Patents
Literature
675 results about "Cryptographic protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
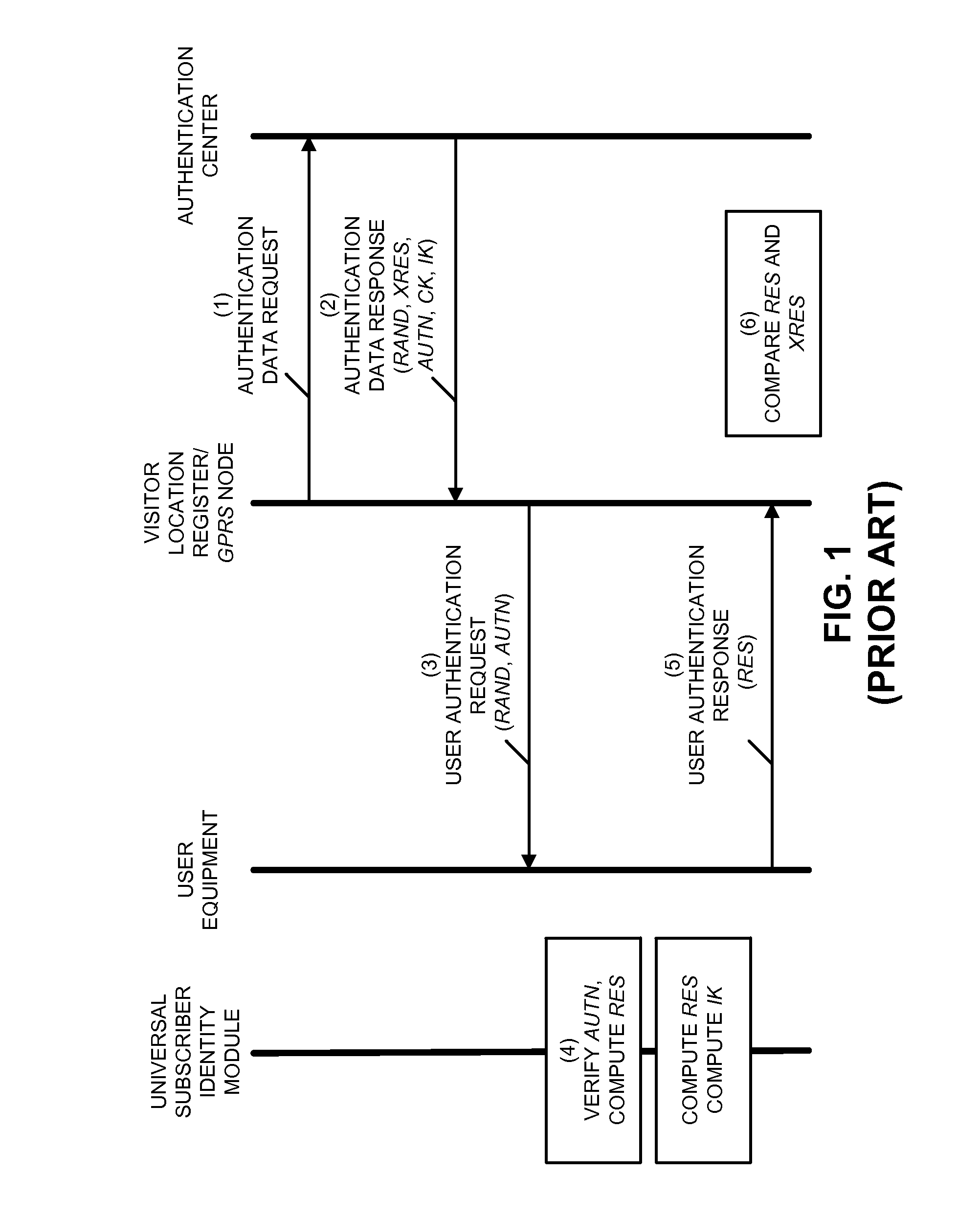
A security protocol (cryptographic protocol or encryption protocol) is an abstract or concrete protocol that performs a security-related function and applies cryptographic methods, often as sequences of cryptographic primitives. A protocol describes how the algorithms should be used. A sufficiently detailed protocol includes details about data structures and representations, at which point it can be used to implement multiple, interoperable versions of a program.
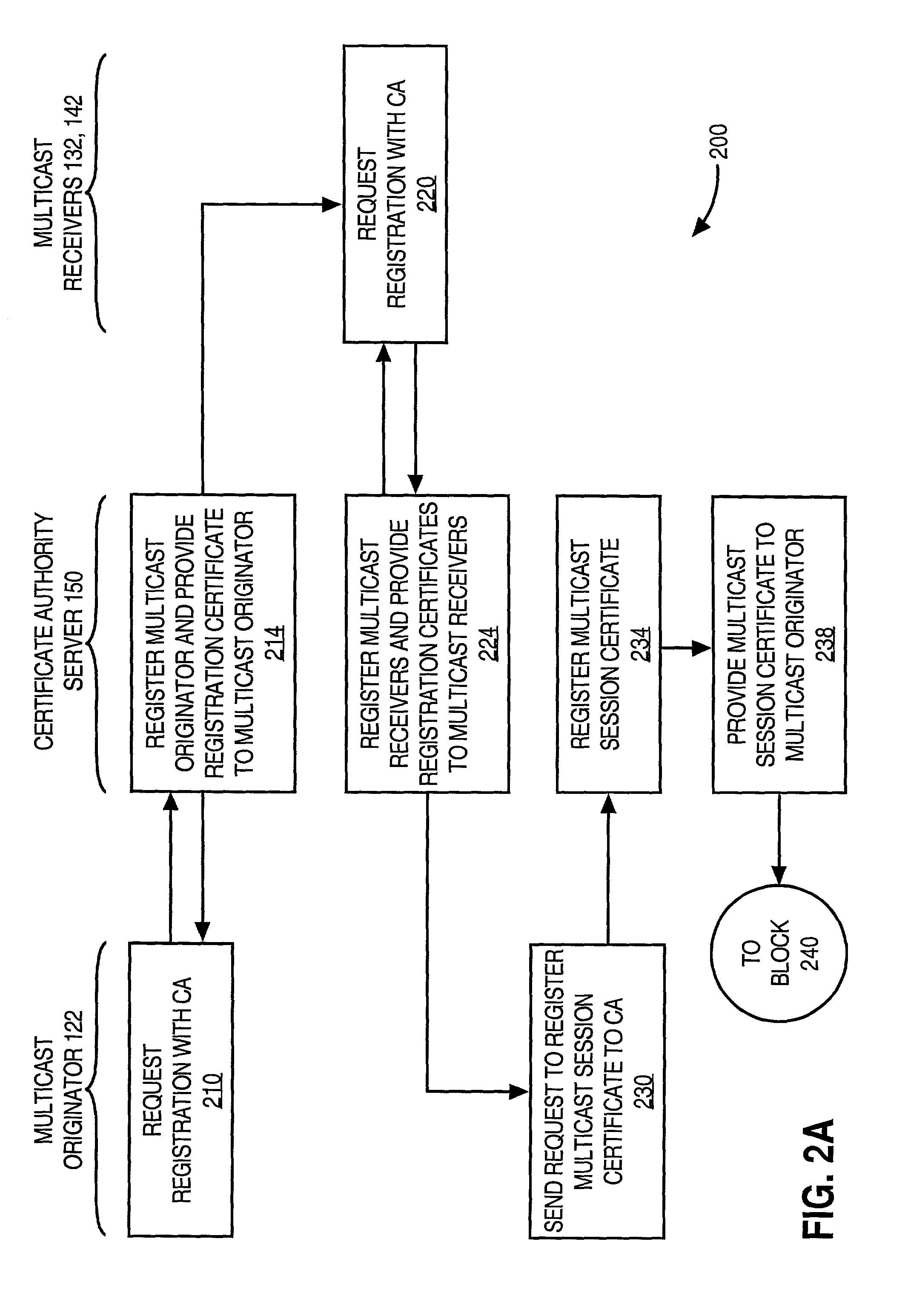
Method and apparatus for remote gaming
InactiveUS6935952B2Apparatus for meter-controlled dispensingVideo gamesCryptographic protocolPersonal computer
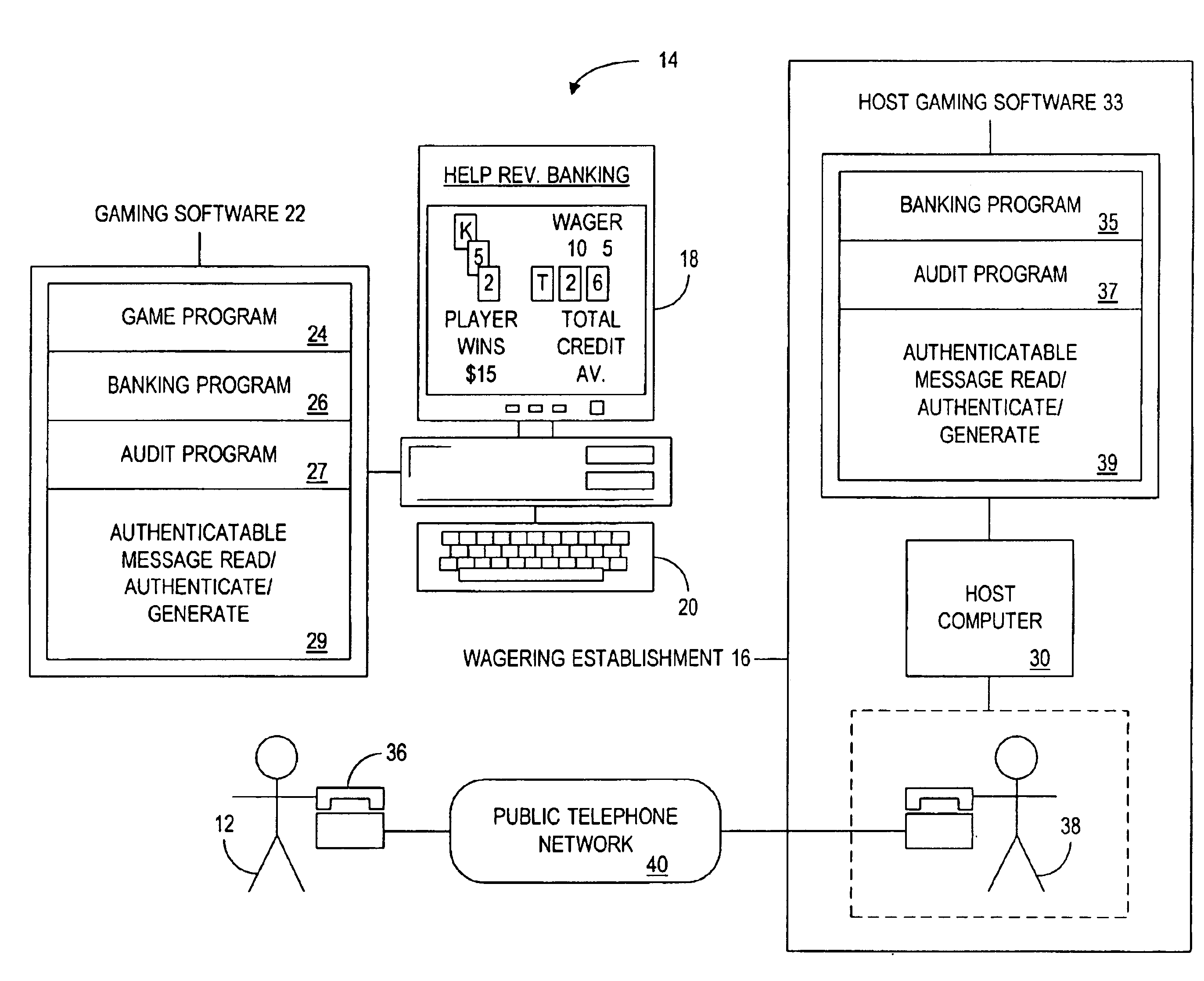
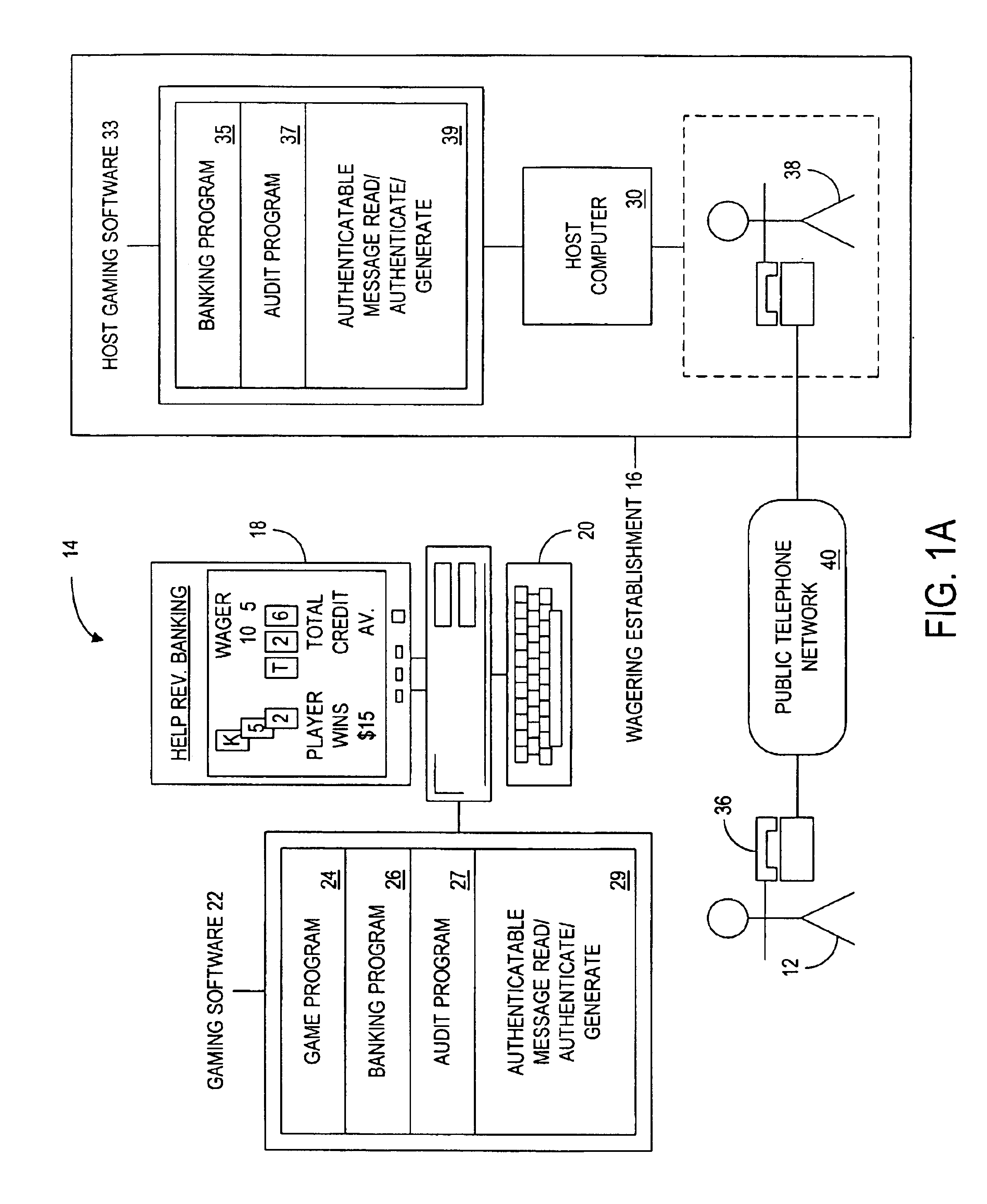
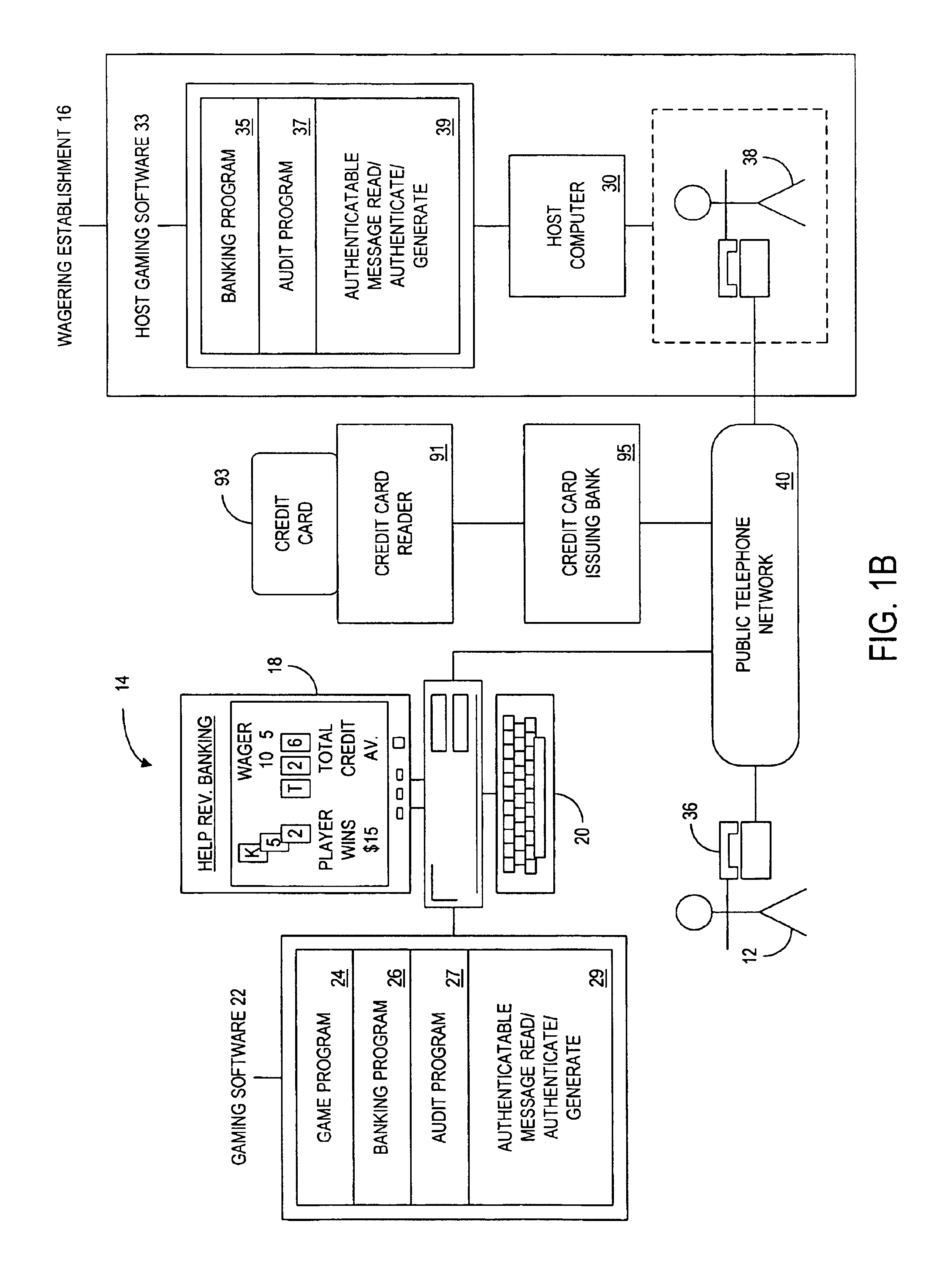
A remote gaming system whereby a player can gamble against a wagering establishment or state-run lottery from a remote location on a personal computer or portable computer device where it is unnecessary to establish an on-line connection with a host computer associated with the wagering establishment, the gaming computer having associated gaming software for providing at least one wagering opportunity and enabling the player to obtain gambling credit and cash-out any resulting winnings, the host computer enabling the player to purchase and redeem gambling credit at the remote location in one embodiment of the invention using cryptographic protocols such as through a series of authenticatable message exchanges between the player and the wagering establishment, the gaming computer and the host computer directly on-line, or the gaming computer having a detachable tamper-resistant or tamper-evident credit module associated therewith or for use with a personal computer being provided to the player with preinstalled or preloaded gambling credit, the gaming system also enabling participation in future events of which the outcome is uncertain such as, for example, a lottery whereby the player makes selections on a gaming computer at a remote location.
Owner:WALKER DIGITAL
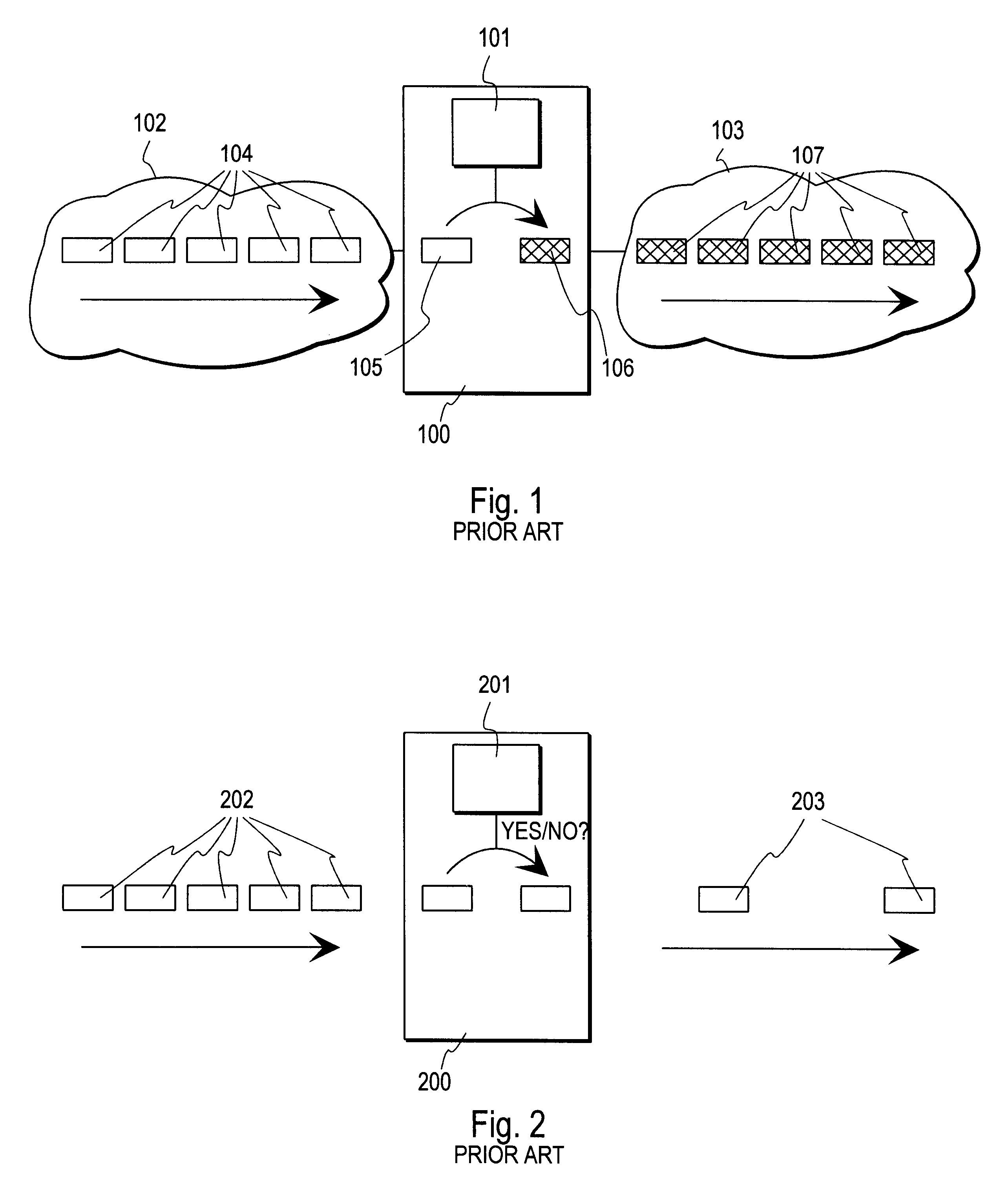
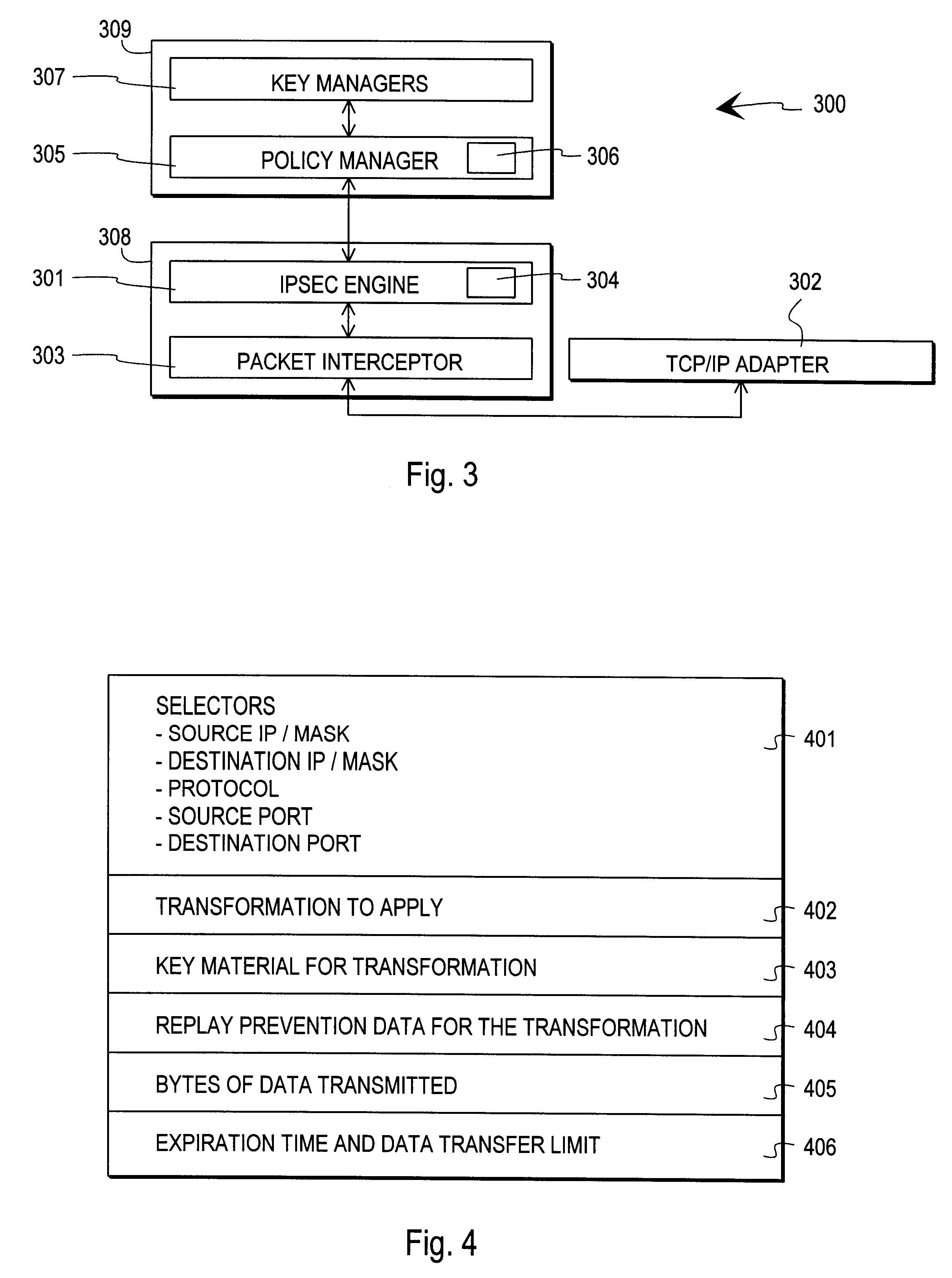
Method and arrangement for implementing IPSEC policy management using filter code
InactiveUS6253321B1User identity/authority verificationData resettingData processing systemComputer network
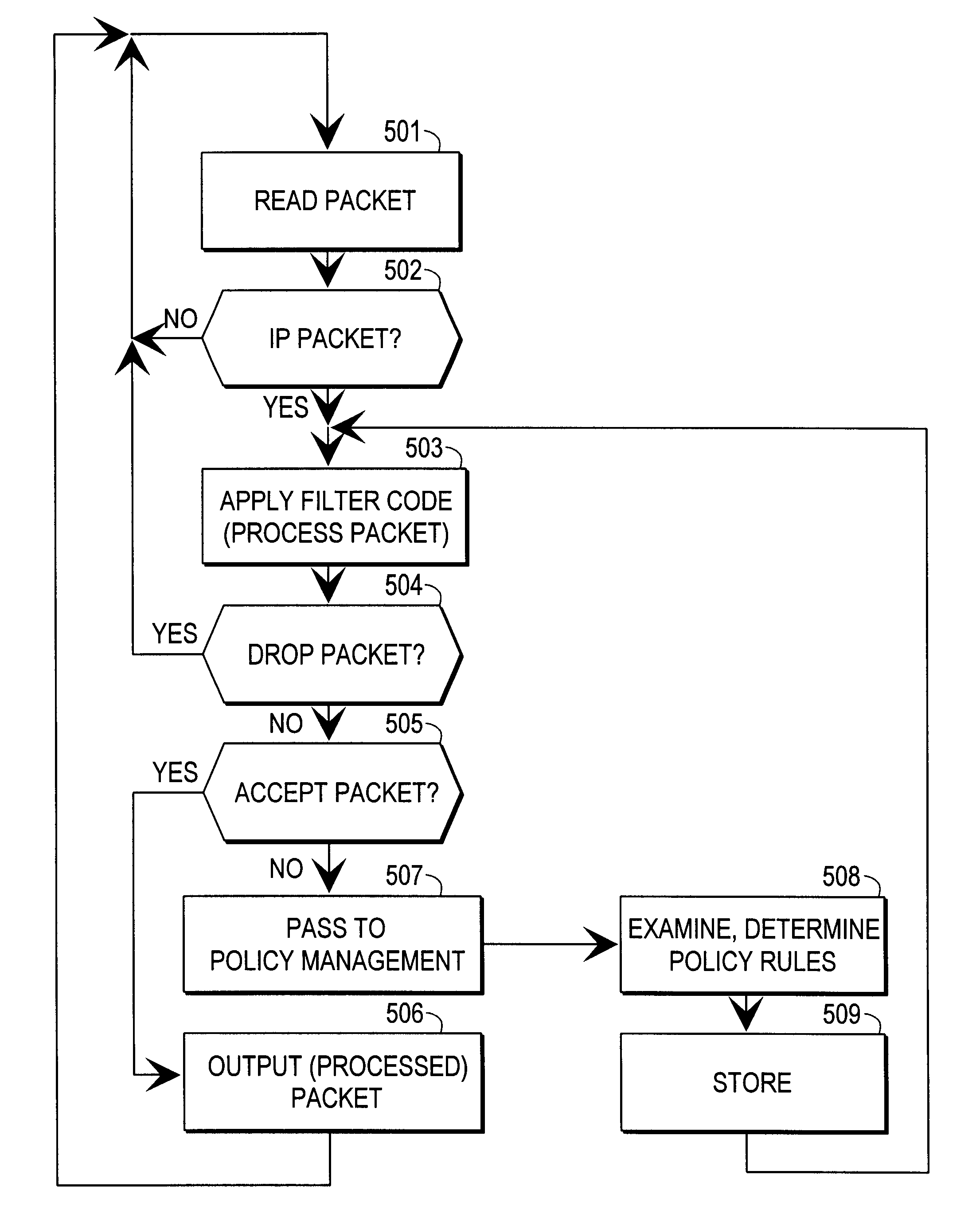
A data processing system implements a security protocol based on processing data in packets. The data processing system comprises processing packets for storing filter code and processing data packets according to stored filter code, and a policy managing function for generating filter code and communicating generated filter code for packet processing. The packet processing function is arranged to examine, whether the stored filter code is applicable for processing a certain packet. If the stored filter code is not applicable for the processing of a packet, the packet is communicated to the policy managing function, which generates filter code applicable for the processing of the packet and communicates the generated filter code for packet processing.
Owner:TECTIA
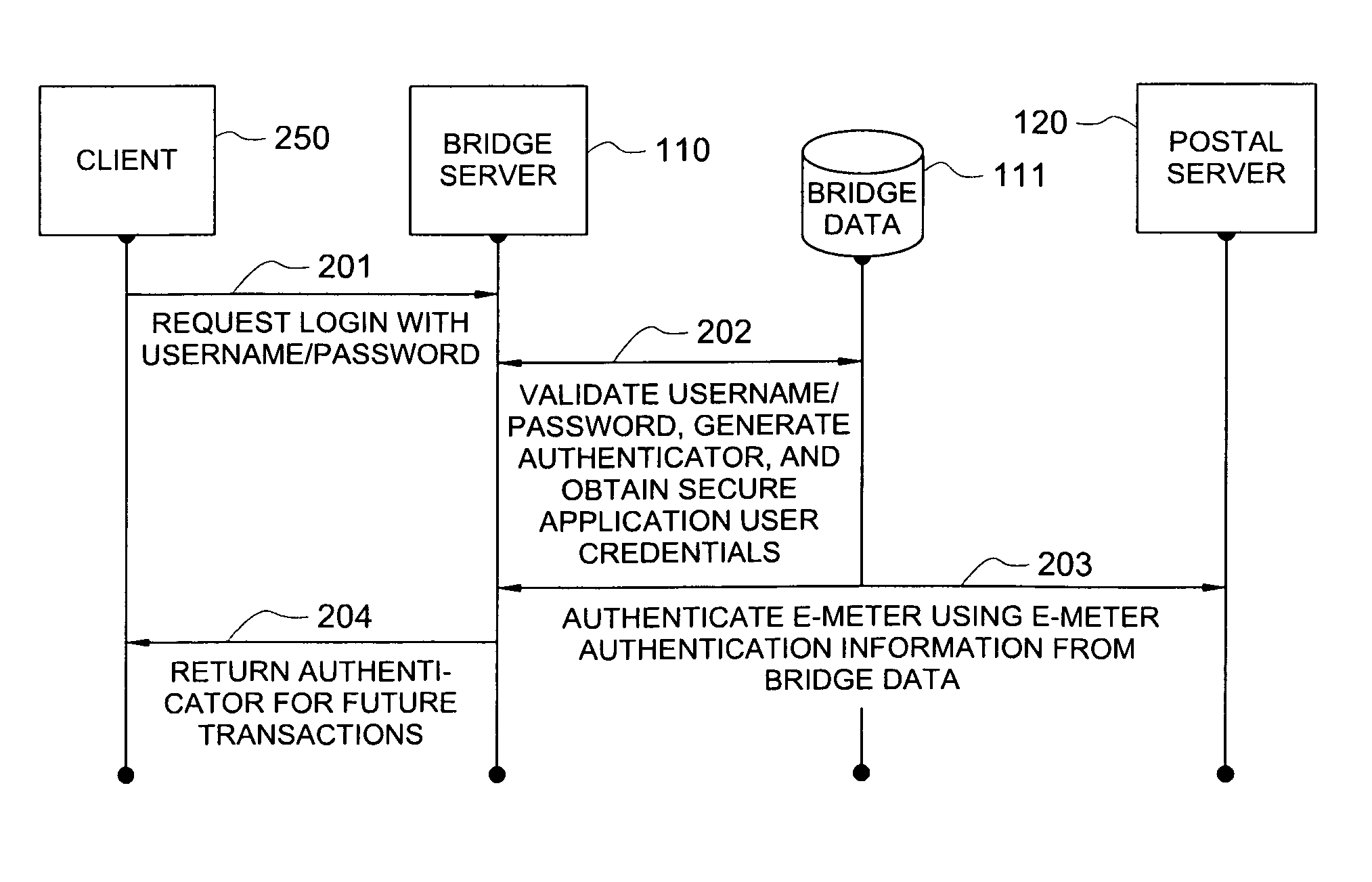
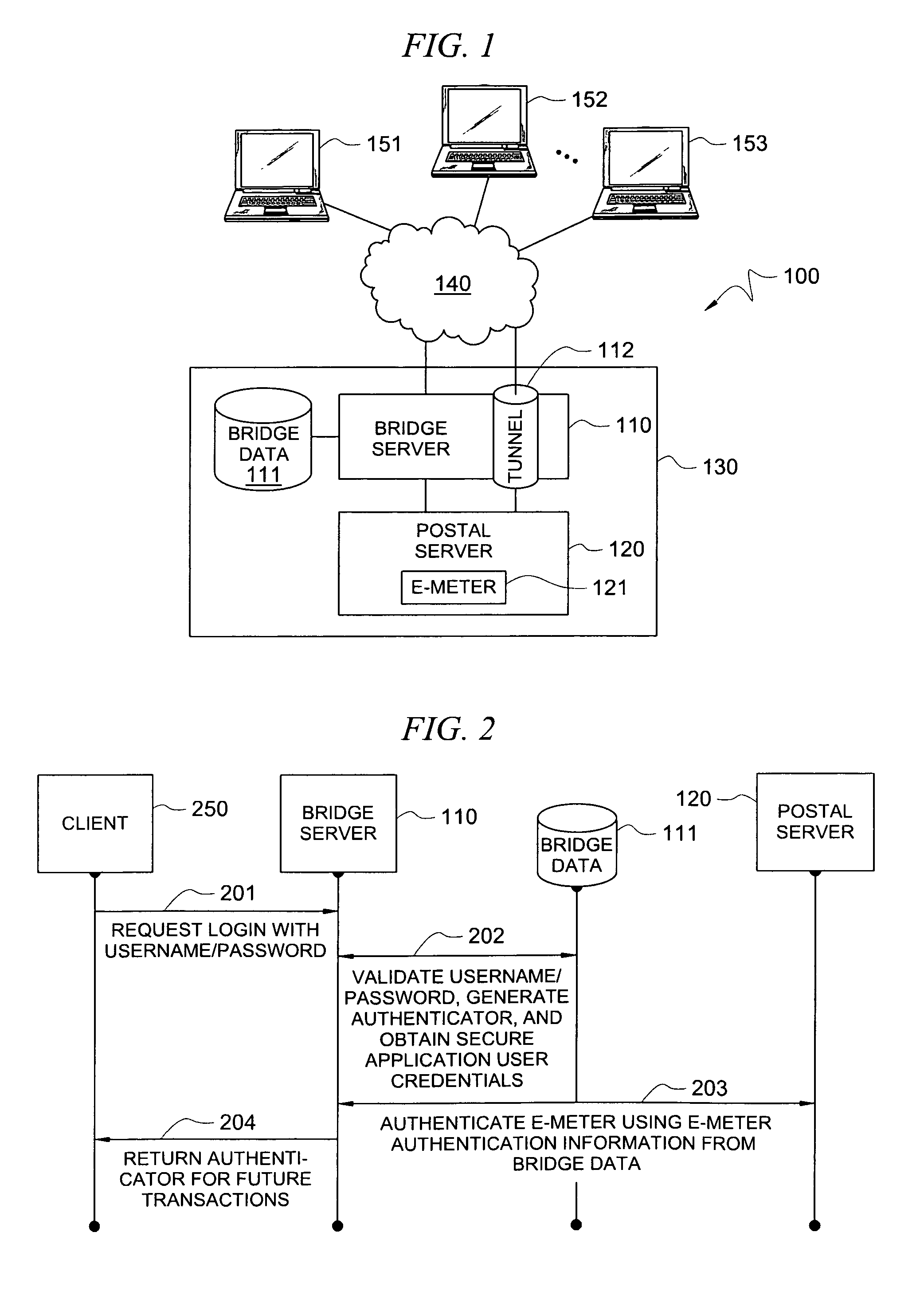
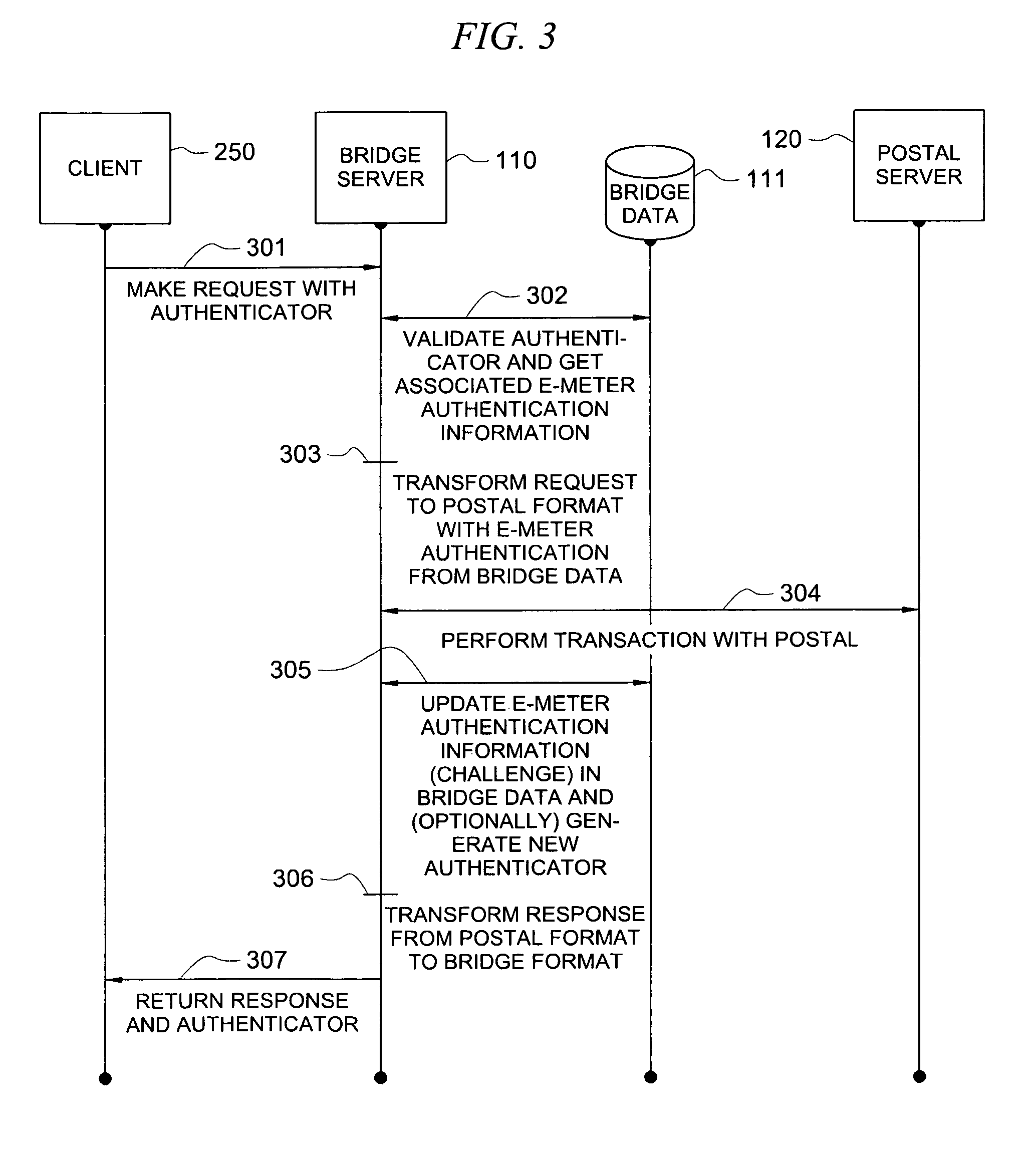
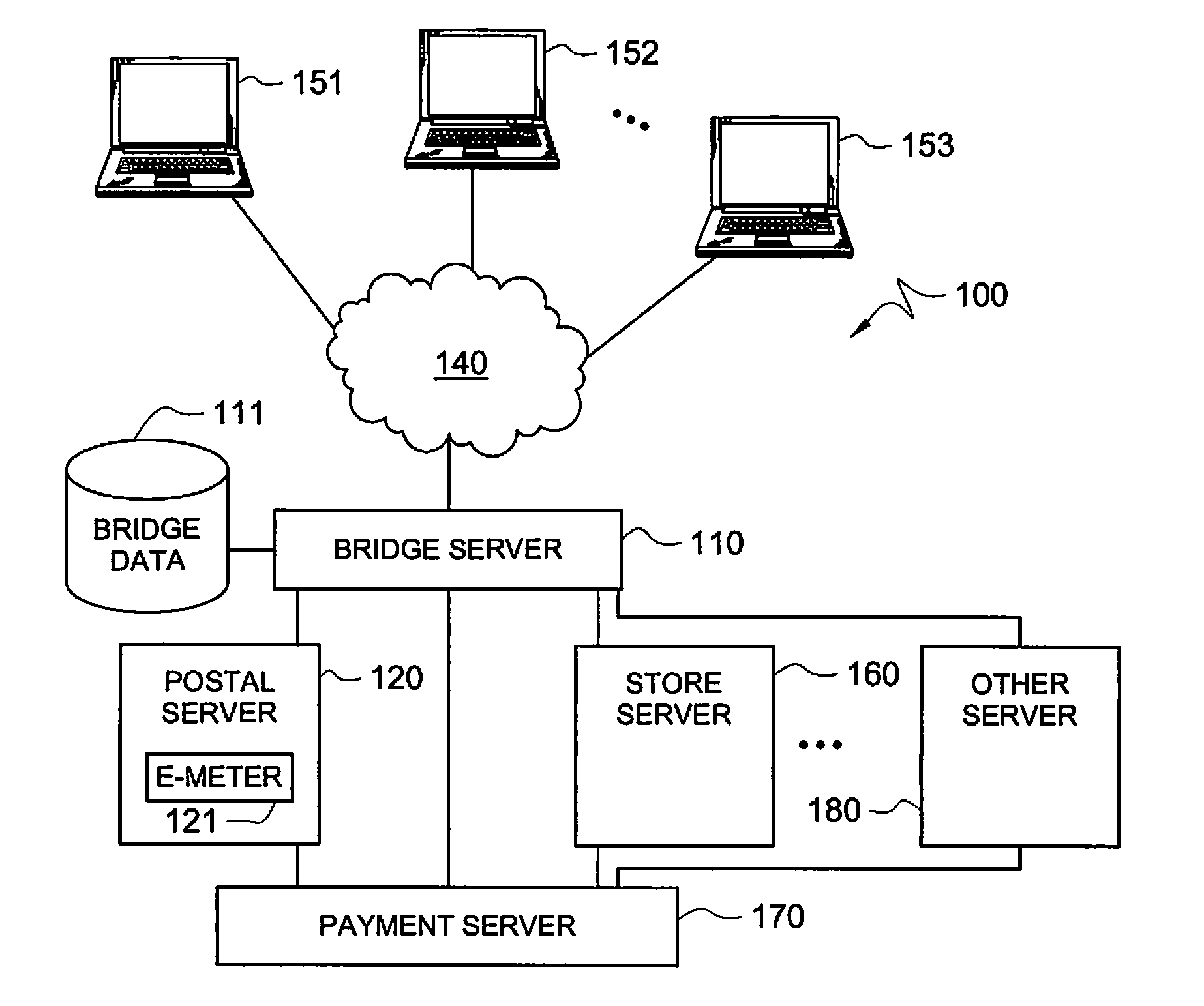
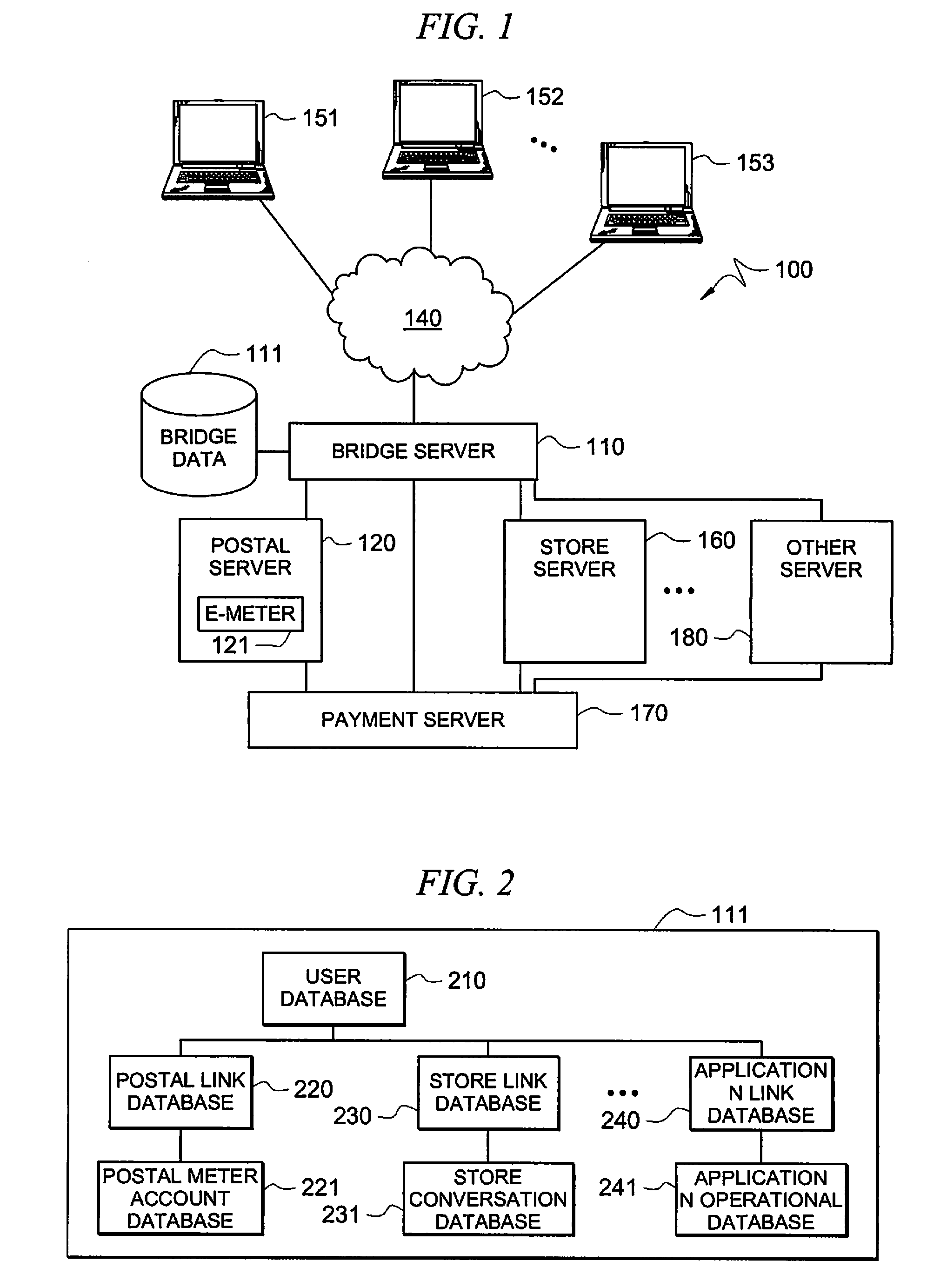
Secure application bridge server
ActiveUS8046823B1Easy to implementConvenient to accommodateDigital data processing detailsComputer security arrangementsApplication serverCryptographic protocol
Systems and methods are provided which implement a bridge server to provide user access to one or more secure applications. A bridge server of embodiments is disposed between a user and a secure application and invokes bridge server security protocols with respect to the user and secure application security protocols with respect to the secure application. In operation according to embodiments, client applications will link into a bridge server, the user will be authenticated by the bridge server, and a valid user will be correlated to an account of the secure application by the bridge server. Bridge servers of embodiments facilitate providing features with respect to secure application user access unavailable using the secure application security protocols.
Owner:AUCTANE INC
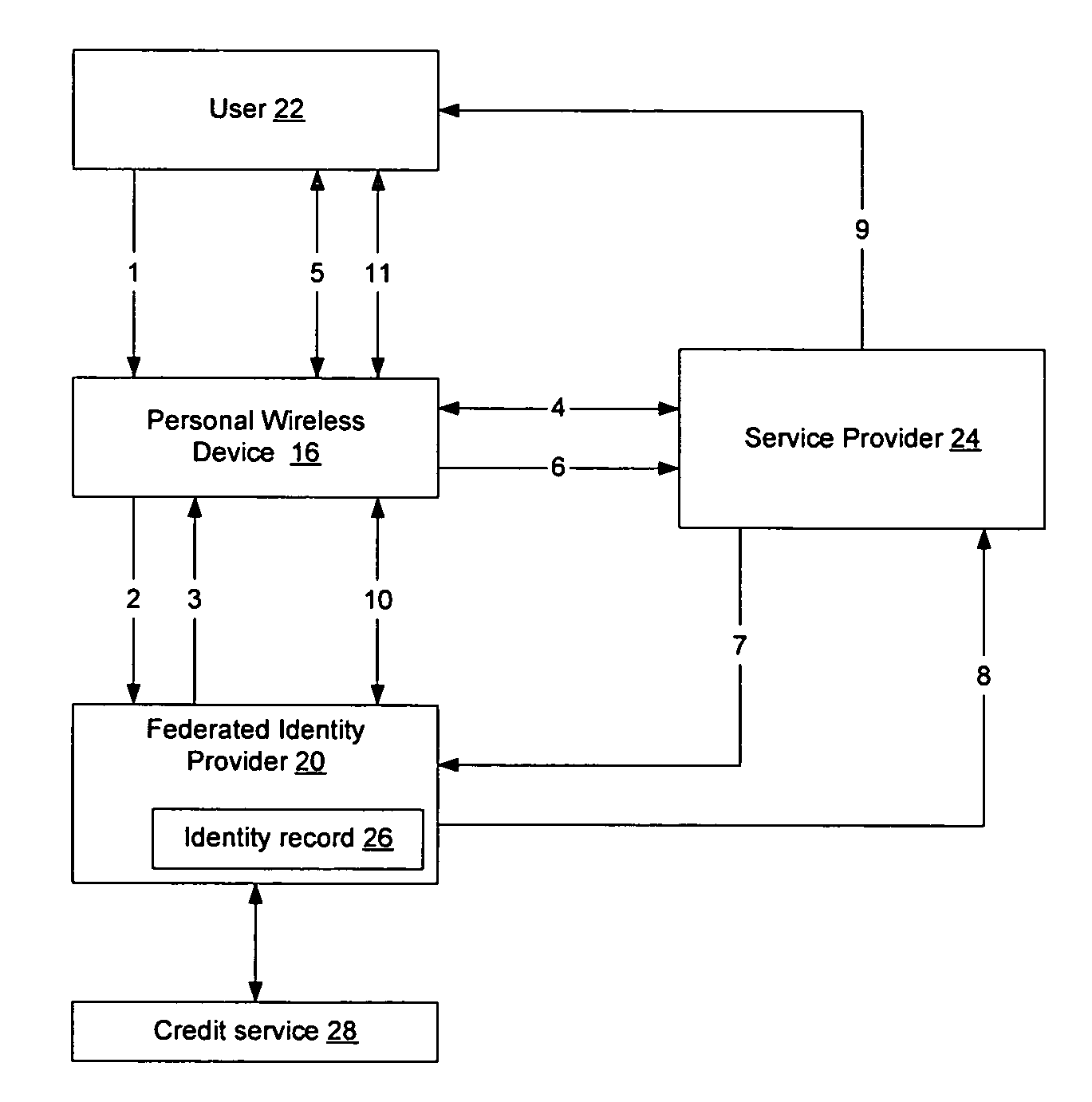
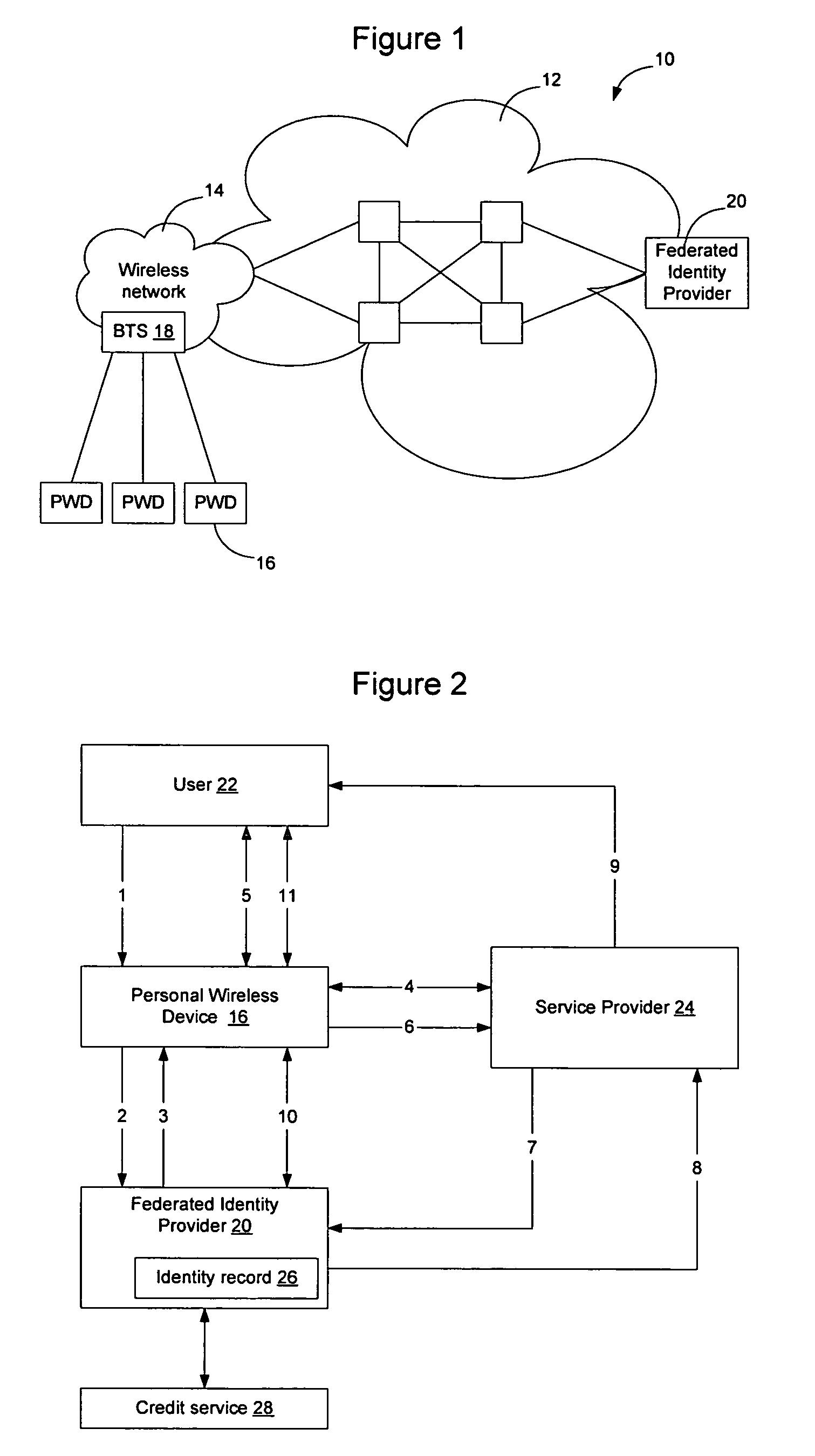
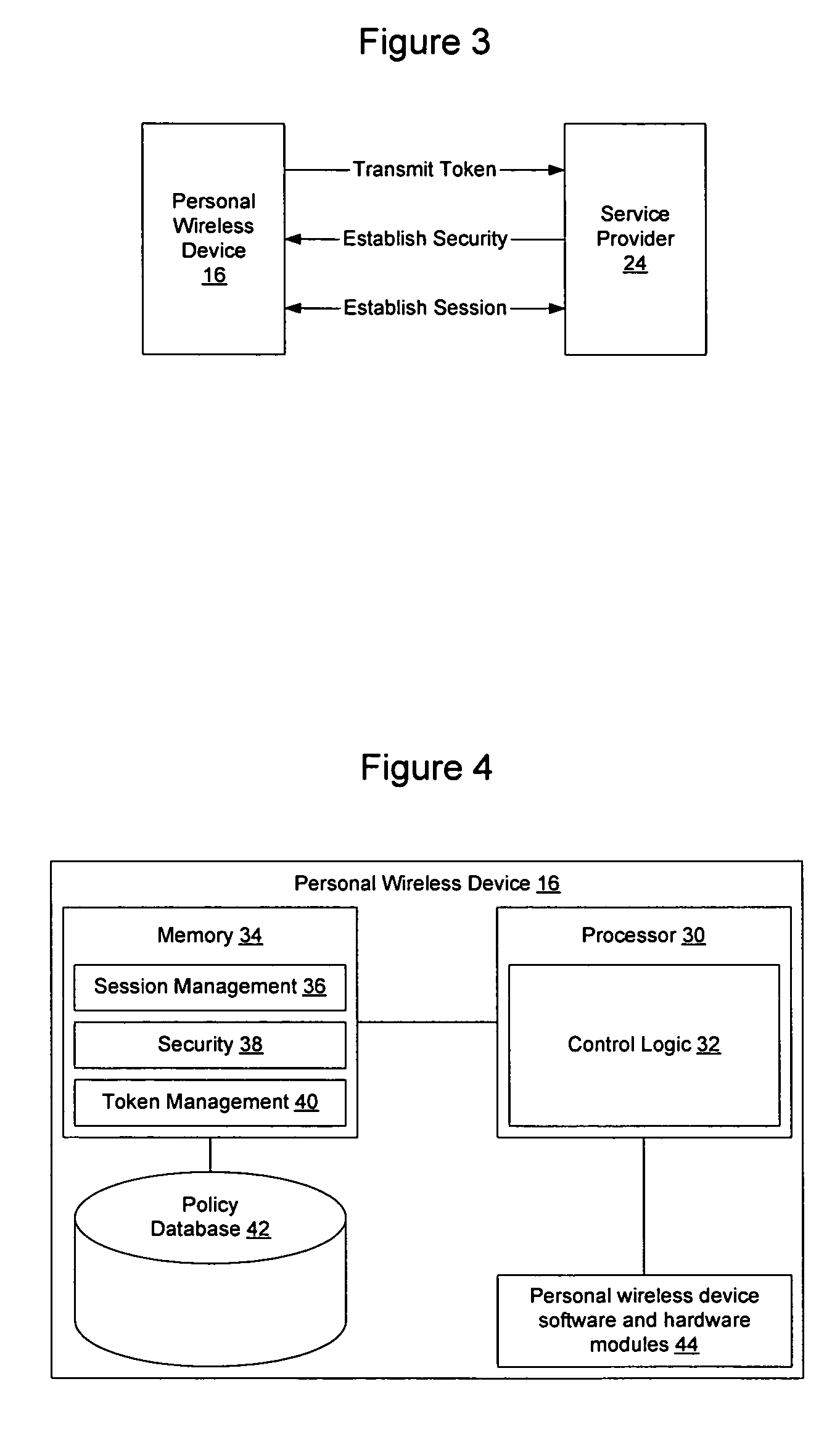
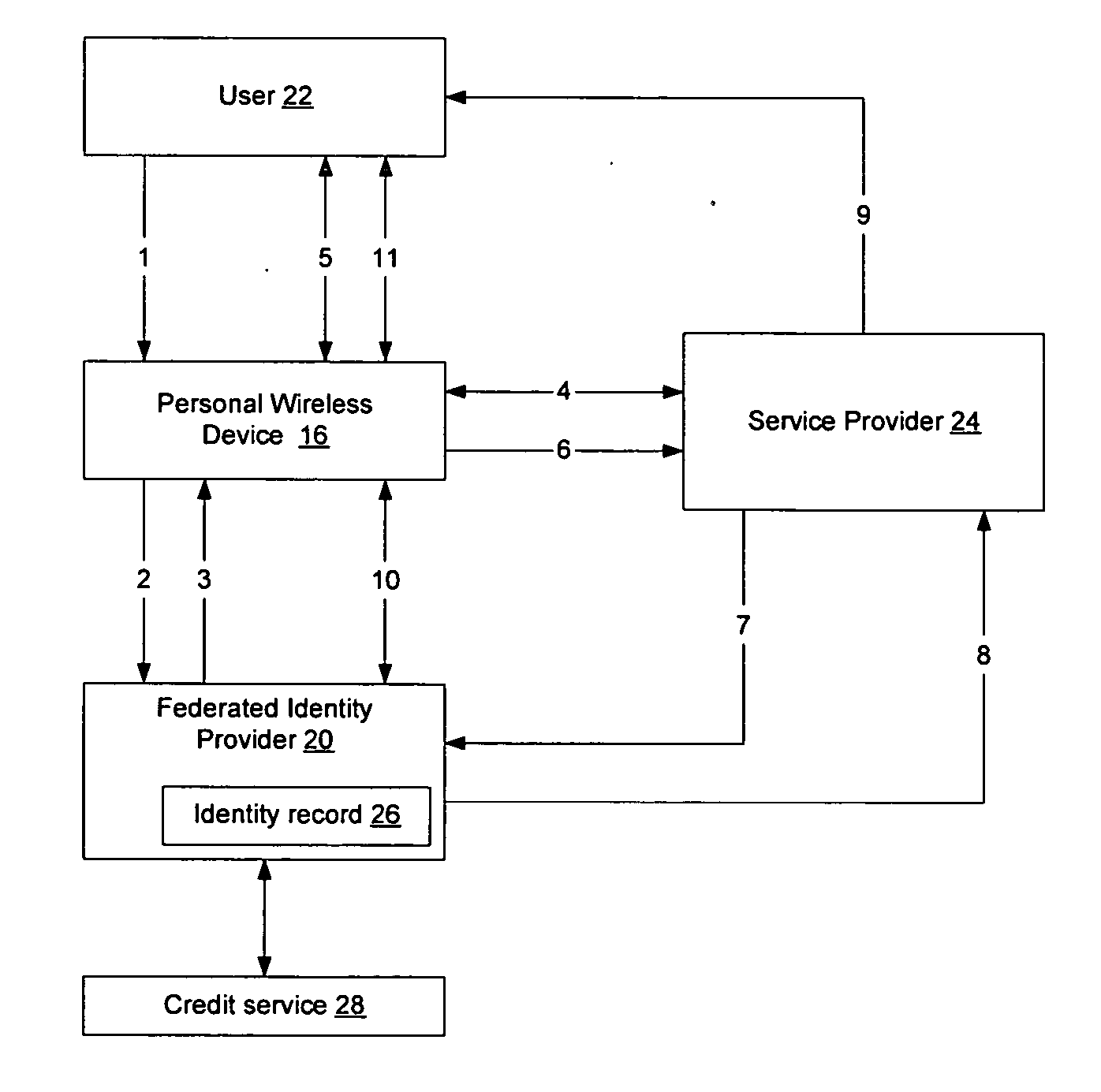
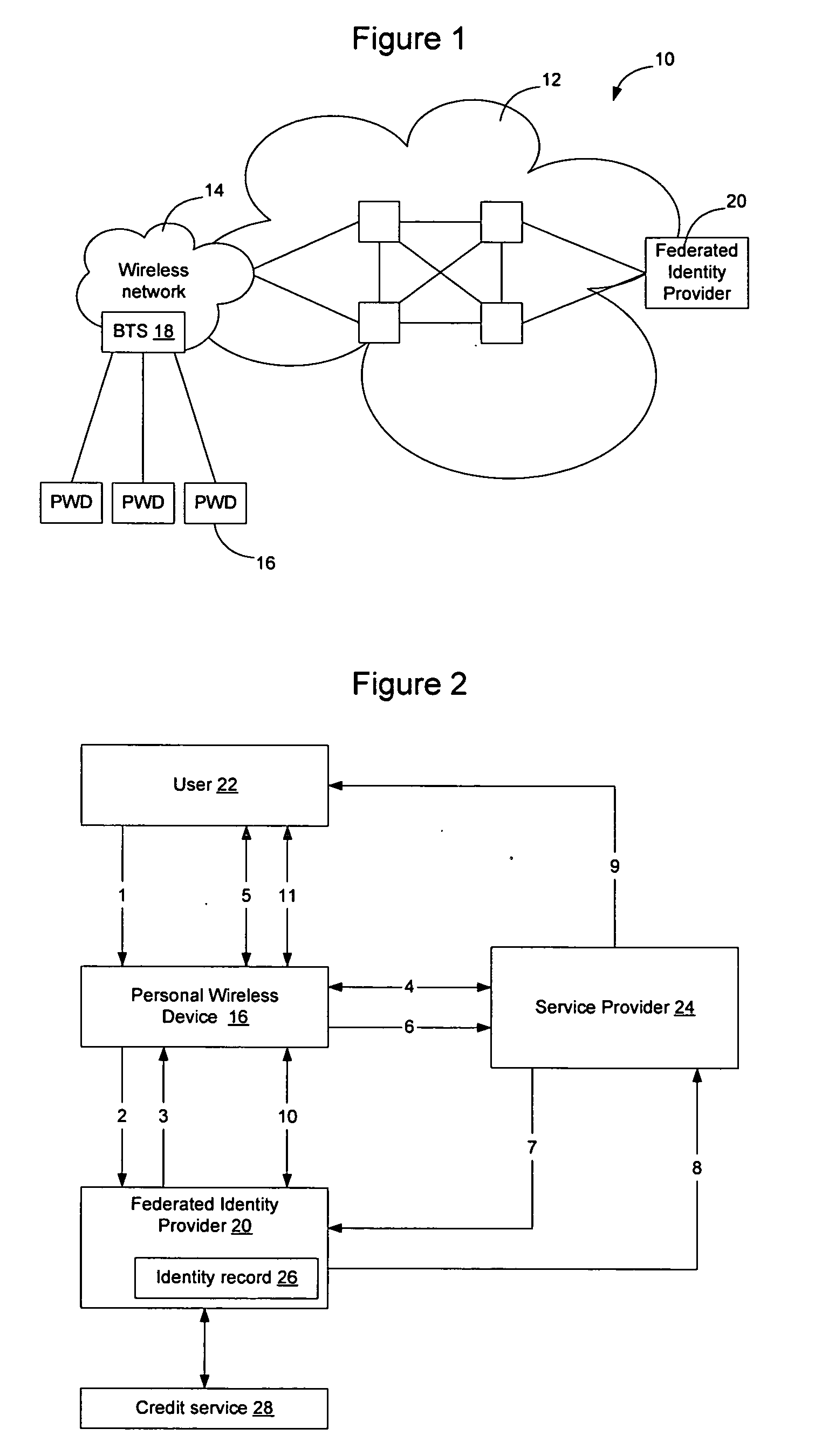
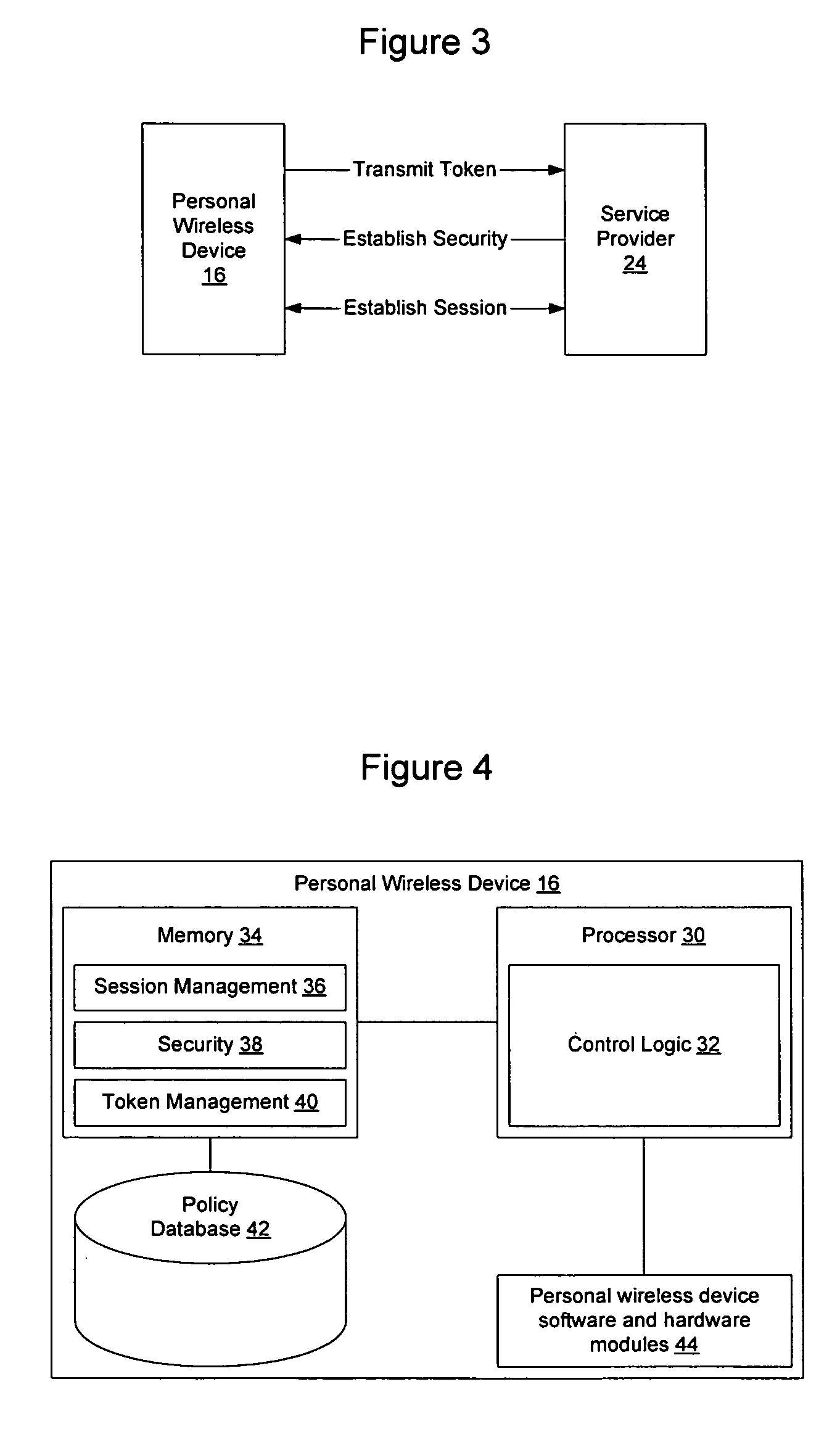
Method and apparatus for establishing a federated identity using a personal wireless device
ActiveUS8522039B2User identity/authority verificationDigital data authenticationCryptographic protocolBluetooth
A federated identity, established through possession of a single sign-on token, will allow a personal wireless device (PWD) to be used in a commercial environment to purchase goods or services, access a building, access a telephone, wireless, or computer network, or in numerous other instances. The token may be obtained by the user authenticating with the PWD and the PWD authenticating with the network. When the PWD comes within range of a service provider, a session is established using a short range wireless protocol, such as Bluetooth or infrared. The session is secured using a security protocol such as SSL, and the service provider authenticates its identity to the PWD. Policy may be implemented regarding transmission of the token to the service provider. Upon receipt of the token, the service provider will validate the token with the federated identity provider, obtain identifying information, and complete the transaction.
Owner:APPLE INC
Mobile transaction device security system
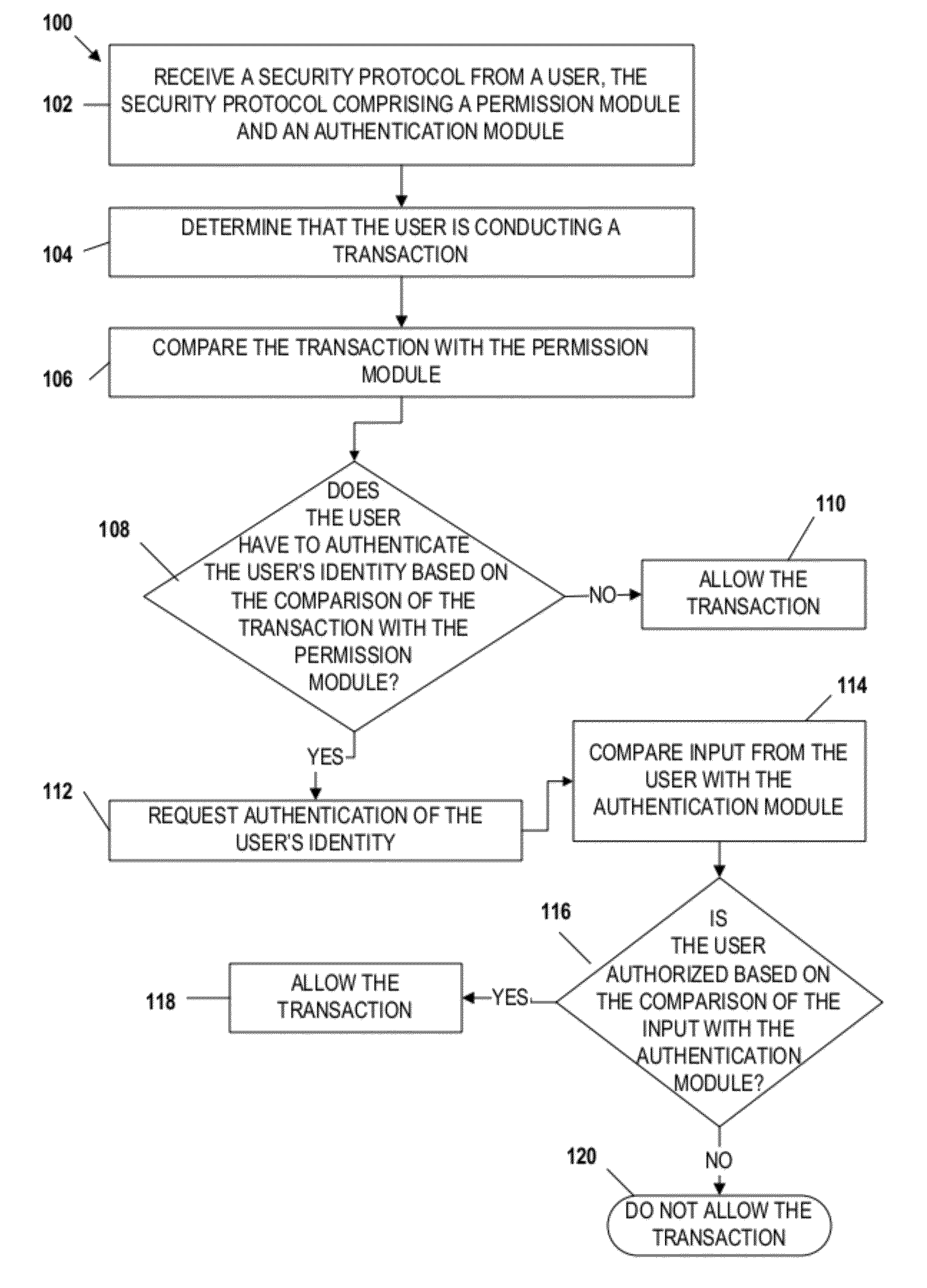
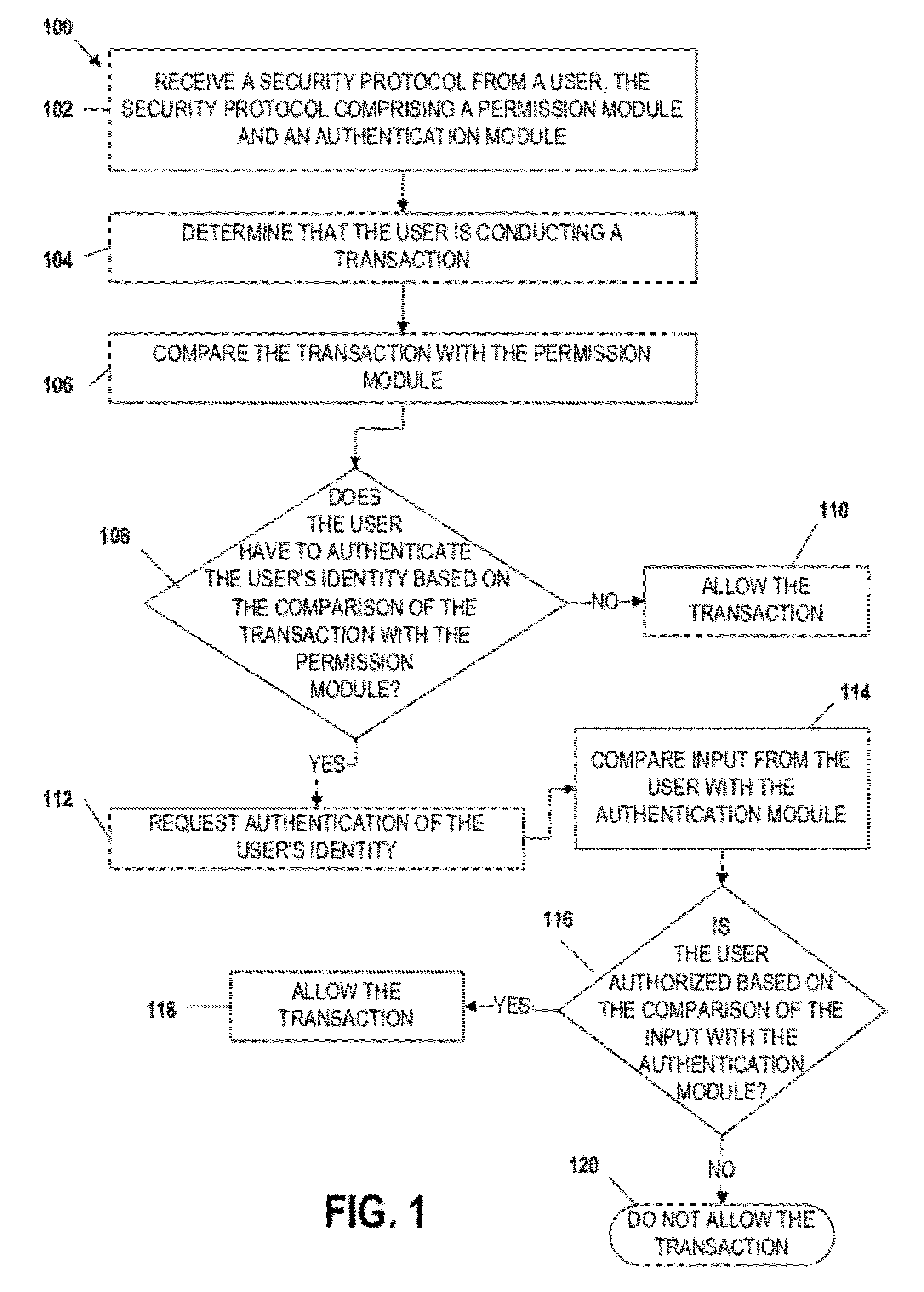
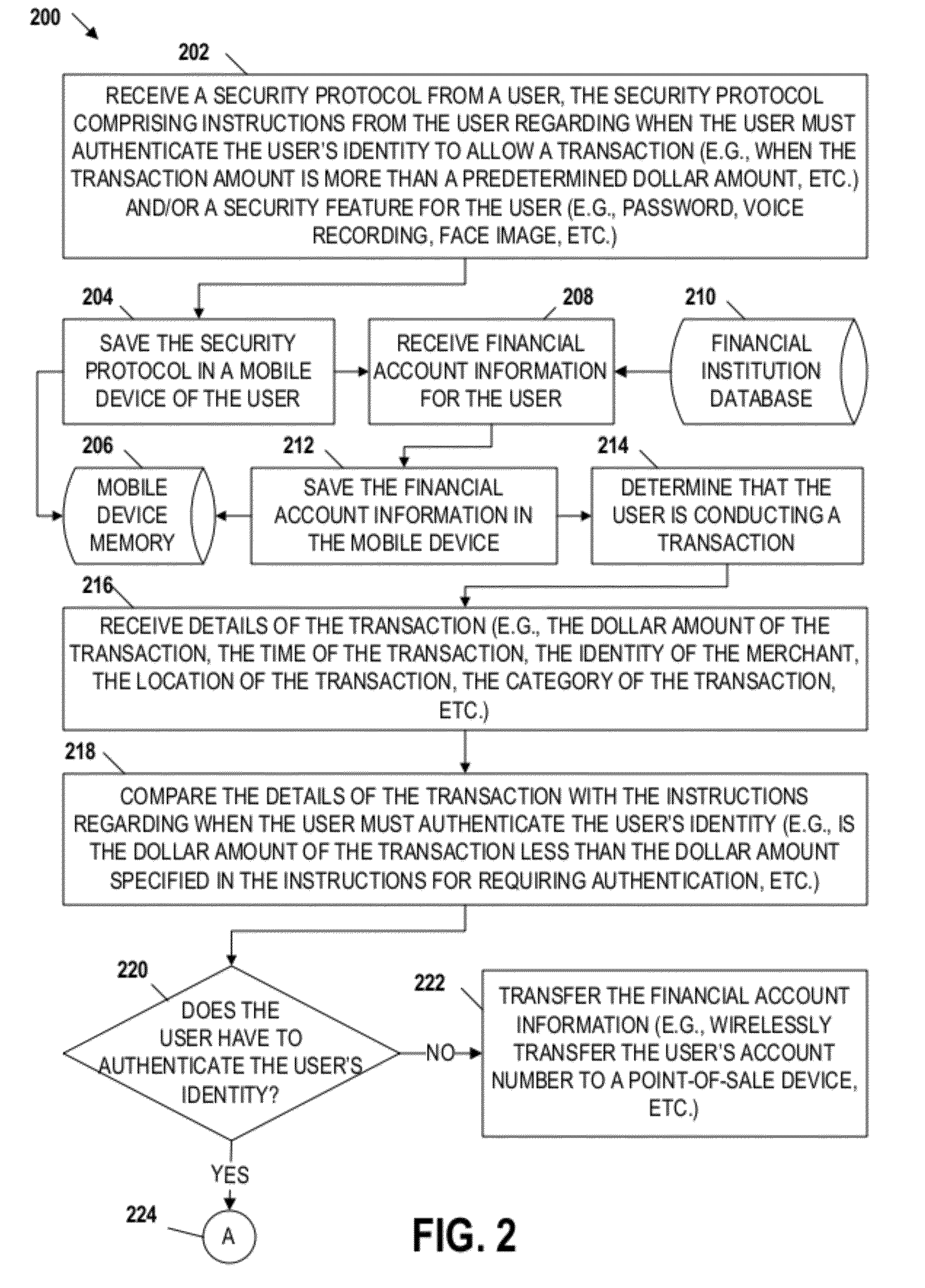
Embodiments of the invention include apparatuses, methods, and computer-program products that provide for a unique financial transaction security system. In one embodiment, the financial transaction security system receives a security protocol from a user. The security protocol includes instructions for allowing transactions without authentication and security features for the user if authentication is necessary. The system then determines that the user is conducting a transaction, compares the transaction to the instructions, and determines whether the transaction can occur without authentication. If the user is required to authenticate his identity, the system requests input from the user, compares the input to the security feature, and determines if the user is authenticated. The user is able to customize both the instructions and the security features to provide greater control over financial transaction security.
Owner:BANK OF AMERICA CORP
Secure communications system for collaborative computing
InactiveUS6901448B2Improve scalabilityEliminate points of failureSpecial service provision for substationMultiple digital computer combinationsCommunications systemPrivate network
A method of distributed collaborative computing is provided. The method includes: partitioning a collaboration function into sub-functions; assigning at least one said sub-function to each of a plurality of logical processes; associating a respective management process with each of said plurality of logical processes, said logical processes configured so that each said logical process is capable of communicating with every other said logical process through said respective management process; communicating between said logical processes using said respective management processes; and monitoring said respective management processes with a single supervisor process; wherein said communicating employs a secure protocol on a dedicated network.
Owner:CISCO TECH INC
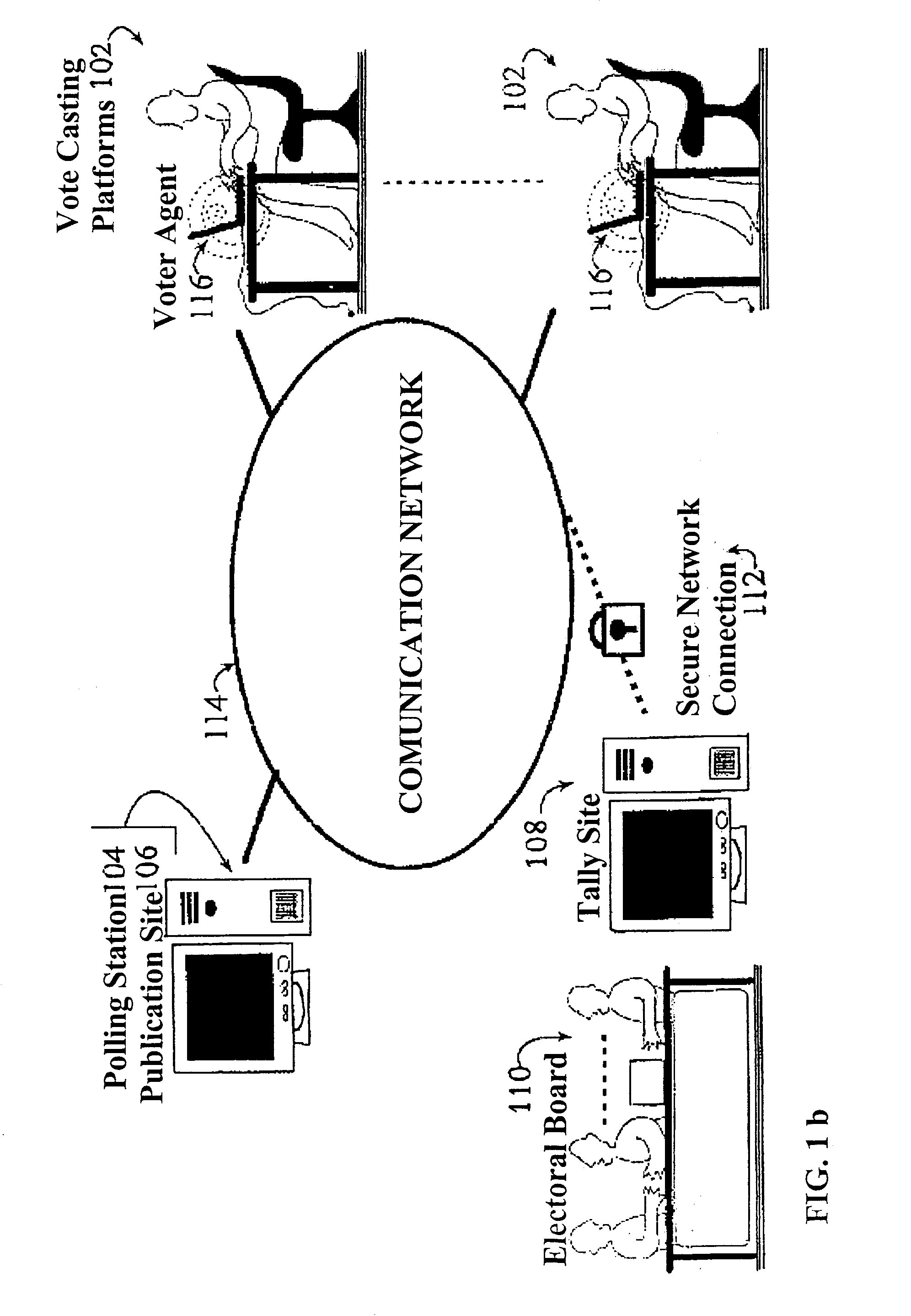
Secure remote electronic voting system and cryptographic protocols and computer programs employed
InactiveUS7260552B2Minimizing confidence levelHindering voters coercionVoting apparatusError detection/correctionCryptographic protocolSurvey result
The method employs interrelated cryptographic processes and protocols to provide reliability to vote casting, ballots recount, and verification of vote or poll results. These cryptographic processes and protocols jointly constitute a cryptographic voting scheme capable of meeting the specific reliability requirements of an electronic voting where voters remotely cast their votes. These reliability requirements include voter authentication and privacy; accurate results, the impossibility of coercion and sale of votes, verifying the final results and, if necessary, the secrecy of intermediate results before completing the vote or poll. The cryptographic voting method minimizes the confidence level to be placed on any of the electronic voting individual party and participants.
Owner:SCYTL ELECTION TECH SL
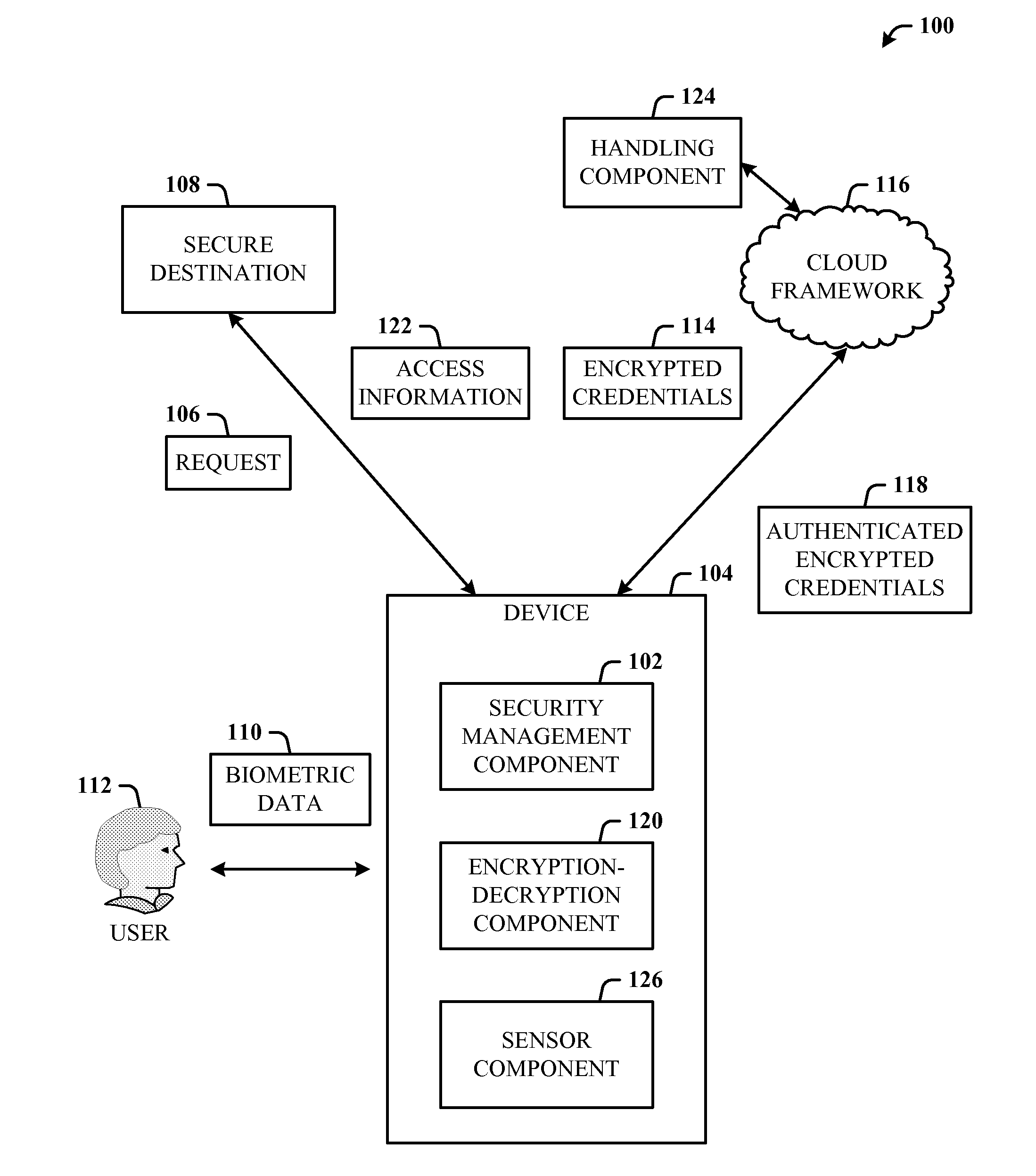
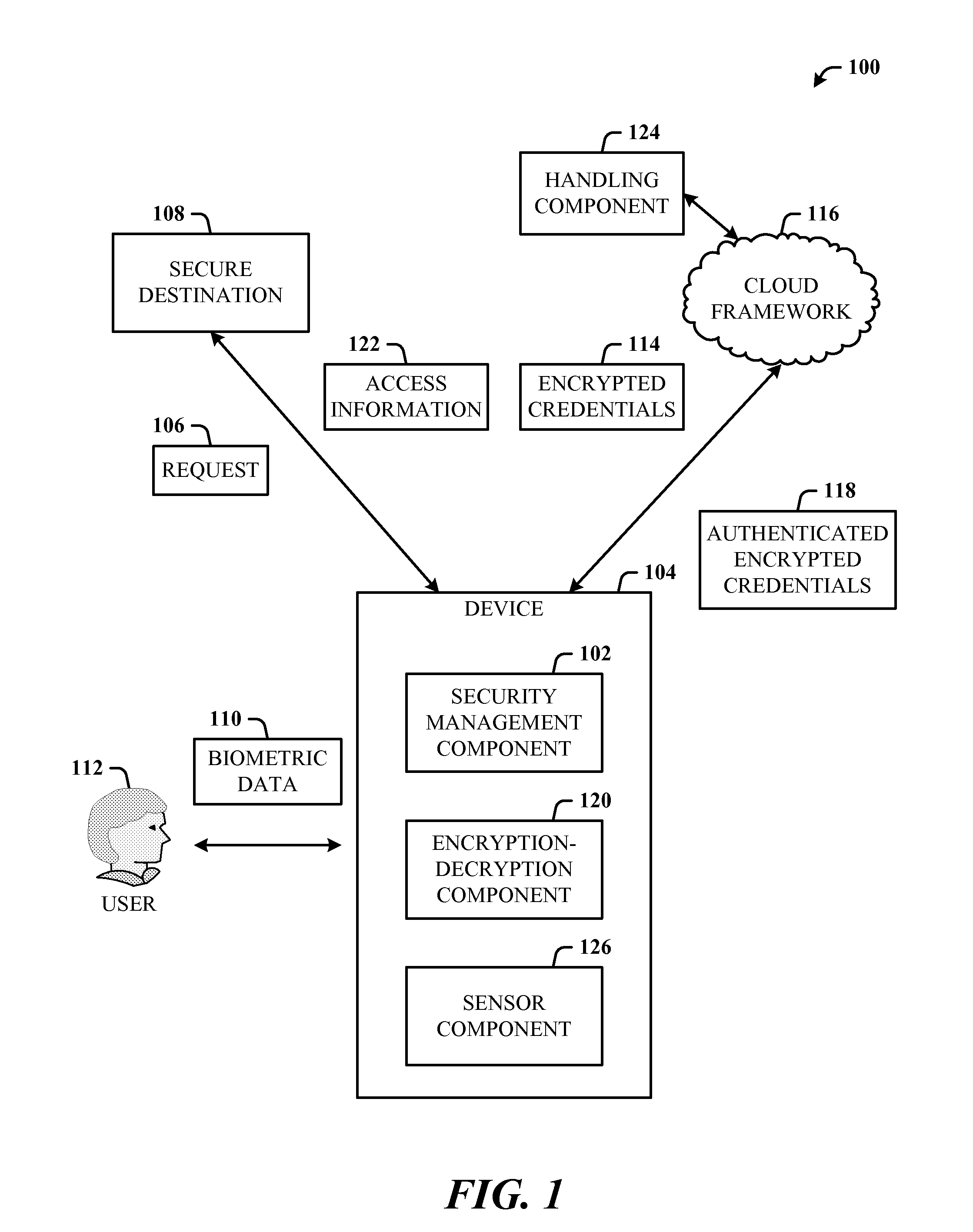
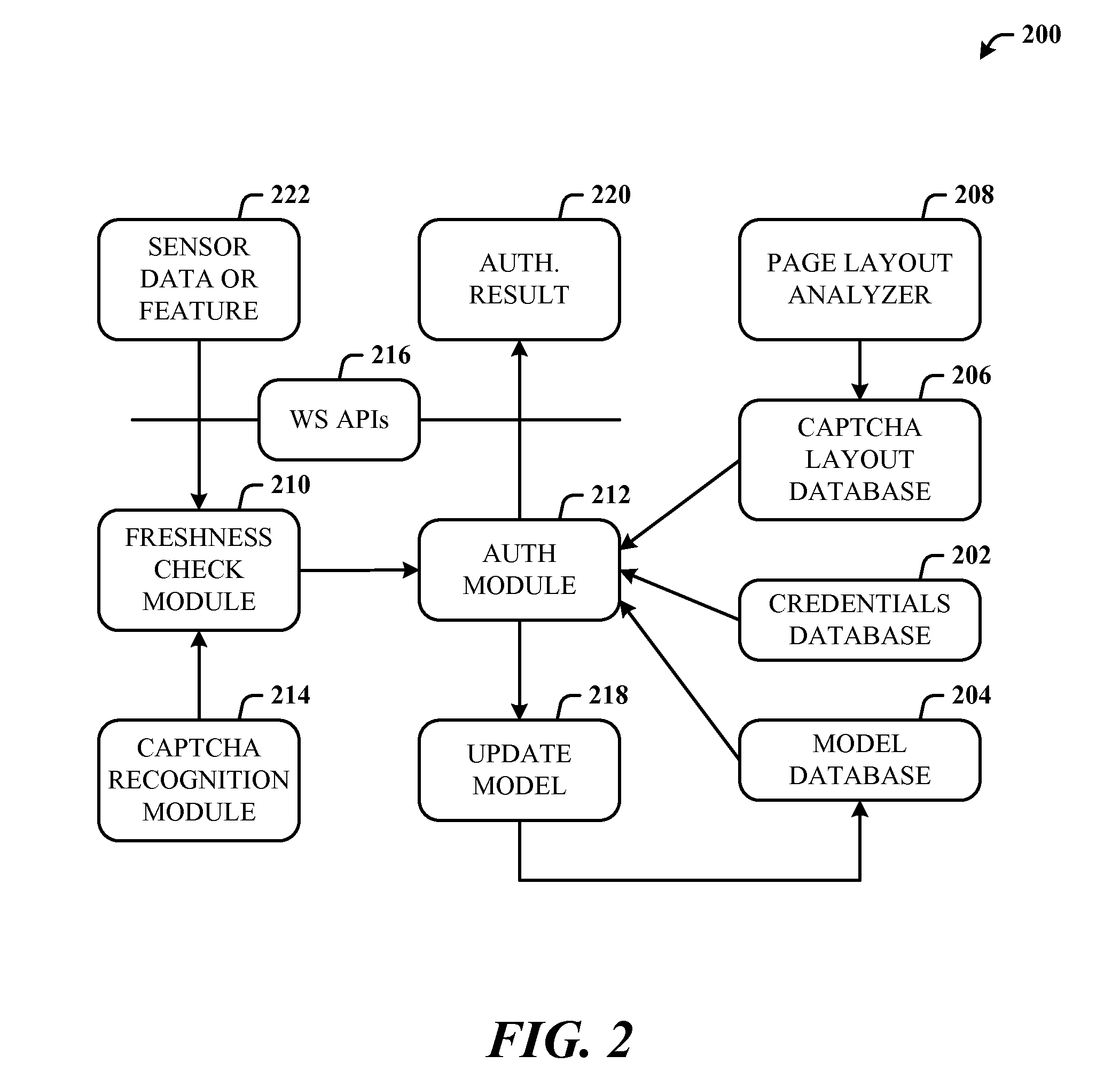
Usable security of online password management with sensor-based authentication
ActiveUS20120297190A1Improve usabilityAuthentication is convenientUser identity/authority verificationDigital data authenticationCryptographic protocolUsability
A multi-party security protocol that incorporates biometric-based authentication and withstands attacks against any single party (e.g., mobile phone, cloud, or the user). The protocol involves the function split between mobile and cloud and the mechanisms to chain-hold the secrets. A key generation mechanisms binds secrets to a specific device or URL (uniform resource locator) by adding salt to a master credential. An inline CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) handling mechanism uses the same sensor modality as the authentication process, which not only improves the usability, but also facilitates the authentication process. This architecture further enhances existing overall system security (e.g., handling untrusted or compromised cloud service, phone being lost, impersonation, etc.) and also improves the usability by automatically handling the CAPTCHA.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for establishing a federated identity using a personal wireless device
A federated identity, established through possession of a single sign-on token, will allow a personal wireless device (PWD) to be used in a commercial environment to purchase goods or services, access a building, access a telephone, wireless, or computer network, or in numerous other instances. The token may be obtained by the user authenticating with the PWD and the PWD authenticating with the network. When the PWD comes within range of a service provider, a session is established using a short range wireless protocol, such as Bluetooth or infrared. The session is secured using a security protocol such as SSL, and the service provider authenticates its identity to the PWD. Policy may be implemented regarding transmission of the token to the service provider. Upon receipt of the token, the service provider will validate the token with the federated identity provider, obtain identifying information, and complete the transaction.
Owner:APPLE INC
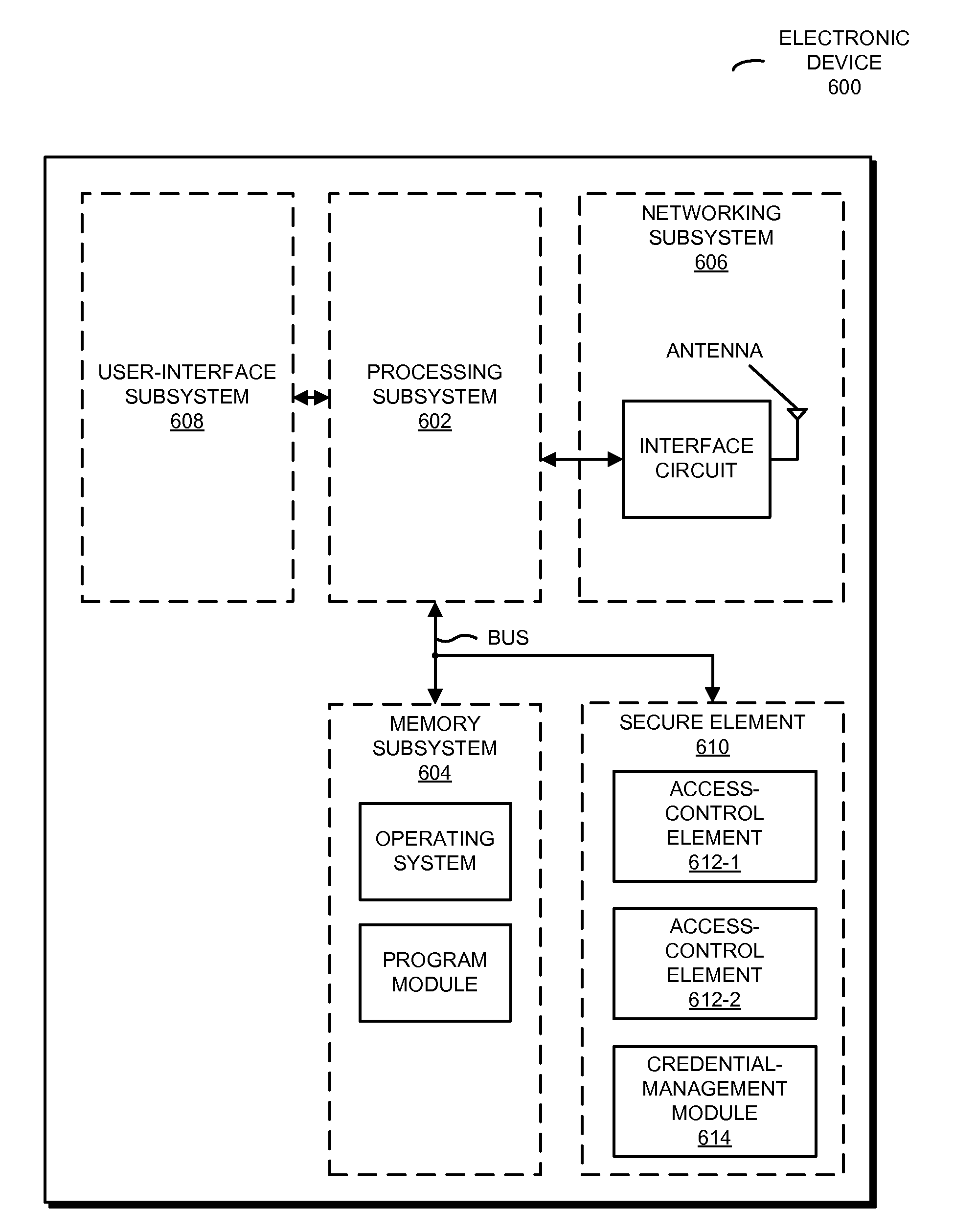
Policy-based techniques for managing access control
ActiveUS20140143826A1Facilitates secure communicationFacilitates privilegeDigital data protectionTransmissionCryptographic protocolMedia access control
A policy-based framework is described. This policy-based framework may be used to specify the privileges for logical entities to perform operations associated with an access-control element (such as an electronic Subscriber Identity Module) located within a secure element in an electronic device. Note that different logical entities may have different privileges for different operations associated with the same or different access-control elements. Moreover, the policy-based framework may specify types of credentials that are used by the logical entities during authentication, so that different types of credentials may be used for different operations and / or by different logical entities. Furthermore, the policy-based framework may specify the security protocols and security levels that are used by the logical entities during authentication, so that different security protocols and security levels may be used for different operations and / or by different logical entities.
Owner:APPLE INC
Cryptographic control for mobile storage means
ActiveUS20090217385A1Digital data processing detailsAnalogue secracy/subscription systemsData operationsCryptographic protocol
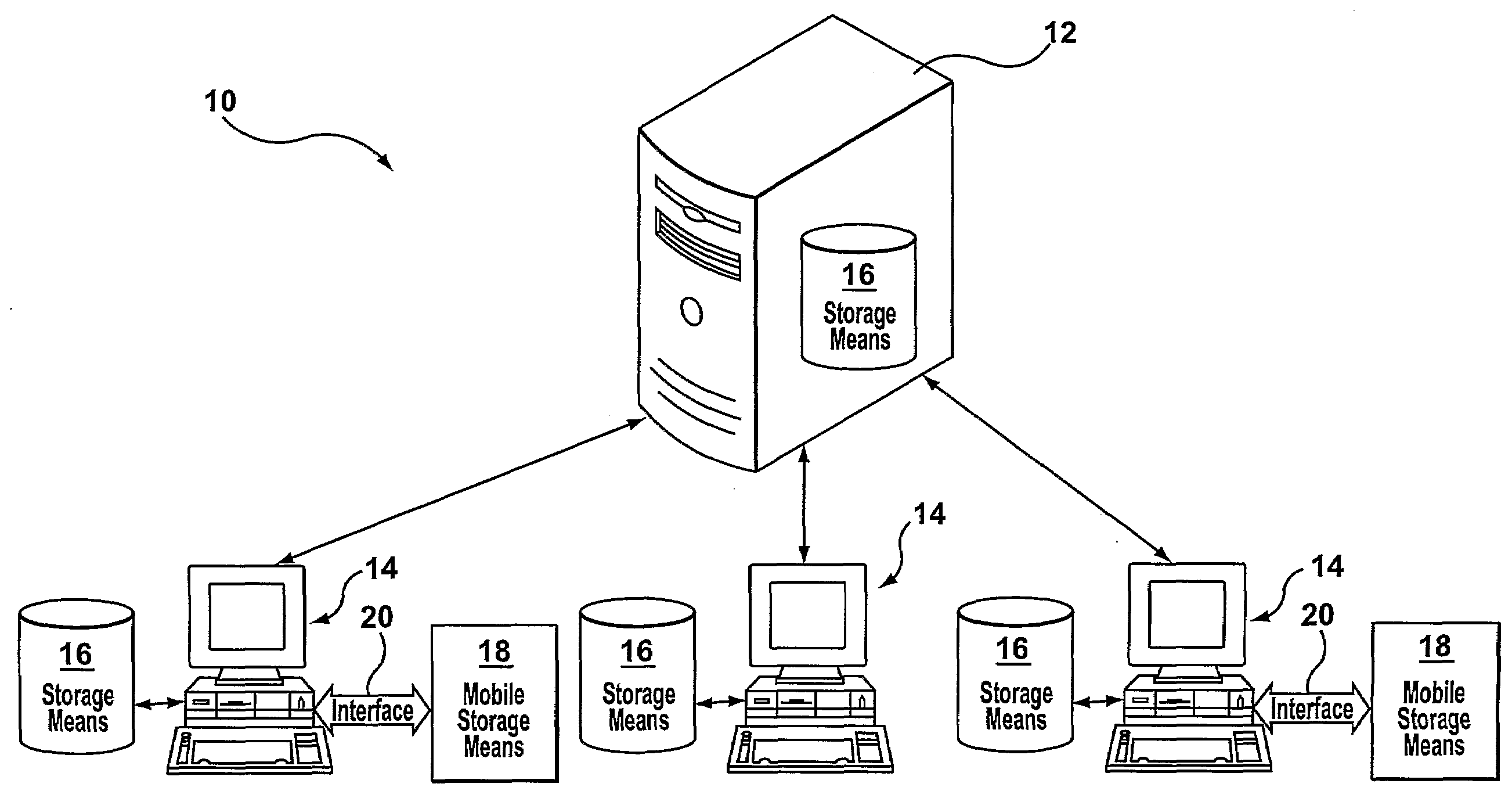
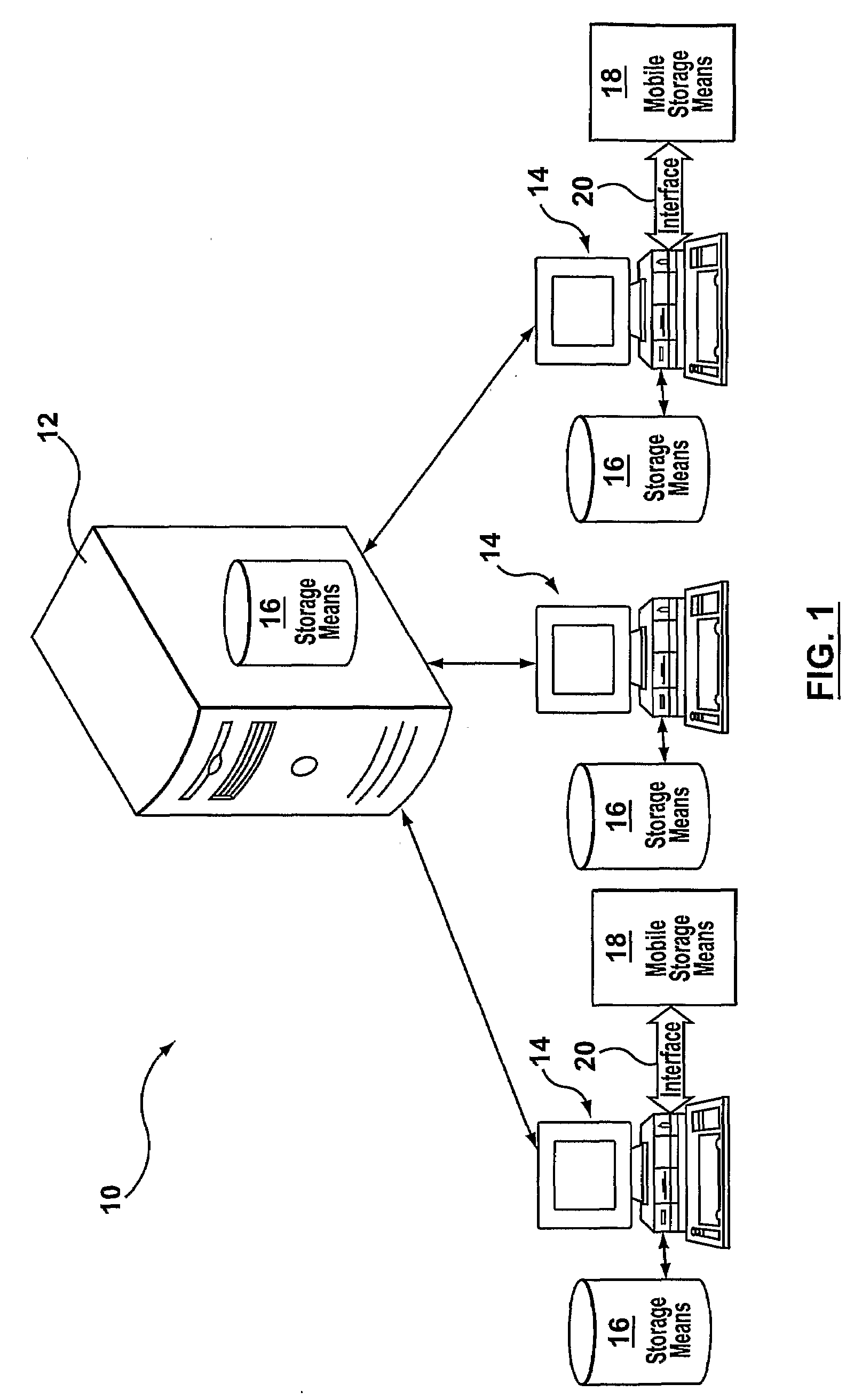
A system and method that regulates the various operations between computing stations and storage devices. Storage devices are the storage means that are contained upon devices that are able to have data stored upon them. Any operation that involves or may lead to the exchange or accessing of content (data) between a storage device and computing station may be regulated by means of a policy which comprise a set of rules. Rules may be defined according to specific criteria, including the type of storage device, the type of content, the attributes of the content, and other attributes associated with the storage device and / or the content. The policy will be dynamically installed upon a computing station for specific user(s) and will regulate the data operations that may take place between the computing stations and storage devices based on evaluation of the policy. Based on the evaluation of the policy, the requested operation is permitted, restricted in some areas, or denied.
Owner:CRYPTOMILL
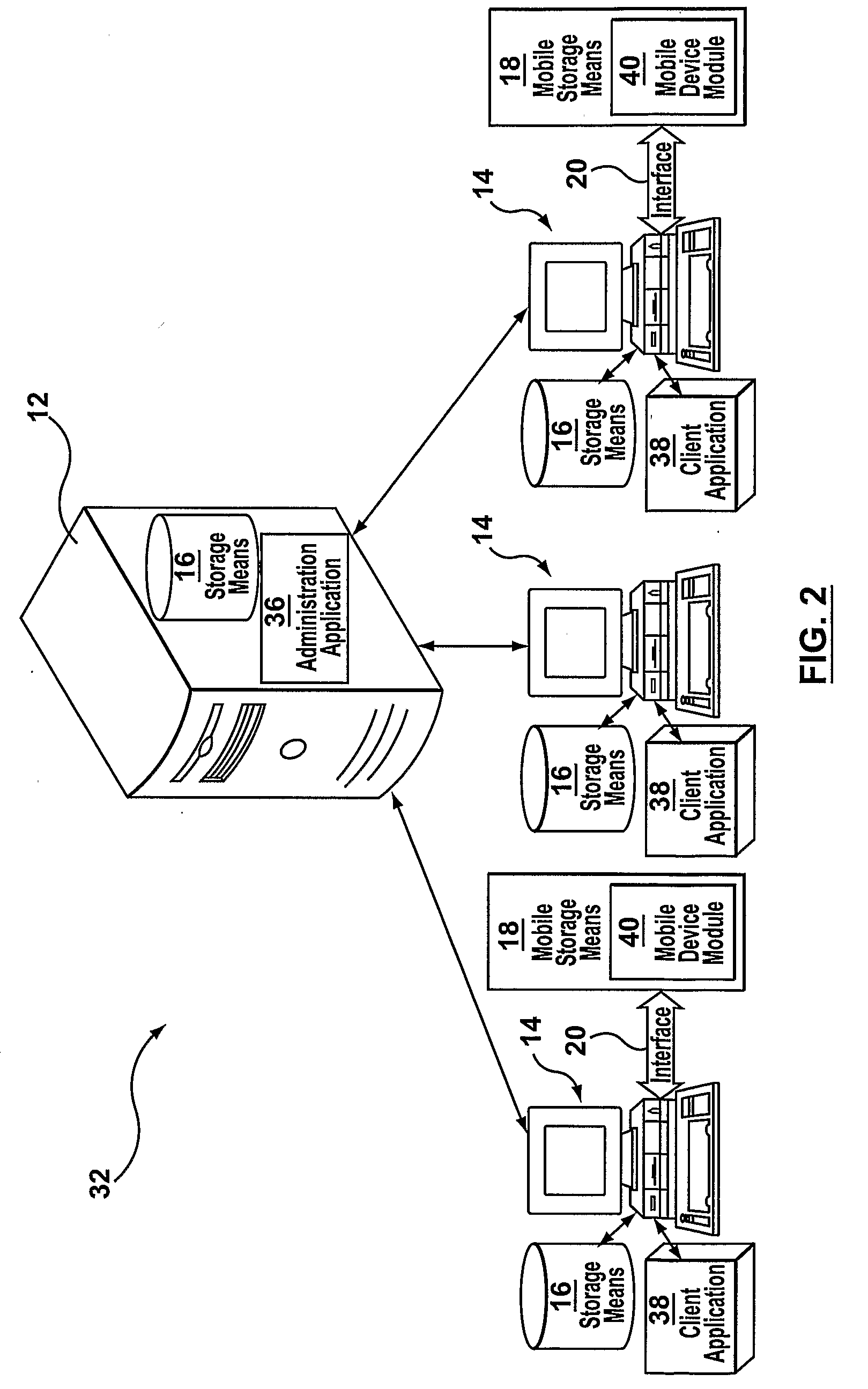
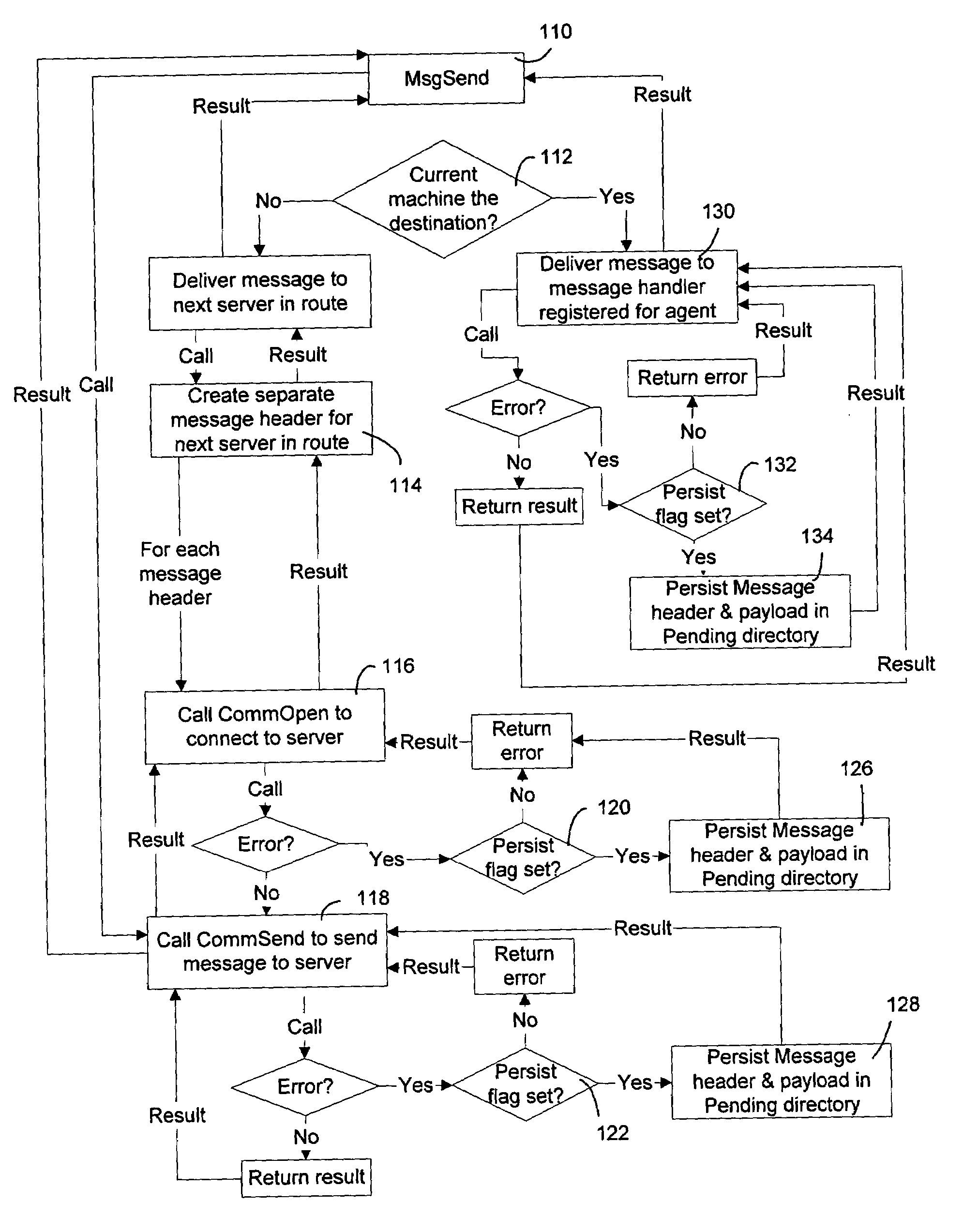
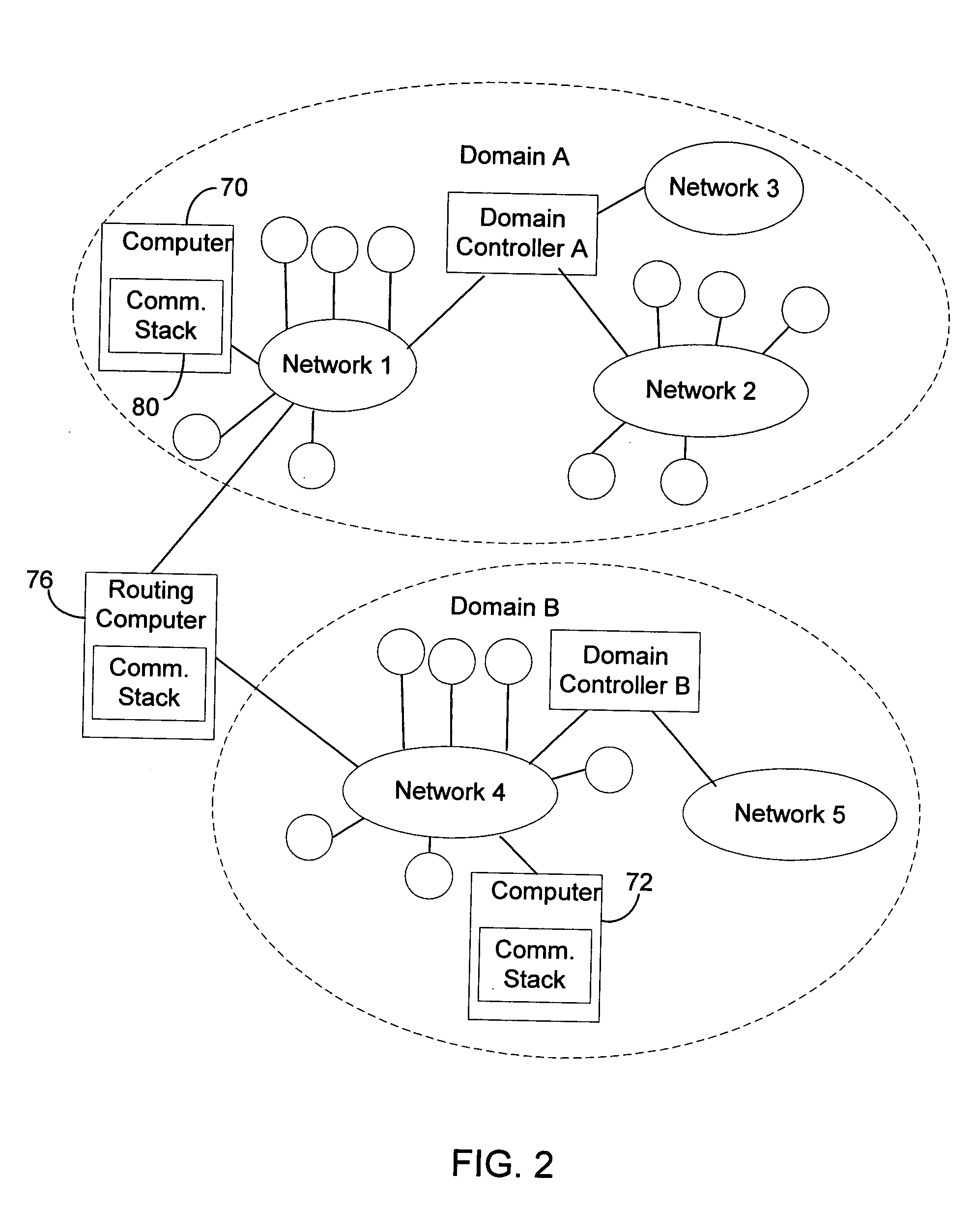
Communication stack for network communication and routing
ActiveUS7191248B2Imparts flexibilityImparts extensibilityMultiple digital computer combinationsSecuring communicationTransmission protocolCryptographic protocol
A communication stack enables computers implementing it to send, receive, or route network communications. The communication stack includes a message layer, a communication layer, a security layer, and a transport protocol layer, with plug-in transport protocol modules and plug-in security protocol modules. Each of the origin computer, target computer, and routing computers involved in delivering a message implements the communication stack. An application on the origin computer calls the message layer of the computer to send messages to a target computer and identifies routing computers on the route for delivering the message to the target computer. The message layer calls the communication layer to establish a connection to the target computer. The communication layer uses the transport protocol layer to establish an initial connection with the target computer, and uses the security layer to negotiate security parameters and to handle secured communications between the origin and target computers.
Owner:MICROSOFT TECH LICENSING LLC
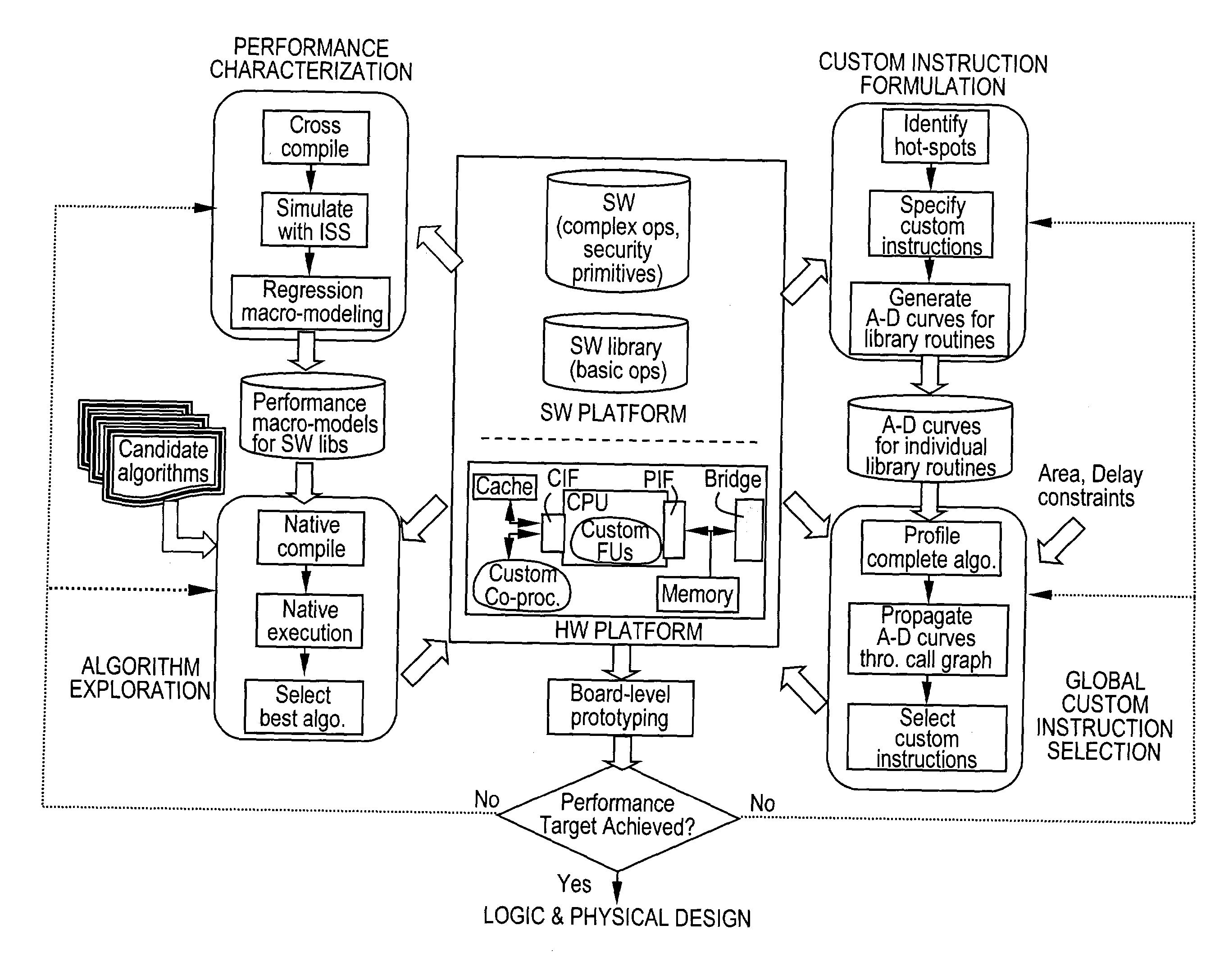
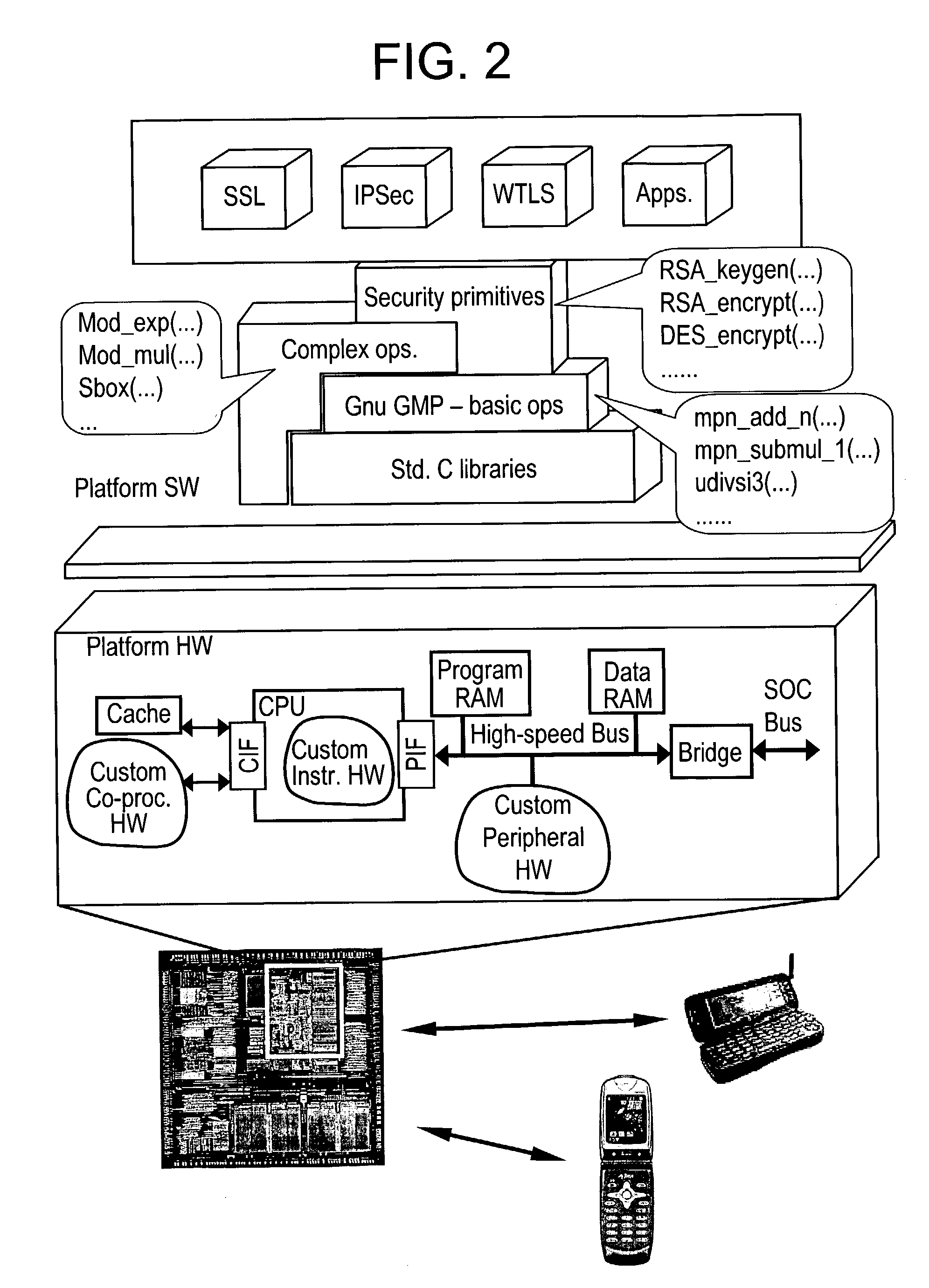
Techniques for efficient security processing
InactiveUS20030142818A1Efficient executionImprove efficiencyInternal/peripheral component protectionCommunication jammingCryptographic protocolSafe handling
A programmable security processor for efficient execution of security protocols, wherein the instruction set of the processor is enhanced to contain at least one instruction that is used to improve the efficiency of a public-key cryptographic algorithm, and at least one instruction that is used to improve the efficiency of a private-key cryptographic algorithm.
Owner:NEC CORP
Systems and methods for single sign-in for multiple accounts
InactiveUS20120227094A1Easy to centralizeEasy to manageDigital data processing detailsUser identity/authority verificationService provisionCryptographic protocol
Systems and methods which facilitate single user sign-in for multiple accounts are shown. Embodiments create a single user base which maps users to multiple accounts. The use of a single set of credentials by the user is provided for according to embodiments irrespective of the applications associated with the various accounts having very different security protocols. A system hosting the shared user base preferably provides a single authentication point for multiple services. Embodiments an authenticator string, as may be passed between a client and bridge server and / or client and application, in order to enable user access, detect attacks with respect to a client conversation, etcetera. In addition to providing a shared user base for single sign-in, embodiments provide additional shared functionality and / or functionality not available from the applications themselves.
Owner:STAMPS COM
IP-based location service within code division multiple access network
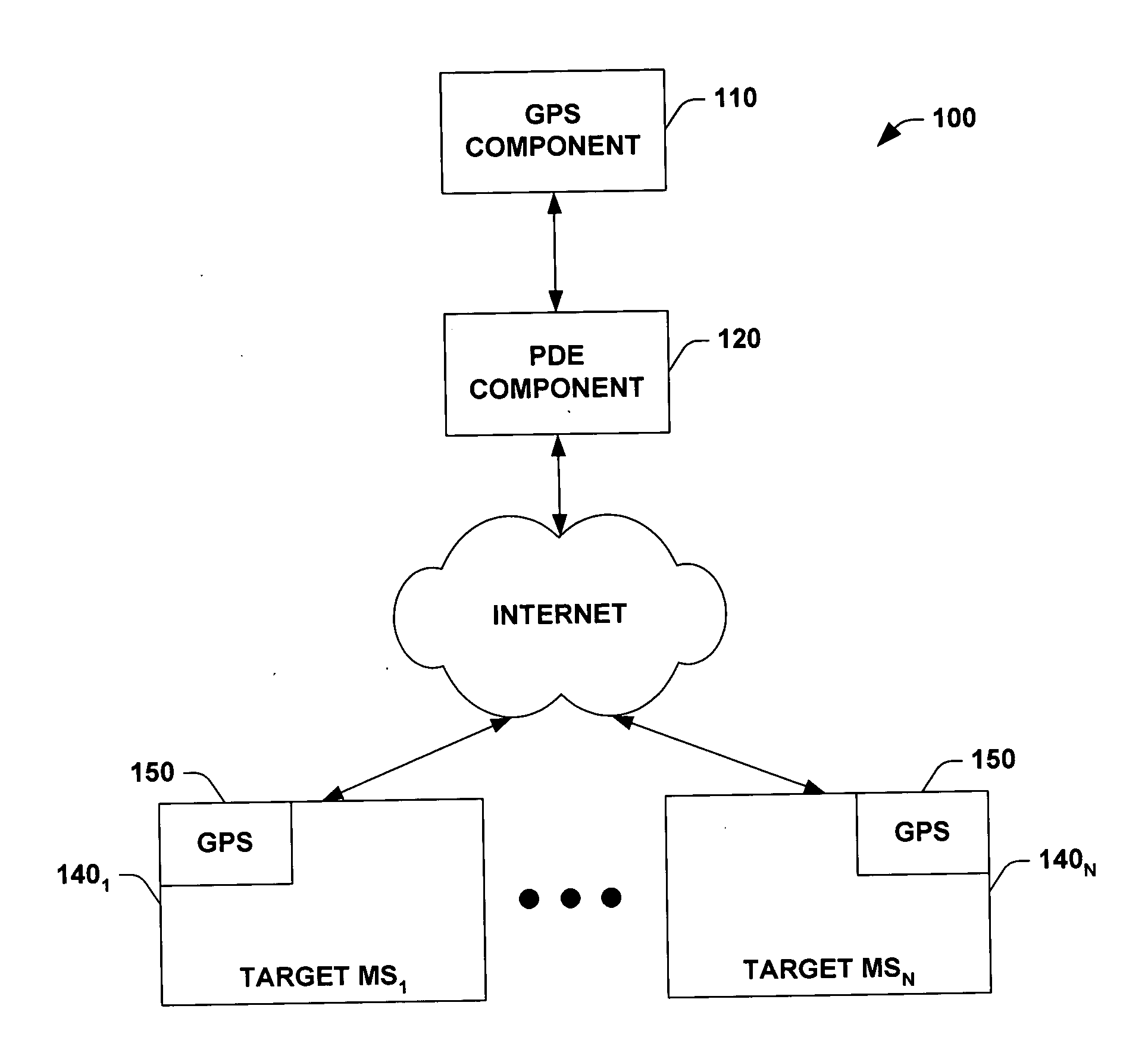
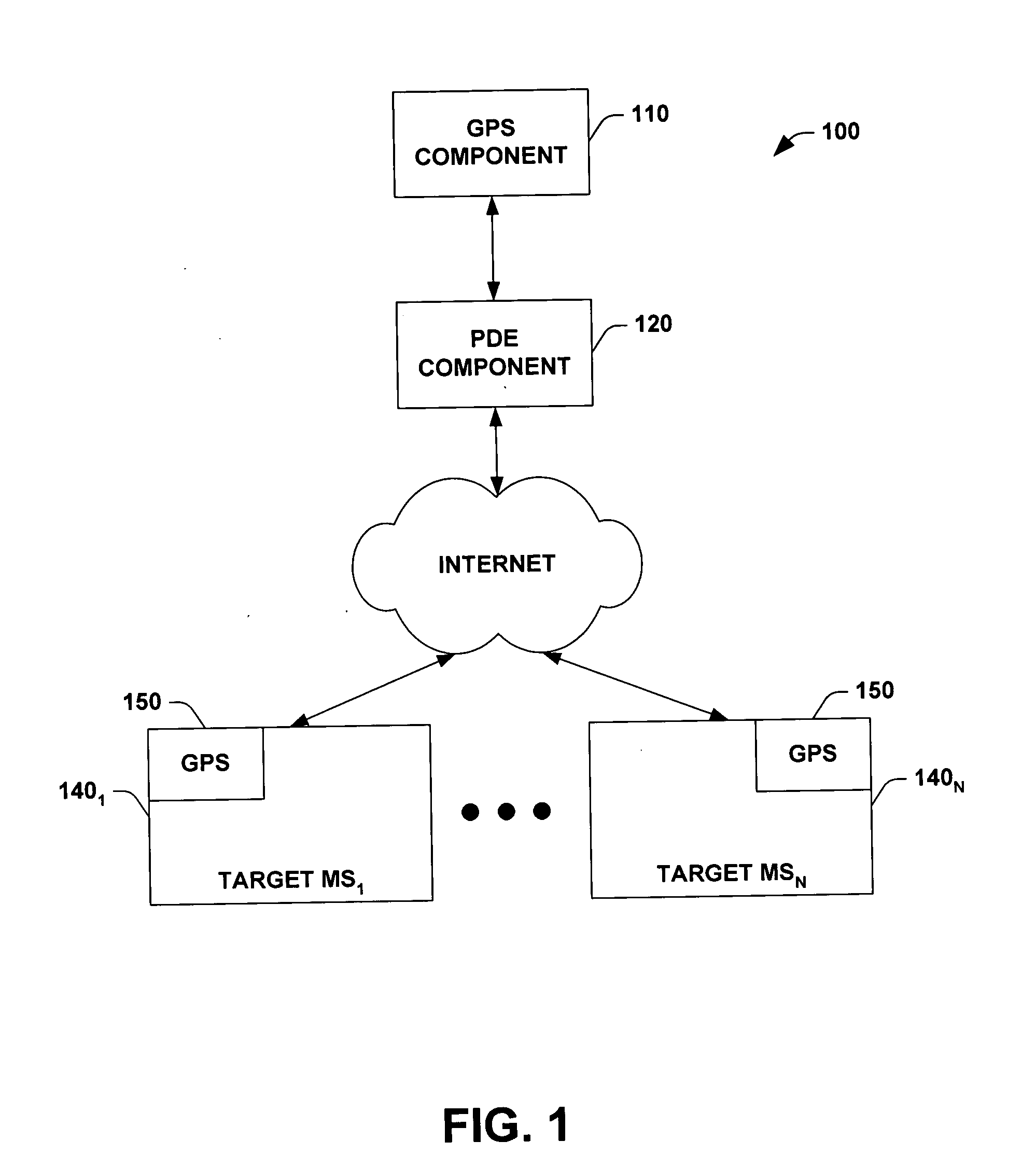
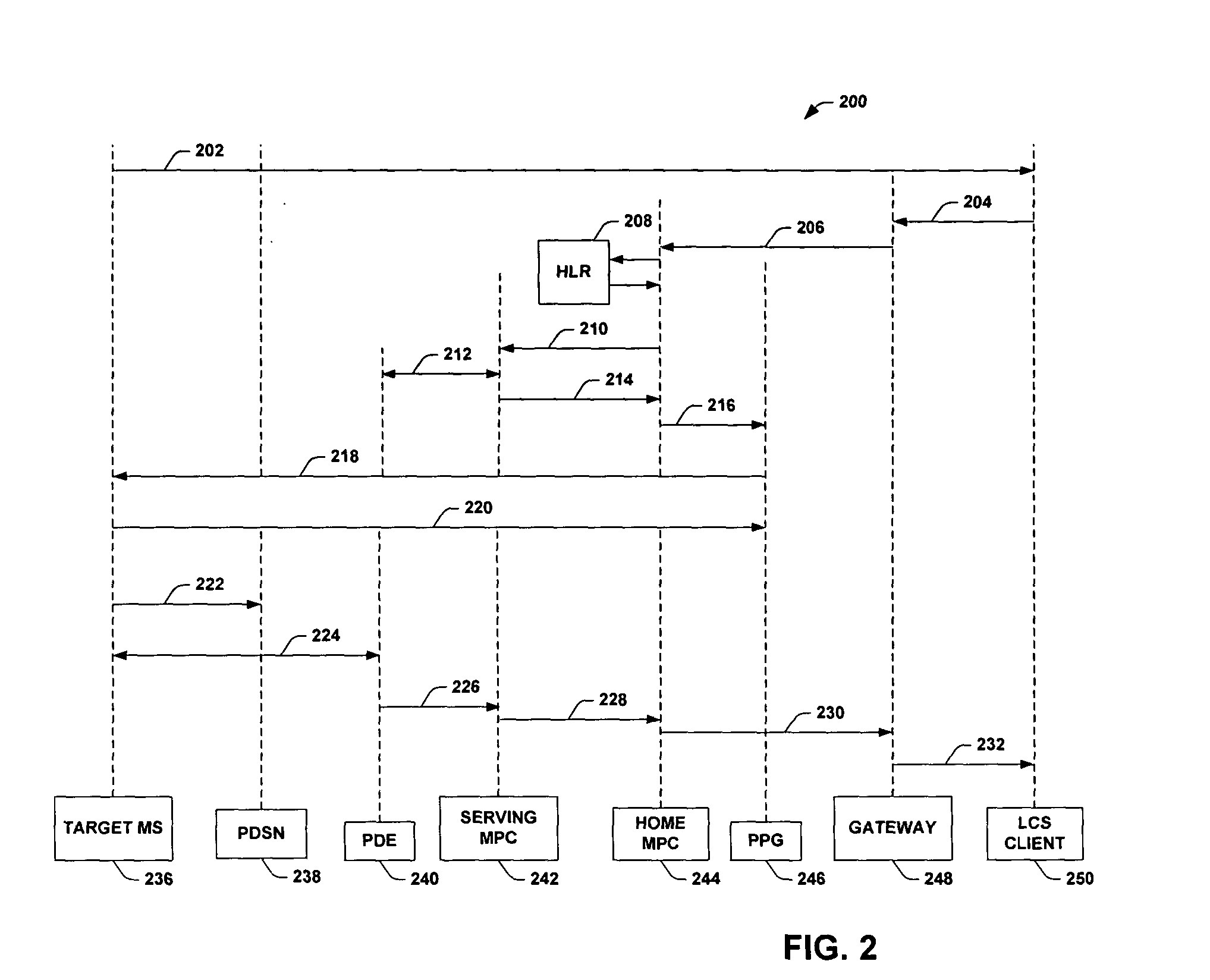
InactiveUS20050066044A1Easy to optimizeFacilitate automated determinationPosition fixationMultiple digital computer combinationsCryptographic protocolMobile station
An Internet protocol (IP) based location system that employs a global positioning system (GPS) component in connection with a position determining entity (PDE) component to determine location of target mobile station(s) via the Internet. As such the system provides an internet protocol based scheme (e.g., UDP) to initiate a location determination session within a CDMA network. The system can provide a location determining service even when the mobile station(s) are not within a home network (e.g., roaming situations). The system can also employ HTTP over TCP / IP so as to facilitate communications between the mobile station(s) and a mobile positioning center (MPC) (e.g., authentication and / or security protocols / schemes). Furthermore, the system can identify a PDE of a plurality of available PDEs that is most suitable for a given state of the mobile station and / or state of the user and / or particular location based application being employed by the mobile station.
Owner:NOKIA CORP
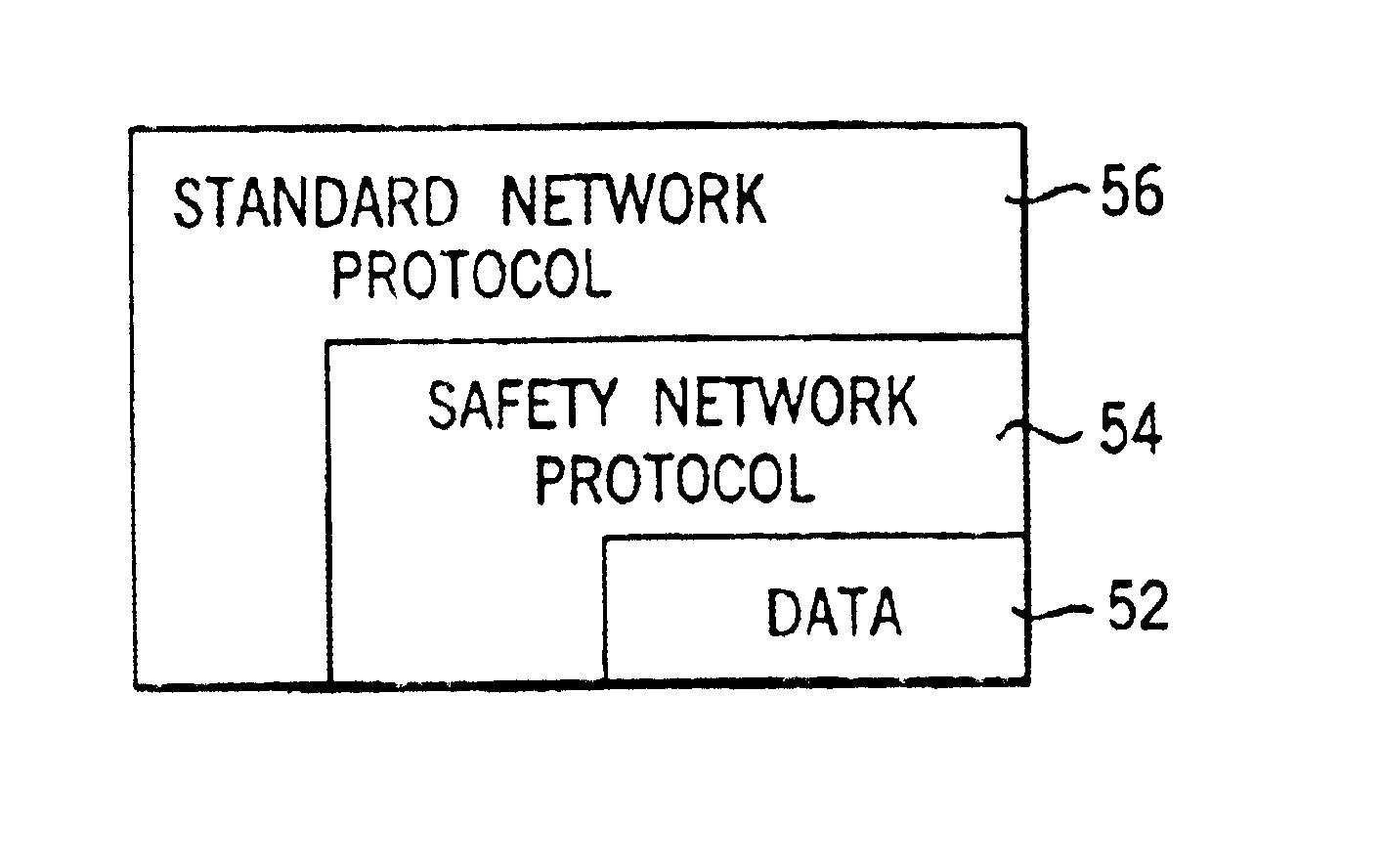
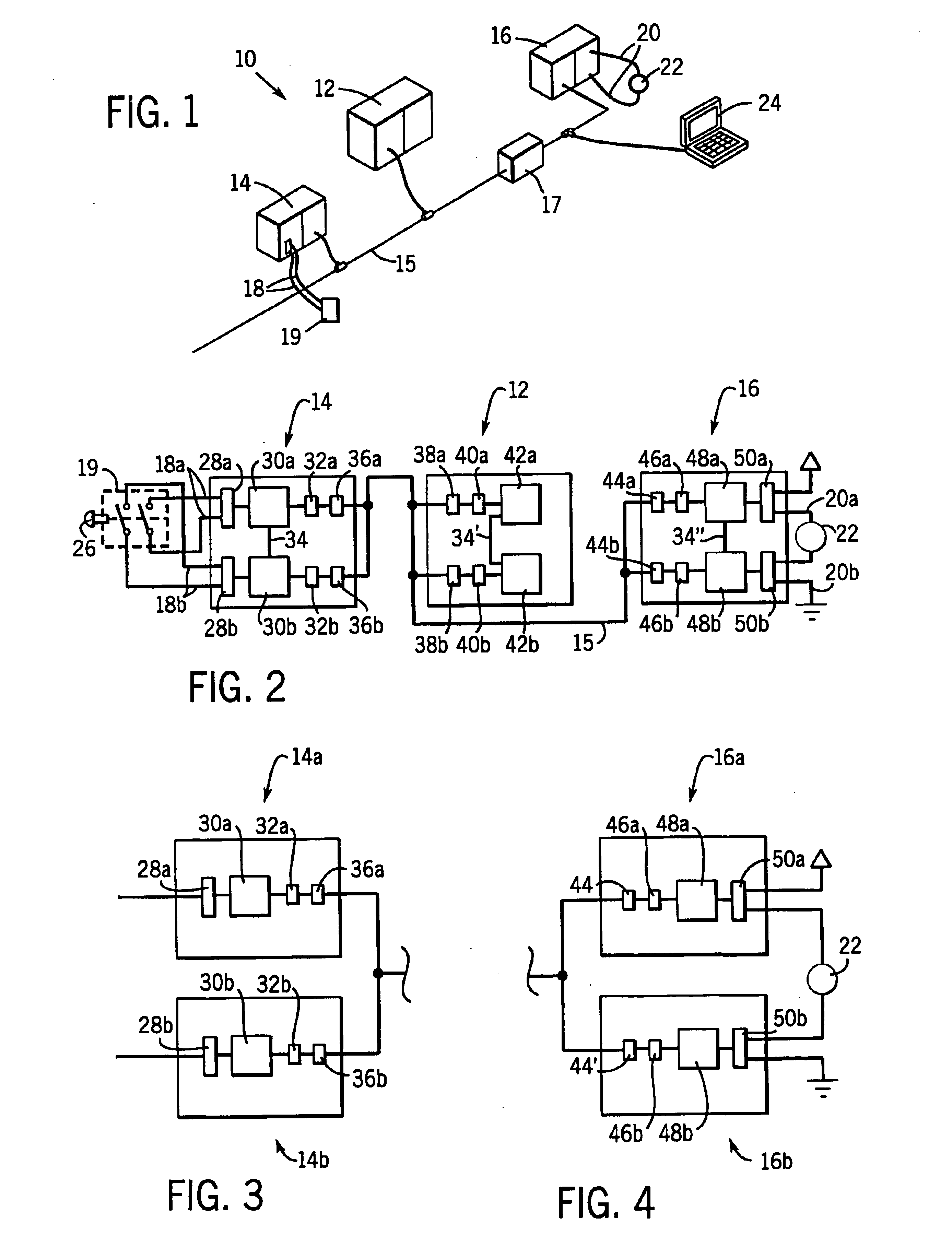
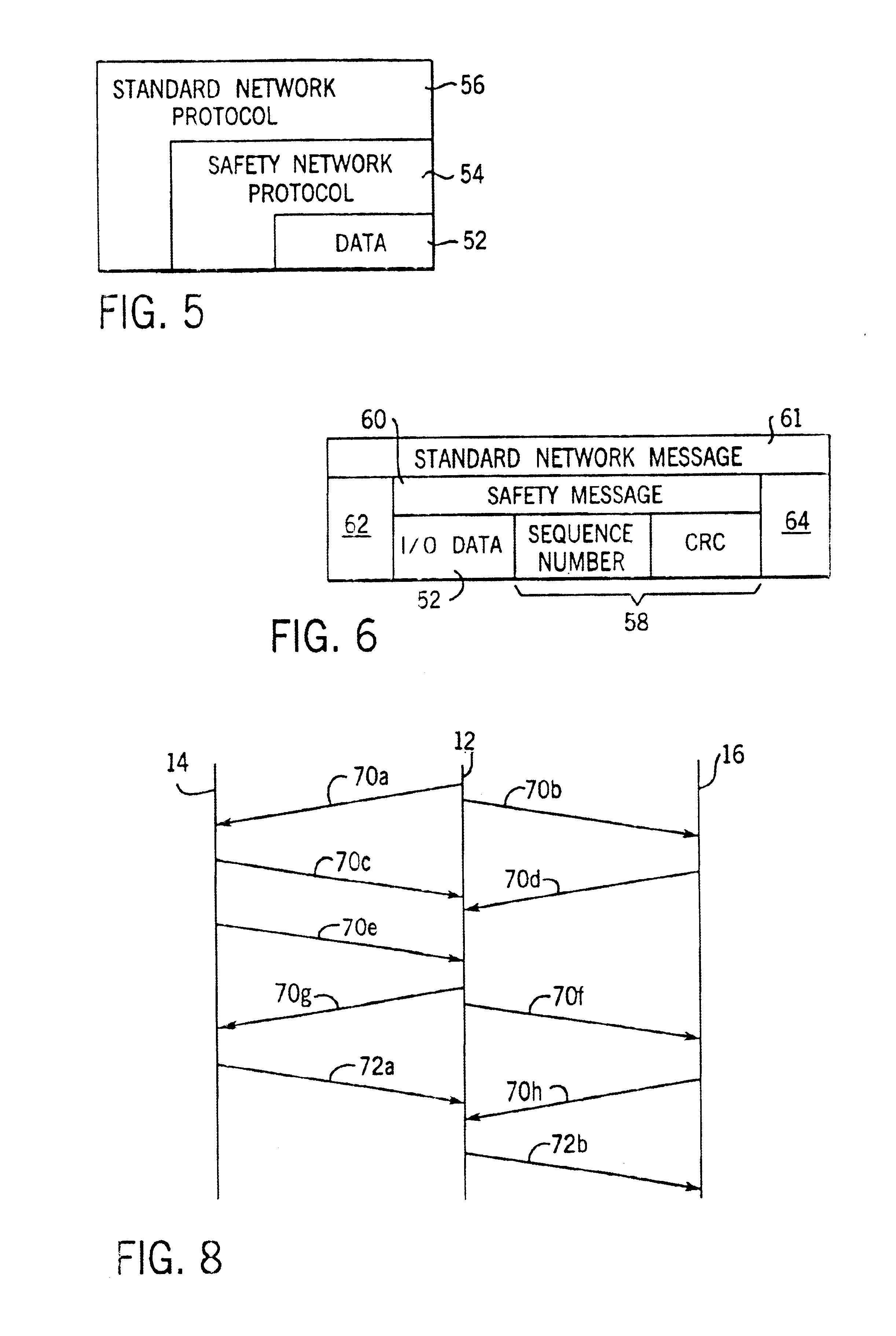
Network independent safety protocol for industrial controller
InactiveUS6891850B1Reduce errorsComputer controlSimulator controlNetworking protocolNetwork generation
A highly reliable industrial control system is produced using a network running a standard serial protocol. A safety protocol is embedded within the standard serial protocol by adding to special error detecting data redundant with the protocol of the standard serial network. In addition an overarching protocol involving timing of messages is imposed to provide the necessary level of reliability in the standard serial network. This approach allows the safety protocol to be used with a wide variety of commercially available serial communication standards without modification of the media or the specialized integrated circuits used for that communication. Safety protocol may be implemented in an additional level for integrated circuits or through firmware changes in programmable aspects of the industrial controller components.
Owner:ROCKWELL TECH
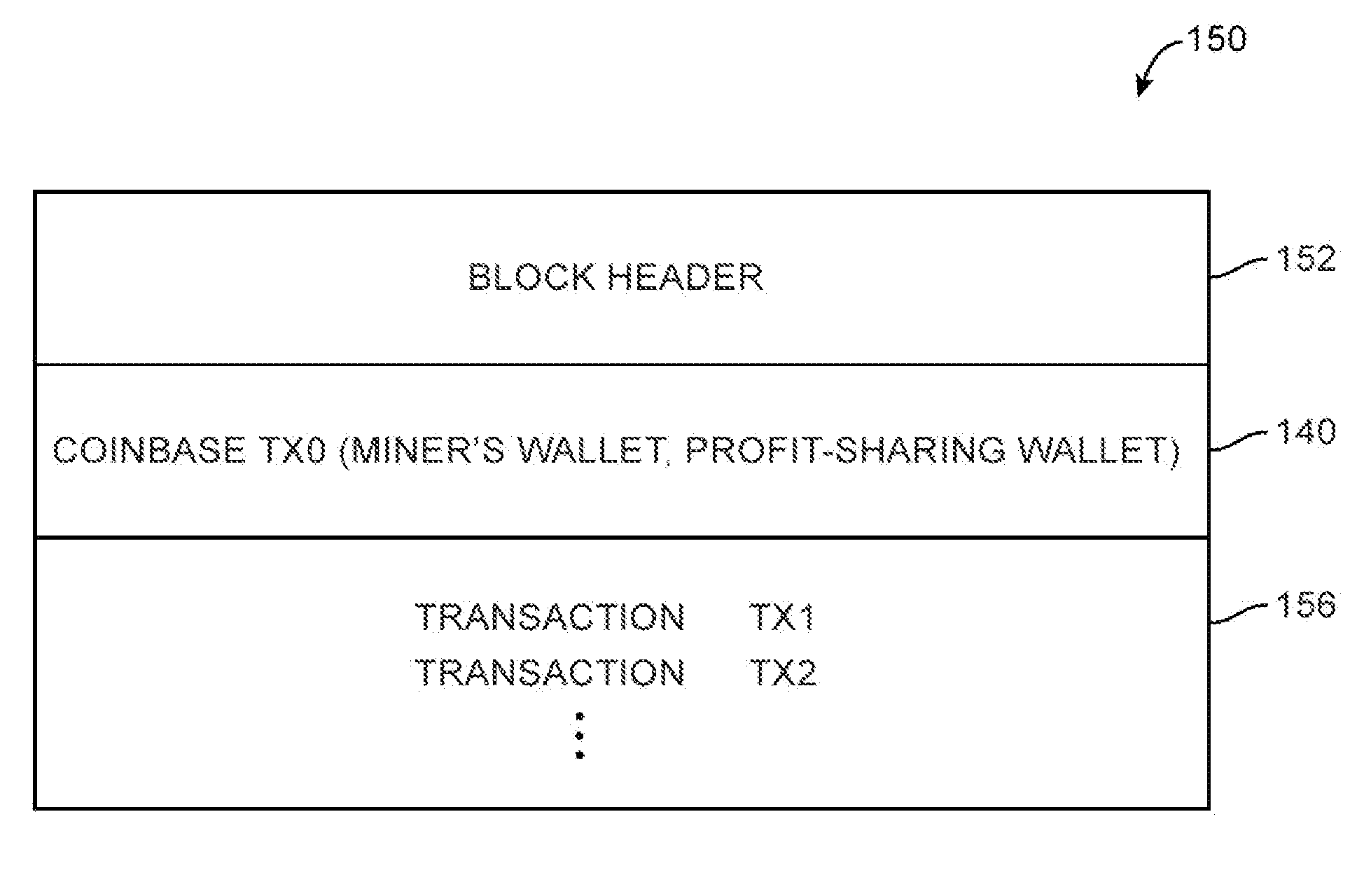
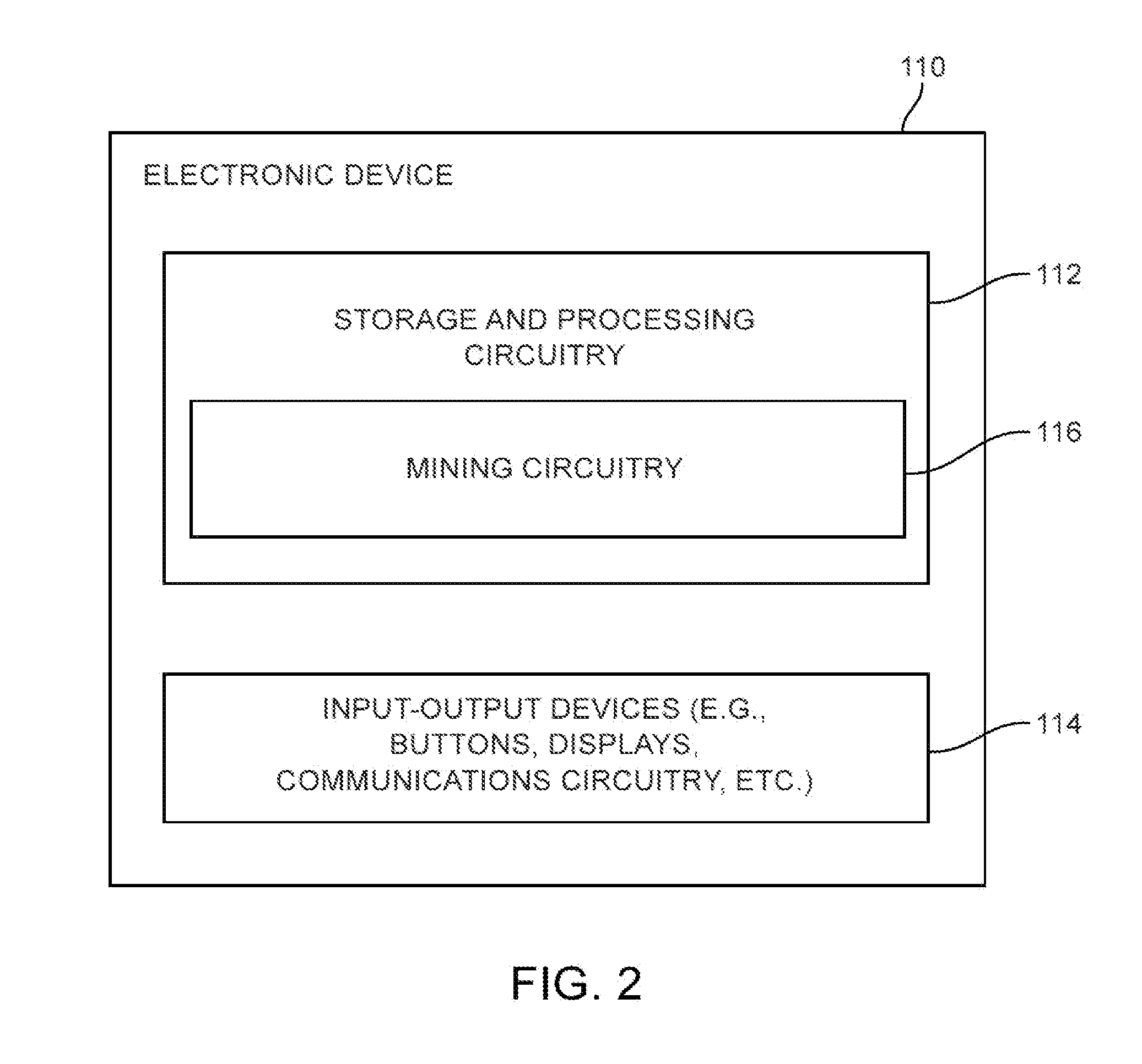
Digital currency mining circuitry with adaptable difficulty compare capabilities
Cryptographic hashing circuitry such as mining circuitry used to mine digital currency may be formed on an integrated circuit. The hashing circuitry may include sequential rounds of register and logic circuitry that perform operations of a cryptographic protocol. A final hash output from the hashing circuitry may be checked using a difficulty comparison circuit to determine whether the hash output satisfies predetermined difficulty criteria. The difficulty comparison circuit may be configured as a hardwired comparison circuit having logic gates for checking only a subset of bits in the hash output. The comparison circuit may be adapted to change the number of bits that is checked based on a target number of bits for comparison set by the Bitcoin protocol. Candidate solutions found using the hardwired comparison circuit may then be fed to a host controller that checks the entire hash output to determine whether the candidate solution is valid.
Owner:COINBASE
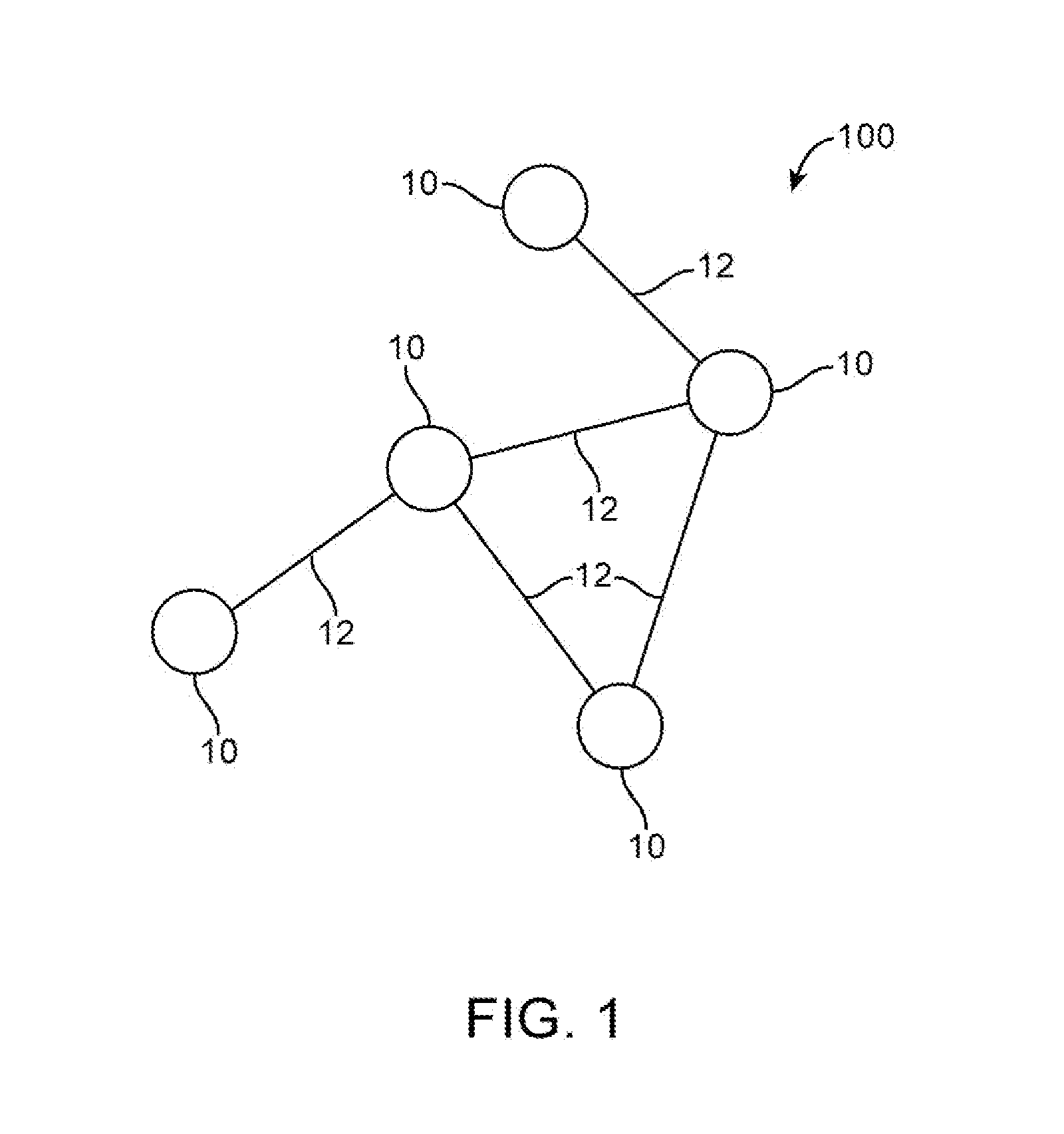
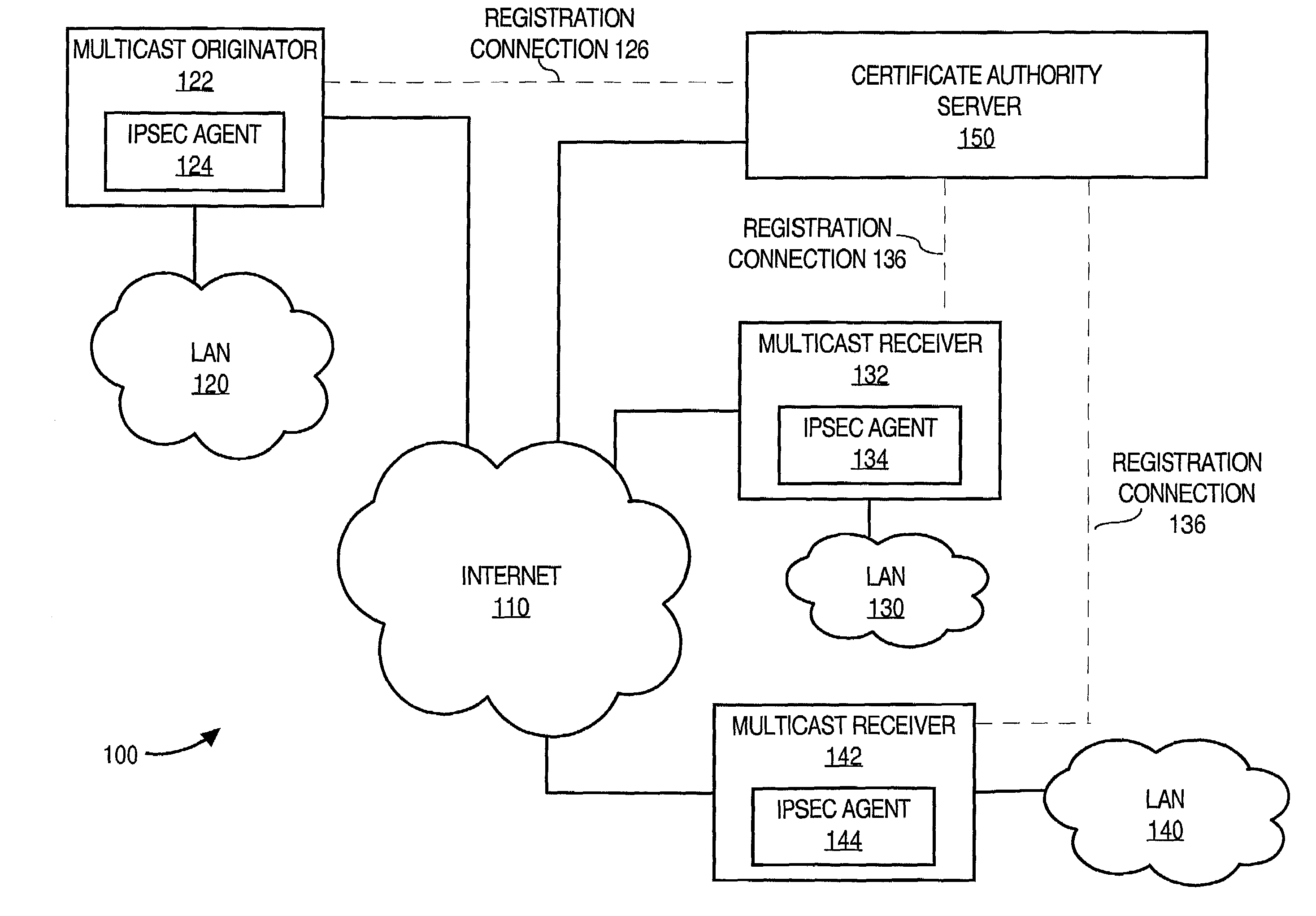
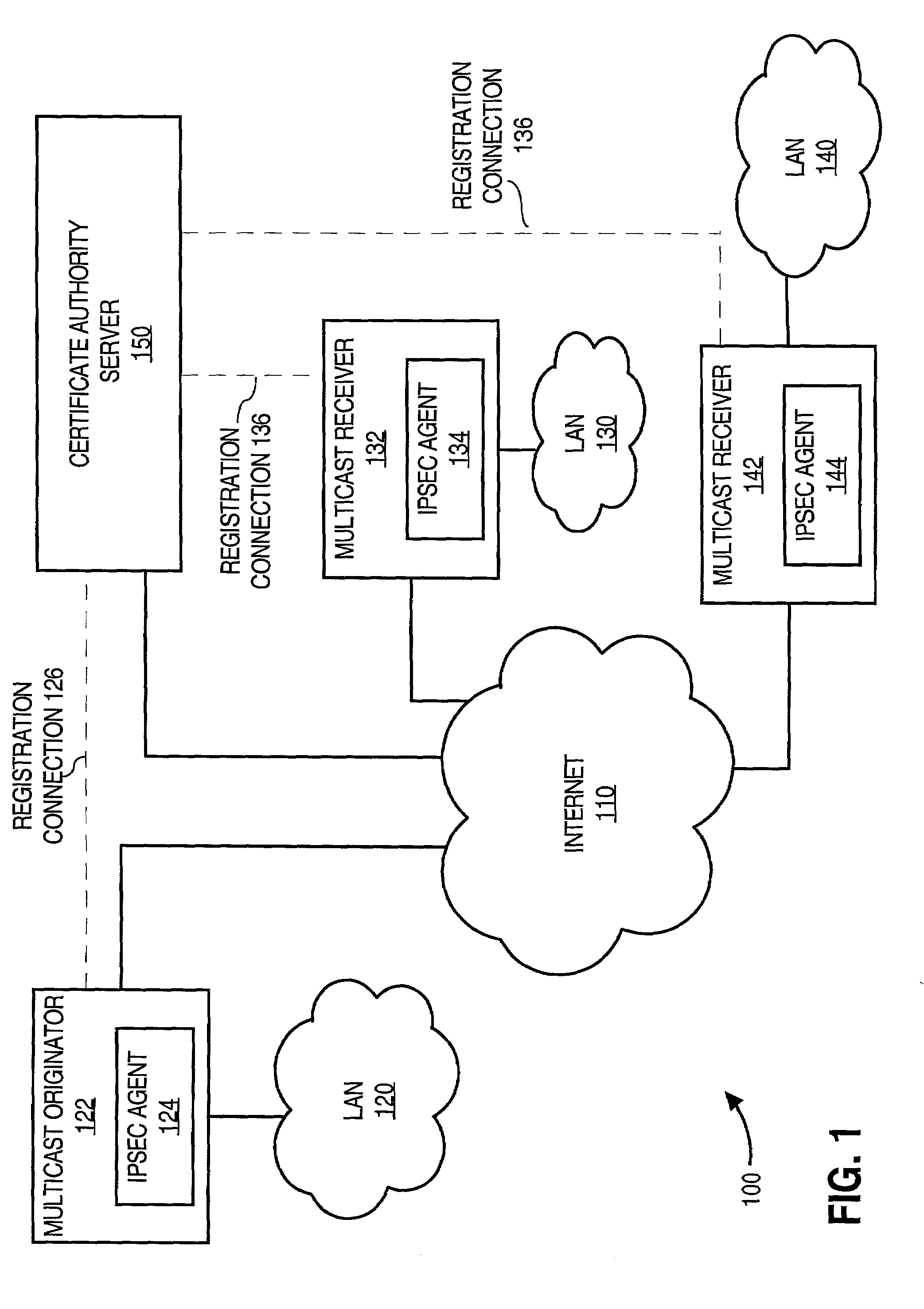
Facilitating secure communications among multicast nodes in a telecommunications network
An approach for facilitating secure communications among multicast nodes in a telecommunications network is disclosed. A source node sends an encryption key and an identifier to an authoritative node that stores the encryption key and associates the identifier with the encryption key. The source node encrypts data using the encryption key and sends the encrypted data with the identifier in a multicast. The multicast destination nodes retrieve the encryption key from the authoritative node based on the identifier and then decrypt the multicast. A list of administrative nodes, a list of authorized nodes, and an expiration time may be used to manage the encryption key. The authoritative node may be a certificate authority or key distribution center, and the source node may encrypt the multicast using the Internet security protocol (IPsec) or secure socket layer (SSL). Thus, communications among multicast nodes may be efficiently secured in a scalable manner.
Owner:CISCO TECH INC
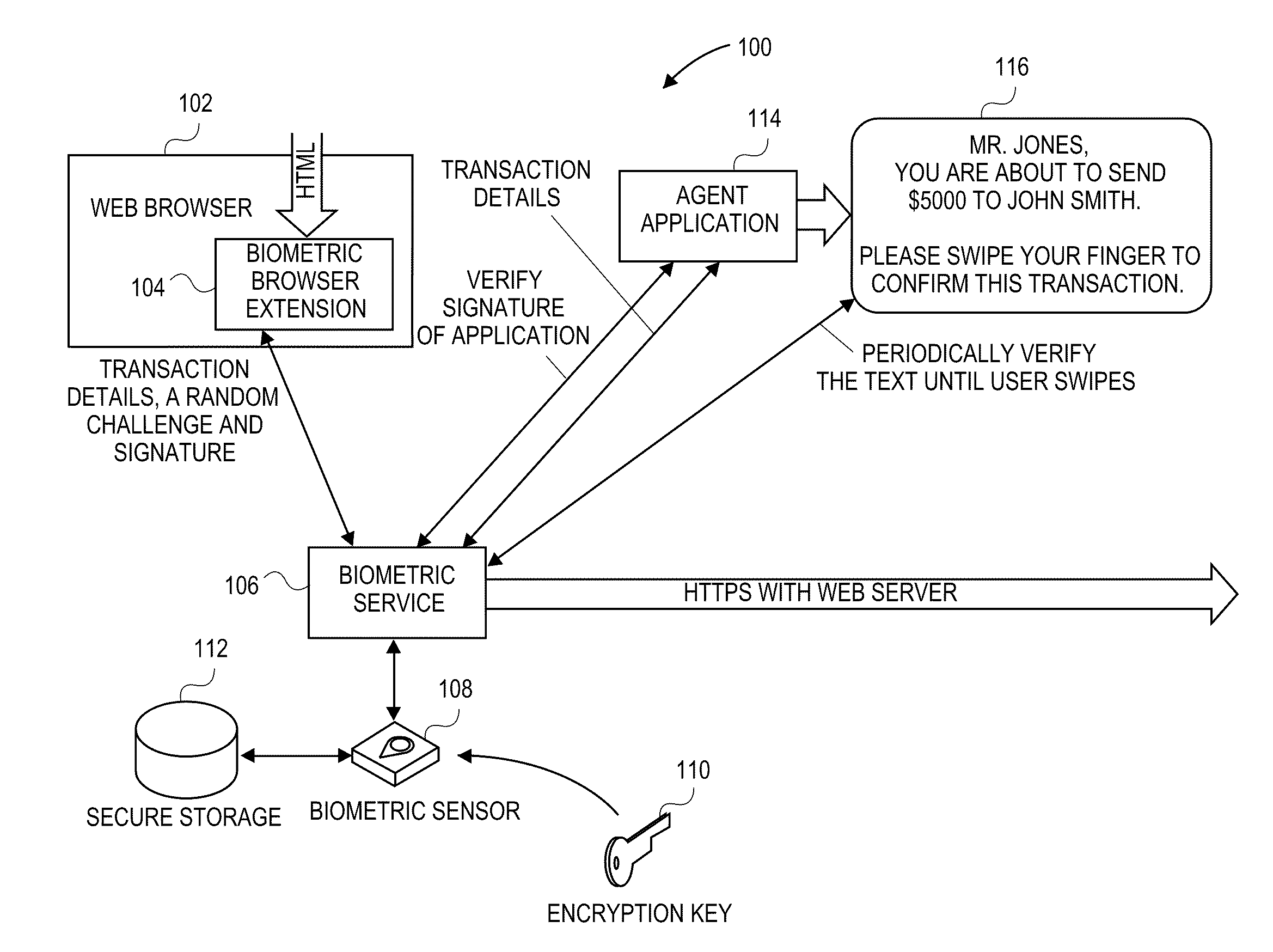
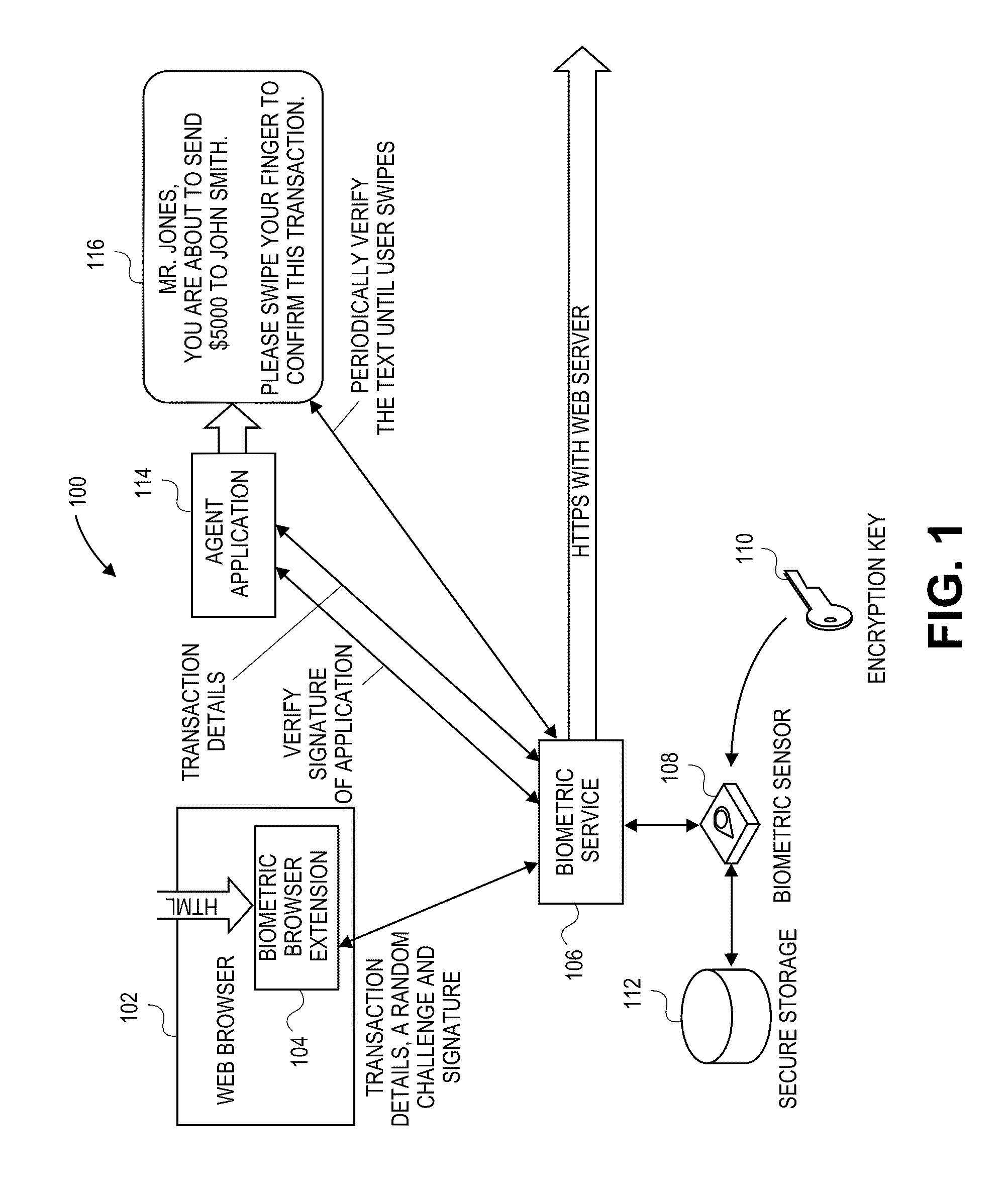
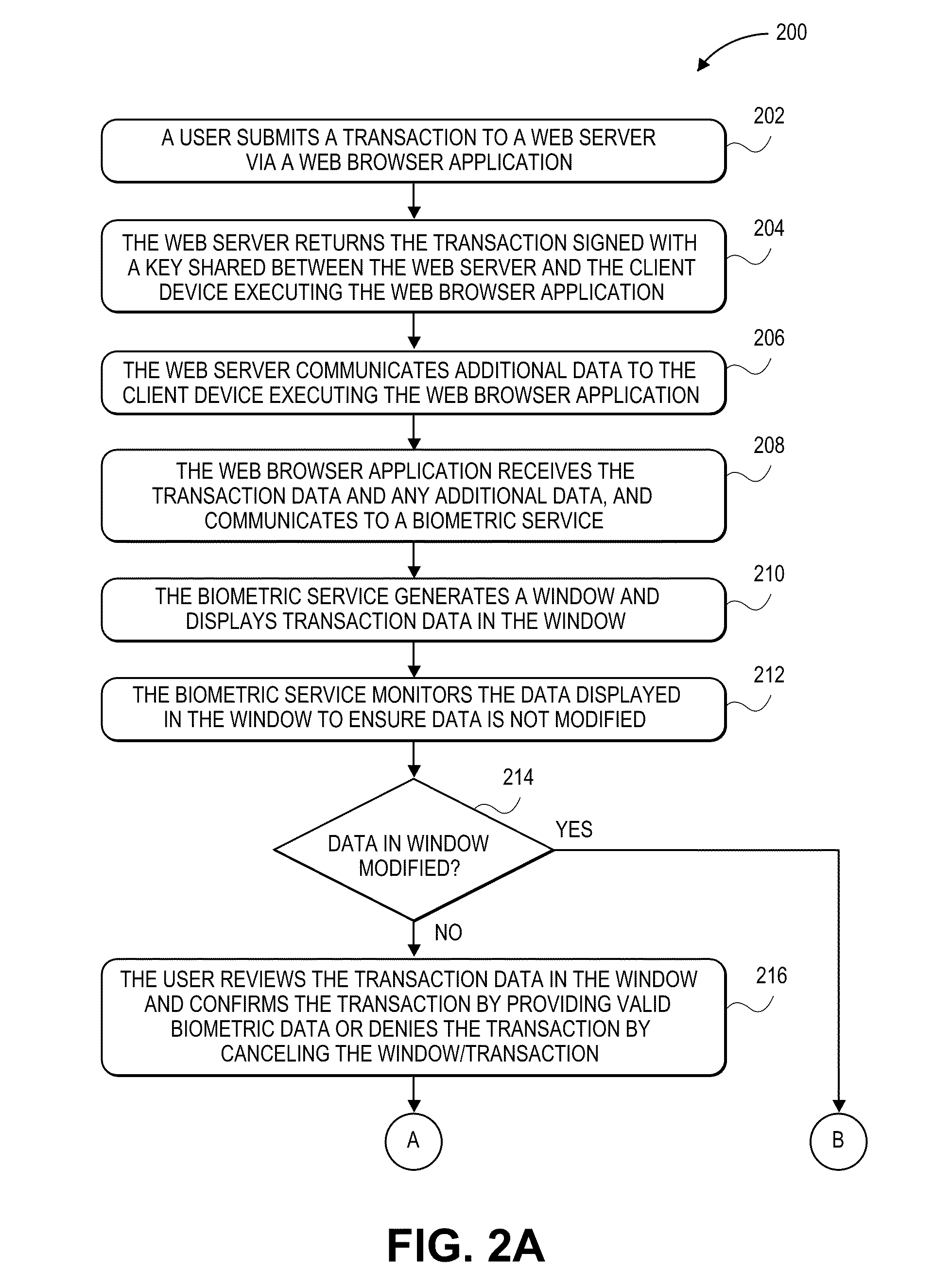
Secure Transaction Systems and Methods using User Authenticating Biometric Information
InactiveUS20110138450A1Digital data processing detailsUser identity/authority verificationBiometric dataWeb browser
A user transaction request is received at a client device. A web browser plug-in communicates the user transaction request to a server that determines whether the user transaction request is a secure transaction. Transaction data is received from the server via the web browser plug-in. If the received transaction data indicates a secure transaction, the user is prompted to provide biometric data from a user using a biometric device and related security protocols. The web browser plug-in then communicates a transaction confirmation to the server.
Owner:SYNAPTICS INC
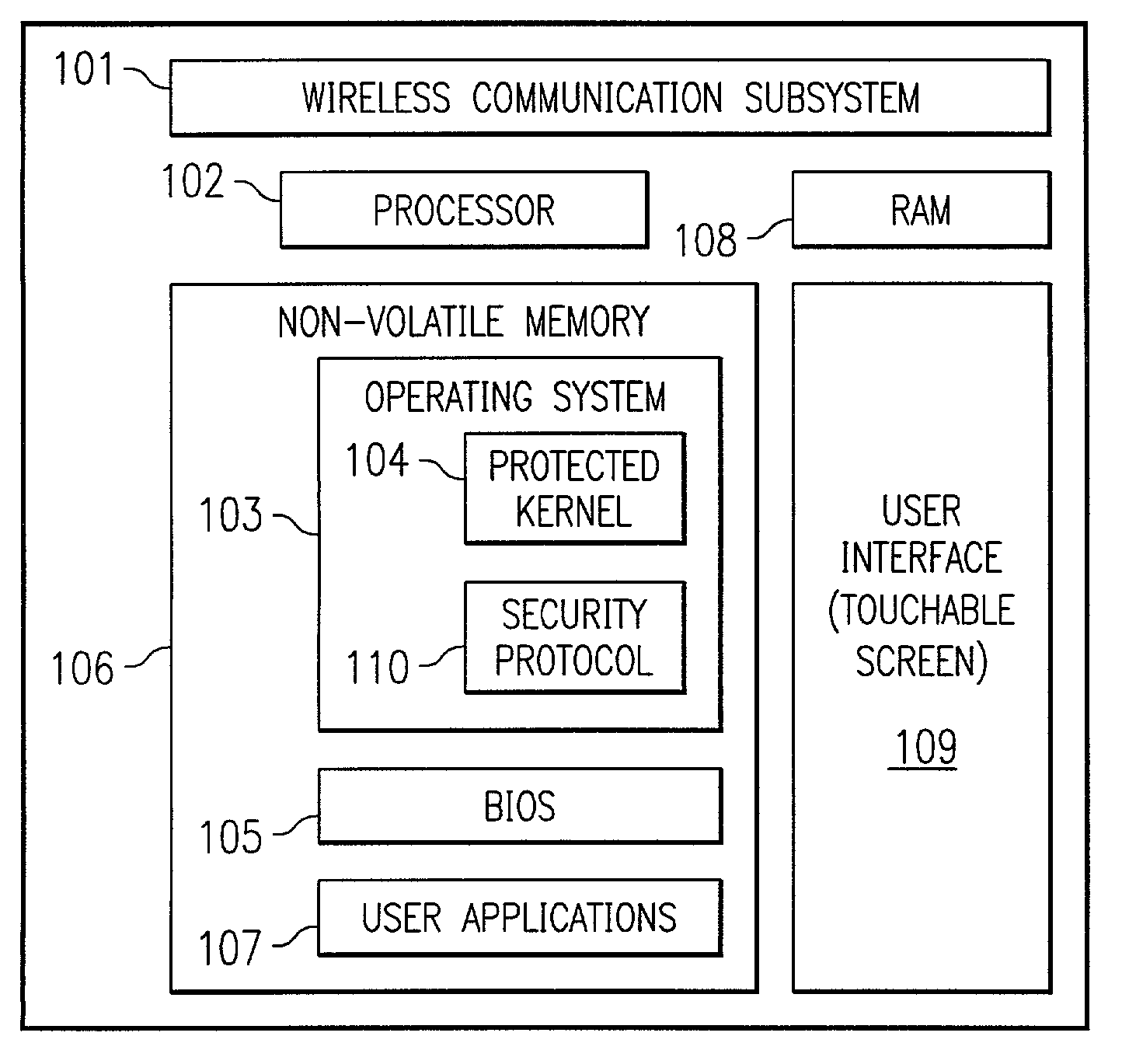
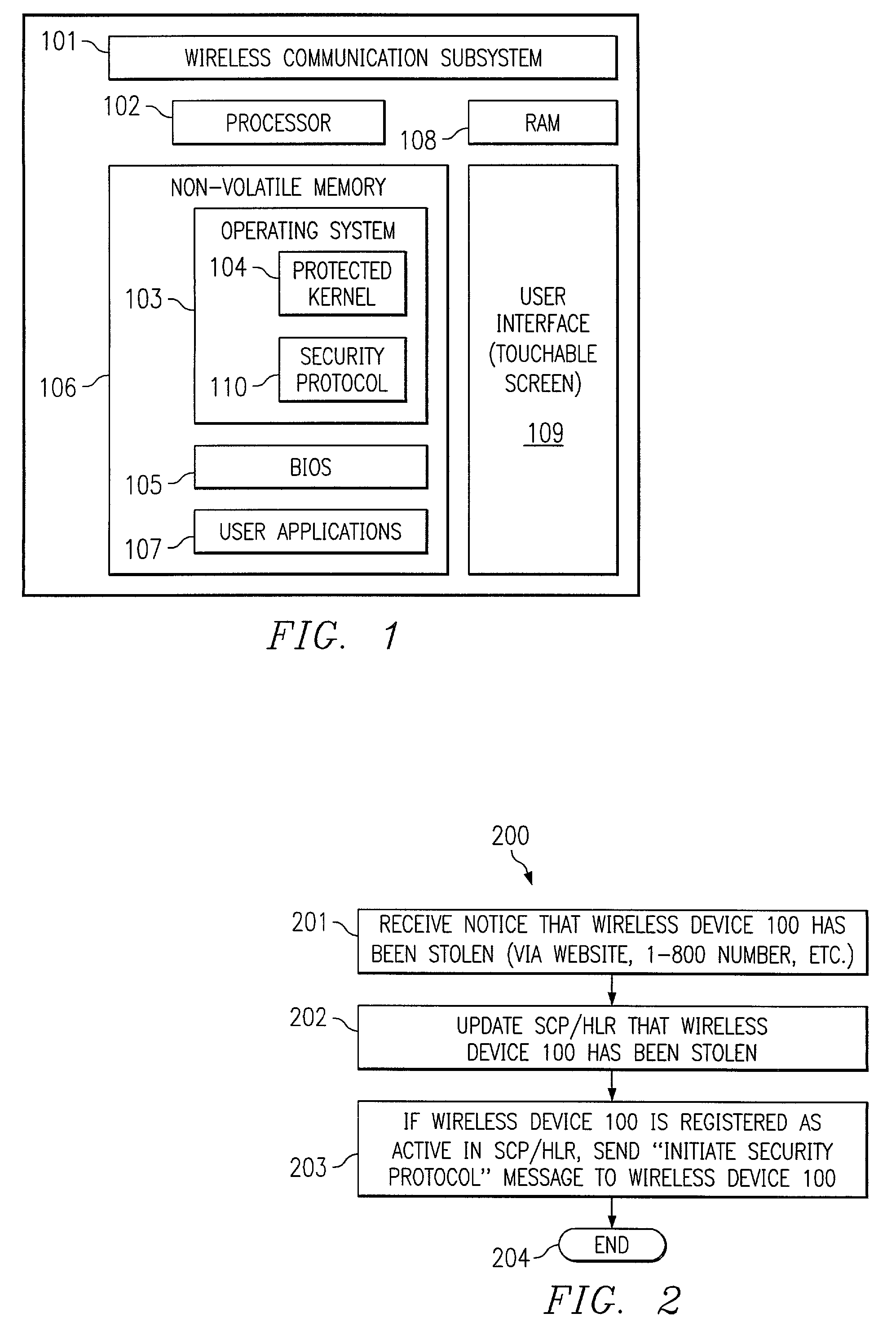
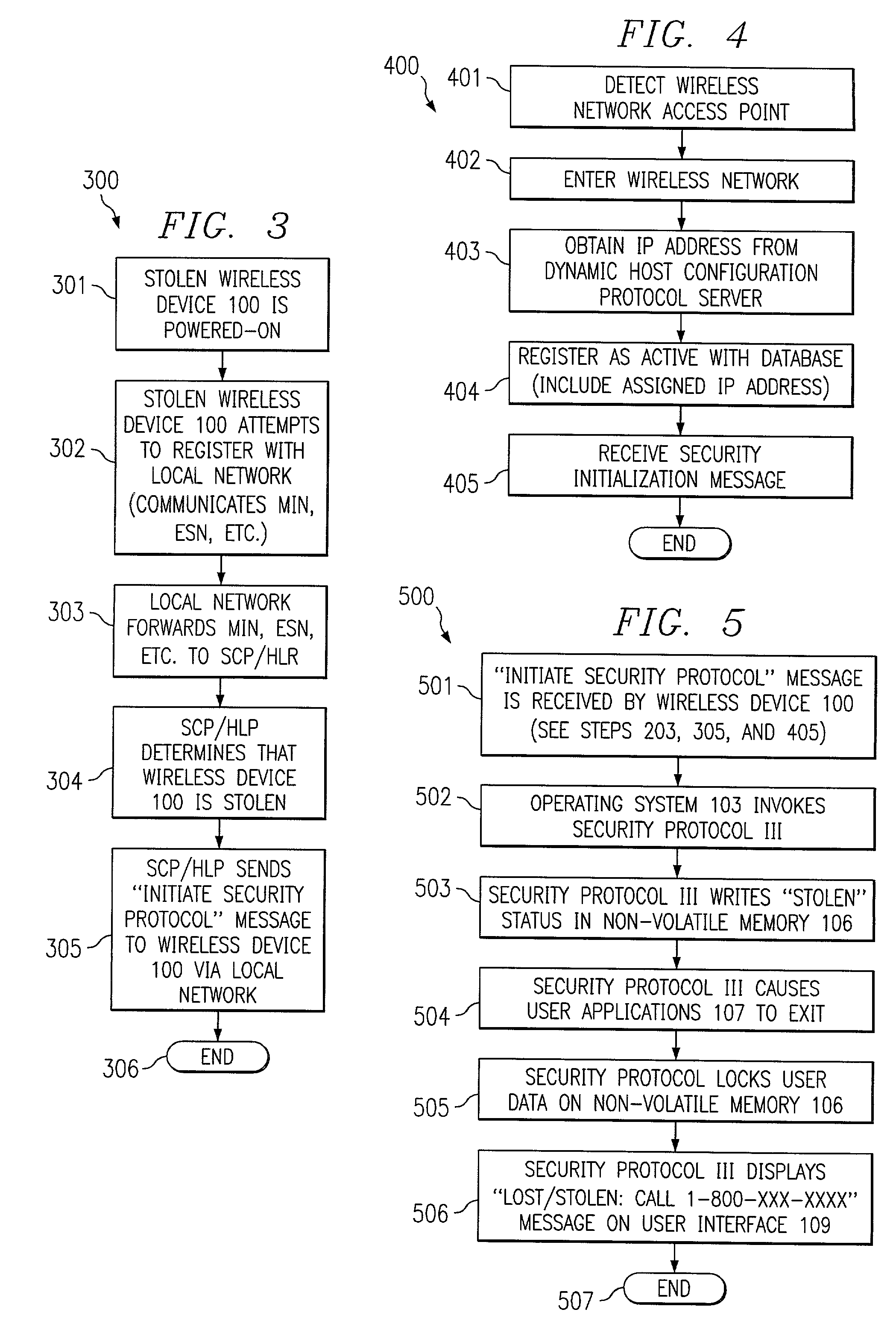
System and method for preventing use of a wireless device
ActiveUS7496957B2Unauthorized useMultiple digital computer combinationsProgram controlComputer hardwareCryptographic protocol
In one embodiment, the present invention is directed to a processor-based device that prevents unauthorized use, comprising a processor for executing software instructions, software instructions defining at least one user application, a wireless communication subsystem that is operable to transmit and receive data utilizing a wireless protocol, and software instructions defining a security protocol process that is operable to prevent execution of the software instructions defining the at least one user application by the processor when a message is received via the wireless communication subsystem, wherein the message indicates that the processor-based device is not in possession of a rightful user.
Owner:QUALCOMM INC
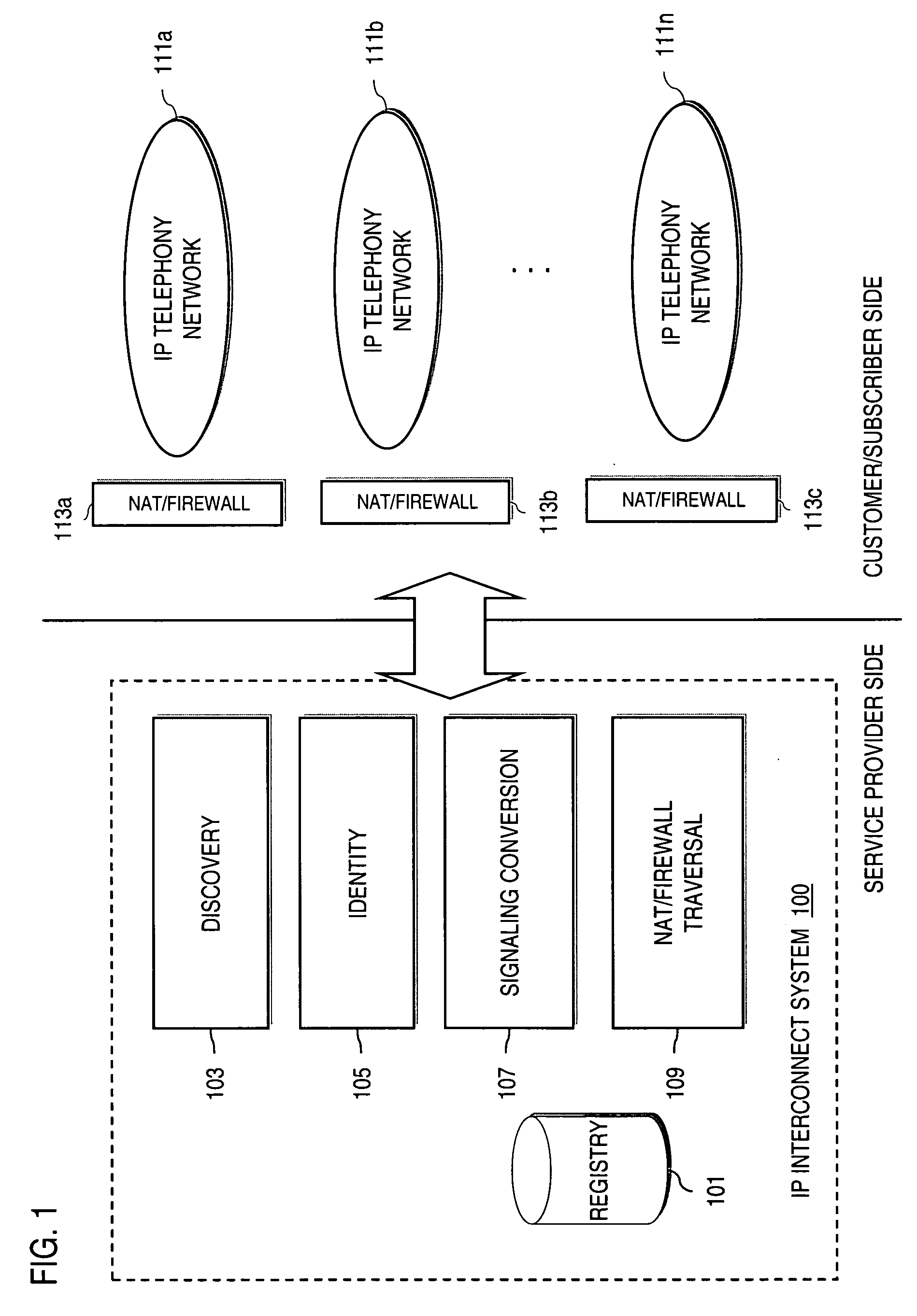
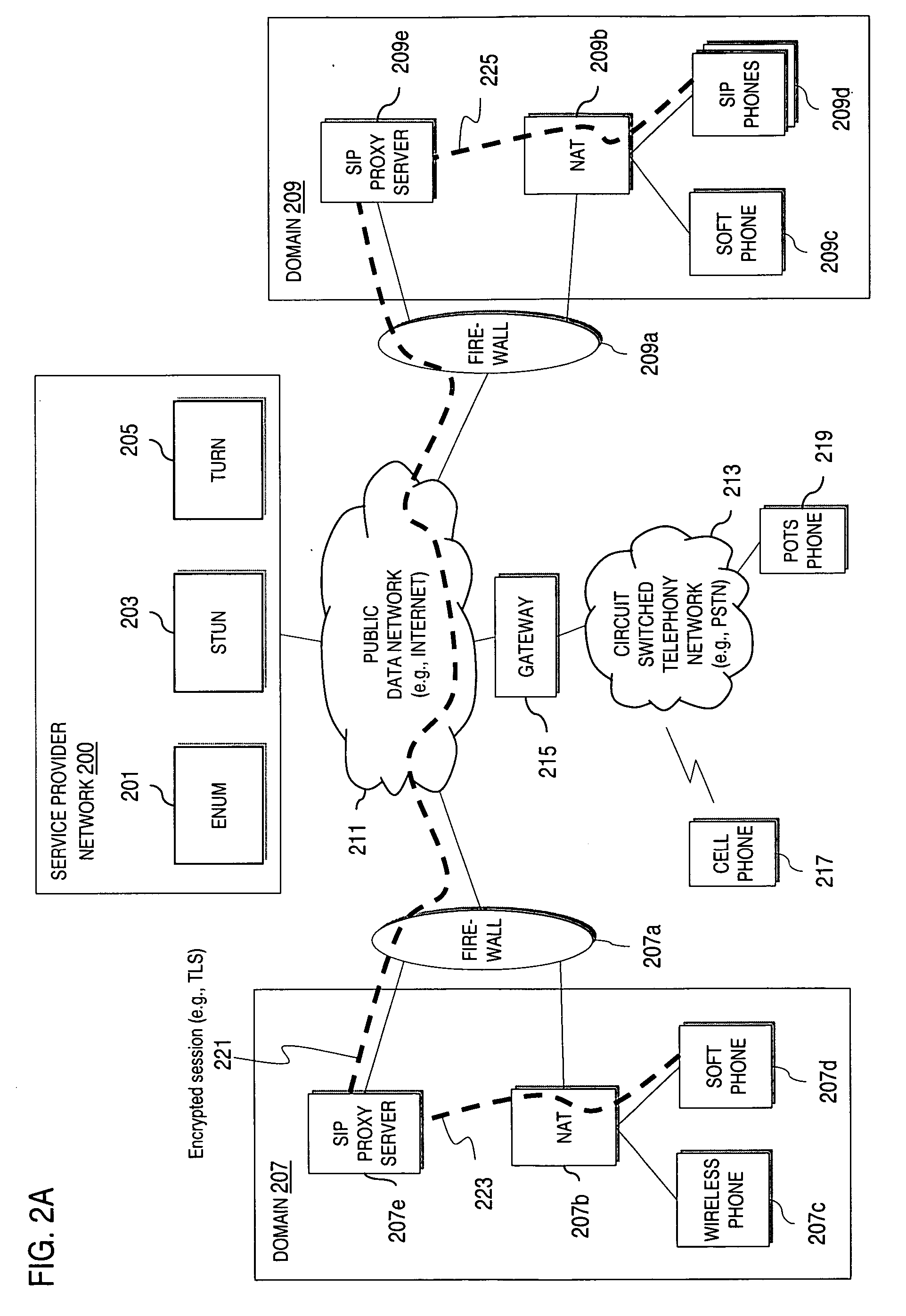
Method and system for providing secure communications between proxy servers in support of interdomain traversal
ActiveUS20070019622A1Time-division multiplexData switching by path configurationSecure communicationService provision
An approach provides interdomain traversal to support packetized voice transmissions. A request is received and specifies a directory number for establishing a communication session from a first endpoint to a second endpoint. The first endpoint is behind a first network address translator of a first domain, and the second endpoint is within a second domain. A service provider network is accessed to determine a network address for communicating with the second endpoint based on the directory number, to determine existence of a second network address translator within the second domain, and to establish, if the network address can be determined, a media path between the first endpoint and the second endpoint based on the network address to support the communication session. An encrypted session is established with a proxy server according to a cryptographic protocol to support the media path. The proxy server resides within the second domain.
Owner:VERIZON PATENT & LICENSING INC
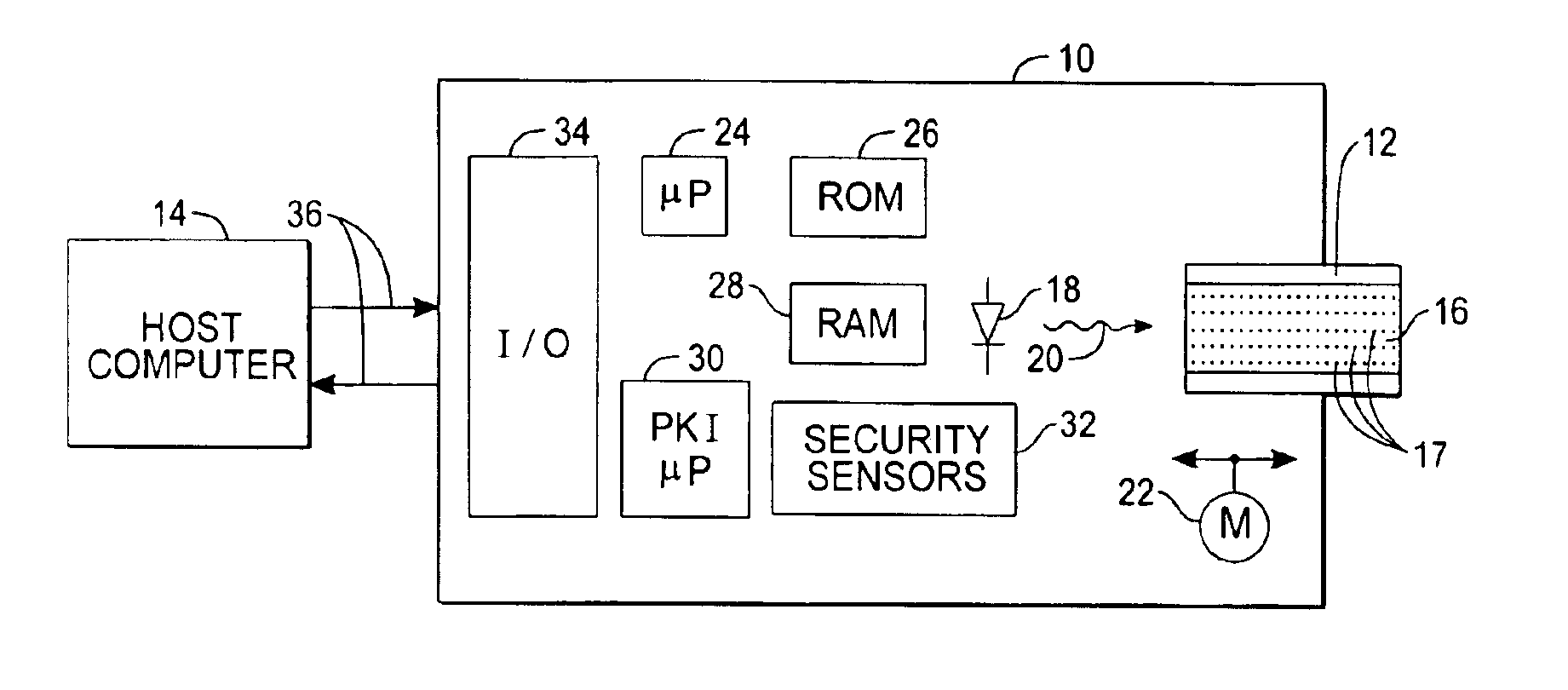
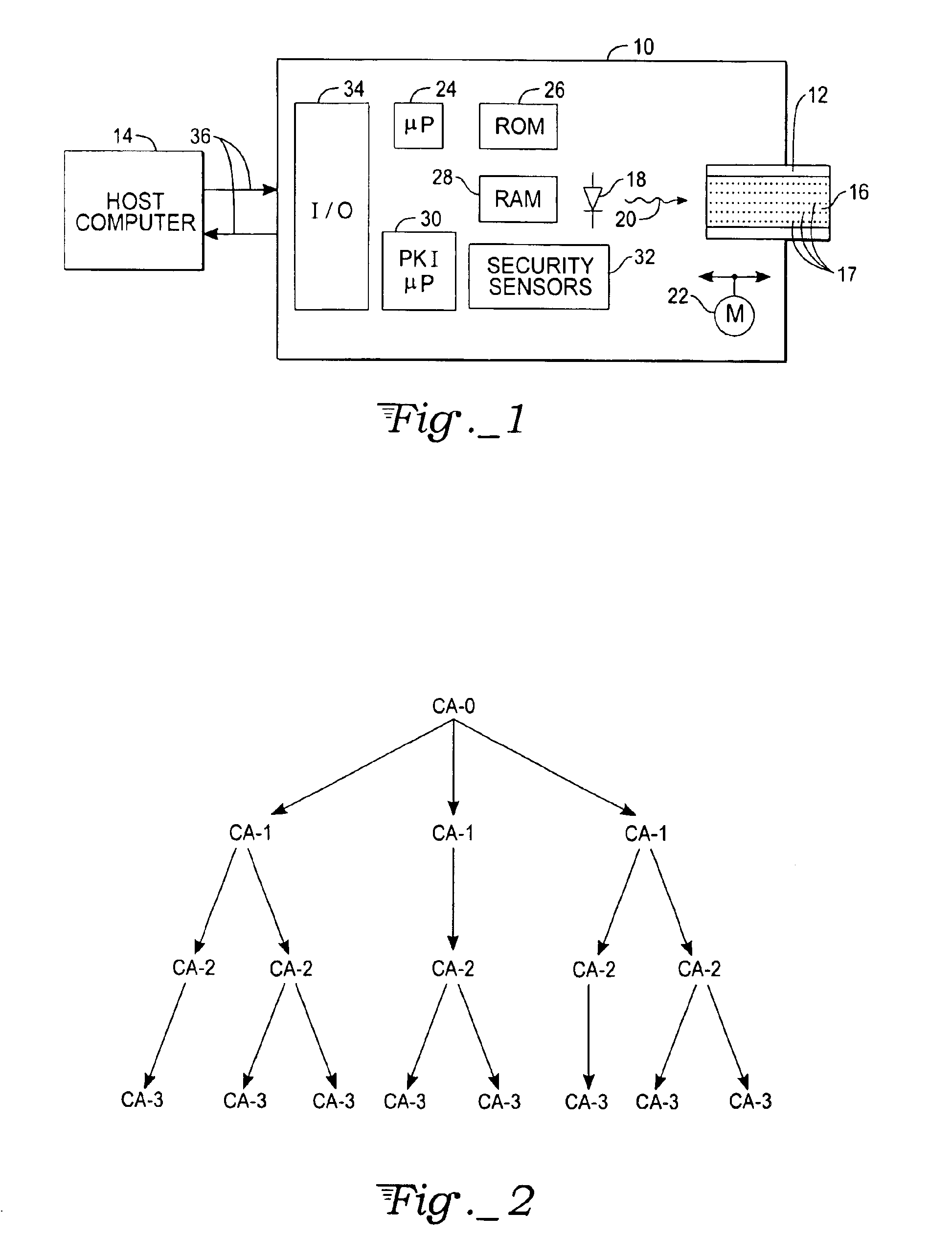
Secure transactions with passive storage media
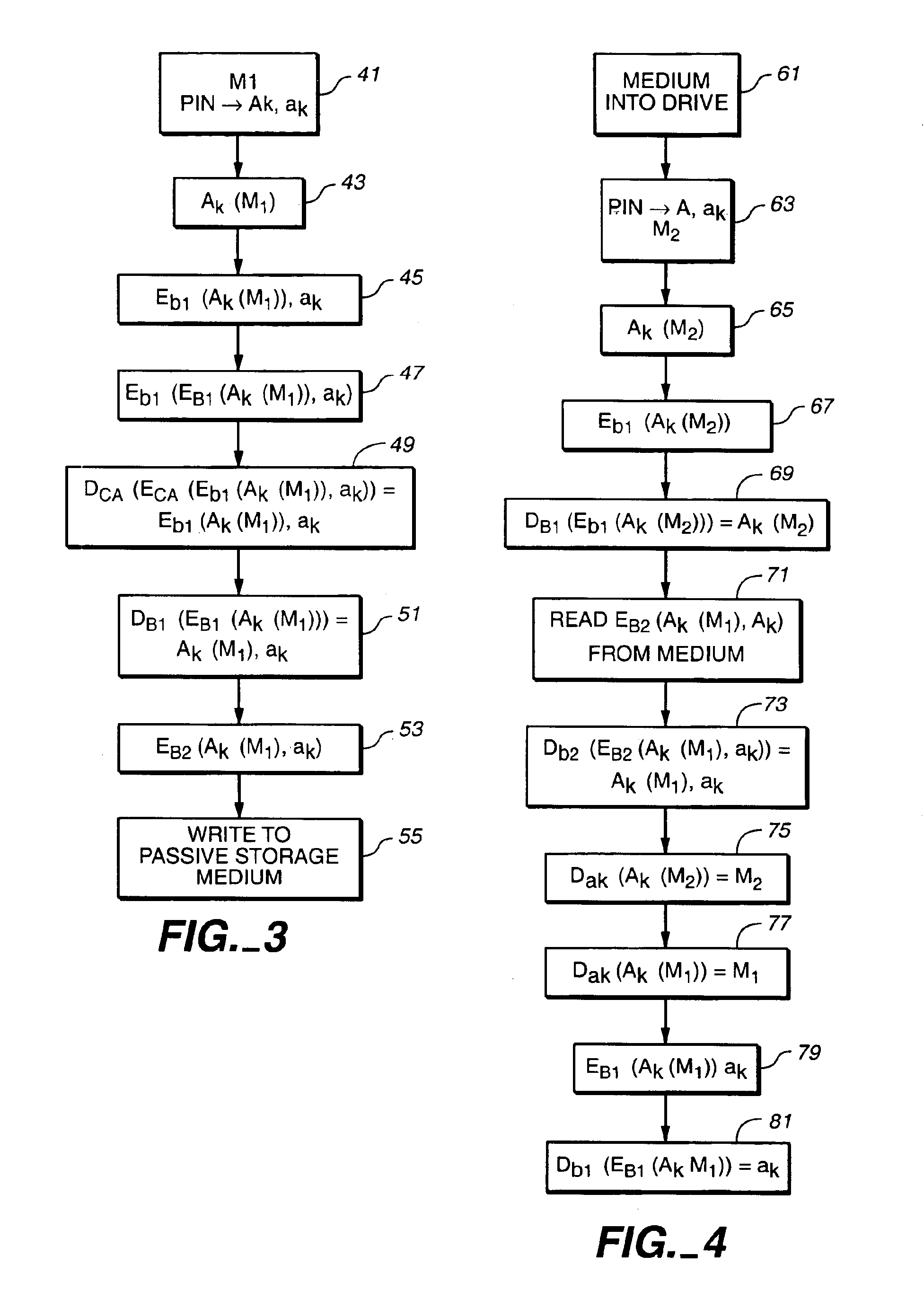
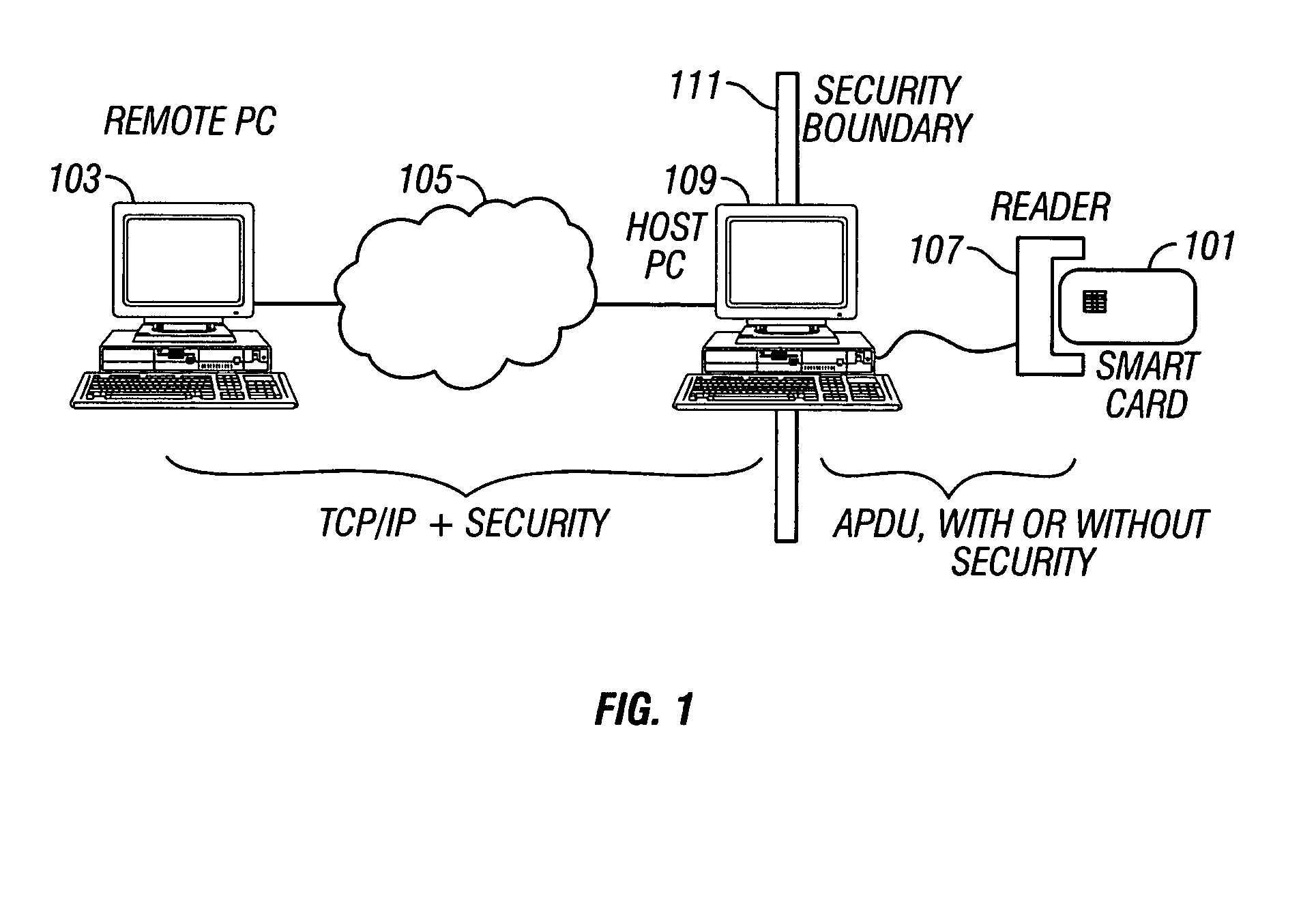
InactiveUS6871278B1User identity/authority verificationUnauthorized memory use protectionBiometric dataPersonal identification number
A transaction system for use with passive data storage media, such as optical memory cards, uses secure protocols involving digital certificates for communication between a read / write drive and the medium and also for communication between the drive and a host computer. The drive is physically secured with tamper resistant features and stores cryptographic keys and firmware for executing the secure protocols. All messages (data or commands) passed between the drive and the passive medium or host computer not only are encrypted but also include at least one digital certificate for authenticating the message. Typically, asymmetric (public-private key) encryption is used and keys may be derived from an authorized user's password, personal identification number, or biometric data. The drive includes sensors to detect any attempted intrusions and a control unit that will destroy the critical information (keys and protocol code) in response to a detected intrusion. The keys and protocols stored in a drive can themselves be changed through appropriate use of a secure protocol involving digital certificates.
Owner:ASSA ABLOY AB
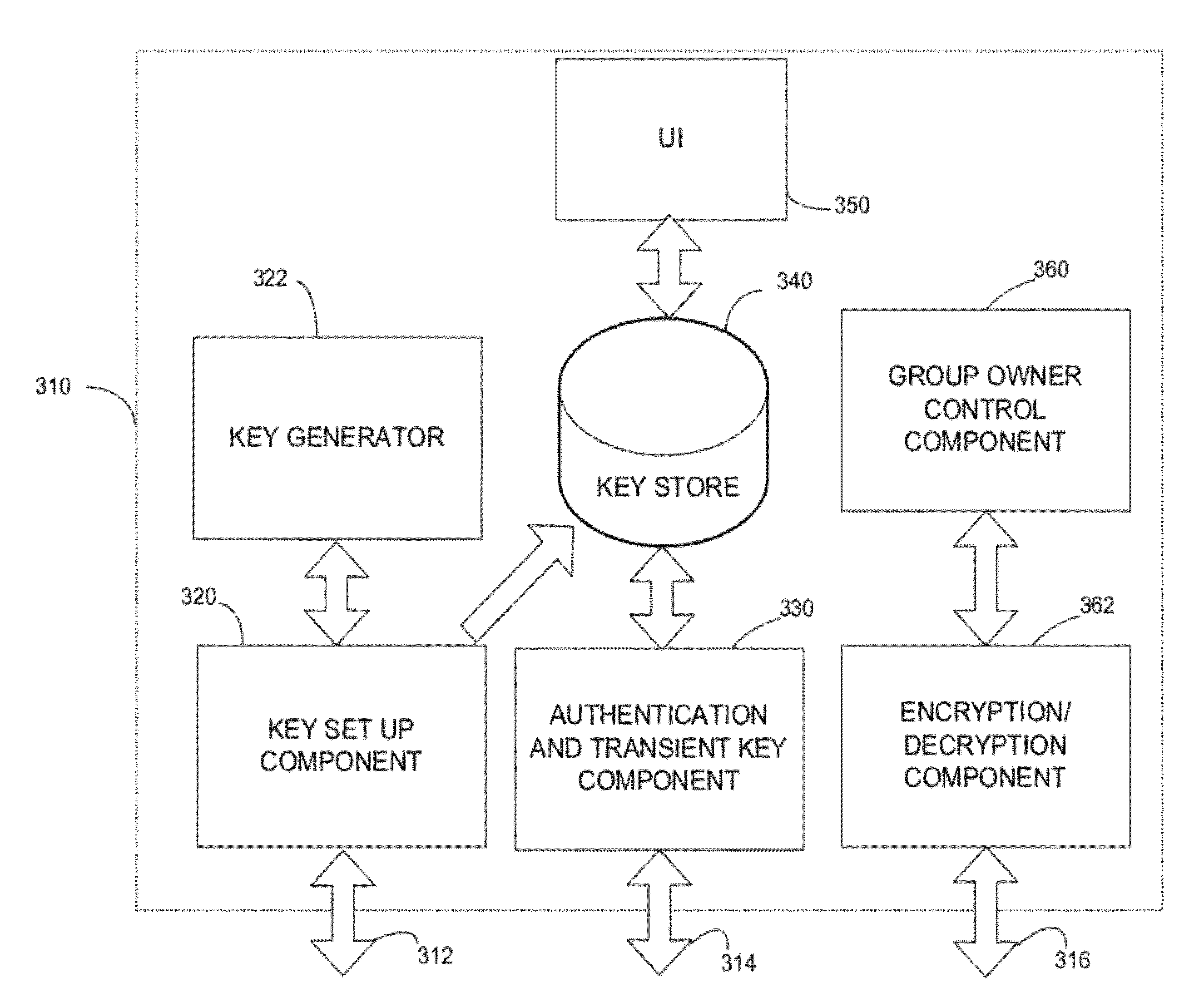
Secure protocol for peer-to-peer network
ActiveUS20120155643A1Reduce the burden onMultiple keys/algorithms usageNetwork topologiesComputer hardwareCryptographic protocol
A wireless computing device operating as a controller of a peer-to-peer group configured to generate unique master keys for each device joining the group. The wireless computing device may use the unique master keys to selectively remove remote devices from the group such that the remote device cannot later rejoin the group. Other remote devices, each possessing a master key that remains valid, can disconnect from the group and later reconnect to the group without express user action. To support such behavior, the wireless device may provide a user interface through which a user may manage connected remote devices by providing commands to selectively disconnect or remove remote devices from the group.
Owner:MICROSOFT TECH LICENSING LLC
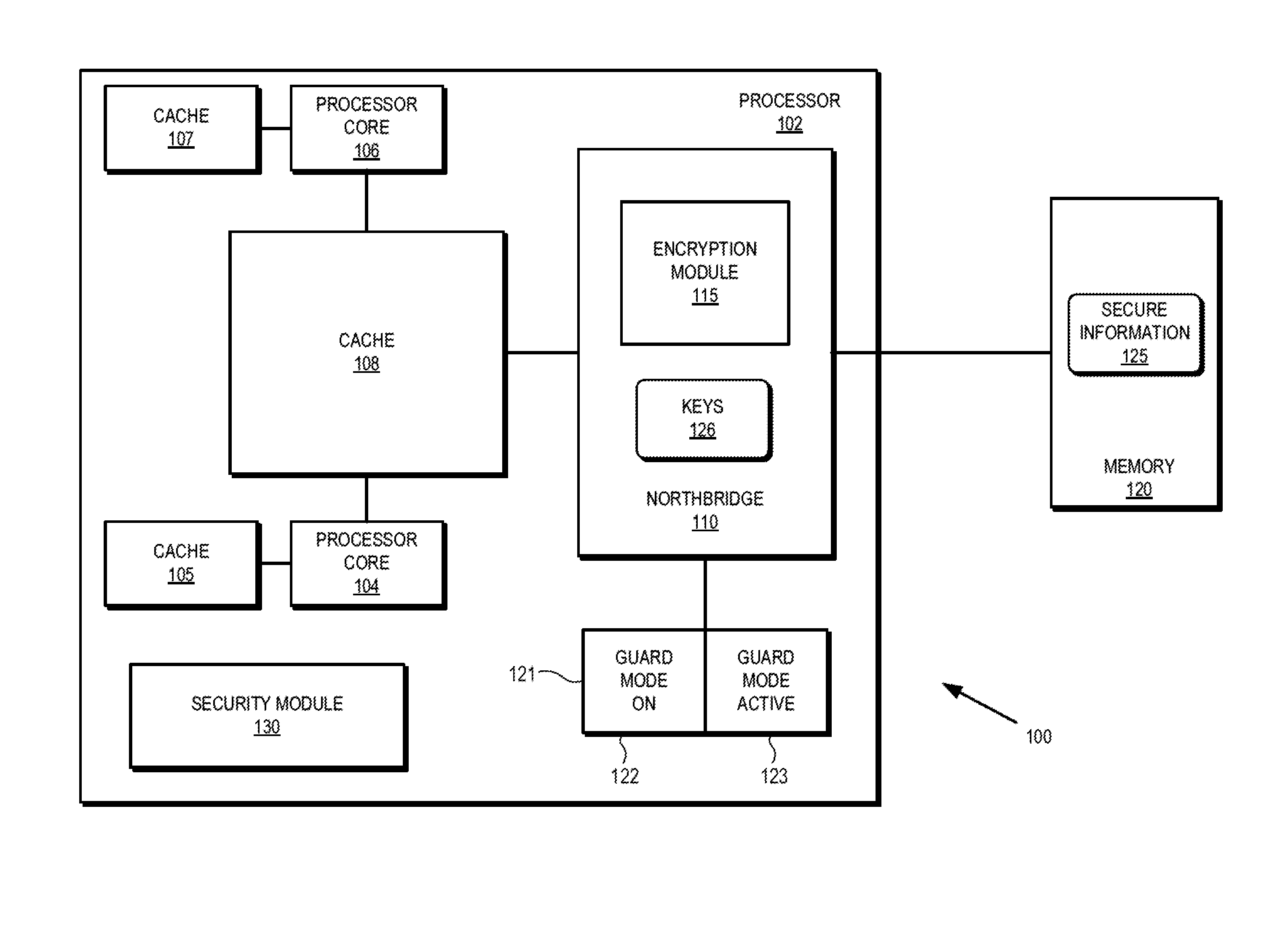
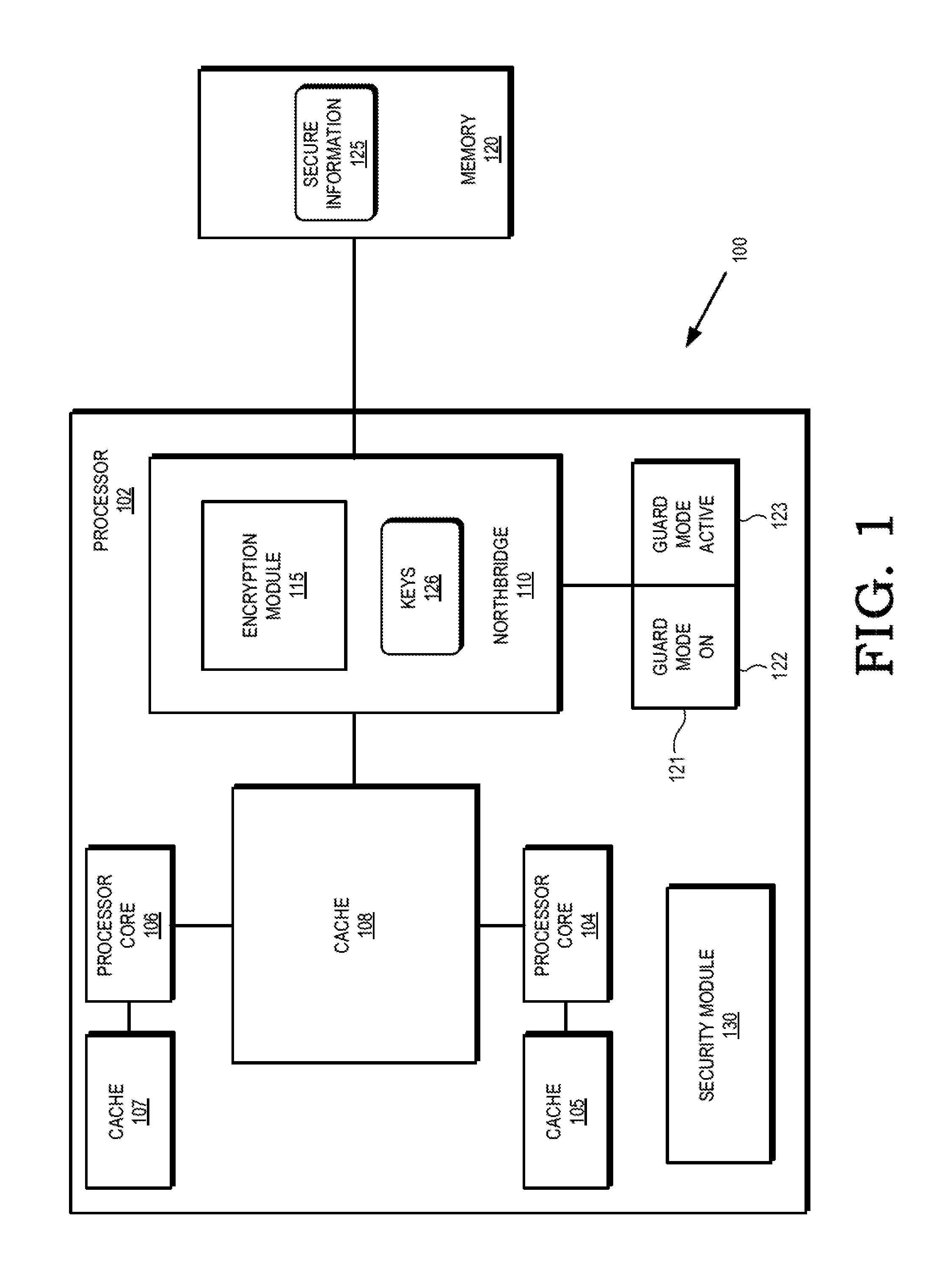
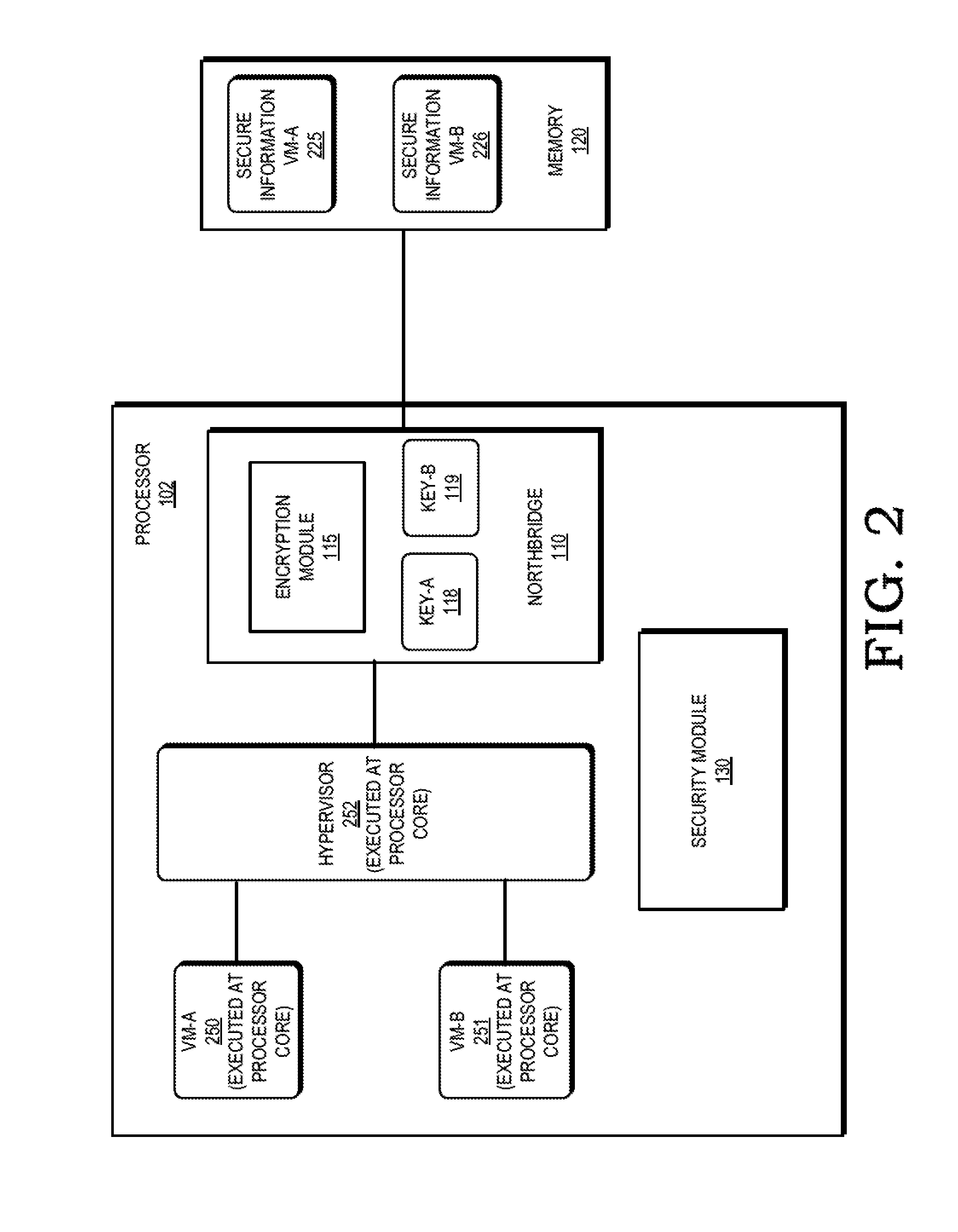
Cryptographic protection of information in a processing system
ActiveUS20150248357A1Memory architecture accessing/allocationUnauthorized memory use protectionComputer hardwareDirect memory access
A processor employs a hardware encryption module in the processor's memory access path to cryptographically isolate secure information. In some embodiments, the encryption module is located at a memory controller (e.g. northbridge) of the processor, and each memory access provided to the memory controller indicates whether the access is a secure memory access, indicating the data associated with the memory access is designated for cryptographic protection, or a non-secure memory access. For secure memory accesses, the encryption module performs encryption (for write accesses) or decryption (for read accesses) of the data associated with the memory access.
Owner:ADVANCED MICRO DEVICES INC
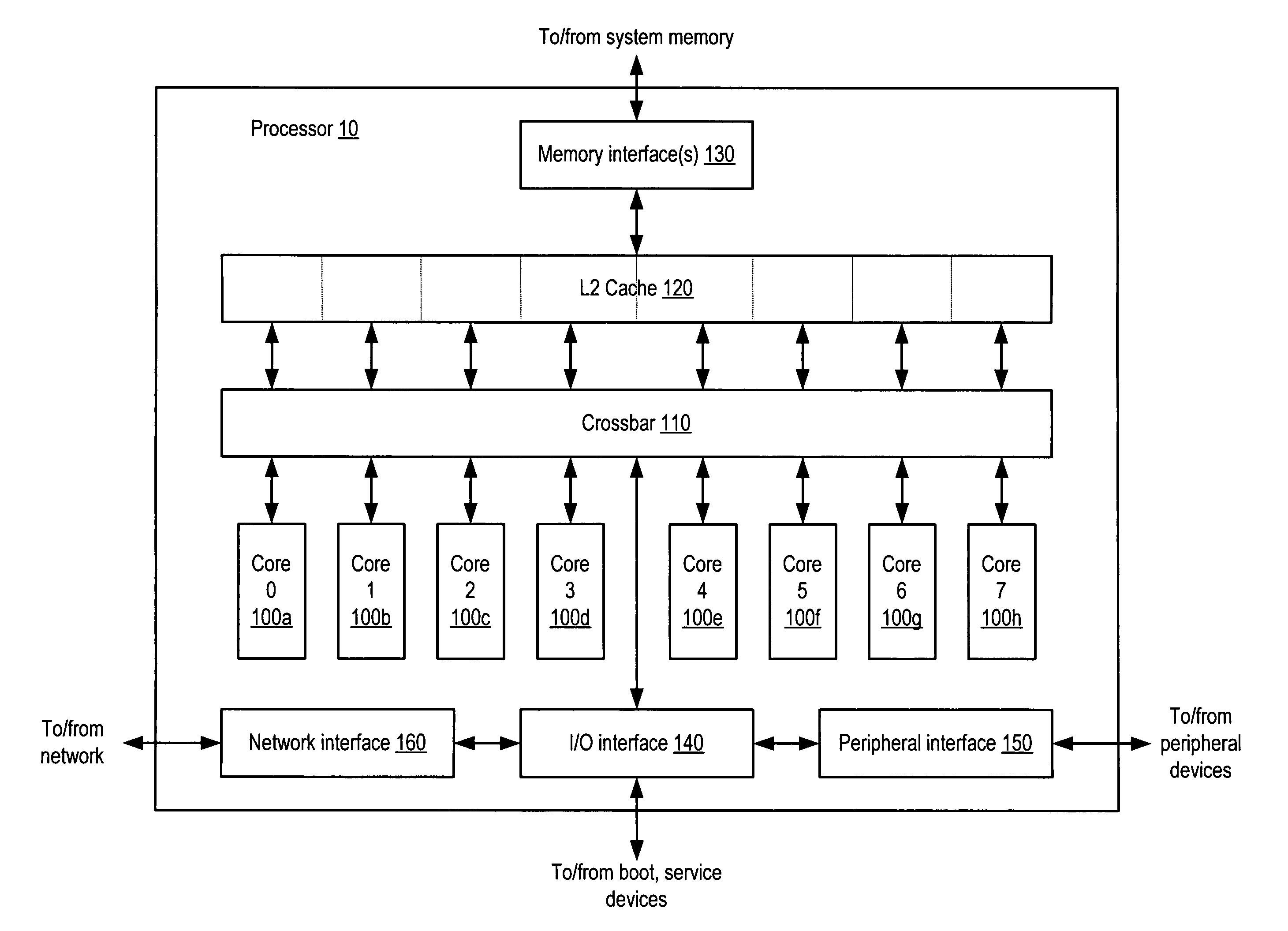
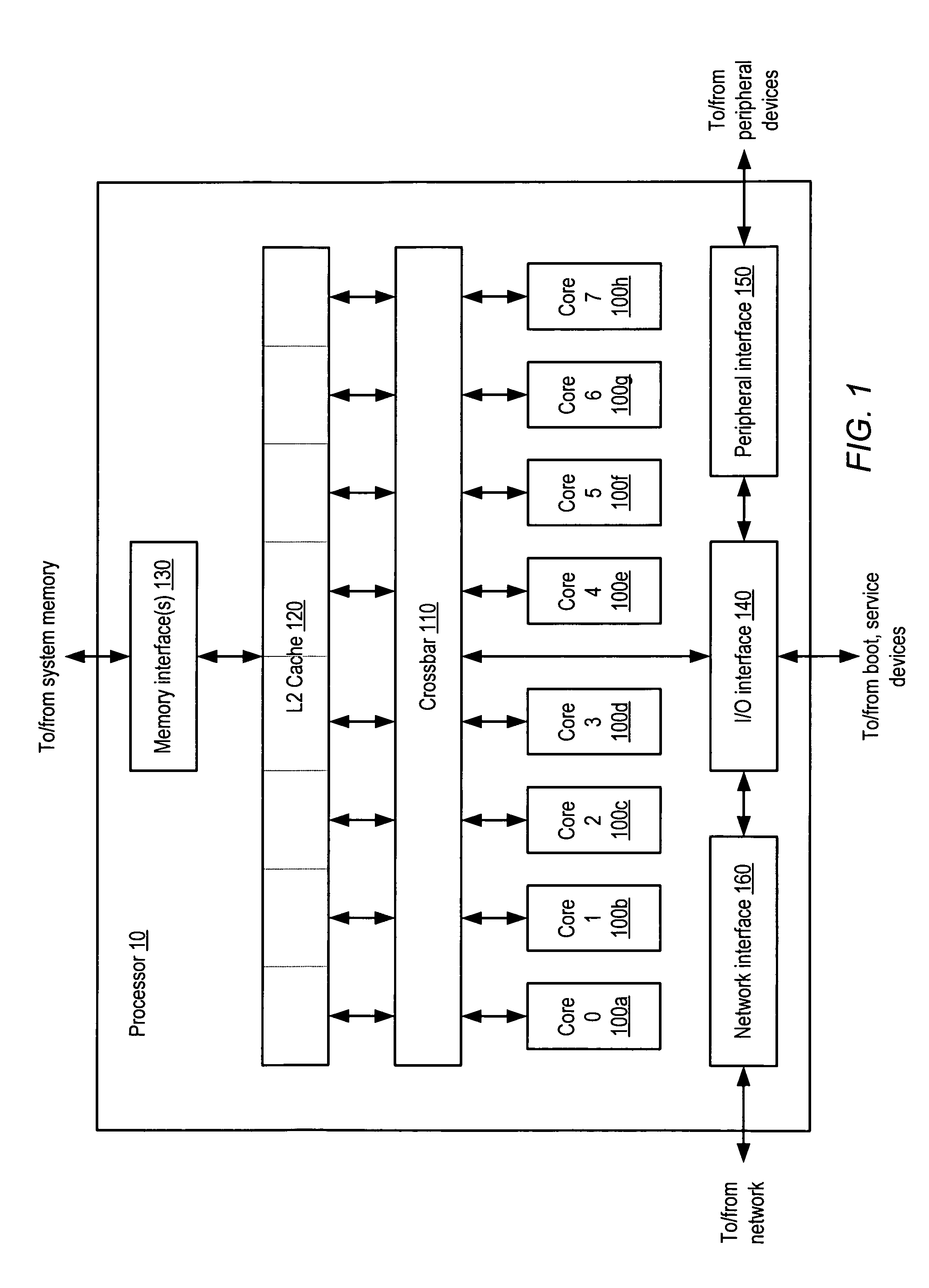
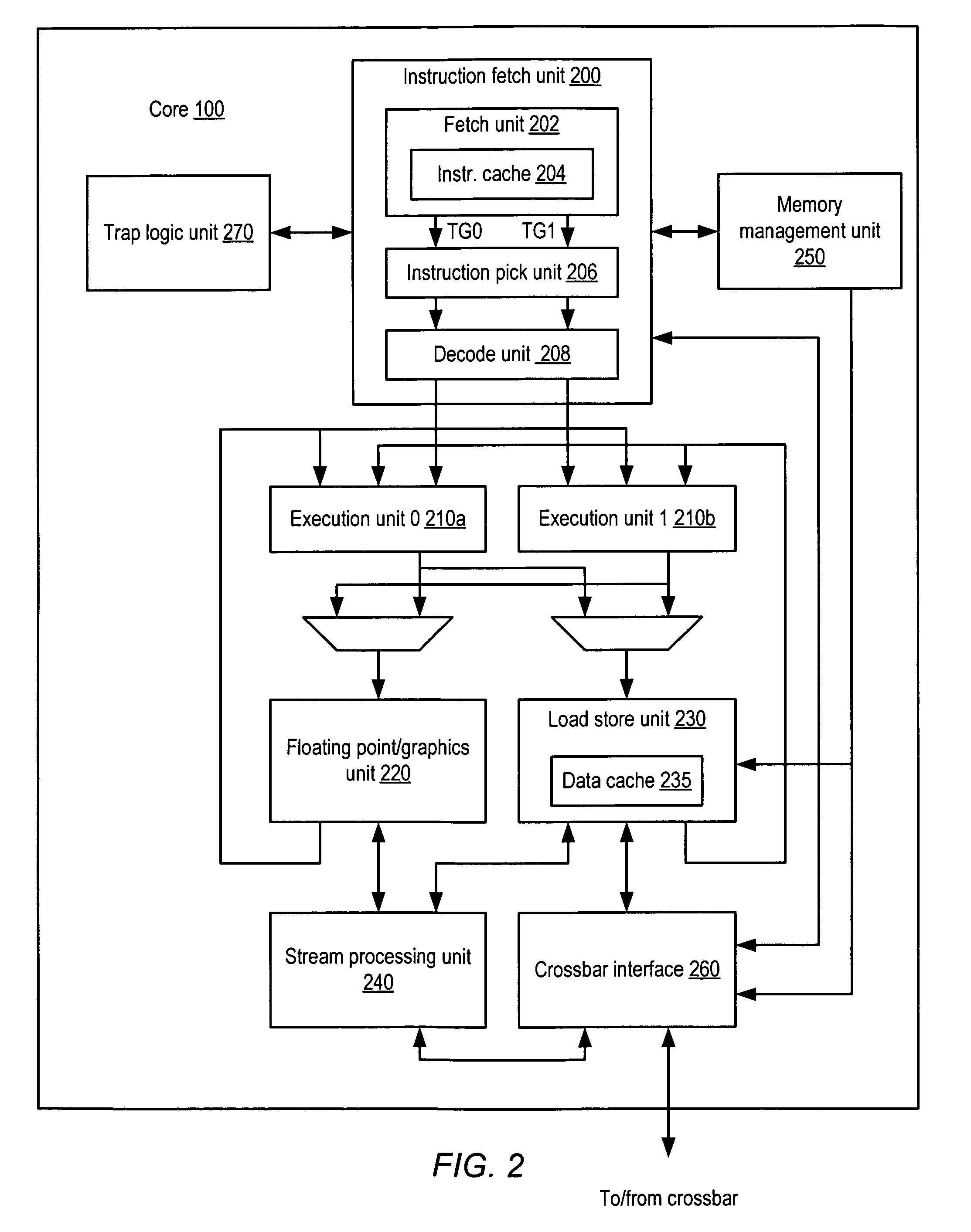
Processor including general-purpose and cryptographic functionality in which cryptographic operations are visible to user-specified software
ActiveUS7620821B1Memory loss protectionDigital data processing detailsGeneral purposeComputer hardware
A processor including general-purpose and cryptographic functionality, in which cryptographic operations are visible to user-specified software. According to one embodiment, a processor may include instruction execution logic configured to execute instructions specified by a user of the processor, where the instructions are compliant with a general-purpose instruction set architecture. The processor may further include a cryptographic functional unit configured to implement a plurality of cryptographic operations, and further configured to process the cryptographic operations independently of the instruction execution logic. A subset of the instructions may be executable to cause individual ones of the cryptographic operations to be processed by the cryptographic functional unit.
Owner:ORACLE INT CORP
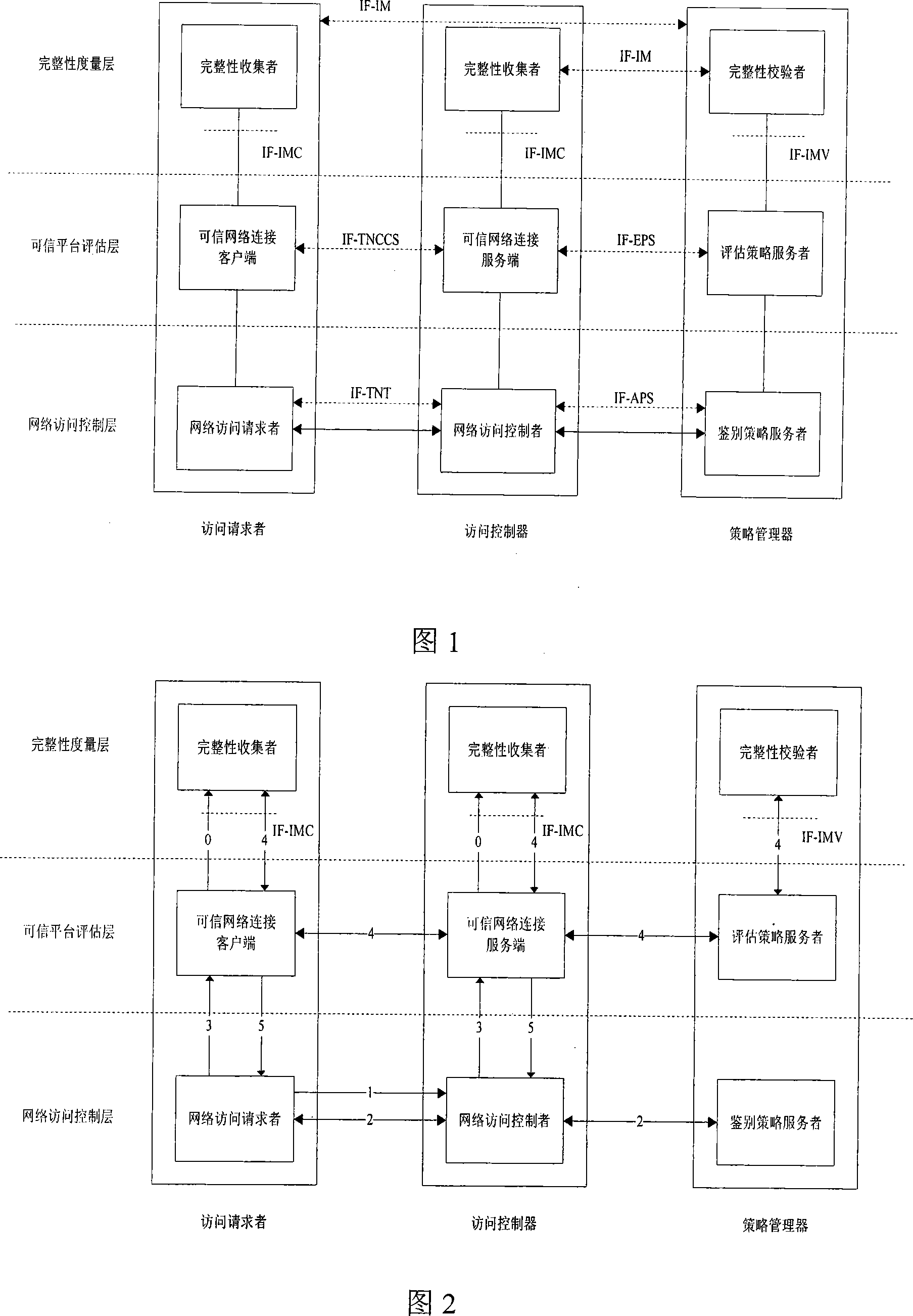
Reliable network access framework
InactiveCN101136928AEasy to manage centrallyImprove distributionData switching by path configurationNetwork connectionsIntegrity assessmentExtensibility
Frame of the invention includes three entities: accessing requestor, accessing controller, and strategy manager. The strategy manager manages the accessing requestor and the accessing controller as well as implements bidirectional user ID authentication between them, and evaluates integrality of platform. Based on decision made from the strategy manager, the accessing requestor and the accessing controller control local ports. Before terminal is connected to network, trusty network connection architecture (TNCA) measures state of platform. Based on secure protocol of trusty third party, the invention implements the said authentication and evaluation of platform so as to guarantee security of TNCA. Introducing strategy manager simplifies key management of the architecture, raises extensibility of the architecture. Features are: higher security for evaluating integrality of platform, centralized verifying integrality, and higher universality.
Owner:BEIJING UNIV OF TECH
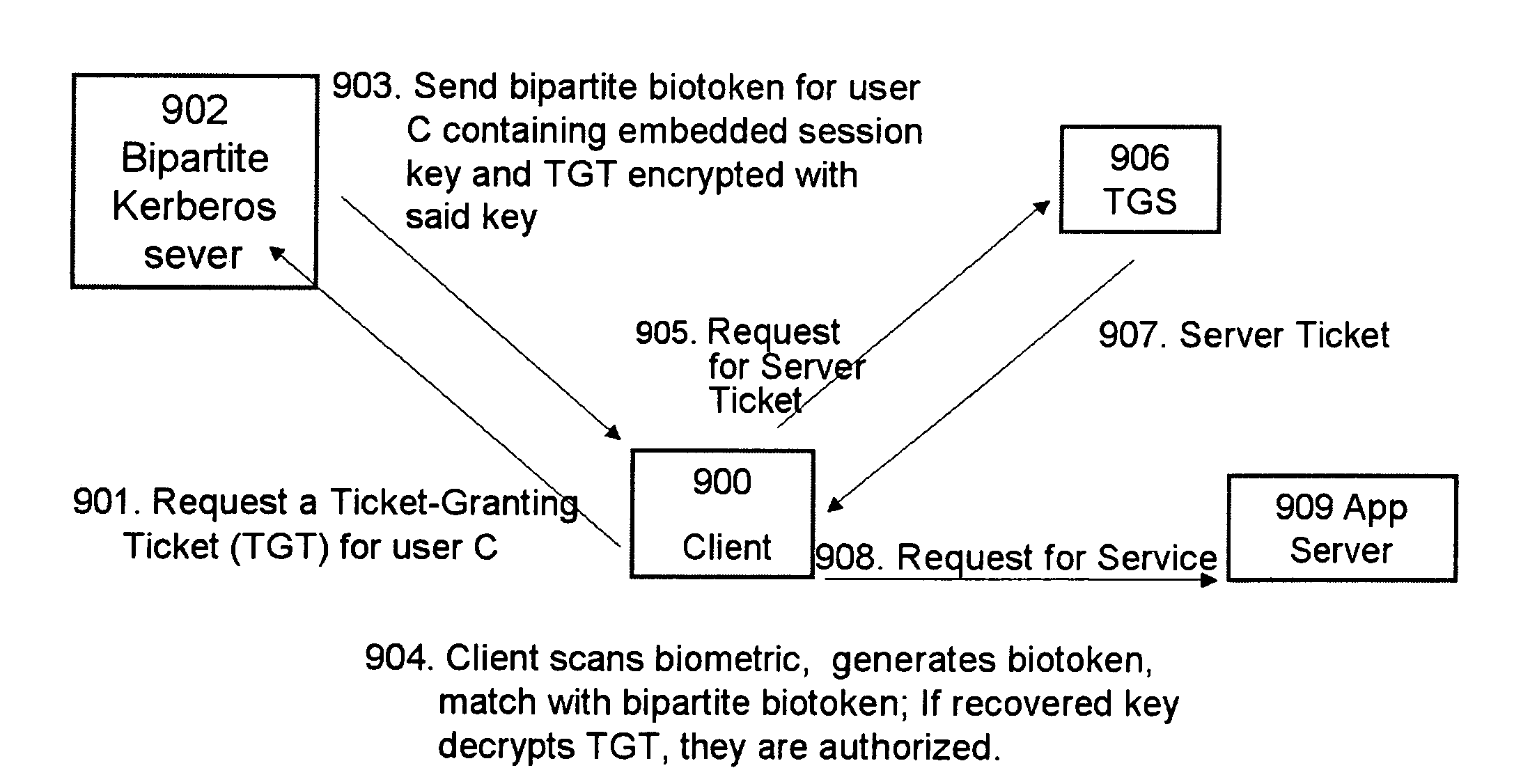
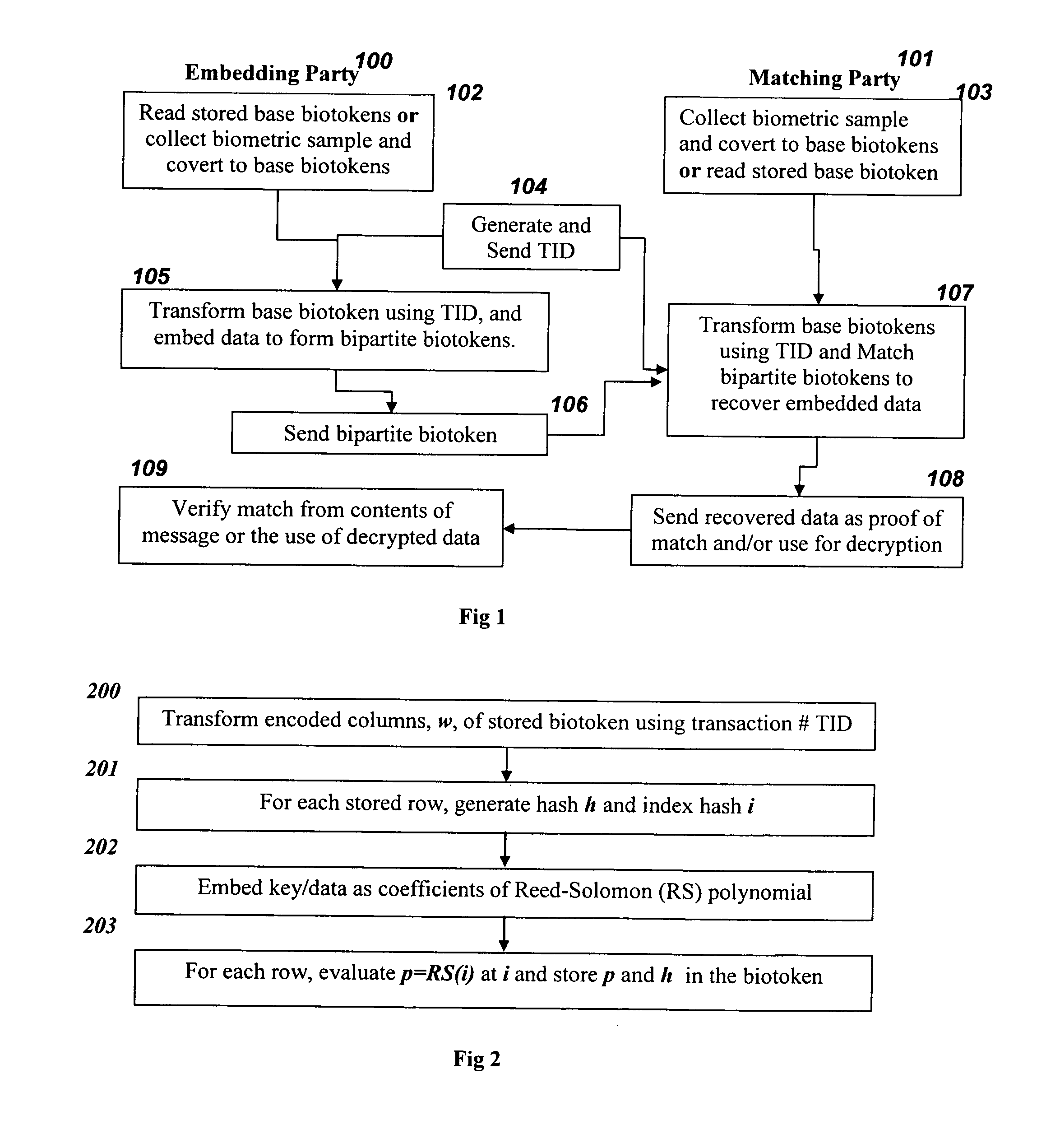
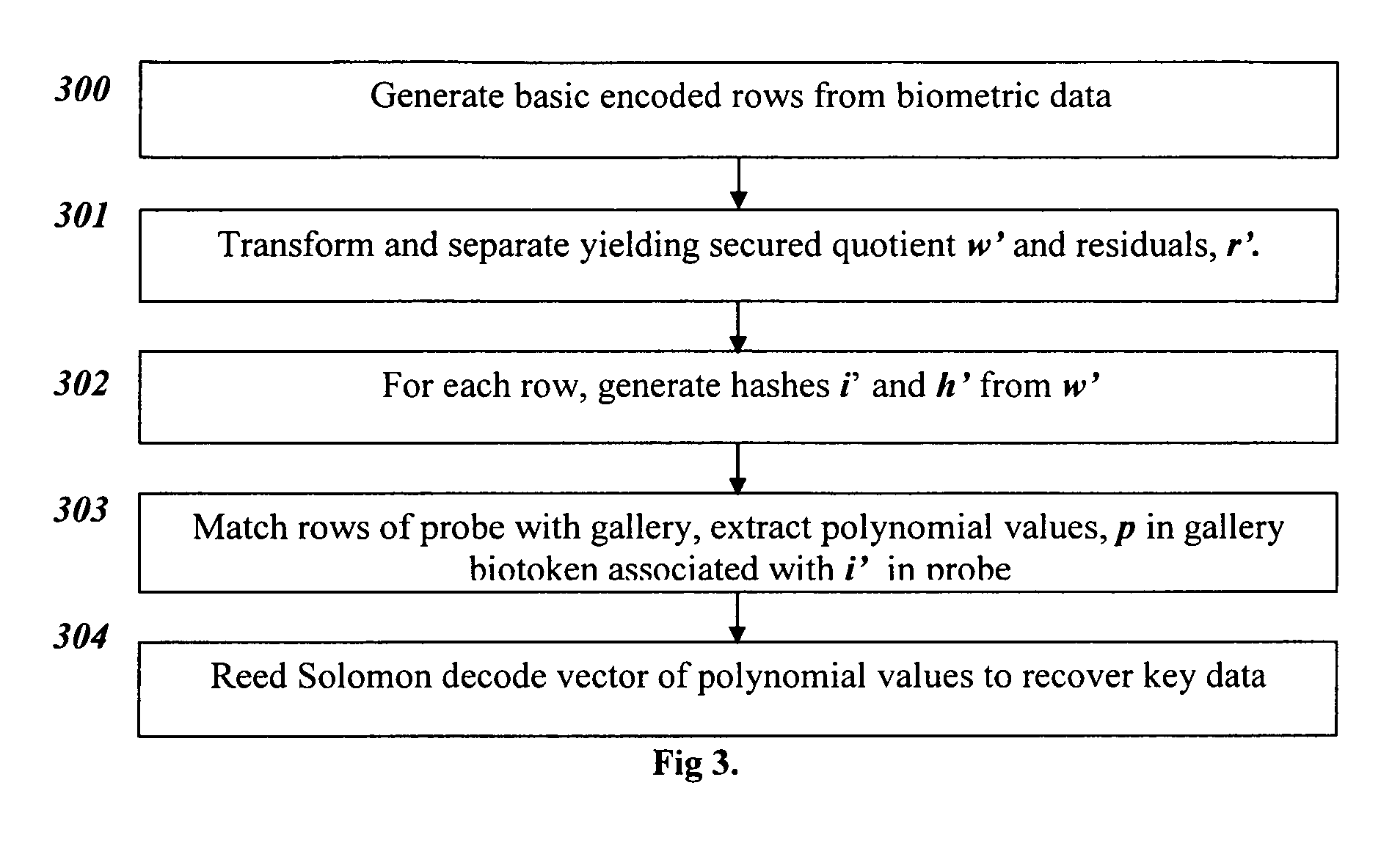
Bio-Cryptograhpy : Secure cryptographic protocols with bipartite biotokens
ActiveUS20090271634A1Improve securityEasy to solveUser identity/authority verificationDigital data authenticationBiotechnologyCryptographic protocol
Techniques, systems and methods are described relating to combining biometric and cryptographic techniques to support securely embedding data within a token and subsequent biometrically-enabled recovery of said data. Various transformation approaches are described that provide a secure means for transforming a stored or live, secure biometric-based identity token, embedding data into such tokens and biometric-based matching to both verify the user's identity and recover the embedded data. Security enhancements to a range of existing protocols are described using the techniques. Systems using novel protocols based on these techniques are described
Owner:UNIV OF COLORADO THE REGENTS OF +1
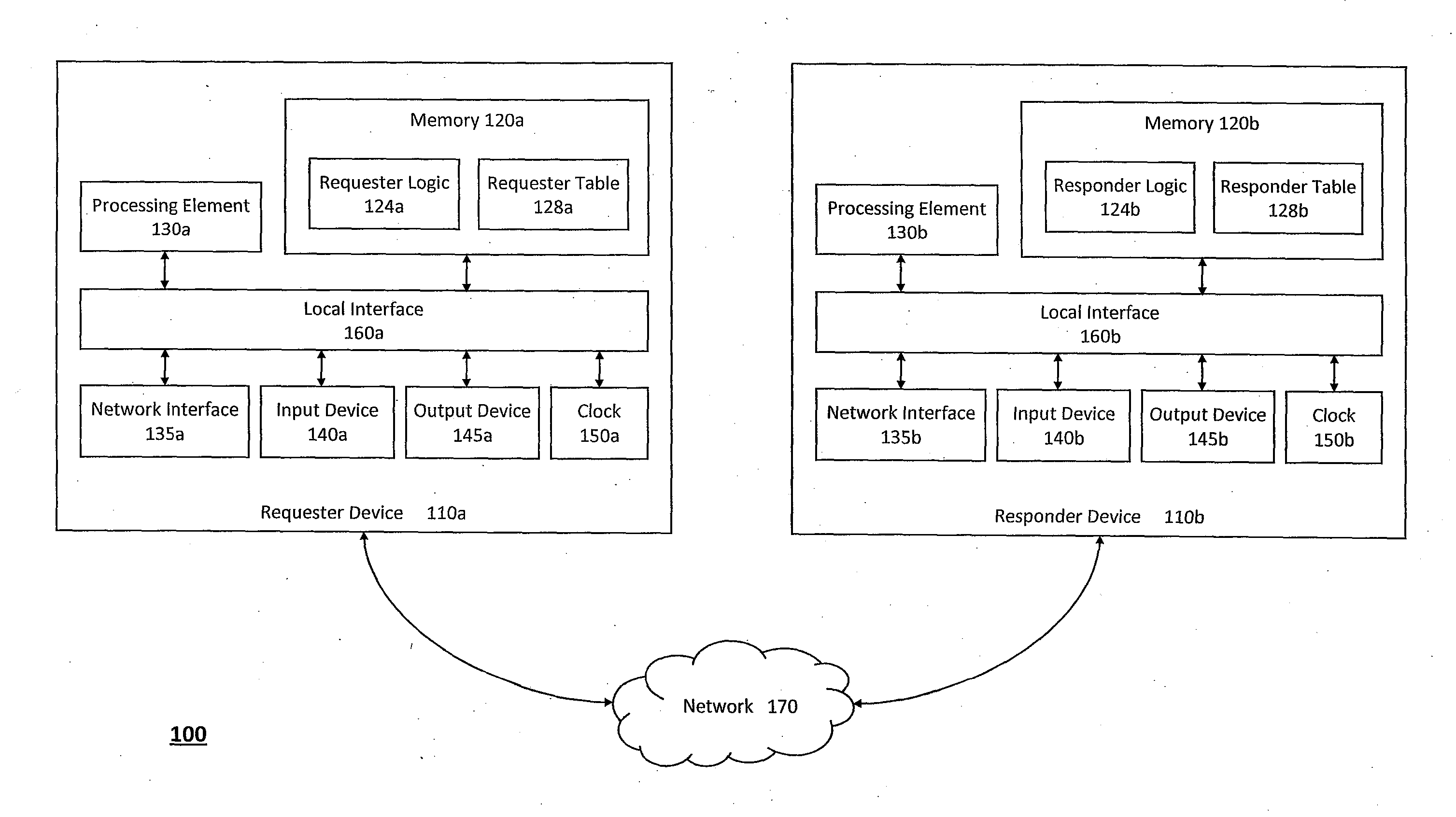
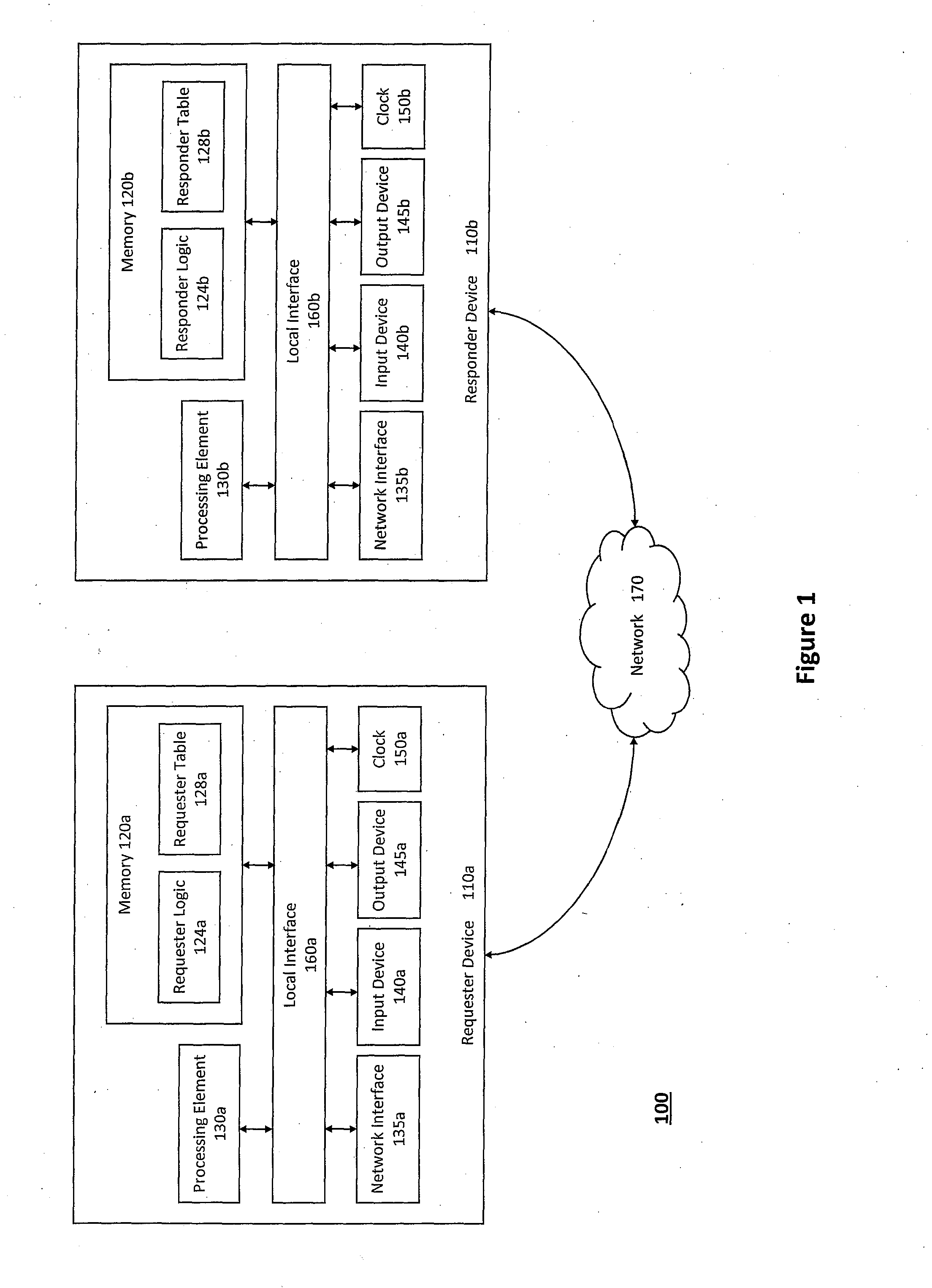
System and method for providing unified transport and security protocols
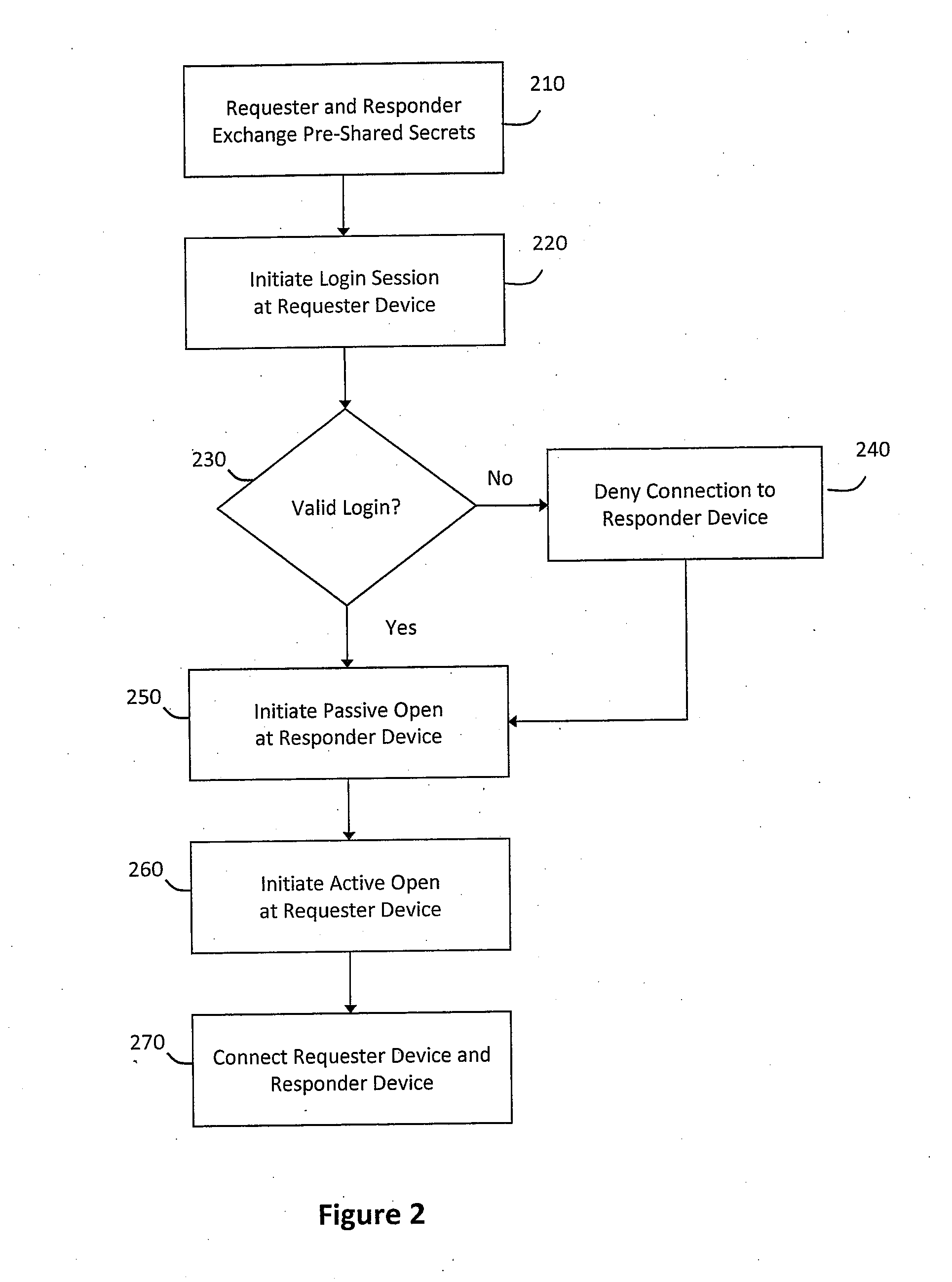
InactiveUS20110099623A1Minimize delayFast and efficientMemory loss protectionError detection/correctionPacket lossMessage frame
The system and method described herein may provide unified transport and security protocols. In particular, the unified transport and security protocols may include a Secure Frame Layer transport and security protocol that includes stages for initially configuring a requester device and a responder device, identifying the requester device and the responder device to one another, and authenticating message frames communicated between the requester device and the responder device. Additionally, the unified transport and security protocols may further include a Secure Persistent User Datagram Protocol that includes modes for processing message frames received at the requester device and the responder device, recovering the requester device in response to packet loss, retransmitting lost packets sent between the requester device and the responder device, and updating location information for the requester device to restore a communications session between the requester device and the responder device.
Owner:AUNIGMA NETWORK SECURITY CORP
Secure networking using a resource-constrained device
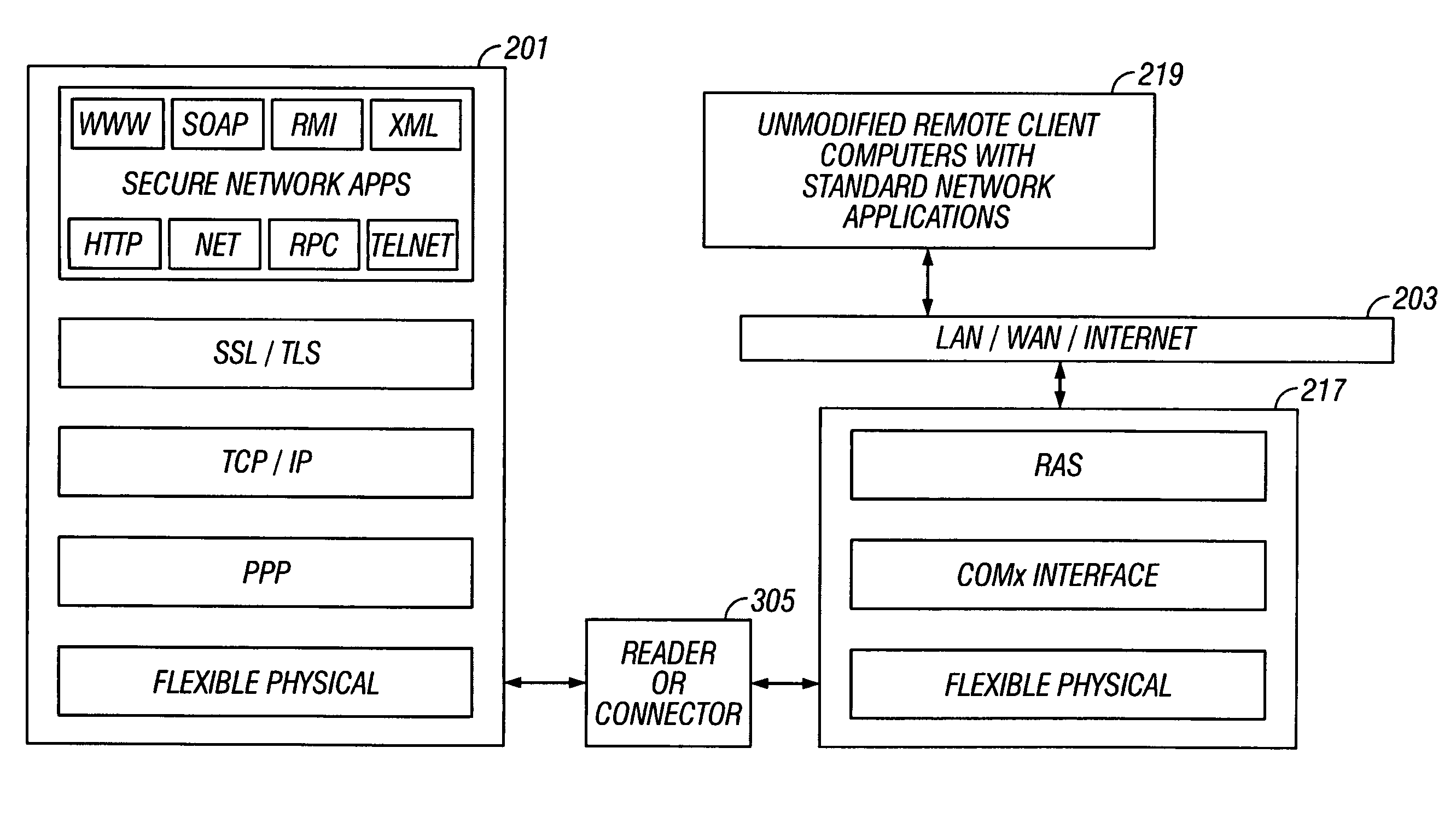
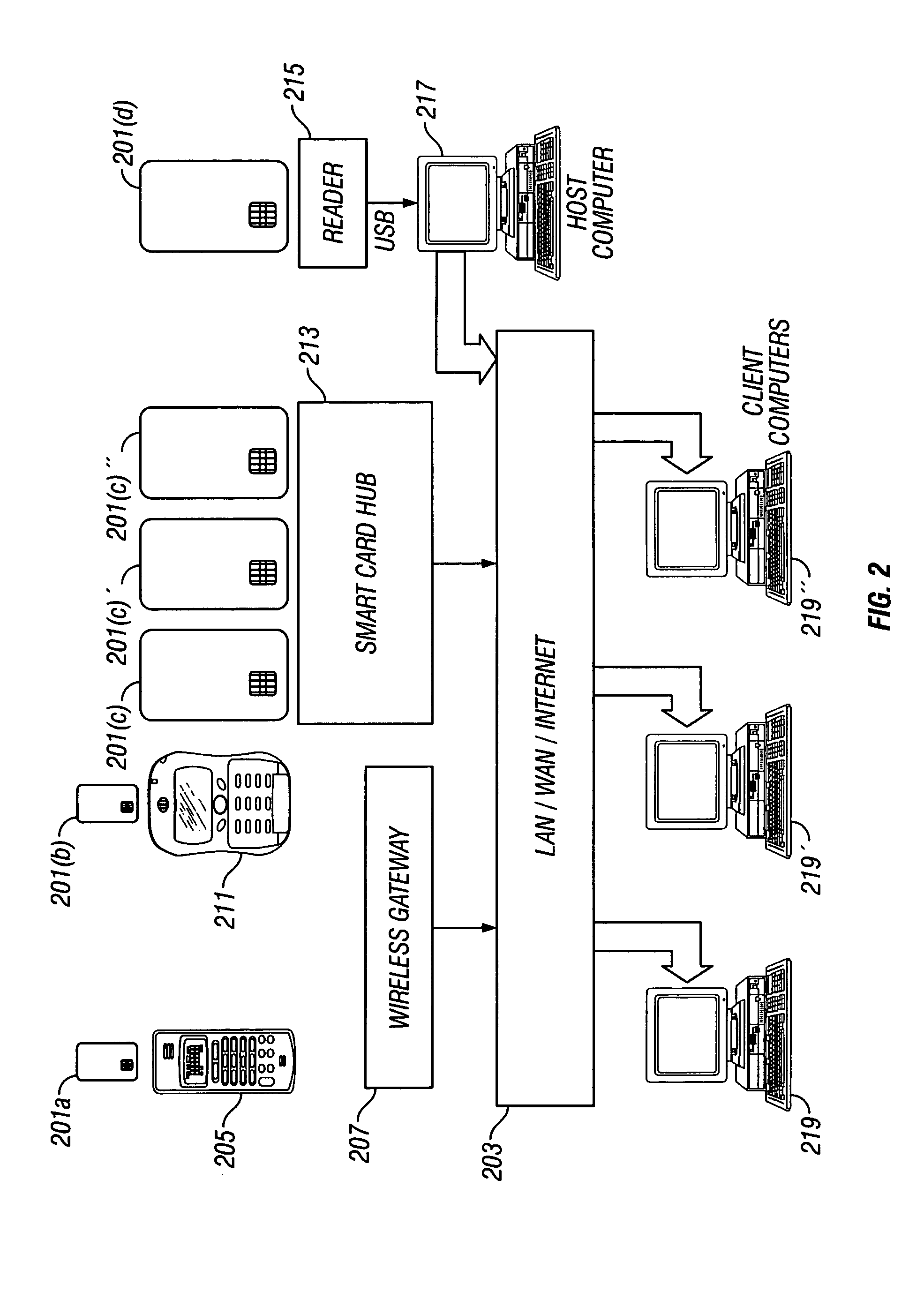
ActiveUS7509487B2Easy to adaptHardware monitoringDigital data authenticationComputer hardwareSecure communication
Secure communication between a resource-constrained device and remote network nodes over a network with the resource-constrained acting as a network node. The remote network nodes communicate with the resource-constrained device using un-modified network clients and servers. Executing on the resource-constrained device, a communications module implements one or more link layer communication protocols, operable to communicate with a host computer, operable to communicate with remote network nodes and operable to implement network security protocols thereby setting a security boundary inside the resource-constrained device.
Owner:THALES DIS USA INC
Prevention of side channel attacks against block cipher implementations and other cryptographic systems
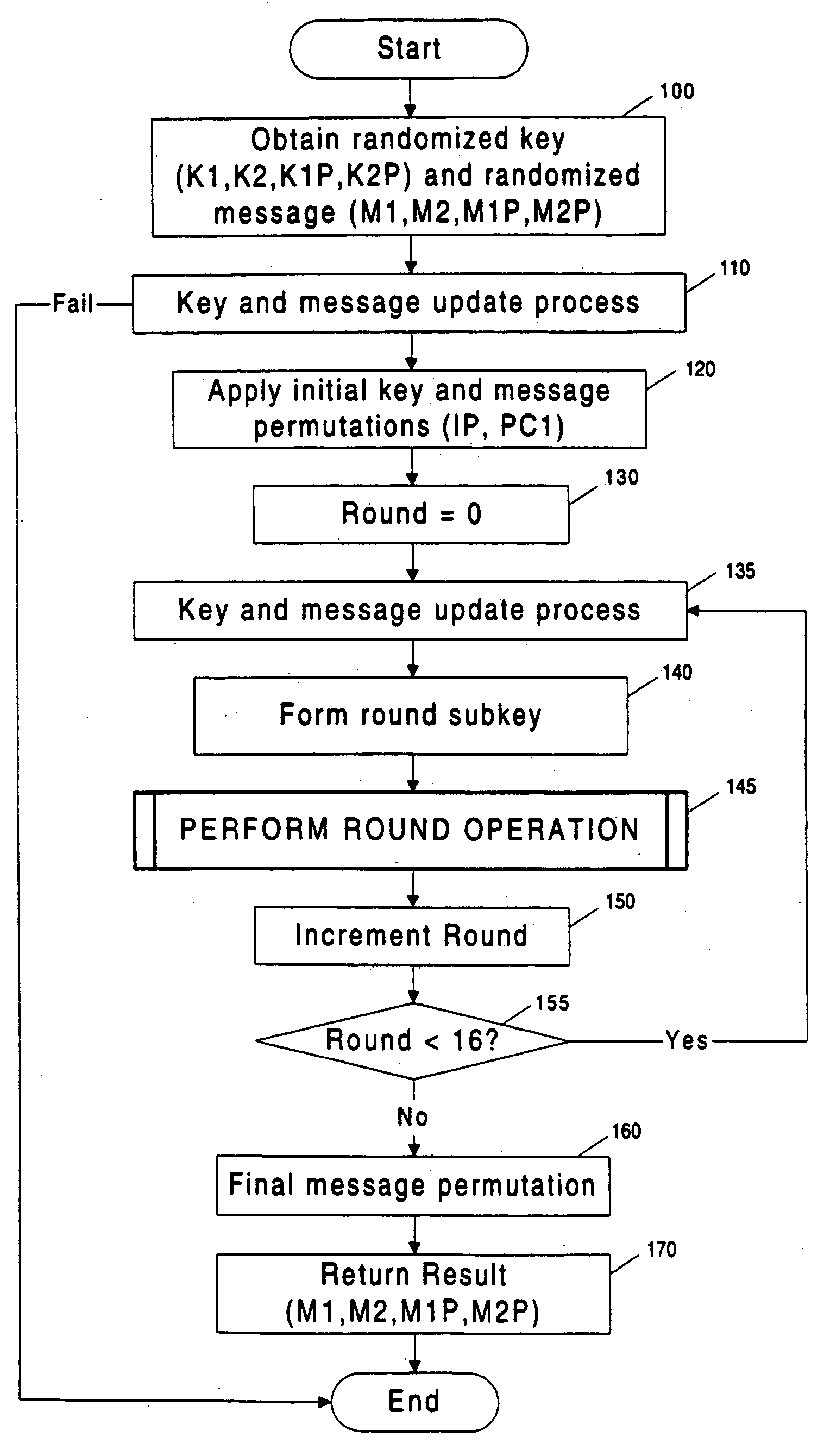
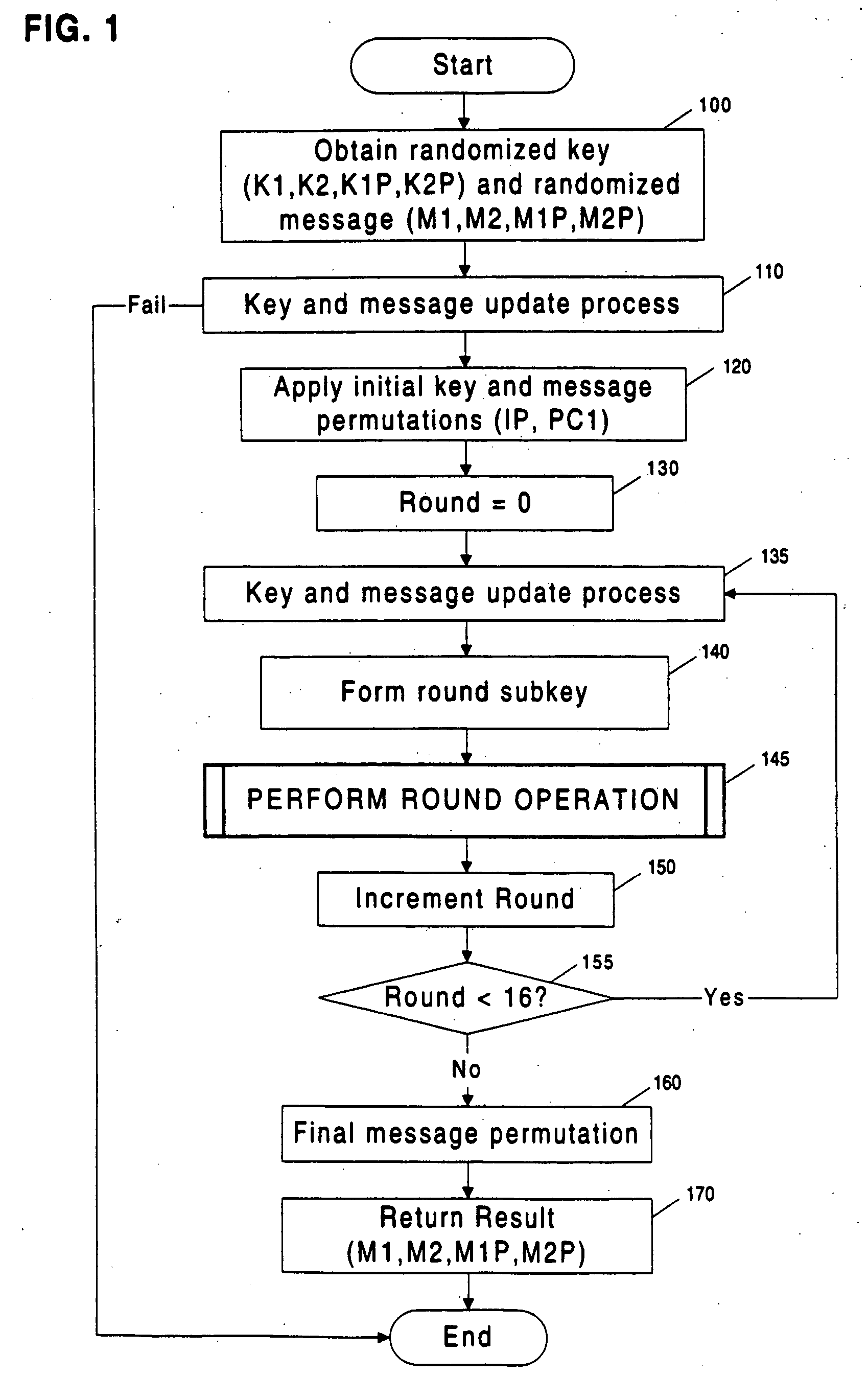
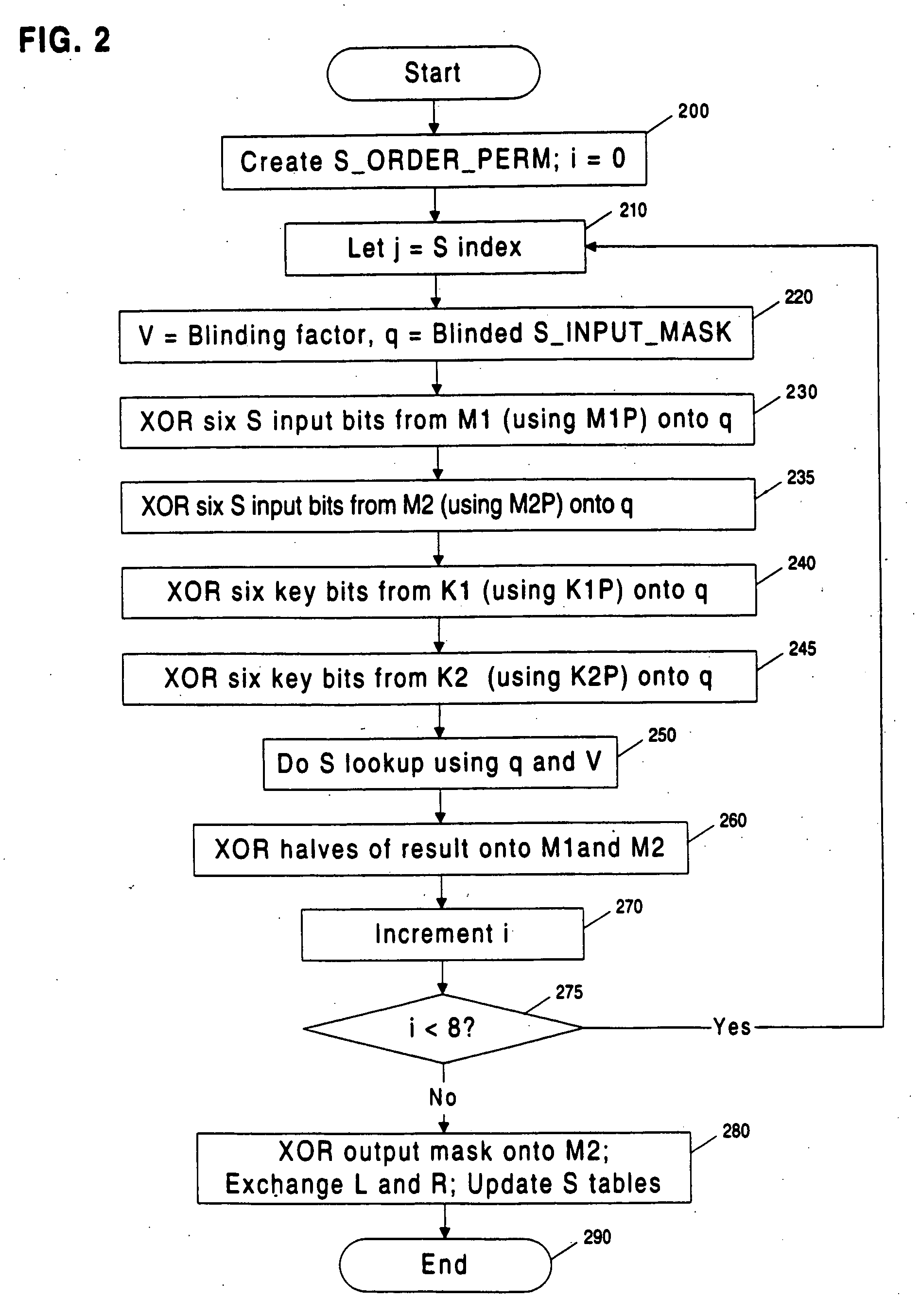
InactiveUS20060045264A1Safe leakageEasy to convertEncryption apparatus with shift registers/memoriesDigital data processing detailsPlaintextSignal-to-noise ratio (imaging)
Methods and apparatuses are disclosed for improving DES and other cryptographic protocols against external monitoring attacks by reducing the amount (and signal-to-noise ratio) of useful information leaked during processing. An improved DES implementation of the invention instead uses two 56-bit keys (K1 and K2) and two 64-bit plaintext messages (M1 and M2), each associated with a permutation (i.e., K1P, K2P and M1P, M2P) such that K1P{K1} XOR K2P{K2} equals the “standard” DES key K, and M1P{M1} XOR M2P{M2} equals the “standard” message. During operation of the device, the tables are preferably periodically updated, by introducing fresh entropy into the tables faster than information leaks out, so that attackers will not be able to obtain the table contents by analysis of measurements. The technique is implementable in cryptographic smartcards, tamper resistant chips, and secure processing systems of all kinds.
Owner:CRYPTOGRAPHY RESEARCH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com