Patents
Literature
1128results about How to "Secure transmission" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
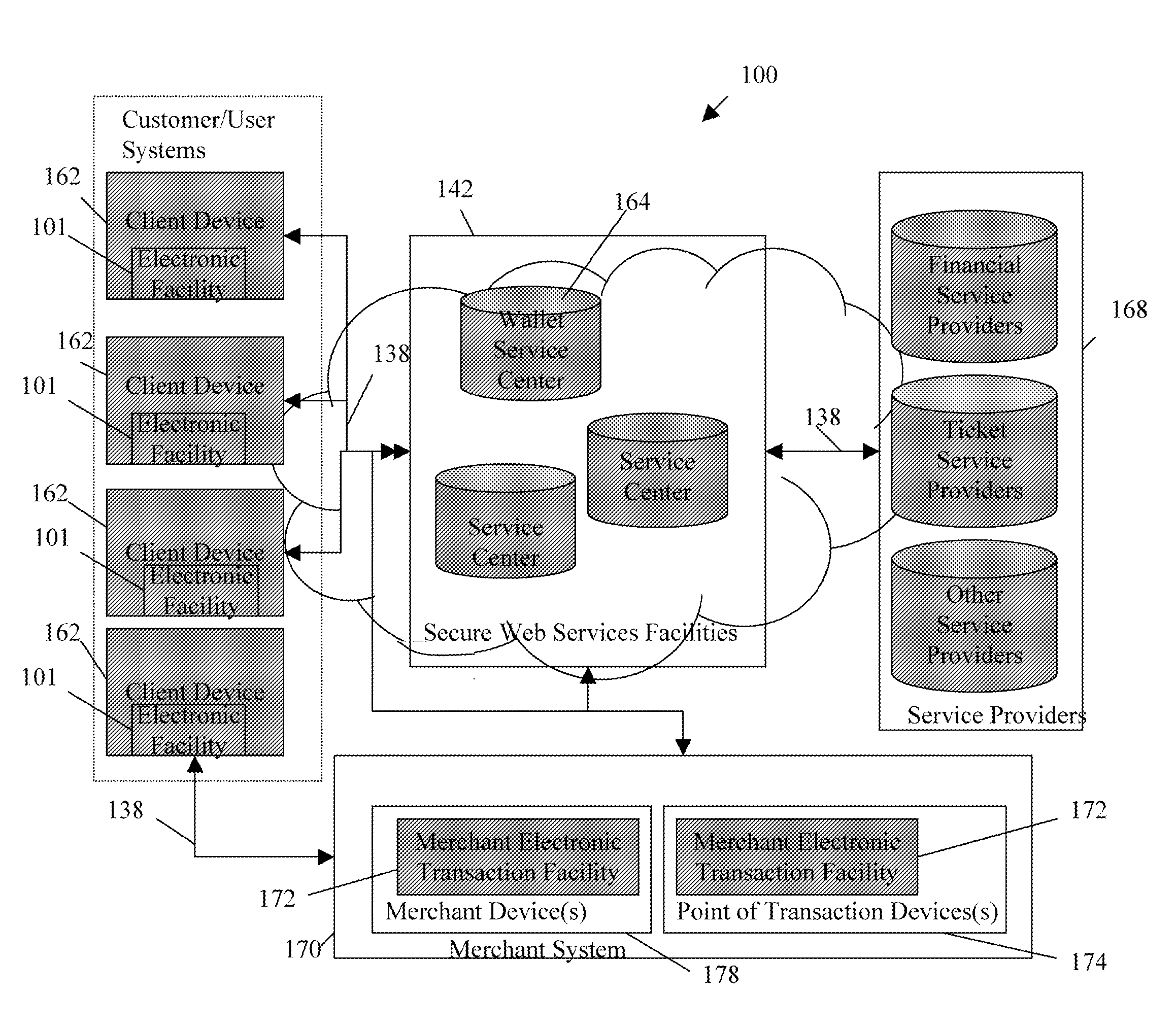
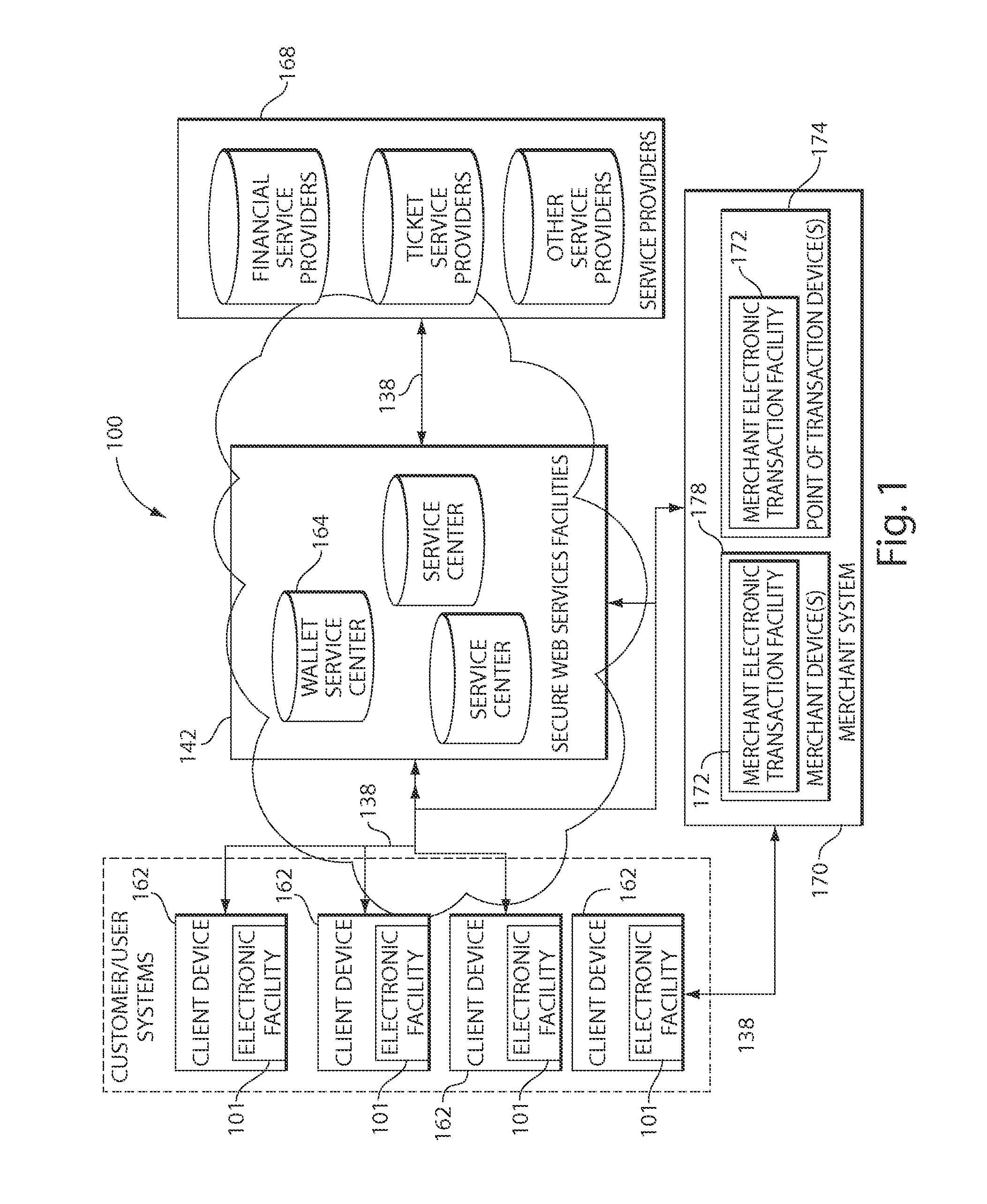
Transactional services
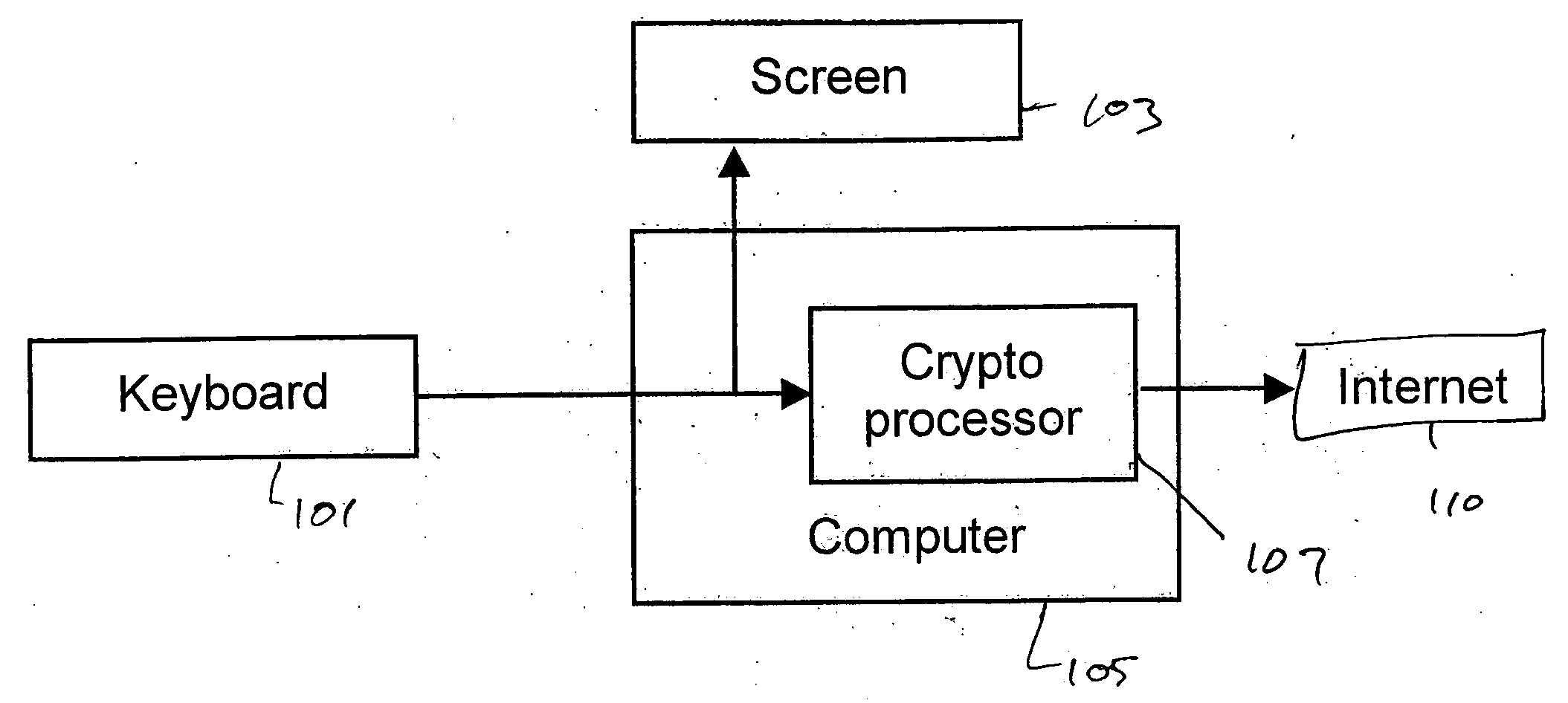
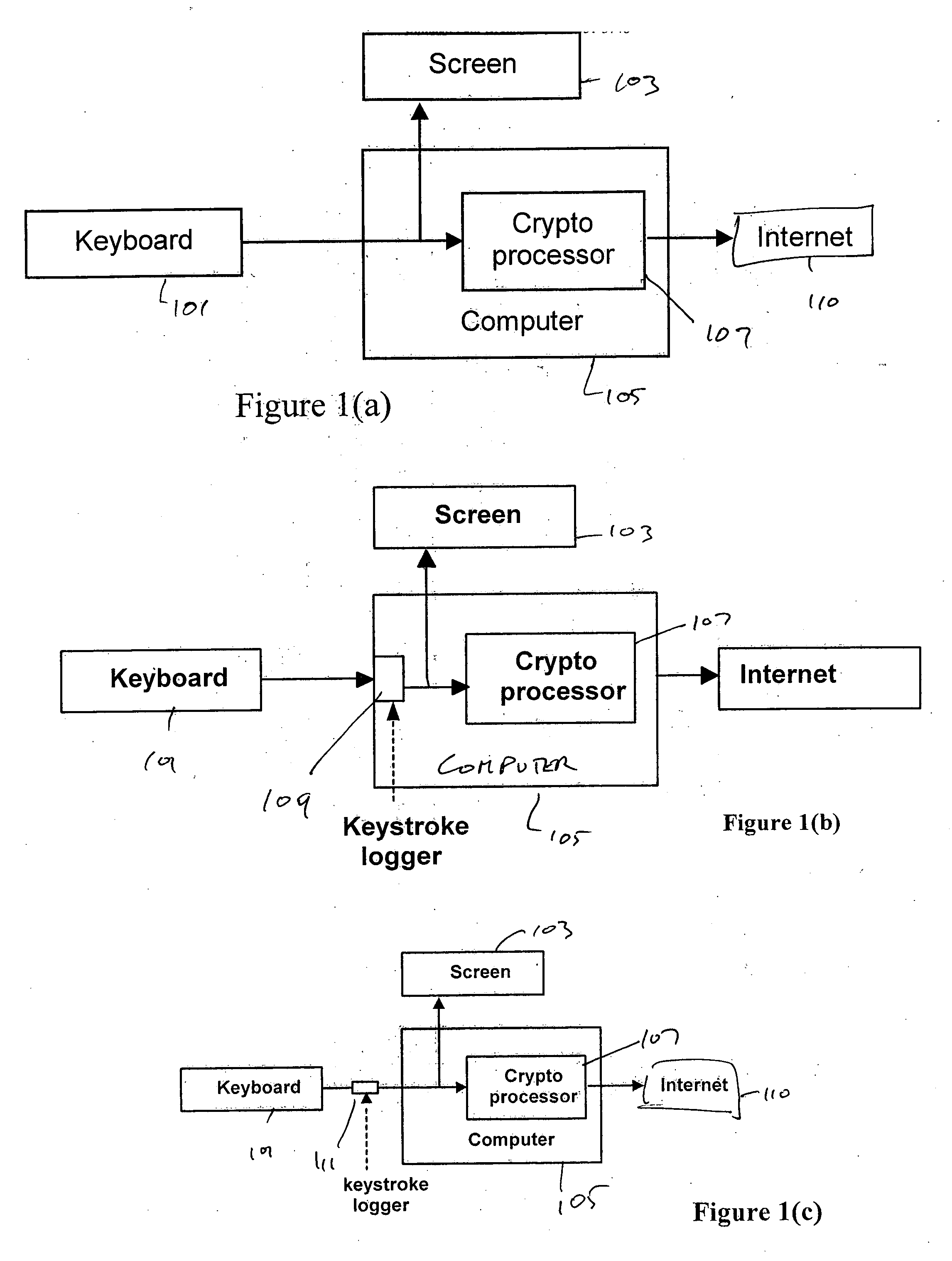
InactiveUS20070198432A1High level of throughputHigh level of efficiencyCryptography processingComputer security arrangementsTransaction serviceDatabase
Owner:MASTERCARD MOBILE TRANSACTIONS SOLUTIONS
System and method for securely transmiting sensitive information
InactiveUS20130194301A1Inhibitory contentSecure transmissionCathode-ray tube indicatorsDigital data protectionComputer hardwareClient-side
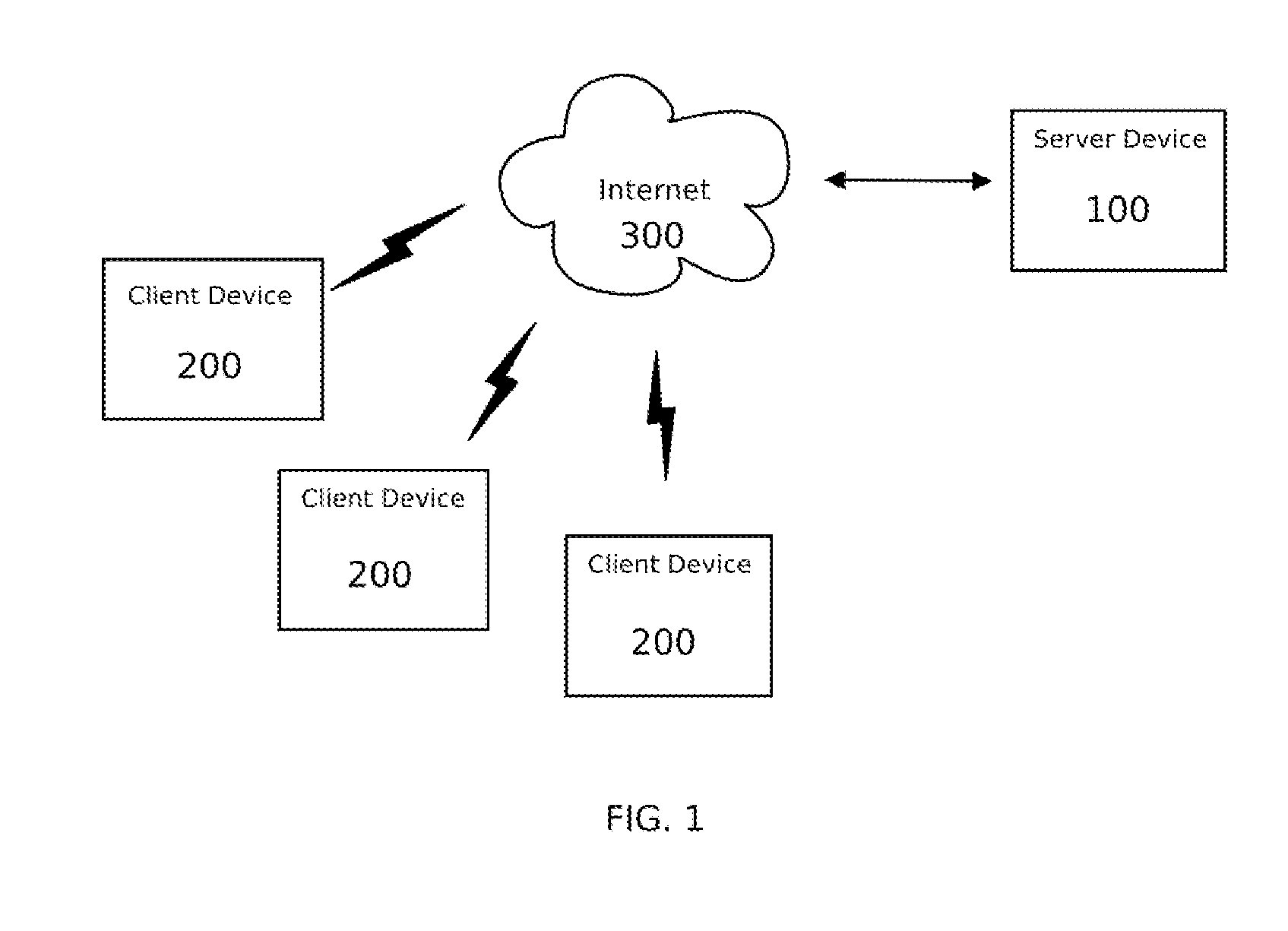
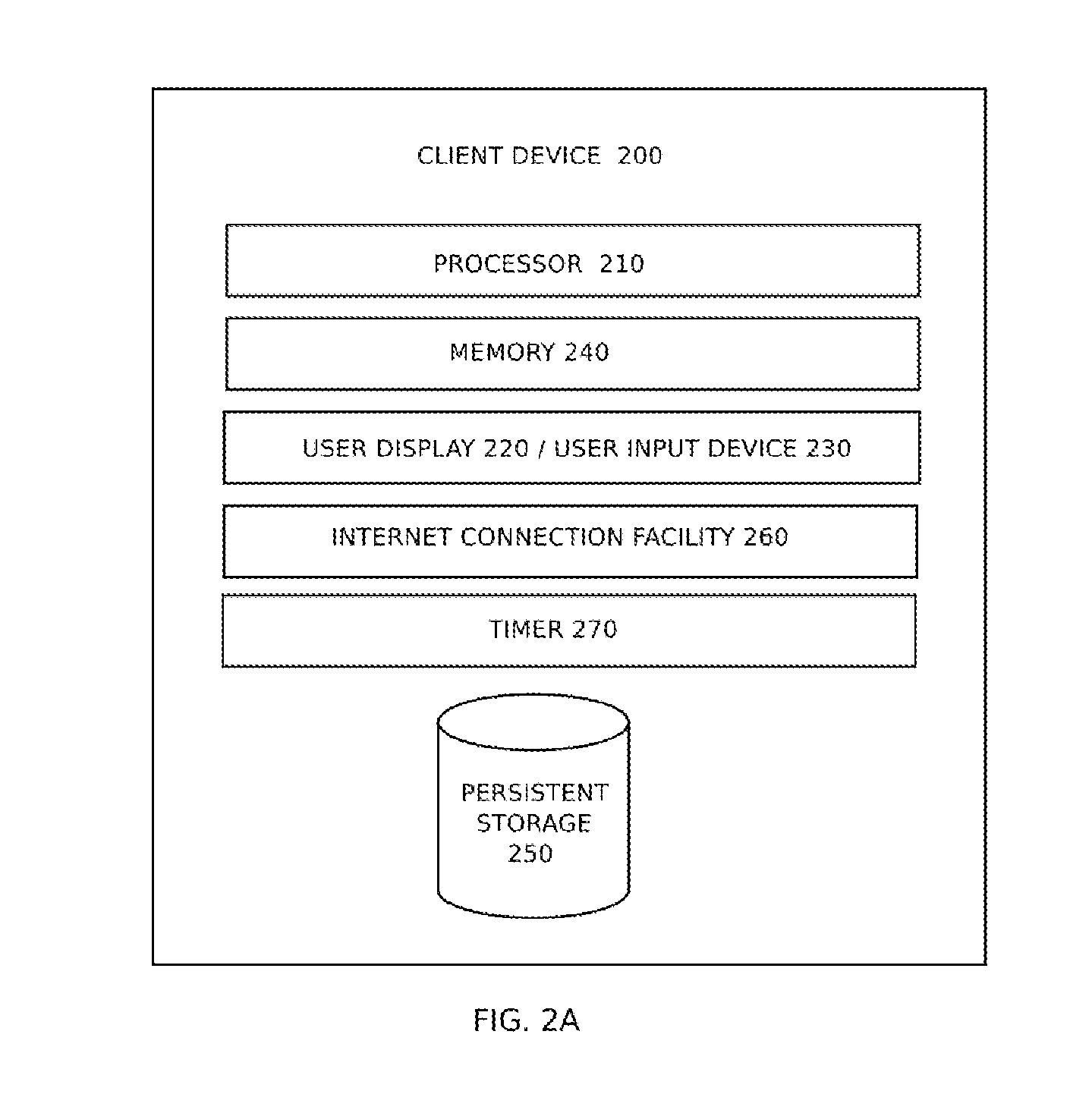
A system and method for securely transmitting information over a communications network comprises receiving a message notification that a recipient has a message on a recipient's client device from a processor based server upon receipt of the message from a sender's client device. The message from the sender's client device is stored in a storage device by the server. The recipient accesses the server to view the message using the recipient's client device. The message is rendered and displayed on the screen by the recipient's client device in accordance with a display method selected by the sender of the message to present only a portion of the message at any given time to the recipient. The prevents the message from being recorded or captured.
Owner:BURN NOTE
System and method for secure message-oriented network communications
InactiveUS6959393B2Minimize threatFacilitate and control accessKey distribution for secure communicationDigital data processing detailsSecurity MeasureNetwork communication
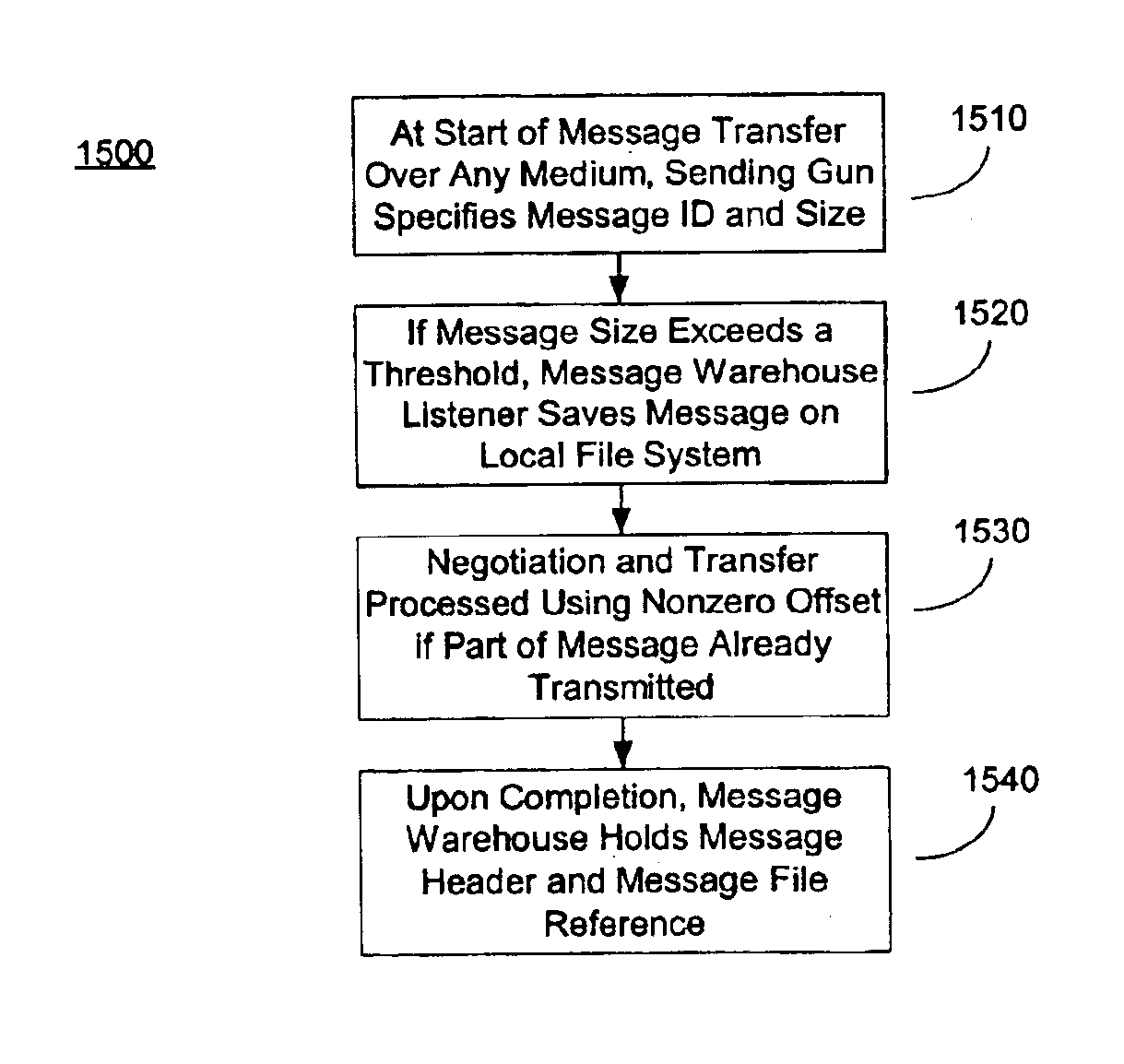
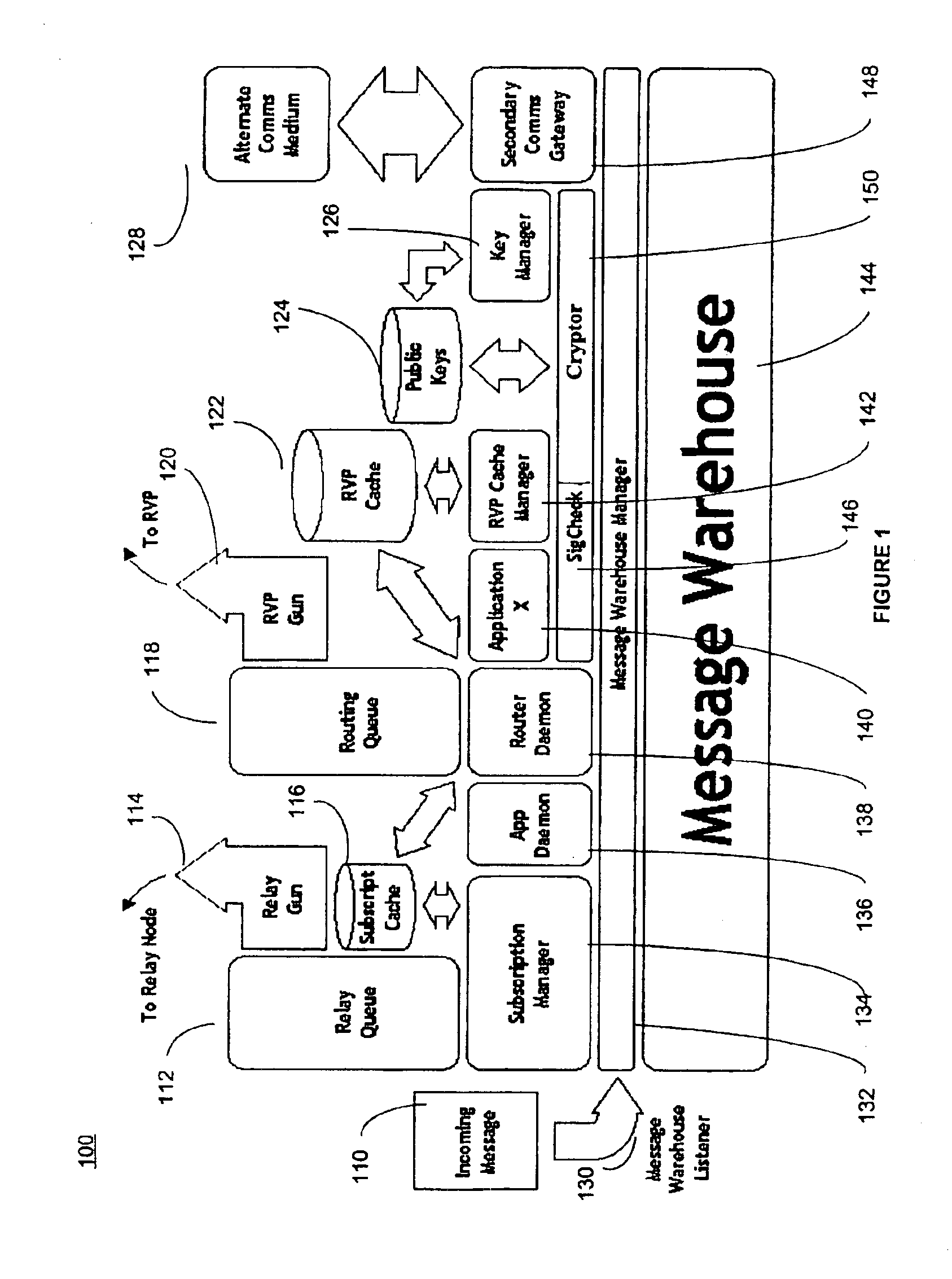
The present invention provides a message-oriented middleware solution for securely transmitting messages and files across public networks unencumbered by intervening network barriers implemented as security measures. It also provides a dynamic, dedicated, application level VPN solution that is facilitated by the message-oriented middleware. Standard encryption algorithms are used to minimize the threat of eavesdropping and an Open-Pull Protocol (OPP) that allows target nodes to pull and verify the credentials of requestors prior to the passing of any data. Messaging can be segregated into multiple and distinct missions that all share the same nodes. The security network's architecture is built to resist and automatically recover from poor, slow, and degrading communications channels. Peers are identifiable by hardware appliance, software agent, and personally identifiable sessions. The security network provides a dynamic, private transport for sensitive data over existing non-secure networks without the overhead and limited security associated with traditional VPN solutions.
Owner:THREATGUARD
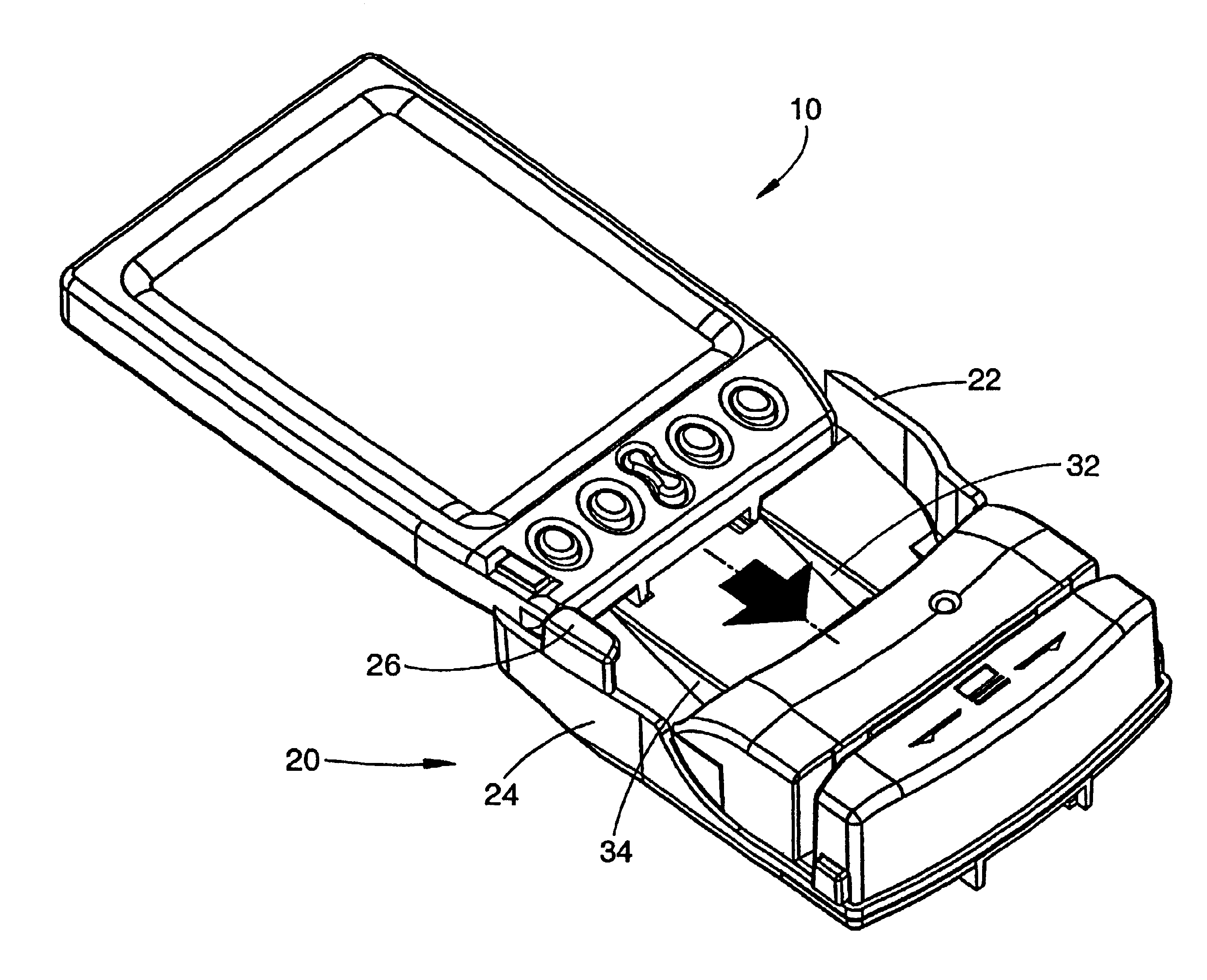
Magnetic stripe reader with power management control for attachment to a PDA device
InactiveUS20050247787A1Easy to operateIncrease powerVolume/mass flow measurementPower supply for data processingEngineeringField service
A magnetic stripe card manual swipe reader (MSR) unit capable of attaching to and communicating with a conventional personal digital assistant (PDA) from various manufacturers, using only the electrical power available as supplied by the PDA device, and capable of effective electrical power management and conservation operations. Additionally, this PDA attachable MSR unit is capable of recognizing multiple magnetic encoding formats and data record formats and converting said formats to a standardized output format, includes the capability of updating and adding new formats while in field service, and is readily allows verifying card data and encoding sensitive material prior to transmission to the PDA. These custom formats can then be used to fulfill current needs in age verification, law enforcement, security, and numerous other applications.
Owner:VERIFONE INC
System and method for secure electronic communication services
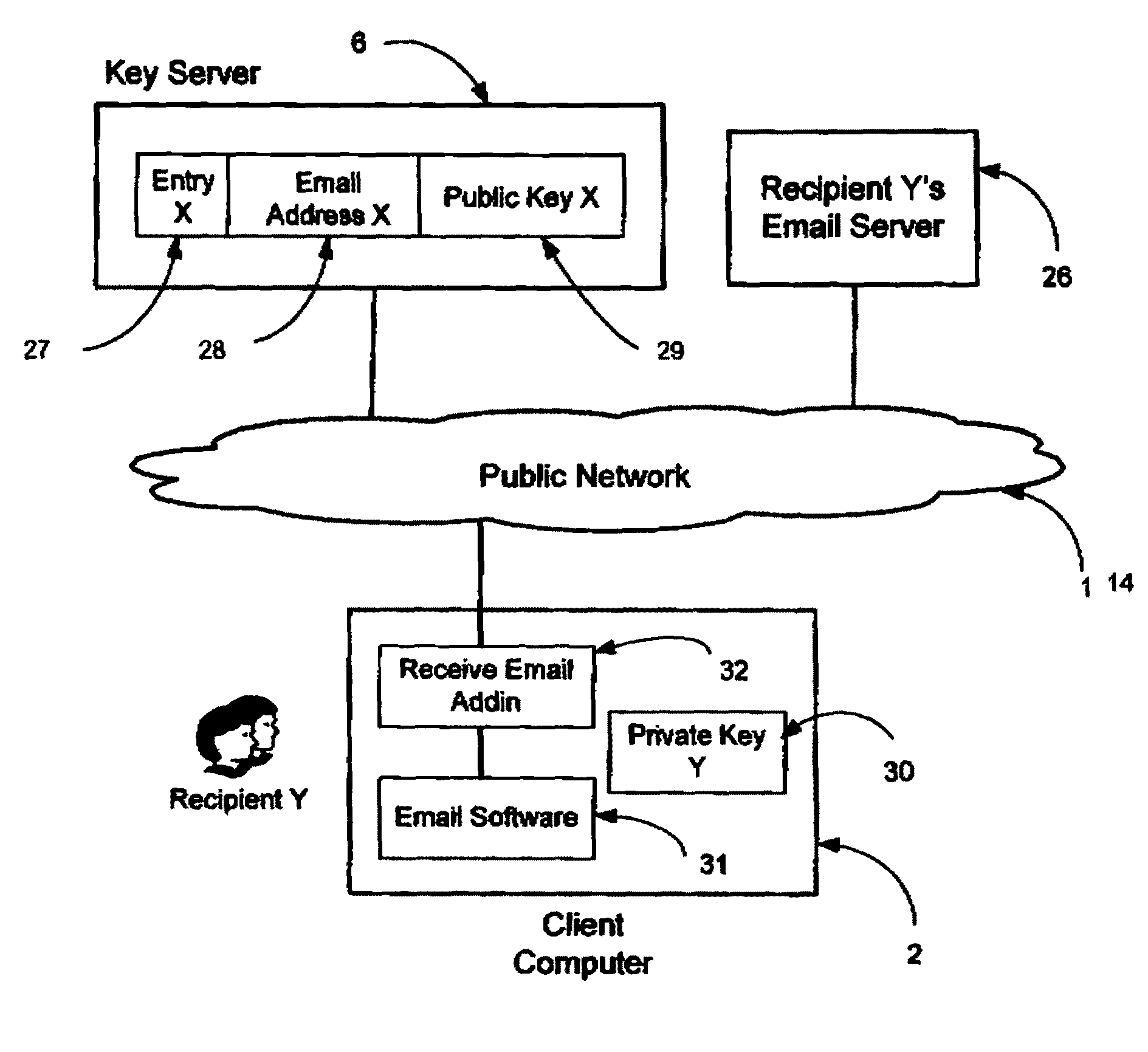
InactiveUS20090198997A1Easy accessSecure transmissionKey distribution for secure communicationMultiple keys/algorithms usageScalable systemEmail address
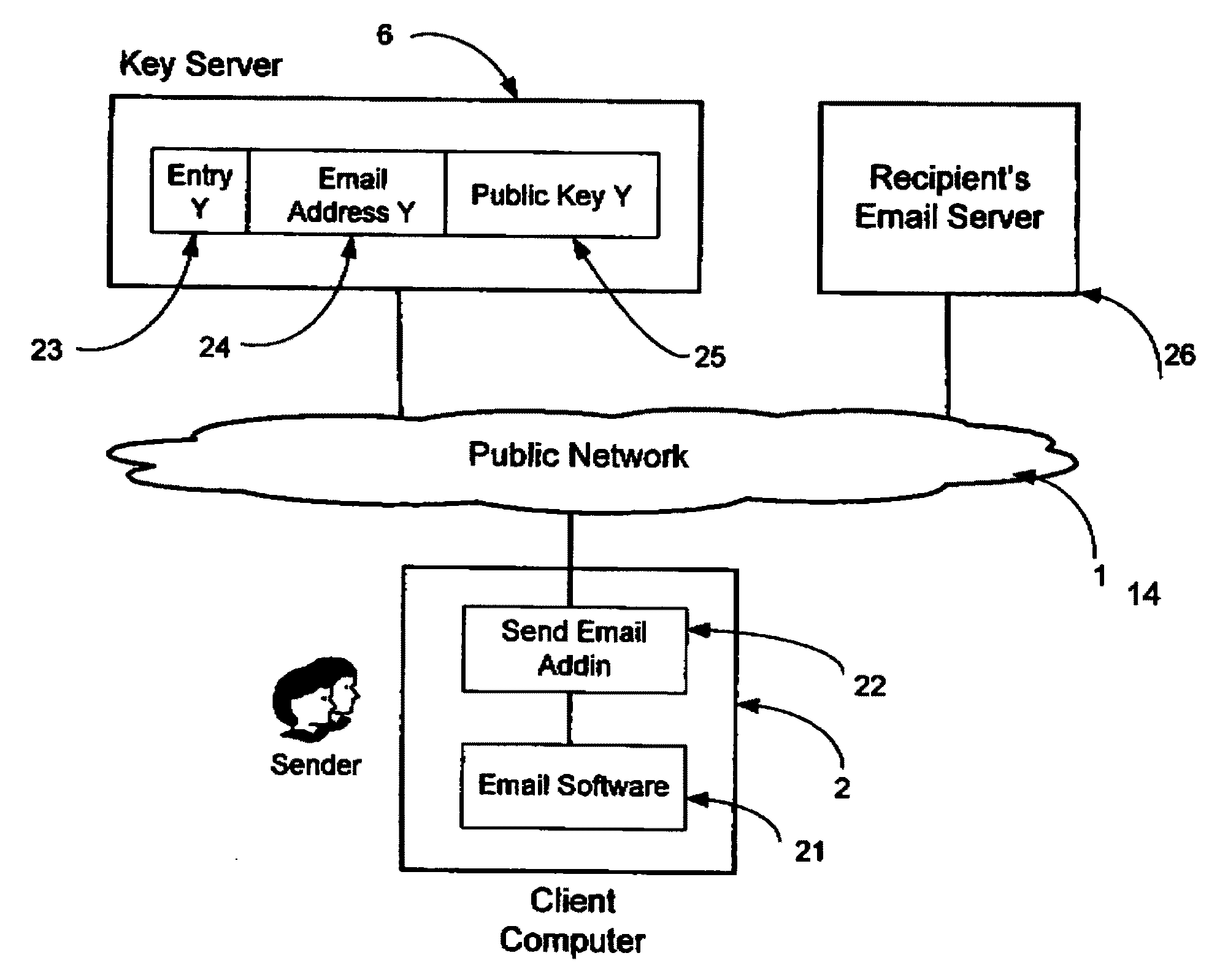
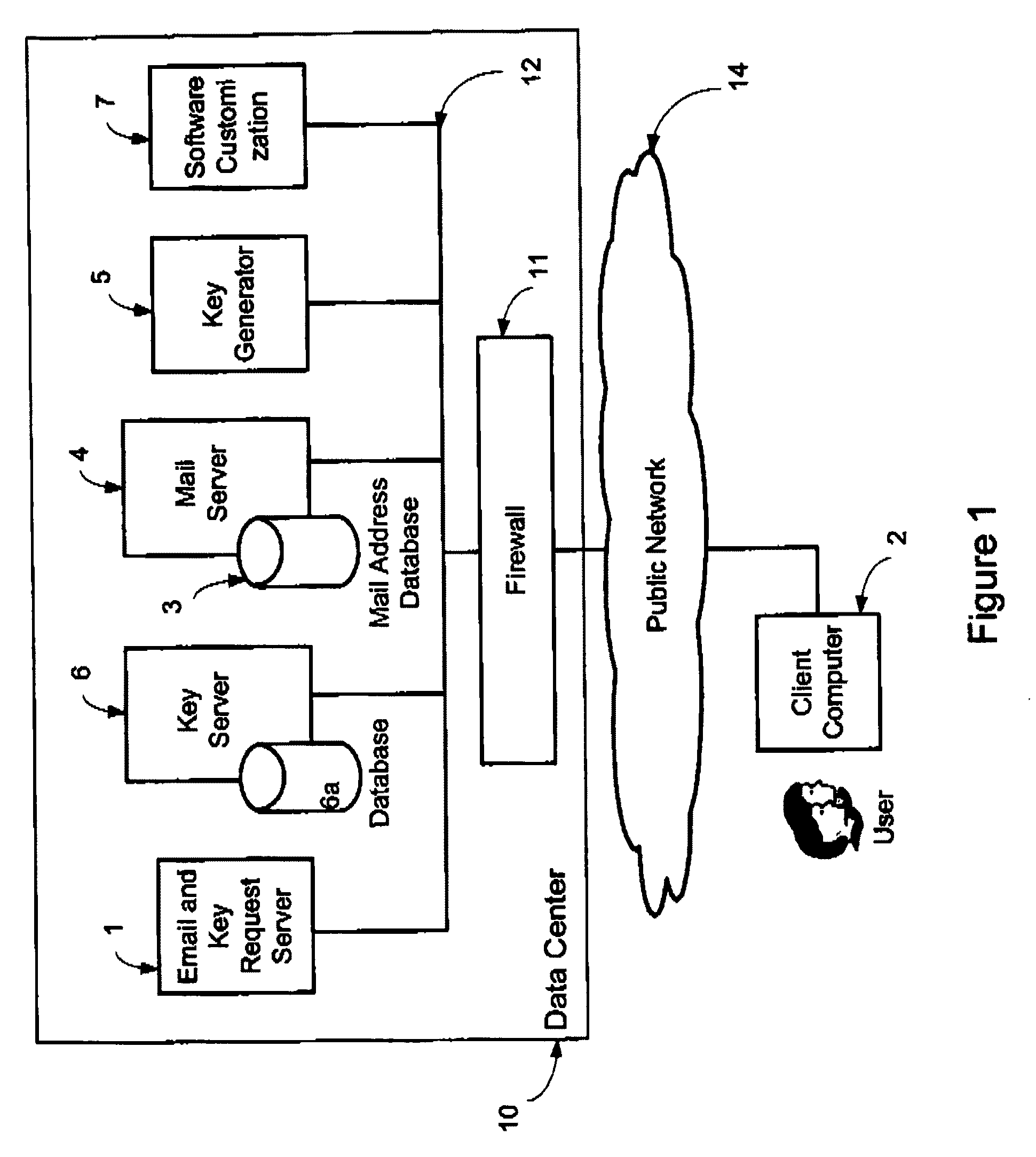
A system, method and software module for secure electronic communication services, wherein a public key (25) of private-public-key pair (30,25) is associated with an email address (24), internet name or other registered unique identifier; the registered user of the unique identifier holds the private-key (30) securely, and the respective public-key (25) is made accessible on a key server (6) for look-up and retrieval by other users, for encryption of communications to be sent to the holder of the private-key, and optionally for message confidentiality, message integrity and authentication of sender and recipient, without requiring certificates. A distributed and scalable system is provided by a server network (600; 401, 501) for registration, key distribution and management preferably using a kDNS server hierarchy (601,602,603) or a key-DNS server hierarchy (701,702,) and associated protocols so that public-keys of recipients can be searched and retrieved over the internet based on the recipients email address or other unique identifier, thus facilitating secure communication between users in different network domains and organizations.
Owner:TOPOSIS CORP
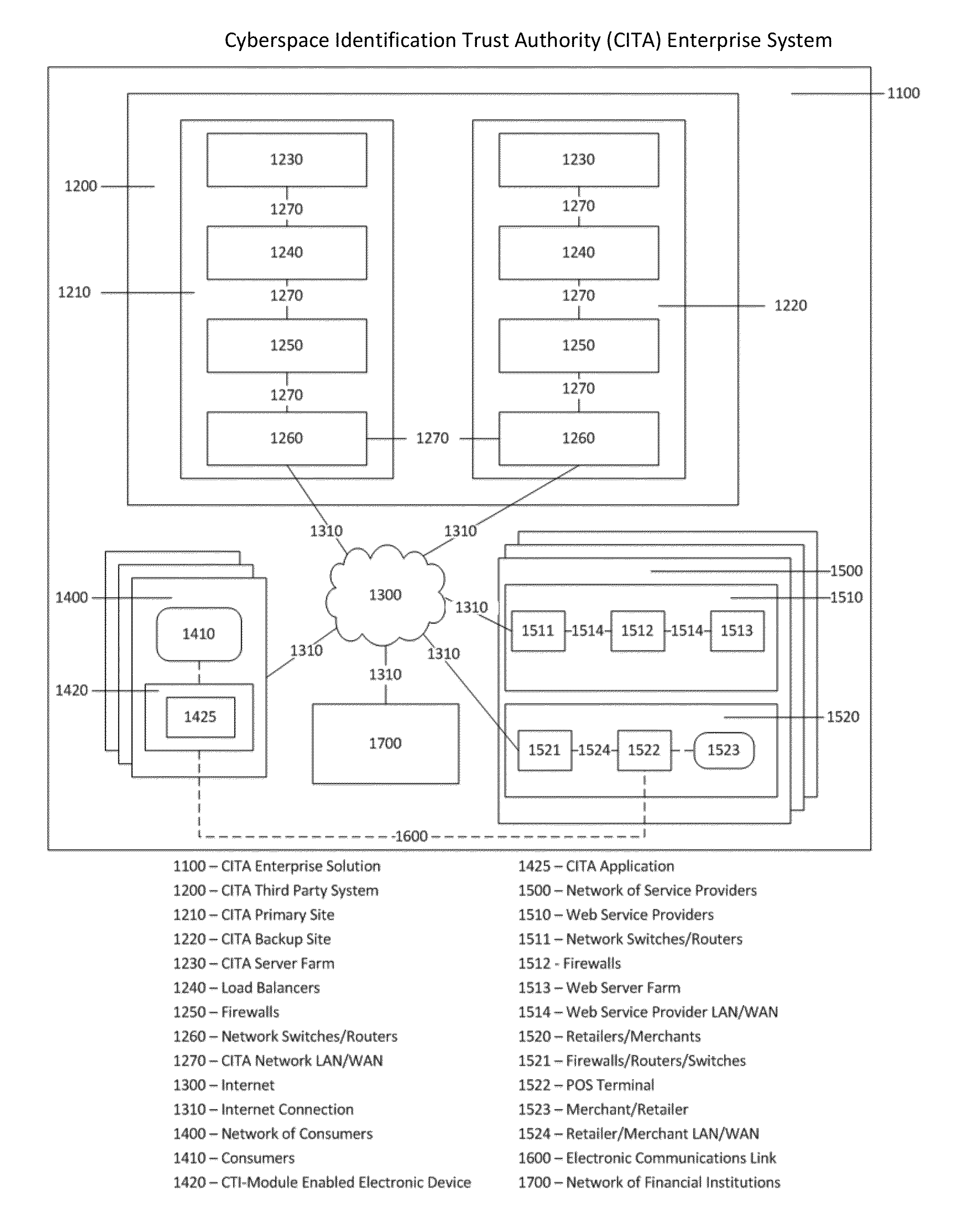
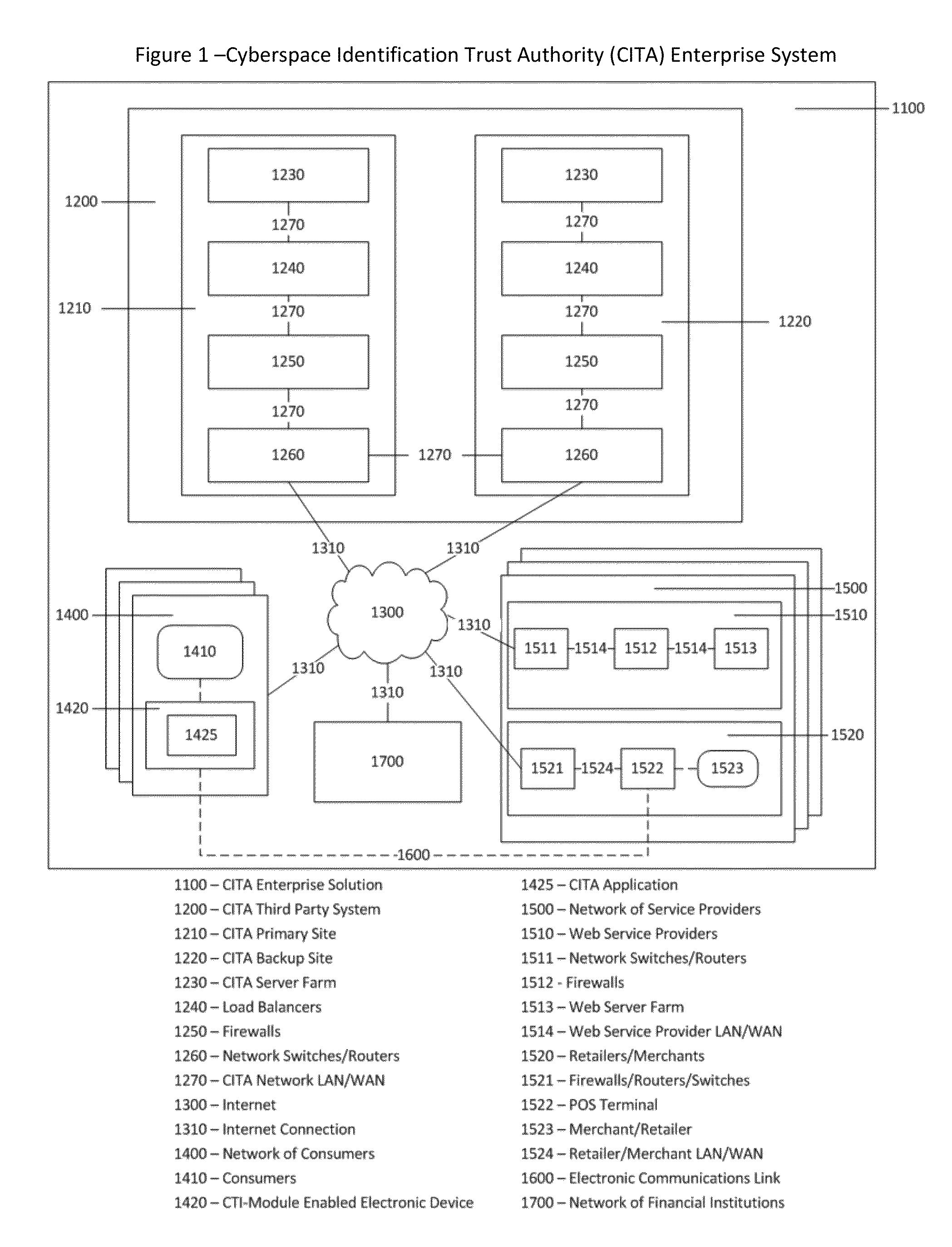
Cyberspace Identification Trust Authority (CITA) System and Method
InactiveUS20130226813A1Eliminate chanceSecure transmissionFinanceProtocol authorisationTrusted authorityPayment
When two parties of a cyberspace transaction register their identity attributes under a CITA system each party is assigned a unique, encrypted and digitally signed identity token. When the consuming party seeks access too, or payment for, cyberspace services, the providing party submits their identity token to the consuming party. The consuming party creates a request token, containing both the consumers' and the providers' identity tokens, and the transaction related information, to the CITA system. The CITA system validates the identity tokens and either creates a payment confirmation token by processing the payment request, or creates an access confirmation token by dynamically defining the minimal consumer identity attributes required to gain access to the provider's service. The confirmation token is encrypted and digitally signed and returned to the consumer, and then forwarded to the provider to complete the transaction without either party openly exchanging personal identity attributes.
Owner:VOLTZ ROBERT MATTHEW
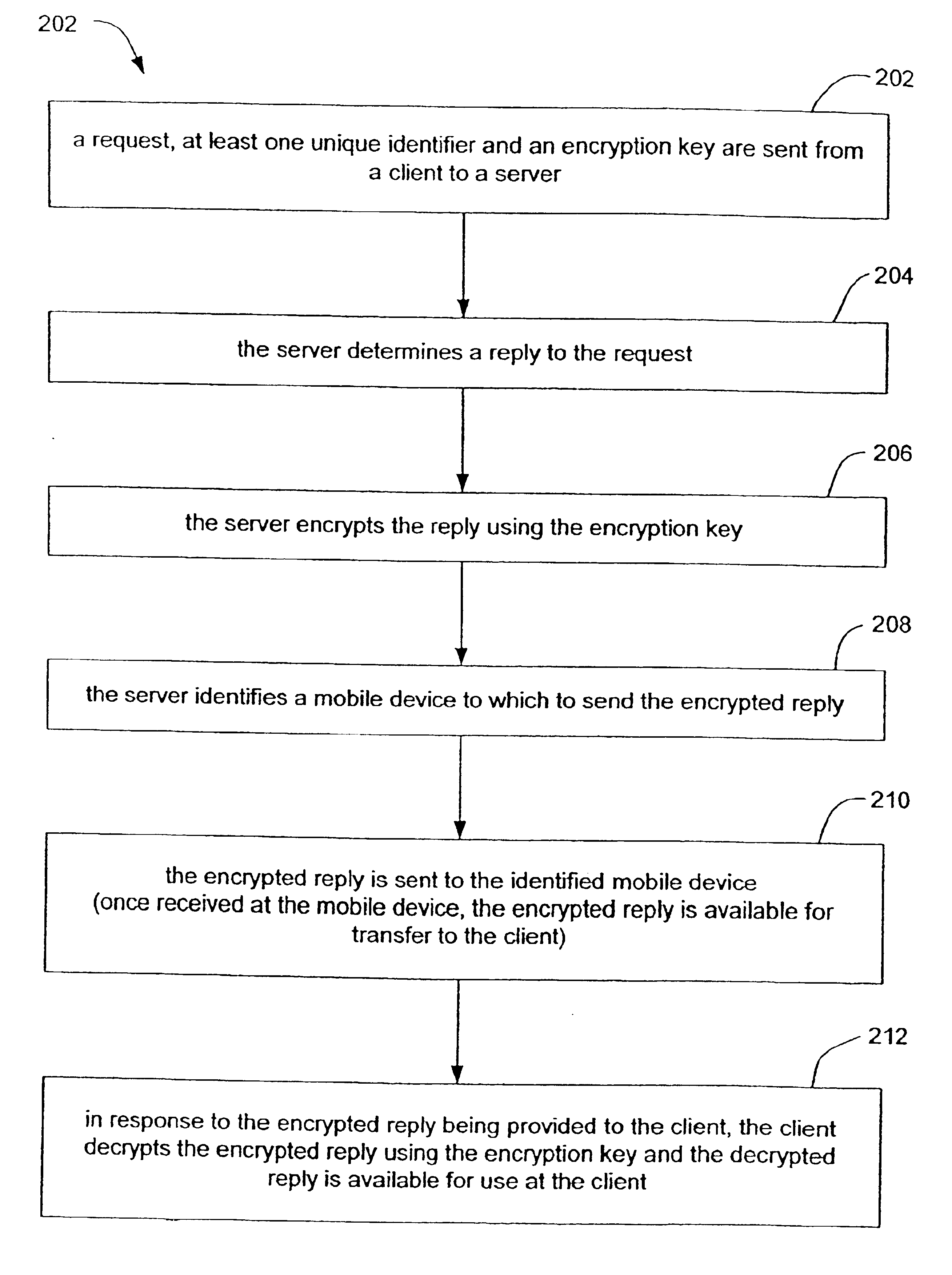
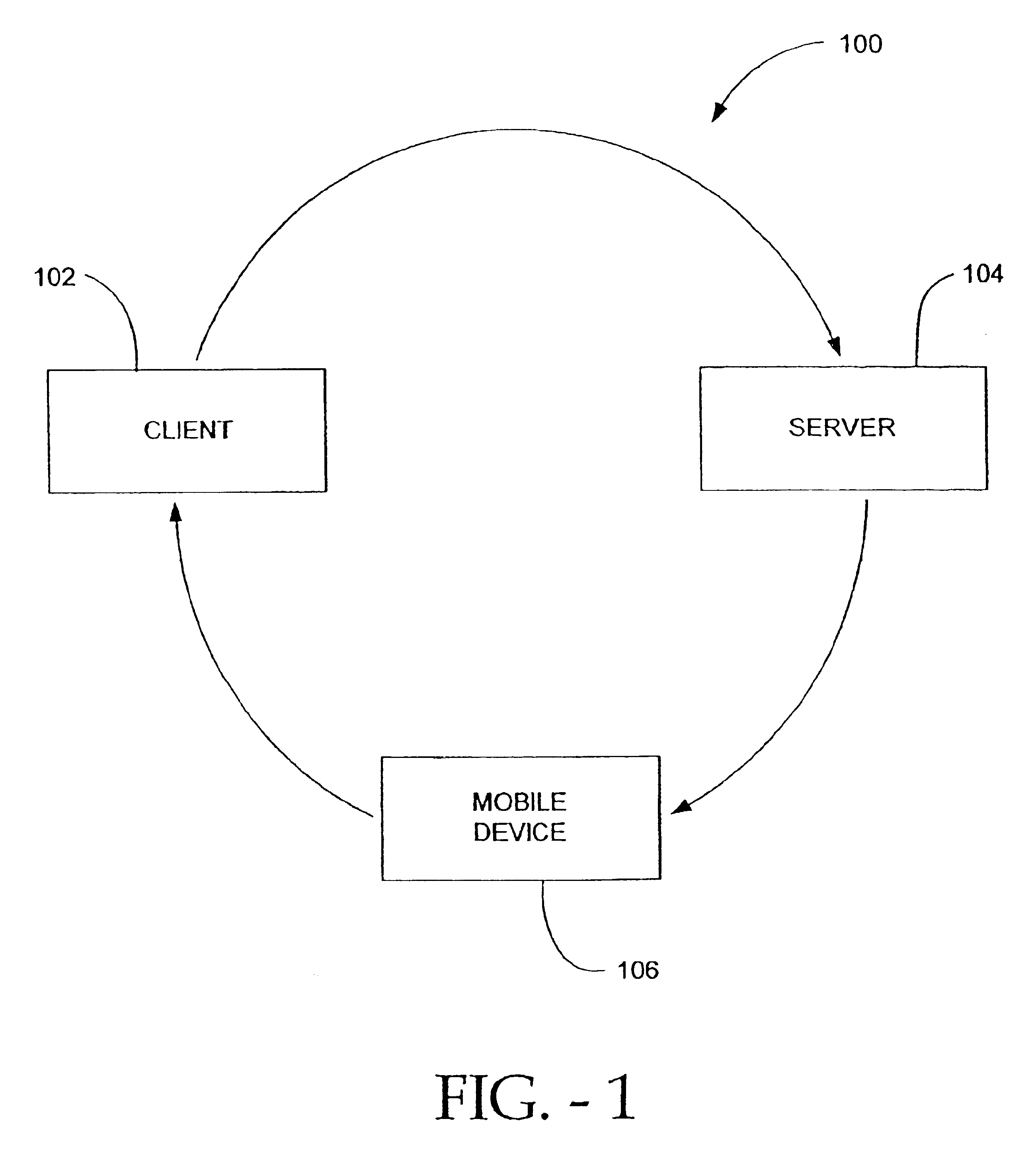
Methods and systems for secure transmission of information using a mobile device
InactiveUS6880079B2Secure transmissionUser identity/authority verificationDigital data authenticationSecure transmissionUnique identifier
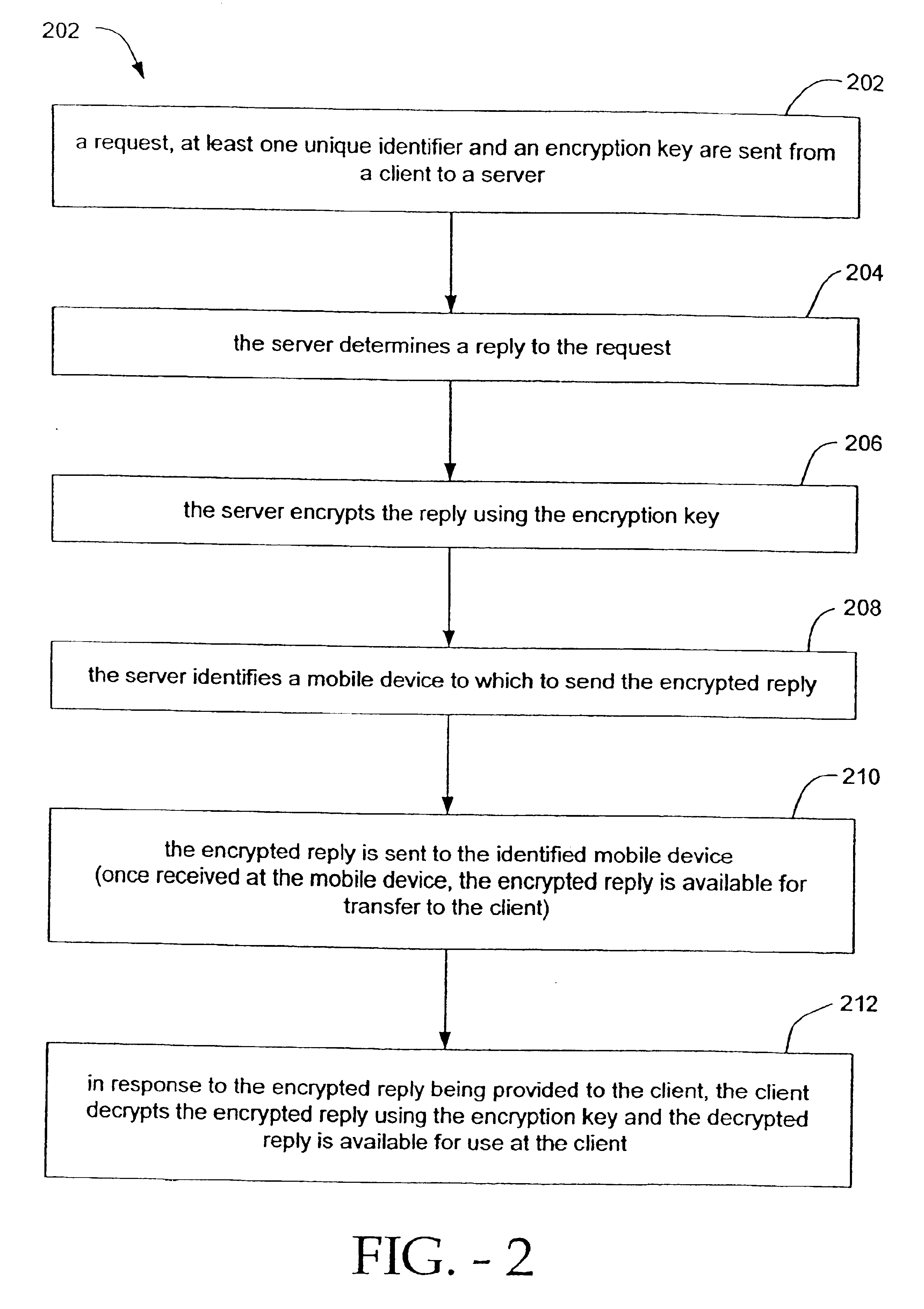
Methods and systems for secure transmission of information are provided. In accordance with a method of the present invention, a client sends to a server, a request, at least one unique identifier and an encryption key. The server generates a reply to the request and identifies a mobile device (based on the at least one unique identifier) to which to send the reply. The server also encrypts the reply, using the encryption key, to thereby produce an encrypted reply. The encrypted reply is then sent from the server to the mobile device (e.g., a mobile phone). Once received by the mobile device, the encrypted reply is available for transfer (automatically or manually) from the mobile device to the client. Once provided to the client, the client can decrypt the encrypted reply using the encryption key. The decrypted reply is then available for use at (e.g., by) the client.
Owner:ONESPAN NORTH AMERICA INC
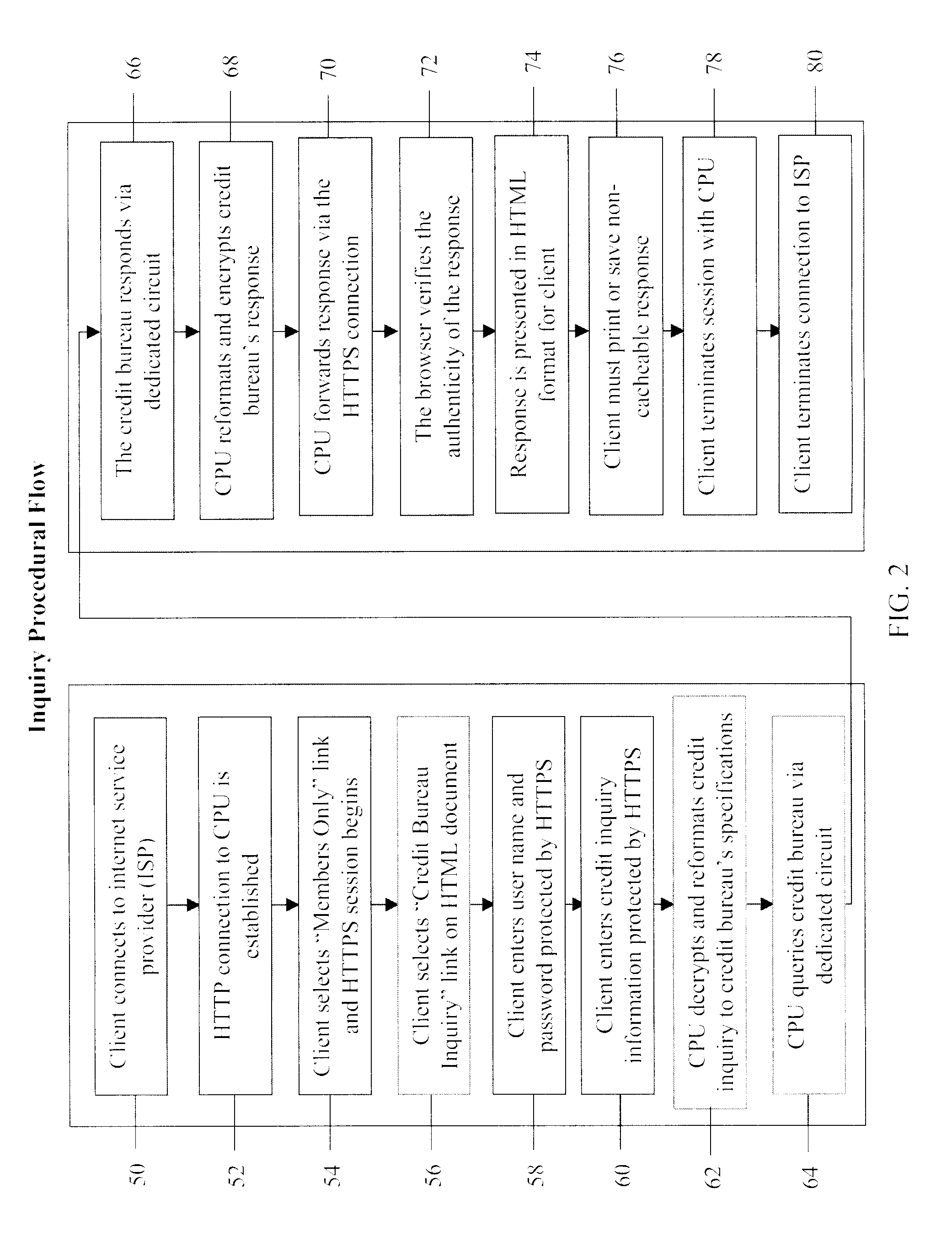
System and method for real-time electronic inquiry, delivery, and reporting of credit information
InactiveUS6988085B2More readable formatSecure transmissionComplete banking machinesFinanceWeb siteWeb browser
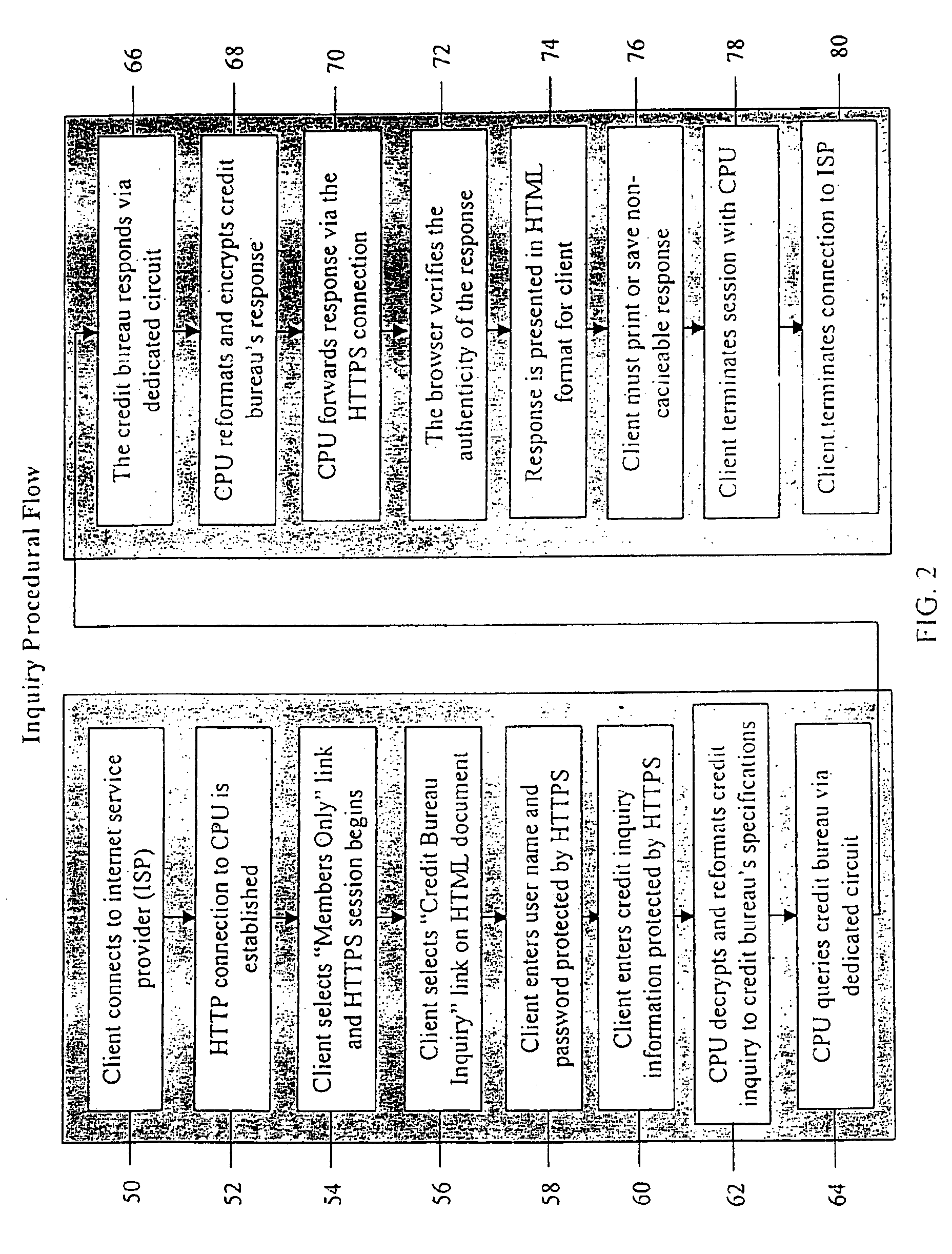
A system and method for providing electronic inquiry, delivery, and reporting of personal credit information to and from credit bureaus, preferably via the Internet. In the preferred embodiment, the system includes a web site that, by using a web browser, allows clients to request credit information from, or provide credit reports to, credit bureaus by entering certain data on pre-built forms in HTML format. The data is encrypted using means for secure transmission, such as a web browser with 128-bit secure socket layer (SSL) technology, then sent to a common gateway interface (CGI) application located on a web server. The CGI application decrypts and reformats the data to a standard format specified by the credit bureau. The CGI application initiates a query. Using a dedicated connection circuit to the credit bureau's computer, the CGI application reformats the response from the credit bureau to an HTML format and encrypts the data using the means for secure transmission. The HTML formatted data is then sent back to the client's computer over the Internet and displayed in the client's web browser in an easily read format.
Owner:F POSZAT HU
System and method for preventing identity theft using a secure computing device
ActiveUS20050071282A1Secure transmissionDigital data processing detailsMultiple digital computer combinationsSecure transmissionIdentity theft
A system and method for effecting secure transactions over a computer network in a manner designed to foil identity theft perpetrated from an untrusted computer. A connection from a client computer to the network wherein the client computer provides a user interface for a user, a connection from a server computer to the network, and a connection from a portable secure computing device to the network provides for secure transmission of private confidential user information from the user to a server. The private information is transmitted directly from the secure computing device to the server over the secure connection without possibility of capture on the computer with which the user is interacting.
Owner:GEMPLU
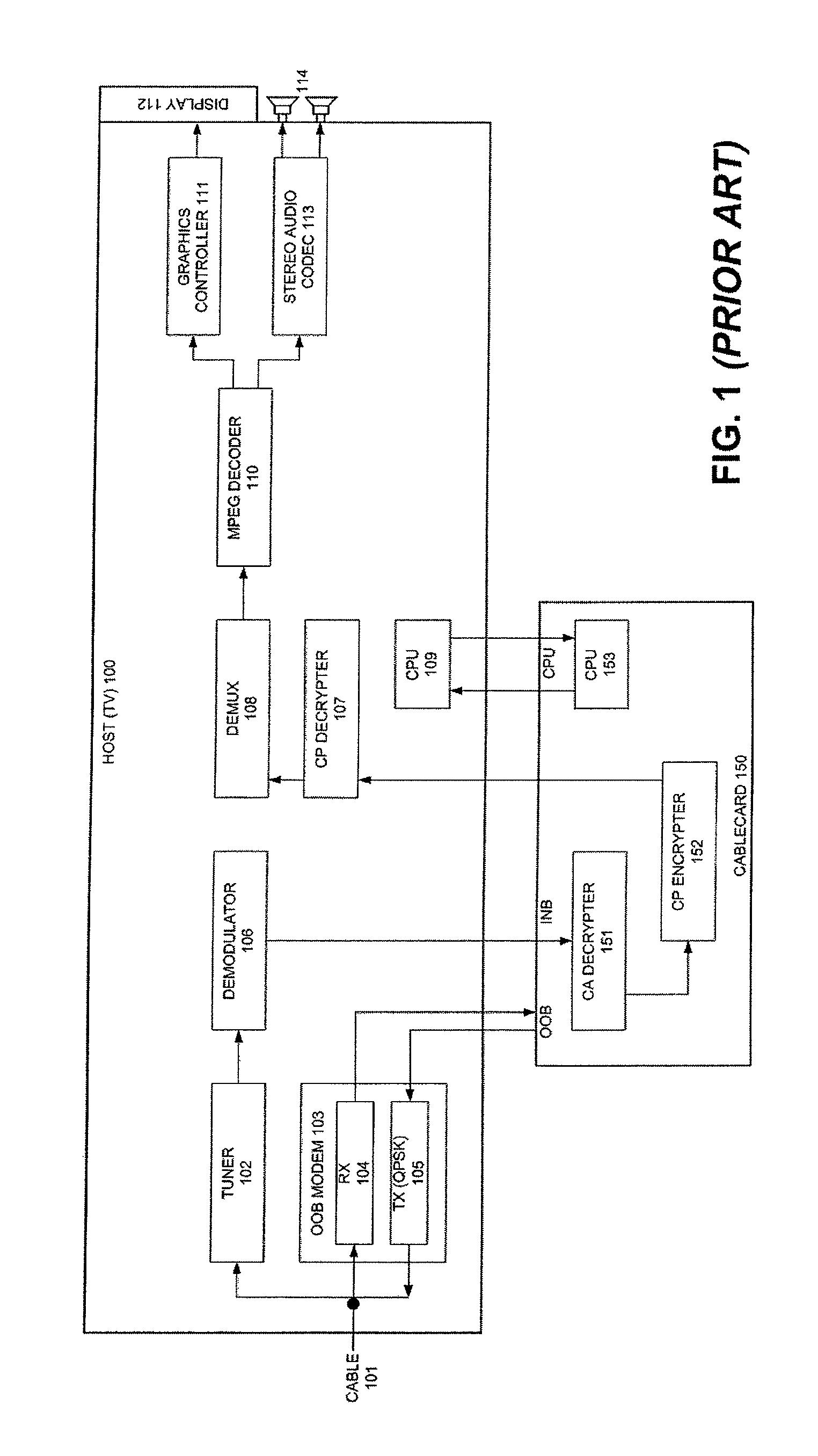
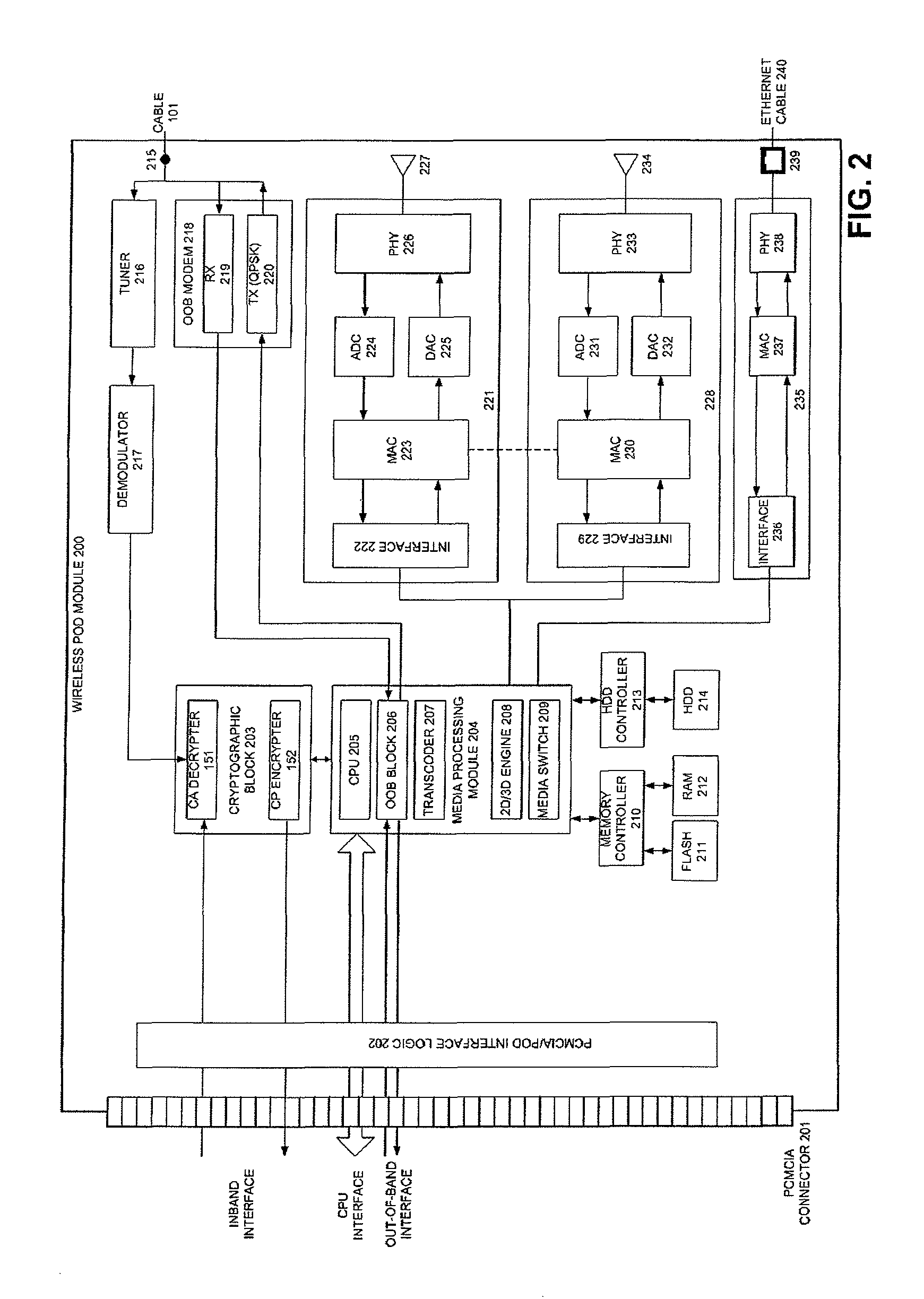
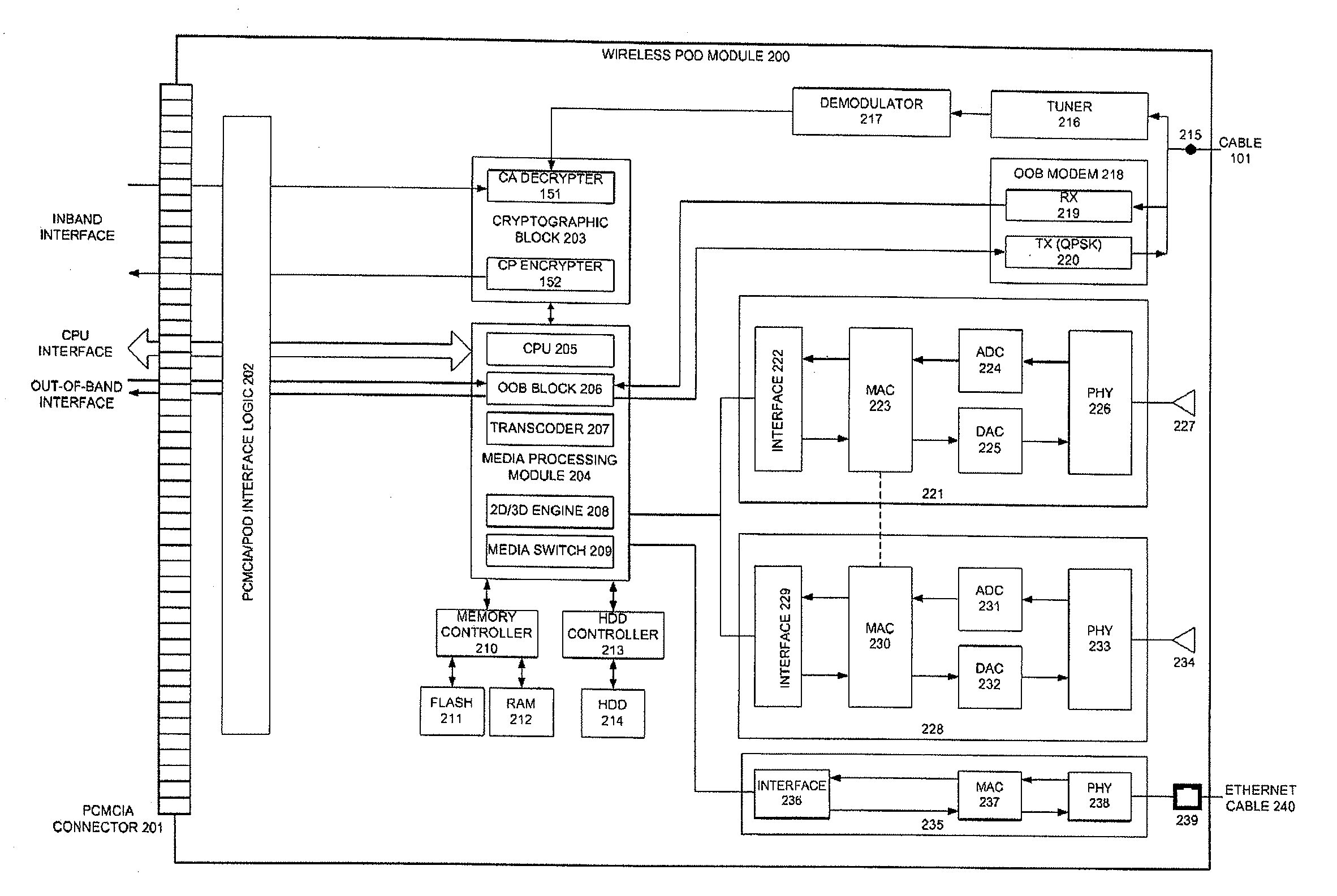
Extended connectivity point-of-deployment apparatus and concomitant method thereof
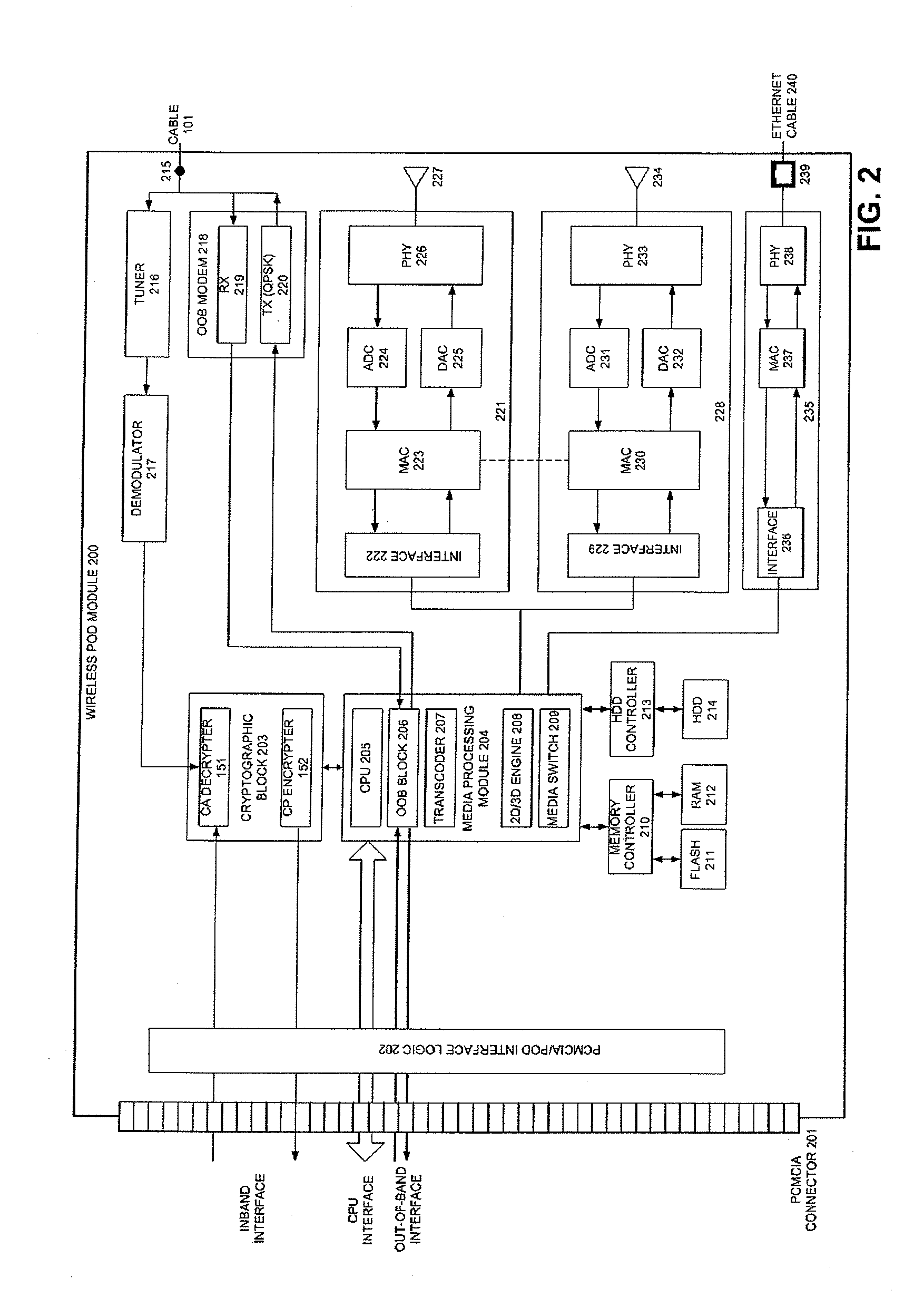
ActiveUS8887212B2Secure transmissionEasy to useNear-field transmissionDigital data processing detailsCoaxial cableComputer module
A POD module system includes a housing, a coaxial cable connector formed on the housing and connectable to a first device to receive a cable signal, a port formed on the housing to receive a wire or wireless signal from a second device, a module unit to process at least one of the cable signal and the at least one of the wireless signal to generate at least one of a copy protection signal and one of video and audio signals, respectively, and a connector formed on the housing and connectable to a third device to transmit the at least one of the copy protection signal and the one of video and audio signals to the third device such that the third device generates at least one of an image and a sound to correspond to the at least one of the copy protection signal and the one of video and audio signals.
Owner:SYNDEFENSE
Pod module and method thereof
ActiveUS20070250872A1Secure transmissionEasy to useAssess restrictionGHz frequency transmissionCoaxial cableEngineering
A POD module system includes a housing, a coaxial cable connector formed on the housing and connectable to a first device to receive a cable signal, a port formed on the housing to receive a wire or wireless signal from a second device, a module unit to process at least one of the cable signal and the at least one of the wireless signal to generate at least one of a copy protection signal and one of video and audio signals, respectively, and a connector formed on the housing and connectable to a third device to transmit the at least one of the copy protection signal and the one of video and audio signals to the third device such that the third device generates at least one of an image and a sound to correspond to the at least one of the copy protection signal and the one of video and audio signals.
Owner:SYNDEFENSE
System and method for delivering encrypted information in a communication network using location identity and key tables
InactiveUS7143289B2Secure transmissionKey distribution for secure communicationDigital data processing detailsSpecific timeComputer security
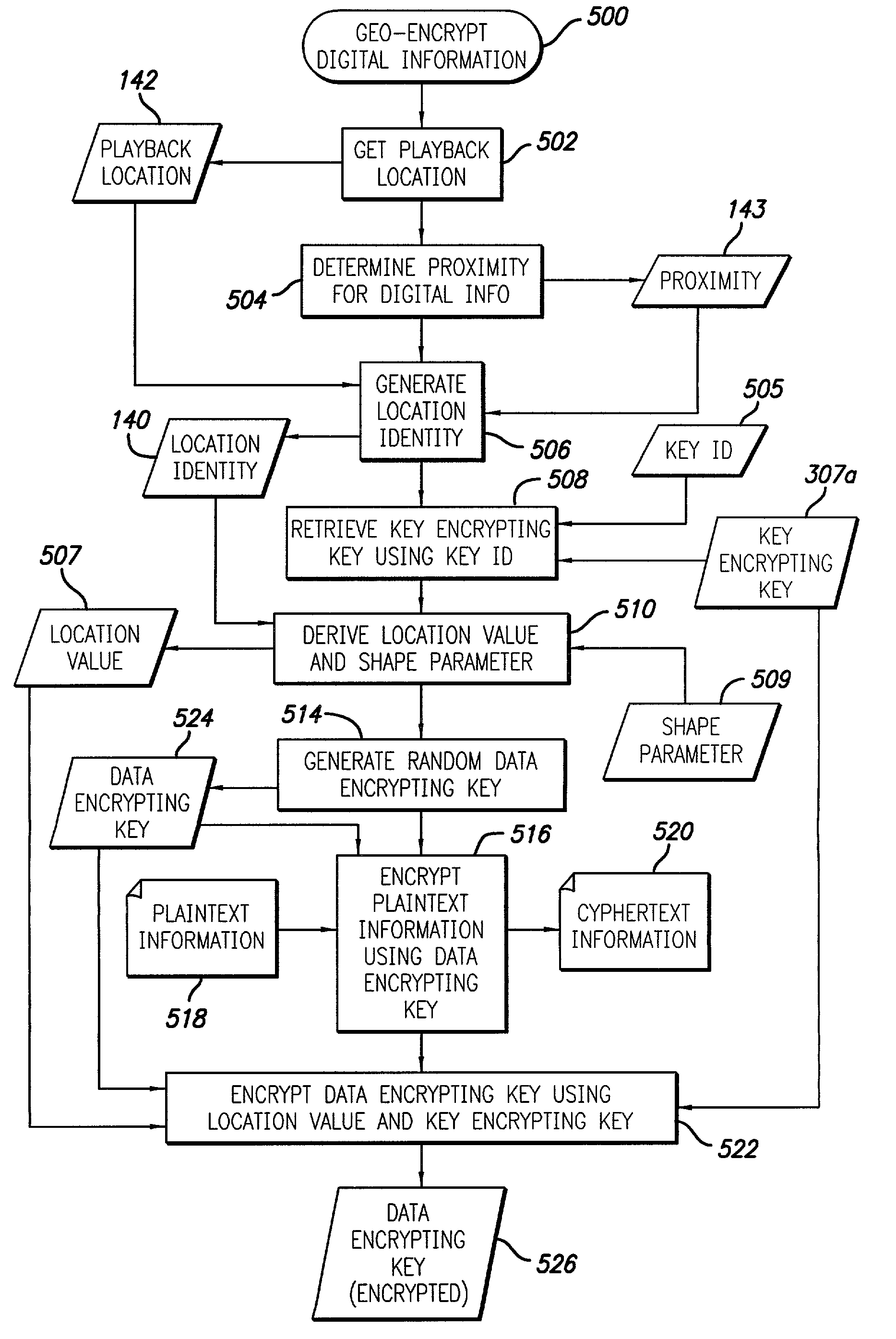
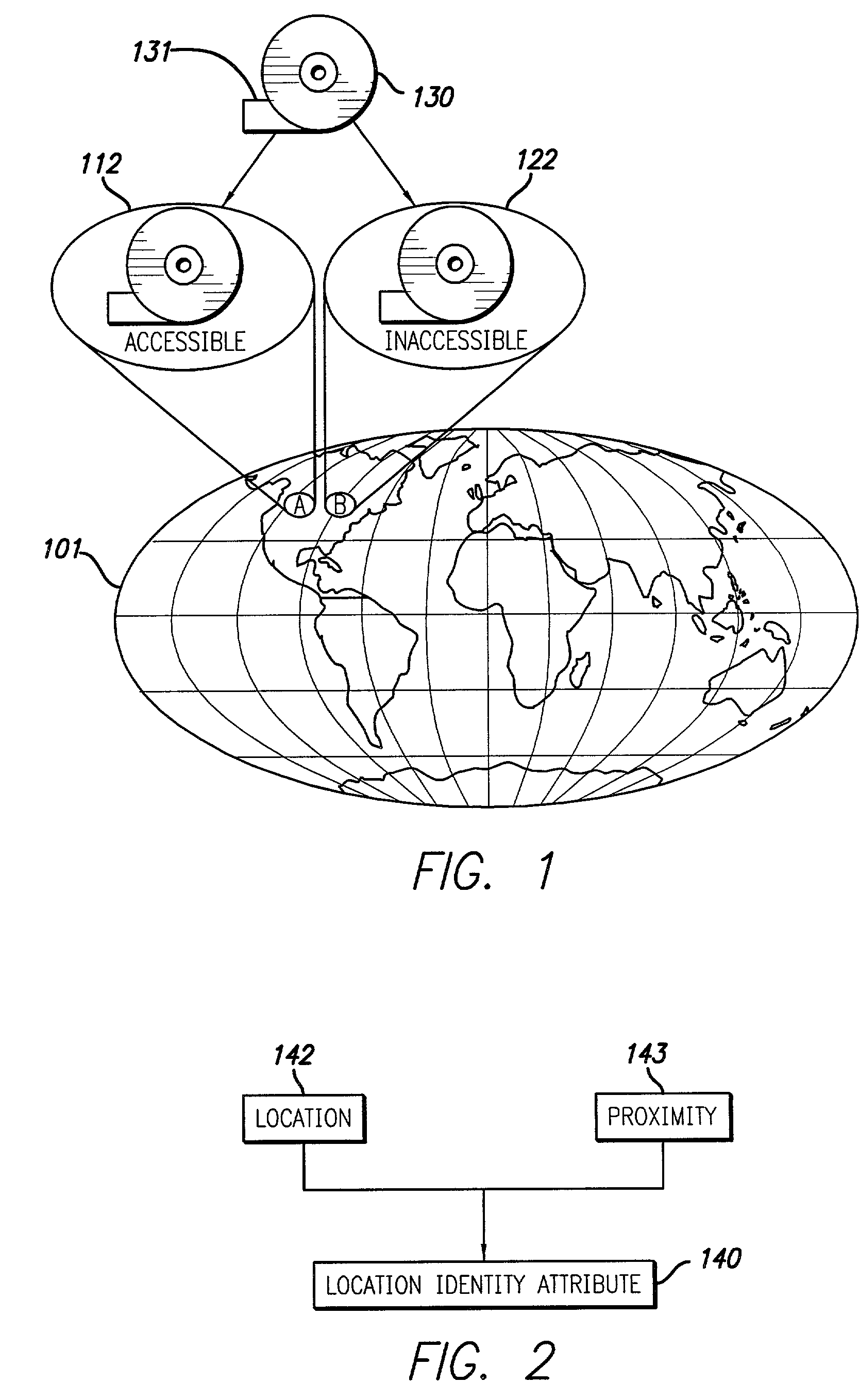
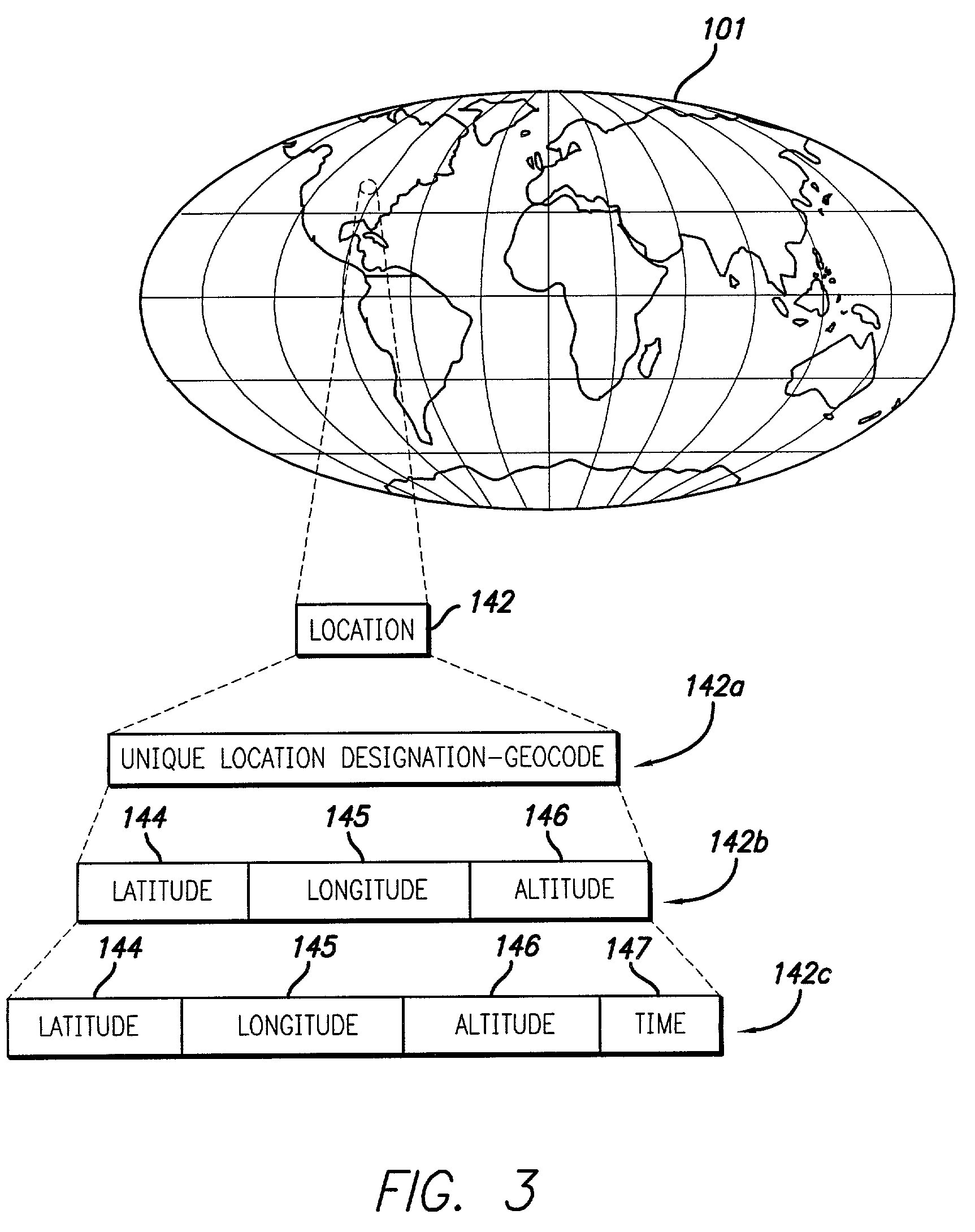
Access to digital data is controlled by encrypting the data in such a manner that, in a single digital data acquisition step, it can be decrypted only at a specified location, within a specific time frame, and with a secret key. Data encrypted in such a manner is said to be geo-encrypted. This geo-encryption process comprises a method in which plaintext data is first encrypted using a data encrypting key that is generated at the time of encryption. The data encrypting key is then encrypted (or locked) using a key encrypting key and information derived from the location of the intended receiver. The encrypted data encrypting key is then transmitted to the receiver along with the ciphertext data. The receiver both must be at the correct location and must have a copy of the corresponding key decrypting key in order to derive the location information and decrypt the data encrypting key. After the data encrypting key is decrypted (or unlocked), it is used to decrypt the ciphertext. If an attempt is made to decrypt the data encrypting key at an incorrect location or using an incorrect secret key, the decryption will fail. If the sender so elects, access to digital data also can be controlled by encrypting it in such a manner that it must traverse a specific route from the sender to the recipient in order to enable decryption of the data. Key management can be handled using either private-key or public-key cryptography. If private-key cryptography is used, the sender can manage the secret key decrypting keys required for decryption in a secure manner that is transparent to the recipient. As a consequence of its ability to manipulate the secret keys, the sender of encrypted data retains the ability to control access to its plaintext even after its initial transmission.
Owner:LONGBEAM TECH LLC
System and Method for Searching for Internet-Accessible Content
InactiveUS20080114739A1Secure transmissionMotivate userWeb data indexingDigital data processing detailsWeb siteWeb browser
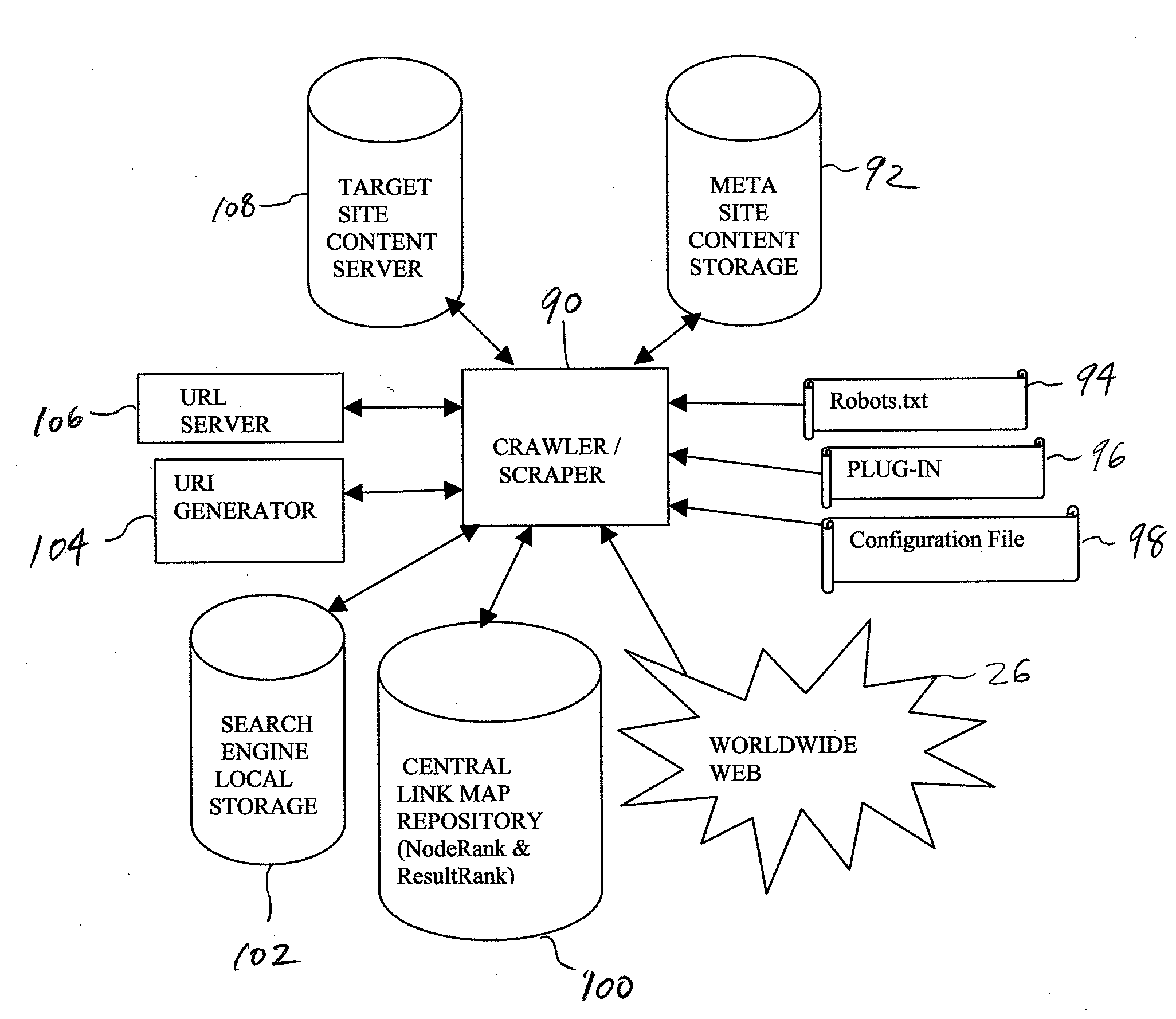
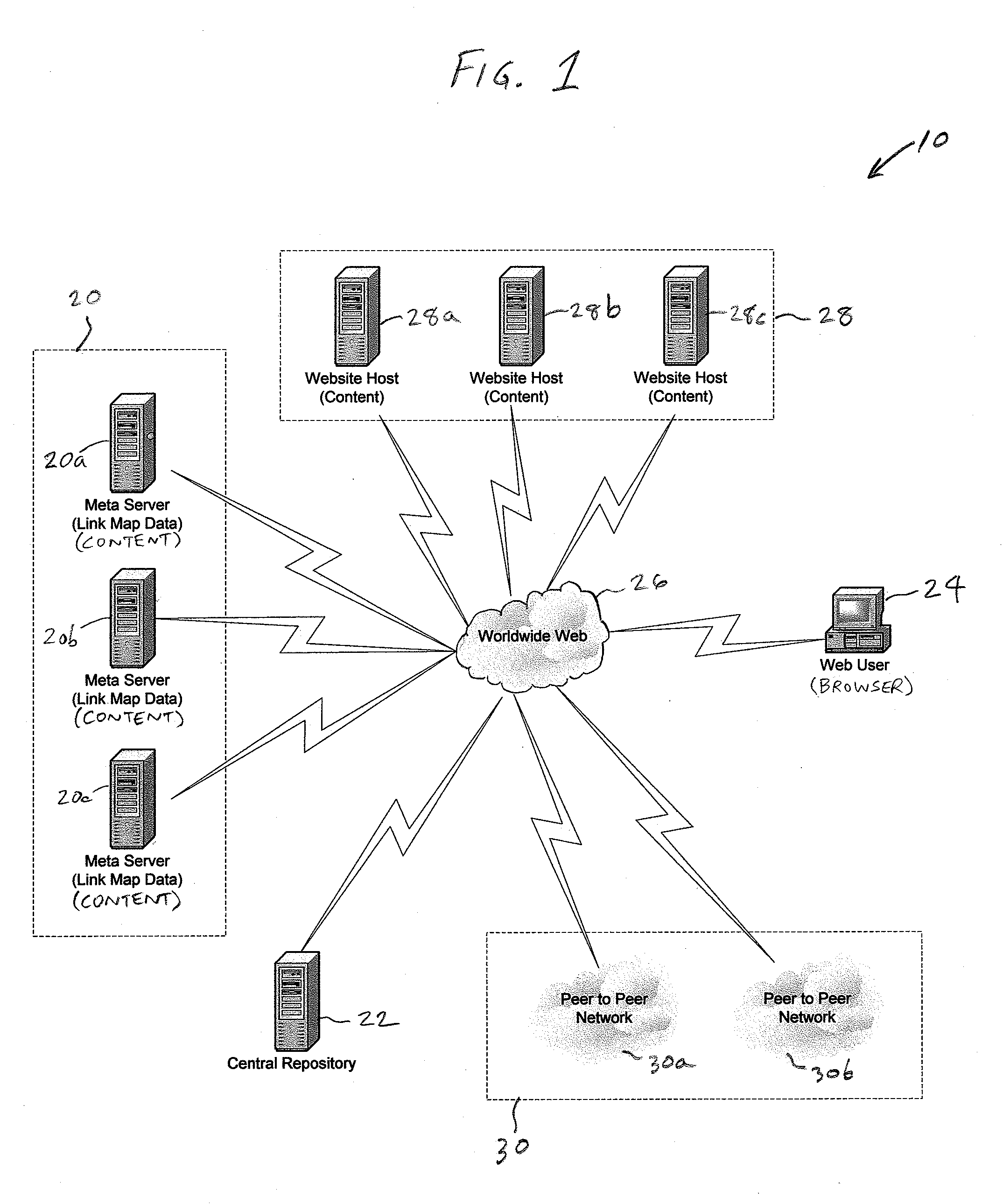
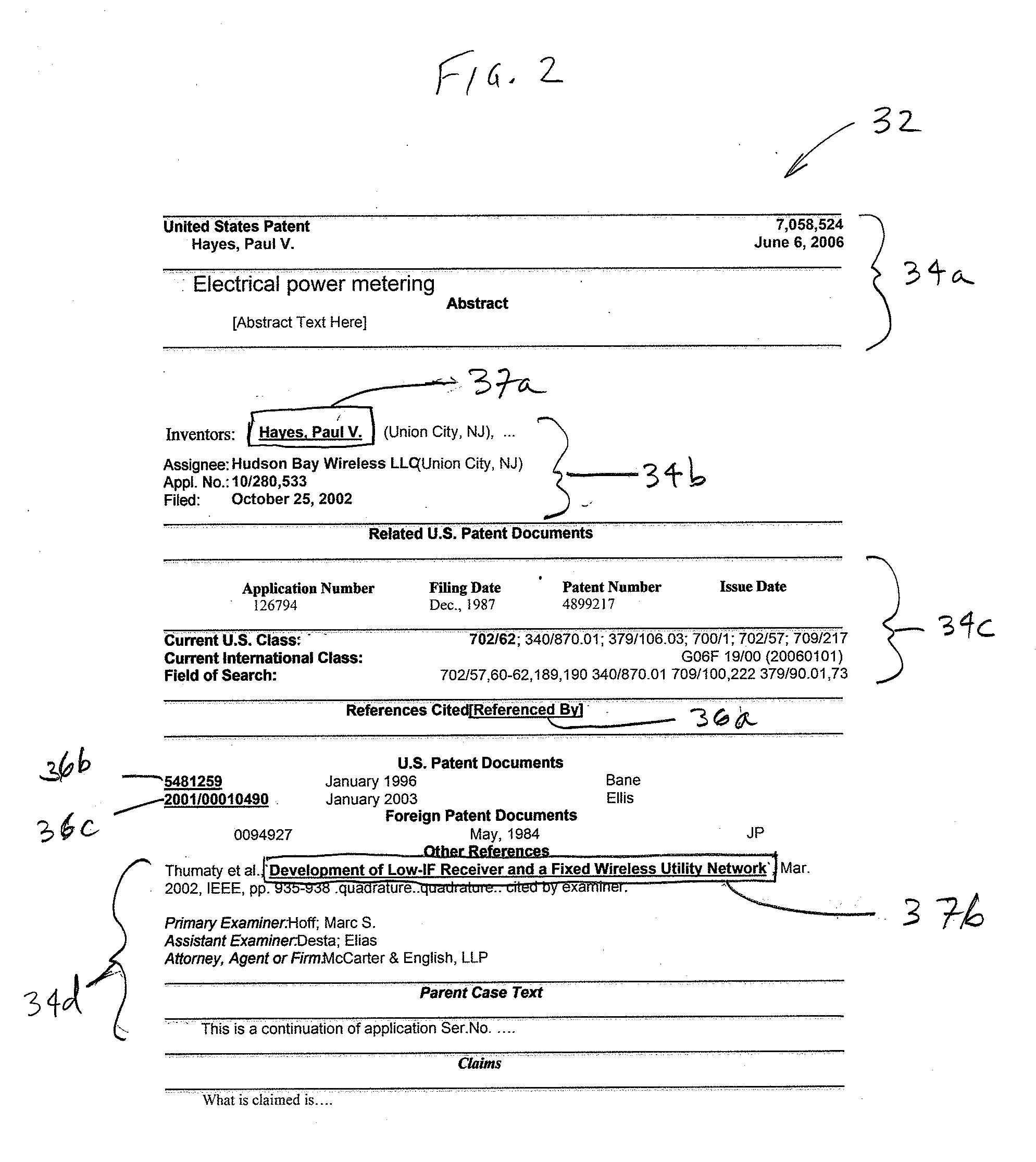
A system and method for searching and voting on Internet-accessible content is presented. One or more meta servers or sites store information about the structure and location of content on one or more Internet host servers. HTML-linked content on the one or more Internet host servers is indexed and stored on the one or more meta servers, and non-HTML content on the one or more Internet host servers is processed by the present invention into HTML content, indexed, and stored on the one or more meta servers. Each meta server includes a local search engine that can be queried by a user. A plurality of different types of queries can be conducted by the user, including local queries, global queries, and peer-to-peer network queries. The user is provided with search results which point to relevant content on one or more of the meta server and / or one or more of the Internet host servers. After viewing the content, the user can cast votes relating to the user's satisfaction with the search results. The present invention also includes a central repository which tracks user votes, query progressions, and information about content on each of the meta sites. The present invention also provides a plurality of enhancement plug-ins for standard web robots, including a toolbar for conventional web browsers. The toolbar can be used to securely solicit and collect authenticated user votes from standard web sites, as well as to vote-check top results returned by supported search engines. The plug-ins facilitate interoperability between existing Internet software (and technology) and the present invention.
Owner:HUDSON BAY WIRELESS
Magnetic strip reader with power management control for attachment to a PDA device
InactiveUS6944782B2Easy to optimizeEasy to doVolume/mass flow measurementPower supply for data processingEngineeringApplication software
A magnetic stripe card manual swipe reader (MSR) unit capable of attaching to and communicating with a conventional personal digital assistant (PDA) from various manufacturers, using only the electrical power available as supplied by the PDA device, and capable of effective electrical power management and conservation operations. Additionally, this PDA attachable MSR unit is capable of recognizing multiple magnetic encoding formats and data record formats and converting said formats to a standardized output format, includes the capability of updating and adding new formats while in field service, and is readily allows verifying card data and encoding sensitive material prior to transmission to the PDA. These custom formats can then be used to fulfill current needs in age verification, law enforcement, security, and numerous other applications.
Owner:VERIFONE INC
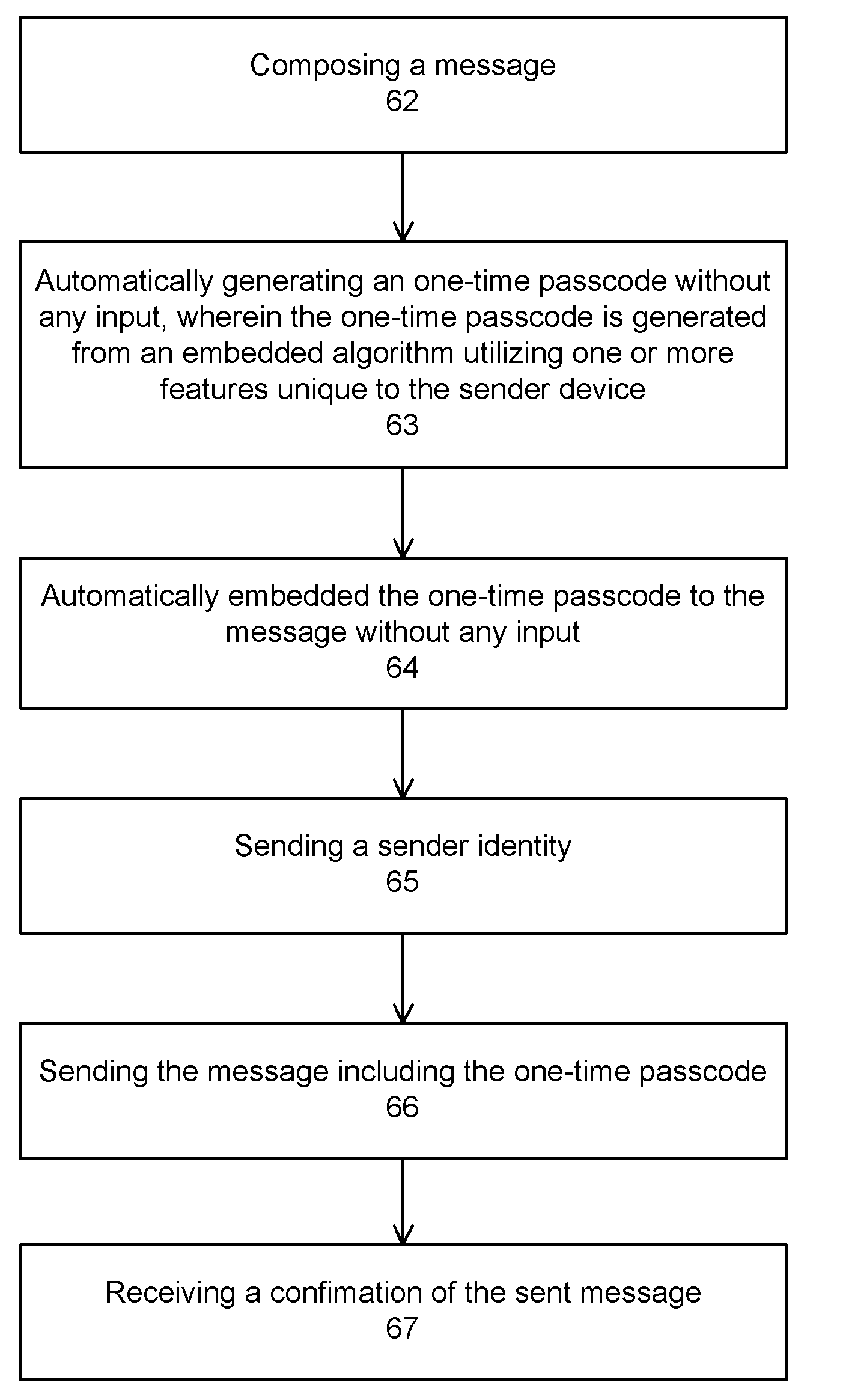
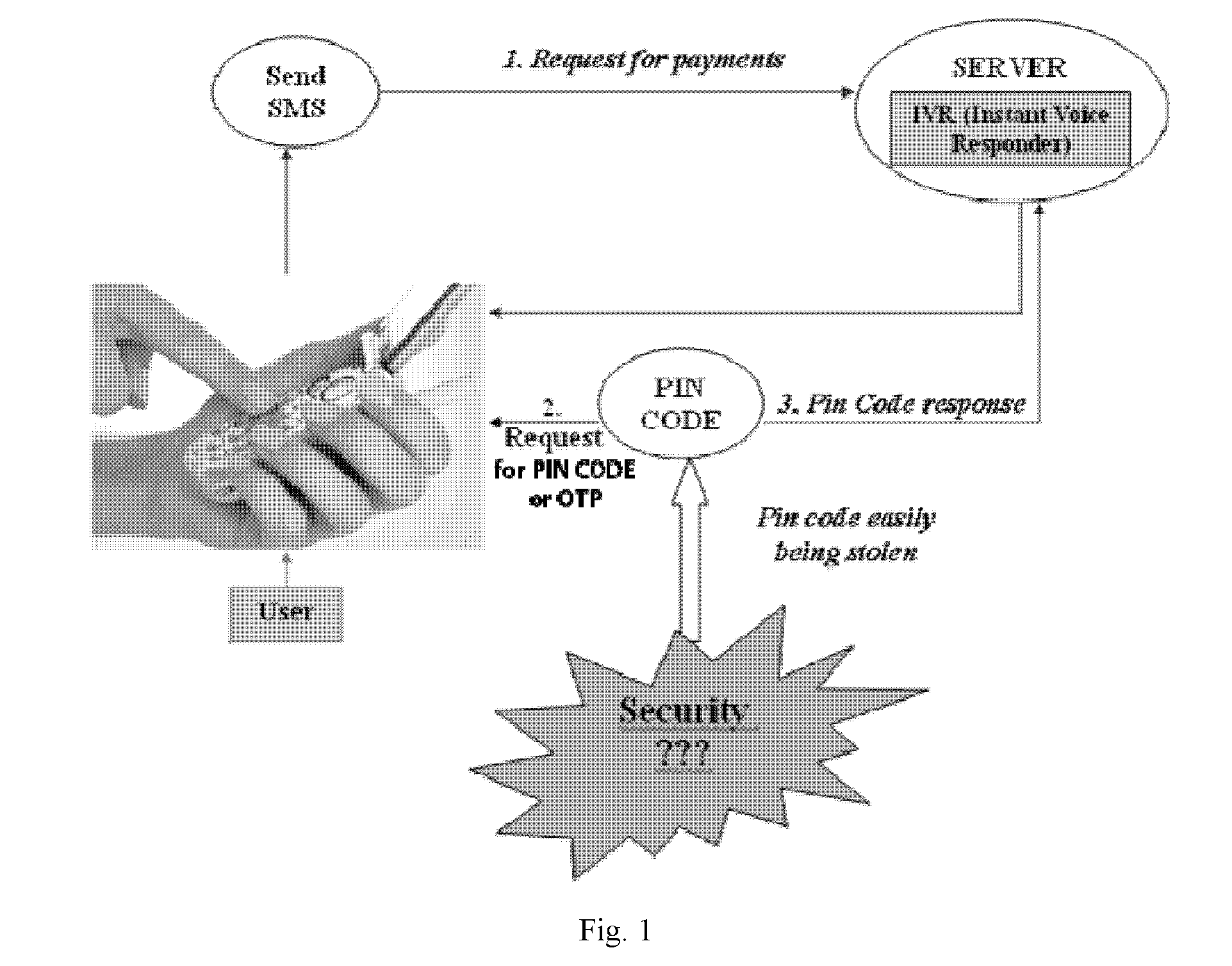
Multi-factor authentication and certification system for electronic transactions
InactiveUS20090172402A1Environment safetyImprove securityFinanceUser identity/authority verificationE-commerceOne-time password
The present invention provides computer-enable certification and authentication in, for example, e-commerce with wireless and mobile devices. The present authentication method offers ease of operation by automatically embedding a one-time passcode to the message without the sender input. A one-time key can also be used to encrypt the message, further providing transmission security. In addition, sensitive information and one-time passcode generator are pre-arranged and stored at both sender and receiver devices, avoiding information comprising in wireless environment transmission.
Owner:TRAN NGUYEN THO
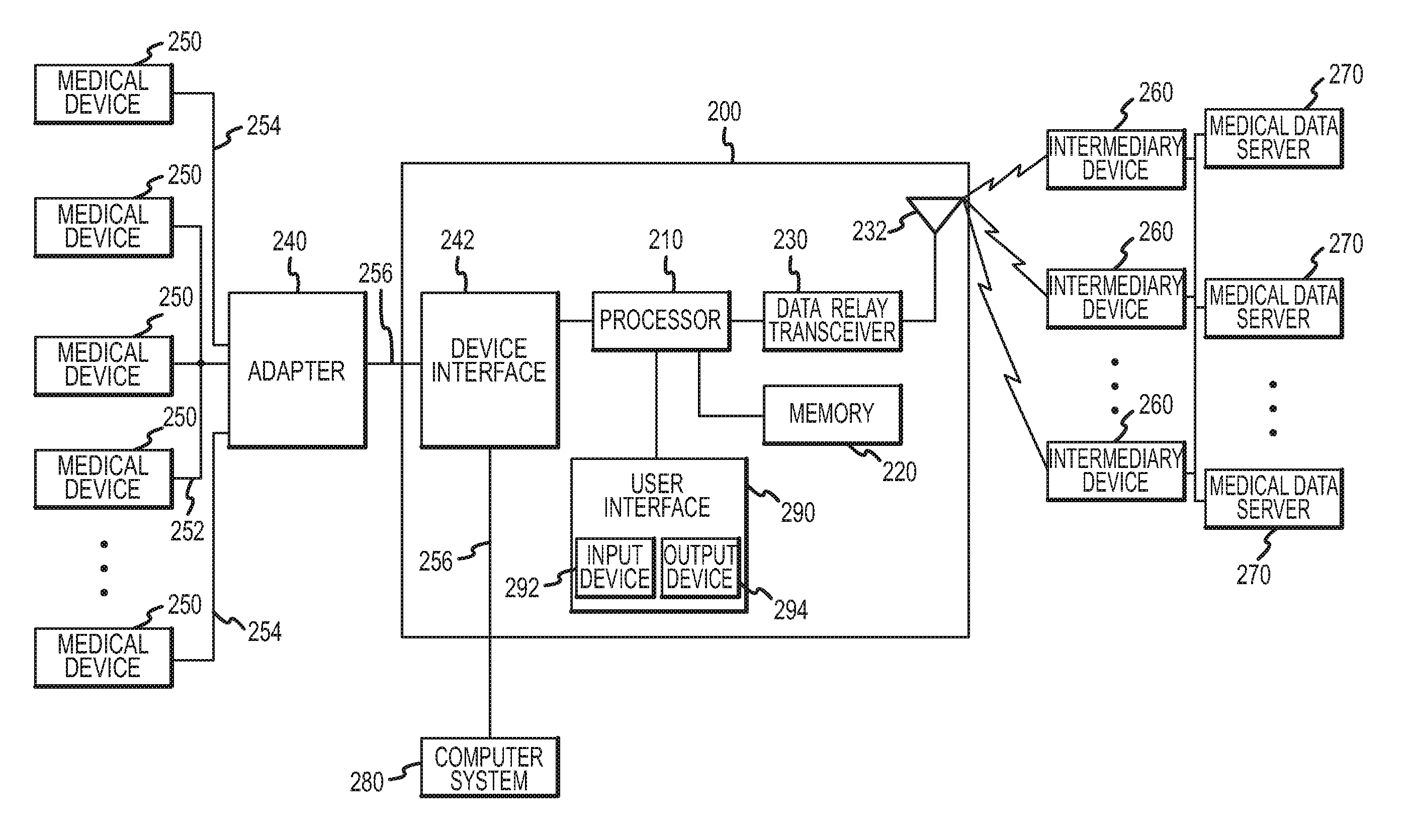
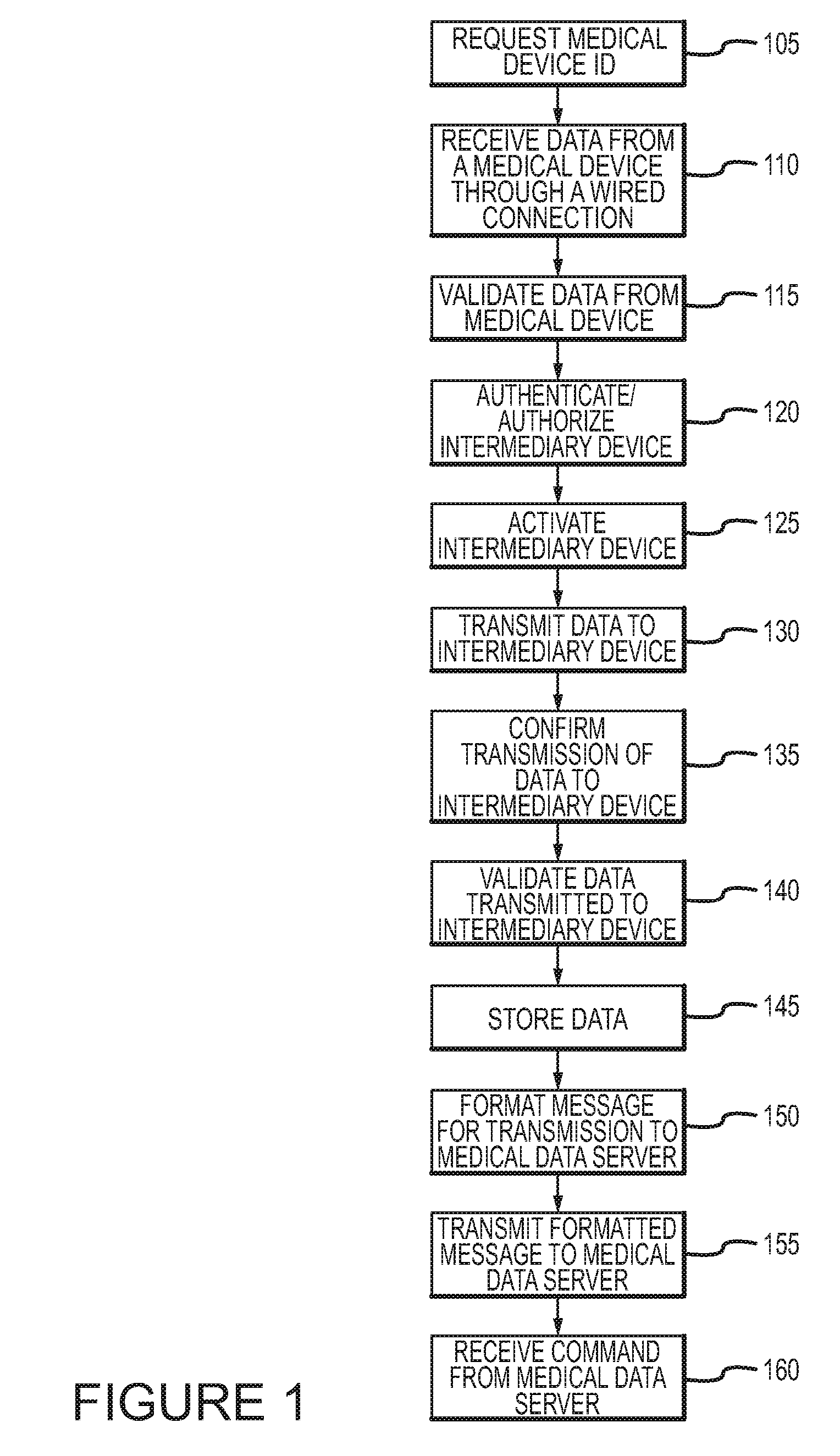
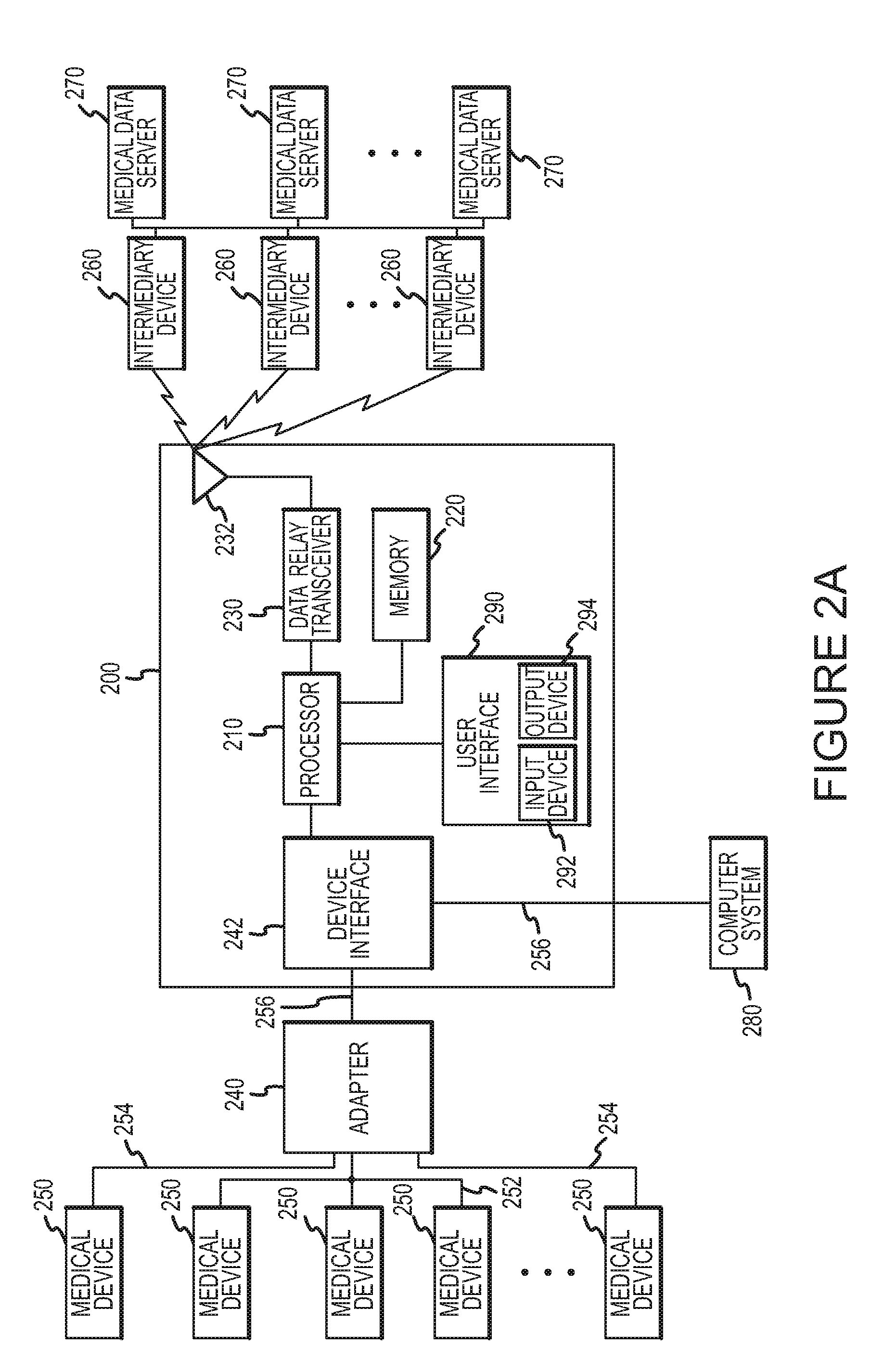
Systems and methods for processing and transmittal of data from a plurality of medical devices
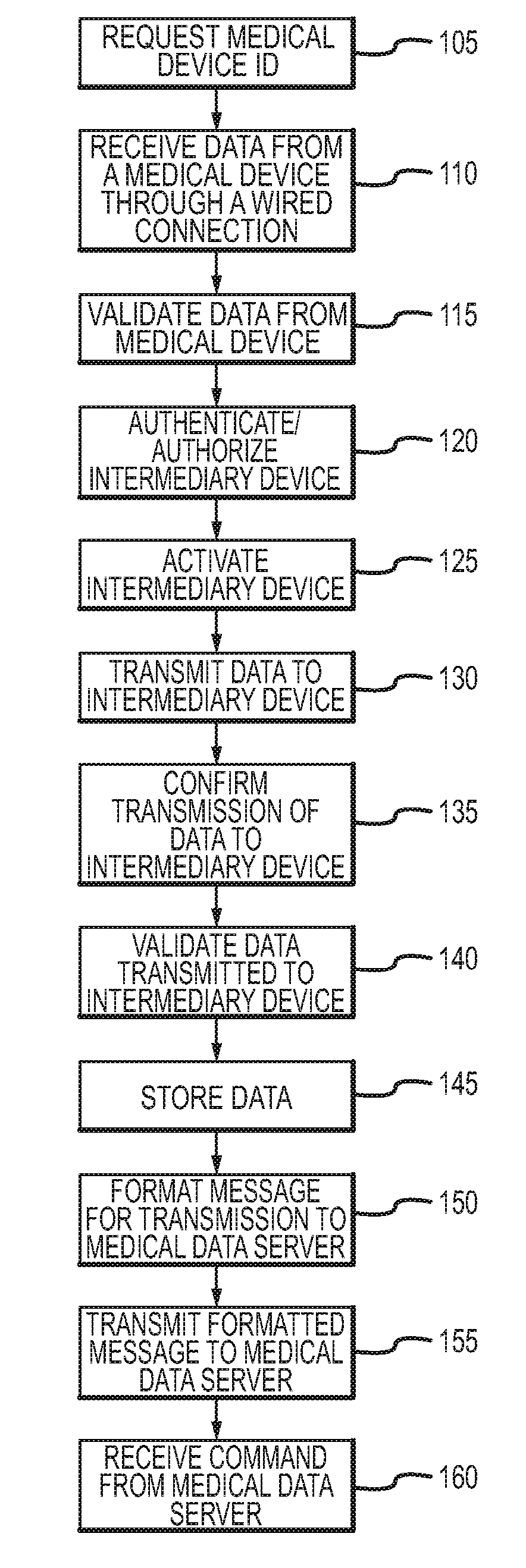
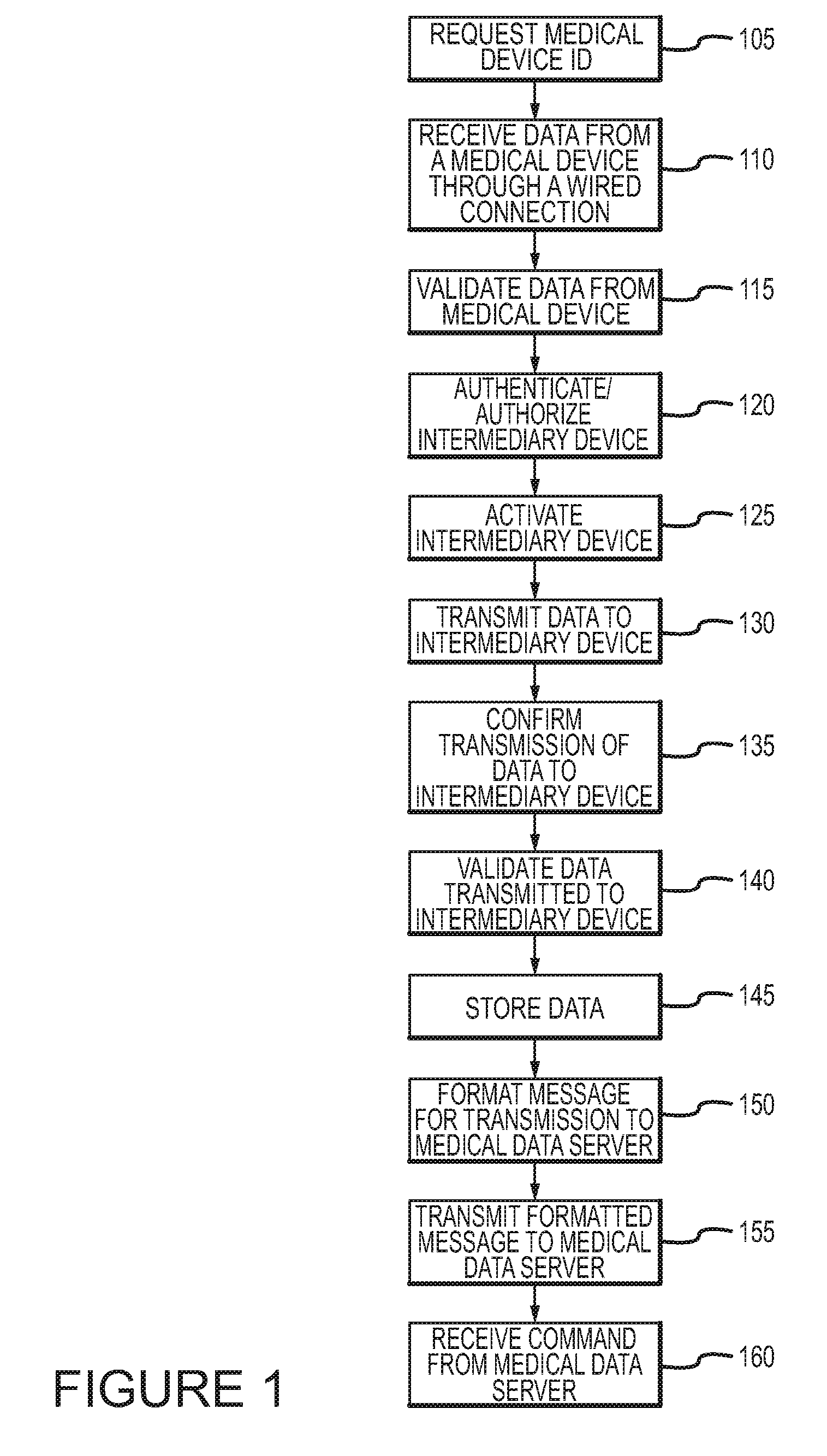
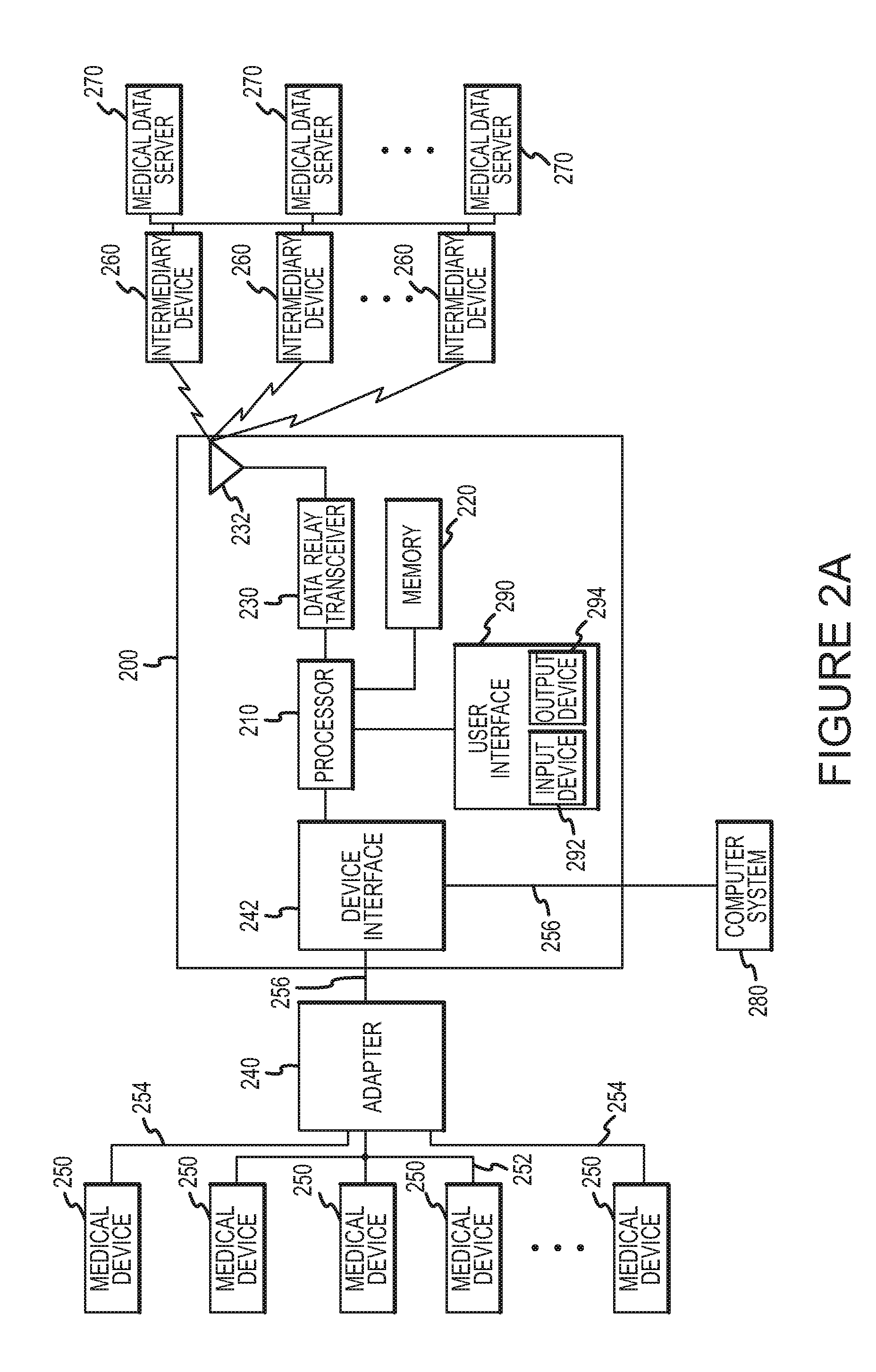
ActiveUS8126729B2Secure transmissionActive lifestyleData processing applicationsLocal control/monitoringMedical deviceOperating system
A method according to an aspect of the present invention includes receiving data from a plurality of medical devices through a wired connection, transmitting the data to an intermediary device, and formatting a message including the received data for transmission to a medical data server. This method can be practiced automatically to allow a medical device for a patient or other subject to be monitored without requiring the patient to manually enter information. This method also allows any number of different medical devices to be monitored, even where such devices each communicate using different wired connections and / or using different communication protocols.
Owner:MEDAPPS
Data transmission of sensors
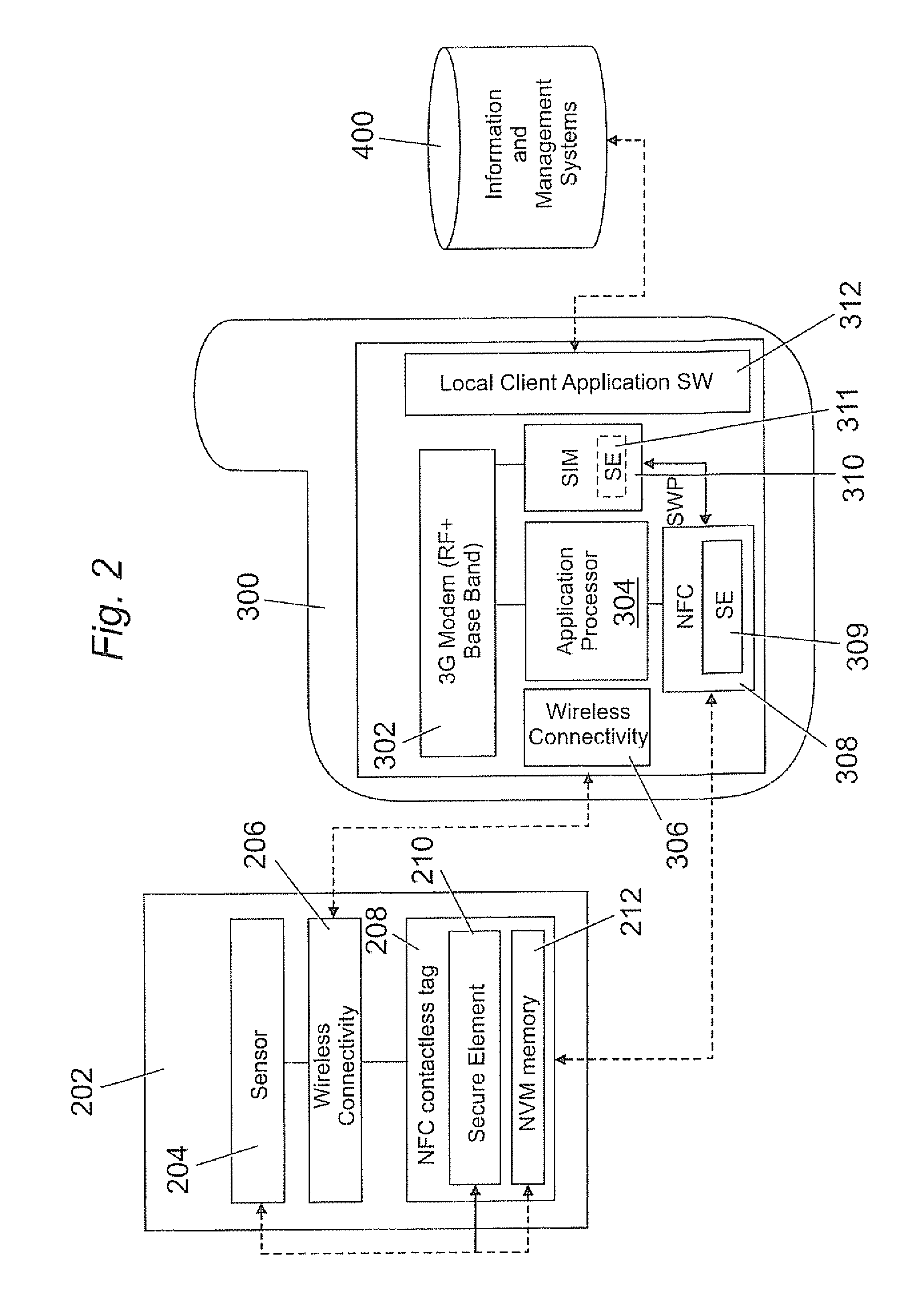
InactiveUS20100045425A1Secure transmissionElectric signal transmission systemsDigital data processing detailsSecure transmissionData transmission
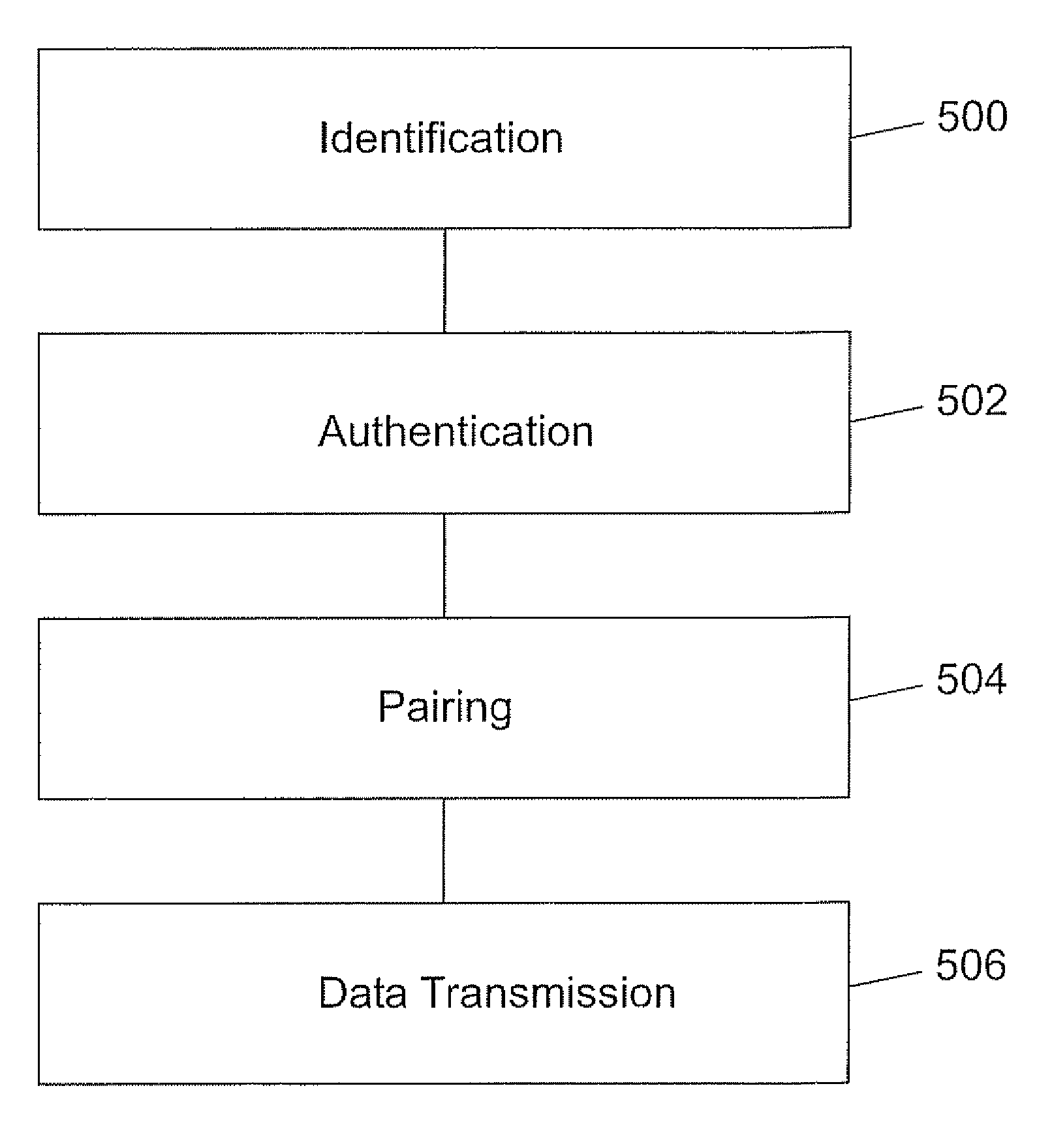
A method for data transmission between a sensor module for measuring and storing data and a mobile device wherein the sensor module and the mobile device have identified each other and, wherein the sensor module comprises a first secure element capable of storing a first security key and the mobile device comprises a second secure element capable of storing a second security key characterized in that the method comprises the steps of an authentication step for carrying out a security process between the sensor module and the mobile device in order to authenticate the sensor module with the mobile device by means of comparing first and second security keys; a pairing step for establishing a communication between the sensor module and the mobile device in order to enable communication therebetween; a transmission step for establishing a secure transmission of data from the sensor module to the mobile device when comparison of the first and second security keys has resulted in authentication.
Owner:CHIVALLIER M LAURENT
Secure intranet access
InactiveUS6950936B2Secure transmissionDigital data processing detailsUser identity/authority verificationAccess methodPrivate network
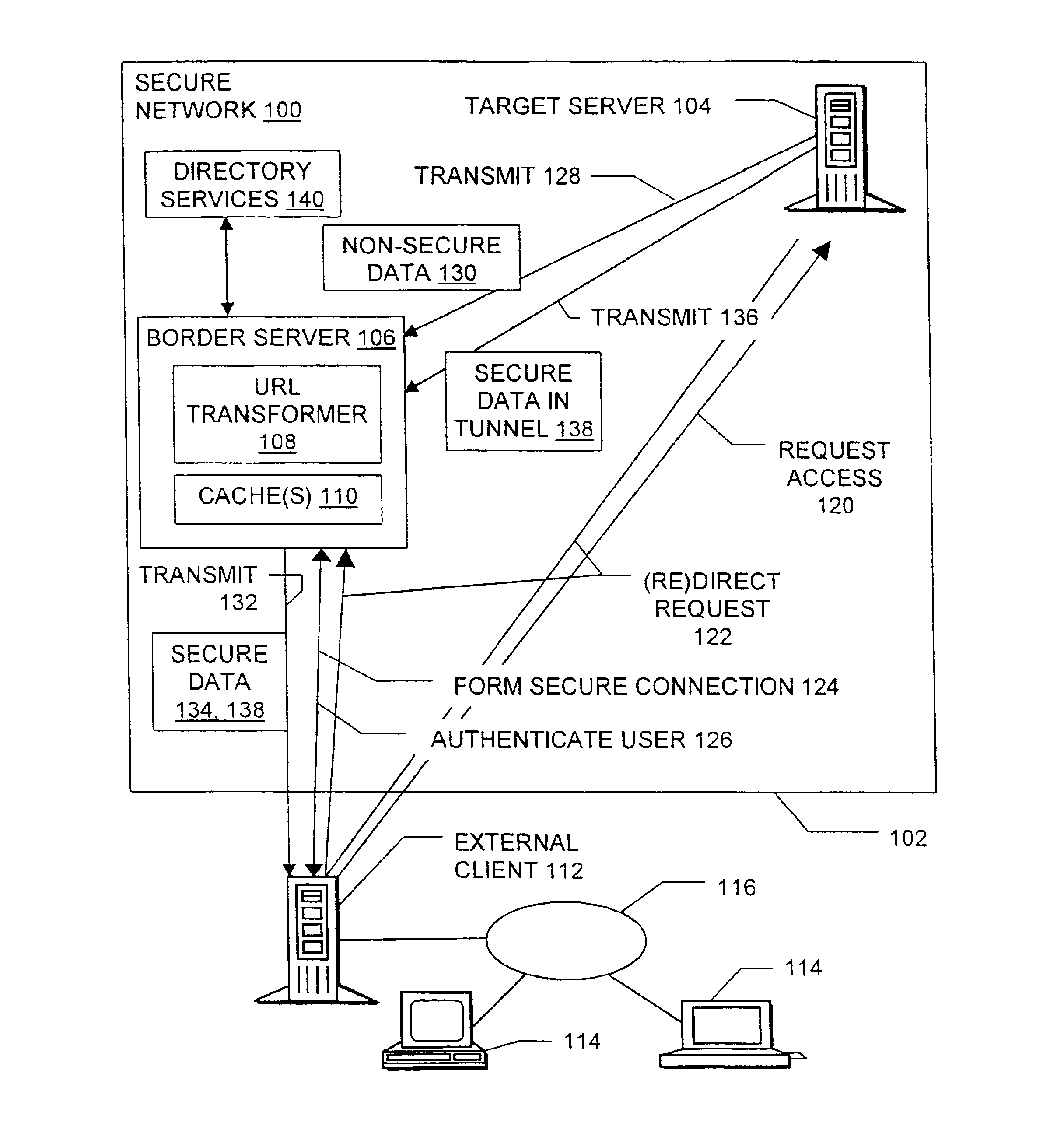
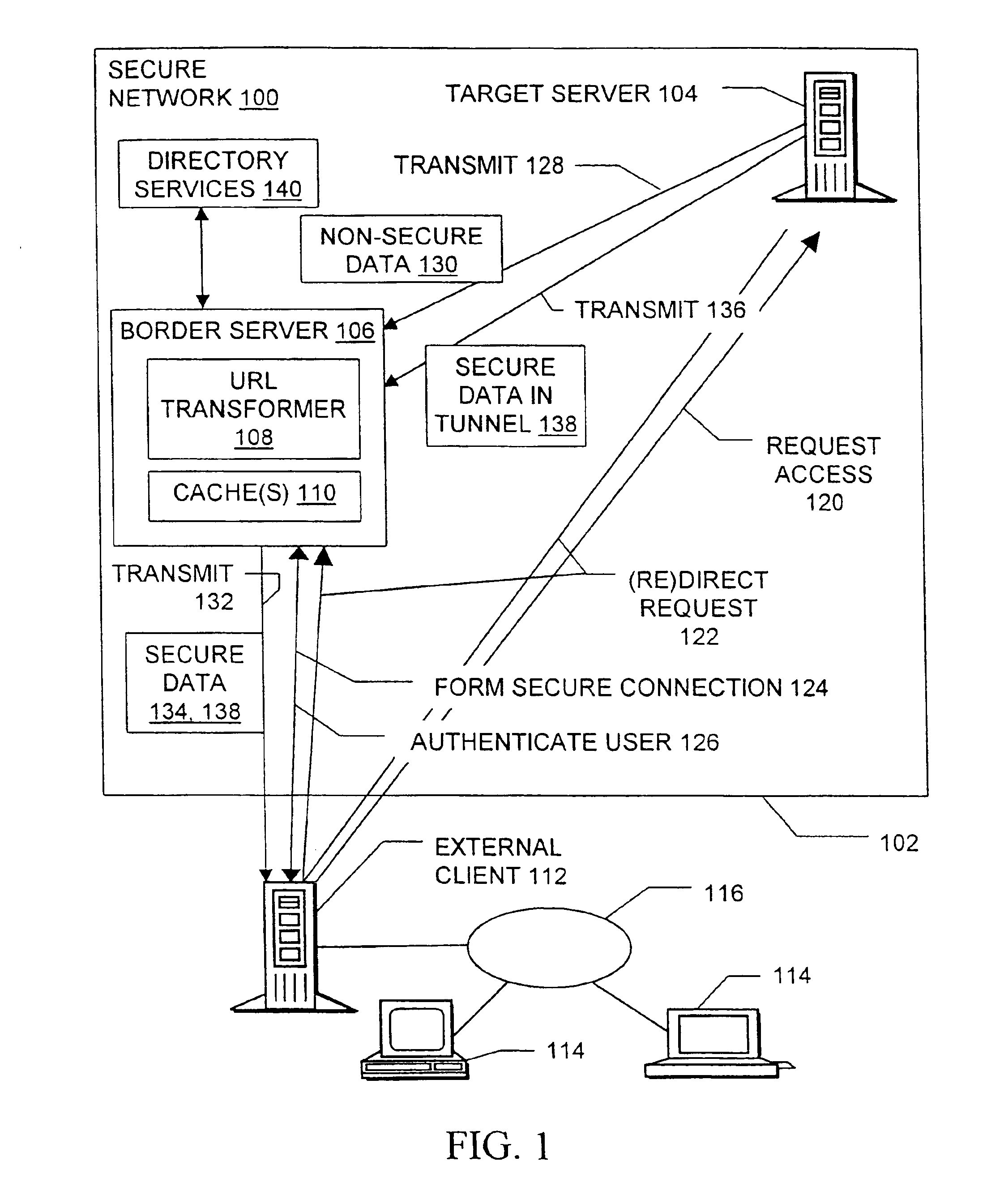
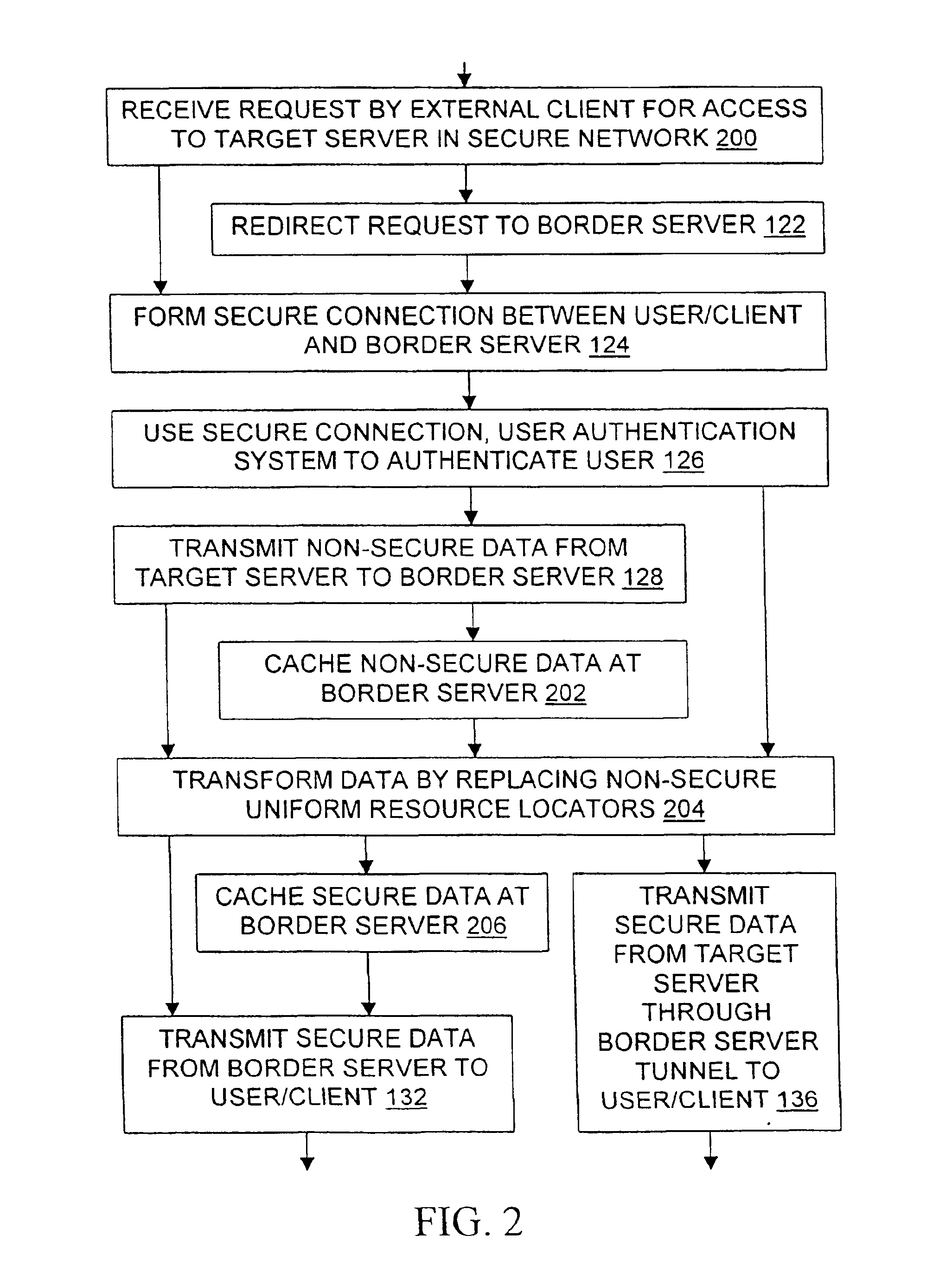
Methods, signals, devices, and systems are provided for secure access to a network from an external client. Requests for access to confidential data may be redirected from a target server to a border server, after which a secure sockets layer connection between the border server and the external client carries user authentication information. After the user is authenticated to the network, requests may be redirected back to the original target server. Web pages sent from the target server to the external client are scanned for non-secure URLs such as those containing “http: / / ” and modified to make them secure. The target server and the border server utilize various combinations of secure and non-secure caches. Although tunneling, may be used, the extensive configuration management burdens imposed by virtual private networks are not required.
Owner:RPX CORP
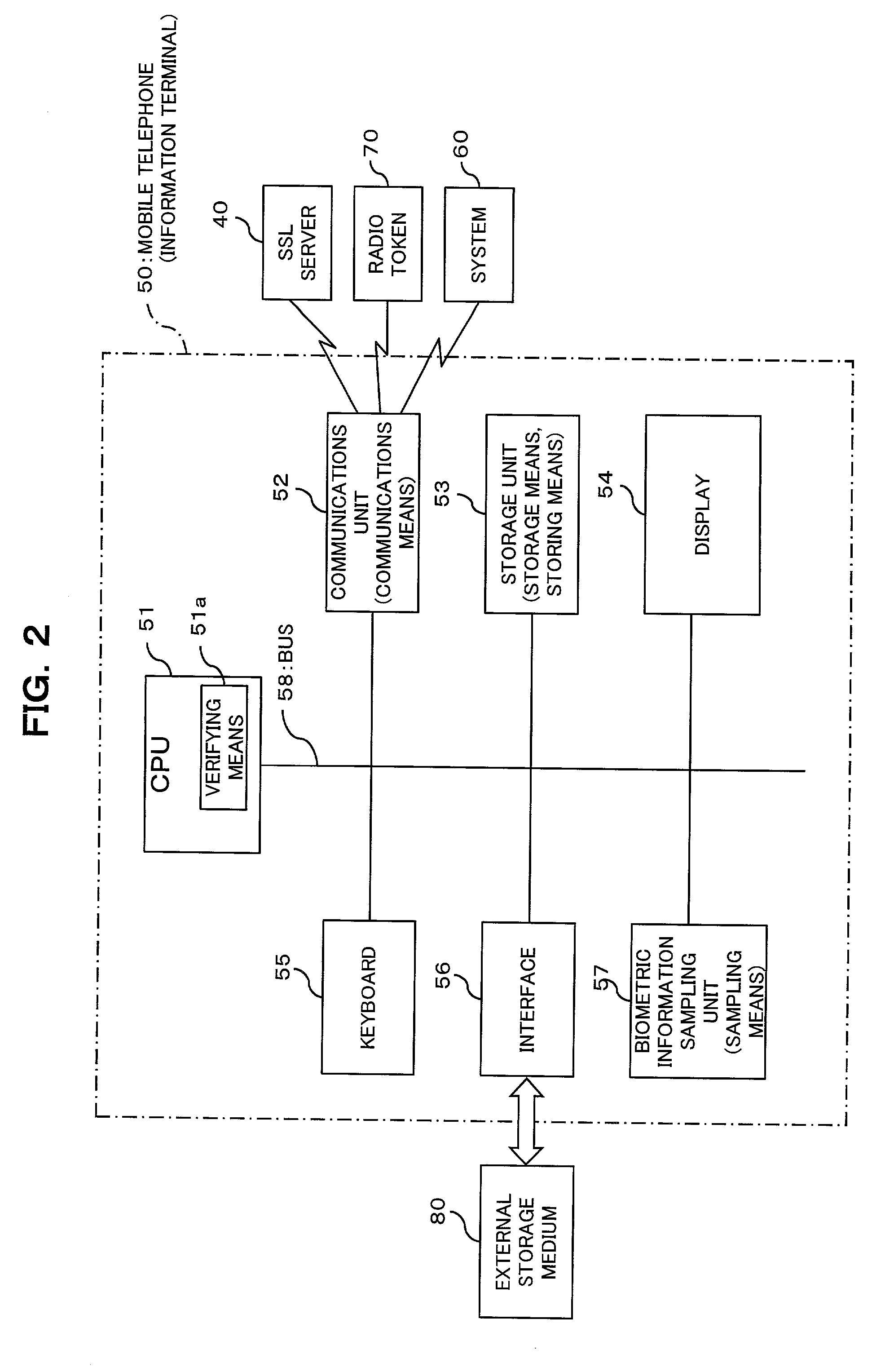
Confidential information management system and information terminal for use in the system
InactiveUS20030004881A1Simplify user operationsAvoid problemsUser identity/authority verificationUnauthorized memory use protectionUser verificationInternet privacy
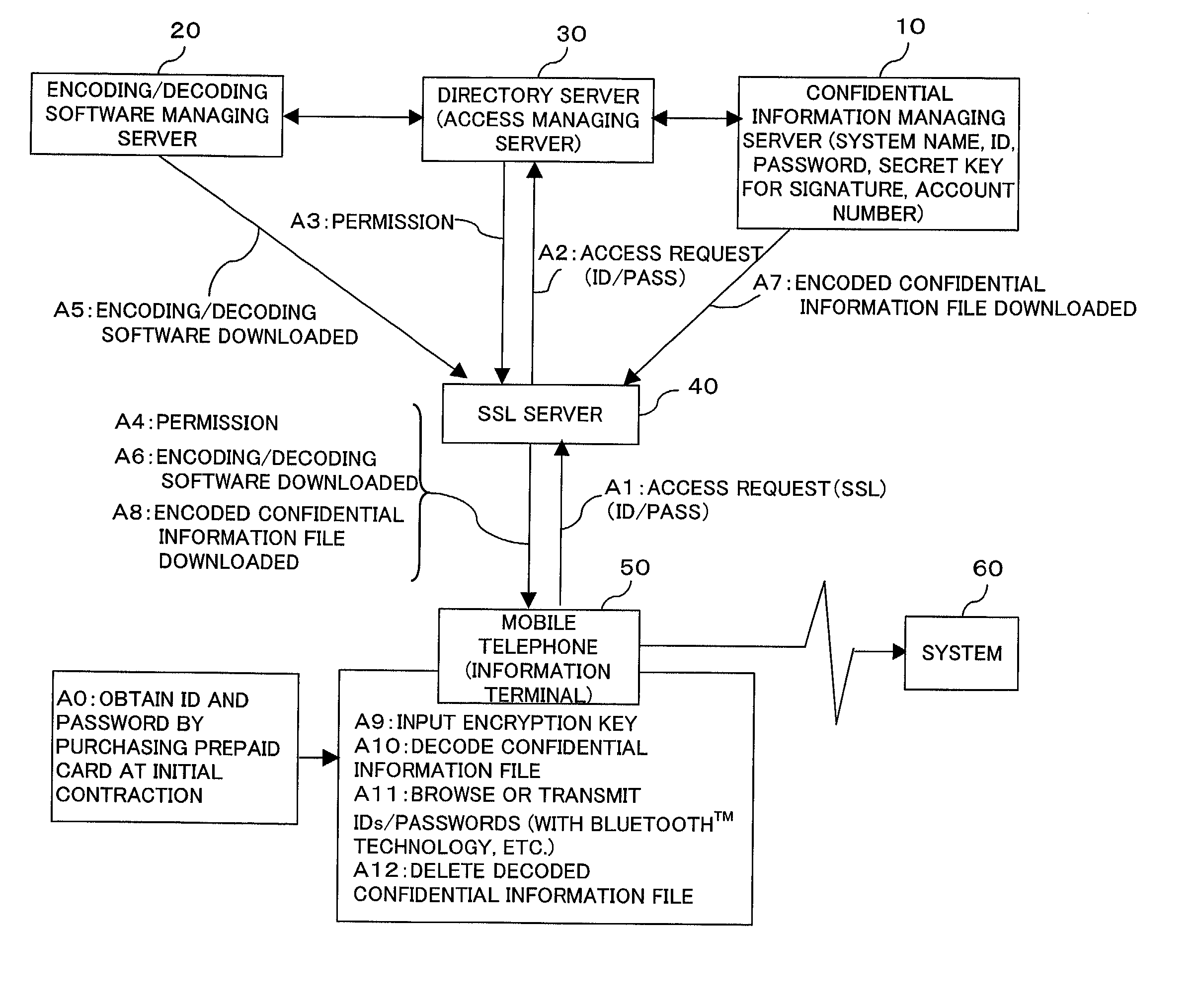
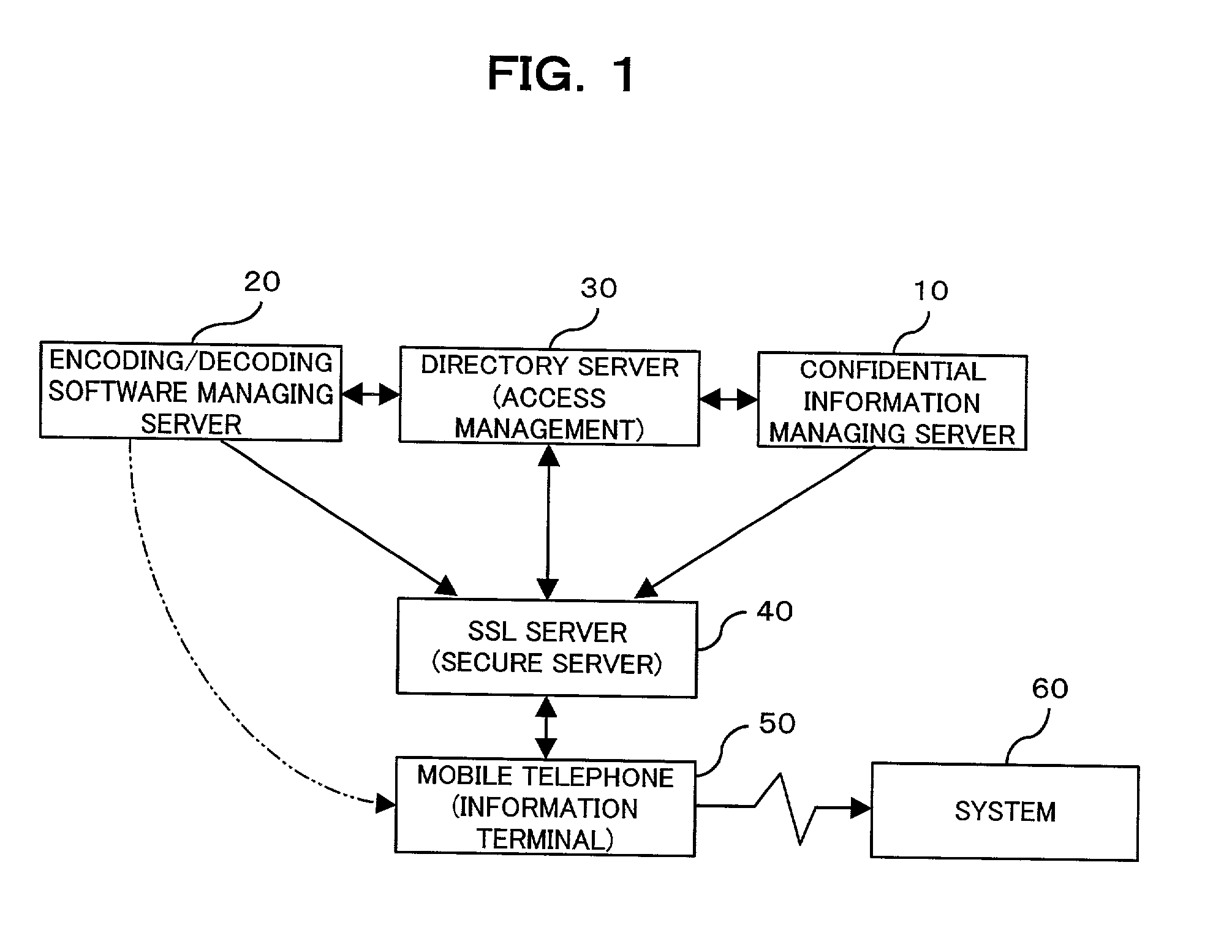
The present invention provides a confidential information management system which allows users to securely obtain confidential information files containing various confidential information, which files are securely stored in the present system, anywhere and anytime, using a minimum of confidential information. A confidential information file and encoding / decoding software are downloaded to an information terminal from a confidential information managing server and an encoding / decoding software managing server, respectively, so that the confidential information file is decoded on the information terminal by using the encoding / decoding software. The present system is applicable to various (computer) systems which store and manage confidential information (ID numbers, passwords, encryption keys, digital certificates, etc.) for use in user verification.
Owner:FUJITSU LTD
System and method for real-time inquiry, delivery, and reporting of credit information
InactiveUS20030041031A1More readableSecure transmissionComplete banking machinesFinanceWeb siteWeb browser
<heading lvl="0">Abstract of Disclosure< / heading> A system and method for providing electronic inquiry, delivery, and reporting of personal credit information to and from credit bureaus, preferably via the Internet. In the preferred embodiment, the system includes a web site that, by using a web browser, allows clients to request credit information from, or provide credit reports to, credit bureaus by entering certain data on pre-built forms in HTML format. The data is encrypted using means for secure transmission, such as a web browser with 128-bit secure socket layer (SSL) technology, then sent to a common gateway interface (CGI) application located on a web server. The CGI application decrypts and reformats the data to a standard format specified by the credit bureau. The CGI application initiates a query. Using a dedicated connection circuit to the credit bureau's computer, the CGI application reformats the response from the credit bureau to an HTML format and encrypts the data using the means for secure transmission. The HTML formatted data is then sent back to the client's computer over the Internet and displayed in the client's web browser in an easily read format.
Owner:F POSZAT HU
Apparatus and method for hard handover in a wireless communication system
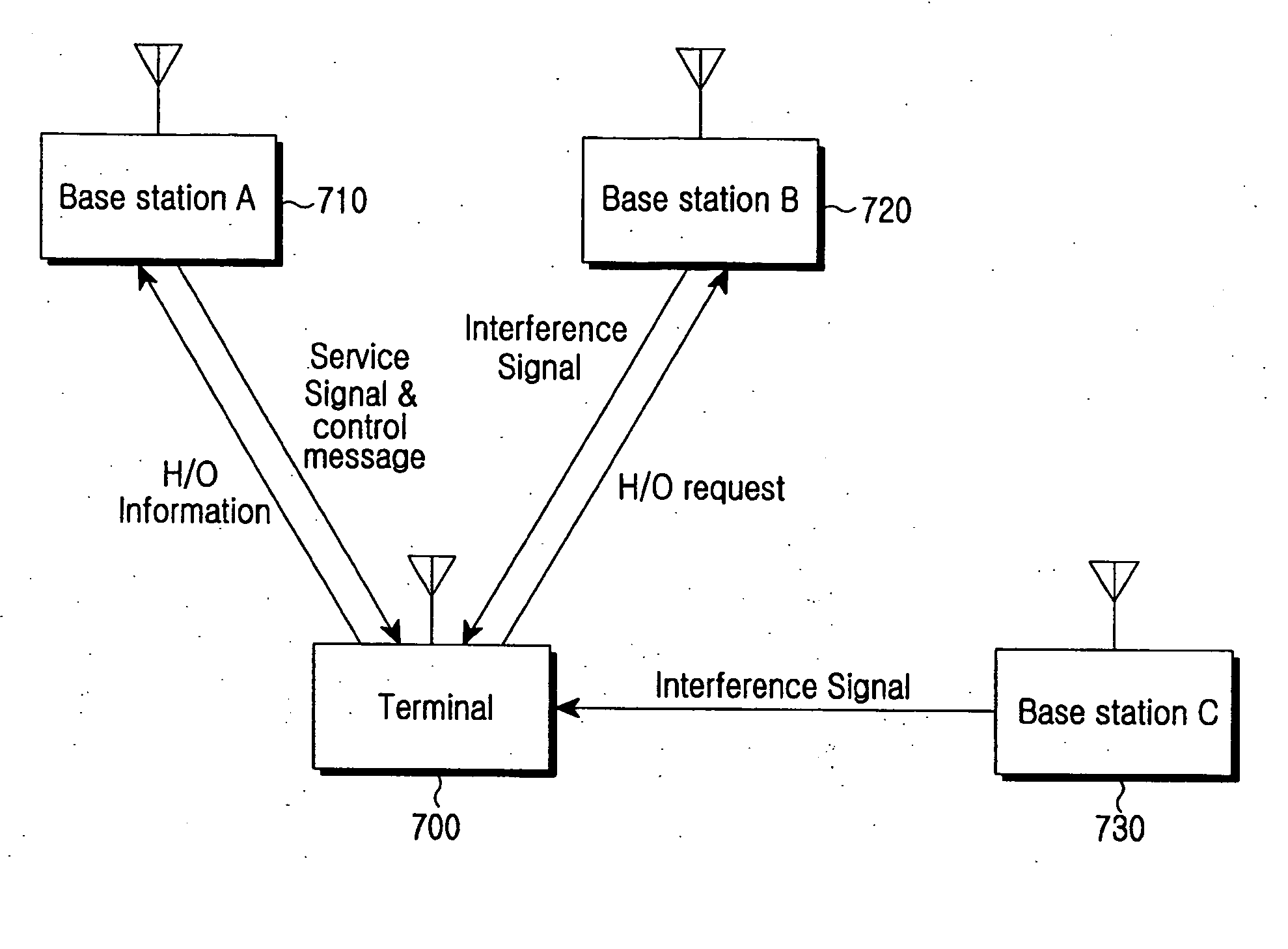
ActiveUS20070135125A1Secure transmissionPreventing a decrease in QoSRadio/inductive link selection arrangementsRadio transmissionCommunications systemSignal-to-noise ratio (imaging)
Provided is a hard handover method in a wireless communication system. The hard handover method includes checking a signal-to-noise ratio (SNR) of a signal received from each of at least one neighboring base station (BS) while in communication with a serving BS, and canceling interference if the SNR of the signal received from each of the at least one neighboring BSs satisfies a select condition; sending a handover request to the serving BS, if a difference between a SNR of the interference-canceled signal and a SNR of the interference signal reaches a handover request threshold; and upon receipt of a handover approval from the serving BS, releasing a communication channel to the serving BS, and connecting a call to a BS that provides an interference signal whose SNR has reached the threshold.
Owner:SAMSUNG ELECTRONICS CO LTD
Security gateway utilizing SSL protocol protection and related method
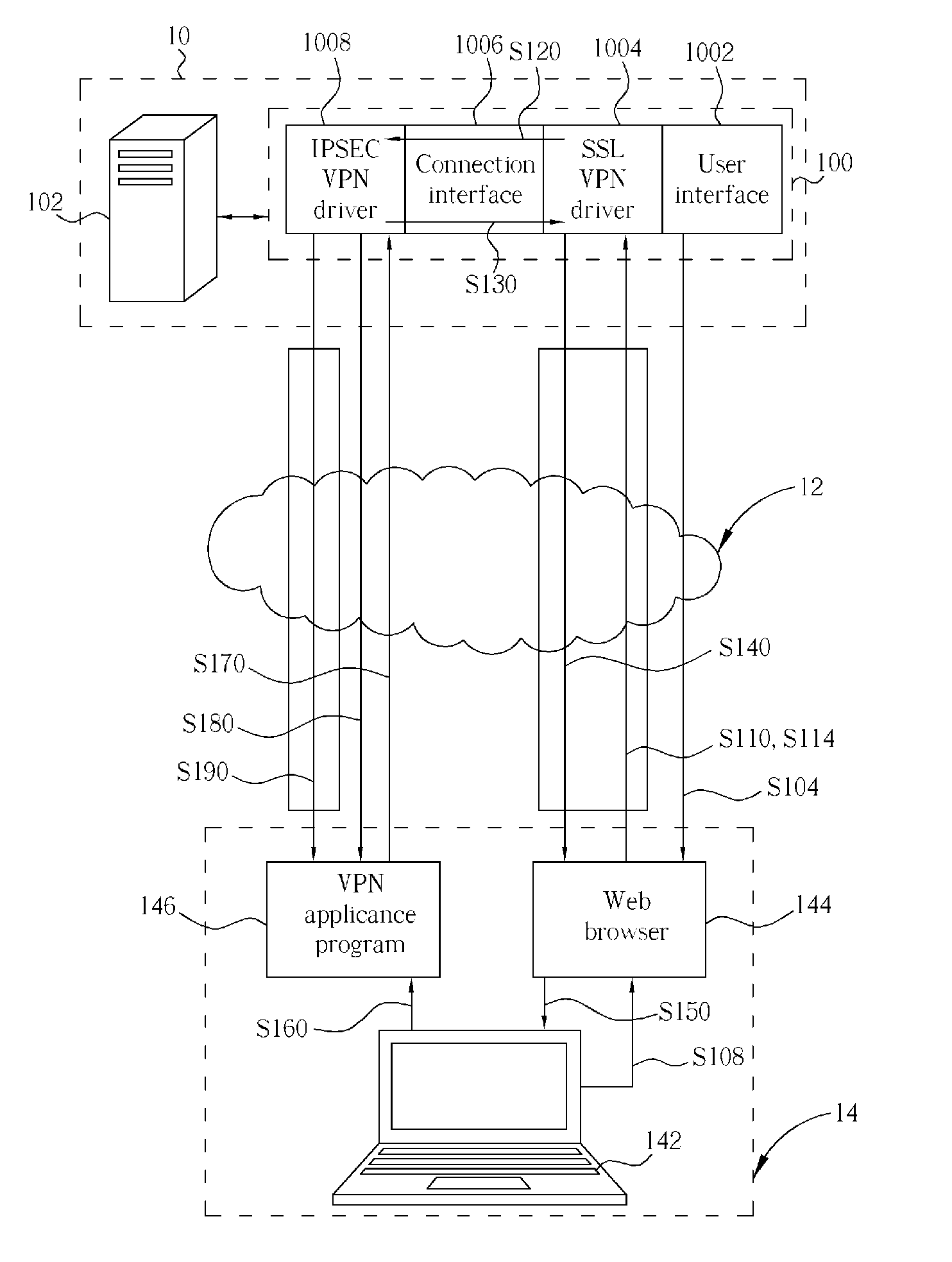
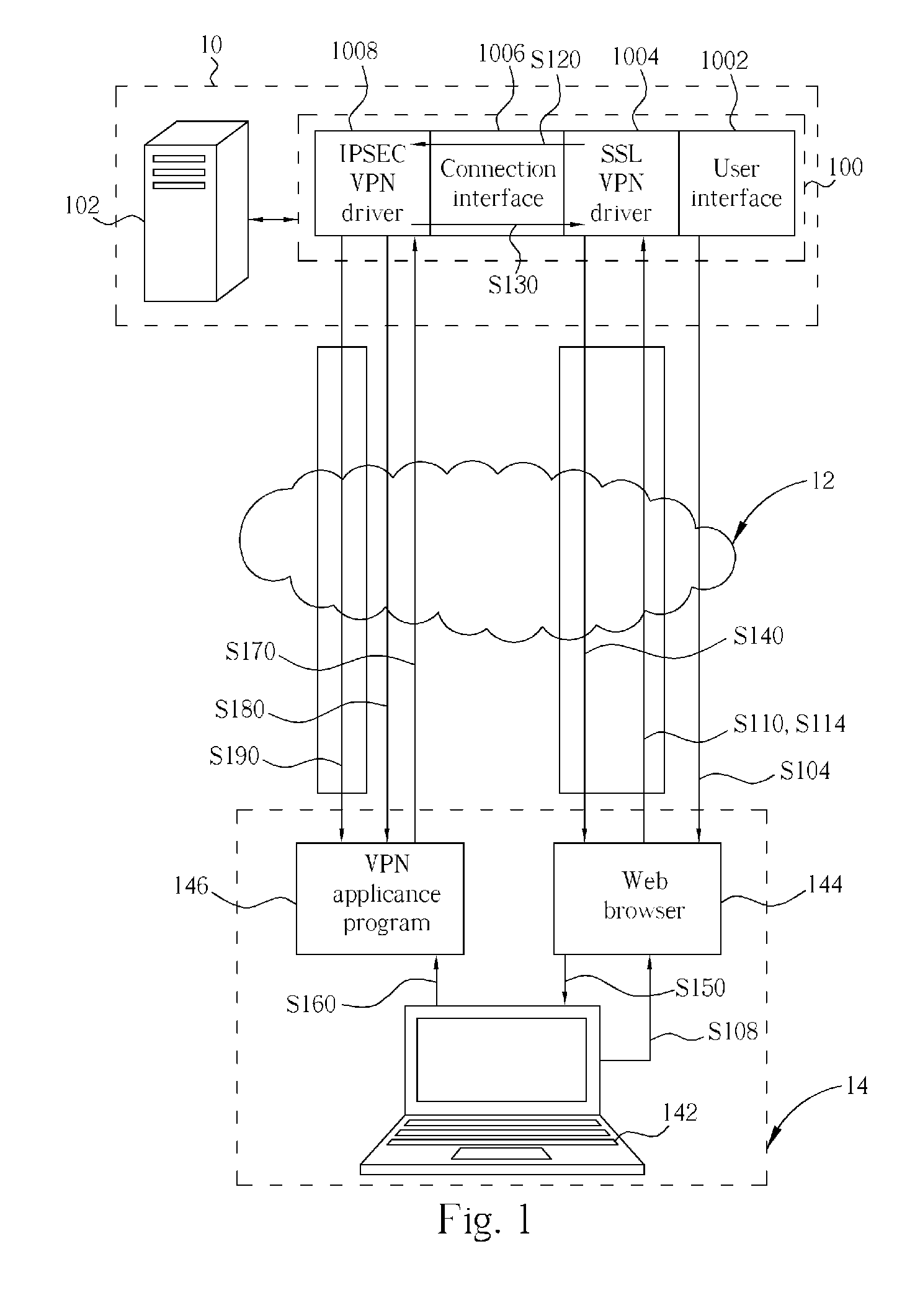
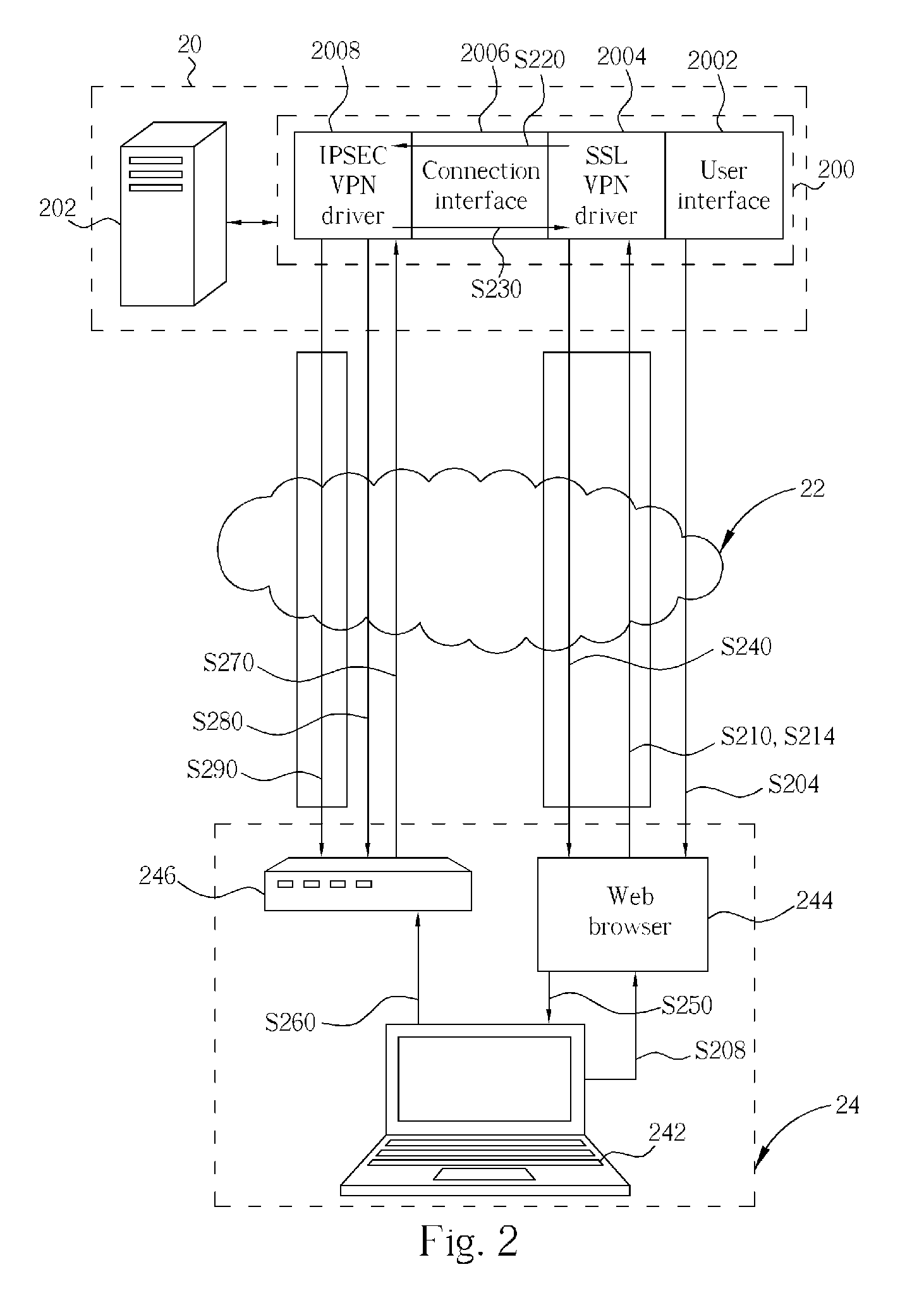
InactiveUS20060005008A1Improve securitySecure transmissionSecuring communicationNetworked systemIPsec
A security gateway, for use in a network system for linking at least a client end and a server end, includes a user interface, a SSL VPN driver, a connection interface and an IPSEC VPN driver. The security gateway supports IPSEC and SSL protocols. Before establishing an IPSEC VPN between a client end and a server end, the security gateway will perform ID authentication for the user of the client end with a widely-used SSL protocol, so as to establish a SSL VPN between a server end and a client end. When the ID of the client end is authorized, a configuration file comprising the SA is generated and then safely sent to the client end through the SSL VPN tunnel. After the client end receives and executes the configuration file having the SA, an IPSEC VPN tunnel between the server end and the client end is established.
Owner:ICP ELECTRONICS
Systems and methods for adapter-based communication with a medical device
ActiveUS8126734B2Secure transmissionActive lifestyleData processing applicationsComputer security arrangementsTransceiverData interchange
Owner:MEDAPPS
Information processing device, information processing method, and computer program
InactiveUS20060168264A1Easily and securely obtainEfficiently obtain informationDigital data protectionMultiple digital computer combinationsInformation processingClient-side
The present invention provides a device and a method enabling a client connected to an external network to efficiently obtain information about servers connected to an internal network. An information processing device serving as an application gateway connected at an interface between the external network and the internal network performs a server information obtaining process about connected servers through the internal network in response to a request for obtaining information about the servers connected to the internal network transmitted from the client connected to the external network, generates a device list based on the obtained server information, and transmits the device list to the client through the external network. With this configuration, the client connected to the external network can efficiently obtain information about the servers connected to the internal network.
Owner:SONY CORP
System and method for secure electronic communication services
InactiveUS8538028B2Easy accessSecure transmissionKey distribution for secure communicationPublic key for secure communicationSecure communicationScalable system
Owner:TOPOSIS CORP
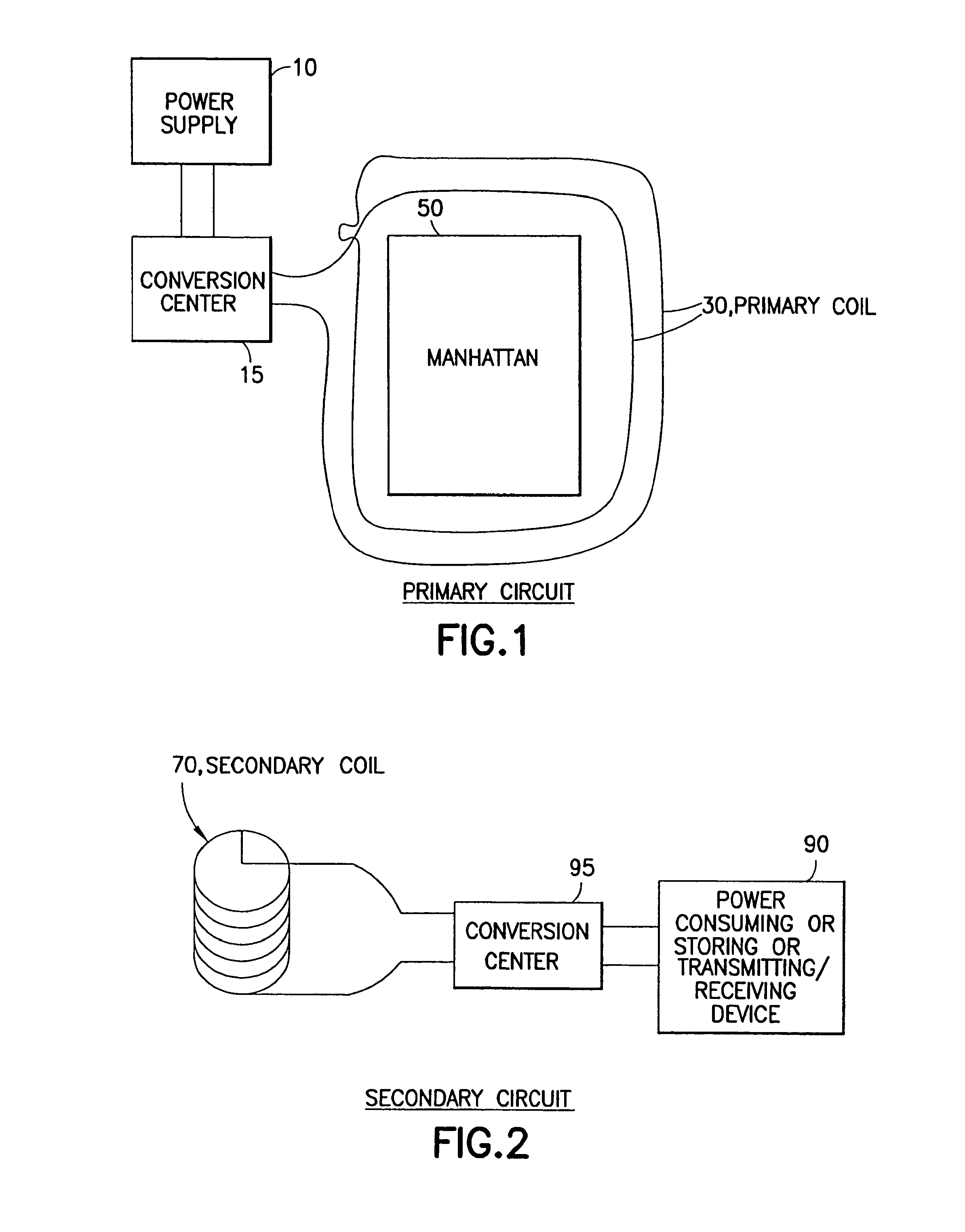
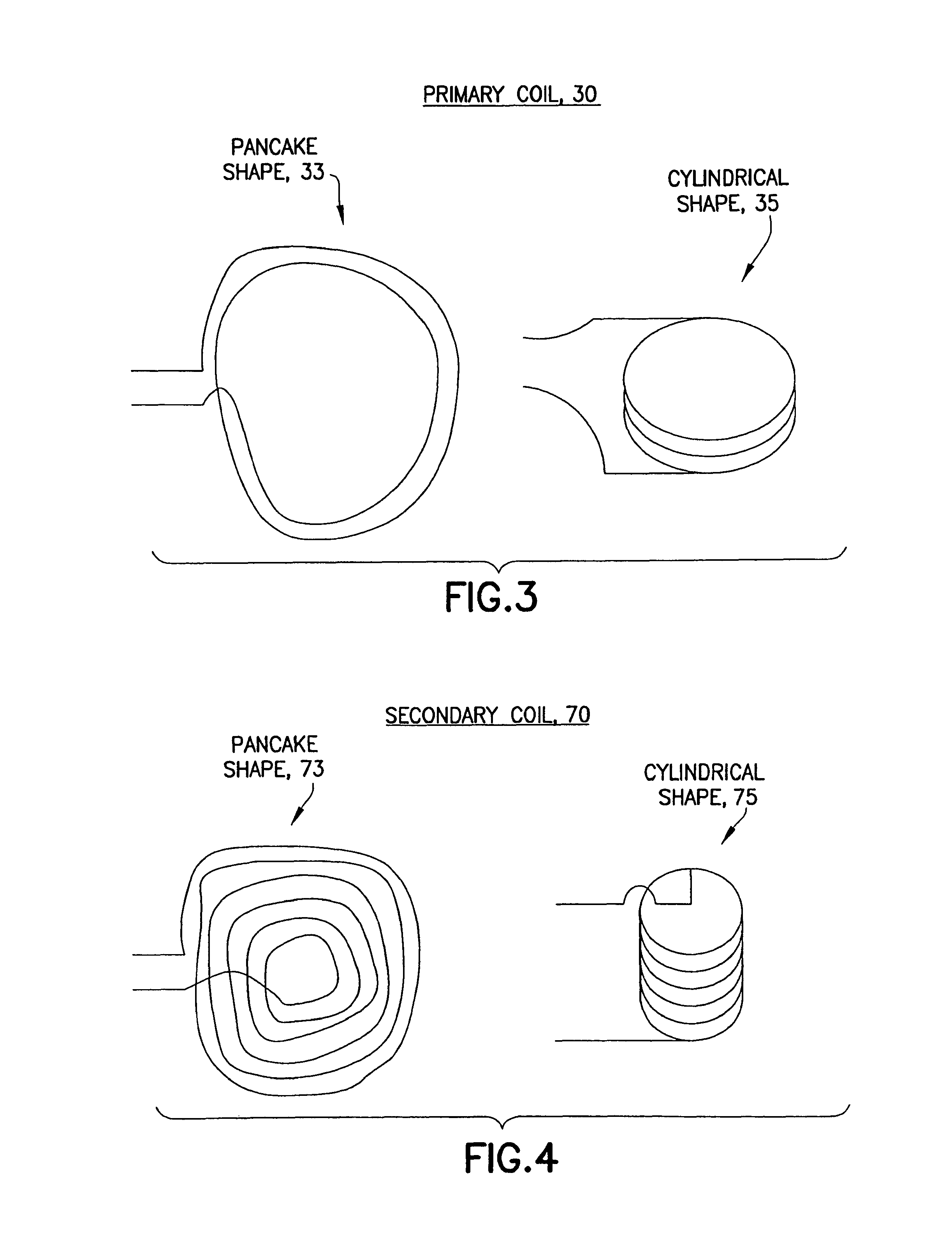
Self-charging electric vehicles and aircraft, and wireless energy distribution system
InactiveUS8890472B2Rapid collection and storageIncrease rangeMobile unit charging stationsPropulsion by batteries/cellsElectric power systemTransmitted power
A method and system for efficient distribution of power using wireless means, and a system and method for wireless power distribution to provide electric devices, such as vehicles with a way to continuously and wirelessly collect, use and charge their power systems and thereby use the transmitted power for operation. The system and method allows a hybrid, simplified and less costly way to charge devices, such as vehicles so that the devices continuously operate while charging / recharging.
Owner:GOVERNING DYNAMICS INVESTMENT +1
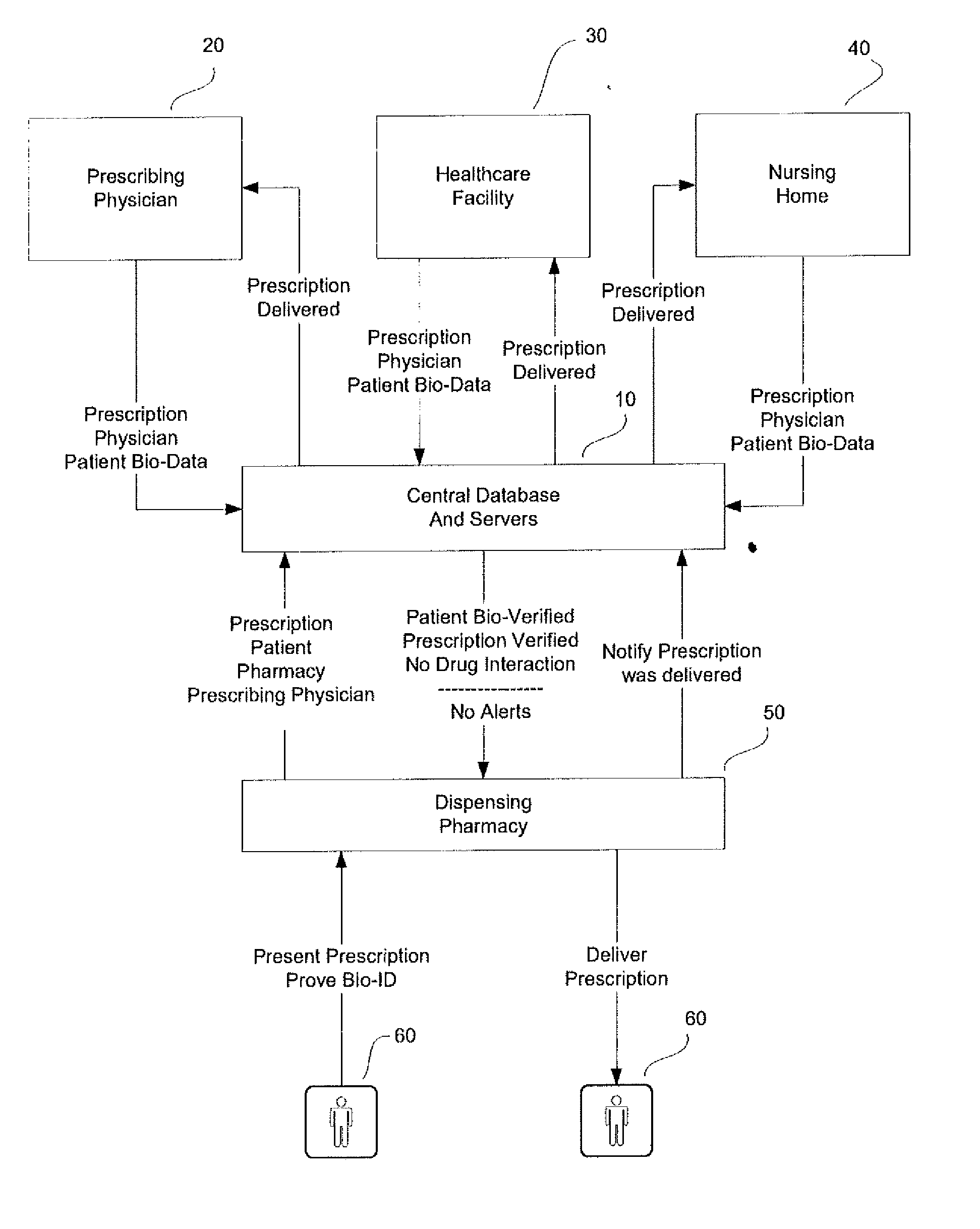
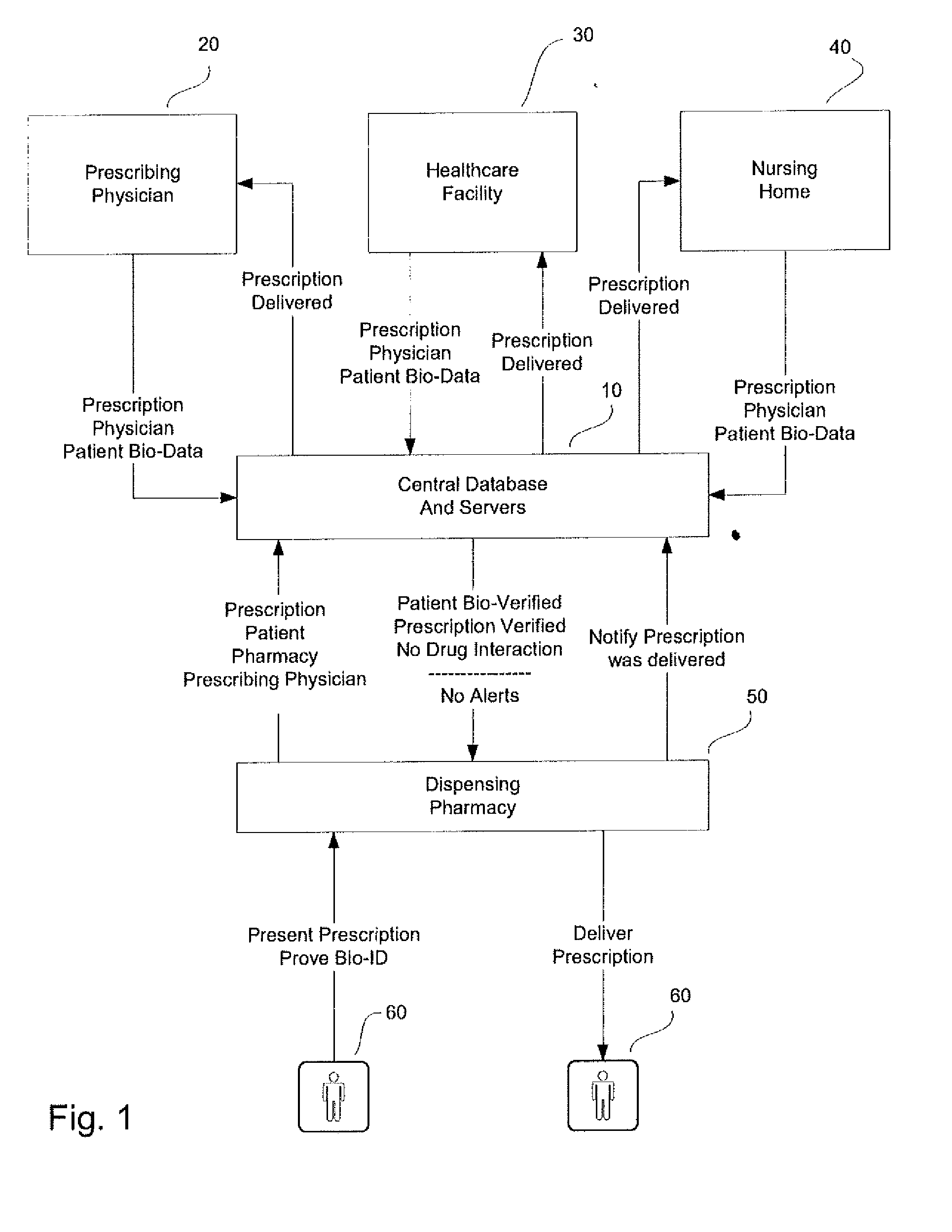
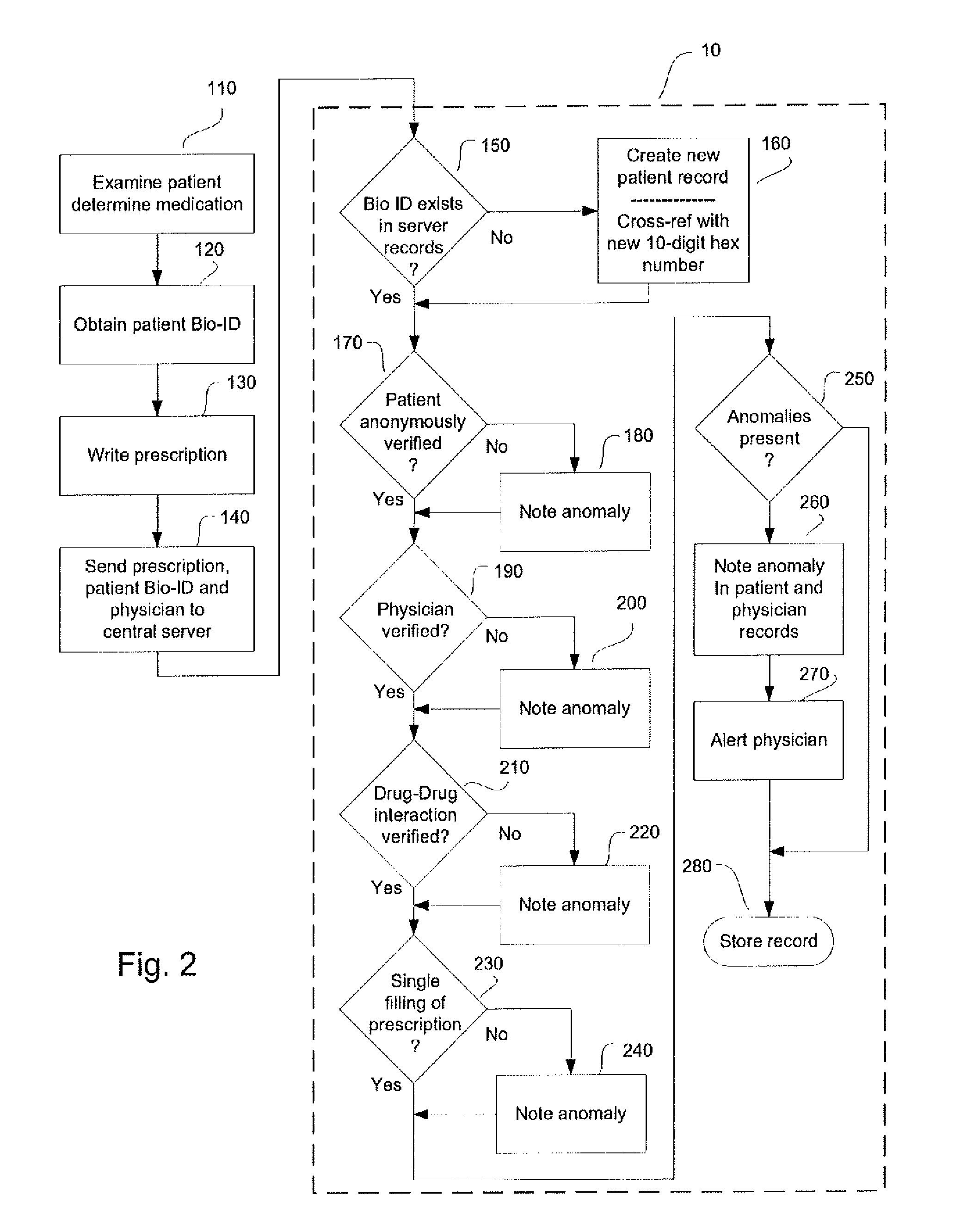
System and method for monitoring medication prescriptions using biometric identification and verification
InactiveUS20100299158A1Quick measurementEasily verifiable biometricDrug and medicationsResourcesBiometric dataDrug interaction
This invention is a system and method for a matching system that cross-references patients anonymously with doctors and pharmacies. The invention uses patient-unique biometrics, such as fingerprinting, retinal scanning, or another such unique identifier, for patient identification and verification without revealing a patient's name or other personal information. The system tracks patient prescriptions and produces alerts to indicate potential problems, such as drug interactions or possible fraudulent behavior. The system utilizes the biometric data of the prescribing physician as authorization of the prescription. The system can produce a traceable paper trail, for investigation or prosecution, and protects the medical industry, patients, and the public from the consequences of doctor shopping.
Owner:BIO TECH MEDICAL SOFTWARE
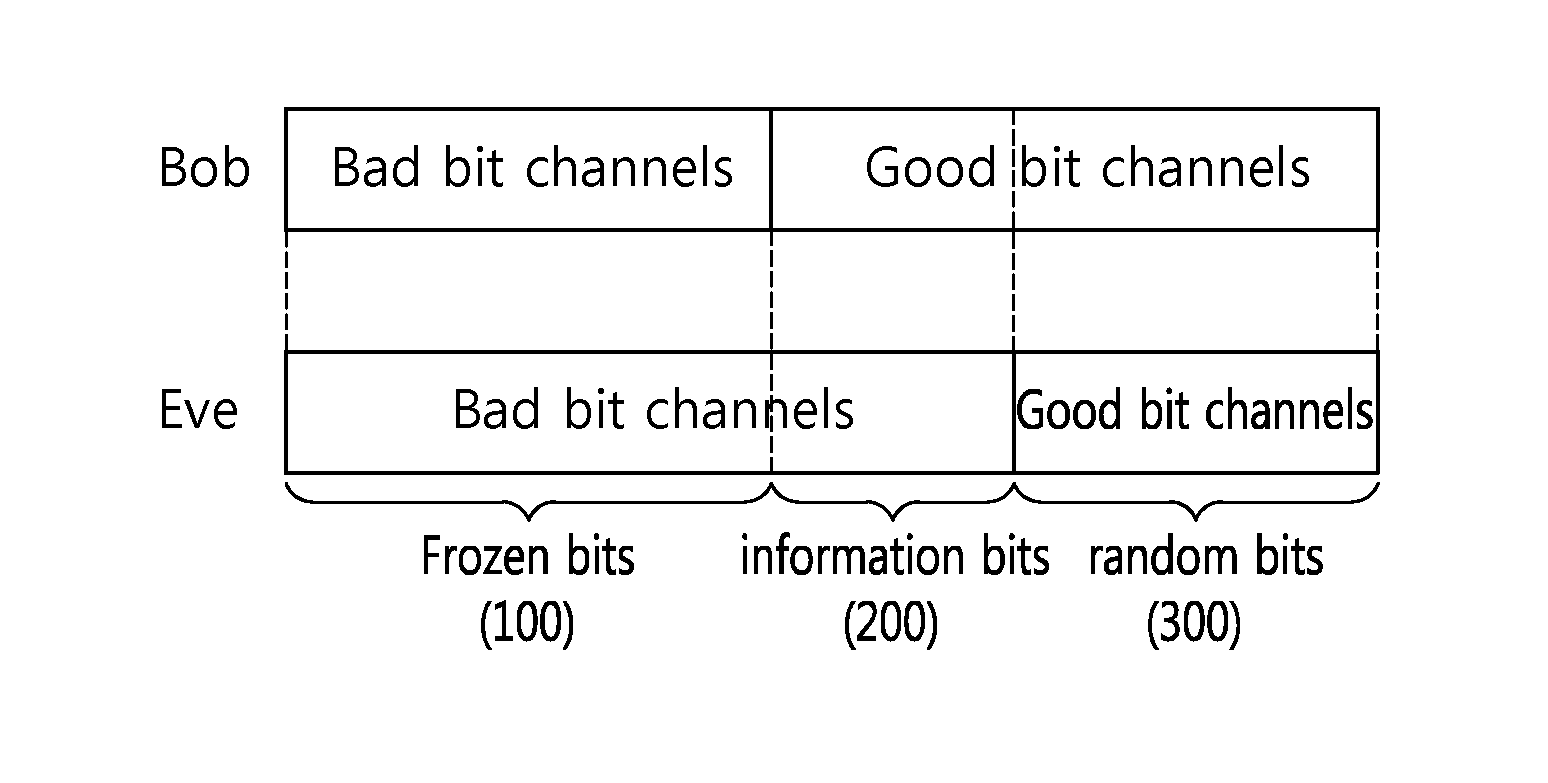
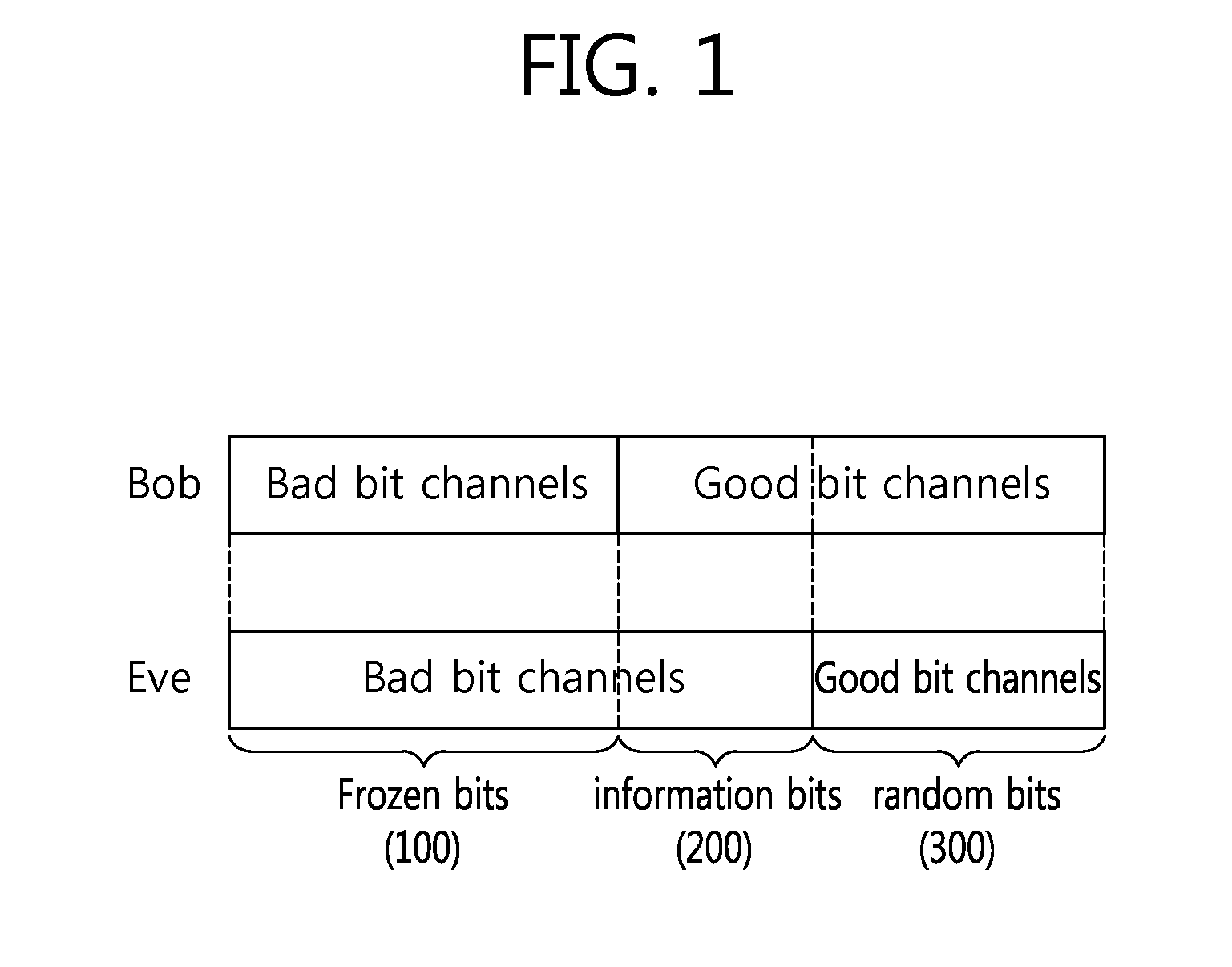
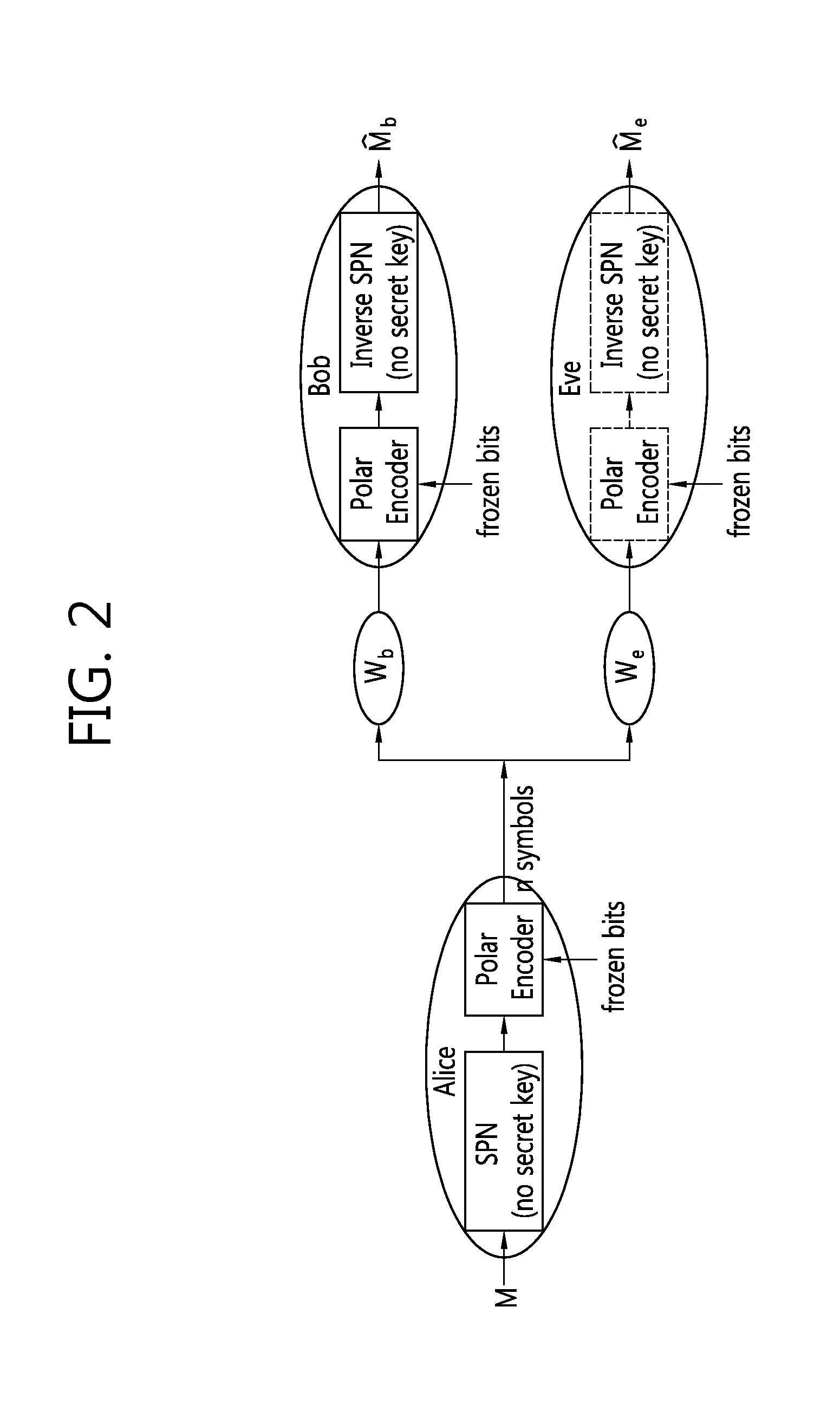
Method and device for providing secure transmission based on polar code
ActiveUS20160164629A1Expand the amount of informationSecure transmissionCode conversionChannel coding adaptationComputer hardwareSecure transmission
A method and apparatus for providing a secure transmission based on a polar code are provided. A device generates an output bit sequence by applying a polar code generator matrix to an input bit sequence and transmits the output bit sequence to a target receiver. The input bit sequence includes first information bits, second information bits and third information bits. The first information bits correspond to gray bit channels for the target receiver and bad bit channels for an eavesdropper. The third information bits correspond to good bit channels for the target receiver and gray bit channels for the eavesdropper.
Owner:LG ELECTRONICS INC
Surgical instrument
InactiveUS7105003B2Secure transmissionEasy to manufactureCannulasShaft for rotary movementSurgical instrumentGeneral surgery
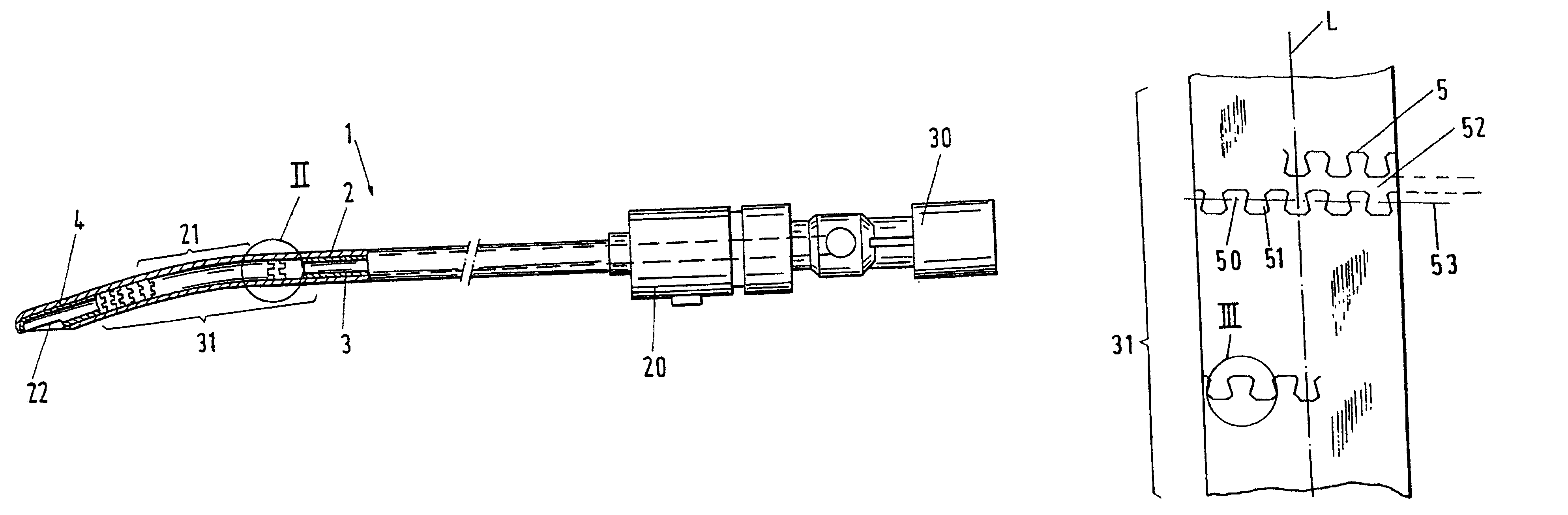
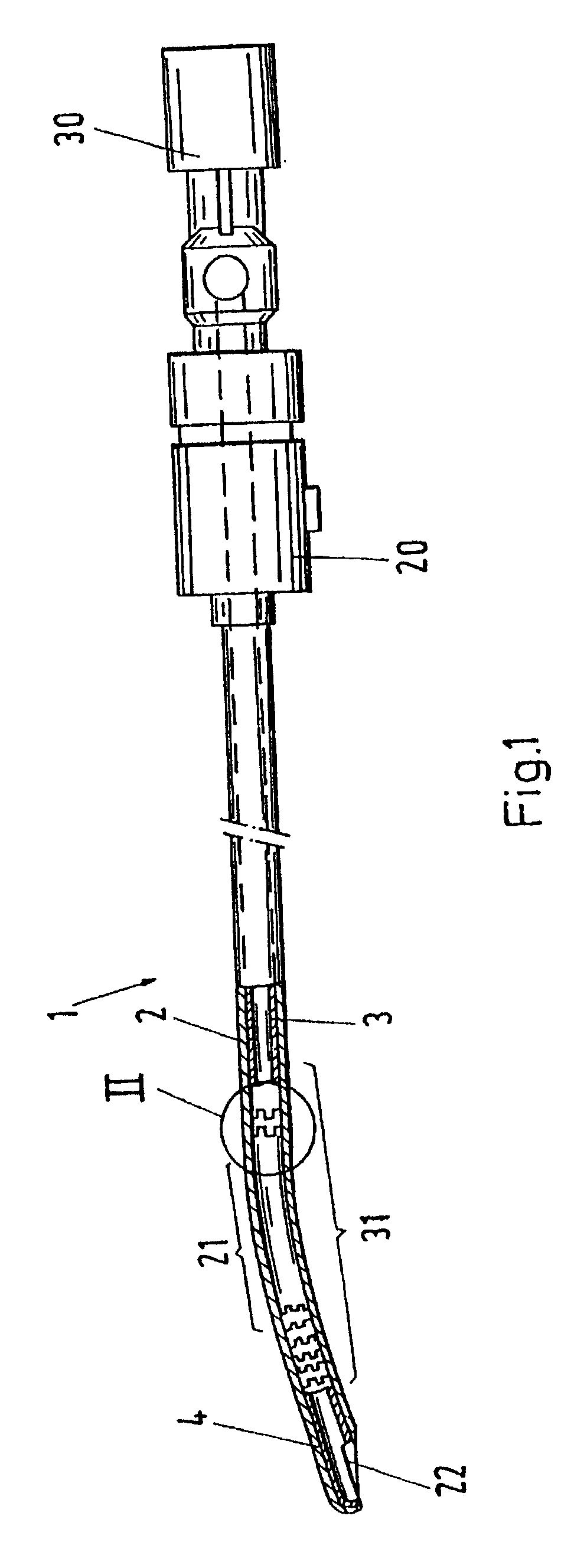
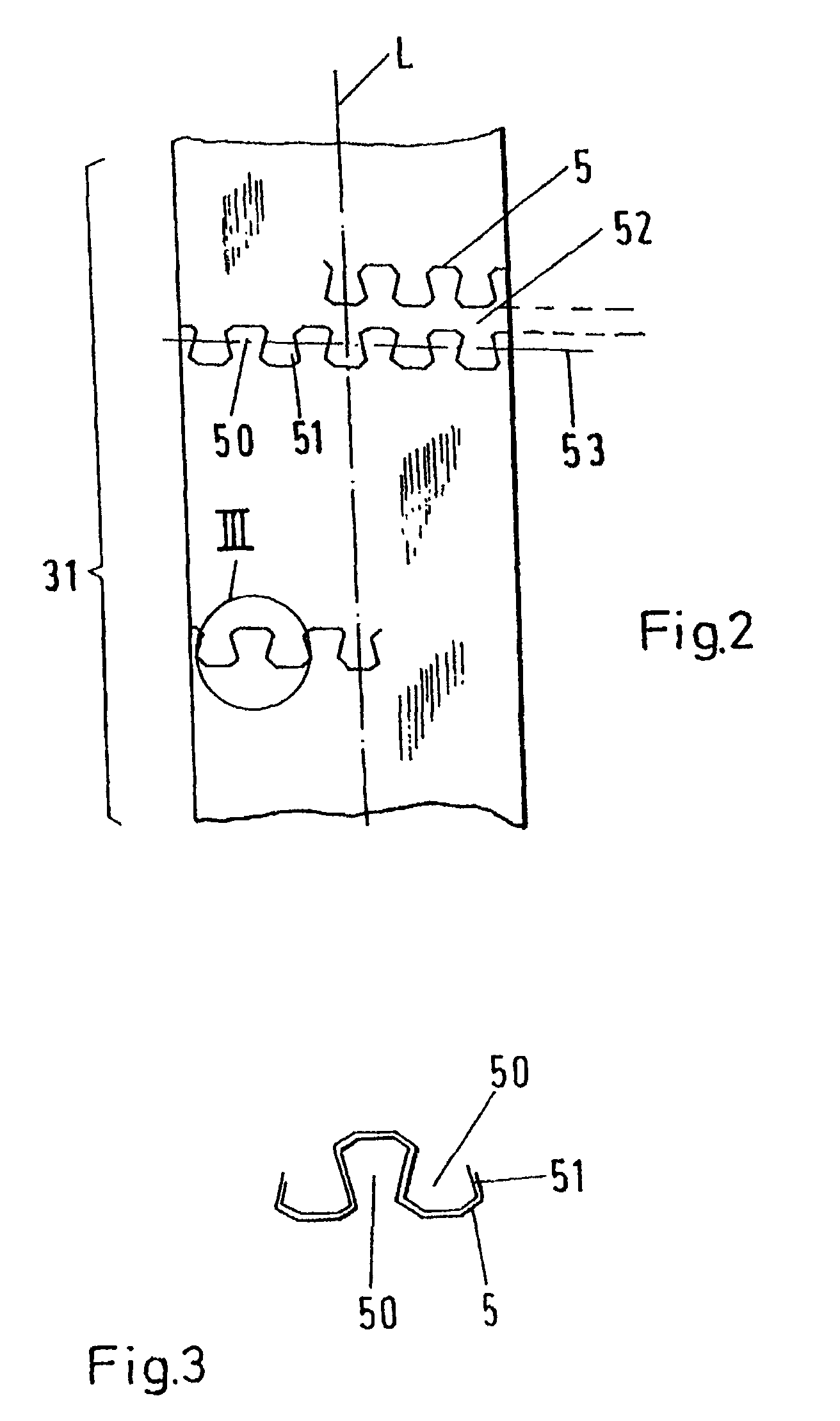
A surgical instrument (1) for the removal of tissue comprises an outer tube (2) having an opening (22) for the removal of tissue, fashioned in a distal region, preferentially in the vicinity of the distal end of the outer tube (2). It further comprises an inner tube (3) disposed in the outer tube (2) and having a rigid proximal region for transferring forces or momenta acting on this proximal region to a distal region of the inner tube (3), preferentially to the distal end of the inner tube (3). The instrument further comprises a cutting tool (4) disposed at the distal region of the inner tube (3), preferentially at the distal end of the inner tube (3), for facilitating cutting of tissue which is subjected to the action of the cutting tool (4) in the vicinity of the opening (22) in the distal region of the outer tube (2), wherein the inner tube (3) has a flexible region (31) located between its rigid proximal region and the cutting tool (4). The inner tube (3) has a slit (5, 5a) in its wall in the flexible region (31) which, as viewed in the longitudinal direction of the inner tube (3) winds in a helical fashion about the longitudinal axis (L) of the inner tube (3) and meanders back and forth with respect to this helical line (52, 52a).
Owner:KARL STORZ GMBH & CO KG
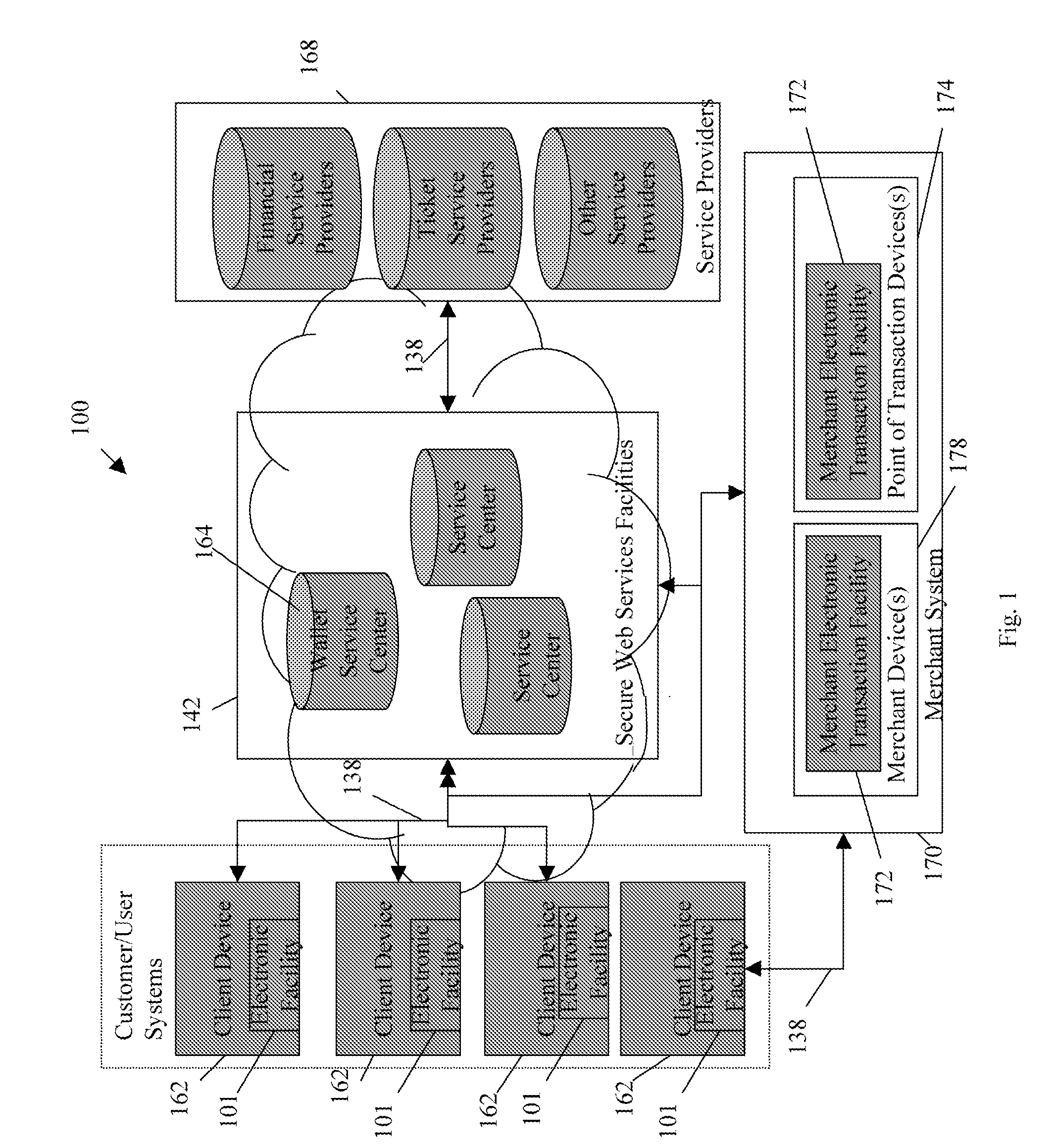
Transactional services
InactiveUS20120005078A1Secure transmissionFinanceCryptography processingService provisionElectronic trading
Owner:MASTERCARD MOBILE TRANSACTIONS SOLUTIONS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com