Patents
Literature
5796 results about "Data objects" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
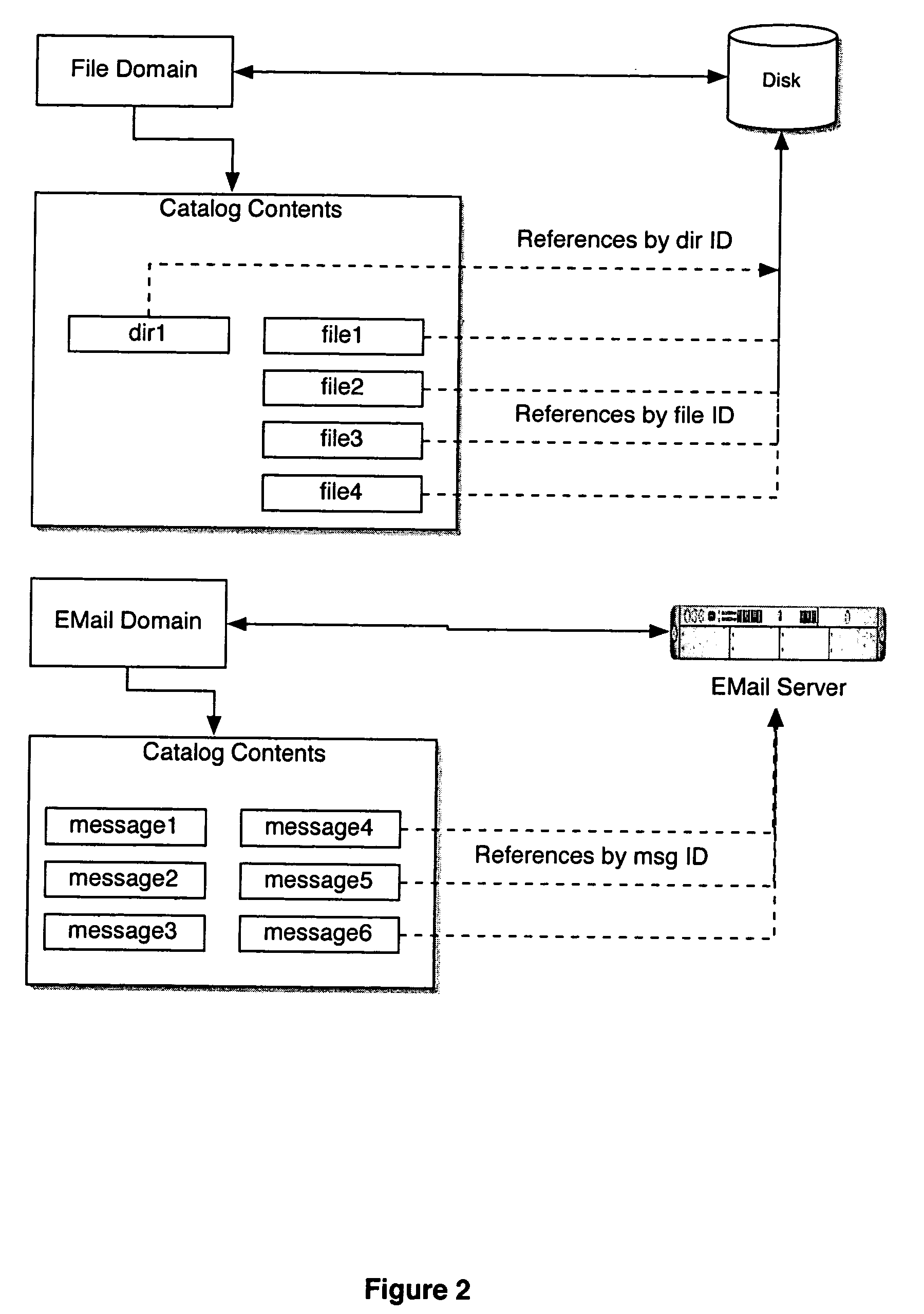
Overview of data objects. A data object is a region of storage that contains a value or group of values. Each value can be accessed using its identifier or a more complex expression that refers to the object.
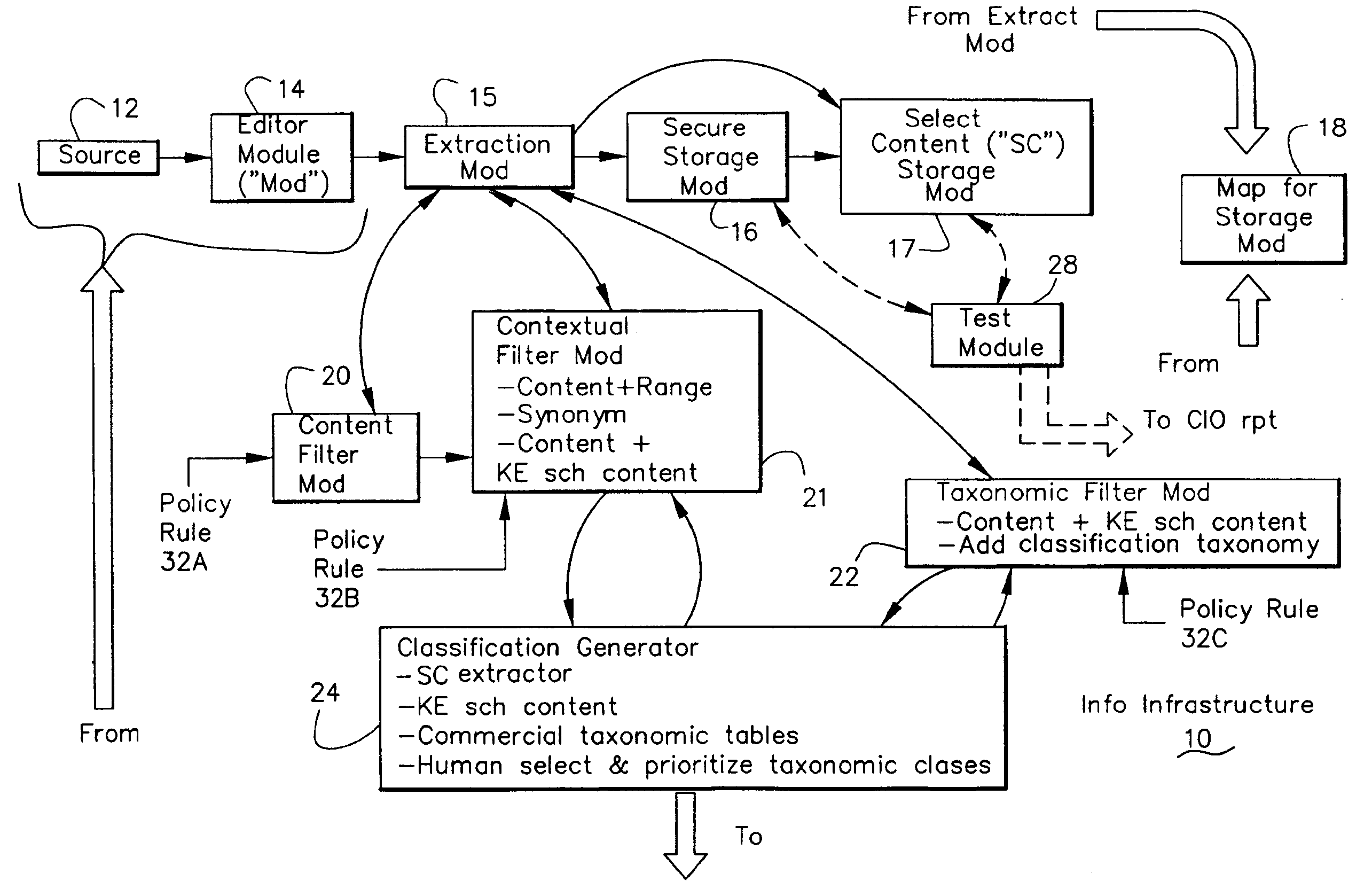
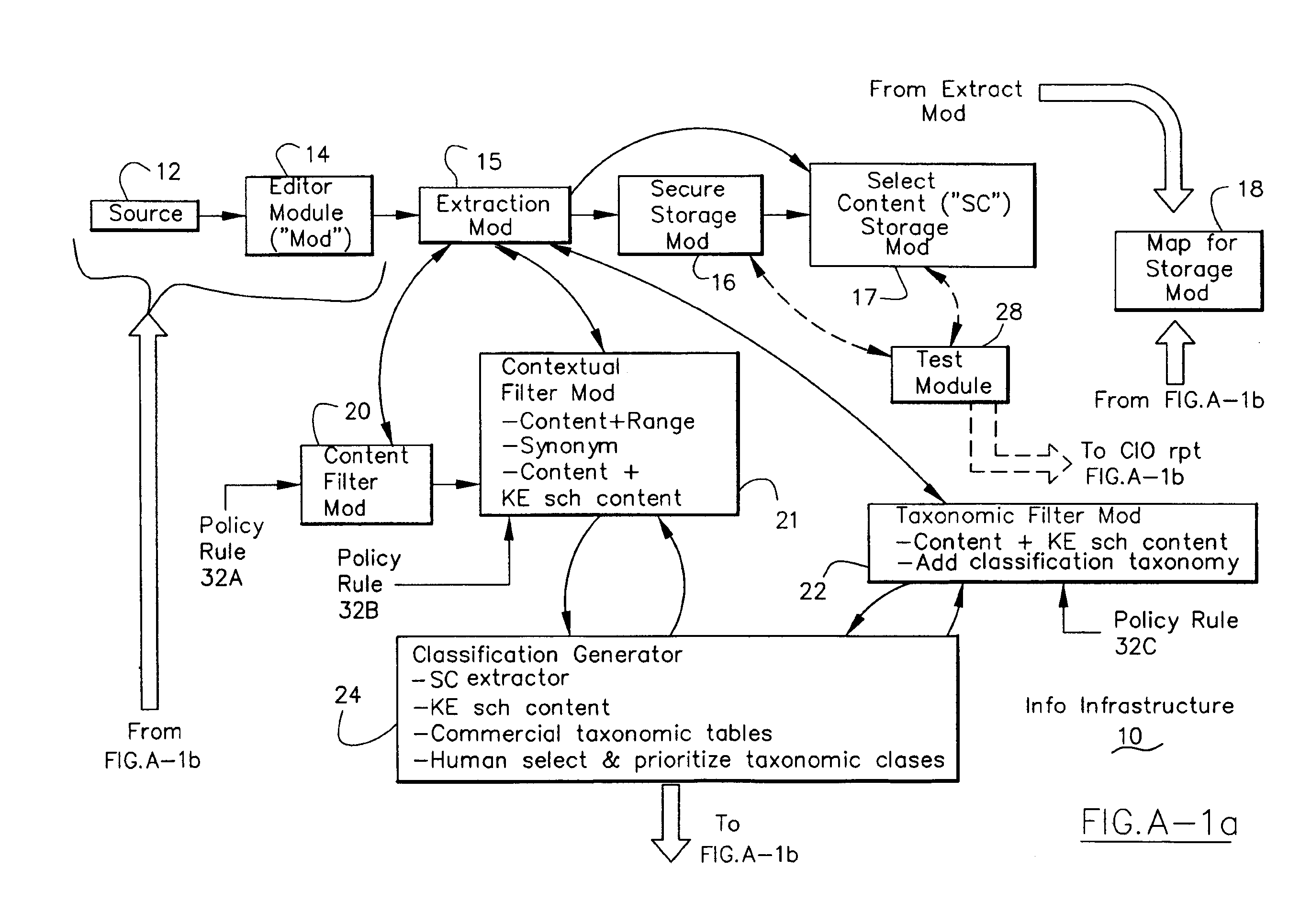
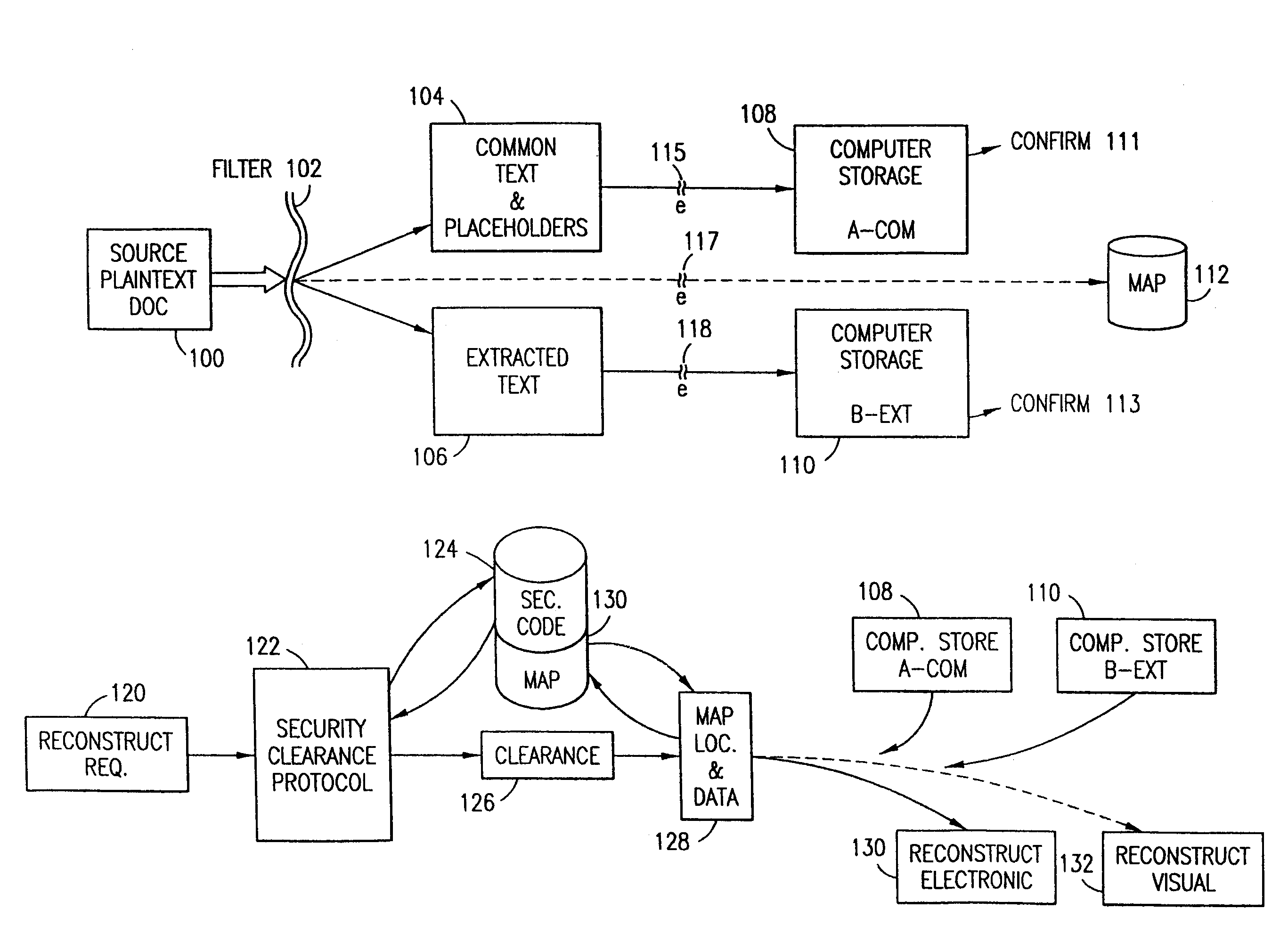
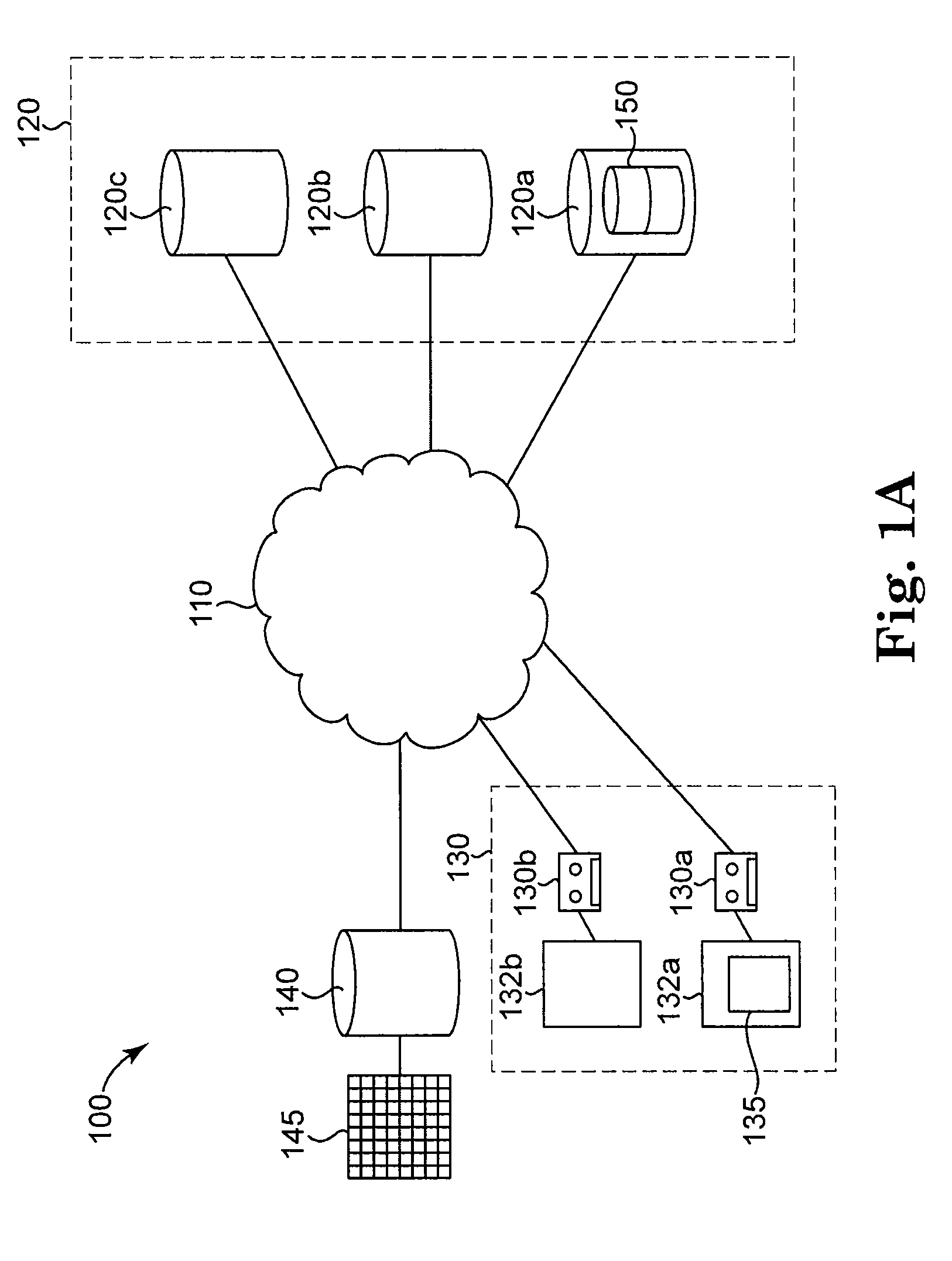
Data security system and method with editor
ActiveUS20050132070A1Ease overhead performanceHigh overhead performanceDigital data processing detailsTelephonic communicationFiltrationPaper document
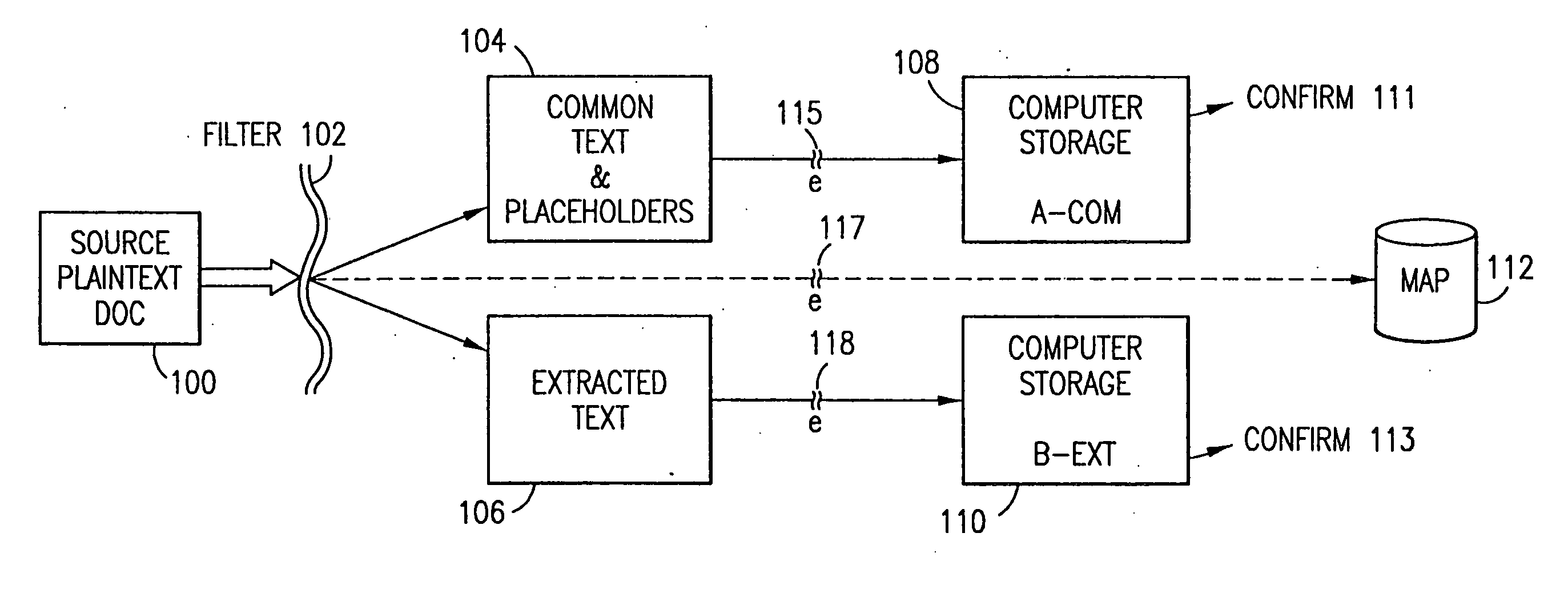
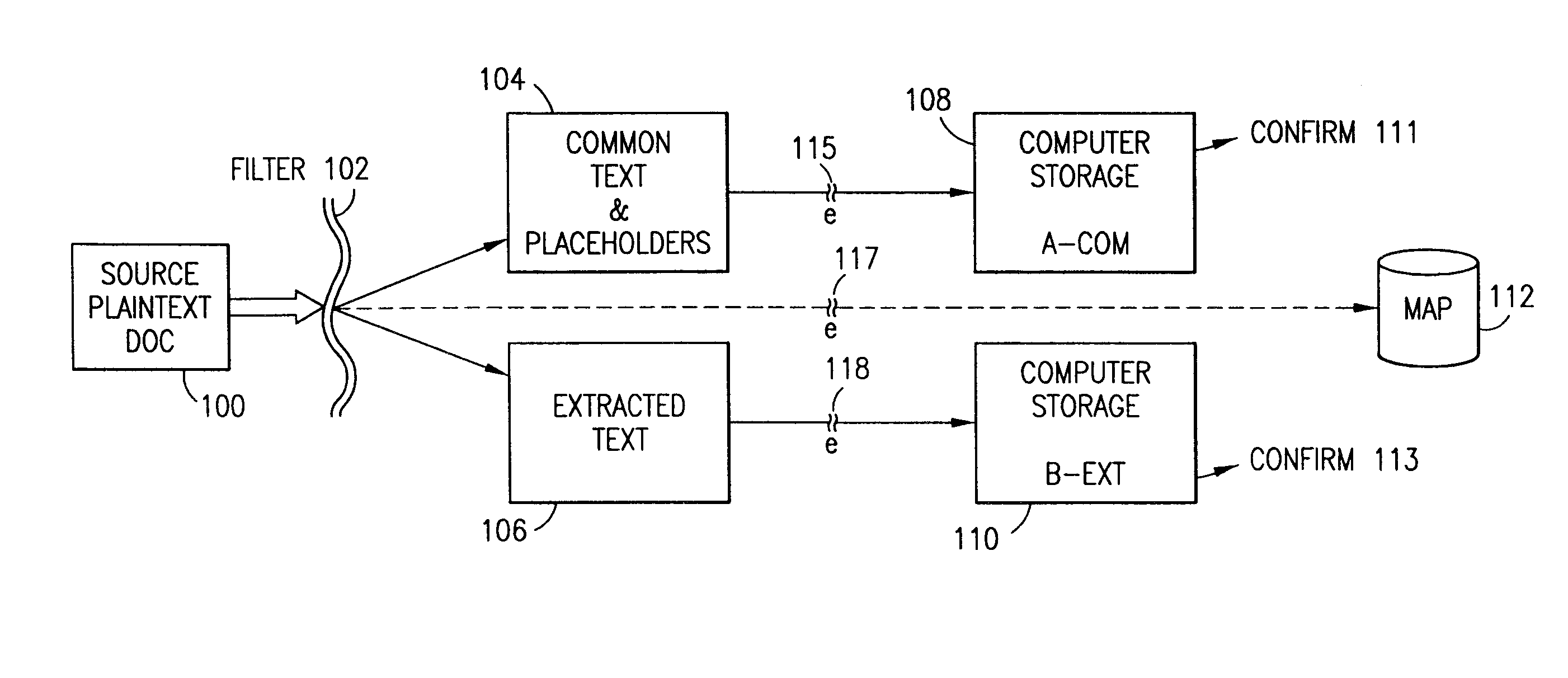
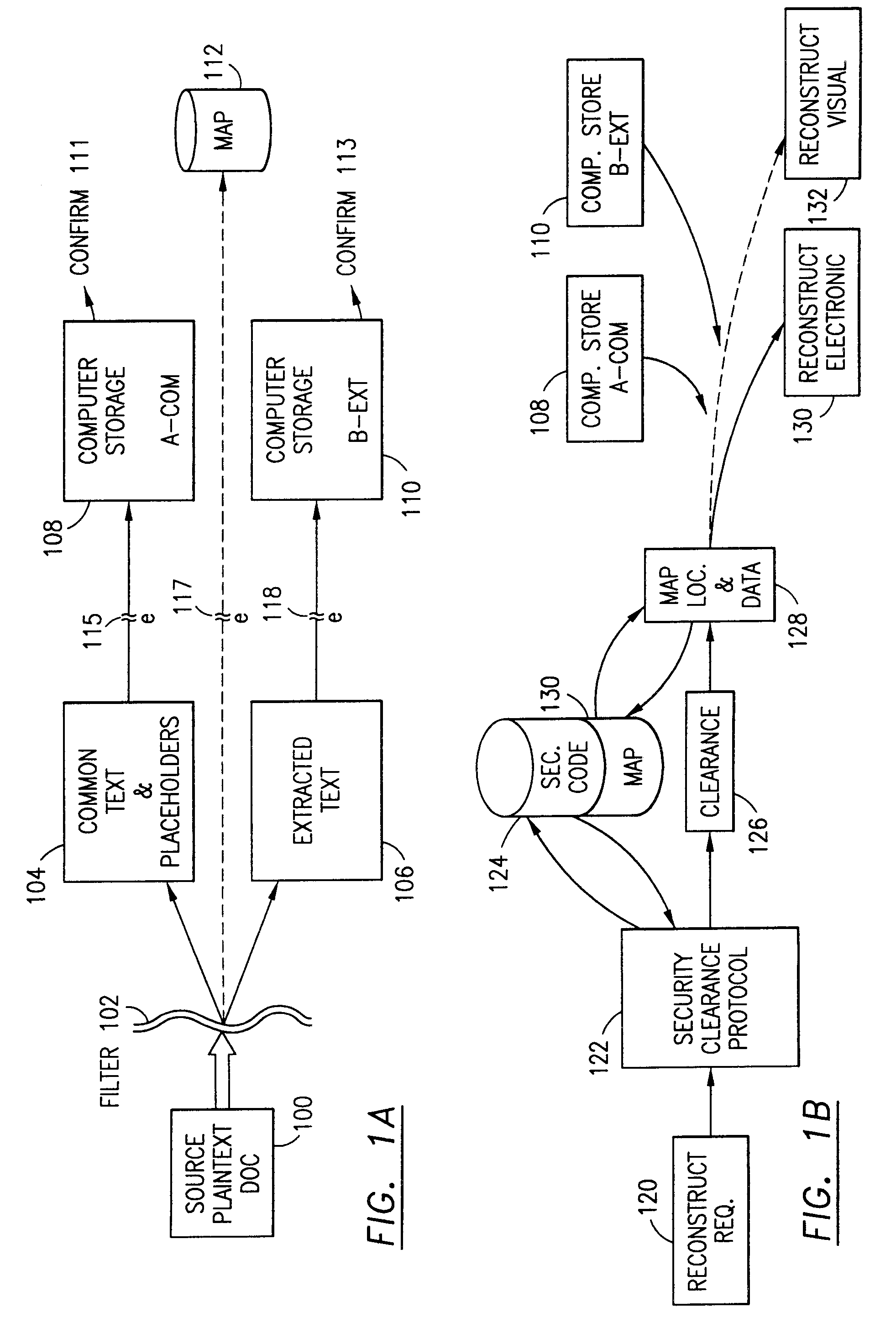
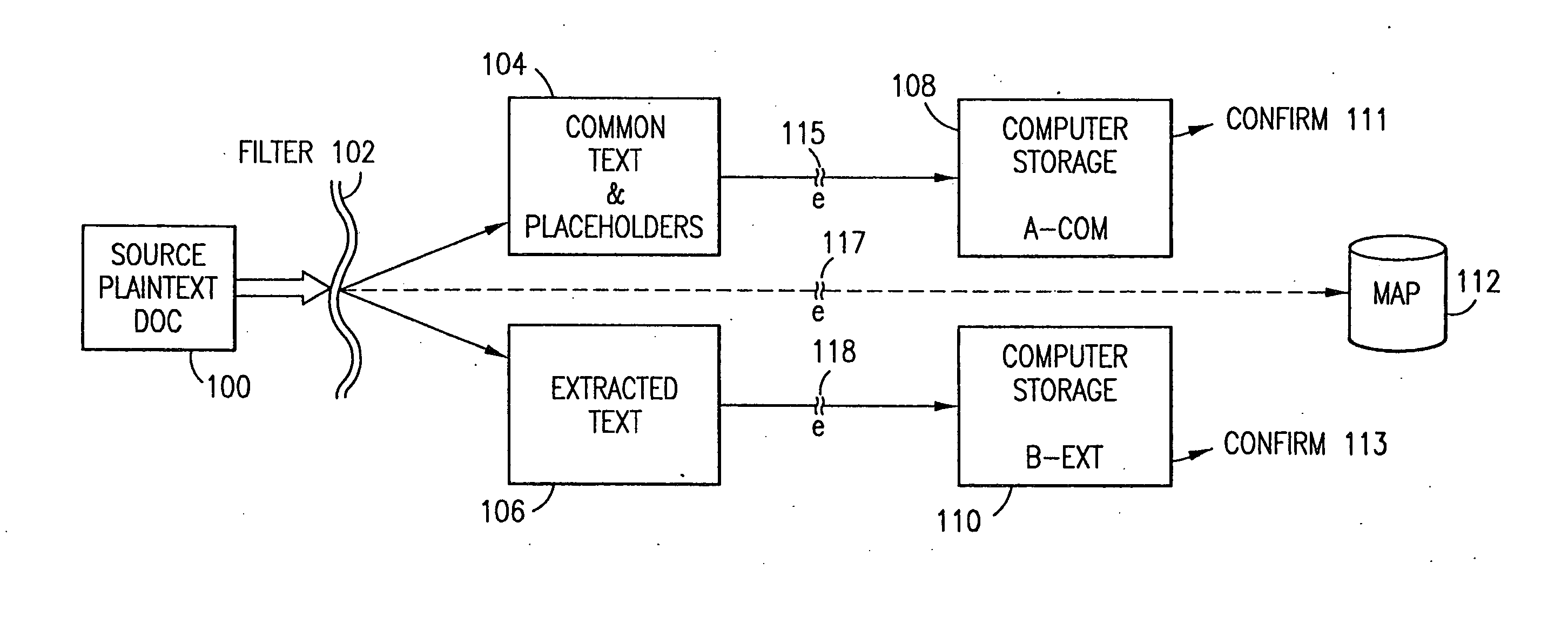
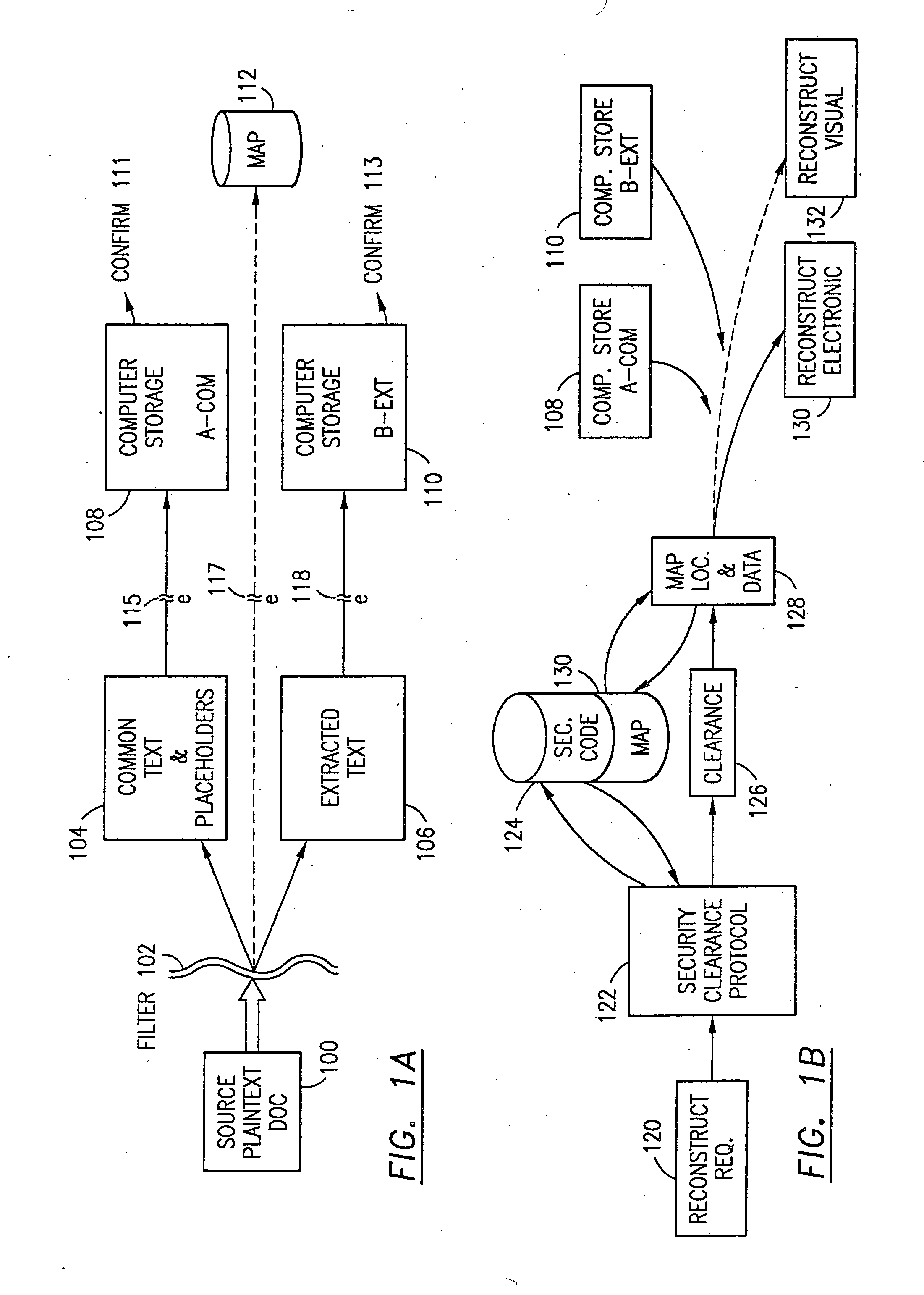
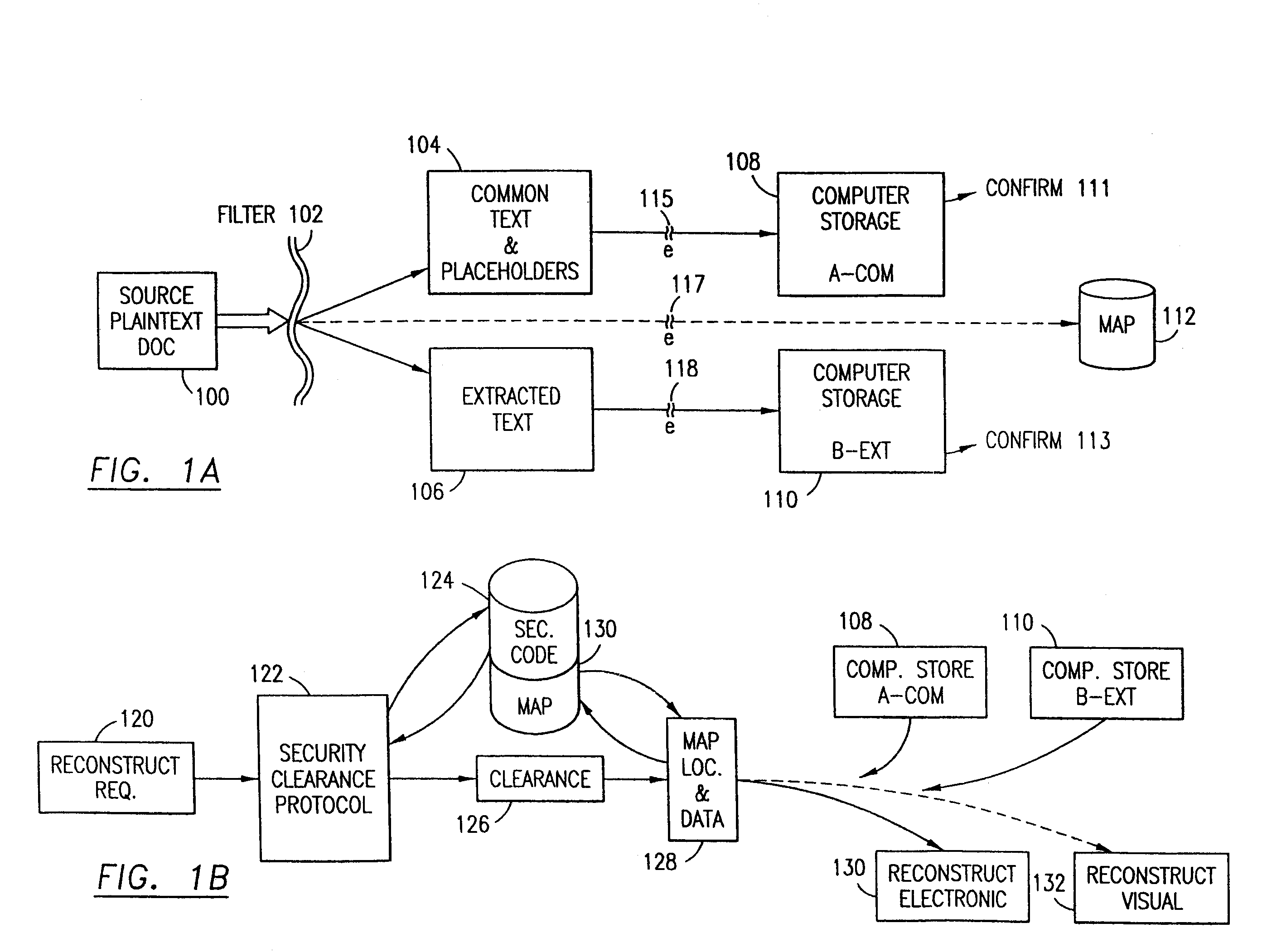
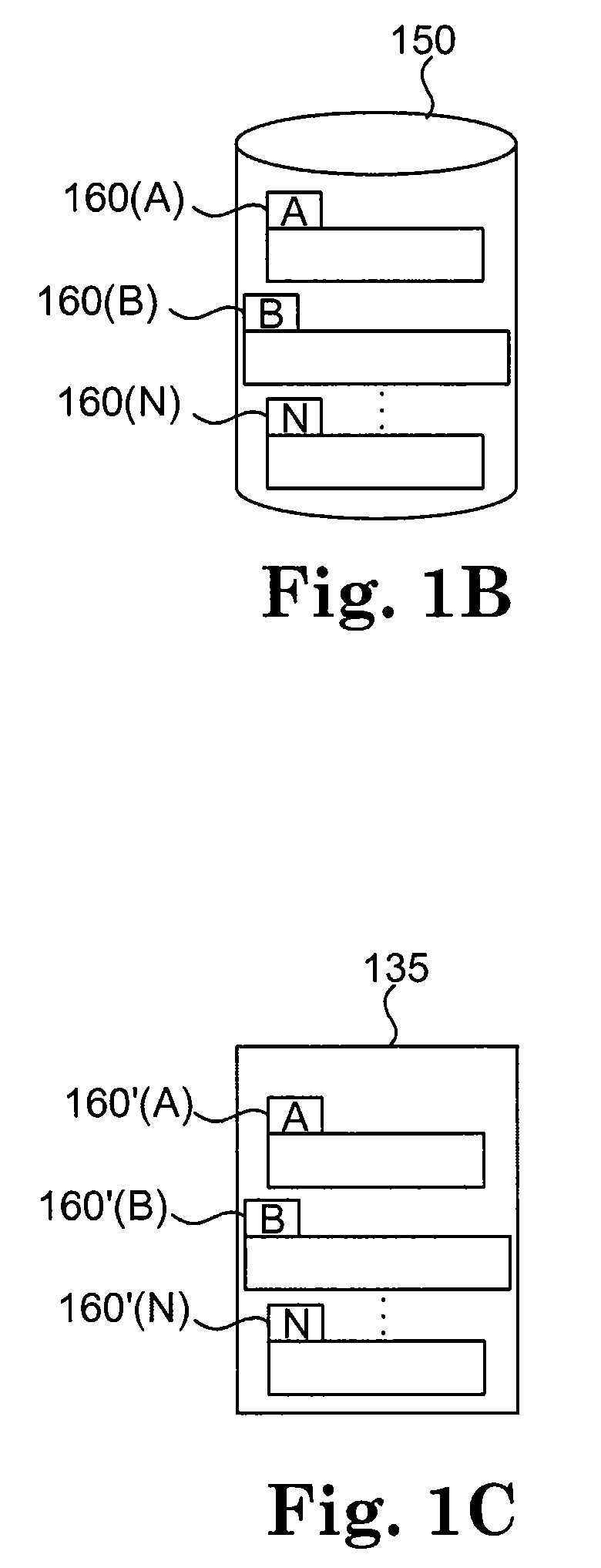
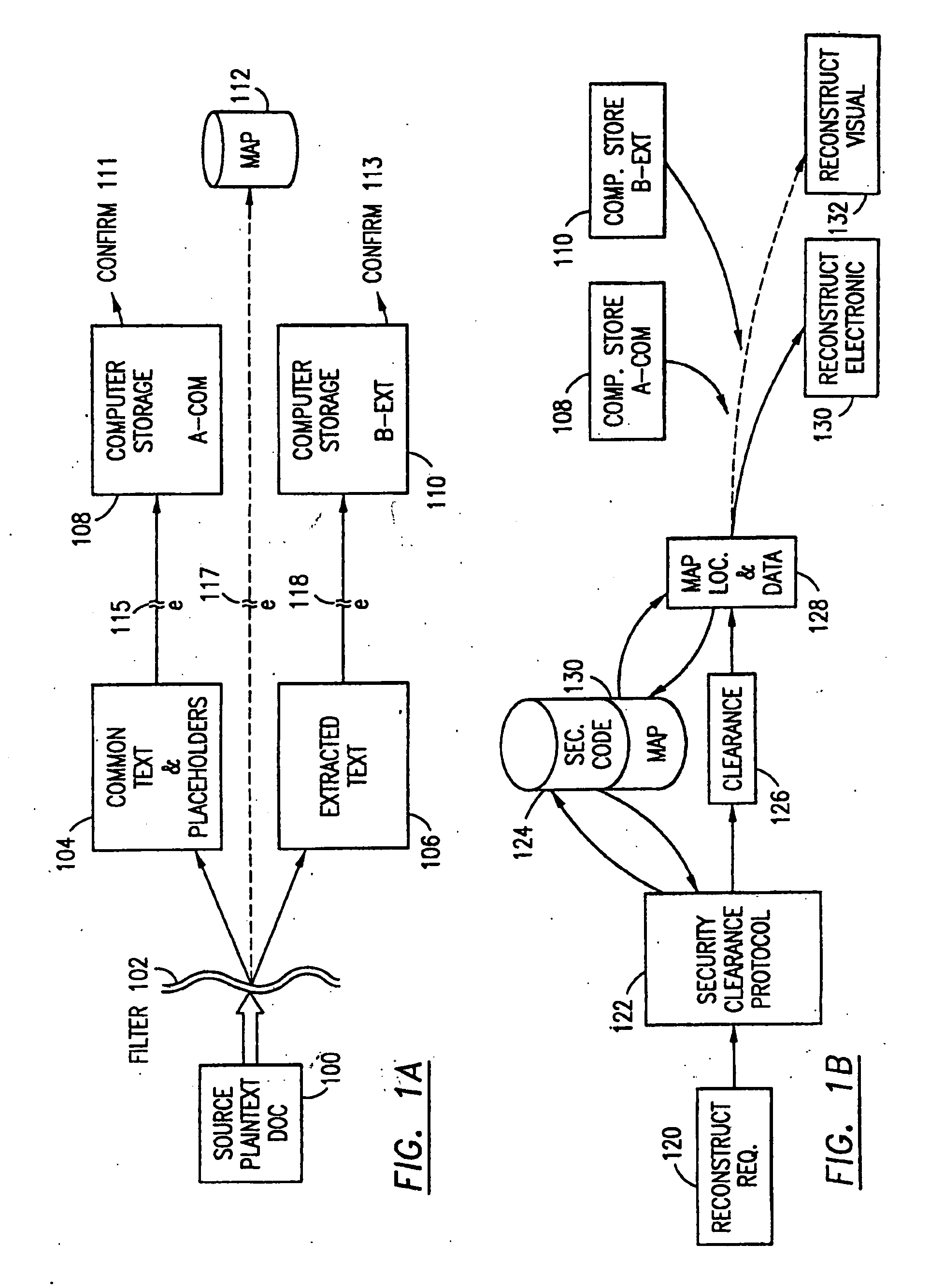
The method, program and system secures sensitive data / objects found in a data source document with an editor. The simple editor identifies and displays, in situ, the sensitive words / objects per each security level. Level tags are inserted and adjunctive words / objects are marked / displayed per the level's protocol. The precursor document is processed to extract sensitive and adjunctive words / objects. The stripped data is either separately stored or partial versions of the secured document are stored per protocol. A comprehensive editor secures content data and meta data contained in a data document object model (DOM). The editor maps the source document root, branch and leaf components as binary files populated with content data and meta data. Security introns, earlier identified based upon the level's informational attributes, are excluded. Security exons are copied from the source content and meta data binary files into a security safe document (template). Filtration, extraction, dispersal and storage follow.
Owner:DIGITAL DOORS
Data security system and method for separation of user communities
InactiveUS7140044B2Multiple keys/algorithms usageDigital data processing detailsInformation processingPlaintext
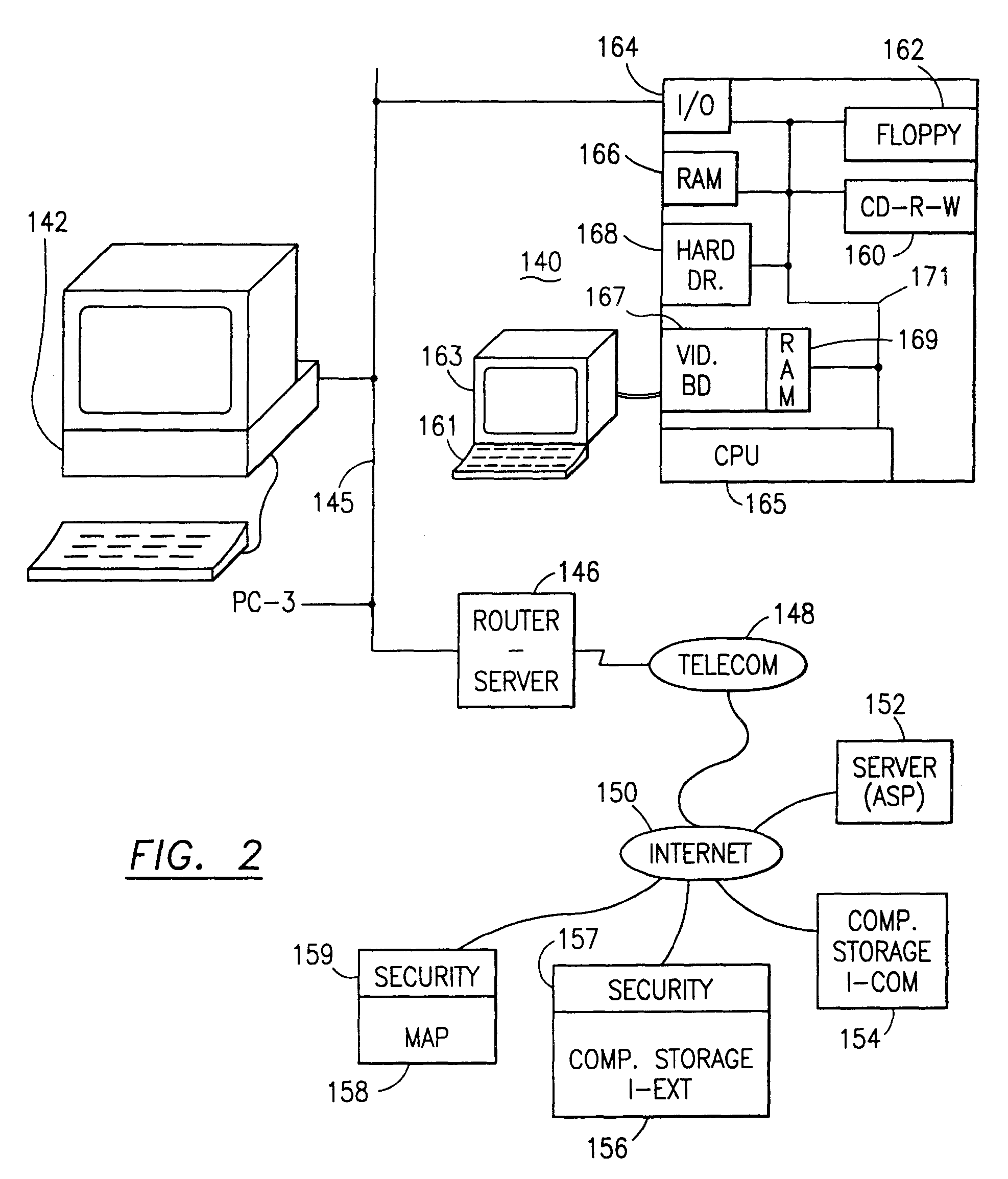
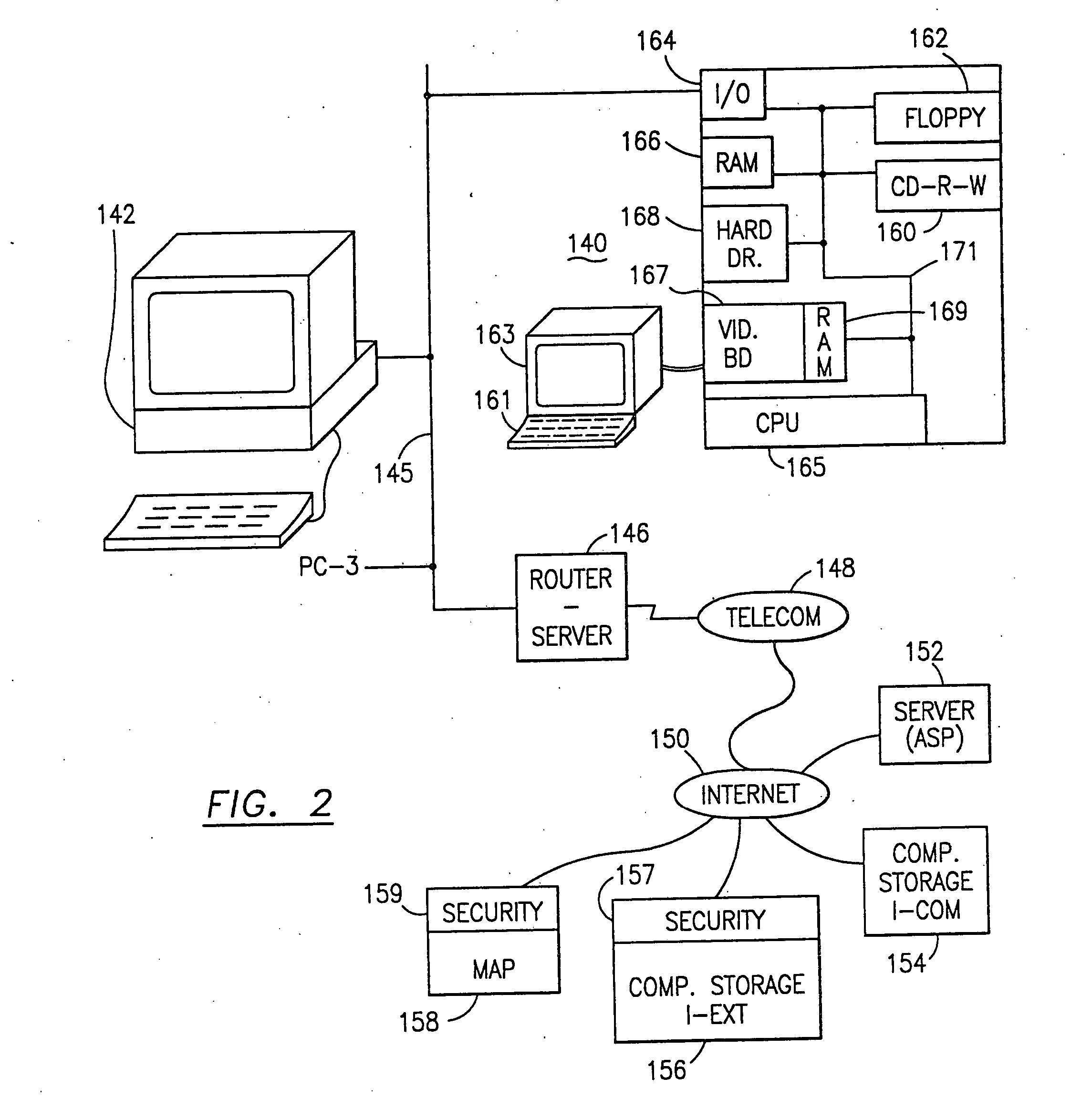
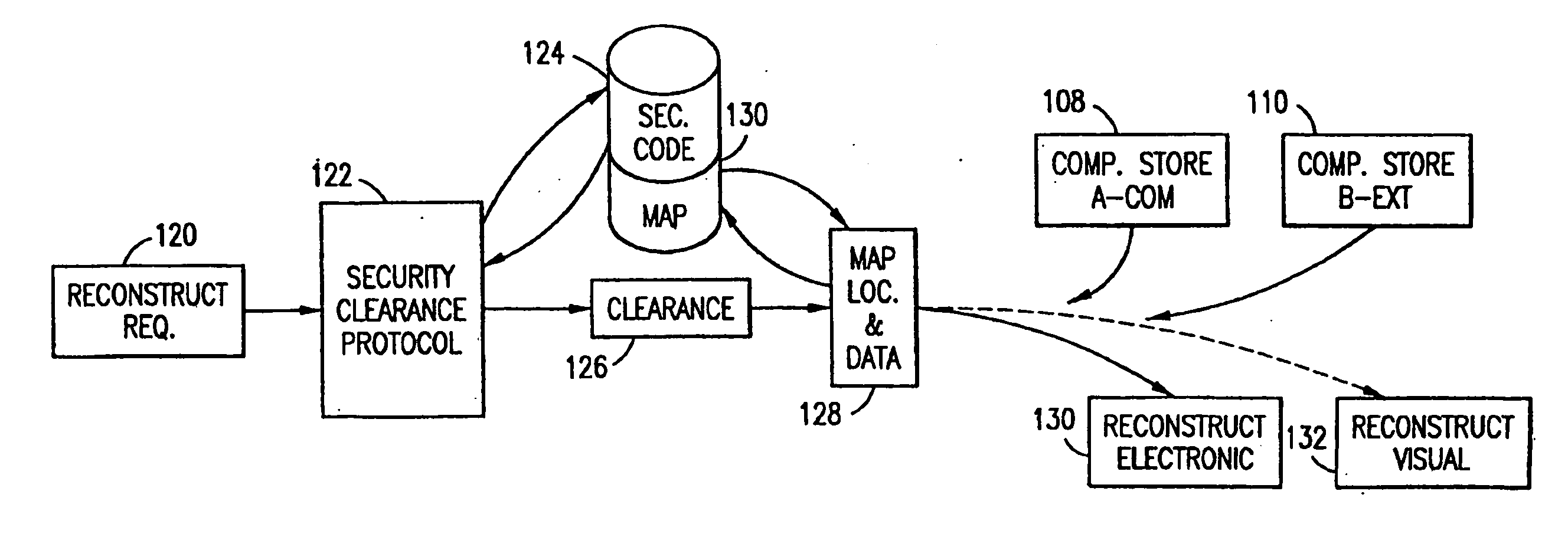
Data is secured in a computer network to transparently establish and manage a separation of user-based communities of interest based upon crypto-graphically separated, need to know, security levels. Data from a source document, data object or data stream is filtered to form subsets of extracted data and remainder data based upon security levels for the communities. Extracts are stored in assigned memories. Full or partial plaintext reconstruction is permitted only in the presence of assigned security clearance for the community of the inquiring party. Encryption, corresponding to security levels, establishes separation of secured data. The information processing system uses a data filter to extract security sensitive words, data objects, etc., a distributed storage system and a compiler is used to reconstruct plaintext based on security clearance. Multiple level encryption in one document is also available.
Owner:DIGITAL DOORS
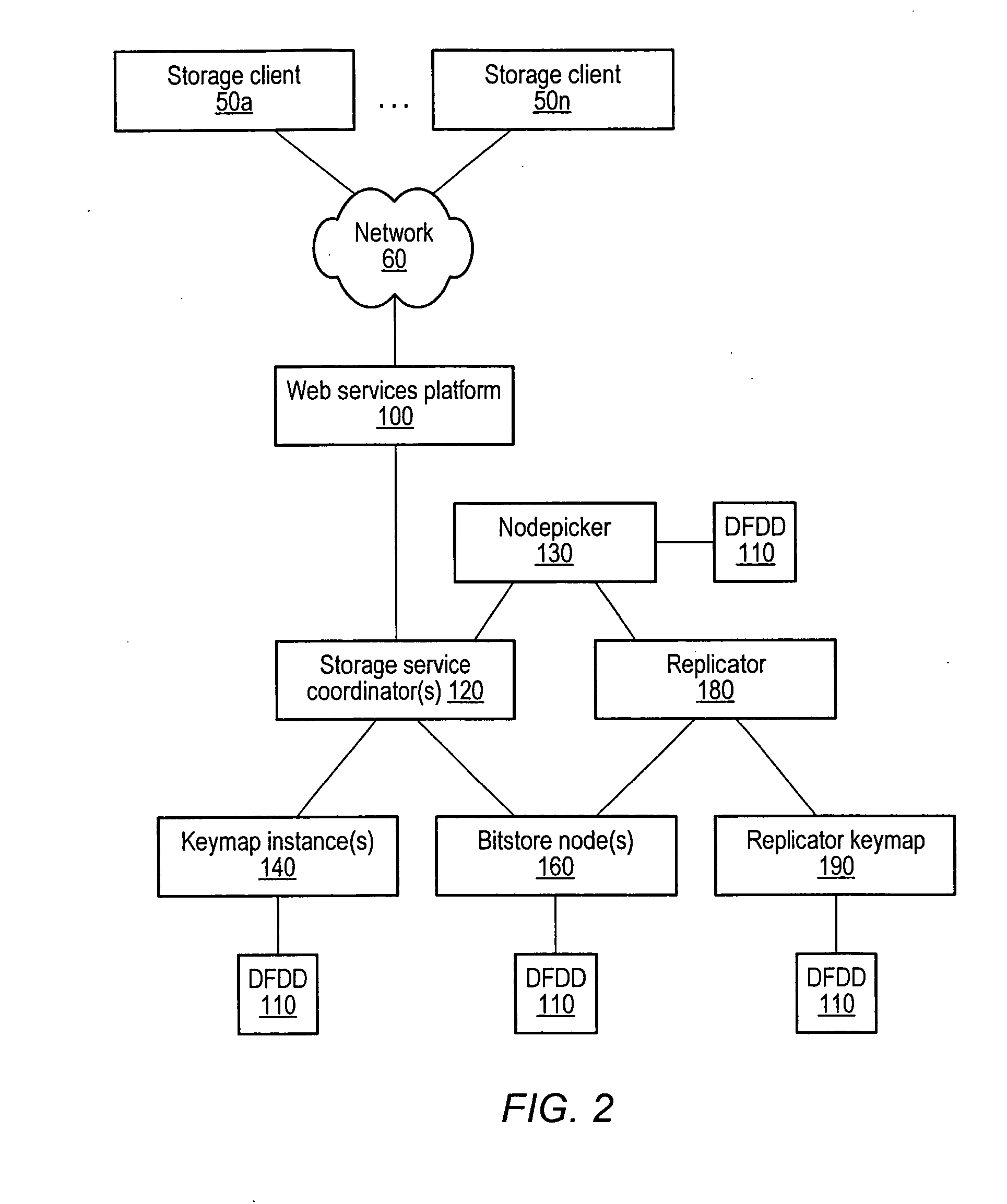
Distributed storage system with web services client interface
ActiveUS20070156842A1Digital data information retrievalMultiple digital computer combinationsWeb serviceClient-side
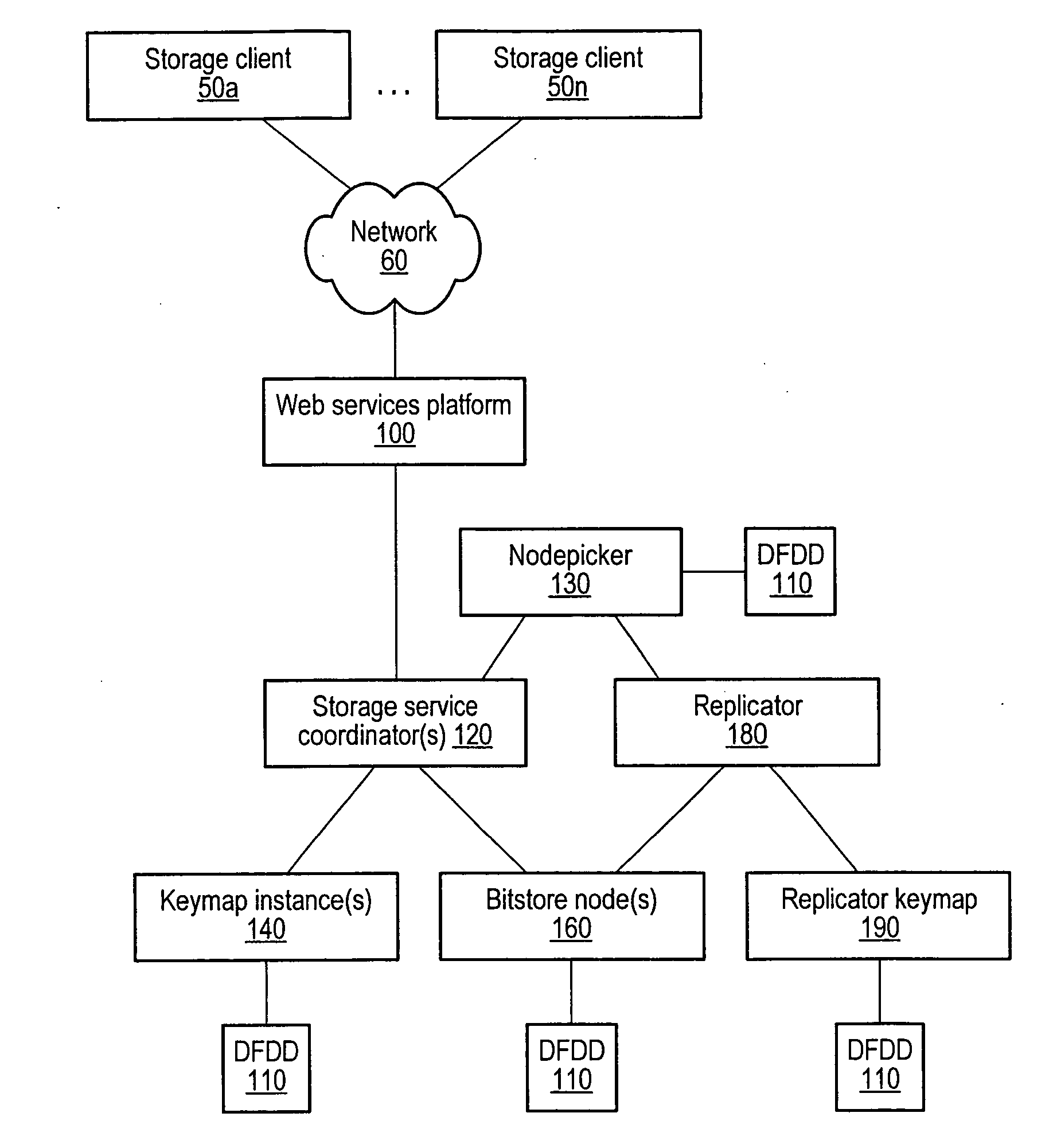
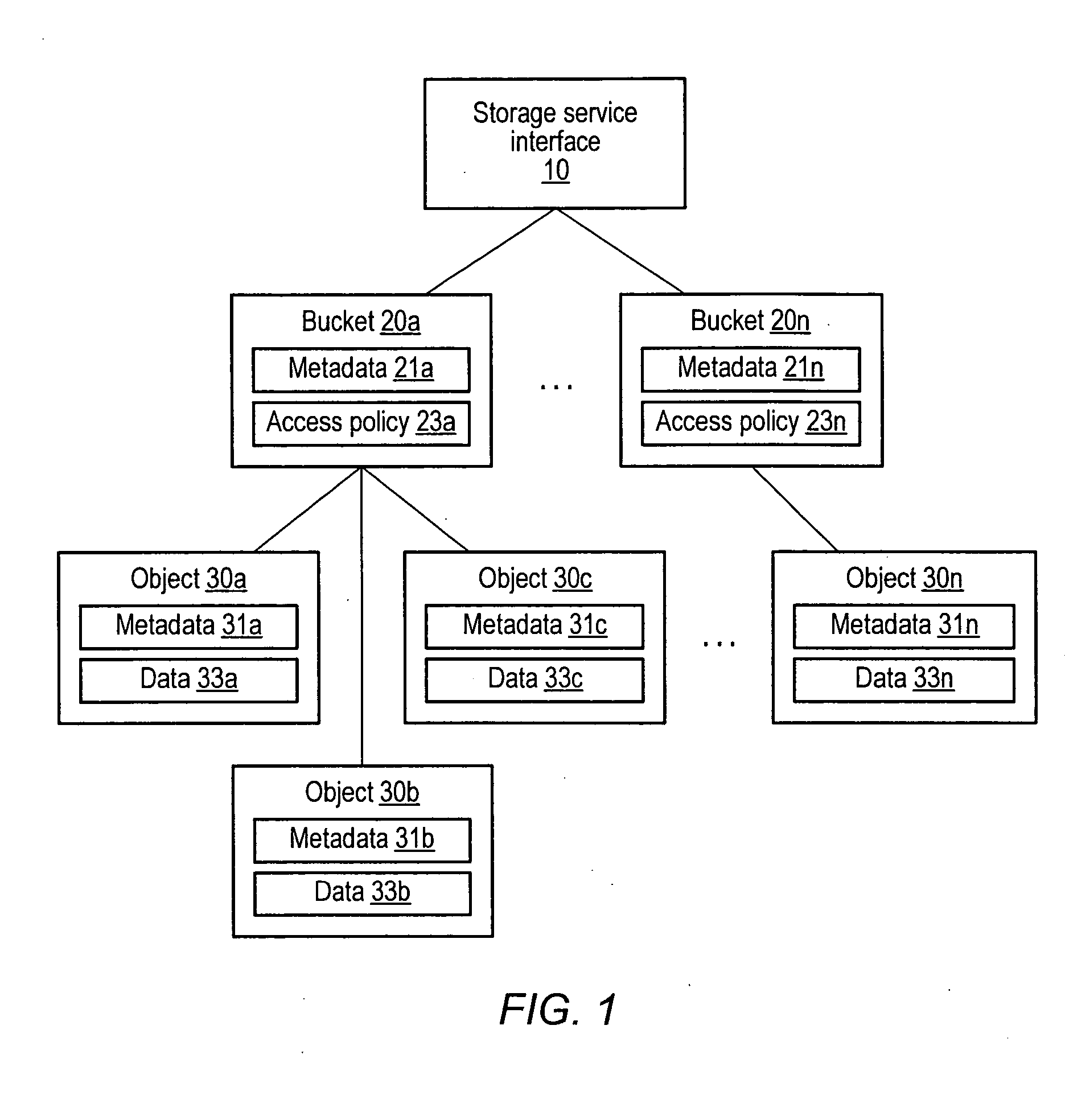
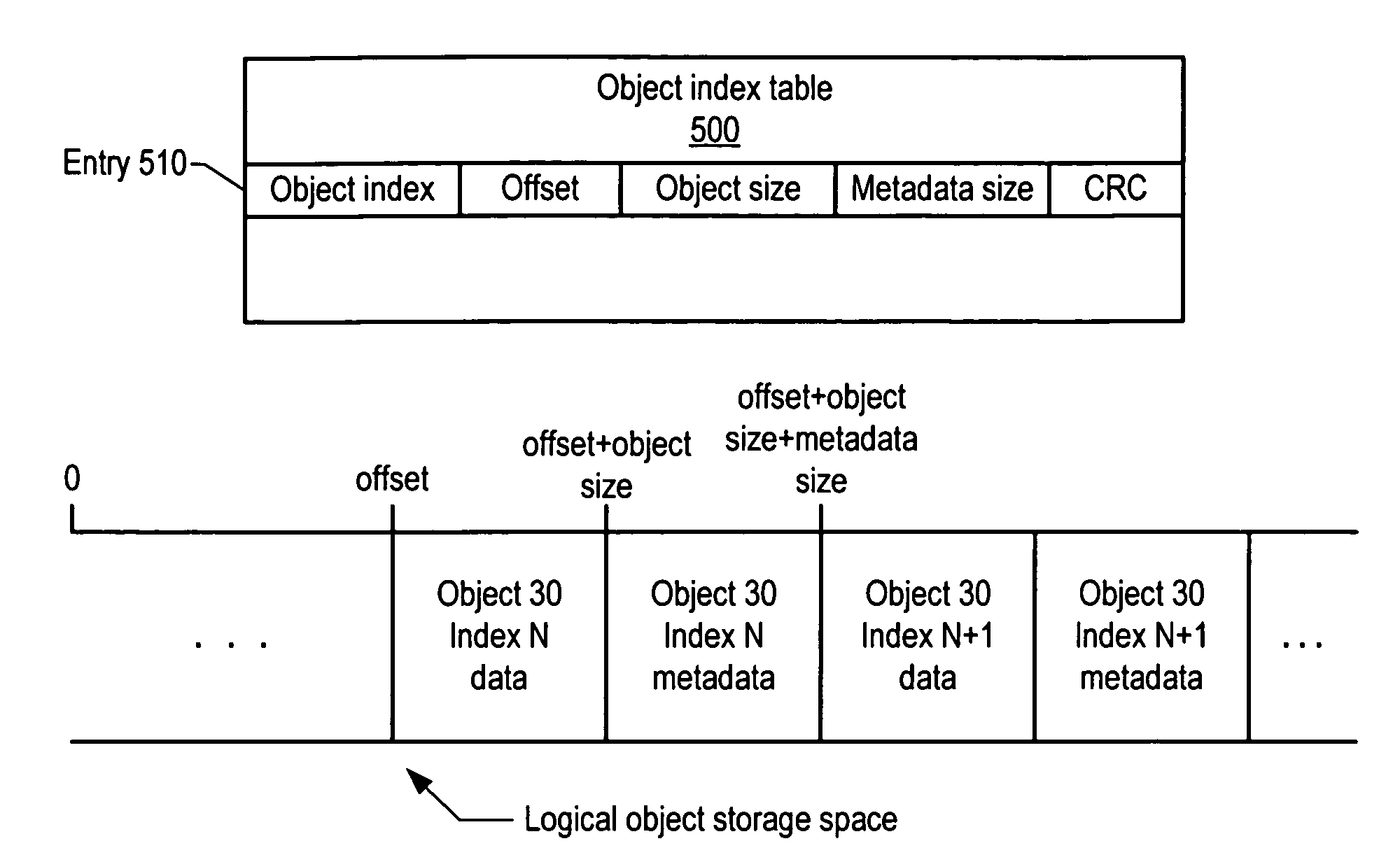
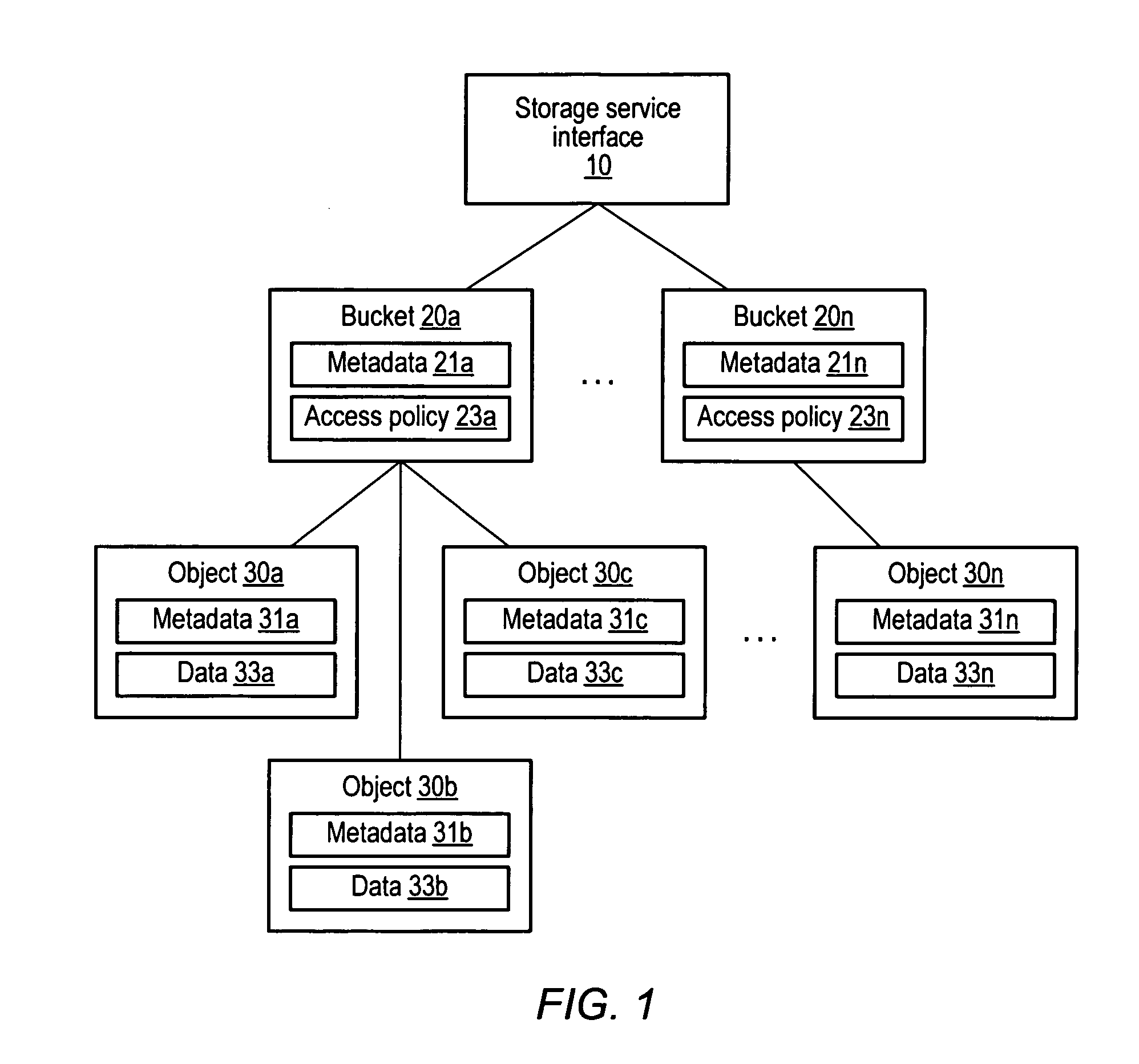
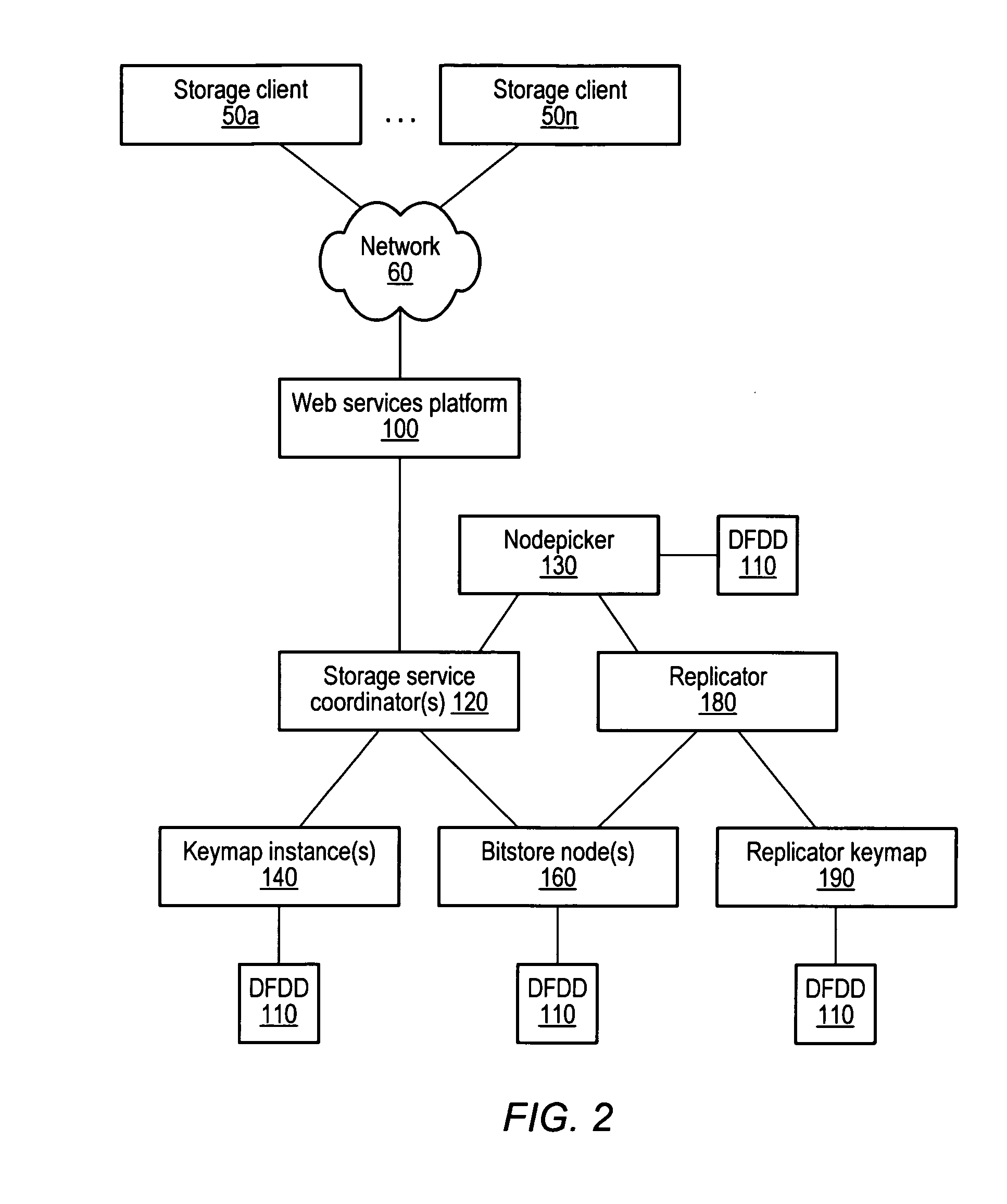
A distributed, web-services based storage system. A system may include a web services interface configured to receive, according to a web services protocol, a given client request for access to a given data object, the request including a key value corresponding to the object. The system may also include storage nodes configured to store replicas of the objects, where each replica is accessible via a respective unique locator value, and a keymap instance configured to store a respective keymap entry for each object. For the given object, the respective keymap entry includes the key value and each locator value corresponding to replicas of the object. A coordinator may receive the given client request from the web services interface, responsively access the keymap instance to identify locator values corresponding to the key value and, for a particular locator value, retrieve a corresponding replica from a corresponding storage node.
Owner:AMAZON TECH INC
System for managing data objects
InactiveUS20020033848A1Television system detailsCo-operative working arrangementsUser inputThumbnail
A device for managing image and audio files displays thumbnails, which are representative of the files, on a screen in different arrangements, depending on the selected layout and order. When the user enters input to indicates that he or she wishes to browse through the thumbnails, the thumbnails move across the screen in sequence, following a path through a focus outline in the center of the screen. The path followed by the thumbnails depends on the selected layout.
Owner:TESSERA ADVANCED TECH
Voice-enabled documents for facilitating operational procedures
InactiveUS20140108010A1Increase productivityImprove efficiencyCharacter and pattern recognitionAutomatic exchangesClient-sideField service
A voice-enabled document system facilitates execution of service delivery operations by eliminating the need for manual or visual interaction during information retrieval by an operator. Access to voice-enabled documents can facilitate operations for mobile vendors, on-site or field-service repairs, medical service providers, food service providers, and the like. Service providers can access the voice-enabled documents by using a client device to retrieve the document, display it on a screen, and, via voice commands initiate playback of selected audio files containing information derived from text data objects selected from the document. Data structures that are components of a voice-enabled document include audio playback files and a logical association that links the audio playback files to user-selectable fields, and to a set of voice commands.
Owner:INTERMEC IP
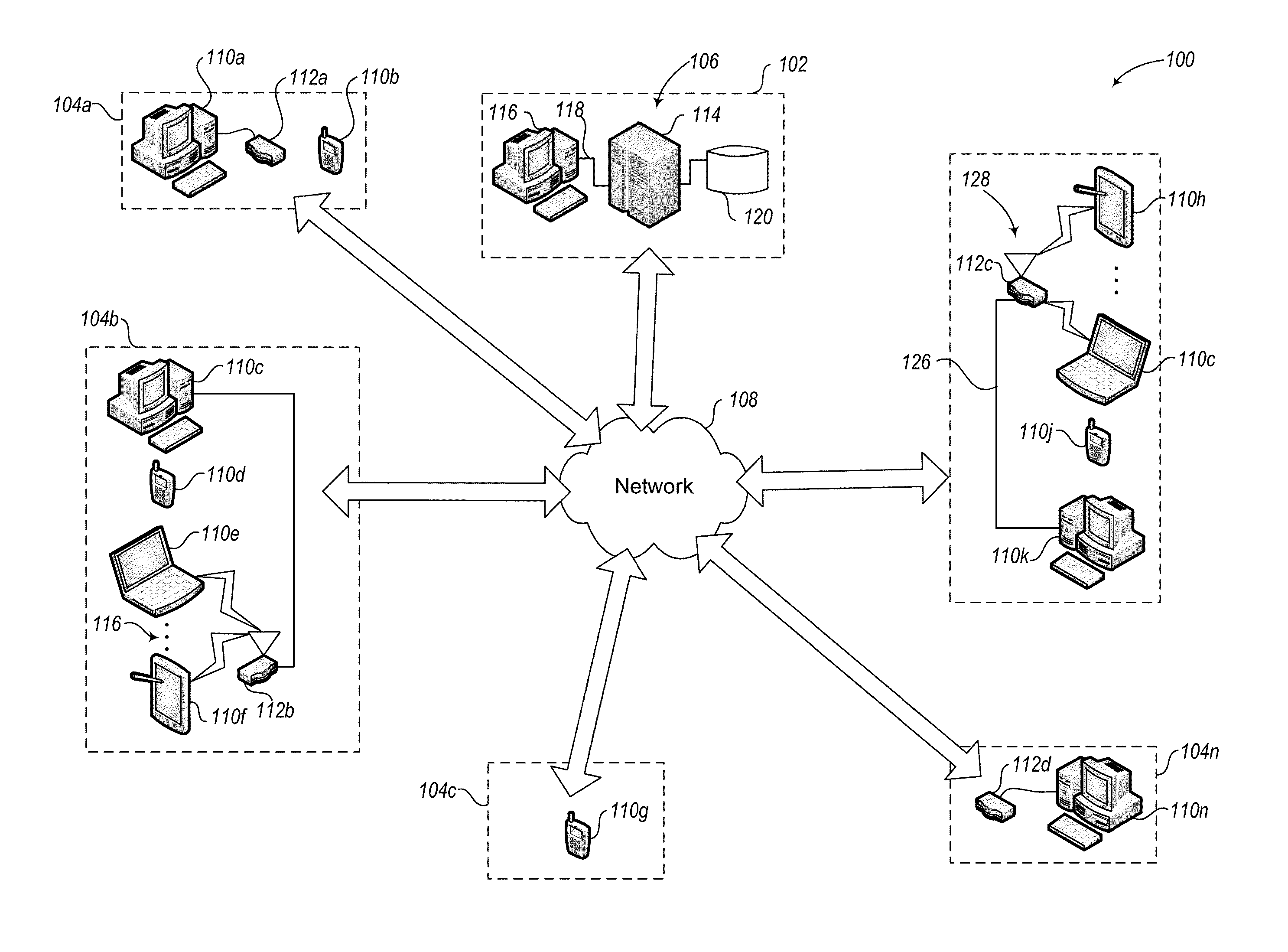
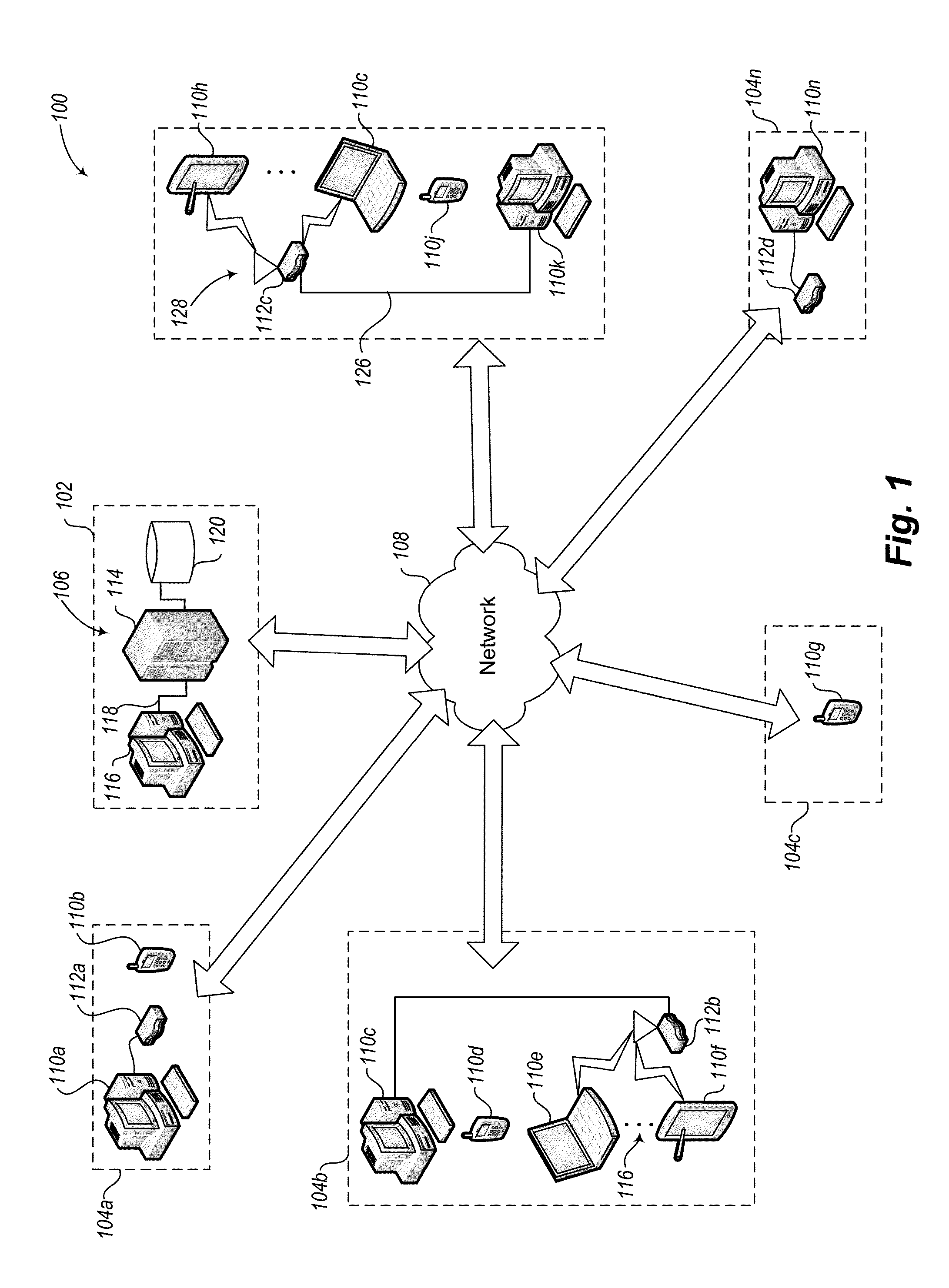
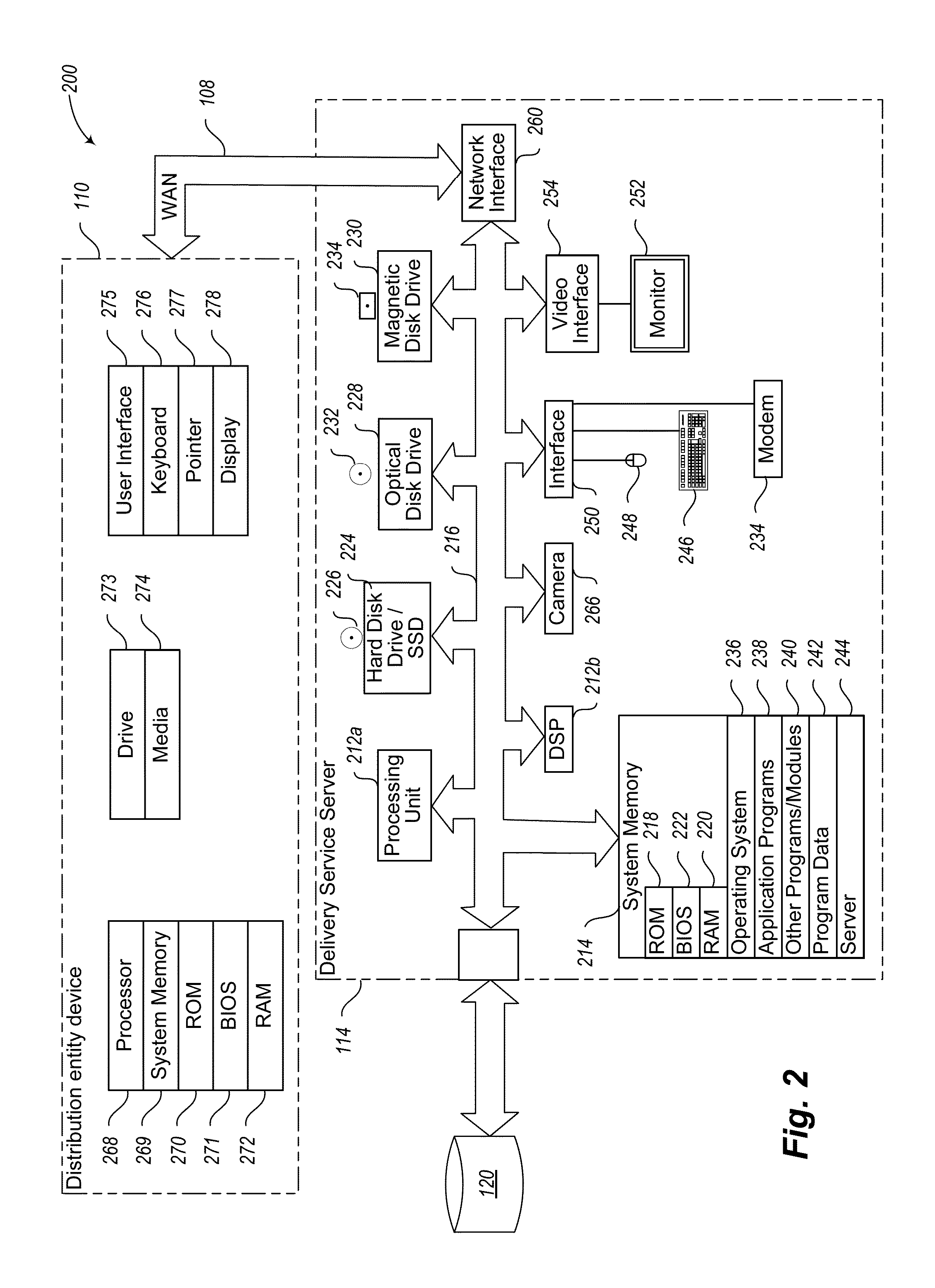
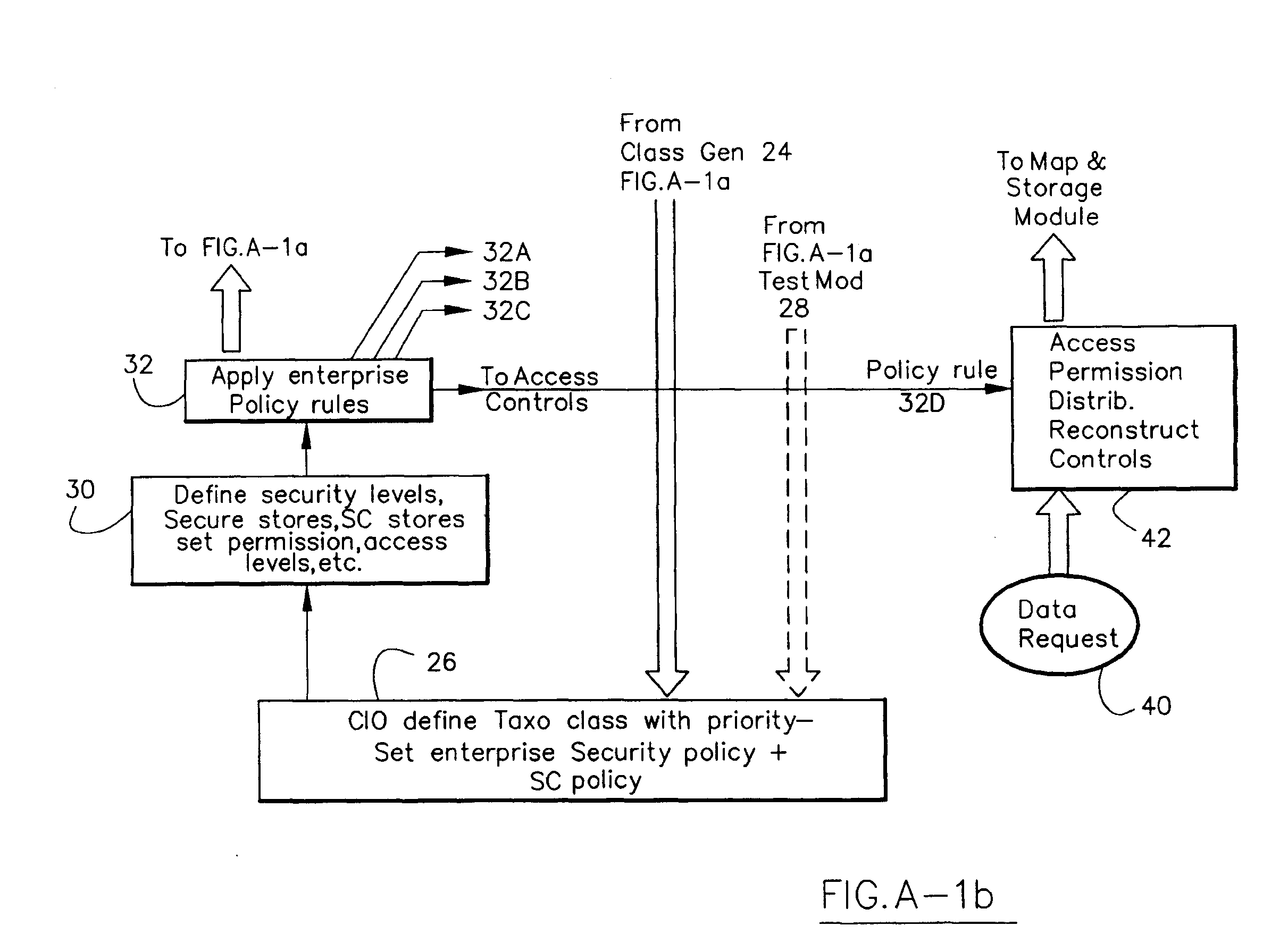
Information Infrastructure Management Tools with Extractor, Secure Storage, Content Analysis and Classification and Method Therefor
The present invention is a method of organizing and processing data in a distributed computing system. The invention is also implemented as a computer program on a computer medium and as a distributed computer system. Software modules can be configured as hardware. The method and system organizes select content which is important to an enterprise operating said distributed computing system. The select content is represented by one or more predetermined words, characters, images, data elements or data objects. The computing system has a plurality of select content data stores for respective ones of a plurality of enterprise designated categorical filters which include content-based filters, contextual filters and taxonomic classification filters, all operatively coupled over a communications network. A data input is processed through at least one activated categorical filter to obtain select content, and contextually associated select content and taxonomically associated select content as aggregated select content. The aggregated select content is stored in the corresponding select content data store. A data process from the group of data processes including a copy process, a data extract process, a data archive process, a data distribution process and a data destruction process is associated with the activated categorical filter and the method and system applies the associated data process to a further data input based upon a result of that further data being processed by the activated categorical filter utilizing the aggregated select content data.
Owner:DIGITAL DOORS
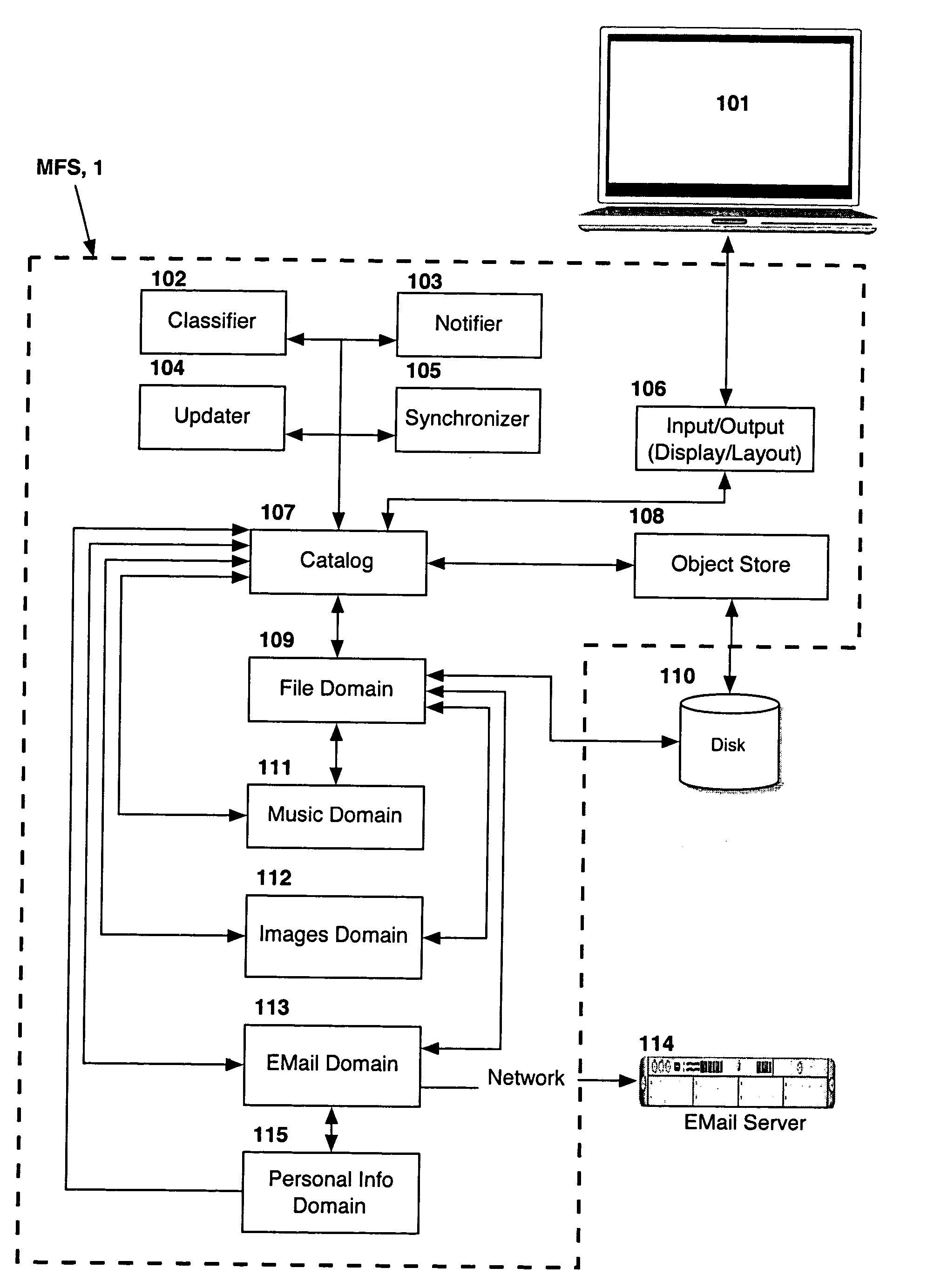
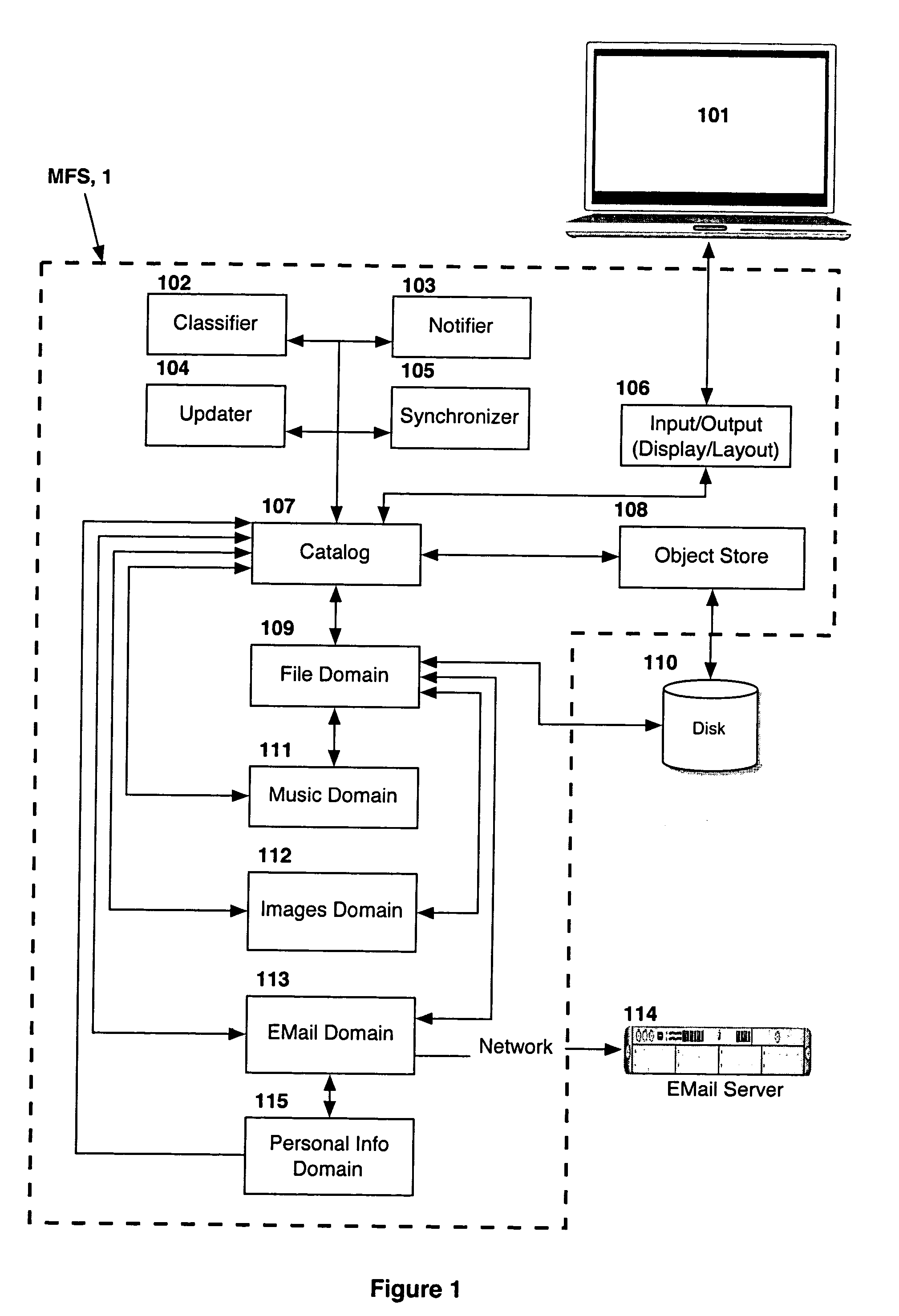
Computer system for automatic organization, indexing and viewing of information from multiple sources
ActiveUS7275063B2Facilitate communicationMultimedia data indexingFile access structuresPathPingSoftware system
Owner:EHIERARCHY LLC
Data security system and method with multiple independent levels of security
InactiveUS20050138110A1Ease overhead performanceHigh overhead performancePeptide/protein ingredientsNGF/TNF-superfamilyInformation processingWorkstation
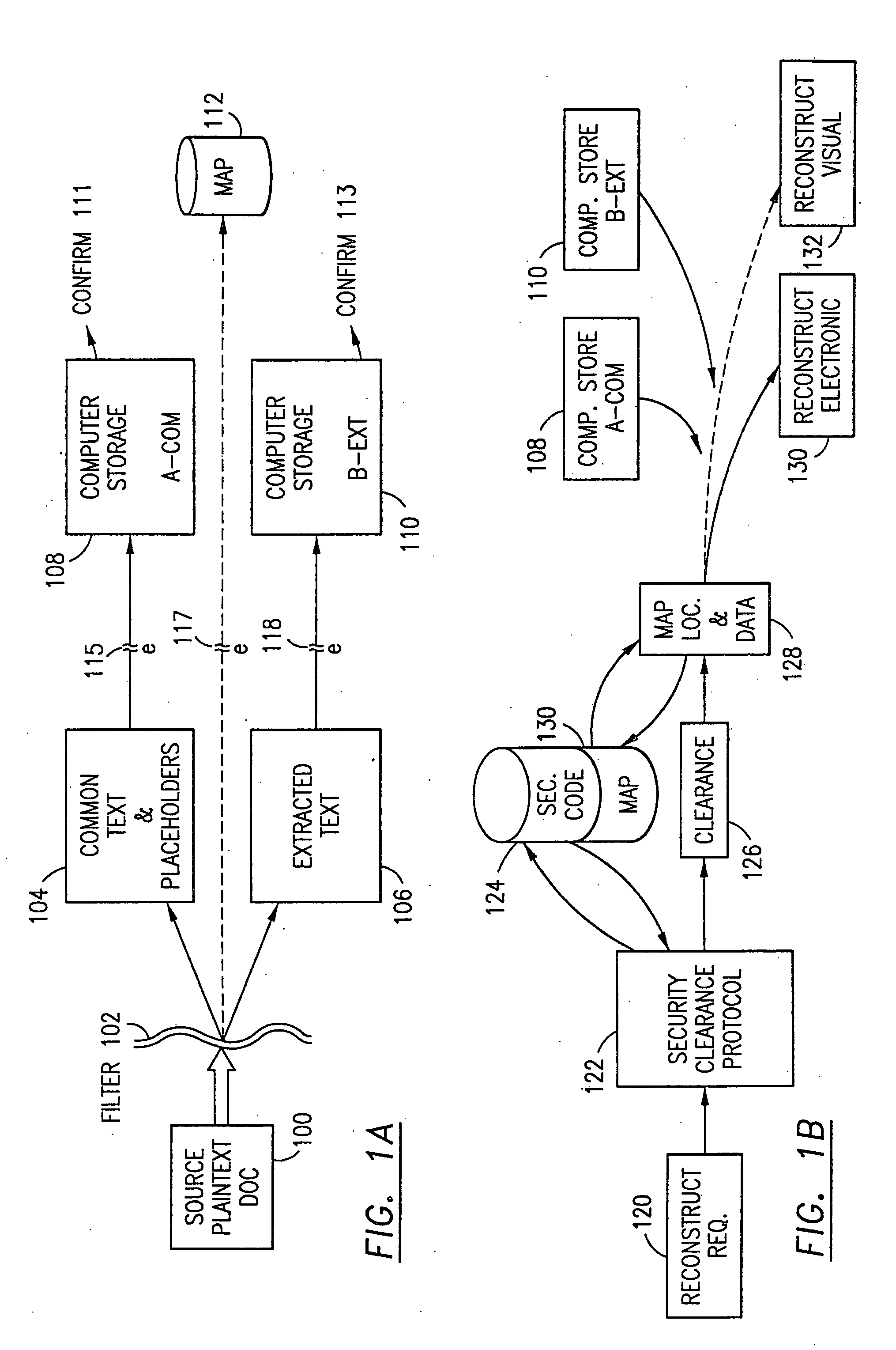
The method, program and information processing system secures data, and particularly security sensitive words, characters or data objects in the data, in a computer system with multiple independent levels of security (MILS). Each level of MILS has a computer sub-network with networked workstations. The MILS sub-networks are connected together via security guard computer(s) and each guard computer has separate memories for each level (TS, S, C, UC(or remainder)). The method extracts the security sensitive words / data (a granular action), from the source document for each MILS level, stores the extracted data in a corresponding extract store for each level and permits reconstruction / reassembly of the dispersed data via said extracted data at each said level of said multiple security levels and remainder data only in the presence of a predetermined security clearance commensurate with each MILS level.
Owner:DIGITAL DOORS
System and method for knowledge retrieval, management, delivery and presentation
InactiveUS20070038610A1Efficient queryWebsite content managementSpecial data processing applicationsAction CodeActive agent
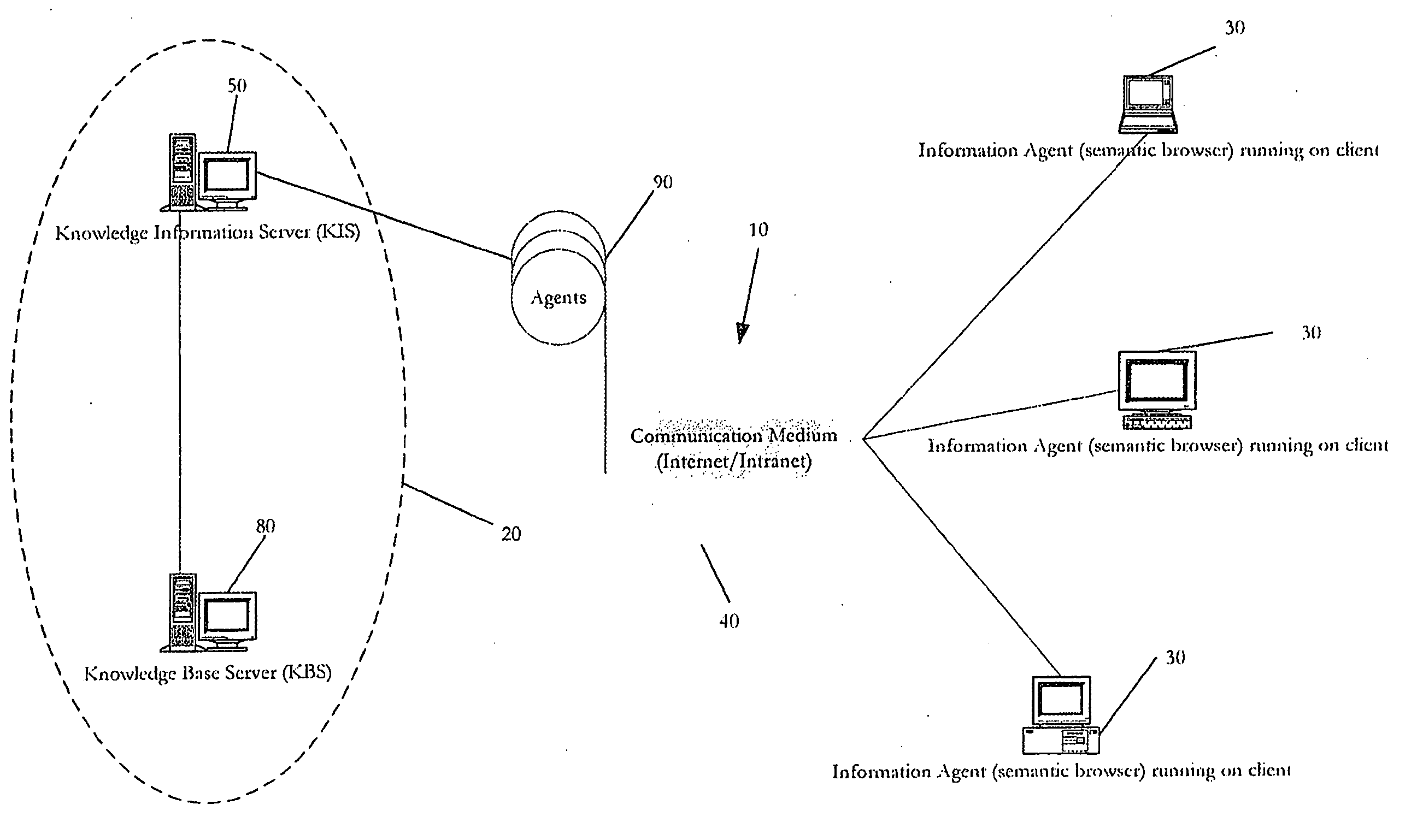
The present invention is directed to an integrated implementation framework and resulting medium for knowledge retrieval, management, delivery and presentation. The system includes a first server component that is responsible for adding and maintaining domain-specific semantic information and a second server component that hosts semantic and other knowledge for use by the first server component that work together to provide context and time-sensitive semantic information retrieval services to clients operating a presentation platform via a communication medium. Within the system, all objects or events in a given hierarchy are active Agents semantically related to each other and representing queries (comprised of underlying action code) that return data objects for presentation to the client according to a predetermined and customizable theme or “Skin.” This system provides various means for the client to customize and “blend” Agents and the underlying related queries to optimize the presentation of the resulting information.
Owner:OMOIGUI NOSA
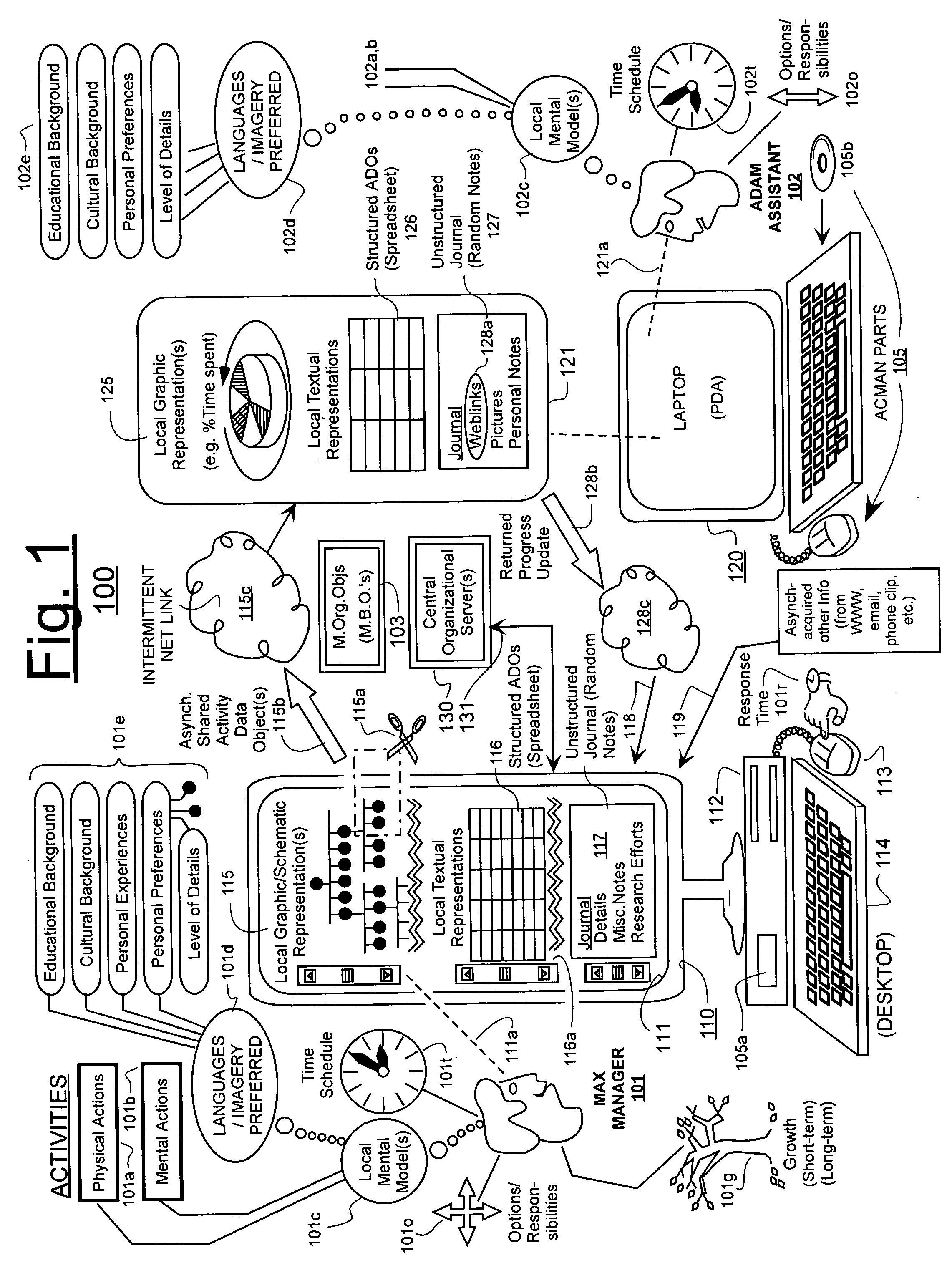
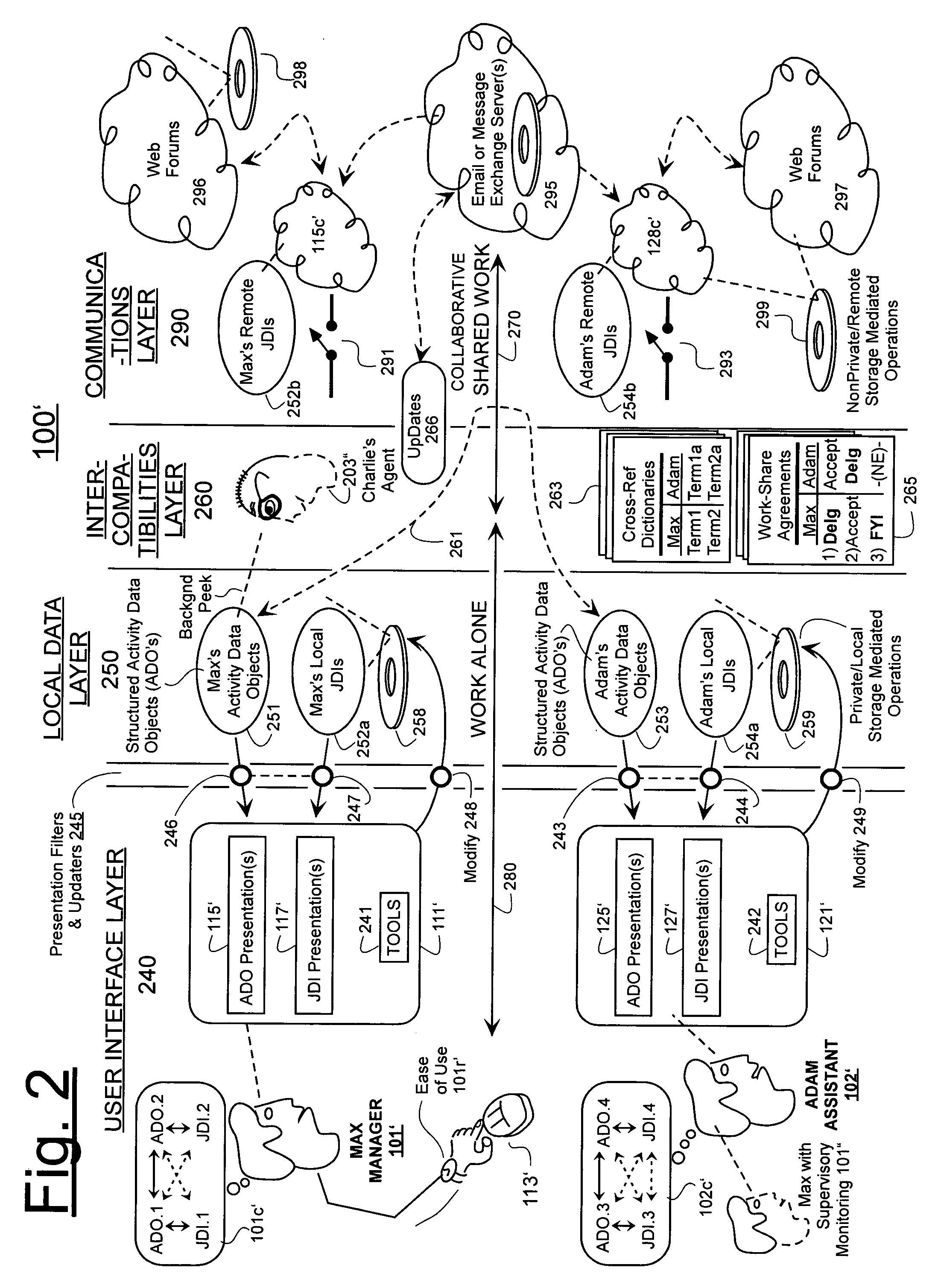
Machine-implemented activity management system using asynchronously shared activity data objects and journal data items
ActiveUS20050182773A1Improve developmentEasy to collectOffice automationBuying/selling/leasing transactionsJob sharingInformation sharing
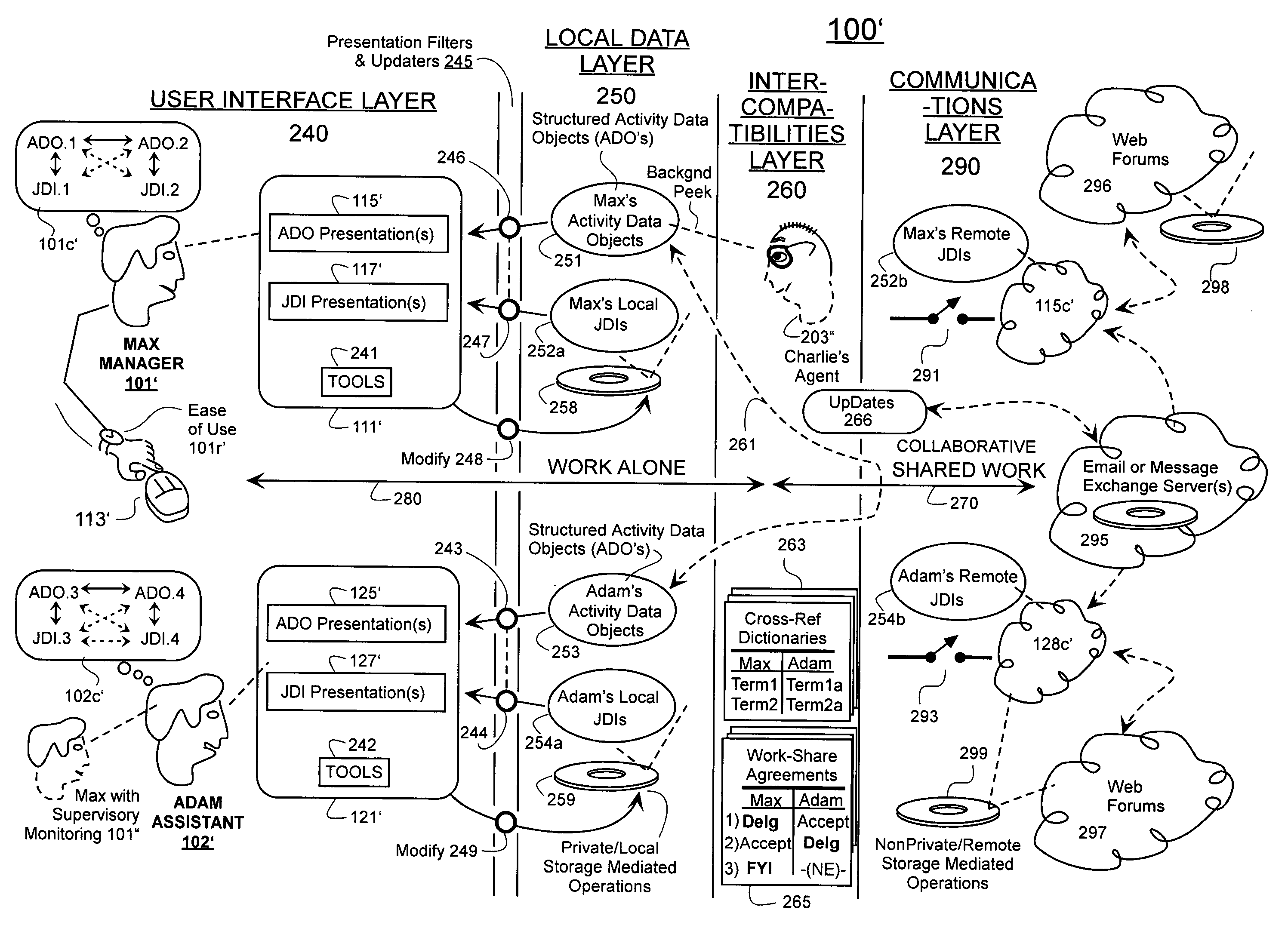
Machine-assisted methods and apparatus are disclosed for allowing individual users to develop and organize respective activity descriptions and supporting journal items according to their respective preferences. Cross-referencing mappings may be created between activity descriptions and journal items in order to find, filter and organize disparate data. Cross-referencing mappings may also be created between the developed activity descriptions of different users so they can better understand each others perspectives and possibly overlapping goals. Different users' activity descriptions can be presented to a user even while the user may be disconnected from communication networks. Hierarchical relationships between activity descriptions may be provided. Machine-assisted means may be provided for creating work-sharing, work-delegating and / or informational sharing agreements between different users. Further machine-implemented means may be provided for automatically and asynchronously updating users on shared activities by other users even though all users are not necessarily connected to one or more respective communication networks at same time.
Owner:CALLAHAN CELLULAR L L C
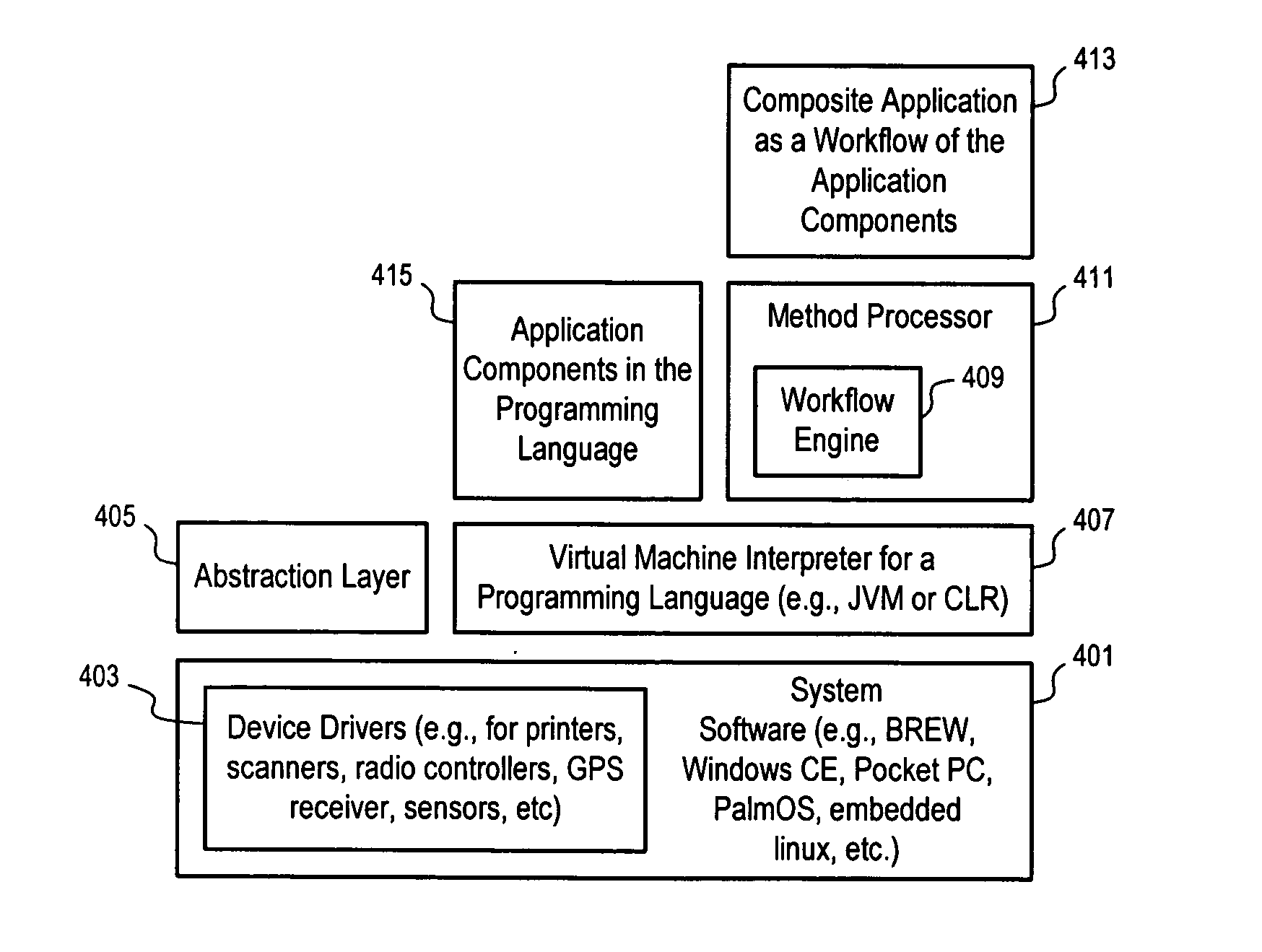
Methods and apparatuses to provide mobile applications
Methods and apparatuses to enable the development, deployment and update of composite applications on mobile devices. In one embodiment, a method processor in a mobile device uses a workflow engine to load modules for execution according to a workflow that specifies the execution flow directions based on the outcomes of the modules. Detached object managers can be used to manage locally data that are checked out from data sources. A object manager can maintain multiple versions of the data locally, receive changes, submit changes, and / or detect conflicts. Conflicts can be resolved over time. Using a check-out check-in model, different devices can work on the same data without having to synchronize with a server sequentially. Data and workflow can be packaged together for transmission over a sometime connected network (e.g., via email) such that a method processor does not have to wait for response if the network connection is not available.
Owner:APACHETA CORP
System and methods for mapping and searching objects in multidimensional space
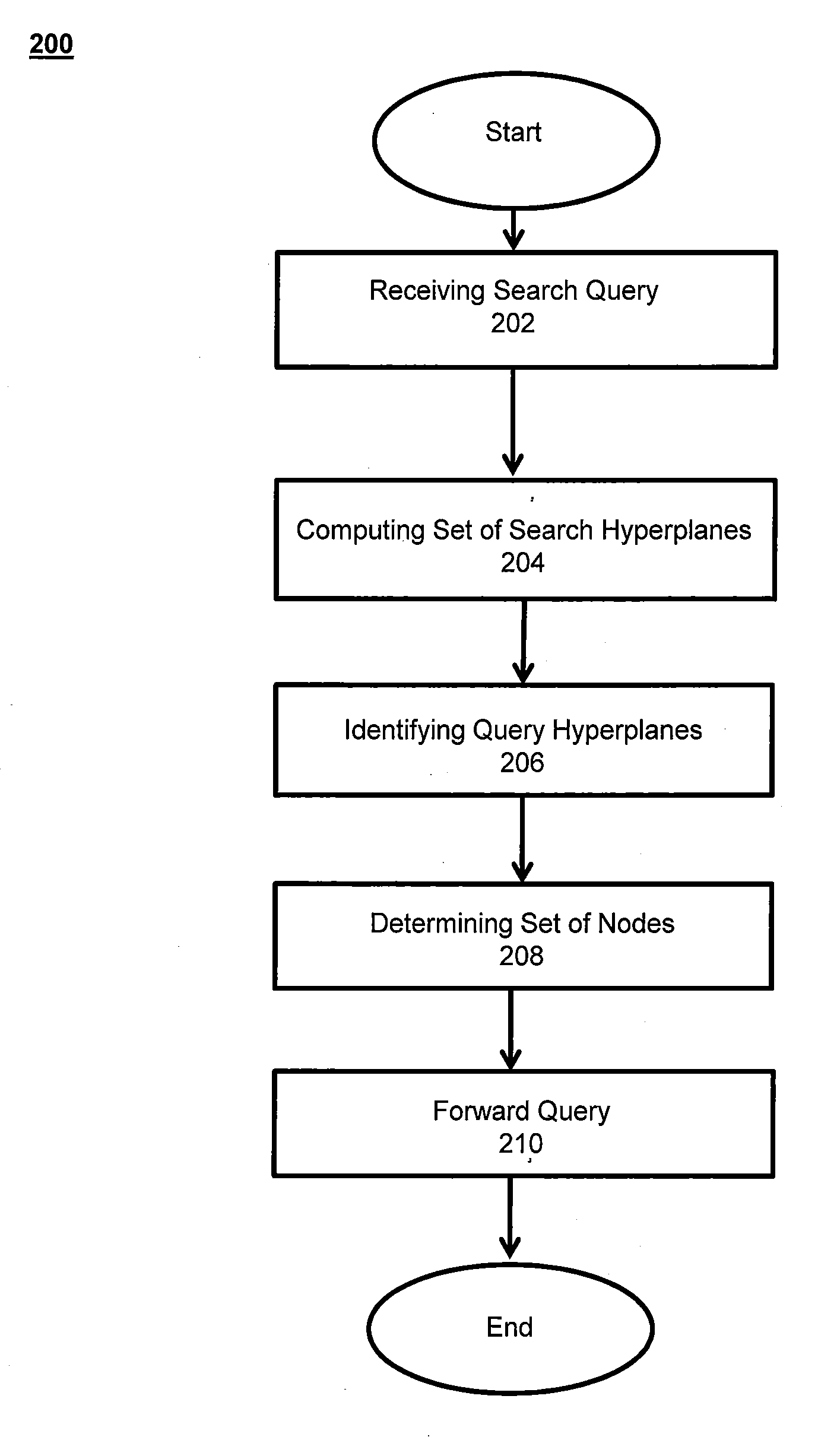
ActiveUS20130138646A1Reduce in quantitySpeed up searchWeb data indexingDigital data processing detailsData miningMultidimensional space
This invention relates to a system and methods for determining the placement of an object in a distributed key-value store by mapping the object to nodes in multidimensional hyperspace. A search function supports efficient object retrieval, even when the search query requests multiple objects and specifies them through non-primary keys. In response to a search query, the search is translated into hyperregions in the hyperspace to determine the set of nodes that hold the queried data object. The number of contacted nodes and the number of scanned objects are significantly reduced in comparison to prior art techniques.
Owner:CORNELL UNIVERSITY
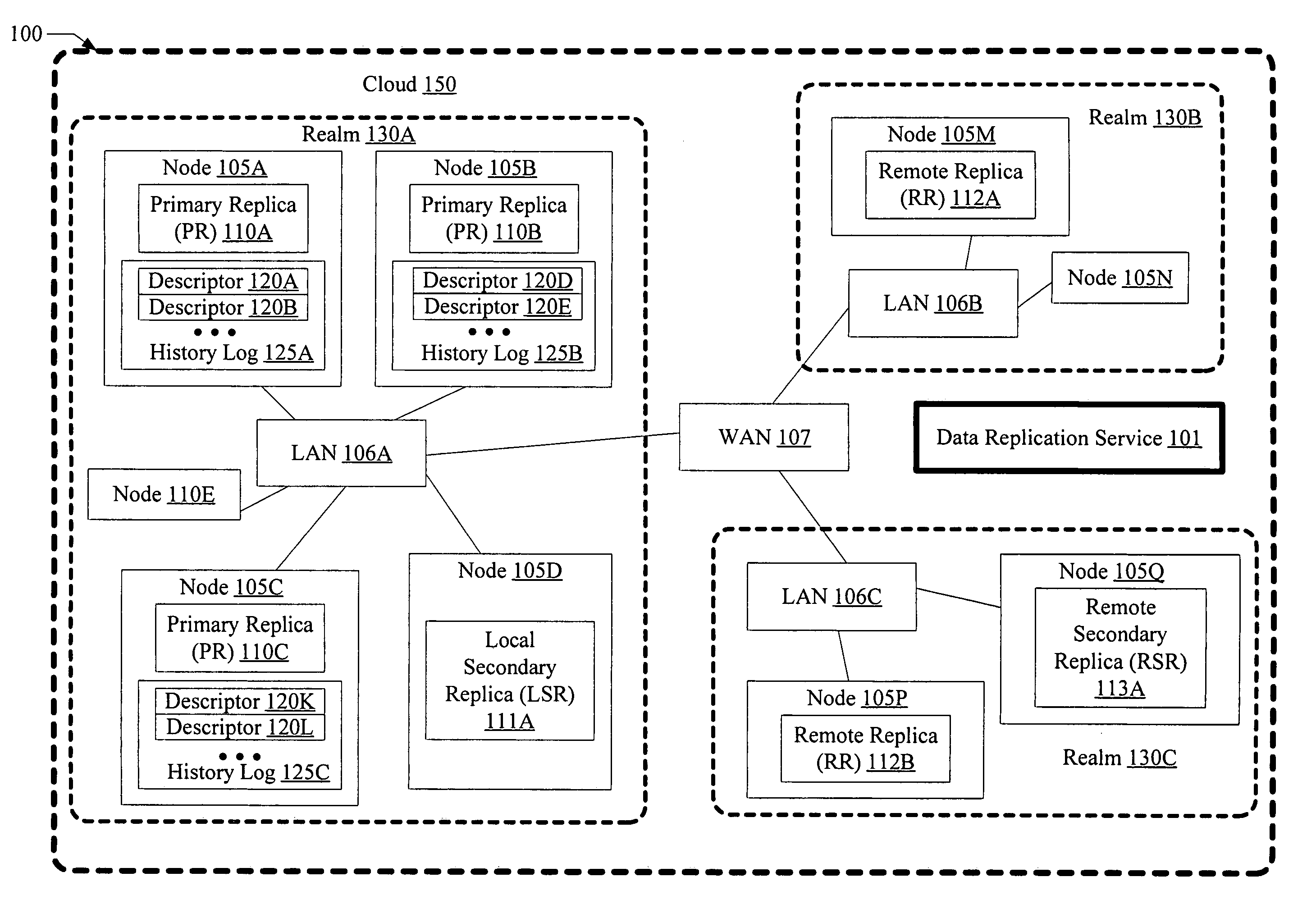
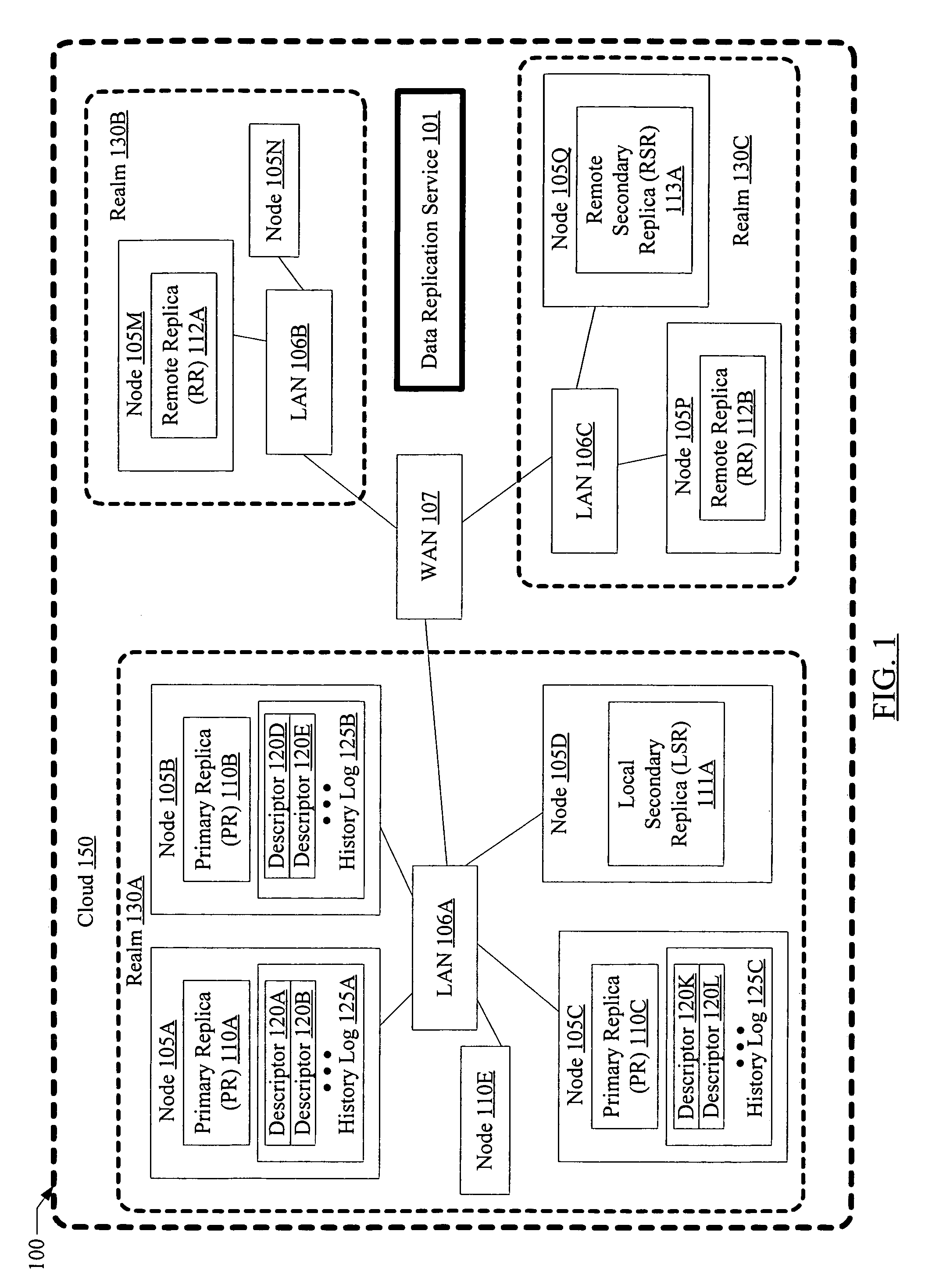
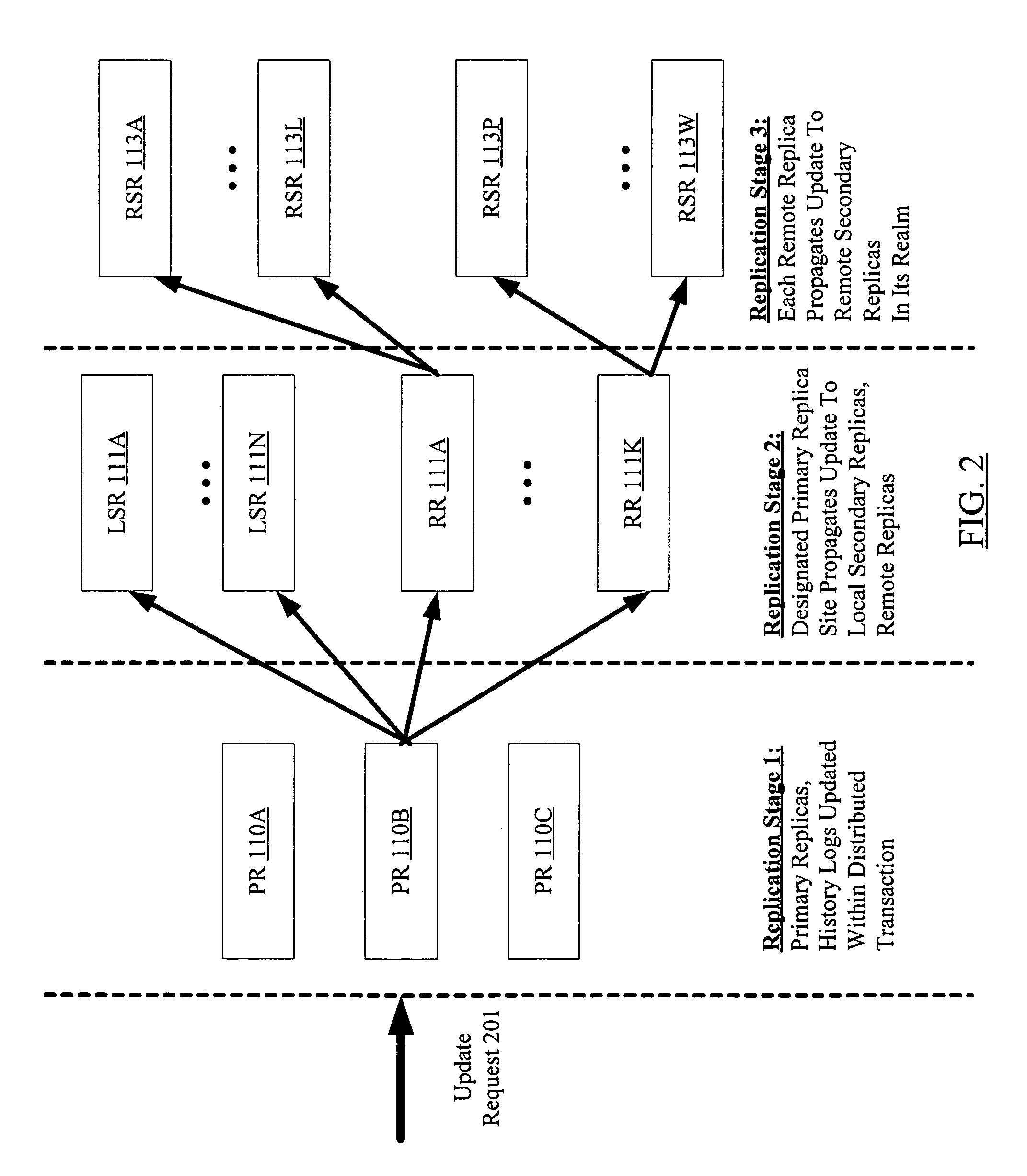
Fault tolerant multi-stage data replication with relaxed coherency guarantees
InactiveUS7653668B1Reduce trafficEasy accessDigital data information retrievalDigital data processing detailsProgram instructionMetadata description
A system for fault tolerant multi-stage data replication with relaxed coherency comprises one or more processors and memory coupled to the processors, where the memory stores program instructions executable by the processors to implement a data replication service. In response to an update request directed at a data object, in a first stage of replication, the data replication service is configured to update respective primary replicas at a plurality of primary replica sites for the data object, and to store metadata descriptors at each of the plurality of primary replica sites. The data replication service is configured to determine whether a notification of the update is to be sent to any other replica sites. In response to identifying such other replica sites, an update notification including contents of a metadata descriptor may be sent to the other replica sites in one or more additional replication stages.
Owner:SYMANTEC OPERATING CORP
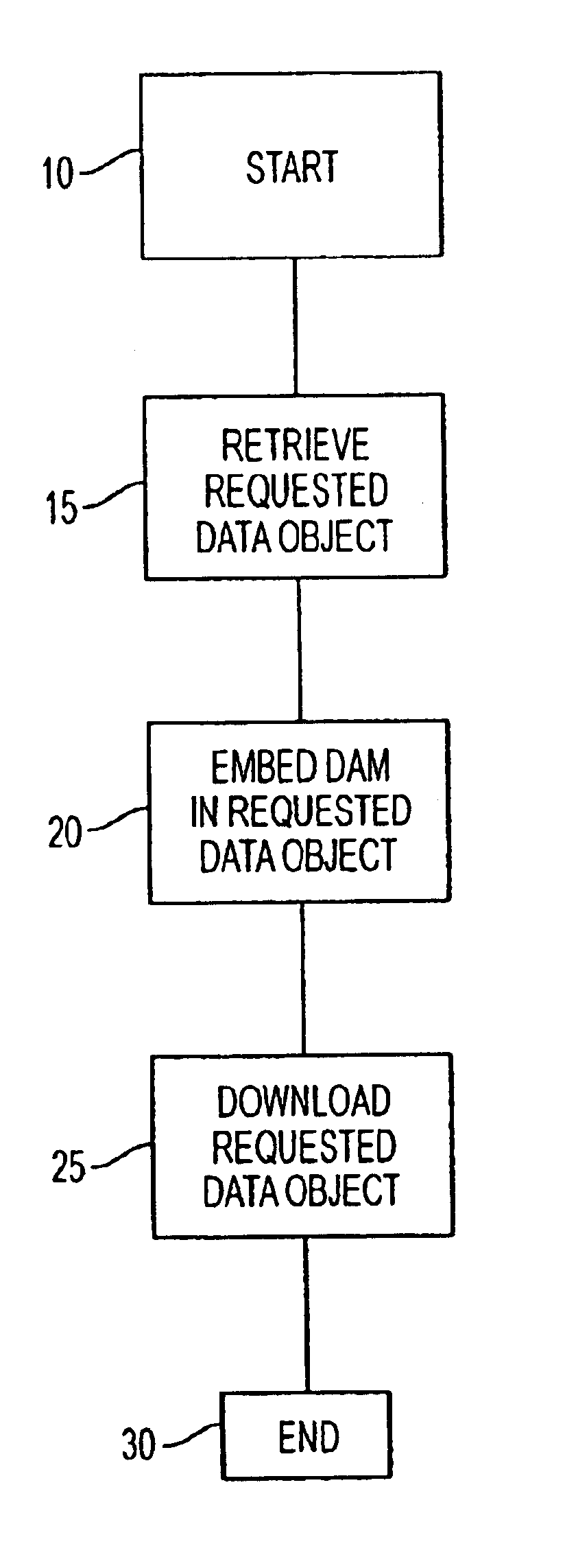
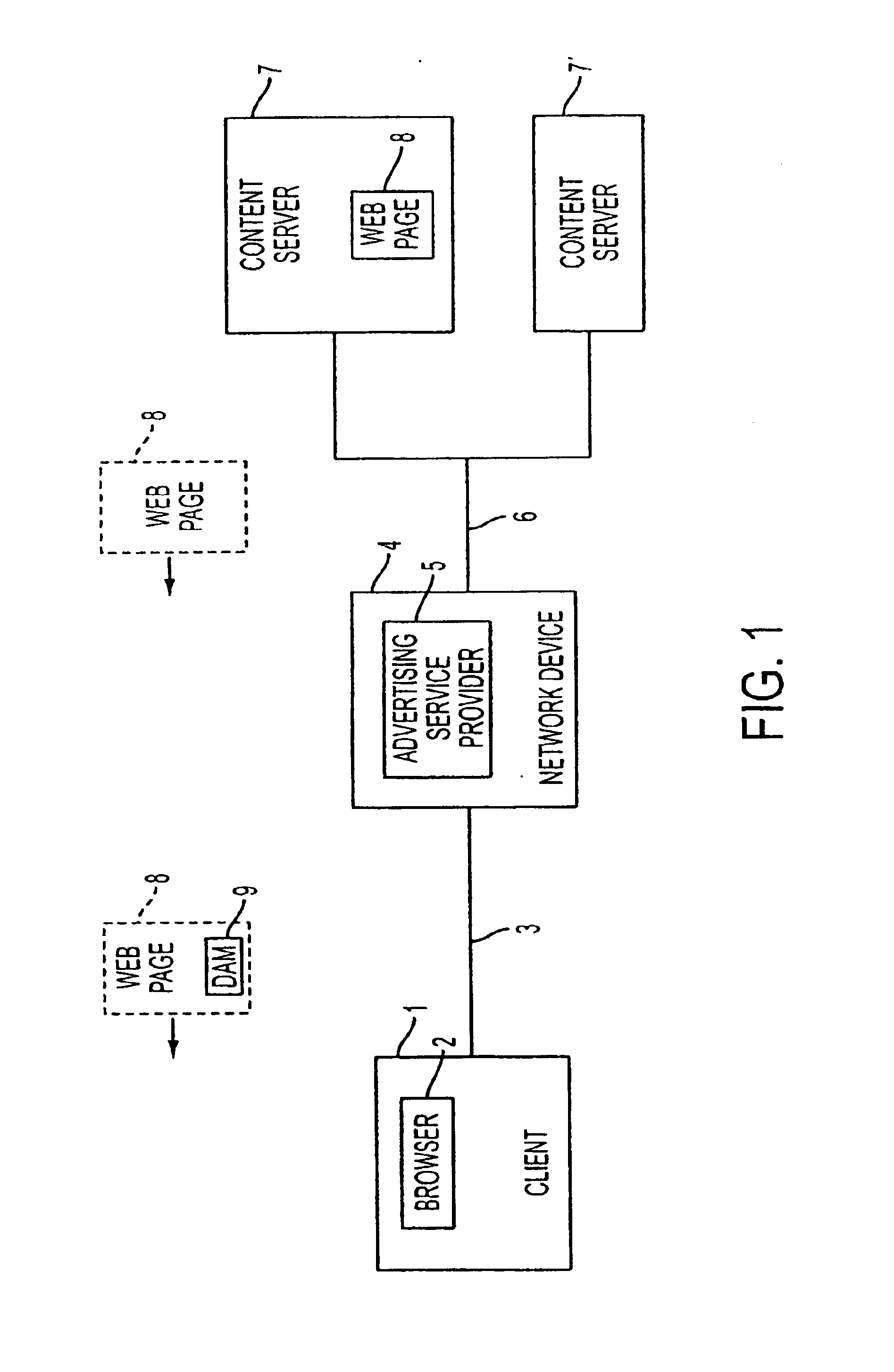
System for delivery of dynamic content to a client device
A system for presenting dynamic content to a user of a client device is implemented in a method including the steps of presenting a requested data object to the user; and automatically presenting dynamic content to the user in addition to the presentation of the requested data object, wherein the dynamic content includes information provided by a dynamic executable module running on the client device.
Owner:INTEL CORP
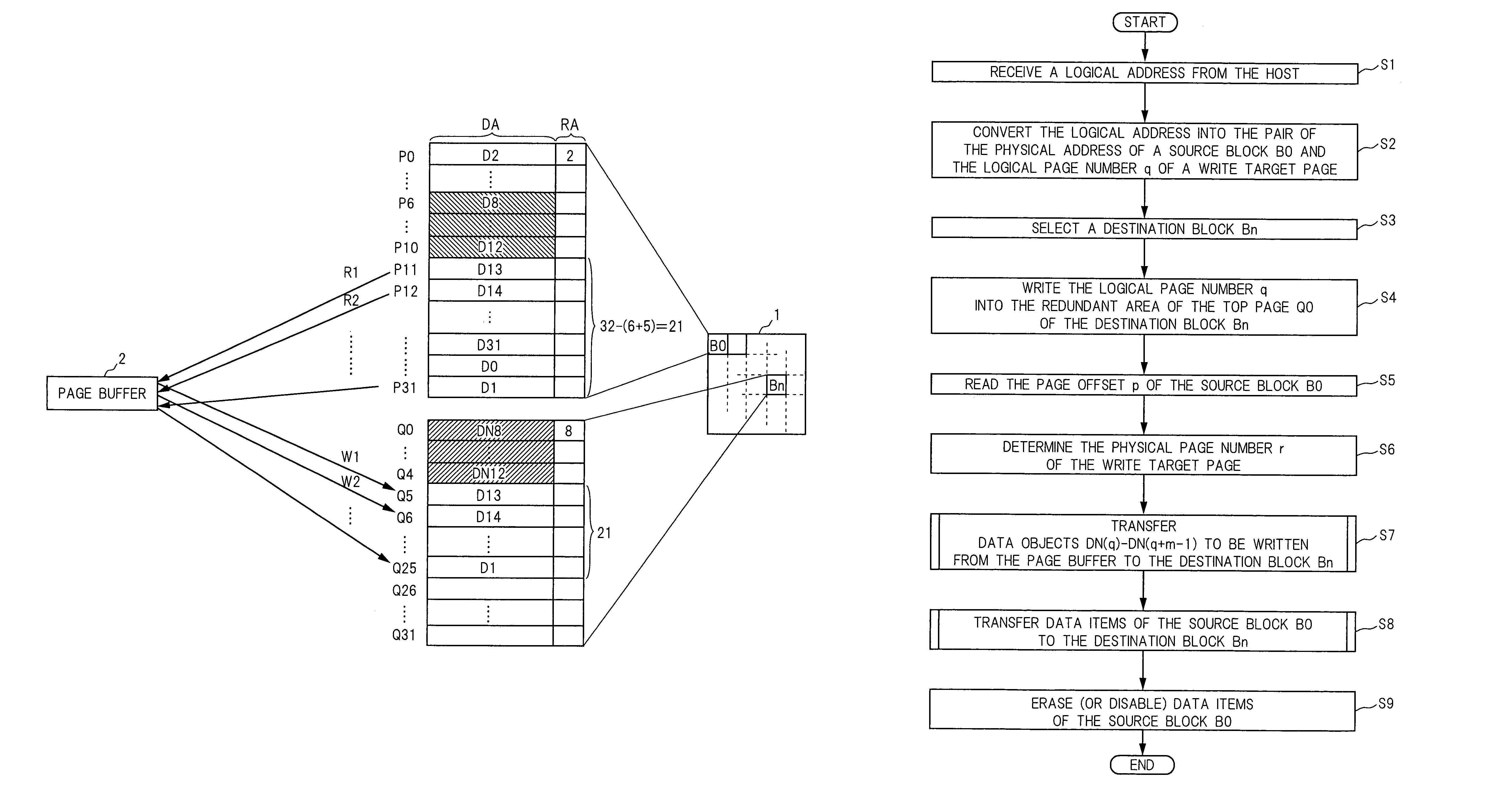
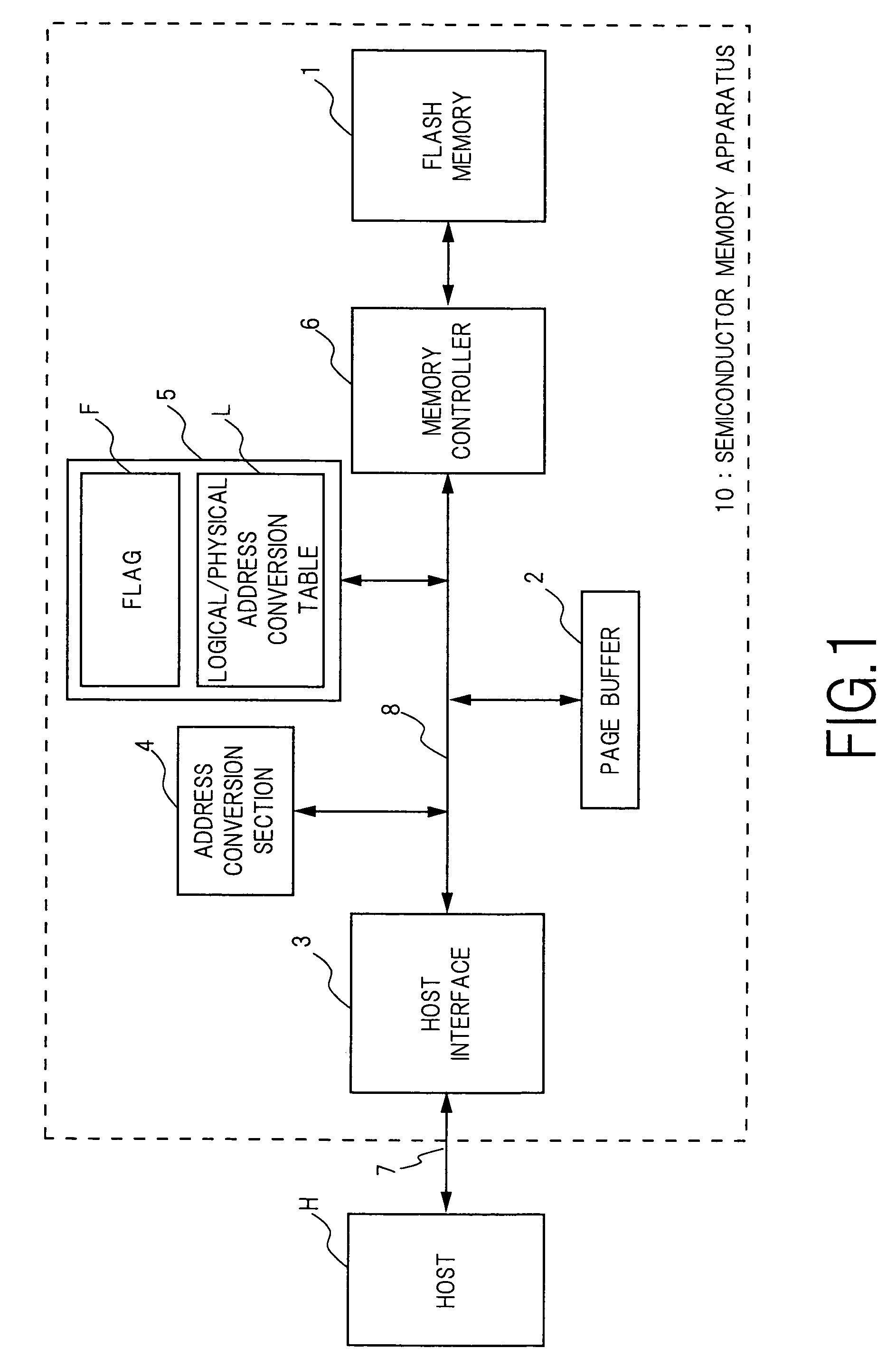
Semiconductor memory device and method for writing data into flash memory
ActiveUS7107389B2Small sizeReduce waiting timeMemory architecture accessing/allocationMemory adressing/allocation/relocationHome pageDatabase
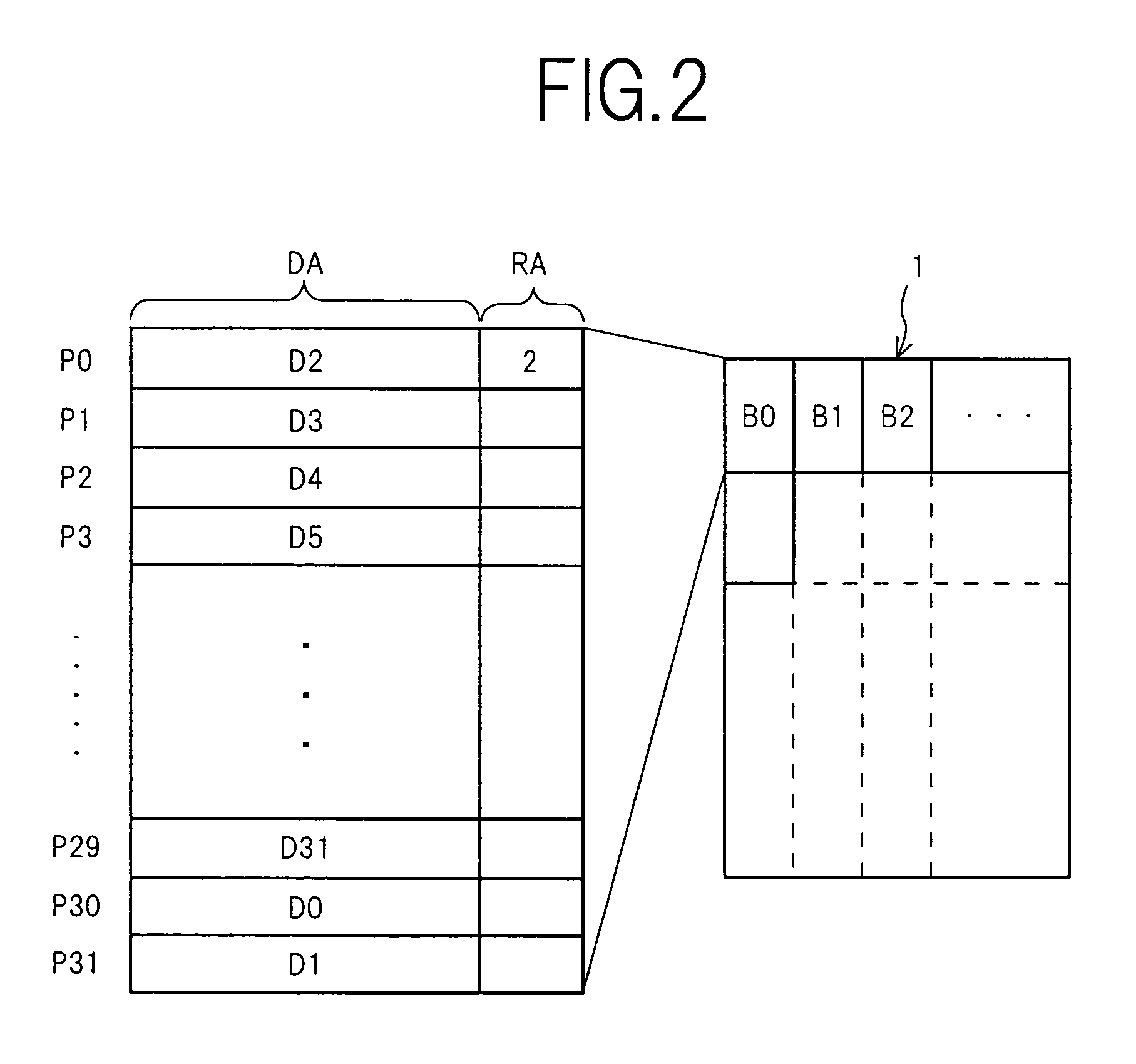
A source block (B0) and the logical page number (“8”) of a write target page are identified from the logical address of the write target page. Data objects (DN8, DN9, . . . , DN12) to be written, which a host stores in a page buffer (2), are written into the data areas (DA) of the pages (Q0, Q1, . . . , Q4) of a destination block (Bn), starting from the top page (Q0) in sequence. The logical page number (“8”) of the write target page is written into the redundant area (RA) of the top page (Q0). The physical page number (“6=8−2”) of the write target page is identified, based on the logical page number (“8”) of the write target page and the page offset (“2”) of the source block (B0). When notified by the host of the end of the sending of the data objects (DN8, . . . , DN12), the data items (D13, . . . , D31, D0, D1, . . . , D7) in the source block (B0) are transferred to the pages (Q5, Q6, . . . , Q31) in the destination block (Bn) via the page buffer (2) sequentially and cyclically, starting from the page (P11) situated cyclically behind the write target page (P6) by the number (“5”) of pages of the data objects (DN8, . . . , DN12).
Owner:PANASONIC CORP
Keymap service architecture for a distributed storage system
A keymap service architecture for a distributed storage system. A system may implement storage nodes configured to store replicas of data objects, where each of the replicas is accessible via a respective locator value, and keymap instances each configured to store keymap entries corresponding respectively to the data objects. A given keymap entry may indicate a mapping from a given key value corresponding to a given data object to each respective locator value of its replicas. Each of the keymap instances may store a replica of the given keymap entry and may index its respective stored keymap entries within a respective index data structure including hierarchically arranged index nodes corresponding to keymap entries. For a given keymap entry having a given corresponding index node, each tag value associated with each ancestor of the given corresponding index node may be a prefix of the given key value.
Owner:AMAZON TECH INC
Data object access system and method using dedicated task object
InactiveUS7818291B2Digital data information retrievalDigital data processing detailsGraphicsApplication software
A task management system for providing a graphically displayable worklist having one or more rows of work items, one or more of the work items each representing one or more data rows to be worked from one or more application data tables that are not a task object table of the task management system, the task management system comprising a task database having at least one task object, a first dedicated task object in said task database, said first dedicated task object having a second metadata associated therewith for graphically displaying information related to said first dedicated task object, a first view object having a first set of instructions for determining a first plurality of data rows of the one or more application data tables and a second set of instructions for creating a first association between each data row of said first plurality of data rows and said first dedicated task object, and a display generator for using said second metadata in initiating generation of display data representing a display image presenting a worklist, said worklist having a first one or more rows of application data table work items, each of said first one or more rows of application data table work items representing at least one data row of said first plurality of data rows.
Owner:GENERAL ELECTRIC CO
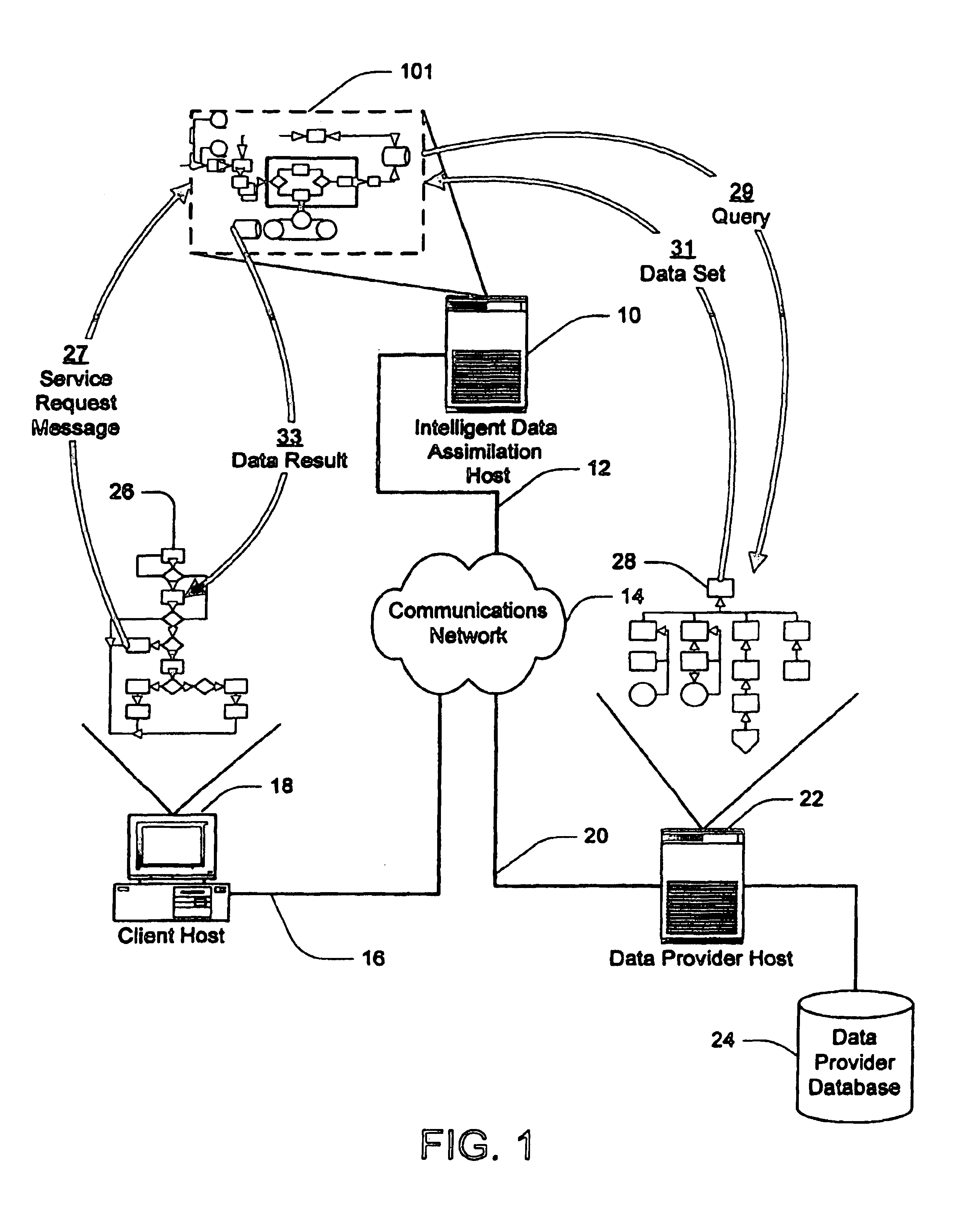
Method and apparatus for intelligent data assimilation
InactiveUS6847974B2Data processing applicationsWebsite content managementGraphical user interfaceApplication server
An intelligent data assimilation system including an ontology description, workflows, and logical search objects. The logical search objects operably connect to external and internal data providers and return search results using an ontology describing atomic data objects and semantic objects. The semantic objects are grouped into larger semantic structures by workflows to create customized services that return search results termed data products. Services are accessed through an application server capable of responding to service requests from different types of data clients. Graphical user interfaces provide facilities for creating logical search objects and aggregating logical search objects into workflows and services.
Owner:US SEARCH COM
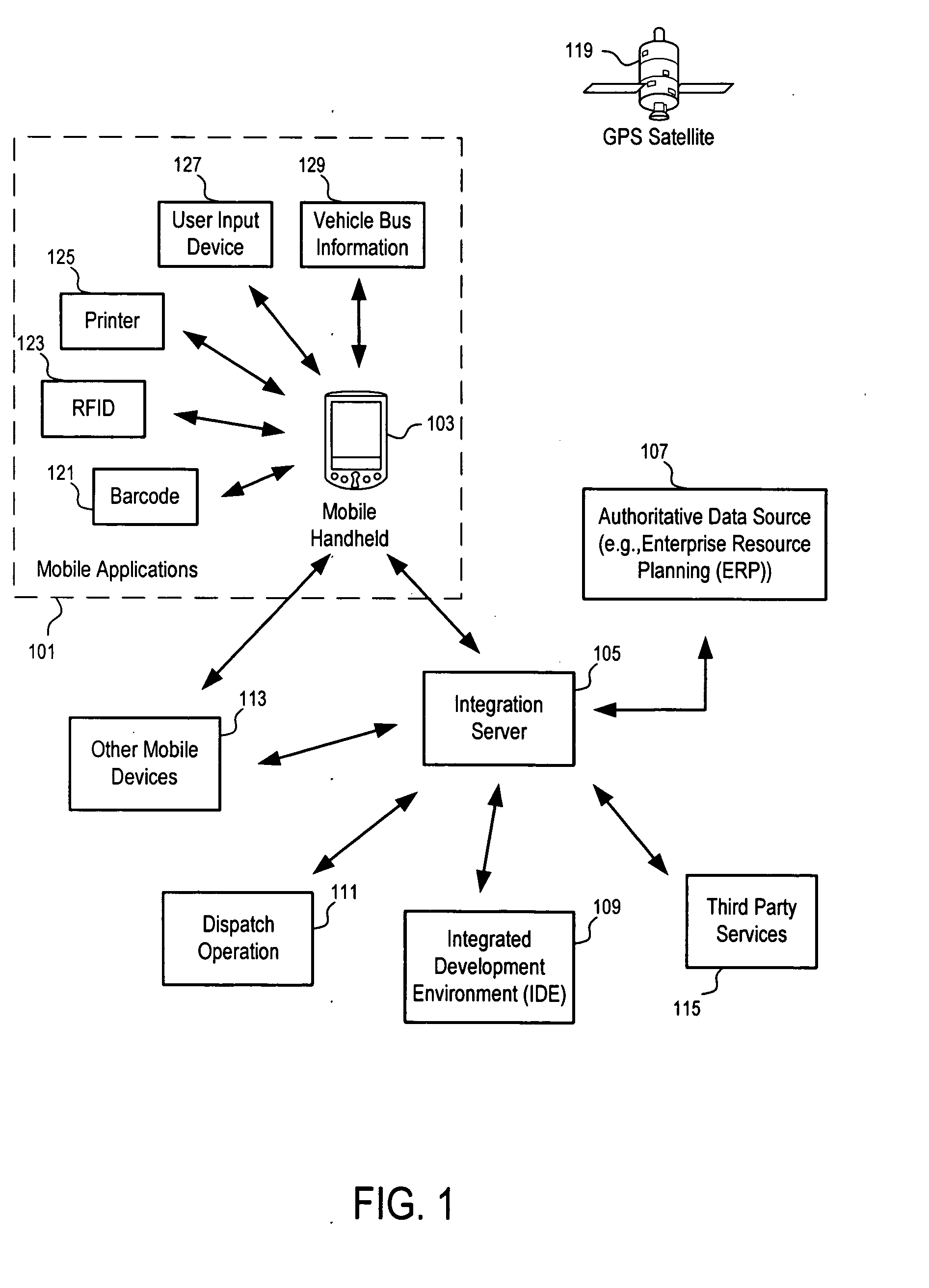
Method and apparatus for the creation of personalized supervisory and control data acquisition systems for the management and integration of real-time enterprise-wide applications and systems
A system and method provide for the creation and operation of real-time enterprise-wide, personalize supervisory and control data acquisition systems. Personalized SCADA applications are constructed from a virtual application service and a personal agent framework using simple drag and drop operations or other high level action. The virtual application service includes a communications gateway that communicates with disparate and non-interoperable systems and external field devices to communicate low level time data collected from such systems into the application environment transforming the collected data in a single common data format. The virtual application service includes application cells that receive the reformatted data and process it to provide high level analysis and context, storing the processed data in an object server. The object server provides a unified, hierarchical object model for all of the data received from the underlying devices and systems. The virtual application service communicates with personal agent frameworks containing presentation cells and service agents. The service agents are representative of the virtual application service, and provide the personal agent framework with access to the object server to receive and send data from the object server to the presentation cells. The presentation cells subscribe to the object server's data objects via the service agent. Presentation cell provide a graphical representation and mapping of data objects and hence underlying devices and systems, to allow a user to manage and control such systems.
Owner:EUTECH CYBERNETICS PTE
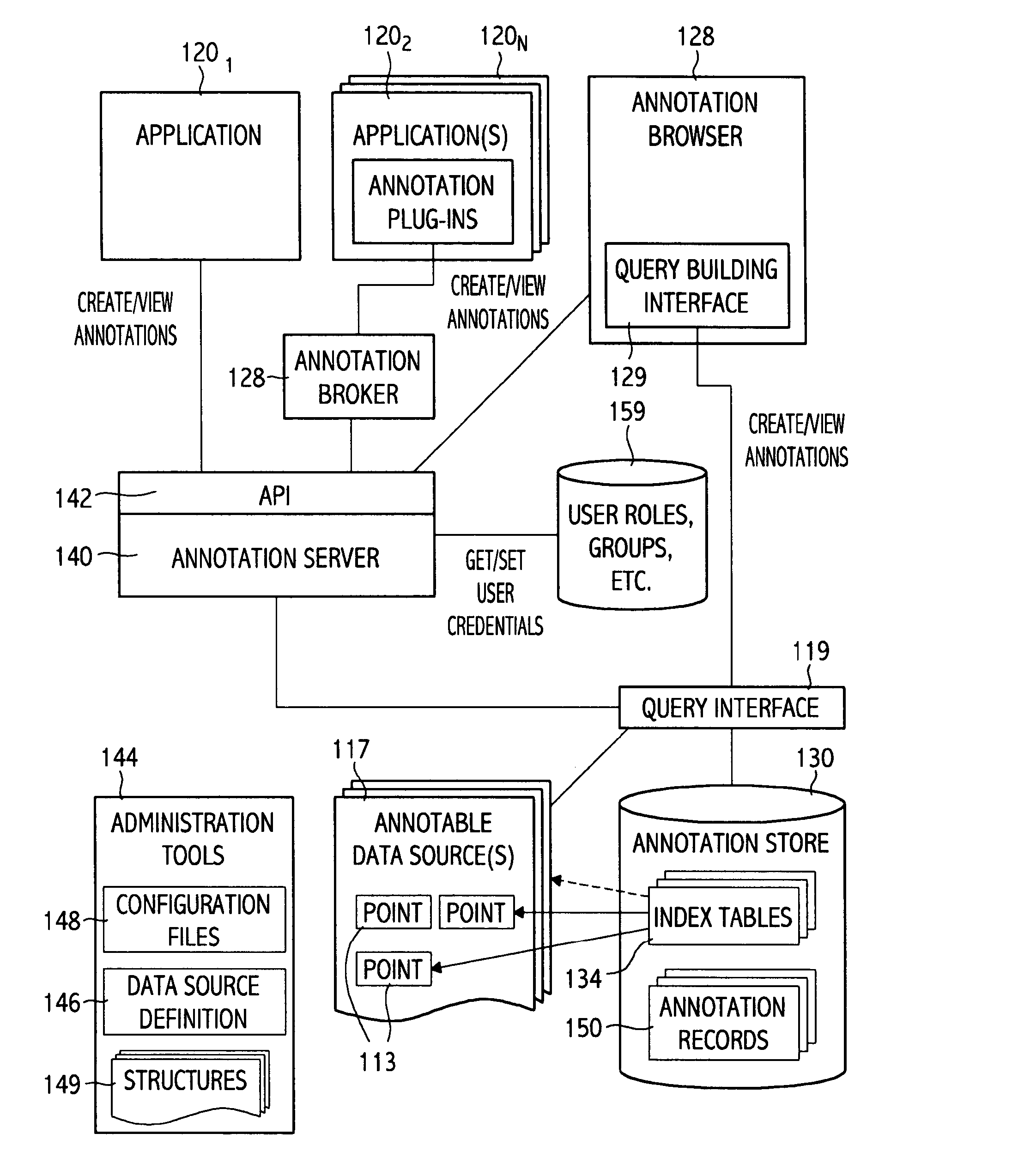
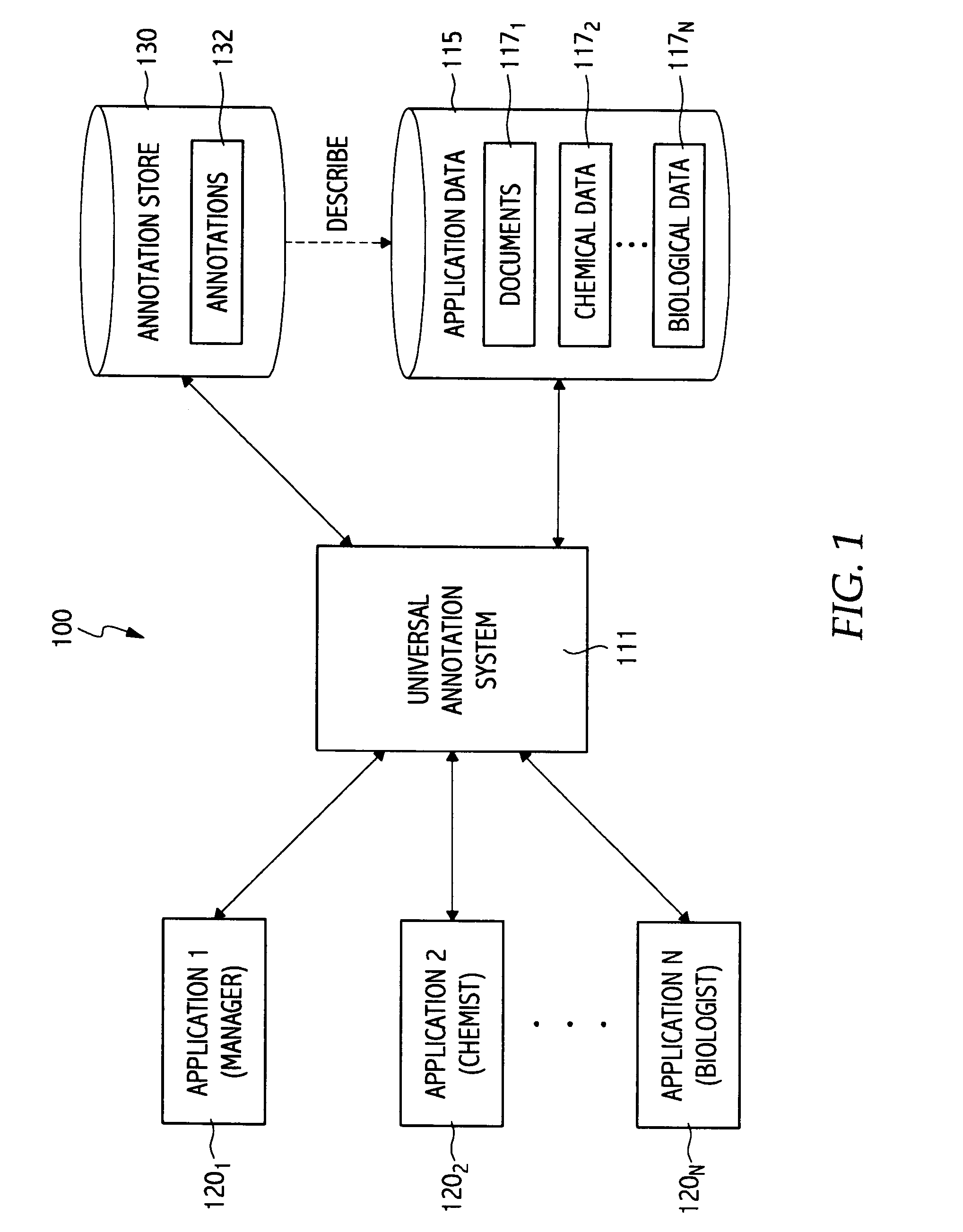
Universal annotation configuration and deployment
InactiveUS20040260702A1Data processing applicationsWeb data navigationTacit knowledgeApplication software
Methods, systems, and articles of manufacture for managing annotations made for a variety of different type data objects manipulated (e.g., created, edited, and viewed) by a variety of different type applications are provided. Some embodiments allow users collaborating on a project to create, view, and edit annotations from within the applications used to manipulate the annotated data objects, which may facilitate and encourage the capturing and sharing of tacit knowledge through annotations. Further, annotations may be stored separate from the application data they describe, decoupling the tacit knowledge captured in the annotations from the applications used to manipulate the annotated data.
Owner:IBM CORP +1
System and method for knowledge retrieval, management, delivery and presentation
InactiveUS20080162498A1Website content managementSpecial data processing applicationsAction CodeActive agent
The present invention is directed to an integrated implementation framework and resulting medium for knowledge retrieval, management, delivery and presentation. The system includes a first server component that is responsible for adding and maintaining domain-specific semantic information and a second server component that hosts semantic and other knowledge for use by the first server component that work together to provide context and time-sensitive semantic information retrieval services to clients operating a presentation platform via a communication medium. Within the system, all objects or events in a given hierarchy are active Agents semantically related to each other and representing queries (comprised of underlying action code) that return data objects for presentation to the client according to a predetermined and customizable theme or “Skin.” This system provides various means for the client to customize and “blend” Agents and the underlying related queries to optimize the presentation of the resulting information.
Owner:OMOIGUI NOSA
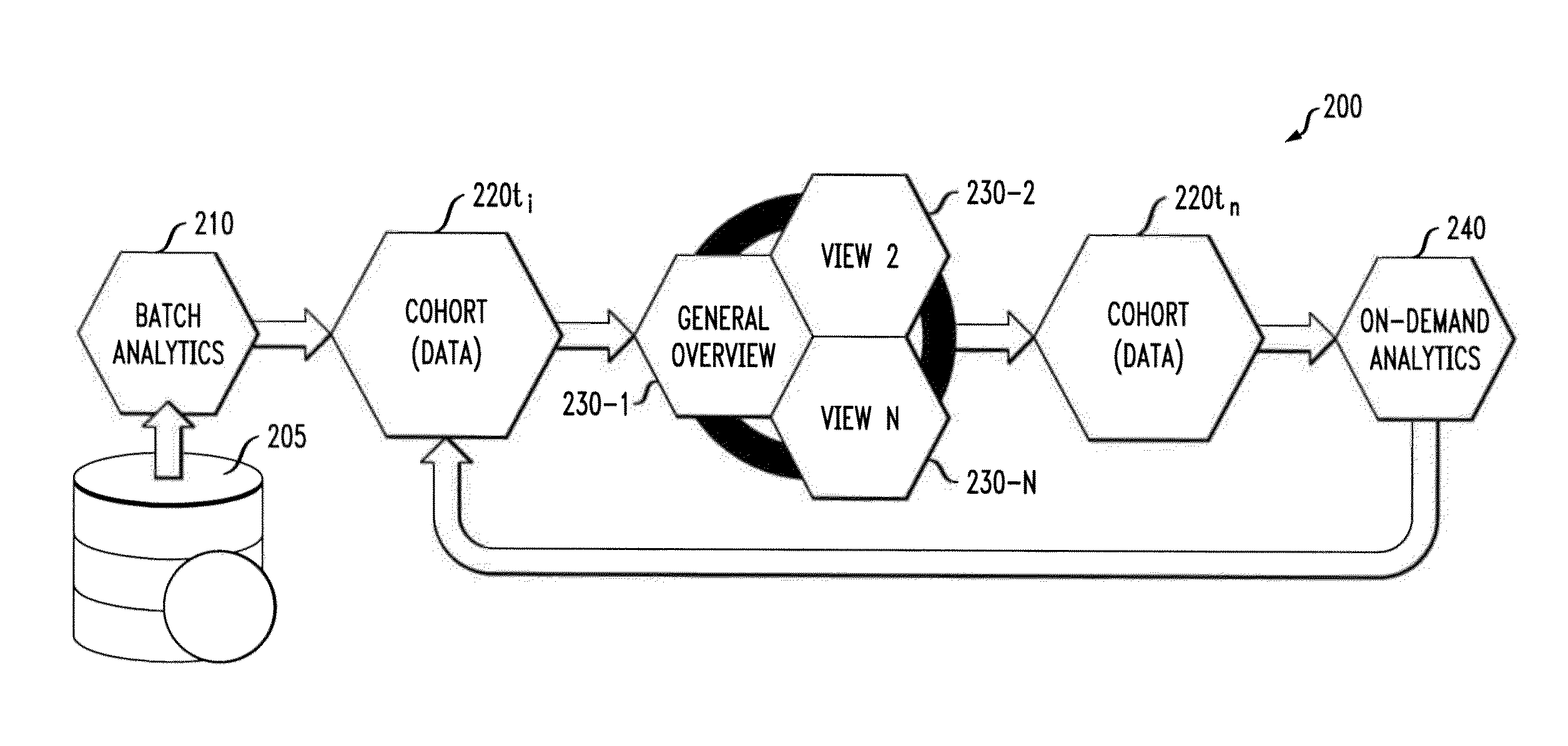
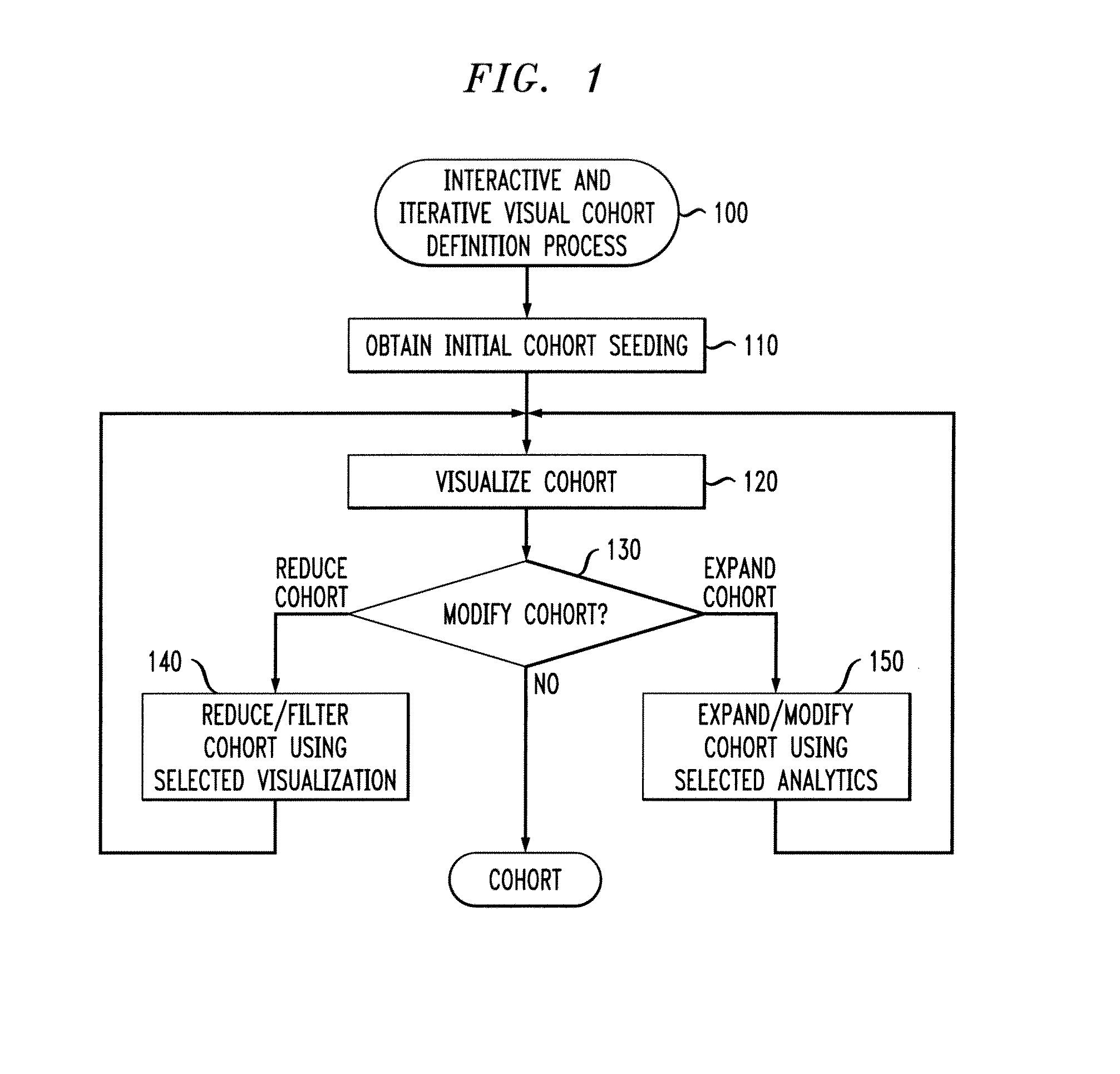
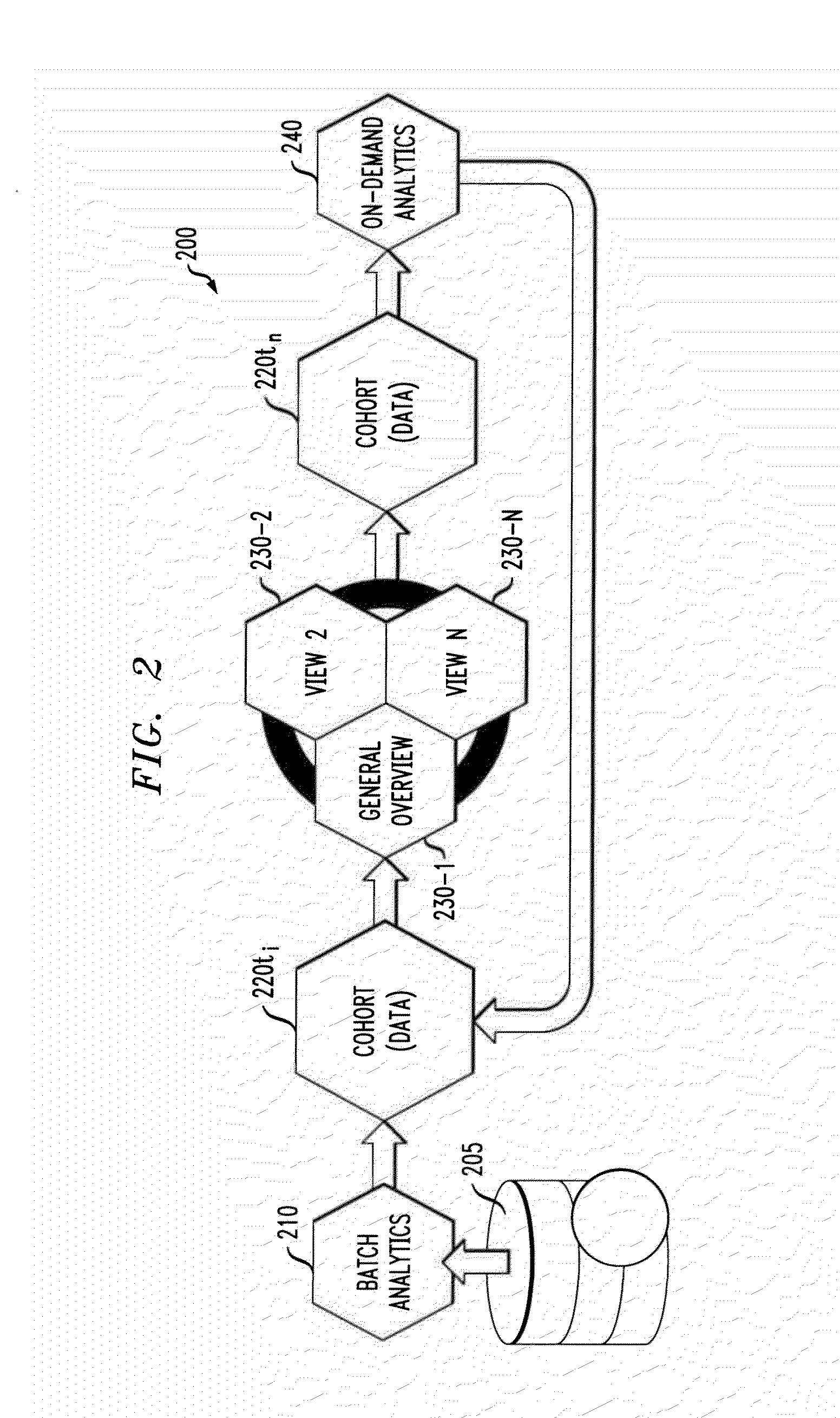
Iterative Refinement of Cohorts Using Visual Exploration and Data Analytics
ActiveUS20140108380A1Cohort can be reducedDigital data processing detailsOther databases browsing/visualisationDrag and dropData profiling
Methods and apparatus are provided for iterative refinement of cohorts using visual exploration and data analytics. A cohort comprised of multiple data objects is defined by obtaining an initial cohort seeding; visualizing the initial cohort using a selected view to present a current cohort; reducing the current cohort using one or more visual filters; visualizing the current cohort using a selected view; expanding the current cohort using one or more selected analytics; and determining whether the current cohort should be further modified using one or more of additional reductions and additional expansions. Cohorts can be passed between views and analytics via drag-and-drop interactions as an analysis unfolds.
Owner:IBM CORP
Data security system and method for portable device
ActiveUS7313825B2Ease overhead performanceHigh overhead performancePeptide/protein ingredientsDigital data processing detailsInformation processingEvent trigger
The method, used with a portable computing device, secures security sensitive words, icons, etc. by determining device location within or without a predetermined region and then extracting the security data from the file, text, data object or whatever. The extracted data is separated from the remainder data and stored either on media in a local drive or remotely, typically via wireless network, to a remote store. Encryption is used to further enhance security levels. Extraction may be automatic, when the portable device is beyond a predetermined territory, or triggered by an event, such a “save document” or a time-out routine. Reconstruction of the data is permitted only in the presence of a predetermined security clearance and within certain geographic territories. A computer readable medium containing programming instructions carrying out the methodology for securing data is also described herein. An information processing system for securing data is also described.
Owner:DIGITAL DOORS
Method and apparatus for sharing common data objects among multiple applications in a client device
InactiveUS6934740B1Readily apparentData processing applicationsMultiple digital computer combinationsObject basedSoftware architecture
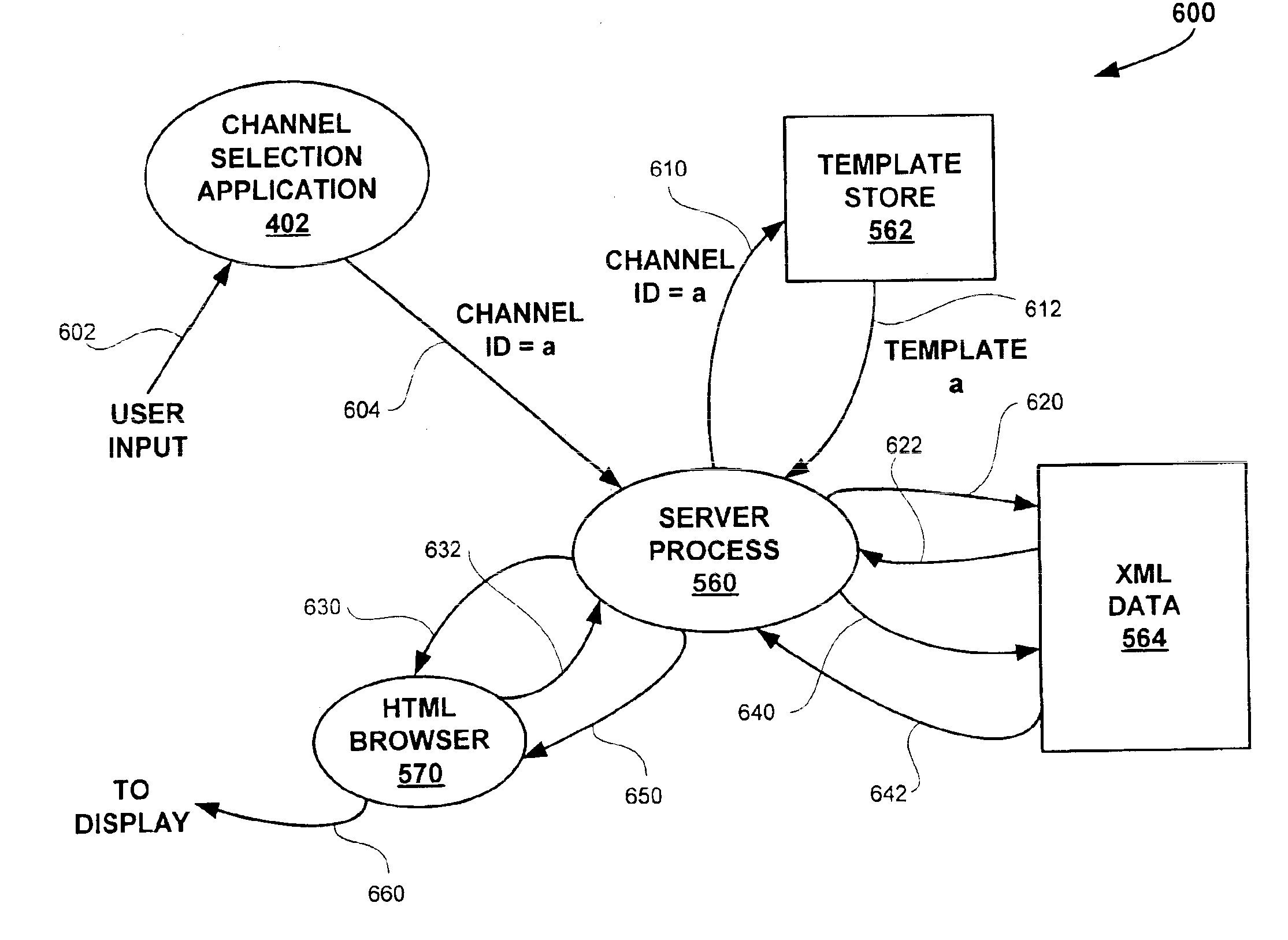
Disclosed is software architecture and method for sharing data objects among multiple applications in a client device. The architecture includes a server process in the client device for processing a template, such as a SHTML template for the Extended Markup Language (XML), based on a template identifier value received from a user application. Each of multiple applications has a template. Each template identifies a series of objects identified by tag values, such as XML entities, that are to be incorporated into a display page. A database of objects, such as a database of XML entities identified by tag values, is maintained that contains data objects for the applications. An update process periodically establishes a communication link with a remote server and requests download of a data document containing content data corresponding to at least a portion of several of the templates. The data document is parsed into the database of objects based on the structure of the data document, which generally conforms to a data type definition. When the server process processes different templates that reference the same data object, it will retrieve the data object from the database. Each template may then be rendered into a page of output data for display to a user. The architecture and method according to the present invention thus permit data objects to be shared by multiple applications and to be automatically updated. Each time a data object is updated, the data will be current for each user application that references the data object.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
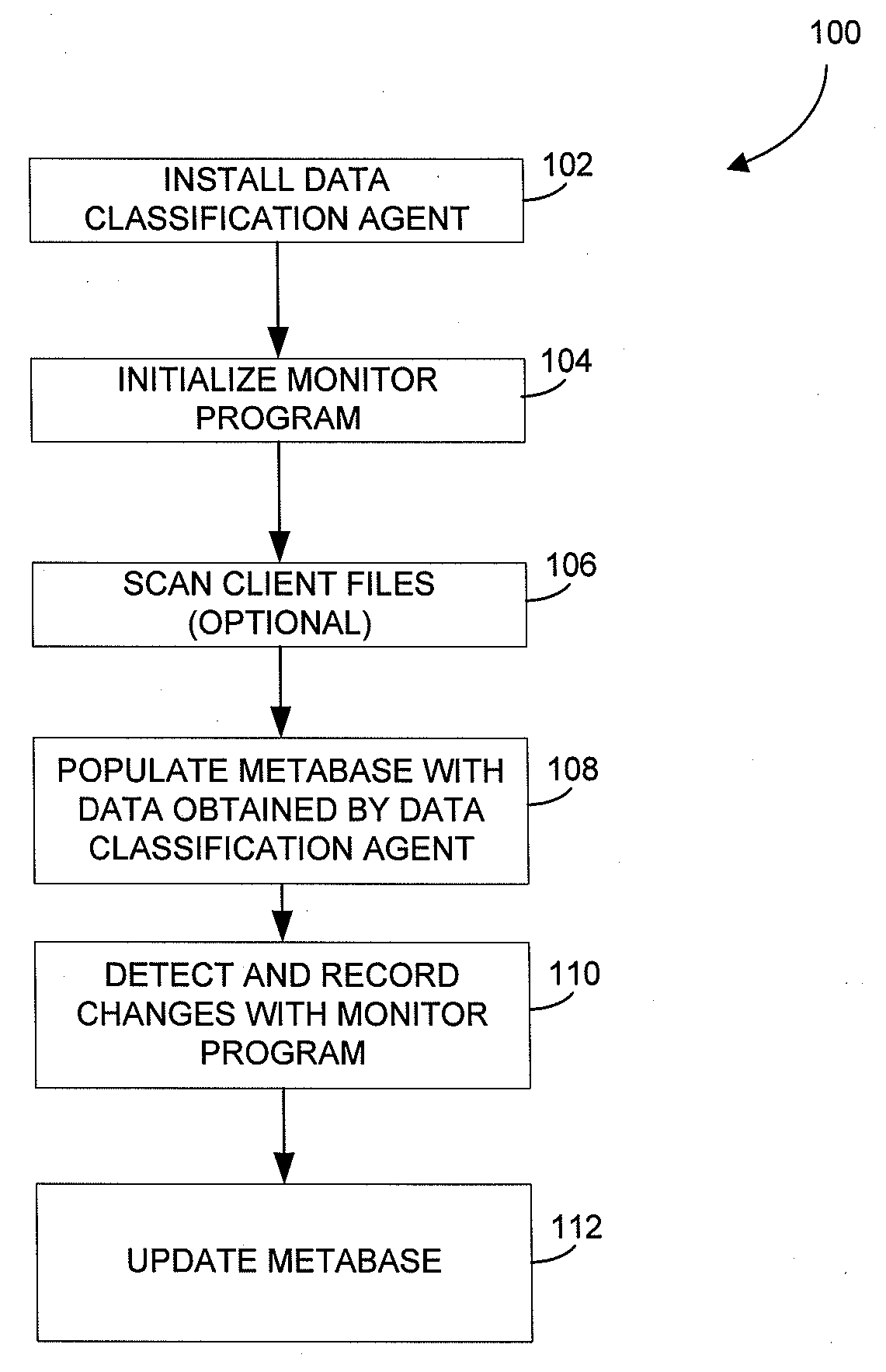
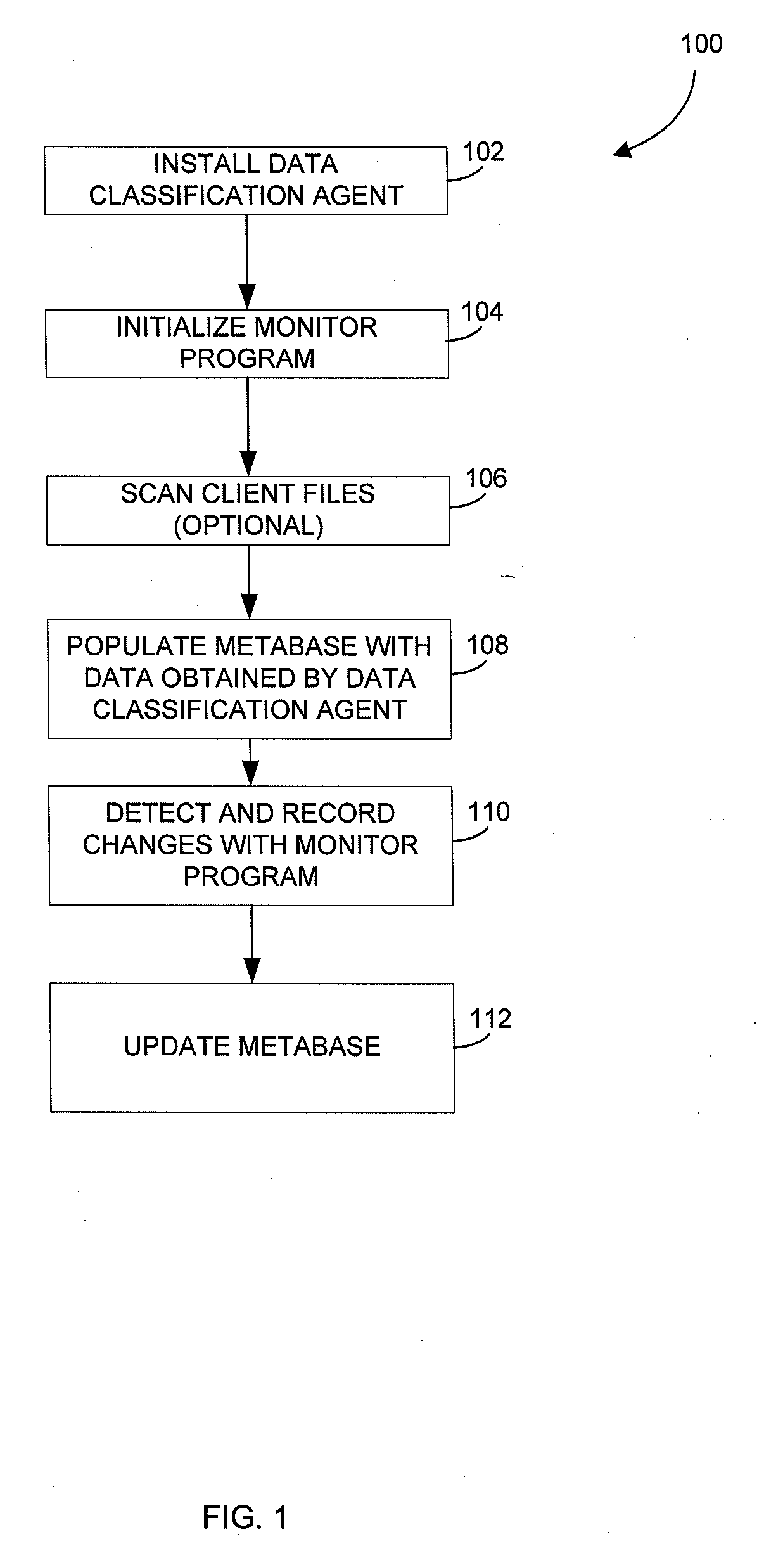
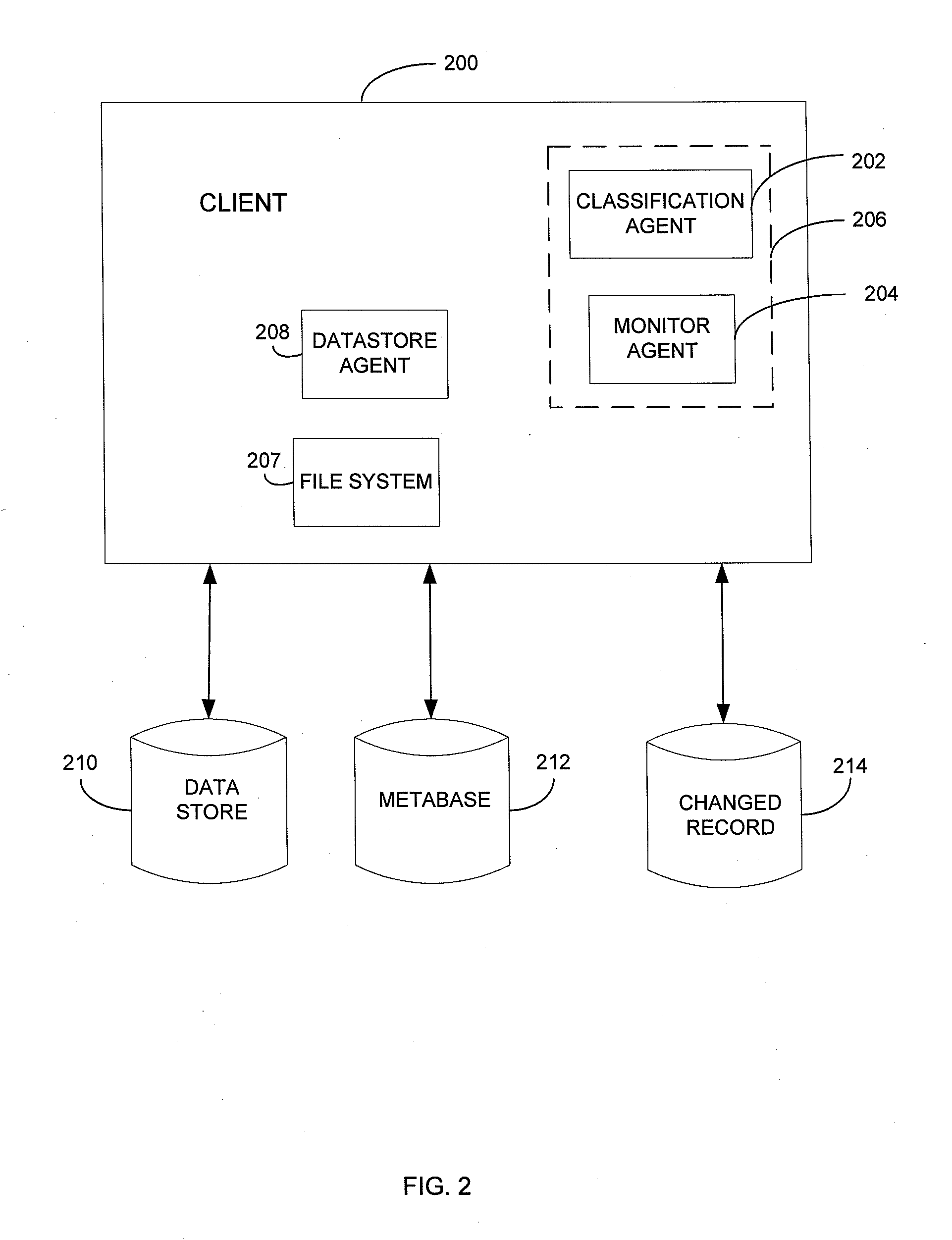
Metabase for facilitating data classification
Systems and methods for managing electronic data are disclosed. Various data management operations can be performed based on a metabase formed from metadata. Such metadata can be identified from an index of data interactions generated by a journaling module, and obtained from their associated data objects stored in one or more storage devices. In various embodiments, such processing of the index and storing of the metadata can facilitate, for example, enhanced data management operations, enhanced data identification operations, enhanced storage operations, data classification for organizing and storing the metadata, cataloging of metadata for the stored metadata, and / or user interfaces for managing data. In various embodiments, the metabase can be configured in different ways. For example, the metabase can be stored separately from the data objects so as to allow obtaining of information about the data objects without accessing the data objects or a data structure used by a file system.
Owner:COMMVAULT SYST INC
System and method for experience-sharing within a computer network
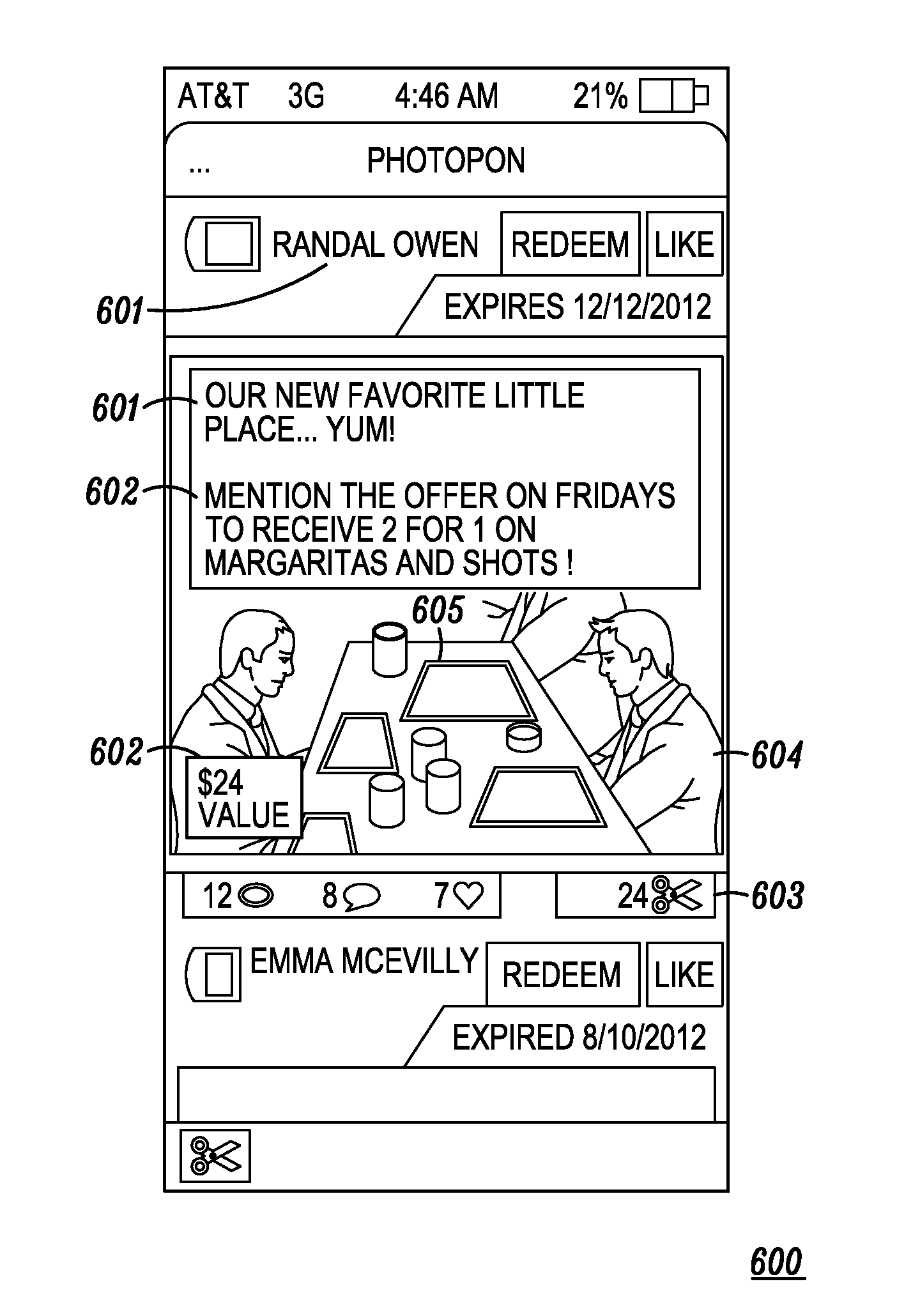
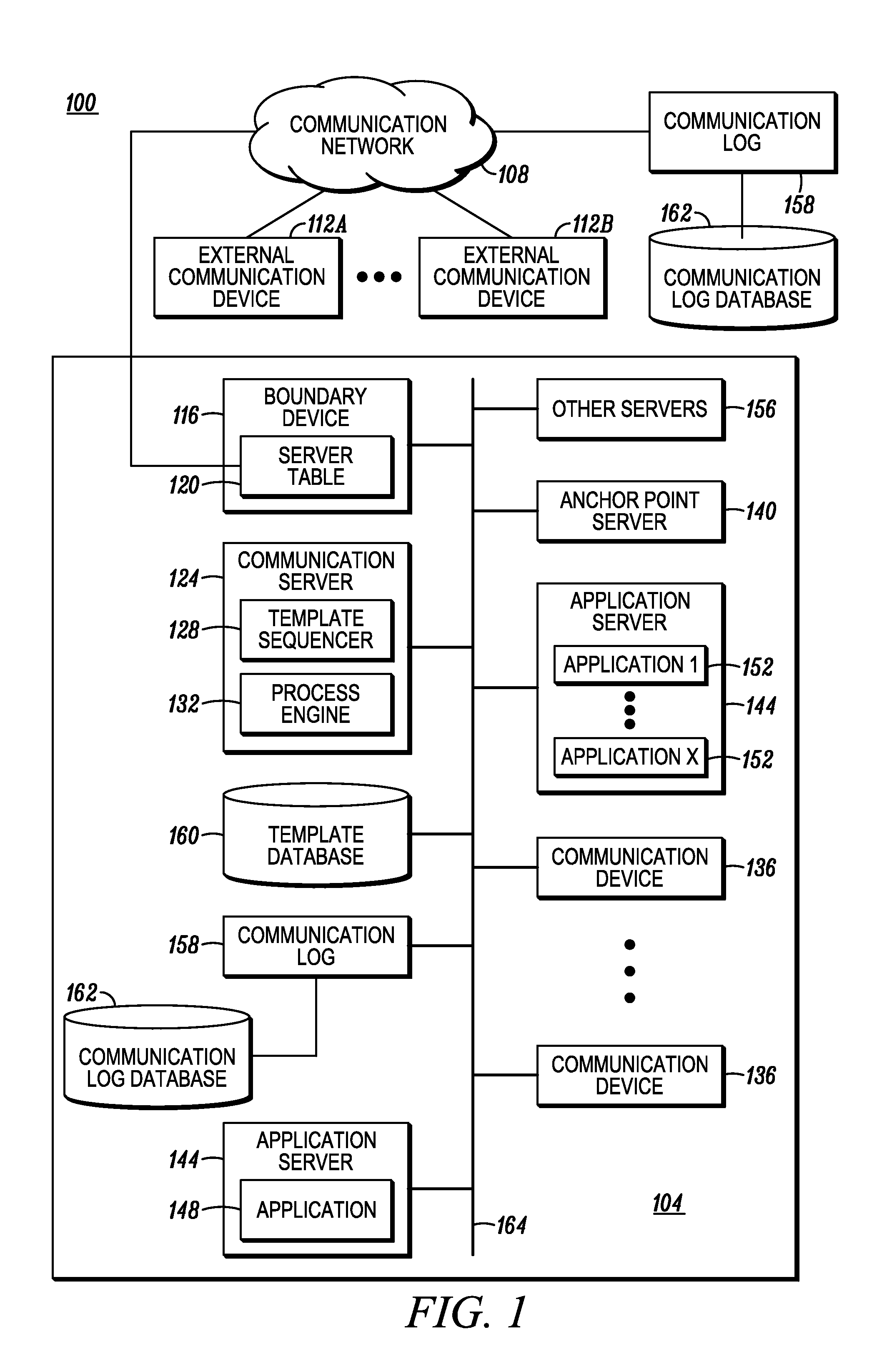
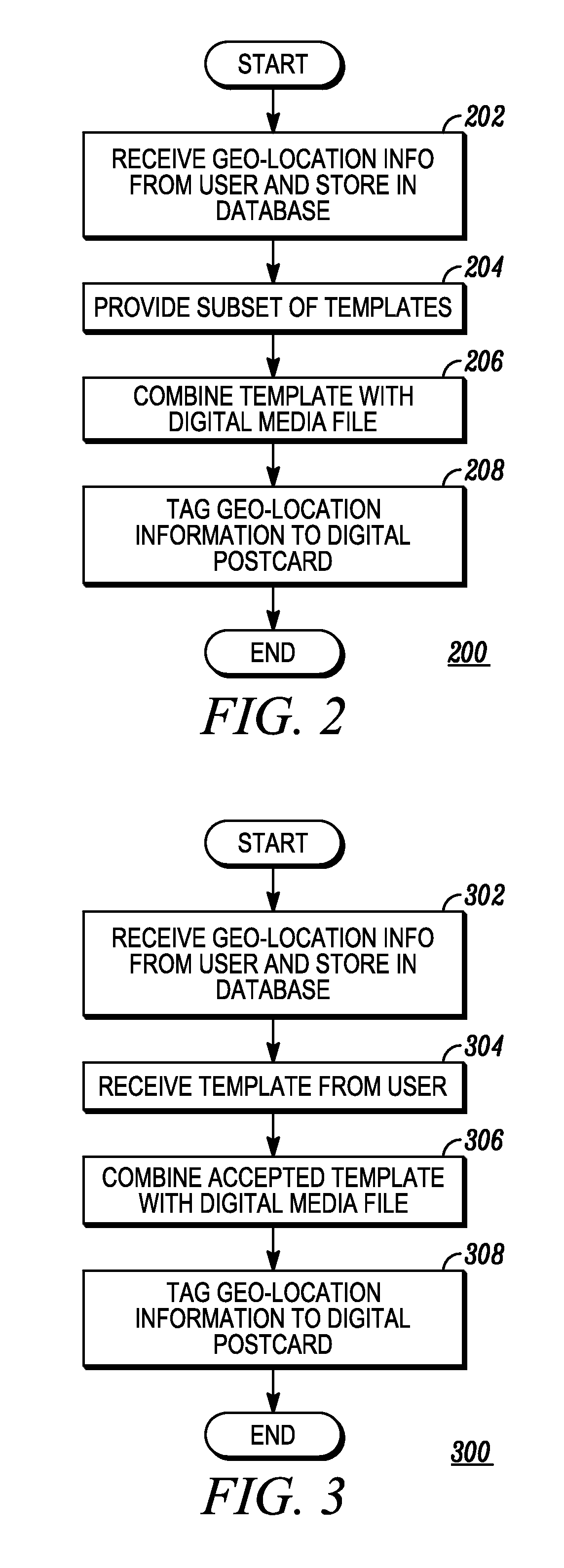
A system and method for providing a communication between users of a computer network are provided, the method including the steps of storing, in a database, received geo-location information, object information, brand information or other information, from a user; providing to the user a subset of previously stored digital media templates from the database for user selection; combining a user-selected digital media template with a user-selected media data object file received from the user; and tagging the geo-location information, object information, brand information or other information, to the combined user-selected digital media template and user-selected media data object file for communicating between users of the computer network.
Owner:PHOTOPON
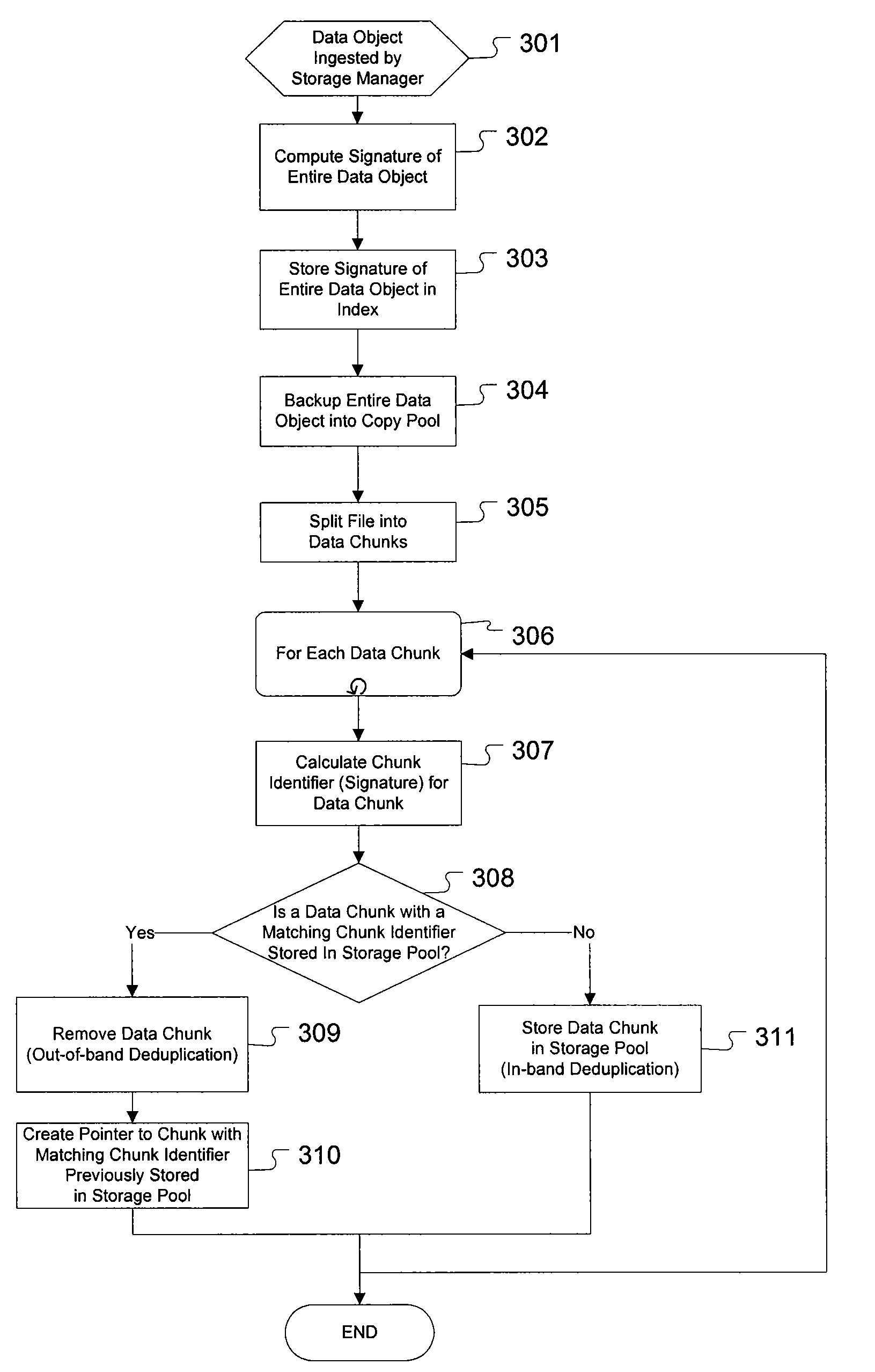
Enhanced method and system for assuring integrity of deduplicated data
ActiveUS20090271454A1Access latencyDigital data information retrievalDigital data processing detailsHash functionDigital signature
The present invention provides for an enhanced method and system for assuring integrity of deduplicated data objects stored within a storage system. A digital signature of the data object is generated to determine if the data object reassembled from a deduplicated state is identical to its pre-deduplication state. In one embodiment, generating the object signature of a data object before deduplication comprises generating an object signature from intermediate hash values computed from a hash function operating on each data chunk within the data object, the hash function also used to determine duplicate data chunks. In an alternative embodiment, generating the object signature of a data object before deduplication comprises generating an object signature on a portion of each data chunk of the data object.
Owner:DROPBOX
Data Security System and with territorial, geographic and triggering event protocol
ActiveUS20090178144A1Ease overhead performanceHigh overhead performanceDigital data processing detailsAnalogue secracy/subscription systemsInformation processingEvent trigger
The method, program and information processing system secures data, and particularly security sensitive words, characters or data objects in the data, in a computer system with territorial, geographic and triggering event protocols. The method and system determines device location within or without a predetermined region and then extracts security data from the file, text, data object or whatever. The extracted data is separated from the remainder data and stored either on media in a local drive or remotely, typically via wireless network, to a remote store. Encryption is used to further enhance security levels. Extraction may be automatic, when the portable device is beyond a predetermined territory, or triggered by an event, such a “save document” or a time-out routine. Reconstruction of the data is permitted only with security clearance and within certain geographic territories. An information processing system for securing data is also described.
Owner:DIGITAL DOORS
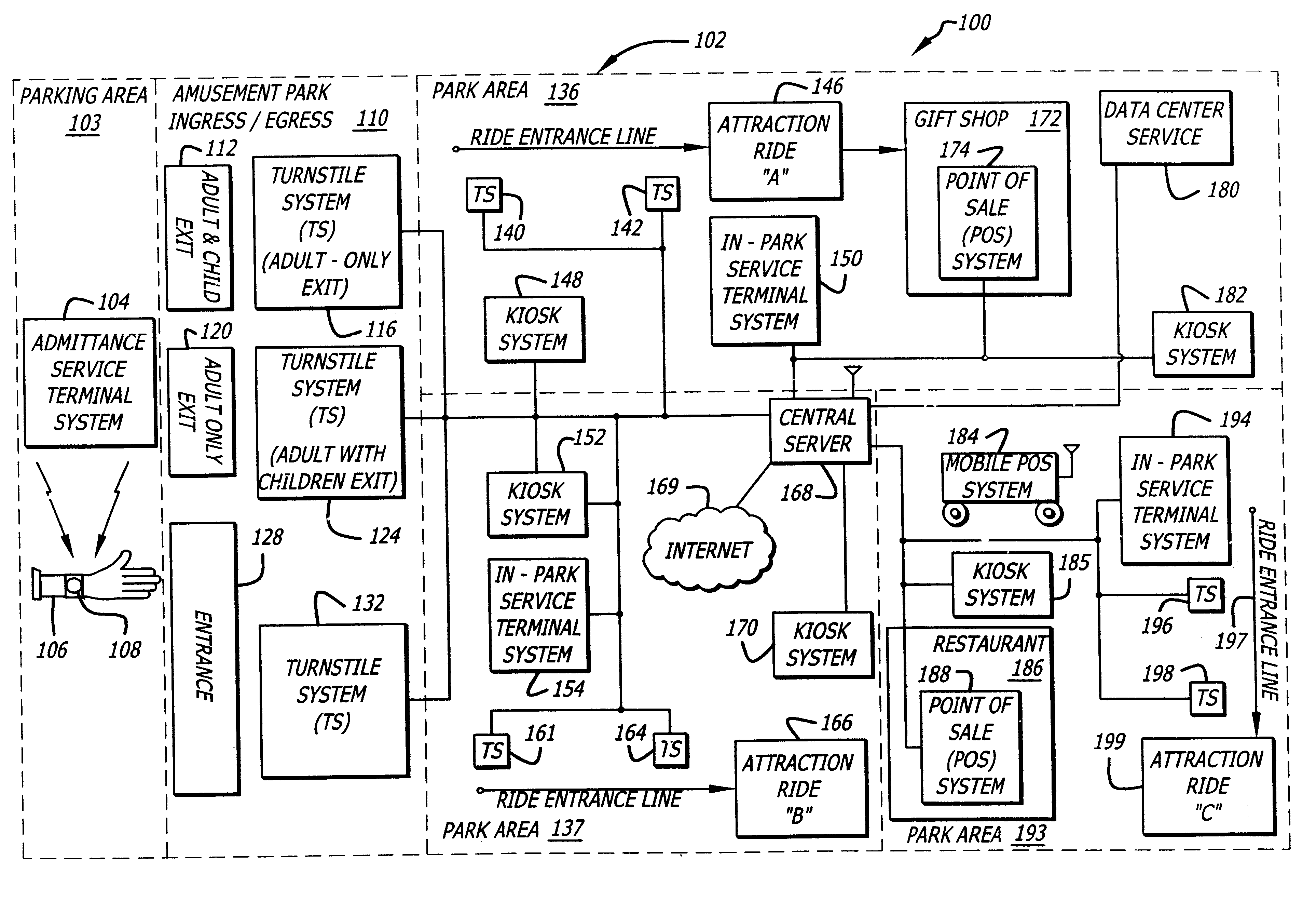
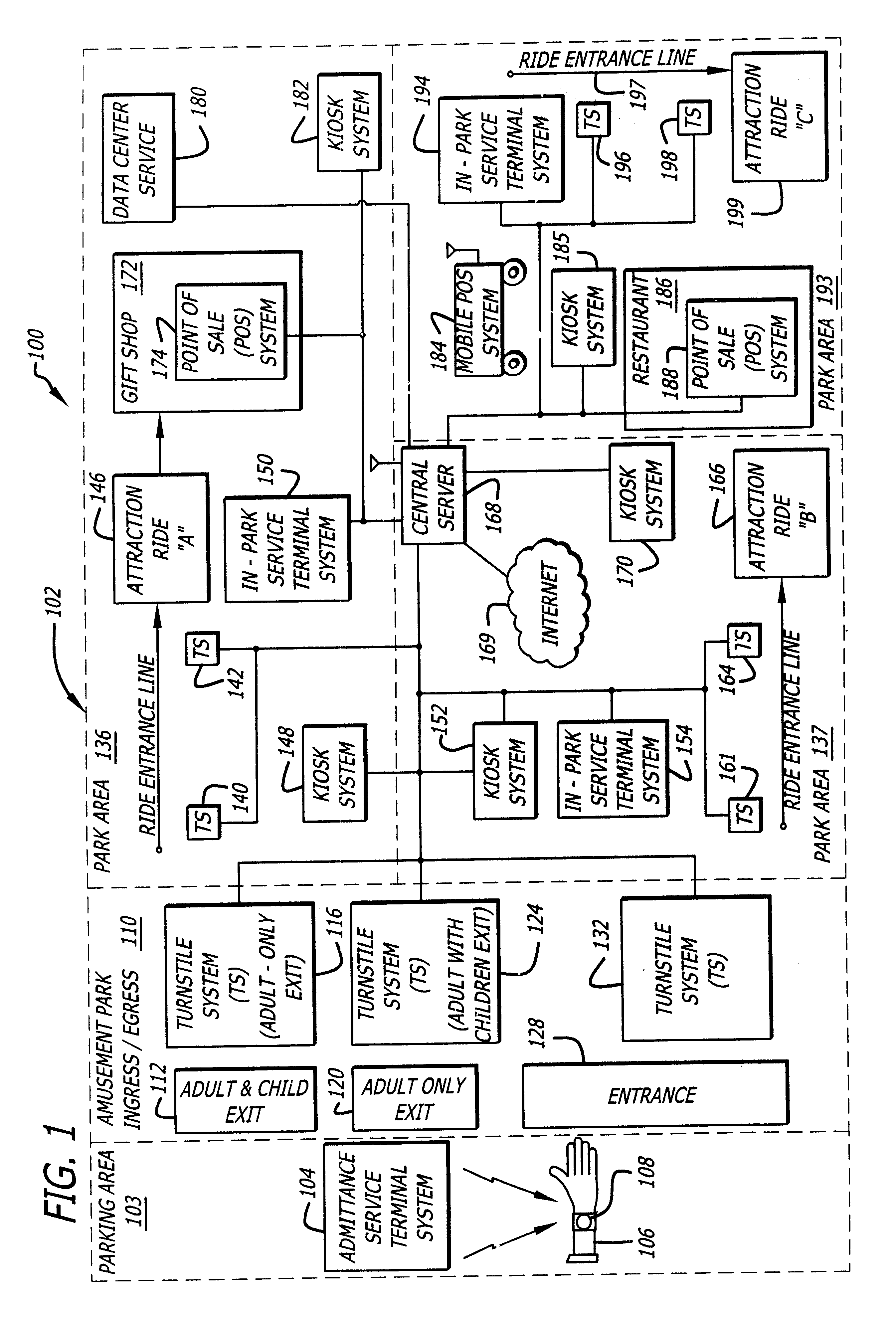
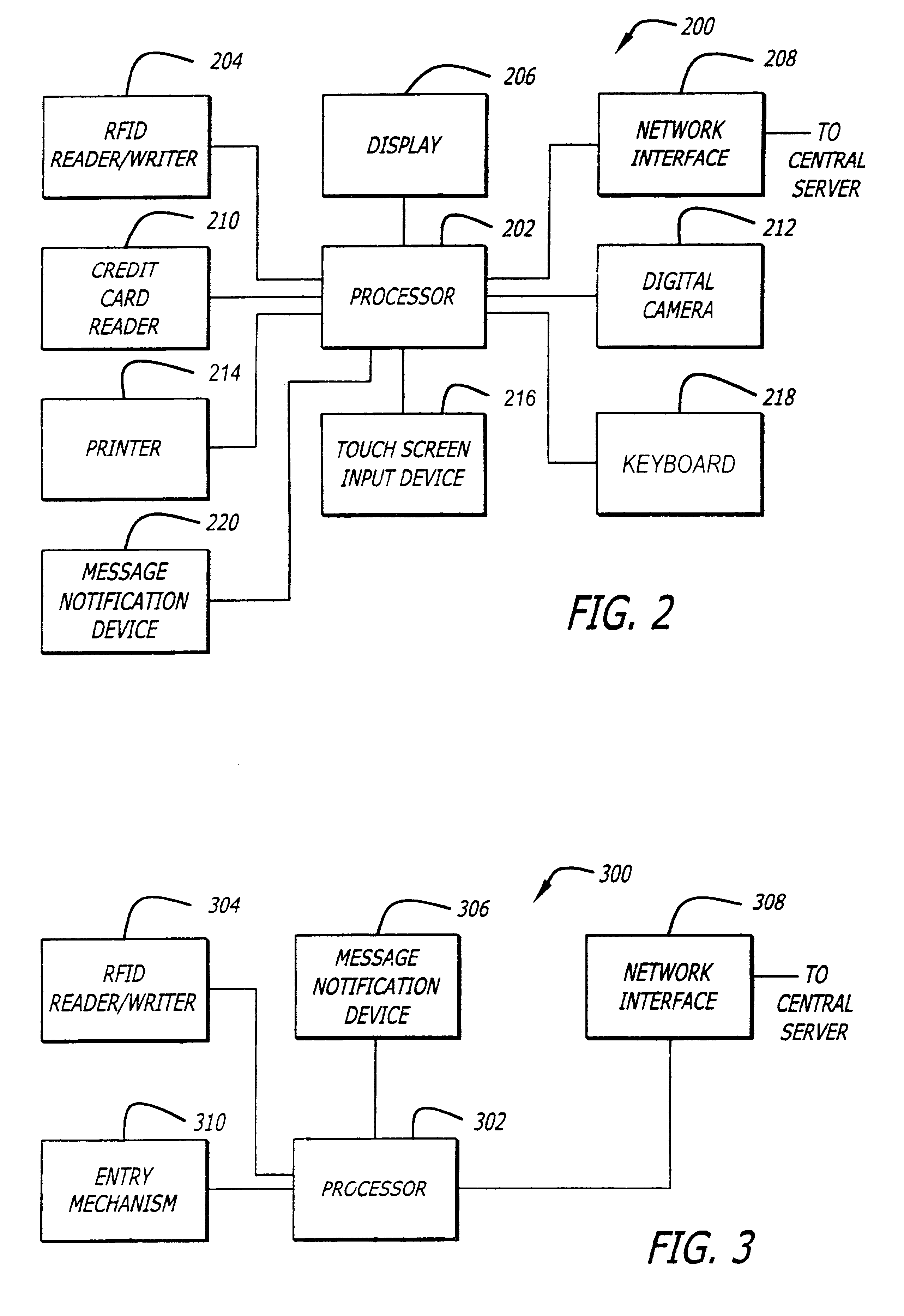
System and method for selectively allowing the passage of a guest through a region within a coverage area
InactiveUS6873260B2Electric signal transmission systemsMultiple keys/algorithms usageControl signalData field
A system and method for selectively allowing the passage of a guest through a region within at a coverage area. The system includes a turnstile system having an RFID reader, a network interface, an entry mechanism and a processor, and a central server having a network interface, a non-volatile memory, and a processor. An RFID reader reads a tag identifier from an RFID tag worn by a guest. The tag identifier is transmitted from the turnstile system to the central server. The central server processor access a guest data object using the tag identifier and reads a data field containing information related to the guest. Based on this information, the central server transmits a control signal to the turnstile system to activate its entry mechanism, thereby allowing the guest to pass through. The information may relate to monetary credits of the guest, statistical information of the guest, and restrictions, disabilities, health conditions and special access of the guest.
Owner:NOBLE LINDA +1
Policy based tiered data deduplication strategy
ActiveUS7567188B1Promote recoveryLeast riskDigital data information retrievalCode conversionData storeData deduplication
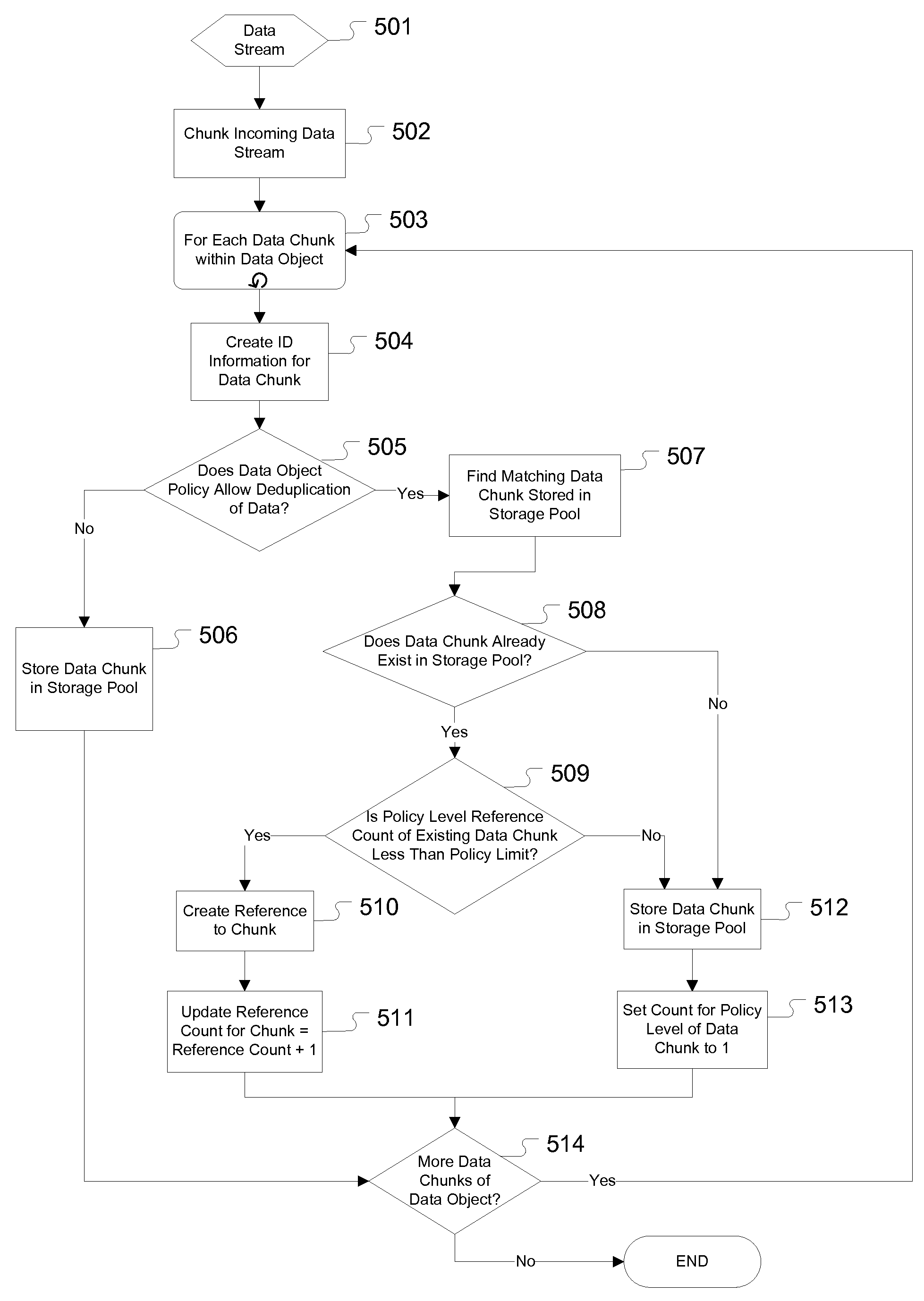
The present invention provides for a method, system, and computer program for the application of data deduplication according to a policy-based strategy of tiered data. The method operates by defining a plurality of data storage policies for data in a deduplication system, policies which may be arranged in tiers. Data objects are classified according to a selected data storage policy and are split into data chunks. If the selected data storage policy for the data object does not allow deduplication, the data chunks are stored in a deduplication pool. If the selected data storage policy for the data object allows deduplication, deduplication is performed. The data storage policy may specify a maximum number of references to data chunks, facilitating storage of new copies of the data chunks when the maximum number of references is met.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com