Cryptographic protection of information in a processing system
a processing system and information technology, applied in the field of processor information security, can solve problems such as data stored in memory modules being subject to theft, data stored therein being subject to unauthorized access, and the hypervisor itself being vulnerable to exploitation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
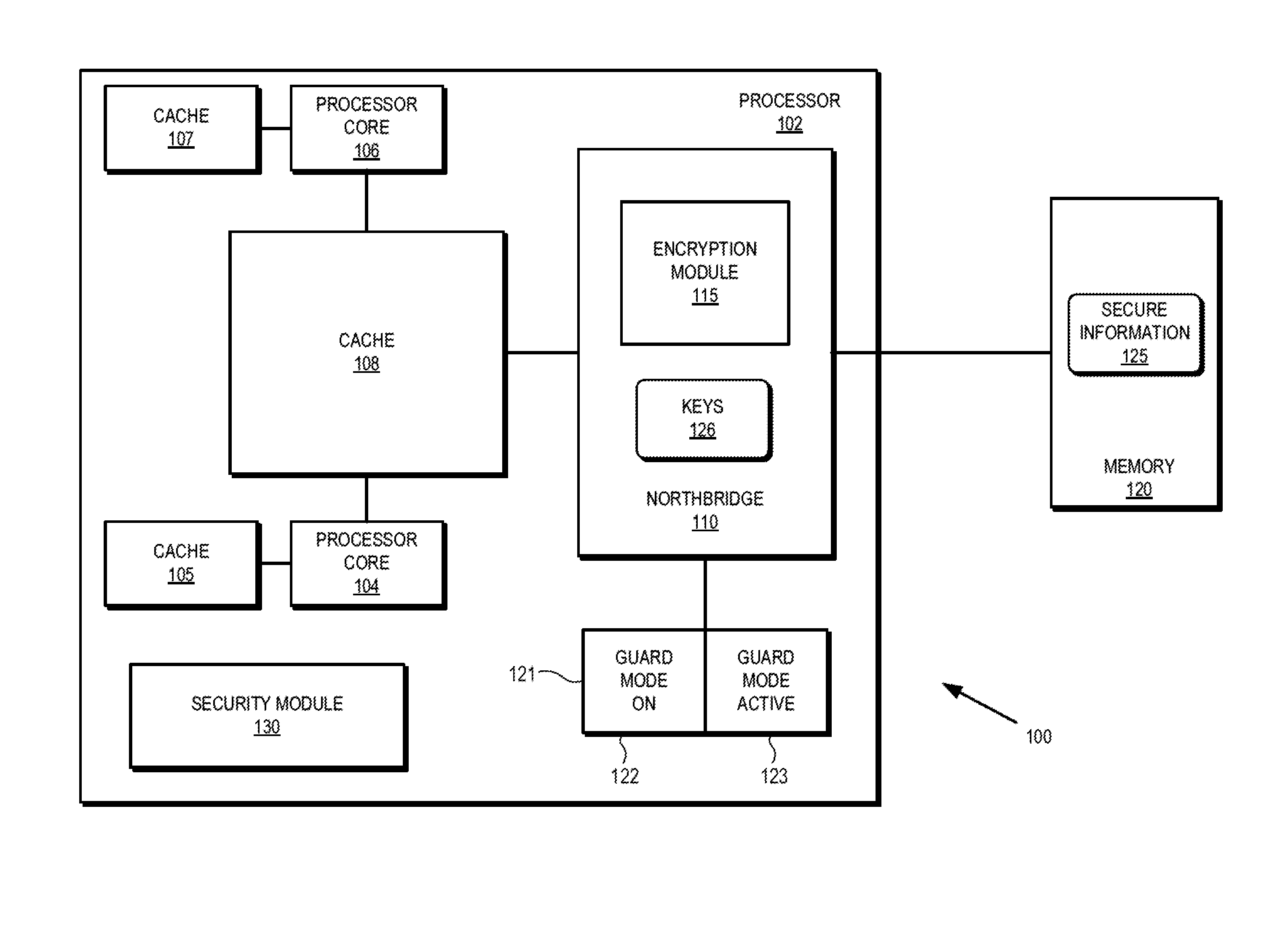
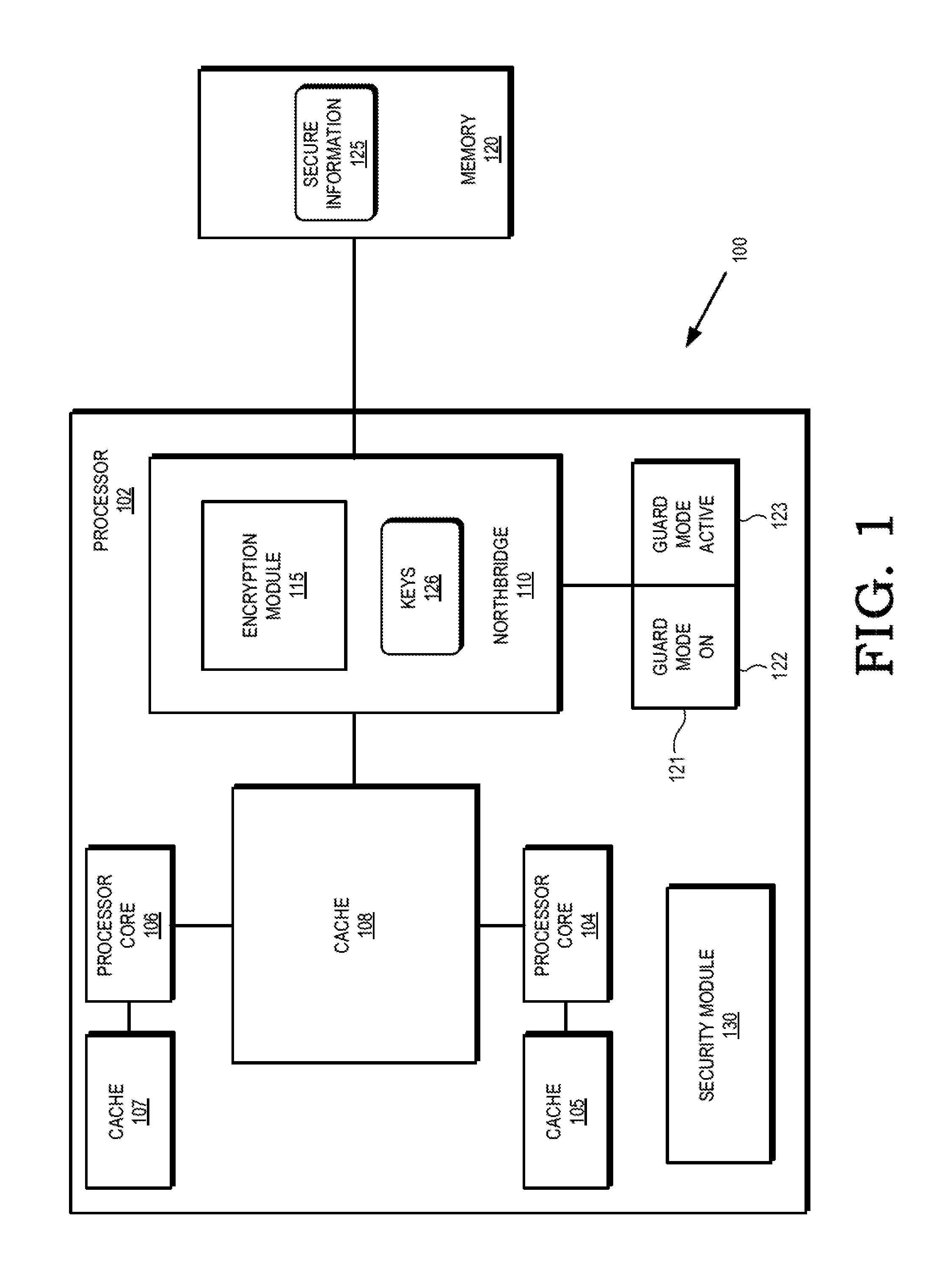
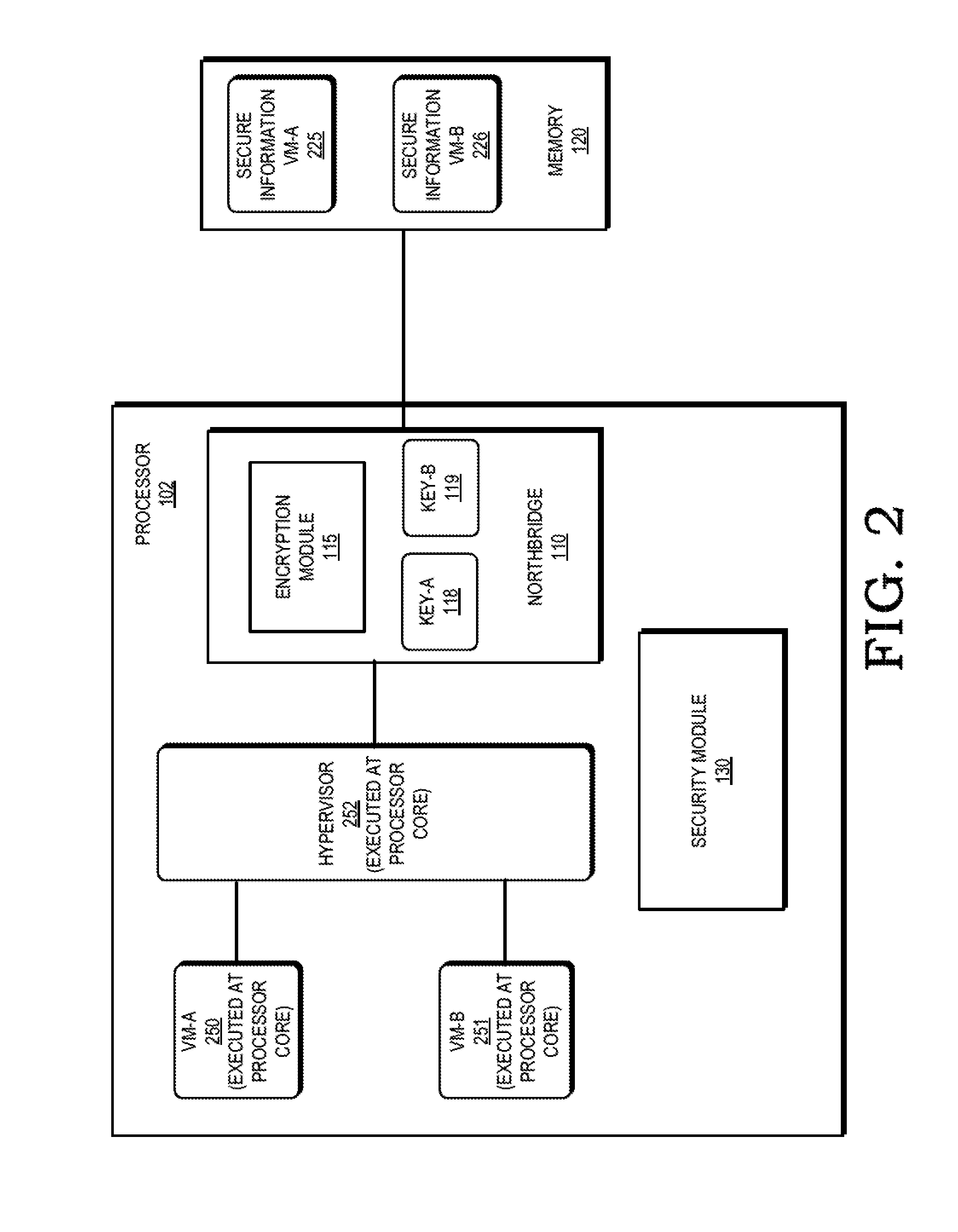
[0017]FIGS. 1-11 illustrate techniques for protecting secure information at a processing system by employing a hardware encryption module in the processor's memory access path to cryptographically isolate the secure information. In some embodiments, the encryption module is located at a memory controller (e.g. northbridge) of the processor, and each memory access provided to the memory controller indicates whether the access is a secure memory access, indicating the information associated with the memory access is designated for cryptographic protection, or a non-secure memory access. For secure memory accesses, the encryption module performs encryption (for write accesses) or decryption (for read accesses) of the data associated with the memory access. Because the encryption is done by hardware in the processor's memory access path, the data stored at the memory is not meaningfully accessible without the correct encryption / decryption key.
[0018]In some embodiments the processor is e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com