Patents
Literature
213 results about "Privilege level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
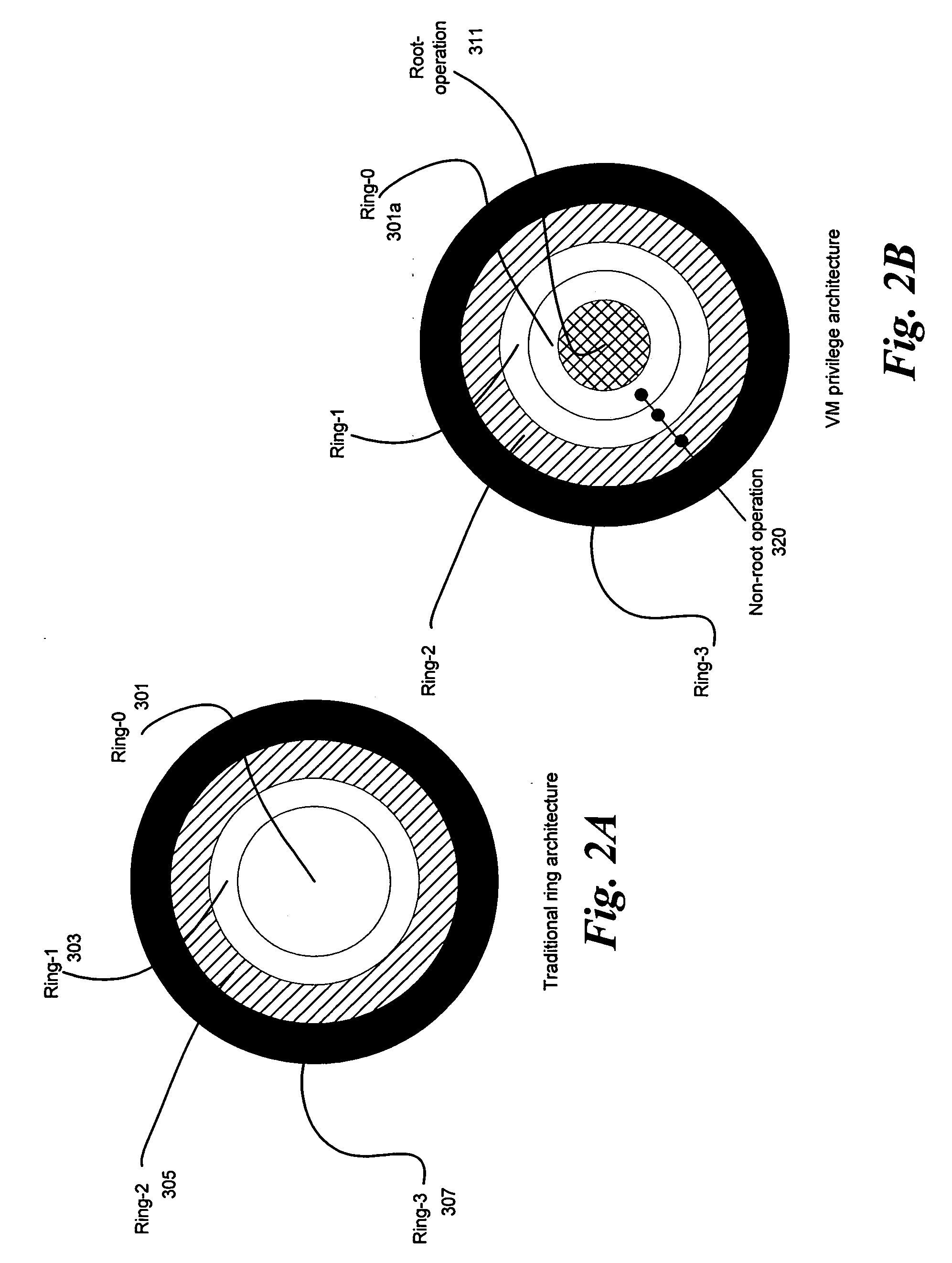
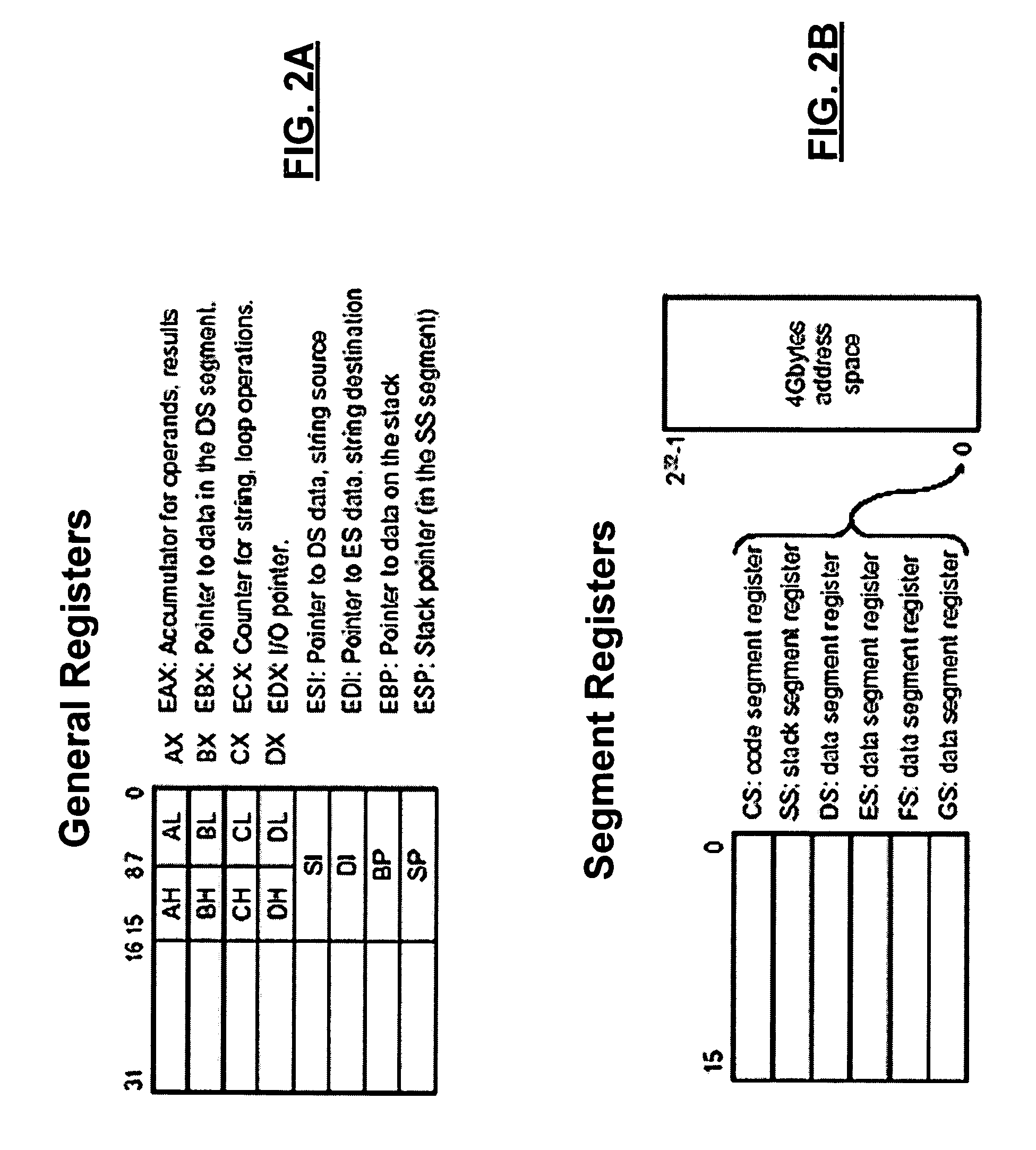
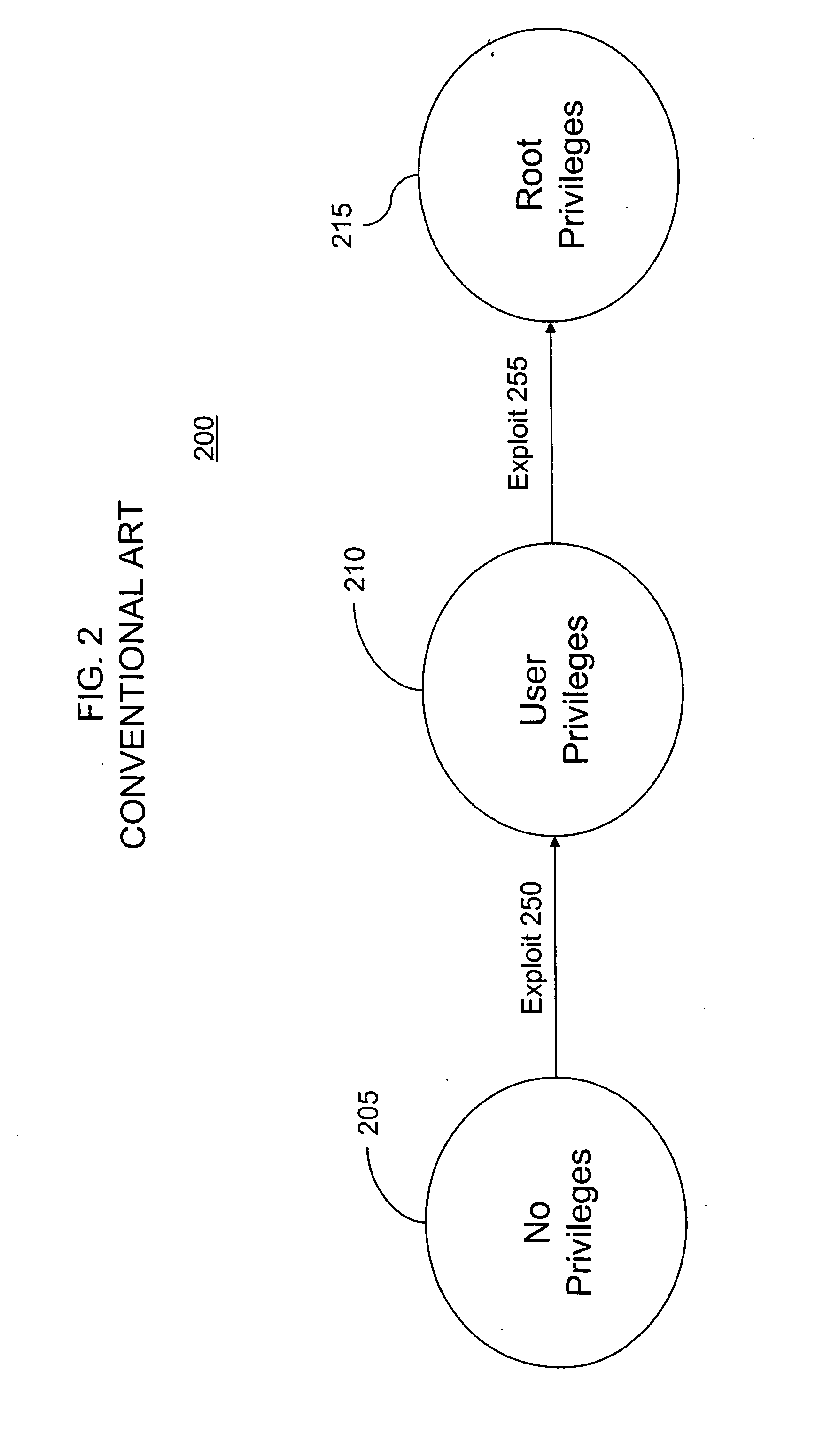
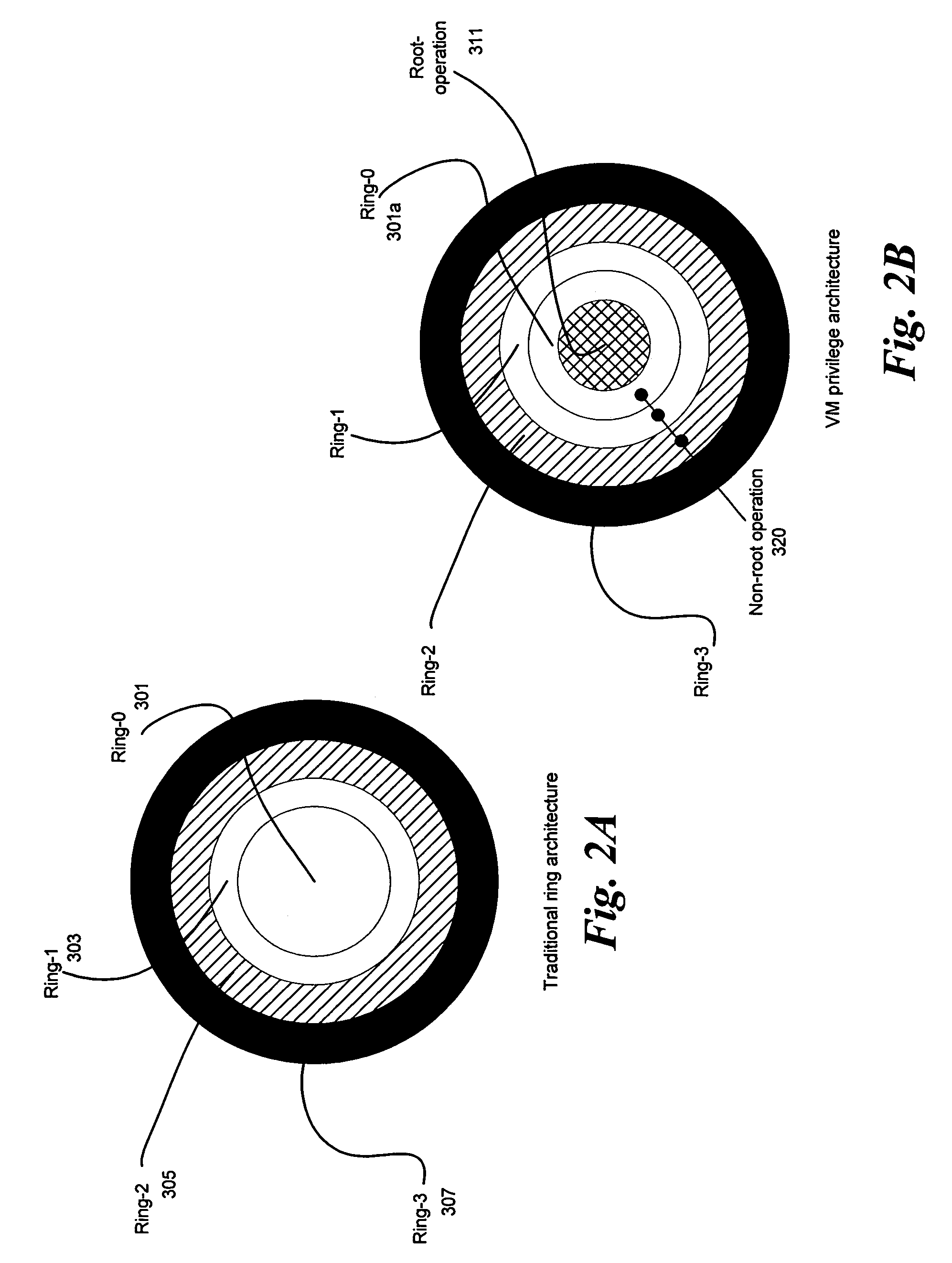
A privilege level in the x86 instruction set controls the access of the program currently running on the processor to resources such as memory regions, I/O ports, and special instructions. There are 4 privilege levels ranging from 0 which is the most privileged, to 3 which is least privileged. Most modern operating systems use level 0 for the kernel/executive, and use level 3 for application programs. Any resource available to level n is also available to level 0..n, so the privilege levels are "rings". It is not necessary to use all four privilege levels. Existing software that was designed to use only one or two levels of privilege can simply ignore the other levels offered by the 80386 and later processors. A one-level system should use privilege level zero; a two-level system should use privilege levels zero and three. Here level zero is called the Supervisor mode while level three is User mode. All versions of Windows below Windows XP use only the two-level system. The real mode programs in 8086 are executed at level 0 whereas virtual mode in 8086 executes all programs at level 3.
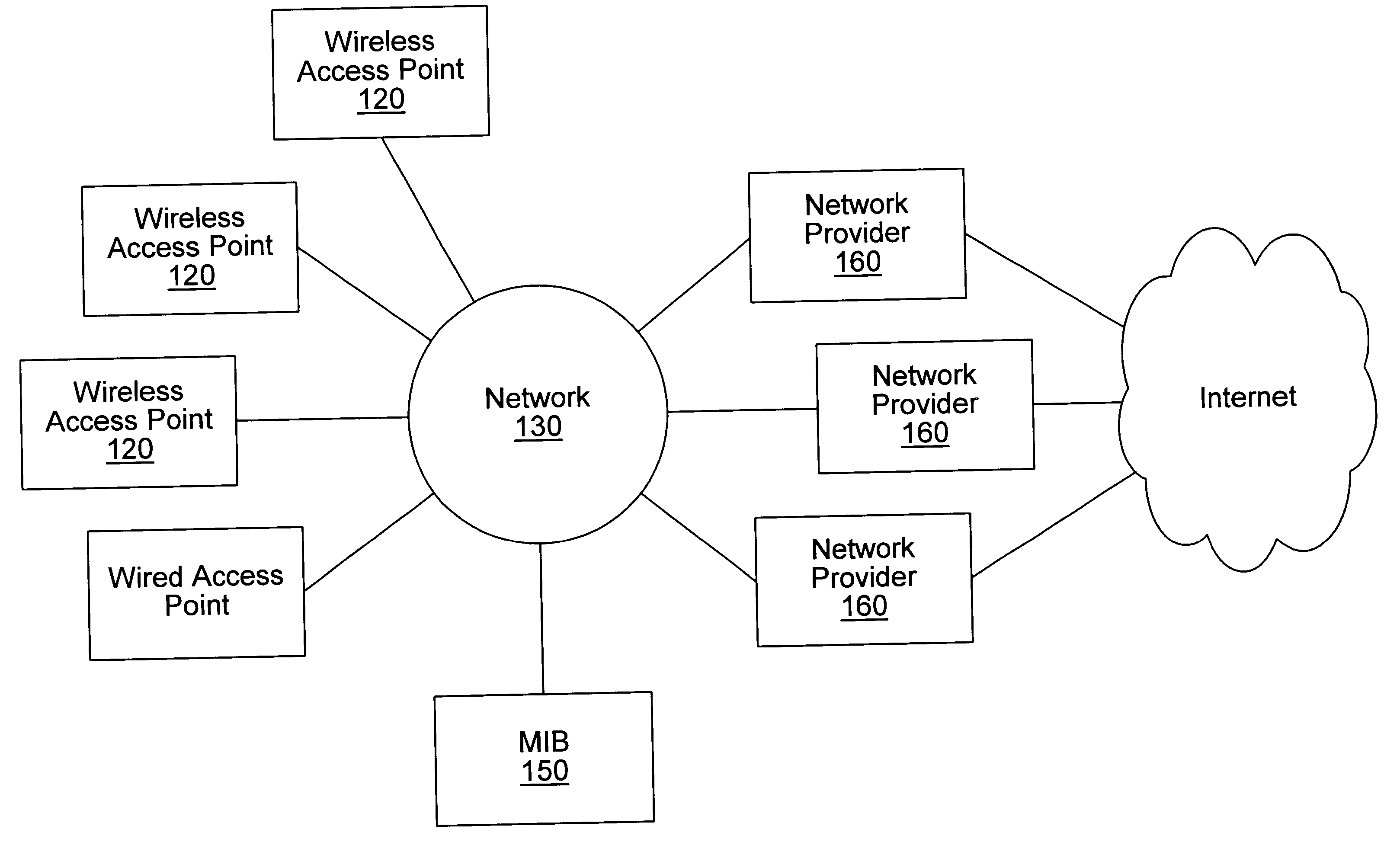
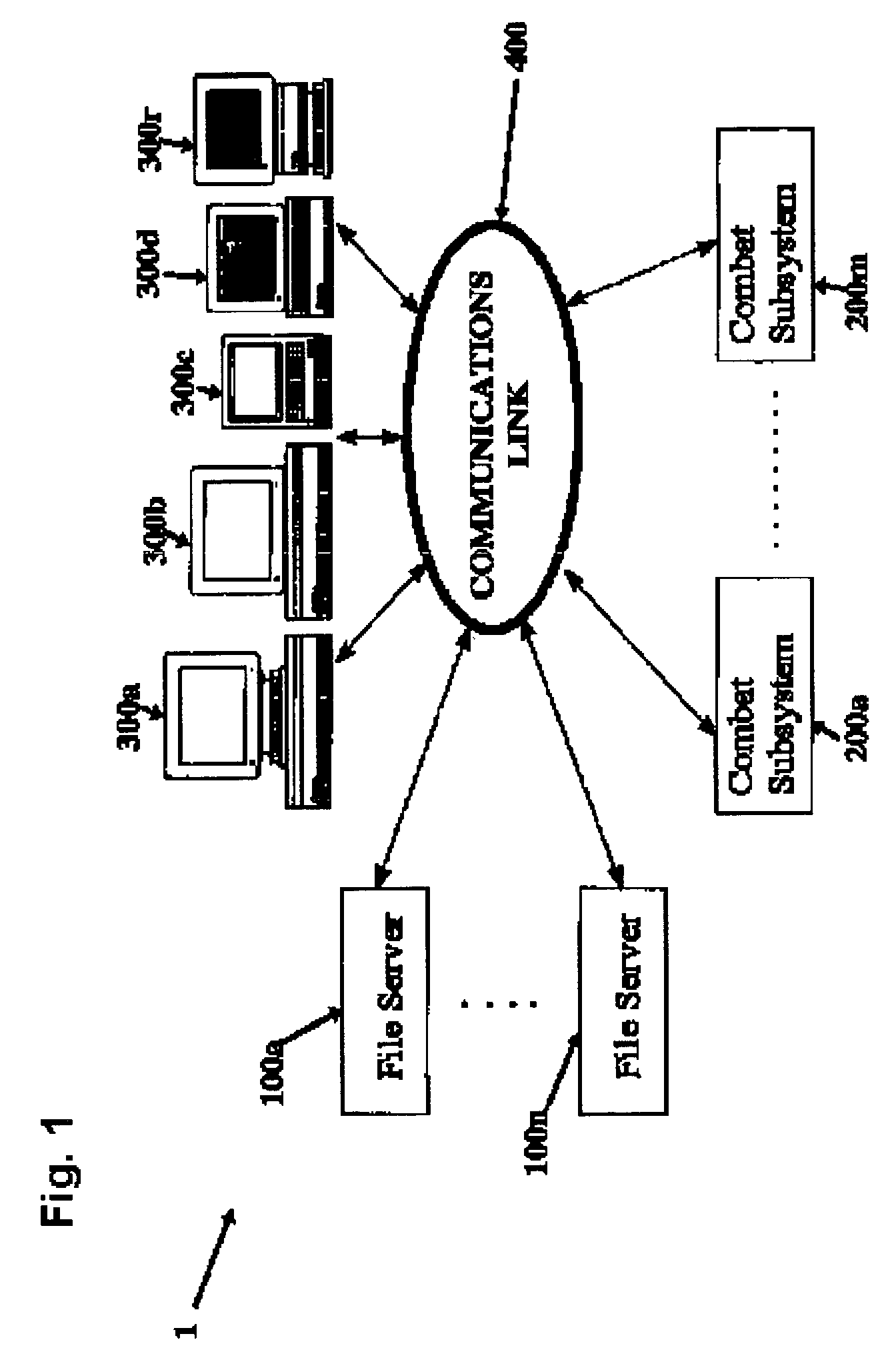
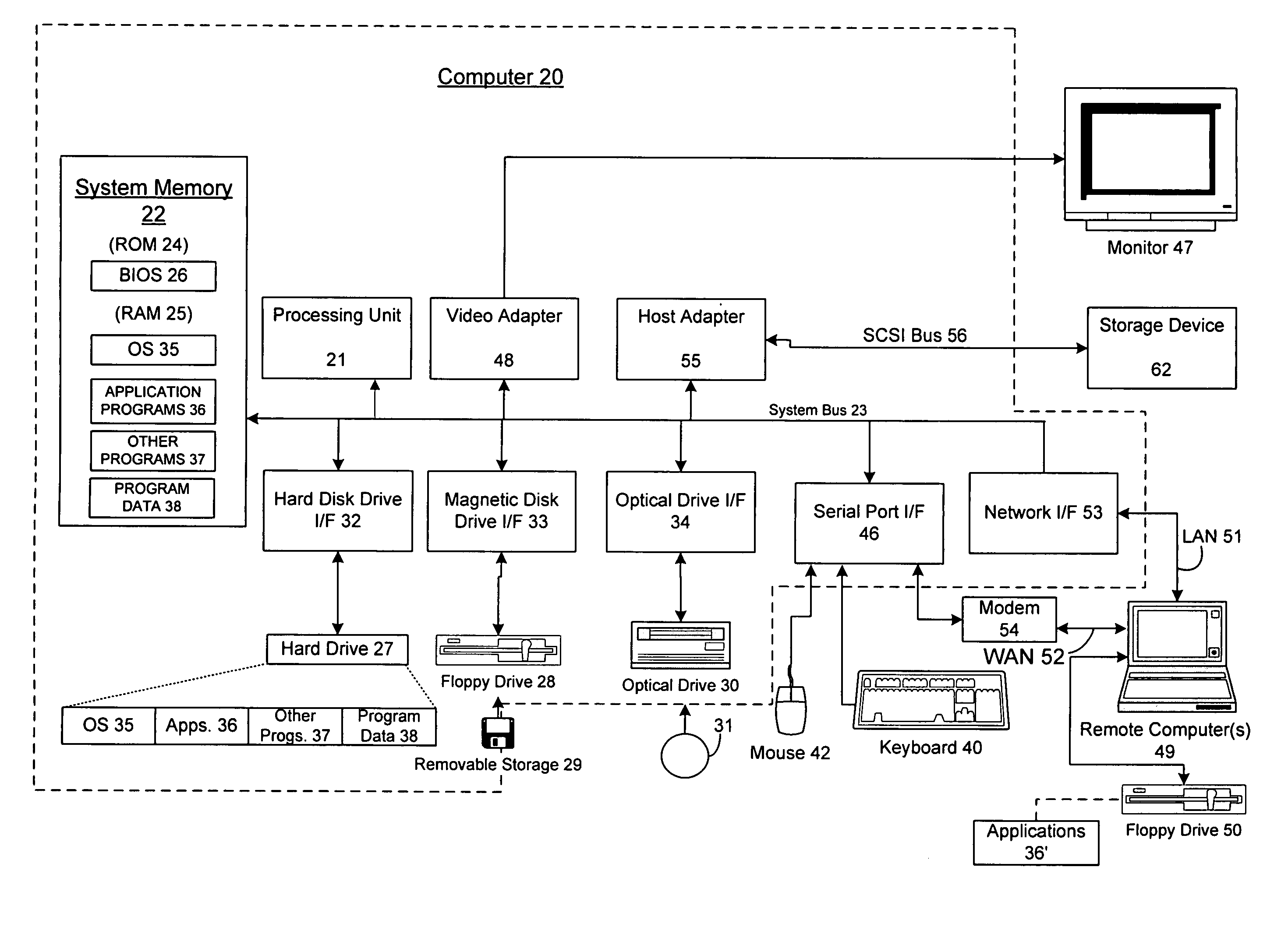
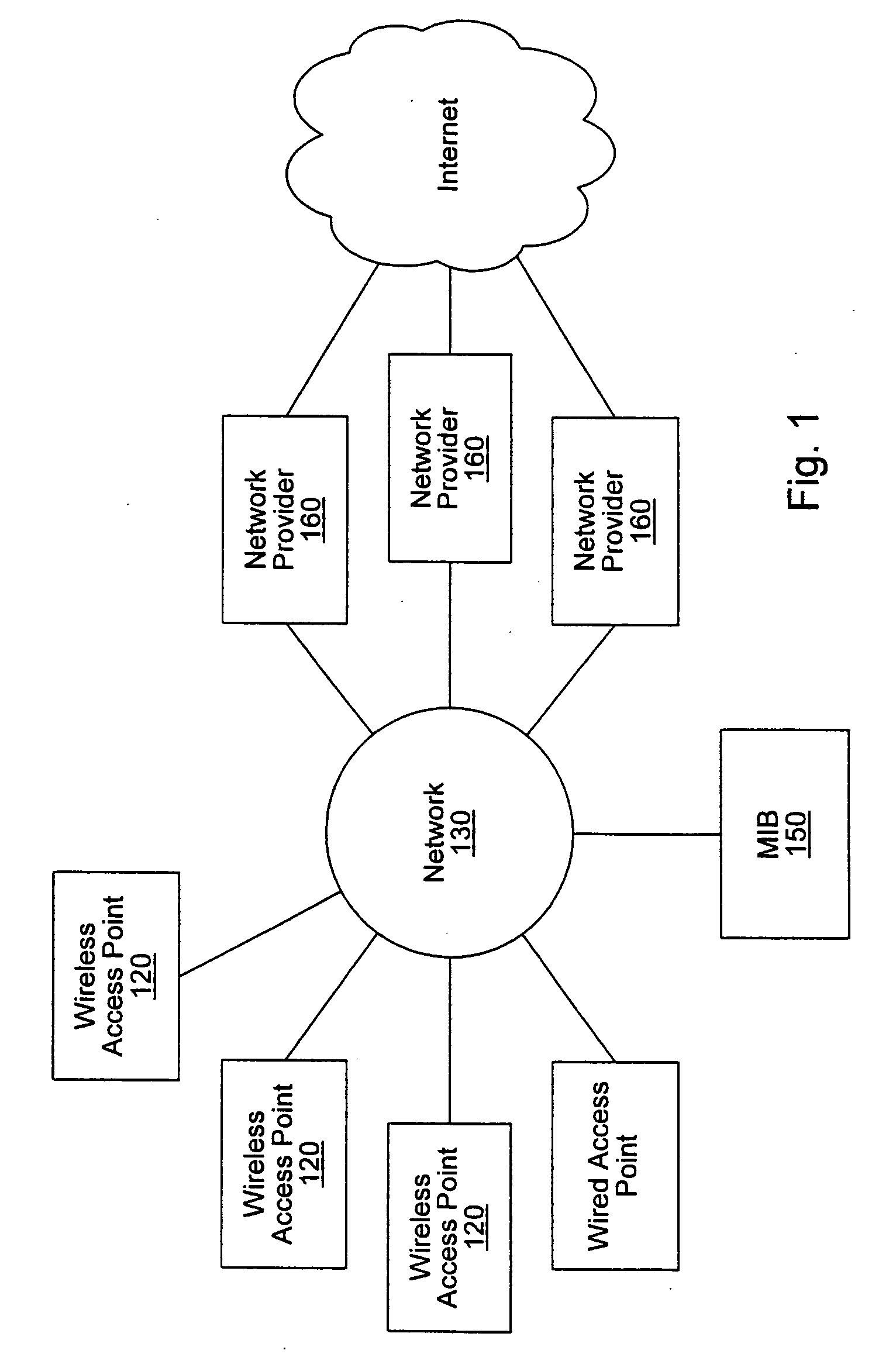
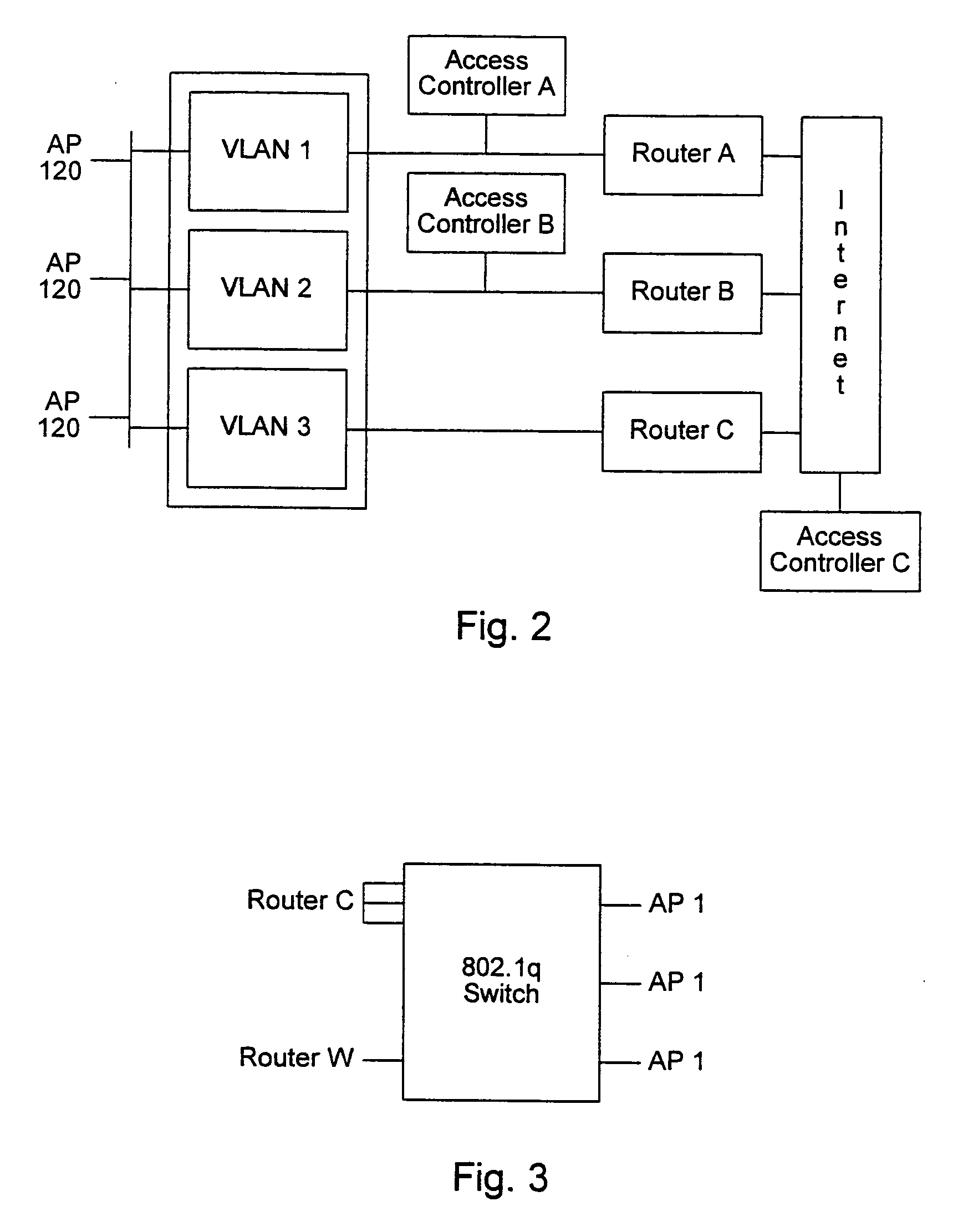
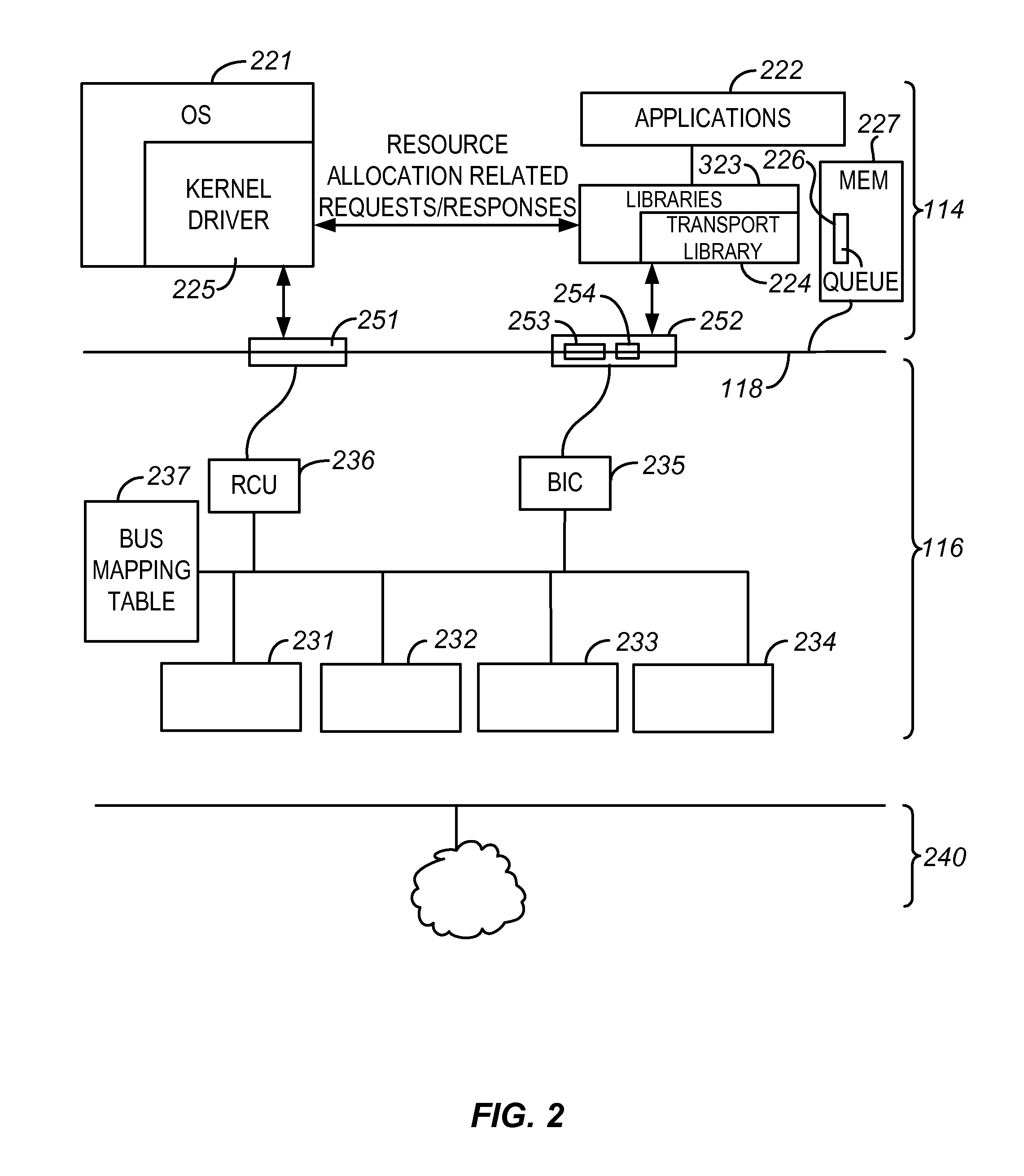
Distributed network communication system which enables multiple network providers to use a common distributed network infrastructure
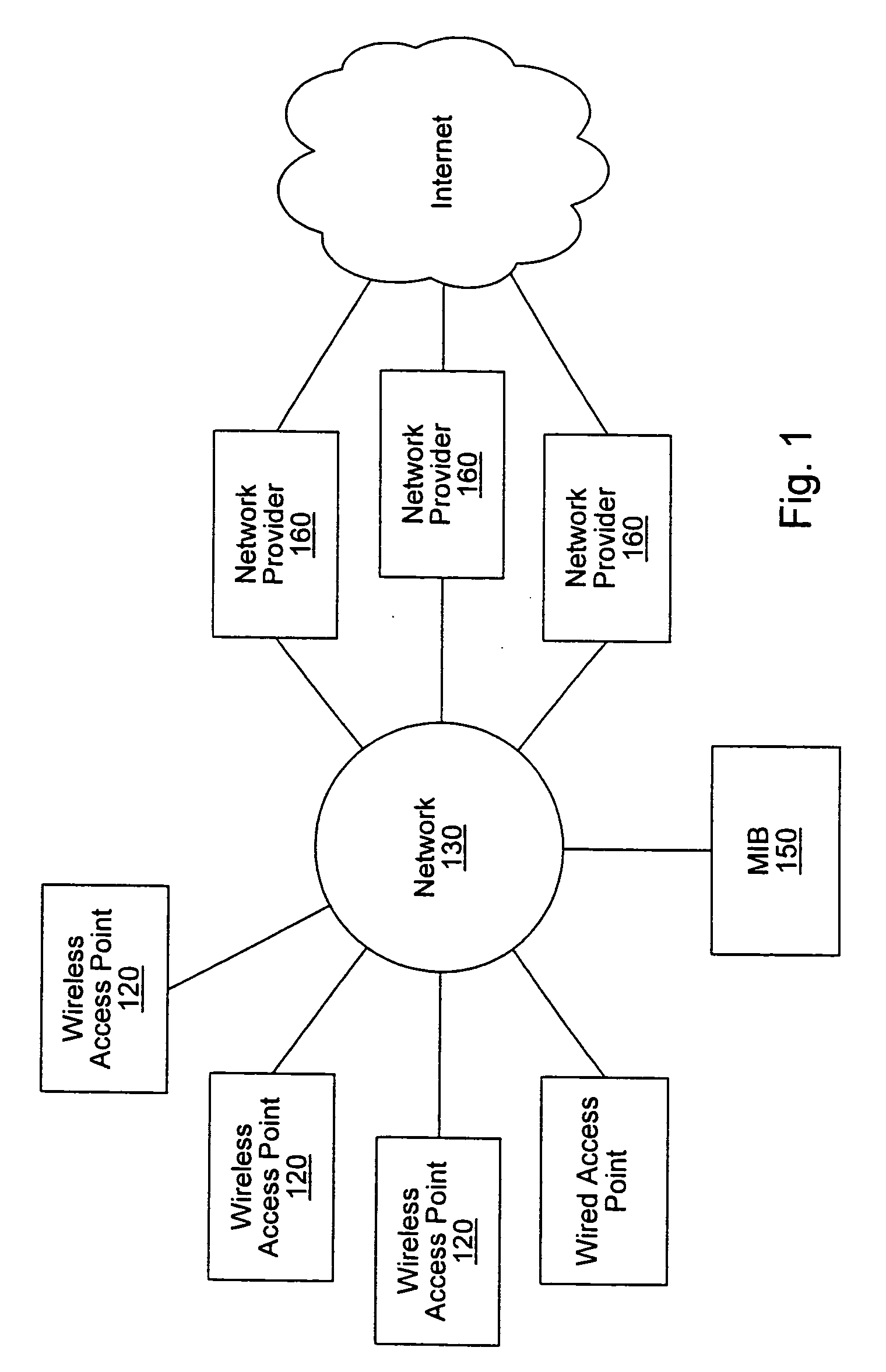
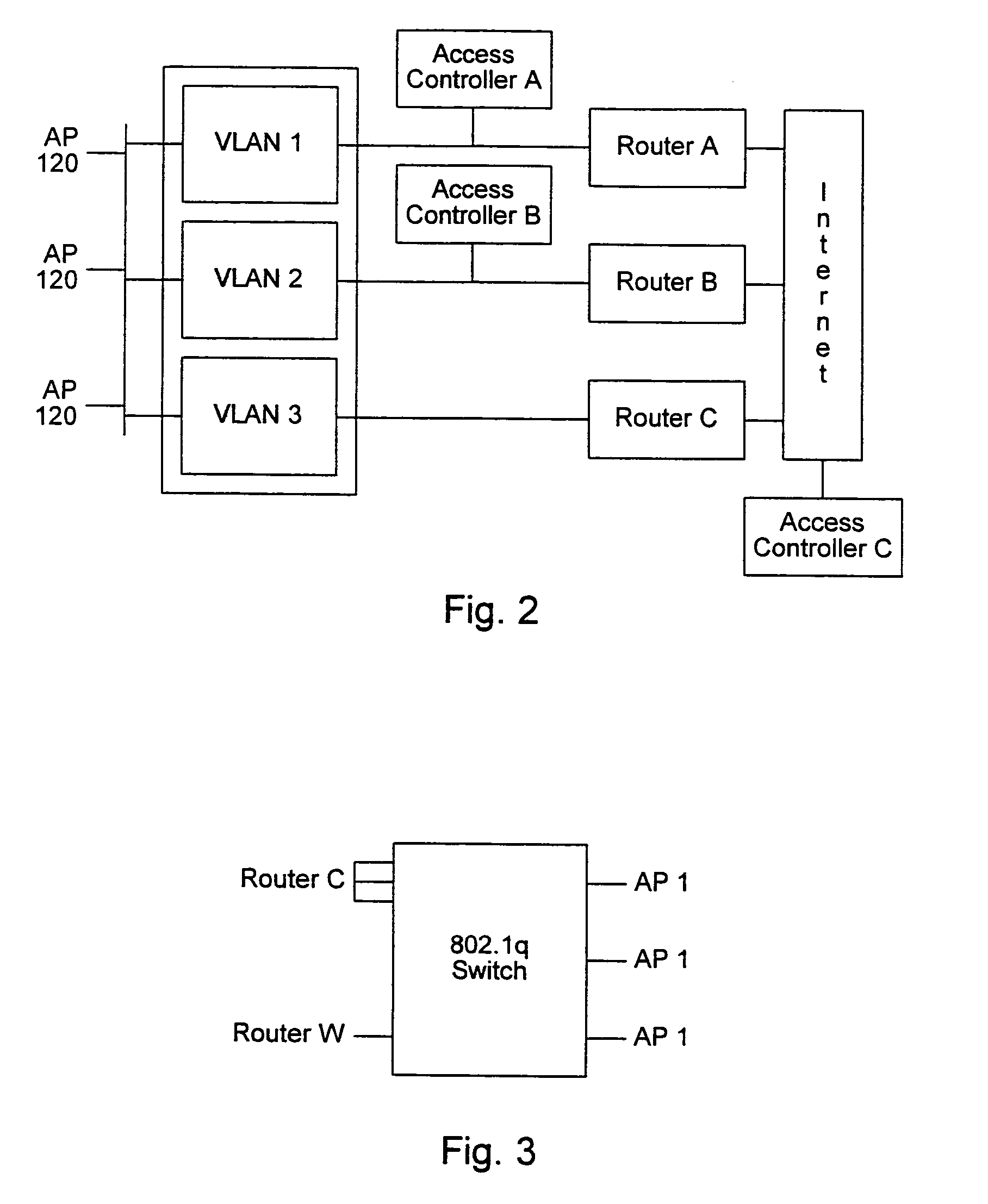
InactiveUS6732176B1Metering/charging/biilling arrangementsMultiple digital computer combinationsCommunications systemNetworked system
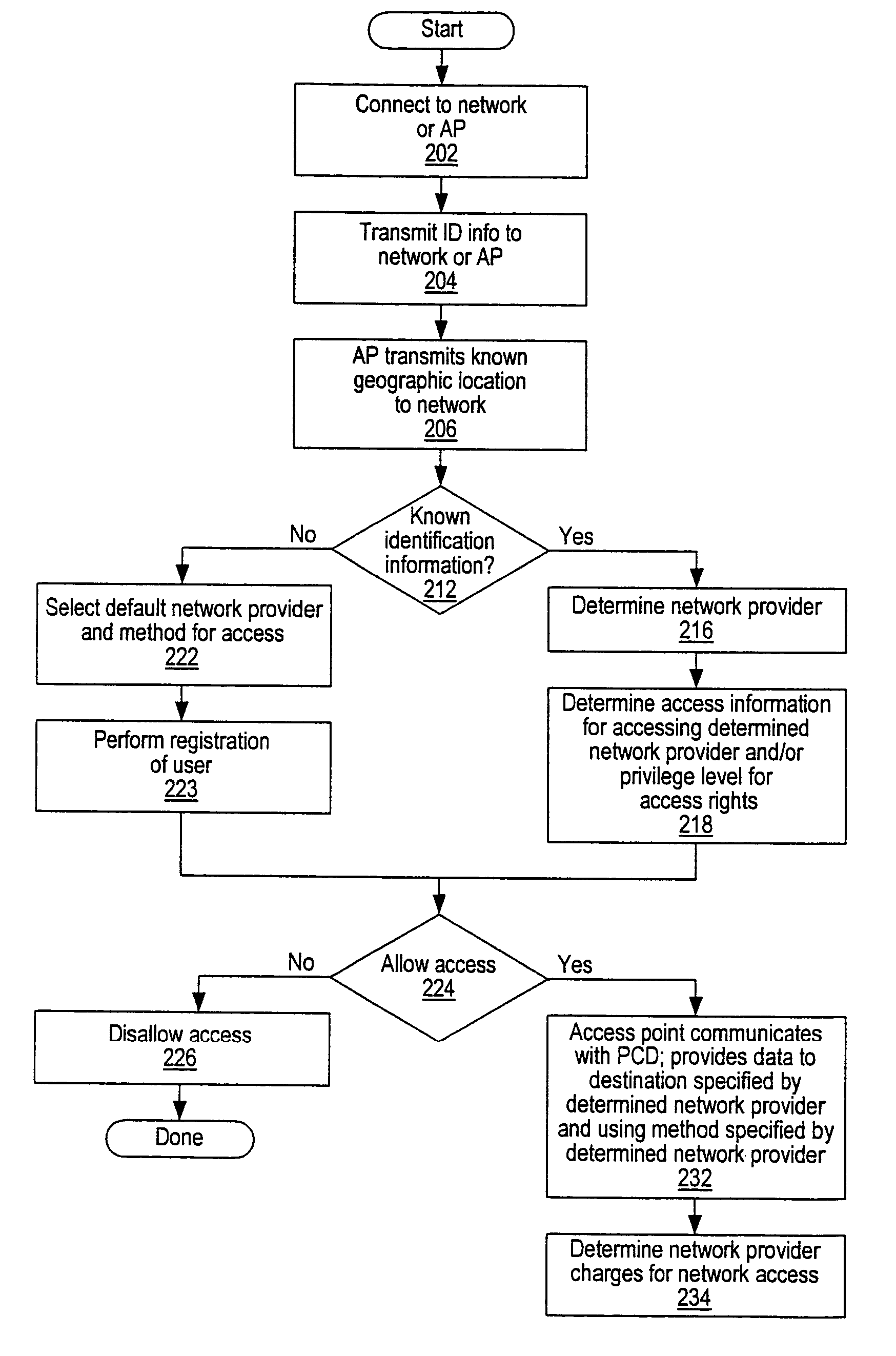
A system and method for providing access and / or roaming features on a network system. The network system includes a plurality of wireless and / or wired access points coupled to a network. A portable computing device (PCD) of a user may store identification information which uniquely indicates a network provider of a plurality of possible network providers. The identification information may also or instead indicate an access or privilege level of the user. When the access point receives the identification information from a PCD of a user, the access point may determine the appropriate network provider for the portable computing device using the identification information. Network access may then be provided to the portable computing device through the determined network provider.
Owner:CISCO TECH INC
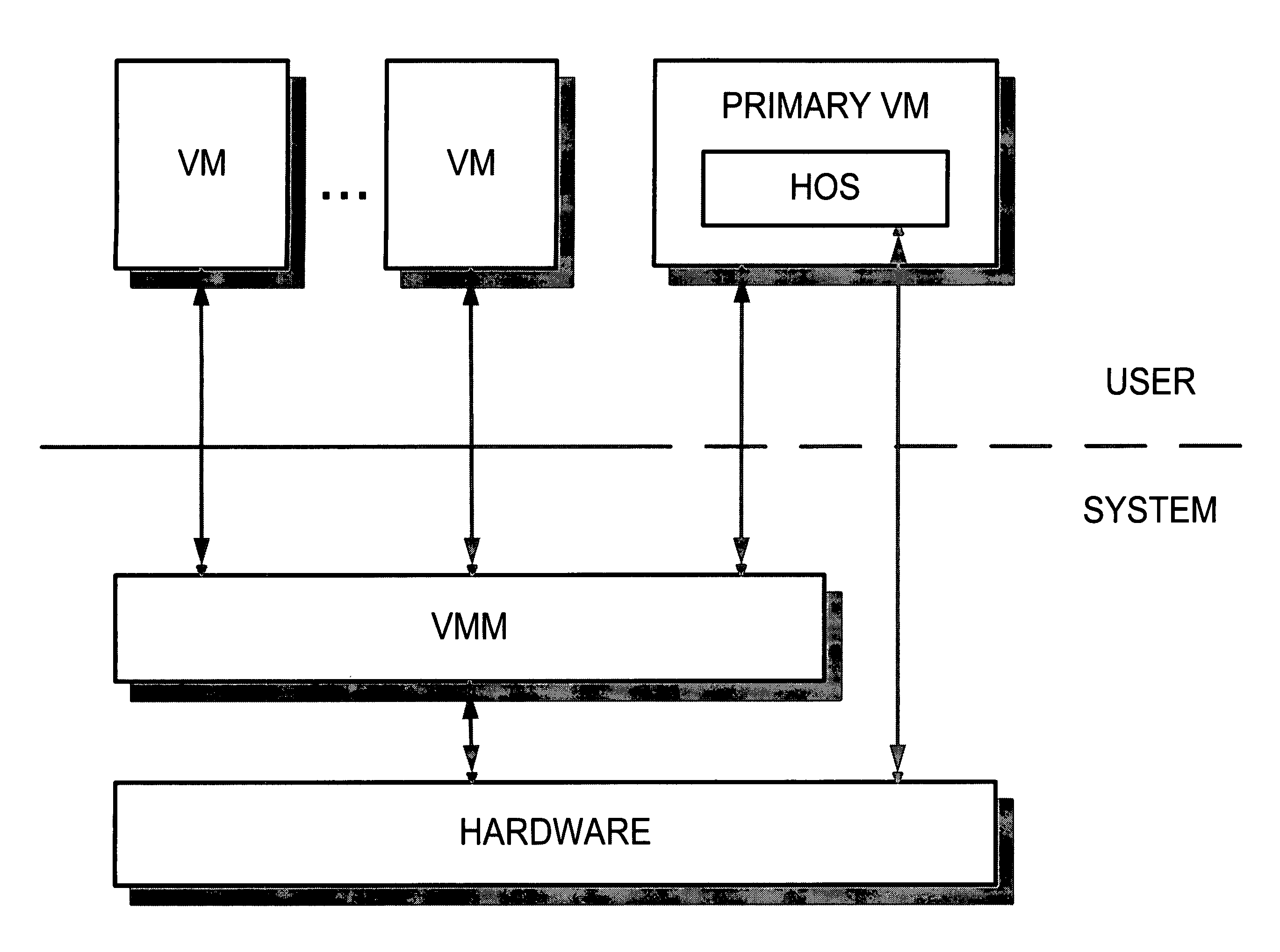
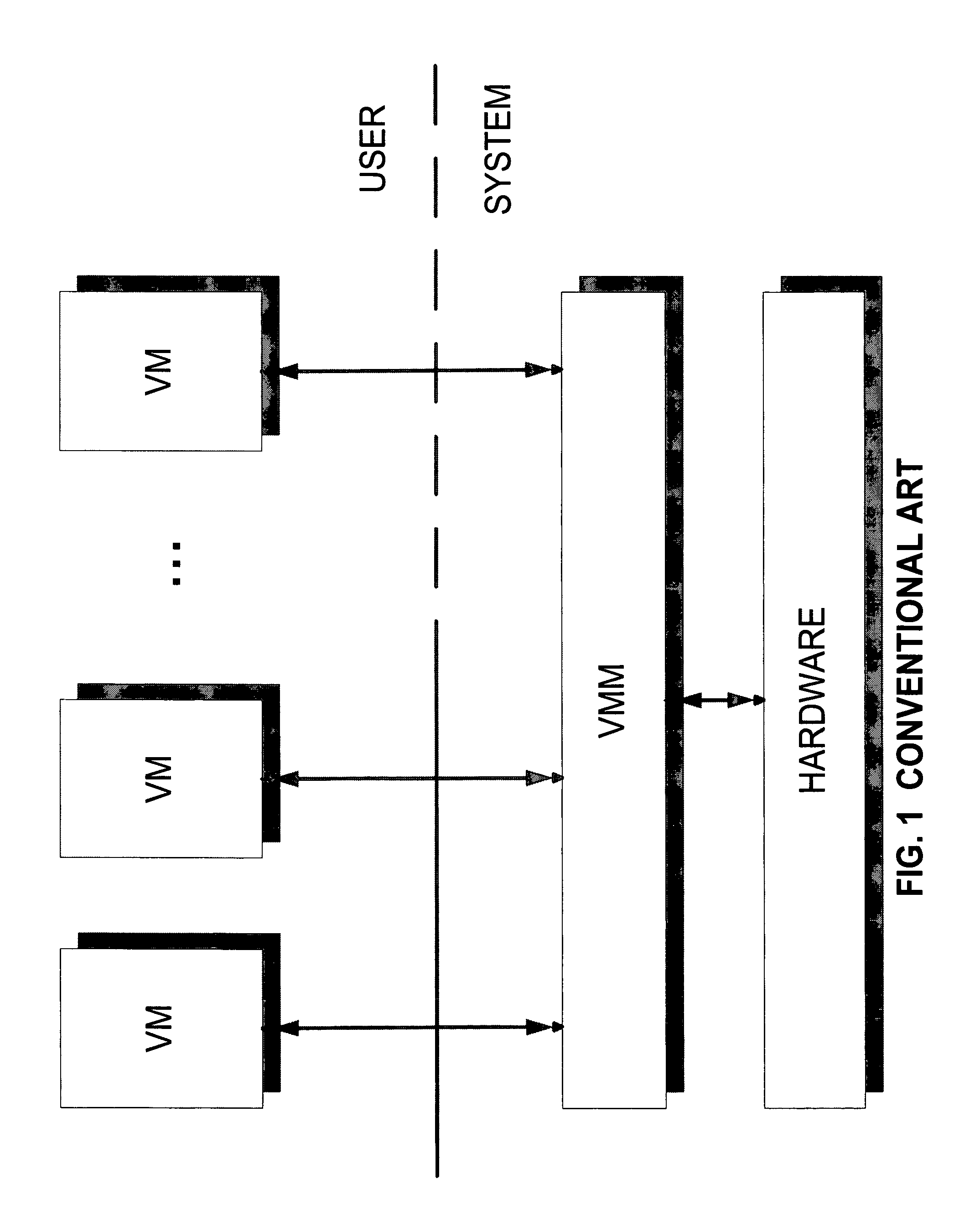
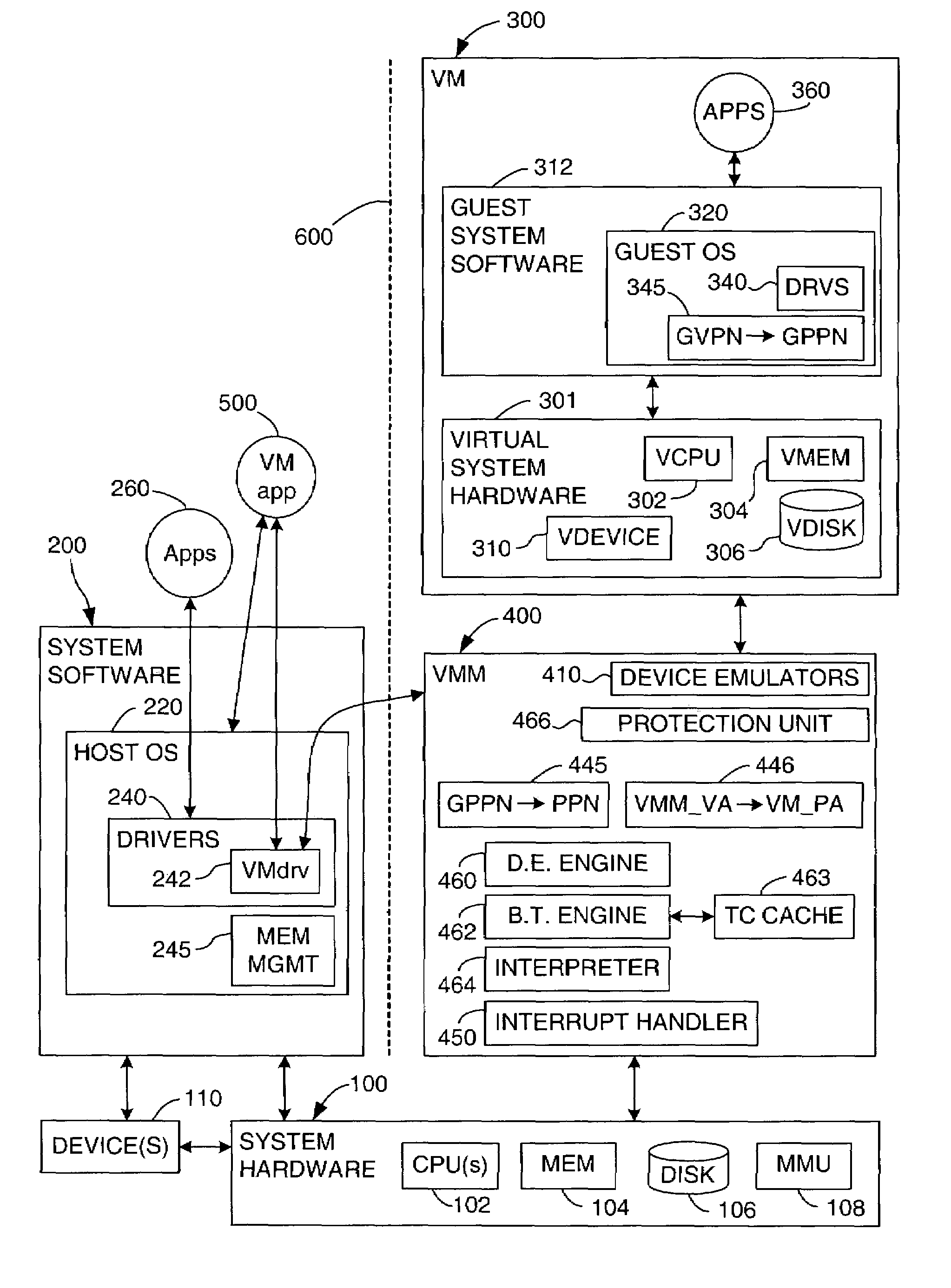
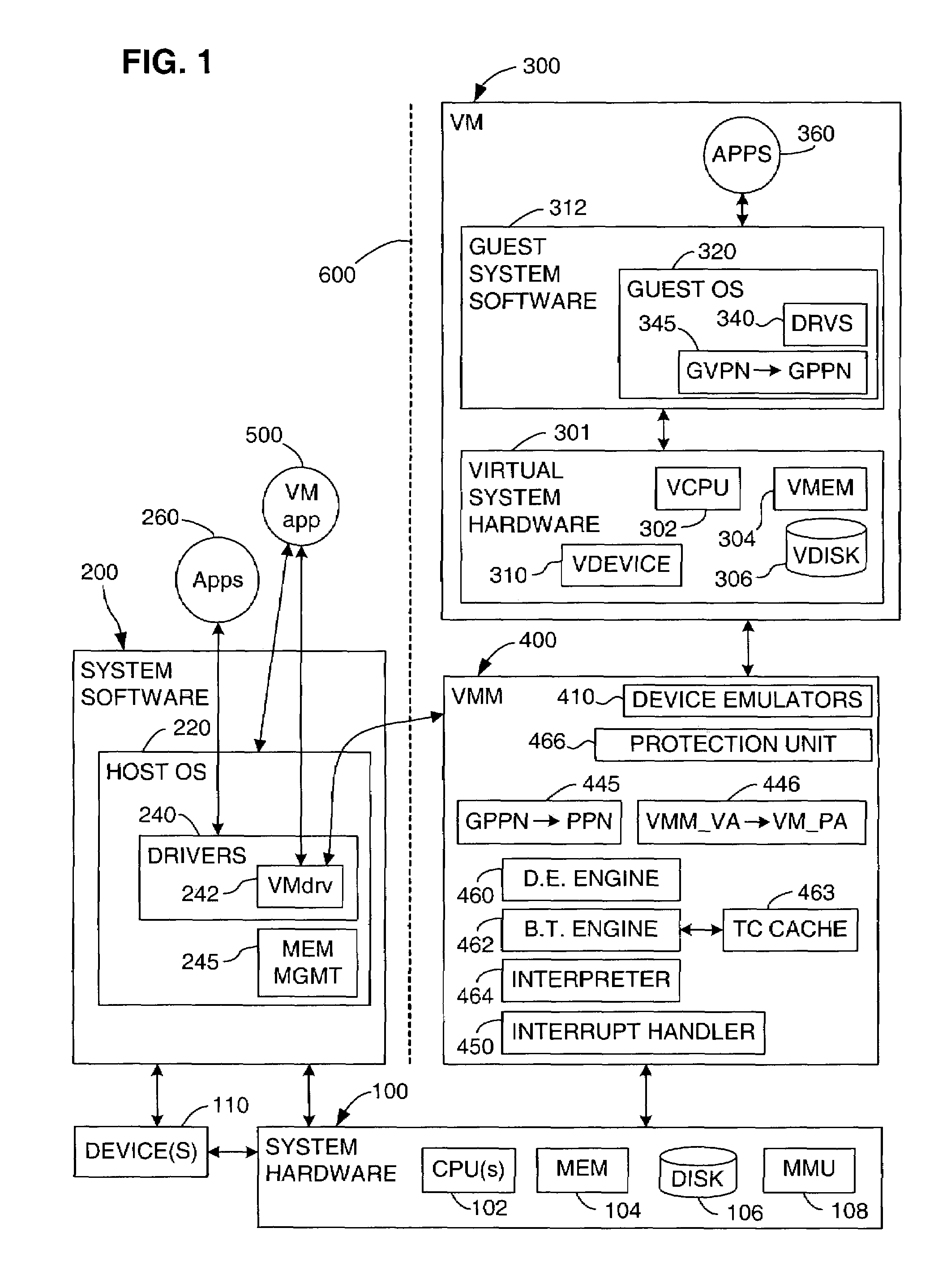
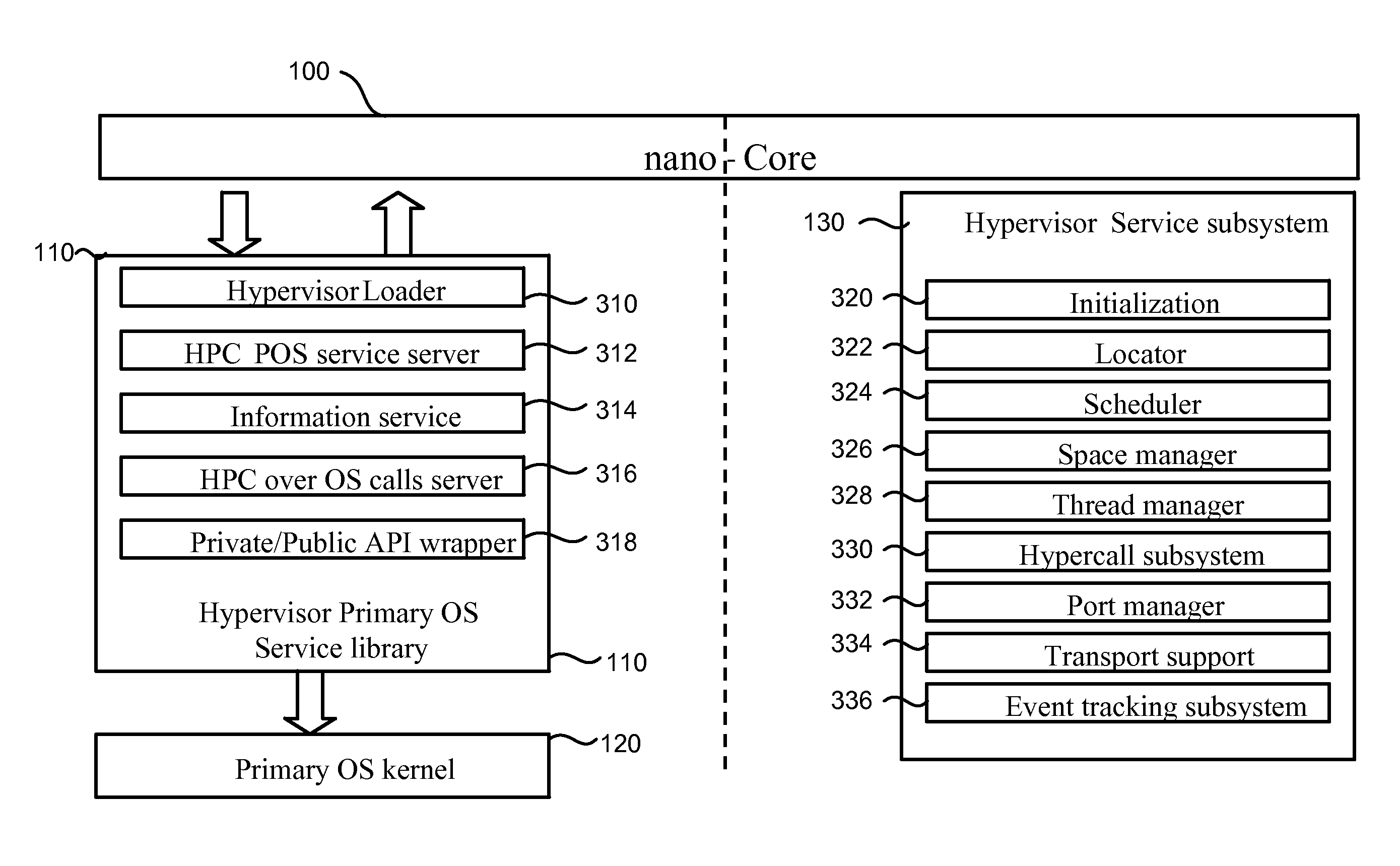
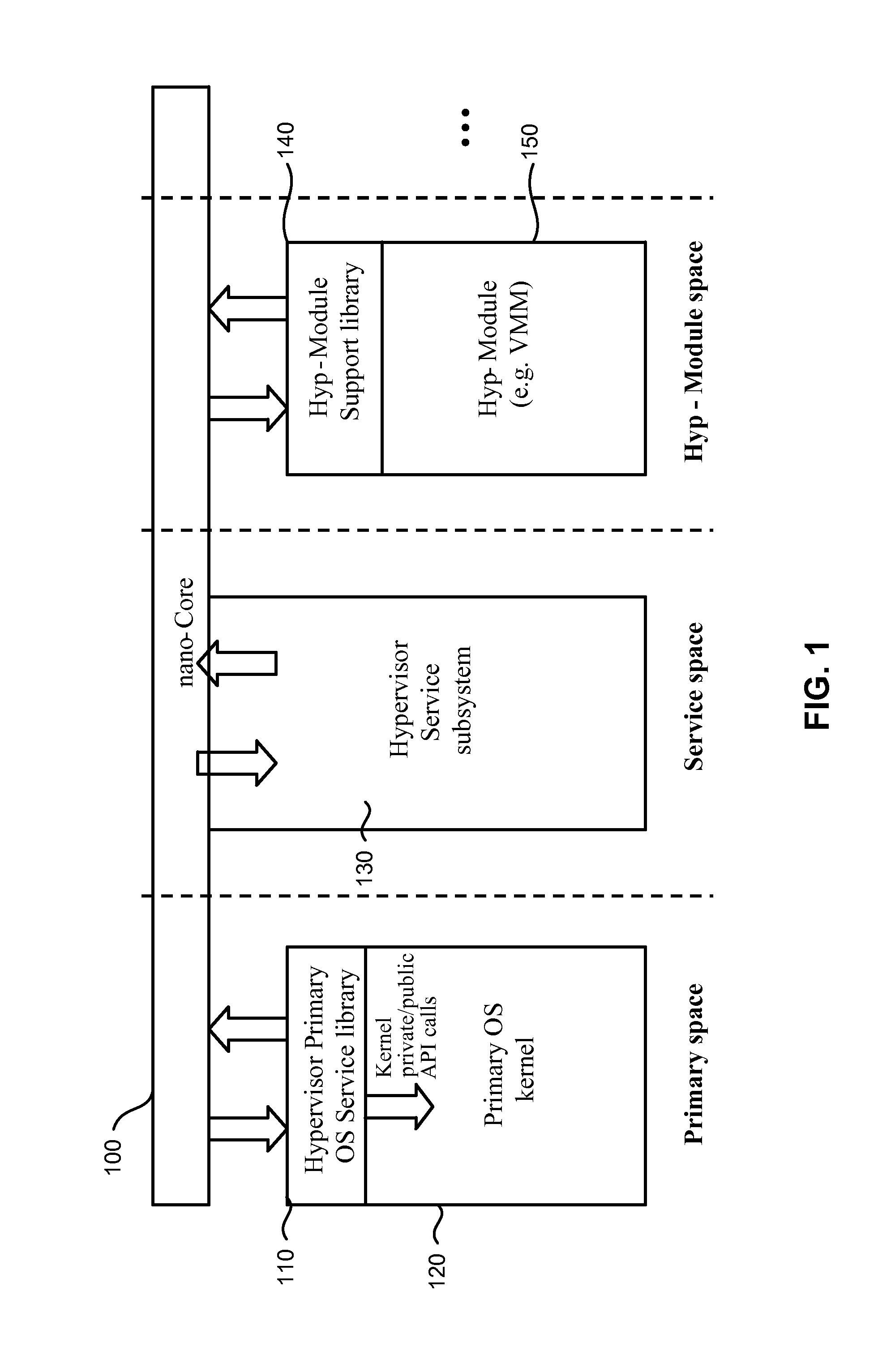
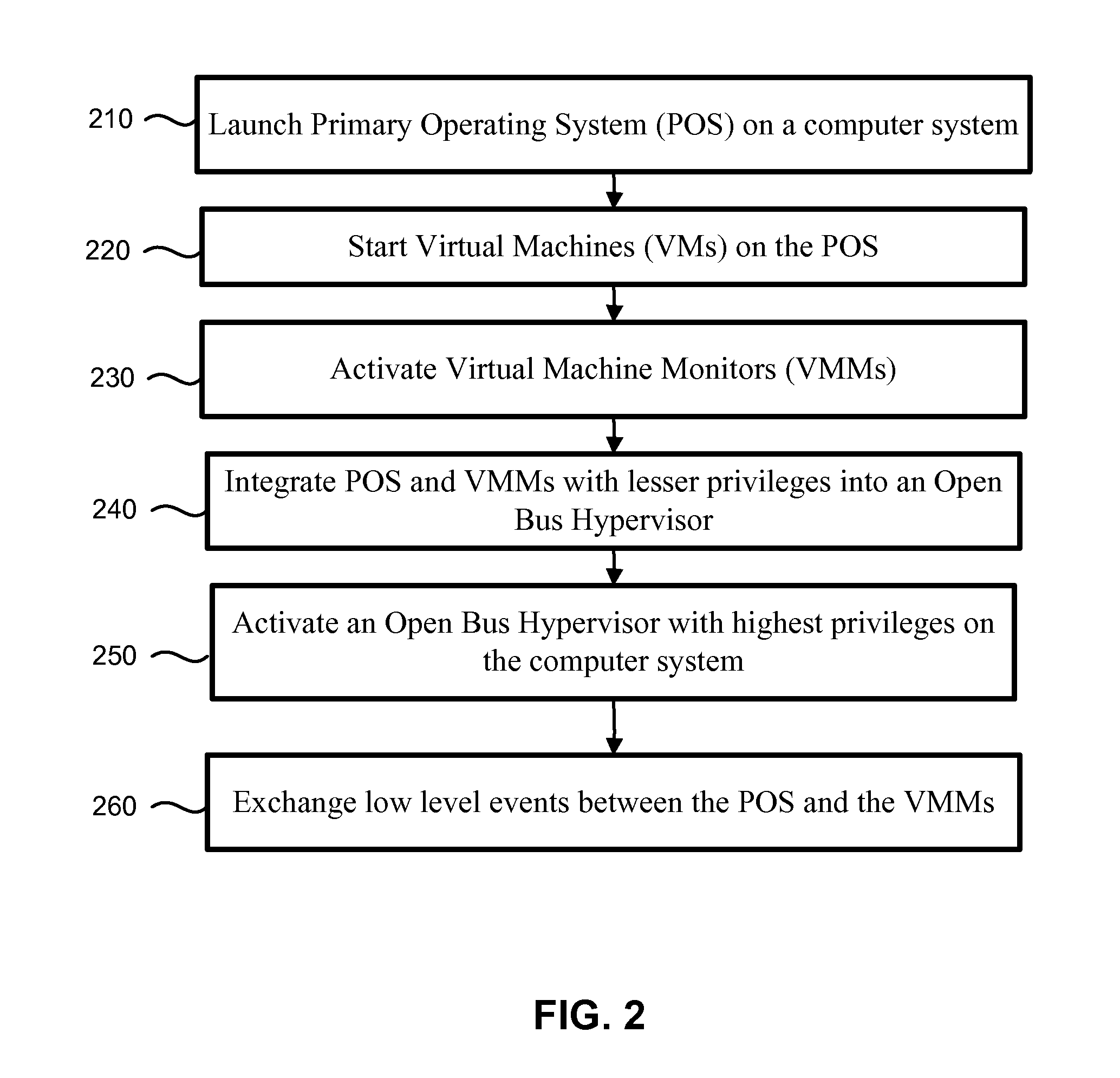
System and method for starting virtual machine monitor in common with already installed operating system
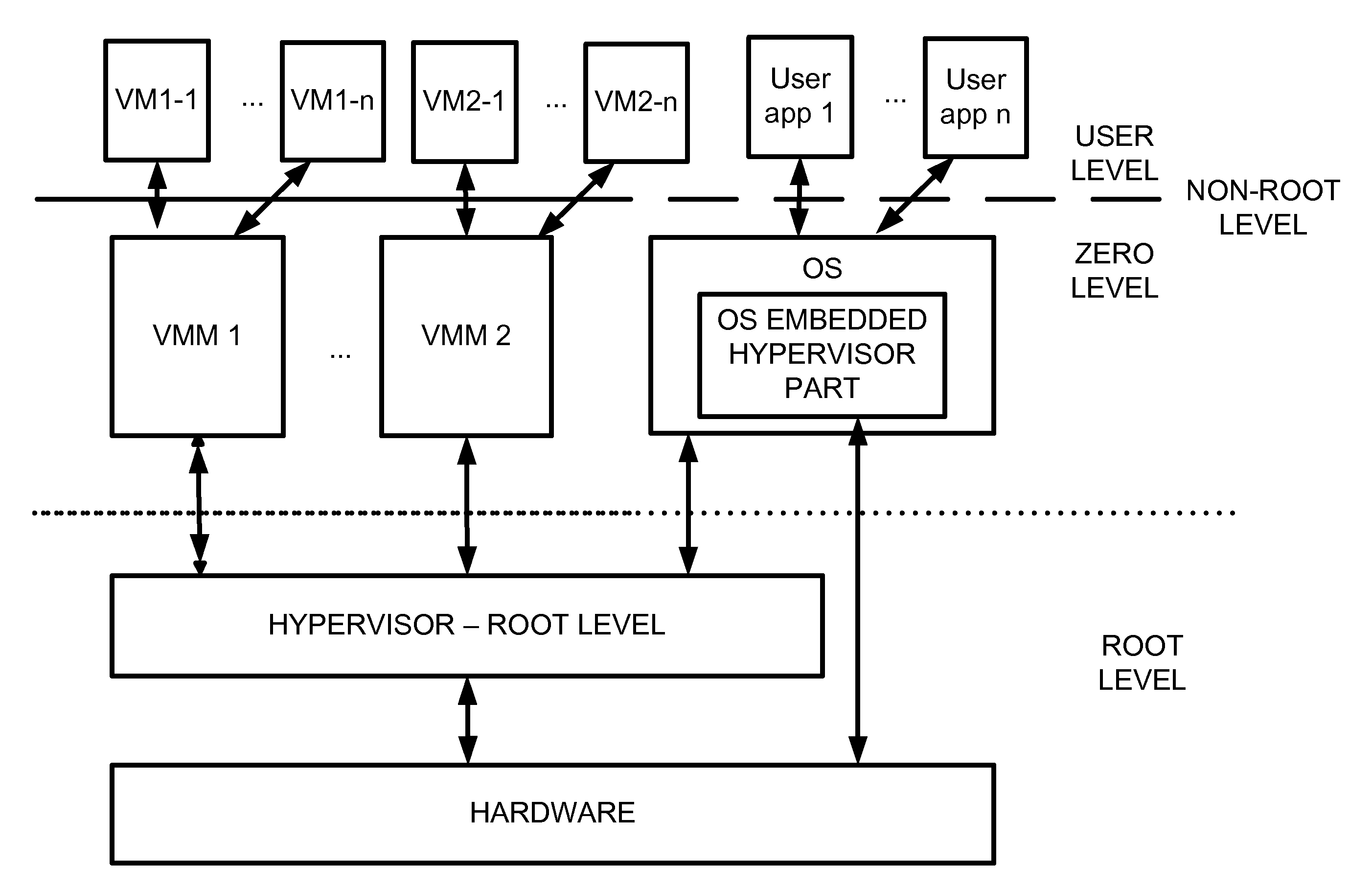
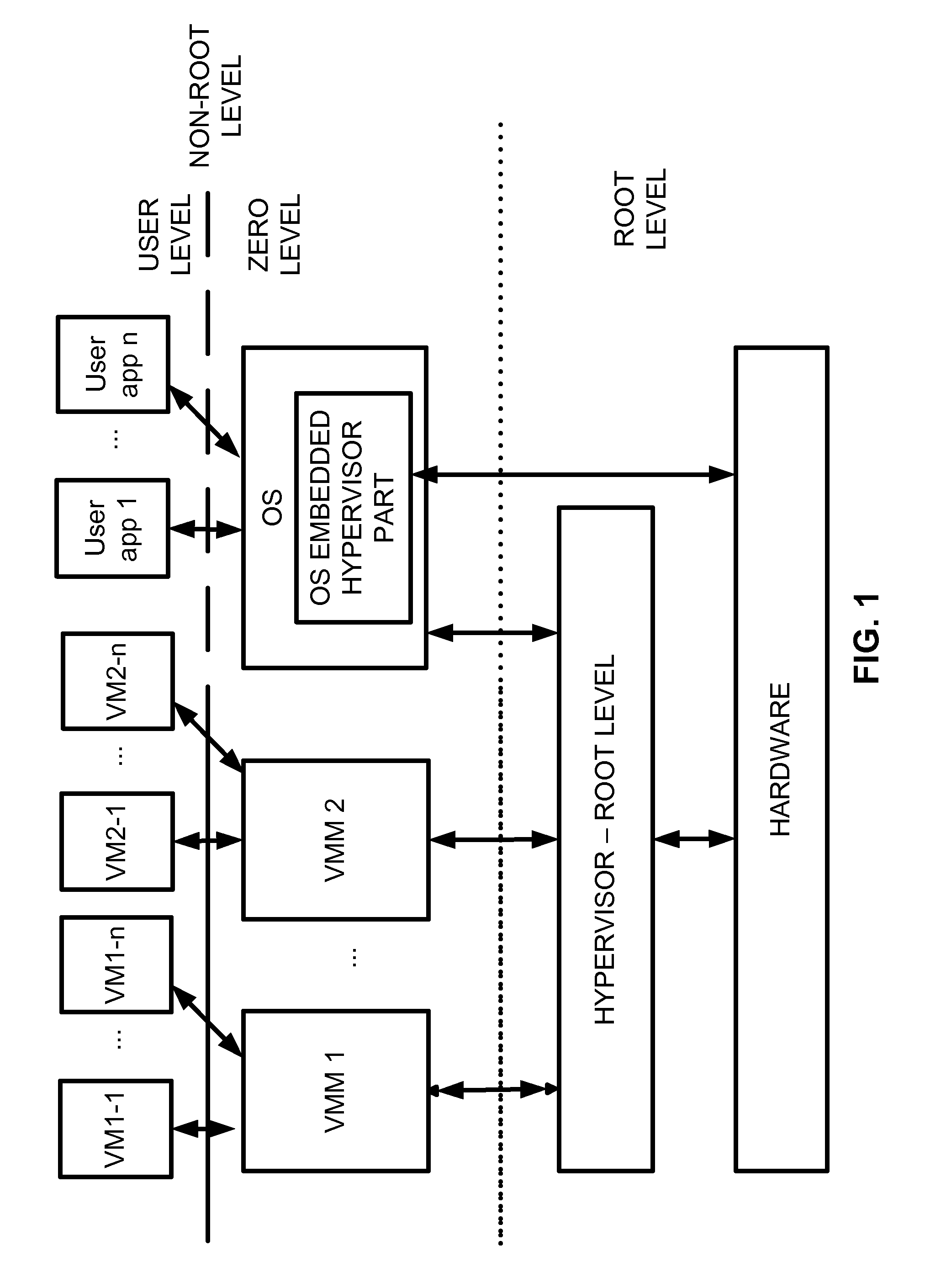
ActiveUS7865893B1Error detection/correctionPlatform integrity maintainanceComputer hardwareComputerized system
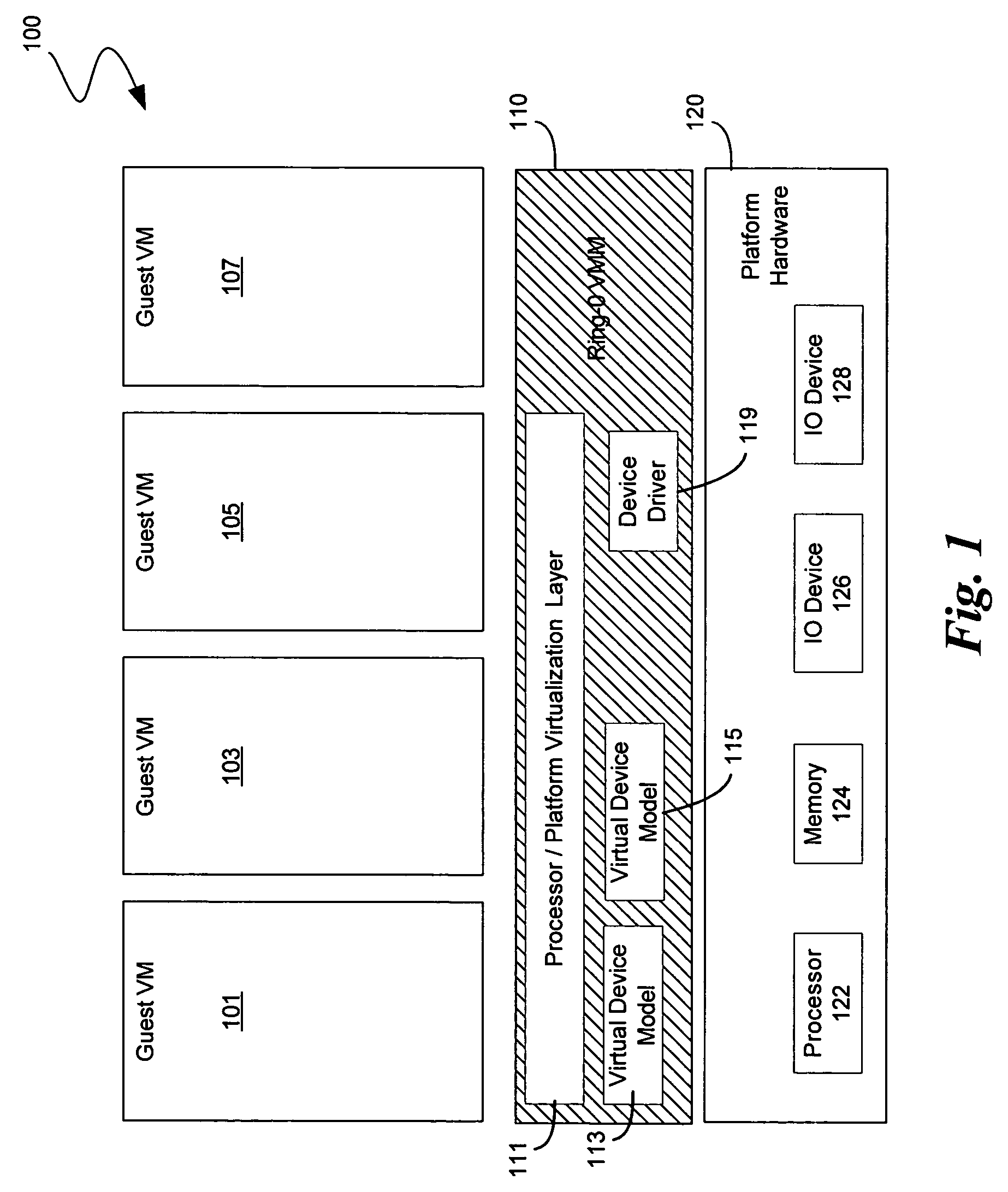
A computer system includes a Hypervisor having the highest privilege level; a Primary Virtual Machine Monitor (VMM) running with the same or fewer privileges than the Hypervisor; and a Primary Virtual Machine (PVM) without system level privileges and having a Primary operating system (POS) running within it. The POS can be the same operating system that ran on the computer system prior to activation of the Hypervisor. The POS can have hardware drivers used by other components for accessing hardware through the POS. The Hypervisor can have hardware drivers used by other components for accessing hardware through the Hypervisor. Alternatively, the POS can have some hardware drivers used by other components for accessing hardware, and the Hypervisor can have other hardware drivers used by the other components for accessing other hardware through the Hypervisor. The POS can have direct access to at least some real hardware devices.
Owner:PARALLELS INT GMBH
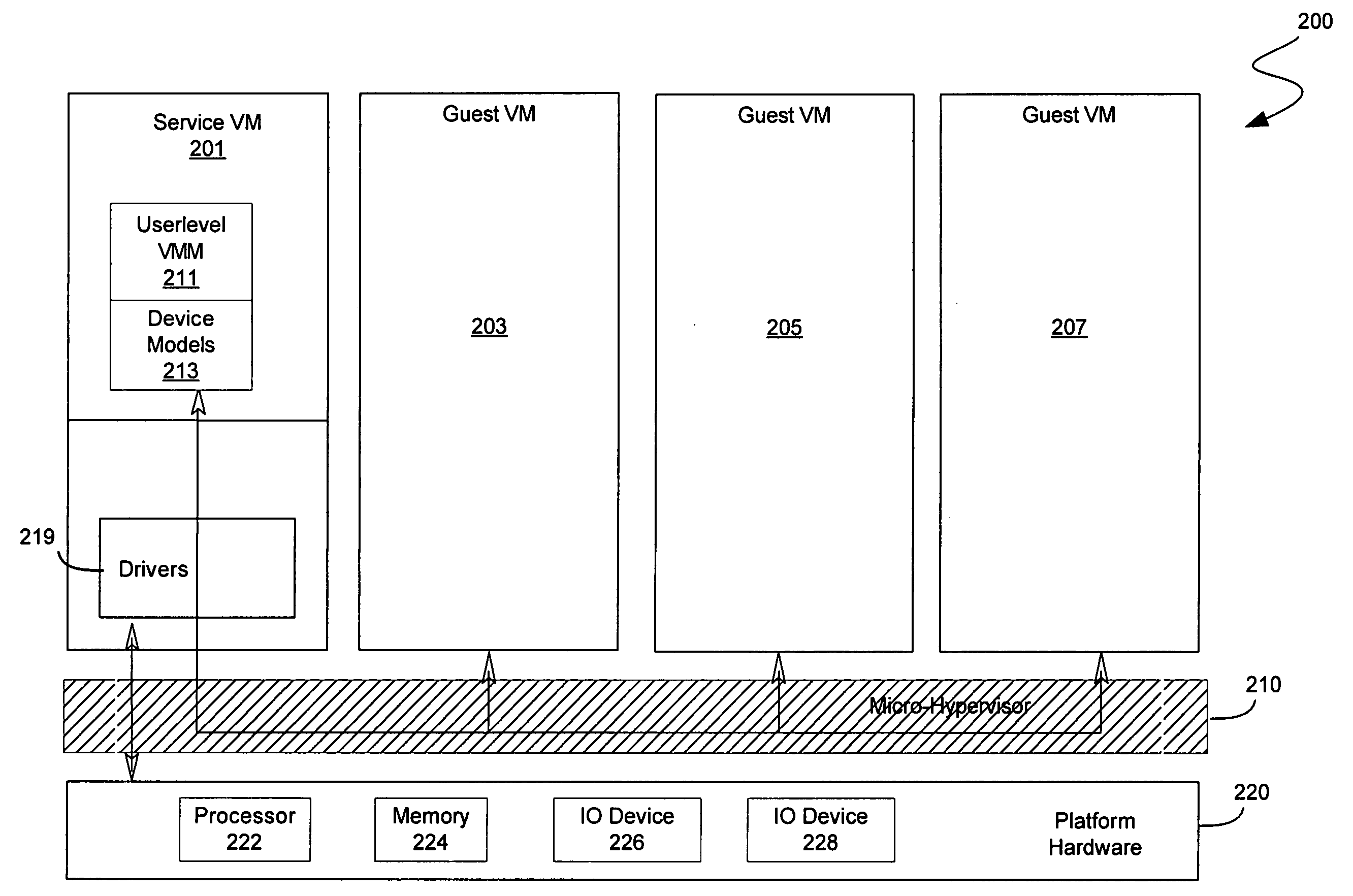
System and method to deprivilege components of a virtual machine monitor
ActiveUS20060130060A1High portability and reliabilityMultiprogramming arrangementsSoftware simulation/interpretation/emulationPrivilege levelHardware virtualization
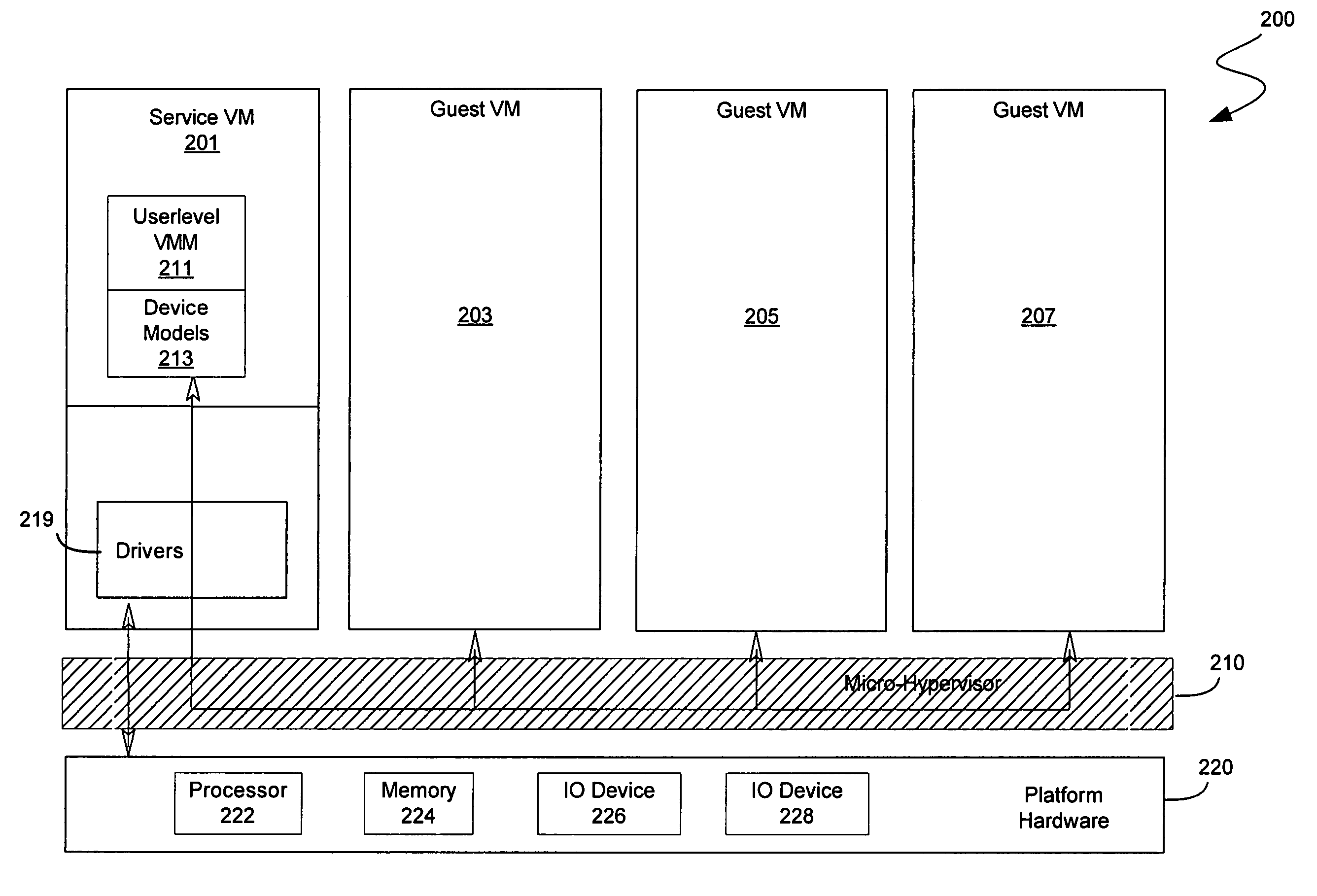
In some embodiments, the invention involves a system to deprivilege components of a virtual machine monitor and enable deprivileged service virtual machines (SVMs) to handle selected trapped events. An embodiment of the invention is a hybrid VMM operating on a platform with hardware virtualization support. The hybrid VMM utilizes features from both hypervisor-based and host-based VMM architectures. In at least one embodiment, the functionality of a traditional VMM is partitioned into a small platform-dependent part called a micro-hypervisor (MH) and one or more platform-independent parts called service virtual machines (SVMs). The micro-hypervisor operates at a higher virtual machine (VM) privilege level than any SVM, while the SVM and other VMs may still have access to any instruction set architecture (ISA) privilege level. Other embodiments are described and claimed.
Owner:INTEL CORP
Secure machine platform that interfaces to operating systems and customized control programs
ActiveUS7073059B2Program initiation/switchingError detection/correctionOperational systemService provision
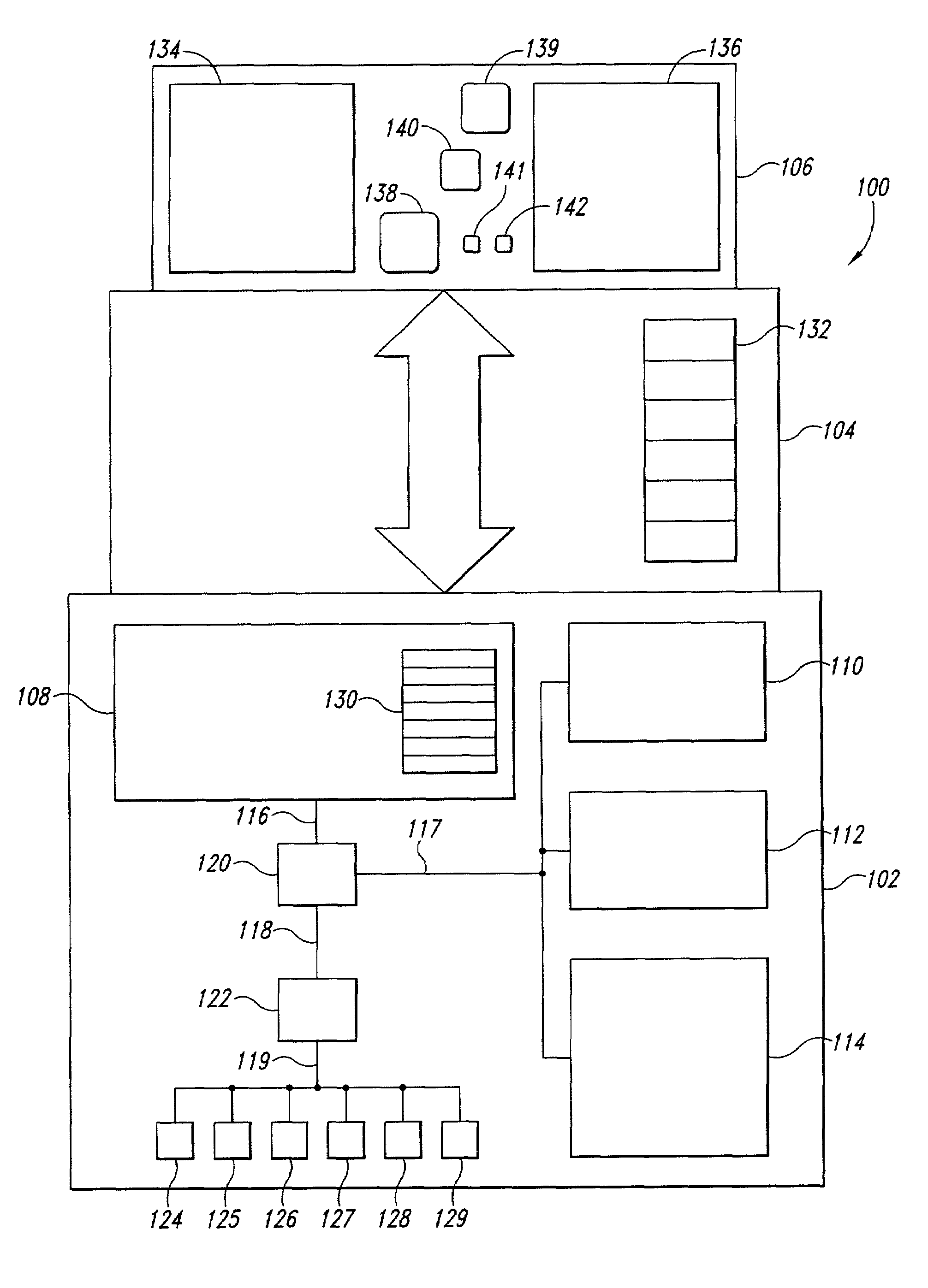
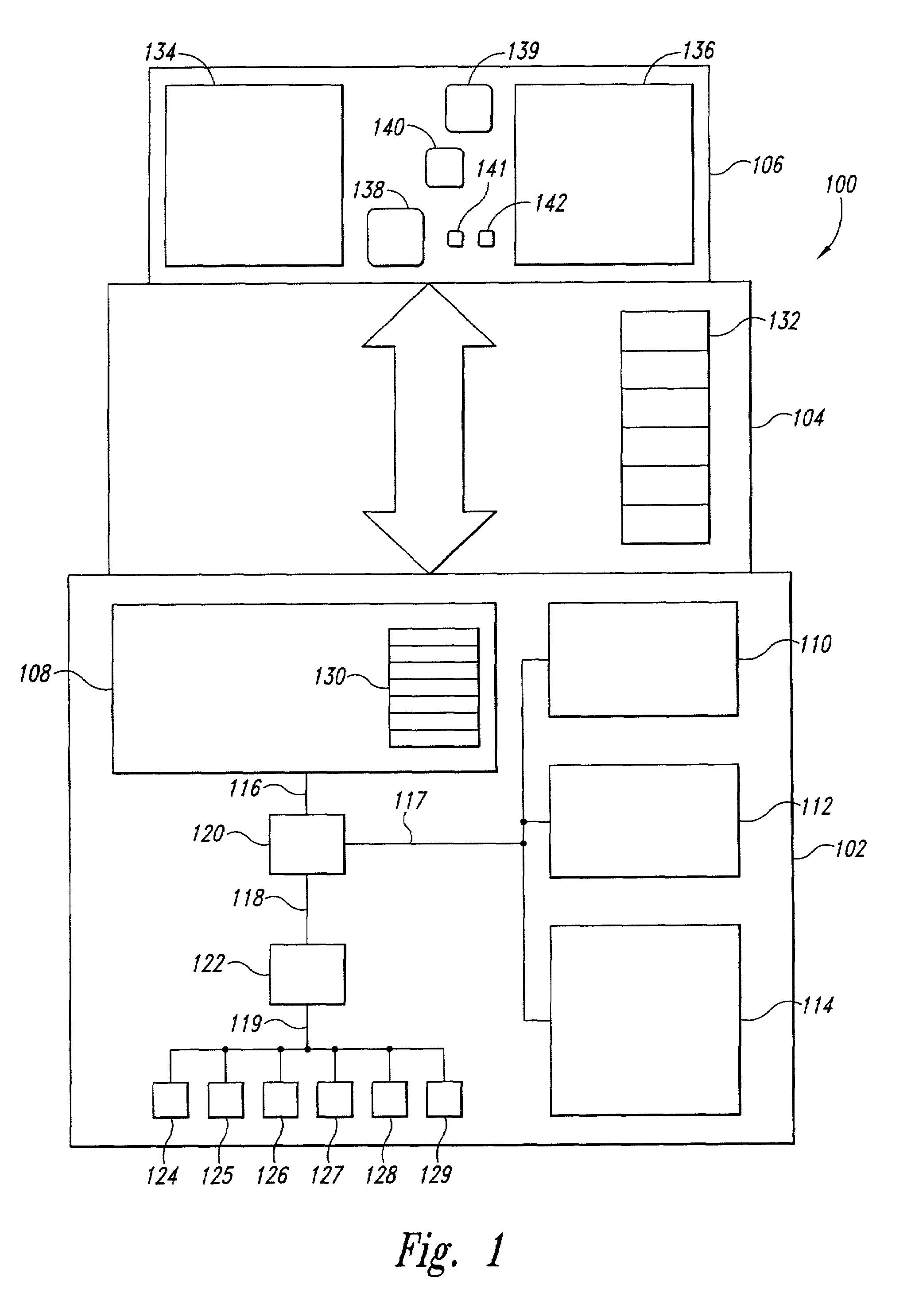
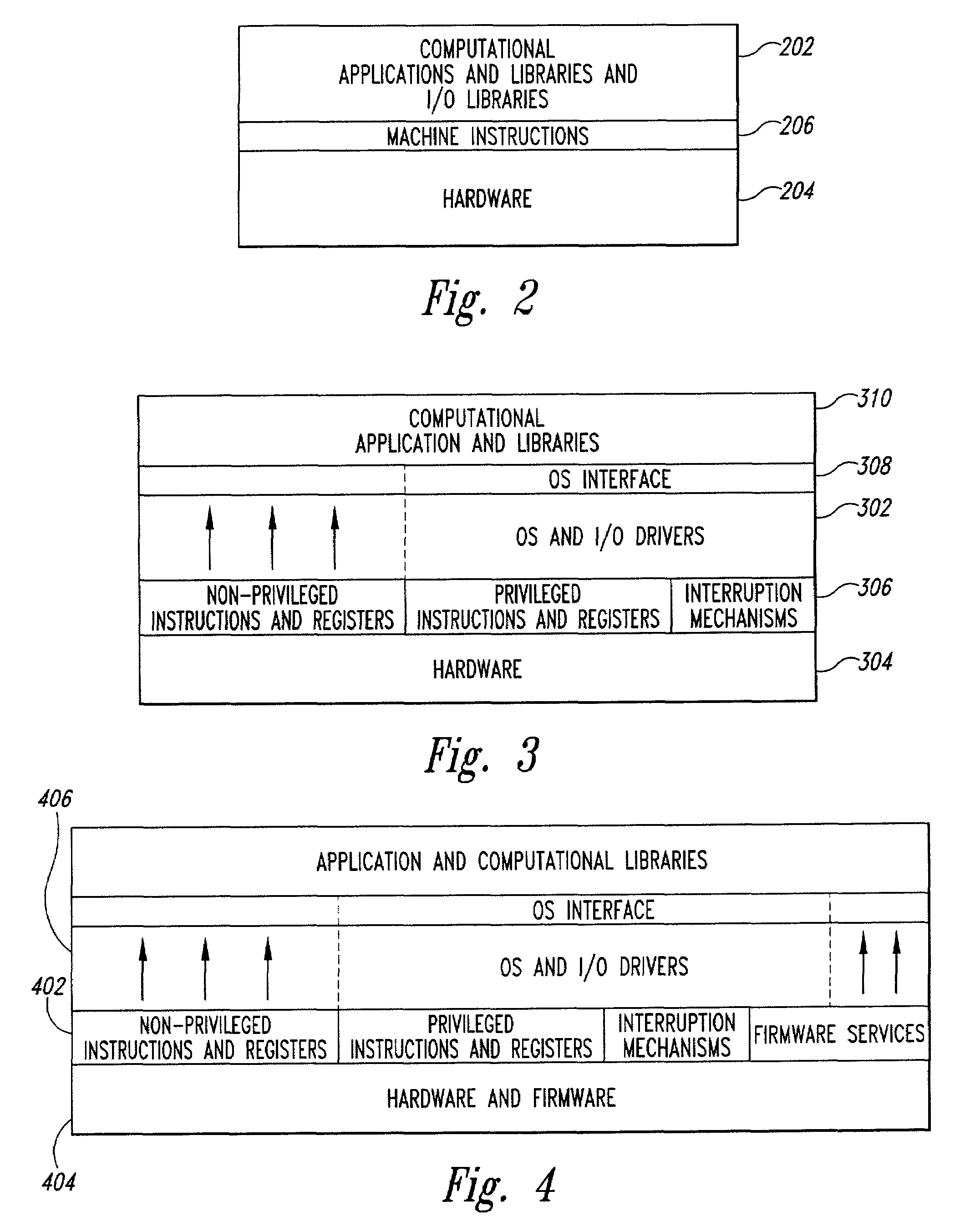
A combined-hardware-and-software secure-platform interface to which operating systems and customized control programs interface within a computer system. The combined-hardware-and-software secure-platform interface employs a hardware platform that provides at least four privilege levels, non-privileged instructions, non-privileged registers, privileged instructions, privileged registers, and firmware interfaces. The combined-hardware-and-software secure-platform interface conceals all privileged instructions, privileged registers, and firmware interfaces and privileged registers from direct access by operating systems and custom control programs, providing to the operating systems and custom control programs the non-privileged instructions and non-privileged registers provided by the hardware platform as well as a set of callable software services. The callable services provide a set of secure-platform management services for operational control of hardware resources that neither exposes privileged instructions, privileged registers, nor firmware interfaces of the hardware nor simulates privileged instructions and privileged registers. The callable services also provide a set of security-management services that employ internally generated secret data, each compartmentalized security-management service managing internal secret data without exposing the internal secret data to computational entities other than the security-management service itself.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
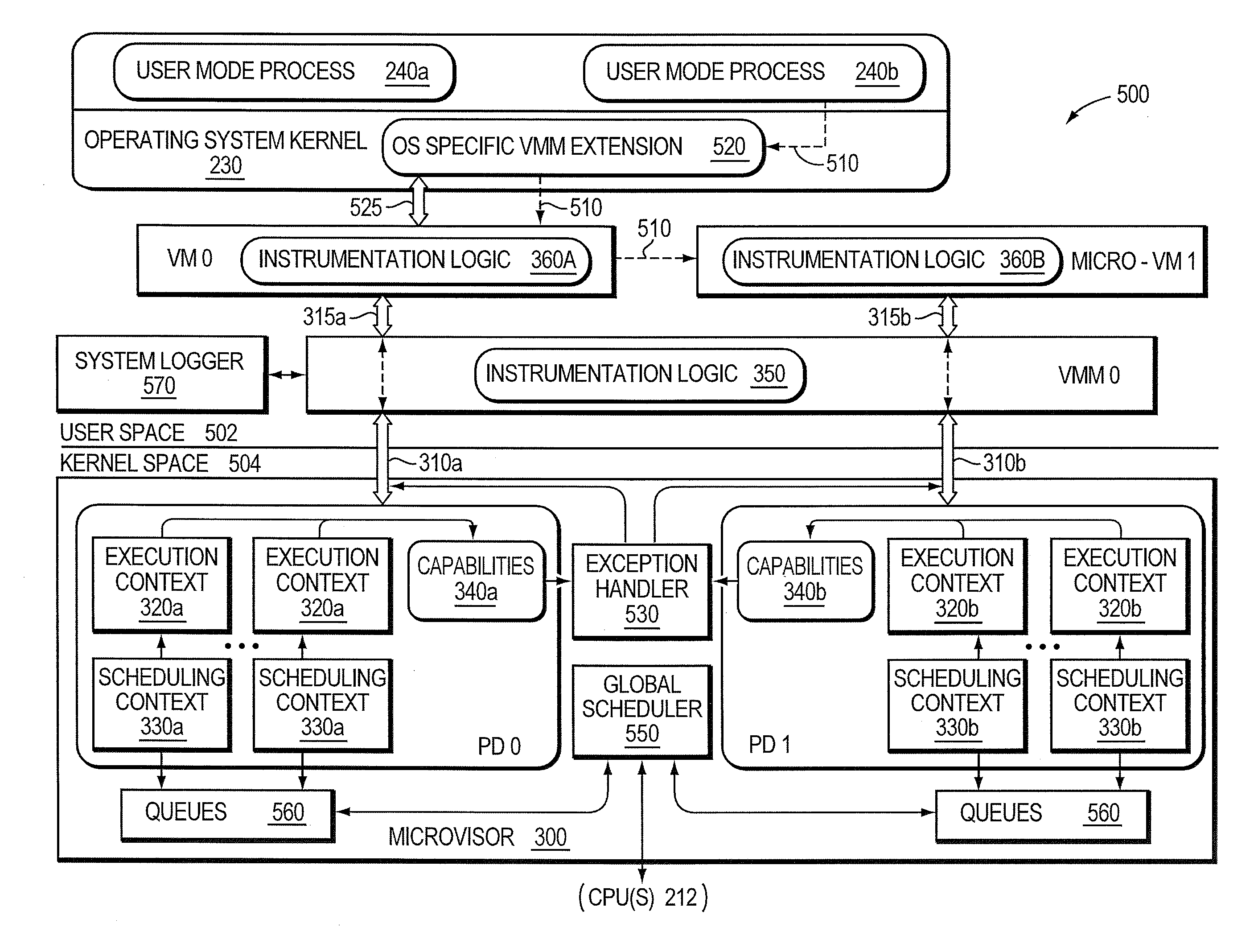
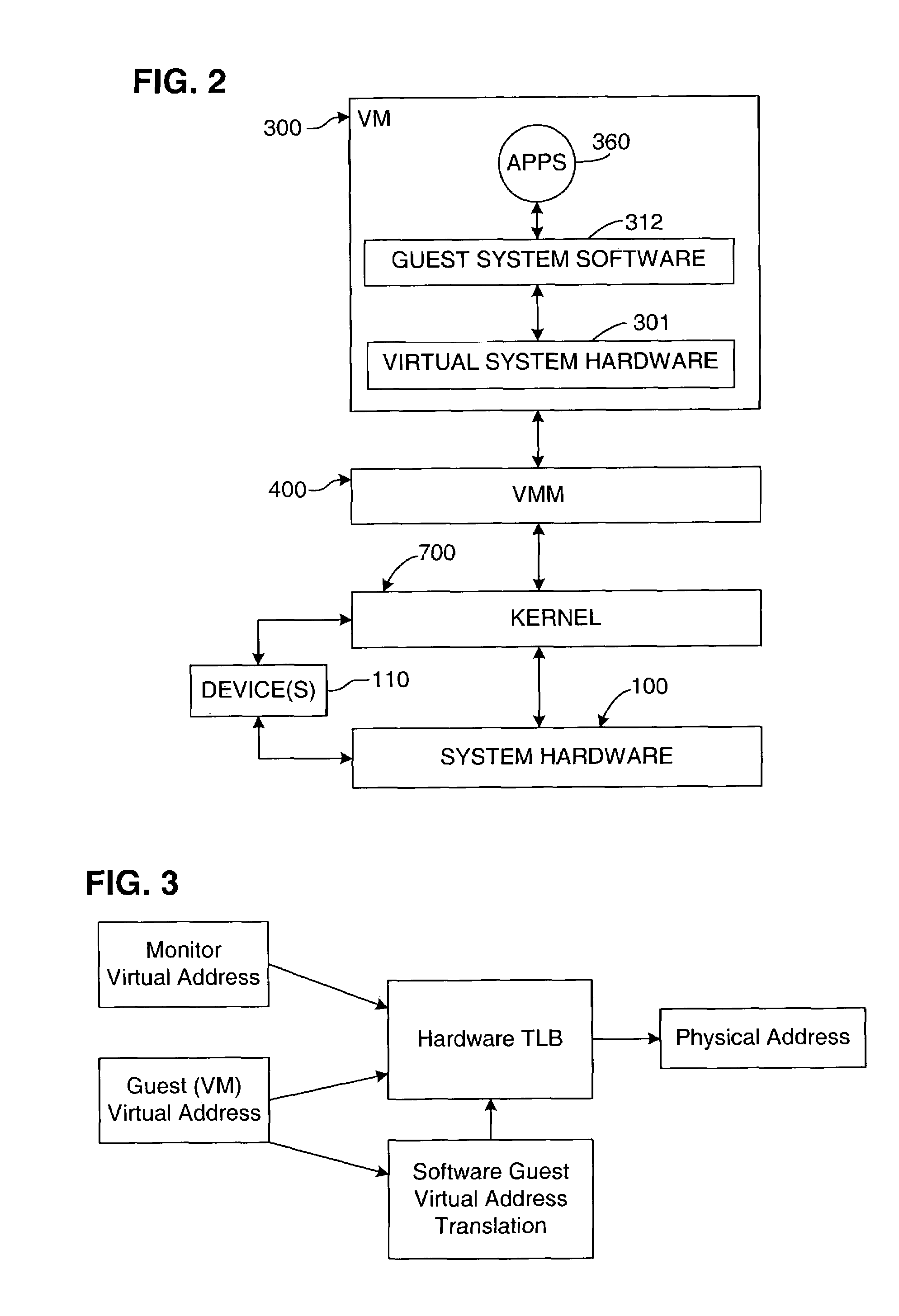
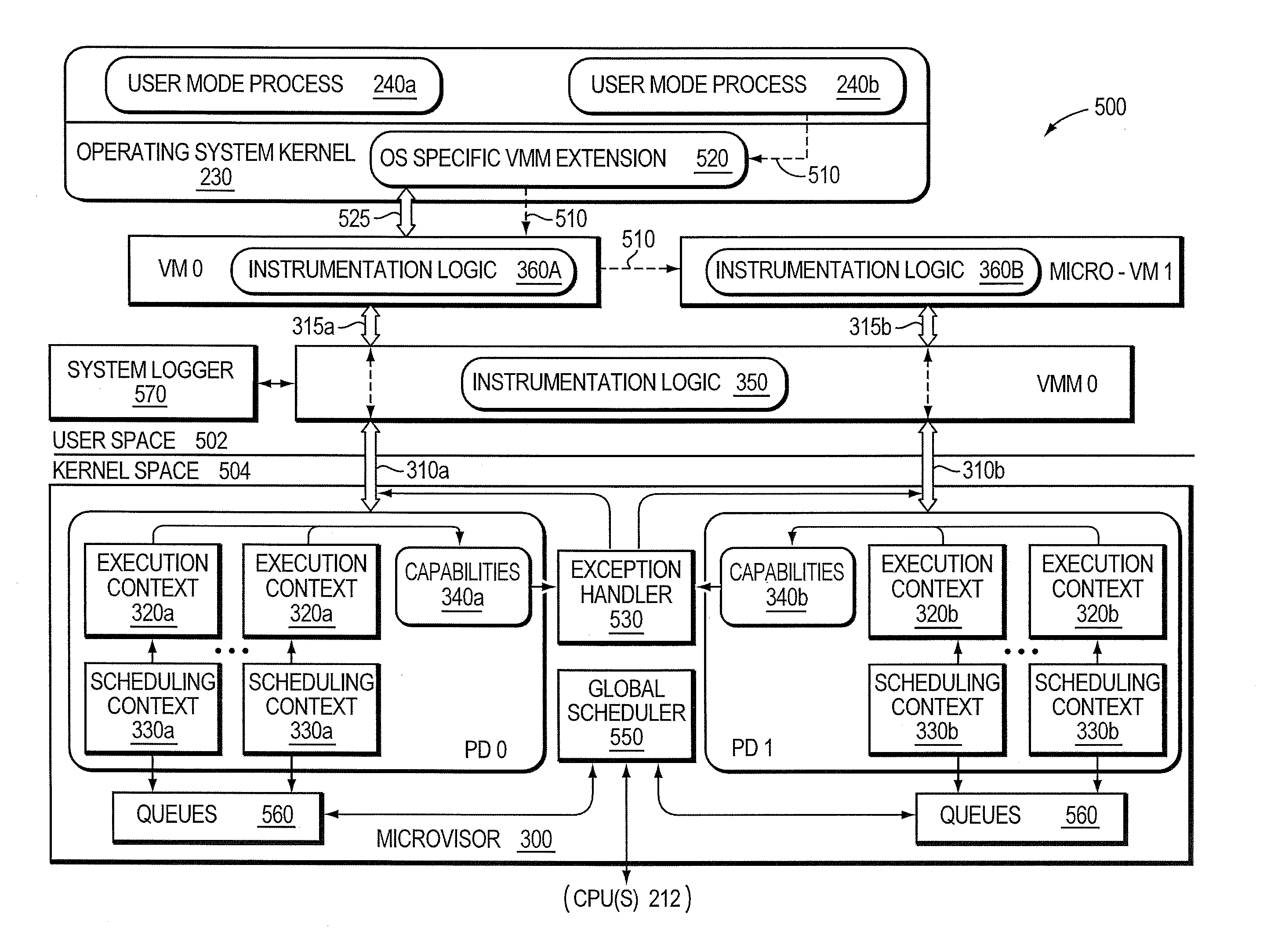
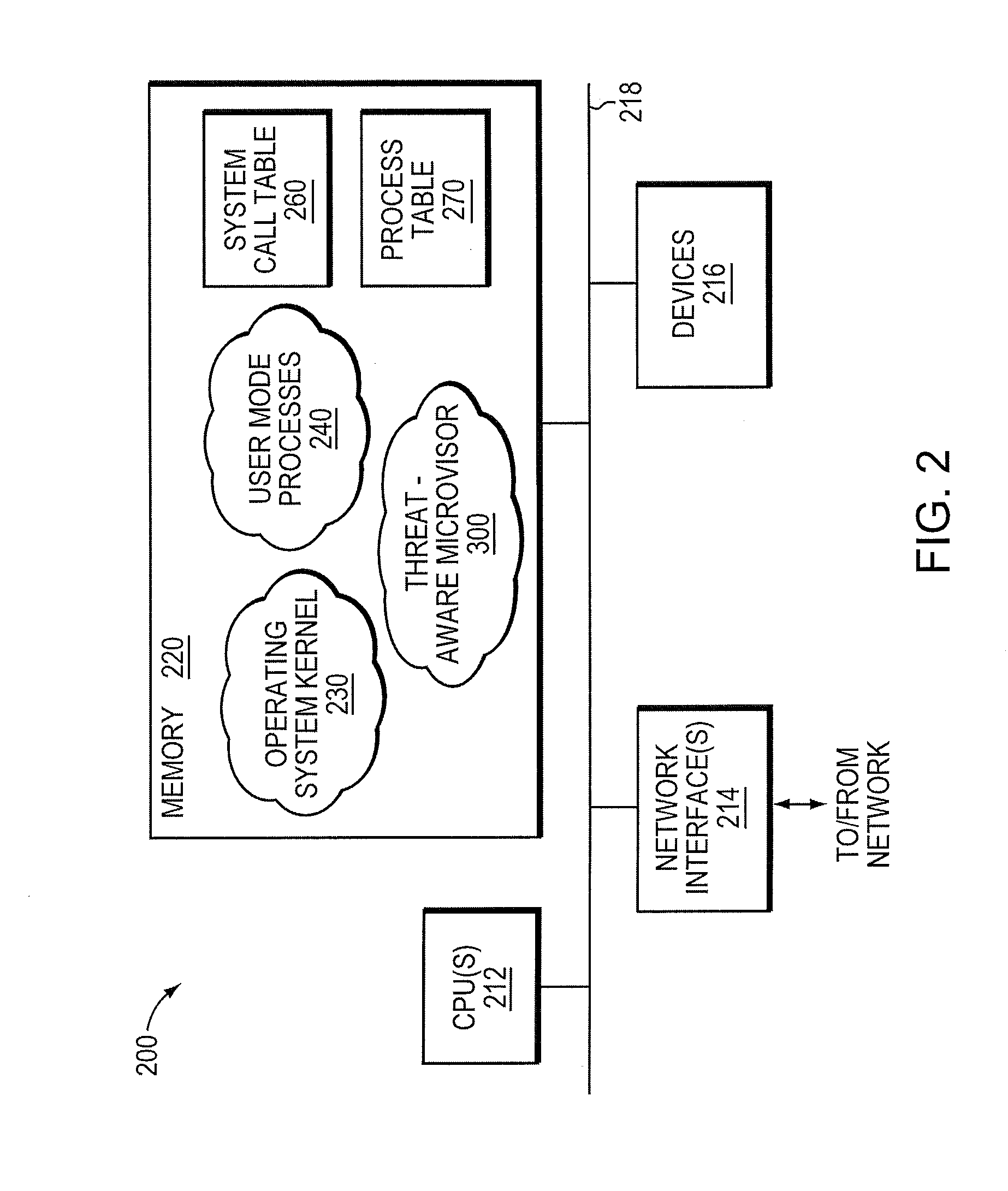
Micro-virtualization architecture for threat-aware microvisor deployment in a node of a network environment
ActiveUS20150199532A1Digital data processing detailsAnalogue secracy/subscription systemsVirtualizationSecurity analysis
A micro-virtualization architecture deploys a threat-aware microvisor as a module of a virtualization system configured to facilitate real-time security analysis, including exploit detection and threat intelligence, of operating system processes executing in a memory of a node in a network environment. The micro-virtualization architecture organizes the memory as a user space and kernel space, wherein the microvisor executes in the kernel space of the architecture, while the operating system processes, an operating system kernel, a virtual machine monitor (VMM) and its spawned virtual machines (VMs) execute in the user space. Notably, the microvisor executes at the highest privilege level of a central processing unit of the node to virtualize access to kernel resources. The operating system kernel executes under control of the microvisor at a privilege level lower than a highest privilege level of the microvisor. The VMM and its spawned VMs execute at the highest privilege level of the microvisor.
Owner:MANDIANT +1
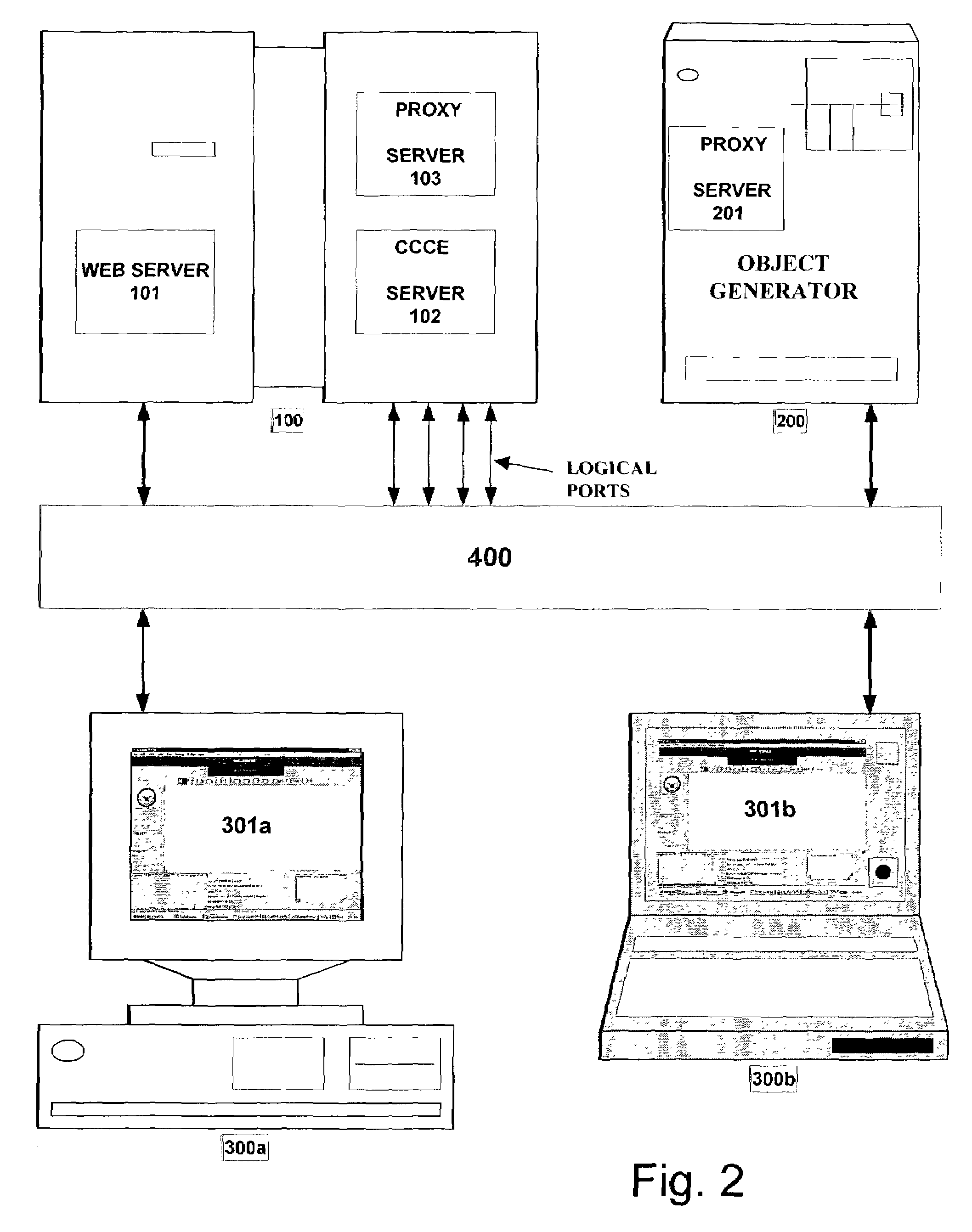
Collaborative environment implemented on a distributed computer network and software therefor
InactiveUS7162528B1Facilitate communicationPromote collaborationDigital data processing detailsAnalogue secracy/subscription systemsClient-sideDistributed computing
A Collaborator computer collaborative environment (CCE) instantiated by a computer network includes N Collaborator CCE clients and a Collaborator CCE server. Each of the N Collaborator CCE clients generates message objects each including a nested group identifier and an associated privilege level; the Collaborator CCE server filters the generated message objects and routes only those message objects to an Nth Collaborator CCE client that is a member of the respective group having the group identifier and that has a privilege greater than or equal to the associated privilege level. Corresponding software is also described.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Virtualization system for computers having multiple protection mechanisms
ActiveUS7278030B1Prevention of memory accessUnauthorized memory use protectionHardware monitoringVirtualizationProtection mechanism
In a virtual computer system, the invention virtualizes a primary protection mechanism, which restricts memory accesses based on the type of access attempted and a current hardware privilege level, using a secondary protection mechanism, which is independent of the hardware privilege level. The invention may be used to virtualize the protection mechanisms of the Intel IA-64 architecture. In this embodiment, virtual access rights settings in a virtual TLB are translated into shadow access rights settings in a hardware TLB, while virtual protection key settings in a virtual PKR cache are translated into shadow protection key settings in a hardware PKR cache, based in part on the virtual access rights settings. The shadow protection key settings are dependent on the guest privilege level, but the shadow access rights settings are not.
Owner:VMWARE INC
Micro-virtualization architecture for threat-aware microvisor deployment in a node of a network environment
ActiveUS9292686B2Digital data protectionPlatform integrity maintainanceVirtualizationOperational system
A micro-virtualization architecture deploys a threat-aware microvisor as a module of a virtualization system configured to facilitate real-time security analysis, including exploit detection and threat intelligence, of operating system processes executing in a memory of a node in a network environment. The micro-virtualization architecture organizes the memory as a user space and kernel space, wherein the microvisor executes in the kernel space of the architecture, while the operating system processes, an operating system kernel, a virtual machine monitor (VMM) and its spawned virtual machines (VMs) execute in the user space. Notably, the microvisor executes at the highest privilege level of a central processing unit of the node to virtualize access to kernel resources. The operating system kernel executes under control of the microvisor at a privilege level lower than a highest privilege level of the microvisor. The VMM and its spawned VMs execute at the highest privilege level of the microvisor.
Owner:MANDIANT +1
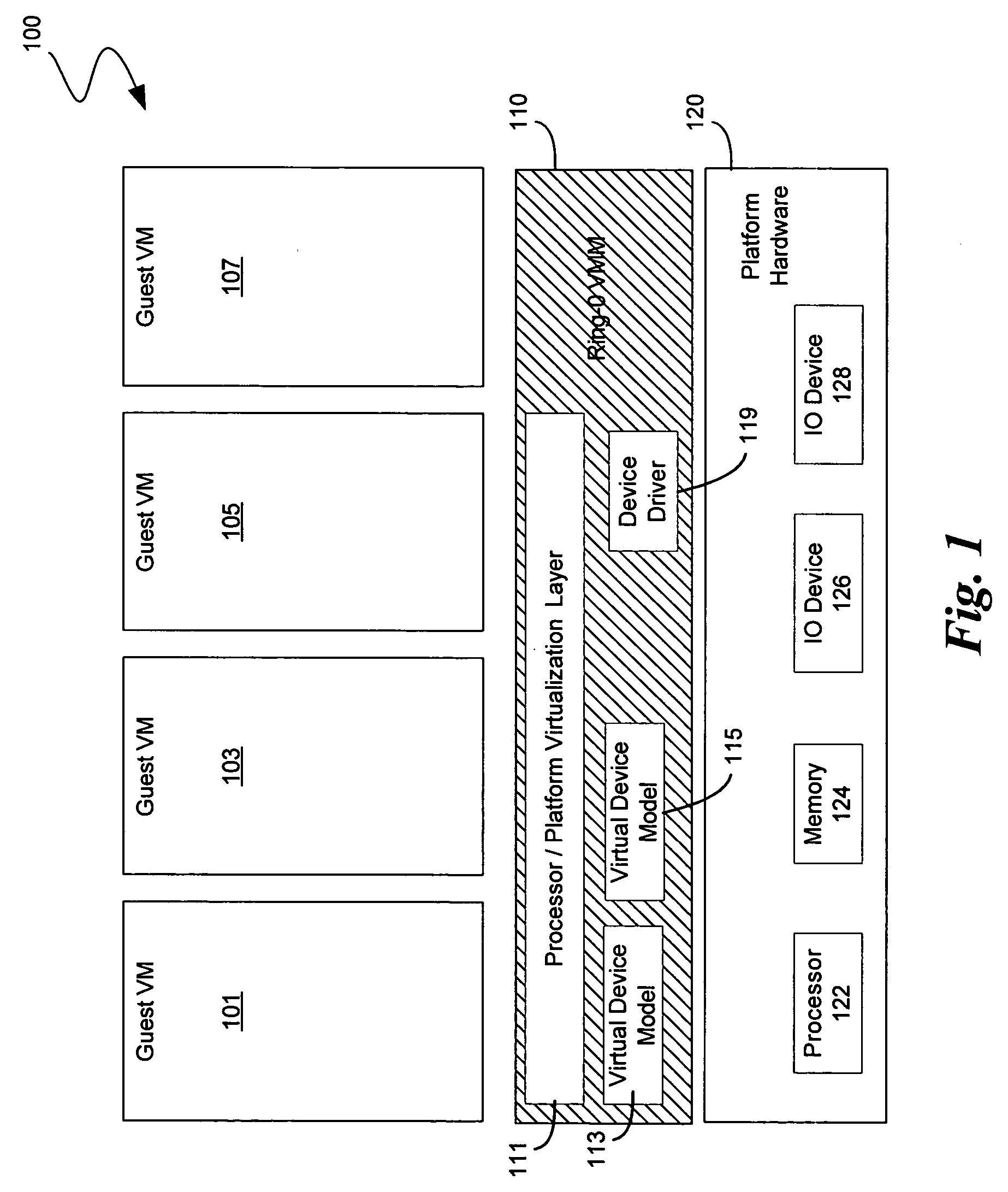
Systems and methods for improving the x86 architecture for processor virtualization, and software systems and methods for utilizing the improvements
InactiveUS20050076186A1Correct shortcomingGeneral purpose stored program computerSoftware simulation/interpretation/emulationSoftware systemProtected mode
The present invention is directed to improvements to the processor architectures, and more specifically the x86 architecture, to correct shortcomings in processor virtualization. Several embodiment of the present invention are directed to the utilization of at least one virtualization control bit to determine whether the execution of a specific instructions cause a privilege-level exception (e.g., GP0) when executed outside of a privilege ring (e.g., outside of ring-0). Several additional embodiments are directed to the utilization of a virtual assist register to implement at least one virtual assist feature. And several additional embodiments are also directed to utilization of a bit for enabling a virtual protected mode that, when a processor in running in a protected mode, causes said processor, which is otherwise executing as if it is running in protected mode, to execute normally with exceptions to handle special virtualization challenges.
Owner:MICROSOFT TECH LICENSING LLC
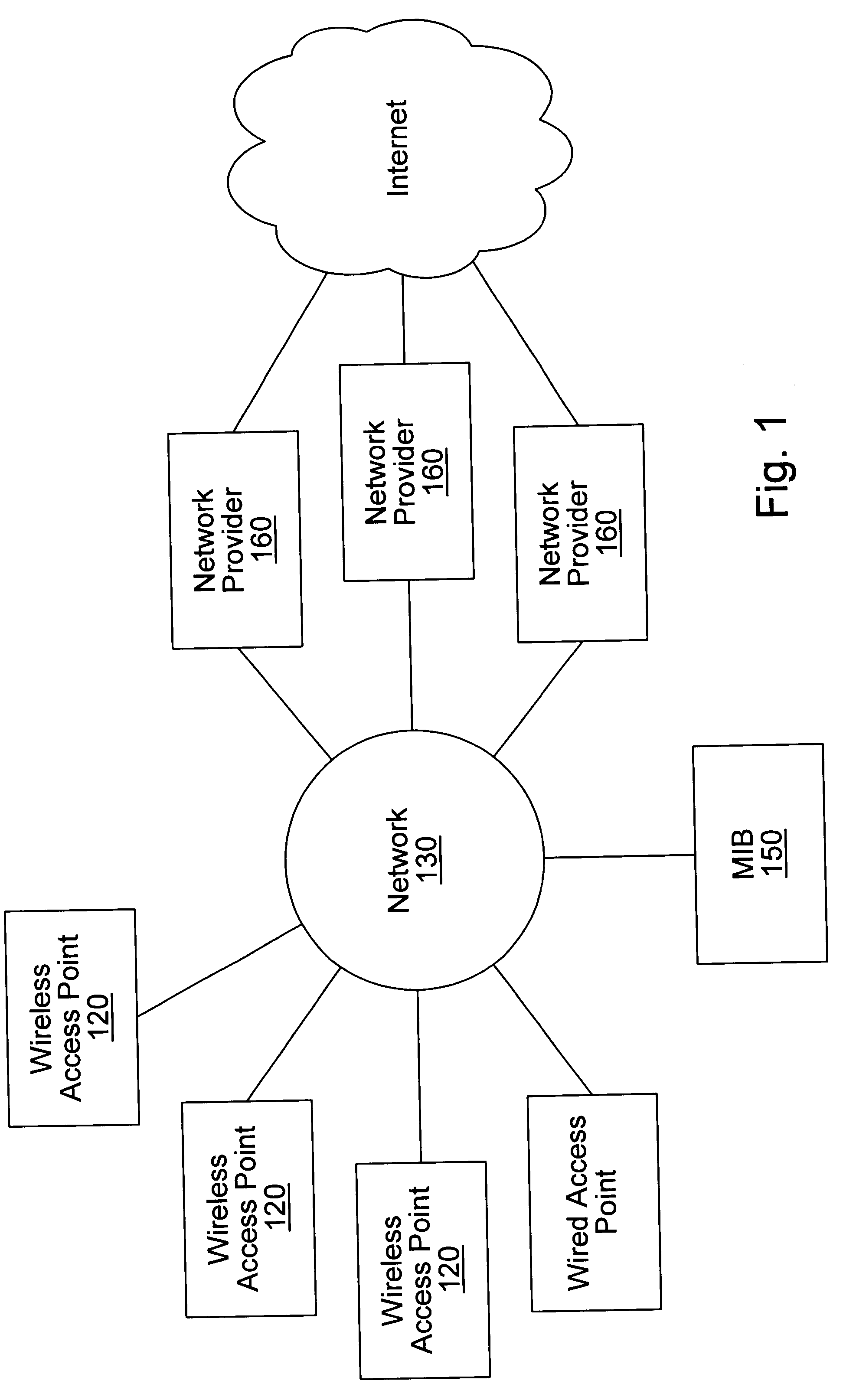
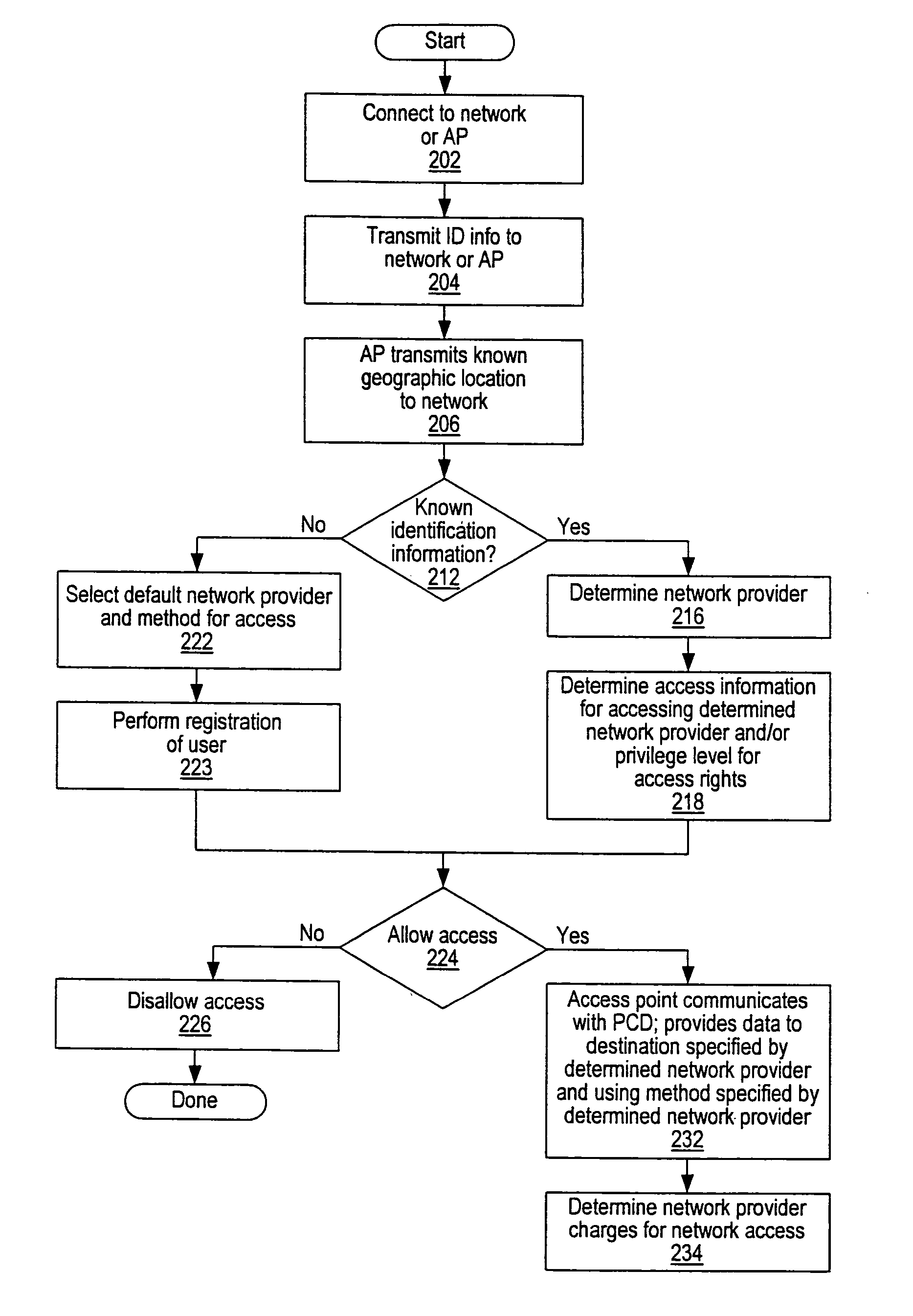
Distributed network communication system which enables multiple network providers to use a common distributed network infrastructure
InactiveUS20040167958A1Metering/charging/biilling arrangementsAssess restrictionCommunications systemNetworked system
A system and method for providing access and / or roaming features on a network system. The network system includes a plurality of wireless and / or wired access points coupled to a network. Access points (APs) for the network may be widely distributed in various facilities, such as airports, mass-transit stations, and various businesses. The network may couple to a wide area network, such as the Internet. In one embodiment, a portable computing device (PCD) of a user may store identification information which uniquely indicates a network provider of a plurality of possible network providers. The identification information may also or instead indicate an access or privilege level of the user. Each of the access points are operable to "listen for" or detect identification information associated with numerous different providers. When the access point receives the identification information from a PCD of a user, the access point may determine the appropriate network provider for the portable computing device using the identification information. Network access may then be provided to the portable computing device through the determined network provider. Thus the network system is useable by subscribers of each of the plurality of possible network providers, thereby enabling subscribers to "roam" on various wireless networks, including networks maintained by other providers. The access information may also include an access level which indicates the user's access or privilege level. Thus, the local network may provide various local resources which are available to users having a first access level, and users with a second access level may not be entitled to view or utilize these network resources on the network, but may be simply provided external Internet access.
Owner:CISCO TECH INC
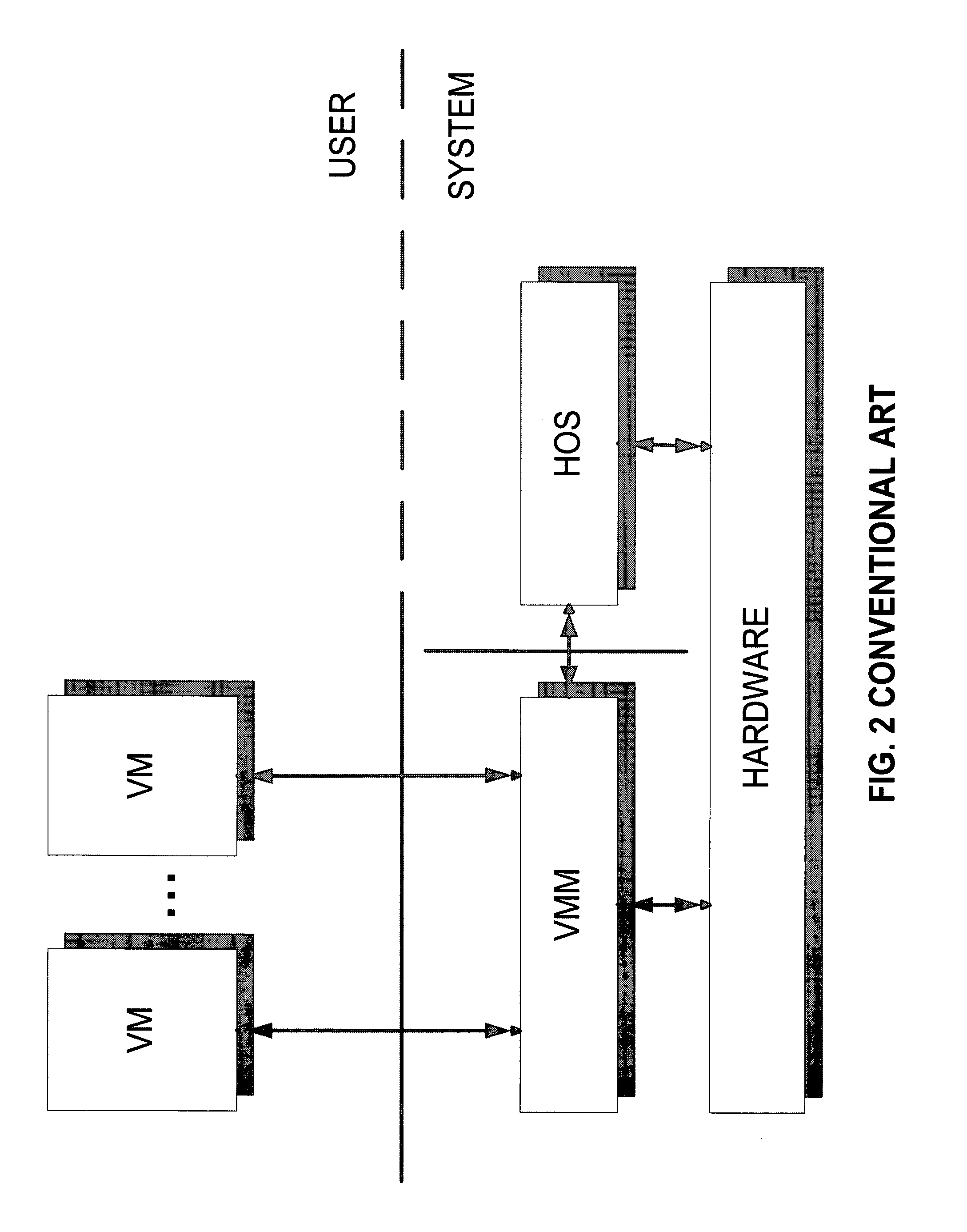
Virtualization system with hypervisor embedded in bios or using extensible firmware interface
A computer system includes a first portion of a Hypervisor is loaded into the memory as a part of an Extensible Firmware Interface upon start up and prior to loading of an operating system. The first portion is responsible for context switching, at least some interrupt handling, and memory protection fault handling. The first portion runs on a root level. An operating system is loaded into a highest privilege level. A second portion of the Hypervisor is loaded into operating system space together with the operating system, and runs on the highest privilege level, and is responsible for (a) servicing the VMM, (b) servicing the VMs, (c) enabling communication between code launched on non-root level with the second portion of the Hypervisor to perform security checks of trusted code portions and to enable root mode for the code portions if allowable. The VMM runs on the highest privilege level. A Virtual Machine is running under control of the VMM. Trusted code runs on non-root level. The first portion of the Hypervisor verifies trusted code portions during their loading or launch time, and the trusted code is executed on root level.
Owner:PARALLELS INT GMBH
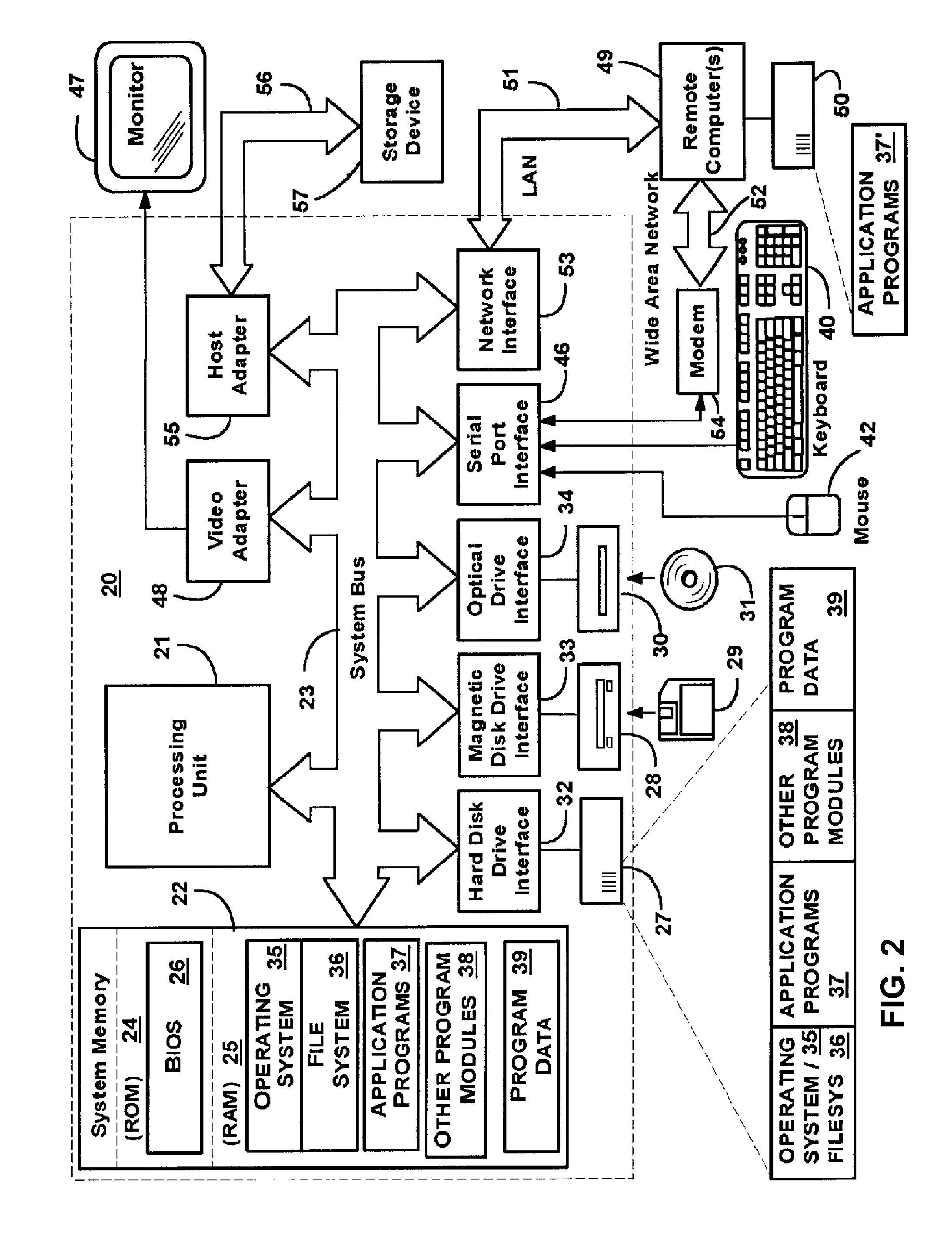
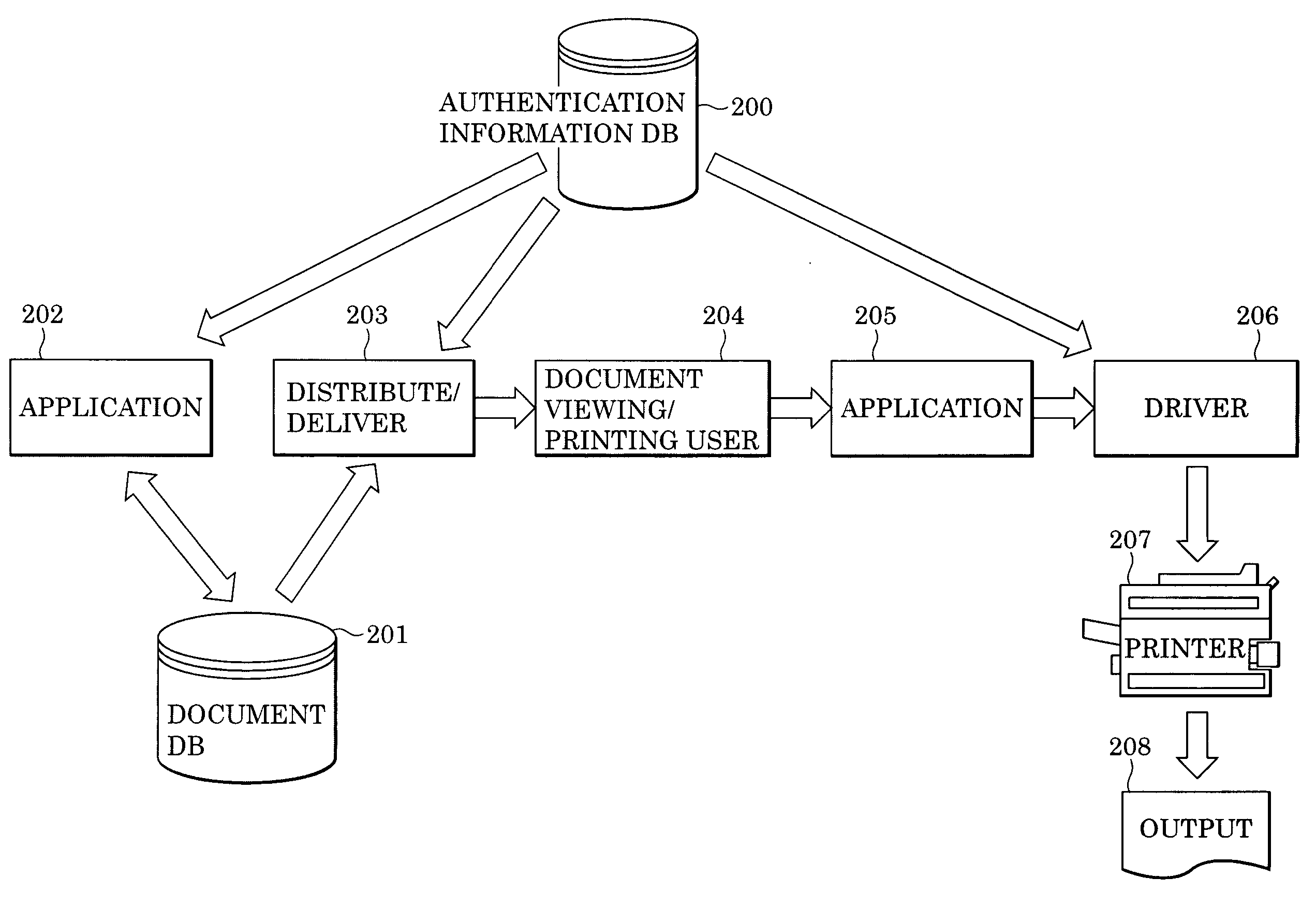
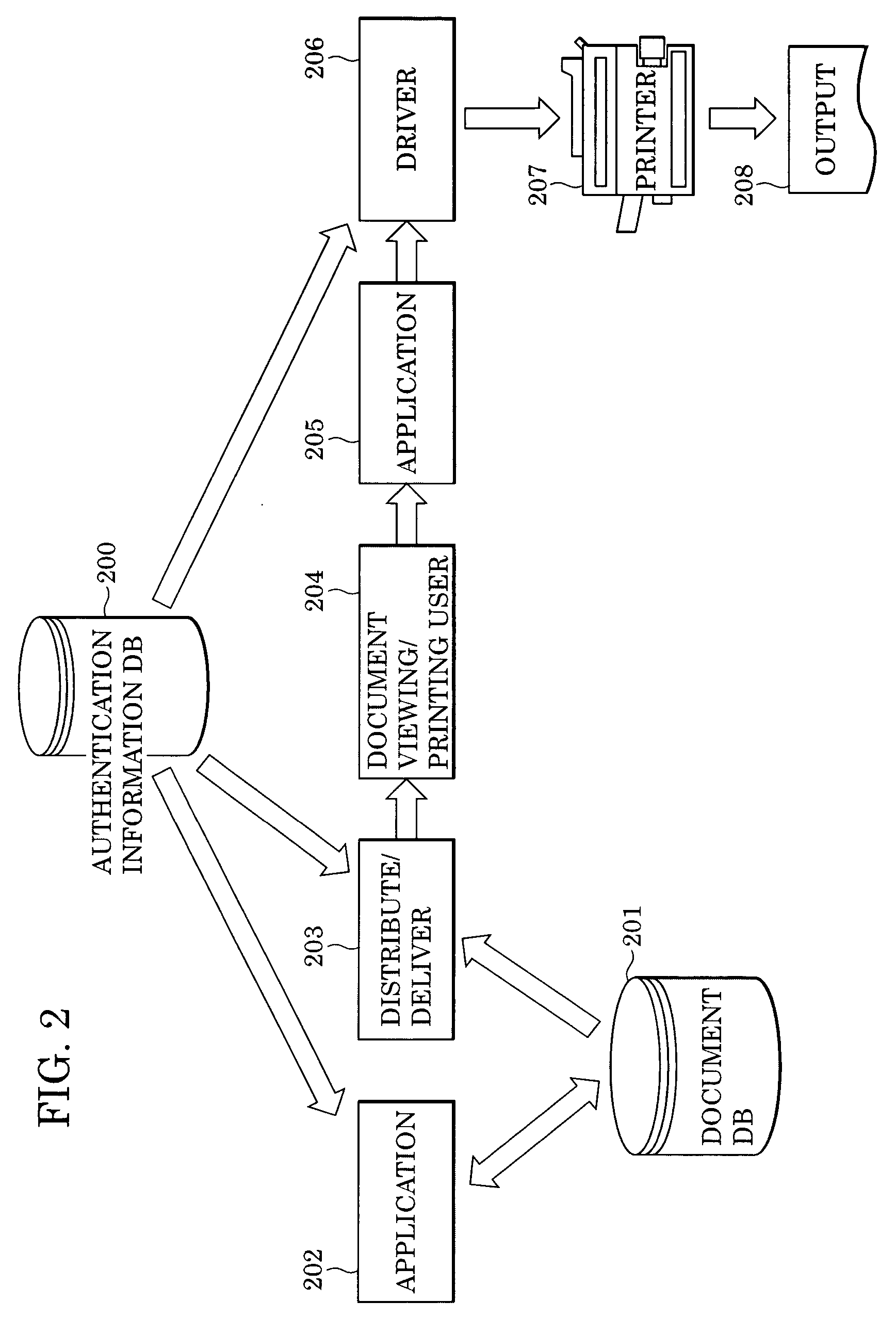
Data processing system, data processing method and apparatus, document printing system, client device, printing device, document printing method, and computer program
InactiveUS20050134896A1Improve printing efficiencyReduce printing costsElectric signal transmission systemsDigital data processing detailsData processing systemUser input
In a network-based printing system having a communication network, such as the Internet or an intranet, printing control information is added to document data or image data, and the document or image data to which the printing control information is added is transmitted to a user designated by an access privilege level that is stored in a server. Printing of the transmitted data is controlled according to authentication information that is input by the user and the printing control information added to the document or image data.
Owner:CANON KK
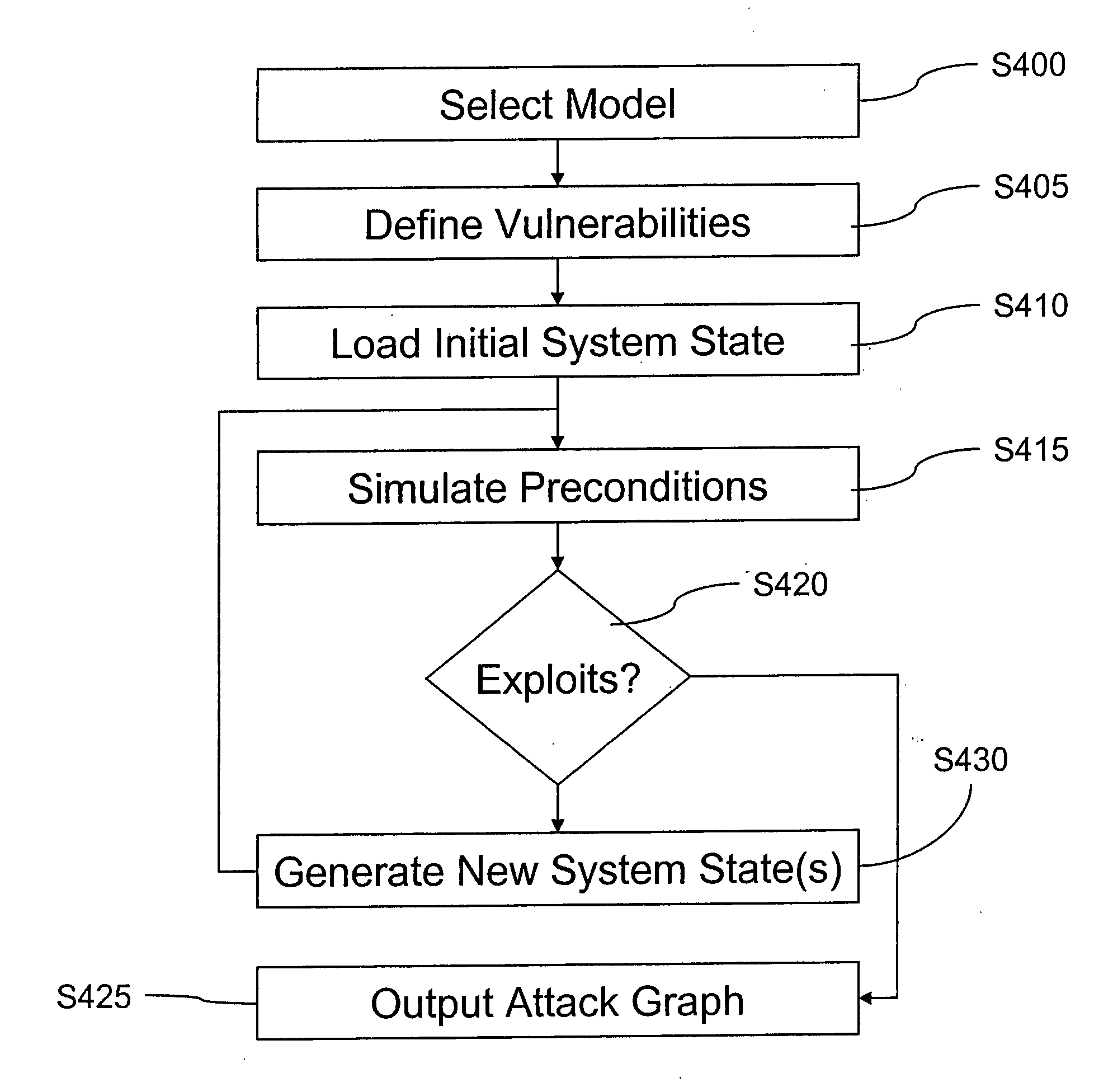
Methods of simulating vulnerability
Methods of simulating vulnerability are provided. In an example, multi-stage vulnerability across multiple systems may be simulated by first simulating a probing of at least one intermediate entity, the at least one intermediate entity connected to a target system, second simulating a probing of the target system if the first simulated probing is successful and generating an attack graph based on the results of the first and second simulating steps. In another example, multi-system vulnerability may be simulated by receiving a plurality of attributes associated with vulnerabilities of a plurality of systems within a network, the plurality of systems including at least one target system and generating an attack graph including one or more attack chains based at least in part on the received plurality of attributes. In another example, system (e.g., single-system) vulnerability may be simulated by first simulating whether vulnerabilities exploited from a first system state cause a transition to a second system state, the second system state having a higher-privilege level than the first system state within a target system and generating an attack graph based at least in part on the results of the simulation.
Owner:LGS INNOVATIONS
System and method to deprivilege components of a virtual machine monitor
ActiveUS7757231B2High portability and reliabilityMultiprogramming arrangementsSoftware simulation/interpretation/emulationPrivilege levelHardware virtualization
In some embodiments, the invention involves a system to deprivilege components of a virtual machine monitor and enable deprivileged service virtual machines (SVMs) to handle selected trapped events. An embodiment of the invention is a hybrid VMM operating on a platform with hardware virtualization support. The hybrid VMM utilizes features from both hypervisor-based and host-based VMM architectures. In at least one embodiment, the functionality of a traditional VMM is partitioned into a small platform-dependent part called a micro-hypervisor (MH) and one or more platform-independent parts called service virtual machines (SVMs). The micro-hypervisor operates at a higher virtual machine (VM) privilege level than any SVM, while the SVM and other VMs may still have access to any instruction set architecture (ISA) privilege level. Other embodiments are described and claimed.
Owner:INTEL CORP
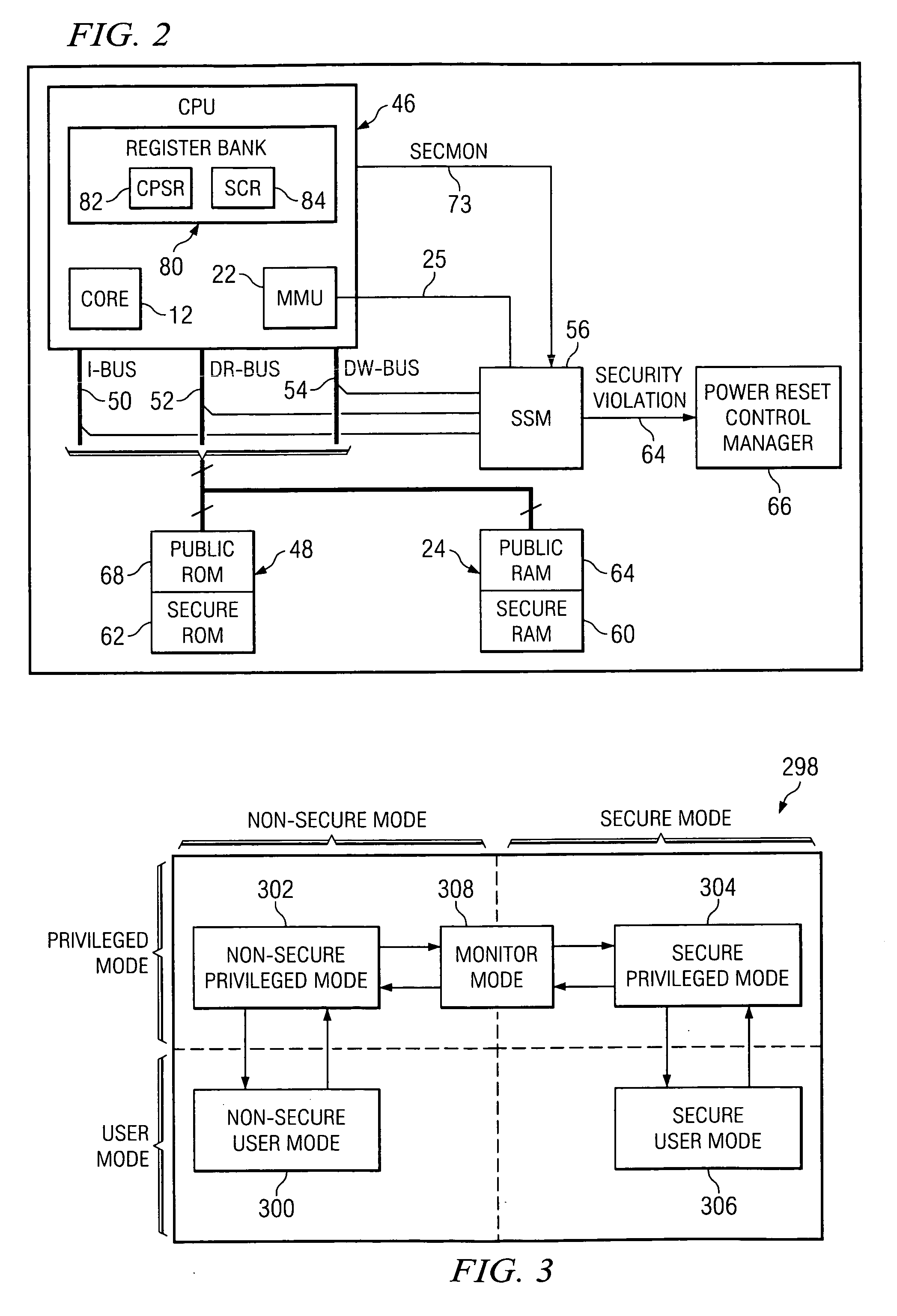
Method and system for preventing unsecure memory accesses
InactiveUS20070067826A1Avoid problemsReduce usageDigital data processing detailsUser identity/authority verificationSecurity ruleMemory management unit
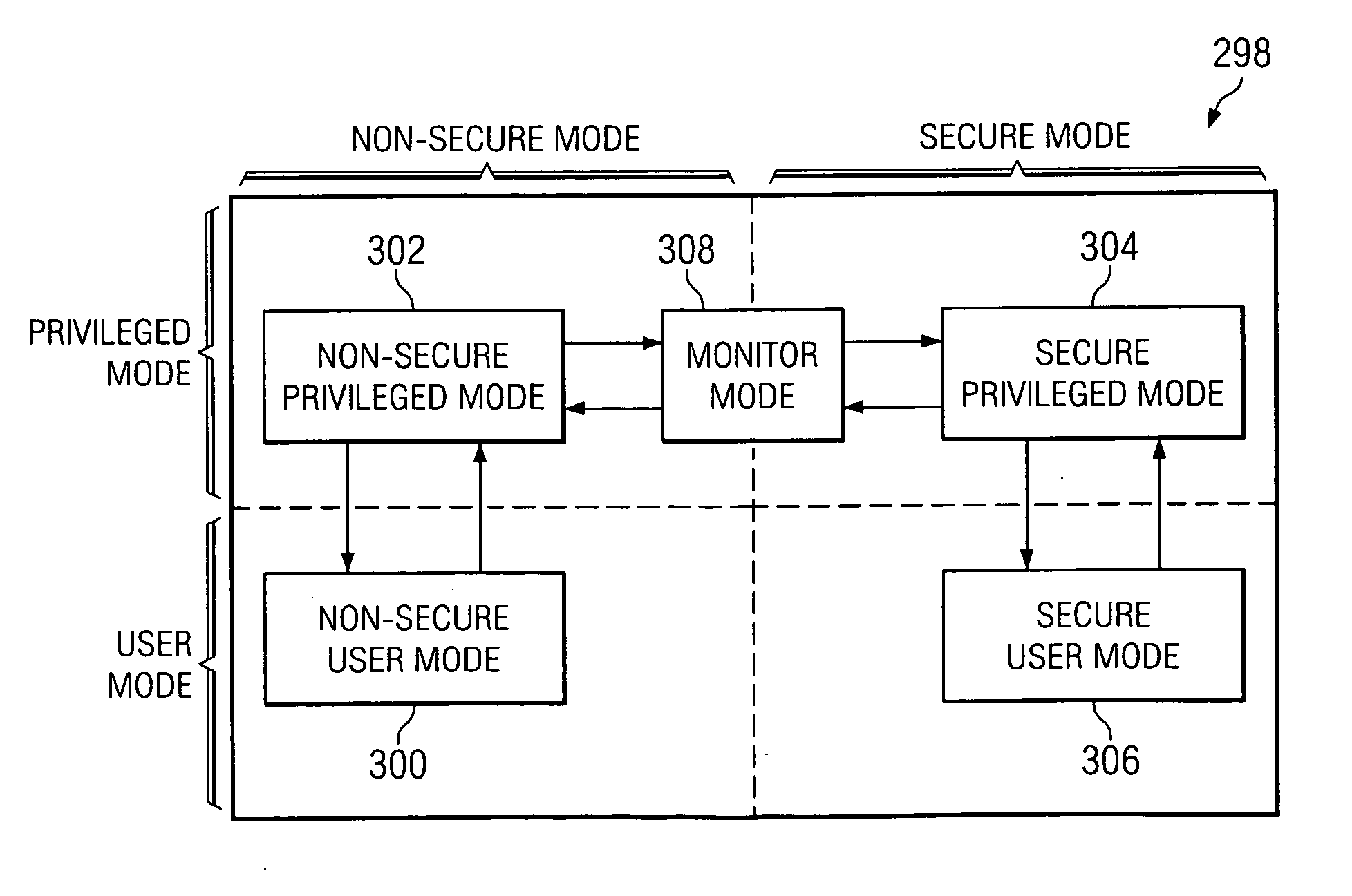
A system comprising a processor adapted to activate multiple privilege levels for the system, a monitoring unit coupled to the processor and employing security rules pertaining to the multiple privilege levels, and a memory management unit (MMU) coupled to the monitoring unit and adapted to partition memory into public and secure memories. If the processor switches privilege levels while the MMU is disabled, the monitoring unit restricts usage of the system. If the processor accesses the public memory while in a privilege level not authorized by the security rules, the monitoring unit restricts usage of the system.
Owner:TEXAS INSTR INC
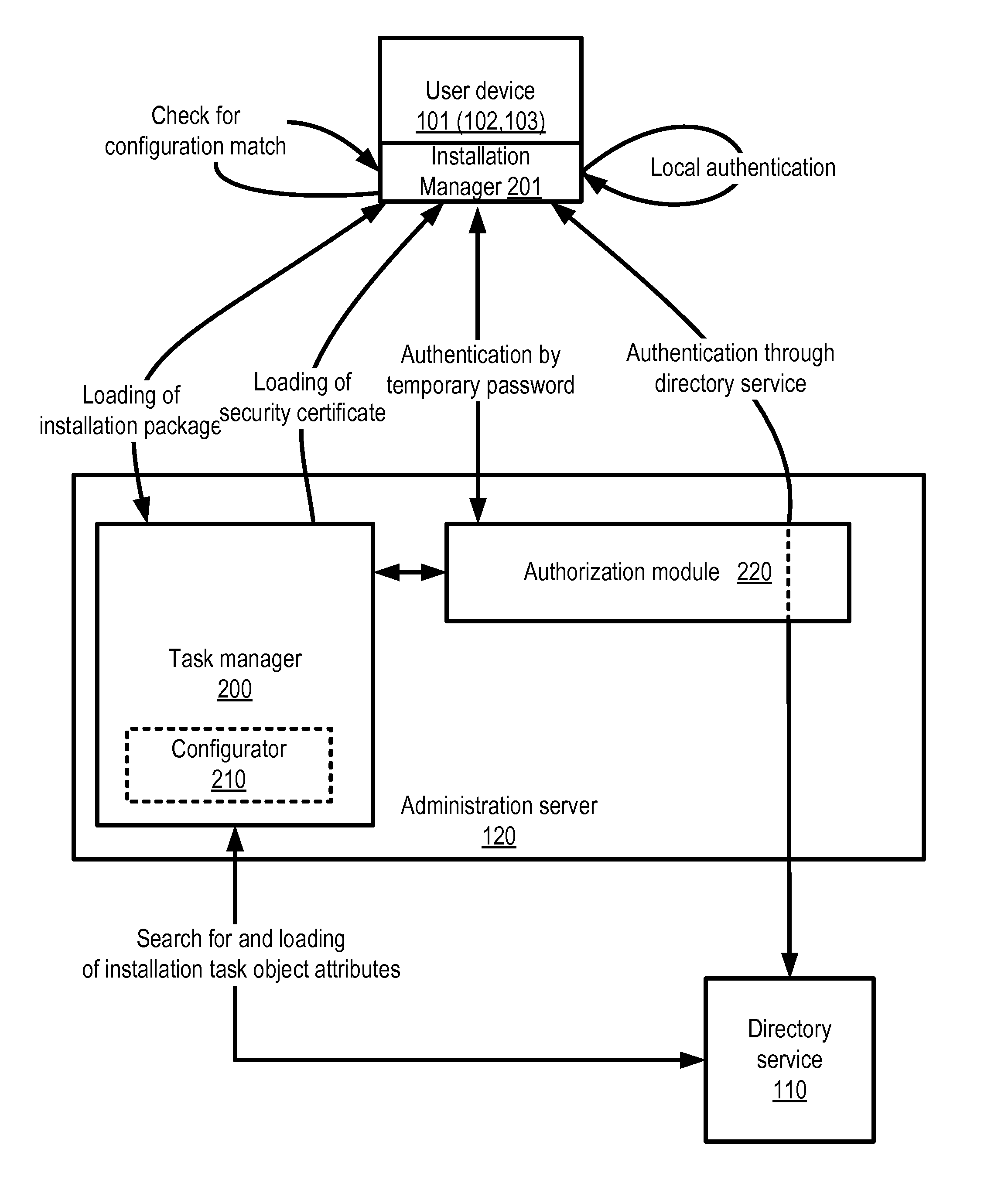
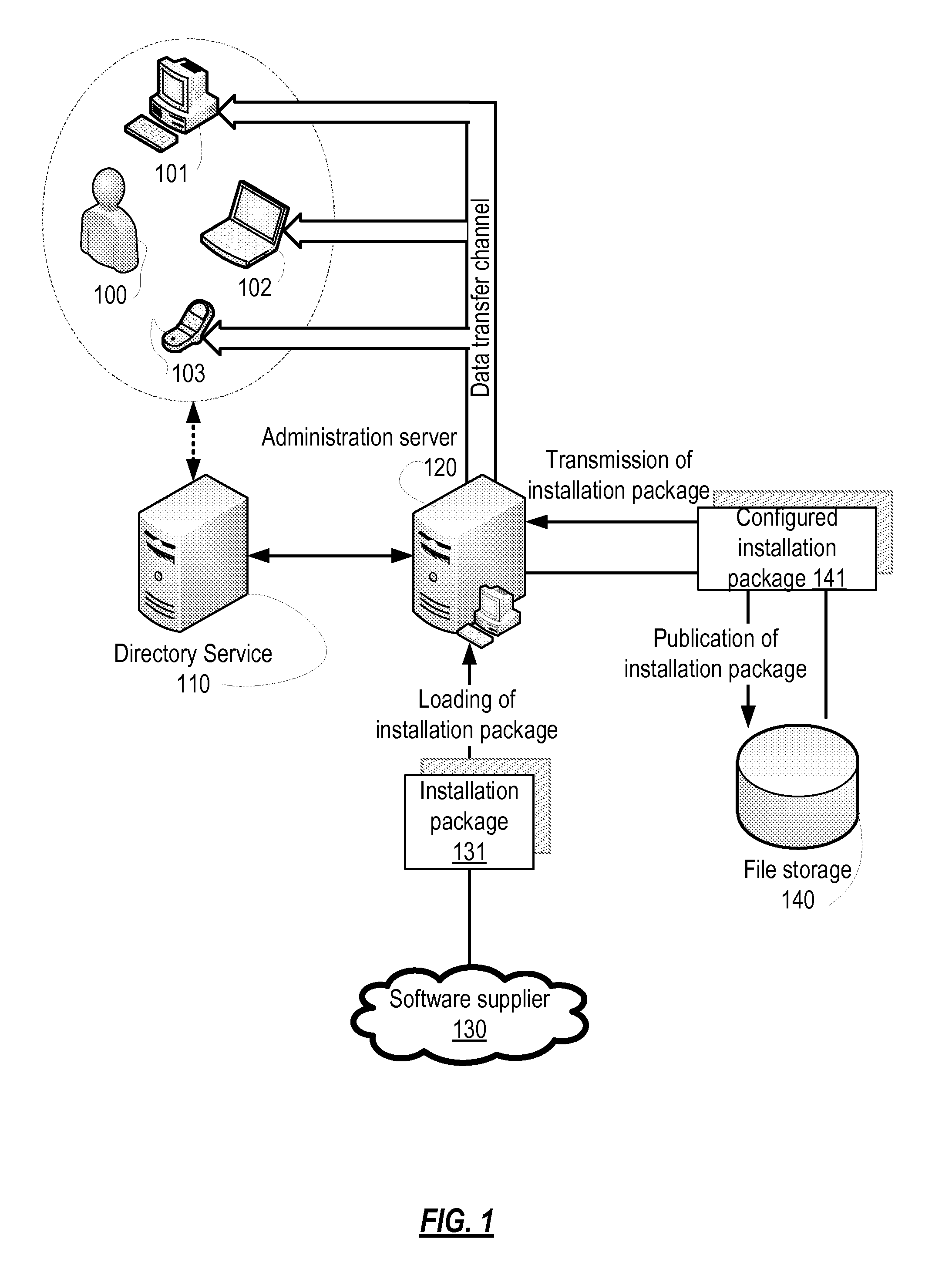
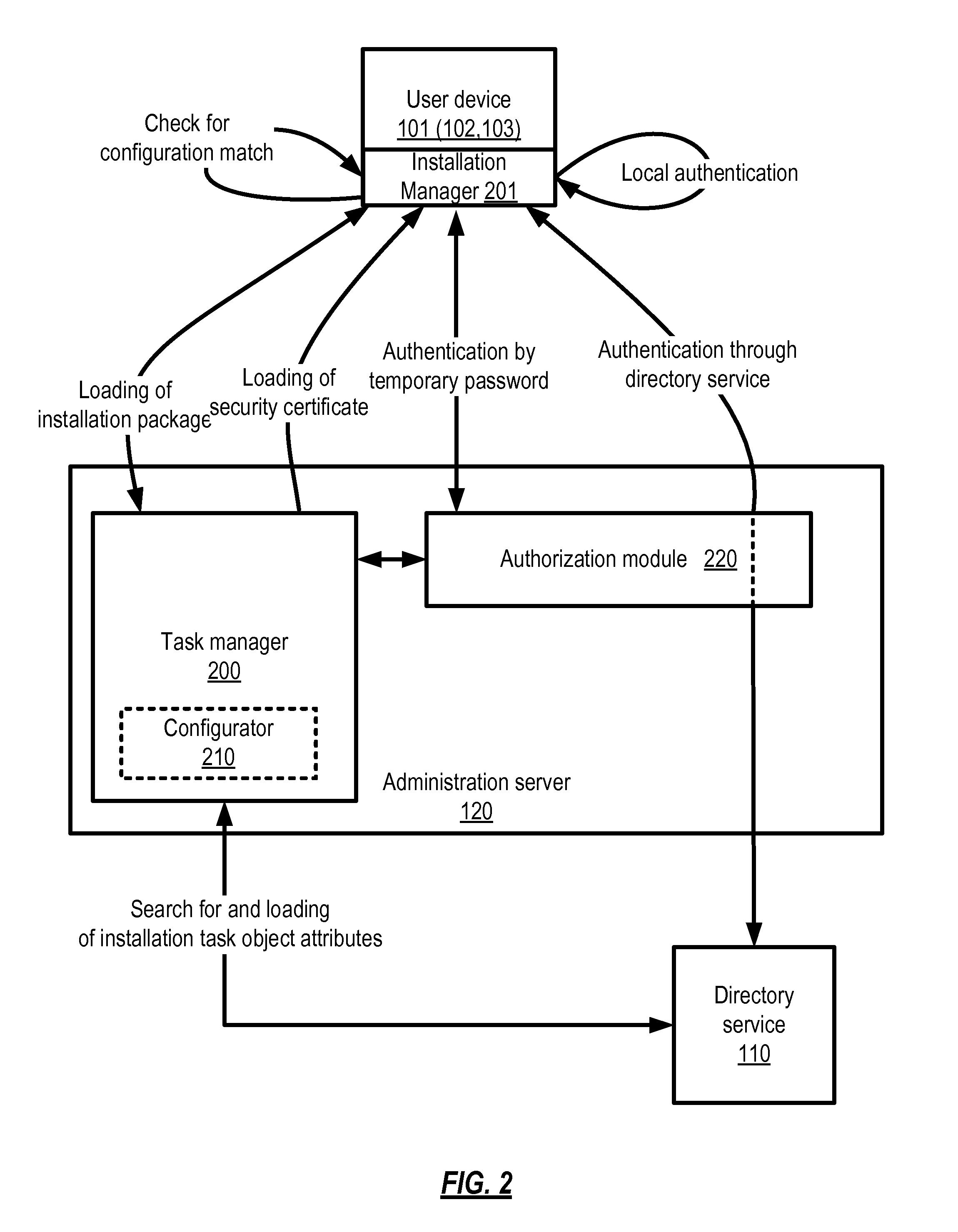
System and method for automated configuration of software installation package
ActiveUS8839234B1Avoid installationDigital data authenticationProgram loading/initiatingUser deviceAuto-configuration
Automated configuration of a software application to be installed via a software installation package onto different user devices for different users. An initial software installation package is obtained, as is information representing (a) associations between the plurality of users and the plurality of user devices, and (b) user attributes from which access privilege level information for individual users is determinable. The initial software installation package is configured for the user devices based on the information representing (a) and (b), to produce a plurality of different specially-configured software installation packages, each one of which corresponds to one or more specific users and one or more specific user devices. Each specially-configured package includes parameters that establish functionality for the software application based on the access privilege level of the users. Each user is authenticated, and completion of installation of the software application is conditioned on a result of the authentication.
Owner:AO KASPERSKY LAB
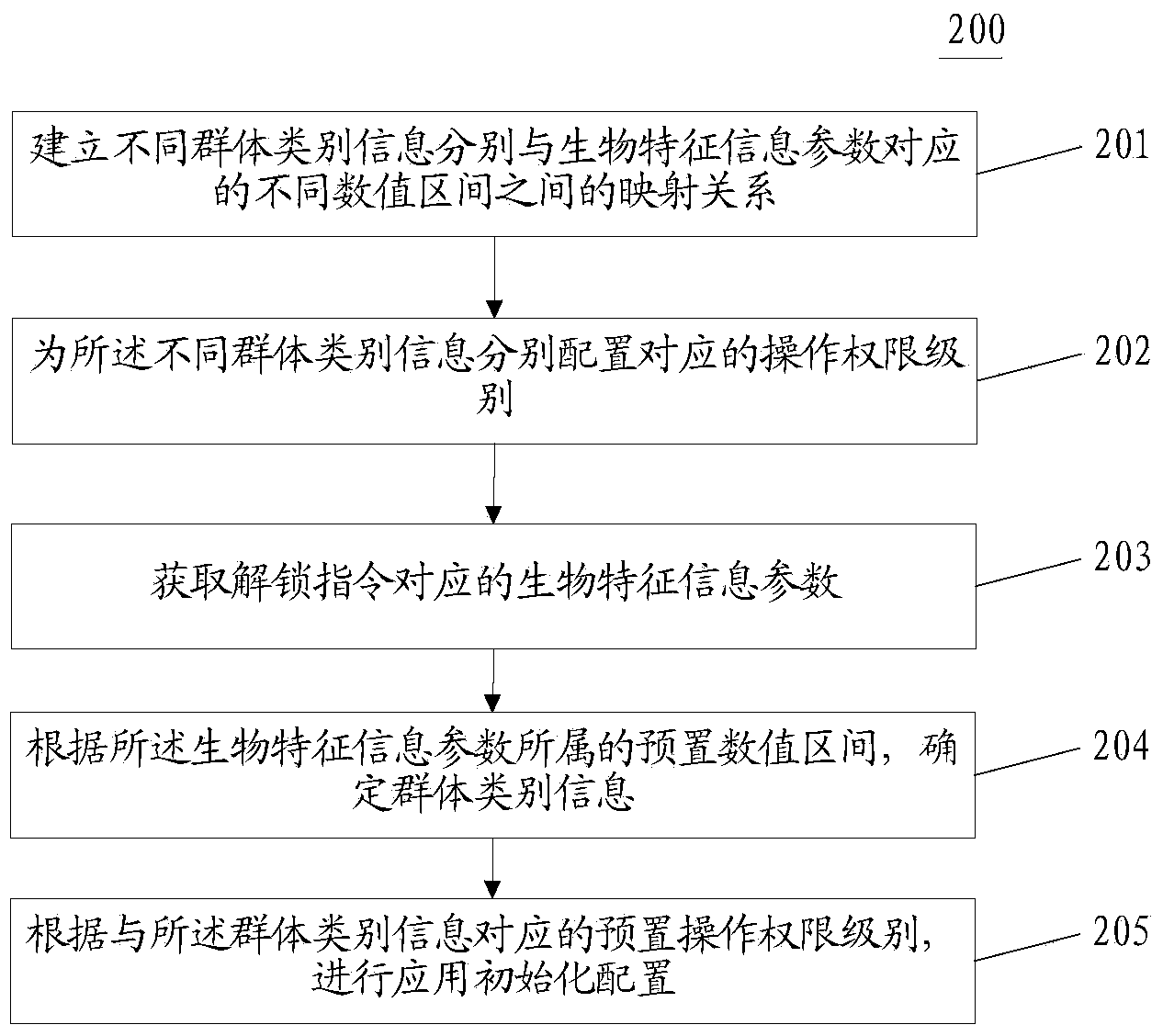
Application customizing method and application customizing device
InactiveCN104239107AAvoid wastingDigital data authenticationProgram loading/initiatingSoftware engineeringComputer terminal
The application discloses an application customizing method and an application customizing device. One specific embodiment of the method comprises the following steps: firstly acquiring biologic feature information parameters which correspond to an unlocking instruction; then, according to a preset numerical value interval to which the biologic feature information parameters belong, determining group class information; finally, according to a preset operation privilege level which corresponds to the group class information, performing application initial configuration. The application initial configuration suitable for different user classes can be performed adaptively, and the goal that different application customizing can be performed by aiming at different groups and the same terminal is achieved, and therefore waste of resources can be avoided.
Owner:SAMSUNG ELECTRONICS CHINA R&D CENT +1
Distributed network communication system which enables multiple network providers to use a common distributed network infrastructure
InactiveUS20040170153A1Metering/charging/biilling arrangementsAssess restrictionNetworked systemNetwork communication
Owner:CISCO TECH INC
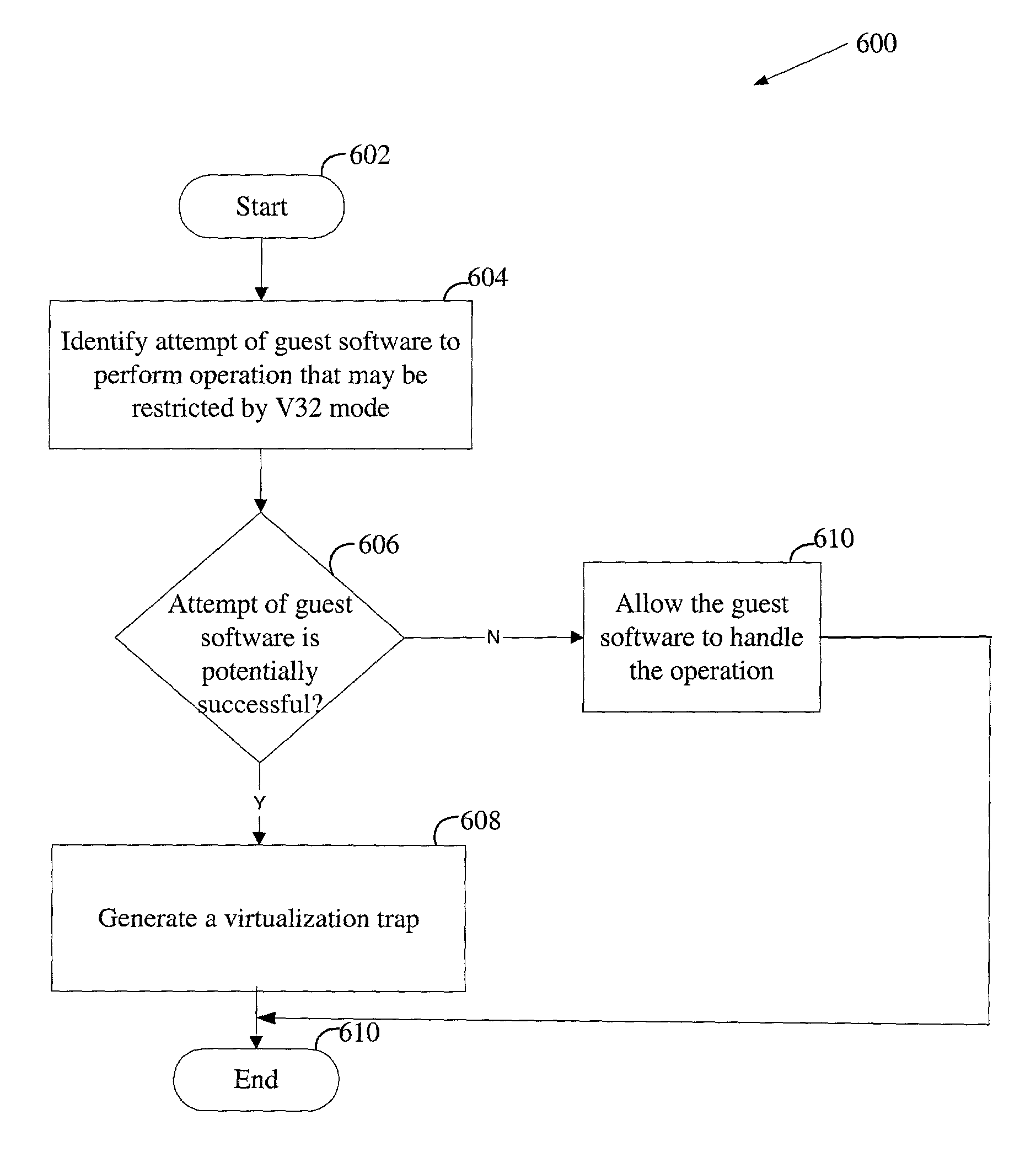
Processor mode for limiting the operation of guest software running on a virtual machine supported by a virtual machine monitor
InactiveUS7818808B1Digital data processing detailsAnalogue secracy/subscription systemsPrivilege levelSoftware
In one embodiment, a processor mode is provided for guest software. The processor mode enables the guest software to operate at a privilege level intended by the guest software. When the guest software attempts to perform an operation restricted by the processor mode, the processor mode is exited to transfer control over the operation to a virtual-machine monitor, which runs outside this processor mode.
Owner:INTEL CORP
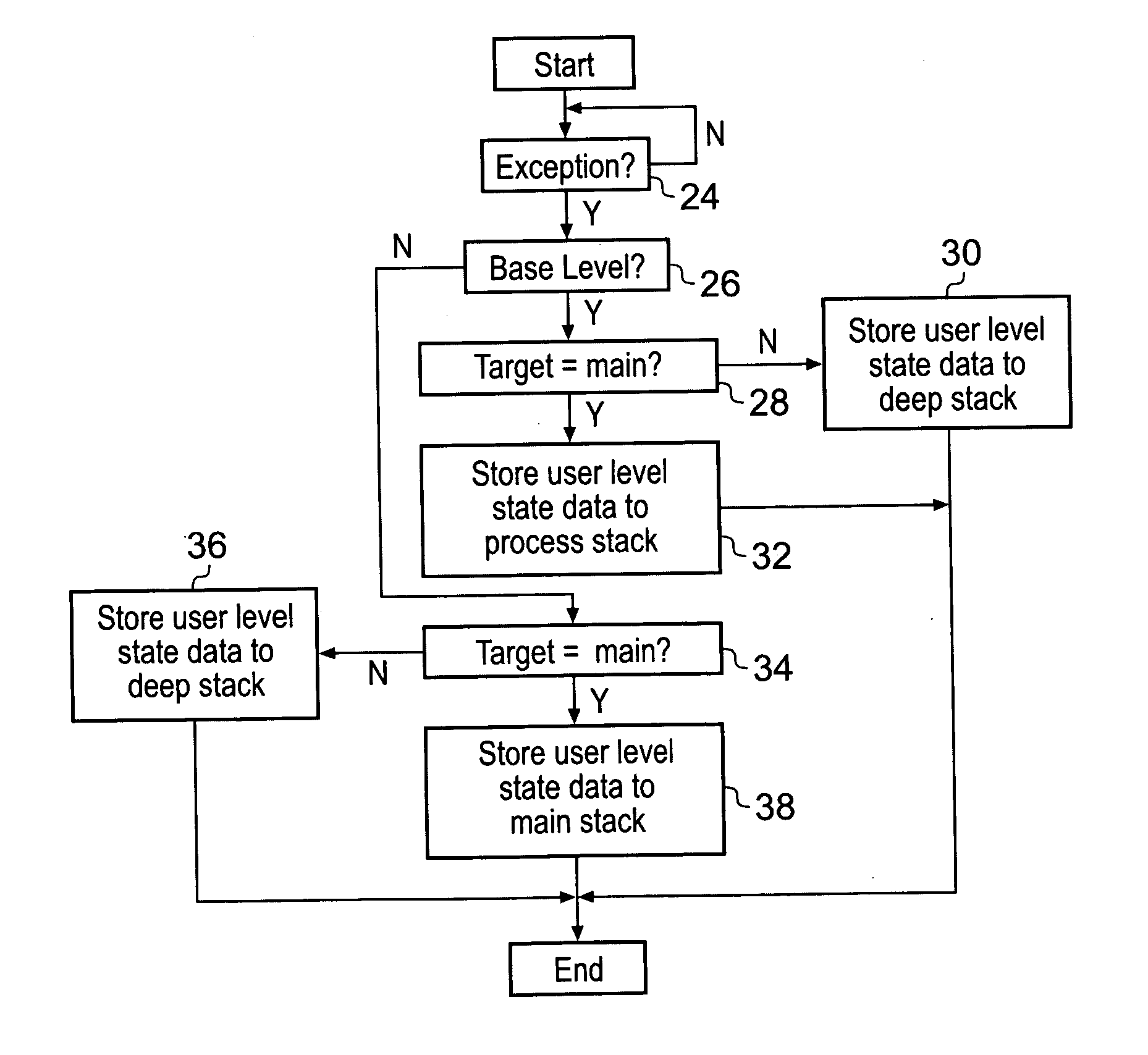
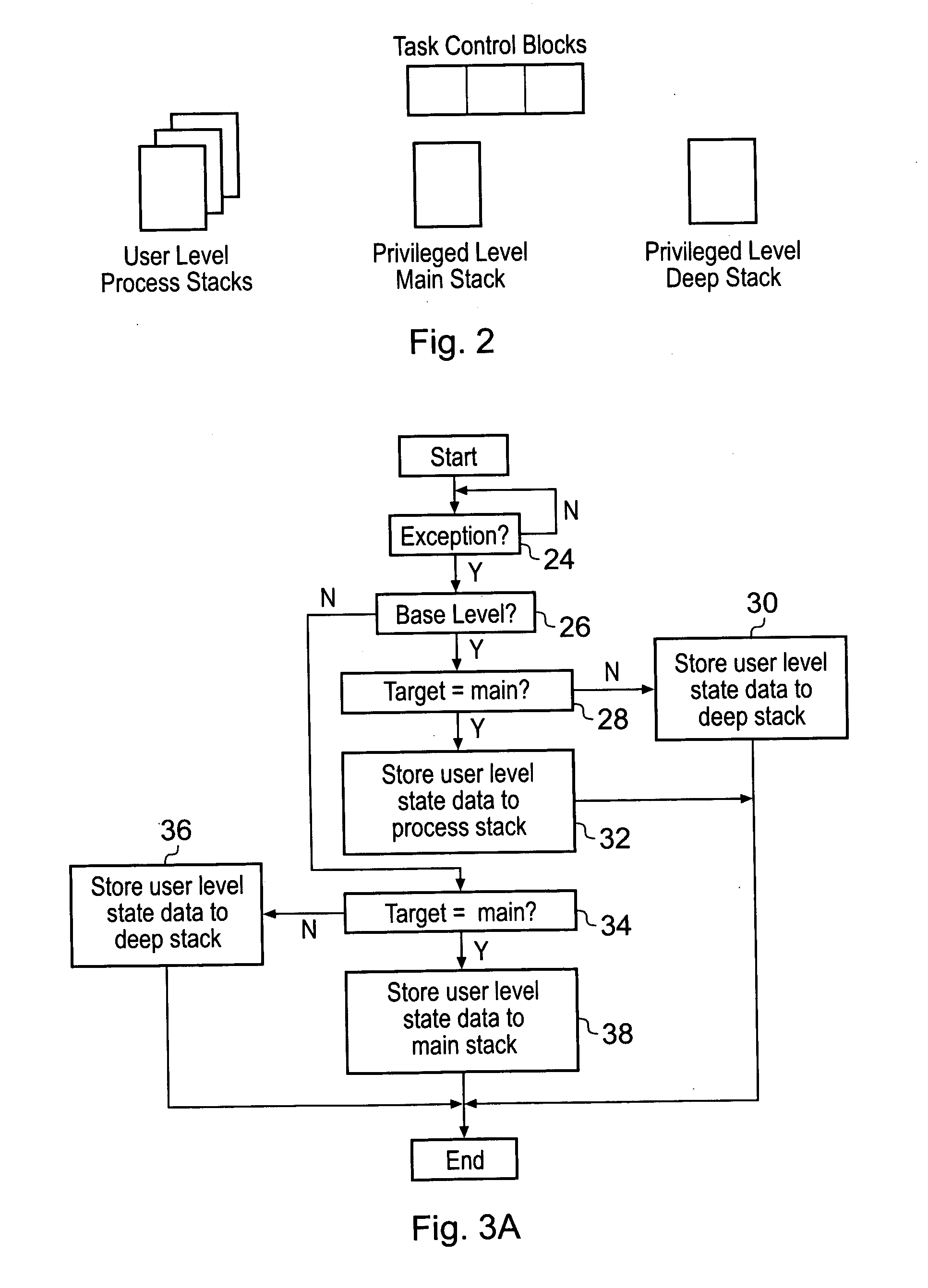
Stack memory selection upon exception in a data processing system
ActiveUS20070266374A1Reduce the possibilityReduce riskSpecific program execution arrangementsMemory systemsHandling CodeData processing system
A data processor 2 has privilege levels associated with it including a user level and a privileged level. The processor 2 also has multiple stack memories which can be used including one or more process stacks, a main stack and a deep stack. The stack memory to be used is de-coupled from the privilege level. An activation level state variable tracking the number of pending exceptions is held by the processor and used to modify which stack memory stores pending state values when an exception occurs. If the system is at a base level of activation, corresponding to currently no pending exceptions, then when an exception occurs the current state data is saved on the process stack with the main stack being available for the exception handling code. Particular exceptions can be flagged as requiring use of a deep stack rather than either the process stack or the main stack. If the system is not at the base level of activation, then the main stack is used to save state variables when an exception occurs rather than the process stack.
Owner:ARM LTD
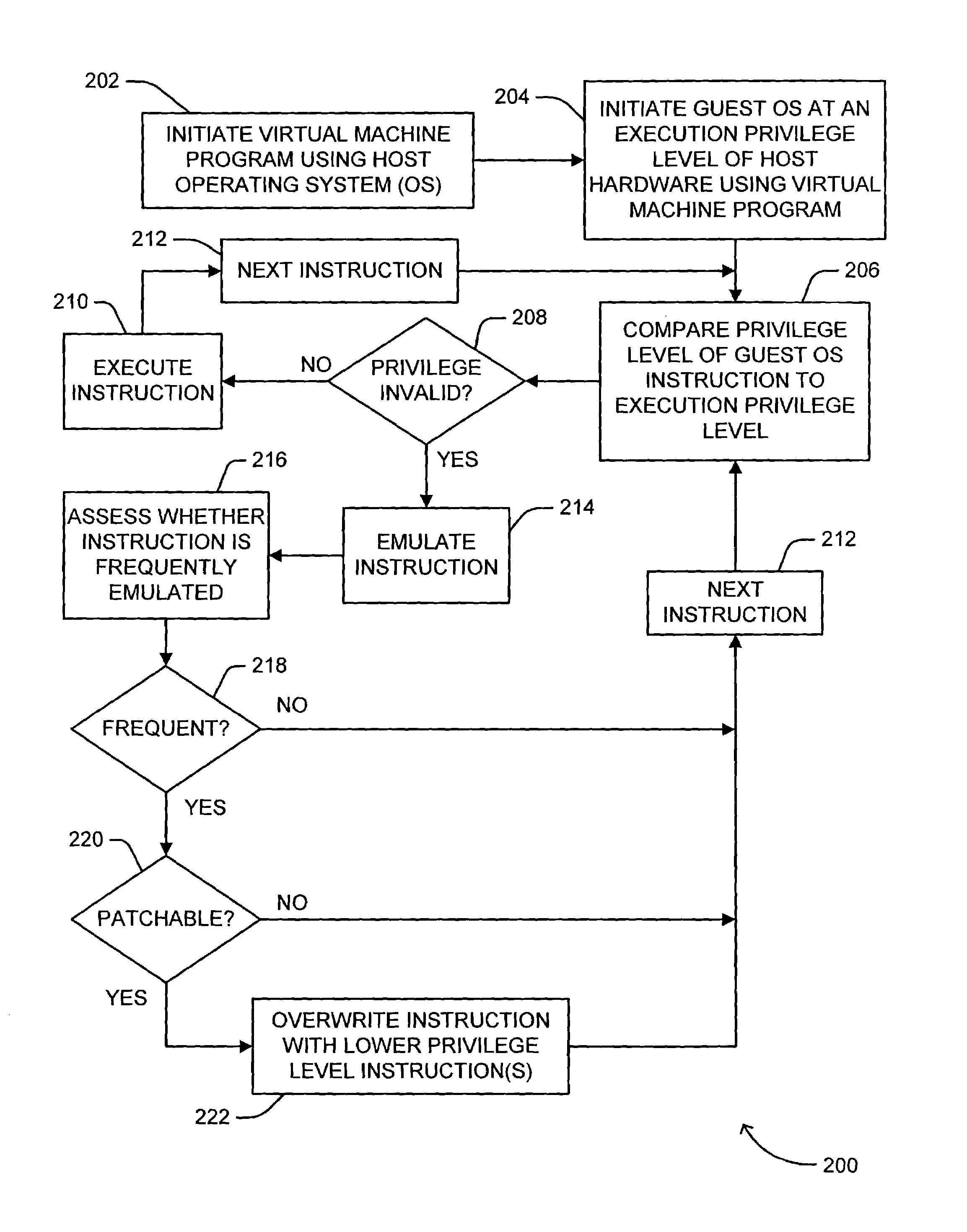
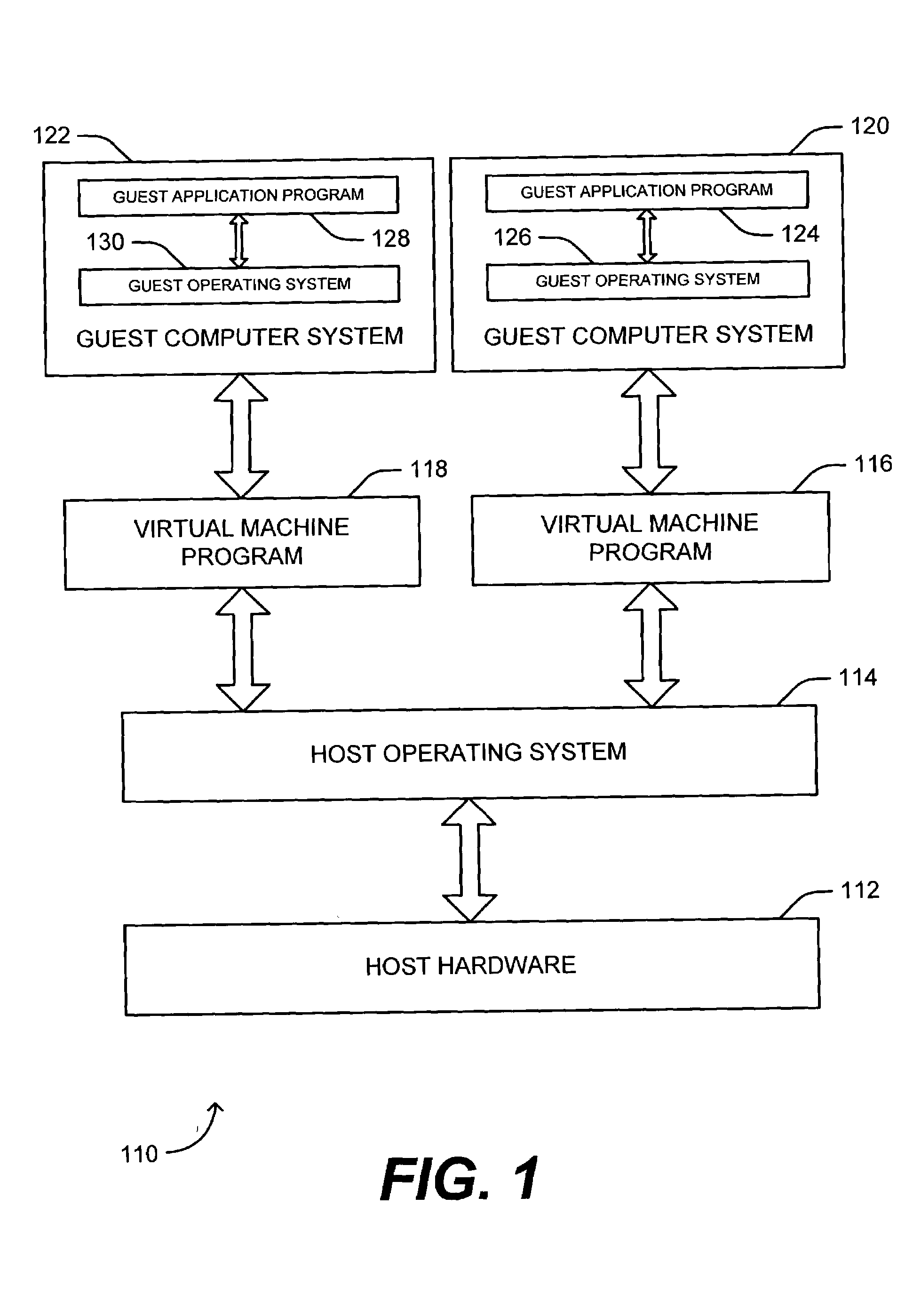
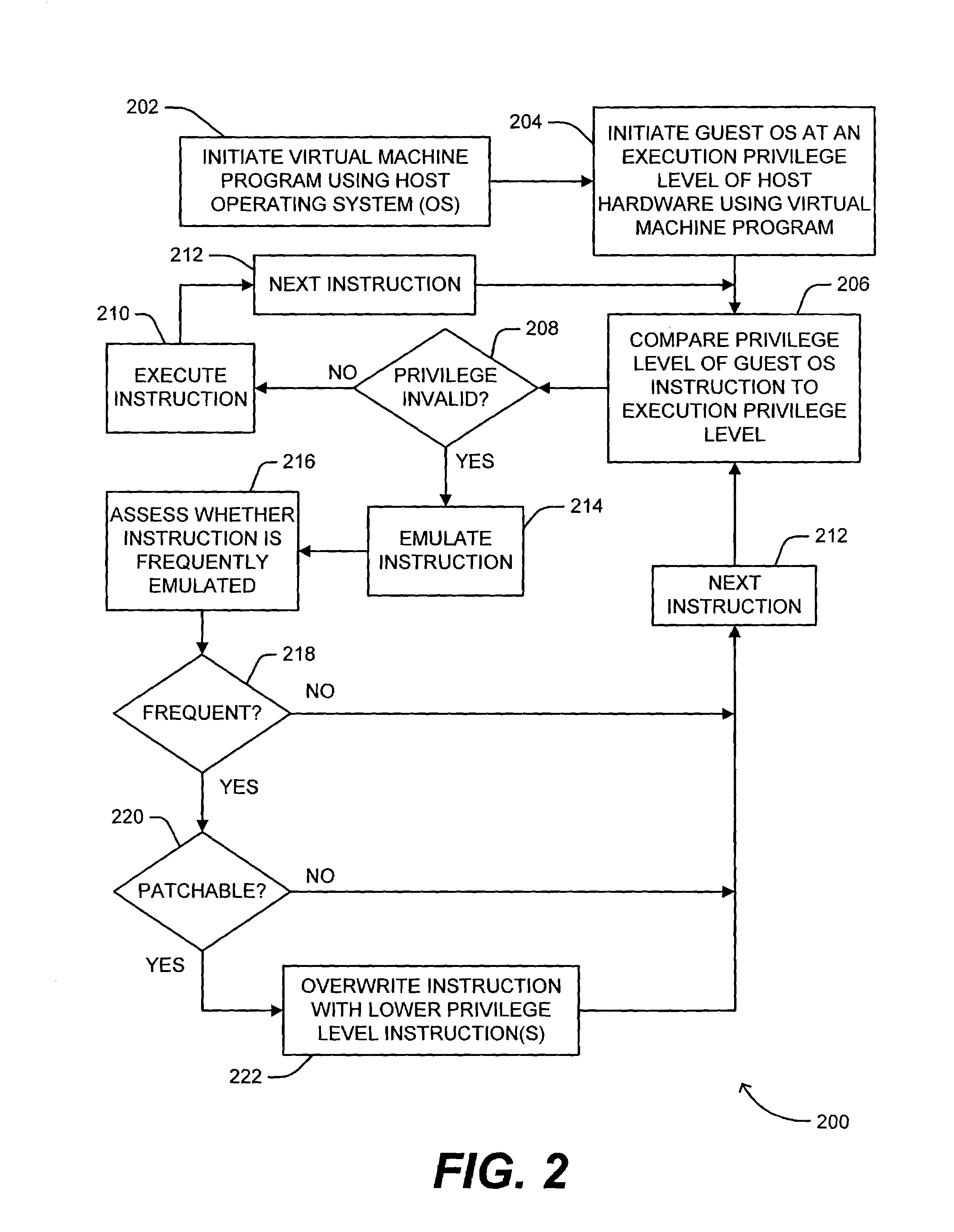
Method for monitoring and emulating privileged instructions of programs in a virtual machine
ActiveUS7210144B2Improve performanceImprove compatibilityError detection/correctionDigital data processing detailsPrivilege levelVirtual machine
A method for monitoring and emulating privileged instructions of a program that is being executed at a privilege level in a virtual machine is disclosed. A privilege level associated with a received instruction is determined. The instruction privilege level is compared to the program execution privilege level. If the instruction privilege level is valid with respect to the program execution privilege level, the instruction is executed. If the instruction privilege level is invalid with respect to the program execution privilege level: the instruction result is emulated; the number of times the instruction has been received from the program is checked; and if the instruction has been received more than a specified number of times, the instruction is overwritten with one or more instructions with a valid privilege level with respect to the program execution privilege level.
Owner:MICROSOFT TECH LICENSING LLC
Packet validation in virtual network interface architecture
ActiveUS20100049876A1Multiple digital computer combinationsTransmissionIp addressNetwork interface device
Roughly described, a network interface device receiving data packets from a computing device for transmission onto a network, the data packets having a certain characteristic, transmits the packet only if the sending queue has authority to send packets having that characteristic. The data packet characteristics can include transport protocol number, source and destination port numbers, source and destination IP addresses, for example. Authorizations can be programmed into the NIC by a kernel routine upon establishment of the transmit queue, based on the privilege level of the process for which the queue is being established. In this way, a user process can use an untrusted user-level protocol stack to initiate data transmission onto the network, while the NIC protects the remainder of the system or network from certain kinds of compromise.
Owner:XILINX INC
System and method for managing relationships with independent multi-dimensional grouping, individualized privileges, and interactive feedback in a social network
A system and method for managing relationships in a social network with independent multi-dimensional groupings, individualized privileges & interactive feedback. The contributing member can assign a privilege level from a sliding scale of at least three levels for each item of information, represented as C1, C2, C3, . . . CN. The contributing member then grants direct privilege levels as they make new friends or grants indirect privilege levels when they join groups or networks. When a requesting user (T) wishes to see contributed information, their privilege level (L) with respect to the contributing member is accessed. The system retrieves all items of information (C), and selectively displays those items of information which have been assigned a privilege level C1, C2, C3, . . . CN matching or less than the privilege level granted to the requesting member TL. A contributing member can also chose to allow ‘friends of friends’ to inherit the privilege level assigned to them by their friends so that ‘friends of friends’ can be granted access to their private information despite the lack of direct connection.
Owner:RIZK HENRI
Dynamic running method for security kernel service of tristate operating system in Feiteng CPU
ActiveCN105022954AReduce security risksImprove safety and reliabilityPlatform integrity maintainanceEcological environmentOperational system
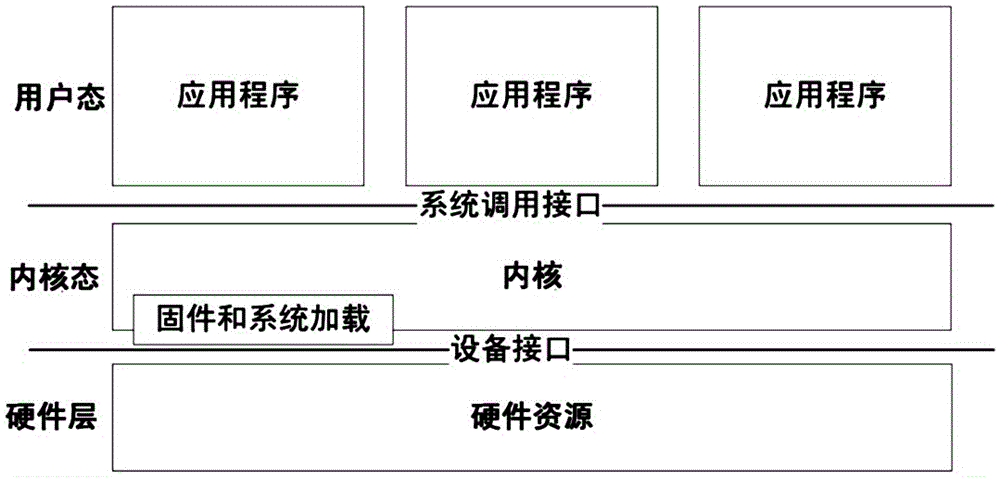
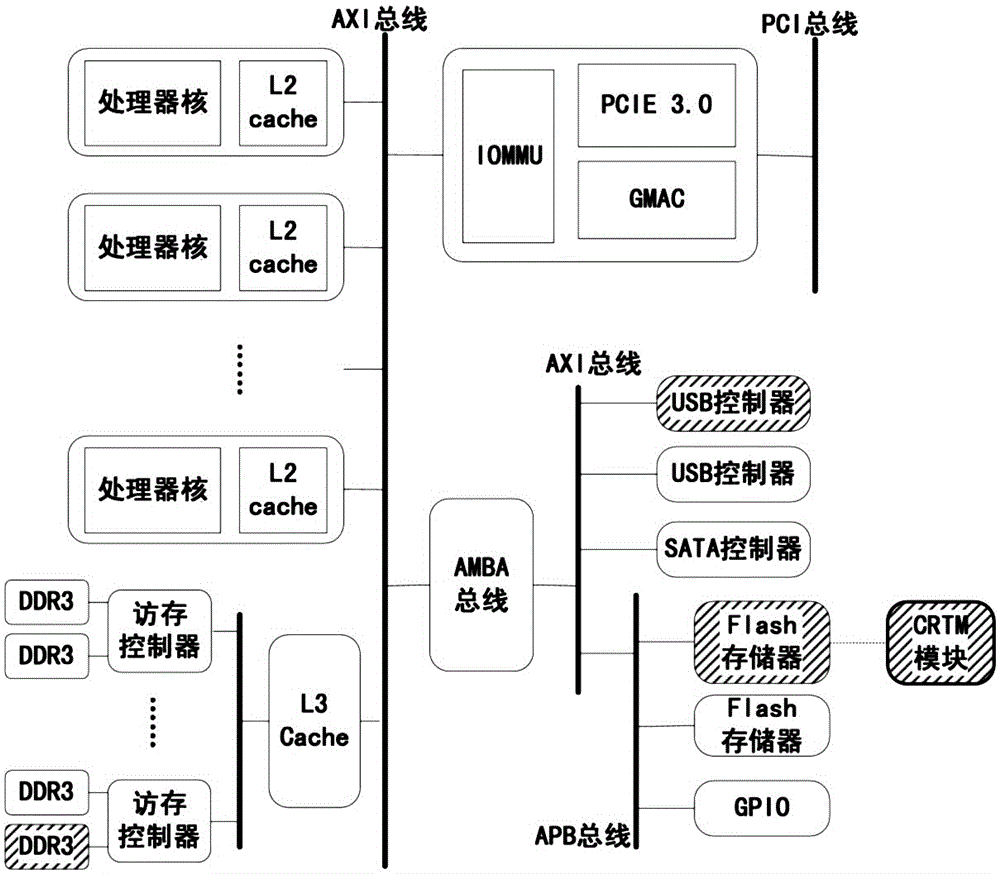
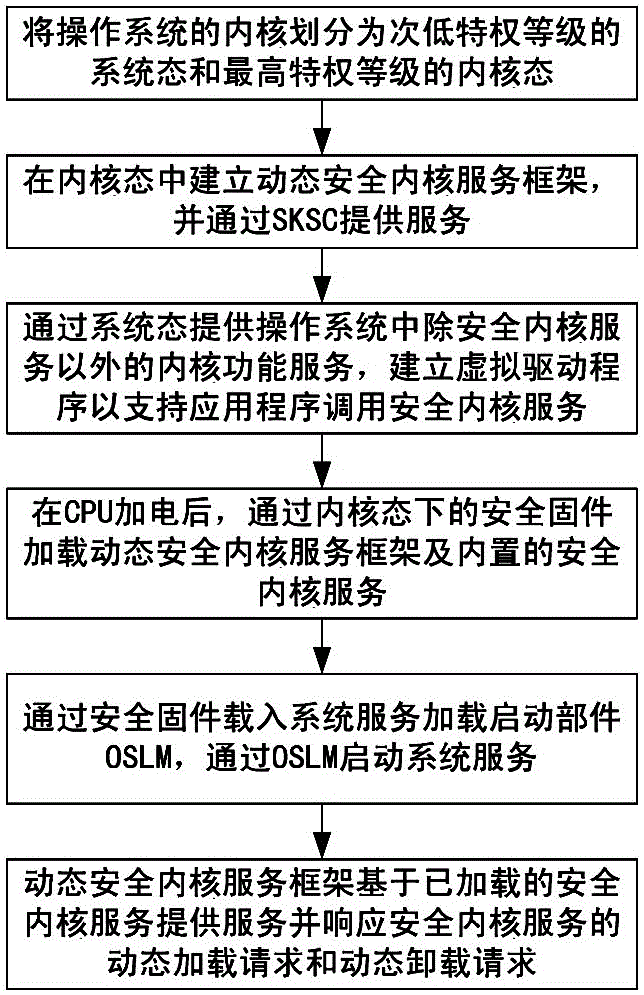
The invention discloses a dynamic running method for a security kernel service of a tristate operating system in a Feiteng CPU. The method comprises the steps of: dividing a kernel into a system state and a kernel state of different privilege levels; establishing a service framework in the kernel state to serve as a container for the security kernel service, and establishing a call interface for the security kernel service; establishing a virtual driving interface in the system state to support a user state to call the security kernel service; loading the service framework and the built-in security kernel service after enabling the CPU to be powered on; and loading a loading part of a system service module and starting a system service, wherein the service framework provides the security kernel service and makes a response to a dynamic loading / unloading request of the security kernel service. The dynamic running method can realize security protection on specific hardware resources of the system, realize security access to a core service of the operating system, efficiently support credibility conformation of the system, effectively improve the system security, lower the security risk of traditional kernel bugs and provide an efficient and flexible credible calculating ecological environment for users.
Owner:TSINGHUA UNIV +1
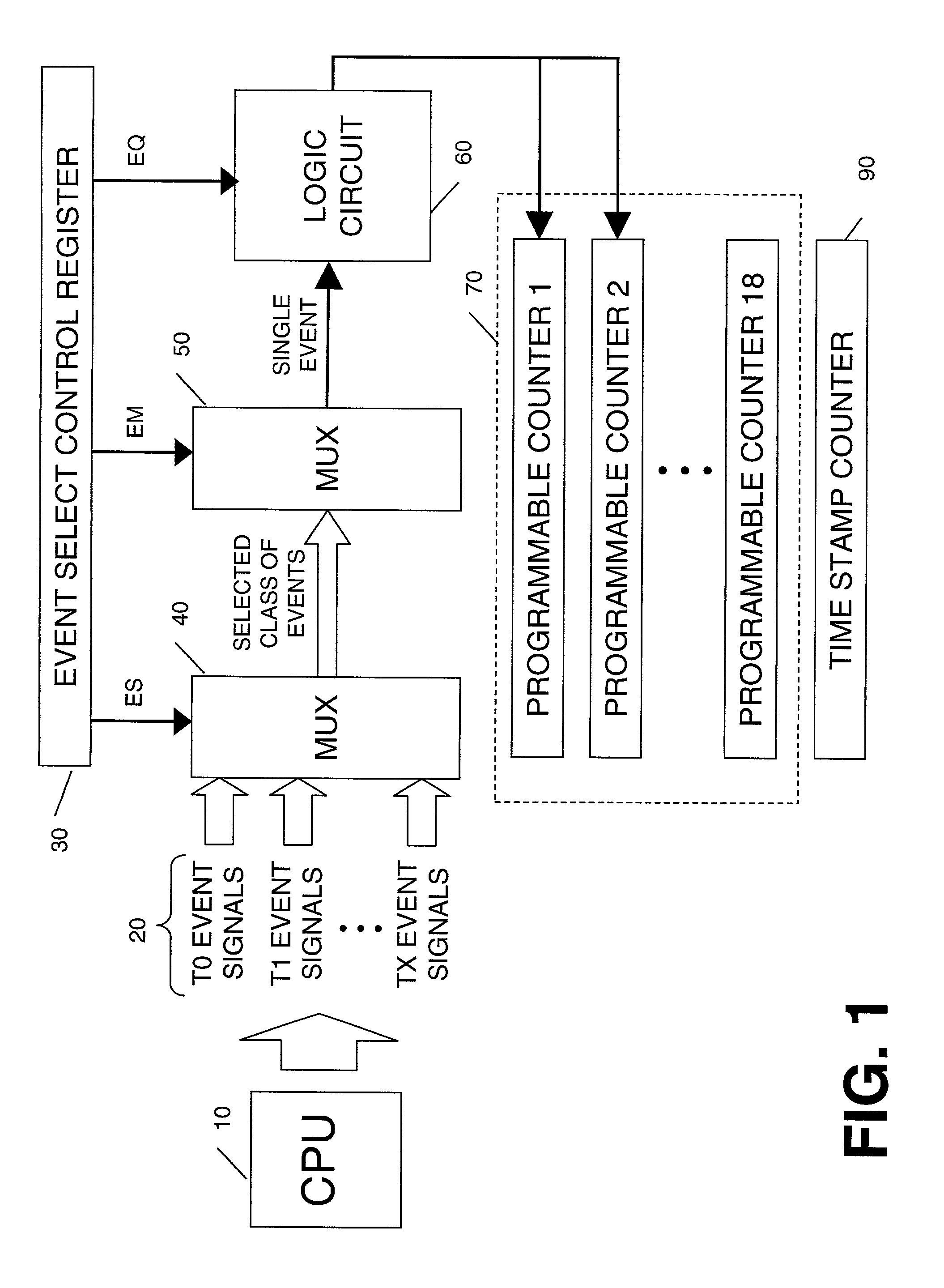
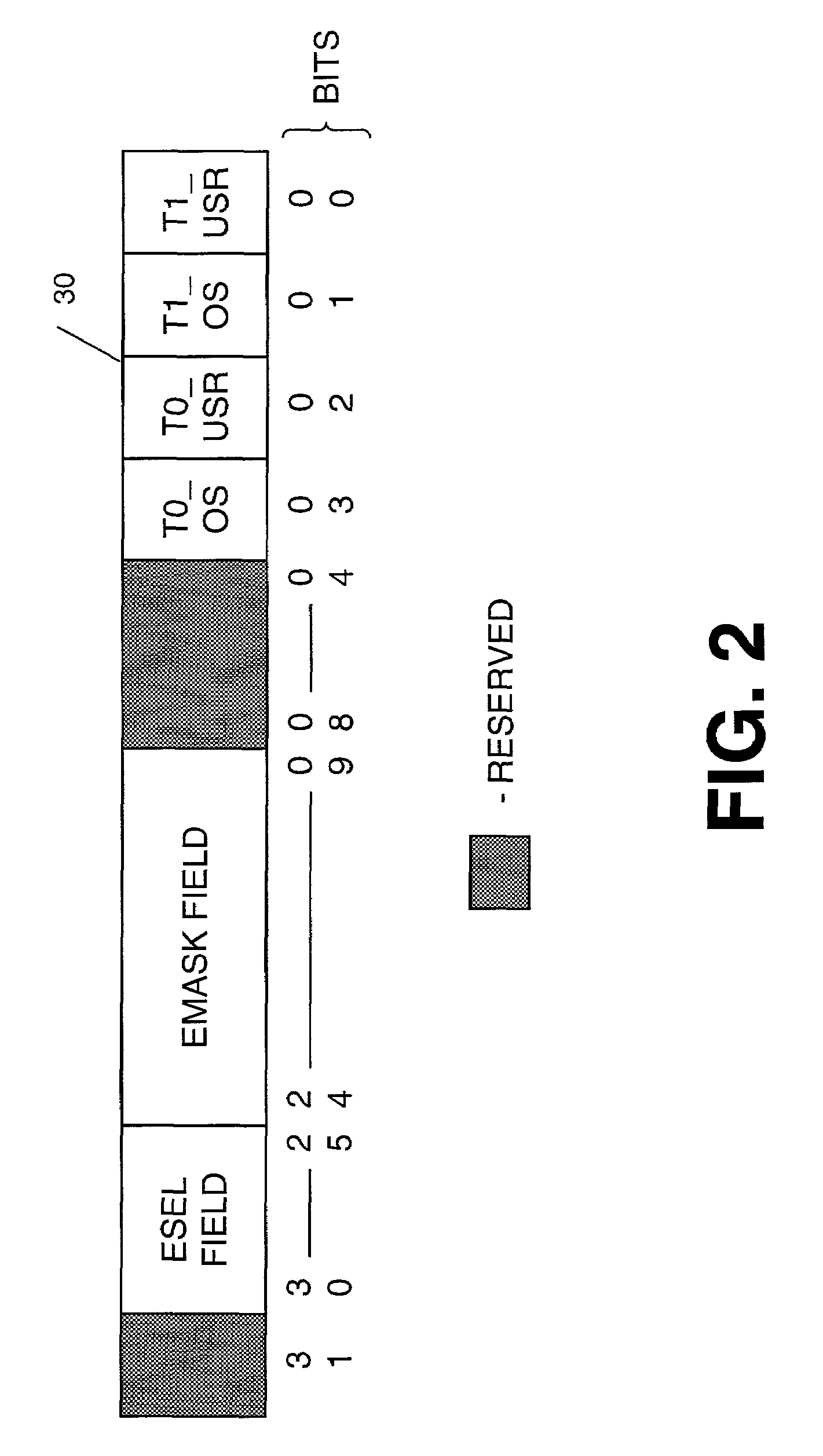
Qualification of event detection by thread ID and thread privilege level
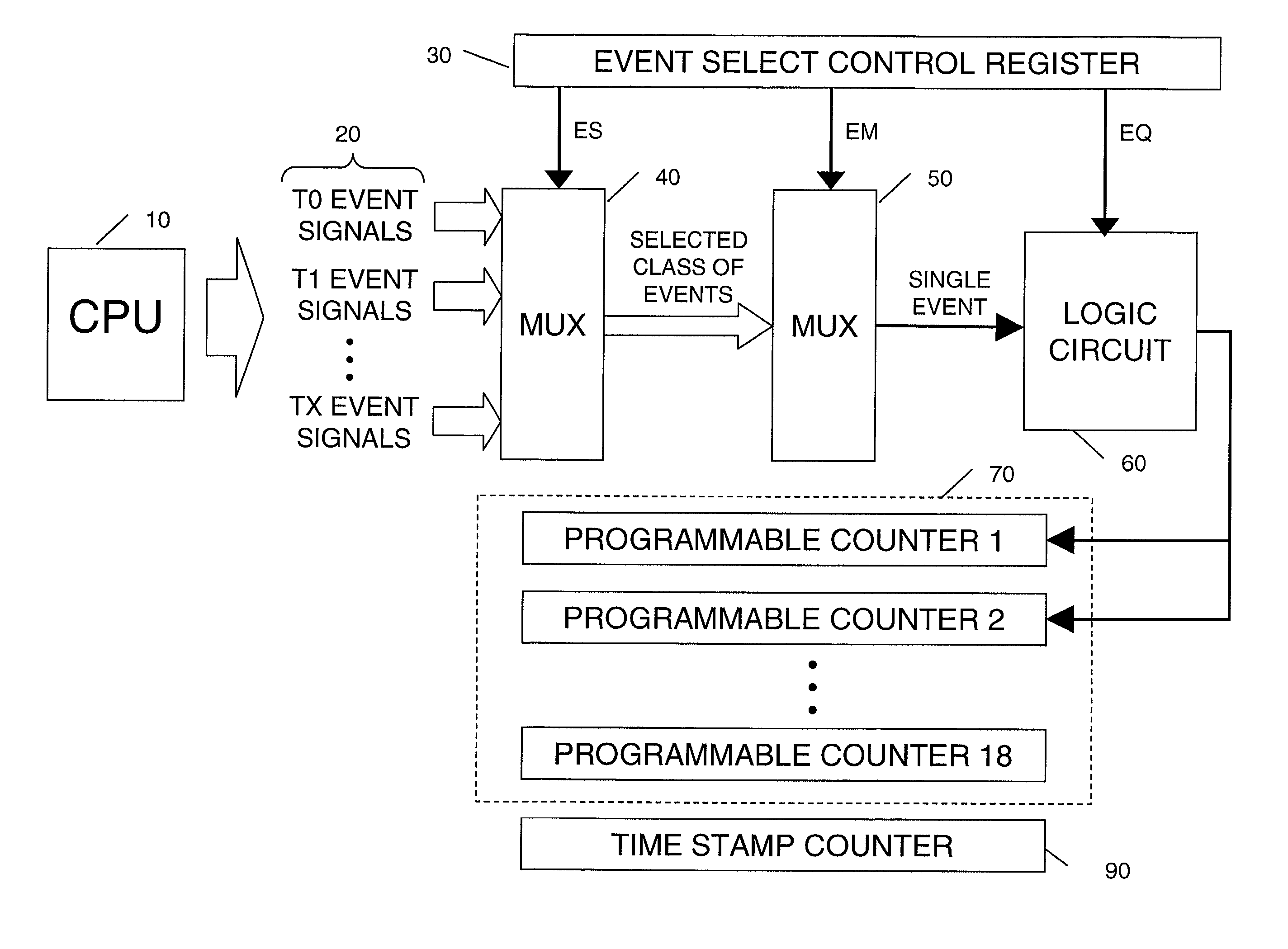
InactiveUS7448025B2Hardware monitoringMultiprogramming arrangementsProgram instructionProcessor register
A method and apparatus for monitoring the performance characteristics of a multithreaded processor executing instructions from two or more threads simultaneously. Event detectors detect the occurrence of specific processor events during the execution of instructions from threads of a multithreaded processor. Specialized event select control registers are programmed to control the selection, masking and qualifying of events to be monitored. Events are qualified according to their thread ID and thread current privilege level (CPL). Each event that is qualified is counted by one of several programmable event counters that keep track of all processor events being monitored. The contents of the event counters can then be accessed and sampled via a program instruction.
Owner:INTEL CORP
Packet validation in virtual network interface architecture
ActiveUS20060248234A1Multiple digital computer combinationsTransmissionIp addressNetwork interface device
Roughly described, a network interface device receiving data packets from a computing device for transmission onto a network, the data packets having a certain characteristic, transmits the packet only if the sending queue has authority to send packets having that characteristic. The data packet characteristics can include transport protocol number, source and destination port numbers, source and destination IP addresses, for example. Authorizations can be programmed into the NIC by a kernel routine upon establishment of the transmit queue, based on the privilege level of the process for which the queue is being established. In this way, a user process can use an untrusted user-level protocol stack to initiate data transmission onto the network, while the NIC protects the remainder of the system or network from certain kinds of compromise.
Owner:XILINX INC
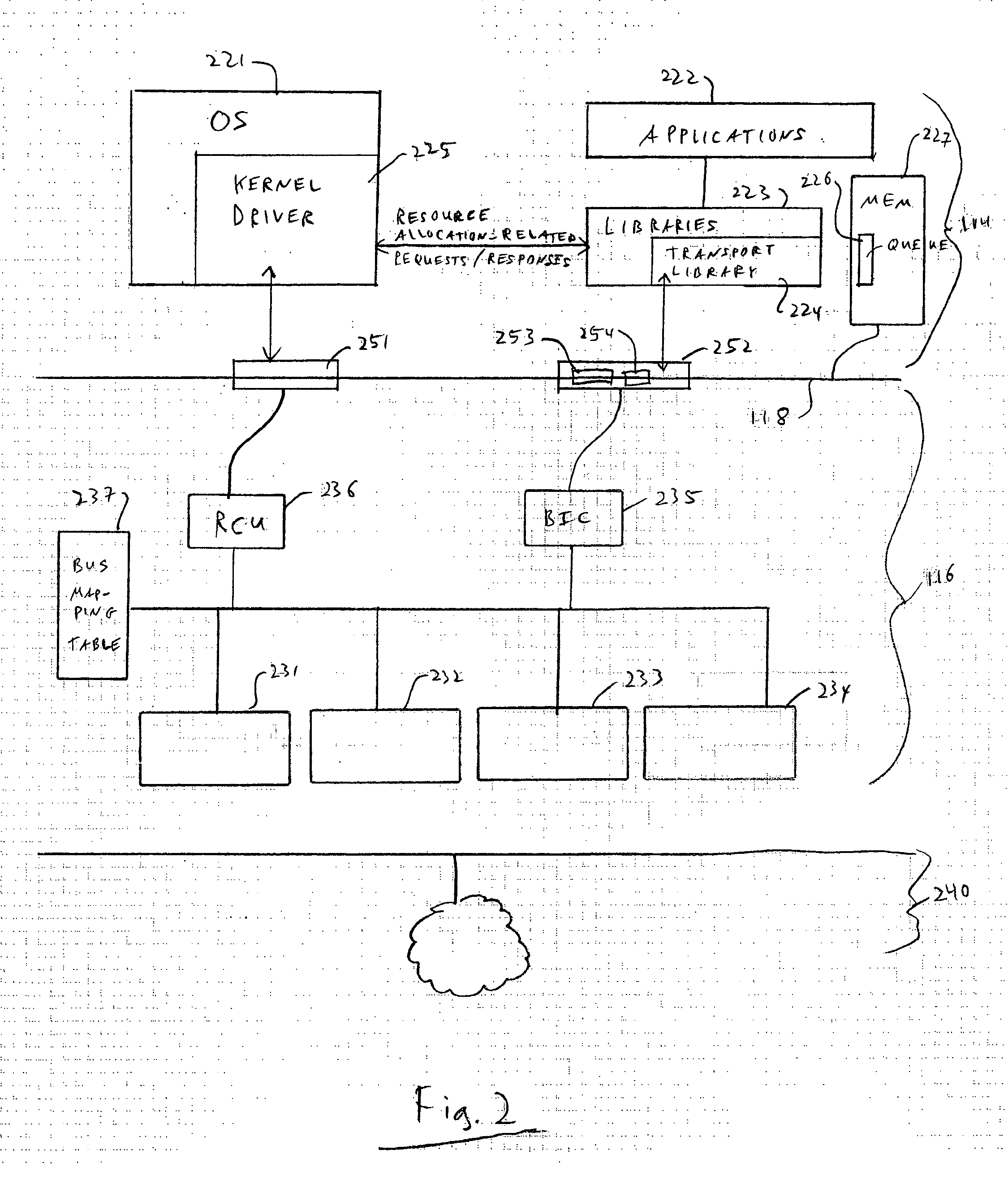
System and method for virtualization using an open bus hypervisor
ActiveUS8091086B1Efficient exchangeMultiprogramming arrangementsSoftware simulation/interpretation/emulationComputer moduleComputerized system
A computer system includes an Open Bus Hypervisor having the highest privilege level. An Open Bus Hypervisor is a set of modules that operate on the root level. The Open Bus Hypervisor provides support for processing, filtering and redirecting of low level events. The Open Bus Hypervisor is used primarily for maintenance and support of computer virtualization features, which are implemented within computer system CPU. Additionally, the Open Bus Hypervisor can be used for supporting new hardware and software modules installed on a computer system. A Virtual Machine Monitor (VMM) runs with fewer privileges than the Open Bus Hypervisor. A Primary Virtual Machine (PVM) runs without system level privileges and has a Primary Operating System (POS) running within it.
Owner:PARALLELS INT GMBH
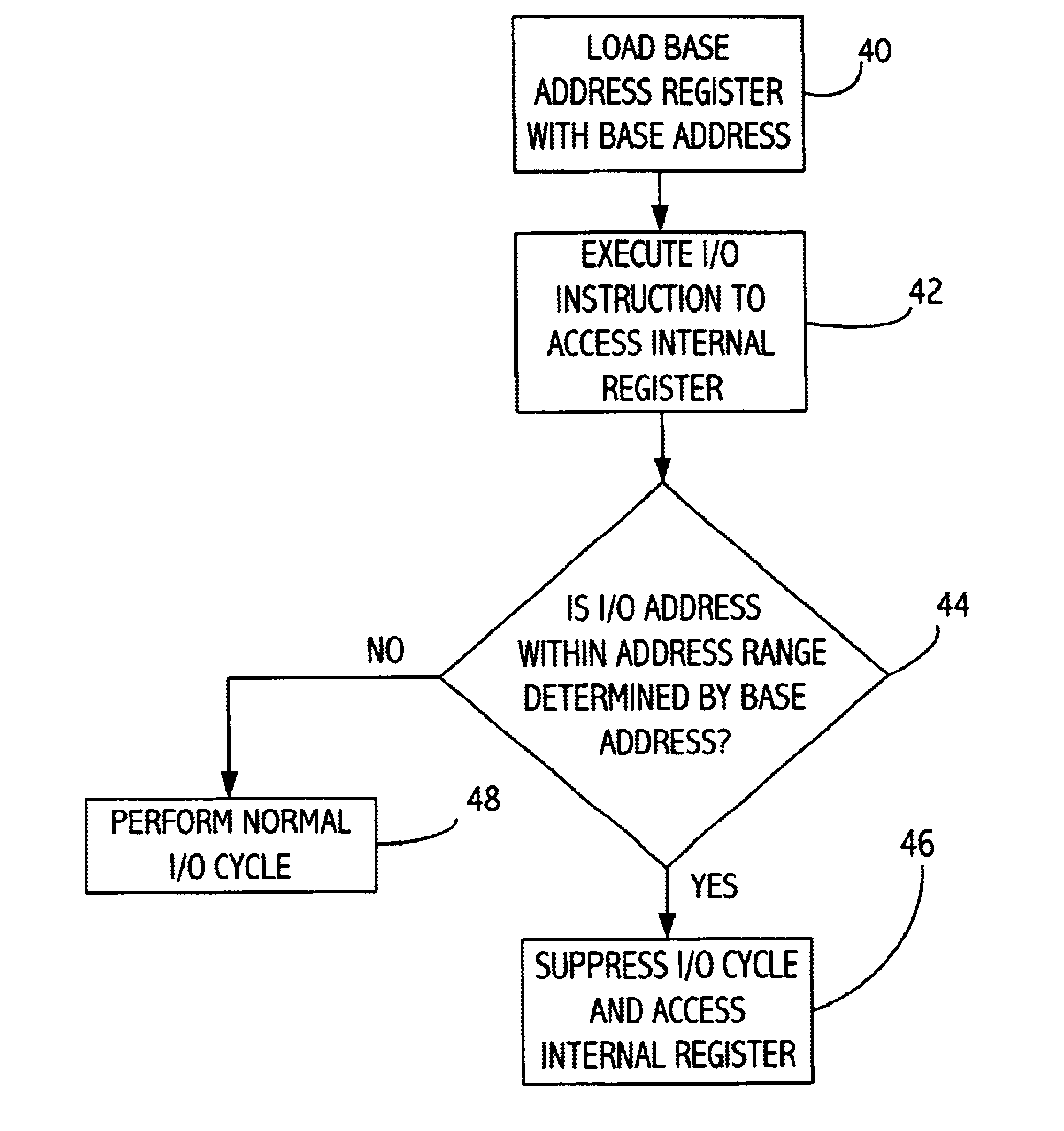
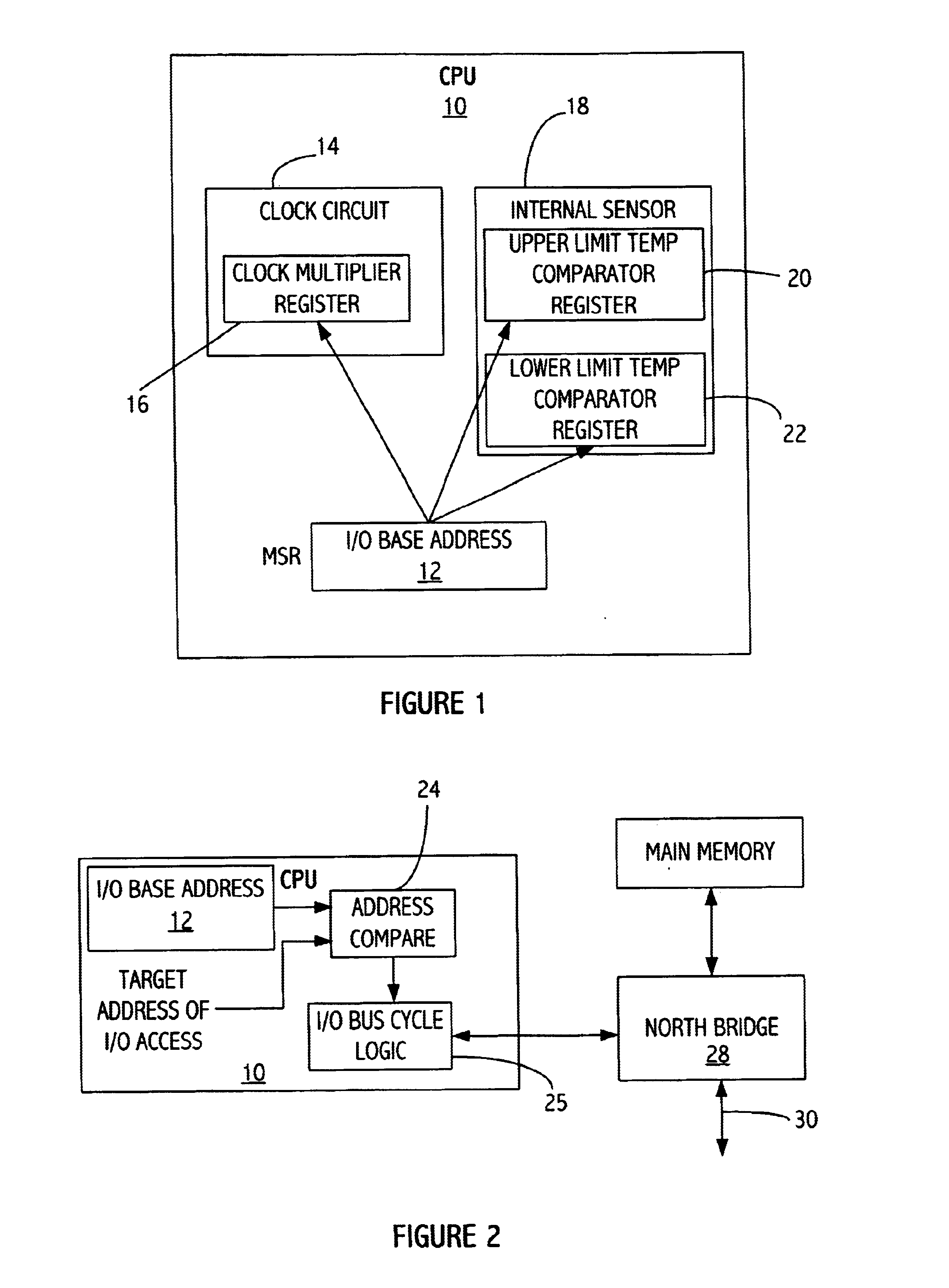
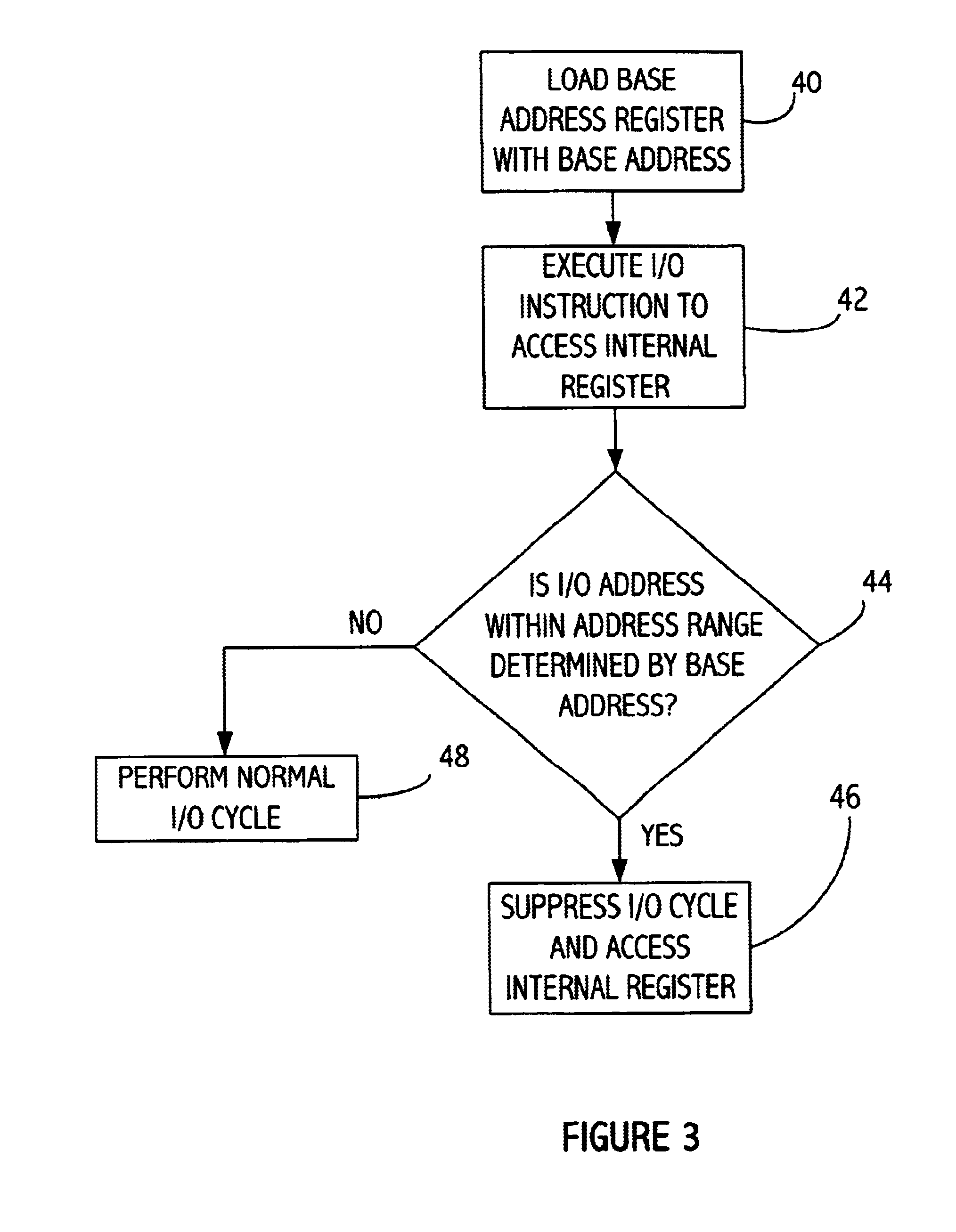
Using a model specific register as a base I/O address register for embedded I/O registers in a processor
InactiveUS6711673B1Memory adressing/allocation/relocationDigital computer detailsPage address registerProcessor register
A processor includes an input / output (I / O) register that is mapped into input / output (I / O) address space. The processor also includes a base address register that is loaded with a base address. The base address register may be a model specific register (MSR). The input / output register is accessed with an input / output instruction at an address determined according to the base address and an offset therefrom. The base address register may be accessible to software operating at a high privilege level and not accessible to software operating at a lower privilege level, while the I / O register is accessible to software operating at the lower privilege level. The processor determines when an I / O access is to the processor I / O register and accesses that I / O register without causing an input / output bus cycle that would otherwise occur.
Owner:GLOBALFOUNDRIES INC
Providing a flexible protection model in a computer system by decoupling protection from computer privilege level
ActiveUS20050172138A1Flexible fine granularityReduce overheadSpecific access rightsDigital data processing detailsOperational systemProtection domain
Methods and systems for providing a flexible protection model in a computer system by decoupling protection from privilege are described. Information describing a relationship between the two or more domains that define types of protection and portions of code is received. The portions of code with the multiple domains that provide fine granularities of protection can be executed in the same privilege level. The relationship is not required to be linear. In addition, the overhead associated with crossing protection domains is relatively low with respect to traditional operating system context switching overhead.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
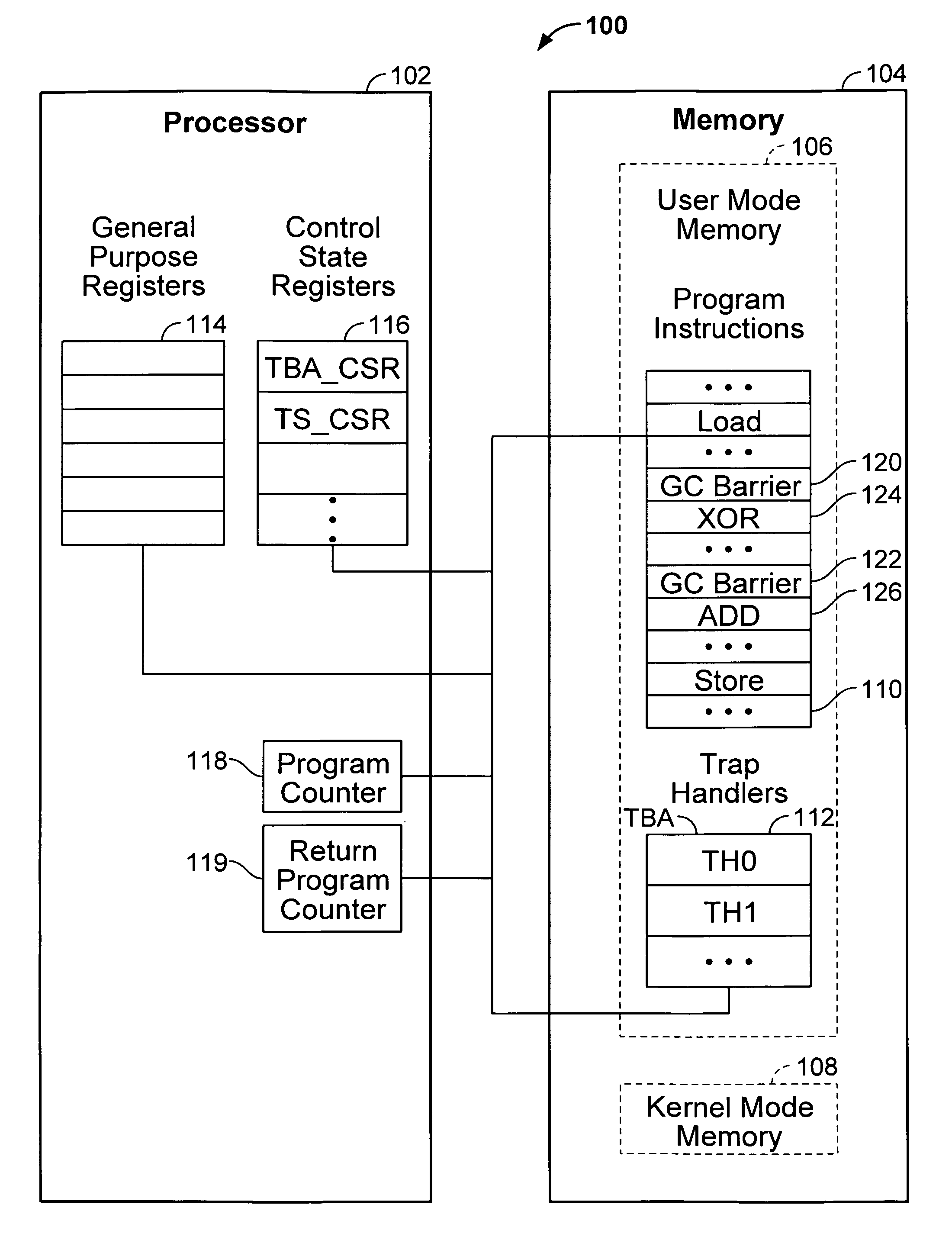
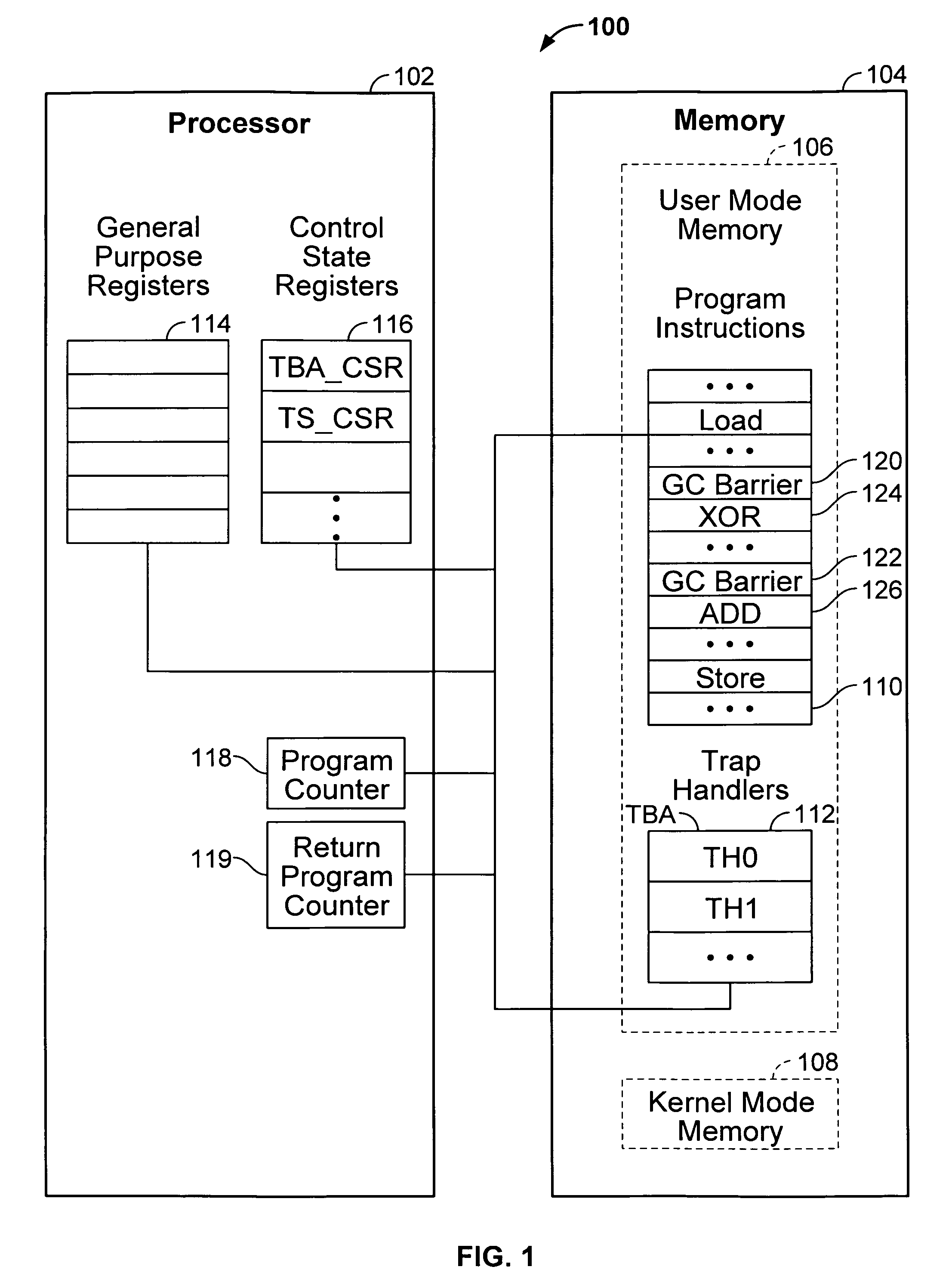
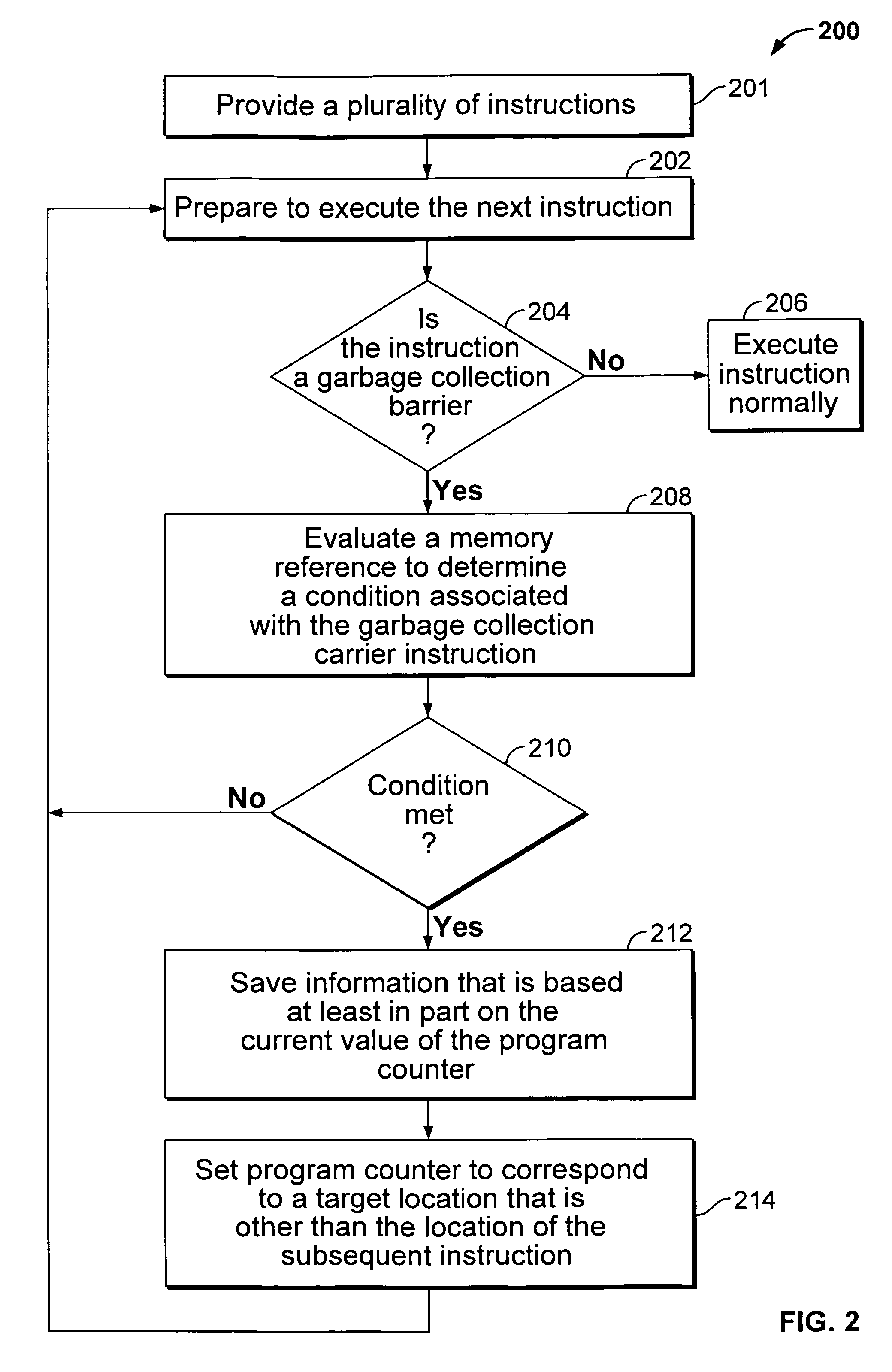
Garbage collection
A computer system includes a processor; and a memory coupled to the processor, configured to provide the processor with a plurality of instructions including a garbage collection barrier instruction and a subsequent instruction that immediately follows the garbage collection barrier instruction; wherein the processor is configured to execute the garbage collection barrier instruction, including by: evaluating a memory reference to determine a condition associated with the garbage collection barrier instruction; and in the event that the condition is met, while maintaining the same privilege level, saving information that is based at least in part on the current value of a program counter, and setting the program counter to correspond to a target location that is other than the location of the subsequent instruction.
Owner:AZUL SYSTEMS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com