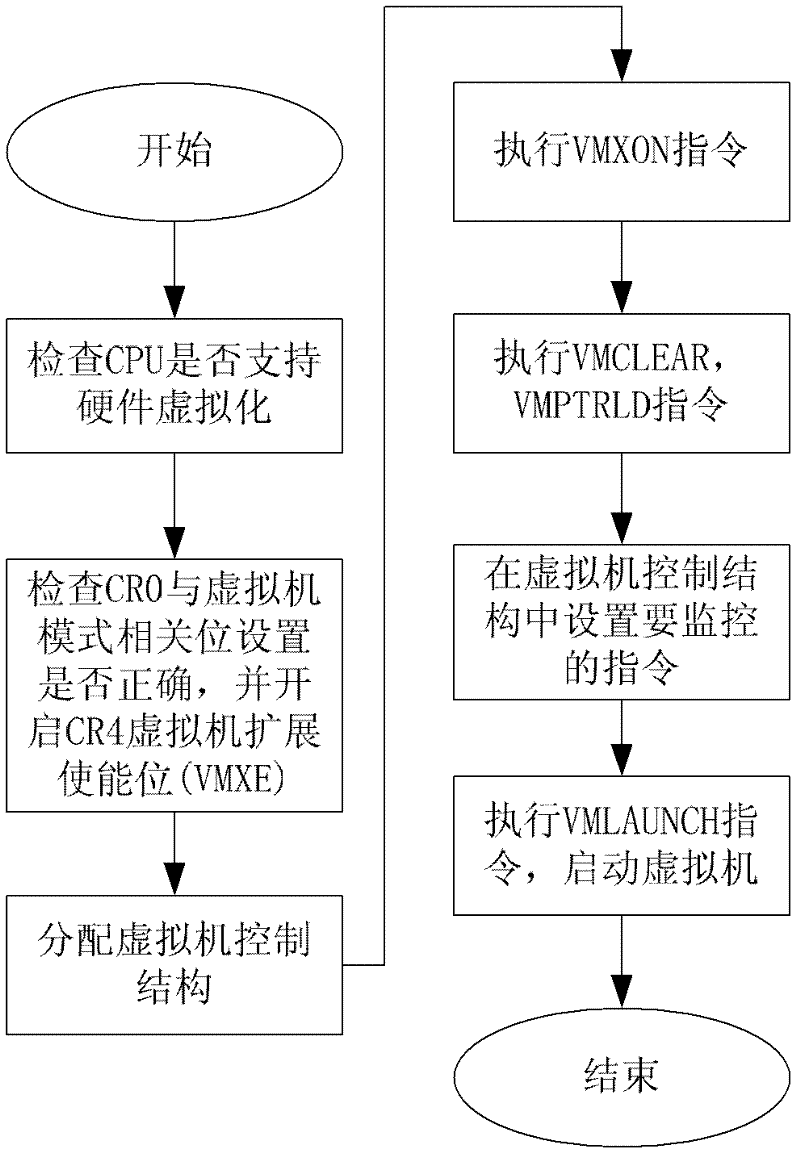
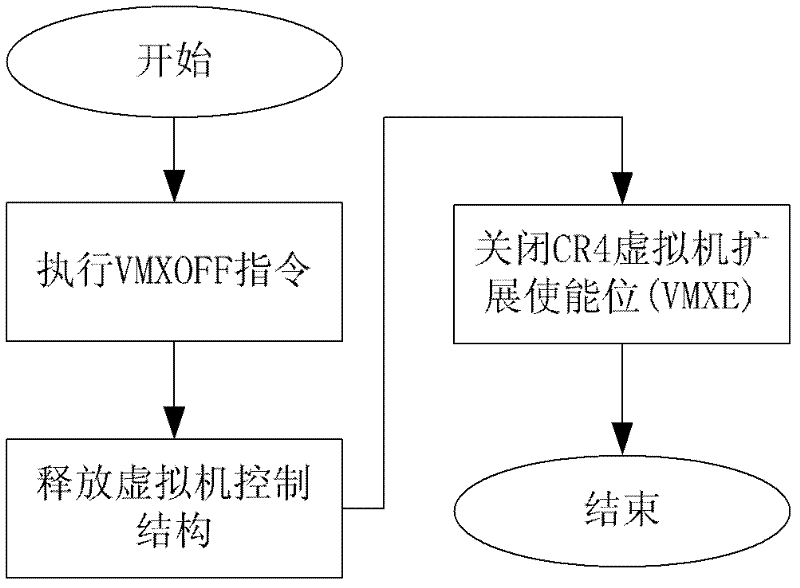
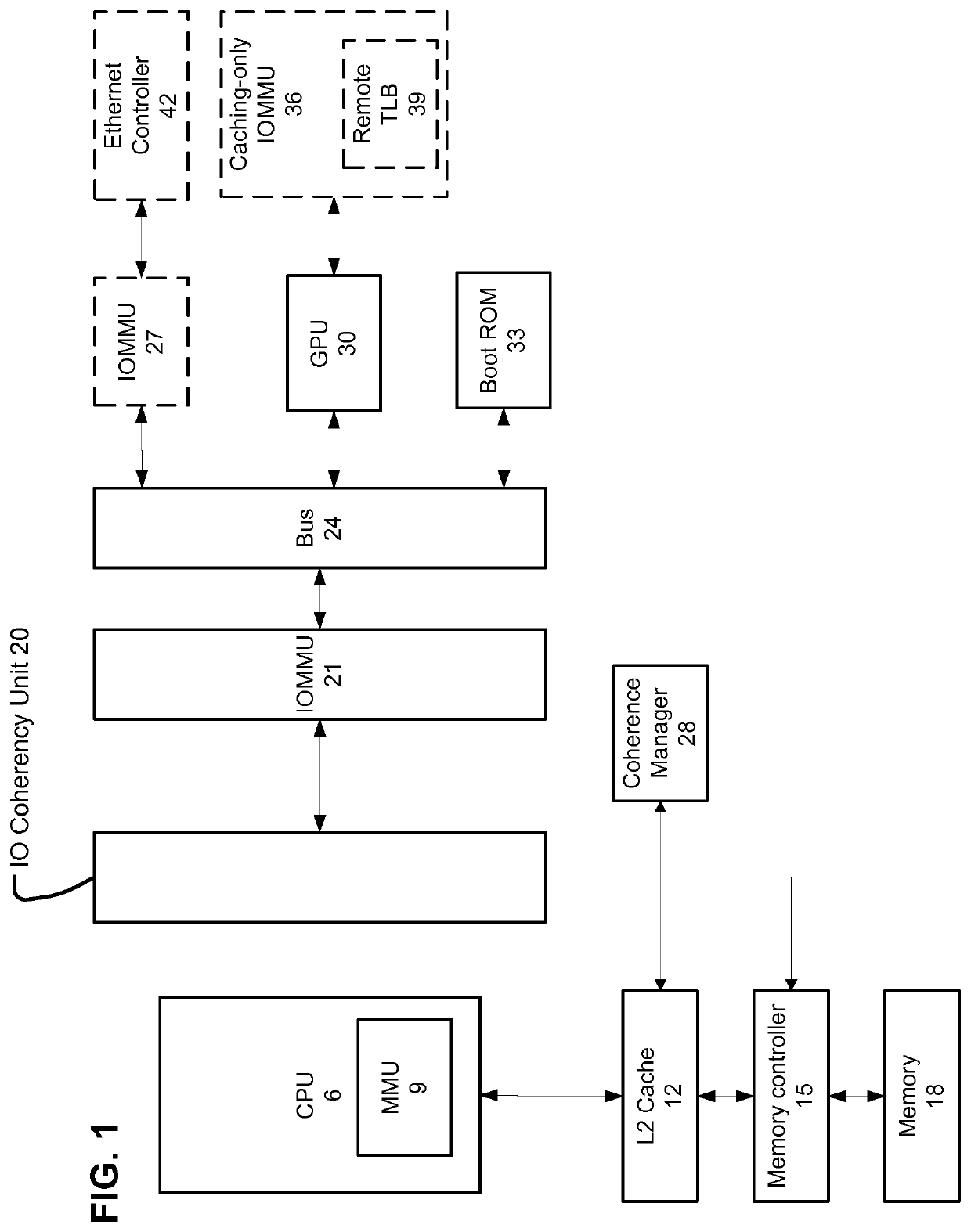
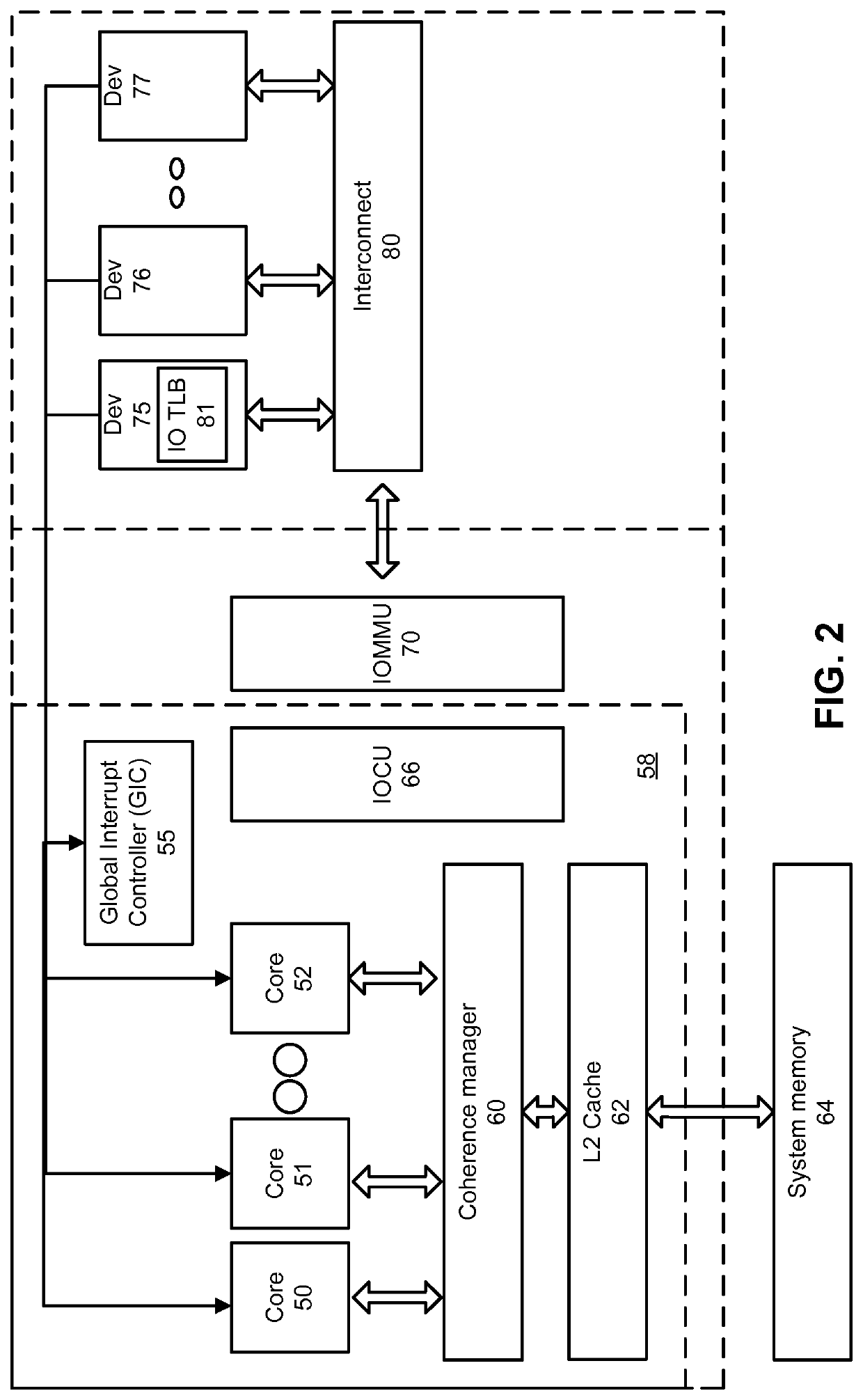
Patents
Literature
158 results about "Hardware virtualization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
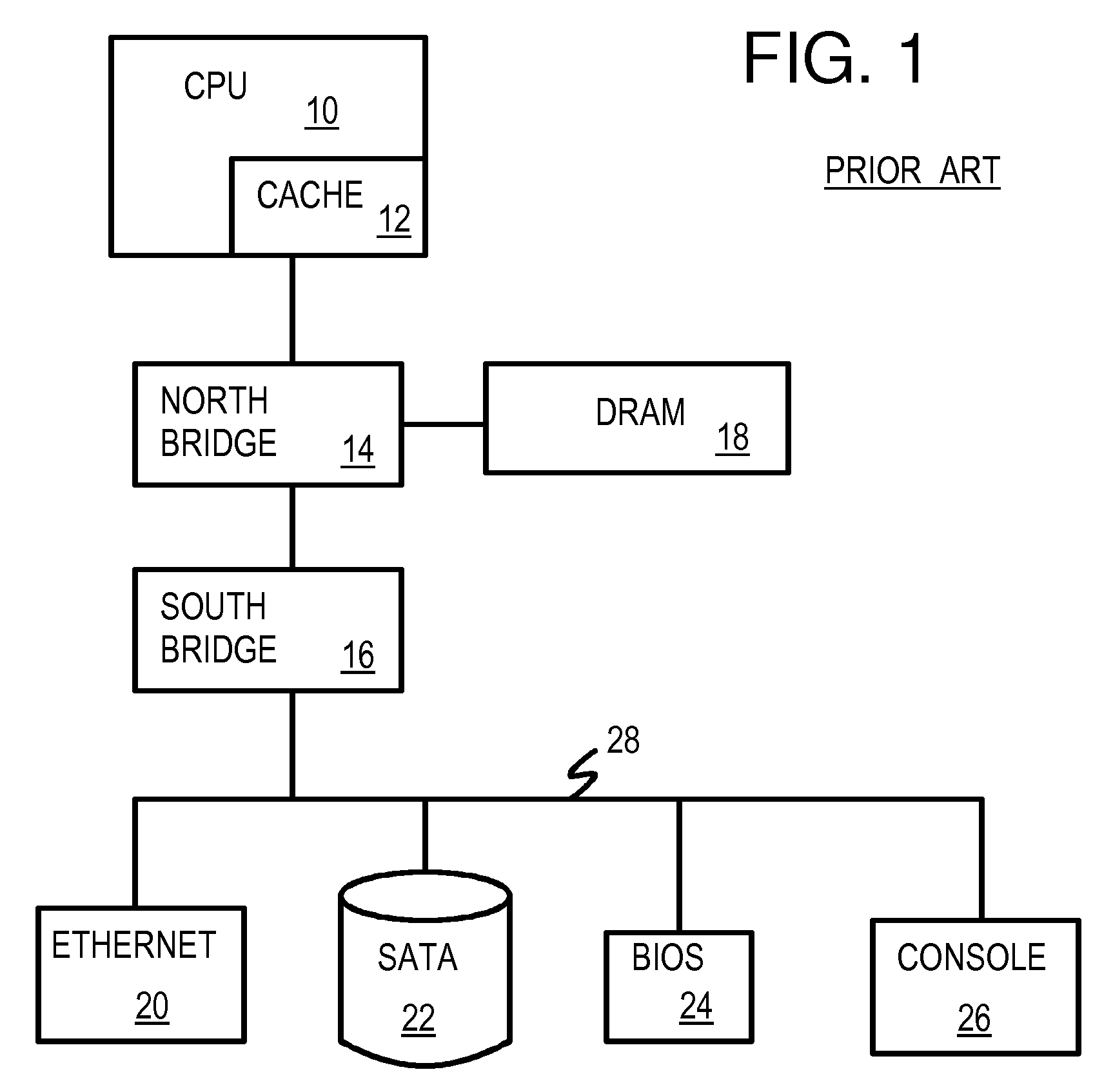
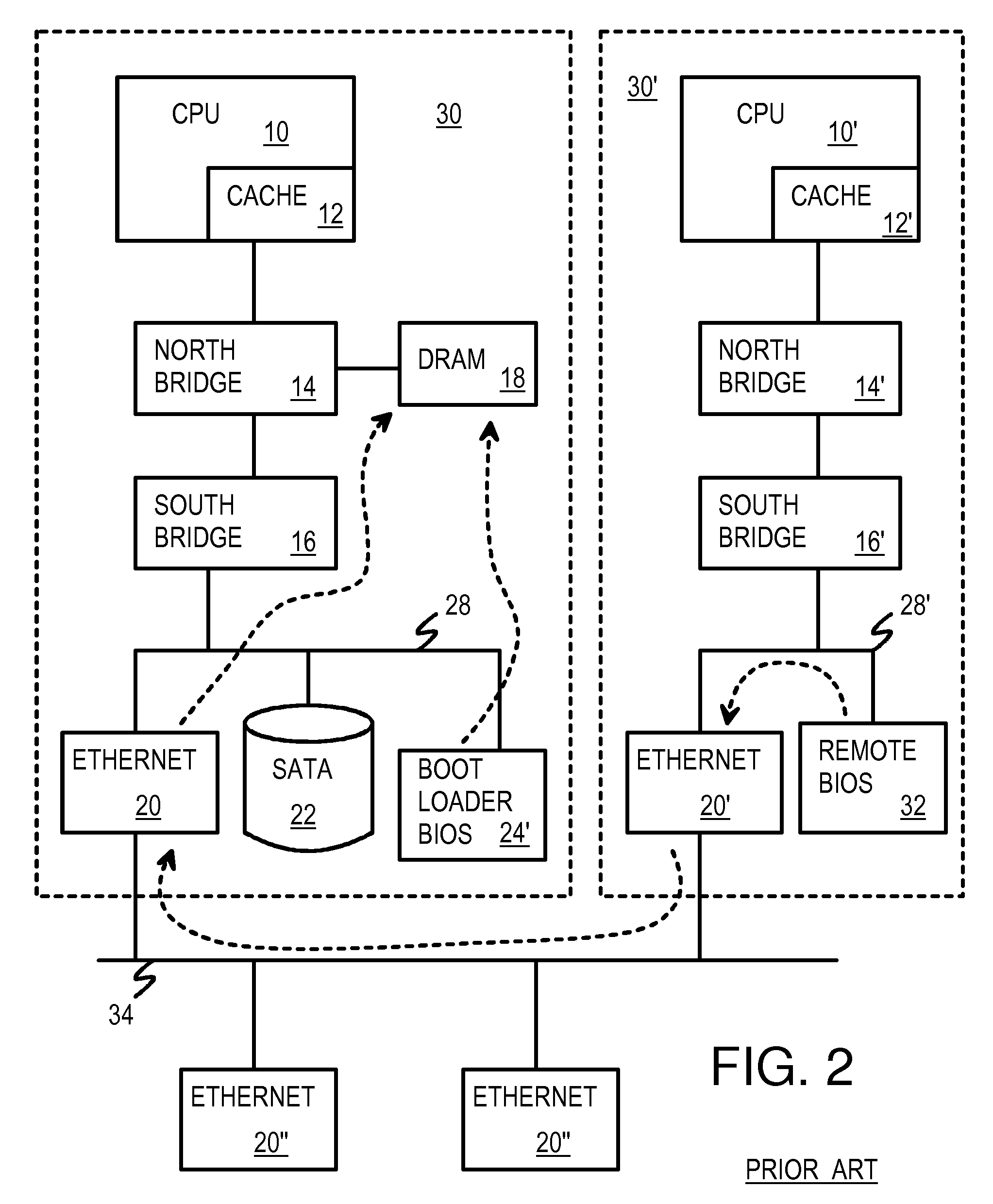
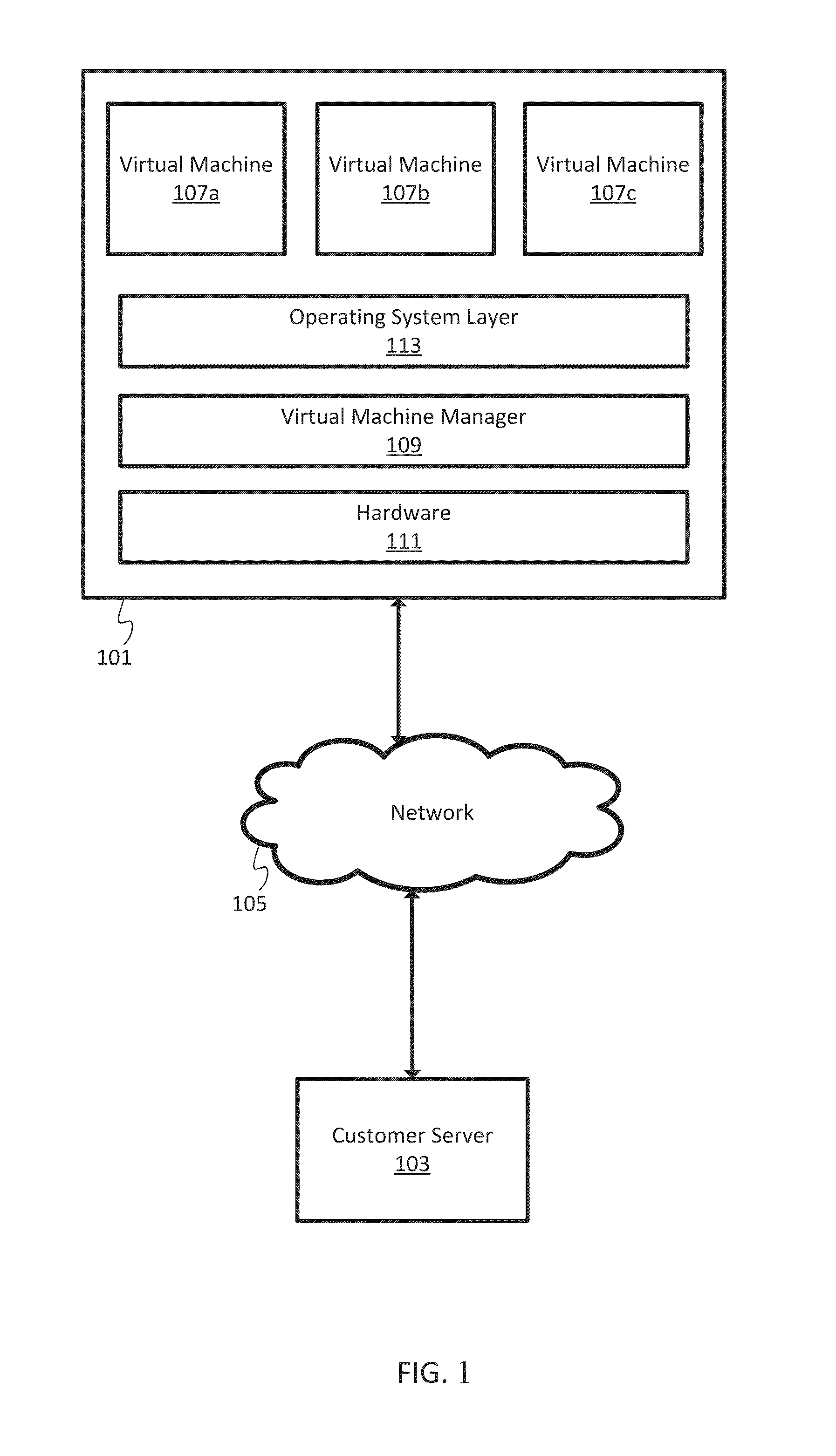
Hardware virtualization is the virtualization of computers as complete hardware platforms, certain logical abstractions of their componentry, or only the functionality required to run various operating systems. Virtualization hides the physical characteristics of a computing platform from the users, presenting instead an abstract computing platform. At its origins, the software that controlled virtualization was called a "control program", but the terms "hypervisor" or "virtual machine monitor" became preferred over time.
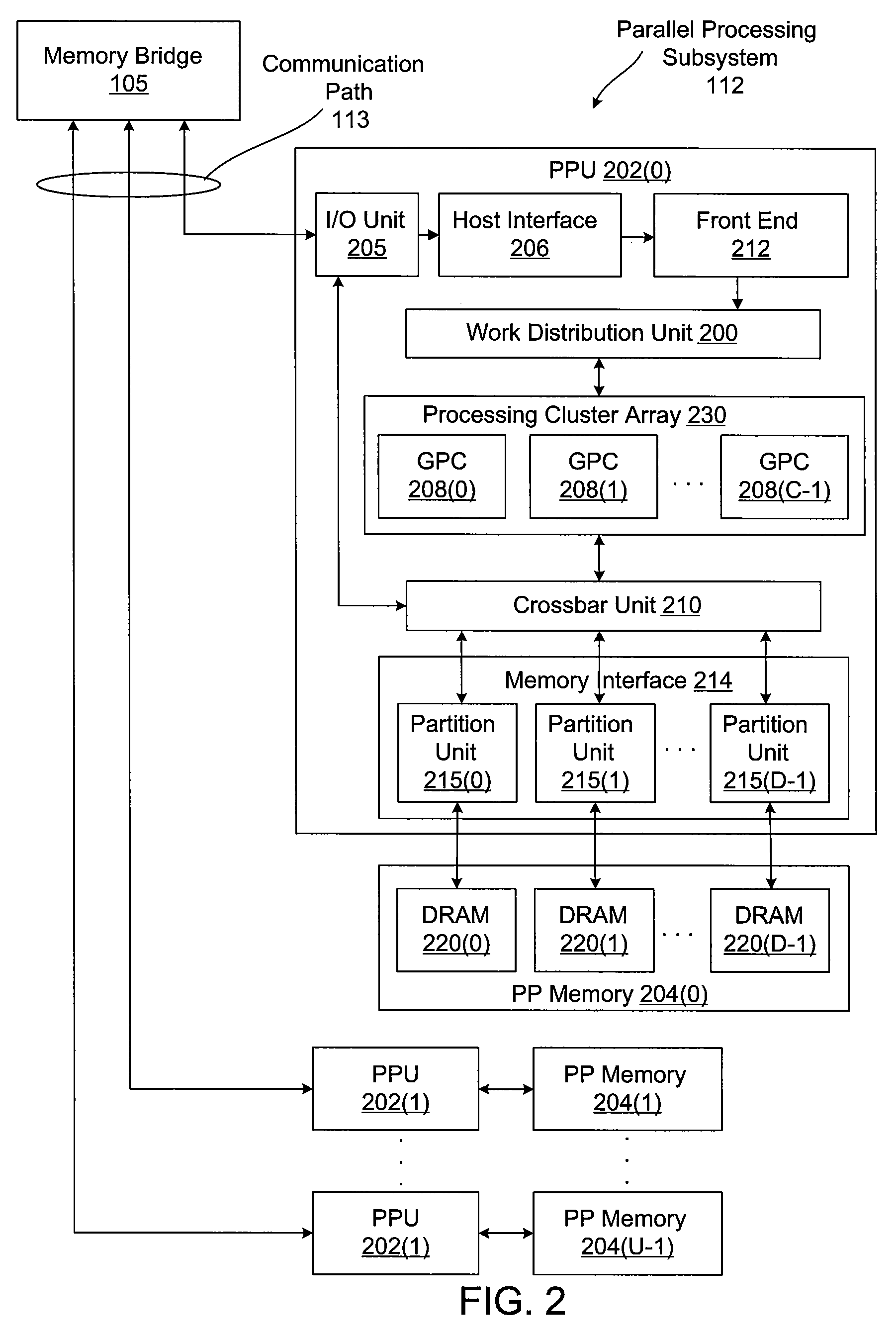
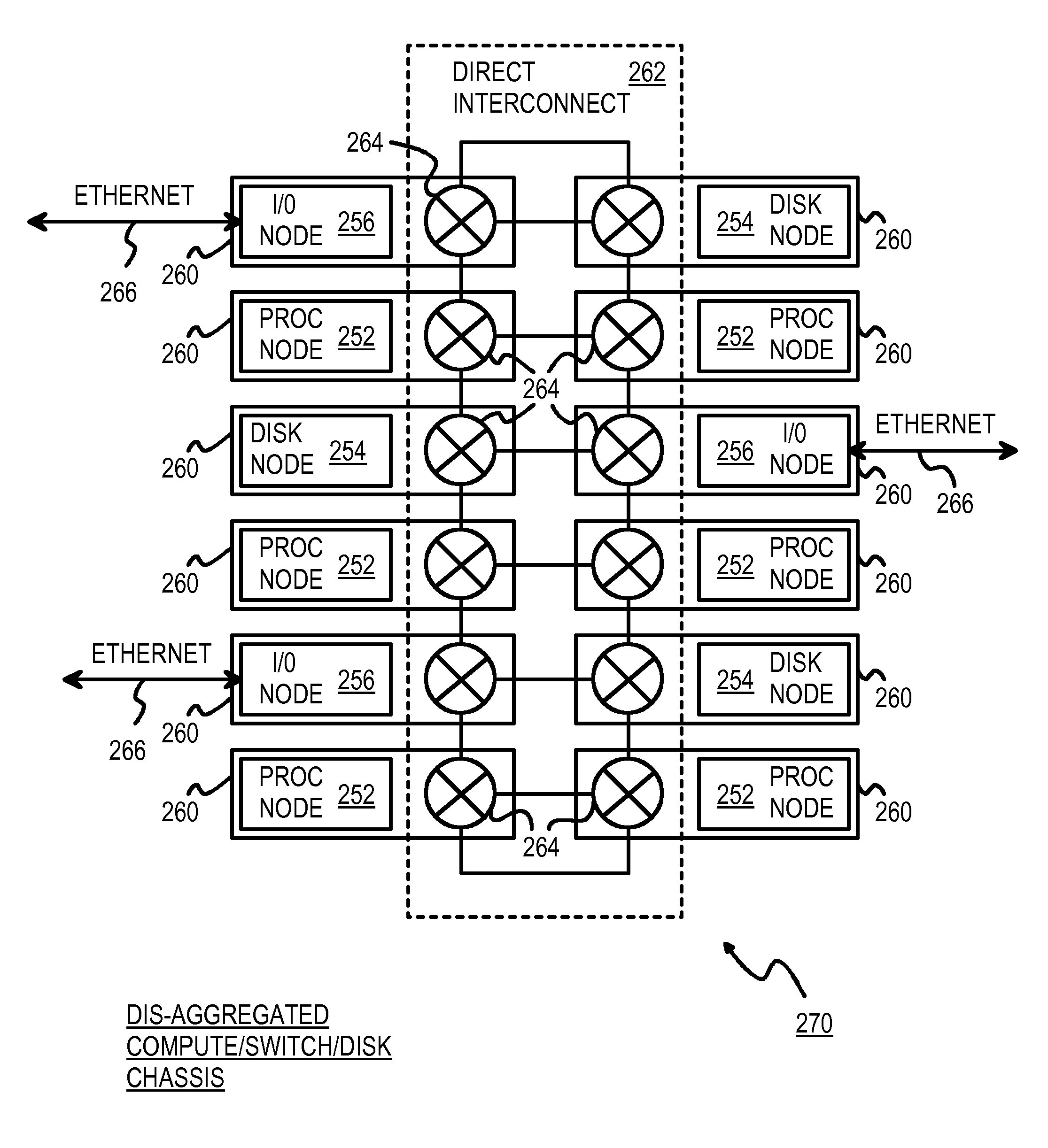
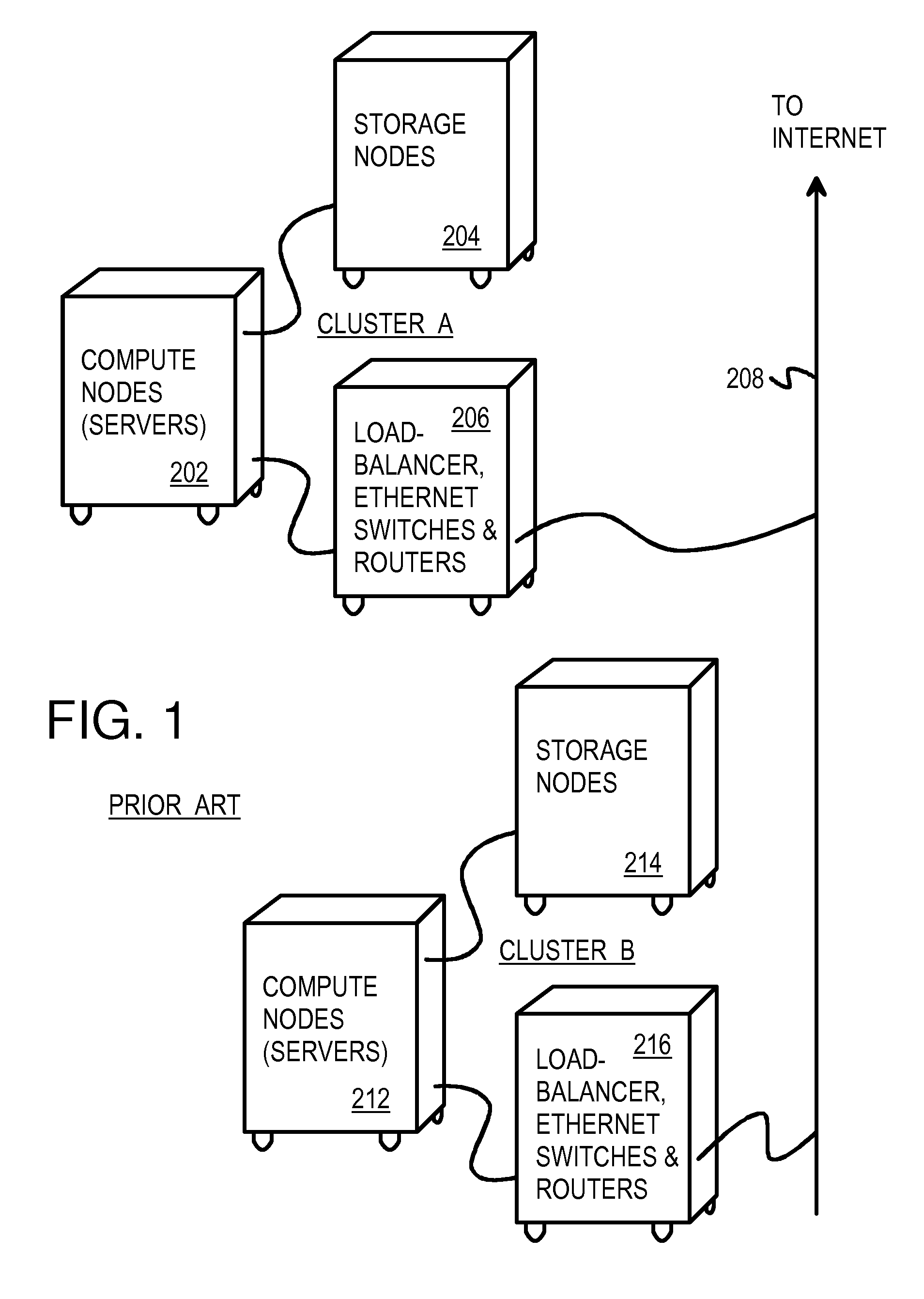
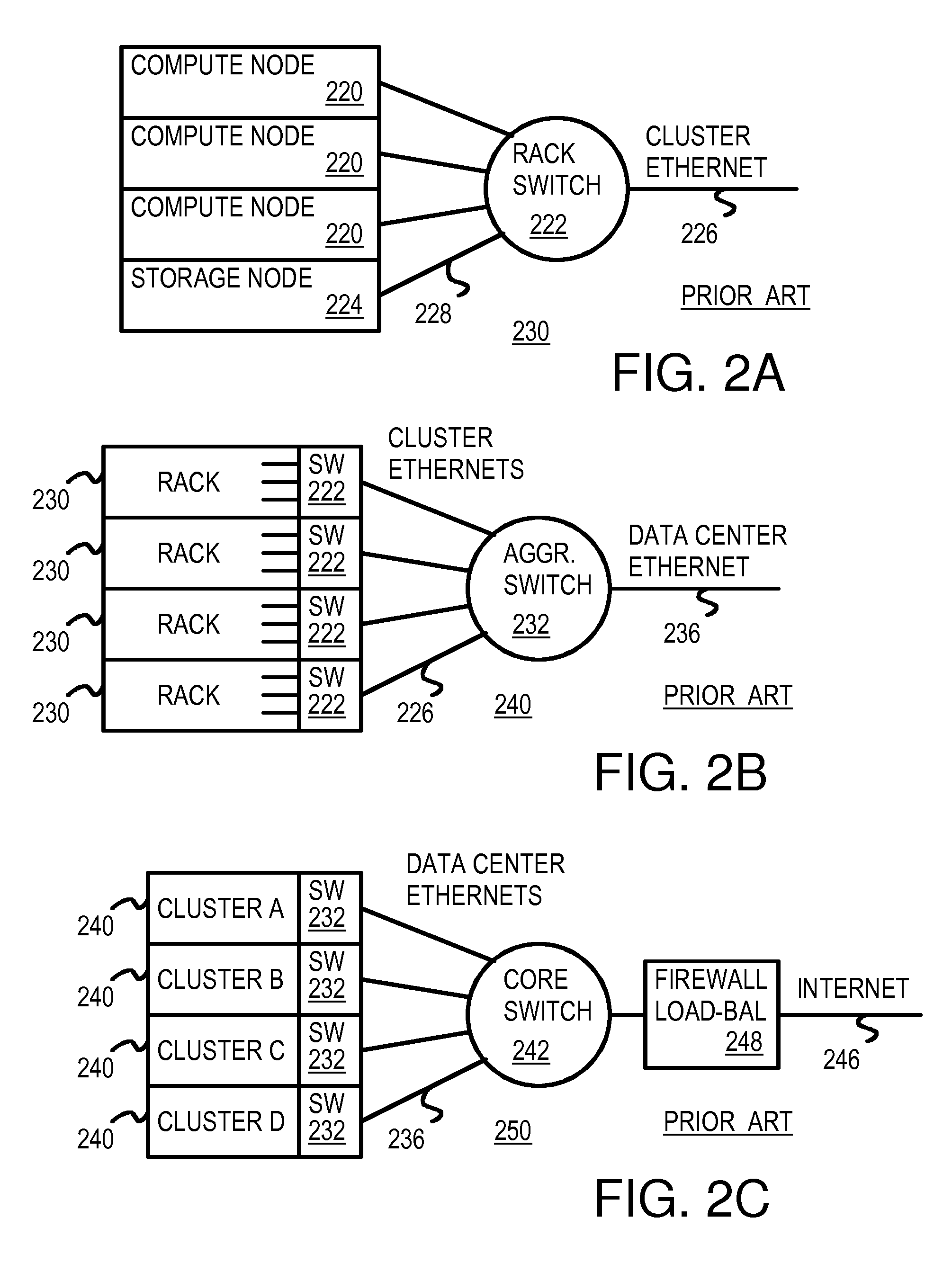
Dis-Aggregated and Distributed Data-Center Architecture Using a Direct Interconnect Fabric
ActiveUS20090216920A1Computer security arrangementsMultiple digital computer combinationsOperational systemData center
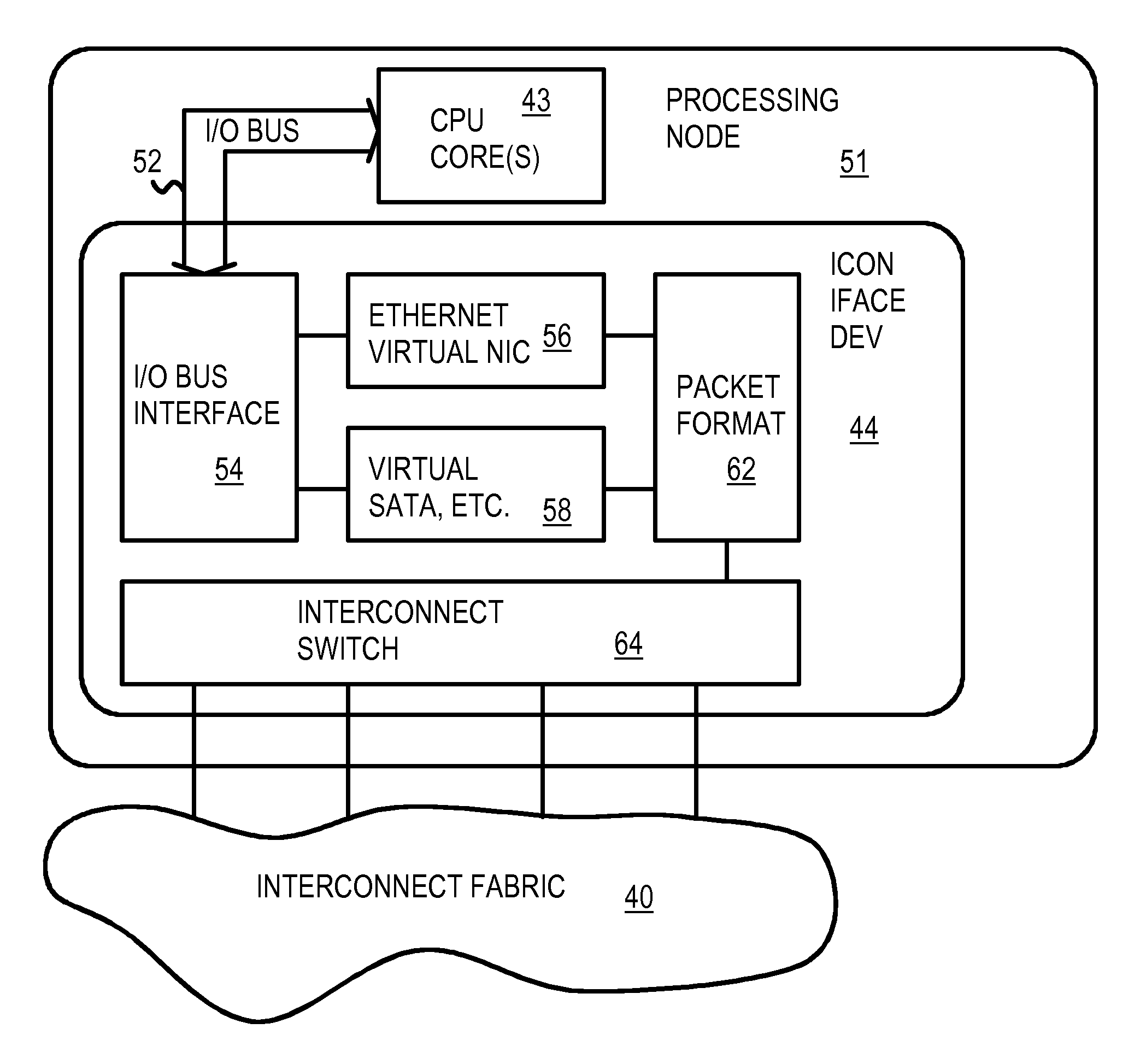
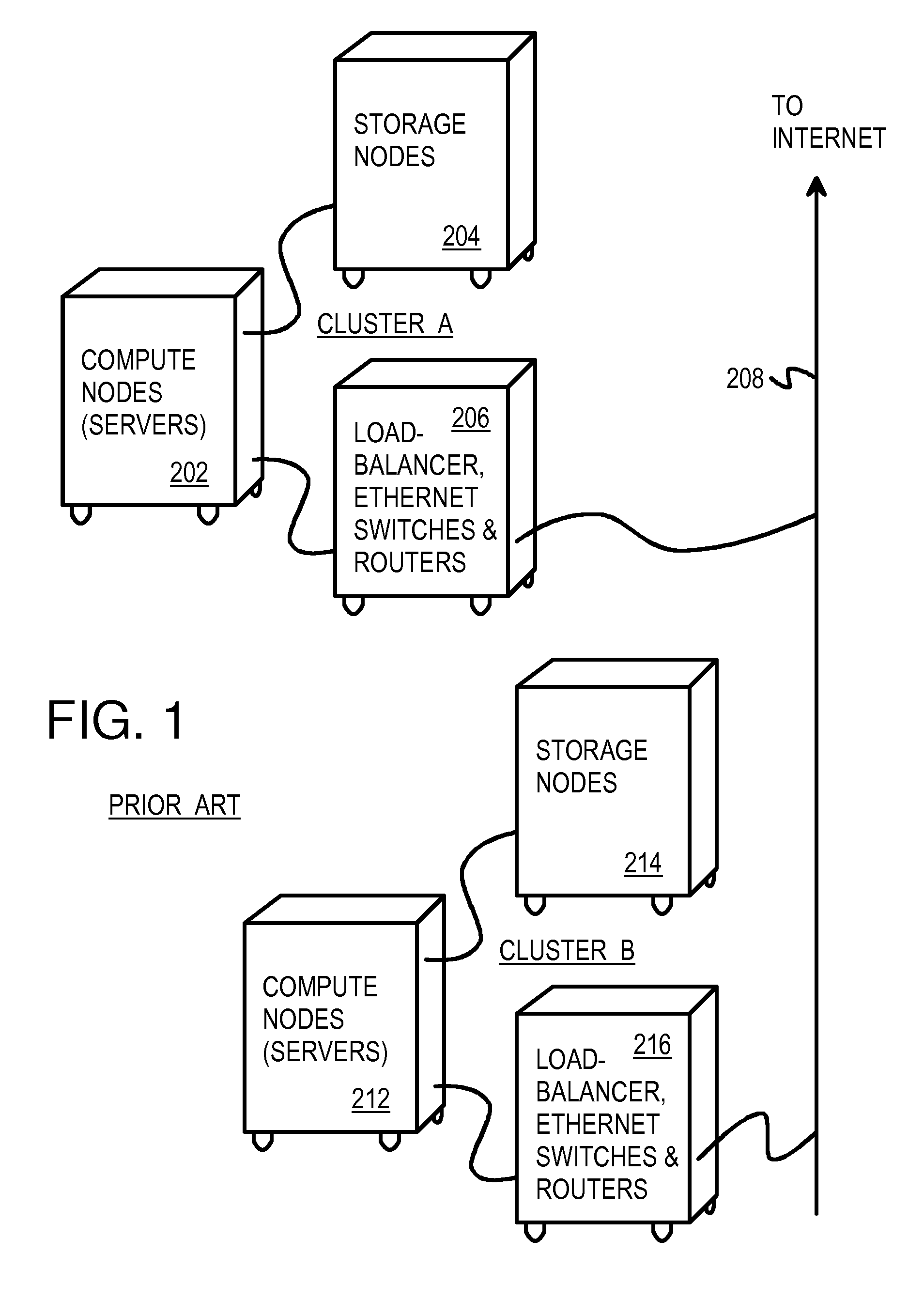
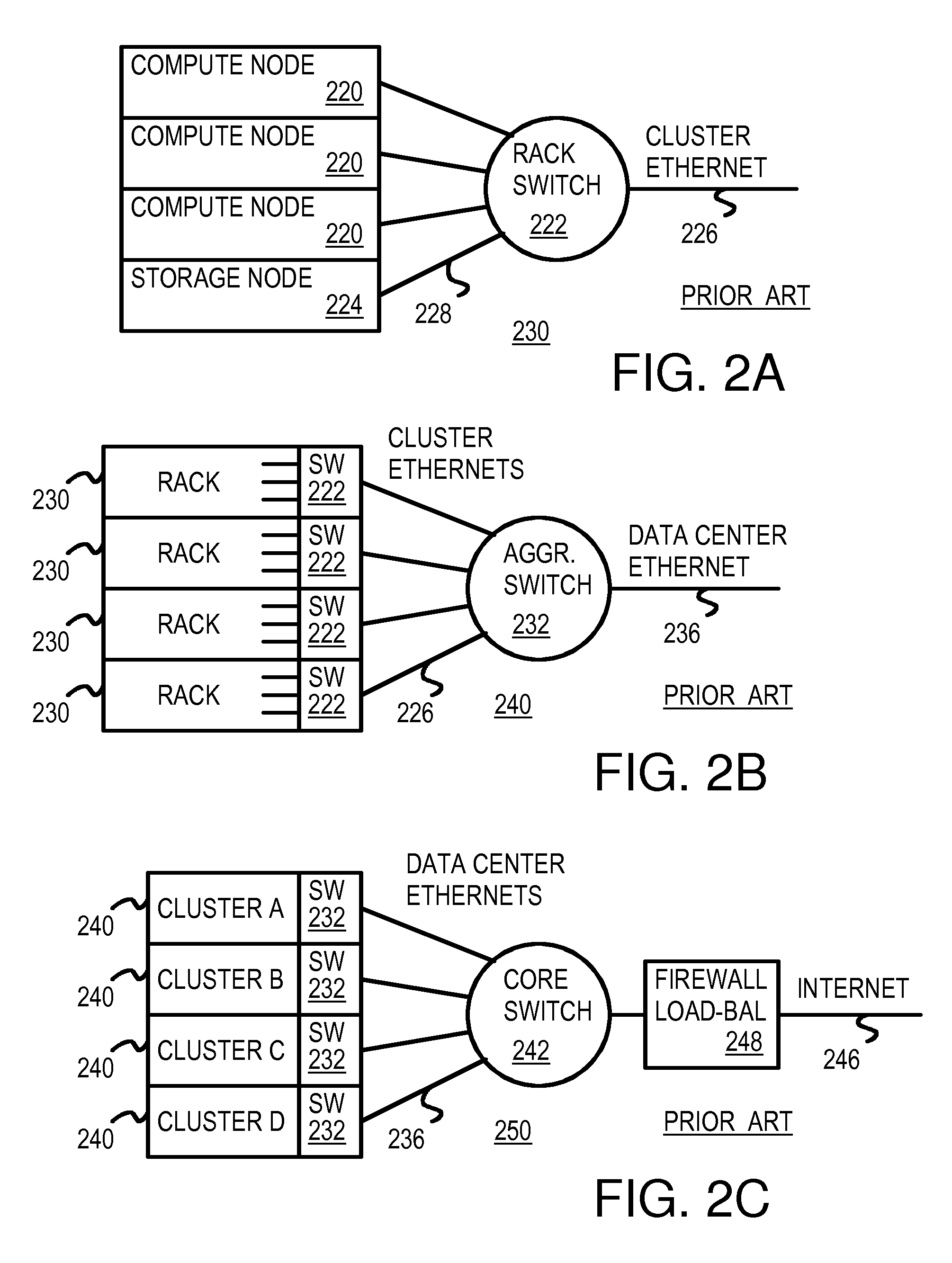
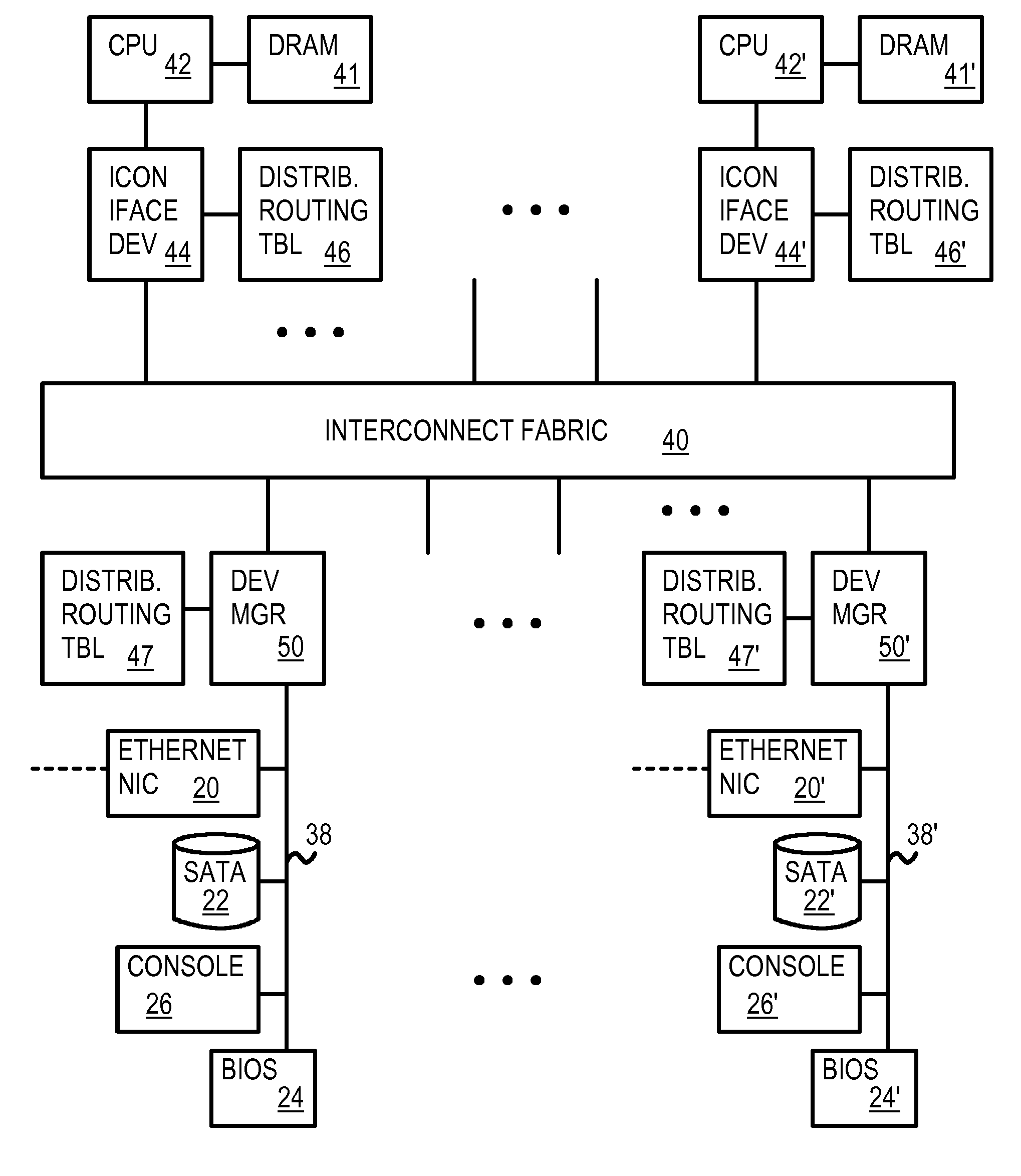
A data center has several dis-aggregated data clusters that connect to the Internet through a firewall and load-balancer. Each dis-aggregated data cluster has several dis-aggregated compute / switch / disk chassis that are connected together by a mesh of Ethernet links. Each dis-aggregated compute / switch / disk chassis has many processing nodes, disk nodes, and I / O nodes on node cards that are inserted into the chassis. These node cards are connected together by a direct interconnect fabric. Using the direct interconnect fabric, remote I / O and disk nodes appear to the operating system to be located on the local processor's own peripheral bus. A virtual Ethernet controller and a virtual generic peripheral act as virtual endpoints for the local processor's peripheral bus. I / O and disk node peripherals are virtualized by hardware without software drivers. Rack and aggregation Ethernet switches are eliminated using the direct interconnect fabric, which provides a flatter, dis-aggregated hierarchy.
Owner:SEAMICRO
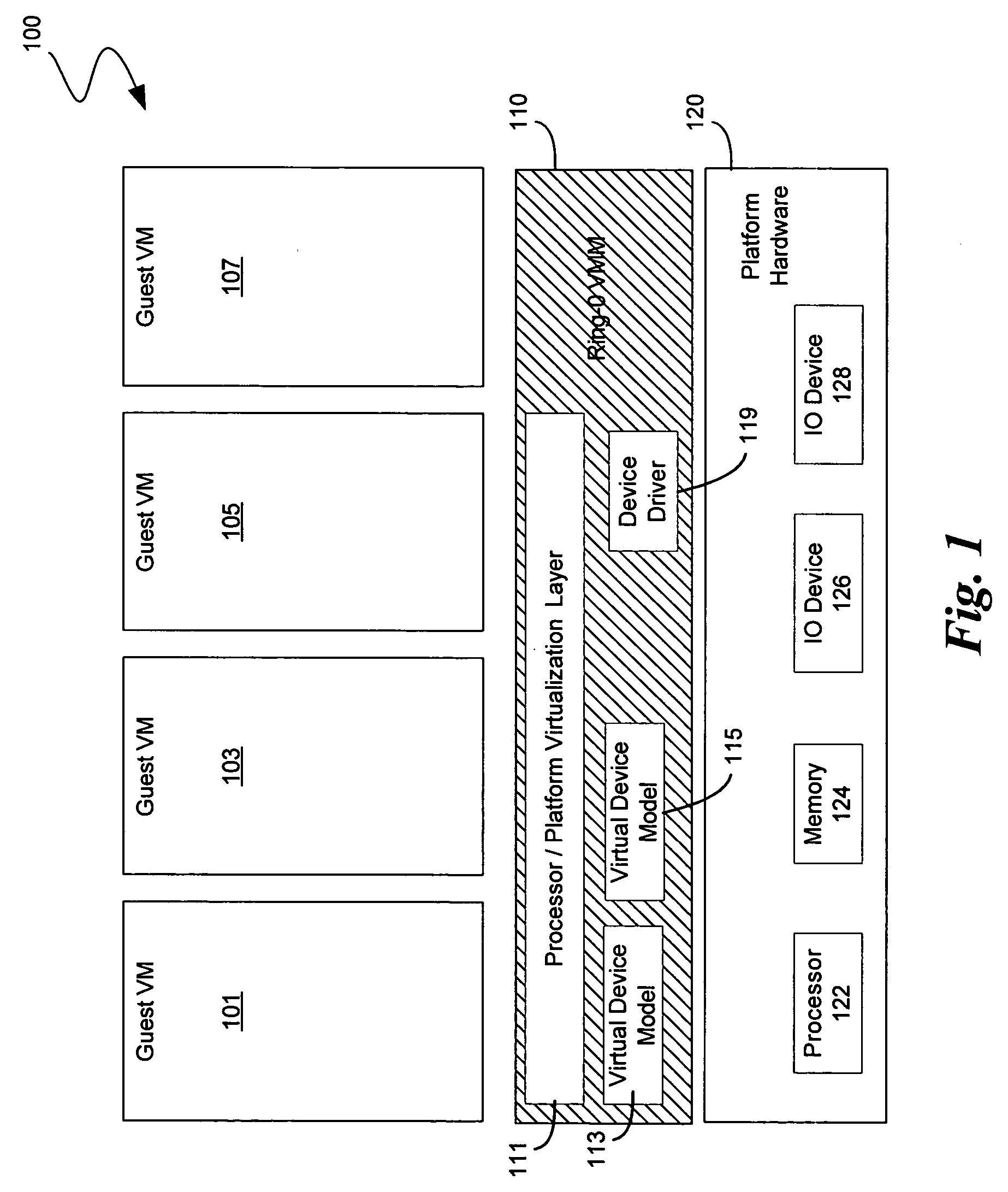
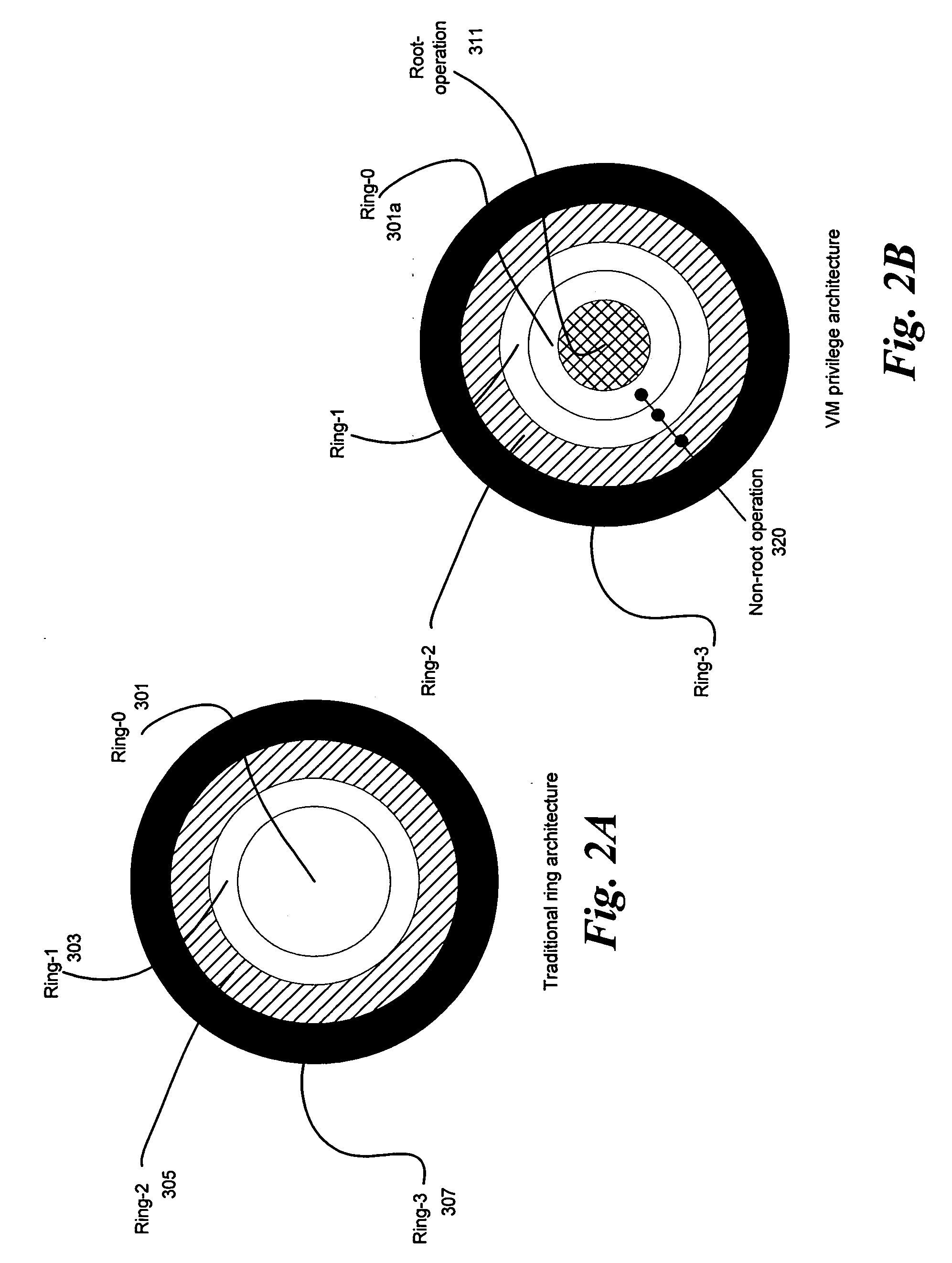
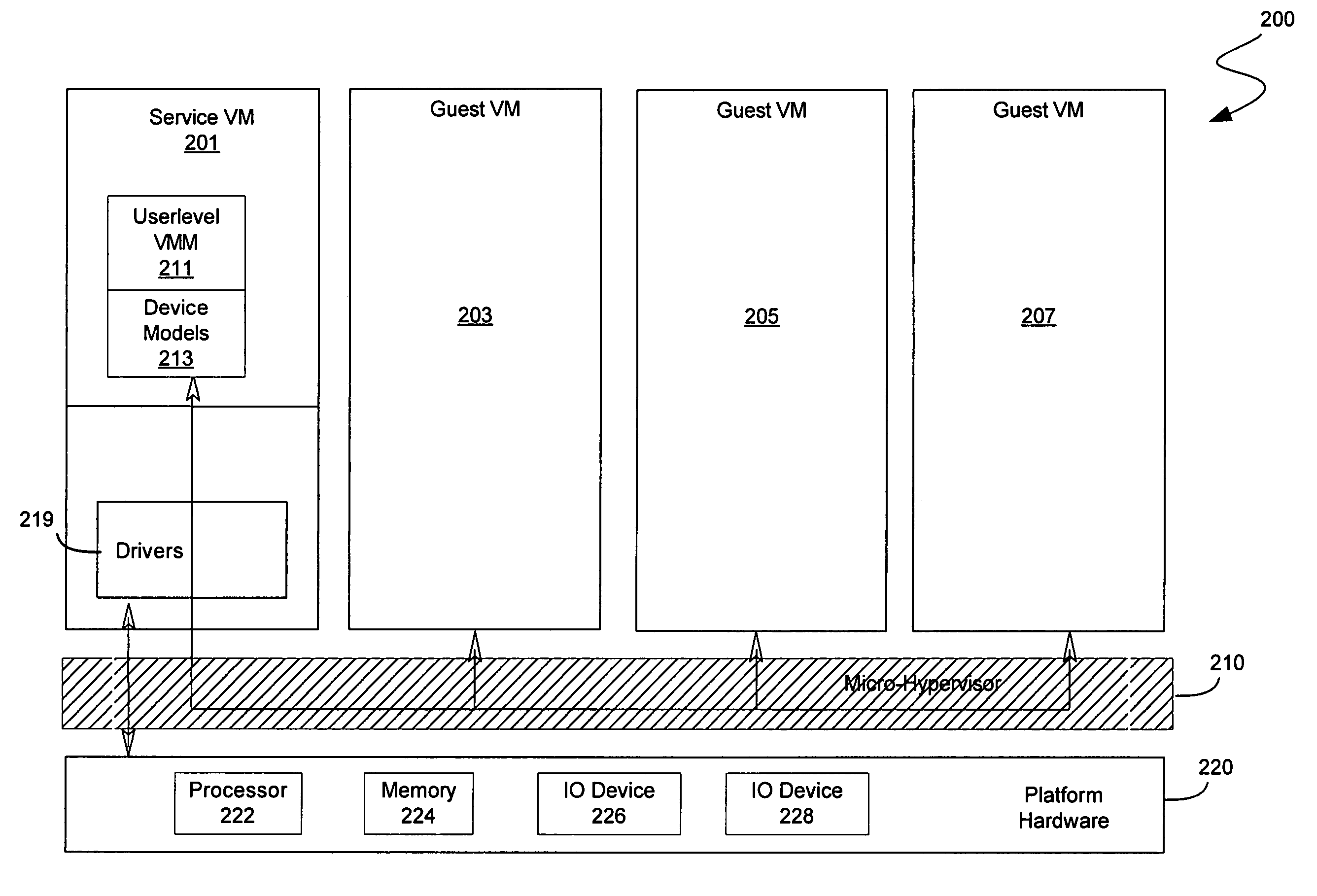
System and method to deprivilege components of a virtual machine monitor
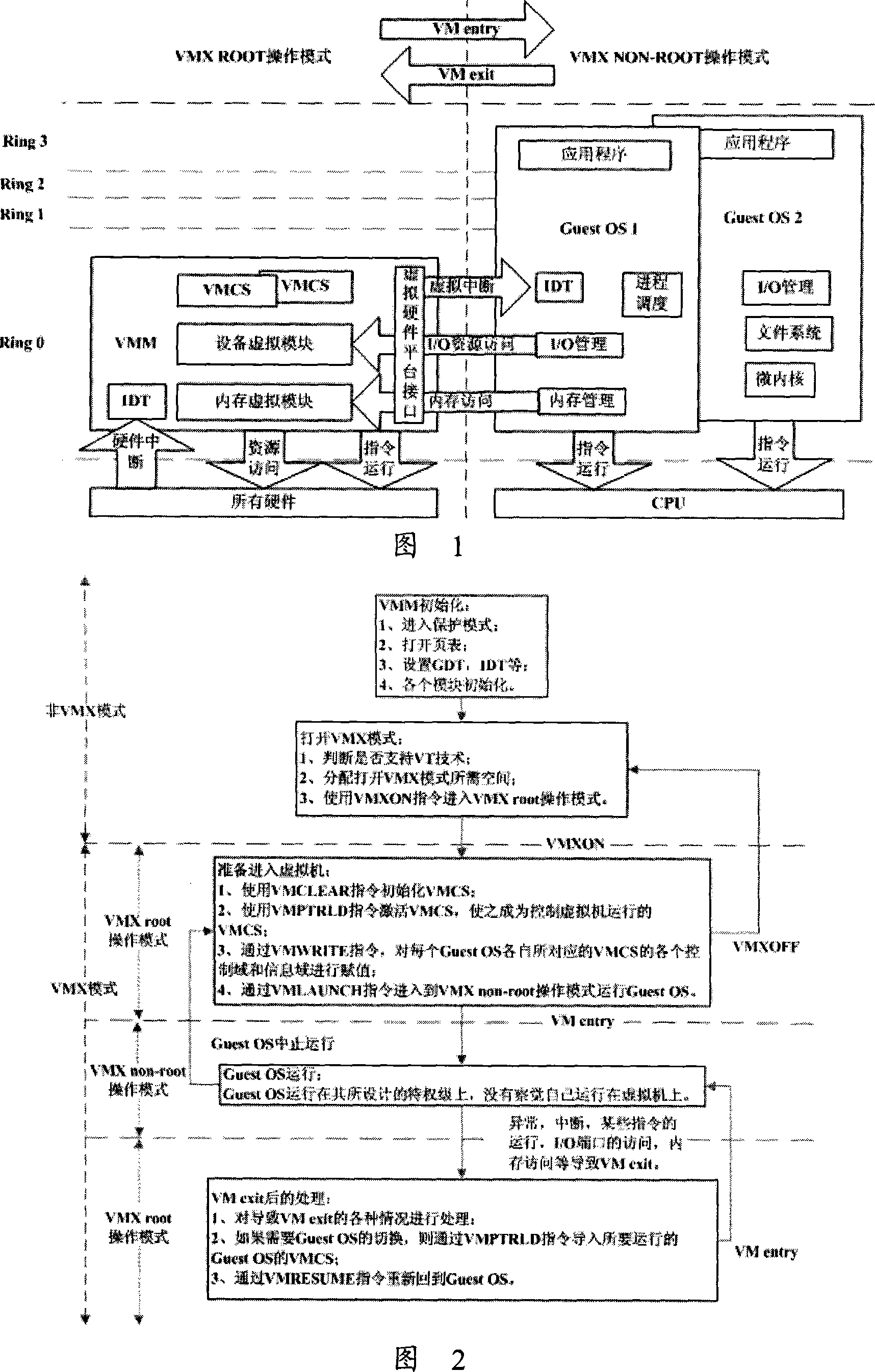
ActiveUS20060130060A1High portability and reliabilityMultiprogramming arrangementsSoftware simulation/interpretation/emulationPrivilege levelHardware virtualization
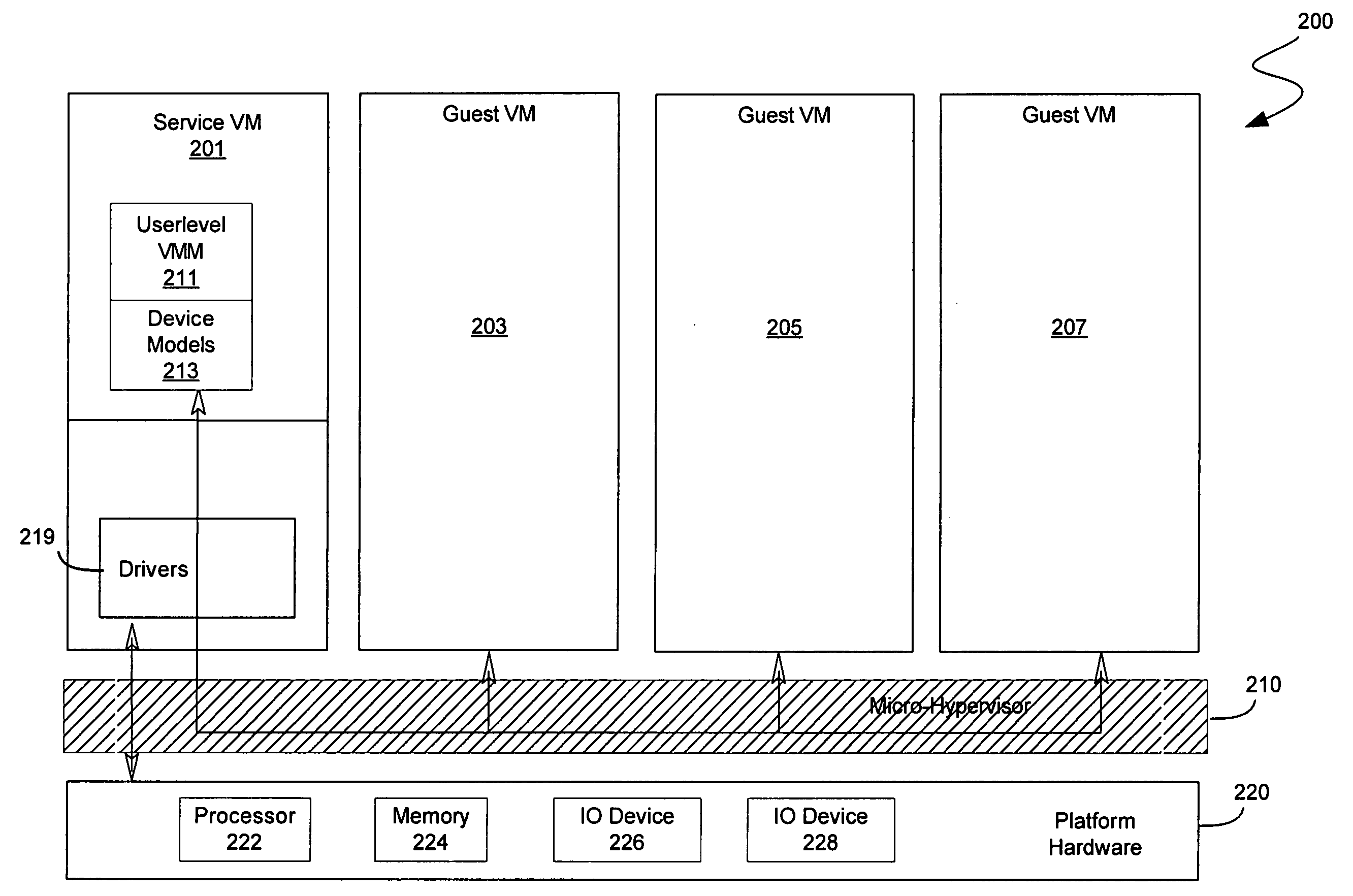
In some embodiments, the invention involves a system to deprivilege components of a virtual machine monitor and enable deprivileged service virtual machines (SVMs) to handle selected trapped events. An embodiment of the invention is a hybrid VMM operating on a platform with hardware virtualization support. The hybrid VMM utilizes features from both hypervisor-based and host-based VMM architectures. In at least one embodiment, the functionality of a traditional VMM is partitioned into a small platform-dependent part called a micro-hypervisor (MH) and one or more platform-independent parts called service virtual machines (SVMs). The micro-hypervisor operates at a higher virtual machine (VM) privilege level than any SVM, while the SVM and other VMs may still have access to any instruction set architecture (ISA) privilege level. Other embodiments are described and claimed.
Owner:INTEL CORP
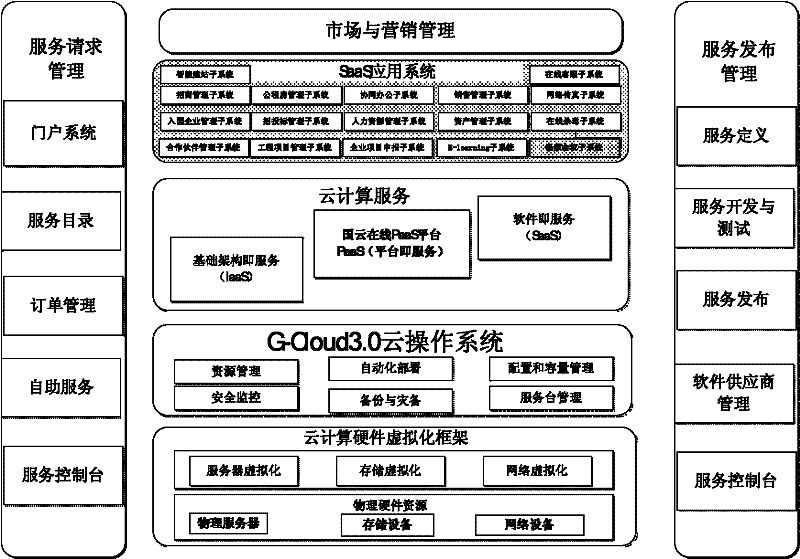
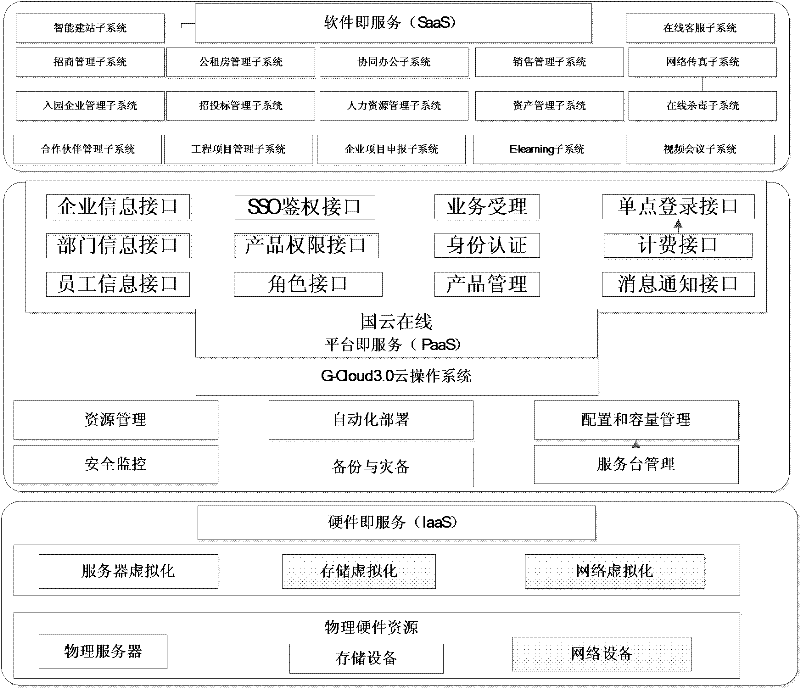
Cloud-computing-based platform as a service (PaaS) platform system and implementation method thereof
The invention relates to the field of cloud computing, in particular to a cloud-computing-based platform as a service (PaaS) platform system and an implementation method thereof. The system comprises a service request management module, a software as a service (SaaS) application system, a service publication system, a cloud operating system, a marketing management system, cloud computing service and a cloud computing hardware virtualization framework. The implementation method comprises the following steps of: performing hardware virtualization on a server cluster by utilizing the cloud operating system, configuring different operating systems according to different requirements of the application system, and dynamically and uniformly allocating and managing hardware resources; and binding users of different systems with different user authentication certificates, adopting the active encryption of real-time encryption and decryption to prevent breach of confidence, and controlling the rights of the application system integrated on a PaaS platform. The problems about the independence, security and high-efficiency resource utilization of the system are solved; and the method can be applied to the cloud-computing-based PaaS platform system.
Owner:G CLOUD TECH
System and method to deprivilege components of a virtual machine monitor
ActiveUS7757231B2High portability and reliabilityMultiprogramming arrangementsSoftware simulation/interpretation/emulationPrivilege levelHardware virtualization
In some embodiments, the invention involves a system to deprivilege components of a virtual machine monitor and enable deprivileged service virtual machines (SVMs) to handle selected trapped events. An embodiment of the invention is a hybrid VMM operating on a platform with hardware virtualization support. The hybrid VMM utilizes features from both hypervisor-based and host-based VMM architectures. In at least one embodiment, the functionality of a traditional VMM is partitioned into a small platform-dependent part called a micro-hypervisor (MH) and one or more platform-independent parts called service virtual machines (SVMs). The micro-hypervisor operates at a higher virtual machine (VM) privilege level than any SVM, while the SVM and other VMs may still have access to any instruction set architecture (ISA) privilege level. Other embodiments are described and claimed.
Owner:INTEL CORP
Partial virtualization on computing device
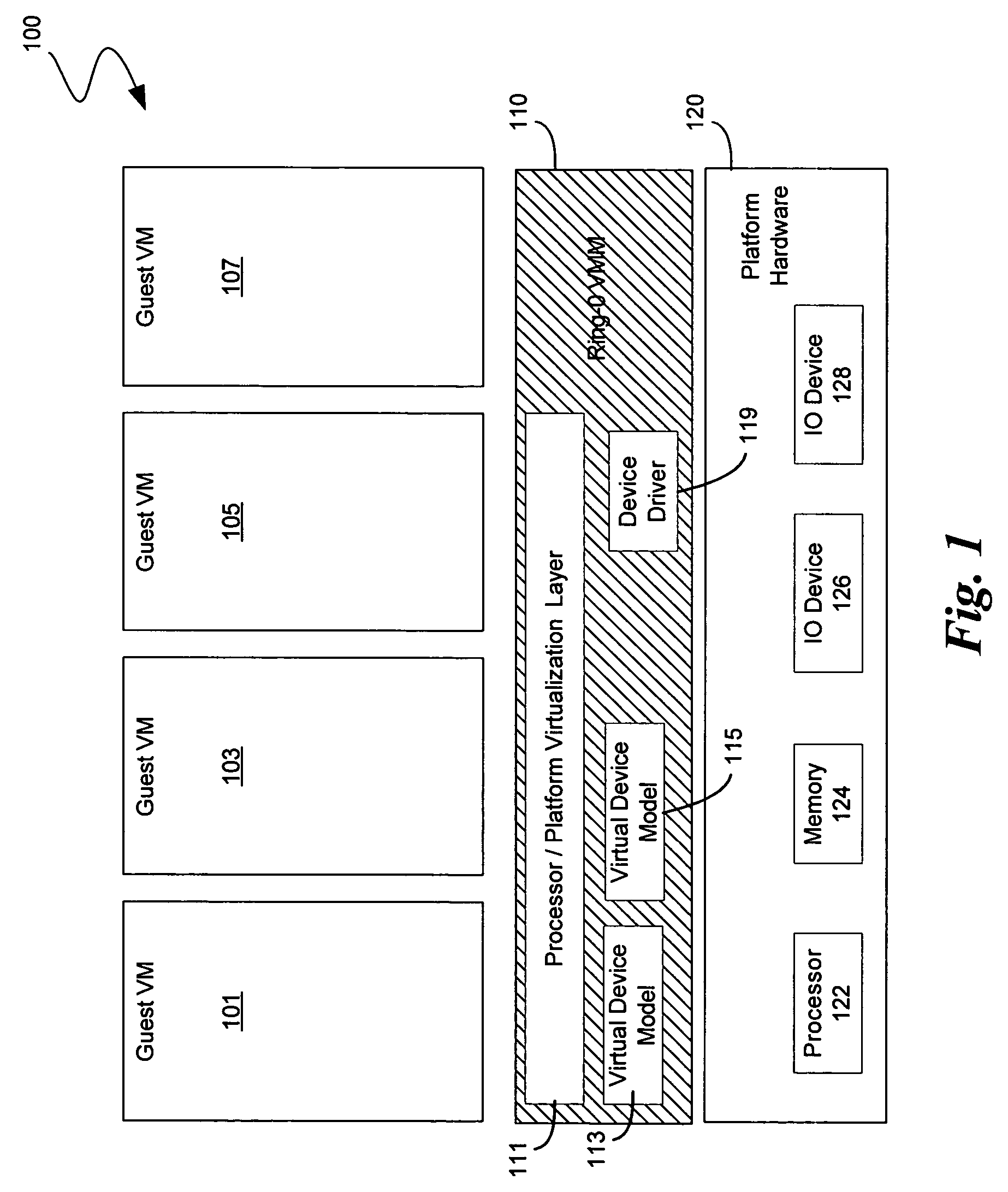
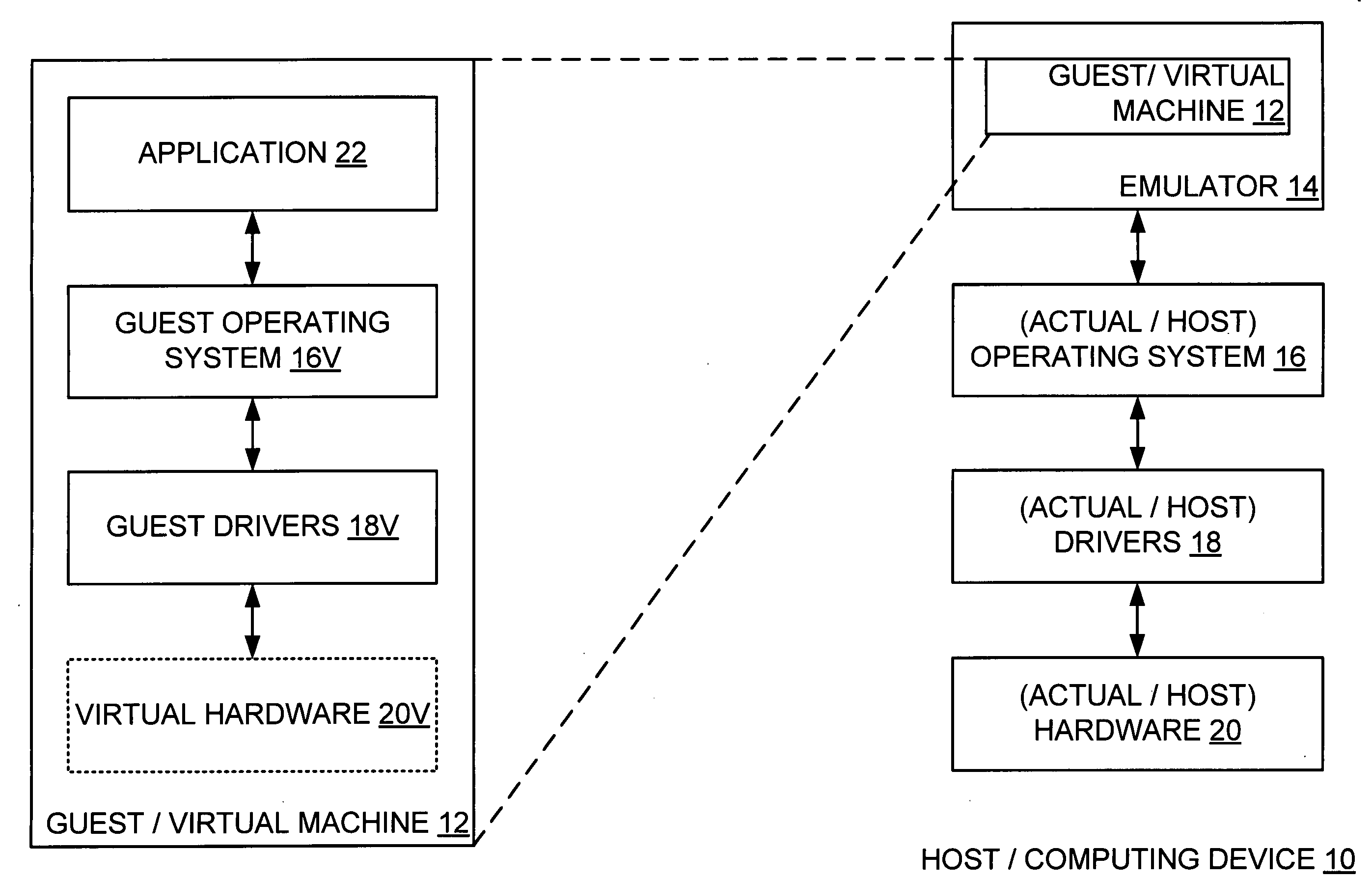
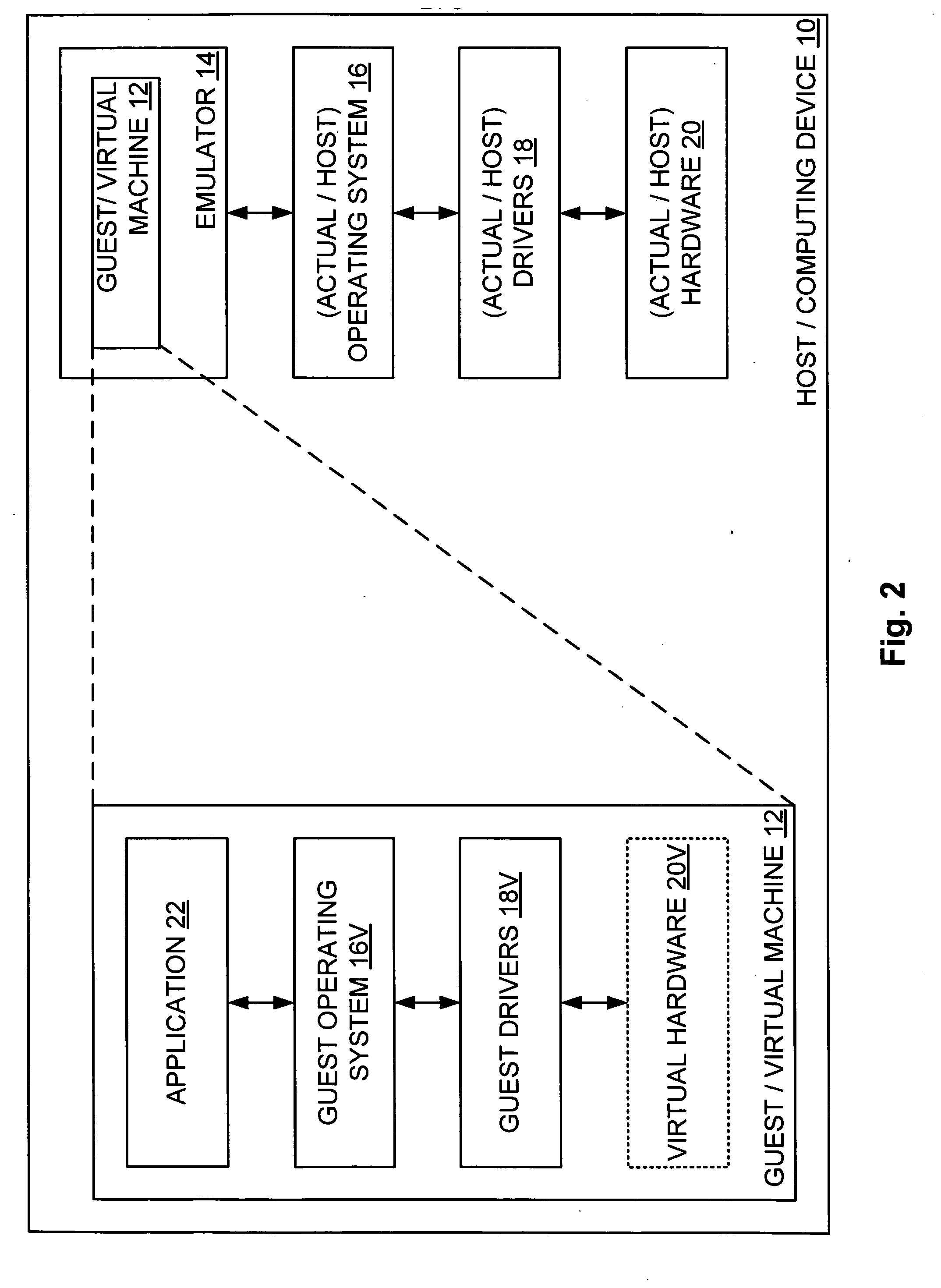
ActiveUS20070288228A1Satisfies needSoftware simulation/interpretation/emulationMemory systemsComputer hardwareOperational system
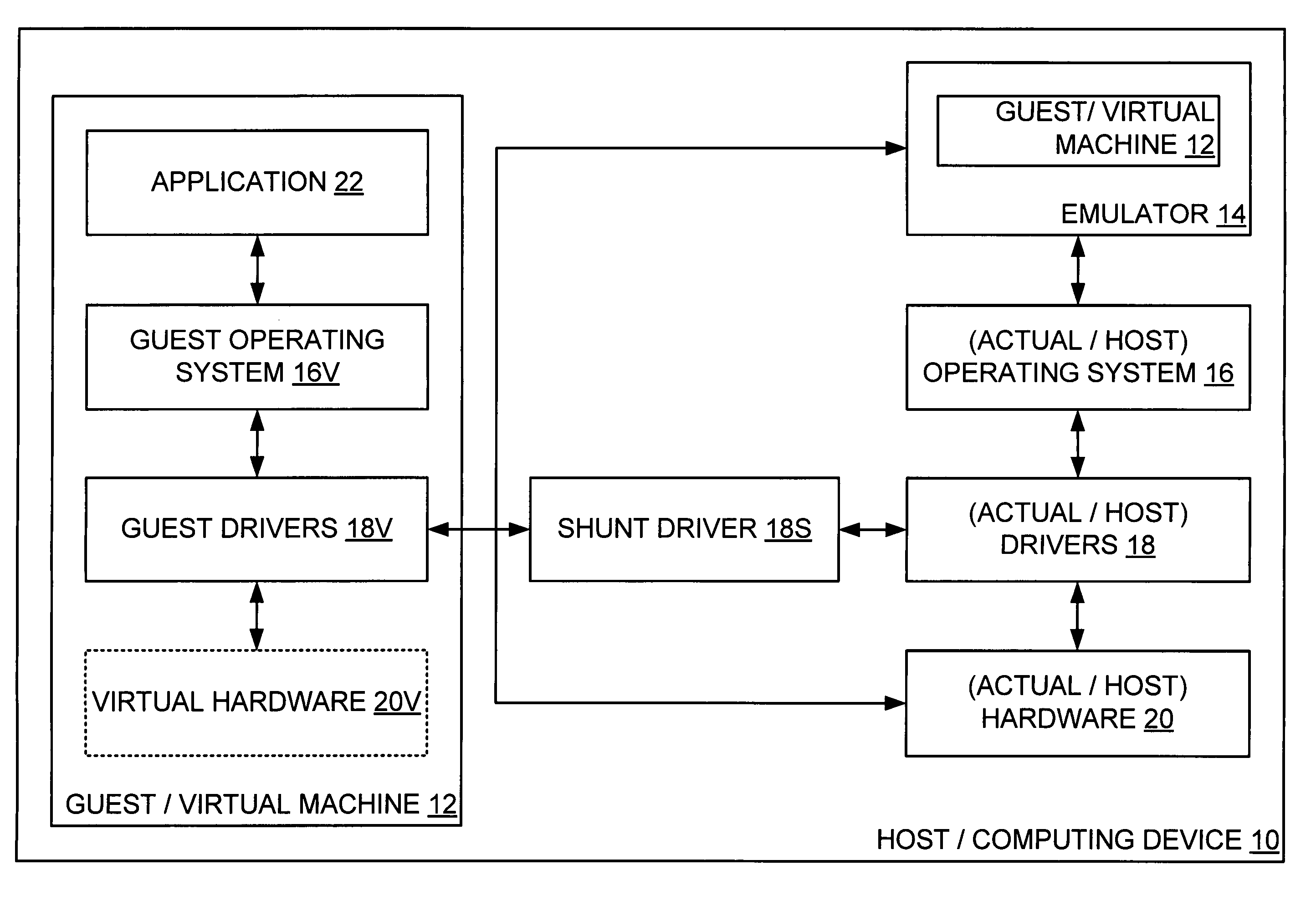
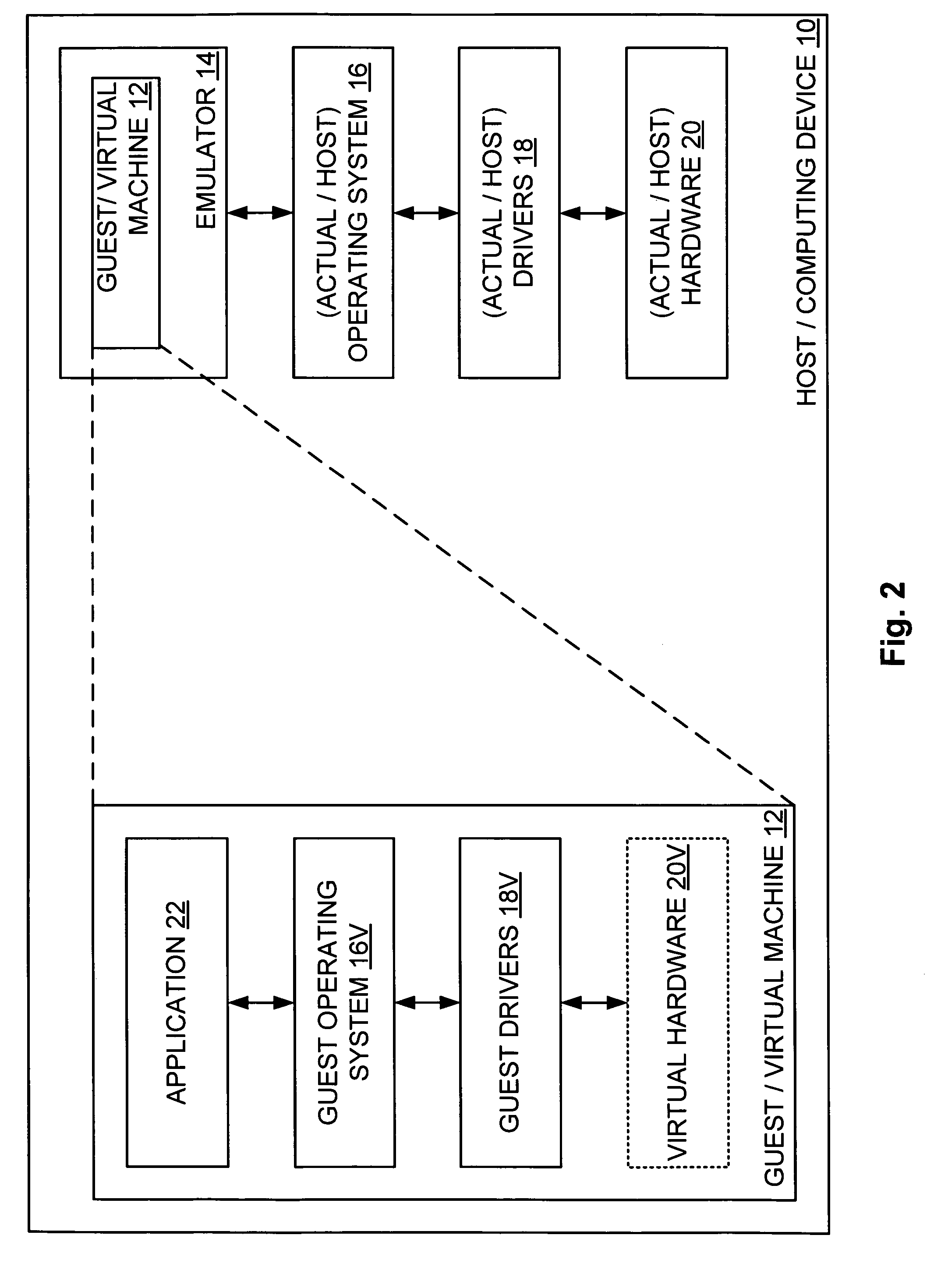
A computing device hosts a virtual machine executing a guest that issues guest hardware requests by way of any of a plurality of paths. Such paths include a path to non-existent virtual hardware, where an emulator intercepts and processes such guest hardware request with a corresponding actual hardware command; a path to an instantiated operating system, where the instantiated operating system processes each such guest hardware request with a corresponding actual hardware request; and a path to device hardware, where the device hardware directly processes each such guest hardware request.
Owner:MICROSOFT TECH LICENSING LLC
Cluster load balance method transparent for operating system
InactiveCN101452406AImplement a load balancing strategyIncrease profitResource allocationVirtualizationOperational system
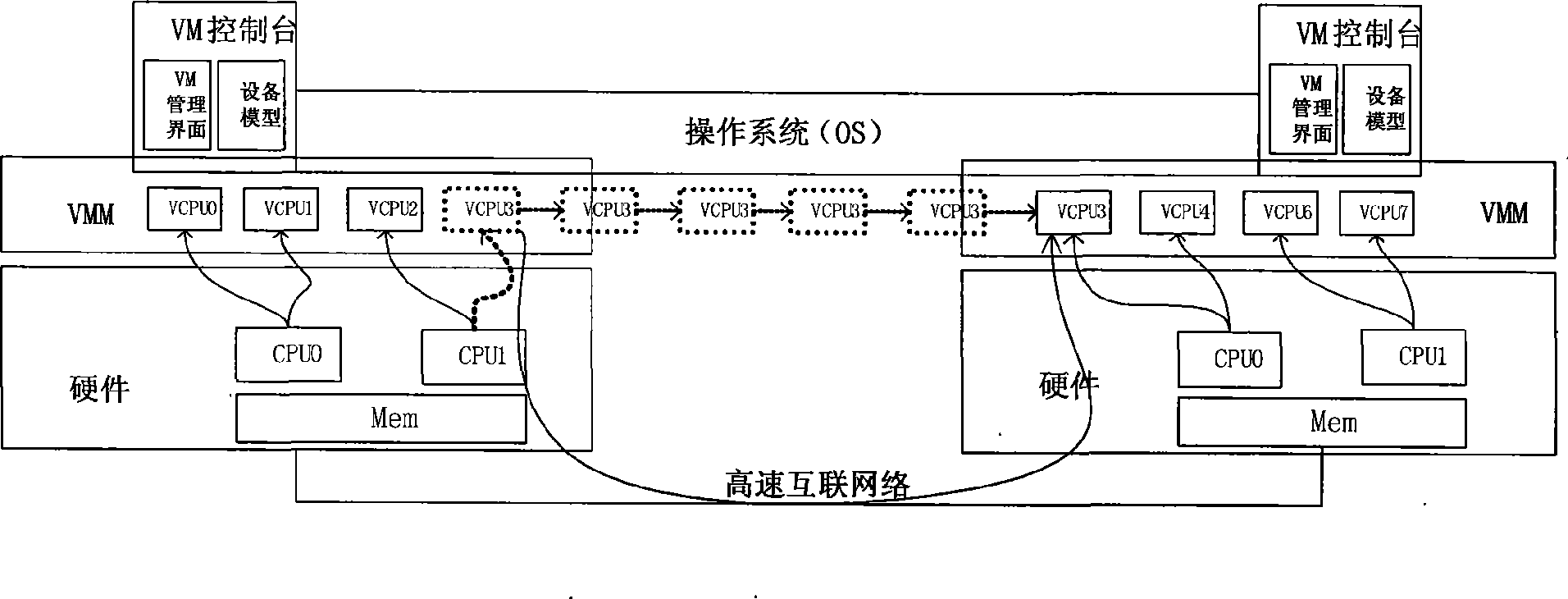
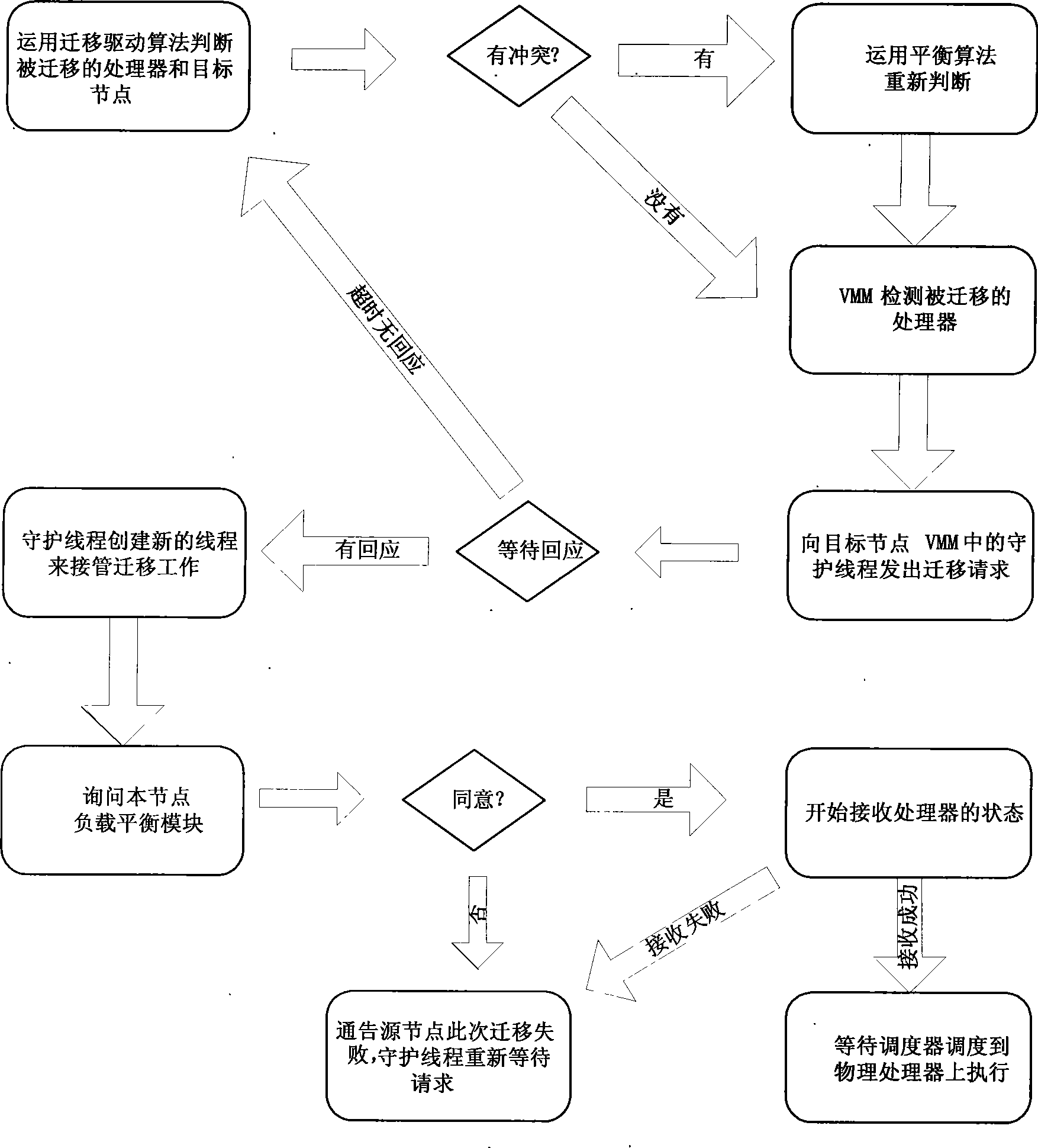
The present invention provides a cluster load balancing method transparent to an operation system. Main functional modules comprise a load balancing module, a processor migrating module and a communication module. The method is characterized by comprising the following steps: 1, driving a virtual processor to migrate; 2, driving balance migration; 3, sending a migrating request to a target node and negotiating; 4, storing and restoring a state of the virtual processor; and 5, communicating. The method better solves the problem of low resource utilization rate of a cluster system. Along with the development of more popularization of the cluster system and the continuous development of hardware virtualization technology in the future, the method can be a good solution for the low resource utilization rate of the cluster system and has good application prospect.
Owner:HUAWEI TECH CO LTD
Centralized device virtualization layer for heterogeneous processing units
ActiveUS8239938B2Operational speed enhancementProgram control using stored programsVirtualizationOperational system
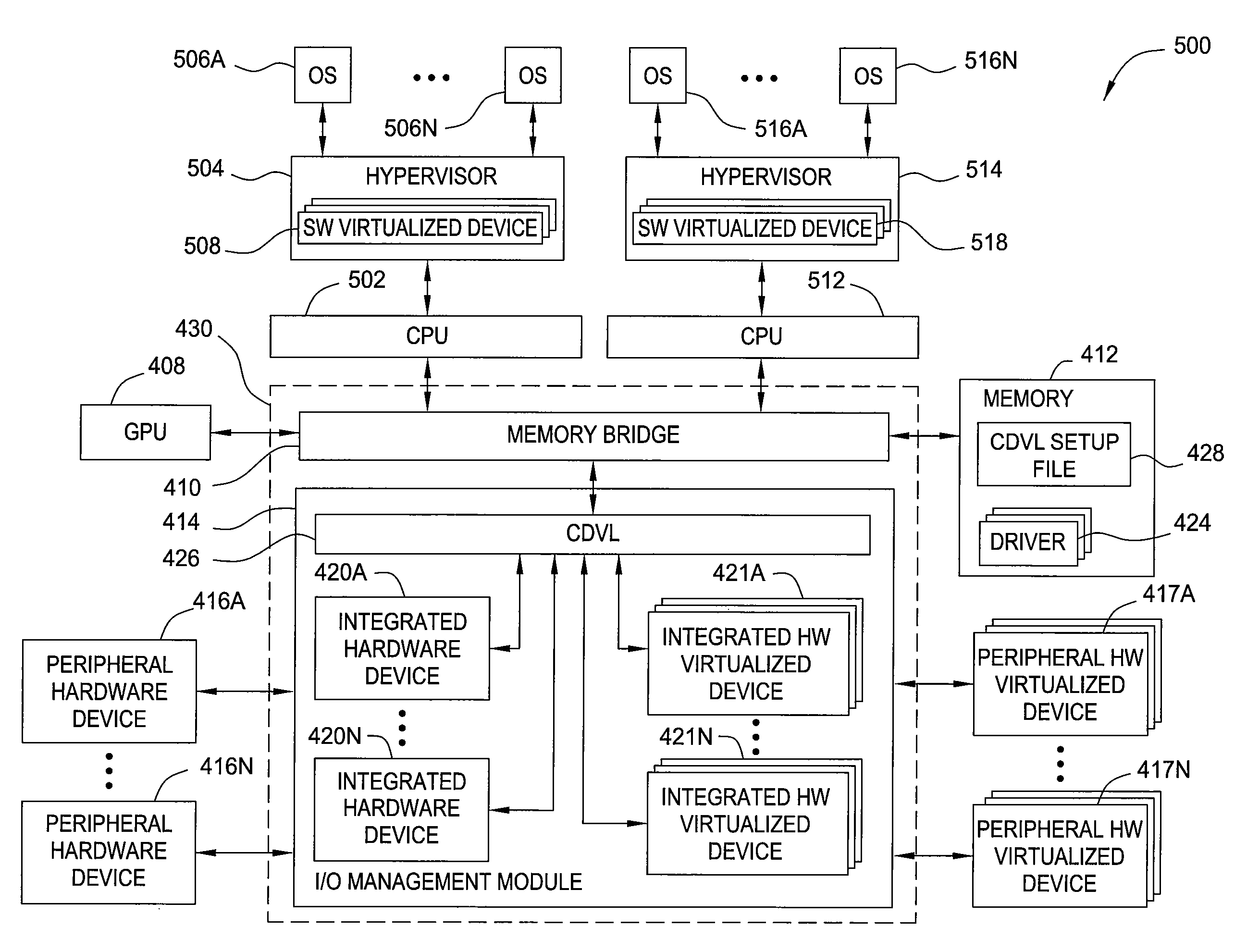
A method for providing an operating system access to devices, including enumerating hardware devices and virtualized devices, where resources associated with a first hardware device are divided into guest physical resources creating a software virtualized device, and multiple instances of resources associated with a second hardware device are advertised thereby creating a hardware virtualized device. First and second permission lists are generated that specify which operating systems are permitted to access the software virtualized device and the hardware virtualized device, respectively. First and second sets of virtual address maps are generated, where each set maps an address space associated with either the software virtualized device or the hardware virtualized device into an address space associated with each operating system included in the corresponding permission list. The method further includes arbitrating access requests from each of the plurality of operating systems based on the permission lists and the virtual address maps.
Owner:NVIDIA CORP
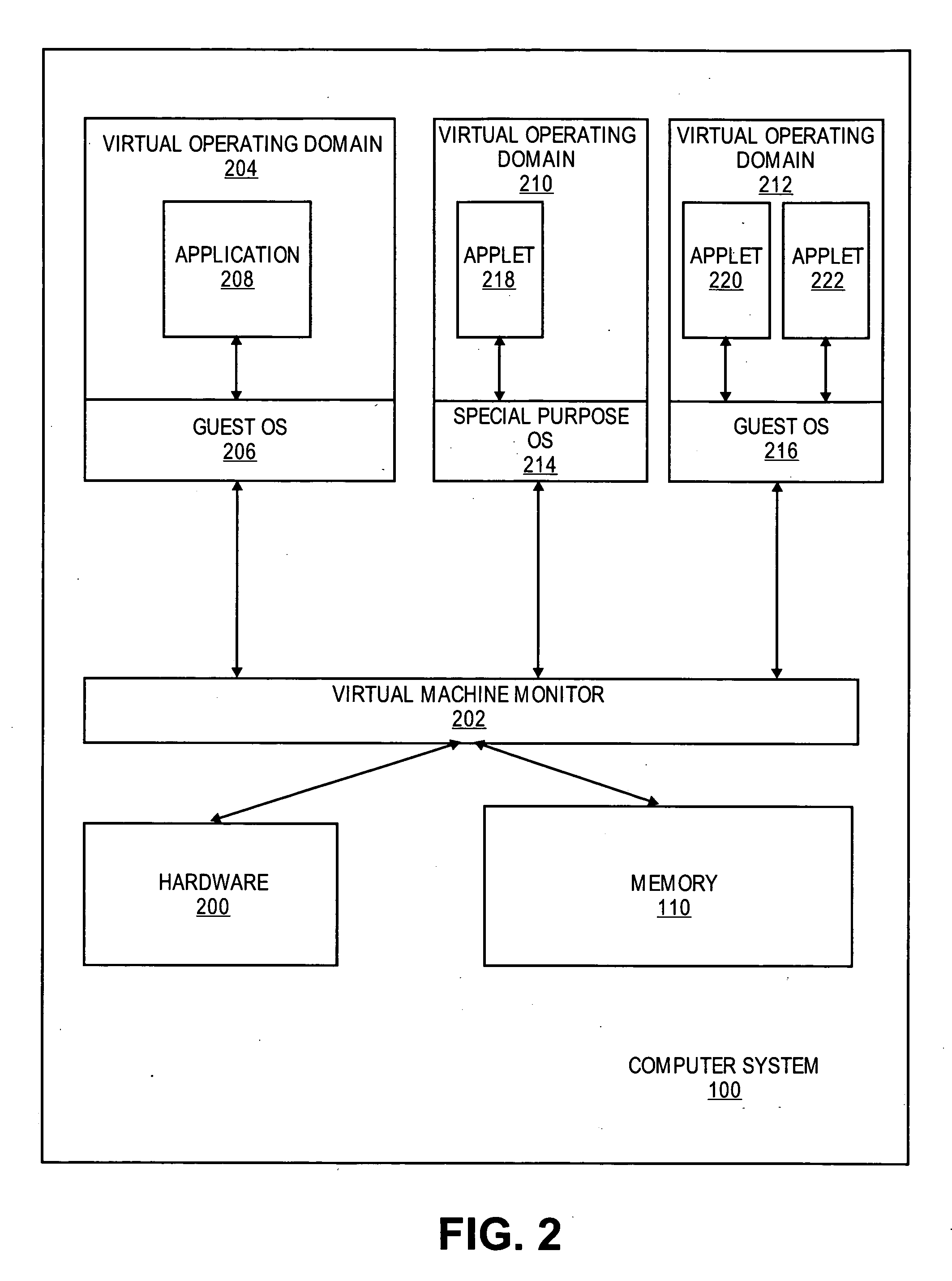
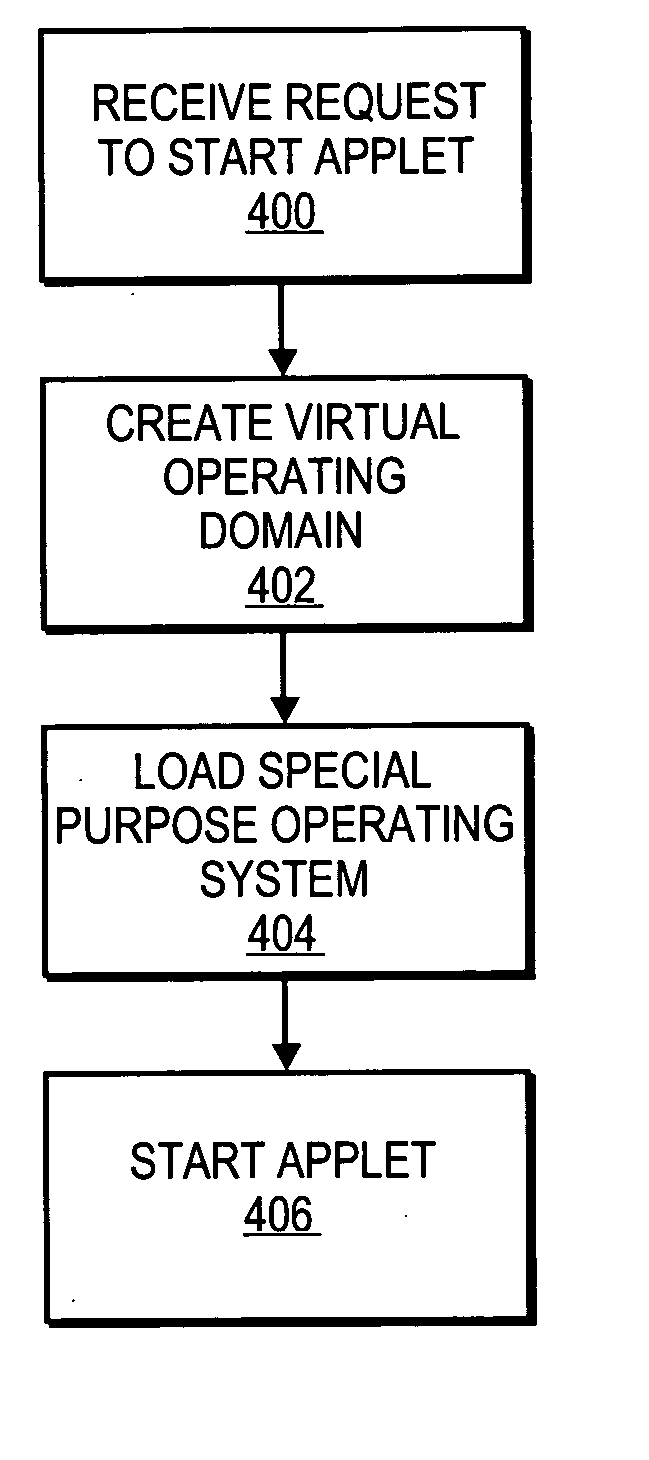
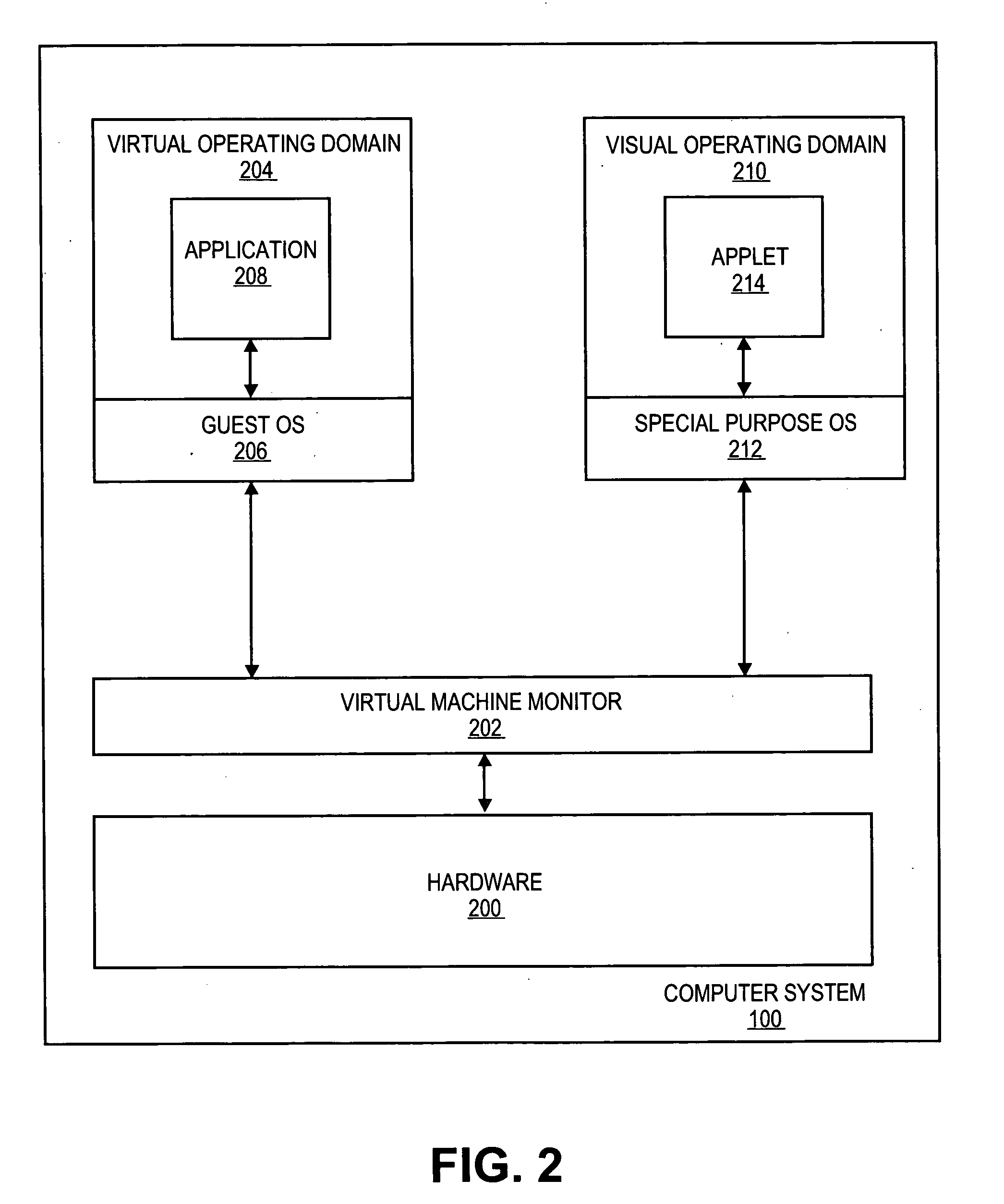
Purpose domain for in-kernel virtual machine for low overhead startup and low resource usage
ActiveUS20070169024A1Software simulation/interpretation/emulationMemory systemsOperational systemAnalog computer
Embodiments of the present invention provide an architecture for securely and efficiently executing byte code generated from a general programming language. In particular, a computer system is divided into a hierarchy comprising multiple types of virtual machines. A thin layer of software, known as a virtual machine monitor, virtualizes the hardware of the computer system and emulates the hardware of the computer system to form a first type of virtual machine. This first type of virtual machine implements a virtual operating domain that allows running its own operating system. Within a virtual operating domain, a byte code interpreter may further implement a second type of virtual machine that executes byte code generated from a program written in a general purpose programming language. The byte code interpreter is incorporated into the operating system running in the virtual operating domain. The byte code interpreter implementing the virtual machine that executes byte code may be divided into a kernel component and one or more user level components. The kernel component of the virtual machine is integrated into the operating system kernel. The user level component provides support for execution of an applet and couples the applet to the operating system. In addition, an operating system running in a virtual operating domain may be configured as a special purpose operating system that is optimized for the functions of a particular byte code interpreter.
Owner:RED HAT
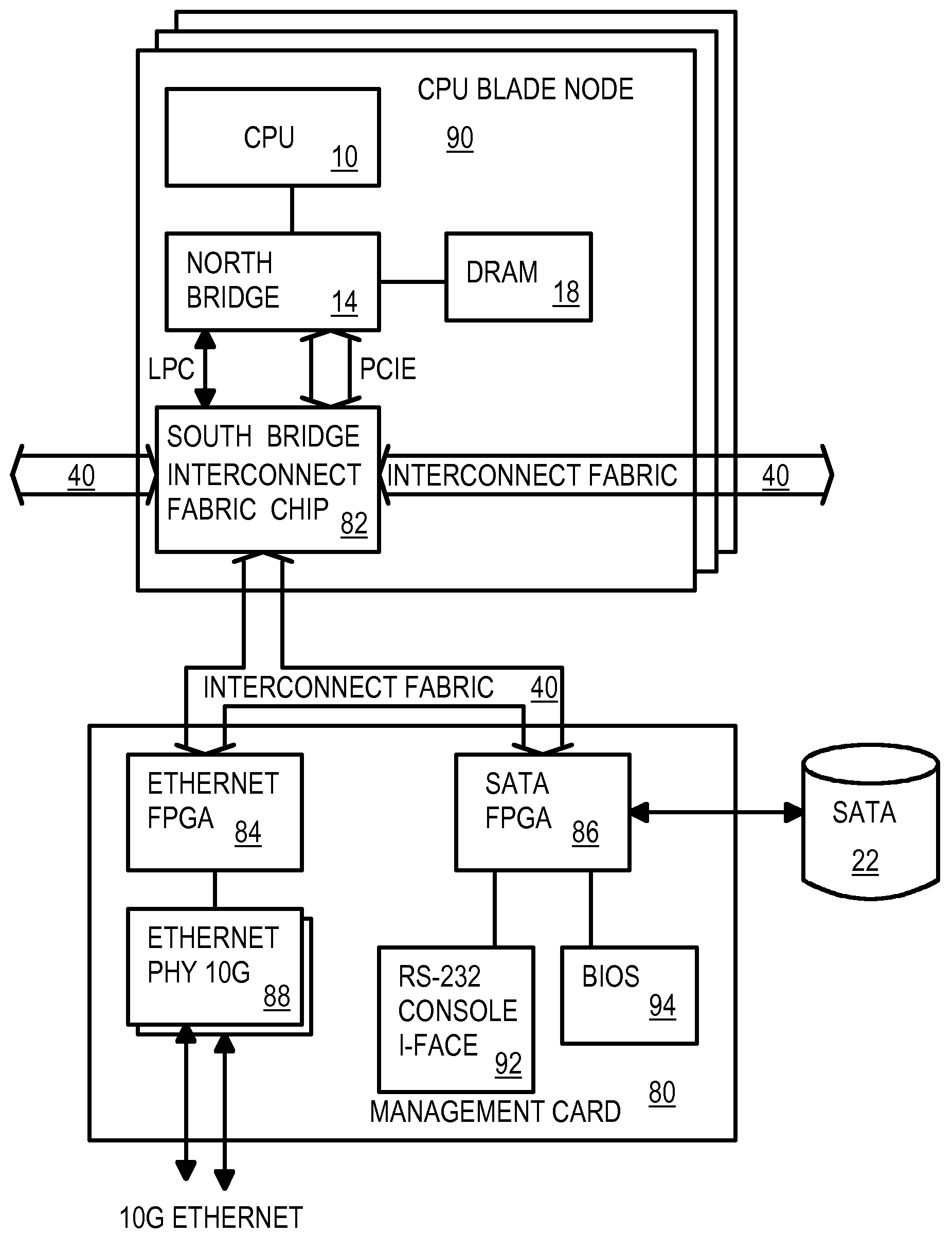
Hardware-Based Virtualization of BIOS, Disks, Network-Interfaces, & Consoles Using a Direct Interconnect Fabric
ActiveUS20080320181A1Program controlInput/output processes for data processingVirtualizationOperational system
A multi-computer system has many processors that share peripherals. The peripherals are virtualized by hardware without software drivers. Remote peripherals appear to the operating system to be located on the local processor's own peripheral bus. A processor, DRAM, and north bridge connect to a south bridge interconnect fabric chip that has a virtual Ethernet controller and a virtual generic peripheral that act as virtual endpoints for the local processor's peripheral bus. Requests received by the virtual endpoints are encapsulated in interconnect packets and sent over an interconnect fabric to a device manager that accesses remote peripherals on a shared remote peripheral bus so that data can be returned. Ethernet Network Interface Cards (NIC), hard disks, consoles, and BIOS are remote peripherals that can be virtualized. Processors can boot entirely from the remote BIOS without additional drivers or a local BIOS. Peripheral costs are reduced by sharing remote peripherals.
Owner:SEAMICRO
Purpose domain for low overhead virtual machines
InactiveUS20070169005A1Multiprogramming arrangementsSoftware simulation/interpretation/emulationOperational systemAnalog computer
Embodiments of the present invention provide an architecture for securely and efficiently executing byte code generated from a general programming language. In particular, a computer system is divided into a hierarchy comprising multiple types of virtual machines. A thin layer of software, known as a virtual machine monitor, virtualizes the hardware of the computer system and emulates the hardware of the computer system to form a first type of virtual machine. This first type of virtual machine implements a virtual operating domain that allows running its own operating system. Within a virtual operating domain, a byte code interpreter may further implement a second type of virtual machine that executes byte code generated from a program written in a general purpose programming language. The byte code interpreter is incorporated into the operating system running in the virtual operating domain. In addition, an operating system running in a virtual operating domain may be configured as a special purpose operating system that is optimized for the functions of a particular byte code interpreter.
Owner:RED HAT
Method for implementing organizational architecture mode of kernel-based virtual machine (KVM)
InactiveCN101968746AEnhanced interactionImprove I/O performanceMultiprogramming arrangementsSoftware simulation/interpretation/emulationVirtualizationData center
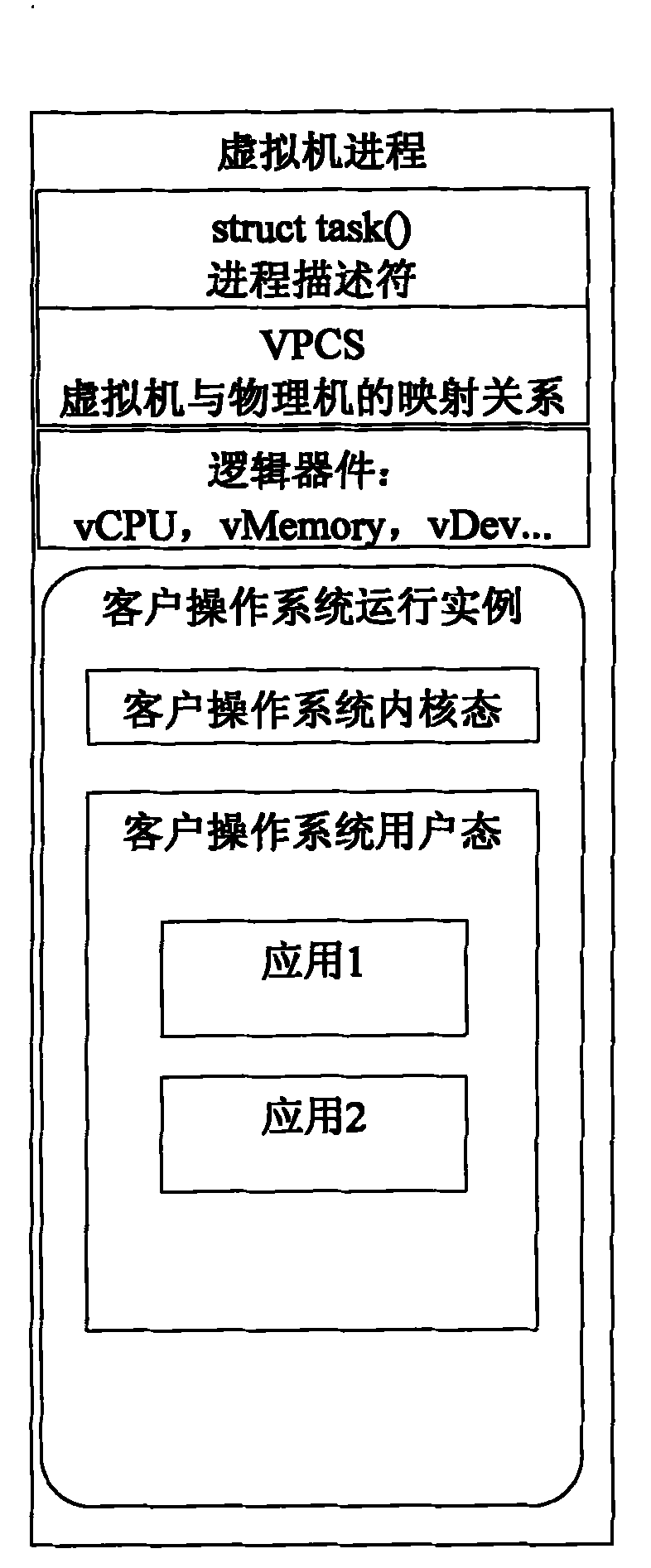
The invention mainly relates to a kernel-based virtual machine (KVM) architecture and an optimization technique thereof. Based on a KVM, the software structure thereof is optimized to fulfill the purposes of reducing the host resource occupied by the virtual machine and providing more efficient virtual machine running mode. In particular, a VPCS (virtual process control structure) created for each virtual machine process provides a good interface for implementing direct mapping between a physical resource and a logic resource. Meanwhile, because the hardware virtualization technique needs the support of a hardware technique, but a big part of servers owned by current large data centers and companies do not support the hardware virtualization technique, the optimization technique enables the virtualization technique to play a greater role in the calculation resource of the part. Therefore, the invention has good application prospect.
Owner:BEIHANG UNIV
Virtualization Hardware For Device Driver Isolation
ActiveUS20080148048A1Solve insufficient computing resourcesSolve insufficient resourcesMultiprogramming arrangementsPlatform integrity maintainanceVirtualizationComputer resources
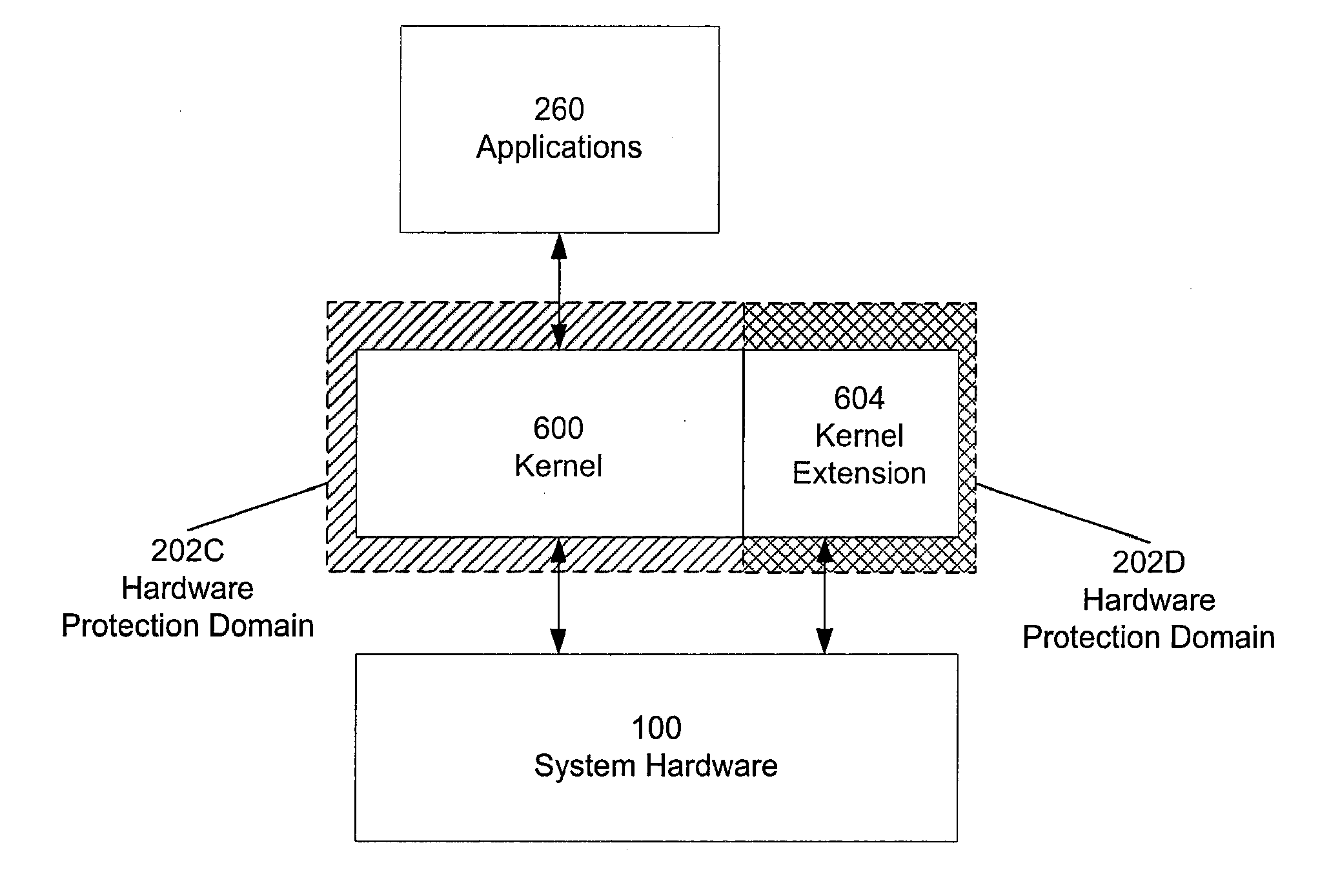
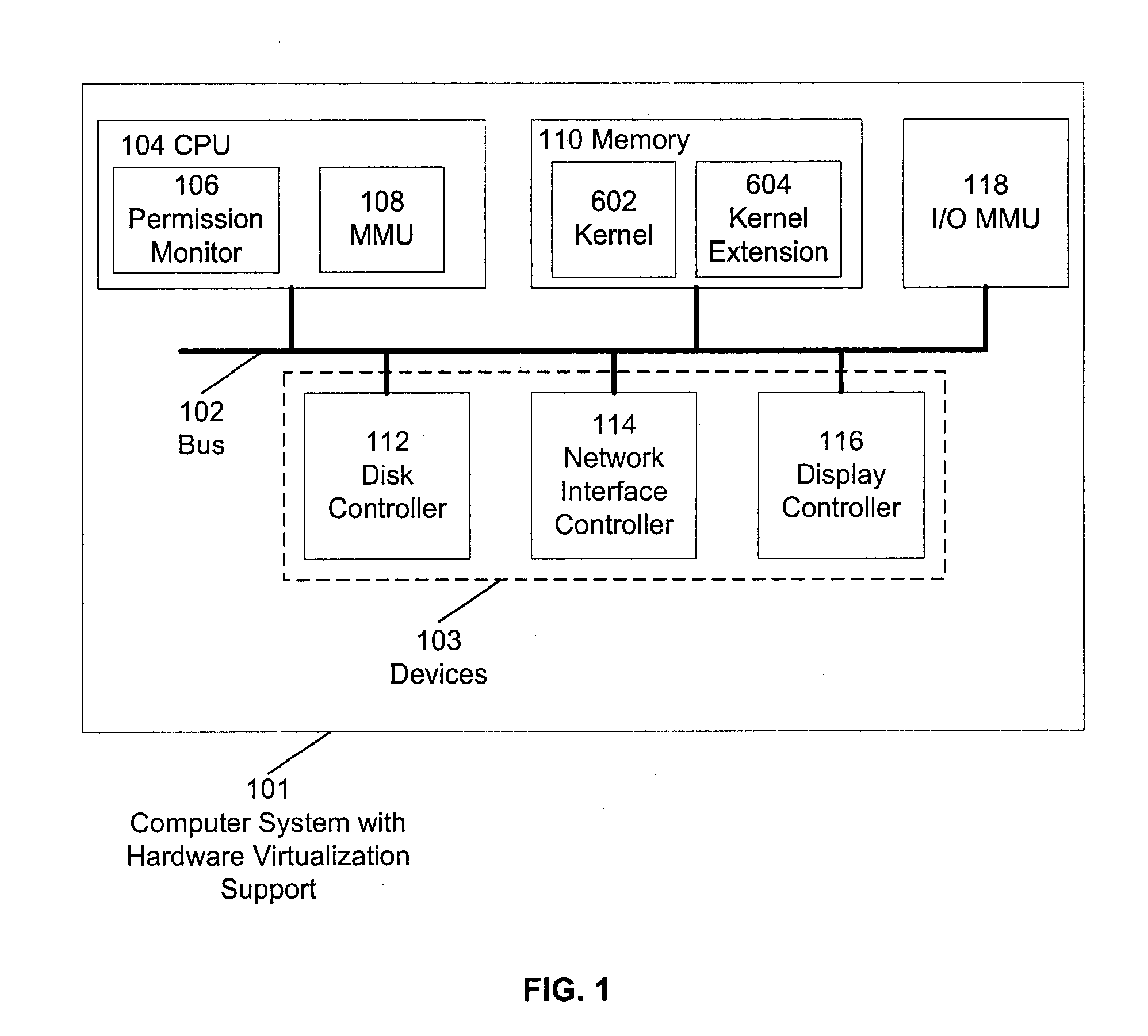
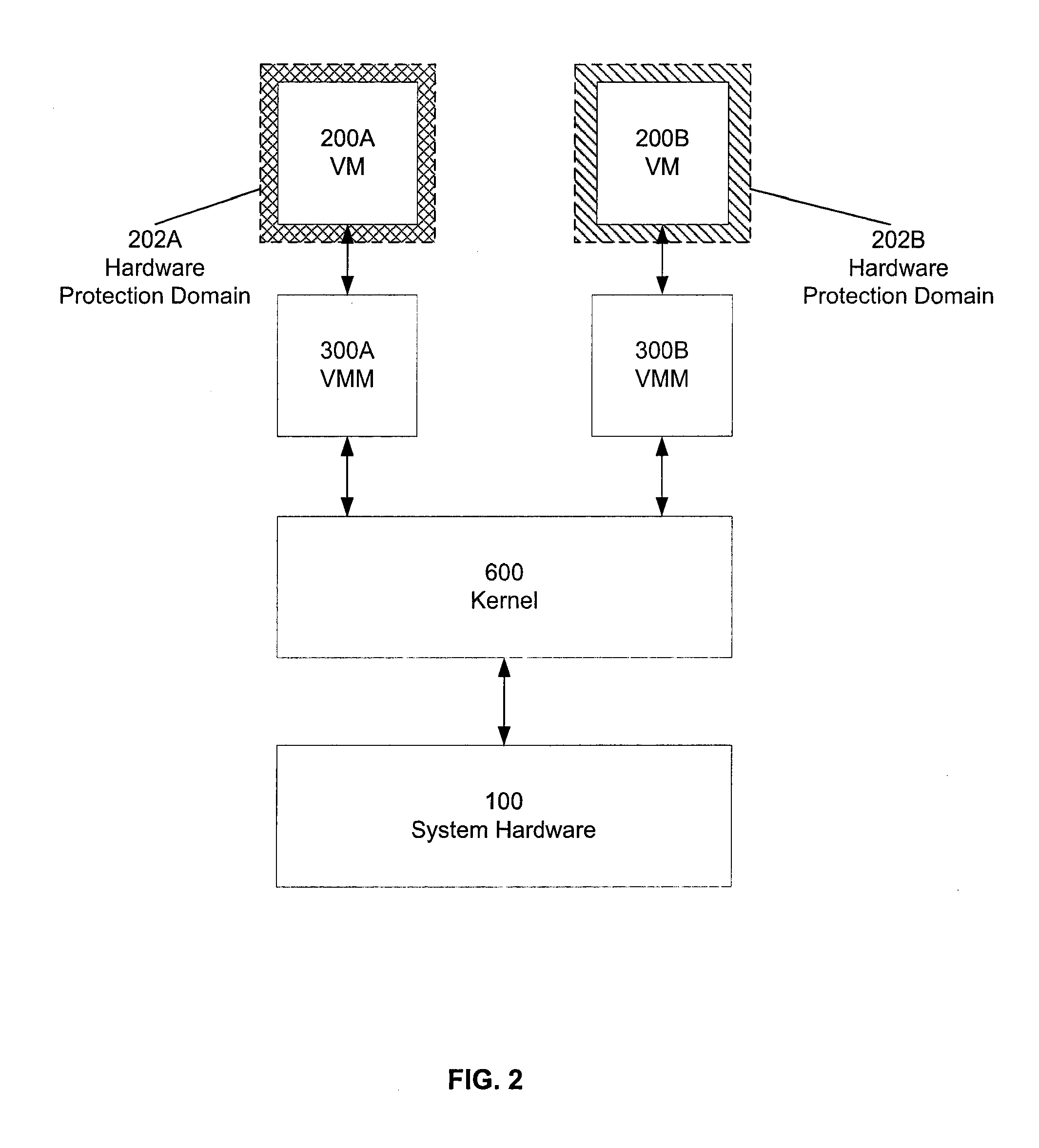
Hardware virtualization support is used to isolate kernel extensions. A kernel and various kernel extensions are executed in a plurality of hardware protection domains. Each hardware protection domain defines computer resource privileges allowed to code executing in that hardware protection domain. Kernel extensions execute with appropriate computer resource privileges to complete tasks without comprising the stability of the computer system.
Owner:VMWARE INC
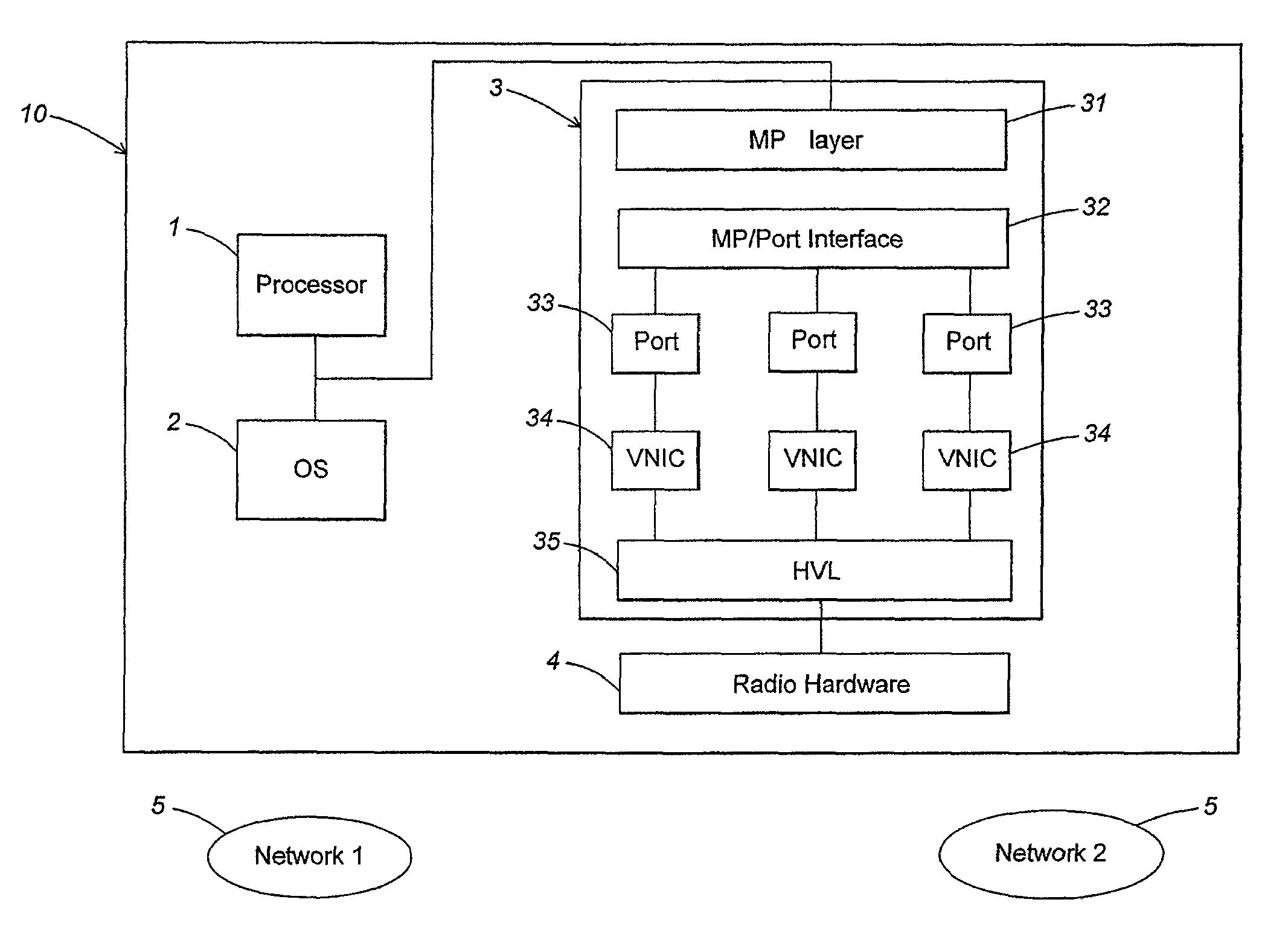
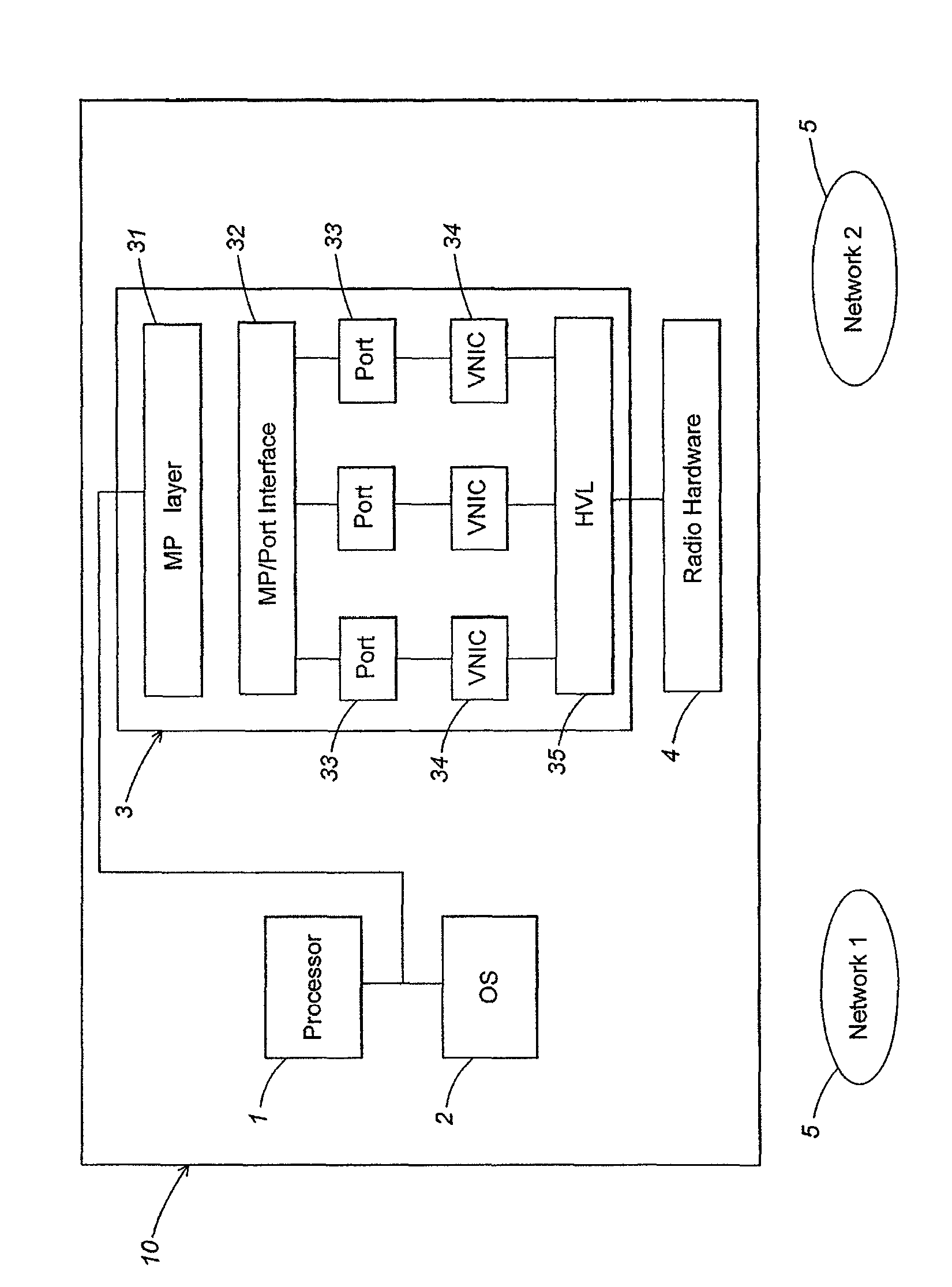
Maintaining multiple, simultaneous wireless network connections using a single radio
ActiveUS20090103481A1Keep in touchTransmission control/equalisingData switching by path configurationVirtualizationNetwork connection
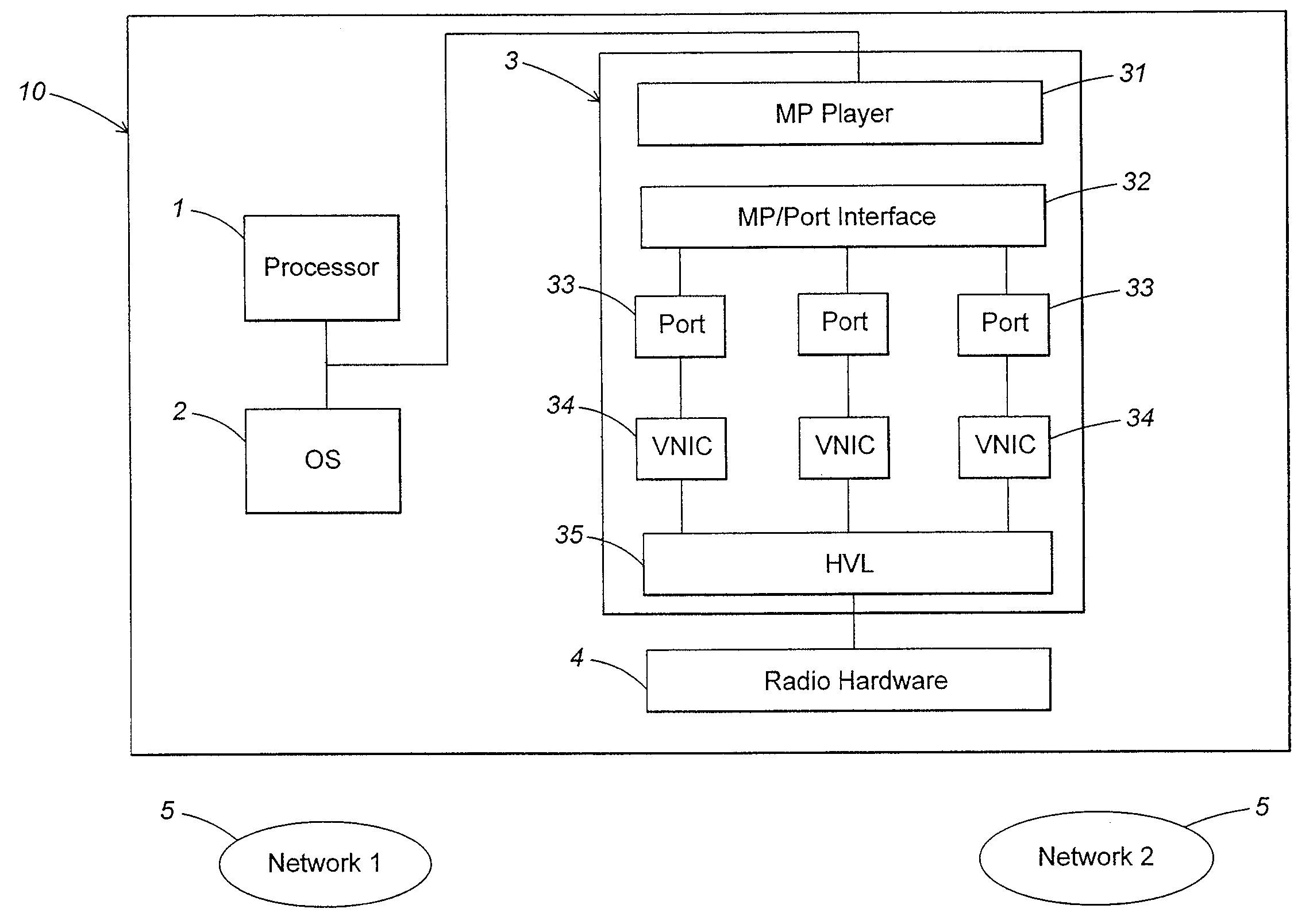
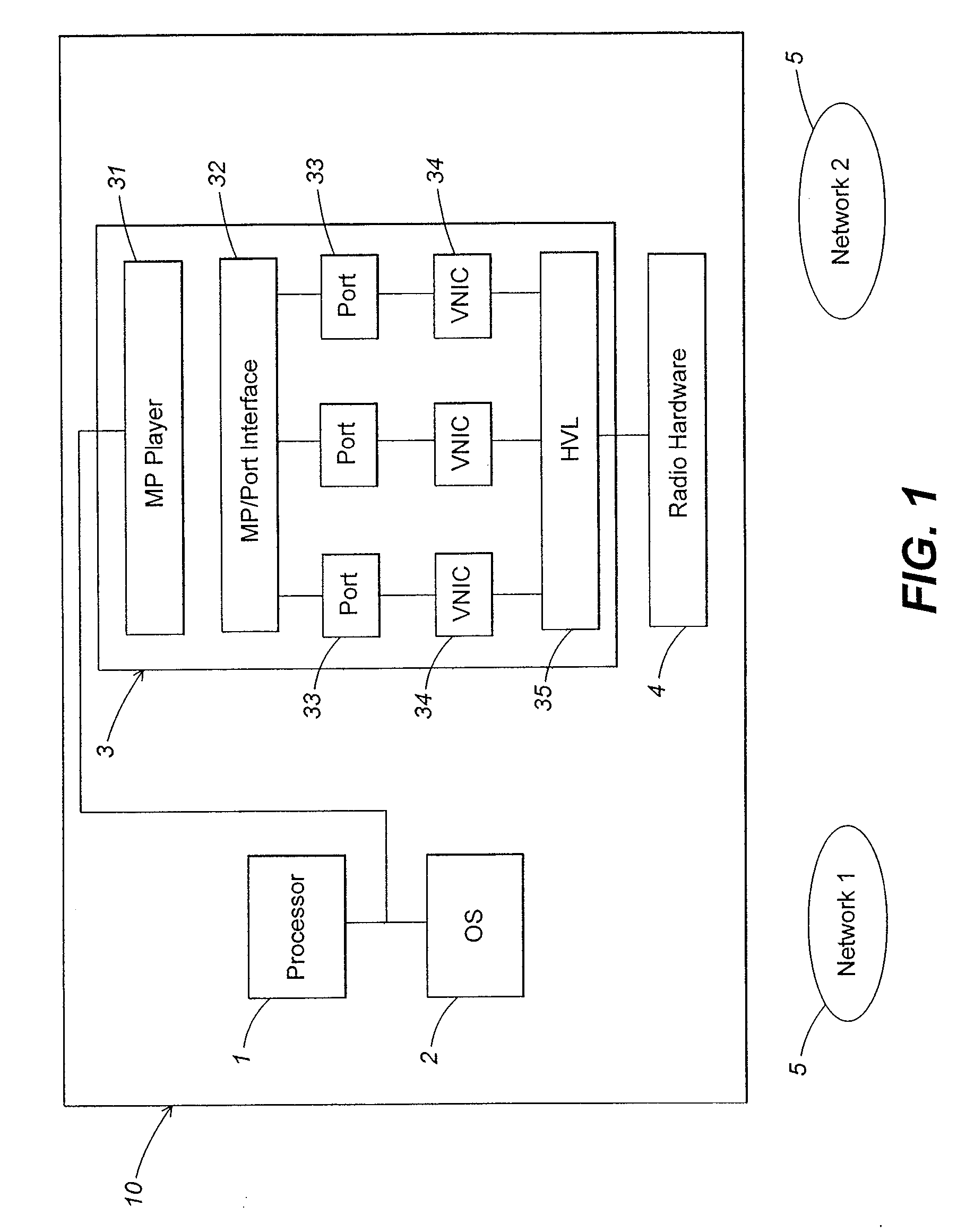
A method and apparatus for managing simultaneous virtual connections with multiple wireless networks. A plurality of ports in a hardware driver may be each associated with a corresponding wireless network and maintain a unique MAC state relative to other ports. Each port may have a corresponding virtual NIC that communicates directly with the radio hardware via a hardware virtualization layer that multiplexes communication between the virtual NICs and the radio hardware. Simultaneous virtual connections may be made with one or more infrastructure networks or adhoc networks, and / or the computer may function as an access point for one or more of the networks.
Owner:MICROSOFT TECH LICENSING LLC
Methods, apparatuses and computer program products for simulating arbitrary unmodified code
InactiveUS8170859B1Error detection/correctionSoftware simulation/interpretation/emulationVirtualizationParallel computing
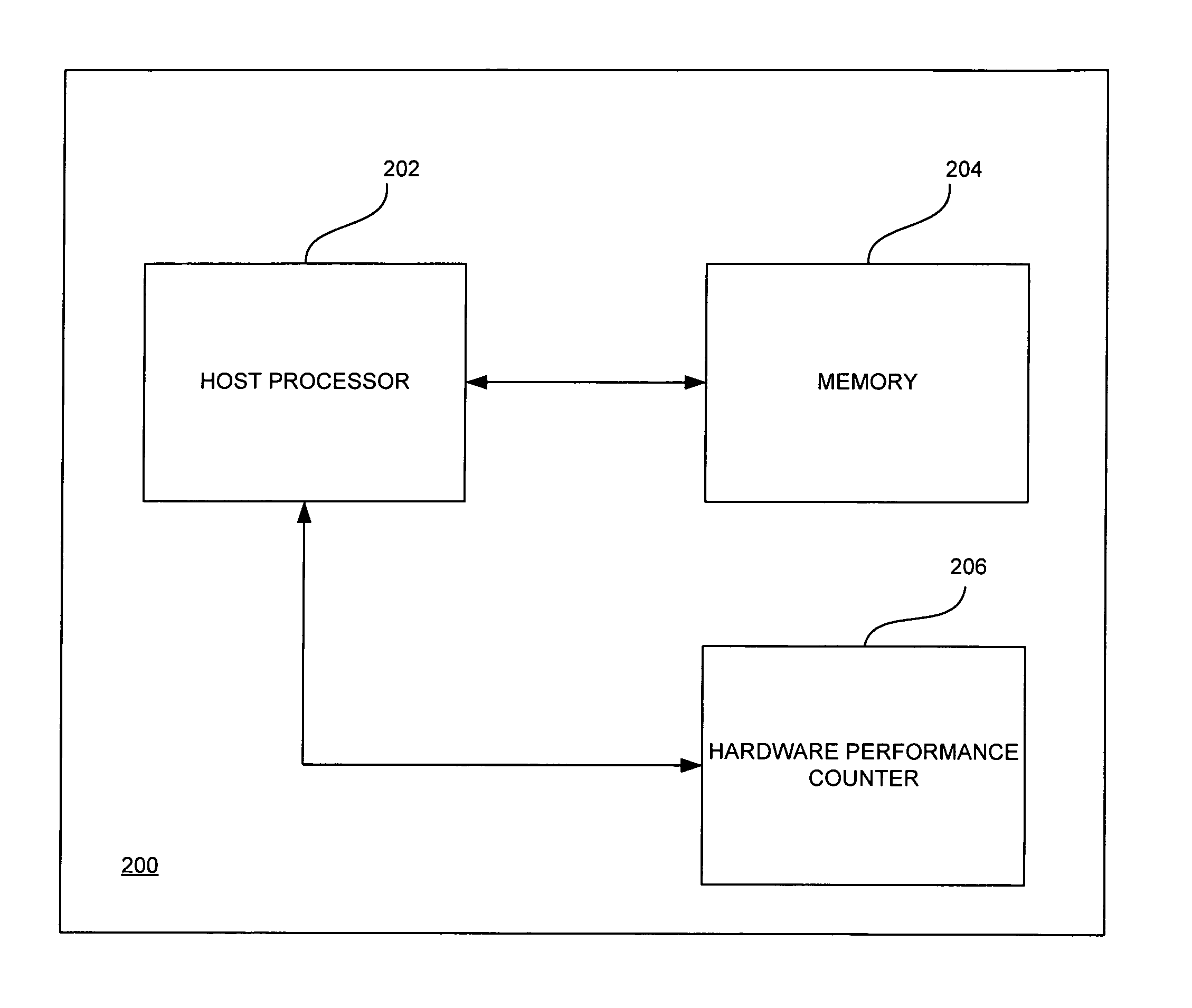
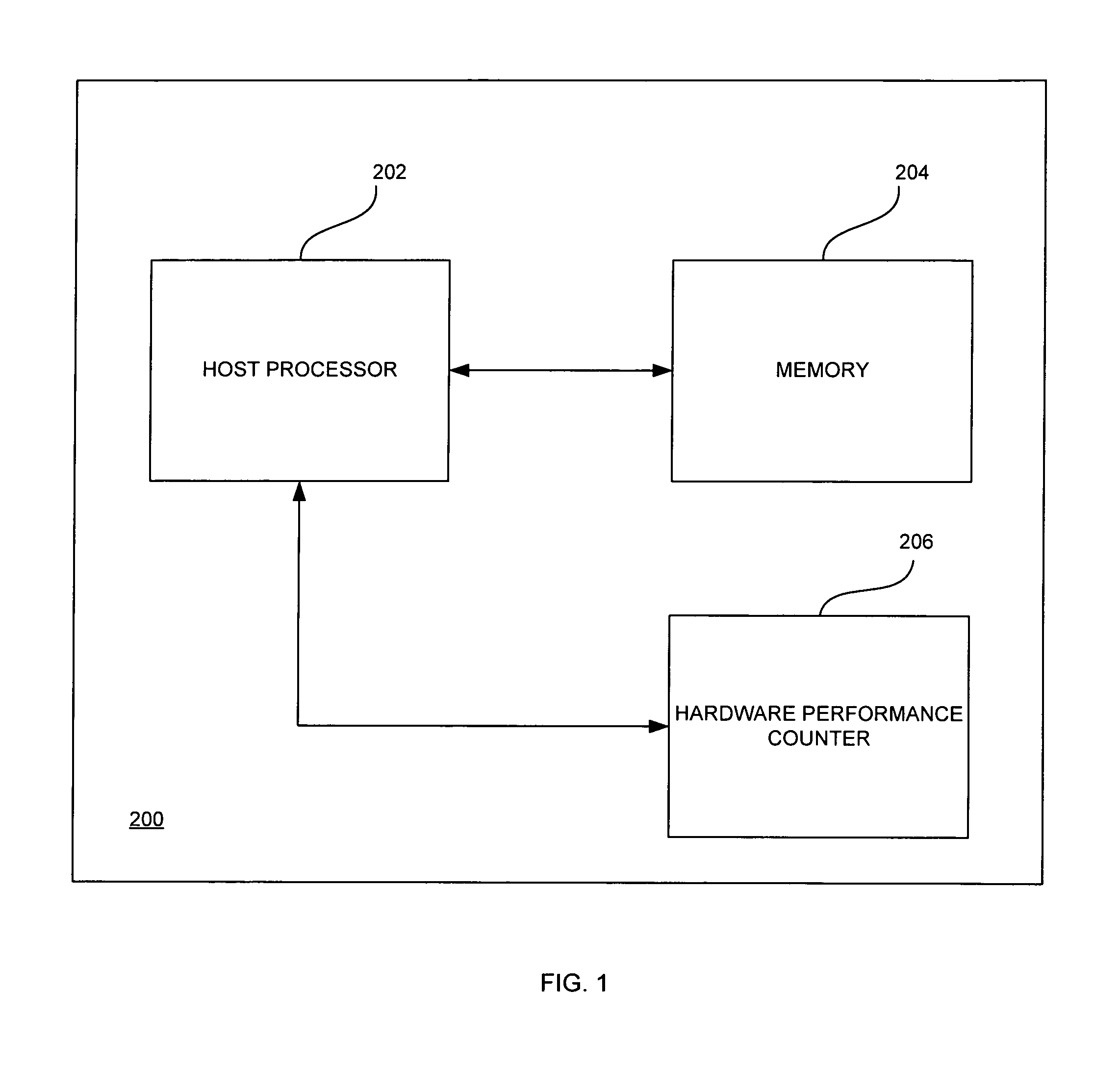
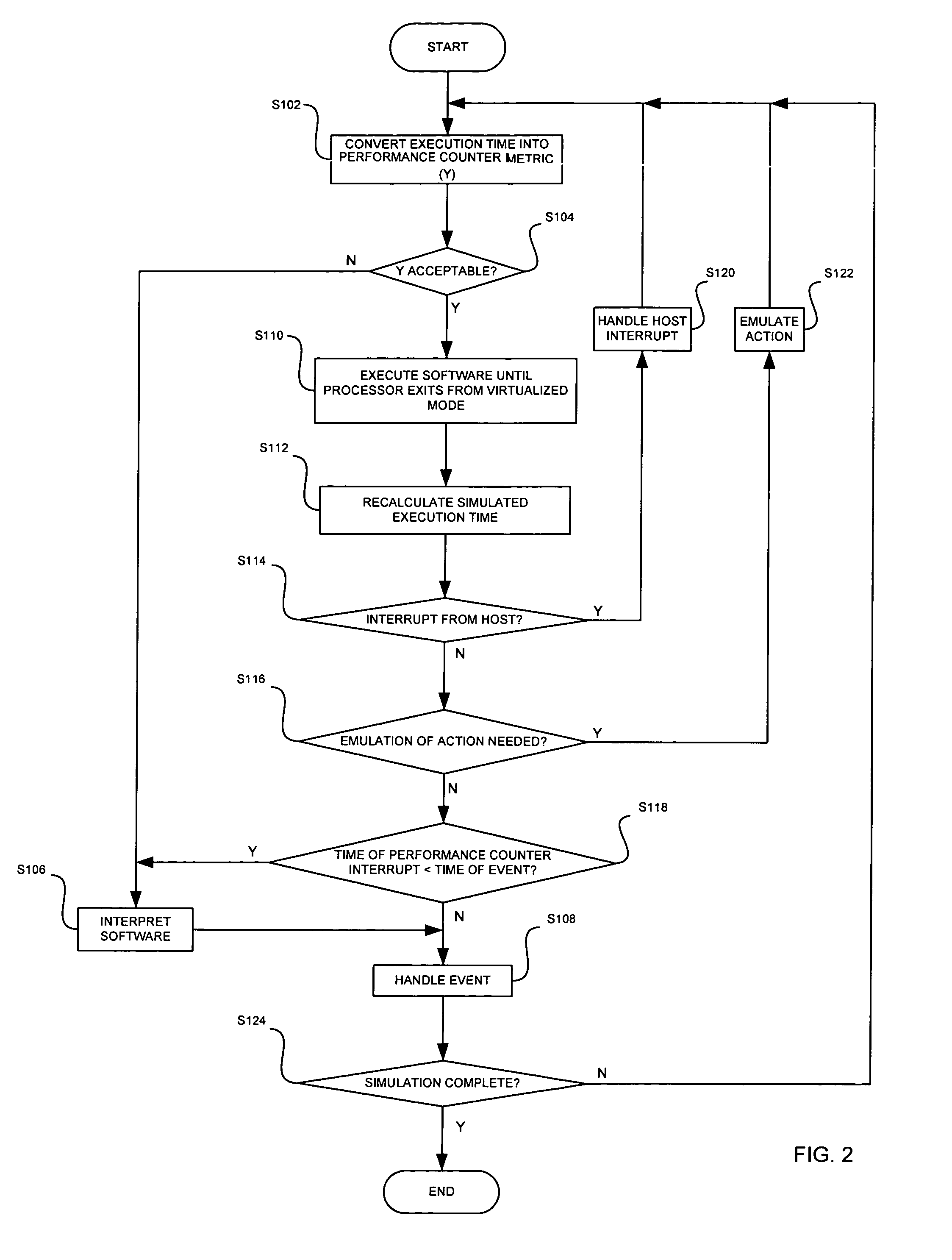
Arbitrary, unmodified code and / or software may be executed directly on a host processor operating in a virtualized mode using hardware virtualization support and performance counters. The arbitrary software may be run on the host processor until the host processor exits from the virtualized mode. An end execution time may be calculated in response to the host processor exiting from the virtualized mode. An event may then be handled based on an execution time at which the host processor exited from the virtualized mode and a time at which a scheduled event was to occur.
Owner:INTEL CORP
Hardware-based virtualization of BIOS, disks, network-interfaces, and consoles using a direct interconnect fabric
ActiveUS7925802B2Program controlInput/output processes for data processingVirtualizationNetwork packet
A multi-computer system has many processors that share peripherals. The peripherals are virtualized by hardware without software drivers. Remote peripherals appear to the operating system to be located on the local processor's own peripheral bus. A processor, DRAM, and north bridge connect to a south bridge interconnect fabric chip that has a virtual Ethernet controller and a virtual generic peripheral that act as virtual endpoints for the local processor's peripheral bus. Requests received by the virtual endpoints are encapsulated in interconnect packets and sent over an interconnect fabric to a device manager that accesses remote peripherals on a shared remote peripheral bus so that data can be returned. Ethernet Network Interface Cards (NIC), hard disks, consoles, and BIOS are remote peripherals that can be virtualized. Processors can boot entirely from the remote BIOS without additional drivers or a local BIOS. Peripheral costs are reduced by sharing remote peripherals.
Owner:SEAMICRO
Server cluster unit system with single system image
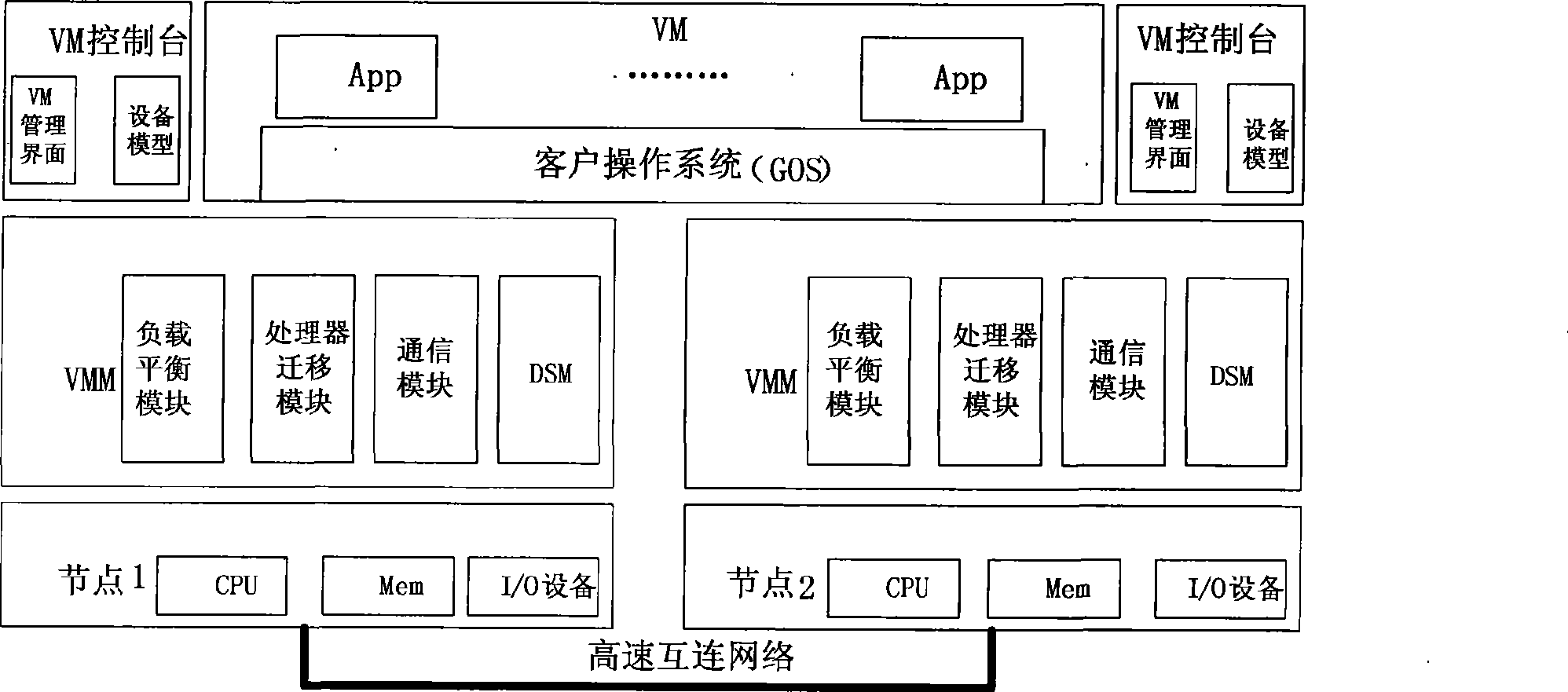
InactiveCN101271401ASingle Point of Control SupportLocation transparentMultiprogramming arrangementsSoftware simulation/interpretation/emulationVirtualizationOperational system
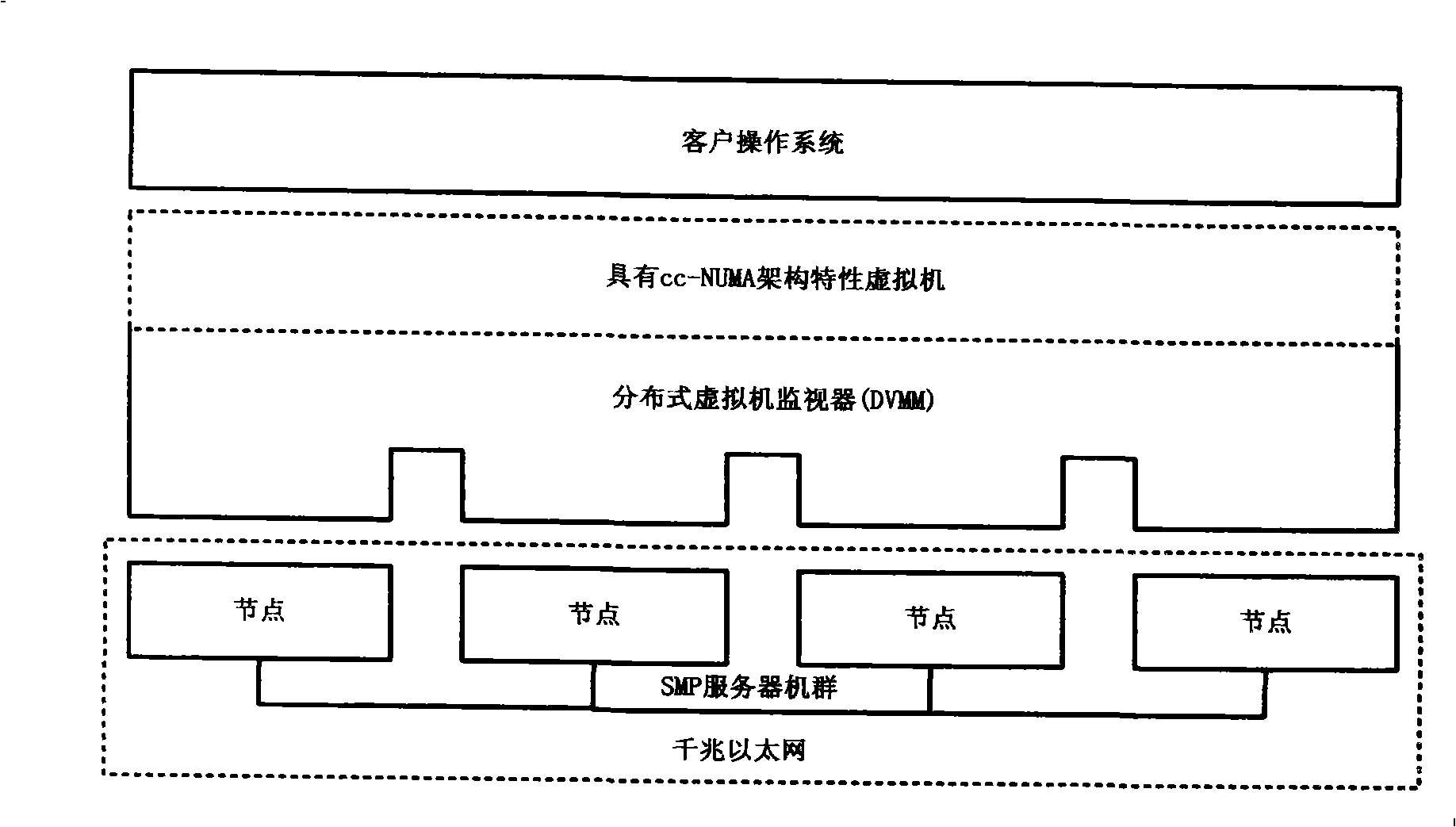
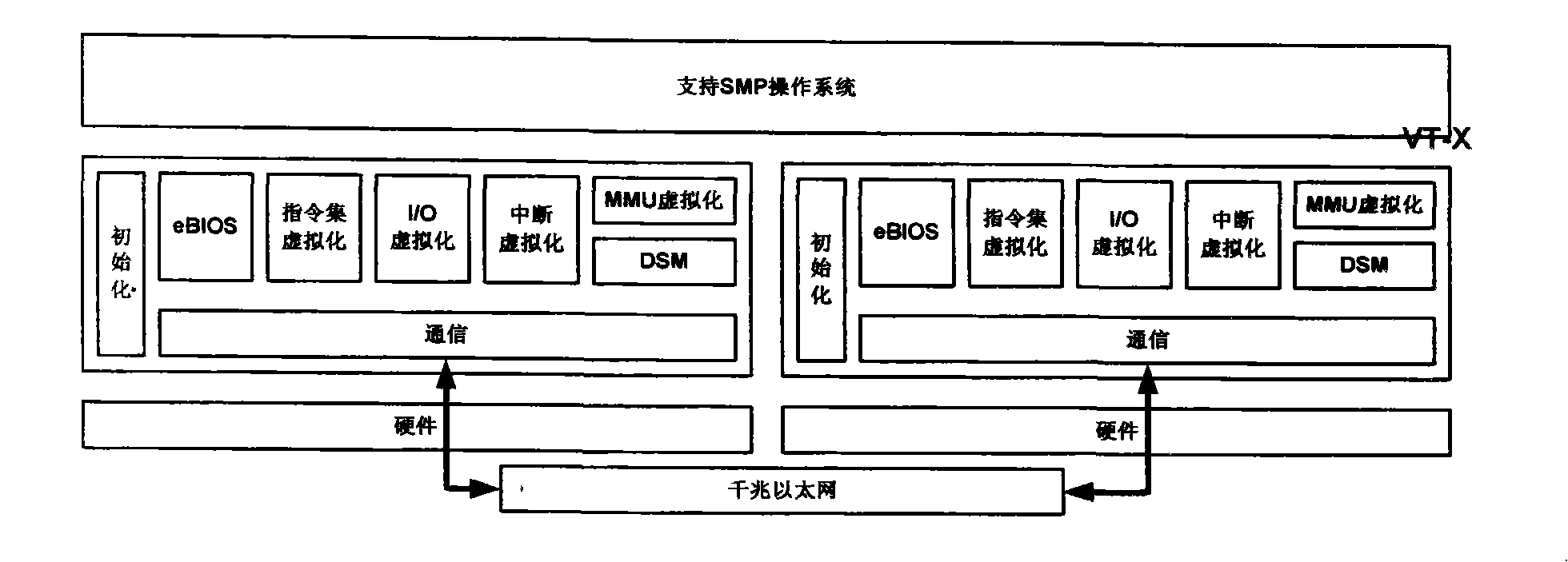
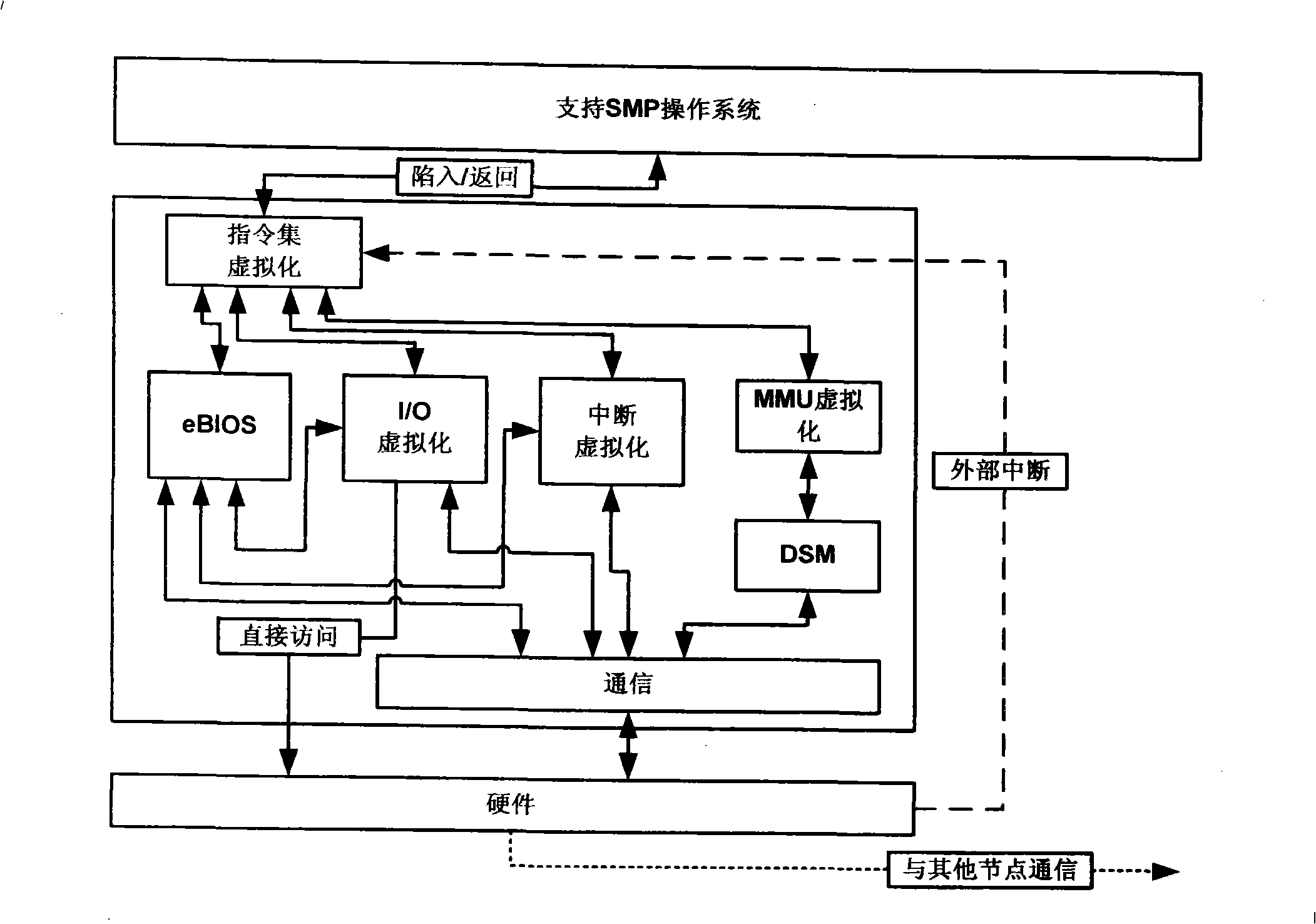
The invention discloses a server group system with single system reflection, including a hardware layer, a distributed virtual machine monitor layer and an operation system layer; wherein, the hardware layer includes a plurality of nodes, a CUP of the nodes supports the hardware virtualization and the nodes are connected via a high-speed network. The distributed virtual machine monitor layer is provided with a virtual machine monitor on the hardware of each node and the virtual machine monitors of the nodes are communicated through bottom communication software and the high-speed network. The operation system layer supports various commercial operation systems of cc-NUMA and existing various cc-NUMA-oriented paralleling software can be operated on the system without modification. Based on the virtualization of the hardware resources, the system achieves the single system reflection of the server group system. The server group system provided by the invention has the advantages of good transparency, high performance, wide application range, moderate realizing difficulty, etc.
Owner:HUAWEI TECH CO LTD
Cross-platform safety protection system based on hardware virtualization
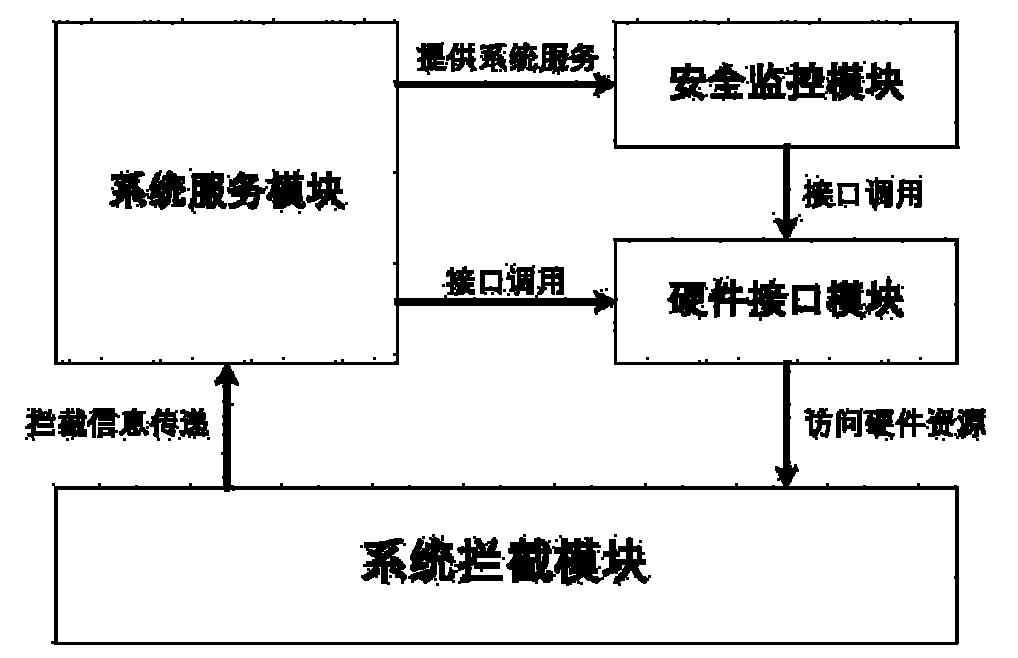
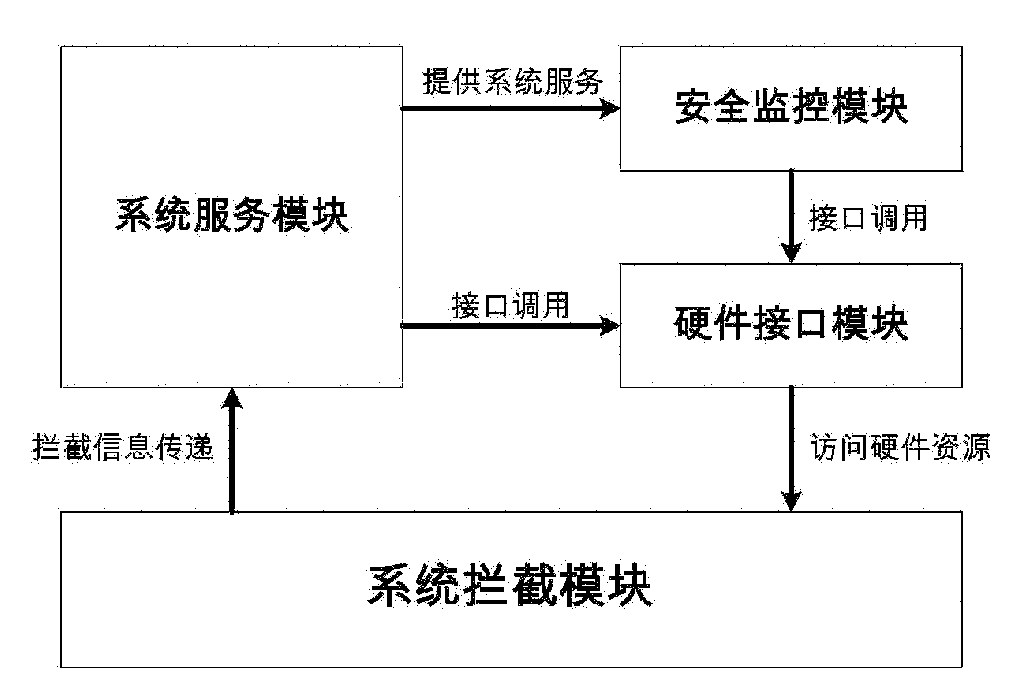
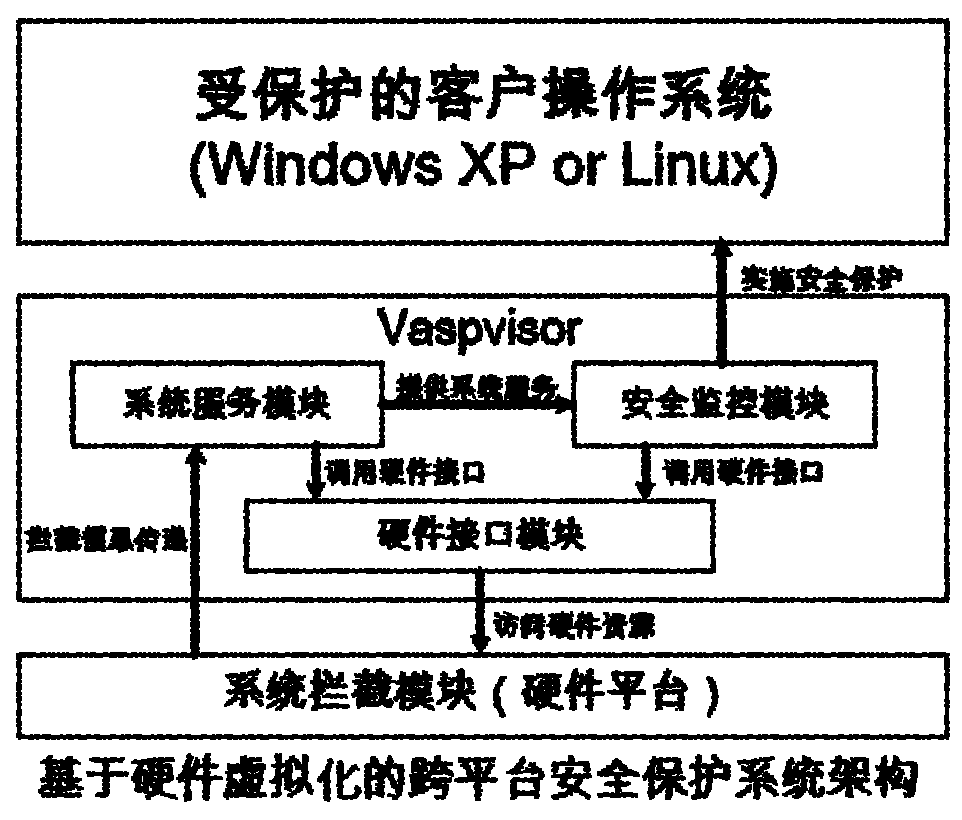
InactiveCN102096786AReduce overheadDoes not affect execution of tasksPlatform integrity maintainanceOperating system securityProtection system
The invention provides a cross-platform safety protection system based on hardware virtualization, which belongs to the technical field of computer safety. The system provided by the invention comprises a system interception module, a hardware interface module, a system service module and a safety monitoring module, wherein the system interception module is used for intercepting the specified operation system sensitive behavior and outputting the intercepted information to the system service module; the system service module determines the corresponding safety protection mechanism according to the information, and outputting a control instruction to the safety monitoring module; the safety monitoring module executes the safety protection operation; and the hardware interface module receives the call instruction of the system service module and the safety monitoring module and achieves the interaction and data transmission with the hardware system. The system can monitor and intercept the sensitive behavior of the operation system through a virtual machine monitoring program, and determine whether the behavior is a bad one or a good one by virtue of the monitoring program according to the source and aim of the behavior so as to prevent or stop the harmful aggressive behavior in time to finally ensure the safe operation of the operation system.
Owner:SHANGHAI JIAO TONG UNIV
System of virtual machine based on virtualizing technique of processor, and implementation method
InactiveCN101093449ASimple structureEasy to useSoftware simulation/interpretation/emulationOperational systemOperation mode
A virtualizer system based on processor virtualization technology consists of processor with virtualization technique, bottom layer hardware, virtualizer monitor and a numbers of virtual operation system. It is featured as switching in one end of virtualizer monitor to various virtual operation systems through virtual hardware platform interface and another end to said bottom layer hardware device except processor and connecting various operation systems directly to processor.
Owner:ZHEJIANG UNIV
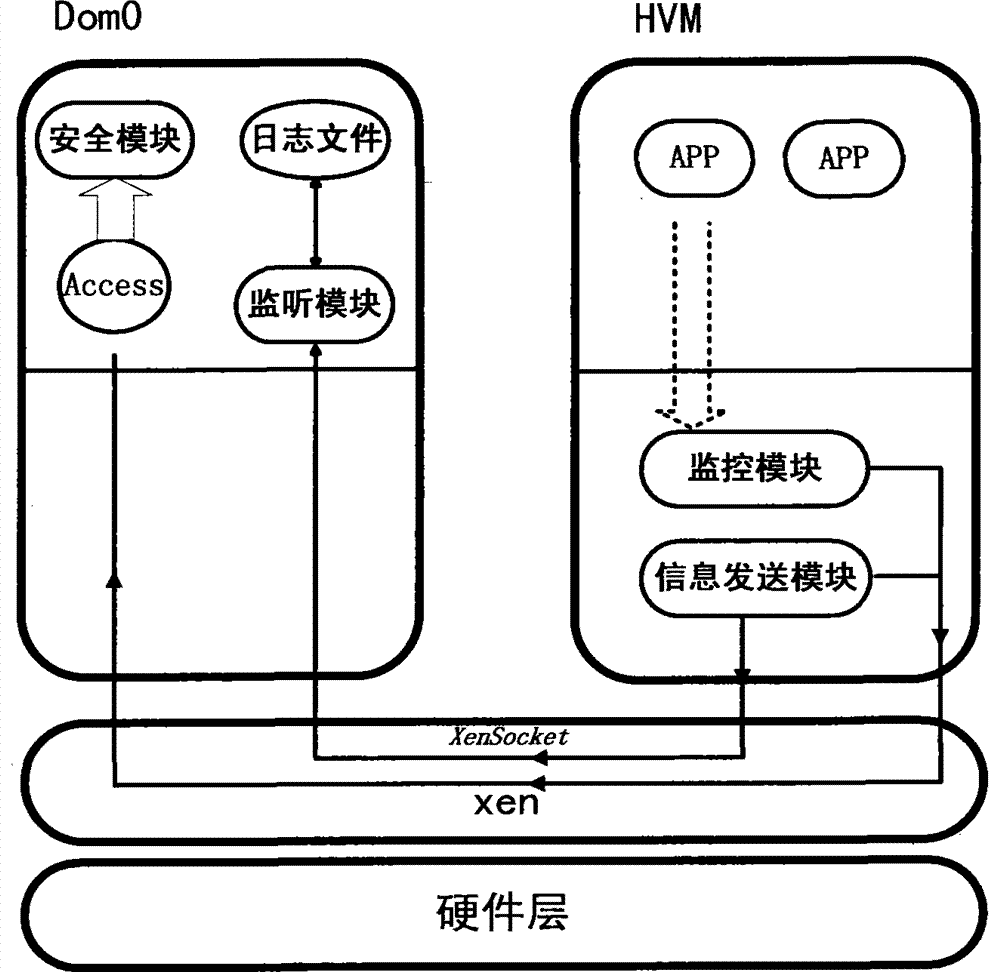
Magnetic disc file operation monitoring system and monitoring method based on Xen hardware virtualization
InactiveCN103399812AMeet the requirements of real-time monitoringOvercome the disadvantage of not being able to monitor file operations in real timeHardware monitoringOperational systemMonitoring system
Provided is a magnetic disc file operation monitoring system based on Xen hardware full virtualization. The magnetic disc file operation monitoring system comprises a supervision module, an information sending module, a monitoring module and a safety module. The supervision module obtains behavior information through interception of magnetic disc file operations of a full-virtualization user operation system so as to achieve the purpose of supervision. The information sending module and the monitoring module enable the behavior information to be transmitted from a domU to a domO. The safety module guarantees operation safety of the information sending module and the monitoring module. The invention provides a monitoring method which includes the steps of intercepting and replacing call of the magnetic disc file operation system in full virtualization, determining types of monitored files, determining whether the files need to be monitored in the operation process, comprehensively determining whether a behavior needs to be monitored according to operation types, the file types and process information, obtaining the behavior information, obtaining an operation target absolute path, sending information, performing information monitoring, and detecting whether the supervision module and the information sending module are attacked when codes are operated, wherein the supervision module and the information sending module are operated under the domU. According to the magnetic disc file operation monitoring system and the monitoring method based on Xen hardware virtualization, real-time monitoring is achieved, and I / O efficiency of an Xen full-virtualization network is improved.
Owner:XIDIAN UNIV
Dis-aggregated and distributed data-center architecture using a direct interconnect fabric
ActiveUS8140719B2Multiple digital computer combinationsTransmissionData centerStructure of Management Information
A data center has several dis-aggregated data clusters that connect to the Internet through a firewall and load-balancer. Each dis-aggregated data cluster has several dis-aggregated compute / switch / disk chassis that are connected together by a mesh of Ethernet links. Each dis-aggregated compute / switch / disk chassis has many processing nodes, disk nodes, and I / O nodes on node cards that are inserted into the chassis. These node cards are connected together by a direct interconnect fabric. Using the direct interconnect fabric, remote I / O and disk nodes appear to the operating system to be located on the local processor's own peripheral bus. A virtual Ethernet controller and a virtual generic peripheral act as virtual endpoints for the local processor's peripheral bus. I / O and disk node peripherals are virtualized by hardware without software drivers. Rack and aggregation Ethernet switches are eliminated using the direct interconnect fabric, which provides a flatter, dis-aggregated hierarchy.
Owner:SEAMICRO
Maintaining multiple, simultaneous wireless network connections using a single radio
ActiveUS8165044B2Transmission control/equalisingData switching by path configurationVirtualizationSelf-organizing network
Owner:MICROSOFT TECH LICENSING LLC
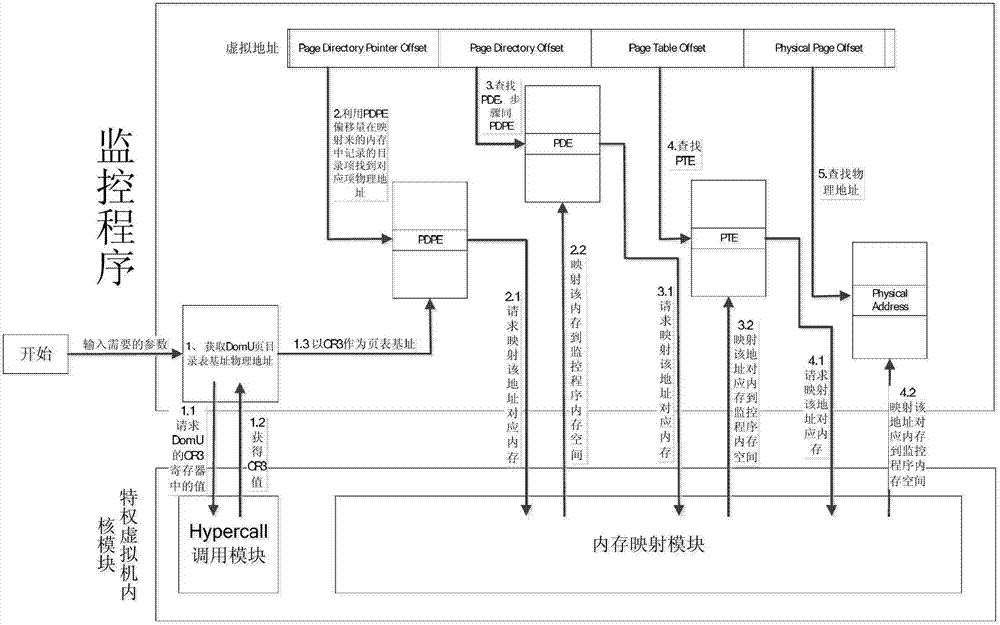
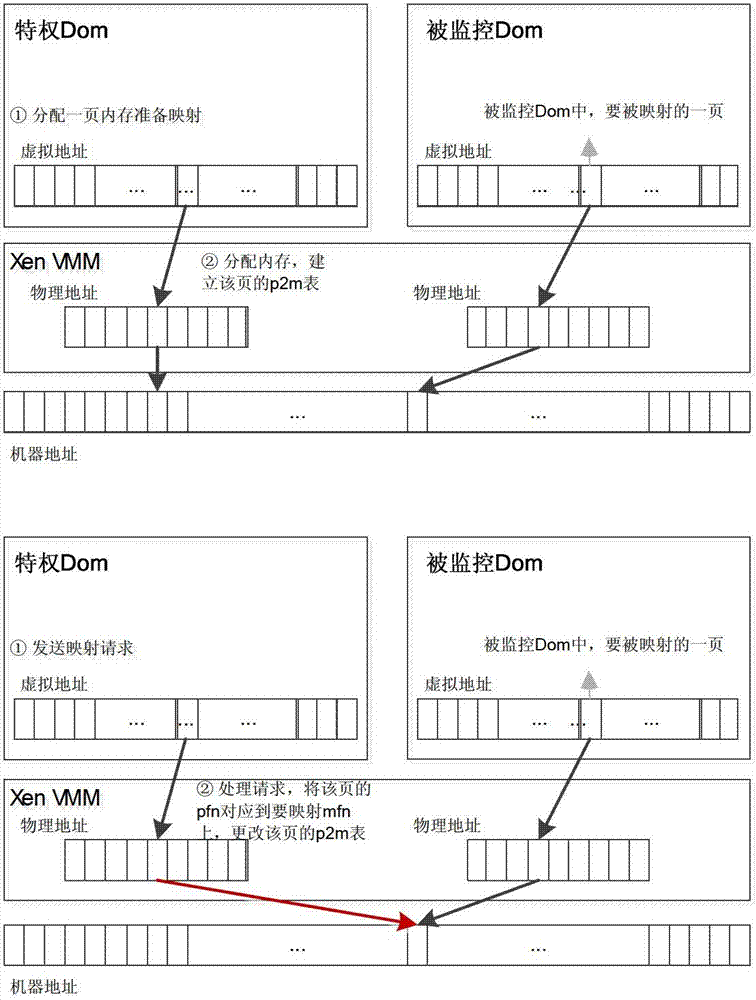
Method and system for monitoring virtualized internal memory of hardware
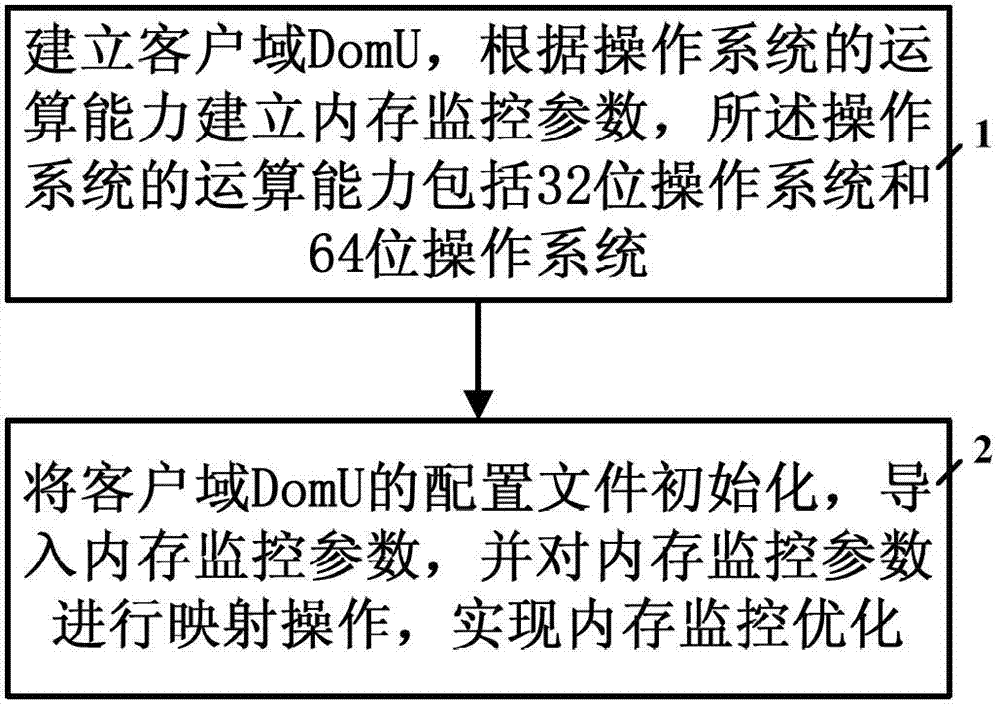
ActiveCN102736969ALighten the performance burdenHardware monitoringSoftware simulation/interpretation/emulationVirtualizationInternal memory
The invention discloses a method and a system for monitoring virtualized internal memory of hardware. The method comprises the following steps: step 1, establishing a customer domain DomU, and establishing memory monitoring parameters according to operational capability of an operation system, wherein the operational capability of the operation system comprises a 32-bit operation system and a 64-bit operation system; step 2, initializing configuration documents of the customer domain DomU, importing the memory monitoring parameters, and performing mapping operation on the memory monitoring parameters, so as to realize optimization of internal memory monitoring.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
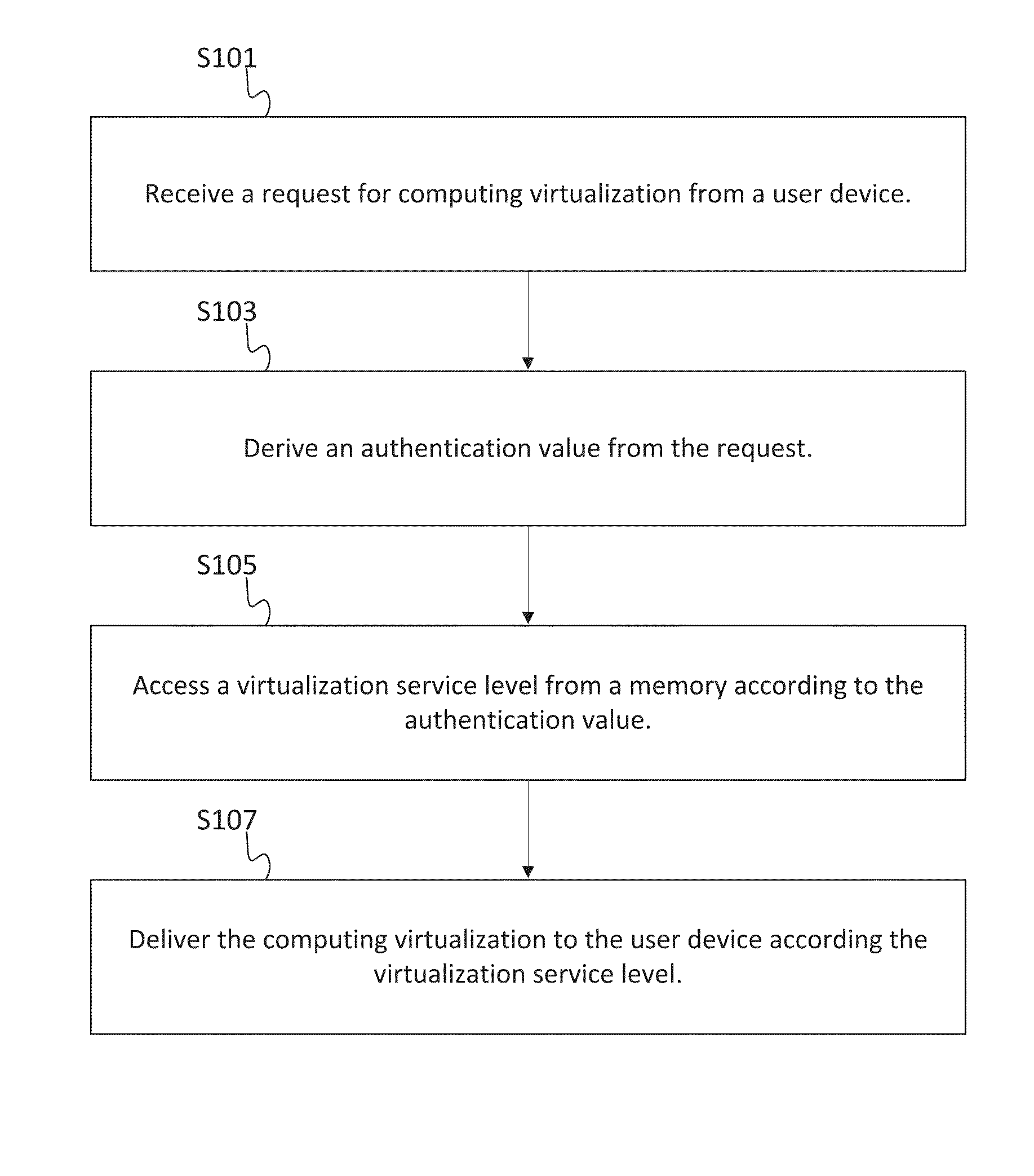
Differentiated service levels in virtualized computing
InactiveUS20140173591A1Software simulation/interpretation/emulationMemory systemsDifferentiated servicesVirtualization
In one implementation, a host provides virtualized computing to one or more customer networks. The virtualized computing may include hardware virtualization quantified in the resources of the virtual machines, services virtualization quantified in the quantity or types of services performed on host, or processing virtualization quantified by process occurrences. When the host receives a request for computing virtualization from a user device, the host derives an authentication value and accesses a virtualization service level from a memory. The host is configured to deliver the computing virtualization to the user device according the virtualization service level.
Owner:CISCO TECH INC
JavaScript virtualization protection method based on front-end bytecode technology
ActiveCN108614960AImprove securityHigh strengthProgram/content distribution protectionData virtualizationSource code
The invention discloses a JavaScript code virtualization protection method based on front-end bytecode technology. According to the method, on the one hand, an idea of code virtualization is introduced, and a code virtualization protection scheme of a JavaScript source code level is provided through studying and borrowing principles of a binary-code virtualization protection method. Execution logic of JavaScript code is protected through analyzing and introducing design details such as a virtual-machine architecture, a virtual instruction set, a virtual interpreter and instruction mapping encoding rules; and on the other hand, the virtual interpreter is realized on the basis of the front-end bytecode technology, and the new front-end bytecode technology is used to carry out improvement andcompilation on the virtual interpreter of the JavaScript virtualization protection scheme to realize a core module of the hidden virtual-machine architecture. Through combination of two aspects of technology, virtualization can be used to improve strength of JavaScript code protection, efficiency of WebAssembly can also be used to reduce additional overheads brought by a virtualization process, and security of front-end key-code can be effectively improved.
Owner:NORTHWEST UNIV(CN)
A method for protecting the interaction integrity and confidentiality of a trusted application and a common application
ActiveCN109558211AAvoid attackImprove securityPlatform integrity maintainanceSoftware simulation/interpretation/emulationVirtualizationConfidentiality
The invention relates to a method for protecting the interaction integrity and confidentiality of a trusted application and a common application. The method comprises the following steps: establishingmemory isolation between a kernel of a rich execution environment and an application by using a virtualization technology; by means of a virtual machine monitor and hardware virtualization support, operations of system calling, interruption and memory page swap-in and swap-out are transparently processed under the condition that a kernel and application codes are not modified; and establishing atrusted application and common application interaction library which is compatible with the original system and is not supported by the kernel drive. Compared with the prior art, the method has the advantages that multiple threads of hardware are supported, the kernel of the rich execution environment does not need to be modified, and more complete protection can be provided for common application.
Owner:SHANGHAI TRUSTKERNEL INFORMATION TECH CO LTD
System and method for providing hardware virtualization in a virtual machine environment
ActiveCN101512488AMultiprogramming arrangementsSoftware simulation/interpretation/emulationOperational systemApplication server
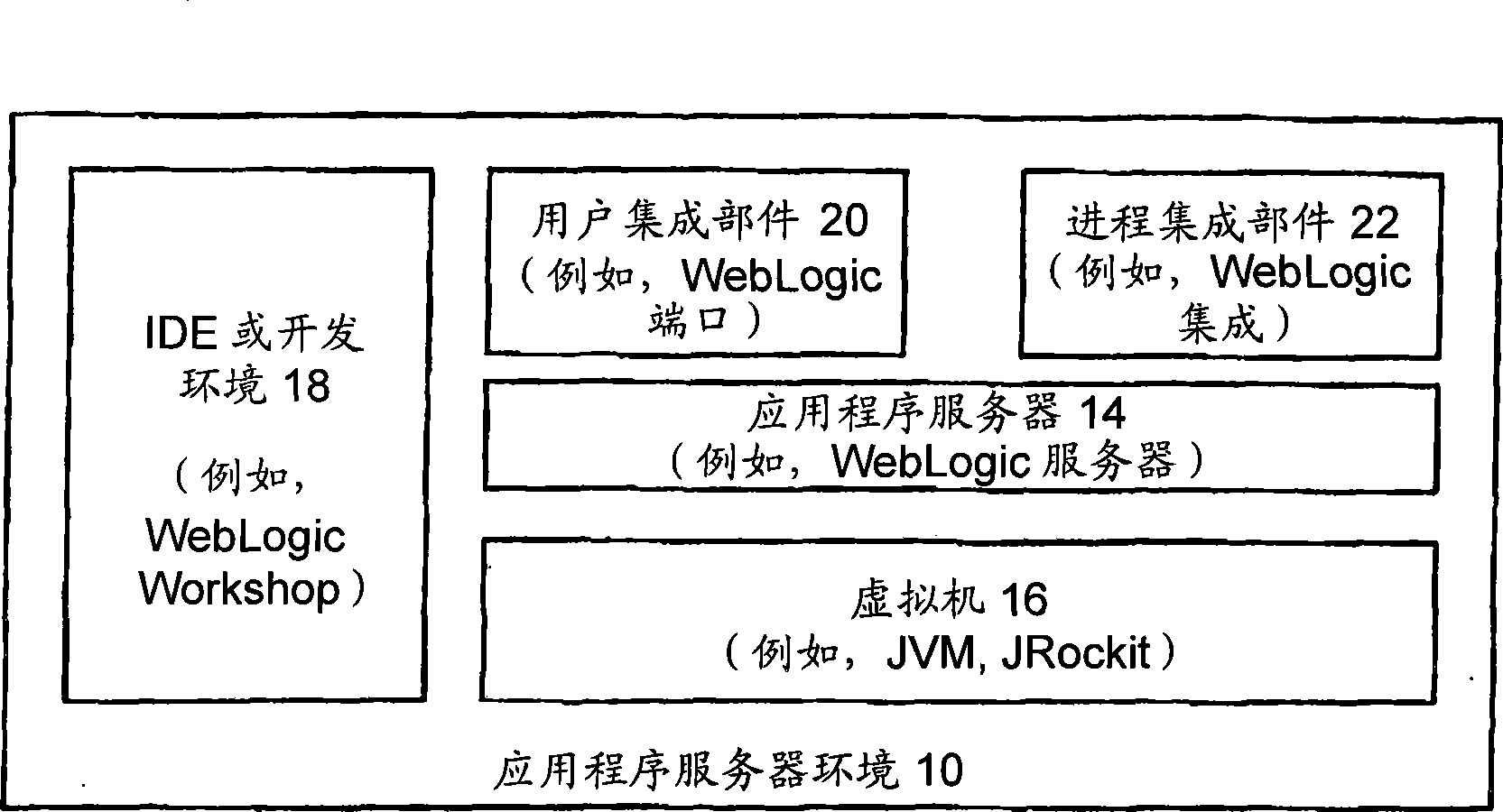
A system and method for providing hardware virtualization and resource management in a virtual machine environment. In accordance with an embodiment, an application server environment includes a computer system, application server, and virtual machine (for example, a Java Virtual Machine or JVM). In accordance with an embodiment, a virtualization layer is provided at each physical machine, including a hypervisor for partitioning virtual machines over the machine. An execution layer runs a single Java-based application, focusing on running that application as efficiently as possible. In accordance with another embodiment, the system comprises two main components: a lower-level, execution environment that replaces the usual operating system; and a higher-level, resource broker that is responsible for handing out new virtual machines to the above layers, and for monitoring the current resource usage of the running virtual machines.
Owner:ORACLE INT CORP
Partial virtualization on computing device
ActiveUS7725305B2Software simulation/interpretation/emulationMemory systemsComputer hardwareOperational system
A computing device hosts a virtual machine executing a guest that issues guest hardware requests by way of any of a plurality of paths. Such paths include a path to non-existent virtual hardware, where an emulator intercepts and processes such guest hardware request with a corresponding actual hardware command; a path to an instantiated operating system, where the instantiated operating system processes each such guest hardware request with a corresponding actual hardware request; and a path to device hardware, where the device hardware directly processes each such guest hardware request.
Owner:MICROSOFT TECH LICENSING LLC
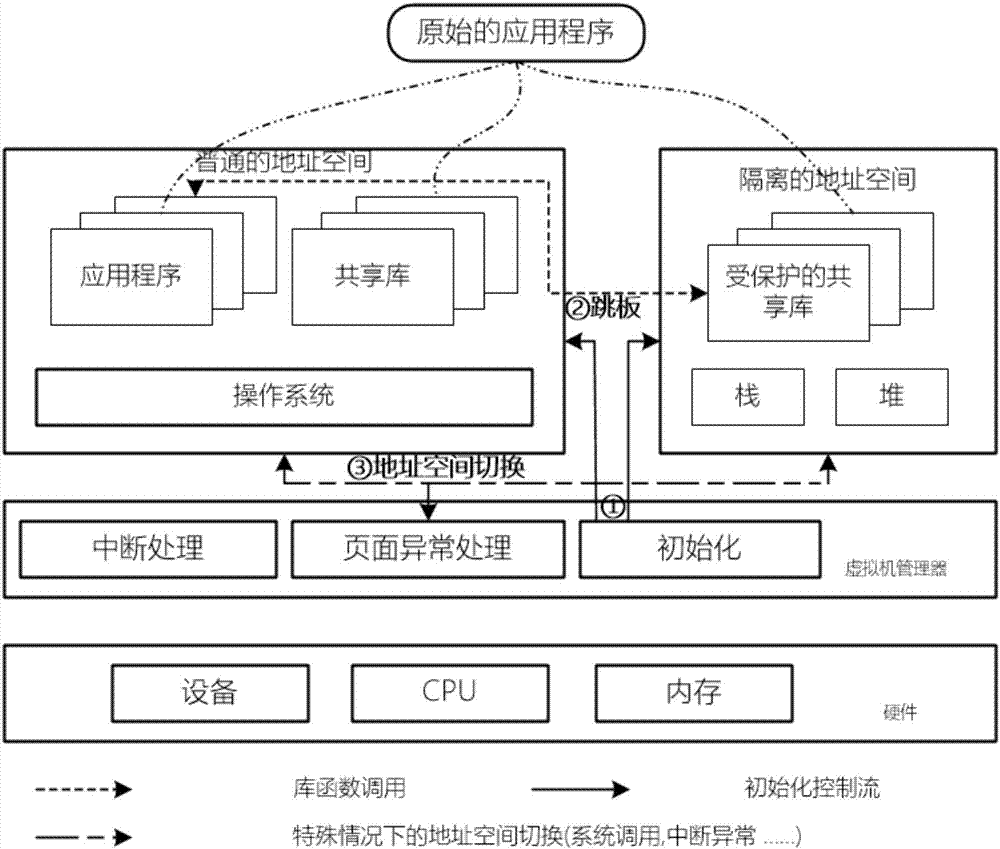
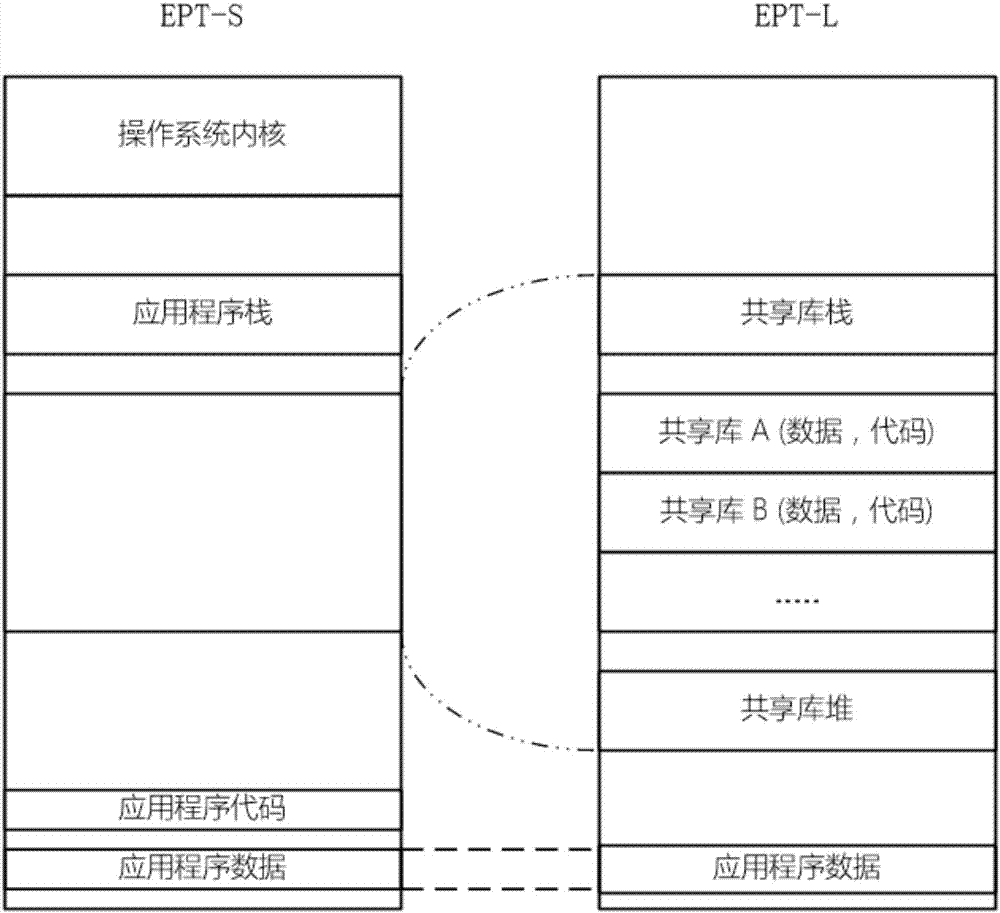
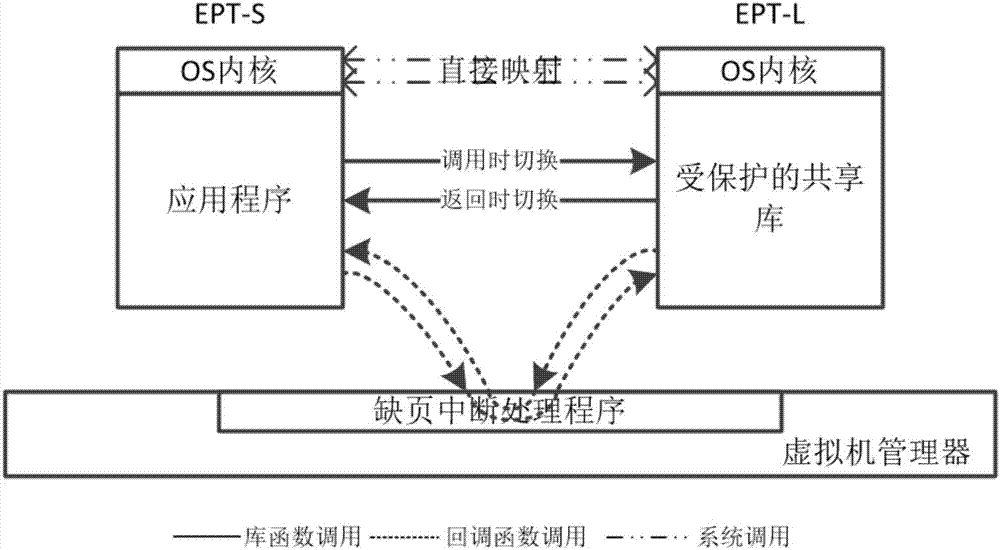
Shared library isolation protection method and system based on hardware virtualization technology
ActiveCN107102888AMaintain shared propertiesImprove versatilityPlatform integrity maintainanceSoftware simulation/interpretation/emulationVirtualizationData access
The invention discloses a shared library isolation protection method based on the hardware virtualization technology. The method includes a novel application address space model is provided, and the memory mapping relationship between an application and a shared library can be more accurately and clearly described; according to the address space model, an isolation mechanism based on the hardware virtualization technology is provided, and the shared library can be efficiently placed in the other isolated address space; an isolated address space interactive control mechanism is provided, the address space is switched when the shared library is in normal interaction with other modules, and at the same time, malicious code execution and data access behaviors occurring during the operation of the shared library are detected. Accordingly, a corresponding system is also provided. The method is suitable for safety isolation and protection of a series of standard and commercial shared libraries, and can avoid the security threats caused by application vulnerabilities to the shared libraries.
Owner:HUAZHONG UNIV OF SCI & TECH
Password protection system based on hardware virtualization
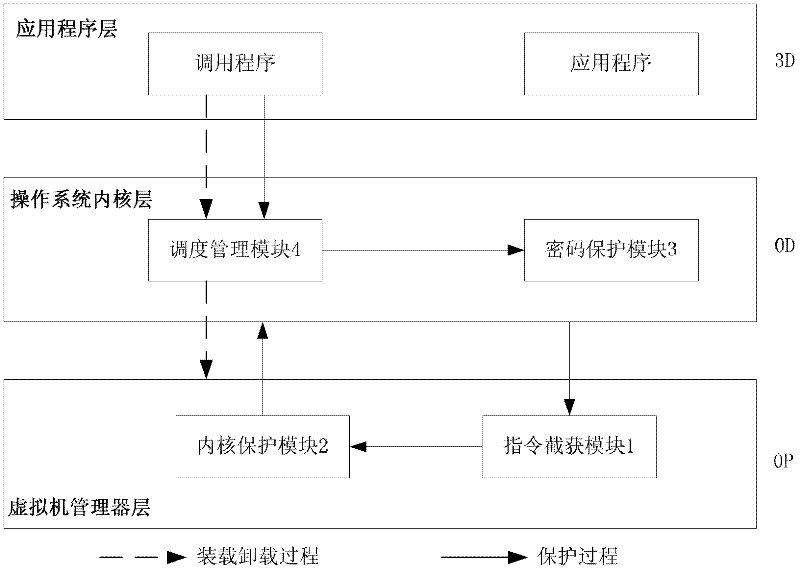
InactiveCN102521531AImprove securityIncrease flexibilityDigital data authenticationOperational systemTrusted Computing
The invention provides a password protection system based on hardware virtualization, which aims at the current situation that a traditional password protection system cannot defend an inner nuclear layer rootkit. The password protection system based on hardware virtualization deploys a password protection module and a scheduling management module in an inner nuclear layer of an operation system, provides a safe input environment and an interactive interface, and simultaneously deploys an instruction intercepting module and an inner core protection module in a manager layer of a virtual machine. The instruction intercepting module is used for intercepting privileged instructions, and transmitting the current privileged instruction information to the inner core protection module so as to lead an execution flow path to enter a manger of the virtual machine from the inner nuclear layer of the operation system. The inner core protection module prevents the rootkit from randomly modifying nuclear data and service in the operation system, and guarantees password protection in the inner nuclear layer of the operation system. The password protection system based on hardware virtualization moves a trusted computing base (TCB) from the inner nuclear layer of the operation system to the manager layer of the virtual machine, thereby achieving lower level and higher safety.
Owner:HUAZHONG UNIV OF SCI & TECH
Hardware virtualized input output memory management unit
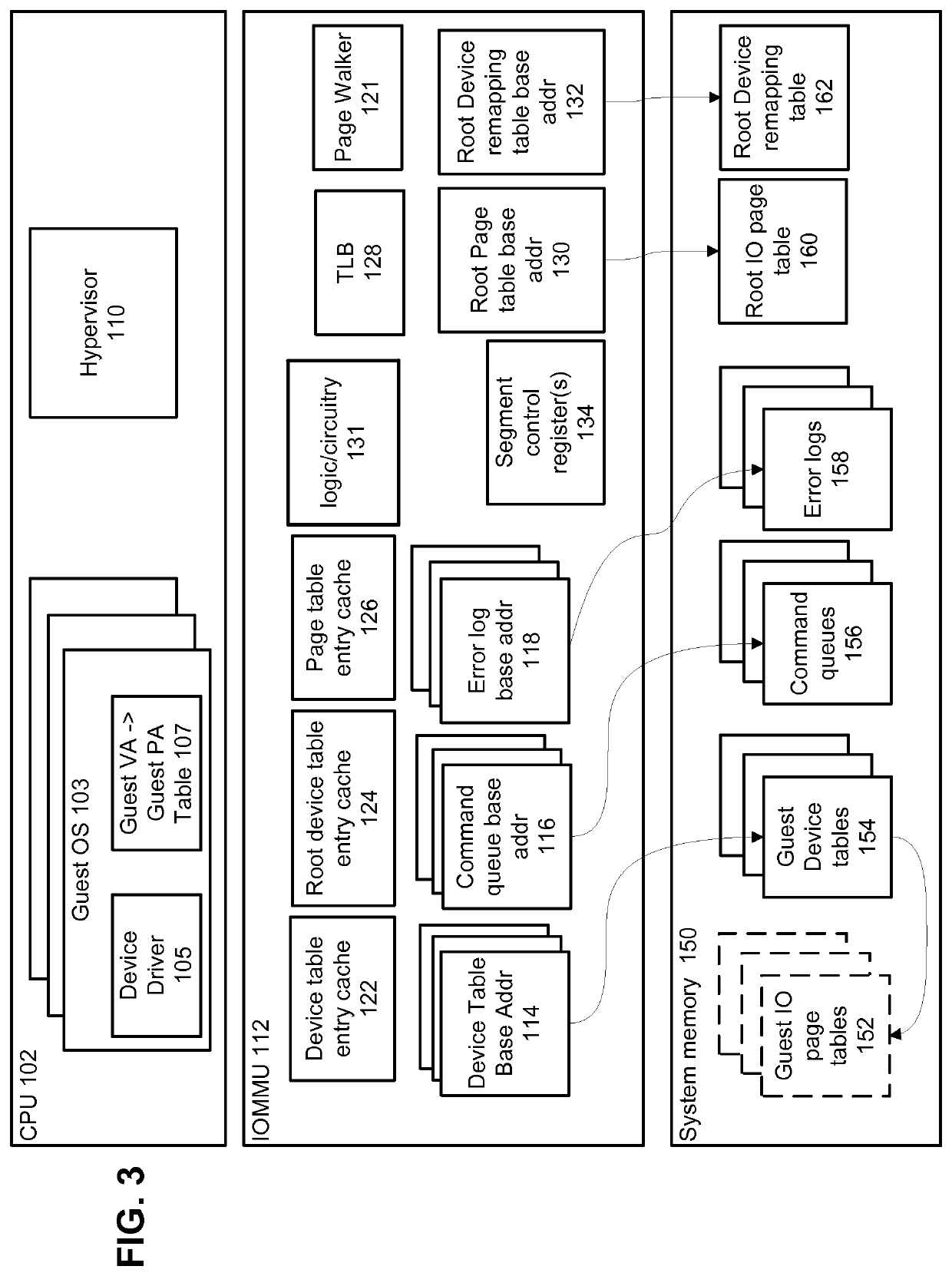
ActiveUS10642501B1Improve performanceIncreased complexityMemory architecture accessing/allocationInput/output to record carriersHardware structureTerm memory
Aspects relate to Input / Output (IO) Memory Management Units (MMUs) that include hardware structures for implementing virtualization. Some implementations allow guests to setup and maintain device IO tables within memory regions to which those guests have been given permissions by a hypervisor. Some implementations provide hardware page table walking capability within the IOMMU, while other implementations provide static tables. Such static tables may be maintained by a hypervisor on behalf of guests. Some implementations reduce a frequency of interrupts or invocation of hypervisor by allowing transactions to be setup by guests without hypervisor involvement within their assigned device IO regions. Devices may communicate with IOMMU to setup the requested memory transaction, and completion thereof may be signaled to the guest without hypervisor involvement. Various other aspects will be evident from the disclosure.
Owner:MIPS TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com