Patents
Literature
138 results about "Operating system security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
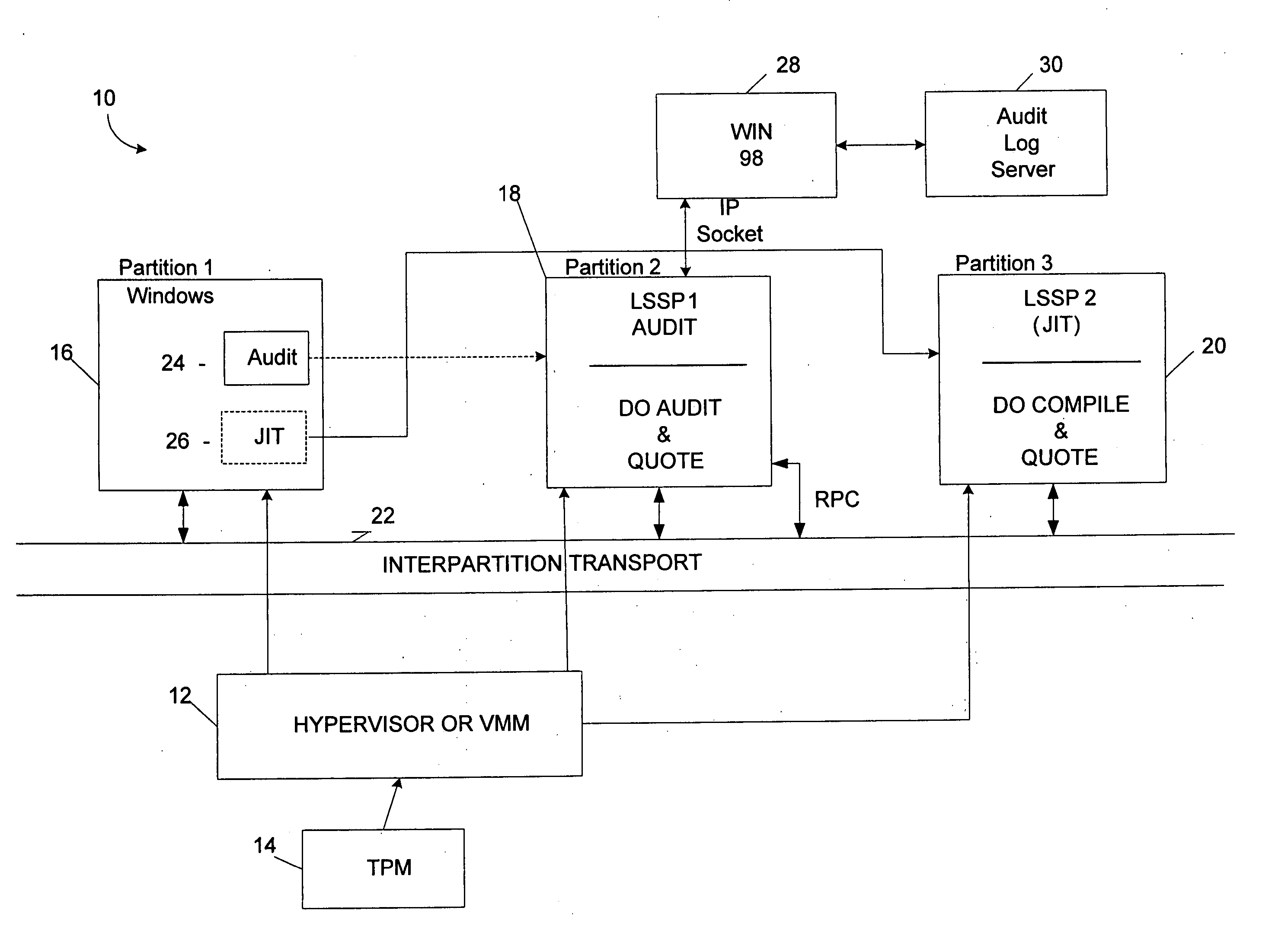
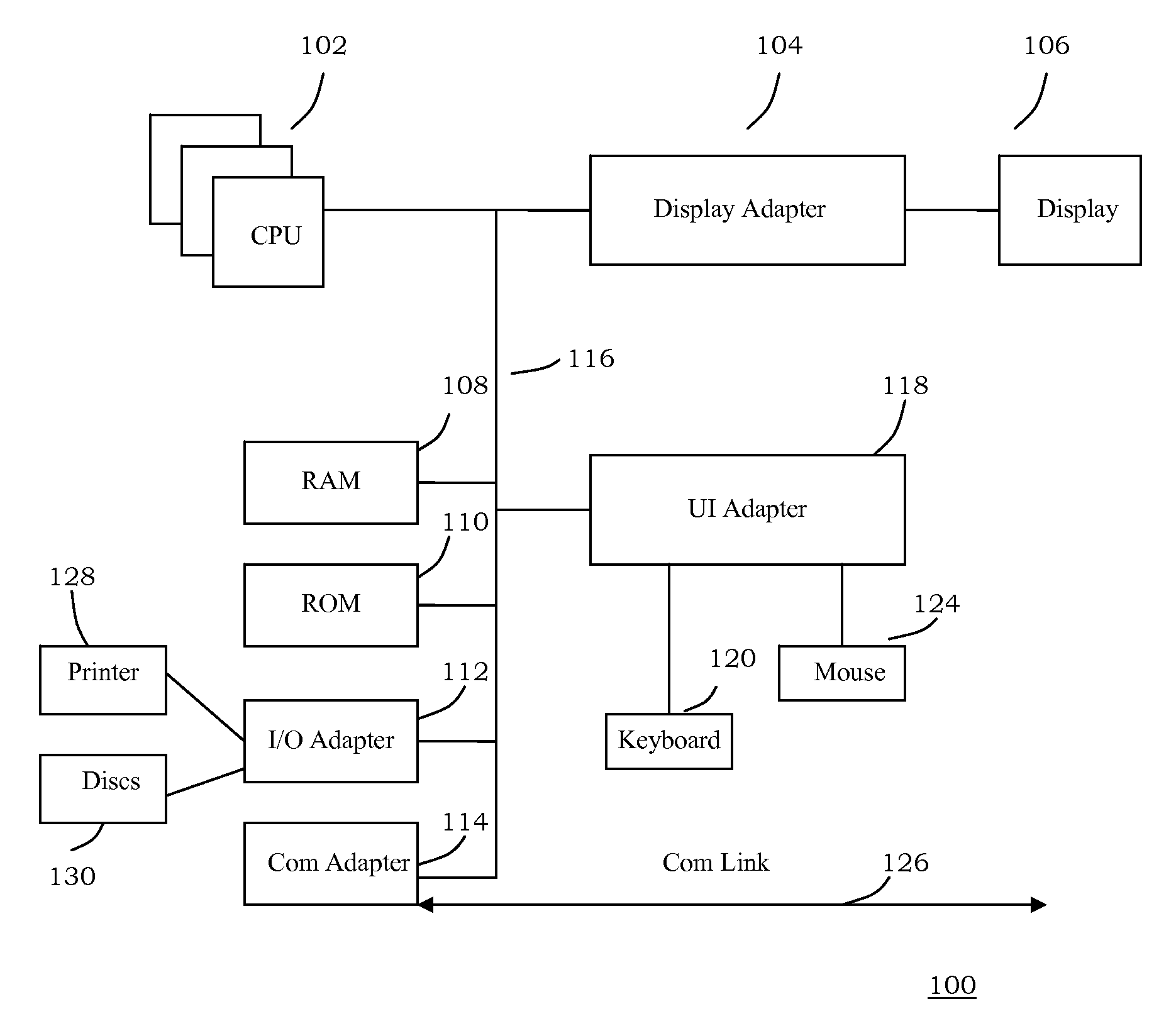
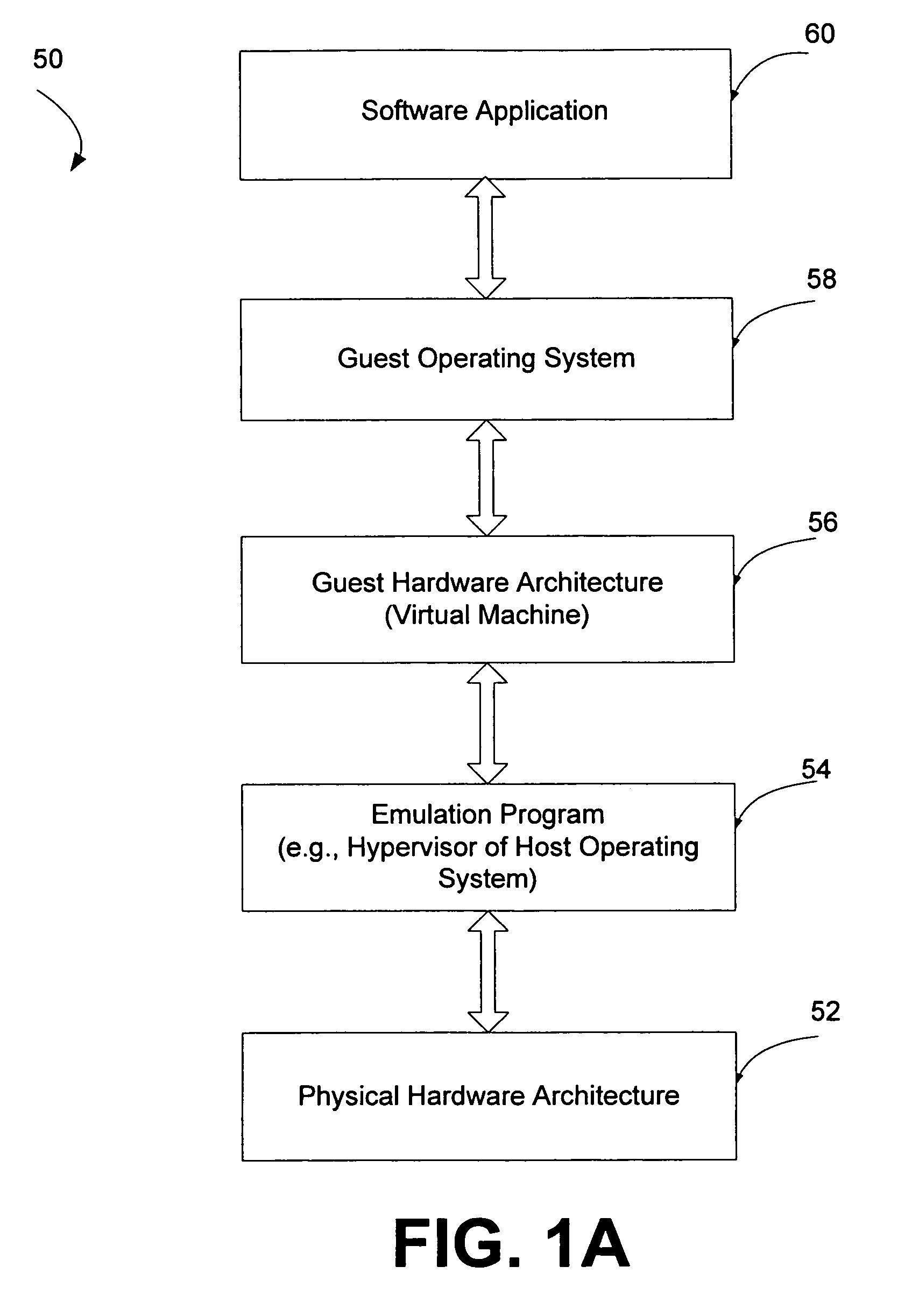
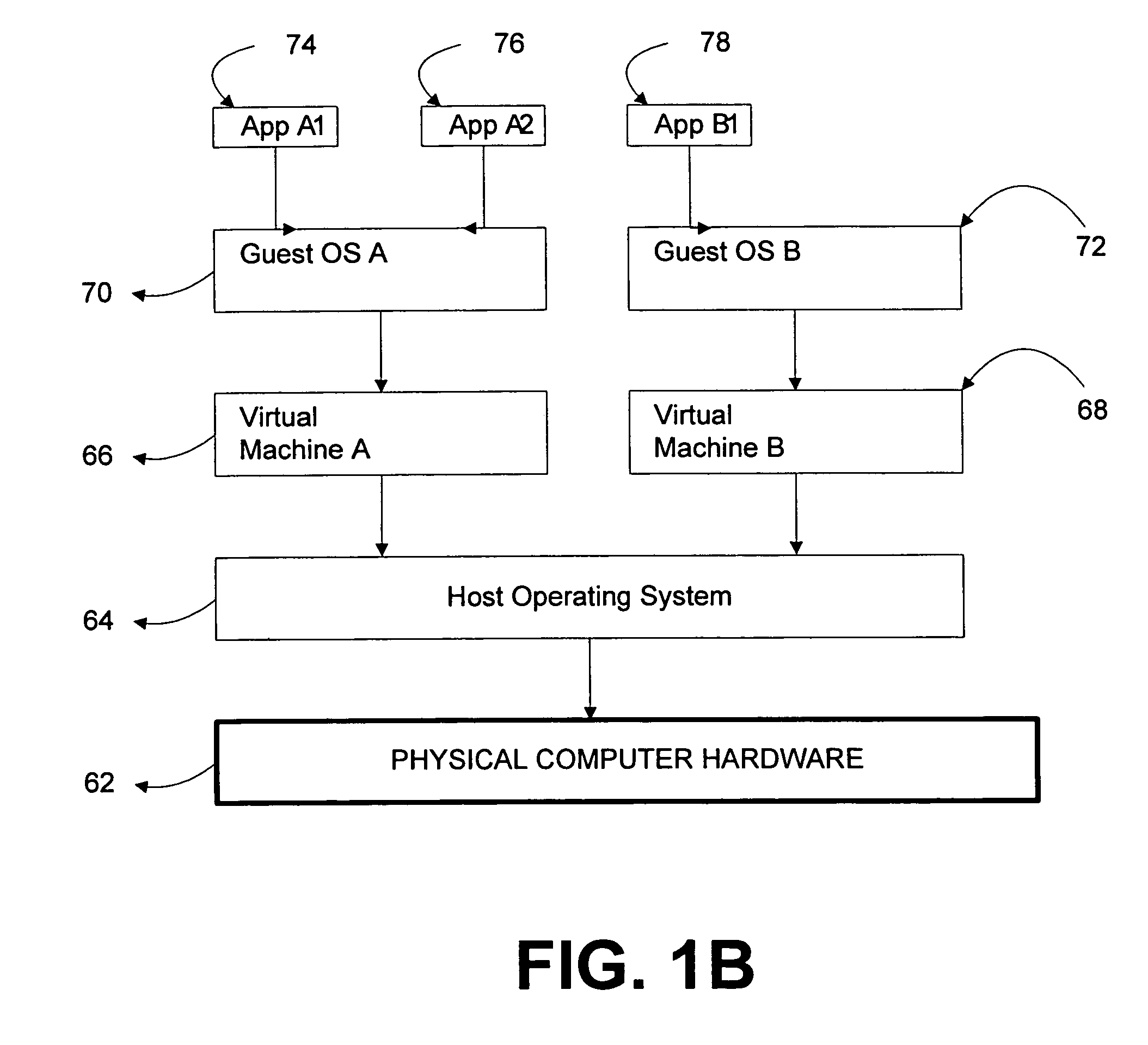
Local secure service partitions for operating system security
ActiveUS20060236127A1Guaranteed growthSmall sizeVolume/mass flow measurementUnauthorized memory use protectionOperational systemOperating system security
Systems and methods provide multiple partitions hosted on an isolation technology such as a hypervisor where at least one of the partitions, a local secure service partition (LSSP), provides security services to other partitions. The service partitions (LSSPs) host those high assurance services that require strict security isolation, where the service can be shared across partitions and accessed even when the user is not connected to a network. The LSSP also can certify the results of any computation using a key signed by a TPM attestation identity key (AIK), or other key held securely by the hypervisor or a service partition. The LSSPs may be configured to provide trusted audit logs, trusted security scans, trusted cryptographic services, trusted compilation and testing, trusted logon services, and the like.
Owner:MICROSOFT TECH LICENSING LLC
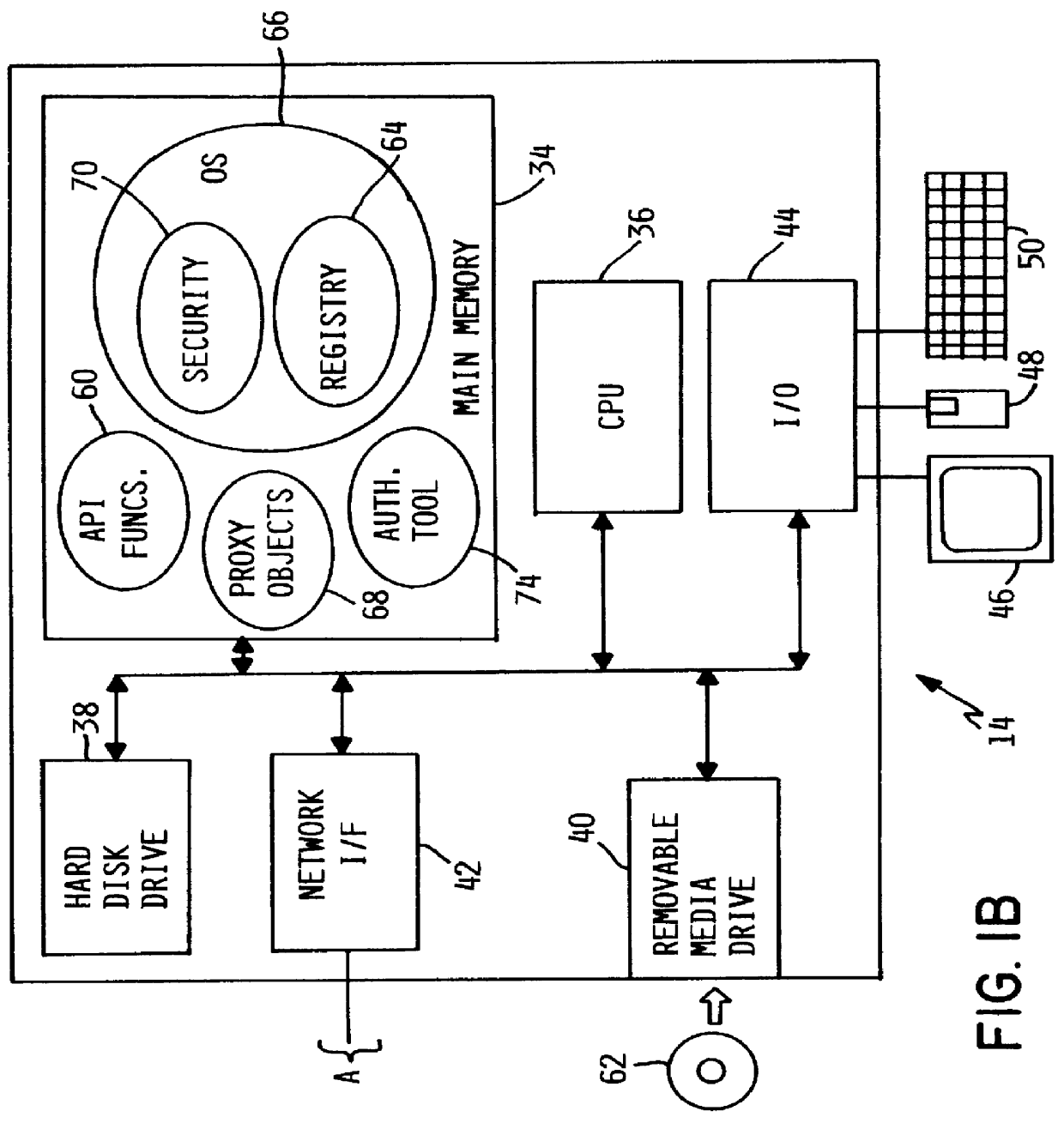
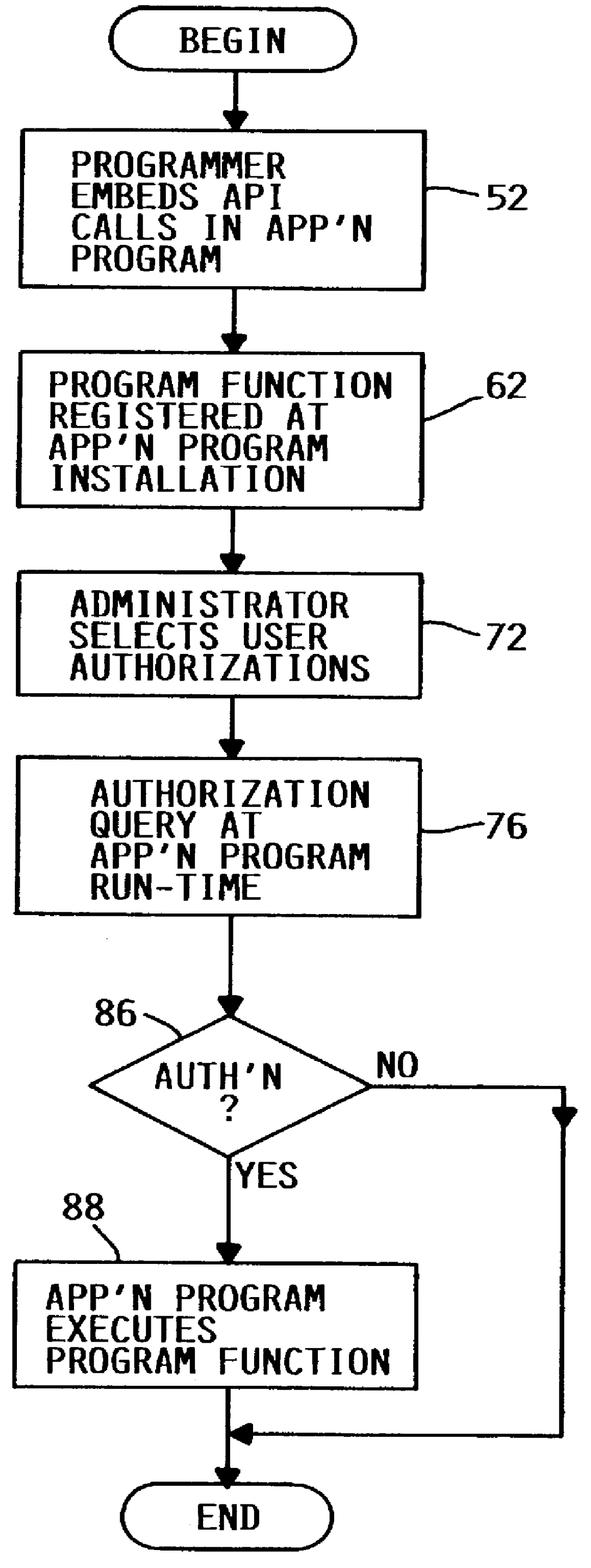
Limit access to program function
InactiveUS6101607ASpecific access rightsDigital data processing detailsOperational systemApplication programming interface
A method, system and computer program product for selectively restricting access to a program function in a computer system having an operating system security mechanism operates via an application programming interface (API) that includes a program function registration API function, an authorization selection API function, and an authorization query API function. In response to a call to the API registration function, the program function is registered in a repository in the computer system. After the program function has been registered, a system administrator can select user authorizations using a software tool that includes calls to the authorization selection API function. The system administrator may select whether a particular user or group of users is authorized to access each registered program function. A programmer can embed a call to the authorization query API function in an application program, which includes or calls the program function. When the application program reaches the call to the authorization query API function, the function is executed and returns an indicator or value indicating whether or not that user is allowed to access the program function.
Owner:IBM CORP
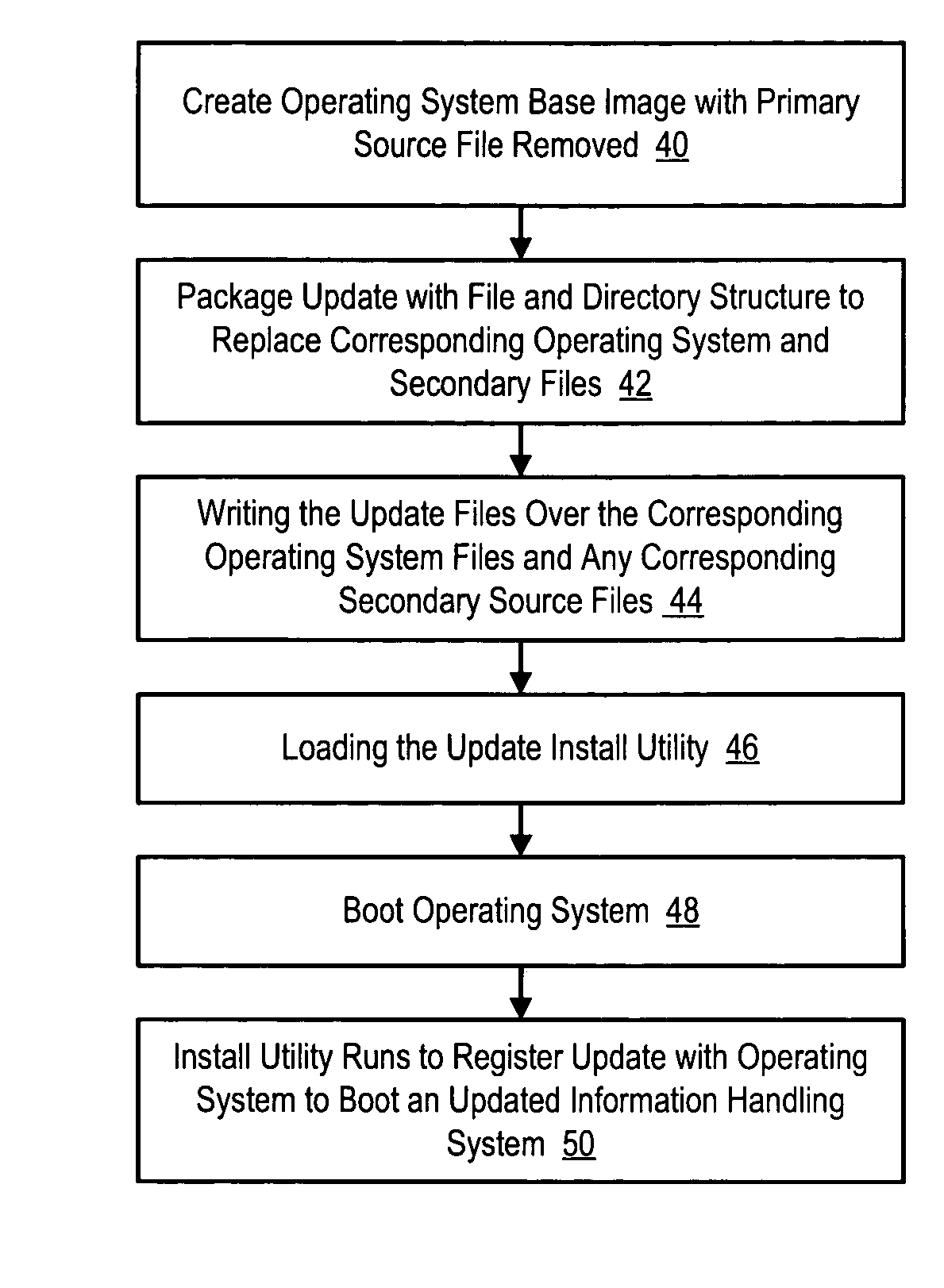
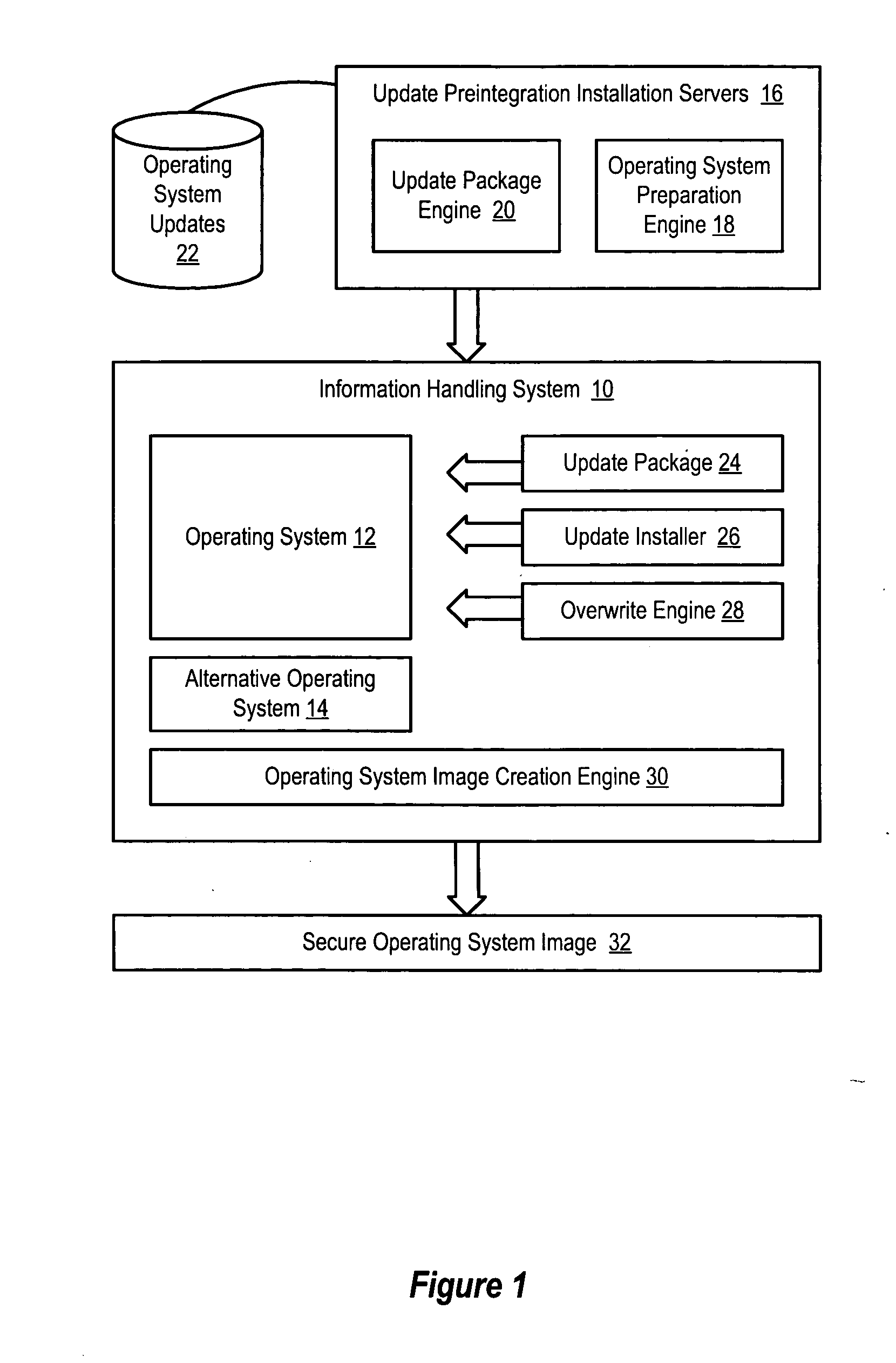
System and method for preintegration of updates to an operating system
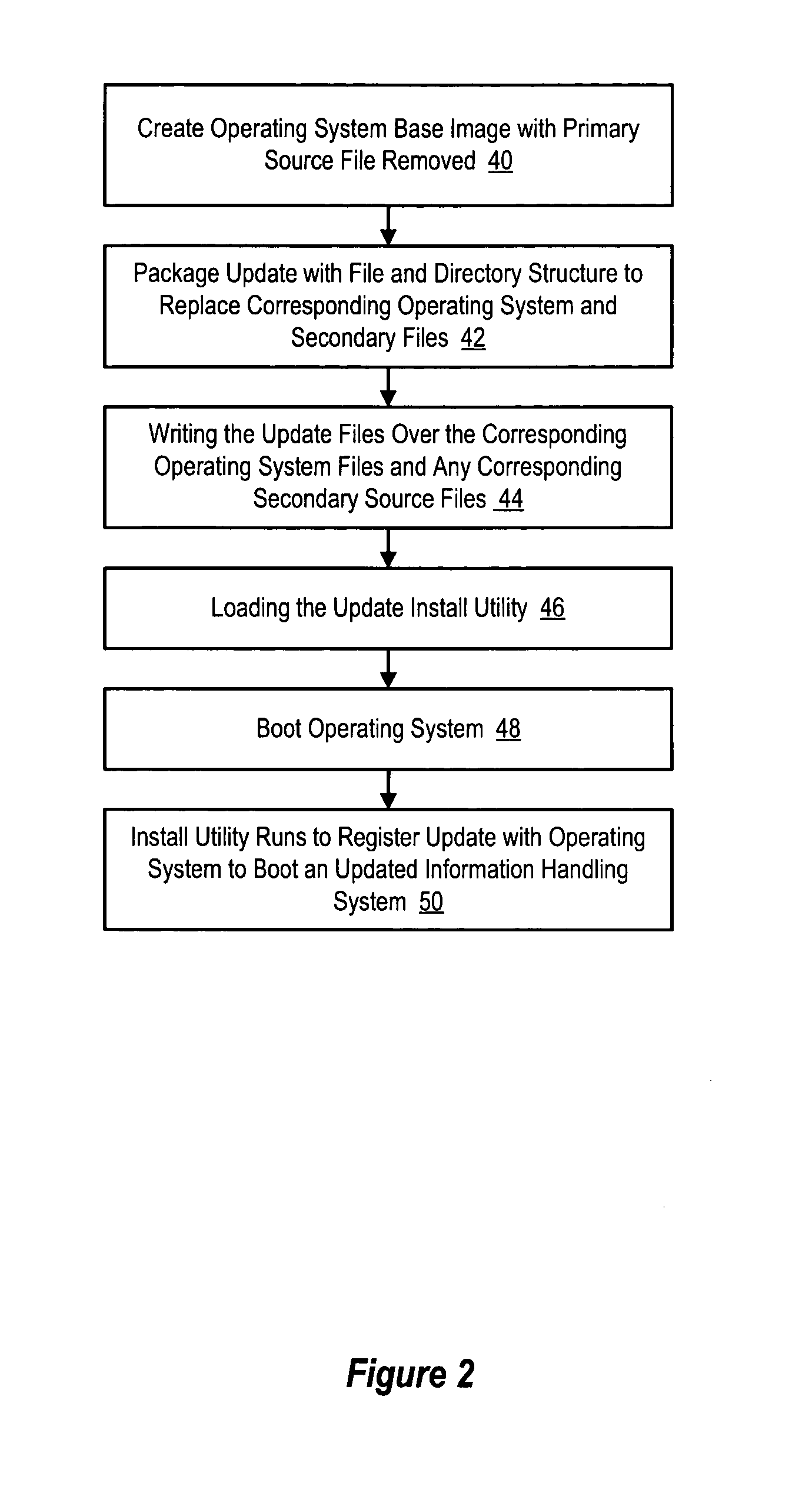
InactiveUS20050172280A1Reduce risk of disruptionReduce disadvantagesPlatform integrity maintainanceProgram loading/initiatingOperational systemOperating system security
An operating system has security updates preintegrated to reduce vulnerability of the operating system to malicious programs, such as worms. Preintegration writes update files over corresponding operating system files before boot of the operating system so that malicious programs are not provided an opportunity to attack the operating system during a post-boot security update. An update package extracts update files, such as QFE files, and prepares the update files within a file and directory structure corresponding to the operating system. An overwrite engine running on an alternative operating system writes the update files to the operating system so that the operating system boots secure from attack by worms that the updates are intended to prevent.
Owner:DELL PROD LP
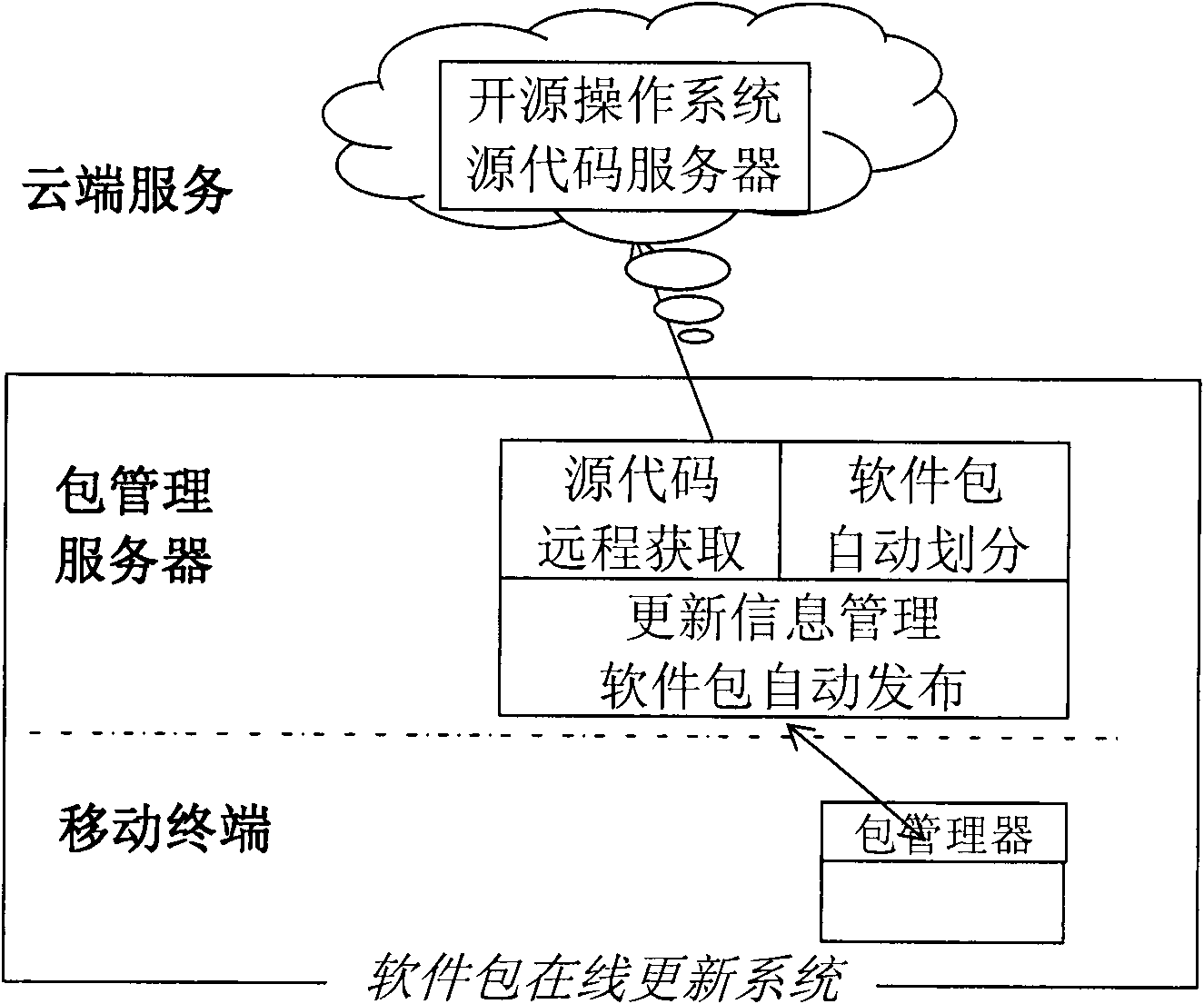
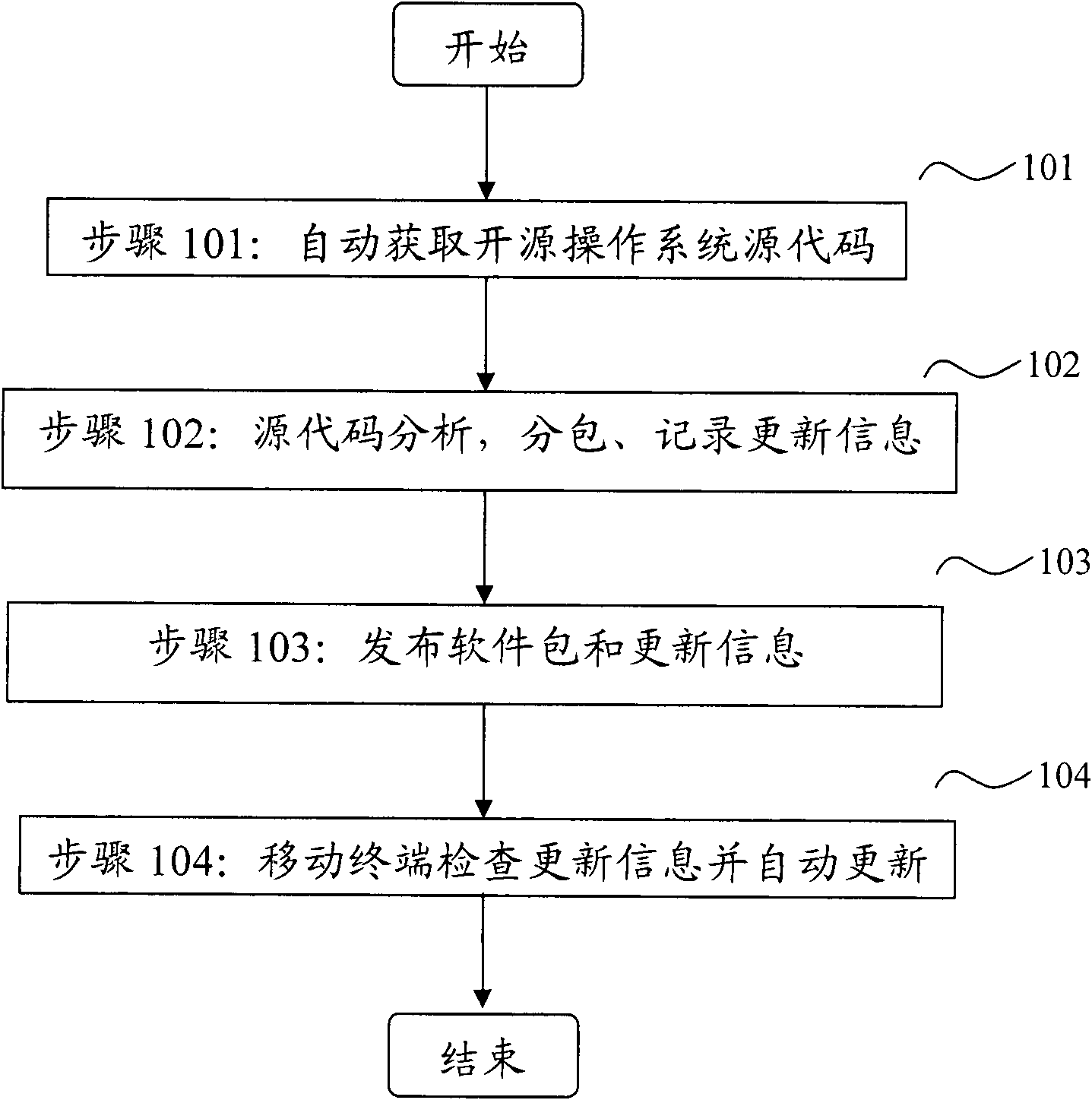
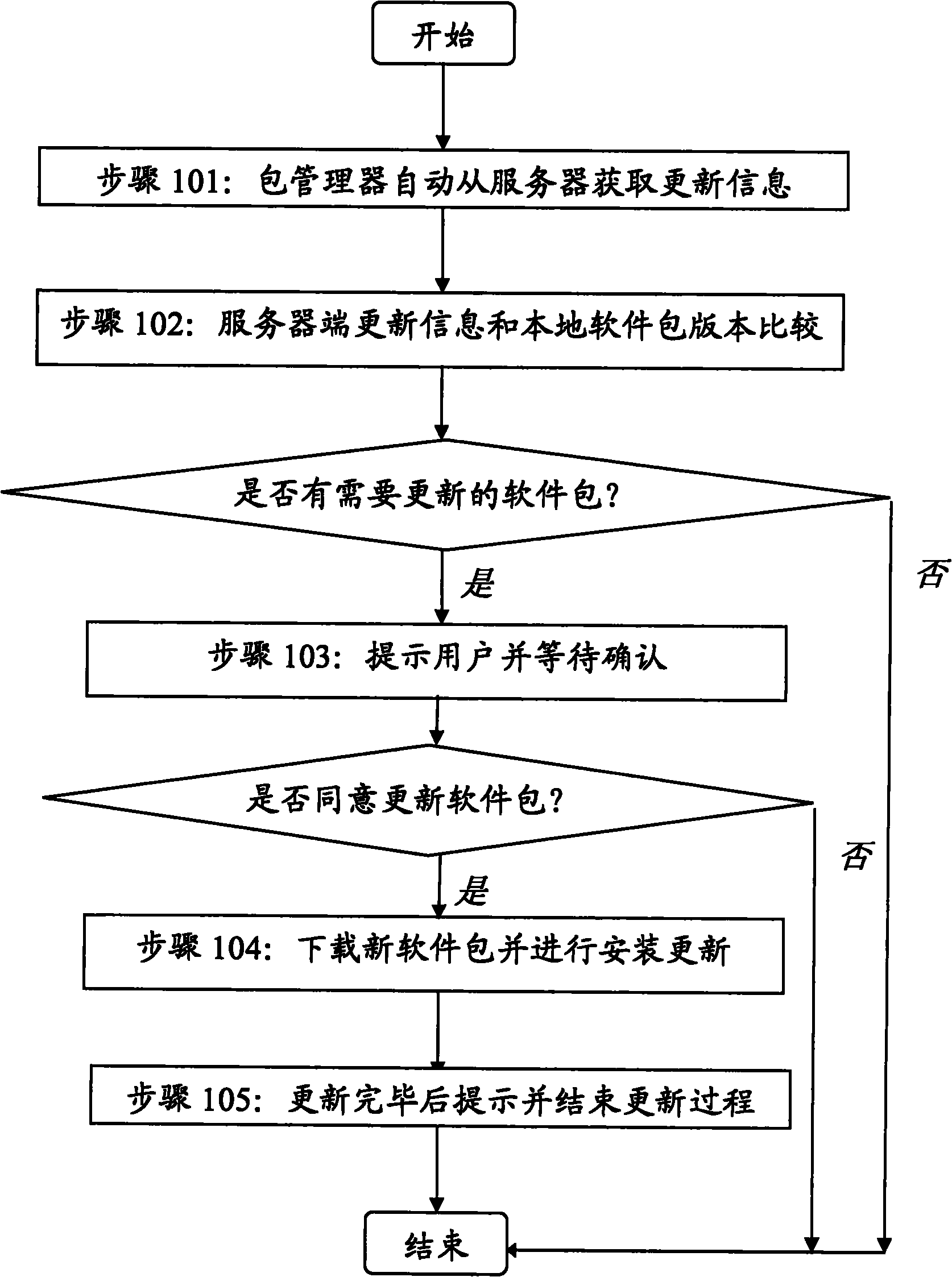
Software package-based online automatic updating method for open source operating system of mobile terminal
ActiveCN102118500AResolve escalationTroubleshoot maintenance management issuesSubstation equipmentProgram loading/initiatingOperational systemNetwork approach
The invention discloses a software package-based online automatic updating method for an open source operating system of a mobile terminal, which relates to the field of mobile terminal software and is applied to the open source operating system of the mobile terminal. By the method, the remote automatic updating of system software can be realized by taking a package as a unit, and convenience isbrought to the rehabilitation of security holes and the installation of the operating system. The method comprises the two aspects that: a server automatically finishes structuring and publishing thesoftware package, acquires all source codes of the operating system from an open source site, automatically divides and structures a proper software package, determines the updating information of the software package according to the version information and dependency of the source codes, and publishes the software package by utilizing a network; and the mobile terminal serving as a software package acquirer and user automatically checks the updating information by client software, and downloads and updates the system by taking the software package as the unit to fulfill the aim of automaticonline updating. The method has the characteristics of high degree of automation and the like, and is easy to deploy in large scale and use.
Owner:TSINGHUA UNIV
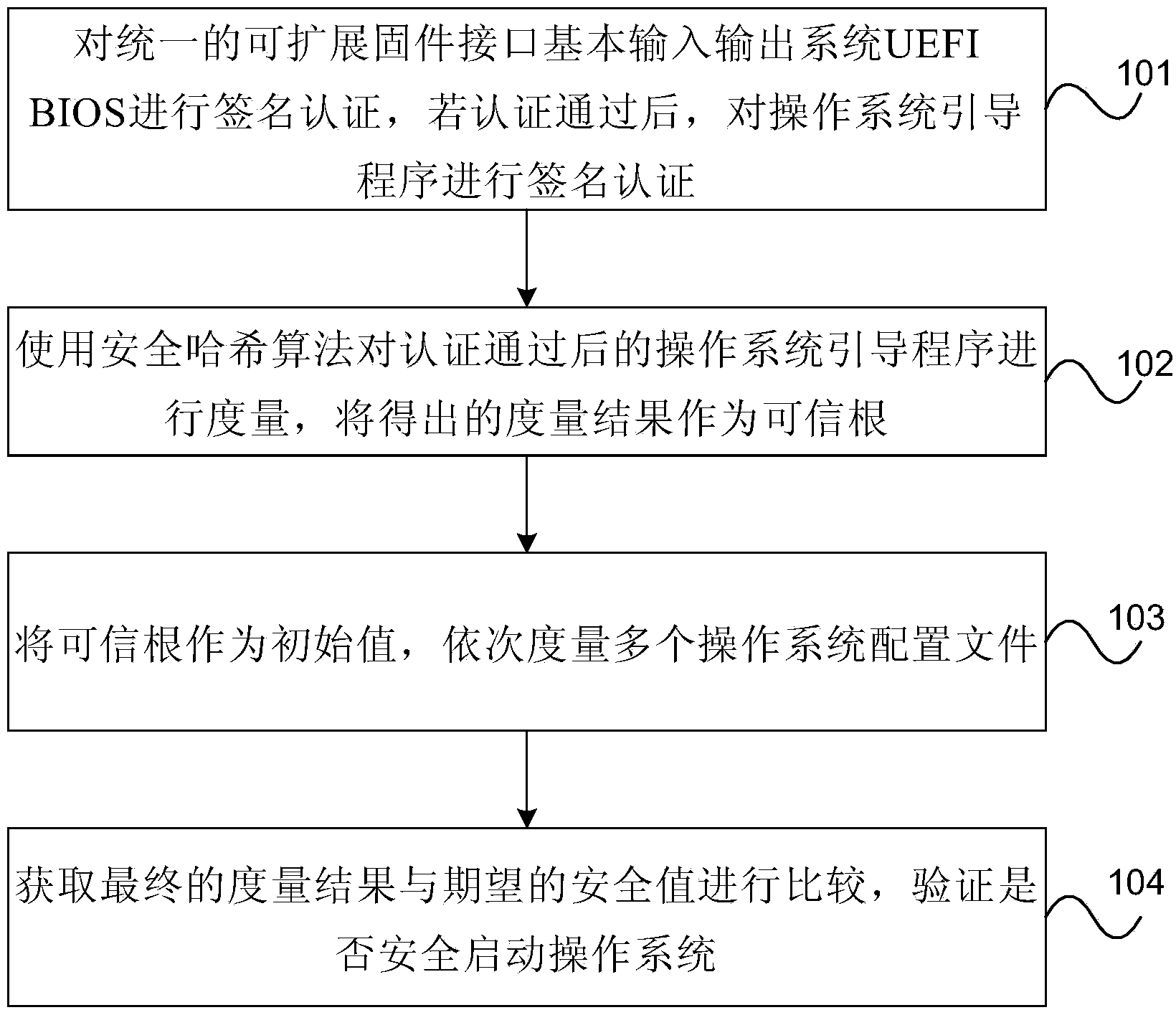
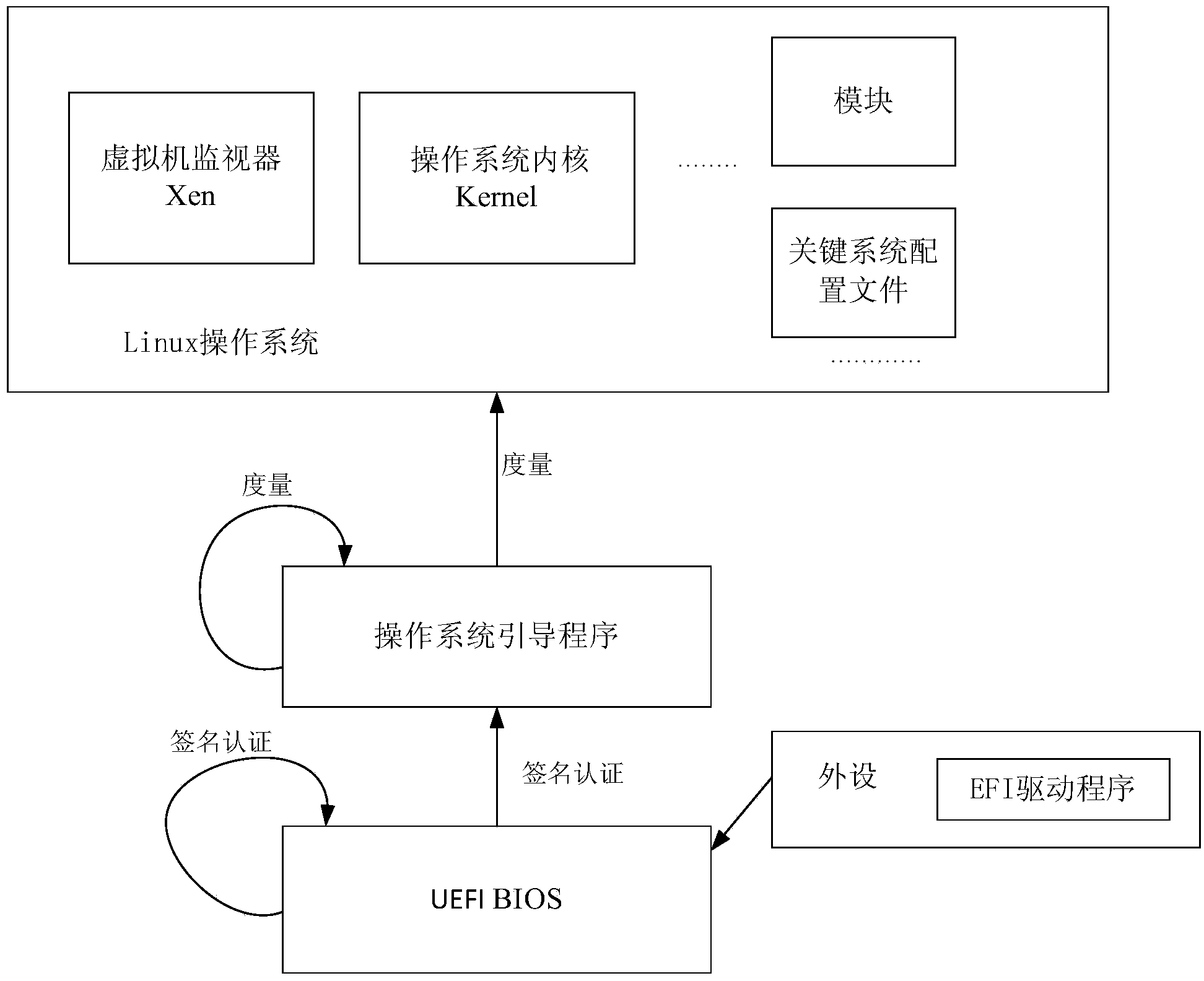
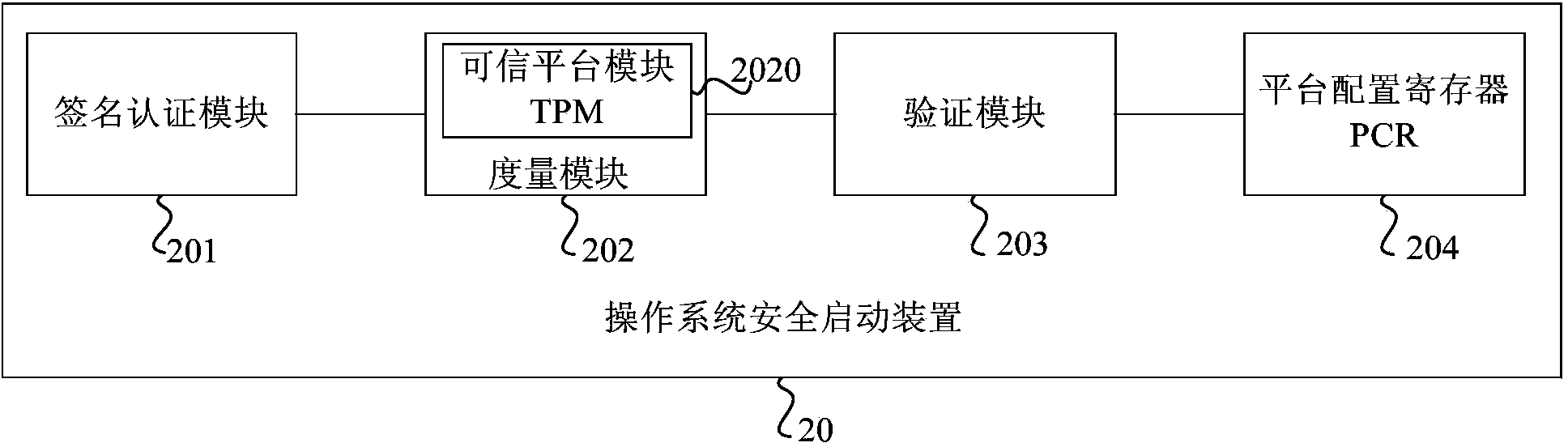
OS secure startup method and device
InactiveCN103927490AAchieving verification securityDigital data authenticationPlatform integrity maintainanceOperational systemDigital signature
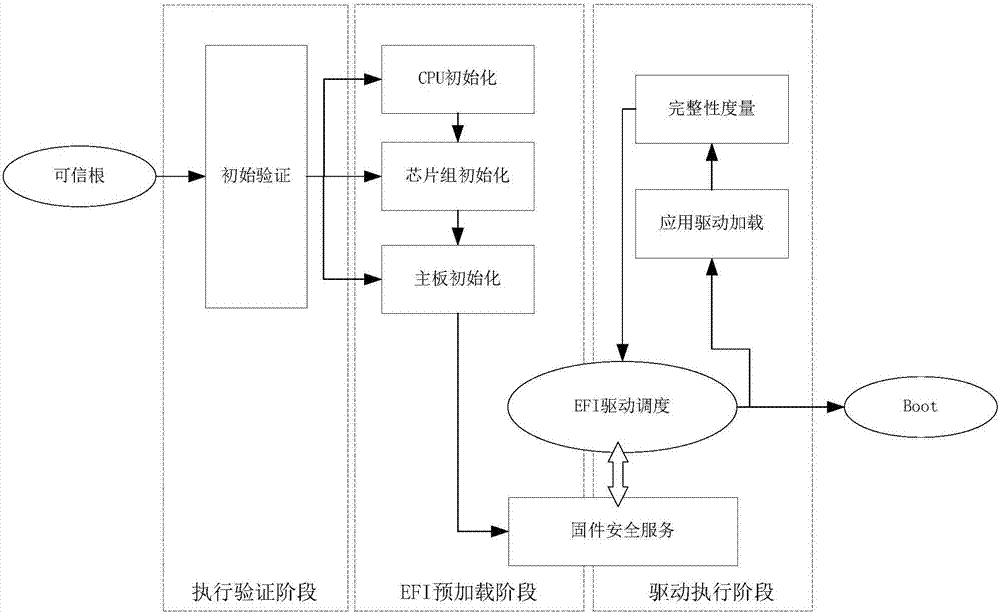
The embodiment of the invention provides an OS secure startup method and device. The method includes the steps that signature verification is conducted on the UEFI BIOS, and signature verification is conducted on guidance programs of an OS if the UEFI BIOS passes the signature verification; the guidance programs, passing the signature verification, of the OS are measured through a secure hash algorithm, and the obtained measurement result serves as a trust root; the trust root serves as an initial value, and multiple configuration files of the OS are sequentially measured; the obtained final measurement result is compared with an expected secure value, and whether the OS is safely started or not is verified. By means of the OS secure startup method and device, security is verified through the method that the guidance programs of the OS pass the digital signature verification, the guidance programs, measured to be secure, of the OS generate the trust root, the OS is measured level by level according to the trust root, a trusted chain extends to the OS from the BIOS, and the problem that in the prior art, security of programs started after the Boot Loader can not be ensured is solved.
Owner:HUAWEI TECH CO LTD
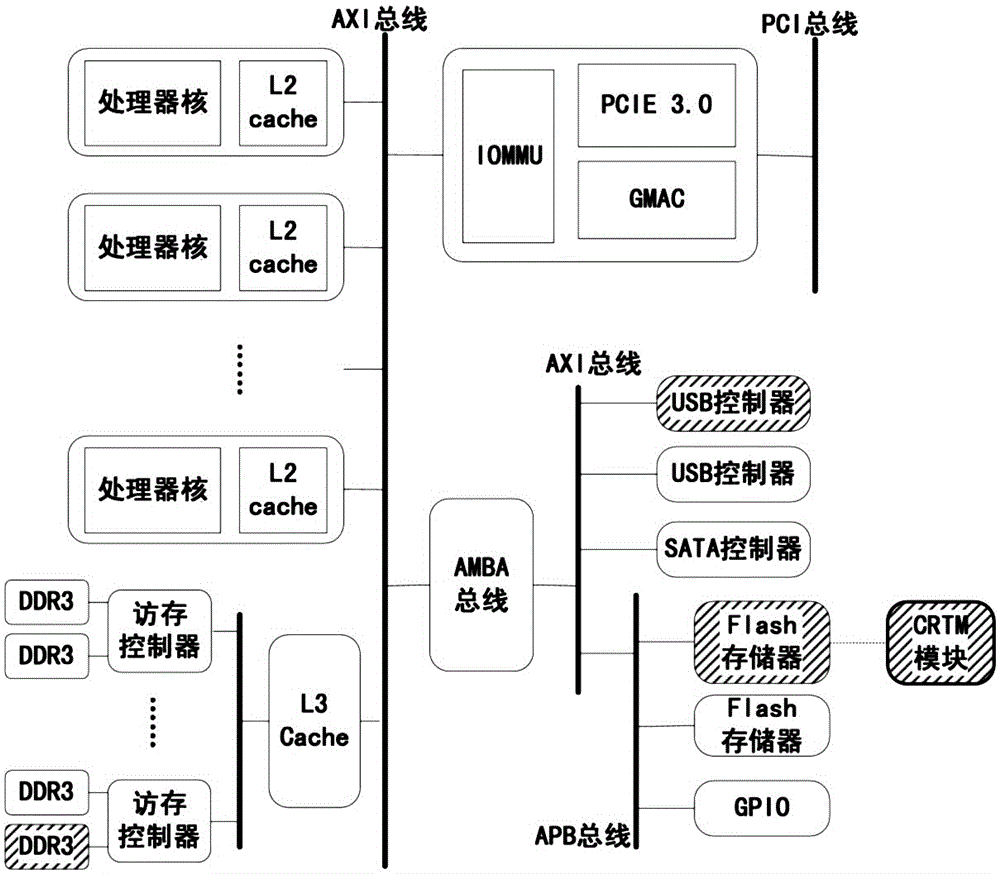
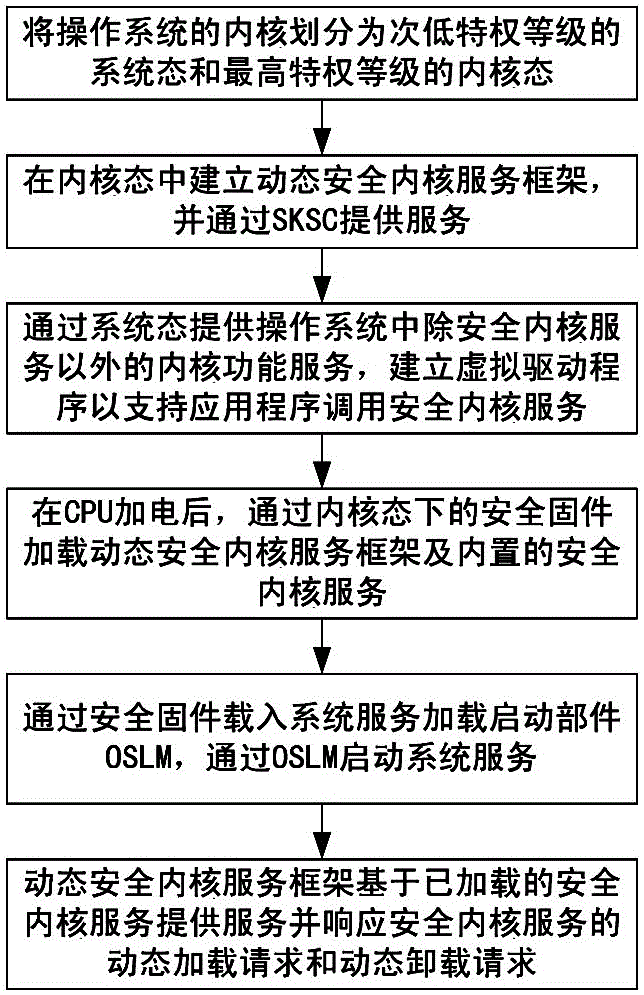
Dynamic running method for security kernel service of tristate operating system in Feiteng CPU
ActiveCN105022954AReduce security risksImprove safety and reliabilityPlatform integrity maintainanceEcological environmentOperational system
The invention discloses a dynamic running method for a security kernel service of a tristate operating system in a Feiteng CPU. The method comprises the steps of: dividing a kernel into a system state and a kernel state of different privilege levels; establishing a service framework in the kernel state to serve as a container for the security kernel service, and establishing a call interface for the security kernel service; establishing a virtual driving interface in the system state to support a user state to call the security kernel service; loading the service framework and the built-in security kernel service after enabling the CPU to be powered on; and loading a loading part of a system service module and starting a system service, wherein the service framework provides the security kernel service and makes a response to a dynamic loading / unloading request of the security kernel service. The dynamic running method can realize security protection on specific hardware resources of the system, realize security access to a core service of the operating system, efficiently support credibility conformation of the system, effectively improve the system security, lower the security risk of traditional kernel bugs and provide an efficient and flexible credible calculating ecological environment for users.
Owner:TSINGHUA UNIV +1
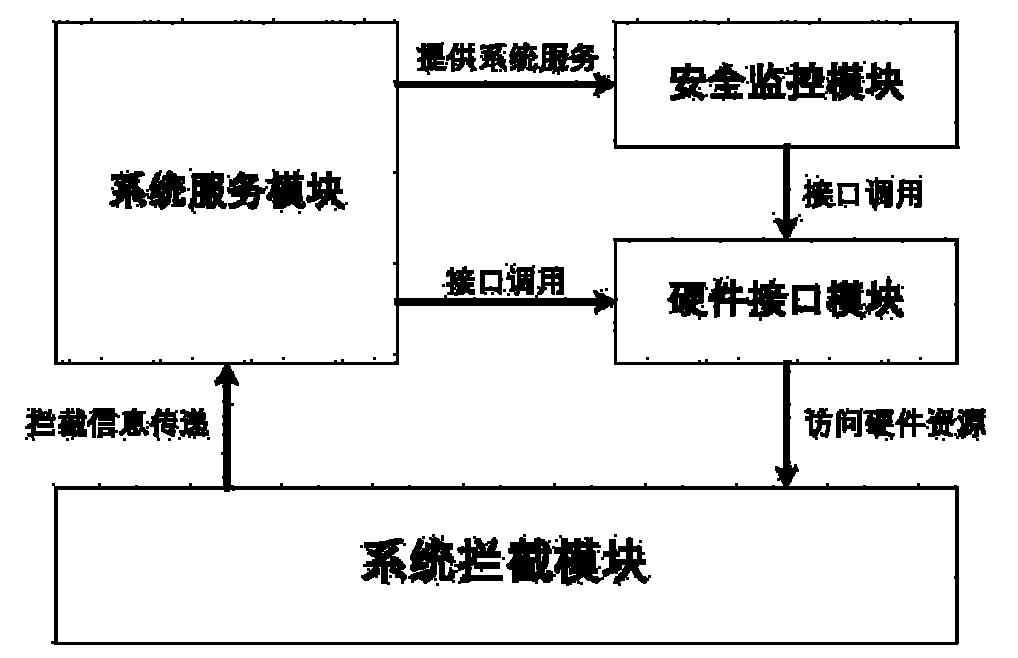
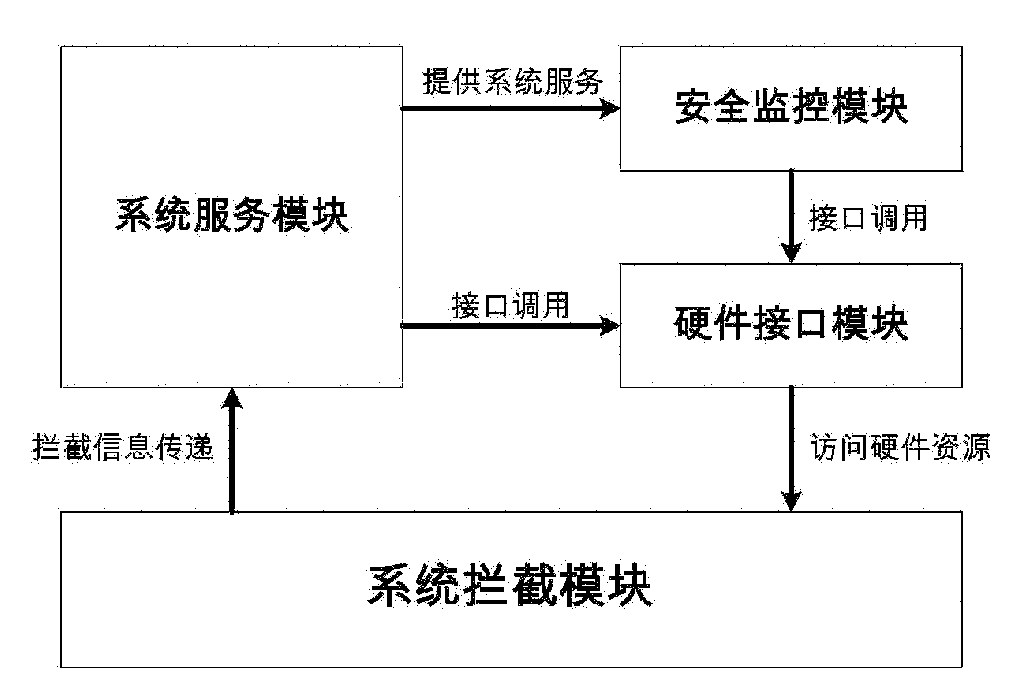
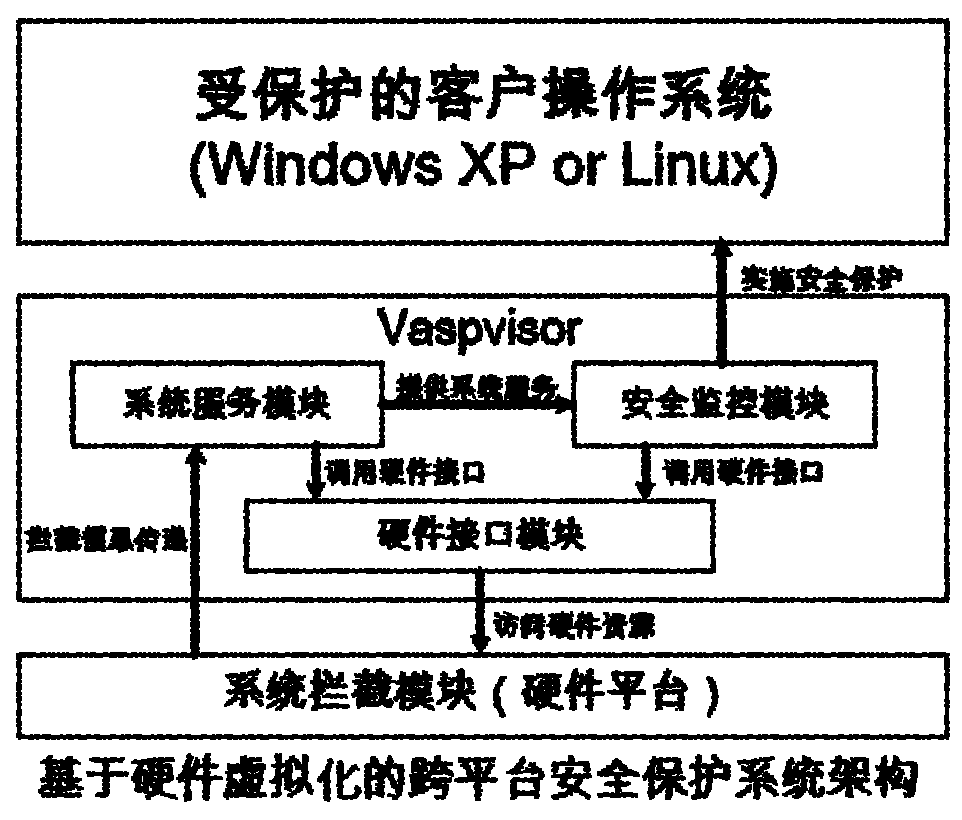
Cross-platform safety protection system based on hardware virtualization
InactiveCN102096786AReduce overheadDoes not affect execution of tasksPlatform integrity maintainanceOperating system securityProtection system
The invention provides a cross-platform safety protection system based on hardware virtualization, which belongs to the technical field of computer safety. The system provided by the invention comprises a system interception module, a hardware interface module, a system service module and a safety monitoring module, wherein the system interception module is used for intercepting the specified operation system sensitive behavior and outputting the intercepted information to the system service module; the system service module determines the corresponding safety protection mechanism according to the information, and outputting a control instruction to the safety monitoring module; the safety monitoring module executes the safety protection operation; and the hardware interface module receives the call instruction of the system service module and the safety monitoring module and achieves the interaction and data transmission with the hardware system. The system can monitor and intercept the sensitive behavior of the operation system through a virtual machine monitoring program, and determine whether the behavior is a bad one or a good one by virtue of the monitoring program according to the source and aim of the behavior so as to prevent or stop the harmful aggressive behavior in time to finally ensure the safe operation of the operation system.
Owner:SHANGHAI JIAO TONG UNIV
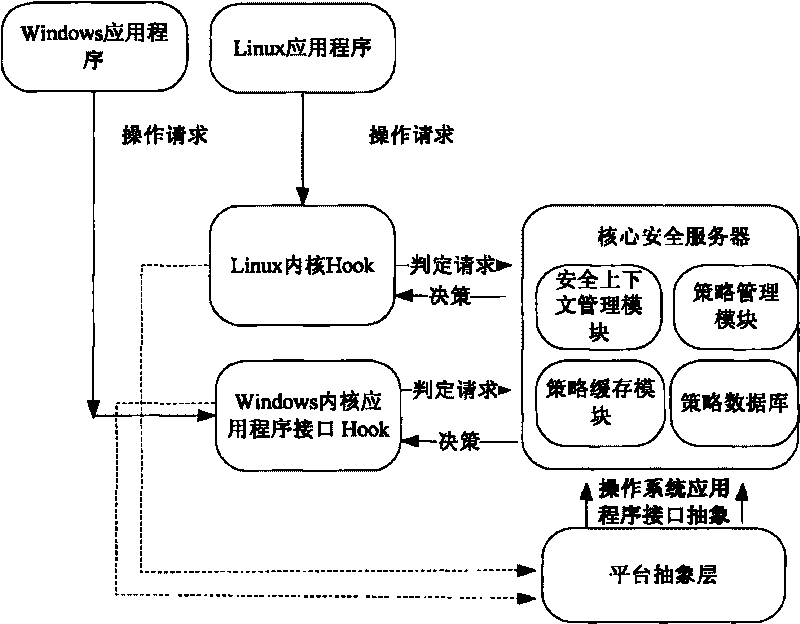
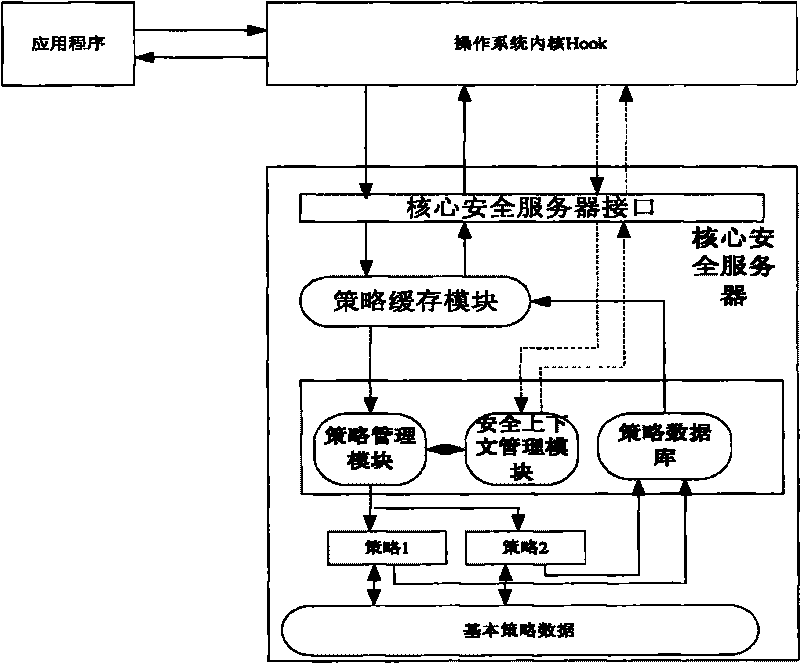
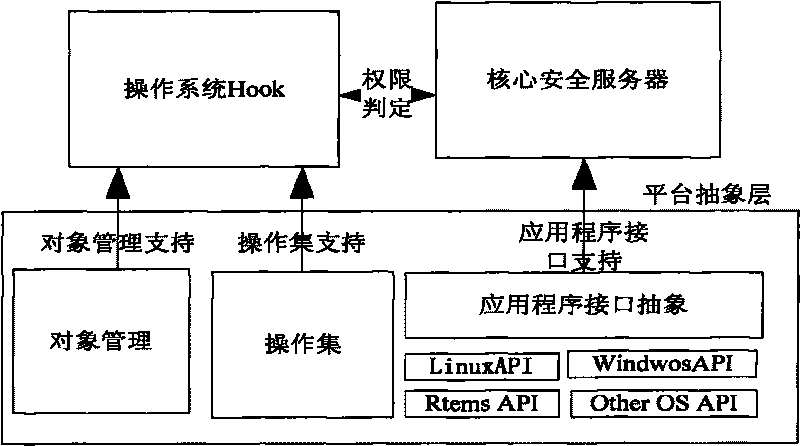
Access control method for operation system and implementation platform thereof
InactiveCN101727555AImplement access control functionsRealize dynamic multi-policyPlatform integrity maintainanceSpecific program execution arrangementsAbstraction layerOperational system
The invention relates to an access control method for an operation system and an implementation platform thereof. The platform comprises an operation system Hook layer, a platform abstraction layer and a core security server. The operation system Hook layer transmits an intercepted request to the core security server; a strategy caching module queries the request, and judges whether the same request exists; if the same request exists, the request is executed; if the same request does not exist, a strategy managing module is queried, whether the access permission of the request exists is judged according to the security rule of the operation system security model which is saved in a strategy database; if the access permission of the request exists, the request is stored in a cache and executed; and if the access permission of the request does not exist, the request is refused. The invention provides the flexible access control platform which can be applied to various operation systems, and provides a unified strategy configuration method which can be conveniently implemented on the various operation systems.
Owner:苏州昂信科技有限公司
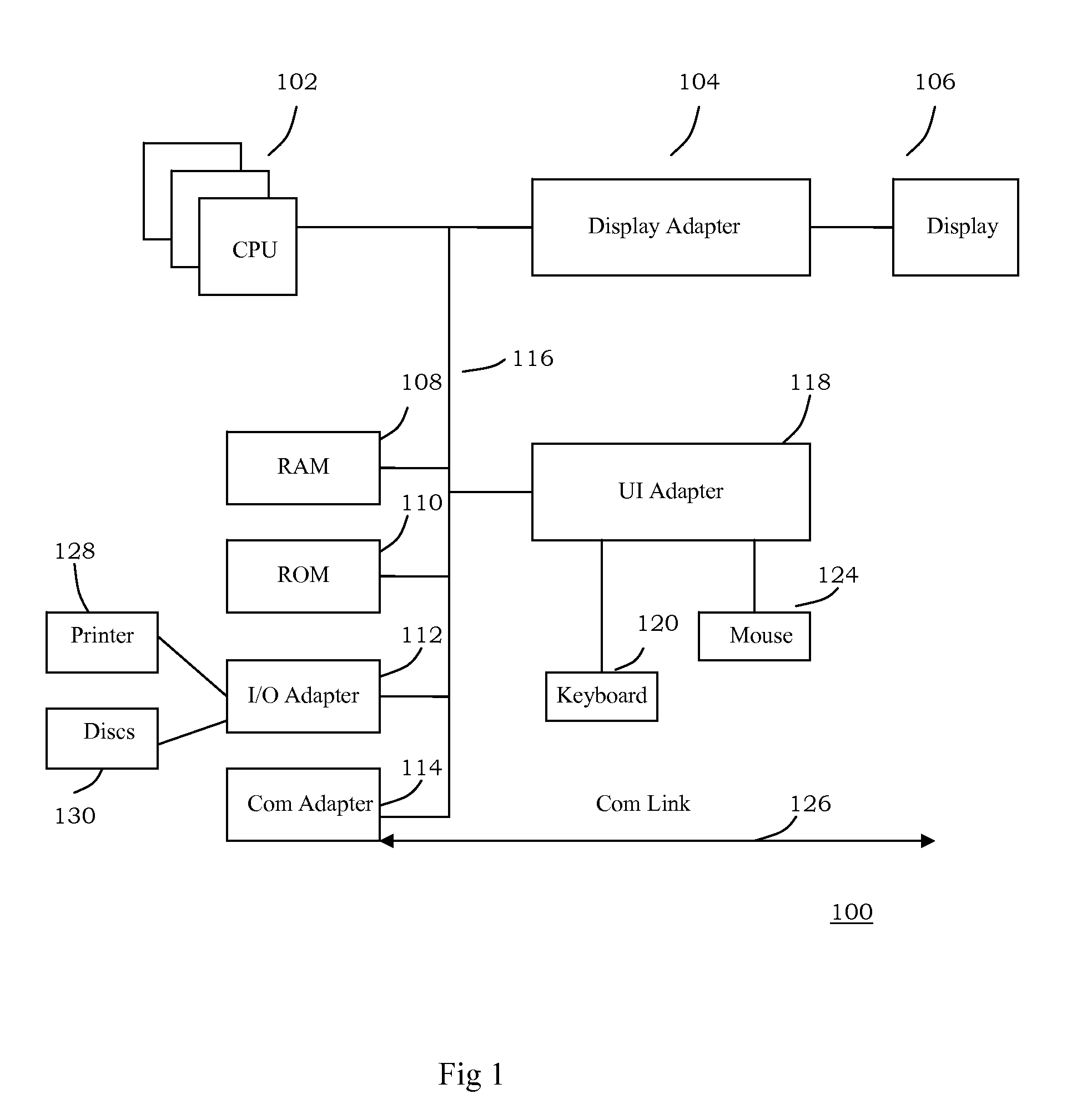
Method and system for securely installing patches for an operating system
InactiveUS20090083727A1Reduce the possibilityPlatform integrity maintainanceTransmissionOperational systemPersonal firewall
A method and a system for securely installing patches for an operating system, wherein the system comprises a personal firewall, for filtering inbound and outbound network traffic; an operating system update agent, for connecting to an update server via the personal firewall to download patches; a policy manager, for invoking respective policies according to respective stages of the operating system; a stage coordinator, for coordinating the policy manager and the operating system update agent for different stages; and a policy database, for storing respective policies for respective stages of the operating system. With the method and system, the possibility of being infected by malicious software is significantly reduced when downloading patches for the operating system from the Internet.
Owner:IBM CORP
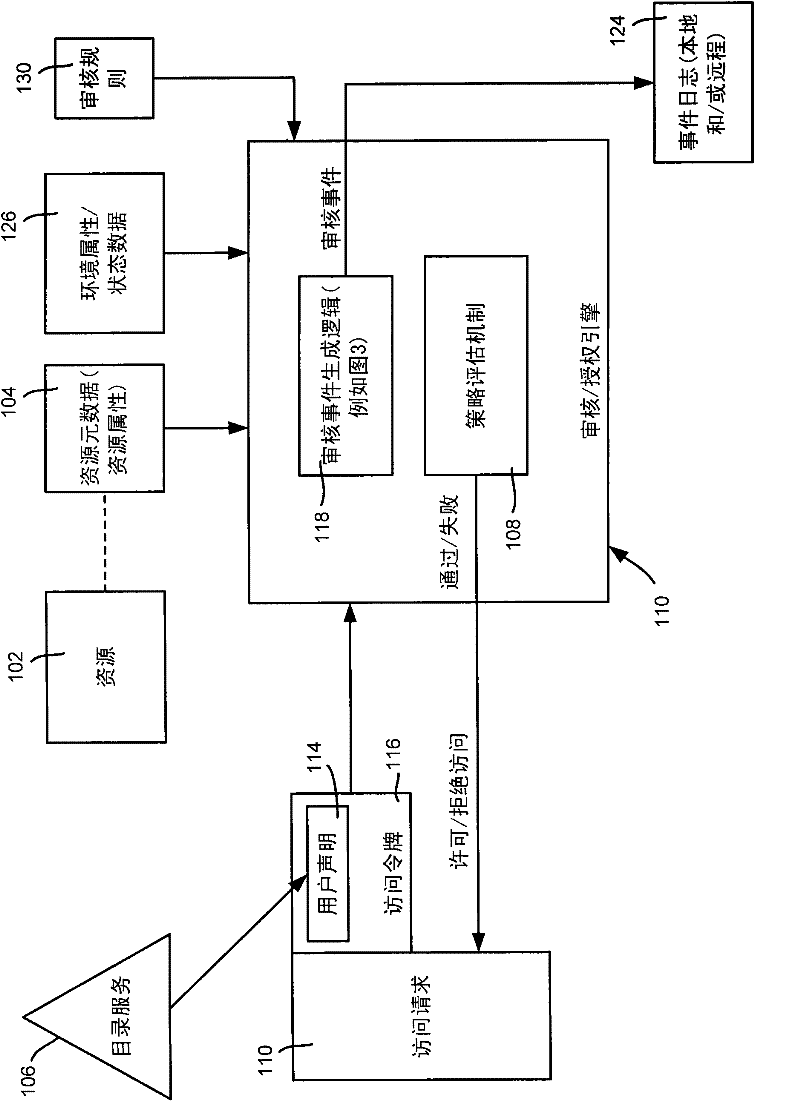
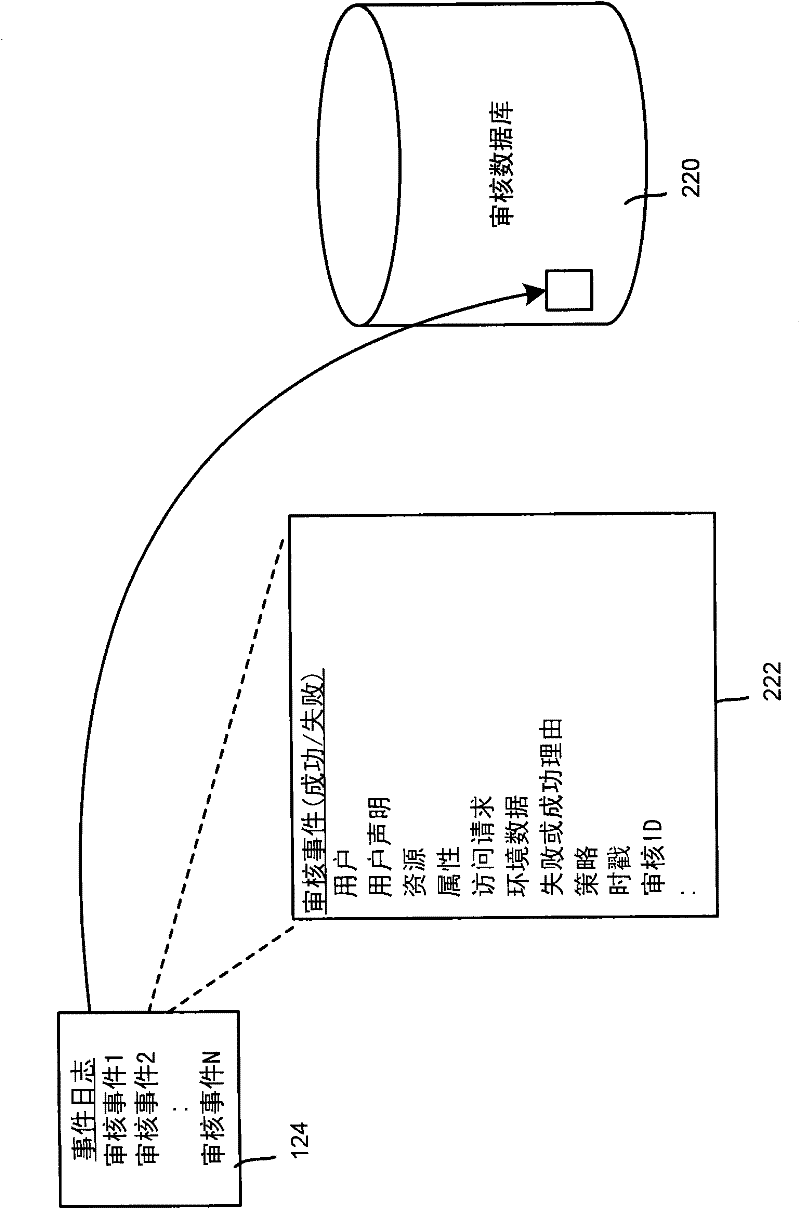
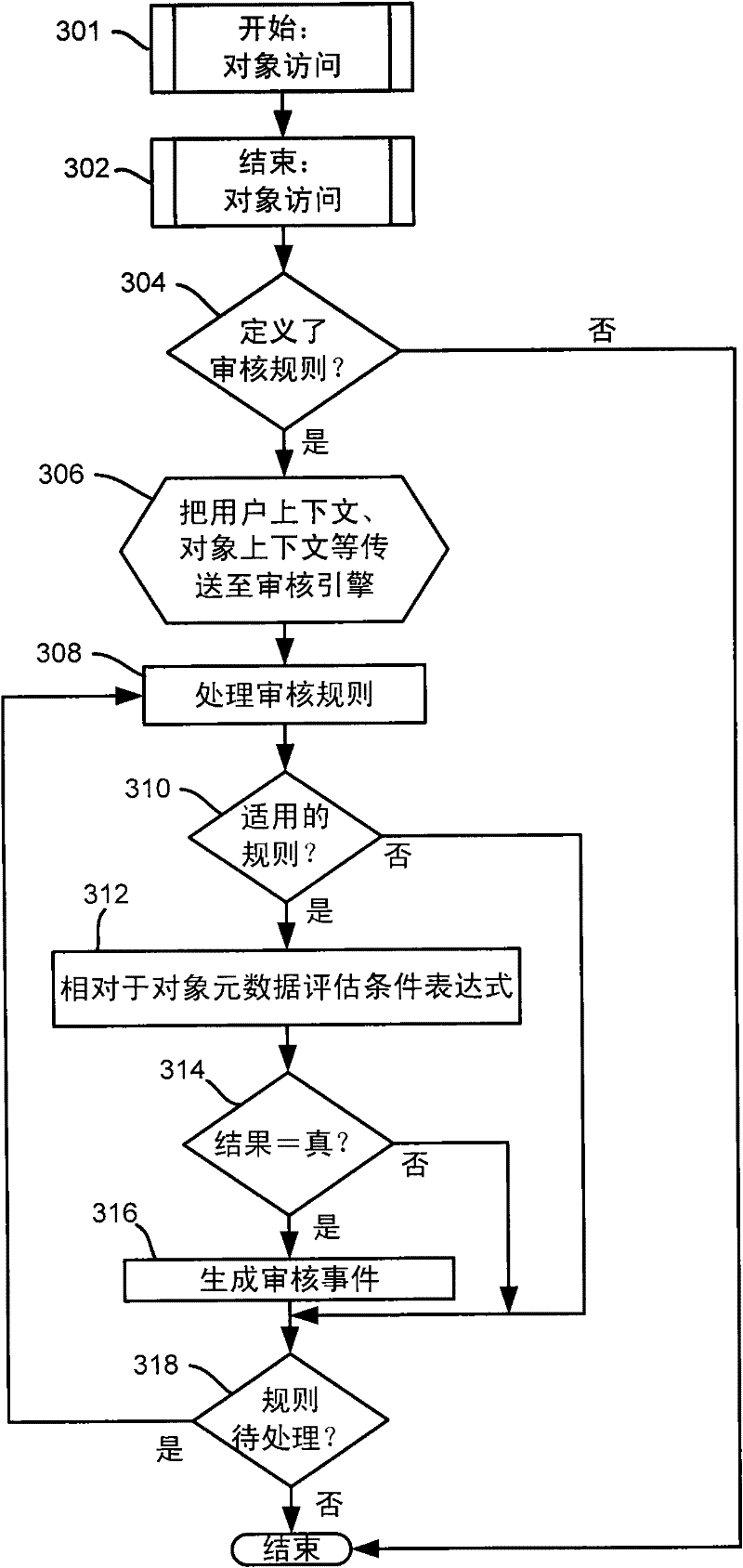
Auditing access to data based on resource properties
The invention relates to an auditing access to data based on resource properties. Described is a technology, such as implemented in an operating system security system, by which a resource's metadata (e.g., including data properties) is evaluated against an audit rule or audit rules associated with that resource (e.g., object). The audit rule may be associated with all such resources corresponding to a resource manager, and / or by a resource-specific audit rule. When a resource is accessed, each audit rule is processed against the metadata to determine whether to generate an audit event for that rule. The audit rule may be in the form of one or more conditional expressions. Audit events may be maintained and queried to obtain audit information for various usage scenarios.
Owner:MICROSOFT TECH LICENSING LLC
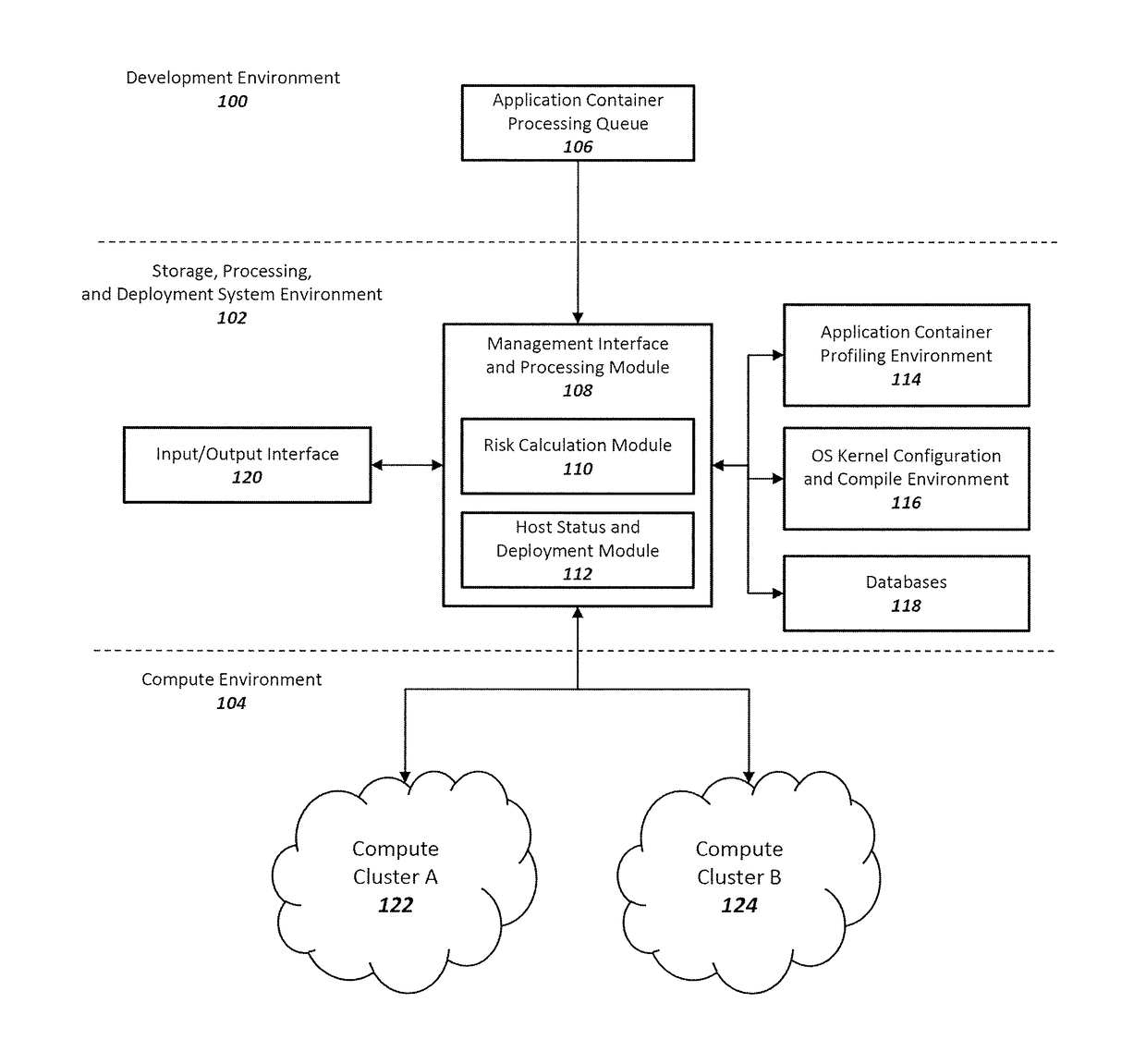
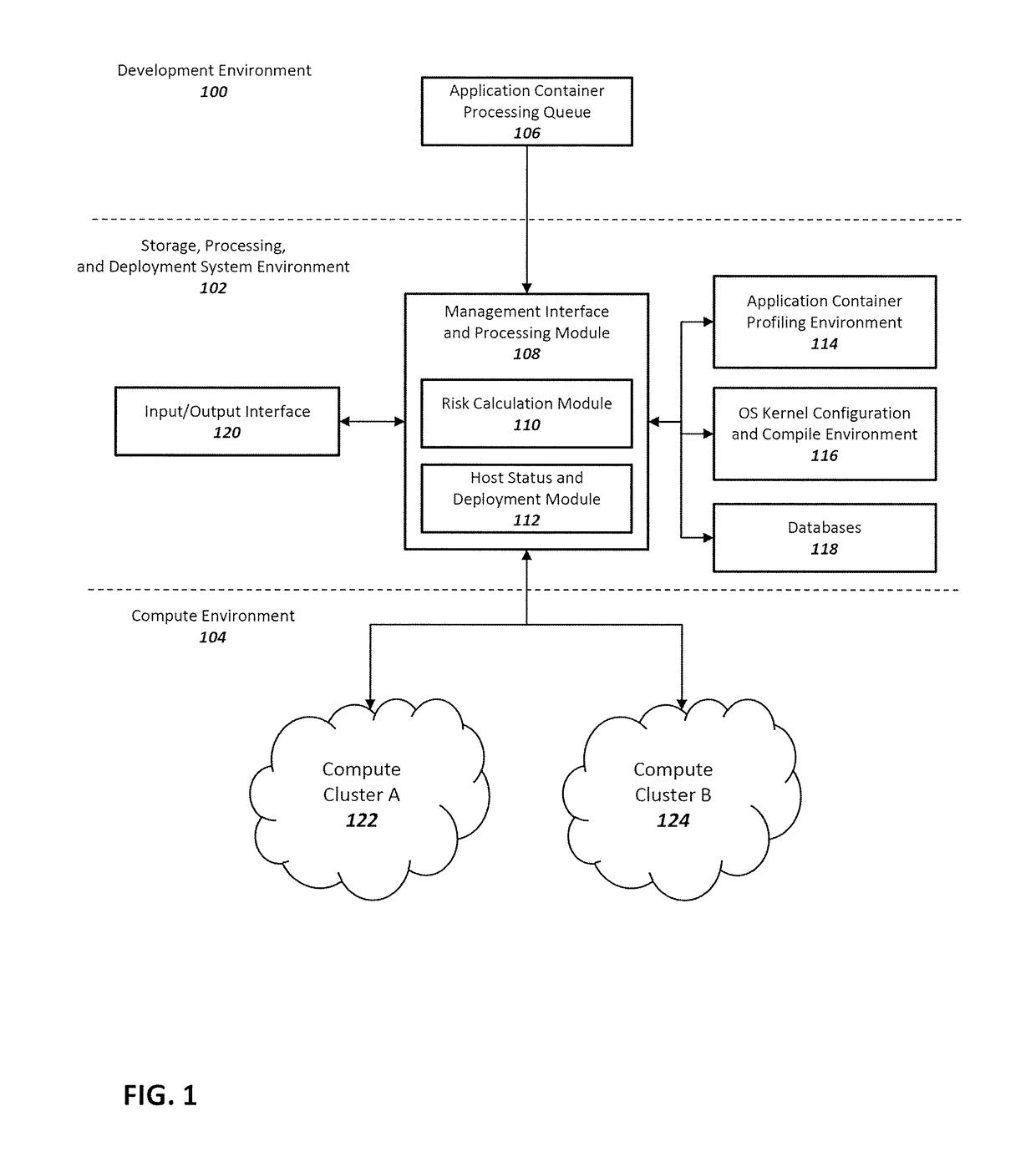
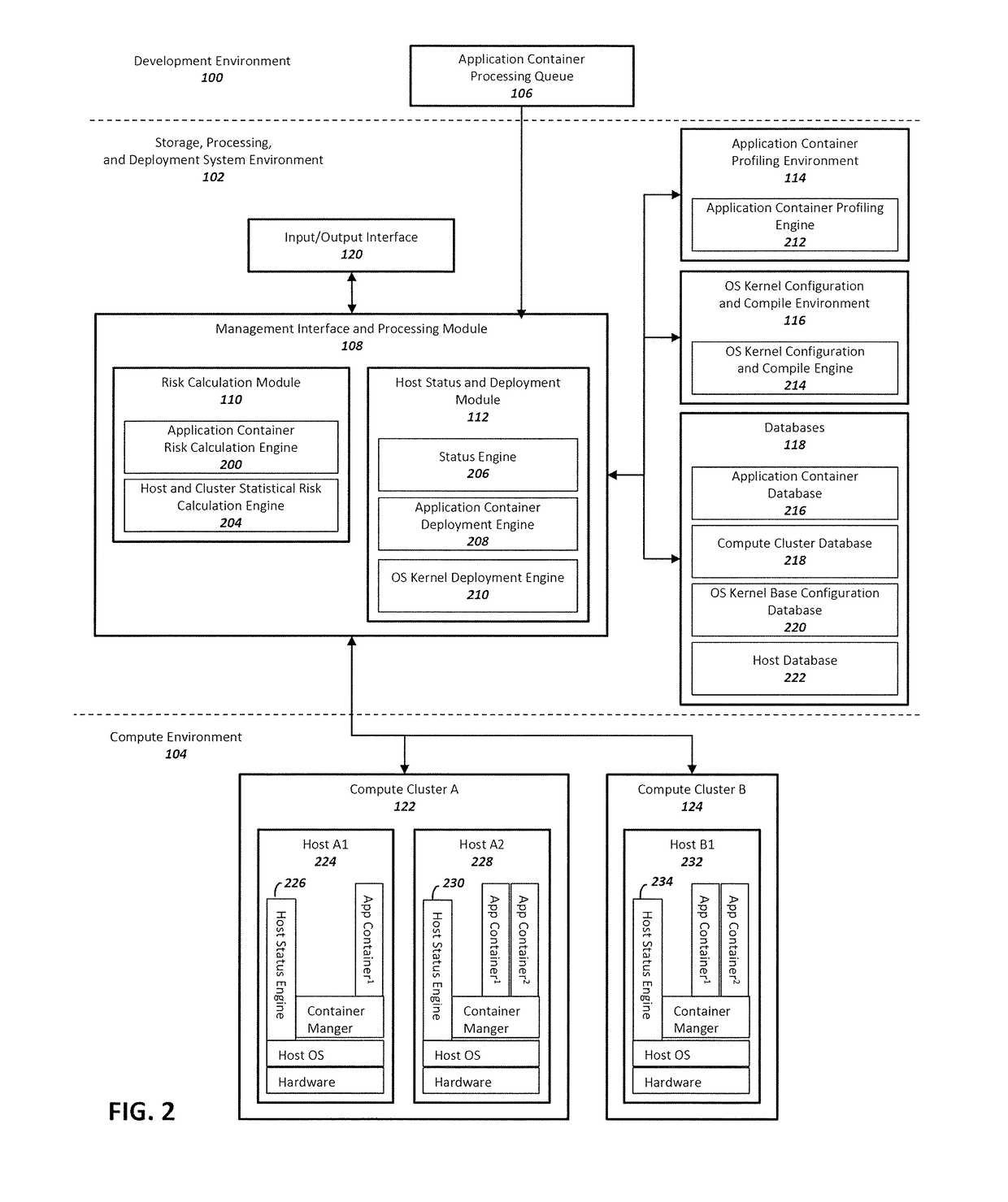
Method and system for enhancing application container and host operating system security in a multi-tenant computing environment
ActiveUS20180046457A1Reliability/availability analysisSoftware testing/debuggingOperating system securityComputerized system
A system for application container security comprising an application container processing and deployment computer system configured to receive an application container, determine operating system kernel requirements of the application container, calculate a risk value based on the operating system kernel requirements of the application container, determine availability of a host computer to host the application container, by determining if the operating system kernel of the host computer meets operational requirements of the application container. The operational requirements including the risk value for the application container. When the operating system kernel of the host computer is determined to meet the operational requirements, pair the application container with the operating system kernel of the host computer. When the operating system kernel of the host computer is determined to not meet the operational requirements, configure and compile a container-specific operating system kernel that meets the operational requirements.
Owner:MAXISIQ INC
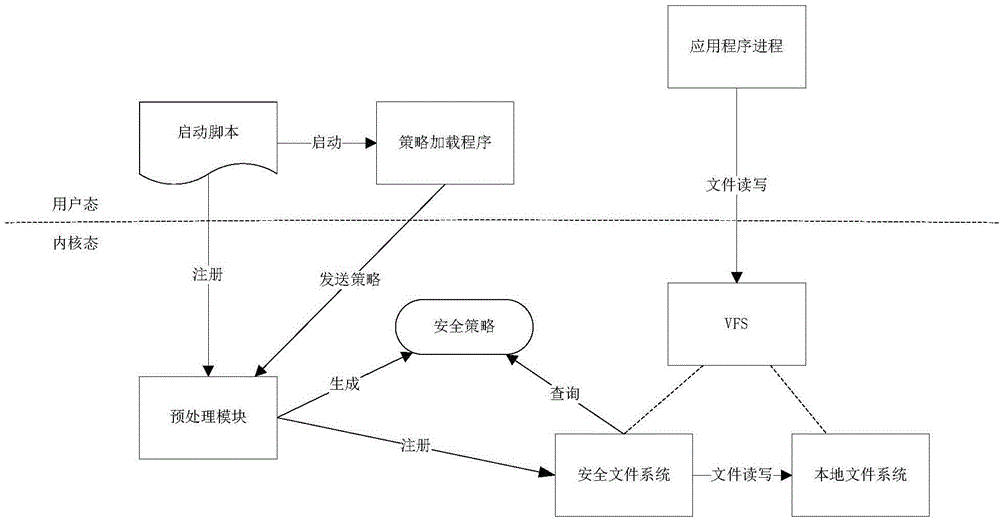
Document safety access control method and device based on Linux kernel
InactiveCN104866778ADigital data protectionPlatform integrity maintainanceOperational systemVirtual file system
The invention belongs to the field of safety of operation systems, and provides a document safety access control method based on a Linux kernel. The document safety access control method comprises the following steps: when a Linux system is started up, the Linux kernel reads startup script registration information, and is registered with a pre-processing module; starting procedure information is read, and a strategy loading module is started up, wherein the pre-processing module runs in the state of the Linux kernel; after the pre-processing module is started up, a safety document system is registered in a VFS (virtual file system), and then a listening port is registered; the strategy loading module reads a local safety strategy file, and a safety strategy is created, and is sent to the listening port of the pre-processing module; the pre-processing module receives the safety strategy, and a safety strategy is created in a memory to be used for the safety file system; when a file is accessed by an application process, the safety file system calls the local file system to complete the operation of the file data according to the safety strategy. According to the method, the efficiency of the file safety access control in the Linux system is improved.
Owner:武汉华工安鼎信息技术有限责任公司
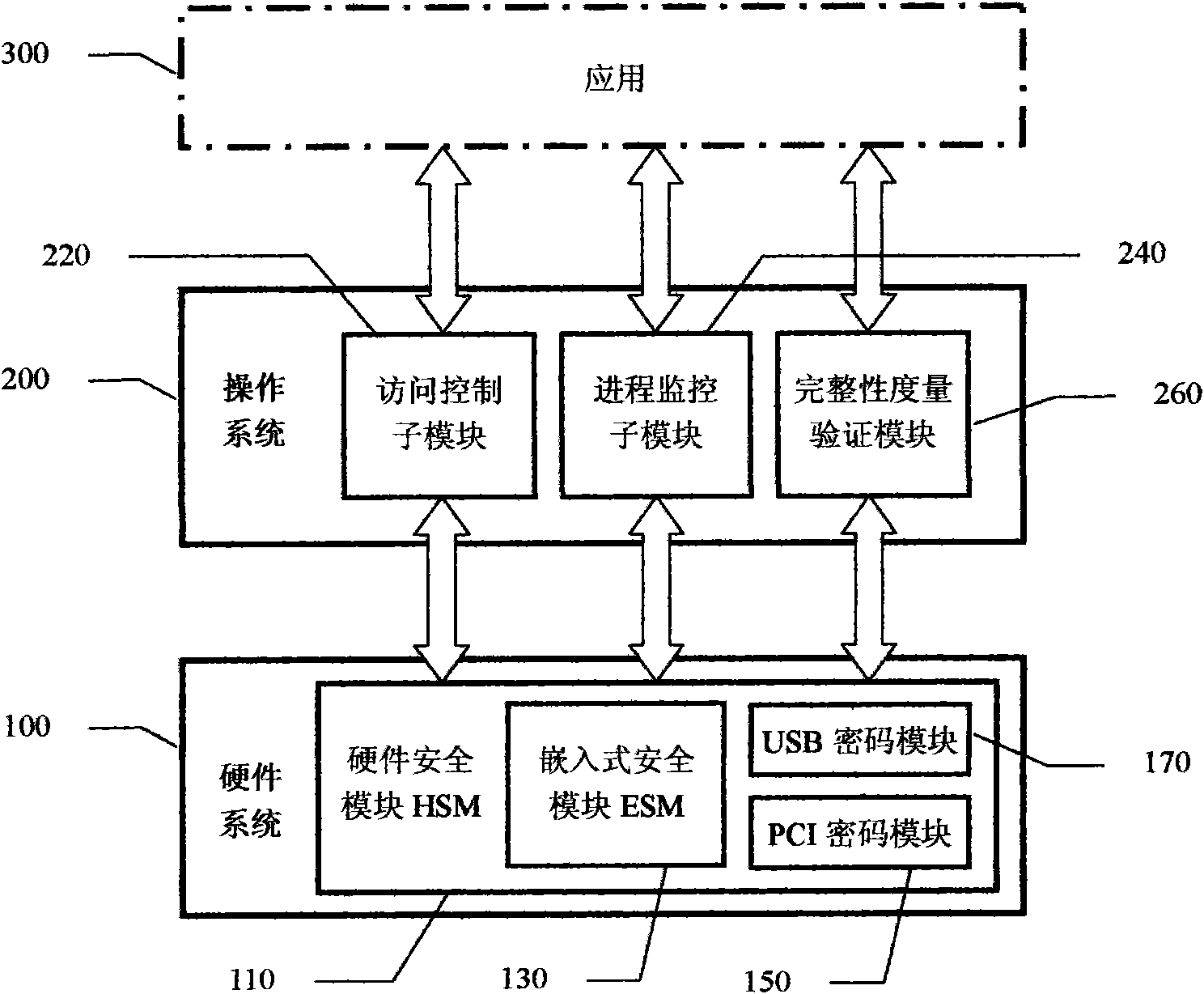
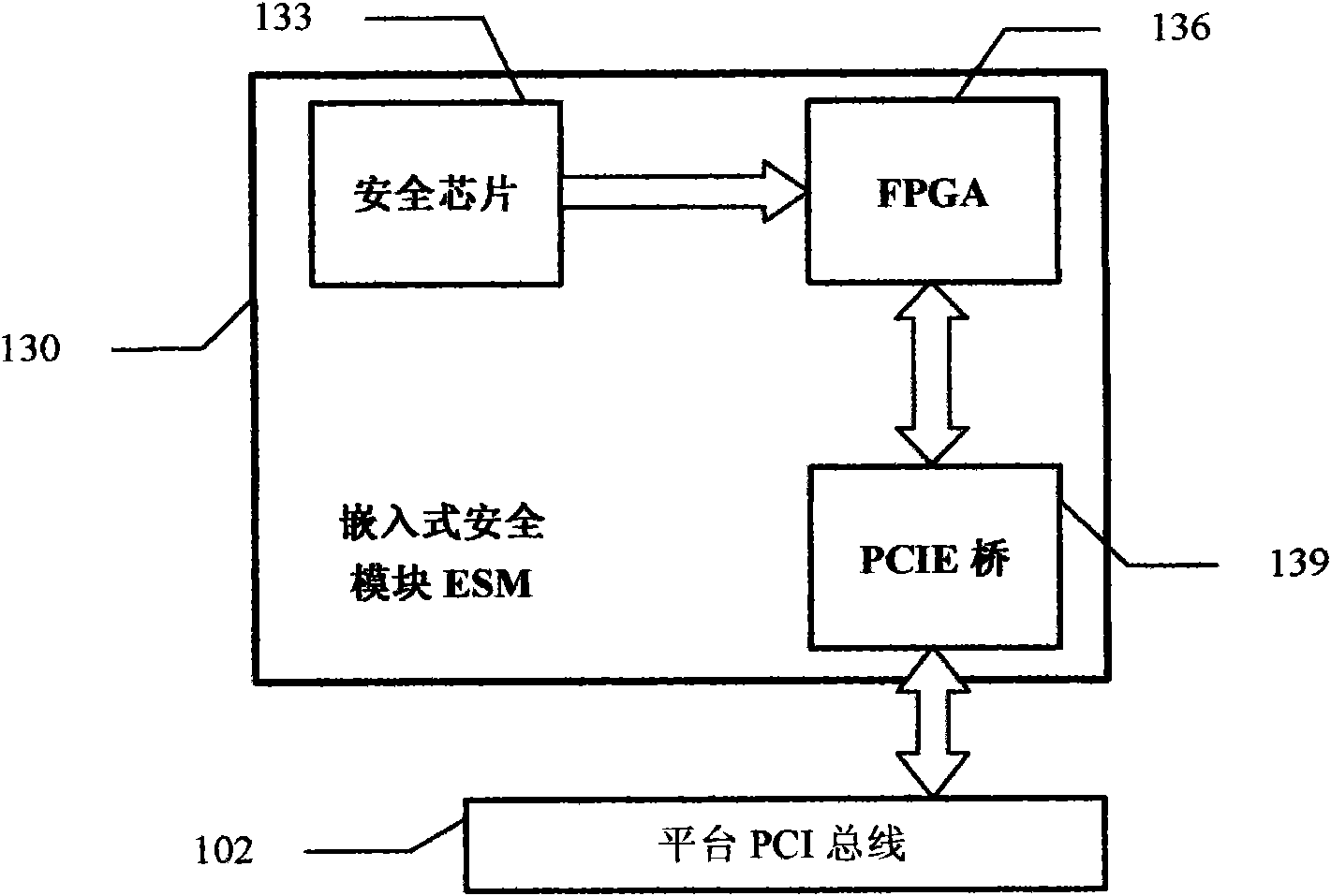
Creditable calculation password platform and realization method thereof
InactiveCN101650764AImprove securityImprove security strengthDigital data protectionEmbedded securityOperational system
The invention relates to a creditable calculation password platform and a realization method thereof, which belong to the technical field of computer safety. The creditable calculation password platform comprises a hardware system and an operation system, wherein the hardware system is connected with the operation system; the hardware system comprises a hardware safety module (HSM); the HSM is bound with the platform and the realization method thereof and comprises an embedded safety module (ESM) or / and an inserted and pulled USB / PCI password module which is connected to a main plate; and theoperation system is provided with an operation system safety module comprising a forced access control submodule, a progress monitoring submodule and an application program integrality measurement identification module. The invention has the advantages of increasing the application range of the creditable calculation password platform and the technique of the realization method thereof, increasingthe self attack resisting degree of the forced access control submodule, the progress monitoring submodule and the integrality measurement identification module, measuring the integrality of the whole platform and the realization method thereof, establishing the creditable environment of the whole platform and the realization method thereof and fully ensuring the benefit of a user of the platformand the realization method thereof.
Owner:瑞达信息安全产业股份有限公司
OS Security Filter
ActiveUS20140283118A1Digital data processing detailsAnalogue secracy/subscription systemsOperational systemData operations
A system and method for protecting against the unauthorized use of operating system level commands is disclosed. The system includes a computer module including: a processor configured for performing data operations; a memory unit configured to store instructions executable by the processor; and an operating system module for supporting basic functions of the computer module, such as scheduling tasks, executing applications, and controlling peripherals. A virtual keyboard is connected to the computer module for creating one or more events or sequences of events recognizable by the operating system module. A system level command filter module is provided for filtering system level commands from the one or more recognizable events or sequences of events.
Owner:ID INTEGRATION
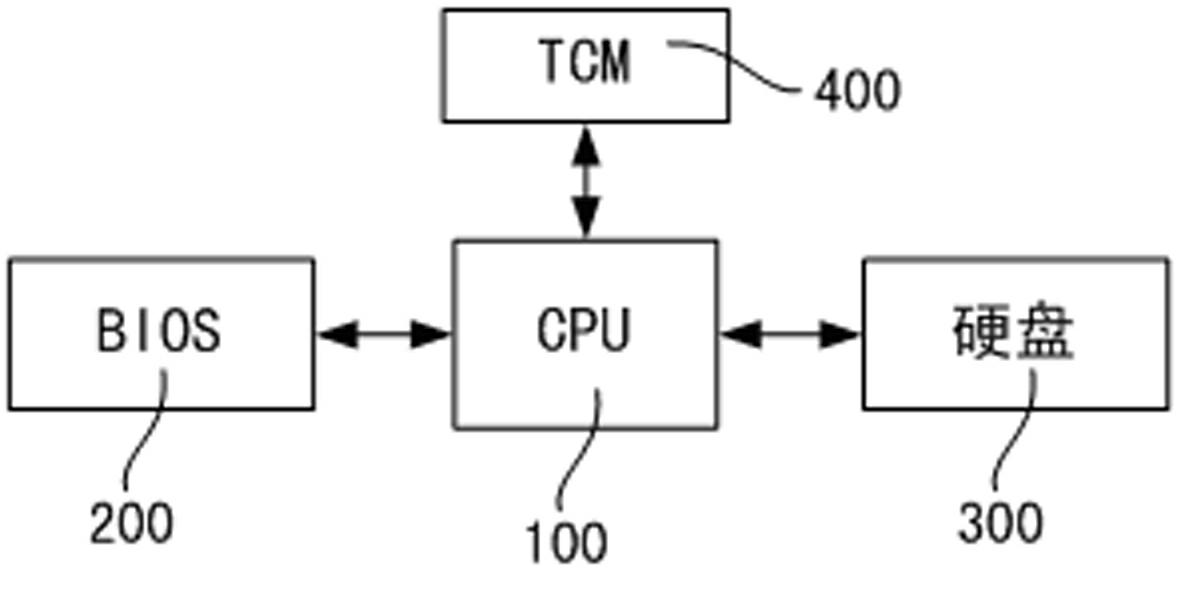
Operation system security bootstrap device and bootstrap device
InactiveCN102650944ANot be tampered with maliciouslyImplement backupProgram loading/initiatingRedundant operation error correctionTrusted ComputingOperating system security
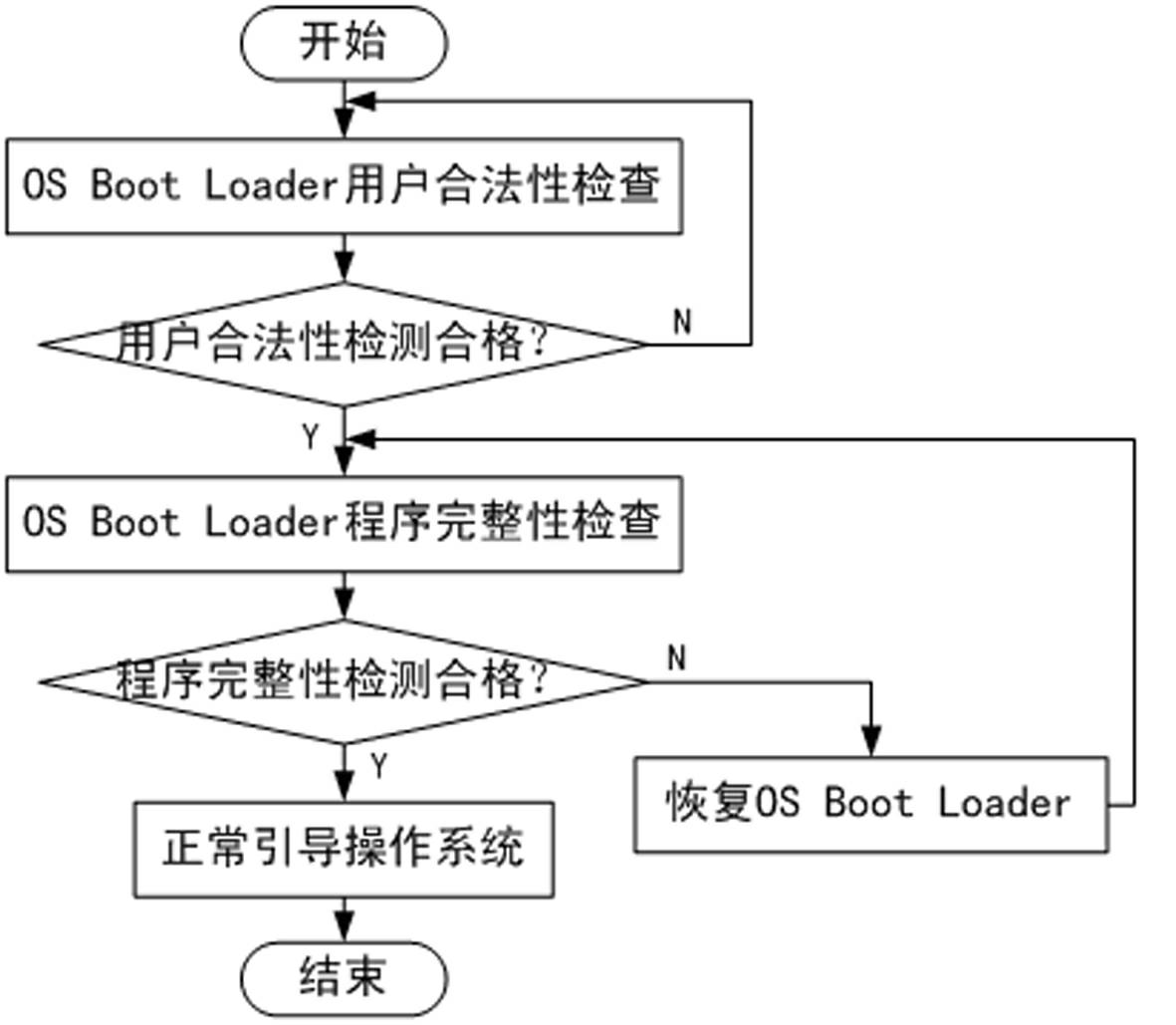
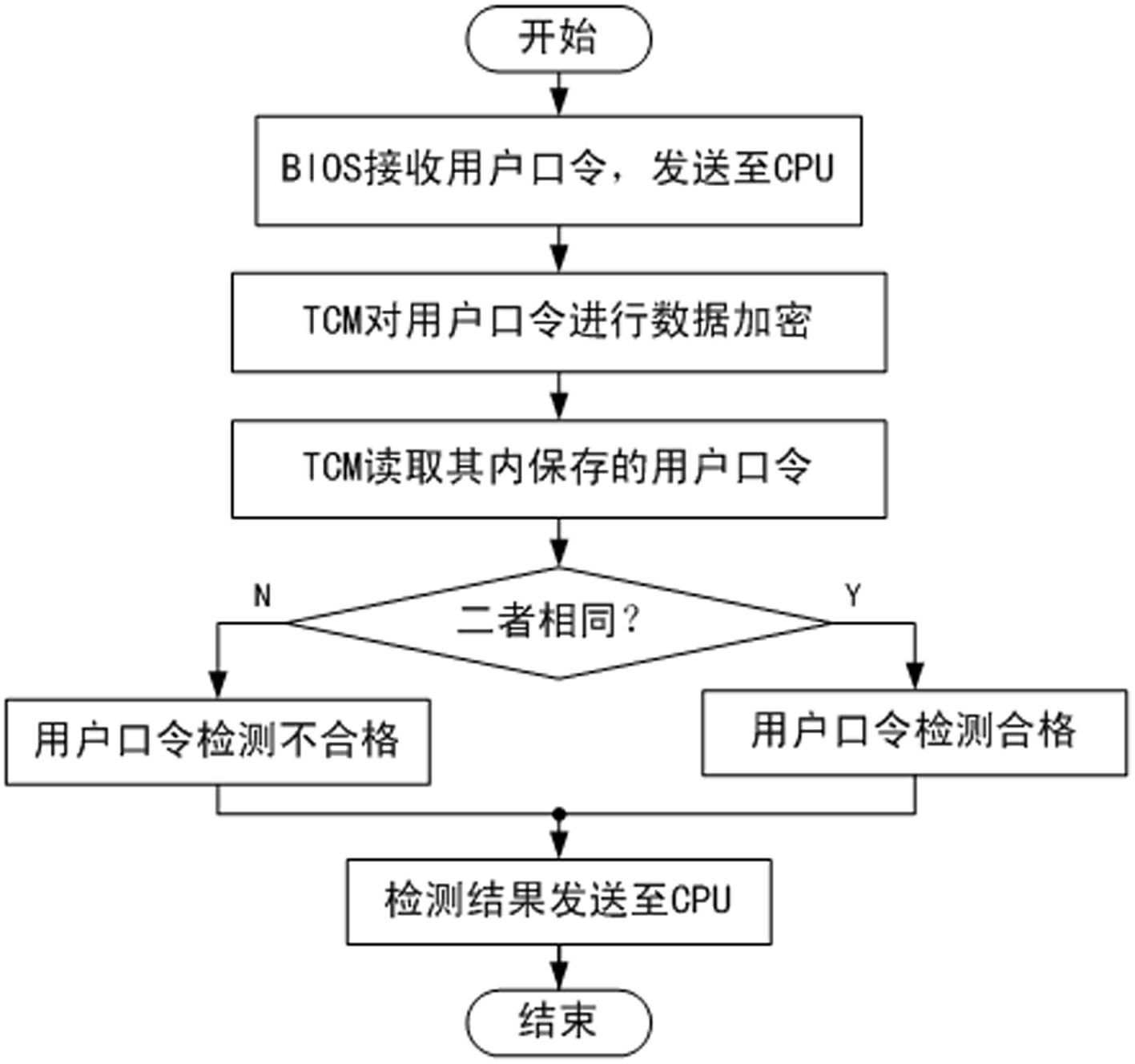
The invention discloses an operation system security bootstrap device, which includes a base input and output system, a central processing unit and a hard disk. The central processing unit is connected with the base input and output system and the hard disk; a bootstrap program is stored in the hard disk to realize the bootstrap to an operation system. Particularly, the bootstrap device further includes a dependable computing cryptographic module which is connected with the central processing unit. The central processing unit controls the dependable computing cryptographic module to verify the legality of an operator and detect the completeness of the bootstrap program, and backups the bootstrap program to realize the restorability of the bootstrap program. The invention further provides a security bootstrap method utilizing the device. Before the operation system is started, the identity of the operator is subjected to legality verification, so as to ensure that the operator is authorized legally; the hard disk bootstrap program is subjected to completeness detection, so as to ensure that the bootstrap program to be not maliciously interpolated; and the backup and restoring mechanism of the bootstrap program can continue the correct bootstrap to the operation system under the condition that the bootstrap program is interpolated.
Owner:NATIONZ TECH INC
Implementation of operating system securing
InactiveUS20090048993A1Computer security arrangementsKnowledge representationOperational systemOperating system security
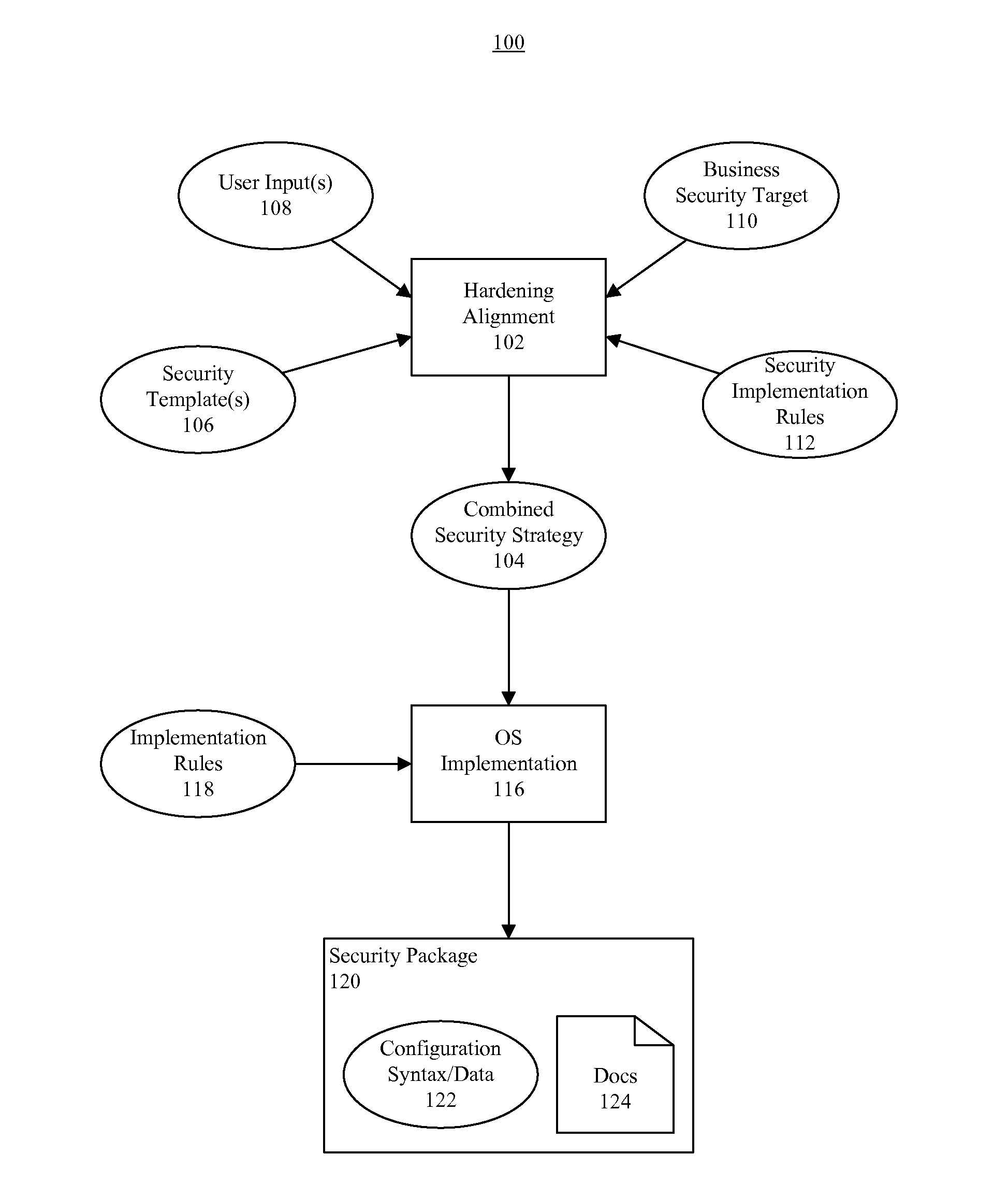
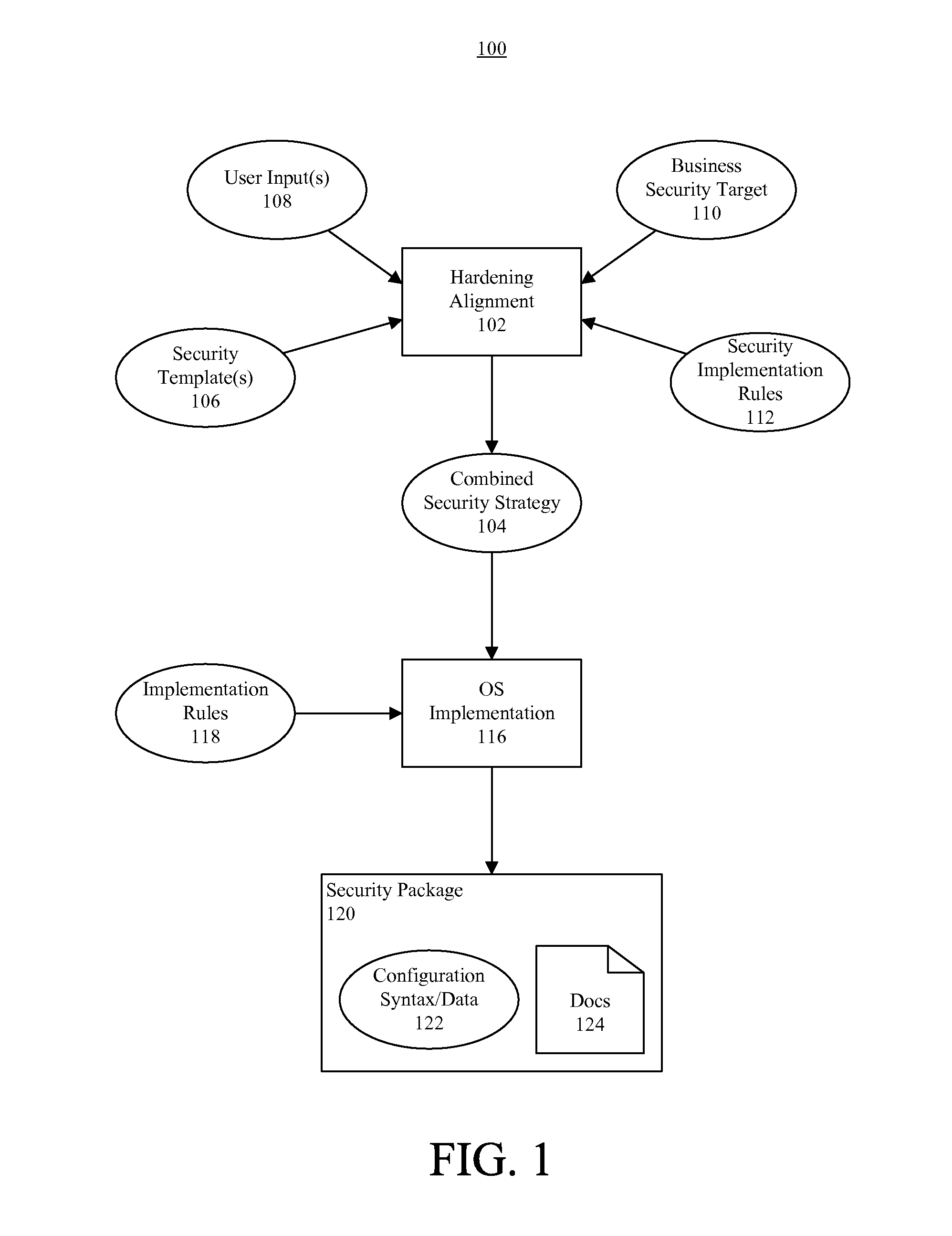
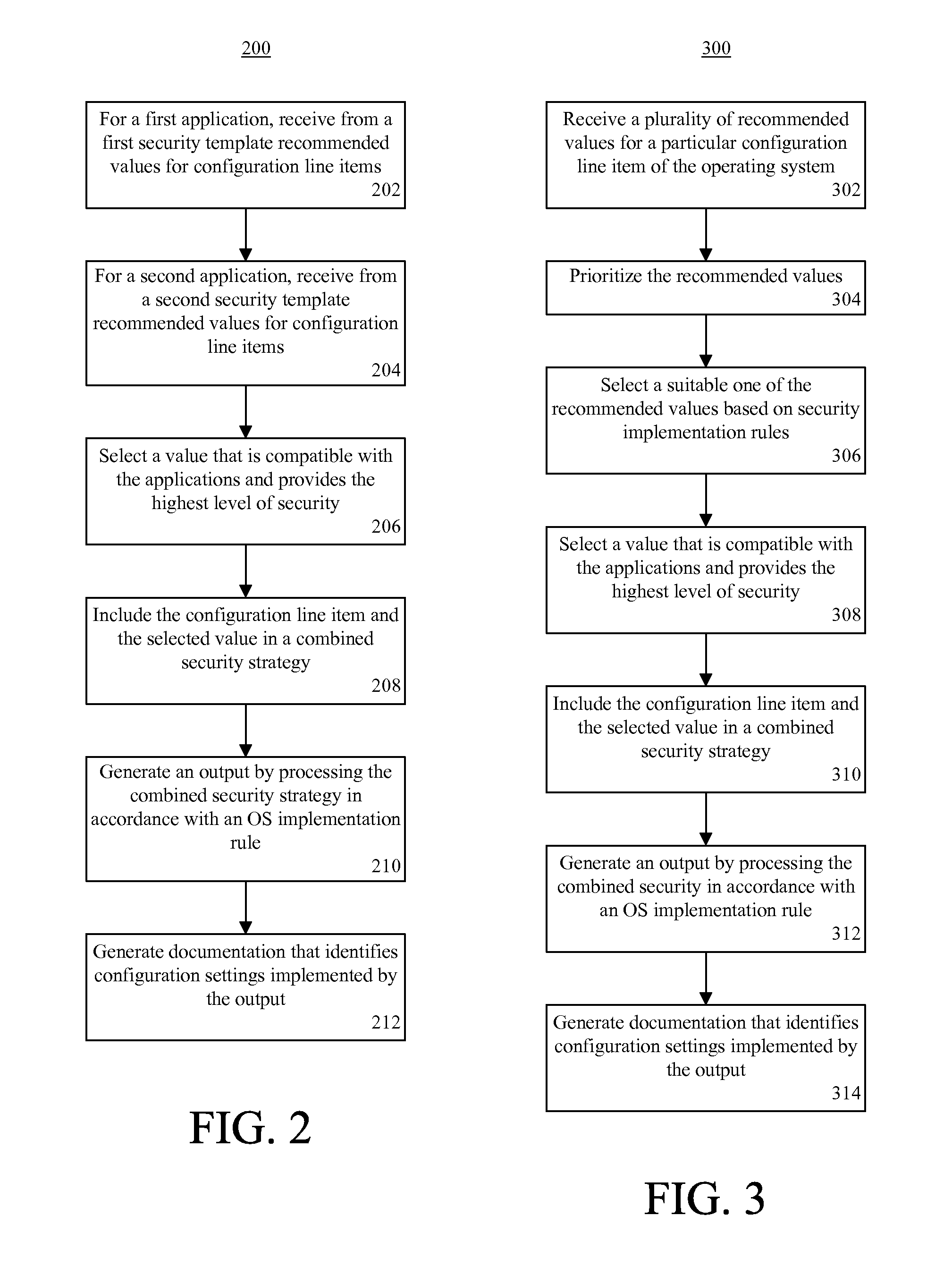
A method (200, 300) of securing an operating system. The method can include, for a first application to be instantiated on the operating system, receiving from a first security template (106) at least a first recommended value for a configuration line item. The method also can include, for a second application to be instantiated on the operating system, receiving a second security template at least a second recommended value for the configuration line item. From among at least the first and second values, at least one value that is compatible with each of the applications can be selected. Further, an output (120) can be generated that automatically updates the configuration line item with the selected at least one value.
Owner:MOTOROLA SOLUTIONS INC
Local secure service partitions for operating system security
ActiveUS8619971B2Small sizeGuaranteed growthError detection/correctionVolume/mass flow measurementOperational systemOperating system security
Systems and methods provide multiple partitions hosted on an isolation technology such as a hypervisor where at least one of the partitions, a local secure service partition (LSSP), provides security services to other partitions. The service partitions (LSSPs) host those high assurance services that require strict security isolation, where the service can be shared across partitions and accessed even when the user is not connected to a network. The LSSP also can certify the results of any computation using a key signed by a TPM attestation identity key (AIK), or other key held securely by the hypervisor or a service partition. The LSSPs may be configured to provide trusted audit logs, trusted security scans, trusted cryptographic services, trusted compilation and testing, trusted logon services, and the like.
Owner:MICROSOFT TECH LICENSING LLC
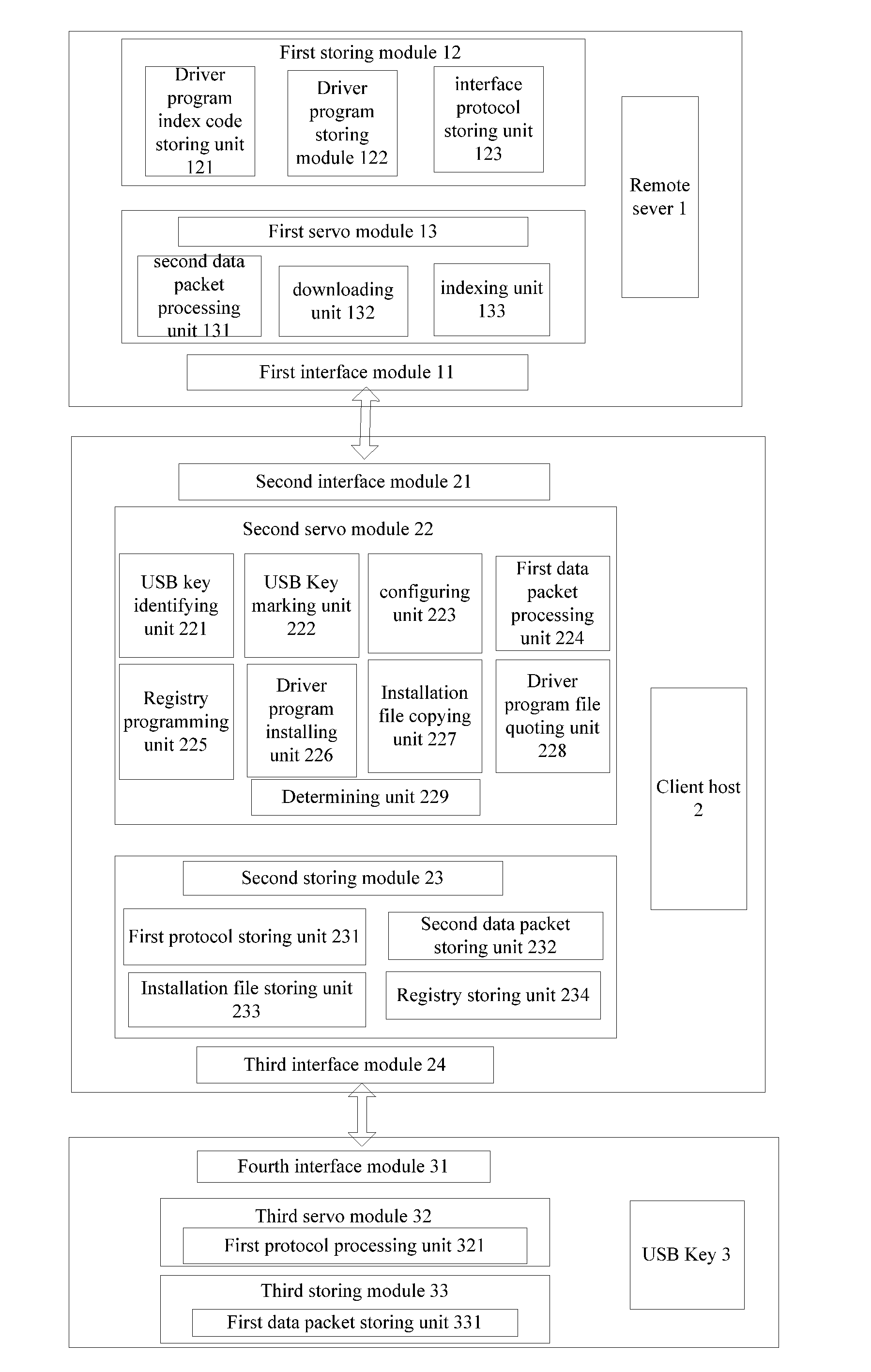
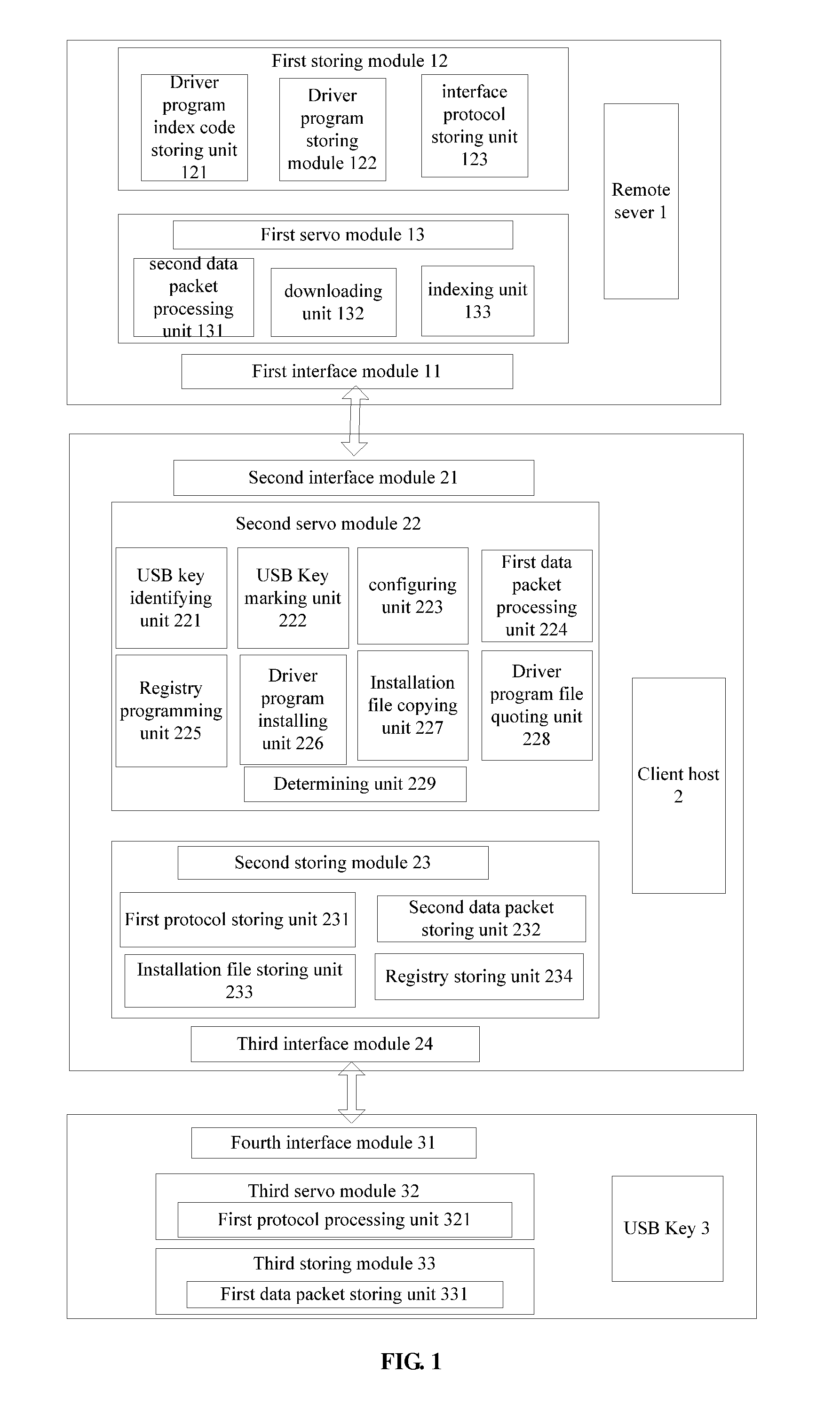
Device and method for automatic driver installation
ActiveUS20120291023A1Avoiding control of userReducing amount of popupMultiple digital computer combinationsProgram loading/initiatingOperational systemDriver/operator
Provided are a device and method for automatic driver installation. The device comprises: a remoter server, a client host and an information security device. The remote server stores driver and interface protocol program downloading service for the client host. The client host is in communication connection with the remote server, receives data information inputted by the information security device, and downloads the driver or interface protocol program from the remote server according to the data information and install or load the driver or interface protocol program. The information security device is in communication connection with the client host and feedbacks data information according to instruction issued by the client host. The present scheme can effectively reduce the number of times user account control (UAC) window pops up and ensure operating system security while installing and deploying middleware, thus simplifying user operation.
Owner:FEITIAN TECHNOLOGIES
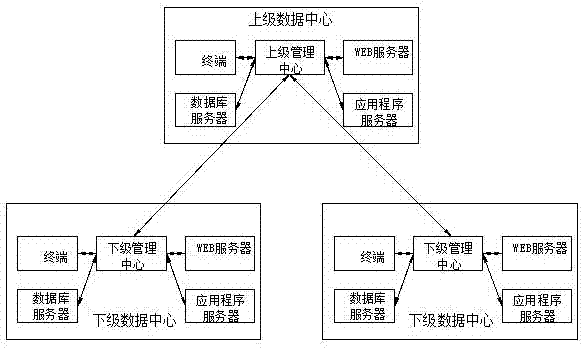
Cascading management system and method for secure network
InactiveCN107276830AReal-time queryImprove securityData switching networksOperational systemData center
The invention discloses a cascading management system and method for a secure network and relates to the field of computer communication and operating system security. Through cascading setting, assert management, strategy management and global monitoring, uniform monitoring and management are carried out on whole network data centers. A superior management center of a superior data center manages subordinate management centers of subordinate data centers; moreover, the superior management center and the subordinate management centers manage terminals at the data centers; the superior management center formulates compulsive strategies or recommendation strategies to the subordinate management centers and issues the strategies in a cascading mode. The subordinate management centers reports statistics and alarm information to the superior management center in the cascading mode. A system manager grasps basic information and security states of the subordinate data centers in real time through the global monitoring of the superior management center. According to the system and the method, the network risk resulting from carrying out connection on all computers and the superior is avoided, the security and compliance of the computers are improved, and the system manager can know the security condition of the whole network computers very conveniently.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Method for managing application programs in SSR centralized management platform
InactiveCN107657171AEasy to managePlatform integrity maintainanceTransmissionTrust levelOperating system security
The invention provides a method for managing application programs in an SSR centralized management platform and belongs to the field of operating system security technology. The method mainly comprises the steps of centralized management, application program list management, strategy management and single-client viewing, wherein application program lists of a plurality of clients under a complicated network are managed in a unified and centralized mode; full-web lists can be checked and trust levels of the full-web lists can be set through an application program list management function; specific application program strategies of the clients are controlled through strategy management; and current operating states of the application programs of the clients are checked and operation is performed through single-client viewing.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
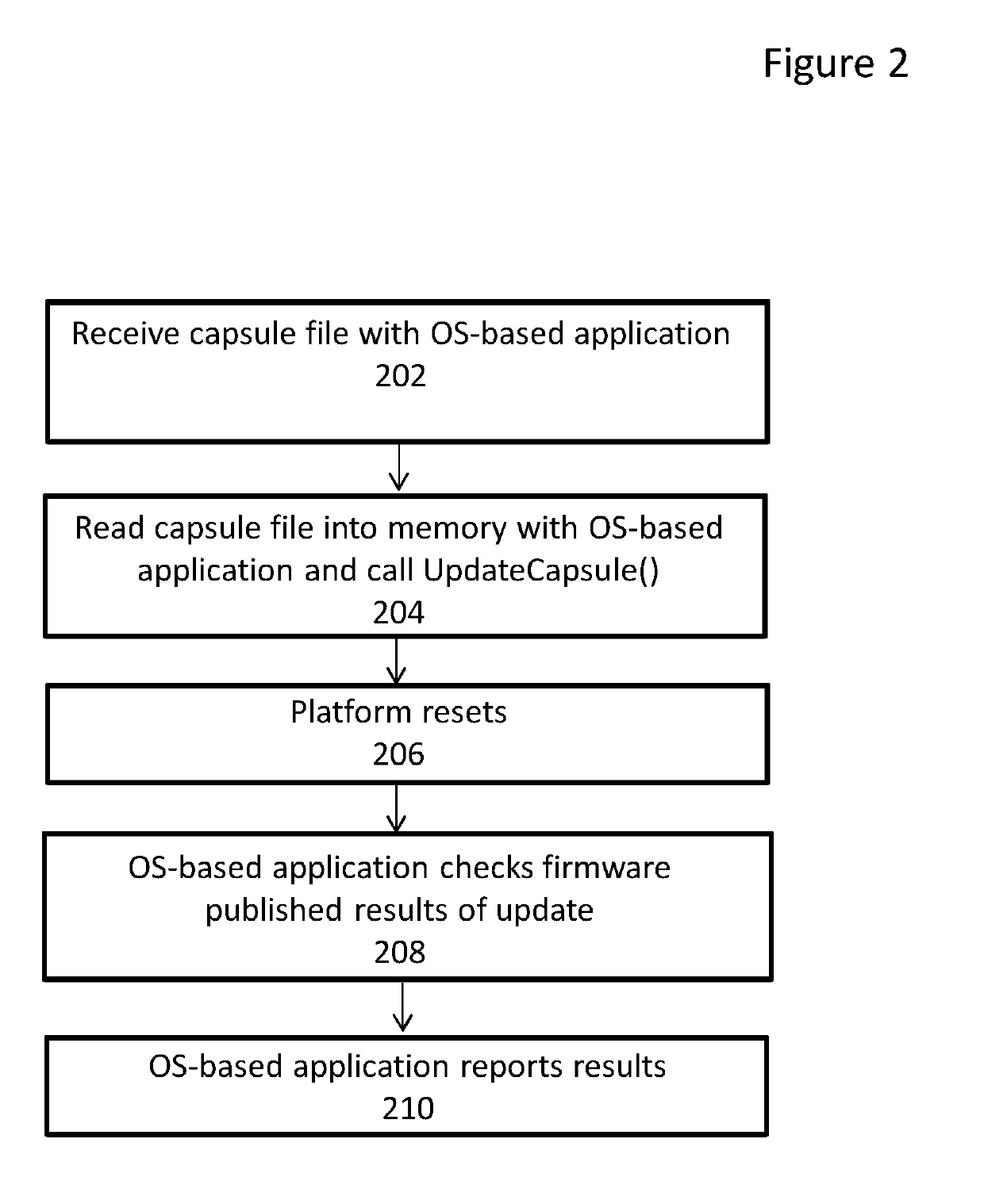
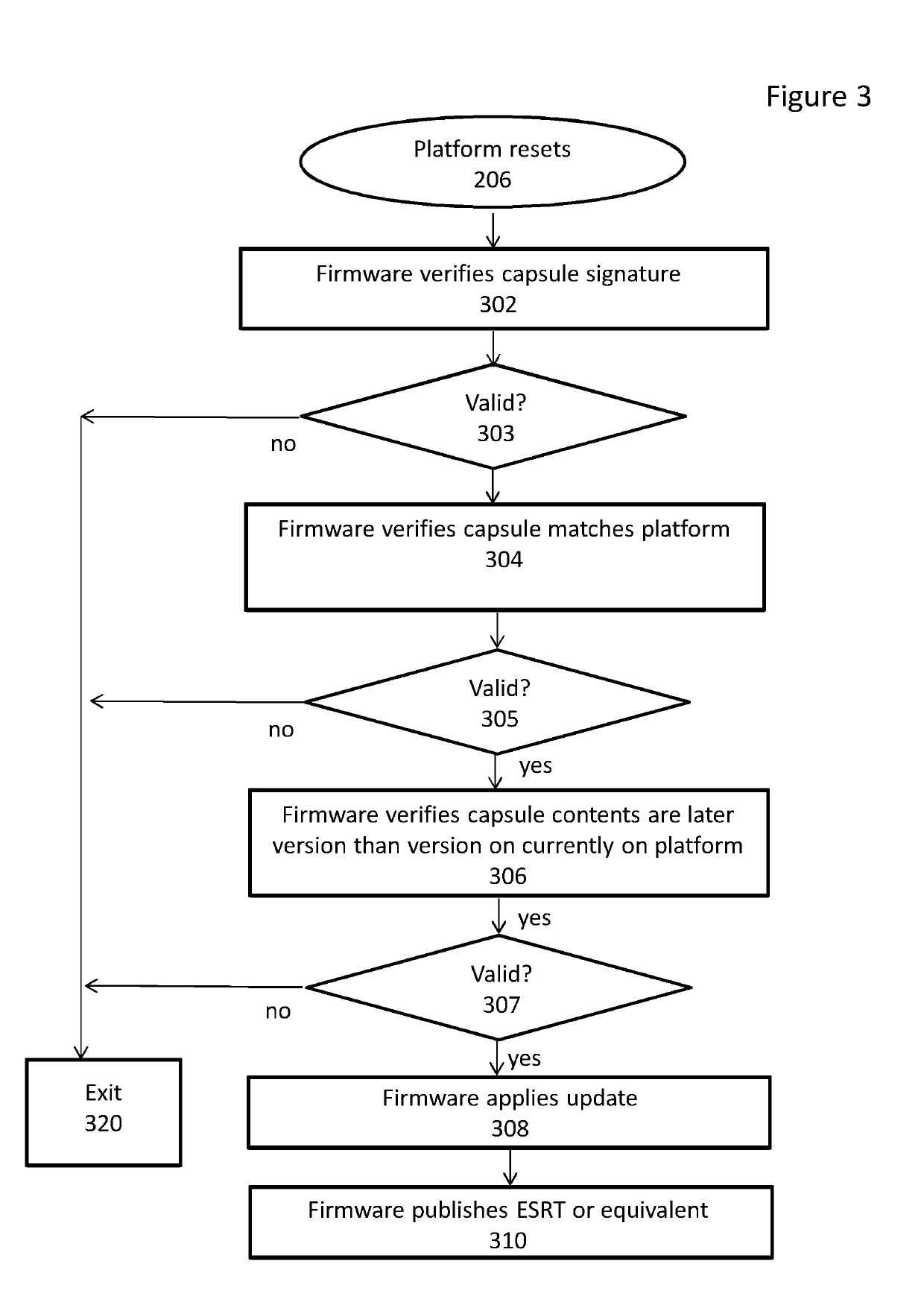
System and method for providing firmware data updates
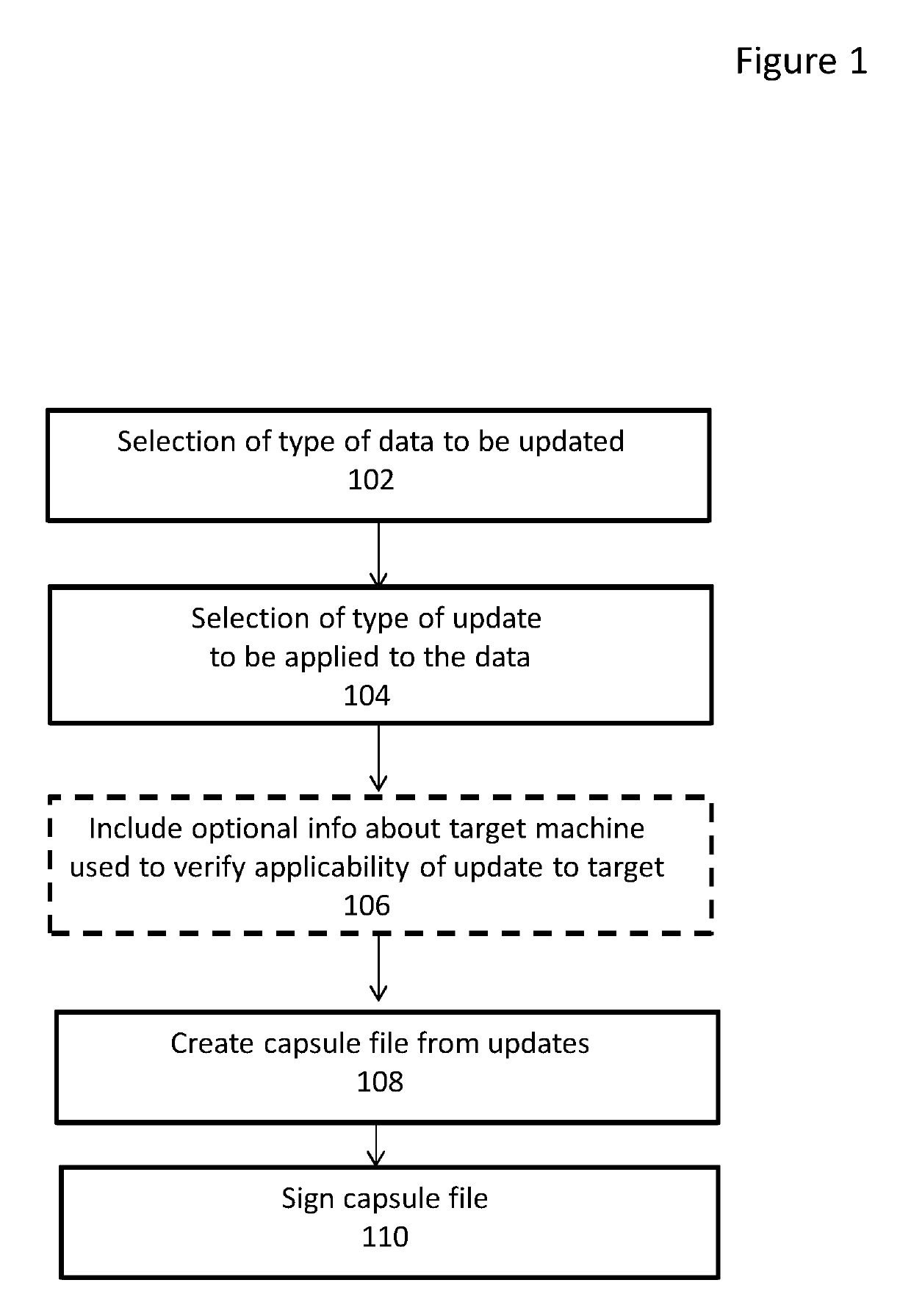
ActiveUS20190243634A1Verify authenticityData resettingPlatform integrity maintainanceOperating system securityMicrocode
A system and method for updating firmware data on a computing platform in response to a firmware update request received in the form of a signed capsule file received via a runtime service is discussed. The firmware update request may be a request to update UEFI firmware and be received using the UpdateCapsule runtime service. The firmware data may include data associated with UEFI protected variables, SMBIOS data, logo data, microcode update data and pre-operating system security policy data.
Owner:INSYDE SOFTWARE
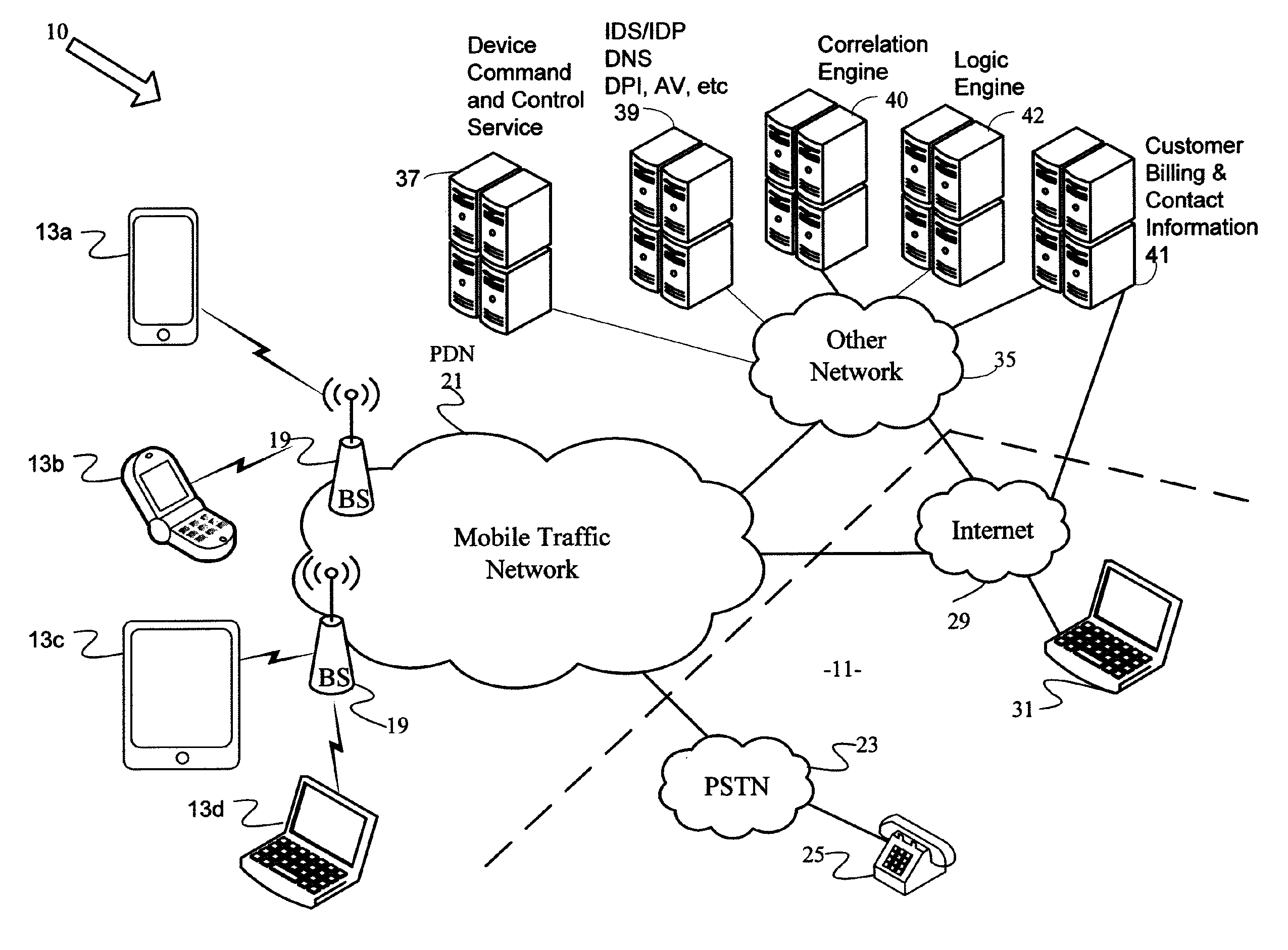
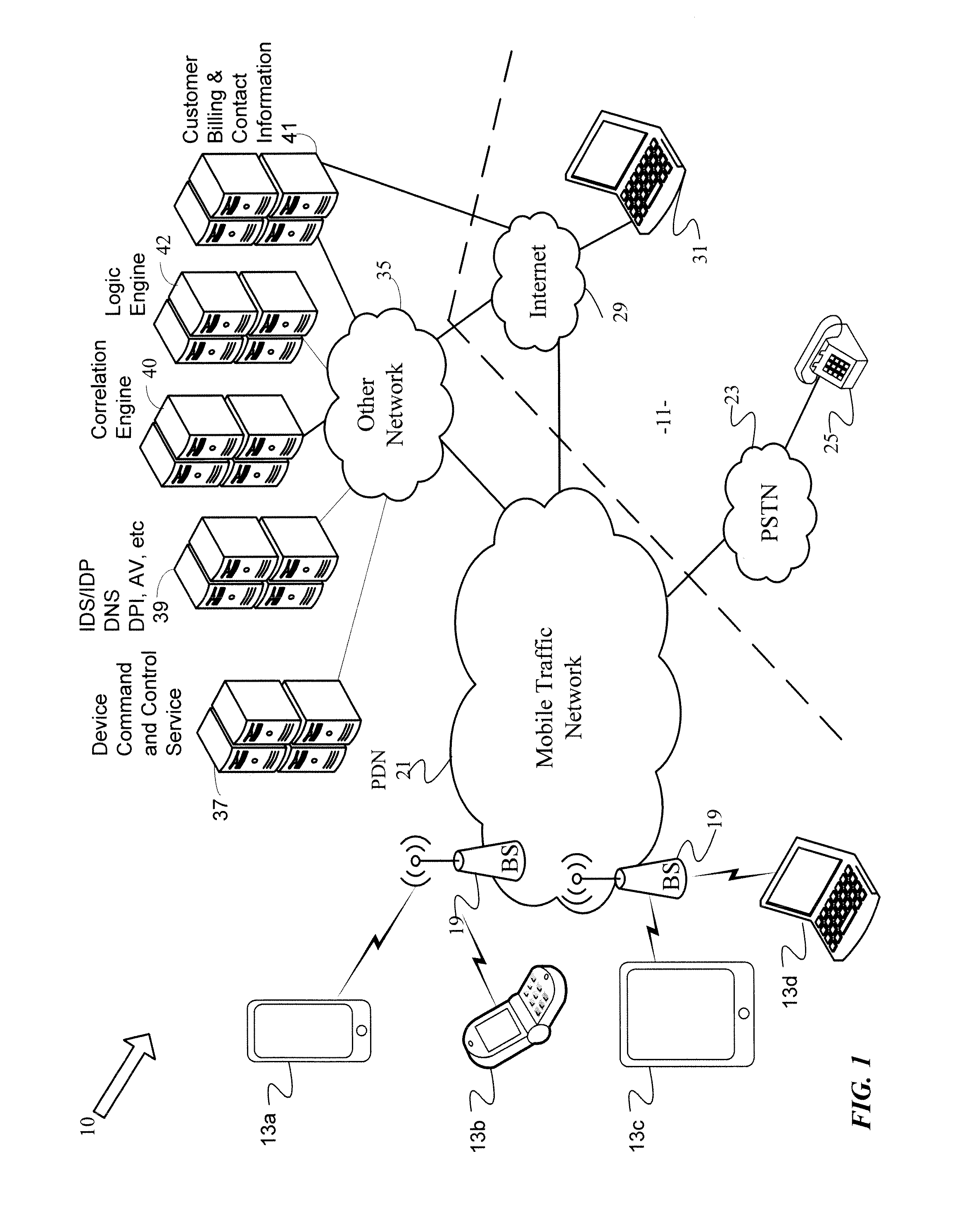
Network based device security and controls
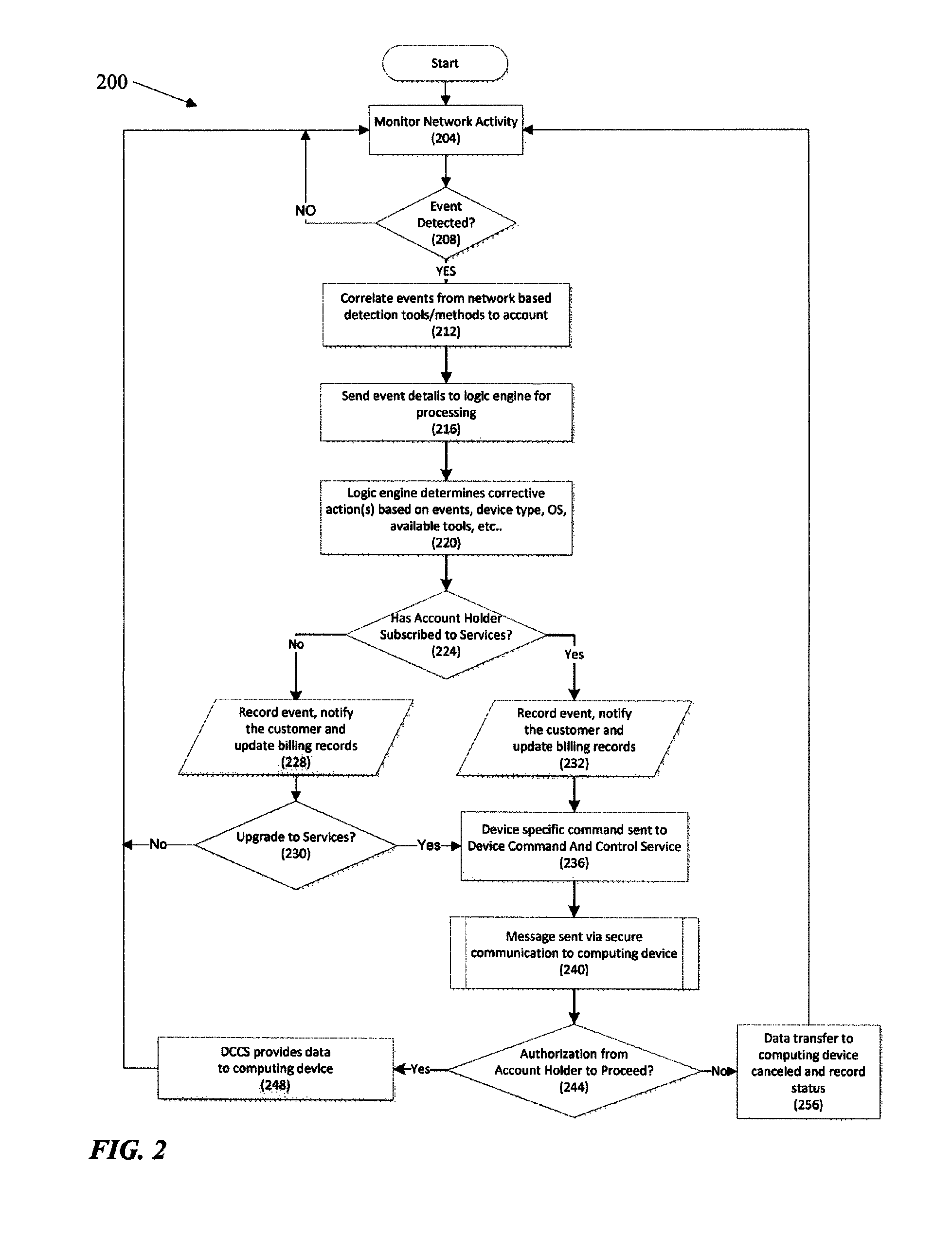
Protection against security attacks involves monitoring network traffic for a computing device security attack and determining whether there is a security event, using one or more network based security tools. Next, it is determined whether an event pattern involving two or more security events meets a predetermined criteria. Upon determining that there is a security attack, corrective action is tailored, based on the type of the computing device, the operating system of the computing device, the type of security attack, and / or the available protection tools. A course of action is performed depending on whether an account of the computing device includes a security protection service. If there is a security protection service, a message is sent over a secure link to the computing device. This message includes the corrective action to cure the computing device from the security attack.
Owner:CELLCO PARTNERSHIP INC +1
User privilege escalation method supporting mandatory access control
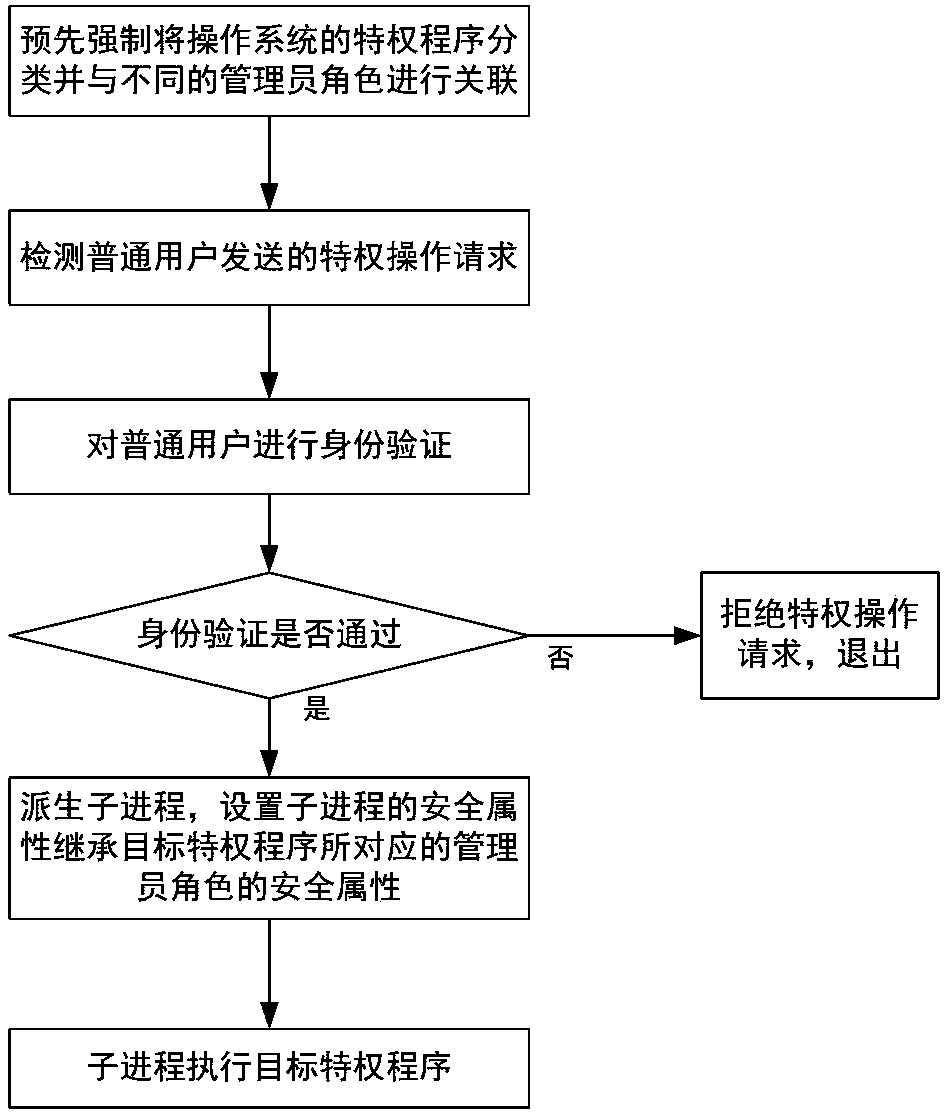
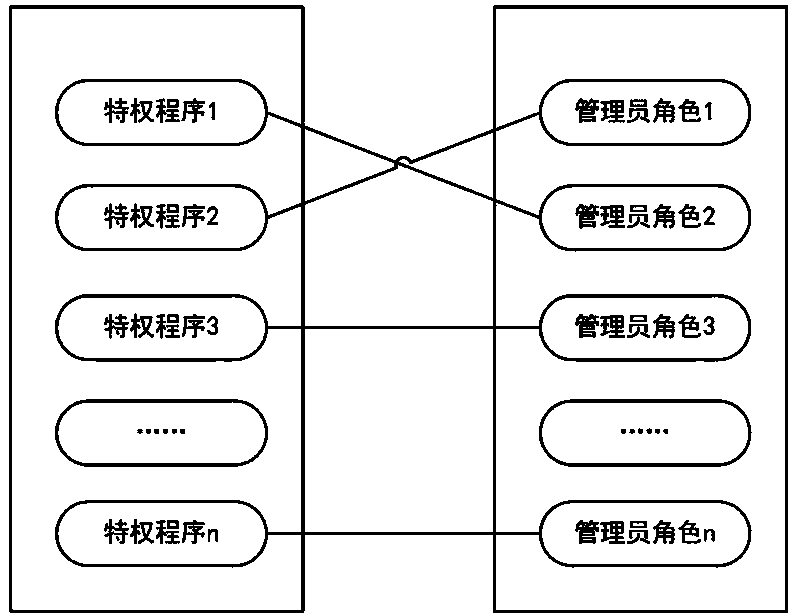
ActiveCN104036166AImprove securityImprove usabilityDigital data authenticationUser PrivilegeOperating system security
The invention discloses a user privilege escalation method supporting mandatory access control. The method comprises the following steps that: (1) privilege programs of an operating system are subjected to mandatory classification in advance and are correlated with different administrator roles; (2) access requests of users are detected, and when a privilege operation request is detected, jumping is carried out to execute the step (3); and (3) a user sending out the privilege operation request is authenticated, if the authentication is passed, a child process is derived, security attributes of the child process are set and are enabled to inherit security attributes of the administrator roles corresponding to the target privilege programs, and the target privilege programs are executed through the child process; and if the authentication is not passed, the privilege operation request of the user is refused, and exiting is carried out. The user privilege escalation method has the advantages that a realization method is simple; the privilege escalation operation of the user can be realized; in addition, the mandatory access control is supported; the safety of the operating system is high; and in addition, the usability is high.
Owner:NAT UNIV OF DEFENSE TECH
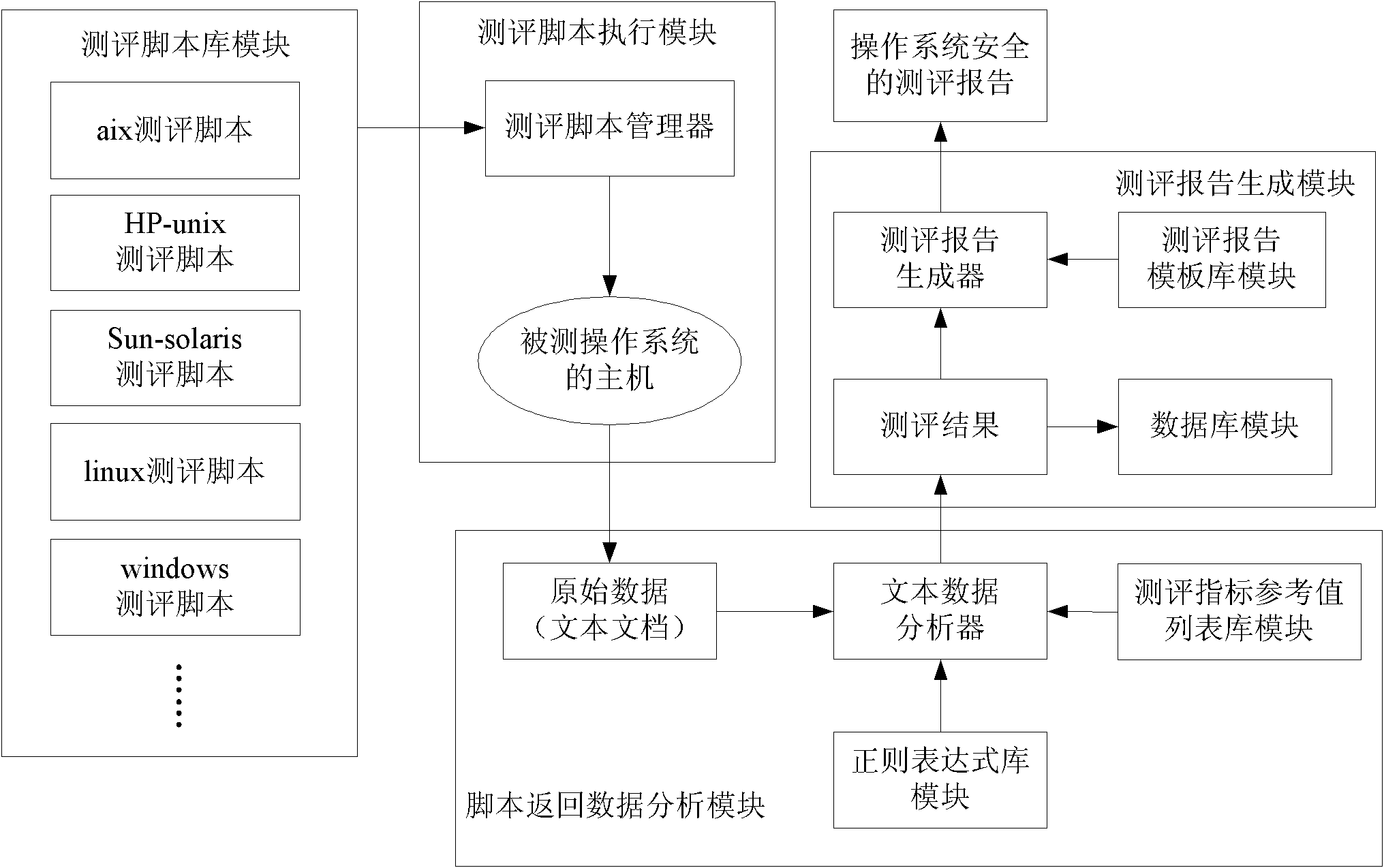
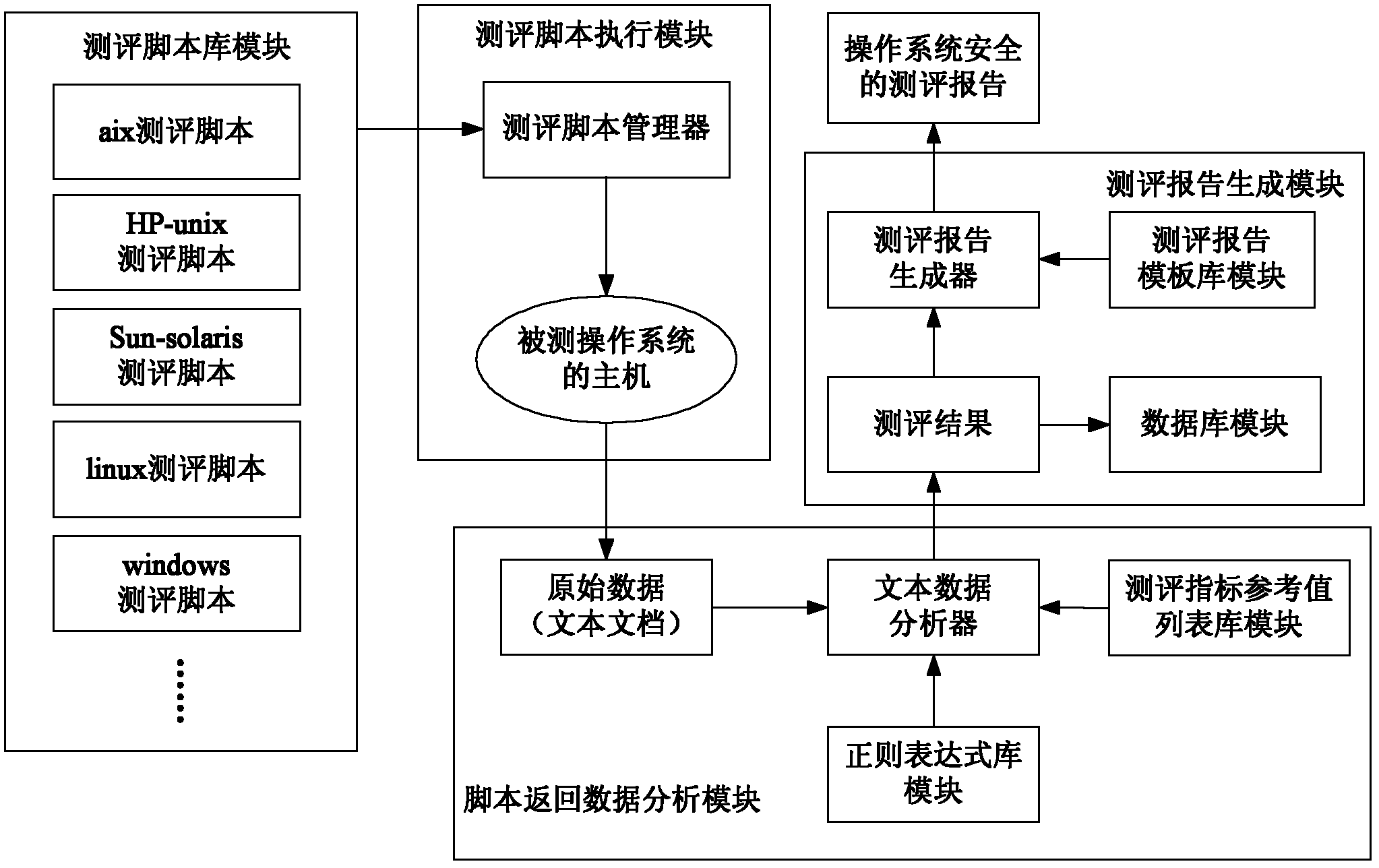
Automatic evaluation method for operation system security in classified protection evaluation and system thereof
InactiveCN102591773AGuaranteed evaluationNormativeSoftware testing/debuggingOperational systemOperating system security
The invention discloses an automatic evaluation method for operation system security in classified protection evaluation. The method comprises the following steps of establishing an evaluation script library capable of checking each security configuration checkpoint of various operation systems; identifying the type of an operated system through an evaluation script executing module, selecting an appropriate evaluation script from the evaluation script library, and executing the evaluation script; analyzing a result executed and returned by the evaluation script through a scrip return data analysis module and forming an evaluation result, and storing the result into a data base; and automatically generating an evaluation report of the operation system security through an evaluation report generation module. The invention further discloses an automatic evaluation system for the operation system security in the classified protection evaluation. The system comprises an evaluation scrip library module, an evaluation scrip executing module, a script return data analysis module and an evaluation report generation module which are sequentially connected. The automatic evaluation method for operation system security in the classified protection evaluation and the system of the automatic evaluation method achieve automatic evaluation on the operation system security and obtain the classified protection evaluation results.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID
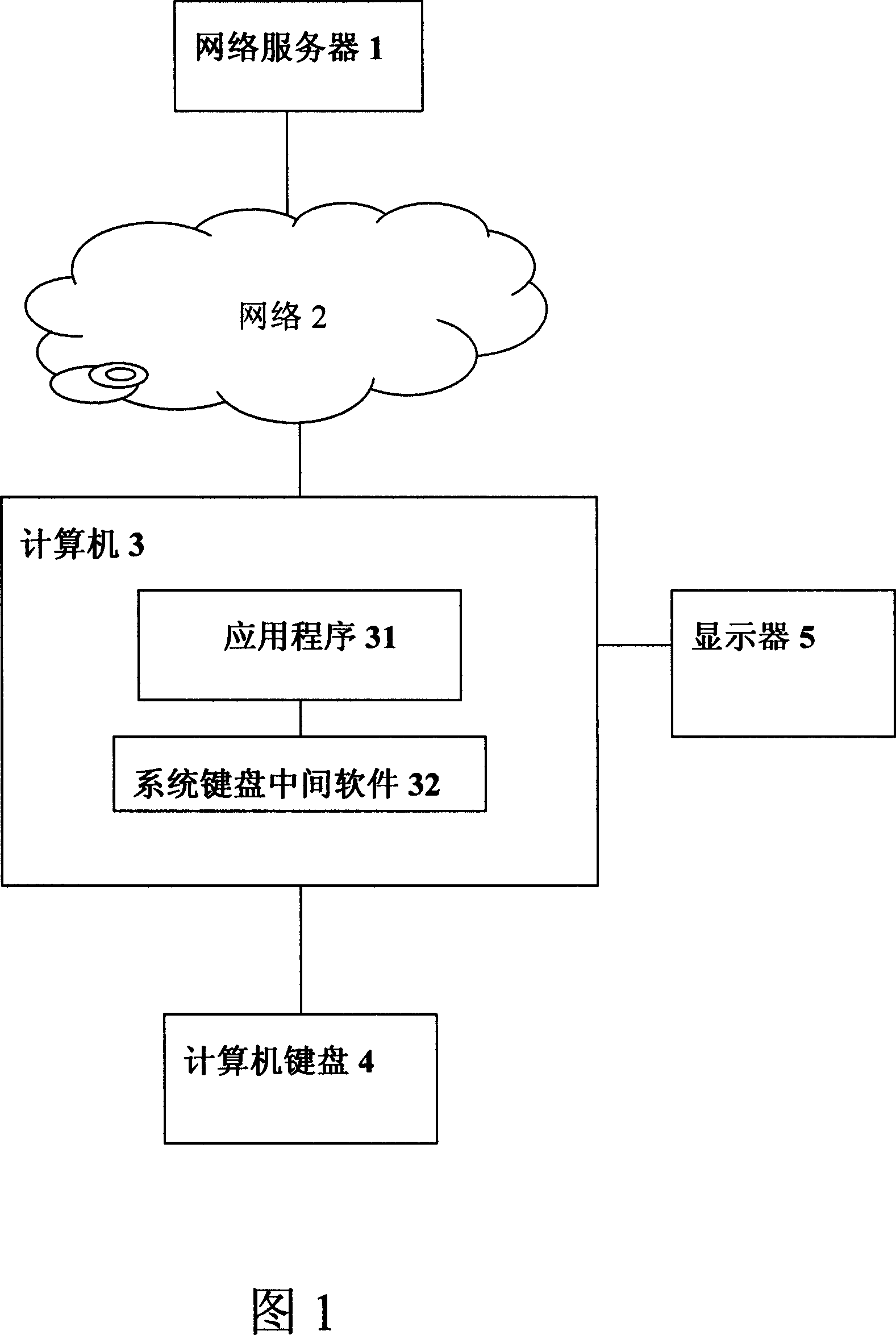
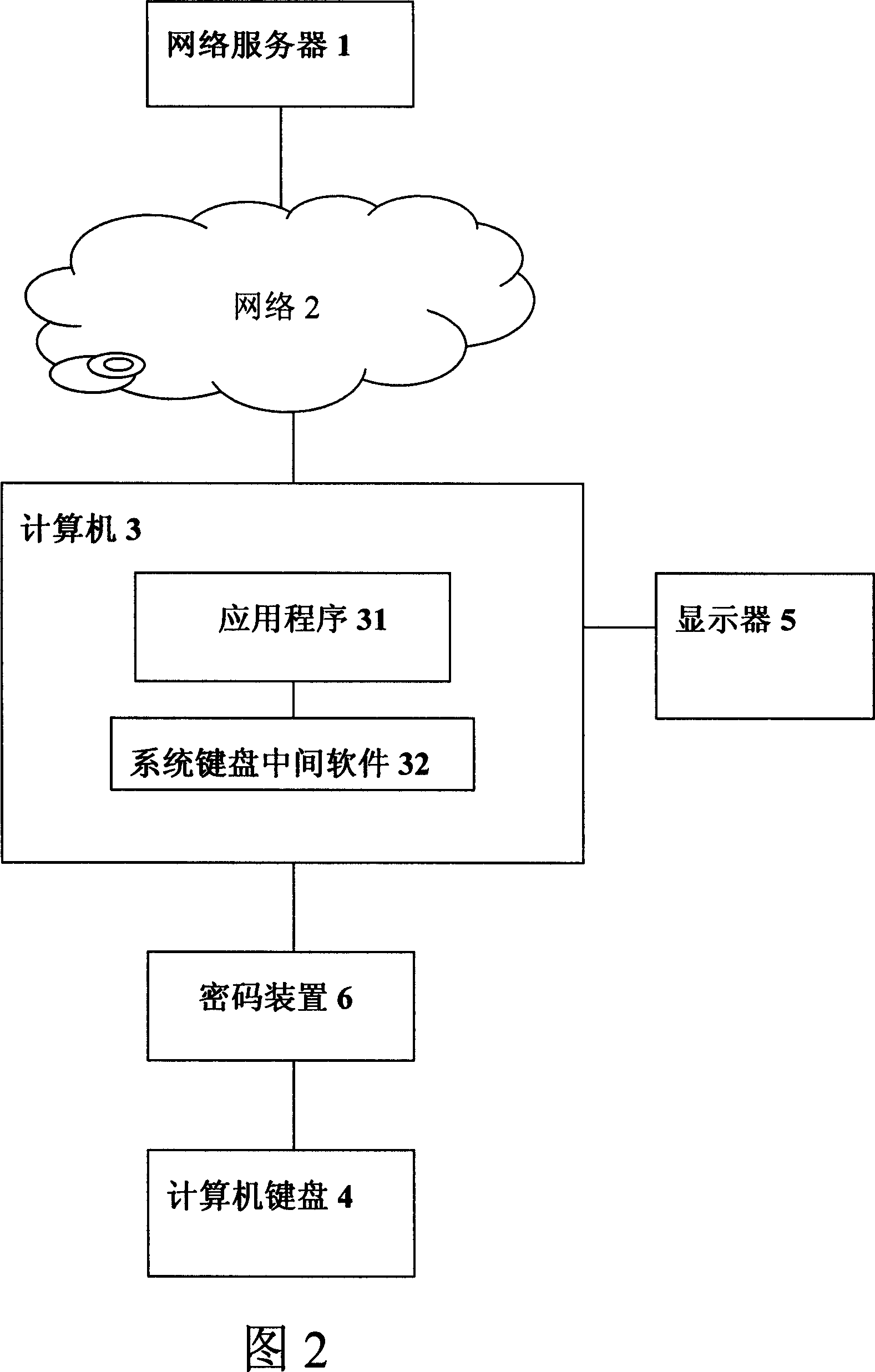
A device and method for secure use of network server service not depending on operating system security
InactiveCN101127605AEasy to useDigital data protectionMechanically effected encryptionOperational systemSecure state
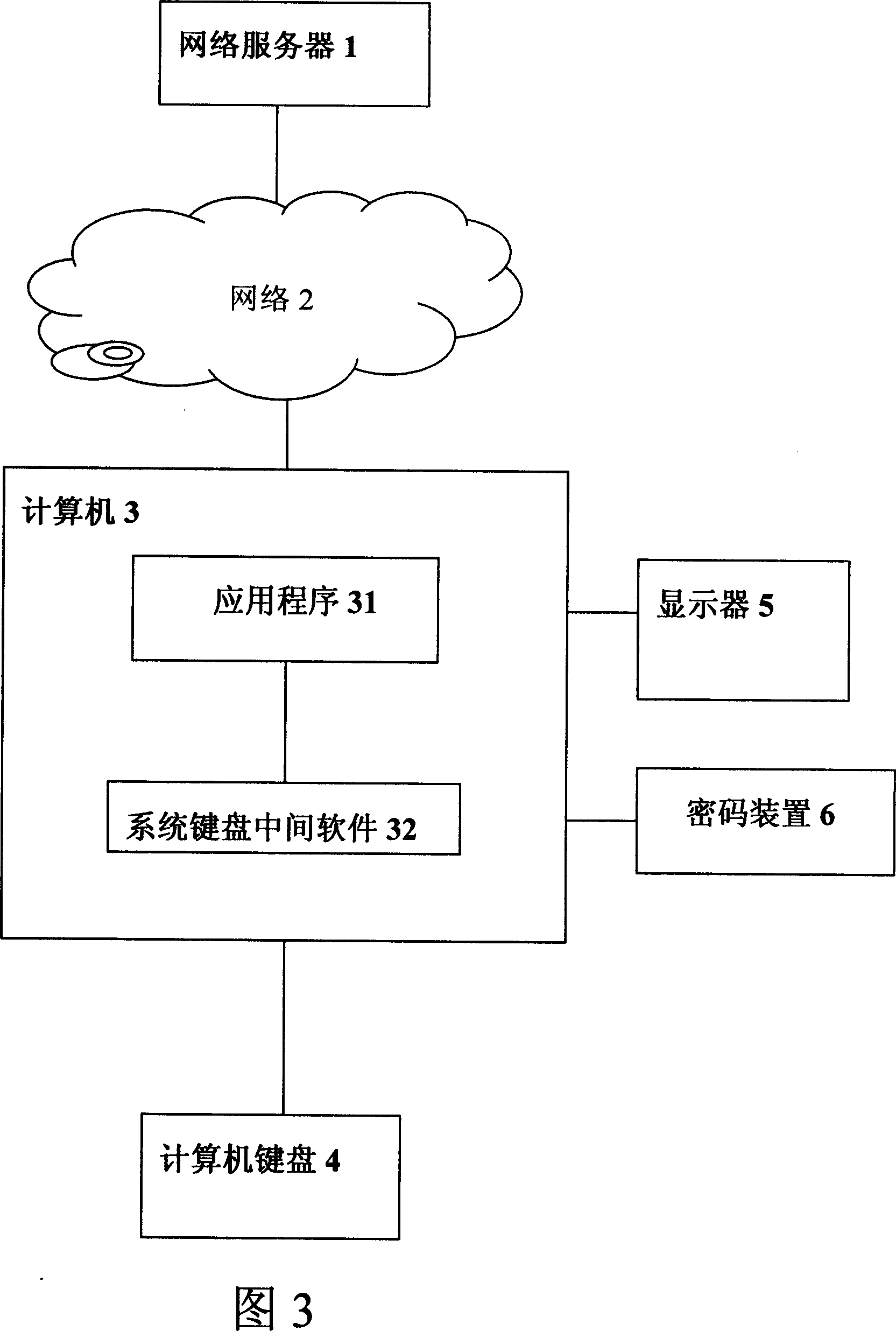
The utility model relates to a specific device and the method for realizing safe use of the network server independent to the safety of the operating system. The utility model has the advantages that utilizing a keyboard, a cryptographic device, a network server and reasonable information flow mode, and combining with good cryptographic protocol can simply and safely realize the device and the method for safely using network server in unsafe computer.
Owner:NANJING E SECURITY TECHNALOGY
Safe remote loading method of operating system
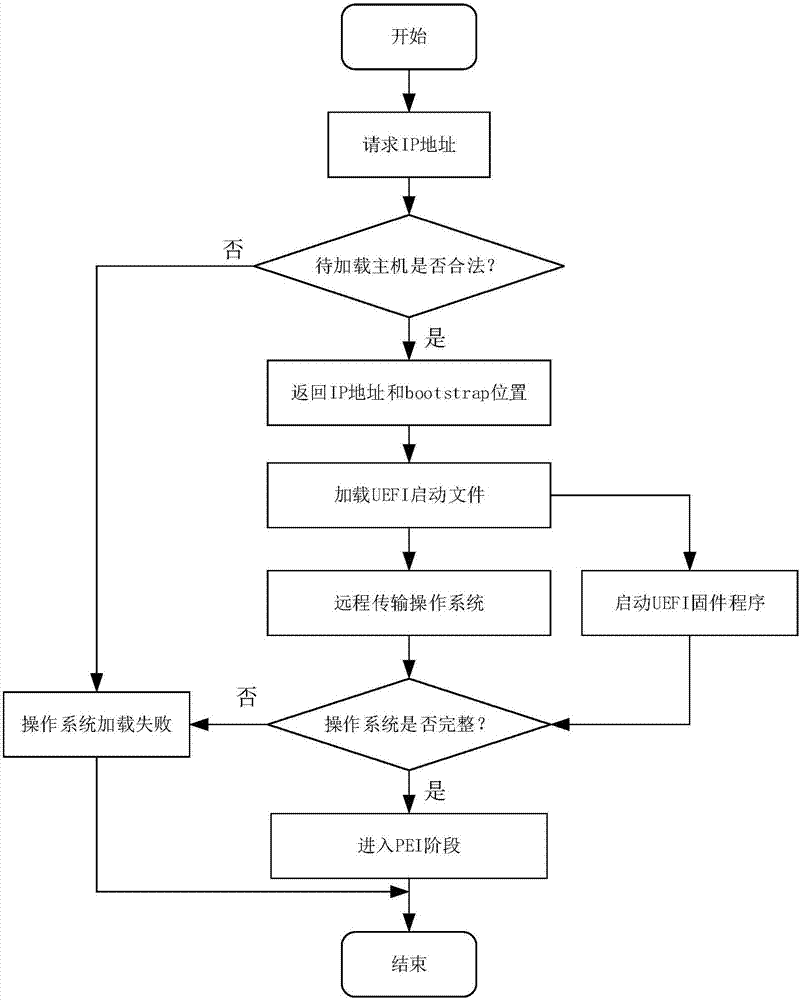
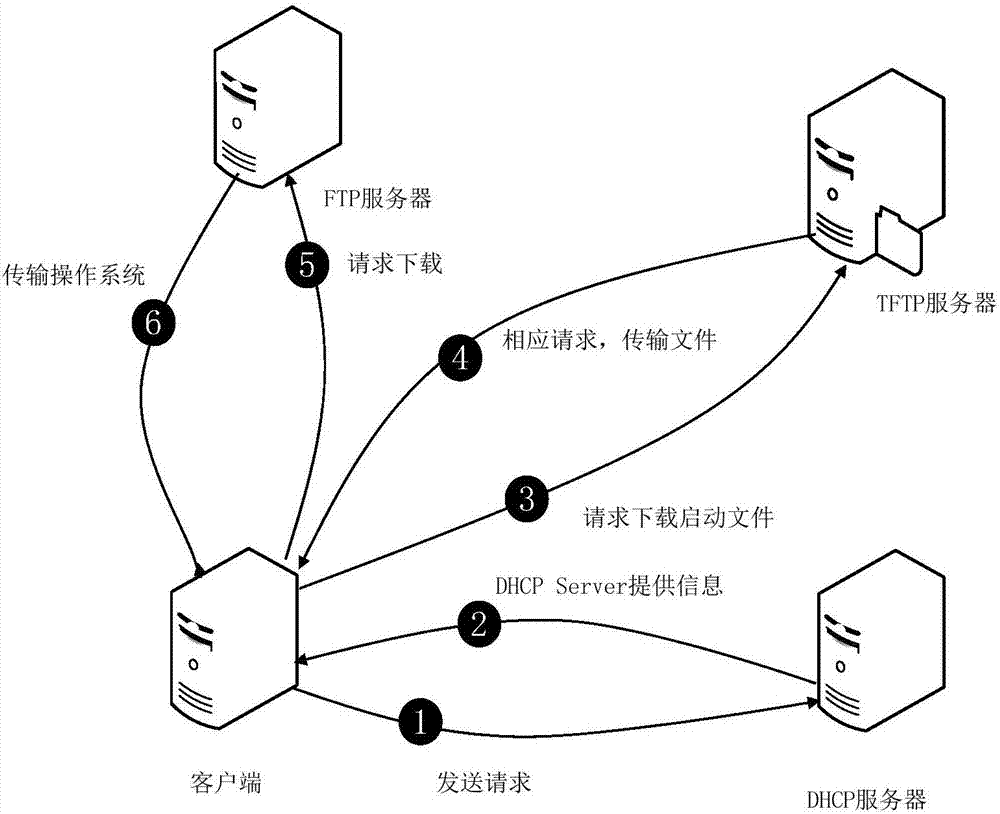
ActiveCN106940769AEnsure safetyDigital data authenticationTransmissionOperational systemSecurity software
The invention discloses a safe remote loading method of an operating system. The safe remote loading method comprises the following steps: (1) a legality verification step of a computer to be subjected to loading; (2) a remote loading step of the operating system; (3) an integrity measurement step of the operating system in a loading process. Aiming at the problem that current security software cannot process operating system-level malicious programs, the integrity of the operating system can be measured before the operating system is started up, so that the environment security before startup is guaranteed.
Owner:GUANGZHOU UNIVERSITY
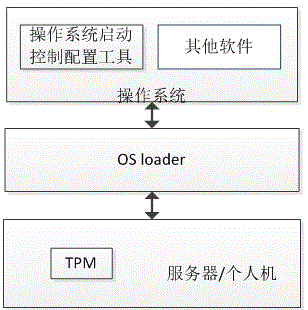
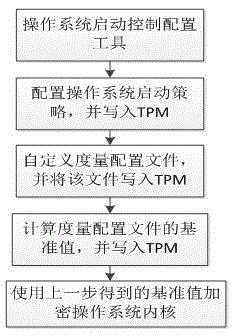
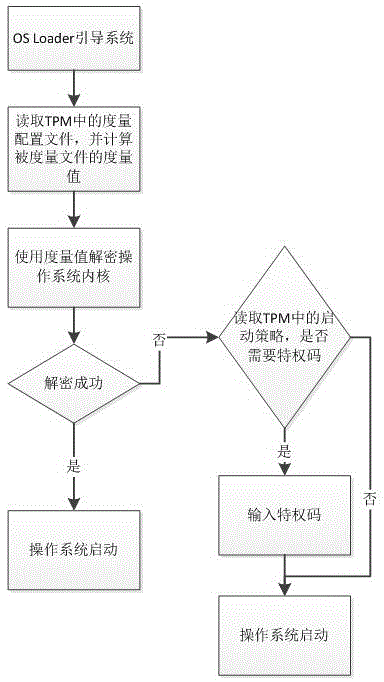
TPM-based control method for safe startup of operating system
ActiveCN105678162AHigh security valuePlatform integrity maintainanceOperational systemTrusted Platform Module
The invention discloses a TPM (Trusted Platform Module)-based control method for safe startup of an operating system, and belongs to the field of trusted computing. According to the invention, a safe startup control policy of the operating system is configured into a TPM chip; the designated measurement configuration file is measured to obtain a reference value for encrypting the operating system core; then when the operating system is started up, combined with guidance of OS Loader, the measurement configuration file in the TPM is read to measure the designated measurement configuration file so as to obtain the measurement value; the measurement value is used for decrypting the operating system core; if decryption fails, the corresponding safe startup control motion can be carried out as per the startup control policy information in the TPM. Therefore, safe startup of the operating system is configurable and controllable.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
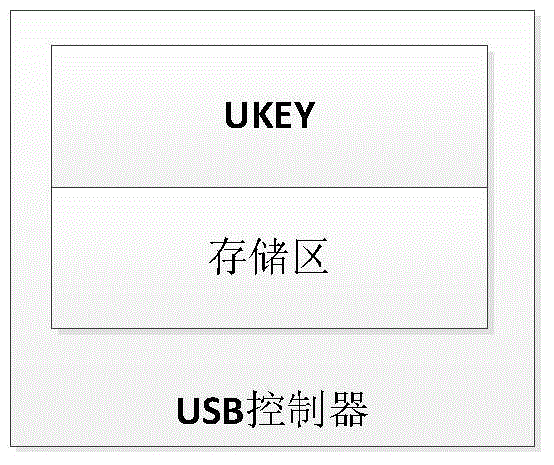
Method for realizing bi-operation system starting of terminal equipment by using USB (universal serial bus) controller
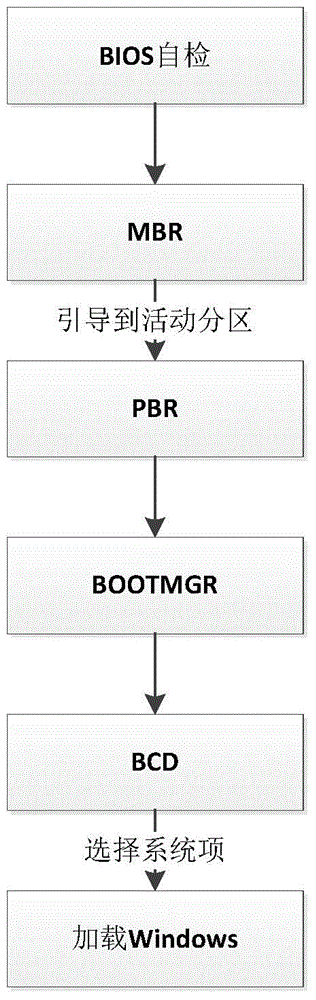
InactiveCN104572093AEnsure safetyLow costSpecific program execution arrangementsOperational systemFree zone
The invention discloses a method for realizing bi-operation system starting of terminal equipment by using a USB (universal serial bus) controller and belongs to the technical field of dual operation system starting of the user terminal equipment. The method is characterized by including on a single hard disk provided with a working area and a free area, judging whether the USB controller is inserted or not by a BIOS (bi-operation system); if yes, executing a modified guide file GRLDR in the USB controller, verifying PIN of a user, loading a secret key, guiding to enter a reserved partition, executing a decryption program to decrypt the working area, and then entering the working area; if not, guiding to enter the free area by an MBR (master boot record), executing a partition boot record (PBR), in the type of BOOTMGR, of the free area, and entering the free area. Different from other methods for realizing bi-operation system starting through double hard disks, the method has the advantages that a mode of realizing bi-operation system starting through the same hard disk and multiple partitions is used, and through an encryption mechanism of a working area operation system, safety of the working area operation system is guaranteed, cost is lowered, and efficiency is improved.
Owner:BEIJING UNIV OF TECH
A system and method for protecting Linux operating system security base on IMA
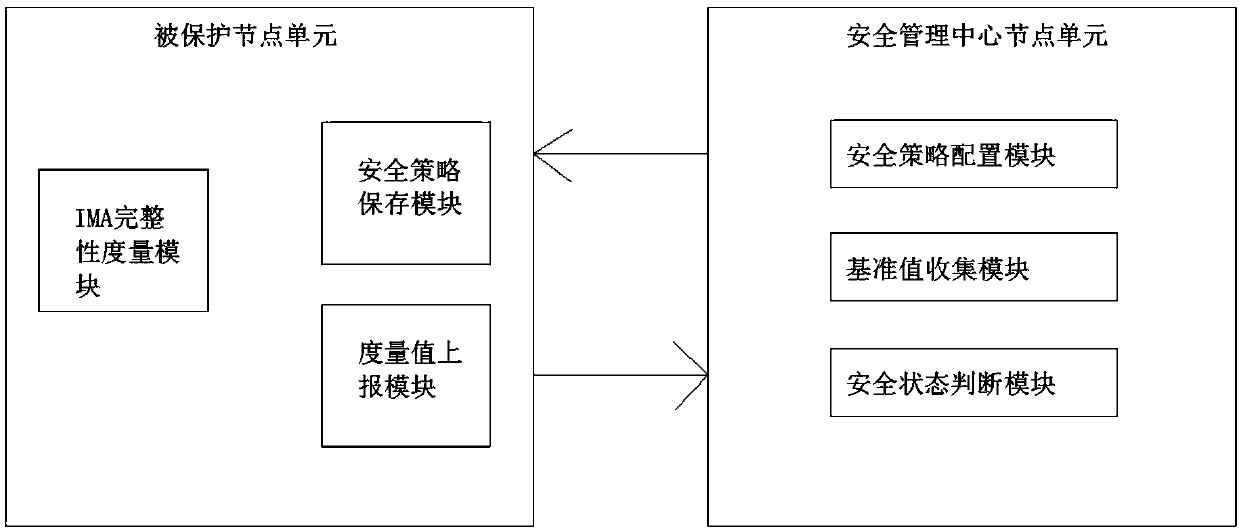
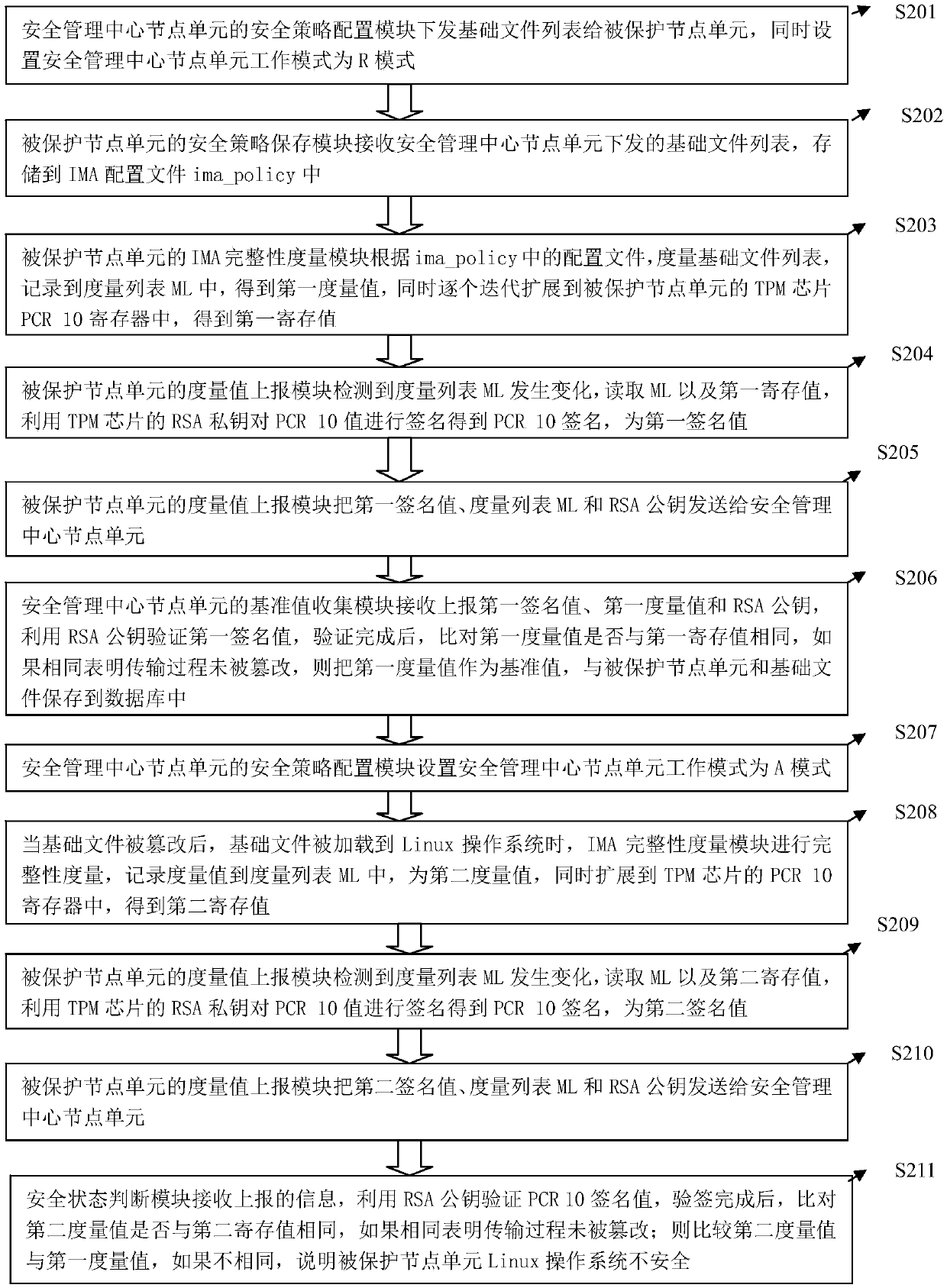
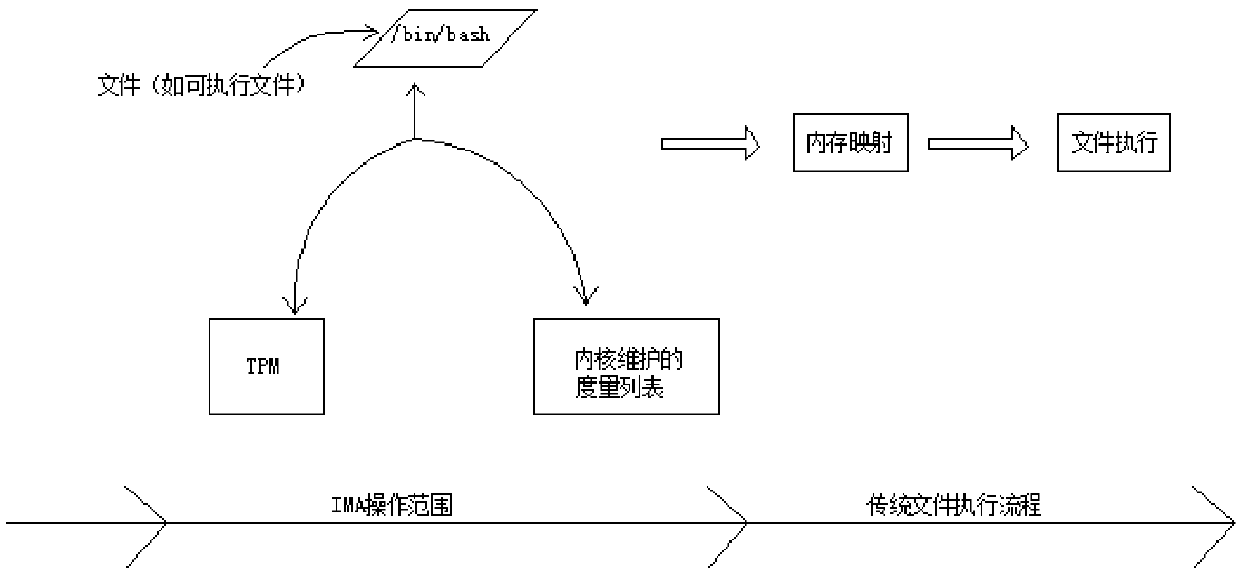
InactiveCN109543413AProtection securityImprove integrityPlatform integrity maintainanceOperational systemGNU/Linux
A system and method for protecting security of Linux operating system base on IMA. At first, that node unit of the security management cent configures a protection policy to the protect node unit, Asthat system executable file, system dynamic link library, System configuration files on the protected node unit need to be run and loaded into the Linux operating system, A measure value of that protected node element is obtain by measuring the object using an IMA technology, and then reporting the measure value to the node unit of the security management center. At last, after that node unit of the security management center analyze and confirms the identity information of the protected node unit, whether the upload metric value is the same as the reference value collected beforehand is compared to judge whether the protected object is tampered with or not, so as to protect the security of the Linux operating system on the protected node unit. The invention protects the integrity of the Linux operating system core system file, enhances the security of the Linux operating system, and the protection cycle will accompany the whole operating system running phase.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Computer operating system safety protecting method
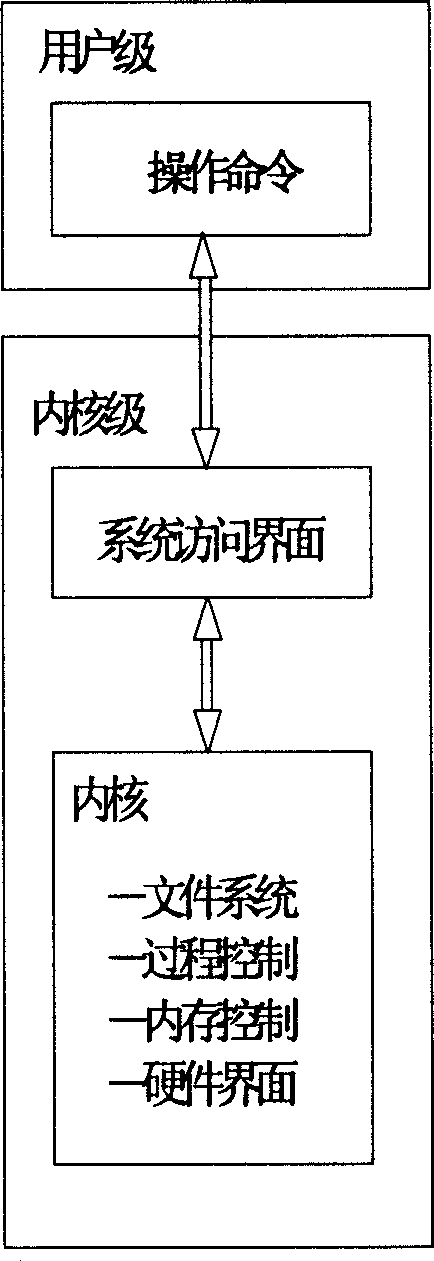
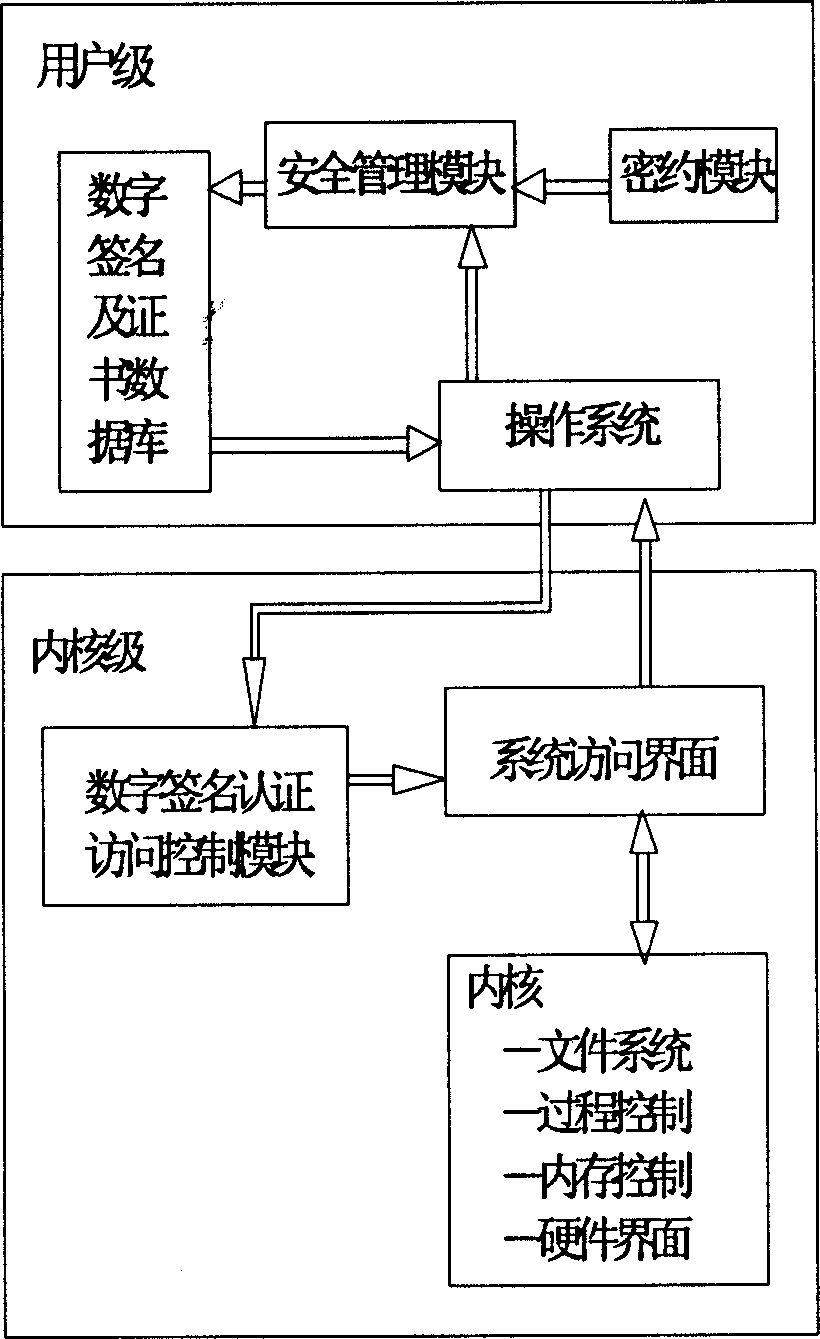
The method adds database of digital signature and certificate, module of security management and module of security agreement on Unix operating system (OS) at user level, and adds an access control module of digital signature authentication on Unix OS at kernel level. Without changing executable files of system and kernel, the method makes the each added module become an effective section of OS so as to be able to carry out security protection and effective control for whole Unix OS under condition of without rewriting operation and condition of transparence. Advantages are: simple, safety, practical and reliable.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com