A device and method for secure use of network server service not depending on operating system security
An input device and encryption device technology, applied in the field of safe use of network server services, can solve problems such as data not being displayed in time, user confusion, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0042] [Example 1] keyboard string dog
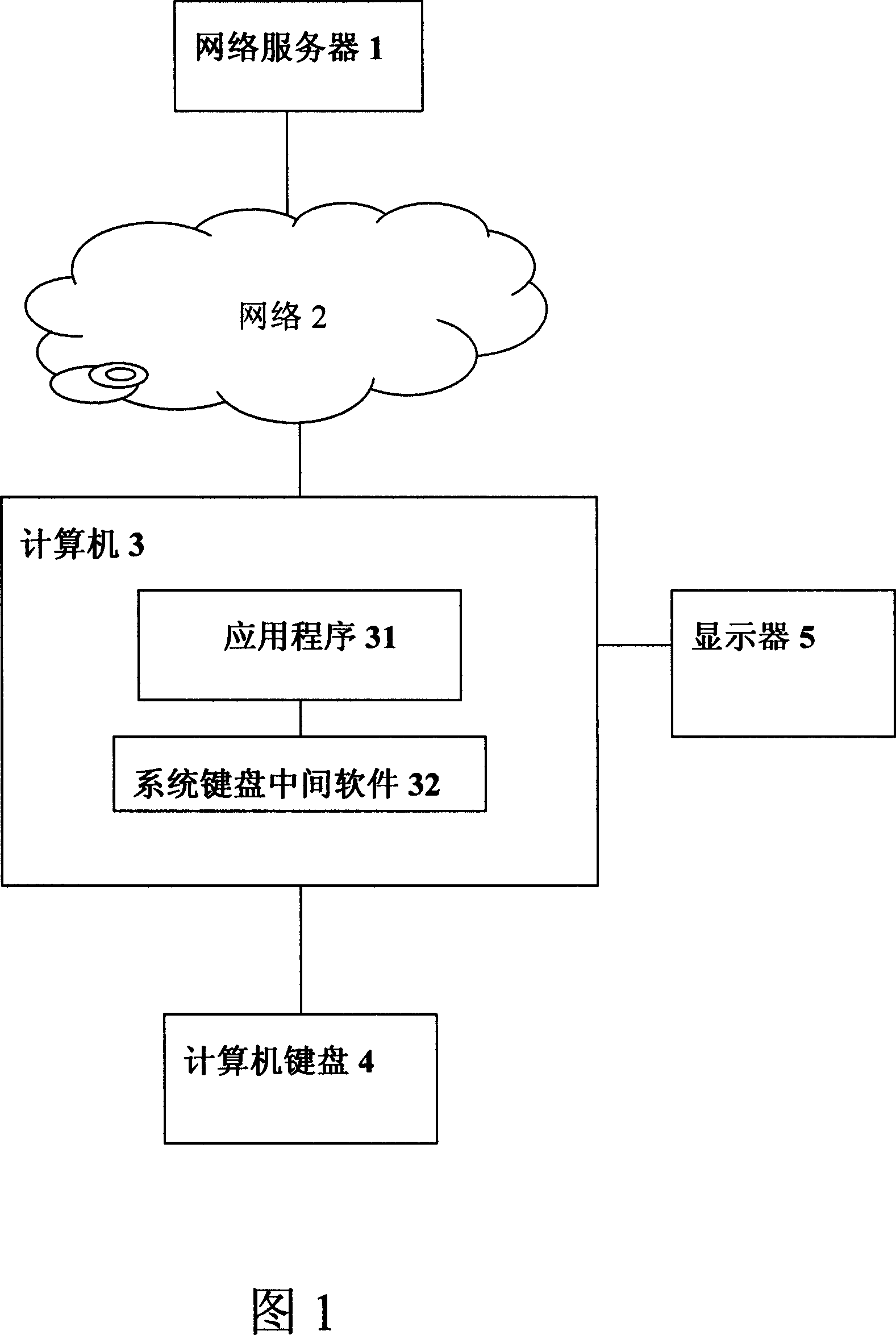
[0043] According to the first embodiment of the present invention, an apparatus and method for realizing safe use of network server services without relying on operating system security are shown in FIG. 2 .
[0044] After the computer normally enters the operating system or the application program 31, when the user enters the key code through the computer keyboard 4, the cryptographic device 6 encrypts the key code according to the obtained key code; then transmits to the system keyboard middleware 32; Send to server 1; Server 1 deciphers this key code, and sends back to system keyboard middleware 32 through network 2; The character of representative is sent to show on display 5 by application program.
[0045] In fact, the application program 31 may be an IE browser, or a client of an online game, or a client of an online bank. When the computer enters the application program 31, it is obvious that the cryptographic device 6 needs t...
Embodiment 2
[0049] [Example 2] USB dog
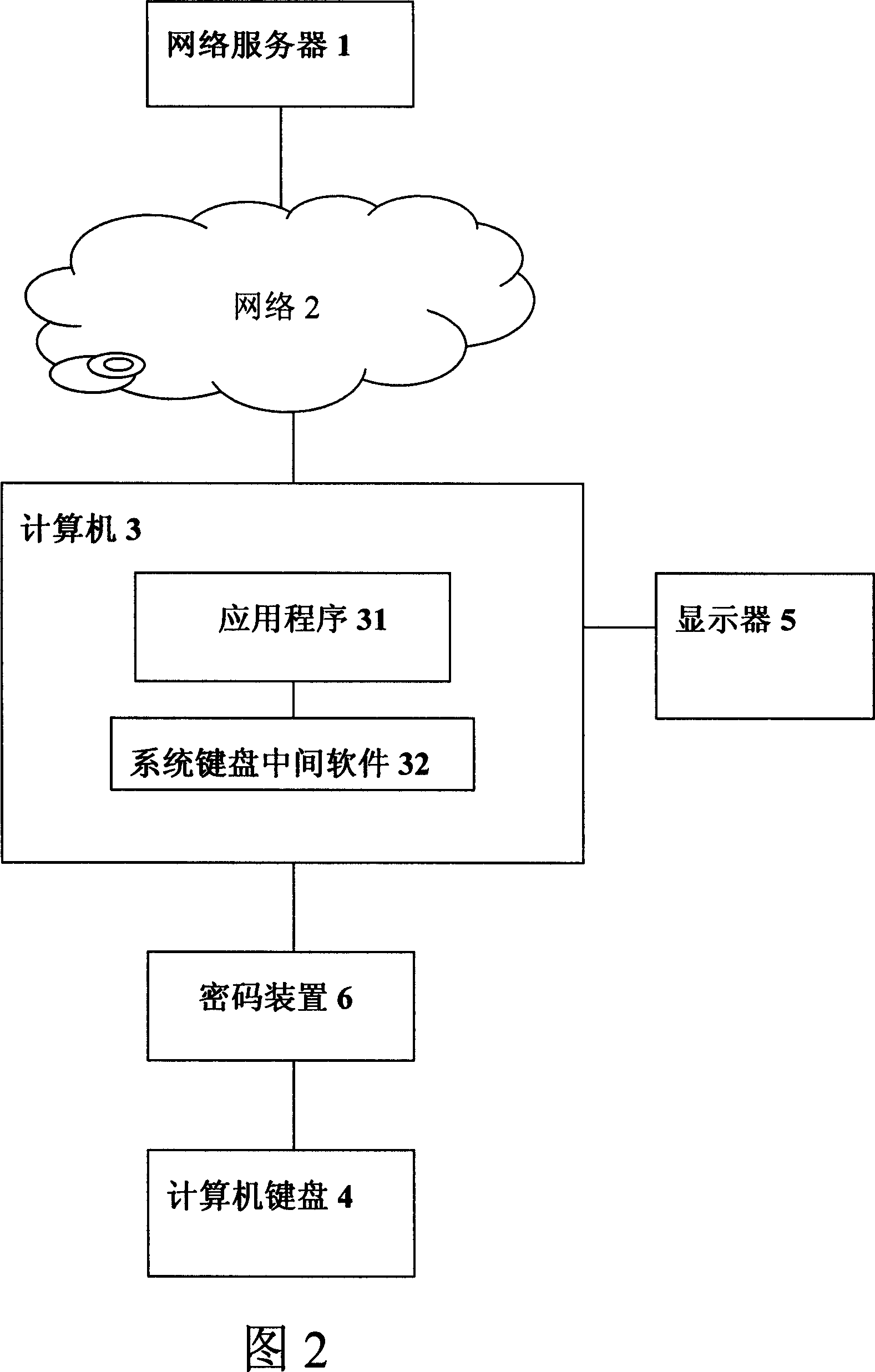
[0050] According to the second embodiment of the present invention, the implementation of the device and method for realizing safe use of network services without relying on computer security is shown in FIG. 3 . In this way, the encryption device 6 is directly connected to a computer interface (for example, a USB interface, a PS2 interface, and a 1394 interface, etc.).
[0051] After the computer normally enters the operating system or the application program 31, when the user enters the key code through the computer keyboard 4, the cryptographic device 6 encrypts the key code according to the obtained key code; then transmits to the system keyboard middleware 32; Send to server 1; Server 1 deciphers this key code, and sends back to keyboard middleware 32 through network 2; The characters are sent to the display 5 by the application program for display. Since the system keyboard middleware 32 can be attacked by a Trojan horse, it may be tampered...
Embodiment 3
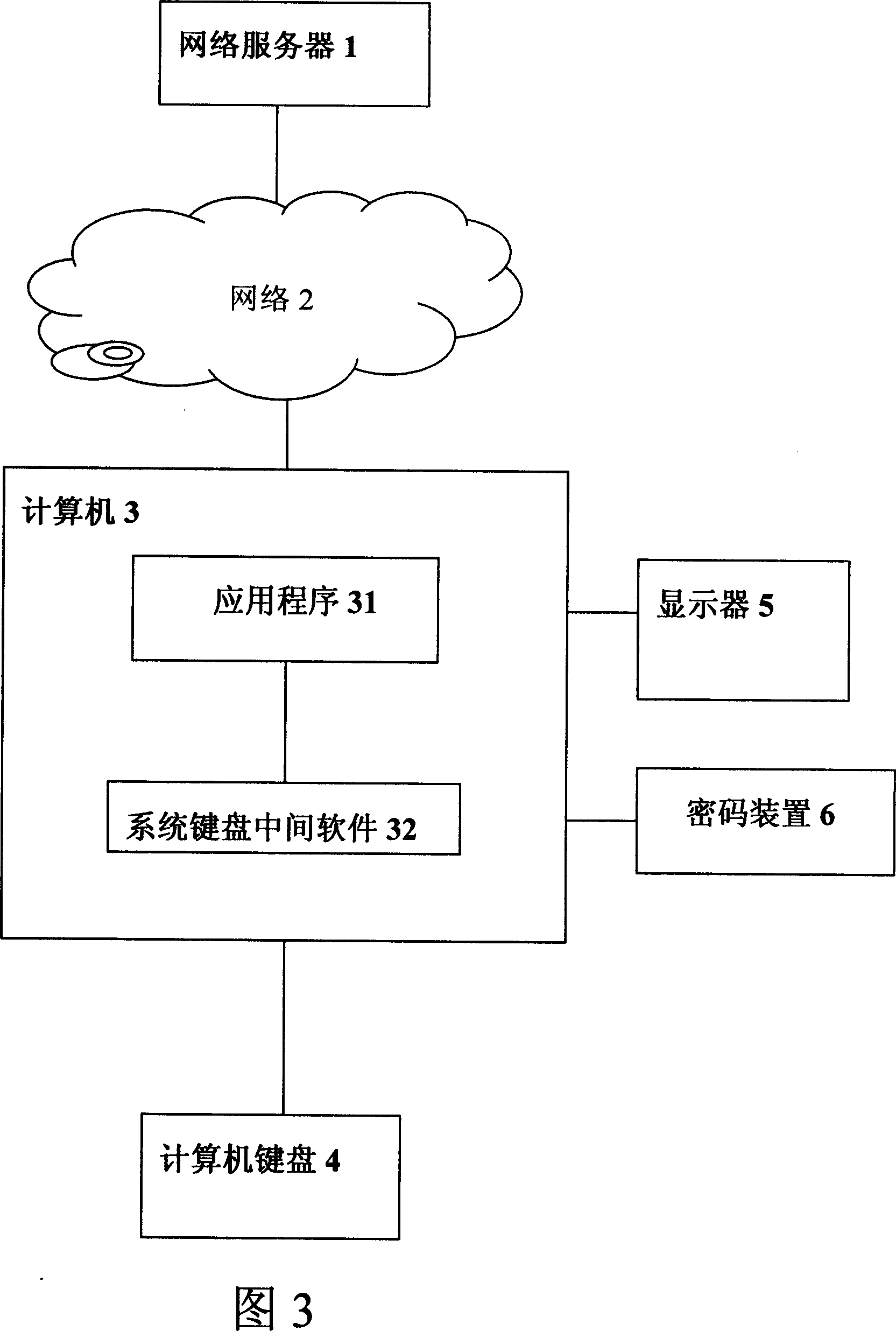
[0054] According to the third embodiment of the present invention, a method for realizing safe use of network services without relying on computer security is shown in FIG. 4 .
[0055] First, the network server and the cryptographic device perform identity authentication; after the authentication is passed, the session key is negotiated, and if the authentication fails, the service will not be provided; when the single-key code is input, it is expanded with a random number; after encryption, it is sent to the middle software of the system keyboard; the system keyboard The intermediate software transmits the single-key code encryption code to the server; the server decrypts the single-key code encryption code and transmits the decrypted key code to the keyboard intermediate software, and records the key code; the system keyboard intermediate software transmits the key code to the application program .
[0056] Embodiment 3 is an information flow chart corresponding to when the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com