Patents
Literature
3378 results about "Complete data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
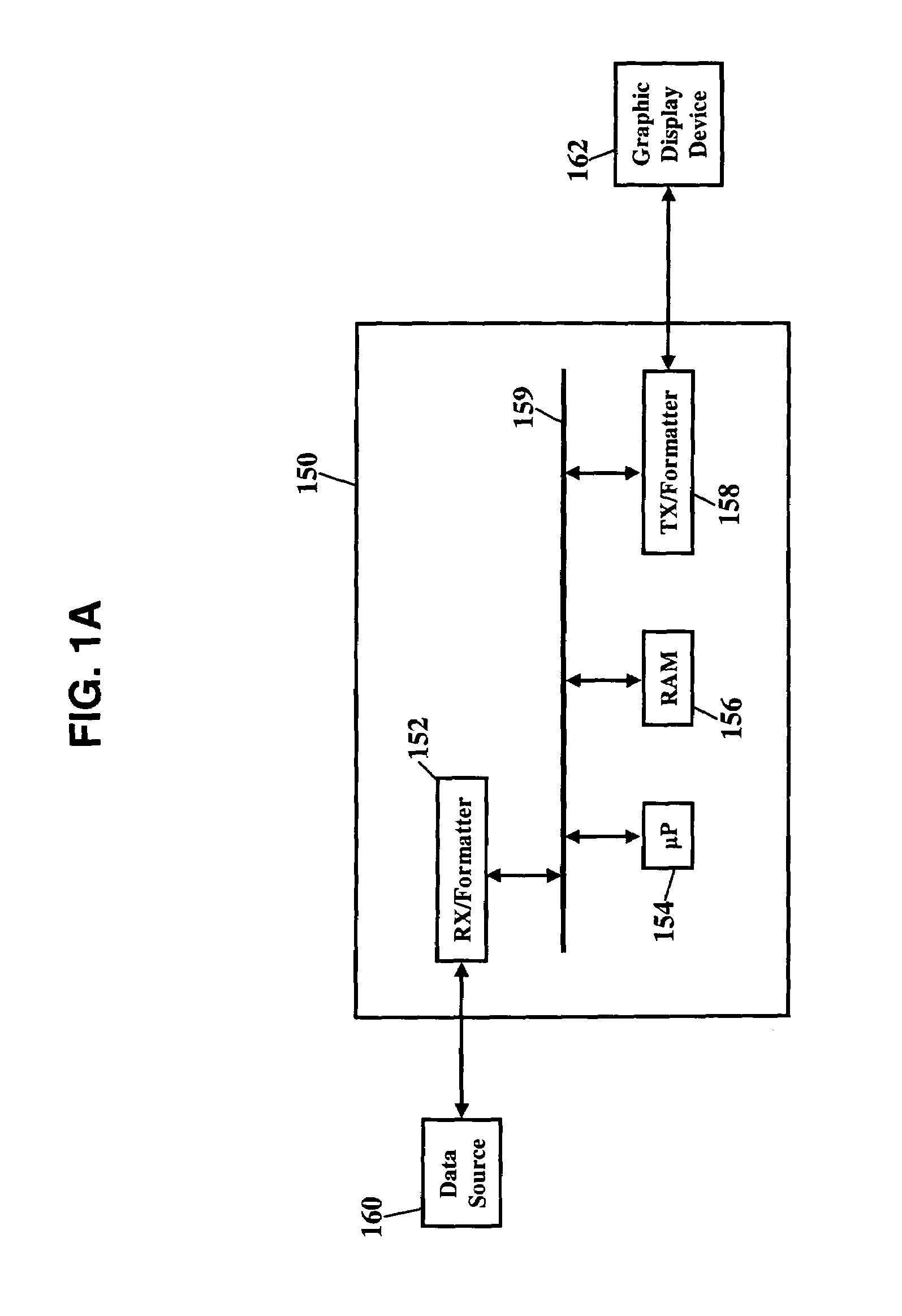
Method for reducing database recovery time
ActiveUS7222133B1Reduce database recovery timeShorten recovery timeData processing applicationsError detection/correctionComplete dataComputer science
Owner:UNISYS CORP
Scheduling with reverse direction grant in wireless communication systems
ActiveUS20070058605A1Reduce power consumptionReduce wasteNetwork topologiesTime-division multiplexComplete dataCommunications system
Systems and methodologies are described that facilitate increased communication channel bandwidth efficiency in association with scheduled time periods that allocate channel access to particular stations. According to various aspects, systems and methods are described that facilitate providing and / or utilizing reverse direction grants in connection with scheduled channel access. Such systems and / or method can mitigate an amount of unused channel access time after a station completes data transmission prior to an end of the allocated period.
Owner:QUALCOMM INC
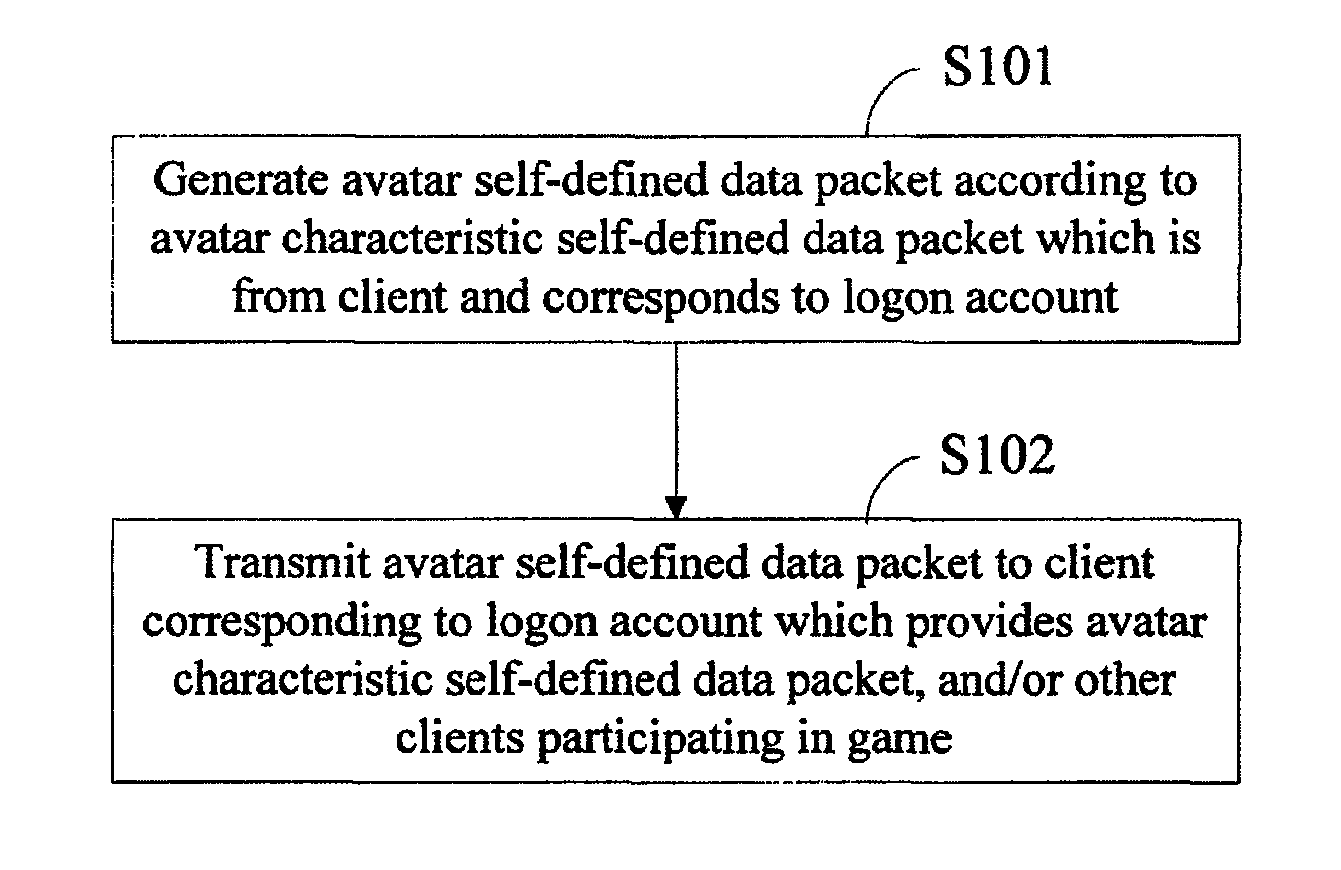
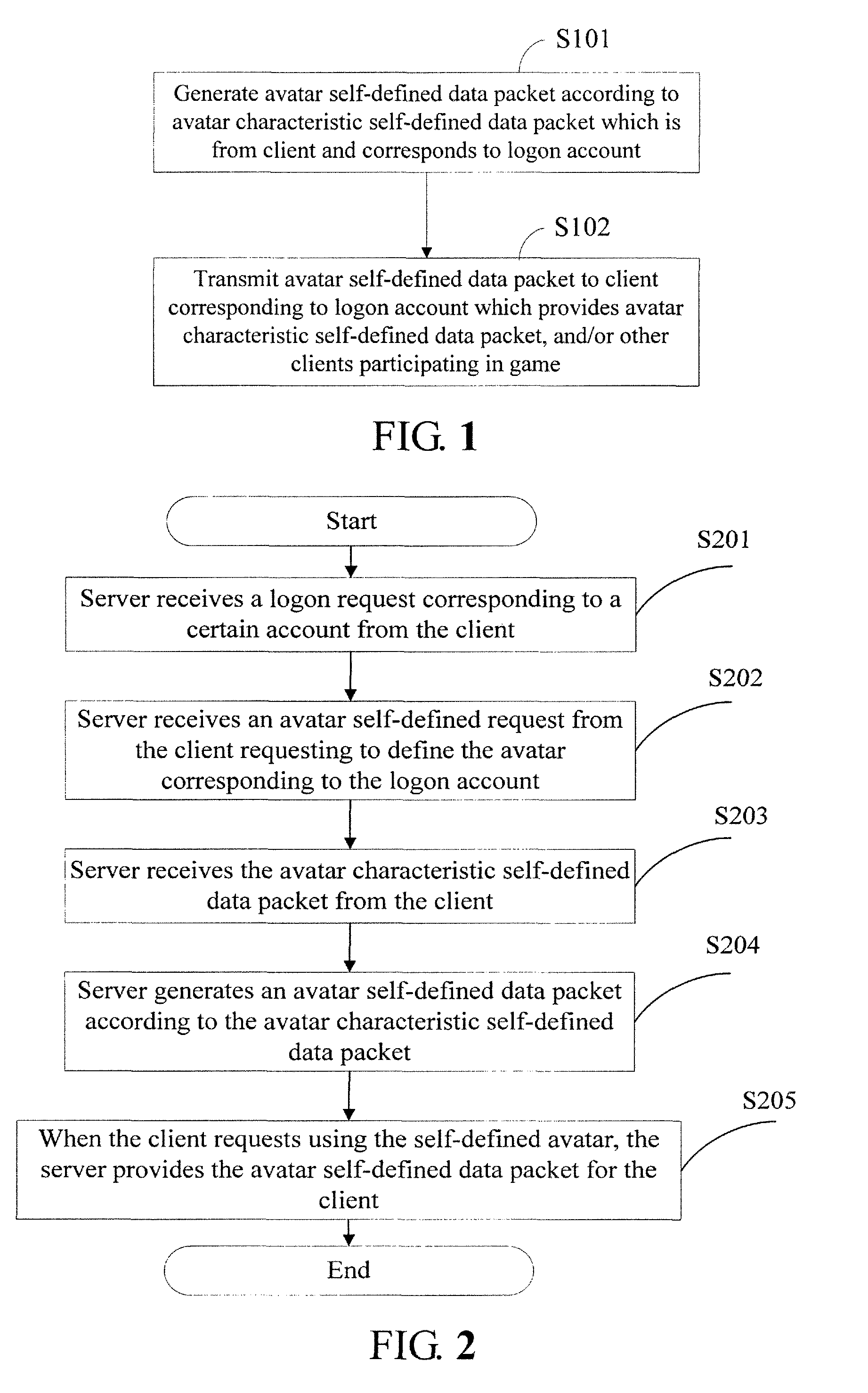
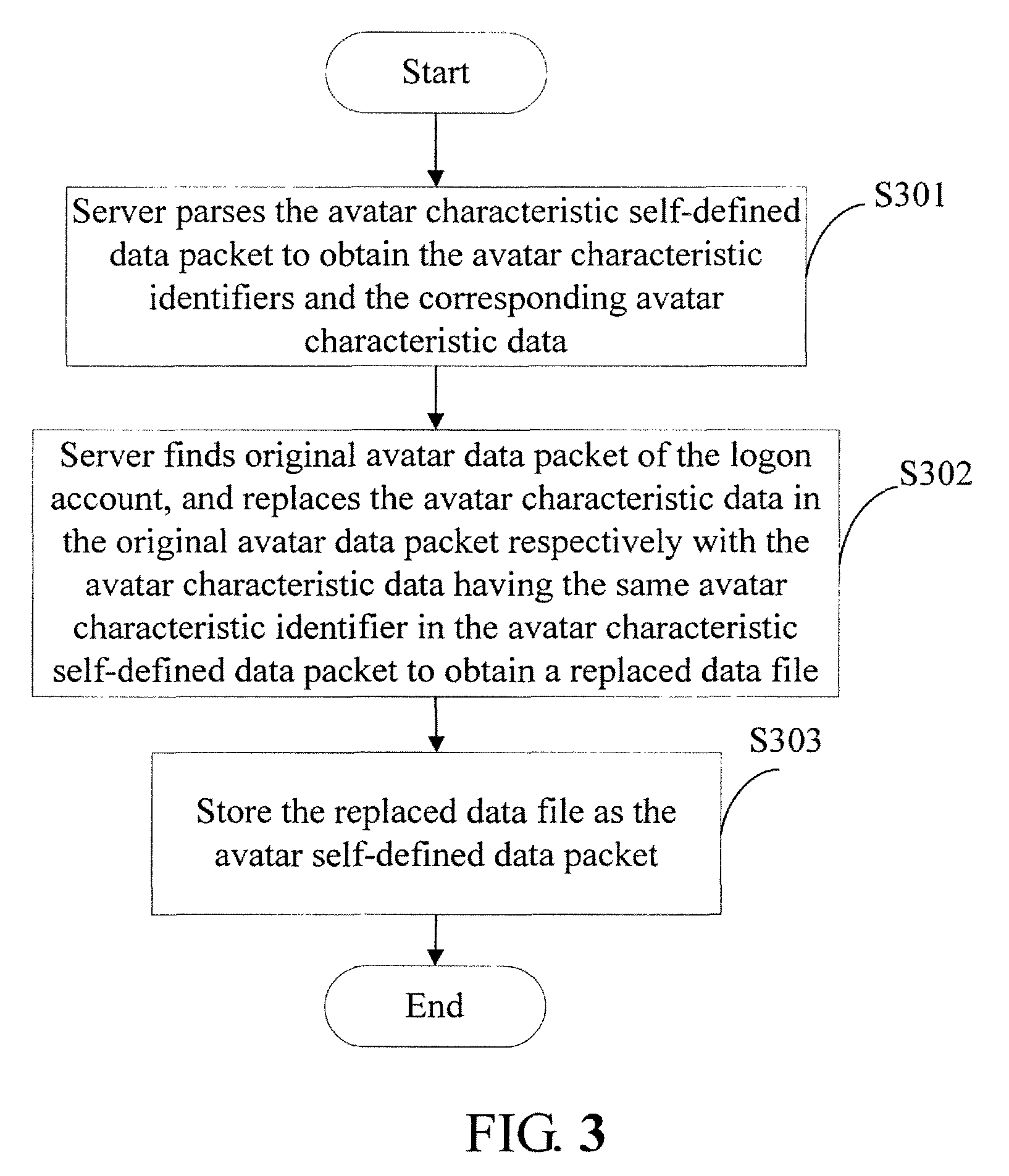
Method, system and apparatus for changing avatar in online game
ActiveUS8601051B2Enhance interestAttract more individuated playersImage enhancementDigital data processing detailsComplete dataNetwork packet
A method for changing an avatar in an online game includes: generating an avatar self-defined data packet comprising complete data of an avatar according to an avatar characteristic self-defined data packet from a client corresponding to a logon account, wherein the avatar characteristic self-defined data packet reflects modification or creation made by a player to the avatar; and transmitting the avatar self-defined data packet to the client corresponding to the logon account providing the avatar characteristic self-defined data packet, and / or a second client participating in the online game. A system and an apparatus for changing an avatar in an online game are also provided.
Owner:TENCENT TECH (SHENZHEN) CO LTD
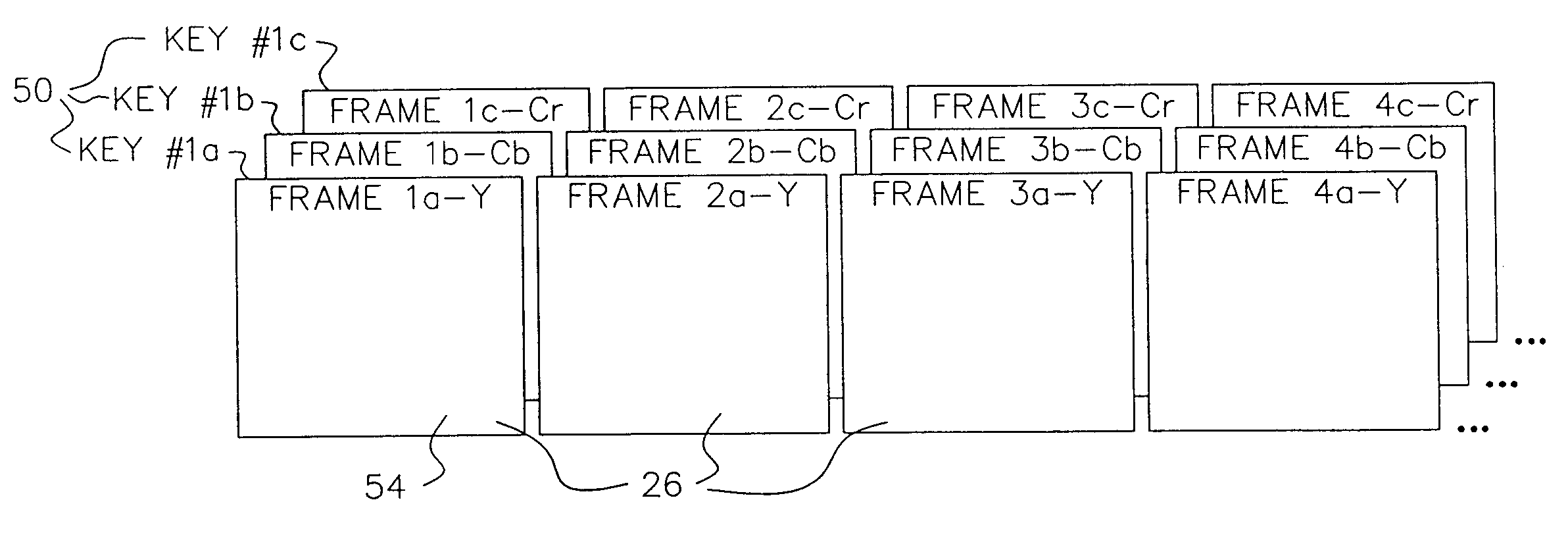
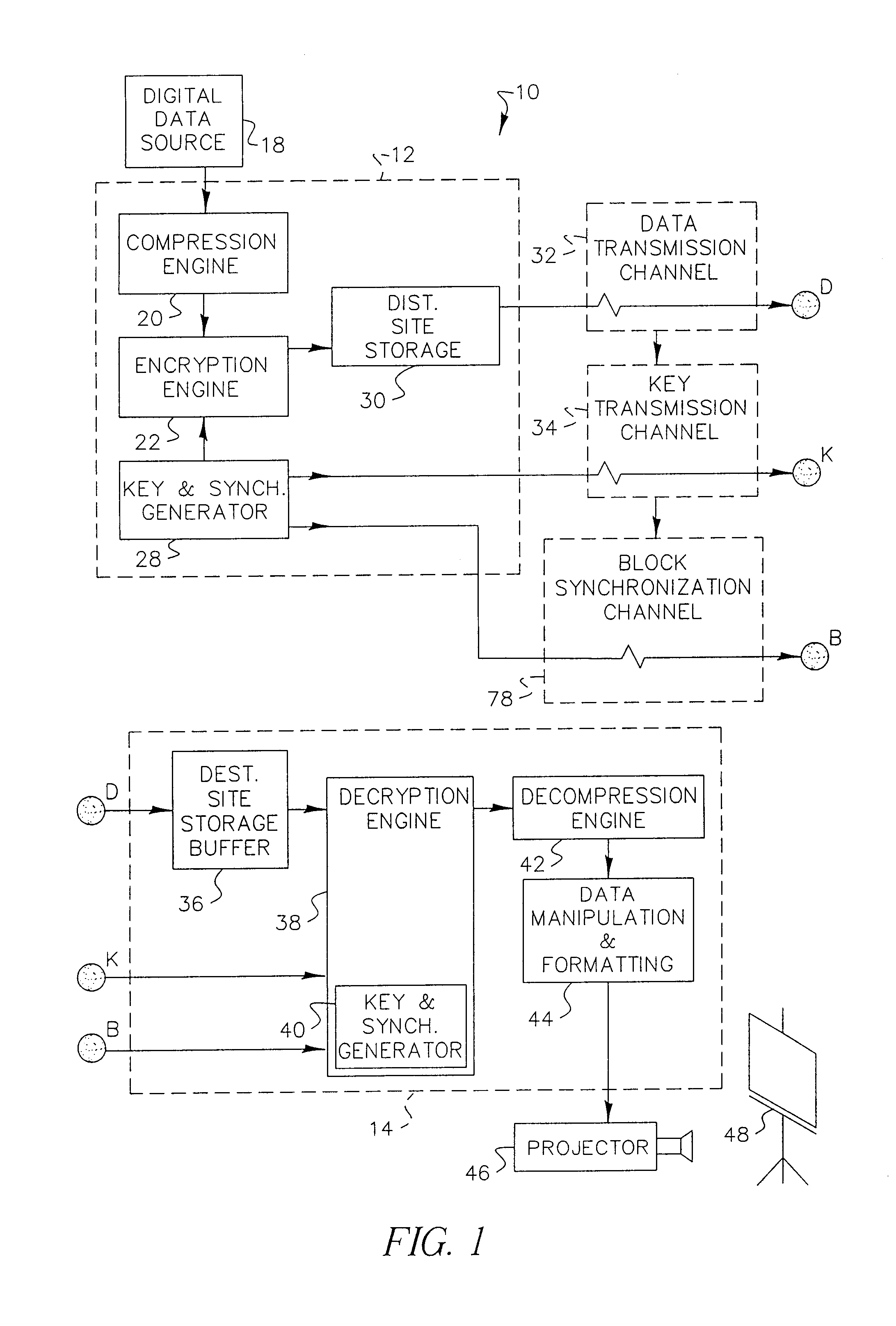
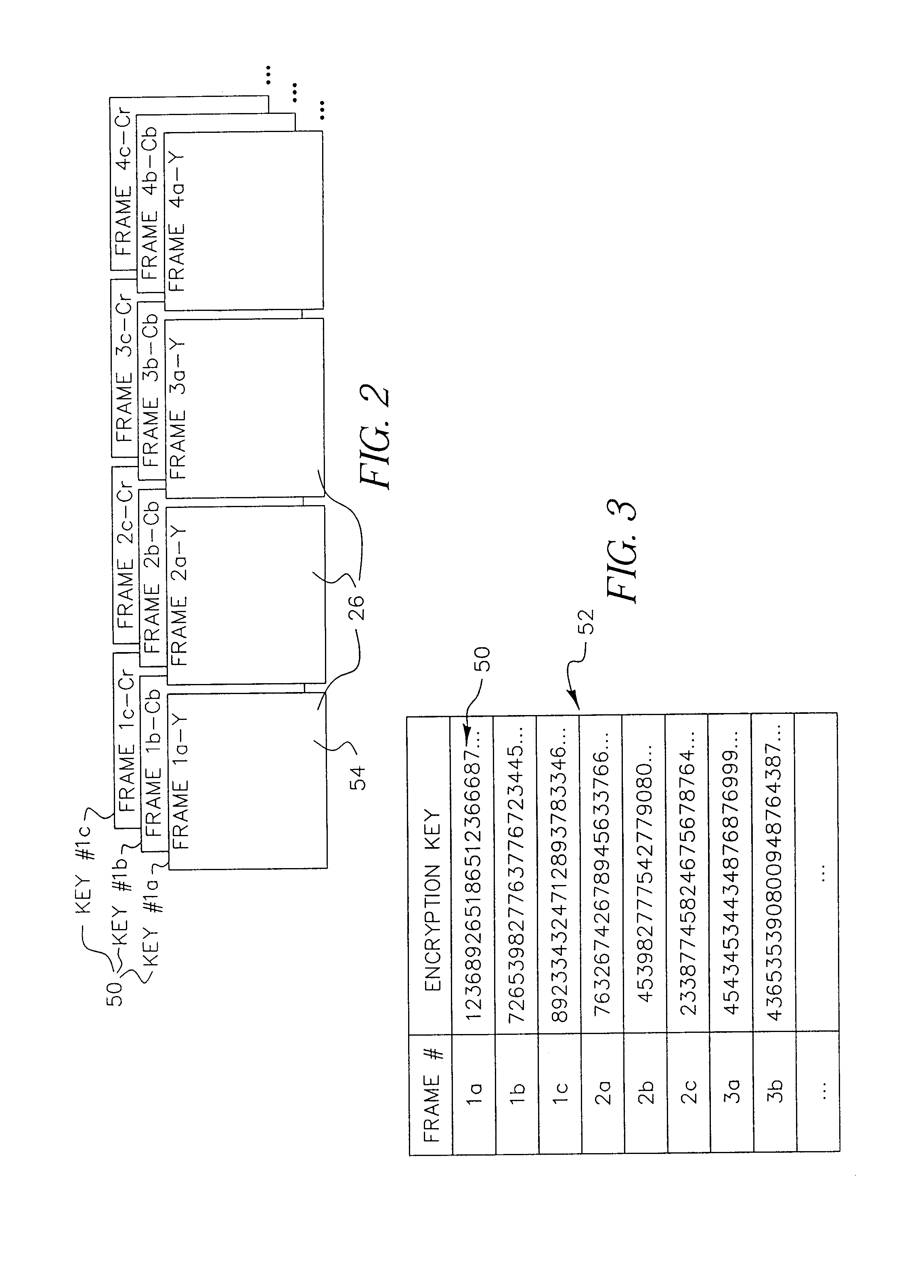
Encryption apparatus and method for synchronizing multiple encryption keys with a data stream
ActiveUS7242772B1Minimized in sizeImprove distributionKey distribution for secure communicationSynchronising transmission/receiving encryption devicesMultiple encryptionComputer hardware
A data stream, such as a digital motion picture, is encrypted in units of one or more blocks, each block having an assigned encryption key. A plurality of encryption keys is assigned to the complete data stream, with a synchronization index provided to map each individual encryption key to its starting data block. Encryption keys and associated synchronization indices are provided separately from the data stream, using one or more additional data transfer mechanisms. An optional offset, randomly generated, allows variation in intervals between data blocks at which encryption by a specific encryption key can be performed.
Owner:MONUMENT PEAK VENTURES LLC
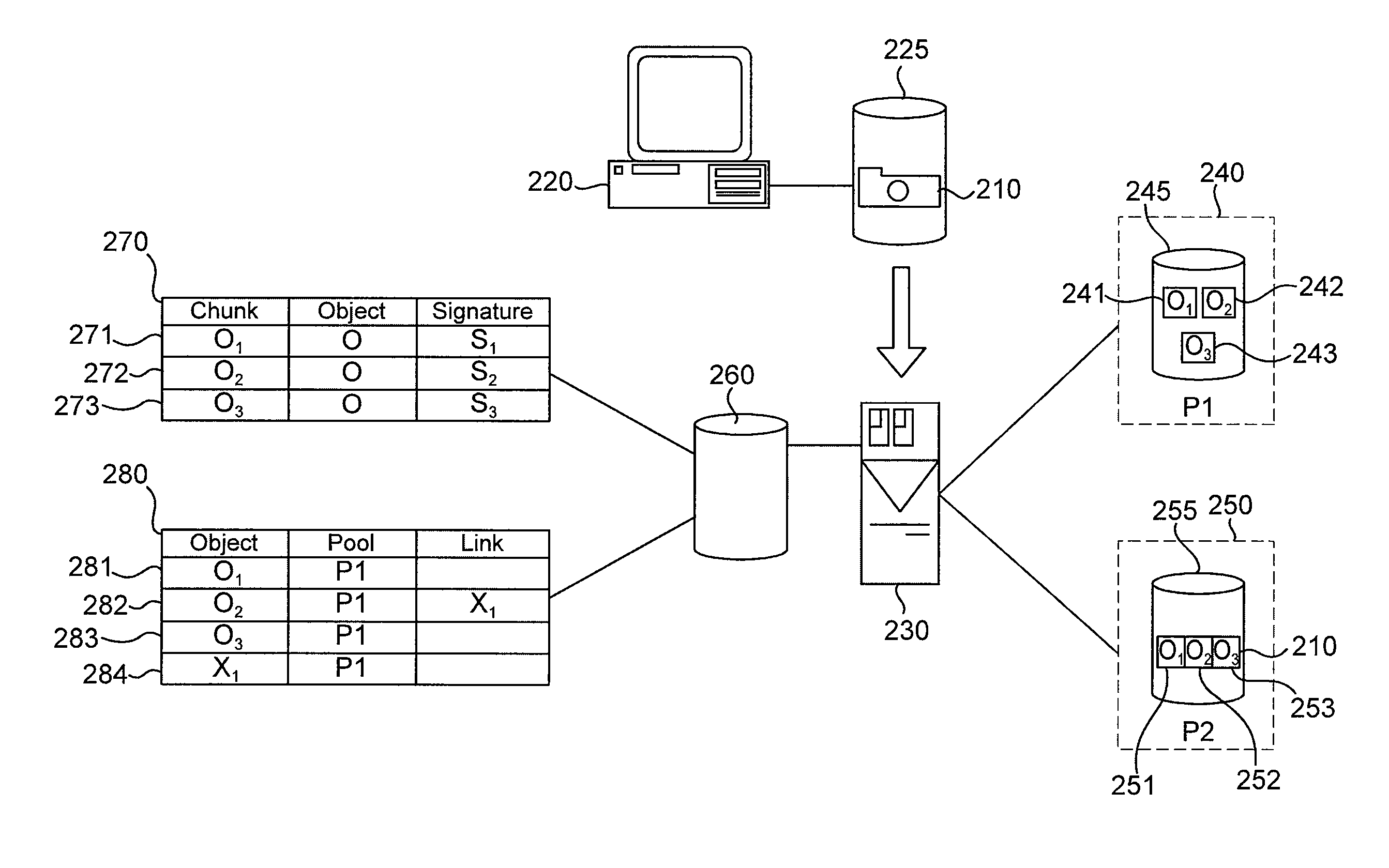
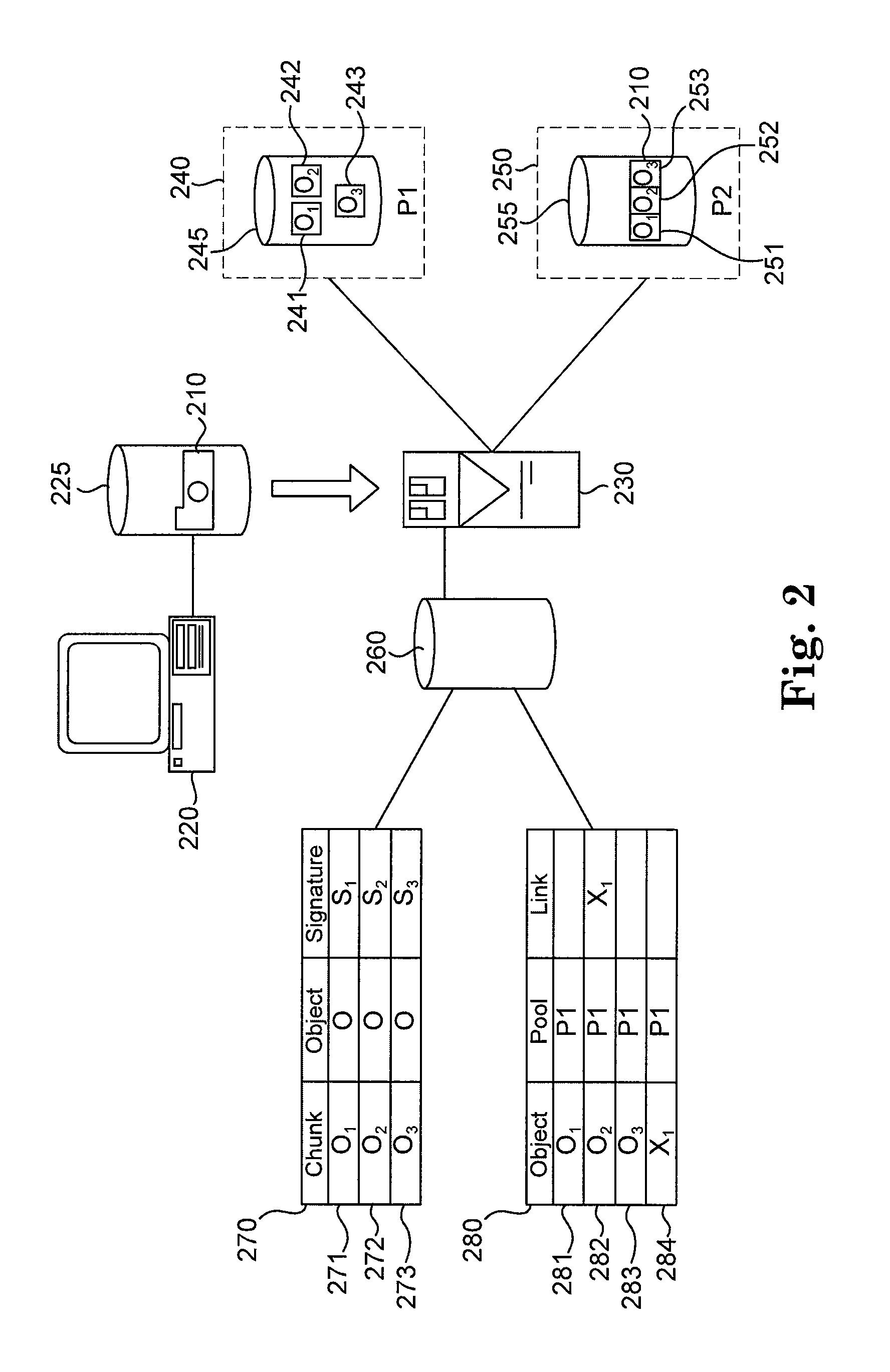
Retrieval and recovery of data chunks from alternate data stores in a deduplicating system
InactiveUS20100070478A1Various limitationPreserve integrityDigital data processing detailsError detection/correctionComplete dataStorage management
One aspect of the present invention includes retrieving and recovering data chunks from alternate data stores in a storage management system which utilizes deduplication. In one embodiment, deduplication information for data chunks of data objects is stored at a system-wide level to enable the transfer and access of data chunks stored among multiple storage pools. When a data object is accessed on a first storage pool that contains damaged or inaccessible data chunks, the undamaged and accessible chunks may be retrieved from the first storage pool, in addition to retrieving an undamaged copy of the damaged or inaccessible data chunks from alternate data storage pools. Thus, a complete data object can be retrieved or recovered with a combination of chunks from the first storage pool and other storage pools within the storage management system, without requiring the entire data object to be retrieved from a backup source.
Owner:IBM CORP
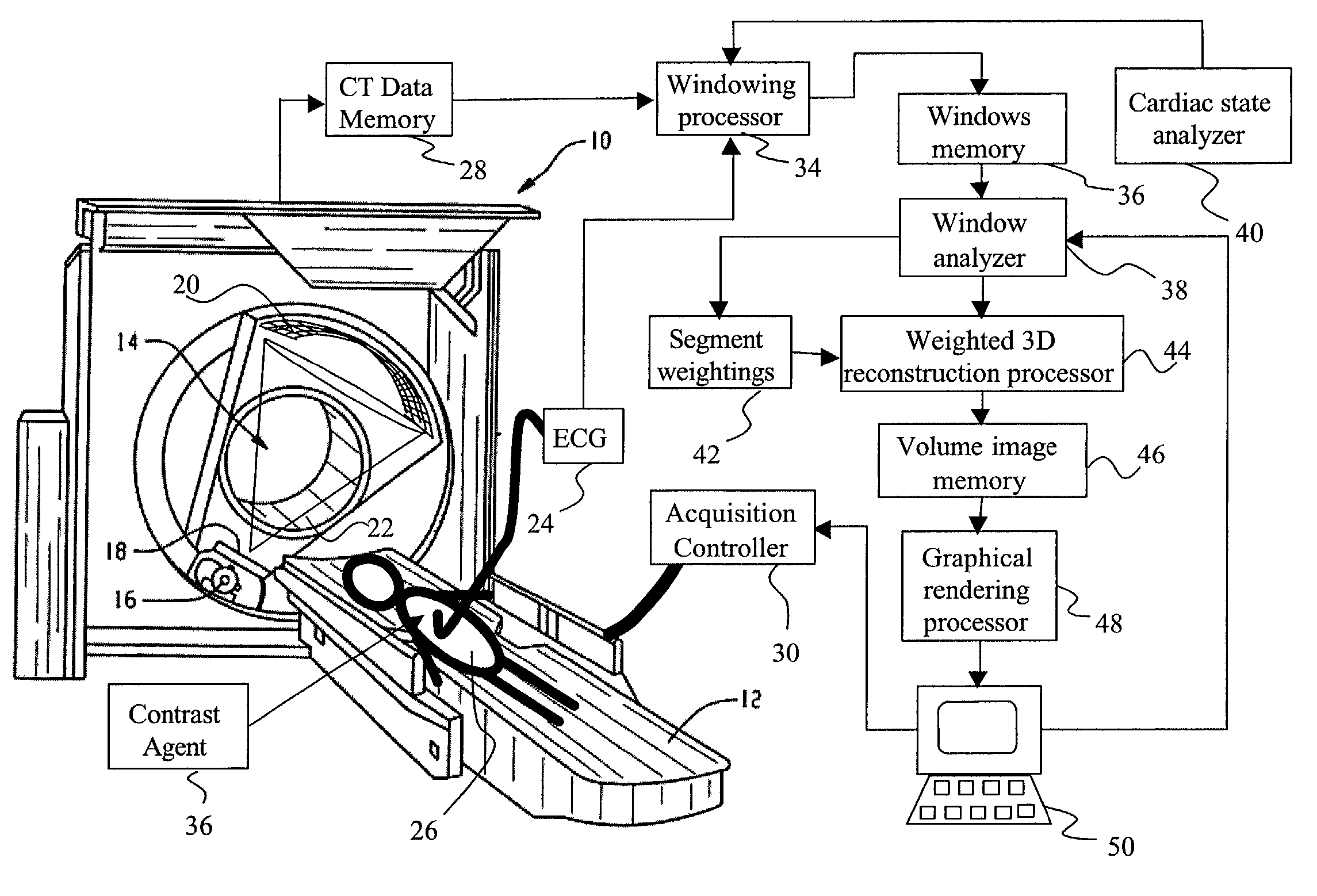
Dynamic computed tomography imaging using positional state modeling
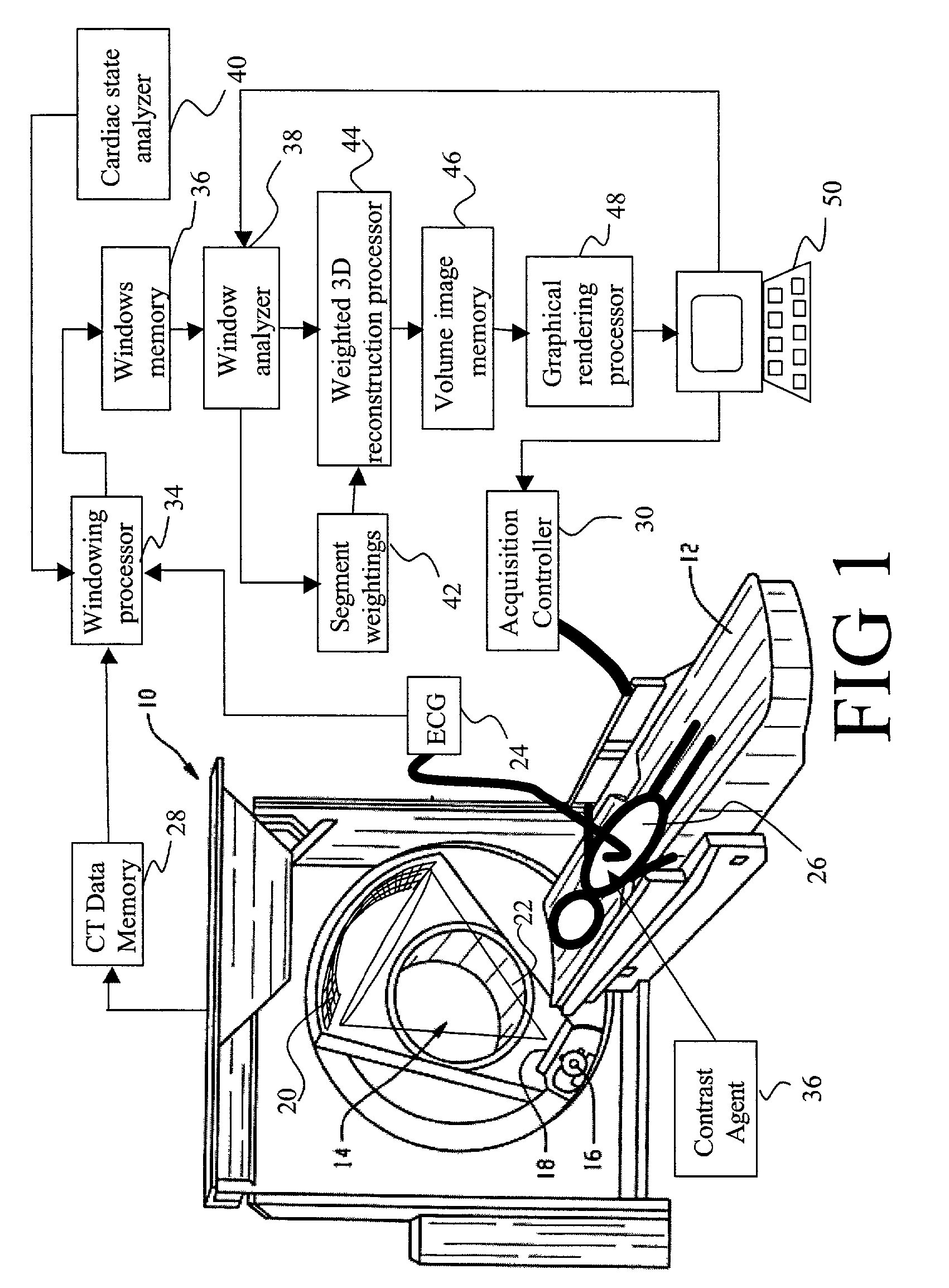
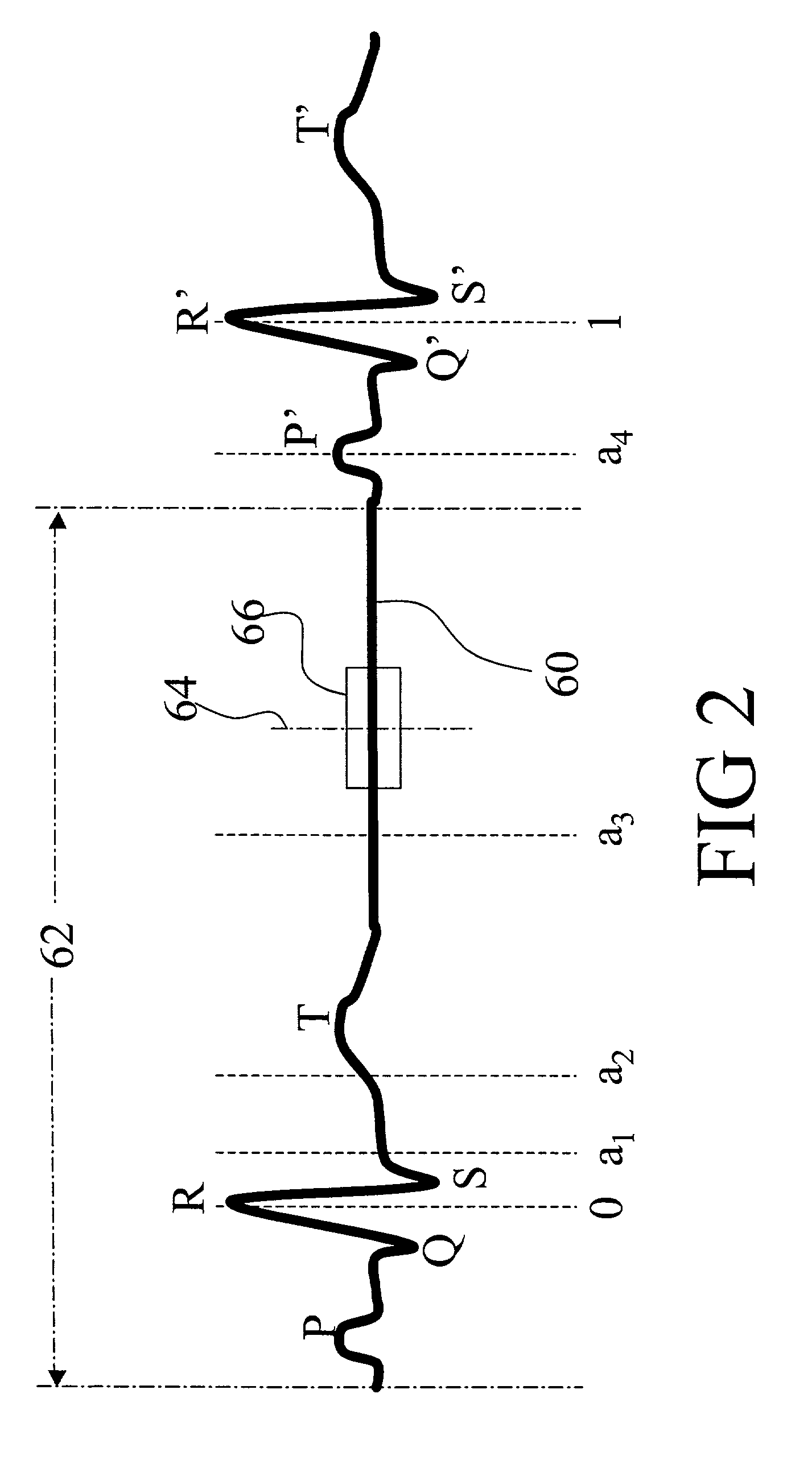
InactiveUS7058440B2Improves temporalImprove spatial resolutionElectrocardiographyMaterial analysis using wave/particle radiationData segmentData set
An apparatus for computed tomography (CT) imaging of a cyclically moving organ includes a positional state monitor (24, 40) that monitors a positional state of the cyclically moving organ such as the heart. A cone-beam CT scanner (10) acquires image data at least within a plurality of time windows. Each time window is centered about an occurrence of a selected positional state of the organ. A window analyzer (38) selects a data segment within each time window such that the data segments combine to form a complete data set covering a selected angular range. A reconstruction processor (44) reconstructs the selected data segments into an image representation.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Method of and system for intravenous volume tomographic digital angiography imaging
InactiveUS6075836AQuality improvementEfficient contrastMaterial analysis using wave/particle radiationRadiation/particle handlingCt scannersData acquisition
Owner:UNIVERSITY OF ROCHESTER
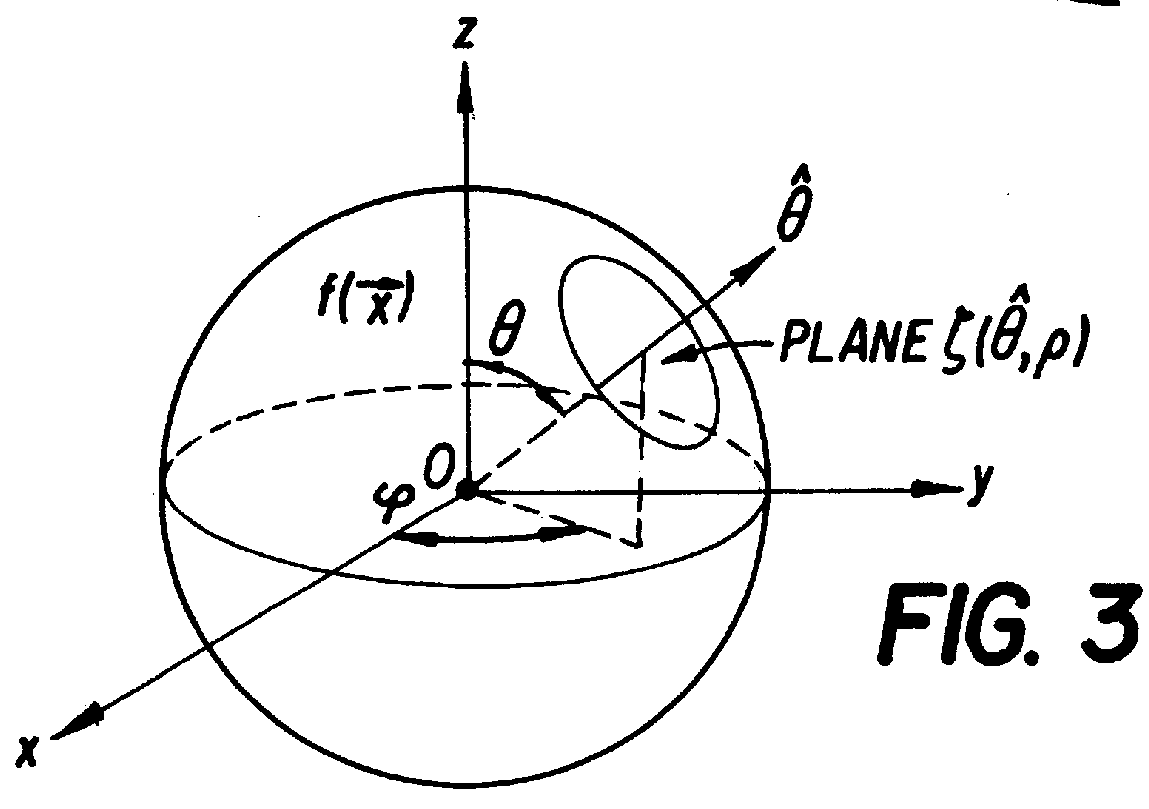
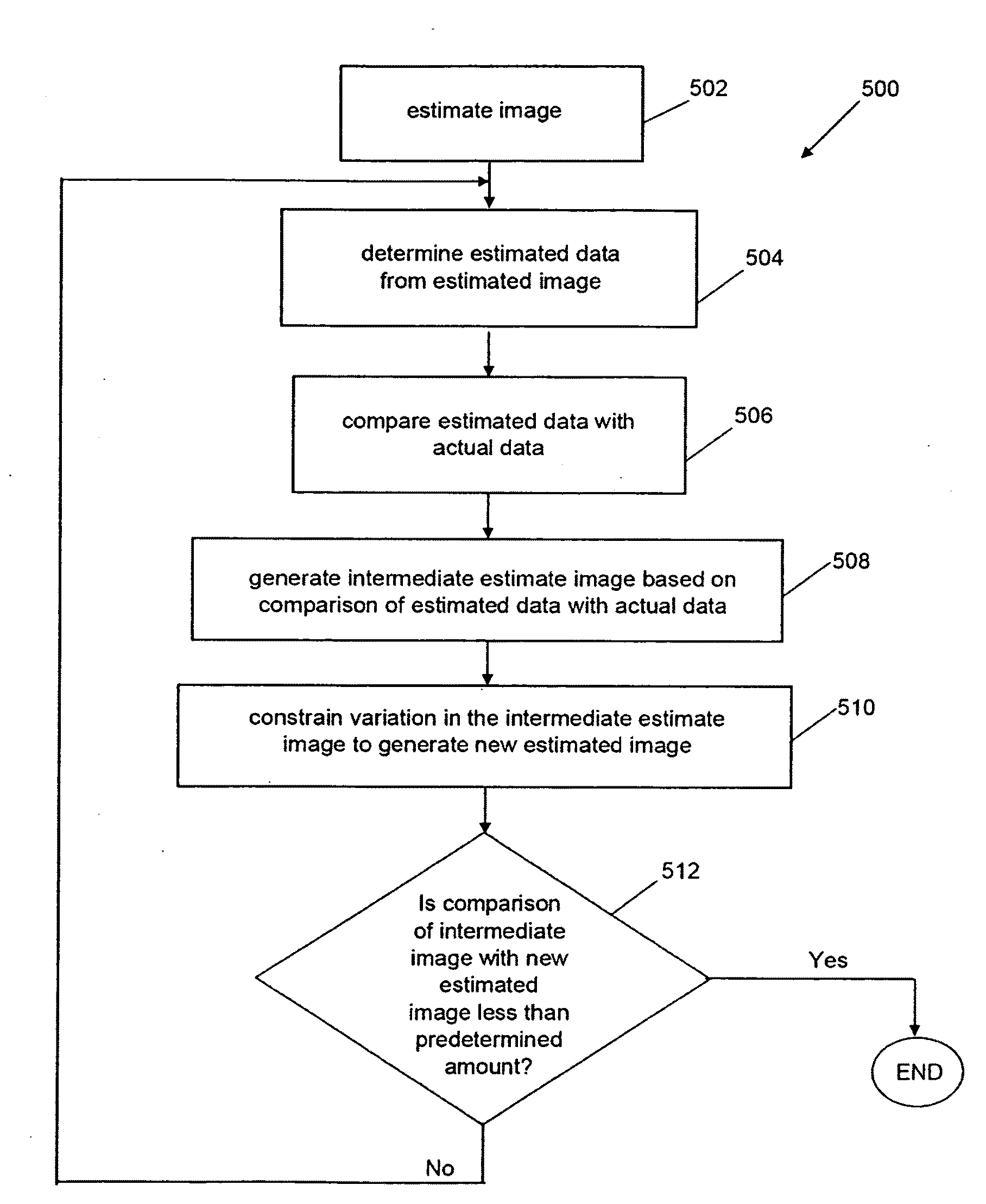
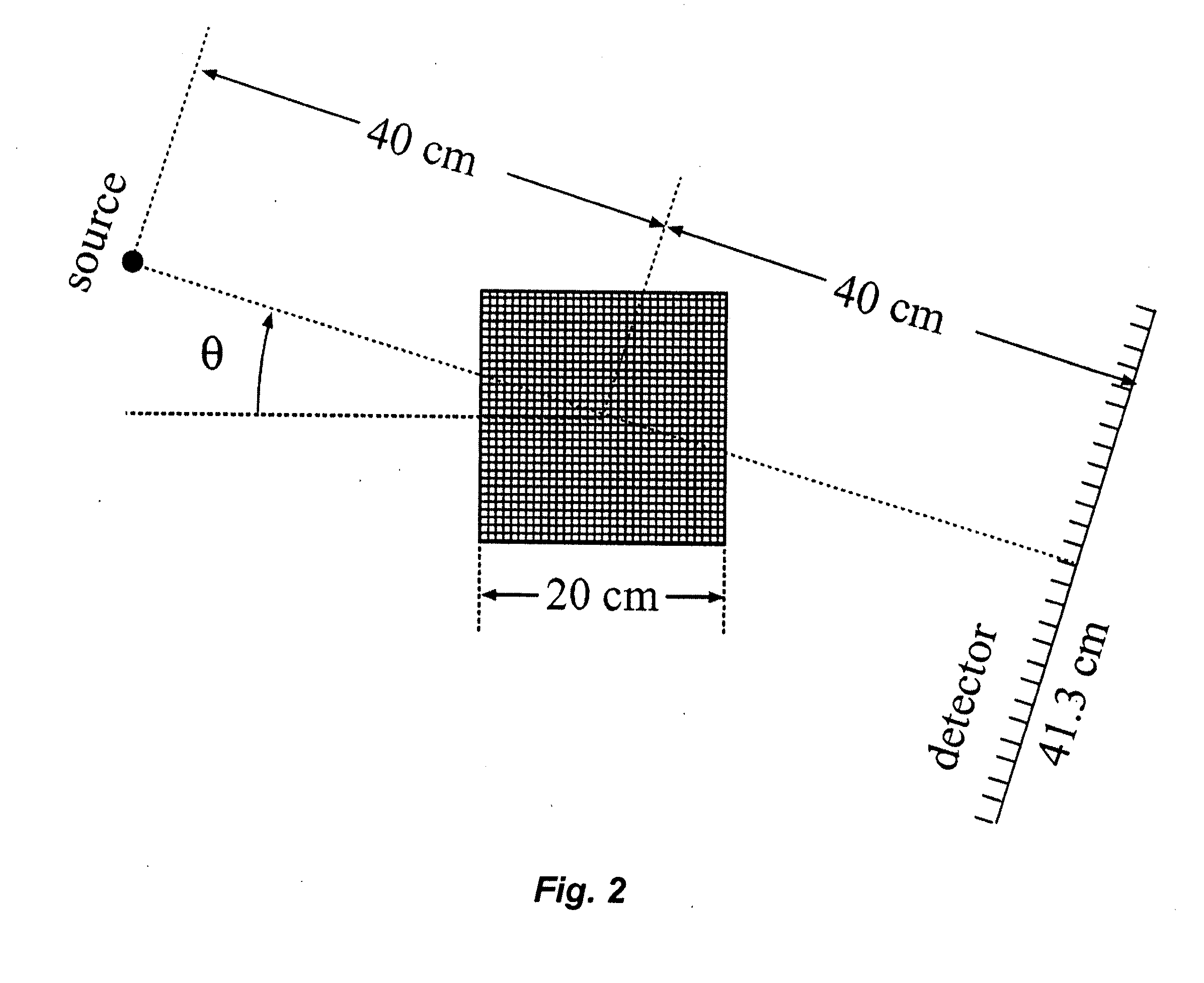
Image Reconstruction From Limited or Incomplete Data
ActiveUS20110044546A1Lessen and reducing total variationReconstruction from projectionCharacter and pattern recognitionComplete dataComputer vision
A system and method are provided for reconstructing images from limited or incomplete data, such as few view data or limited angle data or truncated data (including exterior and interior data) generated from divergent beams. In one aspect of the invention, the method and apparatus iteratively constrains the variation of an estimated image in order to reconstruct the image. As one example, a divergent beam maybe used to generate data (“actual data”). As discussed above, the actual data may be less than sufficient to exactly reconstruct the image by conventional techniques, such as FBP. In order to reconstruct an image, a first estimated image may be generated. Estimated data may be generated from the first estimated image, and compared with the actual data. The comparison of the estimated data with the actual data may include determining a difference between the estimated and actual data. The comparison may then be used to generate a new estimated image. For example, the first estimated image may be combined with an image generated from the difference data to generate a new estimated image. In order to generate the image for the next iteration, the variation of the new estimated image may be constrained. For example, the variation of the new estimated image may be at least partly constrained in order to lessen or reducing the total variation of the image.
Owner:UNIVERSITY OF CHICAGO
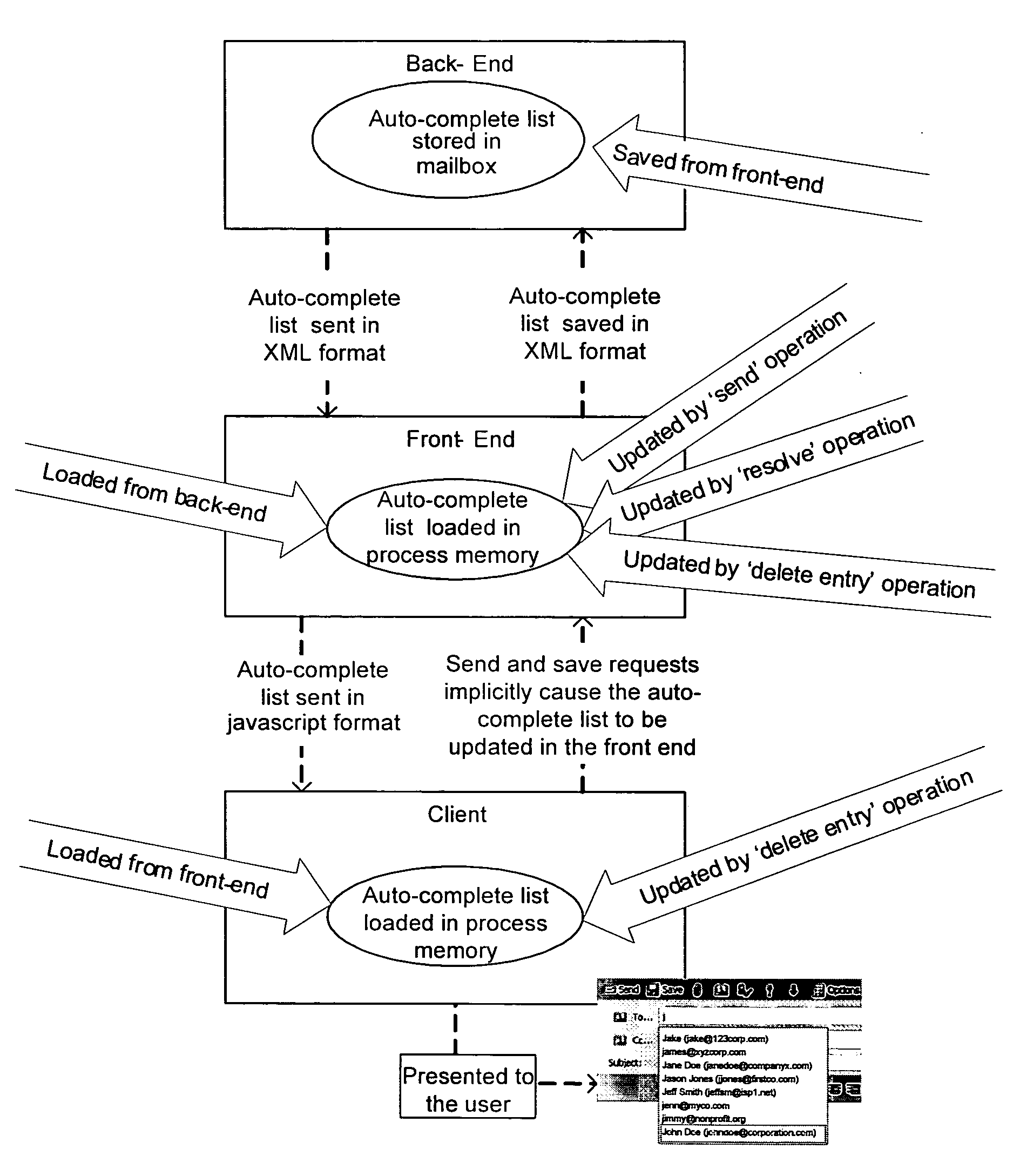
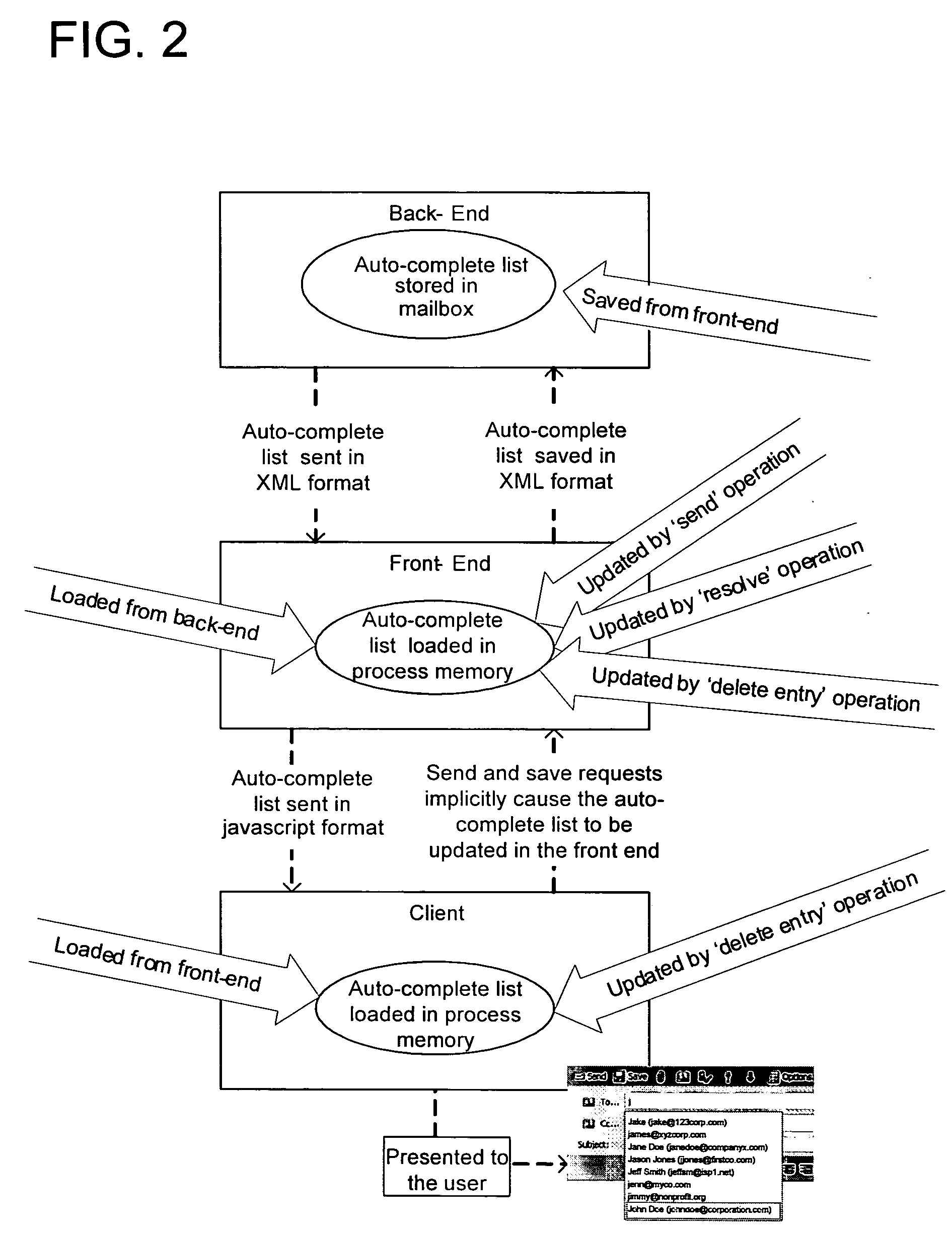
Server-deployed cache list management for presenting an auto-complete list
InactiveUS20060242109A1Natural language data processingSpecial data processing applicationsComplete dataClient-side
Auto-complete lists that are utilized by server-deployed client processes are provided. The auto-complete lists are utilized by a client process to provide a list of potential data records that may match a data record that is partially entered into an input field by a user. The user may either continue to type in a complete data record into the input field, or alternatively, select a displayed data record contained in the auto-complete list for entry in the input field.
Owner:MICROSOFT TECH LICENSING LLC
Secure printing via a wireless internet service
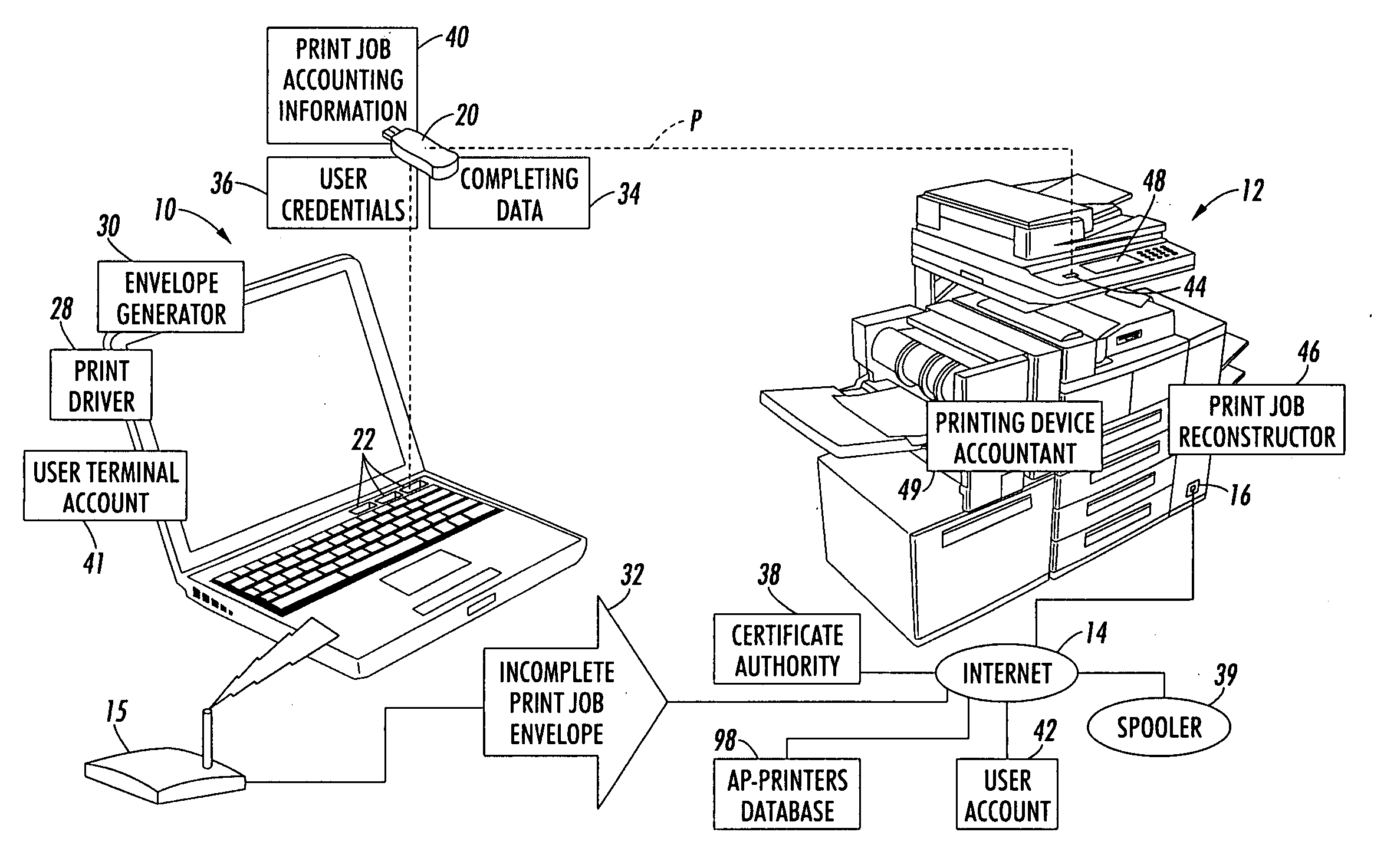
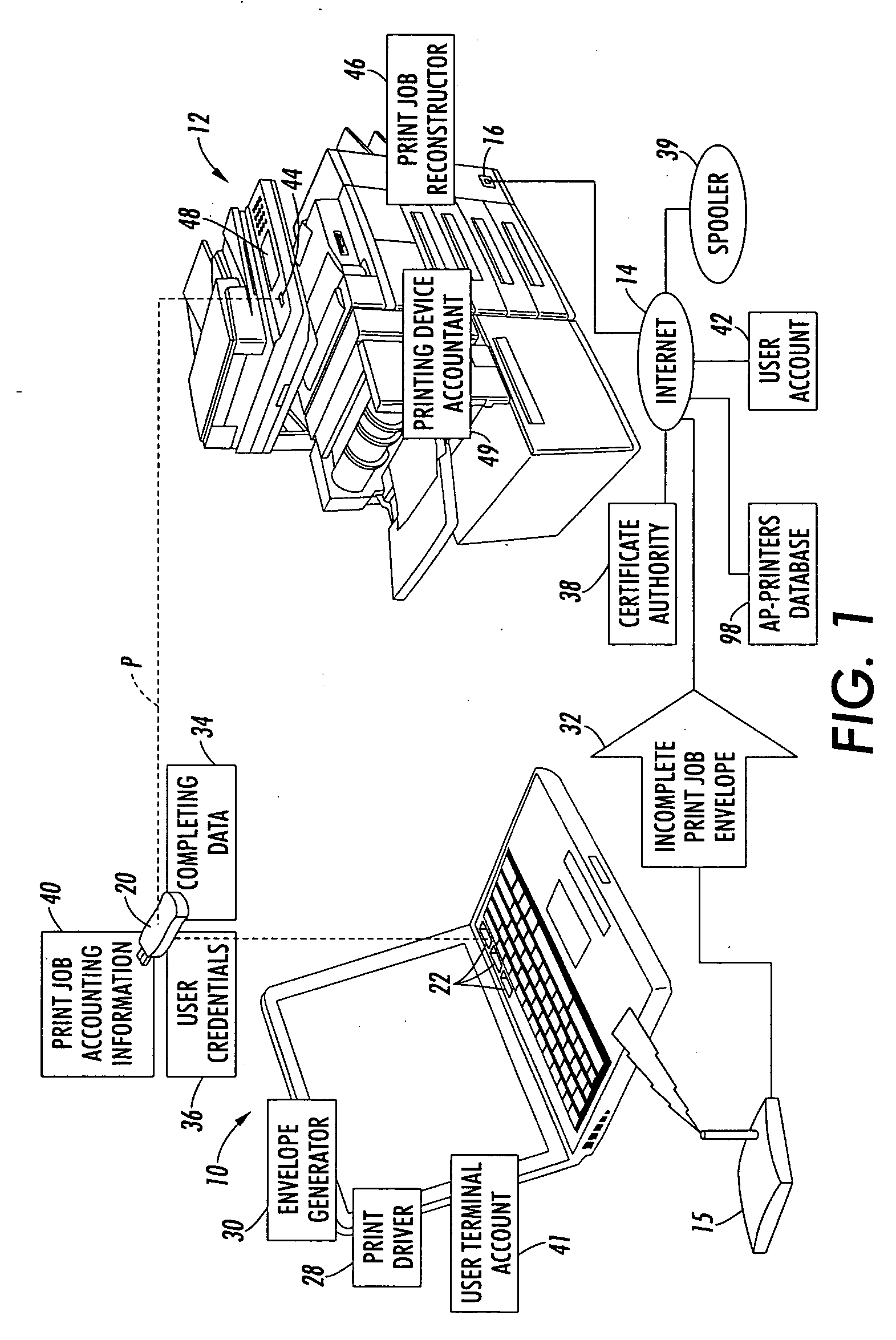
At a user terminal (10) operatively connected with a mobile device (20), a print job is formed into an incomplete print job envelope (32) and completing data (34, 40) including at least print job accounting information (40). The completing data (34, 40) including at least the print job accounting information (40) is stored on the mobile device (20). The incomplete print job envelope (32) is transmitted to a printing device (12). The mobile device (20) is operatively disconnected the from the user terminal (10), and is operatively connected with the printing device (12). After the operative connecting, the print job is re-constructed at the printing device (12), and the re-constructed print job is printed using the printing device (12). A cost of the printing is accounted for based on the print job accounting information (40) stored on the operatively connected mobile device (20).
Owner:XEROX CORP
System and method for providing video services
InactiveUS6961955B1High bandwidthGreater storage savingsTelevision system detailsAnalogue secracy/subscription systemsComputer networkData stream
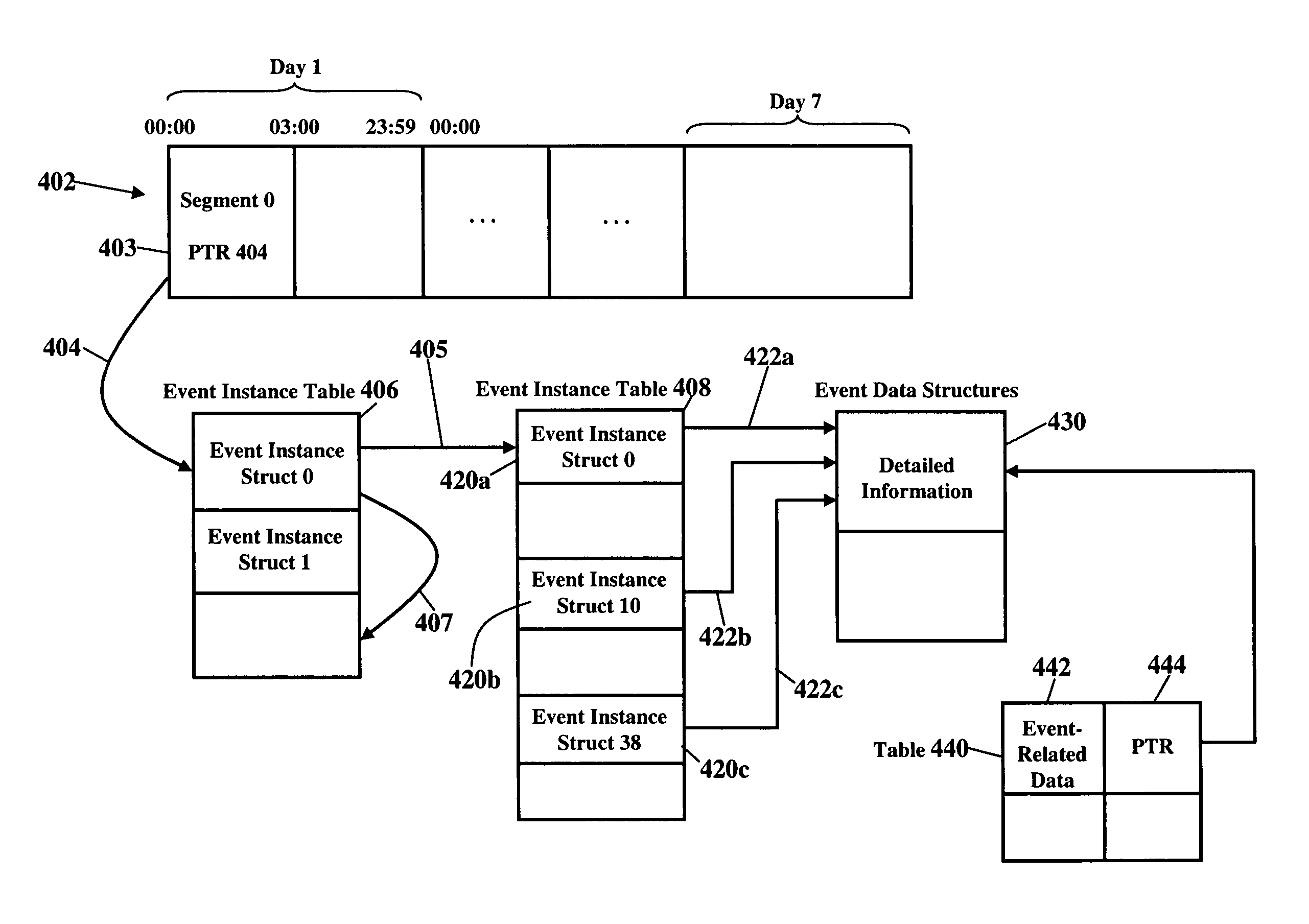
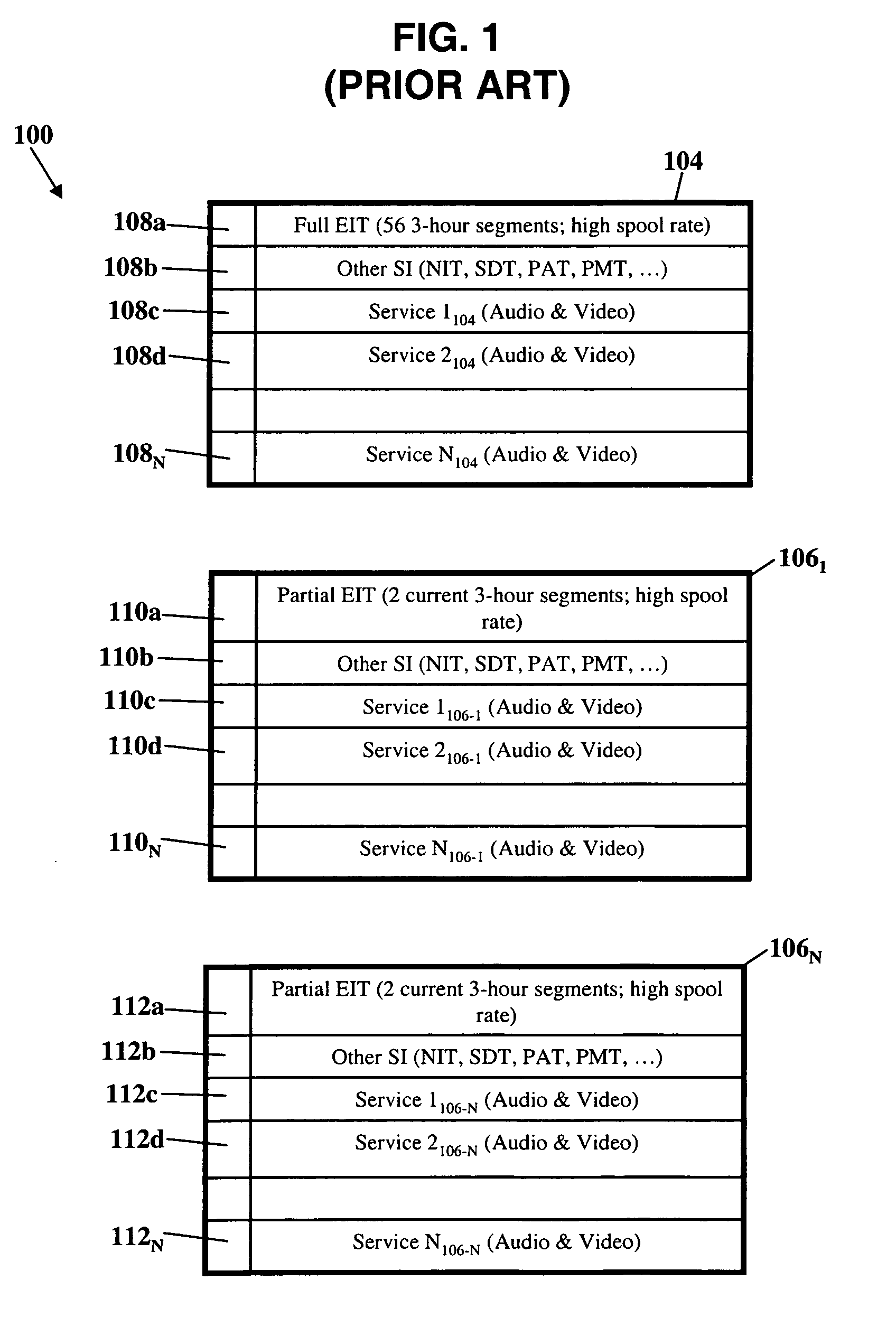
Set top boxes are provided with access to full EIT data streams without having to off-tune from one transport to another. If off-tuning is required, however, a locking mechanism substantially reduces or eliminates service interruption. Data in the additional EIT data streams in the non-home transports is reorganized to be sent by time rather than by service. EIT data is stored in the set top box in an architecture which significantly reduces the redundancy inherent in EIT data, allowing a full 7 days of EIT data to be stored in the set top box memory. The set top box of the present invention is backward compatible with conventional set top boxes.
Owner:BELLSOUTH INTPROP COR
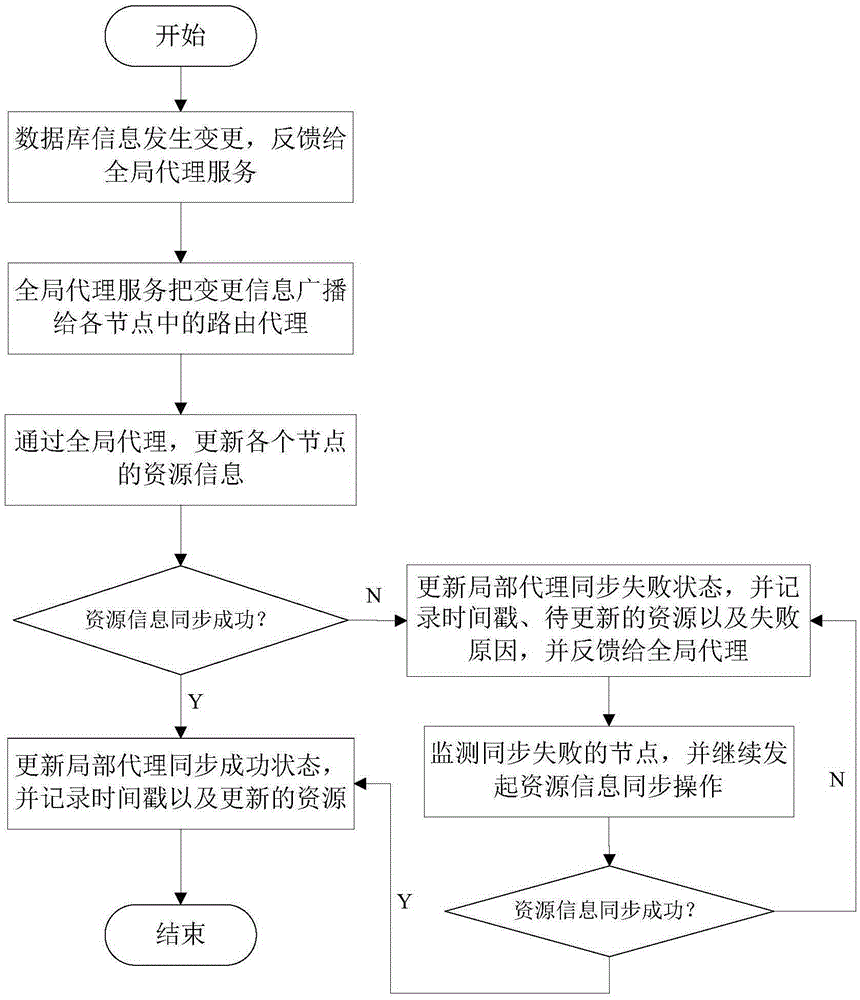
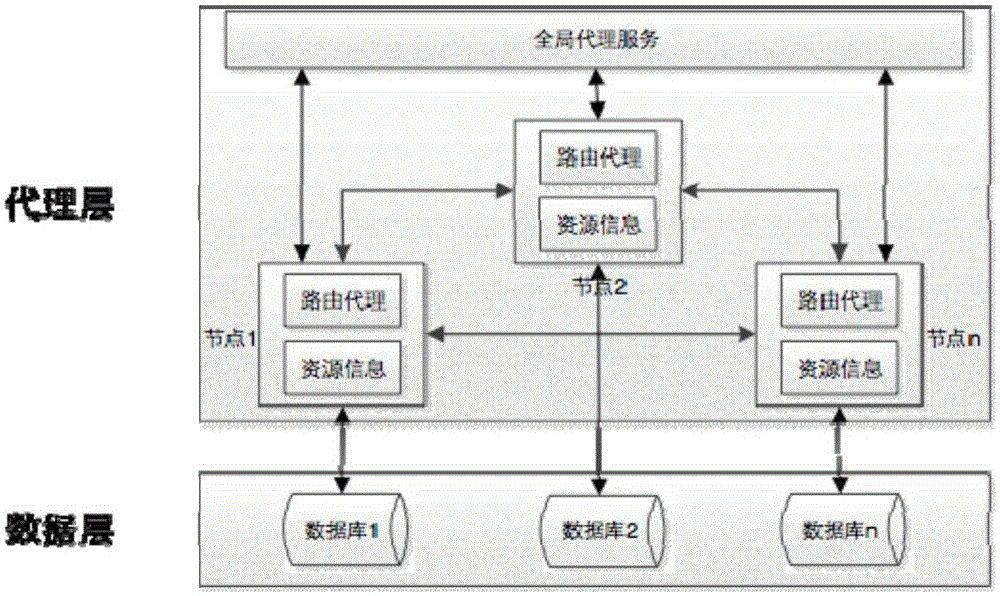
Peer-to-peer network-based heterogeneous database synchronization method
ActiveCN105404701AImprove reliabilityImprove usabilityTransmissionSpecial data processing applicationsTimestampUsability
The invention discloses a peer-to-peer network-based heterogeneous database synchronization method. The method is realized based on a heterogeneous database synchronization device composed of routing nodes and a global proxy server. The method comprises the steps of detecting the information charging condition of a database, feeding back the information changing condition to the global proxy server, broadcasting the changed information to the routing proxies of all nodes by the global proxy server, updating the resource information of each node, recording the timestamp of the updated information, updating the recorded timestamp in a block chain, updating the proxy synchronization state of each node, recording the timestamp thereof and the-be-changed information, and feeding back the updating state to a global proxy. According to the invention, through the decentration process, the self-management of each node is realized. Therefore, the reliability and the usability of database synchronization are greatly improved. The above method is conducted based on the block chain technology and enables the complete data exchange record. Meanwhile, the problem in the prior art that the data exchange in the traditional goal-centered approach cannot be traced is solved.
Owner:浙江图讯科技股份有限公司
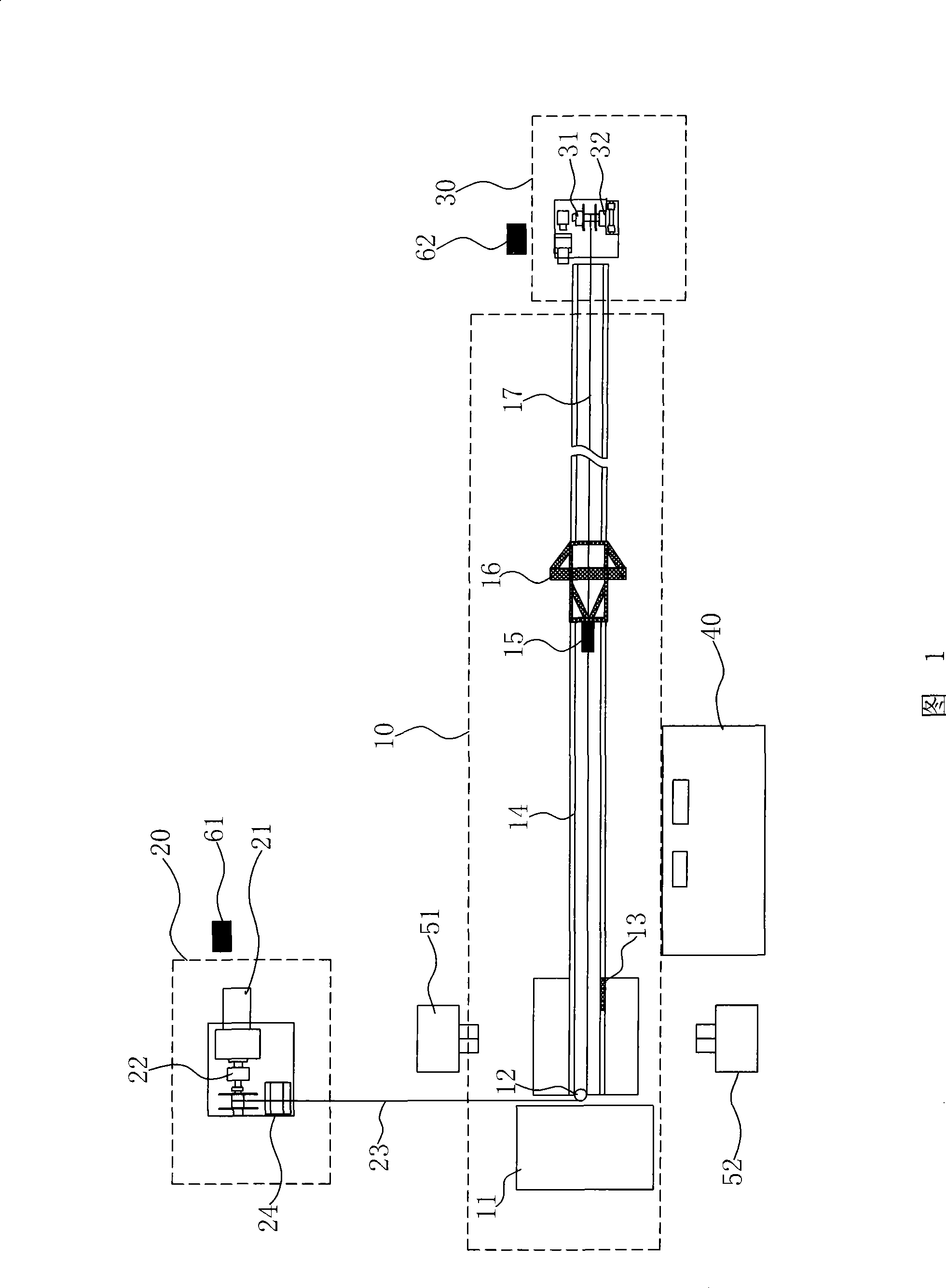
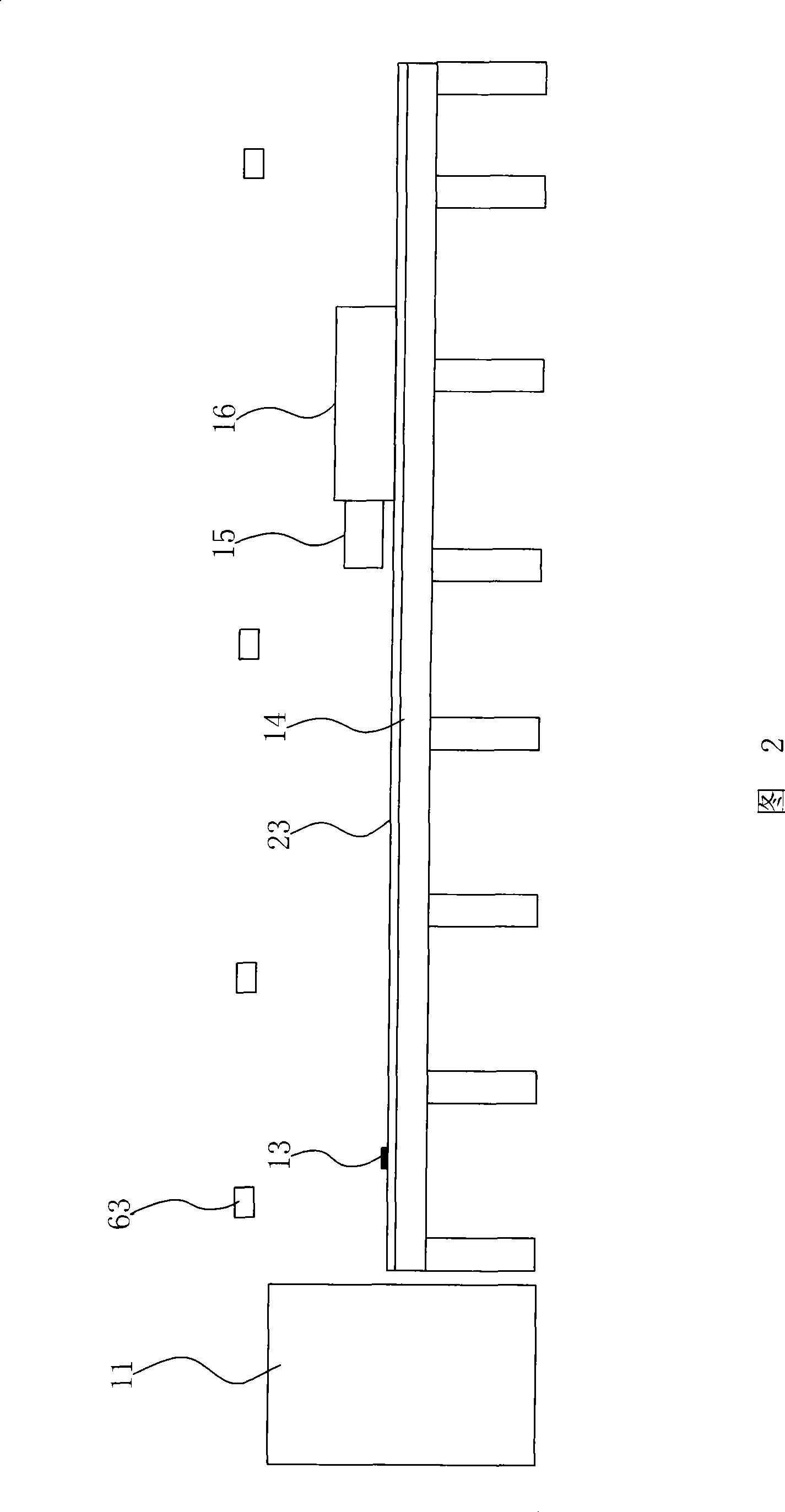
Vehicle component real object collision test method and tester
ActiveCN101430251ADetermination of impact forceDetermination of transient accelerationRailway vehicle testingShock testingComplete dataSpeed test
The invention discloses a test method for real object crash of vehicle components and a test device thereof. The test method comprises the following steps: the vehicle components are fixed on a carrying trolley which can move on a track, the speed of the trolley is increased to a test value by traction with a drive system before preparing for crash an impact wall; when the carrying trolley moves to a set position before the impact wall, a trigger device is started to detach the drive system from the carrying trolley, a test component and the carrying trolley are caused to crash the impact wall without drive power; a vehicle-borne acceleration test system is arranged on the carrying trolley so as to complete data acquisition in real time; and the trigger device triggers a speed test system, an impact force test system and a high-speed camera system at the same time. The test method of the real object crash of the vehicle components and the test device can help measure objective data in real time such as the impact force, a transient acceleration, component deformation and speed output at the moment of crash, and further can record deformation sequence images of the components during the whole crash course so as to get scientific and exact analysis results.
Owner:CENT SOUTH UNIV
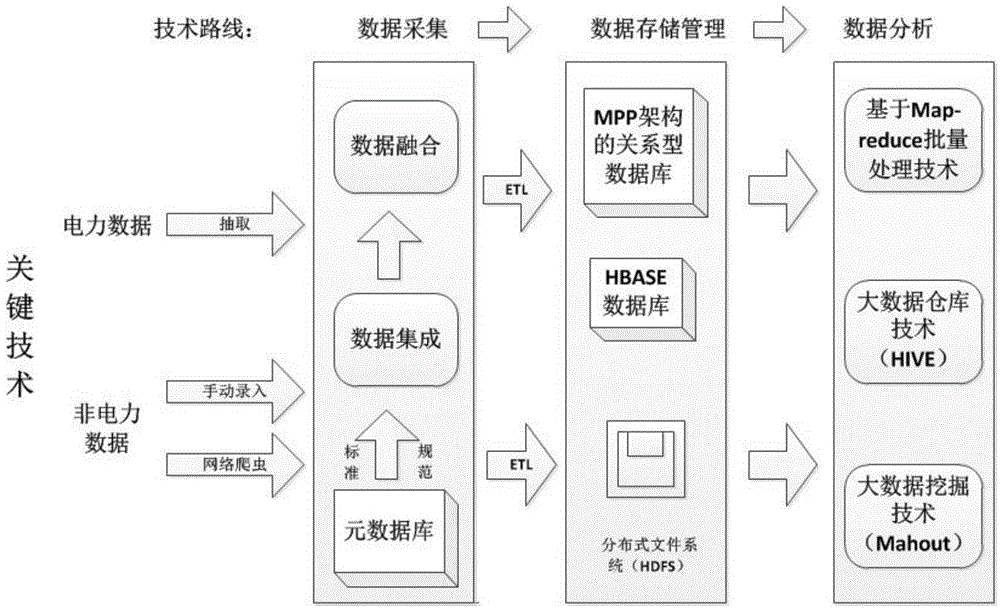
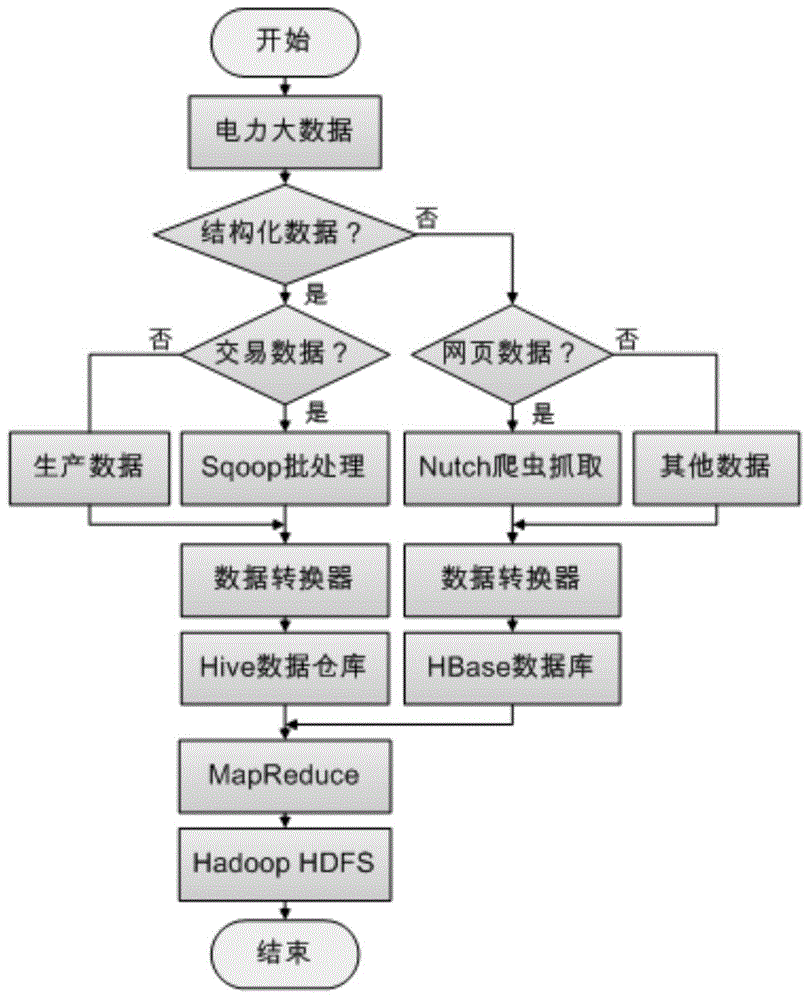
Method for acquiring and storing big data of power information
ActiveCN104820670AFunction is easy to expandGood analysis functionData processing applicationsSpecial data processing applicationsData acquisitionNetwork media
The present invention, belonging to the field of acquisition and storage of big data of power information, relates to a method for acquiring and storing the big data of power information, and solves the problems in the acquisition and storage process of the big data of power information. The method comprises three steps: data acquisition, data storage and management, and data analysis. The method achieves the beneficial effects that the present invention provides the method for acquiring and storing the power information big data; and the problems of low response speed of a service system and long consumed time for waiting of a user, which are generated due to a large cardinal number of power users and a large quantity of information, can be well solved. Meanwhile, for massive information generated by a trading system on the basis of power data, the method can better complete data extension and analysis functions than a traditional database. Moreover, according to the method, massive Internet media data can be acquired, stored and processed so as to better learn about the trade trend; and during the operation process, the storage method has an efficient inquiring function so that retrieval can be rapidly completed when the data volume is increased sharply.
Owner:CENT CHINA GRID +2
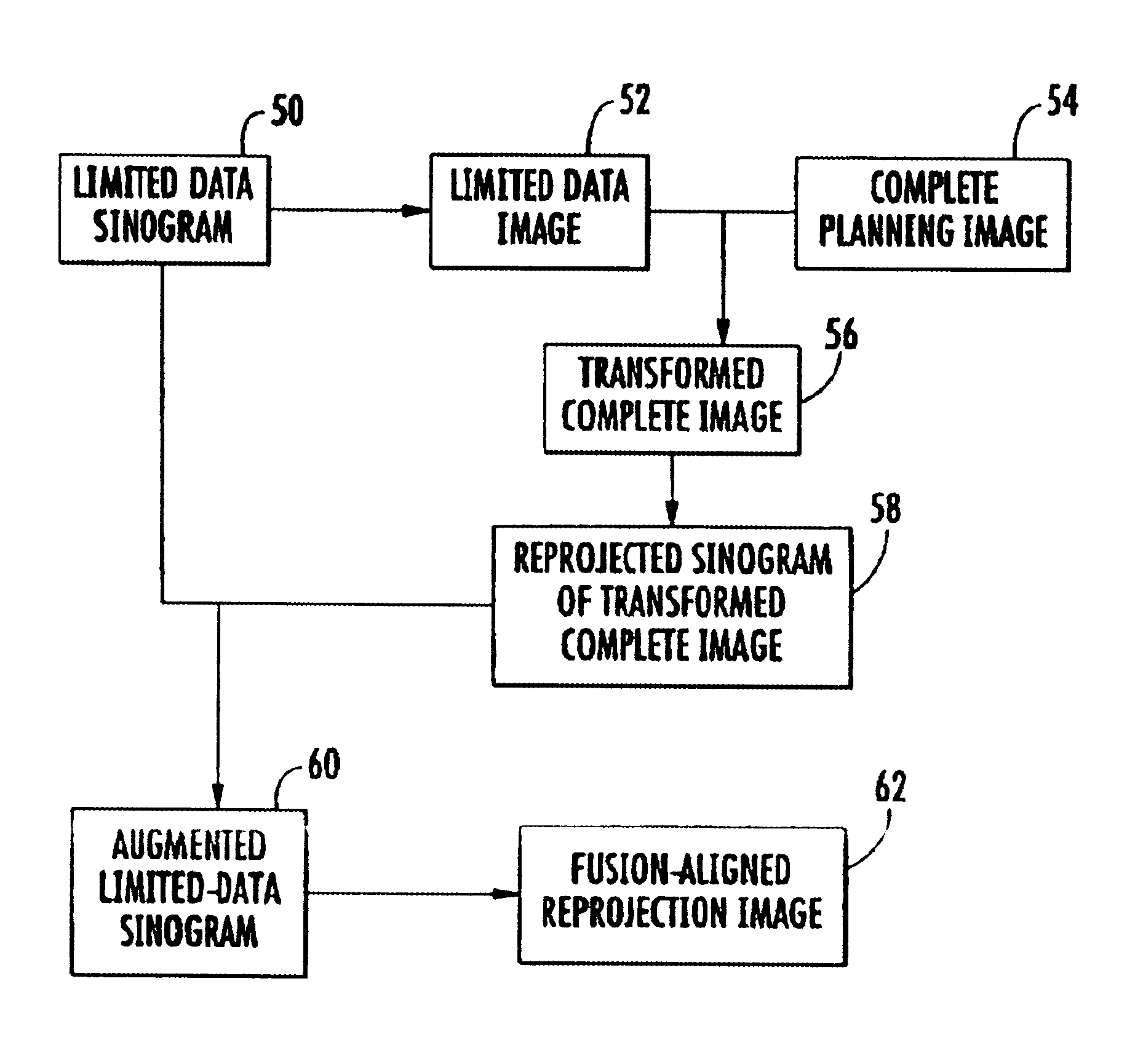
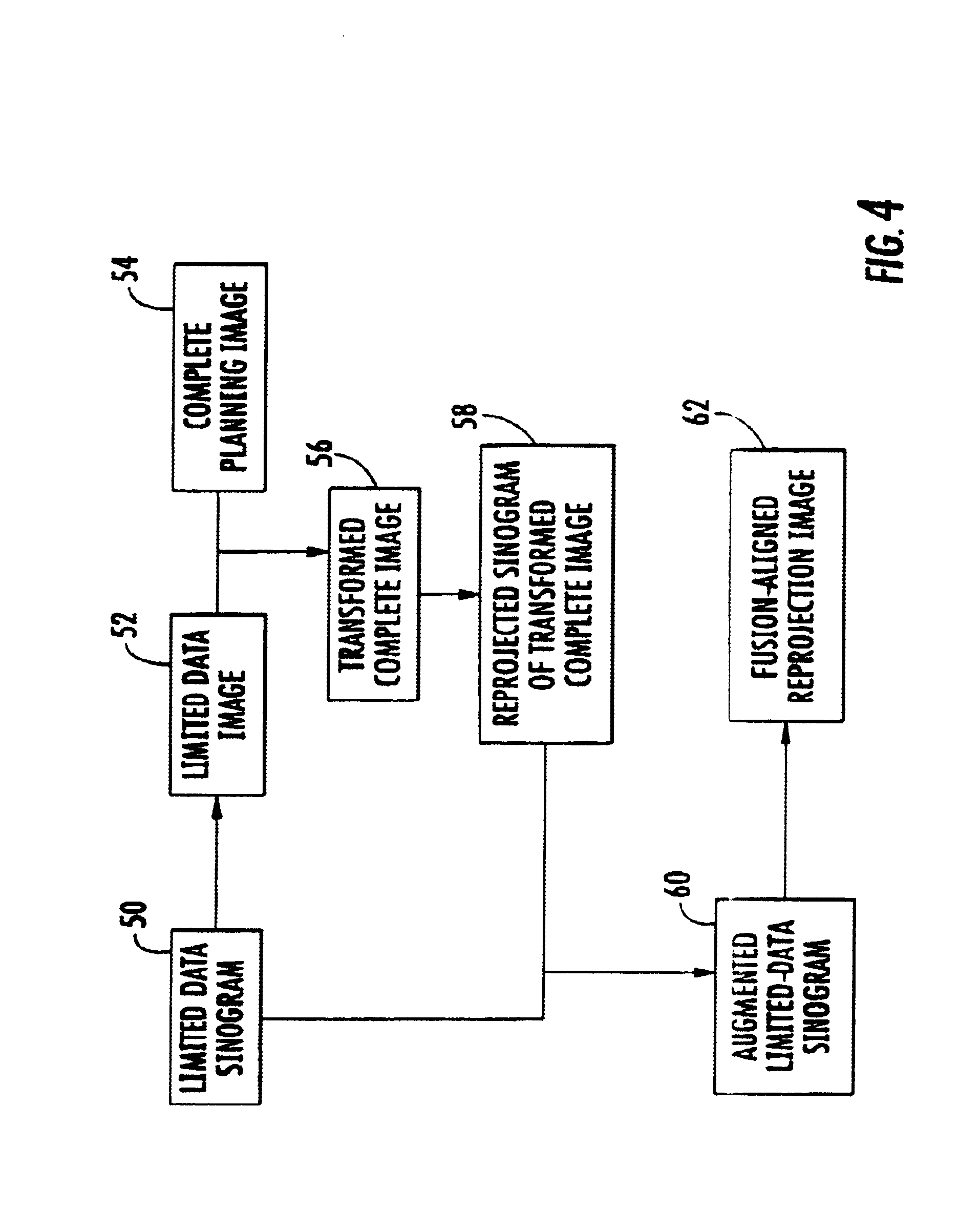
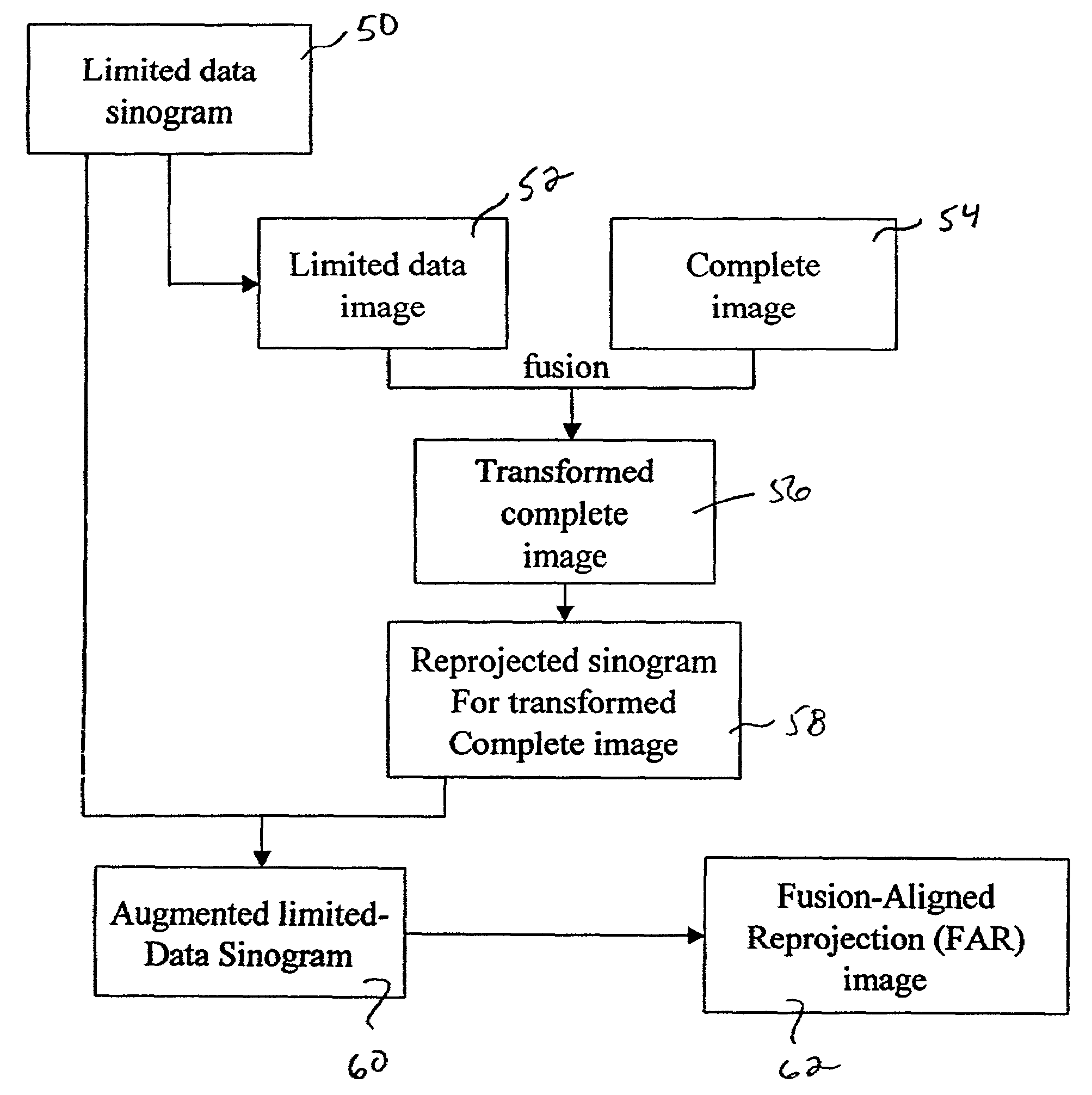
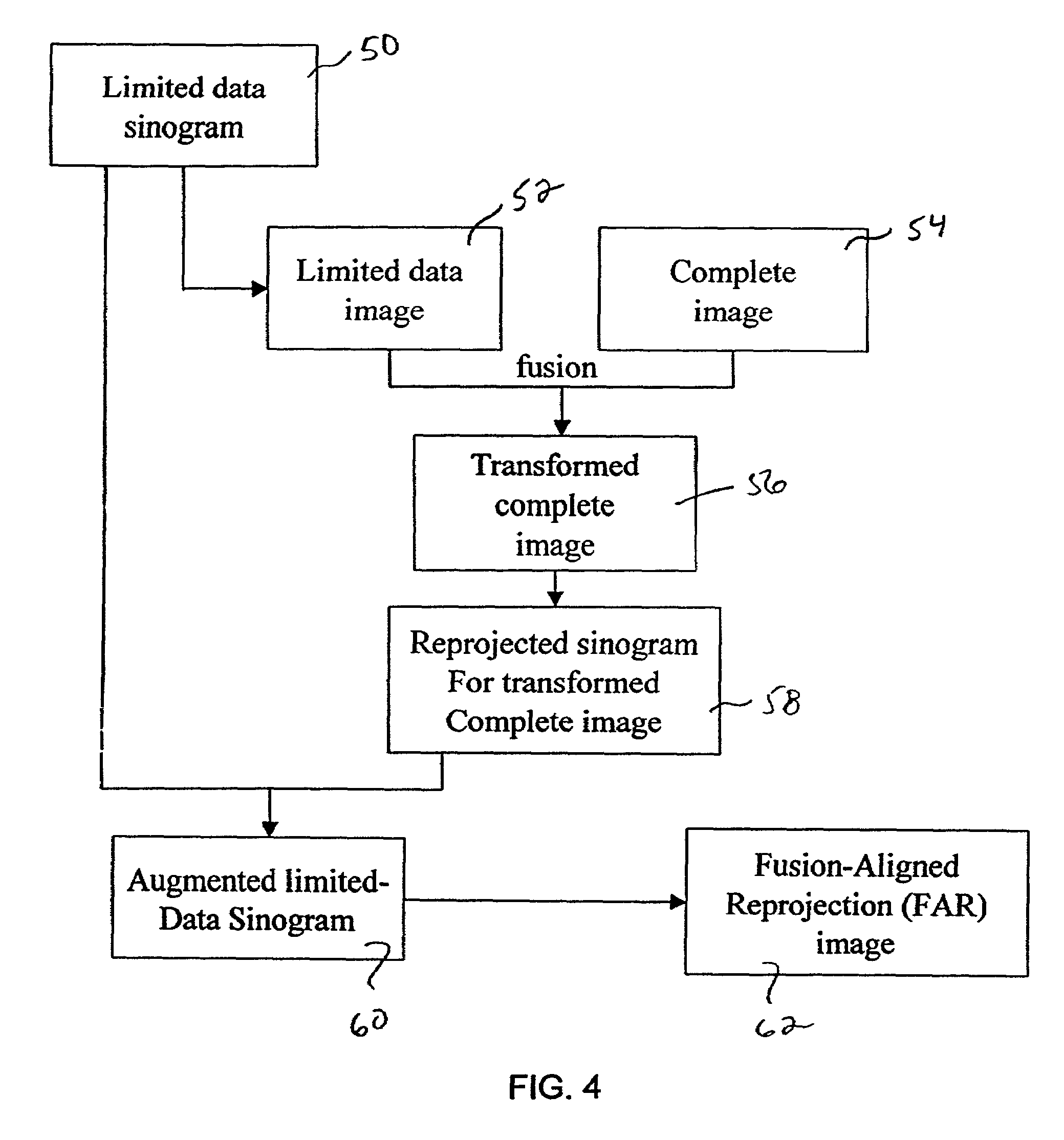
Method for reconstruction of limited data images using fusion-aligned reprojection and normal-error-aligned reprojection
InactiveUS6915005B1Reduce artifactsEnhance the imageReconstruction from projectionCharacter and pattern recognitionComplete dataRadiation therapy
The present invention provides methods of using current but incomplete data to prepare an approximated complete image of a patient potentially undergoing radiation therapy. A complete image of the patient is fused or aligned with a limited patient image using image registration techniques. The aligned image is converted to sinogram data. This sinogram data is compared to sinogram data corresponding to the limited patient image to determine what data exists beyond the scope of the limited sinogram. Any additional data is added to the limited data sinogram to obtain a complete sinogram. This complete sinogram is then reconstructed into an image that approximates the complete image that would have been taken at the time the limited image was obtained.
Owner:TOMOTHERAPY INC
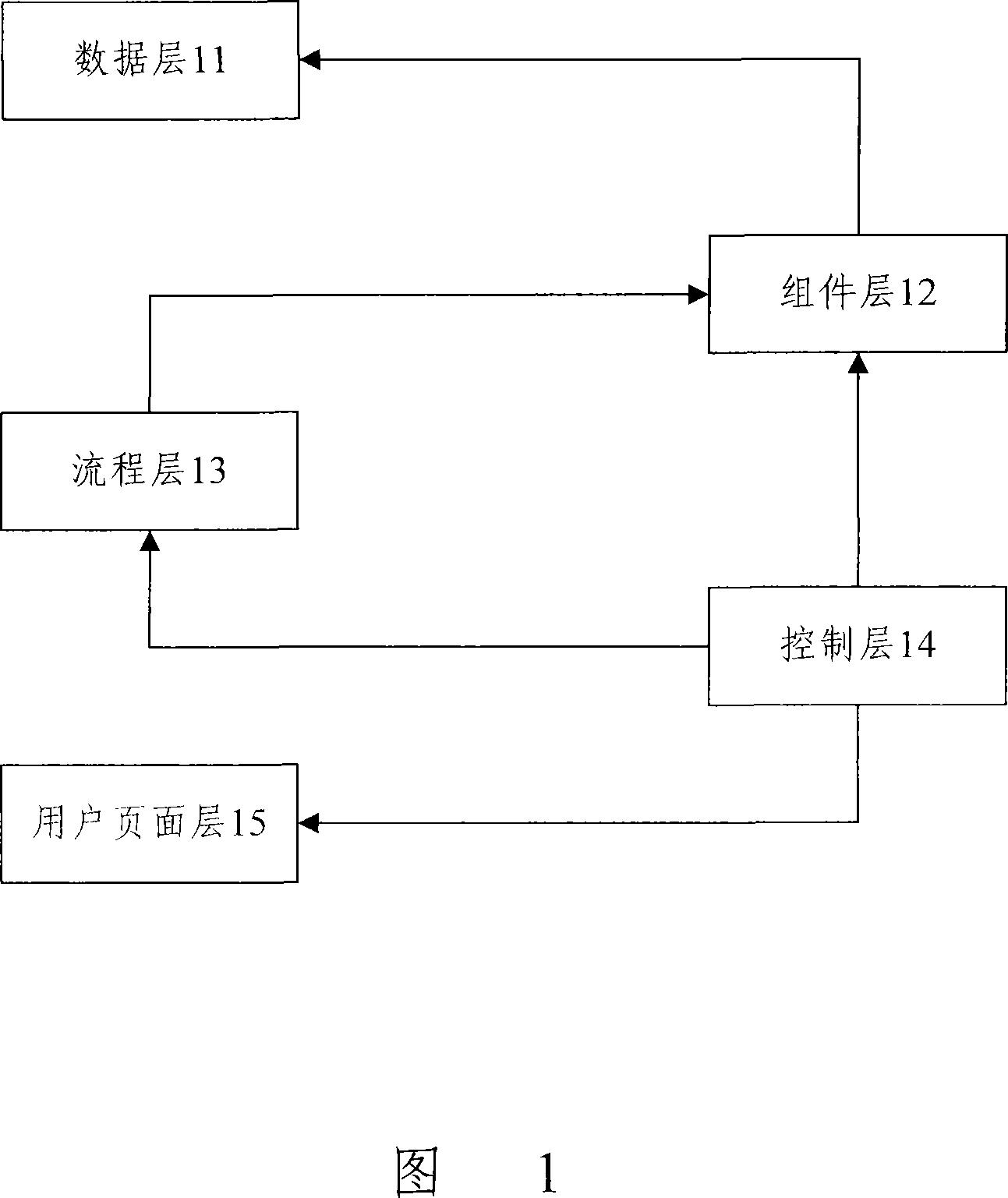
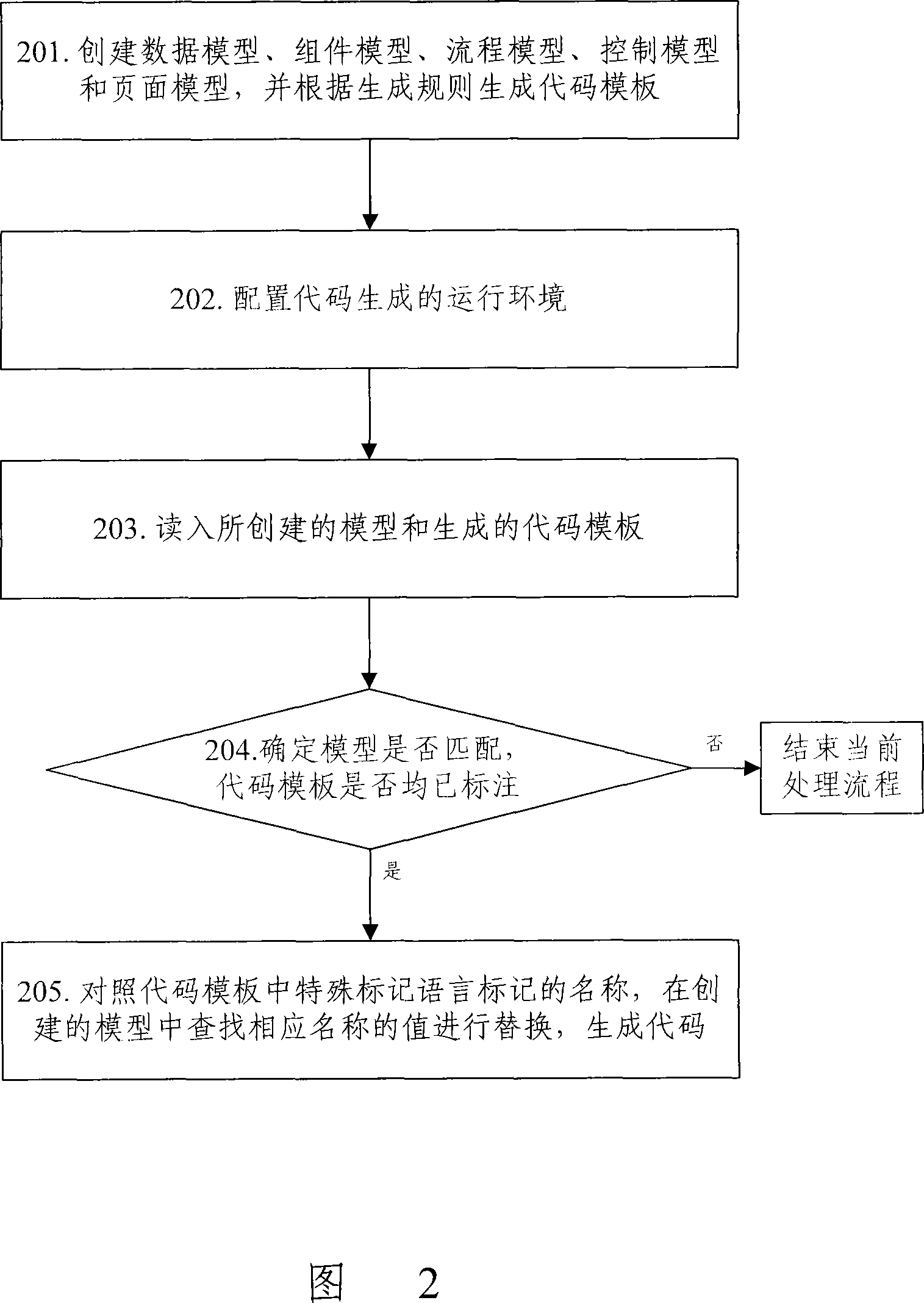
Code automatically generating device based on model component, system and method
InactiveCN101114226AClear structureEasy to implementSpecific program execution arrangementsHandling CodeComplete data
The invention discloses a code automatic generation method used for constructing a code automatic generation device, comprising a data layer, a component layer, a process layer, a control layer and a user interface layer, wherein, the five-layer structure is divided in accordance with functions, and every layer is independent and creates a corresponding processing model to complete data processing, component extraction, flow processing, function control and user interface processing. At the same time, a code template is created based on certain rules, and different processing codes are formed for different business objects. Based on the five-layer model and the code template, a code generating engine controls and calls the model of layers and the code template, which cooperate to complete the code automatic generation process. The invention also discloses a code automatic generation device and system; by adopting the invention, the development efficiency, the reusability and the standardization of software can be enhanced and code quality is improved.
Owner:北京中企开源信息技术有限公司
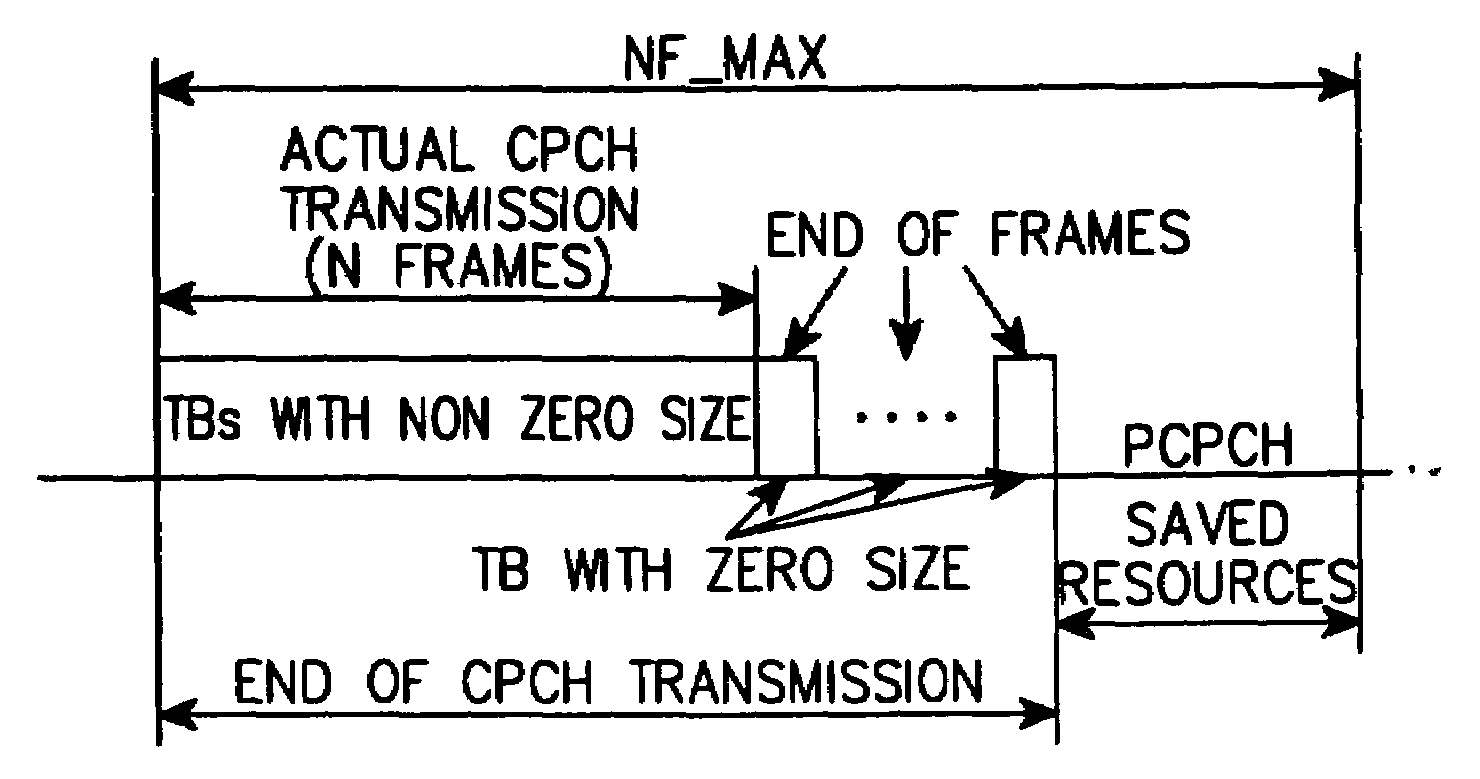
Apparatus and method for assigning a common packet channel in a CDMA communication system
ActiveUS7113496B2Efficient managementImprove reliabilityPower managementNetwork topologiesComplete dataRadio access network
Disclosed is a method for indicating an end of transmitting data frames in order to enable a UTRAN (UMTS (Universal Mobile Telecommunications System) Terrestrial Radio Access Network) to assign a common packet channel to another user equipment (UE) in a UE for a CDMA mobile communication system. The UE requests assignment of any one of a number of common packet channels assignable in the UTRAN; the UE is assigned a common packet channel by the UTRAN in response to the to request; the UE sequentially transmits the data frames and their associated control frames over the assigned common packet channel; and the UE transmits at least one control frame, in an appointed field of which a given bit pattern appointed with the UTRAN is registered, in order to inform the UTRAN of an end of data transmission upon completing data transmission through the data frames.
Owner:NOKIA TECHNOLOGLES OY
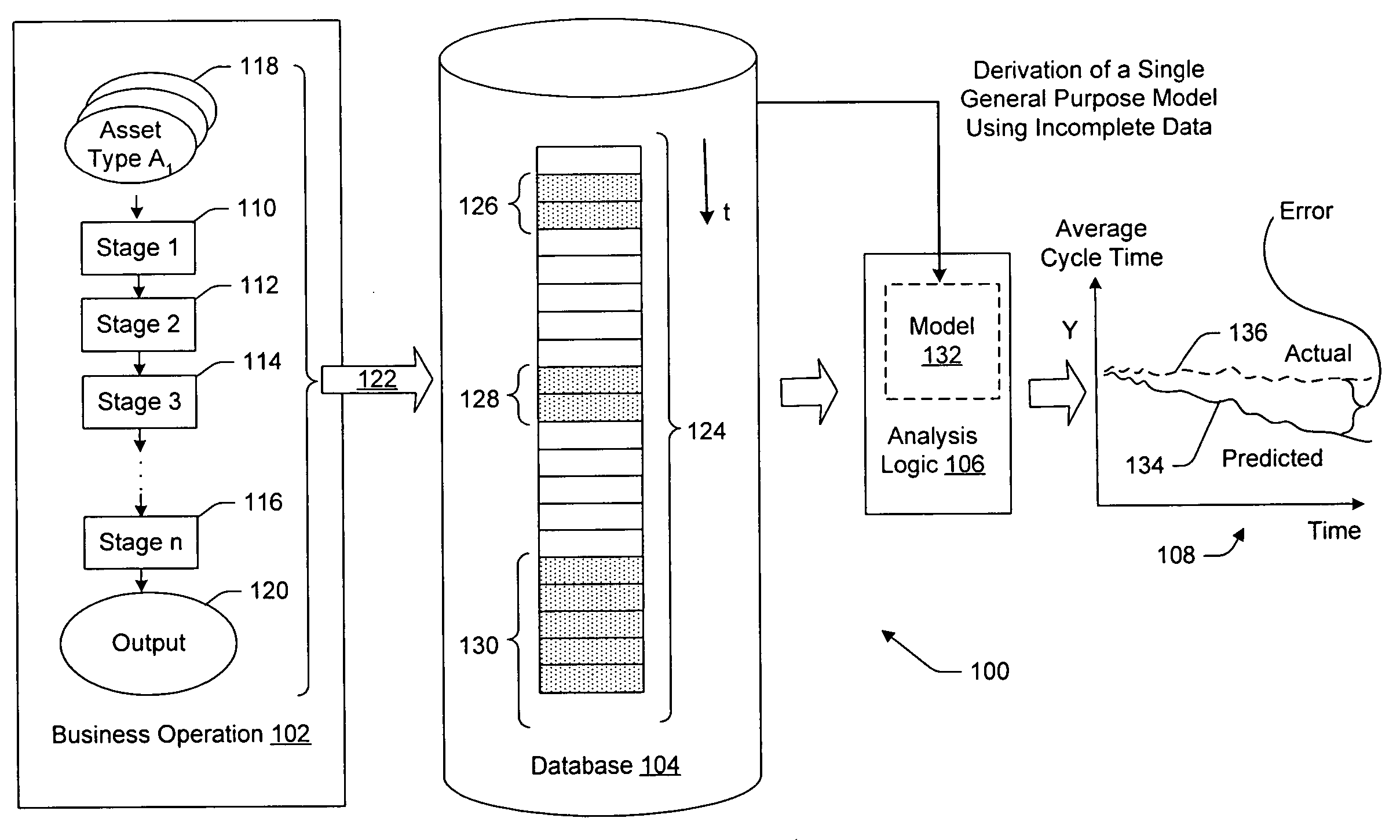
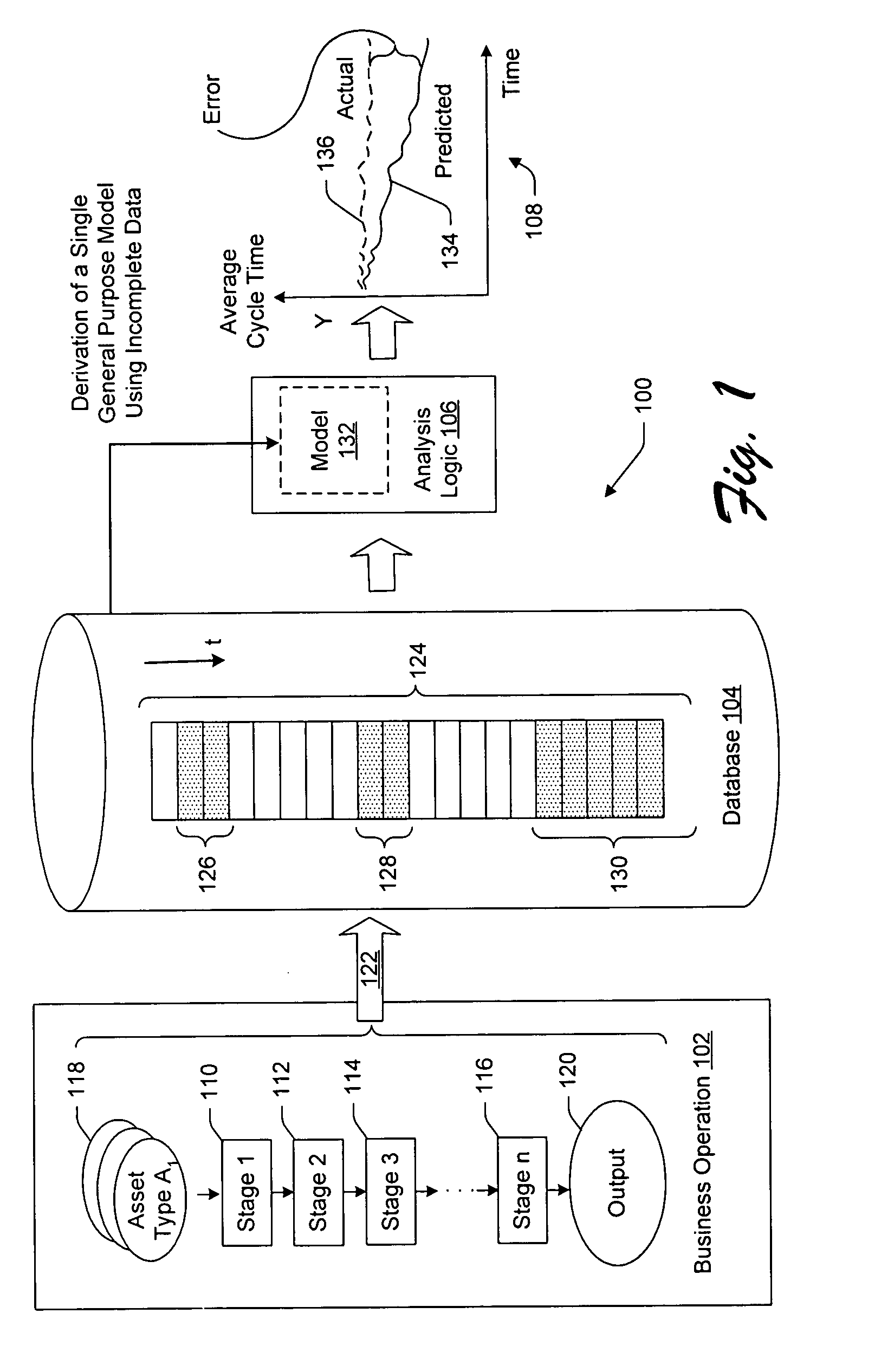
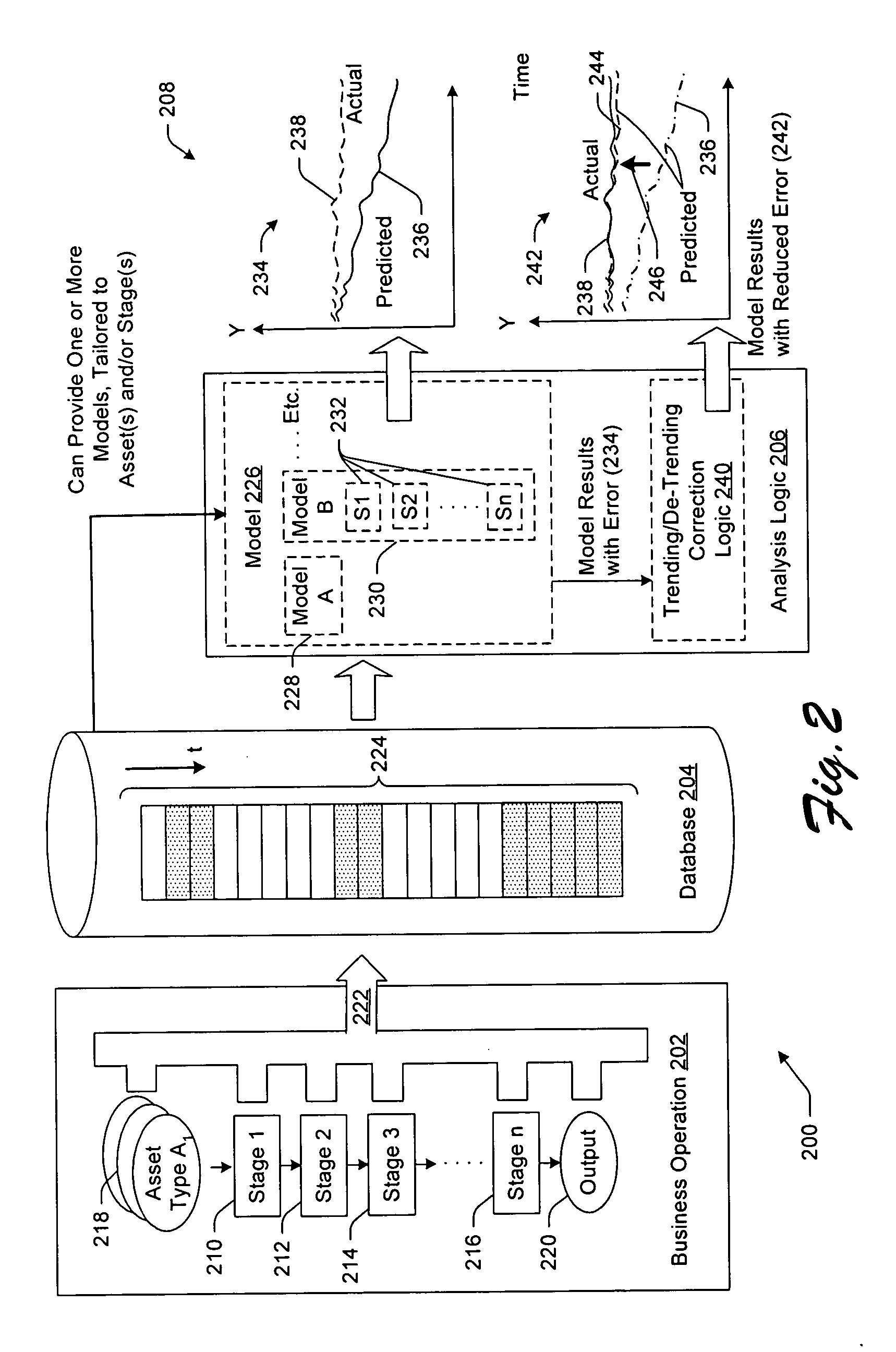
Techniques for performing business analysis based on incomplete and/or stage-based data
Electrical data processing techniques are described for performing business analysis based on datasets that are incomplete (e.g., contain censored data) and / or based on datasets that are derived from a stage-based business operation. A first technique offsets the effects of error caused by the incomplete dataset by performing a trending operation followed by a de-trending operation. A second technique provides a model containing multiple sub-models, where the output of one sub-model serves as the input to another sub-model in recursive fashion. A third technique determines when a specified event is likely to occur with respect to a given asset by first discriminating whether the event is very unlikely to occur; if the asset does not meet this initial test, it is further processed by a second sub-model, which determines the probability that the specified event will occur for each of a specified series of time intervals.
Owner:GENERAL ELECTRIC CO
System and method for downloading application components to a chipcard
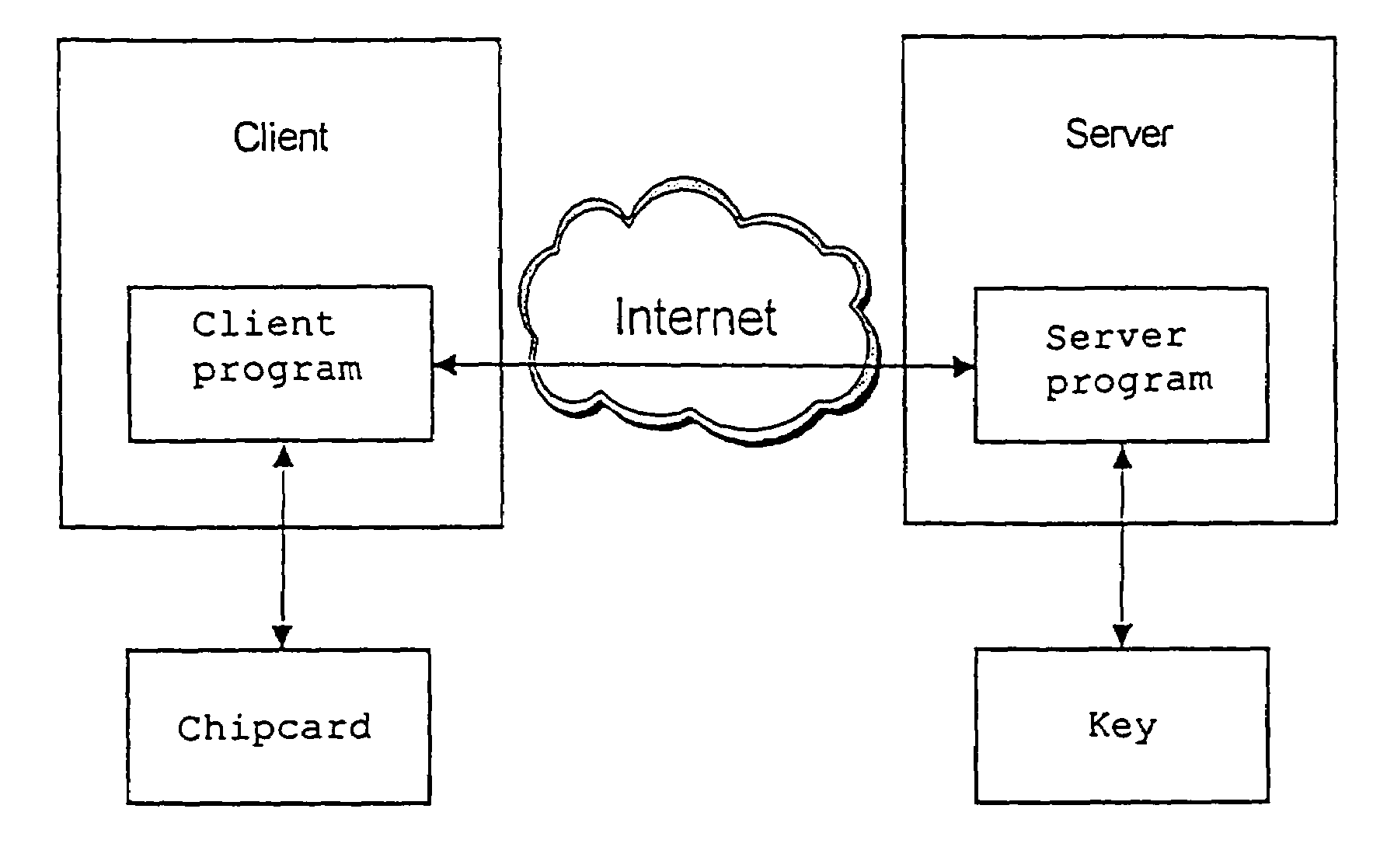
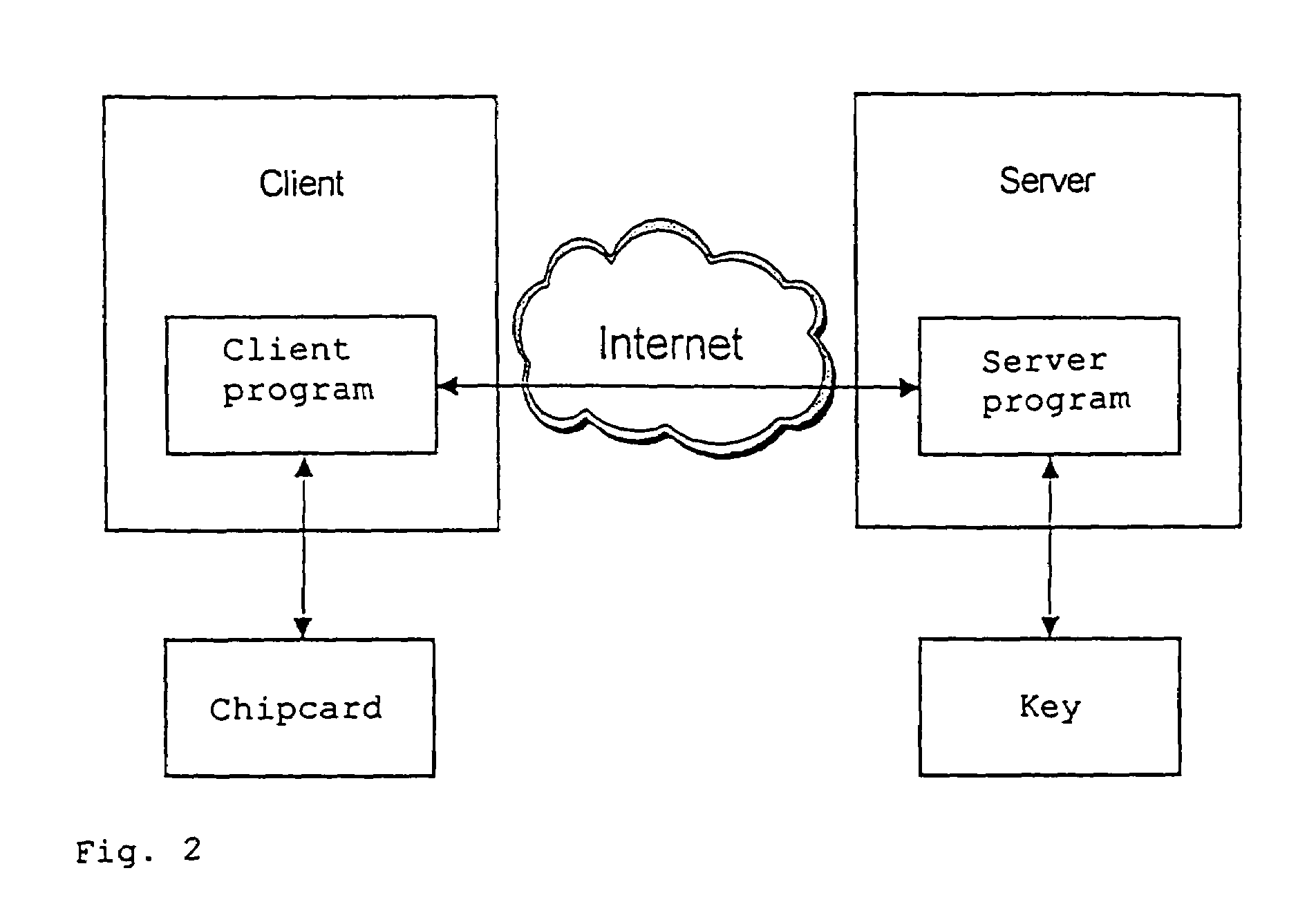
InactiveUS7117364B1Simple wayShorten the timeUser identity/authority verificationPayment architectureComplete dataTTEthernet
The present invention describes a method for downloading application components, so-called on-card application components, from a server via a client to a chipcard, wherein the server and the client communicate with each other via a distributed system, in particular an Intranet or the Internet. The advantages of the present invention lie in the fact that downloading of the application components is divided into two stages: The first stage occurs on the server only, and ensures that not every command to download the application component is sent individually over the network. This is effected by means of a broadband-optimized protocol which bundles the individual commands to download the application component into a command sequence and sends it as a complete data packet over the network. This reduces the time required for downloading application components over the network. Each command within the command sequence is assigned a digital signature and, where appropriate, encrypted. This ensures that only authenticated commands are accepted by the chipcard. In this way this invention meets security requirements for the transfer of data via distributed systems, in particular over the Internet. The second stage occurs between the client and the chipcard, and ensures that the data packets are unpacked and sent individually to the chipcard. All security-relevant keys and certificates are stored on the secure server. Communication between the client and the server runs preferentially via SSL (Secure Sockets Layer) as the transfer protocol. Misuse of the inventive system / method is thereby rendered much more difficult.
Owner:IBM CORP
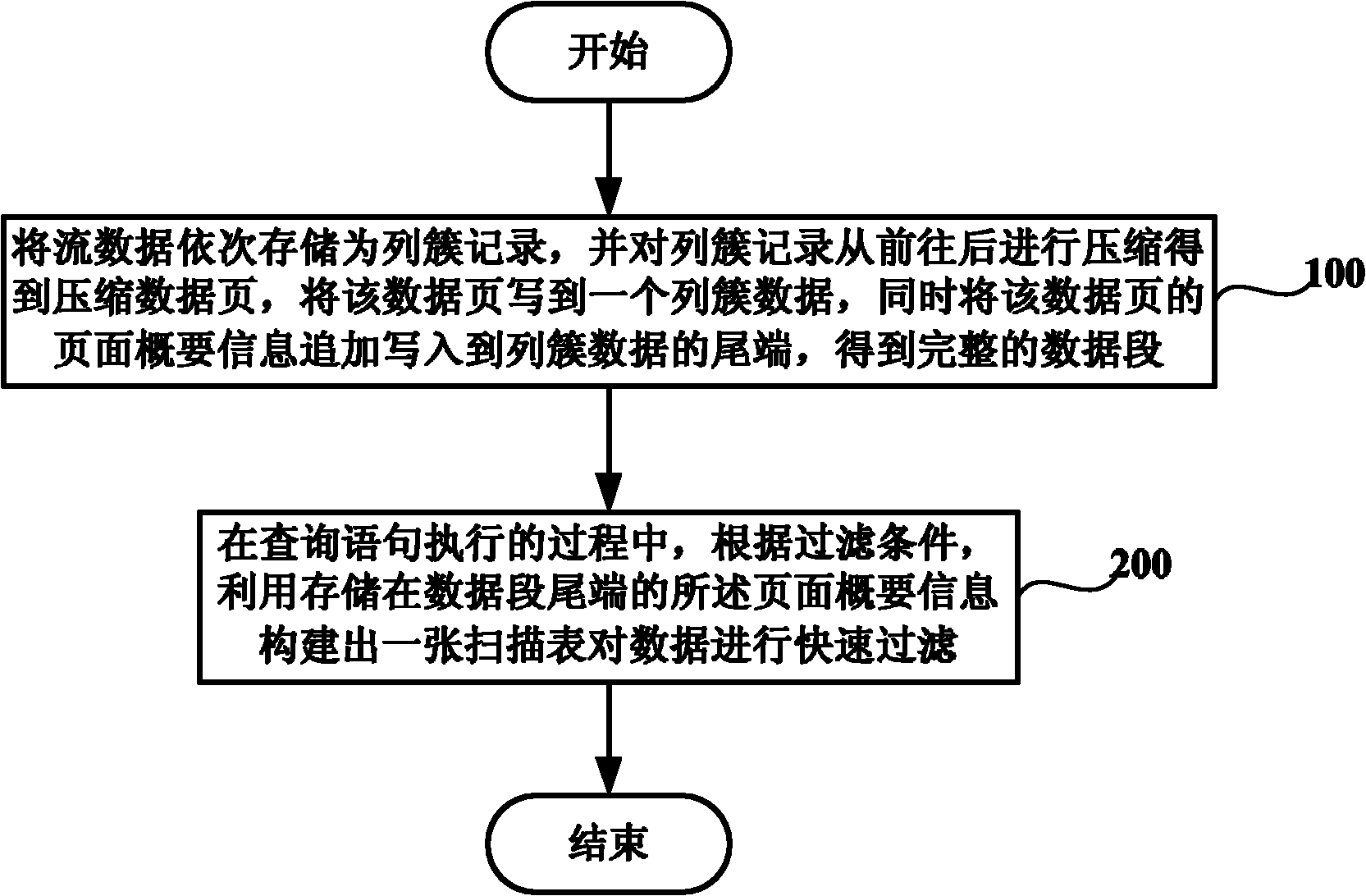
Hadoop-based mass stream data storage and query method and system
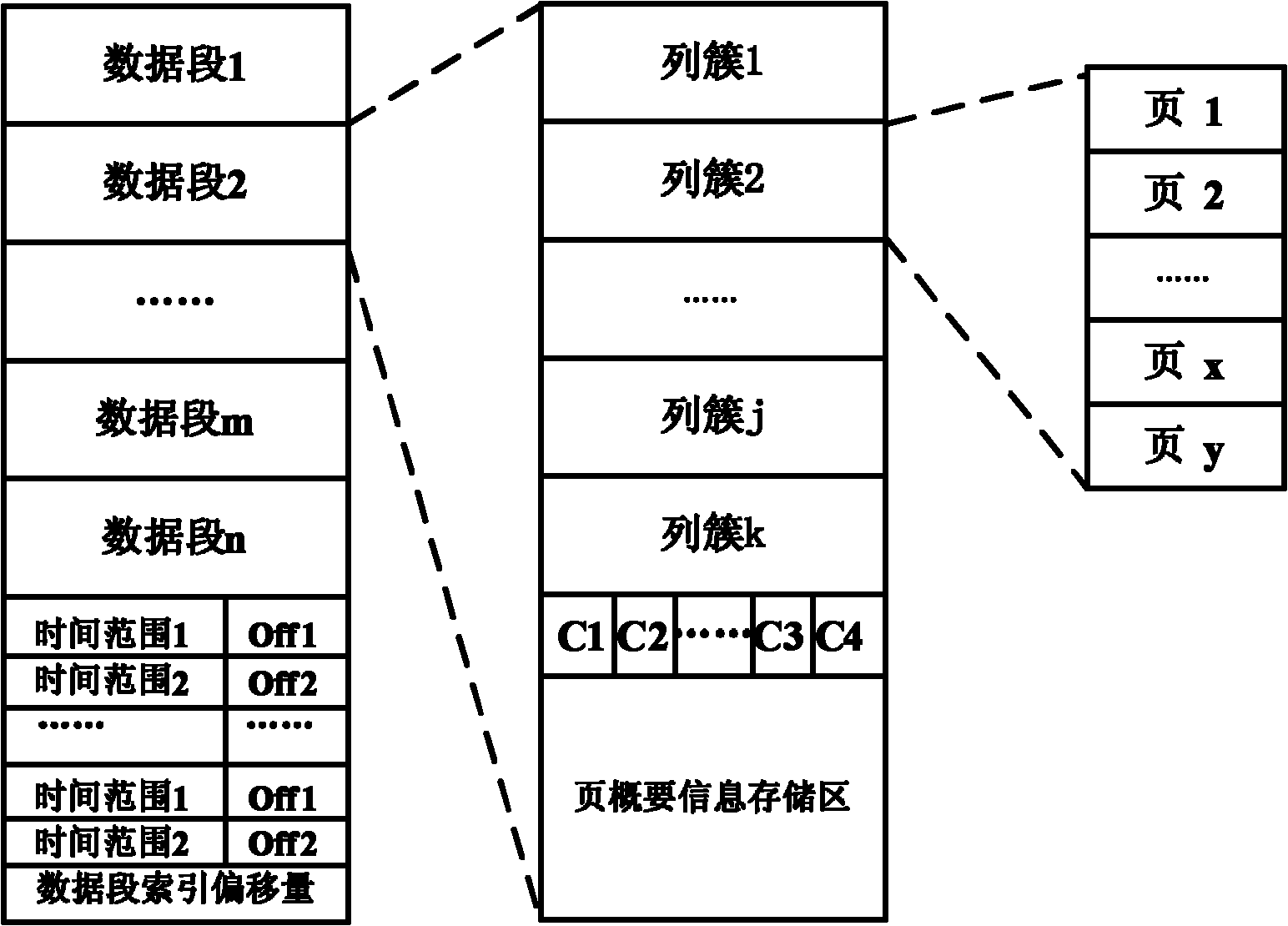
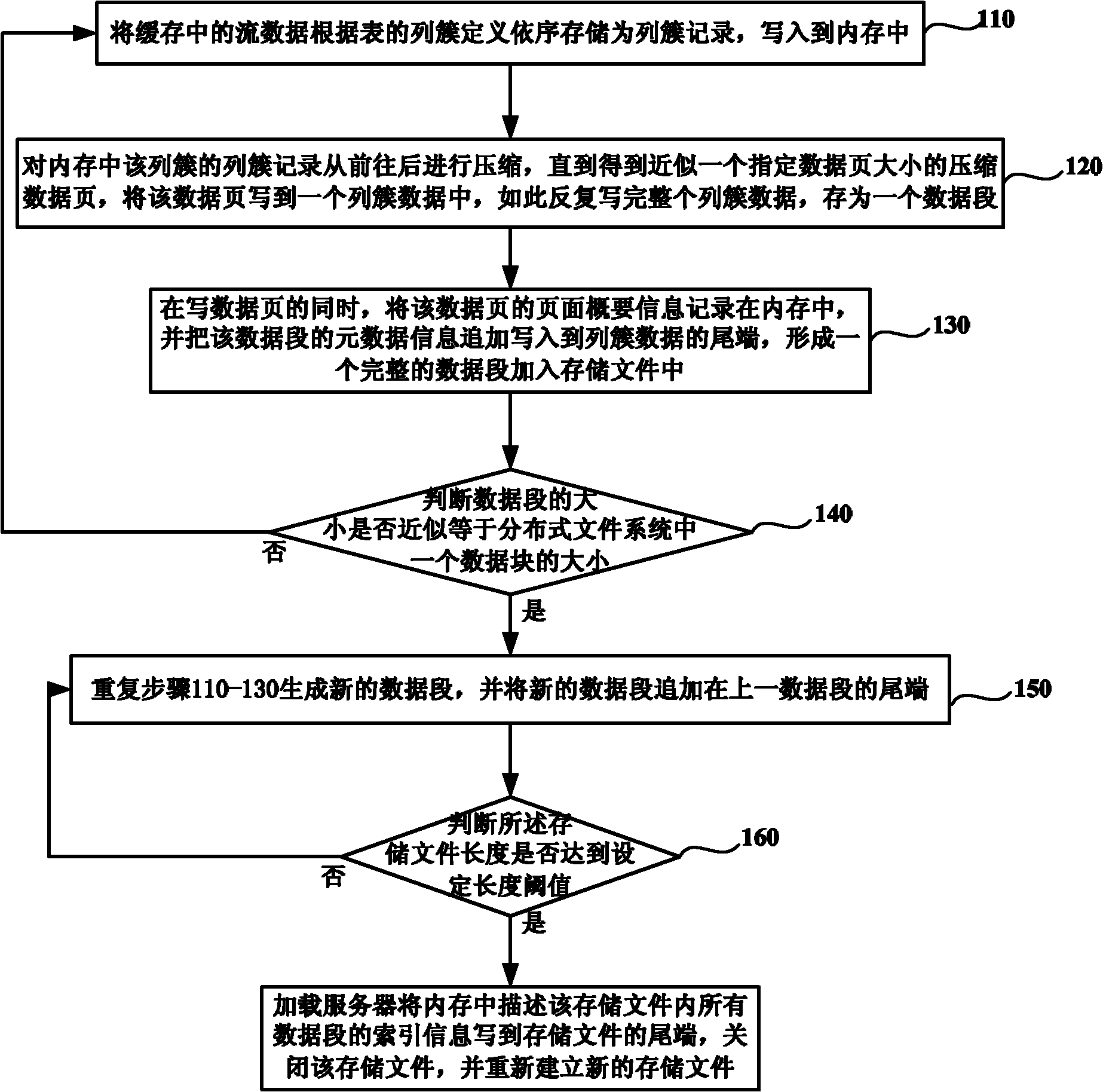
InactiveCN101996250AReduce data volumeQuick filterSpecial data processing applicationsStreaming dataClustered data
The invention discloses a Hadoop-based mass stream data storage and query method and a Hadoop-based mass stream data storage and query system. The method comprises the following steps of: constructing a segmented column cluster type storage structure; sequentially storing stream data as column cluster records, compressing the column cluster records from front to back to obtain compressed data pages, writing each compressed data page into a piece of column cluster data, and simultaneously additionally writing the page outline information of the compressed data pages into the tail ends of the column cluster data to obtain an integrated data segment; and in the process of executing query statements, constructing a scan table according to filtering restraints by utilizing the page outline information at the tail ends of data segments to quickly filter the data.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Method and apparatus for group communication with end-to-end reliability
InactiveUS20050243722A1Avoid packet lossUndesirable characteristicSpecial service provision for substationError preventionComplete dataNetwork packet
The present invention addresses scalability and end-to-end reliability in overlay multicast networks. A simple end-system multicast architecture that is both scalable in throughput and reliable in an end-to-end way is used. In this architecture, the transfers between nodes use TCP with backpressure mechanisms to provide data packet transfers between intermediate nodes having finite-size forwarding buffers. There is also a finite-size backup buffer in each node to store copies of packets which are copied out from the receiver window to the forwarding buffers. These backup buffers are used when TCP connections are re-established to supply copies of data packets for the children nodes after their parent node fails, maintaining a complete sequence of data packets to all nodes within the multicast overlay network. The architecture provides end-to-end reliability, tolerates multiple simultaneous node failures and provides positive throughput for any group size and any buffer size.
Owner:IBM CORP
Method, apparatus and system for data reconstruction in distributed storage system
ActiveCN106662983AInput/output to record carriersError detection/correctionComplete dataComputer hardware
The invention relates to a method, apparatus and system for data reconstruction in a distributed storage system. A main storage node in the distributed storage system performs EC coding on the data to be written to generate an EC stripe; each EC block on the EC stripe is stored on each storage node; when part of the storage nodes cause failure of writing of EC blocks because of faults, the main storage node stores the EC blocks distributed to the storage nodes which fails to write in the local, and generates metadata information required by data reconstruction; and when the faults of the storage nodes recover, the main storage node retransmit the stored EC blocks distributed to the storage nodes and the metadata information corresponding to the EC blocks to the storage nodes so as to enable the storage nodes after recovering the faults to complete data reconstruction. The scheme for data reconstruction in the distributed storage system has the advantages that when part of the storage nodes malfunction, EC reversal coding is not required to recover the data on the fault nodes, but the buffer of main storage node is distributed to the EC blocks with fault nodes; after the fault nodes recover, the buffered EC blocks are retransmitted to the fault nodes to perform data reconstruction, thus avoiding computing resource consumption because of performing EC reversal coding when the storage nodes recover fault to perform data reconstruction, and avoiding consumption of network resource because large amount of data is transmitted during the EC reversal coding process at the same time.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
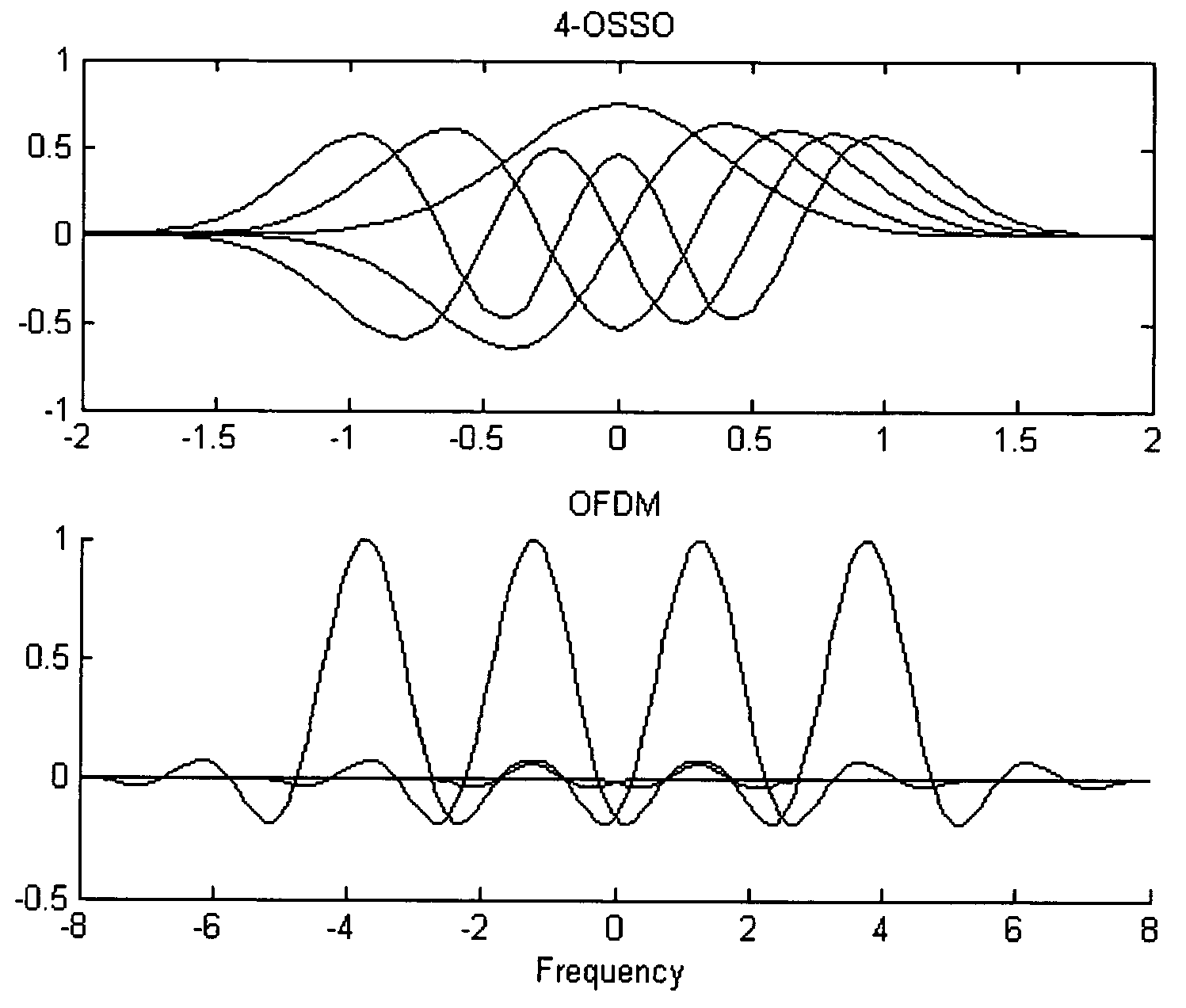
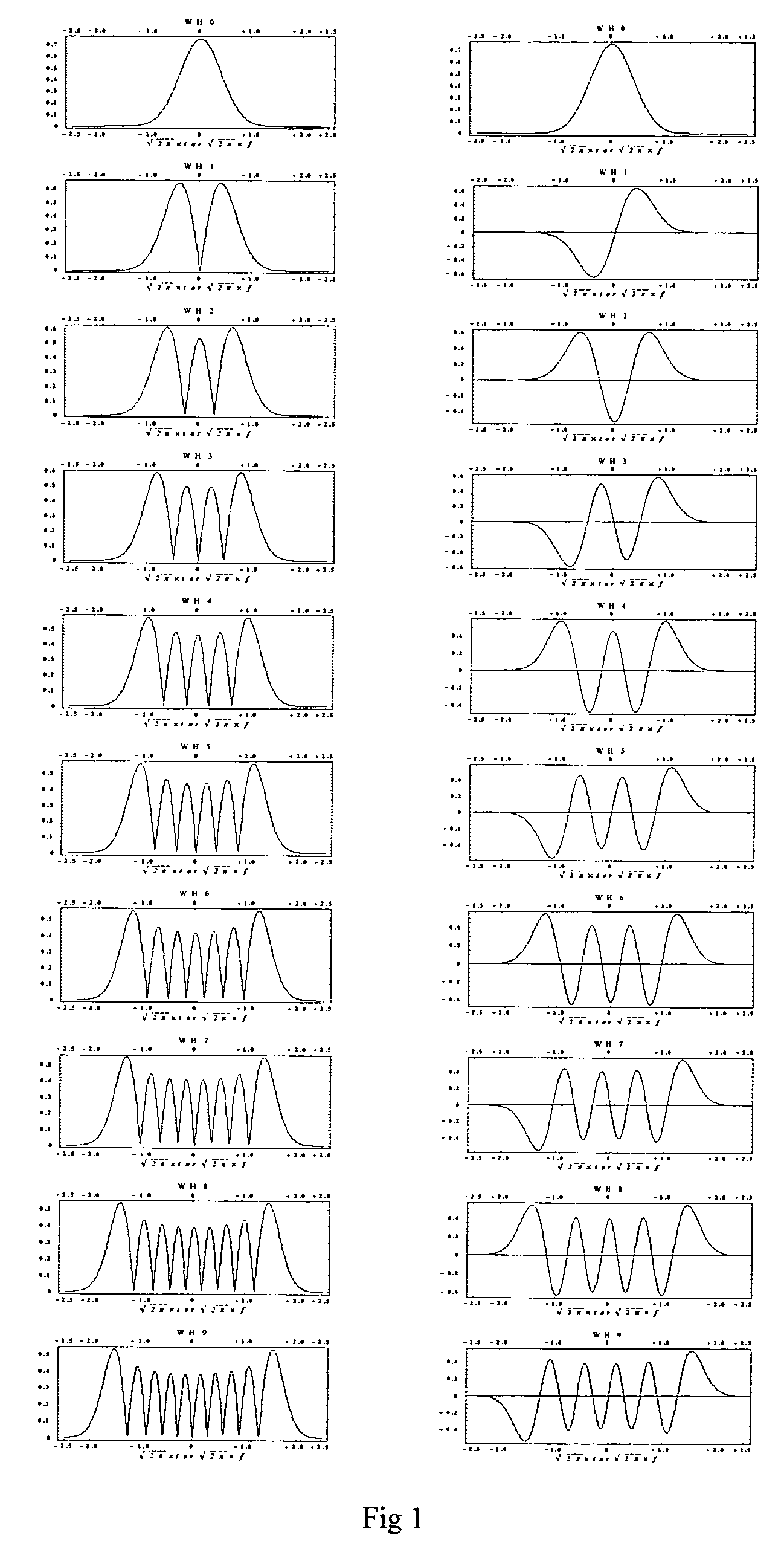
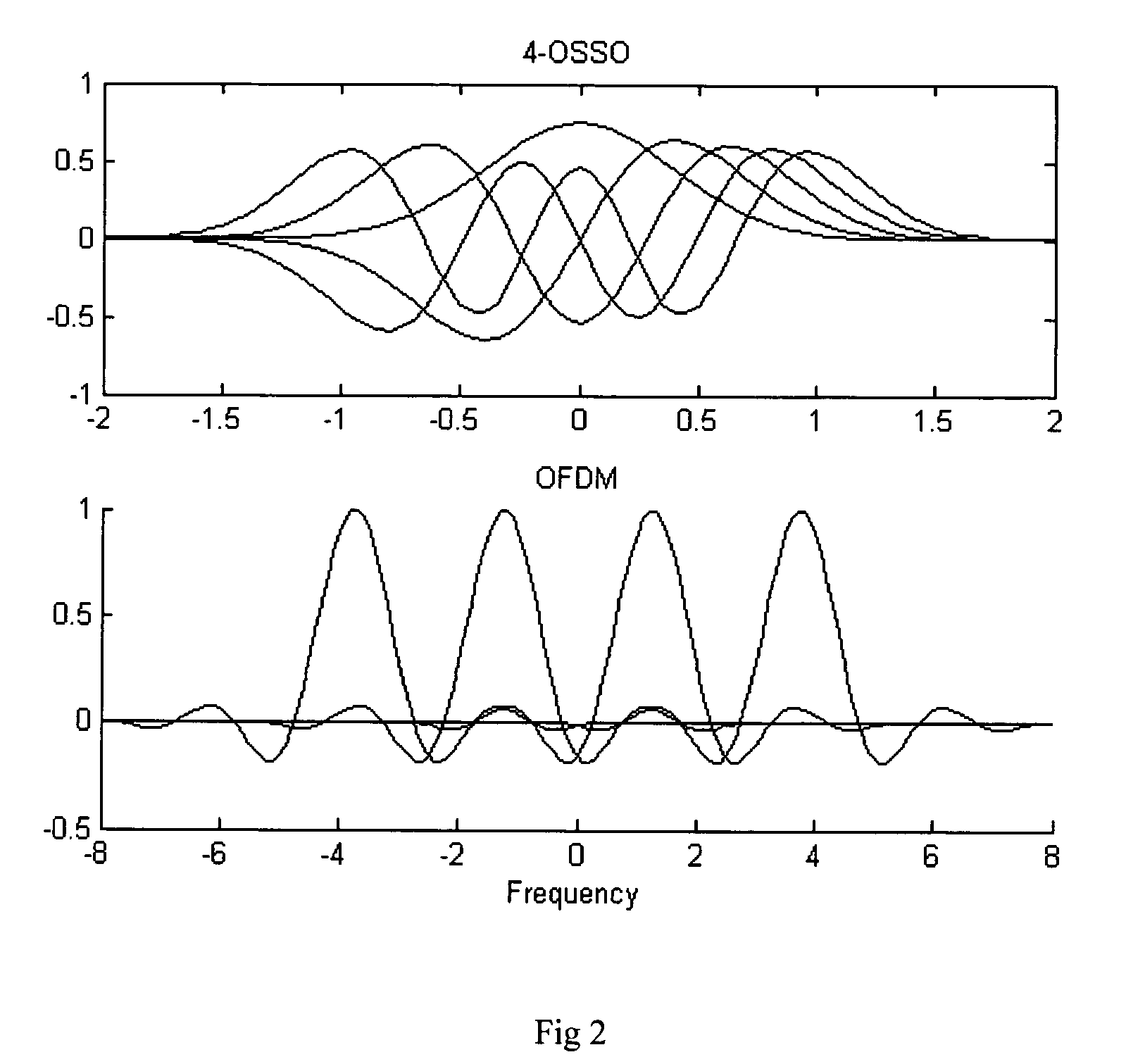
Method and system of orthogonal signal spectrum overlay (OSSO) for communications
InactiveUS7577165B1Improve bandwidth efficiencyIncreasing physical bandwidthTransmission path divisionTime-division multiplexMultiplexingComplete data
A method and system for increasing the effective communications channel bandwidth beyond that of the constrained physical bandwidth of a given channel by orthogonal signal spectrum overlay (OSSO) comprising: decomposing the time-bandwidth product (TBP) of a given symbol in a data stream transmitted through a given bandwidth, expanding the TBP in terms of overlaid orthogonal signals such as Weber-Hermite (WH) functions that constitute the eigensignals of the symbol. The complete data stream is multiplexed to produce a plurality of data channels, each of which is encoded on an orthogonal signal by quadrature amplitude modulation. The overlay of these signals constitutes the OSSO symbol. The OSSO symbols are transmitted in quadrature format (I and Q) and are the result of the addition of orthogonal signals, each of which constitutes a separate overlaid communication channel, occupying the same physical bandwidth.
Owner:BARRETT TERENCE W
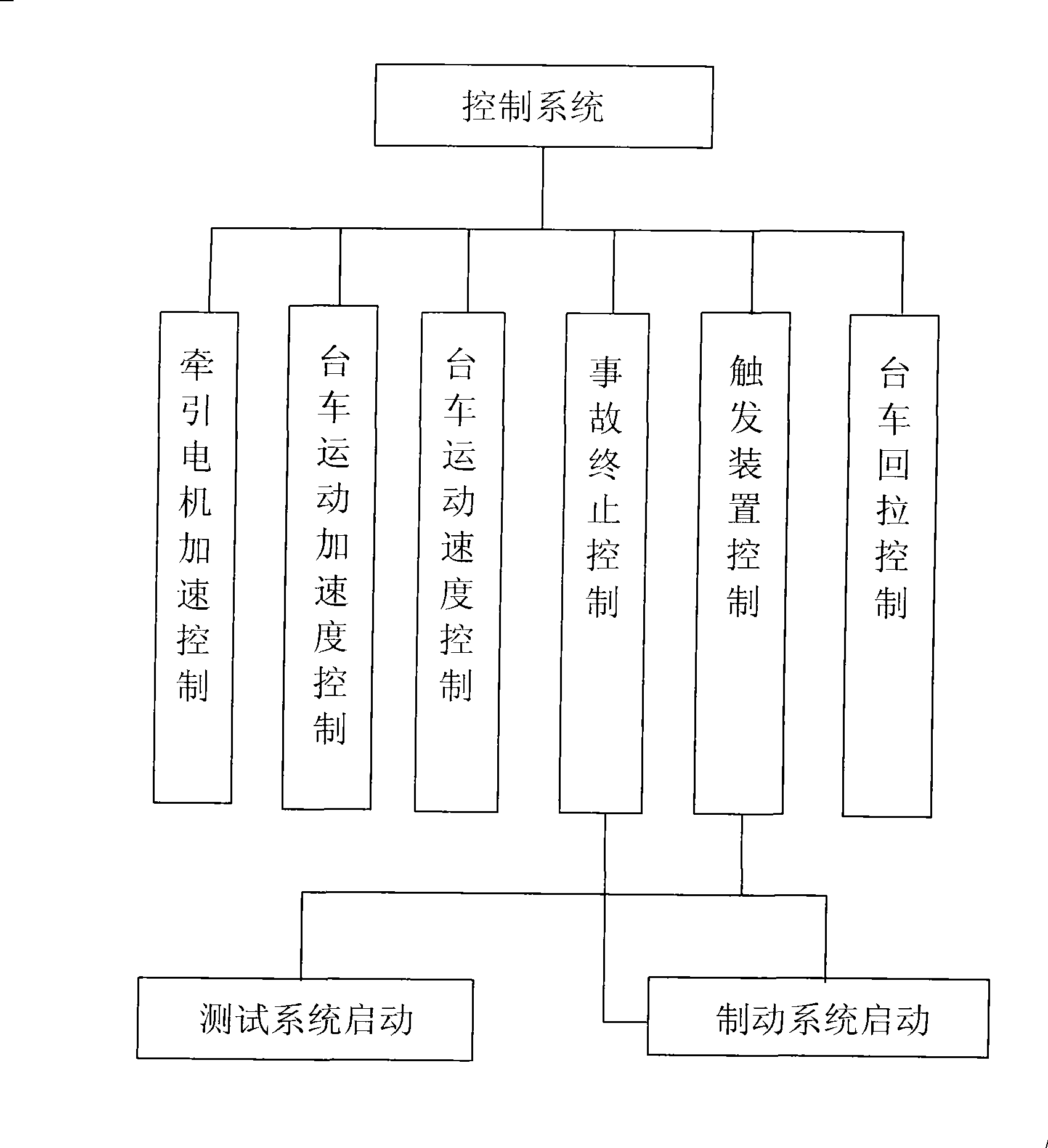
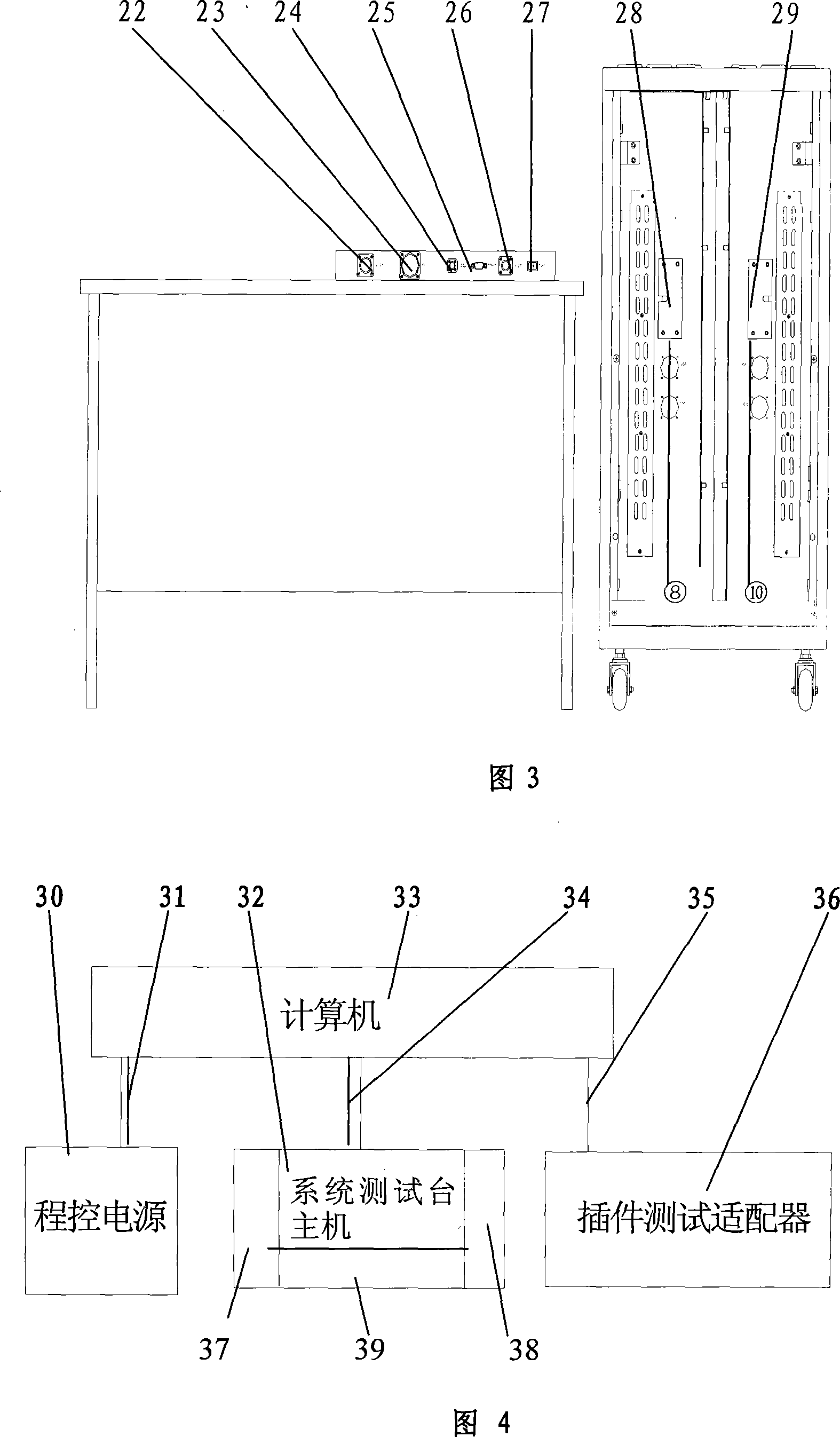
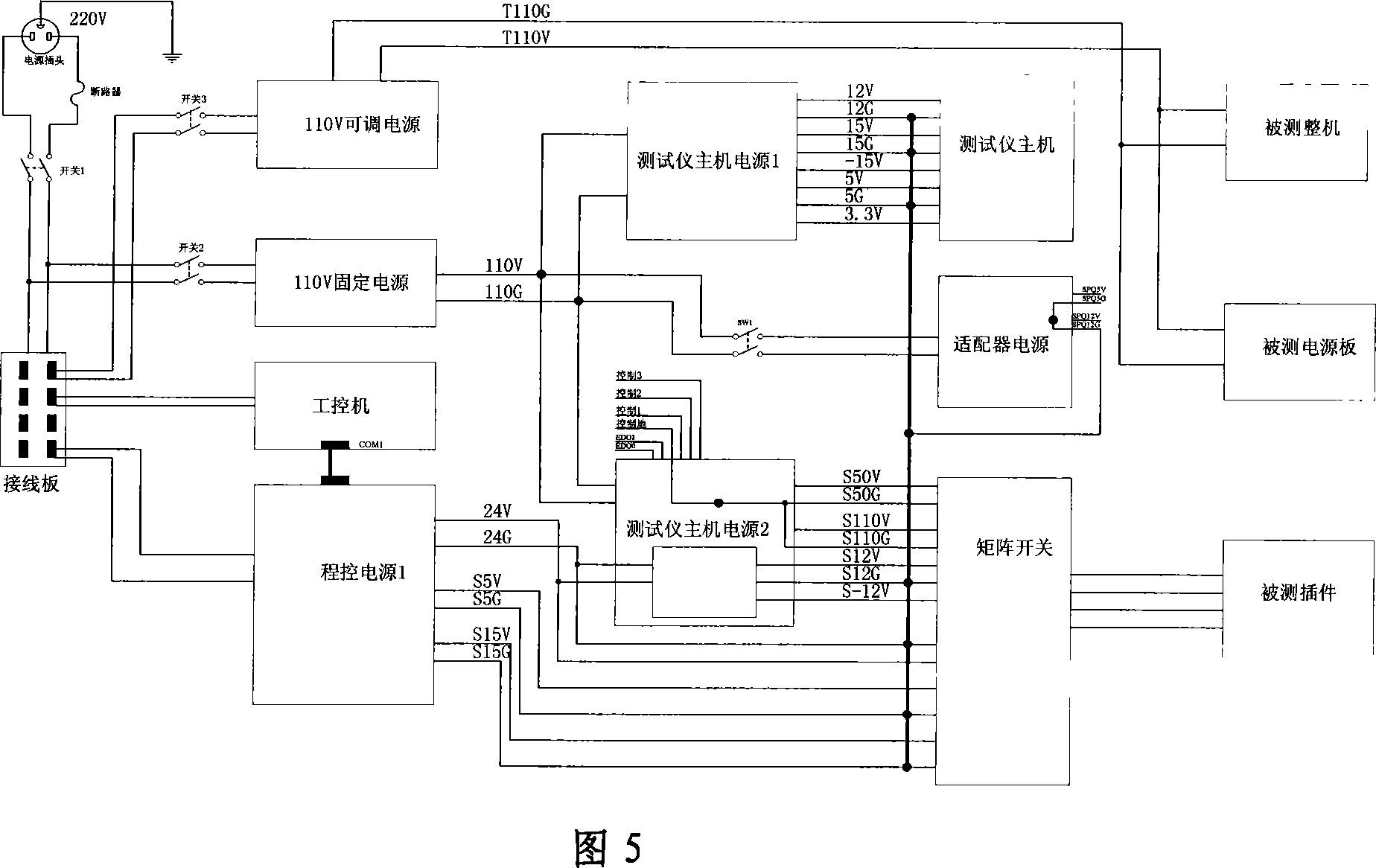
Train running monitoring device comprehensive test method and comprehensive testbench
A comprehensive testing method and testboard of train monitor device. The method is a comprehensive testing system based on computer integrated control. It adopts multi-communication mode to complete data exchange. On one hand, according to the vehicle condition simulated by comprehensive testbord, various high precision actuating signal are generated for normal working of control device, including analog, digital and communication signal. On the other hand, test various output signal of monitor device. Finally, test device by combining function relationship, board and channel grade of tested device. Three objects are communicated by computer directly, including programmed power, testboard host machine and card testing adapter. Communication from computer to programmed power and card testing adapter adopts RS232 mode, to testboard host machine adopts USB1.0 mode. Main control panel and communication management penal in testboard host machine adopts two-gate RAM to change data.
Owner:HUNAN CRRC TIMES SIGNAL & COMM CO LTD
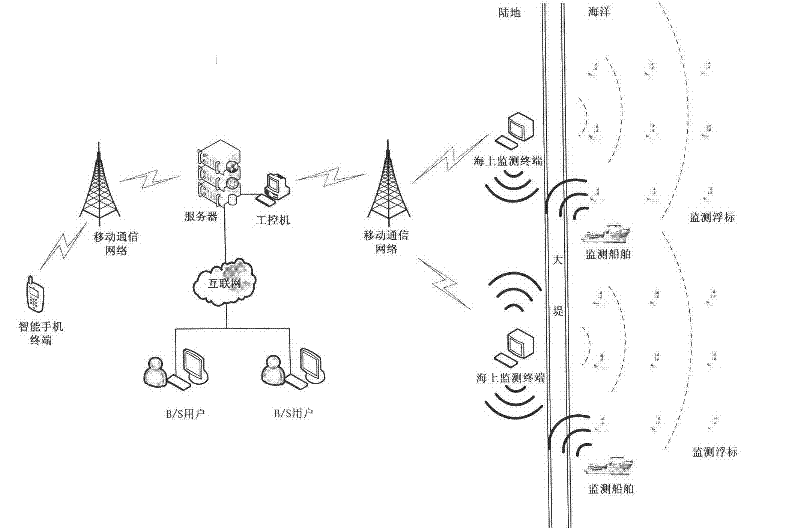
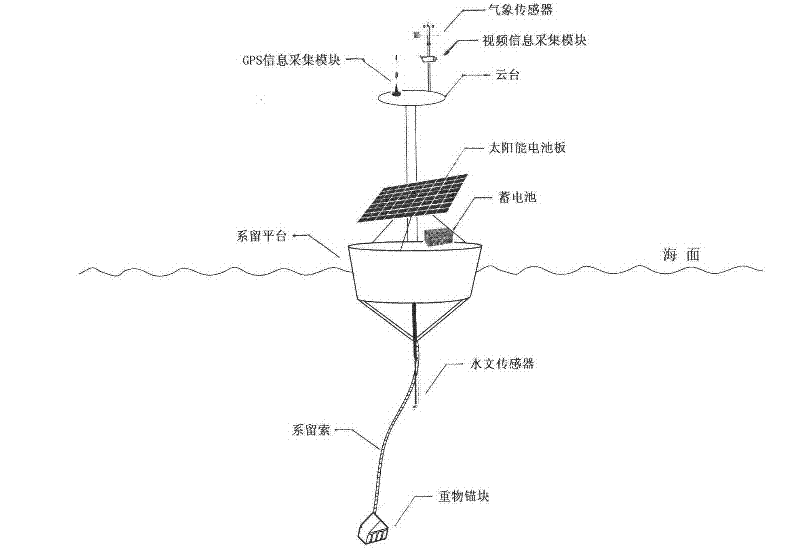
Ocean environment monitoring and early warning system
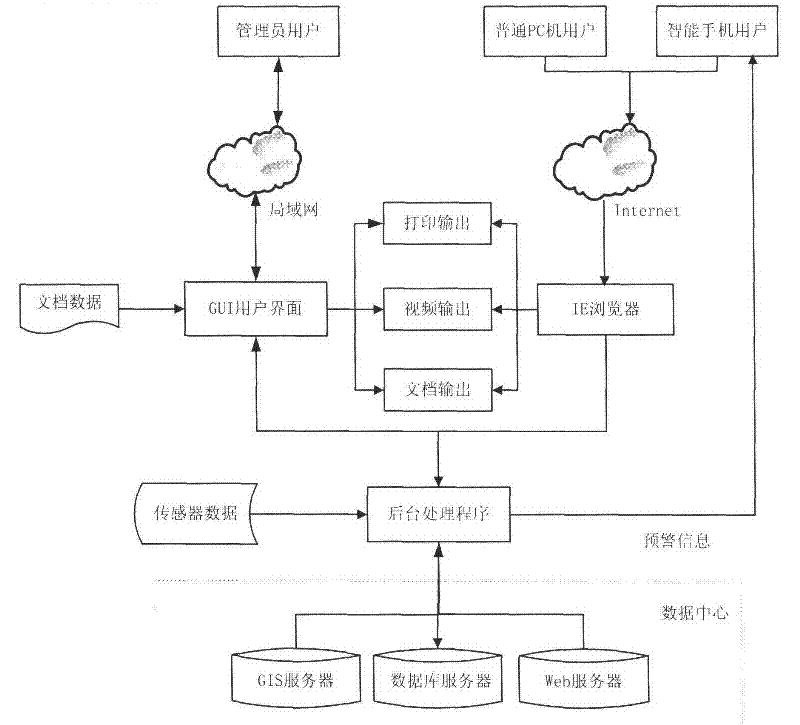
The invention relates to an ocean environment monitoring and early warning system, especially relating to an offshore ocean environment real-time monitoring and calamity early warning system based on Internet of things and a geographical information system. The invention is aimed at realizing on-line real-time dynamic monitoring and solves a practical problem that present ocean environment monitoring technology and method are only established on a sampling analysis base. A monitoring device of the system acquires a meteorological element, a hydrological element, GPS information and video monitoring information. Communication between monitoring buoys is realized through a wireless sensing network, and communication between a monitoring ship and an offshore monitoring terminal and communication between offshore monitoring terminals are realized through a wireless microwave communication network. The offshore monitoring terminal sends data to a remote monitoring center through a mobile communication network, the monitor center completes data reception, storage and management, and publishes GIS service and Web service information. Early warning information is automatically sent to an intelligent mobile phone terminal through a background management program. A monitoring early warning information platform provides related service information to a user for browse access.
Owner:SHANGHAI OCEAN UNIV
Method for performing fault diagnosis by using model conversion
ActiveCN101814114AEasy to useImprove diagnostic accuracyMathematical modelsSpecial data processing applicationsCorresponding conditionalLogic gate
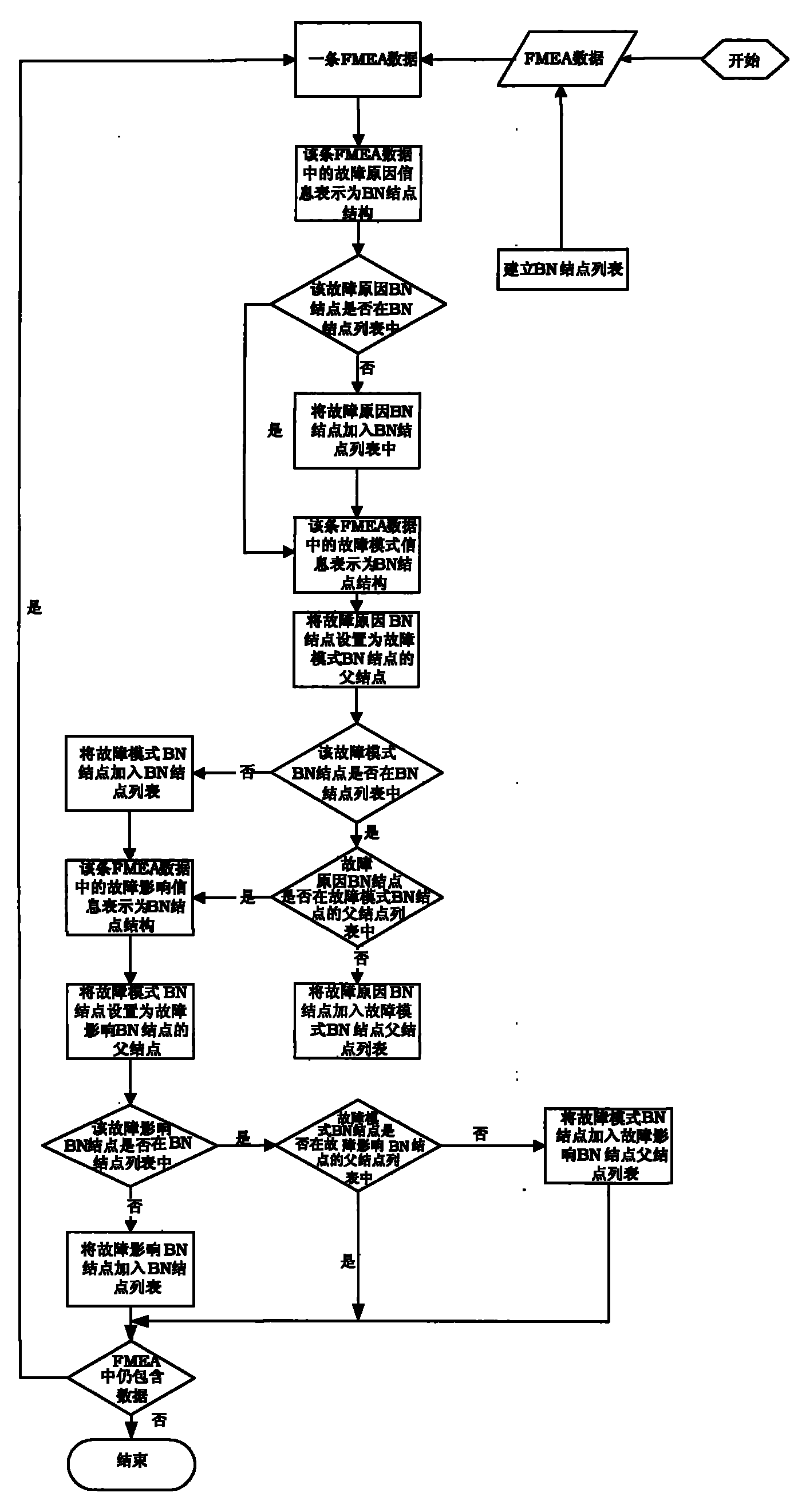
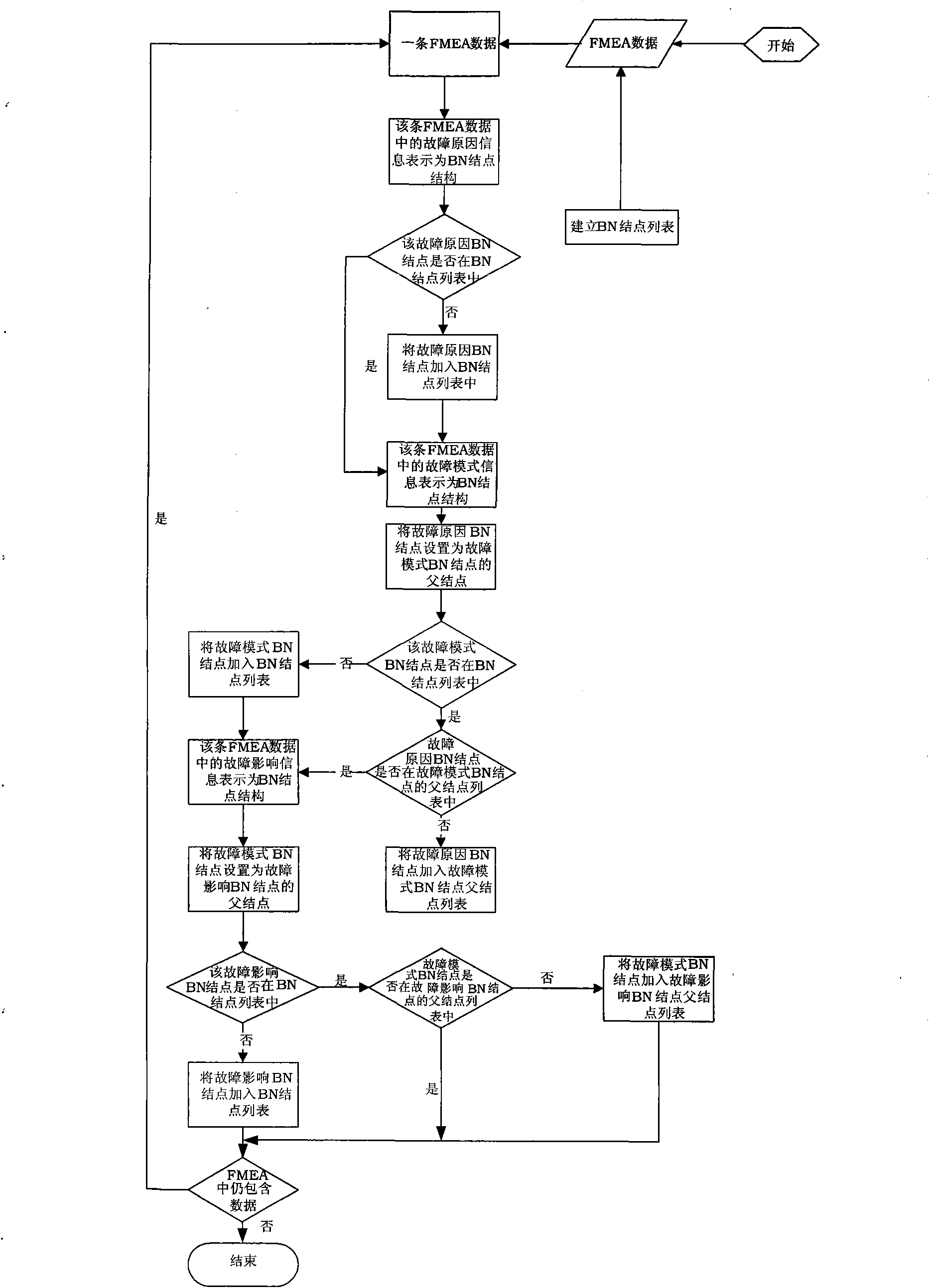
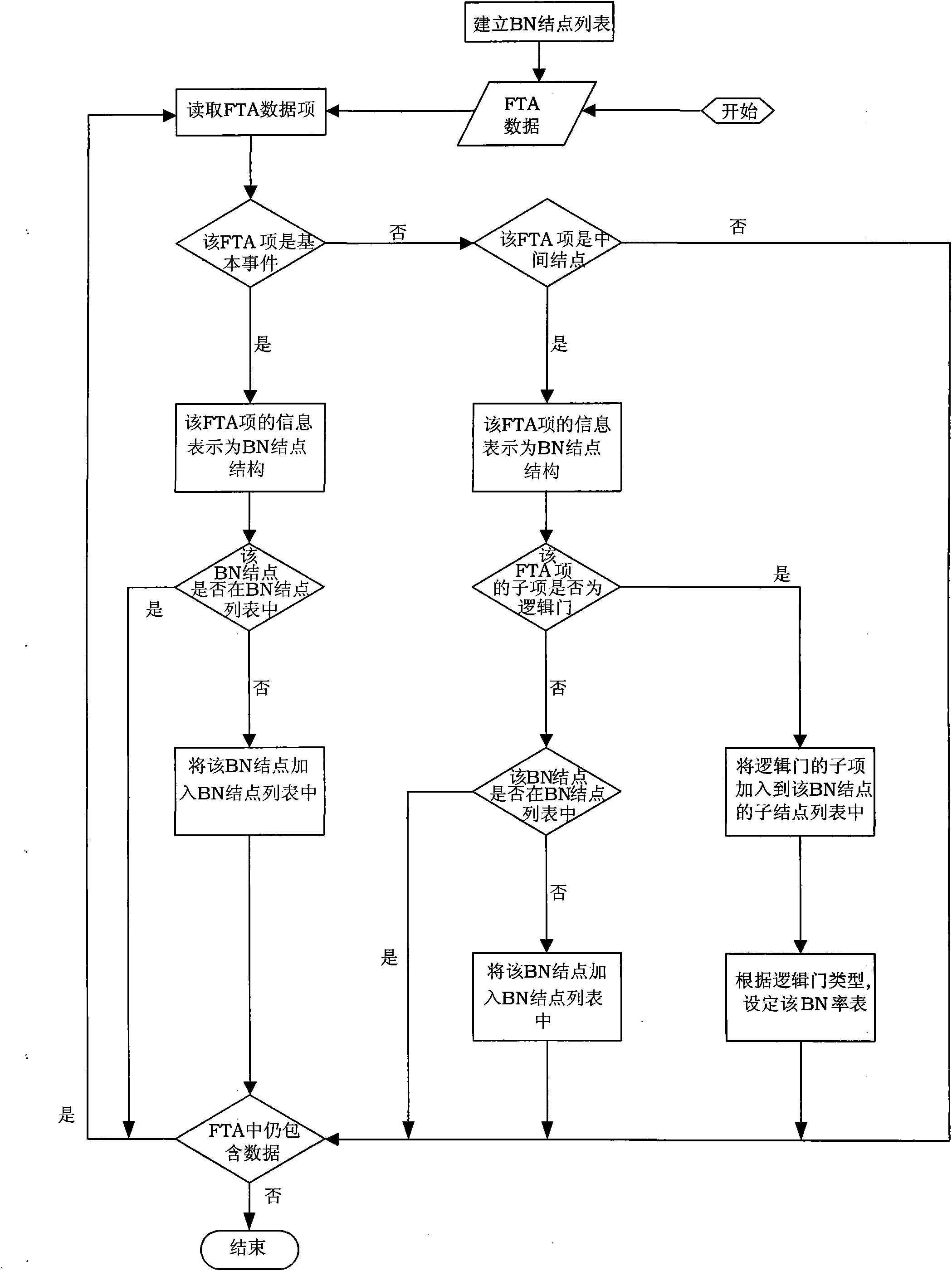
The invention discloses a method for performing fault diagnosis by using model conversion. According to the method, processed related information of a fault mode effect analysis model is converted into a corresponding Bayesian network model by using a self-defined data structure while ensuring complete data, an elementary event, a logic gate and an intermediate event of a fault tree in a fault tree analysis model are converted into nodes in a Bayesian network respectively, and a corresponding conditional probability table in the Bayesian network is set. The fault diagnosis is performed through the converted Bayesian network model. The method of the invention expands the use of the Bayesian network model in the fault diagnosis, improves the diagnosis accuracy of a fault diagnosis model in practical application, ensures the universality of model conversion, and can realize cross-tool conversion among different fault mode effect analysis, fault tree analysis result and the generated Bayesian network.
Owner:BEIHANG UNIV
System and method for fusion-aligned reprojection of incomplete data
InactiveUS7046831B2Precise applicationPrecise positioningReconstruction from projectionCharacter and pattern recognitionComplete dataComputed tomography
The present invention provides a system and method of using current but incomplete data to prepare an approximated complete image of a patient potentially undergoing radiation therapy. A limited patient image, such as that obtained from a CT scan is fused with a complete image of the same area using image registration techniques. The fused image is converted to sinogram data. This data is compared to sinogram data corresponding to the limited patient image to determine what data exists beyond the scope of the limited sinogram. Any additional data is added to the limited data sinogram to obtain a complete sinogram. This is reconstructed into an image that approximates the complete image that would have been taken at the time the limited image was obtained.
Owner:TOMOTHERAPY INC
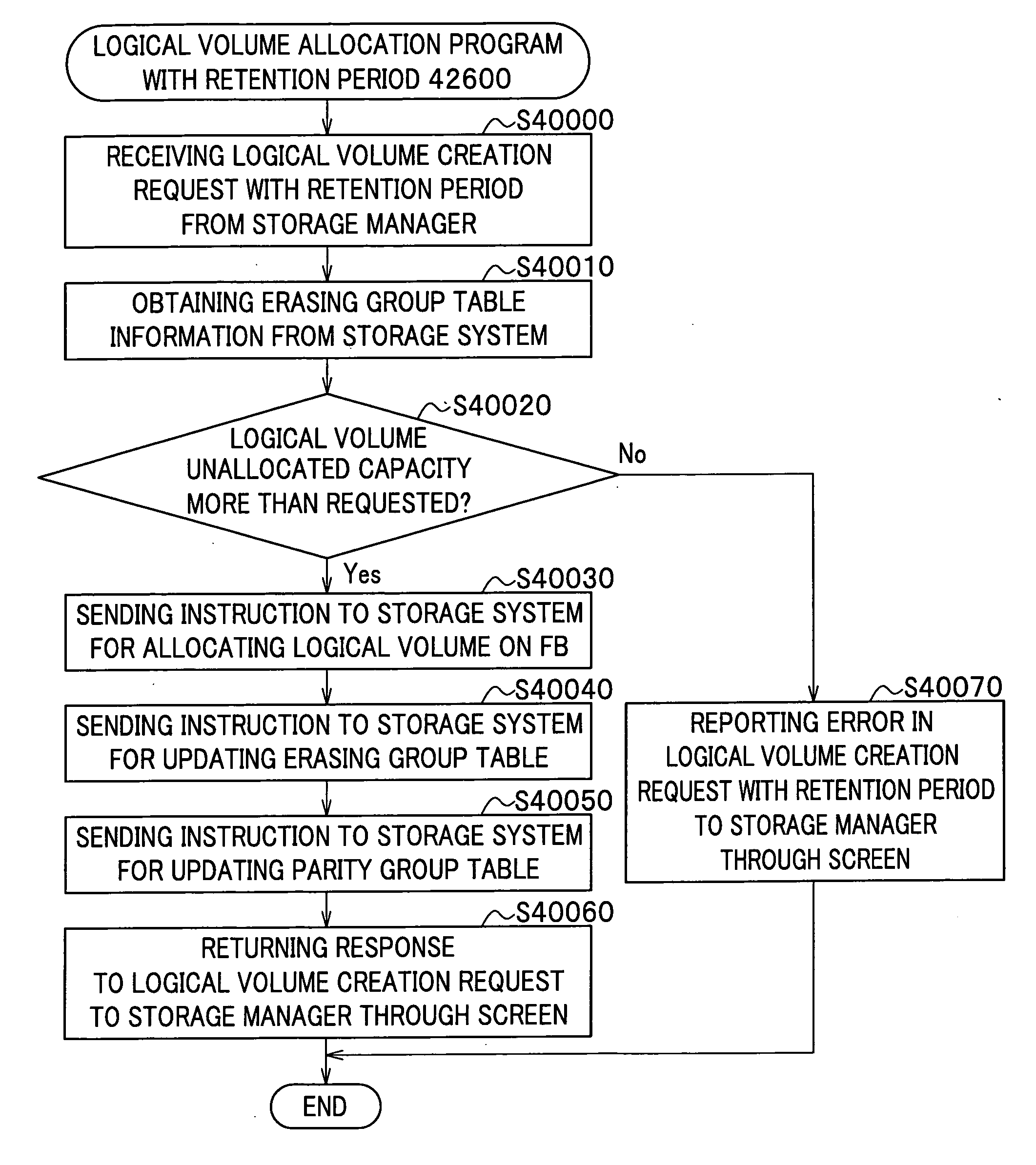
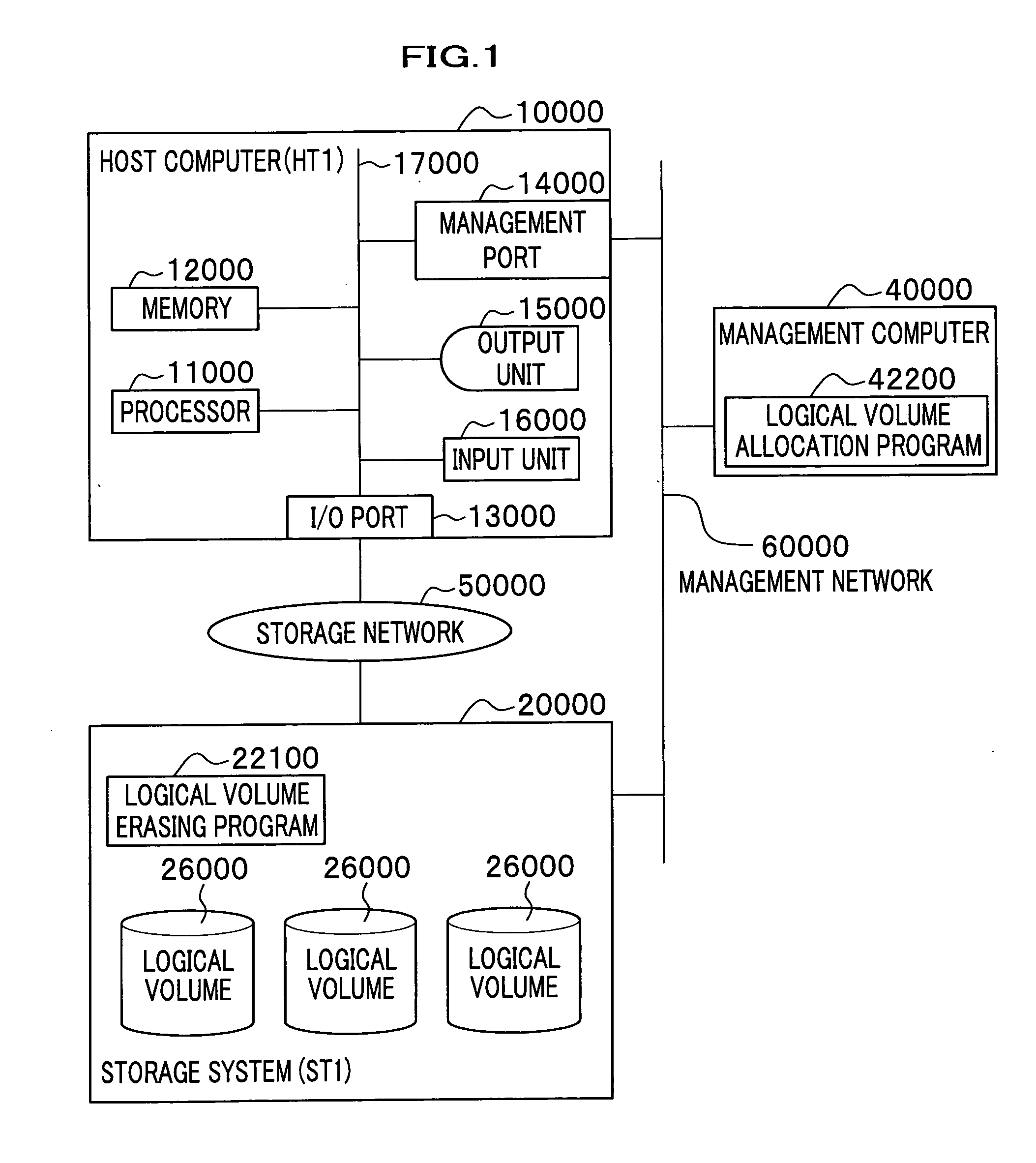
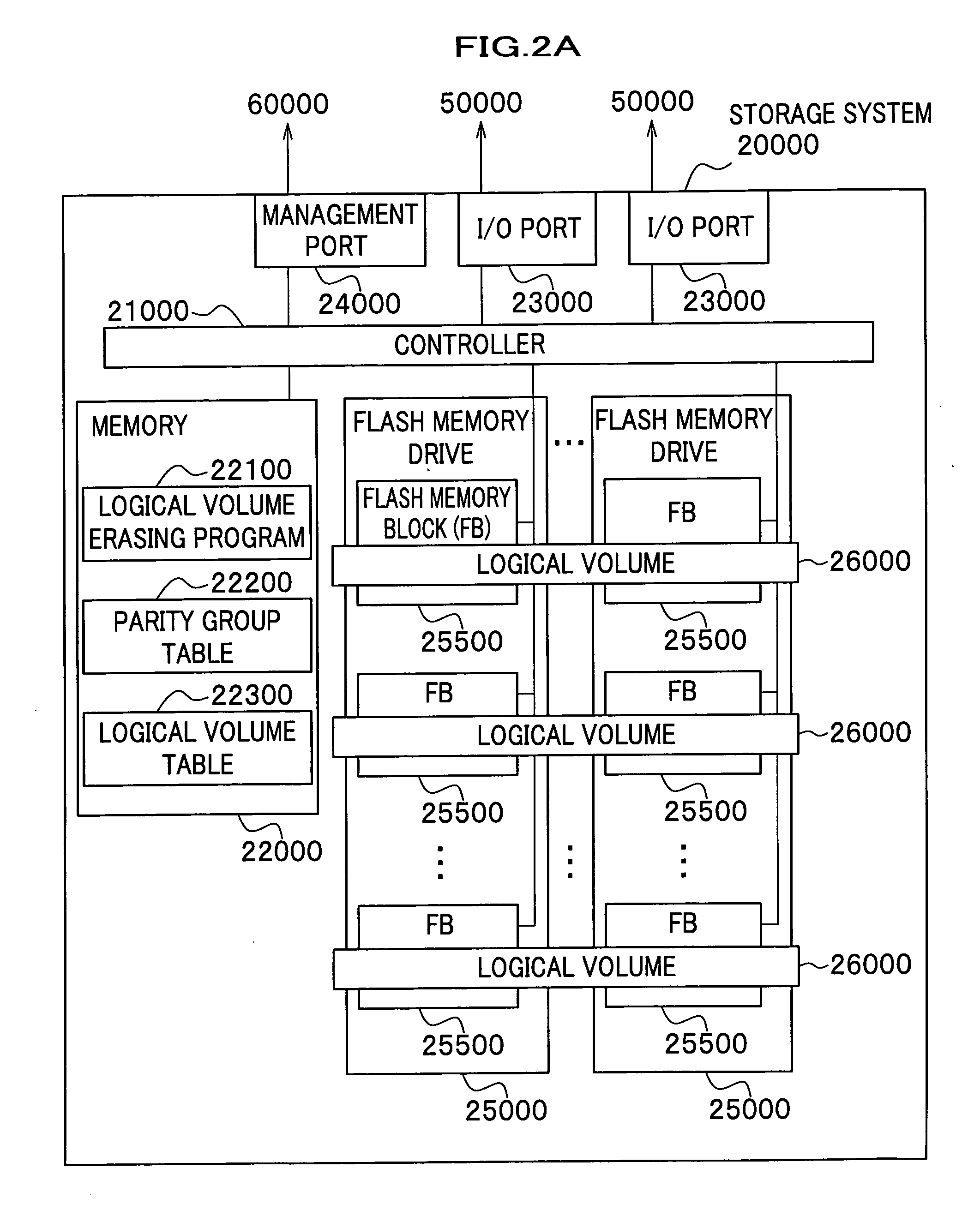
Logical volume management method and logical volume management program
InactiveUS20080065815A1Complete functionDigital data protectionInternal/peripheral component protectionComplete dataSystem usage
There is provided a logical volume management method for storage system. When a logical volume is created on a flash memory drive, a management computer allocates logical volume while flash memory chip border of flash memory drive is taken into account. Specifically, a table for managing a correlation between each parity group and the flash memory chip of the flash memory drive is obtained and the logical volume is allocated in such a manner that a flash memory chip is not shared by a plurality of logical volumes. When complete erasing of logical volume data is performed, the management computer specifies a flash memory chip on which complete data erasing is to be performed, and the storage system completely erases data exclusively on the chip of interest with a use of a function of completely erasing data at a time by chip unit of the flash memory chip (chip erasing).
Owner:HITACHI LTD
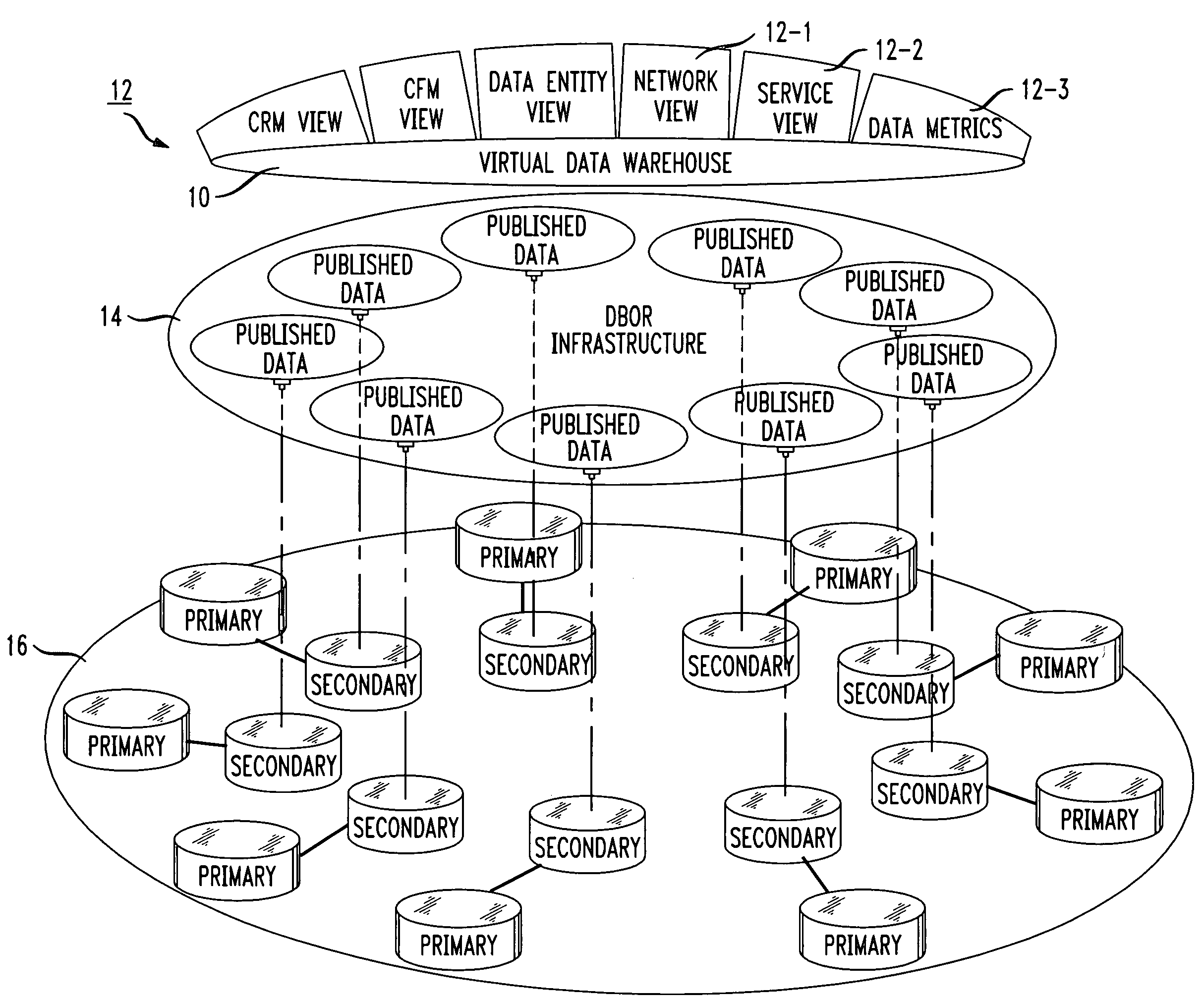
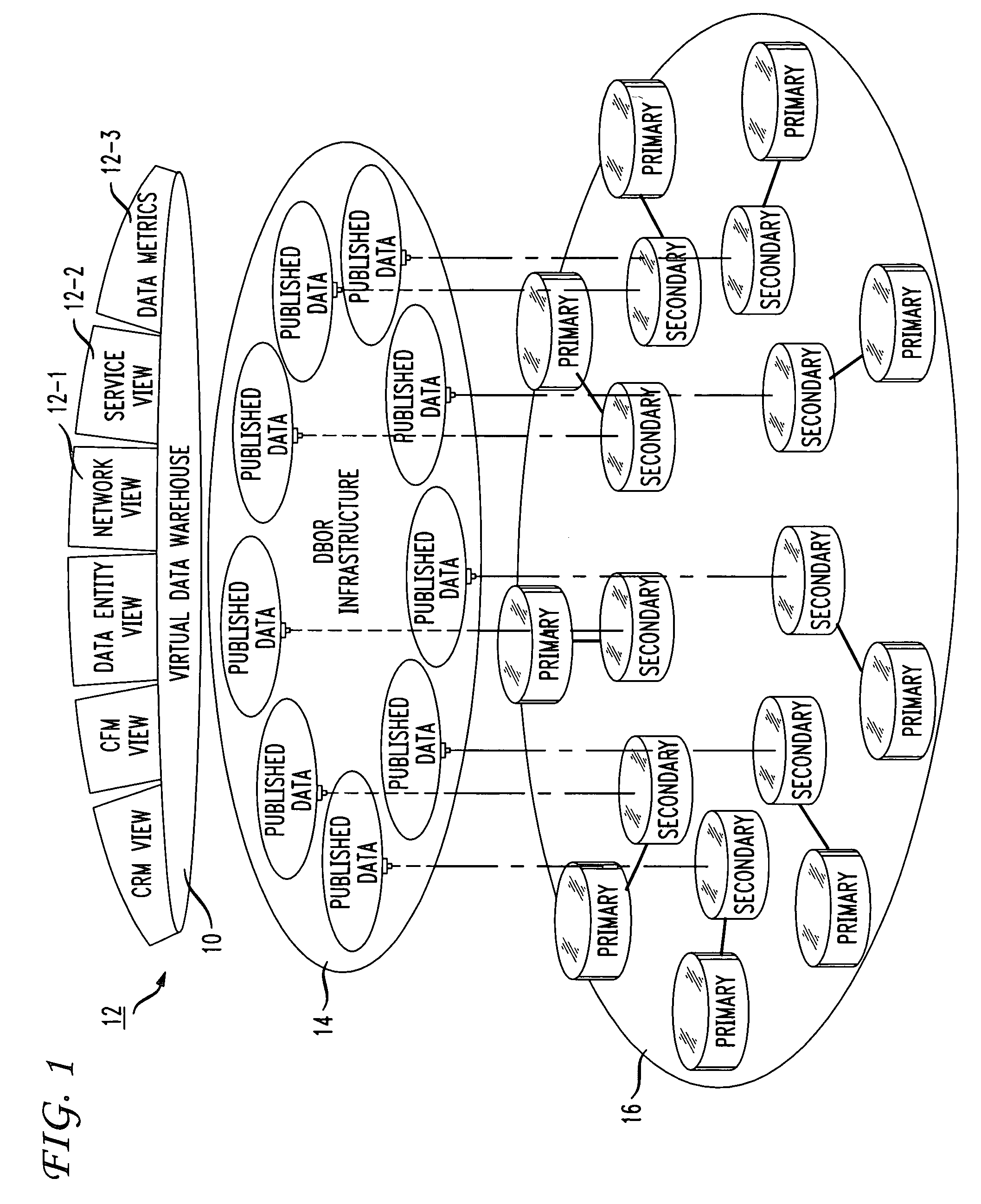
Virtual data warehousing
ActiveUS7280998B1Remove complexityReduce developmentData processing applicationsDigital data information retrievalComplete dataMetadata
A virtual data warehouse (the functional equivalent of a conventional data warehouse) that provides aggregated views of the complete data inventory. The virtual data warehouse contains metadata, which is used to form a logical enterprise data model that is part of the database of record (DBOR) infrastructure. Each legacy back-end database system is published on the infrastructure, with its metadata extracted and used as noted above. The infrastructure software uses standard J2EE, JMS and reusable EJBs, for transactional unit requests, and ETL (extract-transform-load) tools for real-time bulk loading of data.
Owner:TRANSPACIFIC DELTA SCI
Database management system with efficient version control
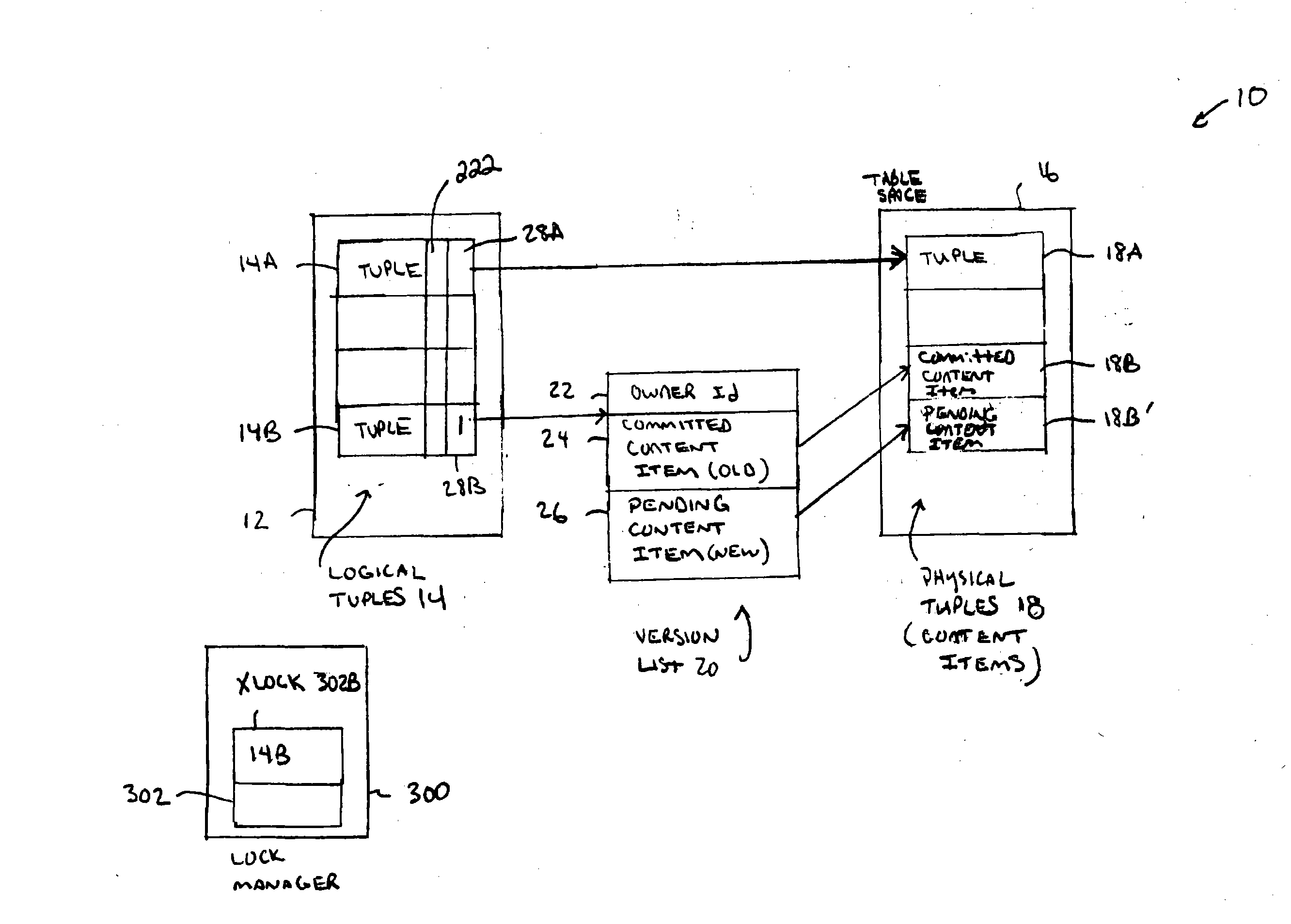
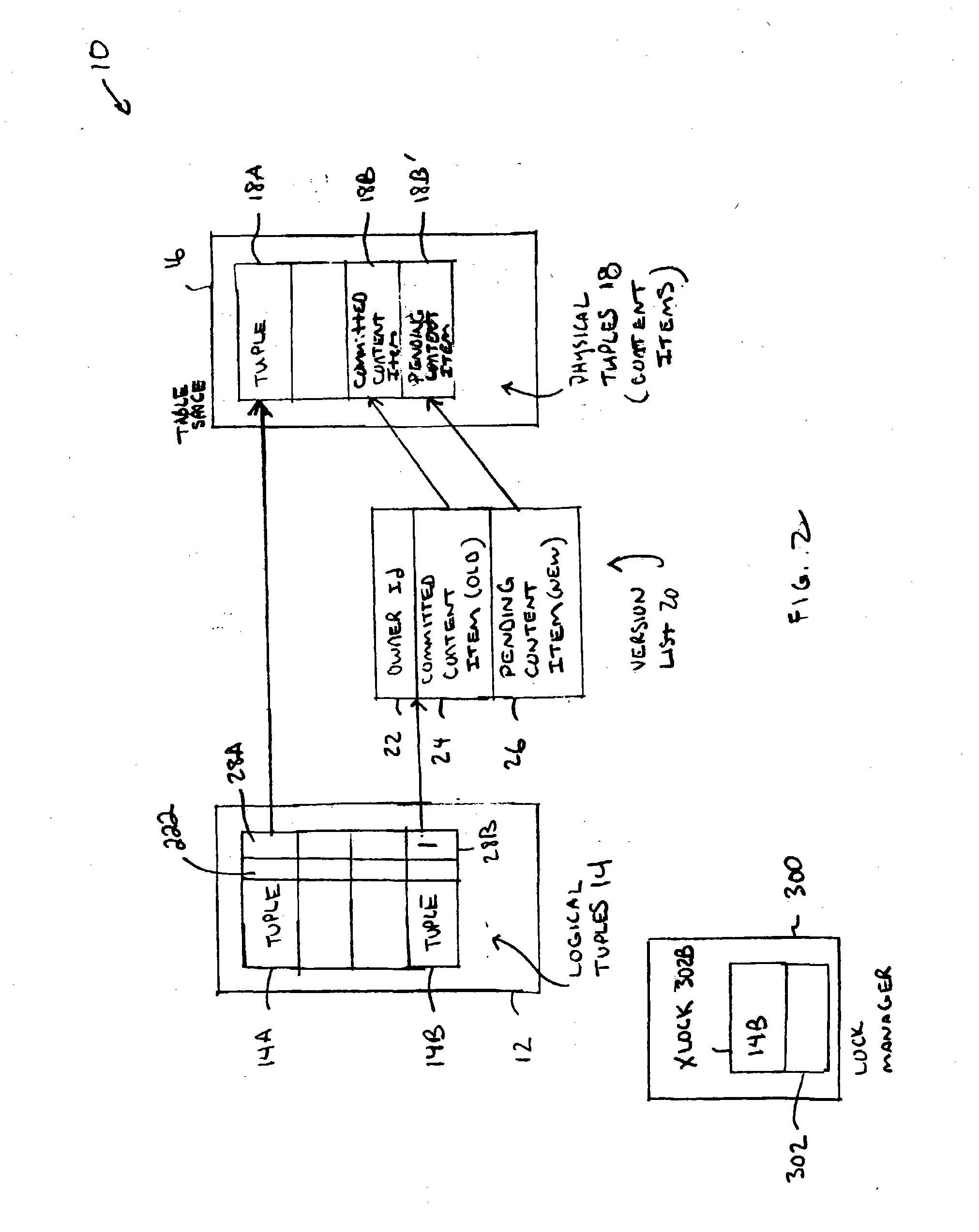
ActiveUS20050033720A1Data processing applicationsDigital data processing detailsComplete dataDatabase
A two copy versioning scheme is proposed. The scheme provides efficient implementation for a high read load database and eliminates read dependencies. The versioning scheme provides efficient implementation for transactions executing under ANSI READ COMMITTED isolation, and is extensible to serializable isolation. The two-copy versioning scheme is garbage free meaning that all versions of data records are used during execution and is adapted to index scanning operations. A “deferred delete” scheme allows read transactions to complete data deallocation operations. Statements that require “snapshots” are efficiently supported.
Owner:TIMES TEN PERFORMANCE SOFTWARE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com