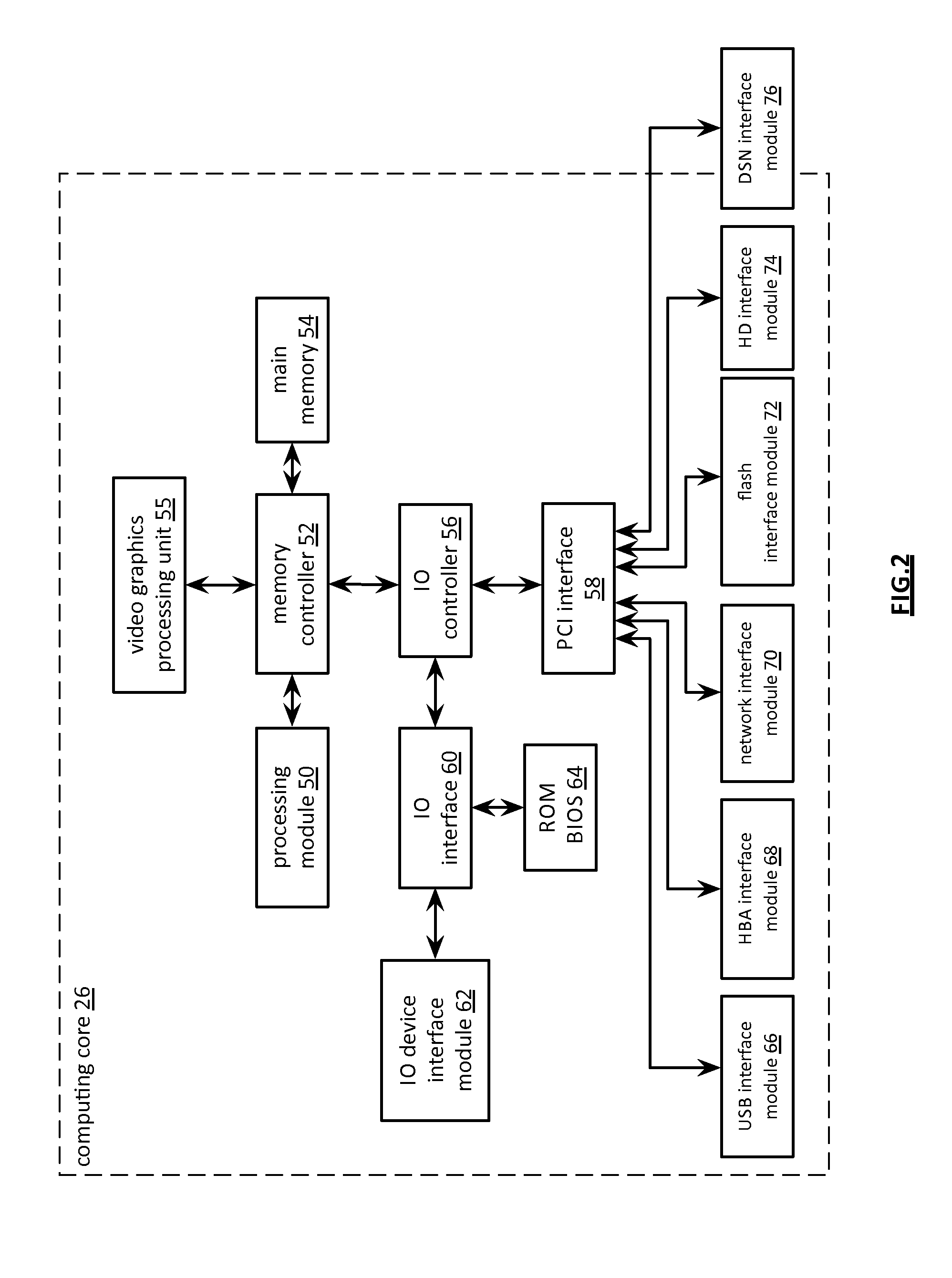
Patents
Literature
804 results about "Threshold number" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Definition of Threshold number. Threshold number means 110% of the number of permanent full-time positions in the base year for the first three-year period in which a business firm is eligible for an enterprise zone incentive grant.
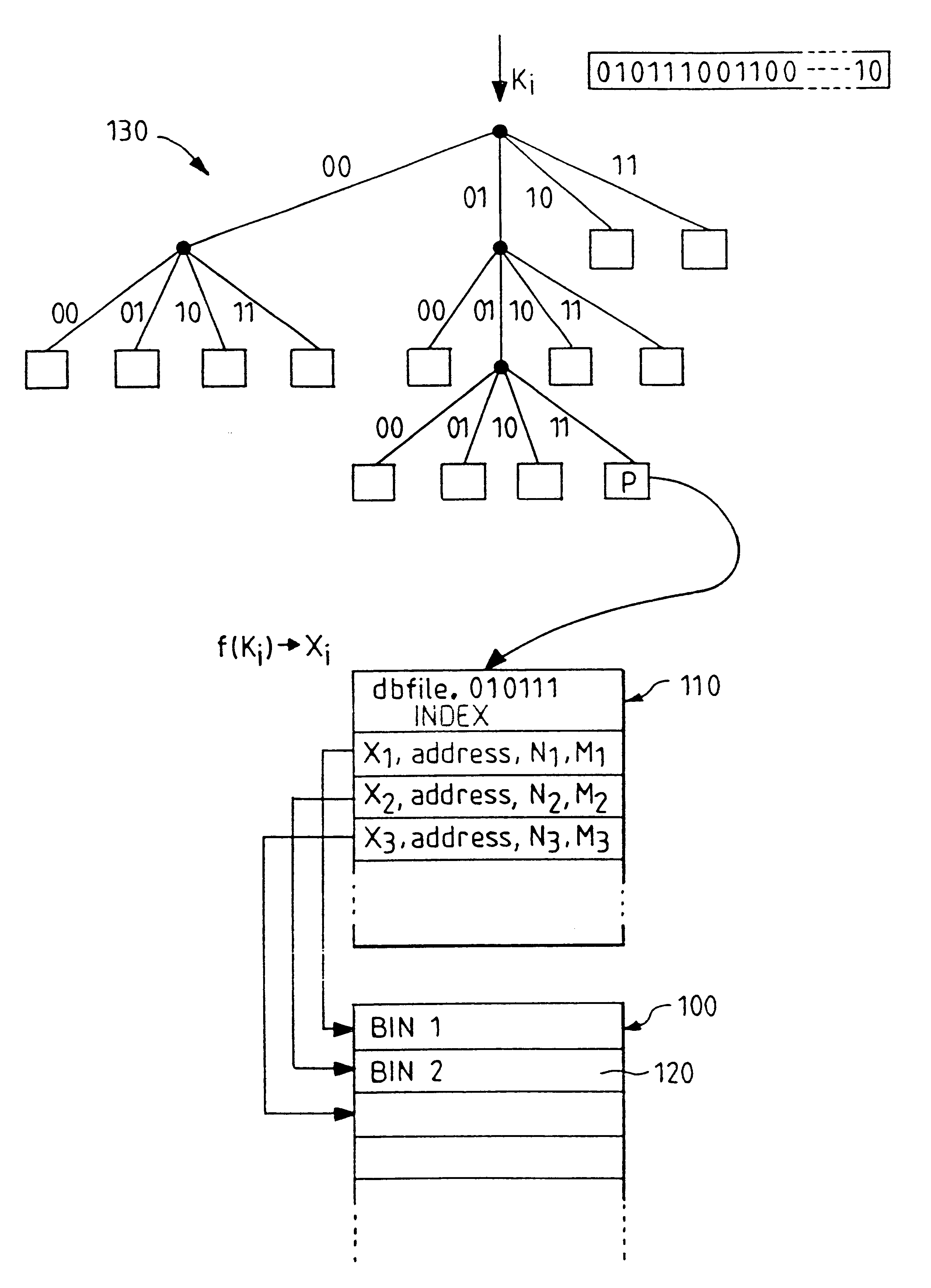
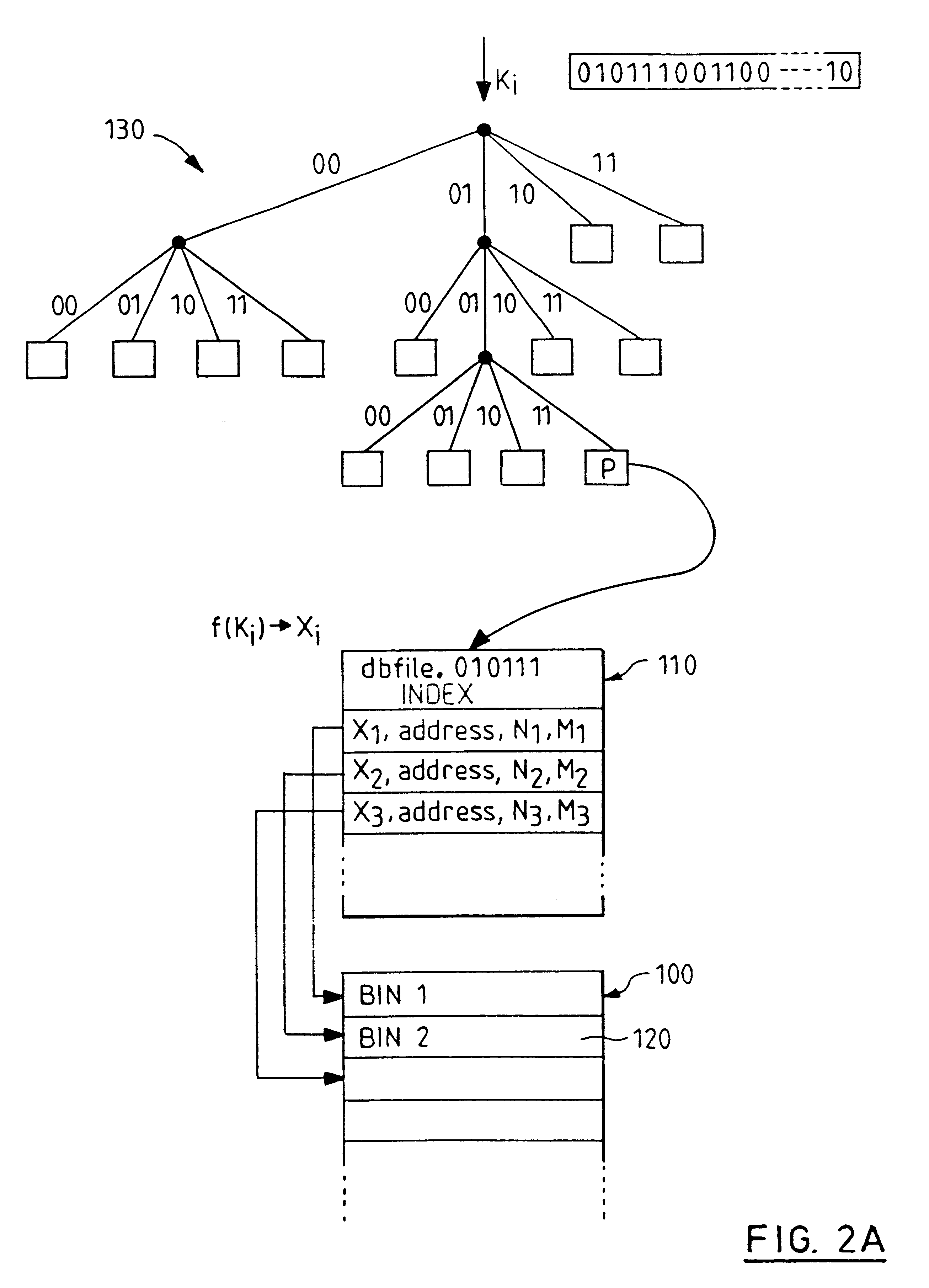
Indexed file system and a method and a mechanism for accessing data records from such a system
InactiveUS6292795B1Efficient access to dataWastefulData processing applicationsDigital data information retrievalExtensibilityCollision detection
A computer filing system includes a data access and allocation mechanism including a directory and a plurality of indexed data files or hash tables. The directory is preferably a radix tree including directory entries which contain pointers to respective ones of the hash tables. Using a plurality of hash tables avoids the whole database ever having to be re-hashed all at once. If a hash table exceeds a preset maximum size as data is added, it is replaced by two hash tables and the directory is updated to include two separate directory entries each containing a pointer to one of the new hash tables. The directory is locally extensible such that new levels are added to the directory only where necessary to distinguish between the hash tables. Local extensibility prevents unnecessary expansion of the size of the directory while also allowing the size of the hash tables to be controlled. This allows optimisation of the data access mechanism such that an optimal combination of directory-look-up and hashing processes is used. Additionally, if the number of keys mapped to an indexed data file is less than a threshold number (corresponding to the number of entries which can be held in a reasonable index), the index for the data file is built with a one-to-one relationship between keys and index entries such that each index entry identifies a data block holding data for only one key. This avoids the overhead of the collision detection of hashing when it ceases to be useful.
Owner:IBM CORP
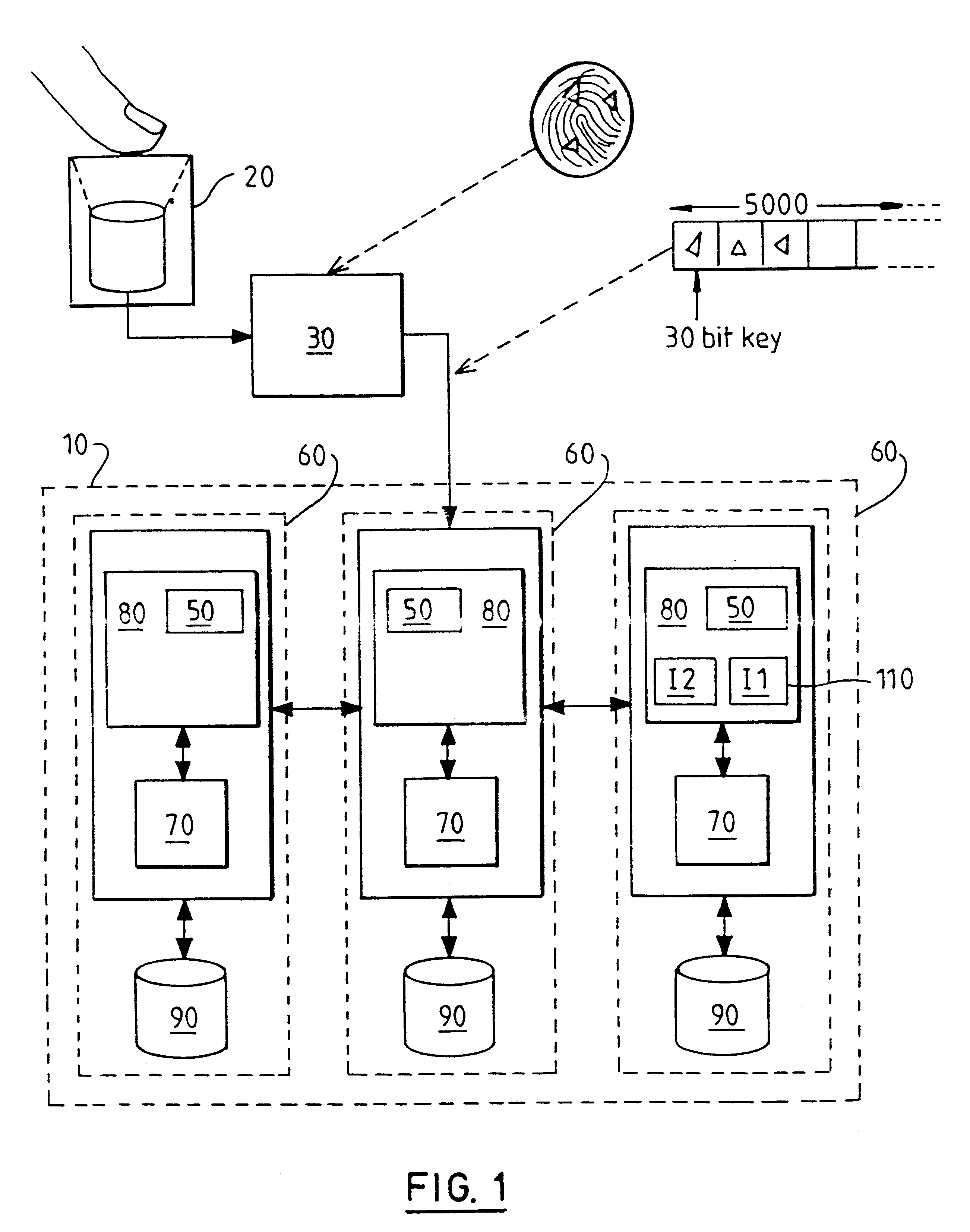
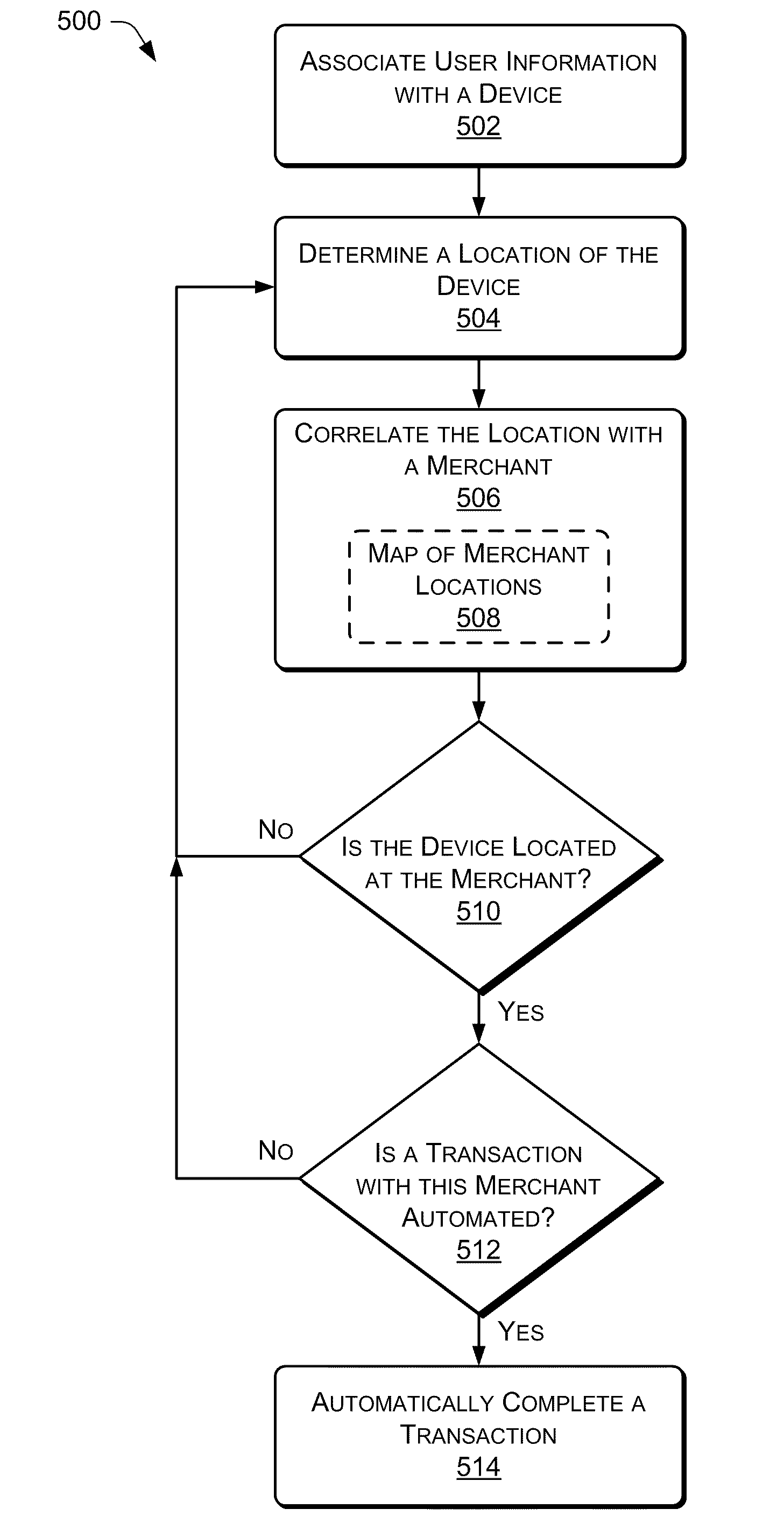
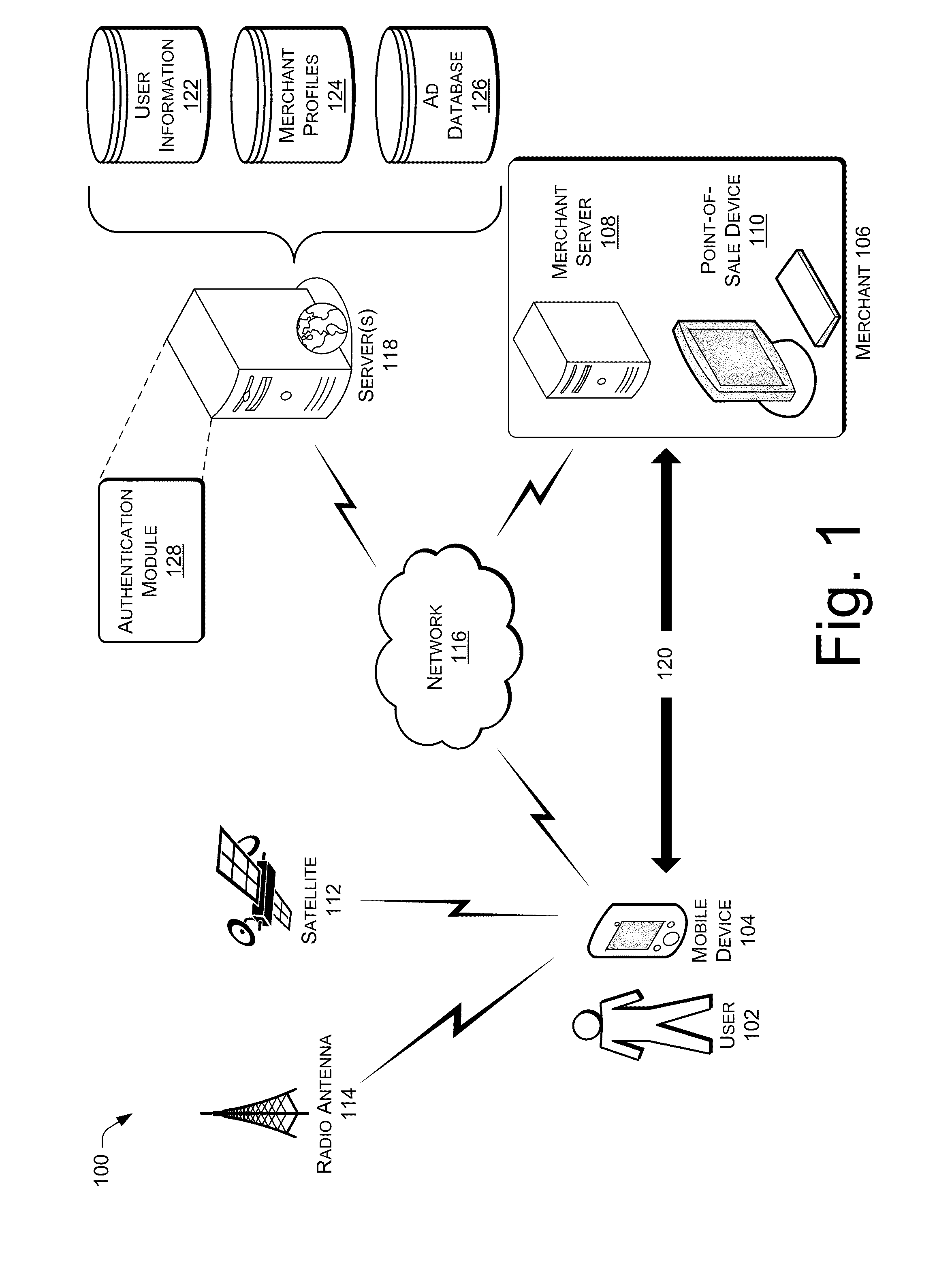
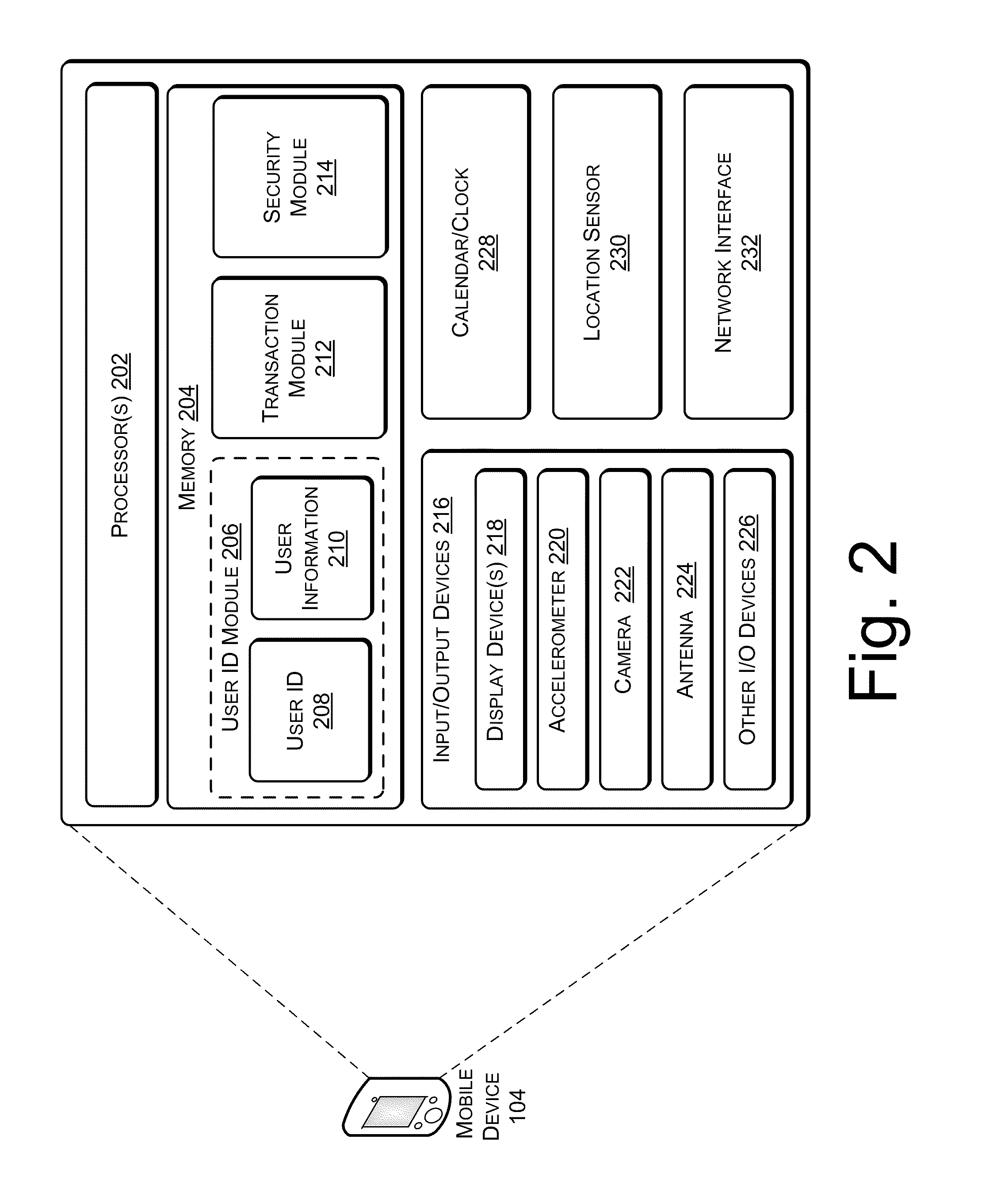
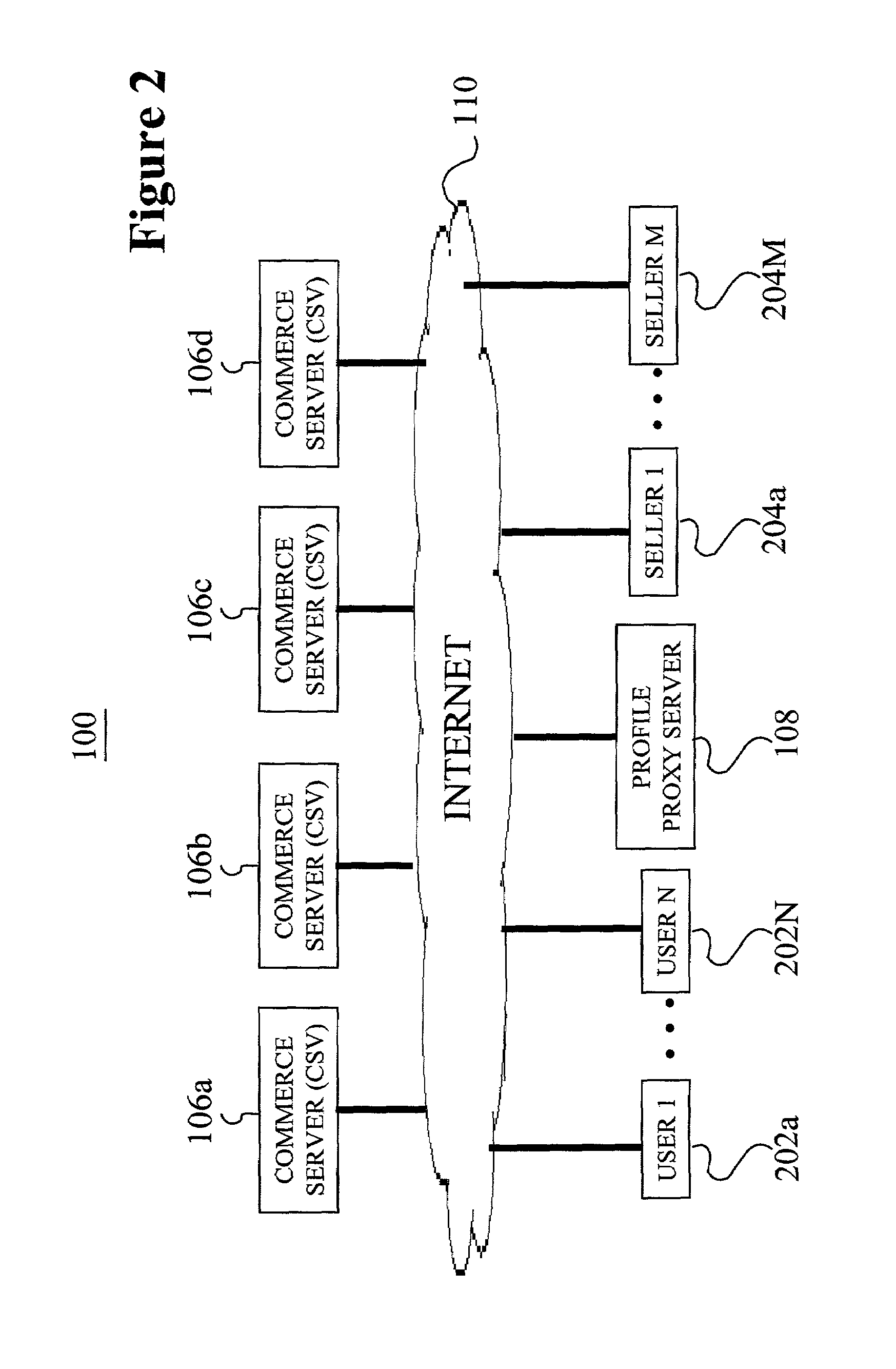
User Profile and Geolocation for Efficient Transactions
Techniques for providing friction-free transactions using geolocation and user identifiers are described herein. These techniques may ascertain a user's location based on a location of a mobile device. A transaction between the user and a merchant may be completed with zero or minimal input from the user based on the geolocation of the mobile device and the user identifiers. In some implementations, a transaction initiated earlier is completed when the mobile device arrives at the merchant. Additionally, a parent-child or similar relationship may be established between multiple devices. Security on the mobile device based may be provided by biometric identification and calculation of variance from regular movement patterns. Advertisements may be sent to the mobile device based on bids from merchants near to the mobile device. Promotions may be sent to the mobile device when more than a threshold number of mobile devices are located at the same merchant.
Owner:AMAZON TECH INC
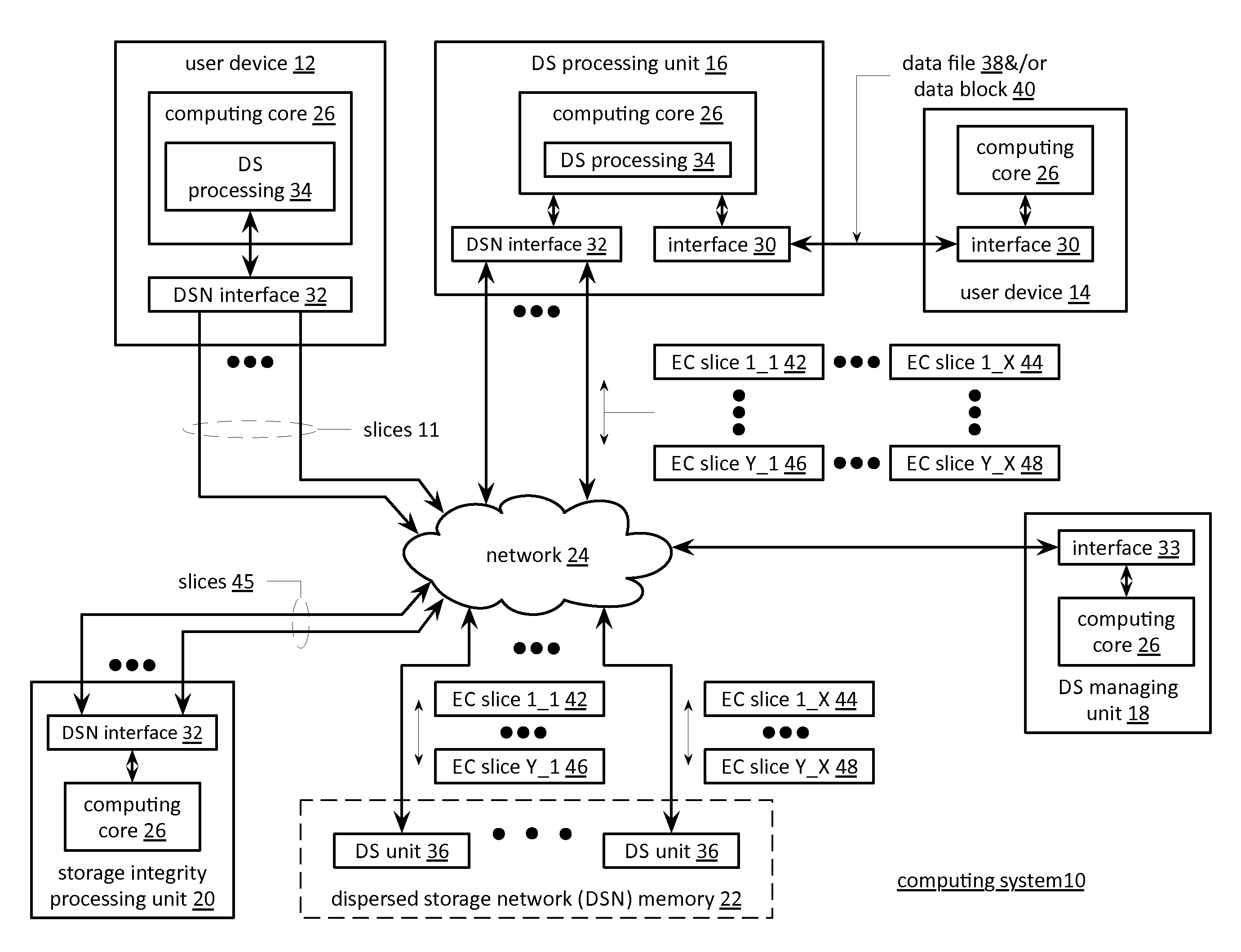
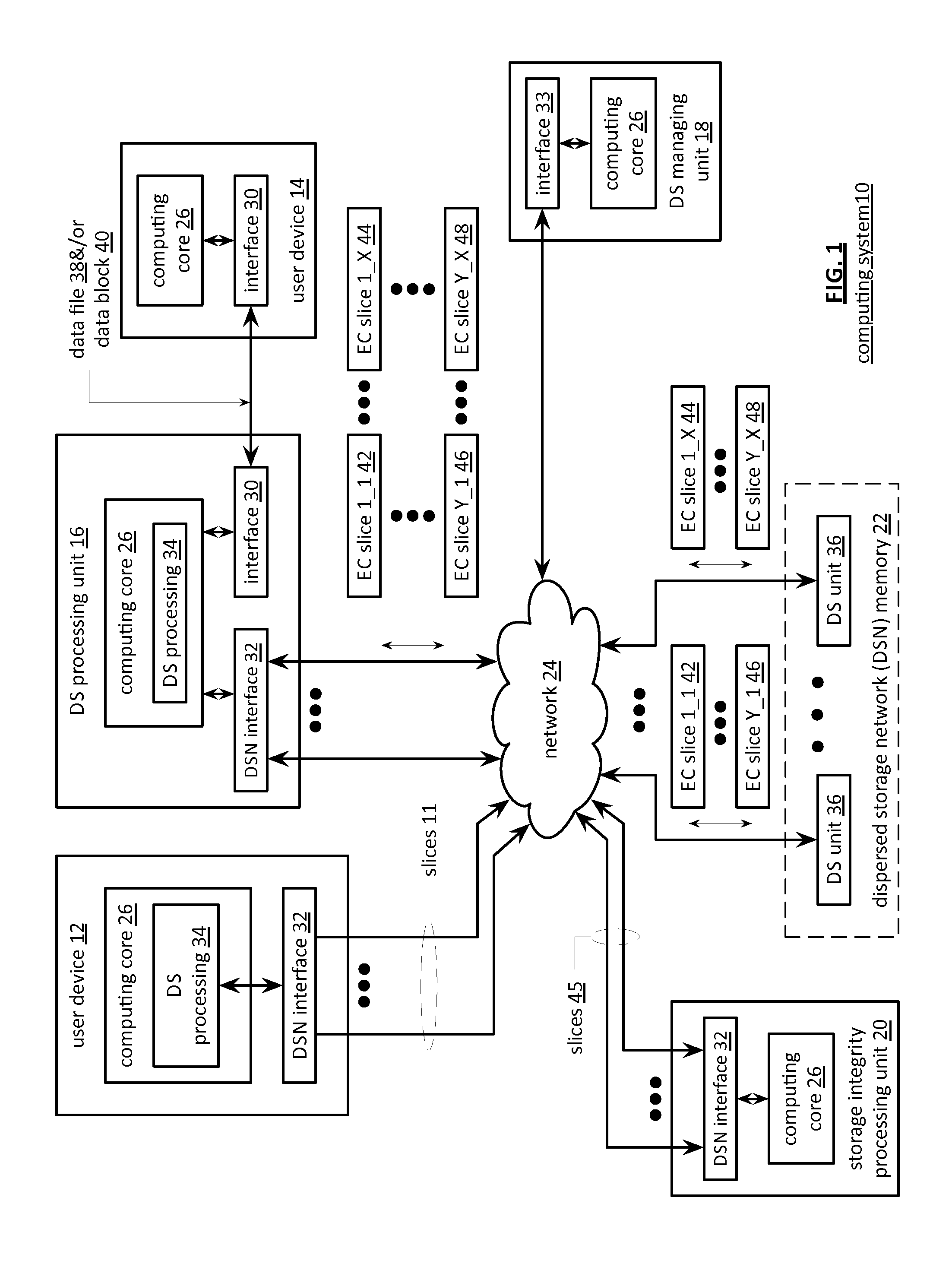
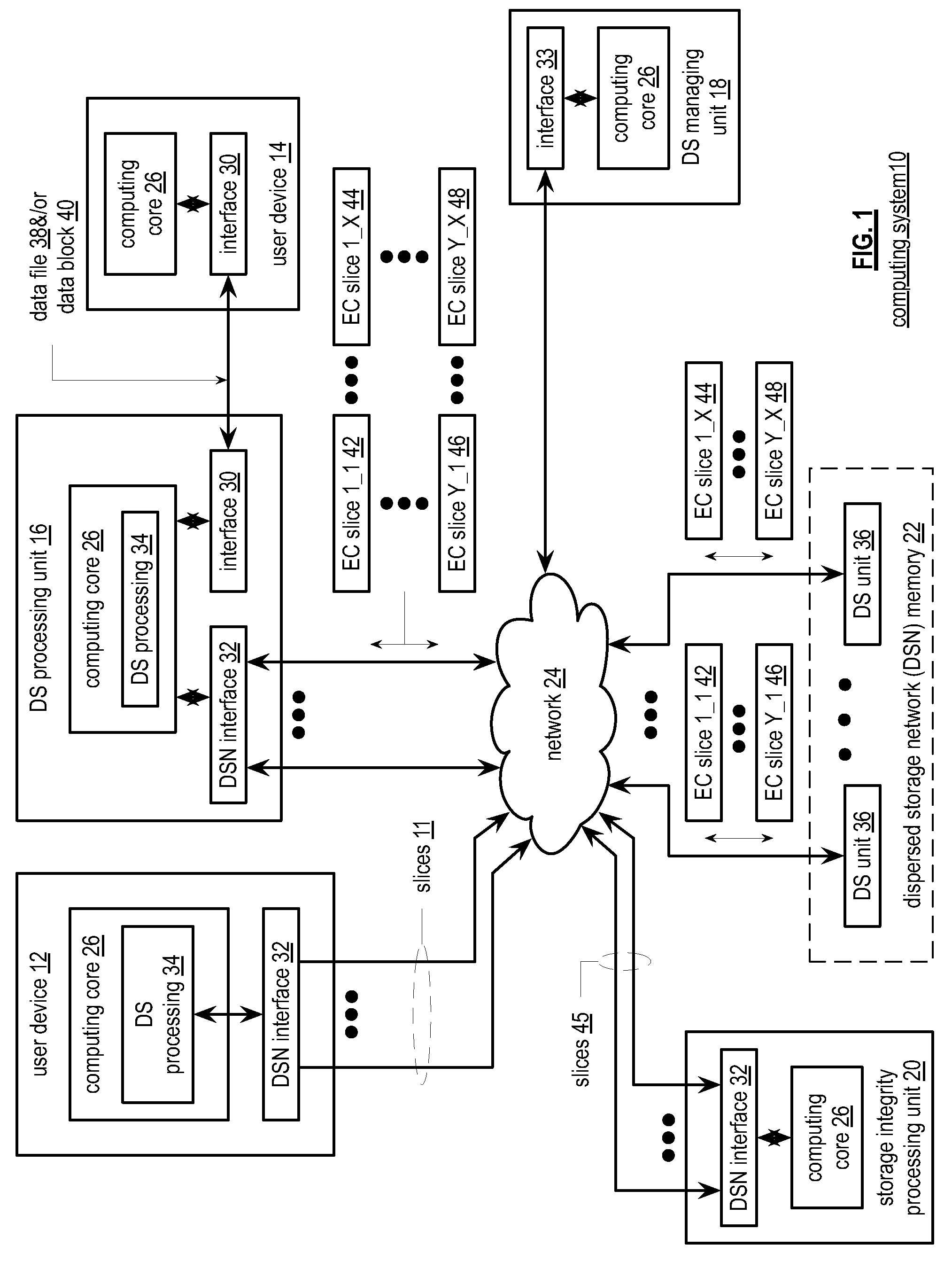
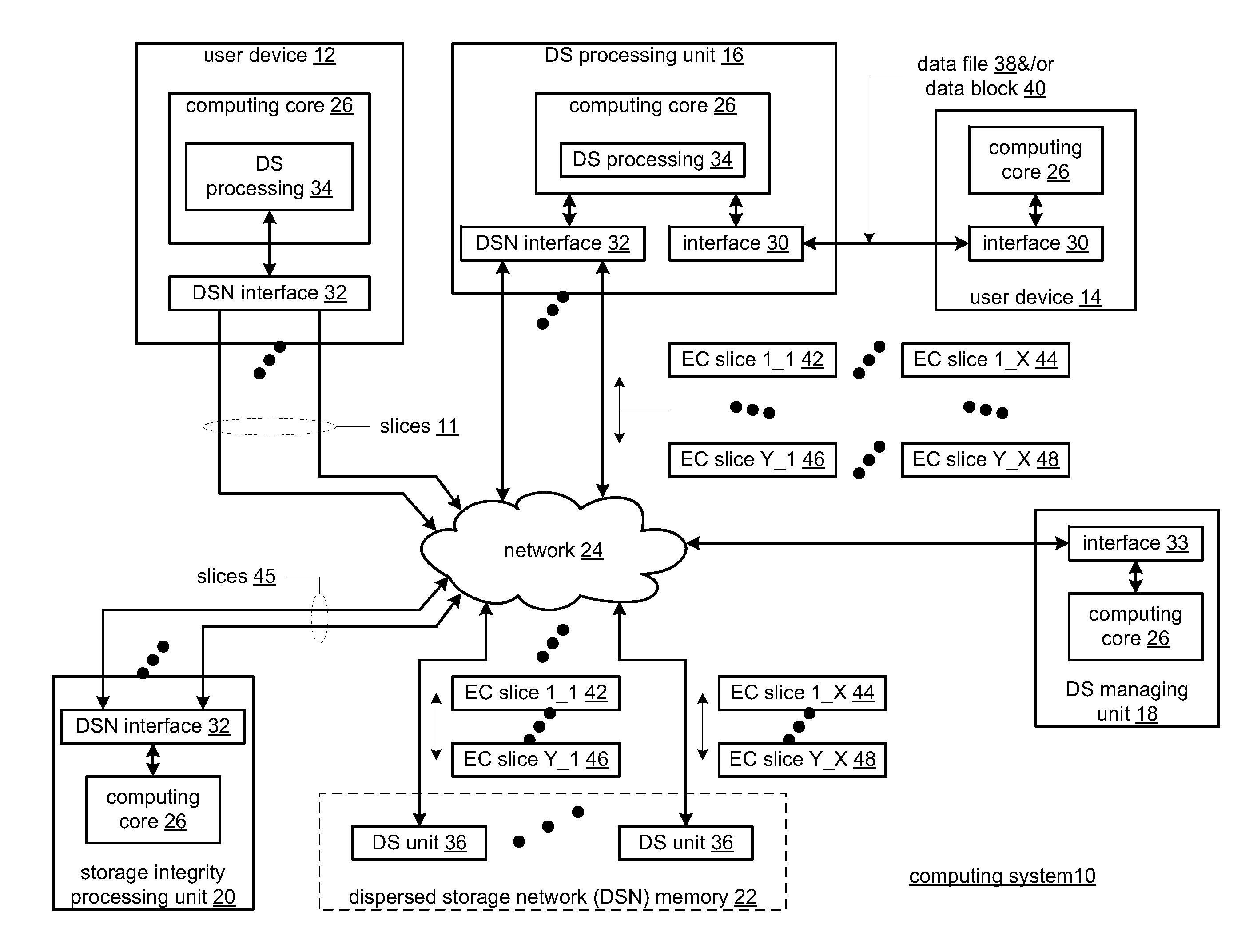
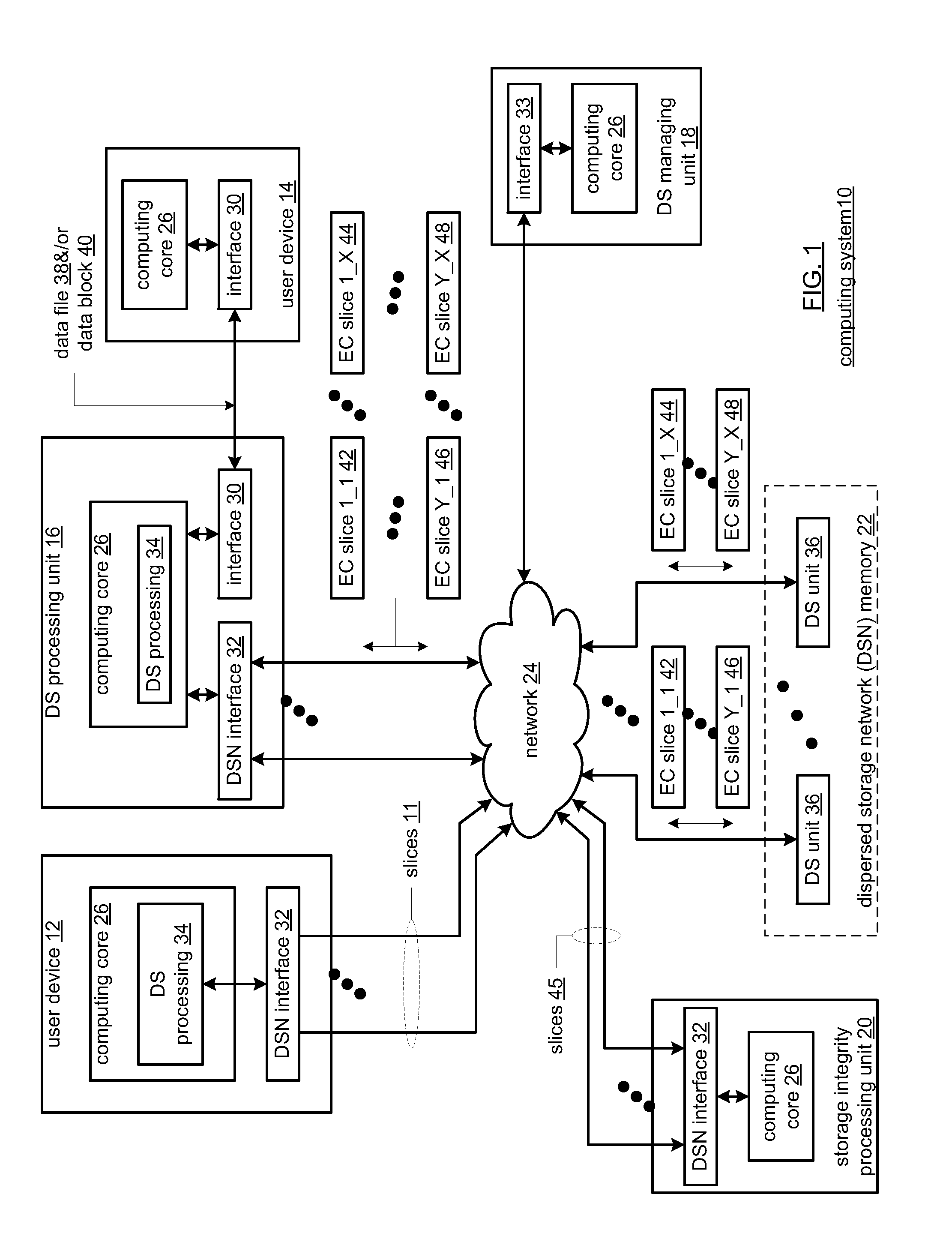
Updating distributed storage network software
ActiveUS20120311557A1Memory architecture accessing/allocationDigital computer detailsManagement unitSoftware update
A method begins by a management unit of a distributed storage network (DSN) sending a software update notice to a plurality of dispersed storage (DS) units, wherein the plurality of DS units supports a plurality of digital storage vaults, and wherein a set of DS units of the plurality of DS units supports a digital storage vault of the plurality of digital storage vaults. The method continues with a DS processing module determining an update strategy for updating software of the plurality of DS units such that at least a decode threshold number of DS units of the set of DS units is continually available to service access requests to the digital storage vault and updating the software of at least some of the plurality of DS units in accordance with the update strategy.
Owner:PURE STORAGE
Upgrading network traffic management devices while maintaining availability
ActiveUS20100042869A1Software engineeringMultiple digital computer combinationsTraffic capacityVirtual cluster
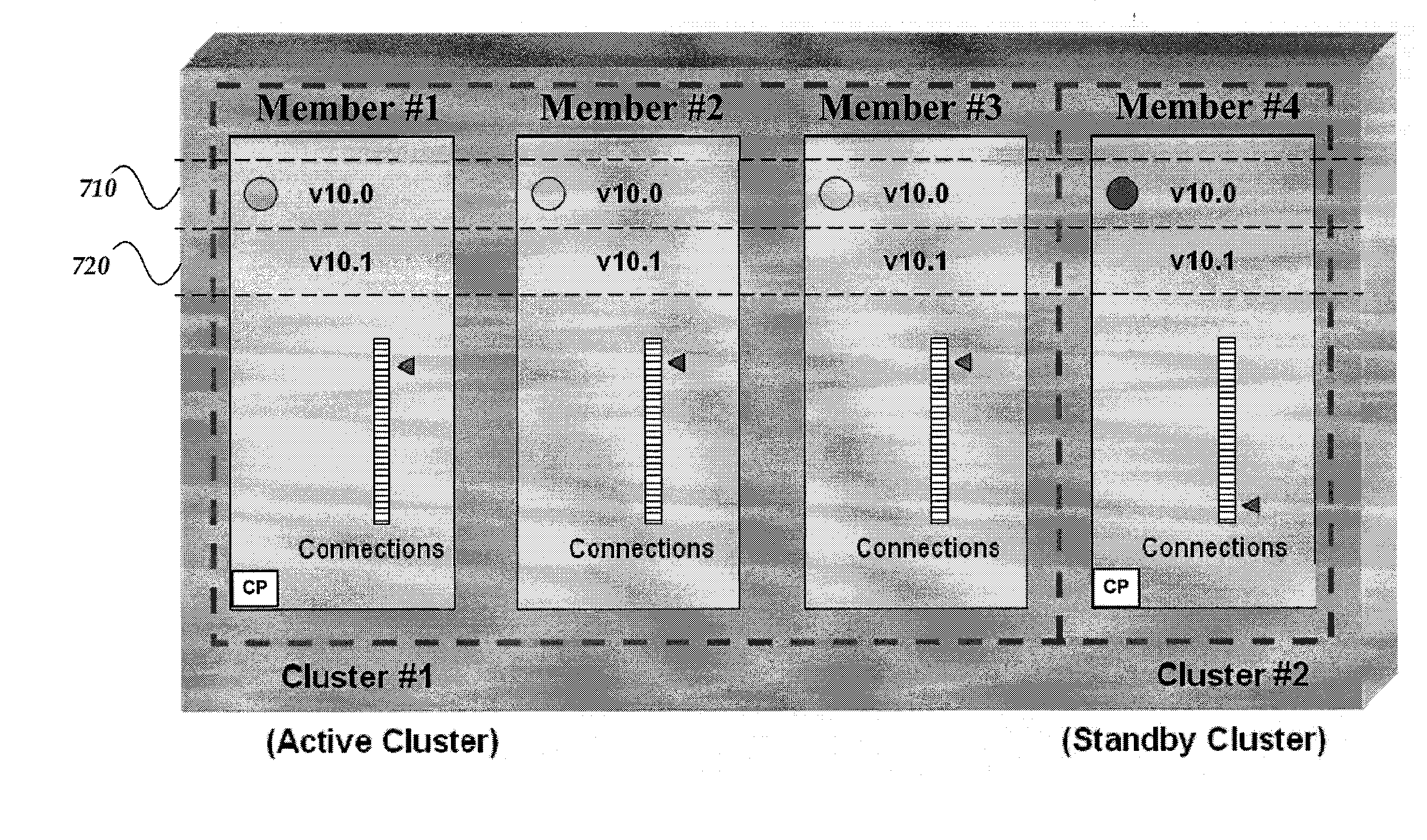
A method, system, machine-readable storage medium, and apparatus are directed towards upgrading a cluster by bifurcating the cluster into two virtual clusters, an “old” virtual cluster (old active cluster) and a “new” virtual cluster (new standby cluster), and iteratively upgrading members of the old cluster while moving them into the new cluster. While members are added to the new cluster, existing connections and new connections are seamlessly processed by the old cluster. Optionally, state mirroring occurs between the old cluster and the new cluster once the number of members of the old and new clusters are approximately equal. Once a threshold number of members have been transferred to the new cluster, control and processing may be taken over by the new cluster. Transfer of control from the old cluster to the new cluster may be performed by failing over connectivity from the old cluster to the new cluster.
Owner:F5 NETWORKS INC
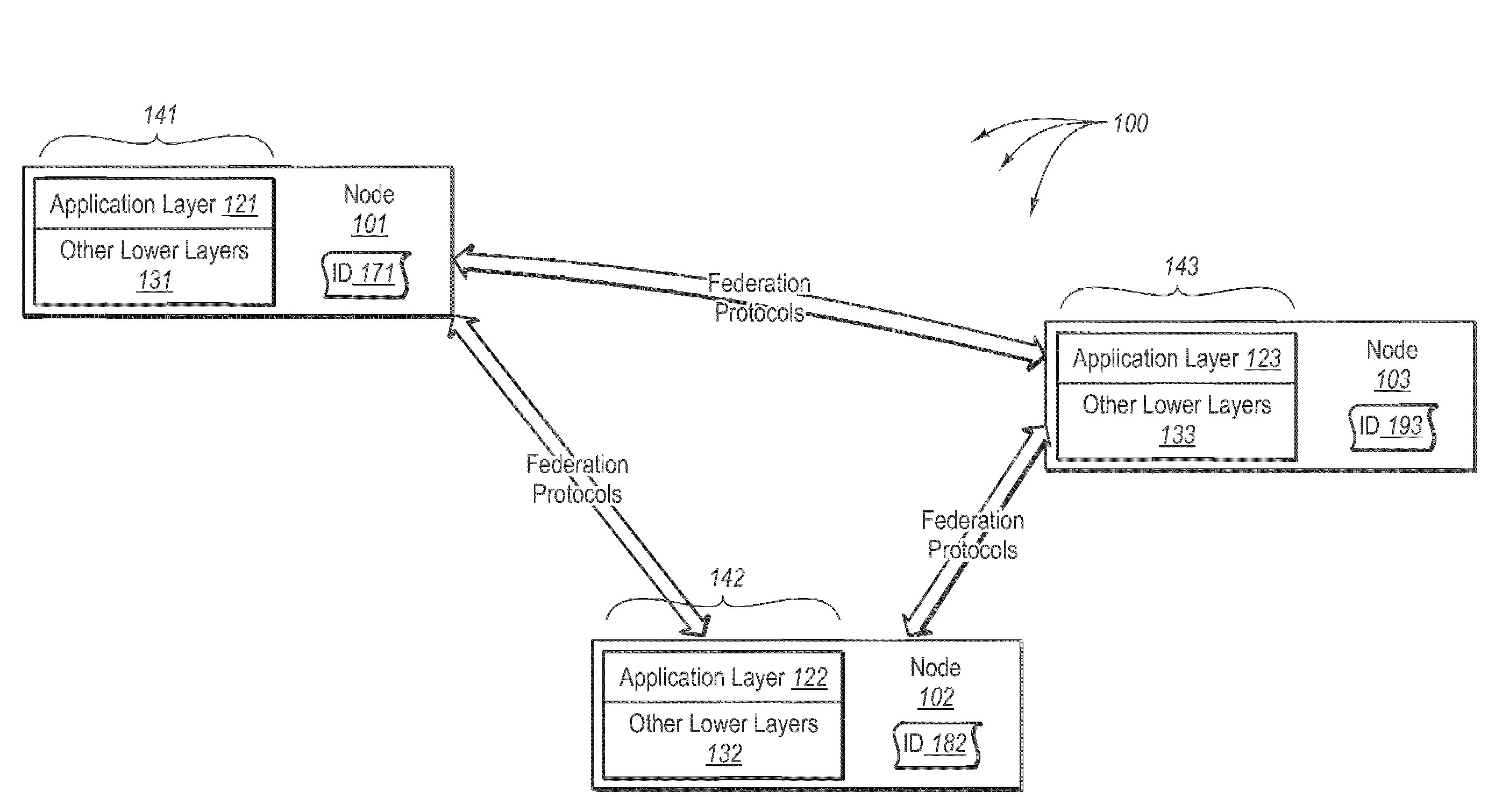
Data consistency within a federation infrastructure
InactiveUS20080288646A1Well formedDigital data information retrievalInput/output to record carriersClient dataClient-side
In some embodiments, it is determined that a primary node has been elected from among a plurality of nodes in a replica set of nodes. The primary node accepts and processes client data access requests. The replica set includes the primary node and other secondary nodes. The primary node receives client data access requests. The primary node assigns a data sequence number to each client data access request that mutates state in the order the client data access requests are received. The data sequence numbers include a linearized processing order that is to be followed by each of the nodes in the replica set. The primary node sends the mutating client data access requests including any corresponding data sequence numbers to the secondary nodes. The primary node receives, from a threshold number of secondary nodes, an acknowledgement indicating reception of the client data access request. The primary node commits the data mutating access request.
Owner:MICROSOFT TECH LICENSING LLC
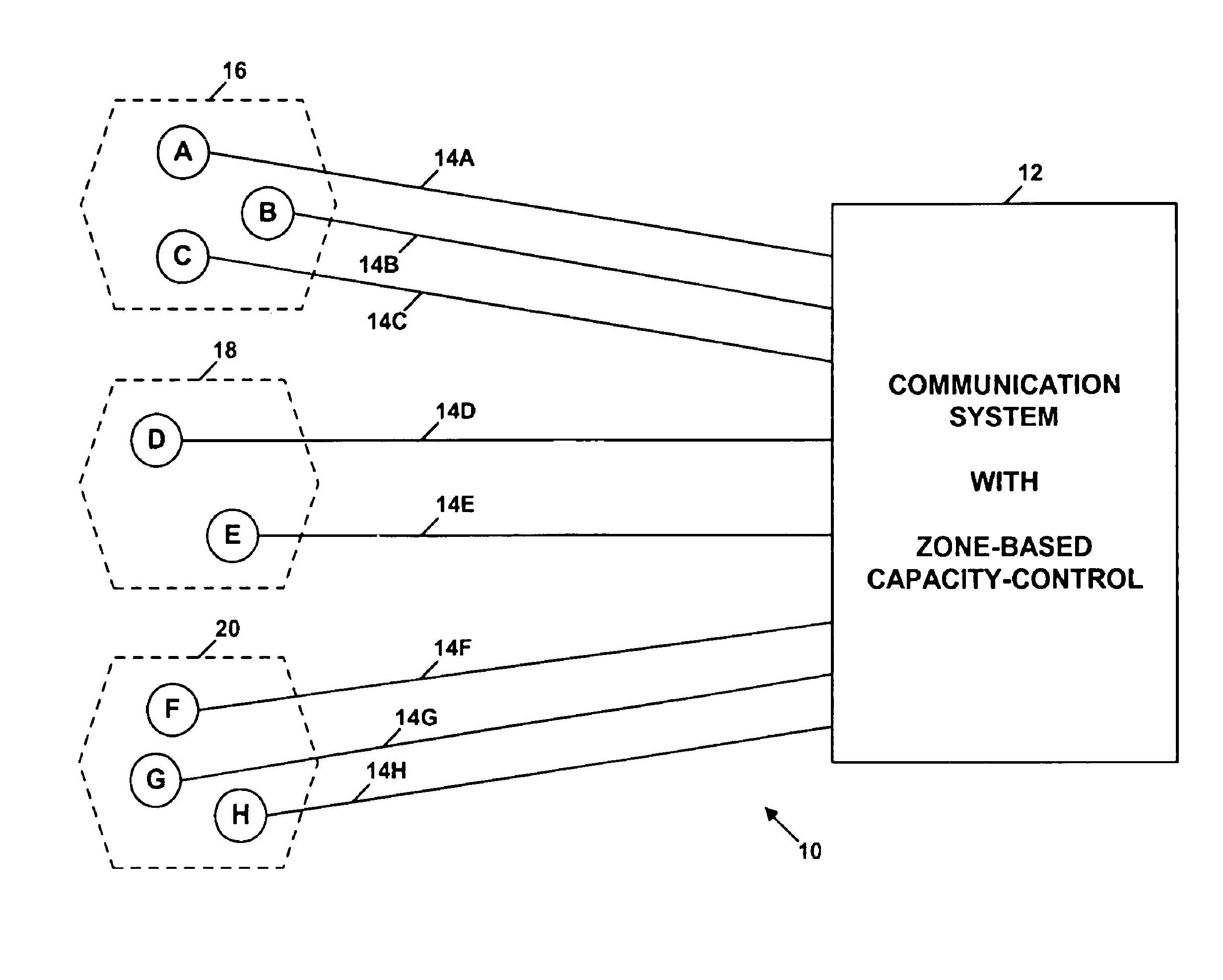
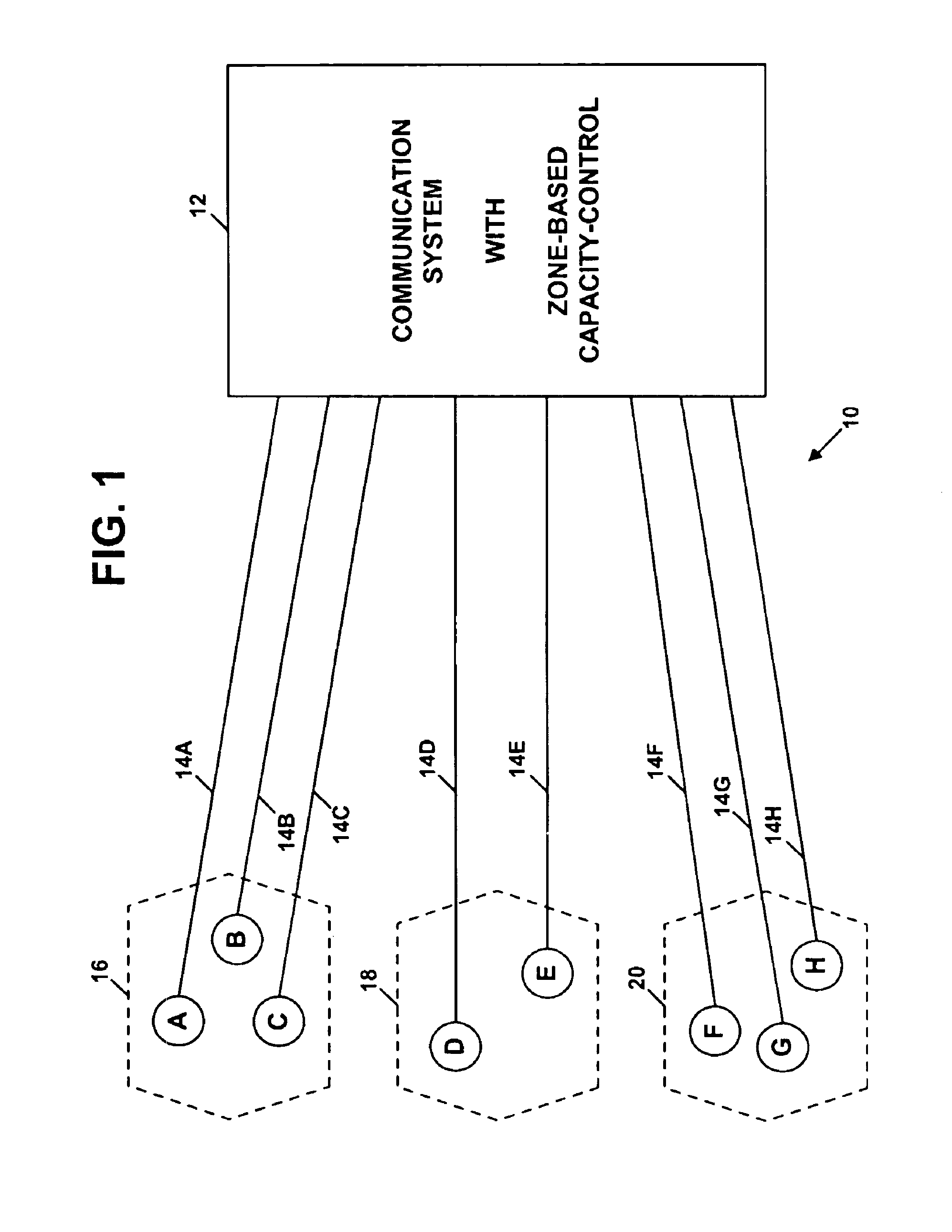
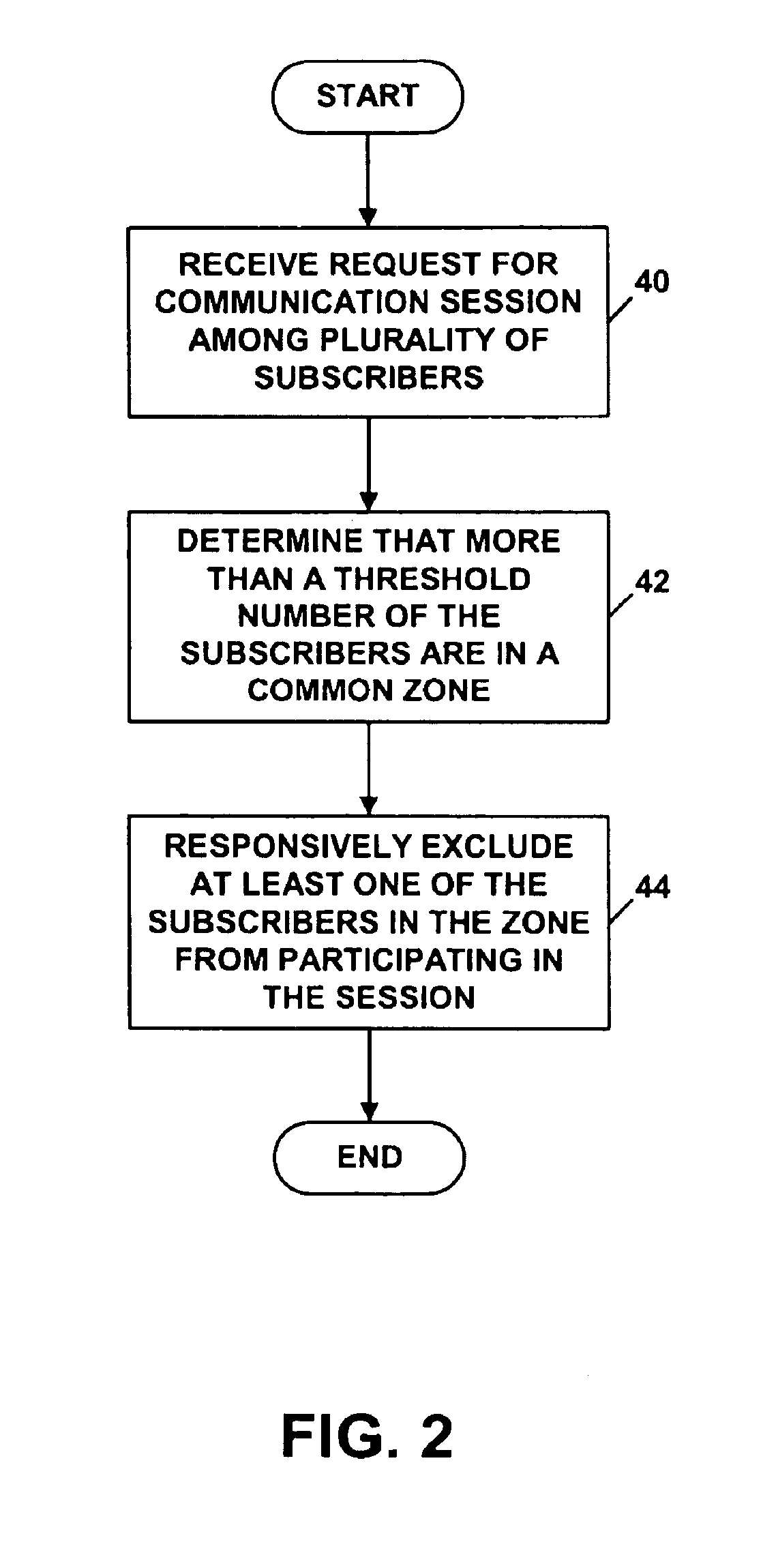
Method and system for zone-based capacity control
InactiveUS6882850B2Avoid accessPreventing situationSpecial service provision for substationMultiplex system selection arrangementsControl communicationsDistributed computing
A mechanism is disclosed for controlling capacity in a communication system, based on zones in which subscribers are located. When a subscriber seeks to establish a communication session among multiple subscribers, a determination is made as to whether more than a threshold number of the subscribers are located in a common zone. If so, the excess subscribers in that zone are excluded from participating in the session.
Owner:SPRINT SPECTRUM LLC
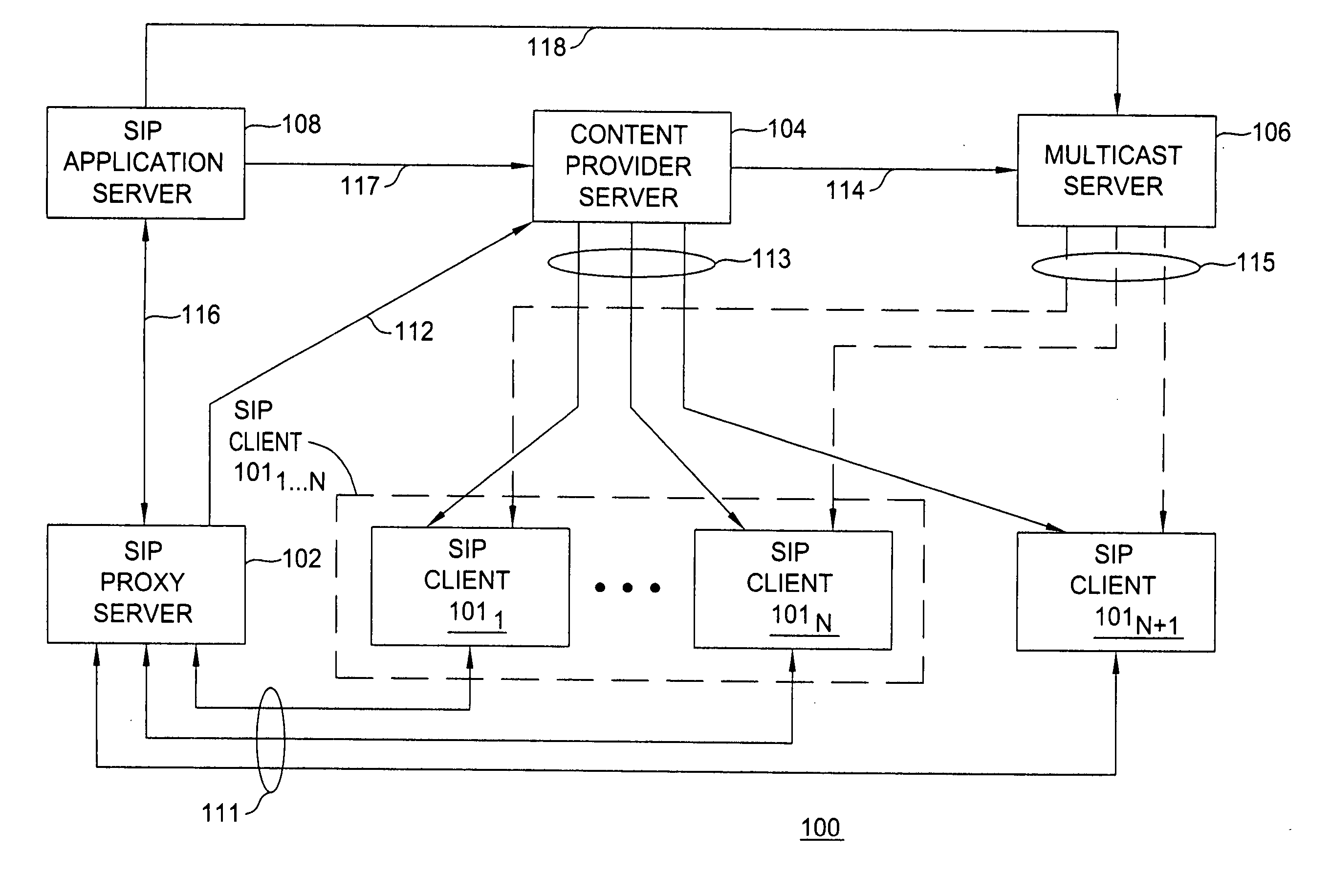
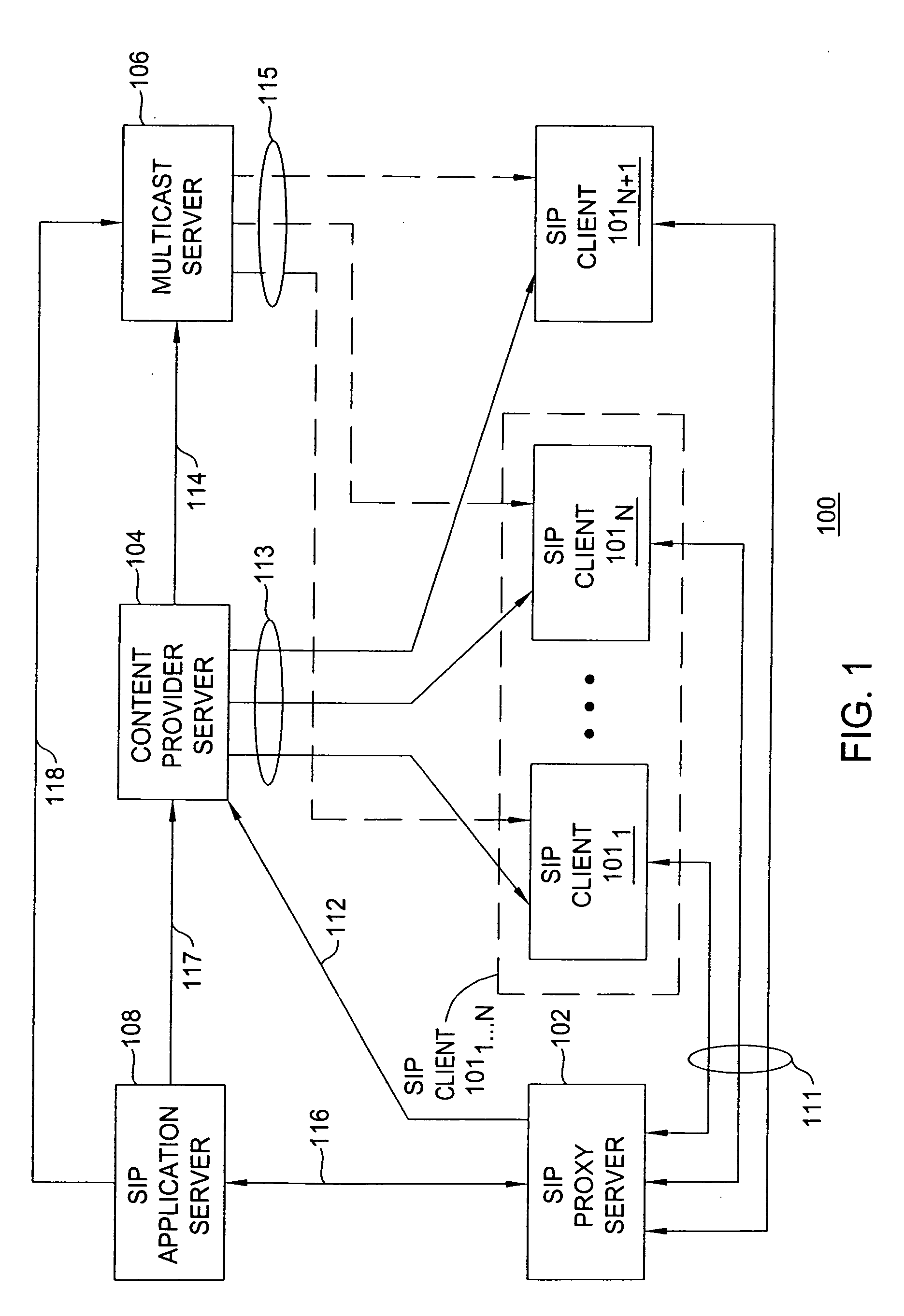
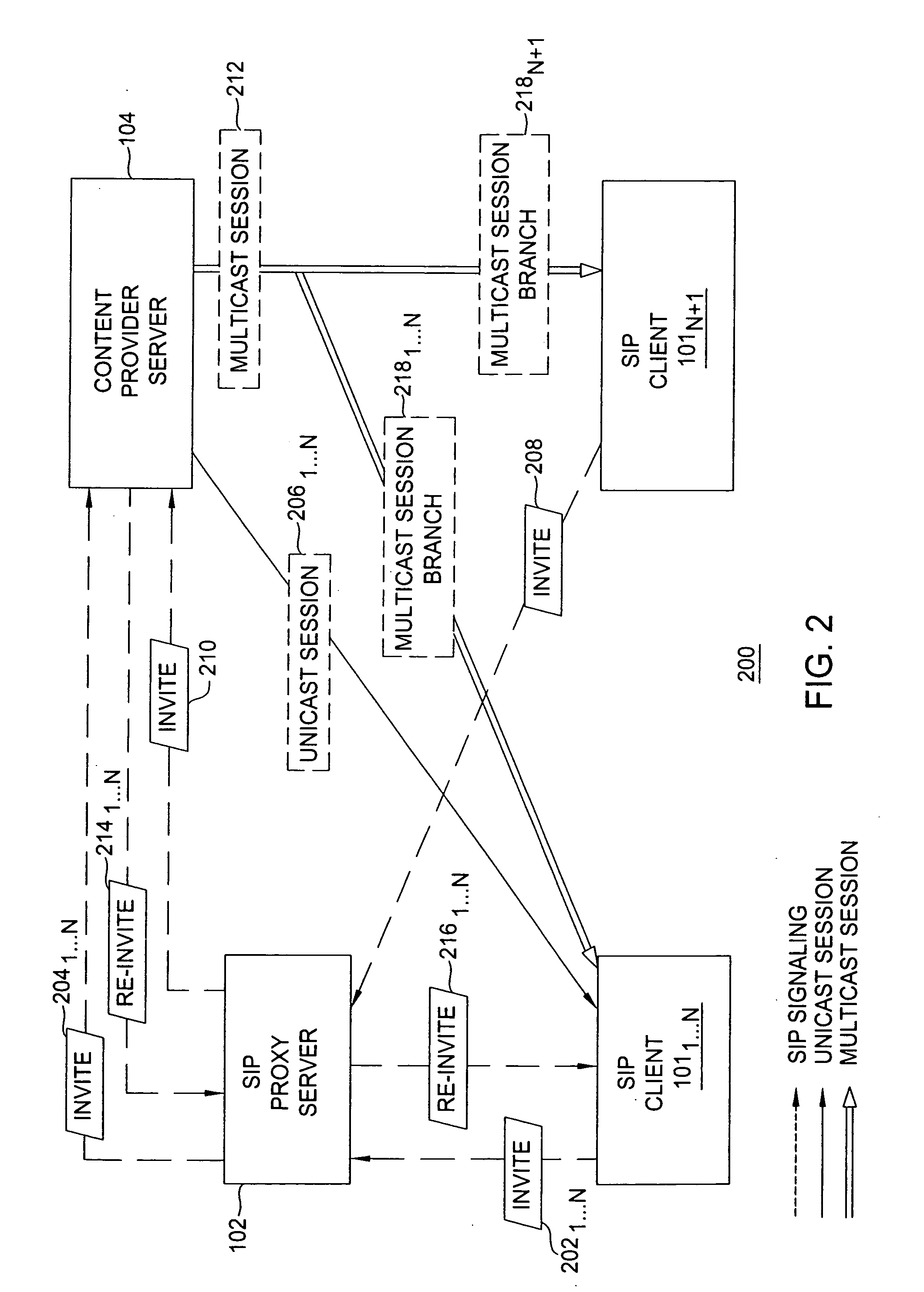
Method for converting between unicast sessions and a multicast session
ActiveUS20070147411A1Special service provision for substationTime-division multiplexComputer networkThreshold number
The invention includes methods for converting between a plurality of unicast sessions and a multicast session. A method for converting from unicast sessions to a multicast session includes receiving a request for establishing a unicast session for delivering content to a first client device, generating a multicast session establishment message adapted for establishing a multicast session with the client device for delivering the content to the client device, and generating at least one multicast session join message for the other client devices, the at least one multicast session join message adapted for enabling the other client devices to join the multicast session. The multicast session establishment message is generated using a threshold number of unicast sessions. A method for converting from a multicast session to a unicast session is provided. A method for converting from a plurality of unicast sessions to a plurality of multicast sessions is provided.
Owner:ALCATEL LUCENT SAS
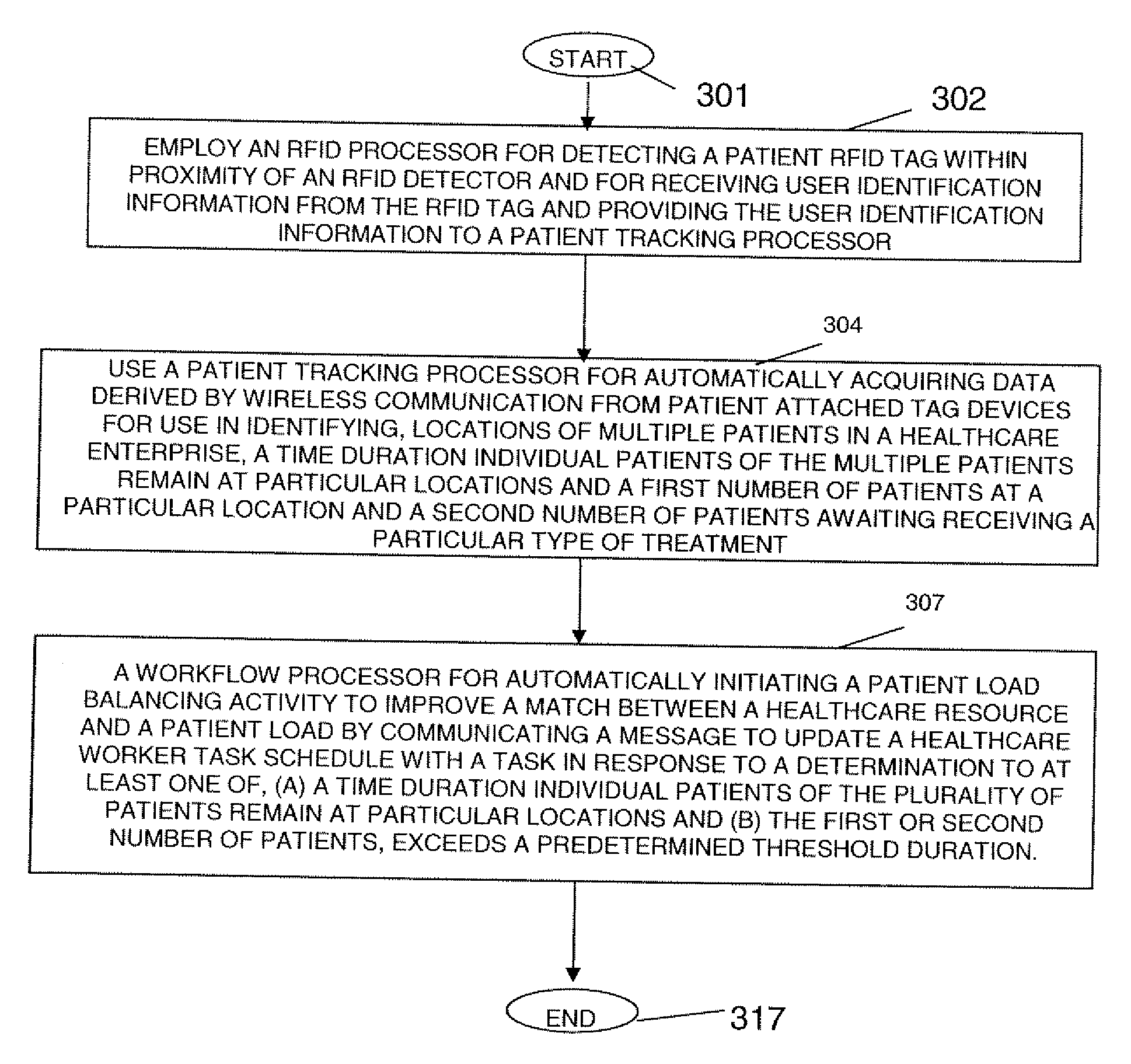
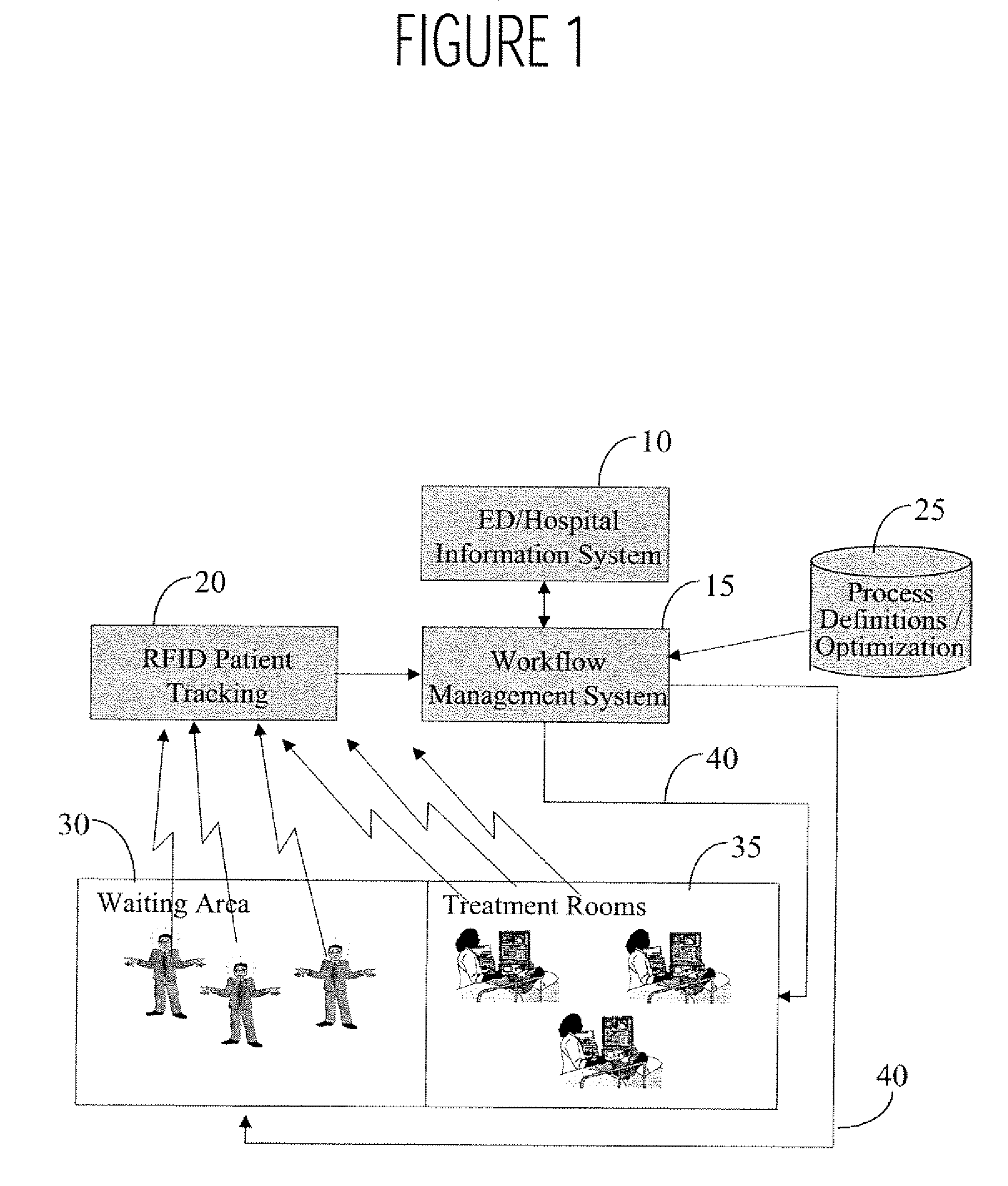
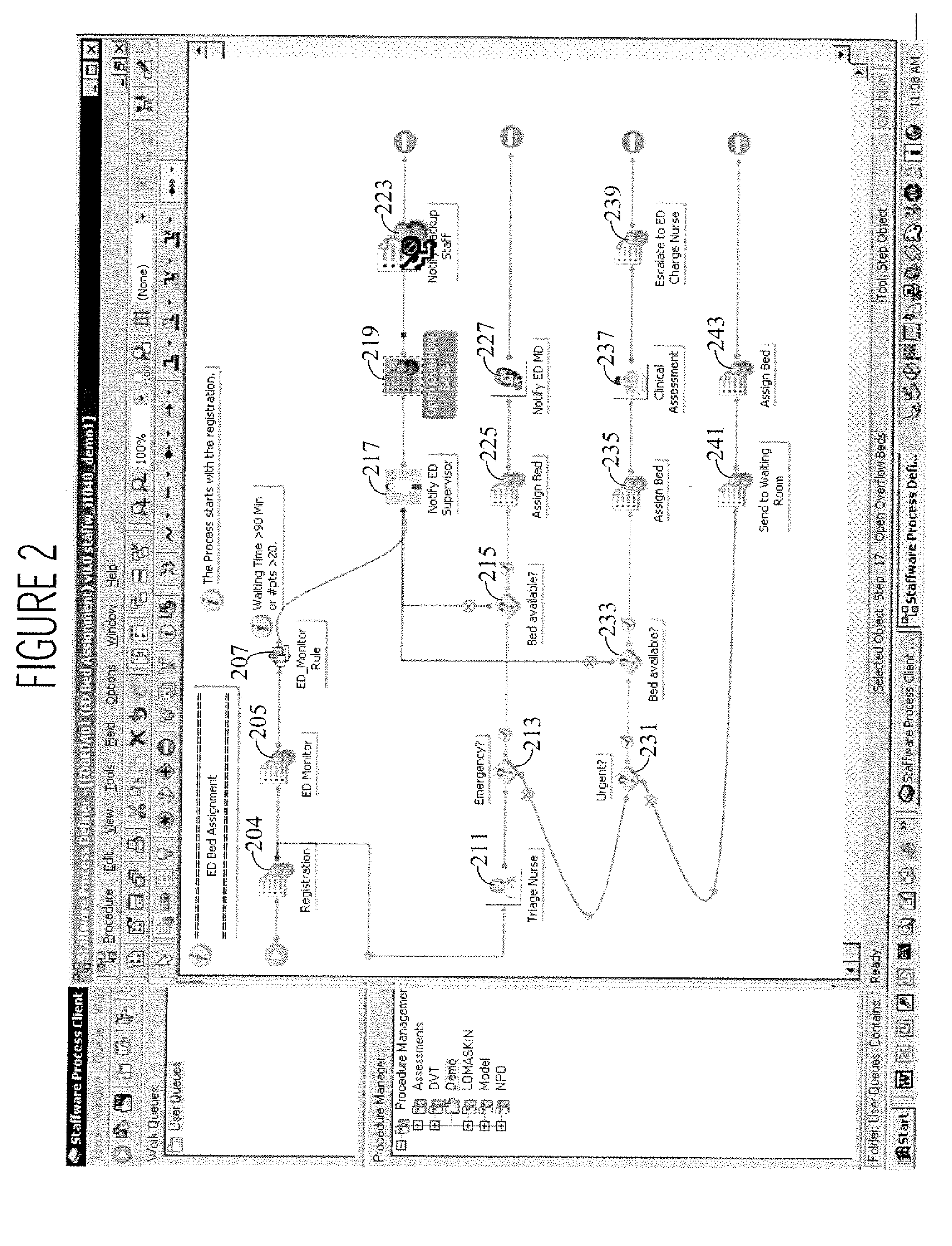
Task and Workflow Management System for Healthcare and other Applications
InactiveUS20070129983A1Improve matchData processing applicationsHealthcare resources and facilitiesMission timeTask management
A task management system uses patient tags (e.g., wireless RFID, Infrared tracking, GPS etc.) for patient location tracking, together with an integrated workflow system to automatically, track patient location how long they have been there and how many patients are at the same location (e.g., waiting room) and manages waiting time and an overall waiting queue, supporting automated adjustment of healthcare staffing, patient flows, and team coordination. A task management system for use in providing healthcare to a patient includes a patient tracking processor and a workflow processor. The patient tracking processor automatically acquires data derived by wireless communication from patient attached tag devices for use in identifying a location of multiple patients in a healthcare enterprise and identifying a first number of patients at a particular location and a second number of patients awaiting receiving a particular type of treatment. The workflow processor automatically initiates a patient load balancing activity to improve a match between a healthcare resource and a patient load by communicating a message to update a healthcare worker task schedule with a task in response to a determination the identified first or second number of patients exceeds a predetermined threshold number.
Owner:SIEMENS AG
Network overload detection and mitigation system and method
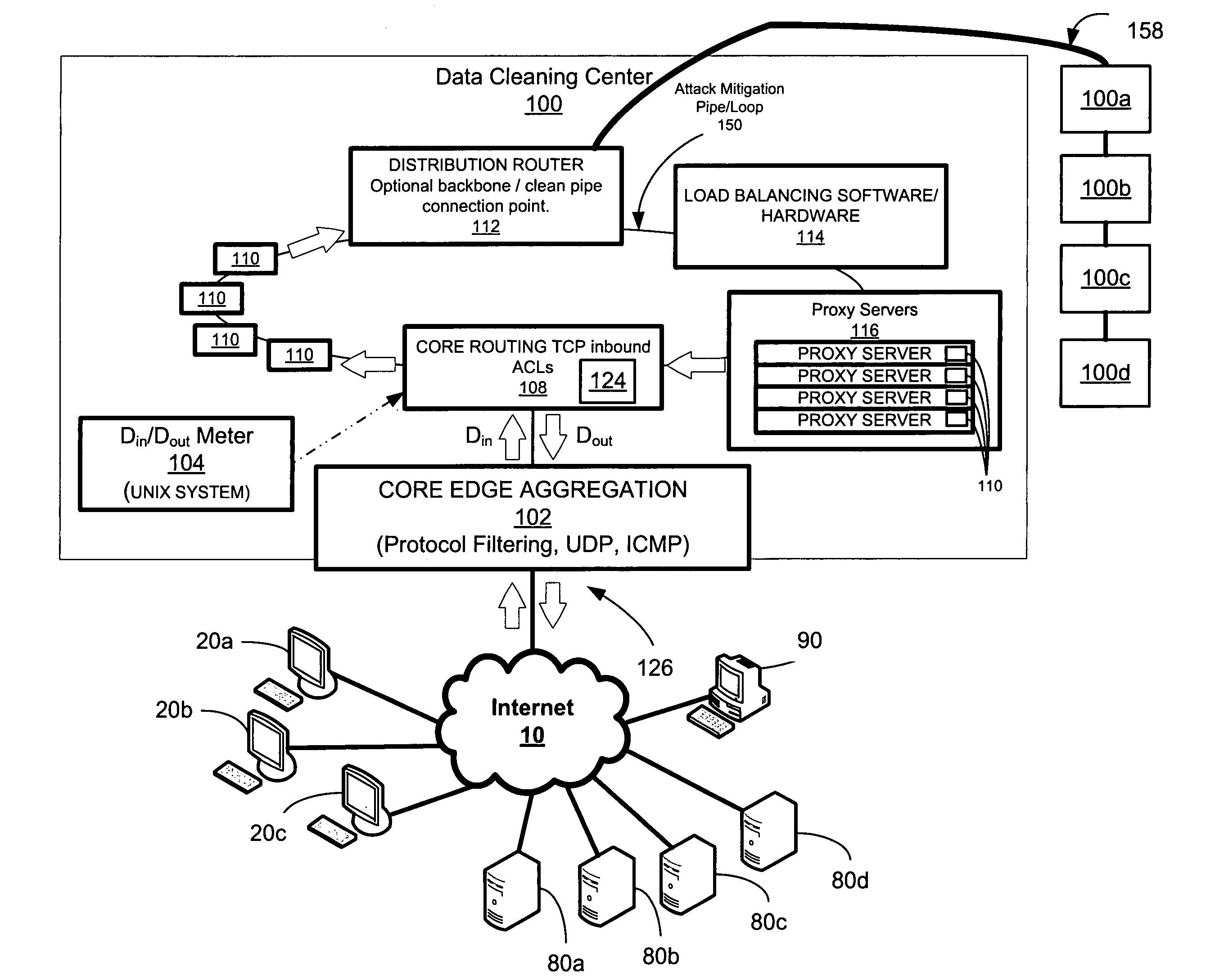
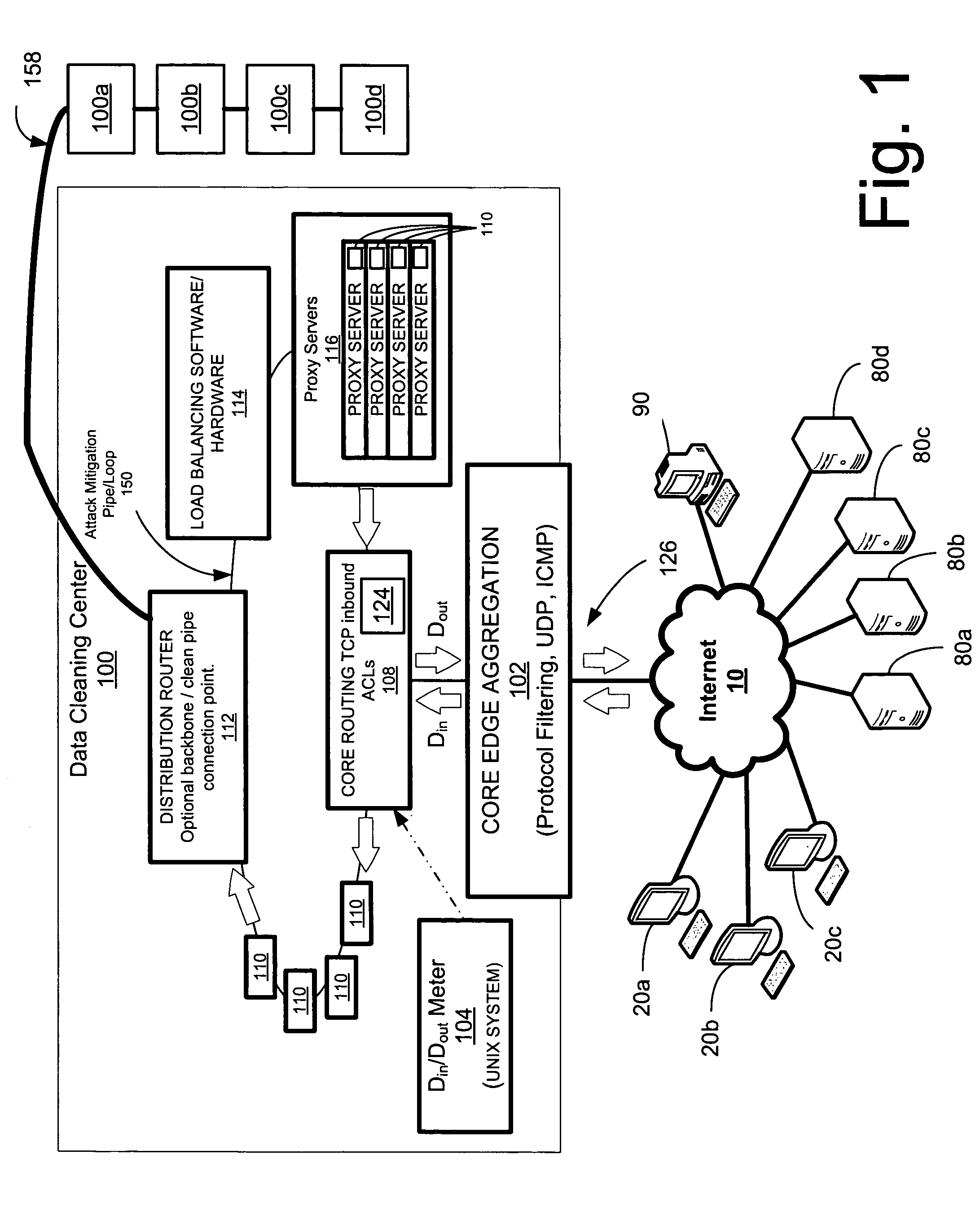
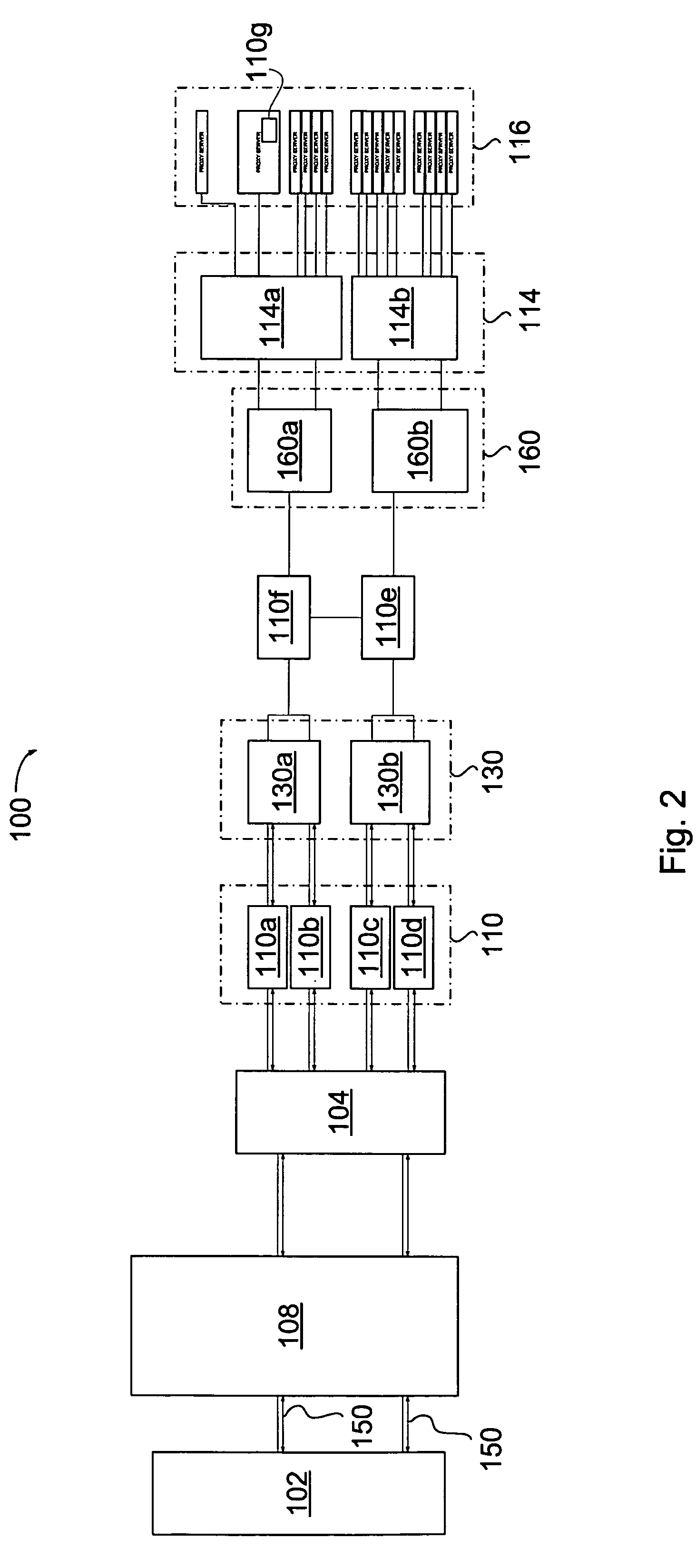
A system and method is disclosed for detecting and / or mitigating an overload condition from one or more first computers, such as a distributed denial of service (DDoS) attack, viral attack, or the like, targeting one or more of a plurality of second computers located on a network. While one or more DDoS attacks are mitigated, a meter, detection apparatus, software, or method, detects the condition being mitigated in a data cleaning center, and provides an alert or notification regarding the mitigated attack.Another preferred embodiment relates, in general terms, to a system and method for detecting and / or mitigating an overload or attempted overload condition targeting a domain name server. A network connection is provided for receiving one or more DNS requests from one or more client computers located on a network. A preferred embodiment includes a processor for providing a response to the one or more DNS requests to the one or more client computers if more than a threshold number of duplicate DNS requests are received.Another preferred embodiment relates, in general terms, to a system and method for detecting and / or mitigating an attempted overload condition targeting a networked computer system that uses a redirection module to divert data until it is deemed to be clean.
Owner:AKAMAI TECH INC
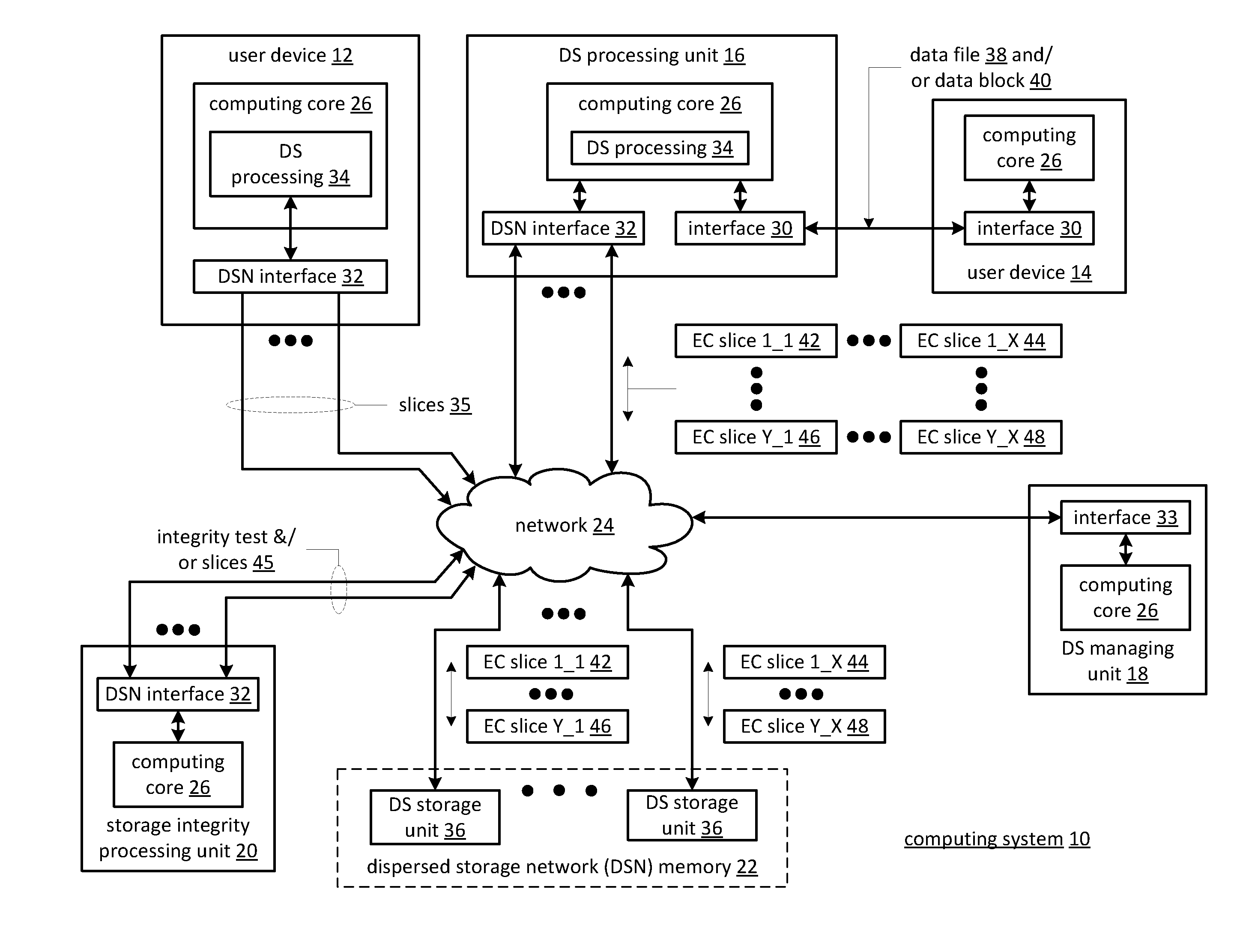
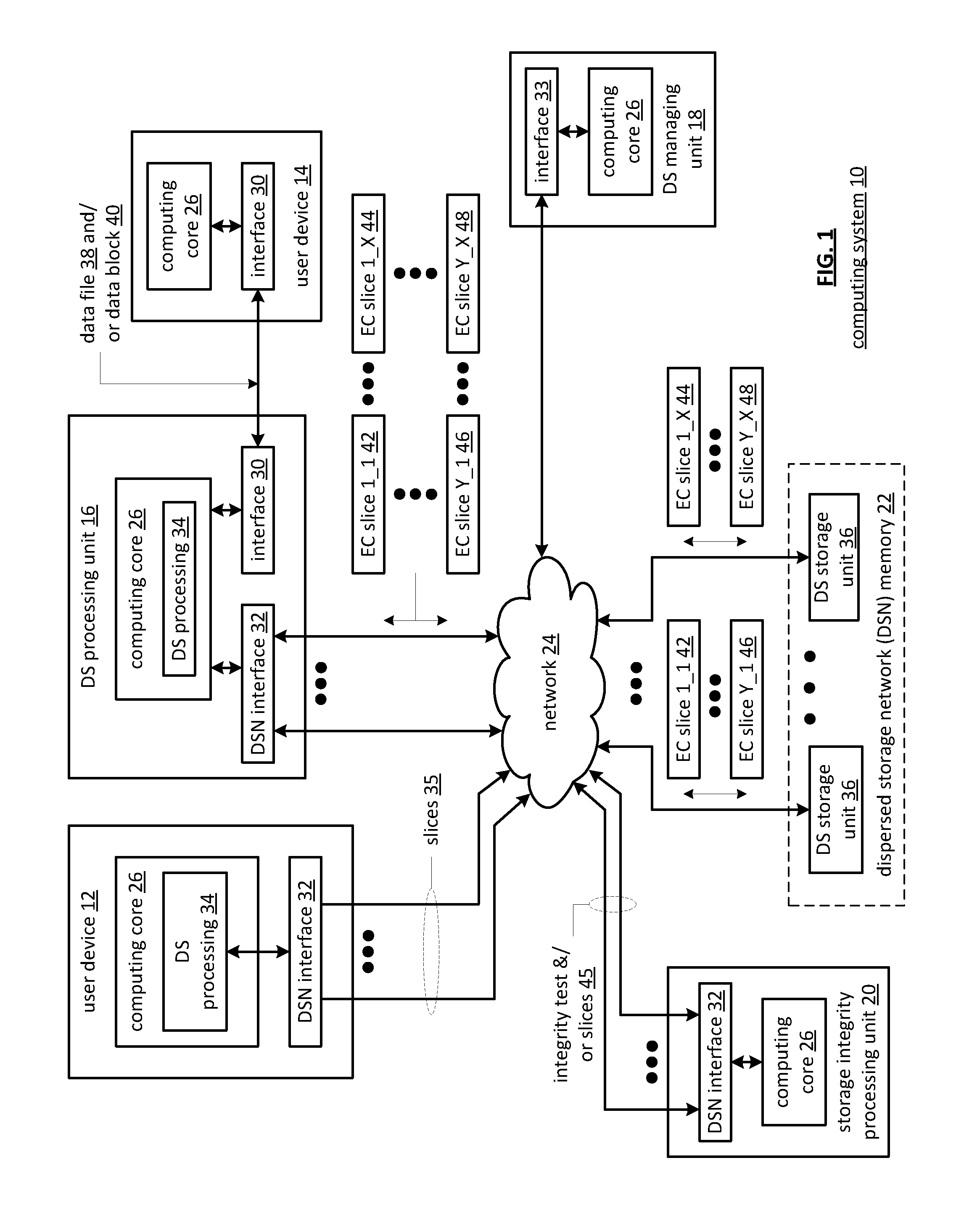
Data revision synchronization in a dispersed storage network
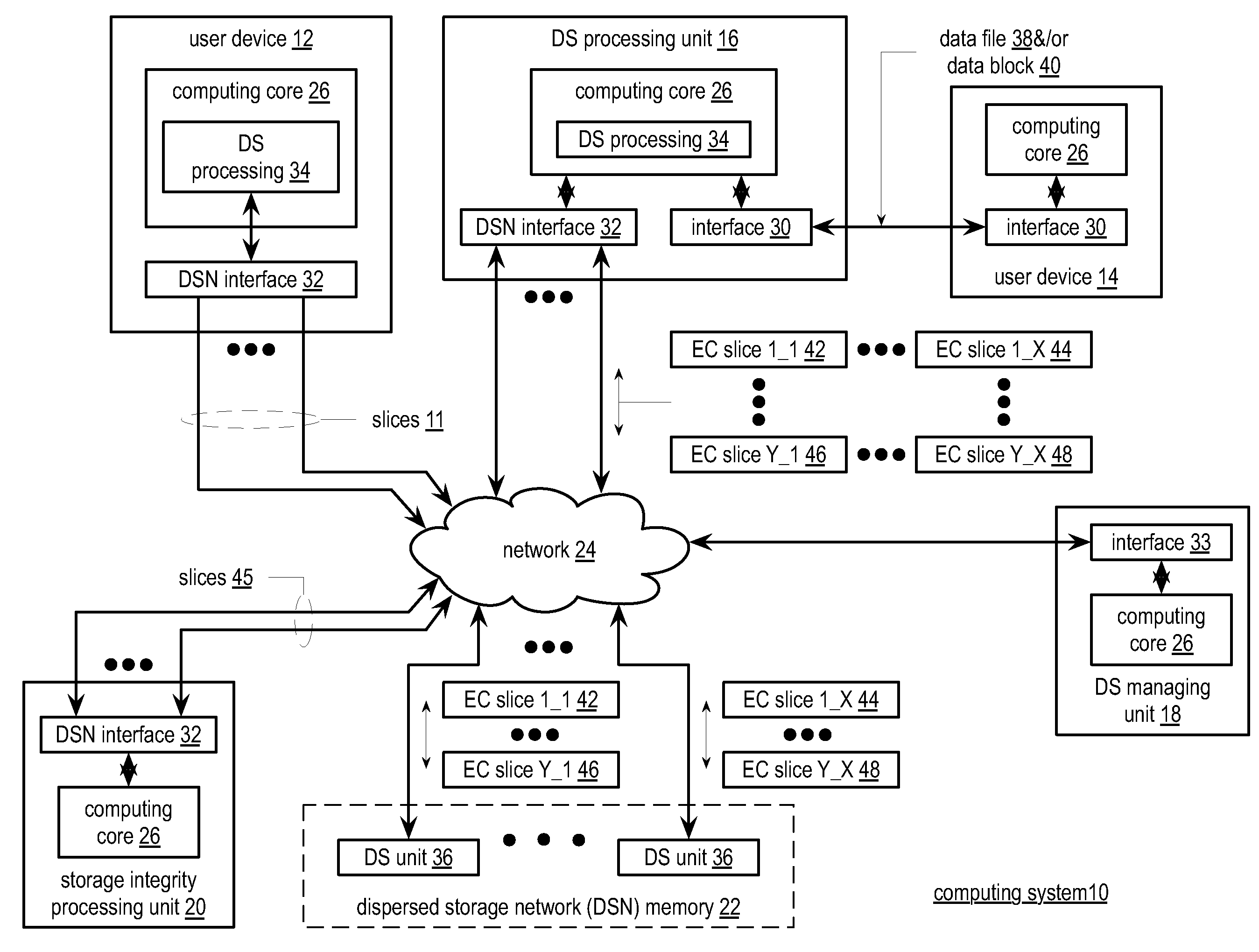
ActiveUS20110071988A1Digital data information retrievalDigital data processing detailsData segmentThreshold number
A method begins by a processing module determining dispersed storage (DS) units that are storing a set of encoded data slices associated with a data segment and sending a revision level check request message to each of the DS units. The method continues with the processing module receiving revision level check response messages from at least some of the DS units within a time period to produce received revision level check response messages and determining concurrency of a revision level of the set of encoded data slices stored by the DS units based on the received revision level check response messages. The method continues with the processing module initiating a revision concurrency process when less than a threshold number of encoded data slices have concurrency of the revision level.
Owner:PURE STORAGE
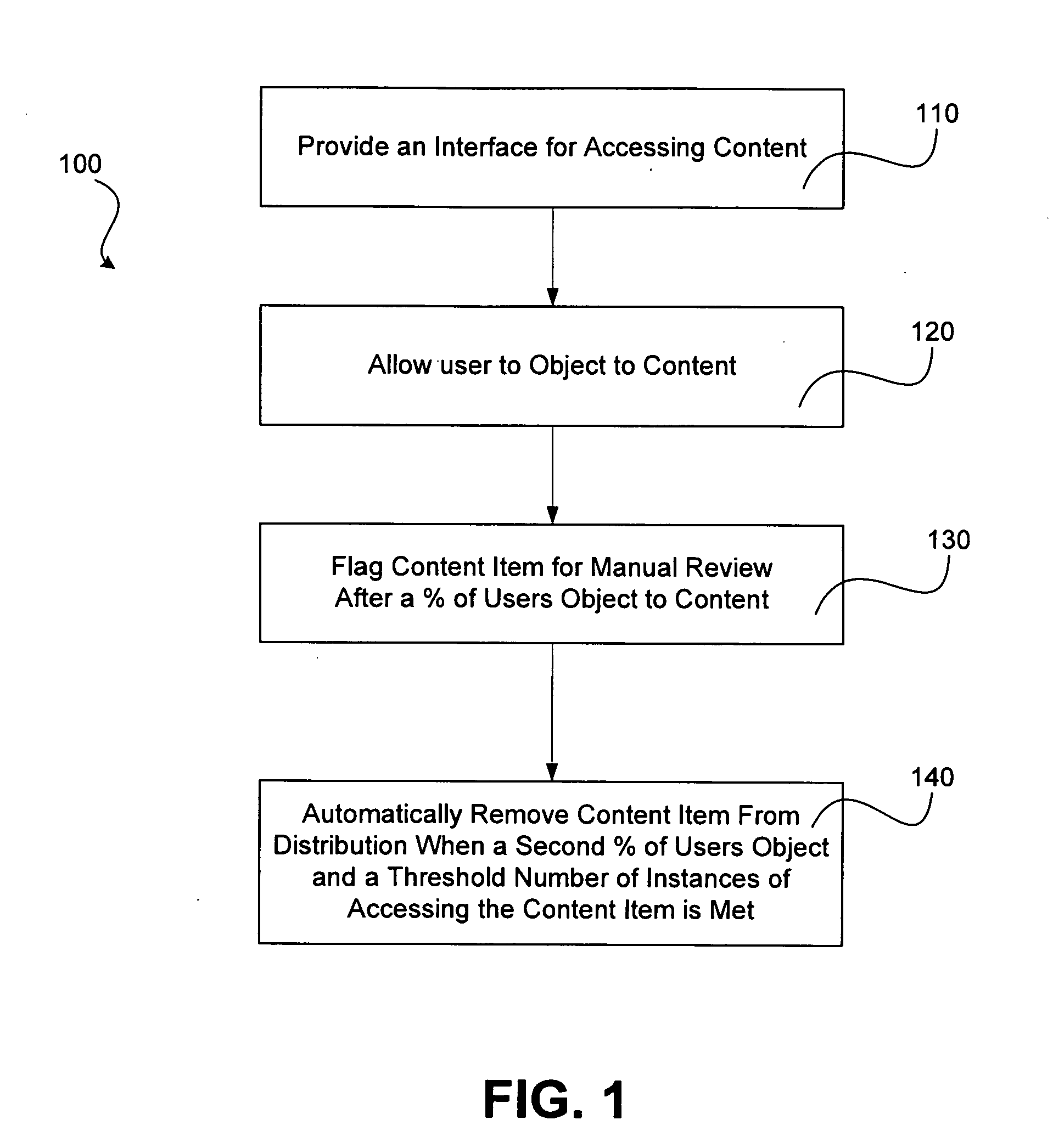
Network Content Objection Handling System and Method
InactiveUS20090012965A1Office automationSpecial data processing applicationsThe InternetHandling system
A system and method for distribution of one or more content items to one or more users over a network, such as the Internet. One or more users that access a content item may provide an indication of objection to the content item. The content item may be flagged for manual review when a first threshold percentage of indications of objection is met. The content item is automatically removed from distribution when a second threshold percentage of indications of objection is met and a threshold number of instances of access is met.
Owner:DECISION ACQUISITION
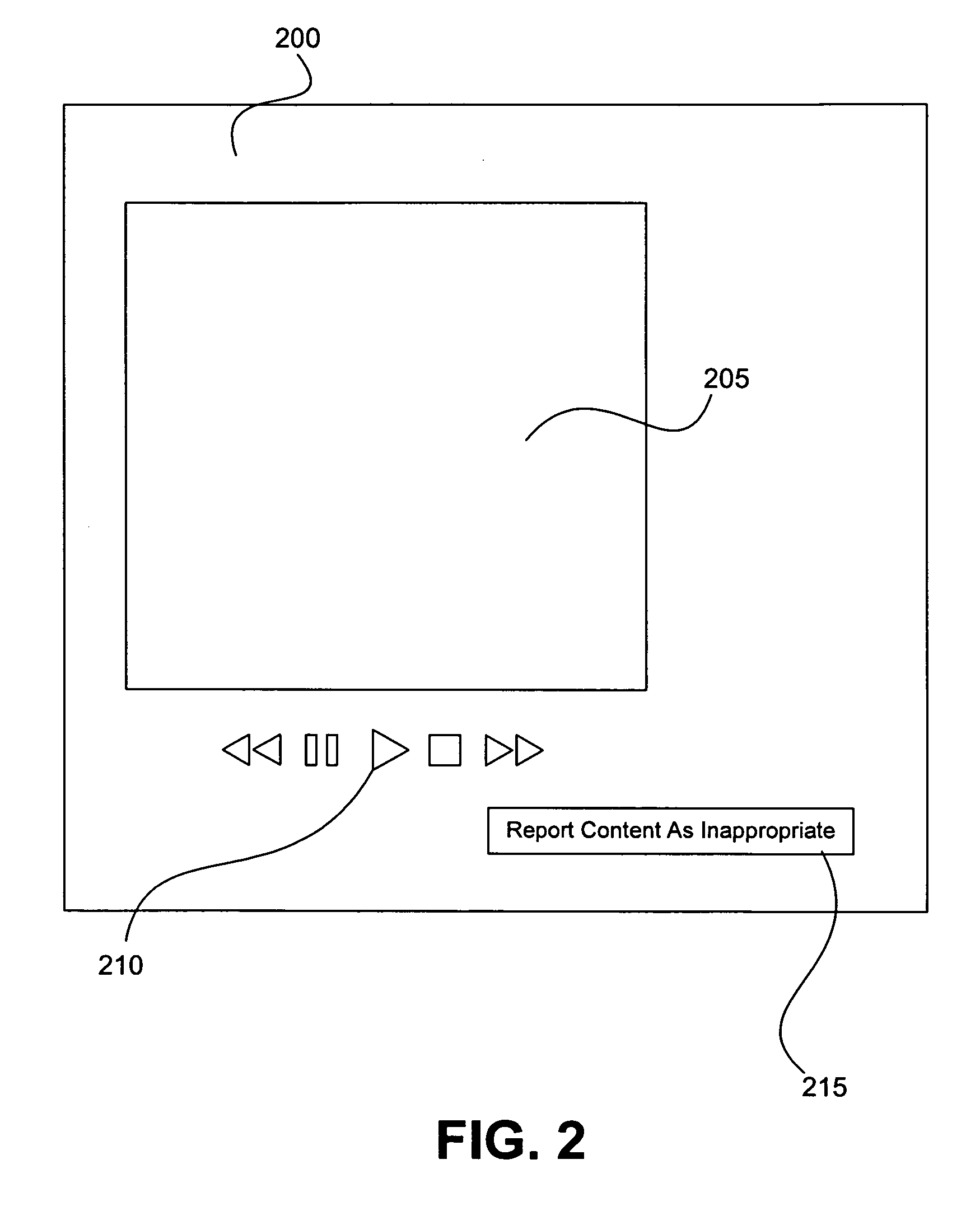
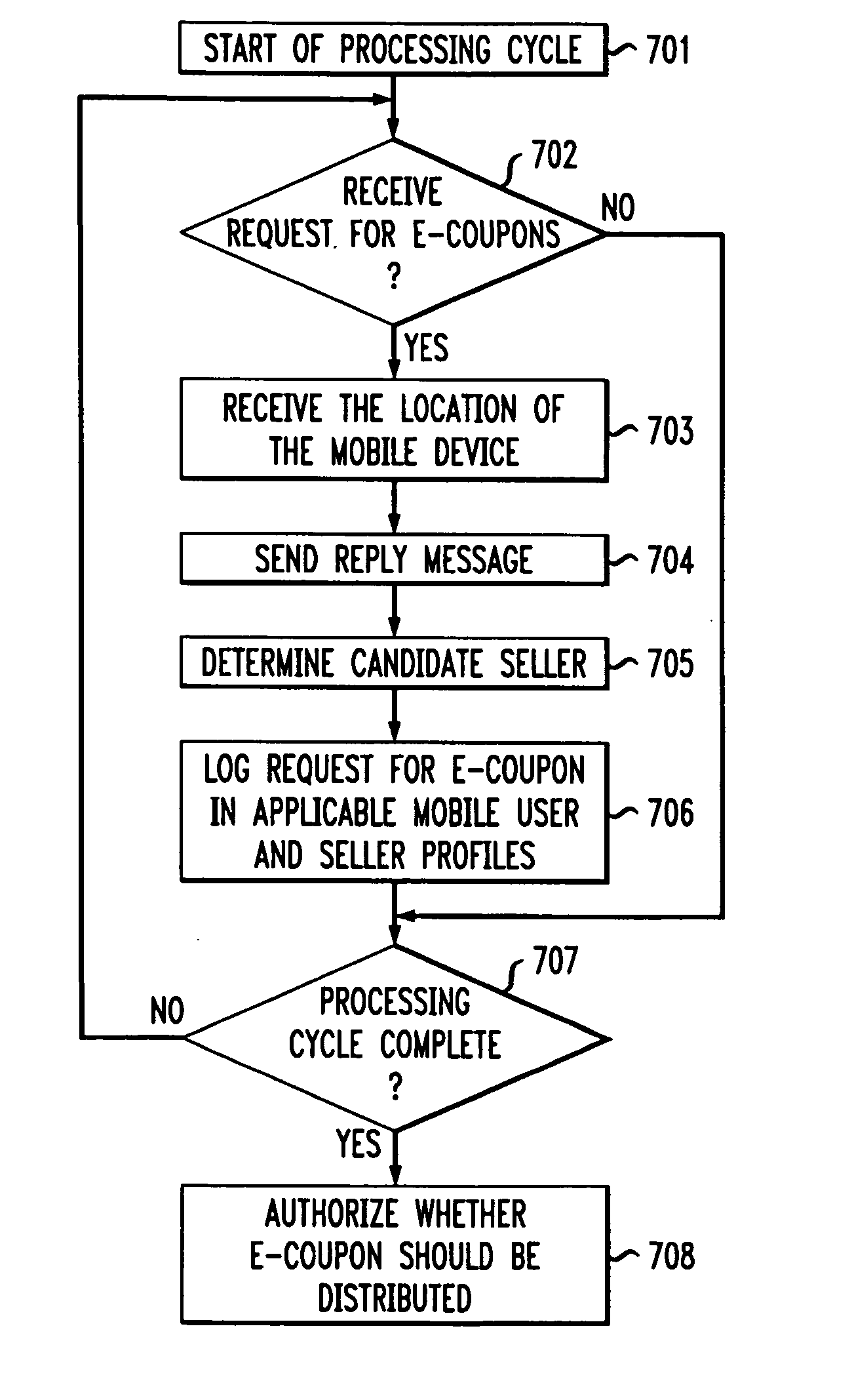
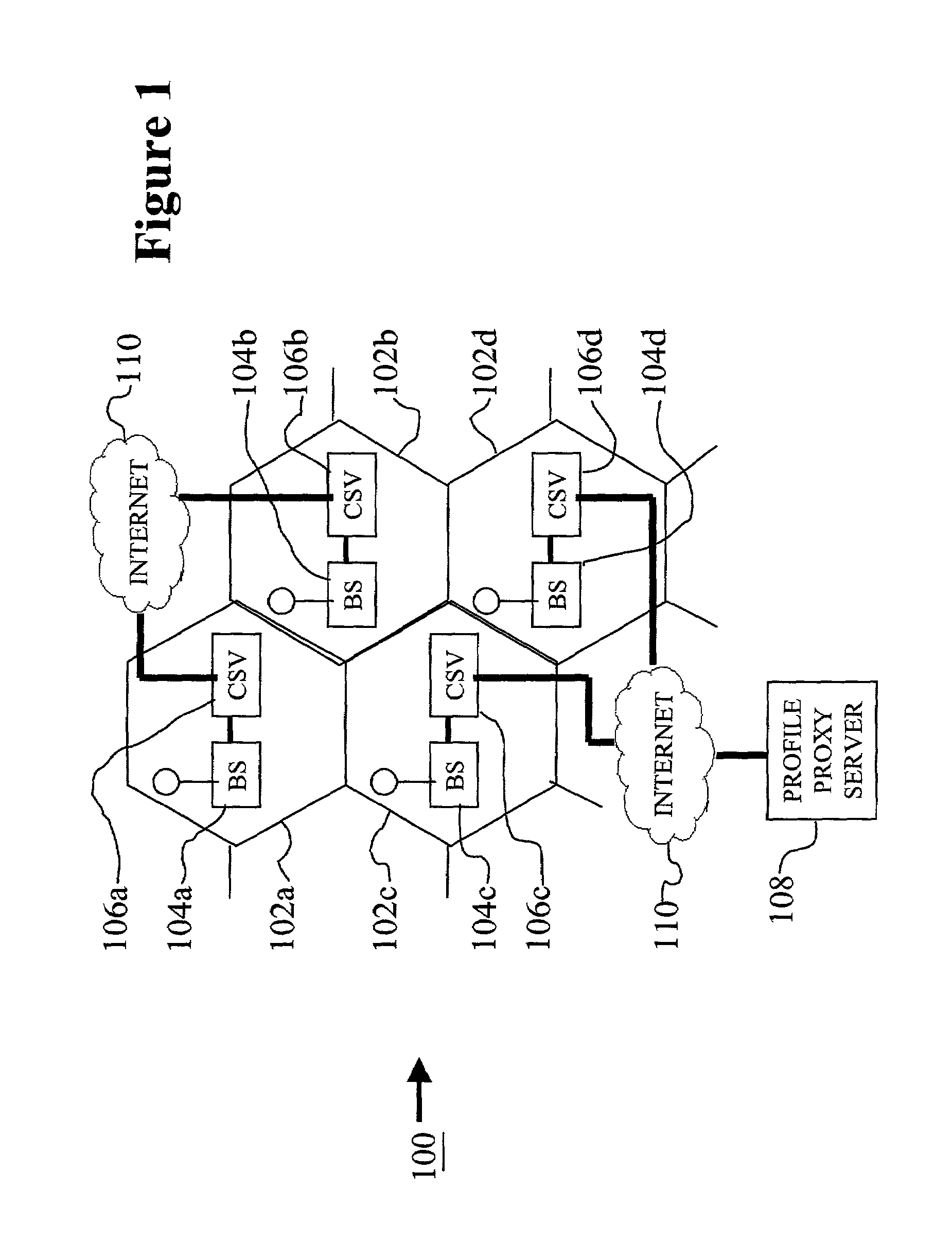
E-coupon service for location-aware mobile commerce which determines whether to supply requested e-coupons based on the number of requests received in a processing cycle, and a threshold number of requests required to make expected returns from redeemed coupons greater than advertising fees
InactiveUS20060036491A1Improve efficiencySufficient freedomDiscounts/incentivesCash registersDistribution methodLocation aware
A conditional e-coupon distribution method distributes e-coupons predefined by sellers to mobile users only if the number of mobile users requesting such e-coupons equals or exceeds a threshold. The method receives a request to browse e-coupons from a mobile user. The method receives the location of the mobile user and determines a plurality of sellers local to the mobile electronic device and a plurality of corresponding e-coupons available from the local sellers. The method receives a request for a particular e-coupon from a seller and authorizes the provision of said e-coupon to the mobile user. At the end of a processing cycle, the mobile user receives the requested e-coupon if all conditions, such as a period of time and threshold, have been met. A computer-usable medium having computer-readable program code embodied therein allows for storage of the method.
Owner:AT&T INTPROP II L P
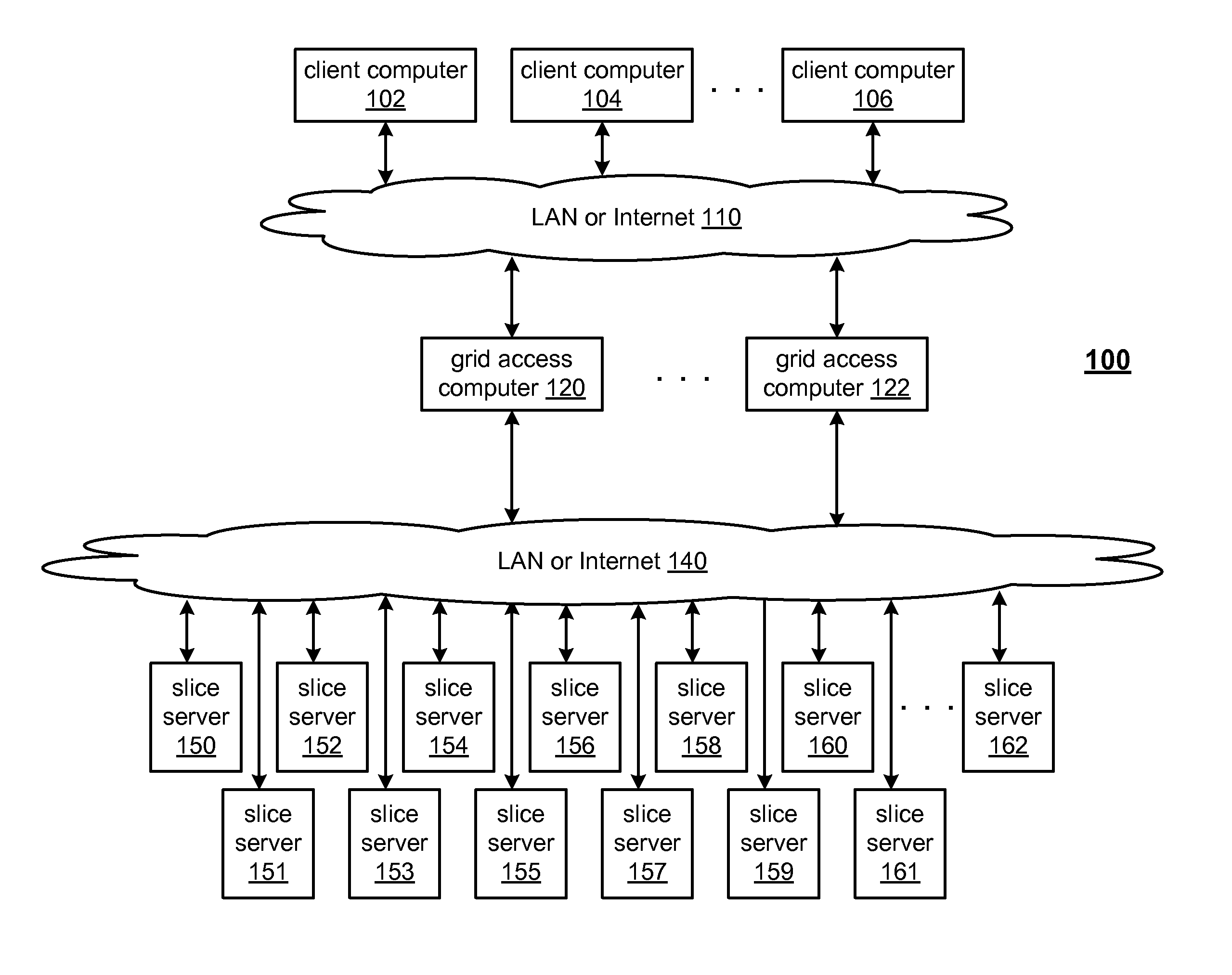
Smart access to a dispersed data storage network
ActiveUS20100115063A1Error detection/correctionDigital data processing detailsData segmentData store
A method for reading data from a dispersed data storage network that includes a plurality of slice servers. The method begins by accessing a list of slice servers of the plurality of slice servers, wherein each slice server on the list stores at least one data slice associated with a data segment of the data. The method continues by transmitting read requests to at least some of the slice servers on the list. The method continues by receiving a data slice from a slice server on the list. The method continues by determining whether a threshold number of data slices has been received. The method continues, when the threshold number of data slices has been received, assembling the data segment from at least the threshold number of data slices.
Owner:PURE STORAGE
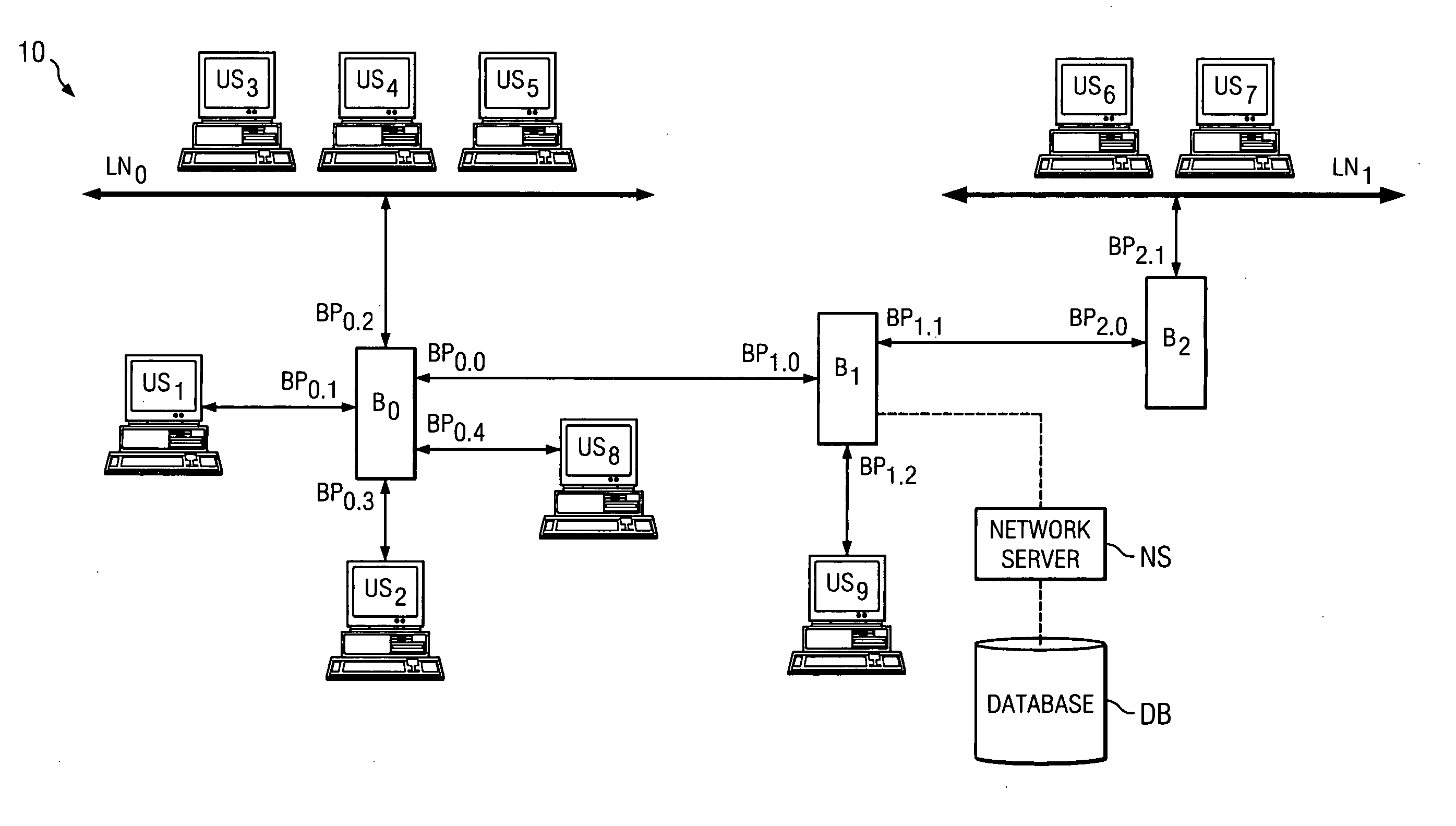
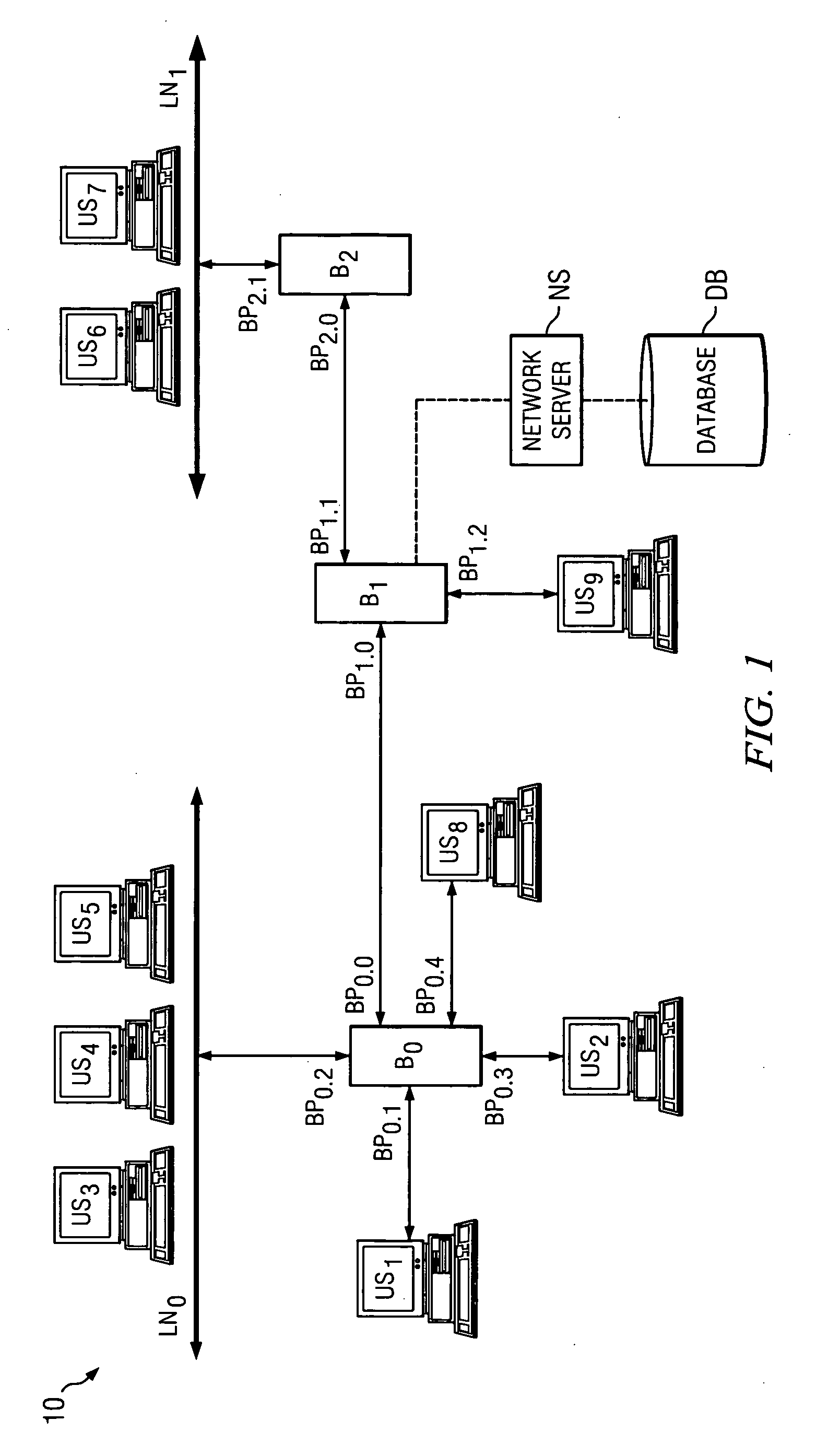
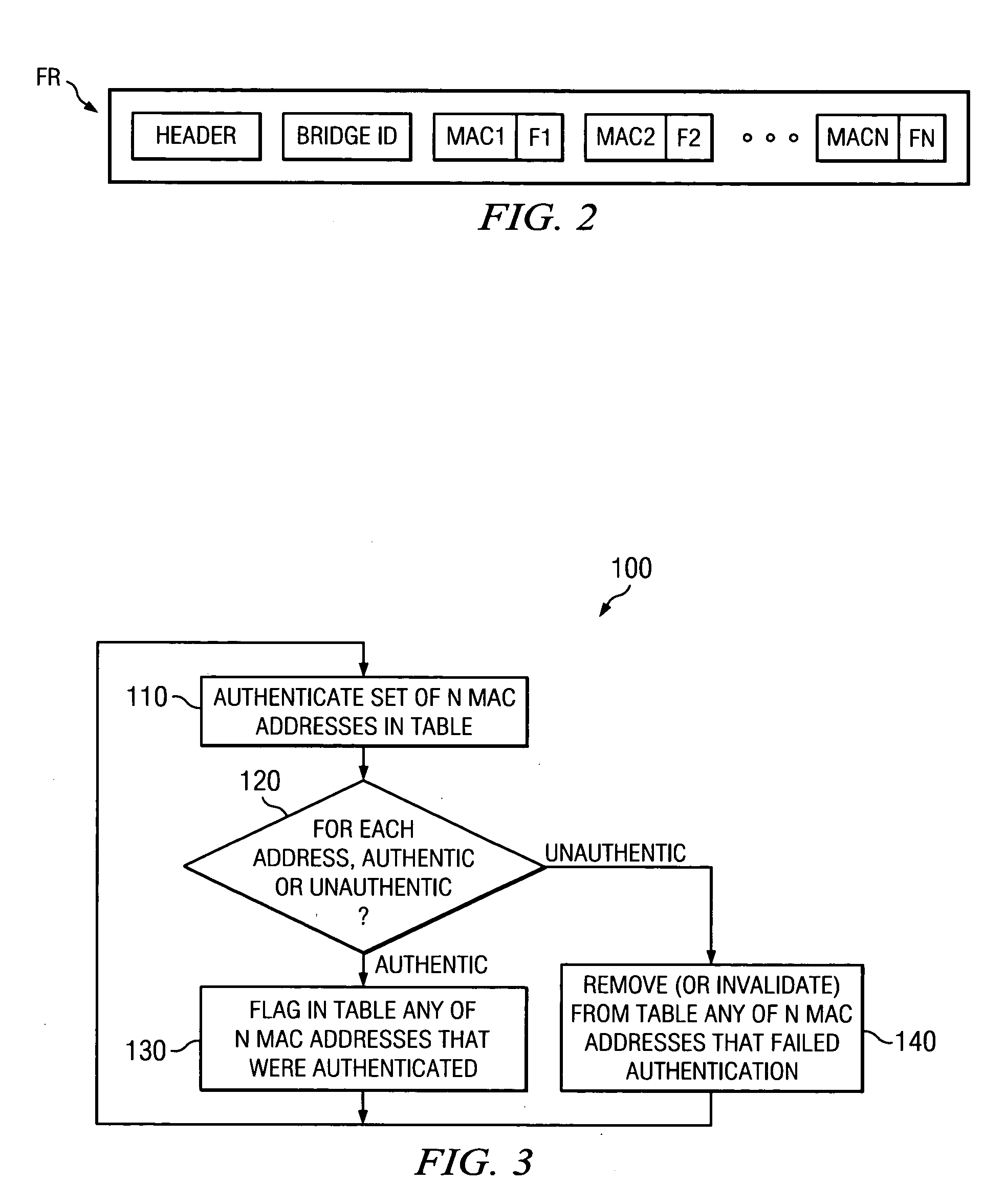
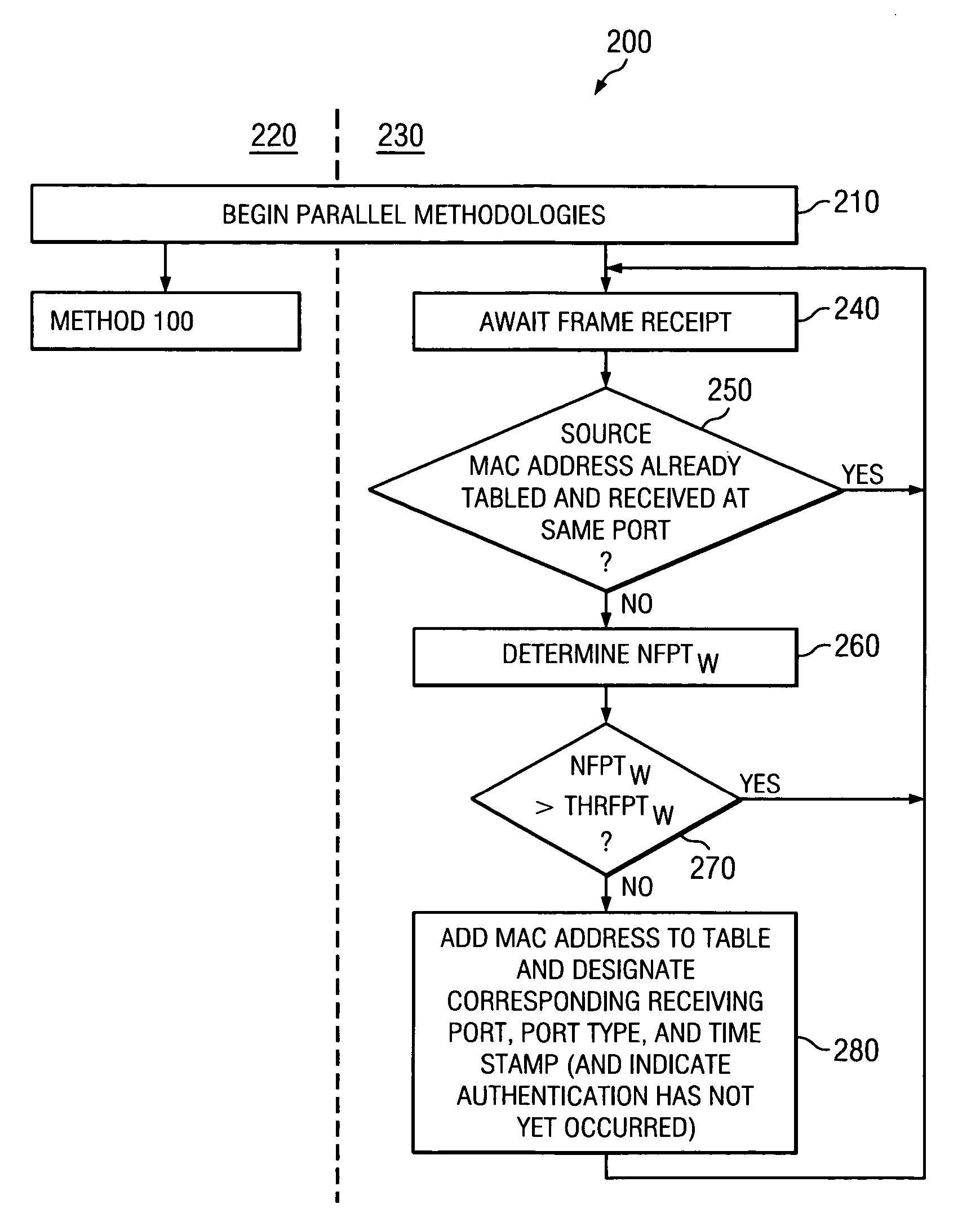
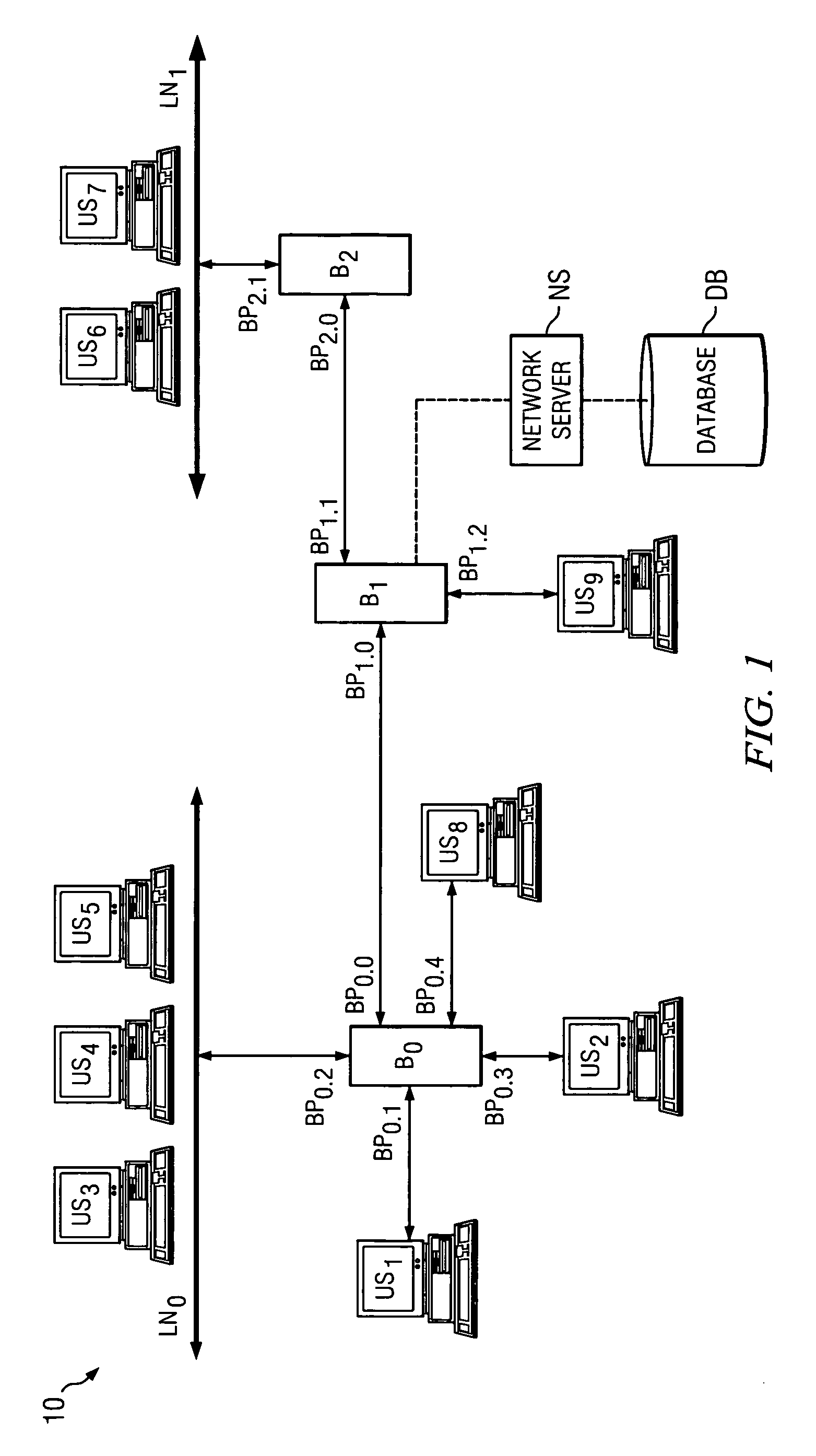
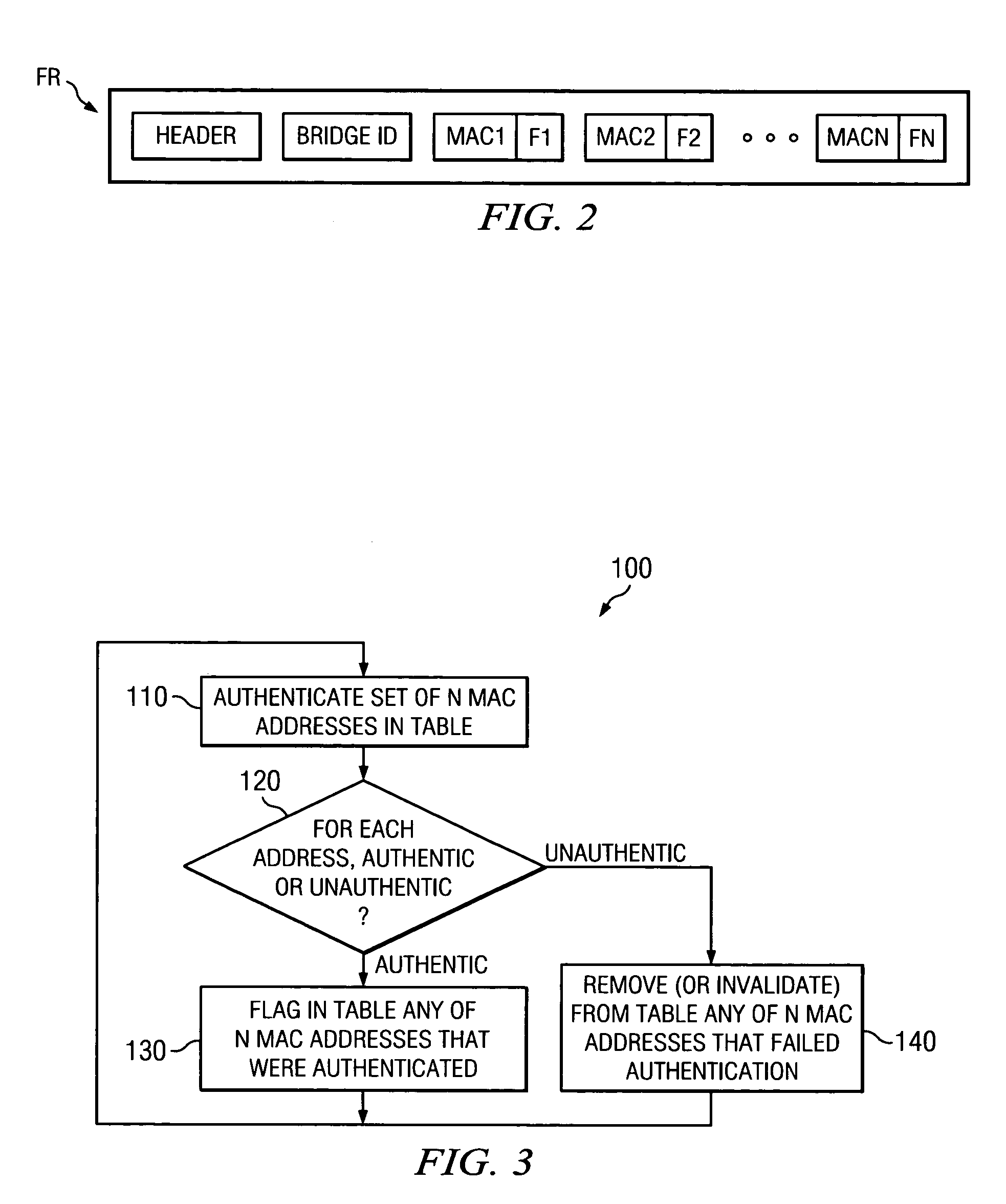
Network with MAC table overflow protection
A method of operating a bridge node (B0) in a network system. The bridge node comprises a plurality of ports (BP0.x). The method comprises a step of receiving a frame (240), from a device in the network system and other than the bridge node, at a port in the plurality of ports. The frame comprises a source network address. The method is also responsive to at least one condition (250, 260) associated with the port in that the method stores the source address in a forwarding table associated with the bridge if the at least one condition is satisfied. The at least one condition comprises whether the frame was received within a time window Tw of when a threshold number of previous frames were received at the port and their respective source network addresses were stored in the table.
Owner:PROVEN NETWORKS LLC
Method and apparatus for slice partial rebuilding in a dispersed storage network
ActiveUS20110029711A1Input/output to record carriersMemory adressing/allocation/relocationData segmentAlgorithm
A dispersed storage system includes a plurality of storage units that each include a partial rebuild grid module. The partial rebuild grid module includes partial rebuilding functionality to reconstruct one of a plurality of encoded data slices wherein the plurality of encoded data slices are generated from a data segment based on an error encoding dispersal function. In the partial rebuilding process, a data slice is rebuilt by combining in any order slice partials generated from at least a threshold number T of the plurality of data slices.
Owner:PURE STORAGE
Method and system for governing resource consumption in a multi-tenant system
ActiveUS20080086479A1Improve performanceDigital data processing detailsDatabase distribution/replicationResource consumptionDistributed computing
A database system includes servers configured to receive requests from user systems. Each server includes a local and a global store. Each local store stores the number of requests received by its server. The system includes a processor configured to receive the number of requests from servers. The processor is configured to determine the number of requests received by all of the servers, and send this number of requests to each server. The global store stores the number of requests received from the processor. A given server is configured to compare the number of requests received by the servers with a threshold number. If this number is greater than the threshold number, then the given server is configured to send a message to the user systems that the number of threshold requests has been exceeded and / or the given server will discontinue accepting requests.
Owner:SALESFORCE COM INC
Apparatus with segemented bitscan for verification of programming
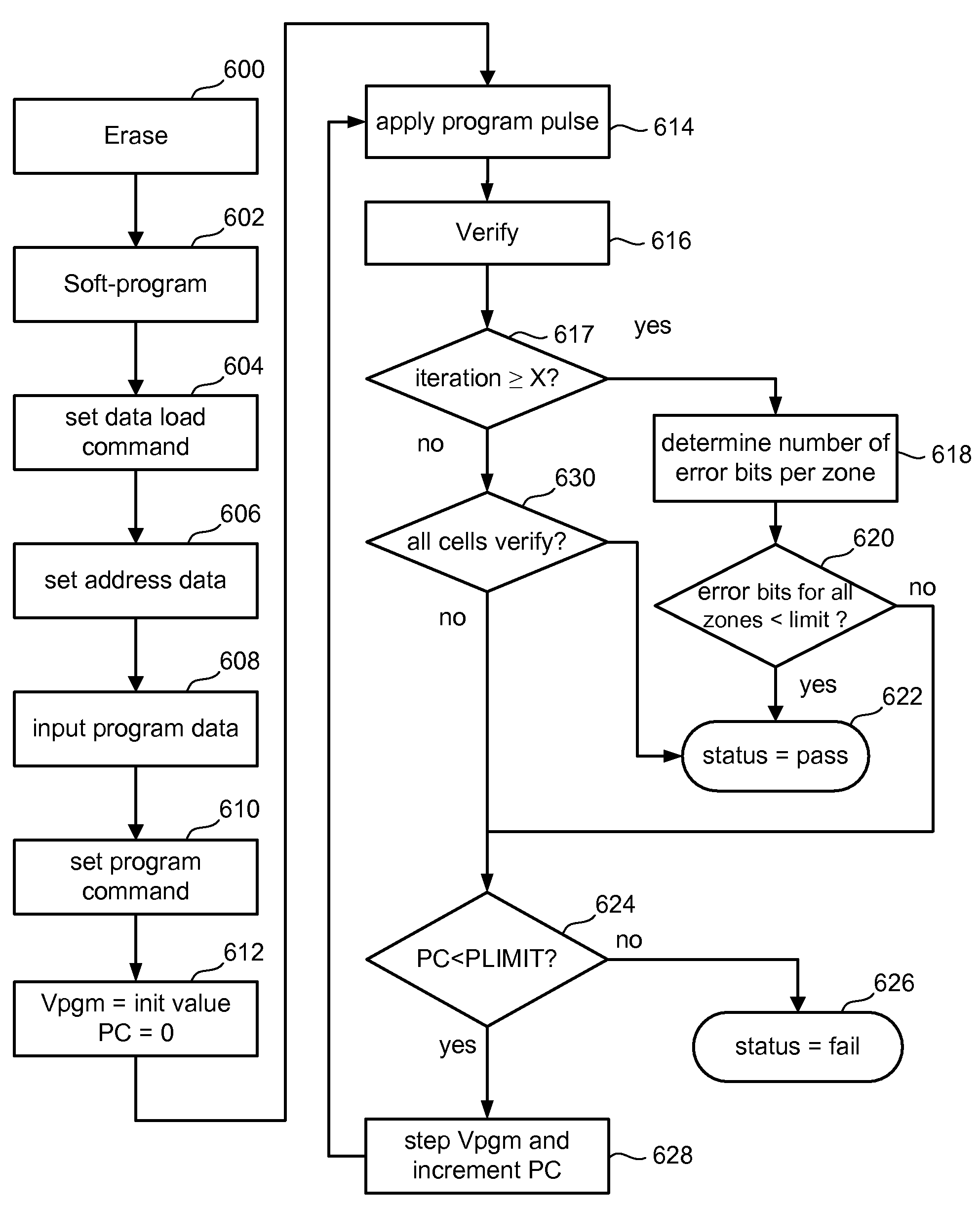
ActiveUS20080127104A1Bit errorError can not be correctedError detection/correctionRead-only memoriesProgramming languageProgramming process
A set non-volatile storage elements are subjected to a programming process in order to store a set of data. During the programming process, one or more verification operations are performed to determine whether the non-volatile storage elements have reached their target condition to store the appropriate data. Decisions about whether to continue programming or whether the programming is successful are made based on whether overlapping groups of the non-volatile storage elements have less than a threshold number of non-volatile storage elements that are not properly programmed.
Owner:SANDISK TECH LLC
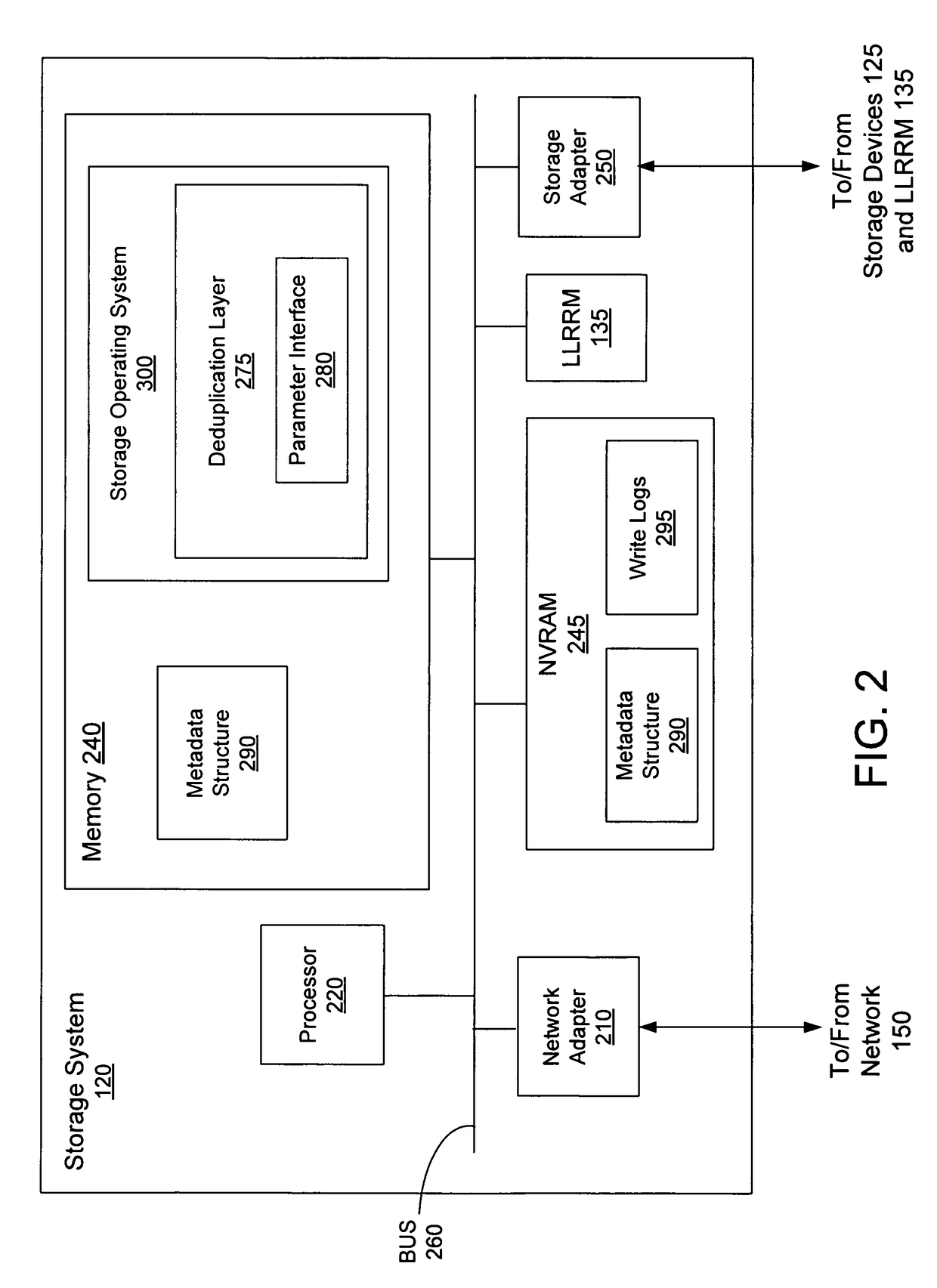
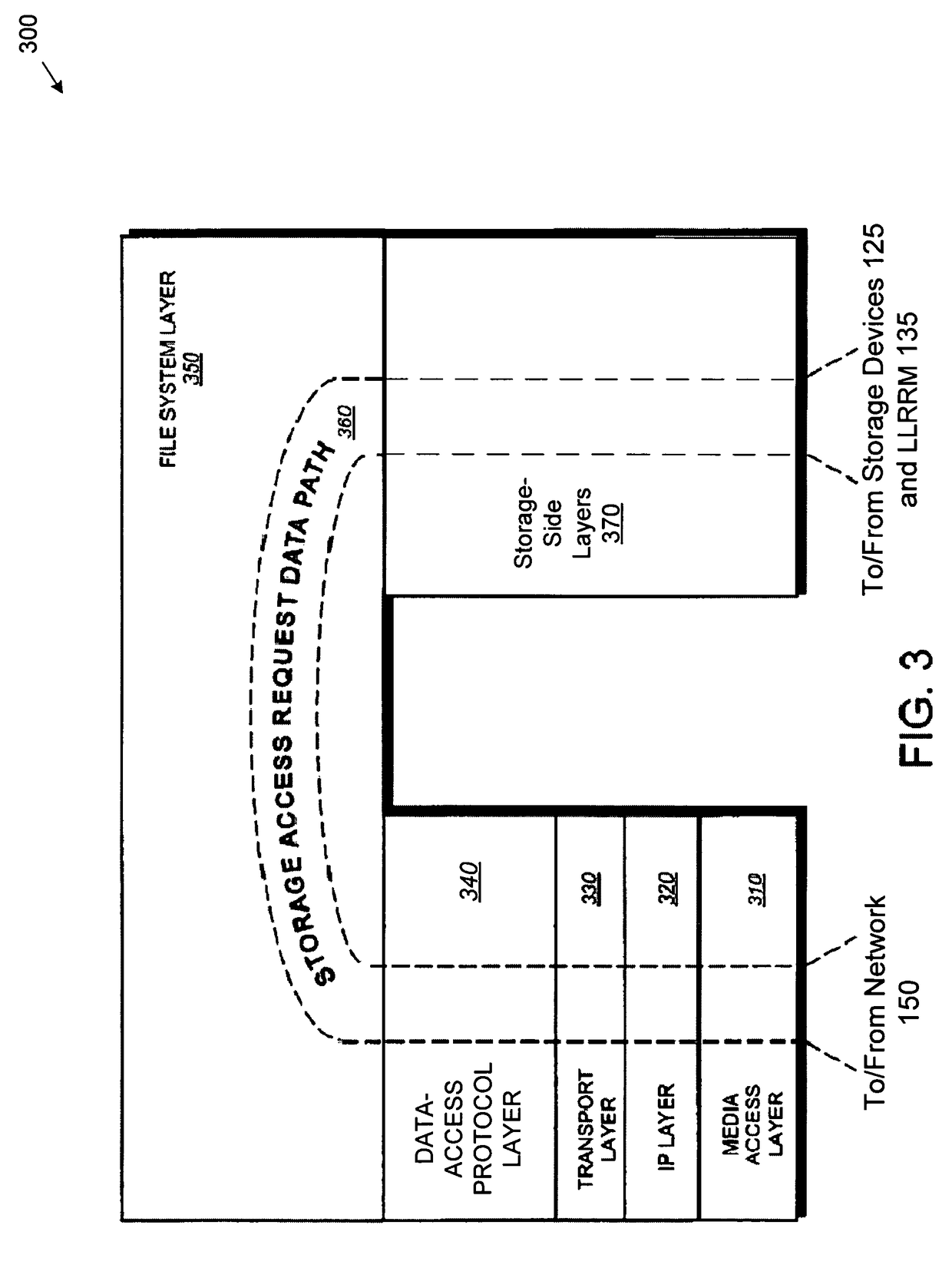
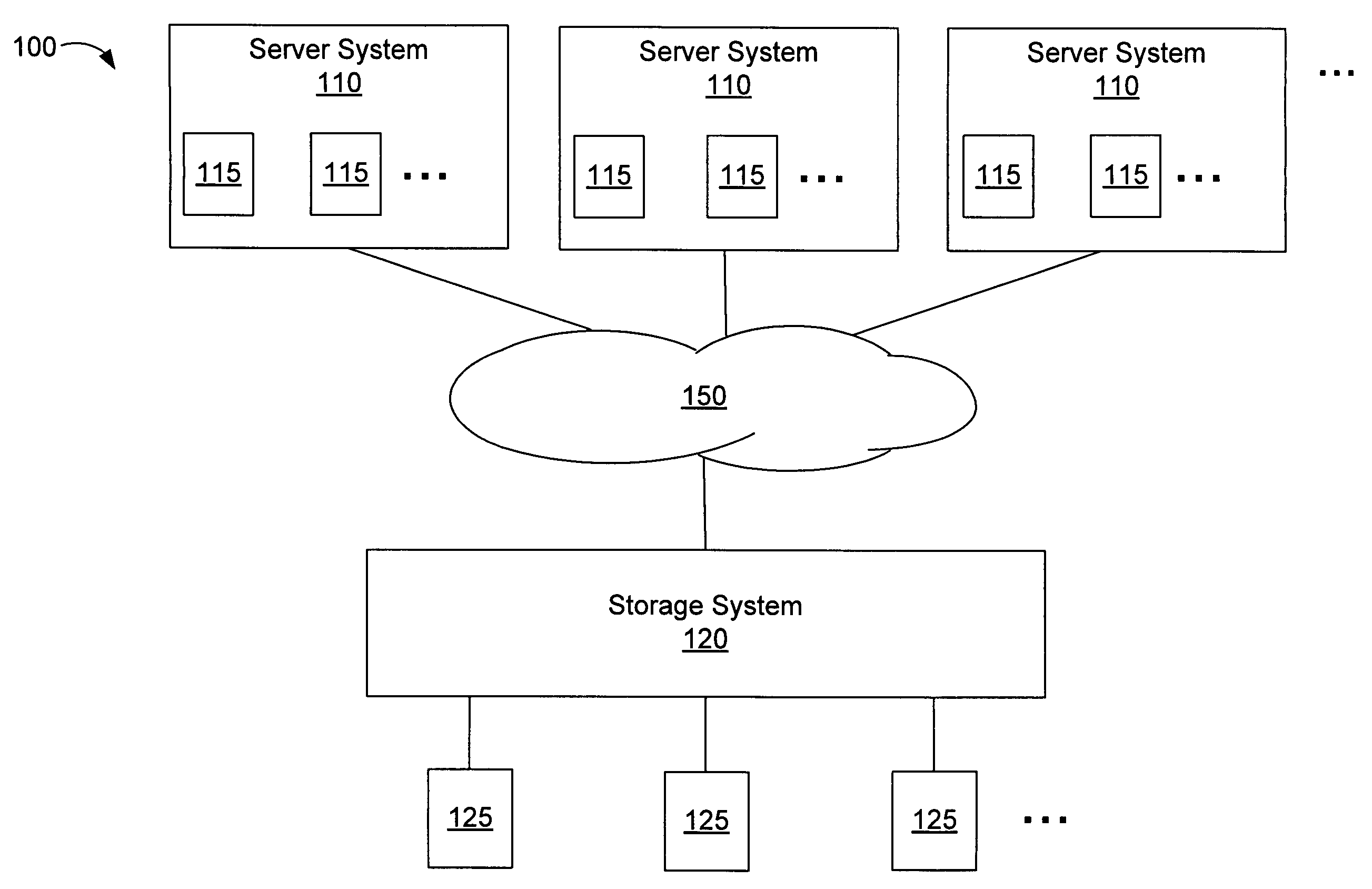
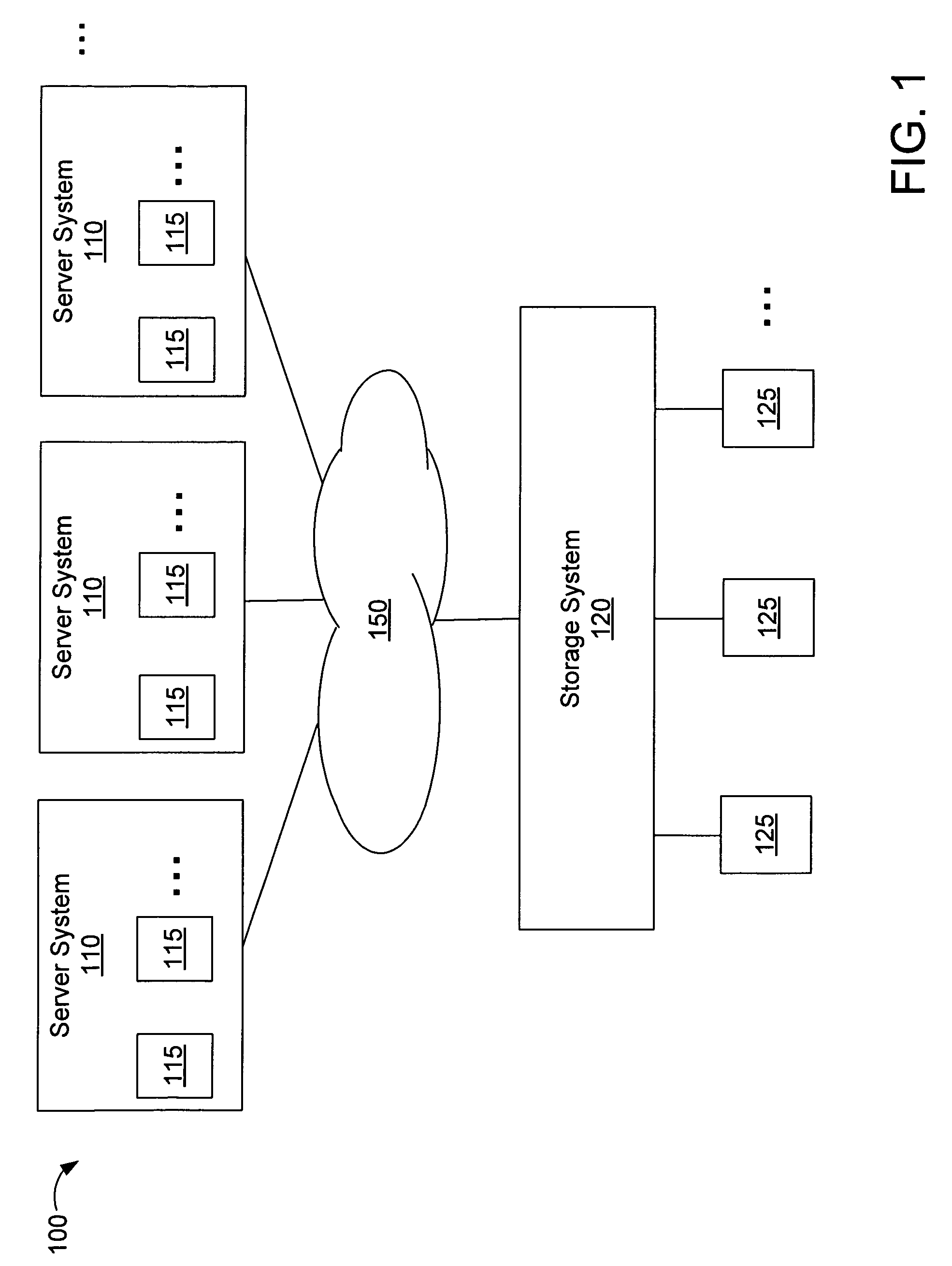
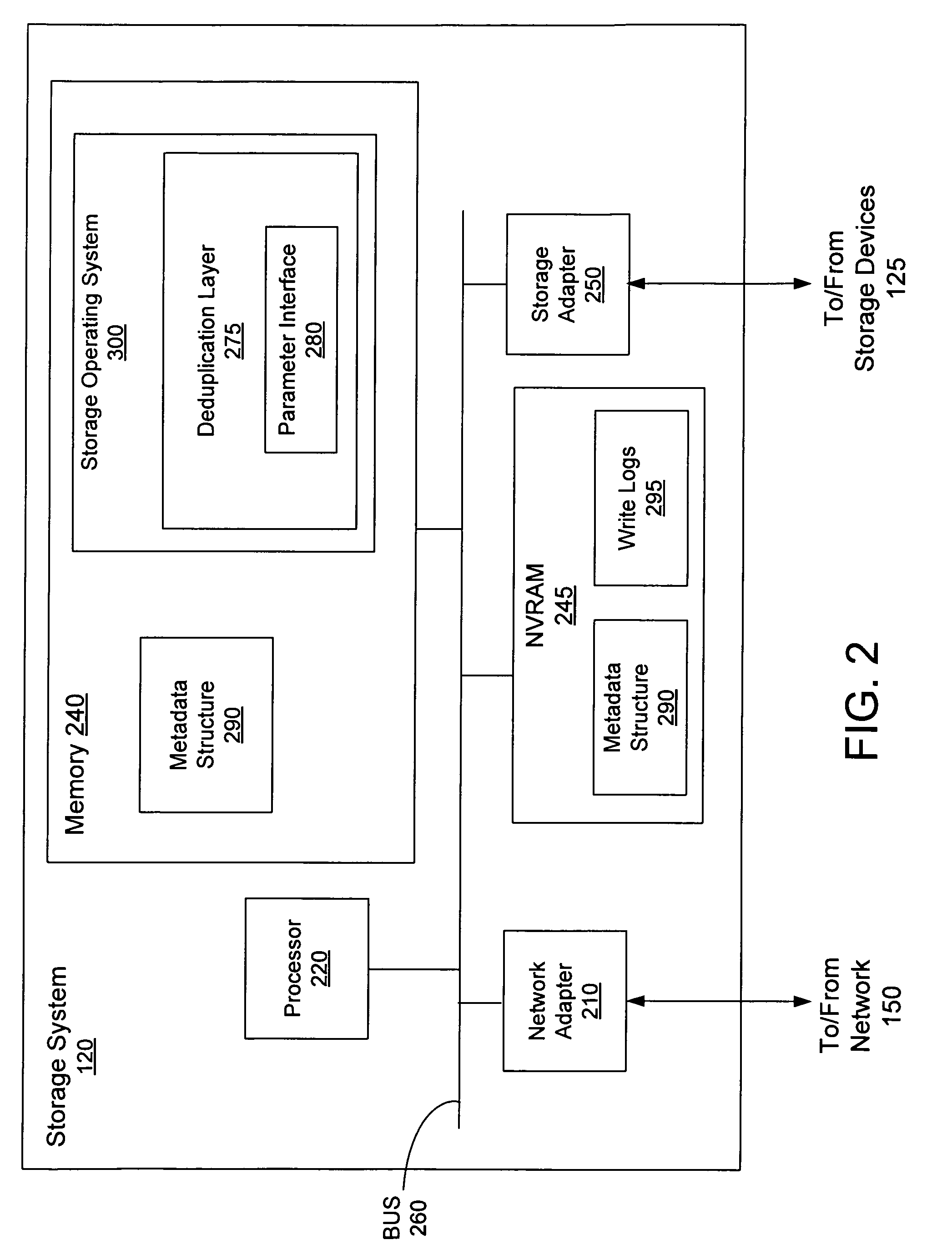
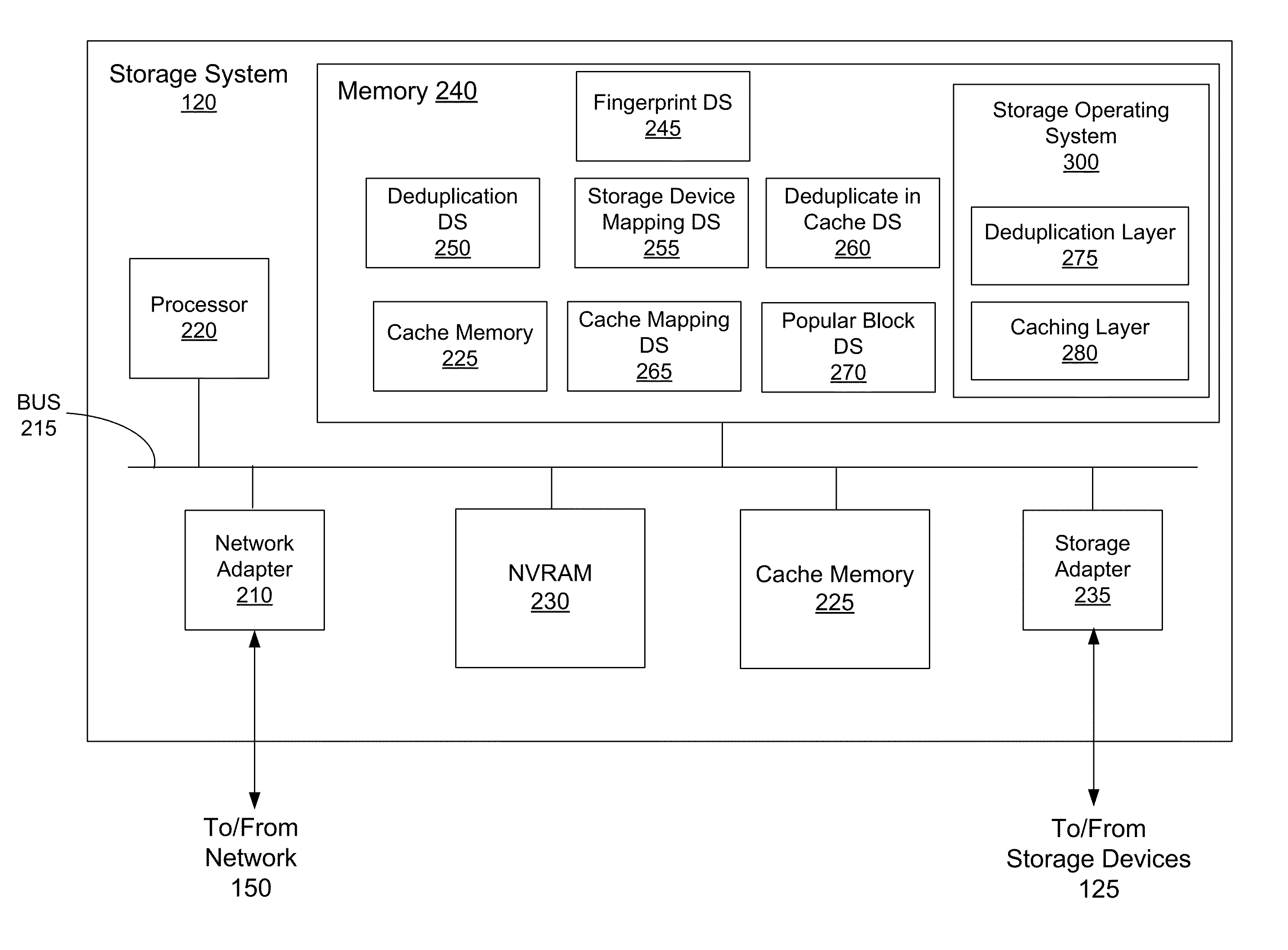
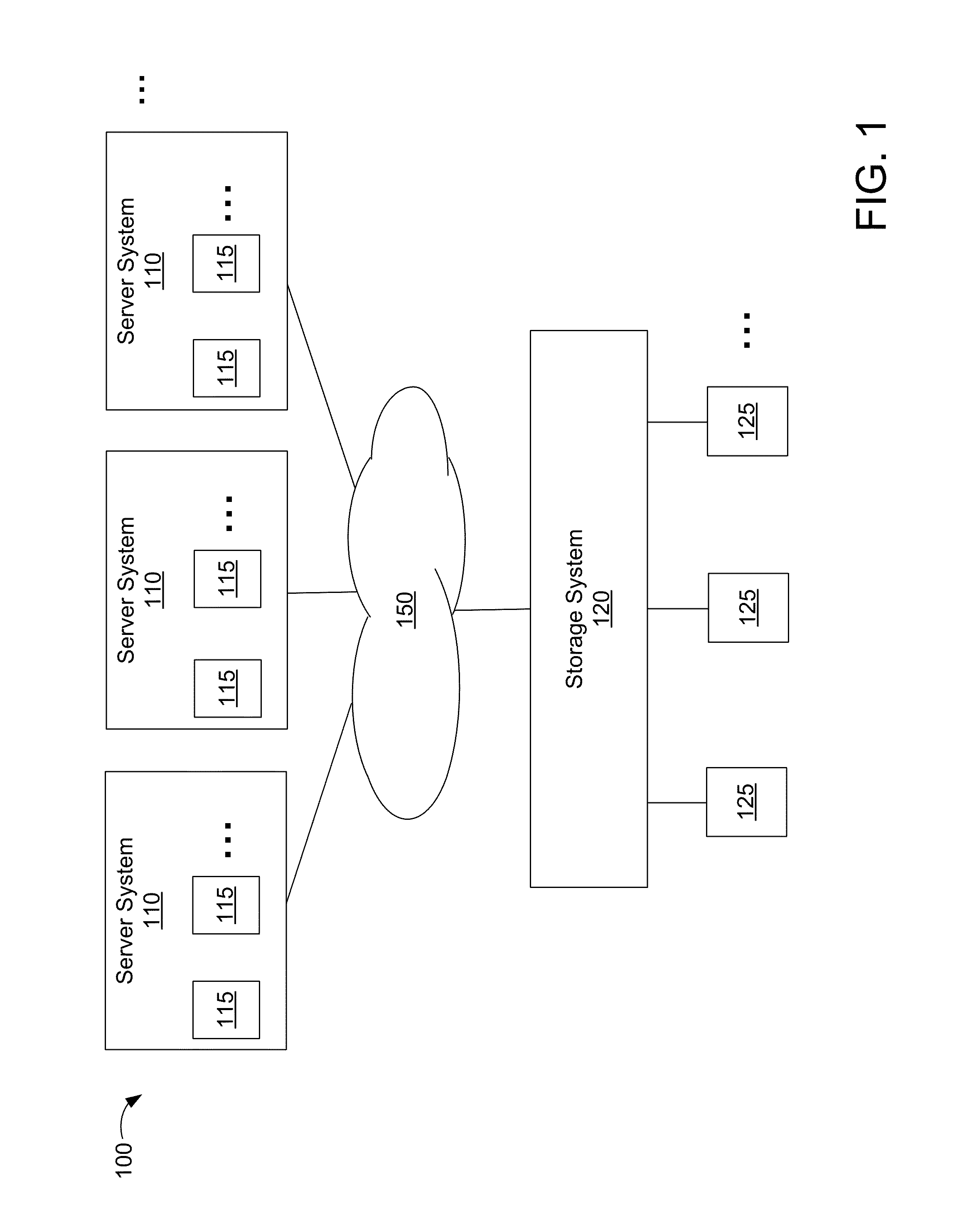
Deduplication of data on disk devices using low-latency random read memory
InactiveUS7908436B1Lower latencyReduce performanceMemory adressing/allocation/relocationFile access structuresLatency (engineering)Memory deduplication
Deduplication of data using a low-latency random read memory (LLRRM) is described herein. Upon receiving a block, if a matching block stored on a disk device is found, the received block is deduplicated by producing an index to the address location of the matching block. In some embodiments, a matching block having a predetermined threshold number of associated indexes that reference the matching block is transferred to LLRRM, the threshold number being one or greater. Associated indexes may be modified to reflect the new address location in LLRRM. Deduplication may be performed using a mapping mechanism containing mappings of deduplicated blocks to matching blocks, the mappings being used for performing read requests. Deduplication described herein may reduce read latency as LLRRM has relatively low latency in performing random read requests relative to disk devices.
Owner:NETWORK APPLIANCE INC
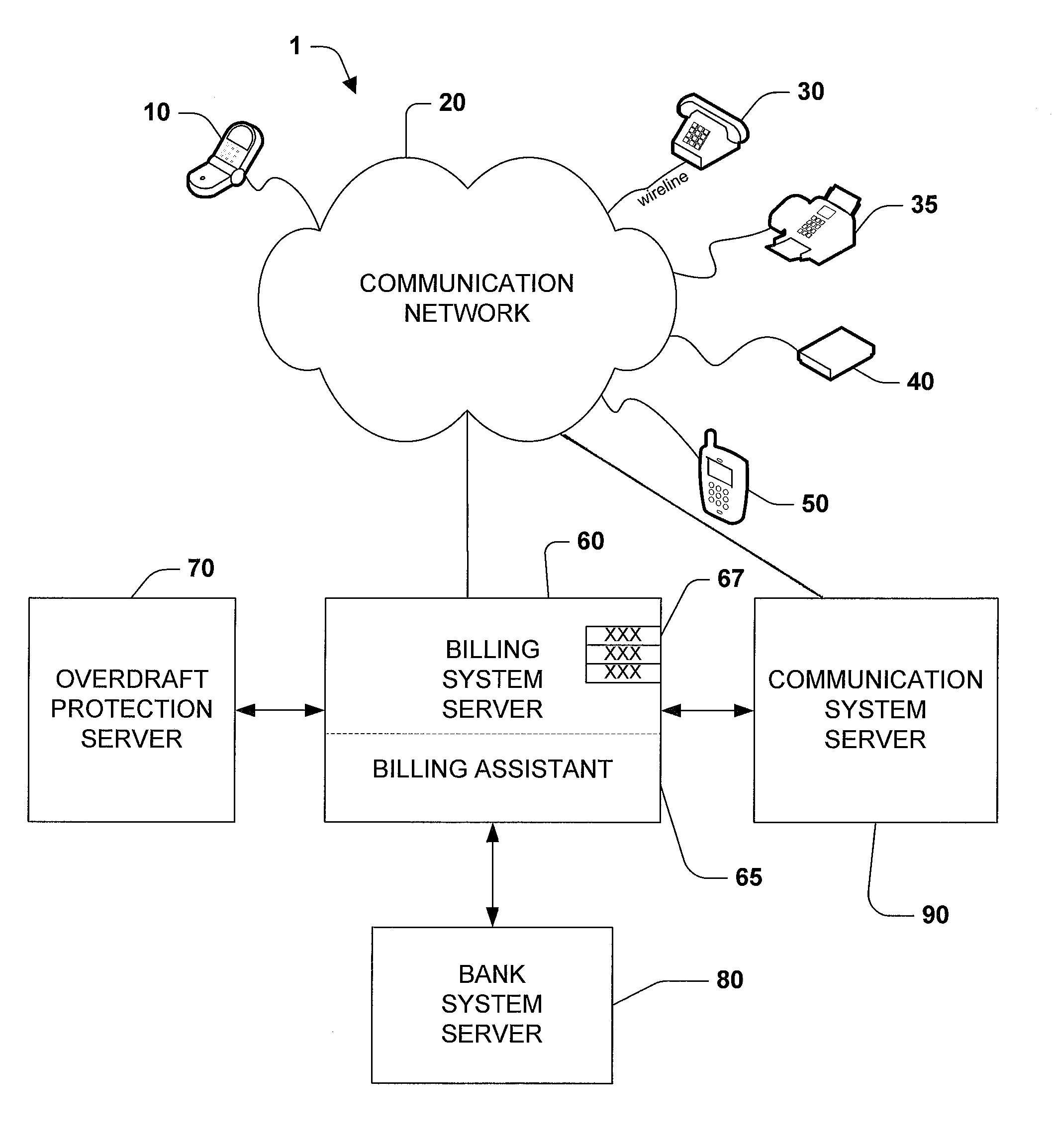
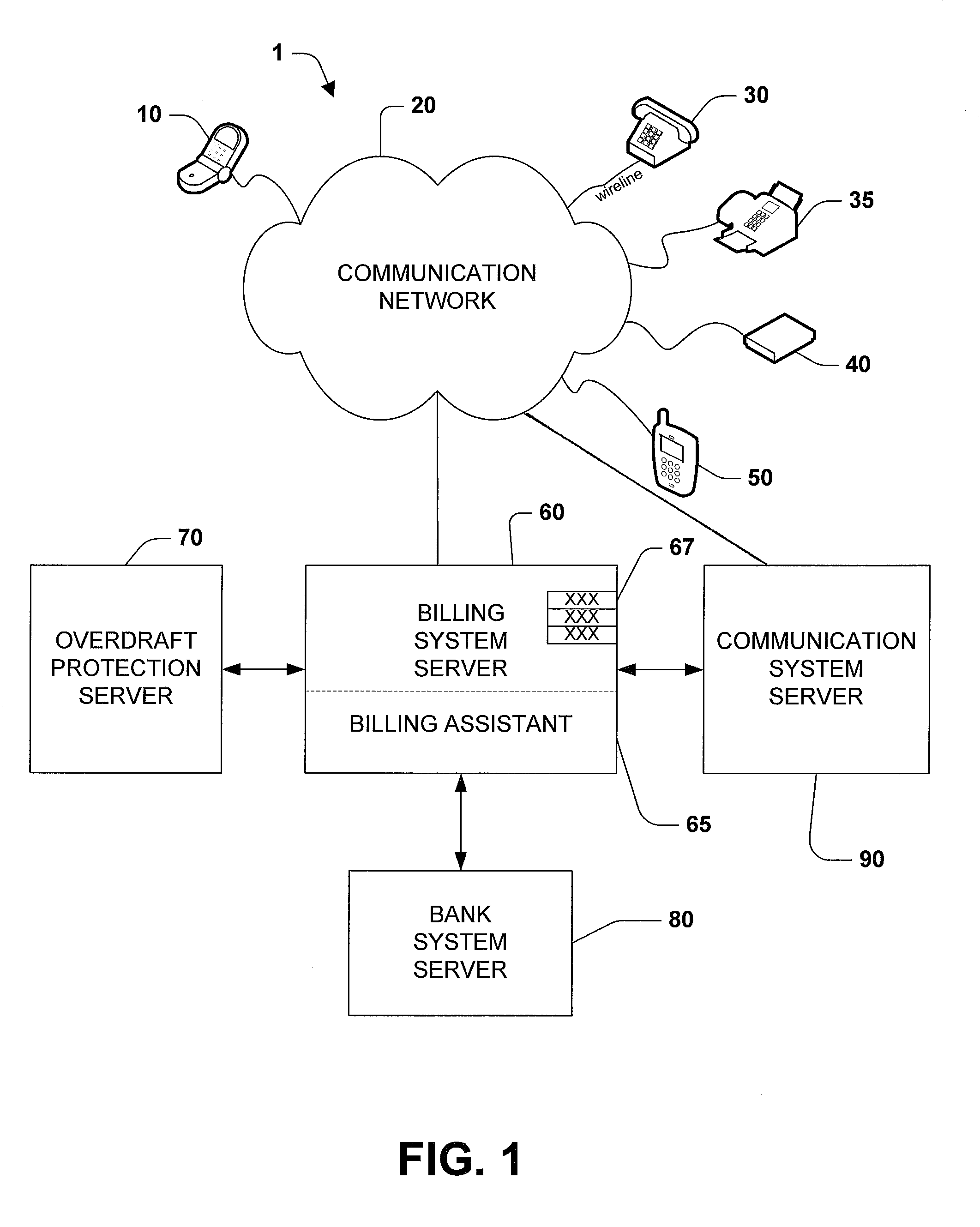
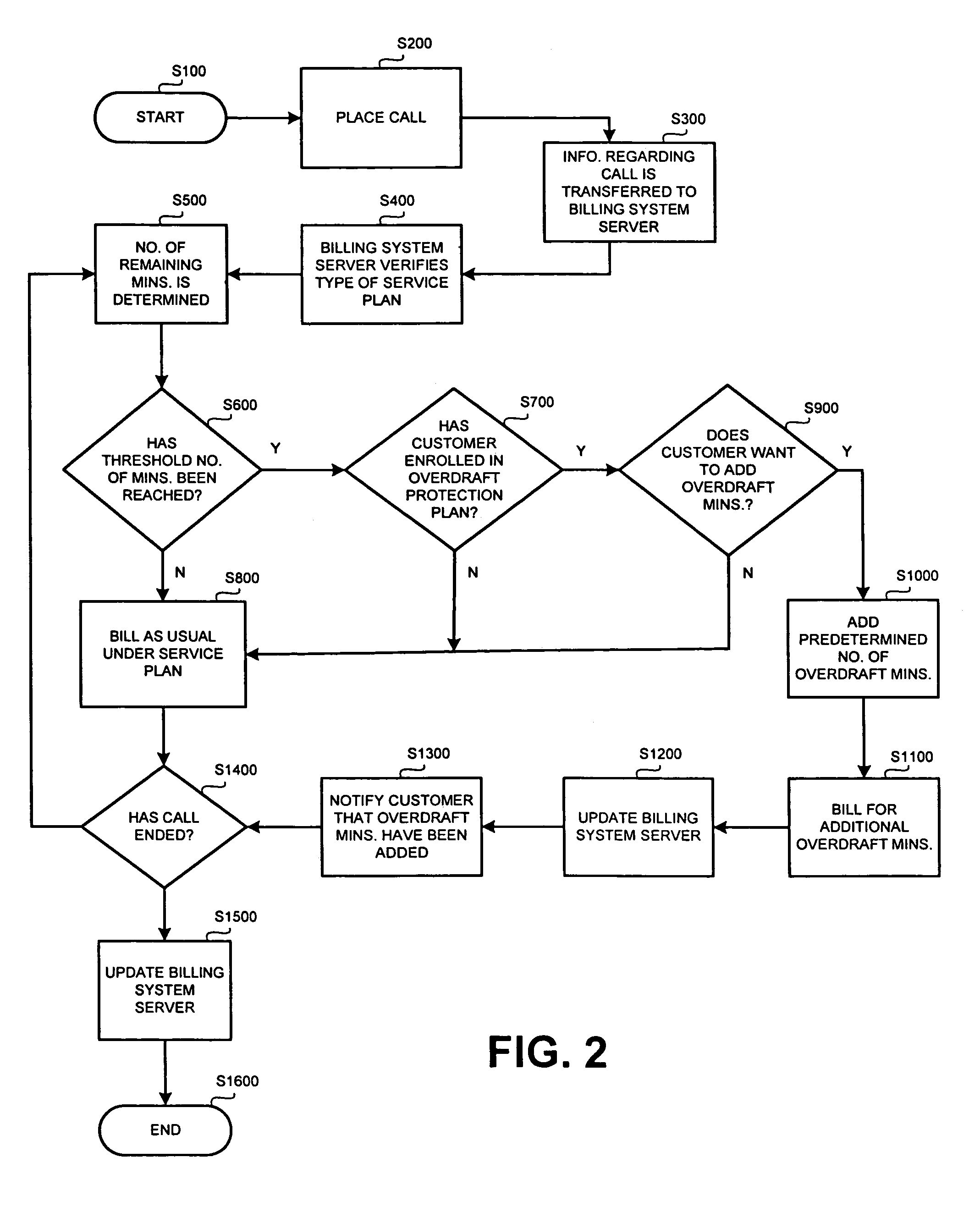
Methods for providing overdraft protection for post-paid communication service plans
ActiveUS7450928B1Cost controlIncreased overage costMetering/charging/biilling arrangementsAccounting/billing servicesCommunication PlanIndustrial engineering
Methods for adding minutes to a calling plan having a calling plan period. The methods including determining whether a threshold number of minutes have been reached during the calling plan period; and incrementally adding minutes to the calling plan when the threshold number of minutes has been reached. The cost per minute of the added minutes is less than the high-cost per minute rate normally associated with exceeding the threshold number of minutes during the calling plan period.
Owner:CINGULAR WIRELESS II LLC
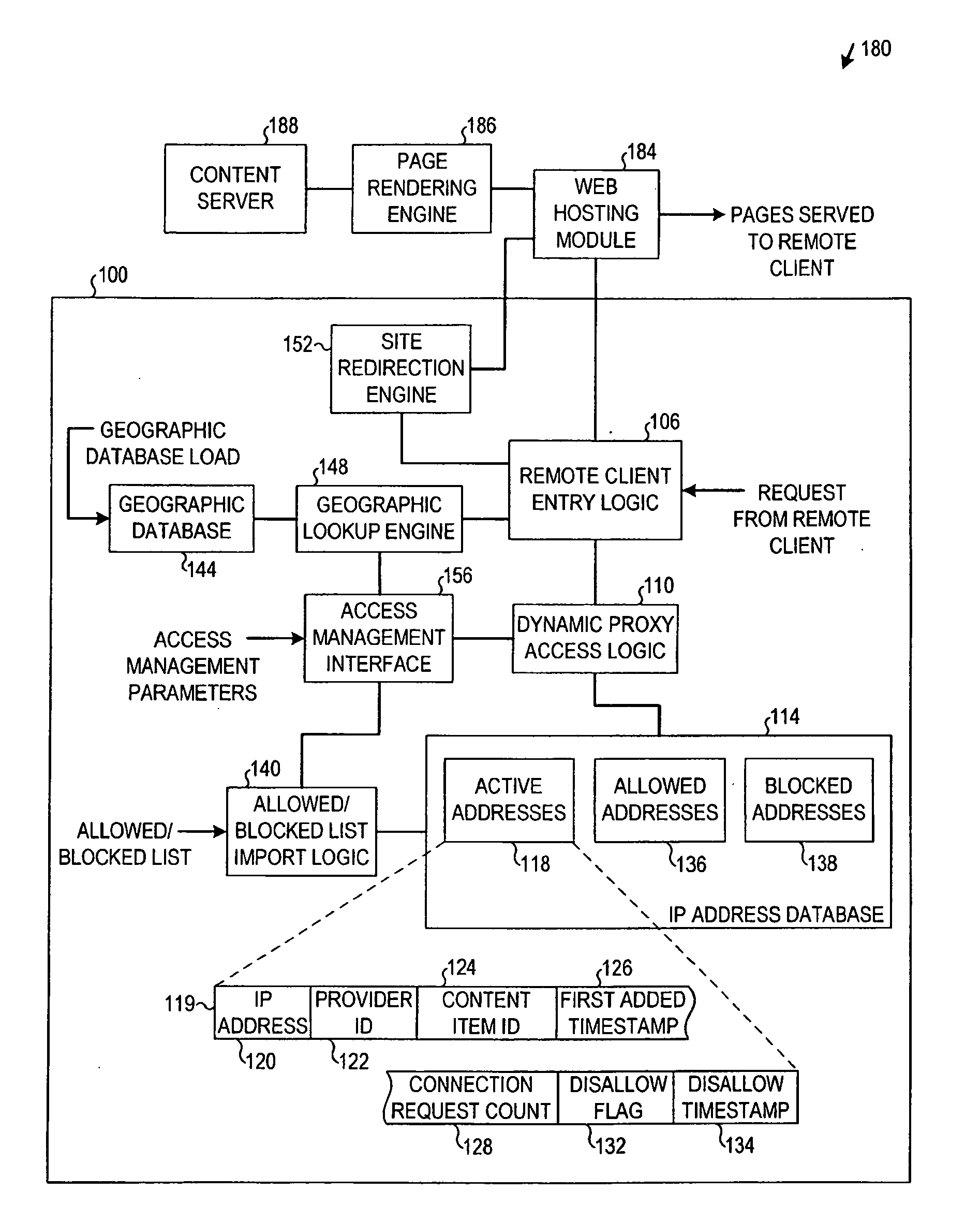
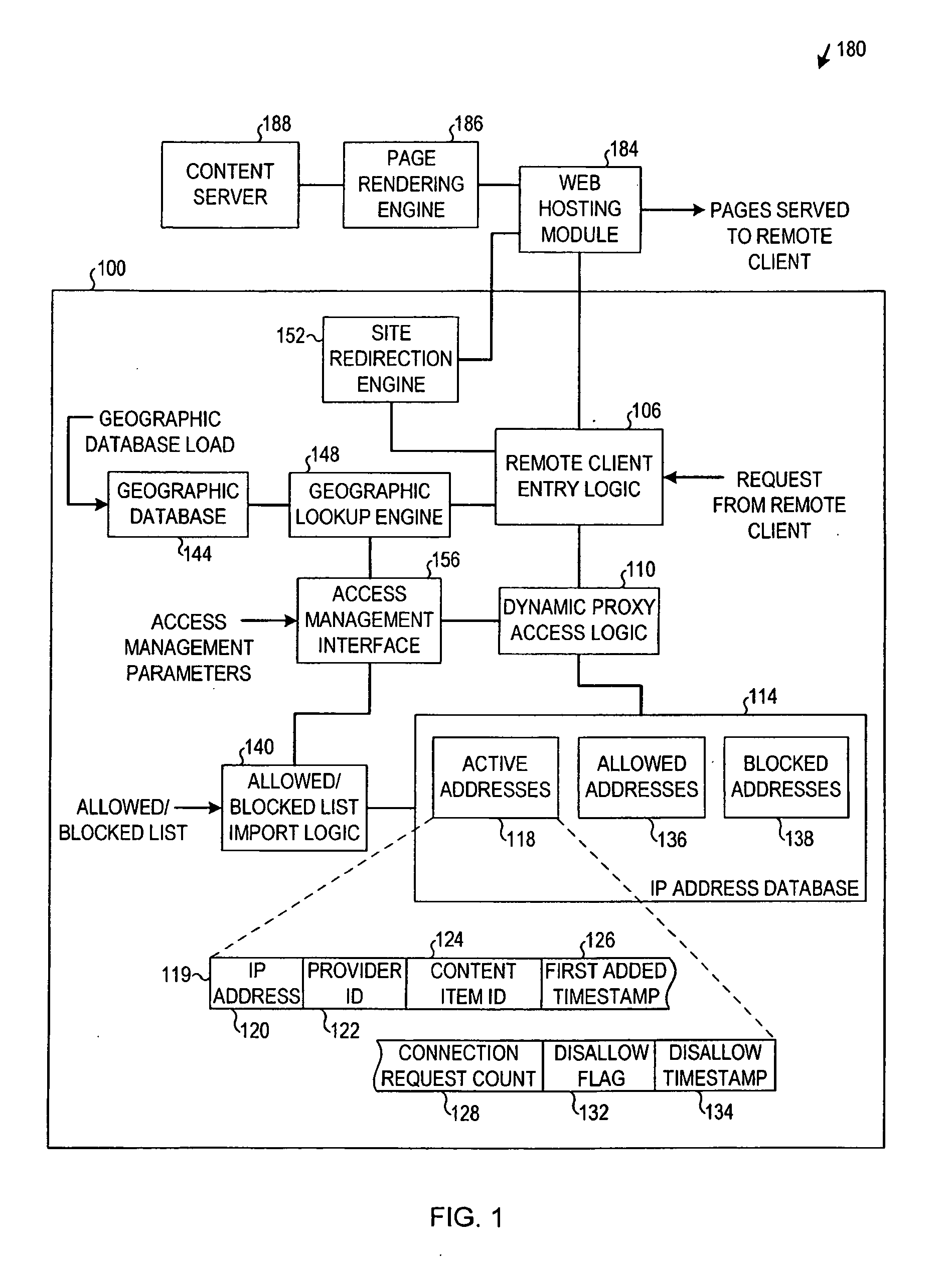
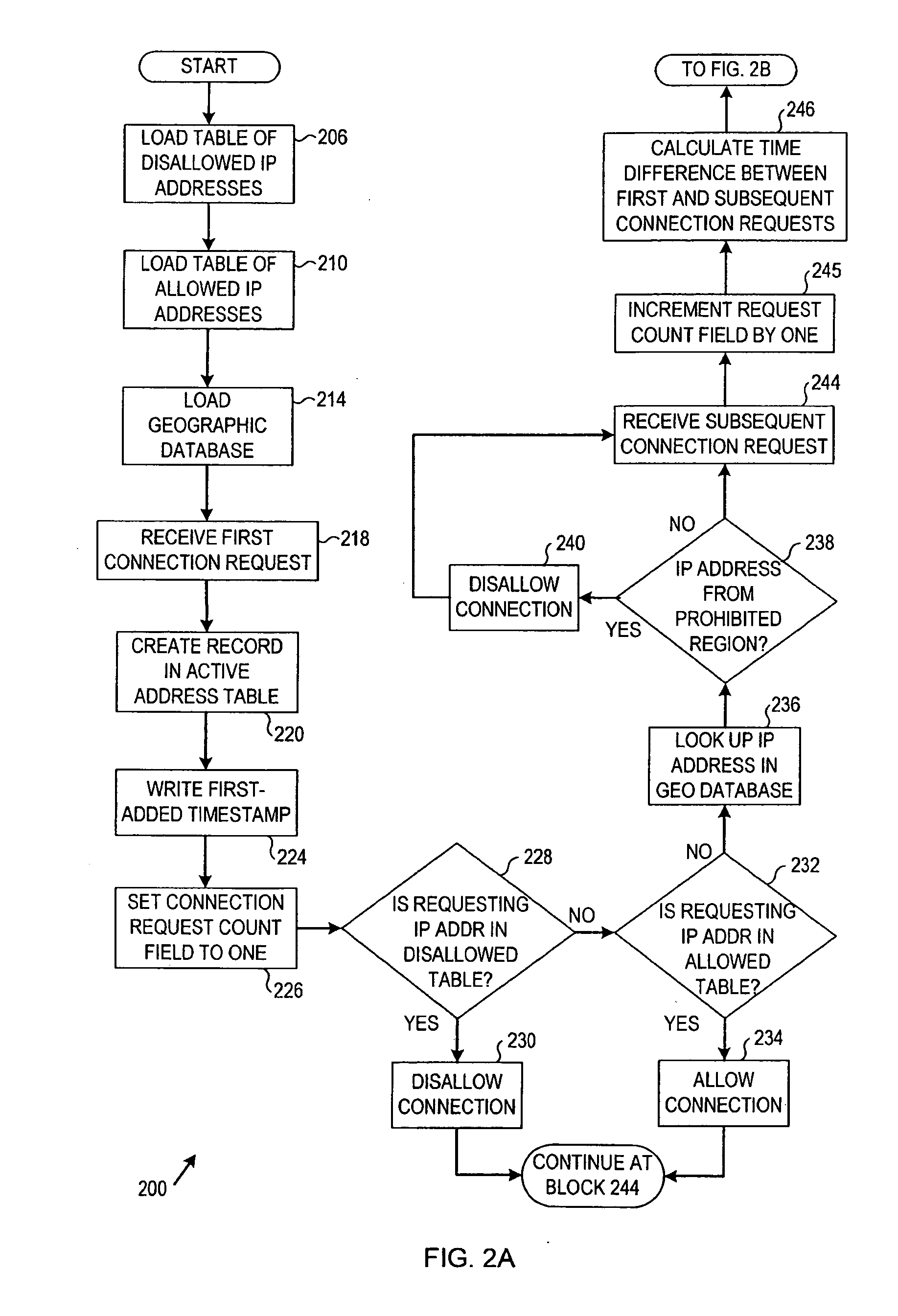
Proxy server access restriction apparatus, systems, and methods
InactiveUS20100042734A1Connection managementMultiple digital computer combinationsIp addressClient-side
Apparatus, systems, and methods disclosed herein disallow connections from one or more remote clients associated with an Internet protocol (IP) address for a period of disallowance if a number of connection requests from the one or more clients associated with the IP address exceeds a threshold number during a threshold time period. Other embodiments are described and claimed.
Owner:IRDETO USA
Deduplication of Data on Disk Devices Based on a Threshold Number of Sequential Blocks
ActiveUS20090271402A1Reduce latencyReduce settingsDigital data information retrievalDigital data processing detailsTime costMetadata
Deduplication of data on disk devices based on a threshold number (THN) of sequential blocks is described herein, the threshold number being two or greater. Deduplication may be performed when a series of THN or more received blocks (THN series) match a sequence of THN or more stored blocks (THN sequence), whereby a sequence comprises blocks stored on the same track of a disk device. Deduplication may be performed using a block-comparison mechanism comprising metadata entries of stored blocks and a mapping mechanism containing mappings of deduplicated blocks to their matching blocks. The mapping mechanism may be used to perform later read requests received for the deduplicated blocks. The deduplication described herein may reduce the read latency as the number of seeks between tracks may be reduced. Also, when a seek to a different track is performed, the seek time cost is spread over THN or more blocks.
Owner:NETWORK APPLIANCE INC
Network with MAC table overflow protection
Owner:PROVEN NETWORKS LLC
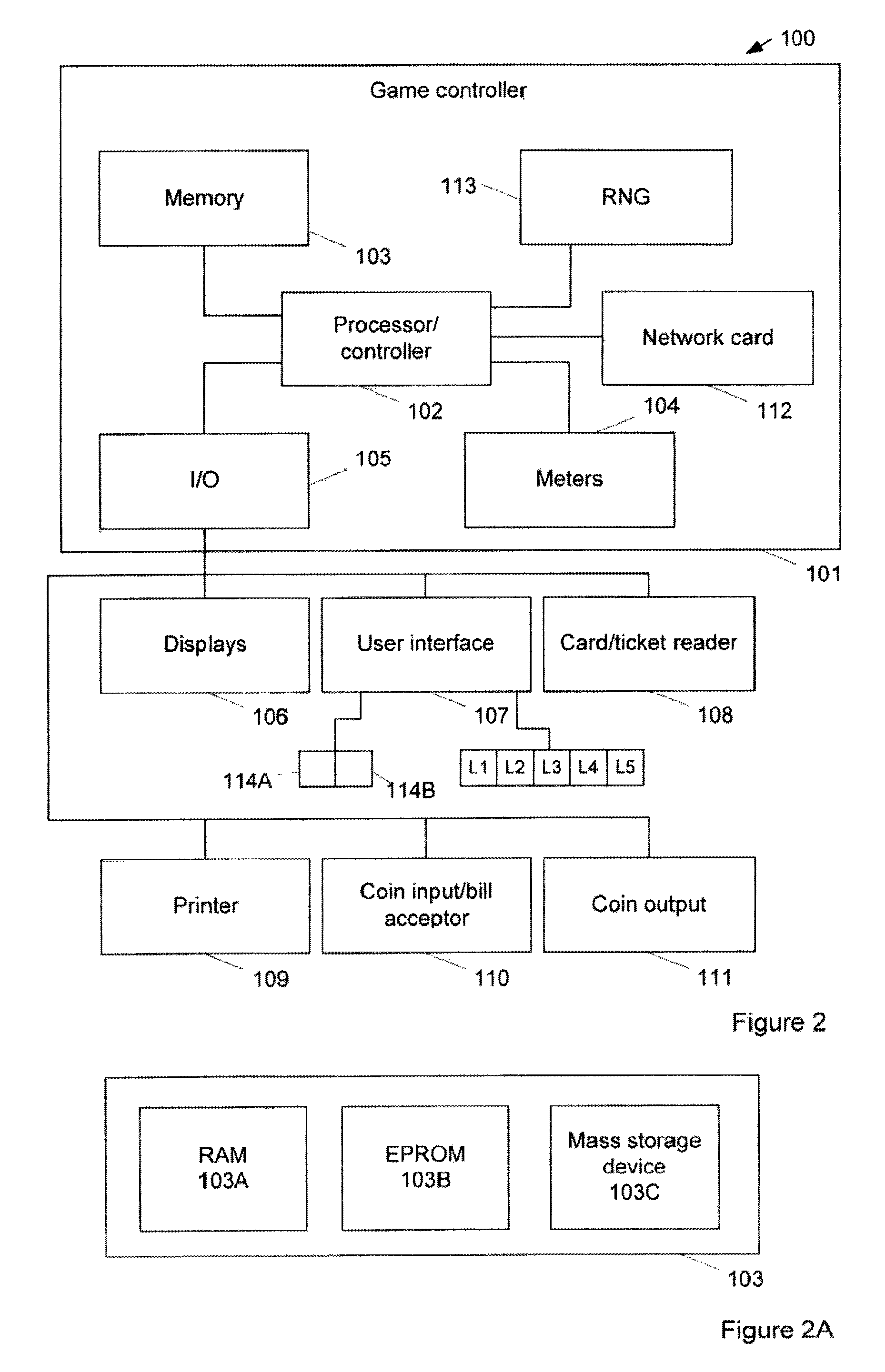
Gaming machine with modified prize feature
ActiveUS8287367B2Low chanceCard gamesApparatus for meter-controlled dispensingArtificial intelligenceOperations research
A gaming system is provided having a display and a game controller. The system implements a game wherein random events are caused to be displayed on the display and, if a predefined winning event results, the system awards a prize. A feature game of the gaming system includes a series of prize outcomes and a series of intervening games, which provide a player with a chance of advancing to a subsequent prize outcome in the event of a winning outcome in an intervening game. A monitoring means may be provided for monitoring and indicating the number of non-winning game outcomes and triggering a penalty event in the event of the non-winning outcomes exceeding a threshold number. In another aspect, a prize outcome of a feature is a progressive prize and a progressive prize modifier for modifying the progressive prize before awarding the prize.
Owner:ARISTOCRAT TECH AUSTRALIA PTY LTD
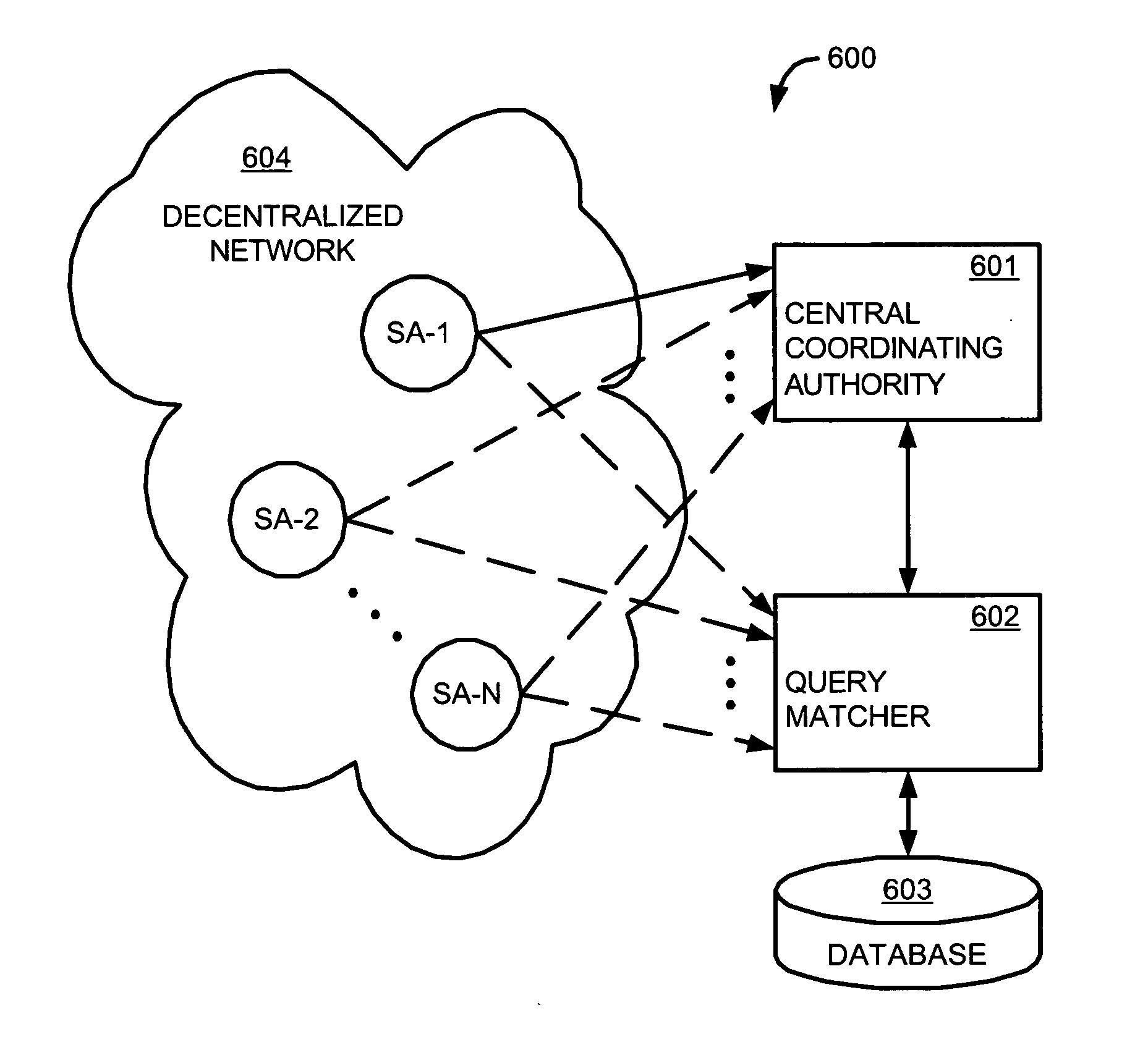
Demand based method for interdiction of unauthorized copying in a decentralized network
InactiveUS20050114709A1Digital data processing detailsUnauthorized memory use protectionDecoyNetwork communication
A multi-level and / or demand based method and apparatus for interdicting unauthorized copying in a decentralized network are described. In their preferred embodiments, the method and apparatus start out by performing search result manipulation to interdict unauthorized copying of protected files. If a trigger event is detected in network communications, however, such as a threshold number of requests being exceeded for a protected file by a network node, then the method floods that node with decoys of the protected file to enhance interdiction efforts.
Owner:MACROVISION CORP
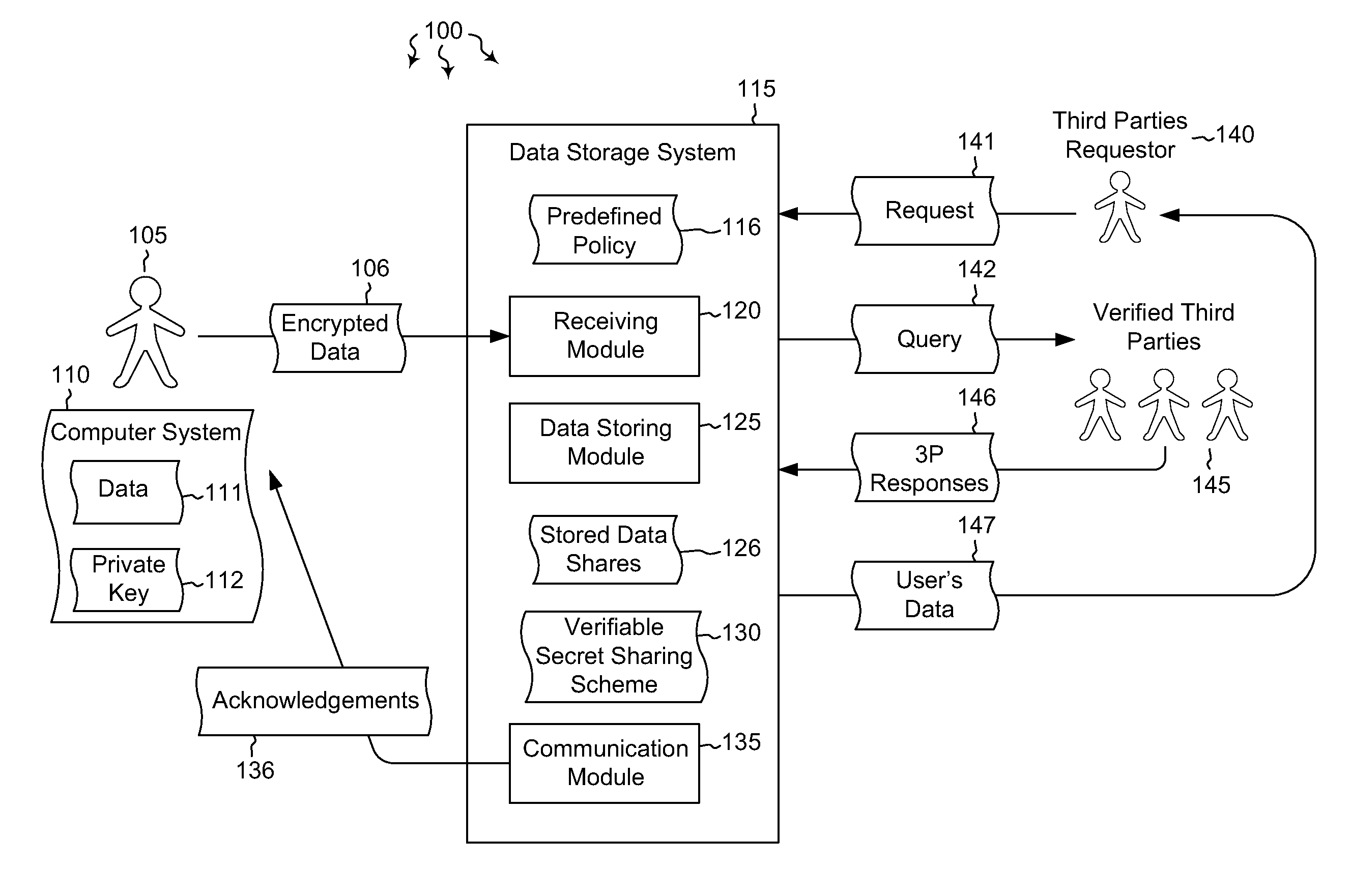
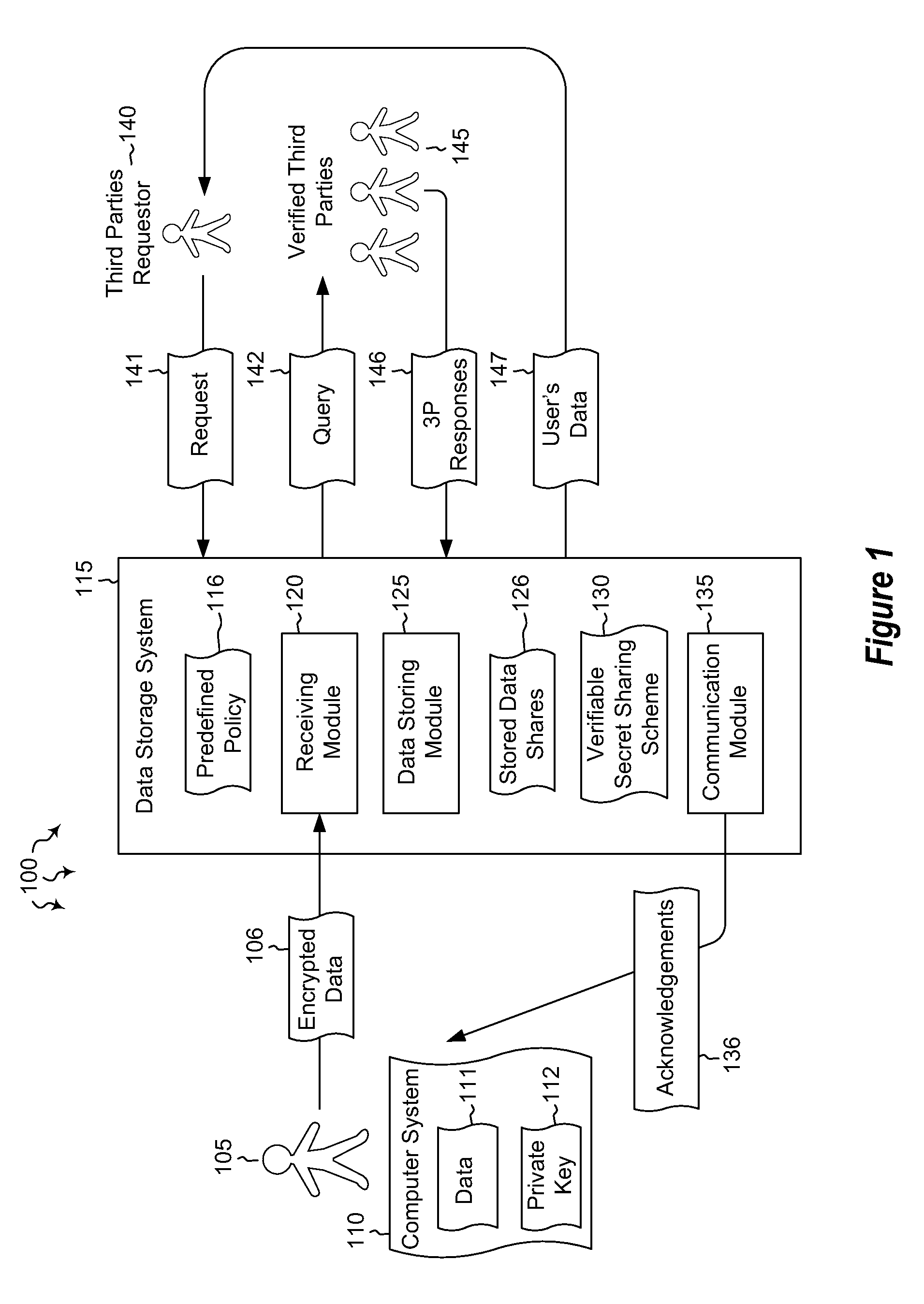
Cloud key escrow system
ActiveUS20120321086A1Data augmentationKey distribution for secure communicationDigital data processing detailsThird partyData access
Owner:MICROSOFT TECH LICENSING LLC
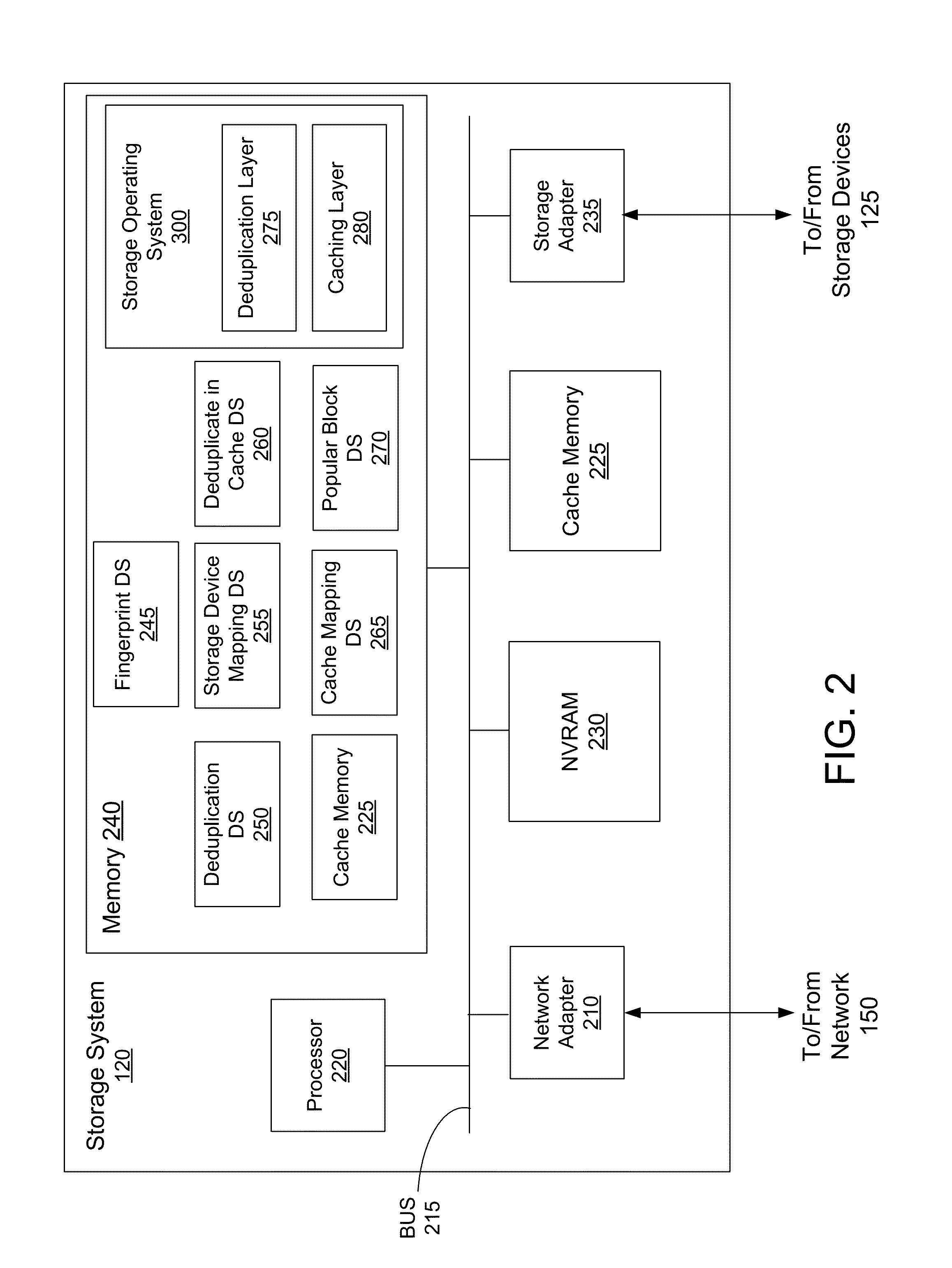
Deduplication of data blocks on storage devices
ActiveUS8732403B1Save on storageHigh trafficMemory adressing/allocation/relocationInput/output processes for data processingOperational systemData deduplication
A storage system comprises a cache for caching data blocks and storage devices for storing blocks. A storage operating system may deduplicate sets of redundant blocks on the storage devices based on a deduplication requirement. Blocks in cache are typically deduplicated based on the deduplication on the storage devices. Sets of redundant blocks that have not met the deduplication requirement for storage devices and have not been deduplicated on the storage devices and cache are targeted for further deduplication processing. Sets of redundant blocks may be further deduplicated based on their popularity (number of accesses) in cache. If a set of redundant blocks in cache is determined to have a combined number of accesses being greater than a predetermined threshold number of accesses, the set of redundant blocks is determined to be “popular.” Popular sets of redundant blocks are selected for deduplication in cache and the storage devices.
Owner:NETWORK APPLIANCE INC
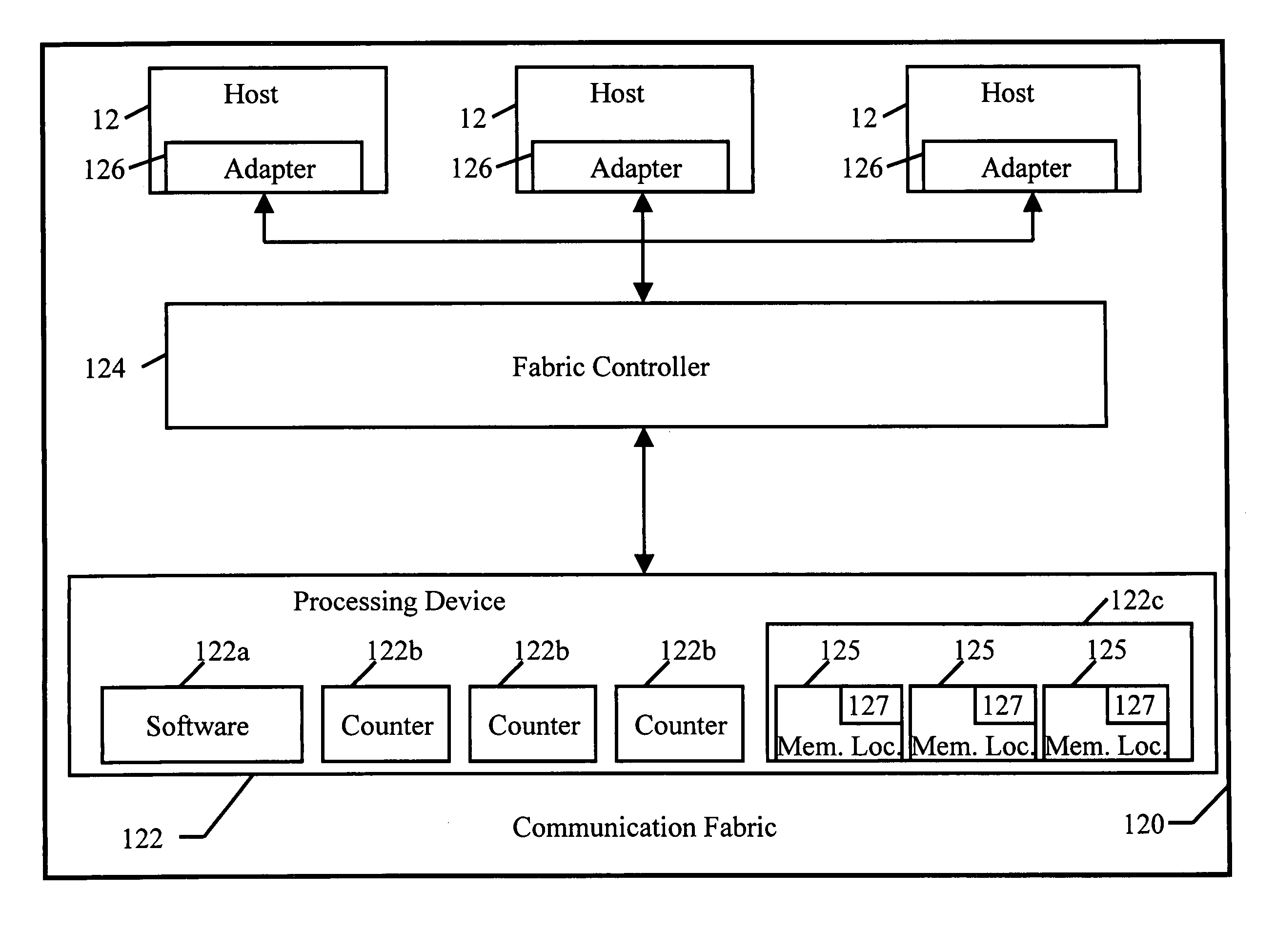
Dynamic threshold scaling in a communication system
A computer system including an error recovery system establishes error threshold inversely proportional to the number of a like kind of system resources, such as host adapters. When a host adapter is initialized or deactivated, a software subcomponent of a processing device calculates a new threshold number and writes it to a memory location associated with each host adapter. When a number of errors exceeds the threshold number, the host adapter is reset, quiesced for repair, or fenced for replacement.
Owner:IBM CORP
Method for Voting with Secret Shares in a Distributed System
ActiveUS20110022883A1Eliminate pointLess reliableKey distribution for secure communicationDigital data processing detailsFailoverSecret share
A replicated decentralized storage system comprises a plurality of servers that locally store disk images for locally running virtual machines as well as disk images, for failover purposes, for remotely running virtual machines. To ensure that disk images stored for failover purposes are properly replicated upon an update of the disk image on the server running the virtual machine, a hash of a unique value known only to the server running the virtual machine is used to verify the origin of update operations that have been transmitted by the server to the other servers storing replications of the disk image for failover purposes. If verified, the update operations are added to such failover disk images. To enable the replicated decentralized system to recover from a failure of the primary server, the master secret is subdivided into parts and distributed to other servers in the cluster. Upon a failure of the primary server, a secondary server receives a threshold number of the parts and is able to recreate the master secret and failover virtual machines that were running in the failed primary server.
Owner:VMWARE INC
Distributed storage network for modification of a data object
In a dispersed storage network, data objects are dispersed storage error encoded into pluralities of sets of encoded data slices that are each stored in corresponding sets of storage units. To recover a data object, a read threshold number of encoded data slices from each set of encoded data slices of the plurality of sets of encoded data slices are required. Upon determining that an update is available for the storage units, a dispersed storage managing unit determines an updating sequence pattern that ensures that while one or more storage units are taken off line for the update, a sufficient number of storage units remain on line such that at least the read threshold number of encoded data slices are available for each set of encoded data slices.
Owner:PURE STORAGE
E-coupon service for location-aware mobile commerce which determines whether to supply requested e-coupons based on the number of requests received in a processing cycle, and a threshold number of requests required to make expected returns from redeemed coupons greater than advertising fees
ActiveUS6996579B2Improve advertising effectivenessImprove cost-efficiencyDiscounts/incentivesSpecial data processing applicationsDistribution methodMobile electronics
A conditional e-coupon distribution method distributes e-coupons predefined by sellers to mobile users only if the number of mobile users requesting such e-coupons equals or exceeds a threshold. The method receives a request to browse e-coupons from a mobile user. The method receives the location of the mobile user and determines a plurality of sellers local to the mobile electronic device and a plurality of corresponding e-coupons available from the local sellers. The method receives a request for a particular e-coupon from a seller and authorizes the provision of said e-coupon to the mobile user. At the end of a processing cycle, the mobile user receives the requested e-coupon if all conditions, such as a period of time and threshold, have been met. A computer-usable medium having computer-readable program code embodied therein allows for storage of the method.
Owner:AT&T INTPROP I L P
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com