Patents
Literature
973 results about "User verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
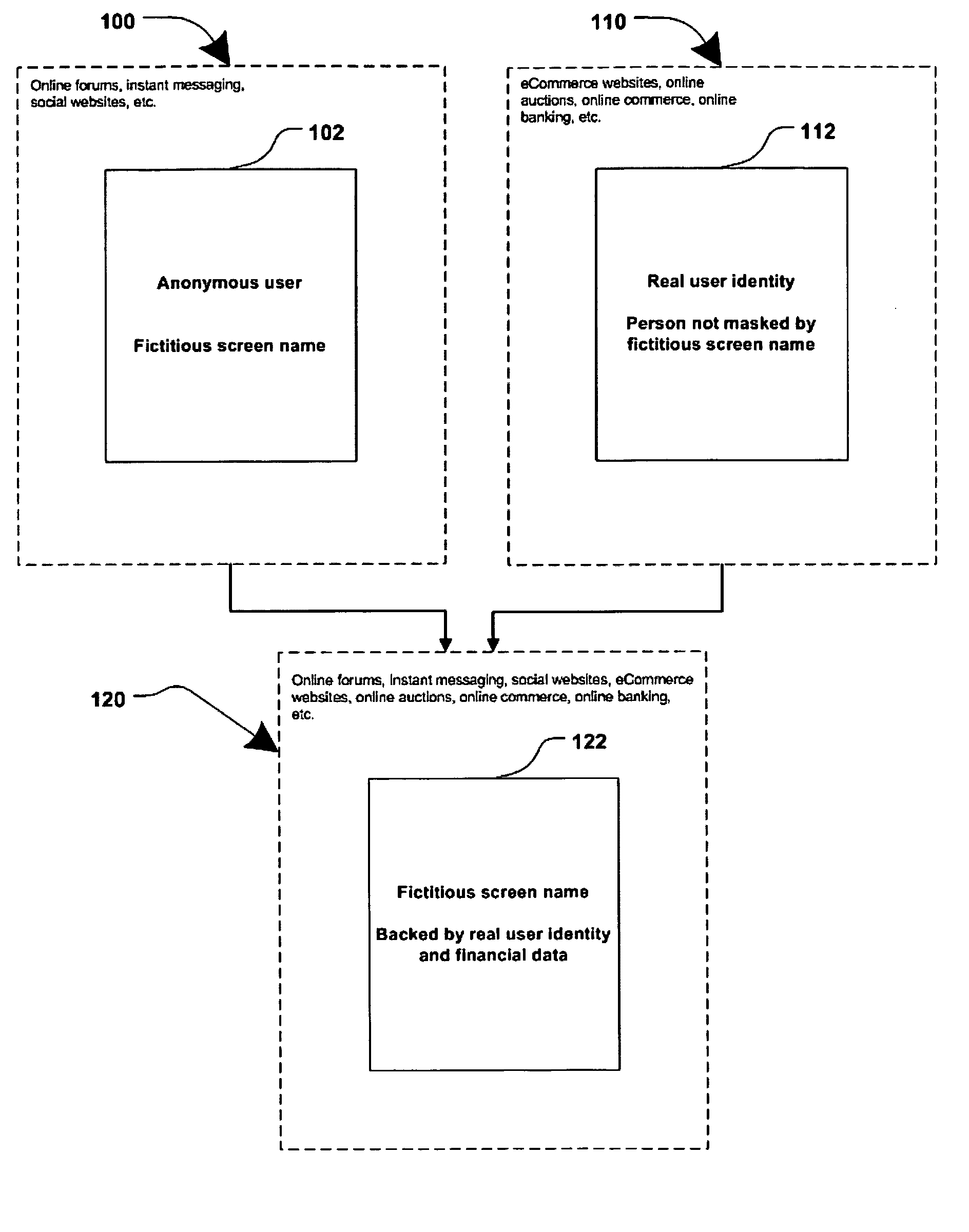
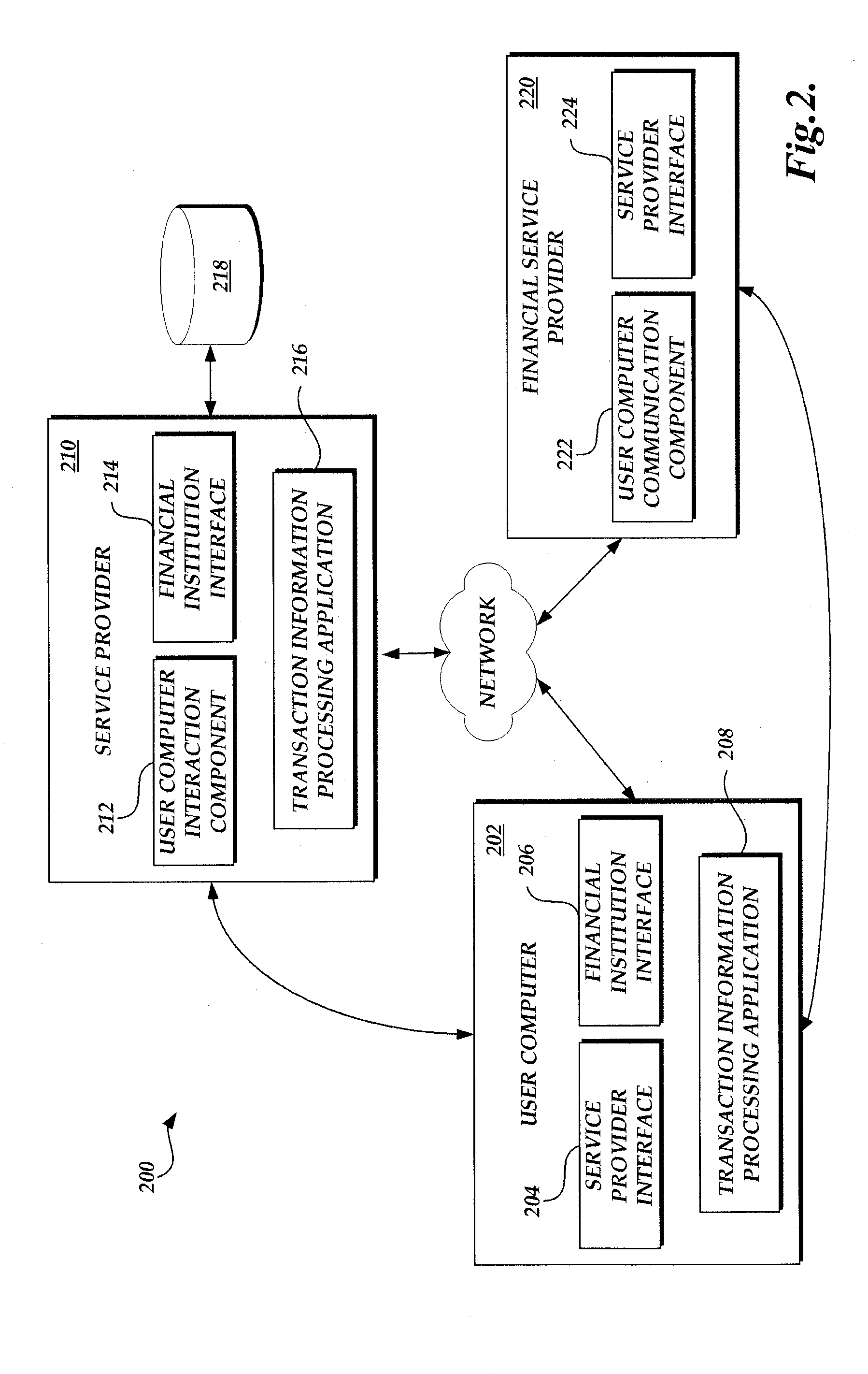
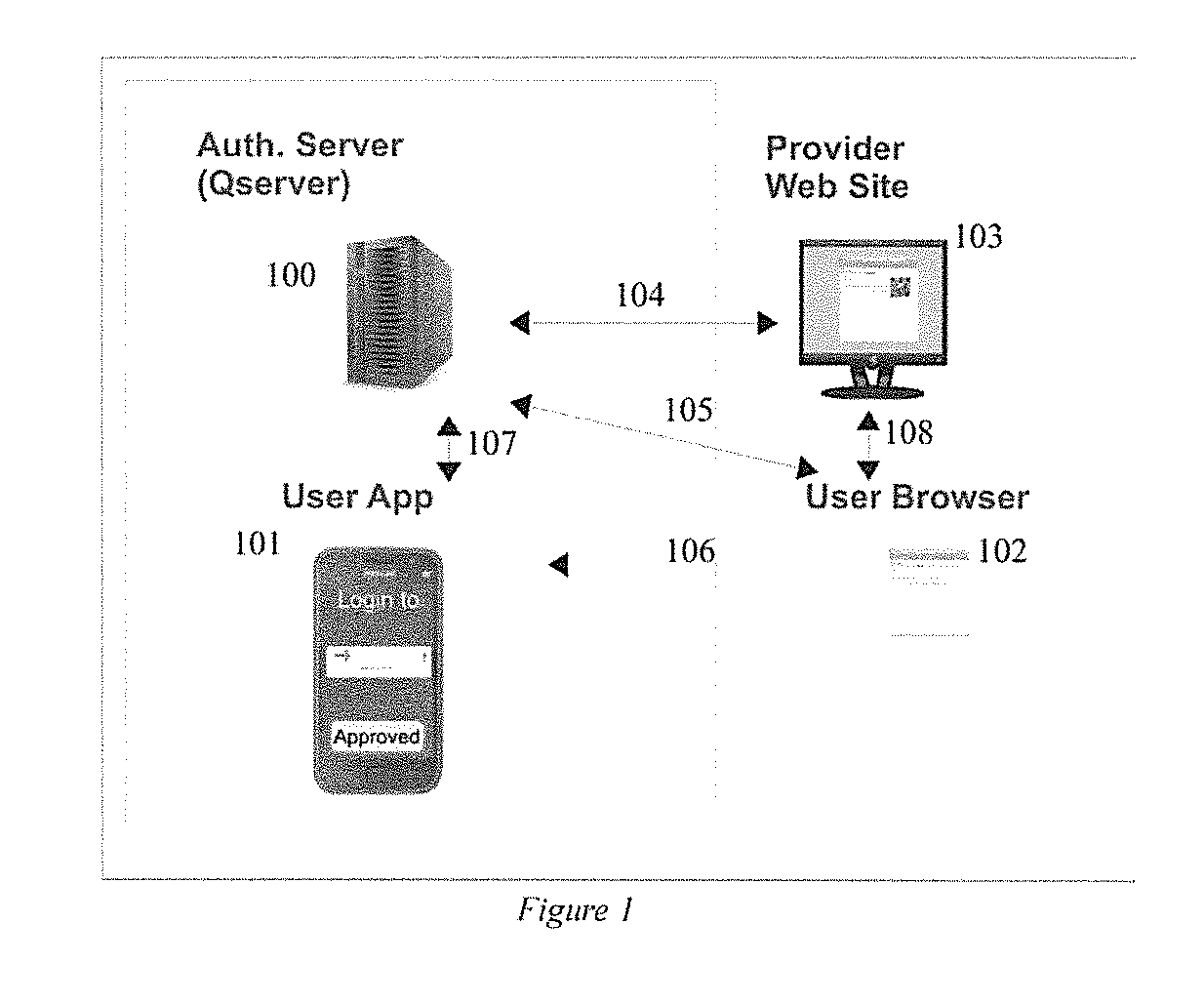
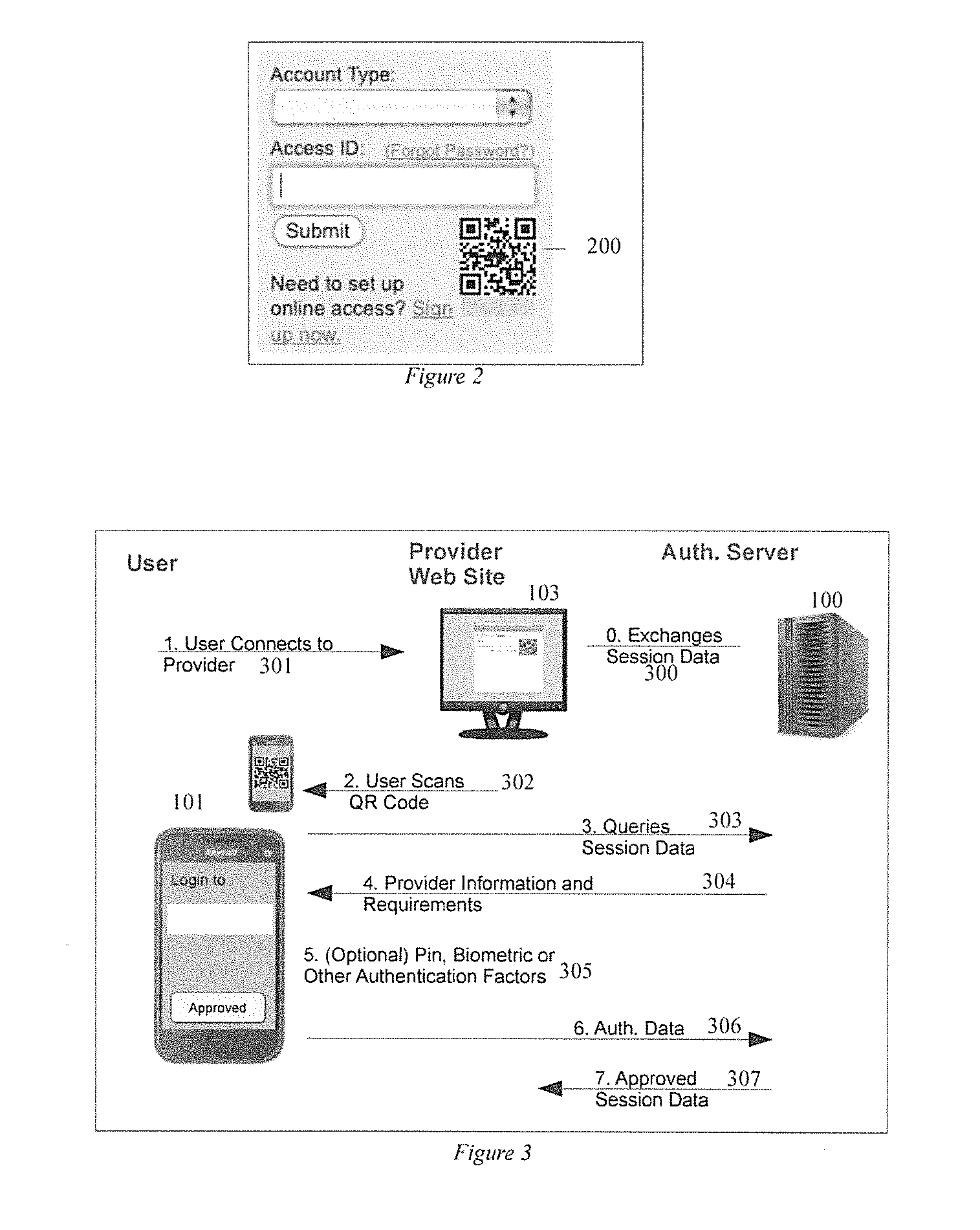
Method and system for securing online identities
InactiveUS8646103B2Targeted optimizationDigital data processing detailsUser identity/authority verificationUser verificationElectronic communication
Owner:JAKOBSON GABRIEL +1
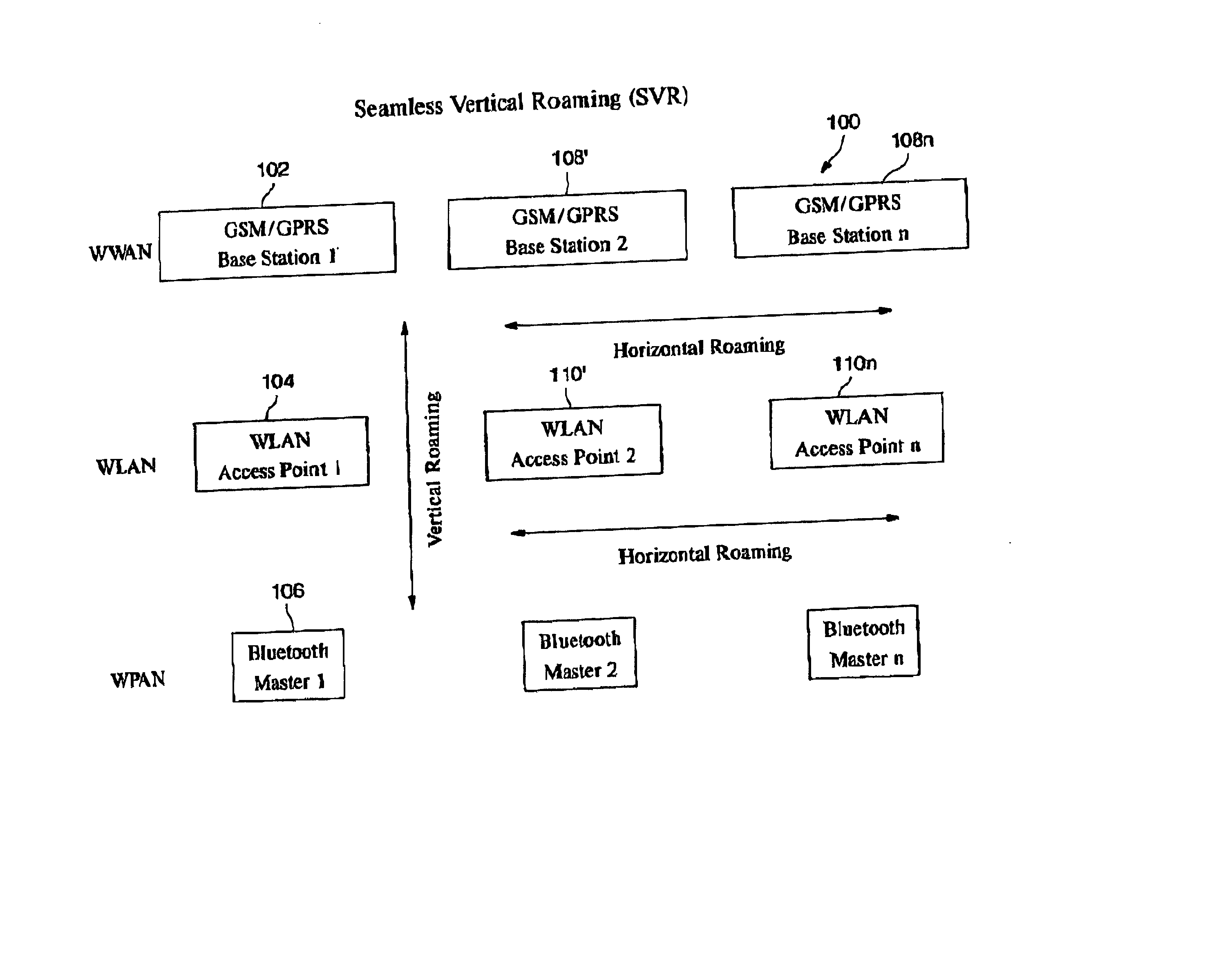
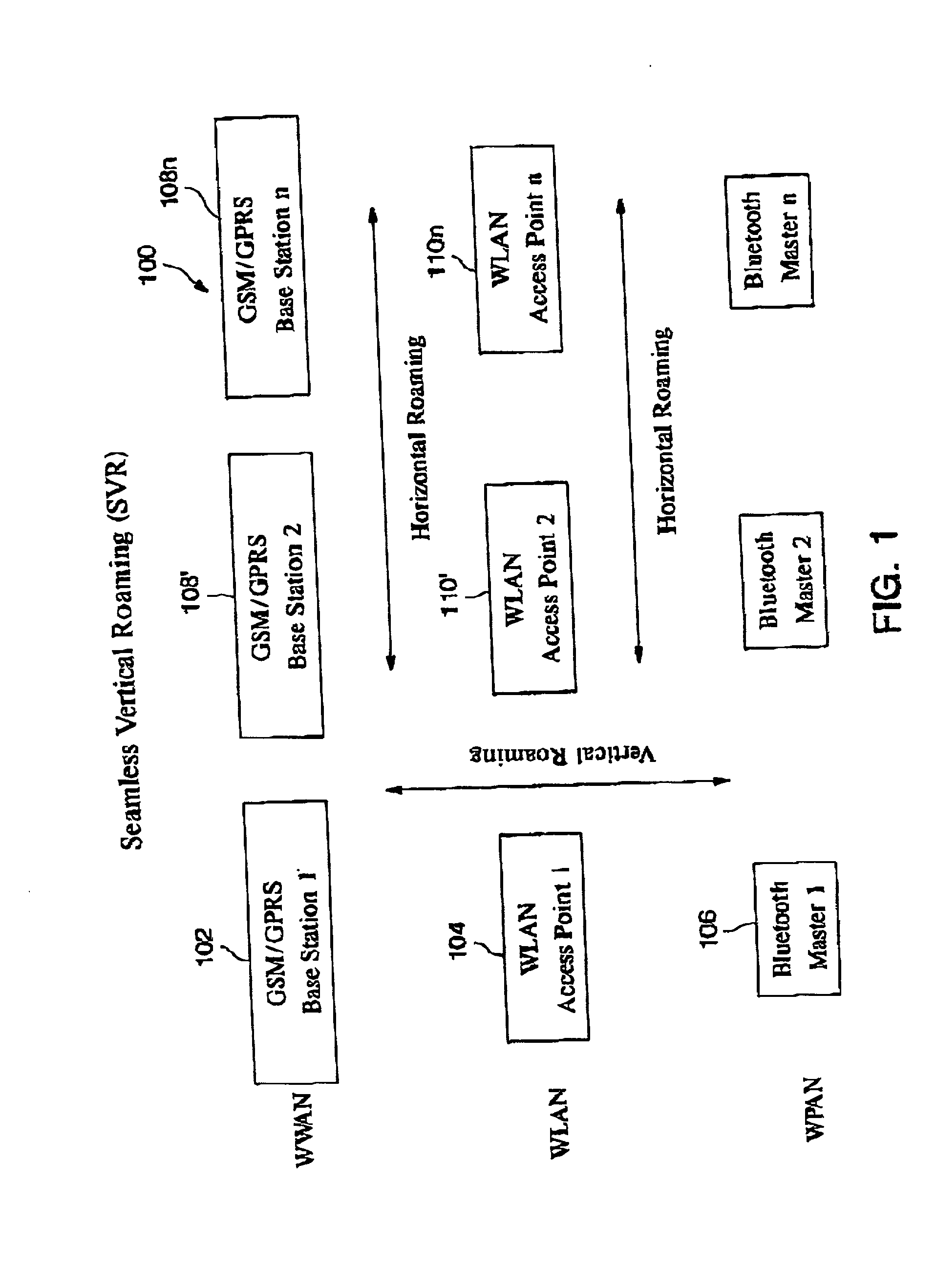
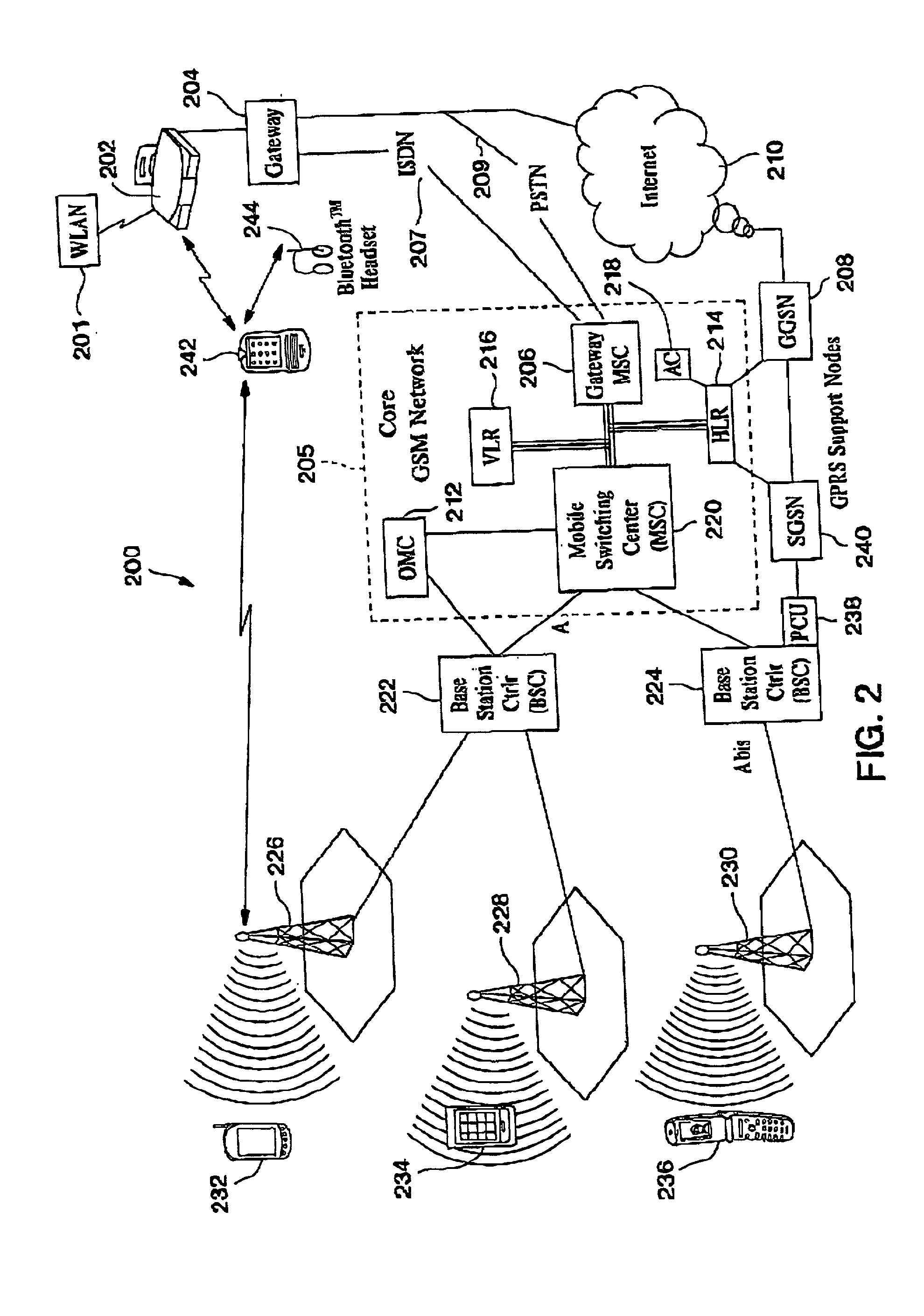
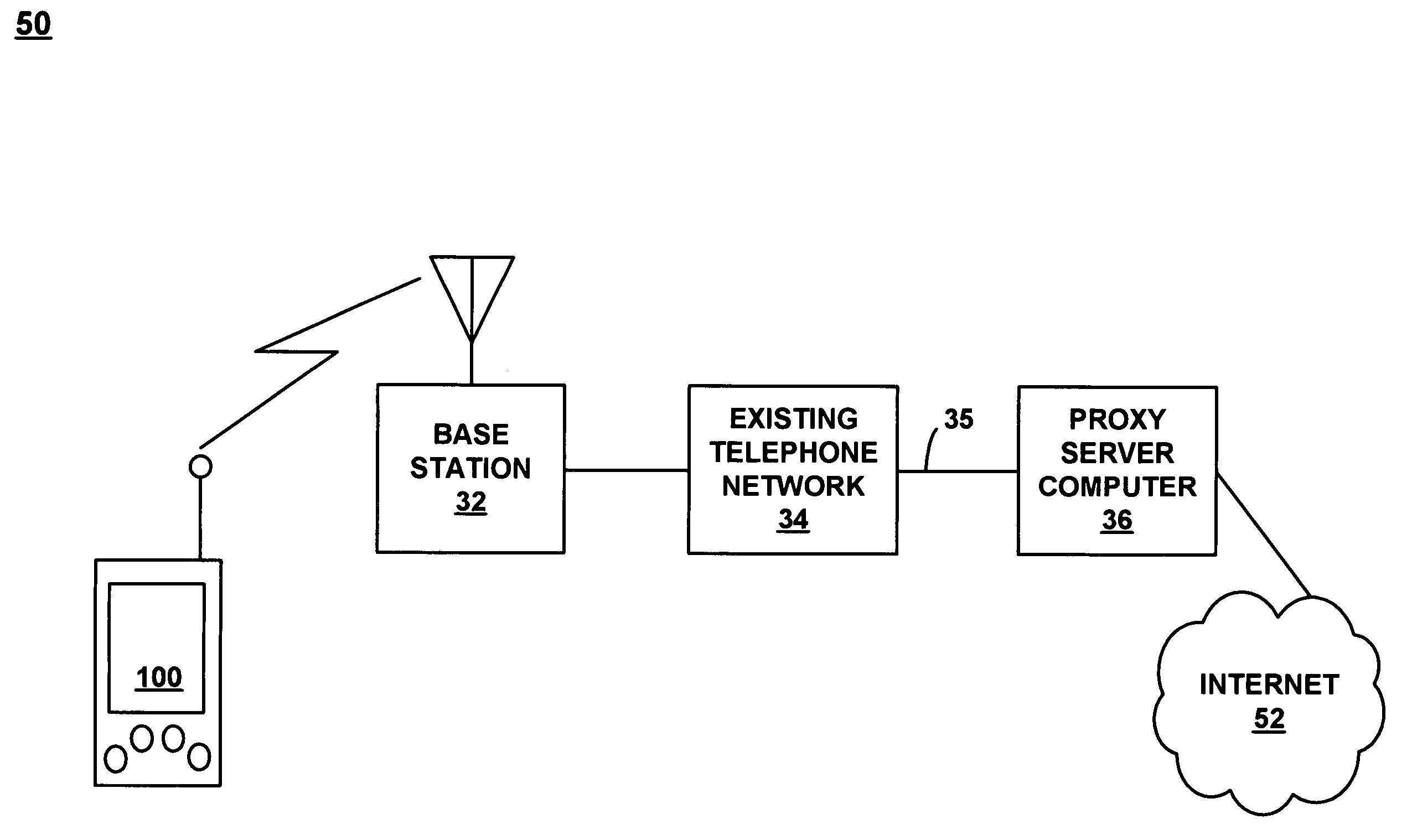
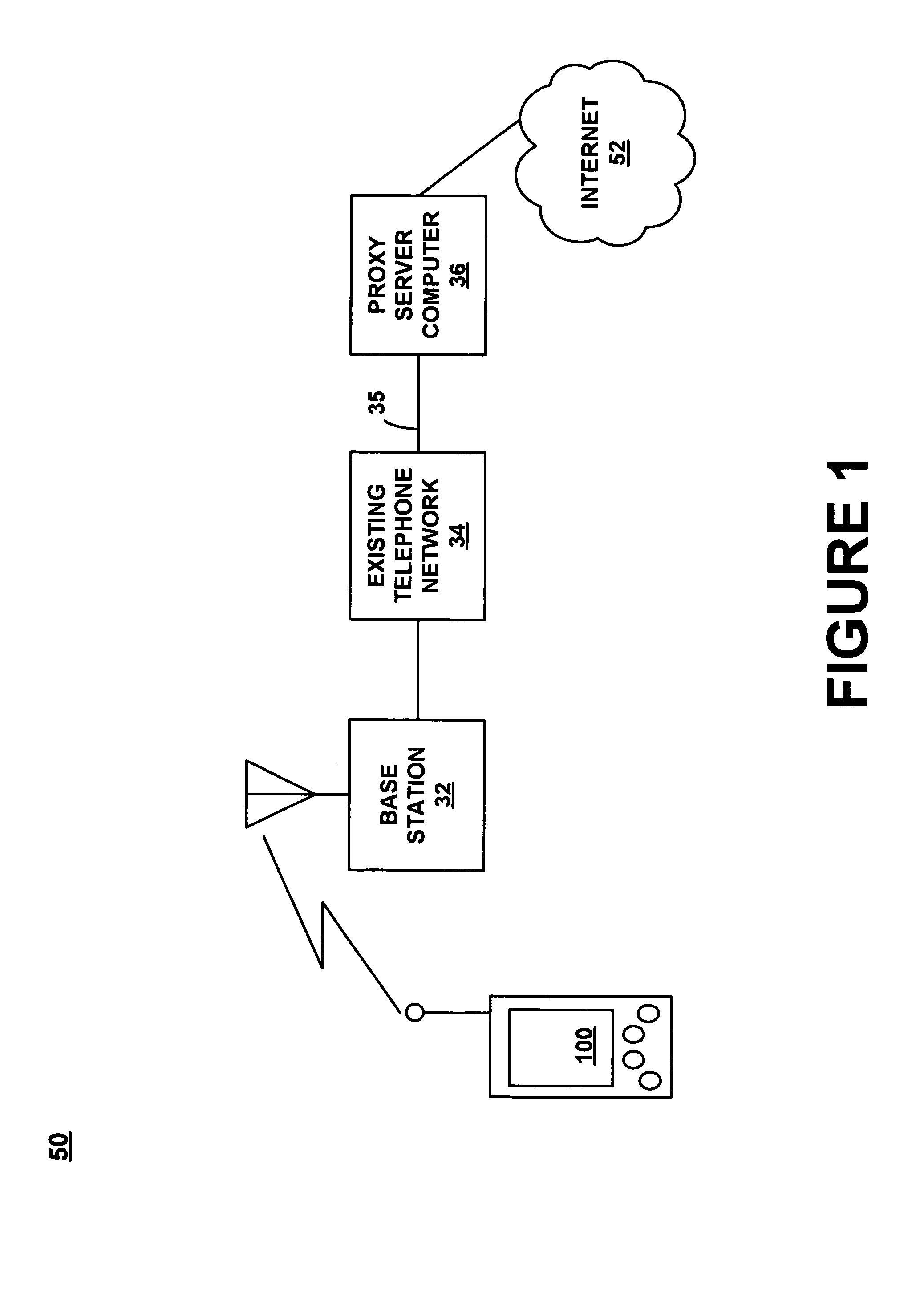
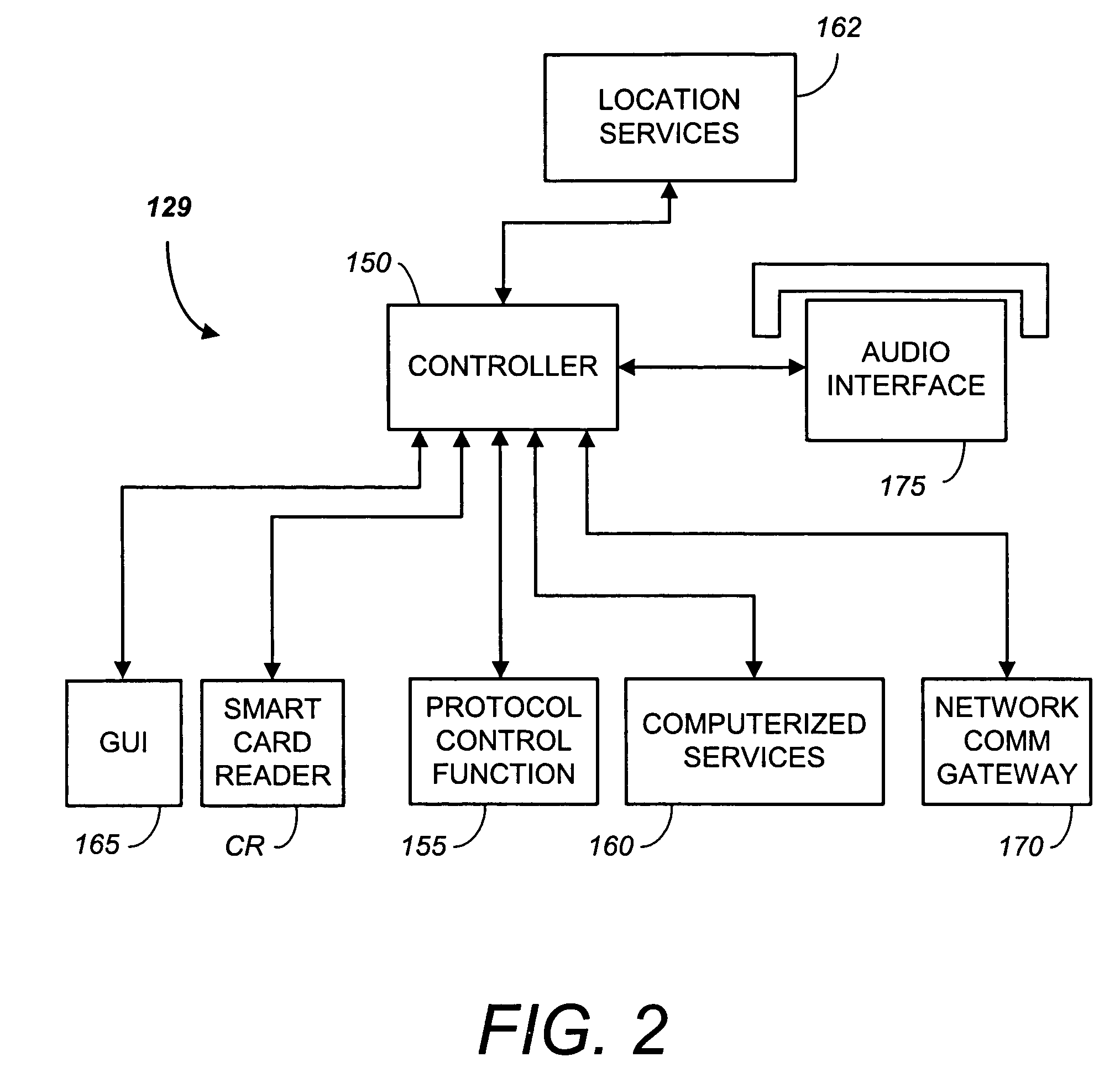
Automatic and seamless vertical roaming between wireless local area network (WLAN) and wireless wide area network (WWAN) while maintaining an active voice or streaming data connection: systems, methods and program products
ActiveUS20020085516A1Data switching by path configurationRadio/inductive link selection arrangementsData connectionUser verification
A Mobile Station (MS) is able to vertically roam in either direction between two different network, i.e. WWAN and WLAN. The MS is equipped with a dual mode Radio for WWAN and WLAN transmissions. The WLAN Radio is linked to a WLAN Enterprise Gateway Controller (EGC) via a first air link and the WWAN Radio is linked to a WWAN Base Transceiver Station (BTS) via a second air link. The EGC is connected to a Mobile Switching Center (MSC) which is in turn connected to the BTS. An outgoing VoIP call from the WLAN Radio to a remote party on the WWAN will transition or seamlessly switch over to a WWAN connection when the MS detects packet error rates, frequent scale back or consistent signal degradation. Upon such conditions, the WLAN Radio requests the EGC to request an Explicit Call Transfer via the MSC to the MS integrated WWAN Radio portion which automatically accepts the call based on referenced information stored in the user's subscriber identification module (SIM). Once the WWAN Radio is confirmed connected to the remote party on the WWAN, the WLAN Radio drops the WLAN connection. An incoming call between the MS and a remote user via the WWAN will transition to the WLAN Radio when the MS enters WLAN coverage. The MS issues an ECT to the WLAN. After user verification by the WLAN Radio and the EGC signals acceptance of the call, the WWAN Radio connection is dropped and the call is now established between the WLAN Radio and the remote party on the WWAN.
Owner:SYMBOL TECH LLC
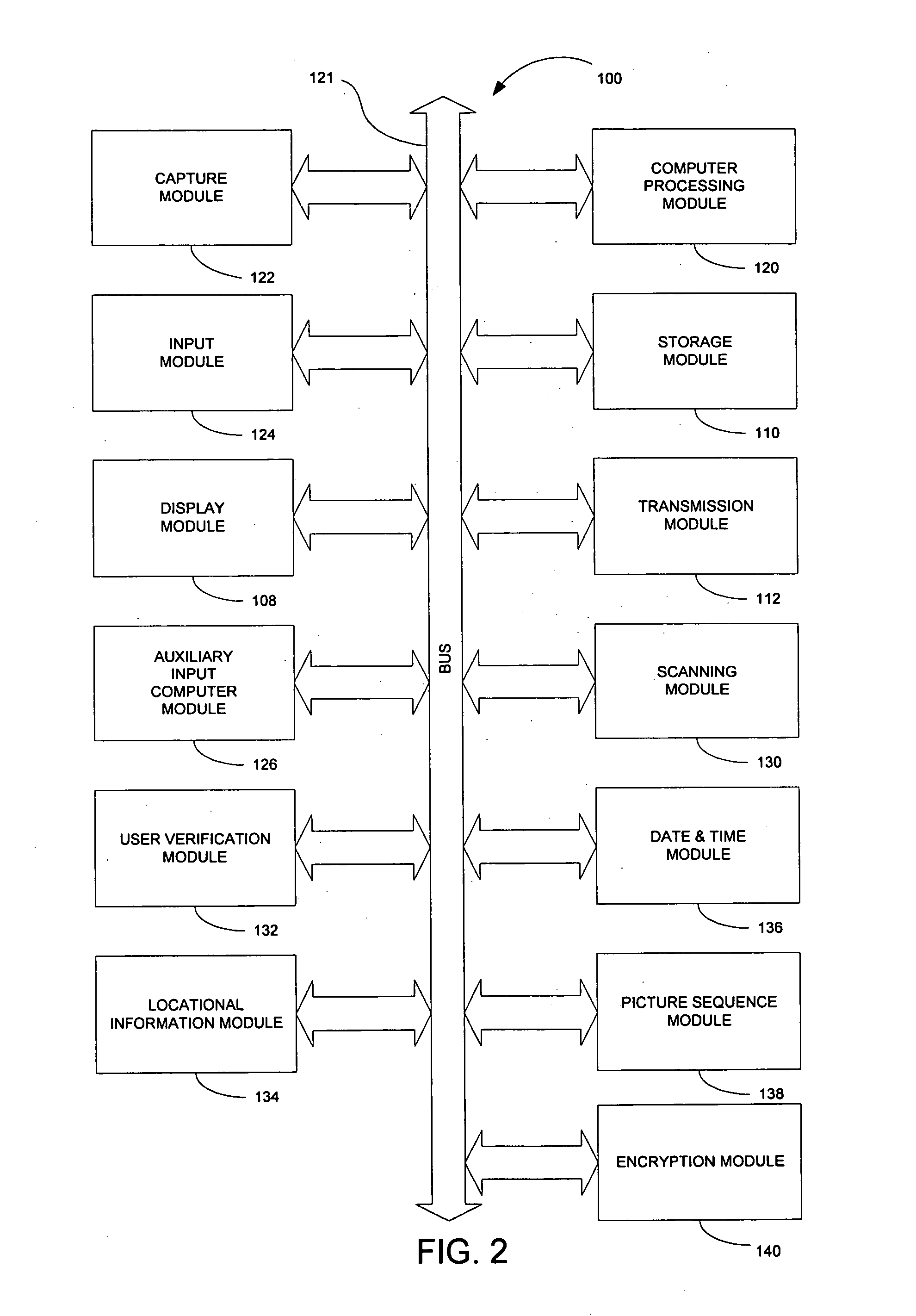
Device and method for embedding and retrieving information in digital images
InactiveUS20060114338A1Facilitate embedding informationTelevision system detailsColor television detailsUser verificationDigital imaging
A digital imaging device and method for embedding and retrieving of information in digital images are provided. The digital imaging device includes a capture module for capturing an image and creating a digital image file; a locational information module for determining a location of the device when capturing the image; and a processing module for associating the location information to the digital image file. The device further includes a user verification module for verifying an identity of a user of the device at a time of image capture and an encryption module for encrypting the digital image file and associated information. The method provides for securing information associated with the digital images and for verifying activities of a user.
Owner:ROTHSCHILD DIGITAL CONFIRMATION LLC
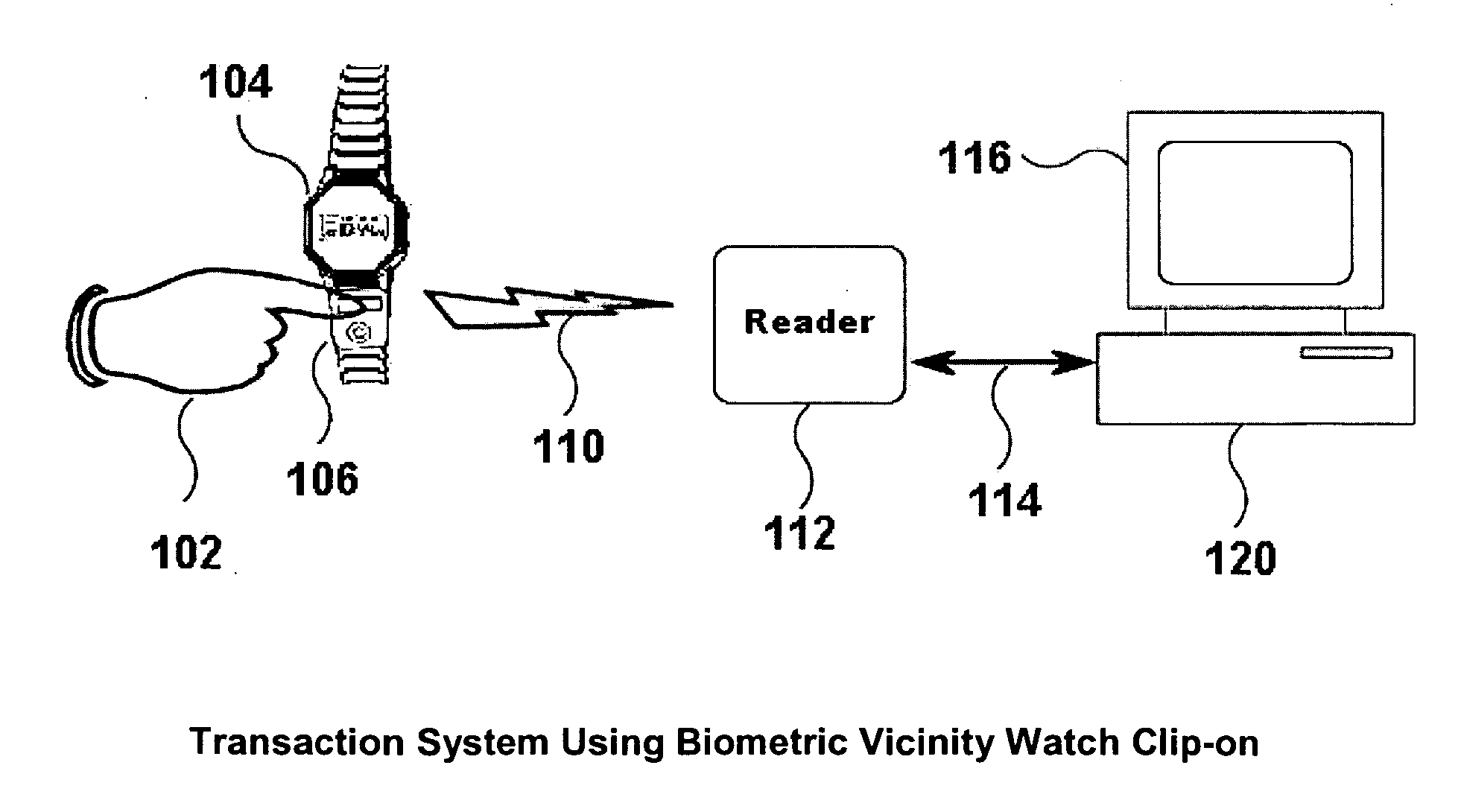
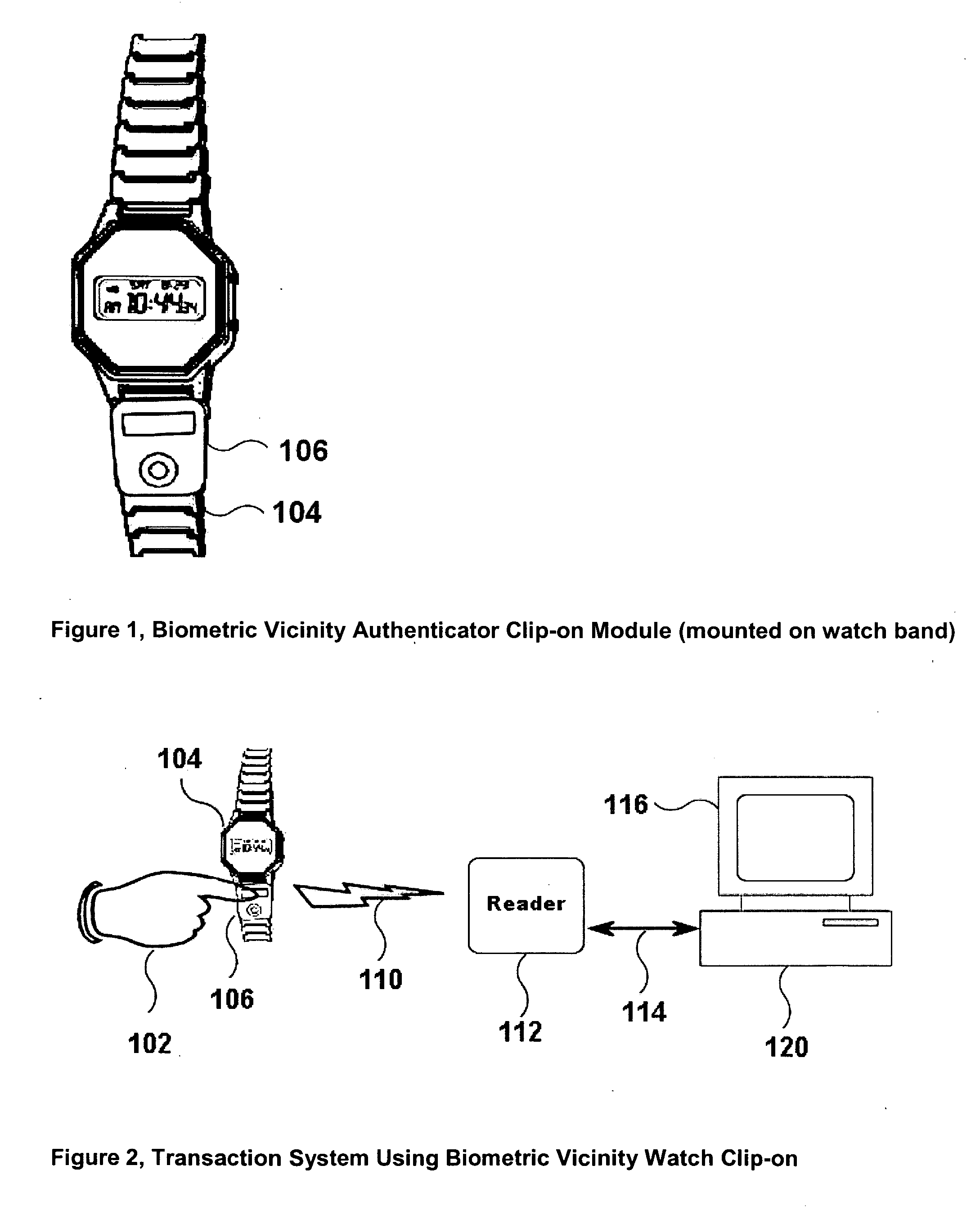
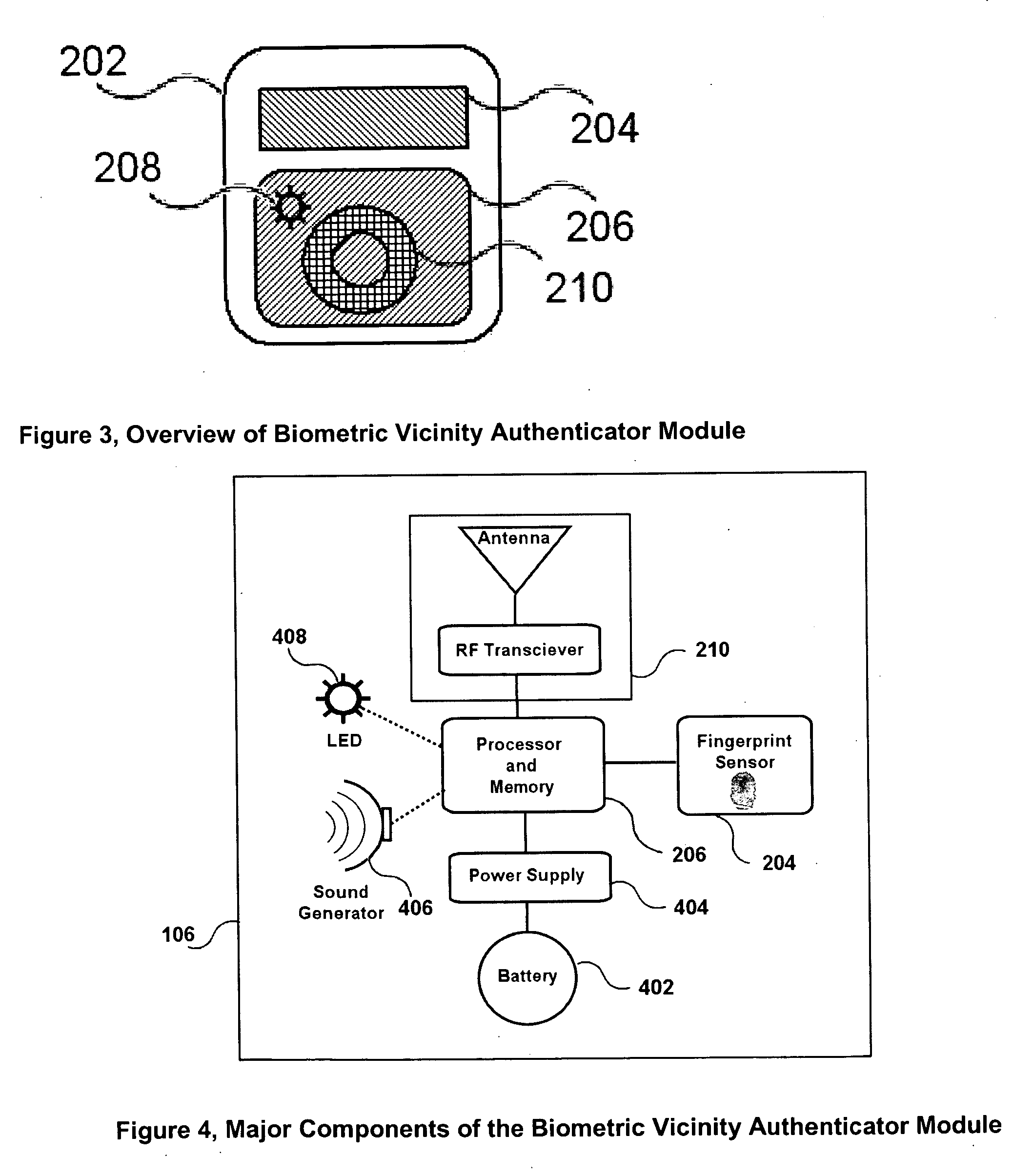
Attachable biometric authentication apparatus for watchbands and other personal items
InactiveUS20060288233A1Improve securityFacilitate user authenticationDigital data authenticationSecret communicationUser verificationTransceiver
The “first apparatus” disclosed is an ergonomic, removably-attachable biometric user authentication module, attachable onto a wristwatch band (or other surface) directly proximate to a user. This first apparatus includes (1) an attaching subsystem (e.g., bendable tabs, Velcro™ straps, etc.); and (2) a biometric authentication subsystem module. The first apparatus attaches onto any convenient “target” surface, but wristwatch bands are ideal for many users. The invention method, is a secure wireless protocol for communicating “successful biometric authentication” messages from the first apparatus, to a verification transceiver / reader (a “second apparatus”) which grants or denies user(s) access to transaction(s) and / or controlled resource(s), facilities, etc. The transceiver / reader is an “access governance” device that ensures only authorized users can access controlled (e.g., financial, physical, logical, etc.) resources. The system of the invention combines these first and second apparatuses and this method, plus includes embedded software for granting user access to controlled resources.
Owner:BIOMETRIC ASSOCS LP
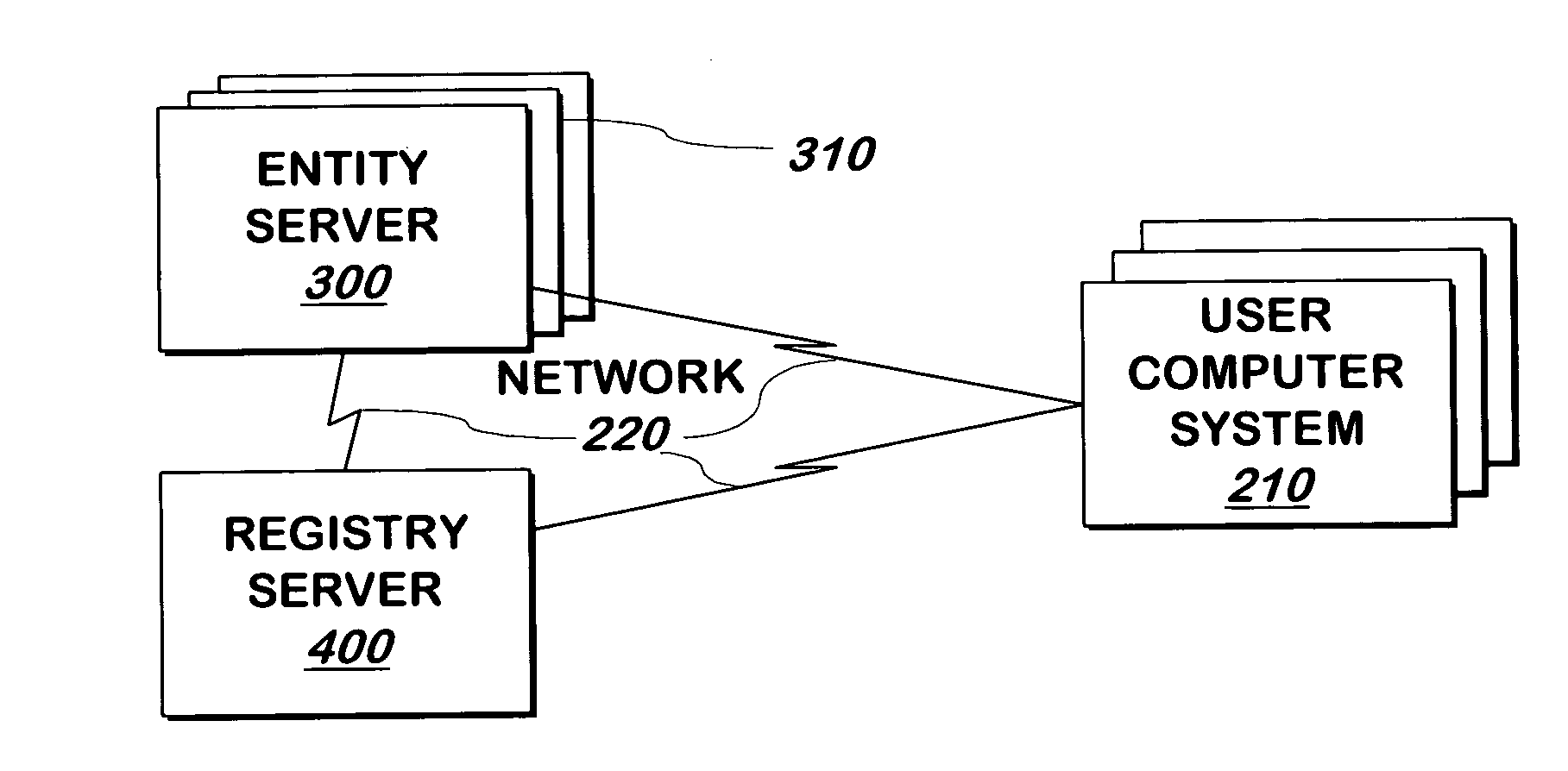
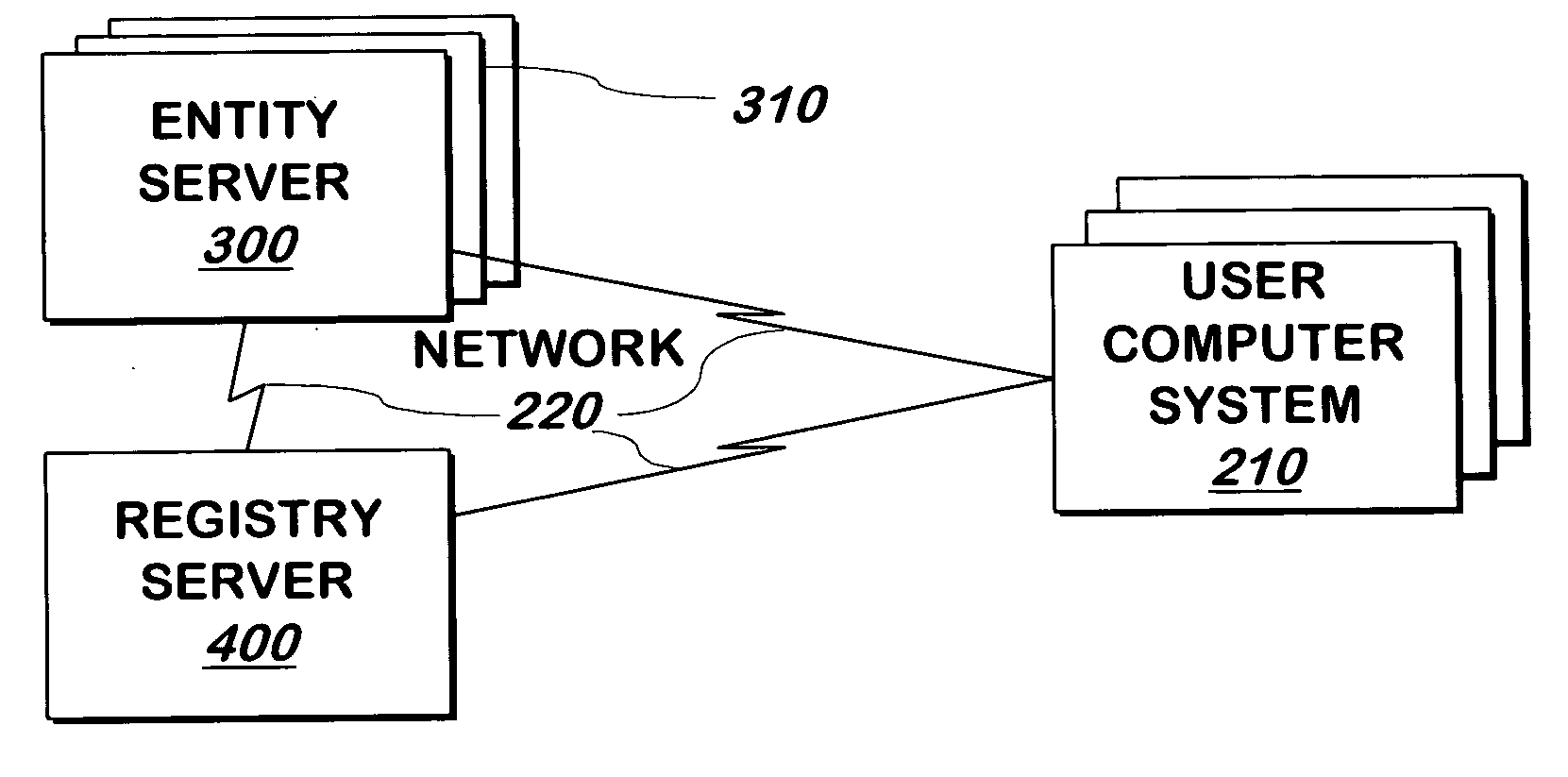
System and method for authenticating entities to users
InactiveUS7562222B2Digital data processing detailsUser identity/authority verificationUser verificationWindows Registry
A system and method communicates information from an entity that a registry can use to authenticate the entity to a user. If the registry authenticates the entity, it displays information that represents a shared secret between the registry and the user.
Owner:EMC IP HLDG CO LLC
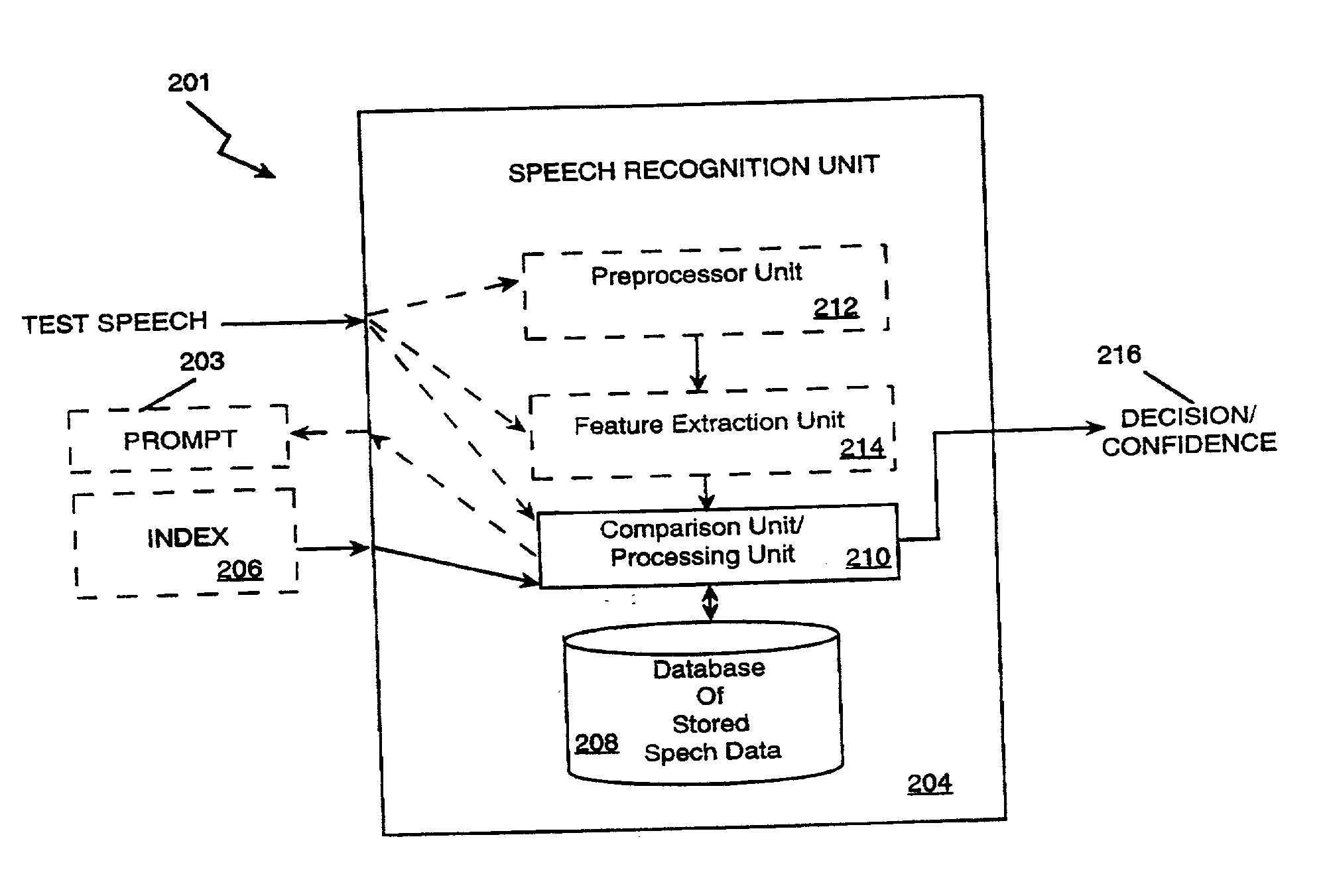
User validation for information system access and transaction processing
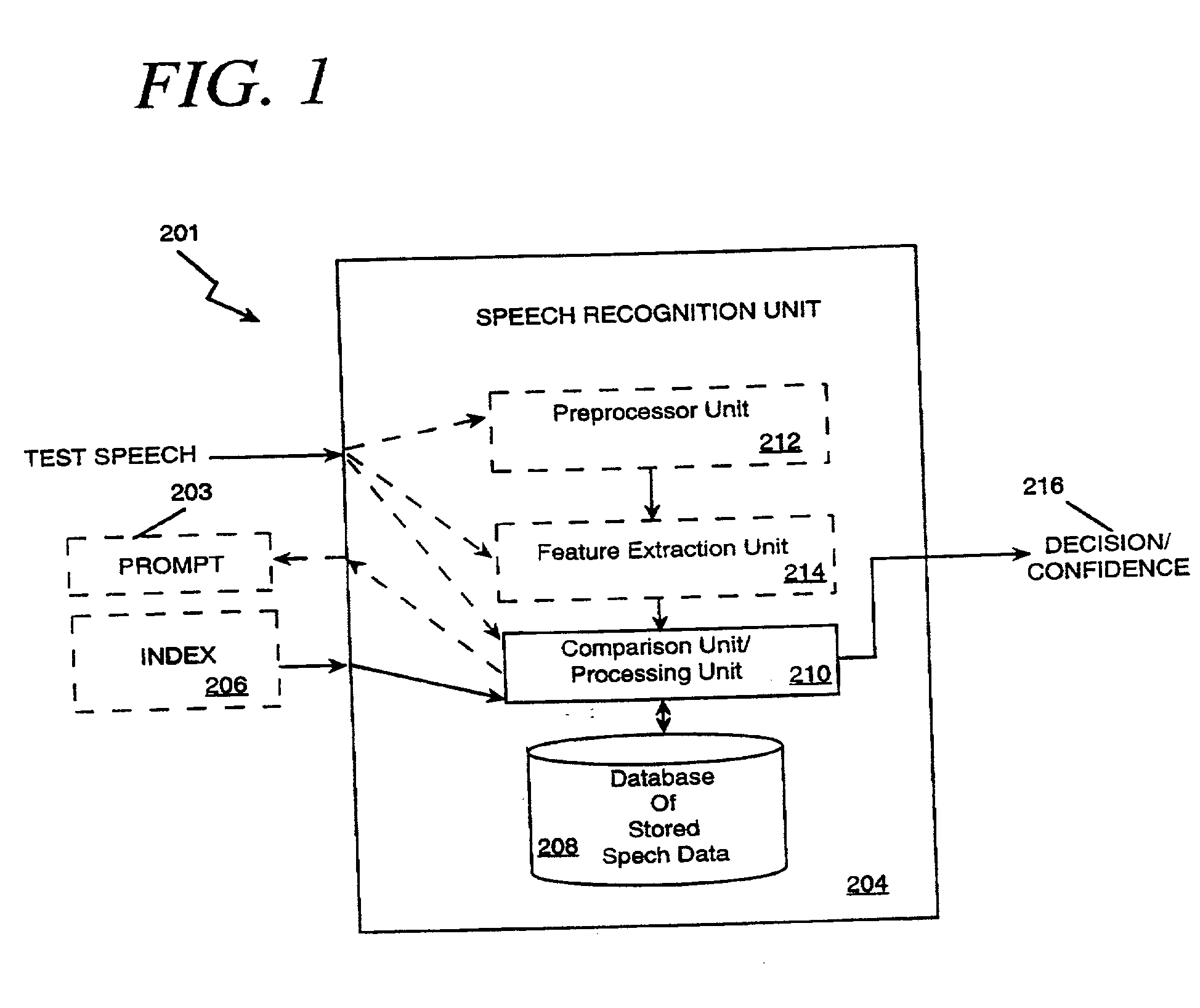
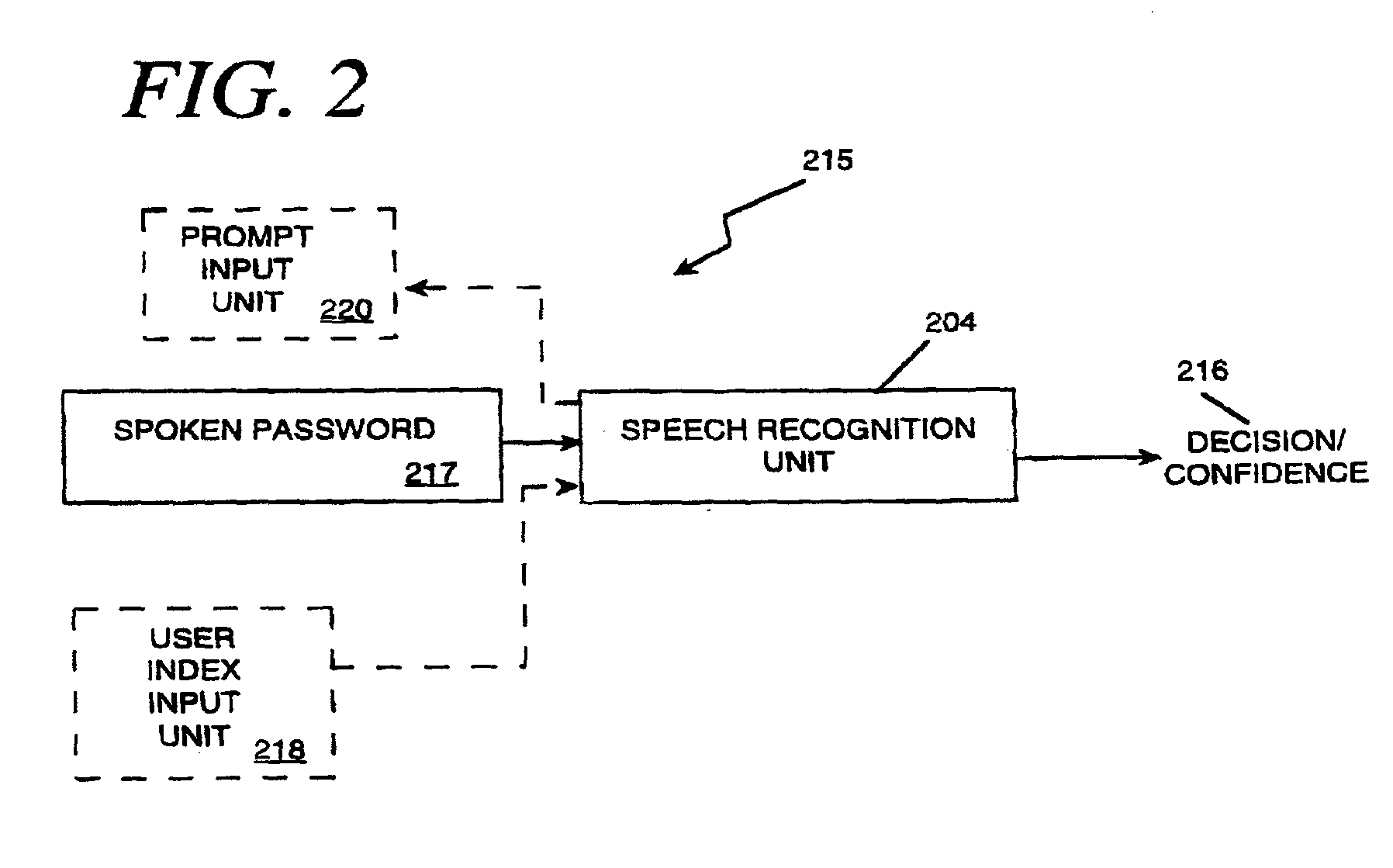
InactiveUS20030046083A1Robust methodPayment architectureDigital data authenticationUser verificationSpeech identification
The present invention applies speech recognition technology to remote access, verification, and identification applications. Speech recognition is used to raise the security level of many types of transaction systems which previously had serious safety drawbacks, including: point of sale systems, home authorization systems, systems for establishing a call to a called party (including prison telephone systems), internet access systems, web site access systems, systems for obtaining access to protected computer networks, systems for accessing a restricted hyperlink, desktop computer security systems, and systems for gaining access to a networked server. A general speech recognition system using communication is also presented. Further, different types of speech recognition methodologies are useful with the present invention, such as "simple" security methods and systems, multi-tiered security methods and systems, conditional multi-tiered security methods and systems, and randomly prompted voice token methods and systems.
Owner:BANK ONE COLORADO NA AS AGENT +1
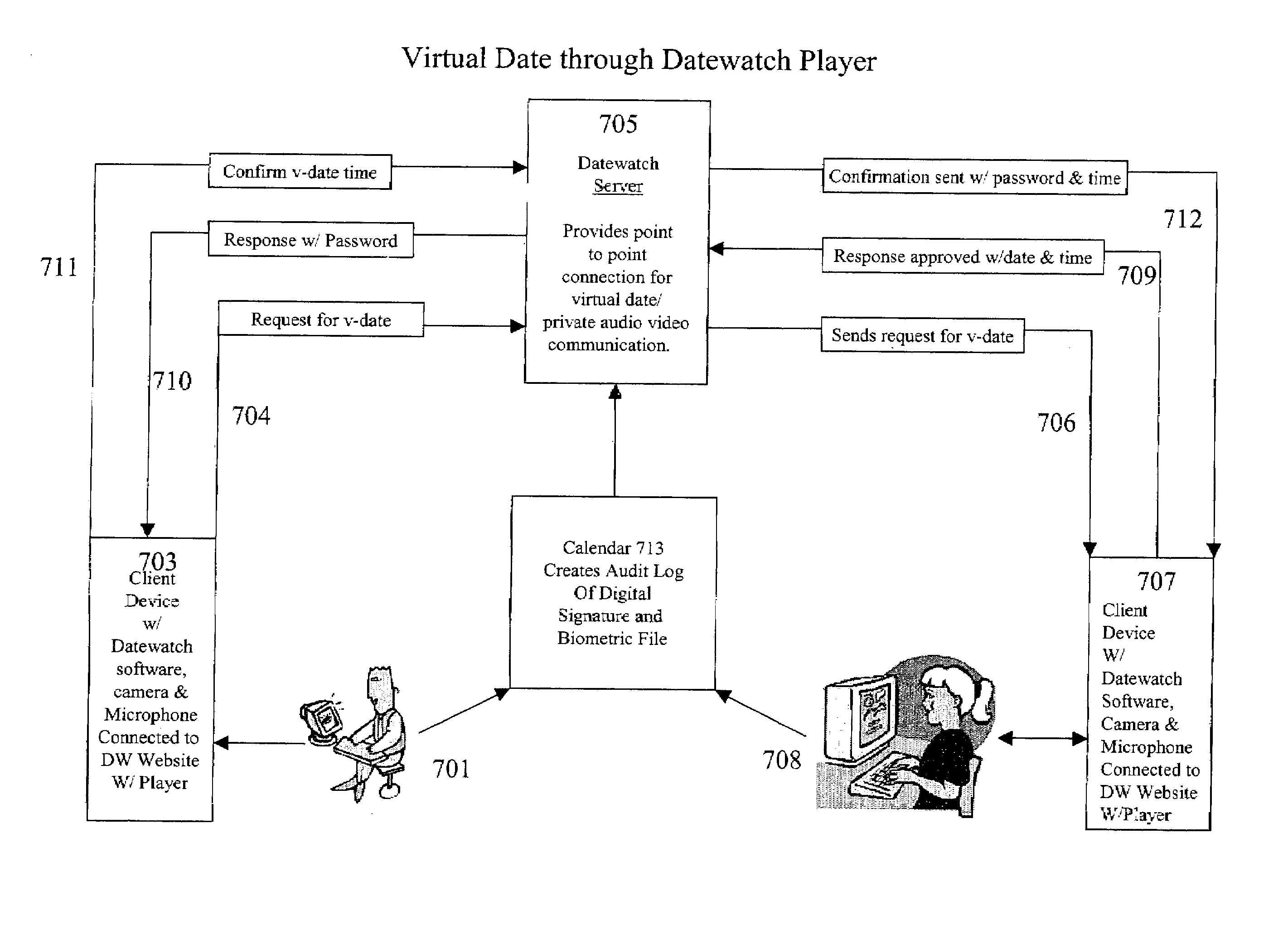
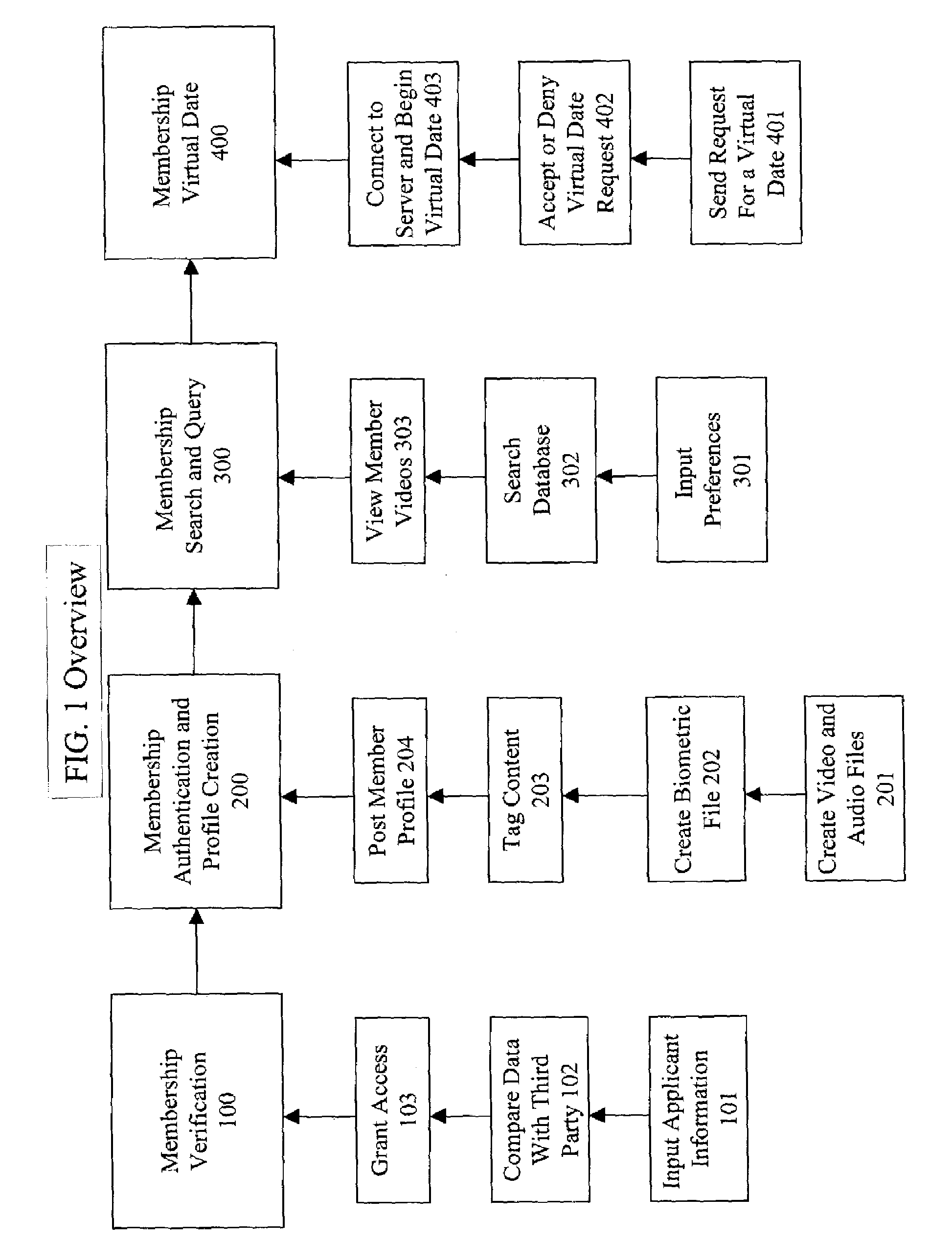
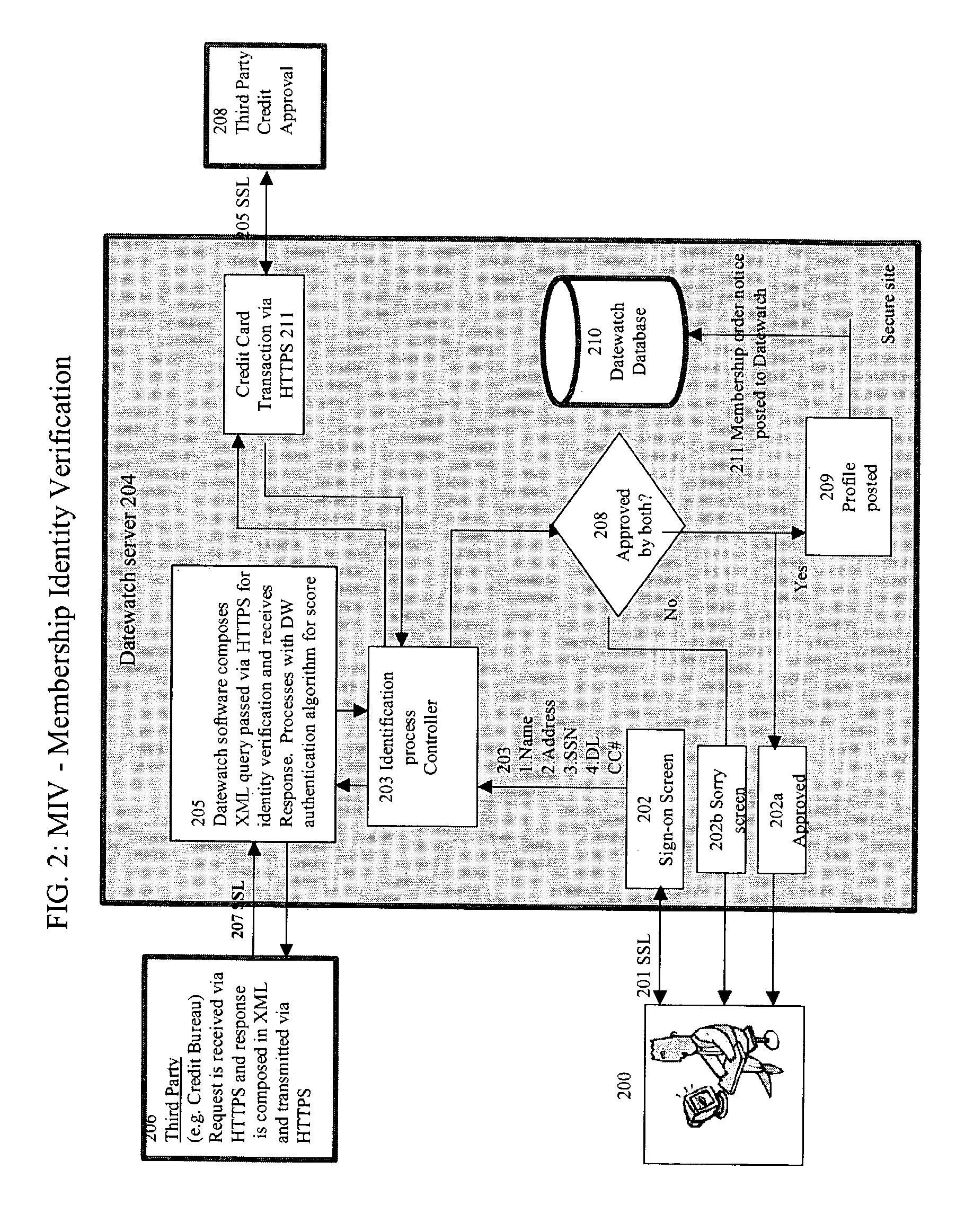
Method for user verification and authentication and multimedia processing for interactive database management and method for viewing the multimedia
InactiveUS7162475B2Improve audio qualityImprove video qualityDigital computer detailsDigital data authenticationUser verificationDigital video
A method for verifying specific profile, legal, and social preference data responses for generating a selectively approved membership database. Membership security is completed with a biometric security authentication of each member upon member logon. A media player is used for recording and delivering video on demand; live video broadcast communications, and video / audio relational database management as well as searching the database for Digital video and audio content defined by indexed unique hint track data. Live video conferencing is available utilizing bandwidth scheduling methods for quality video control and creating audit logs for member accountability and content control.
Owner:INTERNET BIOMETRIC SECURITY SYST
Computer user interface for product selection
InactiveUS6920614B1Quality improvementLow costTelevision system detailsColor television detailsUser verificationDisplay device
An entertainment system has a personal computer as the heart of the system with a large screen VGA quality monitor as the display of choice. The system has digital satellite broadcast reception, decompression and display capability with multiple radio frequency remote control devices which transmit self identifying signals and have power adjustment capabilities. These capabilities are used to provide context sensitive groups of keys which may be defined to affect only selected applications running in a windowing environment. In addition, the remote control devices combine television and VCR controls with standard personal computer keyboard controls. A keyboard remote also integrates a touchpad which is food contamination resistant and may also be used for user verification. Included in the system is the ability to recognize verbal communications in video signals and maintain a database of such text which is searchable to help identify desired programming in real time.
Owner:GATEWAY
System and method for authenticating entities to users
InactiveUS20050268100A1Digital data processing detailsUser identity/authority verificationUser verificationWindows Registry
A system and method communicates information from an entity that a registry can use to authenticate the entity to a user. If the registry authenticates the entity, it displays information that represents a shared secret between the registry and the user.
Owner:EMC IP HLDG CO LLC
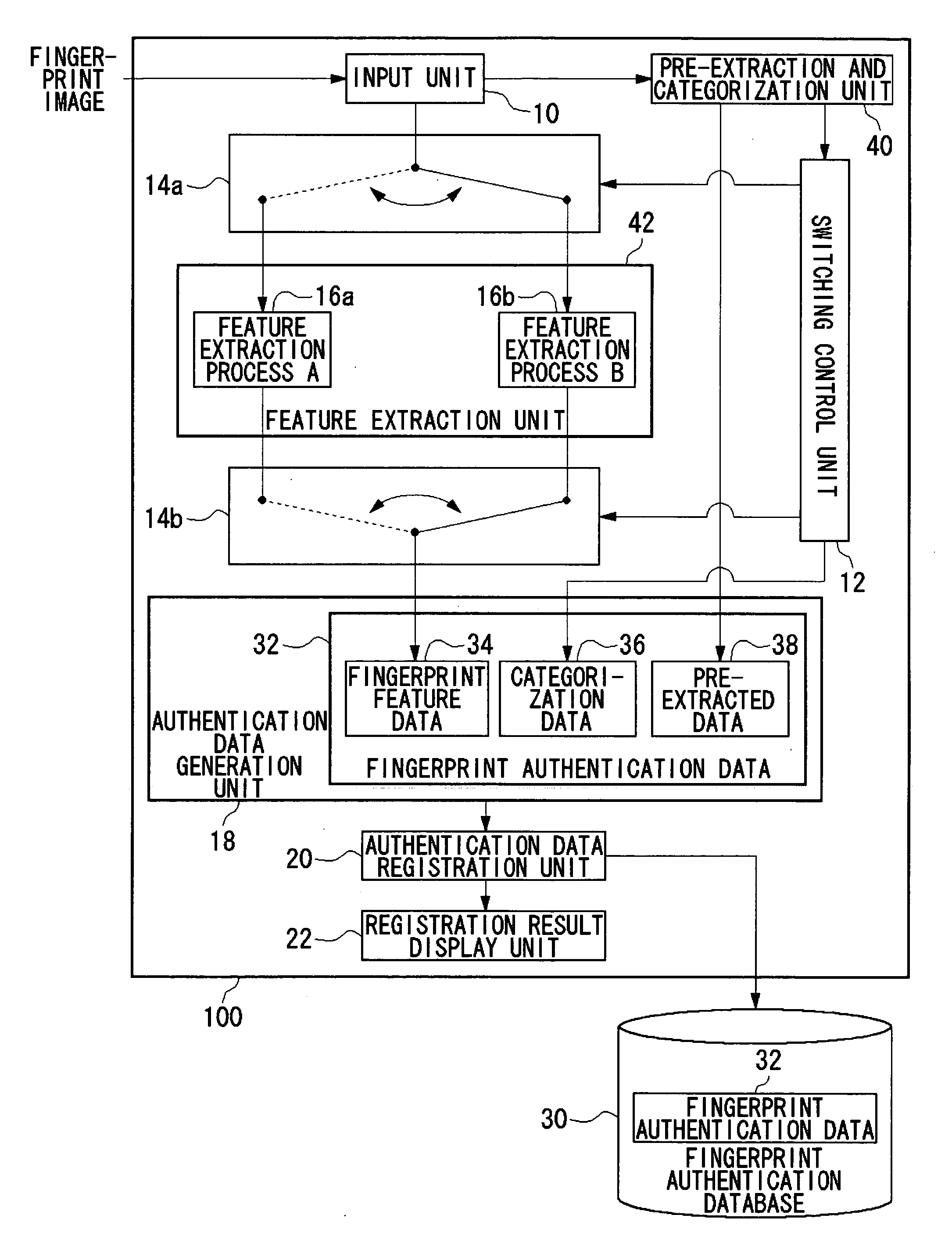
User authentication using biometric information
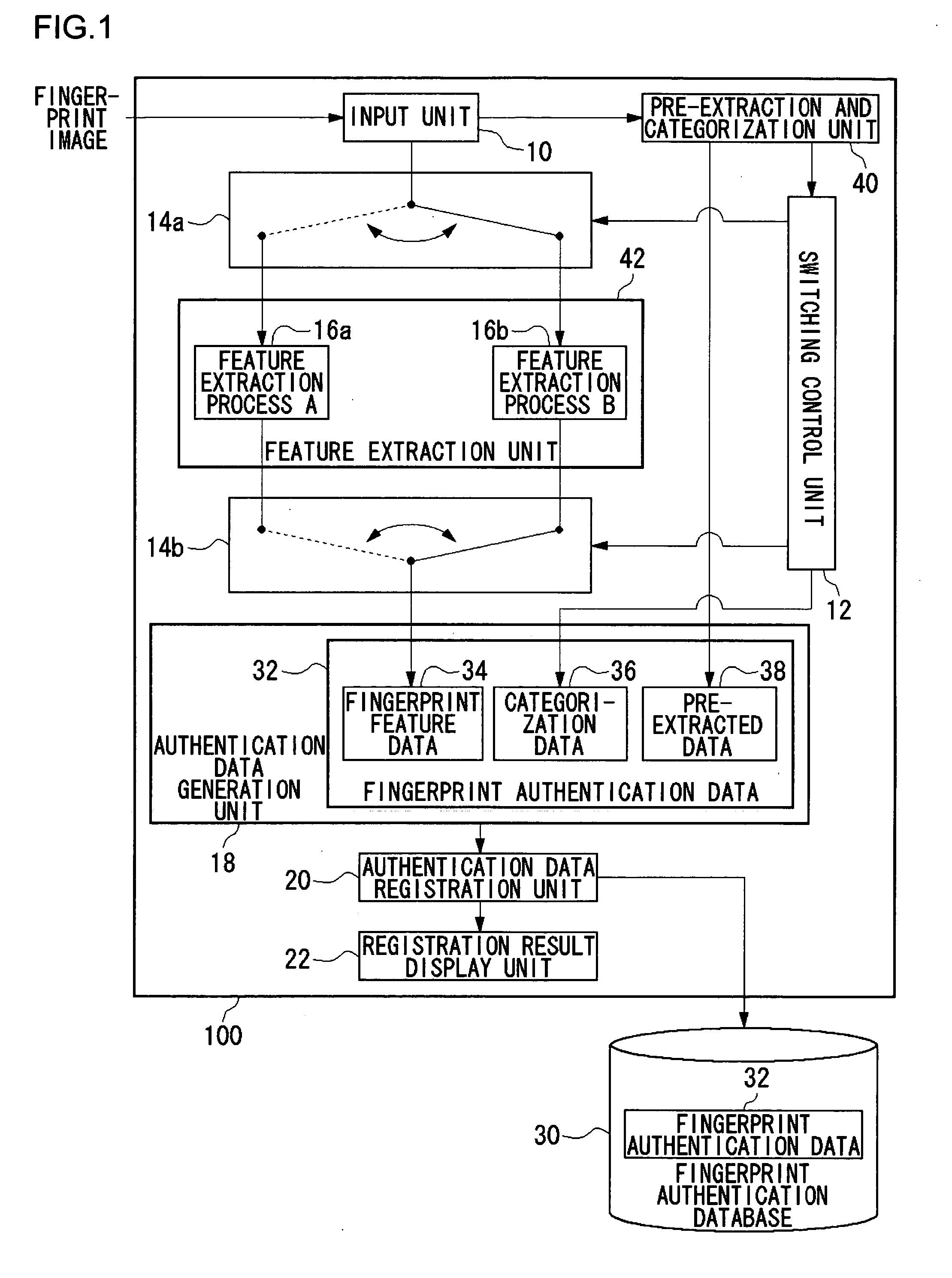
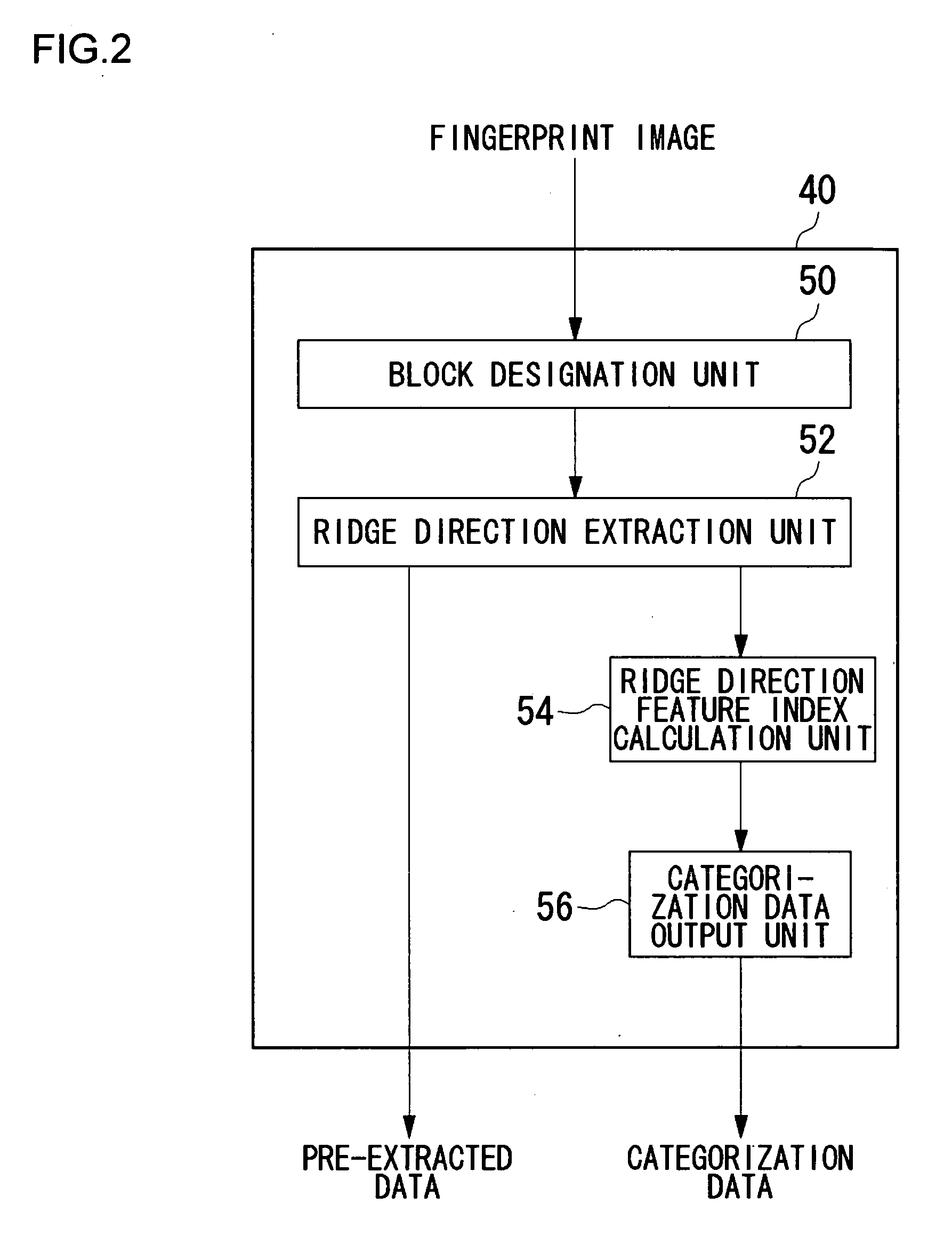
InactiveUS20070036400A1High precisionEfficiently retrieve the reference biometric informationCharacter and pattern recognitionData matchingUser verification
An input unit accepts a fingerprint image of a user. A pre-extraction and categorization unit generates pre-extracted data from the fingerprint image and uses the data to categorize the input fingerprint image into one of multiple groups. A feature extraction unit extracts fingerprint feature data from the fingerprint image by processing methods defined for the respective groups. A feature data matching processing unit matches the fingerprint feature data against fingerprint authentication data registered in a fingerprint authentication database by processing methods defined for the respective groups. An integrated authentication unit authenticates a user with the input fingerprint image based upon a result of matching.
Owner:SANYO ELECTRIC CO LTD
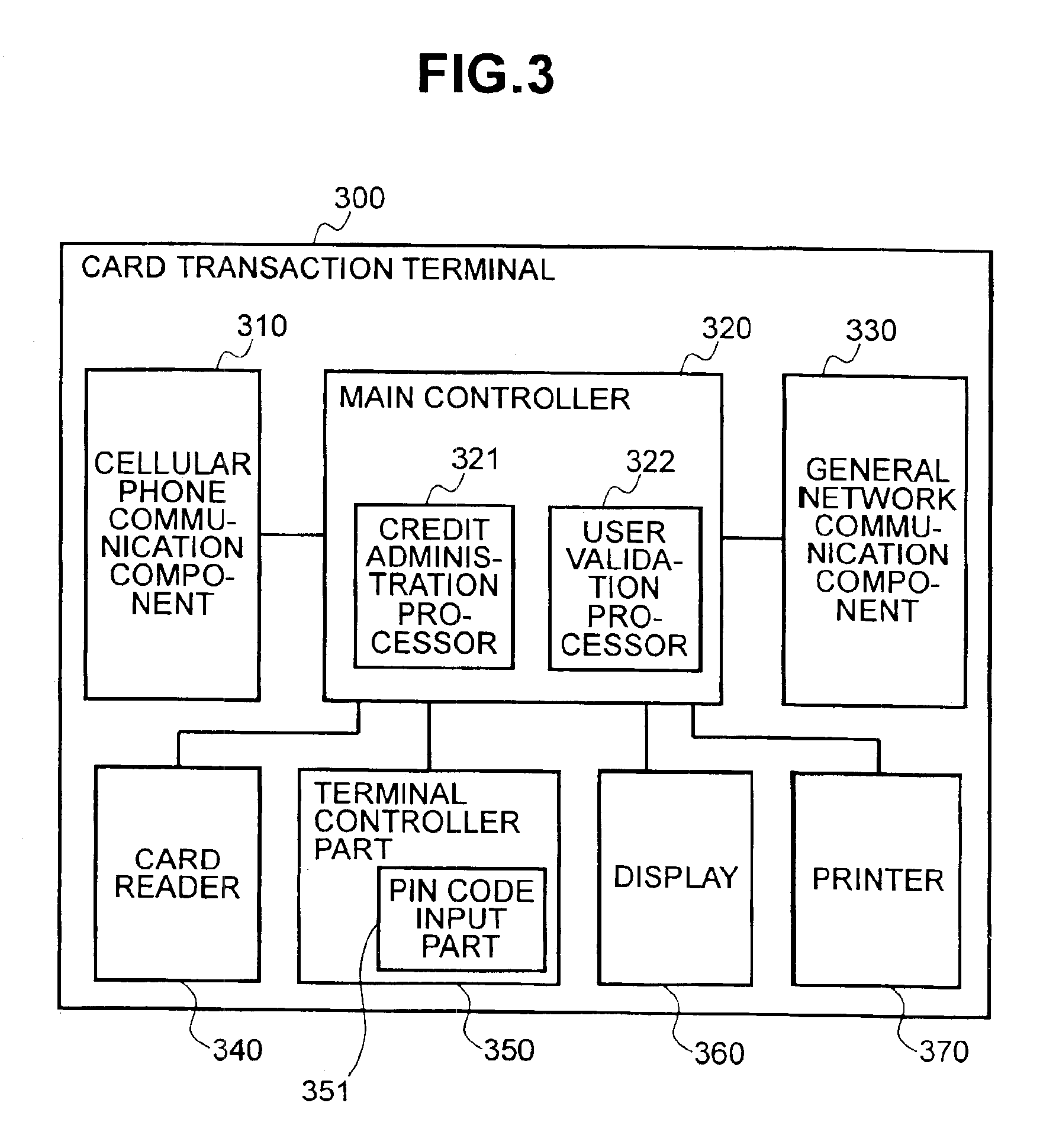
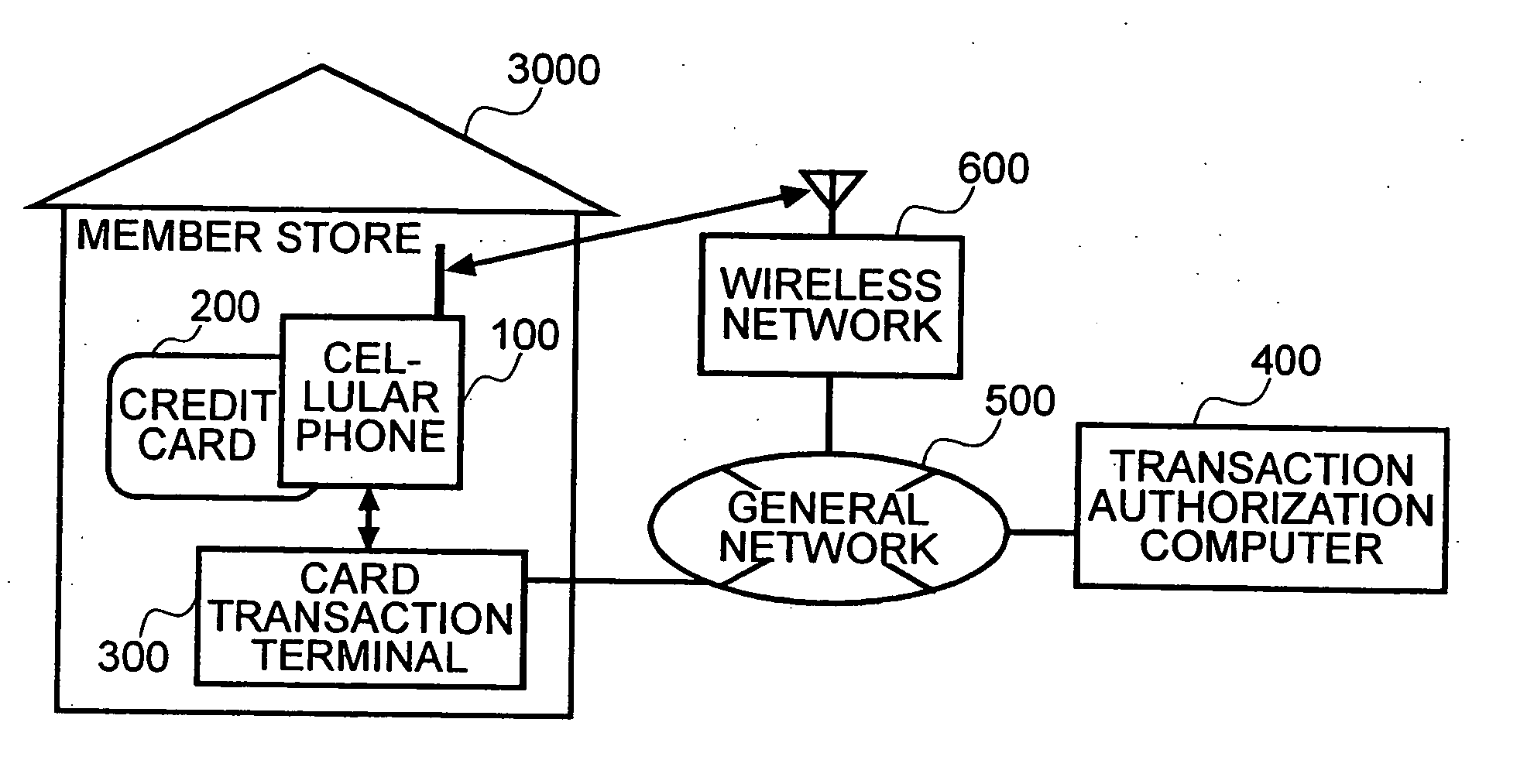
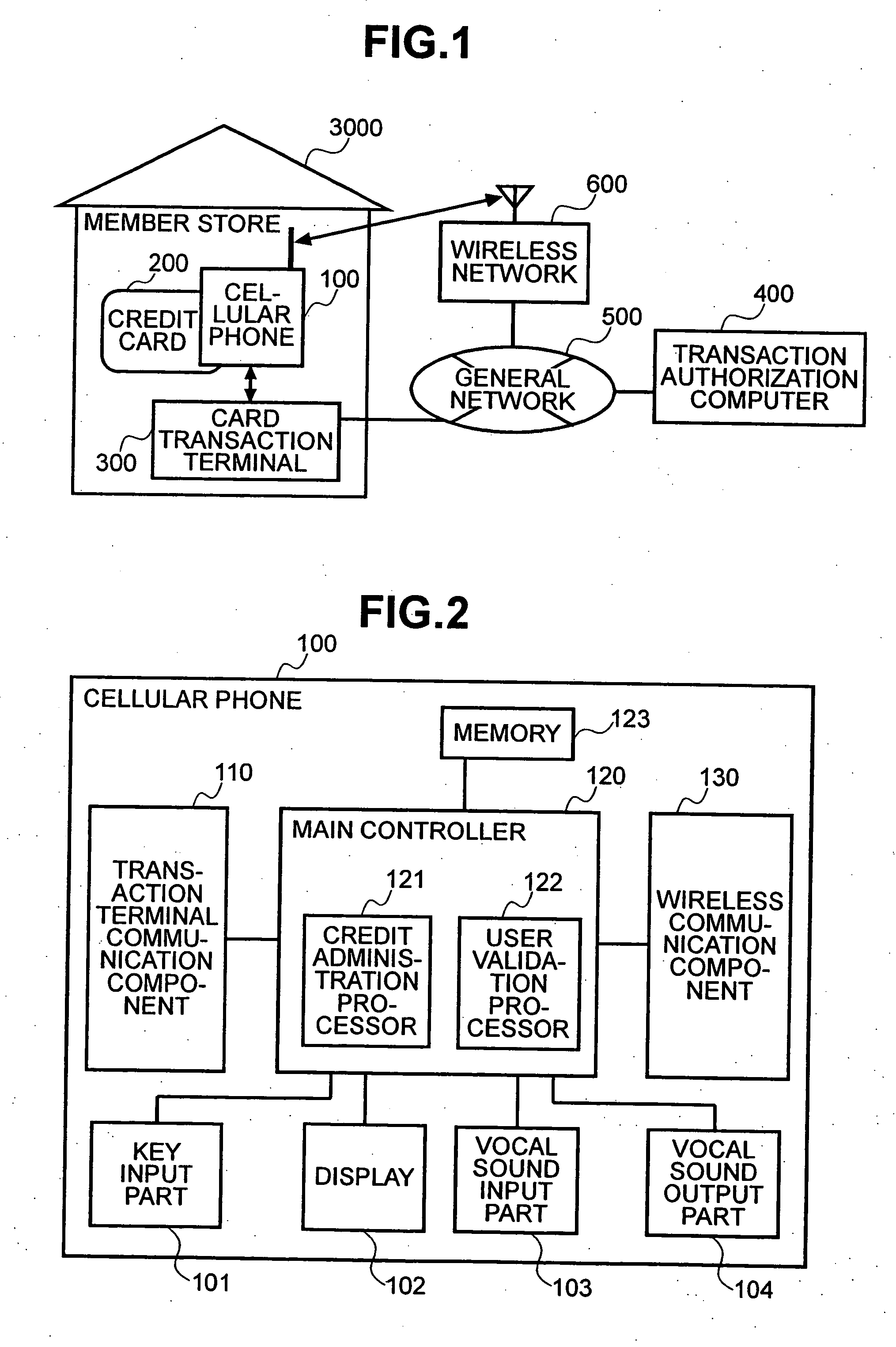
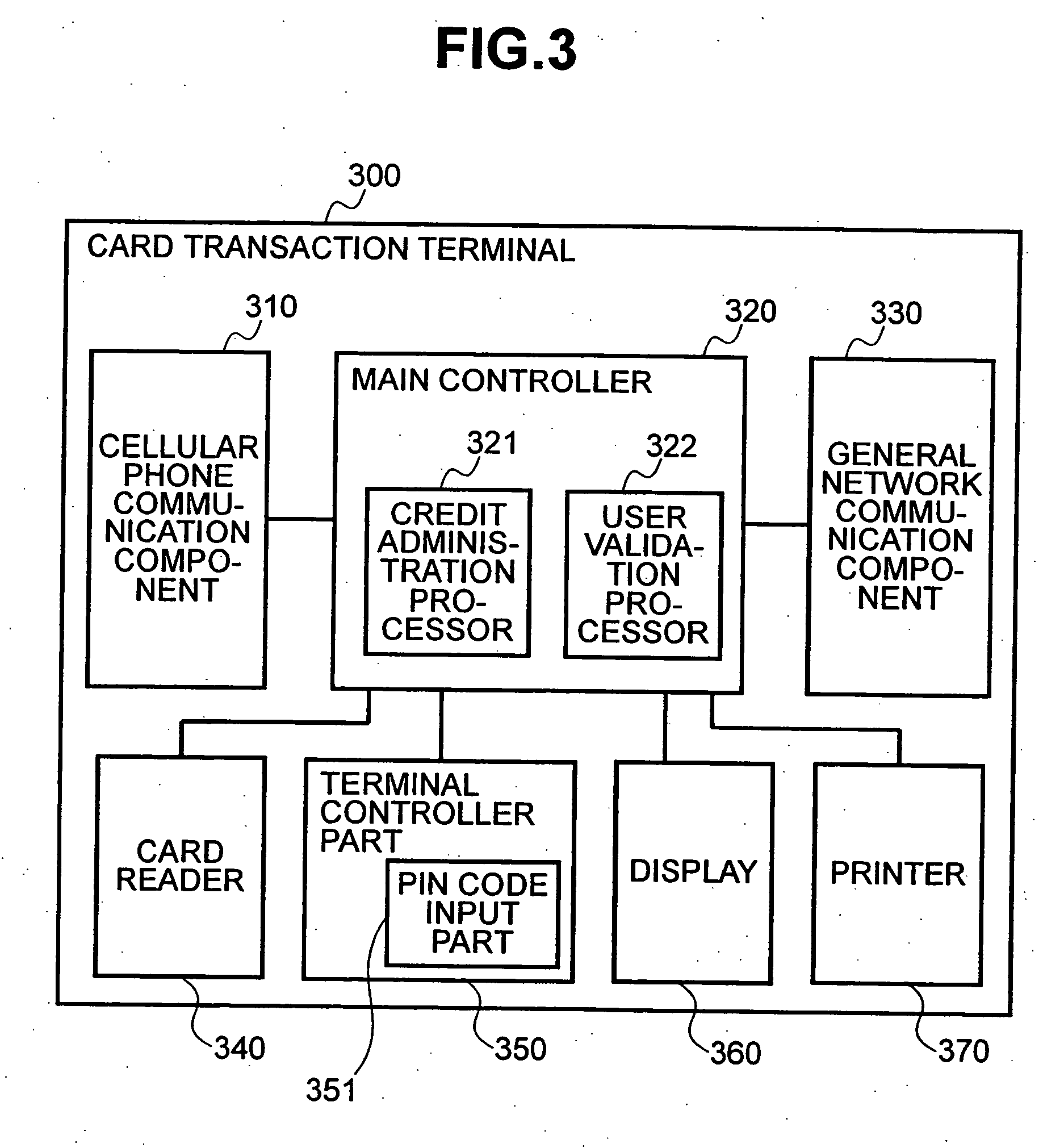
Method and system to prevent fraudulent payment in credit/debit card transactions, and terminals therefor
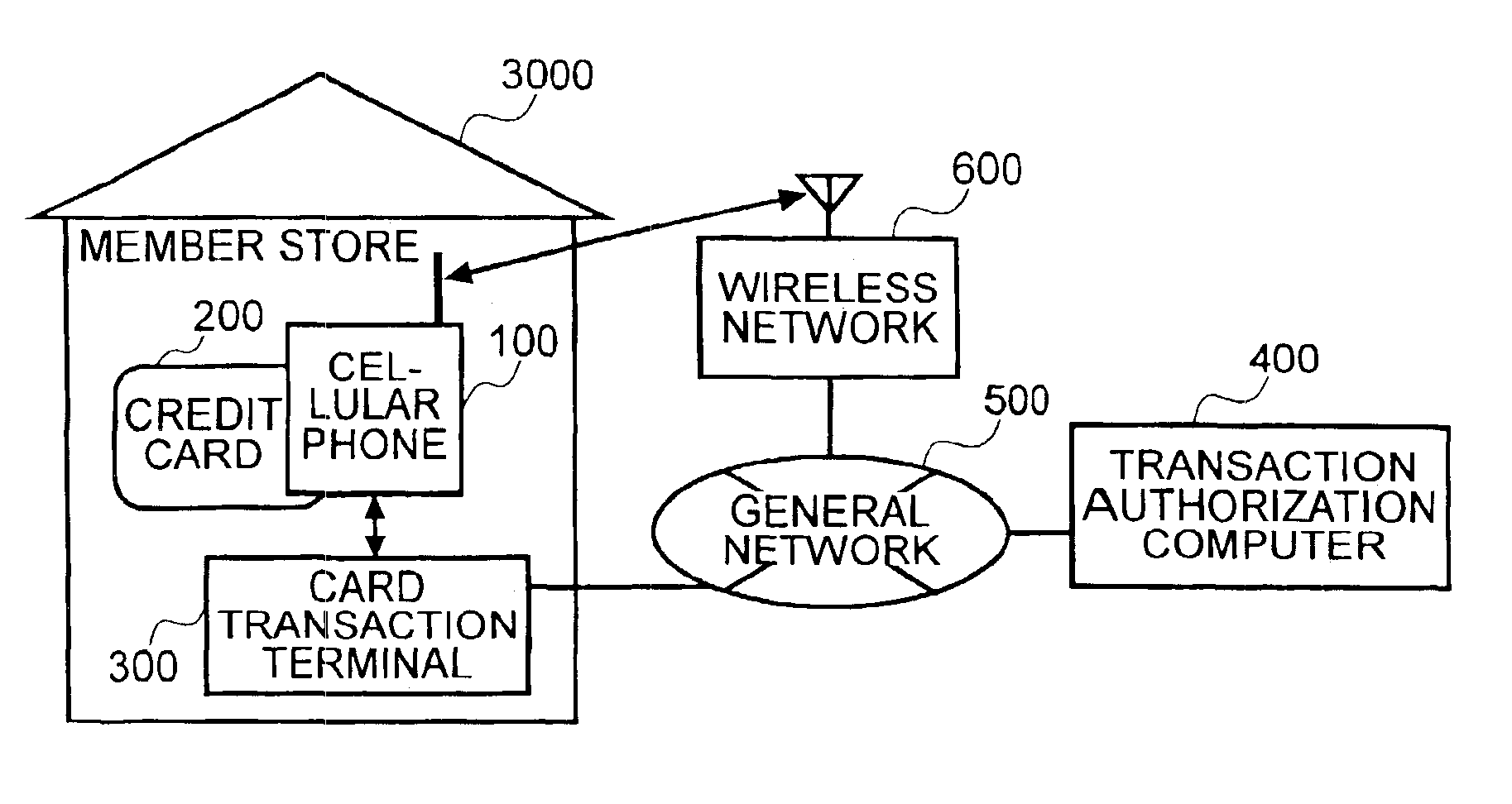
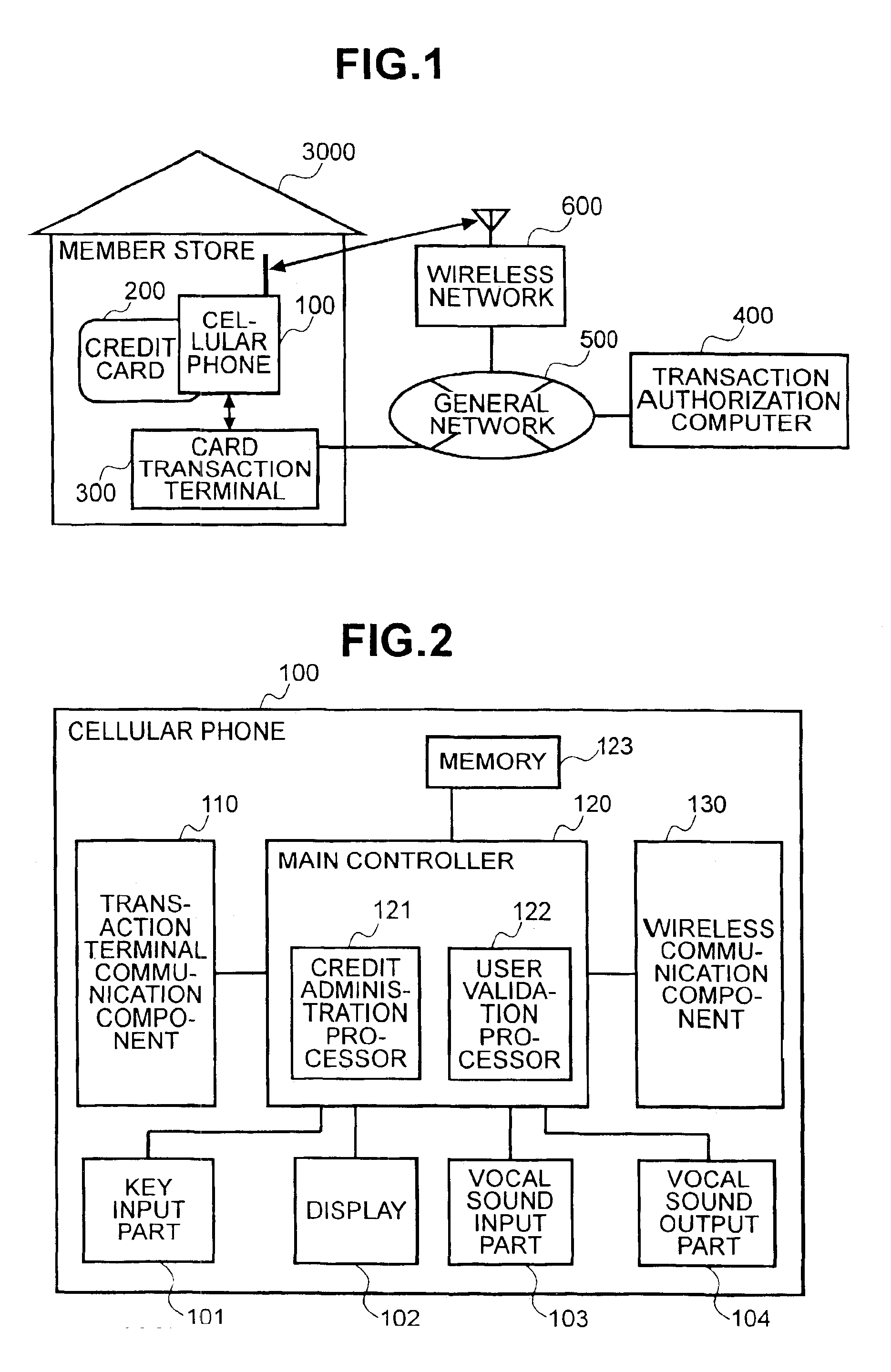
InactiveUS6913194B2Transaction can be blockedEliminate dangerBuying/selling/leasing transactionsVerifying markings correctnessUser verificationComputer terminal
The present invention enables secure, valid card payments in credit transactions to be performed, preventing fraudulent card use even in cases of loss or theft of a card or of information theft. During a transaction authorization process using a transaction terminal disposed in a credit transaction member store and connected with a host computer, user validation or credit administration is carried out by using a portable communication terminal to input to the host computer identity information which has been previously registered in the portable communication terminal and / or location information for the portable communication terminal.
Owner:MAXELL HLDG LTD
Transaction authentication card
InactiveUS20070220273A1Electric signal transmission systemsImage analysisUser verificationComputer hardware
A transaction authentication card uses a biometric input and a wireless output. The biometric input may be a sensor pad on the transaction authentication card that measures blood flow patterns, temperature, and / or fingerprint patterns to identify a user to permit access. The transaction authentication card is preferably substantially rigid, but may be formed to have some flexibility. Power to the transaction authentication card may be accomplished through an internal battery that is optionally rechargeable. Biometric data is stored on the card only and used for user verification. Biometric data will not be transferred from the card. If authorized biometric data is authenticated the card will transmit a wireless access code to a proximity reader or transaction equipment.
Owner:RESILENT
System and method for enabling a user of an E-commerce system to visually view and/or configure a product for purchase
InactiveUS6985876B1Increase incomeReduce in quantityAcutation objectsBuying/selling/leasing transactionsUser verificationGraphics
A system and method that enables a user to configure a customizable product for purchase in an E-Commerce system. A user may launch a web browser on a client computer system to access a vendor's web site to purchase a customizable product. The user may customize the product for purchase by selecting one or more customizable components of the product. A user may select one or more customizable components of the product by using a forms / menu interface or a visual graphical user interface. The vendor's web site may receive the one or more user selections for the customized product and may, in response, send data and information to client computer system to visually depict the ‘as purchased’ customized product for user verification and product checkout.
Owner:NATIONAL INSTRUMENTS
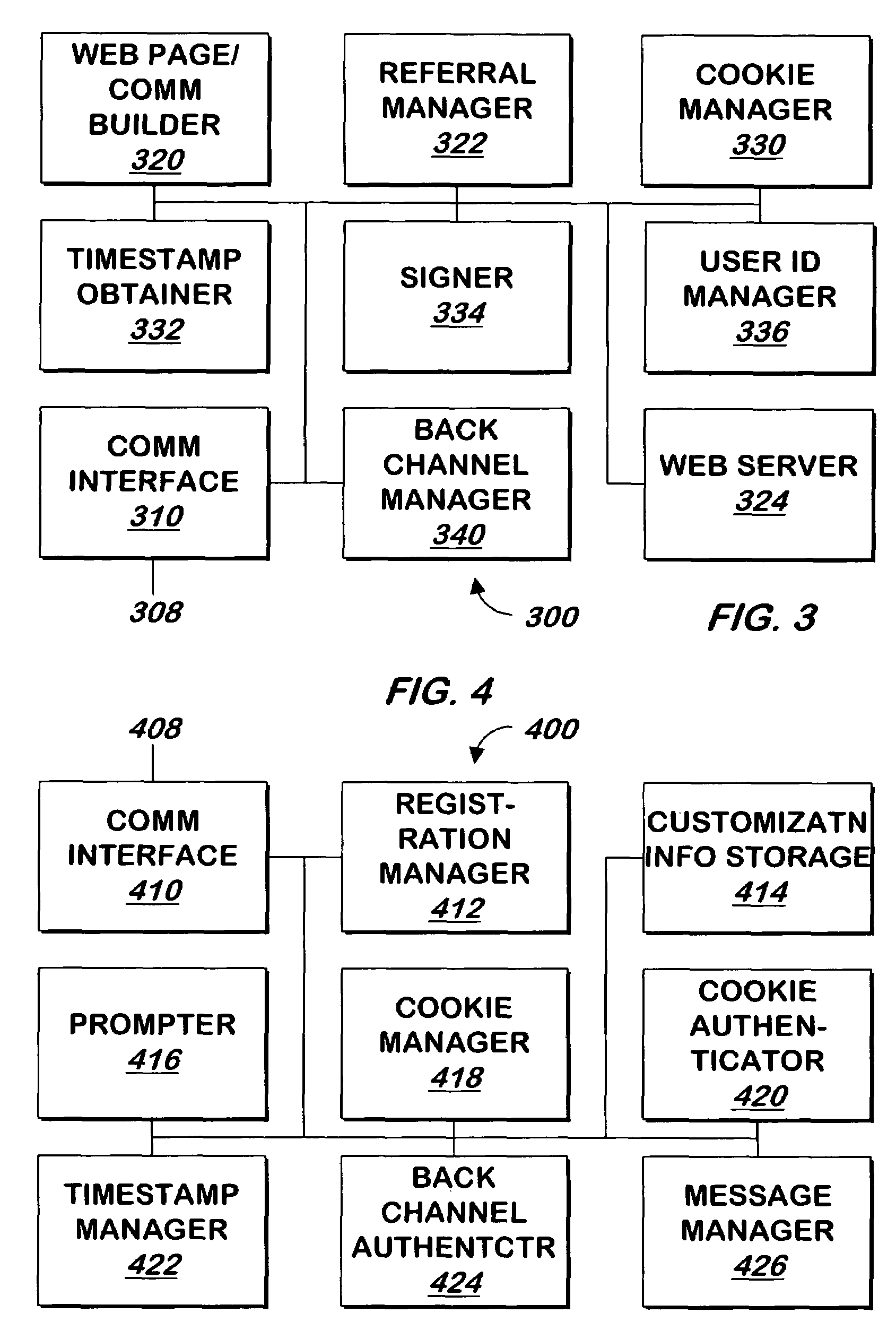
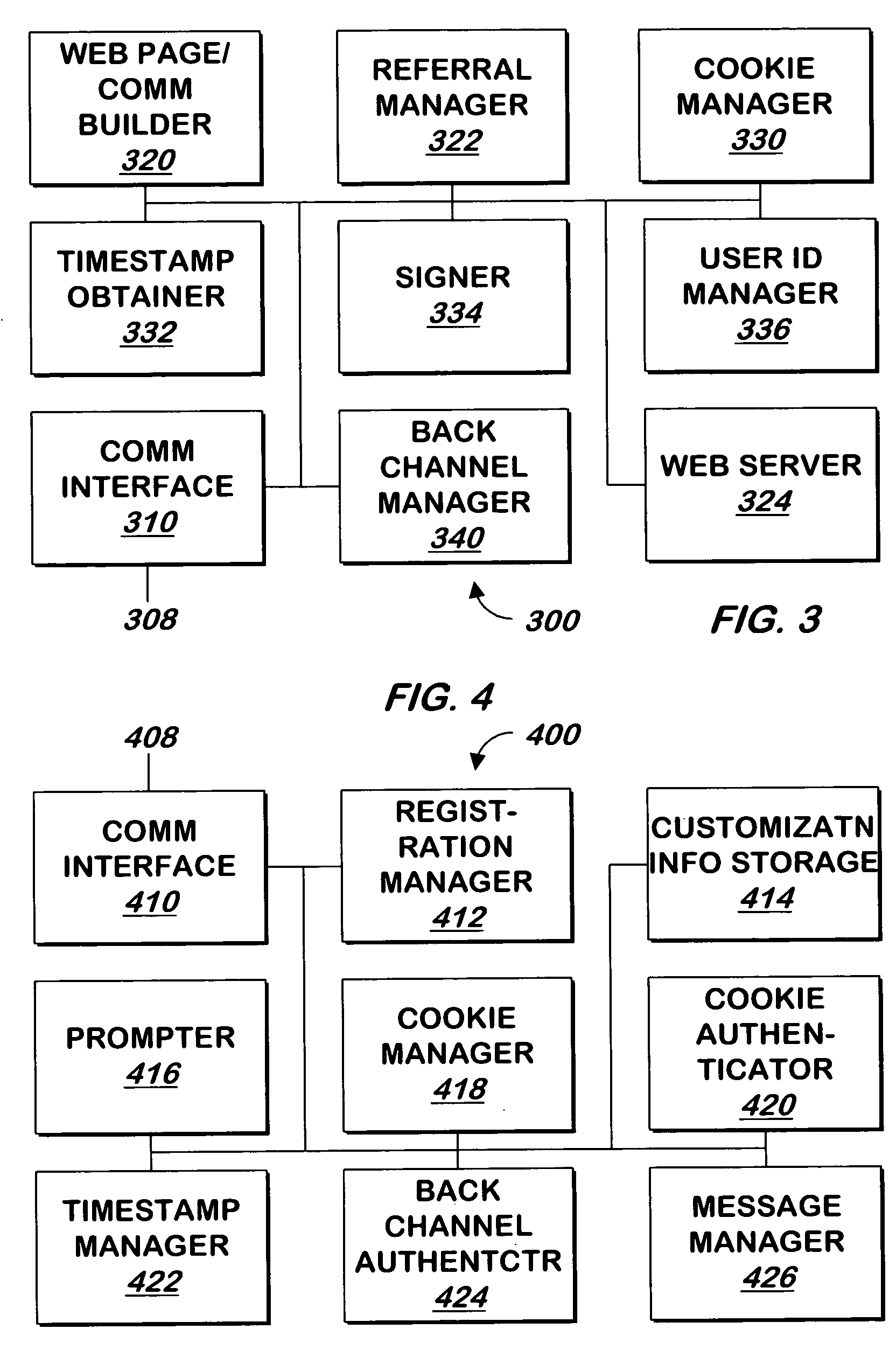
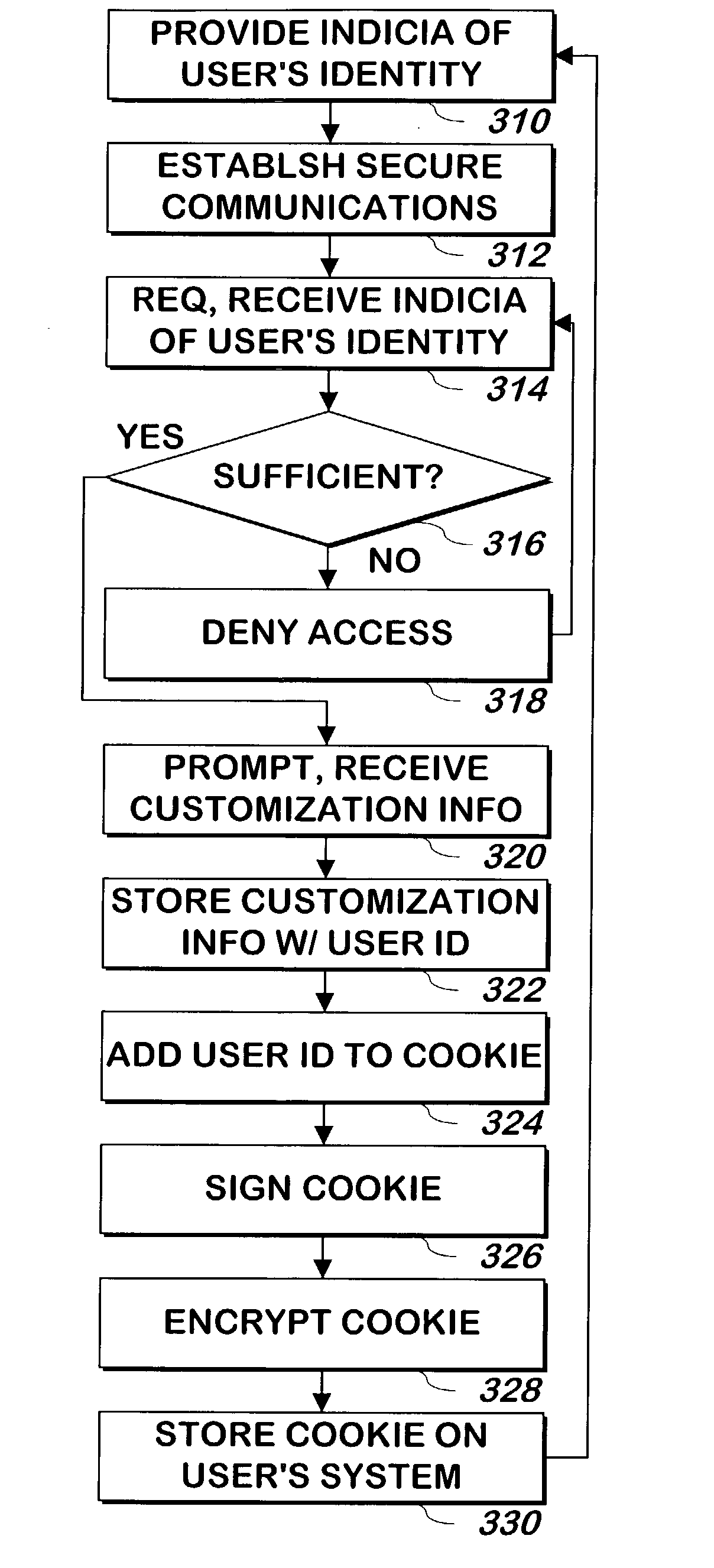
Method and apparatus for authentication of users and web sites
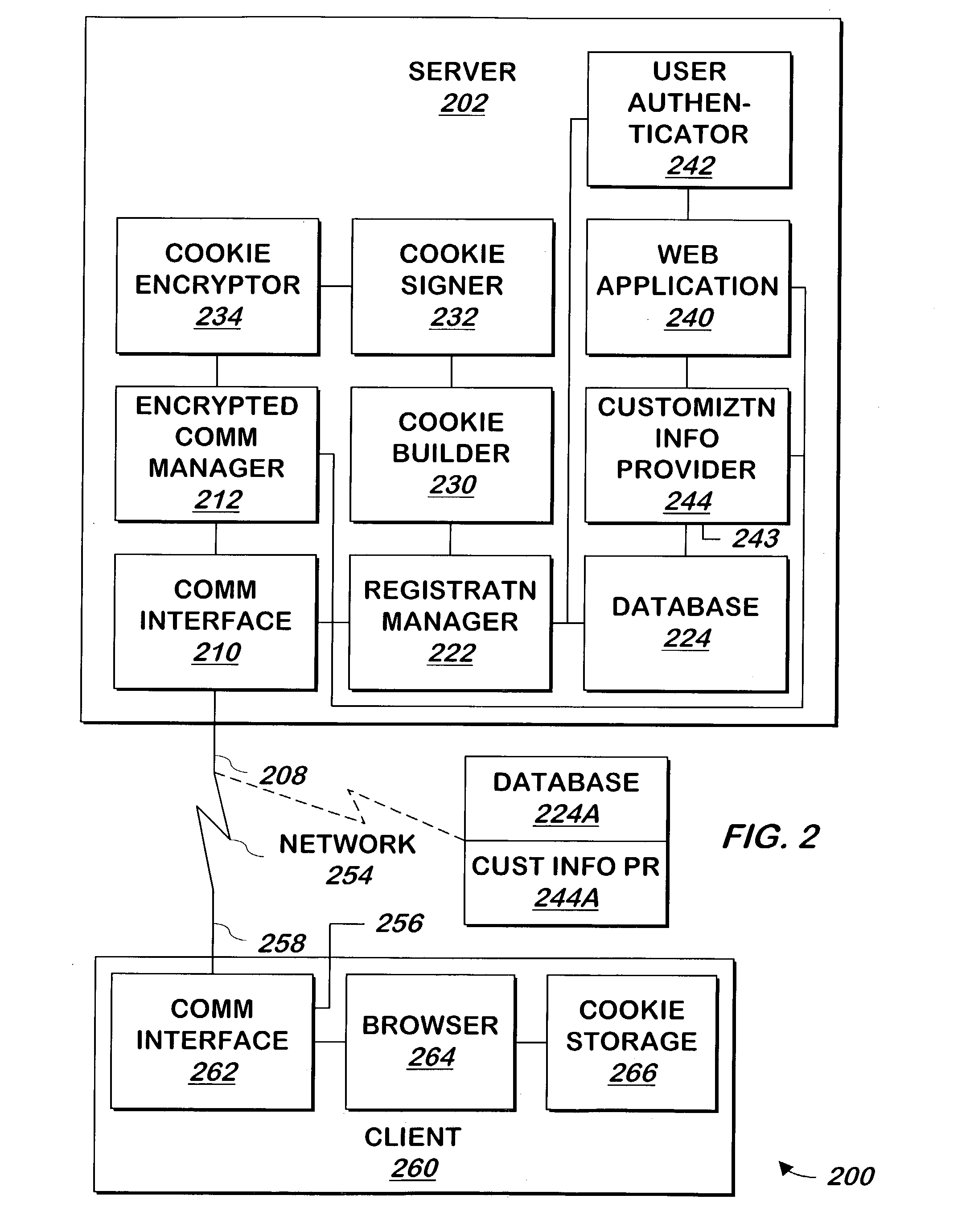
InactiveUS20040168083A1Digital data processing detailsUser identity/authority verificationWeb siteWeb page
A system and method allows a user to authenticate a web site, a web site to authenticate a user, or both. When a user requests a web page from the web site, customization information that is recognizable to the user is provided to allow the user to authenticate the web site. A signed, encrypted cookie stored on the user's system allows the web site to authenticate the user.
Owner:EMC IP HLDG CO LLC
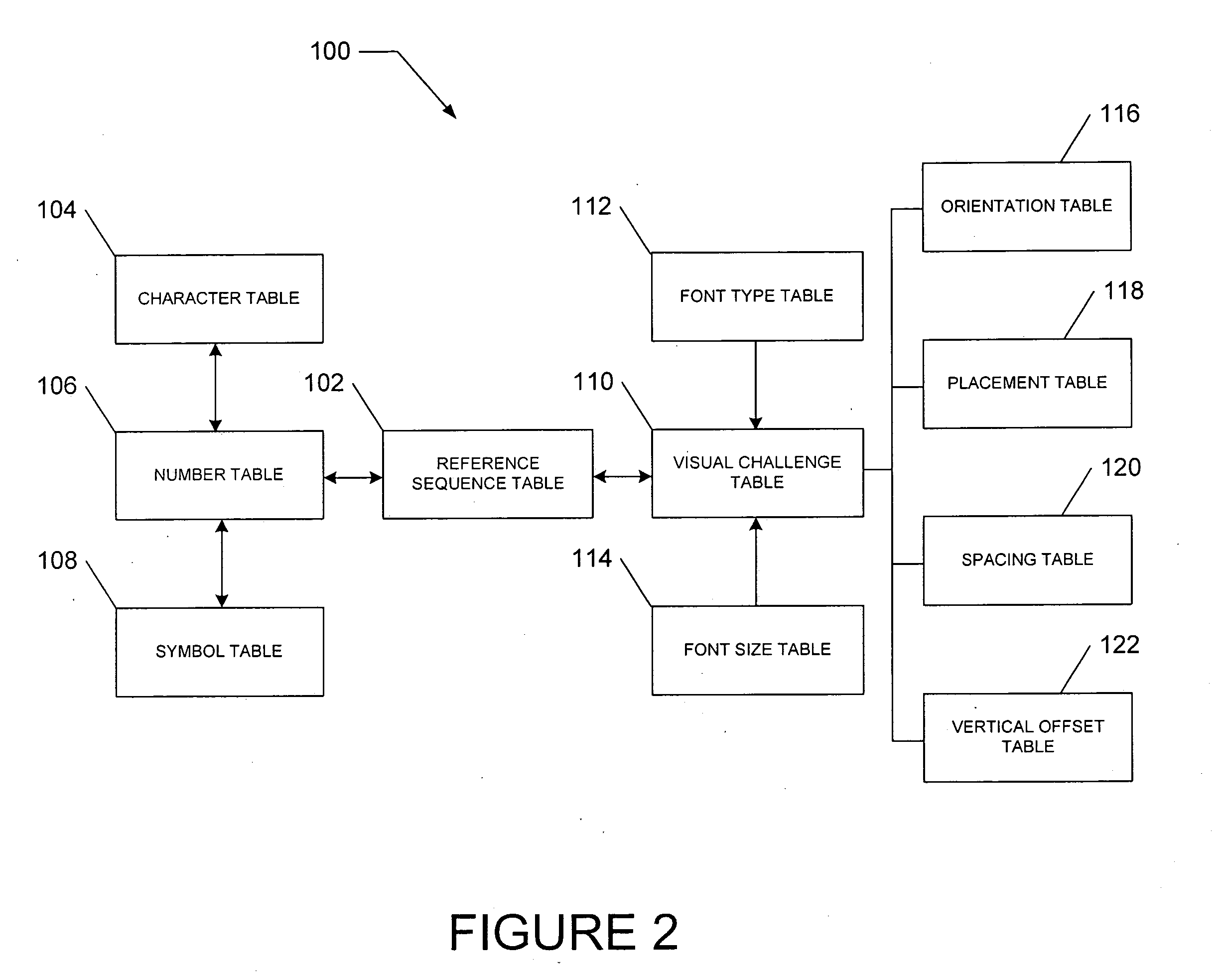
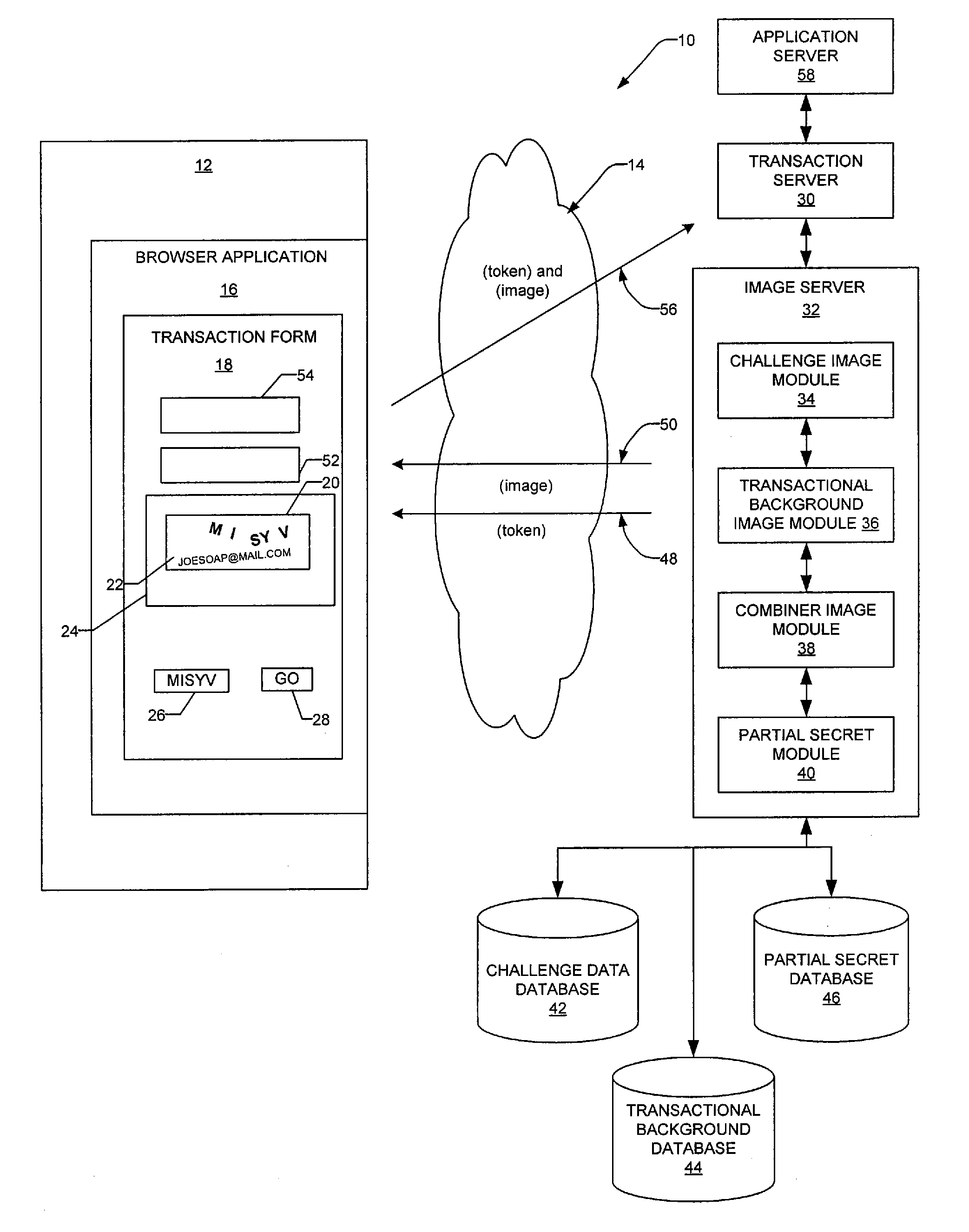
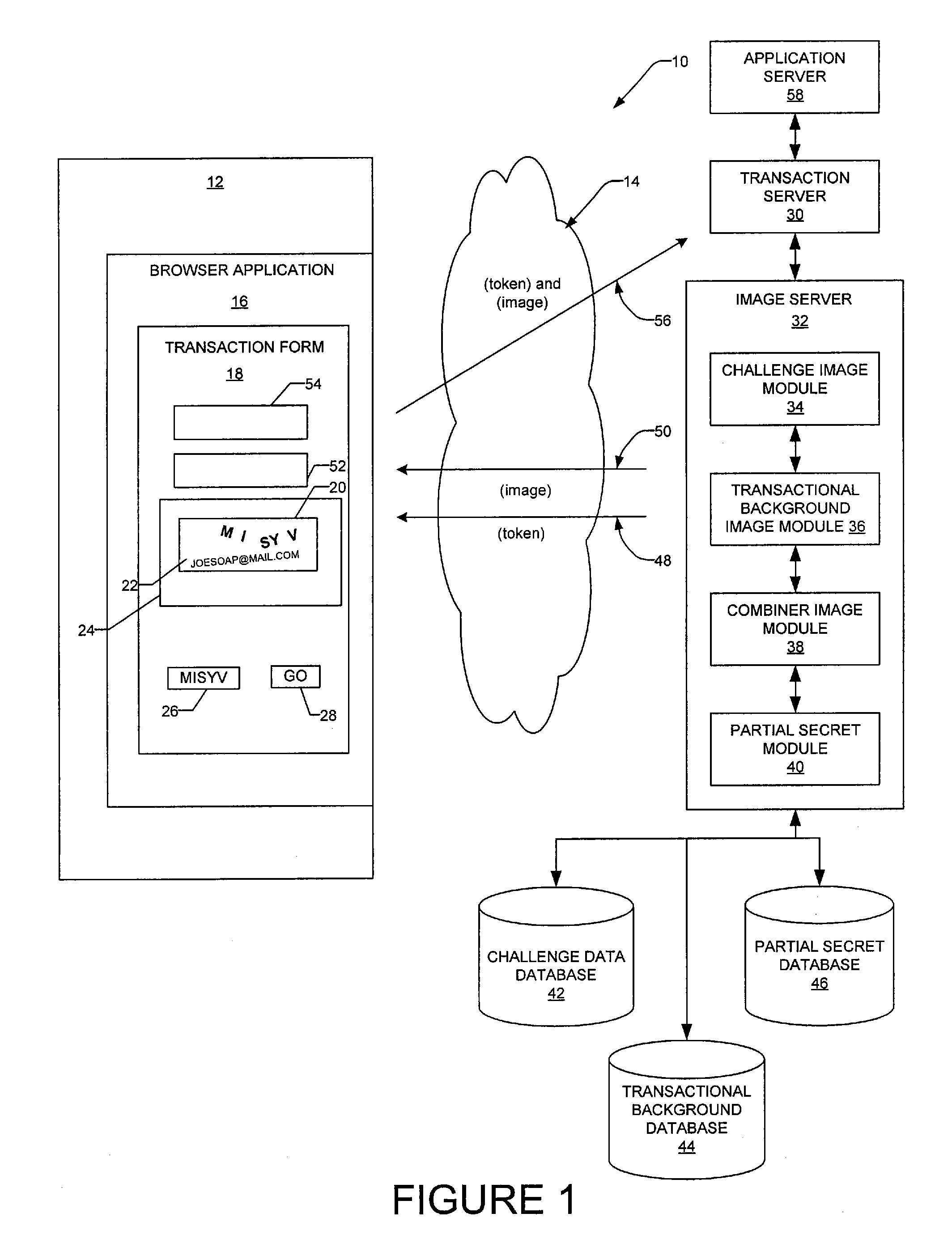
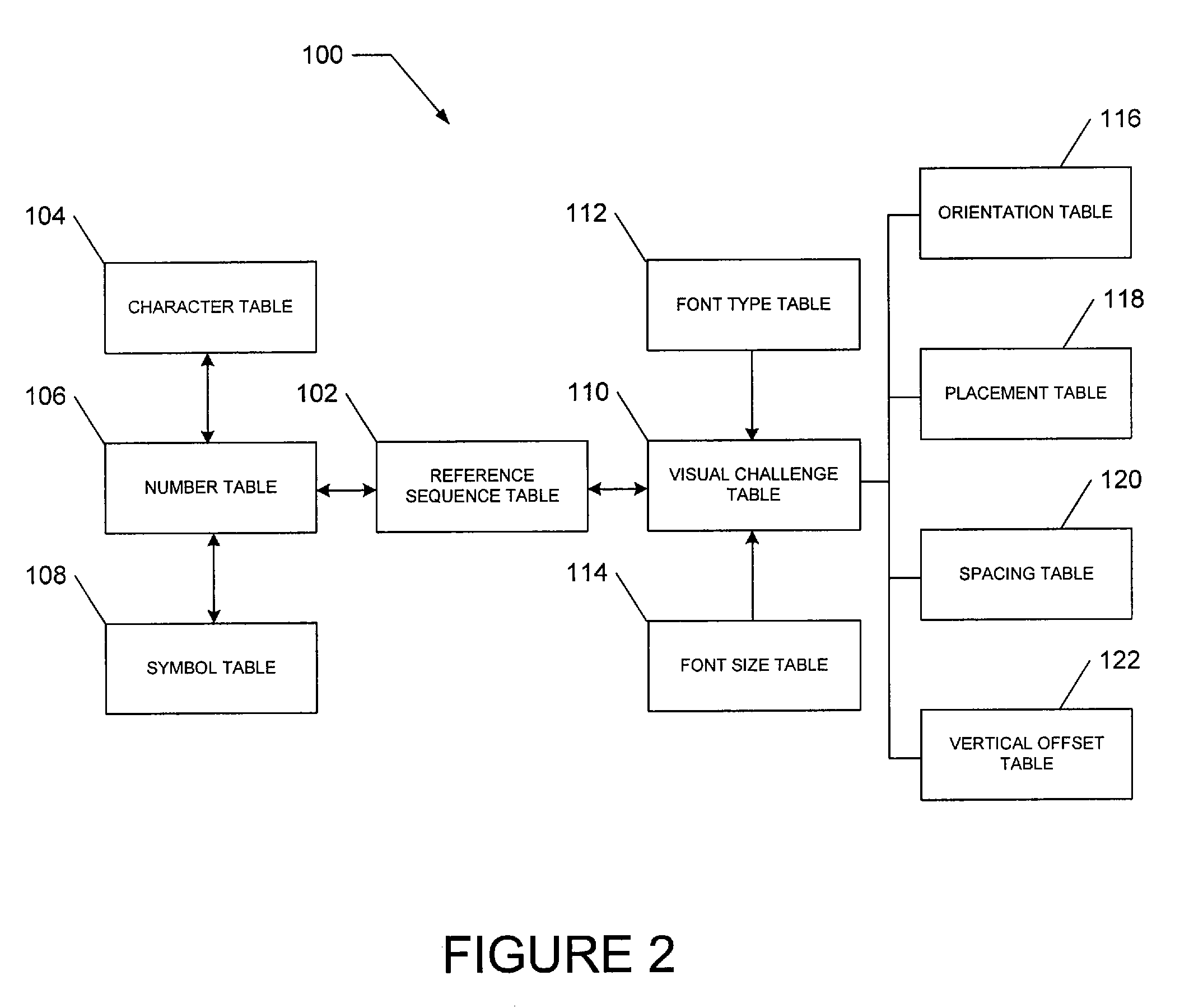
Contextual visual challenge image for user verification
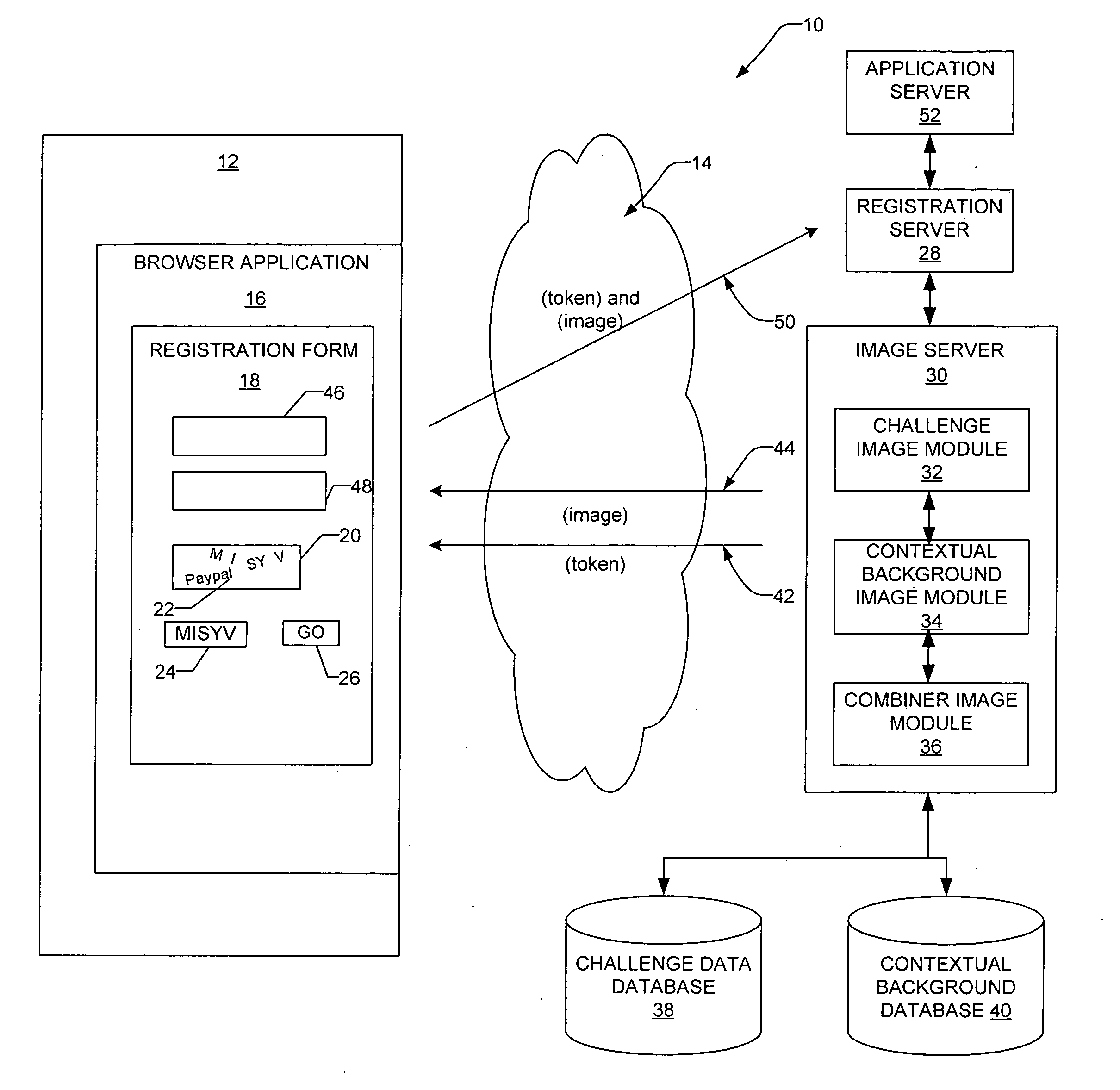
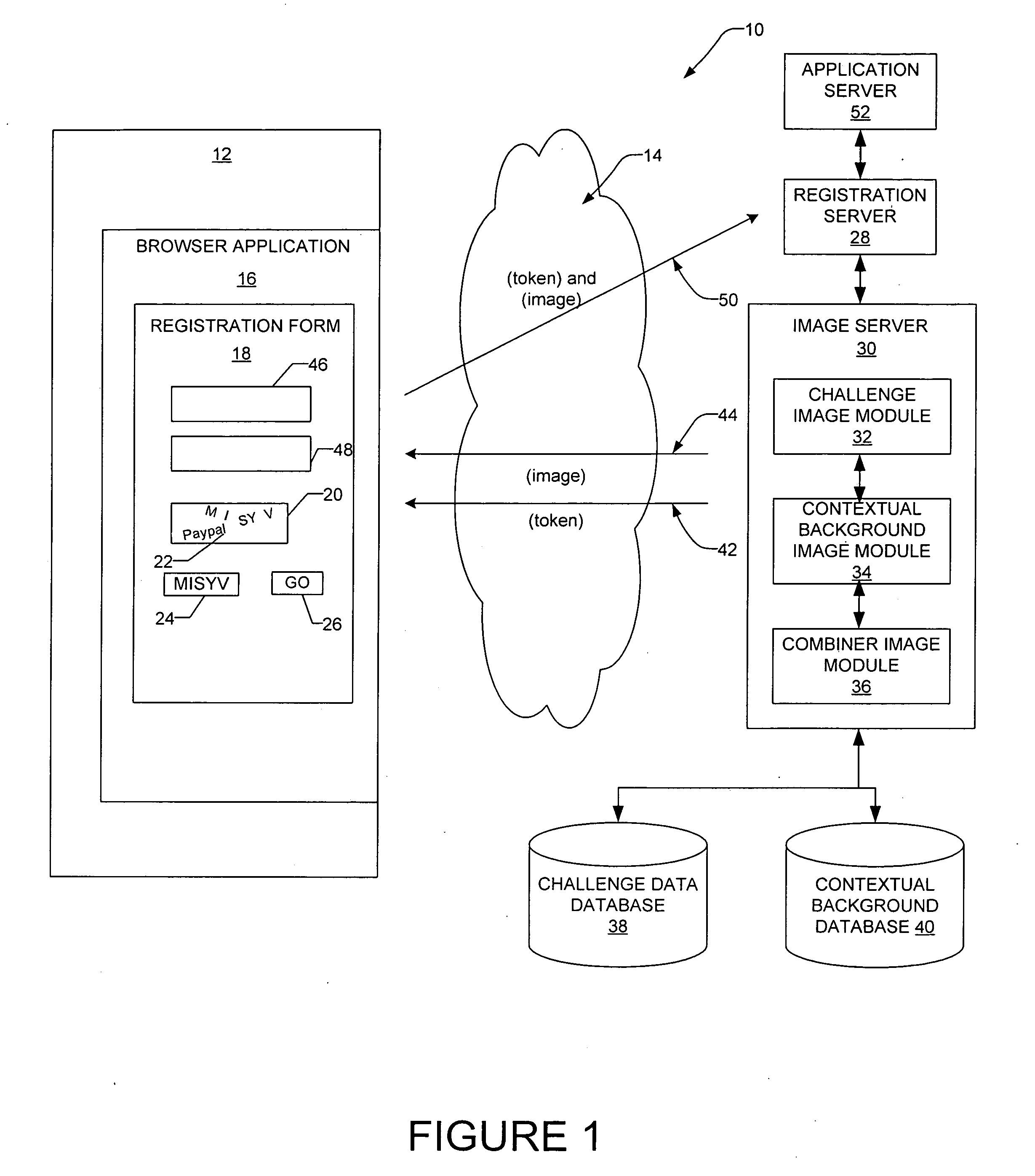
InactiveUS20080072293A1Digital data processing detailsUser identity/authority verificationUser verificationHuman–computer interaction
A method and a system generate a contextual visual challenge image to be presented to a user thereby to verify that the user is human. For example, an image module generates a visual challenge to be presented to a user as part of a challenge-response to verify that the user is human. A contextual background module identifies a contextual background that is contextual to a specific environment and a combiner image module combines the visual challenge and the contextual background into an image which is to be presented to the user in the specific environment, the contextual background associating the visual challenge with the specific environment.
Owner:EBAY INC
Method and system to prevent fraudulent payment in credit/debit card transactions, and terminals therefor
InactiveUS20050242173A1Transaction can be blockedEliminate dangerBuying/selling/leasing transactionsVerifying markings correctnessUser verificationComputer terminal
The present invention enables secure, valid card payments in credit transactions to be performed, preventing fraudulent card use even in cases of loss or theft of a card or of information theft. During a transaction authorization process using a transaction terminal disposed in a credit transaction member store and connected with a host computer, user validation or credit administration is carried out by using a portable communication terminal to input to the host computer identity information which has been previously registered in the portable communication terminal and / or location information for the portable communication terminal.
Owner:MAXELL HLDG LTD
Transactional visual challenge image for user verification
InactiveUS20080209223A1User identity/authority verificationDigital data authenticationUser verificationInternet privacy
A method and a system generate a transactional visual challenge image to be presented to a user thereby to verify that the user is human. For example, an image module generates a visual challenge to be presented to a user as part of a challenge-response to verify that the user is human. A transactional background image module identifies a transactional background that is associated with a specific transaction and a combiner image module combines the visual challenge and the transactional background into an image which is to be presented to the user during transaction authorization, the transactional background associating the visual challenge with the particular transaction.
Owner:EBAY INC
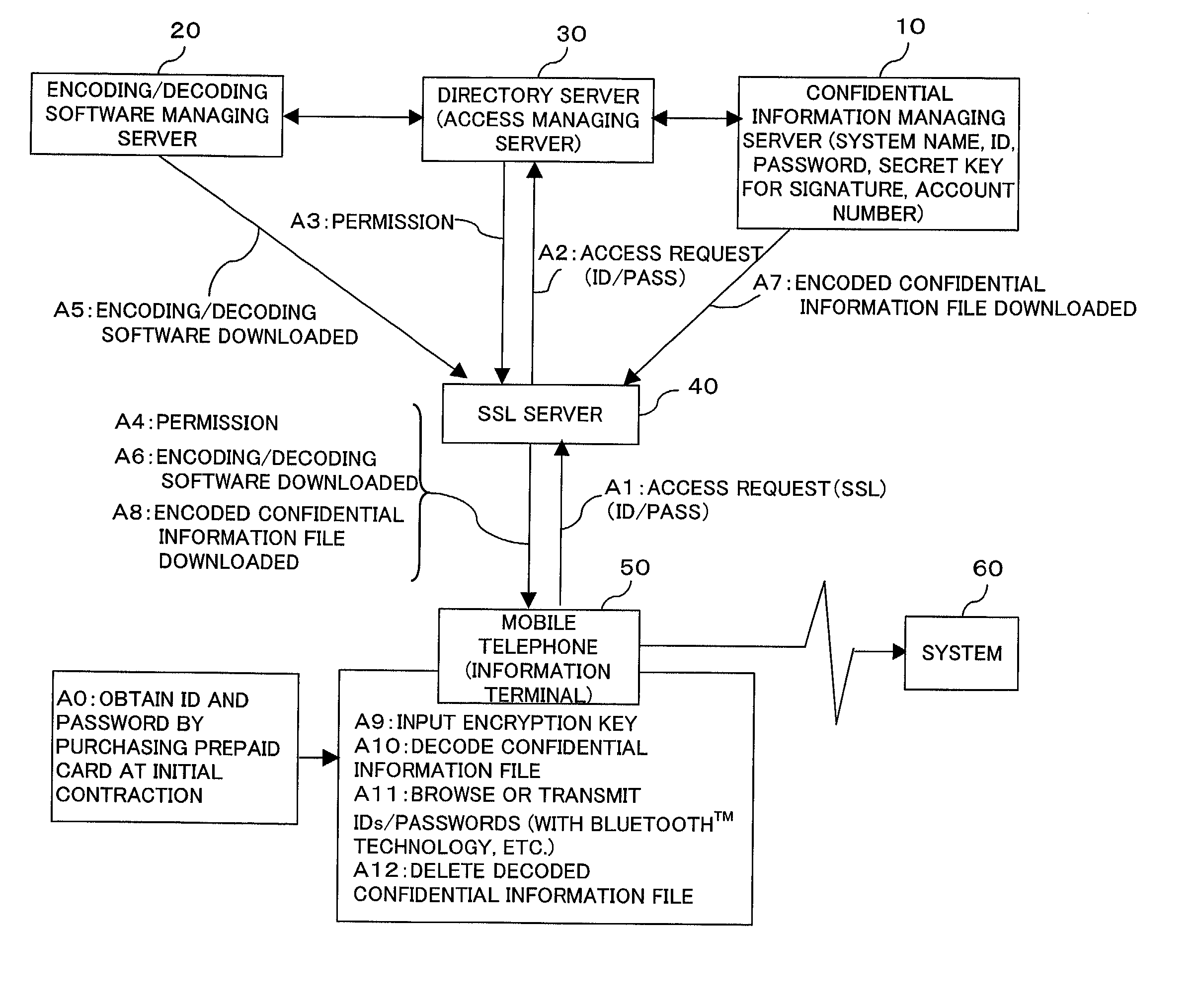
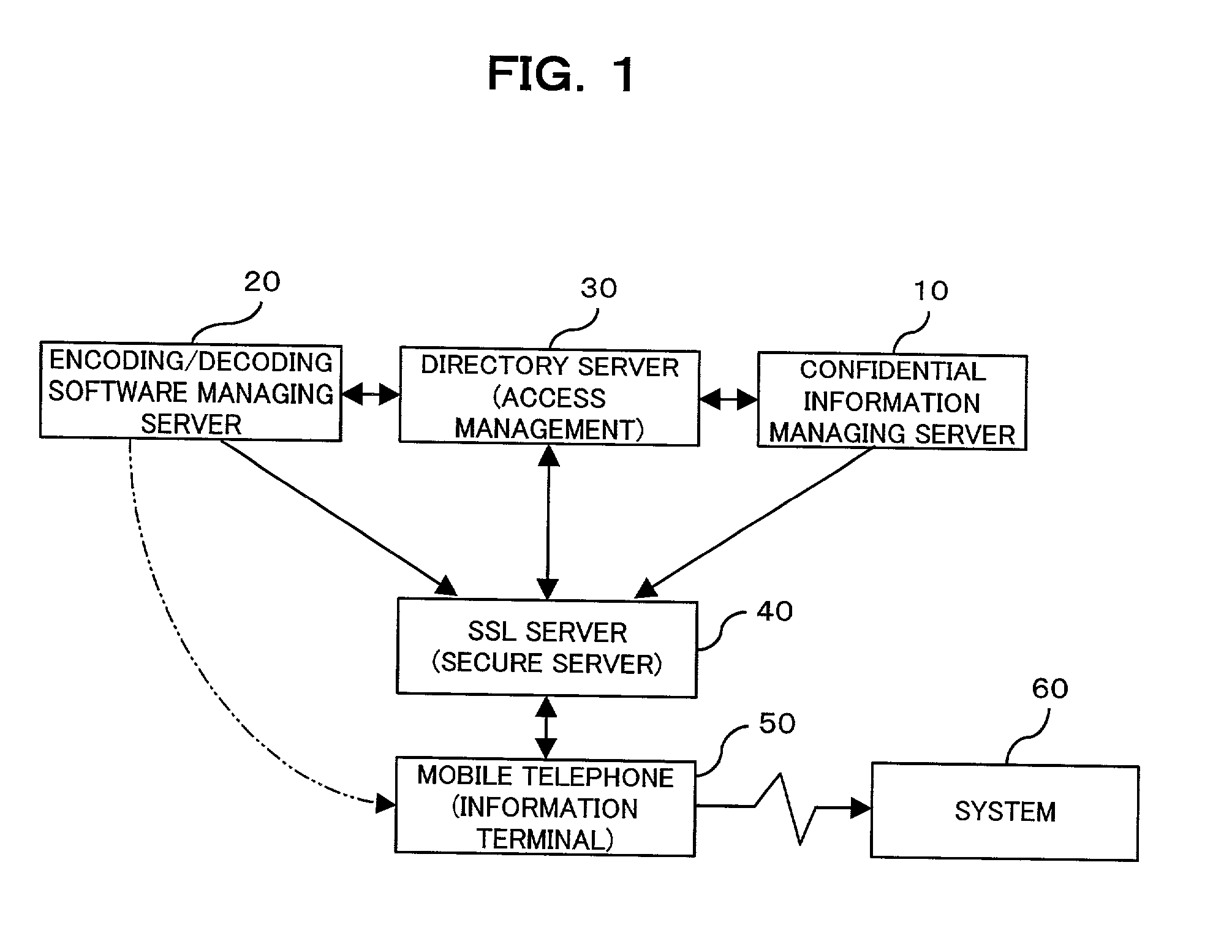
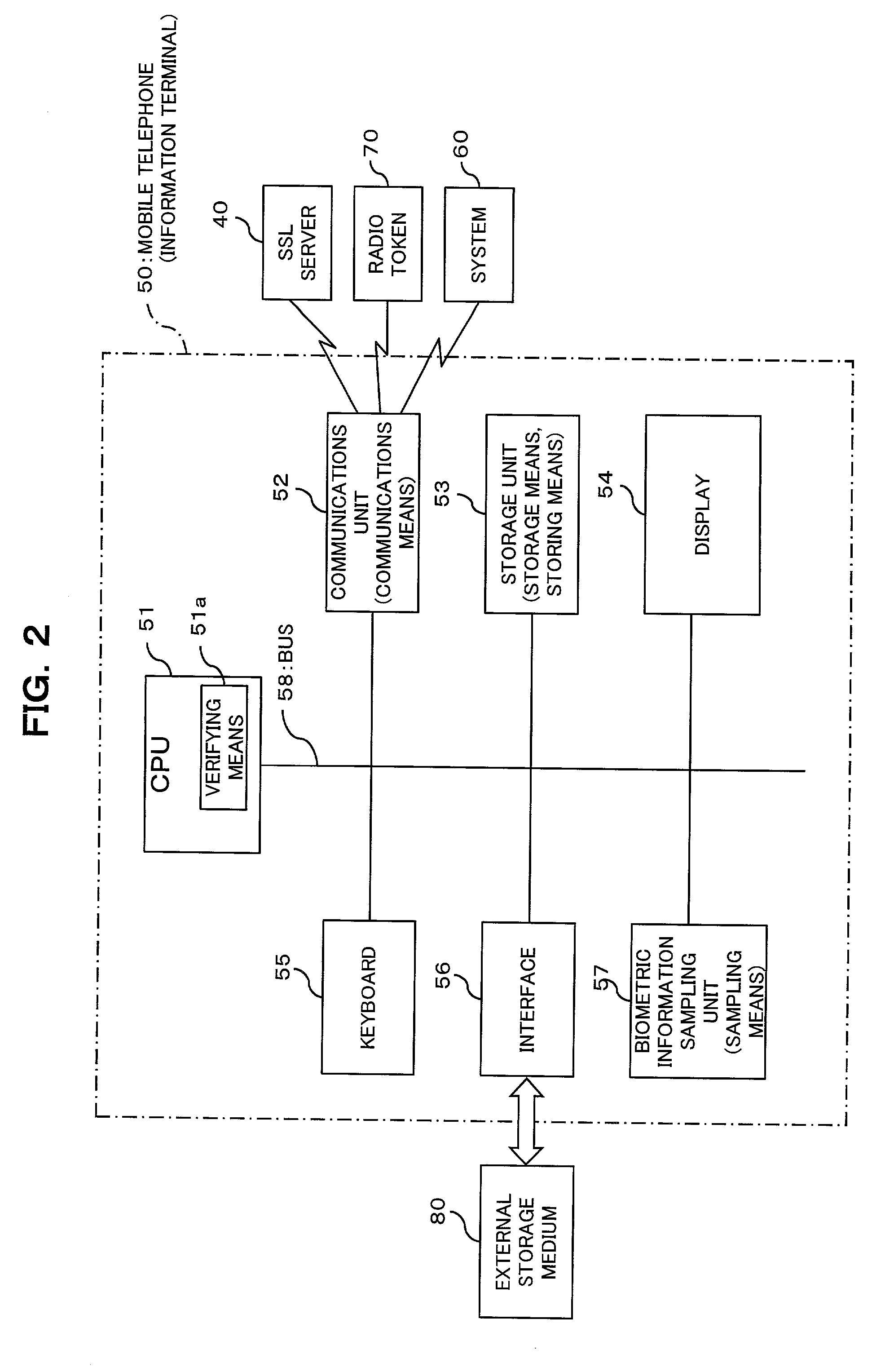
Confidential information management system and information terminal for use in the system
InactiveUS20030004881A1Simplify user operationsAvoid problemsUser identity/authority verificationUnauthorized memory use protectionUser verificationInternet privacy
The present invention provides a confidential information management system which allows users to securely obtain confidential information files containing various confidential information, which files are securely stored in the present system, anywhere and anytime, using a minimum of confidential information. A confidential information file and encoding / decoding software are downloaded to an information terminal from a confidential information managing server and an encoding / decoding software managing server, respectively, so that the confidential information file is decoded on the information terminal by using the encoding / decoding software. The present system is applicable to various (computer) systems which store and manage confidential information (ID numbers, passwords, encryption keys, digital certificates, etc.) for use in user verification.
Owner:FUJITSU LTD
Managing transaction accounts
Owner:AMAZON TECH INC
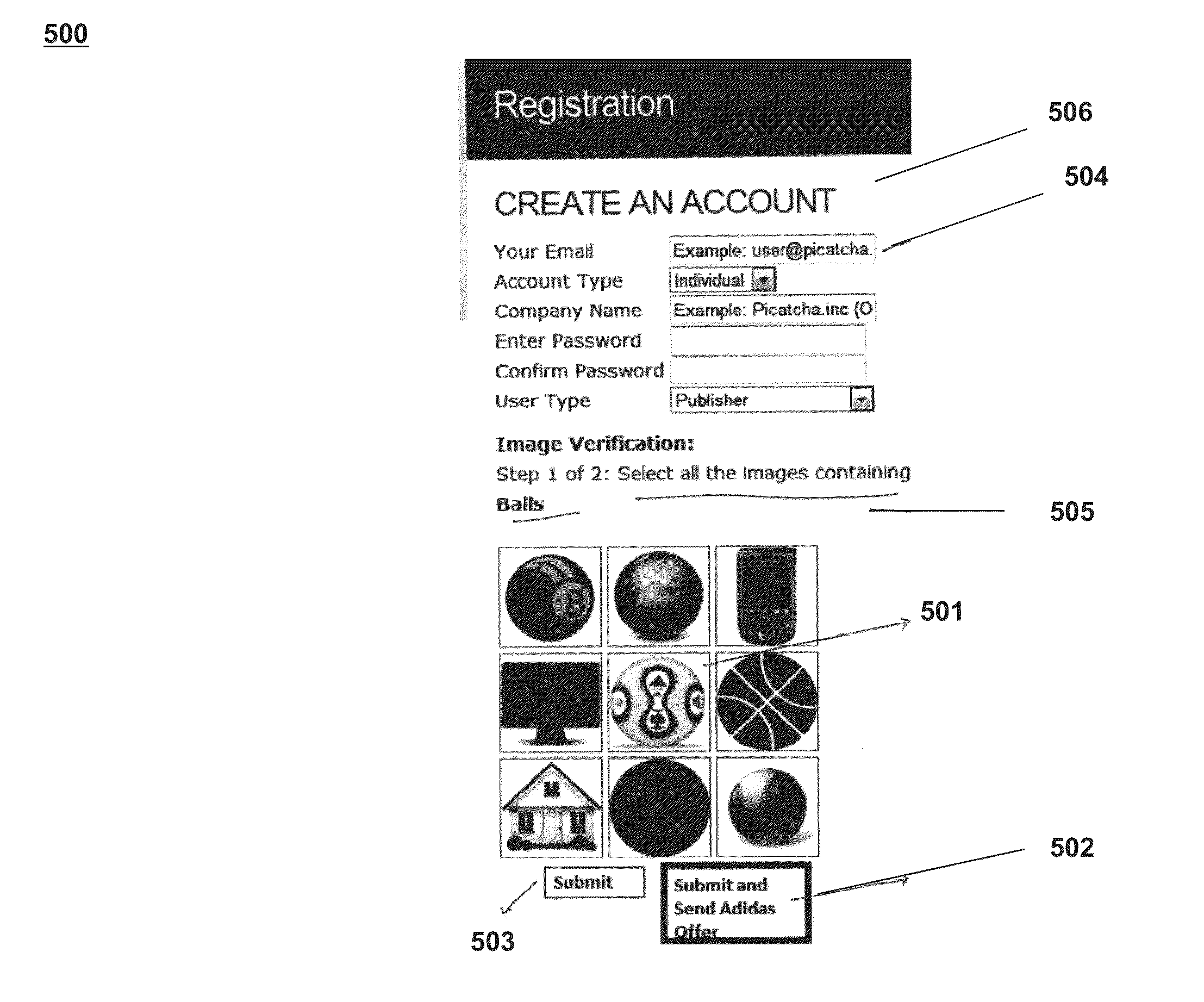
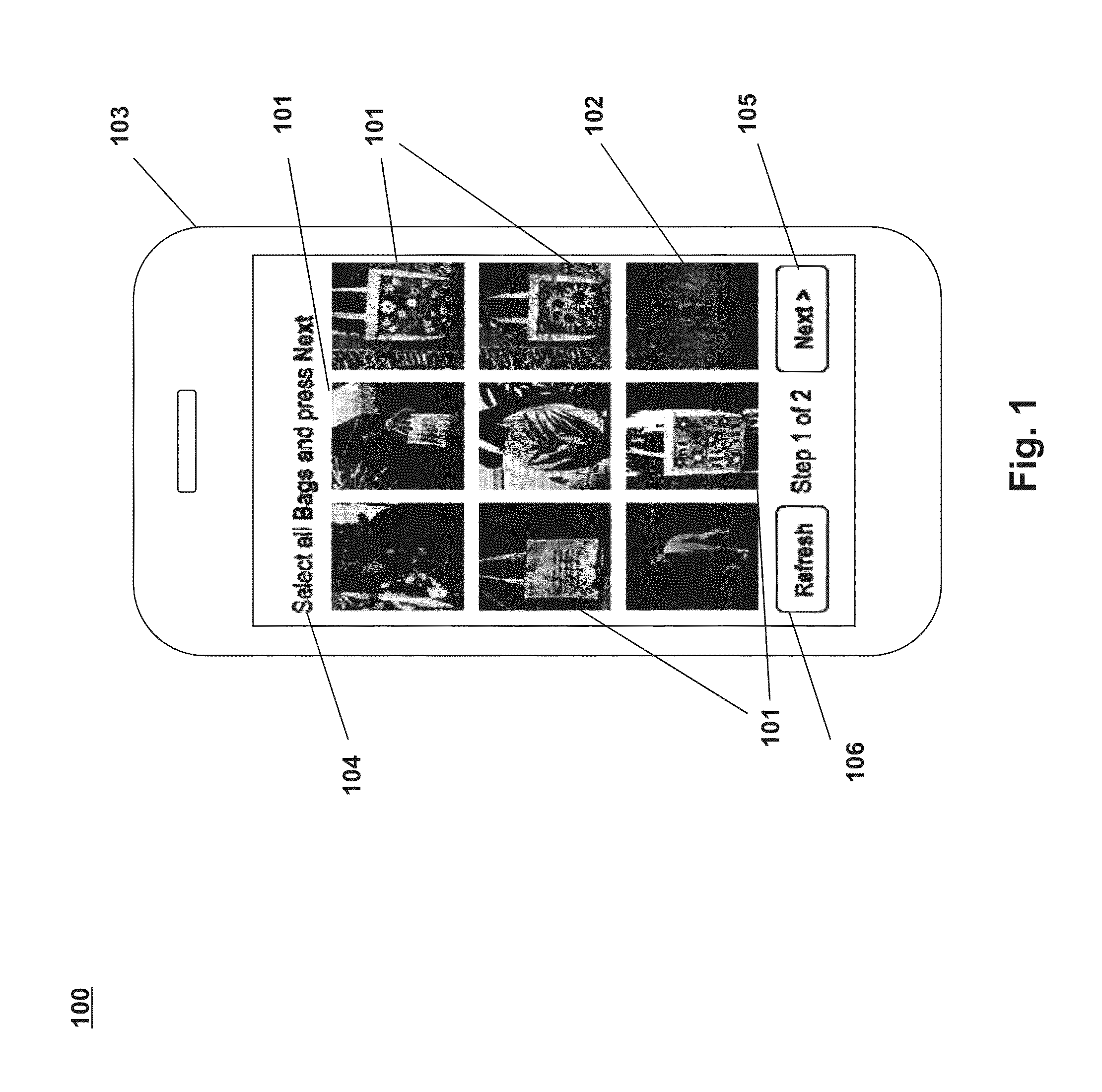
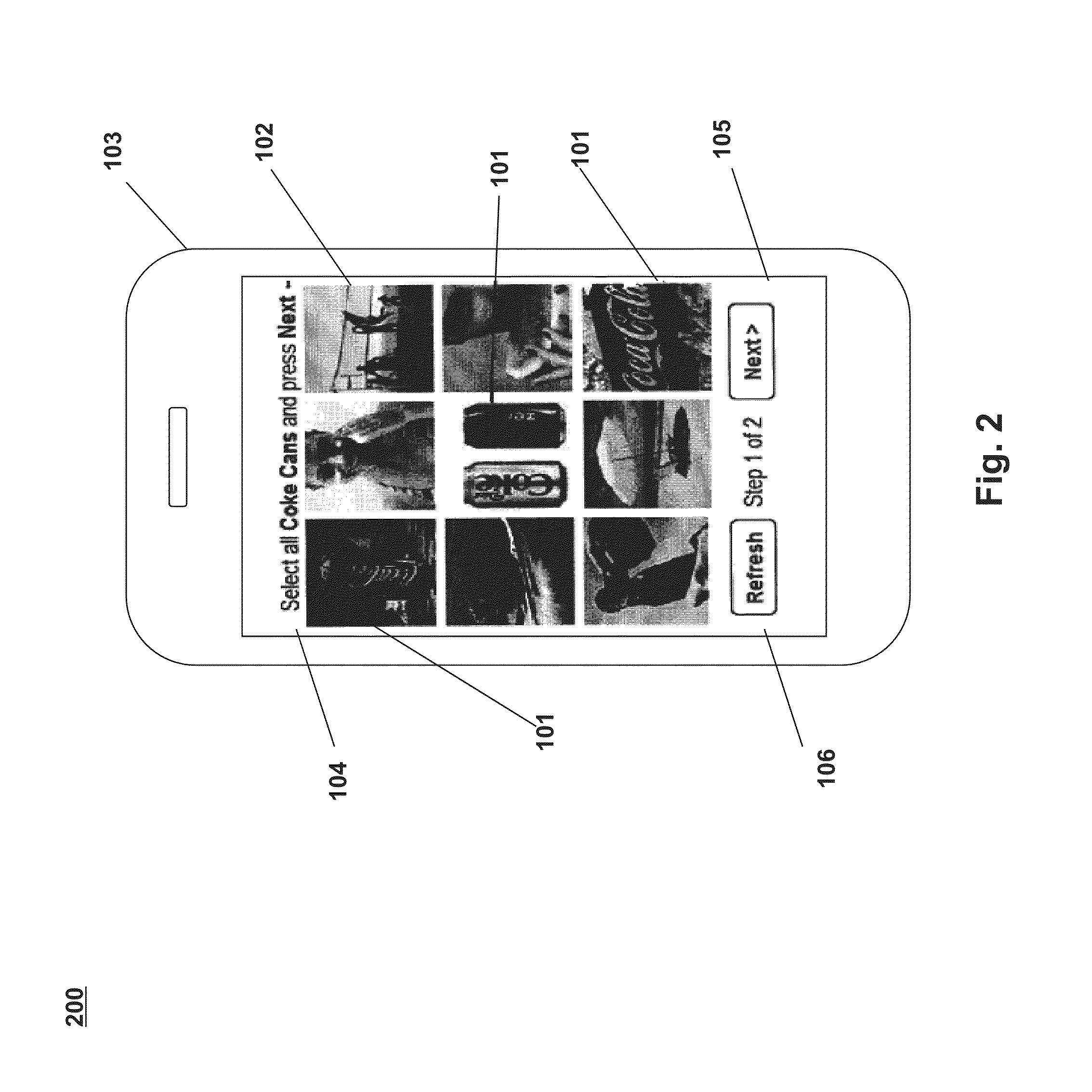
Captcha authentication processes and systems using visual object identification
InactiveUS20130145441A1Accurate identificationDigital data processing detailsMultiple digital computer combinationsUser verificationEngineering
Systems and processes for performing user verification using an imaged-based CAPTCHA are disclosed. The verification process can include receiving a request from a user to access restricted content. In response to the request, a plurality of images may be presented to the user. A challenge question or command that identifies one or more of the displayed plurality of images may also be presented to a user. A selection of one or more of the plurality images may then be received from the user. The user's selection may be reviewed to determine the accuracy of the selection with respect to the challenge question or command. If the user correctly identifies a threshold number of images, then the user may be authenticated and allowed to access the restricted content. However, if the user does not correctly identify the threshold number of images, then the user may be denied access the restricted content.
Owner:PICATCHA
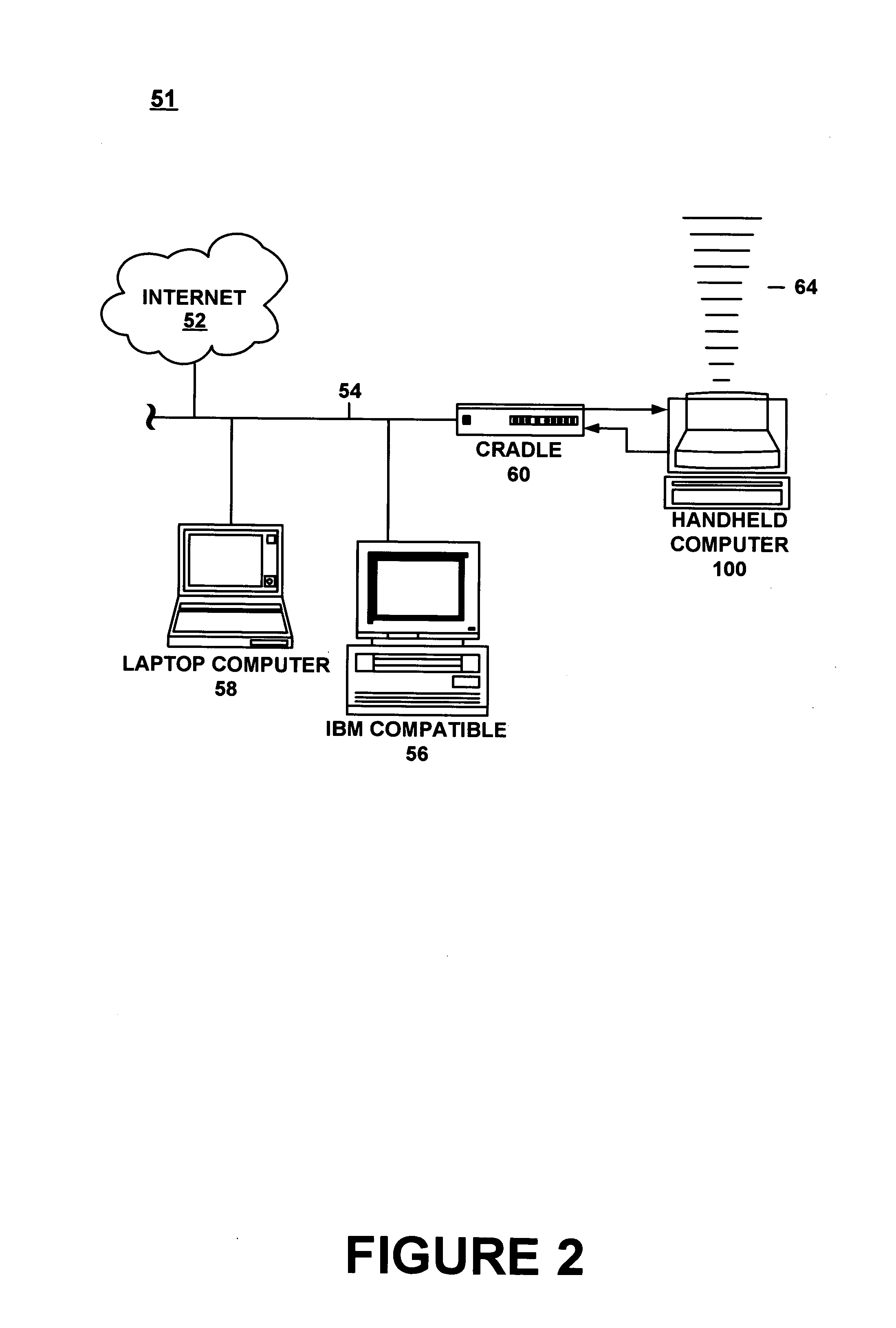
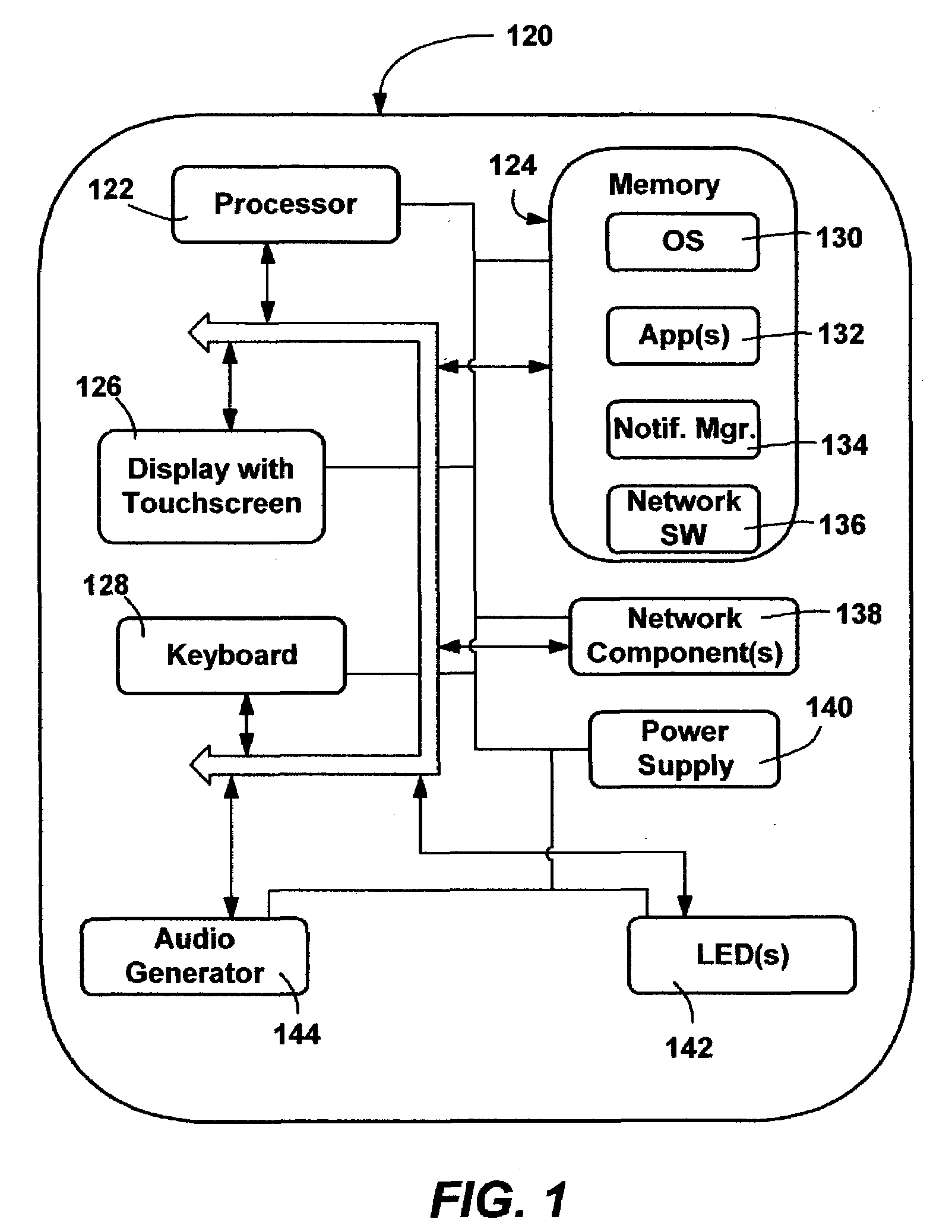
Handheld computer system configured to authenticate a user and power-up in response to a single action by the user
InactiveUS7124300B1Easy accessImprove user experienceElectric signal transmission systemsImage analysisUser verificationElectricity
A computer system configured to authenticate a user and to power-up in response to a single action by the user is described. In particular, the computer system includes a user verification device which interacts with the user. In an embodiment, the user verification device includes a biometric sensor which captures biometric data from the user. The biometric data can be of any type. The user verification device is configured to capture biometric data in response to an action by the user desiring access to the computer system. The user verification device can have a button-shape for receiving the finger, thumb, or any other part of the user.
Owner:QUALCOMM INC
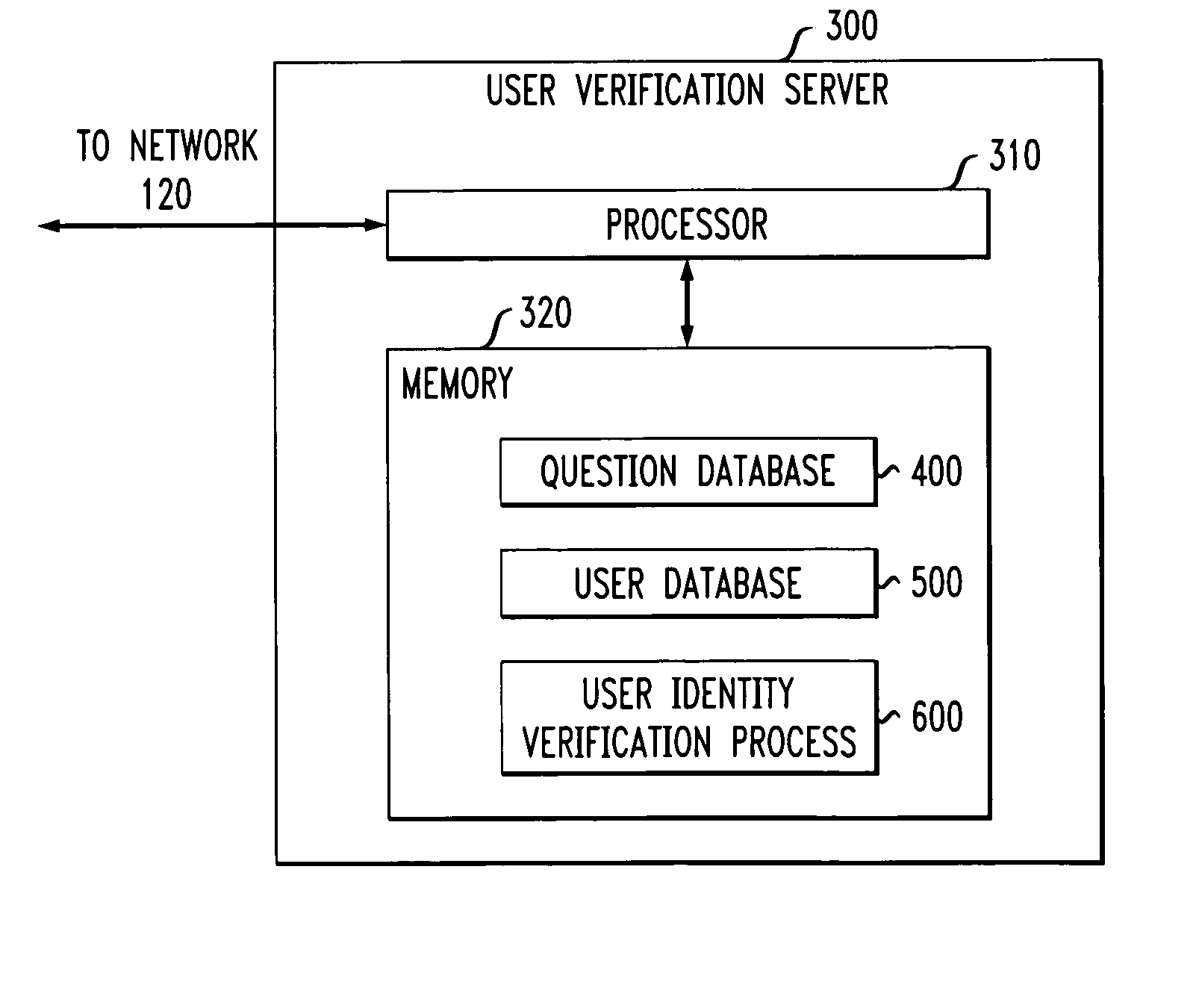
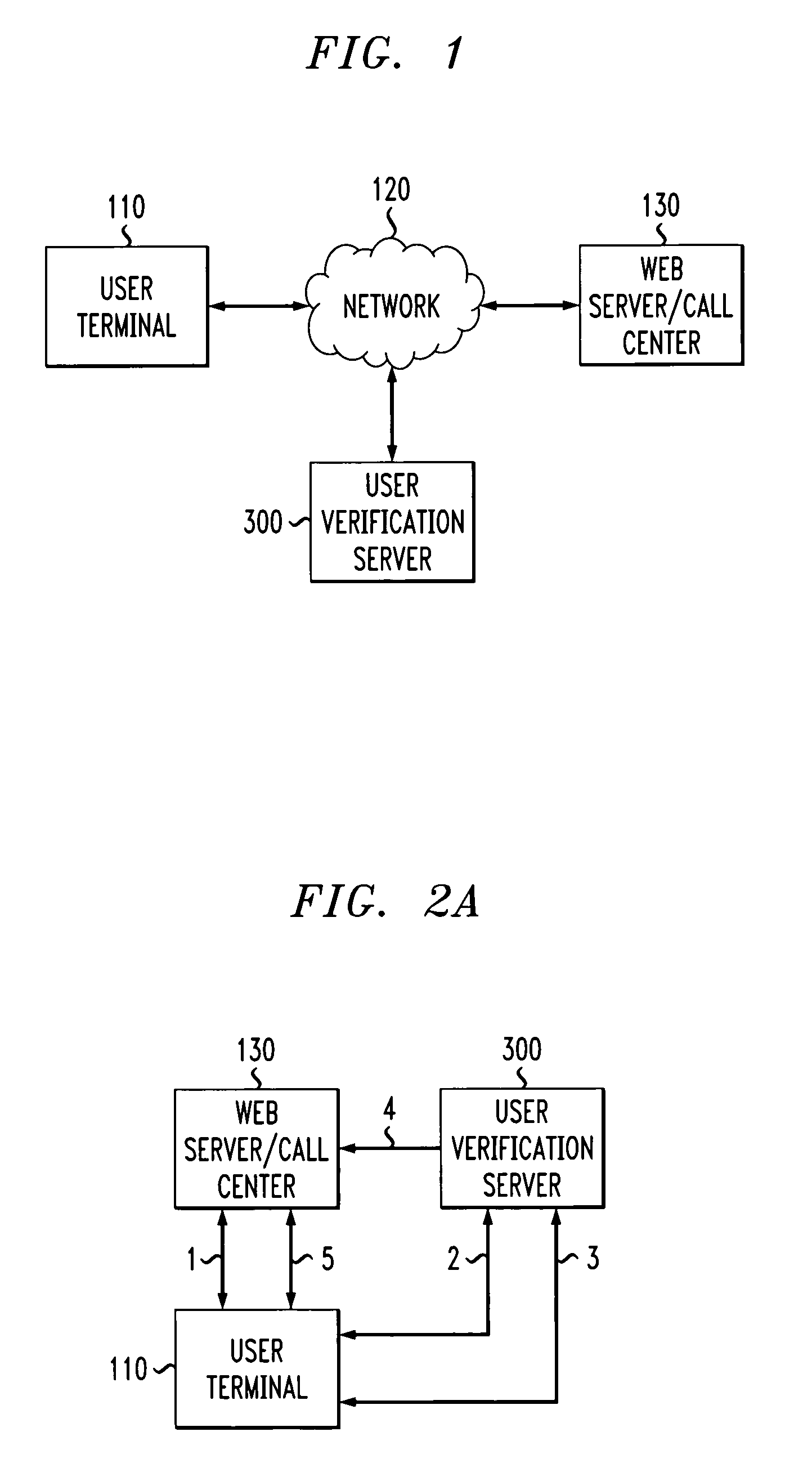
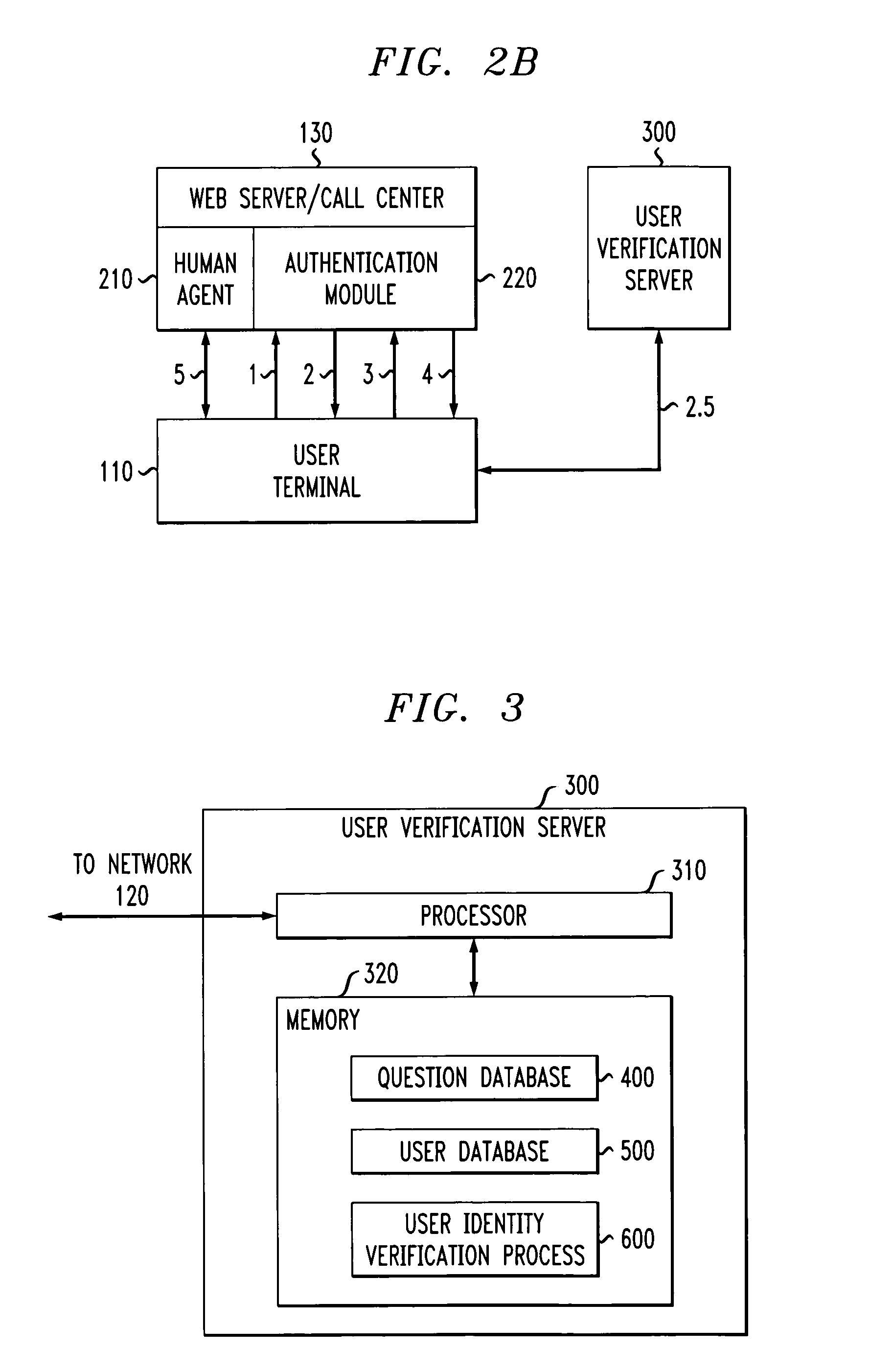
Method and apparatus for authenticating a user using three party question protocol
InactiveUS20050039056A1Digital data processing detailsSpecial service for subscribersUser verificationHuman agent
A three party authenticating protocol is disclosed. During an enrollment phase, a user contacts a call center and is directed to a user verification server. The user verification server instructs the user to select and answer a number of questions that will be used for verification. The selected questions along with identifying indices for each question are stored at the user's location and at the user verification server. The user verification server sends the question indices to the call center, which in turn sends these indices to the user to obtain answer indices for each question. During a verification phase, the user contacts the call center and an authentication module asks the user to provide an asserted identity. The authentication module provides a random selection of question indices from those selected by the user. The user provides answer indices for each question to the authentication module. If the number of correctly matching answers exceeds a threshold, then the user is verified. Otherwise, the user fails verification. After verification, the user is transferred from the authentication module of the call center to a human agent for further processing.
Owner:AVAYA INC
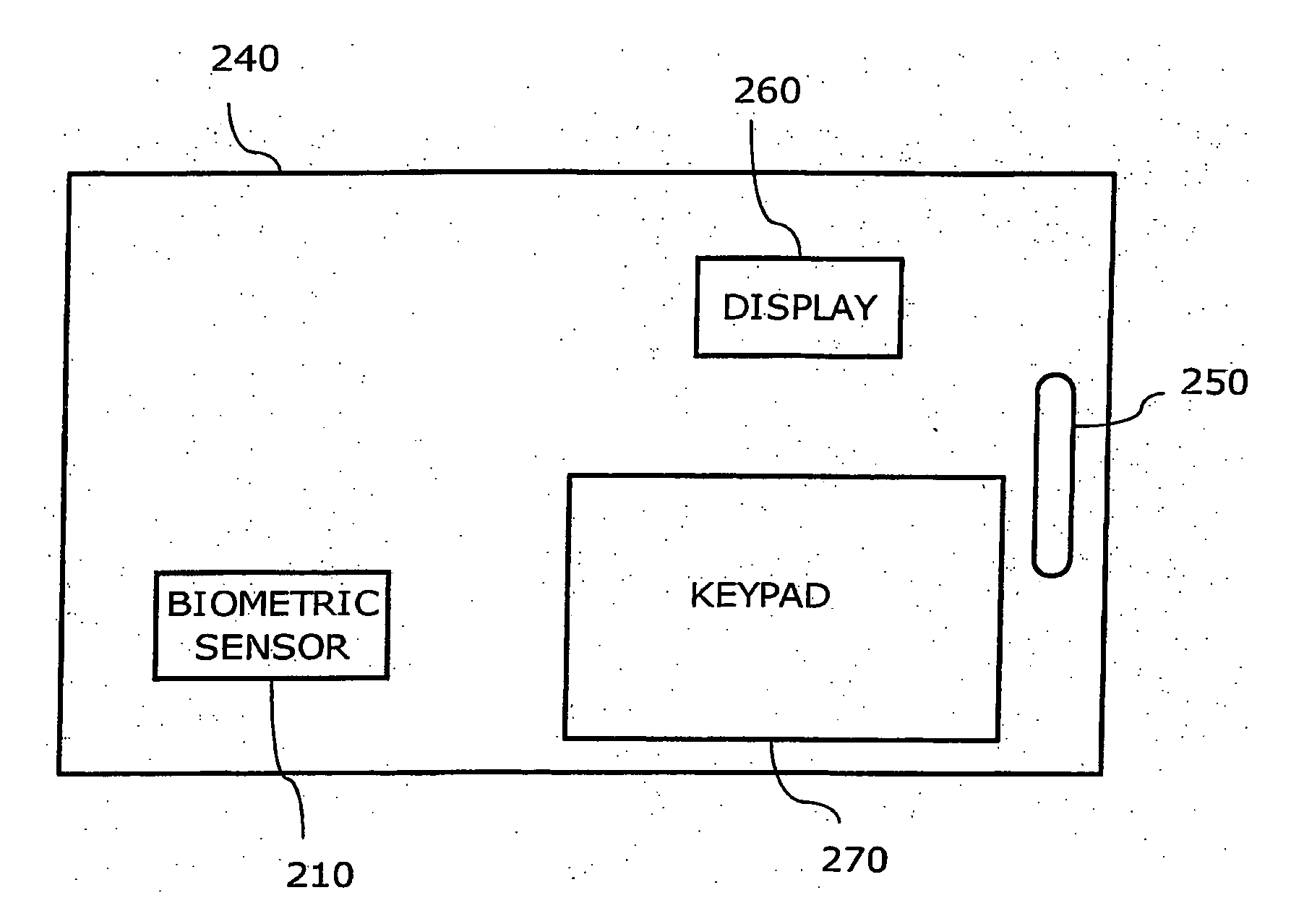
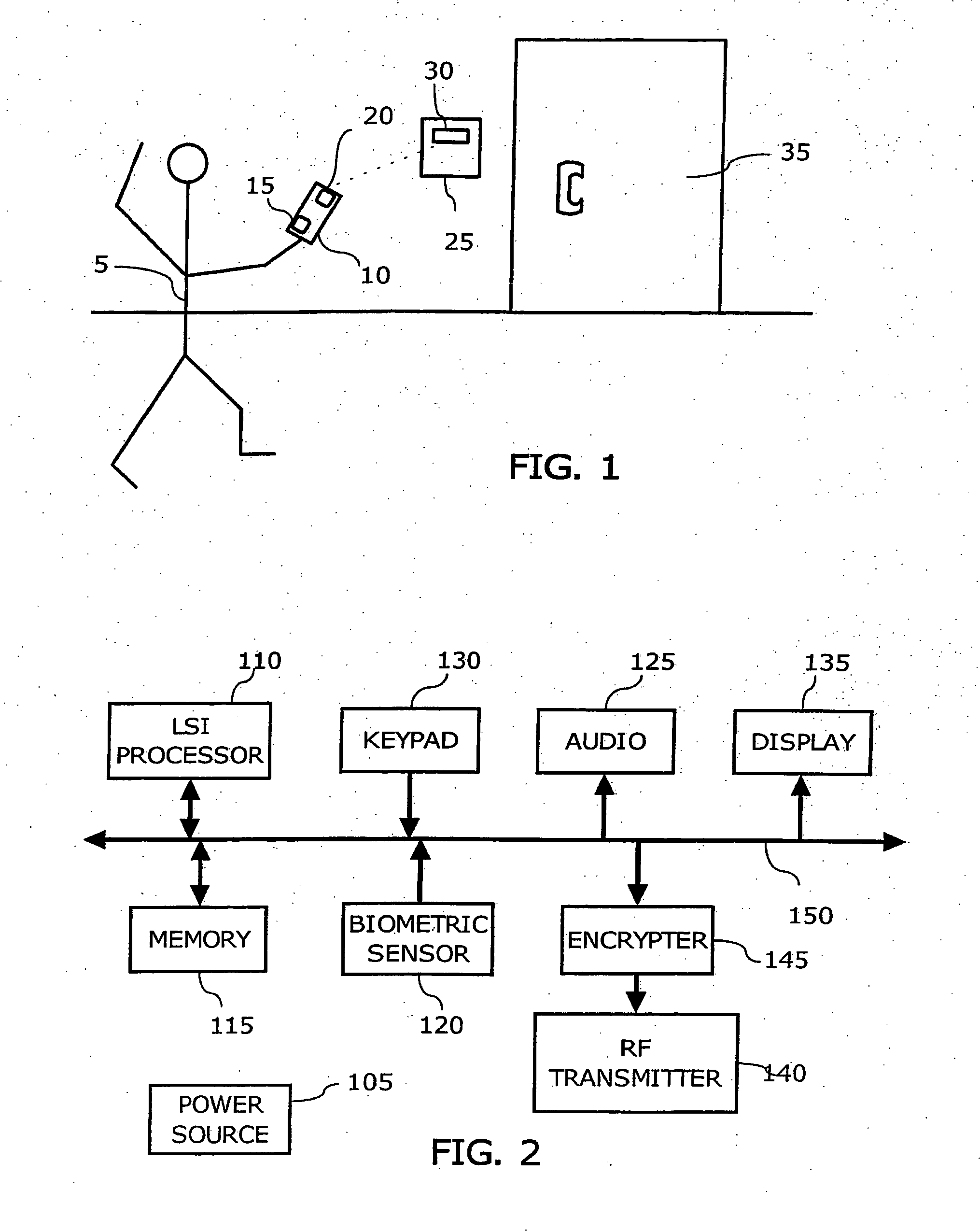
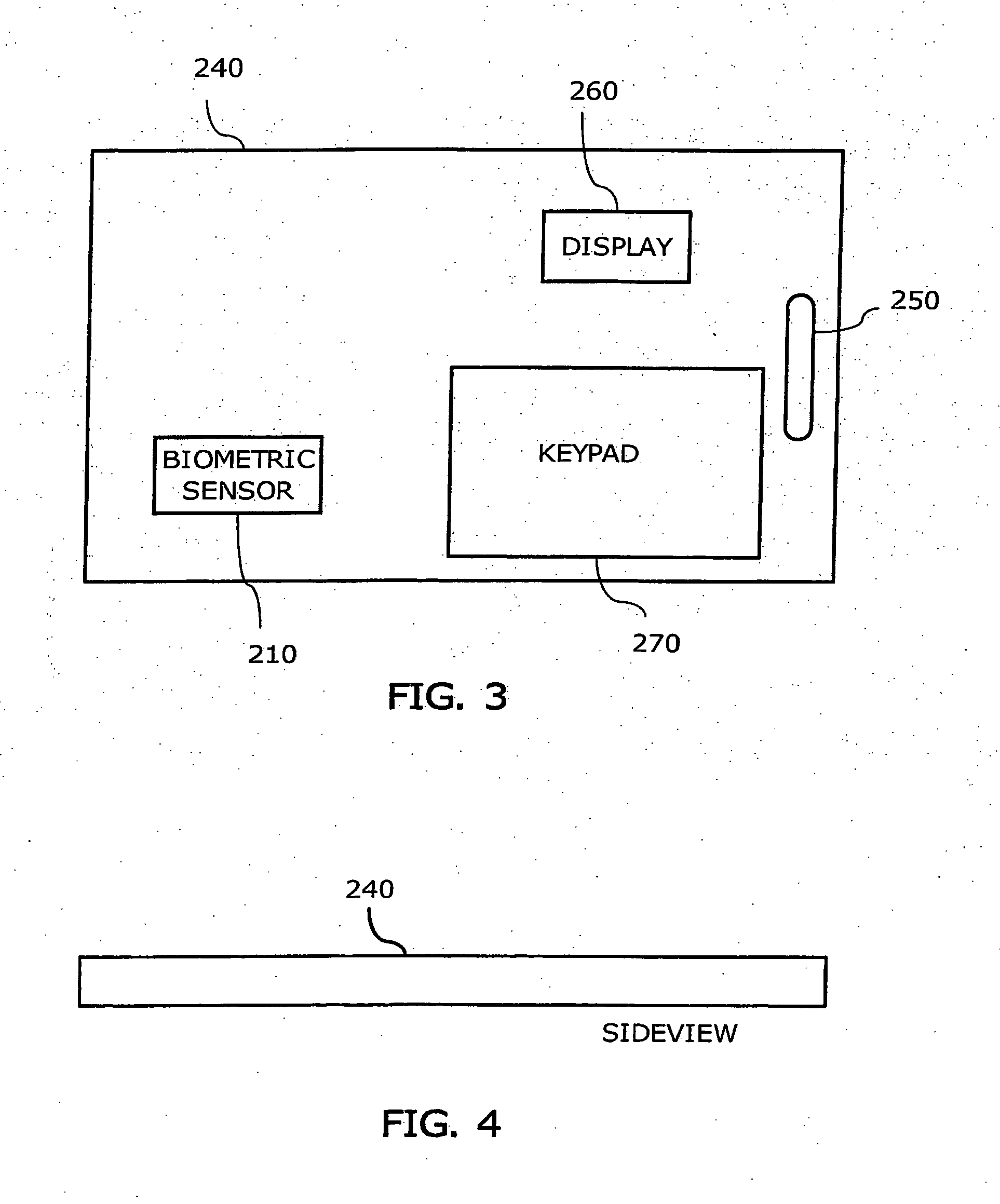
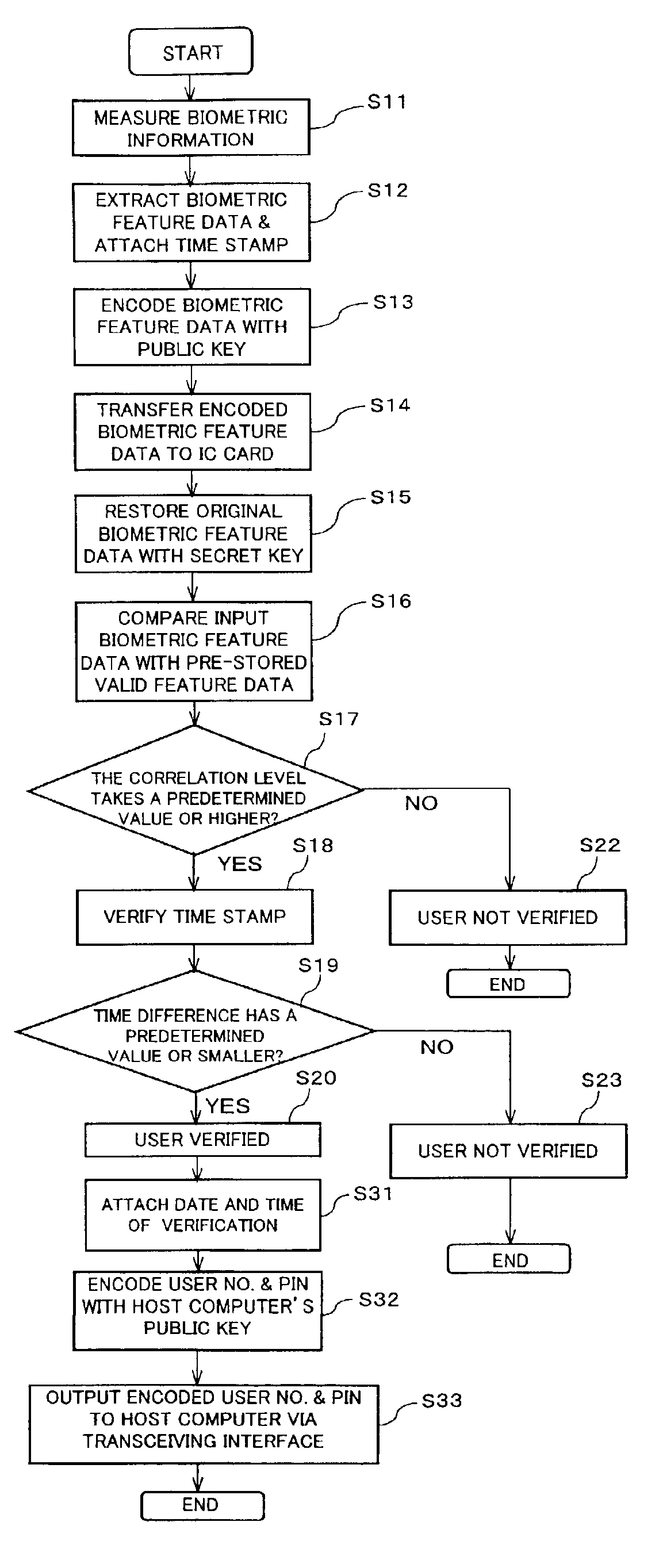
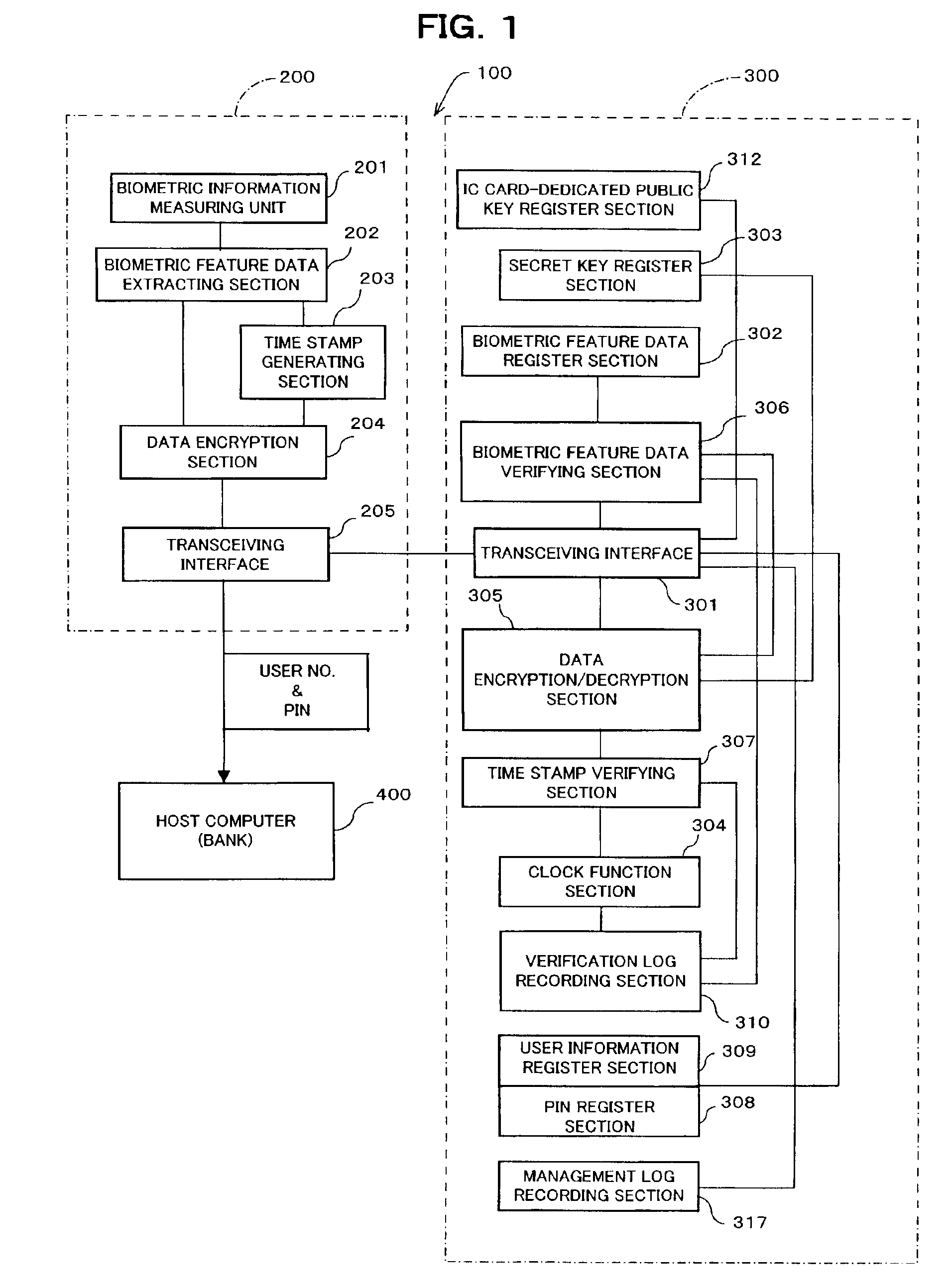
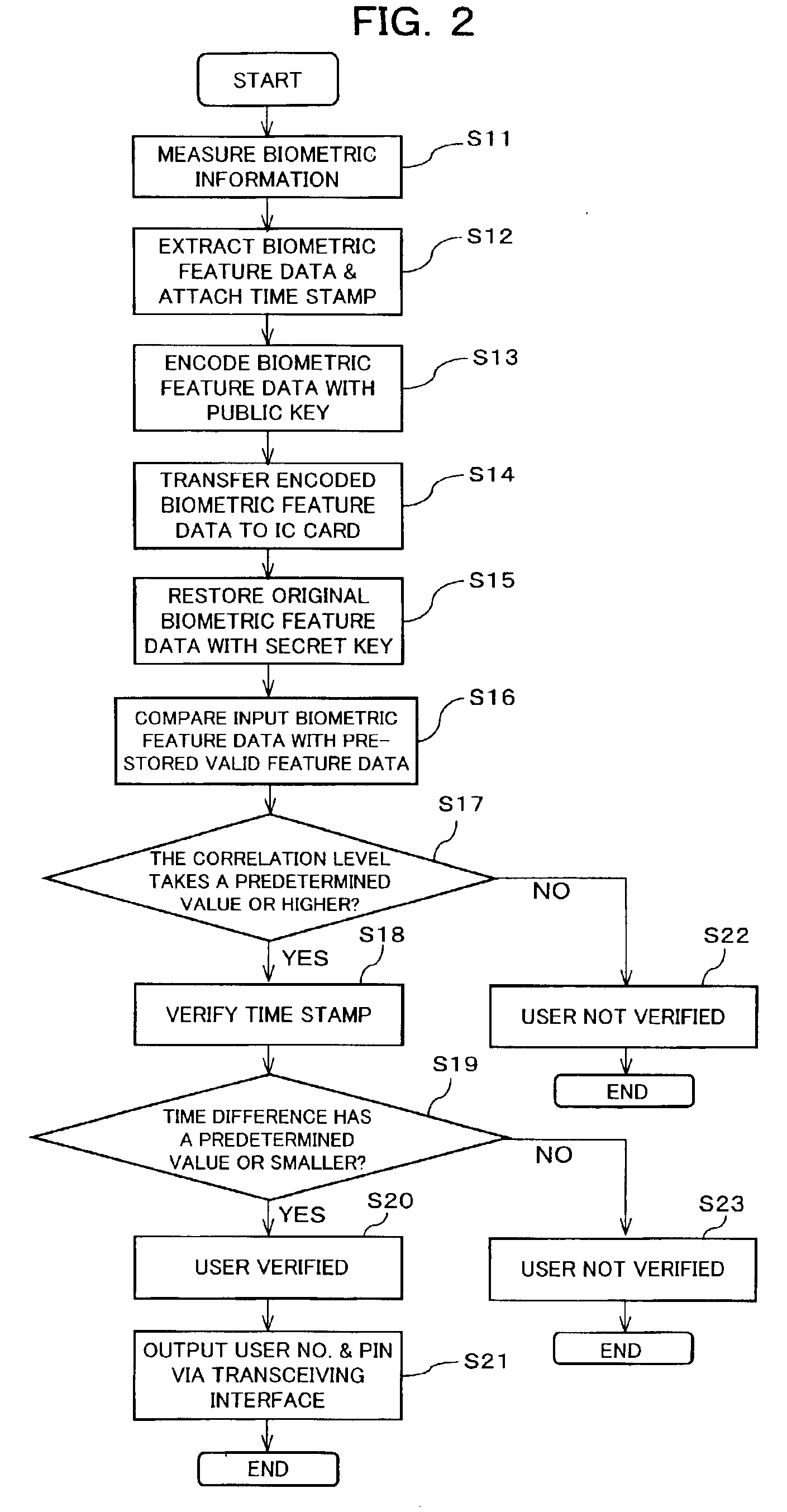
User verification system, and portable electronic device with user verification function utilizing biometric information
InactiveUS6957339B2Risk minimizationPrevent leakageDigital data processing detailsUser identity/authority verificationUser verificationComputer hardware
In a system (e.g., debit card) where a PIN is entered as verification, the PIN and biometric information, which is free of being stolen or faked, are combined to realize secure user verification. The leakage and the theft of a PIN is reliably prevented, thereby realizing a high security ability. To-be-verified biometric feature data is transmitted from first transceiving interface (205) of data processing device (200) to portable electronic device (300). Biometric feature data verifying section (306) of portable electronic device (300) compares the to-be-verified biometric feature data, which has been received by second transceiving interface (301), with valid biometric feature data. If a predetermined matching condition between the to-be-verified biometric feature data and the valid biometric feature data is satisfied, a PIN stored in portable electronic device (300) is transmitted from second transceiving interface (301) to management device (400) via first transceiving interface (205) of data processing device (200).
Owner:FUJITSU LTD
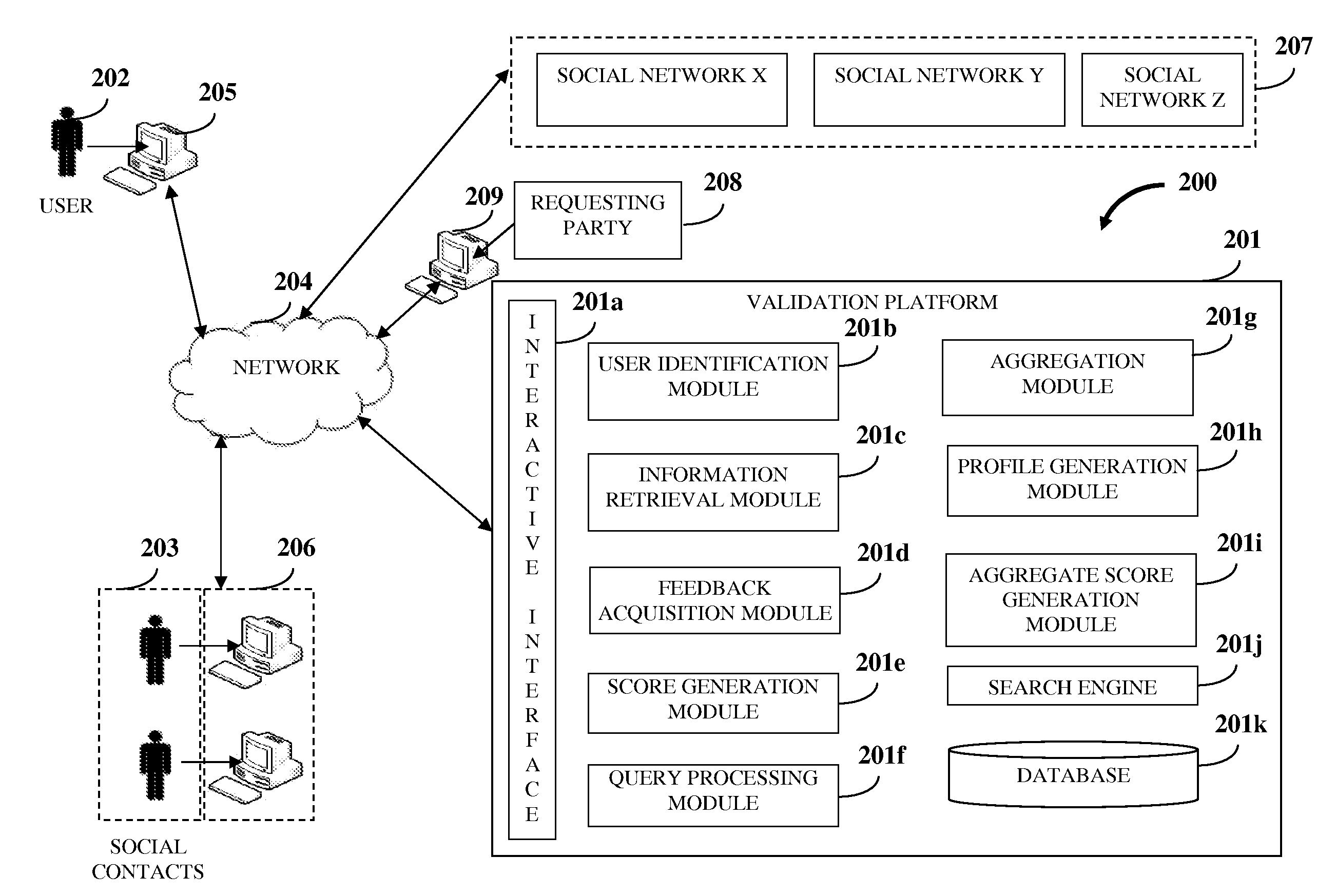
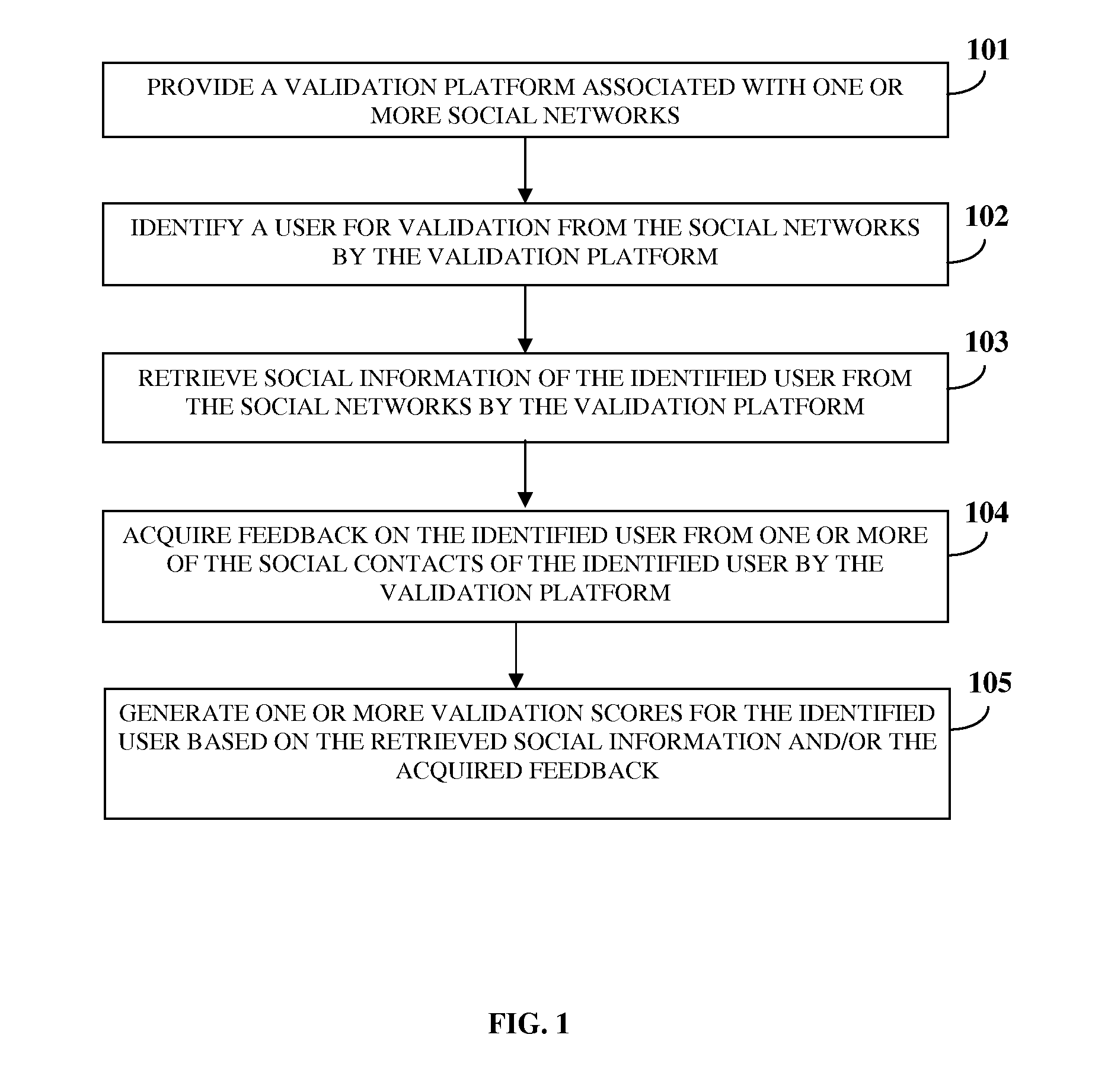
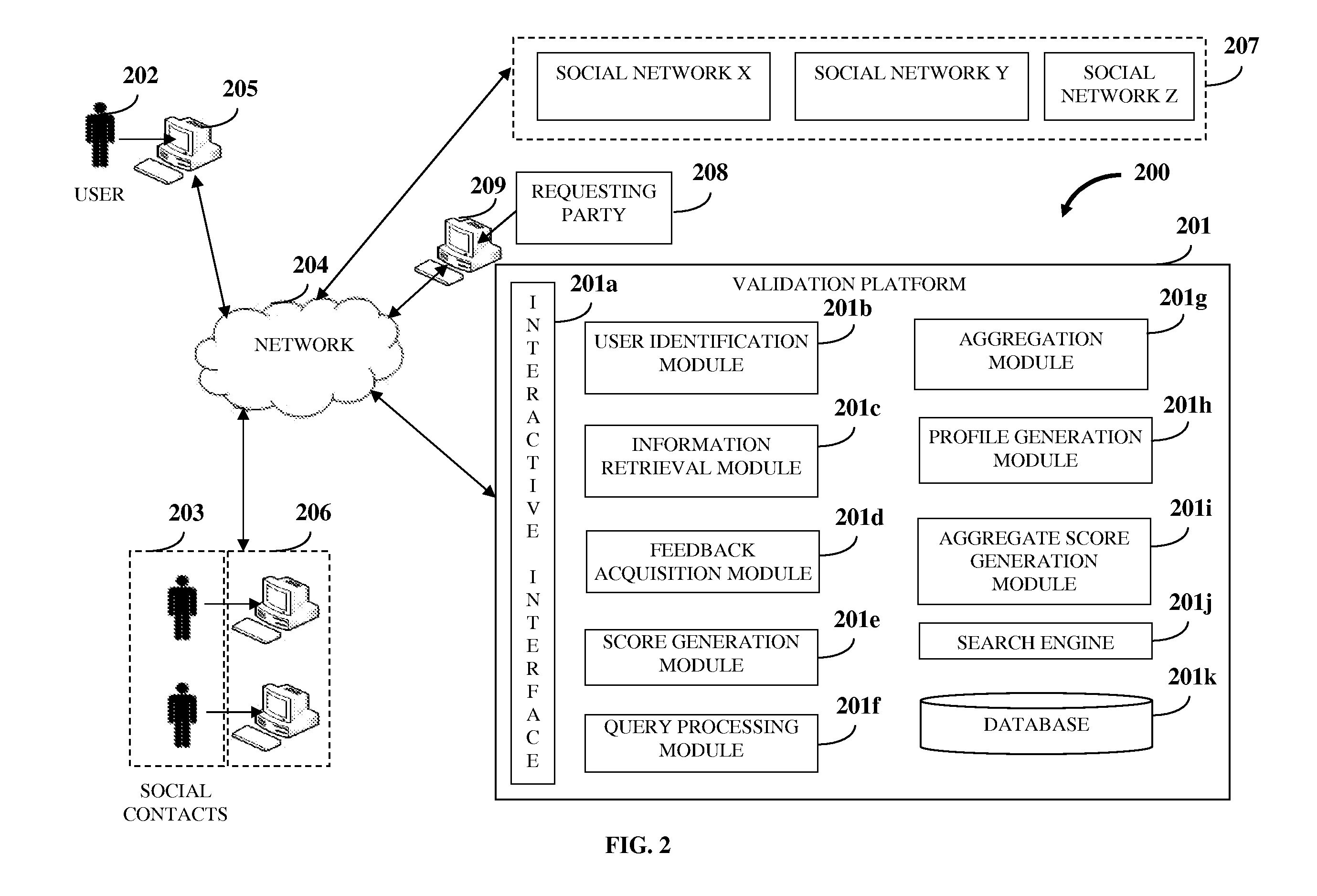
User Validation In A Social Network
ActiveUS20120226701A1Data processing applicationsDigital data processing detailsUser verificationUser authentication
A computer implemented method and system is provided for validating a user associated with one or more social networks. A validation platform associated with the social networks is provided. The validation platform identifies a user for the validation from the social networks. The validation platform retrieves social information of the identified user from the social networks. The social information comprises relationship information of and between the identified user and social contacts of the identified user on the social networks. The validation platform acquires feedback on the identified user from one or more of the social contacts. The validation platform generates one or more validation scores, for example, an evaluation score, a feedback authentication score, a user authentication score, a composite score, etc., for the identified user based on the retrieved social information and / or the acquired feedback. The generated validation scores enable validation of the user associated with the social networks.
Owner:SINGH PUNEET
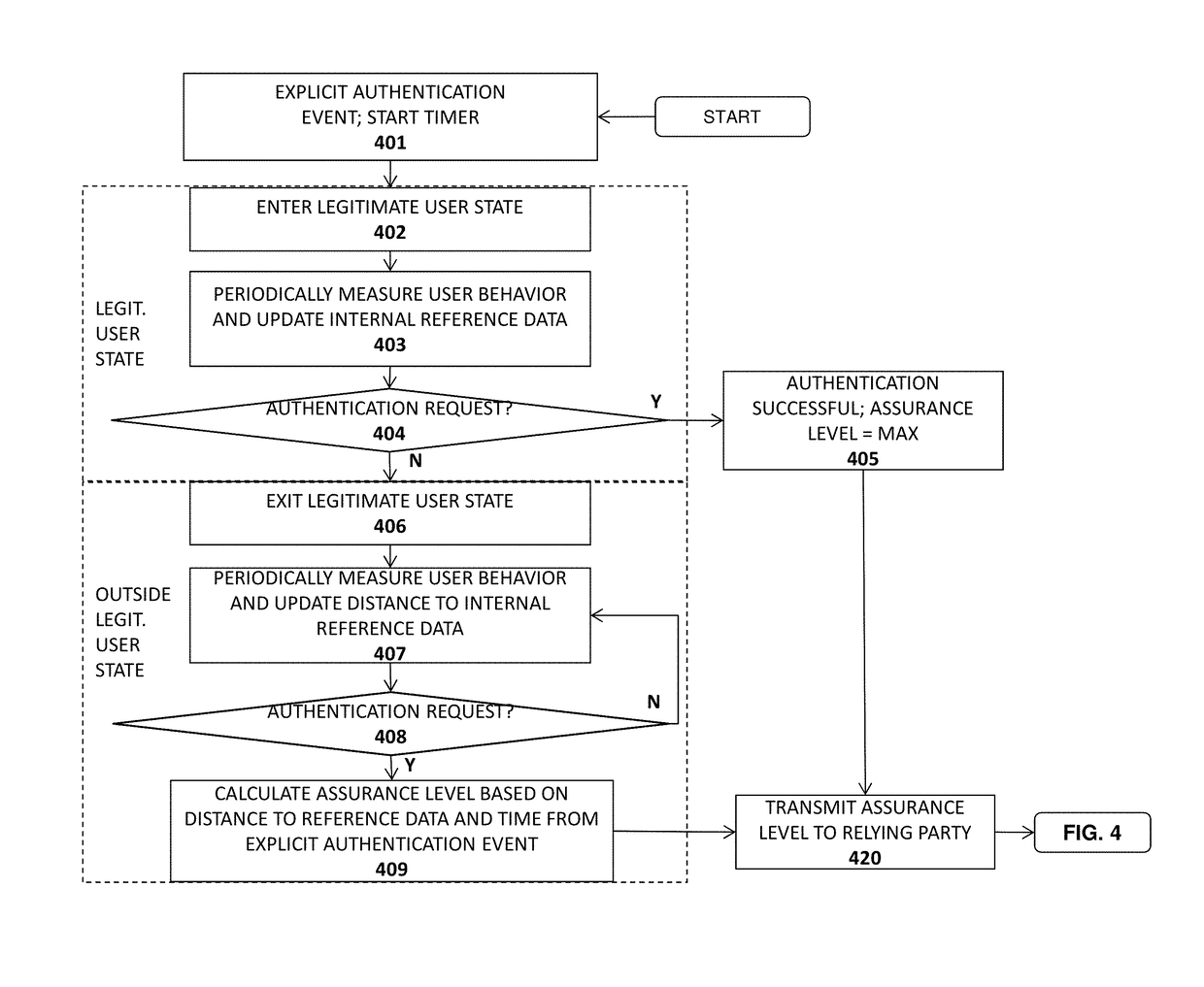
System and method for bootstrapping a user binding
A system, apparatus, method, and machine readable medium are described for bootstrapping an authenticator. For example, one embodiment of a method comprising: confirming an identity of a user by a first relying party using a first identity verification technique responsive to the user acquiring a device having an authenticator; generating or collecting initial user verification reference data upon verifying the identity of the user through the first identity verification technique; securely providing the initial user verification reference data or data derived from the initial user verification reference data to the authenticator; the authenticator implementing a second identity verification technique by comparing the initial user verification reference data or data derived from the initial user verification reference data to data collected from the user or data collected from a device provided to the user; and providing proof of a successful verification of the identity of the user to a second relying party during a registration request of the authenticator with the second relying party.
Owner:NOK NOK LABS
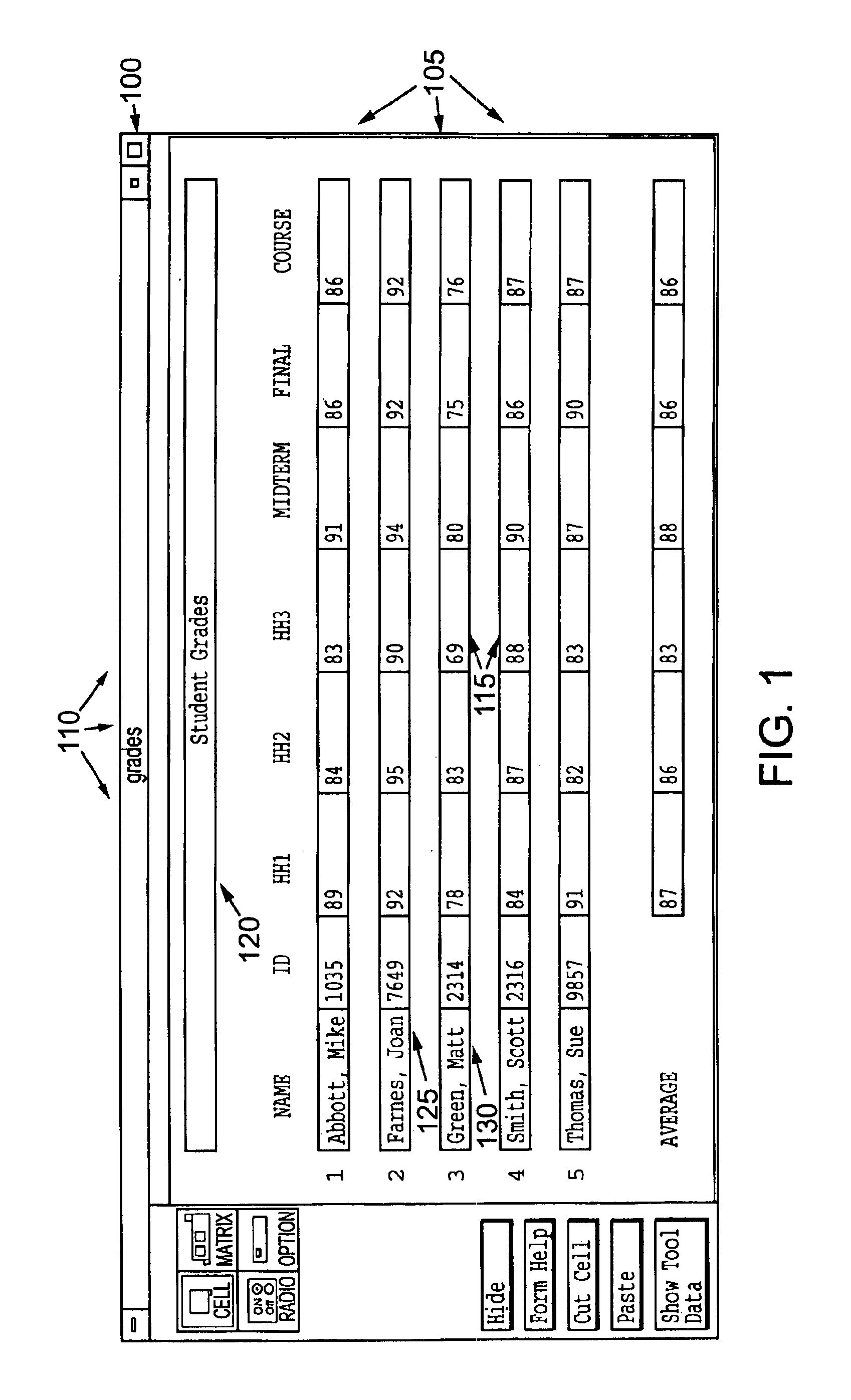
Methodology for testing spreadsheets
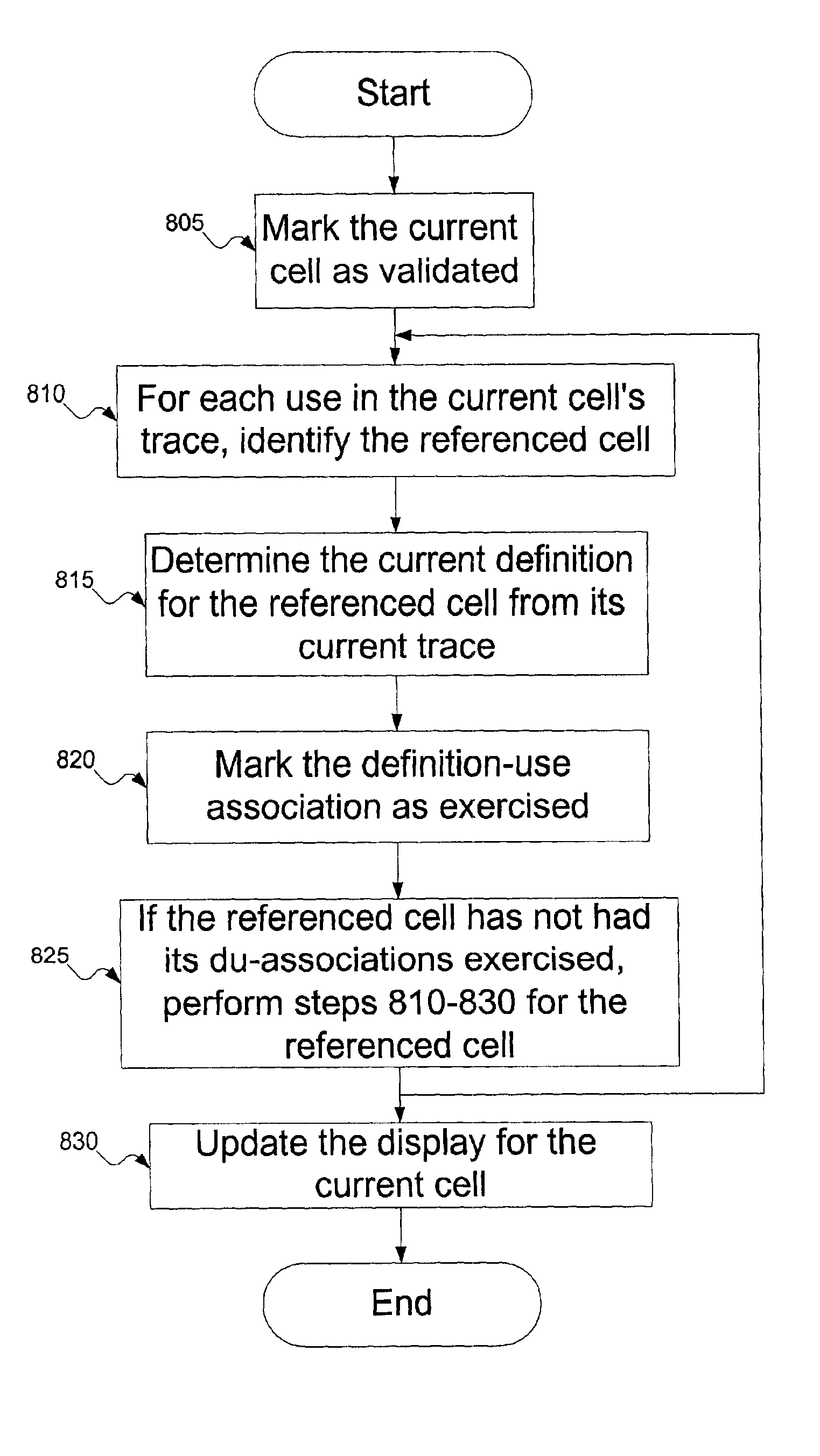
InactiveUS6948154B1Text processingSpecific program execution arrangementsTheoretical computer scienceTest element
The invention includes a method for testing a spreadsheet cell. Du-associations are collected for the spreadsheet cell. The cell's execution trace is tracked. After the user validates the cell, the du-associations that participated in the execution trace are marked as executed. Du-associations for other cells that are affected by the testing a spreadsheet cell are similarly marking as exercised. If the user changes a cell's contents, the collected du-associations for the cell are discarded and the steps of collecting test elements, tracking execution traces, and marking are repeated. Cells that depend on the changed cell also repeat these steps. After the user marks a cell as validated, a validation symbol is shown on the cell. If the cell's validation status is later brought into question, the validation symbol can change or be removed entirely. The invention also includes a method for providing a user with feedback of the testedness of the spreadsheet cells. The du-associations for each spreadsheet cell are maintained, and the subset of du-associations that have been exercised is identified. Using the numbers of tested and untested du-associations, a testedness measure is calculated for the cell, which is provided to the user.
Owner:UNIV OREGON STATE
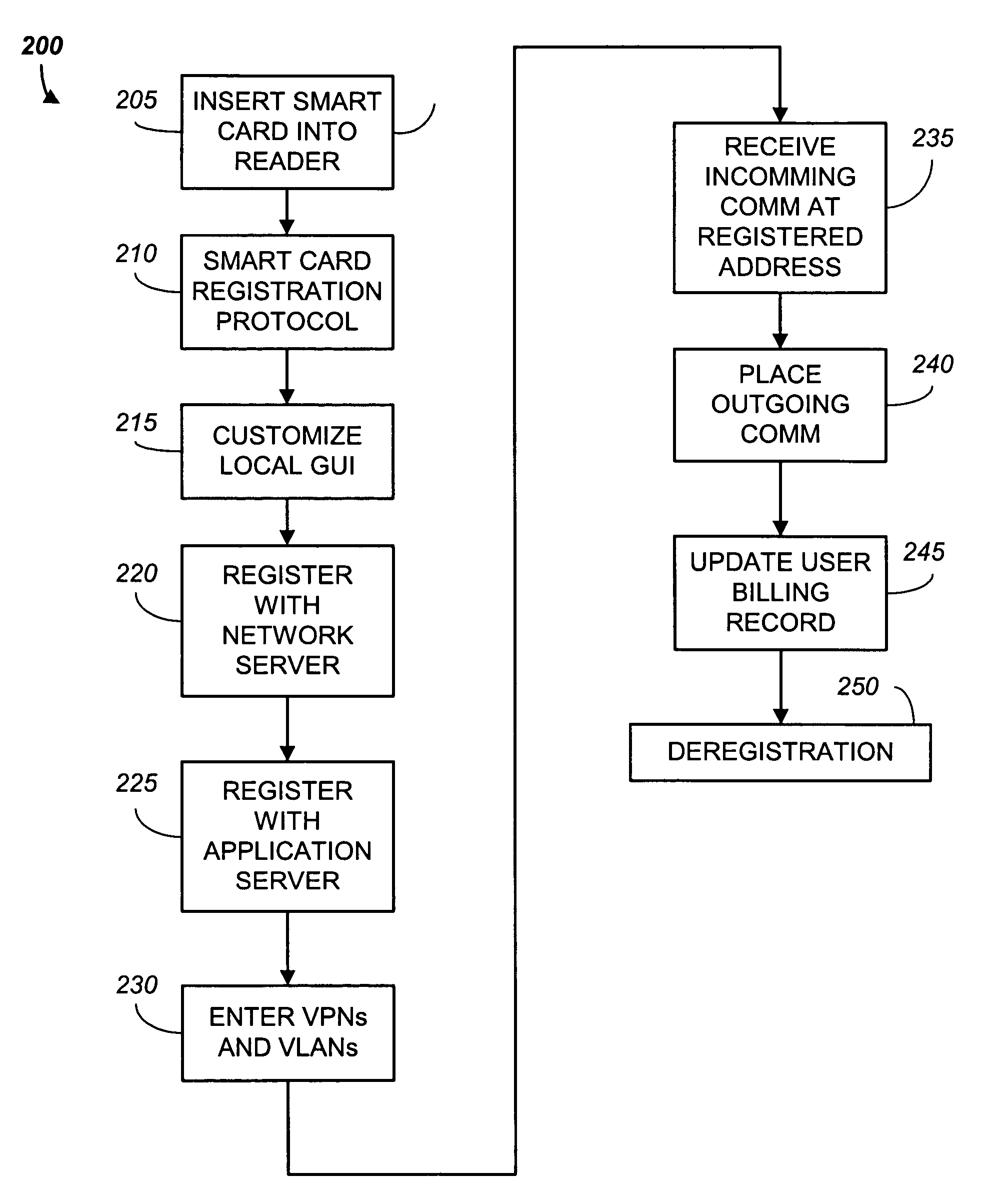
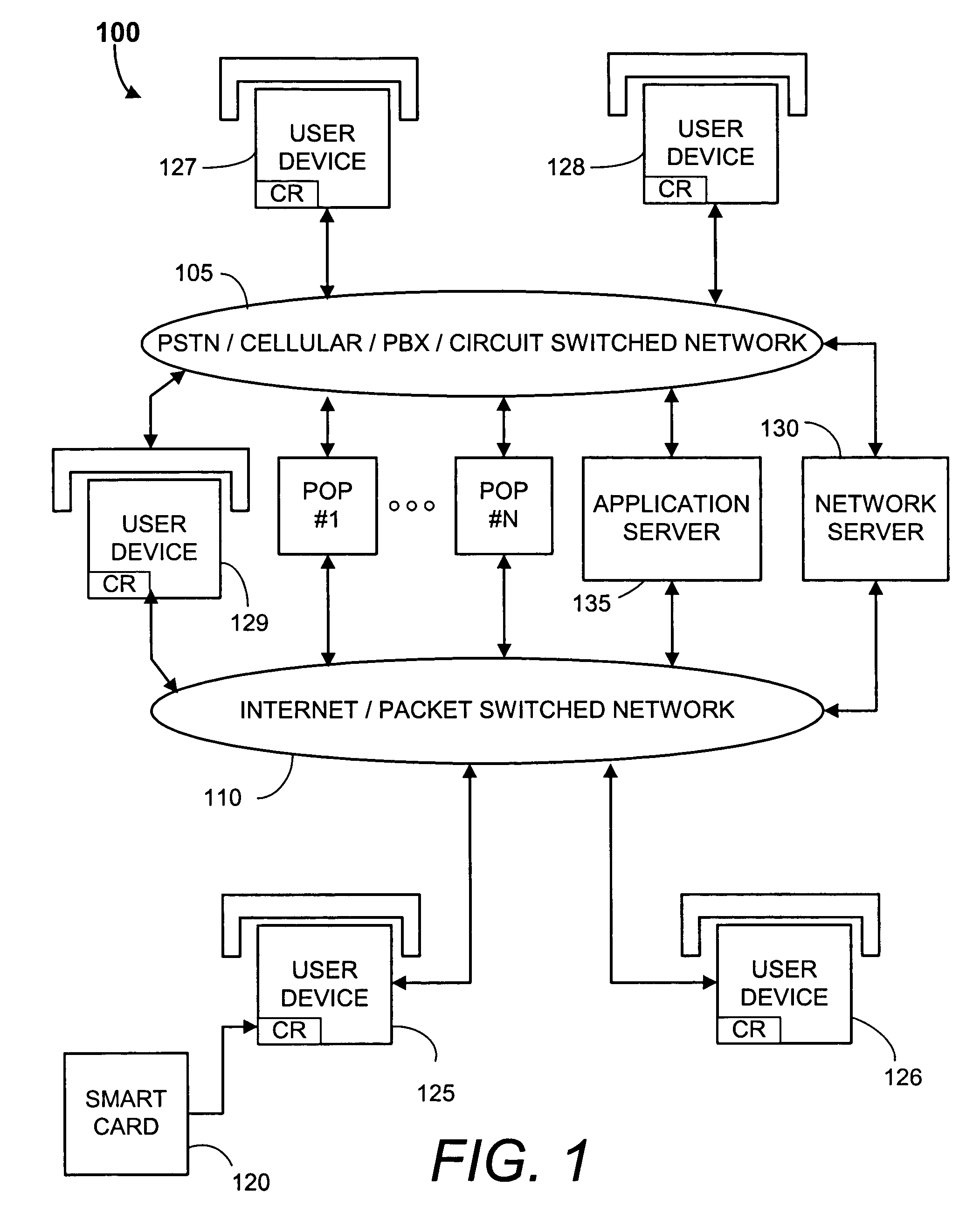
Methods, smart cards, and systems for providing portable computer, VoIP, and application services
InactiveUS7451921B2Devices with card reading facilitySpecial service for subscribersUser authenticationSmart card
A smart card is used with a network based system to providing portable telecommunication and computing services. In an exemplary embodiment the smart card holds a user authentication code and user telephony account information. The smart card transfers the user authentication code and the account information to one of a plurality of geographically dispersed card readers which are each connected to a local telephony device. When the smart card is plugged into a first card reader, telephone calls directed to the smart card user's follow-me telephone number are received at a first local telephony device. When the smart card is plugged into a second smart card reader, telephone calls directed to the follow-me telephone number are received at a second telephony local device. Hence the user is enabled to receive and place calls using any of the geographically dispersed telephony devices as though they were his / her own personal landline or cellular telephone supplied by his / her telephony services provider.
Owner:INTERNET COMM SOLUTIONS
Intelligent entrance guard system for mobile terminal user verification
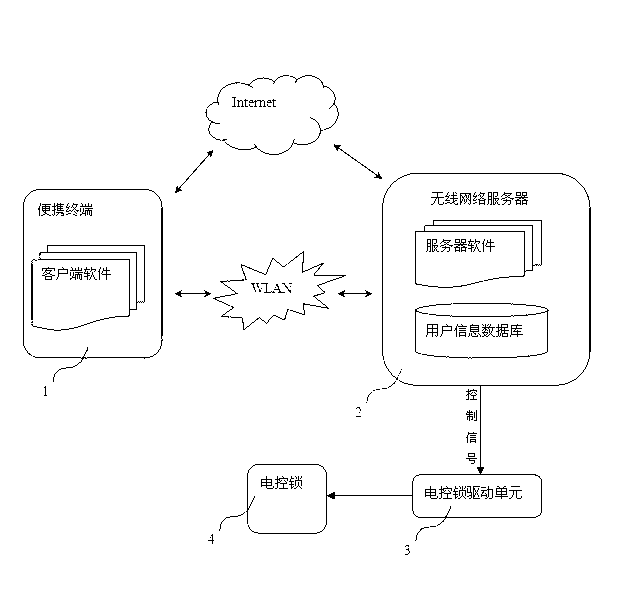
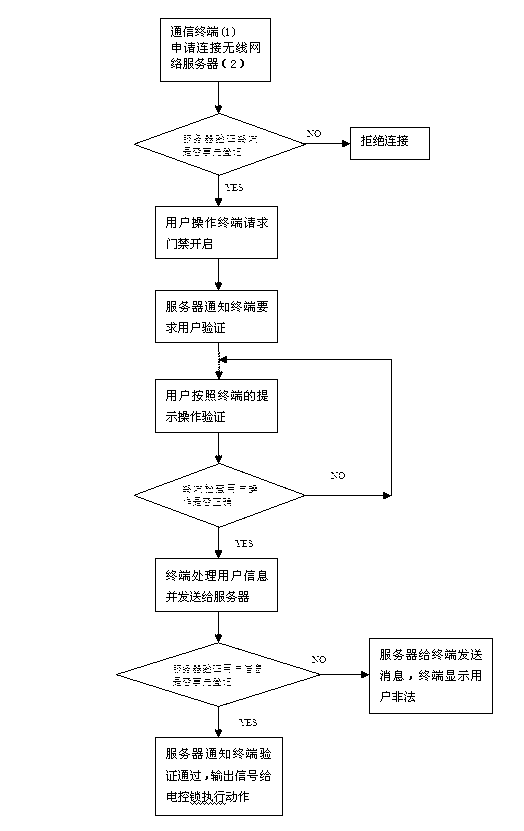
InactiveCN103021045AWith technical effectPracticalUser identity/authority verificationIndividual entry/exit registersUser verificationThe Internet
The invention provides an intelligent entrance guard system which uses mobile phones and other mobile communication terminals as user information reading and communication devices, utilizes a wireless network communication, and realizes dual verification for the terminals and the user identities. The system provided by the invention is composed of a mobile intelligent communication terminal, a wireless network server, an electronically controlled lock drive unit, and an electronically controlled lock, wherein the terminal is accessed to the Internet through a wireless LAN or a GPRS mobile telephone network, and builds a wireless communication connection verified by the terminal with the server; a client software of the terminal provides a human-computer interaction interface, and reads, entries, analyzes and identifies the user information; and a server software of the wireless network server realizes user verification, database management and controlling motions of the electronically controlled lock. The entrance guard system is low in cost, high in safety and convenient to use.
Owner:边高伟
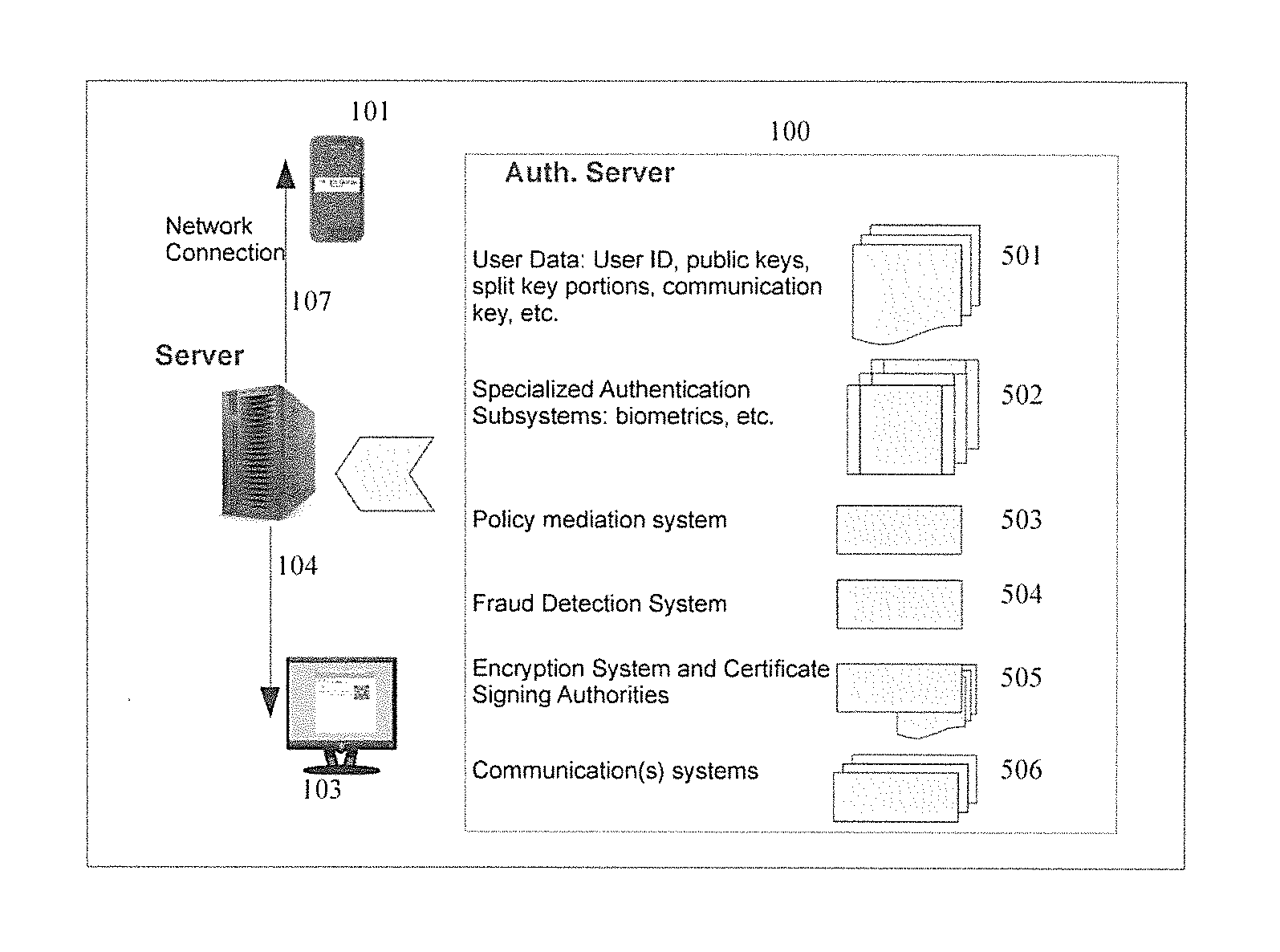
Secure authentication in a multi-party system
ActiveUS20130263211A1Easy to modifyWeb data indexingDigital data processing detailsUser verificationInternet privacy
An authentication server transmits a random number to and receives a other information from a service provider. Later, the first random number is received from a requester and a provider identifier, the received other information and provider authentication policy requirements are transmitted to the requester. A user identifier and validation information are received from the requester. The received validation information is determined to correspond to the provider authentication policy requirements, and compared with stored user validation information associated with the received user identifier to authenticate the requester. A message, including both the random number and other information, signed with a credential of the requesting user is received and transmitted to the first provider.
Owner:PAYFONE
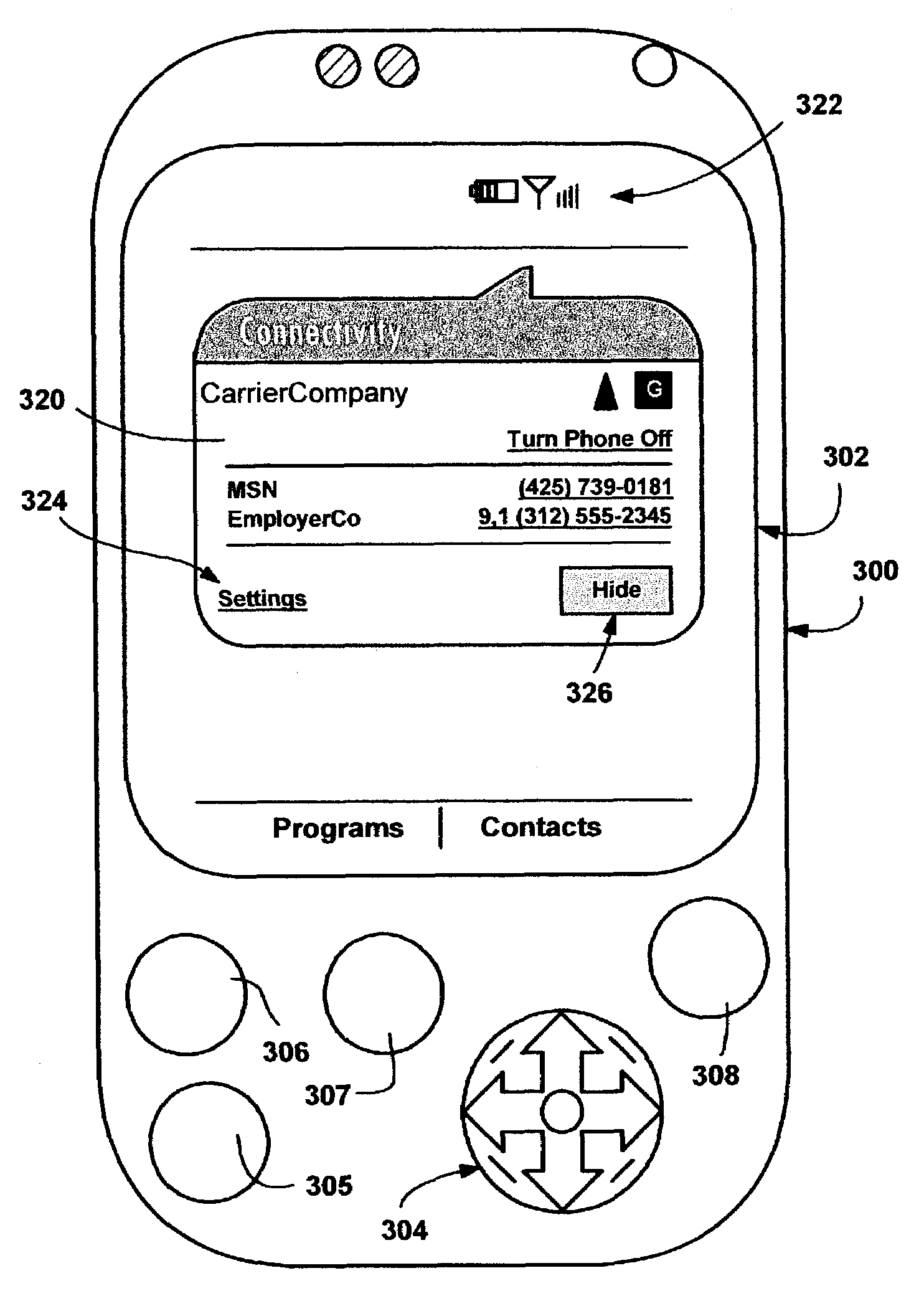
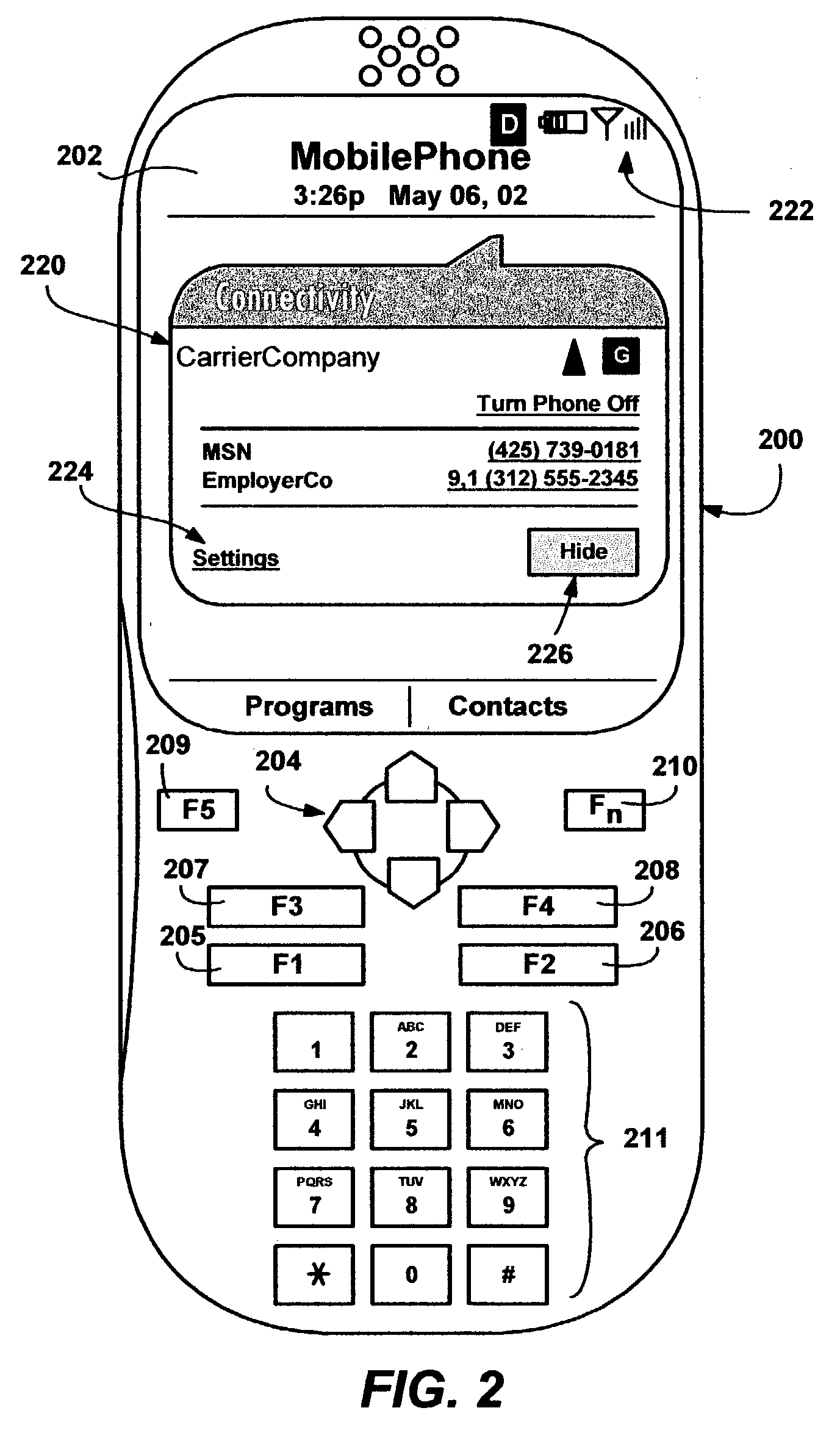
Connectivity notification displaying path to connection
ActiveUS7369850B2Quickly remedyConveniently performedAssess restrictionMultiple digital computer combinationsUser verificationNetwork connection
A system and method in a connectivity user interface of a mobile device that enables a user to inspect and select a connection from among available network connections and methods of connecting. If the user alternatively wants a connection to be automatically selected by the device, the connectivity user interface allows the user to verify the connection that will be made when required. An easily accessible connectivity dialog displays configured connections, and connection data. Before a connection is established, the connection data may describe a type of connection, such as the telephone number for a dial-up connection. After a connection is established, the connection data may describe the connection's status, such as the amount of time the connection has been in use. A link in the connectivity user interface enables the user to efficiently configure or reconfigure a connection.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com