Patents
Literature
1275 results about "Host processor" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Host processor. [′hōst ¦prä‚ses·ər] (computer science) The central computer in a hierarchical distributed processing system, which is typically located at some central site where it serves as a focal point for the collection of data, and often for the provision of services which cannot economically be distributed.
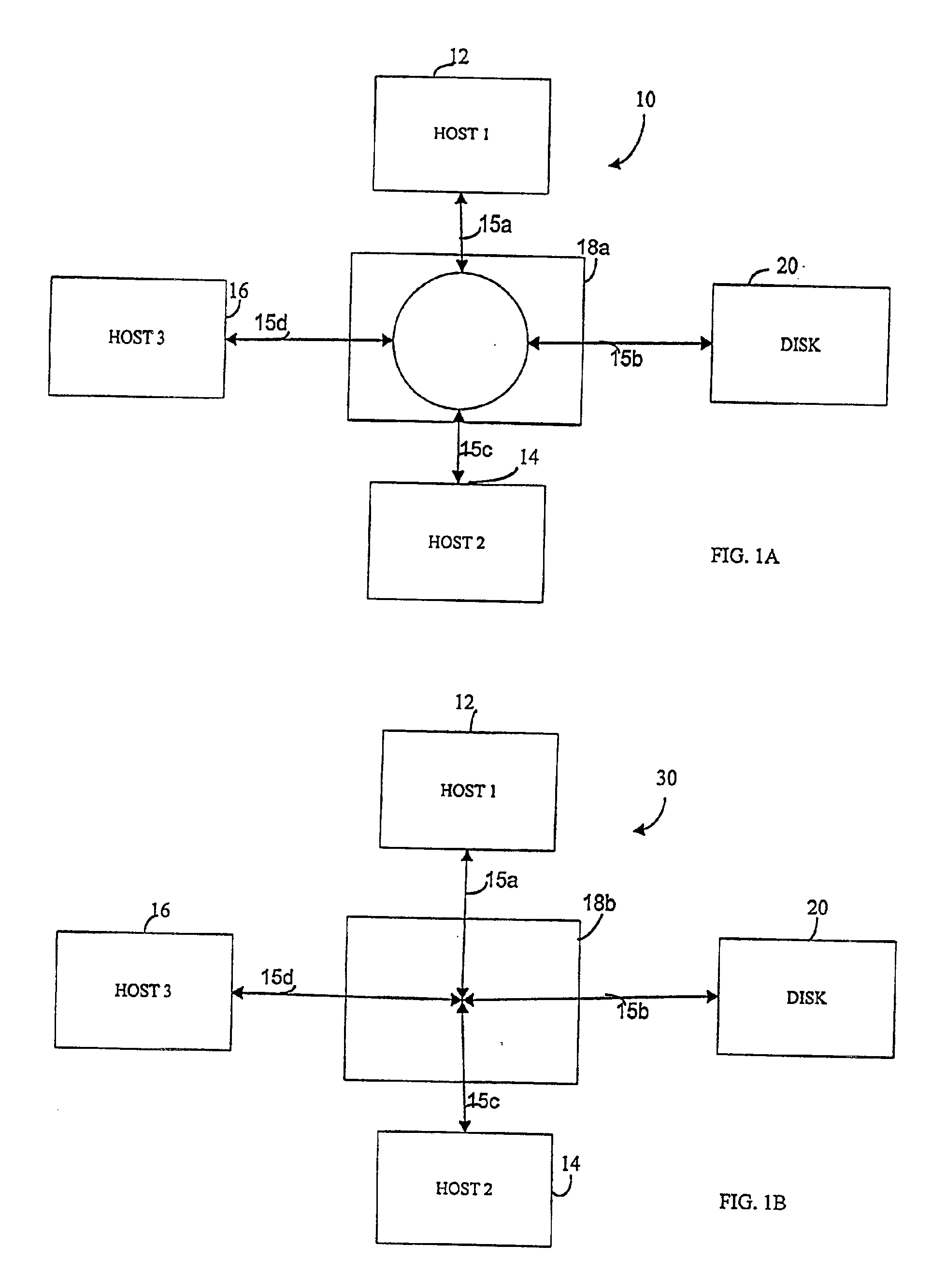
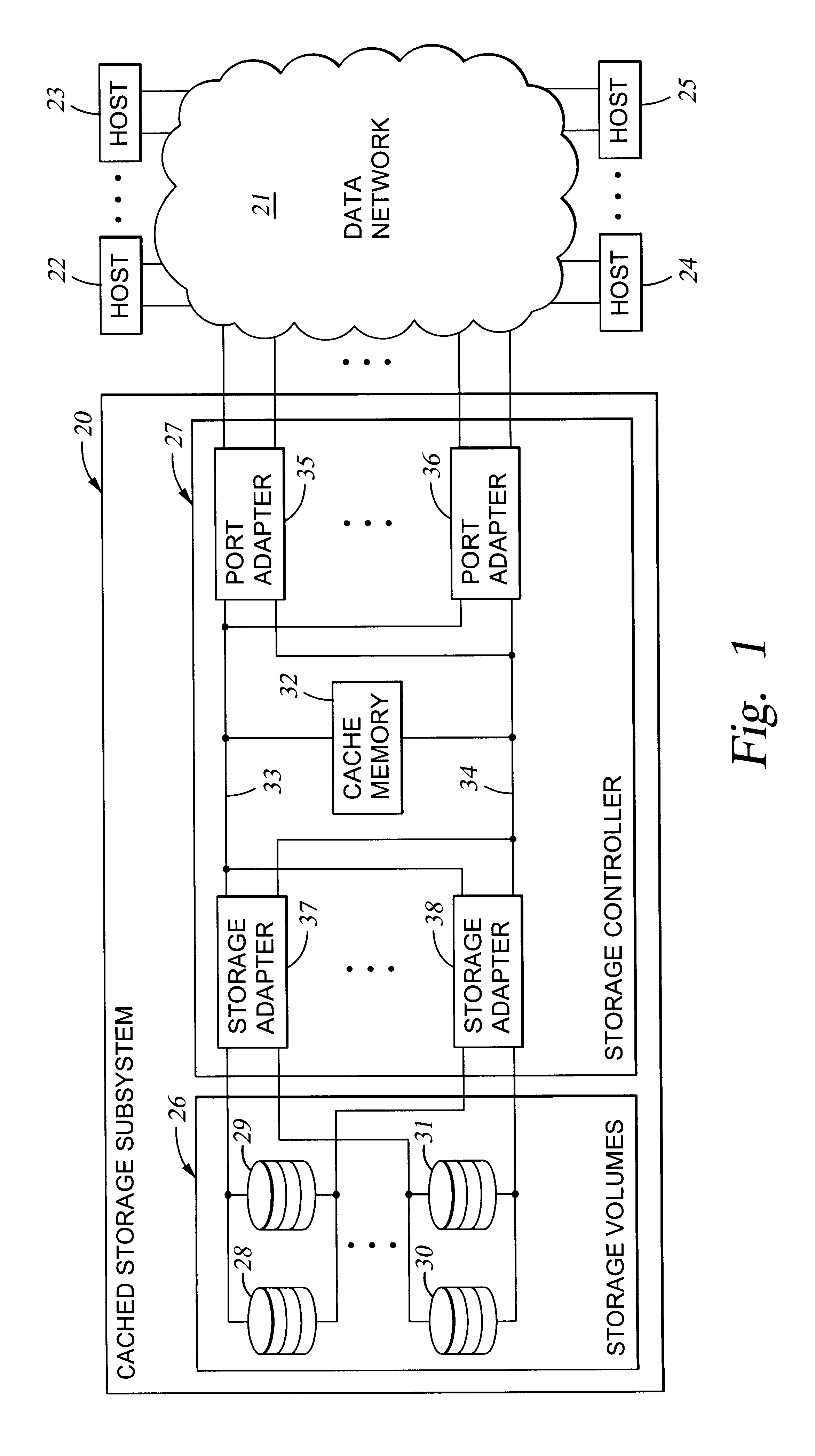
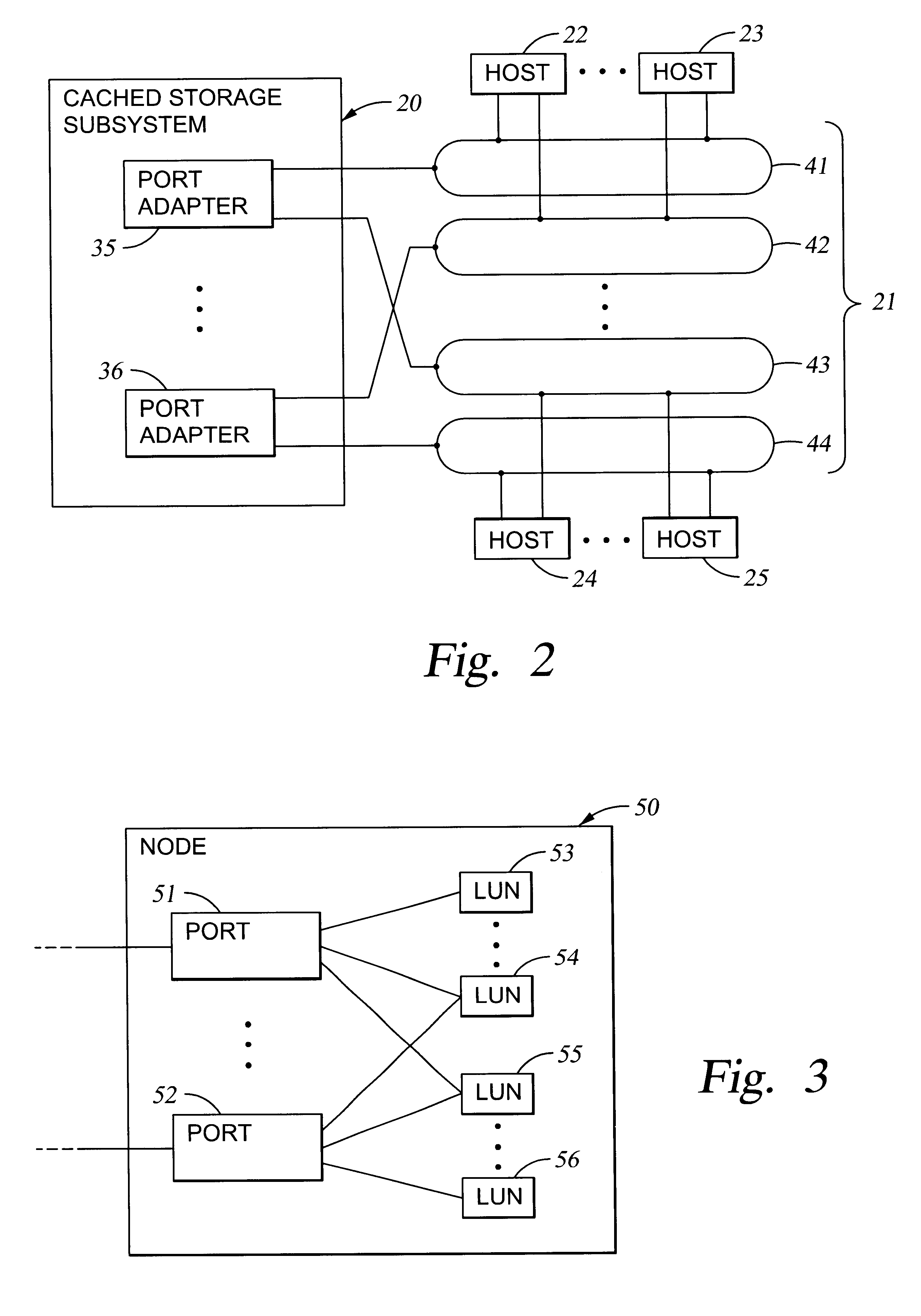
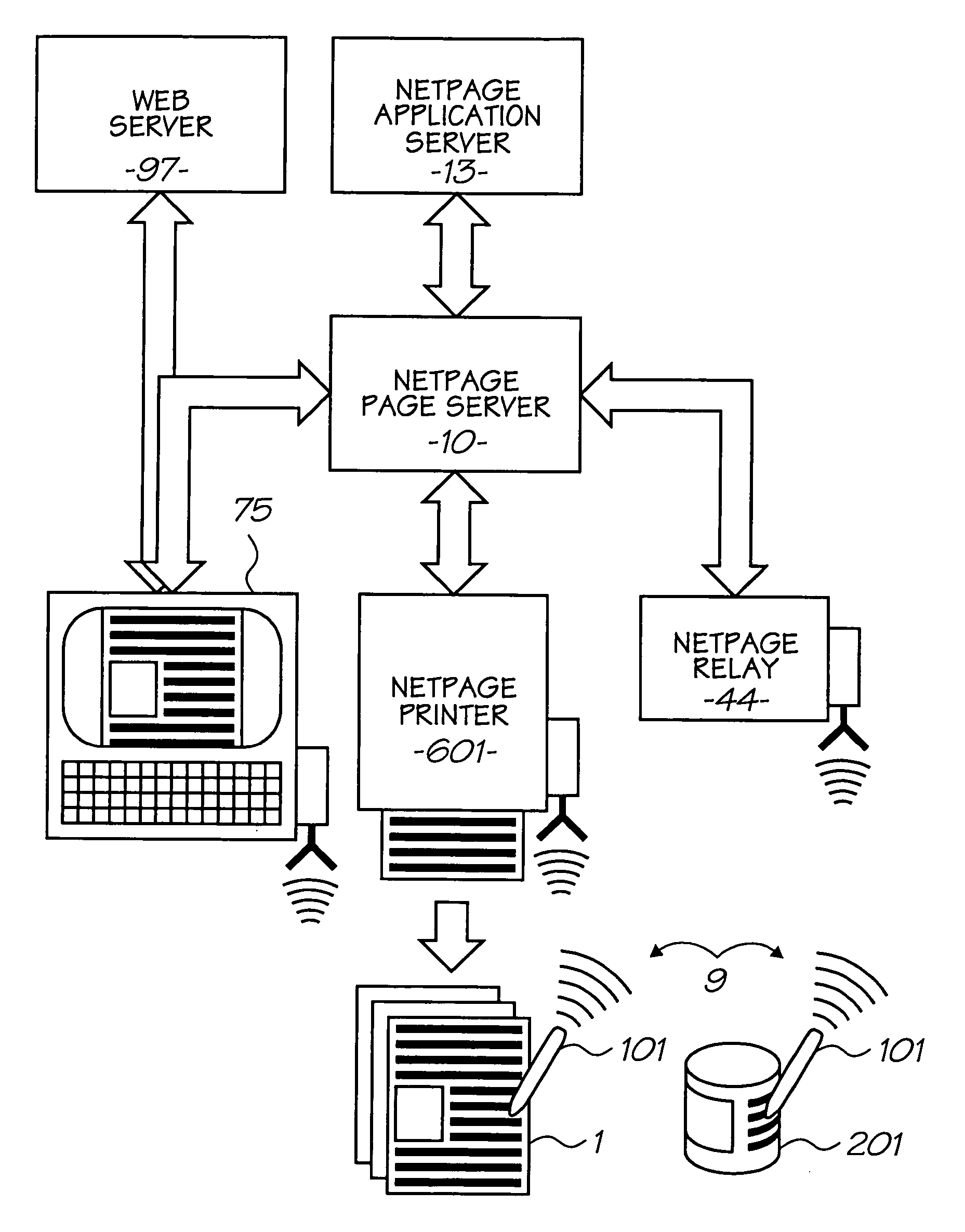
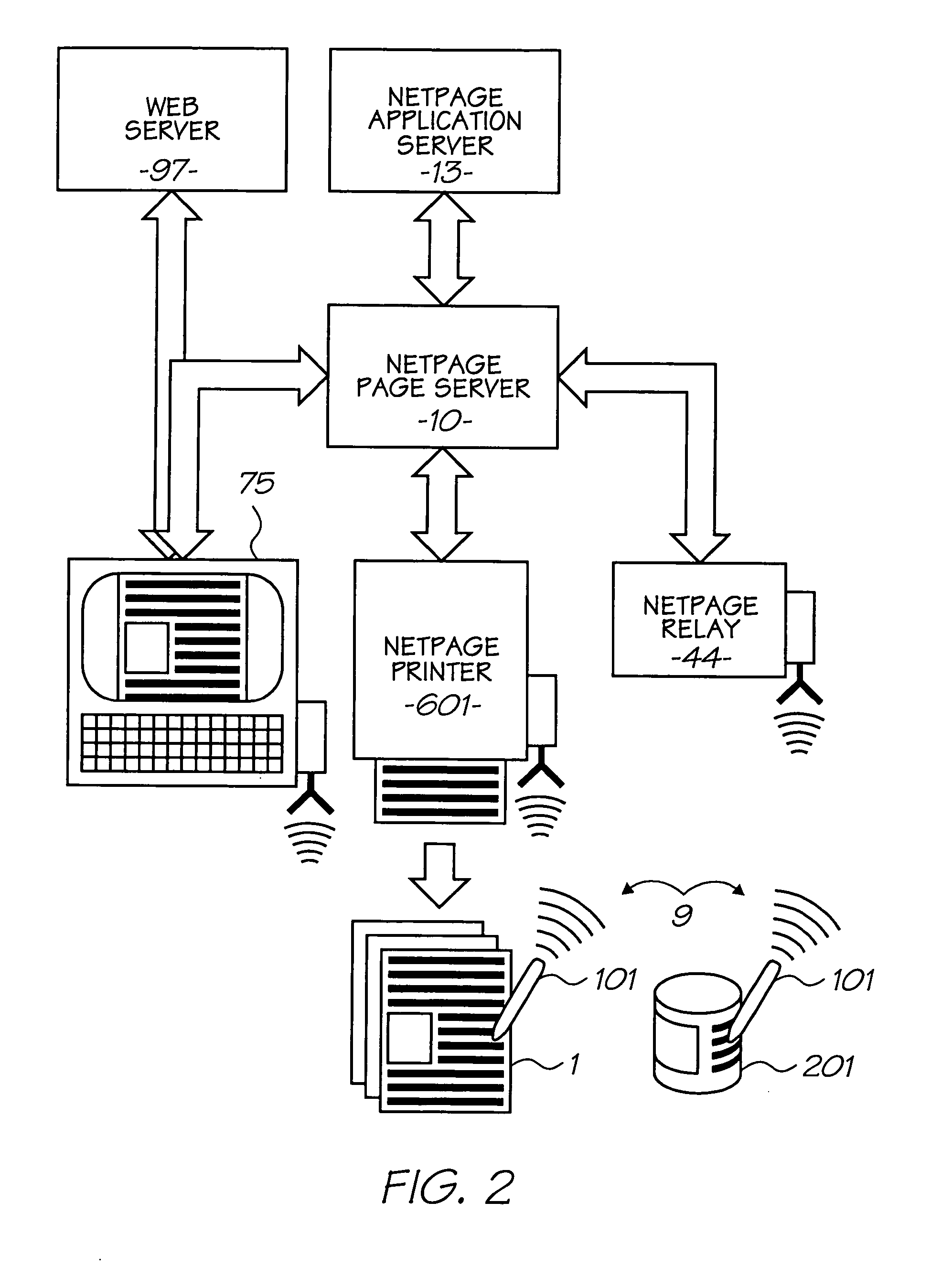
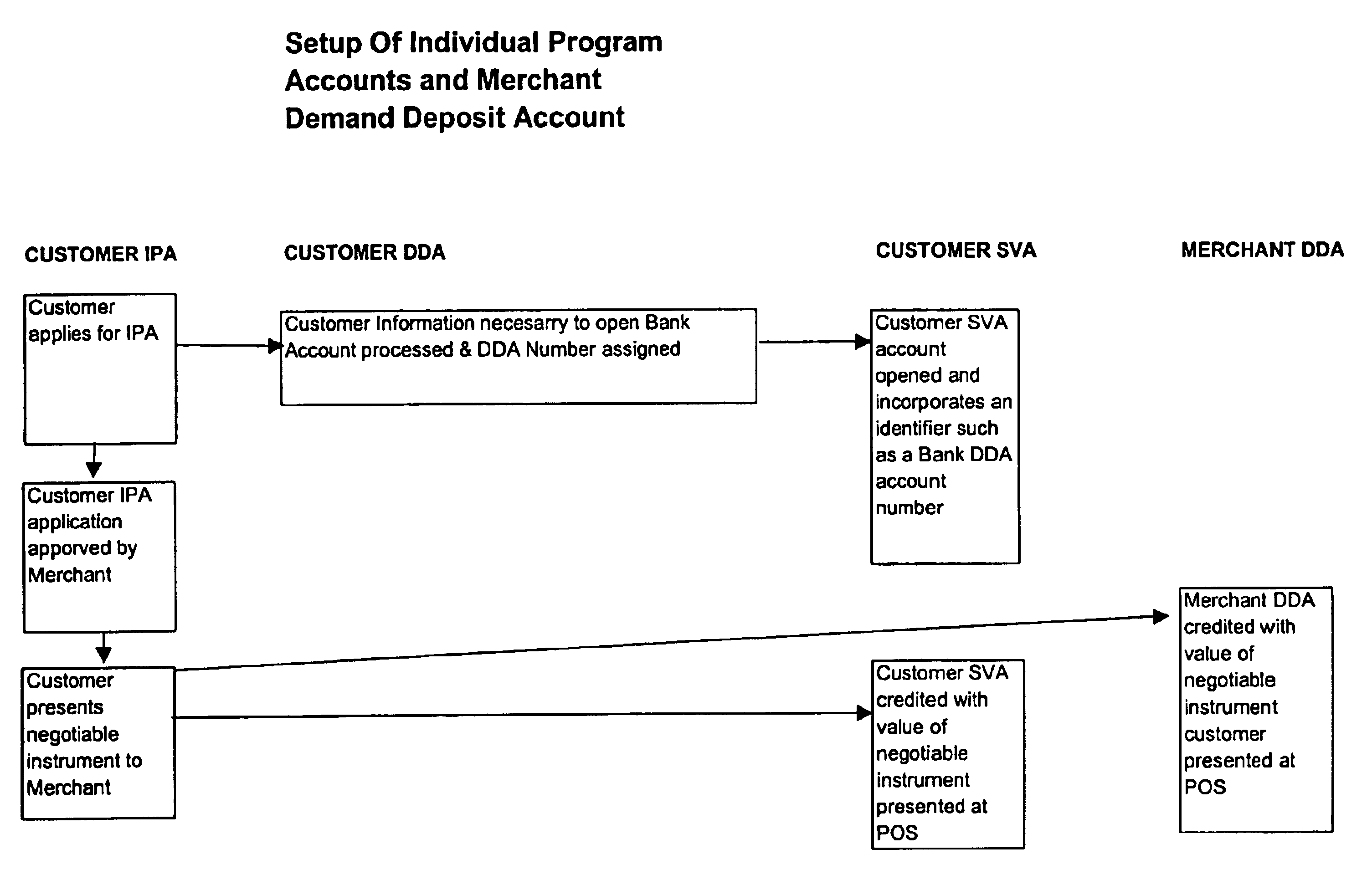
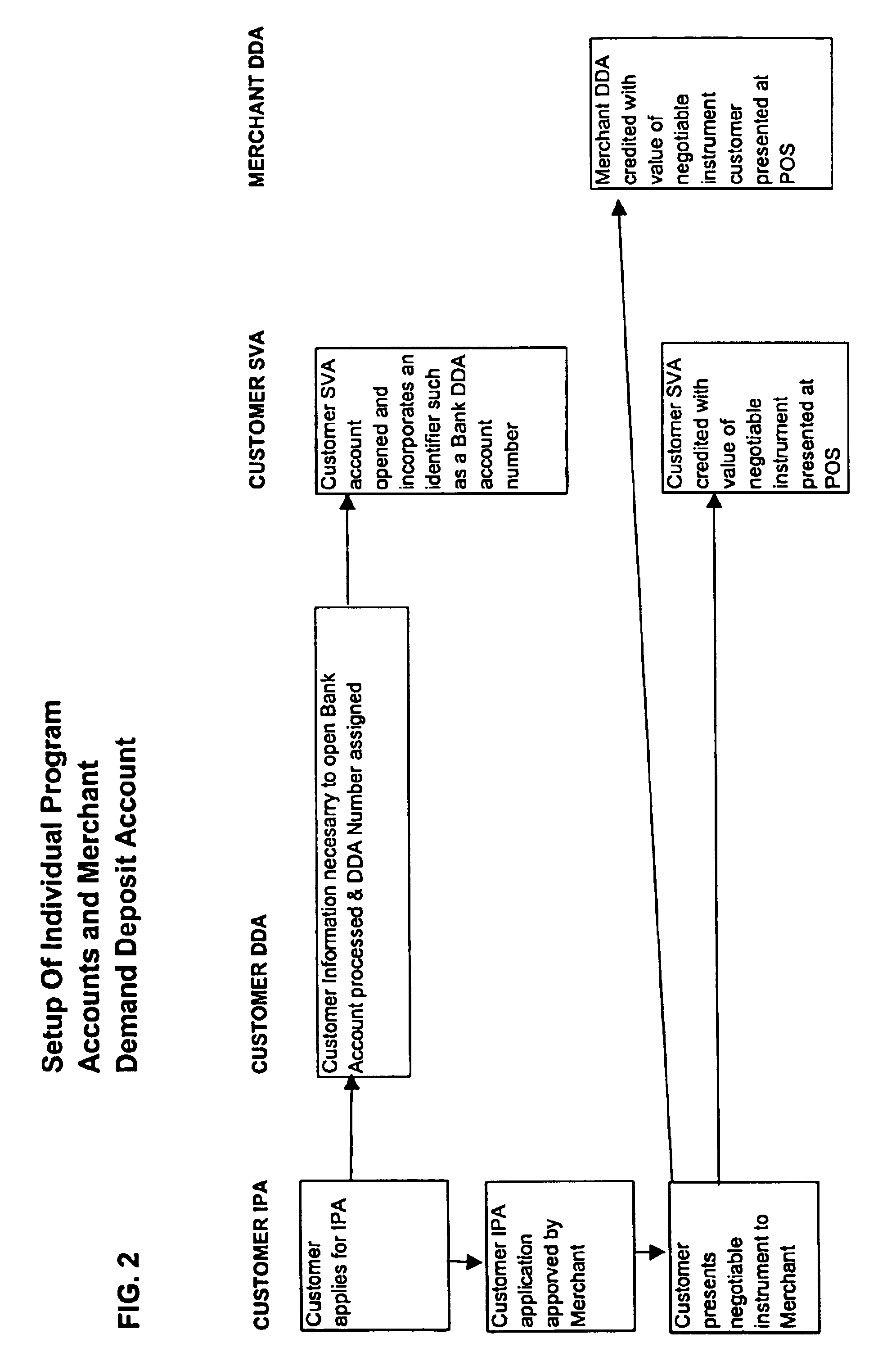
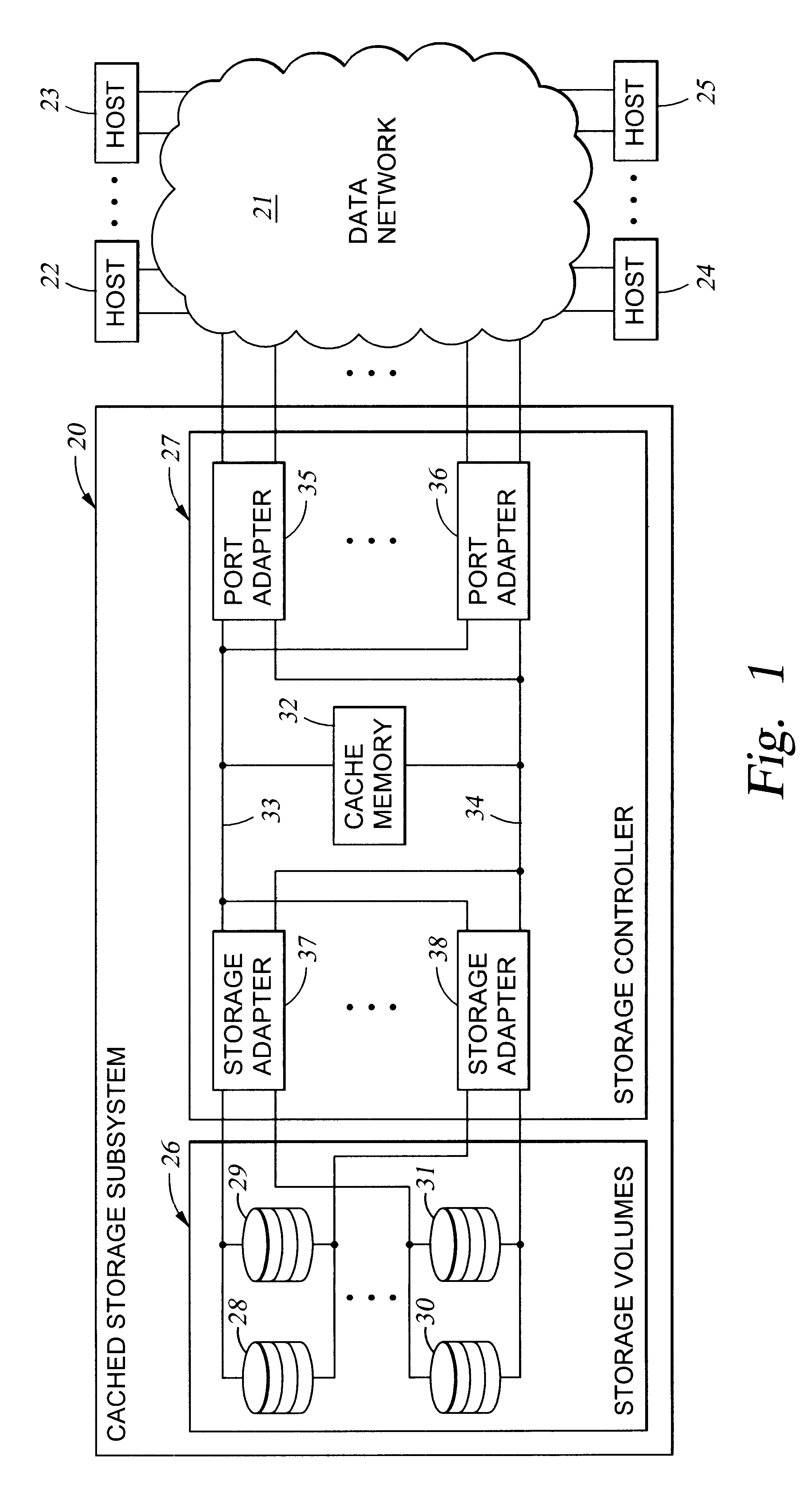
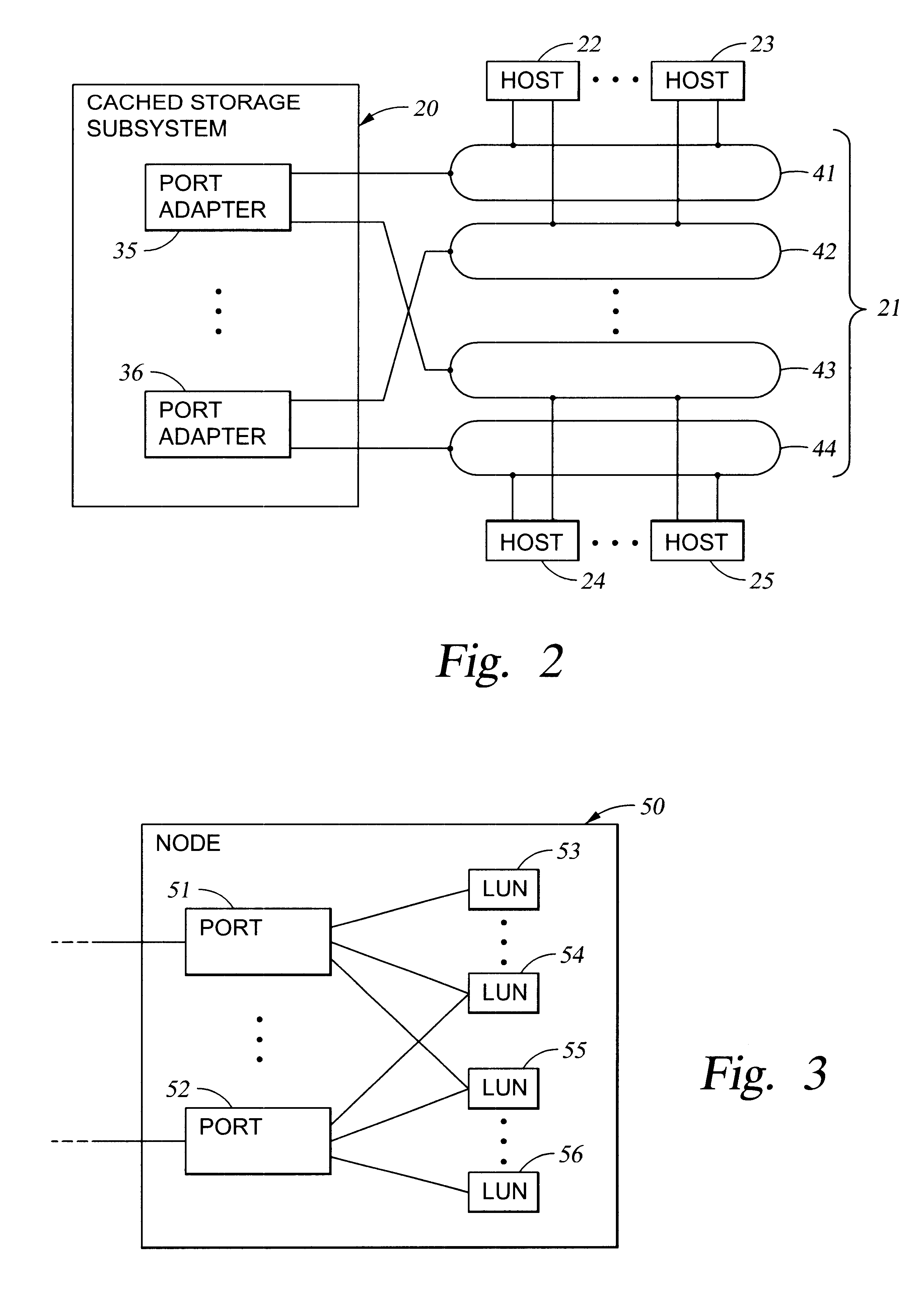
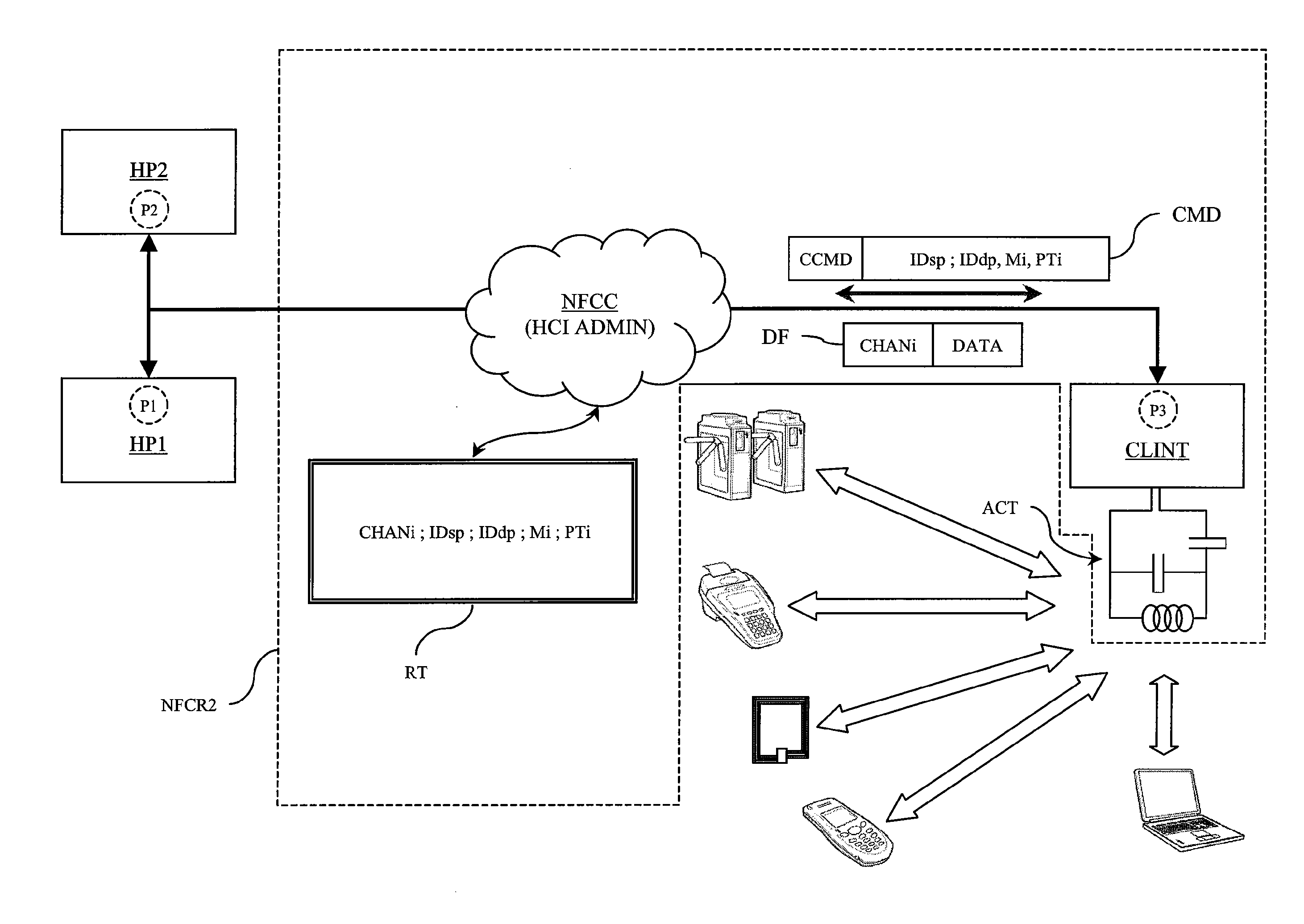
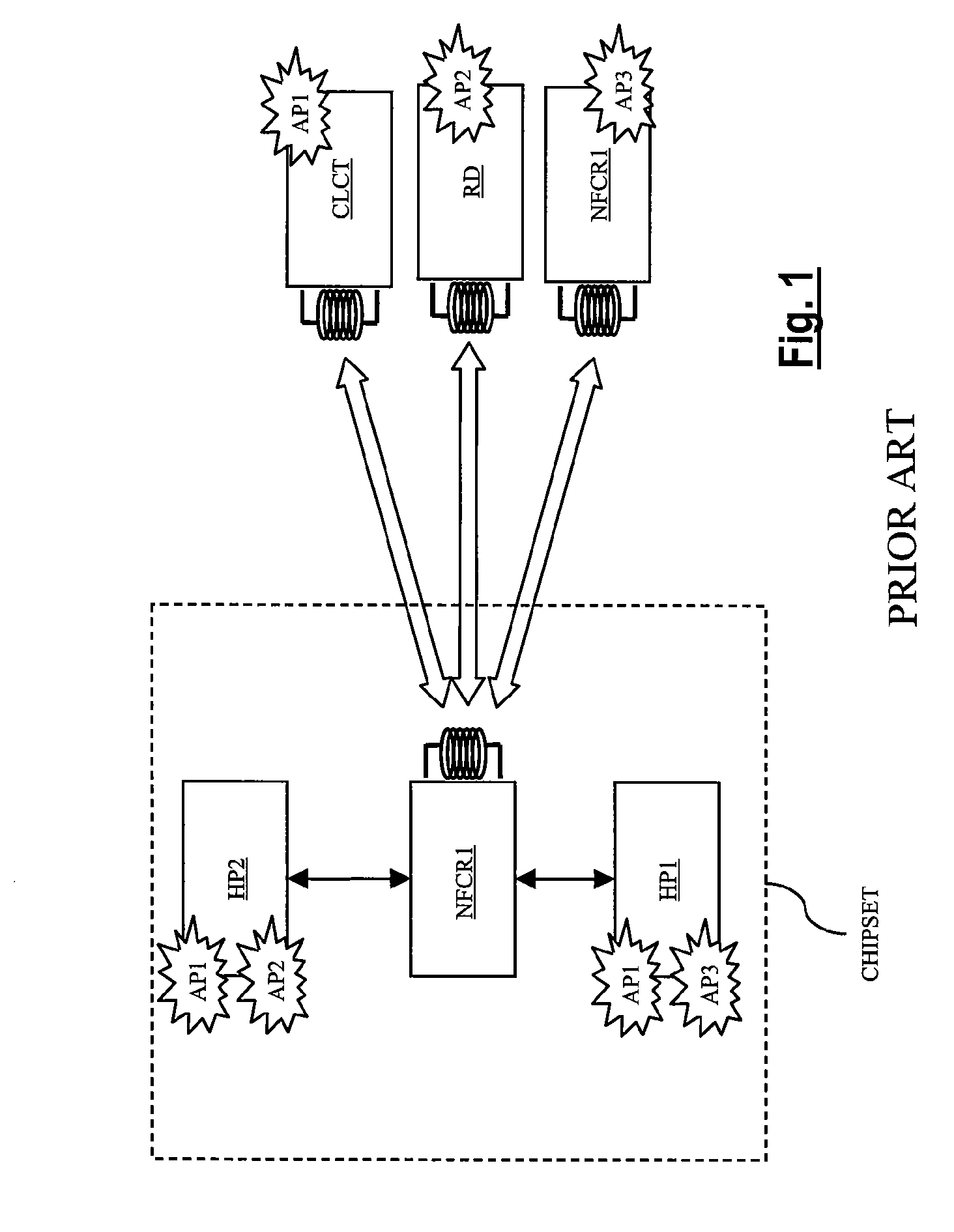
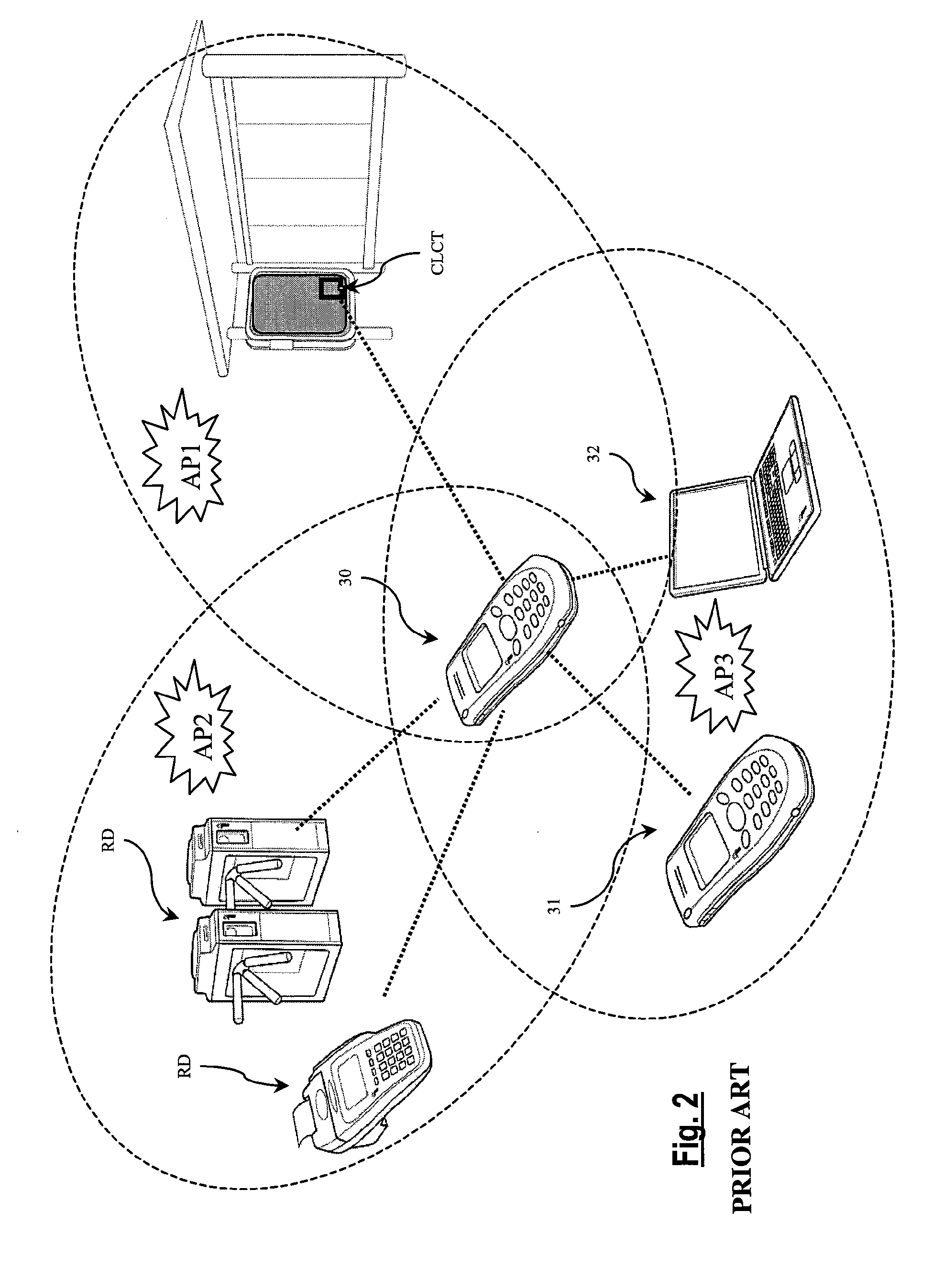
Virtual ports for data transferring of a data storage system
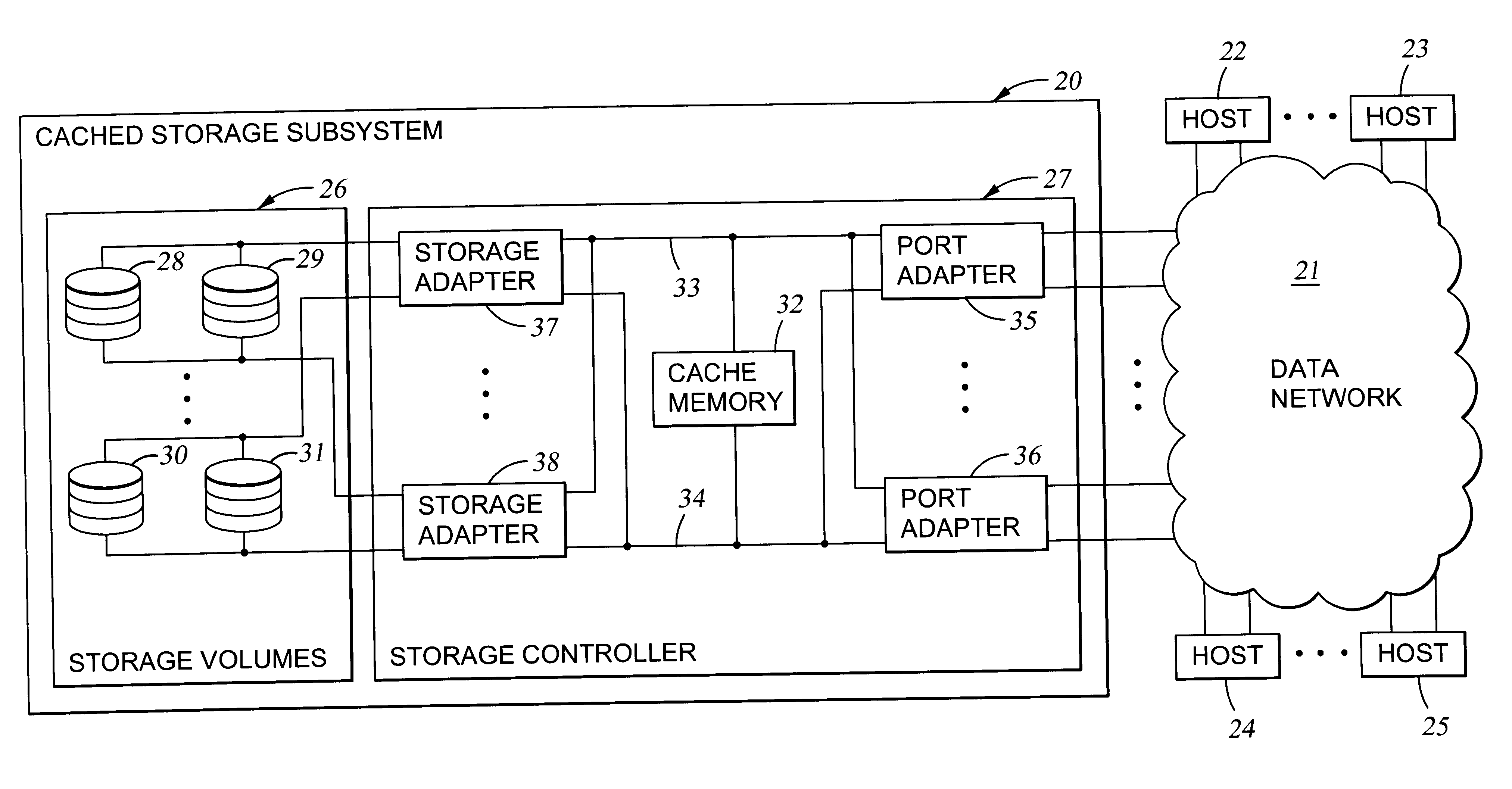
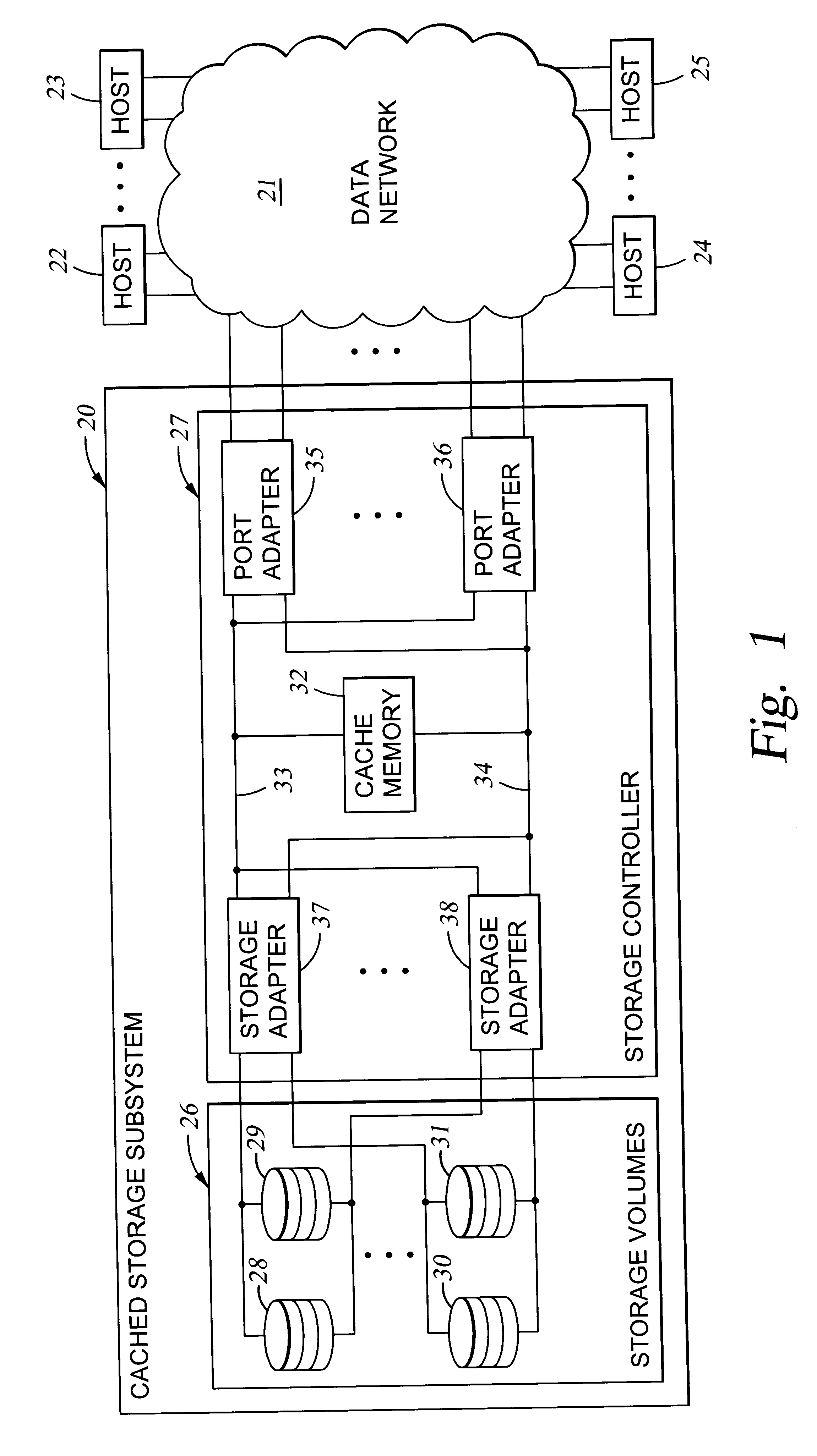
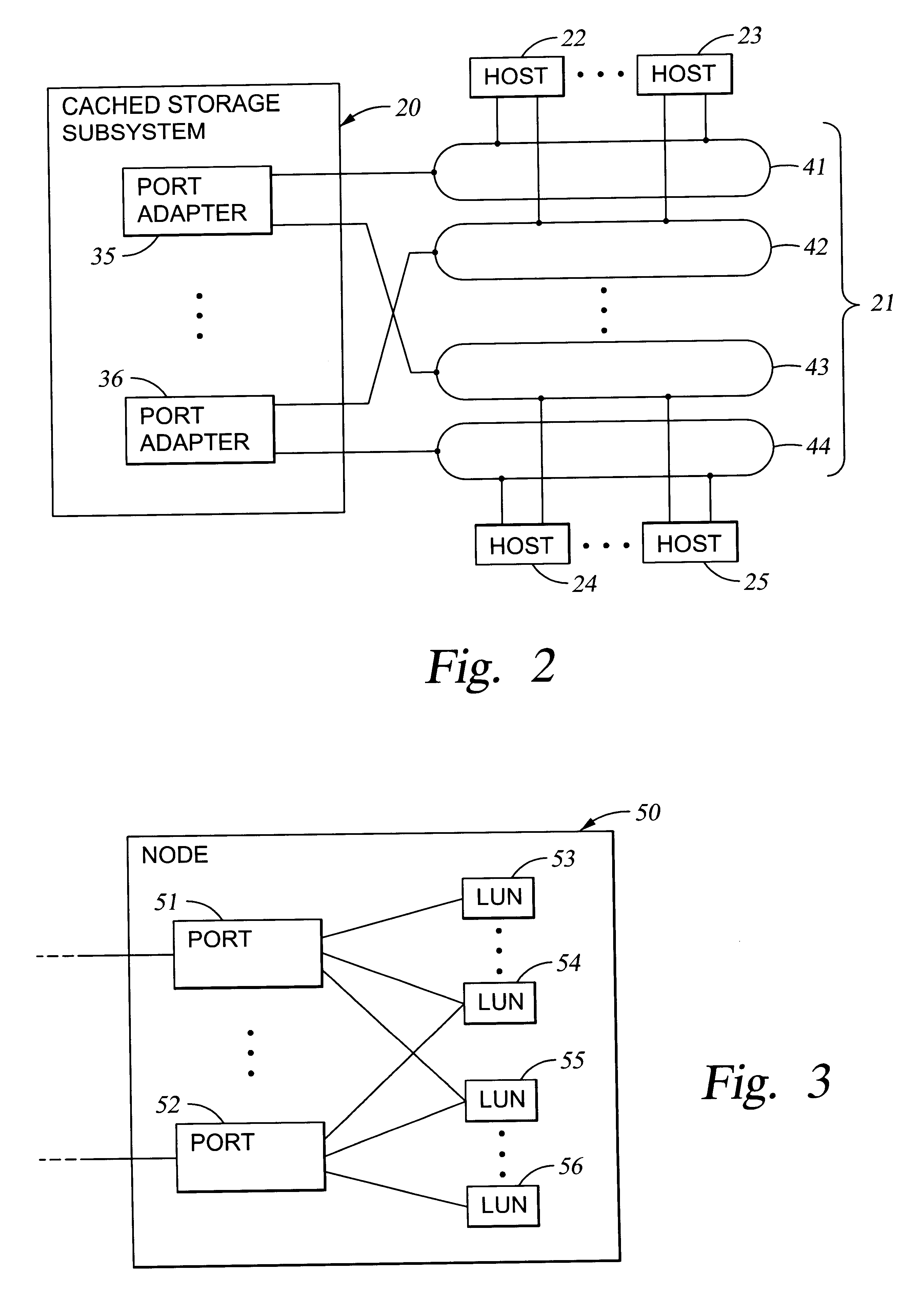
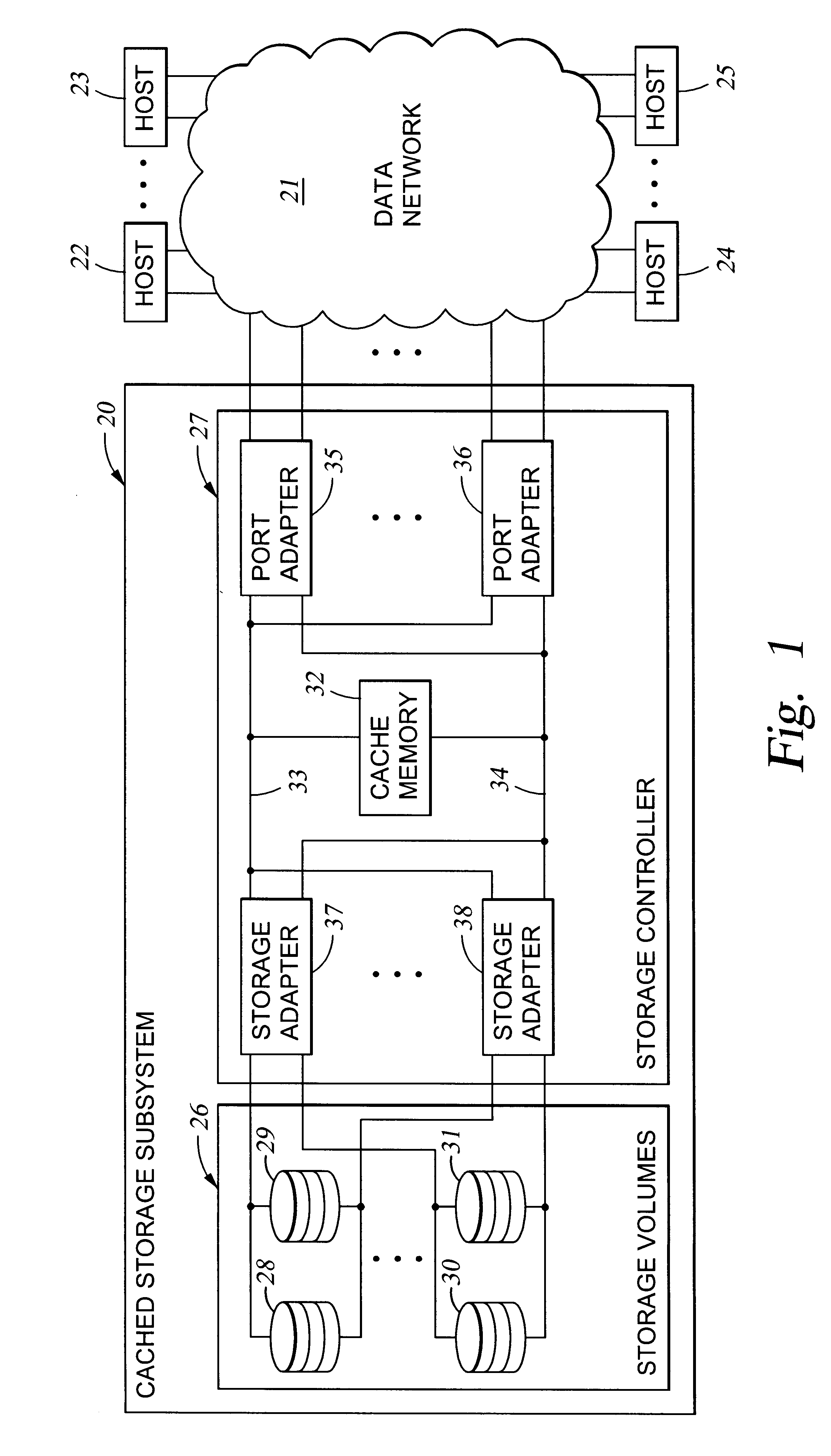
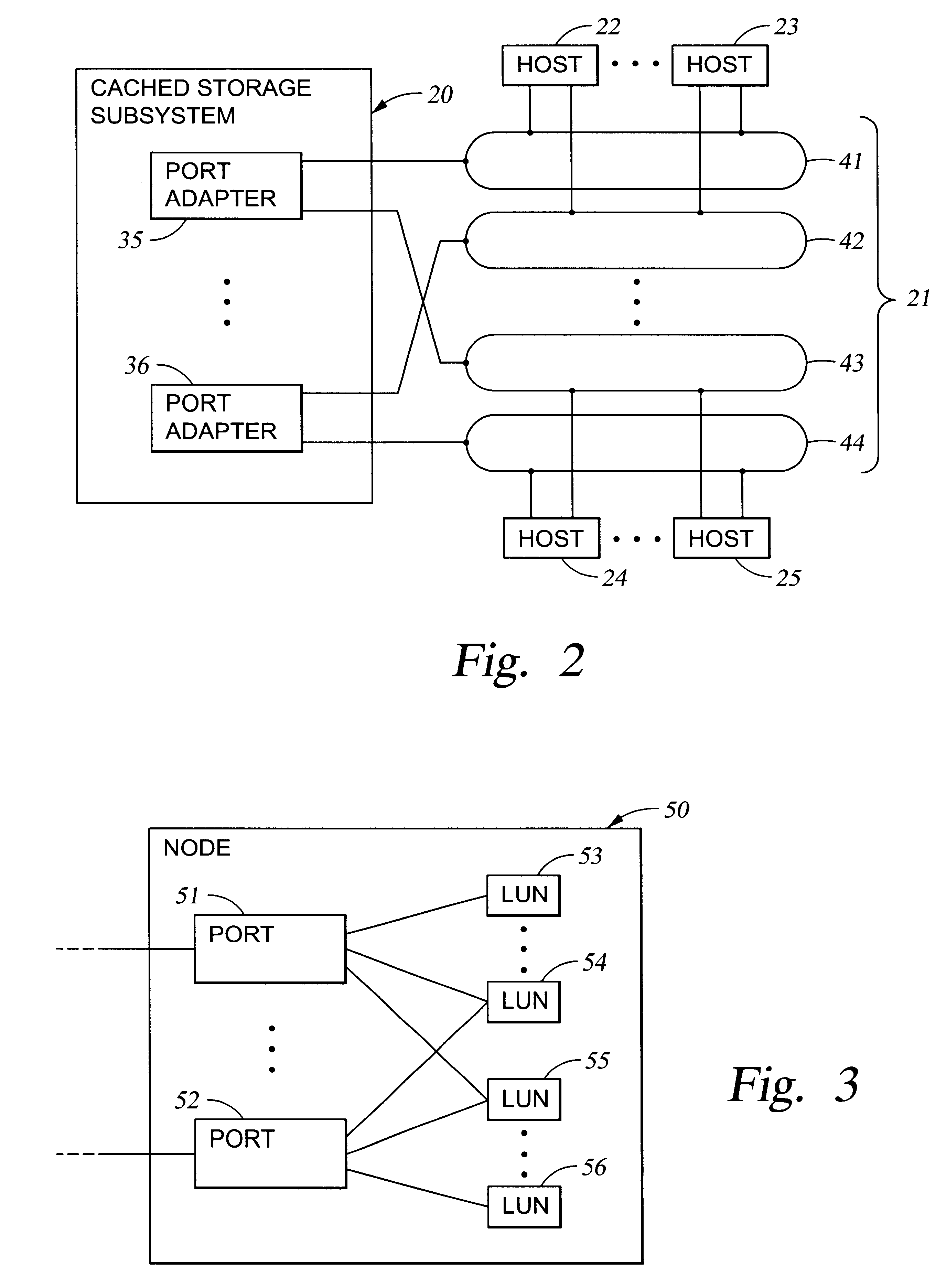
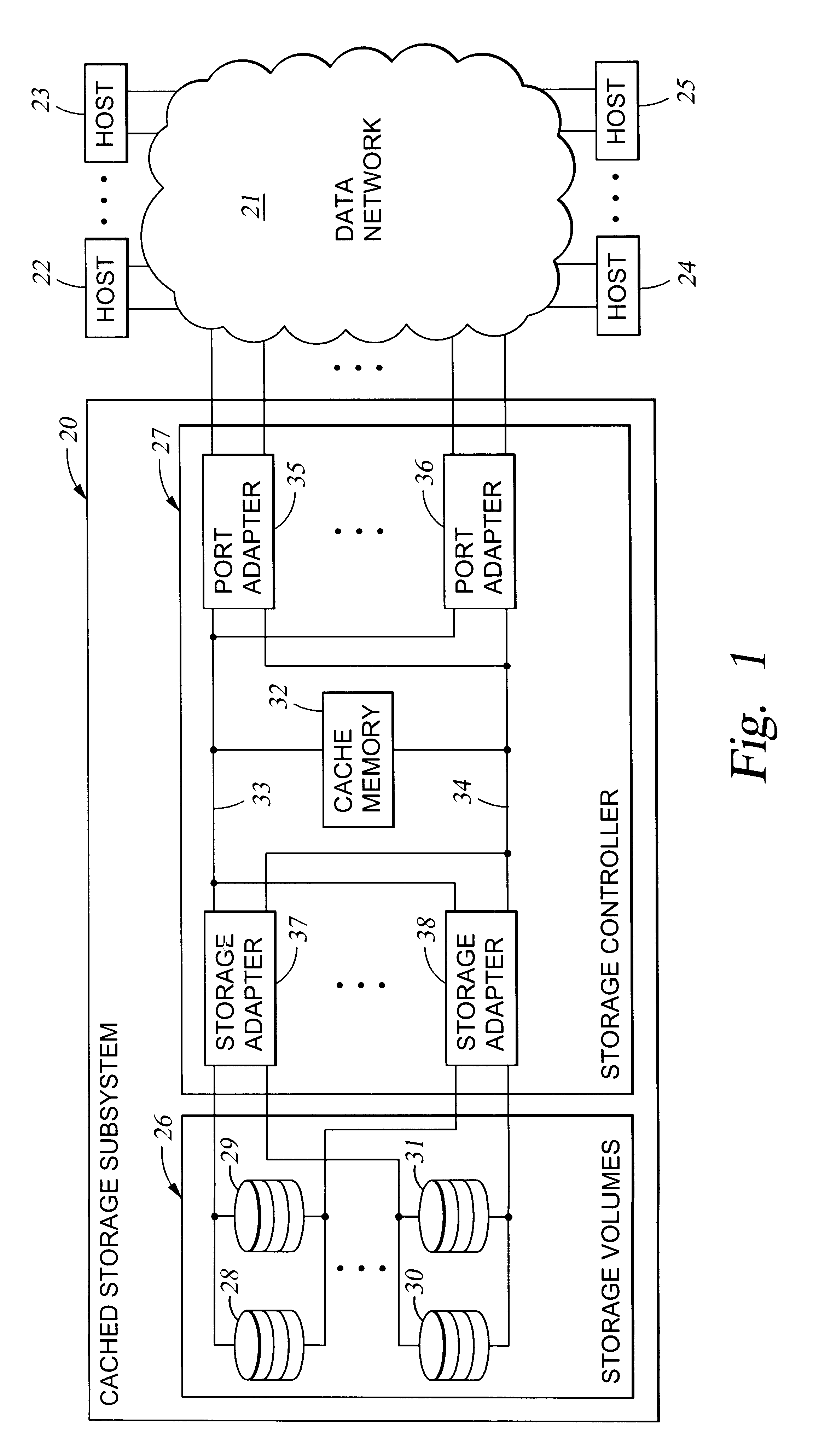
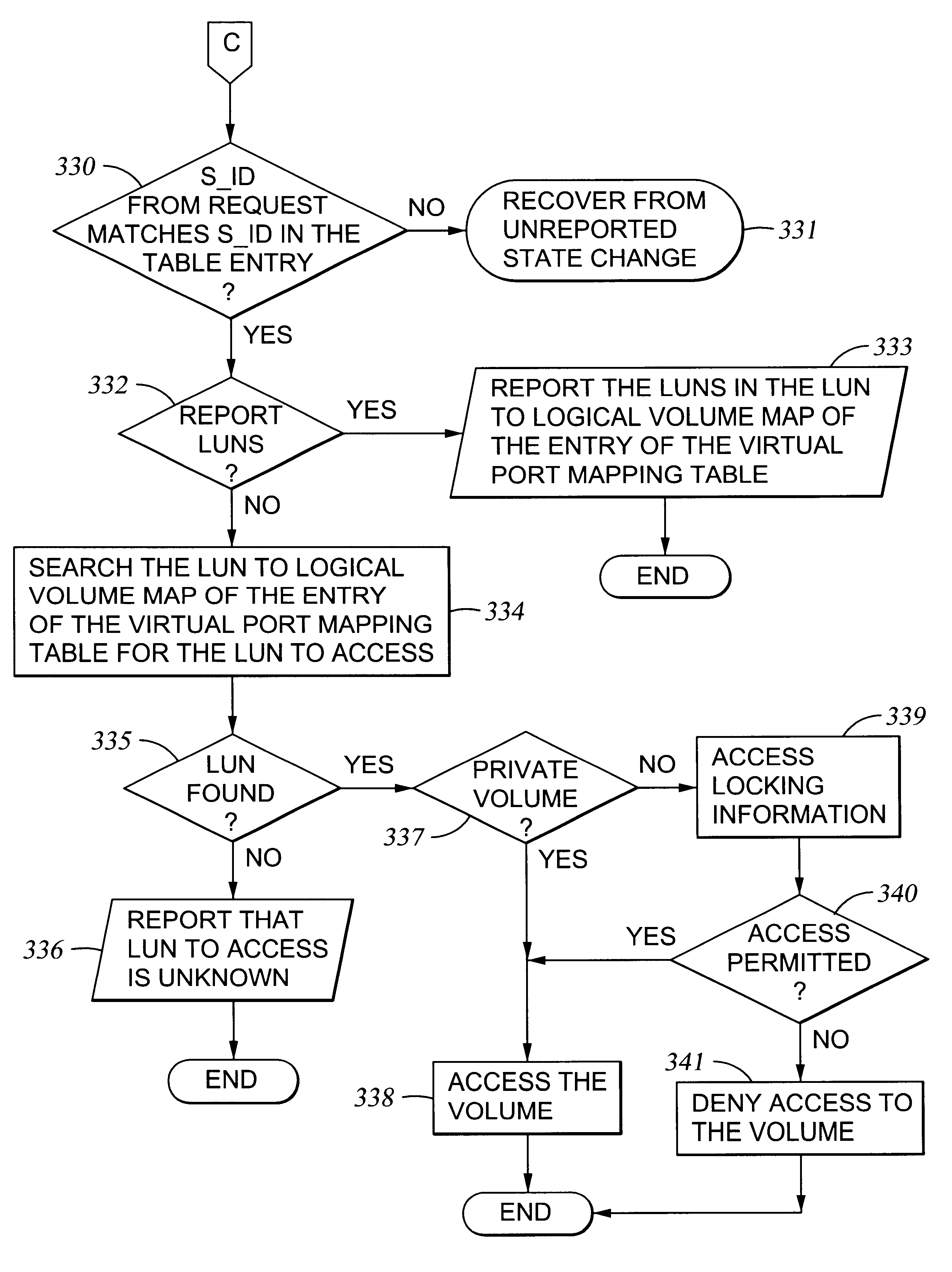
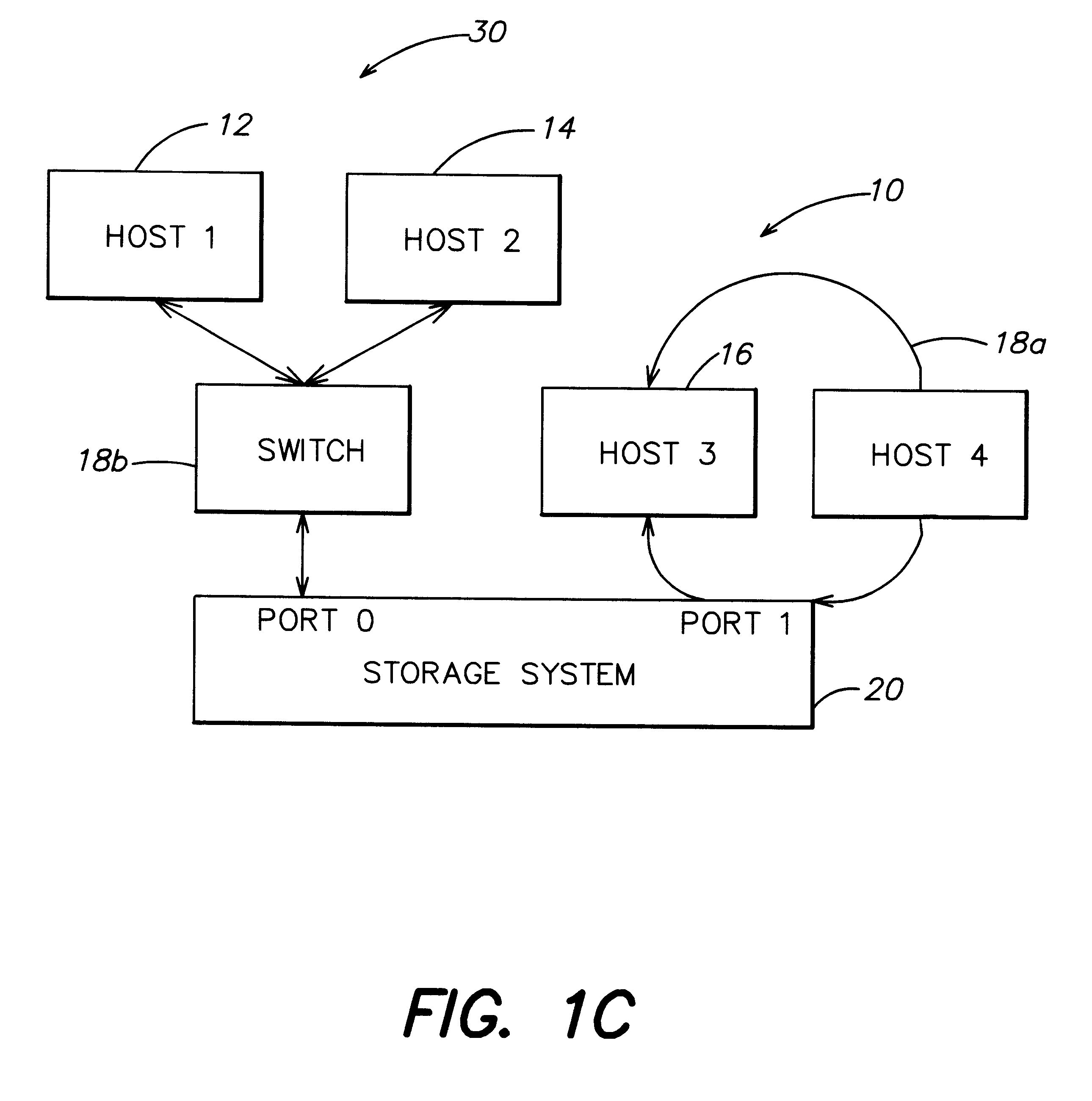
A storage controller has at least one physical data port for a data network including host processors. The storage controller is programmed to provide a plurality of virtual ports for access to storage, and a virtual switch for routing storage access requests from the physical port to the virtual ports. The virtual ports and the virtual switch are defined by software. The virtual ports appear to the hosts as physical ports in the data network. For example, in a Fiber-Channel network, the virtual ports have World Wide Names (WWNs) and are assigned temporary addresses (S_Ds), and the virtual switch provides a name server identifying the WWNs and S_IDs of the virtual ports. For convenient partitioning of storage among host processors, one or more virtual ports are assigned to each host, and a set of storage volumes are made accessible from each virtual port. A host can access storage at a virtual port only if the virtual port has been assigned to the host. Preferably, storage can be accessed through each virtual port by no more than one assigned host, although a shared volume may be accessible from more than one virtual port. The storage controller may provide a service for reporting to a host the virtual ports through which the host can access storage, and the storage volumes that are accessible to the host through each of the virtual ports.
Owner:EMC IP HLDG CO LLC
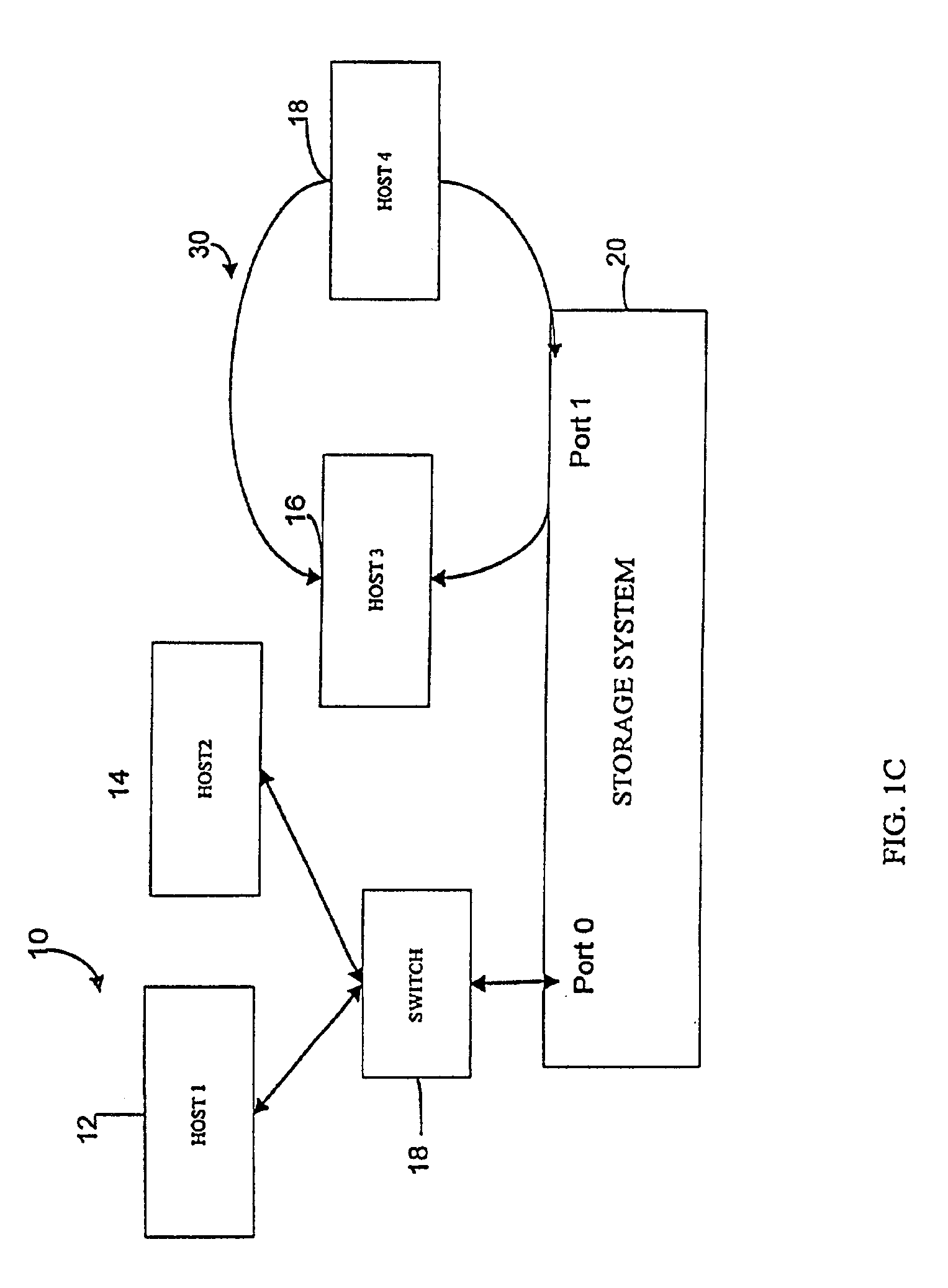
Storage mapping and partitioning among multiple host processors in the presence of login state changes and host controller replacement
InactiveUS6260120B1Input/output to record carriersData processing applicationsData portControl store
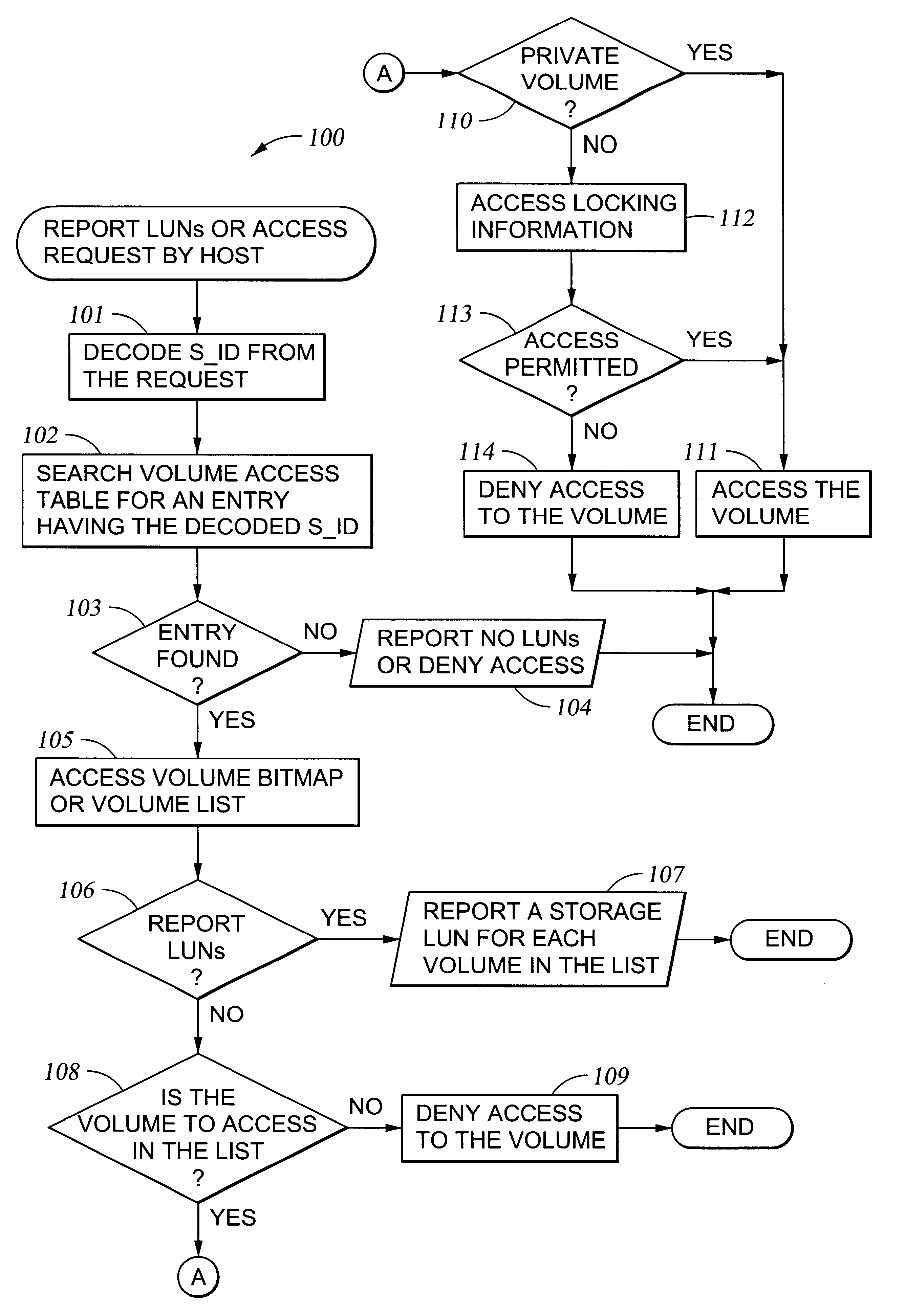
A storage controller for controling access to data storage has a memory and at least one data port for a data network including host processors. The memory is programmed to define a respective specification for each host processor of a respective subset of the data storage to which access by the host processor is restricted, and each specification is associated with a host identifier stored in the memory. When the storage controller receives a data access request from a host processor, it decodes a host identifier from the data access request, and searches the memory for a host identifier matching the host identifier decoded from the request. Upon finding a match, the respective specification of the respective subset for the host processor is accessed to determine whether or not storage specified by the storage access request is contained in the respective subset. If so, then storage access can continue, and otherwise, storage access is denied. Preferably the host identifier decoded from the request is a temporary address assigned by the network, and also stored in the memory in association with each respective specification is a relatively permanent identifier for the host processor.
Owner:EMC IP HLDG CO LLC
Systems and methods for virtualizing graphics subsystems
ActiveUS20060146057A1Program control using stored programsProcessor architectures/configurationVirtualizationOperational system
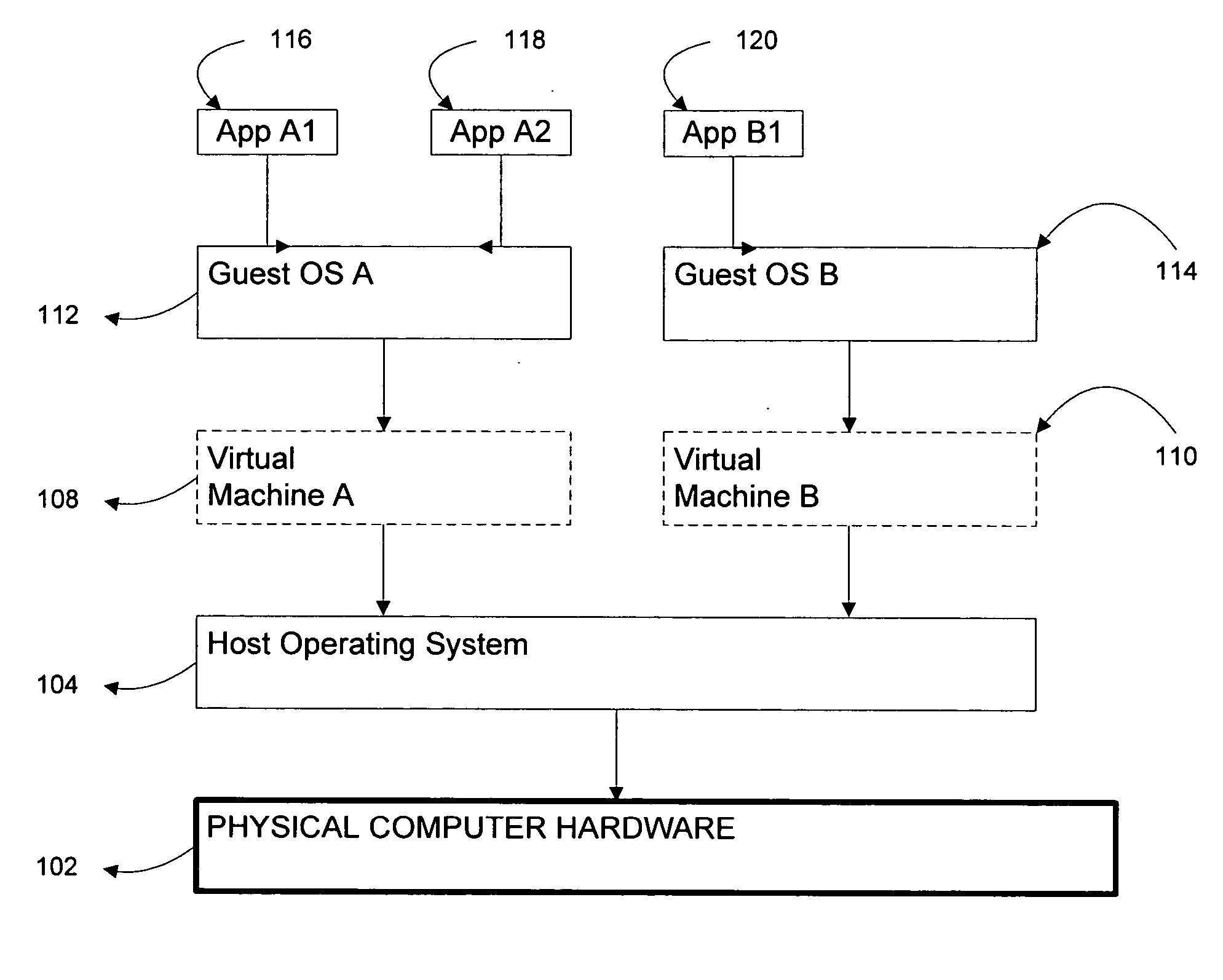
Systems and methods for applying virtual machines to graphics hardware are provided. In various embodiments of the invention, while supervisory code runs on the CPU, the actual graphics work items are run directly on the graphics hardware and the supervisory code is structured as a graphics virtual machine monitor. Application compatibility is retained using virtual machine monitor (VMM) technology to run a first operating system (OS), such as an original OS version, simultaneously with a second OS, such as a new version OS, in separate virtual machines (VMs). VMM technology applied to host processors is extended to graphics processing units (GPUs) to allow hardware access to graphics accelerators, ensuring that legacy applications operate at full performance. The invention also provides methods to make the user experience cosmetically seamless while running multiple applications in different VMs. In other aspects of the invention, by employing VMM technology, the virtualized graphics architecture of the invention is extended to provide trusted services and content protection.
Owner:MICROSOFT TECH LICENSING LLC
Secure NFC data authentication
ActiveUS20140256251A1Near-field systems using receiversPayment architectureTransceiverWireless transceiver
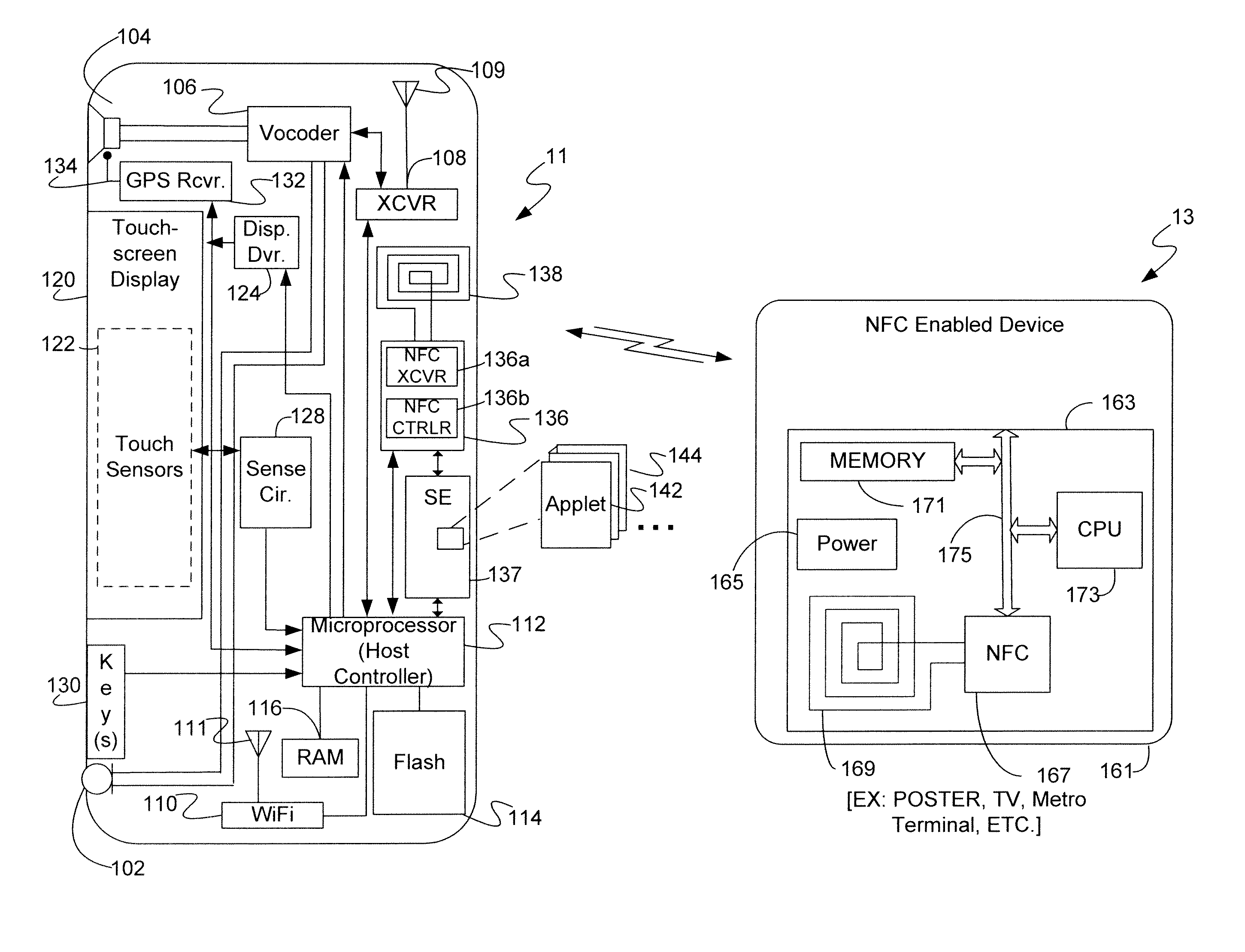
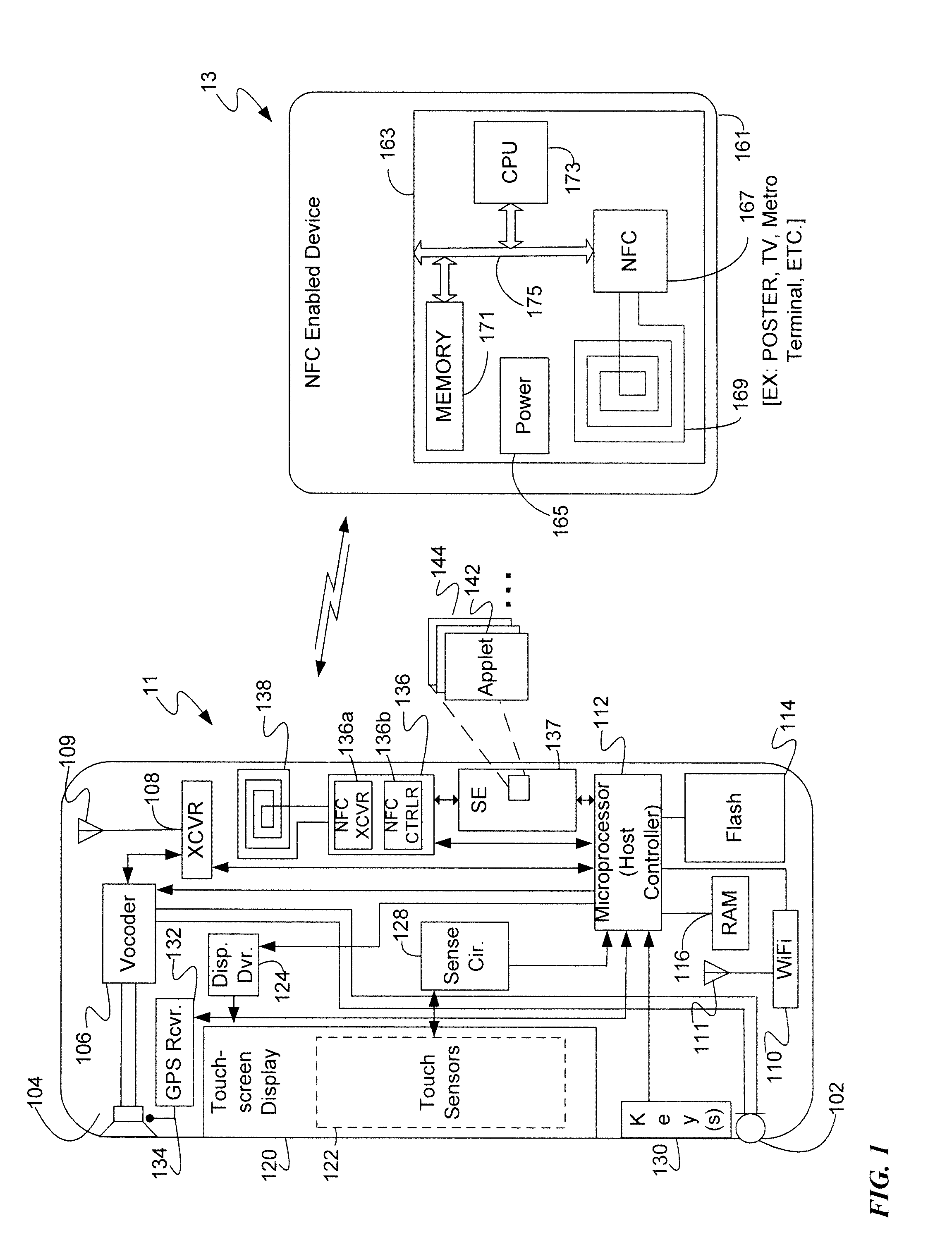
A mobile device includes a wireless transceiver, a host processor, a secure element (SE), and a near field communication (NFC) system having an NFC transceiver and an NFC controller implementing a contactless front end. The contactless front end routes a near field communication related to a payment transaction between the NFC system and the SE without going to or from the host processor. The contactless front end routes a near field communication not related to a payment transaction, but requiring a security function, between the NFC system and the SE without going to or from the host processor. The contactless front end routes a near field communication not related to a payment transaction, and not requiring a security function, between the NFC system and host processor without going to or from the SE.
Owner:CELLCO PARTNERSHIP INC
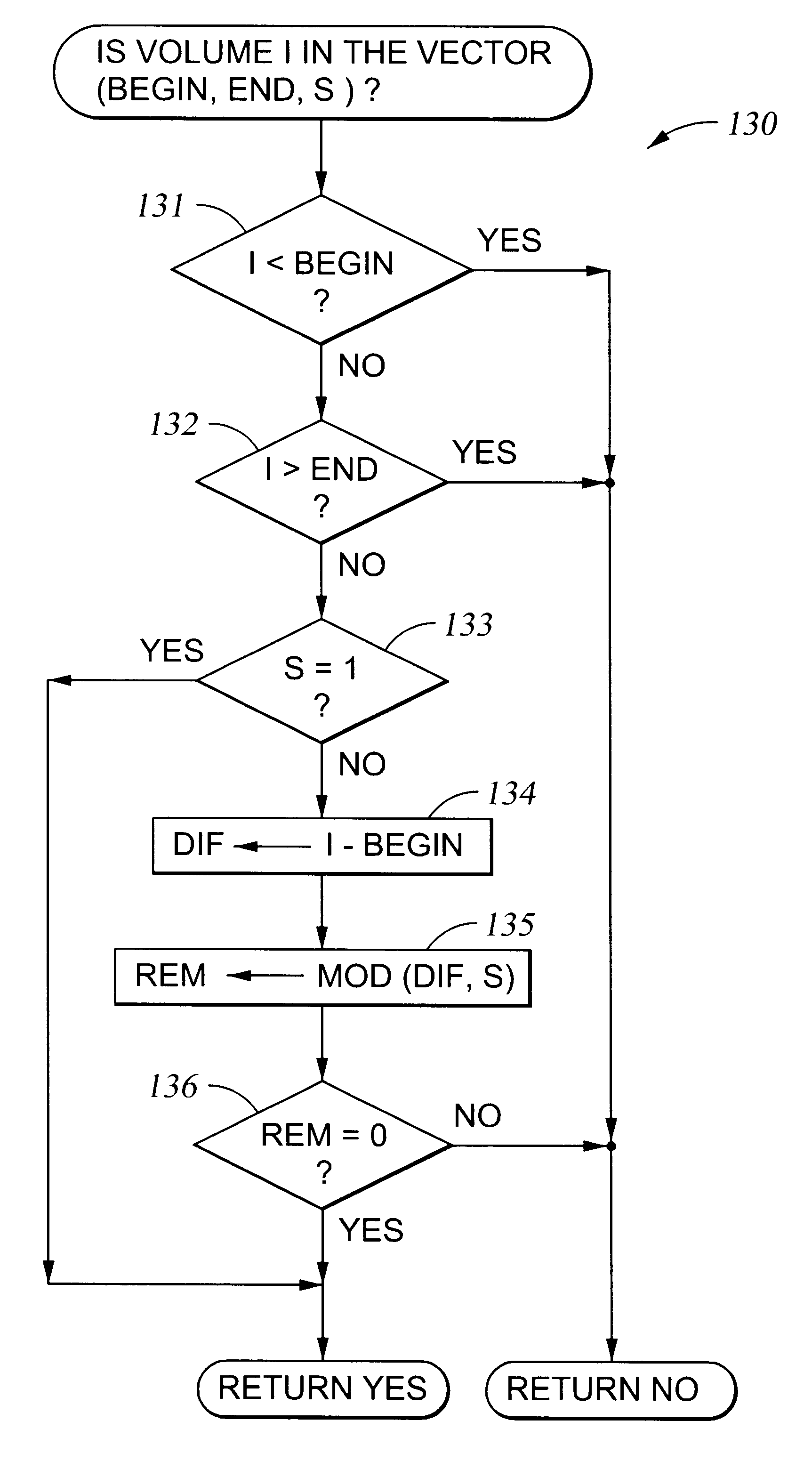
Configuring vectors of logical storage units for data storage partitioning and sharing
InactiveUS6295575B1Input/output to record carriersMemory adressing/allocation/relocationTheoretical computer scienceData store
In a data storage subsystem providing data storage to host processors, a process of configuration defines a subset of the data storage that each host may access. A vector specification is a convenient mechanism for specifying a set of storage volumes that a host may access. For example, for each host processor, there is stored in memory of the data storage subsystem a list of contiguous ranges or vectors of the storage volumes that the host may access. To determine whether or not a specified logical volume number is included in the vector, a modulus of the stride of the vector is computed from the difference between the address of the specified logical volume and the beginning address of the vector, and the modulus is compared to zero. To provide a mapping between logical unit numbers specified by the host and the logical volumes, a contiguous range of logical unit numbers may also be specified for each contiguous range or vector of storage volumes. The logical volume number is computed from a specified logical unit number by computing a difference between the specified logical unit number and the beginning logical unit number, multiplying the difference by the stride of the vector to produce a product, and adding the product to the beginning address of the vector.
Owner:EMC IP HLDG CO LLC
User interface for managing storage in a storage system coupled to a network
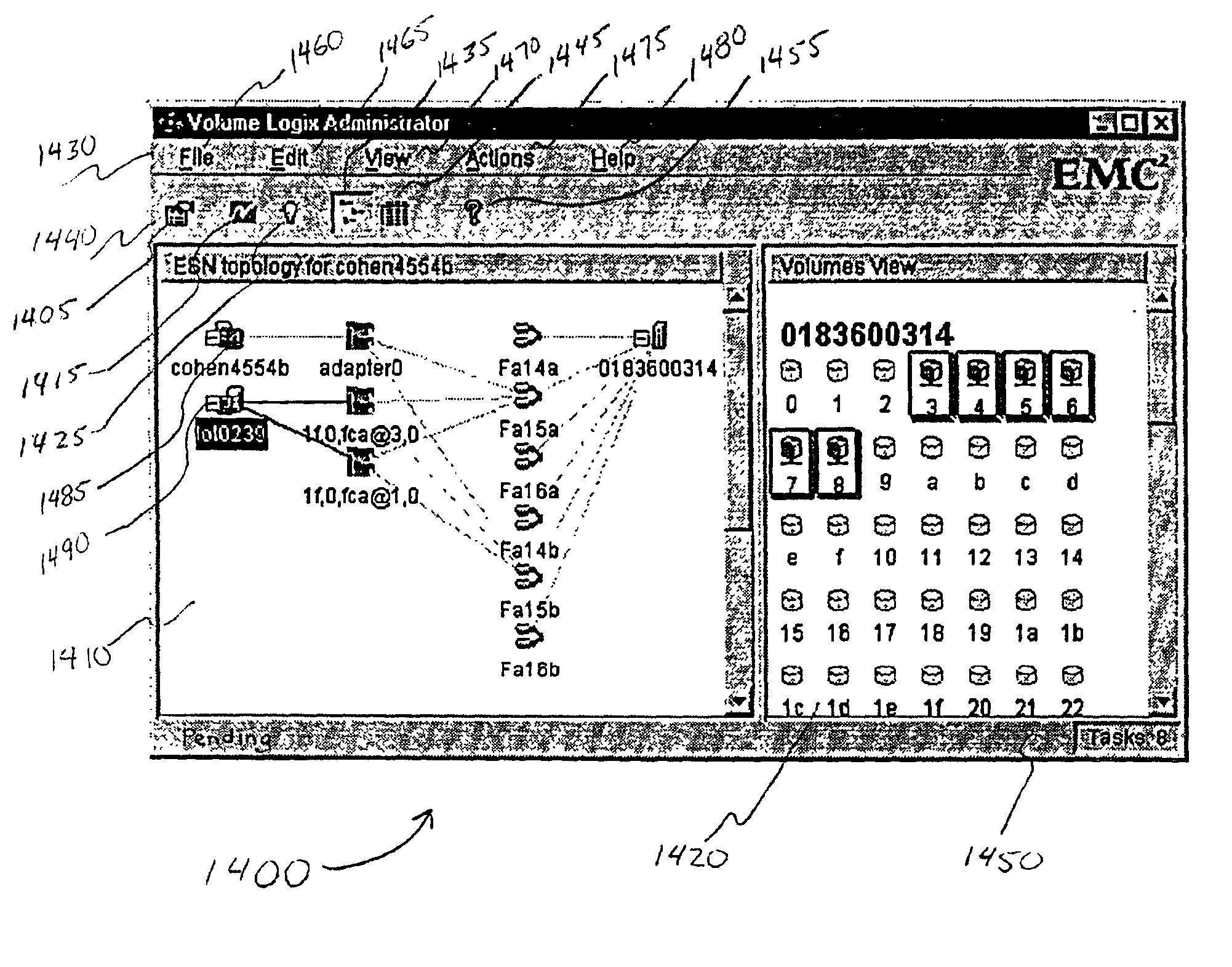
A method and apparatus for managing the availability and assignment of data in a storage system that is coupled to a network. A user interface is provided that executes on a host processor that is coupled to the storage system over the network. The user interface communicates with a configuration database in the storage system to identify host processors that are logged into the storage system over the network, to identify storage volumes on the storage system, to identify whether access to a particular storage volume on the storage system is permitted from a particular host processor, and to identify a network path by which host processors are logged into the storage system over the network. In one embodiment, a graphical user interface is provided that can be used to graphically represent host processors, host bus adapters, storage systems, and storage system adapters and storage volumes on the storage system. The graphical representation provided by the graphical user interface permits a user to graphically view a topology of the network at varying levels of detail, selectable by the user. The graphical user interface also permits a user to allow or deny access to storage systems or a particular storage volume on storage system from one or more of the host processors, host bus adapters, etc., by selecting and manipulating graphical representations thereof. In another embodiment, a command line user interface is provided with similar functionality.
Owner:EMC IP HLDG CO LLC
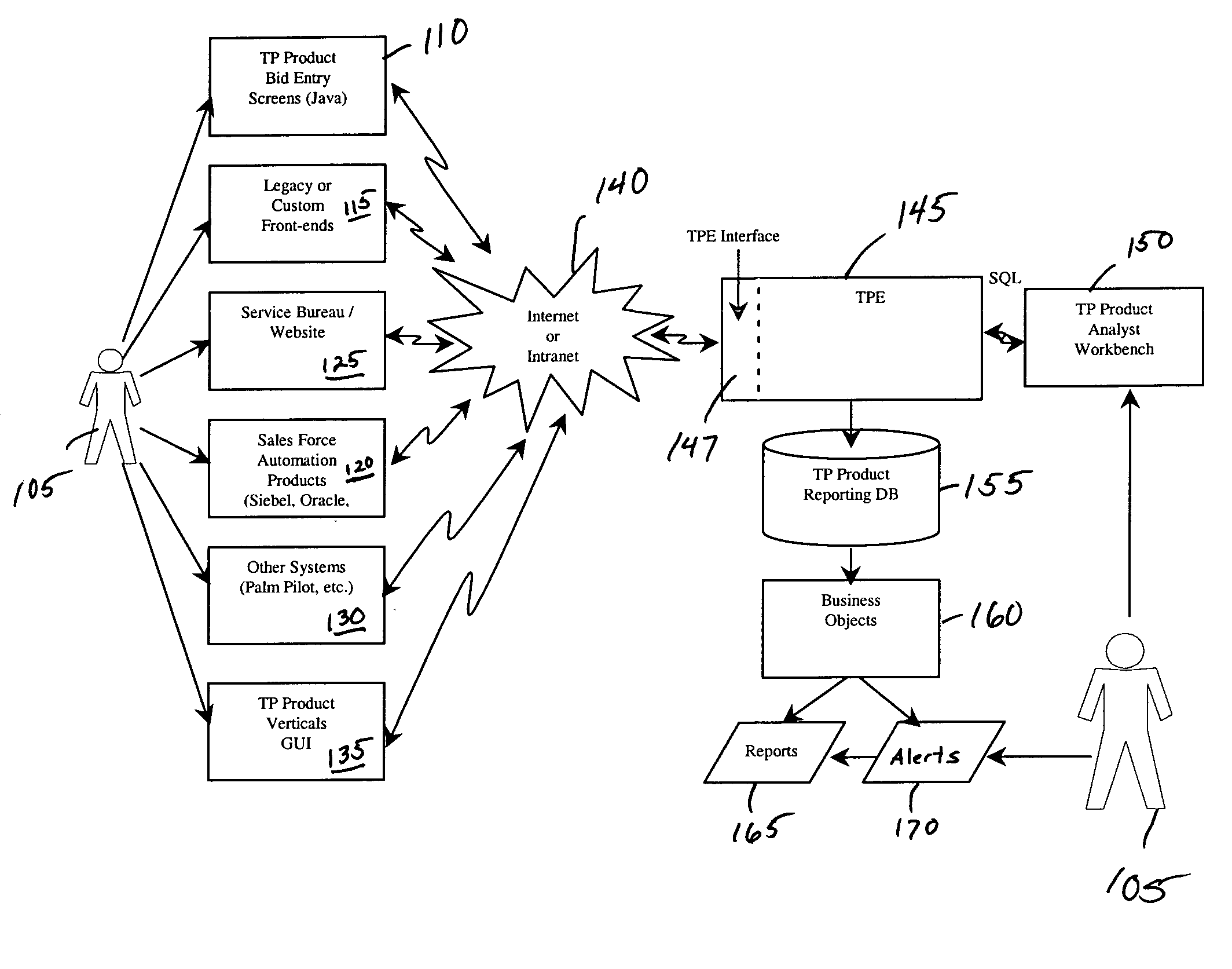
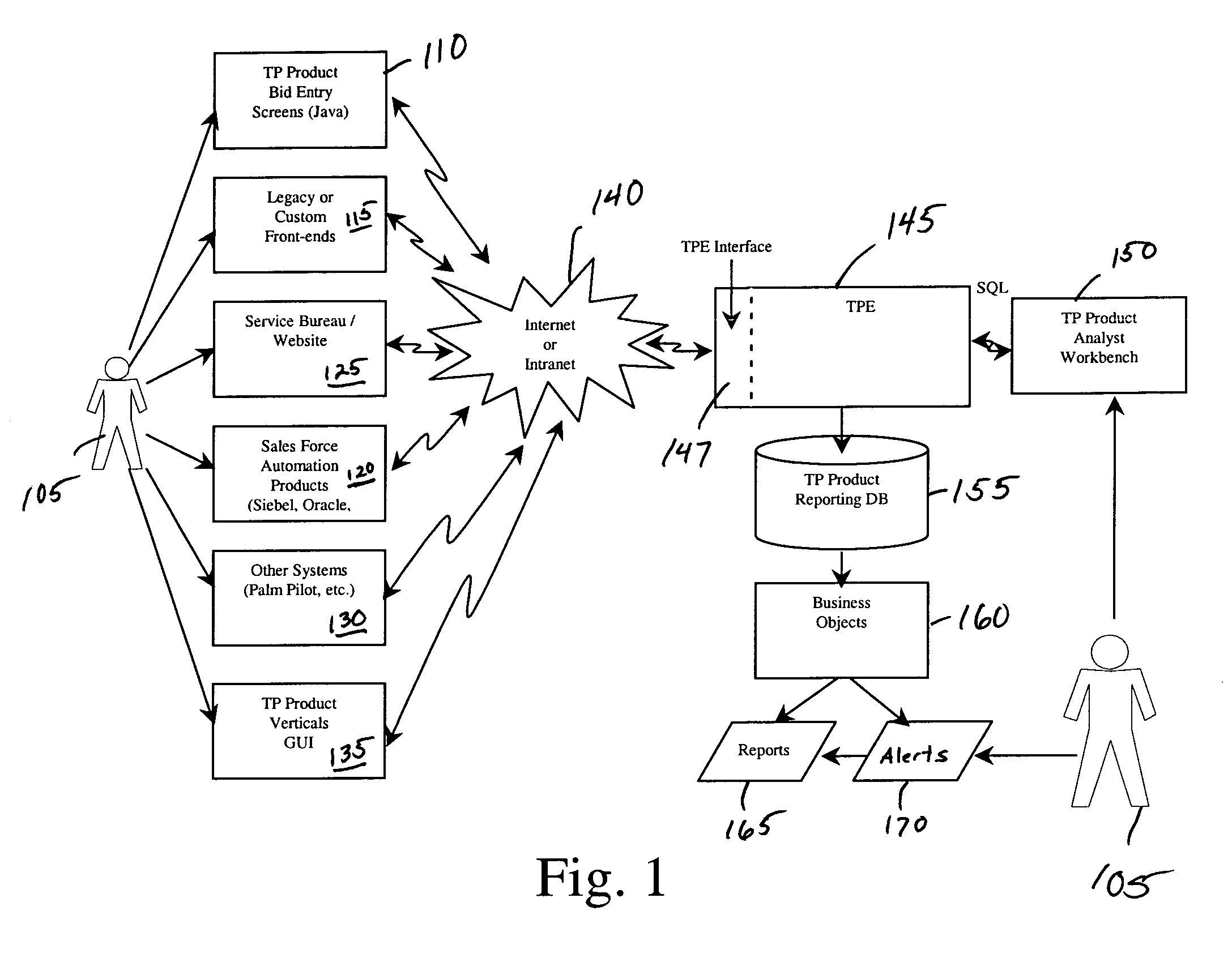
Target pricing system
InactiveUS6963854B1Increase profitMaximize expected financial contributionFinanceFlags/bannersComputerized systemData storing
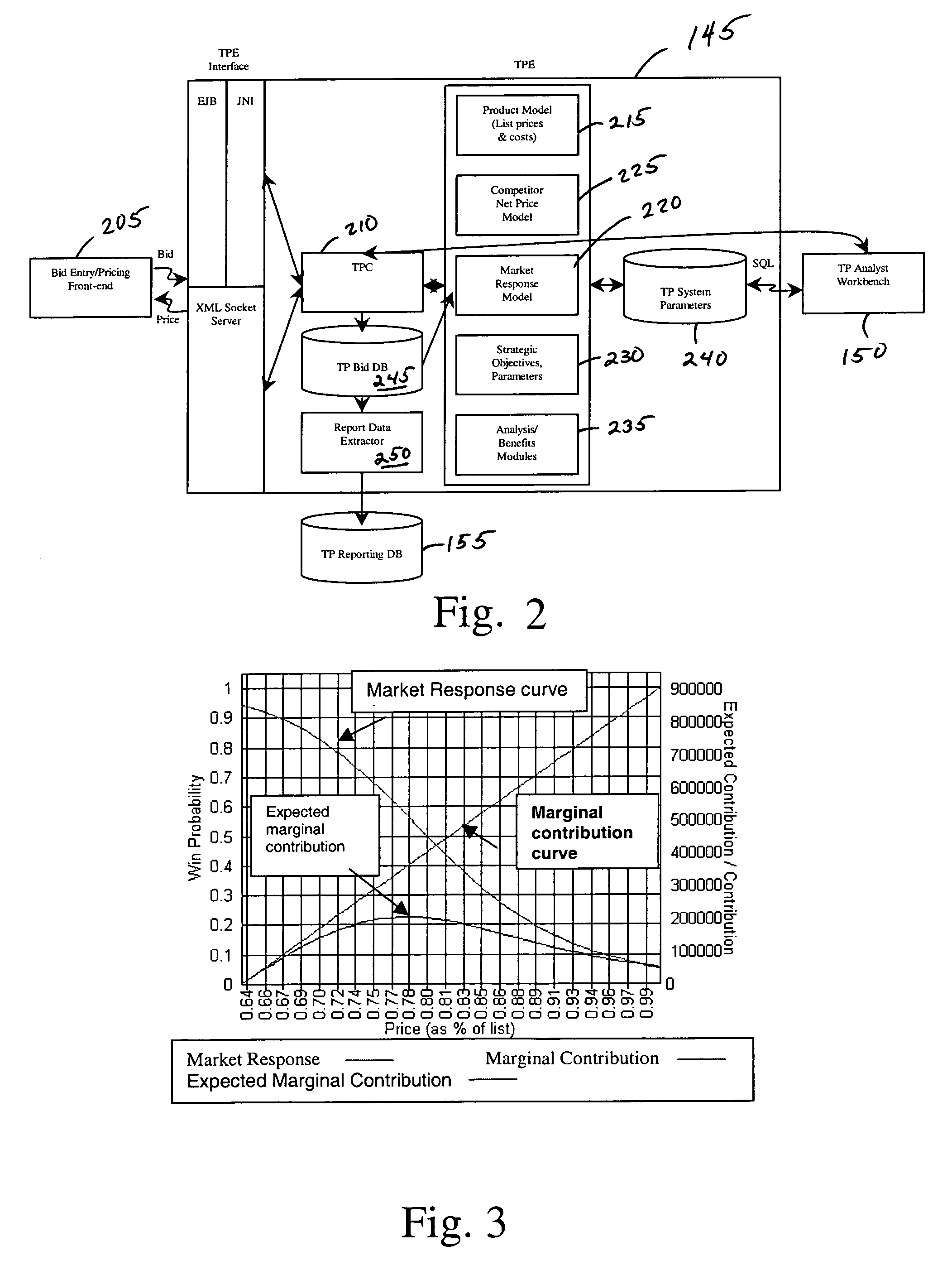
A business process and computer system known as the “Target Pricing System” (TPS) that generates an optimum bid or value for a competitively bid good or service. The system is resident on one or more host processors in connection with one or more data stores, and includes a product model that defines list values for the bid using stored price data and costs the values using stored cost data, a competitor net price model that calculates an equivalent competitor net price for the value, anda market response model that calculates the probability of winning with the value as a function of price. The system further preferably includesan optimization model that computes the target price of an optimal value that maximizes expected contribution for the bid or value. The system alternately further includes a benefits model for calculating the benefits of using target pricing over a pre-existing approach, and strategic objects which each affect the target price.
Owner:JDA SOFTWARE GROUP
Integrated pharmaceutical accounts management system and method
InactiveUS20020002495A1Facilitate real-time adjudicationEasy to processHand manipulated computer devicesDrug and medicationsData warehouseDrug interaction
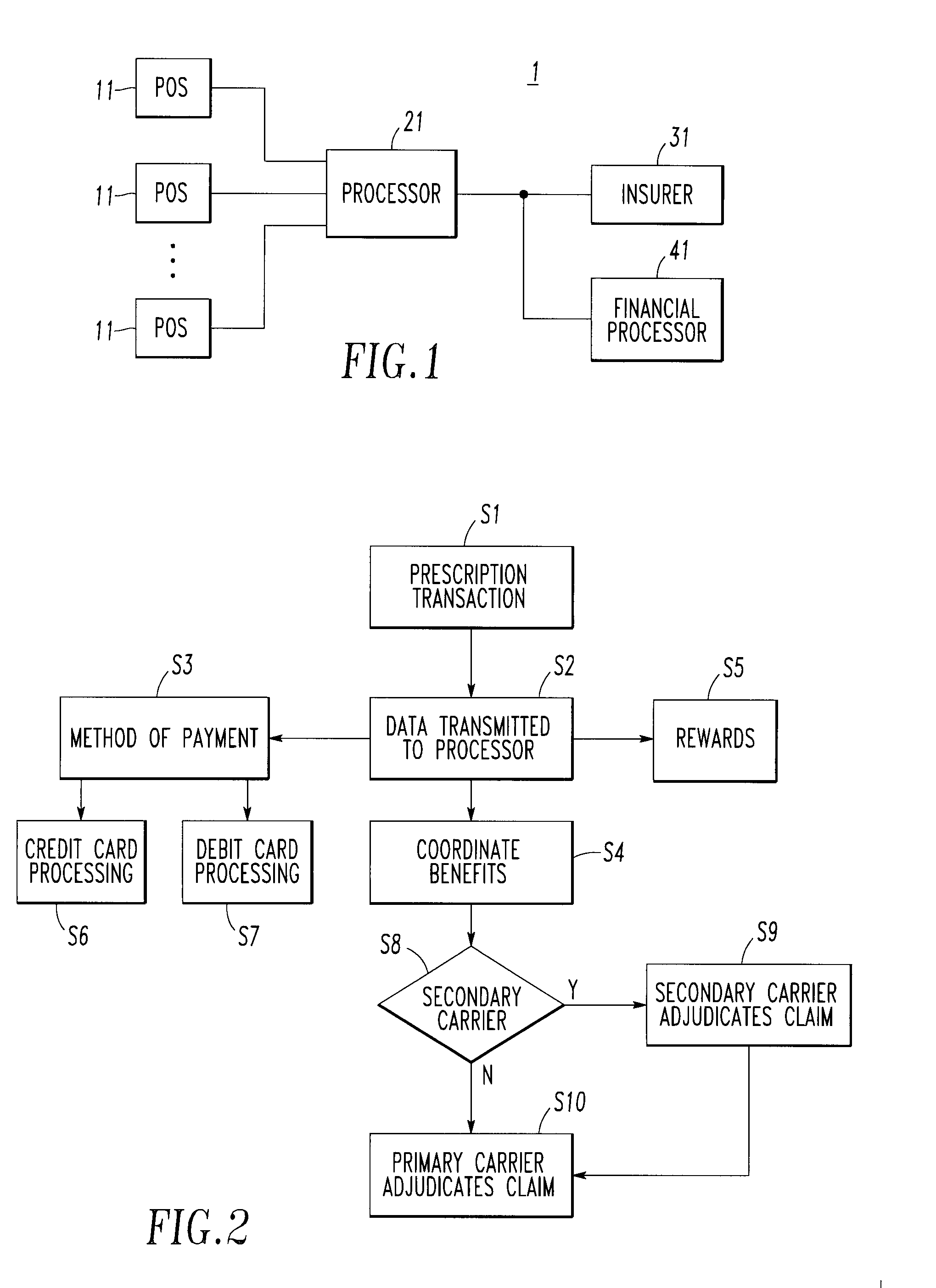
<heading lvl="0">Abstract of Disclosure< / heading> An integrated suite of services for consumers, service providers and manufacturers in the pharmaceutical industry is disclosed. The present invention utilizes one or more of the NCPDP standard formats and adopts the switch for an integrated system of, for example, instant adjudication of prescriptions, consumer data warehousing and / or incentive rewards for the consumer. A participating consumer with one card, can instantly purchase pharmaceuticals and charge the transaction to a credit card and earn and apply savings dollars redeemable for pharmaceutical purchases. For a participating service provider, instant adjudication and instant validation of consumer eligibility can be performed. Moreover, a service provider may receive messages related to the patient's medications. Significantly, data is recorded for consumers even when consumers make the pharmaceutical purchase with cash. The system includes a unique card issued to participating consumers. The card is adapted to encode conventional credit or debit card information specific to the participating consumer so that the consumer can consummate a transaction for the purchase of pharmaceuticals without possession of an additional credit card. The system further includes a host processor coupled to the point of sale at the service provider through a leased line or public switch network or the like. When a customer performs a pharmaceutical transaction at the point of sale of the service provider, the host processor coordinates any benefits and data with other prescription benefit management systems through messages transmitted and received from any primary or secondary carrier systems. The host processor further is adapted to facilitate real-time adjudication of claims and checks for any dangerous drug-to-drug interactions. The host processor additionally facilitates any financial processing including the accumulation and redemption of any bonus dollars earned by the consumer. Furthermore, since the card used by the consumer can be encoded with credit or debit card information, the host processor determines the desired payment method and performs the actual financial transaction. Even if the transaction at the point of sale is a cash purchase, the consumer may desire to use his unique card for the accrual of bonus dollars. Therefore, data concerning the transaction (i.e., pharmacy number, prescription number, etc.) can be recorded even for transactions conducted with cash.
Owner:NPAX
Media processing method and device
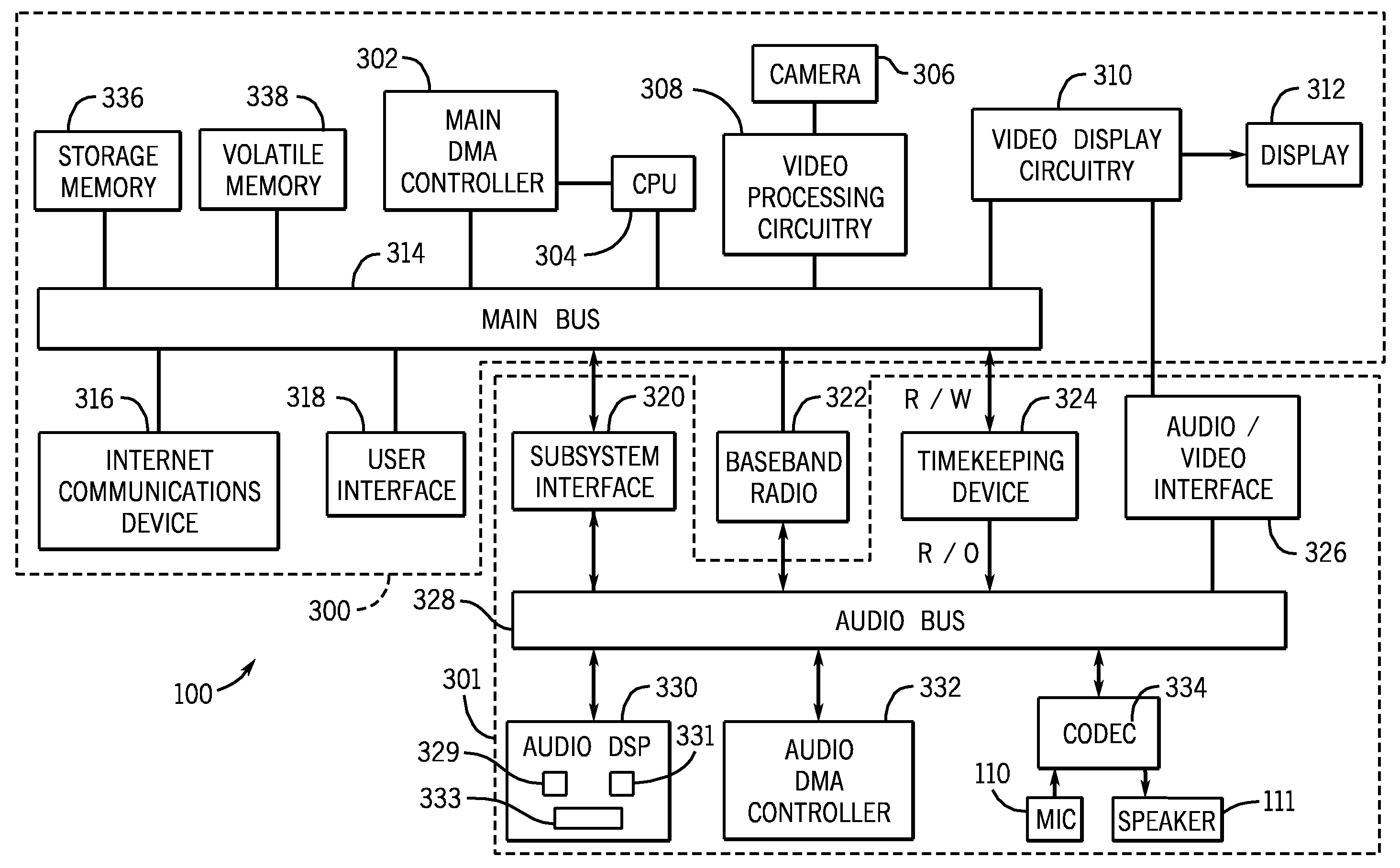
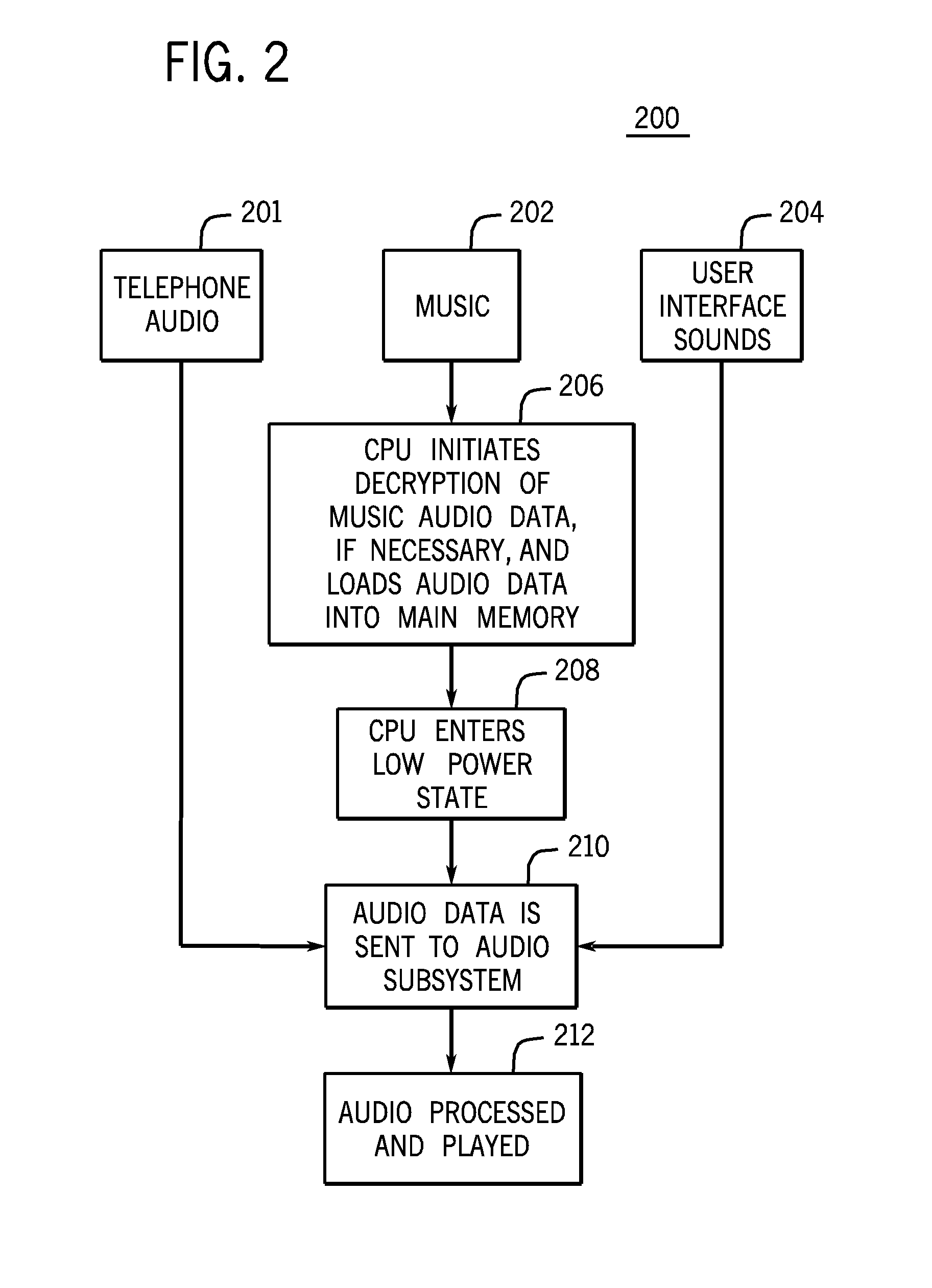
A media processing system and device with improved power usage characteristics, improved audio functionality and improved media security is provided. Embodiments of the media processing system include an audio processing subsystem that operates independently of the host processor for long periods of time, allowing the host processor to enter a low power state. Other aspects of the media processing system provide for enhanced audio effects such as mixing stored audio samples into real-time telephone audio. Still other aspects of the media processing system provide for improved media security due to the isolation of decrypted audio data from the host processor.
Owner:APPLE INC
Apparent network interface for and between embedded and host processors
InactiveUS6058434ASignificant comprehensive benefitsMultiple digital computer combinationsElectric digital data processingPerformance enhancementWeb service
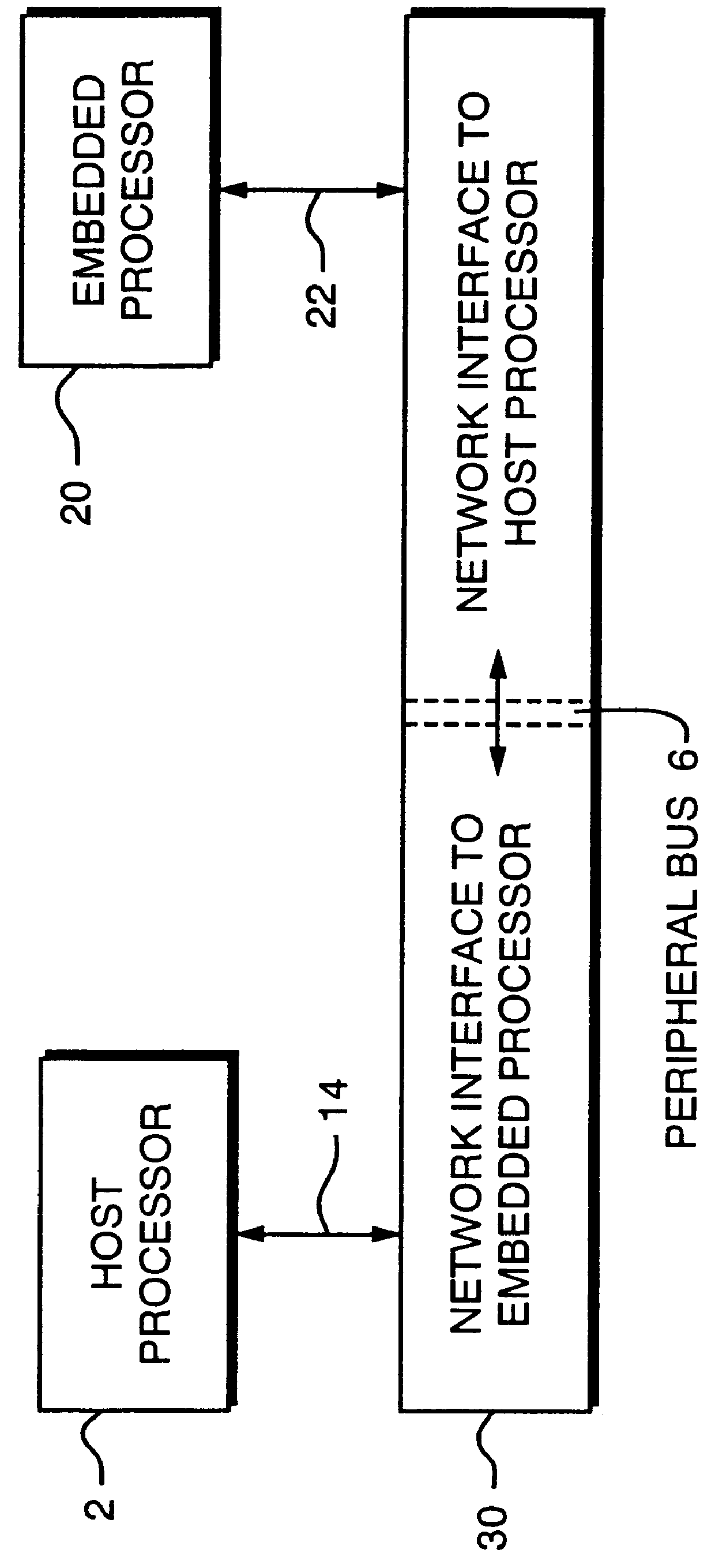
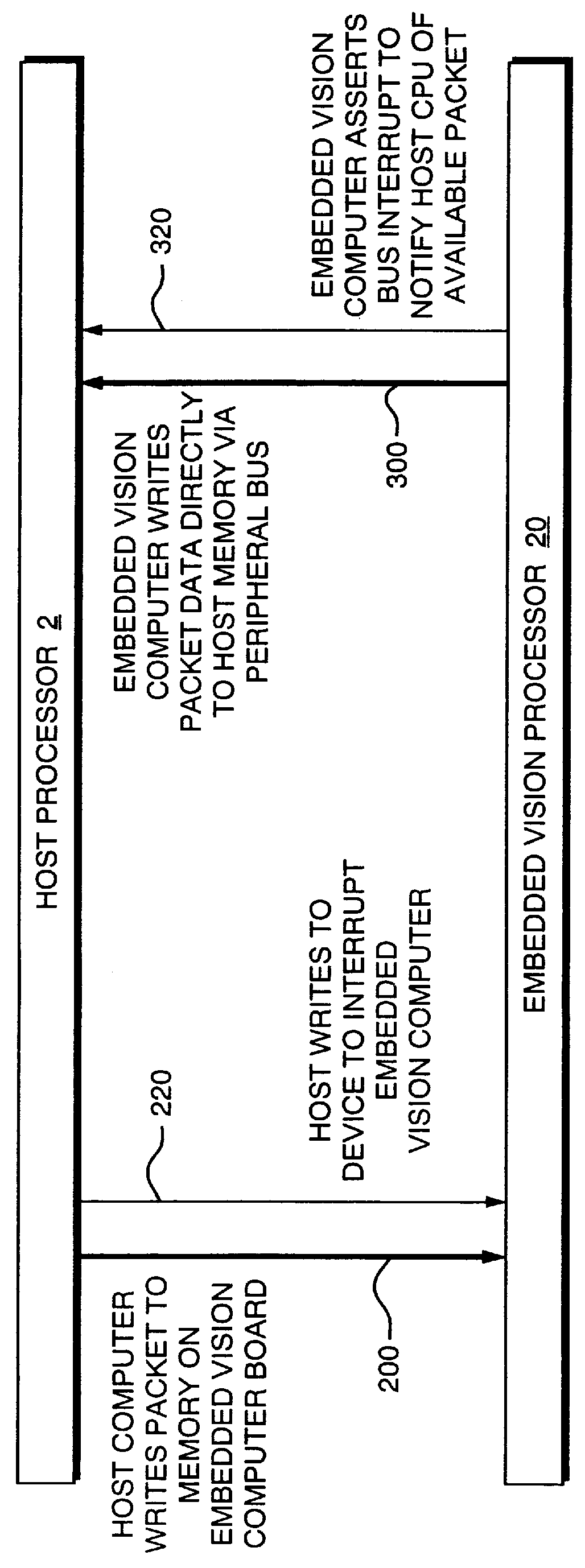
An apparent network interface permits one processor such as a processor embedded within a larger processing system (an embedded processor) to communicate to a host processor or other processors and devices on the network to which the embedded processor is attached, using standard network communication mechanisms / protocols such as TCP / IP, NFS, FTP, HTTP, etc. The web server protocol HTTP is particularly useful because it permits the embedded computer to publish a user interface for remote monitoring and remote control using a standard web browser application. The invention provides the host computer with an apparent network interface that appears to be a standard network device, such as an Ethernet interface card. This apparent interface communicates directly with the embedded processor, which appears to be a device on this apparent network. Significant cost savings and performance enhancements are realized by implementing the communication directly over the host computer's peripheral bus rather than using standard network hardware such as Ethernet hardware.
Owner:MICROSCAN SYSTEMS
Storage mapping and partitioning among multiple host processors
InactiveUS6799255B1Input/output to record carriersData processing applicationsData portControl store
A storage controller for controling access to data storage has a memory and at least one data port for a data network including host processors. The memory is programmed to define a respective specification for each host processor of a respective subset of the data storage to which access by the host processor is restricted, and each specification is associated with a host identifier stored in the memory. When the storage controller receives a data access request from a host processor, it decodes a host identifier from the data access request, and searches the memory for a host identifier matching the host identifier decoded from the request. Upon finding a match, the respective specification of the respective subset for the host processor is accessed to determine whether or not storage specified by the storage access request is contained in the respective subset. If so, then storage access can continue, and otherwise, storage access is denied. Preferably the host identifier decoded from the request is a temporary address assigned by the network, and also stored in the memory in association with each respective specification is a relatively permanent identifier for the host processor.
Owner:EMC IP HLDG CO LLC
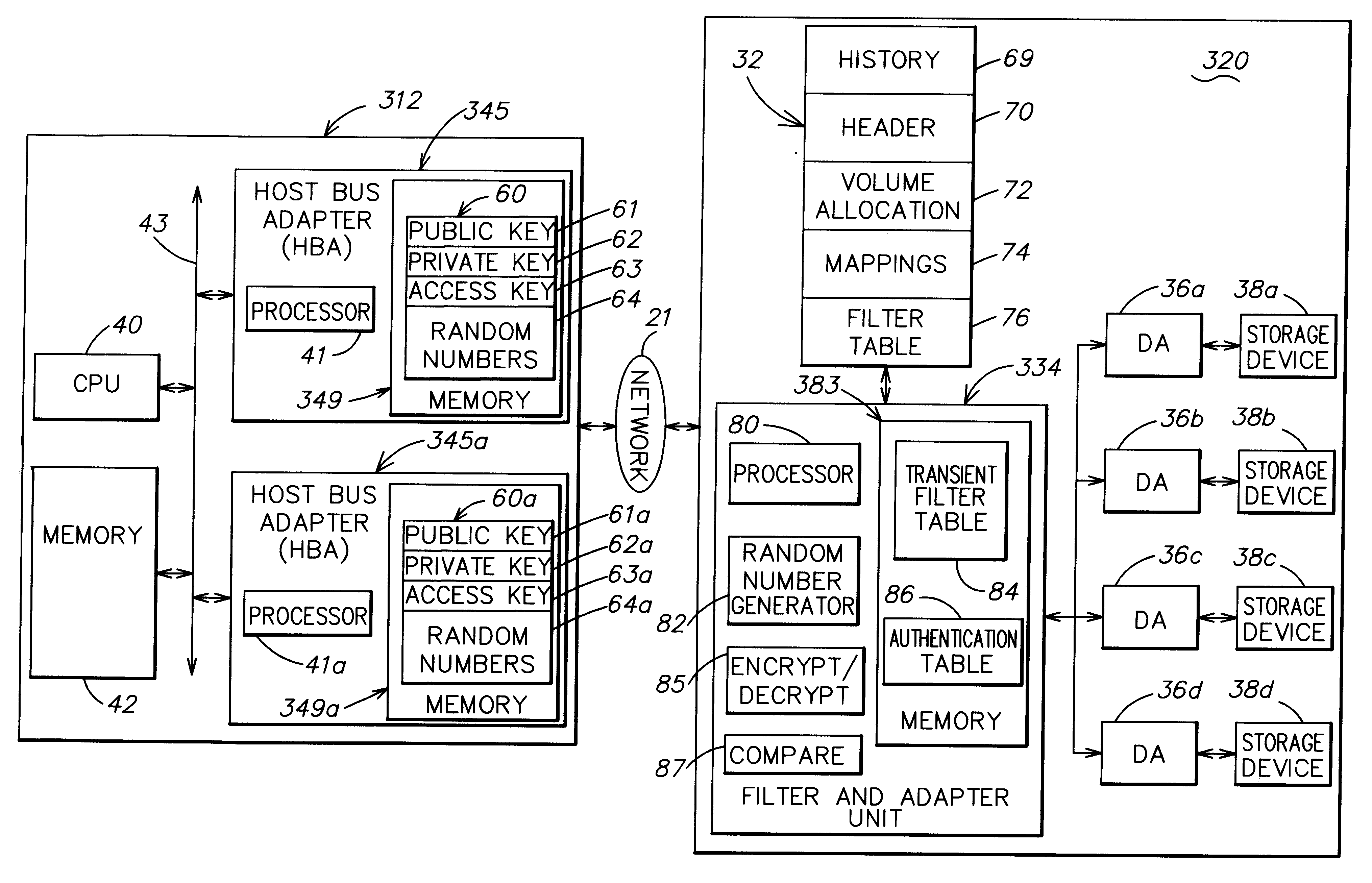
Method and apparatus for authenticating connections to a storage system coupled to a network
InactiveUS6263445B1Key distribution for secure communicationInput/output to record carriersData accessData management
A data management technique for managing accesses to data at a shared storage system includes a filter at the storage system. The filter is coupled to a configuration table, which identifies which of a number of coupled host processors have accesses to each of the resources at the device. During operation, requests received from the host devices are filtered by the filter, and only those requests to resources that the individual host devices have privilege to access are serviced. Advantageously, data security is further enhanced by authenticating each of the requests received by the storage system to verify that the host processor that is represented as forwarding the request is the indicated host processor. In addition, transfers of data between the storage system and the host processor may be validated to ensure that data was not corrupted during the data transfer.
Owner:EMC IP HLDG CO LLC
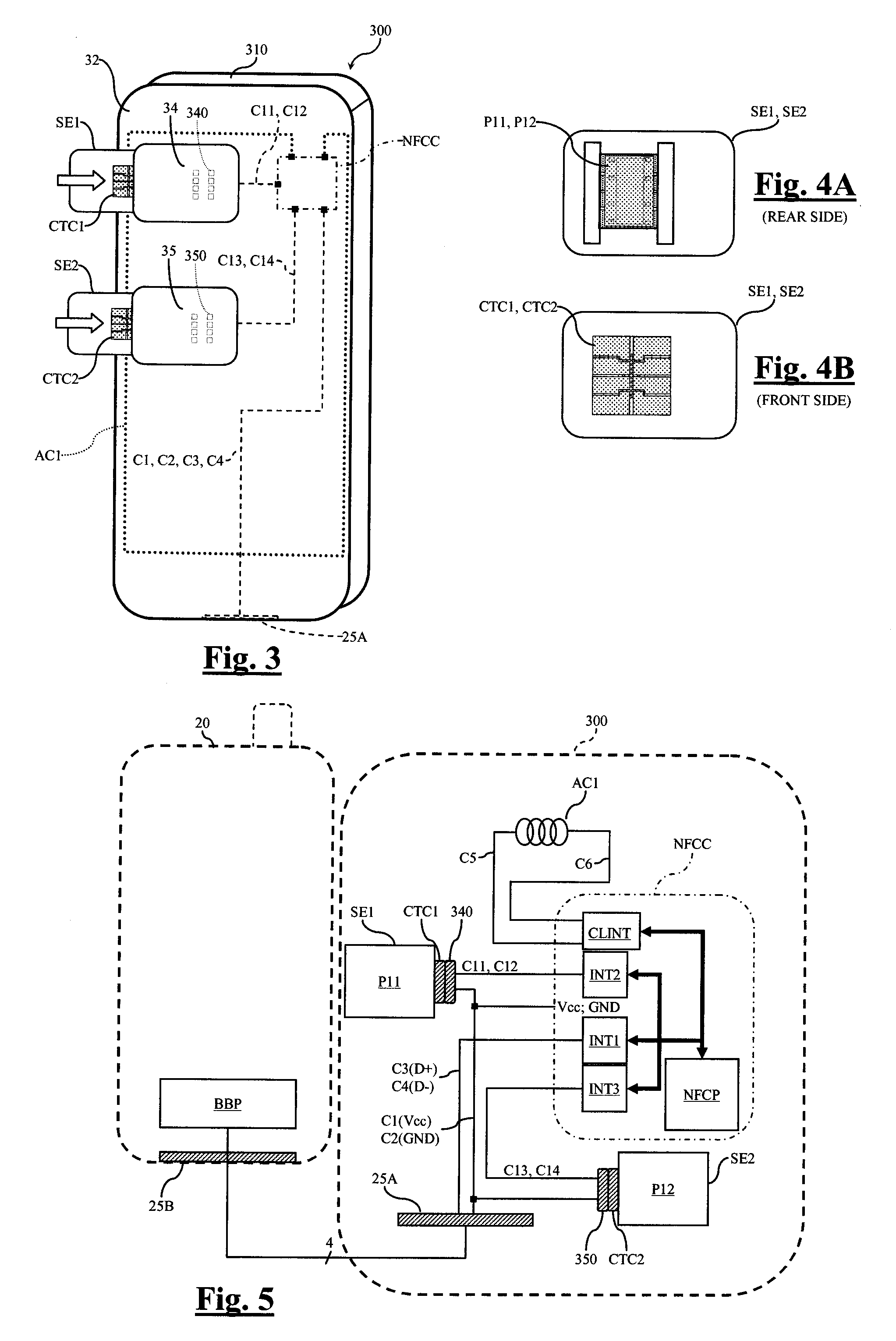
Protective envelope for a handheld electronic device
A protective envelope for a handheld electronic device is shaped to cover at least 40% of a surface of the handheld device. The protective envelope includes at least a first housing having at least one first host processor or being suitable for receiving at least one first host processor, at least one main antenna, and an assembly for linking the host processor to the main antenna.
Owner:INSIDE CONTACTLESS SA
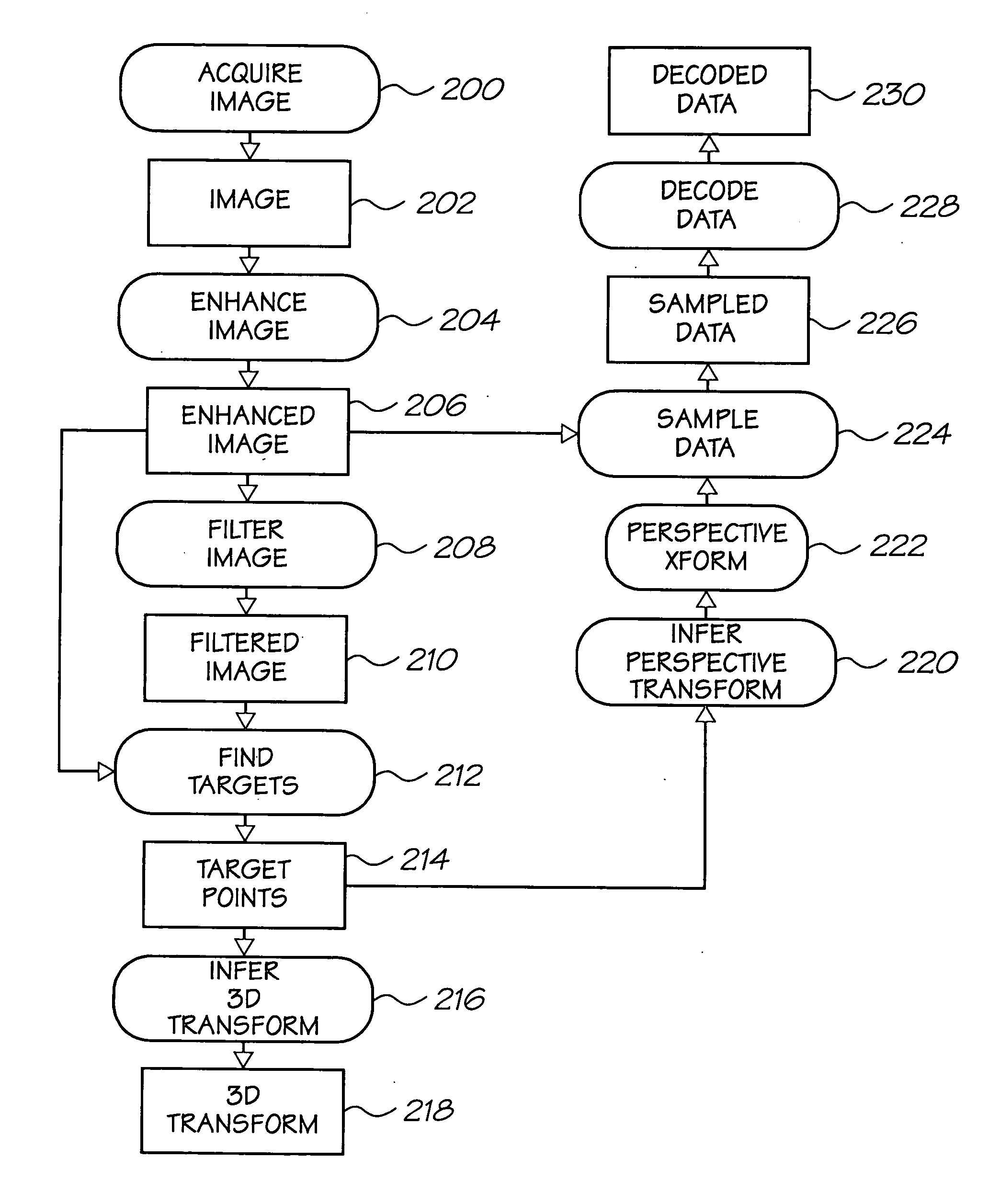
Scanning device for coded data
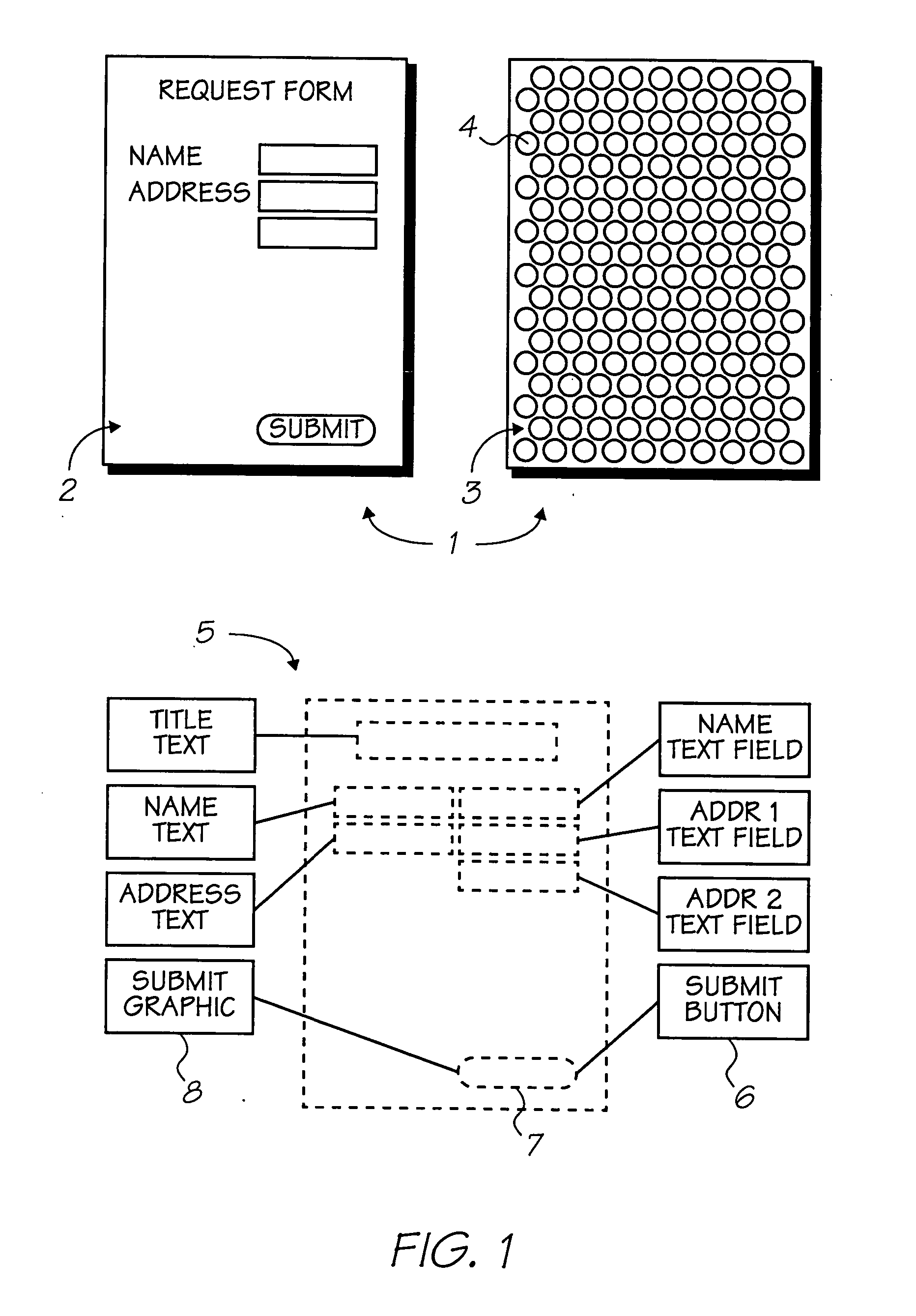
InactiveUS7128270B2Input/output for user-computer interactionDigital data processing detailsPhotovoltaic detectorsPhotodetector
A scanning device for scanning coded data indicative of a plurality of locations disposed on a surface is provided. The device generates interaction data based on the sensed coded data. The scanning device comprises a laser source for exposing a coded data portion, a photodetector, an analog to digital converter, a framestore, an image processor and a host processor.
Owner:SILVERBROOK RES PTY LTD
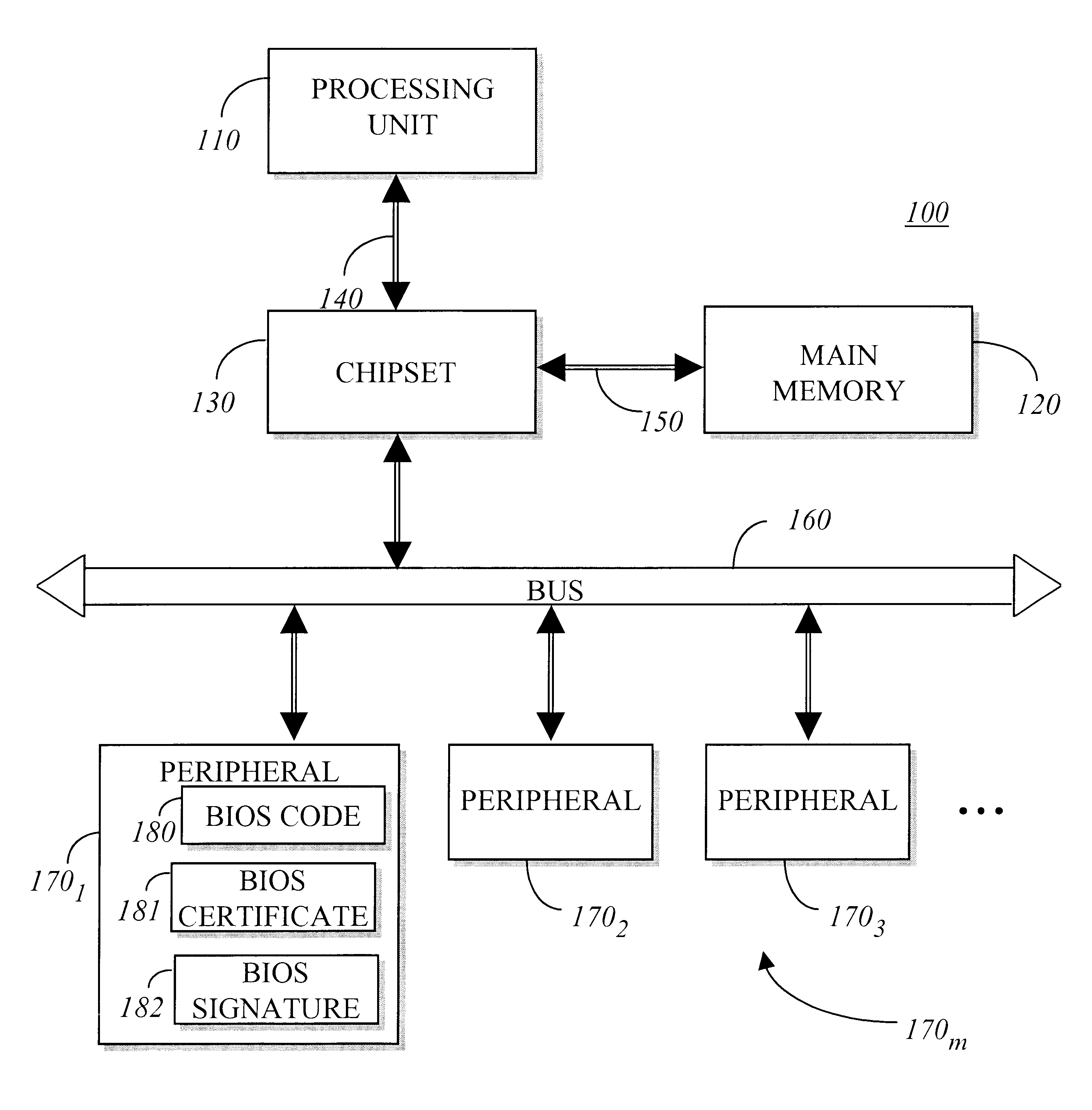
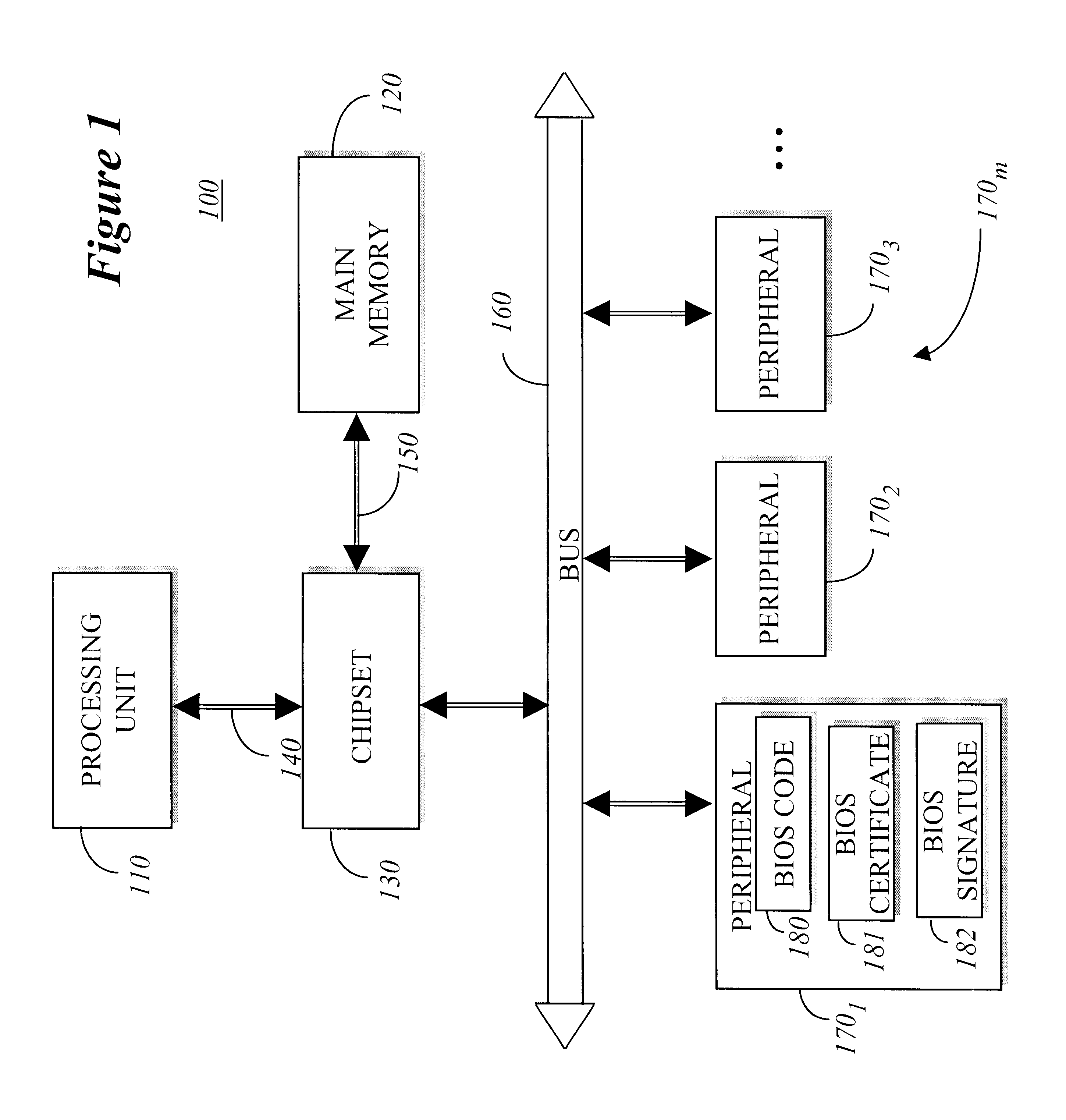
Method for BIOS authentication prior to BIOS execution
InactiveUS6401208B2User identity/authority verificationUnauthorized memory use protectionPower-on resetBIOS
Owner:INTEL CORP
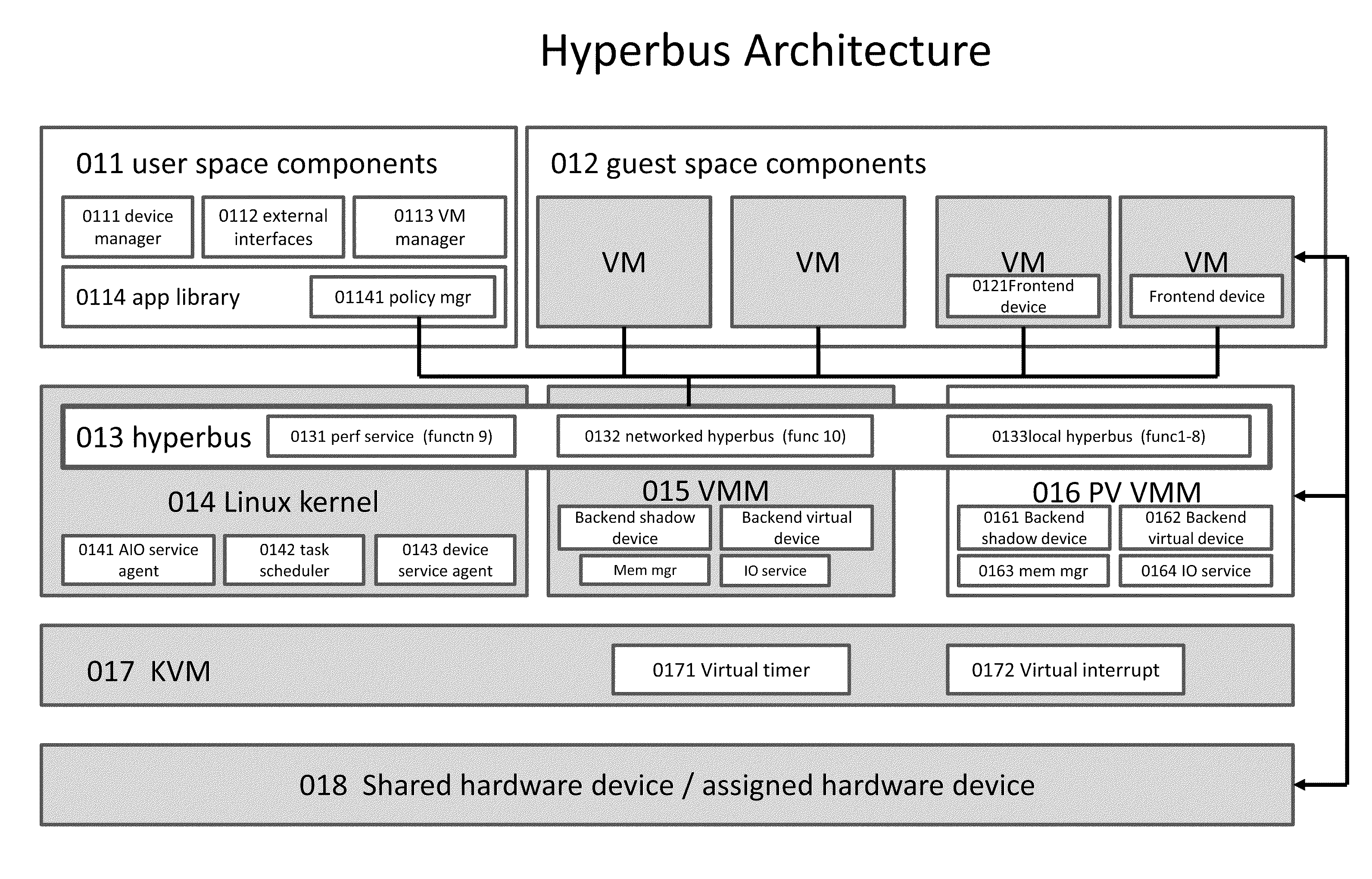
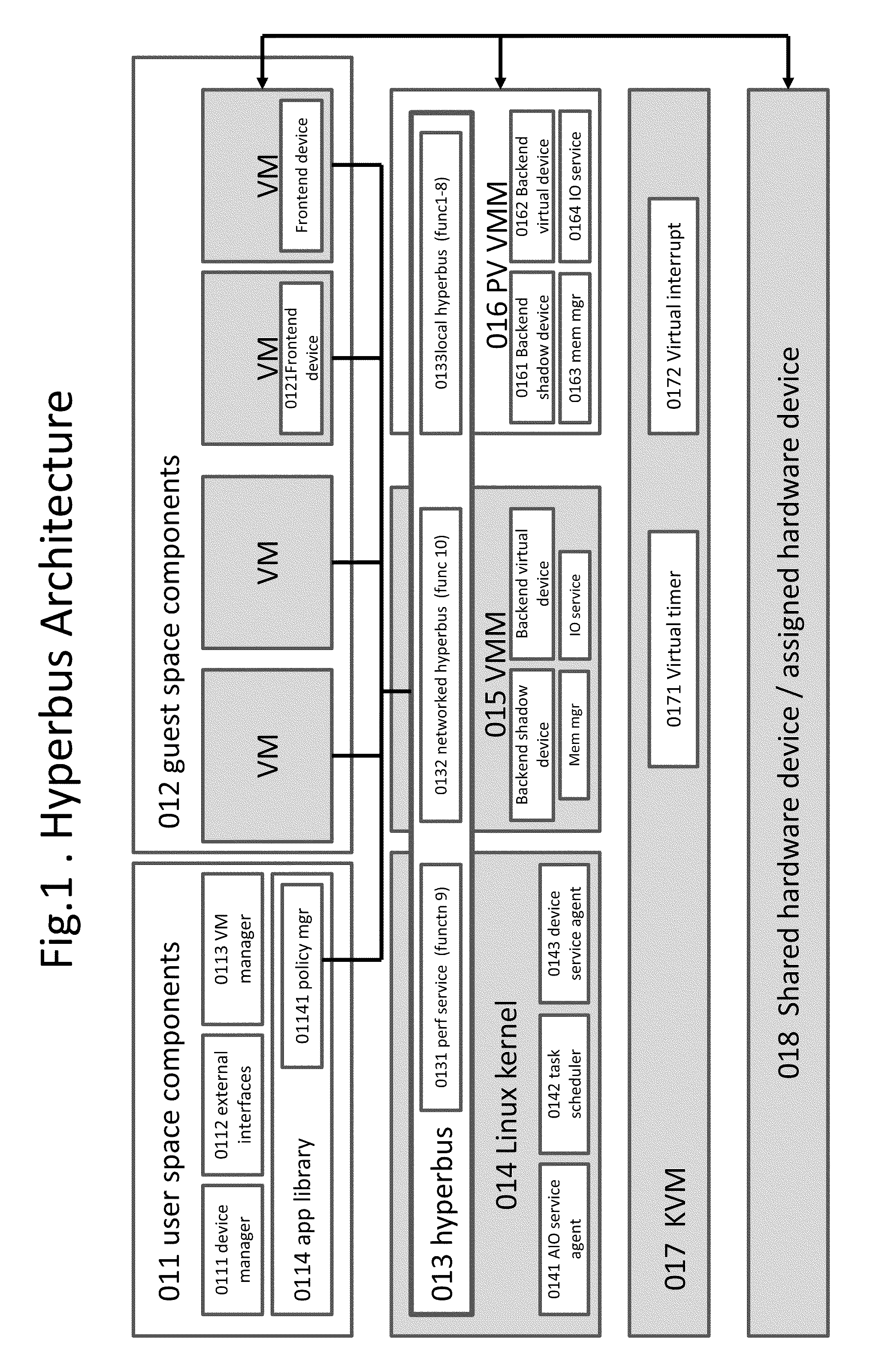
Kernel Bus System to Build Virtual Machine Monitor and the Performance Service Framework and Method Therefor
InactiveUS20110296411A1Fast deliveryImprove performanceSoftware simulation/interpretation/emulationMemory systemsVirtualizationSystem configuration
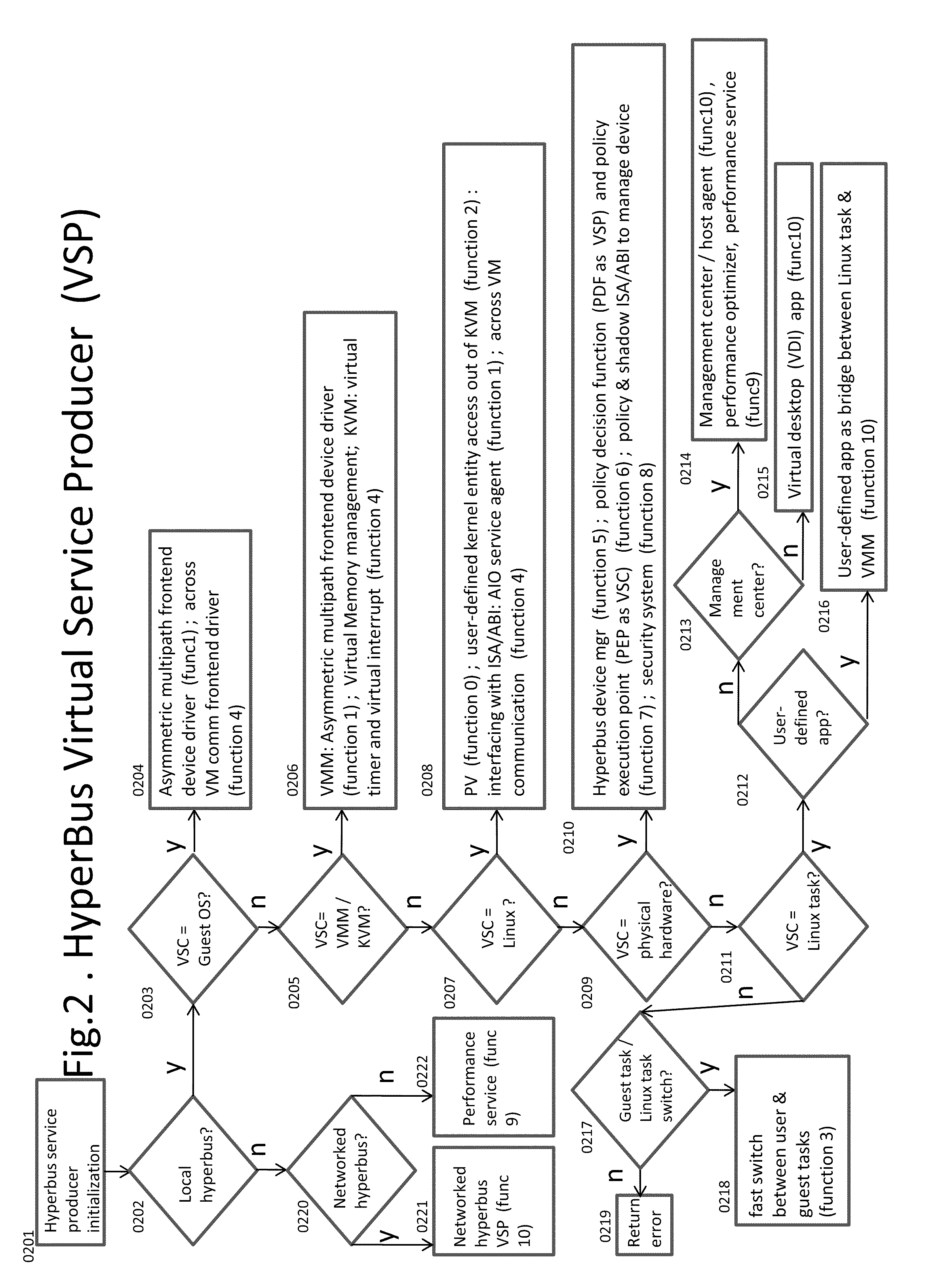
Some embodiments concern a kernel bus system for building at least one virtual machine monitor. The kernel bus system is based on kernel-based virtual machine. The kernel bus system is configured to run on a host computer. The host computer comprising one or more processors, one or more hardware devices, and memory. The kernel bus system can include: (a) a hyperbus; (b) one or more user space components; (c) one or more guest space components configured to interact with the one or more user space components via the hyperbus; (d) one or more VMM components having one or more frontend devices configure to perform I / O operations with the one or more hardware devices of the host computer using a zero-copy method or non-pass-thru method; (e) one or more para-virtualization components having (1) a virtual interrupt configured to use one or more processor instructions to swap the one or more processors of the host computer between a kernel space and a guest space; and (2) a virtual I / O driver configured to enable synchronous I / O signaling, asynchronous I / O signaling and payload delivery, and pass-through delivery independent an QEMU emulation; and (f) one or more KVM components. The hyperbus, the one or more user space components, the one or more guest space components, the one or more VMM components, the one or more para-virtualization components, and the one or more KVM components are configured to run on the one or more processors of the host computer. Other embodiments are disclosed.
Owner:TRANSOFT
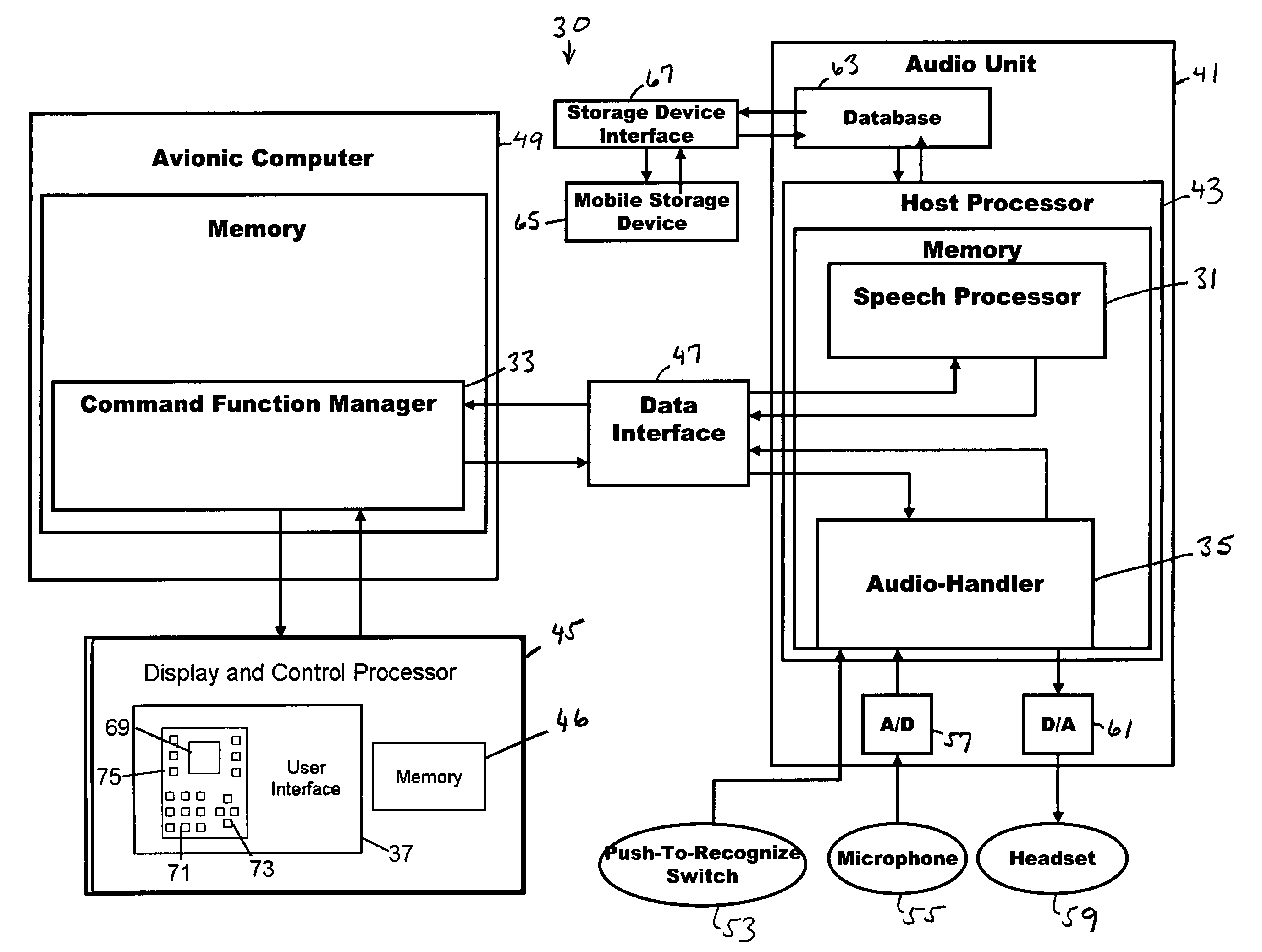
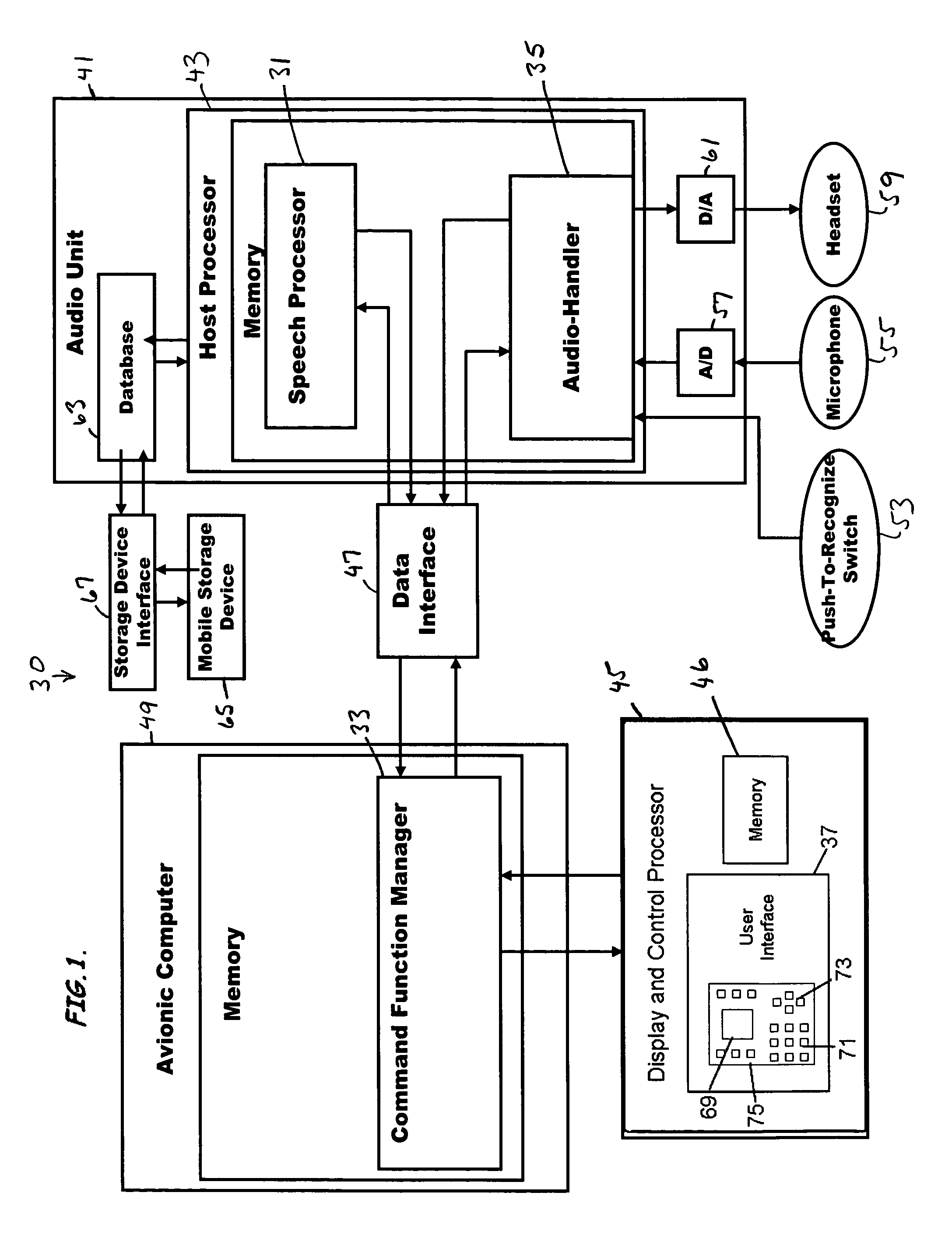
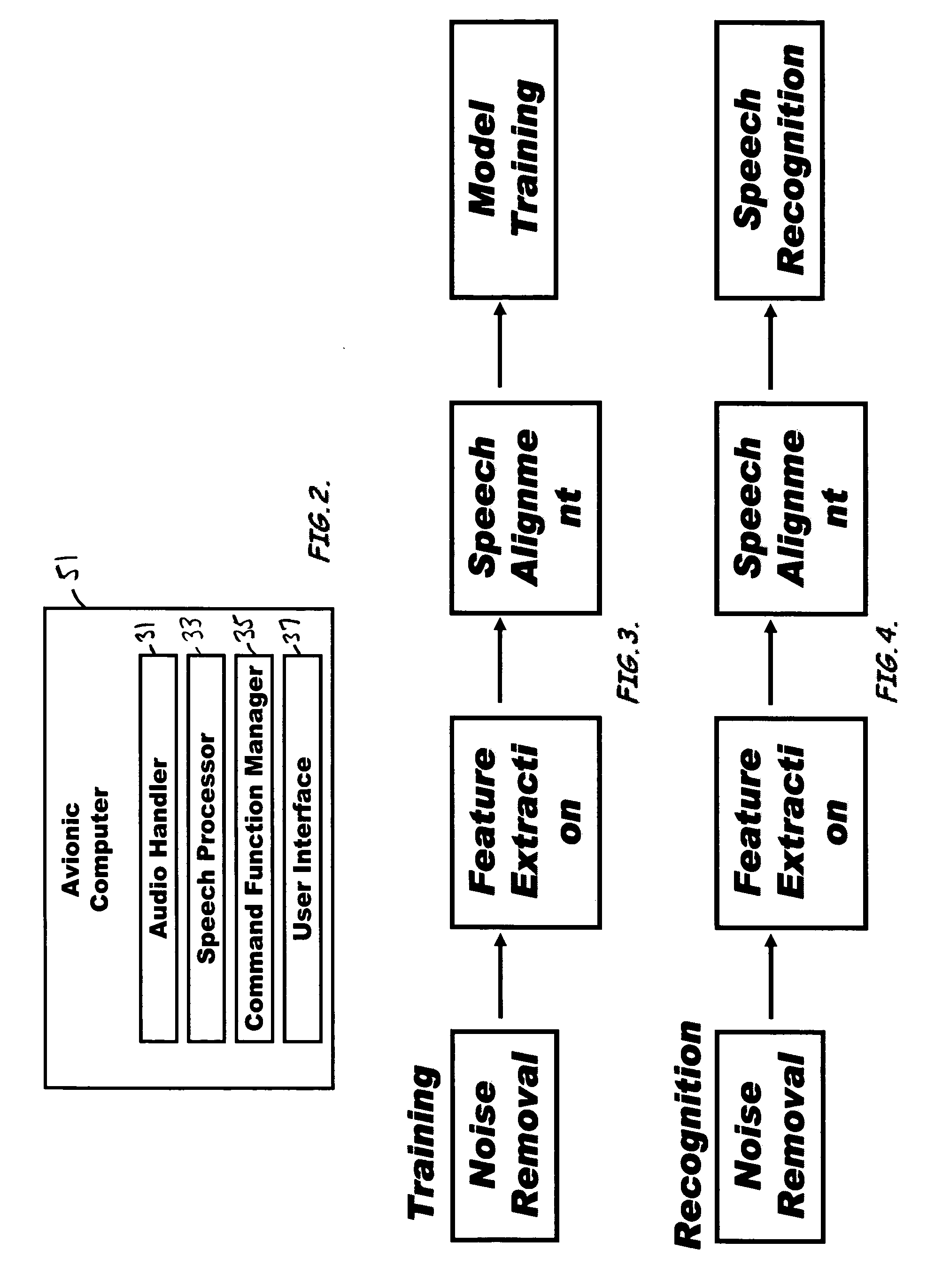
Speech activated control system and related methods
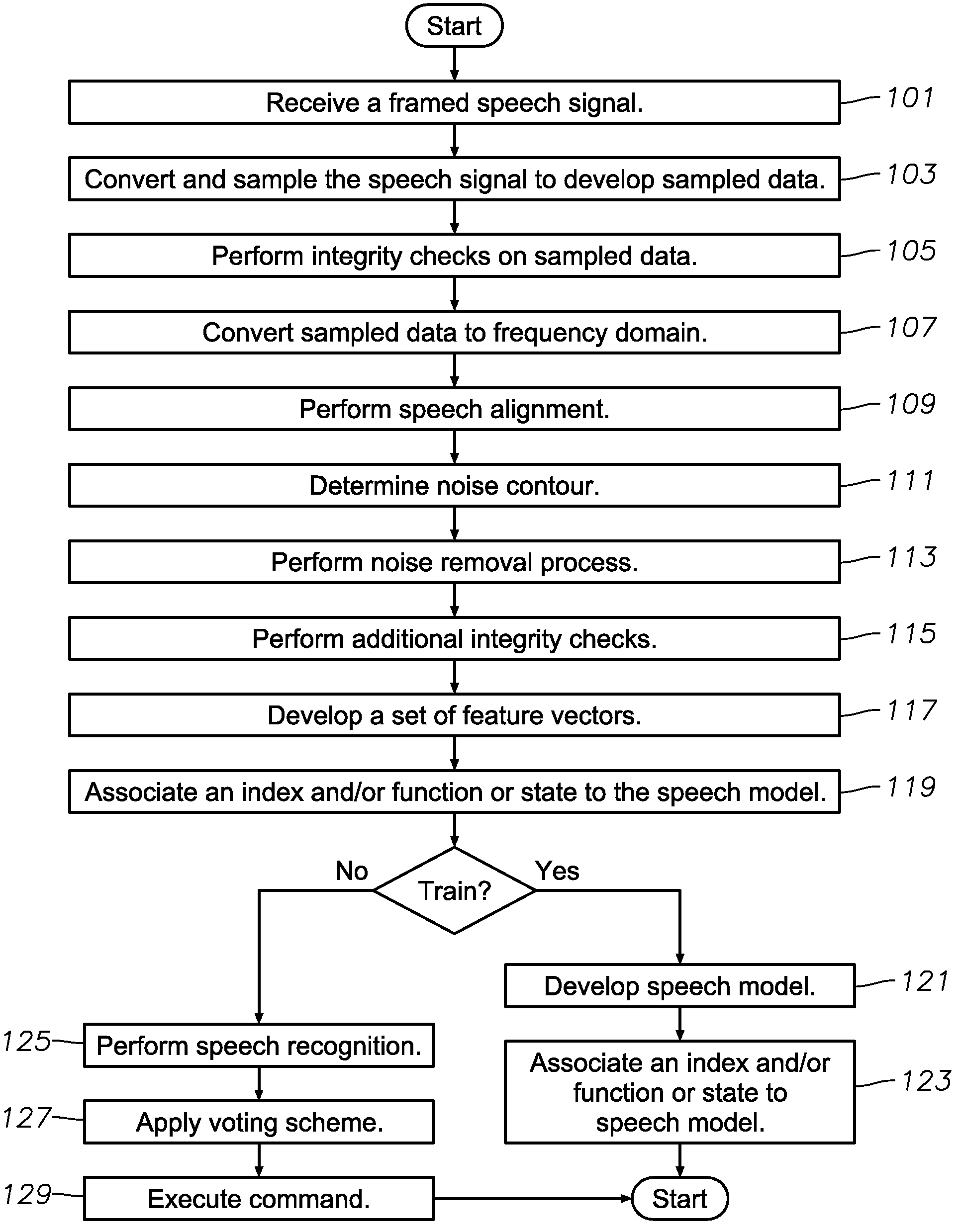
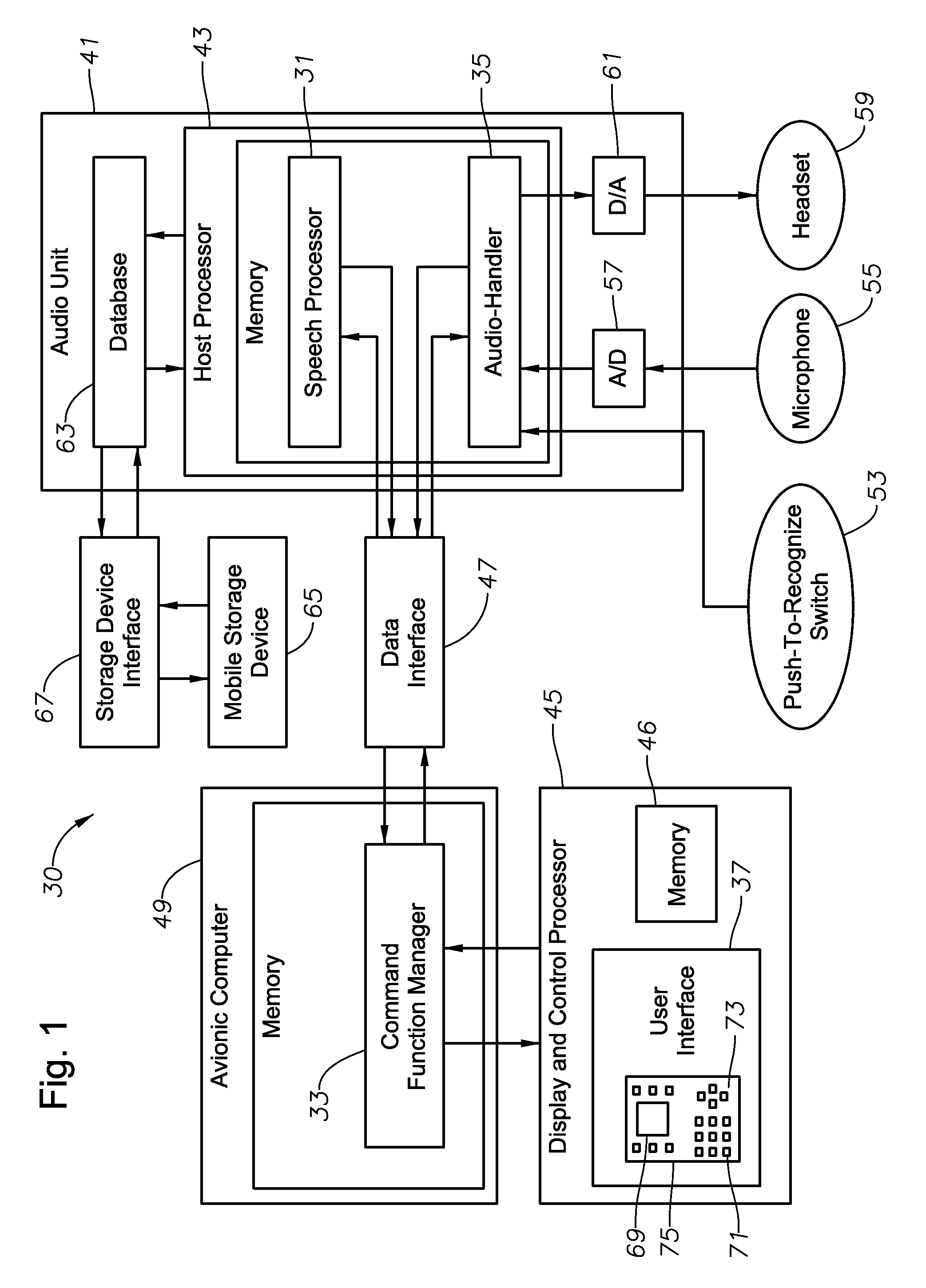
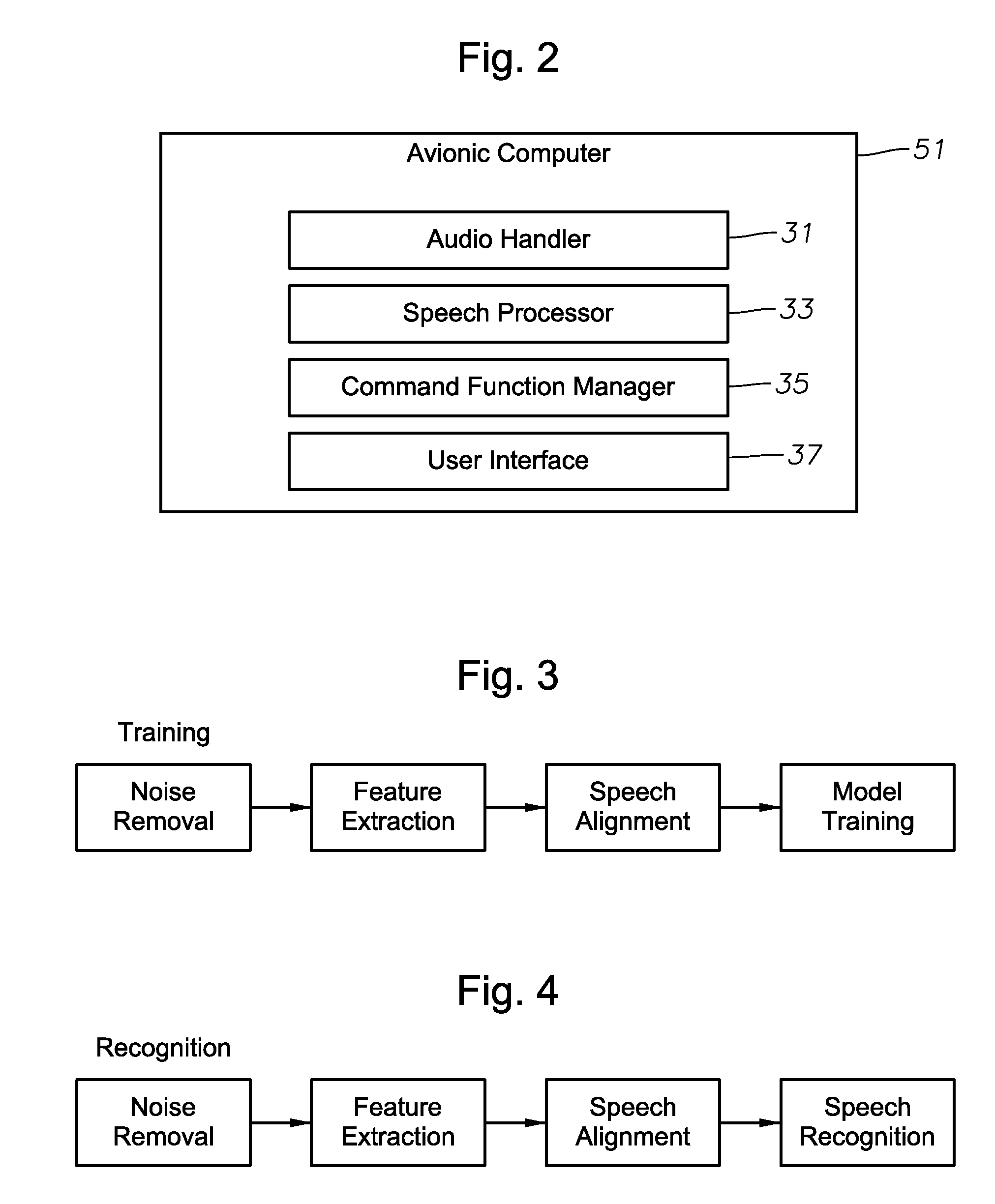
InactiveUS7774202B2Improve recognition accuracySmall vocabulary sizeSpeech recognitionControl systemSpeech identification
A speech activated control system for controlling aerial vehicle components, program product, and associated methods are provided. The system can include a host processor adapted to develop speech recognition models and to provide speech command recognition. The host processor can be positioned in communication with a database for storing and retrieving speech recognition models. The system can include an avionic computer in communication with the host processor and adapted to provide command function management, a display and control processor in communication with the avionic computer adapted to provide a user interface between a user and the avionic computer, and a data interface positioned in communication with the avionic computer and the host processor provided to divorce speech command recognition functionality from vehicle or aircraft-related speech-command functionality. The system can also include speech actuated command program product at least partially stored in the memory of the host processor and adapted to provide the speech recognition model training and speech recognition model recognition functionality.
Owner:LOCKHEED MARTIN CORP
Financial management system
A financial transaction network includes a customer network serviced by a host processor. The financial transaction network provides customers with a plurality of diverse and interchangeable financial products and financial services that customers may utilize to directly manage their financial assets. The host processor acts as a communications switch validating incoming transaction requests and routing them to specialized subsystems. The host processor maintains central records that can be accessed by network participants. The financial transaction network enables customers to continually interchange account values relating to any financial product, or financial service within the network. With its accessibility, speed and finality of settlement, the network permits these interchanges to be accomplished with maximum efficiency.
Owner:KIOBA PROCESSING LLC
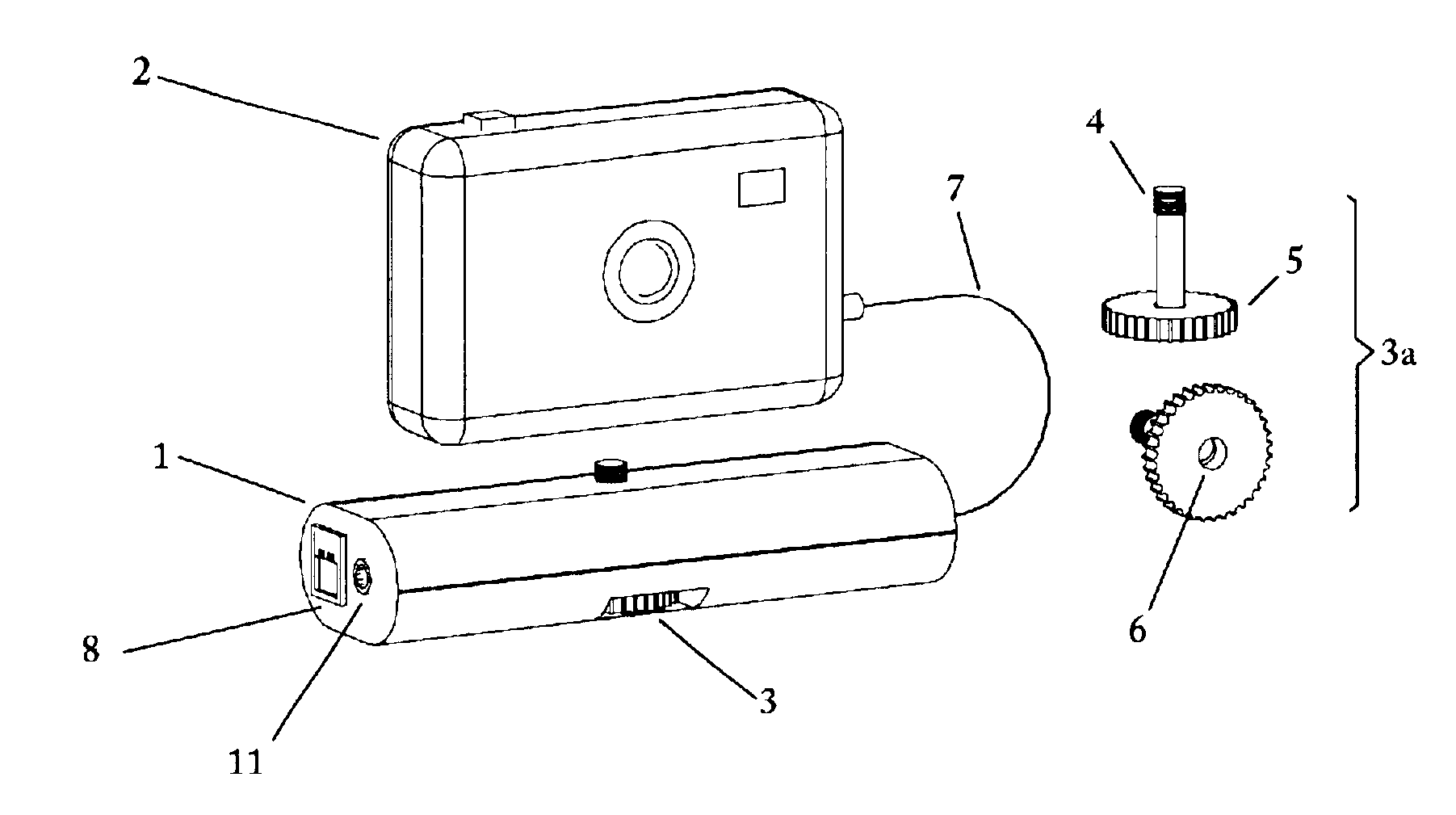
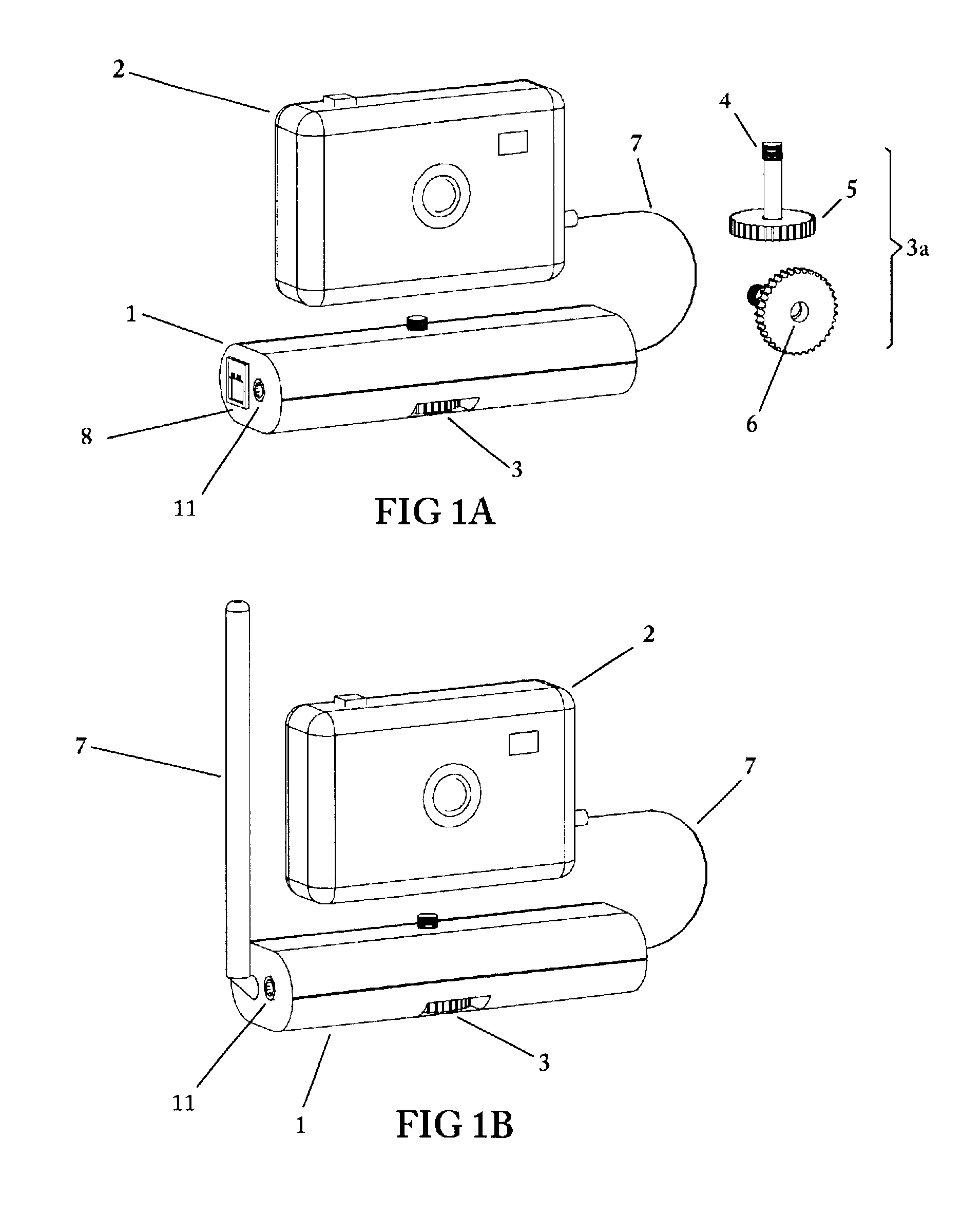
Remote camera relay controller method and apparatus
InactiveUS6400903B1Reduce transmit powerReduction in Eb/NoTelevision system detailsProjector film strip handlingModem deviceTelecommunications link
A remote camera relay method and apparatus for remotely operating a self-contained, unattended digital camera over a communications link. Format conversion means are included for transparently relaying control signals and remote image data between a local host processor and the remotely located digital camera, independently of specific camera command and image protocols. It thereby functions as a universal remote image transmission adapter, operable as an attachment for use with self-contained digital cameras. A portable enclosure is provided for accommodating the remote relay communications and control electronics and for attaching a hand-held digital camera thereto. Further means are included for remotely actuating the pan and tilt orientation of the camera in accordance with field-of-view selection commands. Data rate conversion and error correction coding are included for providing reliable, low power image forwarding. The communications channel could be a dial-up telephone system, a network connection, modem, an infra-red link or a wireless RF link, for example. Additional control means are provided for remotely selecting the camera field of view for image capture, and includes the ability to access only those subsets of image scenes for which viewing permissions are authorized. A further mode of operation includes protocol training whereby host photographing commands are captured by the remote relay invention during on-line operation, then replayed at programmed times resulting in automatic scheduled remote image capture. Power management is provided for maximizing operating time when used in low power, portable, battery operation.
Owner:CONOVAL PAUL
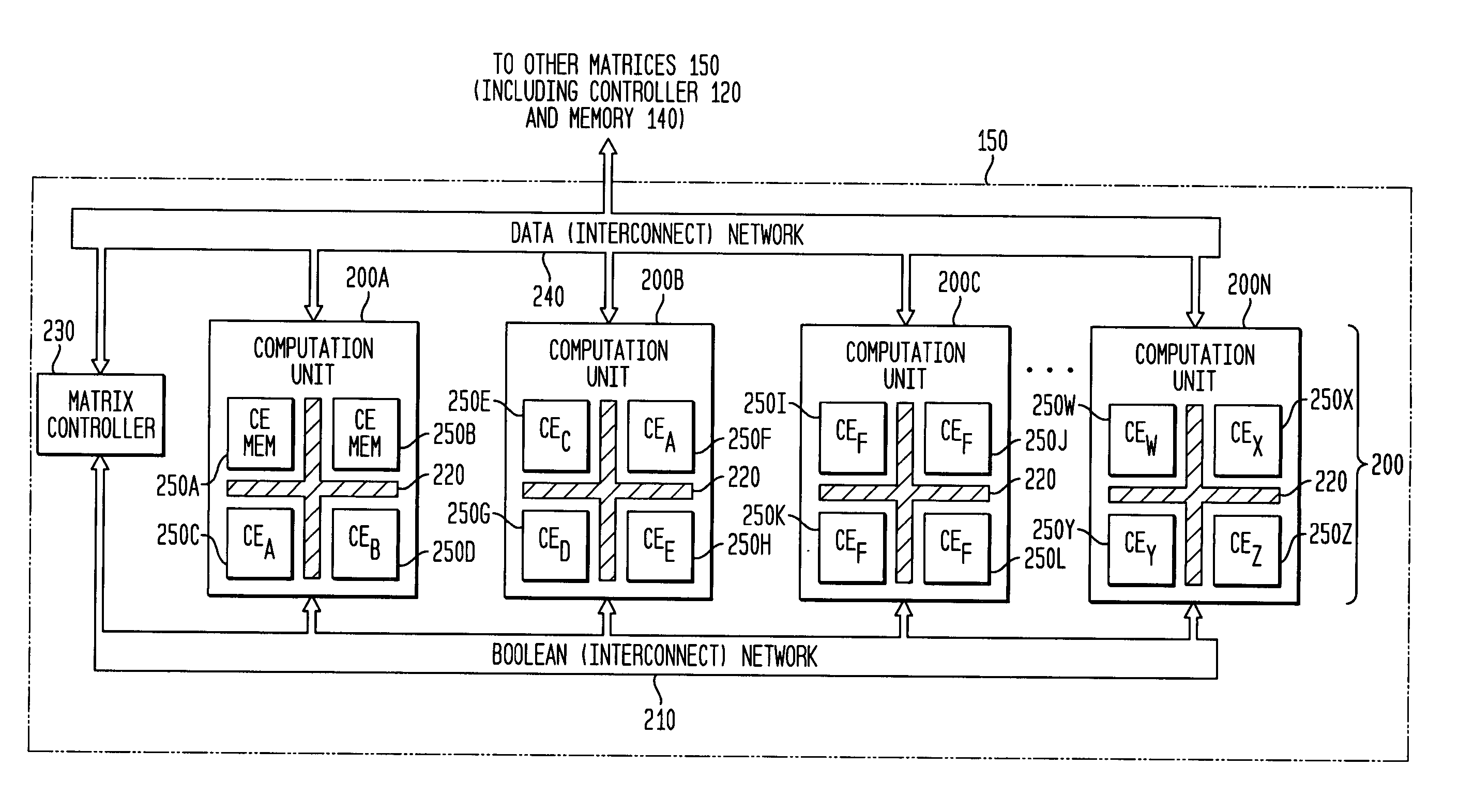
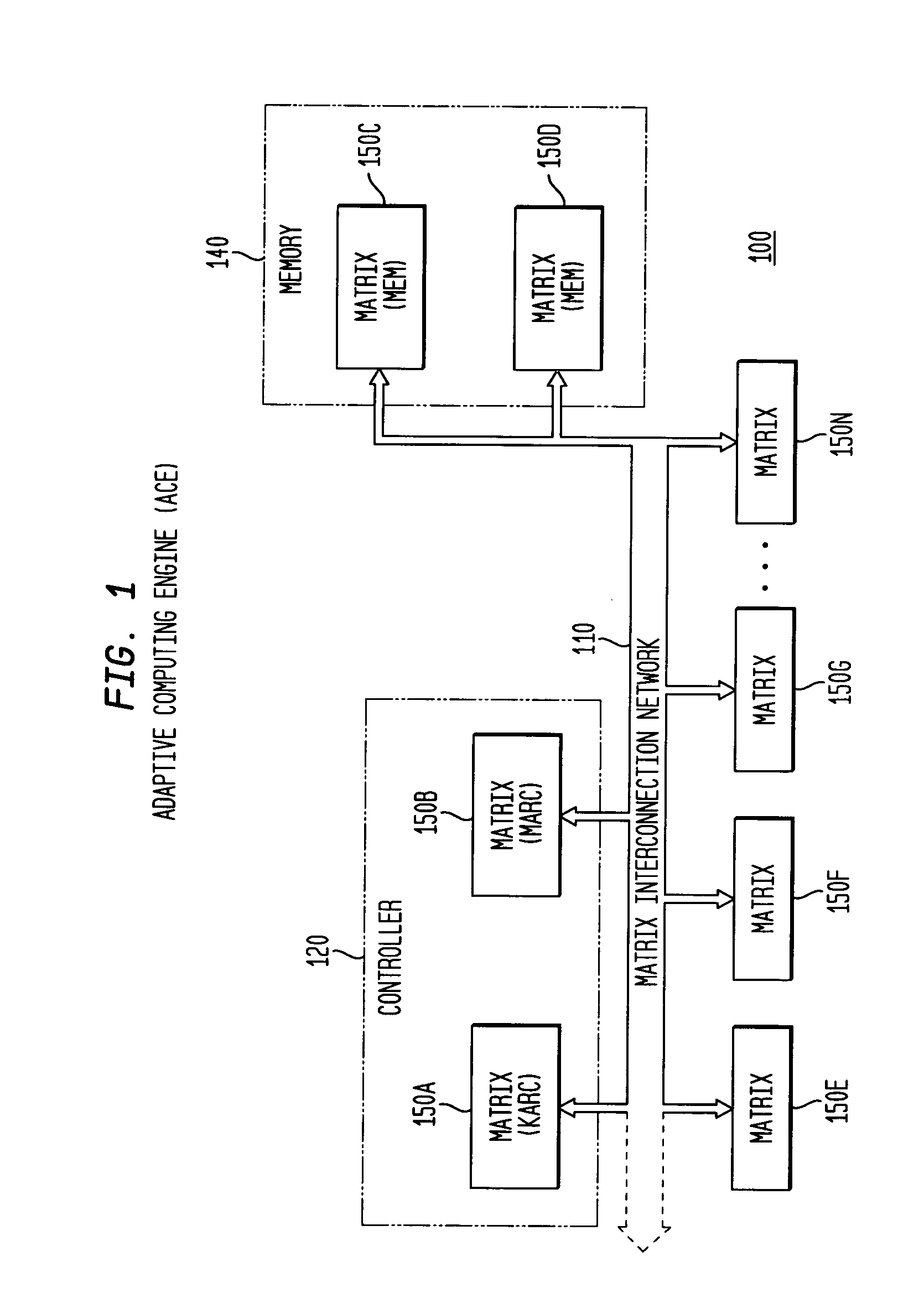
Asynchronous, independent and multiple process shared memory system in an adaptive computing architecture
The present invention provides a system and method for implementation and use of a shared memory. The shared memory may be accessed both independently and asynchronously by one or more processes at corresponding nodes, allowing data to be streamed to multiple processes and nodes without regard to synchronization of the plurality of processes. The various nodes may be adaptive computing nodes, kernel or controller nodes, or one or more host processor nodes. The present invention maintains memory integrity, not allowing memory overruns, underruns, or deadlocks. The present invention also provides for “push back” after a memory read, for applications in which it is desirable to “unread” some elements previously read from the memory.
Owner:NVIDIA CORP
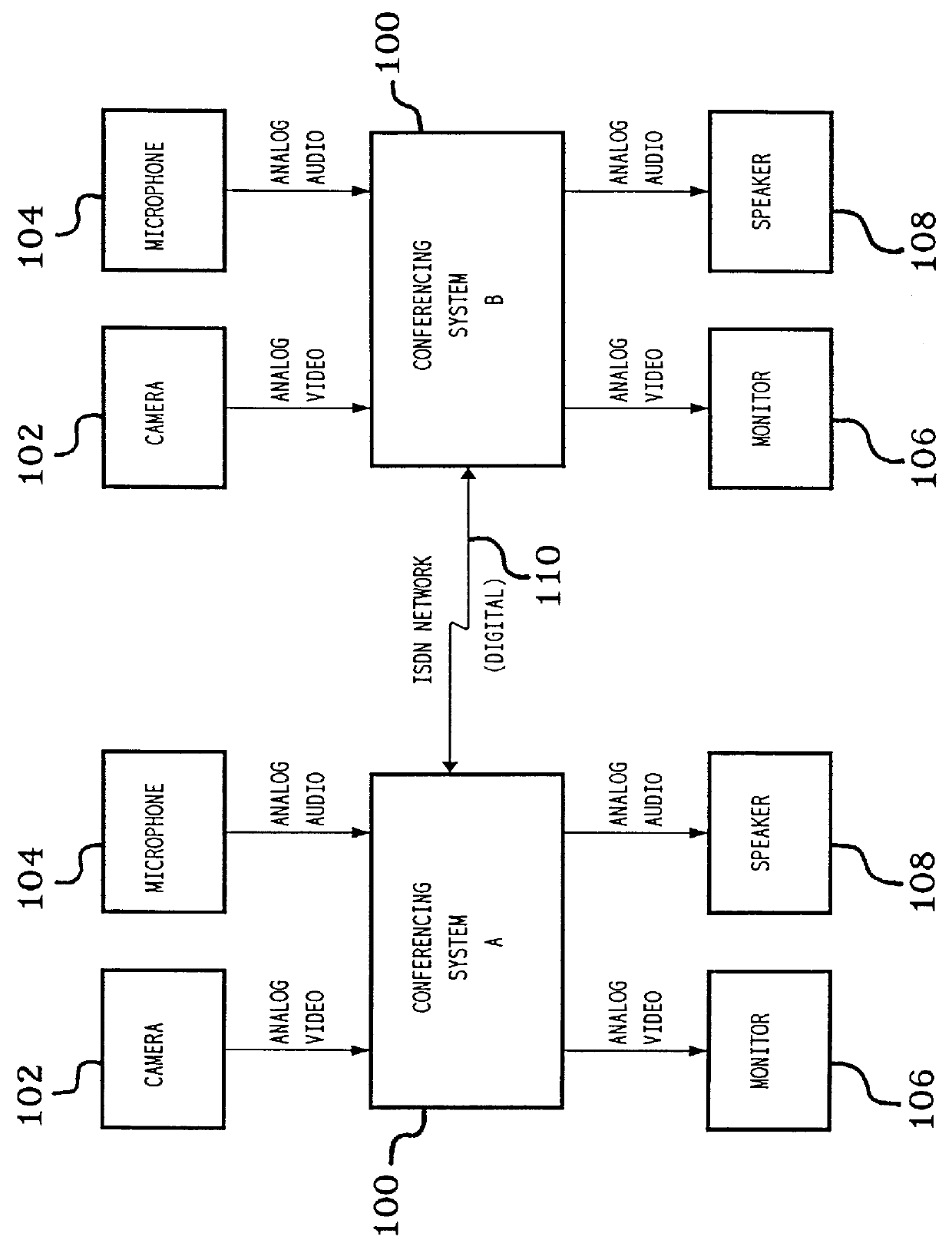
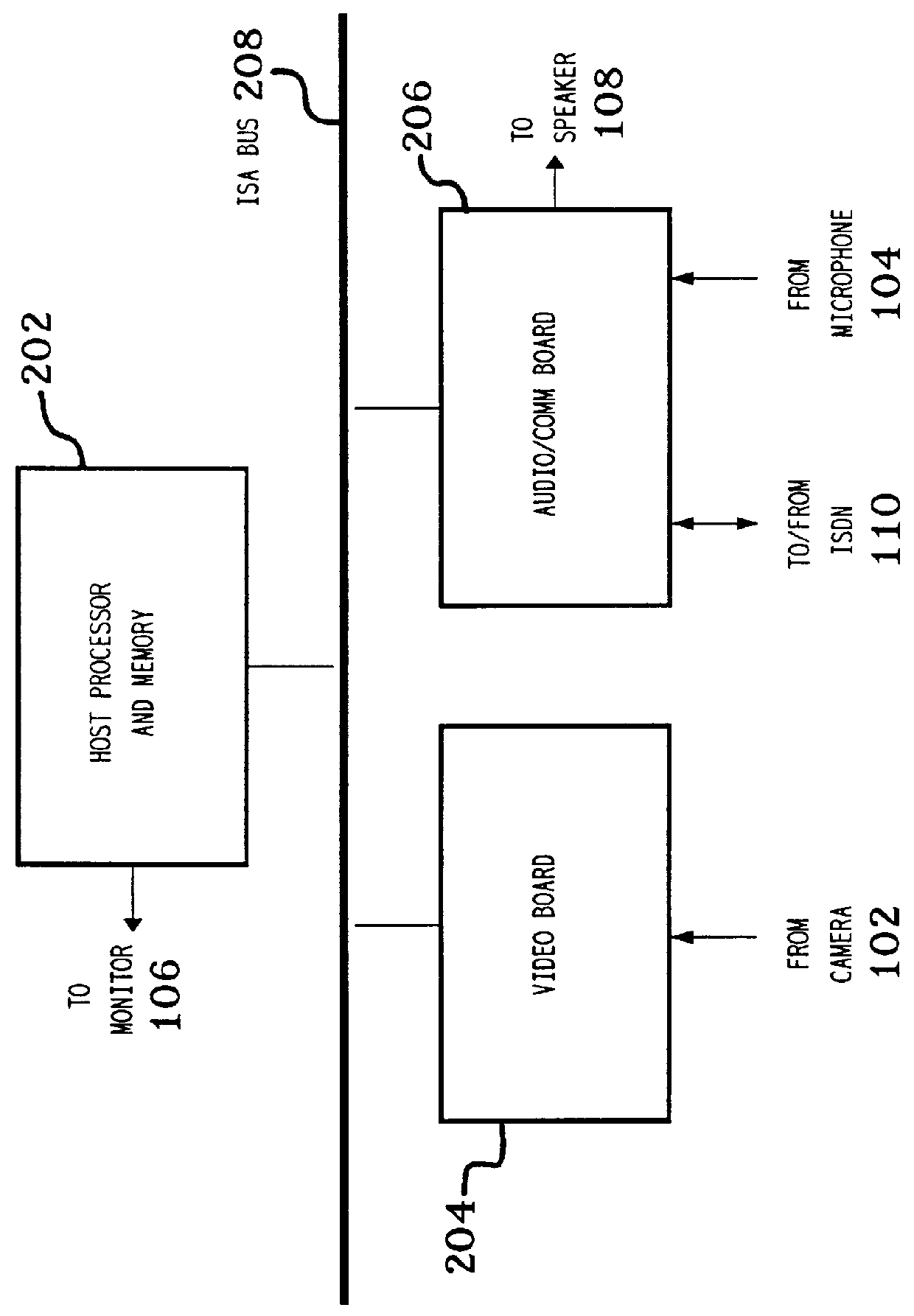
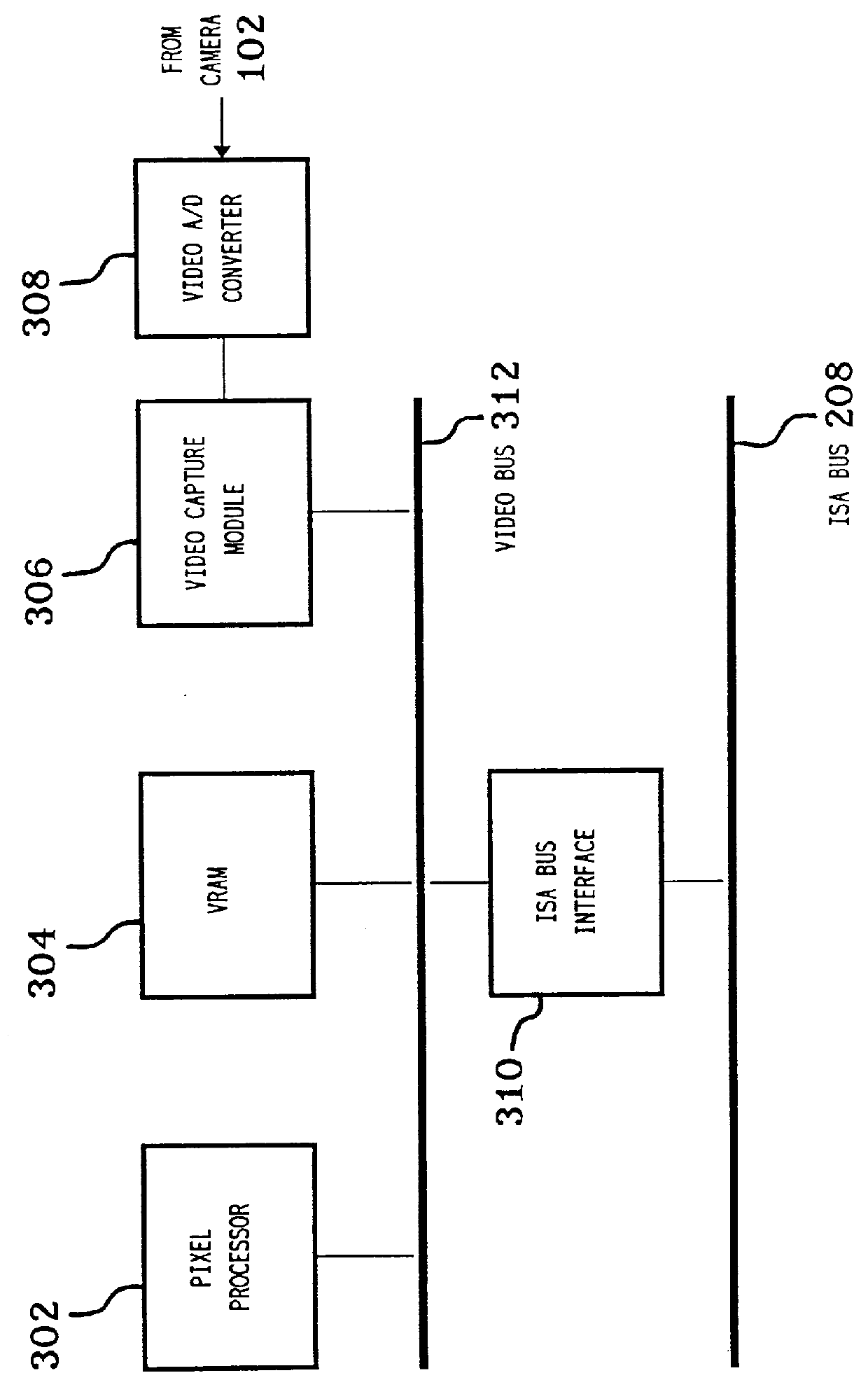
Communications subsystem for computer-based conferencing system using both ISDN B channels for transmission
InactiveUS6125398ASpecial service provision for substationMultiplex system selection arrangementsTelecommunications linkCommunication link
A communications task resides on an audio / communications board of the computer conferencing system. A communications manager and a communications application programming interface reside on a general-purpose host-processor of the computer conferencing system. The communications manager receives local compressed video signals from a video subsystem of the computer conferencing system and passes the local compressed video signals to the communications task. The communications task receives local compressed audio signals from an audio task of the computer conferencing system, the audio task residing on the audio / communications board. The communications task transmits the local compressed video signals and the local compressed audio signals over a communications link to a remote computer conferencing system. The communications task receives remote compressed video signals and remote compressed audio signals over the communications link from the remote computer conferencing system. The communications task passes the remote compressed audio signals directly to the audio task for decompression and playback processing. The communications task passes the remote compressed video signals to the video subsystem for decompression and playback processing.
Owner:INTEL CORP
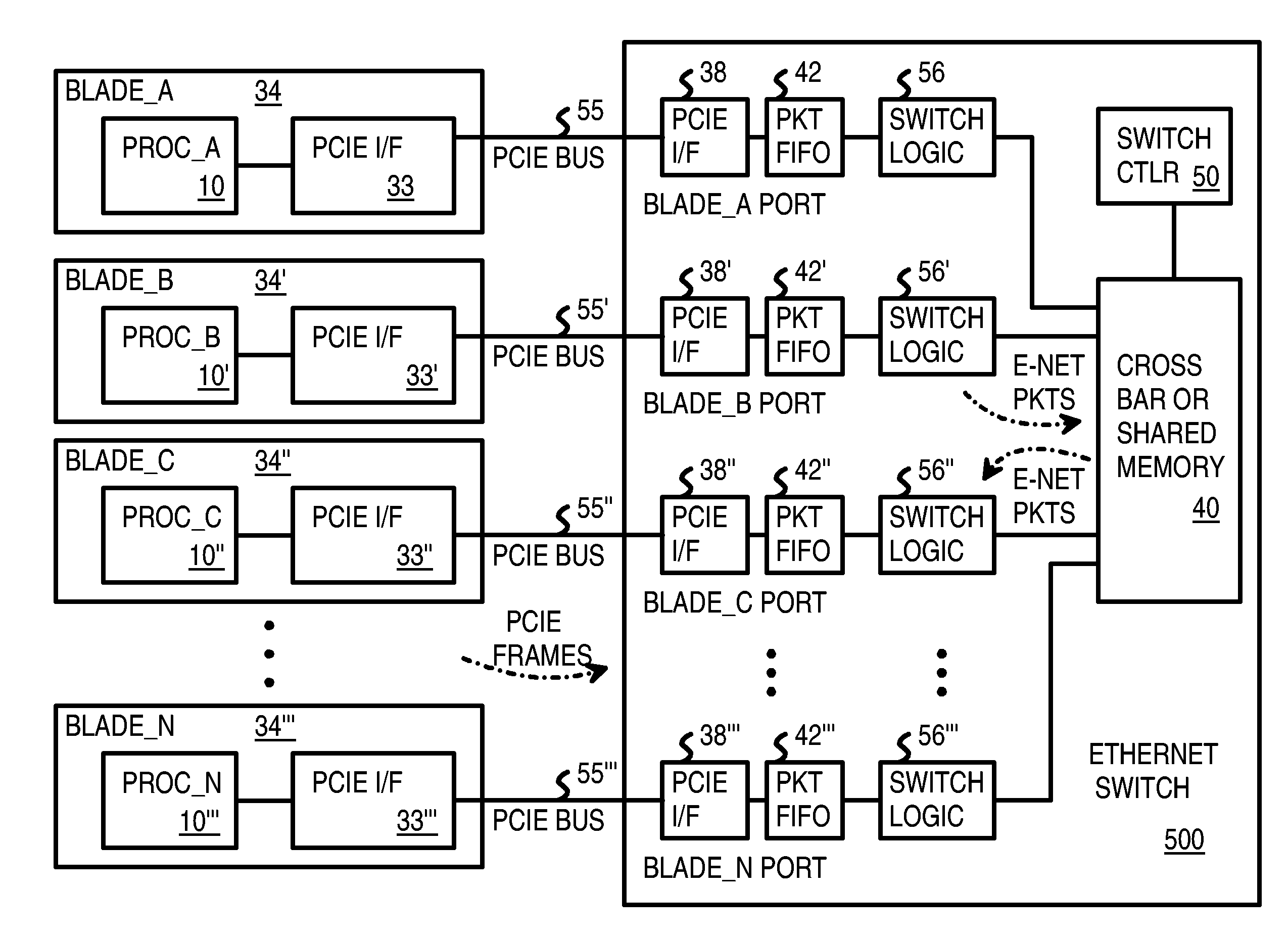
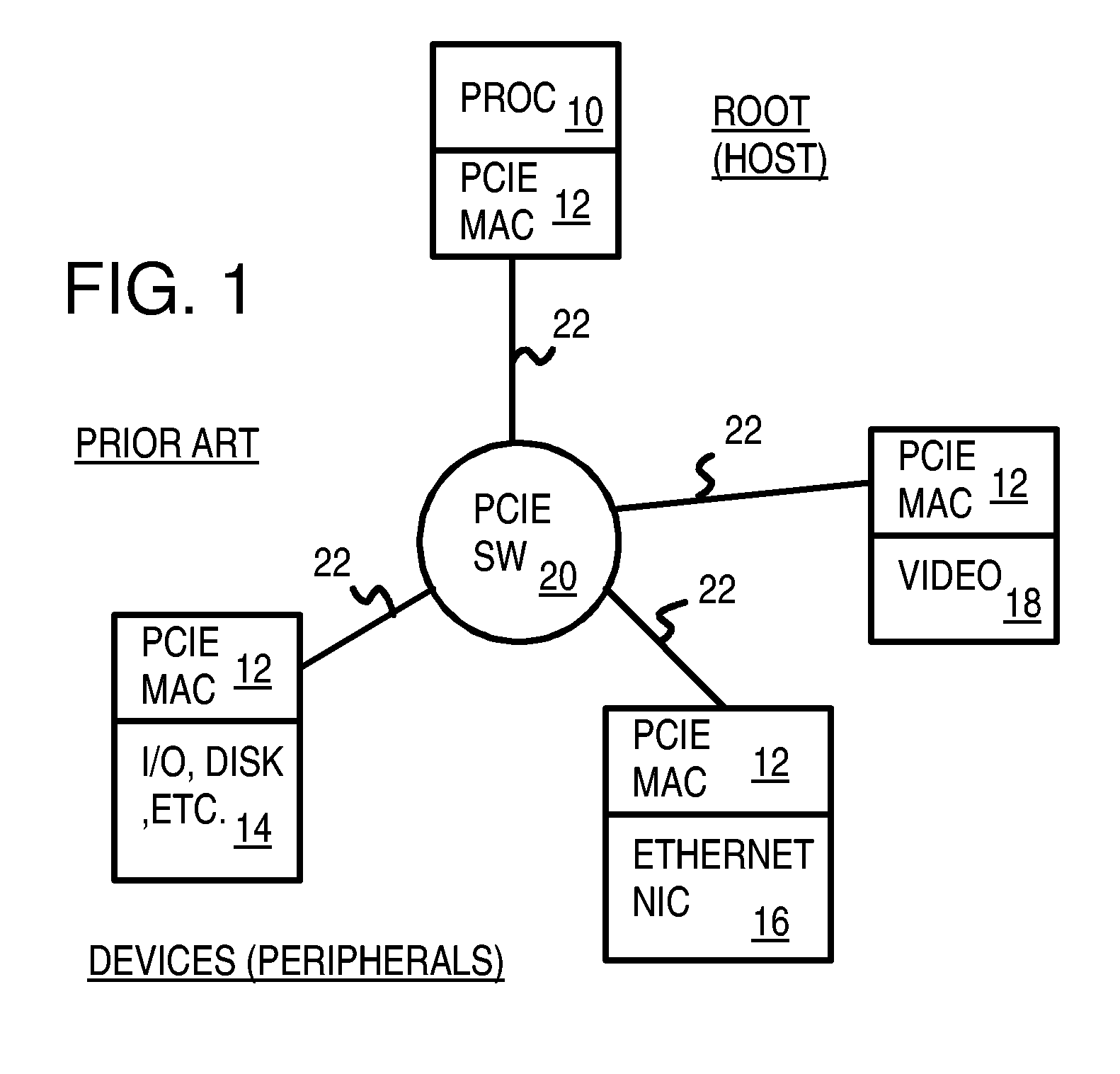
Pseudo-ethernet switch without ethernet media-access-controllers (MAC's) that copies ethernet context registers between PCI-express ports
A Pseudo-Ethernet switch has a routing table that uses Ethernet media-access controller (MAC) addresses to route Ethernet packets through a switch fabric between an input port and an output port. However, the input port and output port have Peripheral Component Interconnect Express (PCIE) interfaces that read and write PCI-Express packets to and from host-processor memories. When used in a blade system, host processor boards have PCIE physical links that connect to the PCIE ports on the Pseudo-Ethernet switch. The Pseudo-Ethernet switch does not have Ethernet MAC and Ethernet physical layers, saving considerable hardware. The switch fabric can be a cross-bar switch or can be a shared memory that stores Ethernet packet data embedded in the PCIE packets. Write and read pointers for a buffer storing an Ethernet packet in the shared memory can be passed from input to output port to perform packet switching.
Owner:DIODES INC
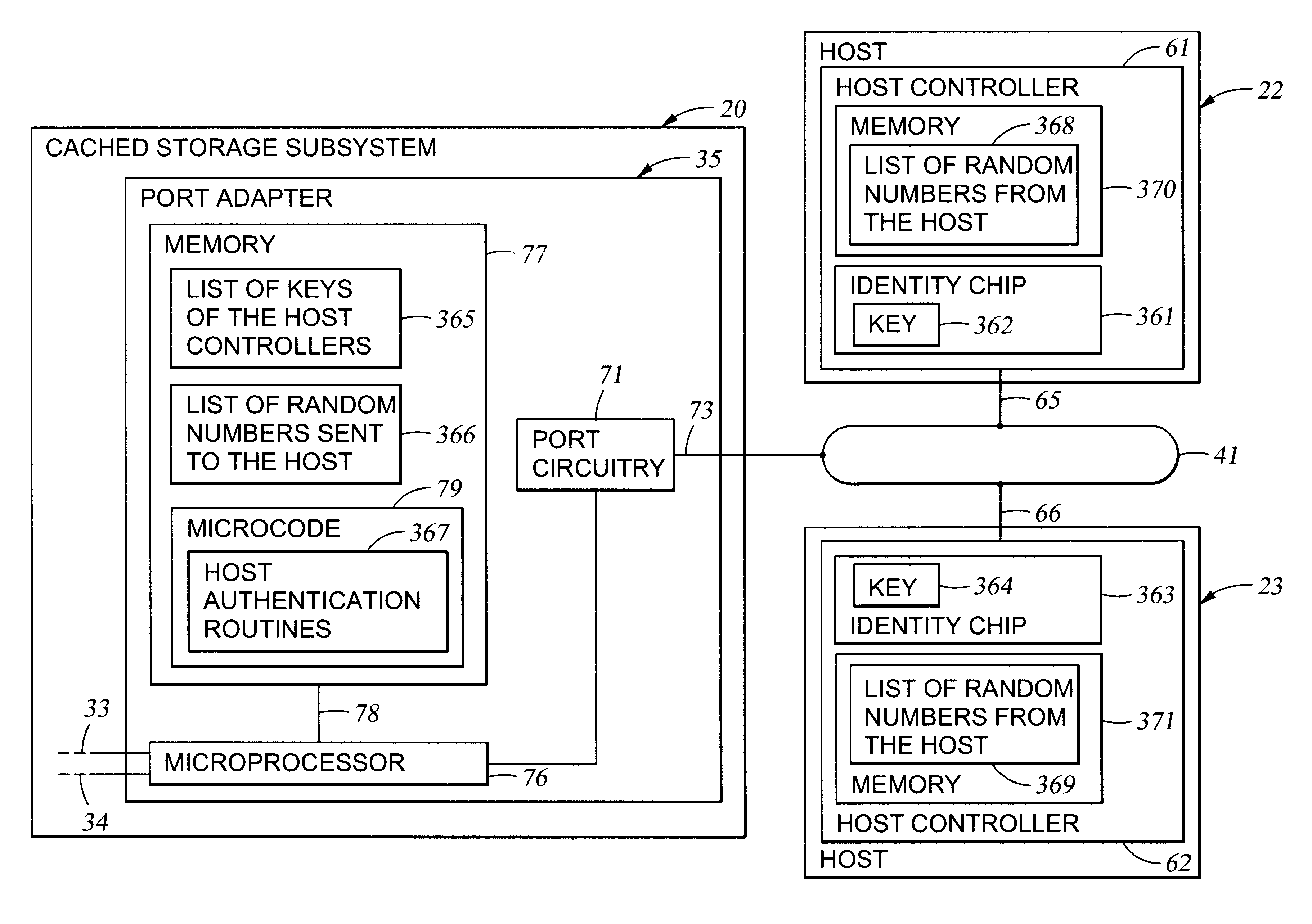
Authentication of a host processor requesting service in a data processing network
InactiveUS6493825B1Key distribution for secure communicationPublic key for secure communicationData processing systemVisual inspection
An object is authenticated by transmitting a random number to the object. The object has an integrated circuit chip including a memory and encryption circuitry. The memory stores information defining an encryption scheme preassigned to the object. The encryption circuitry reads the memory, and encrypts the random number according to the encryption scheme defined by the information read from the memory to produce encrypted data. The memory cannot be read from any output of the integrated chip, and the chip is constructed so that it is virtually impossible to recover the information contained in the memory by visual inspection, probing, or disassembly of the chip. The object is authenticated by checking whether the encrypted data is a correct result of encrypting the data using the encryption scheme pressigned to the object. The method can be used in a data processing system to authenticate each message transmitted by a host processor to a data processing device. For example, when a host logs into the data processing device, the data processing device transmits a series of random numbers to the host. The host encrypts the random numbers to produce a series of encrypted data, and the data processing device concurrently encrypts the random numbers to produce a series of encrypted values. The host inserts respective encrypted data into each message, and the data processing device authenticates each message by comparing the encrypted data in the message to a corresponding encrypted value.
Owner:EMC IP HLDG CO LLC
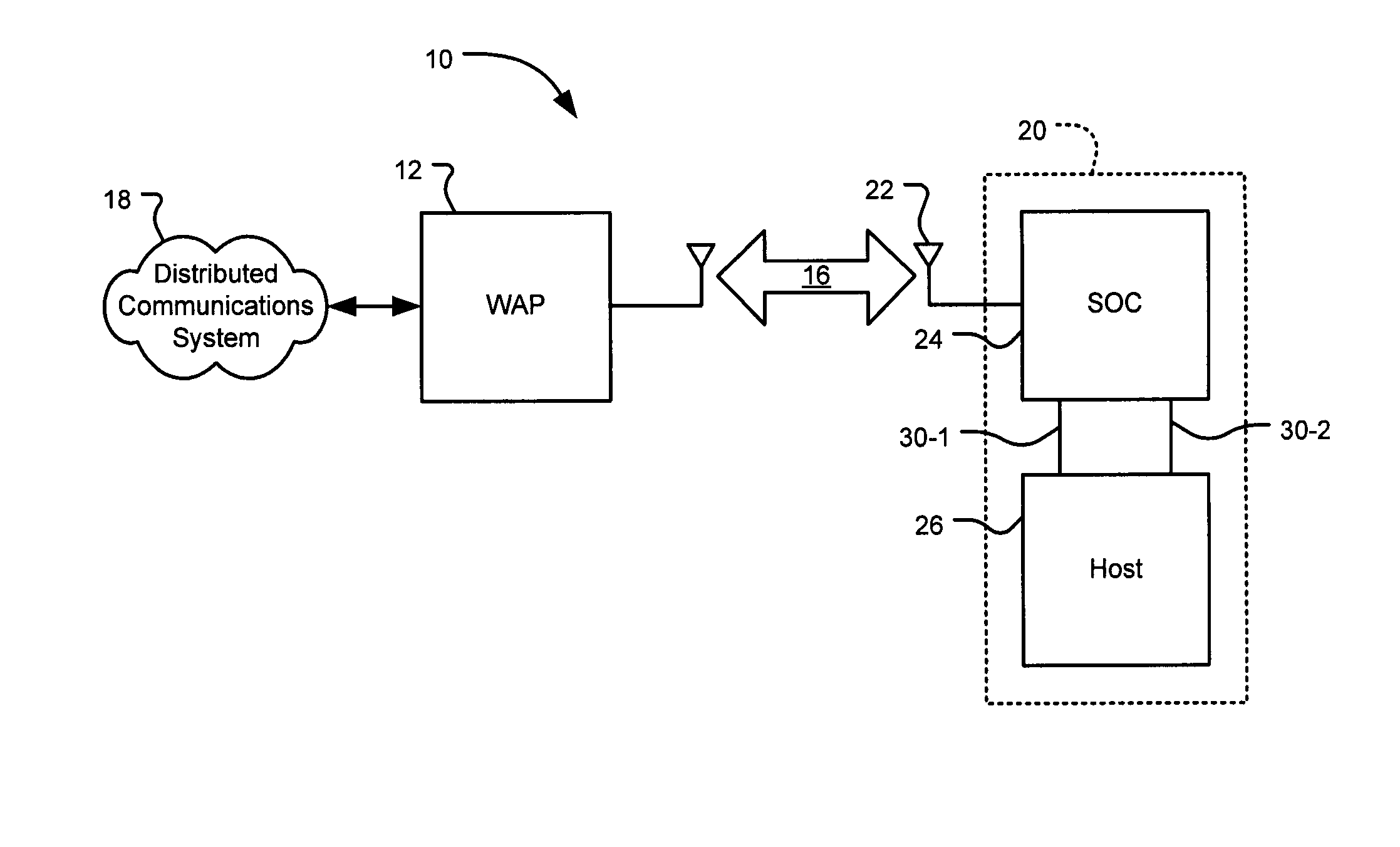
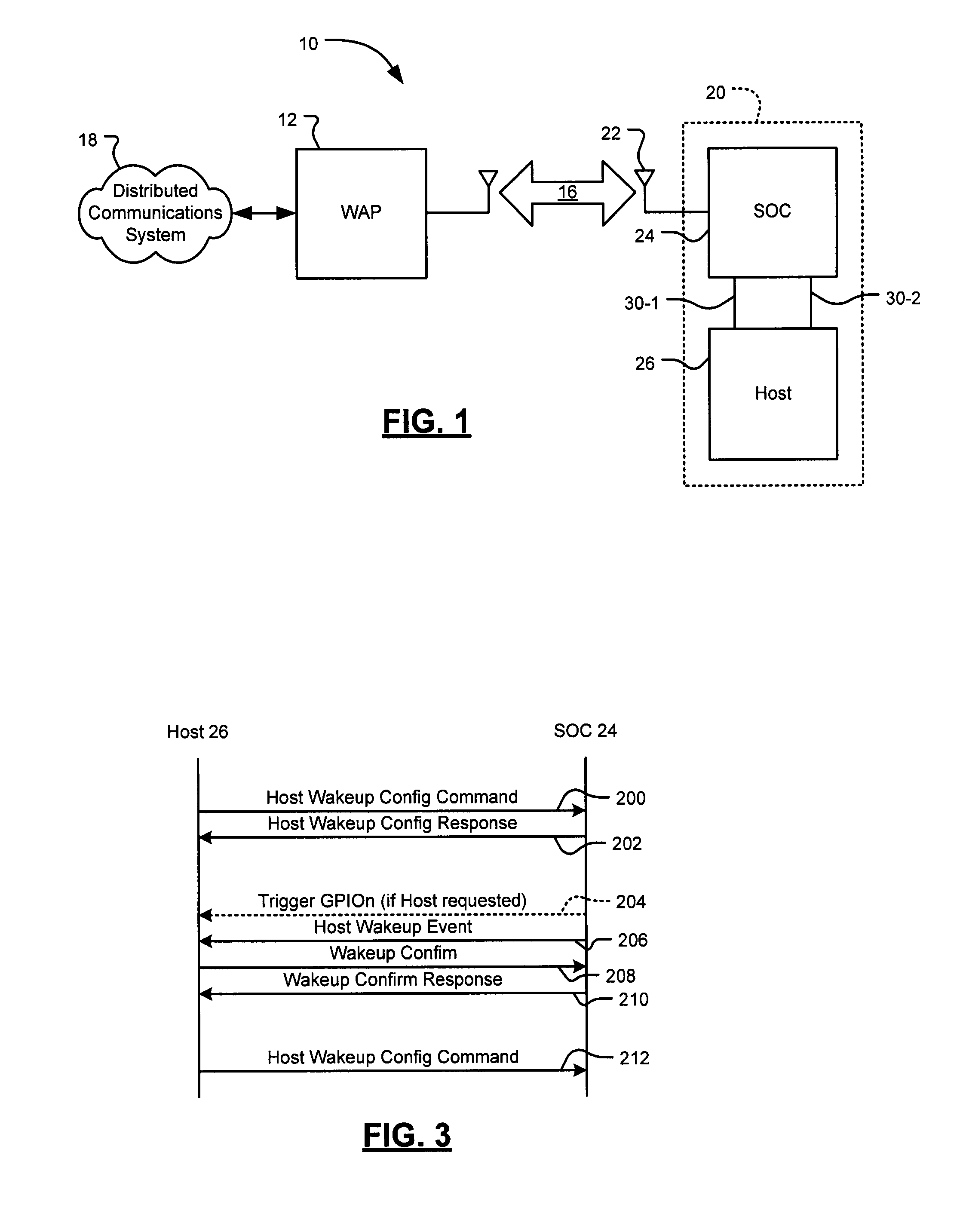
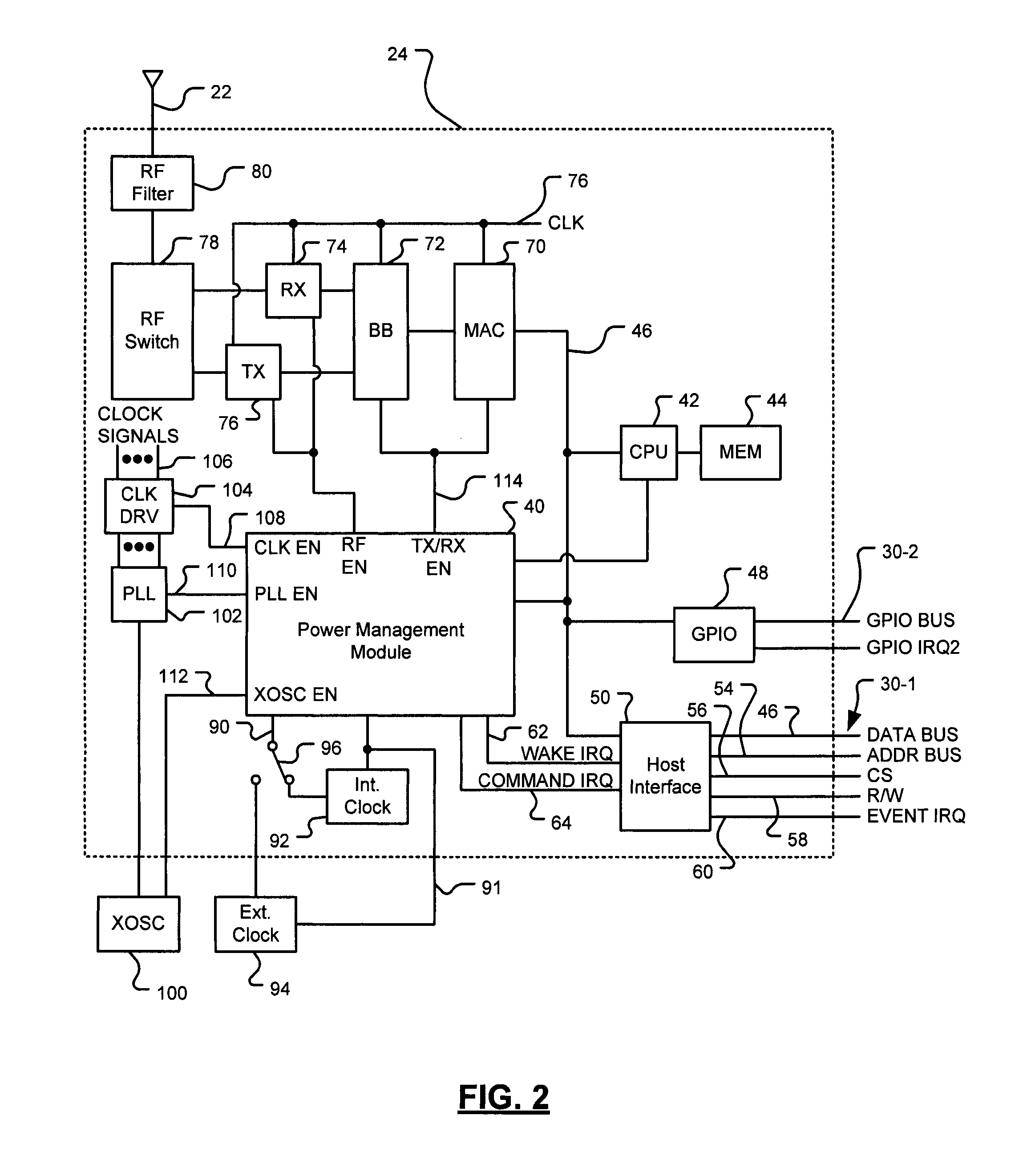
Wake on wireless LAN schemes
A system includes a host interface module and a power management module. The host interface module is configured to receive configuration information from a host processor of a wireless device. The configuration information indicates that the host processor is to (i) operate in a power save mode, and (ii) in response to the wireless device receiving data of a predetermined category from a wireless network, transition from the power save mode to an active mode. The power management module is configured to generate a first signal in response to the wireless device receiving data of the predetermined category from the wireless network. The first signal transitions the host processor from the power save mode to the active mode in which the host processor processes the data of the predetermined category.
Owner:NXP USA INC
Speech recognition and control system, program product, and related methods
InactiveUS20070288242A1Improve recognition accuracySmall vocabulary sizeSpeech recognitionCapability managementControl system
A speech activated control system for controlling aerial vehicle components, program product, and associated methods are provided. The system can include a host processor adapted to develop speech recognition models and to provide speech command recognition. The host processor can be positioned in communication with a database for storing and retrieving speech recognition models. The system can include an avionic computer in communication with the host processor and adapted to provide command function management, a display and control processor in communication with the avionic computer adapted to provide a user interface between a user and the avionic computer, and a data interface positioned in communication with the avionic computer and the host processor provided to divorce speech command recognition functionality from vehicle or aircraft-related speech-command functionality. The system can also include speech actuated command program product at least partially stored in the memory of the host processor and adapted to provide the speech recognition model training and speech recognition model recognition functionality.
Owner:LOCKHEED MARTIN CORP
Method and apparatus for adjusting overflow buffers and flow control watermark levels
InactiveUS6084856AReduce congestionHigh trafficError prevention/detection by using return channelTransmission systemsShared memory architectureTraffic capacity
A network switch having a shared memory architecture for storing data frames includes configuration registers that are programmable by a host processor to adaptively adjust overflow buffer locations and flow control watermark levels based on monitored network traffic. The host processor allocates shared resources by setting memory configuration registers corresponding to an external memory, where the network switch uses the external memory for storing received data frames, Management Information Base (MIB) counter values, and output port overflow data. The host processor periodically reads the MIB counter values from the external memory, and adjusts flow control watermark levels or the memory configuration registers in the network switch based on rate-based network traffic derived from the MIB counter values. PCI burst transfers between the host processor and the external memory via the network switch ensure that stored data is not lost during reconfiguration of the external memory. The disclosed arrangement enables resources used by the network switch to be adjusted to minimize congestion by borrowing resources from network ports serving idle stations.
Owner:GLOBALFOUNDRIES INC
Method of conducting a transaction using an NFC device
ActiveUS20110226853A1Multiplex system selection arrangementsNear-field transmissionEngineeringIntegrated circuit
The invention relates to a method of conducting a transaction between an NFC device and a contactless integrated circuit of the passive reader type. The method includes providing, in the contactless integrated circuit, at least one reader application emulation program and, by an intermediary unit of the NFC device, establishing a communication with the contactless integrated circuit, receiving from the contactless integrated circuit reader application commands and transferring the commands to the first host processor, and receiving card application responses supplied by the first host processor and transferring the responses to the contactless integrated circuit.
Owner:VERIMATRIX INC
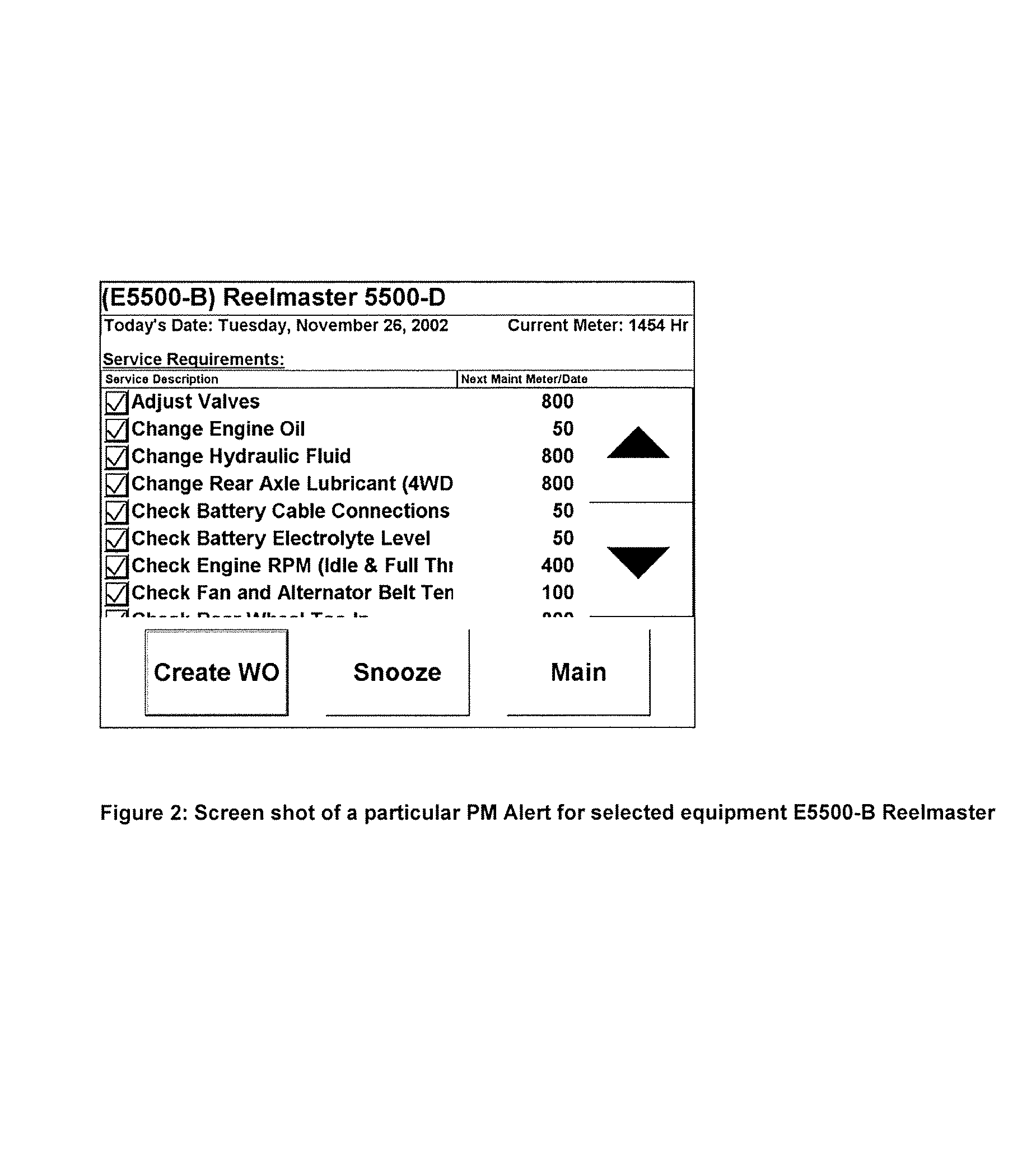
Integrated system for routine maintenance of mechanized equipment
ActiveUS7356393B1Easy accessEffective maintenanceVehicle testingRegistering/indicating working of vehiclesComputerized systemMaster processor
An apparatus and method for managing the preventative maintenance requirements and unscheduled repairs on a fleet of vehicles. The apparatus includes a computer system having a host processor and a database accessible by the host processor, and at least one maintenance response station communicating with the host processor. The database contains vehicle specific maintenance schedules indicating recommended maintenance intervals for scheduled maintenance, where each scheduled maintenance has associated maintenance tasks. The method involves periodically receiving signals at the host processor containing maintenance trigger data associated with a specific vehicle in the fleet of vehicles, comparing the received maintenance trigger data to maintenance schedule data contained in the database, and for each comparison, determining whether maintenance is indicated, and if so, identifying the vehicle at a vehicle response station.
Owner:TURFCENTRIC
Method for routing incoming and outgoing data in an NFC chipset
A method for routing data in a chipset comprising at least two host processors and one RFID-type contactless data send / receive interface configurable according to several operating modes and according to several contactless communication protocols includes routing, to at least one of the host processors, data received by the contactless data send / receive interface via a contactless data transmission channel. The method further includes determining a destination point of the data in a host processor using as criteria to determine the destination point the operating mode and the contactless communication protocol used by the contactless data send / receive interface to create the contactless data transmission channel through which the data are received.
Owner:VERIMATRIX INC
Scanning device for coded data
InactiveUS20050254106A9Input/output for user-computer interactionDigital data processing detailsGratingPhotodetector
A scanning device for: scanning coded data disposed on a surface; and generating interaction data based on the sensed coded data, the interaction data being indicative of interaction of the scanning device with the surface; the coded data including, at a plurality of locations on the interface surface, a corresponding plurality of coded data portions, the scanning device comprising: (a) a laser source and scan optics configured to emit a scanning beam through an aperture in a housing of the scanning device, the scanning beam being directed in first and second orthogonal directions to thereby generate a raster scan pattern over a scanning patch, the scanning patch being positioned to cause the exposure of the at least one coded data portion when the surface and the sensing device are positioned operatively with respect to each other; (b) a photodetector for detecting reflection of the scanning beam from the surface, thereby to capture sample information; (c) at least one analog to digital converter for converting the captured sample information into sample data; (d) a first framestore for storing successive sample data as image data; (e) an image processor for processing the image data to generate processed image data; (e) a host processor for generating the interaction data based at least partially on the processed image data.
Owner:SILVERBROOK RES PTY LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com