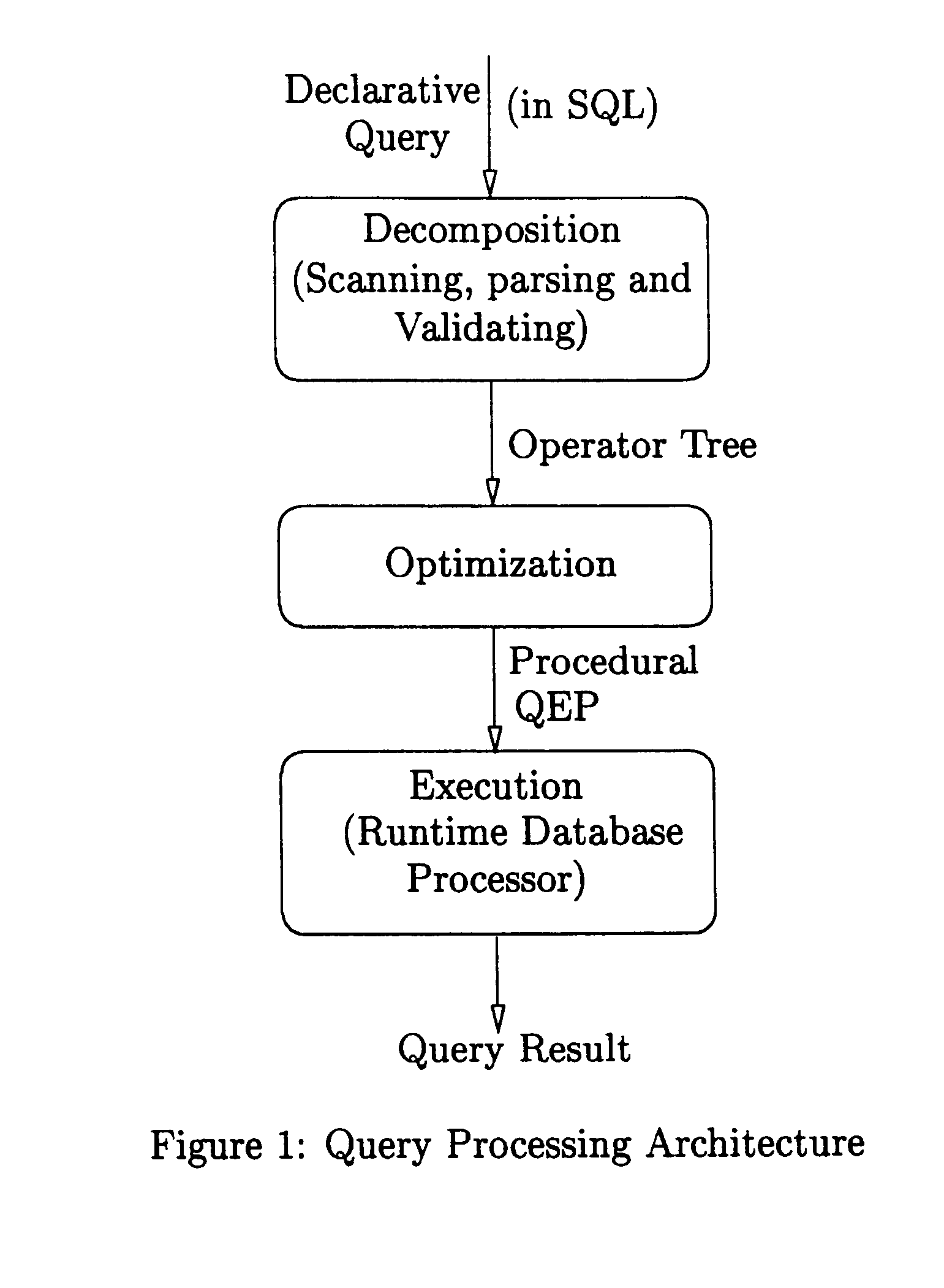
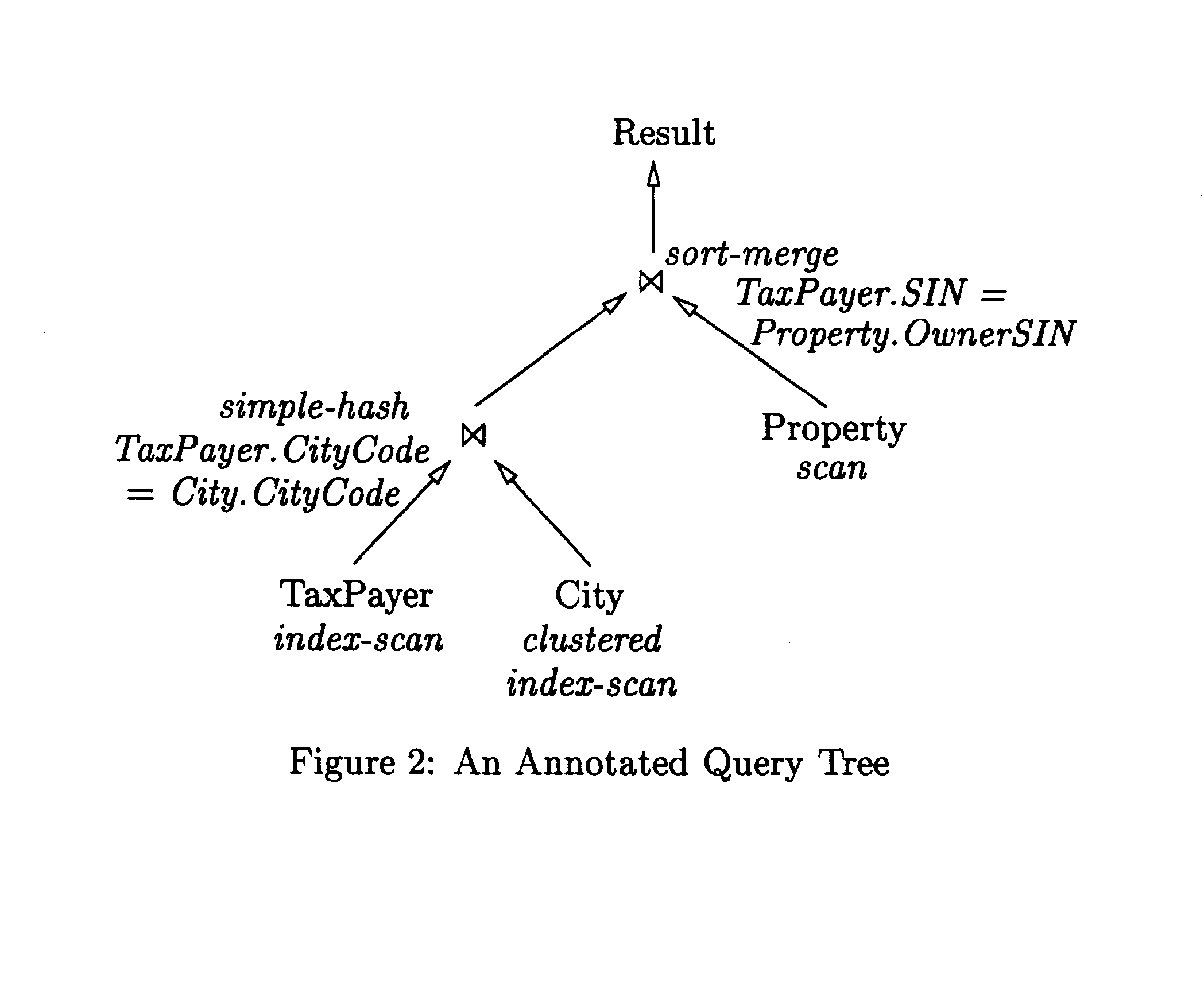
Patents
Literature
1170 results about "Base Number" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A positive integer (sometimes called the radix or scale) that establishes the counting numbers and place values in a number system.
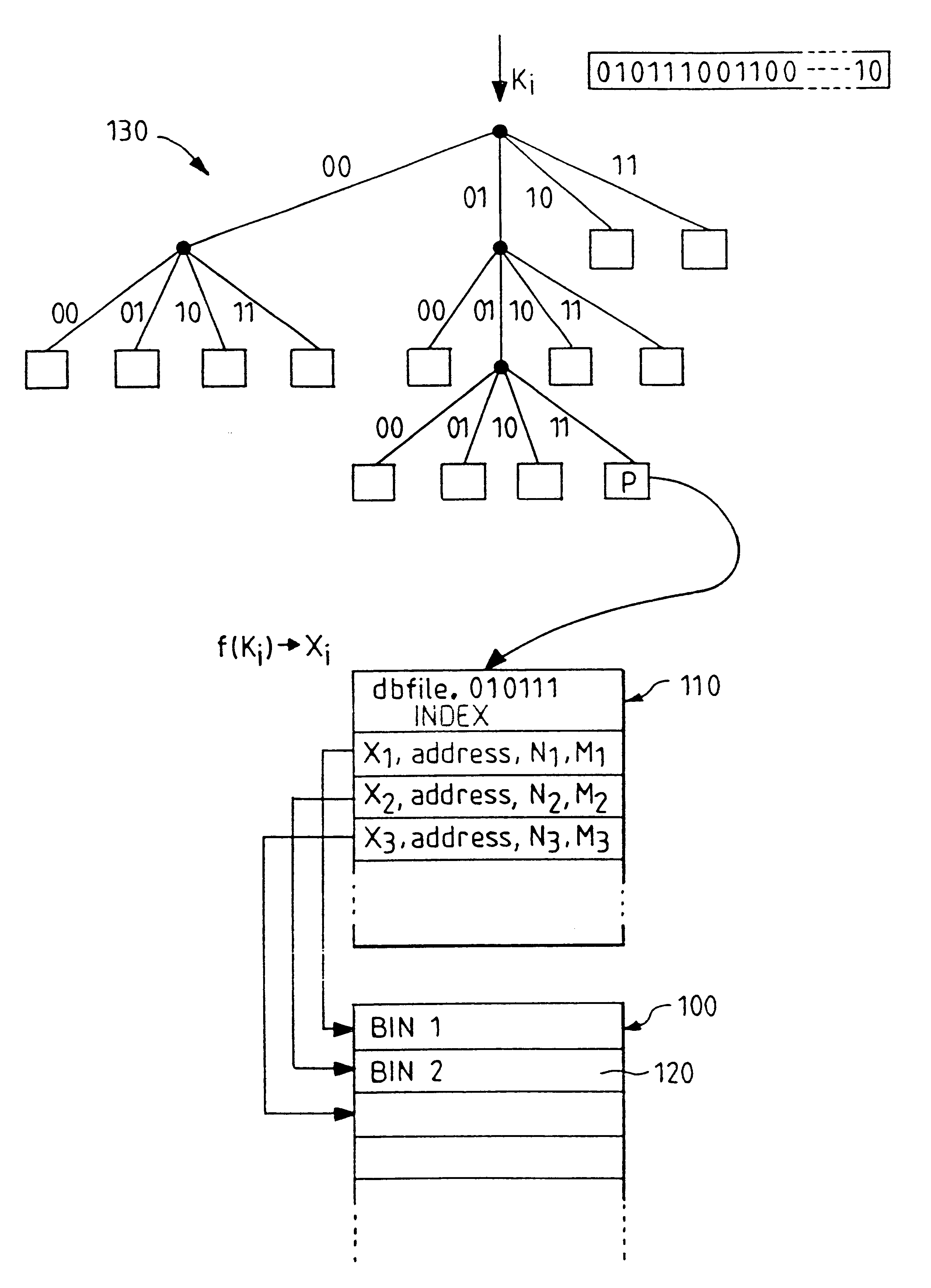
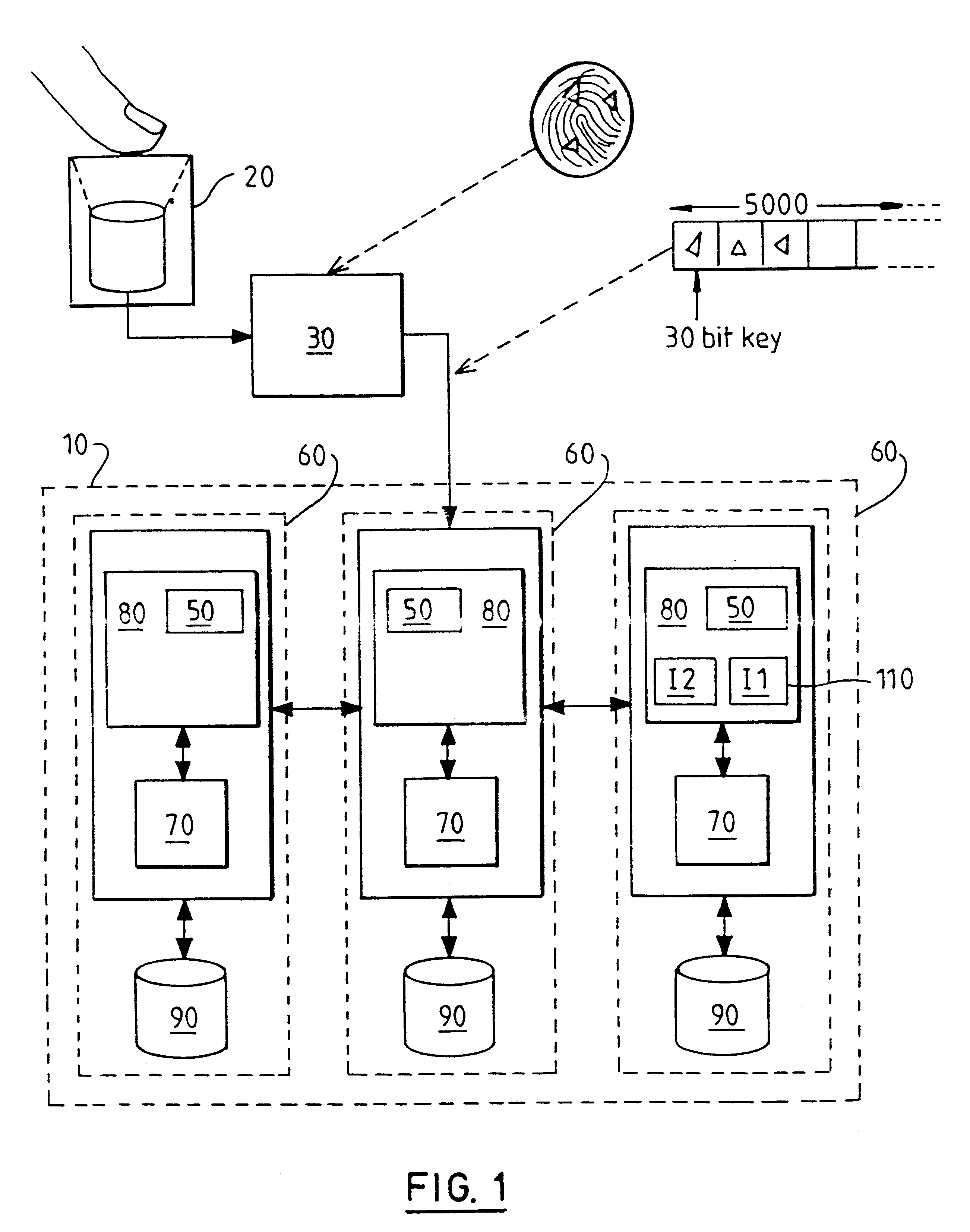
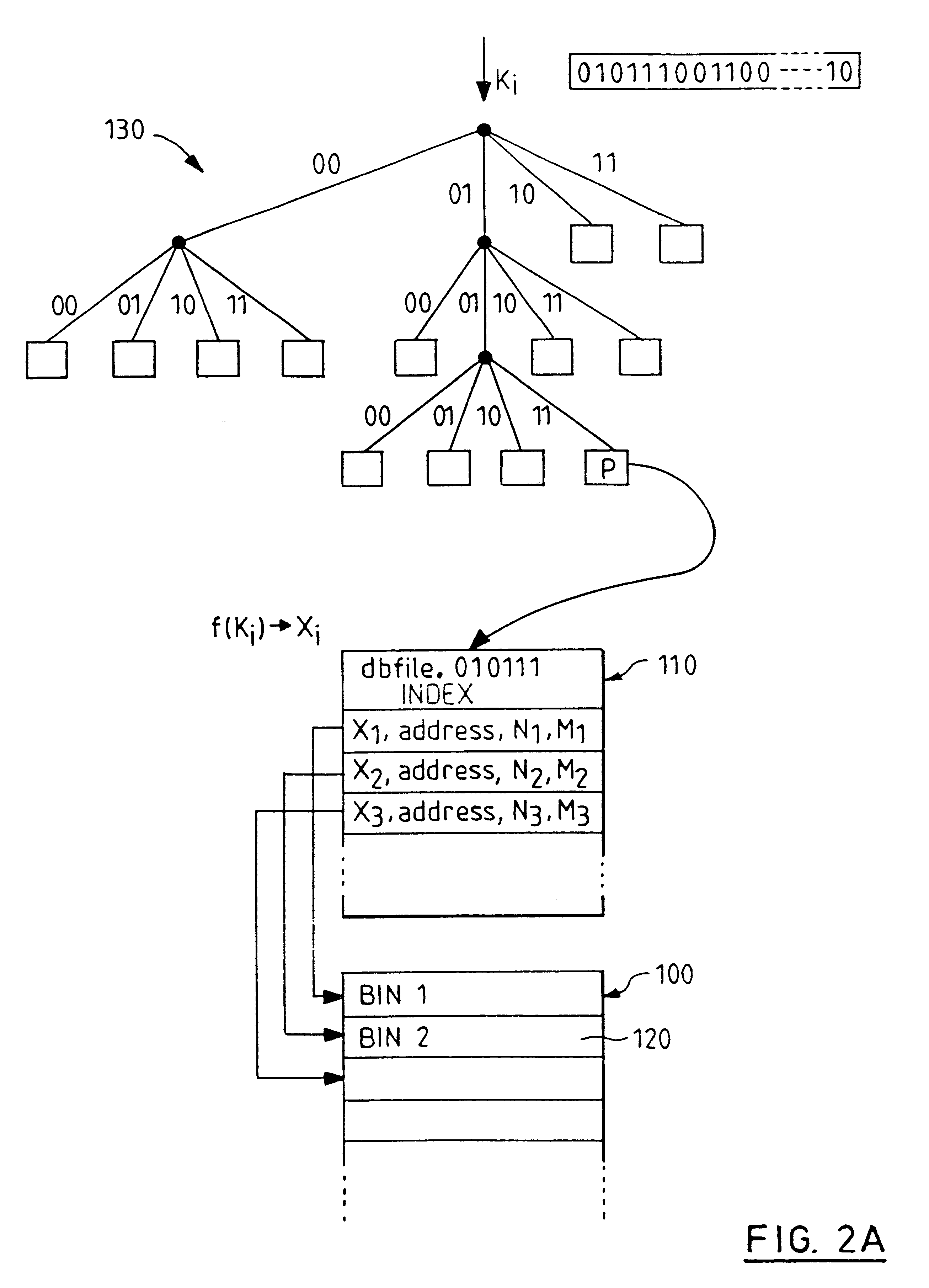
Indexed file system and a method and a mechanism for accessing data records from such a system
InactiveUS6292795B1Efficient access to dataWastefulData processing applicationsDigital data information retrievalExtensibilityCollision detection
A computer filing system includes a data access and allocation mechanism including a directory and a plurality of indexed data files or hash tables. The directory is preferably a radix tree including directory entries which contain pointers to respective ones of the hash tables. Using a plurality of hash tables avoids the whole database ever having to be re-hashed all at once. If a hash table exceeds a preset maximum size as data is added, it is replaced by two hash tables and the directory is updated to include two separate directory entries each containing a pointer to one of the new hash tables. The directory is locally extensible such that new levels are added to the directory only where necessary to distinguish between the hash tables. Local extensibility prevents unnecessary expansion of the size of the directory while also allowing the size of the hash tables to be controlled. This allows optimisation of the data access mechanism such that an optimal combination of directory-look-up and hashing processes is used. Additionally, if the number of keys mapped to an indexed data file is less than a threshold number (corresponding to the number of entries which can be held in a reasonable index), the index for the data file is built with a one-to-one relationship between keys and index entries such that each index entry identifies a data block holding data for only one key. This avoids the overhead of the collision detection of hashing when it ceases to be useful.
Owner:IBM CORP
Method of generating attribute cardinality maps
InactiveUS6865567B1The result is accurateSmall sizeData processing applicationsDigital data information retrievalResource consumptionAlgorithm
This invention provides a novel means for creating a histogram for use in minimizing response time and resource consumption when optimizing a query in a database, and other like structures, the histogram being created by placing ordered elements into specific range until the next element to be considered for inclusion in the range is a predetermined distance from the (generalized) mean value associated with the elements within the range, whereupon that next element is placed in the following range. Similarly, the following ranges are closed when the next element to be considered for inclusion in the range is greater than a predetermined distance from the (generalized) mean value associated with the elements in that range, whereupon that next element is placed in the following range. For each range, the location and size of the range is recorded with, for example, the mean value, the slope or other attribute characterizing one or more elements in the range. The invention has also applications in pattern recognition, message routing, and in actuarial sciences.
Owner:OOMMEN BASANTKUMAR JOHN +1
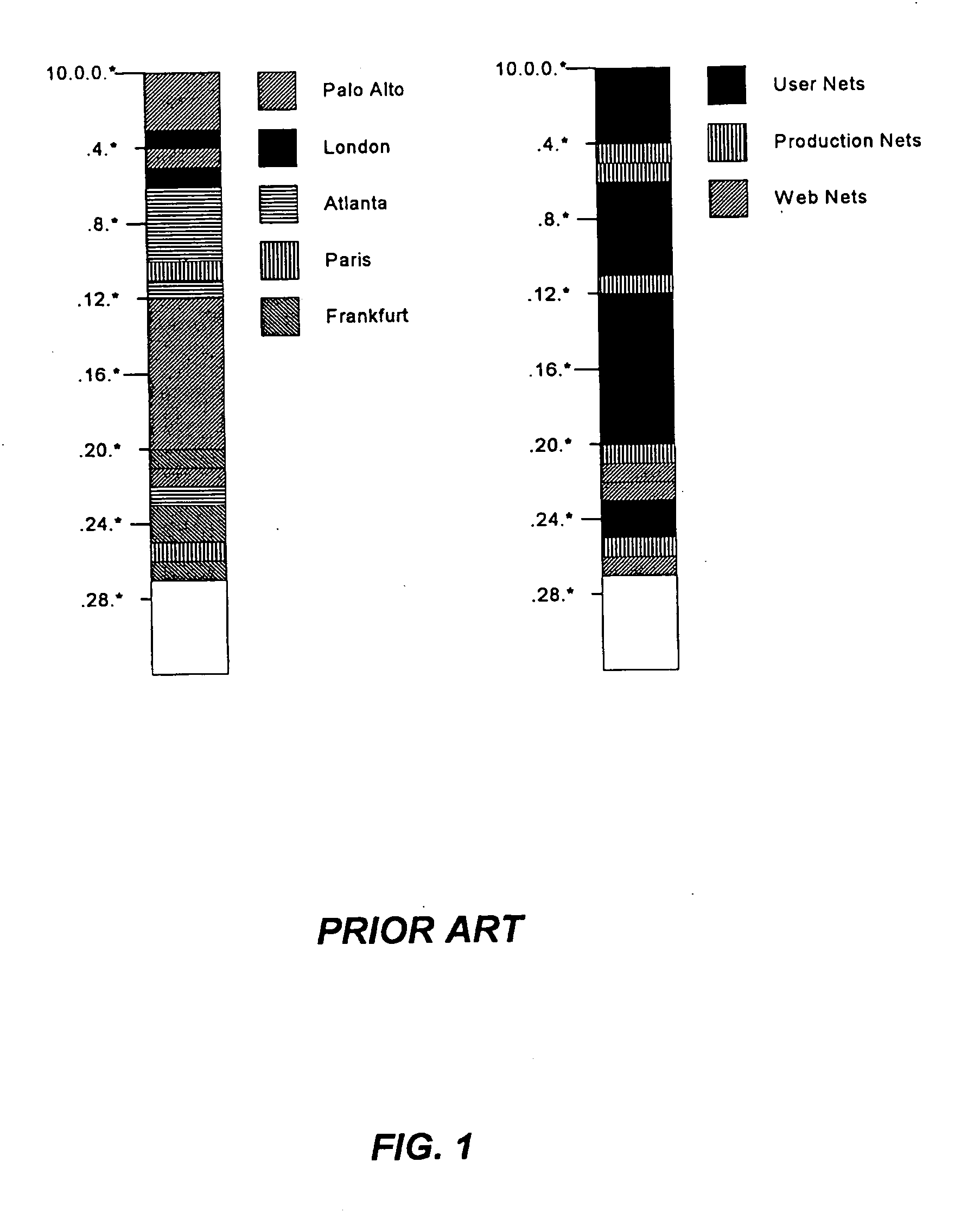
System and method of aggregating discontiguous address ranges into addresses and masks using a plurality of repeating address blocks
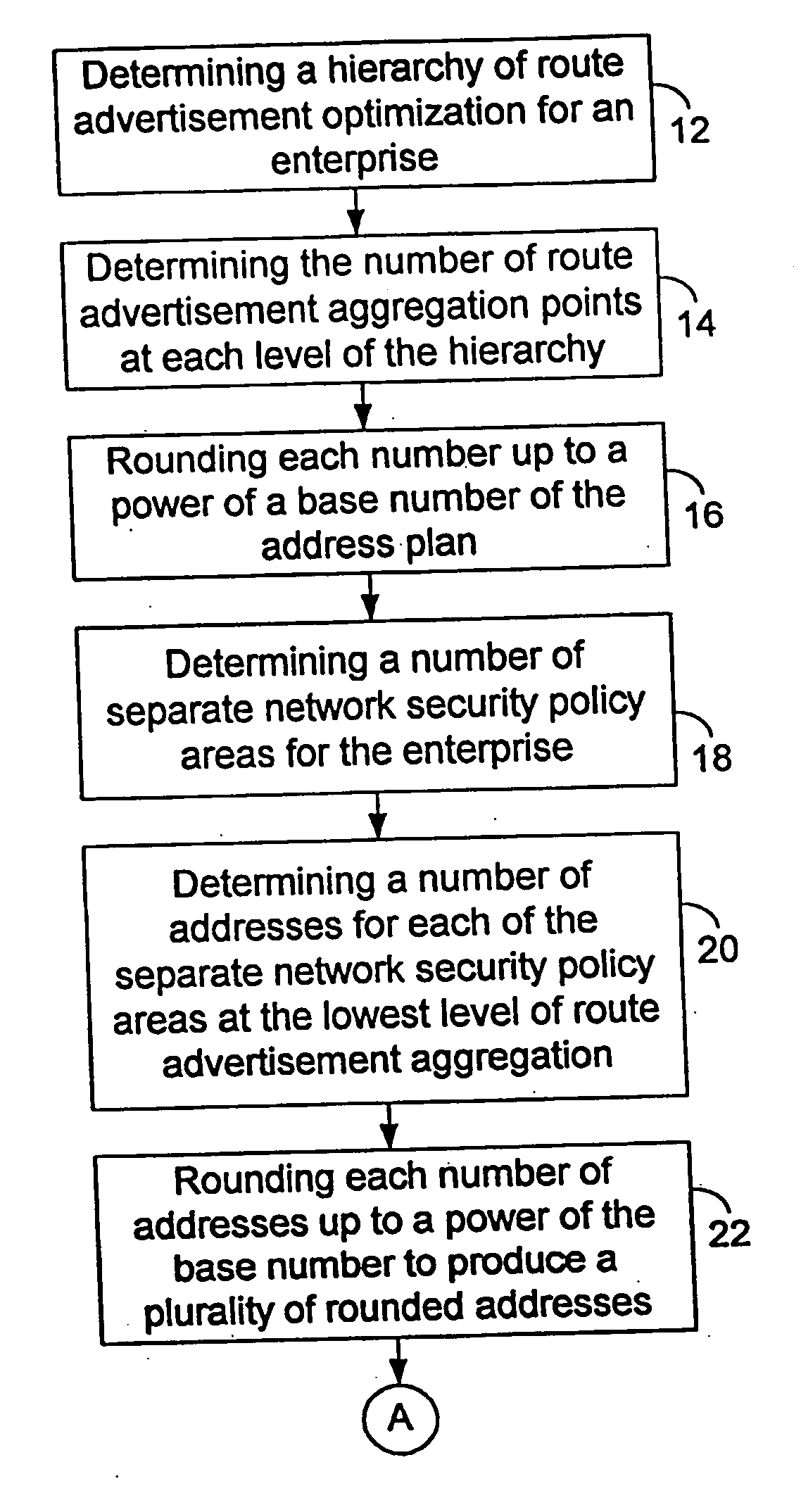
A method of creating a discontiguous address plan for an enterprise is provided which includes determining a hierarchy of routing optimization for an enterprise, determining a number of route advertisement aggregation points at each level of the hierarchy, determining a number of network security policy areas for the enterprise, and determining a number of addresses for each of the network security policy areas. The number of addresses is rounded up to a power of the address scheme base number to produce a plurality of rounded addresses. The method further includes allocating an address range for each of the plurality of rounded addresses so that a starting address of the address range begins on a power of the base number and determining a size of the plurality of address ranges. The size of the plurality of address ranges is rounded up to a power of the base number to produce the size of a repeating policy pattern. The method further includes assigning an instance of the repeating policy pattern to each of the route advertisement aggregation points at each hierarchy, and determining an address and a mask for each of the network security policy areas in the repeating policy pattern.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Inverse inference engine for high performance web search
InactiveUS7051017B2Eliminate needIncrease computing speedData processing applicationsDigital data processing detailsDecompositionOrthogonal basis
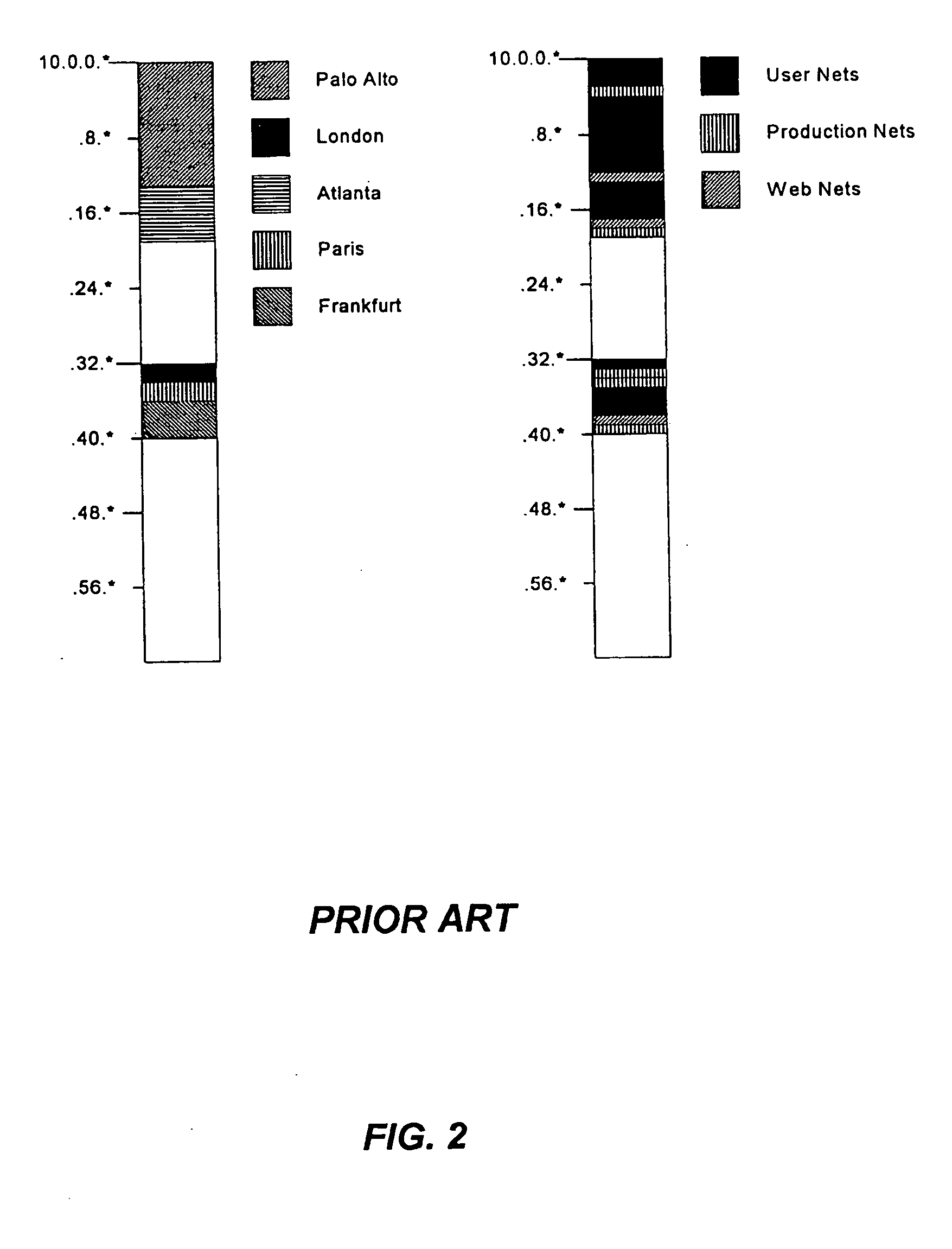
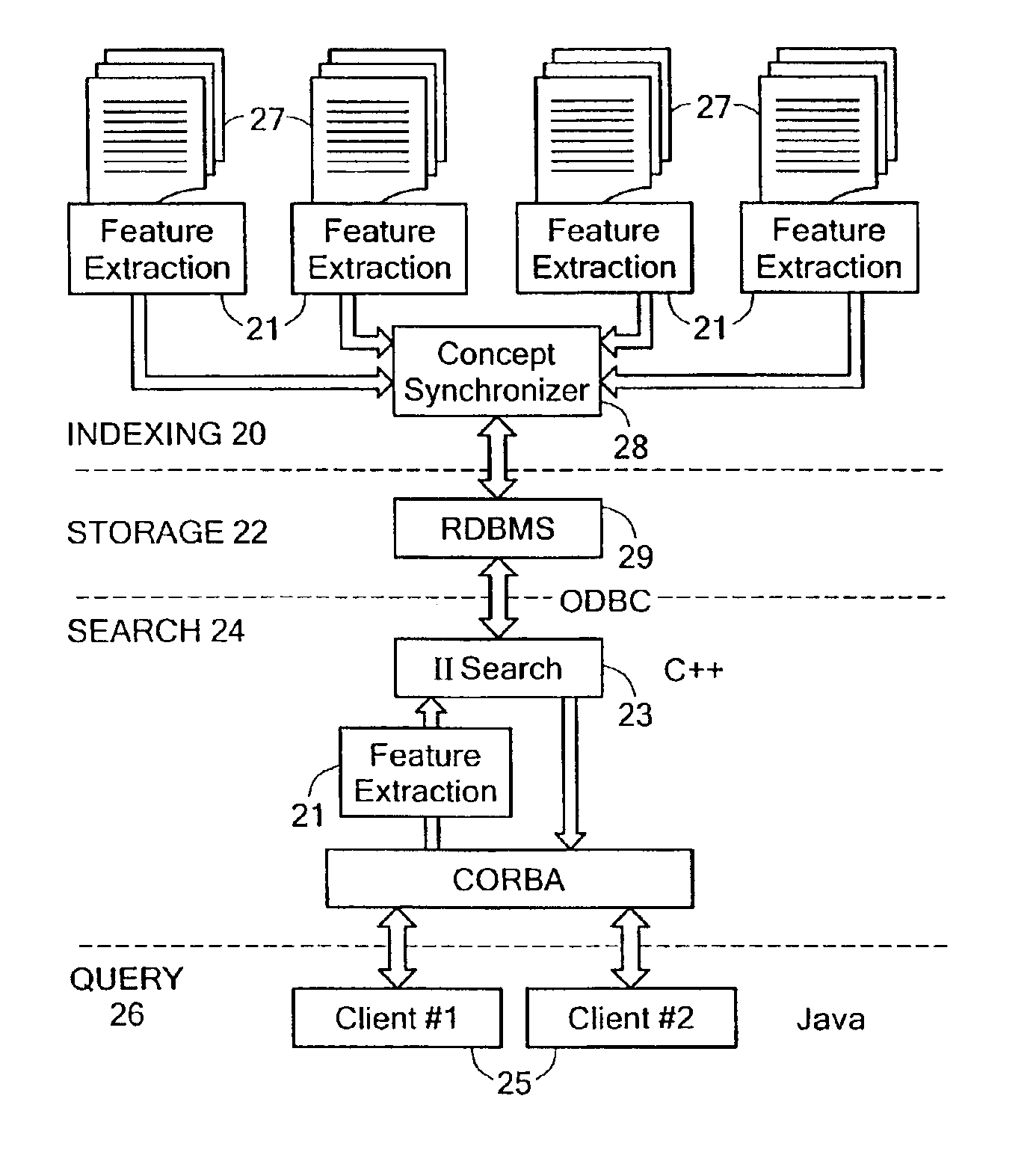
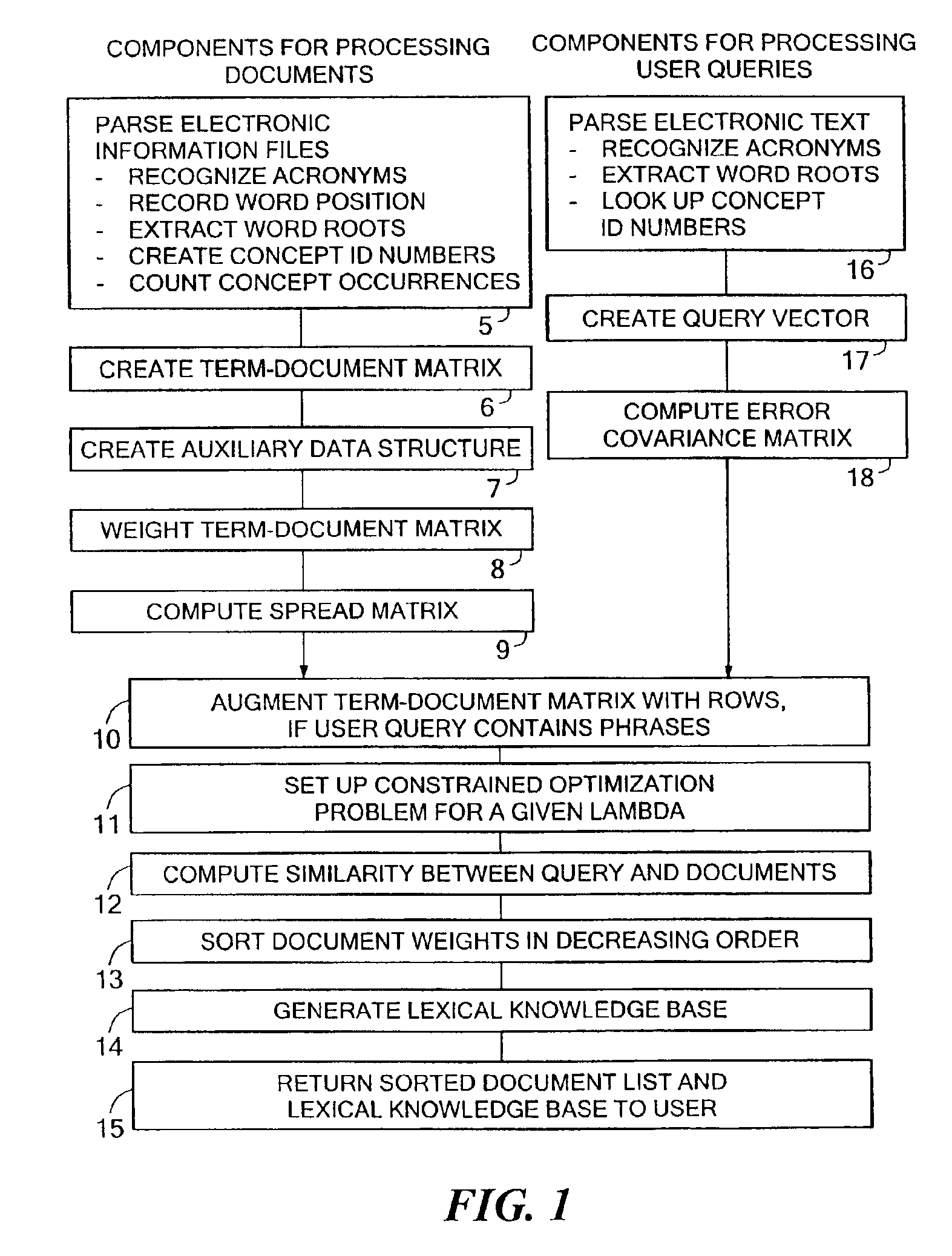
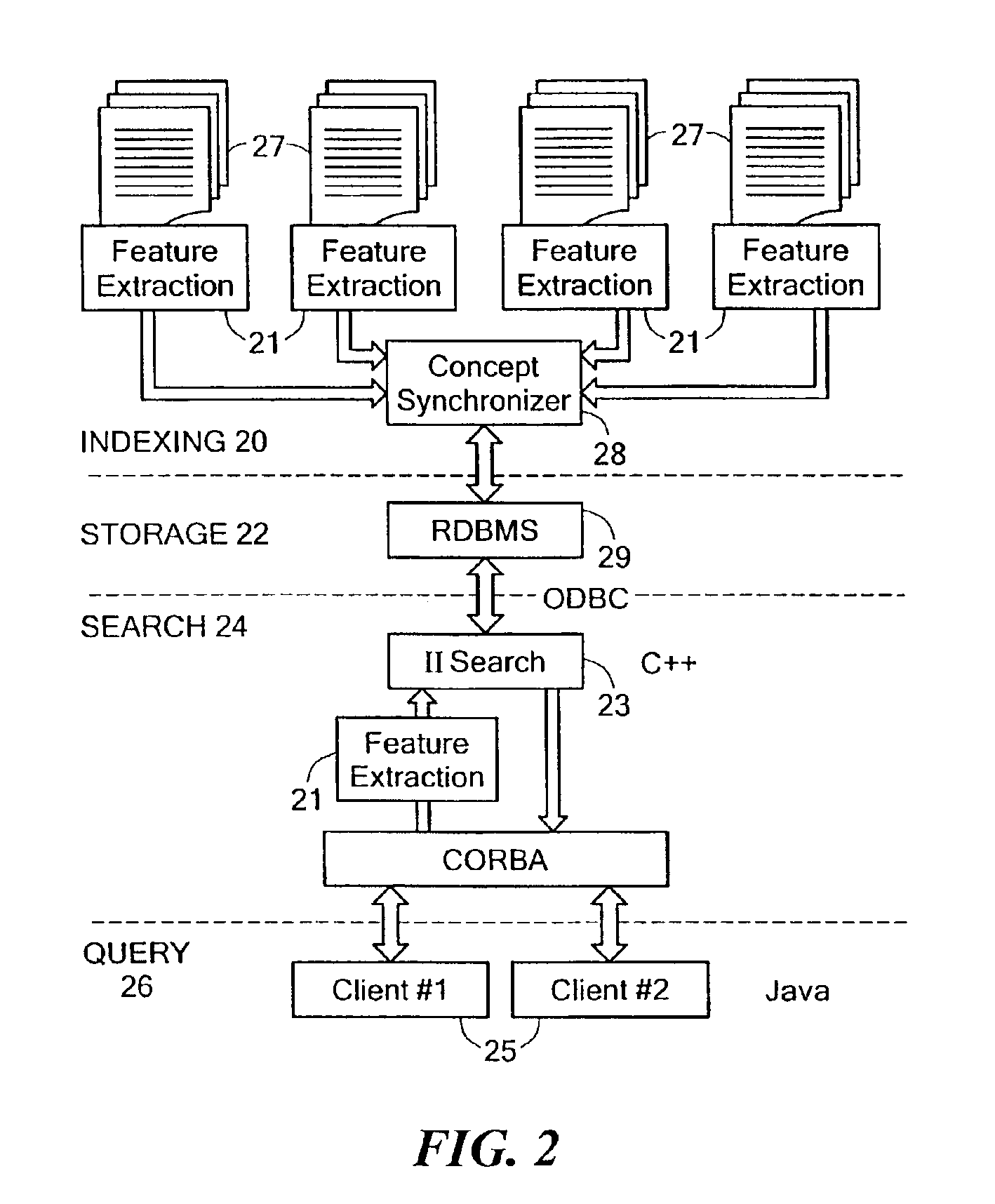
An information retrieval system that deals with the problems of synonymy, polysemy, and retrieval by concept by allowing for a wide margin of uncertainty in the initial choice of keywords in a query. For each input query vector and an information matrix, the disclosed system solves an optimization problem which maximizes the stability of a solution at a given level of misfit. The disclosed system may include a decomposition of the information matrix in terms of orthogonal basis functions. Each basis encodes groups of conceptually related keywords. The bases are arranged in order of decreasing statistical relevance to a query. The disclosed search engine approximates the input query with a weighted sum of the first few bases. Other commercial applications than the disclosed search engine can also be built on the disclosed techniques.
Owner:FIVER LLC
Method and apparatus for exploiting statistics on query expressions for optimization
ActiveUS6947927B2Improve accuracyData processing applicationsDigital data information retrievalQuery planExecution plan
A method for evaluating a user query on a relational database having records stored therein, a workload made up of a set of queries that have been executed on the database, and a query optimizer that generates a query execution plan for the user query. Each query plan includes a plurality of intermediate query plan components that verify a subset of records from the database meeting query criteria. The method accesses the query plan and a set of stored intermediate statistics for records verified by query components, such as histograms that summarize the cardinality of the records that verify the query component. The method forms a transformed query plan based on the selected intermediate statistics (possibly by rewriting the query plan) and estimates the cardinality of the transformed query plan to arrive at a more accurate cardinality estimate for the query. If additional intermediate statistics are necessary, a pool of intermediate statistics may be generated based on the queries in the workload by evaluating the benefit of a given statistic over the workload and adding intermediate statistics to the pool that provide relatively great benefit.
Owner:MICROSOFT TECH LICENSING LLC
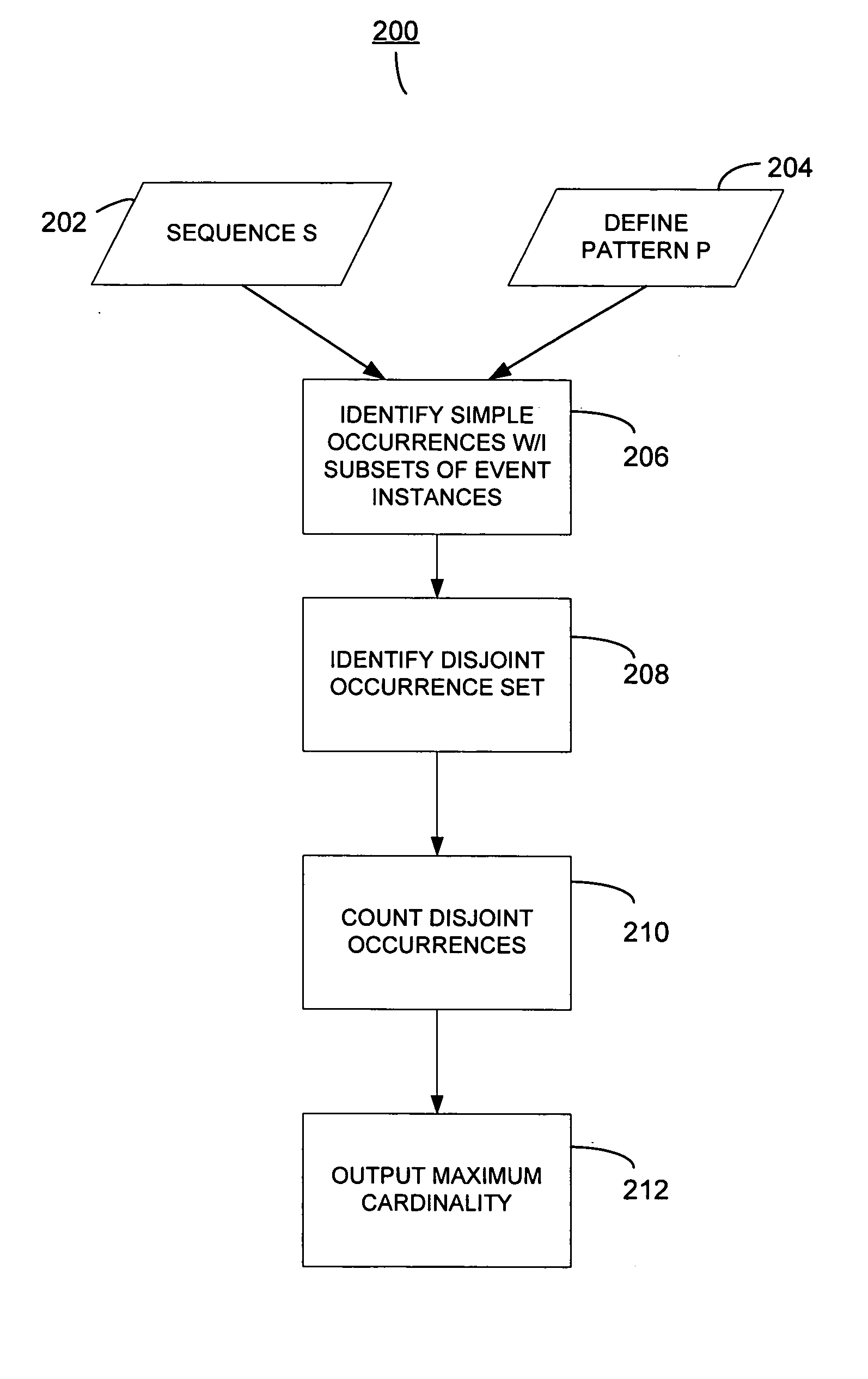
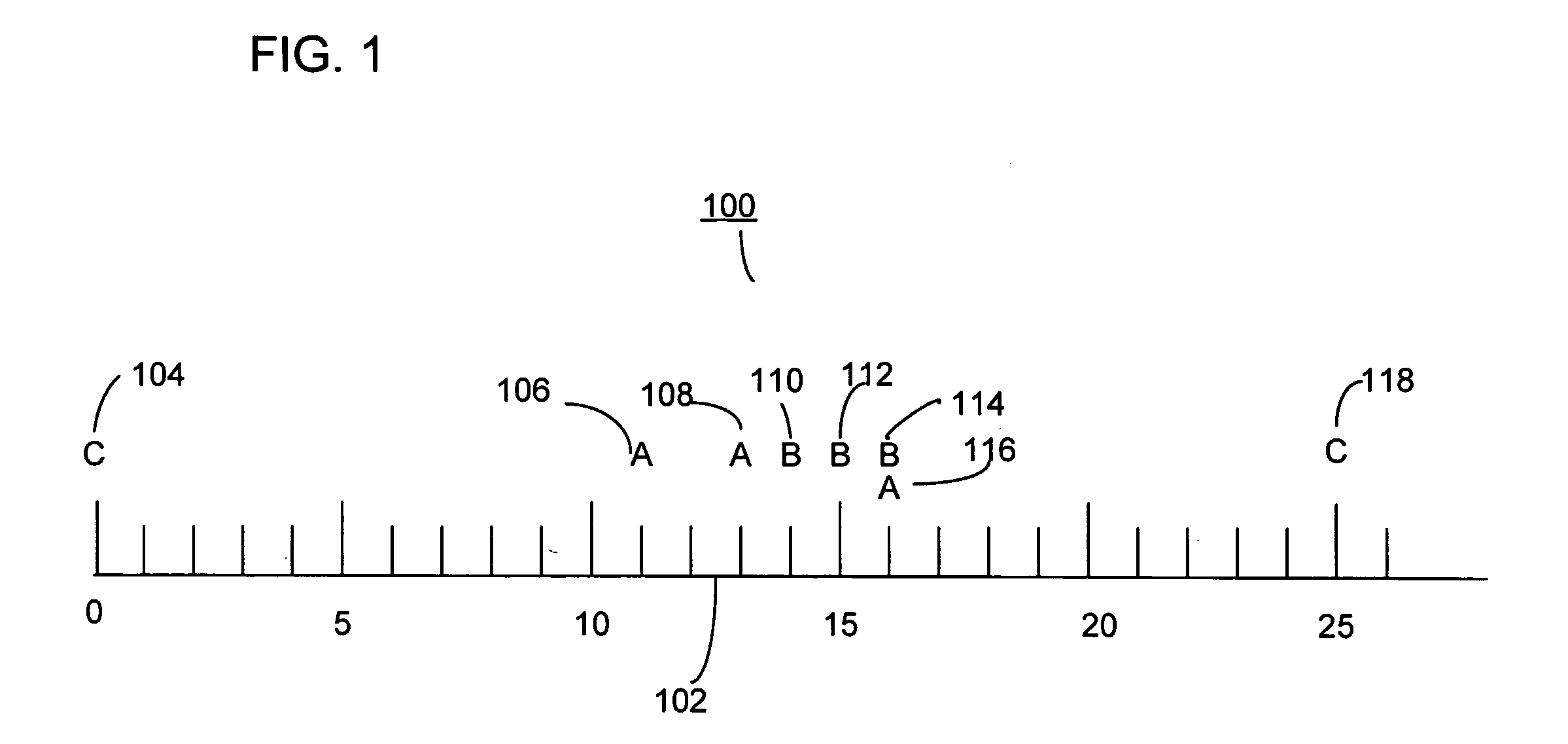
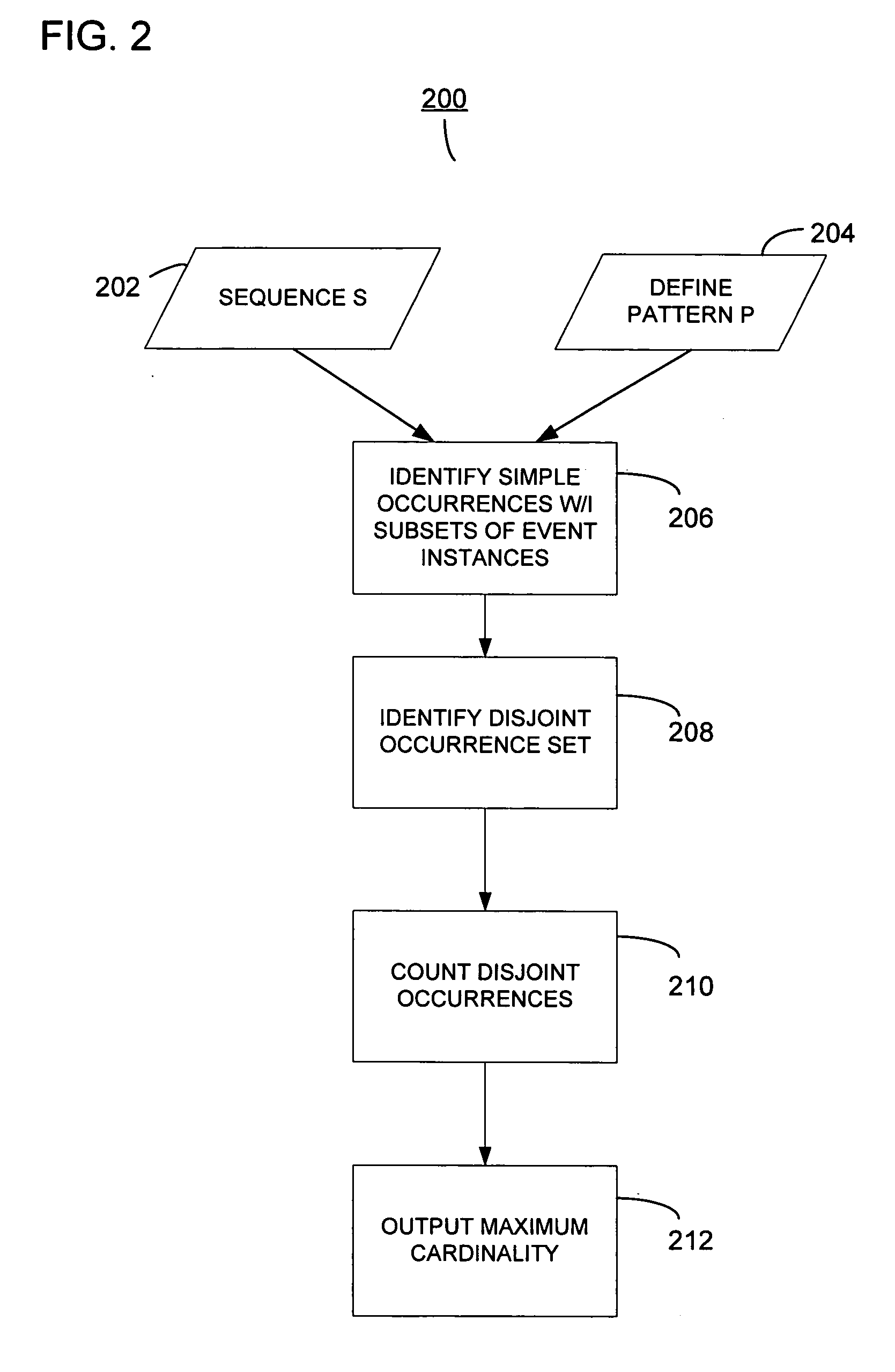
System and method for analyzing a pattern in a time-stamped event sequence
InactiveUS20050235356A1Improved efficiency and effectivenessIncrease opportunitiesDigital data information retrievalMemory loss protectionData miningBase Number
Preferred embodiments and implementations include a system and method for determining distinct occurrences of a pattern in a sequence of time-stamped event instances by determining a maximum cardinality of disjoint occurrences of the pattern in the one or more sequences. The invention also includes estimating an expected quantity of distinct occurrences of a pattern in a sequence of time-stamped events assigned to event categories. The invention further includes identifying a surprise pattern within a sequence of time-stamped events.
Owner:THE BOEING CO
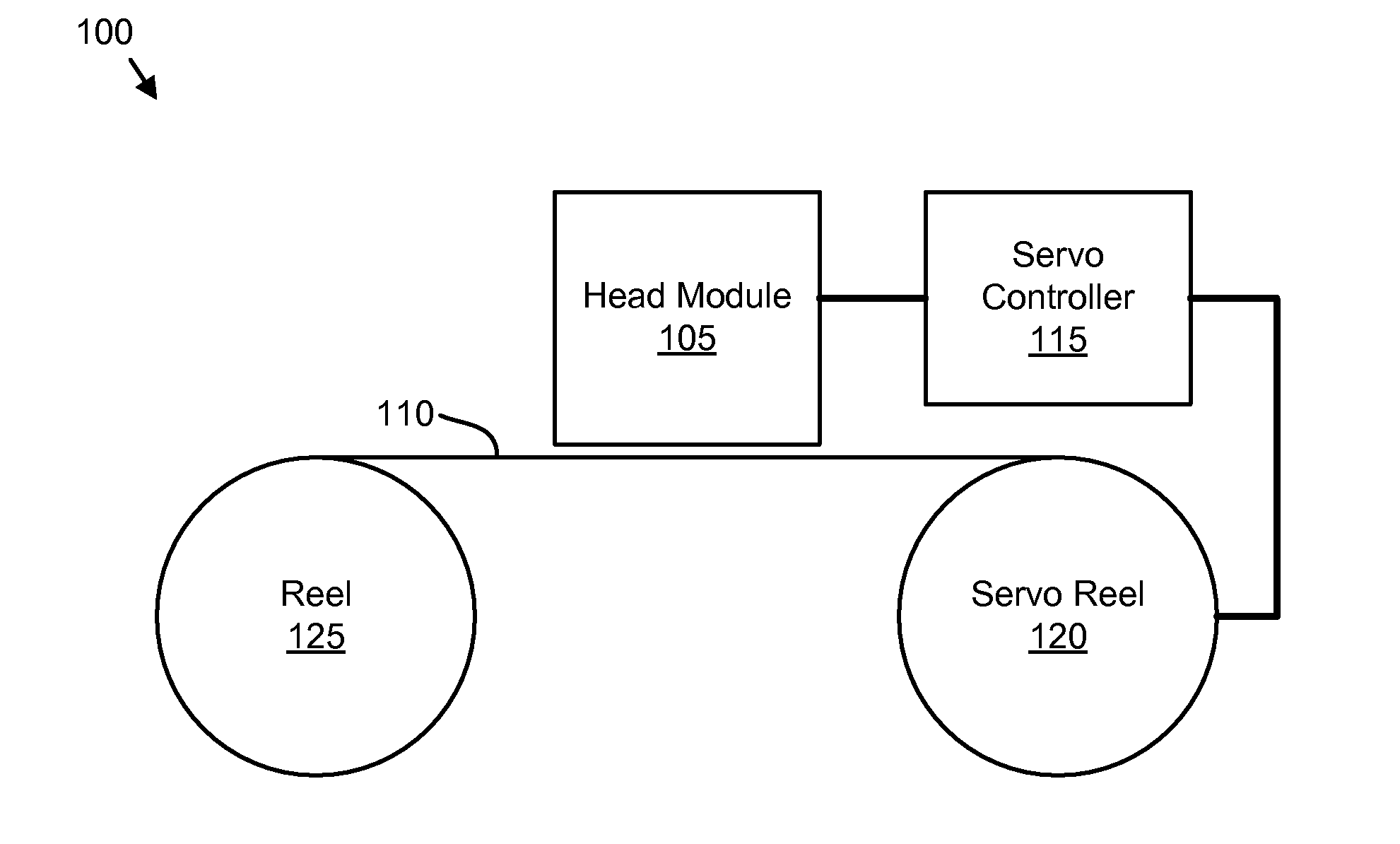
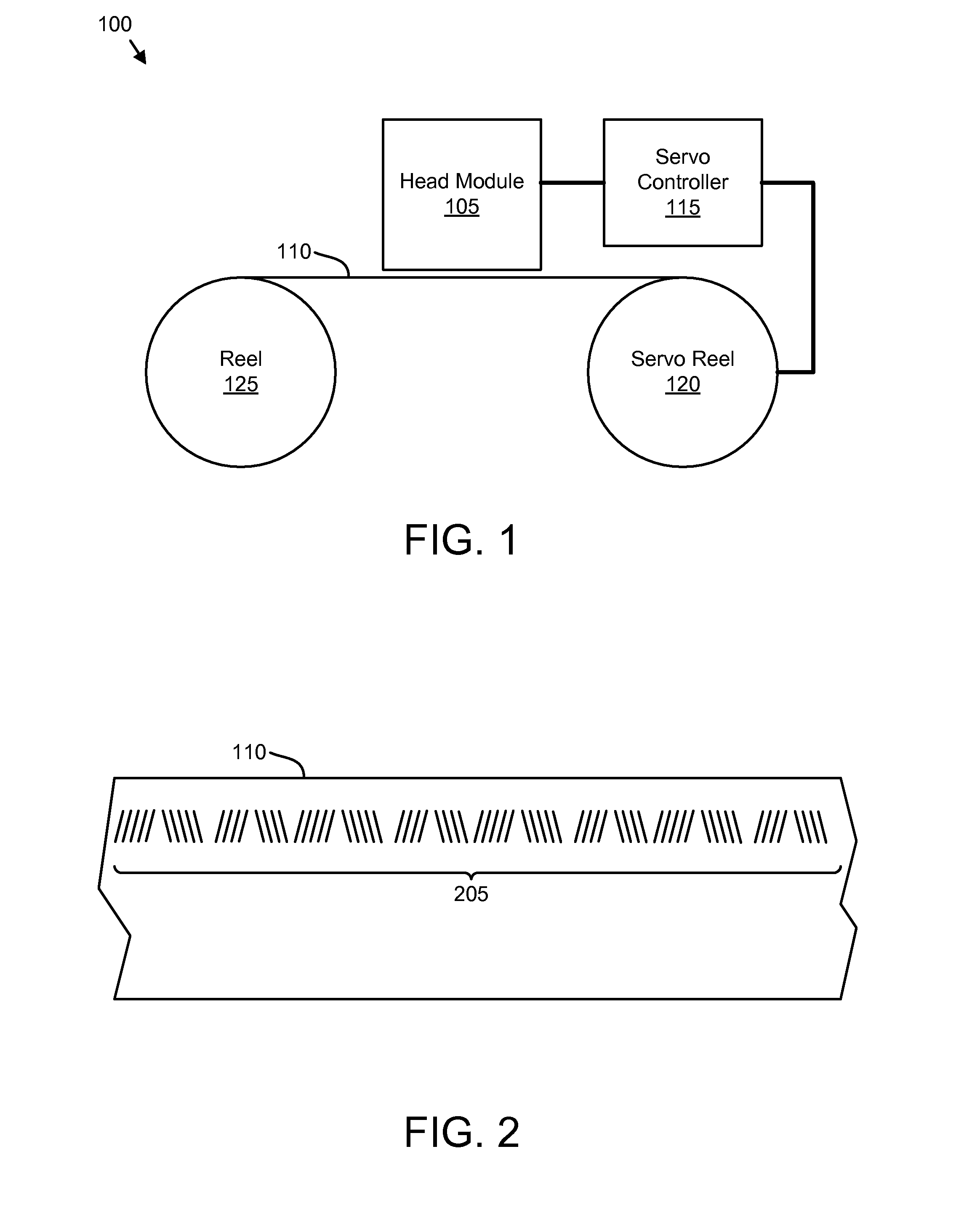
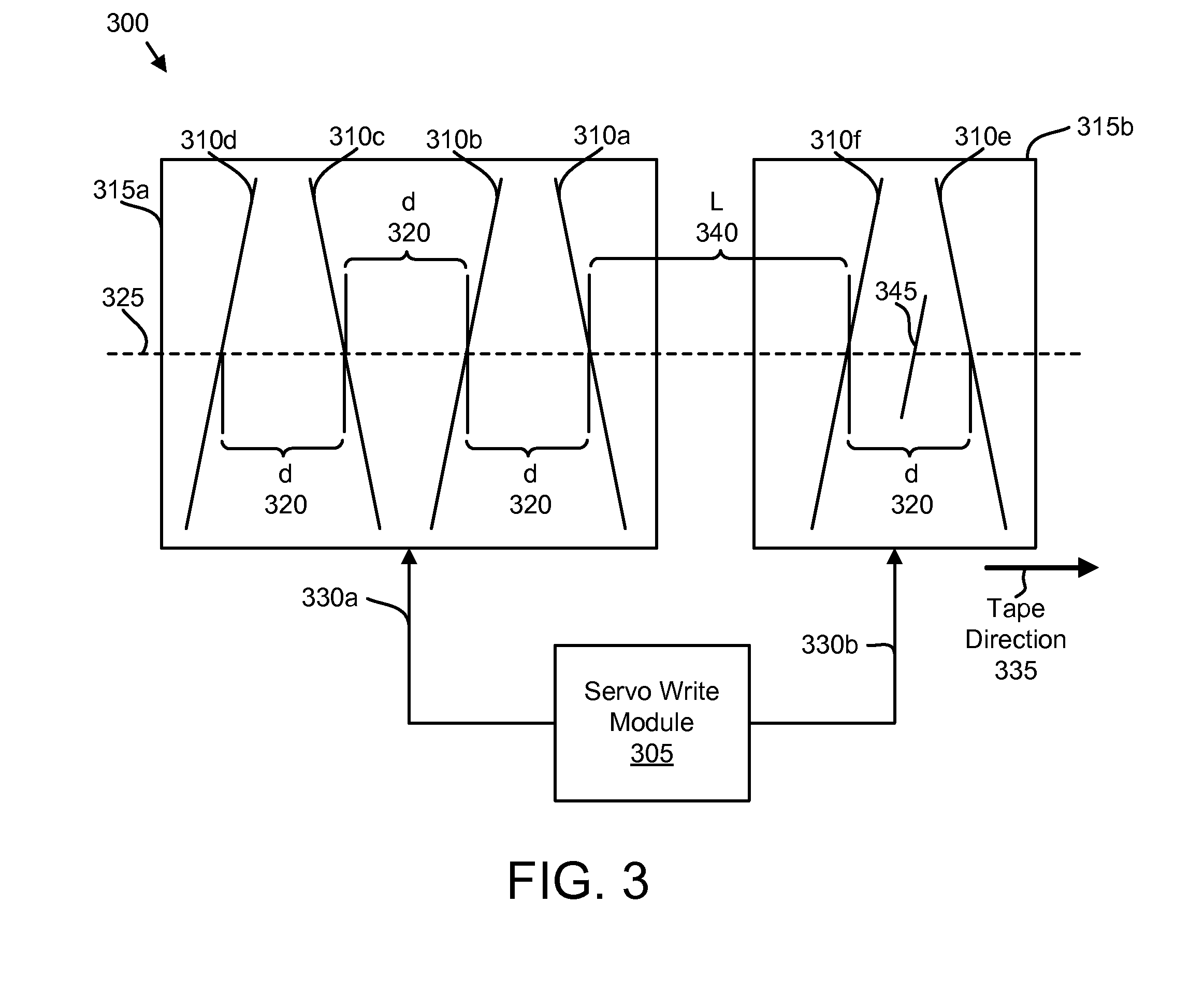
Apparatus, system, and method for timing based servo tape formating
InactiveUS20080174897A1Reduce readReduce write errorDriving/moving recording headsAlignment for track following on tapesMagnetic tapeComputer science
An apparatus, system, and method are disclosed for formatting a timing-based servo pattern on a magnetic tape. A first write head concurrently writes a base number of stripes to a plurality of first stripe patterns with a first and third element and writes the base number of stripes to a plurality of second stripe patterns with a second and fourth element of a first write head in response to at least one first write signal. A second write head concurrently writes an incremental number of stripes to a specified first stripe pattern to form a first incremental stripe pattern with a fifth write element and writes the incremental number of stripes to a specified second stripe pattern to form a second incremental stripe pattern with a sixth write element.
Owner:IBM CORP
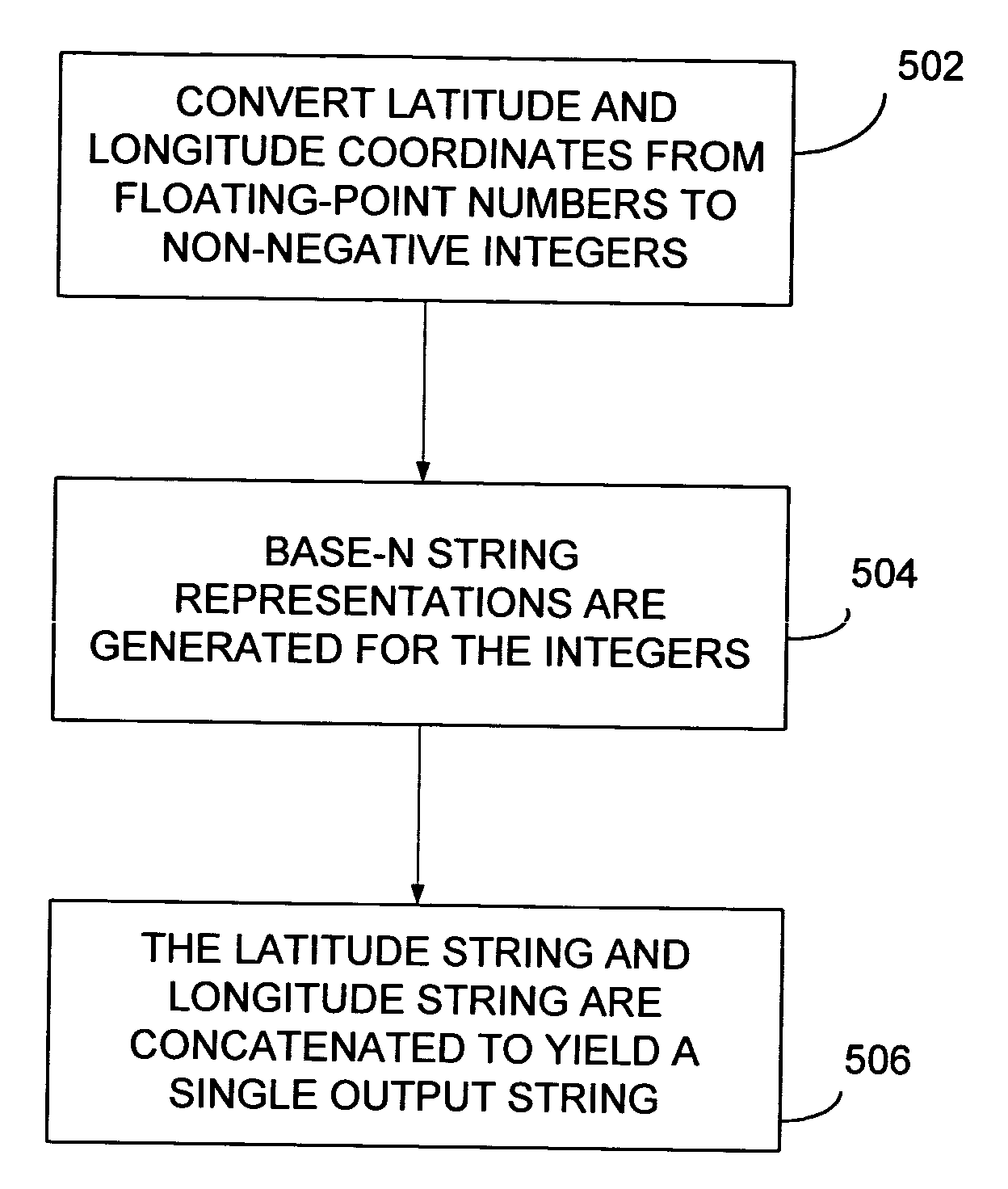
Compact text encoding of latitude/longitude coordinates
InactiveUS20050023524A1Data processing applicationsDigital data information retrievalTheoretical computer scienceLongitude
Methods are disclosed for encoding latitude / longitude coordinates within a URL in a relatively compact form. The method includes converting latitude and longitude coordinates from floating-point numbers to non-negative integers. A set of base-N string representations are generated for the integers (N represents the number of characters in an implementation-defined character set being utilized). The latitude string and longitude string are then concatenated to yield a single output string. The output string is utilized as a geographic indicator with a URL.
Owner:MICROSOFT TECH LICENSING LLC
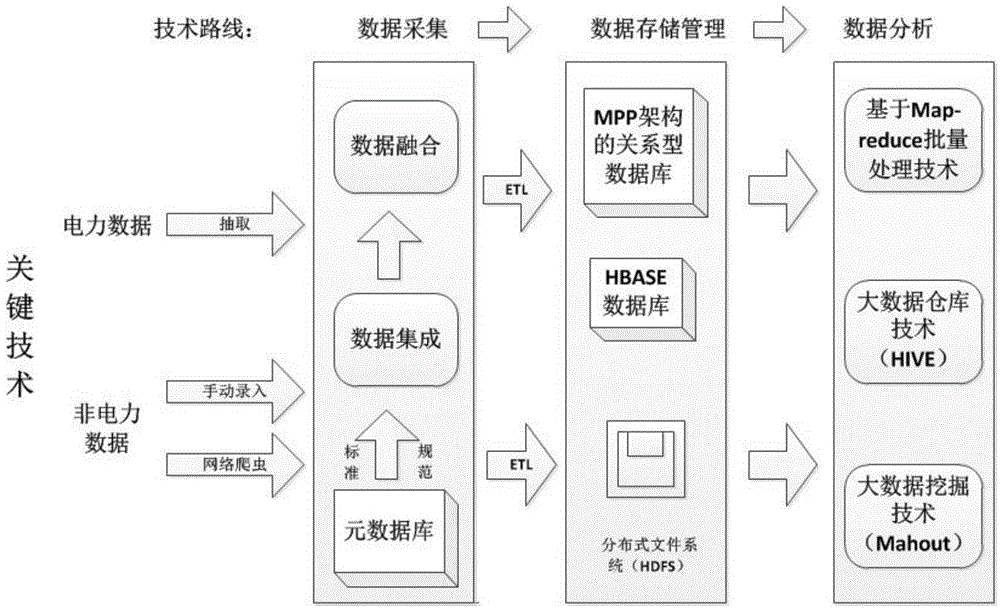
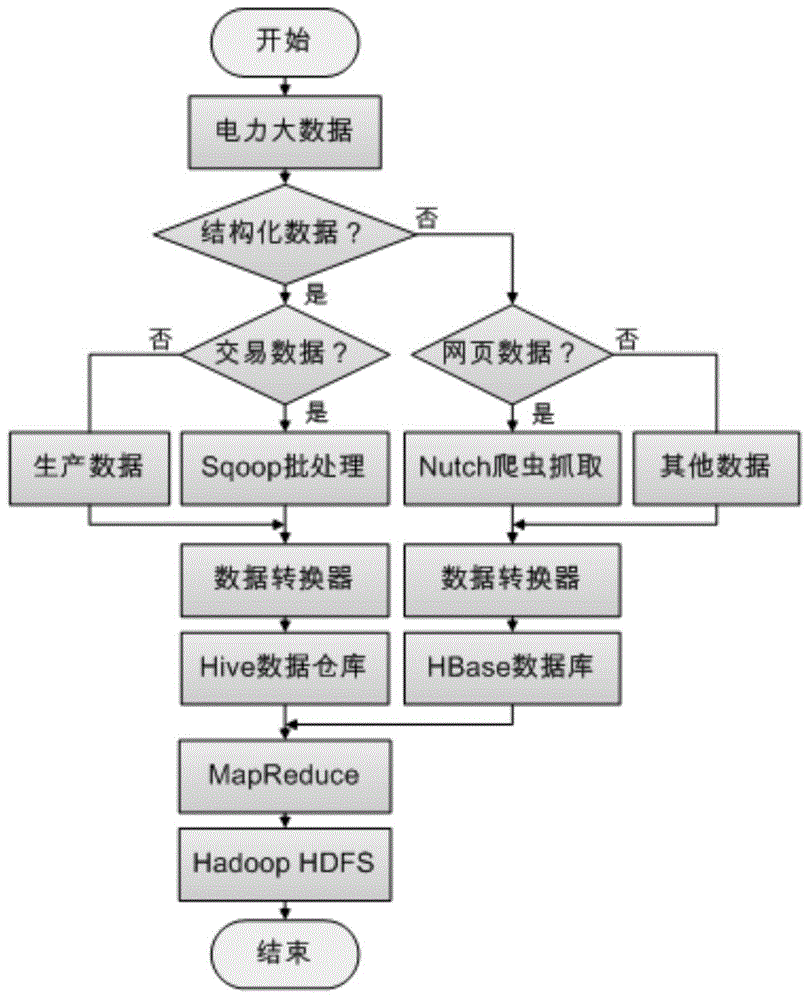
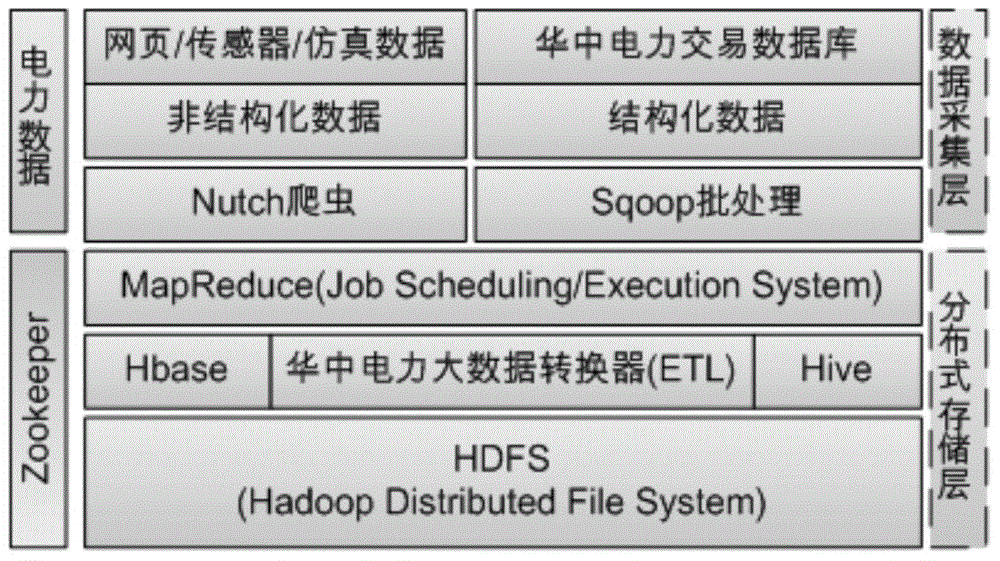
Method for acquiring and storing big data of power information
ActiveCN104820670AFunction is easy to expandGood analysis functionData processing applicationsSpecial data processing applicationsData acquisitionNetwork media
The present invention, belonging to the field of acquisition and storage of big data of power information, relates to a method for acquiring and storing the big data of power information, and solves the problems in the acquisition and storage process of the big data of power information. The method comprises three steps: data acquisition, data storage and management, and data analysis. The method achieves the beneficial effects that the present invention provides the method for acquiring and storing the power information big data; and the problems of low response speed of a service system and long consumed time for waiting of a user, which are generated due to a large cardinal number of power users and a large quantity of information, can be well solved. Meanwhile, for massive information generated by a trading system on the basis of power data, the method can better complete data extension and analysis functions than a traditional database. Moreover, according to the method, massive Internet media data can be acquired, stored and processed so as to better learn about the trade trend; and during the operation process, the storage method has an efficient inquiring function so that retrieval can be rapidly completed when the data volume is increased sharply.
Owner:CENT CHINA GRID +2
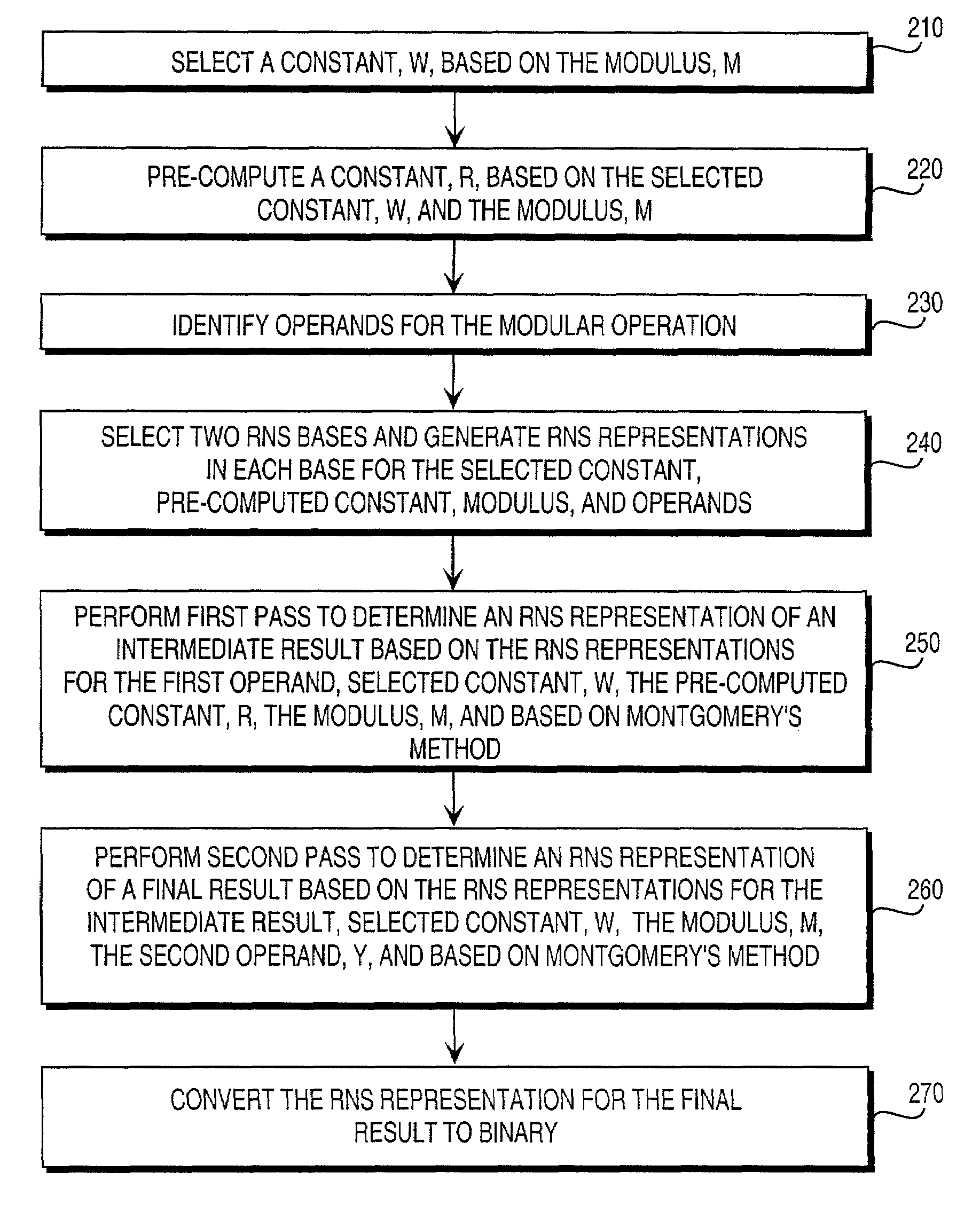
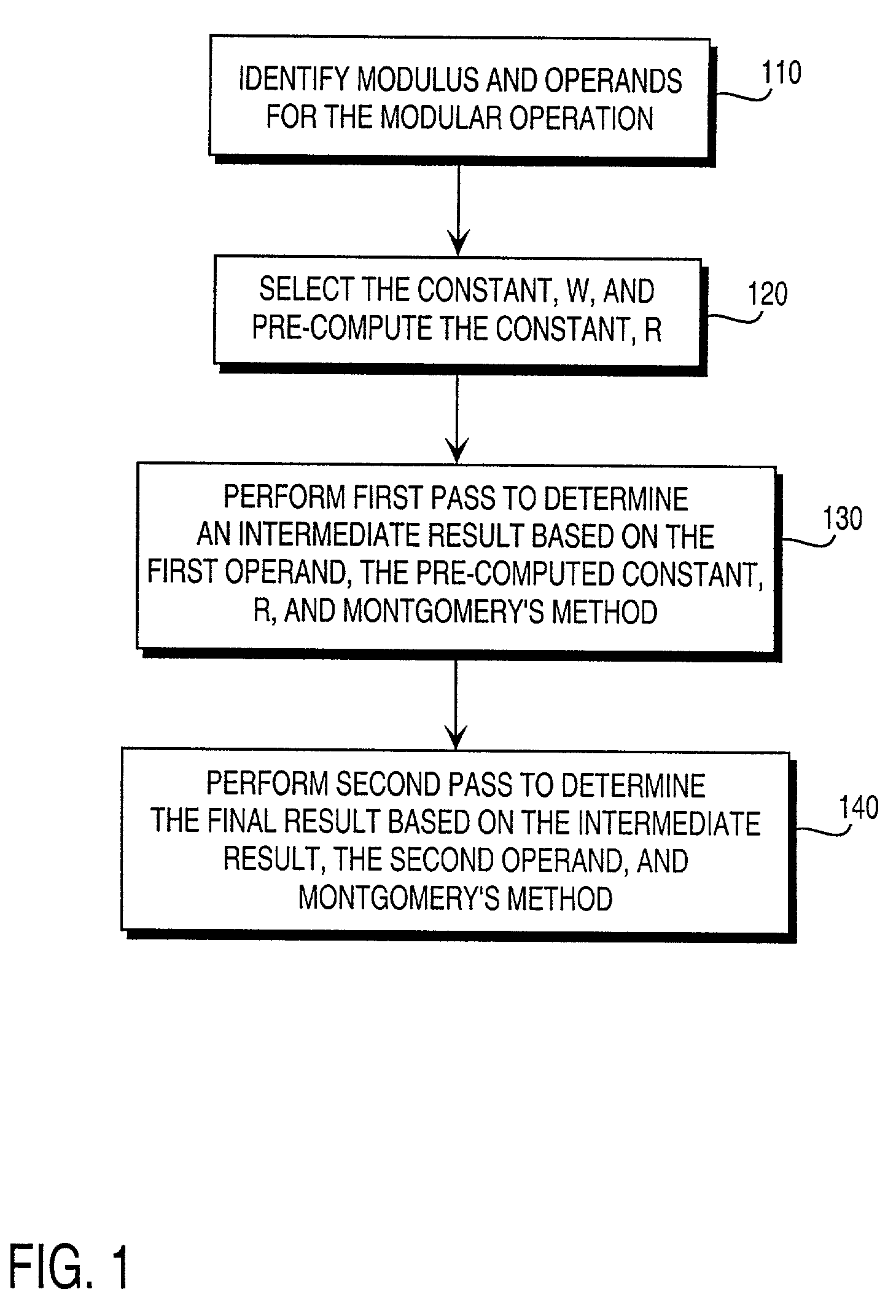
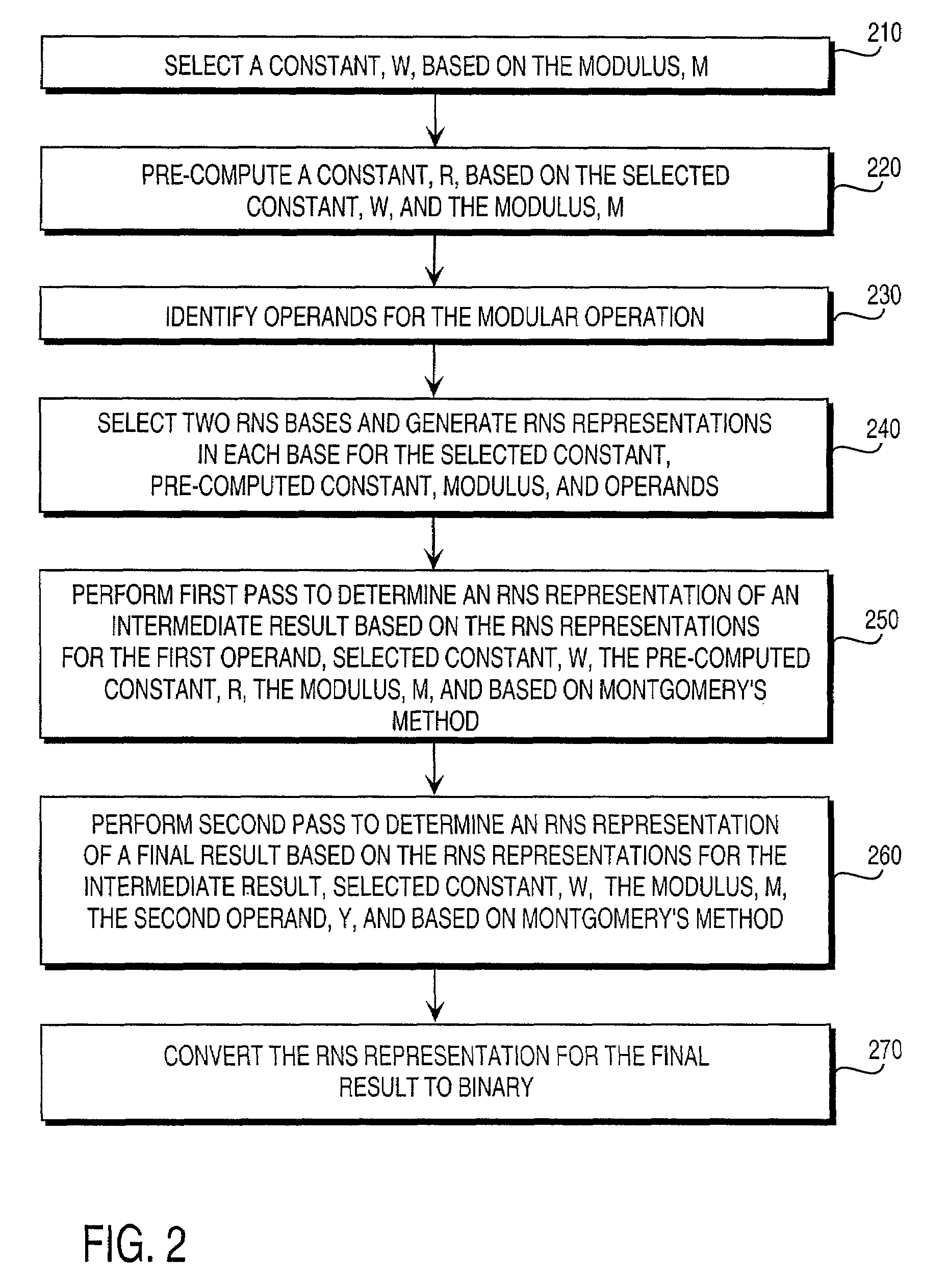
Residue number system based pre-computation and dual-pass arithmetic modular operation approach to implement encryption protocols efficiently in electronic integrated circuits
InactiveUS7027598B1Computations using contact-making devicesComputation using non-contact making devicesProcessor registerModularity
A pre-computation and dual-pass modular operation approach to implement encryption protocols efficiently in electronic integrated circuits is disclosed. An encrypted electronic message is received and another electronic message generated based on the encryption protocol. Two passes of Montgomery's method are used for a modular operation that is associated with the encryption protocol along with pre-computation of a constant based on a modulus. The modular operation may be a modular multiplication or a modular exponentiation. Modular arithmetic may be performed using the residue number system (RNS) and two RNS bases with conversions between the two RNS bases. A minimal number of register files are used for the computations along with an array of multiplier circuits and an array of modular reduction circuits. The approach described allows for high throughput for large encryption keys with a relatively small number of logical gates.
Owner:CISCO TECH INC
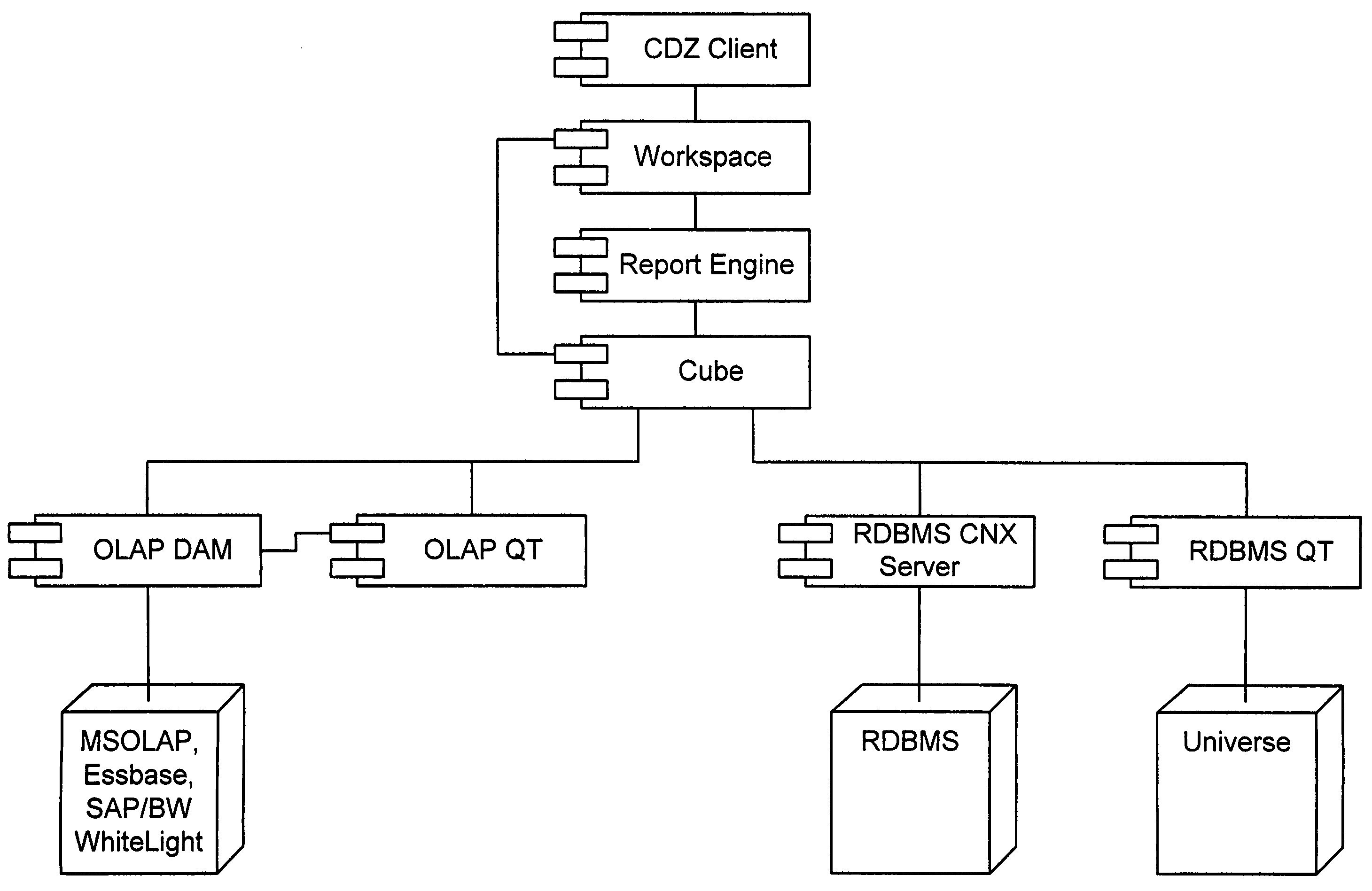
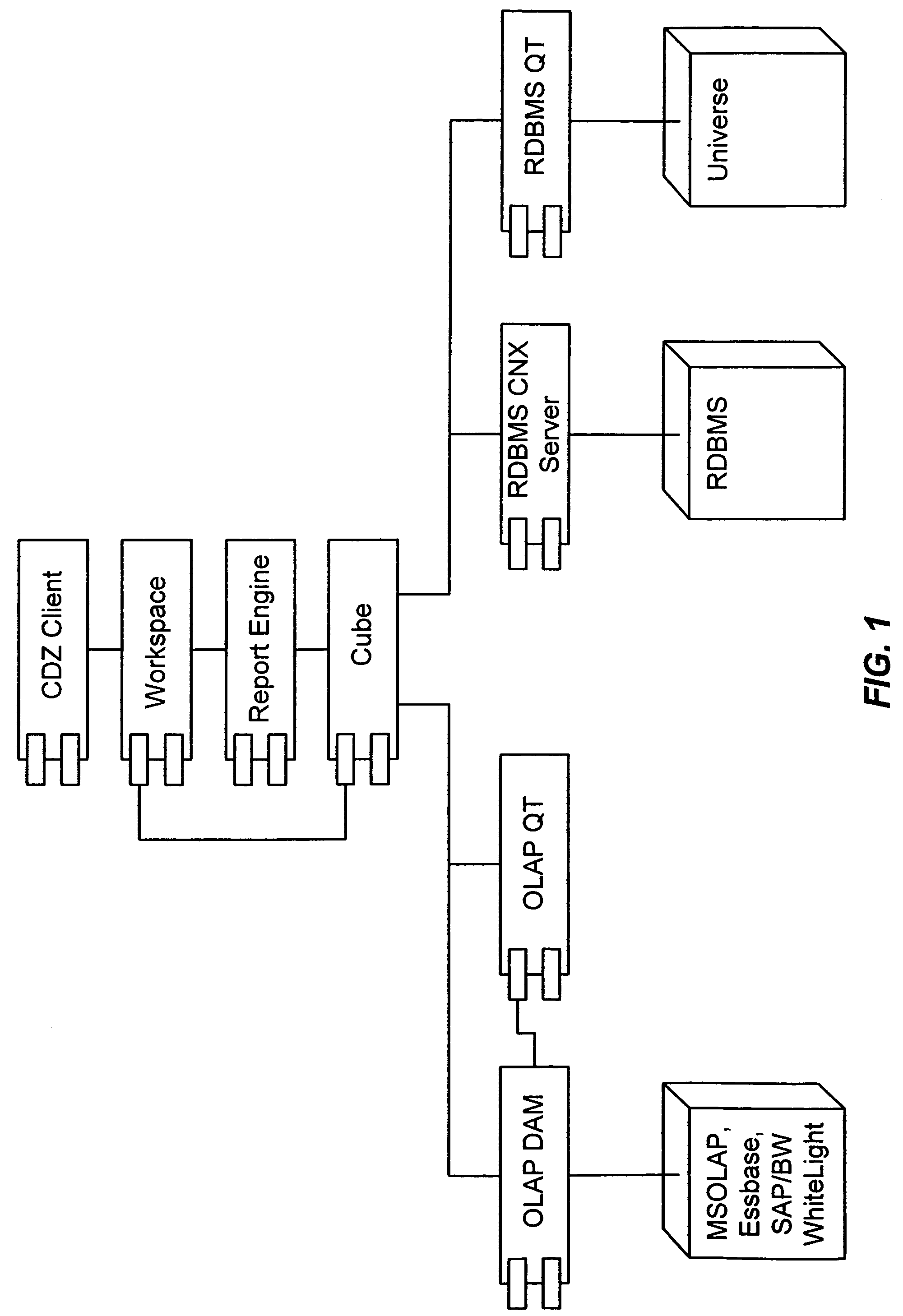
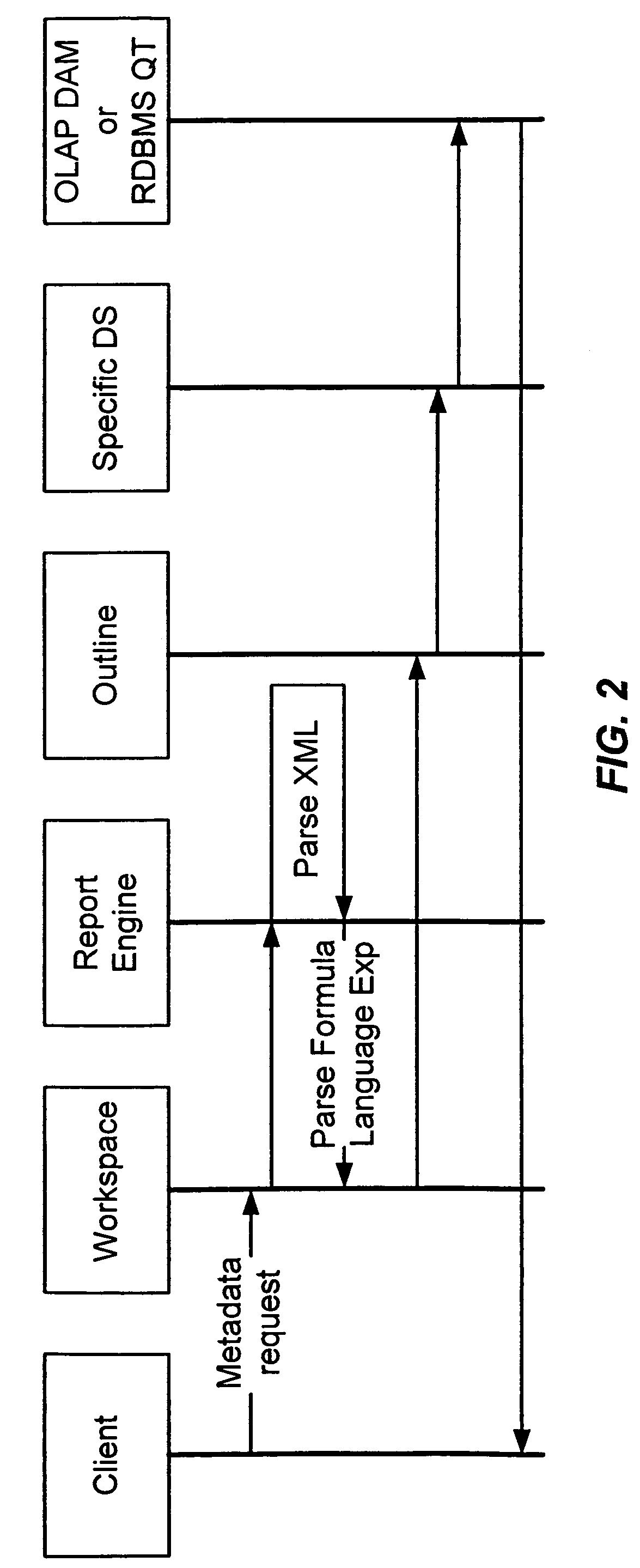
Mapping of an RDBMS schema onto a multidimensional data model
InactiveUS7181440B2Functional dependencyEasy to createData processing applicationsDigital computer detailsRelational modelMultidimensional data
A Relational Database Management System (RDBMS) having any arbitrary structure is translated into a multi-dimensional data model suitable for performing OLAP operations upon. If a relational table defining the relational model includes any tables with cardinality of 1,1 or 0,1, the tables are merged into a single table. If the relational table is not normalized, then normalization is performed and a relationship between the original table and the normalized table is created. If the relational table is normalized, but not by dependence between columns, such as in the dimension table in a snowflake schema, the normalization process is performed using the foreign key in order to generate the normalized table. Once the normalized table is generated, OLAP measures are derived from the normalized relational table by an automated method. In addition, OLAP dimensions are derived from the normalized relational table and the results of the OLAP measures derivation by an automated method according to the present invention. According to an aspect, it is possible to associate a member of a dimension to another member of the same or another dimension. According to another aspect, it is possible to create a new dimension of analysis, the members of which are all the different values that a scalar expression can take on. According to yet another aspect, it is possible to access the various instances of a Reporting Object as members in an OLAP dimension. According to the yet another aspect, it is possible to apply opaque filters or a combination of them to the data that underlies analysis.
Owner:BUSINESS OBJECTS SOFTWARE
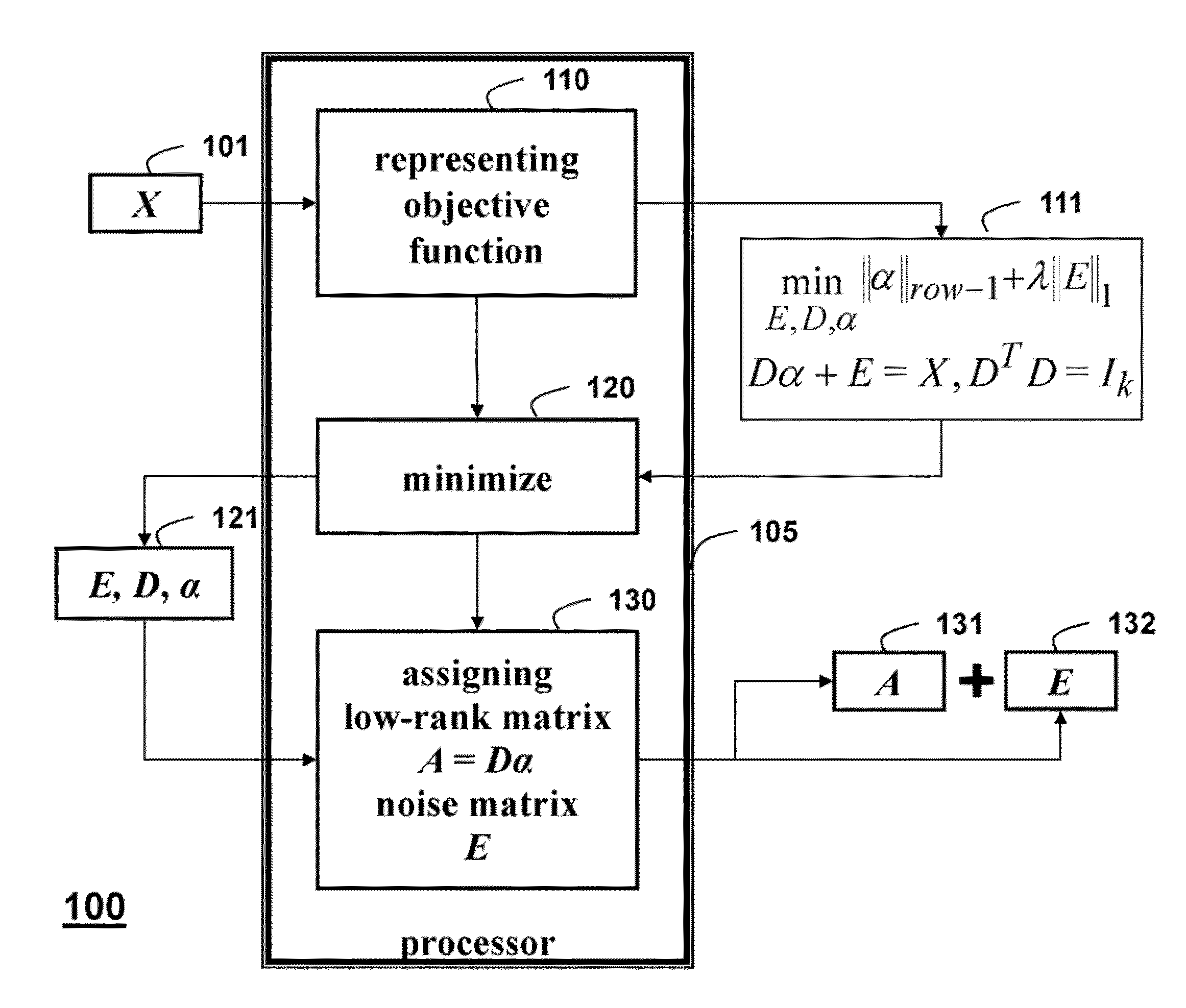
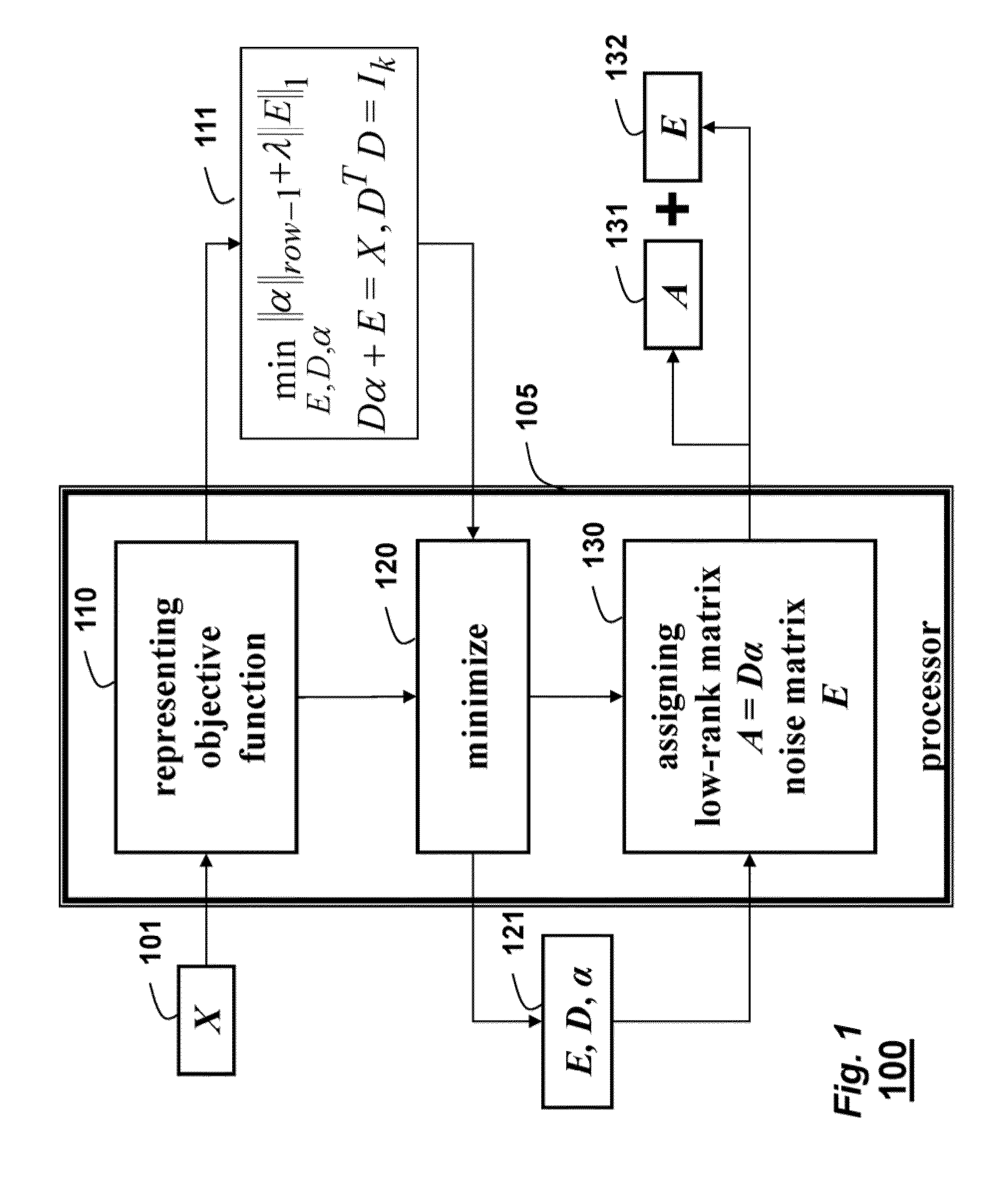
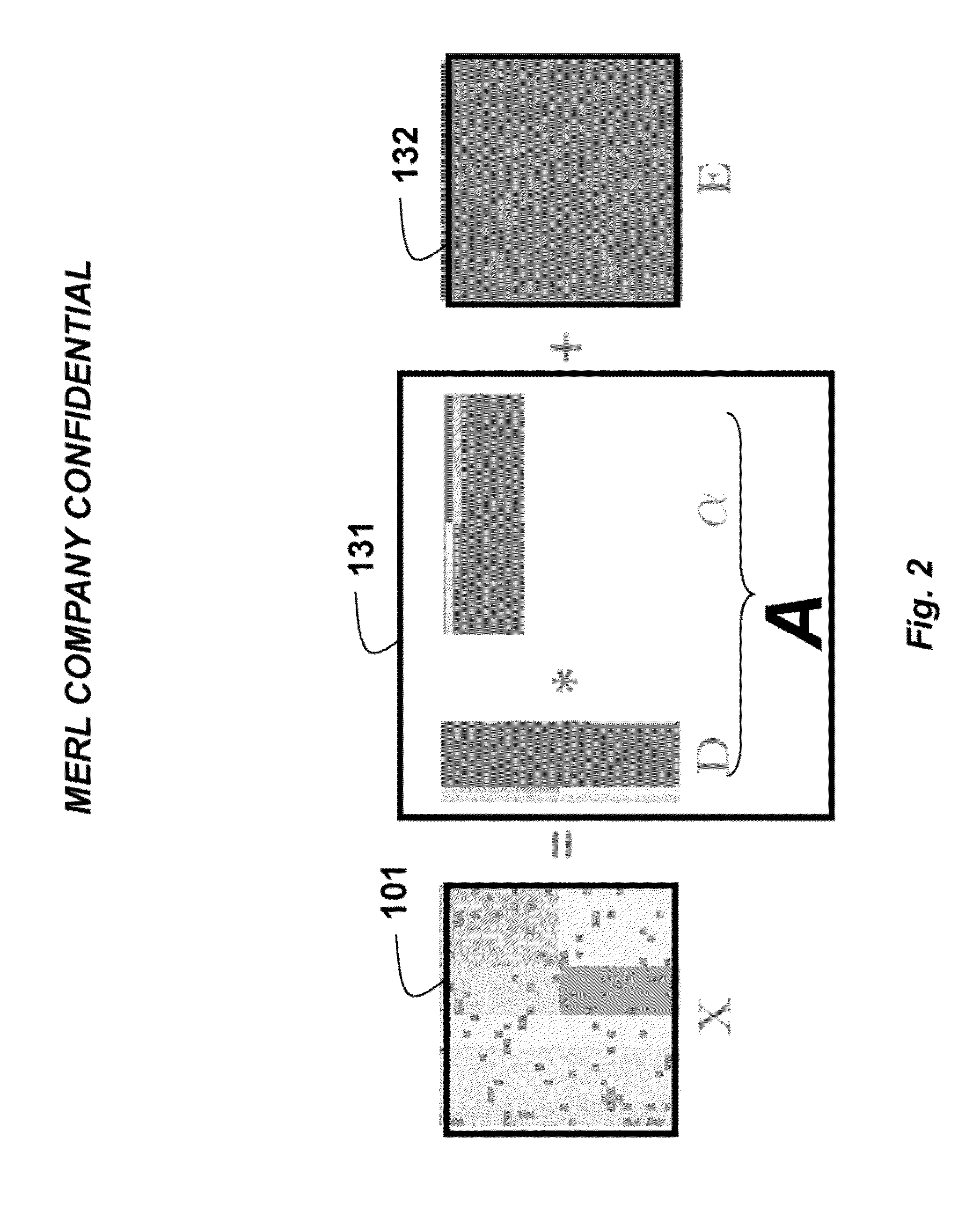
Method for Recovering Low-Rank Matrices and Subspaces from Data in High-Dimensional Matrices
InactiveUS20130191425A1Effective recoveryFaster robust low-rank recoveryDigital data processing detailsDigital computer detailsAugmented lagrange multiplierAlgorithm
A method recovers an uncorrupted low-rank matrix, noise in corrupted data and a subspace from the data in a form of a high-dimensional matrix. An objective function minimizes the noise to solve for the low-rank matrix and the subspace without estimating the rank of the low-rank matrix. The method uses group sparsity and the subspace is orthogonal. Random subsampling of the data can recover subspace bases and their coefficients from a much smaller matrix to improve performance. Convergence efficiency can also be improved by applying an augmented Lagrange multiplier, and an alternating stepwise coordinate descent. The Lagrange function is solved by an alternating direction method.
Owner:MITSUBISHI ELECTRIC RES LAB INC
Lubricating oil composition
ActiveUS20080110799A1Excellent in thermal/oxidation stabilityInhibit of acid numberLiquid carbonaceous fuelsAdditivesInternal combustion engineSoot
The present invention provide a lubricating oil composition suitable for internal combustion engines, which composition is excellent in thermal / oxidation stability and can inhibit the increases of the viscosity and acid number even in the presence of NOx and can be used for a long period of time or provide a lubricating oil composition particularly suitable for diesel or direct injection engines equipped with an exhaust-gas after-treatment device such as DPF or various catalysts, which composition is excellent in high-temperature detergency and base number retention properties and further can achieve the effect of inhibit wear caused by soot contamination in the oil occurring significantly when the content of phosphorus compounds such as ZnDTP is decreased, at a high level and can inhibit the exhaust-gas after-treatment device from being adversely affected. The lubricating oil composition comprises a lubricating base oil containing, a specific amount of a base oil with specific properties, and two or more types of additives selected from specific additives.
Owner:NIPPON OIL CORP
Value-instance connectivity computer-implemented database
InactiveUS20080059412A1Reduce memory usageShorten the timeMulti-dimensional databasesSpecial data processing applicationsMulti dimensional dataData value
A computer-implemented database and method providing an efficient, ordered reduced space representation of multi-dimensional data. The data values for each attribute are stored in a manner that provides an advantage in, for example, space usage and / or speed of access, such as in condensed form and / or sort order. Instances of each data value for an attribute are identified by instance elements, each of which is associated with one data value. Connectivity information is provided for each instance element that uniquely associates each instance element with a specific instance of a data value for another attribute. In accordance with one aspect of the invention, low cardinality fields (attributes) may be combined into a single field (referred to as a “combined field”) having values representing the various combinations of the original fields. In accordance with another aspect of the invention, the data values for several fields may be stored in a single value list (referred to as a “union column”). Still another aspect of the invention is to apply redundancy elimination techniques, utilizing in some cases union columns, possibly together with combined fields, in order to reduce the space needed to store the database.
Owner:TARIN STEPHEN A
Flexible Radix Switch
ActiveUS20130083701A1High trafficImprove the level ofData switching by path configurationNetwork structureInterconnection
A system and method for interconnecting nodes and routing data packets in high radix networks includes constructing or redefining a network structure to provide improved performance. Computation and data storage nodes are connected to a network of switching nodes that provide near optimum bandwidth and latency for networks of any size. Specialized interconnection patterns and addressing methods ensure reliable data delivery in very large networks with high data traffic volume.
Owner:THE J SCOTT BENSON LIVING TRUST
Mapping of an RDBMS schema onto a multidimensional data model
InactiveUS20050015360A1Functional dependencyEasy to createData processing applicationsDigital data processing detailsSnowflake schemaRelational model
A Relational Database Management System (RDBMS) having any arbitrary structure is translated into a multi-dimensional data model suitable for performing OLAP operations upon. If a relational table defining the relational model includes any tables with cardinality of 1,1 or 0,1, the tables are merged into a single table. If the relational table is not normalized, then normalization is performed and a relationship between the original table and the normalized table is created. If the relational table is normalized, but not by dependence between columns, such as in the dimension table in a snowflake schema, the normalization process is performed using the foreign key in order to generate the normalized table. Once the normalized table is generated, OLAP measures are derived from the normalized relational table by an automated method. In addition, OLAP dimensions are derived from the normalized relational table and the results of the OLAP measures derivation by an automated method according to the present invention. According to an aspect, it is possible to associate a member of a dimension to another member of the same or another dimension. According to another aspect, it is possible to create a new dimension of analysis, the members of which are all the different values that a scalar expression can take on. According to yet another aspect, it is possible to access the various instances of a Reporting Object as members in an OLAP dimension. According to the yet another aspect, it is possible to apply opaque filters or a combination of them to the data that underlies analysis.
Owner:BUSINESS OBJECTS SOFTWARE
Systems for and methods of determining likelihood of mobility of reference points in a positioning system
Systems for and methods of determining likelihood of mobility of reference points in a positioning system are disclosed. A method of determining a measure of likelihood that a designated wireless device is a mobile device includes determining a set of reference points associated with a designated wireless device. The reference points are a geographic position at which signals from the device were detected and / or another wireless device from which signals were also detected by a receiver within a selected period of time during which the signals from the designated device were detected. The method also includes retrieving statistical information about a temporal distribution of detection of signals of reference points, a spatial distribution of the reference points, and / or a cardinality of the reference points. The method includes determining a measure of likelihood that the designated wireless device is a mobile wireless device based on the statistical information.
Owner:SKYHOOK WIRELESS
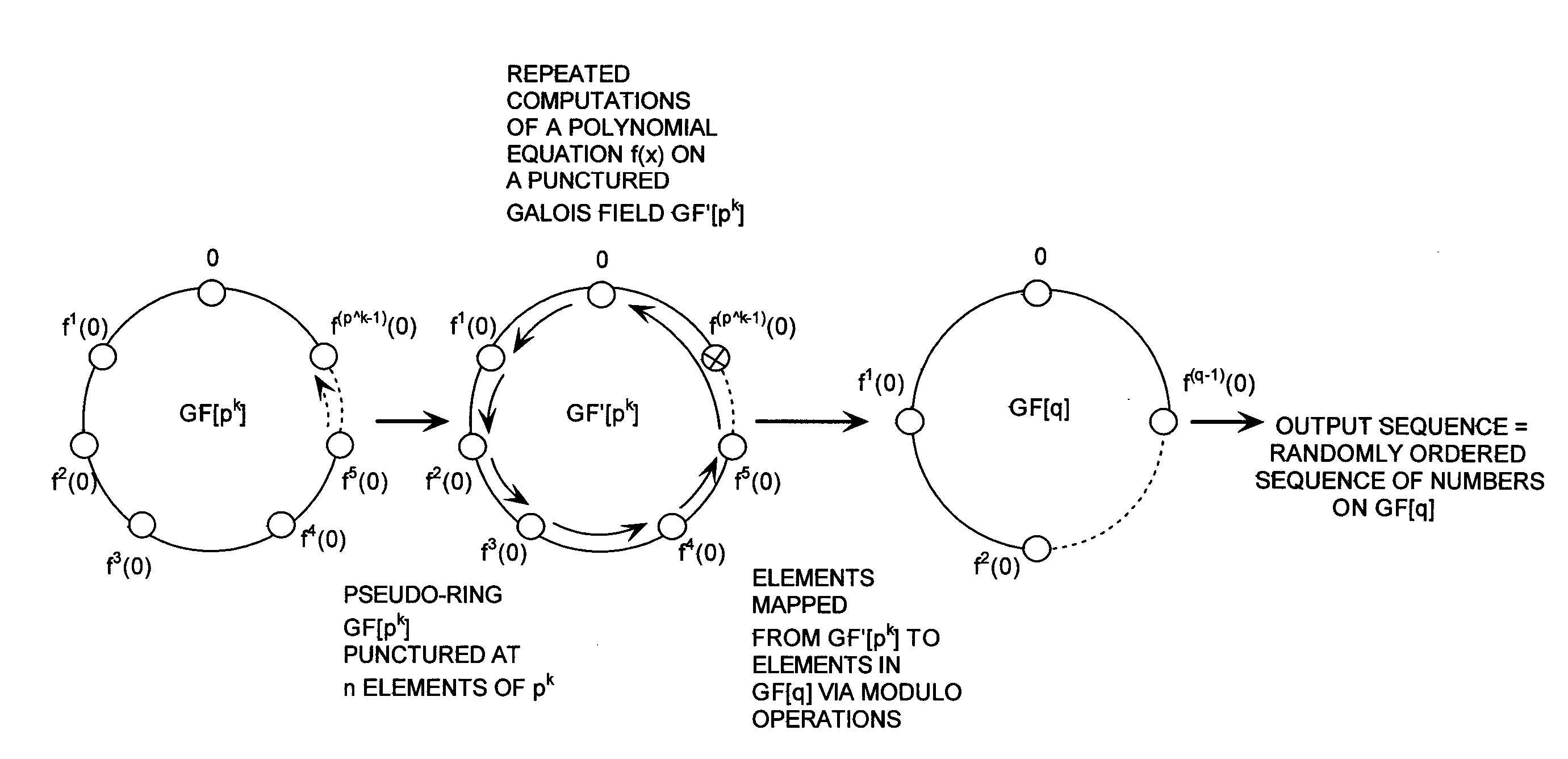
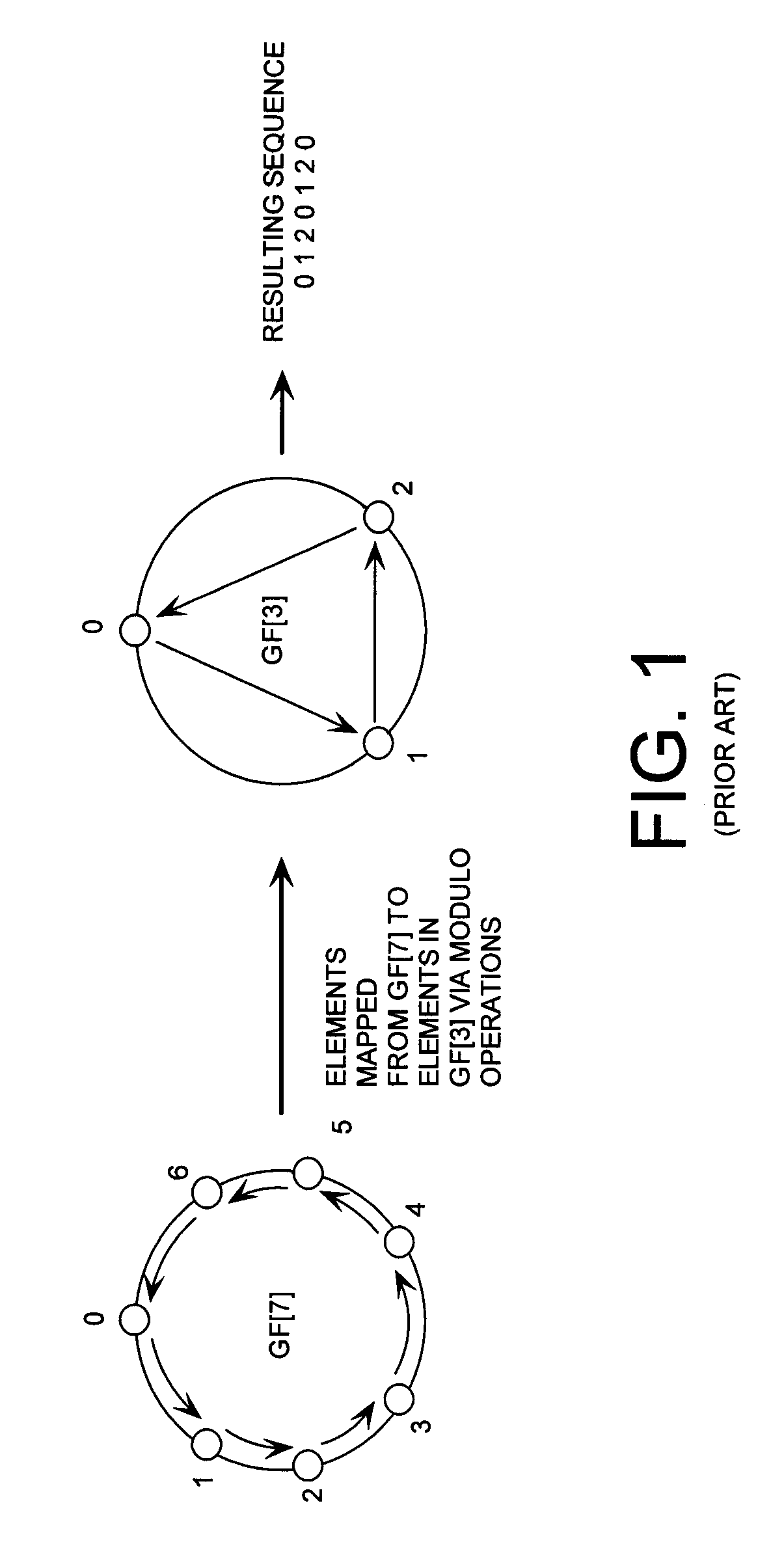
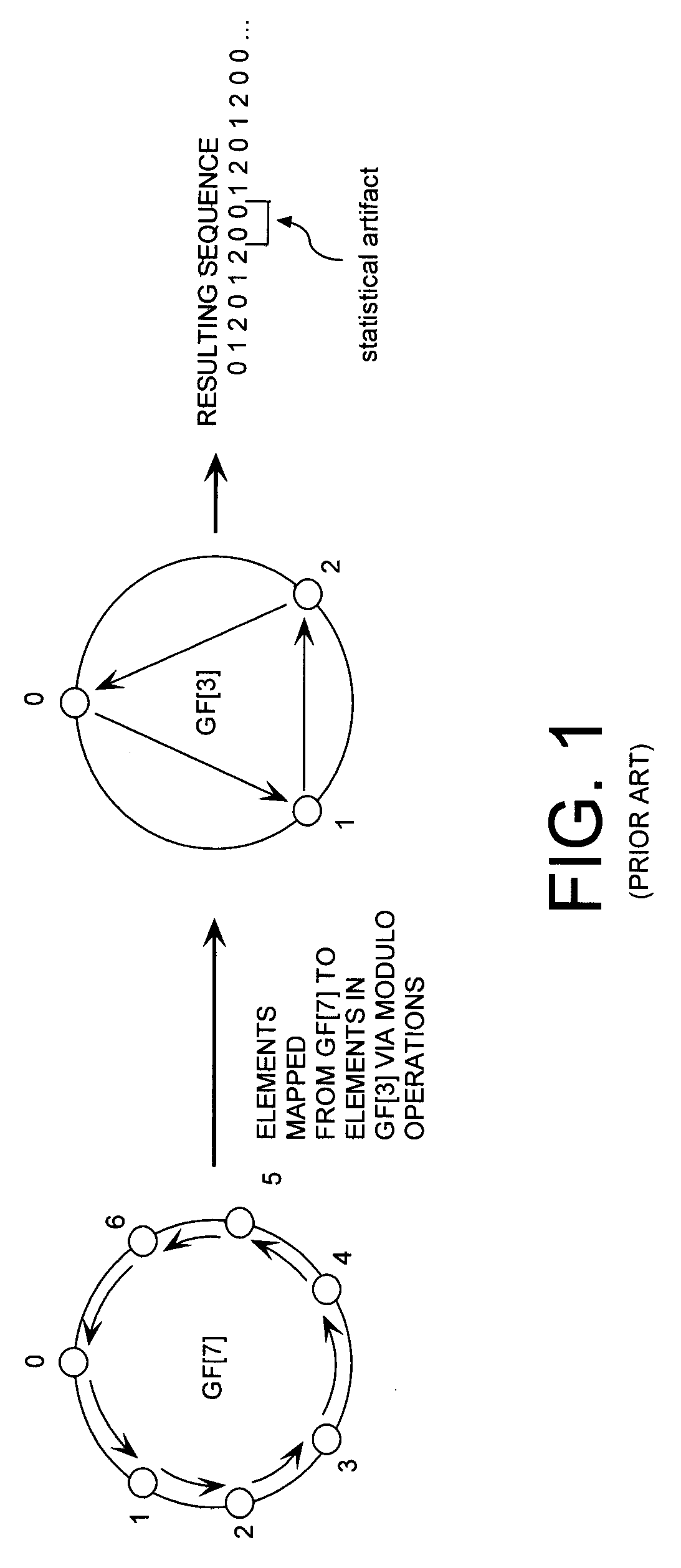
Cryptographic system configured to perform a mixed radix conversion with a priori defined statistical artifacts
ActiveUS20090202067A1Eliminate artifactsRandom number generatorsDigital computer detailsData streamComputer science
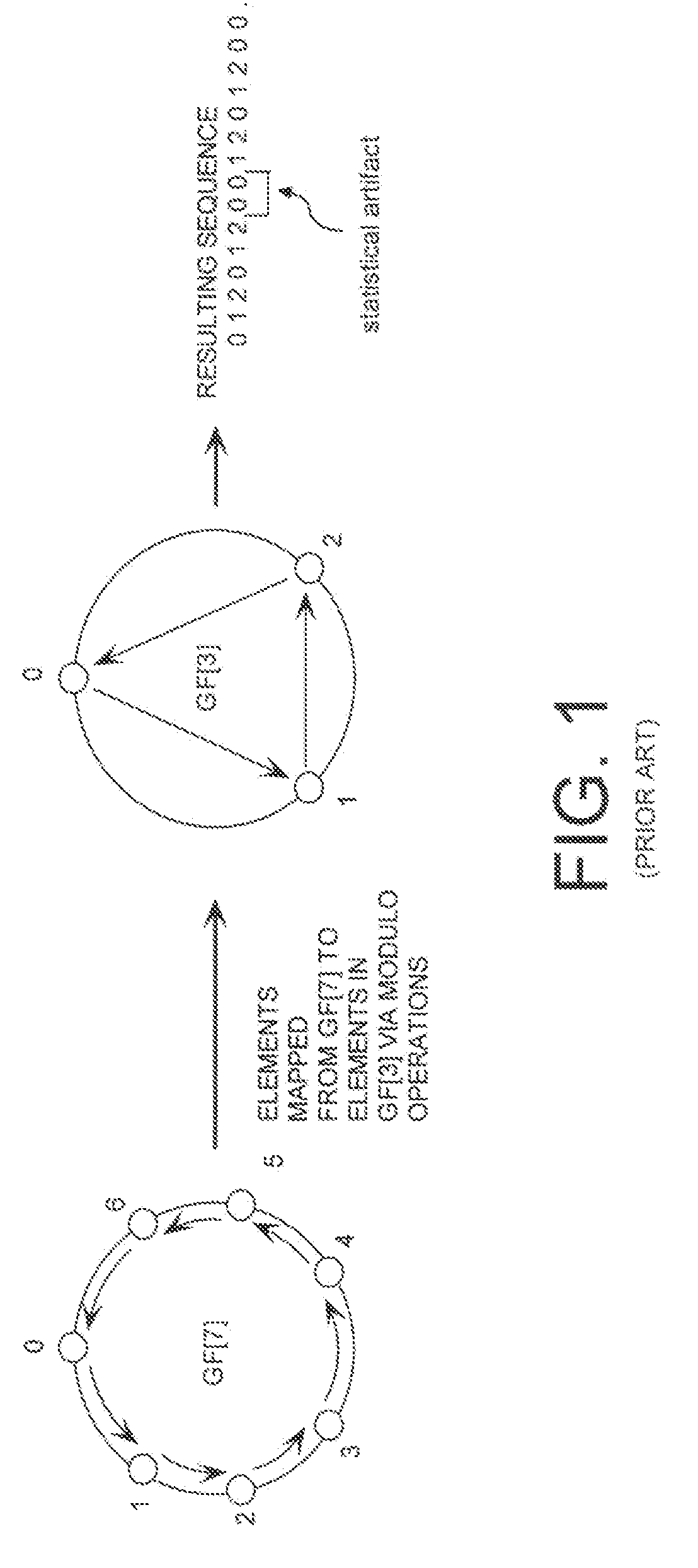
A cryptographic system (CS) is provided. The CS (800) comprises a data stream receiving means (DSRM), a generator (702), a mixed radix converter (MRC) and an encryptor (908). The DSRM (902) is configured to receive a data stream (DS). The generator is configured to selectively generate a random number sequence (RNS) utilizing a punctured ring structure. The MRC (704) is coupled to the generator and configured to perform a mixed radix conversion to convert the RNS from a first number base to a second number base. The encryptor is coupled to the DSRM and MRC. The encryptor is configured to generate an altered data stream by combining the RNS in the second number base with the DS. The punctured ring structure and the MRC are configured in combination to produce an RNS in the second number base which contains a priori defined statistical artifacts after the mixed radix conversion.
Owner:HARRIS CORP
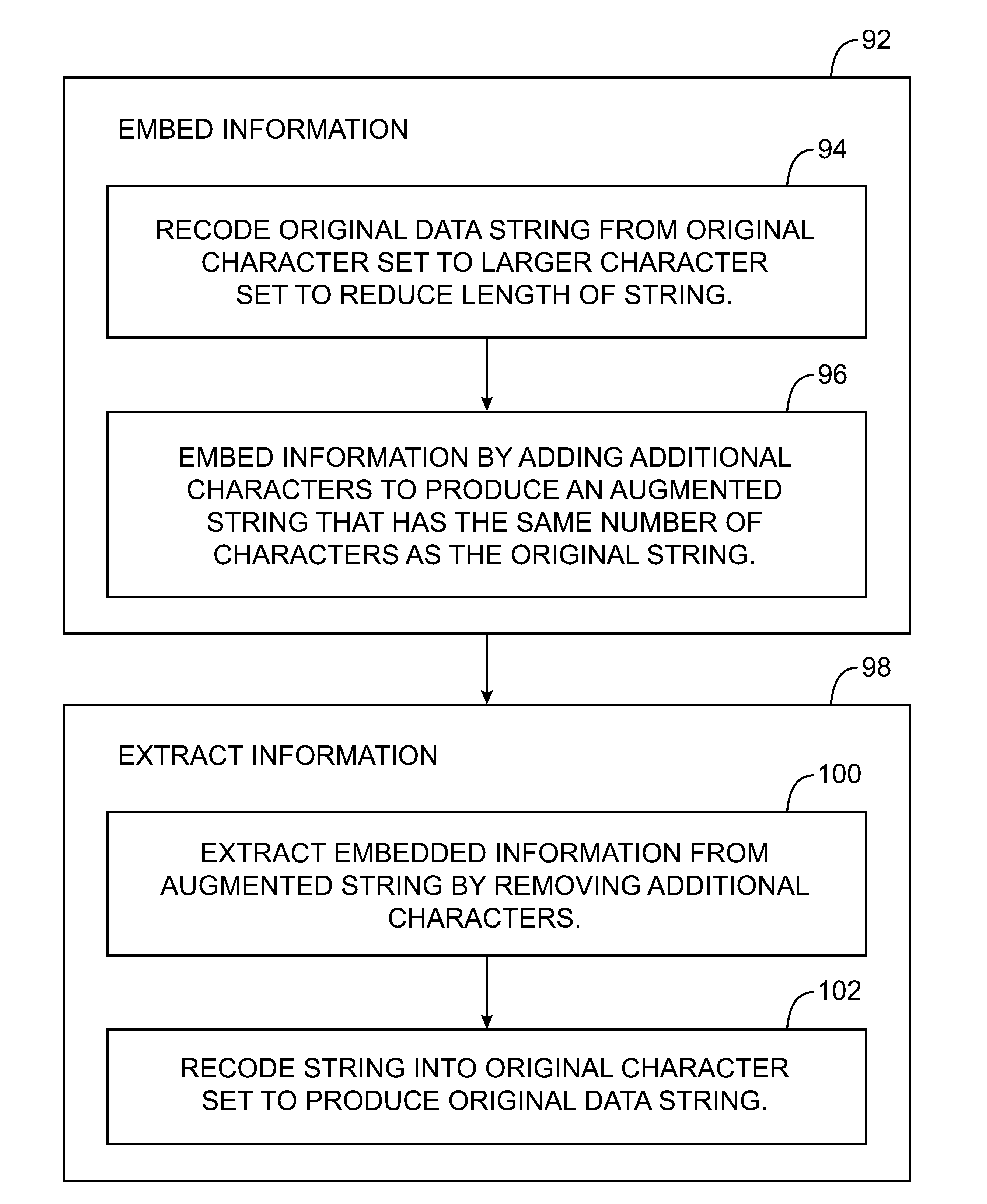
Systems for embedding information in data strings
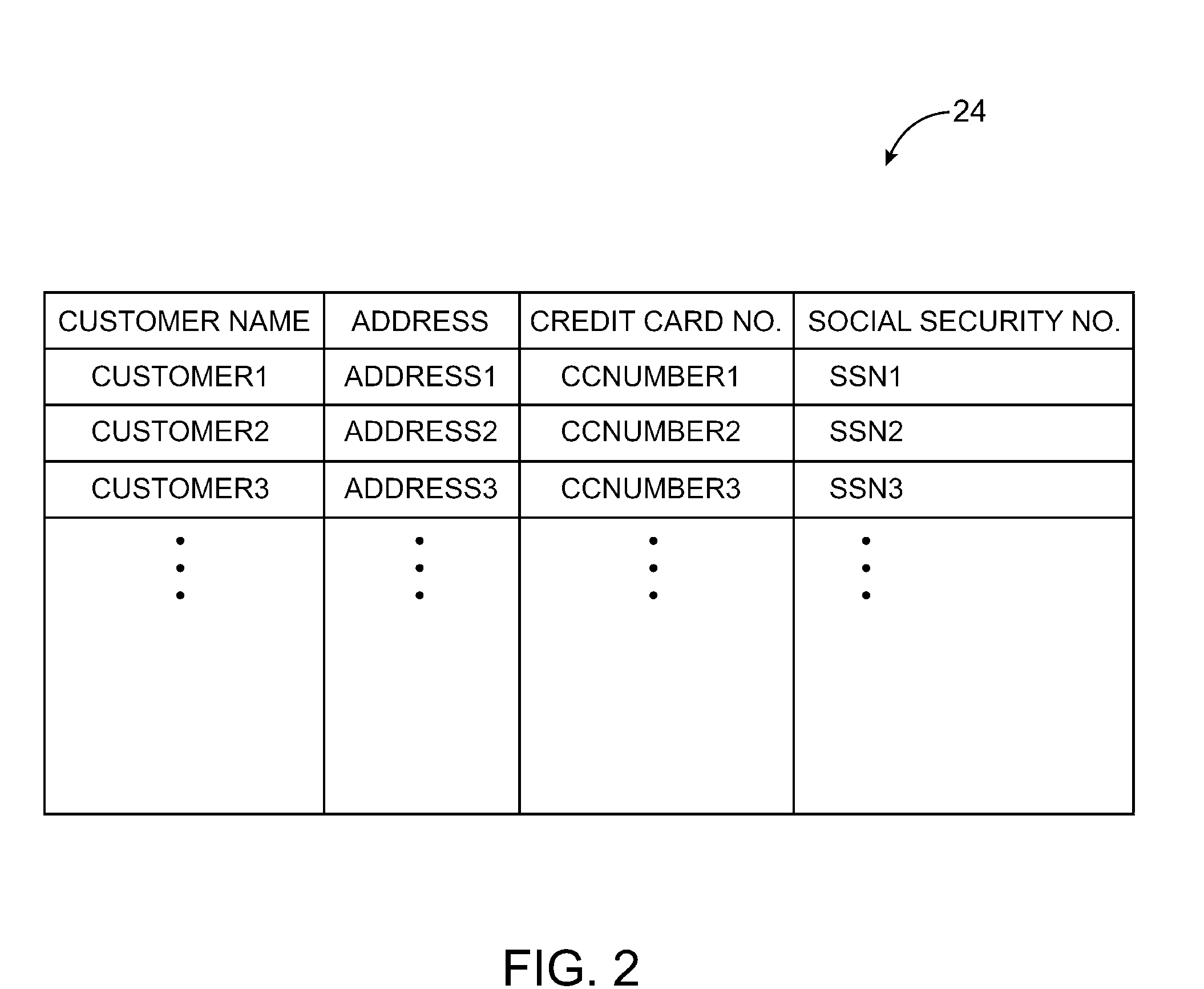
ActiveUS20100284532A1Information be useCode conversionComputer security arrangementsData processing systemBase Number
A data processing system is provided that includes applications, databases, encryption engines, and decryption engines. Encryption and decryption engines may be used to perform format-preserving encryption on data strings stored in a database. Applications may be used to embed information in data strings. Information may be embedded by using a character set that is larger than a character set being used by a data string. A data string may be converted into a larger character set, analogous to converting a number from a lower base to higher base. Such a conversion may shorten a data string, allowing information to be embedded as appended characters.
Owner:MICRO FOCUS LLC
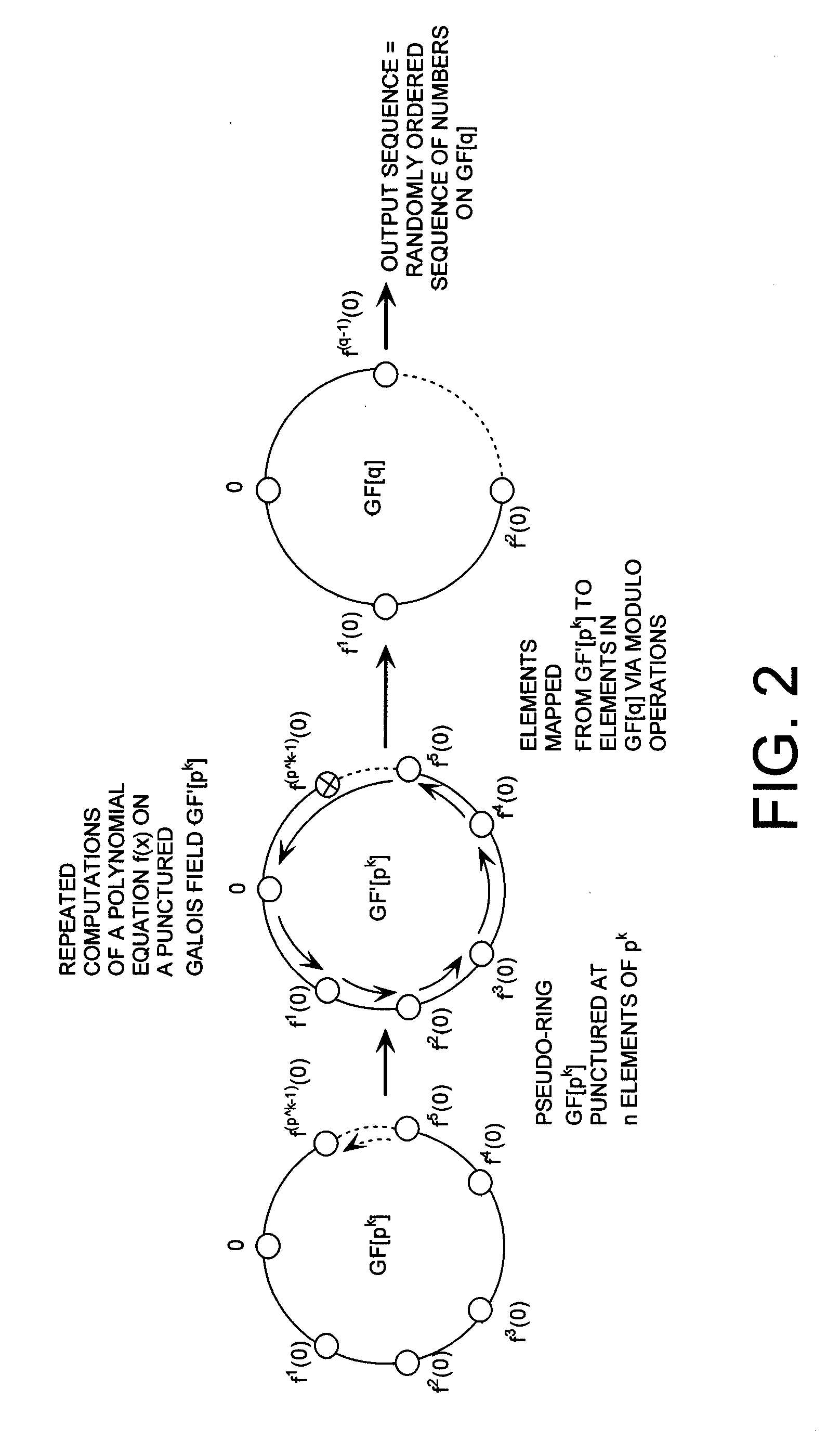
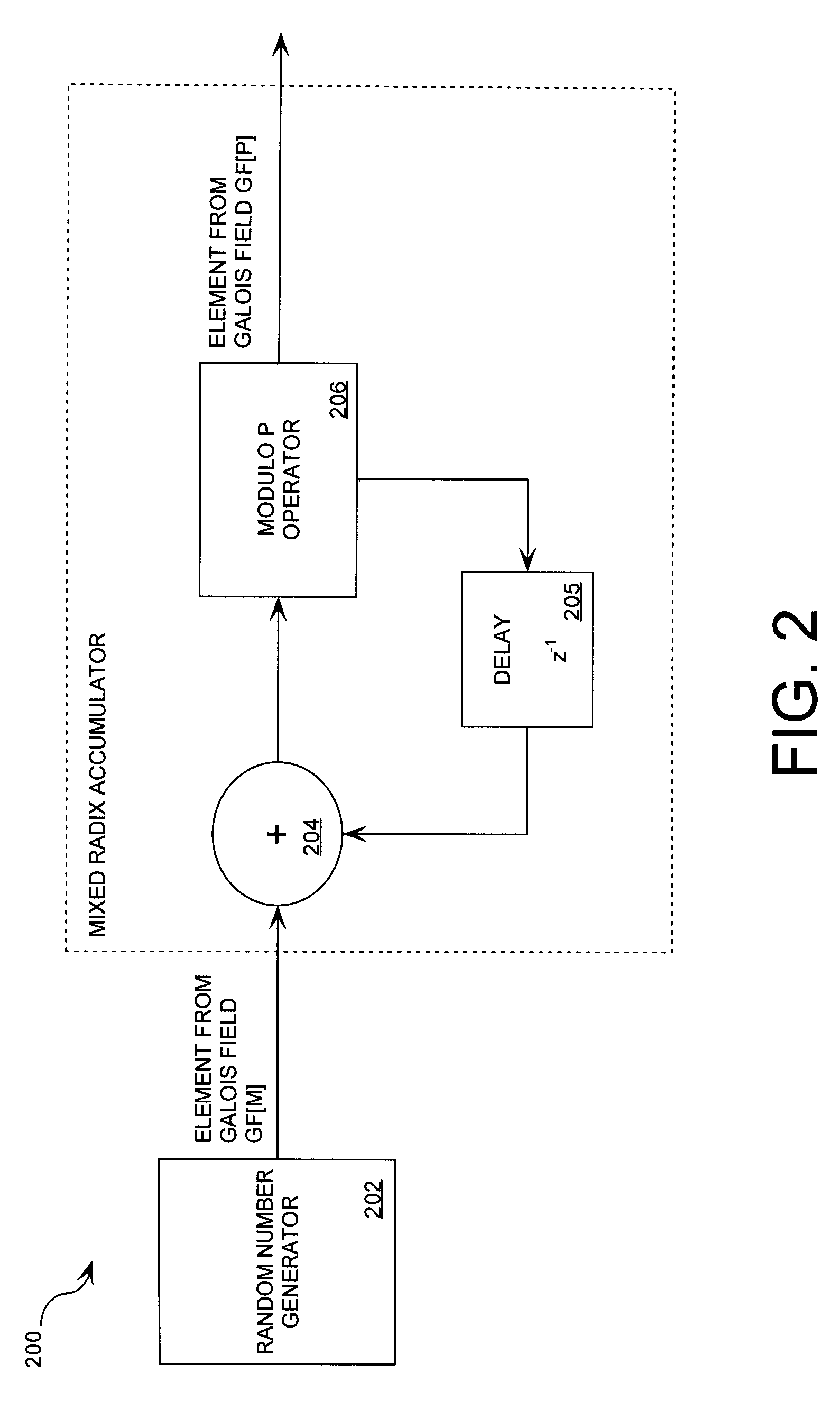
Mixed Radix Number Generator with Chosen Statistical Artifacts
Owner:HARRIS CORP
Cryptographic system including a mixed radix number generator with chosen statistical artifacts
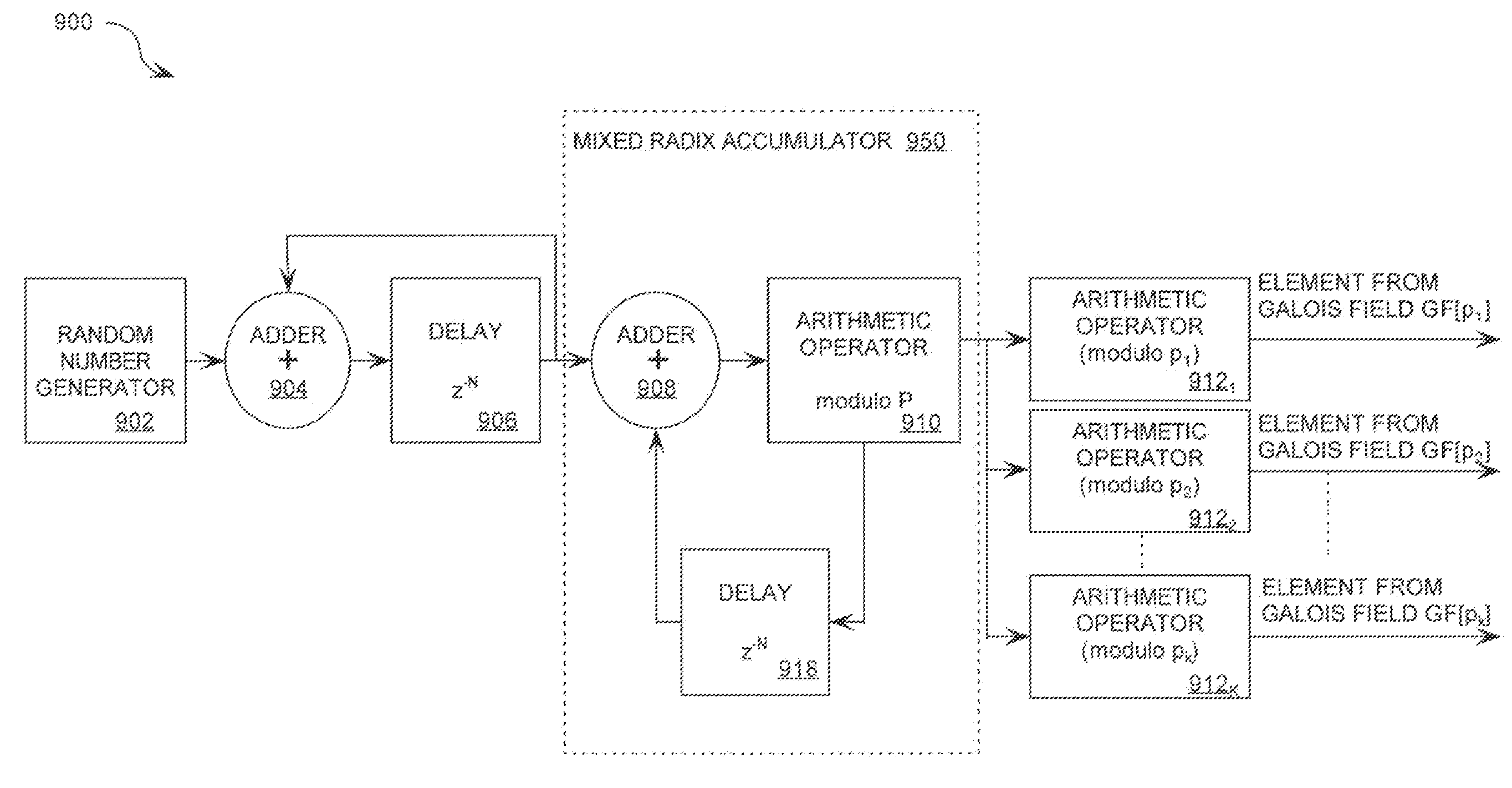
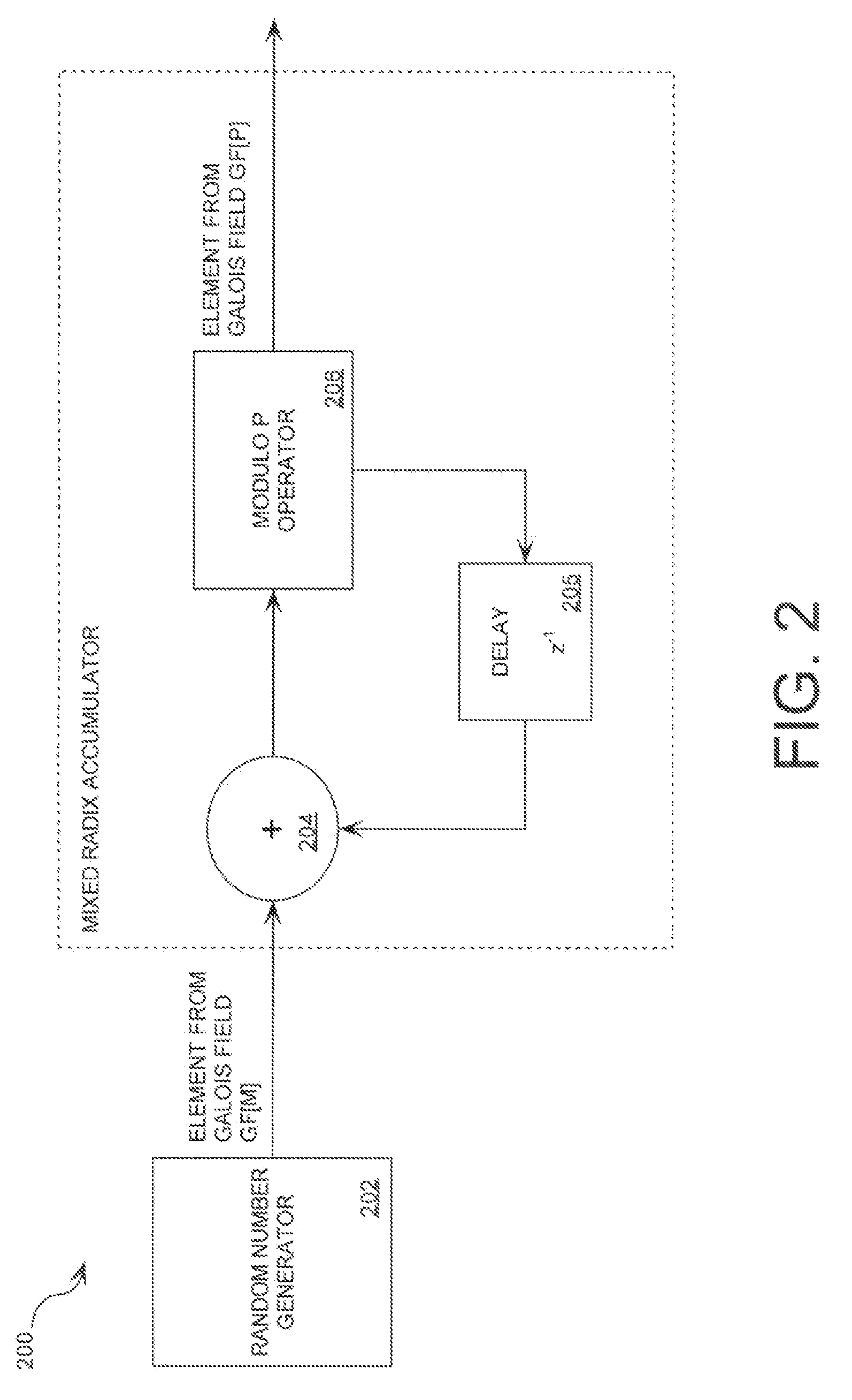
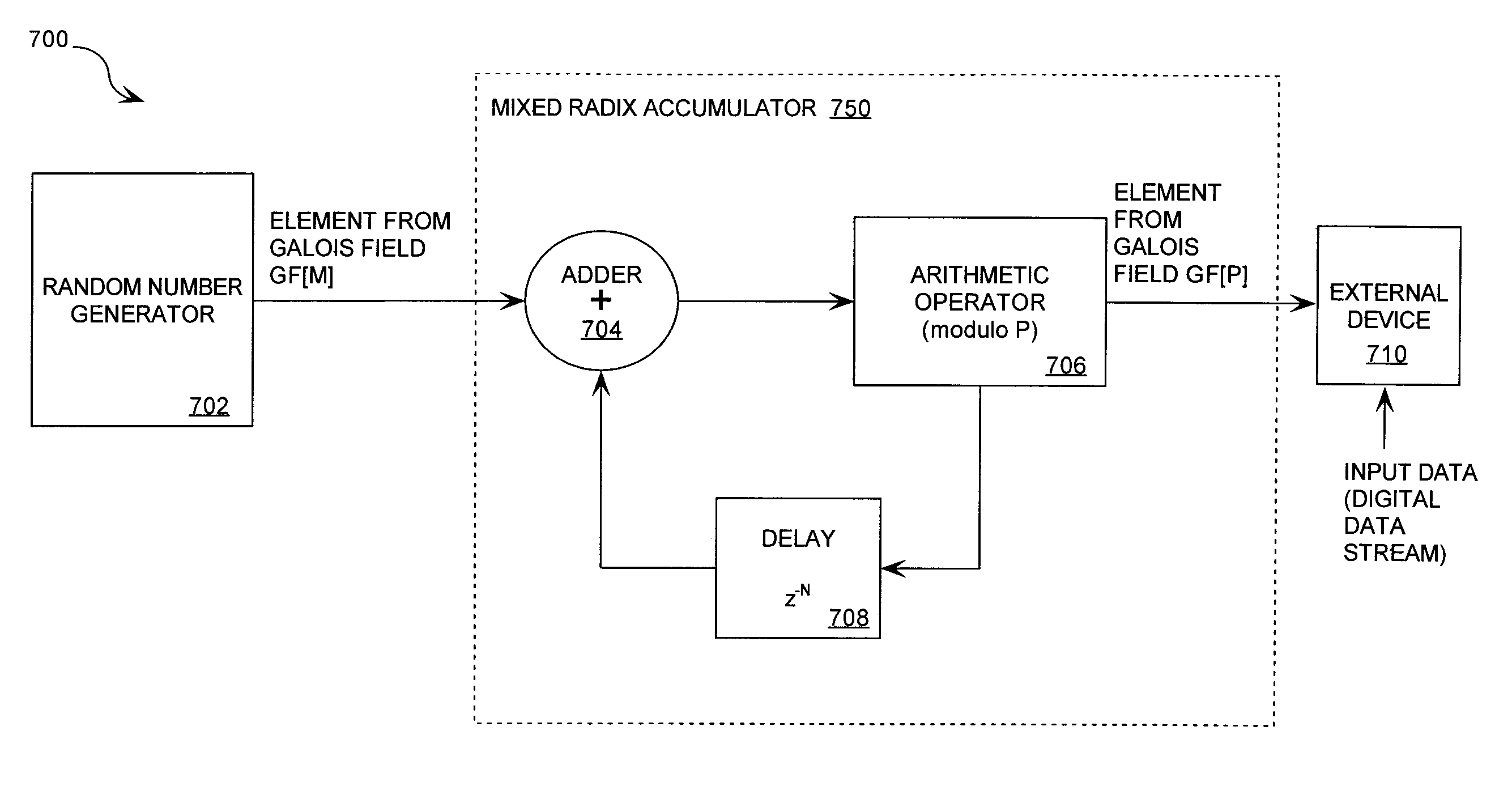
A cryptographic system (1000) is provided. The cryptographic system includes a data stream receiving means (DSRM), a number generator (NG), a mixed radix accumulator (MRA) and an encryptor. The DSRM (1002) receives a data stream (DS). The NG (702) generates a first number sequence (FNS) contained within a Galois Field GF[M]. The MRA (750) is configured to perform a first modification to a first number (FN) in FNS. The first modification involves summing the FN with a result of a modulo P operation performed on a second number in FNS that proceeds FN. The MRA is also configured to perform a second modification to FN utilizing a modulo P operation. The MRA is further configured to repeat the first and second modification for numbers in FNS to generate a second number sequence (SNS). The encryptor (1004) is configured to generate a modified data stream by combining SNS and DS.
Owner:HARRIS CORP
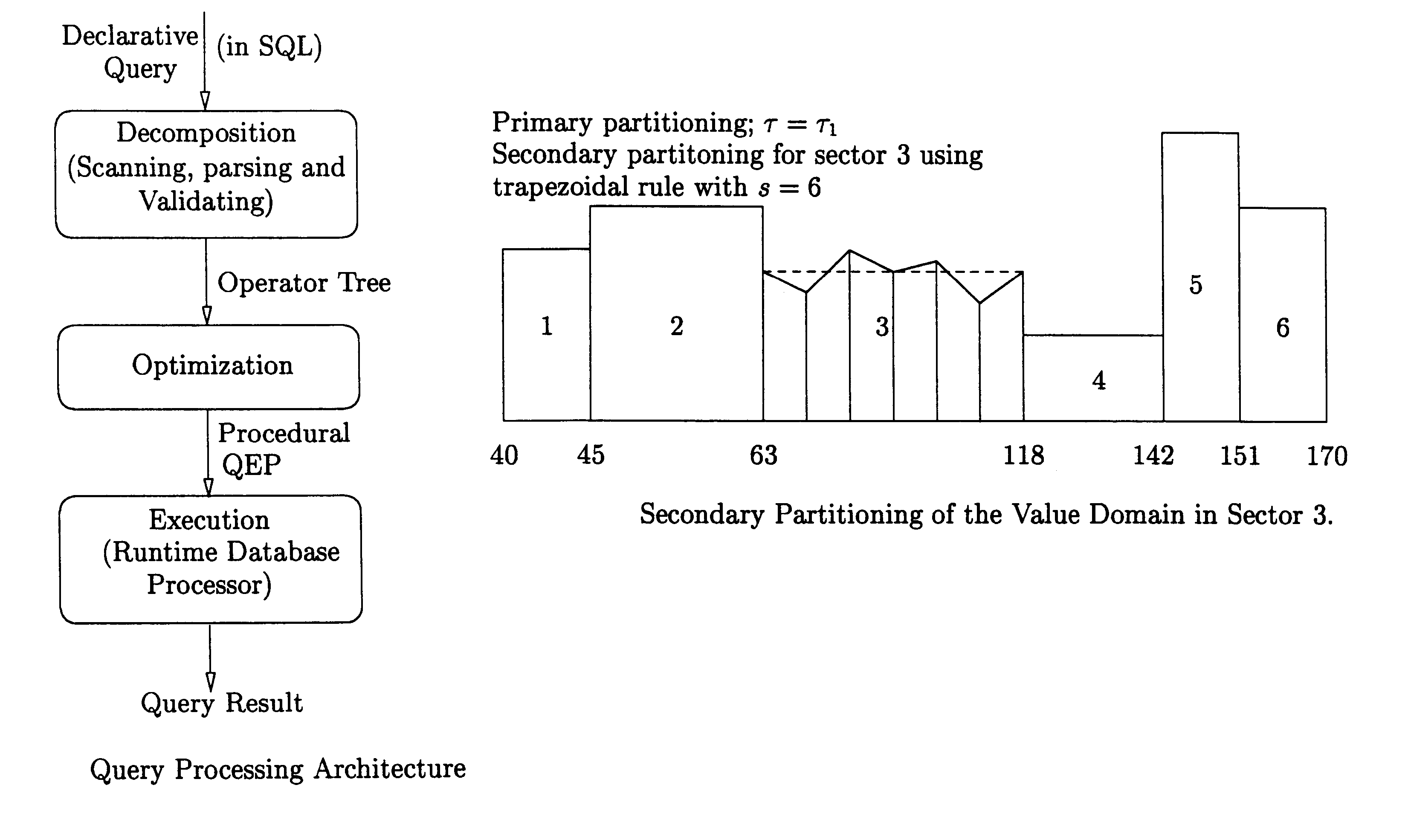
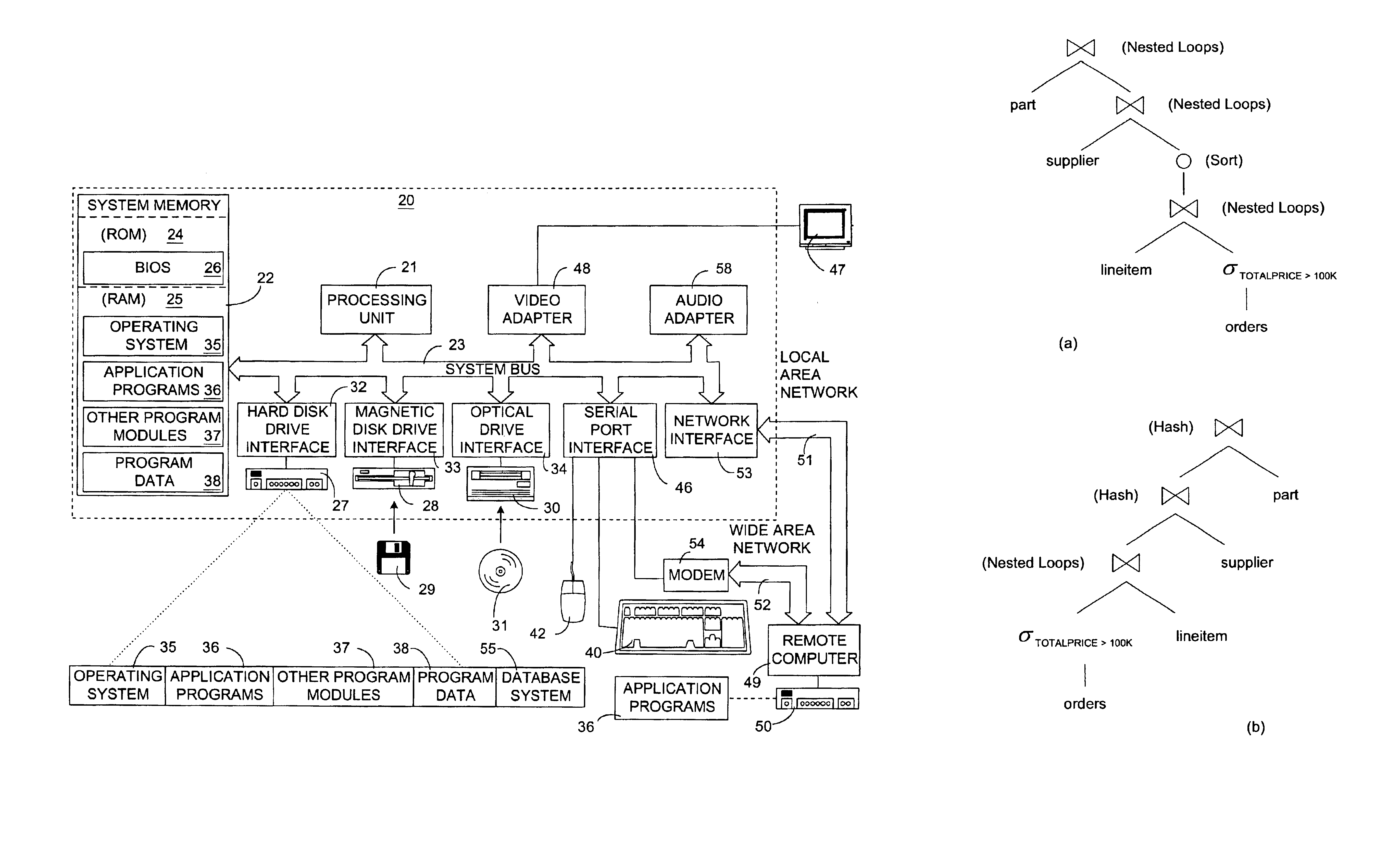
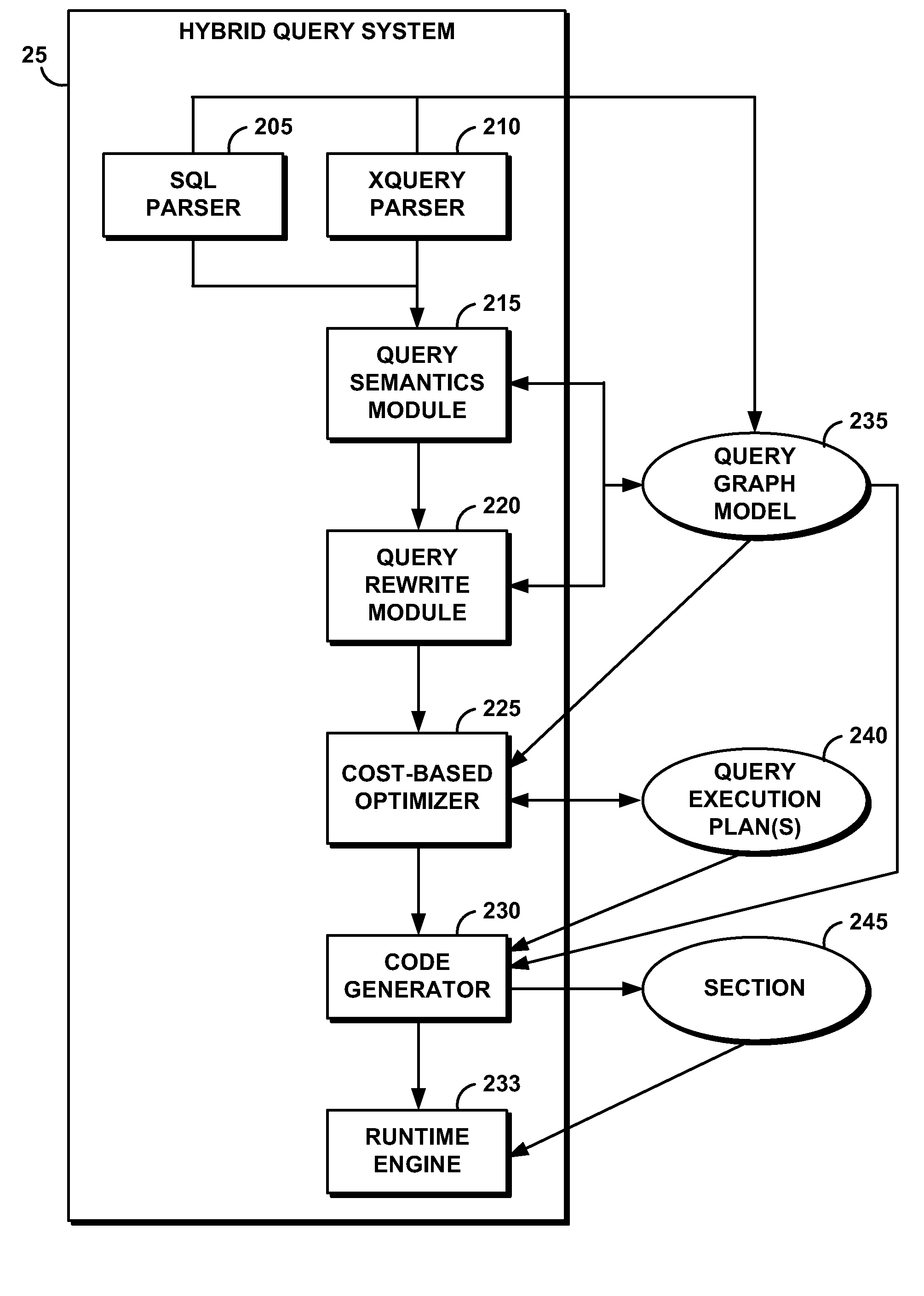
System and Method for Optimizing Query Access to a Database Comprising Hierarchically-Organized Data
InactiveUS20080222087A1Easy accessDigital data information retrievalSpecial data processing applicationsExecution planTheoretical computer science
An cost based optimizer optimizes access to at least a portion of hierarchically-organized documents, such as those formatted using eXtensible Markup Language (XML), by estimating a number of results produced by the access of the hierarchically-organized documents. Estimating the number of results comprises computing the cardinality of each operator executing query language expressions and further computing a sequence size of sequences of hierarchically-organized nodes produced by the query language expressions. Access to the hierarchically-organized documents is optimized using the structure of the query expression and / or path statistics involving the hierarchically-organized data. The cardinality and the sequence size are used to calculate a cost estimation for execution of alternate query execution plans. Based on the cost estimation, an optimal query execution plan is selected from among the alternate query execution plans.
Owner:IBM CORP
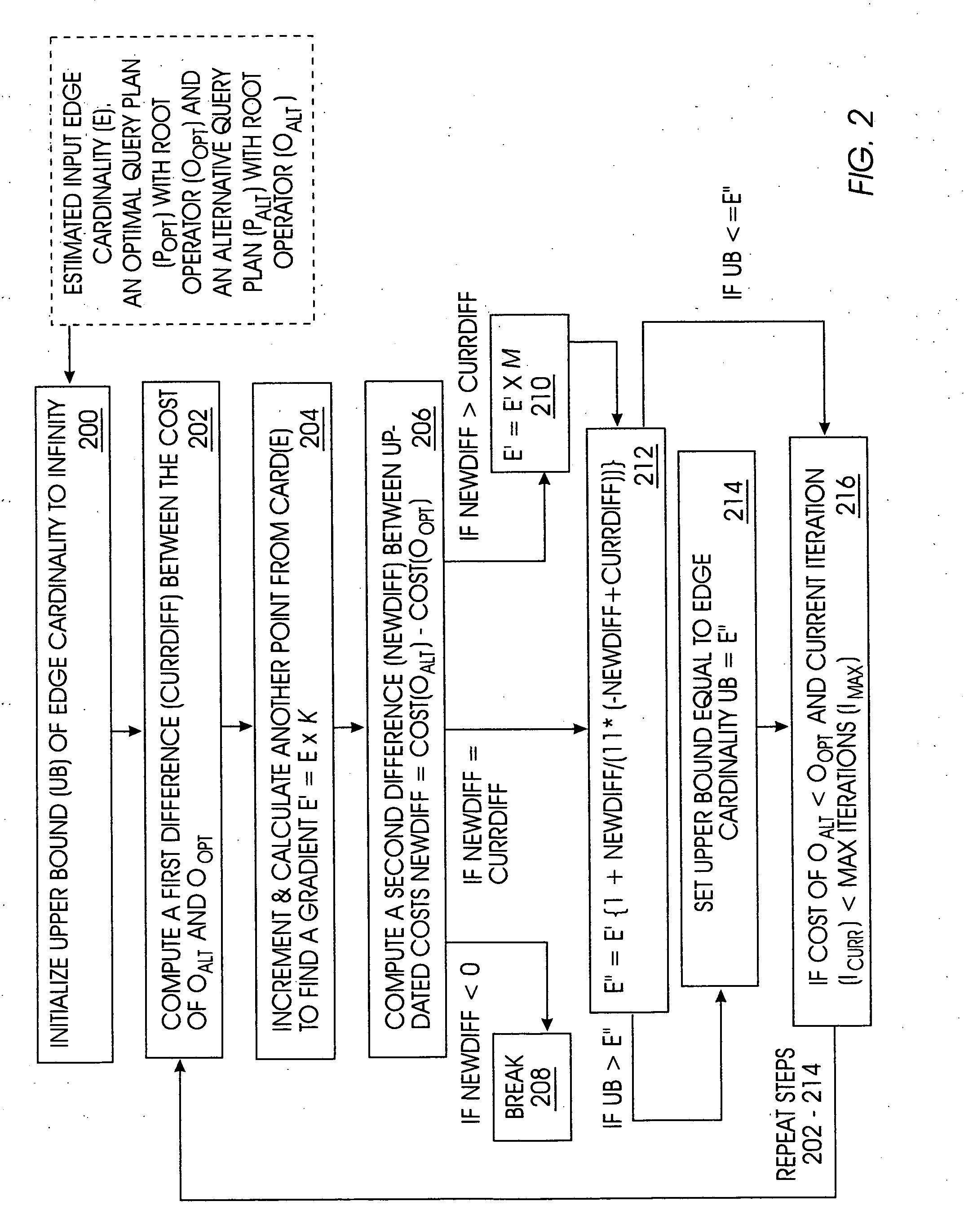
Determining validity ranges of query plans based on suboptimality
InactiveUS20050267866A1Improve robustnessAccurate thresholdData processing applicationsDigital data information retrievalQuery planAlgorithm
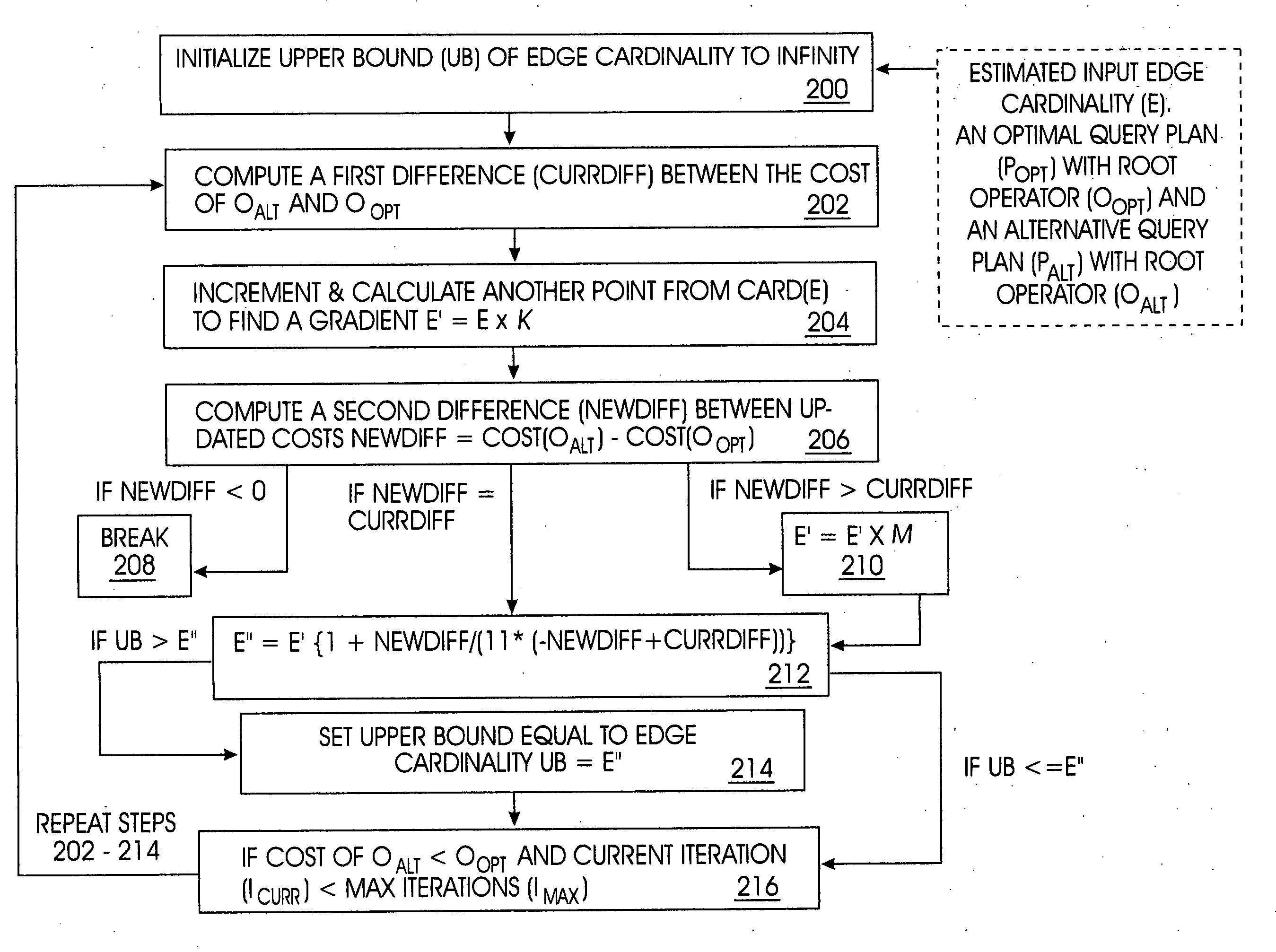
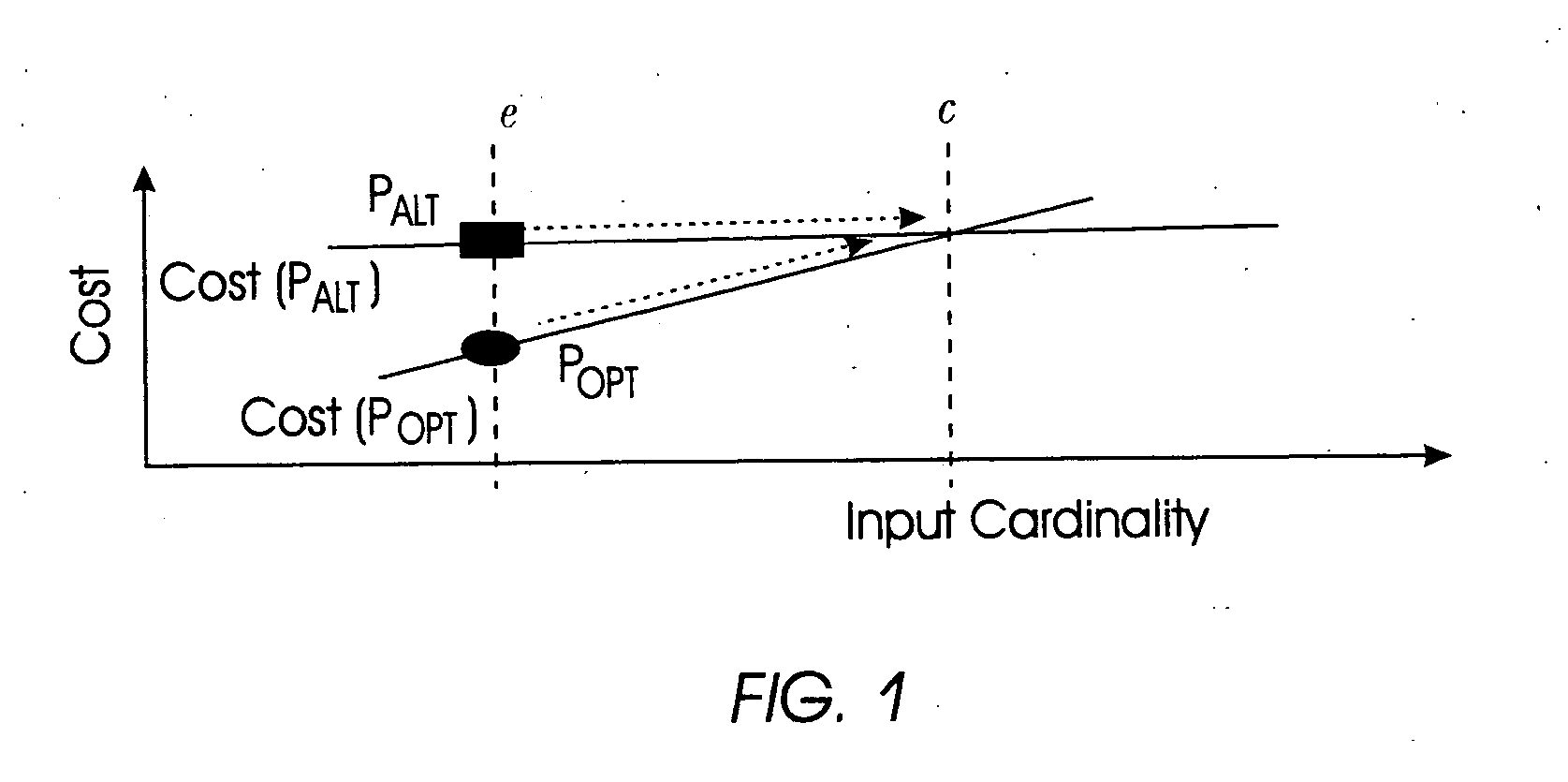
“Determining Validity Ranges of Query Plans Based on Suboptimality” A method for approximating a validity range for a domain of cardinalities of input to an optimal query plan is provided. Such a validity range is iteratively approximated using a modified Newton-Raphson method to find roots of cost functions for optimal and alternative query plans, respectively. The Newton-Raphson method is combined with a method of incrementing roots of cost functions, known as input cardinalities, such that discontinuous and non-differentiable points in cost functions are avoided. In this manner, input cardinalities remain within a domain for which a valid range can be specified. Additionally, a robustness measure is determined by a sensitivity analysis performed on an approximated validity range. Using a robustness measure provided by a sensitivity analysis and resultant validity range and, query plan sub-optimality detection is simplified, re-optimization is selectively triggered, and robustness information is provided to a system or user performing corrective actions.
Owner:IBM CORP
Data communication method and the use of the method in a system for remotely reading meters
InactiveUS6357034B1Reduce occupancyProbability of collisionError preventionTransmission systemsComputer scienceBase Number
A method of communicating data in a system having a plurality of transmitters each adapted to transmit a radio signal, and a receiver situated at a distance from the transmitters to receive and process the signals transmitted by the transmitters, information for transmission being subdivided into N-bit symbols, the method consisting in:giving a numerical value to each symbol; andcompressing the data using a CHIP encoding technique in which the values of the symbols are transposed to an encoded value having x digits in a base B, each digit subsequently being represented in the form of n chips, the base B, the number n of chips, and the number x of digits for an encoded value satisfying the following conditions: so that the total number of chips x.n representing the coded value is less than 2.N.
Owner:UBS AG STAMFORD BRANCH AS ADMINISTATIVE AGENT +1
High base number composite calcium sulfonate lubricating grease and its preparation method
A composite lubricating grease contains high-basicity petroleum calcium sulfonate or synthetic calcium sulfonate, acetic acid, C12-C22 hydroxy fatty acid, boric acid, arylamine-type antioxidizing agent and basic lubricating oil. Its advantages are excellent extreme-pressure resistance to friction, water, salt fog and corrosion, high drop point and thermal stability, good viscosity and long service life.
Owner:SINOPEC LUBRICANTS TIANJIN
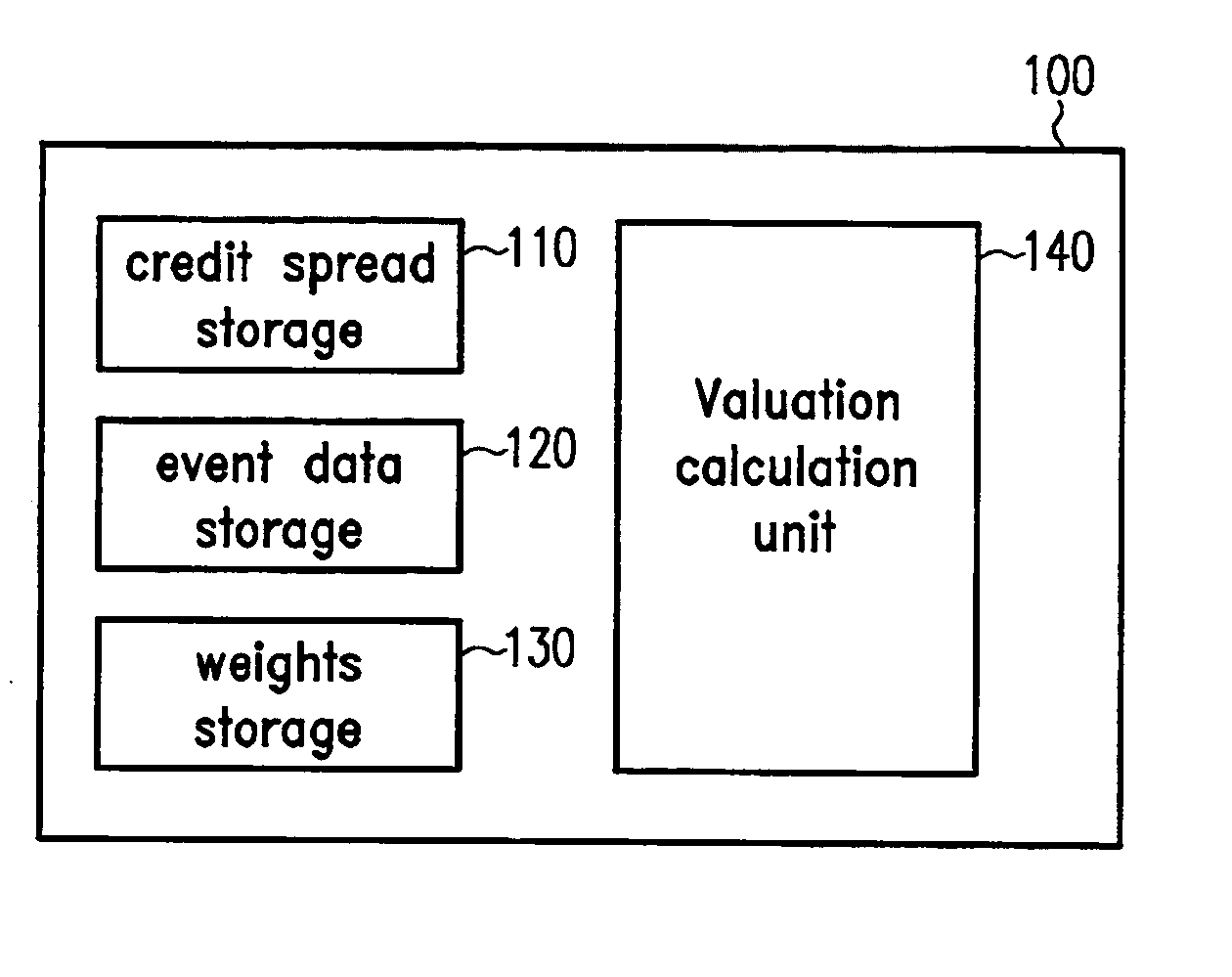
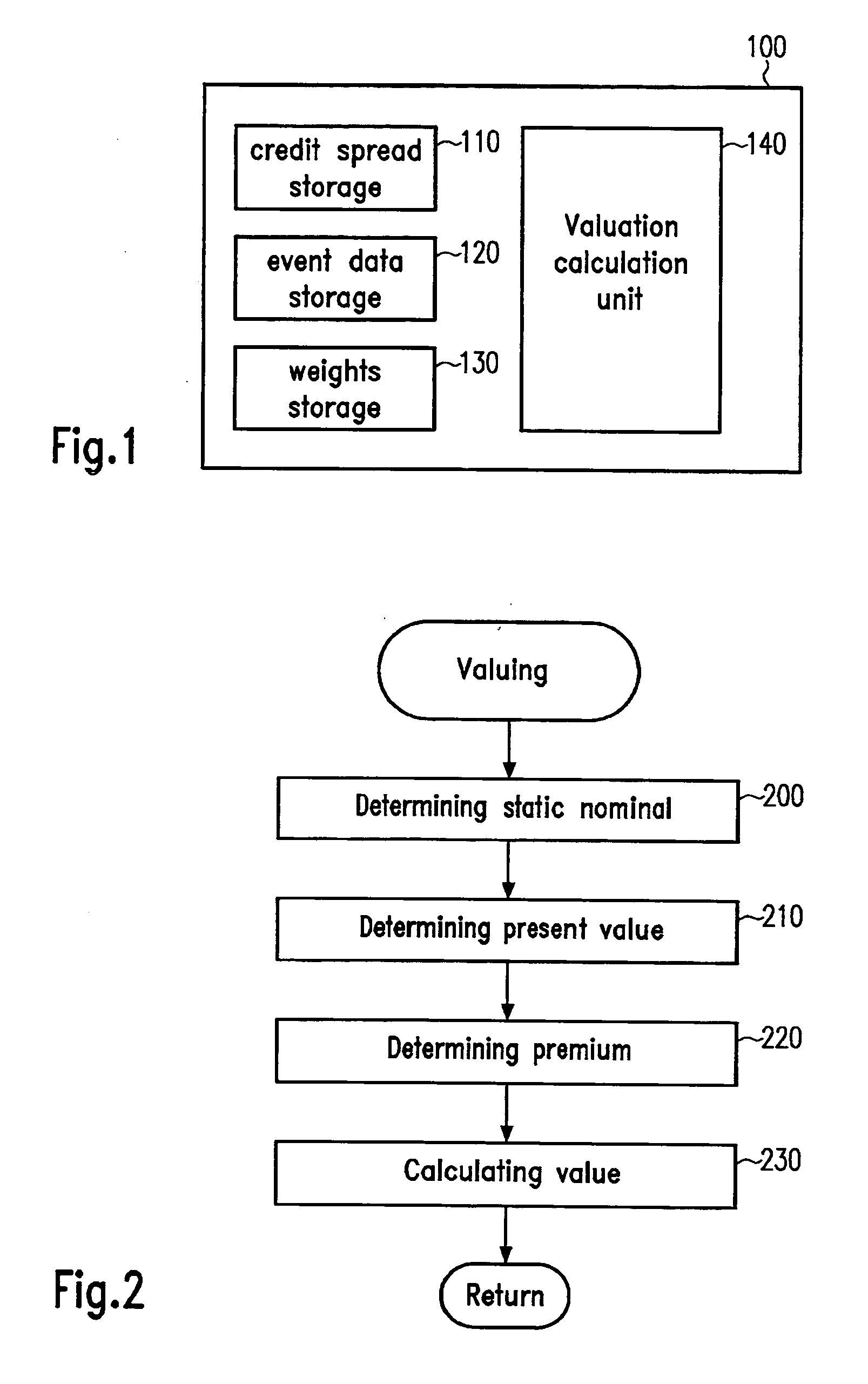
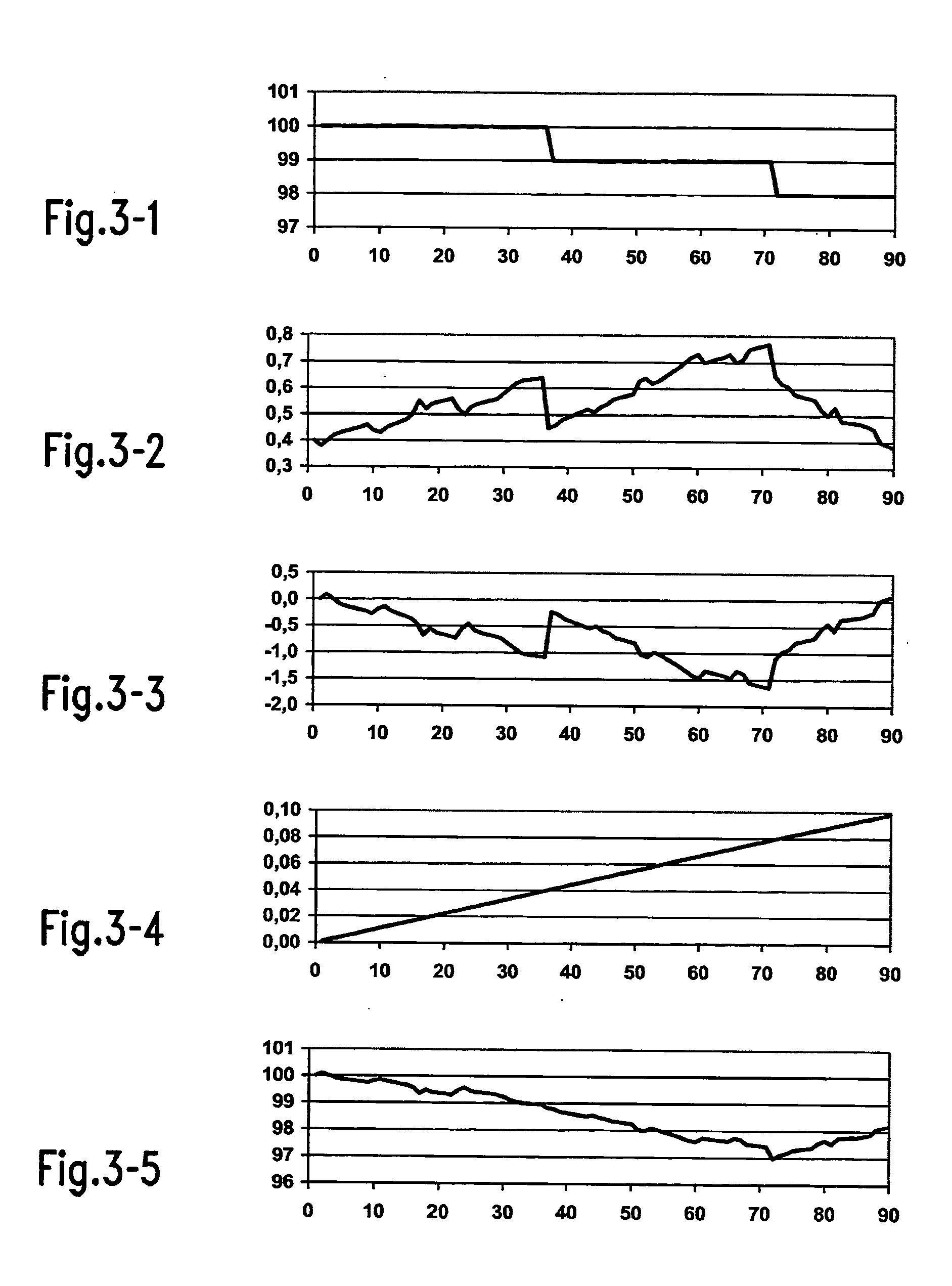
Unsteadiness compensation in valuation systems and methods
There is provided a data processing system and method for valuing a bundle of constructs that may individually fail, in case of a separation event causing the bundle of constructs to separate a failing construct from the bundle. A present value determination unit applies a predefined model to determine a present value of the bundle of constructs after having separated the failing construct from the bundle. Further, a static value determination unit determines a static value by reducing a static base number each time a separation event occurs. Furthermore, a calculation unit calculates a value of the bundle of constructs based on the determined present value and the determined static value. The calculation unit is adapted to calculate a sum of the determined present value and the determined static value. In an embodiment, the bundle of constructs is a basket of credit default swaps.
Owner:DEUT BORSE
Method and apparatus for calibrating color temperature of color display devices
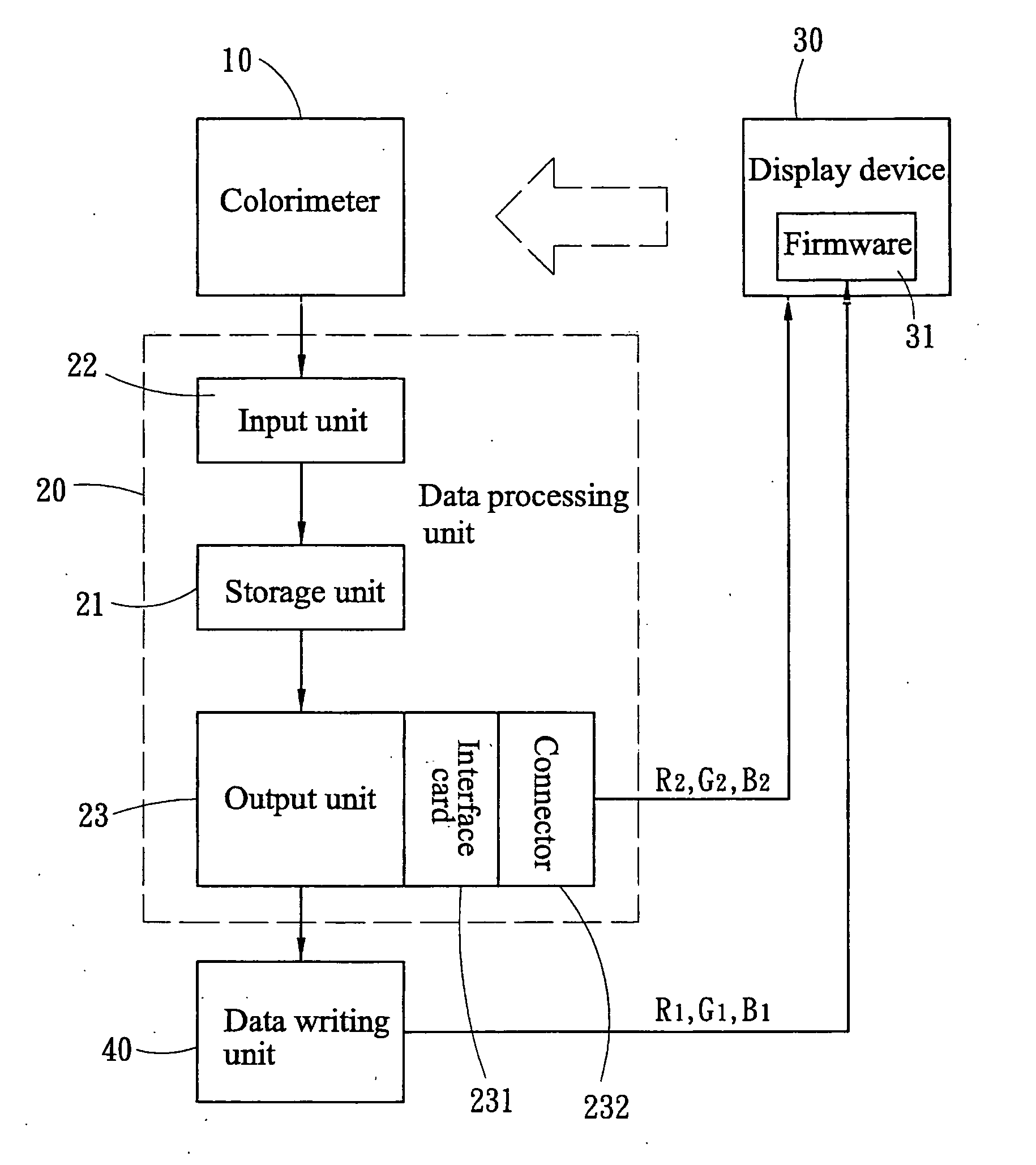
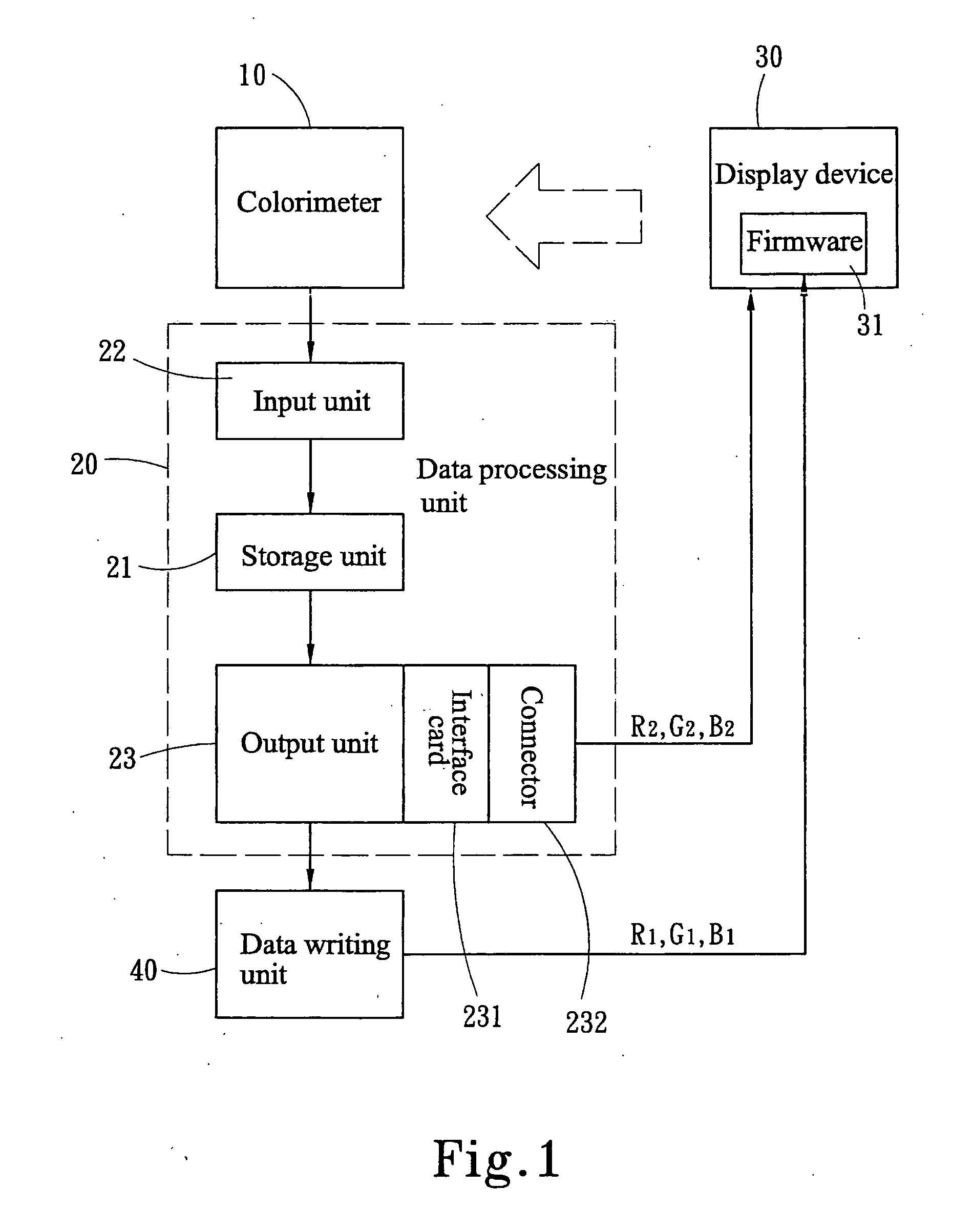
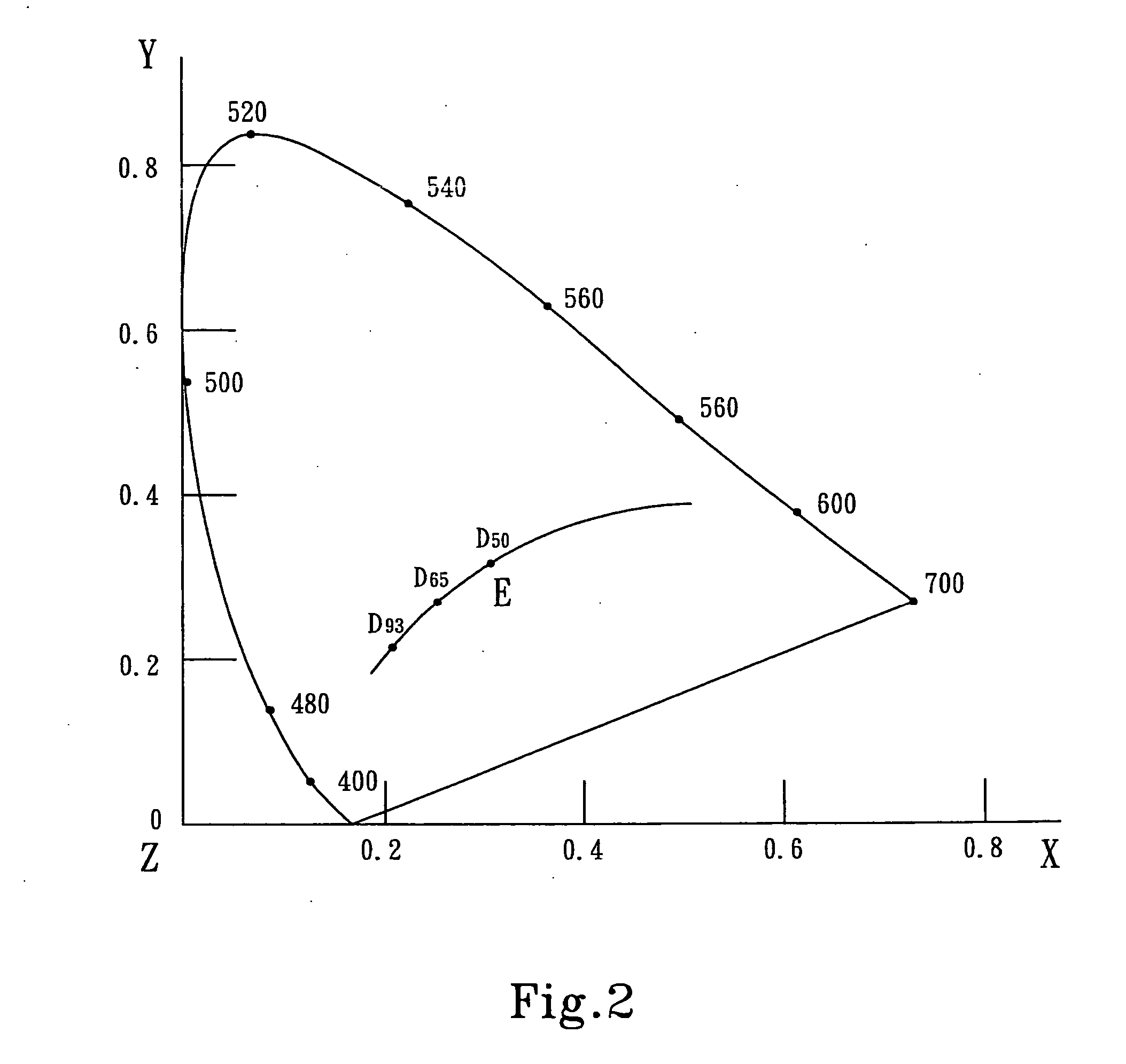
ActiveUS20050275912A1Color signal processing circuitsCathode-ray tube indicatorsPattern recognitionDisplay device
A method and apparatus for calibrating color temperature of color display devices aims to calibrate output bases of RGB three original color lights of a color display device so that different color display devices can radiate the same color temperature in the same color temperature settings. The method of the invention uses a colorimeter to obtain current chromaticity value radiated from the color display device in a standard color representation system and in the condition of known output bases of the current three original color light signals, and through calculation to obtain the proportional relationship of the current radiating color temperature and an objective color temperature in the same standard color representation system, and based on which to derive the output bases of the required three original color light signals corresponding to the objective color temperature to be calibrated. The results are written through the apparatus into a color profile of the color display device.
Owner:TCL CHINA STAR OPTOELECTRONICS TECH CO LTD
Method and Apparatus for Low Power Modulation and Massive Medium Access Control
ActiveUS20090051496A1Save powerIncrease processing gainElectric signal transmission systemsTime-division multiplexPower modulationCommunications system
An ultra low power, low complexity, low collision, deterministic modulation method that also works as a massive medium access mechanism for communication systems is based on positioning data in a communication resource space, such as time and frequency, such that the position of a symbol in that space determines its value and its access to the medium. The number base of the symbol is determined by the size of the subset of the resource space it is positioning itself in and, thereby, a few sparsely located symbols can convey a large value, while the remainder of the space can be simultaneously and massively used by other sparsely resource using members of the network.
Owner:TAGARRAY
Systems for and methods of determining likelihood of reference point identity duplication in a positioning system
Systems for and methods of determining likelihood of reference point identity duplication in a positioning system are disclosed. A method of determining a measure of likelihood that a designated identifier is shared by wireless devices includes determining reference points associated with any wireless device having a designated identifier. The reference points are a geographic position at which signals from any of the wireless devices were detected and / or wireless devices from which signals were also detected within a selected period of time during which the signals from any of the wireless devices having the designated identifier were detected. The method also includes determining statistical information about a temporal distribution of detection of signals of reference points, a spatial distribution of the reference points, and / or a cardinality of the reference points and determining a measure of likelihood that the designated identifier is shared by wireless devices is based on the statistical information.
Owner:SKYHOOK WIRELESS
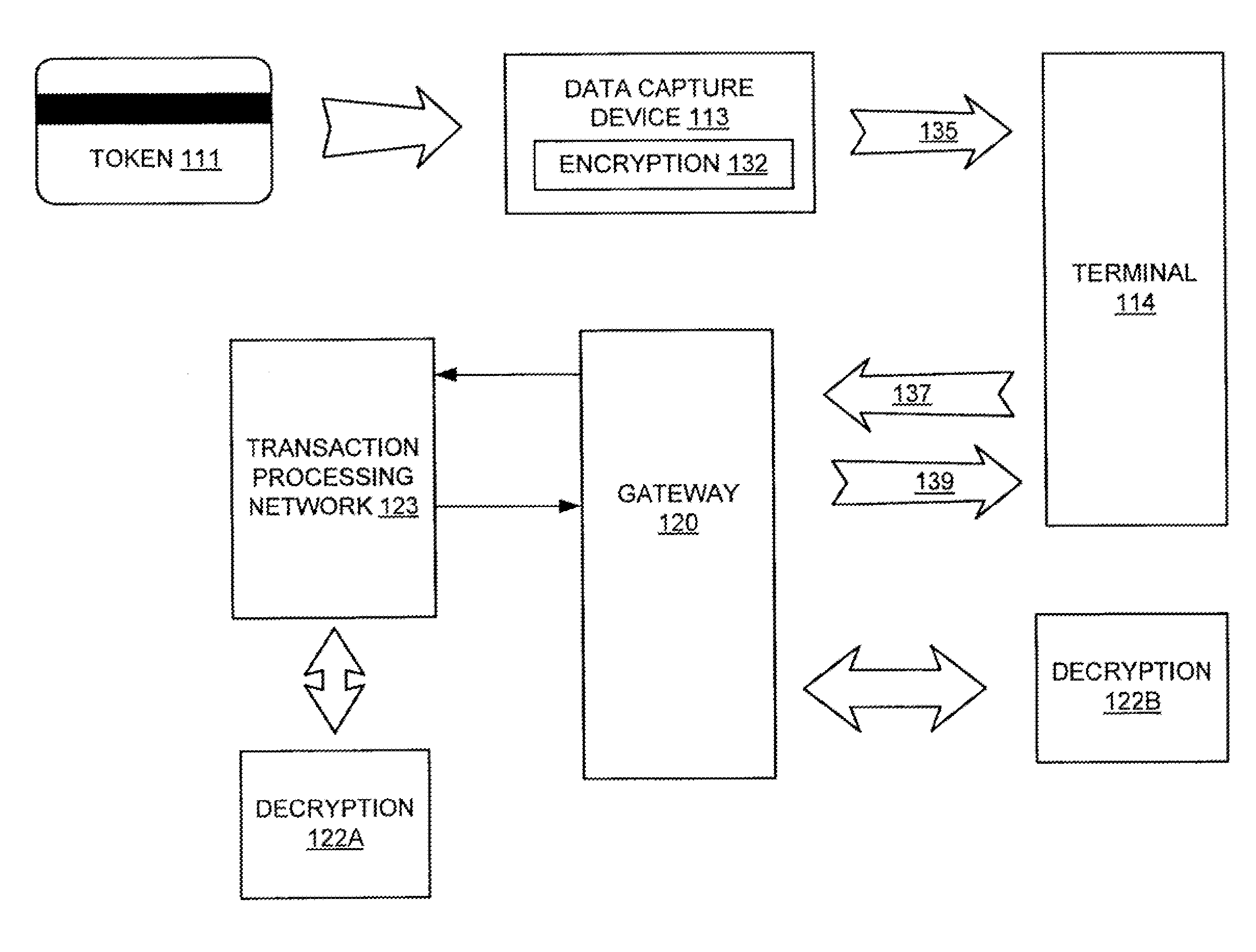
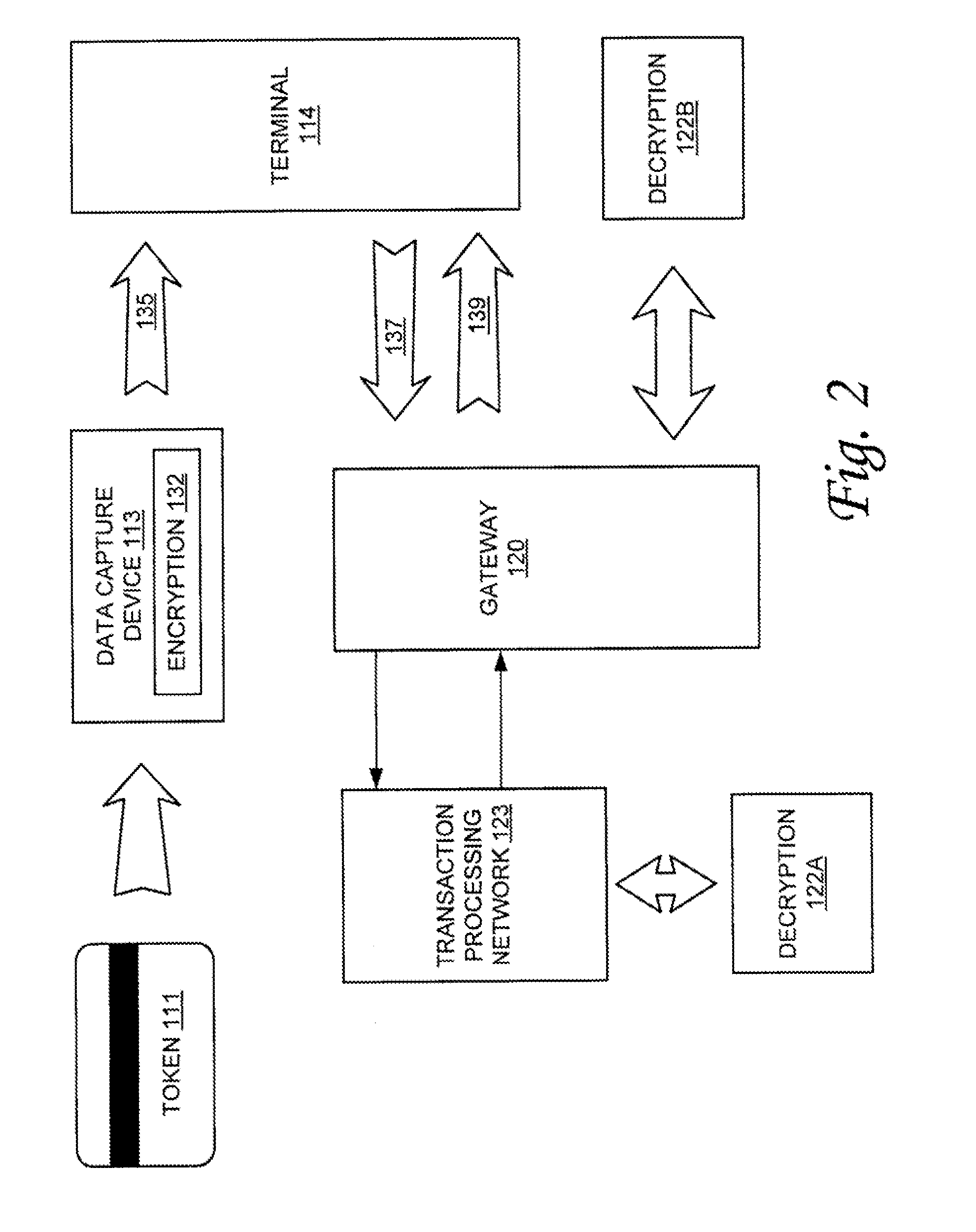
Format preserving cipher system and method
InactiveUS20130168450A1Improve securityComplete security measuresSecret communicationSensing record carriersPlaintextDefining length
Systems and methods for enciphering data are provided. In one embodiment, information is enciphered using a variable block length cipher that returns the encrypted symbol set in any defined symbol set with a radix greater than or equal to the plaintext format. The cipher can be based on DES, AES or other block ciphers. In one example implementation a method for enciphering token information the invention provides for enciphering token information by constructing a tweak of a defined length using token information; converting the tweak to a bit string of a defined size to form a first parameter; converting a number of digits of plaintext to a byte string of a defined size to form a second parameter, wherein the number of digits converted varies; defining a data encryption standard key; applying the data encryption standard key to the first and second parameters; computing a specified number of encryption rounds; and receiving enciphered token information.
Owner:VON MUELLER CLAY W +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com