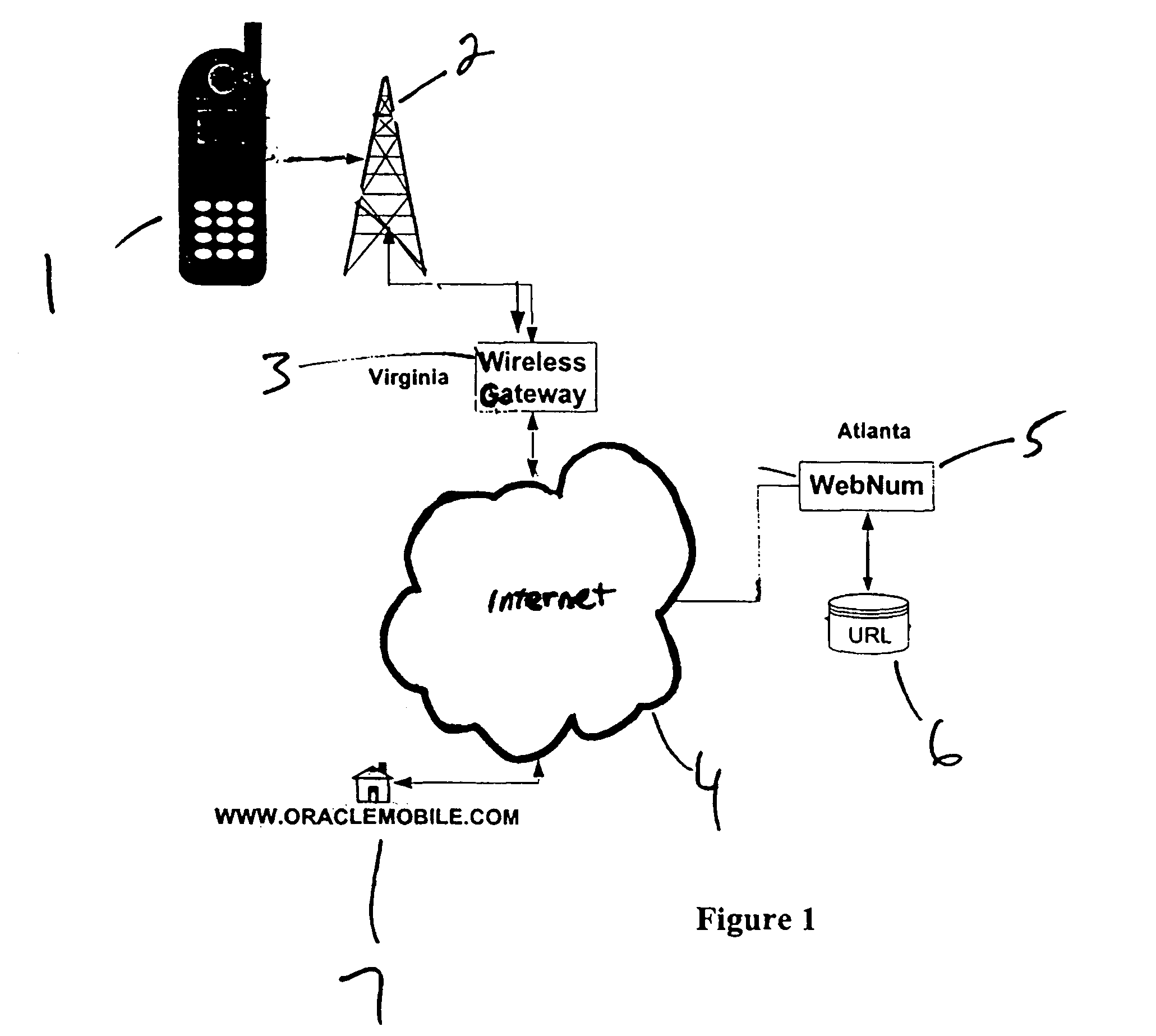
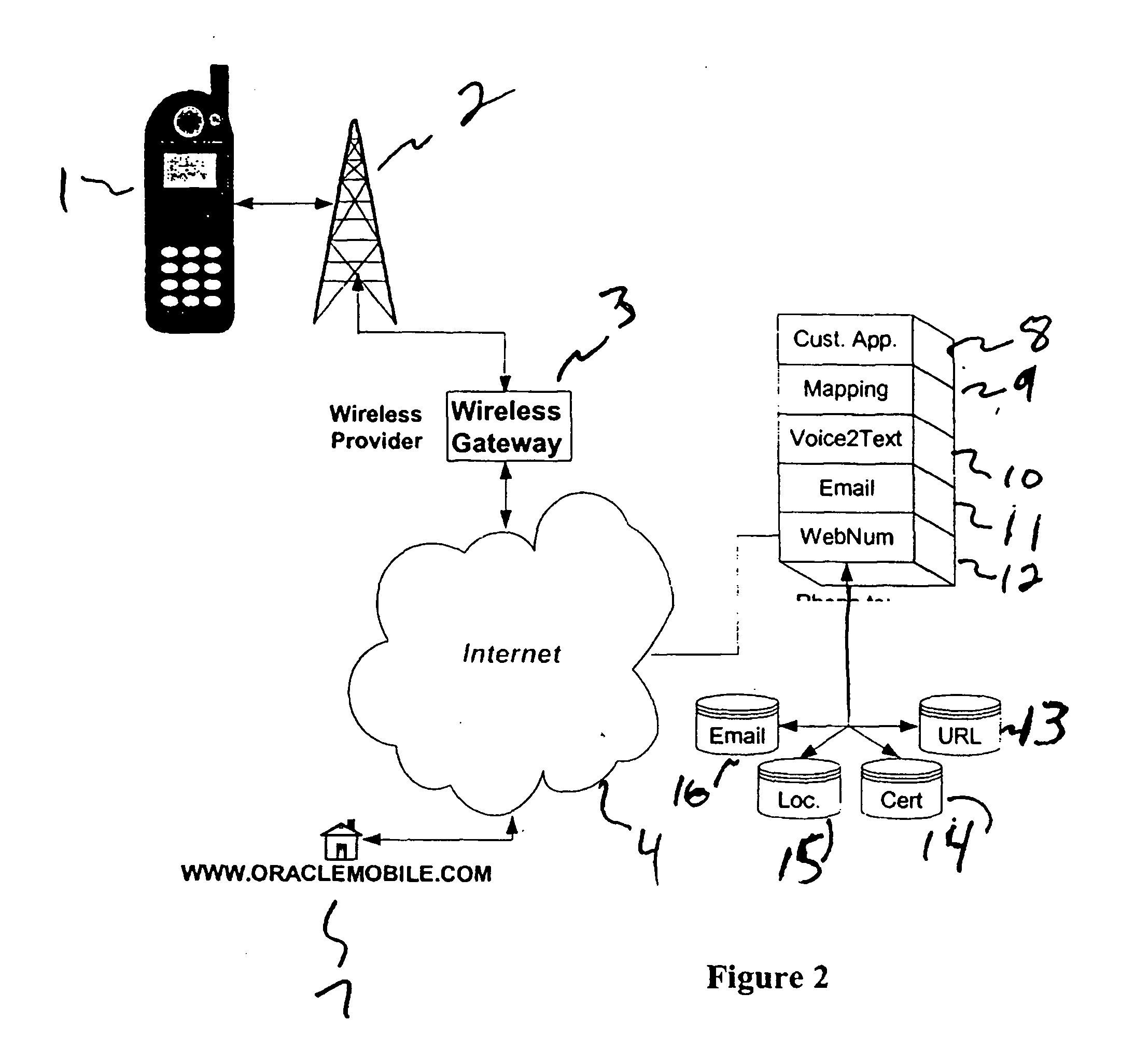
A system that provides users of both fixed and wireless Internet devices, a method of entering numbers instead of the text characters of Internet Uniform Resource Locators (URLs) and other Internet identifiers to access Internet resources and functions, such as Web sites, e-mail services, individual documents or files, location services, etc. When the user enters a WebNum, the digits of the WebNum are sent to a database on a system that is accessible over the Internet. The database maps the WebNum back to a Uniform Resource Locator (URL), which contains a hostname in the Internet domain name structure. This would subsequently be resolved through the Internet Domain Name System (DNS) to an IP address to identify the IP address of the Web site. The cell phone provider or WID network provider would then retrieve the home page of the Web site over the Internet, to return content to the cell phone or WID display.
Owner:DEPUY SPINE INC (US) +1
Bulk tuning of frequency-modulated video signals
InactiveUS20050289623A1Analogue secracy/subscription systemsTwo-way working systemsFiberMarket place
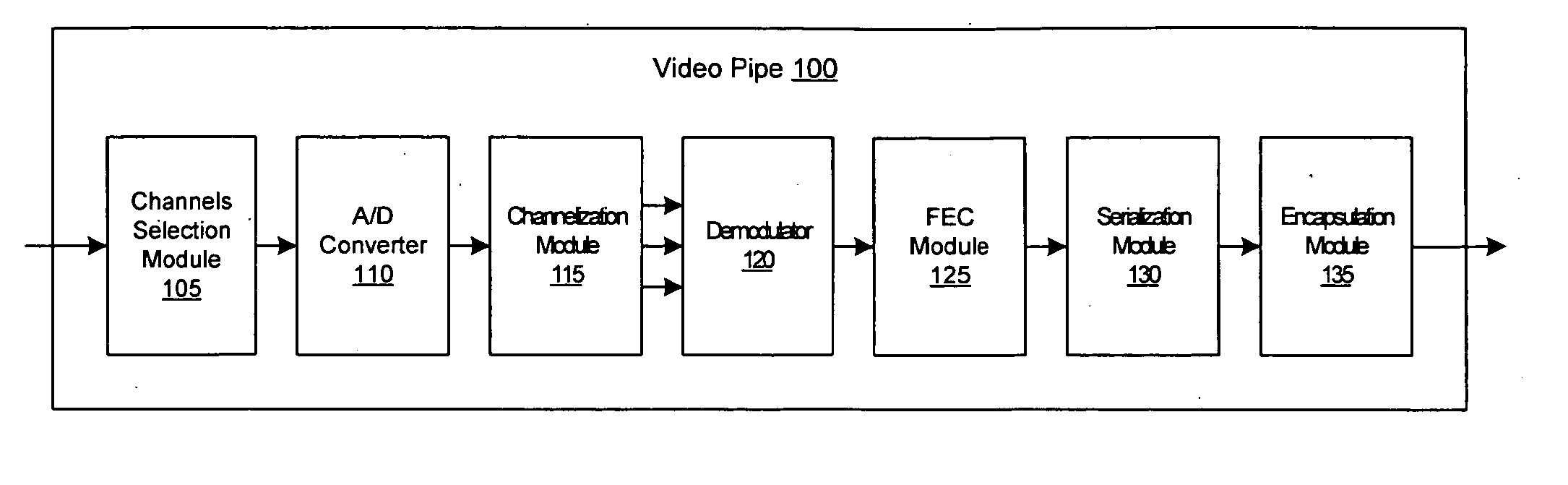
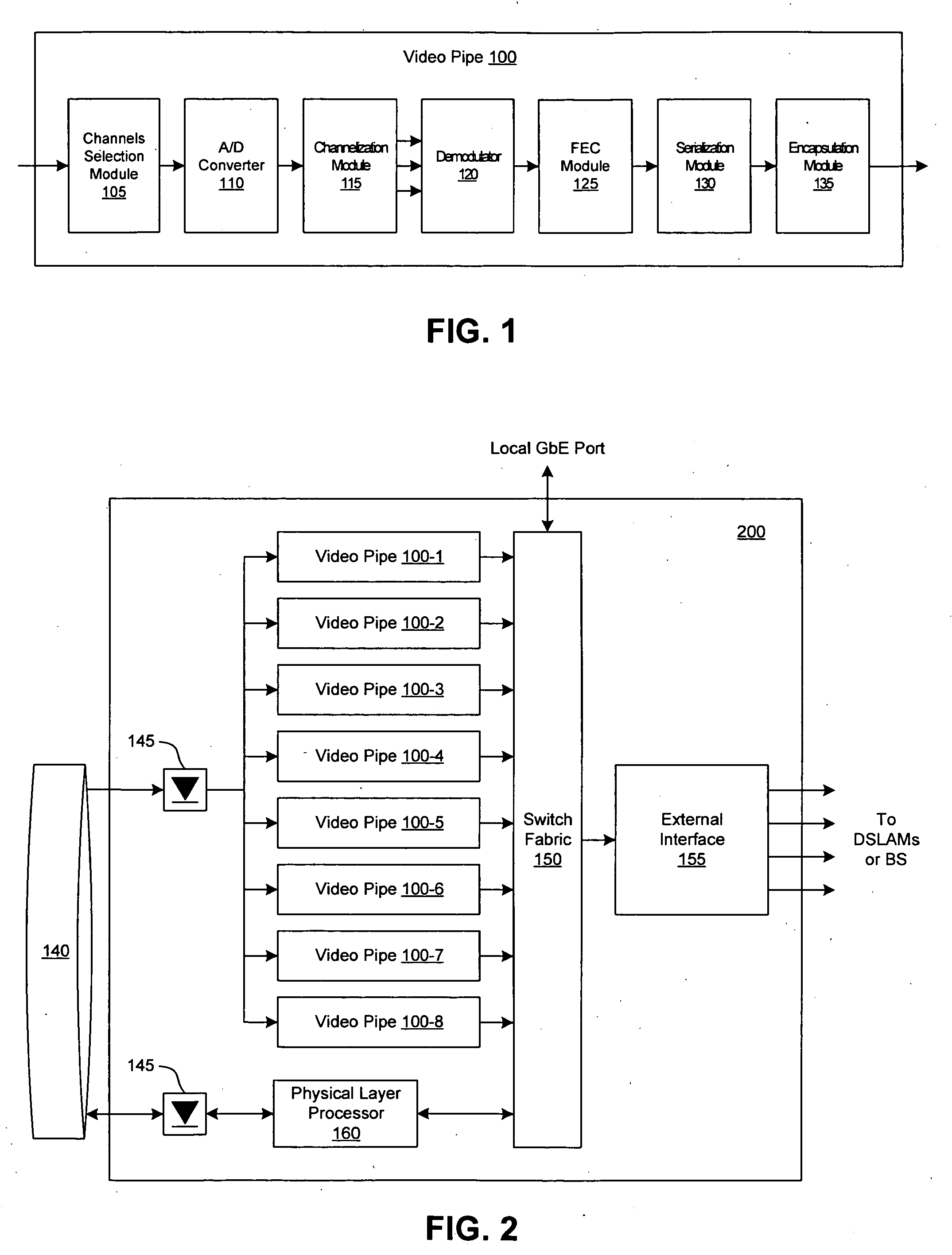
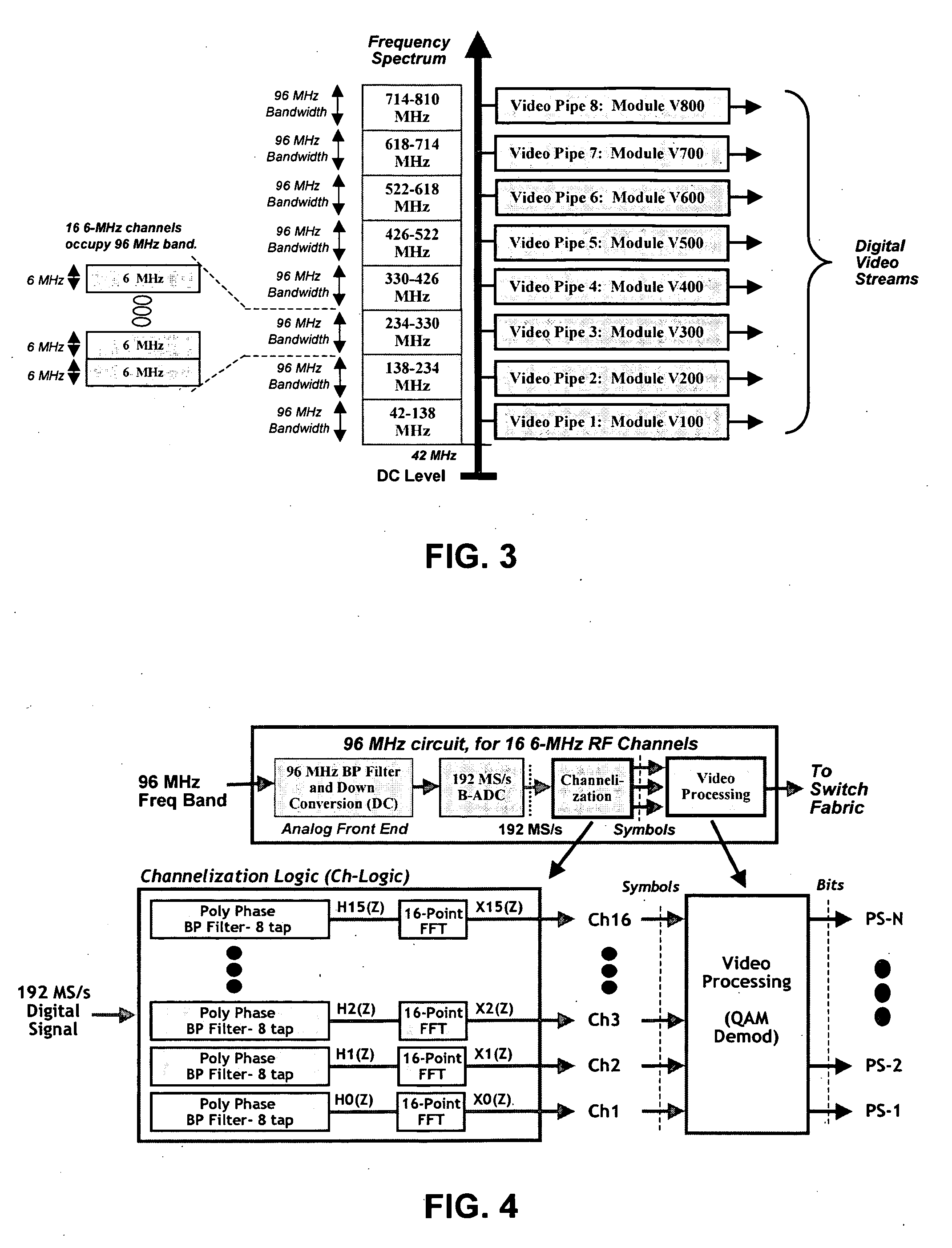
A video processing engine terminates frequency-modulated video signals transported over the so-called third mile (the network segment from the head-end to the access network) for delivery to an end user. In various network architectures, these signals are received at a central office (CO), for the telephone companies; at a fiber node (FN), for MSOs; or at a satellite dish, for satellite networks. By terminating these signals appropriately, high-quality video service can be delivered efficiently to customers over the last mile. Systems and methods for processing these video streams as well as various network architectures that allow the network providers to offer cost effective video services to the mass market are described.
Owner:MIDANI MOWAFFAK +2
Fiber optic cabling for multi-dwelling unit (MDU) and commercial building deployments
Owner:COMMSCOPE TECH LLC
Network device with a distributed switch fabric timing system
InactiveUS6876652B1Low costMultiplex system selection arrangementsSynchronisation information channelsEngineeringTiming system
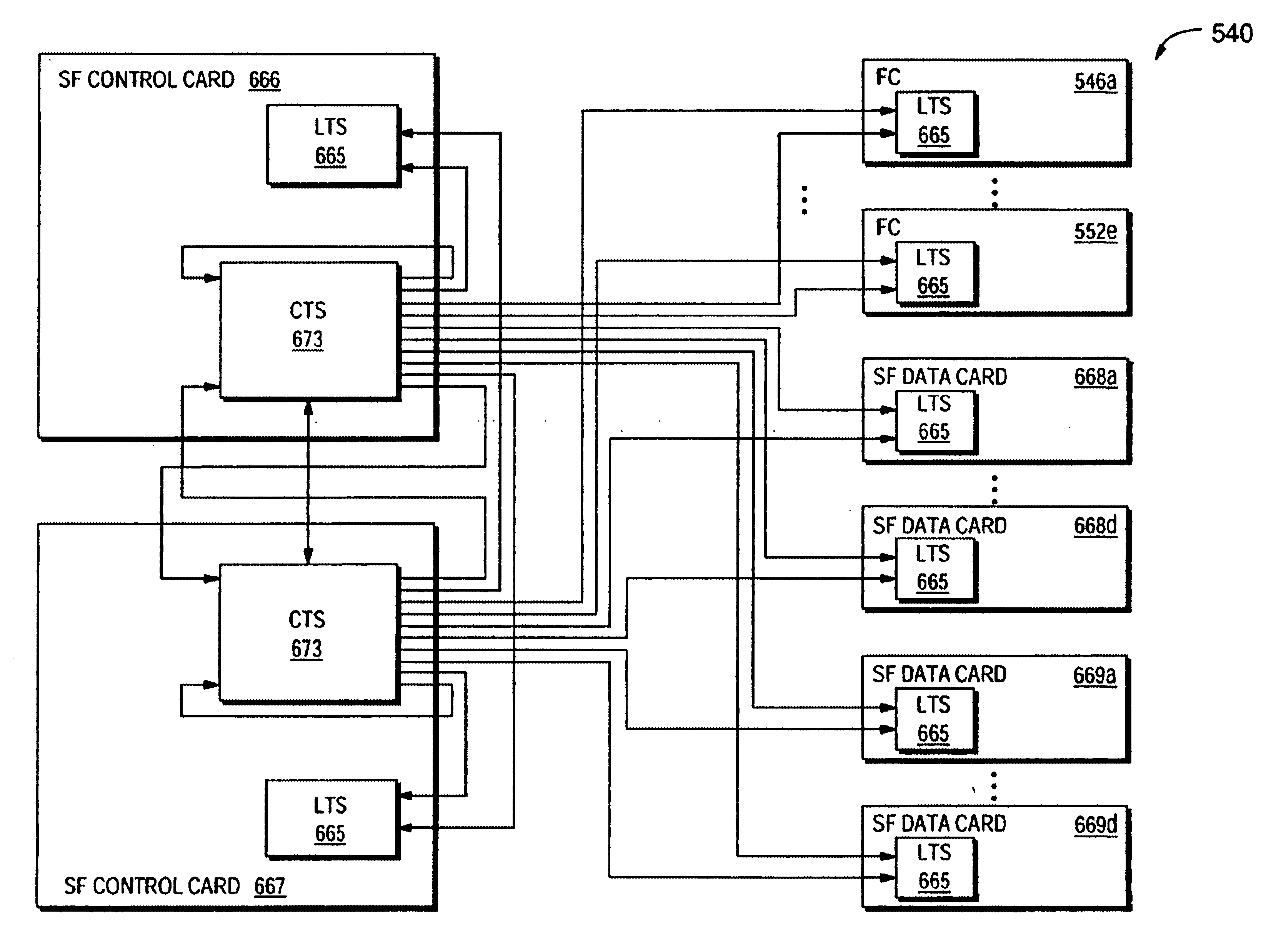
The present invention provides a central switch fabric timing subsystem and distributed switch fabric timing subsystems. Distributed switch fabric subsystems reduce the cost of a minimally configured network device by providing a network device with a distributed switch fabric. Such a network device locates a portion of the switch fabric functionality on each forwarding card allowing the minimal network device configuration to include less than the entire switch fabric functionality. The cost of the minimal configuration is, therefore, reduced allowing network service providers to more quickly recover the initial cost of the network device. As new services are requested, additional functionality, including both forwarding cards and universal port cards may be added to the network device to handle the new requests, and the fees for the new services may be applied to the cost of the additional functionality. Consequently, the cost of the network device more closely tracks the service fees received by network providers.
Owner:CIENA
Trust inheritance in network authentication
InactiveUS20050198534A1Digital data processing detailsUser identity/authority verificationUnique identifierOne-time password
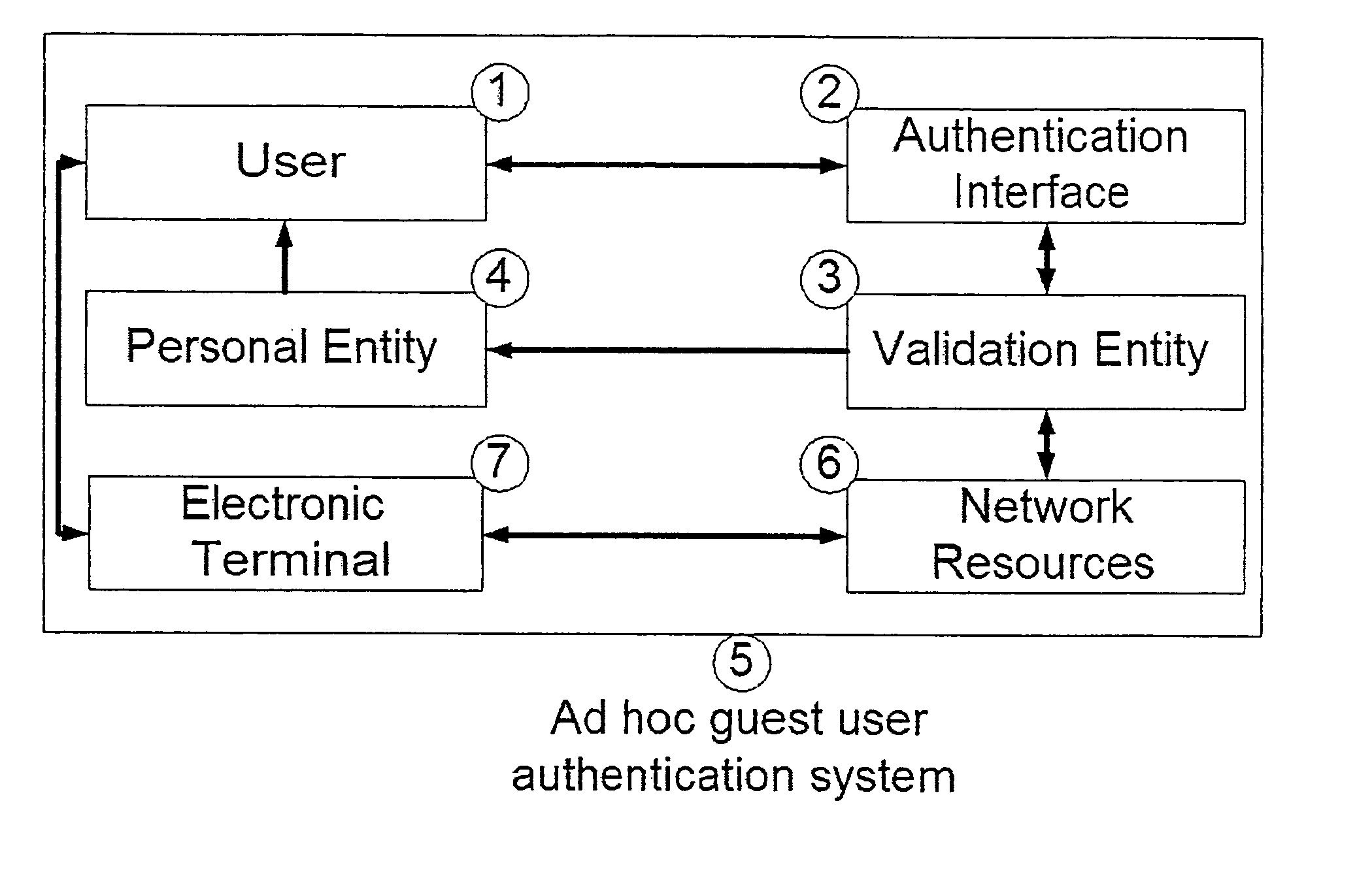
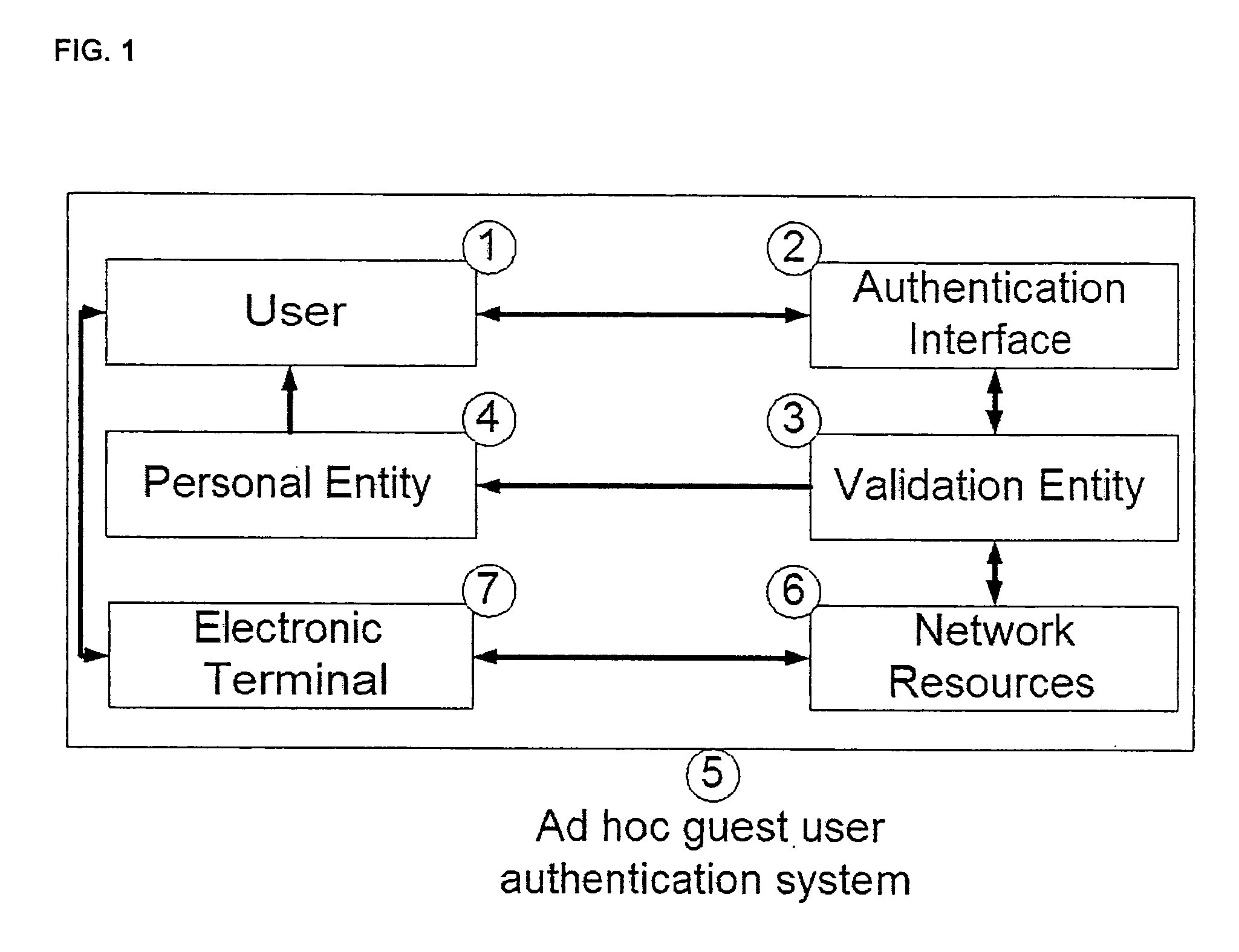
A system and method for providing ad hoc controlled user access to wireless and wireline IP communication networks while maintaining privacy for users and traceability for network providers. The method includes an authentication interface accepting user credentials, and a validation entity for credential verification and access authorization. The credentials include a unique identifier and a system generated password. The unique identifier is associated with a personal entity of the user such as a cellular telephone. The password is transmitted to the user through a SMS message to his cellular telephone. The user's Internet session is monitored by the system and all records are indexed by his cellular telephone number. The system and method therefore permit fast and traceable access for guest users at networks where they are were not previously known. Alternatively, users do not provide their unique identifiers such as cellular telephone numbers which are instead already stored in the system. A user provides a username and a one time password is generated by the system and sent to the user by SMS. This enables the system to validate the user's identity as well as the user to validate the Internet resources' identity.
Owner:SESAME NETWORKS +1
Global network computers
InactiveUS20060177226A1High potential economic savingOptimize networkMultiple digital computer combinationsProgram controlBroadband transmissionThe Internet
This invention generally relates to one or more computer networks having computers like personal computers or network servers with microprocessors linked by broadband transmission means and having hardware, software, firmware, and other means such that at least one parallel processing operation occurs that involve at least two computers in the network. More particularly, this invention relates to one or more large networks composed of smaller networks and large numbers of computers connected, like the Internet, wherein more than one separate parallel processing operation involving more than one different set of computers occurs simultaneously and wherein ongoing processing linkages can be established between virtually any microprocessors of separate computers connected to the network. Still more particularly, this invention relates to business arrangements enabling the shared used of network microprocessors for parallel and other processing, wherein personal computer owners provide microprocessor processing power to a network, preferably for parallel processing, in exchange for network linkage to other personal and other computers supplied by network providers, including linkage to other microprocessors for parallel or other processing; the basis of the exchange between owners and providers being whatever terms to which the parties agree, subject to governing laws, regulations, or rules, including payment from either party to the other based on periodic measurement of net use or provision of processing power.
Owner:ELLIS III FRAMPTON E
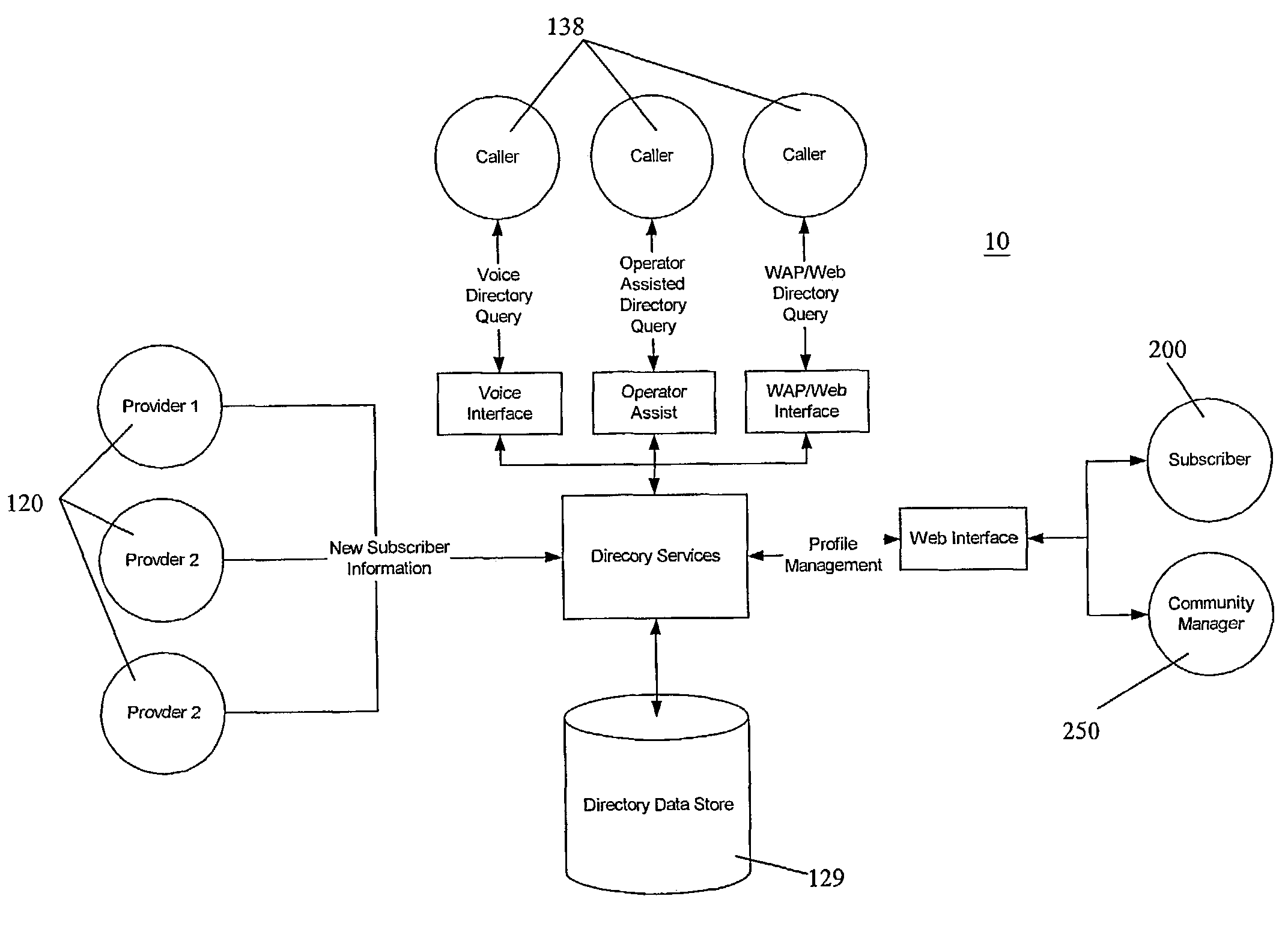
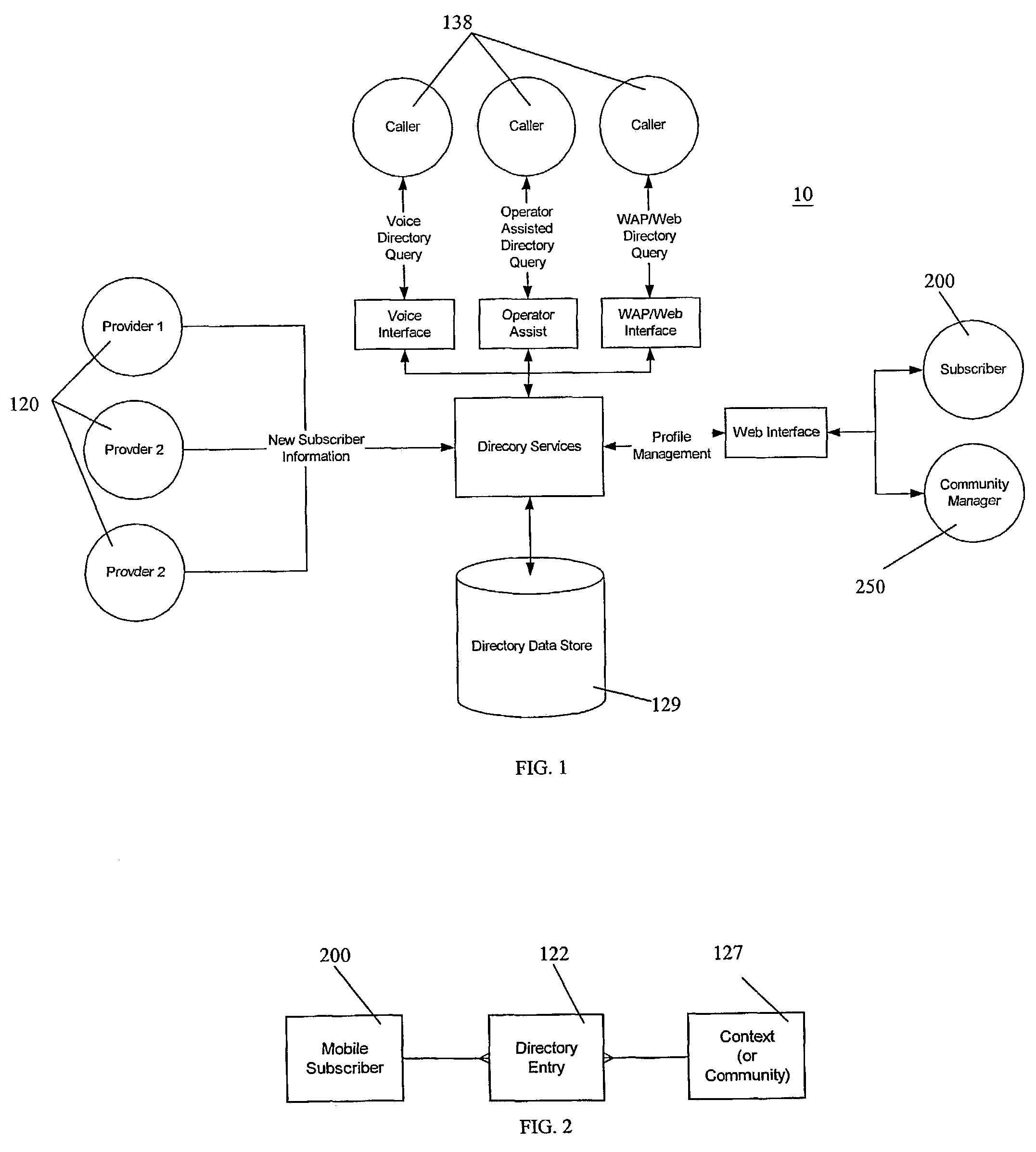
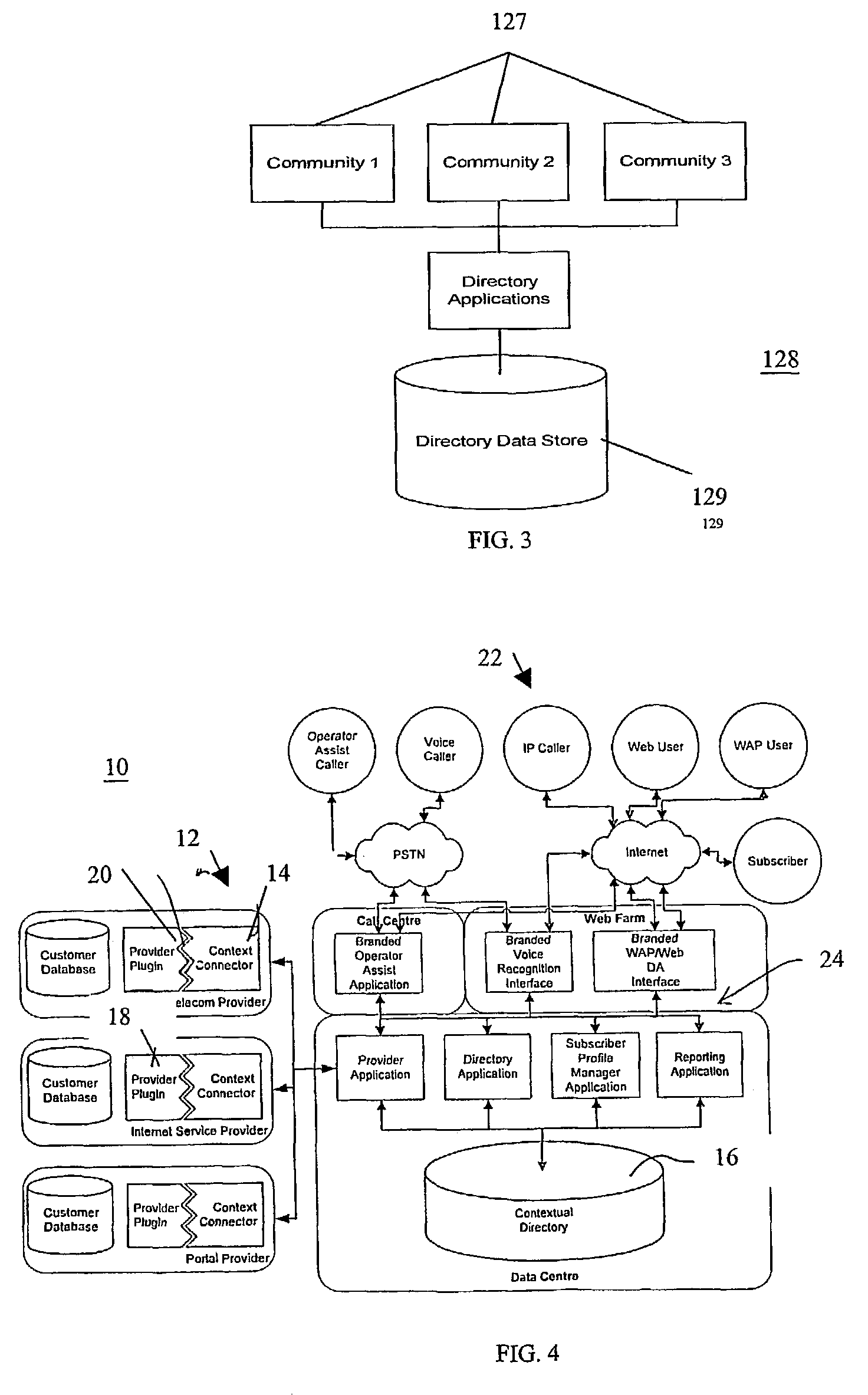
System and method for directory services and e-commerce across multi-provider networks
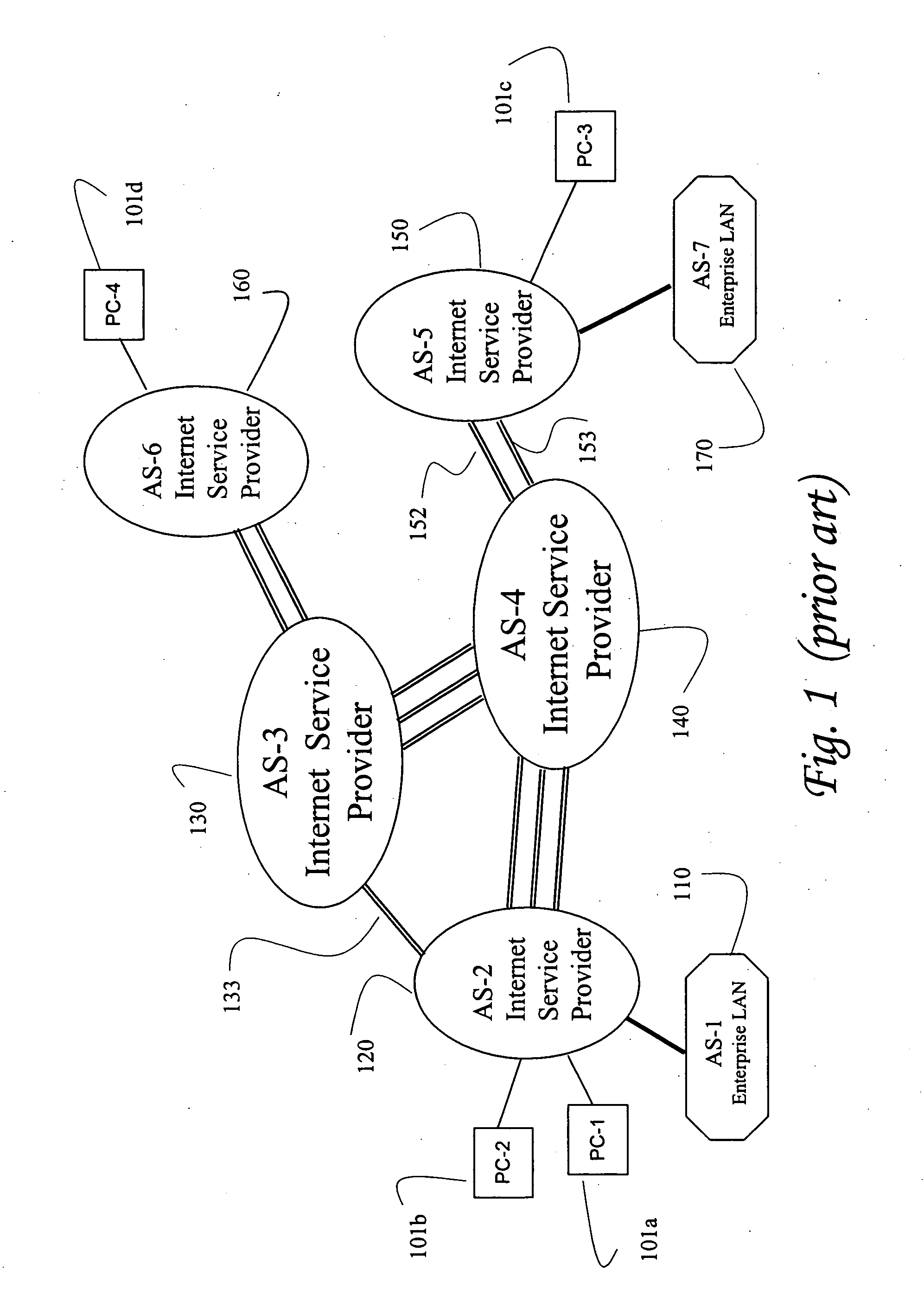
InactiveUS7340048B2Easy to identifyEasy to findTelephone data network interconnectionsAccounting/billing servicesNetwork providersWeb system
The present invention solves the problem of cross-provider access proprietary information between unaffiliated and competing network providers, but not allow that information to be disclosed to competing providers. The invention provides a system that allows increased utilization and revenue by allowing information from one provider to be accessed and used to complete a transaction or make a connection with subscribers in another carrier or network system without that information being disclosed. The description of the invention for use in wireless or cellular directory assistance is for convenience and illustration of the features of the invention. It is to be understood that the invention has many embodiments and can be applied to any system where confidential and secure access to an entity or services are needed.
Owner:WALMART APOLLO LLC
Distributed network communication system which enables multiple network providers to use a common distributed network infrastructure
InactiveUS20040167958A1Metering/charging/biilling arrangementsAssess restrictionCommunications systemNetworked system
A system and method for providing access and / or roaming features on a network system. The network system includes a plurality of wireless and / or wired access points coupled to a network. Access points (APs) for the network may be widely distributed in various facilities, such as airports, mass-transit stations, and various businesses. The network may couple to a wide area network, such as the Internet. In one embodiment, a portable computing device (PCD) of a user may store identification information which uniquely indicates a network provider of a plurality of possible network providers. The identification information may also or instead indicate an access or privilege level of the user. Each of the access points are operable to "listen for" or detect identification information associated with numerous different providers. When the access point receives the identification information from a PCD of a user, the access point may determine the appropriate network provider for the portable computing device using the identification information. Network access may then be provided to the portable computing device through the determined network provider. Thus the network system is useable by subscribers of each of the plurality of possible network providers, thereby enabling subscribers to "roam" on various wireless networks, including networks maintained by other providers. The access information may also include an access level which indicates the user's access or privilege level. Thus, the local network may provide various local resources which are available to users having a first access level, and users with a second access level may not be entitled to view or utilize these network resources on the network, but may be simply provided external Internet access.
Owner:CISCO TECH INC
System, method and program product for delivery of digital content offerings at a retail establishment
ActiveUS20080097858A1Recover installationRecover maintenanceMetering/charging/biilling arrangementsDiscounts/incentivesGraphicsDigital content
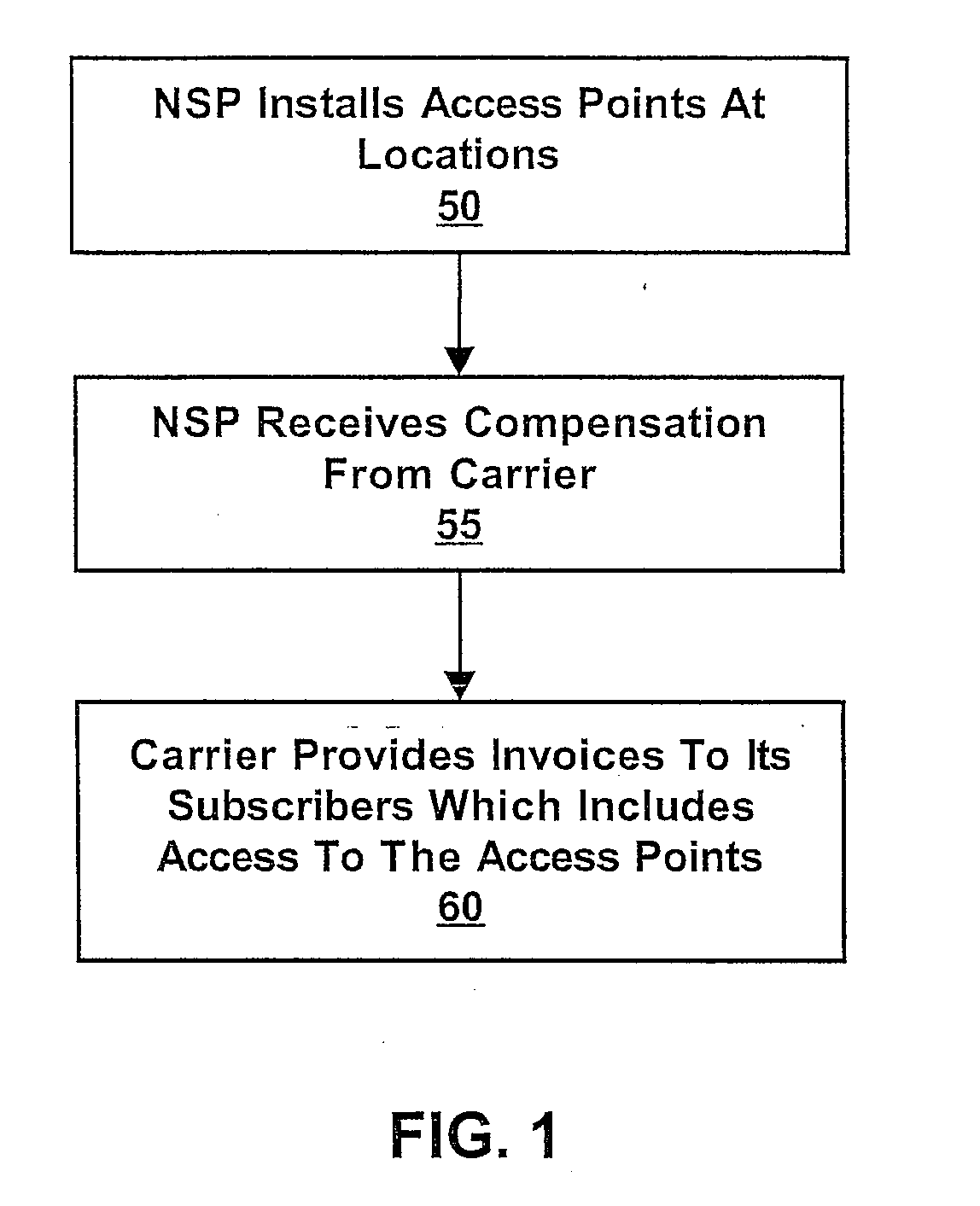
A method and system for providing distributed network access point installation and management. A network provider installs and / or operates a plurality of access points at locations of a retail entity. Each access point may provide services such as Internet access, and / or content such as audio, video, text, and / or graphics, among other types of services. A carrier, such as a telephone or cable company, may compensate the network service provider for installation and operation of the access points. The carrier may in turn charge its subscribers for network access at the retail entity locations. A plurality of different carriers may provide compensation and allow respective subscriber access. The network access points may be configured to allow each carrier to present a point of presence to its subscribers at the retail entity locations. The installed network may also provide service for retail entity back office functions.
Owner:WAYPORT
Method and system for processing downstream packets of an optical network
InactiveUS20030086140A1Efficient disseminationMultiplex system selection arrangementsWavelength-division multiplex systemsQuality of serviceTransceiver
Unlike the conventional art which polices data at the entry points of a network, a transceiver node can police or monitor downstream bandwidths for quality of service at exit portions of an optical network. That is, the transceiver node can police downstream communication traffic near the outer edges of an optical network that are physically close to the subscribers of the optical network. In this way, a network provider can control the volume or content (or both) of downstream communications that are received by subscribers of the optical network. In addition to controlling the volume of communications that can be received by a subscriber, the transceiver node employs a plurality of priority assignment values for communication traffic. Some priority assignment values are part of a weighted random early discard algorithm that enables an output buffer to determine whether to drop data packets that are destined for a particular subscriber. In one exemplary embodiment, a weighted random early discard (WRED) priority value can be assigned according to the type of communication traffic supported by a packet.
Owner:ARRIS SOLUTIONS
Client-based context-based billing for wireless networks
ActiveUS7620383B2Precise positioningMetering/charging/biilling arrangementsAccounting/billing servicesService provisionContext based
The invention increases billing options for a wireless service provider by allowing the provider to make billing decisions based upon what a client or mobile station application does both on and off the network. This type of billing, based on context, generates a billing record of events whether or not a particular client accesses the wireless network or not. The invention also provides transmission quality data allowing the wireless network provider to improve user experience in a wireless network. The invention captures the context, including content, quantity, and / or quality of data processed by a mobile station using a client-based application rather than a network-based application. The client-based application causes the mobile station to transmit a billing record corresponding to the captured context to a user monitoring server. The user monitoring server processes the billing record for determining billing and for generating engineering reports.
Owner:U S CELLULAR
Securing Communications of a Wireless Access Point and a Mobile Device
ActiveUS20130103939A1User identity/authority verificationNetwork topologiesSecure communicationCommunications security
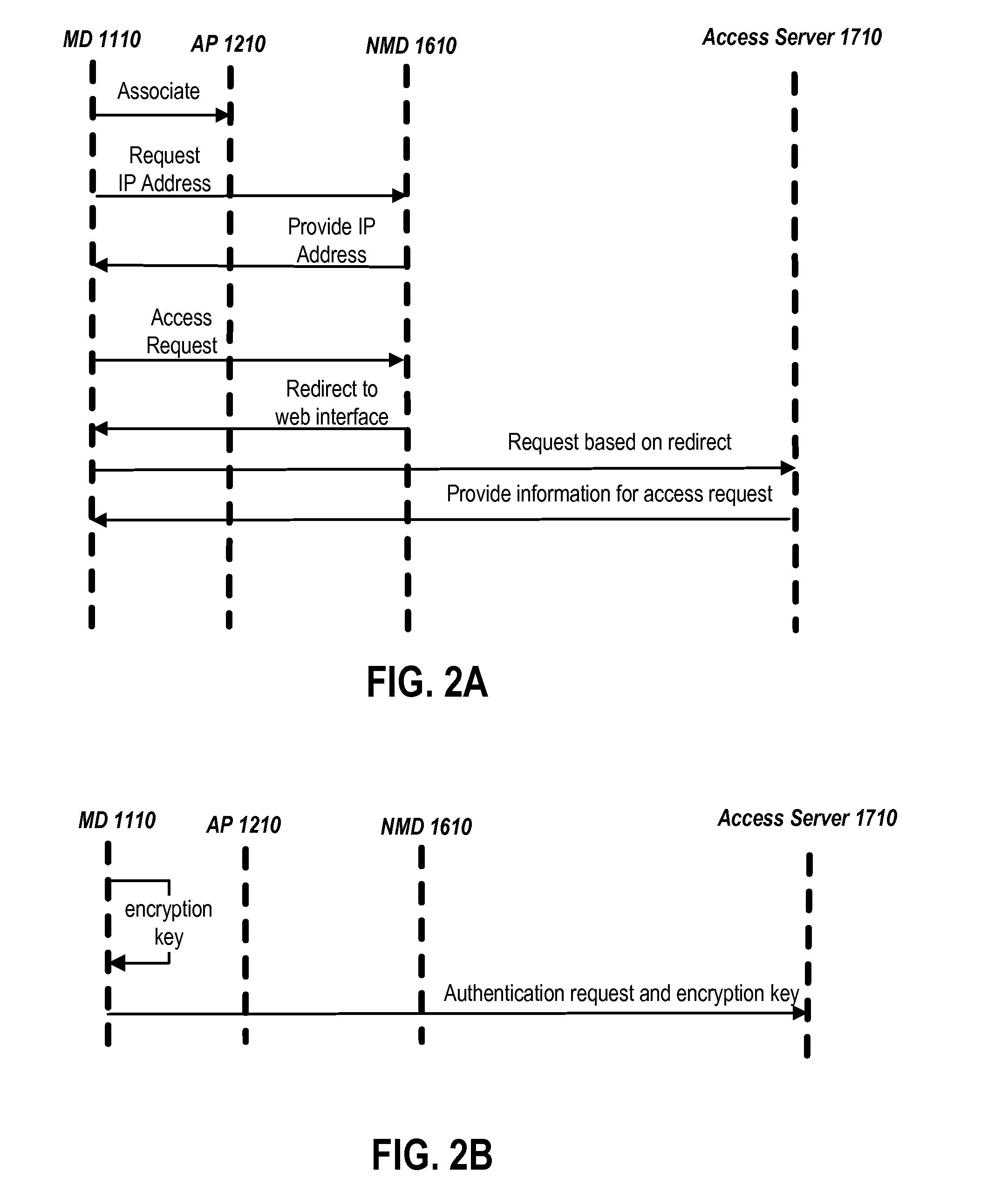
In one or more embodiments, a network provider can receive a request to access a public network via a wireless network implemented via one or more wireless access points. The network provider can receive, via an unsecured wireless communication from a mobile device utilizing the wireless network and via a hypertext transfer protocol secure (HTTPS), an encryption key usable to secure wireless communications from the mobile device utilizing the wireless network. The encryption key can be encrypted via a public encryption key, received from the network provider or previously stored by the mobile device, associated with the network provider. The network provider can decrypt the encryption key and can provide the encryption key to a wireless access point implementing the wireless network and communicating with the mobile device. The wireless access point and the mobile device can communicate in a secure fashion based on the encryption key.
Owner:AT&T INTPROP I L P
Systems and methods for traffic management between autonomous systems in the Internet
InactiveUS20060165009A1Error preventionFrequency-division multiplex detailsTraffic capacityBorder Gateway Protocol
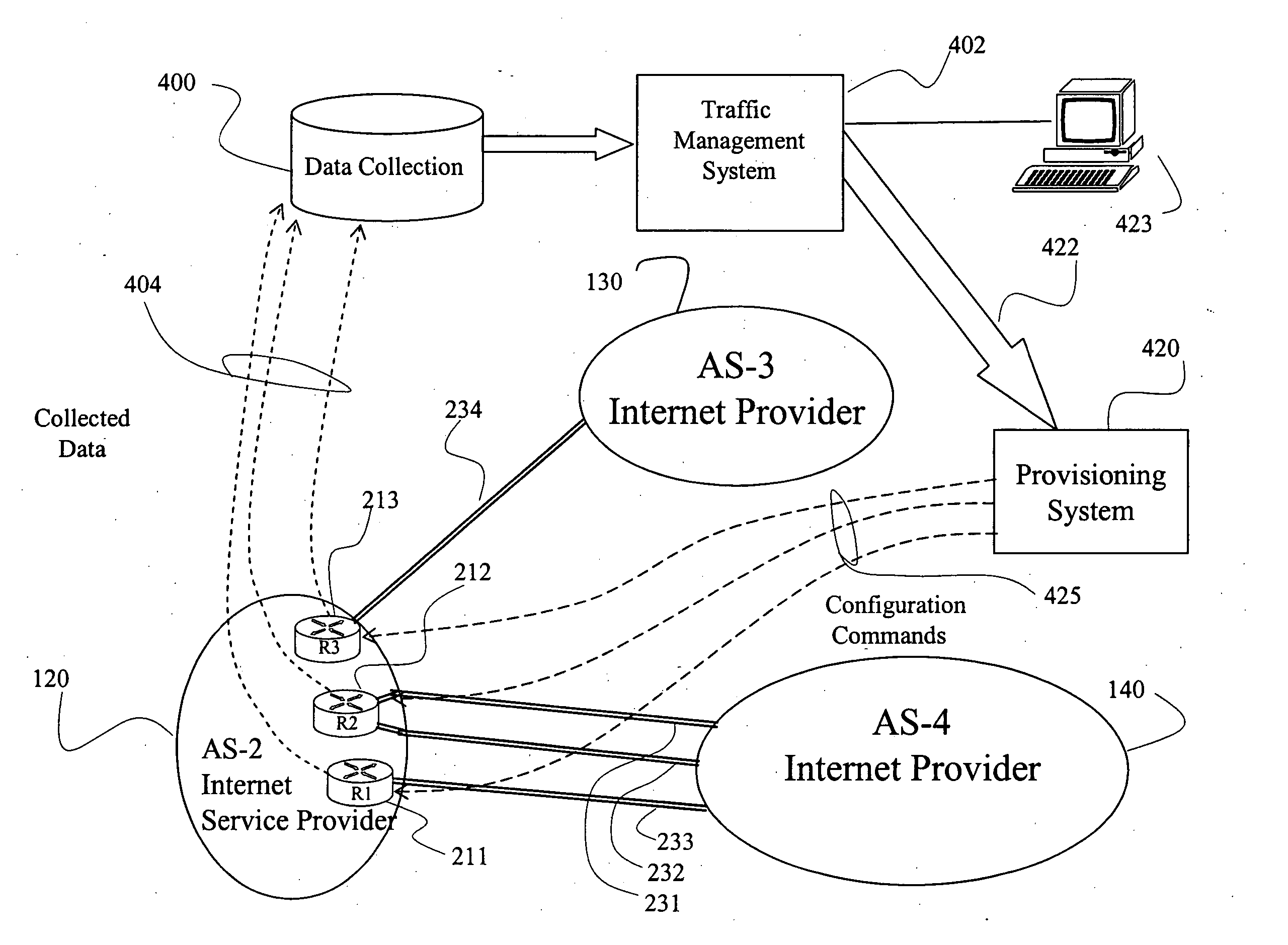
Systems and methods are disclosed for managing the traffic between autonomous systems in the Internet. Data on links on border routers between autonomous systems is collected and analyzed at certain traffic times. Once determined, traffic on various customer facing interfaces at that time is associated with an Internet Prefix. Then, the aggregate traffic volume for each Internet Prefix is allocated to a first link on a primary routing basis and to a second link on a secondary routing basis. These routes are announced to a provisioning system that in turn, configures various border routers, which in turn announce the new routes using the Internet Border Gateway Protocol. In this manner, inter-autonomous traffic is managed to facilitate traffic distribution on the links according to criteria defined by network provider, allowing resources to be better utilized and network traffic to be maintained if a link fails.
Owner:ZVOLVE
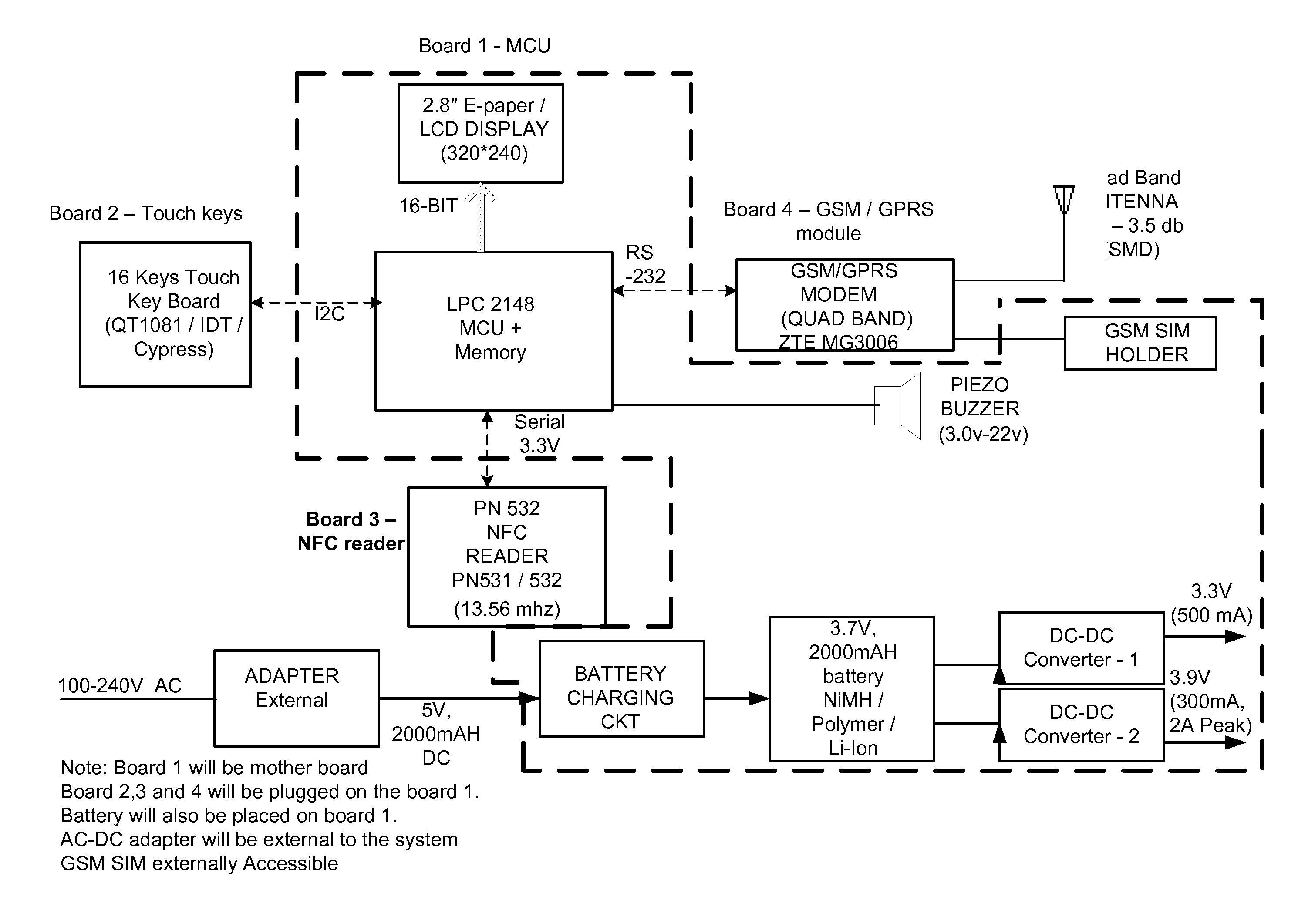
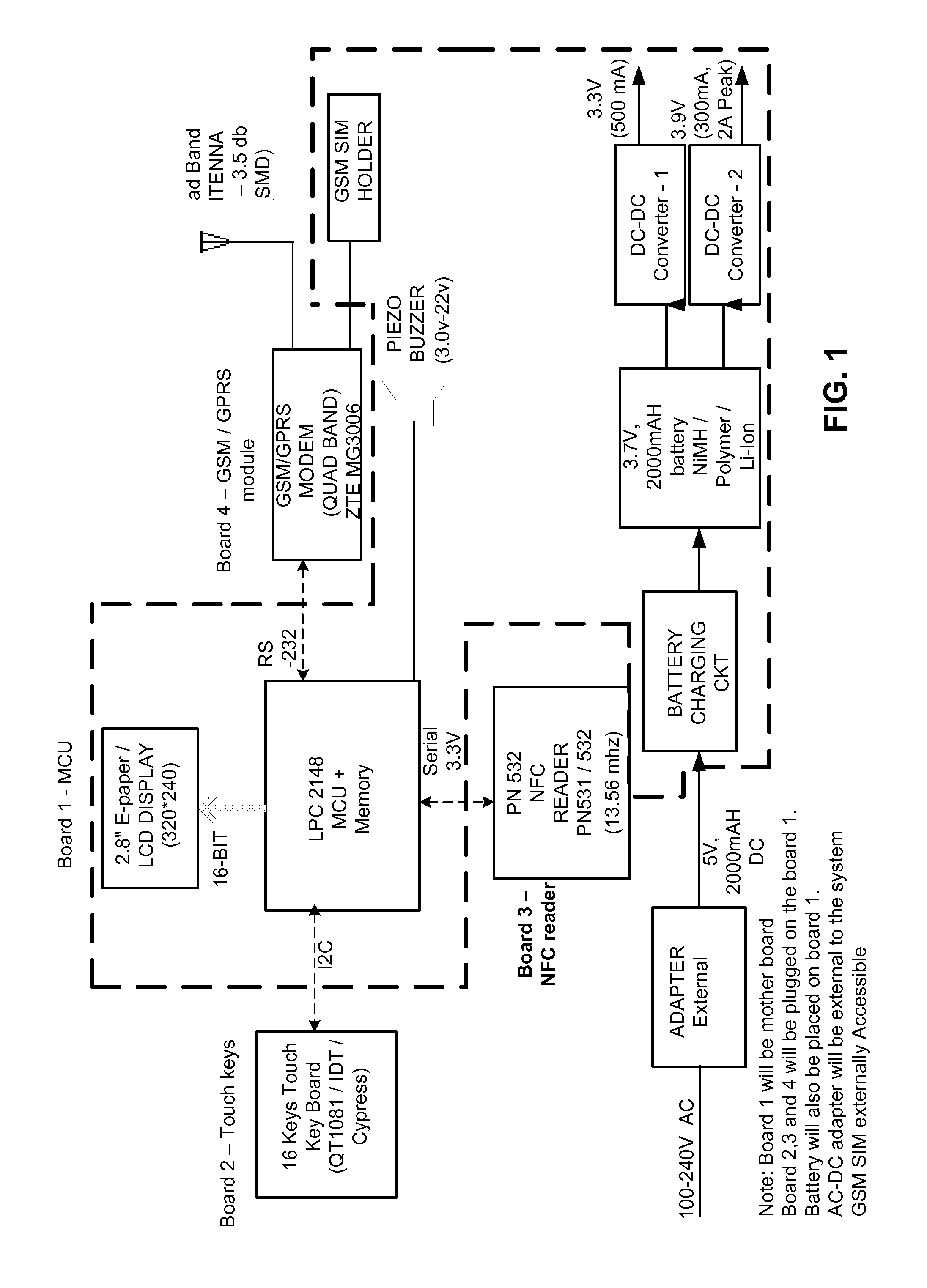
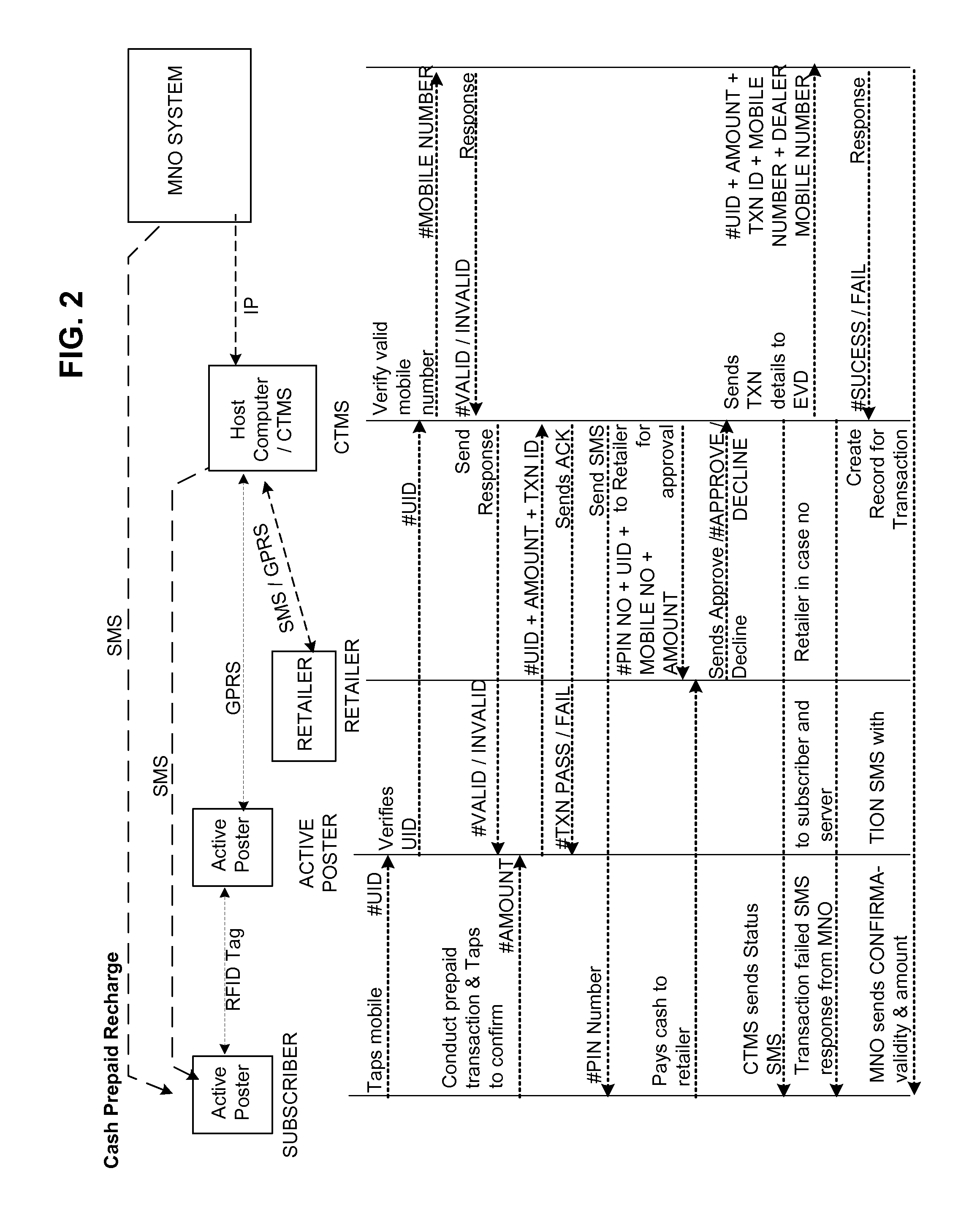
Integrated system and method for enabling mobile commerce transactions using active posters and contactless identity modules
A method, integrated system and Active Poster for processing mobile touch transactions. The integration consists of an RFID or other near field communication enabled device which may be standalone, affixed to, or part of a mobile or hand held portable wireless communication device (optionally using a Contact Less (CL) SIM with near field communication capability), a touch sensitive Active Poster also with near field communication capability, an issuer's or mobile network provider's system and application and a host computer with networking capability.
Owner:XIUS CORP
Network Access Via Telephony Services
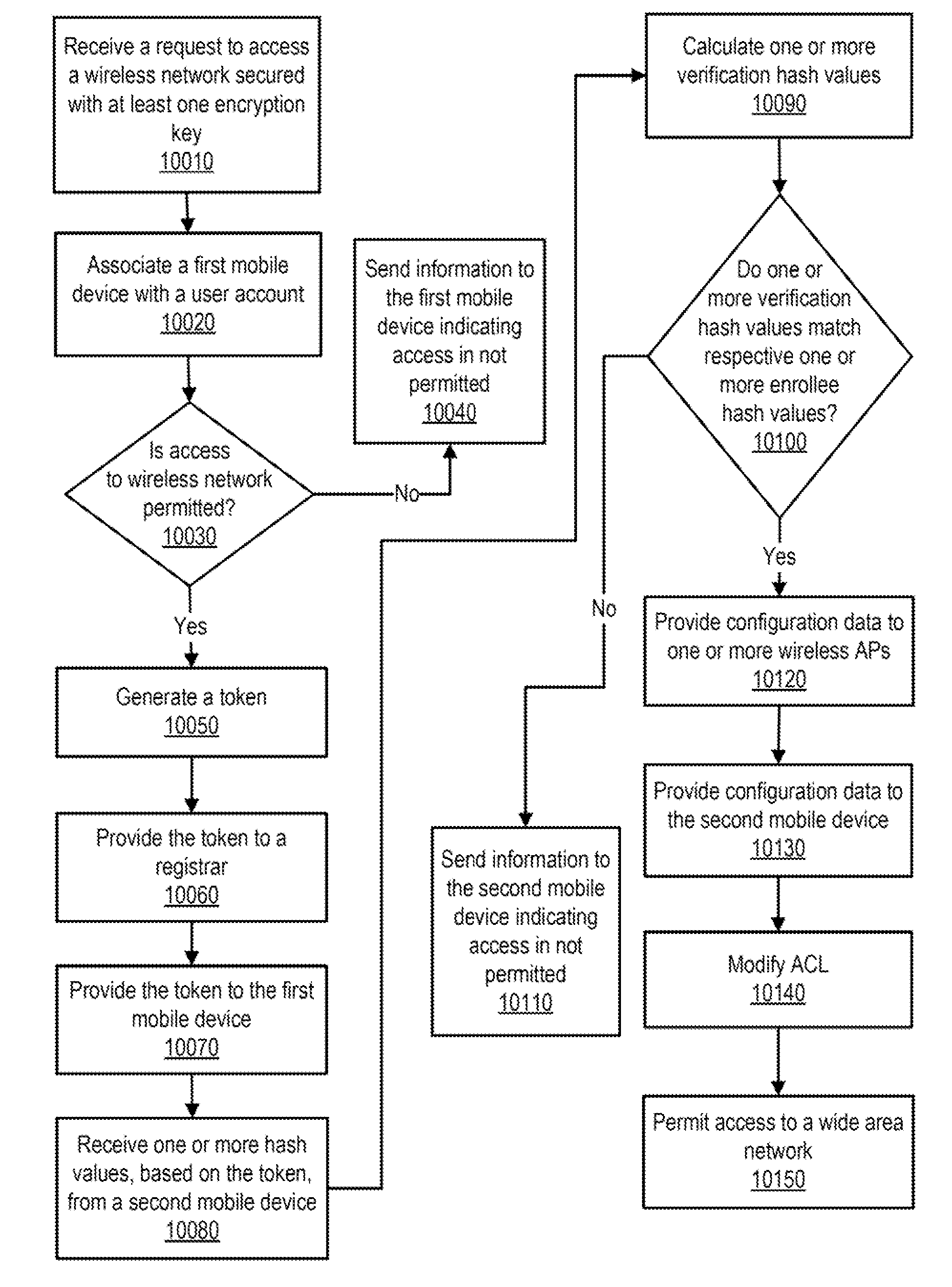
A network provider can receive a request, via a first mobile device and a mobile wireless telephone network, for access to a wireless network secured with at least one encryption key and implemented by at least one wireless access point. In response to the request, the network provider can associate the first mobile device with a user account of a user and can provide a token to a registrar and to the first mobile device via the mobile wireless telephone network. The registrar can receive, from the first mobile device or a second mobile device associated the user via the wireless access point. After determining, based on the one or more hash values, that the first or second mobile device has possession of the token, the registrar can provide the encryption key to that mobile device.
Owner:AT&T INTPROP I L P
Method and system for detecting of errors within streaming audio/video data
The rapid proliferation of streamed audio-visual services to users via the Internet, especially fee-based services, has increased the importance for content providers in establishing, maintaining, improving and validating the quality of service and experience they provide to the subscribers or users of their services. Accordingly, there is provided a method of determining quality metric data at the user's display in response to a provided digital multimedia stream. The quality metric data being stored for subsequent transmission to a remote server for aggregation and correlation with other quality metric data and defect related data of provided digital multimedia streams to provide service and network providers with quantified data relating to the quality of experience of users of Internet based audio-visual services. As such the quality metric data may be applied to discrete or continuous audio-visual content facilitating quality determinations for streamed content.
Owner:CLARESTOW CORP
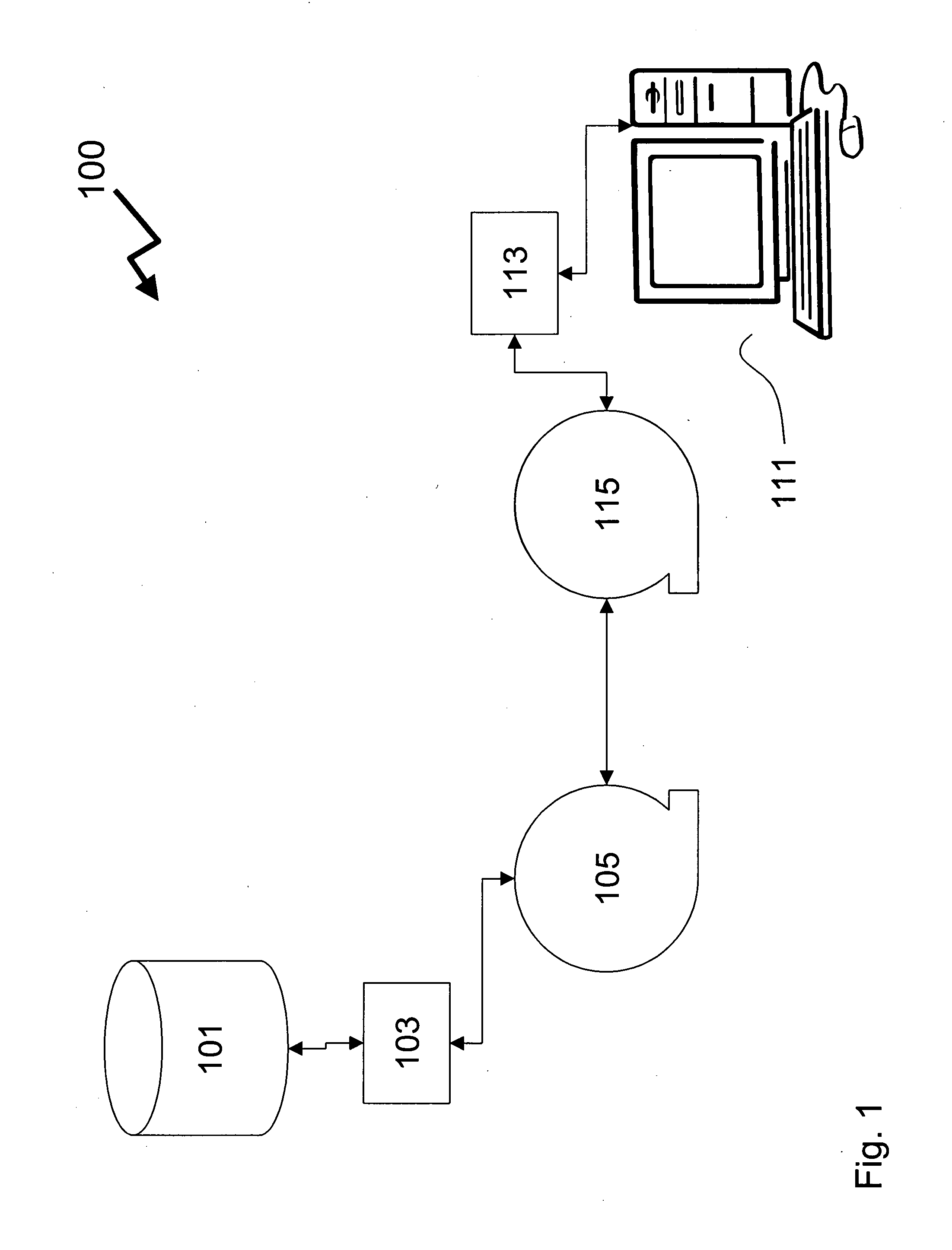
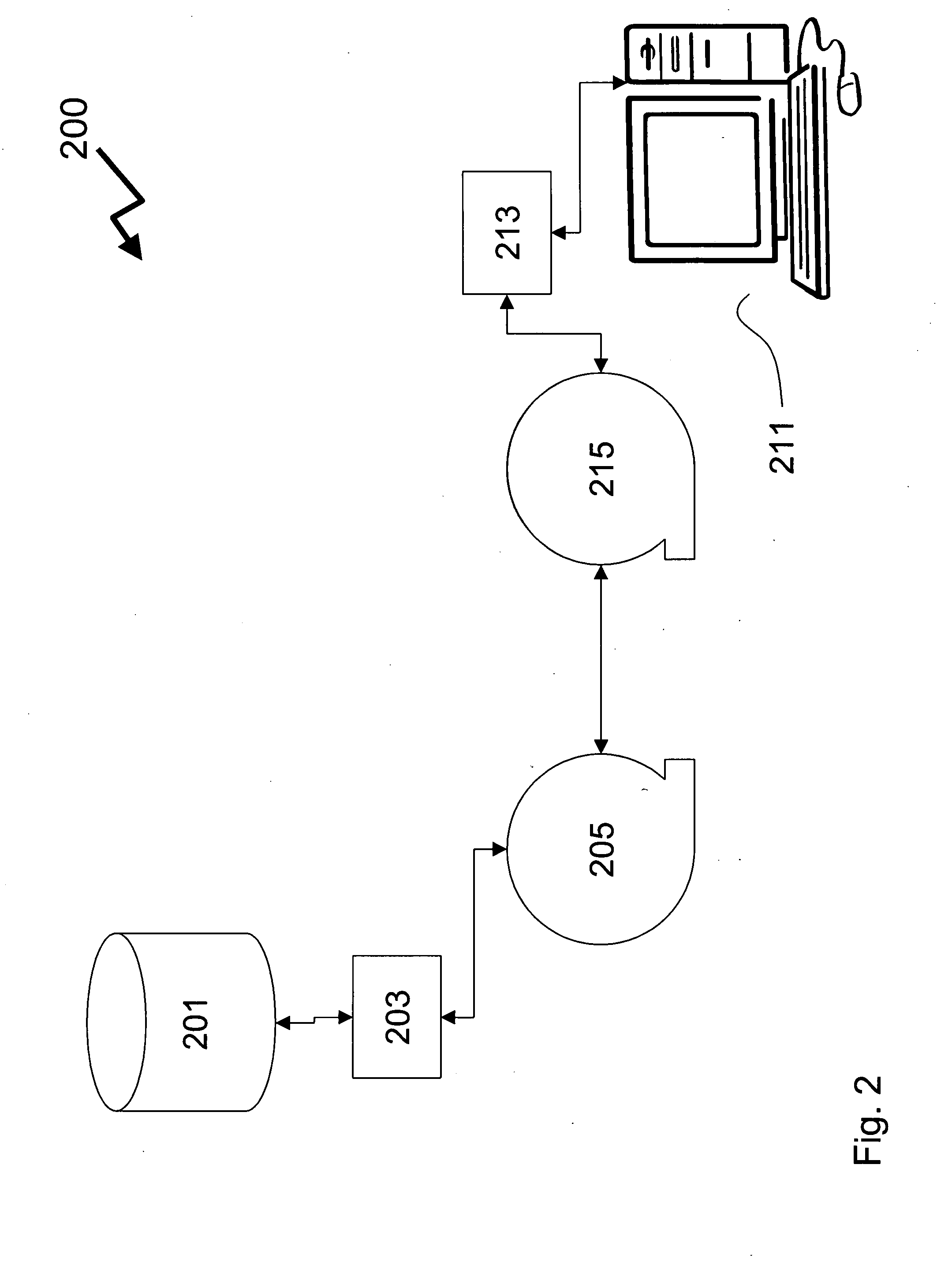
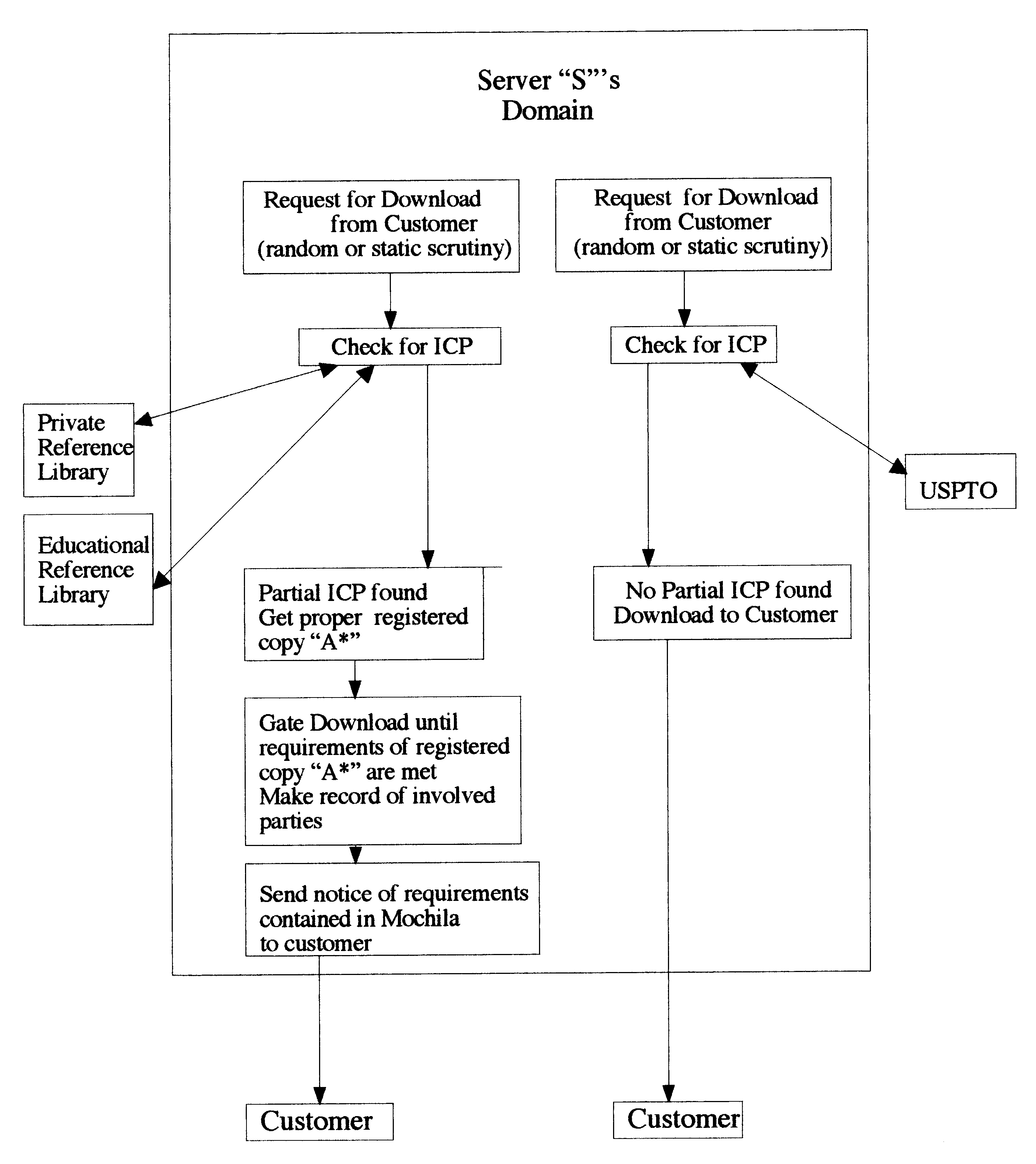
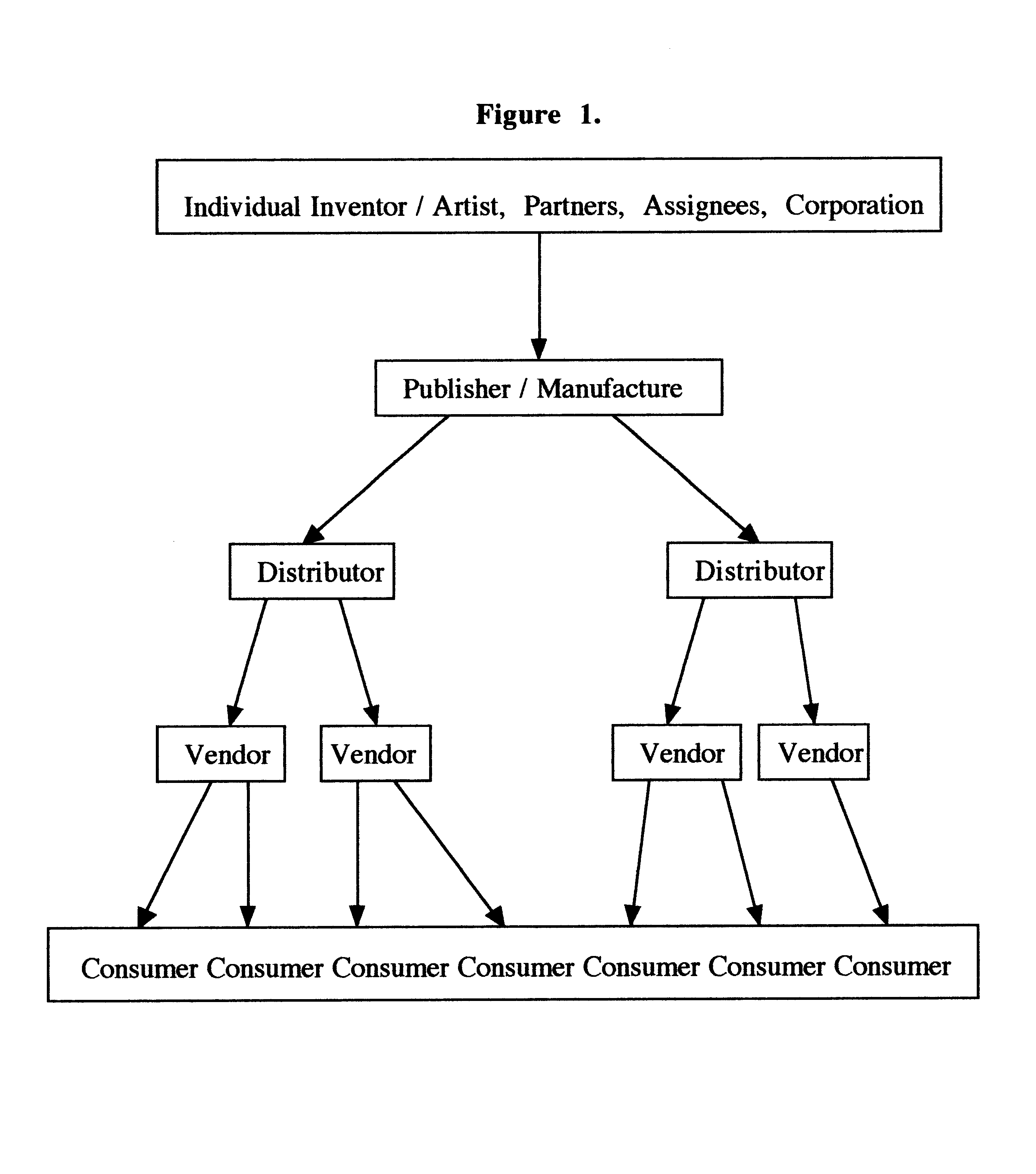
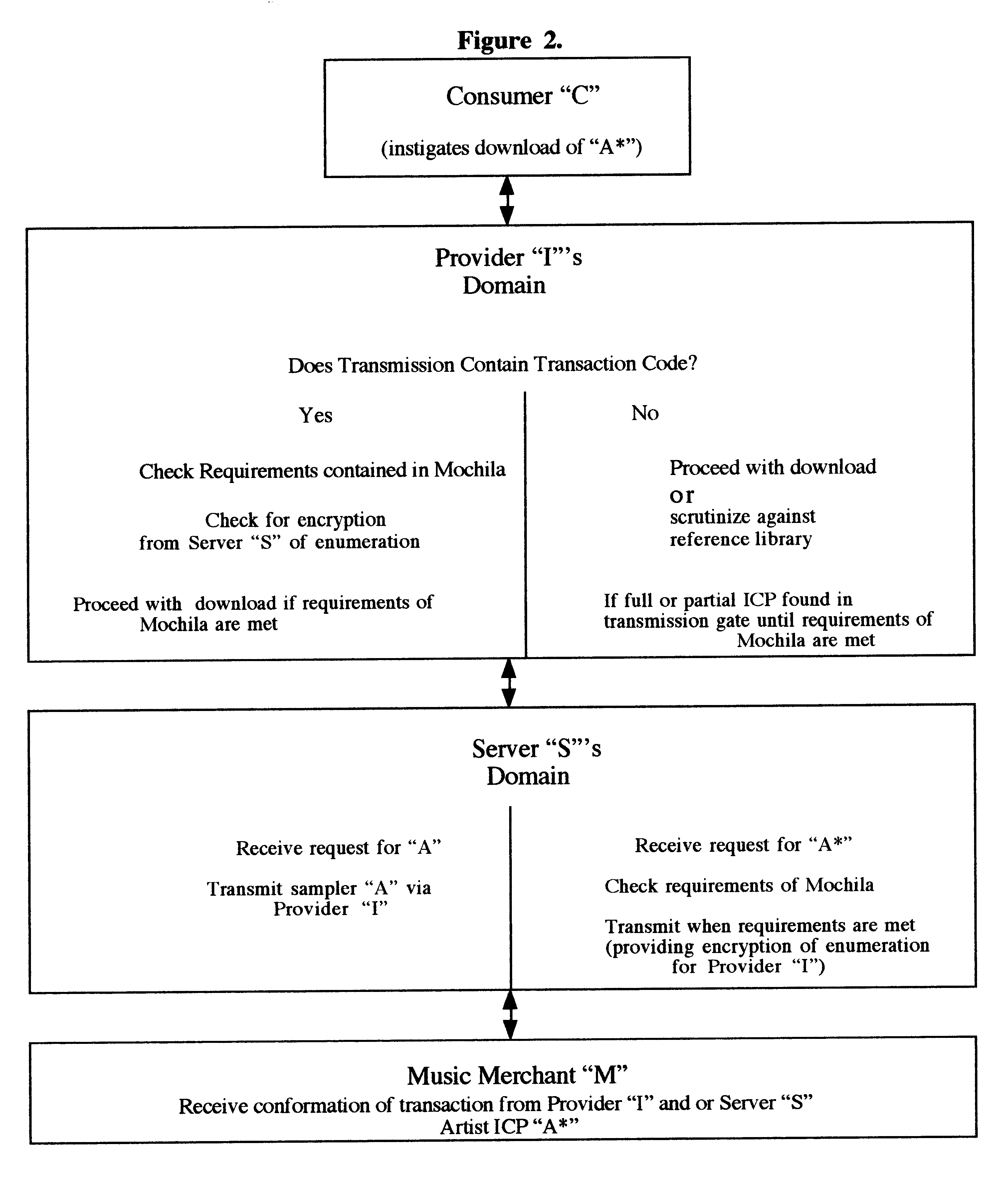
Distribution, recognition and accountability system for intellectual and copy written properties in digital media's
InactiveUS6947909B1Increase market shareIncrease dominanceComputer security arrangementsCommerceIntellectual propertyE-commerce
A method for distribution, recognition and accountability for Intellectual and Copy written Properties in digital media's by associating a Transaction Code Identifier or Designator and further bundled information which distinguishes digital files as Intellectual or Copy written Property, and therefore unique and bound to restrictions with regard to transfer, ownership, proliferation and electronic commerce. The employment of said transaction code identifier further promotes novel distribution scenarios for electronic commerce. Further delineated is the role of network providers and servers in promoting the interests of owners of Intellectual and Copy written Property in accordance with the present invention.
Owner:HOKE JR CLARE L
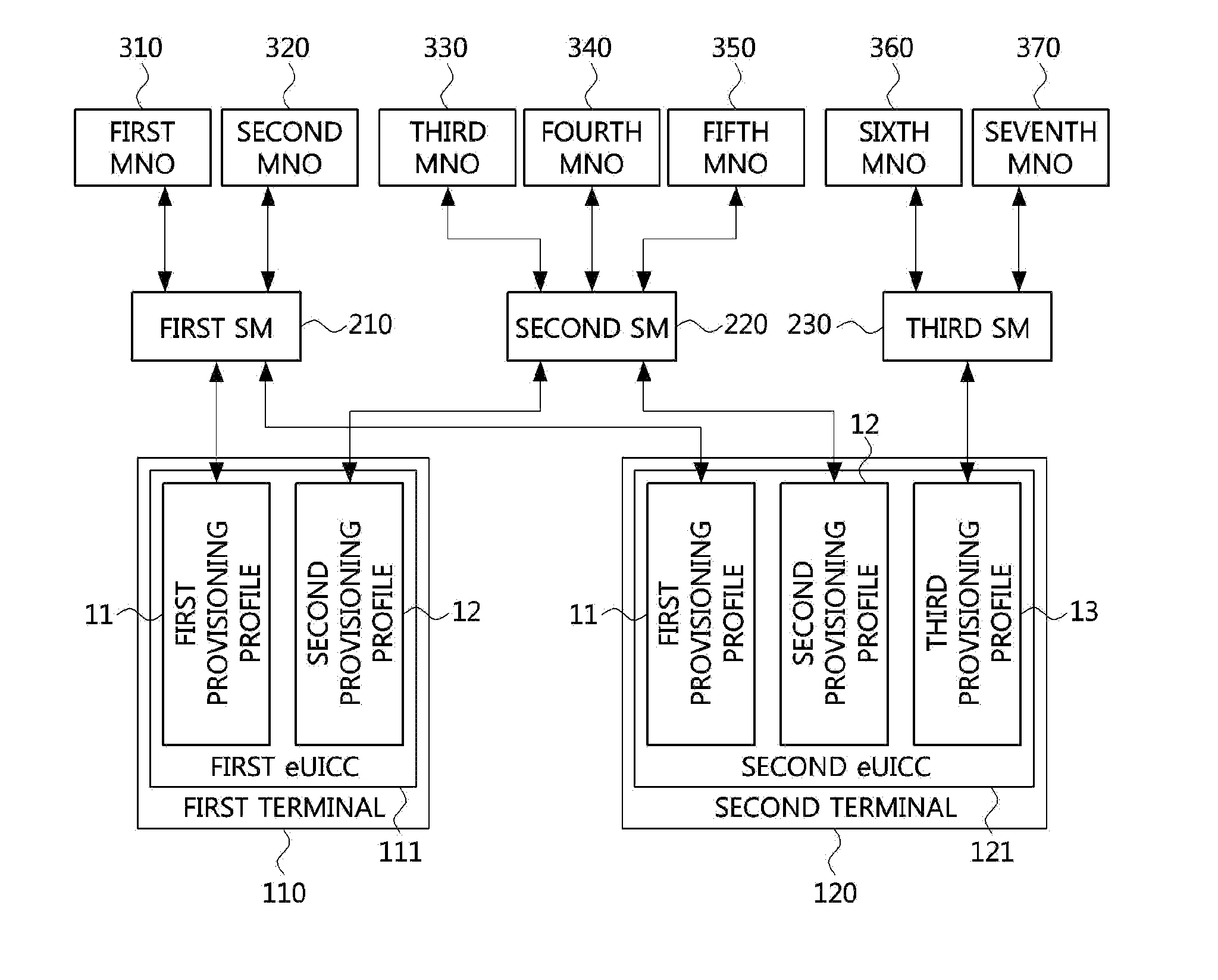
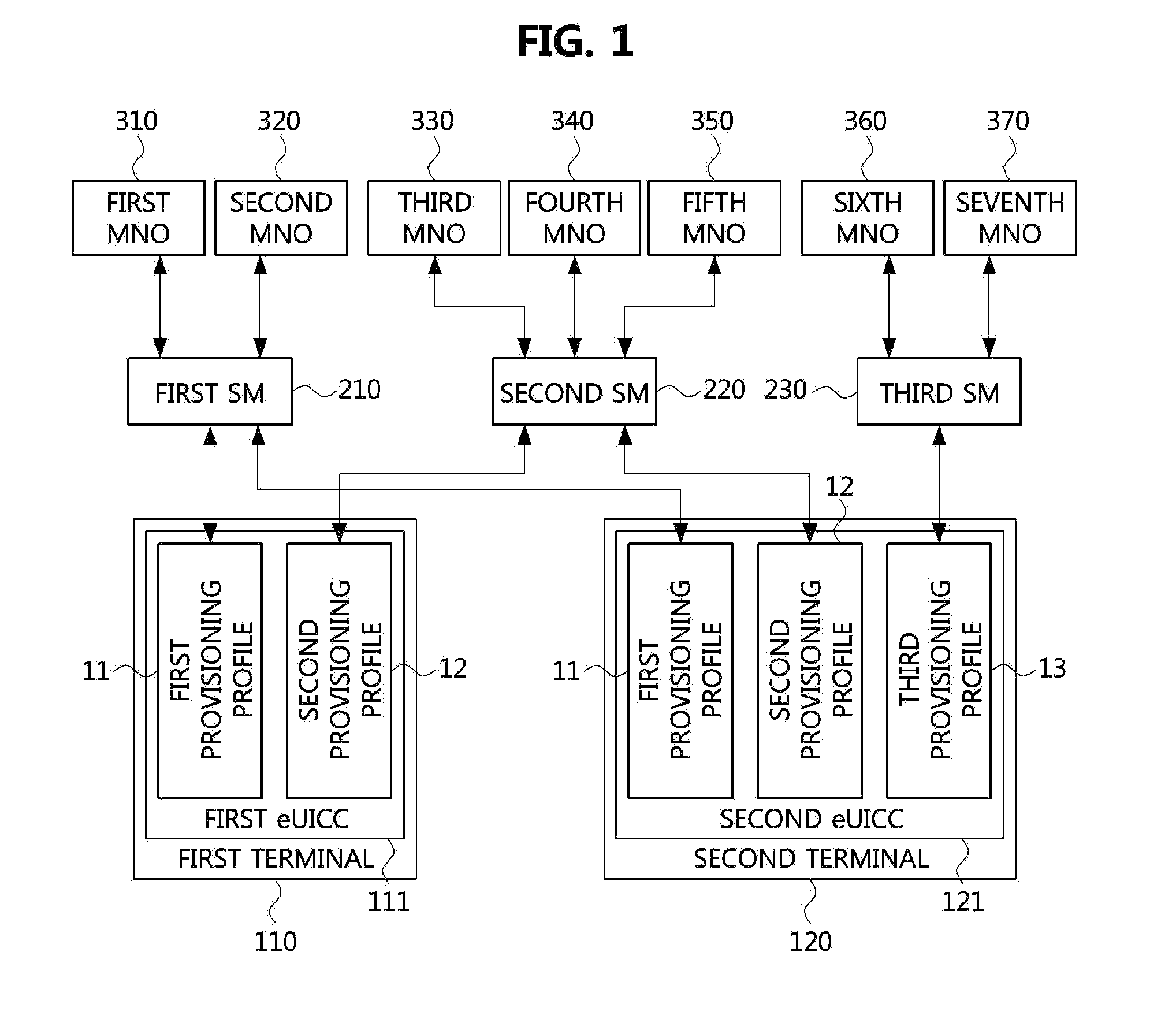
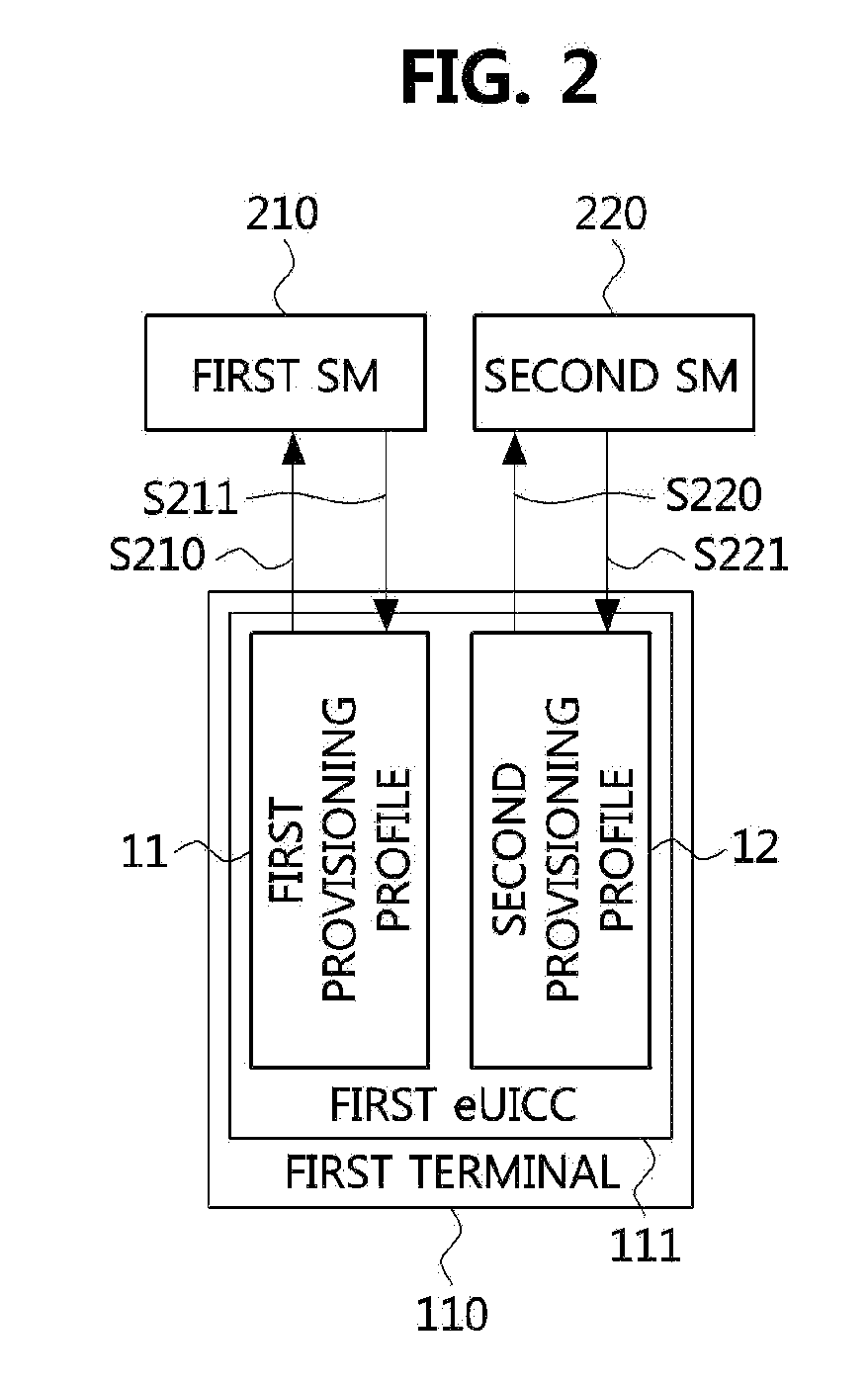
Method for selecting mobile communication network provider using provisioning profile, and apparatus using same
ActiveUS20150349825A1Easy to set upAssess restrictionConnection managementComputer hardwareMobile communication network
Owner:SAMSUNG ELECTRONICS CO LTD
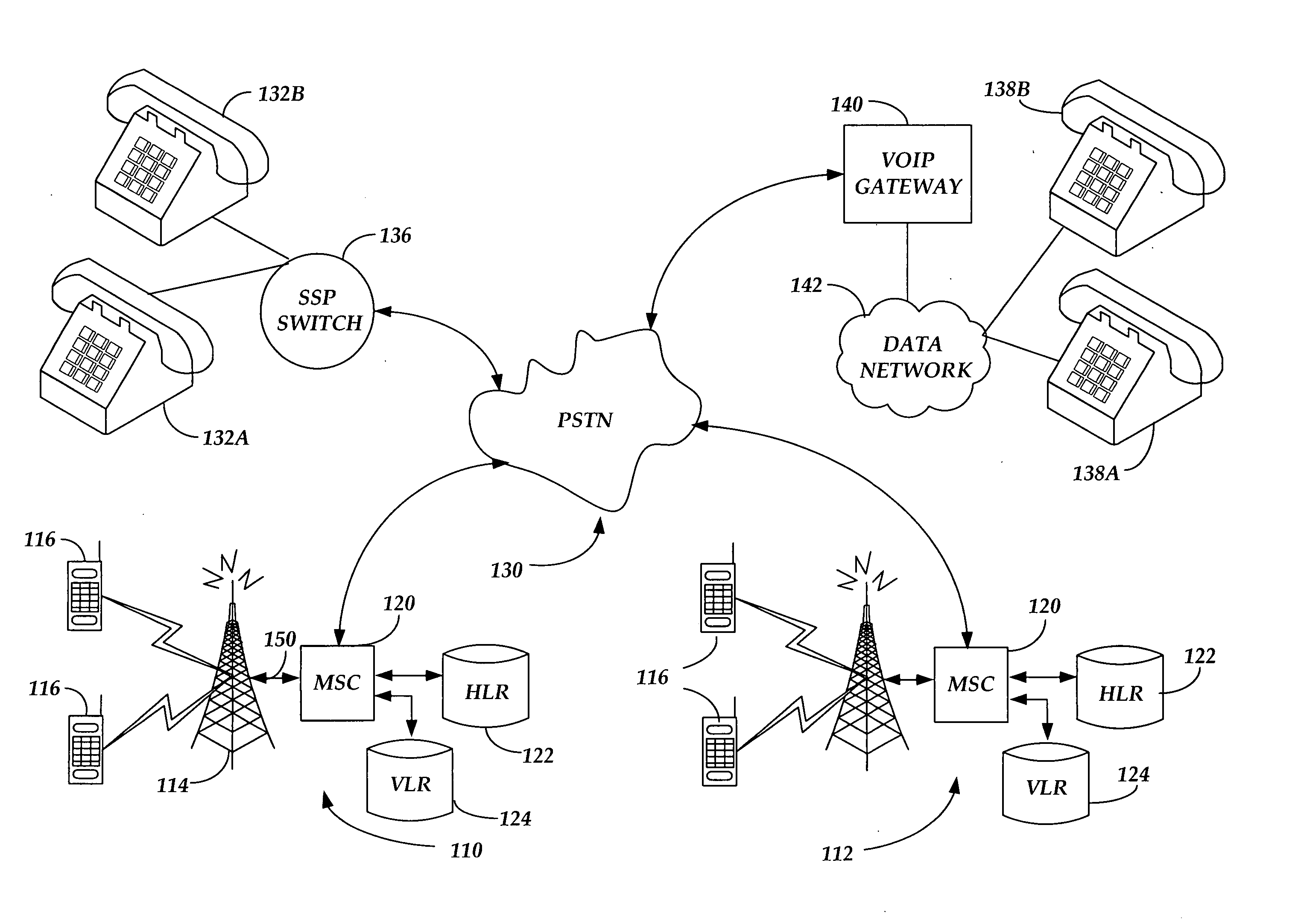
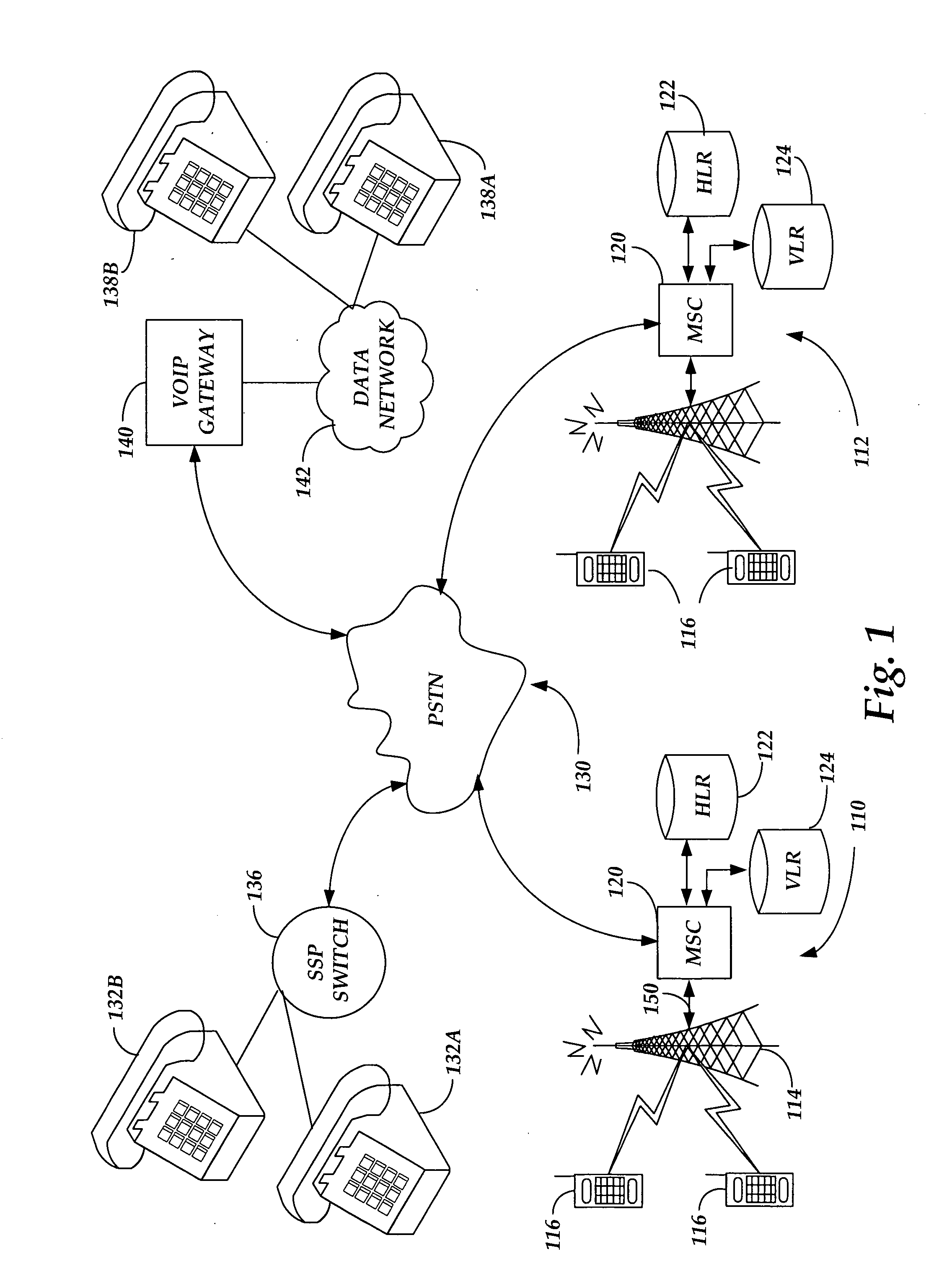
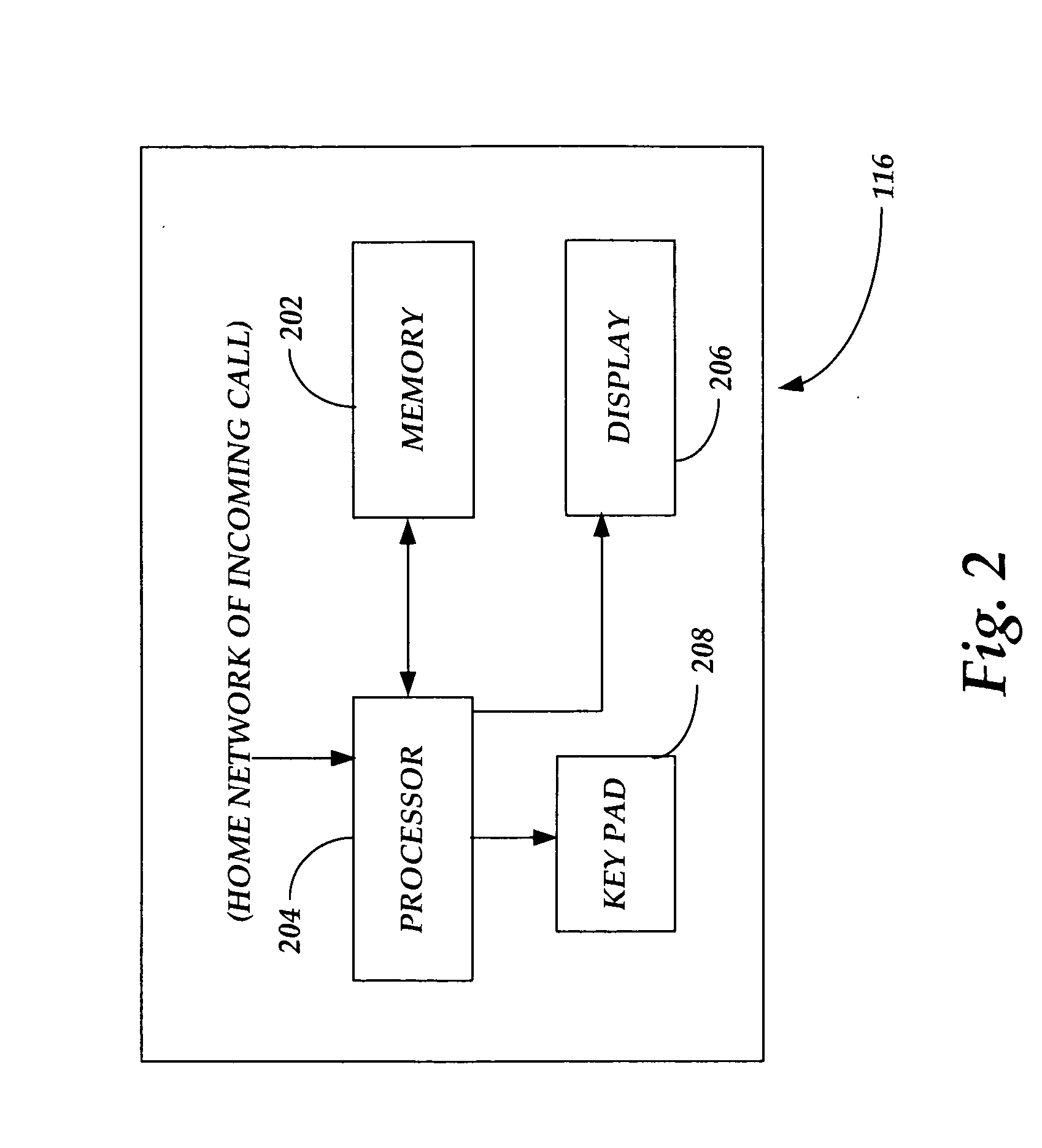
Methods and apparatus for recognizing home network provider of incoming wireless calls
InactiveUS20070111714A1Readily apparentSpecial service for subscribersServices signallingWirelessHandset
In a cellular wireless system, a handset identifies and displays the home network provider for an incoming call. If that home network provider is different from the home network provider for the called handset, the user of that handset is notified and may decide not to accept an incoming call that may incur an airtime charge.
Owner:BELLSOUTH INTPROP COR
Sending a communications header with voice recording to send metadata for use in speech recognition and formatting in mobile dictation application
In embodiments of the present invention improved capabilities are described for sending a communications header with voice recording to send metadata for use in speech recognition and formatting when converting voice to text on a mobile communication facility comprising capturing speech presented by a user using a resident capture facility on the mobile communication facility; transmitting a communications header to a speech recognition facility from the mobile communication facility via a wireless communications facility, wherein the communications header includes at least one of device name, network provider, network type, audio source, a display parameter for the wireless communications facility, geographic location, and phone number information; transmitting at least a portion of the captured speech as data through a wireless communication facility to a speech recognition facility; generating speech-to-text results for the captured speech utilizing the speech recognition facility based at least in part on the communications header; transmitting the text results from the speech recognition facility to the mobile communications facility; and entering the text results into a text field on the mobile communication facility.
Owner:VLINGO CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com