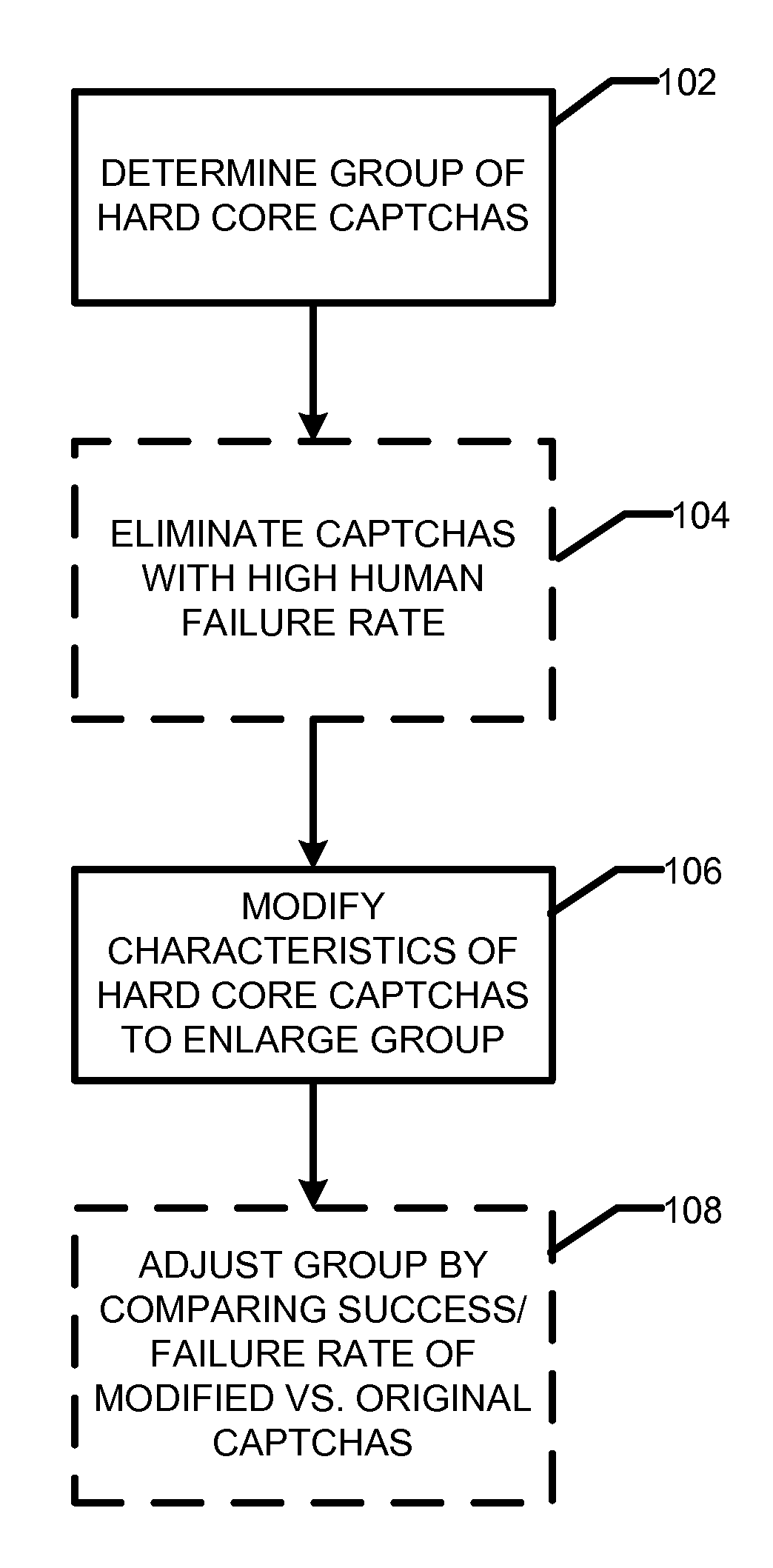
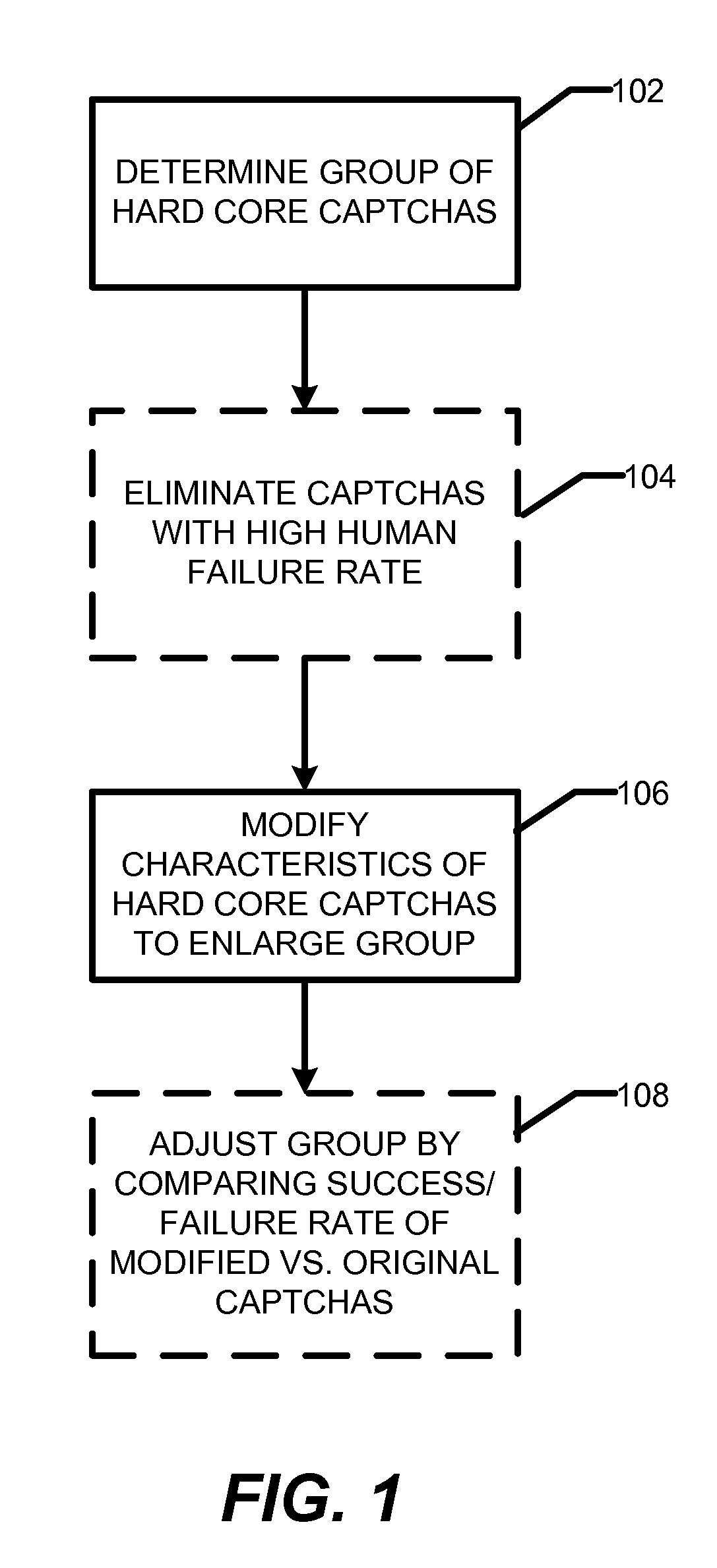
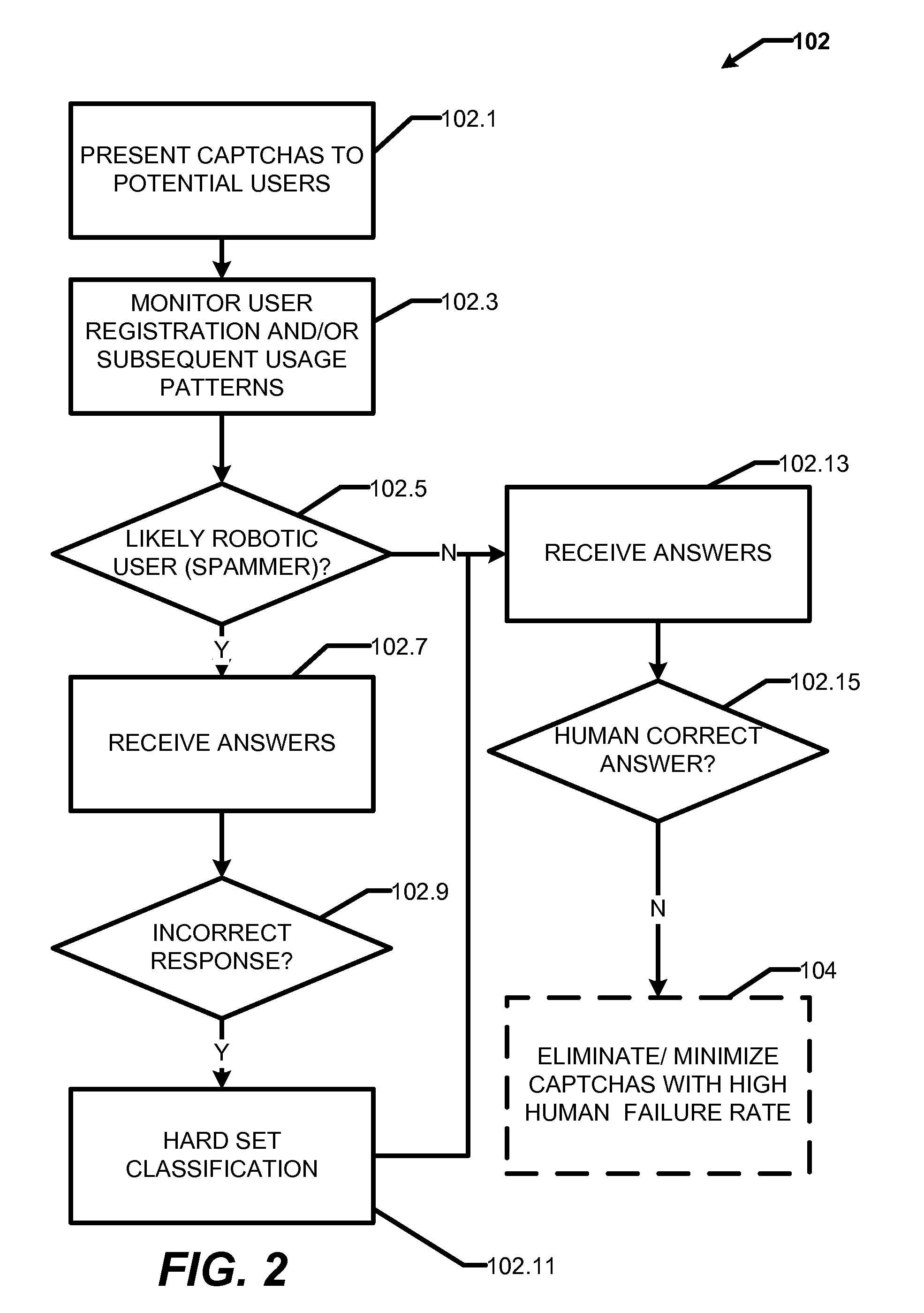
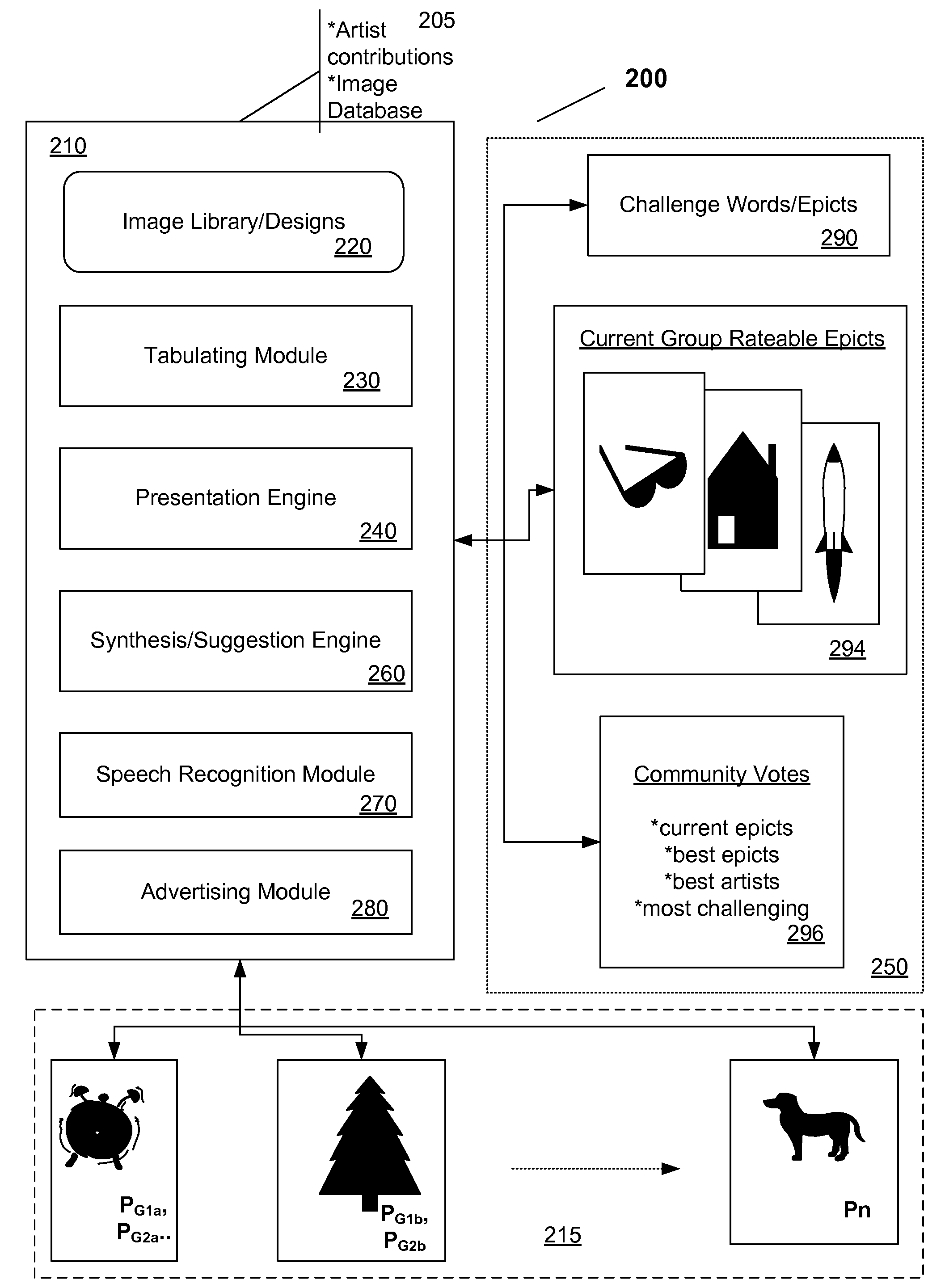
Patents
Literature
301 results about "CAPTCHA" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
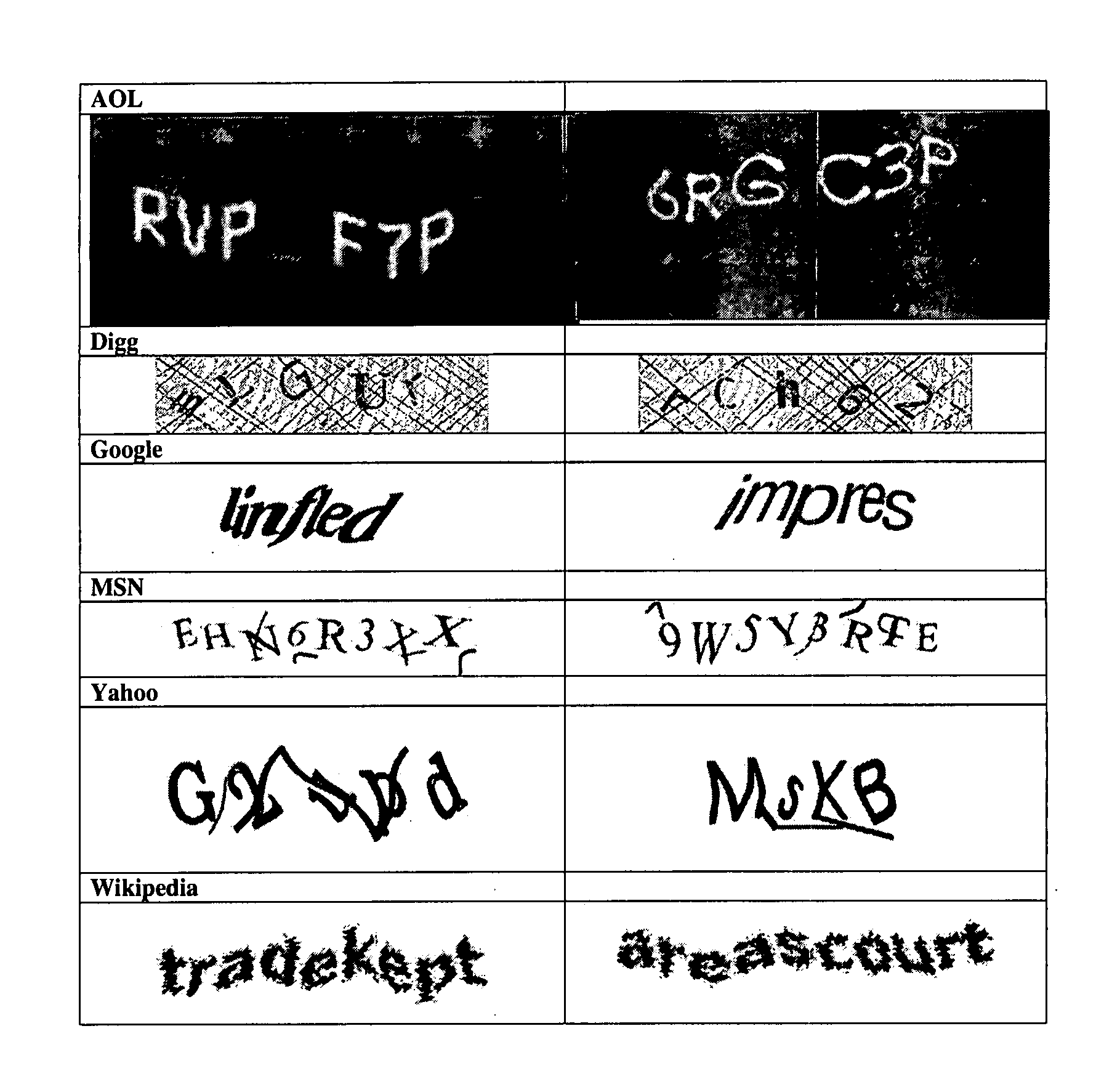
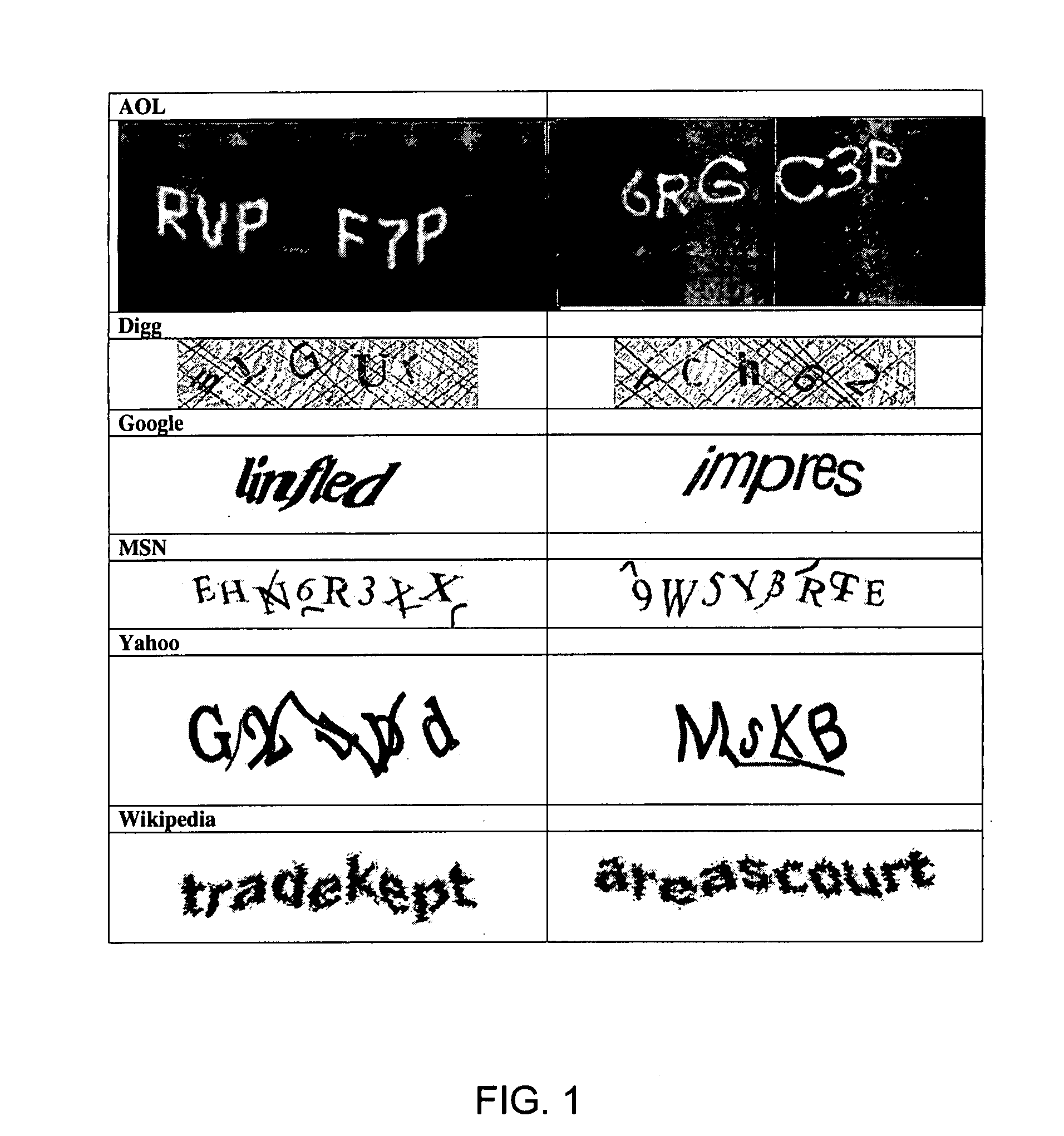
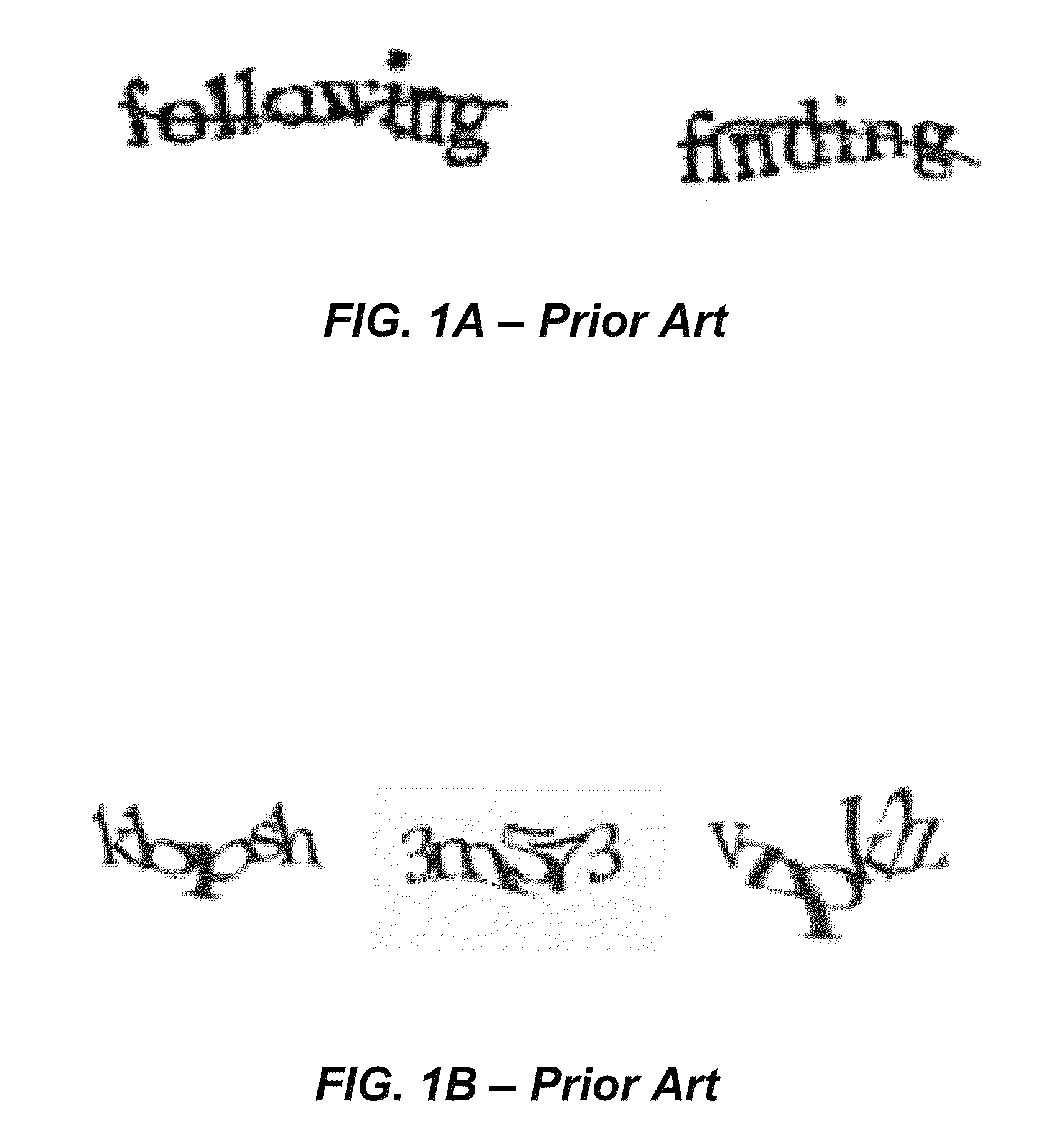
A CAPTCHA (/kæp.tʃə/, an acronym for "Completely Automated Public Turing test to tell Computers and Humans Apart") is a type of challenge–response test used in computing to determine whether or not the user is human.
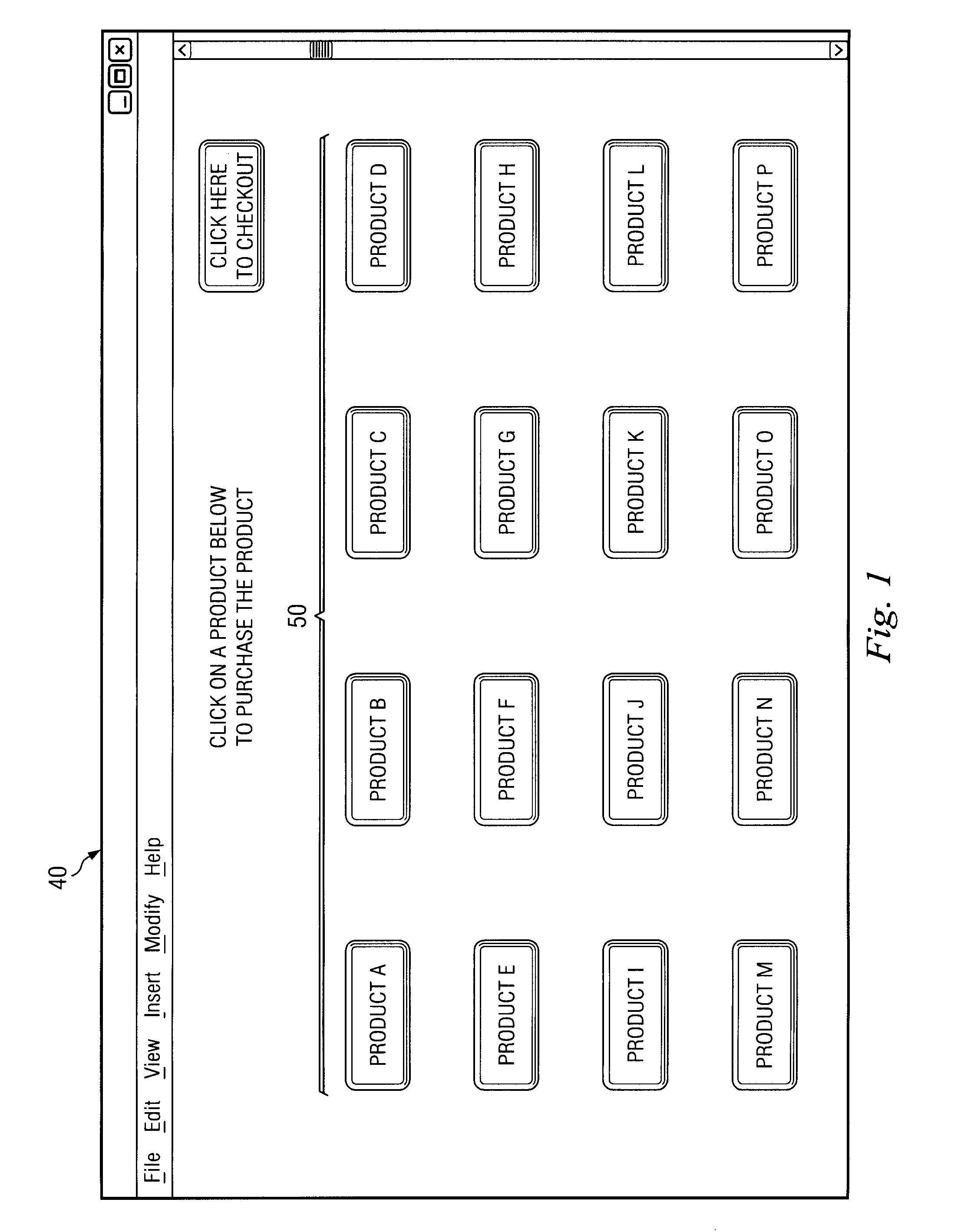
Image-based captcha system
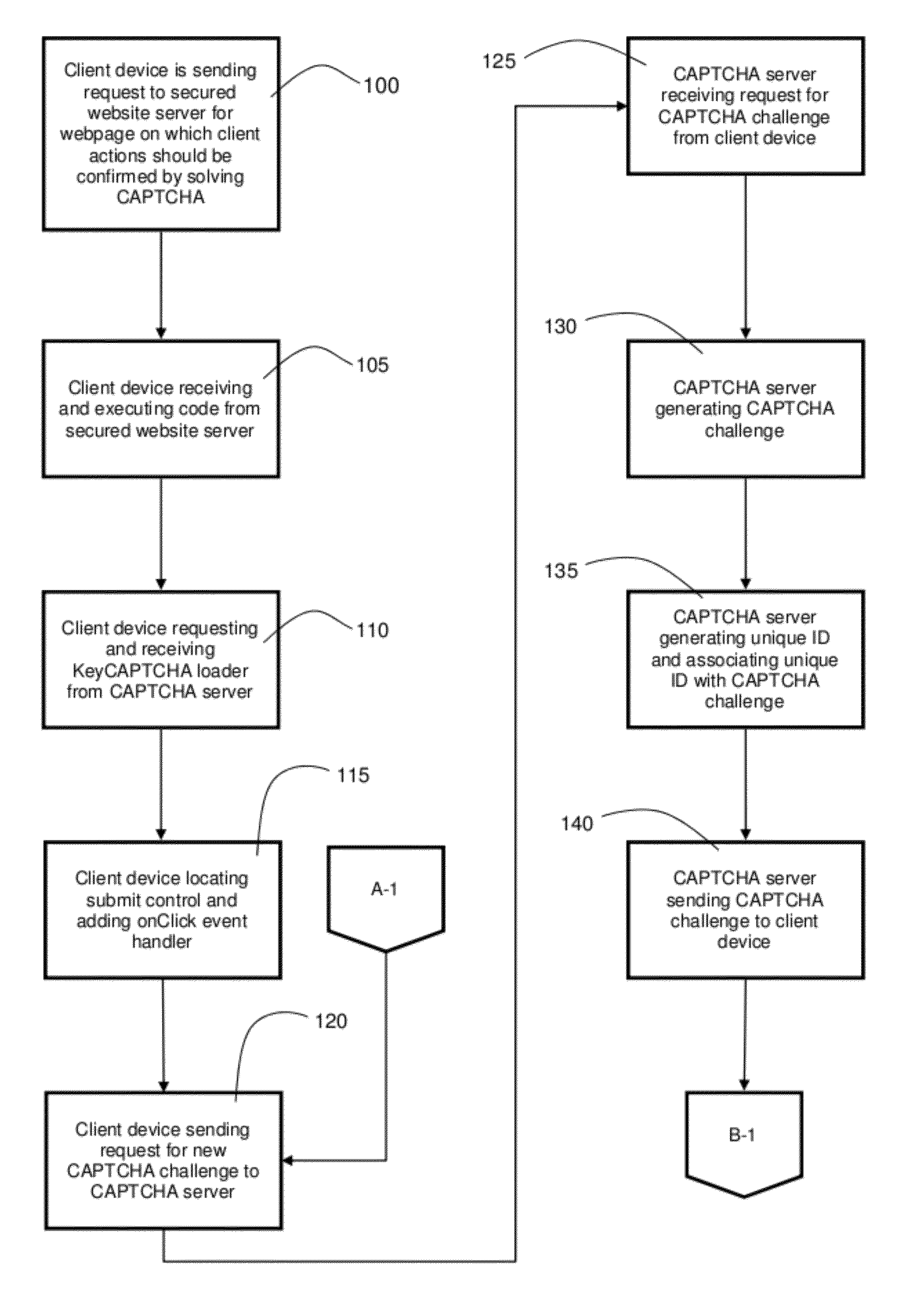
InactiveUS20120323700A1Convenient verificationDigital data processing detailsUser identity/authority verificationHuman interactionCAPTCHA
A system and method for remote verification of human interaction without requiring the entering of alpha numeric characters using a keyboard.
Owner:MERSANE
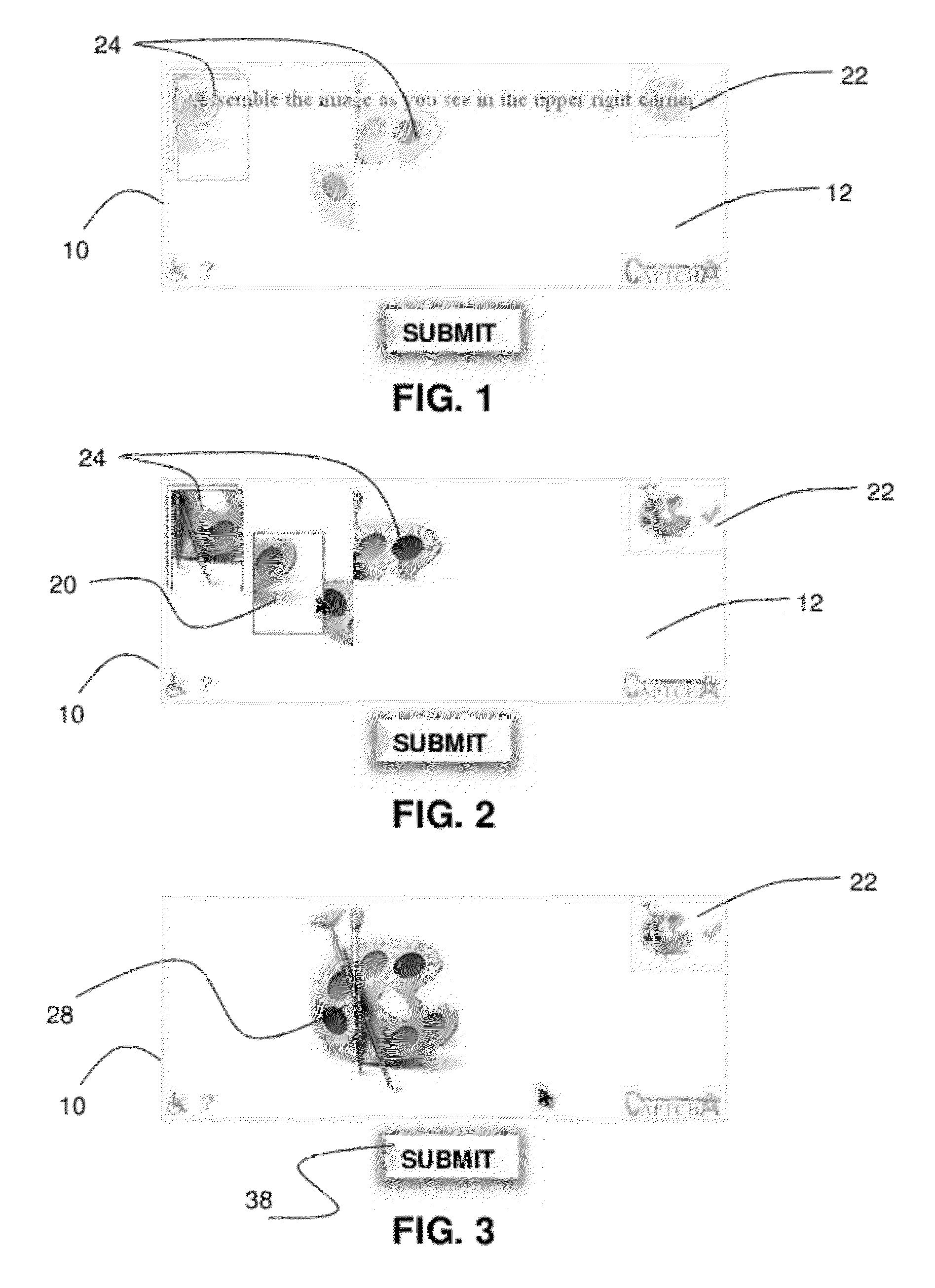
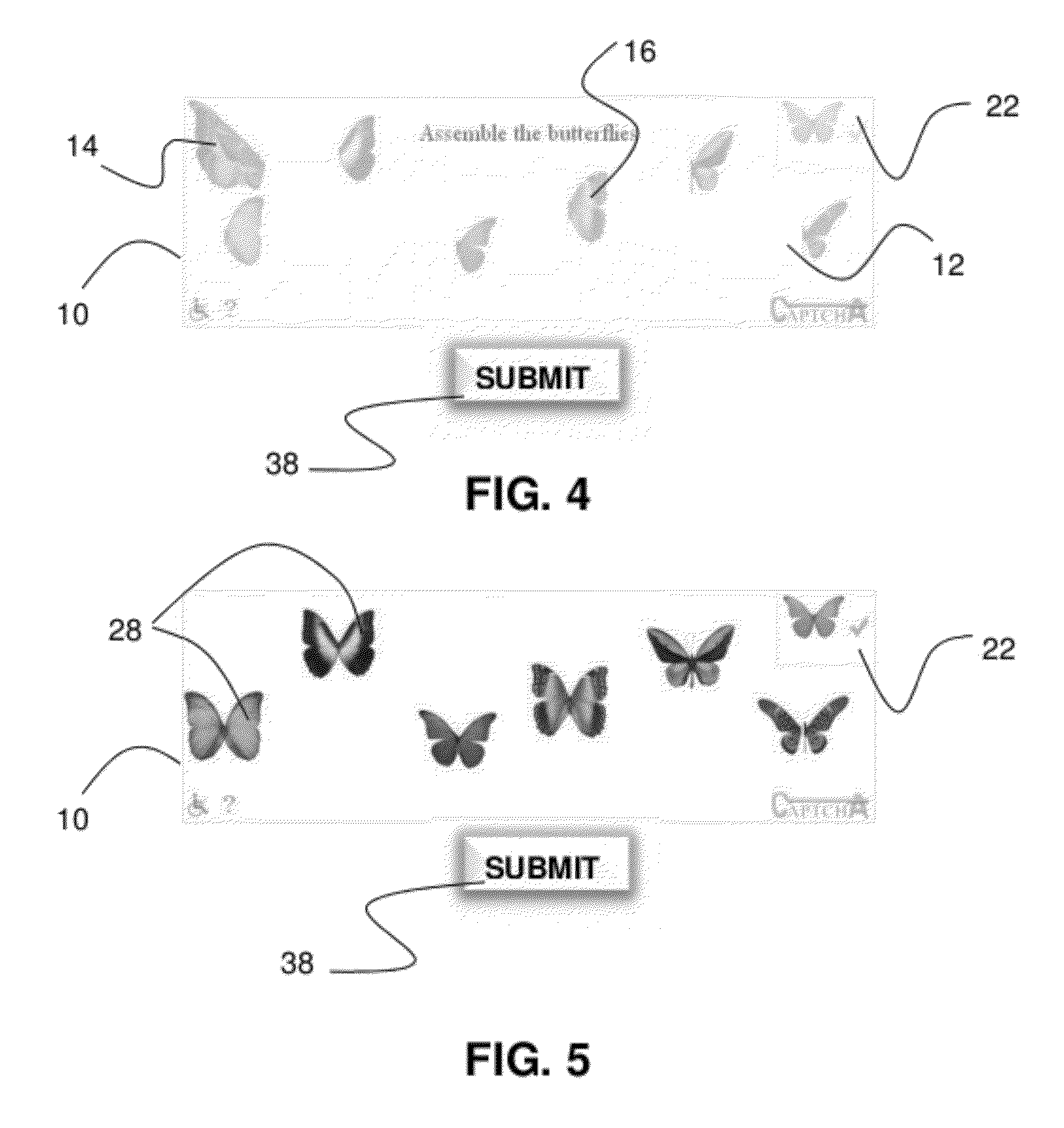
Image-based CAPTCHA generation system
InactiveUS7929805B2Digital data processing detailsUnauthorized memory use protectionHigh resistanceAmbiguity
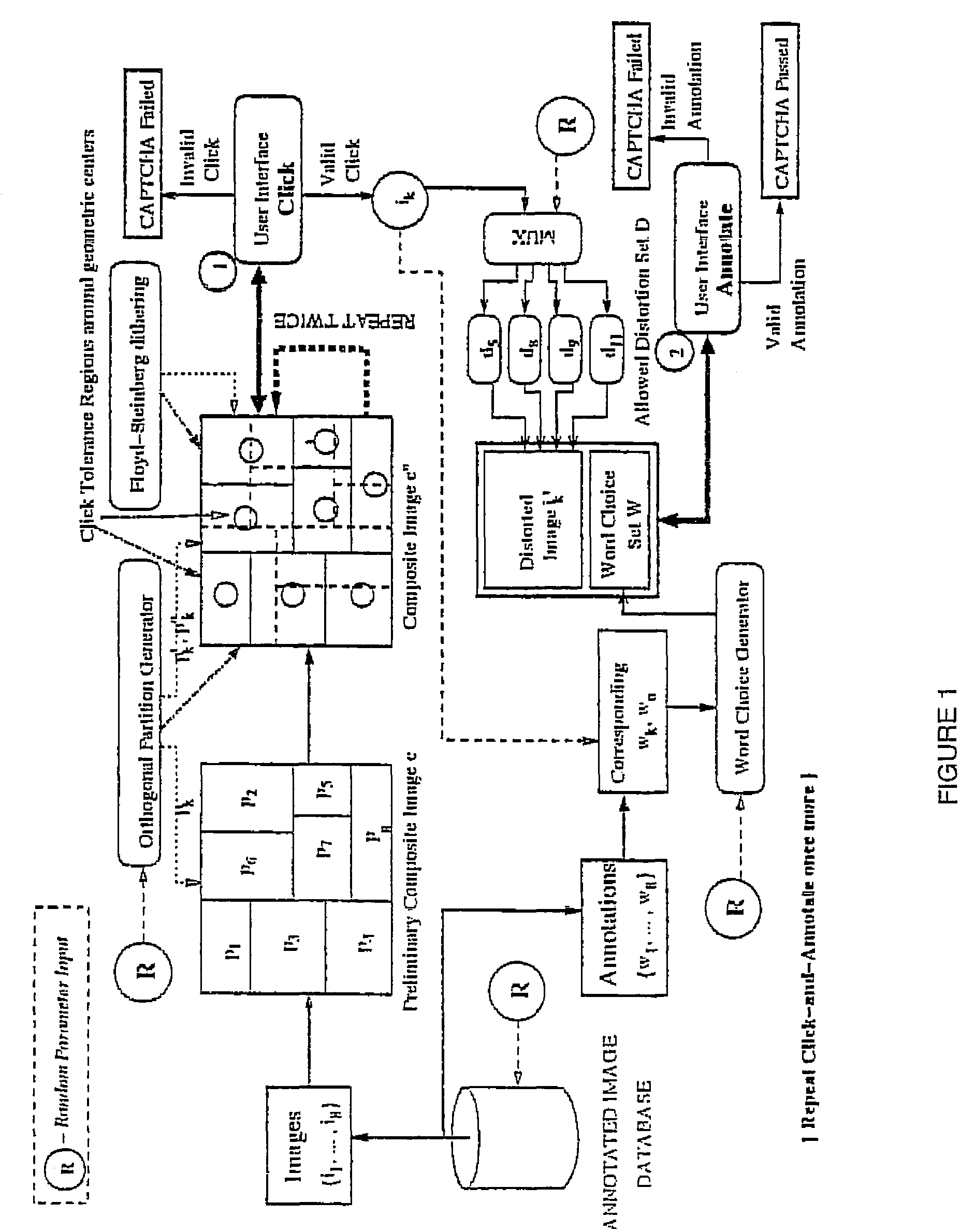
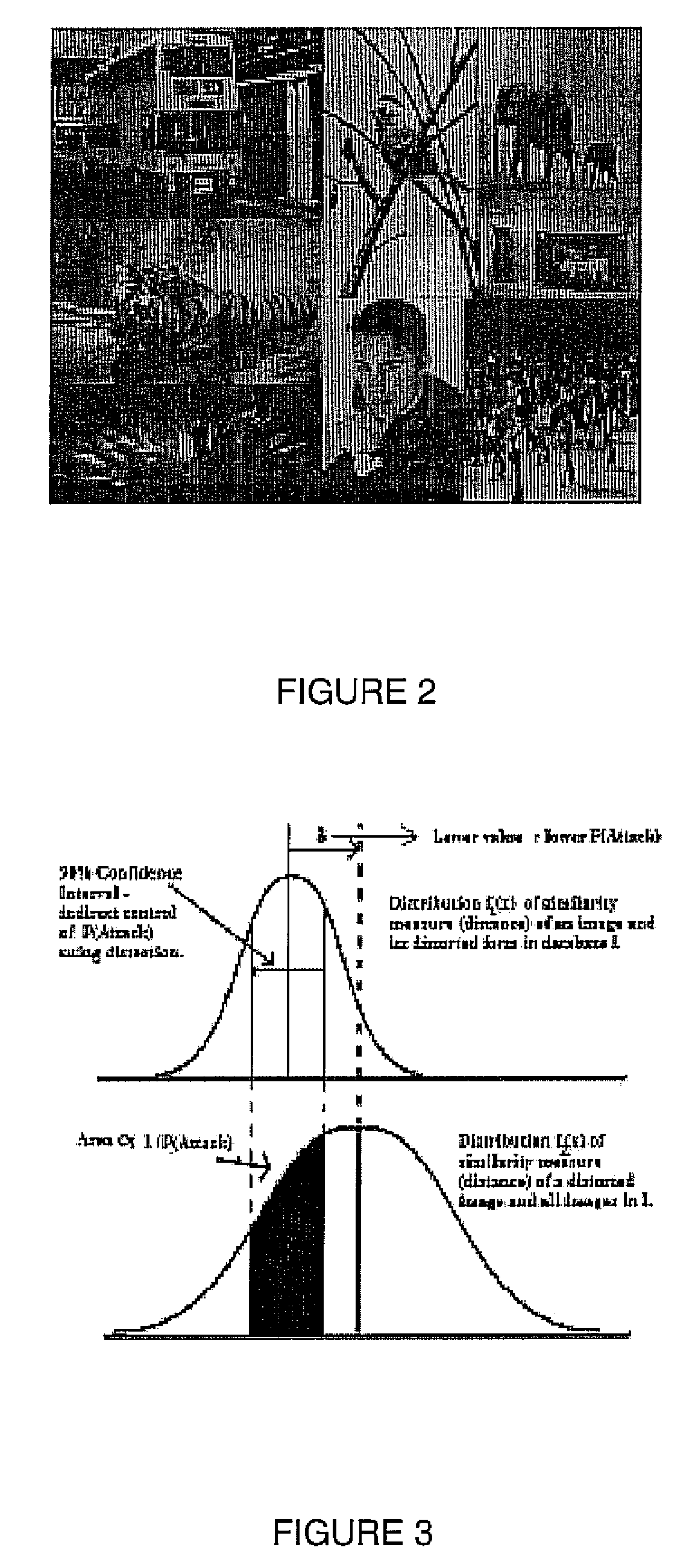
In a system and method for the generation of attack-resistant, user-friendly, image-based CAPTCHAs (Completely Automated Public test to Tell Computers and Humans Apart), controlled distortions are applied to randomly chosen images and presented to a user for annotation from a given list of words. An image is presented that contains multiple connected but independent images with the borders between them distorted or otherwise visually obfuscated in a way that a computer cannot distinguish the borders and a user selects near the center of one of the images. The distortions are performed in a way that satisfies the incongruous requirements of low perceptual degradation and high resistance to attack by content-based image retrieval systems. Word choices are carefully generated to avoid ambiguity as well as to avoid attacks based on the choices themselves.
Owner:PENN STATE RES FOUND
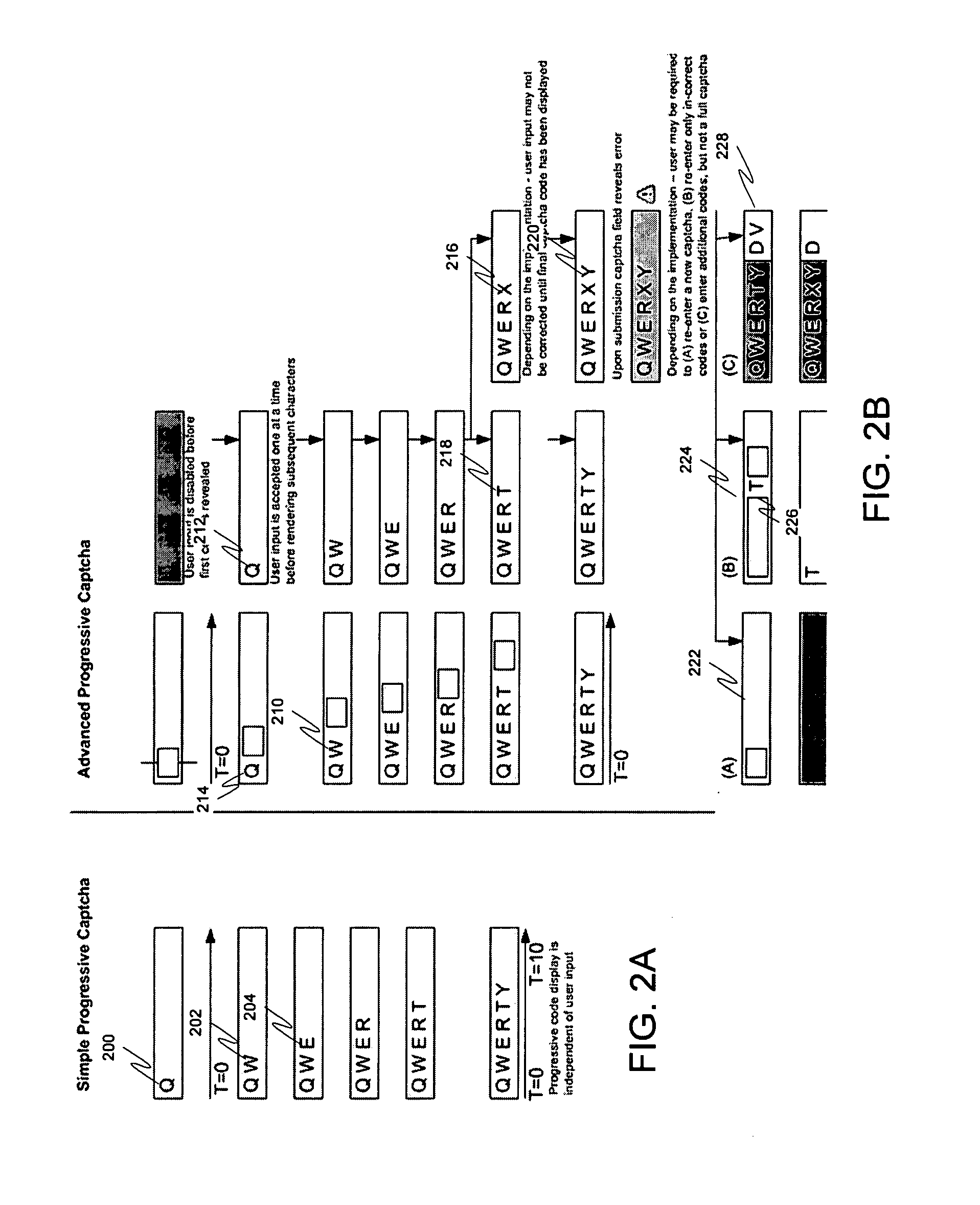
Progressive captcha
InactiveUS20090113294A1Natural language data processingDigital data authenticationDisplay deviceCAPTCHA
Validating that a user is a human may be accomplished through various techniques. In one embodiment, a first portion of a captcha is displayed at a first time. A second portion of the captcha image is displayed on the display at a second time, wherein the second time is subsequent to the first time. In another embodiment, an interactive task is presented on a display for a user to perform. Then a captcha image is displayed on the display once the user completes the interactive task. In either embodiment, a user may be accepted as human if input from the user matches predefined input corresponding to the captcha image.
Owner:OATH INC
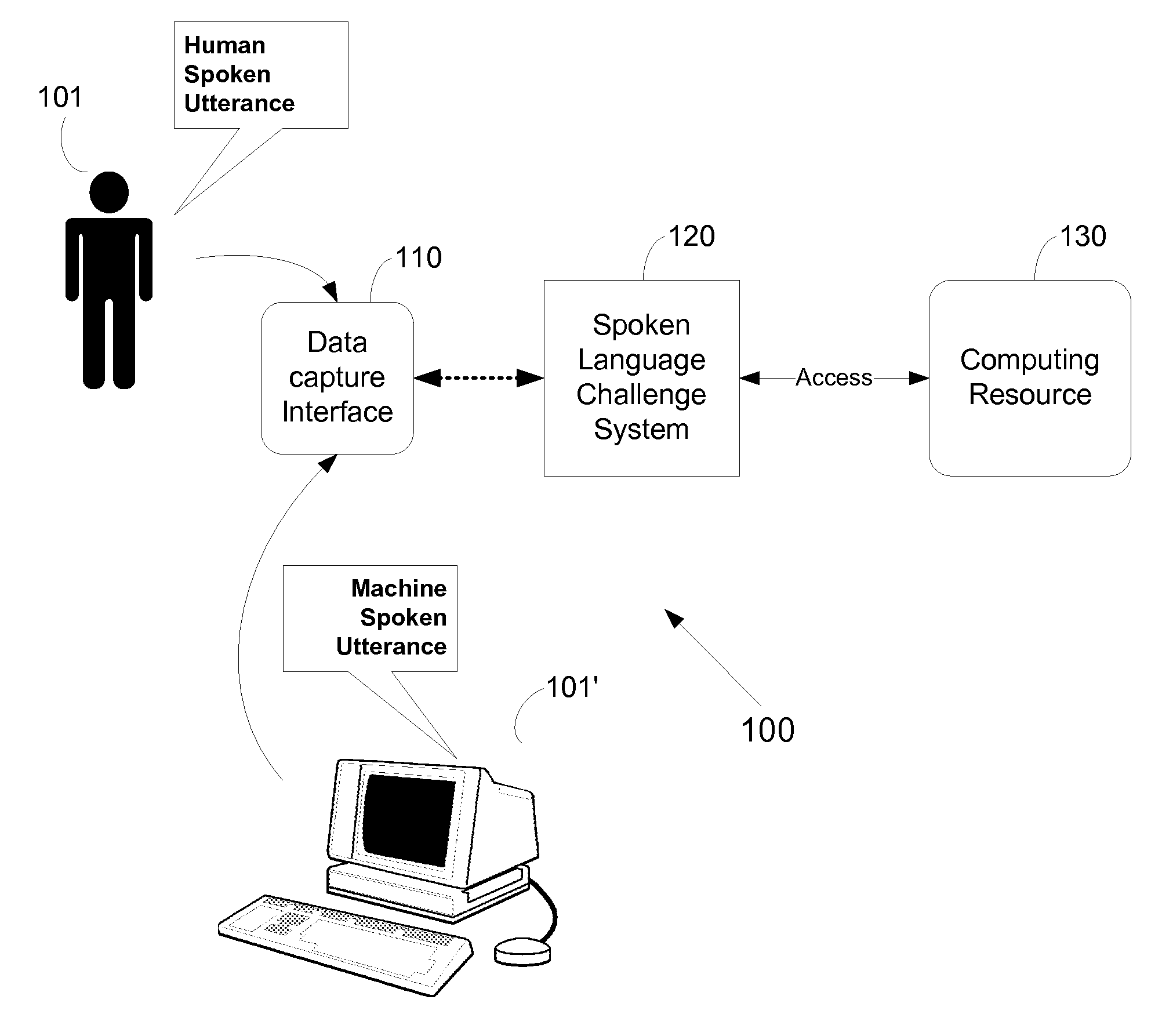
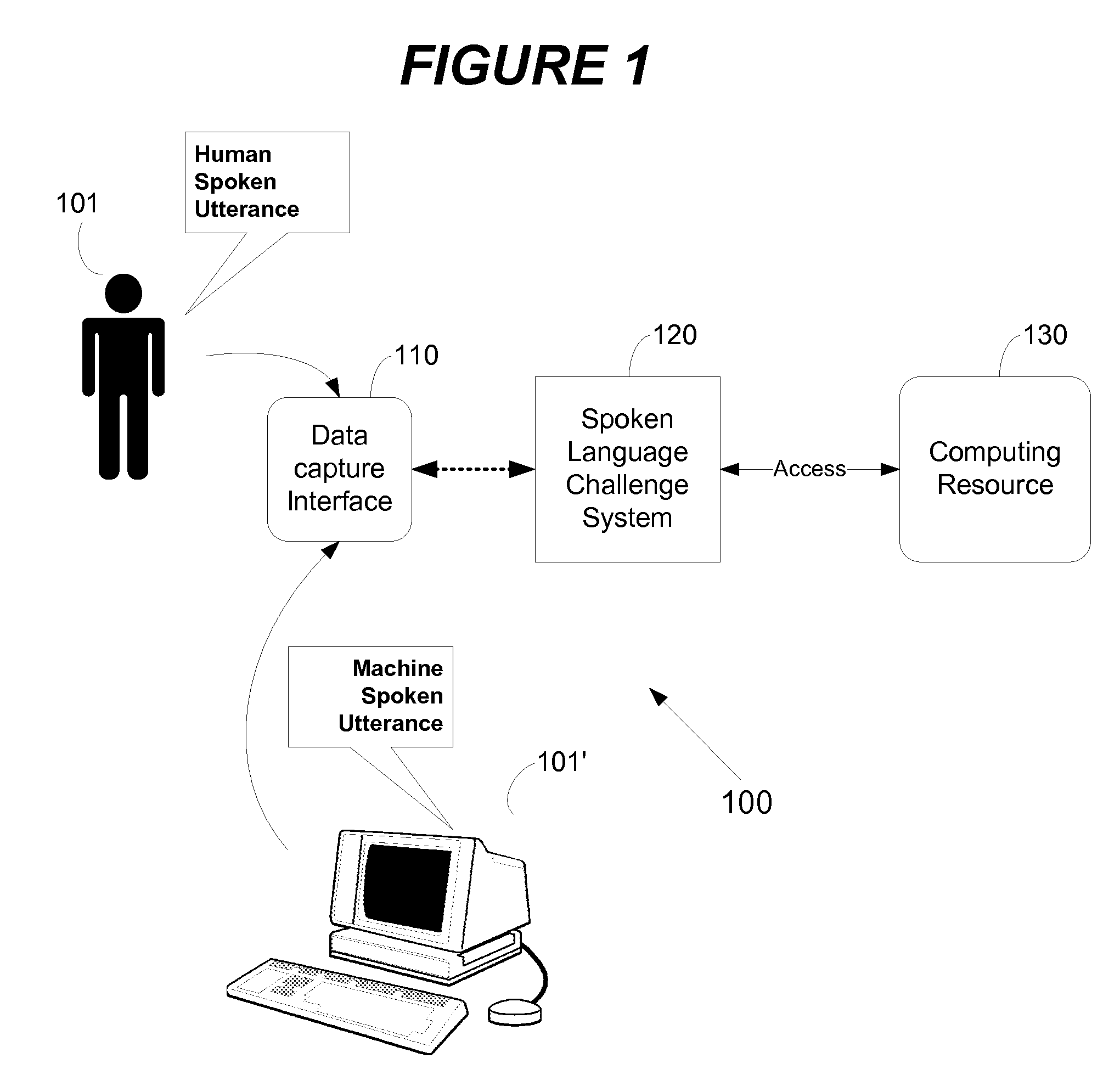
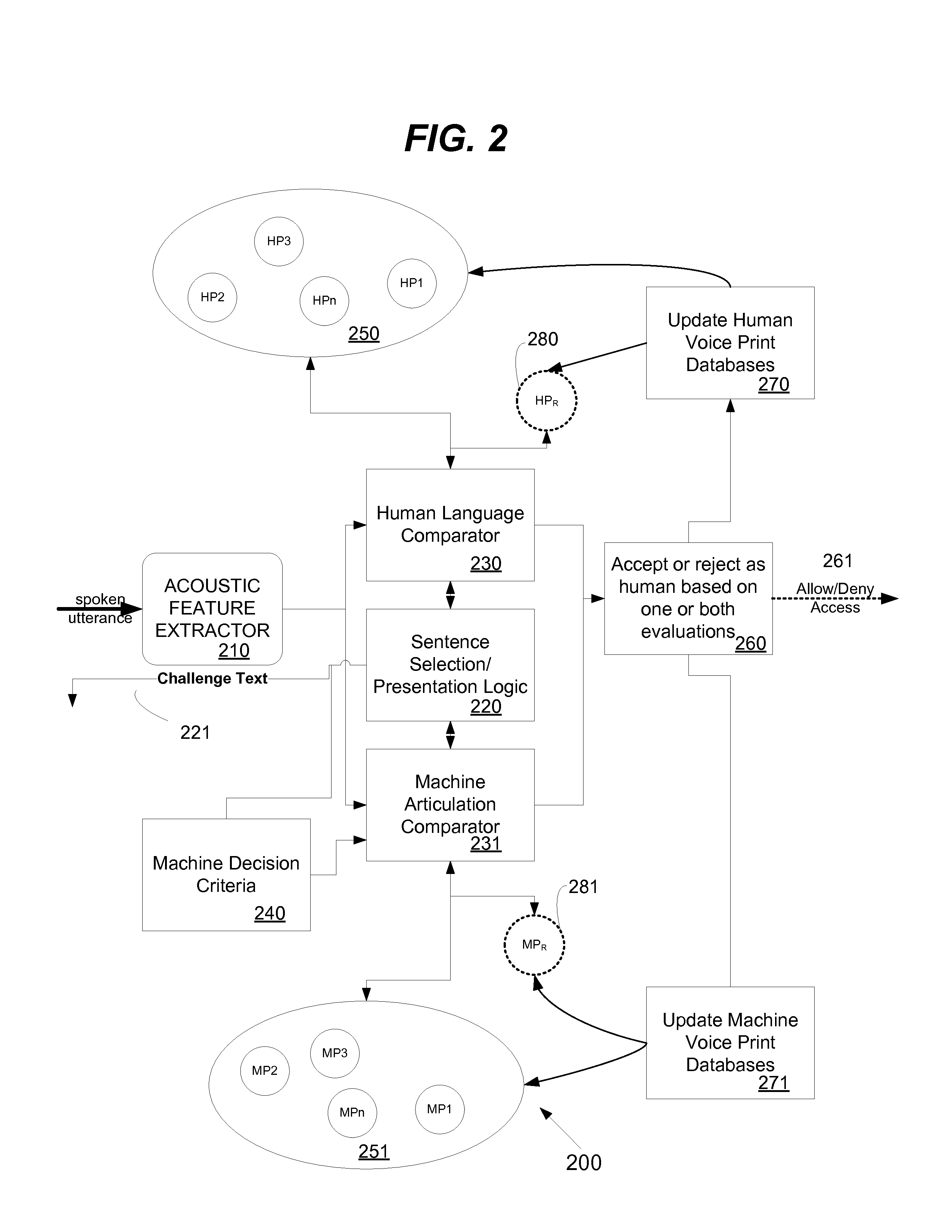
CAPTCHA Using Challenges Optimized for Distinguishing Between Humans and Machines
ActiveUS20090319270A1Special service provision for substationInterconnection arrangementsNatural language processingCAPTCHA
An audible based electronic challenge system is used to control access to a computing resource by using a test to identify an origin of a voice. The test is based on analyzing a spoken utterance using optimized challenge items selected for their discrimination capability to determine if it was articulated by an unauthorized human or a text to speech (TTS) system.
Owner:KNAPP INVESTMENT
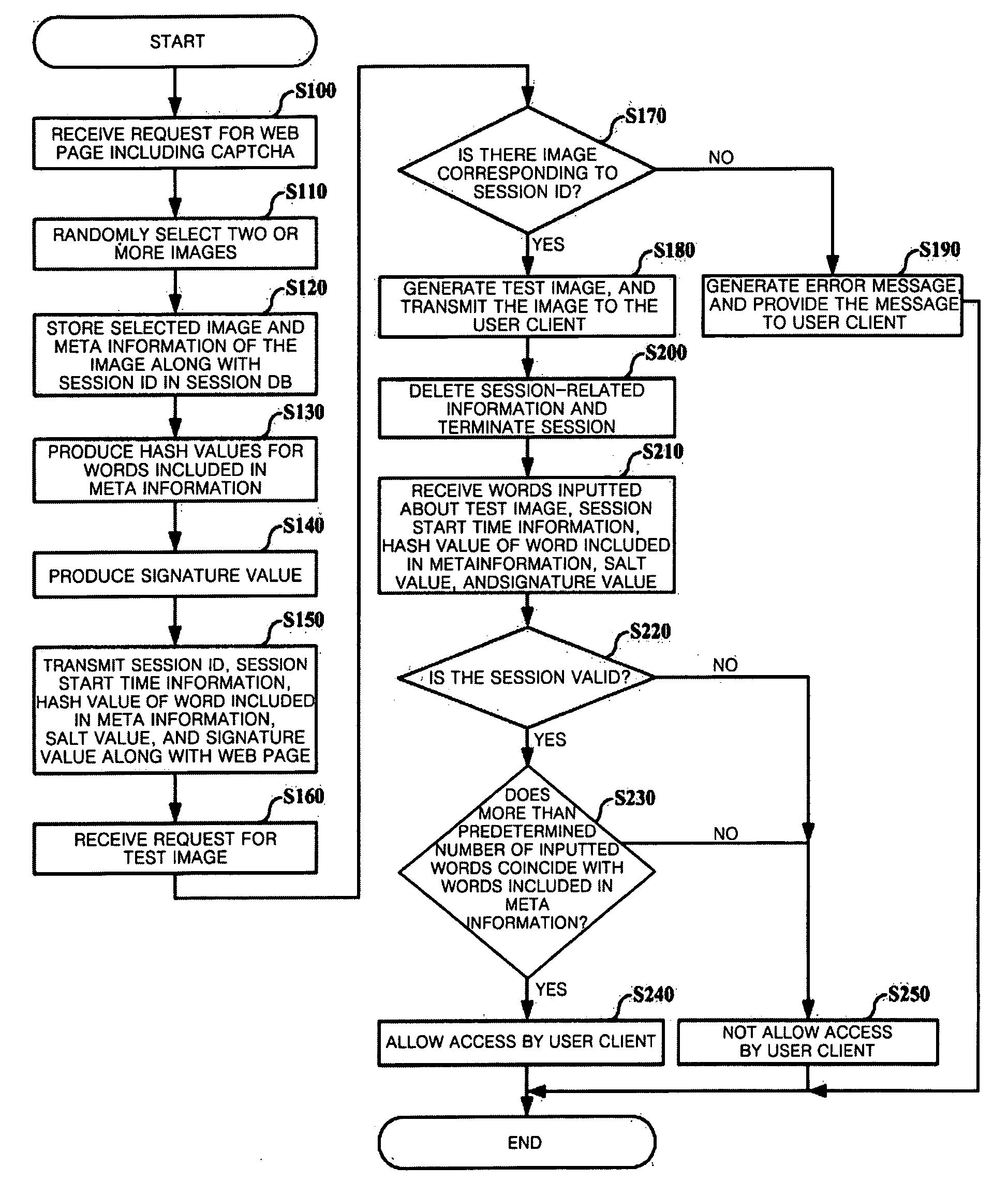
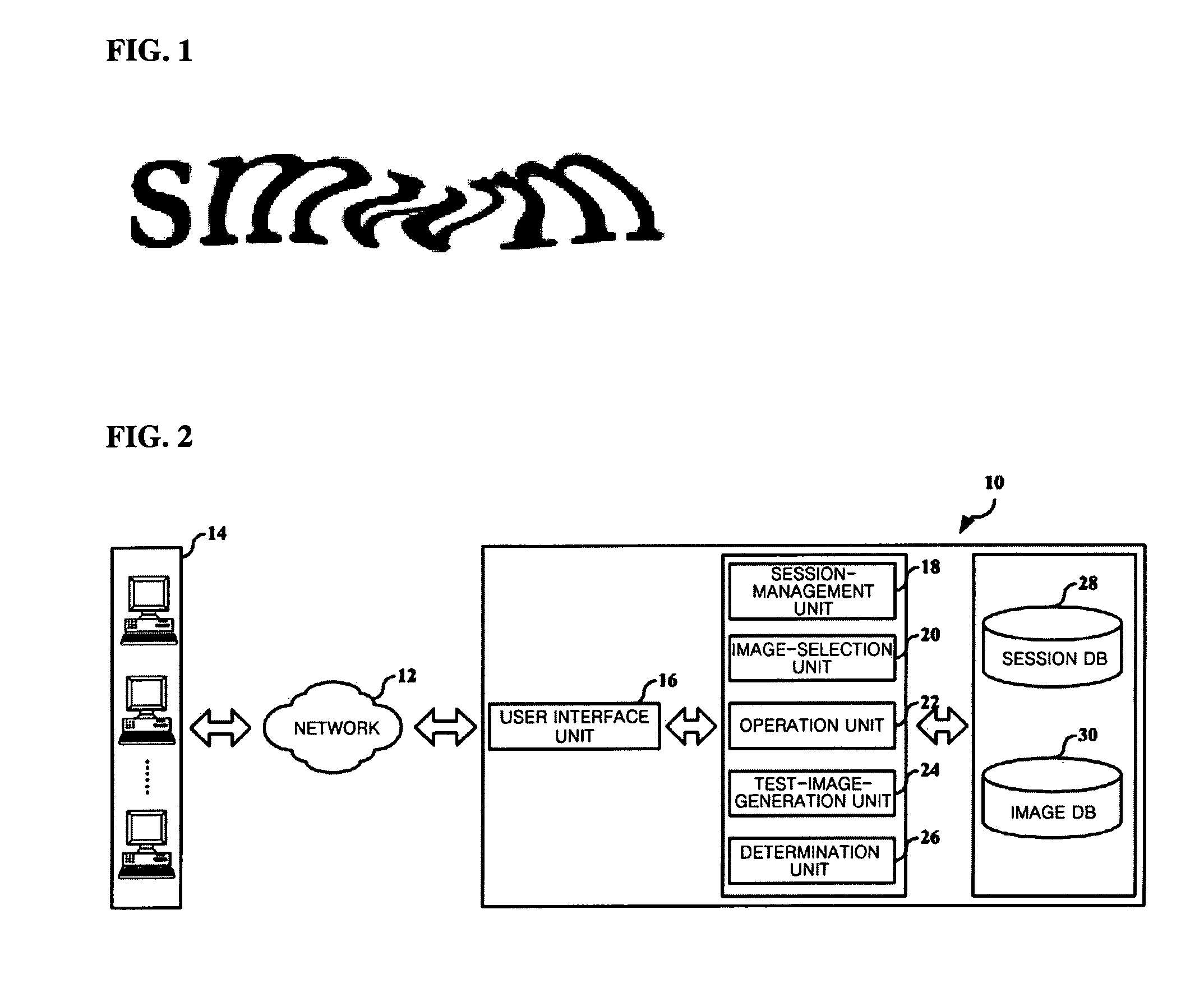
Method of providing completely automated public turing test to tell computer and human apart based on image
Disclosed is a method of providing a completely automated public turing test to tell a computer and a human apart (CAPTCHA) based on image. The method comprises the steps of: storing a plurality of randomly-selected images by session when a request for a web page is received from a user client; providing the web page and a session ID to the user client; generating a test image by mixing the plurality of images when a request for a test image corresponding to the session ID is received from the user client; transmitting the generated test image to the user client; receiving at least one of first identification information inputted by the user about the test image from the user client; and comparing the first identification information with second identification information included in Meta information of the test image.
Owner:INHA UNIV RES & BUSINESS FOUNDATION
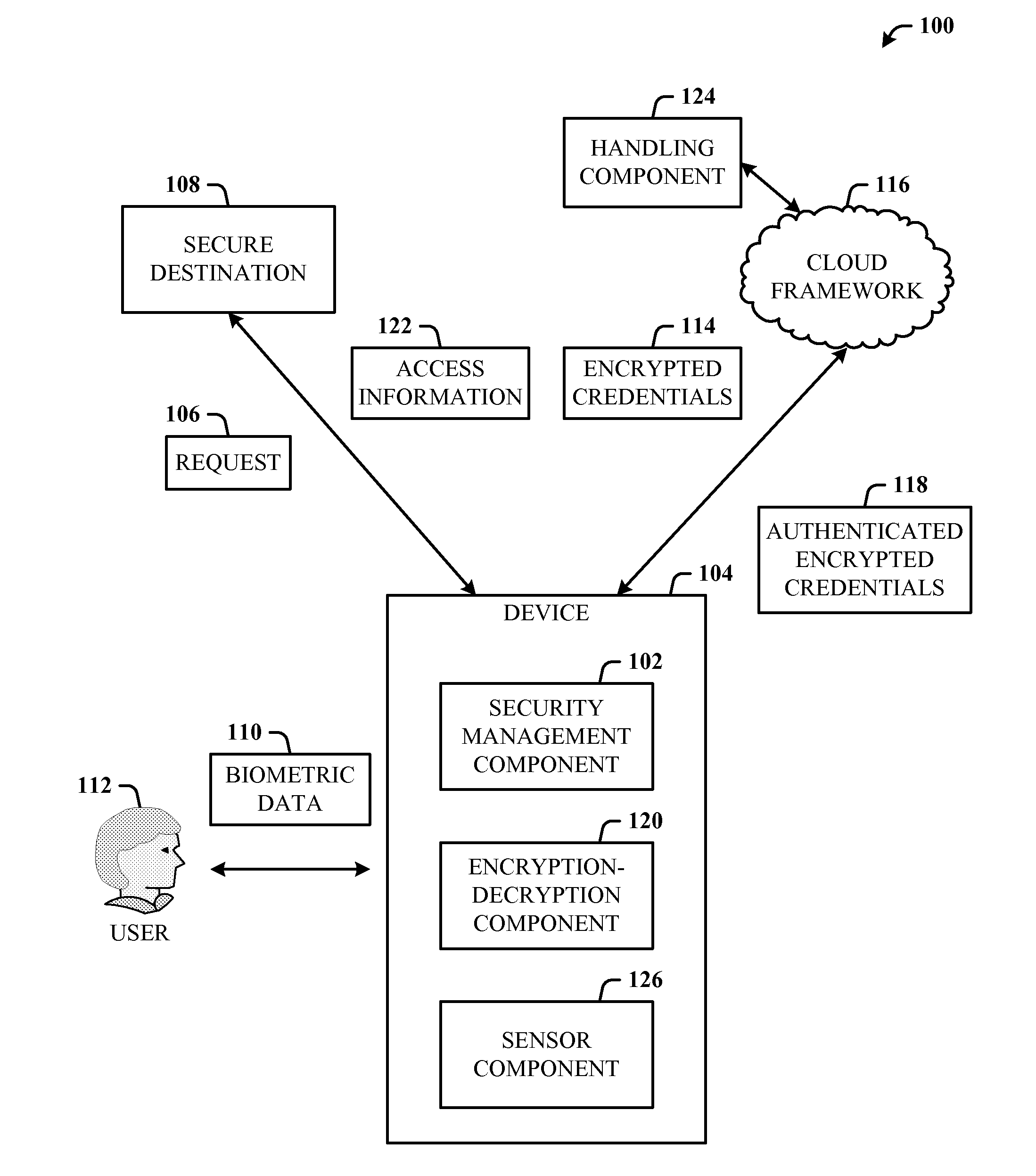
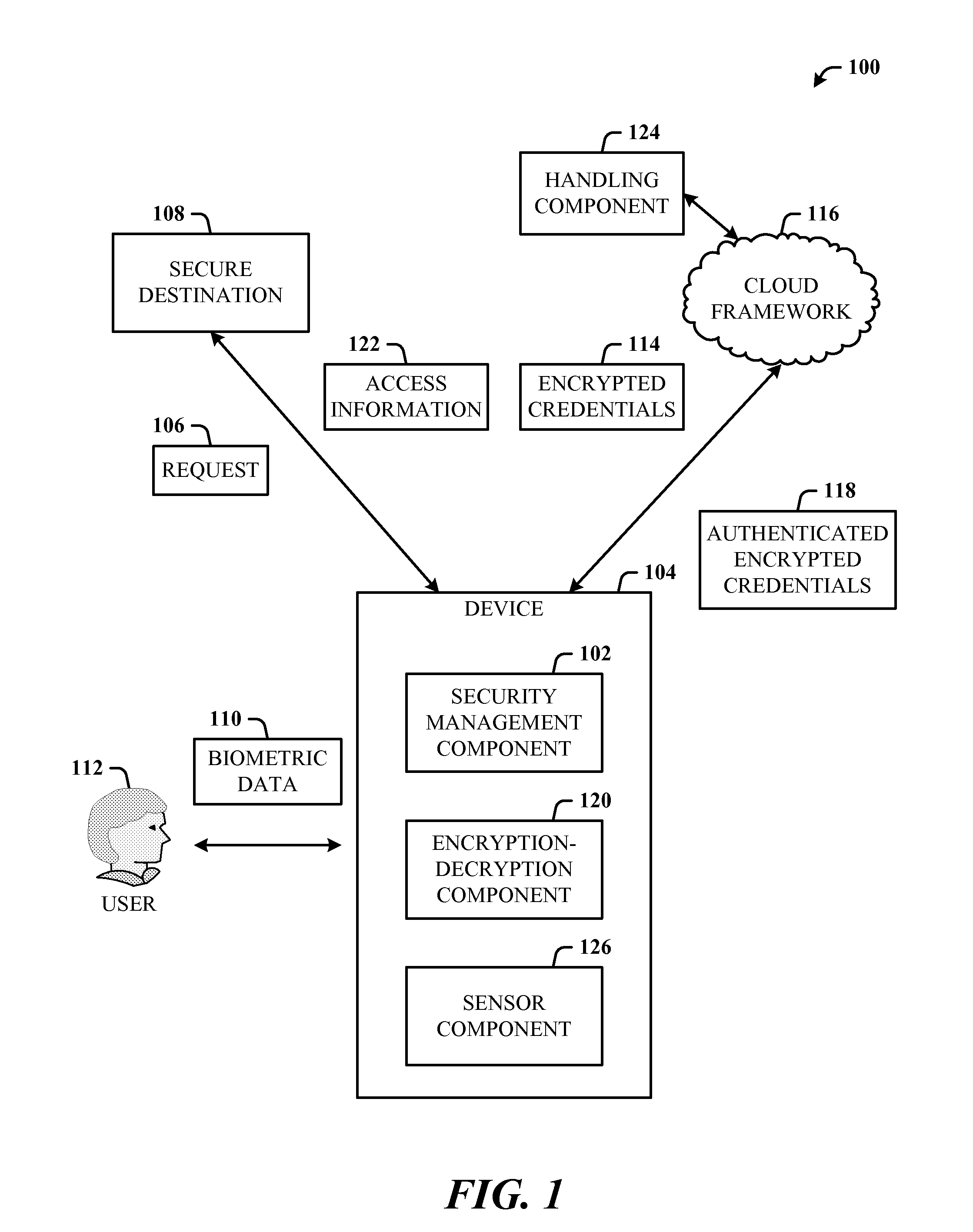
Usable security of online password management with sensor-based authentication
ActiveUS20120297190A1Improve usabilityAuthentication is convenientUser identity/authority verificationDigital data authenticationCryptographic protocolUsability
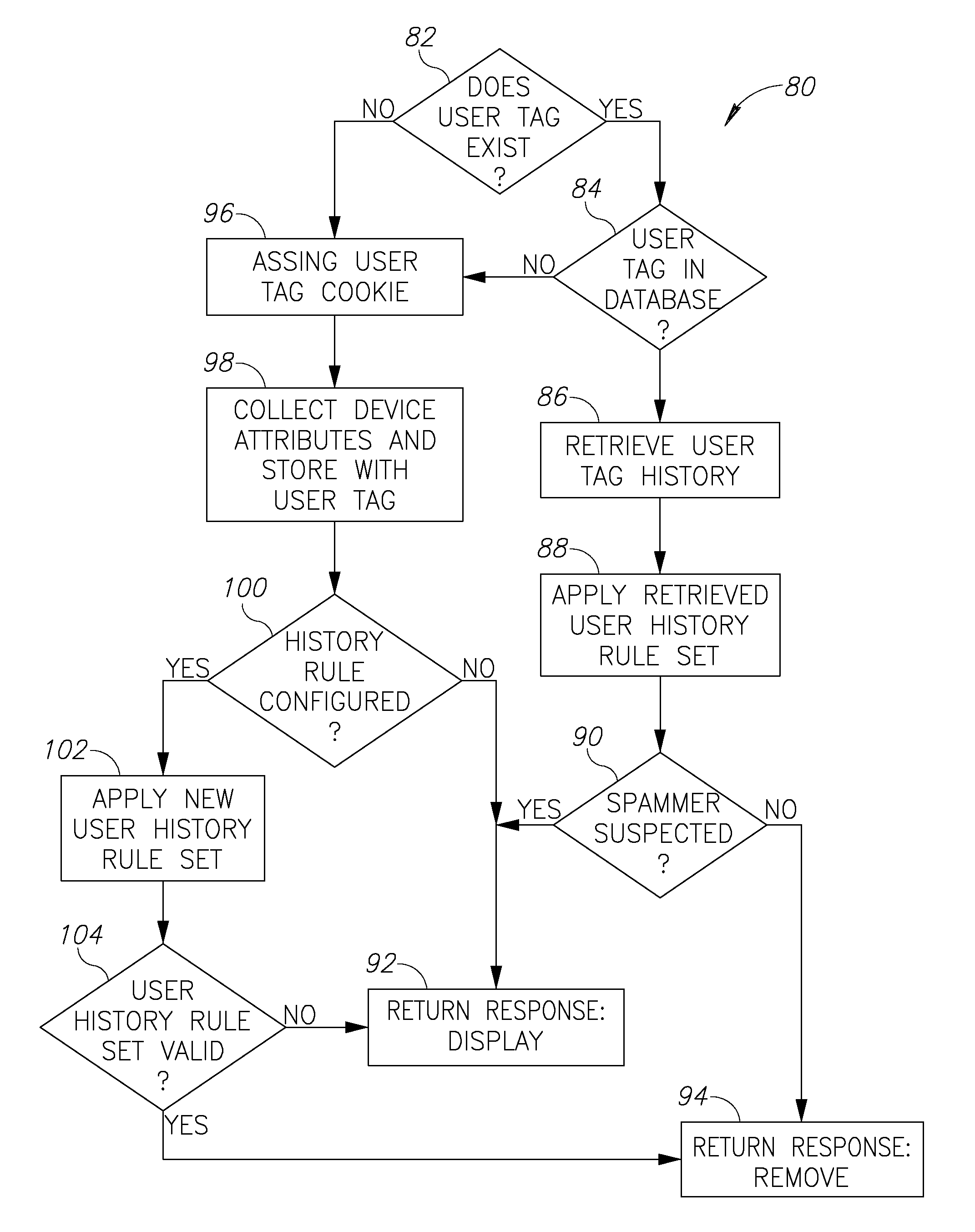
A multi-party security protocol that incorporates biometric-based authentication and withstands attacks against any single party (e.g., mobile phone, cloud, or the user). The protocol involves the function split between mobile and cloud and the mechanisms to chain-hold the secrets. A key generation mechanisms binds secrets to a specific device or URL (uniform resource locator) by adding salt to a master credential. An inline CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) handling mechanism uses the same sensor modality as the authentication process, which not only improves the usability, but also facilitates the authentication process. This architecture further enhances existing overall system security (e.g., handling untrusted or compromised cloud service, phone being lost, impersonation, etc.) and also improves the usability by automatically handling the CAPTCHA.
Owner:MICROSOFT TECH LICENSING LLC
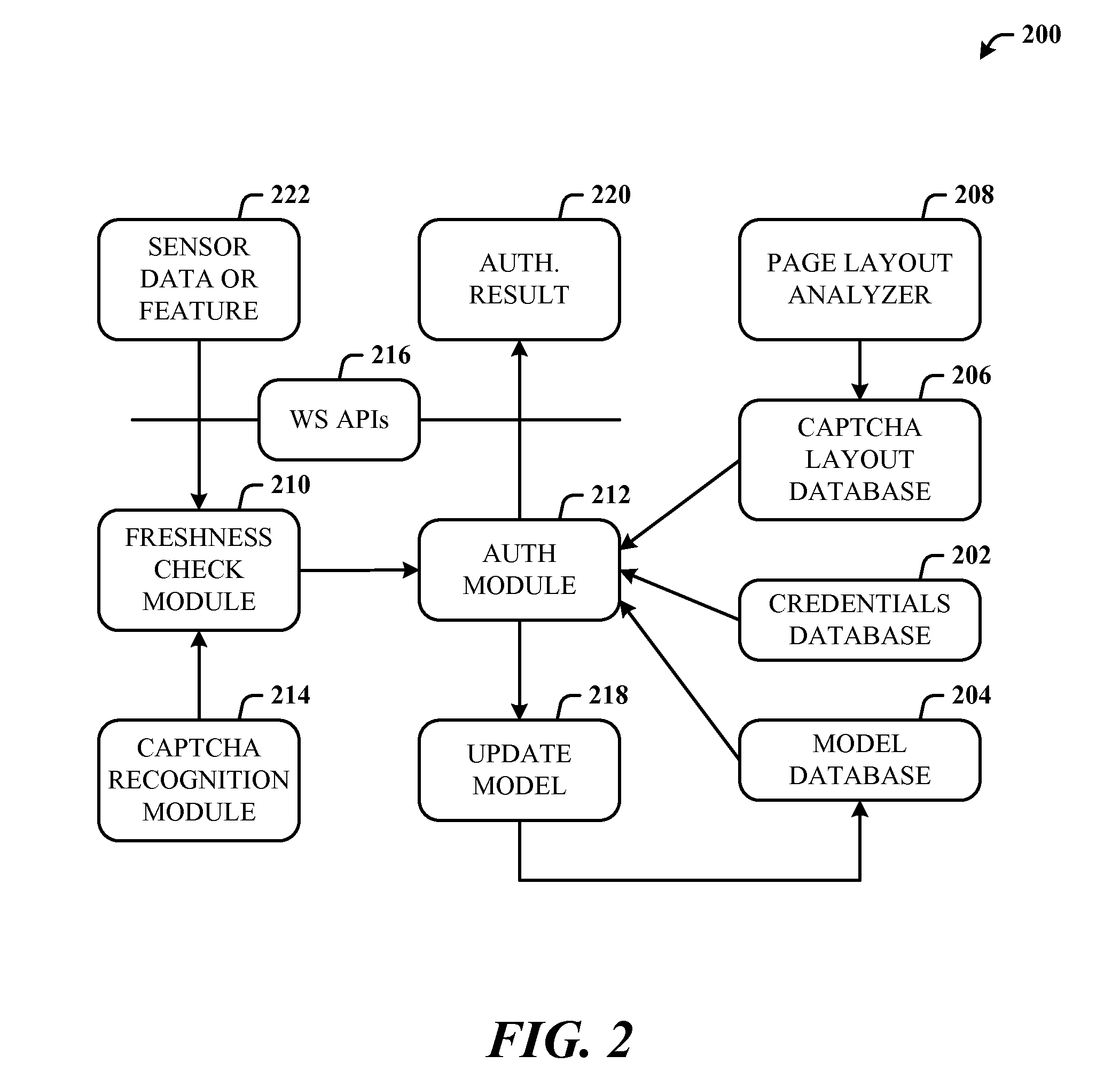
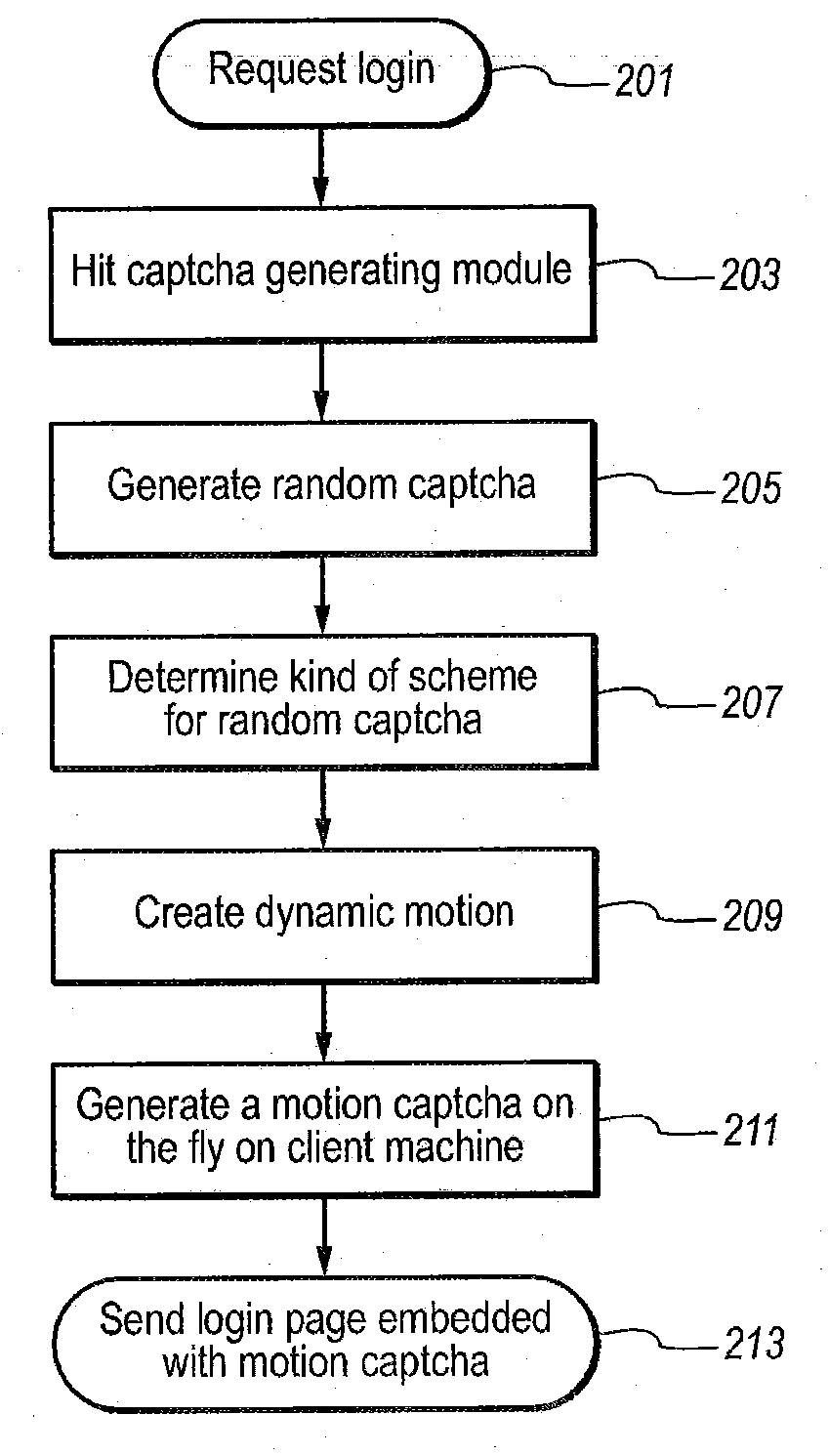
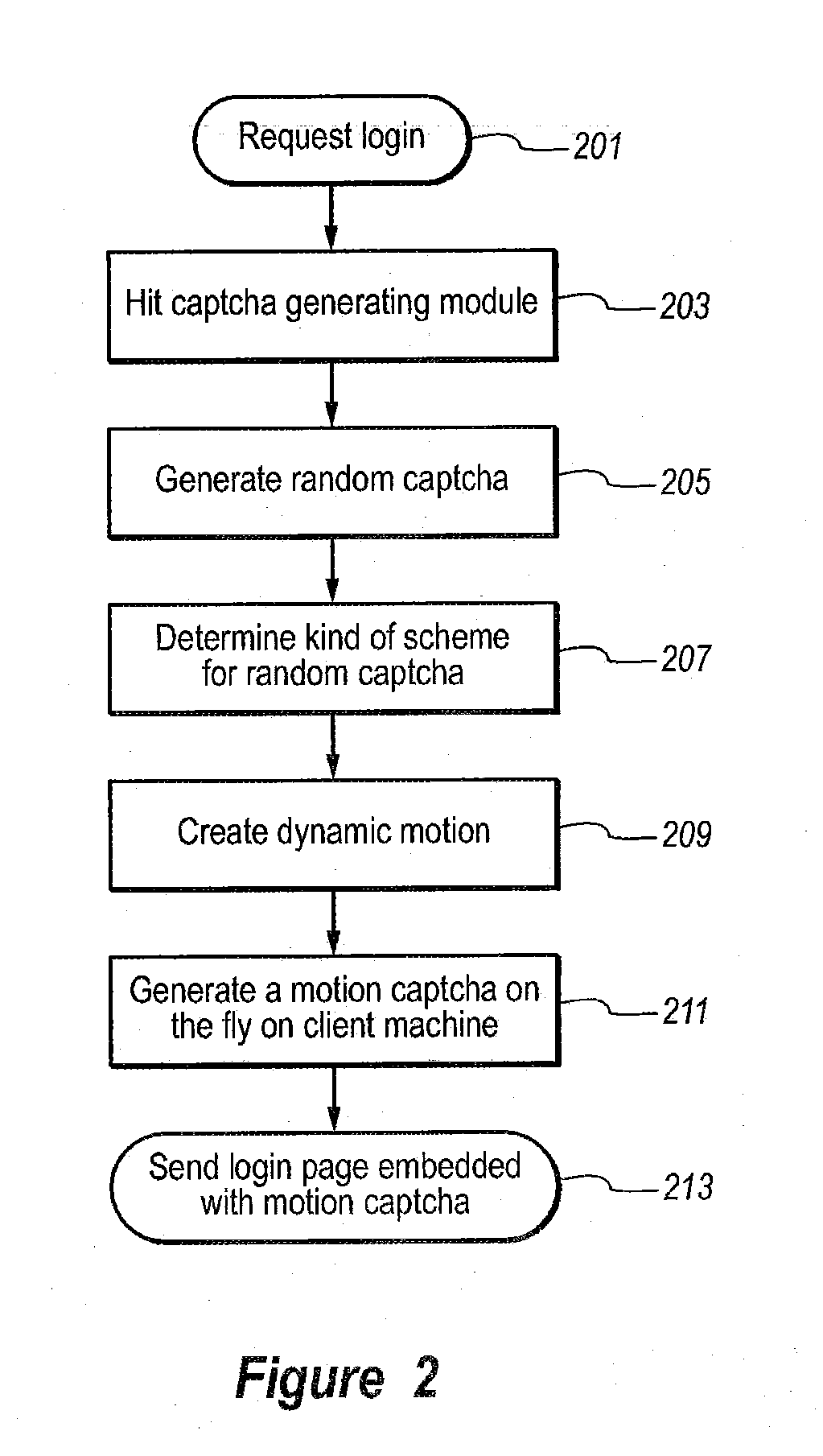
System and method for monitoring human interaction
InactiveUS20090150983A1Well formedDigital data processing detailsUser identity/authority verificationHuman interactionWeb service
A method and system to authenticate human interactive proof (HIP) are described here. In response to a request from a web server, a motion random HIP in the form of motion-captcha is generated. The web server can then display the generated the motion random HIP in a requested web page. The web page is accompanied with a request from the user to provide the response for the generated motion captcha. After evaluation and verification of response received from the particular user, the authentication system determine whether the response to the HIP challenge is from human or from other source like computer software scripted agent.
Owner:INFOSYS TECH LTD (IN)
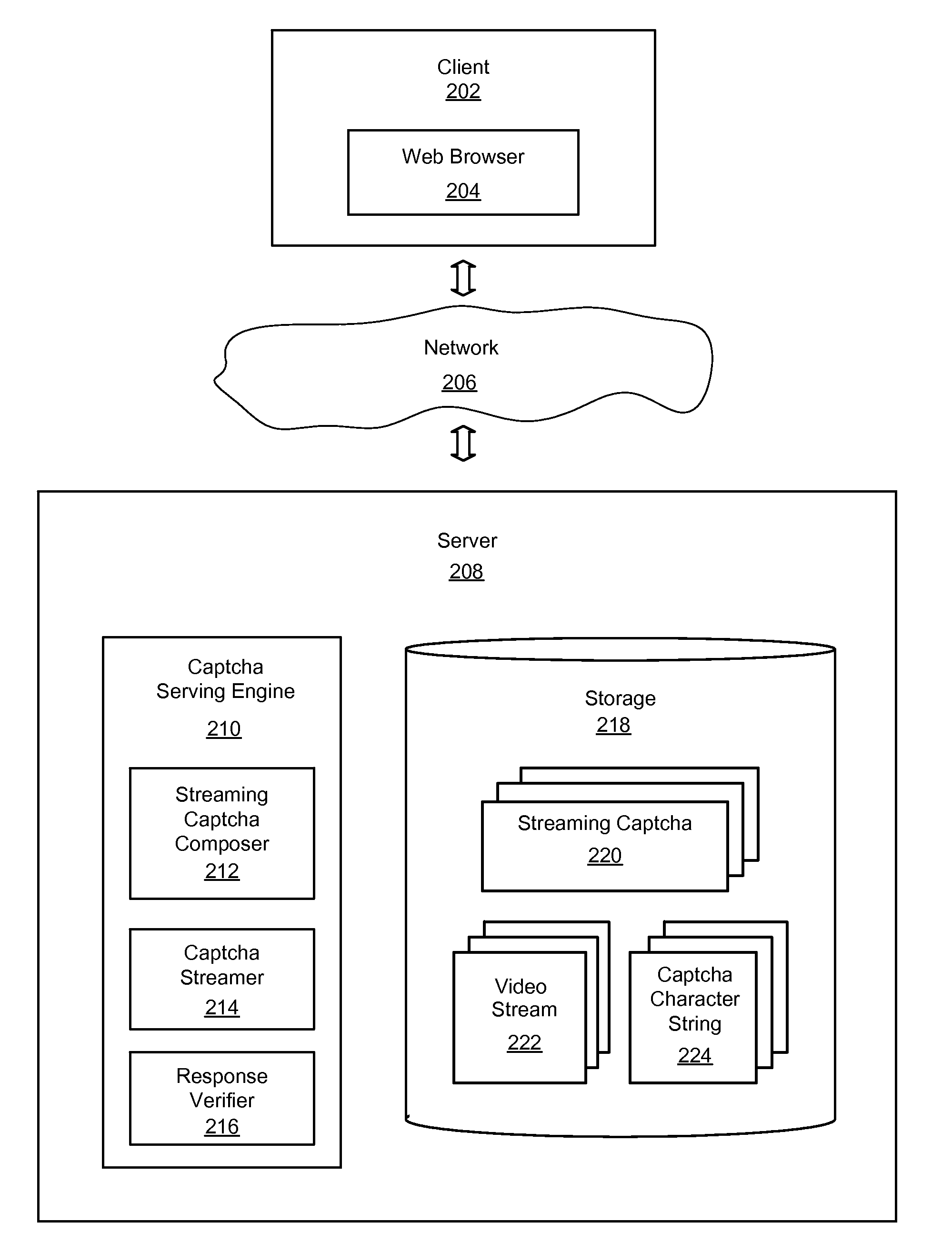
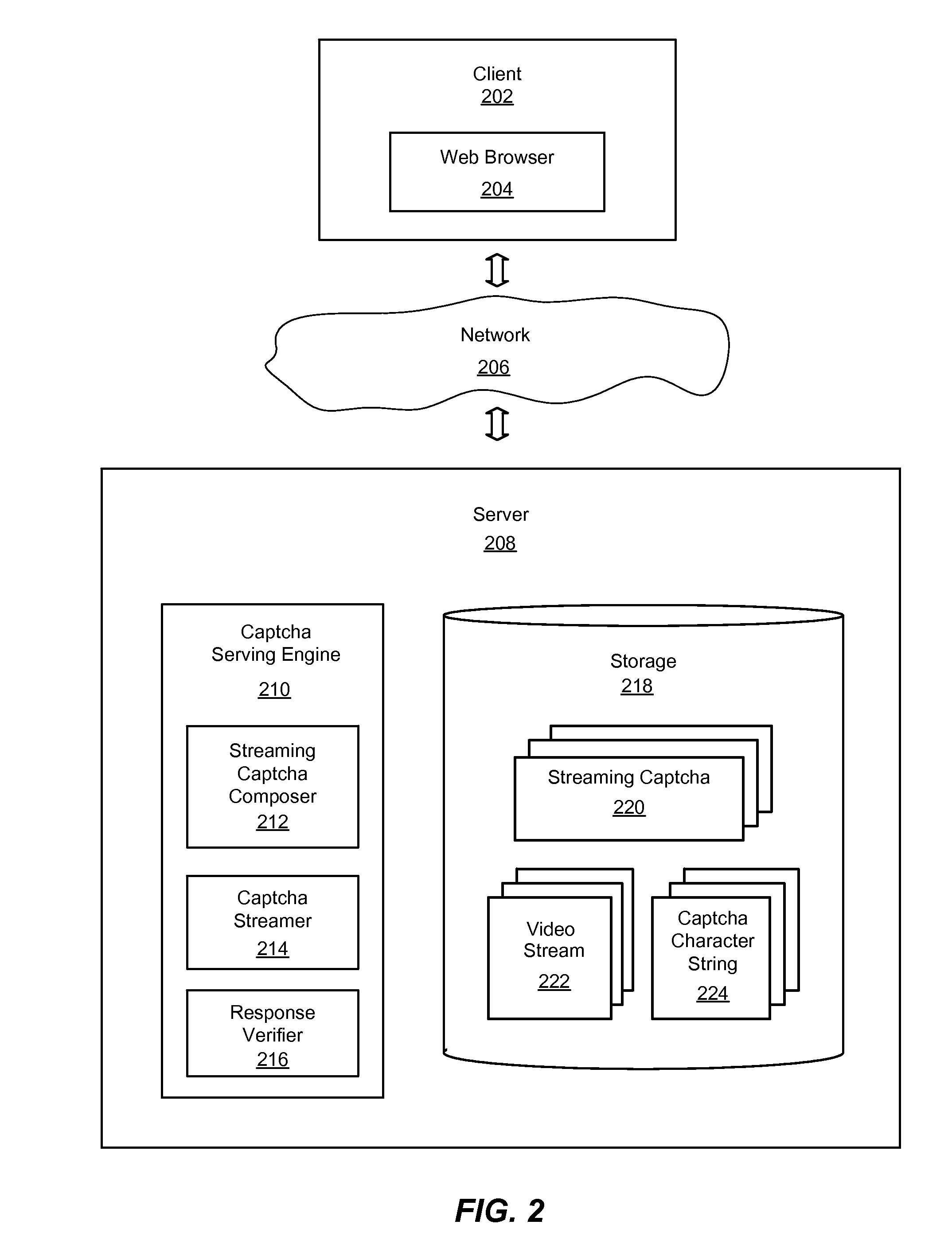
System and method using streaming captcha for online verification
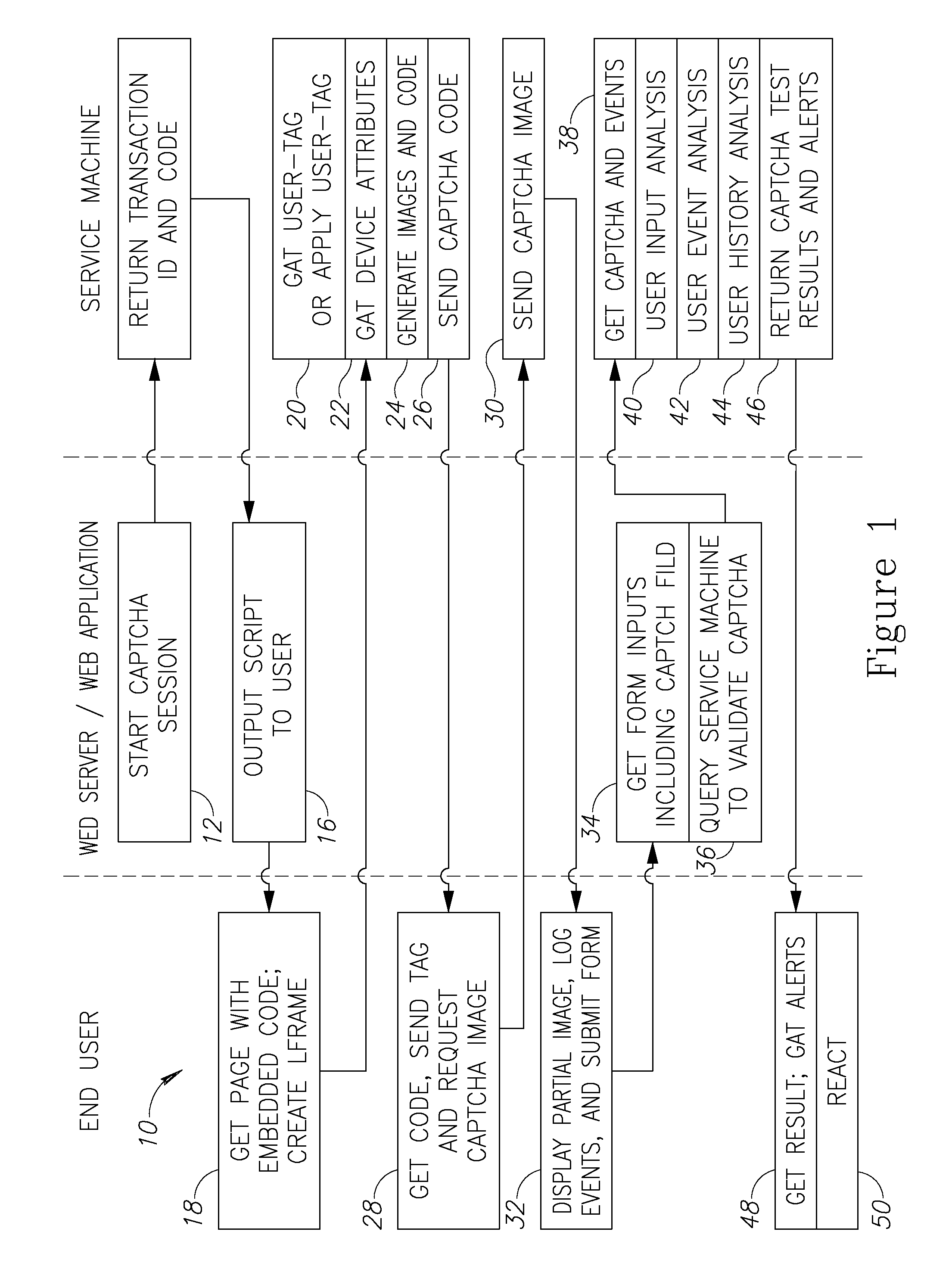
InactiveUS20090328163A1Easy to decipherDifficult to defeatDigital data processing detailsUser identity/authority verificationUser inputClient-side
An improved system and method using a streaming captcha for online verification is provided. A request sent by a client device may be received by a server to serve a streaming captcha to the client device. A server may compose a streaming captcha by superimposing a captcha character string on a video. The streaming captcha may be streamed to the client device. The streaming captcha may be displayed on the client device, and a character string input by a user may be received in response to display of the streaming captcha. The character string received may be sent to the server for verification. The server may verify that the character string received is the same as the captcha character string displayed in the streaming captcha. The server may then send an indication of the verification to the client device.
Owner:OATH INC
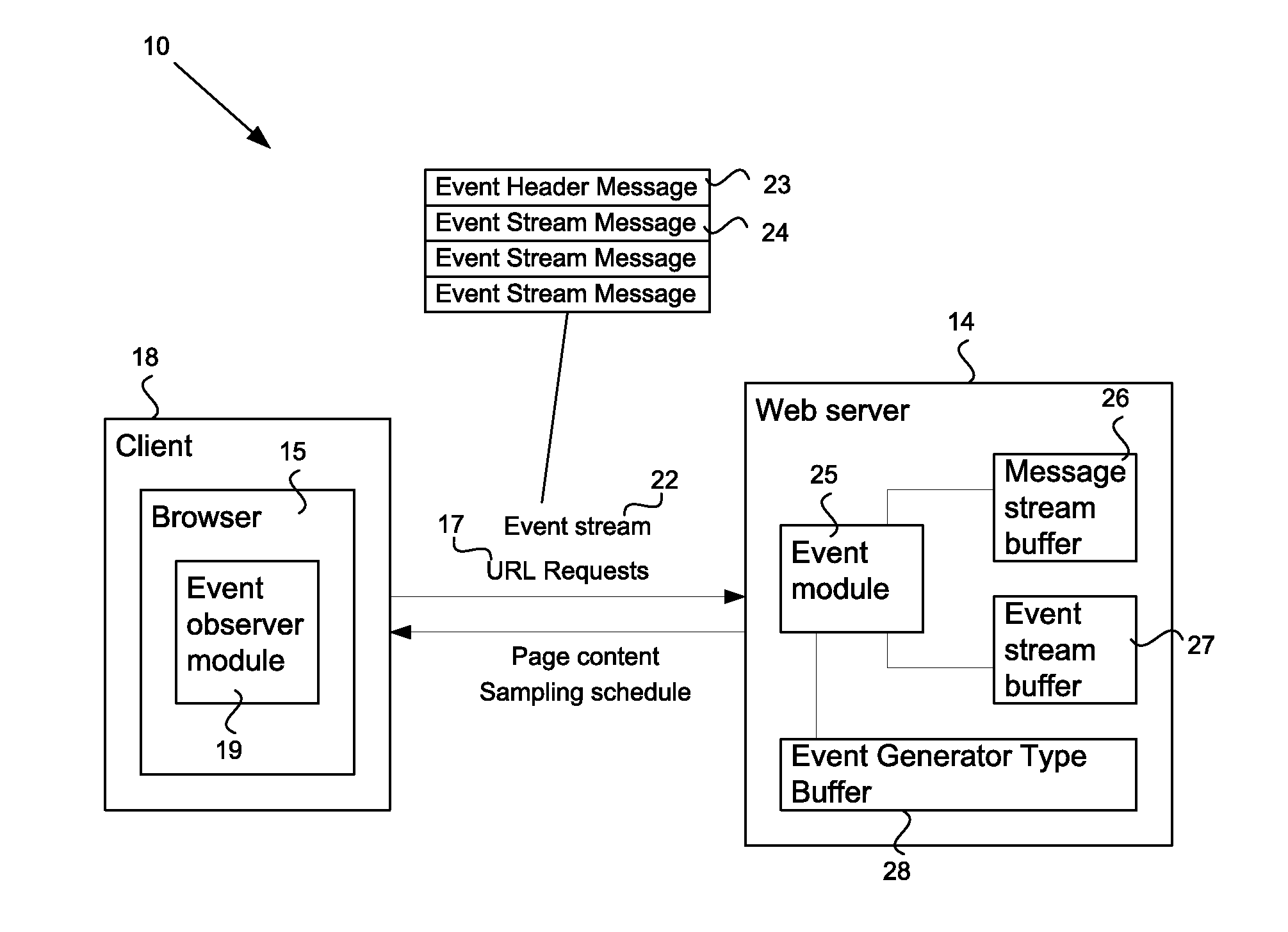
System and method for processing user interface events
ActiveUS20100287229A1Multiple digital computer combinationsDigital data authenticationHuman behaviorHuman interaction
A system and method to detect and prevent non-human interaction between a client and a web server invokes an effect to change the event generation behavior at the client. Subsequent event streams from the client to the server are analyzed to determine whether the event streams contain events corresponding to expected reactions of a human operator at the client to the effect. Indications of non-human behavior may invoke more direct human testing, for example using a dynamic CAPTCHA application, or may cause a termination of the client / URL interaction.
Owner:ORACLE INT CORP
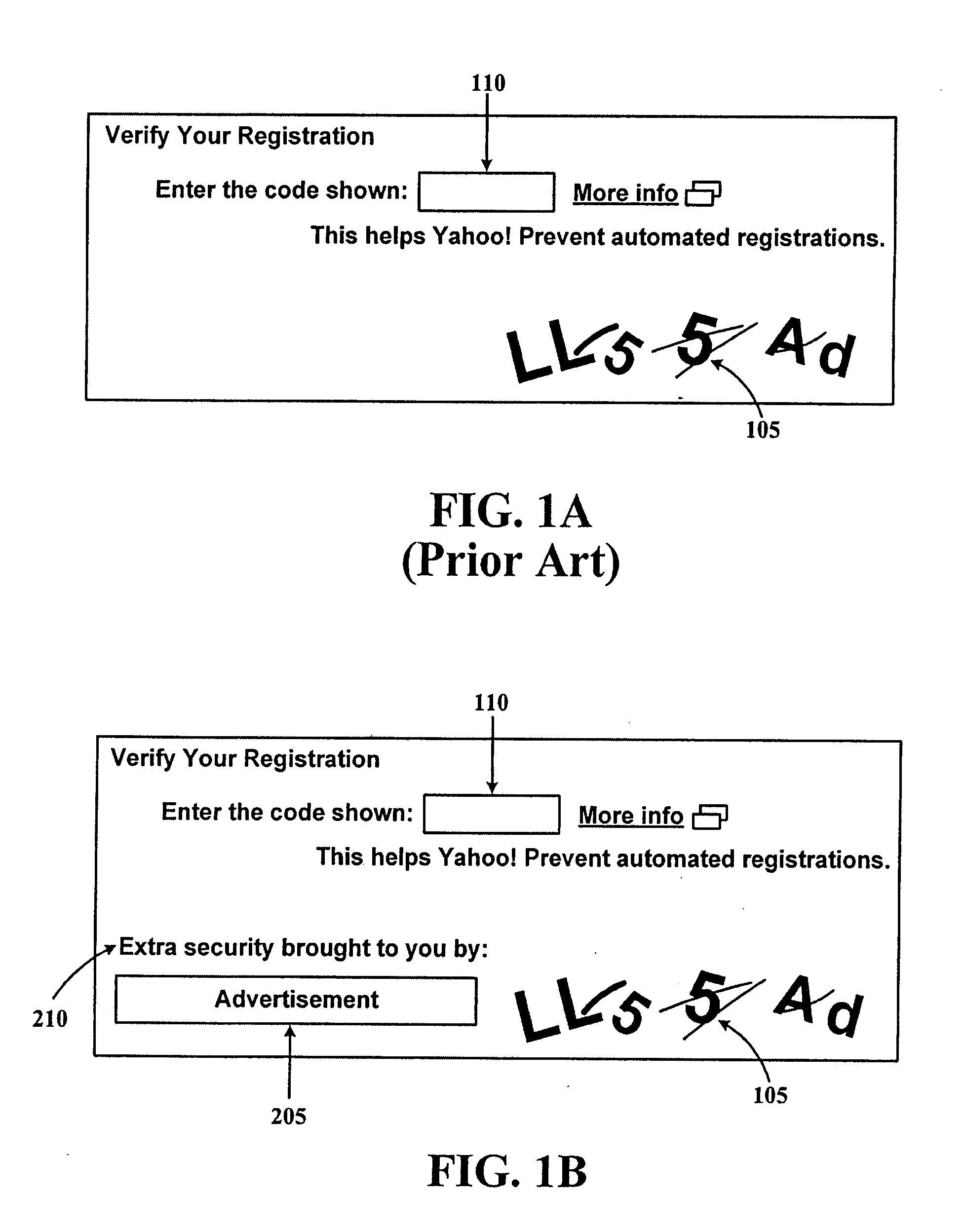
System and method of using captchas as ads
A method of using advertisements in a Completely Automatic Public Turing test to tell Computers and Humans Apart (CAPTCHA) challenge / response transaction. In accordance with one aspect, a server allows access to some resource if the response to the ad / CAPTCHA challenge is an acceptable response.
Owner:OATH INC
Captcha authentication processes and systems using visual object identification
InactiveUS20130145441A1Accurate identificationDigital data processing detailsMultiple digital computer combinationsUser verificationEngineering
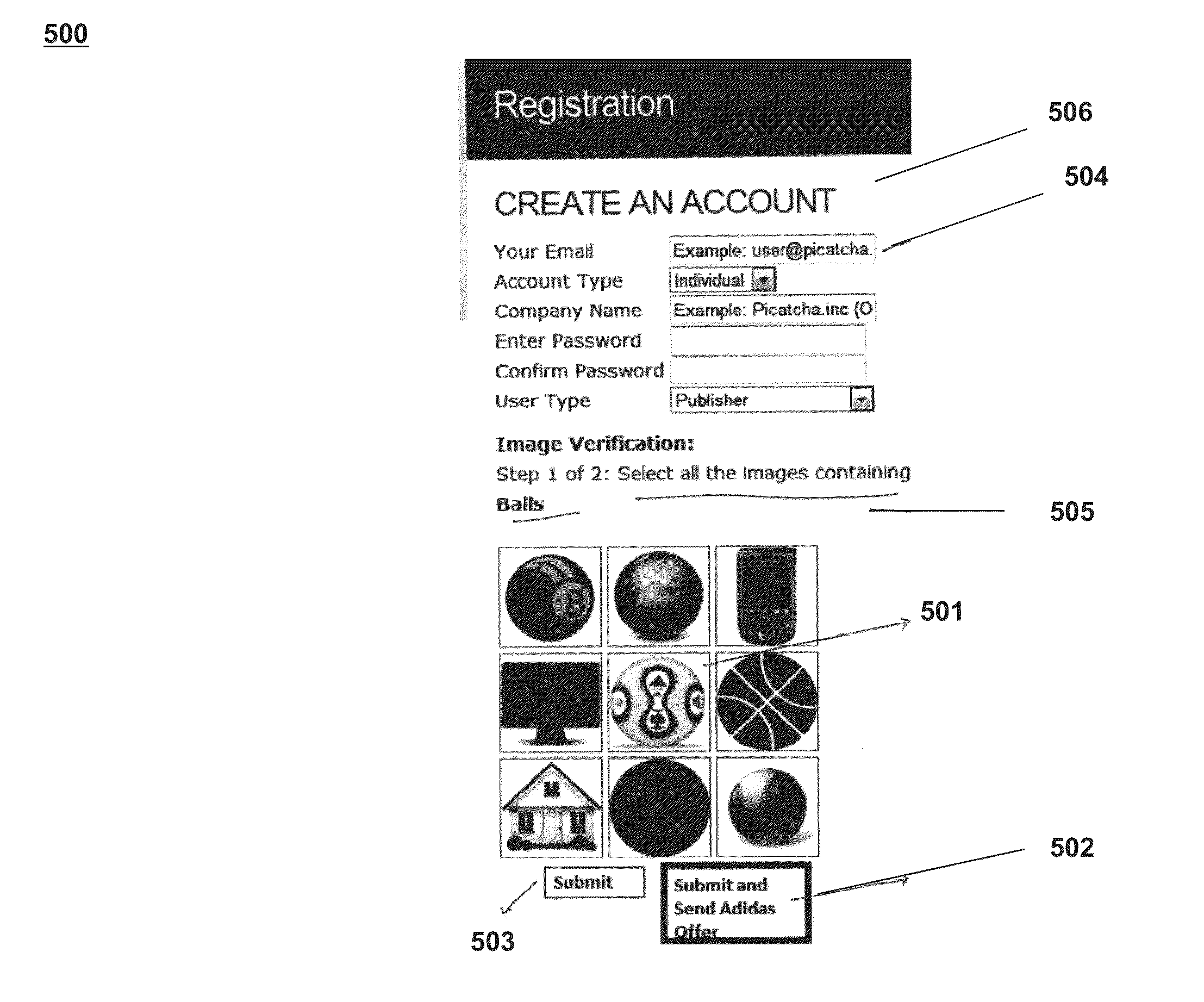
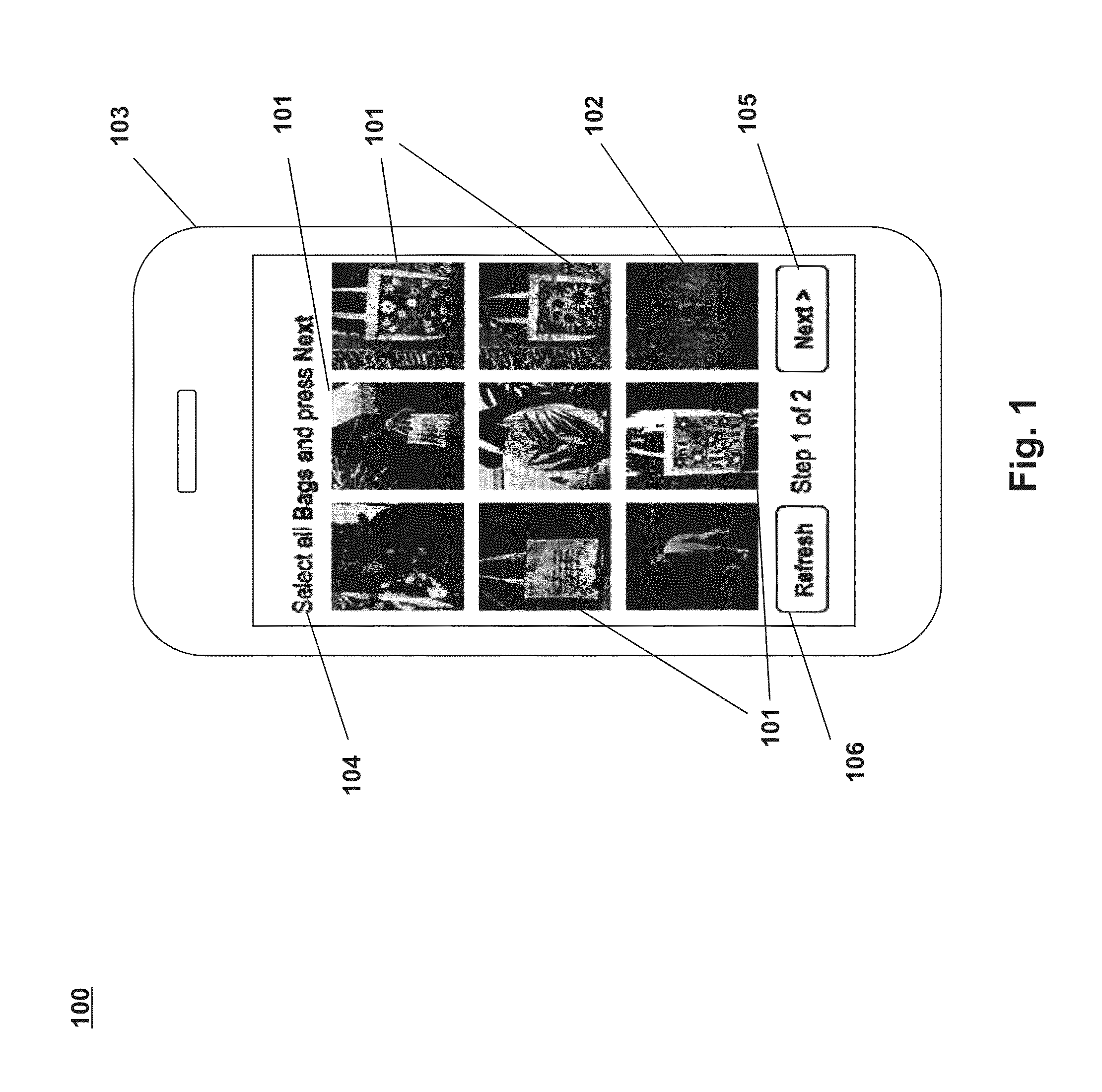
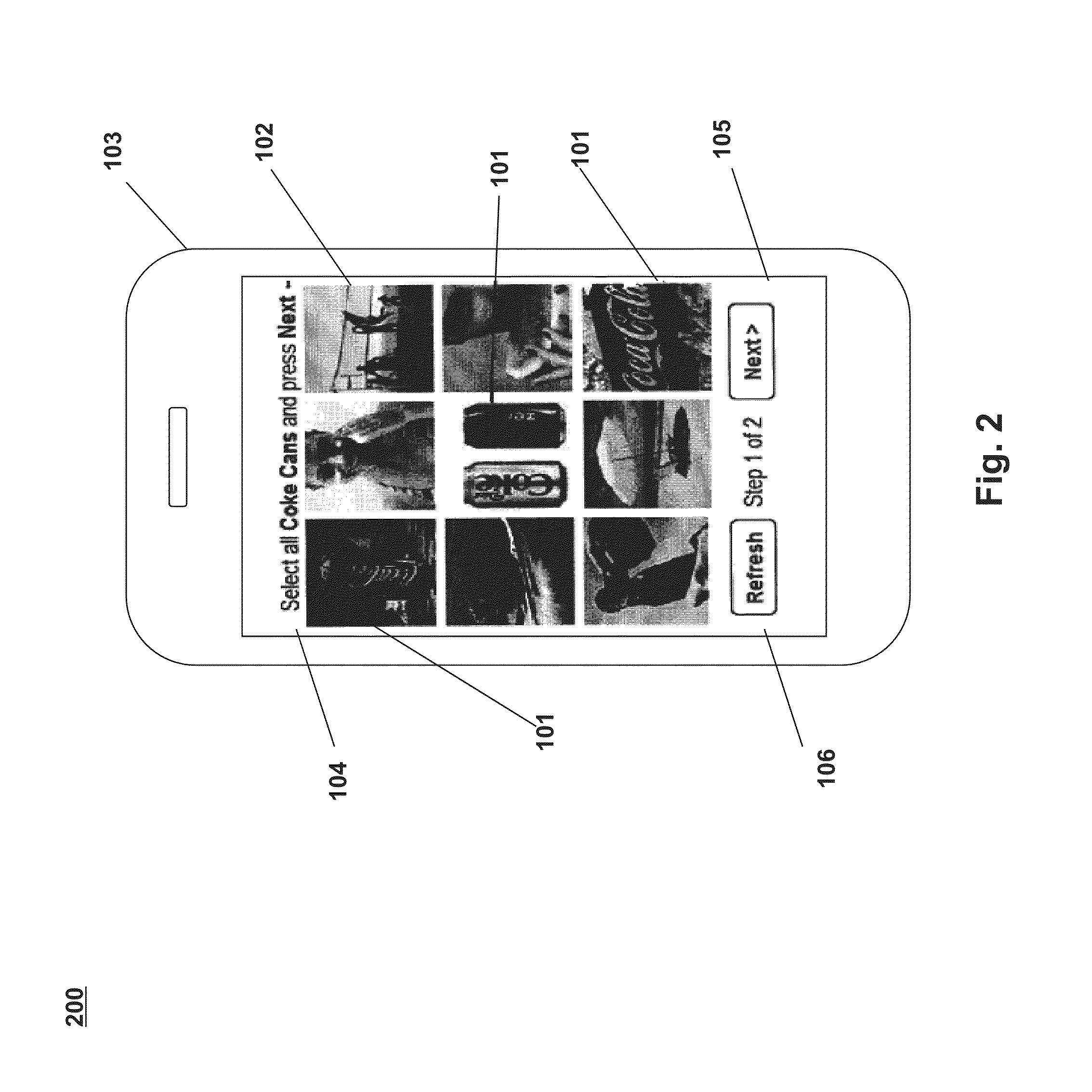
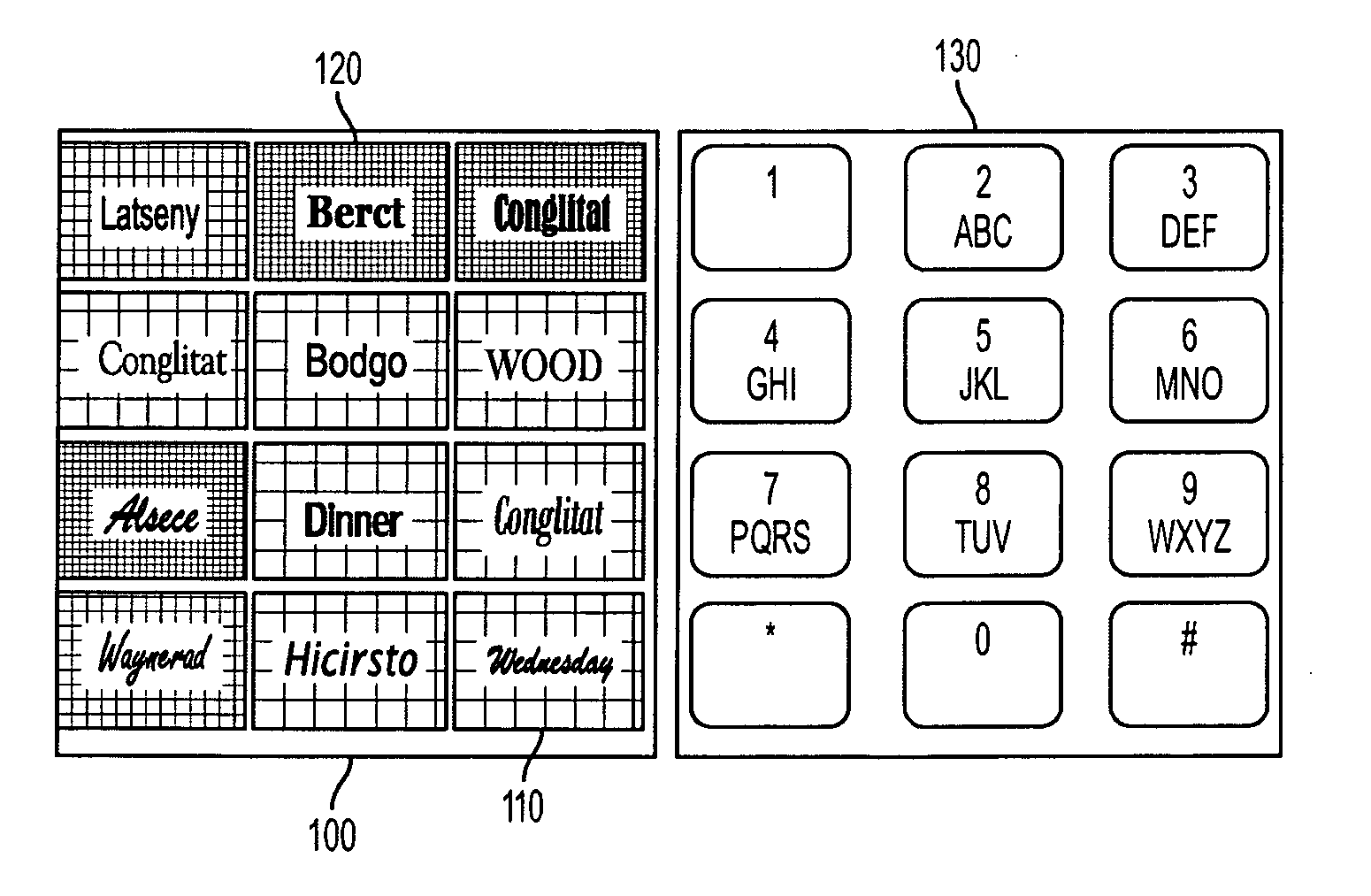
Systems and processes for performing user verification using an imaged-based CAPTCHA are disclosed. The verification process can include receiving a request from a user to access restricted content. In response to the request, a plurality of images may be presented to the user. A challenge question or command that identifies one or more of the displayed plurality of images may also be presented to a user. A selection of one or more of the plurality images may then be received from the user. The user's selection may be reviewed to determine the accuracy of the selection with respect to the challenge question or command. If the user correctly identifies a threshold number of images, then the user may be authenticated and allowed to access the restricted content. However, if the user does not correctly identify the threshold number of images, then the user may be denied access the restricted content.
Owner:PICATCHA
DISTINGUISH VALID USERS FROM BOTS, OCRs AND THIRD PARTY SOLVERS WHEN PRESENTING CAPTCHA
ActiveUS20140250538A1Digital data processing detailsAnalogue secracy/subscription systemsThird partyTuring test
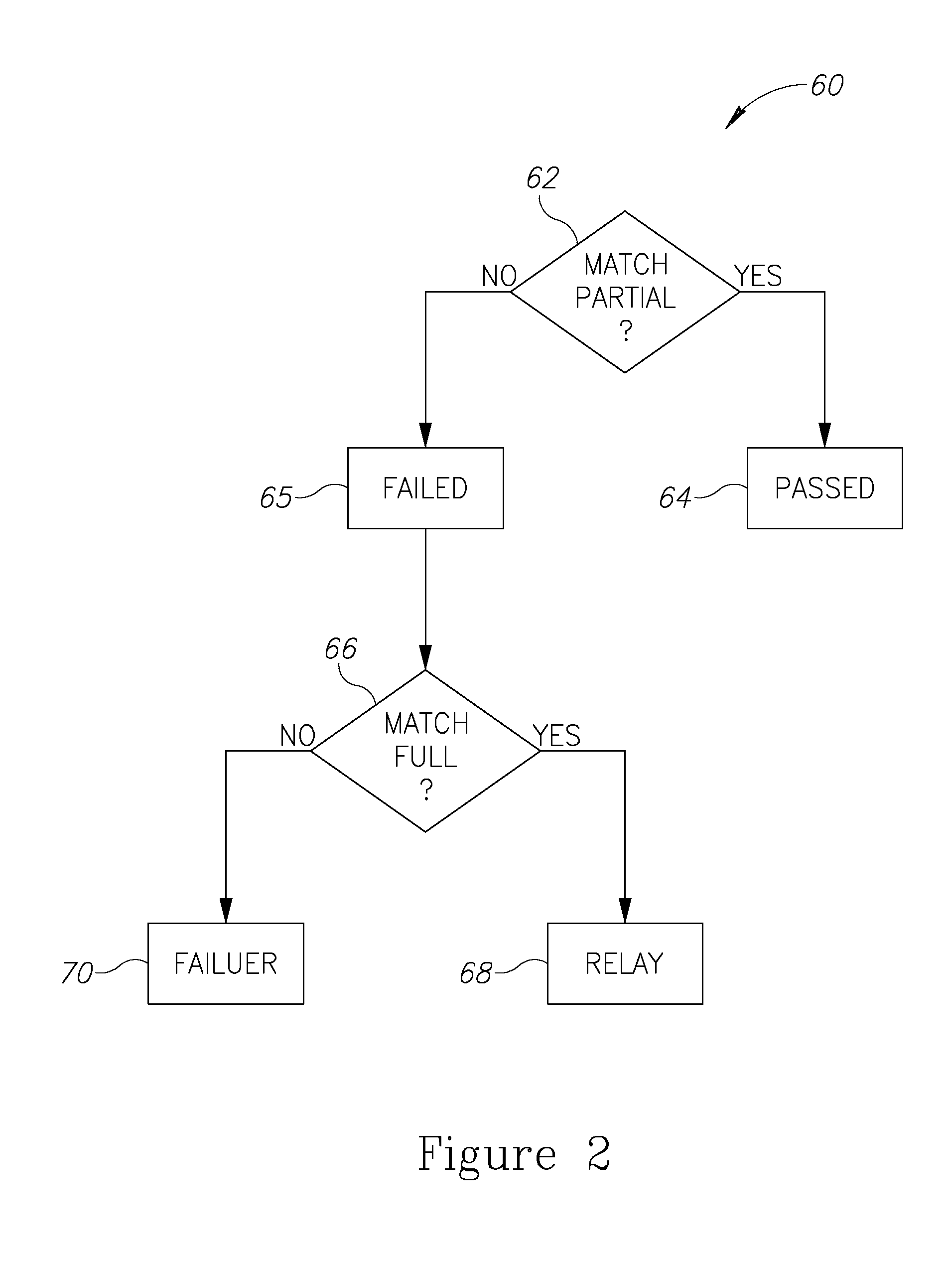
Embodiments of the present invention relate to a method of providing an automated public Turing test to a client display system. The method includes providing an image having a plurality of random characters, as well as providing a browser code to the client, whereby the browser code is adapted to restrict display of the image to only a predetermined portion of the image. The method further includes detecting a client response to receiving the predetermined portion of said image.
Owner:FIREBLADE HLDG LLC
Captcha image authentication method and system
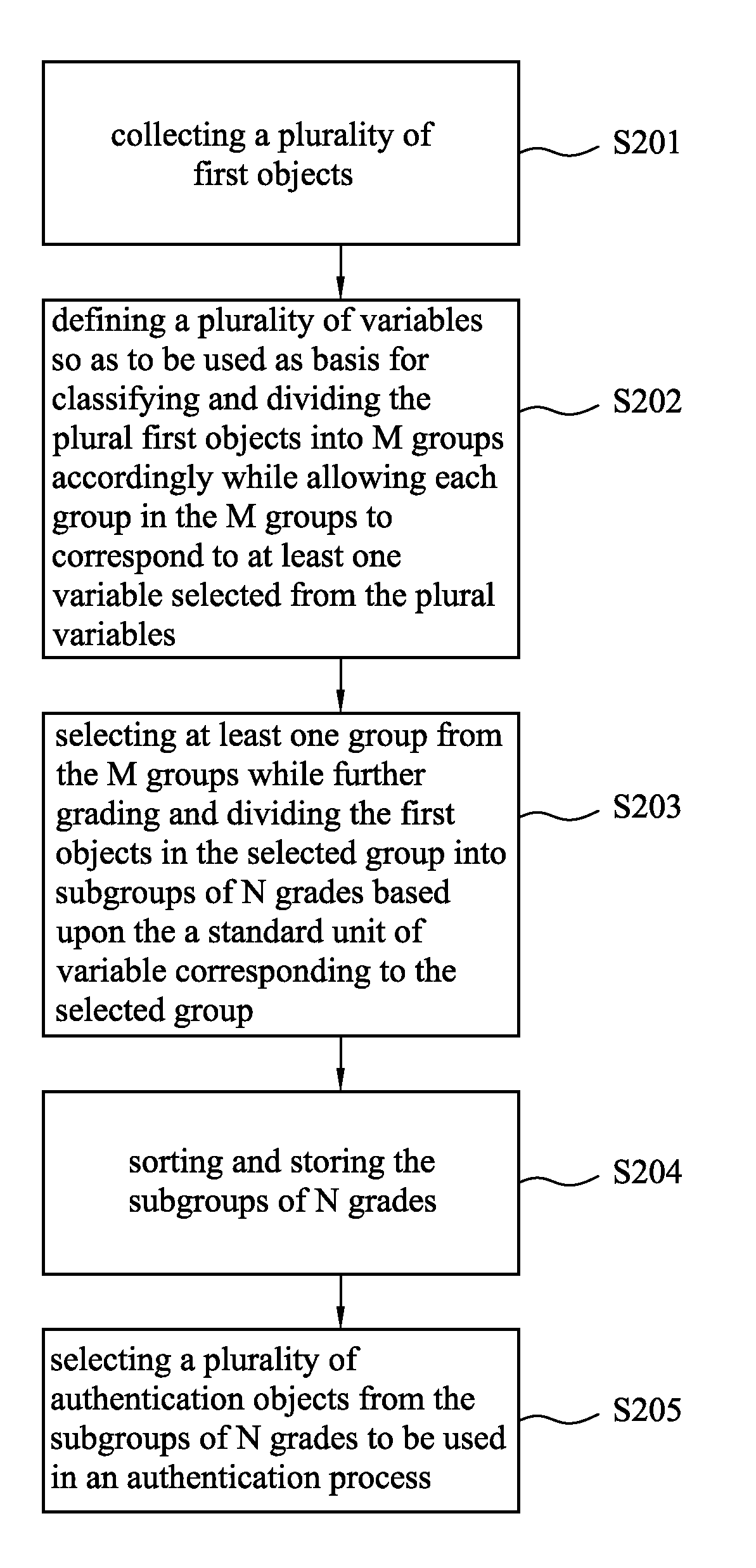
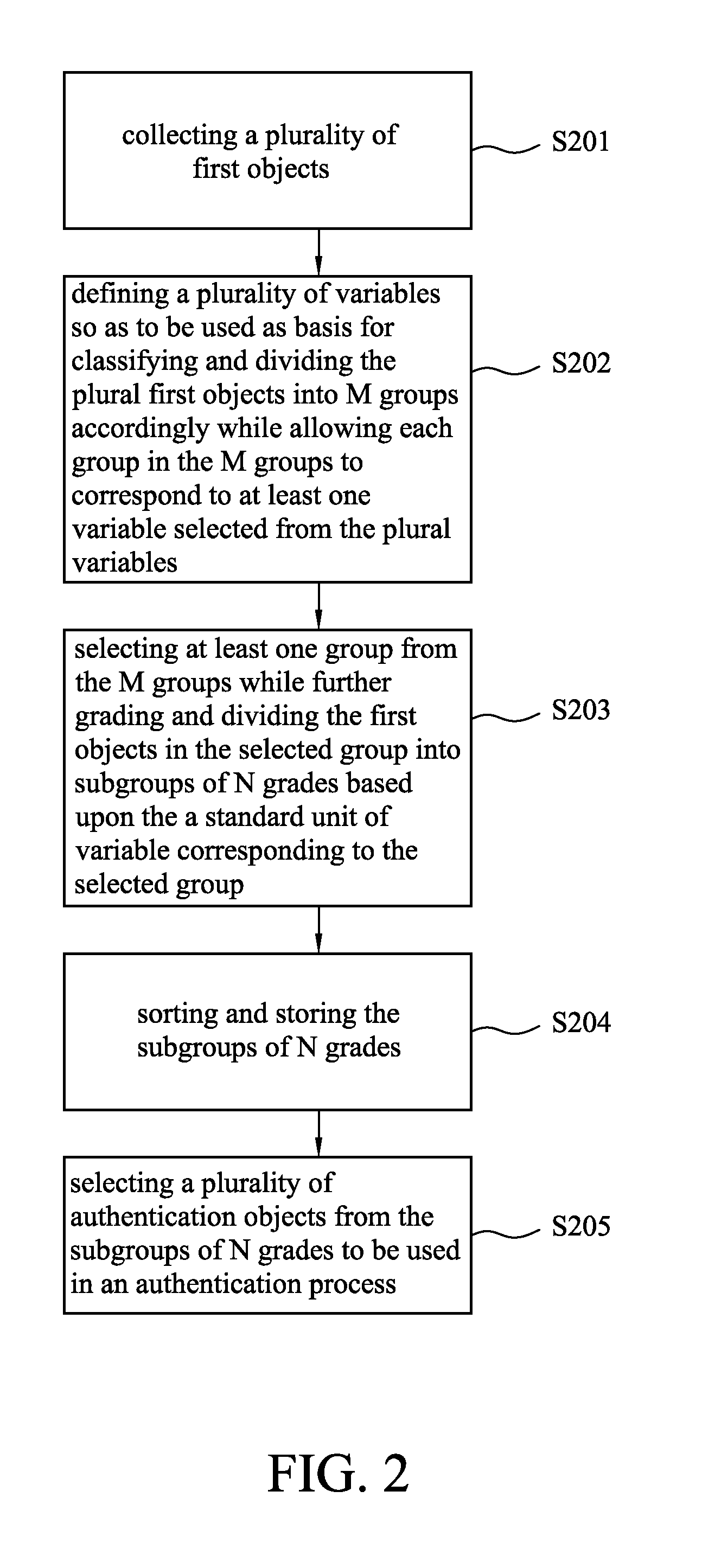
ActiveUS20130019278A1Digital data processing detailsUnauthorized memory use protectionTuring testCAPTCHA
The present disclosure relates to a Completely Automated Public Turing Test to tell Computers and Humans Apart (CAPTCHA) image authentication method and system. The CAPTCHA image authentication method comprises the steps of: collecting a plurality of first objects; defining a plurality of variables so as to be used as basis for classifying and dividing the plural first objects into M groups accordingly while allowing each group in the M groups to correspond to at least one variable selected from the plural variables; selecting at least one group from the M groups while further grading and dividing the first objects in the selected group into subgroups of N grades based upon a standard unit of the variable corresponding to the selected group; sorting and storing the subgroups of N grades; and selecting a plurality of authentication objects from the subgroups of N grades to be used in an authentication process.
Owner:IND TECH RES INST
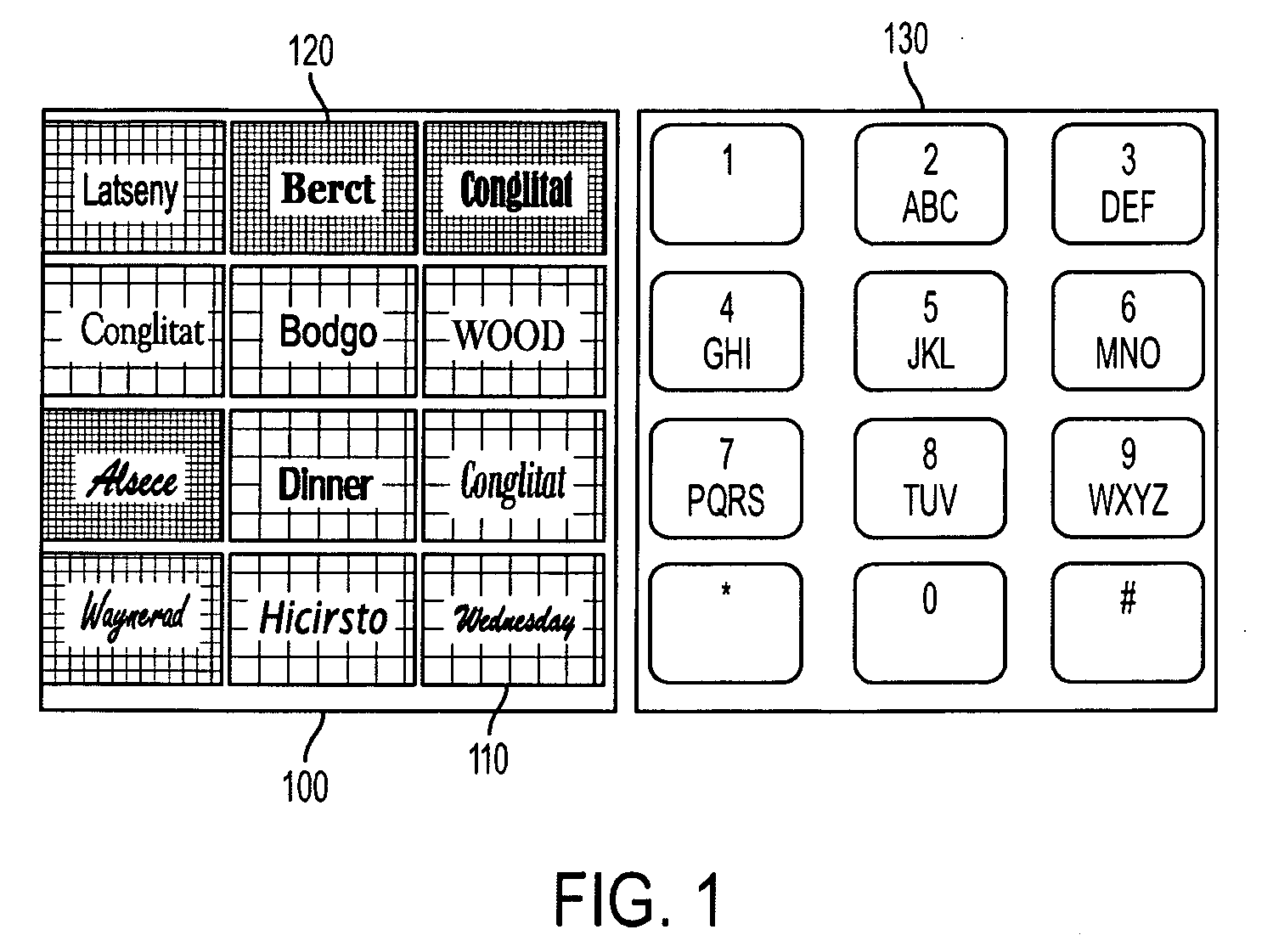
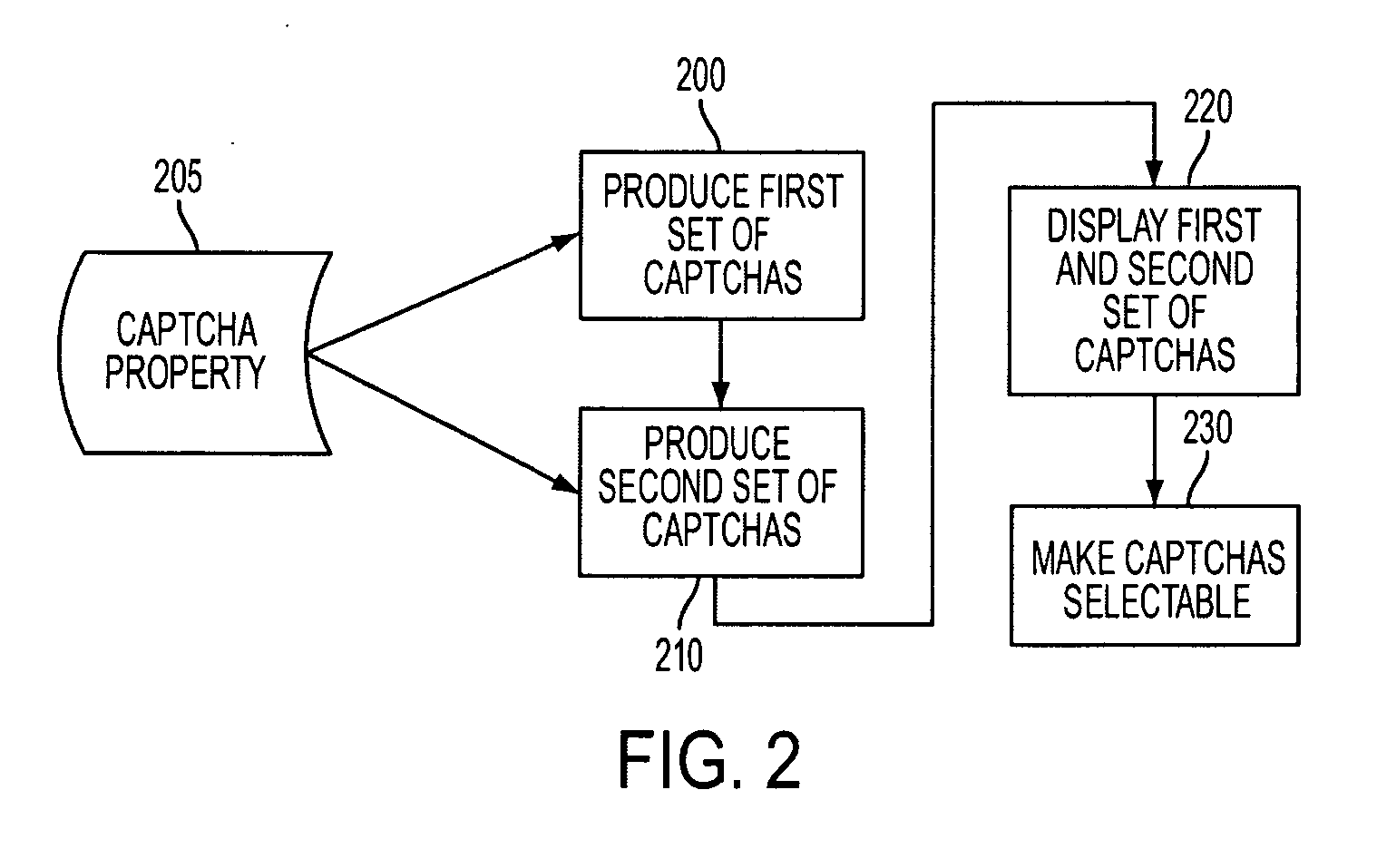
Selectable captchas
ActiveUS20090235327A1Easily pass CAPTCHA challengeDigital data processing detailsUser identity/authority verificationCAPTCHAComputer science
A system for displaying a set of selectable CAPTCHAs produces a first set of CAPTCHAs whose images are based at least partially on an alphanumeric sequence, where a respective CAPTCHA in the first set is associated with a CAPTCHA property. The system also produces a second set of CAPTCHAs whose images are based at least partially on an alphanumeric sequence, where a respective CAPTCHA in the second set is not associated with a CAPTCHA property. Next, the system displays the first and second sets of CAPTCHAs. Finally, the system makes respective CAPTCHAs in the first and second sets of CAPTCHAs selectable, thereby allowing a user to pass a CAPTCHA challenge by distinguishing the first set of CAPTCHAs from the second set of CAPTCHAs without typing the words associated with the images.
Owner:XEROX CORP
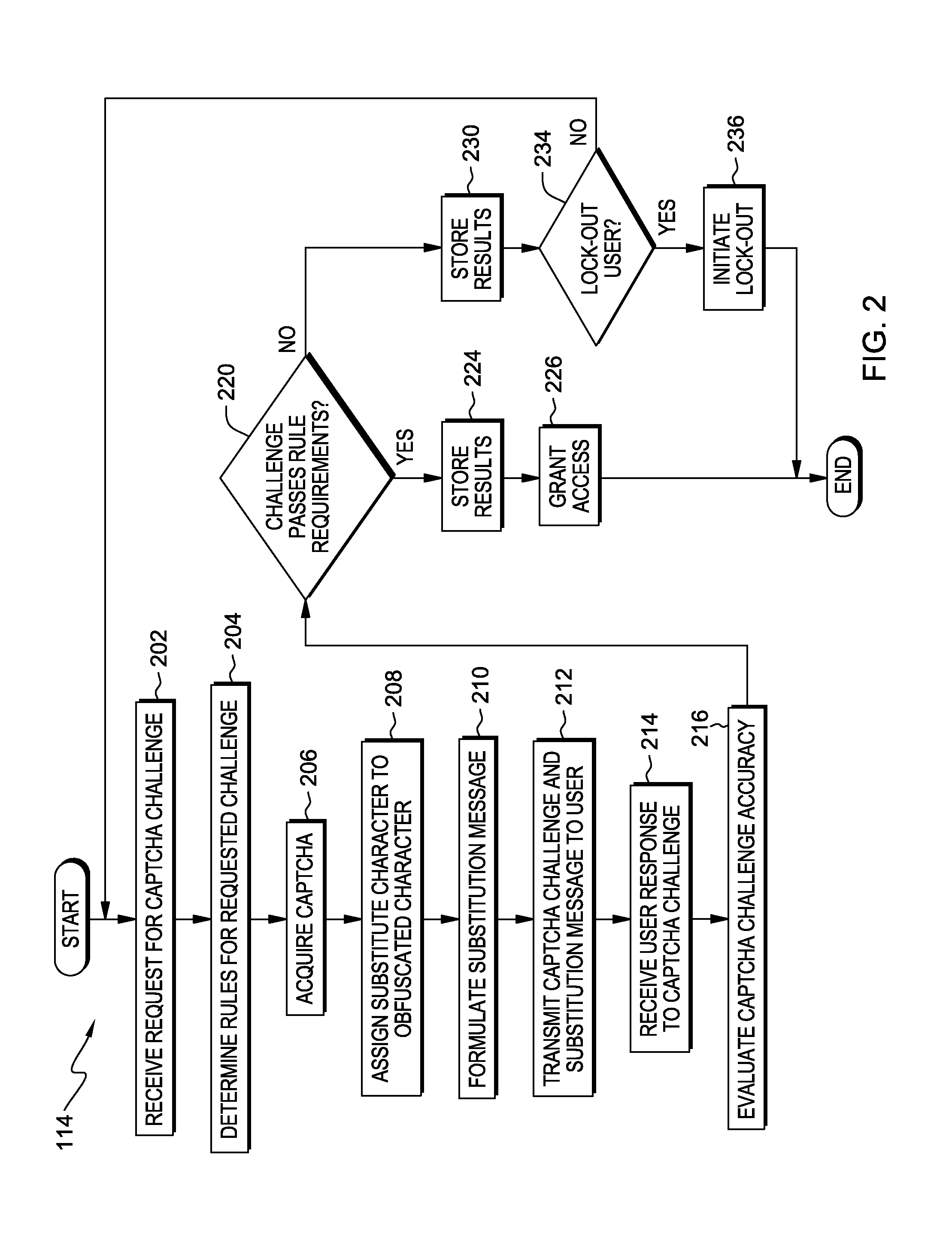
Captcha challenge incorporating obfuscated characters
InactiveUS20150365401A1Digital data processing detailsMultiple digital computer combinationsAlgorithmSoftware engineering
A method for determining if a user of a computer system is a human. A processor receives an indication that a computer security program is needed and acquires at least one image depicting a first string of characters including at least a first and second set of one or more characters. A processor assigns a substitute character to be used as input for each of the second set of one or more characters. A processor presents the at least one image and an indication of the substitute character and when to use the substitute character to the user. A processor receives a second string of characters from the user. A processor determines whether the second string of characters substantially matches the first string of characters based on the substitute character assigned to each of the second set of one or more characters and determines whether the user is a human.
Owner:KYNDRYL INC
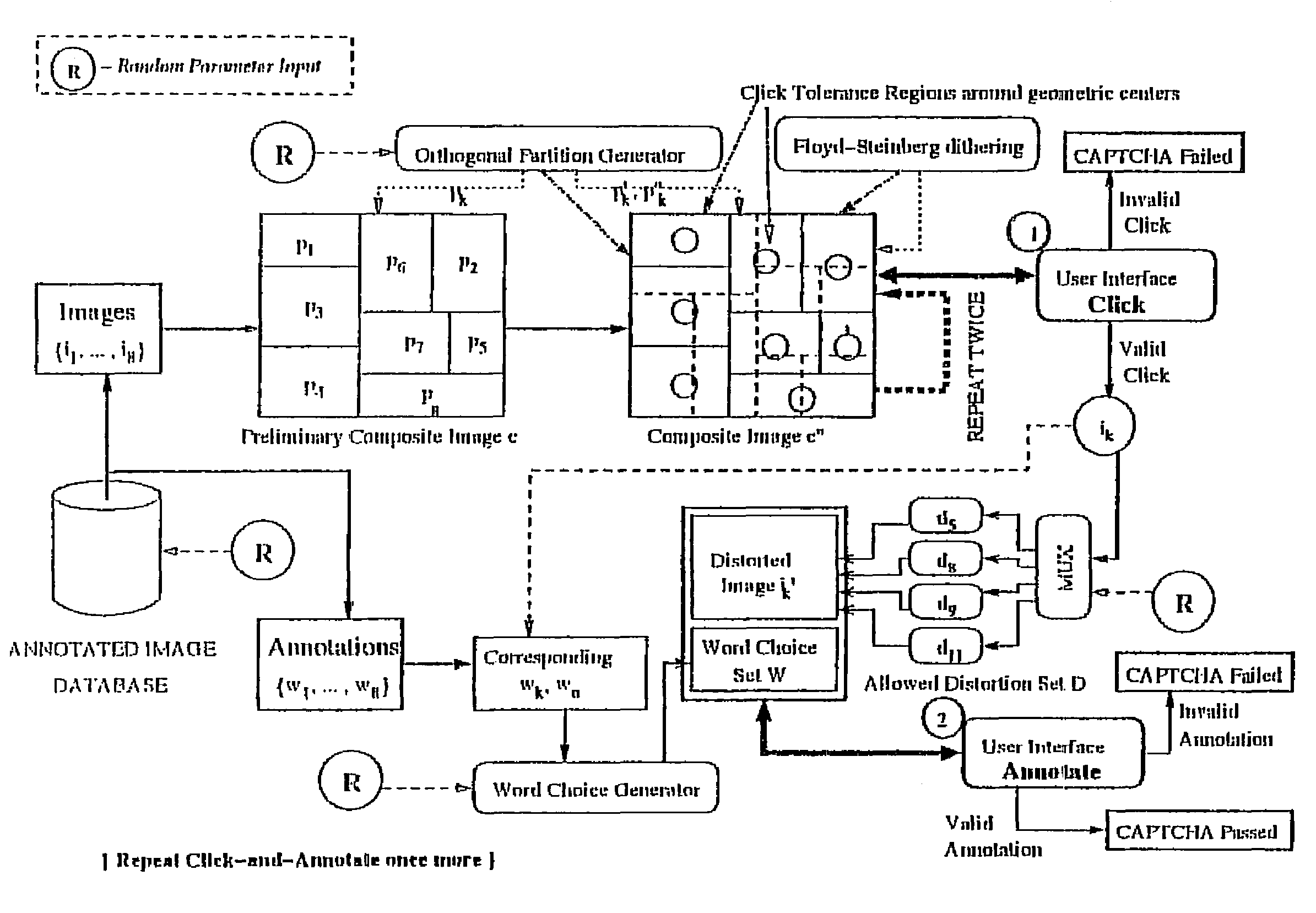
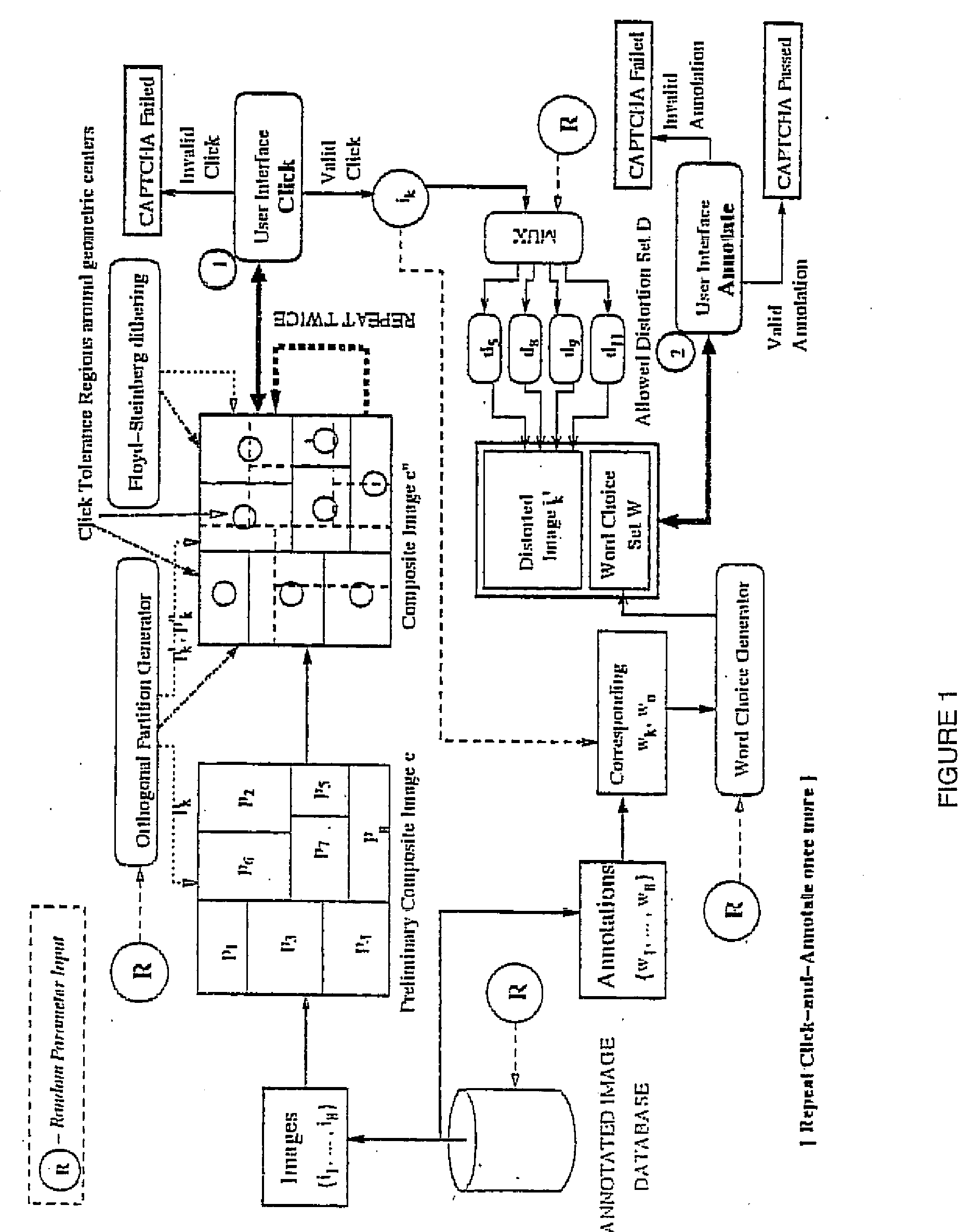
Image-based captcha generation system
InactiveUS20070201745A1Avoid ambiguityIncrease resistanceDigital data processing detailsUnauthorized memory use protectionHigh resistanceAmbiguity
In a system and method for the generation of attack-resistant, user-friendly, image-based CAPTCHAs (Completely Automated Public test to Tell Computers and Humans Apart), controlled distortions are applied to randomly chosen images and presented to a user for annotation from a given list of words. An image is presented that contains multiple connected but independent images with the borders between them distorted or otherwise visually obfuscated in a way that a computer cannot distinguish the borders and a user selects near the center of one of the images The distortions are performed in a way that satisfies the incongruous requirements of low perceptual degradation and high resistance to attack by content-based image retrieval systems. Word choices are carefully generated to avoid ambiguity as well as to avoid attacks based on the choices themselves.
Owner:PENN STATE RES FOUND
Authentication
InactiveUS20120047563A1Improve securityDigital data processing detailsUser identity/authority verificationComputer hardwarePassword
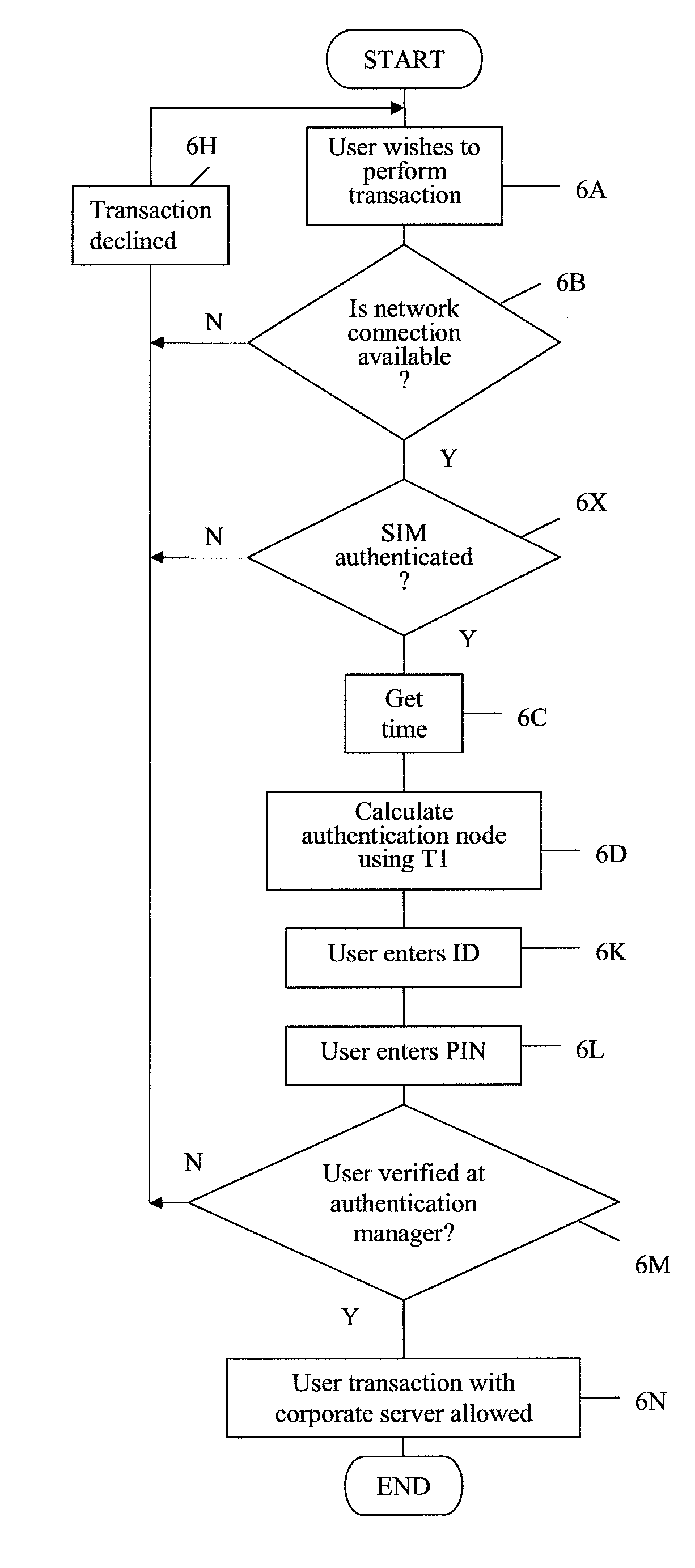
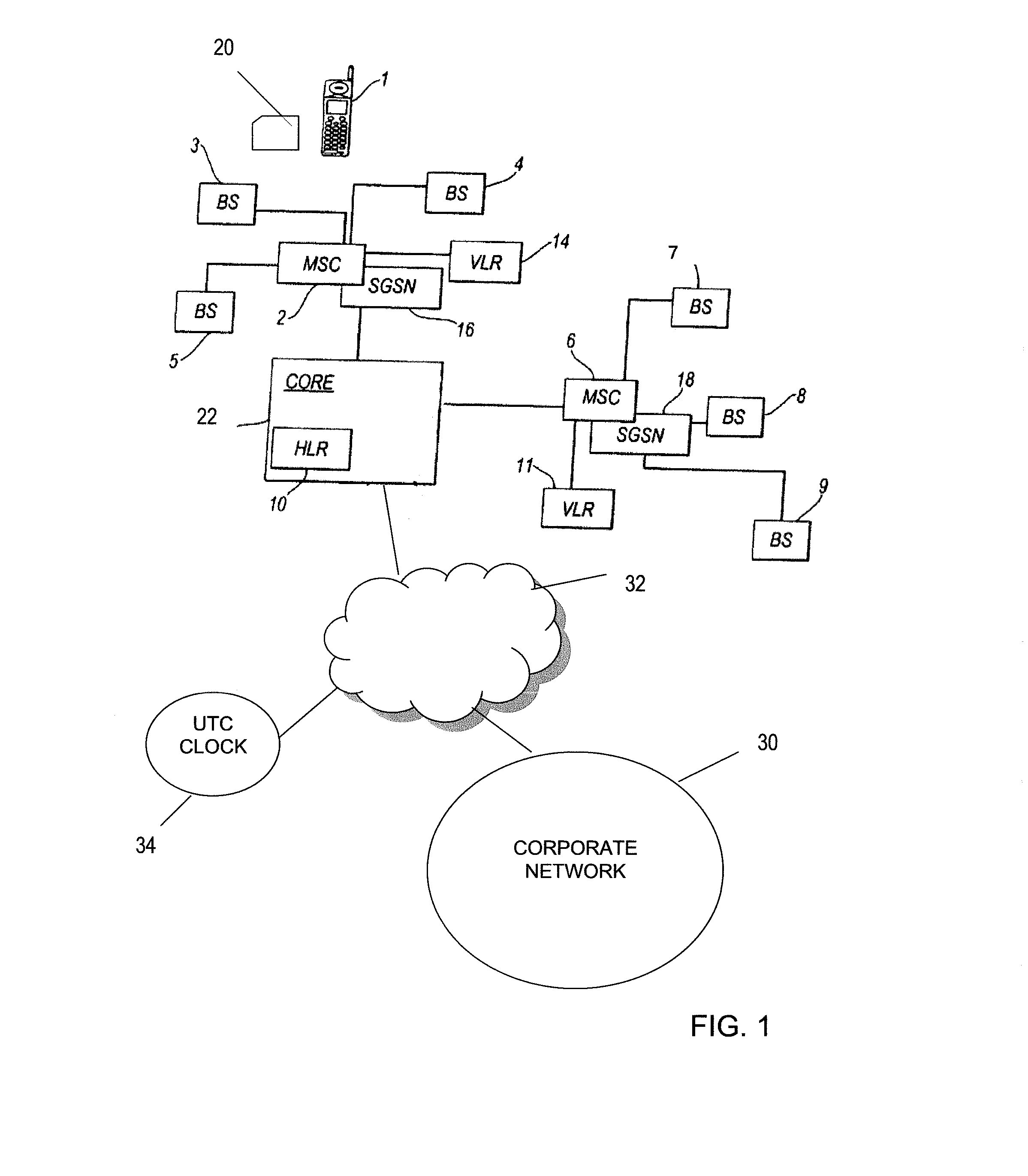
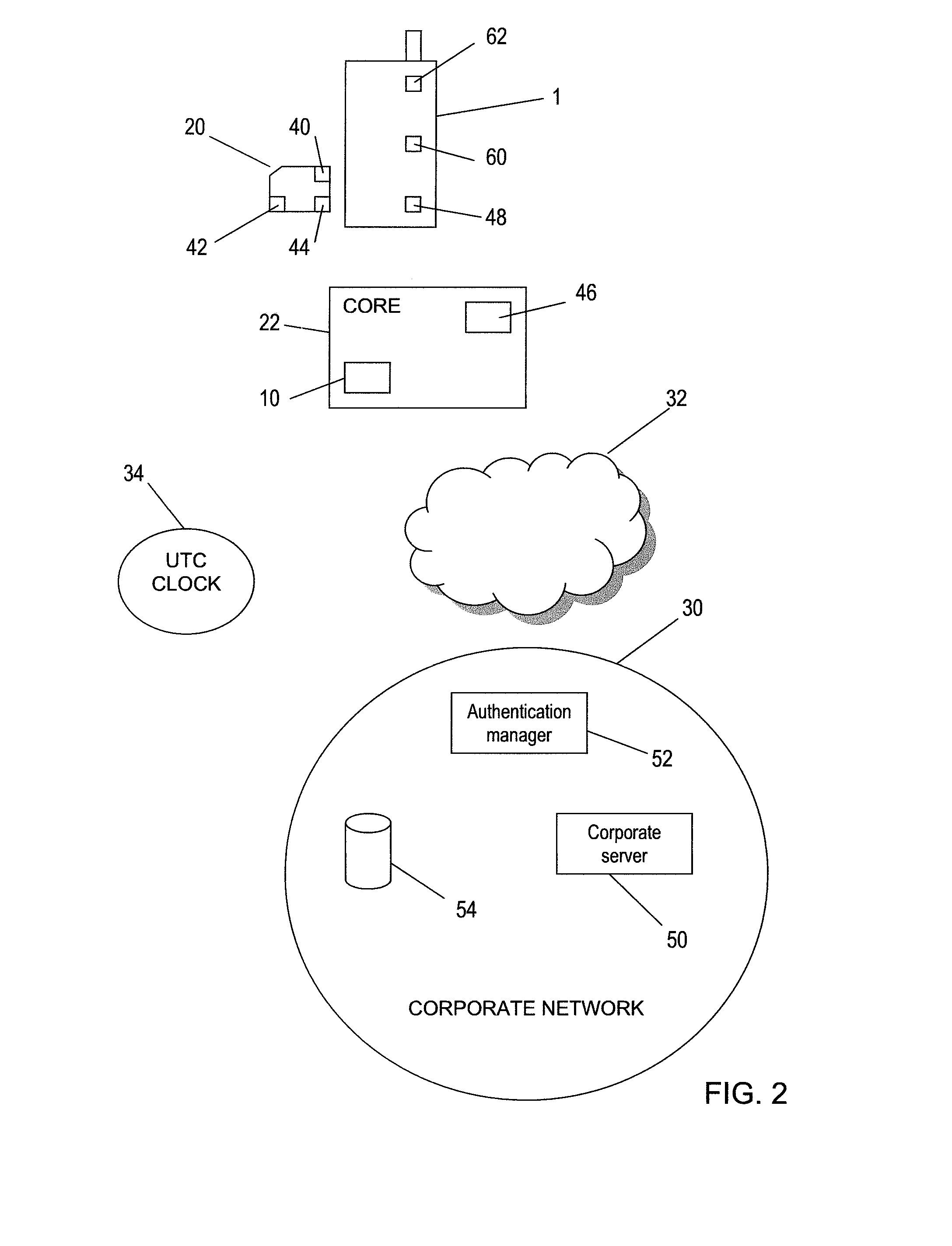
An arrangement for authenticating a transaction between a user's mobile device and an entity such as a corporate server is disclosed. The user's universal integrated circuit card (UICC) is adapted to generate a time-dependent authentication code which is dependent on a time value and which is usable to authenticate the transaction only during a predetermined period. A time verification processor verifies a time value to ensure that the time-dependent authentication code was generated based on the correct time value. The time value is based on the UTC time obtained from UTC clock. The verified time is used to generate a “one-time” password (authentication code) by the authentication code calculator of the UICC. This is used to authenticate a transaction with the corporate network.
Owner:VODAFONE IP LICENSING
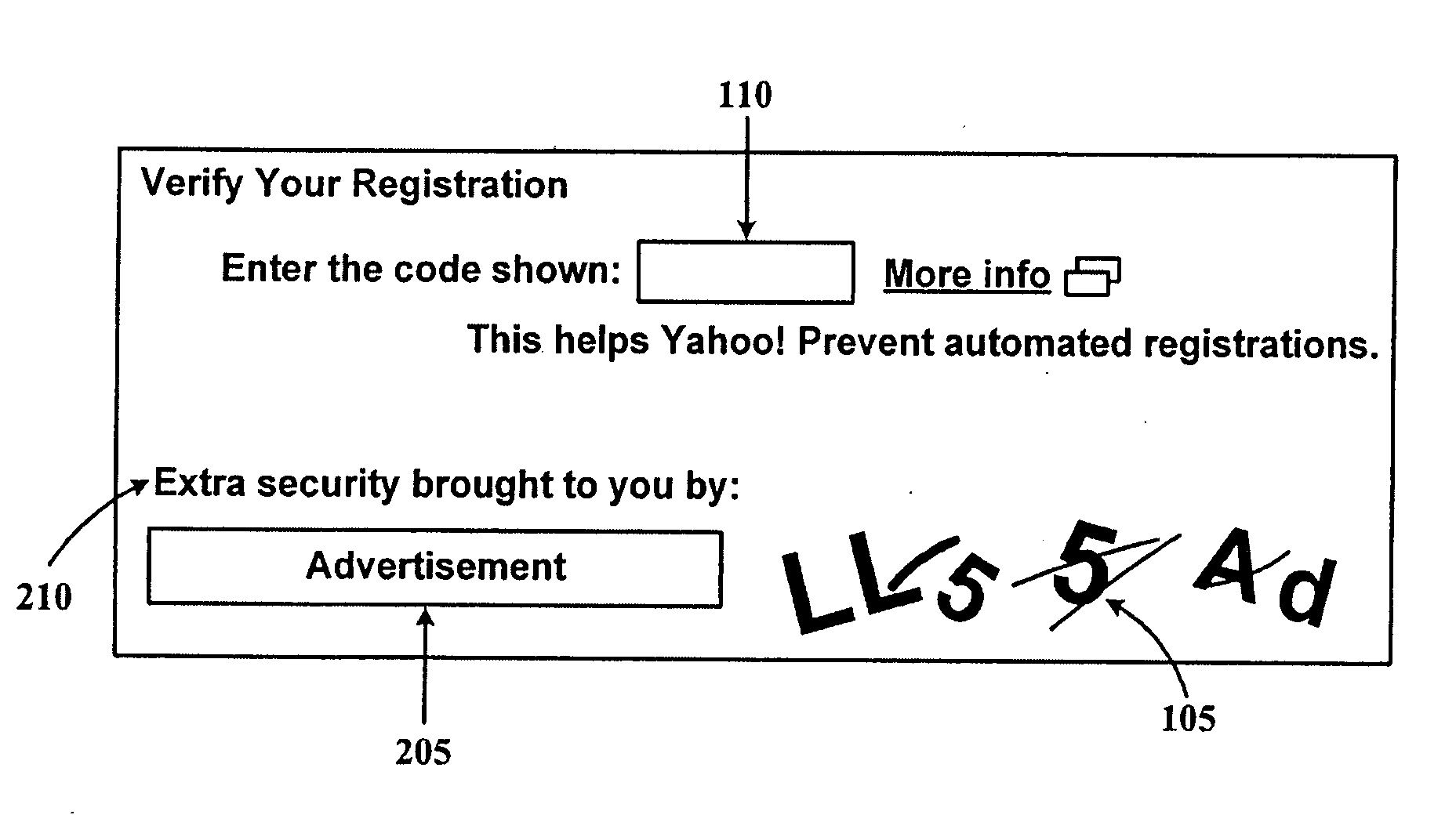
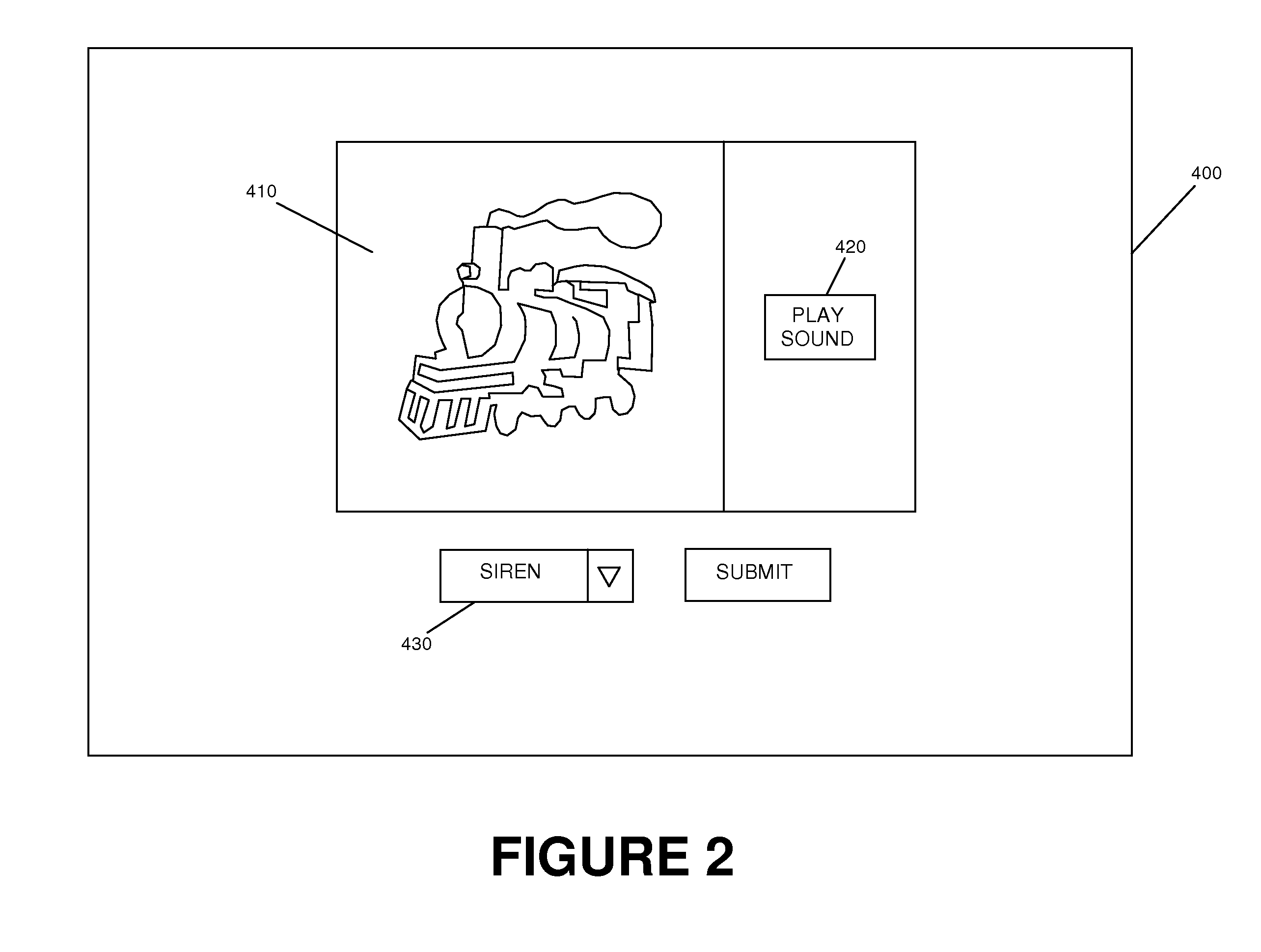
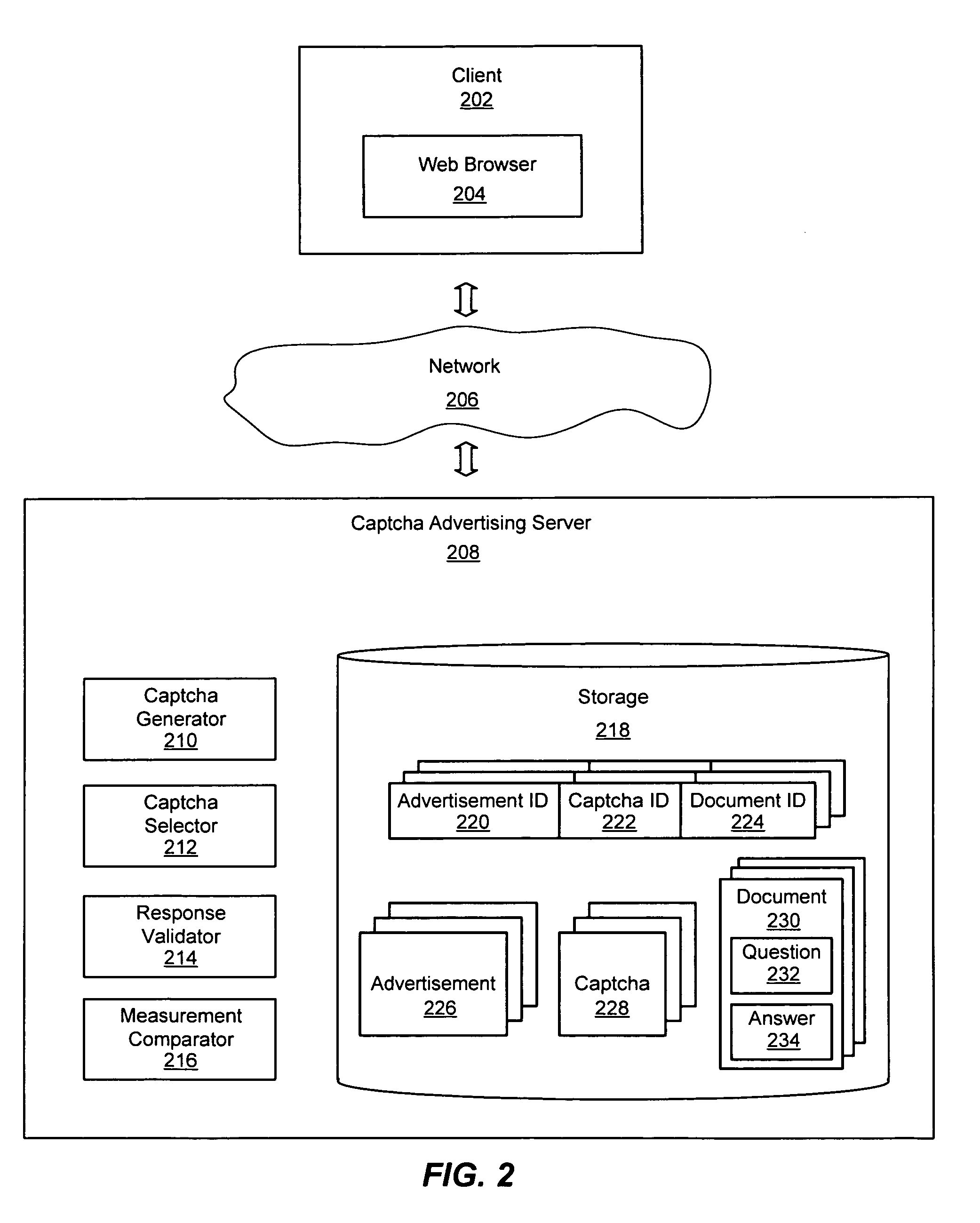
System and method for providing semantic captchas for online advertising
InactiveUS20080133347A1Efficient measurementAdvertisementsWeb data indexingWeb browserNative advertising
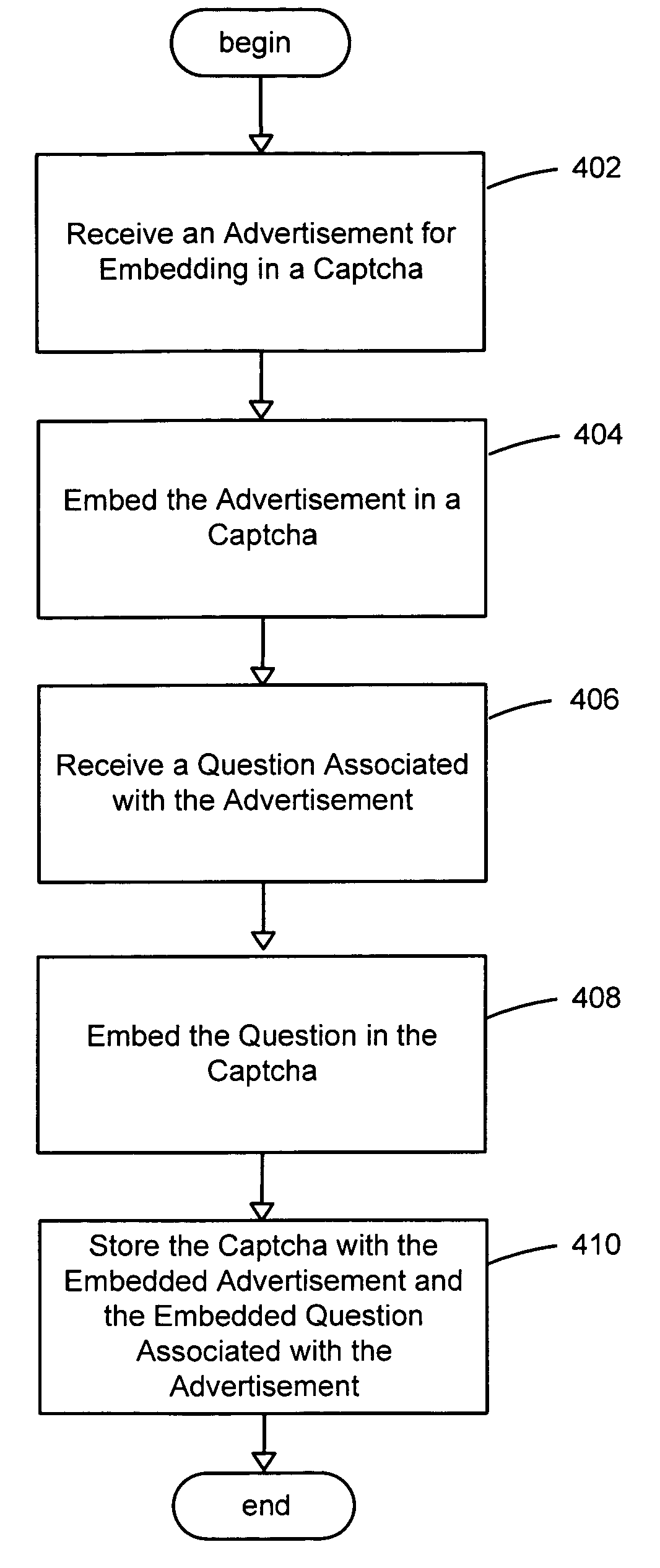
An improved system and method for providing and using captchas for online advertising is provided. An advertisement may be received, embedded in a captcha and stored for use in online advertising. A question about the advertisement may also be stored along with a valid answer for use in verifying a user has received an impression of the advertisement. In response to a request received for sending a captcha with an embedded advertisement to a web browser operating on a client, a captcha with an embedded advertisement may be selected and sent to the web browser for display as part of a web page. Upon verifying the response to the question from the user is a valid answer, receipt of an impression of the advertisement may be recorded. Additionally, the awareness of an online advertisement may be measured for a target audience and reported to advertisers.
Owner:OATH INC
Universally usable human-interaction proof
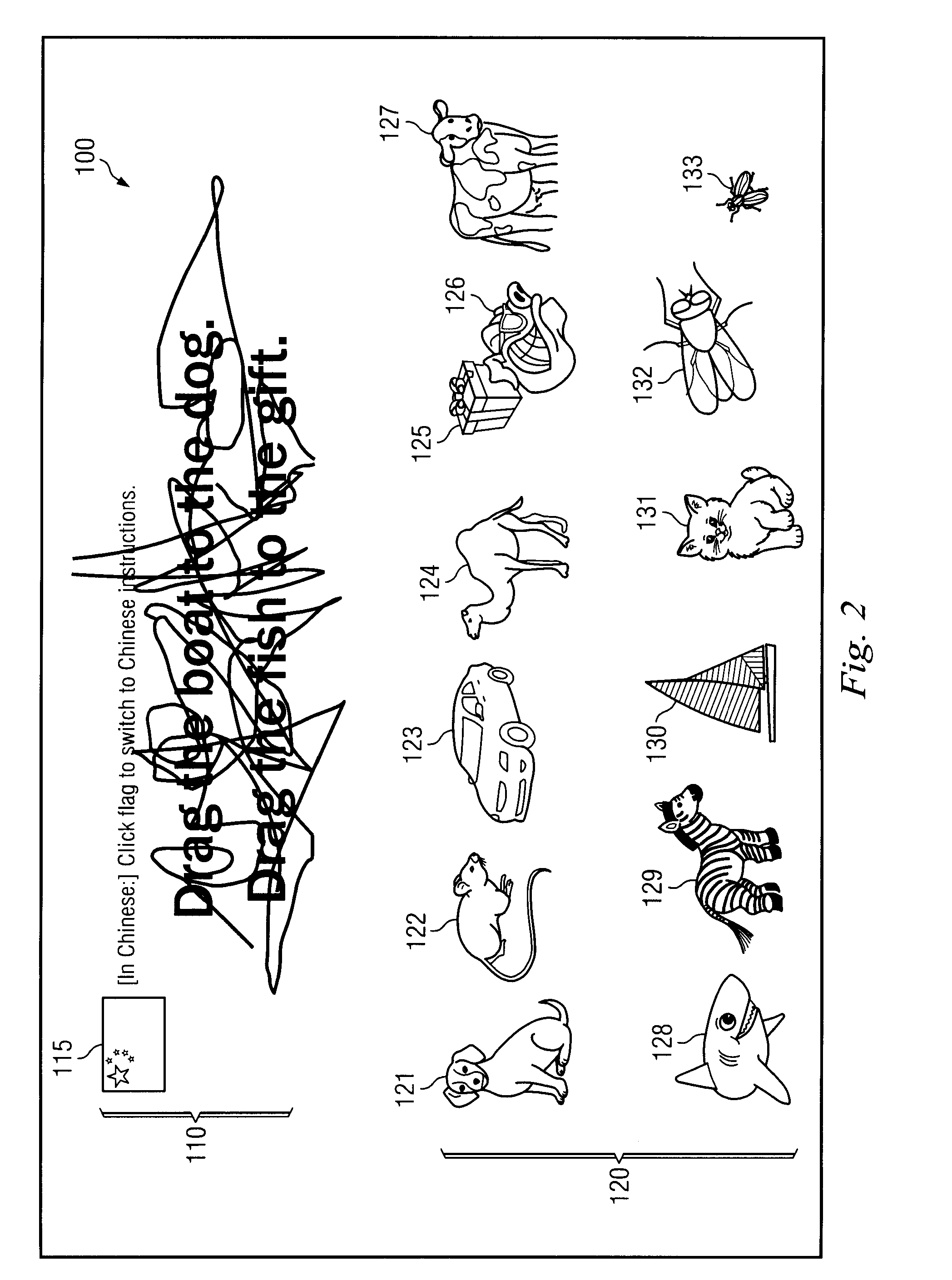
InactiveUS20100095350A1Easy to adaptEasy to internationalizeDigital data processing detailsMultiple digital computer combinationsHuman interactionInternet privacy
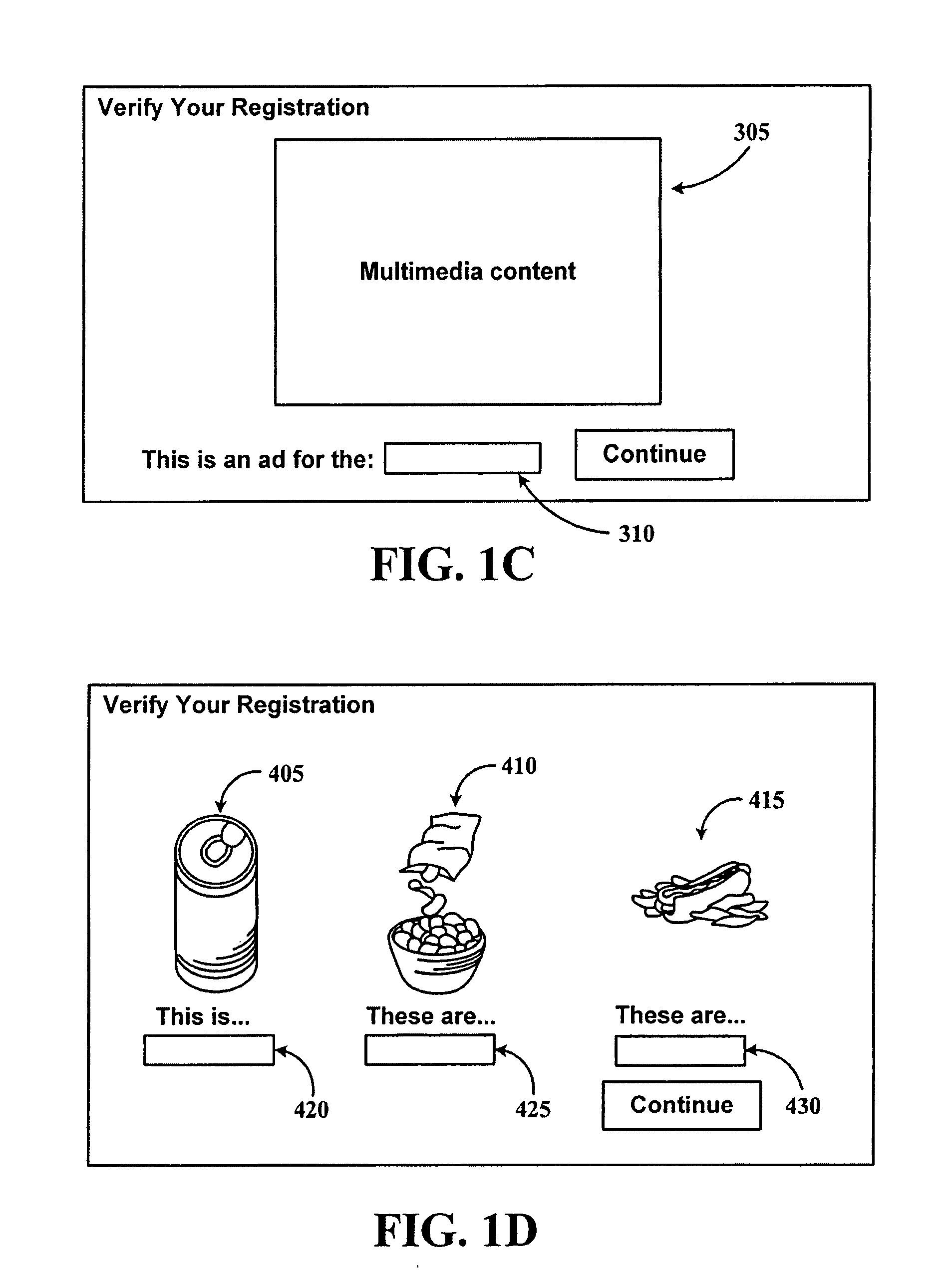
Disclosed is a system and method for generating a universally usable, completely automated public turing test to tell a computer and a human apart (CAPTCHA). The universally usable CAPTCHA uses contextually related pictures and sounds to present concepts to a user. The pictures allow the CAPTCHA to be used by someone who could see, and the audio would allow the CAPTCHA to be used by someone who could not see. This combination of sound and images should make the CAPTCHA more universally usable for a larger population of users than previously known CAPTCHAs.
Owner:TOWSON UNIVERSITY
System and method for delivering online advertisements using captchas
An improved system and method for providing and using captchas for online advertising is provided. An advertisement may be received, embedded in a captcha and stored for use in online advertising. A question about the advertisement may also be stored along with a valid answer for use in verifying a user has received an impression of the advertisement. In response to a request received for sending a captcha with an embedded advertisement to a web browser operating on a client, a captcha with an embedded advertisement may be selected and sent to the web browser for display as part of a web page. Upon verifying the response to the question from the user is a valid answer, receipt of an impression of the advertisement may be recorded. Additionally, the awareness of an online advertisement may be measured for a target audience and reported to advertisers.
Owner:OATH INC
Captcha image generation
InactiveUS20100077210A1Traffic minimizationAccurate distinctionUser identity/authority verificationDigital computer detailsSoftware engineeringCAPTCHA
Owner:OATH INC
Progressive Pictorial & Motion Based CAPTCHAs
A CAPTCHA system uses images / pictures and / or motion for granting access to a computing system. The images can be culled from examples used in pictorial games, and can progressively presented to increase the strength of the CAPTCHA challenges. Speech recognition, motion and touch sensing can also be employed as parts of the challenge.
Owner:HUMAN DIFFERENTIAL INTELLIGENCE LLC
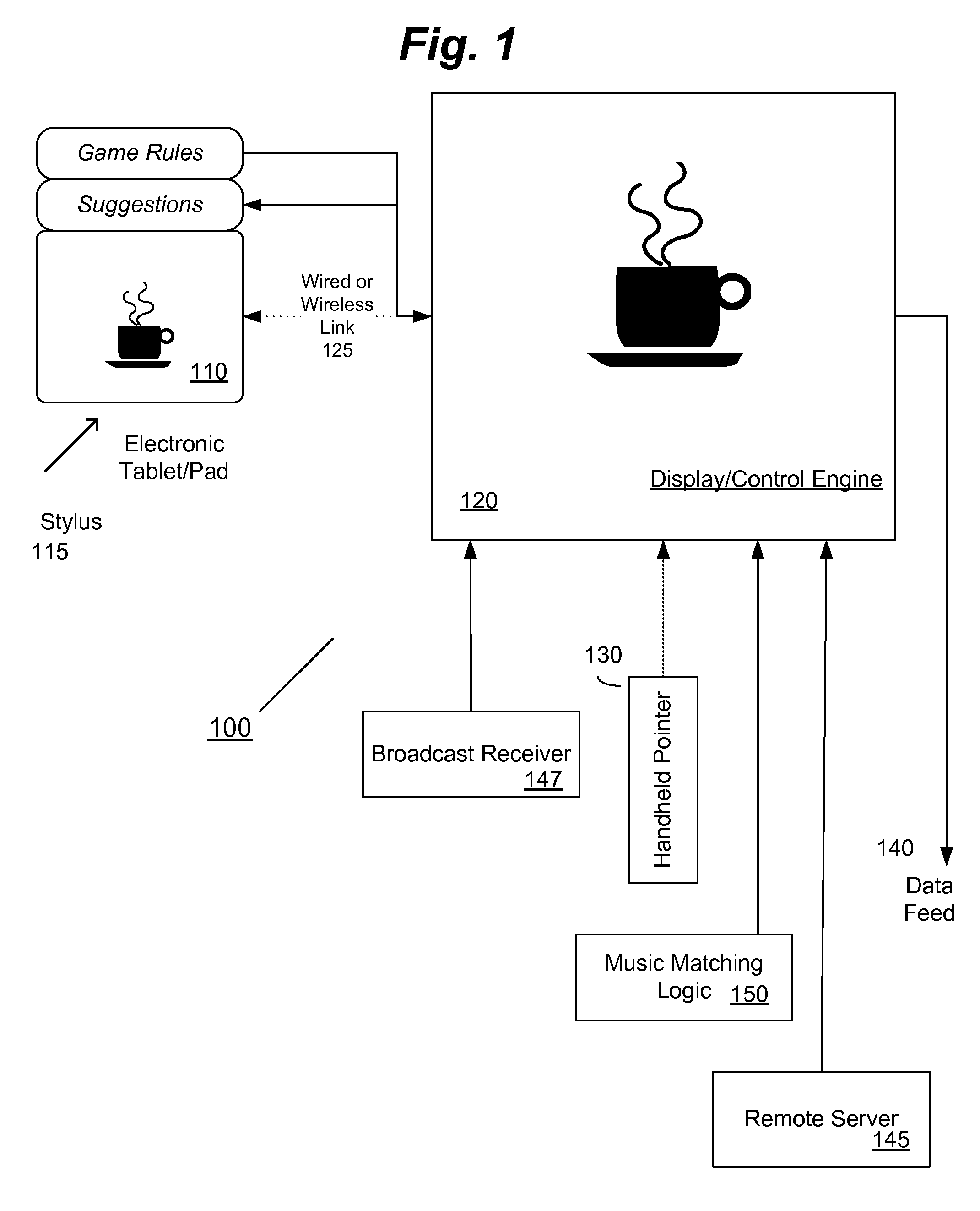
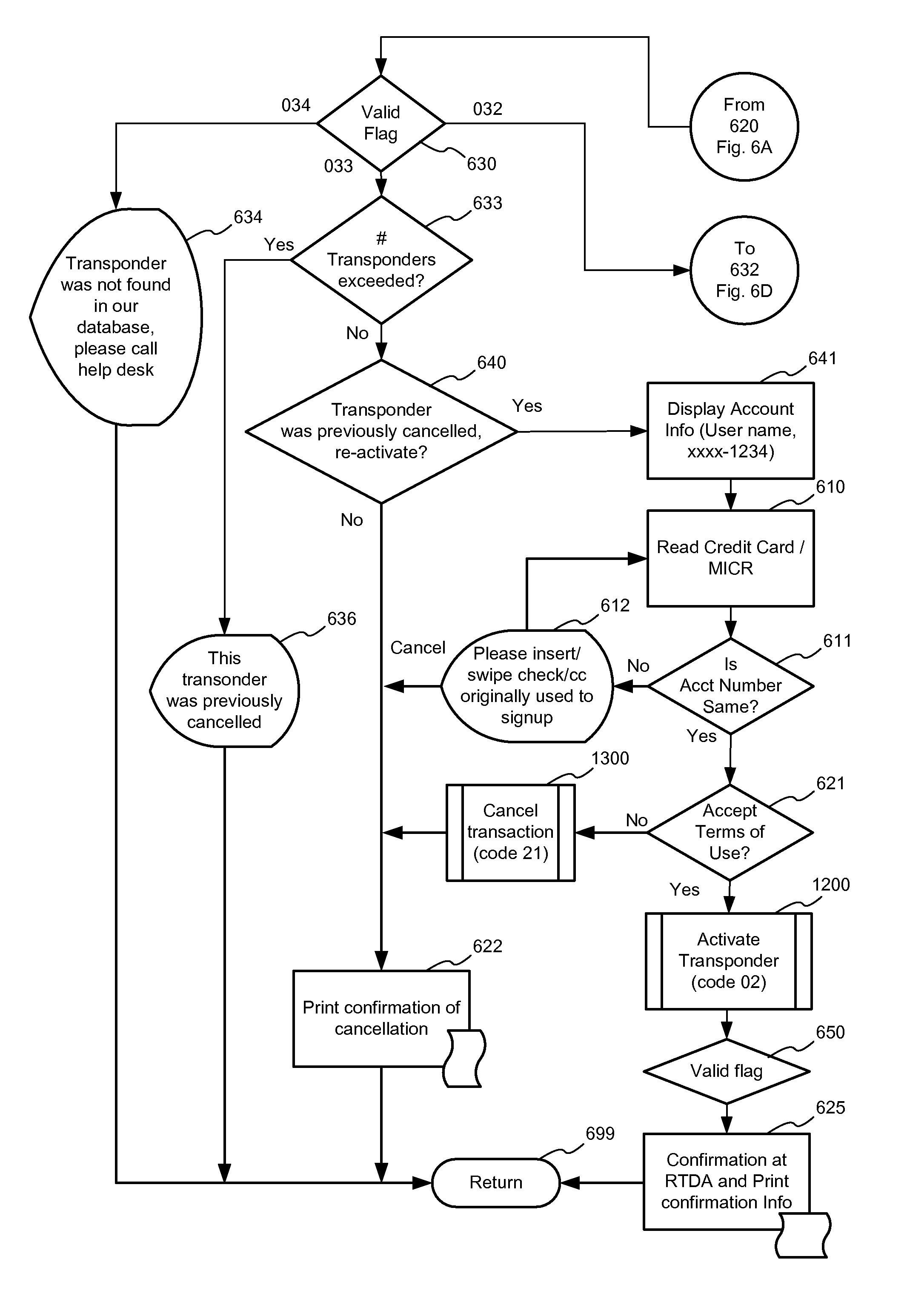
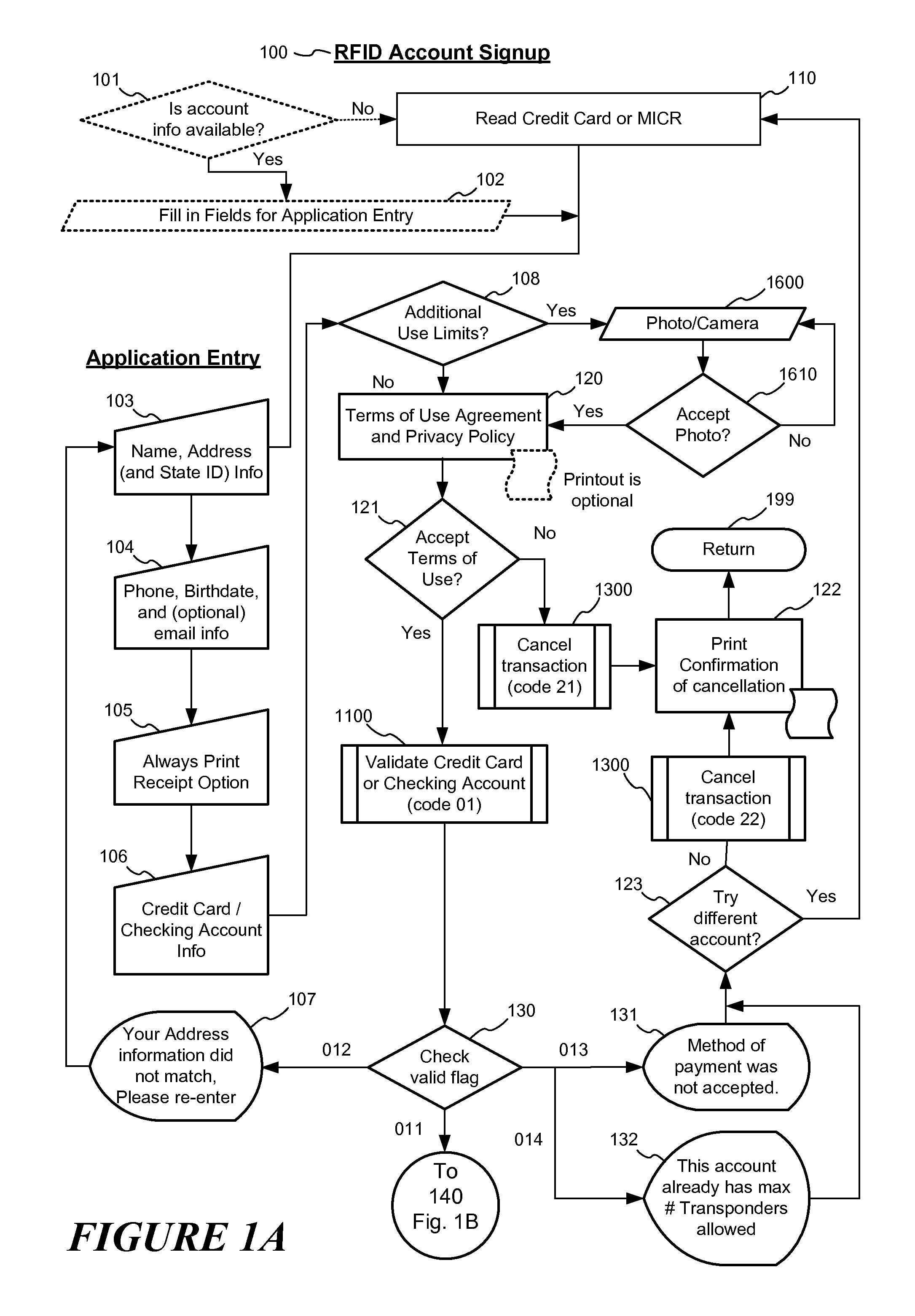
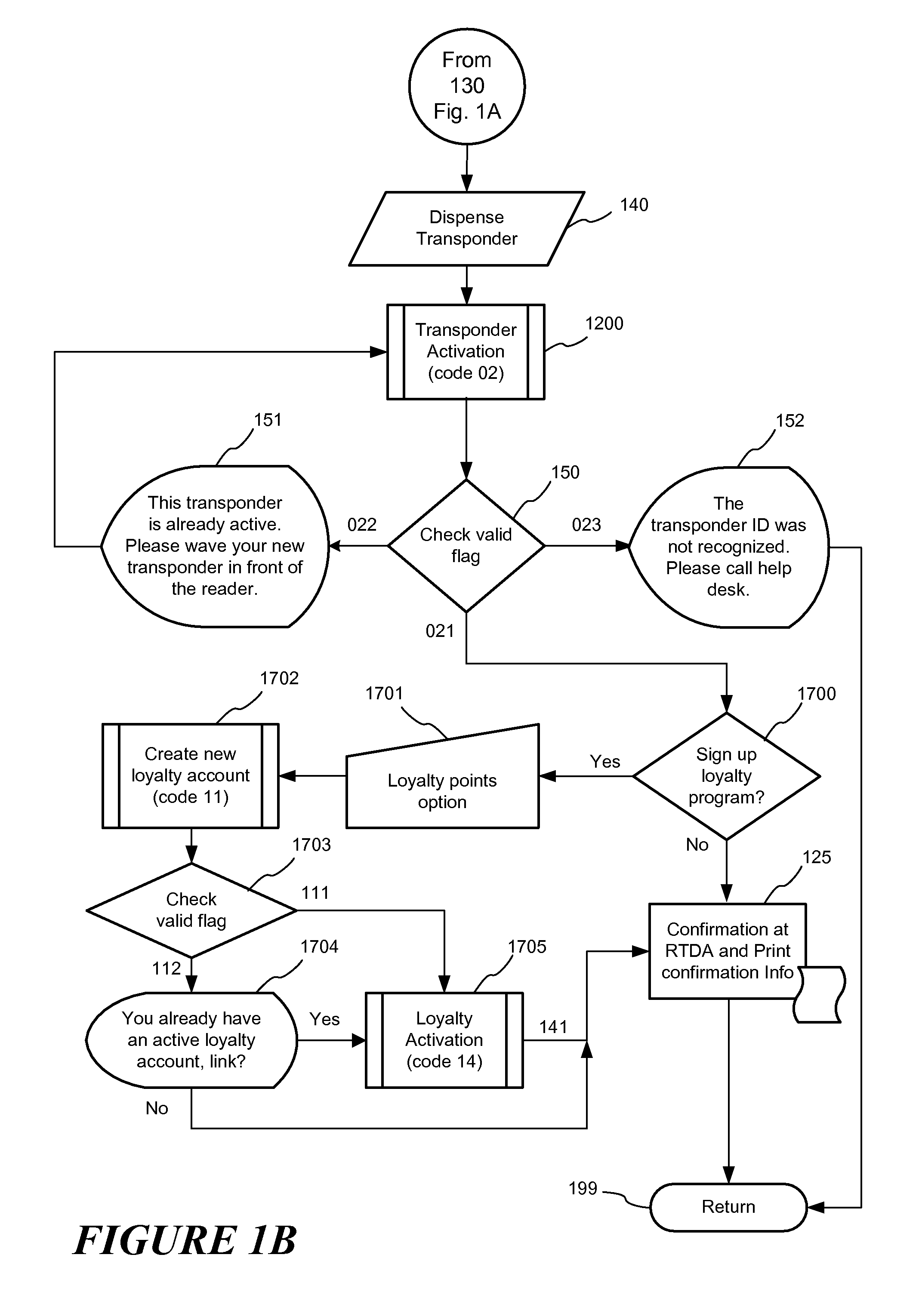
RFID transponder dispenser and authorizer
InactiveUS7069251B1Shorten the timeFacilitate the processAcutation objectsApparatus for meter-controlled dispensingData validationSource Data Verification
A RFID transponder dispenser and authorizer (RTDA) system for distributing and activating an RFID Transponder at a point of purchase. The system has a storage for Transponders and Transponders in the storage. It also has at least one electronic data reader, network access to a processor system, and an application for customer data verification, electronic data and account data verification across the network at the processor, an interface to the RTDA apparatus to control dispensing of Transponders, and receiving an account verification code and an activation confirmation code from the processor. The RTDA reads customer electronic account data, verifies same and verifies the account is valid, dispenses a Transponder to a customer, reads the Transponder ID code, and associates the Transponder ID code with the customer's electronic account data in a unique customer record in an RFID database, and receives an account activation confirmation code and displays confirmation of activation to the customer.
Owner:ACC CORP
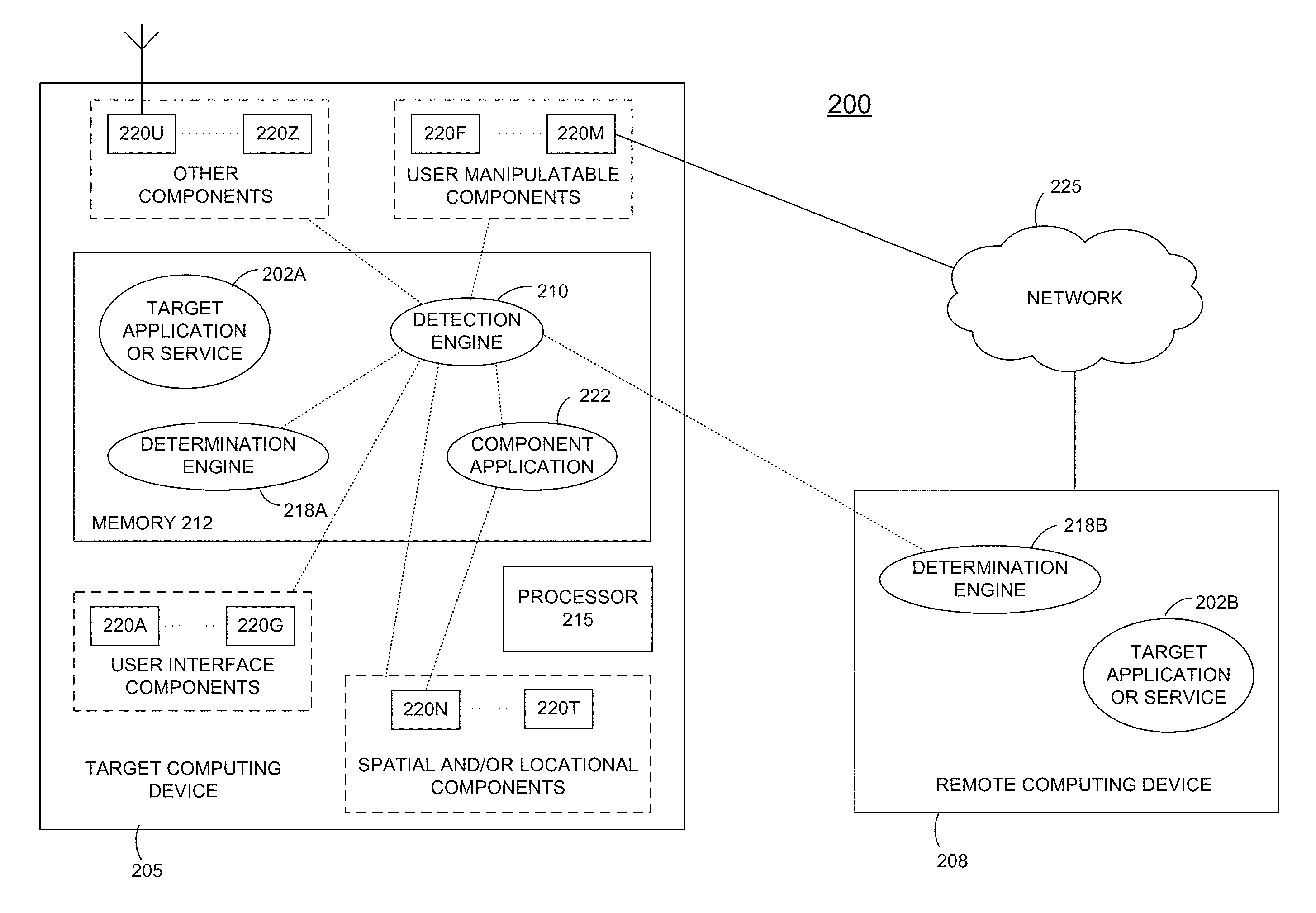
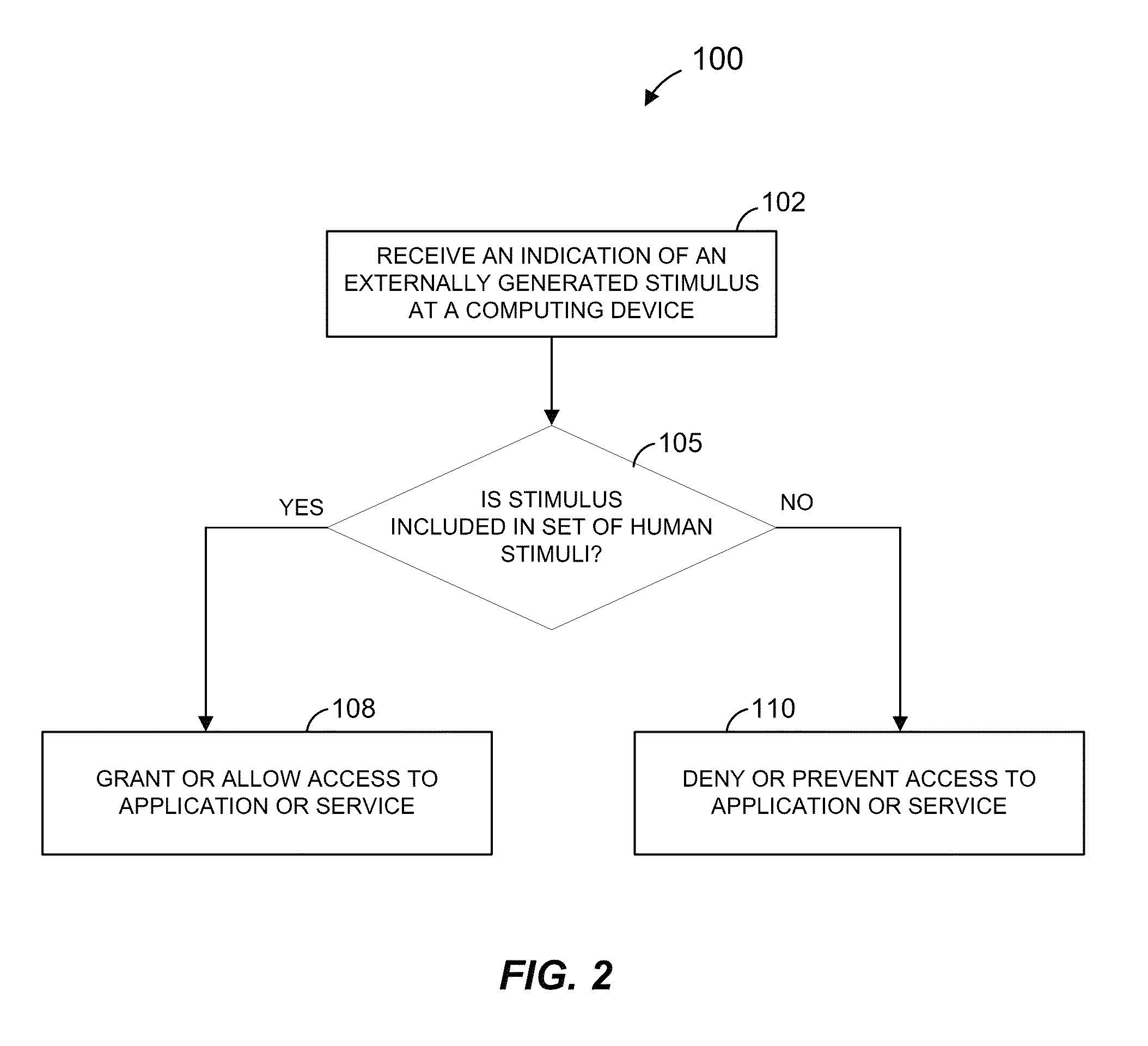
Determining human stimuli at computing devices
ActiveUS9147065B2Character and pattern recognitionDigital data authenticationSpatial OrientationsHuman–computer interaction
Techniques for granting access to an application or service based on a detected human stimulus at a computing device include detecting a stimulus that is generated by an external entity and independent of a CAPTCHA or CAPTCHA-like challenge. If the stimulus is included in a set of human stimuli, access to the application or service may be granted. Otherwise, access may be denied. The detected stimulus may be ad-hoc, or may be a response to an explicit challenge other than a CAPTCHA or CAPTCHA-like challenge. A background application may continuously test over time for ad-hoc stimuli that are consistent with a human presence, and may maintain or deny access accordingly. The detected stimulus may include changes in states of components of the computing device that are related to spatial orientation and / or location. Access to the application or service may be granted / denied based on the detected stimulus and an additional criteria.
Owner:GOGO BUSINESS AVIATION LLC
Method and apparatus for watermarking images
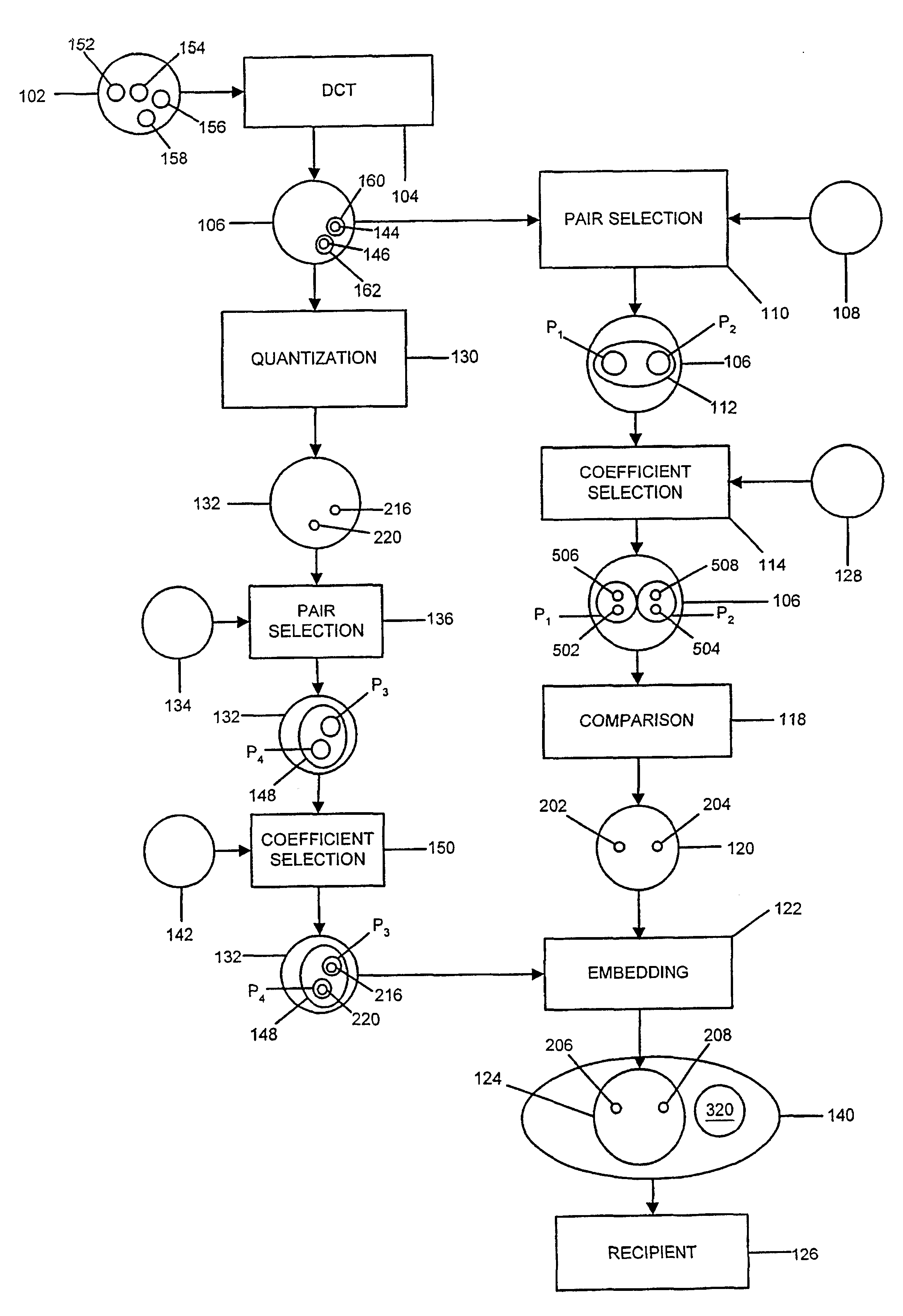
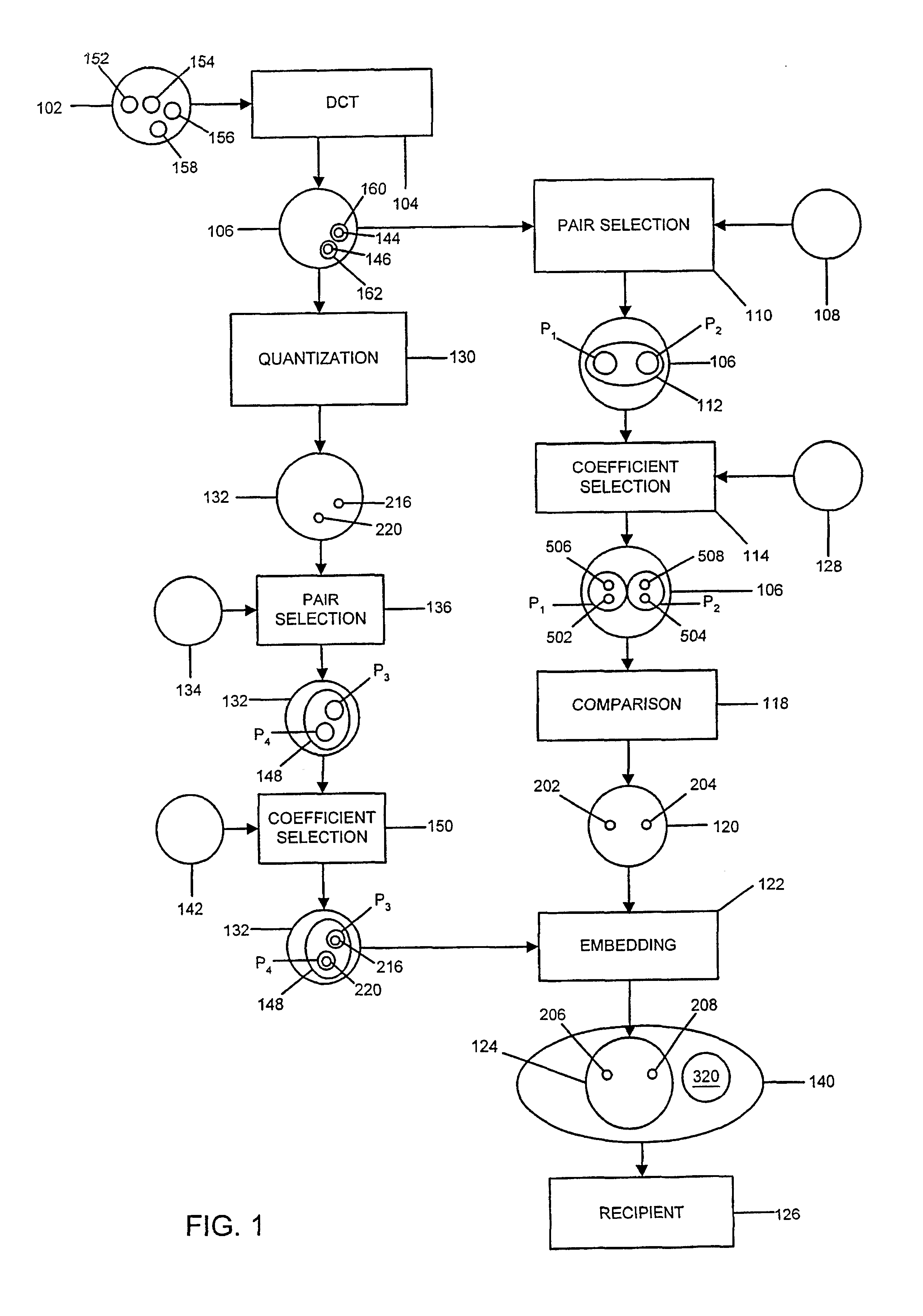
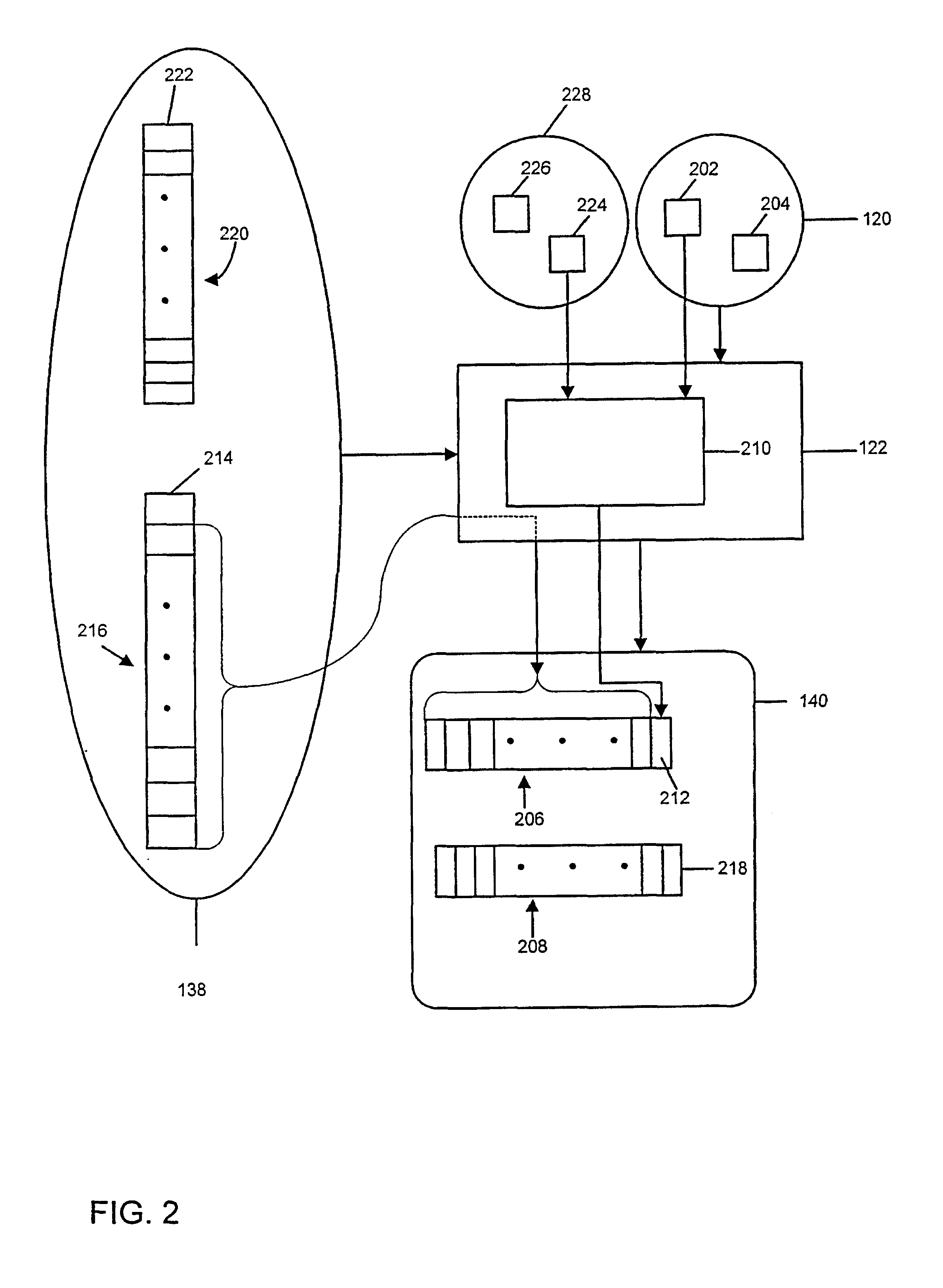
InactiveUS6879703B2User identity/authority verificationCharacter and pattern recognitionComputer hardwareCAPTCHA
Digital watermarks are embedded in image data (102)in order to enable authentication of the image data and / or replacement of rejected portions of the image data. Authentication codes are derived by comparing selected discrete cosine transform (DCT) (104) coefficients within DCT data (106) derived from the original, spatial-domain image data. The authentication codes thus generated are embedded in DCT coefficients (612) other than the ones which were used to derive the authentication codes. The resulting, watermarked data can be sent or made available to one or more recipients who can compress or otherwise use the watermarked data. Image data derived from the watermarked data—e.g, compressed versions of the watermarked data—can be authenticated by: extracting the embedded authentication codes, comparing DCT coefficients derived from the coefficients from which the original authentication codes were generated; and determining whether the compared DCT coefficients are consistent with the extracted authentication codes.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
Interactive CAPTCHA
InactiveUS20130007875A1Digital data processing detailsUser identity/authority verificationCAPTCHAHuman–computer interaction
Owner:PAYPAL INC
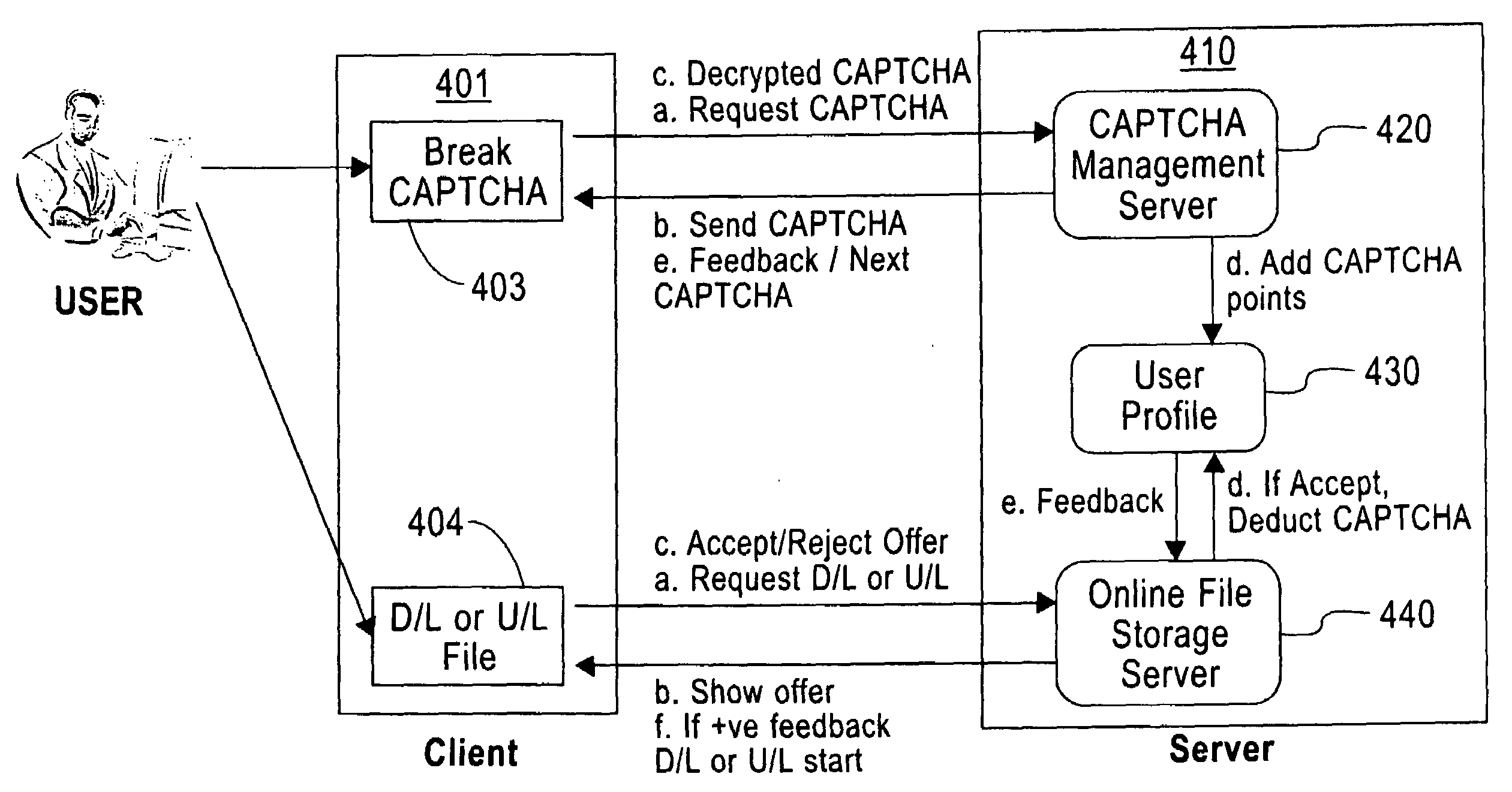
Efficient, Peer-to-Peer Captcha-Based Verification and Demand Management for Online Services
ActiveUS20090260068A1Maintain integrityMaintaining purposeDigital data processing detailsUser identity/authority verificationRequirements managementCAPTCHA
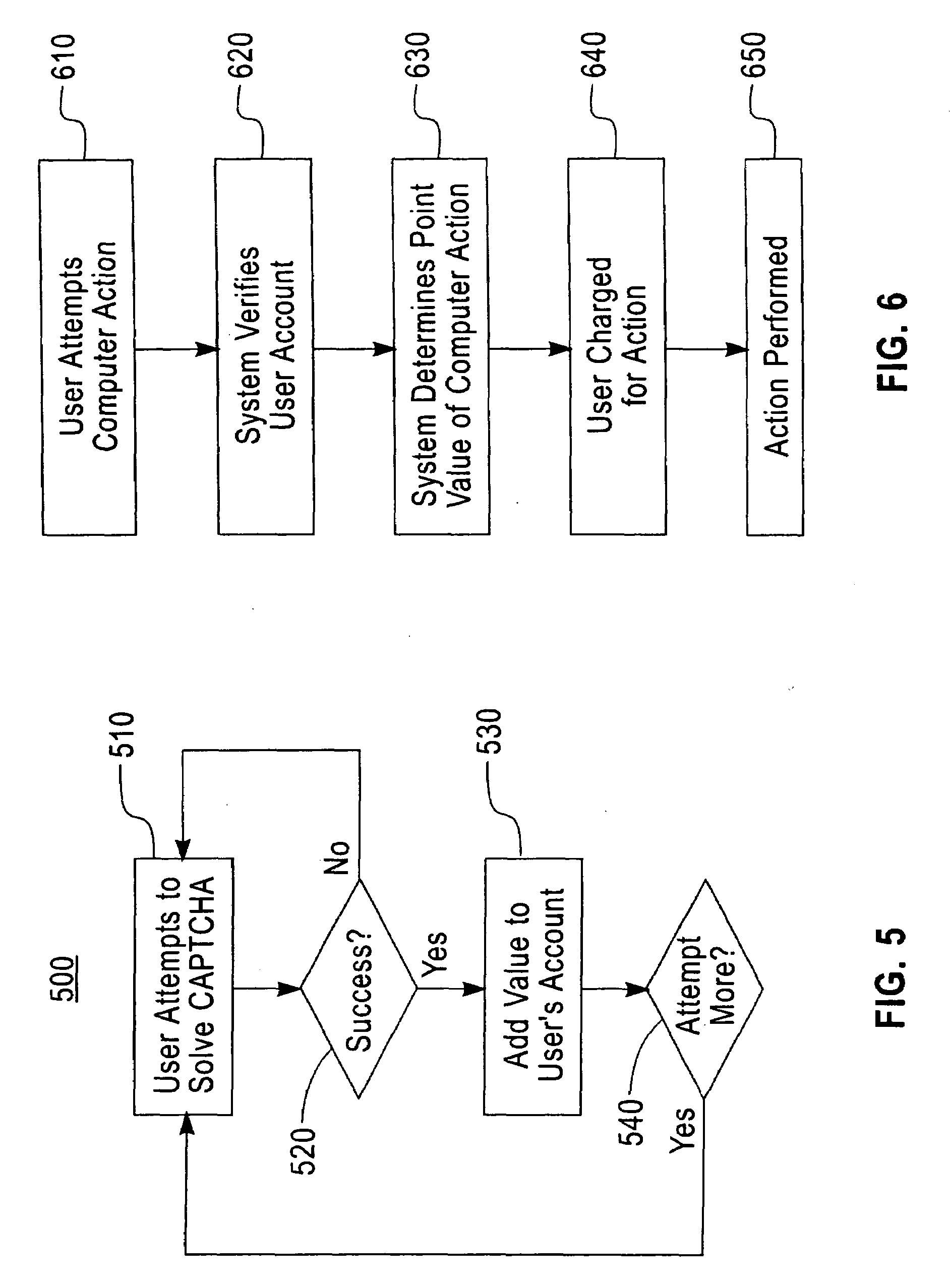
A system and method configured that may allow performing a human-computer verification including crediting a verified task from a first user to a second user. In additional embodiments, may allow the user to perform a computer operation that require human-computer verification based upon an amount of credits that the user has been provided.
Owner:IBM CORP
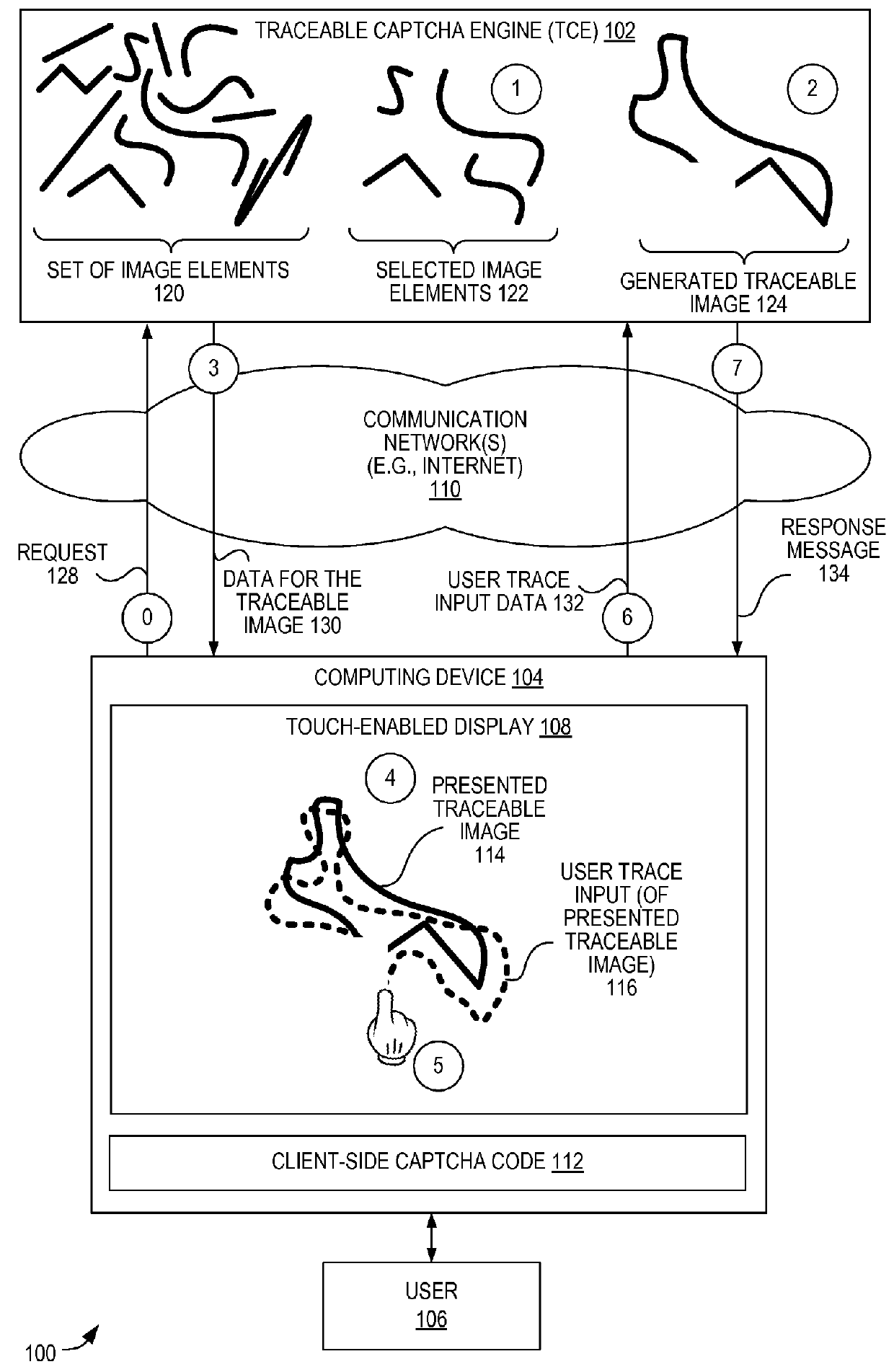
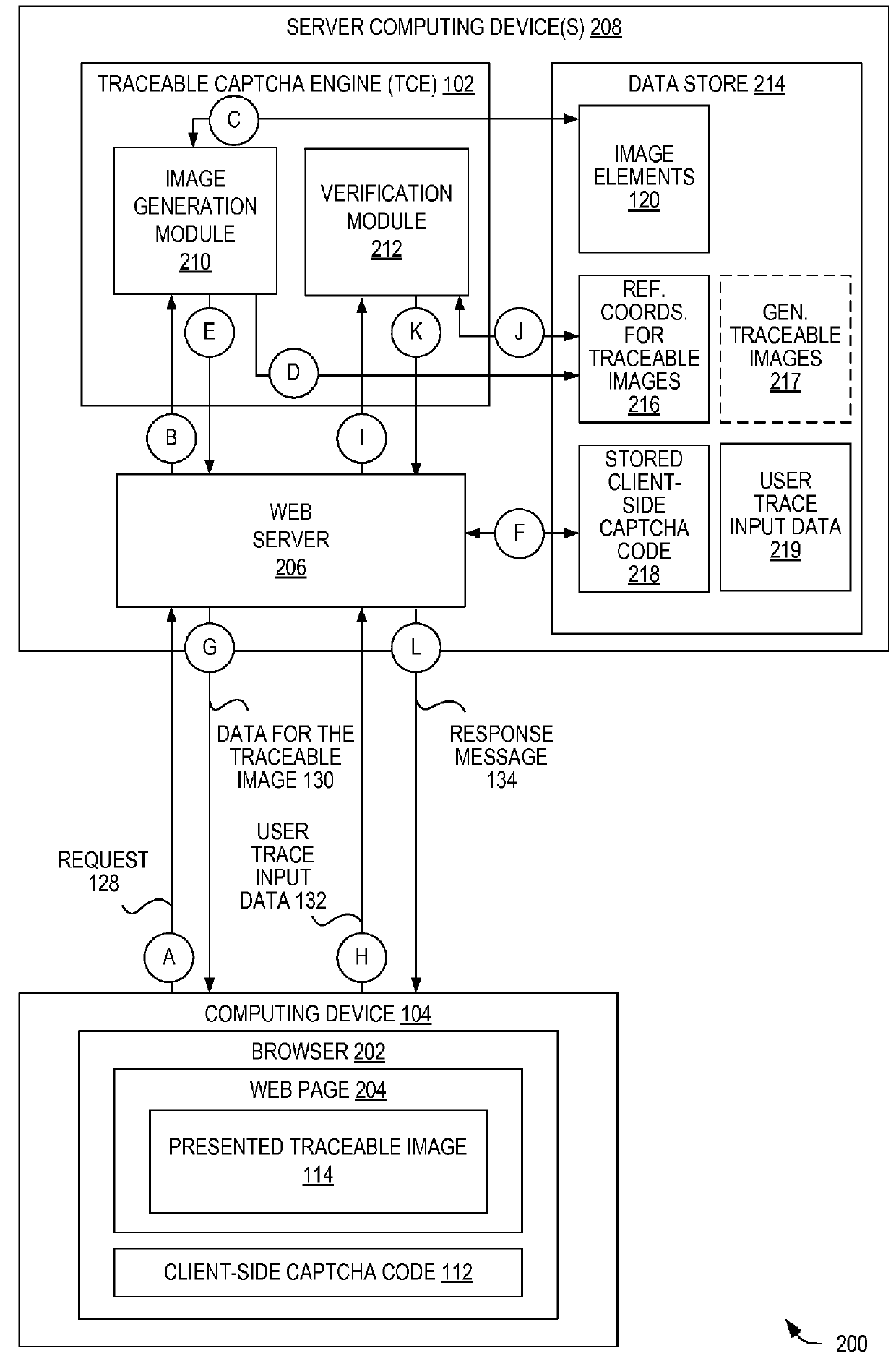
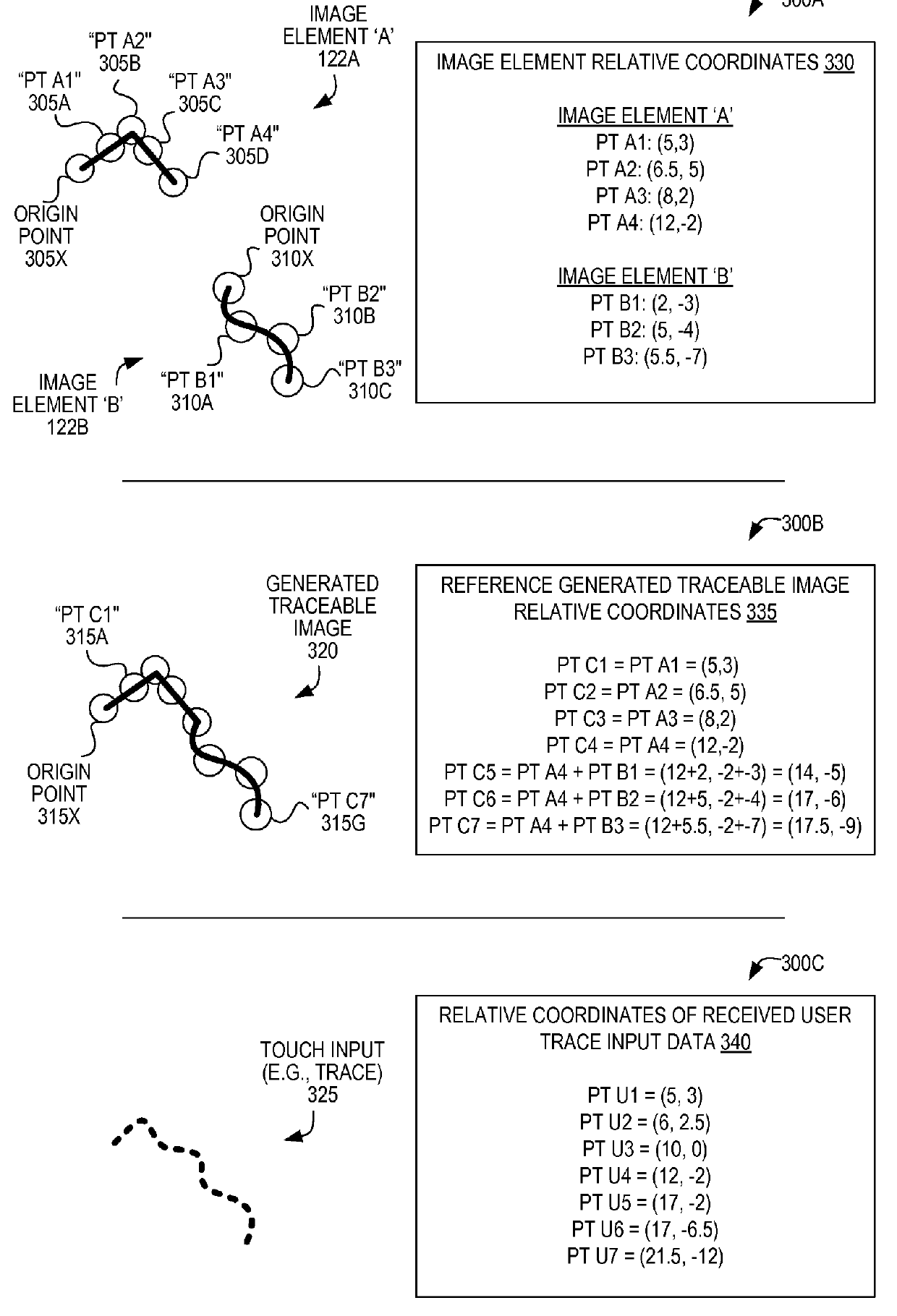
Captcha techniques utilizing traceable images
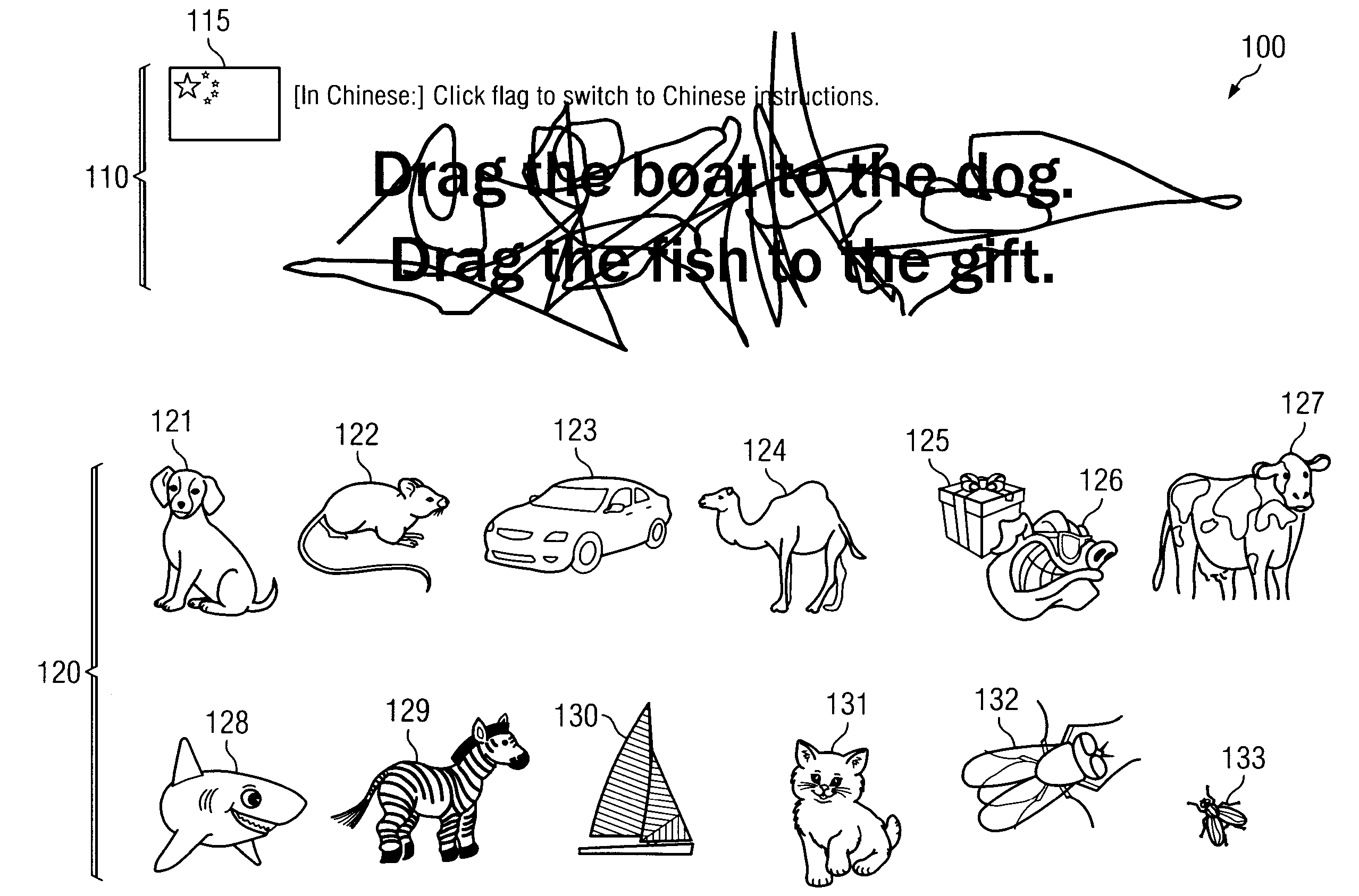
ActiveUS20160055329A1Drawing from basic elementsDigital data processing detailsDisplay deviceImaging technique
Techniques are disclosed for generating, utilizing, and validating traceable image CAPTCHAs. In certain embodiments, a traceable image is displayed, and a trace of the image is analyzed to determine whether a user providing the trace is human. In certain embodiments, a computing device receives a request for an image, and in response, creates a traceable image based upon a plurality of image elements. The computing device transmits data representing the traceable image to cause a second computing device to display the traceable image via a touch-enabled display. The computing device receives a user trace input data generated responsive to a trace made at the second computing device, and determines whether the trace is within an error tolerance range of the set of coordinates associated with the traceable image. The computing device then sends a result of the determination.
Owner:ORACLE INT CORP
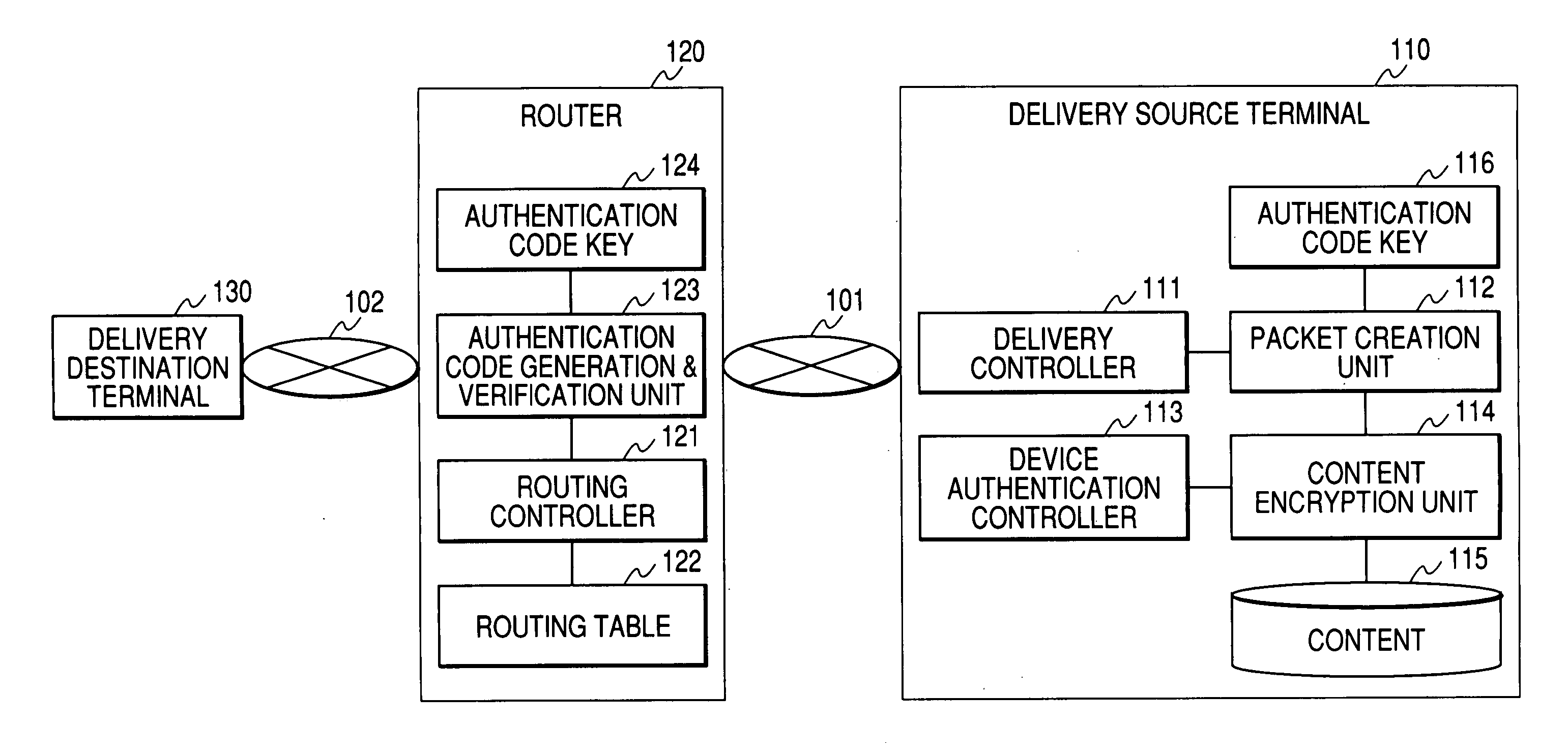
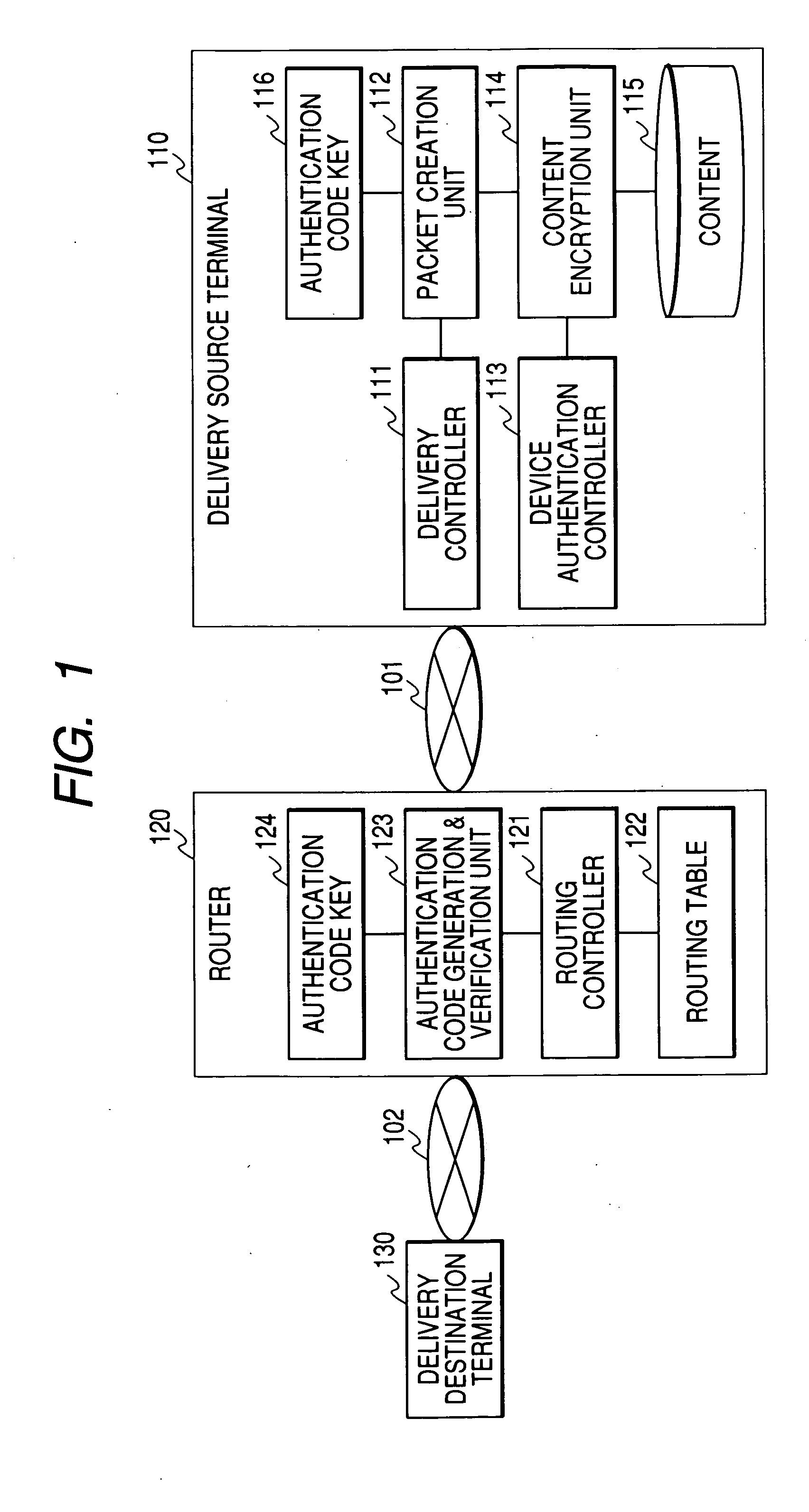
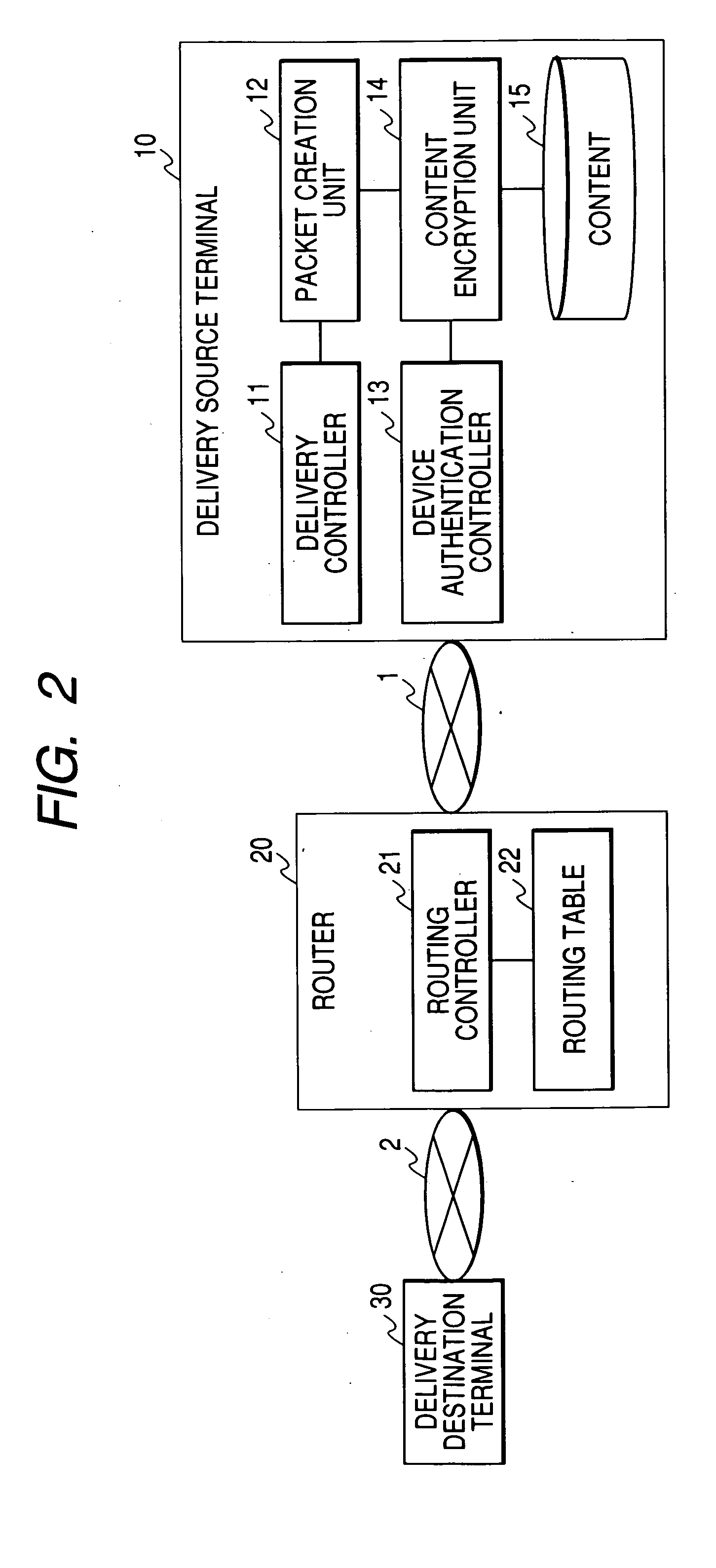
Content transmission control device, content distribution device and content receiving device
ActiveUS20050216730A1Falsification of possible number can be preventedSlow changeDigital data processing detailsAnalogue secracy/subscription systemsComputer terminalCAPTCHA
A delivery of content to the unspecified number of persons is prevented by limiting the content delivery range. A delivery source terminal 110 generates an authentication code based on the number of possible transmission times of content and an authentication code key 116, and configures the number of possible transmission times and the generated authentication code in a packet. The delivery source terminal 110 transmits the packet to a delivery destination terminal 130. A router 120 verifies whether the authentication code generated based on the number of possible transmission times and the authentication code key 124 that are received agrees with the authentication code received from the delivery source terminal 110, updates the number of possible transmission times when the two codes agree, generates a new authentication code, and configures it in the packet. The router 120 transmits the packet thus generated to the delivery destination terminal 130.
Owner:MAXELL HLDG LTD
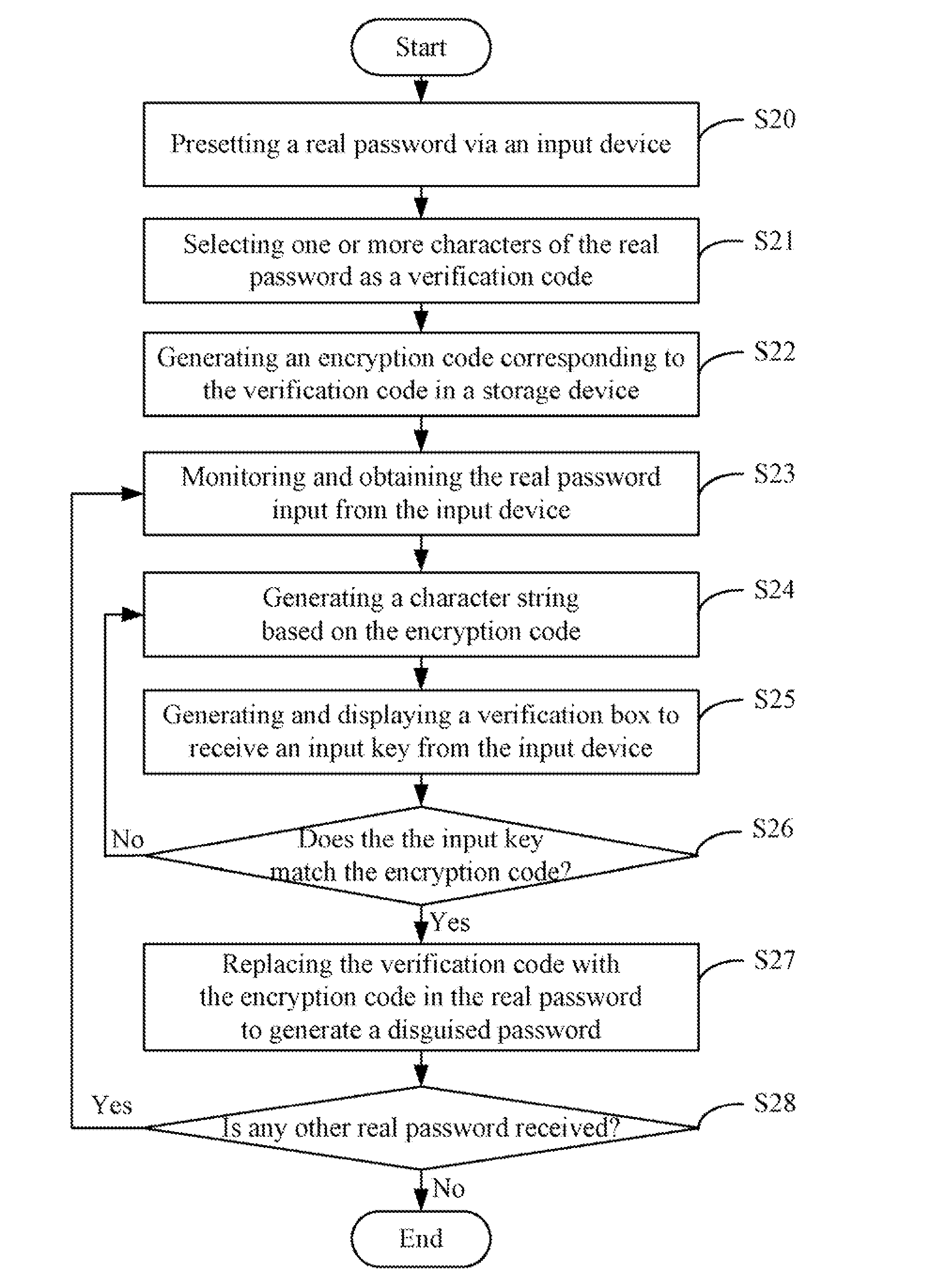
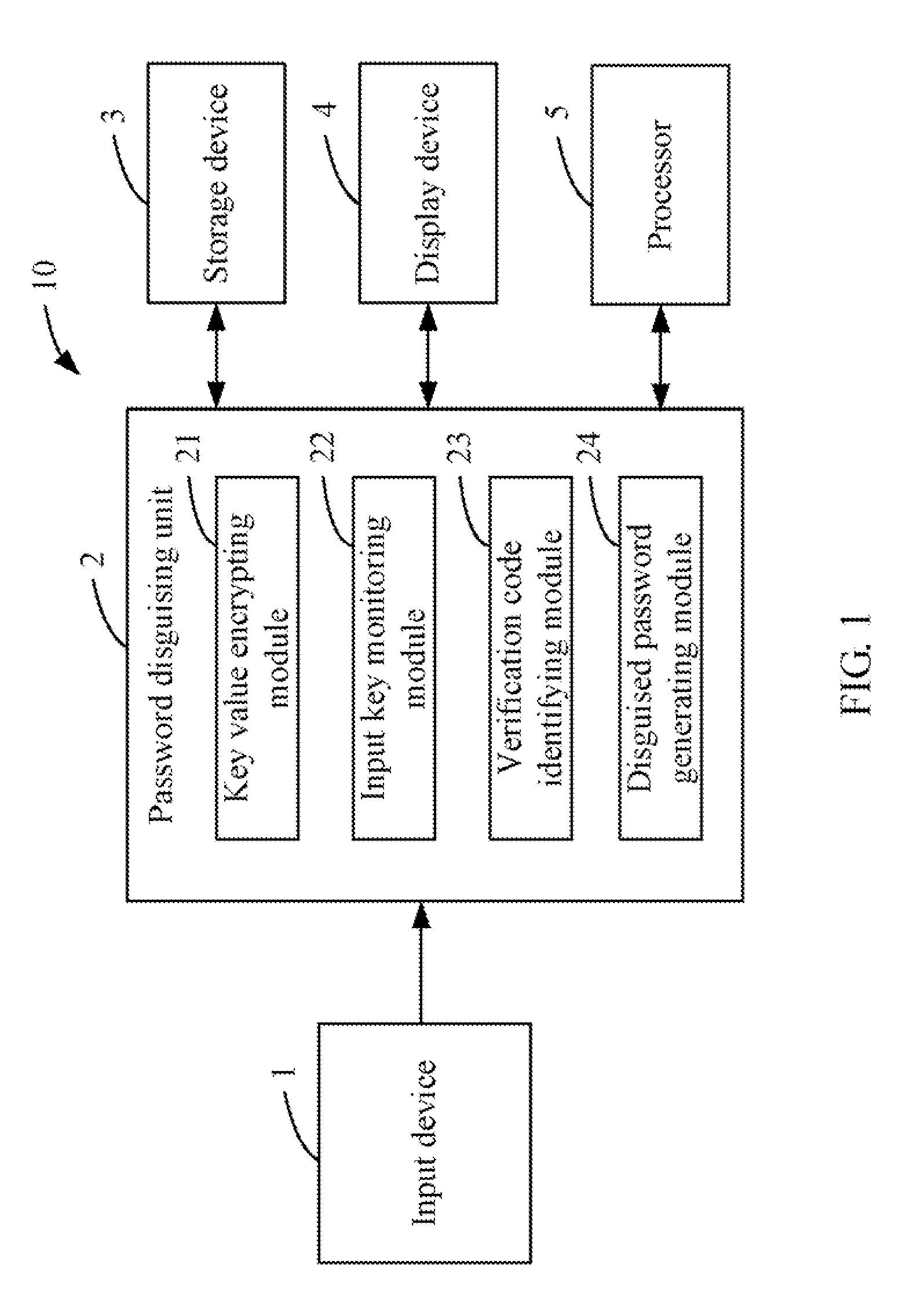
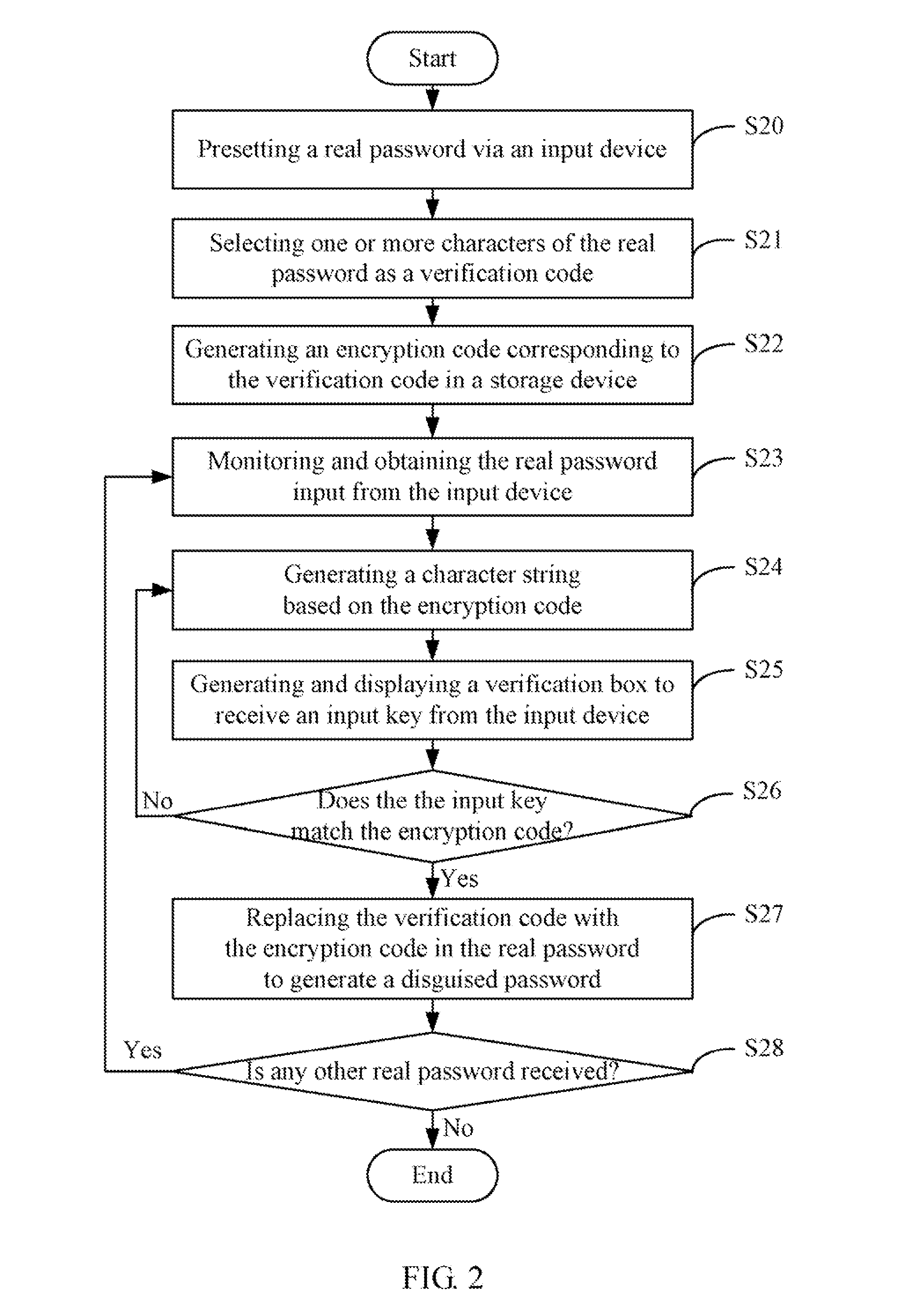
System and method for generating a disguised password based on a real password
InactiveUS20100318807A1Digital data processing detailsUser identity/authority verificationPasswordCAPTCHA
A system and method for generating a disguised password are provided. The method presets a real password via an input device, selects one or more characters from the real password as a verification code. The method further generates an encryption code corresponding to the verification code according to an encryption algorithm, generates a character string based on the encryption code, and displays a verification box on a display screen to receive an input key from the input device. In addition, the method determines whether the input key matches the encryption code of the character string, and generates a disguised password by replacing the verification code with the encryption code in the real password if the input key matches the encryption code of the character string.
Owner:HON HAI PRECISION IND CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com