Patents
Literature
92results about How to "Complete security measures" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
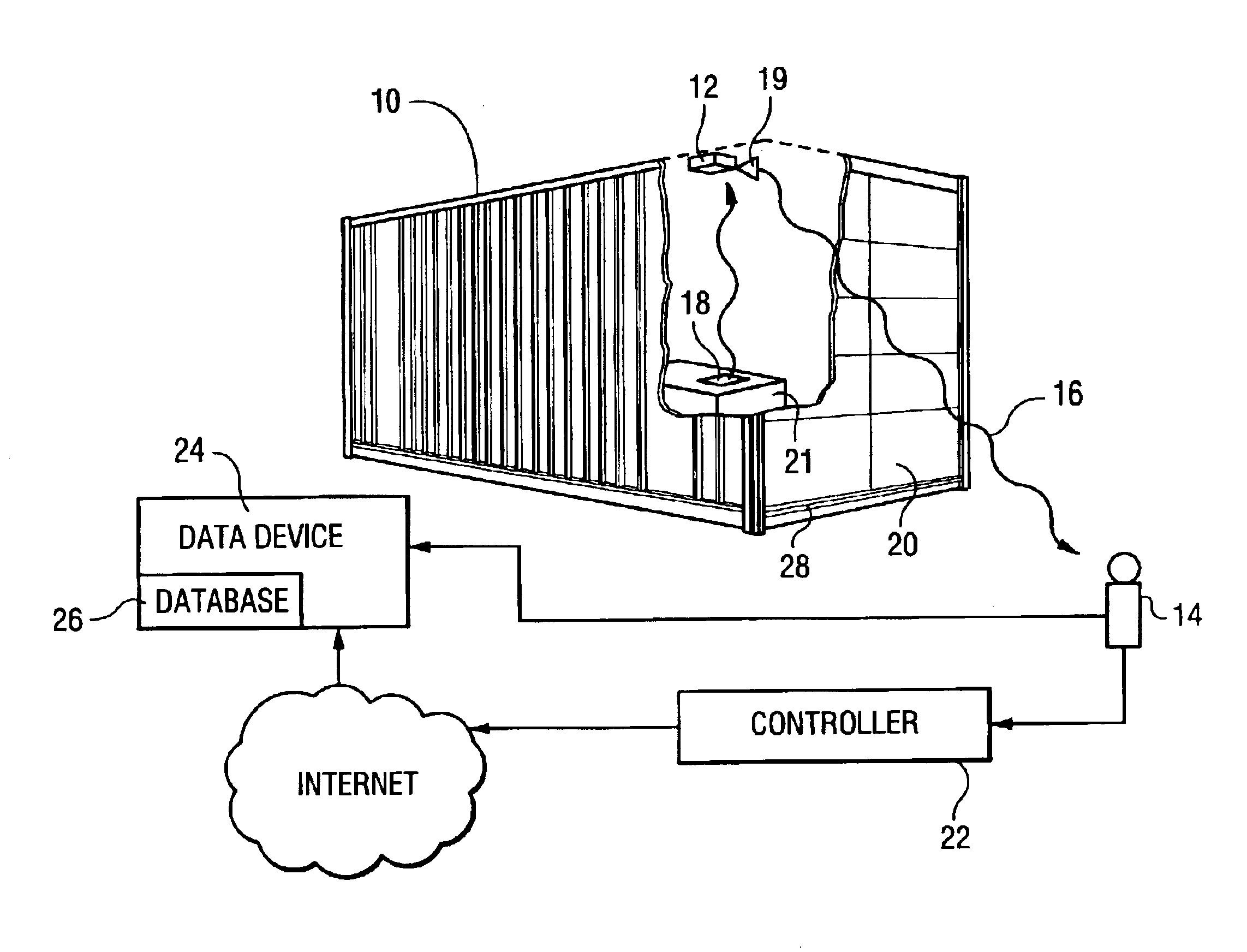
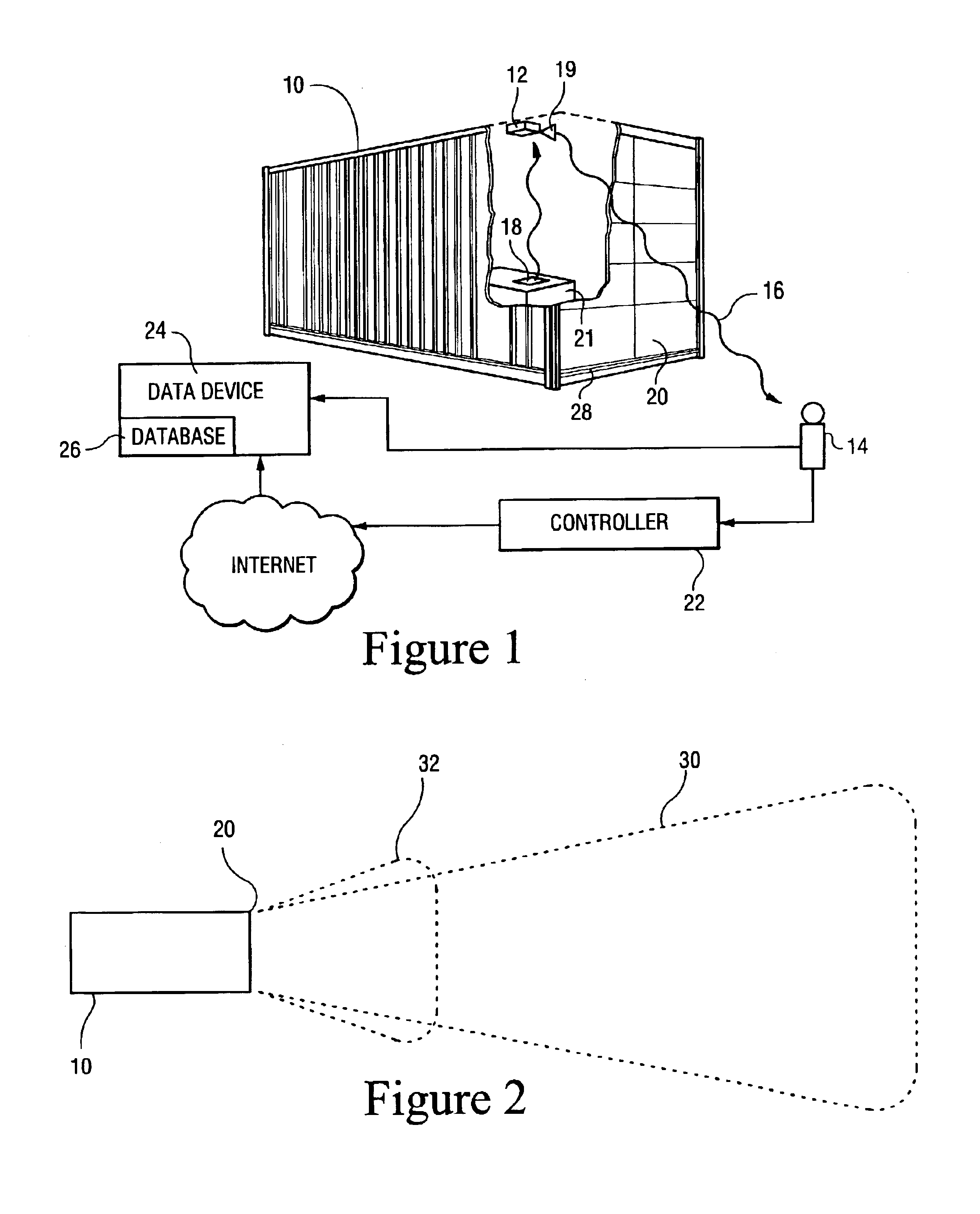
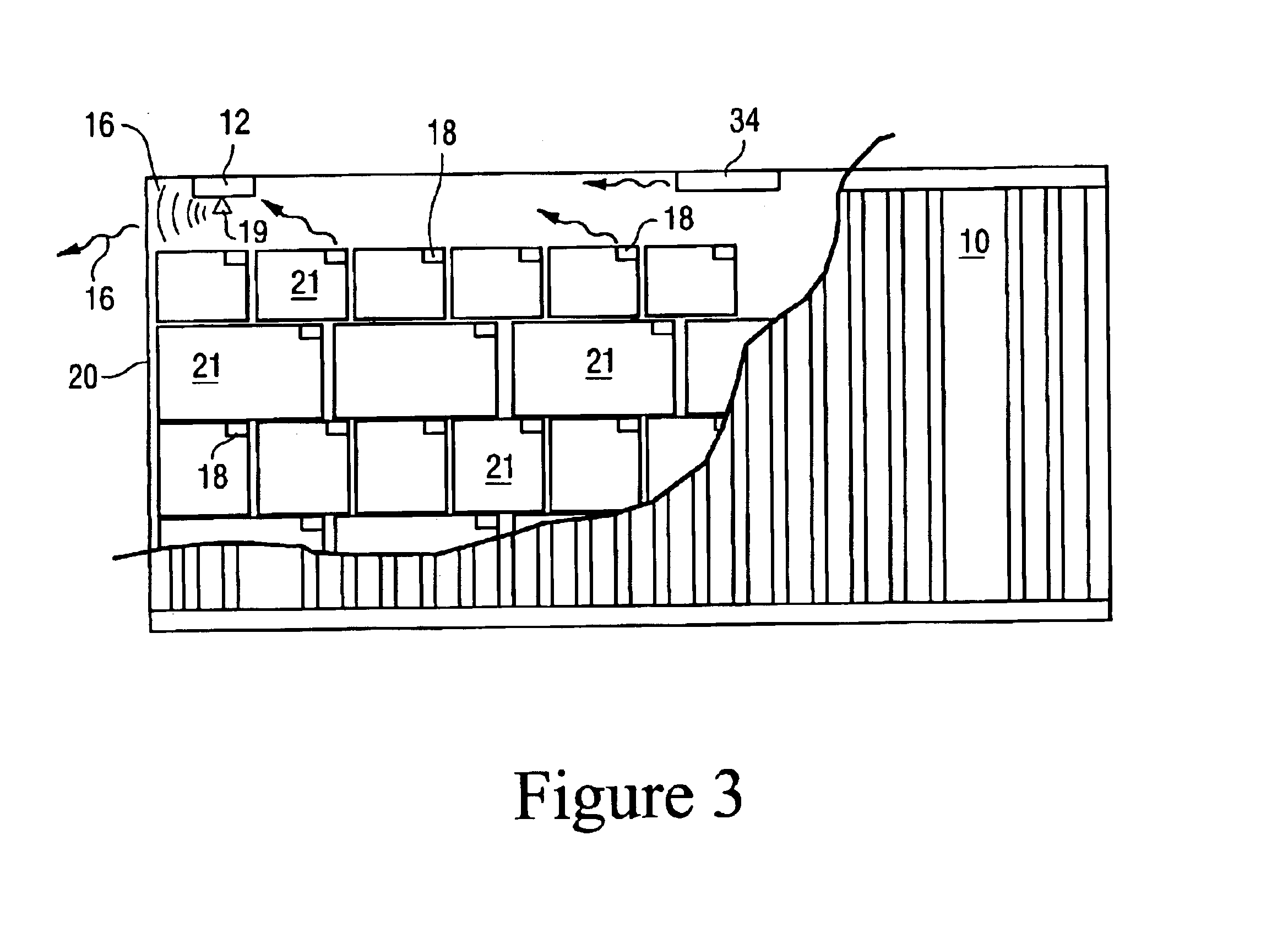
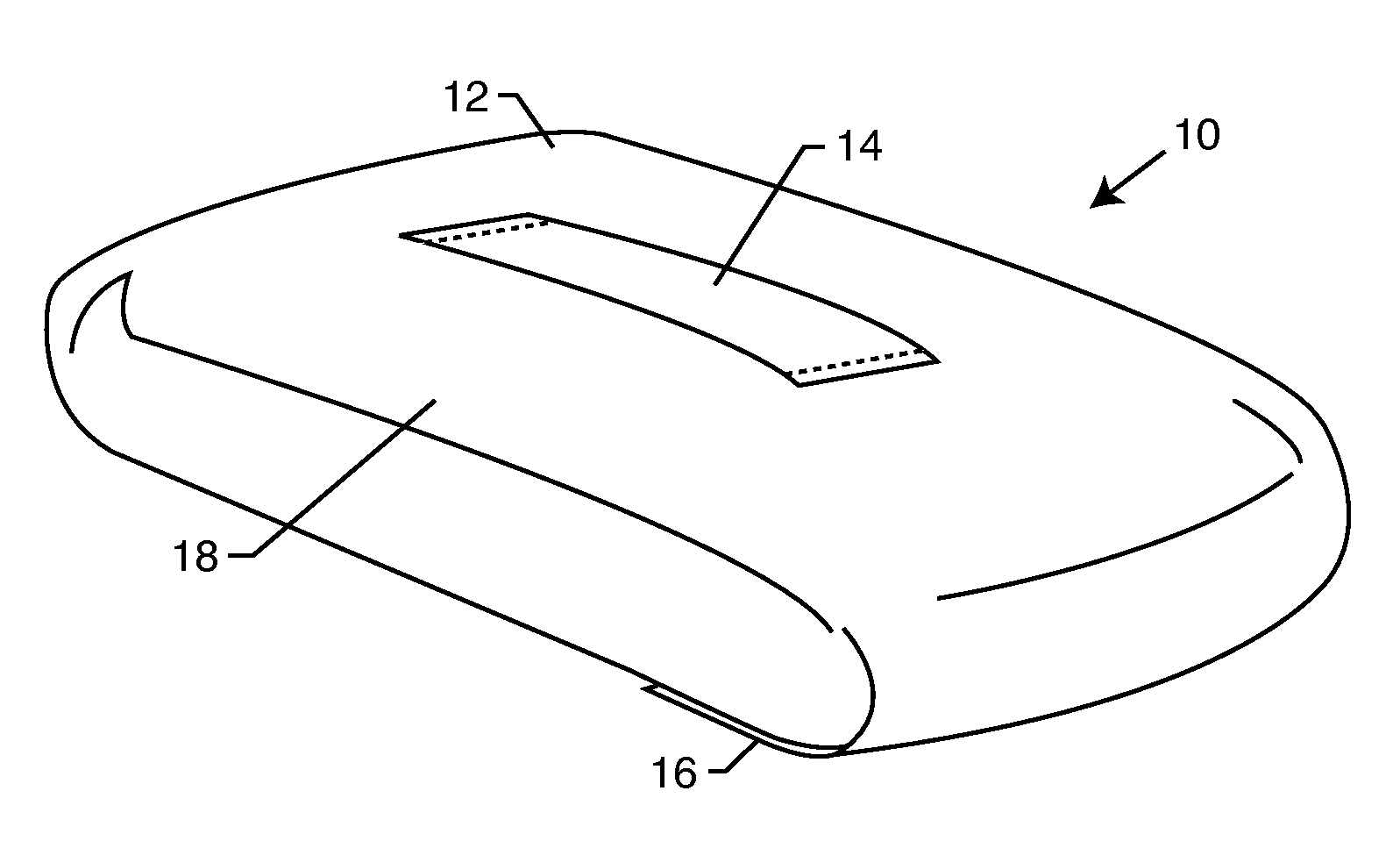
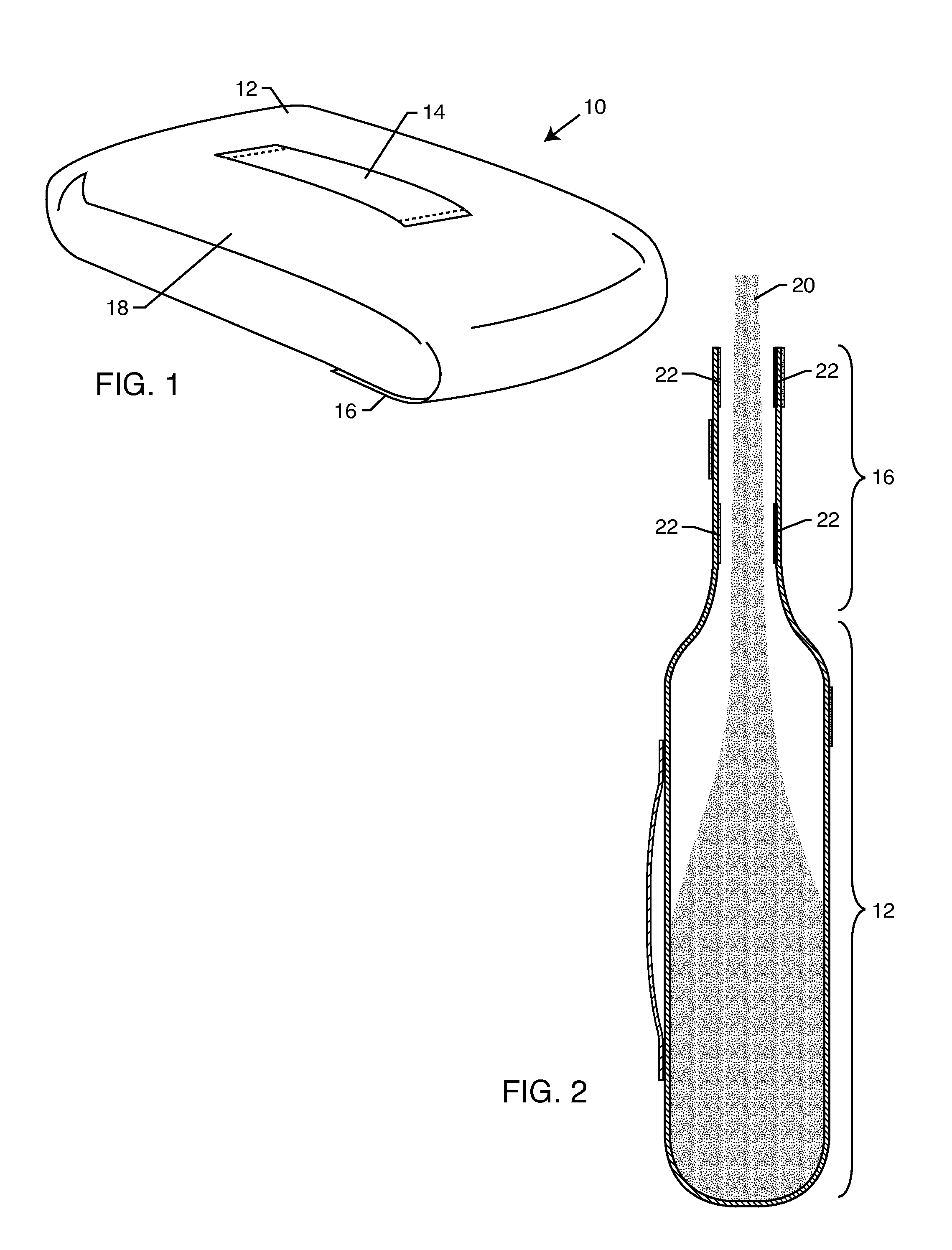
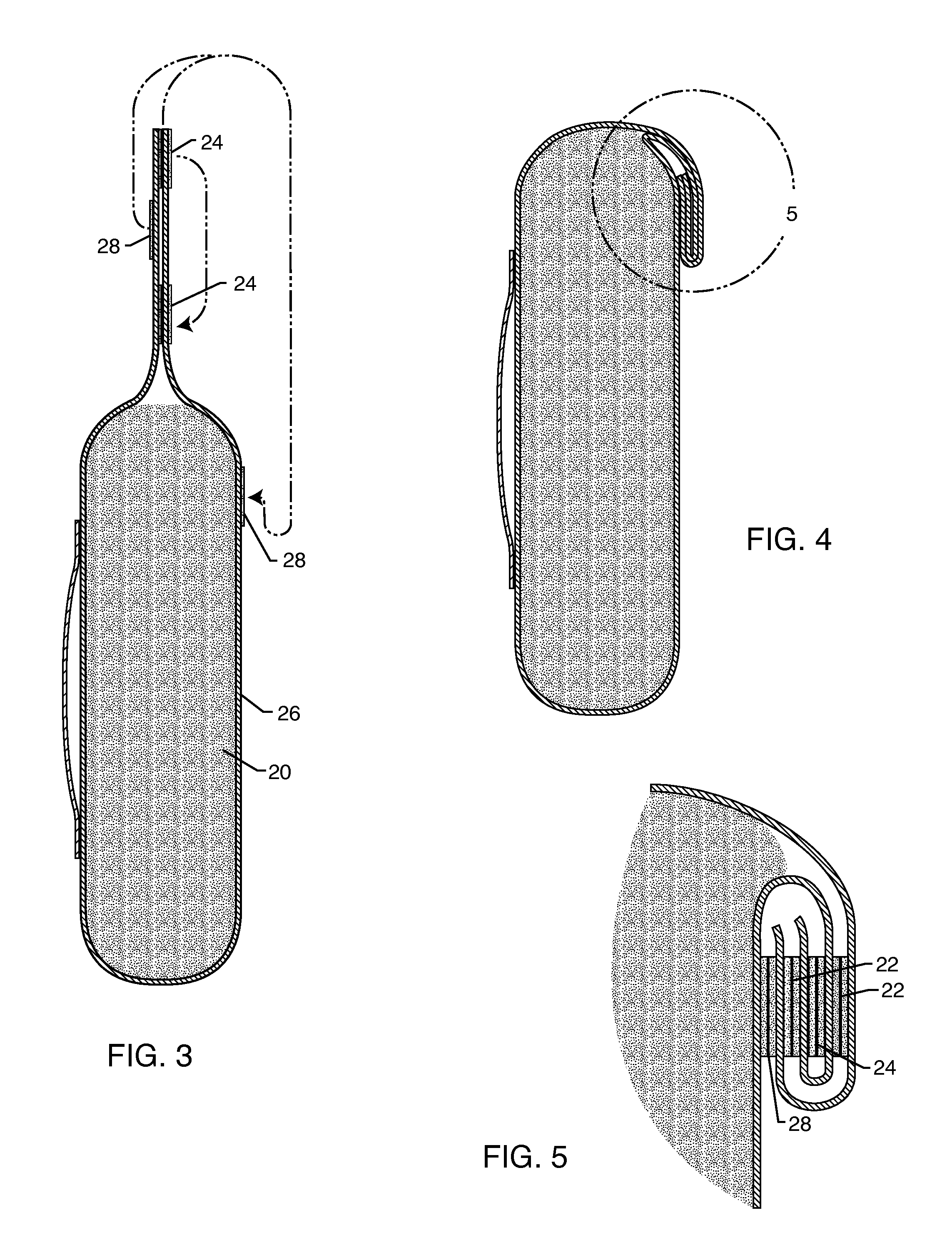
Method for enabling communication and condition monitoring from inside of a sealed shipping container using impulse radio wireless techniques
InactiveUS6927688B2Complete security measuresOvercome difficultiesFire alarmsSensing record carriersRadio receptionRadiotransmitter
A system to capture data regarding conditions in a sealed metal shipping container having: a sensor unit mountable inside the container and adapted to sense a condition inside of the container; an impulse radio transmitter receiving data from the sensor regarding the condition and transmitting an impulse radio wireless signal inside of the container; an impulse radio receiver external to the container and proximate the container, wherein the receiver is adapted to receive the impulse radio wireless signal propagating through the sealed metal shipping container, and a data device in communication with the receiver to capture the data from the sensor unit regarding the condition inside of the container.
Owner:CACI INT
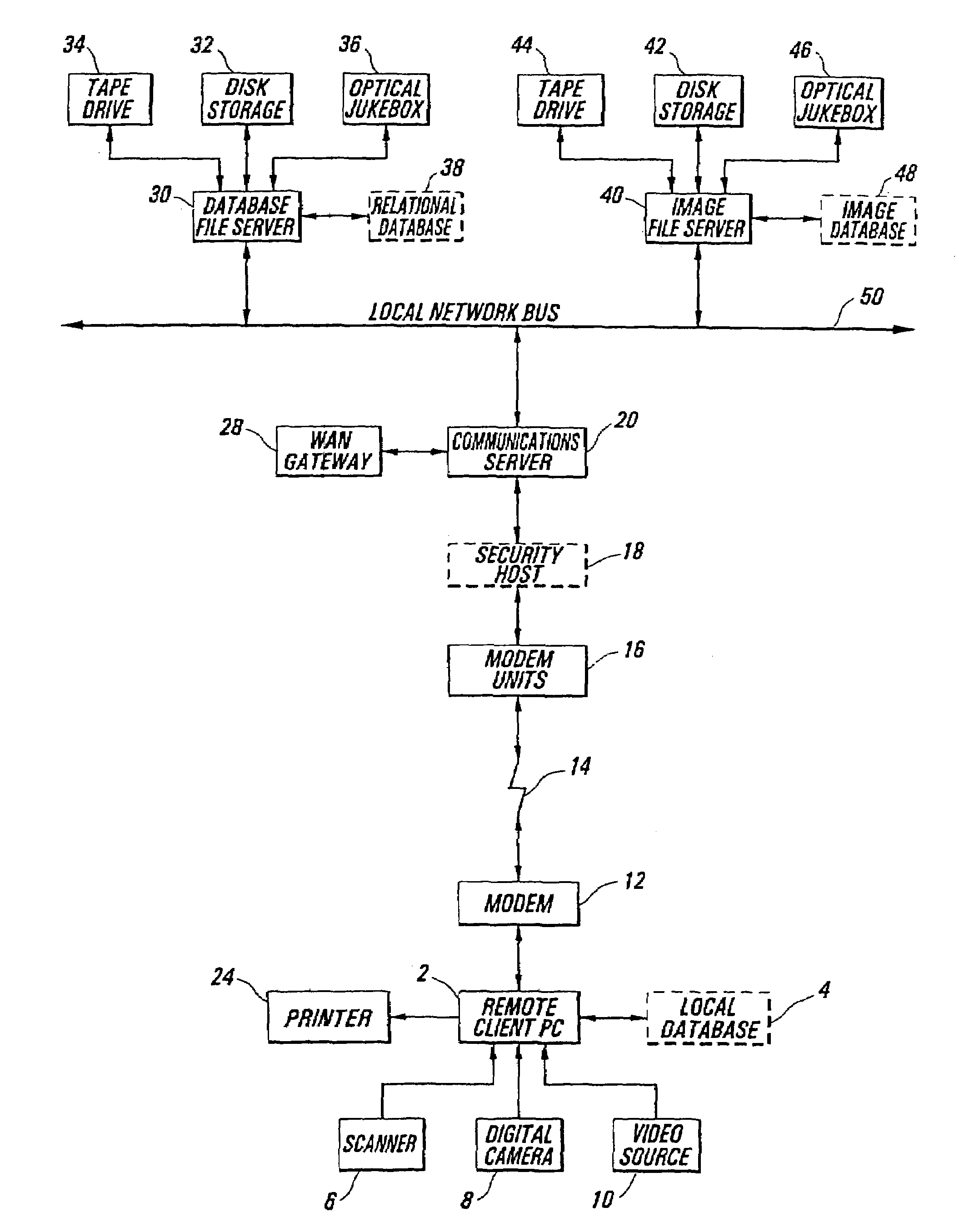
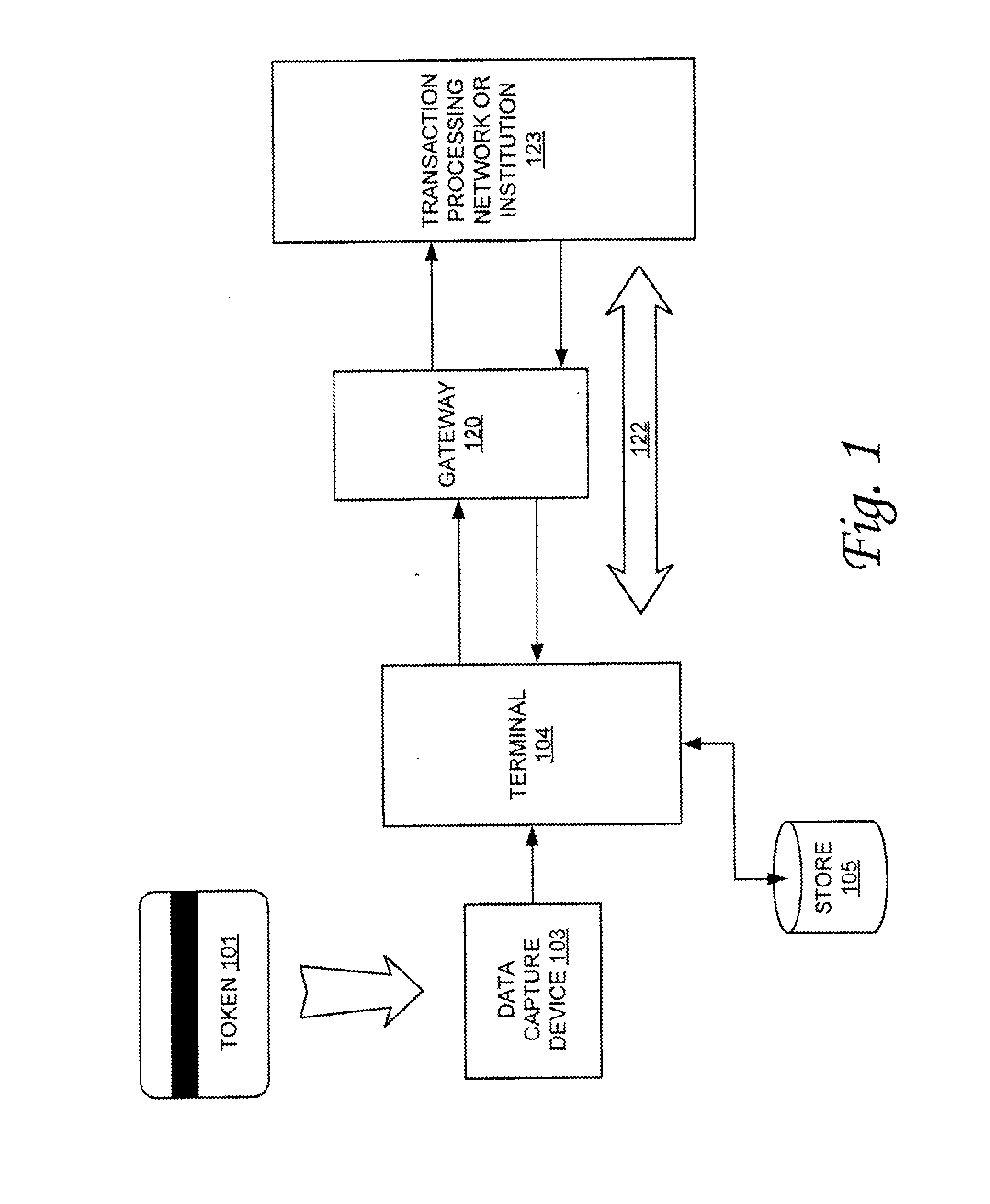
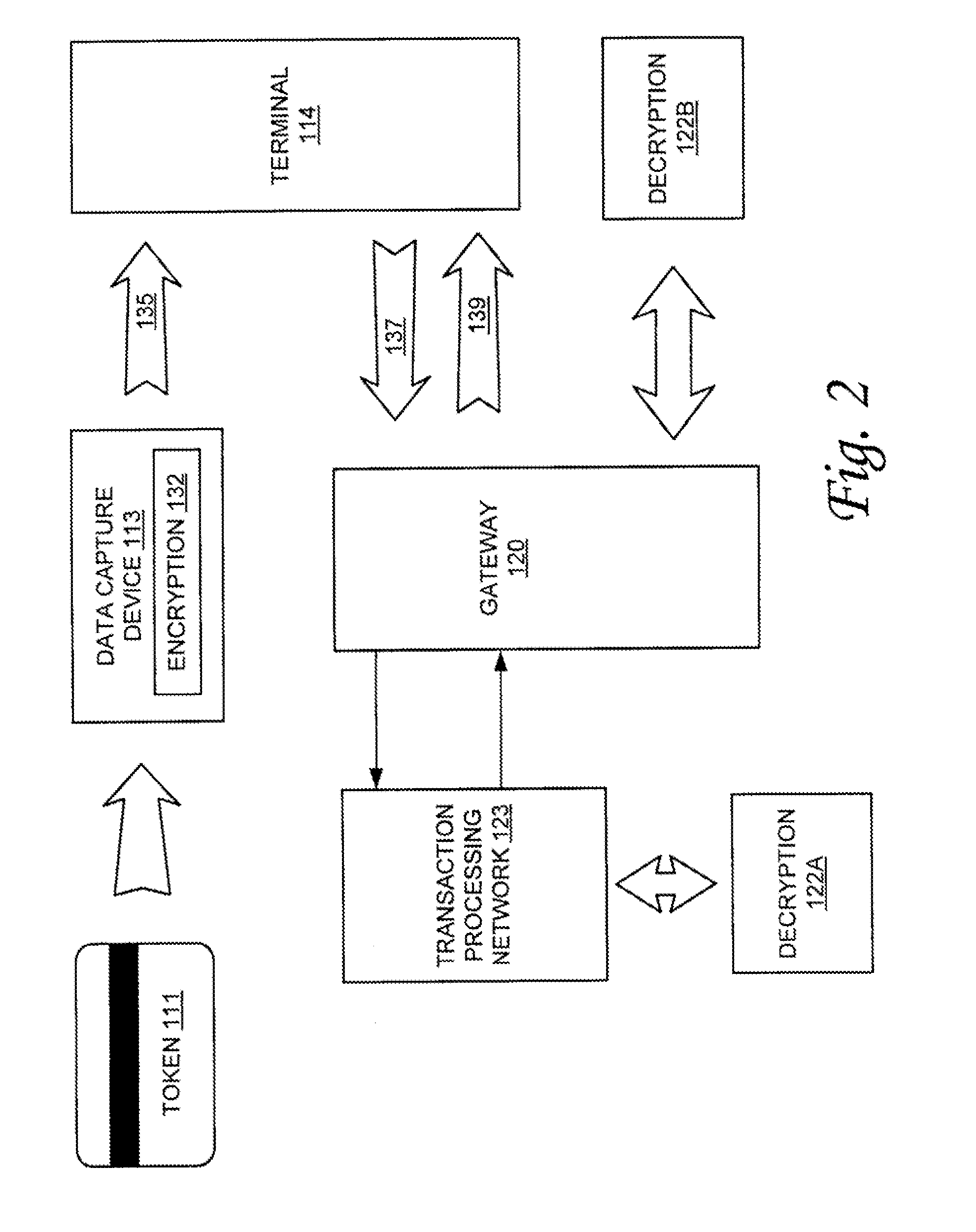
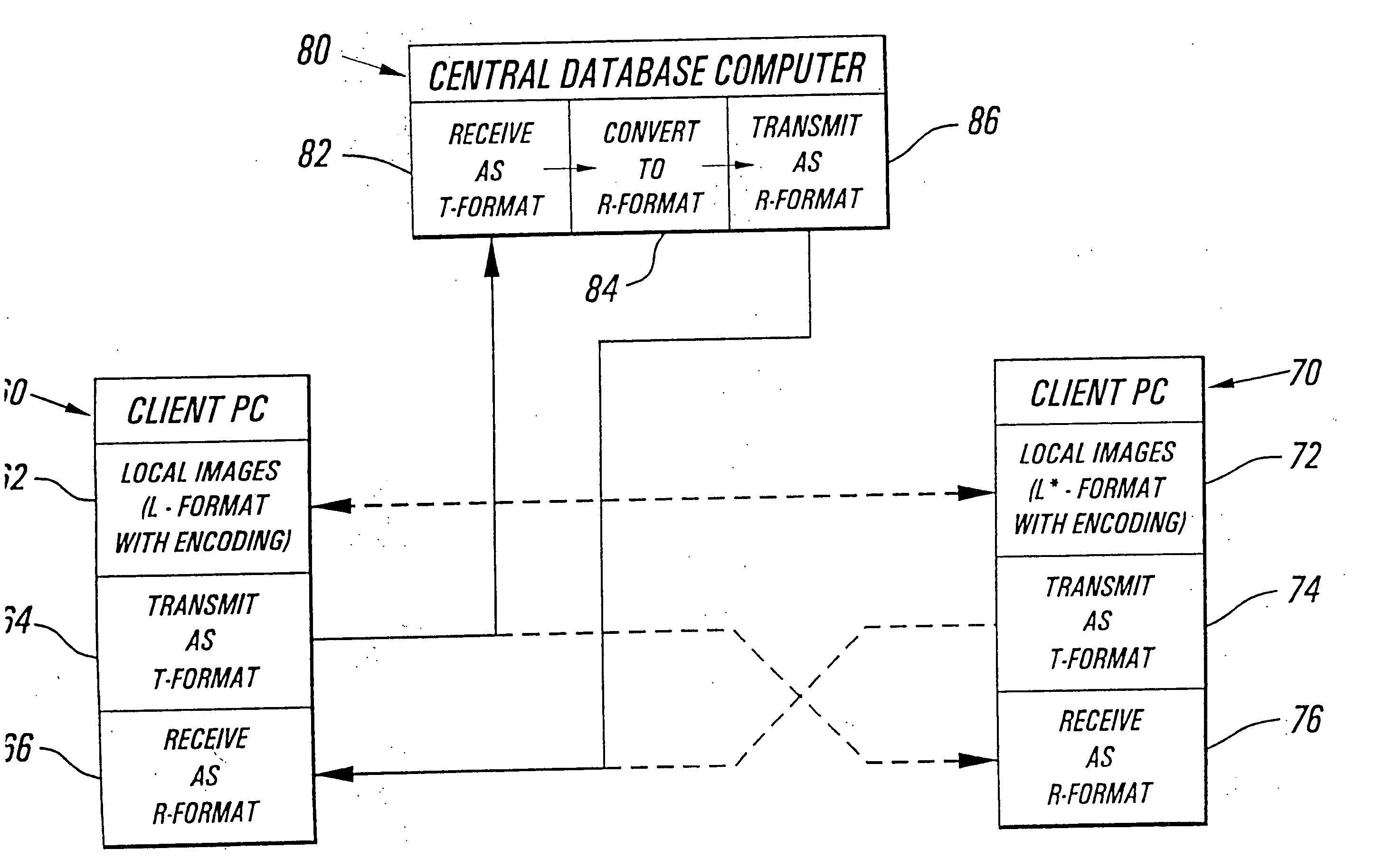
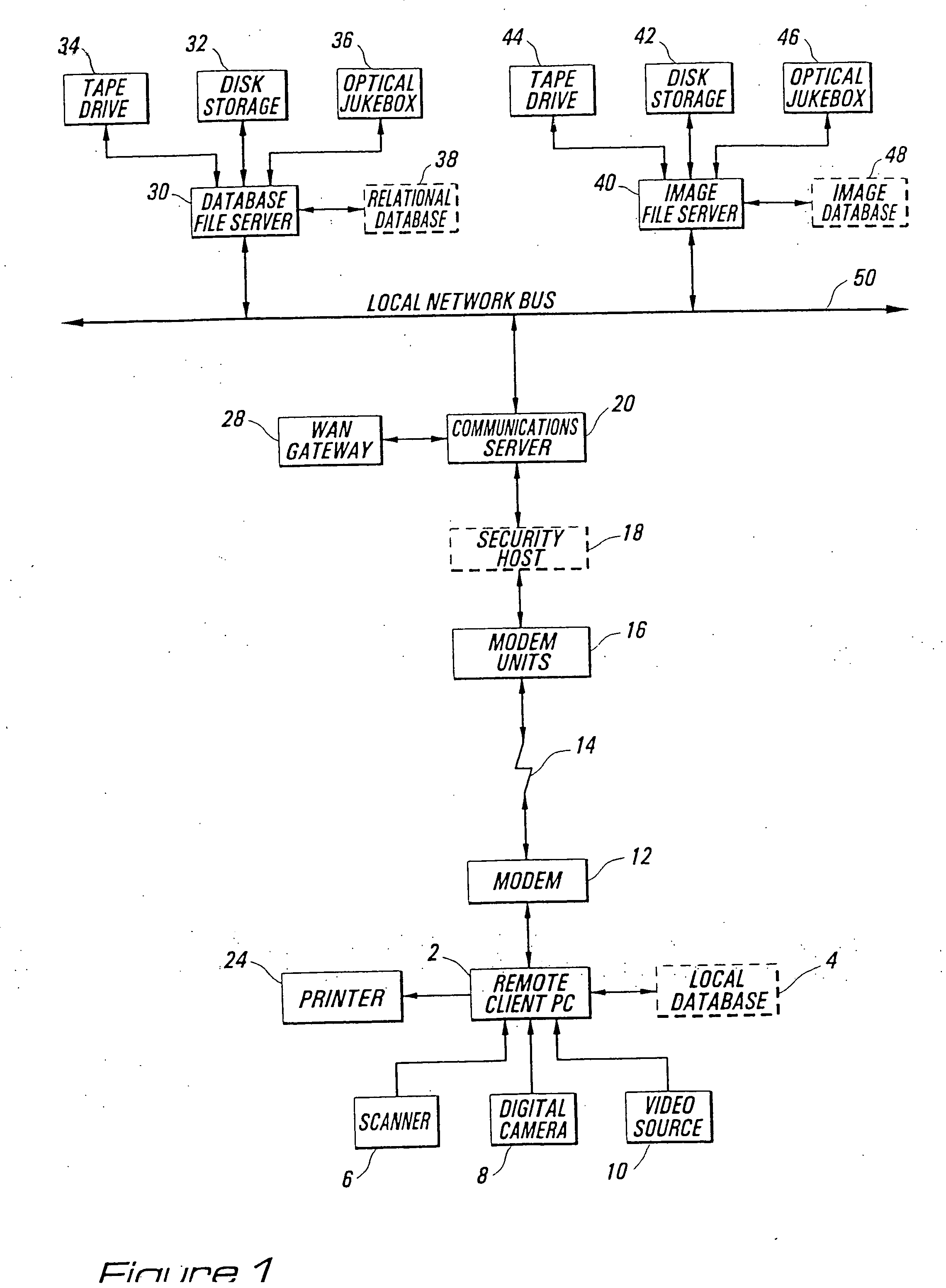
Secure identification system
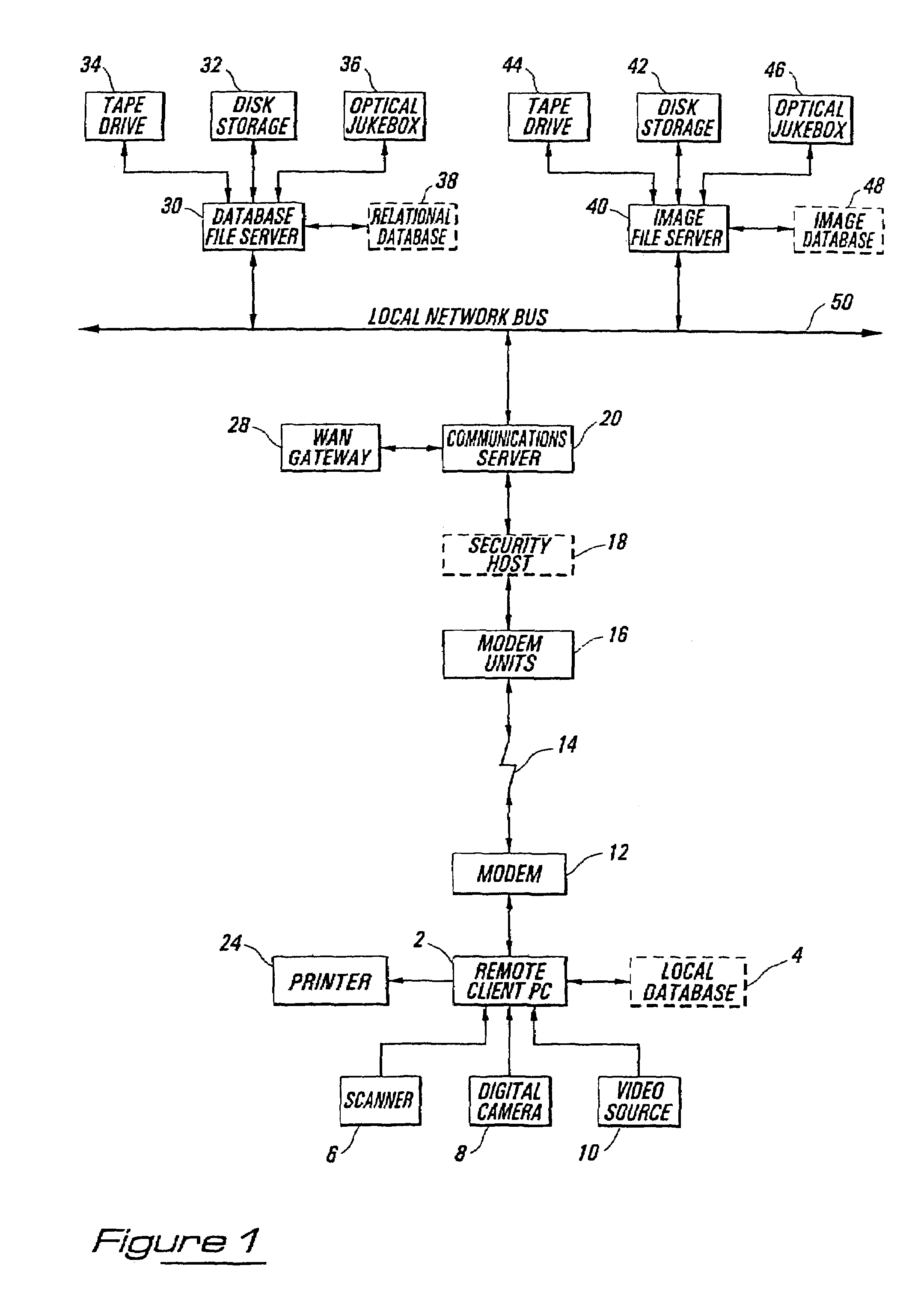
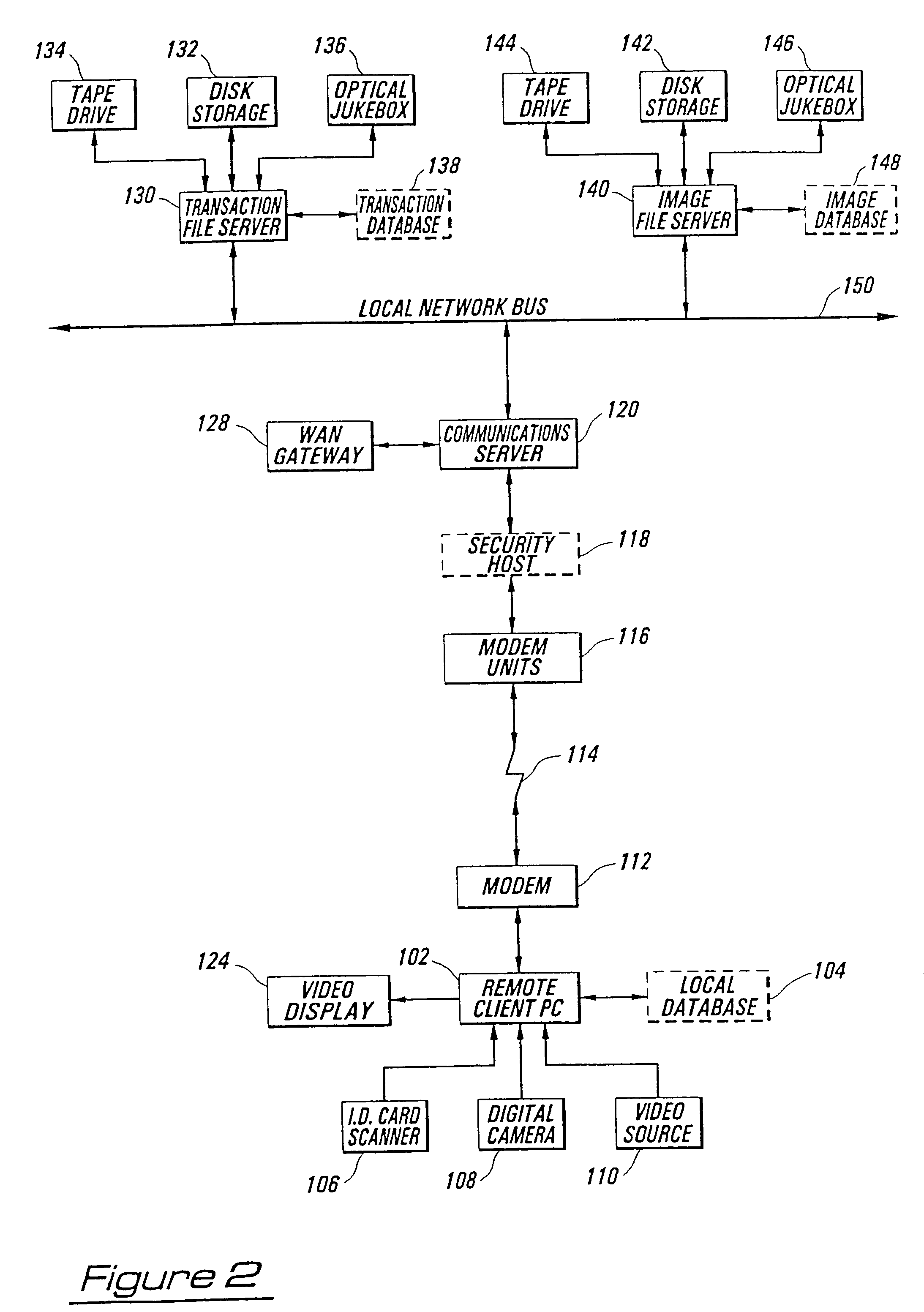
InactiveUS7418474B2Complete security measuresOvercome limitationsKey distribution for secure communicationMultiple digital computer combinationsData integrityRelational database
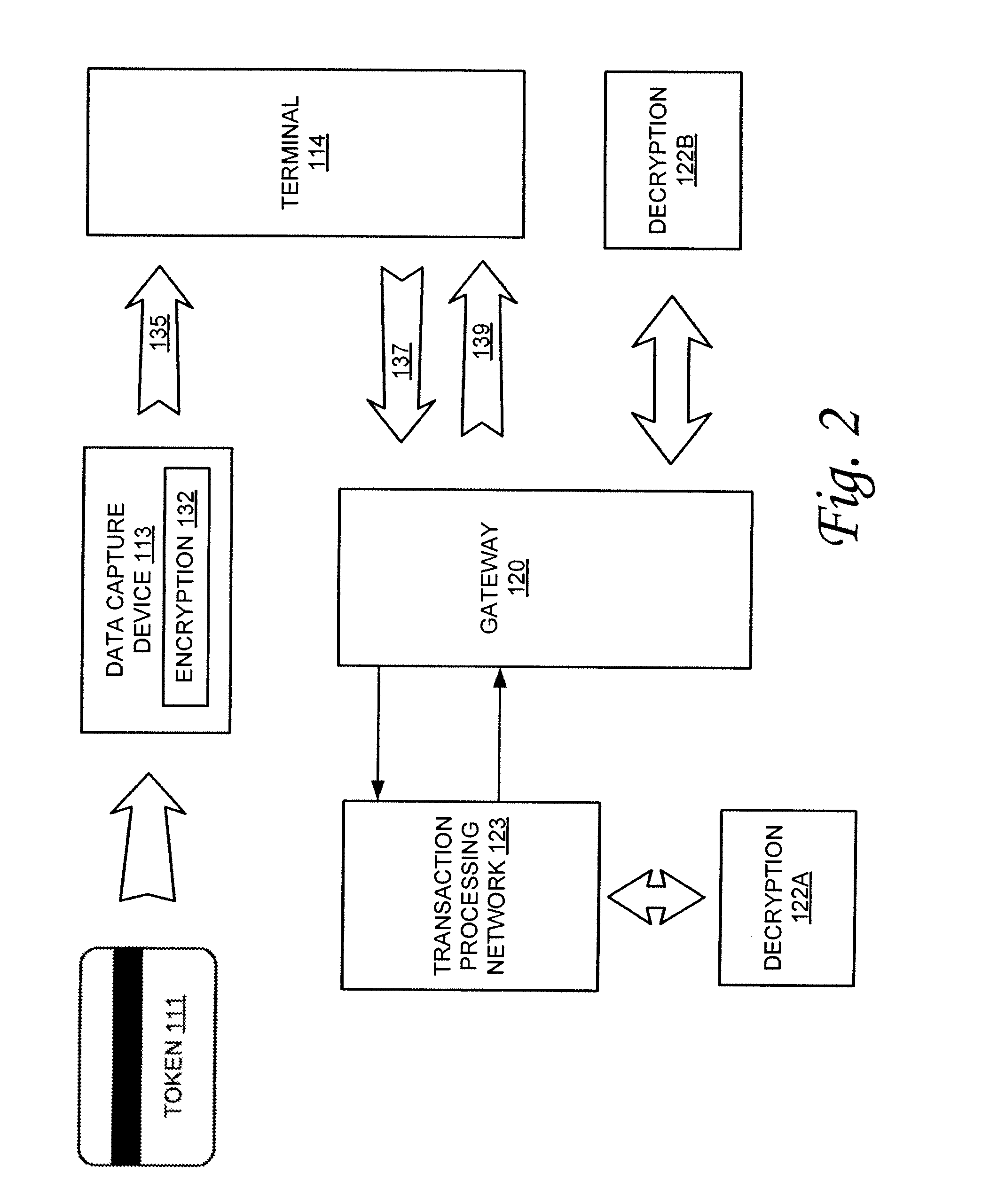
Methods and apparatus are described which provide secure interactive communication of text and image information between a central server computer and one or more client computers located at remote sites for the purpose of storing and retrieving files describing and identifying unique products, services, or individuals. Textual information and image data from one or more of the remote sites are stored separately at the location of the central server computer, with the image data being in compressed form, and with the textual information being included in a relational database with identifiers associated with any related image data. Means are provided at the central computer for management of all textural information and image data received to ensure that all information may be independently retrieved. Requests are entered from remote terminals specifying particular subject matter, and the system is capable of responding to multiple simultaneous requests. Textural information is recalled and downloaded for review, along with any subsequently requested image data, to be displayed at a remote site. Various modes of data and image formatting are also disclosed, including encryption techniques to fortify data integrity. The server computers may be interfaced with other computers to effect financial transactions, and images representing the subjects of transactions may be uploaded to the server computer to create temporary or permanent records of financial or legal transactions. A further feature of the system is the ability to associate an identification image with a plurality of accounts, transactions, or records.
Owner:SCHWAB BARRY H
Variable-length cipher system and method
ActiveUS20090310778A1Improve securityComplete security measuresAcutation objectsPayment architectureDefining lengthVariable length
Systems and methods for enciphering data are provided. In one embodiment, information is enciphered using a variable block length cipher that returns the encrypted symbol set in the same format as the plaintext symbol set. The cipher can be based on DES, AES or other block ciphers. In one example implementation a method for enciphering token information the invention provides for enciphering token information by constructing a tweak of a defined length using token information; converting the tweak to a bit string of a defined size to form a first parameter; converting a number of digits of plaintext to a byte string of a defined size to form a second parameter, wherein the number of digits converted varies; defining a data encryption standard key; applying the data encryption standard key to the first and second parameters; computing a specified number of encryption rounds; and receiving enciphered token information.
Owner:VERIFONE INC
Systems and Methods for Providing a Point of Sale Platform
InactiveUS20160034876A1Increase security measureComplete security measuresHand manipulated computer devicesBuying/selling/leasing transactionsObject storageObject based
This disclosure describes systems, methods, and computer-readable media related to providing a point of sale platform. In some embodiment, a point of sale (POS) device may receive information associated with an order and payment information associated with the order. The POS device may generate a first object based at least in part on the information associated with the order and a second object based at least in part on the payment information. The POS device may store the first object and the second object in a queue. The POS device may transmit the first object and the second object to a remote server.
Owner:FIRST DATA
Format preserving cipher system and method
InactiveUS20130168450A1Improve securityComplete security measuresSecret communicationSensing record carriersPlaintextDefining length
Systems and methods for enciphering data are provided. In one embodiment, information is enciphered using a variable block length cipher that returns the encrypted symbol set in any defined symbol set with a radix greater than or equal to the plaintext format. The cipher can be based on DES, AES or other block ciphers. In one example implementation a method for enciphering token information the invention provides for enciphering token information by constructing a tweak of a defined length using token information; converting the tweak to a bit string of a defined size to form a first parameter; converting a number of digits of plaintext to a byte string of a defined size to form a second parameter, wherein the number of digits converted varies; defining a data encryption standard key; applying the data encryption standard key to the first and second parameters; computing a specified number of encryption rounds; and receiving enciphered token information.
Owner:VON MUELLER CLAY W +1
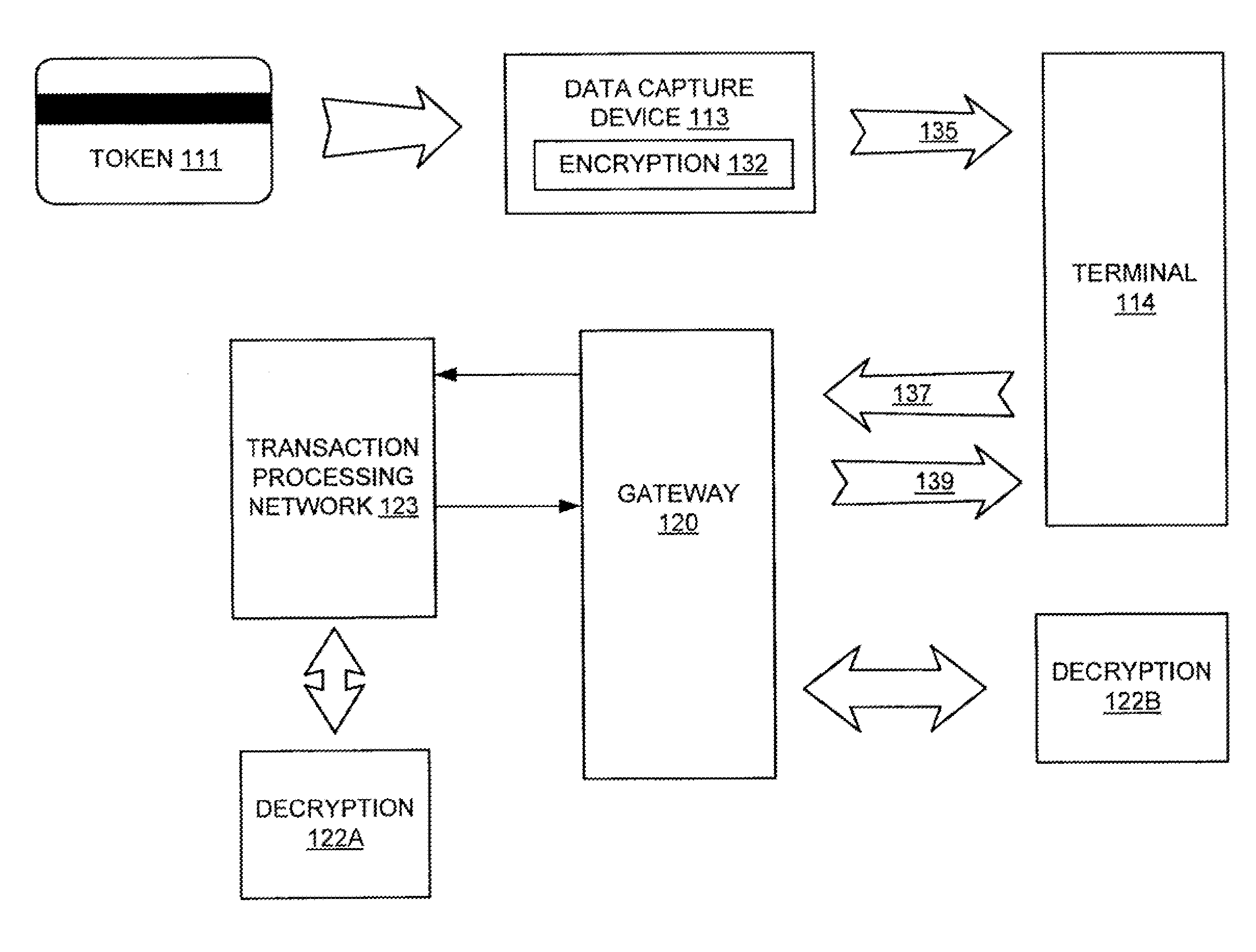
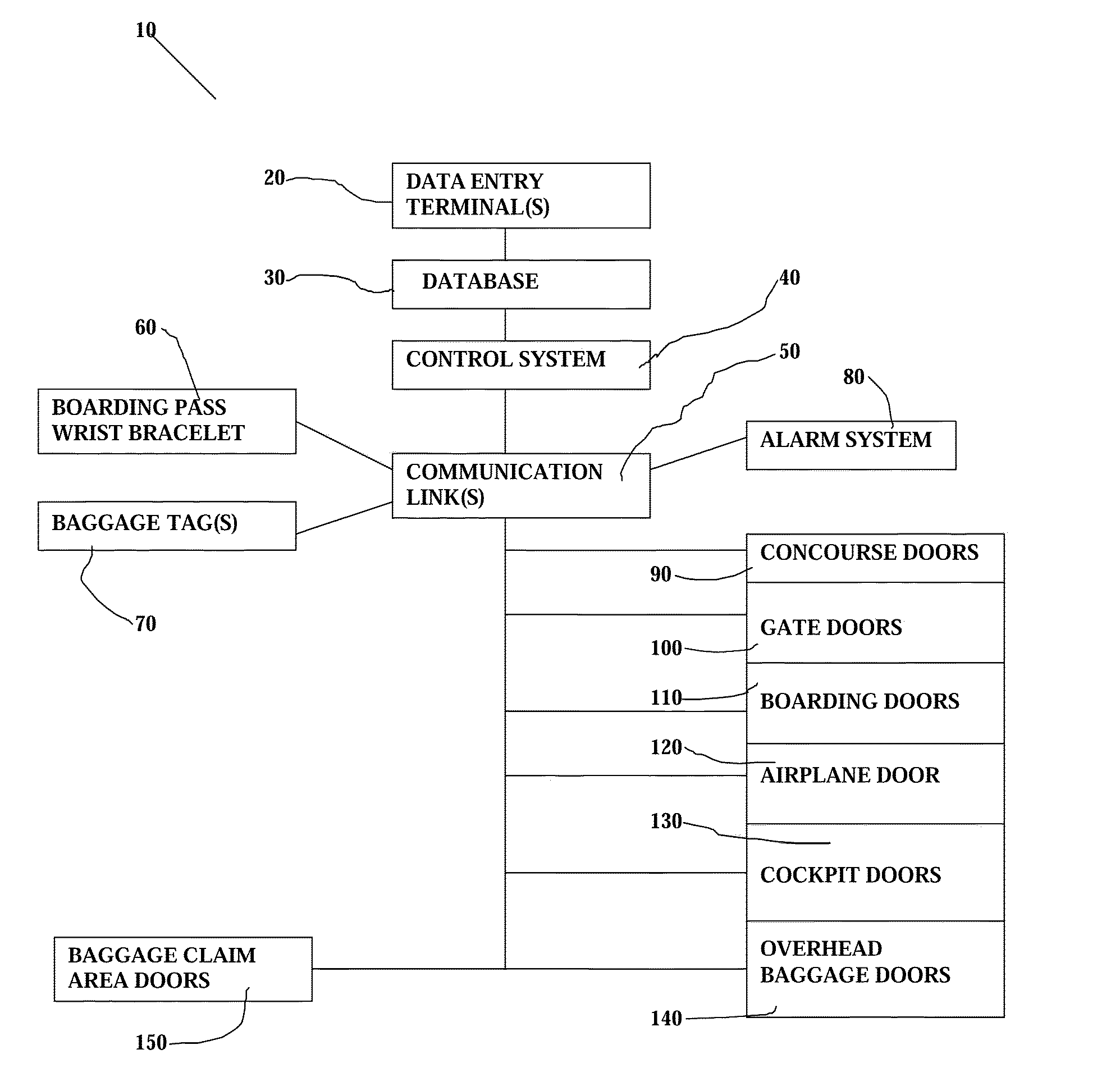
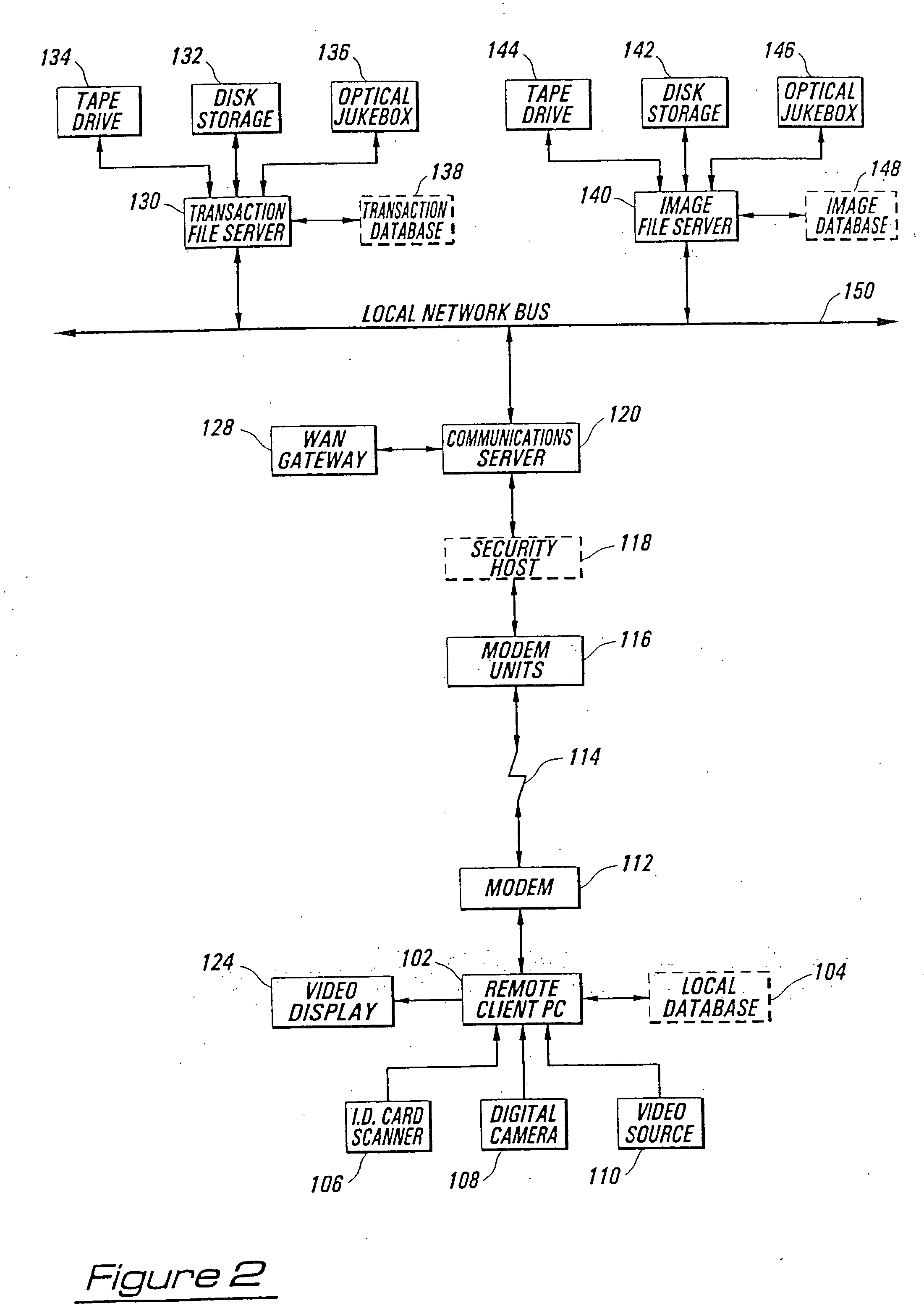
Security systems
InactiveUS20050083171A1Avoid easy removalAvoid security breachesProgramme controlElectric signal transmission systemsData displayTelecommunications link
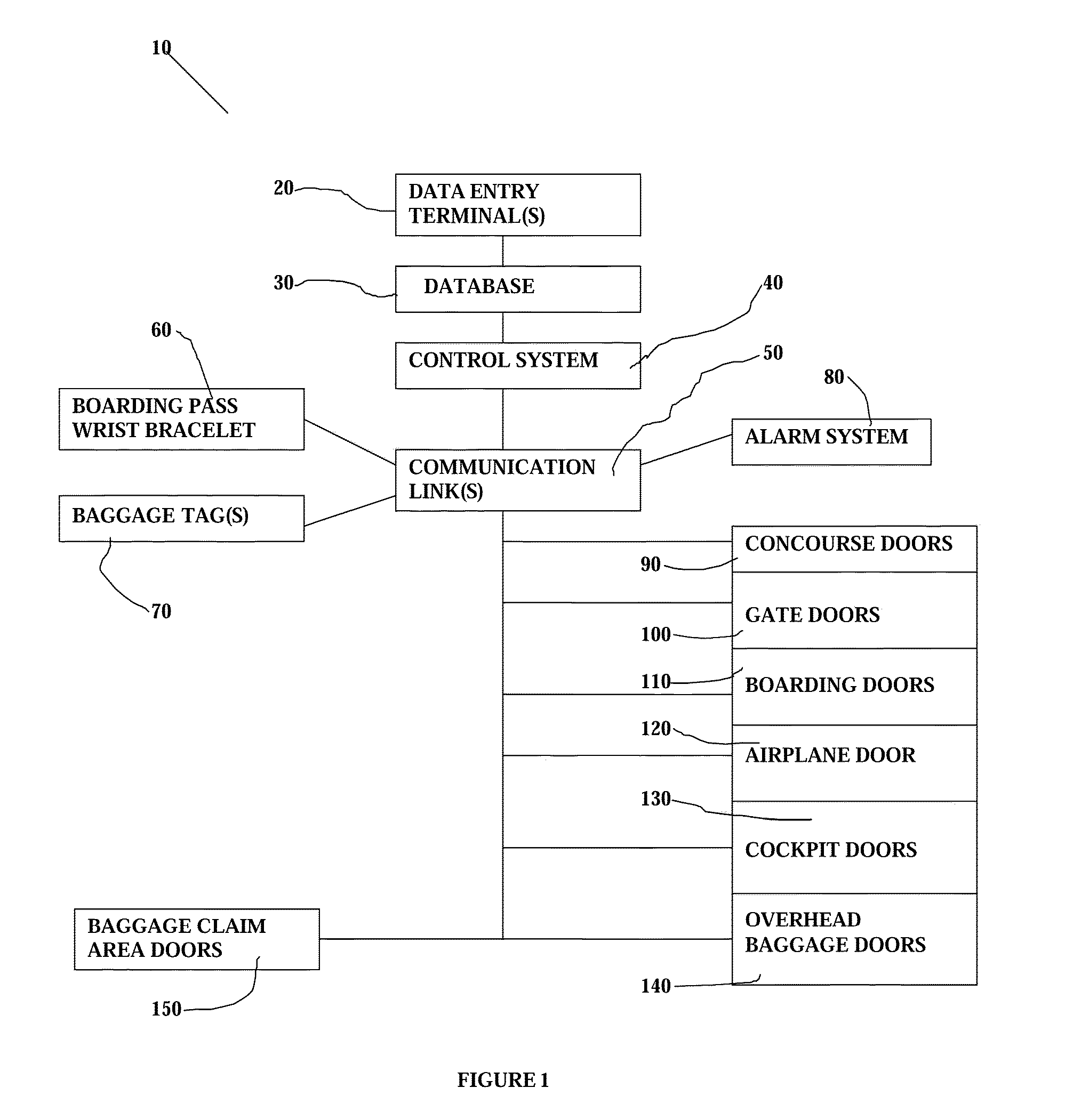
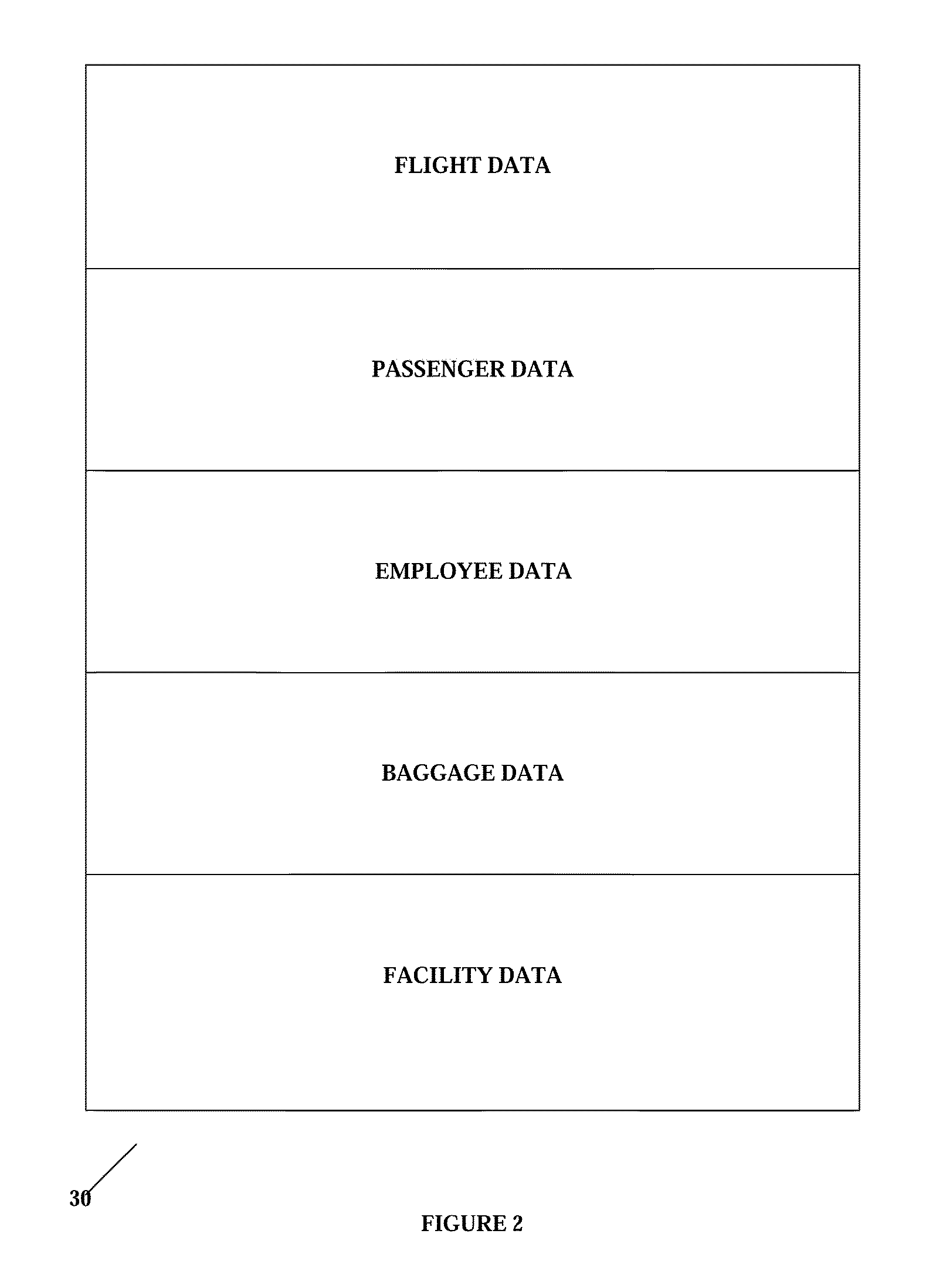
A security system includes machine readable passenger and employee wrist bracelets and baggage tags in conjunction with a computerized control system, electrically remotely actuated locks, alarms, and communications links to monitor and control the movement of passengers, employees, and baggage. The system prevents security breaches through lost security badges, misplaced keys, or access codes being given to or obtained by unauthorized individuals, and may include double doors having remotely actuated locks to selectively detain unauthorized individuals between a pair of locked double doors. The wrist bracelets and baggage tags are preferably constructed so as to be difficult to remove and may include electronic circuitry to provide an indication of tampering or removal. The system preferably includes a database associated with at least one data display and input terminal to maintain information pertaining to flight data, passenger data, employee data, baggage data, and facility data. The system may employ a relational type of database structure to provide convenient access to all types of data pertaining to a particular individual, flight, bag, or facility. The system may include GPS sensors to enable current real time display of status and location information associated with a particular bag, flight, or individual.
Owner:HAMILTON SHARON
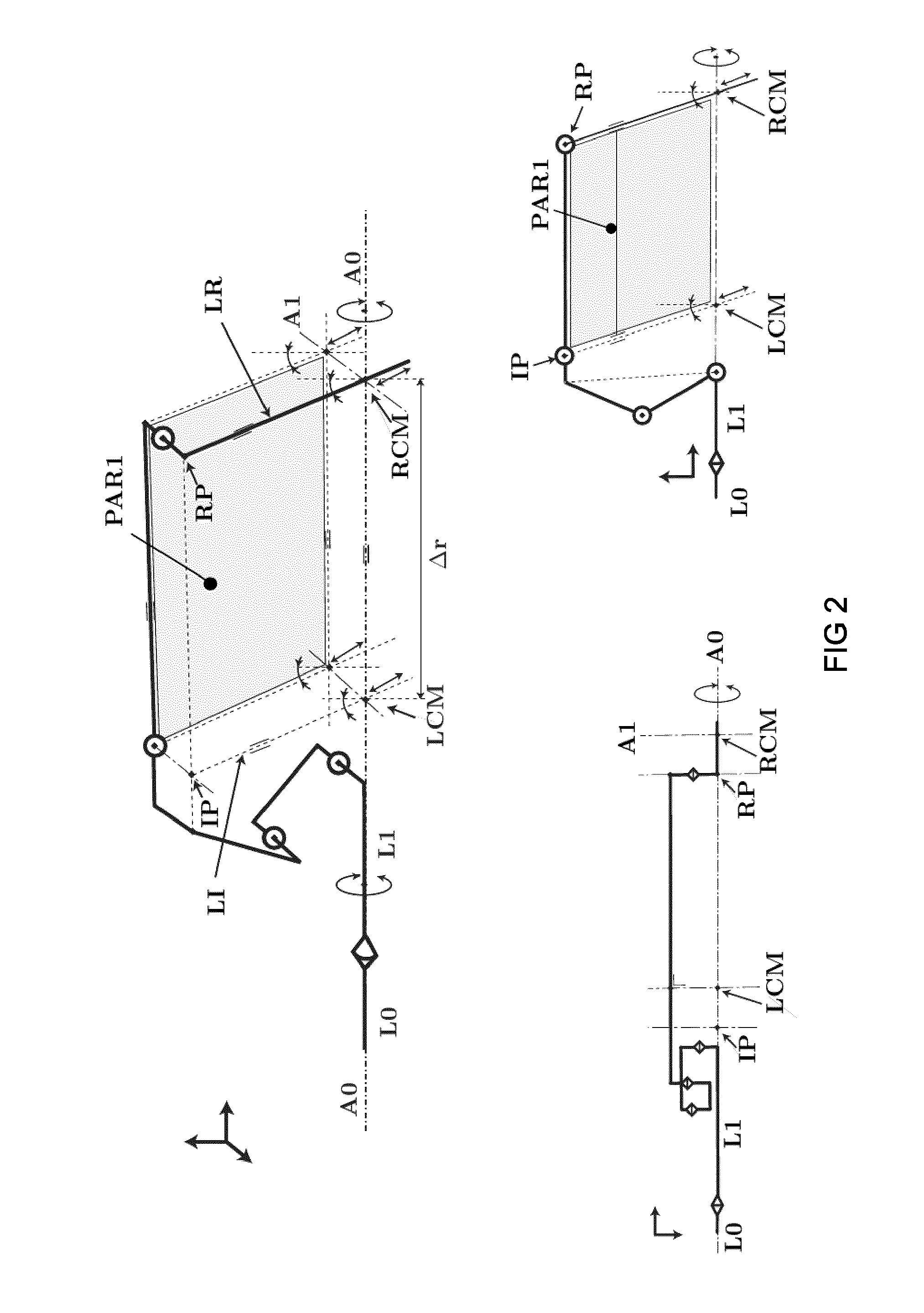
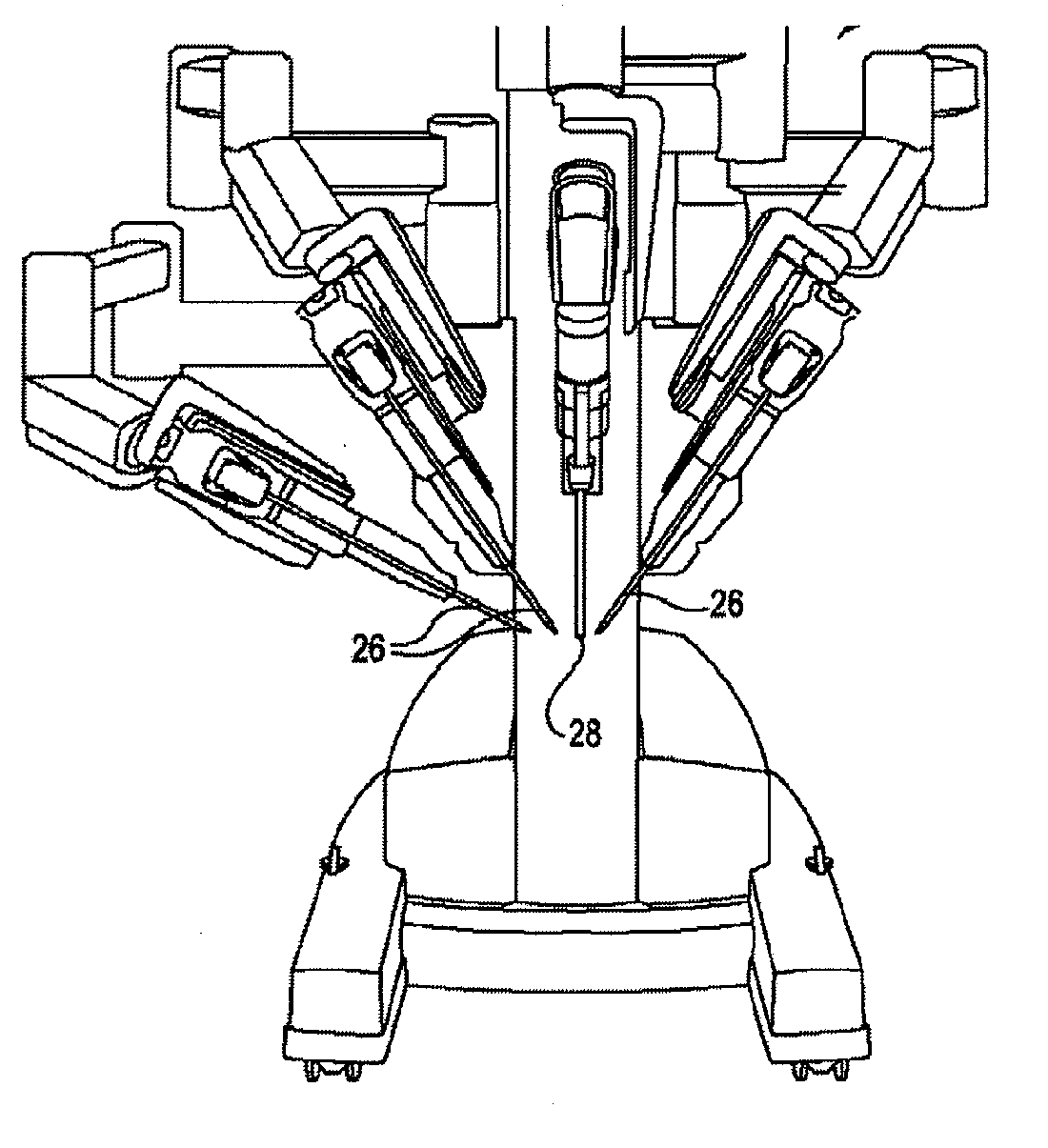
An apparatus for generating motion around a remote centre of motion
ActiveUS20150351857A1Easy to controlEasy to manufactureProgramme-controlled manipulatorDiagnosticsEngineeringTarsal Joint
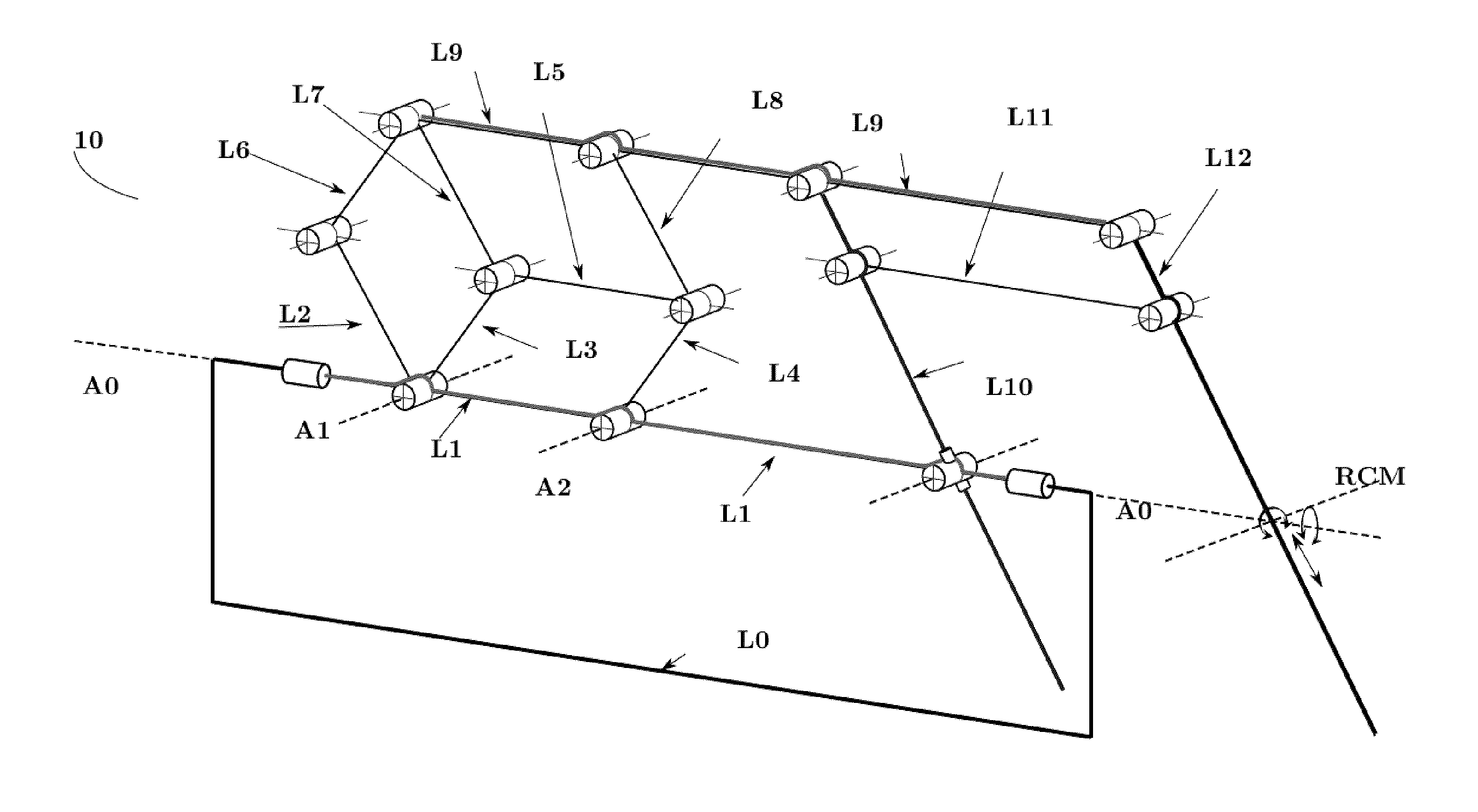
Apparatus (10) for generating motion around a remote center of motion (RCM), comprising a distal link (L12, LR) arranged to revolve about the remote center of motion and to translate through the remote center of motion, a proximal link (L10, LI) arranged to revolve about a proximal center of motion (LCM), coupled to a base link, through a rotational joint (150) and a sliding joint (181), a first mechanism comprising a first link (L9, BE) pivotally coupled to the proximal link (L10) and to the distal link (L12) and operable to transfer motion of the proximal link relative to the proximal center of motion to a motion of the distal link relative to the remote center of motion by maintaining a parallelogram (PAR1), and a second mechanism operable to move the first link with two degrees of freedom in a plane parallel to the plane of motion of the proximal link, characterised in that the second mechanism comprises one link or a serial connection of links (L4, L8, L3, L7, L2, L6) connecting the base link to the first link, configured to have an orientation of instant motion which is different from an orientation of instant motion of the proximal link (L10), relative to the base link.
Owner:KATHOLIEKE UNIV LEUVEN
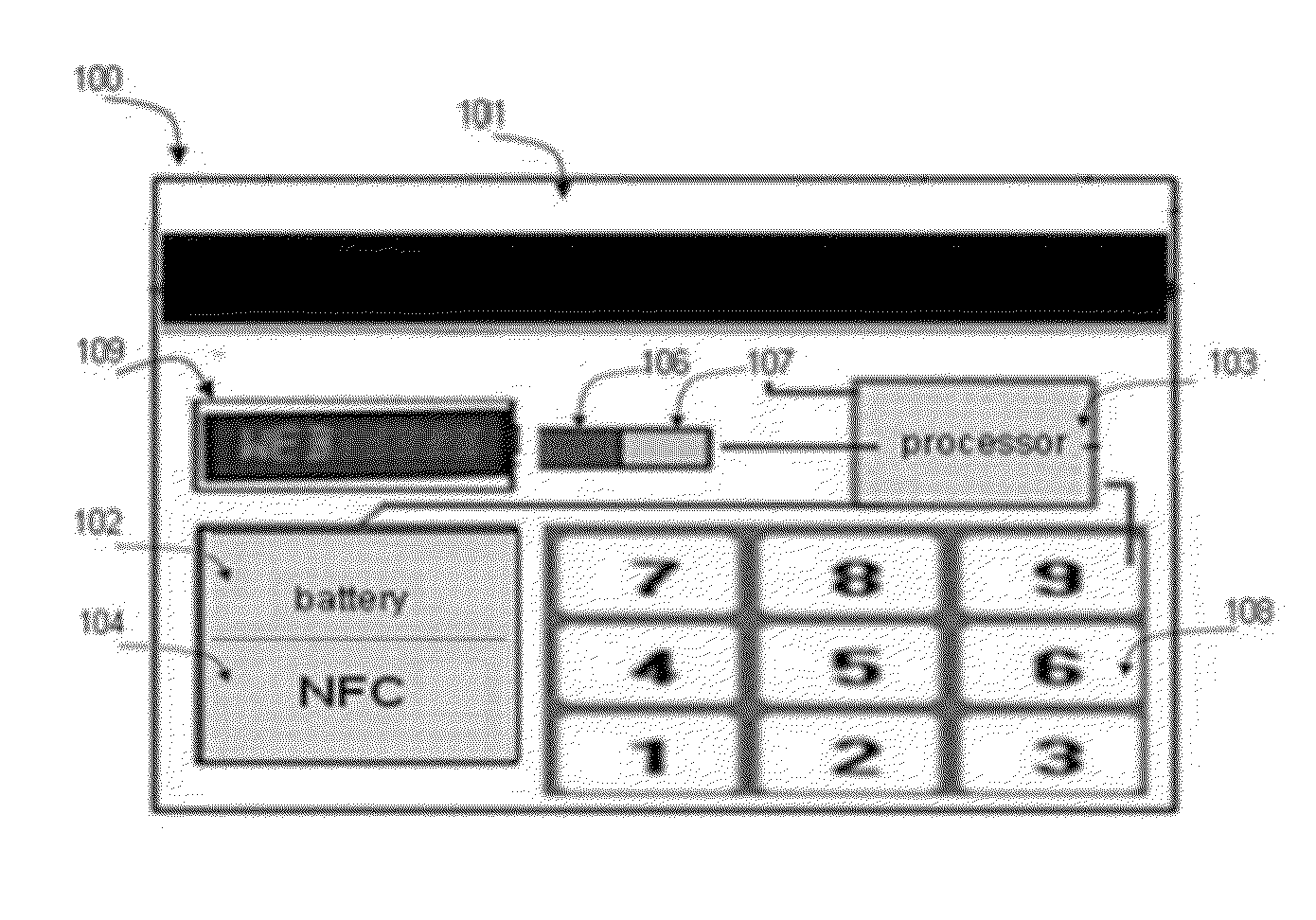
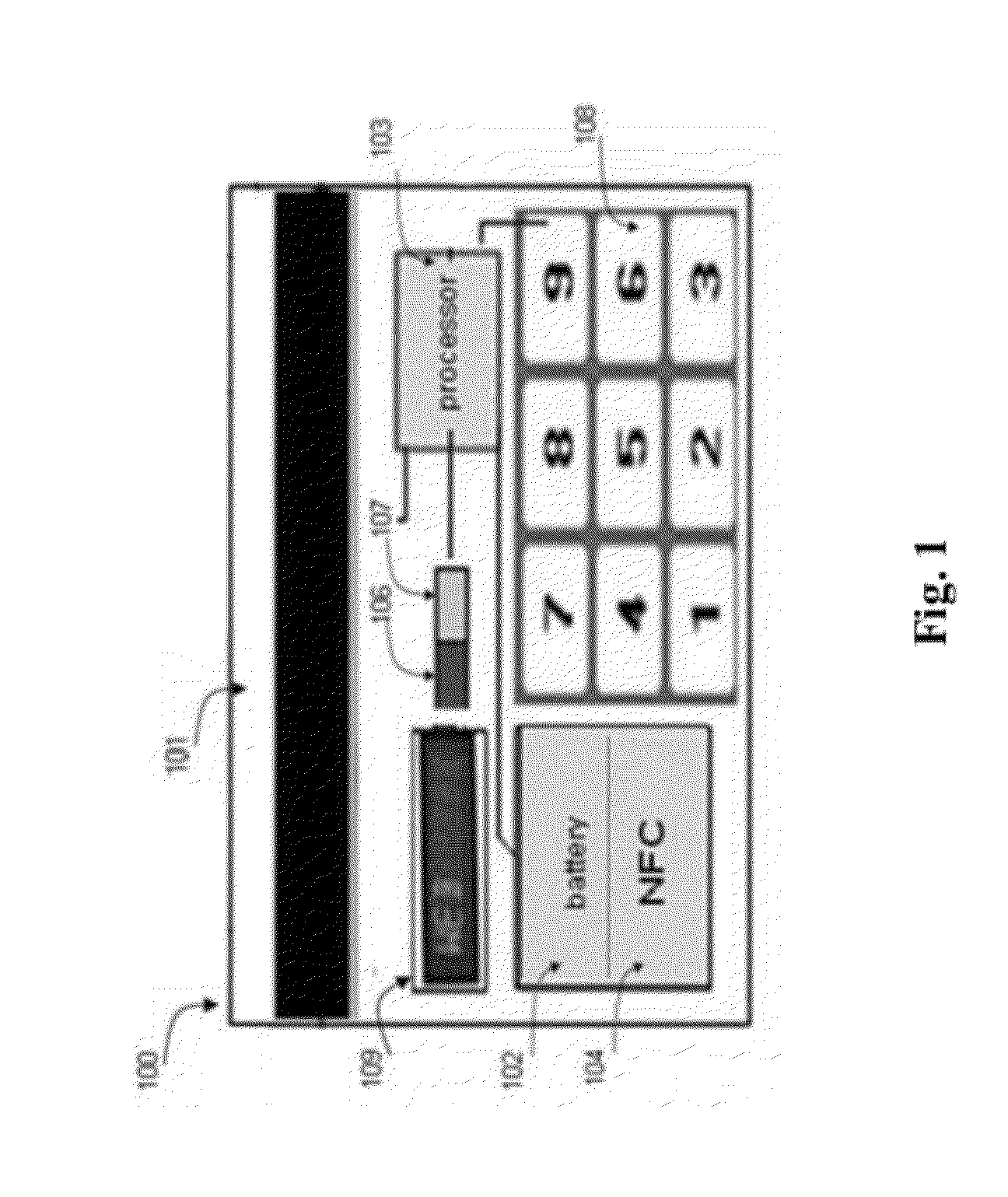
Transaction Card with dynamic CVV
InactiveUS20120153028A1Easy to useComplete security measuresAcutation objectsPayment architectureComputer hardwareLiquid-crystal display
The transaction card of the invention comprises a Card Verification Value (CVV) generator unit that generates a new CVV code each time the card user is invited to enter his CVV code, typically in a remote transaction. The CVV code is displayed on a screen on the transaction card. The screen can be a liquid crystal display (LCD) screen or any similar or newer display technology.
Owner:POZNANSKY AMIR +1
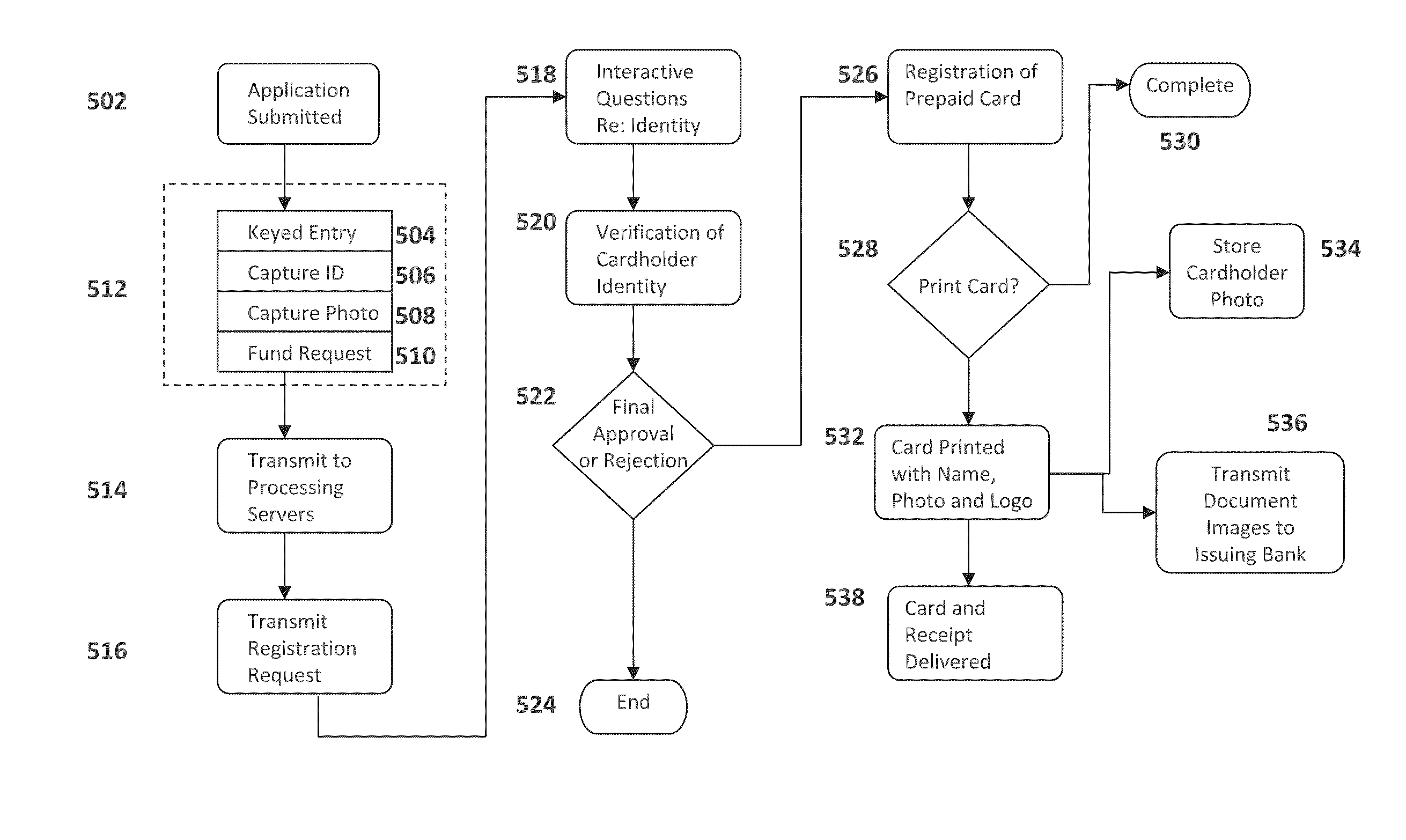
System and method for immediate issuance of an activated prepaid card with improved security measures
InactiveUS20110196753A1Complete security measuresEliminate useAcutation objectsFinanceSecurity MeasureCustomer identification
A system and method for immediate issuance of a prepaid transaction card having increased security measures. The identity of the applicant is verified and checked against a database in accordance with Customer Identification Program, Sarbanes-Oxley and the USA Patriot Act in real time. Authorized applicants receive a printed prepaid debit card bearing name and photograph immediately at the point of sale.
Owner:PAY O MATIC +1
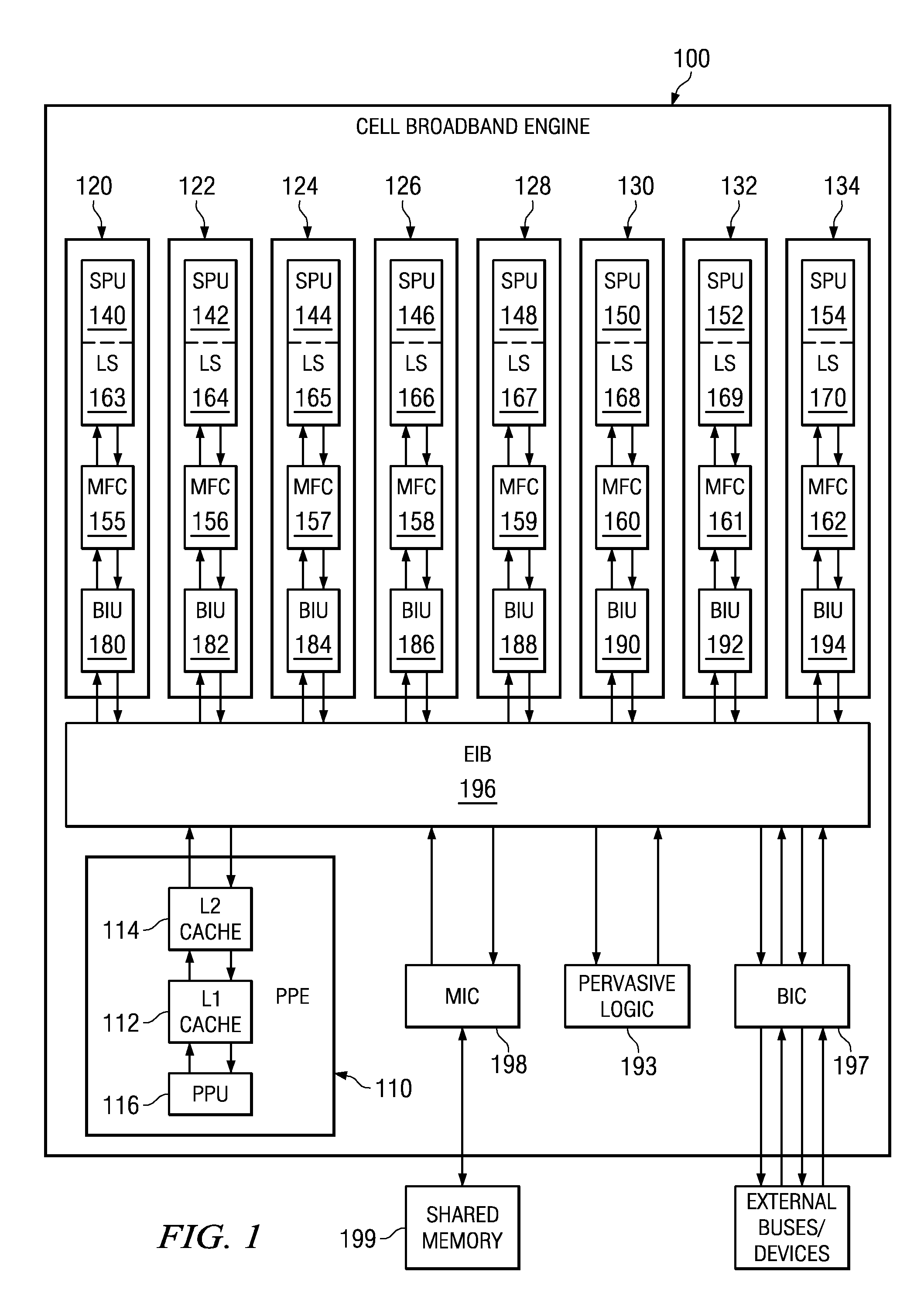
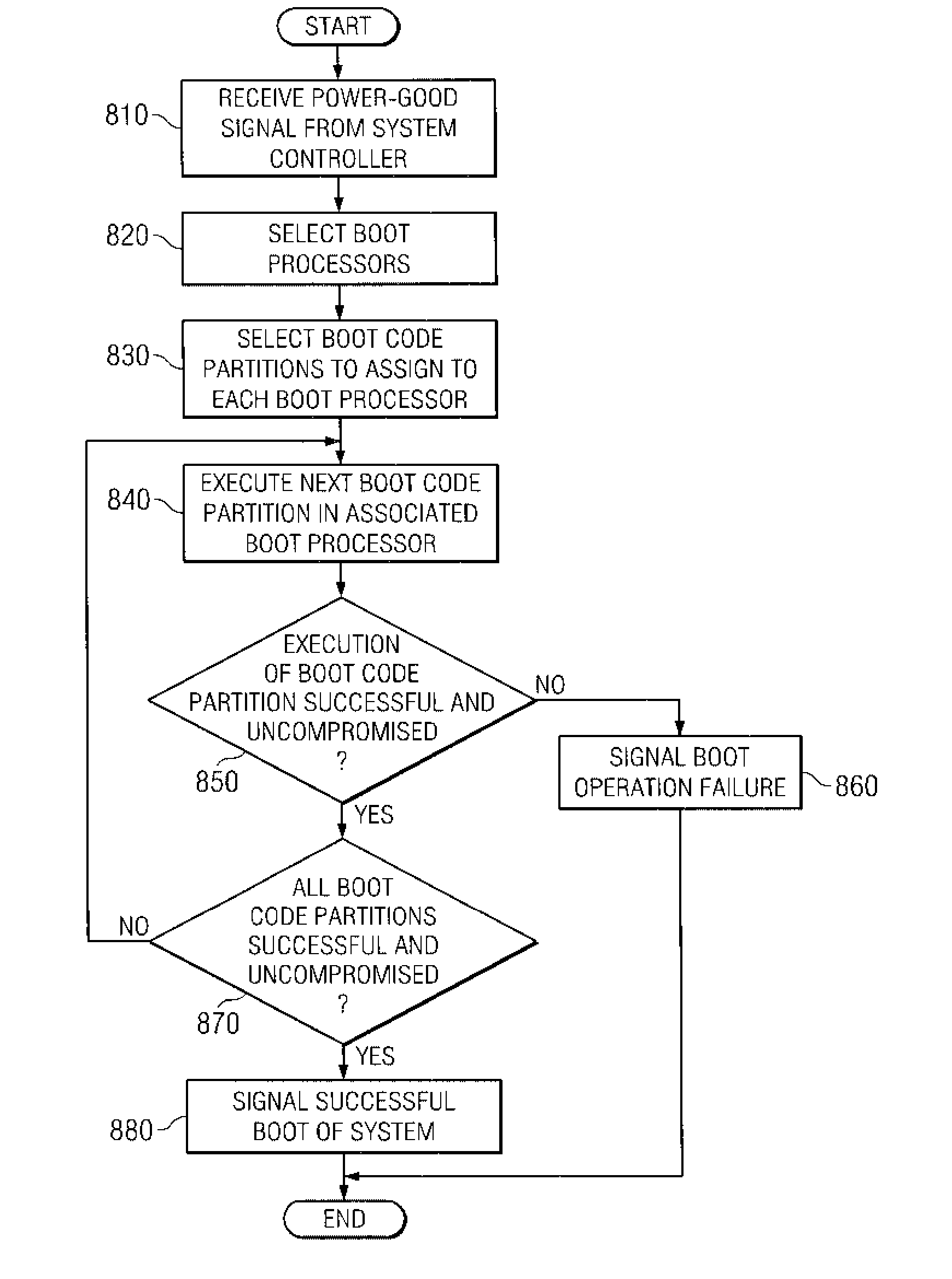
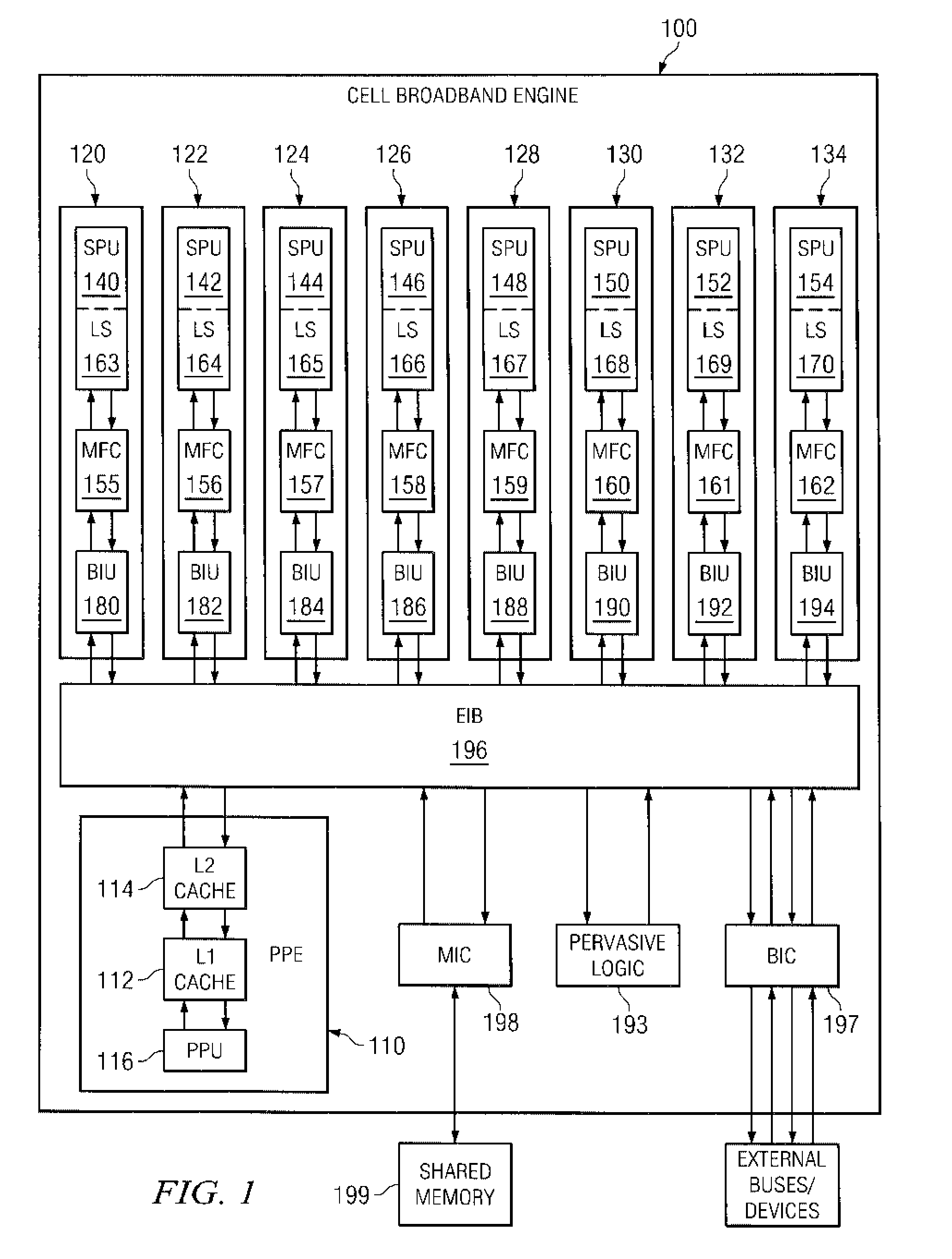
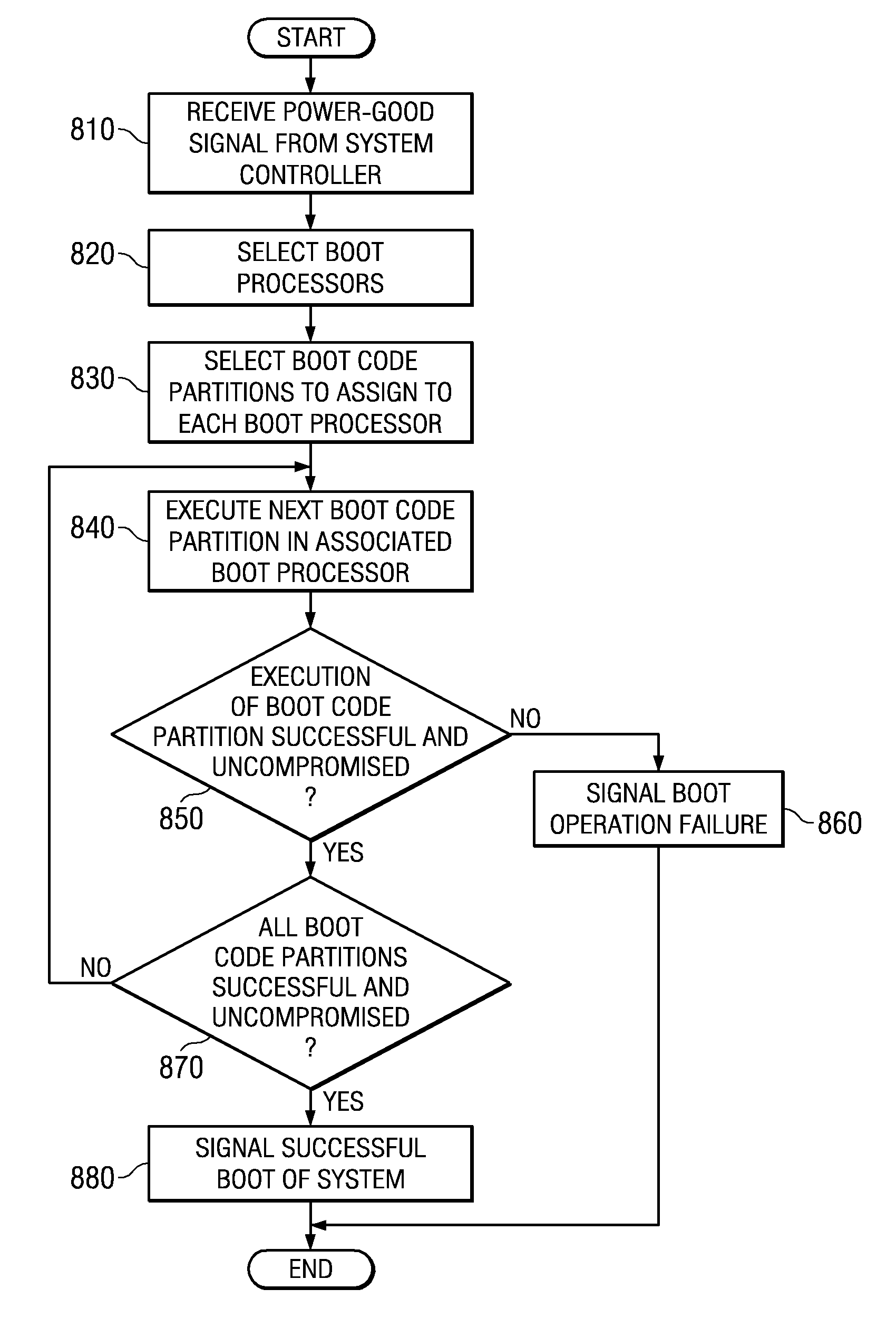
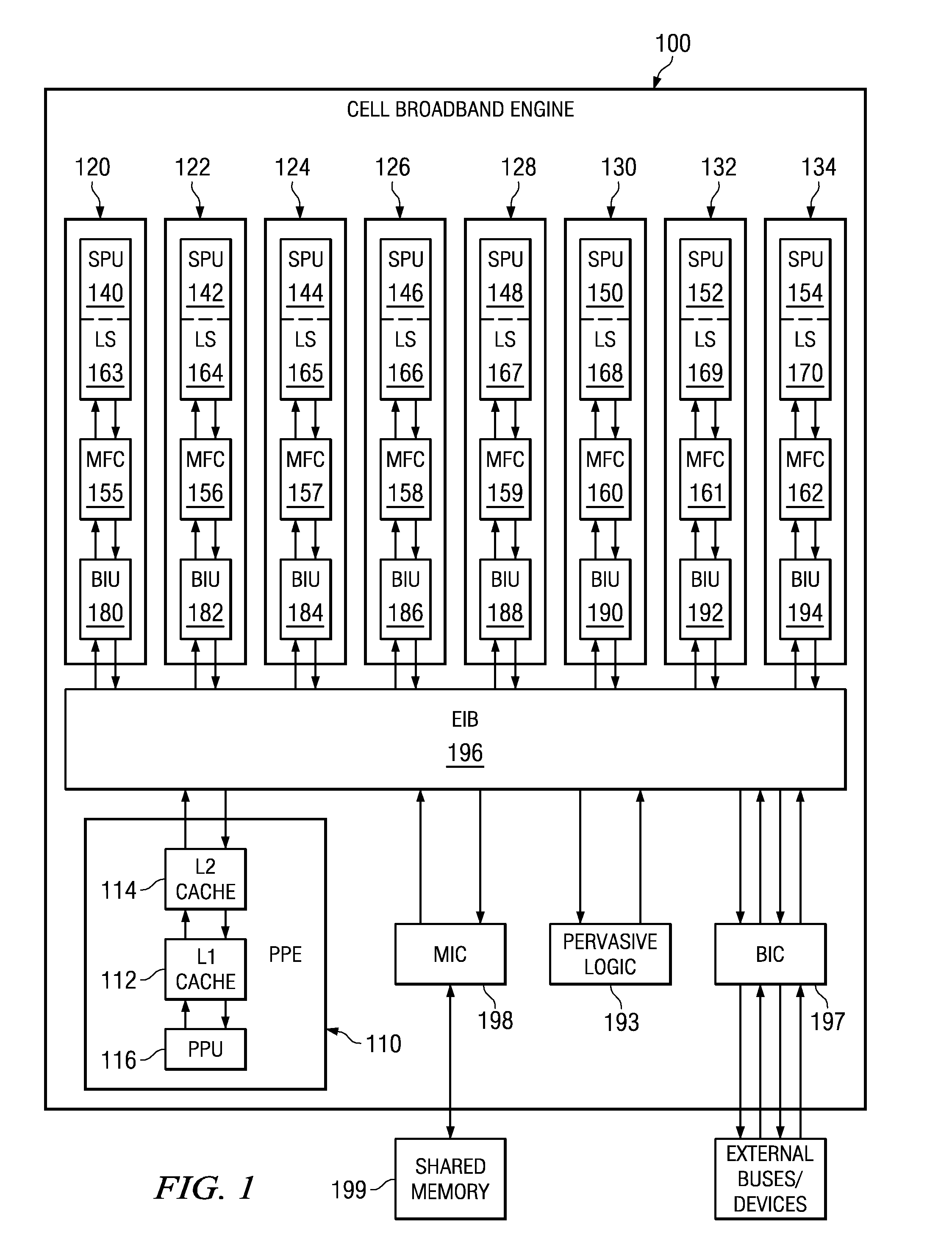
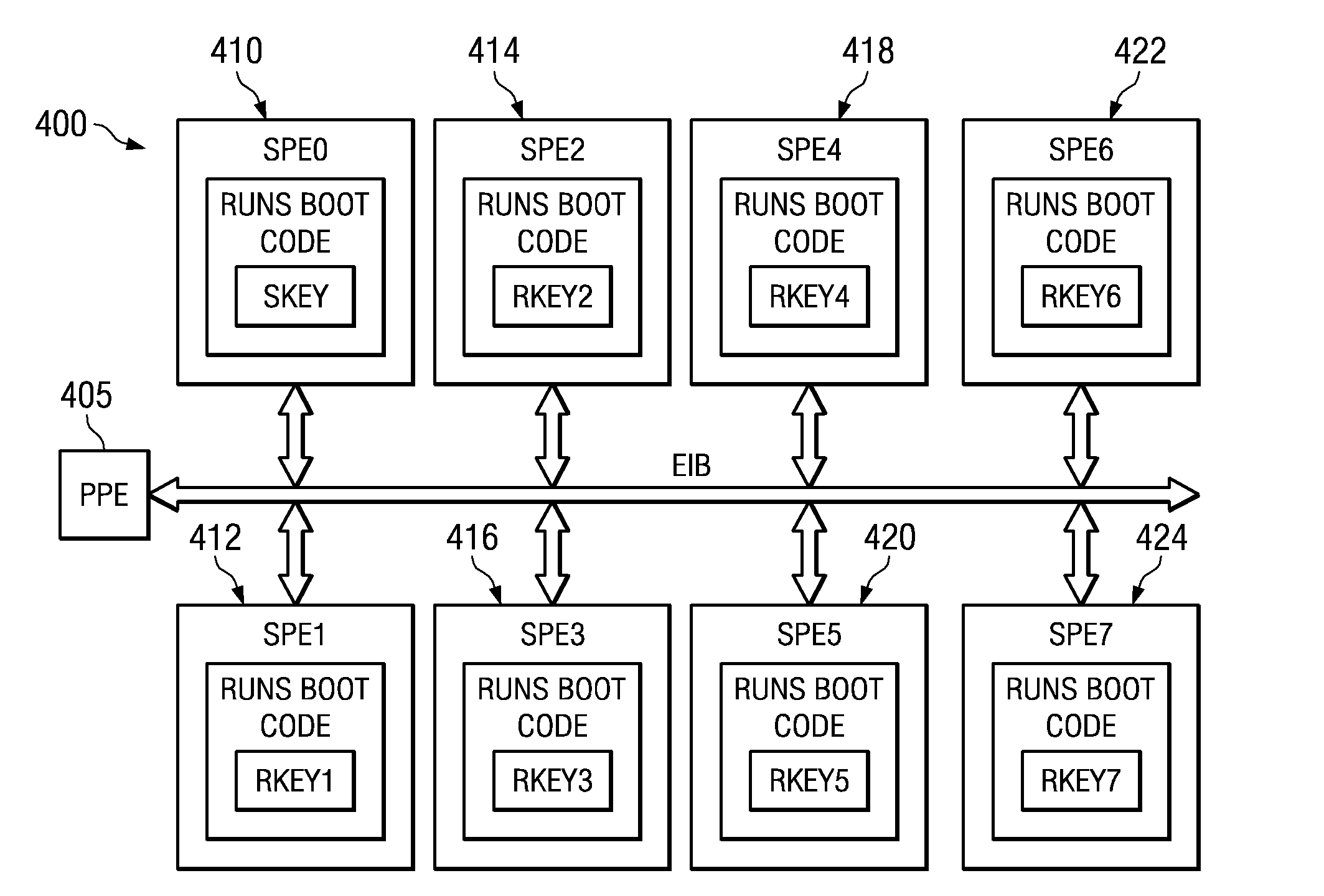
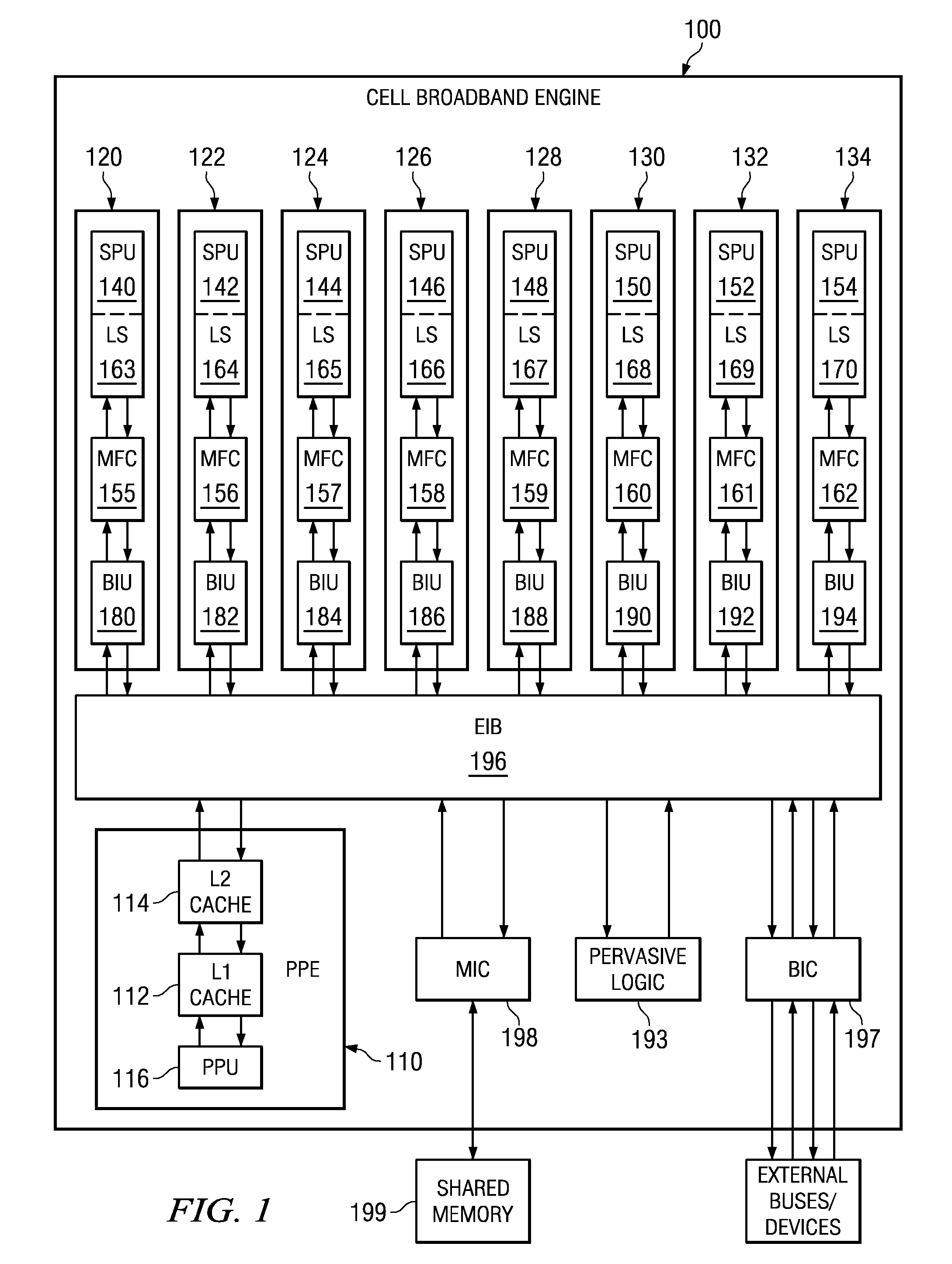
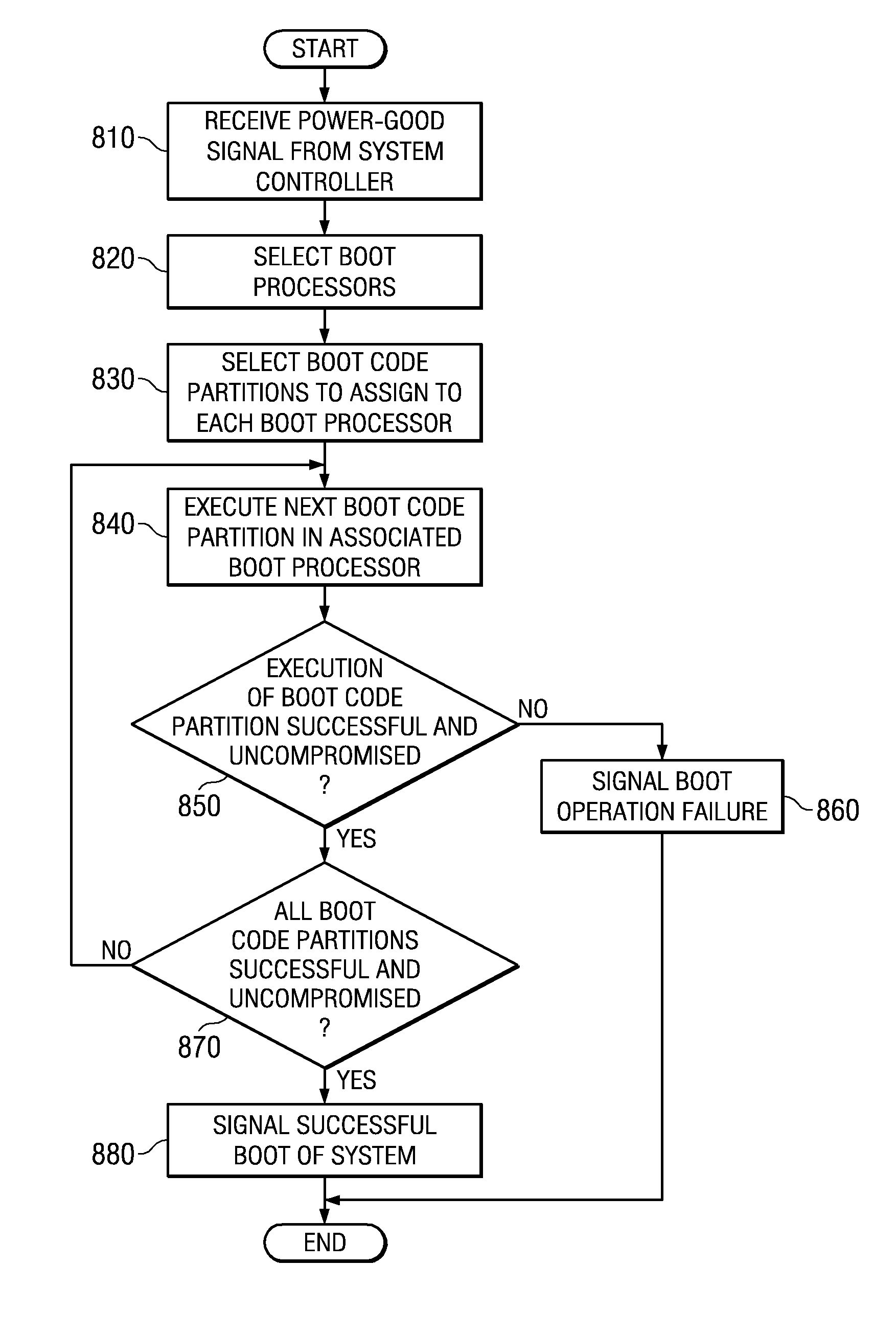
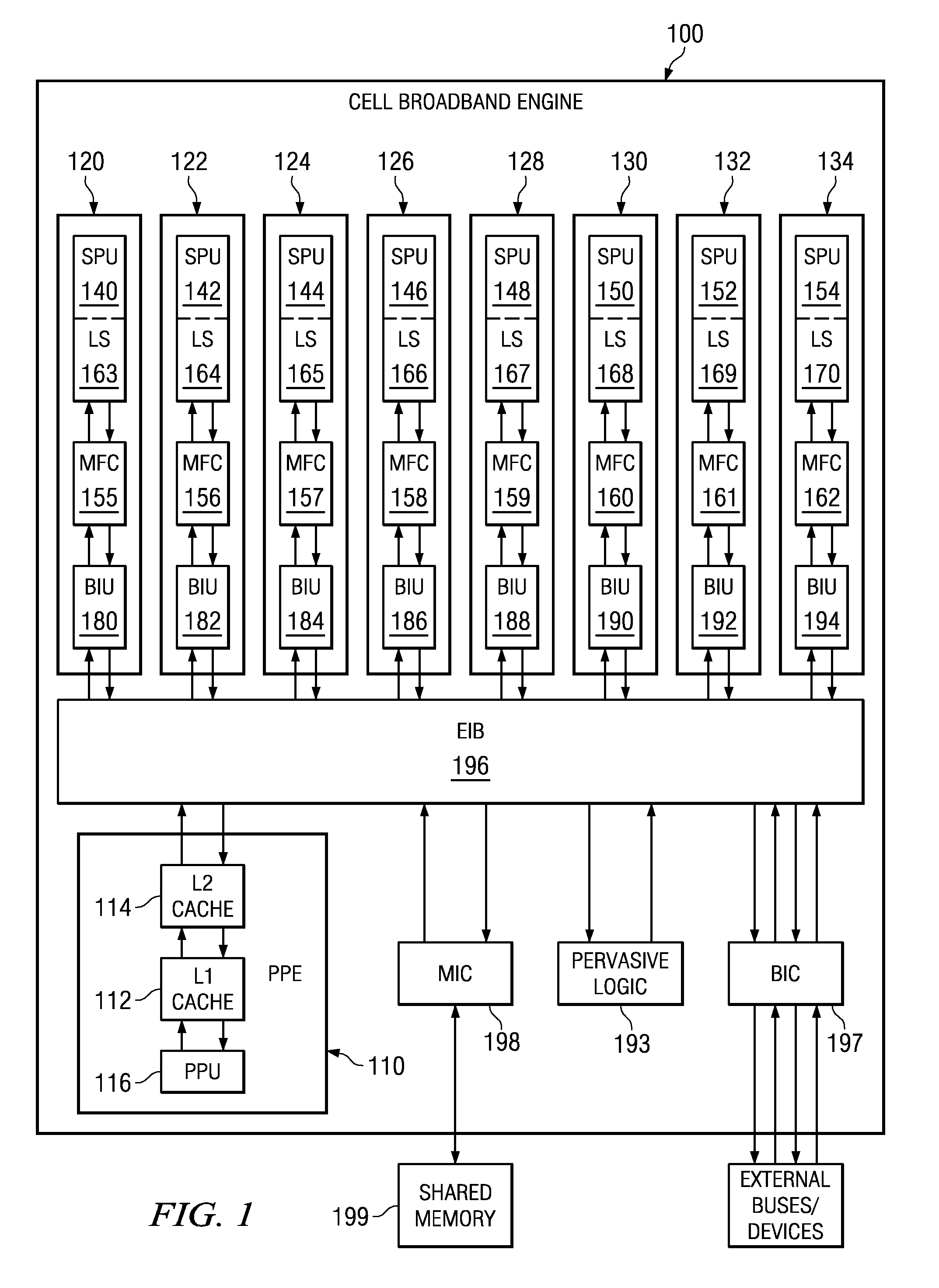
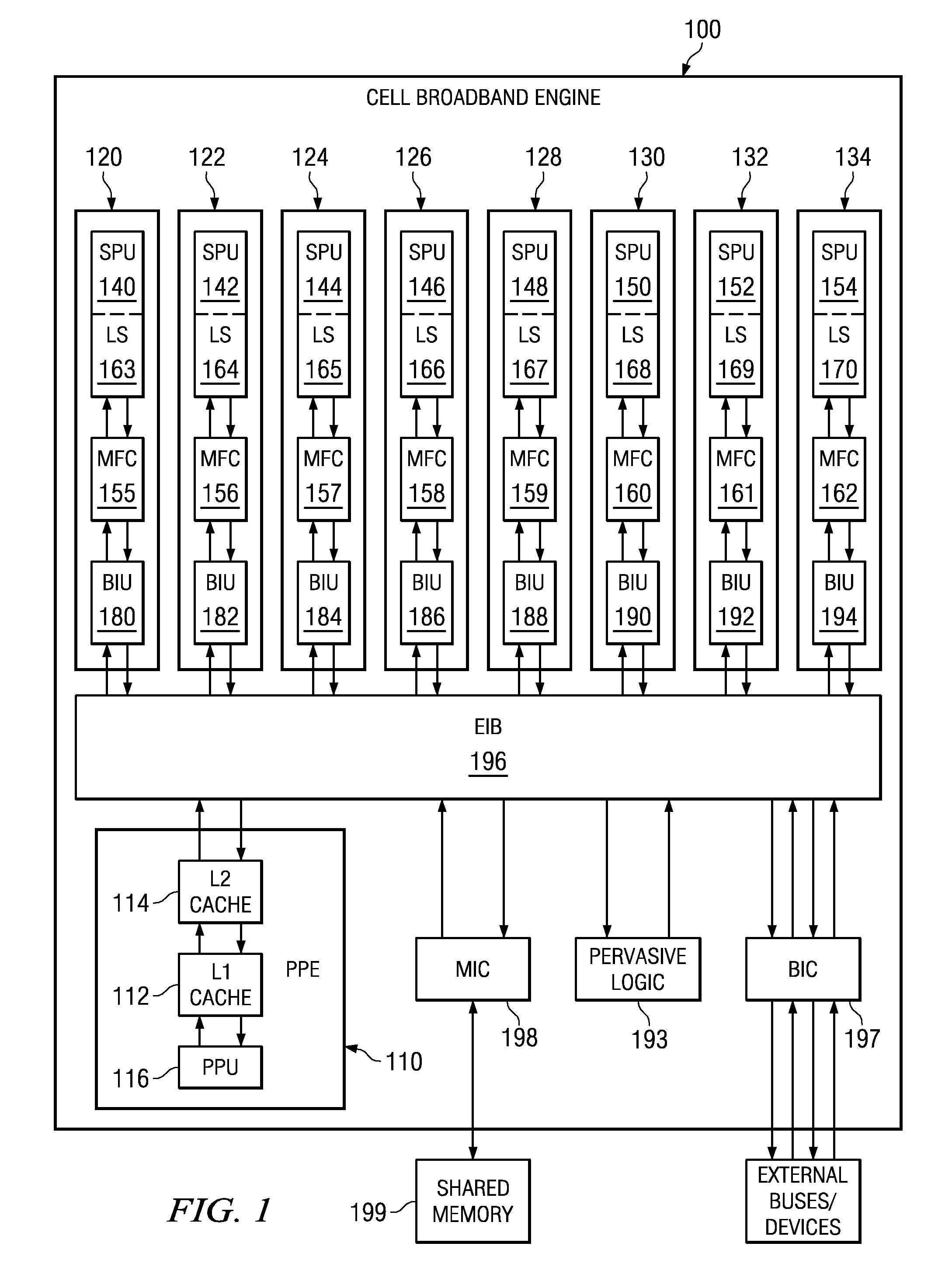
Secure Boot Across a Plurality of Processors
InactiveUS20080229092A1Complete security measuresIncrease the number ofDigital computer detailsComputer security arrangementsSuccessful completionMulti processor
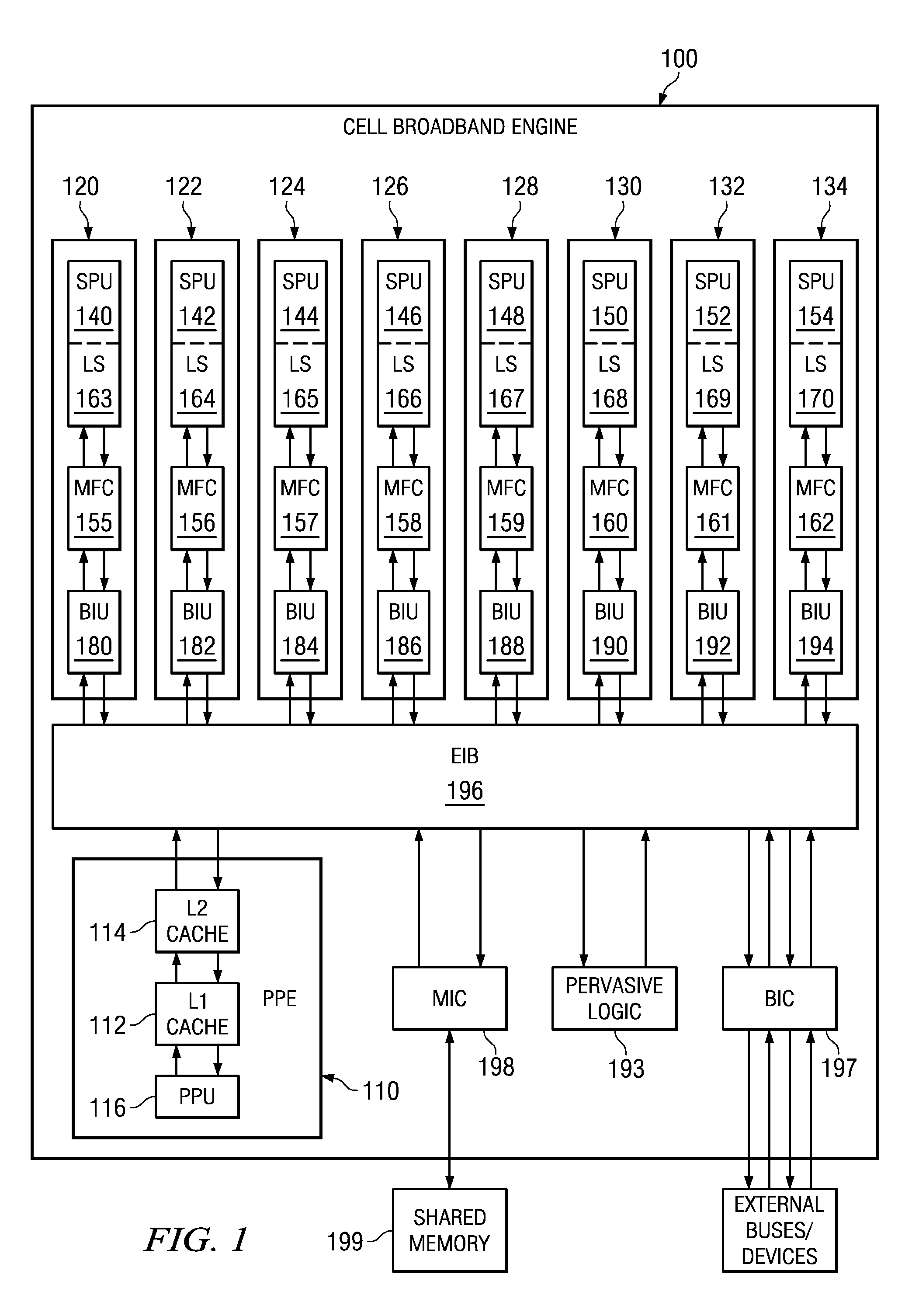
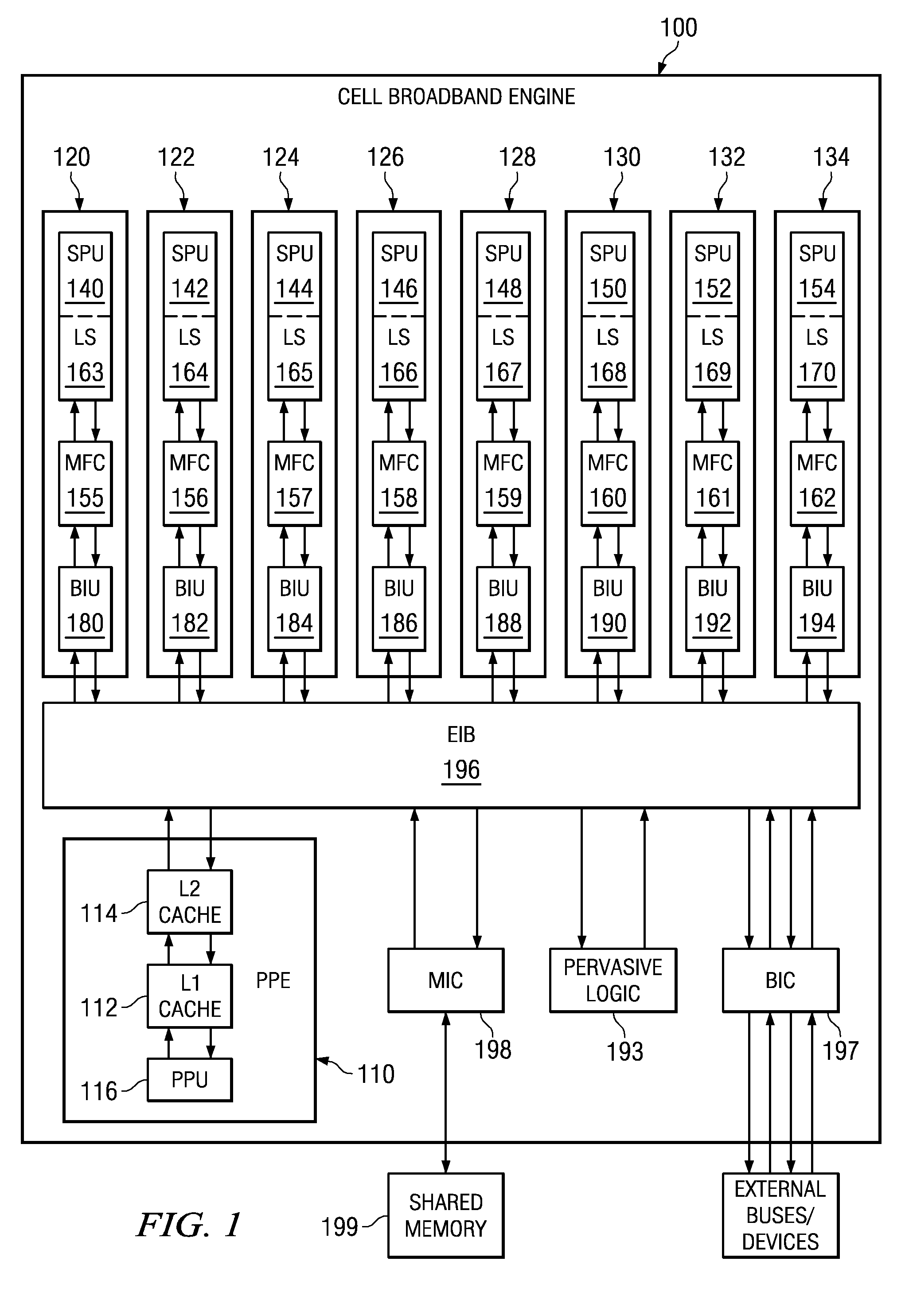
Boot code is partitioned into a plurality of boot code partitions. Processors of a multiprocessor system are selected to be boot processors and are each provided with a boot code partition to execute in a predetermined boot code sequence. Each processor executes its boot code partition in accordance with the boot code sequence and signals to a next processor the successful and uncompromised execution of its boot code partition. If any of the processors does not signal successful completion and / or uncompromised execution of its boot code partition, the boot operation fails. The processors may be arranged, with regard to the boot operation, in a daisy chain, ring, or master / slave arrangement, for example.
Owner:IBM CORP
Data security in a semantic data model
InactiveUS20060149739A1Simple definitionComplete security measuresDigital data processing detailsComputer security arrangementsGranularitySemantic search
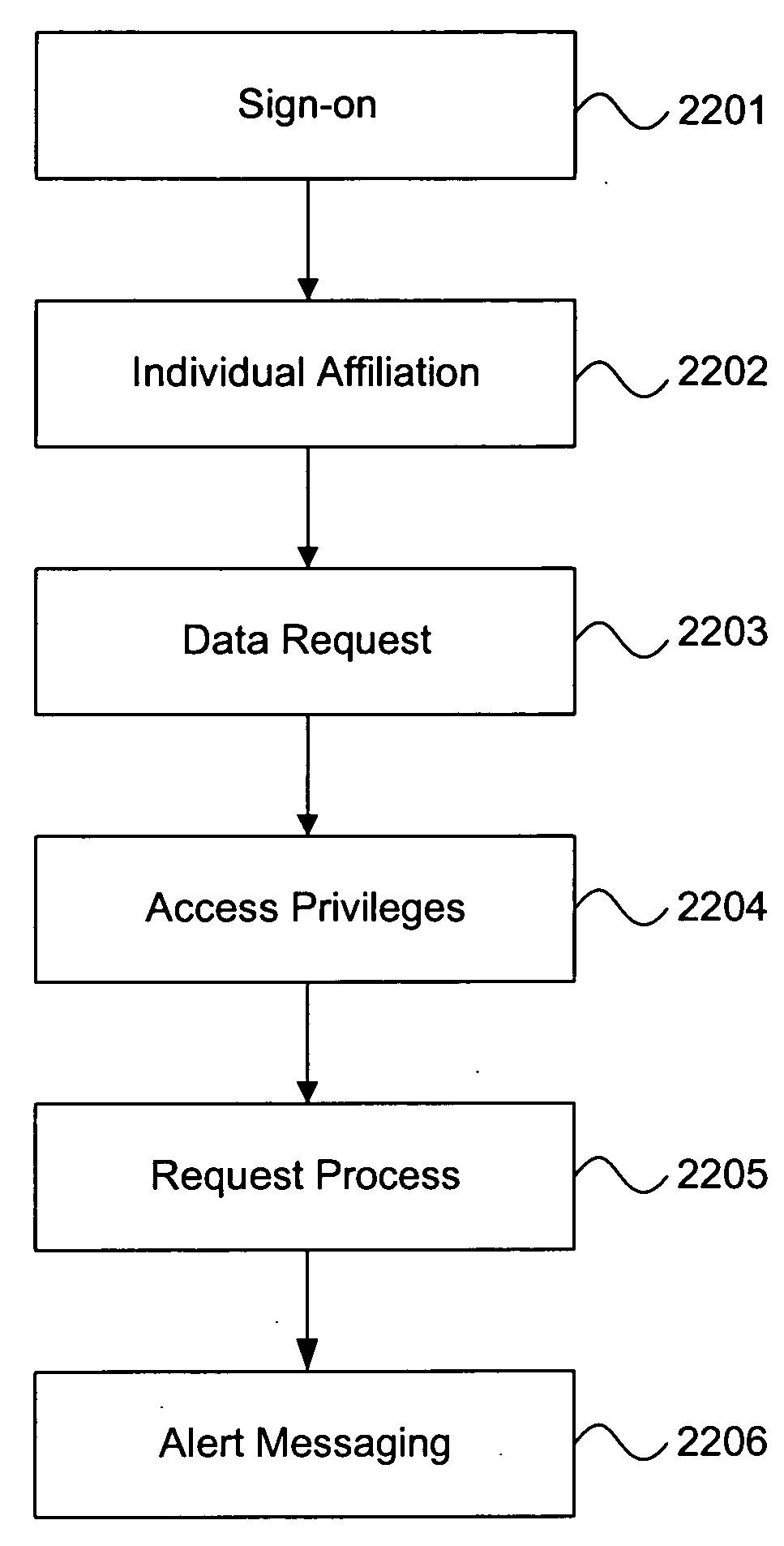
A data dependency path calculator for a semantic search engine is provided. A body of semantically related data is modeled according to a semantic data model. A user is presented a list of data elements from which they may select desired data elements. The system automatically calculates all of the possible paths through the database that may be used to retrieve meaningful data based on the selected data elements. The available data dependency paths are returned to the user for selection. The system further provides a type of data permission that allows restricted data elements to be used as a pass-through data element for relating, connecting and retrieving non-restricted data. Thus, a user can use restricted data to create data dependency paths to retrieve meaningful data. The system further provides for defining access privileges for all levels of data structures, allowing data to be secured with an increased level of granularity than previously possible.
Owner:METADATA
Automatic push-out to avoid range of motion limits
ActiveUS10028793B2High strengthComplete security measuresProgramme-controlled manipulatorMachine supportsRange of motionControl system
Robotic and / or surgical devices, systems, and methods include kinematic linkage structures and associated control systems configured to facilitate preparation of the system for use. In some embodiments, actively driven joints will move a platform structure that supports multiple manipulators in response to movement of one of the manipulators, facilitating and expediting the arrangement of the overall system by moving those multiple manipulators as a unit into alignment with the workspace. Systems and methods are also provided to keep one, some, or all joints of the kinematic chain off a hardstop or physical range of motion limit associated with the joint or to otherwise maintain a desired range of motion for one, some, or all joints of the kinematic chain when exiting a set-up mode.
Owner:INTUITIVE SURGICAL OPERATIONS INC
Automatic Push-Out to Avoid Range of Motion Limits
ActiveUS20170112580A1High strengthComplete security measuresProgramme-controlled manipulatorMachine supportsRange of motionControl system
Robotic and / or surgical devices, systems, and methods include kinematic linkage structures and associated control systems configured to facilitate preparation of the system for use. In some embodiments, actively driven joints will move a platform structure that supports multiple manipulators in response to movement of one of the manipulators, facilitating and expediting the arrangement of the overall system by moving those multiple manipulators as a unit into alignment with the workspace. Systems and methods are also provided to keep one, some, or all joints of the kinematic chain off a hardstop or physical range of motion limit associated with the joint or to otherwise maintain a desired range of motion for one, some, or all joints of the kinematic chain when exiting a set-up mode.
Owner:INTUITIVE SURGICAL OPERATIONS INC
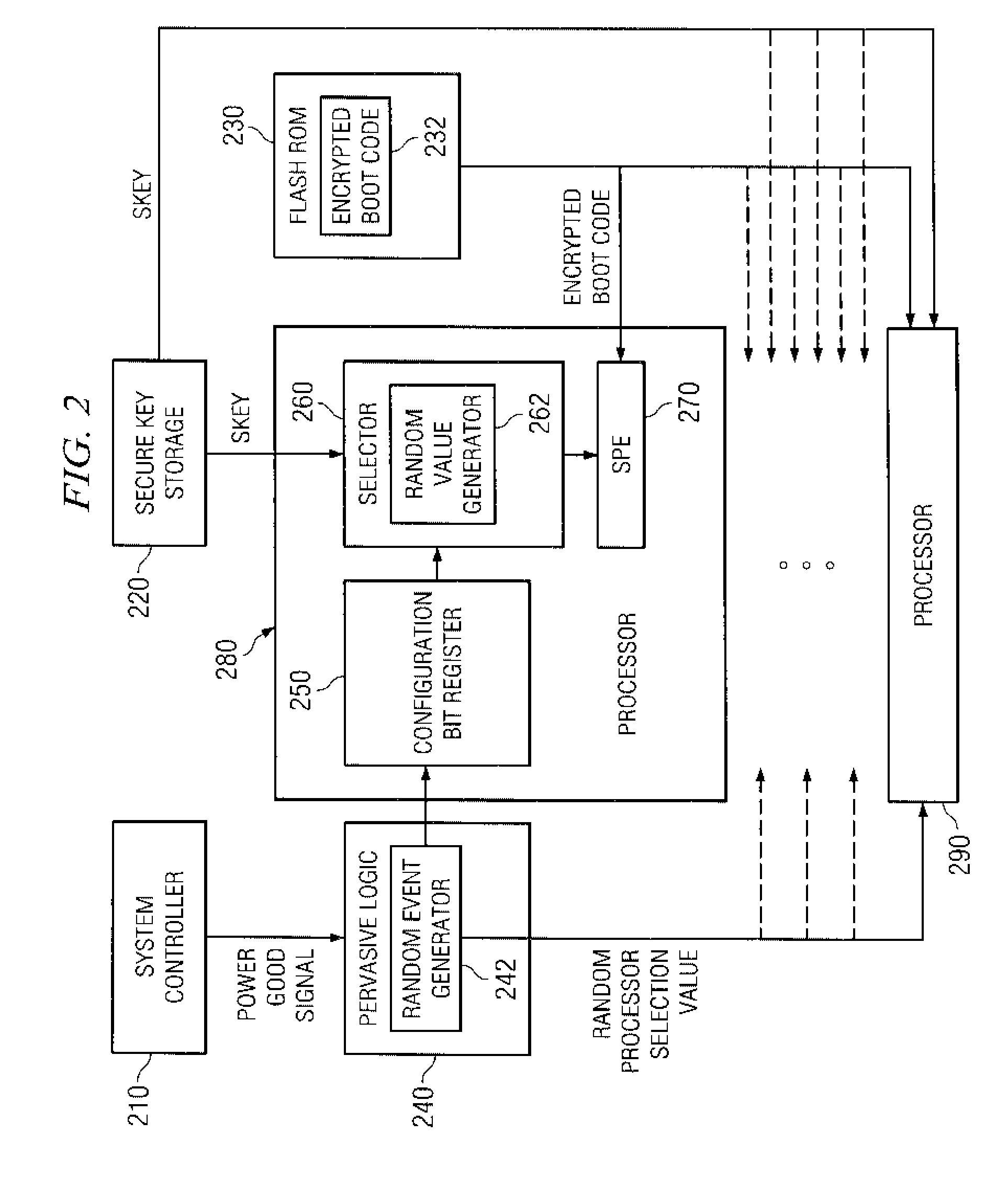
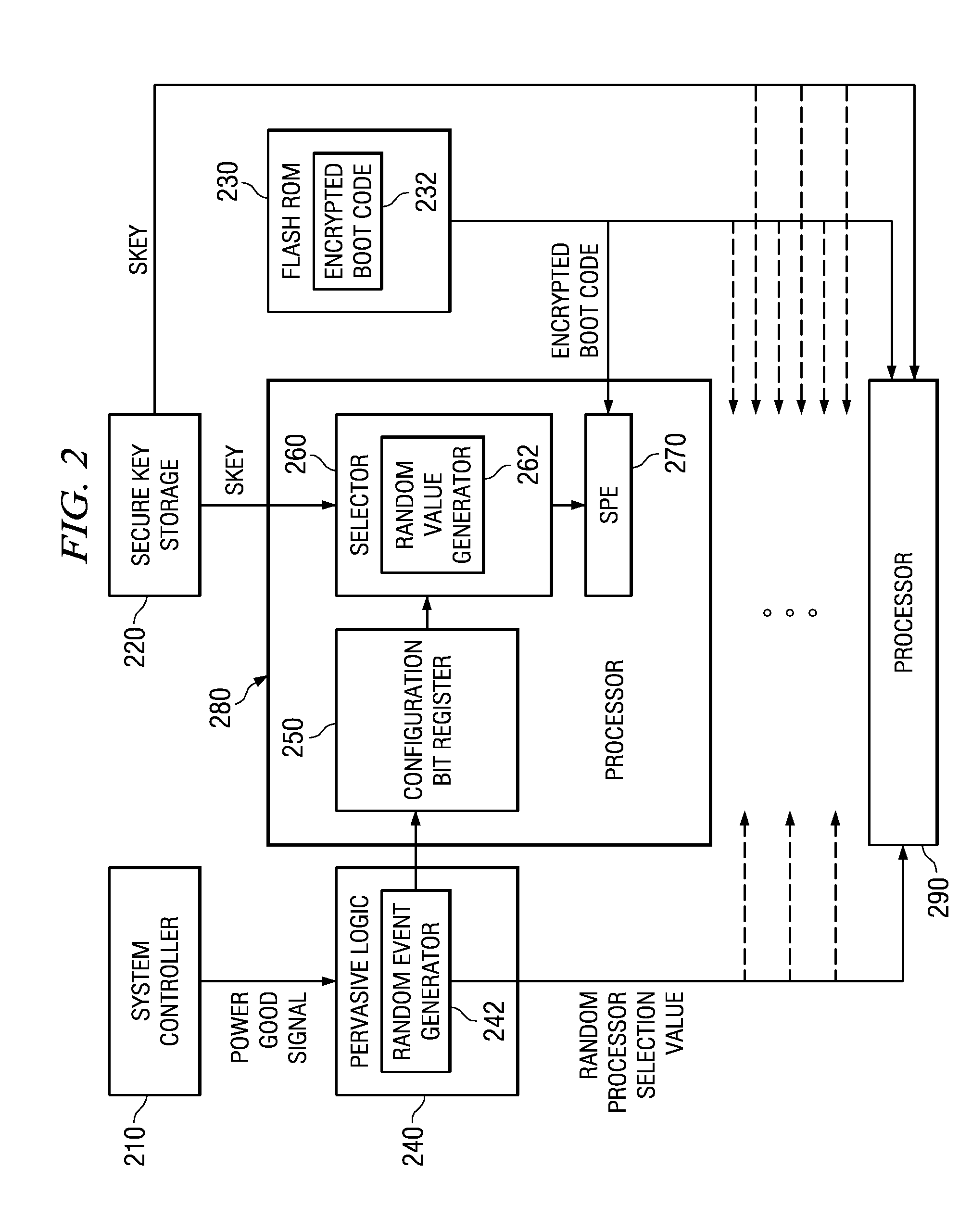
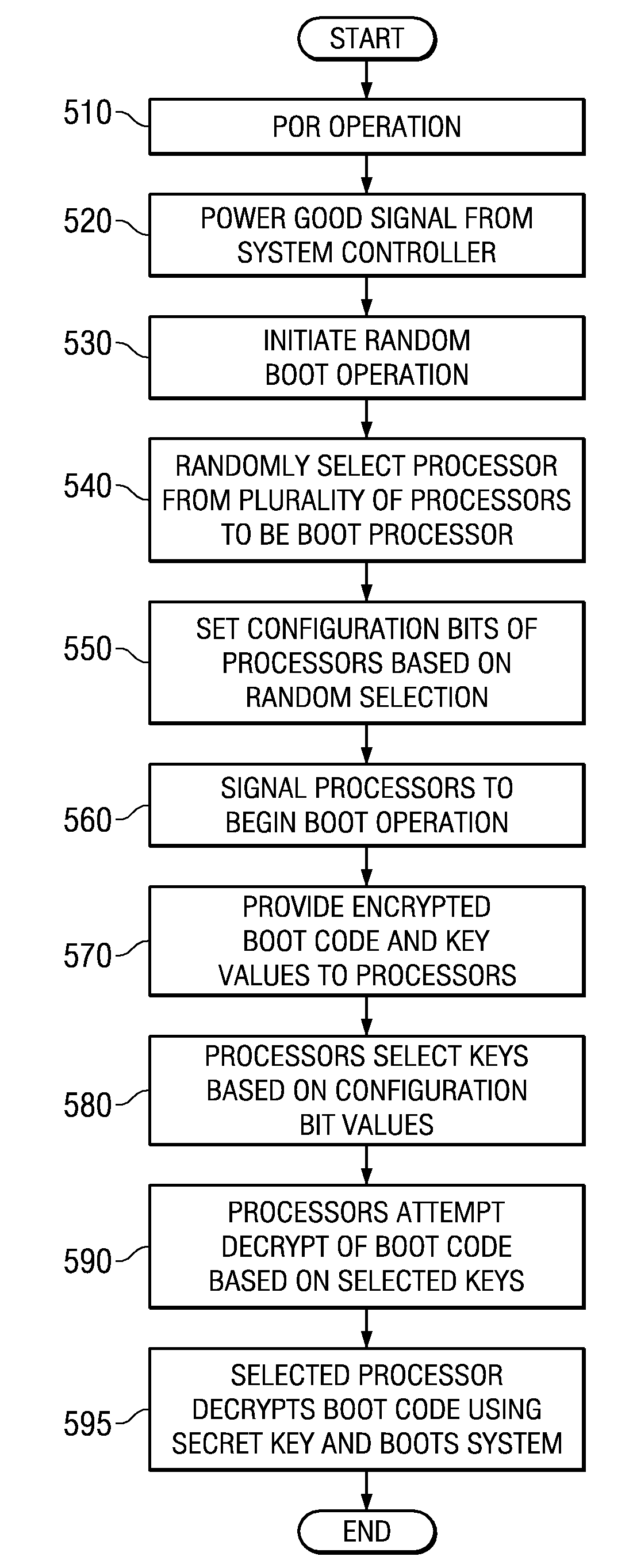
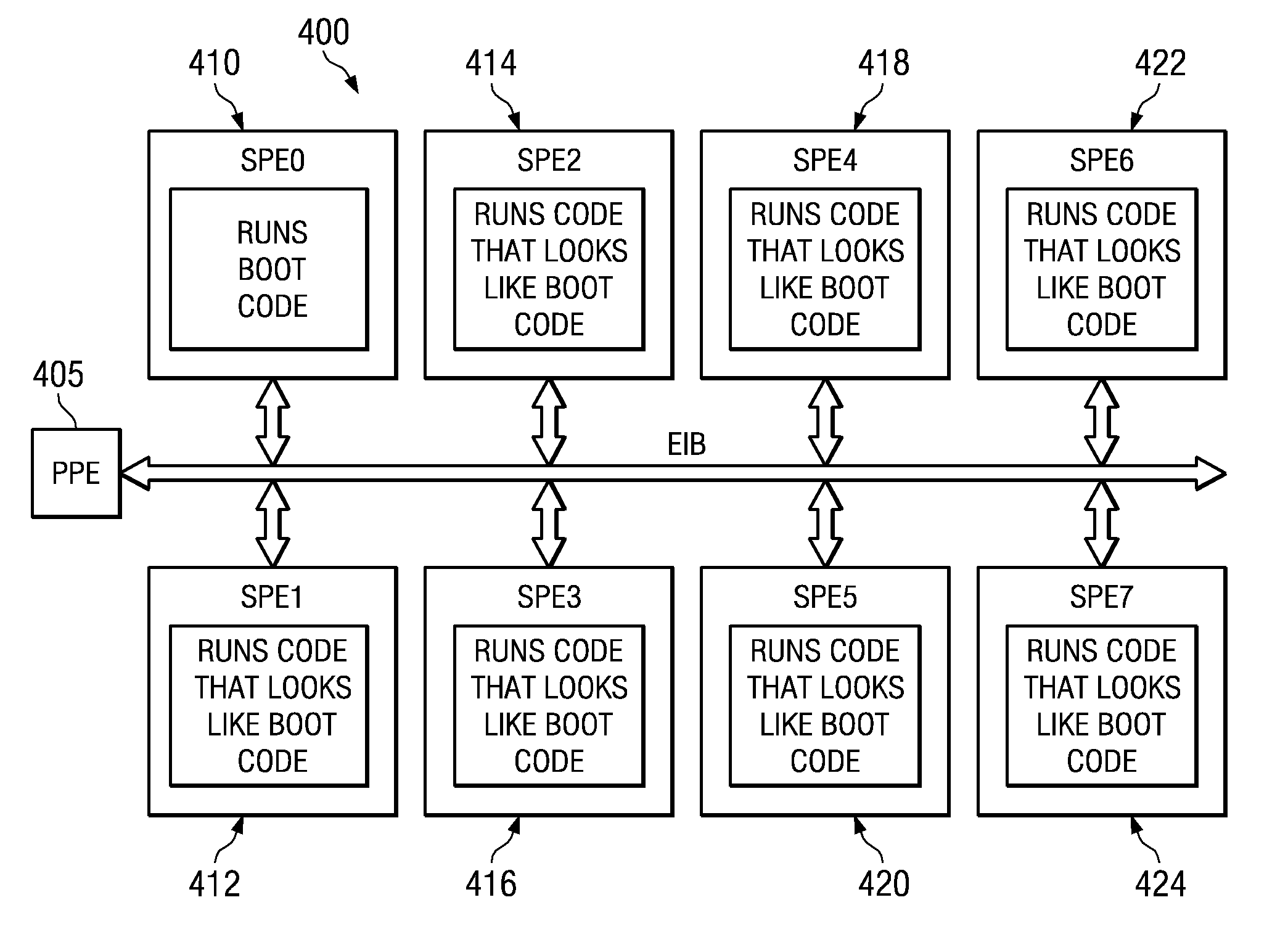
System and method for selecting a random processor to boot on a multiprocessor system
InactiveUS20070288738A1Complete security measuresIncrease the number ofDigital computer detailsComputer security arrangementsMulti processorVirtual Processor
A system and method for masking a boot sequence by providing a dummy processor are provided. With the system and method, one of the processors of a multiprocessor system is chosen to be a boot processor. The other processors of the multiprocessor system execute masking code that generates electromagnetic and / or thermal signatures that mask the electromagnetic and / or thermal signatures of the actual boot processor. The execution of the masking code on the non-boot processors preferably generates electromagnetic and / or thermal signatures that approximate the signatures of the actual boot code execution on the boot processor. One of the non-boot processors is selected to execute masking code that is different from the other masking code sequence to thereby generate a electromagnetic and / or thermal signature that appears to be unique from an external monitoring perspective.
Owner:IBM CORP
Secure identification system
InactiveUS20070112968A1Complete security measuresOvercome limitationsKey distribution for secure communicationMultiple digital computer combinationsData integrityRelational database
Methods and apparatus are described which provide secure interactive communication of text and image information between a central server computer and one or more client computers located at remote sites for the purpose of storing and retrieving files describing and identifying unique products, services, or individuals. Textual information and image data from one or more of the remote sites are stored separately at the location of the central server computer, with the image data being in compressed form, and with the textual information being included in a relational database with identifiers associated with any related image data. Means are provided at the central computer for management of all textural information and image data received to ensure that all information may be independently retrieved. Requests are entered from remote terminals specifying particular subject matter, and the system is capable of responding to multiple simultaneous requests. Textural information is recalled and downloaded for review, along with any subsequently requested image data, to be displayed at a remote site. Various modes of data and image formatting are also disclosed, including encryption techniques to fortify data integrity. The server computers may be interfaced with other computers to effect financial transactions, and images representing the subjects of transactions may be uploaded to the server computer to create temporary or permanent records of financial or legal transactions. A further feature of the system is the ability to associate an identification image with a plurality of accounts, transactions, or records.
Owner:SCHWAB BARRY H
System and method for secure boot across a plurality of processors
InactiveUS20070288740A1Complete security measuresIncrease the number ofDigital computer detailsComputer security arrangementsSuccessful completionMulti processor
A system and method for secure boot across a plurality of processors are provided. With the system and method, boot code is partitioned into a plurality of boot code partitions. Processors of a multiprocessor system are selected to be boot processors and are each provided with a boot code partition to execute in a predetermined boot code sequence. Each processor executes its boot code partition in accordance with the boot code sequence and signals to a next processor the successful and uncompromised execution of its boot code partition. If any of the processors does not signal successful completion and / or uncompromised execution of its boot code partition, the boot operation fails. The processors may be arranged, with regard to the boot operation, in a daisy chain, ring, or master / slave arrangement, for example.
Owner:IBM CORP
Medical indication device and identification method
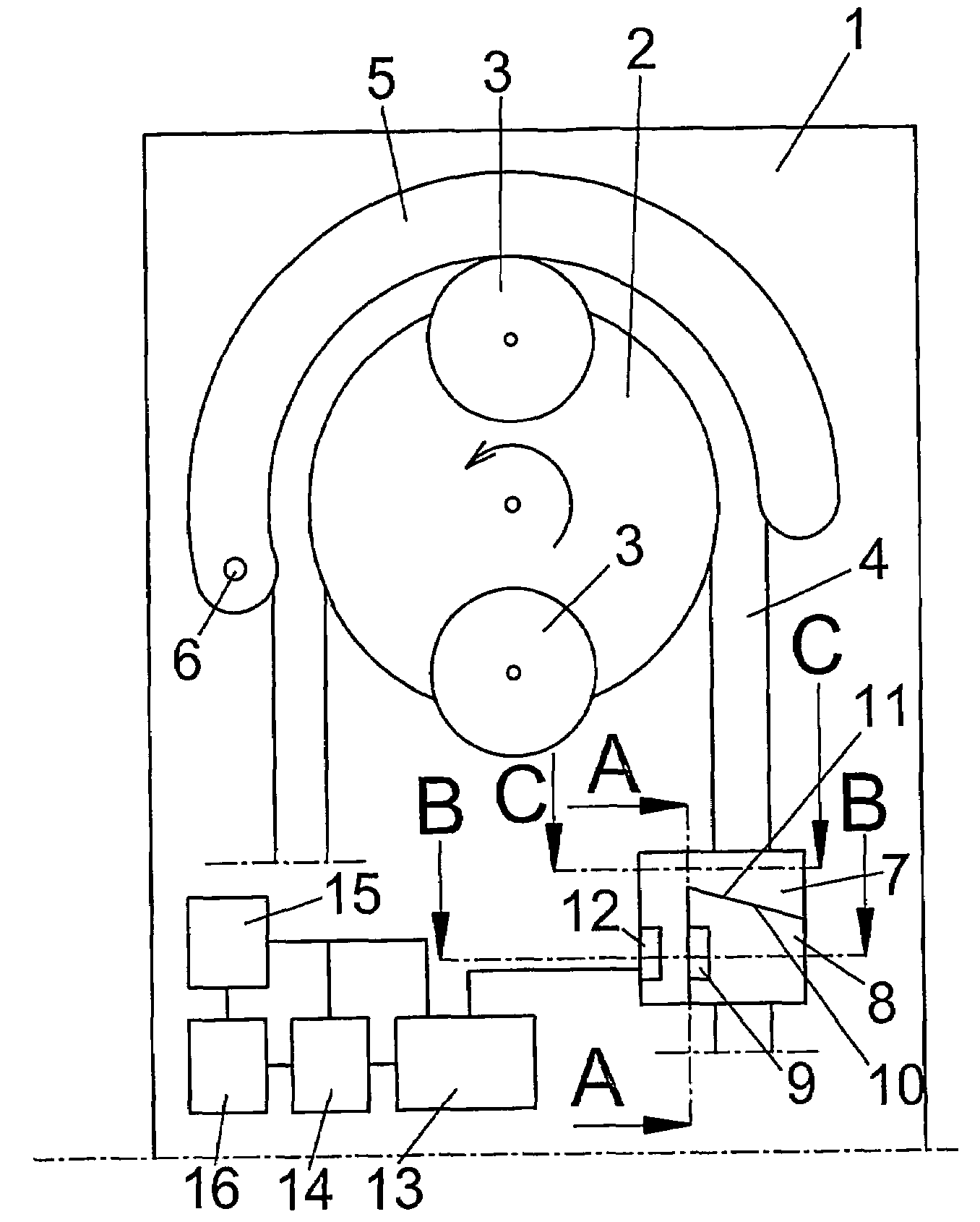
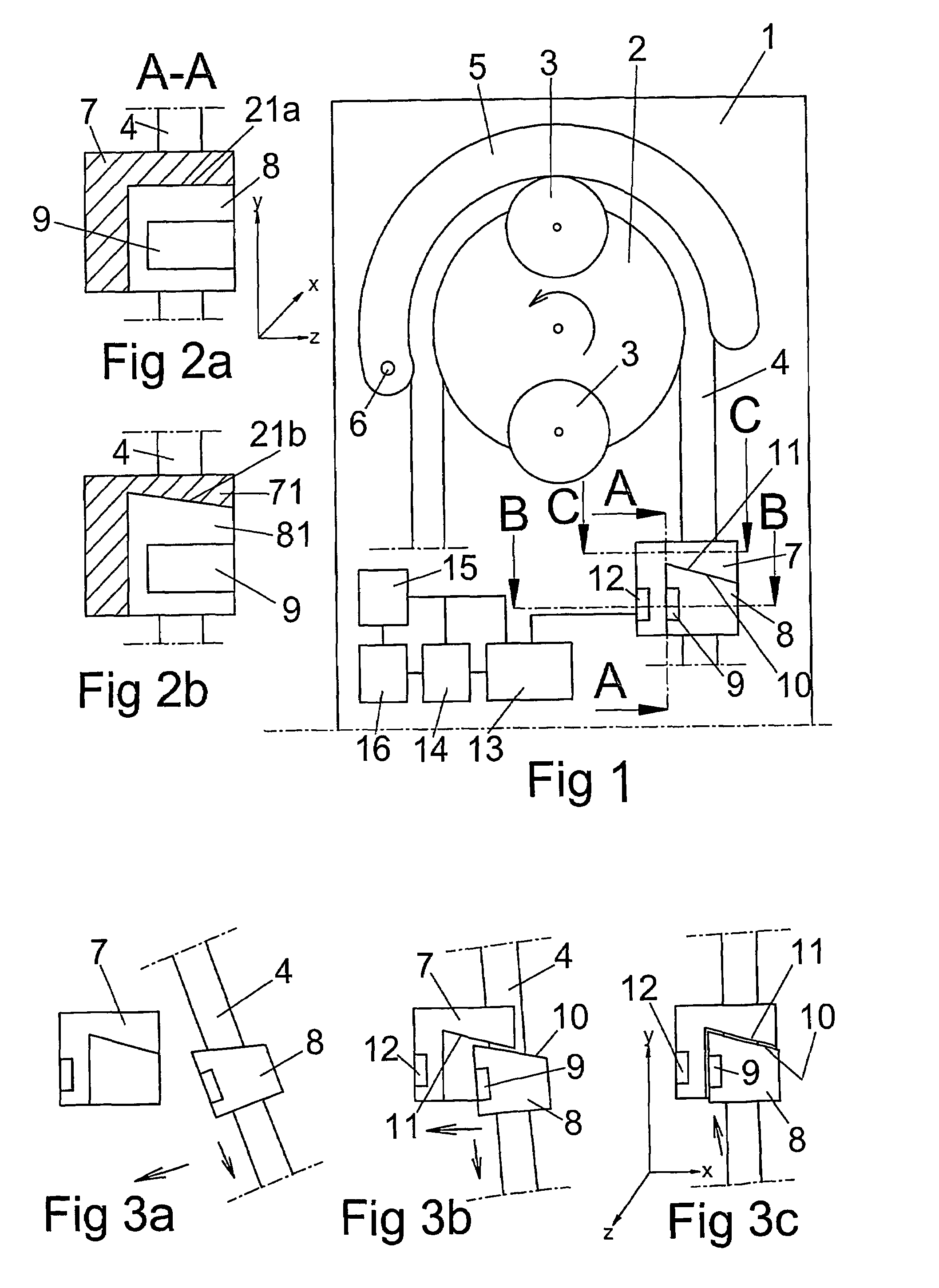
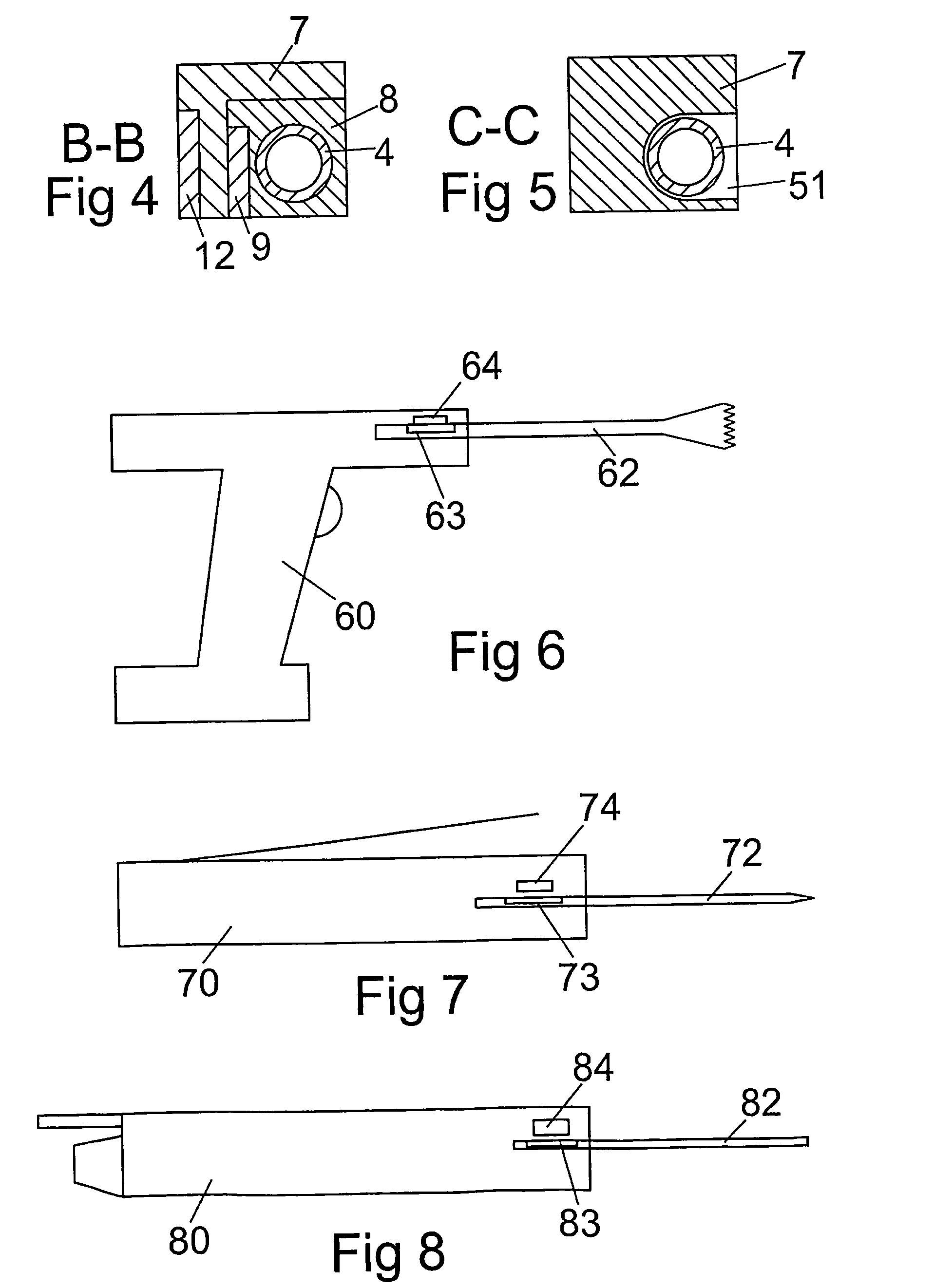
InactiveUS7661582B2Inhibit functioningComplete security measuresDigital data processing detailsMedical devicesIdentification deviceMedical device
The present invention relates to a medical-technical identification device for identifying a sterile product (4, 62, 72, 82), and to a method of identifying such a product, for example a product intended for one-time-use only, when connected to a piece of medical equipment (1, 60, 70, 80), wherein the sterile product (4, 62, 72, 82) includes a fixedly mounted information carrier (9, 63, 73, 83) which is adapted to deliver or to offer specific product information in a contactless fashion to a reading element (12, 64, 74, 84) connected to the equipment (1, 60, 70, 80).
Owner:INSIGHTRA MEDICAL INC
Hunting garment and saftey harness system
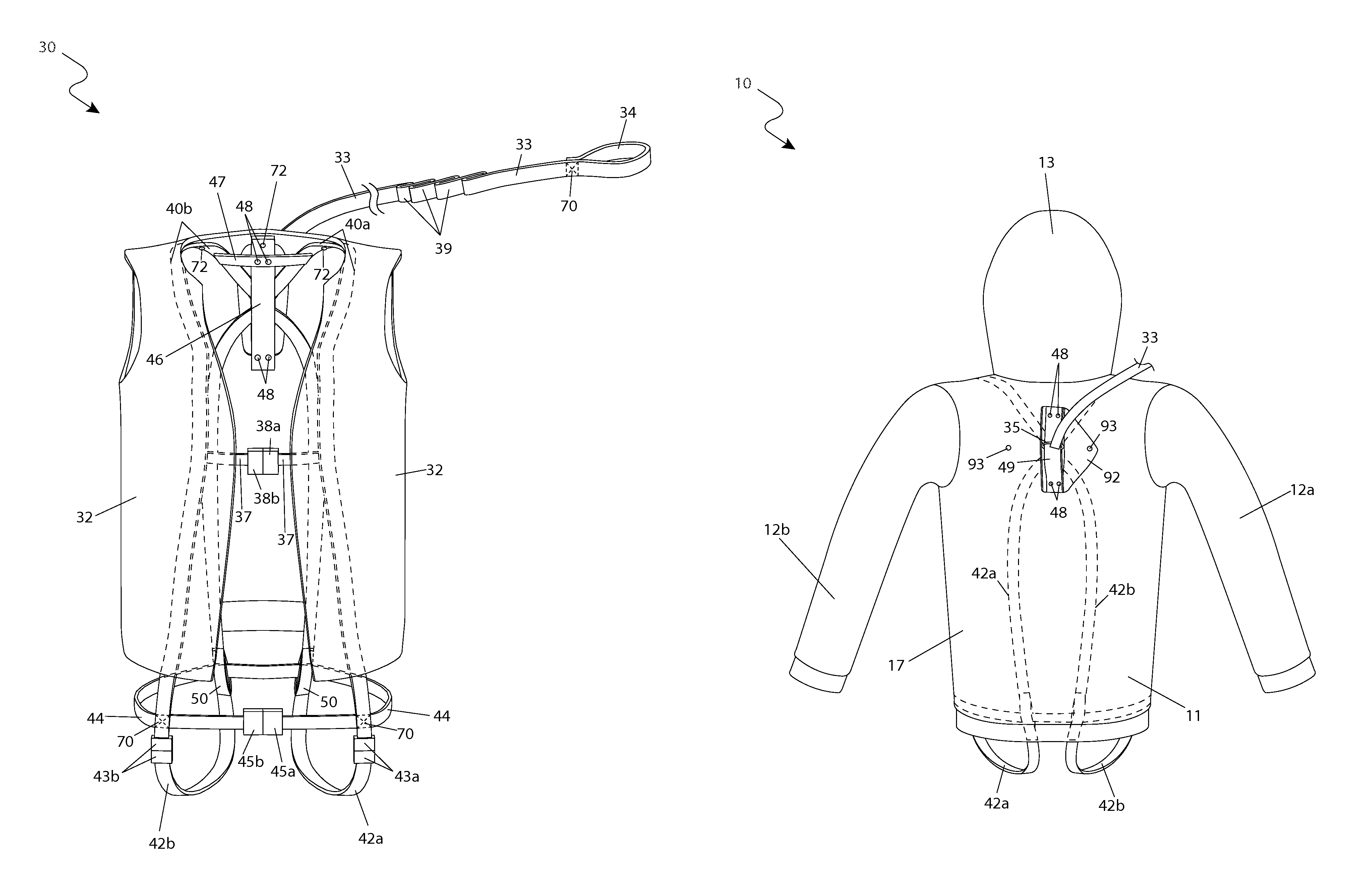
ActiveUS8776266B1Complete security measuresQuick and easy and effectiveOvergarmentsProtective garmentTree standEngineering
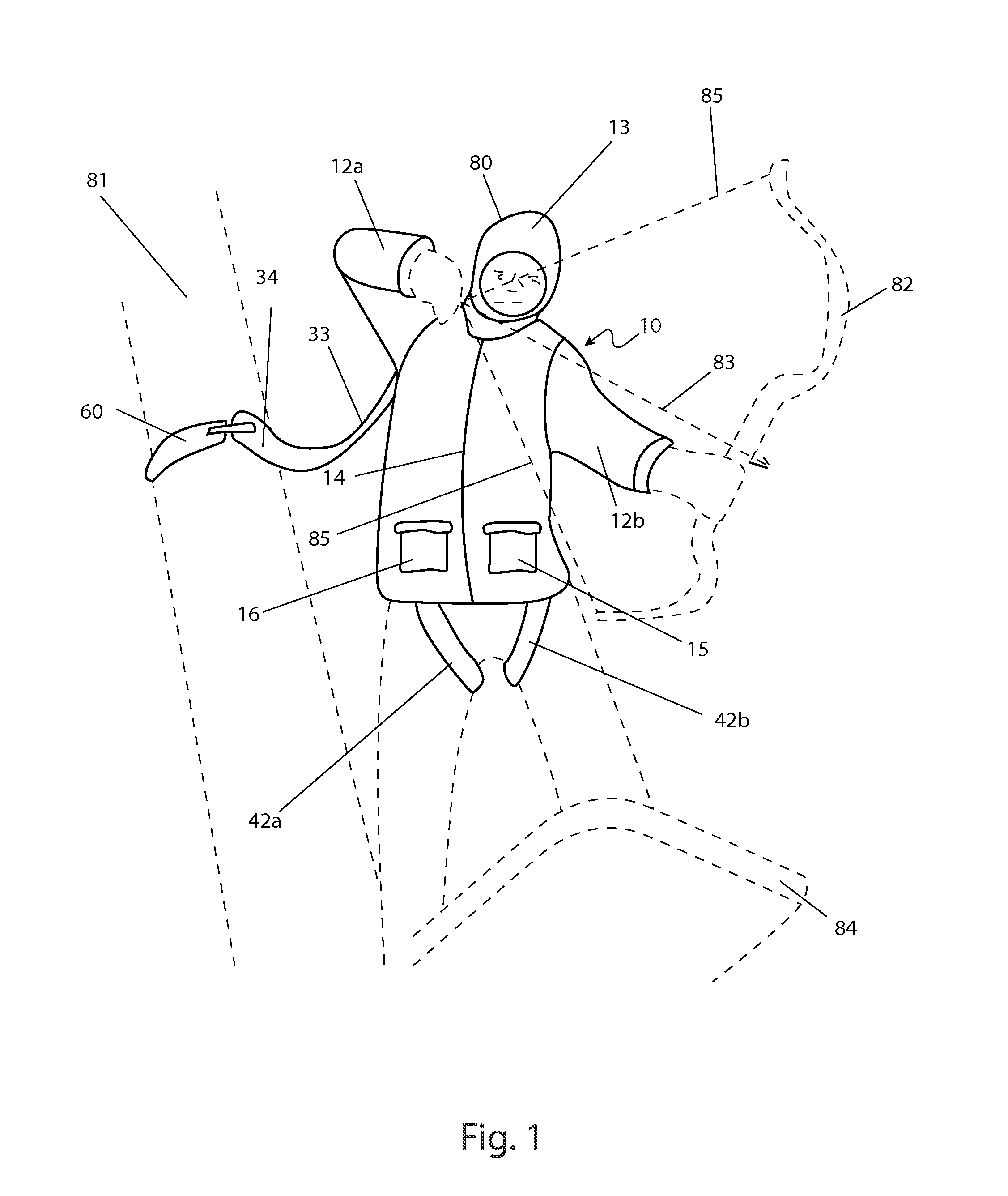
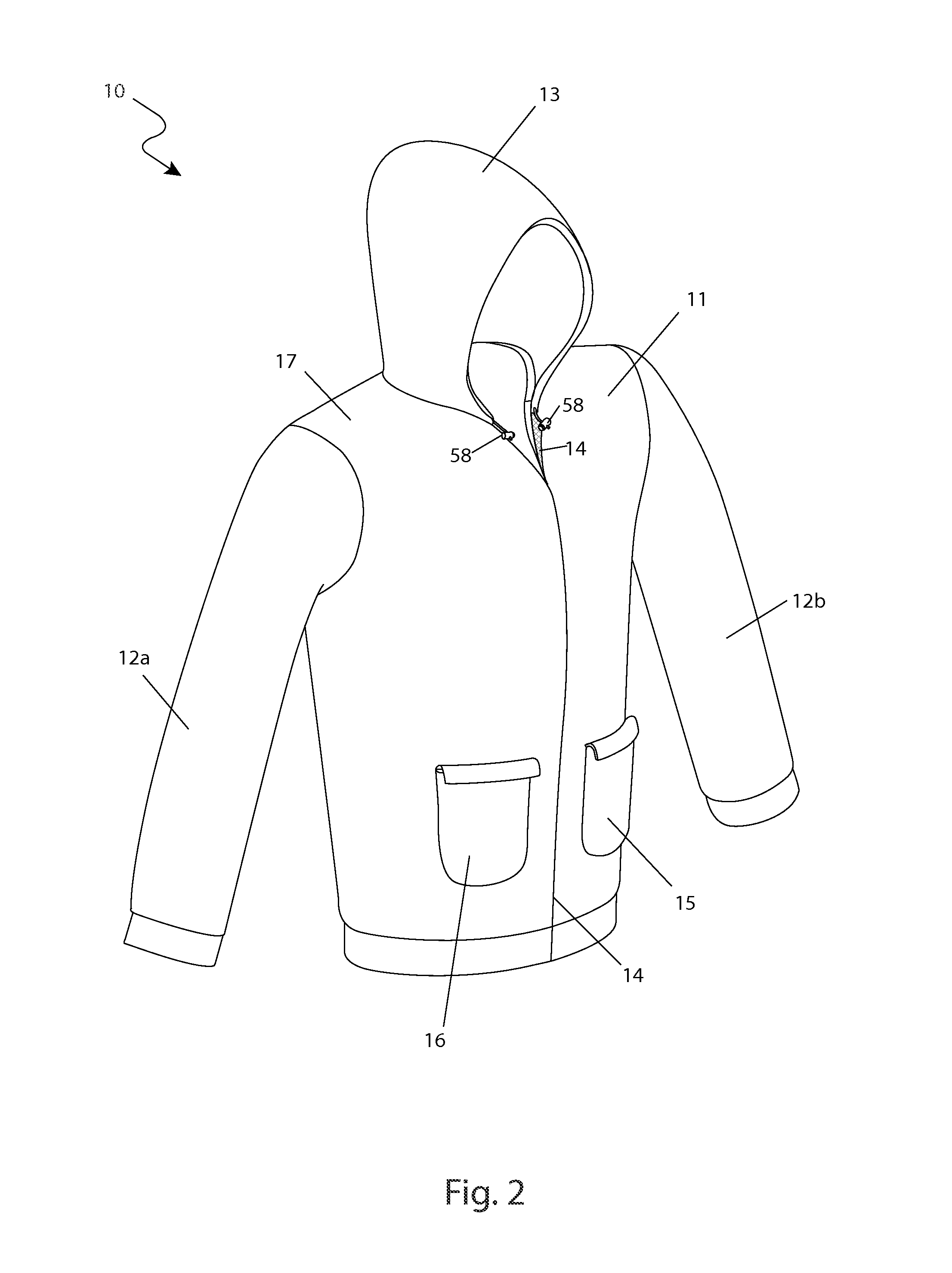
A hunting garment system including a safety harness which restrains a hunter while perched on a tree stand, an outer member, and an inner member. Both the inner member and the outer member include detachable sleeves and a detachable hood allowing the hunter to select a particular weather-conforming configuration. The safety harness is designed to be safely anchored onto a tree and is worn alone, beneath the outer member, beneath the inner member, beneath an outer vest, beneath an inner vest, or in combination with an assembly of the outer member over the inner member.
Owner:METZ JOHNATHAN
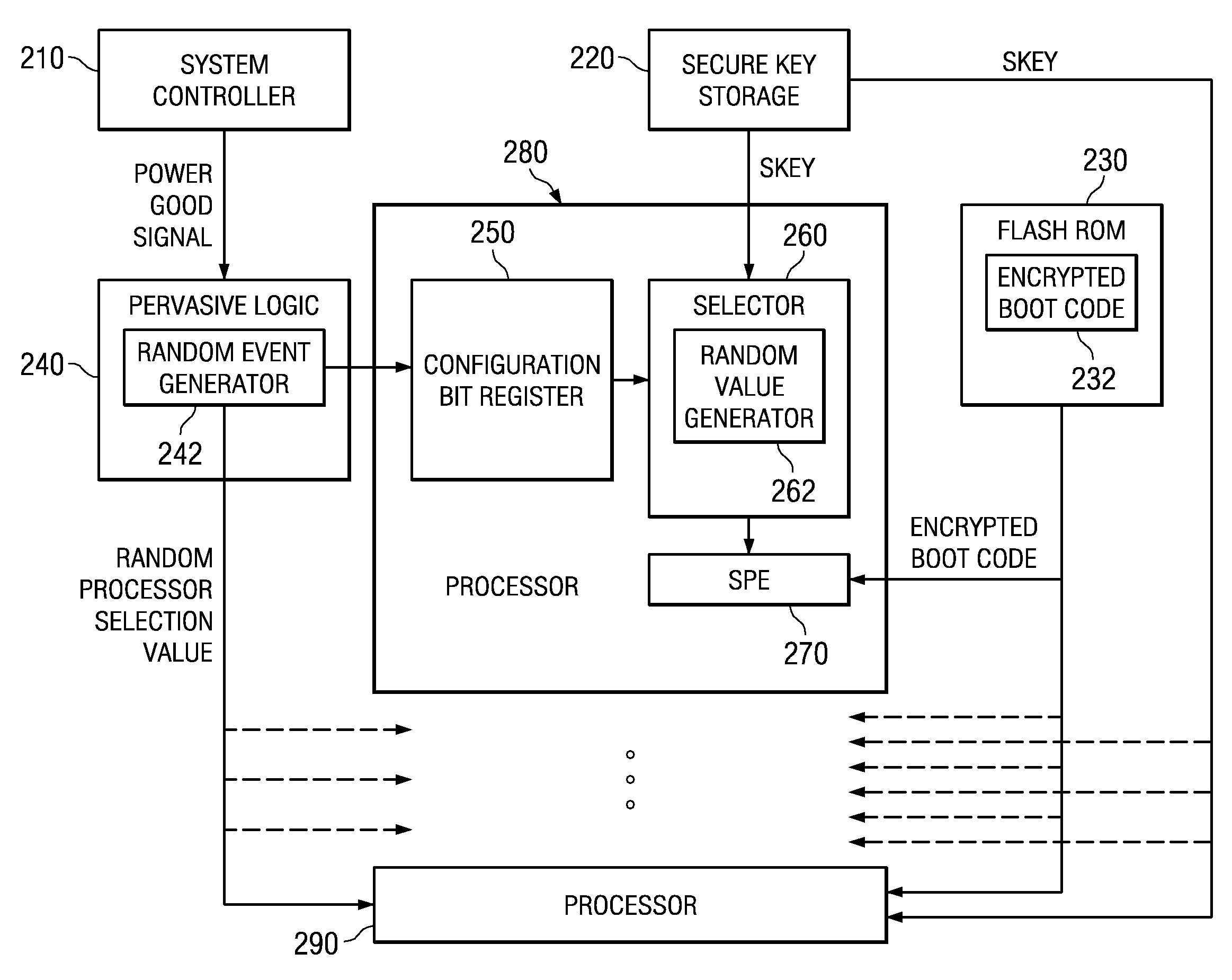
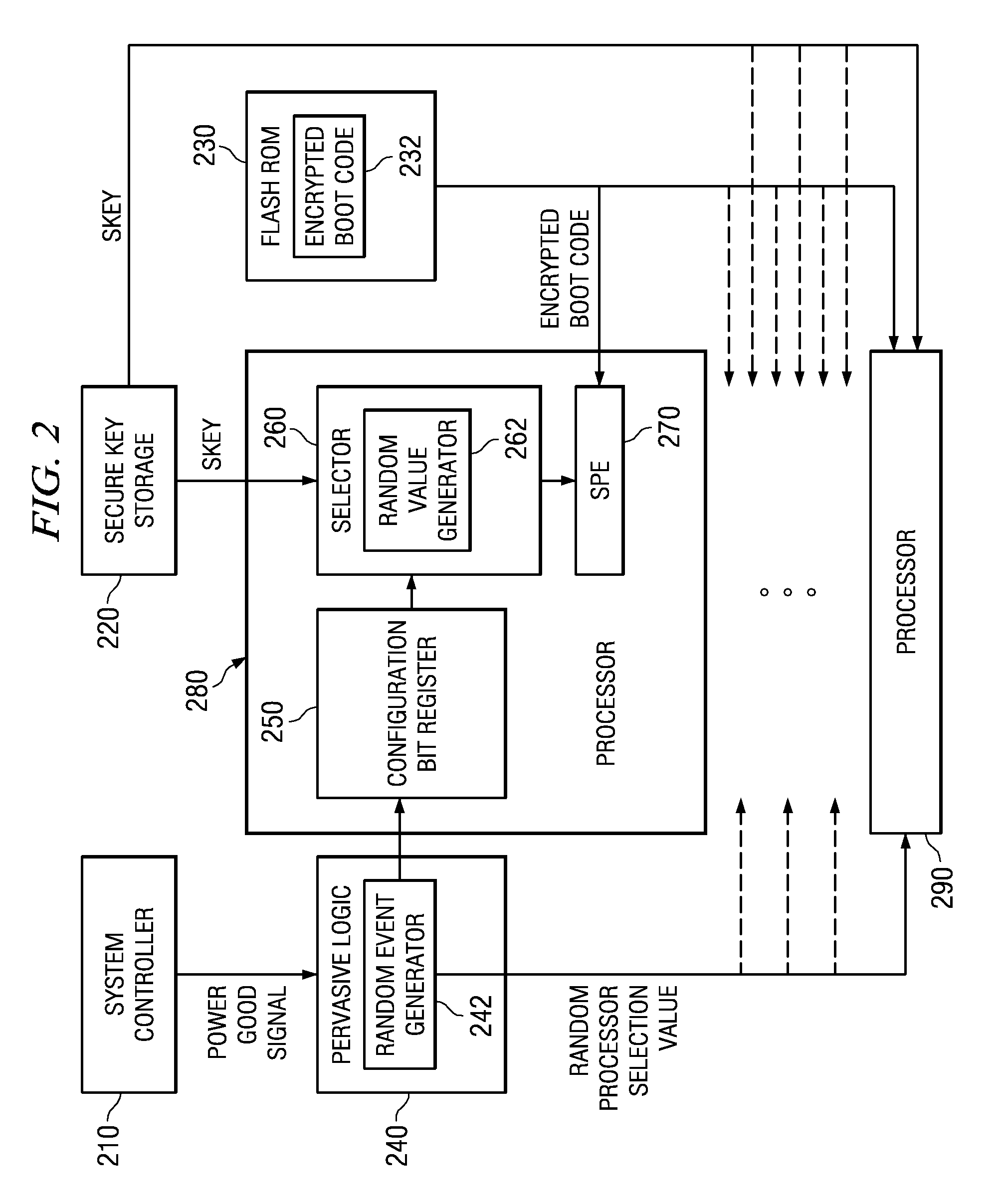
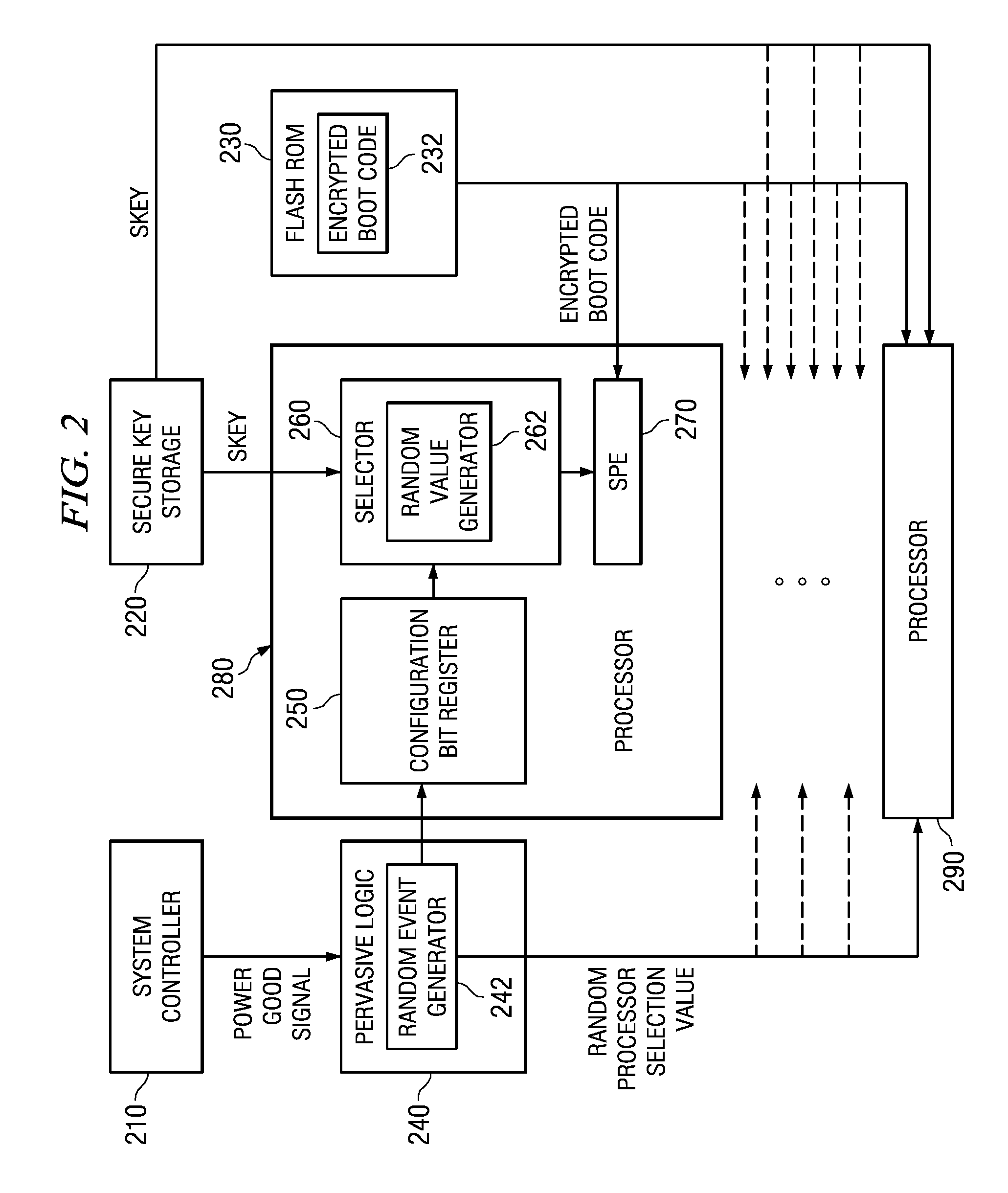
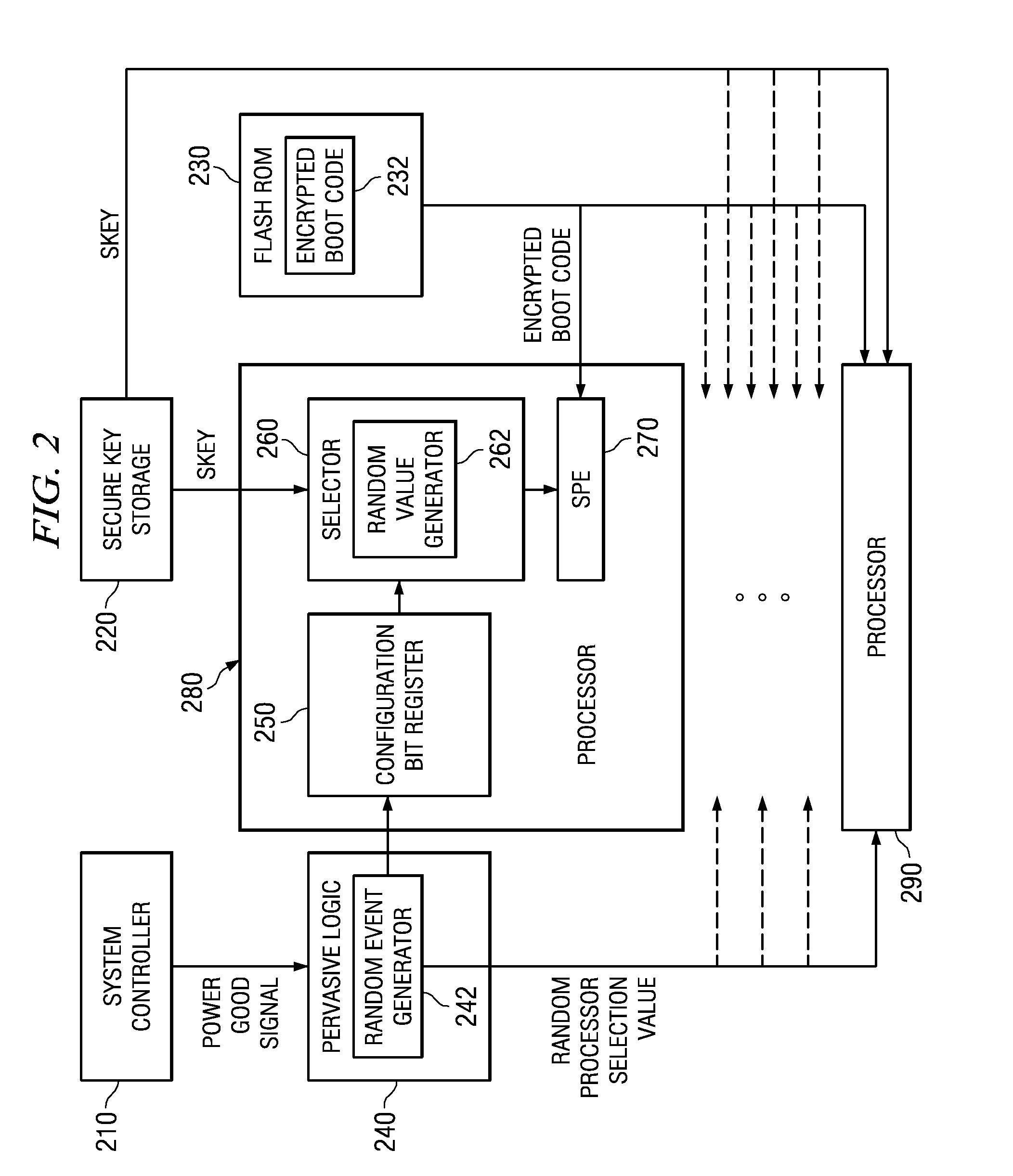
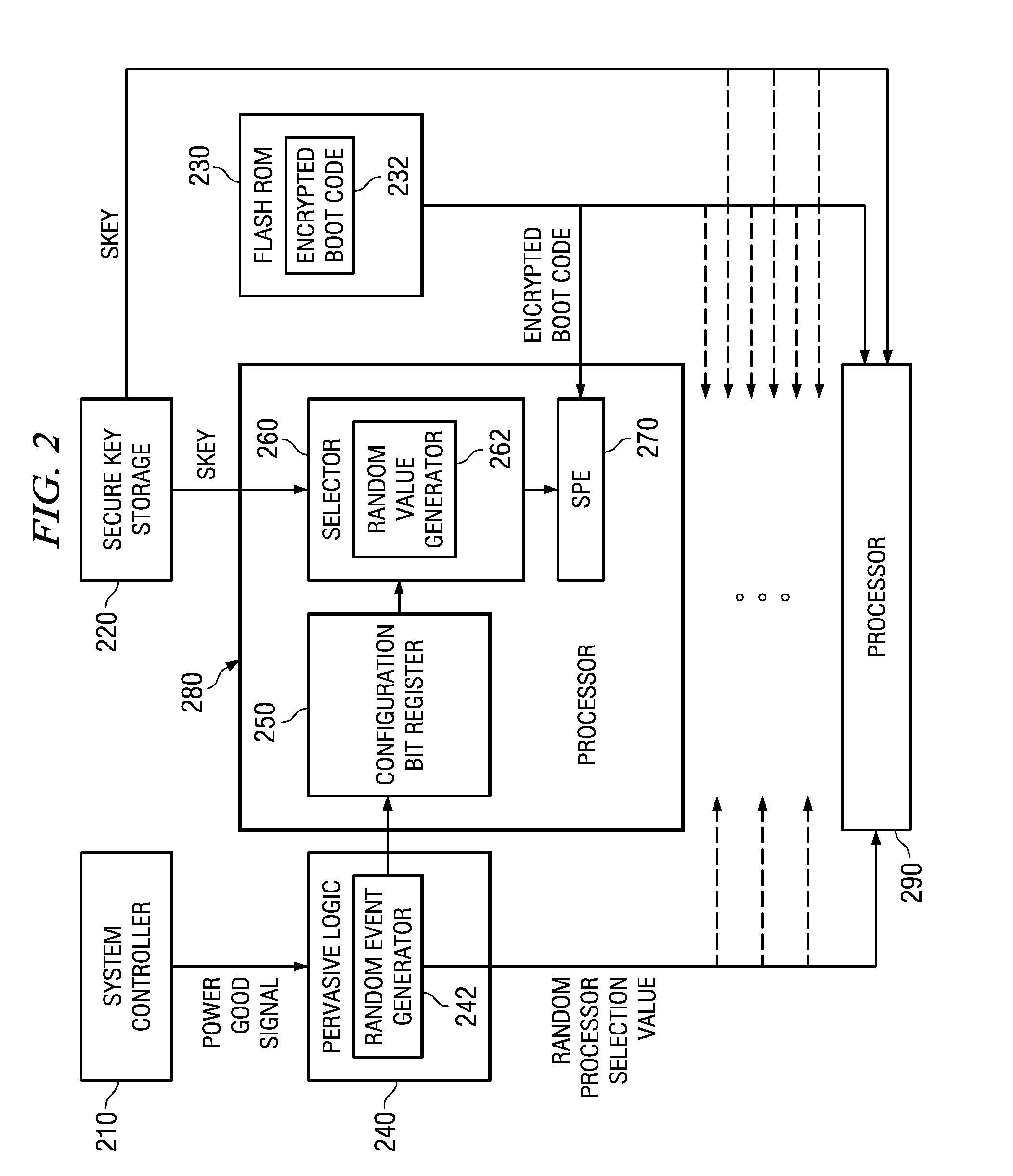
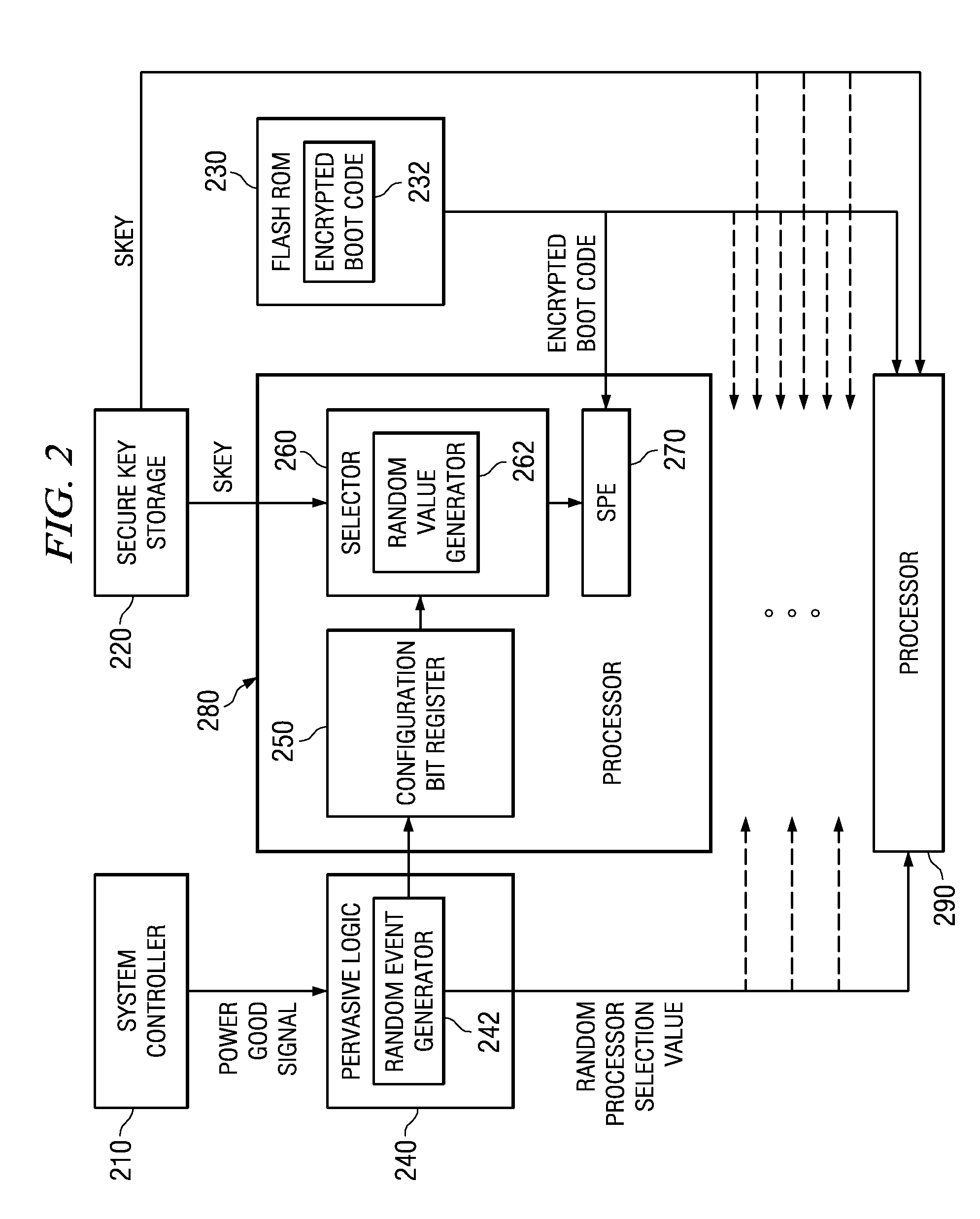
Selecting a Random Processor to Boot on a Multiprocessor System
InactiveUS20090327680A1Complete security measuresIncrease the number ofDigital computer detailsUnauthorized memory use protectionMulti processorEvent generator
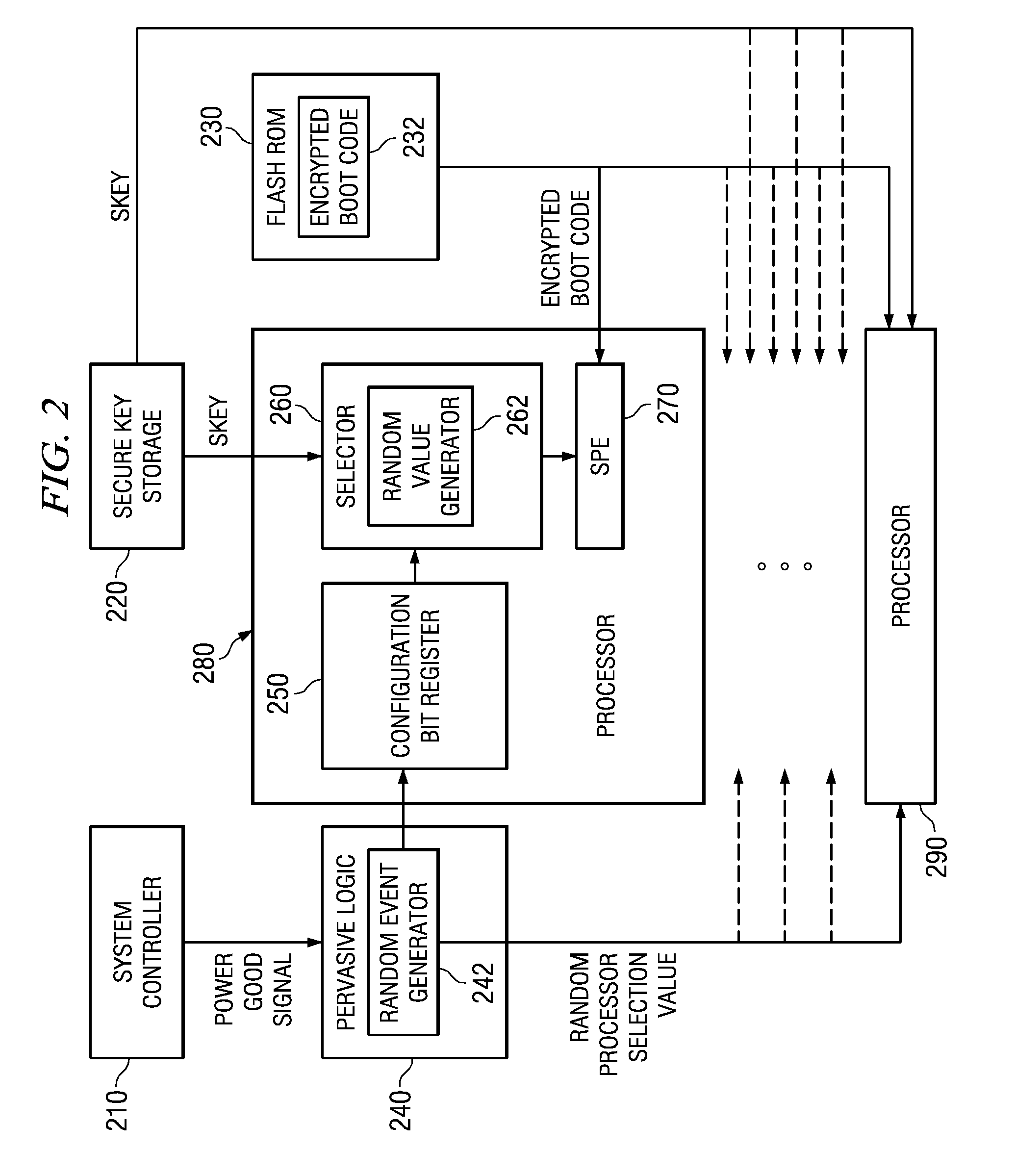
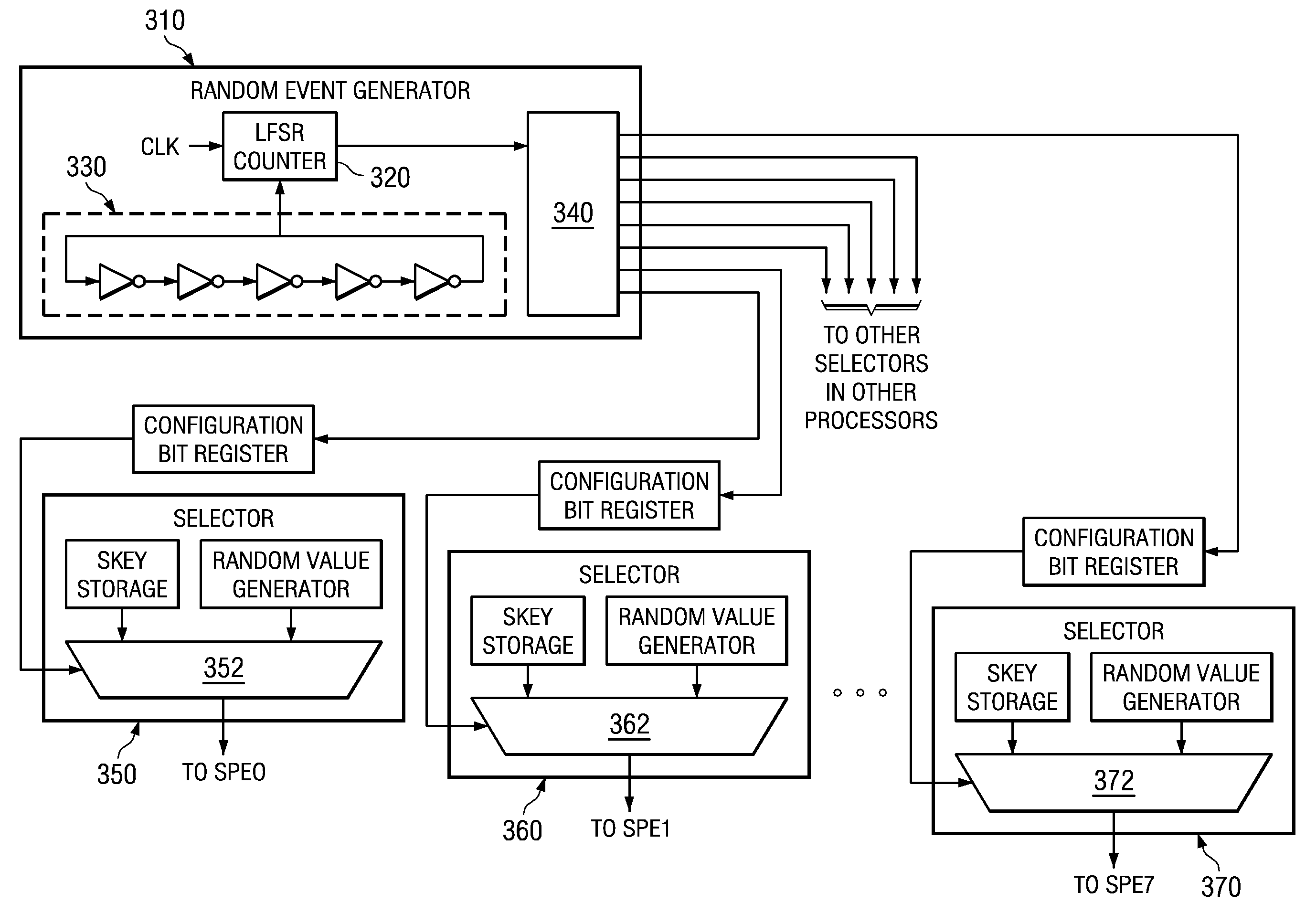
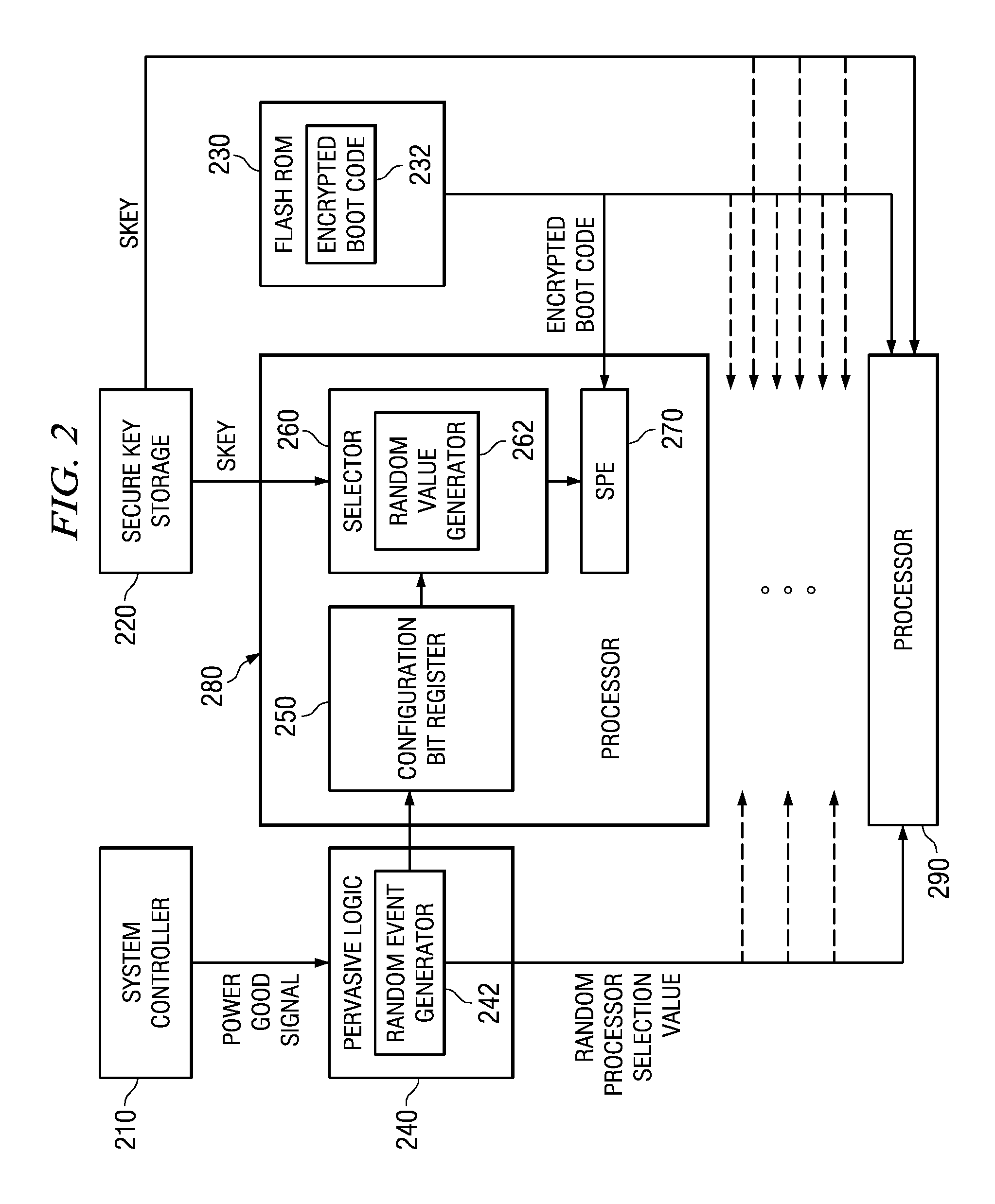
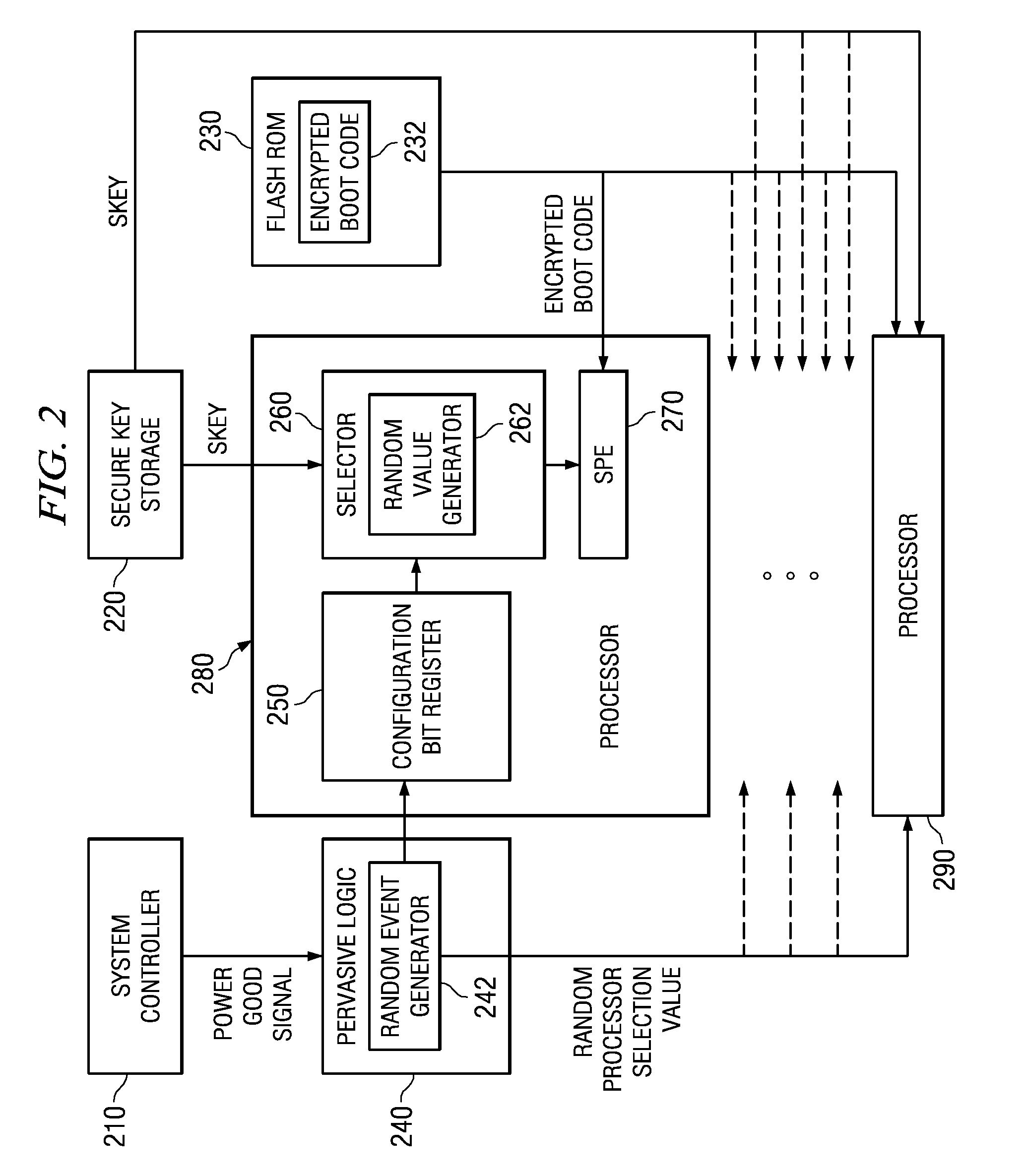
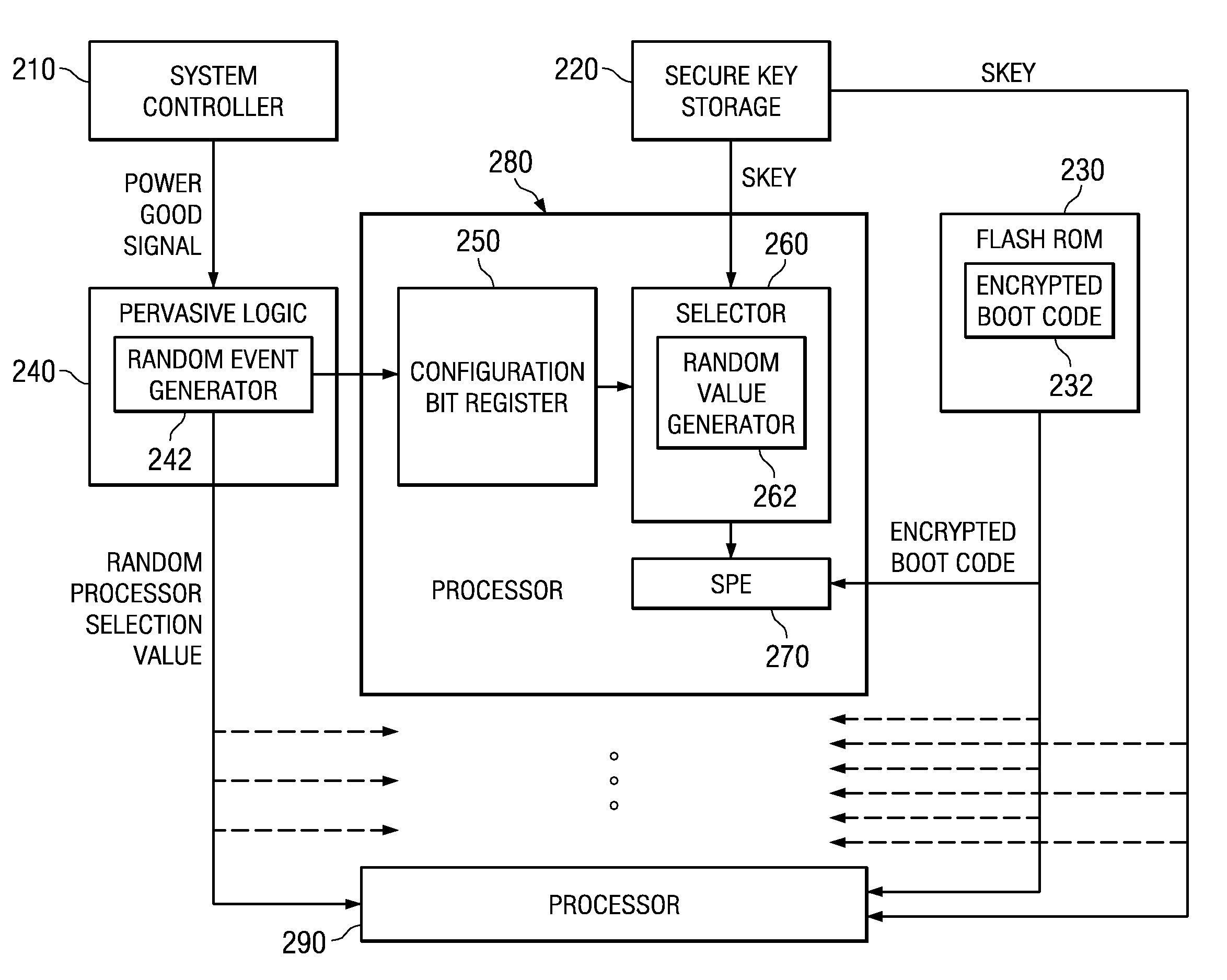
Pervasive logic is provided that includes a random event generator. The random event generator randomly selects which processor of a plurality of processors in the multiprocessor system is to be a boot processor for the multiprocessor system. A corresponding configuration bit for the randomly selected processor is set to identify the processor as a boot processor. Based on the setting of the configuration bits for each processor in the plurality of processors, a selection of a security key is made. The security key is then used to decrypt the boot code for booting the multiprocessor system. Only the randomly selected boot processor is able to select the correct security key for correctly decrypting the boot code, which it then executes to bring the system to an operational state.
Owner:IBM CORP
System and Method for Booting a Multiprocessor Device Based on Selection of Encryption Keys to be Provided to Processors
InactiveUS20080256366A1Complete security measuresIncrease the number ofMultiple keys/algorithms usageDigital computer detailsMulti processorEncryption
A system and method for booting a multiprocessor device based on selection of encryption keys to be provided to the processors are provided. With the system and method, a security key and one or more randomly generated key values are provided to a selector mechanism of each processor of the multiprocessor device. A random selection mechanism is provided in pervasive logic that randomly selects one of the processors to be a boot processor and thereby, provides a select signal to the selector of the boot processor such that the boot processor selects the security key. All other processors select one of the one or more randomly generated key values. As a result, only the randomly selected boot processor is able to use the proper security key to decrypt the boot code for execution.
Owner:INT BUSINESS MASCH CORP
Resistance exercise trainer having portable hand-held weights
ActiveUS20120058863A1Complete security measuresLow densityDumb-bellsSpace saving gamesMuscle groupHand held
The soft weight strength trainer includes a selectively fillable pouch with a strap positioned so that a person can fit a hand or foot in-between the strap and the fillable pouch. The soft weight strength trainer can be utilized in a variety of exercises that strengthen various muscle groups. None of the exercises that are performed with the soft weight strength trainer require a close fisted grip, which makes the soft weight strength trainer ideal for use by a person with reduced hand strength due to age or injury. Additionally, the soft weight strength trainer will not cause damage or injury if inadvertently dropped due to its non-rigid construction.
Owner:BRIZARD CYRIL +1
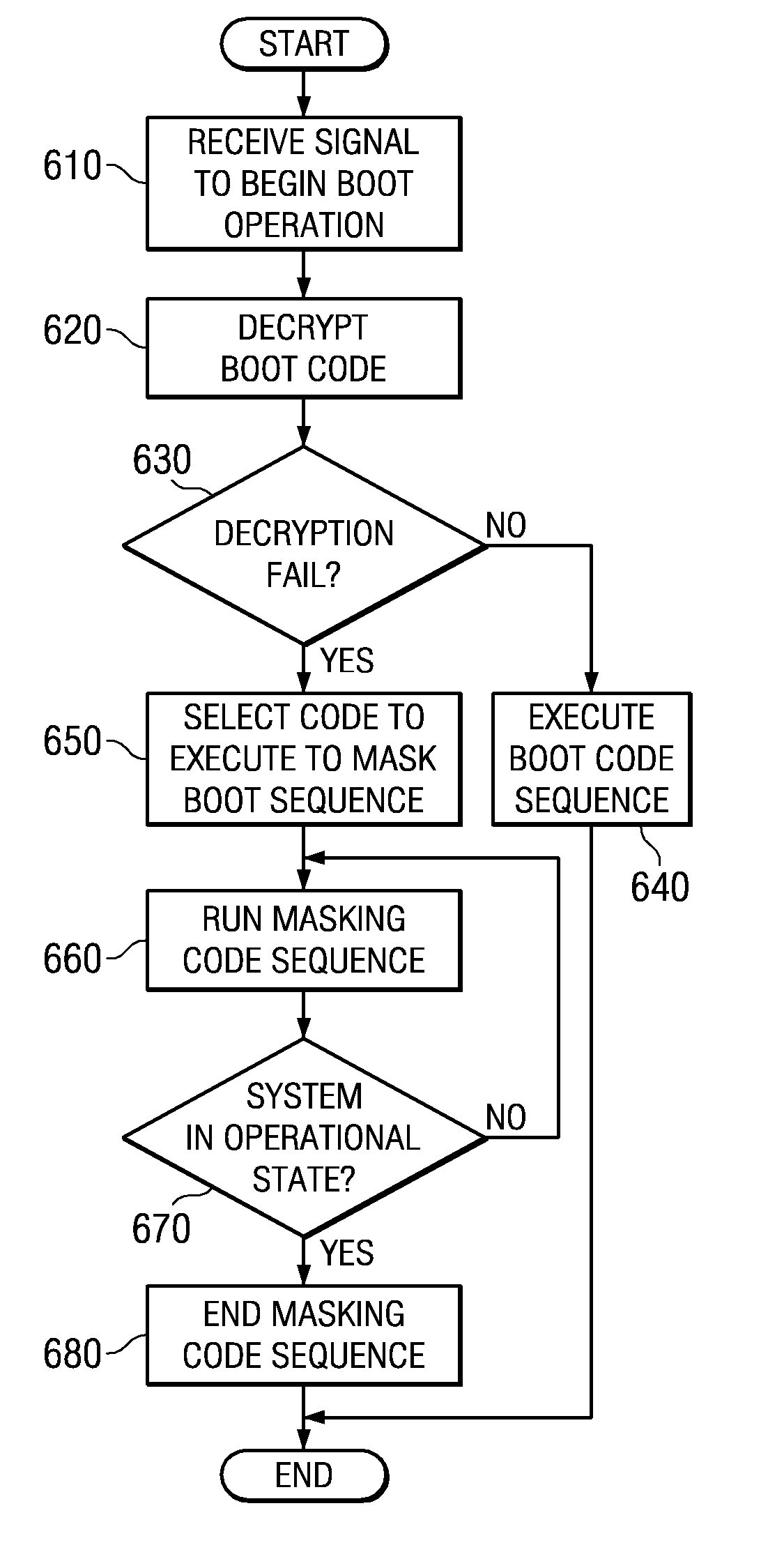
System and method for masking a hardware boot sequence
InactiveUS7594104B2Complete security measuresIncrease the number ofKey distribution for secure communicationDigital data processing detailsMulti processorSecurity information
A system and method for masking a hardware boot sequence are provided. With the system and method, one of the processors of a multiprocessor system is chosen to be a boot processor. The other processors of the multiprocessor system execute masking code that generates electromagnetic and / or thermal signatures that mask the electromagnetic and / or thermal signatures of the actual boot processor. Such masking may involve running the same boot code as the boot processor but without obtaining access to security information, such as the security key for accessing the system. The electromagnetic and / or thermal signatures generated by the execution of the masking code preferably approximate the electromagnetic and / or thermal signatures of the actual boot code executing on the boot processor. In this way, it is difficult to distinguish which processor is the actual boot processor.
Owner:INT BUSINESS MASCH CORP
System and method for masking a boot sequence by providing a dummy processor
InactiveUS20070288762A1Complete security measuresIncrease the number ofKey distribution for secure communicationVolume/mass flow measurementMulti processorMethod selection
A system and method for masking a boot sequence by providing a dummy processor are provided. With the system and method, one of the processors of a multiprocessor system is chosen to be a boot processor. The other processors of the multiprocessor system execute masking code that generates electromagnetic and / or thermal signatures that mask the electromagnetic and / or thermal signatures of the actual boot processor. The execution of the masking code on the non-boot processors preferably generates electromagnetic and / or thermal signatures that approximate the signatures of the actual boot code execution on the boot processor. One of the non-boot processors is selected to execute masking code that is different from the other masking code sequence to thereby generate a electromagnetic and / or thermal signature that appears to be unique from an external monitoring perspective.
Owner:IBM CORP
Air treatment apparatus and method
InactiveUS20170097163A1Improve air qualityEfficient executionMechanical apparatusDispersed particle filtrationAir treatmentAir purification
An air treatment apparatus and method are disclosed in the present invention, wherein, at least one air treatment unit is included. The unit comprises air inlet, air outlet, air treatment devices and connecting components. The air treatment device is located between the air inlet and the air outlet. The air treatment device comprises at least one of the following components: component for air purification and filtering, blow-through fan, draw-through fan, pump, component for heating, component for dehumidifying, component for humidifying, component for air-cooling. The air treatment unit can be used alone for improving the air quality of the environment. When more than one unit are connected together with the connecting components, the units are teamed up and work together, and an air treatment system is formed.
Owner:AKOS R&D
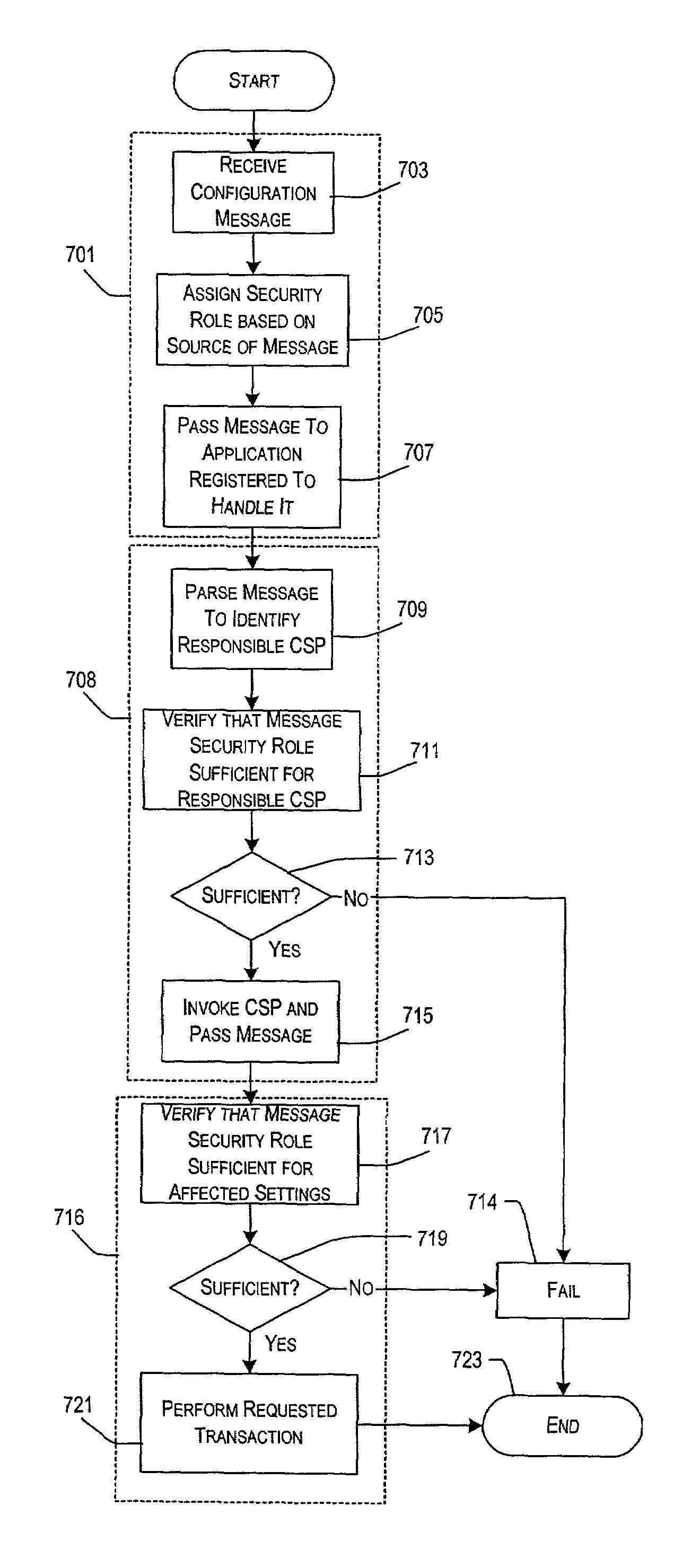
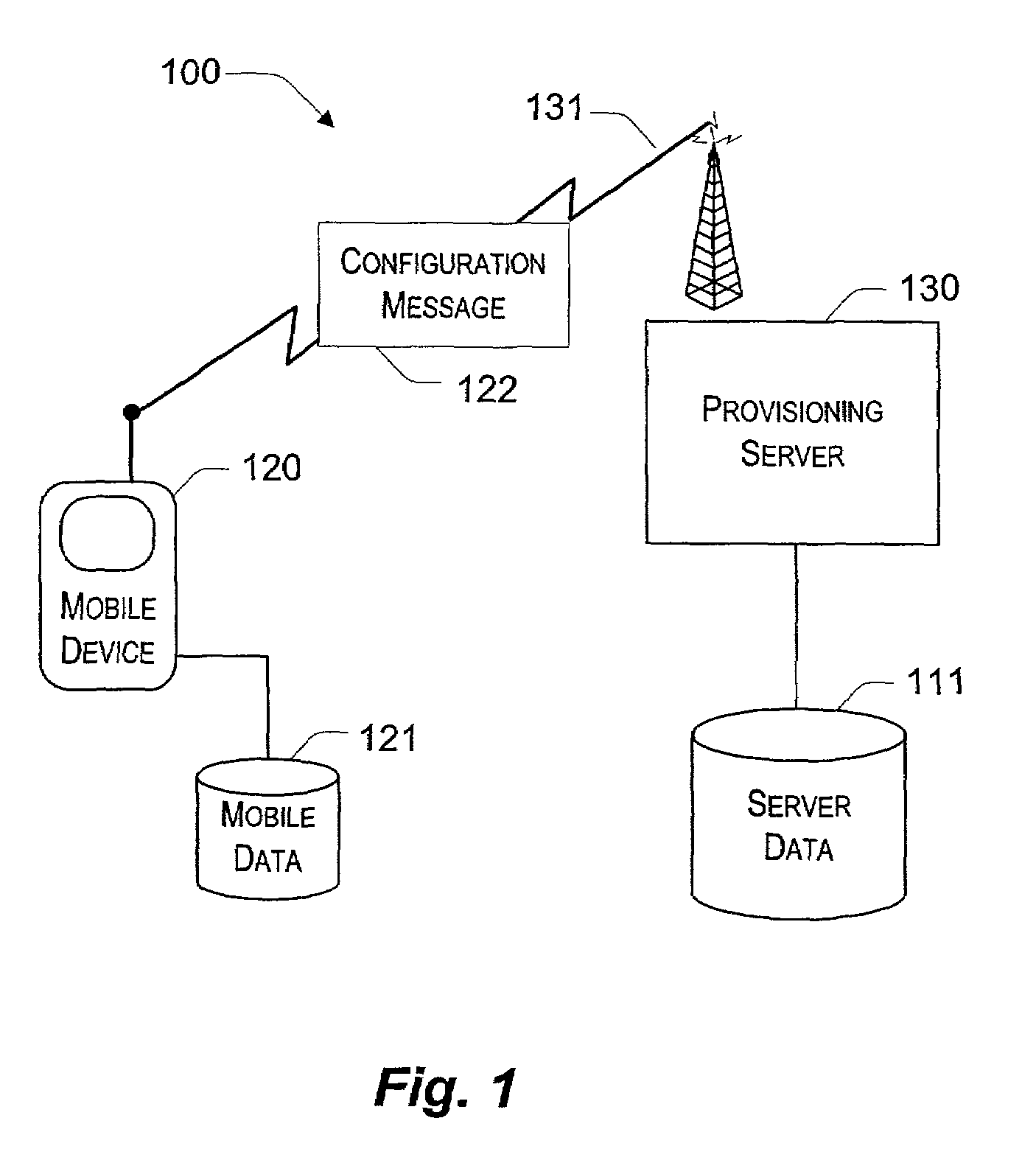
System and method for over the air configuration security
InactiveUS7188243B2Improve security measuresGreat peace of mindDigital data processing detailsUser identity/authority verificationComputer securityOver the Air
A system and method for assigning security credentials to particular components within a mobile device, and for ensuring that only configuration messages having sufficient access privilege to those components are allowed access, based on the security credentials. The security credentials or “roles” describe which settings a particular configuration message has authority to modify or query. Access is disallowed to settings for which a message does not have adequate security credentials.
Owner:MICROSOFT TECH LICENSING LLC
System and method for masking a hardware boot sequence
InactiveUS20070300053A1Complete security measuresIncrease the number ofKey distribution for secure communicationDigital data processing detailsMulti processorSecurity information
A system and method for masking a hardware boot sequence are provided. With the system and method, one of the processors of a multiprocessor system is chosen to be a boot processor. The other processors of the multiprocessor system execute masking code that generates electromagnetic and / or thermal signatures that mask the electromagnetic and / or thermal signatures of the actual boot processor. Such masking may involve running the same boot code as the boot processor but without obtaining access to security information, such as the security key for accessing the system. The electromagnetic and / or thermal signatures generated by the execution of the masking code preferably approximate the electromagnetic and / or thermal signatures of the actual boot code executing on the boot processor. In this way, it is difficult to distinguish which processor is the actual boot processor.
Owner:IBM CORP
Masking a Hardware Boot Sequence
InactiveUS20090055640A1Complete security measuresIncrease the number ofKey distribution for secure communicationDigital computer detailsMulti processorSecurity information
One of the processors of a multiprocessor system is chosen to be a boot processor. The other processors of the multiprocessor system execute masking code that generates electromagnetic and / or thermal signatures that mask the electromagnetic and / or thermal signatures of the actual boot processor. Such masking may involve running the same boot code as the boot processor but without obtaining access to security information, such as the security key for accessing the system. The electromagnetic and / or thermal signatures generated by the execution of the masking code preferably approximate the electromagnetic and / or thermal signatures of the actual boot code executing on the boot processor. In this way, it is difficult to distinguish which processor is the actual boot processor.
Owner:IBM CORP
Air treatment apparatus and method
InactiveUS20190056126A1Improve air qualityEfficient executionMechanical apparatusSpace heating and ventilation safety systemsWi-FiAir treatment
An air treatment apparatus and method are disclosed in the present invention, wherein, at least one air treatment unit is included. The air treatment device has at least one of the following components: component for air purification and filtering, blow-through fan, draw-through fan, pump, component for heating, component for dehumidifying, component for humidifying, component for air-cooling. The air treatment unit can be used alone for improving the air quality of the environment. When more than one unit are connected together with the connecting components, the units are teamed up and work together, and an air treatment system is formed. The connecting components further have at least one of the following components, a Wi-Fi module, a Infra-red transmission modules, a Bluetooth Modules.
Owner:AKOS R&D
System and Method for Quick Authentication between Bluetooth Devices
ActiveUS20120171961A1Fast authenticationSimplify the authentication processSynchronisation arrangementNetwork topologiesBluetoothAuthentication
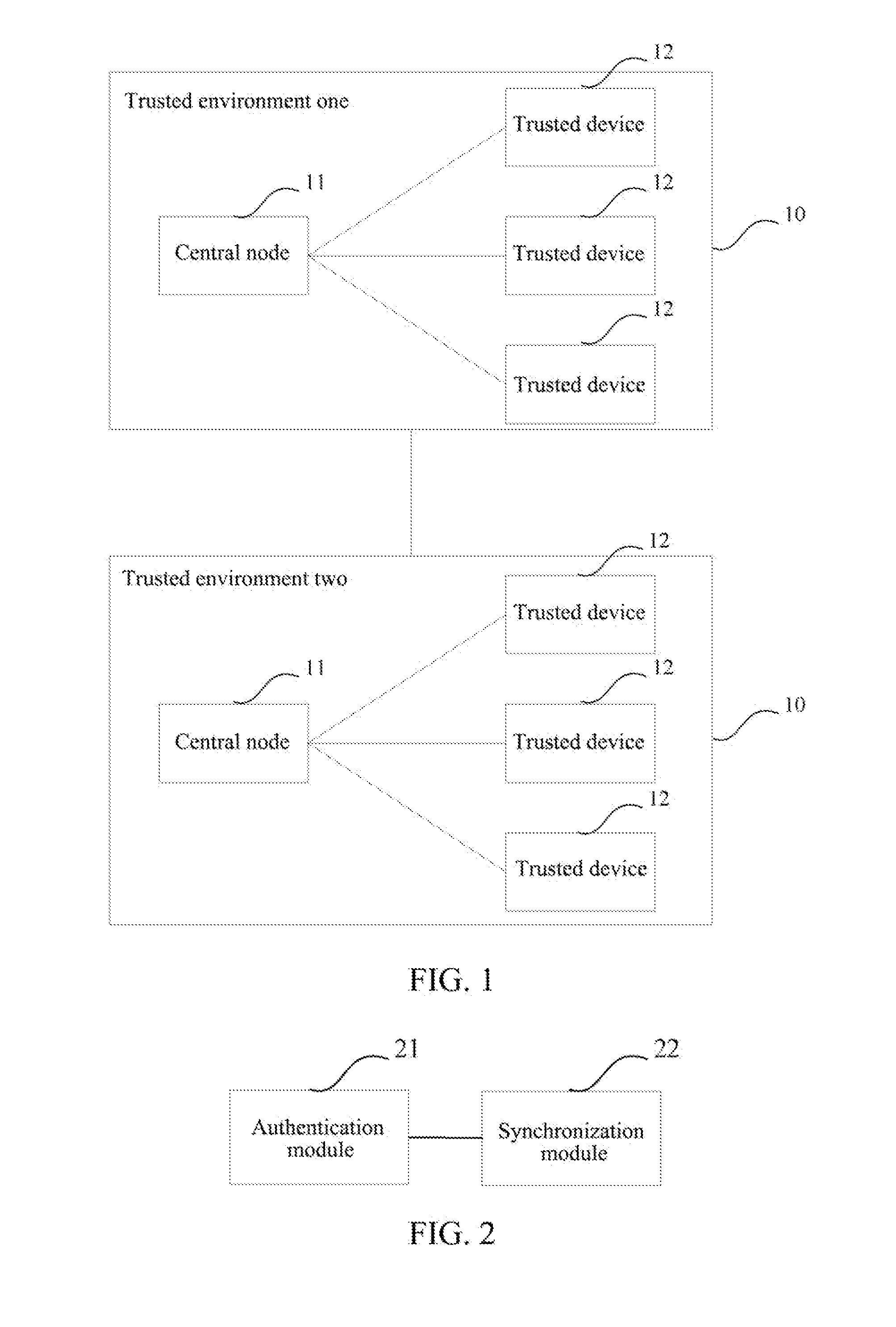
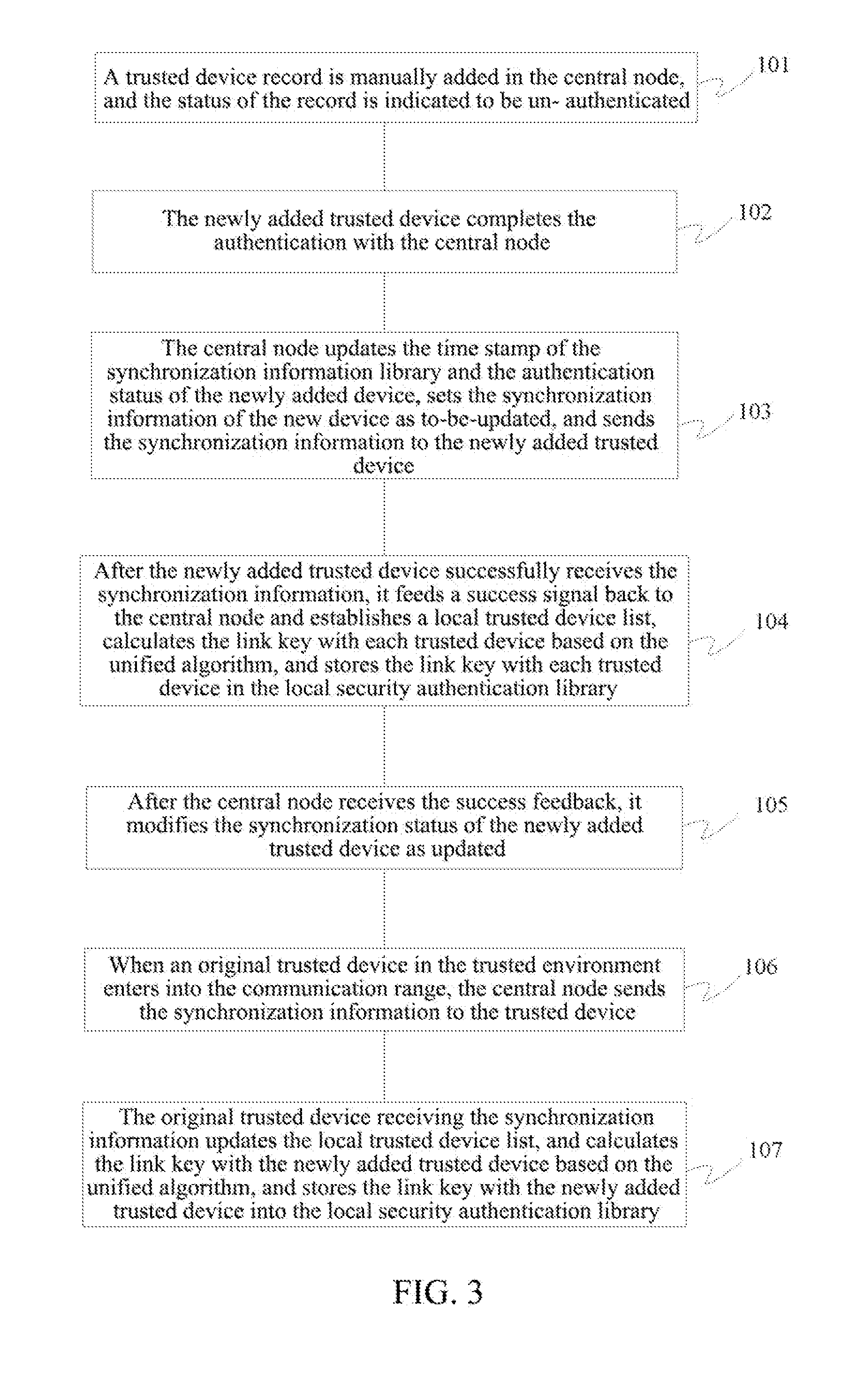
A system and method for quick authentication between Bluetooth devices are disclosed. The method includes: adding a central node (11) in a trusted environment (10, 13) of a Bluetooth device, wherein, said control node makes authentication with each trusted device (12) in the trusted environment and stores an information list containing information of each trusted device; after the information of a trusted device in the trusted environment is updated, the central node sends synchronization information to the trusted device that needs to update the synchronization information, and the trusted device receiving the synchronization information implements the update of the synchronization information.
Owner:DRNC HLDG INC
System and Method for Masking a Boot Sequence by Providing a Dummy Processor
InactiveUS20080215874A1Complete security measuresIncrease the number ofKey distribution for secure communicationDigital data processing detailsMulti processorComputer science
A system and method for masking a boot sequence by providing a dummy processor are provided. With the system and method, one of the processors of a multiprocessor system is chosen to be a boot processor. The other processors of the multiprocessor system execute masking code that generates electromagnetic and / or thermal signatures that mask the electromagnetic and / or thermal signatures of the actual boot processor. The execution of the masking code on the non-boot processors preferably generates electromagnetic and / or thermal signatures that approximate the signatures of the actual boot code execution on the boot processor. One of the non-boot processors is selected to execute masking code that is different from the other masking code sequence to thereby generate a electromagnetic and / or thermal signature that appears to be unique from an external monitoring perspective.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com