Patents
Literature
3427 results about "Storage management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
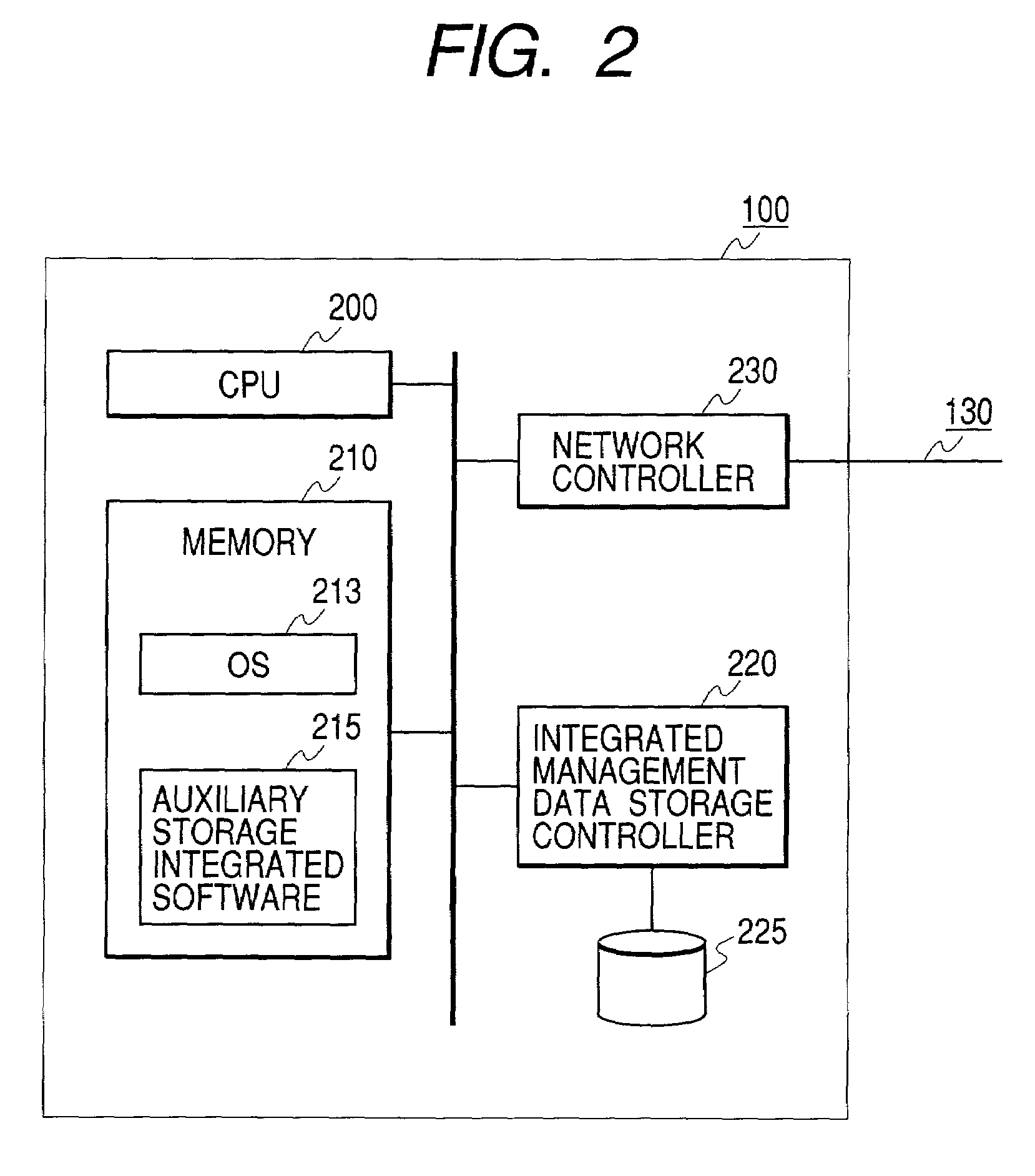
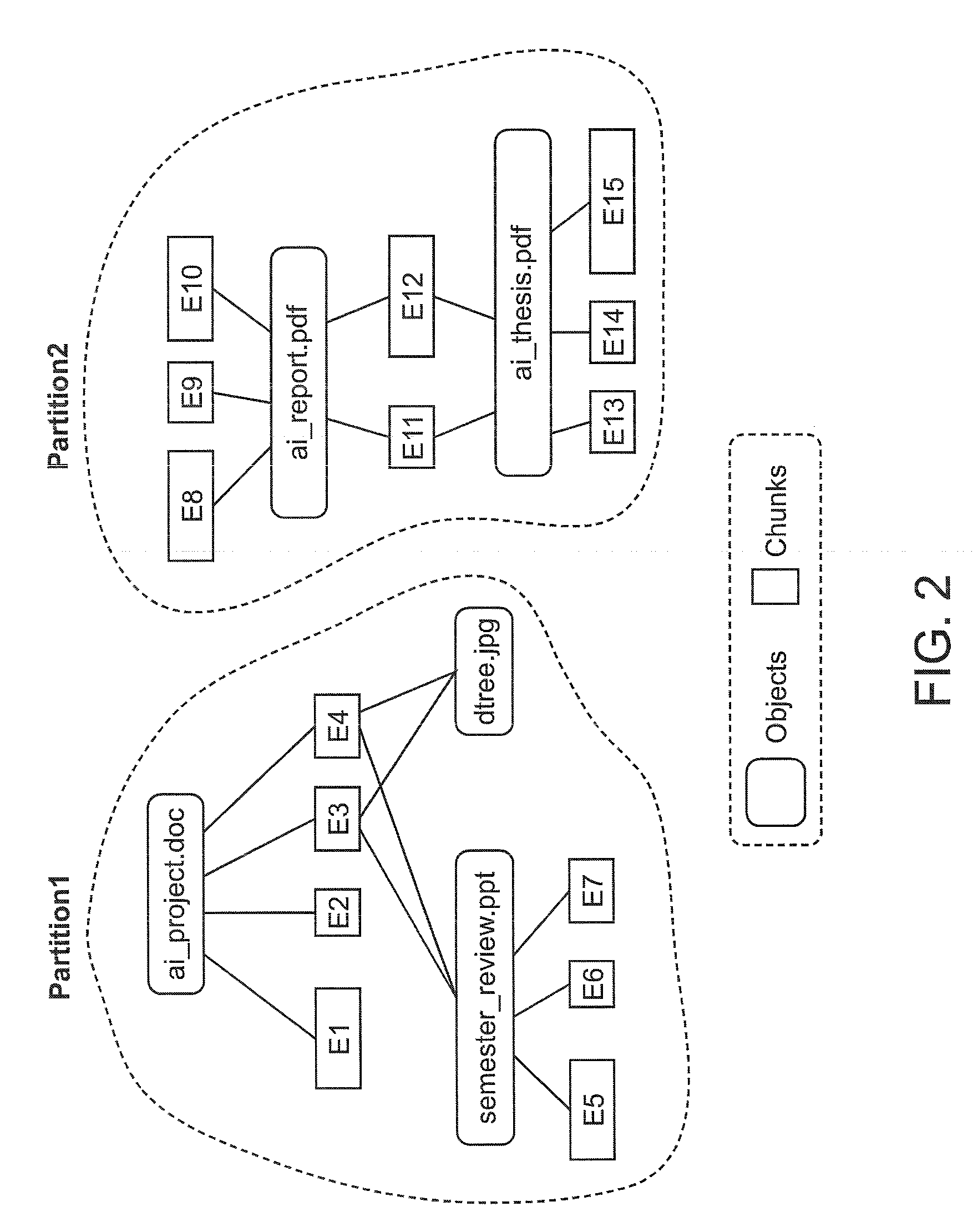
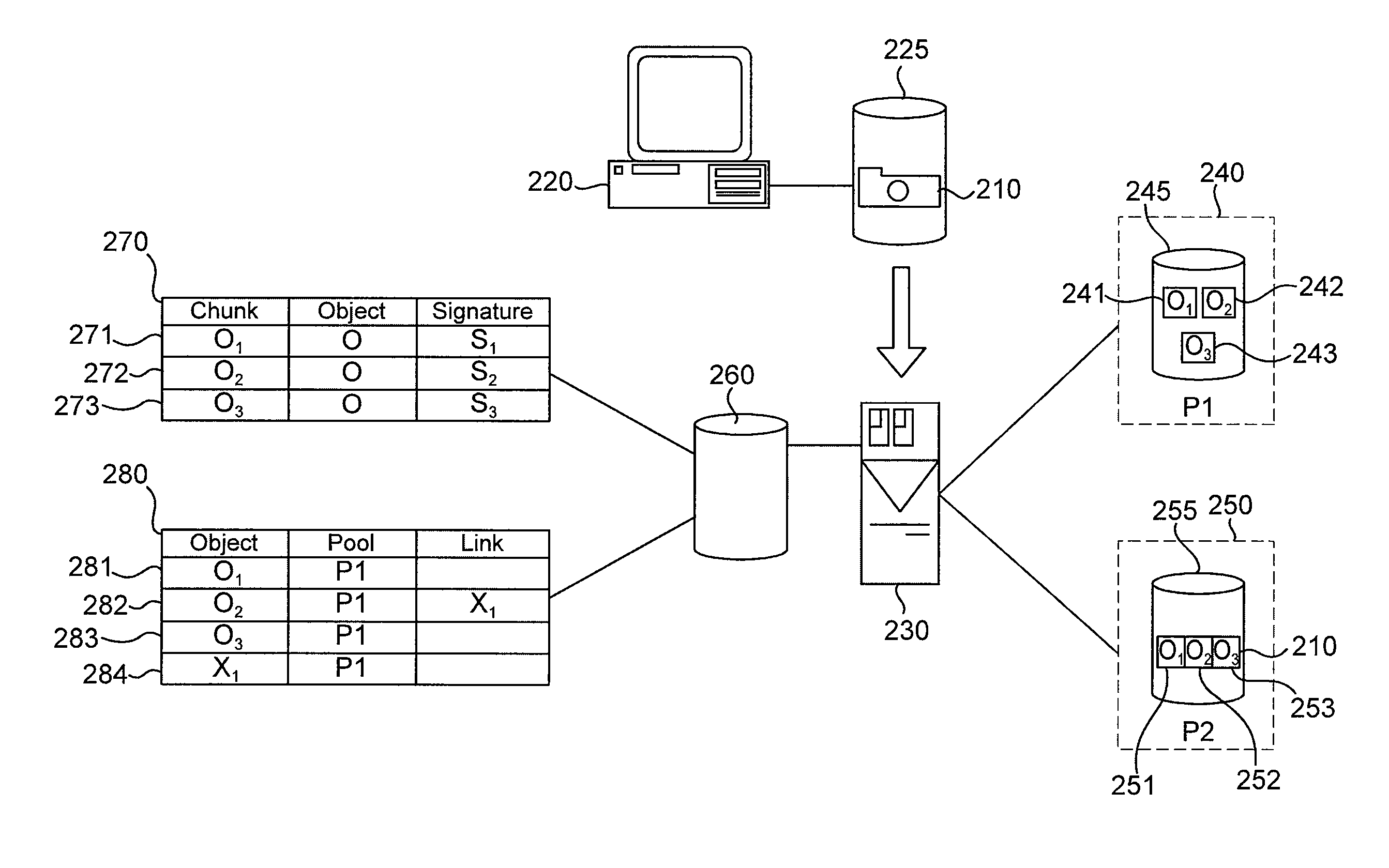
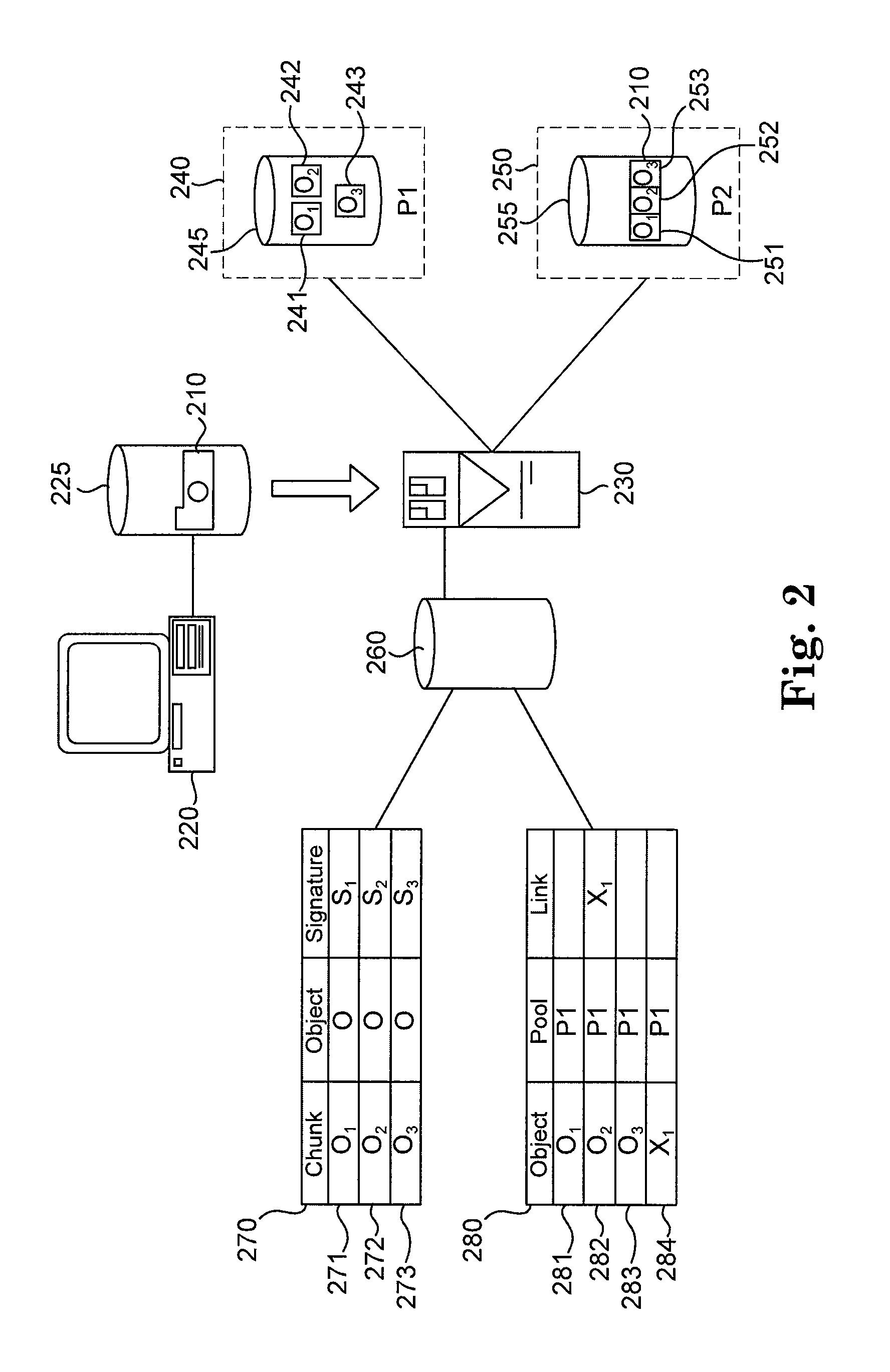
Storage system and a storage management system
InactiveUS20060047907A1Improve matchMemory loss protectionMultiple digital computer combinationsData packStorage management
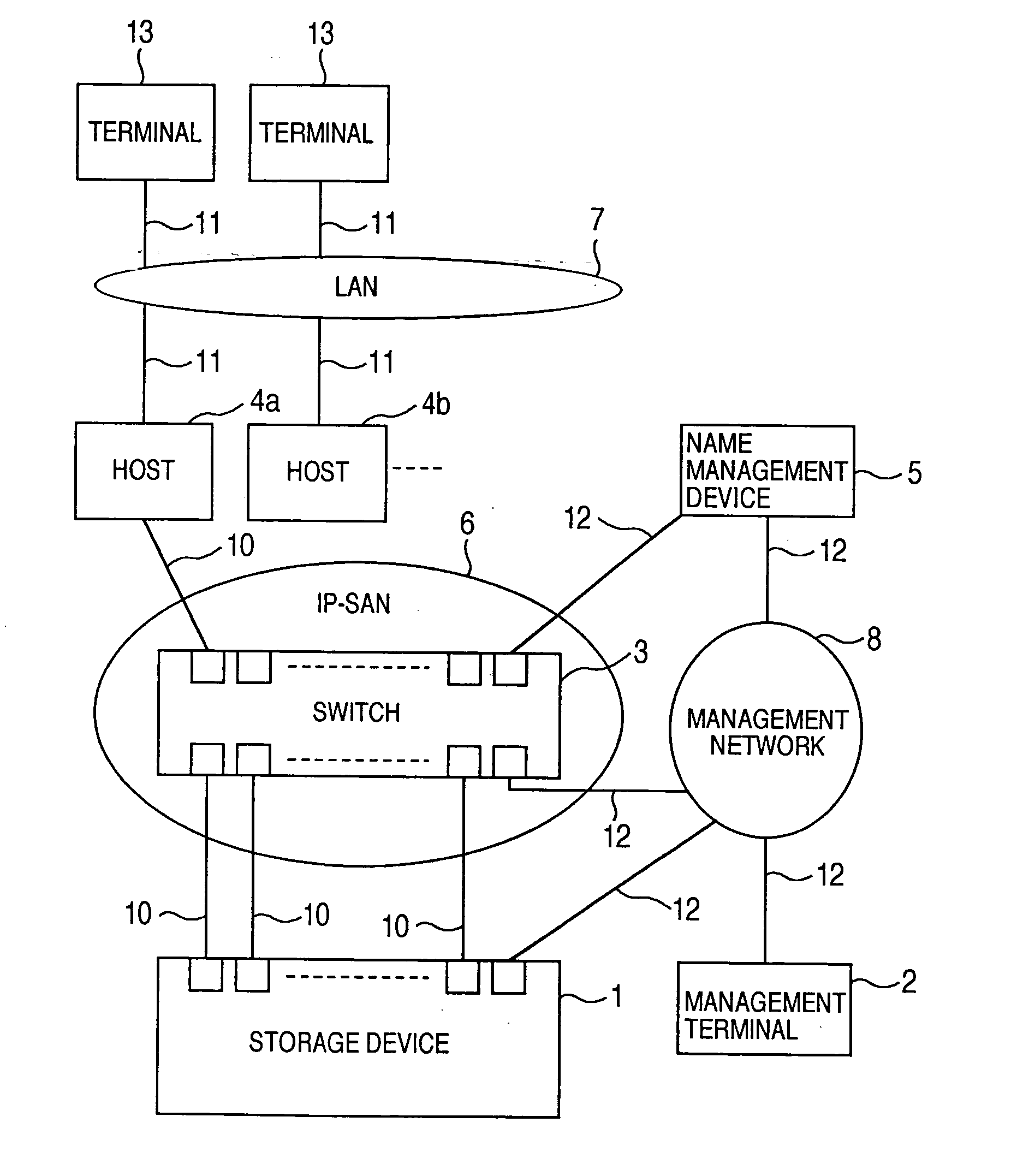
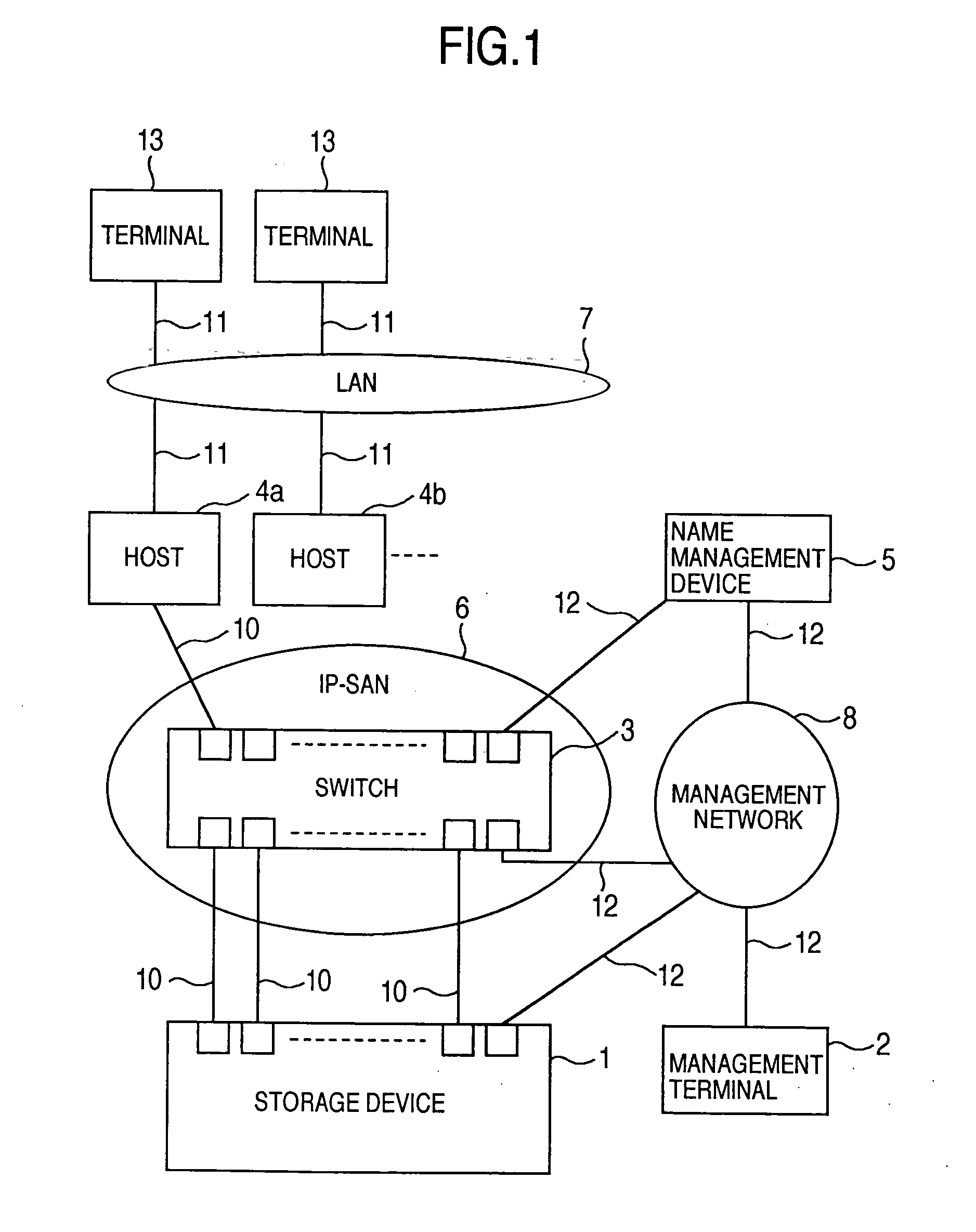
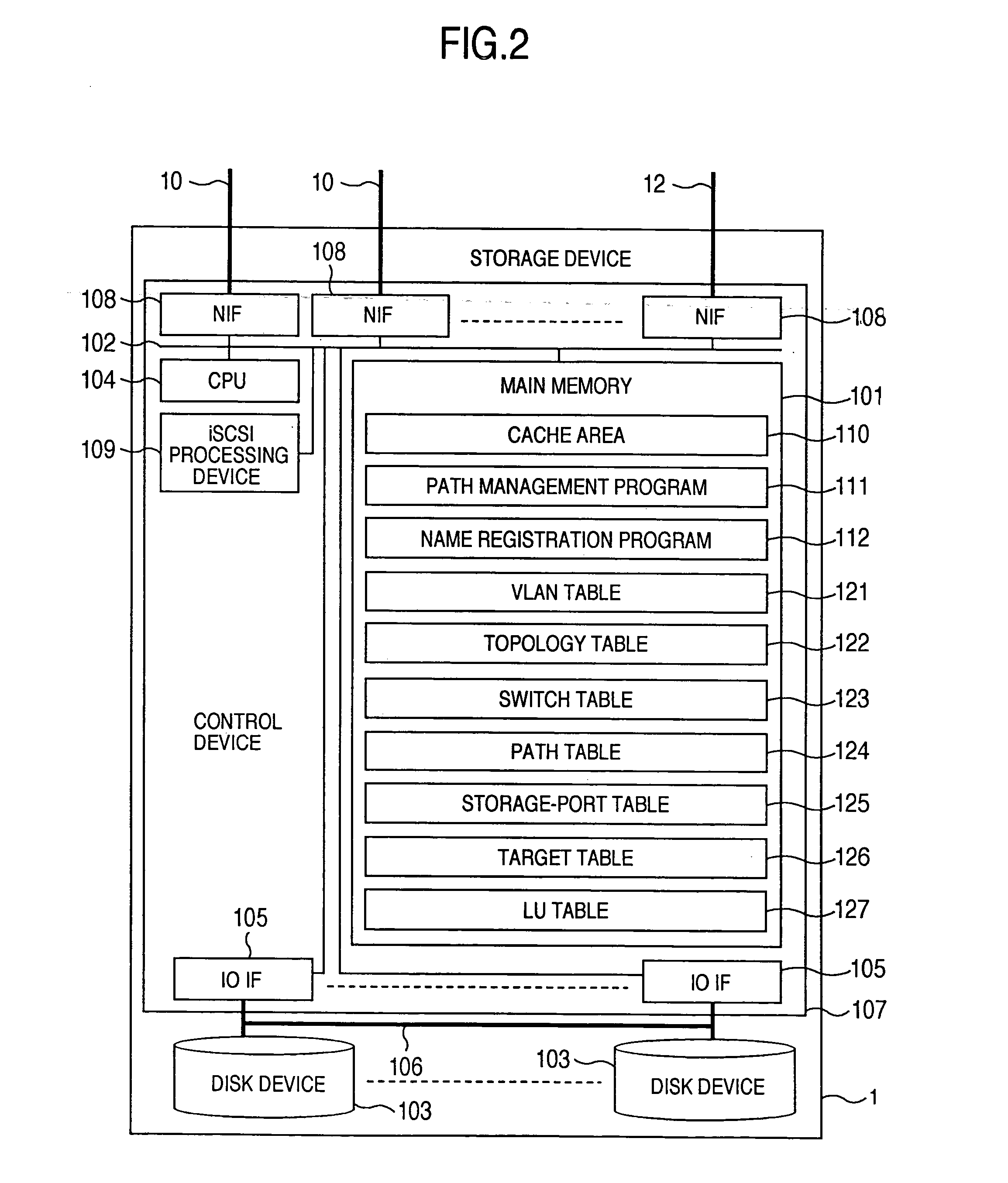
A storage device managing one or more logical volumes is connected with a name management device through an IP-SAN 6 composed of a switch. The storage device stores a topology table saving connecting relation among physical ports of host, physical ports of the storage device and physical ports of the switch, reads an identifier of the host and an identifier of the logical volume, selects a unused first physical port of the switch by referring to the topology table, selects a second physical port of the switch connected with the storage device, registers a group composed of the host and the logical volume with the name management device, and executes a configuration of allowing packets to be transferred between the first and the second physical ports with respect to the switch.
Owner:GOOGLE LLC
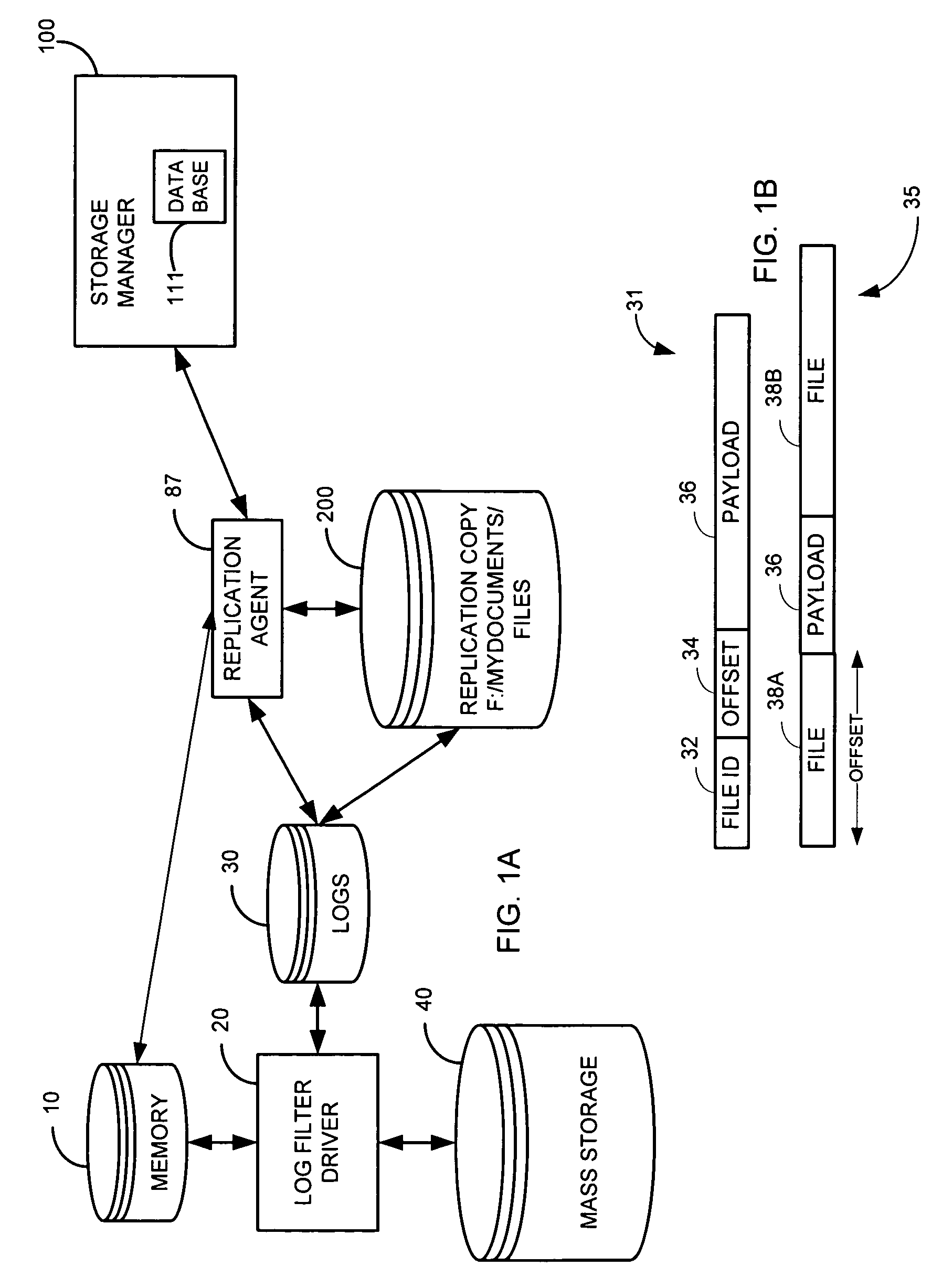
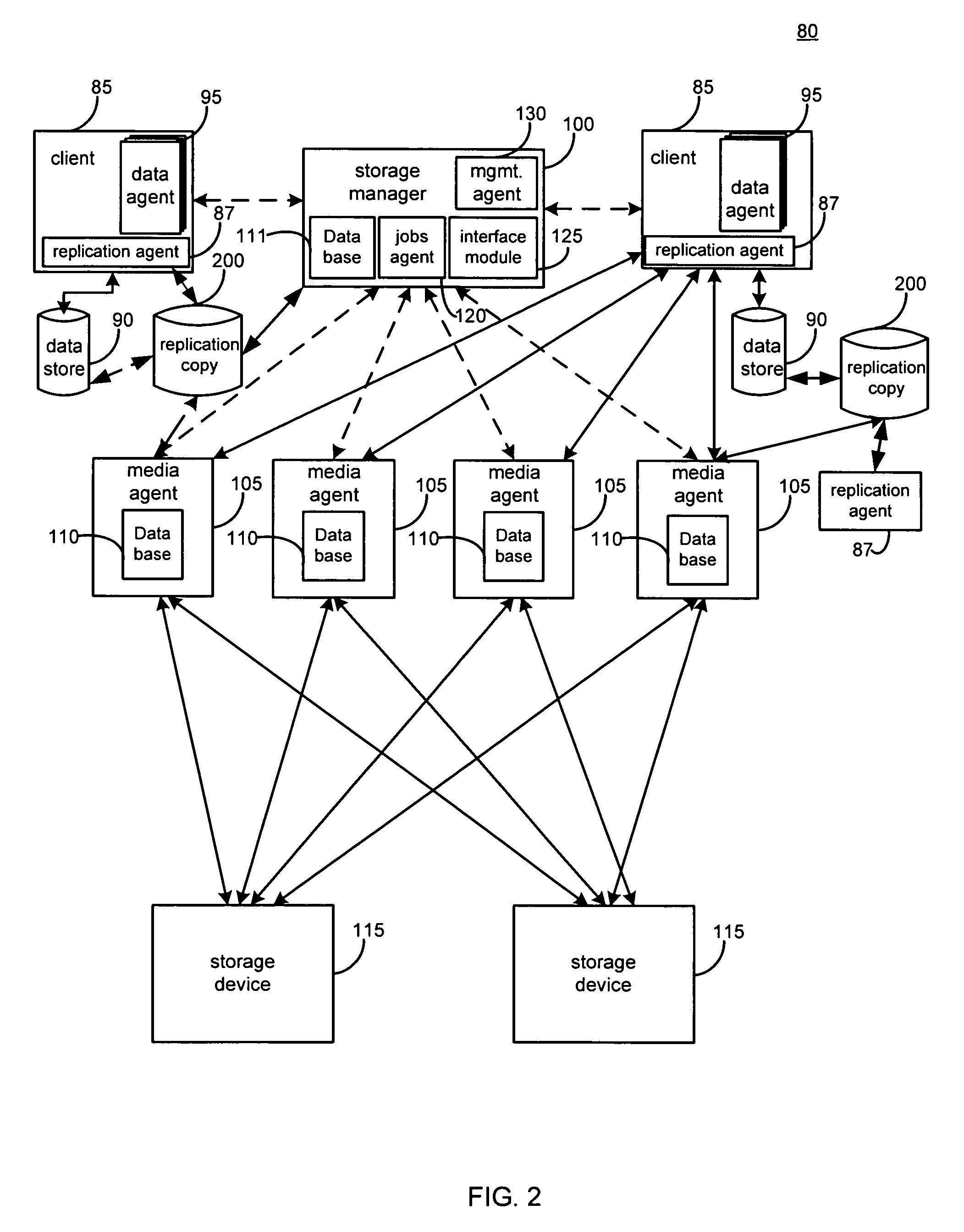
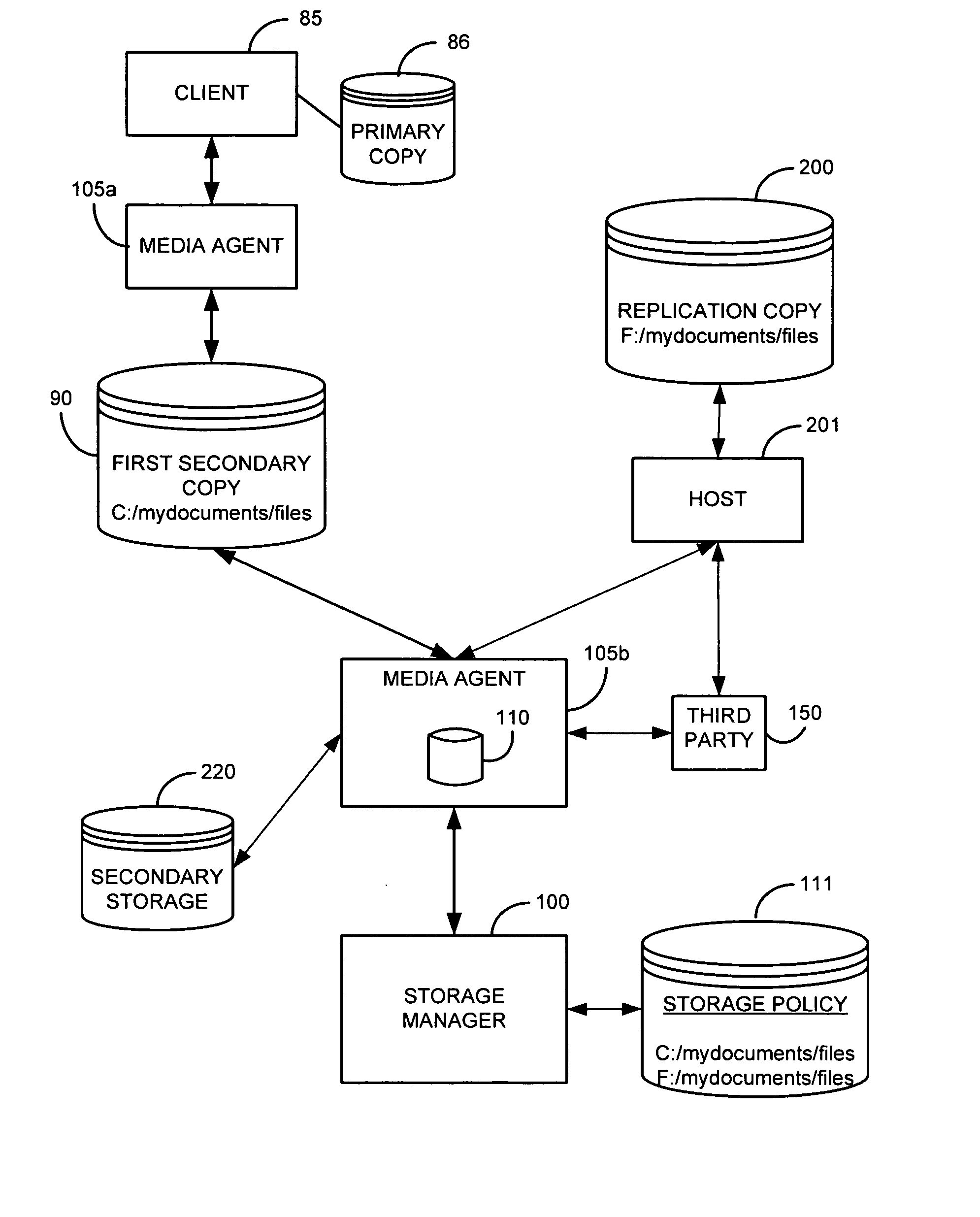
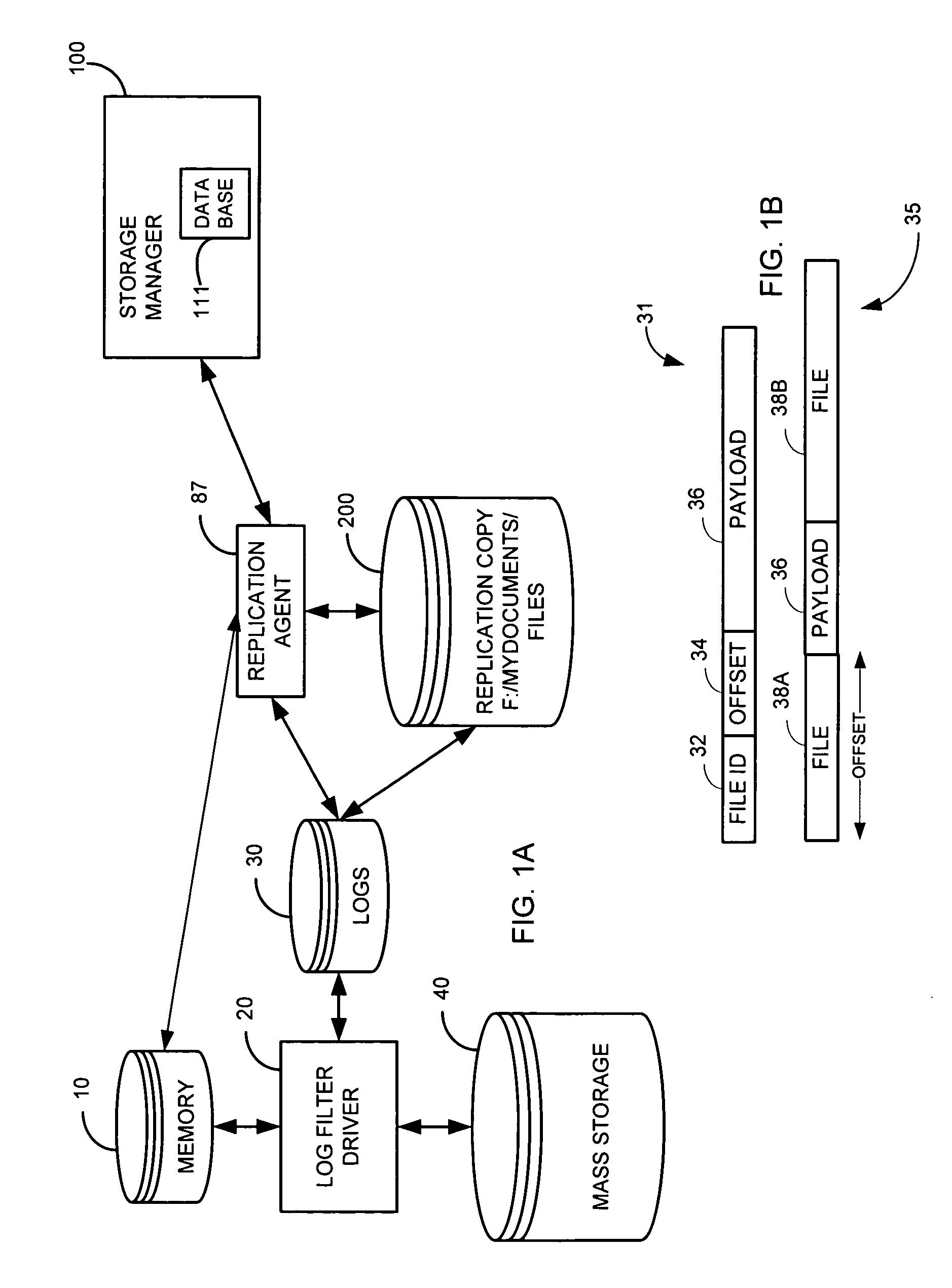
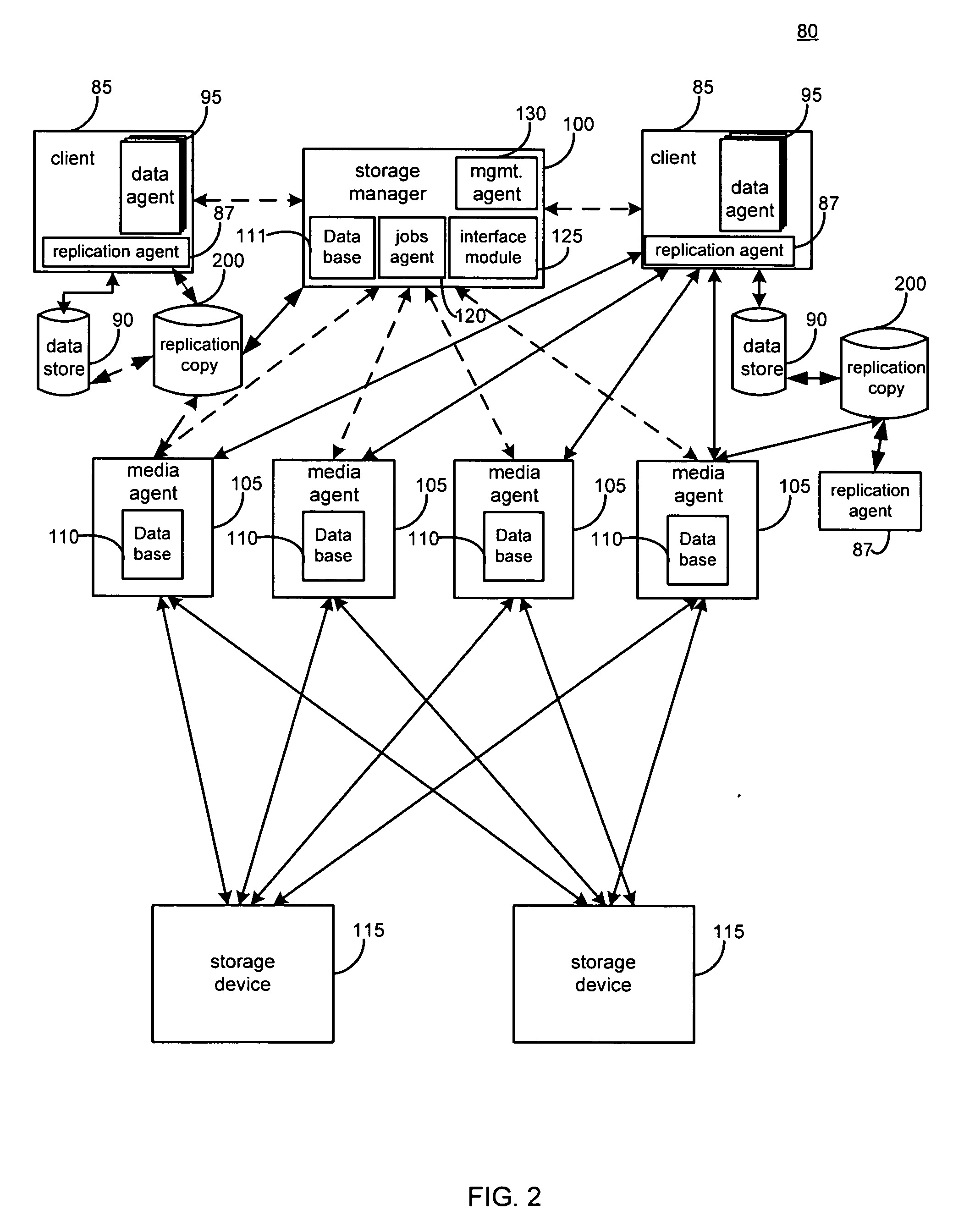
System and method for performing replication copy storage operations
InactiveUS7606844B2Data processing applicationsDatabase distribution/replicationThird partyEngineering
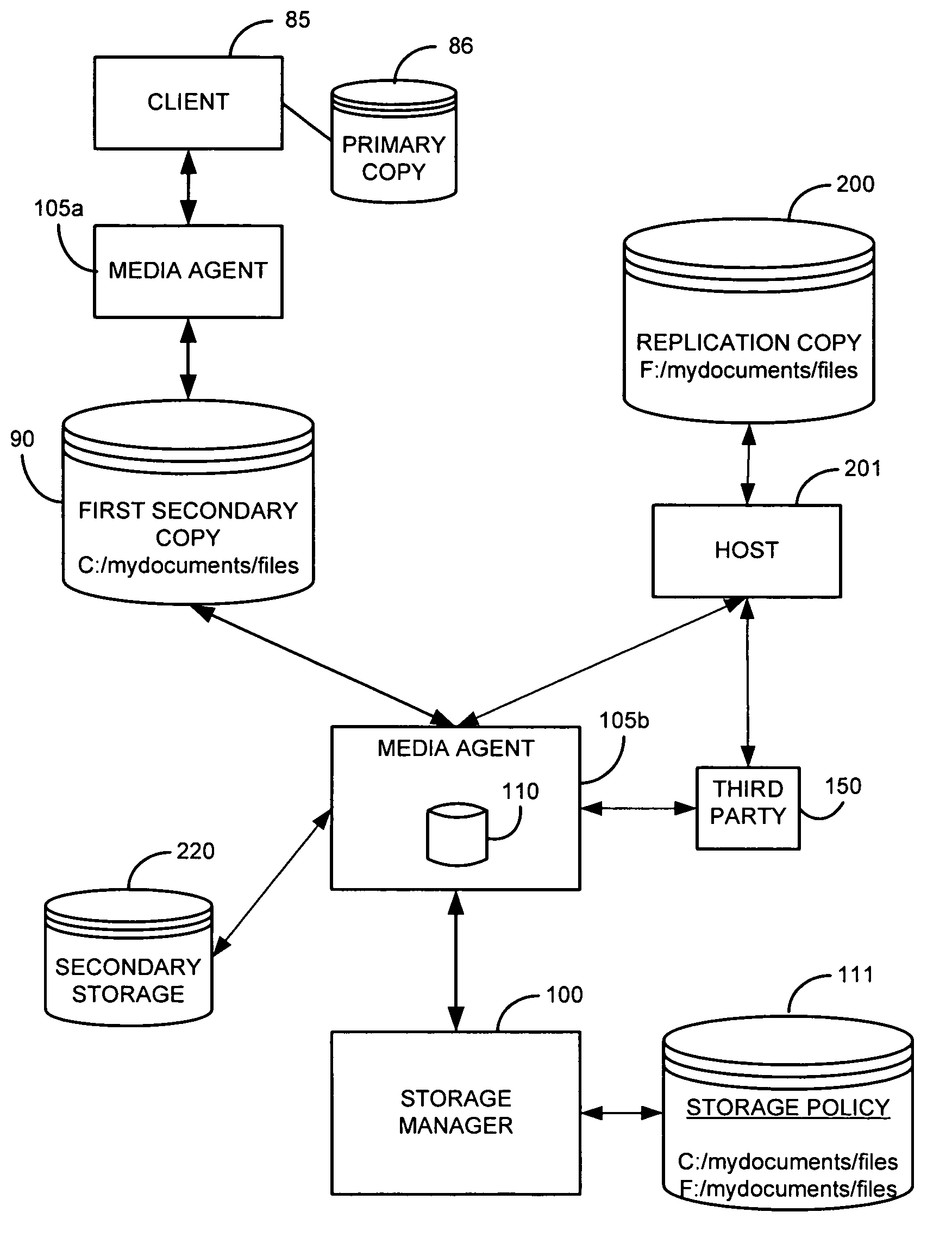
A system and method are provided for performing storage operations relating to a first secondary copy of electronic data. A storage policy or storage preferences may dictate that a replication copy should be used in storage operations performed to a particular client, sub-client, data, media or other item. Based on the storage policy, when a new client, sub-client, data, media or other item is received, a media agent determines whether there is a replication copy of the item. In the absence of a replication copy, one may be created. The replication copy may be provided by a third party application, or created by the client or a storage management system component. Information regarding the replication copy and its corresponding first secondary copy may be stored in a database. To optimize use of system resources, storage operations relating to the first secondary copy may be performed using the replication copy instead of the first secondary copy.
Owner:COMMVAULT SYST INC
Method and system for using multi-function cards for storing, managing and aggregating reward points
InactiveUS20050021400A1Decreasing (if not eliminating) reliance on a central server systemDiscounts/incentivesFinanceCredit cardMultimedia
A system and method for operating a reward points accumulation and redemption program wherein a user earns reward points from a plurality of independent reward points issuing entities, with each tracking the user's earned reward points in a user reward point account stored on a multi-function card (such as a frequent flyer account or a credit card loyalty account). The multi-function card is adapted to aggregate some or all of the user's earned reward points from the reward accounts and credit the aggregated points into a single reward exchange account on the multi-function card. The user may then select an item for purchase with the accumulated reward points from the multi-function card. The item is provided to the user in exchange for a subset or all of the reward points from the multi-function card.
Owner:SIGNATURE SYST
Page based management of flash storage
InactiveUS20110055458A1Memory architecture accessing/allocationMemory adressing/allocation/relocationControl signalPaging
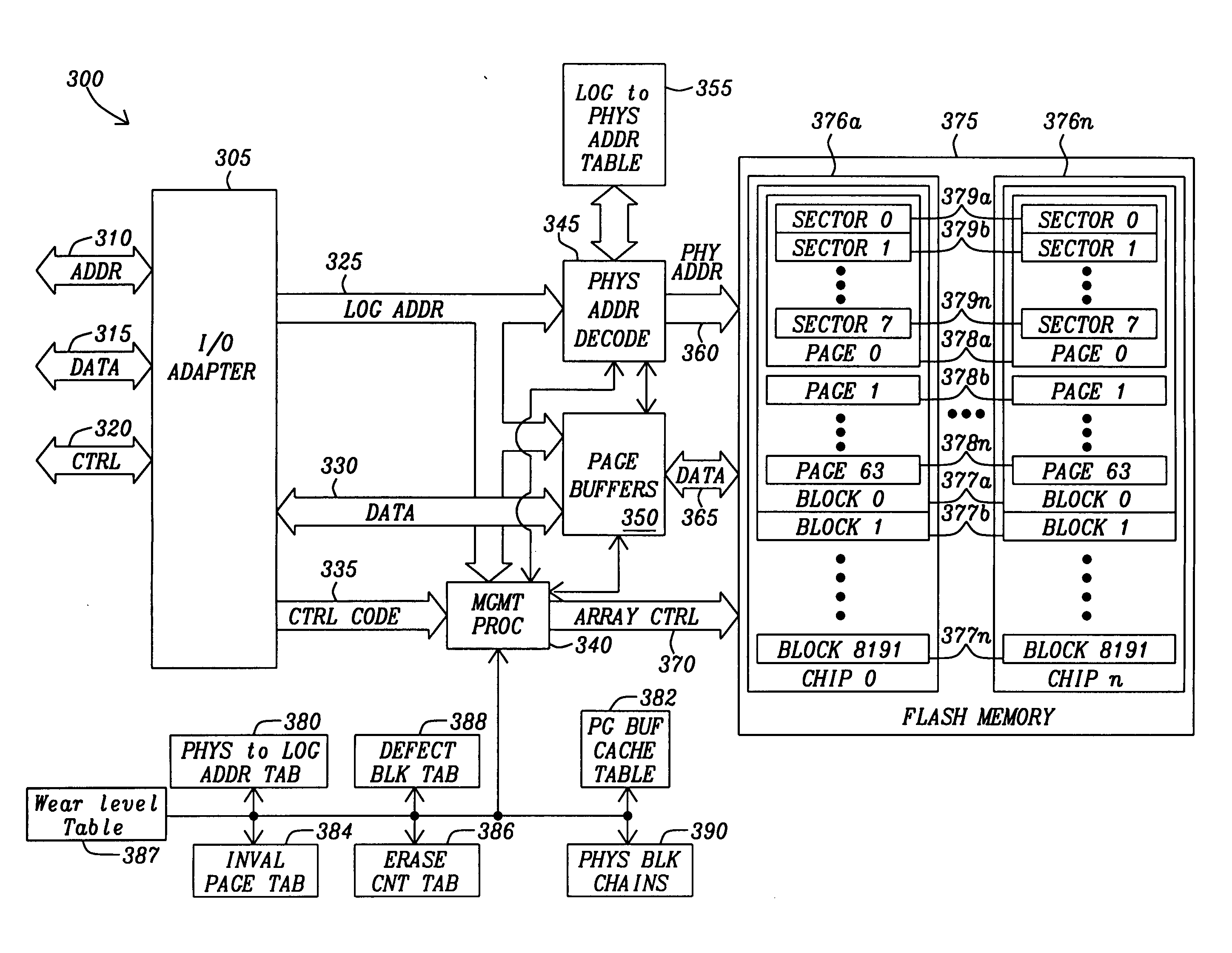
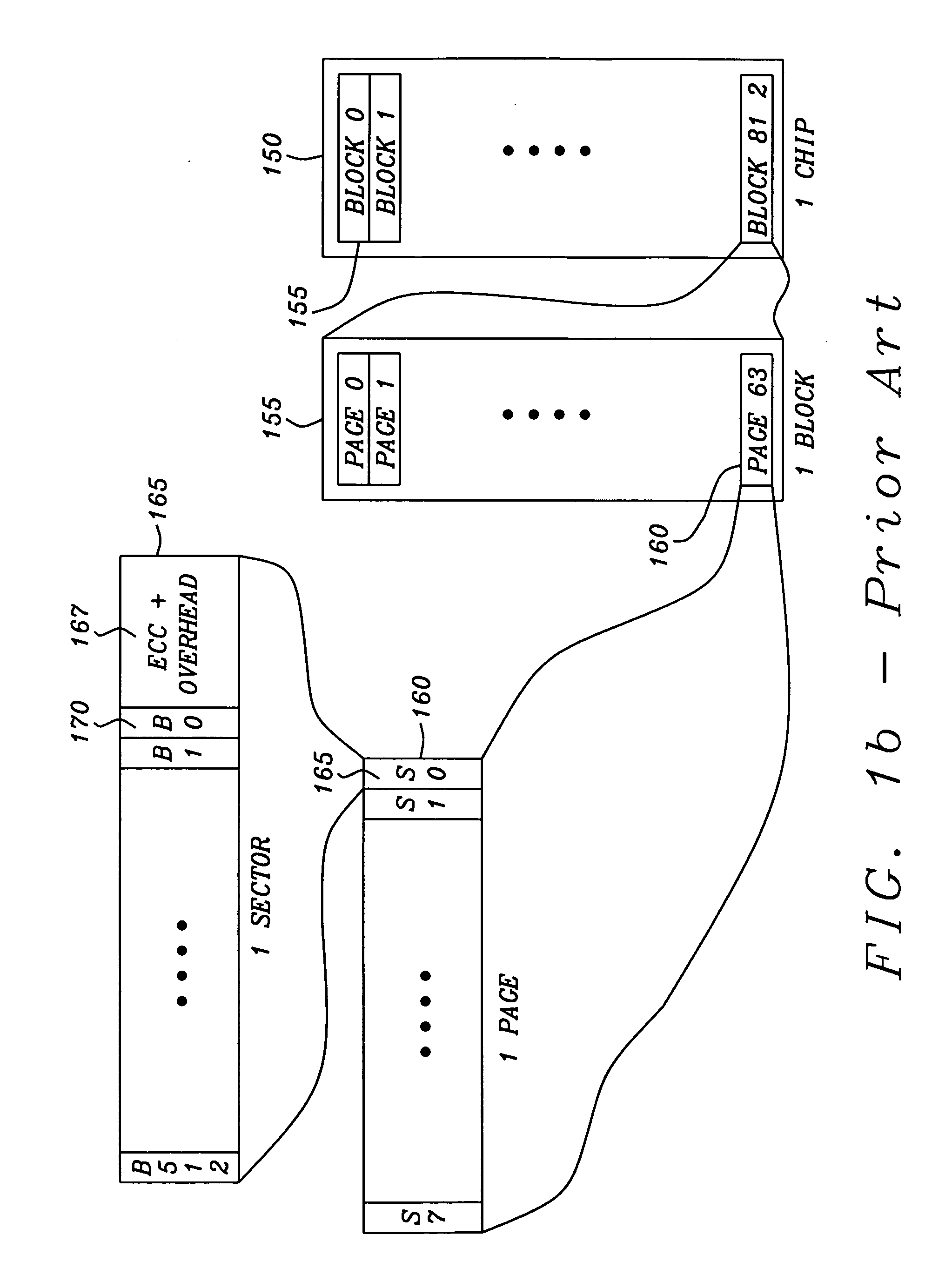
Methods and circuits for page based management of an array of Flash RAM nonvolatile memory devices provide paged base reading and writing and block erasure of a flash storage system. The memory management system includes a management processor, a page buffer, and a logical-to-physical translation table. The management processor is in communication with an array of nonvolatile memory devices within the flash storage system to provide control signals for the programming of selected pages, erasing selected blocks, and reading selected pages of the array of nonvolatile memory devices.
Owner:PIONEER CHIP TECH
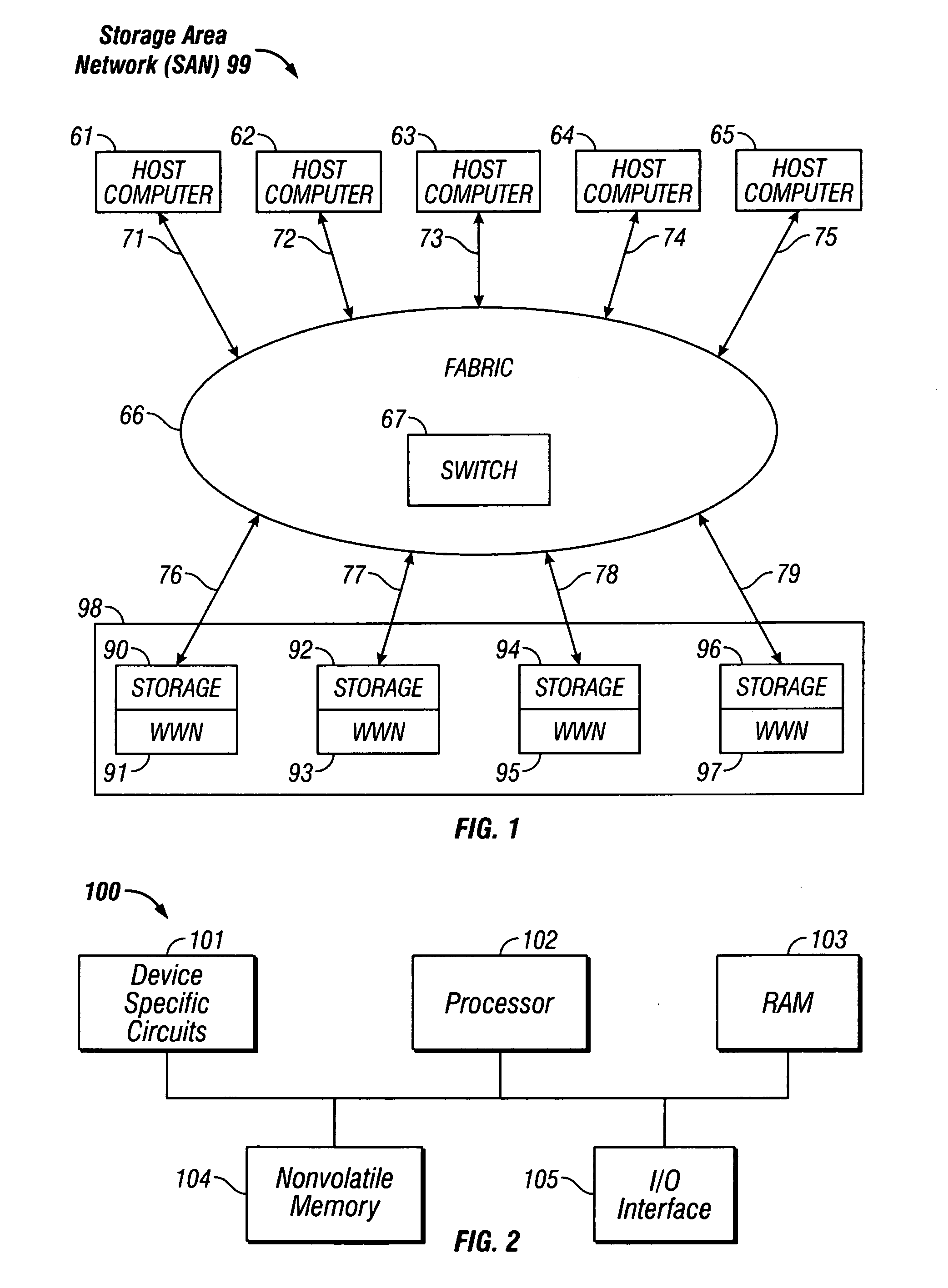
Switching system method for discovering and accessing SCSI devices in response to query
InactiveUS7089293B2Simple processRobust systemSpecial service provision for substationMultiplex system selection arrangementsStorage managementComputer engineering
Owner:ORACLE INT CORP
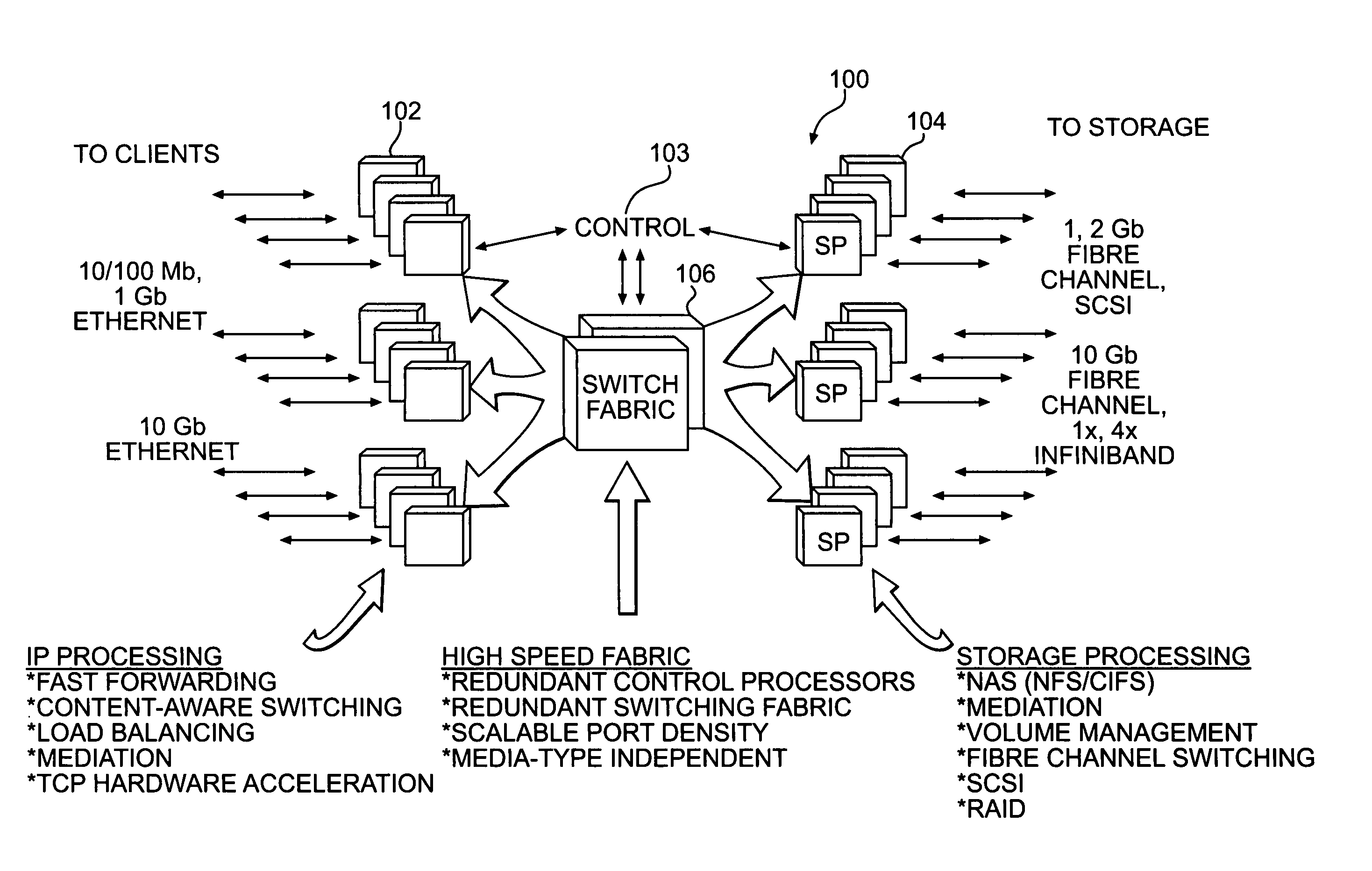
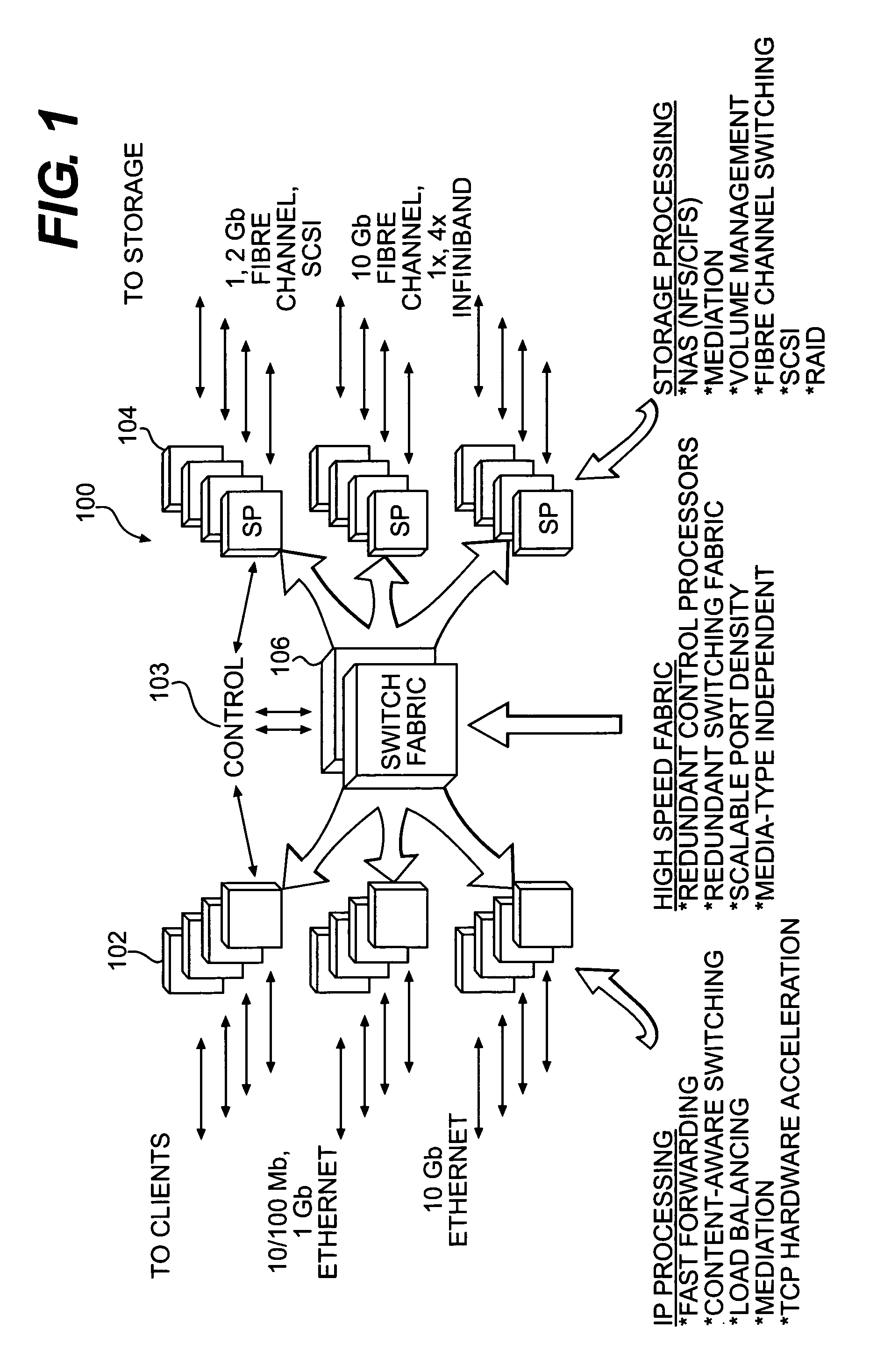
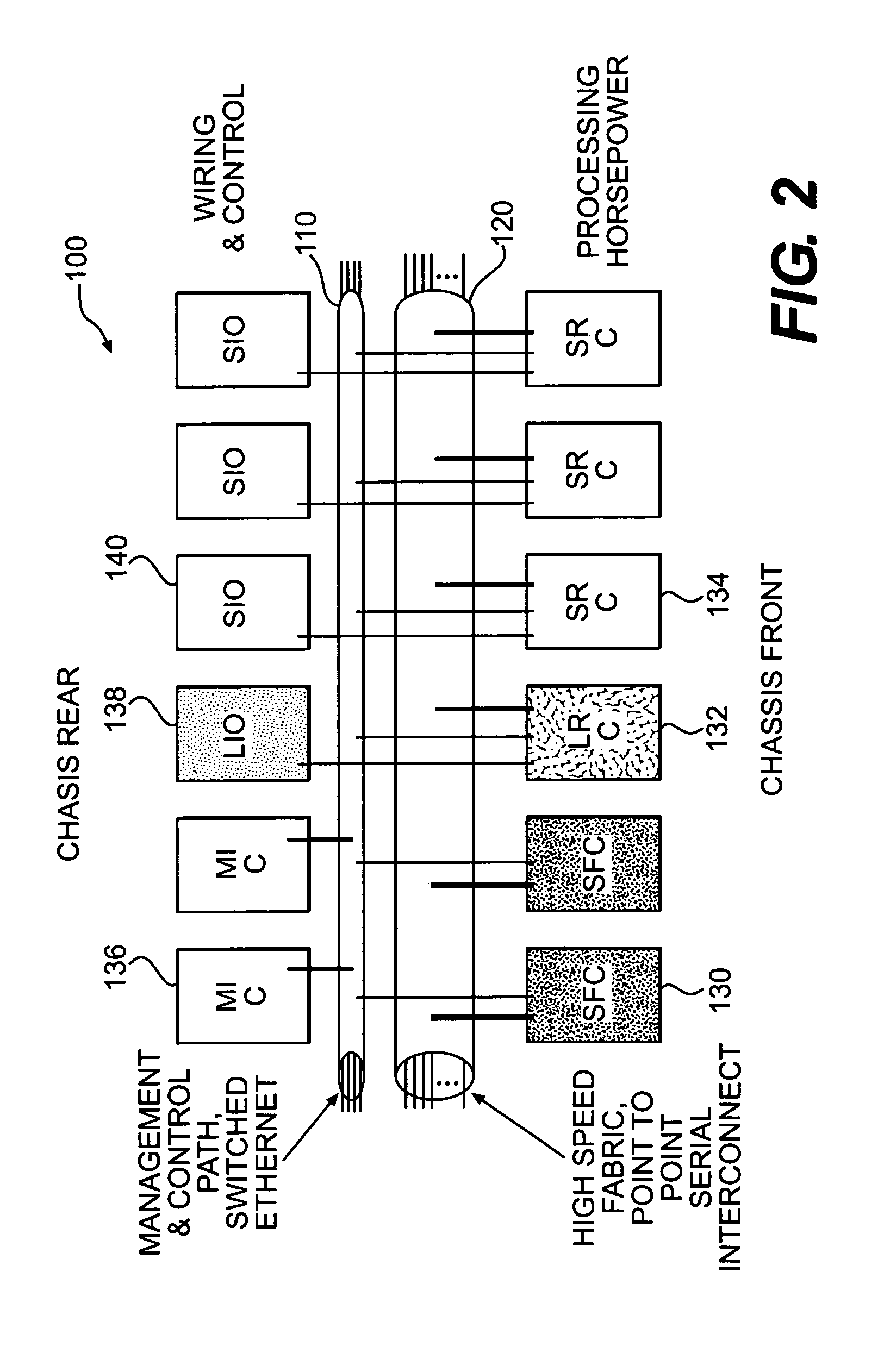
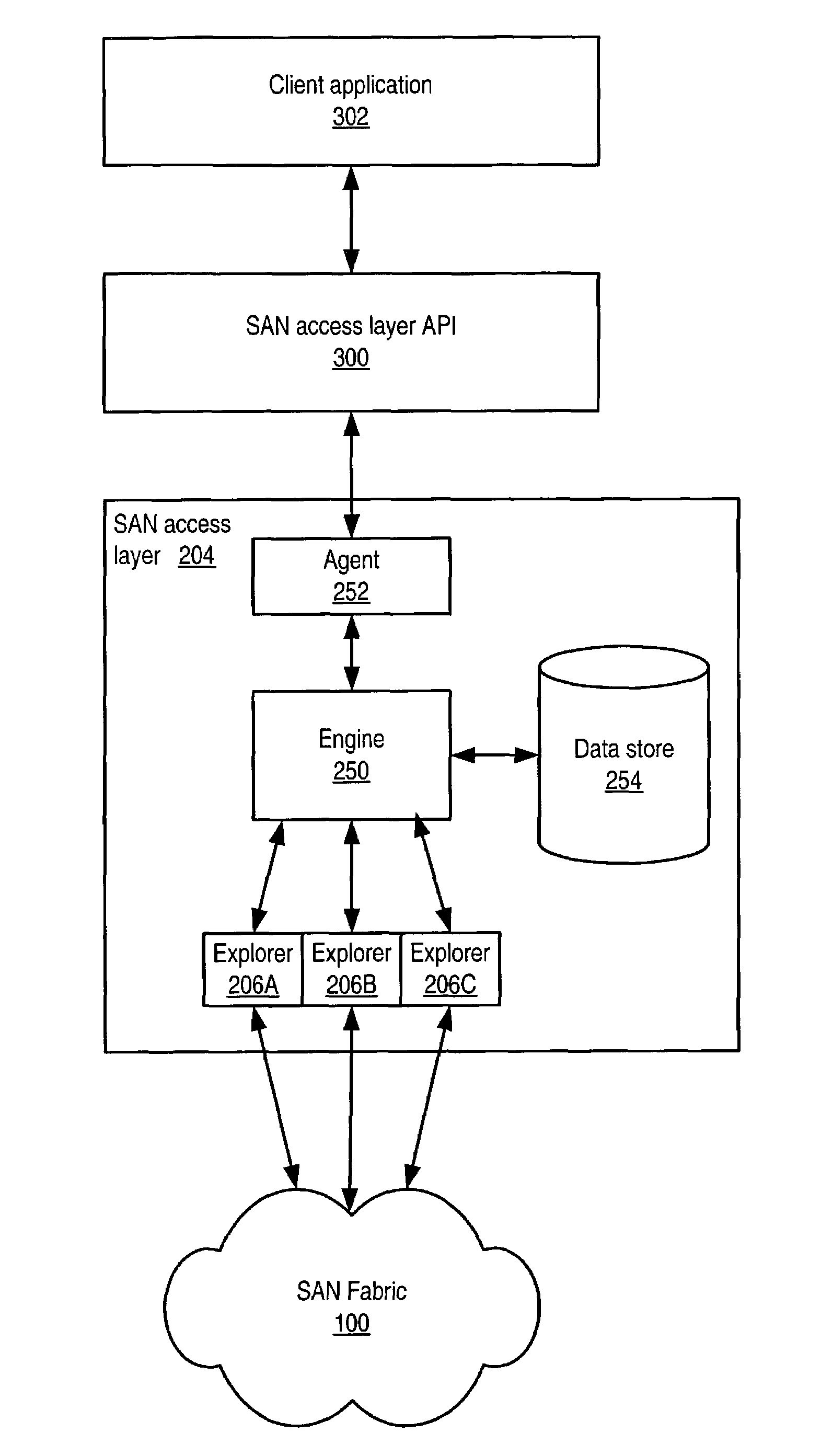
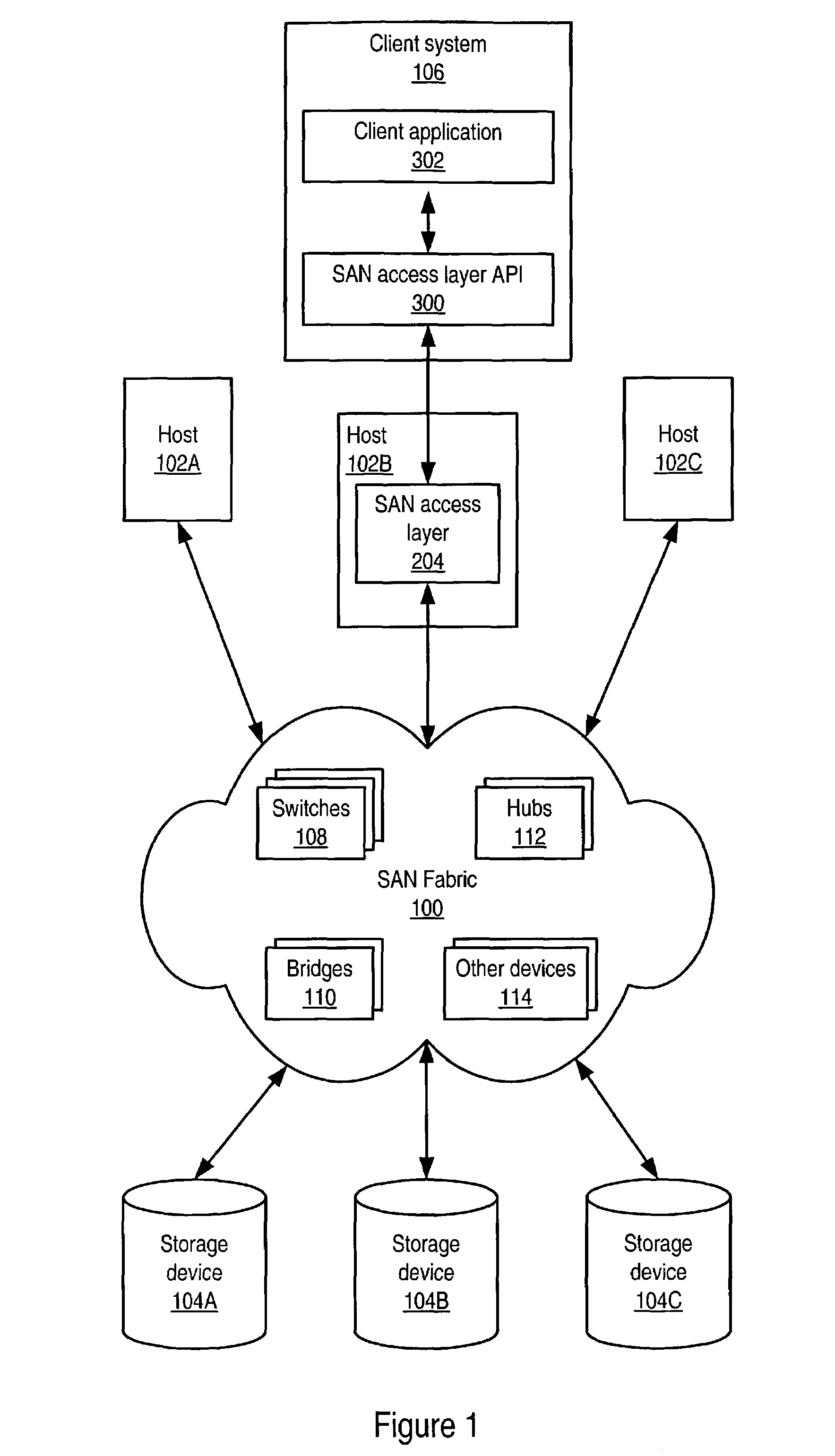
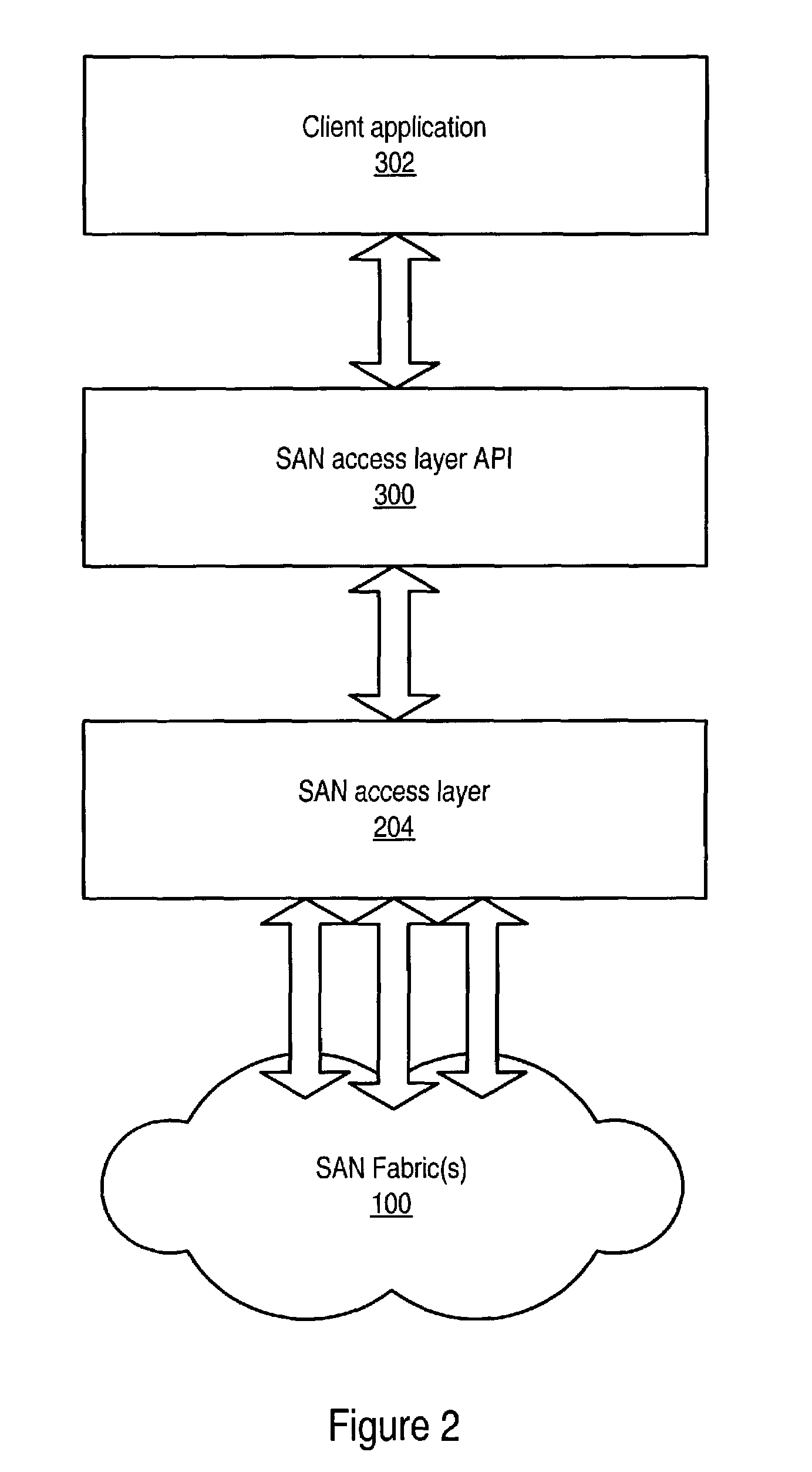
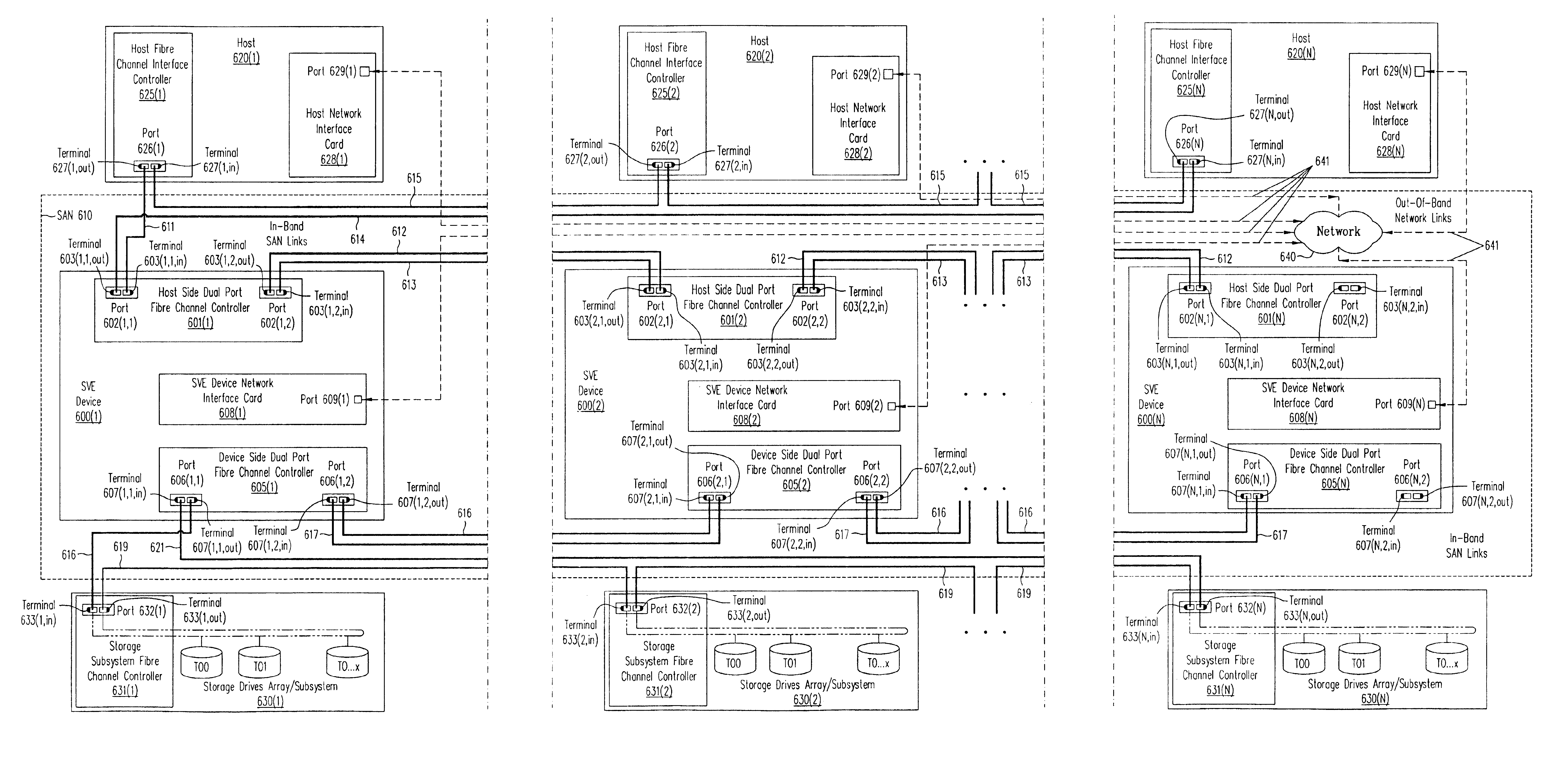
System and method for an access layer application programming interface for managing heterogeneous components of a storage area network
ActiveUS7401338B1Easy programmingDigital data processing detailsUser identity/authority verificationStorage area networkApplication programming interface
Embodiments of an application programming interface (API) for a Storage Area Network (SAN) access layer. A SAN may include a SAN access layer as an interface between SAN components and client applications. A SAN access layer API may be provided which enables a client application to access SAN access layer functionality such as storage management and configuration services. Through the SAN access layer API, a client application may invoke some or all of the functionalities of the SAN access layer. The SAN access layer may provide SAN information gathered from the SAN to the client application through the SAN access layer API. Embodiments of the SAN access layer API may provide security and licensing restrictions to client applications. Embodiments of the SAN access layer API may encapsulate message conversion and network transport functions so that client application developers are not required to implement these functions.
Owner:SYMANTEC OPERATING CORP
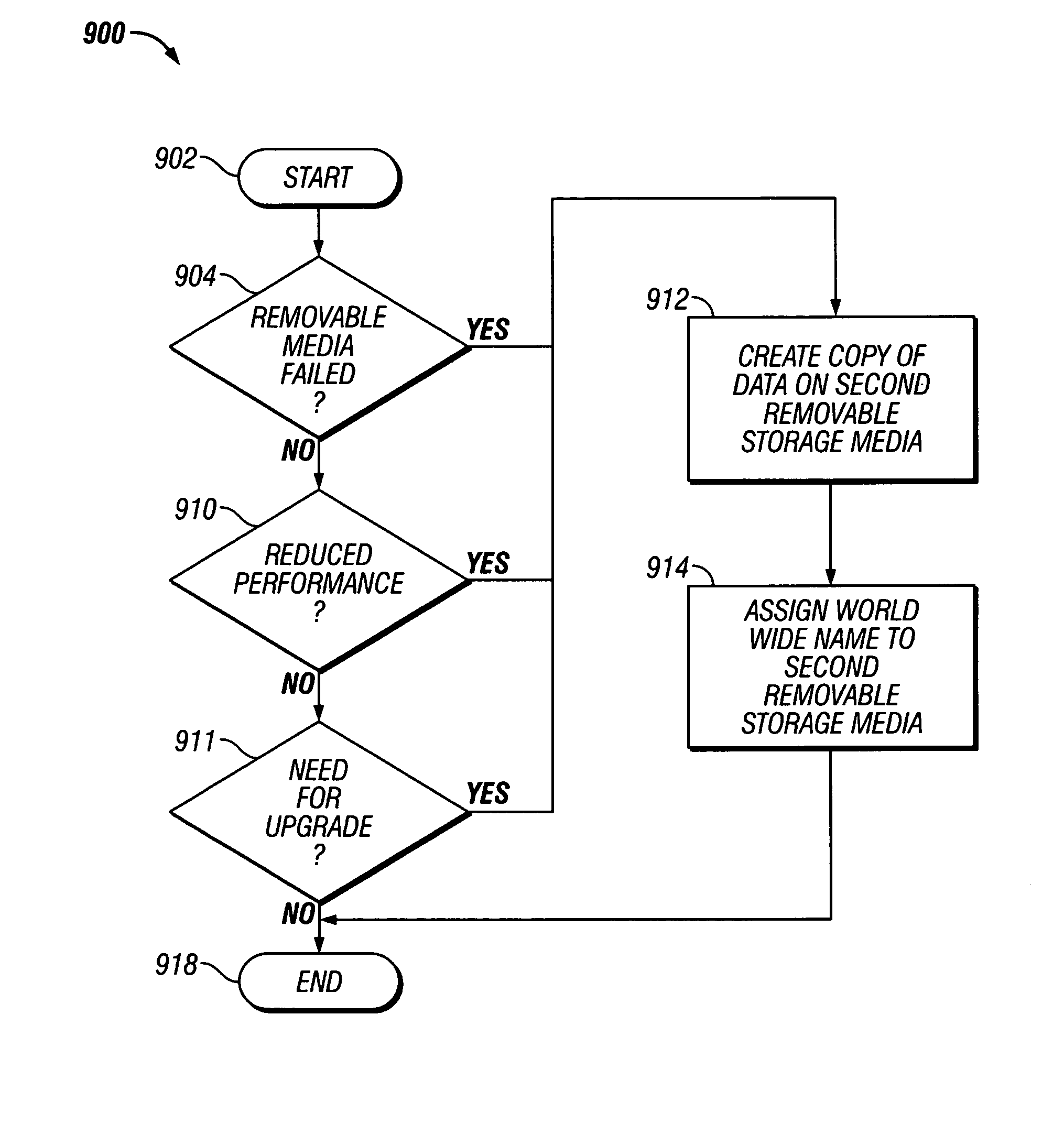
Persistent worldwide names assigned to removable media storage
InactiveUS20050188246A1Enhances storage area network (SAN) storage managementEasy storage managementMemory loss protectionError detection/correctionRemovable mediaStorage management
Disclosed are a system, a method, and article of manufacture to provide for managing removable storage media that is identified by a persistent worldwide name. SAN storage management is enhanced by preserving the persistent worldwide names assigned to removable storage media when it is necessary to replace the removable storage media. Exemplary embodiments include determining that a first removable storage media identified by a persistent worldwide name needs to be replaced, creating a copy of the data from the first removable storage media and assigning the persistent worldwide name to the second removable storage media.
Owner:IBM CORP
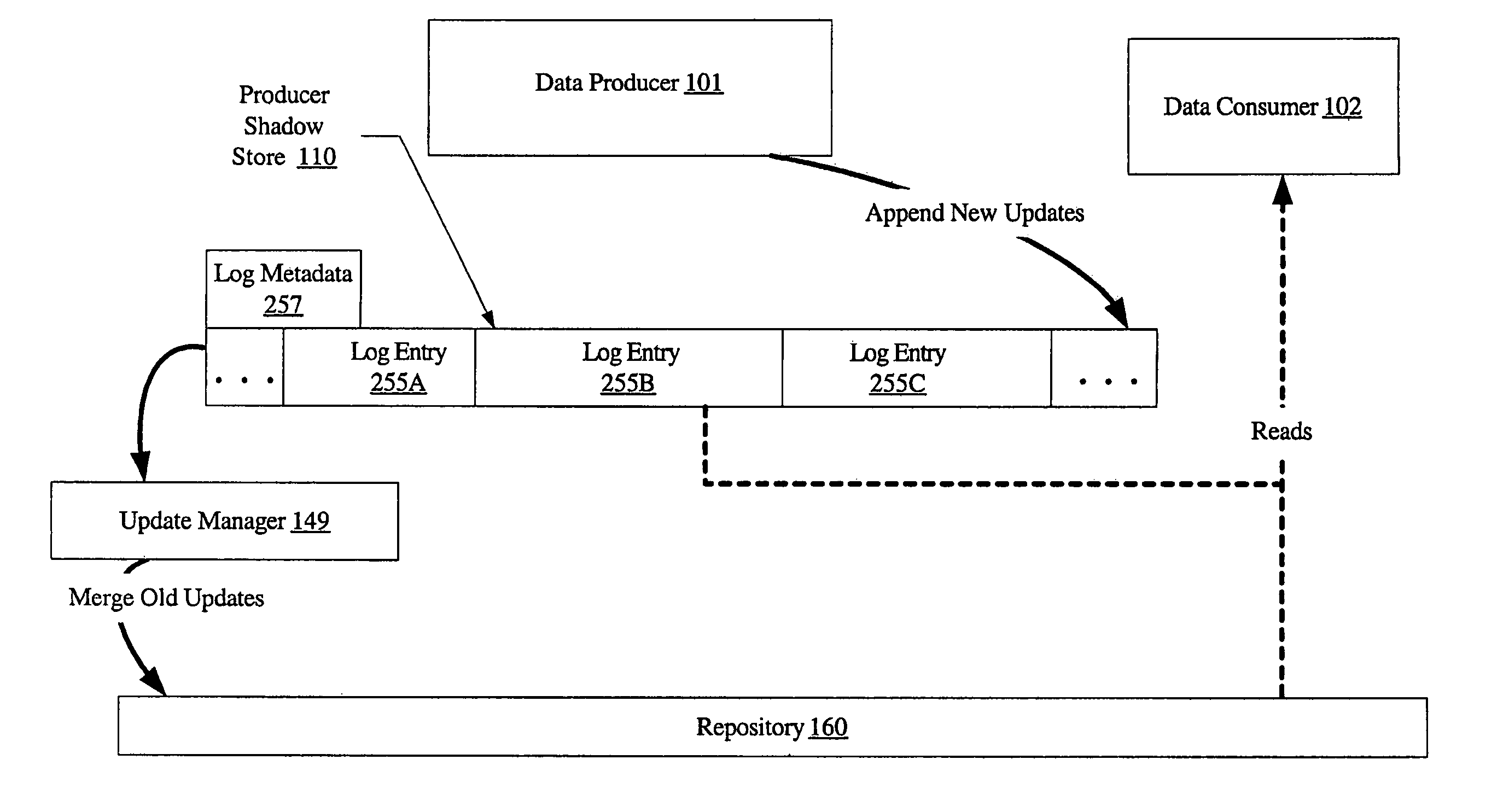
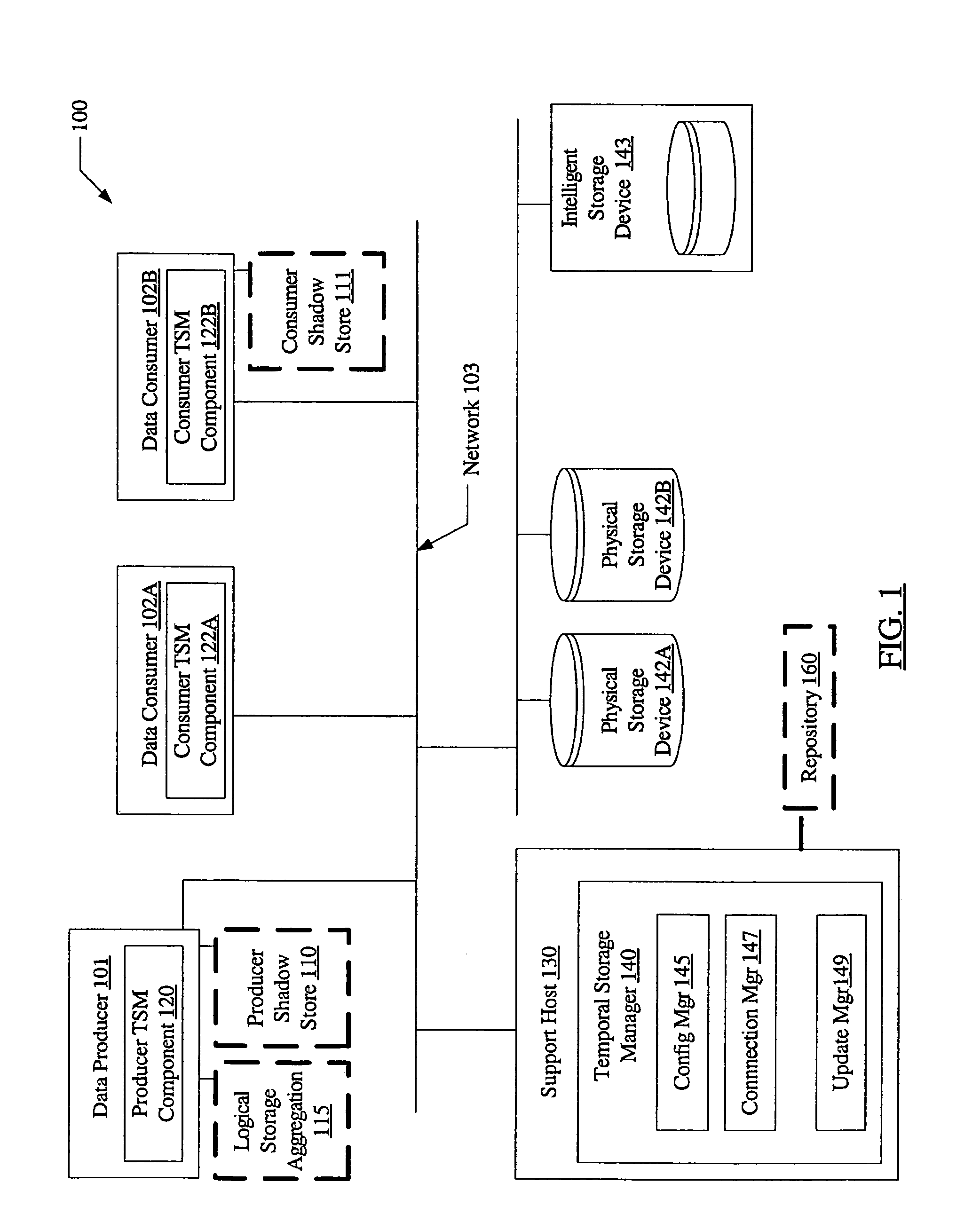
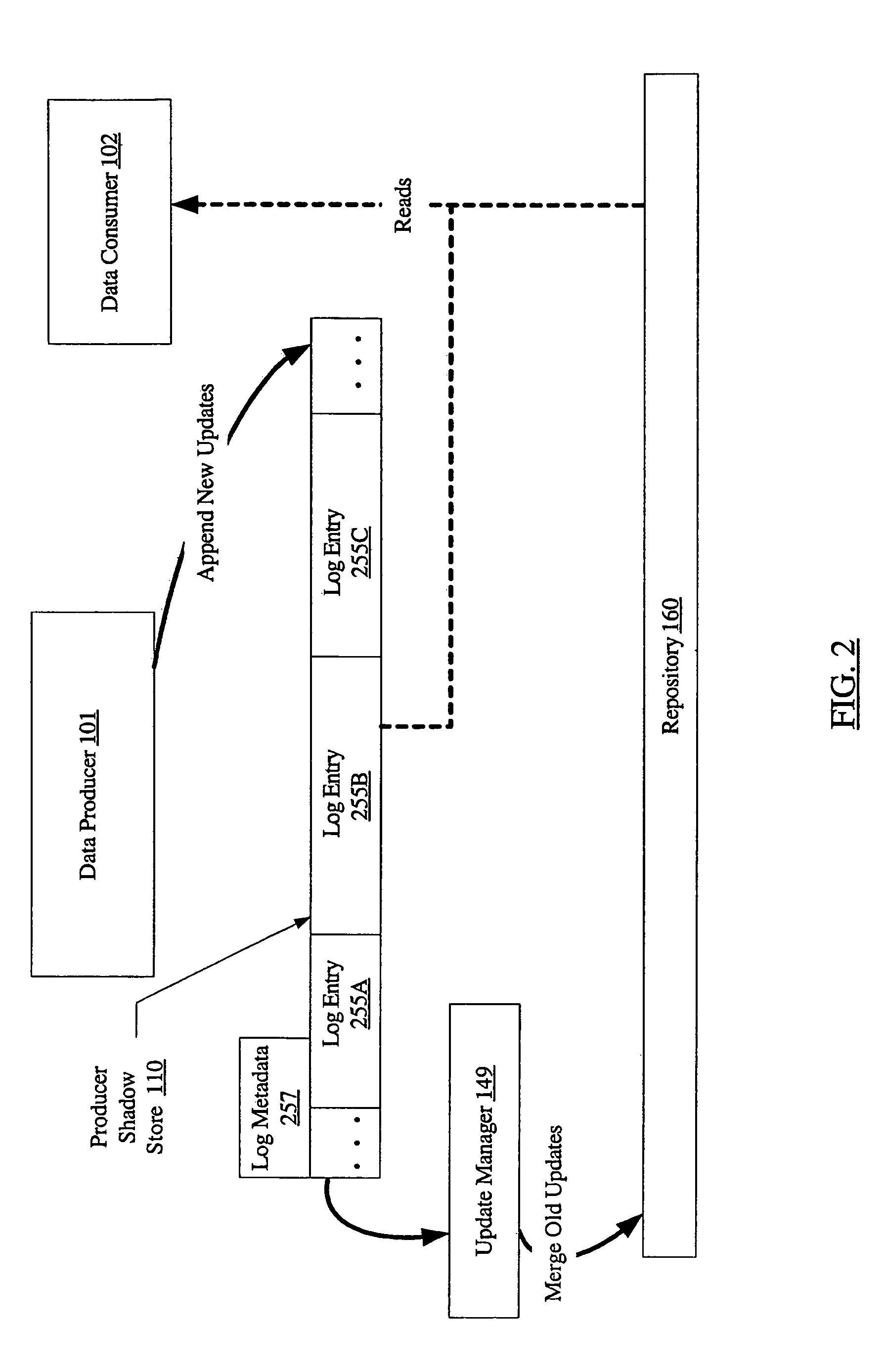
System and method for loosely coupled temporal storage management
ActiveUS7257689B1Prevent corruptionHigh degreeData processing applicationsDigital data information retrievalStorage managementDatabase
A system for loosely coupled temporal storage management includes a logical storage aggregation including a plurality of data blocks, a data producer, one or more data consumers, and a temporal storage manager. The temporal storage manager may be configured to maintain a producer shadow store including entries stored in a log-structured logical volume, where each entry is indicative of one or more data blocks of the logical storage aggregation that have been modified by the data producer. The temporal storage manager may also be configured to maintain a repository containing a baseline version of the logical storage aggregation, and to provide the data consumers with read-only access to the producer shadow store and the repository.
Owner:SYMANTEC OPERATING CORP
Method and apparatus for efficient scalable storage management
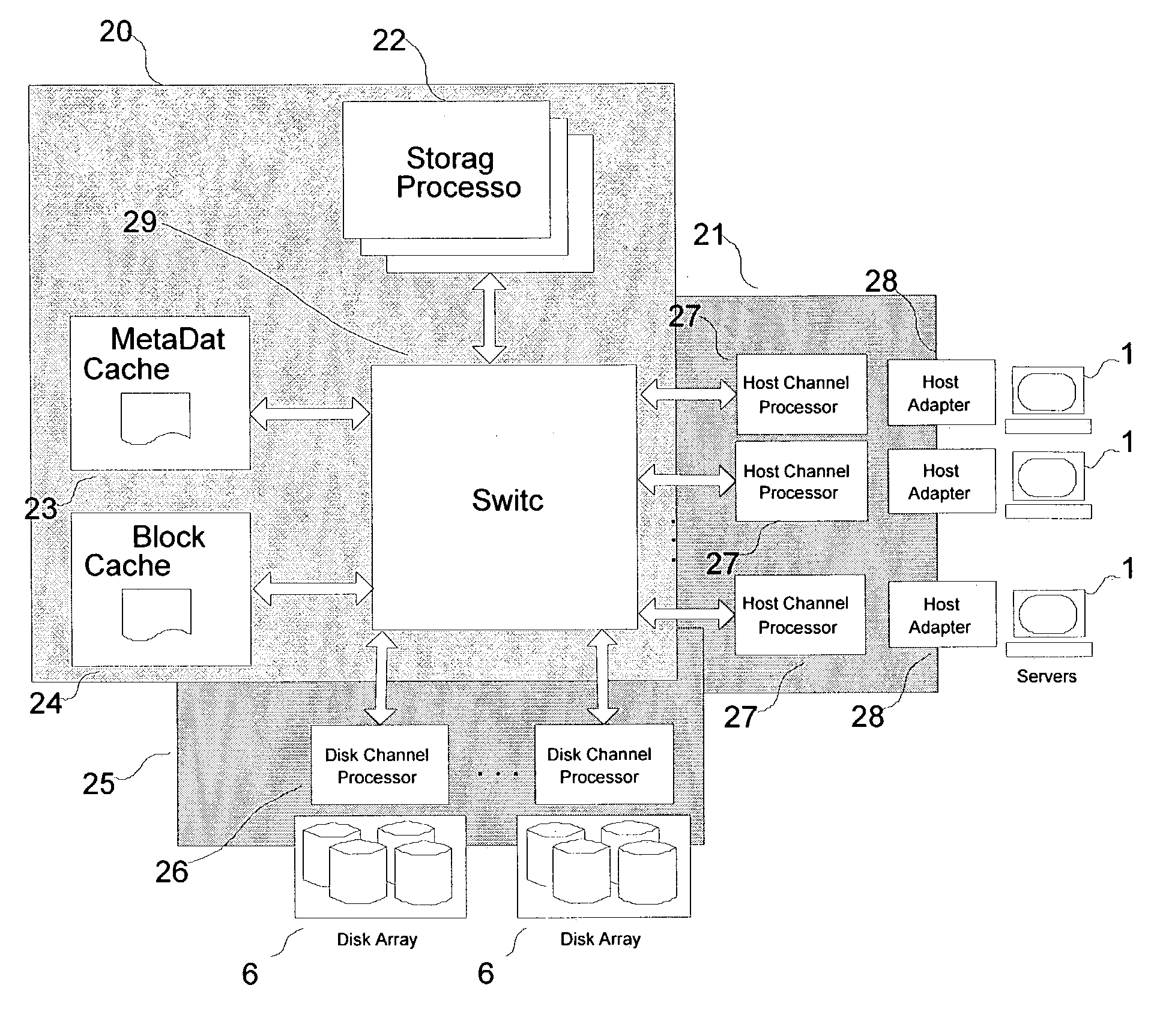
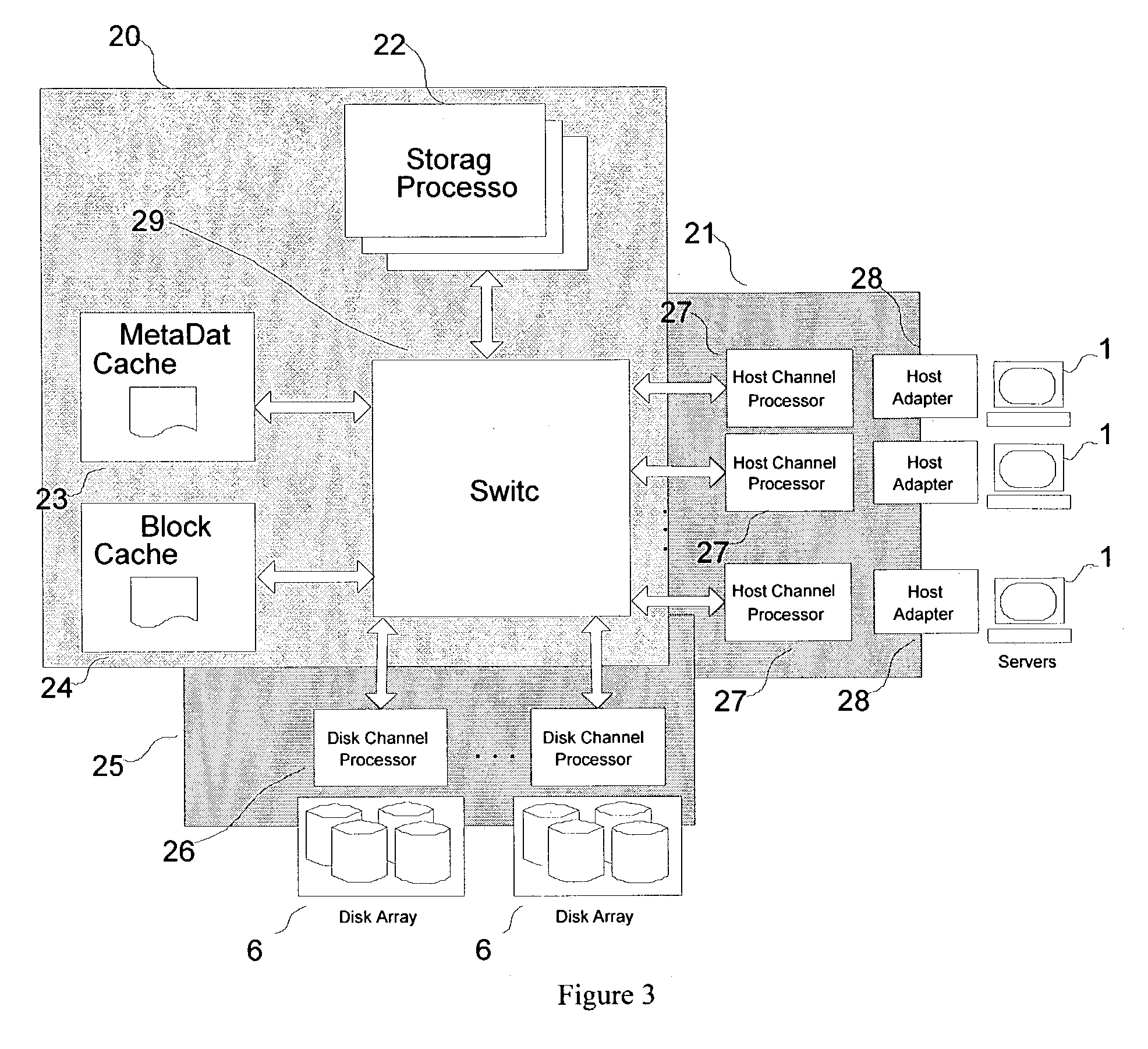
ActiveUS7181578B1Improve performanceSolve the lack of spaceMemory systemsInput/output processes for data processingHandling systemDatapath
A hybrid centralized and distributed processing system includes a switching device that connects a storage processor to one or more servers through a host channel processor. The switching device also connects the storage processor to one or more storage devices such as disk drive arrays, and to a metadata cache and a block data cache memory. The storage processor processes access request from one or more servers in the form of a logical volume or logical block address and accesses the metadata cache to determine the physical data address. The storage processor monitors the performance of the storage system and performs automatic tuning by reallocating the logical volume, load balancing, hot spot removal, and dynamic expansion of storage volume. The storage processor also provides fault-tolerant access and provides parallel high performance data paths for fail over. The storage processor also provides faster access by providing parallel data paths for, making local copies and providing remote data copies, and by selecting data from a storage device that retrieves the data the earliest.
Owner:COPAN SYST INC +1
Snapshot storage and management system with indexing and user interface
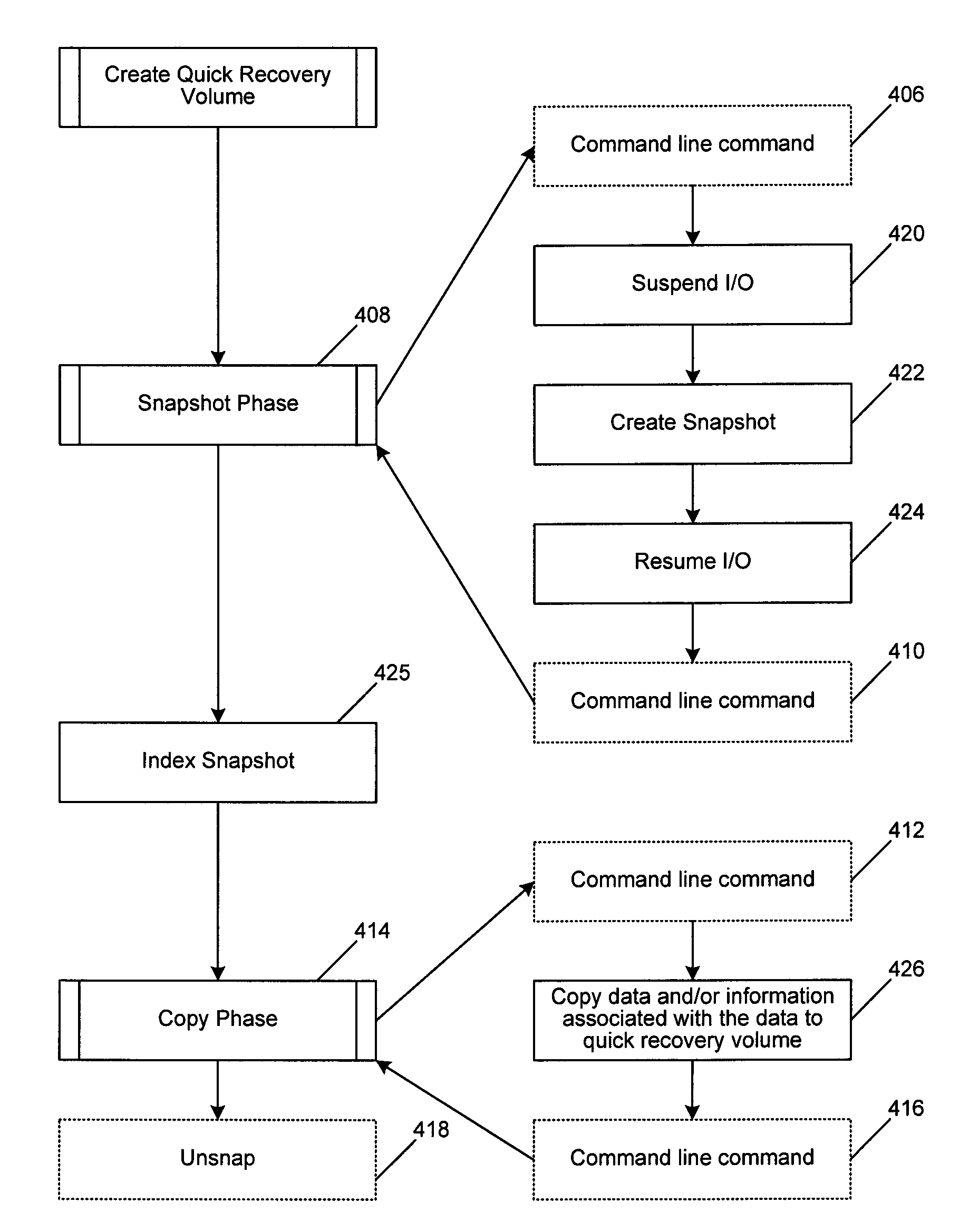
InactiveUS7568080B2Create efficientlyEfficient managementData processing applicationsInput/output to record carriersStorage managementApplication software
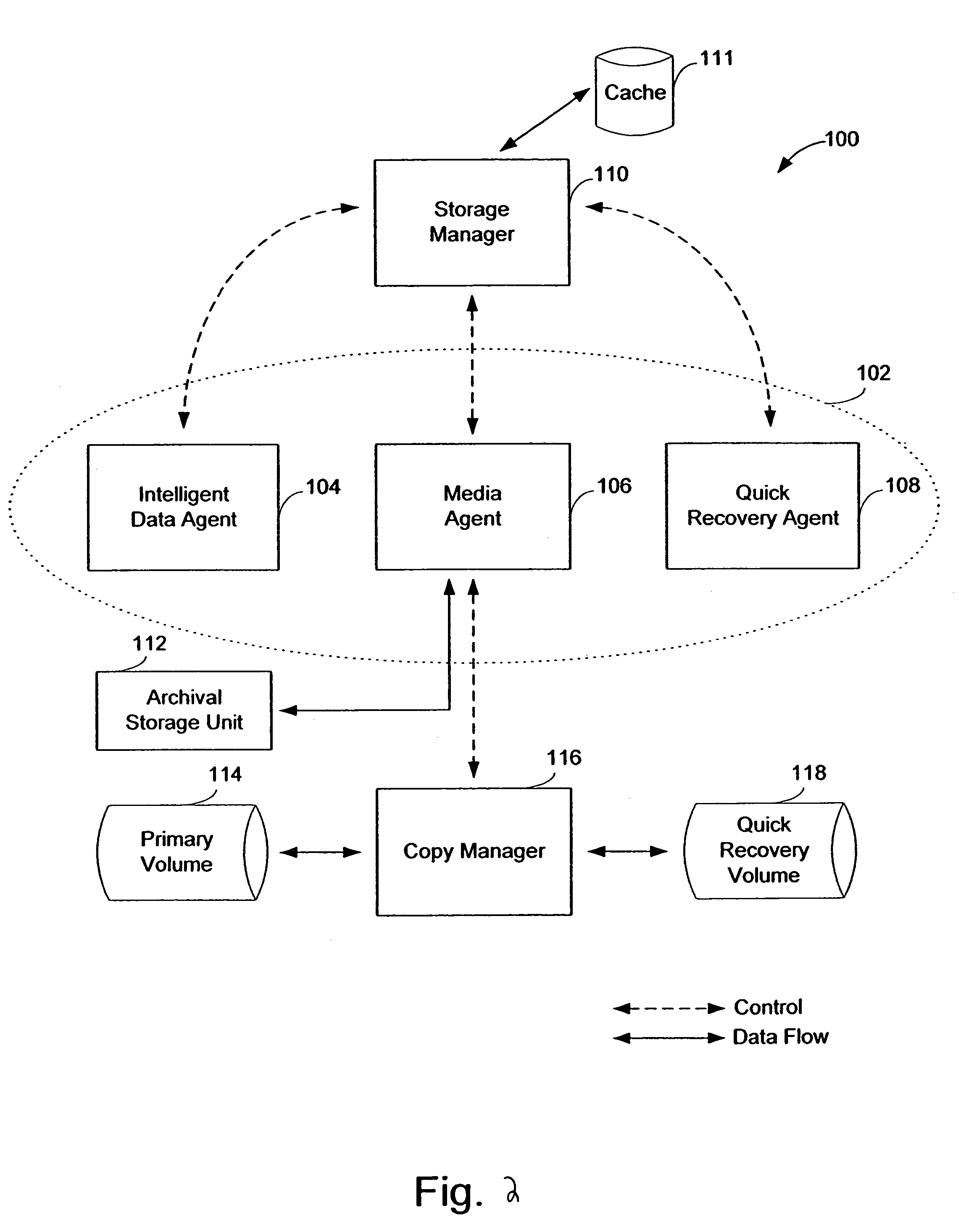
A system and method of managing stored data in a storage management system. The storage management system includes a storage manager, a media agent connected to the storage manager, and a primary volume connected to the media agent. A plurality of snapshots are taken of the primary volume. The snapshots are indexed by associating respective information with the snapshot. The indexed snapshots are copied to a recovery volume. In this way, browsing features are enabled for the user. The user may view the snapshots in a hierarchical format, and may even view snapshot data in association with the corresponding application. The resultant recovery volume may be used to replace a primary volume.
Owner:COMMVAULT SYST INC
Storage management integrated system and storage control method for storage management integrated system
InactiveUS7120757B2Easy to implementImprove fitInput/output to record carriersDigital computer detailsStorage managementAccessibility
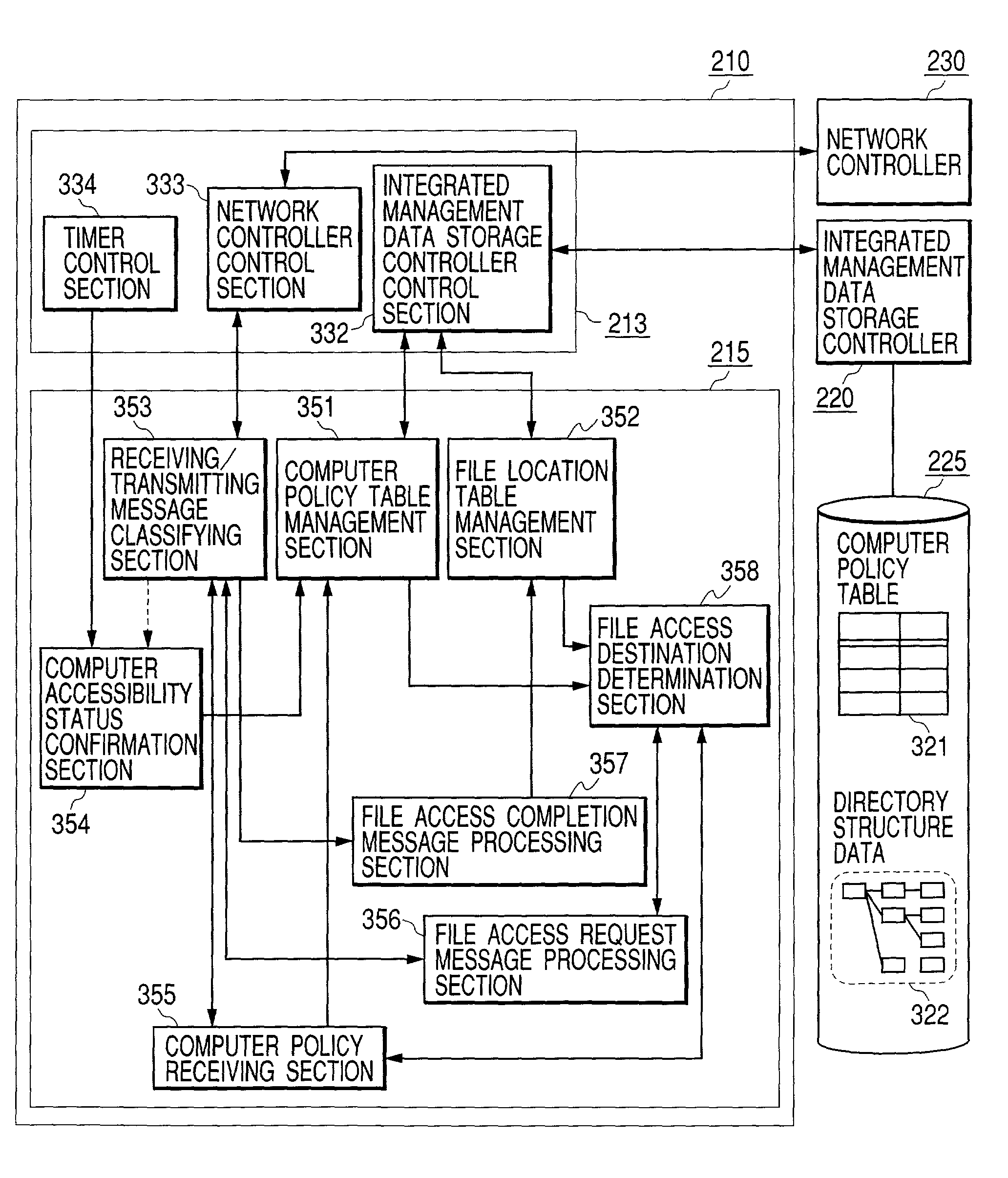
It is intended to achieve an arrangement wherein, when file information of shared disks which are distributed in a plurality of computers connected to a network are used, operating conditions at the time of accessing shared disks can be defined, thus enabling users to easily share files without being bothered by setting-up, or operations of computers located on the other side when they are to perform file sharing.In order to achieve the above-stated arrangement, a storage management integrated server 100 is provided in a network, and respective computers register conditions, an accessibility states and use types pertaining to shared volume to be offered to the server. Thereafter, when a certain computer is to make a file accessing to a shared volume, the computer makes an inquiry to the storage management integrated server for an adequate access destination, determines, on the basis of a response from the server, computers which are suitable to the access source, and makes direct accesses to such computers.
Owner:HITACHI LTD
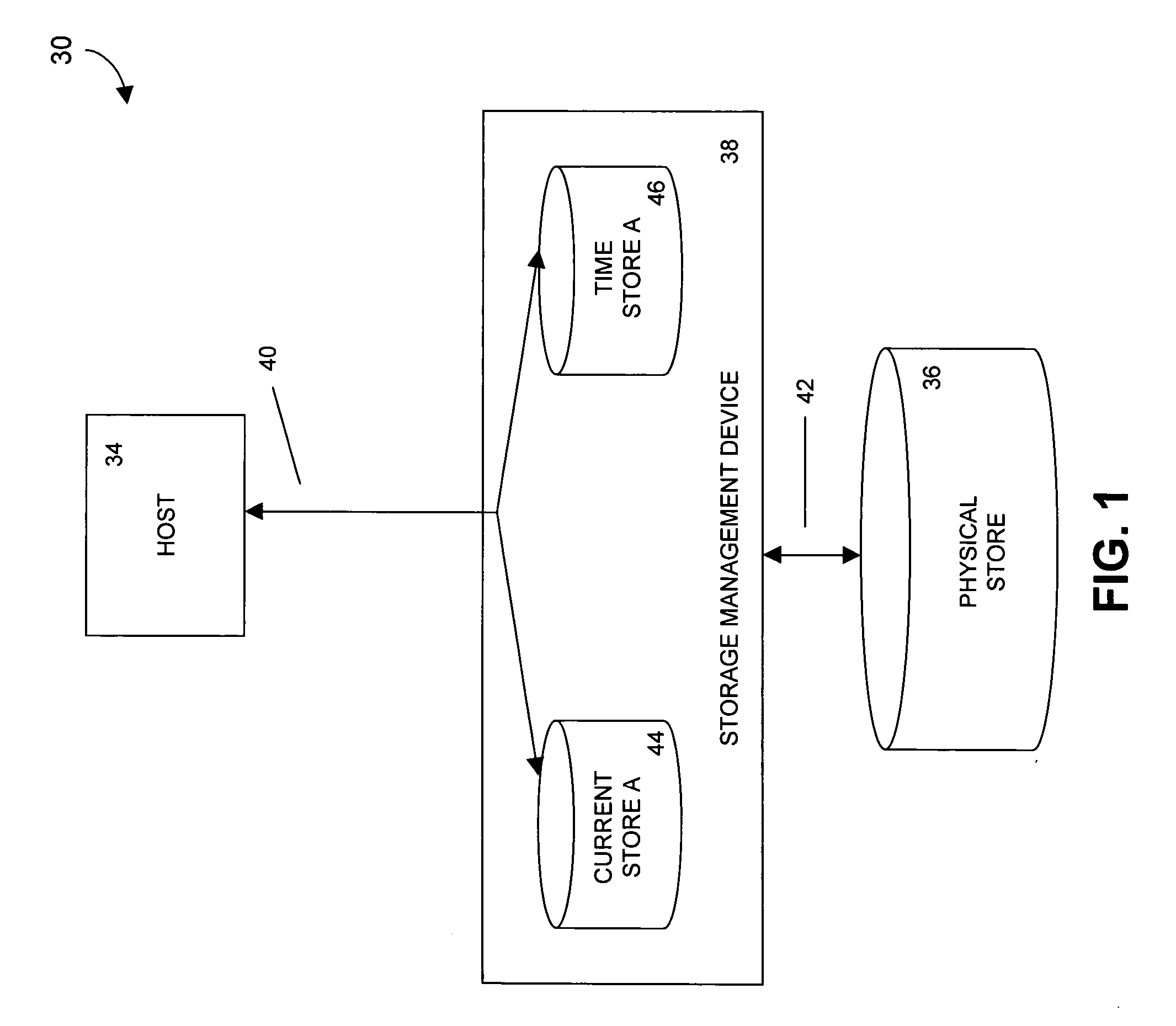
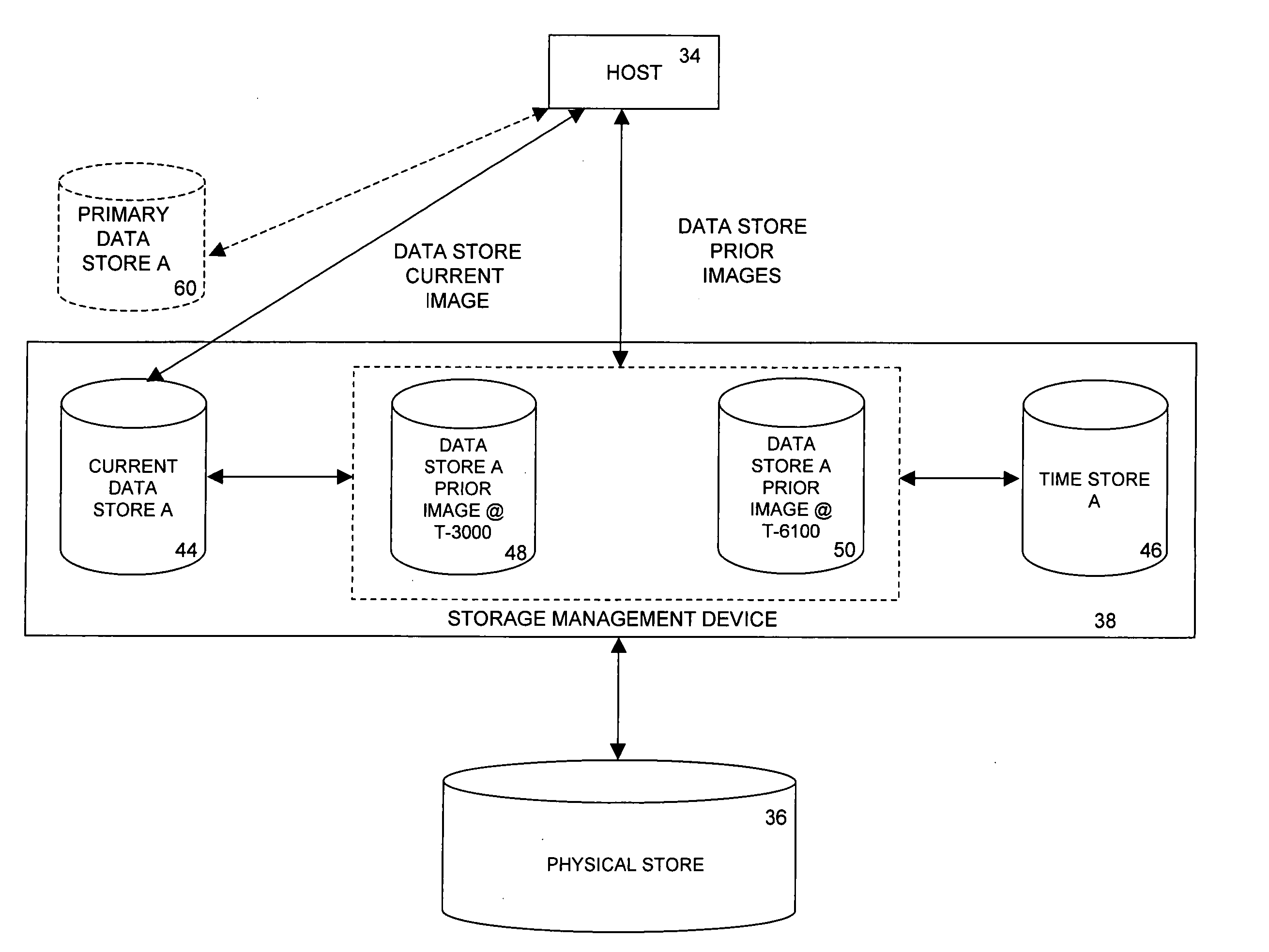
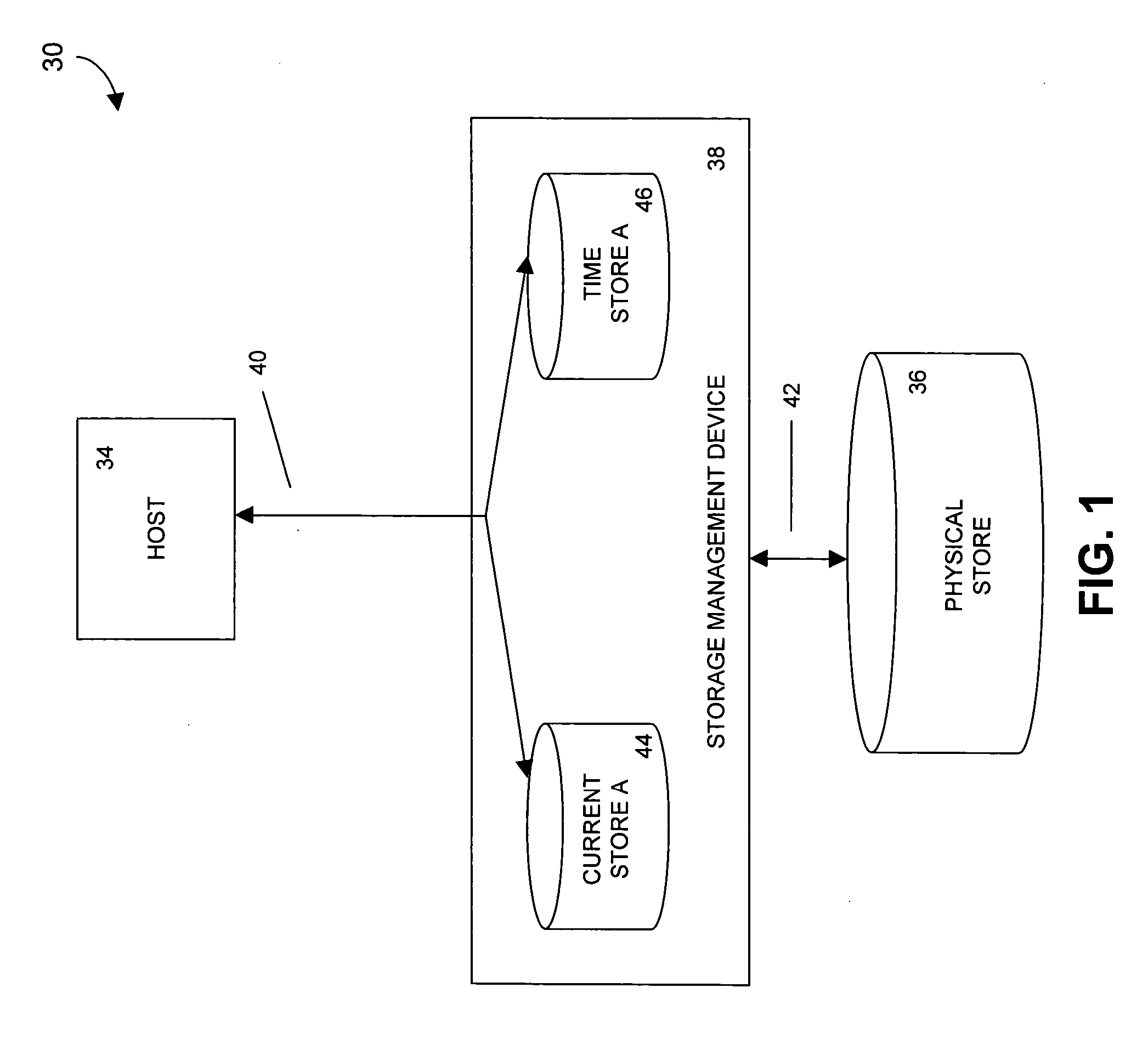
Methods and apparatus for recording write requests directed to a data store
InactiveUS20050066118A1Promote recoveryData storage is convenientMemory loss protectionDigital data processing detailsStorage managementData store
A storage management device records write requests that are directed to a data store. In one embodiment, the storage management device records a plurality of write request entries, each one of which includes information relating to a write request, in at least one first database table, and maintains, for each first database table, at least one record in a second database table. The one or more records in the second database table include data representing the effects of the write requests on a state of at least one portion of the data store. In one such embodiment, each time that one write request entry is recorded in one first database table, the storage management device updates at least one record in the second database table.
Owner:SYMANTEC OPERATING CORP
System and method for performing replication copy storage operations
InactiveUS20070143371A1Data processing applicationsDatabase distribution/replicationThird partyStorage management
A system and method are provided for performing storage operations relating to a first secondary copy of electronic data. A storage policy or storage preferences may dictate that a replication copy should be used in storage operations performed to a particular client, sub-client, data, media or other item. Based on the storage policy, when a new client, sub-client, data, media or other item is received, a media agent determines whether there is a replication copy of the item. In the absence of a replication copy, one may be created. The replication copy may be provided by a third party application, or created by the client or a storage management system component. Information regarding the replication copy and its corresponding first secondary copy may be stored in a database. To optimize use of system resources, storage operations relating to the first secondary copy may be performed using the replication copy instead of the first secondary copy.
Owner:COMMVAULT SYST INC
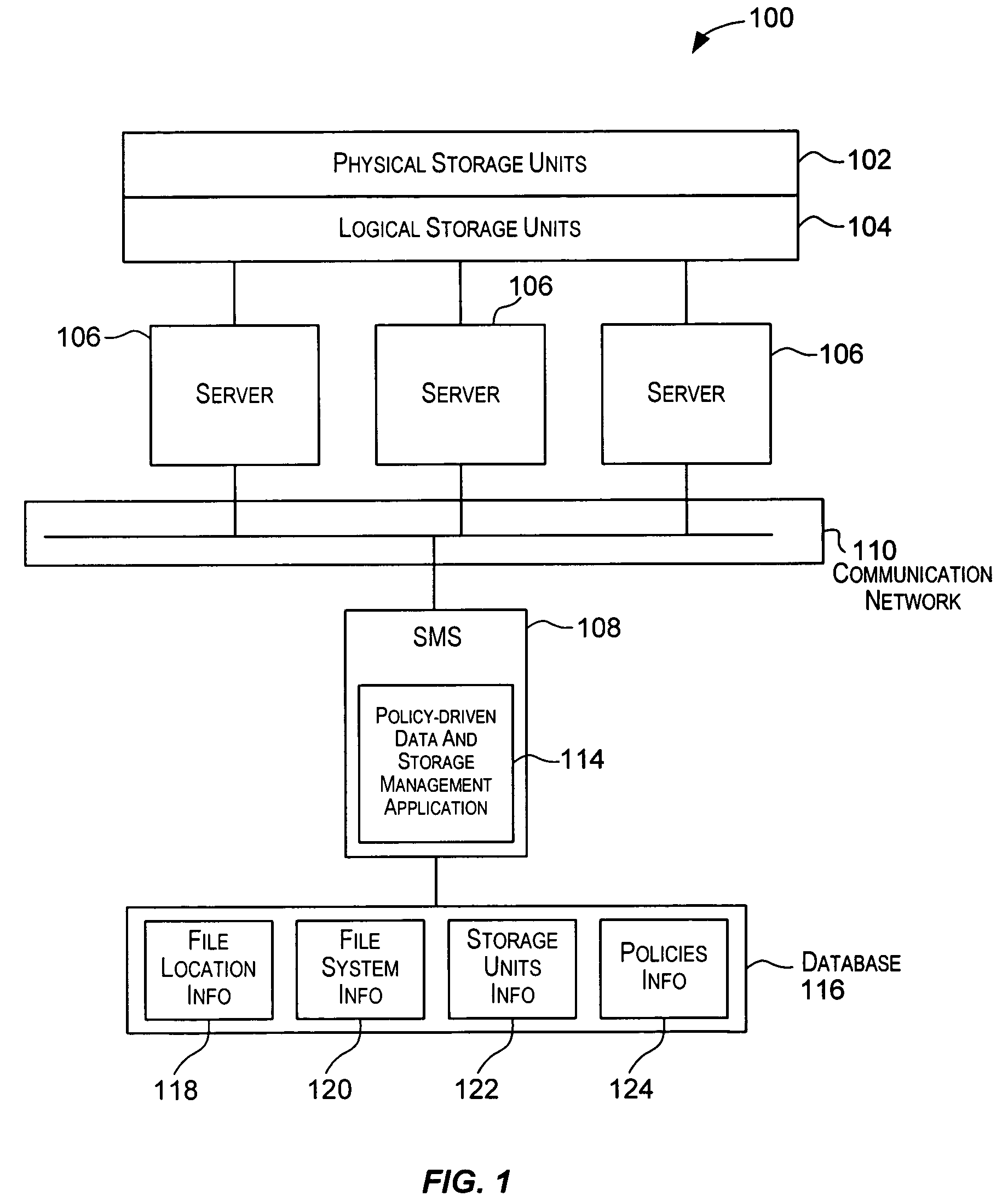
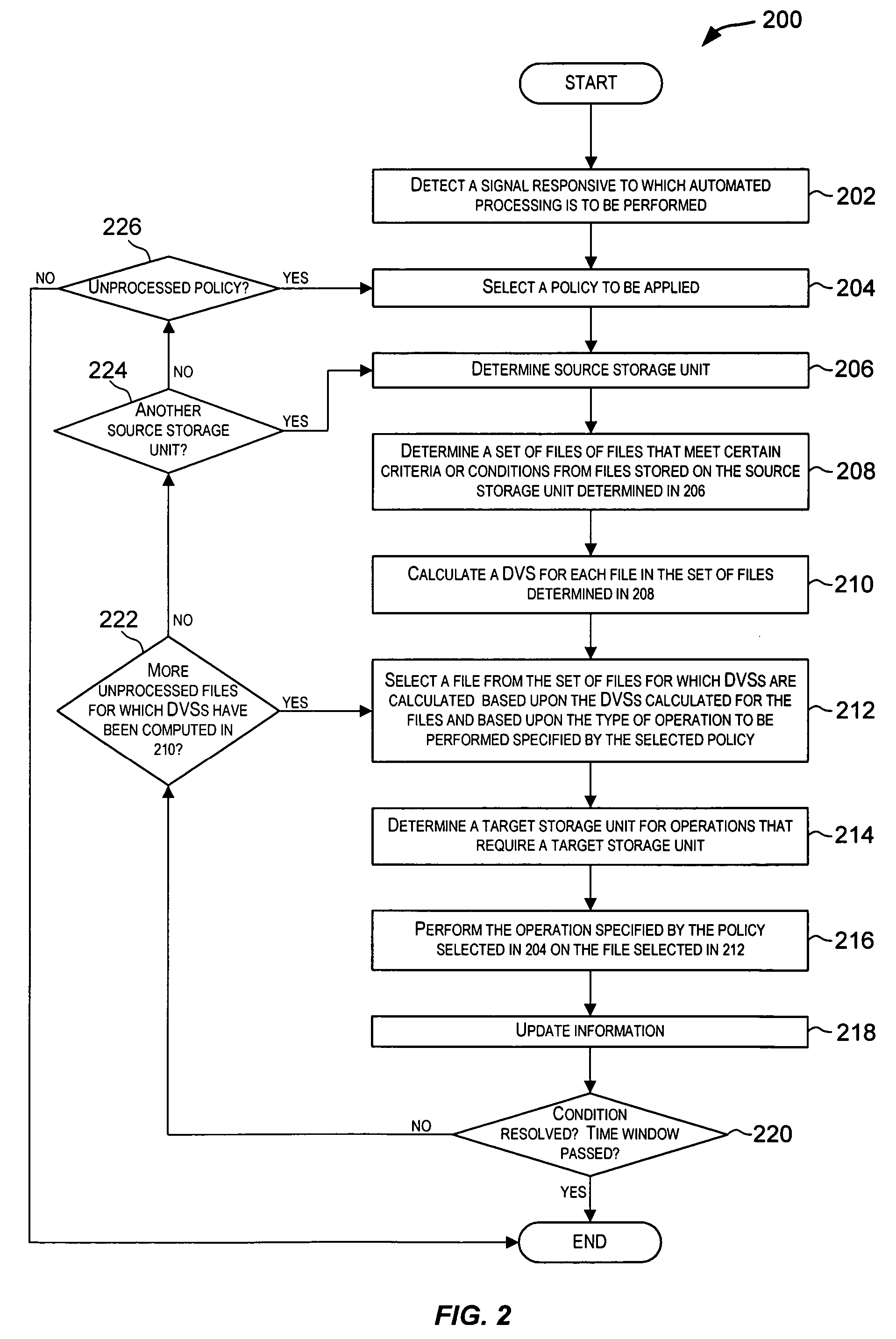
Techniques for performing policy automated operations
ActiveUS7509316B2Data processing applicationsDigital data processing detailsStorage managementDatabase
Techniques for automatically performing various data and storage management operations in a storage environment. The operations to be performed are automatically determined based upon policies configured for the data and storage environment. For a selected operation, one or more files on which the operation is to be performed are also automatically determined. The one or more files may be selected using different techniques based upon characteristics of the files and also based upon the operation to be performed. Target storage units, if need for the operation, are also automatically determined. The operations are then performed on the selected files. Examples of policy-driven operations include copying a file, moving a file, deleting a file, archiving a file, backing-up a file, restoring a file, migrating a file, recalling a file, etc.
Owner:ROCKET SOFTWARE
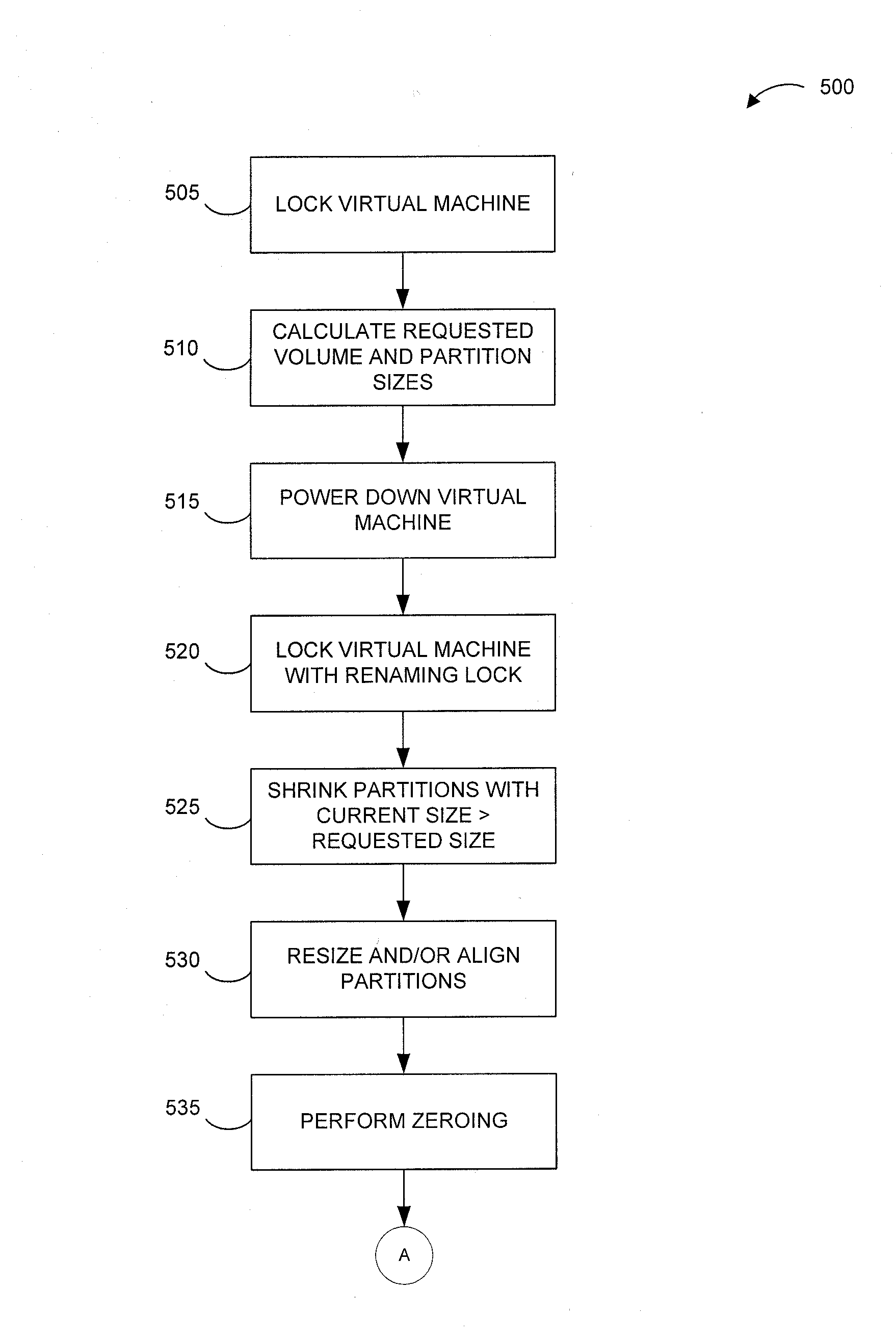
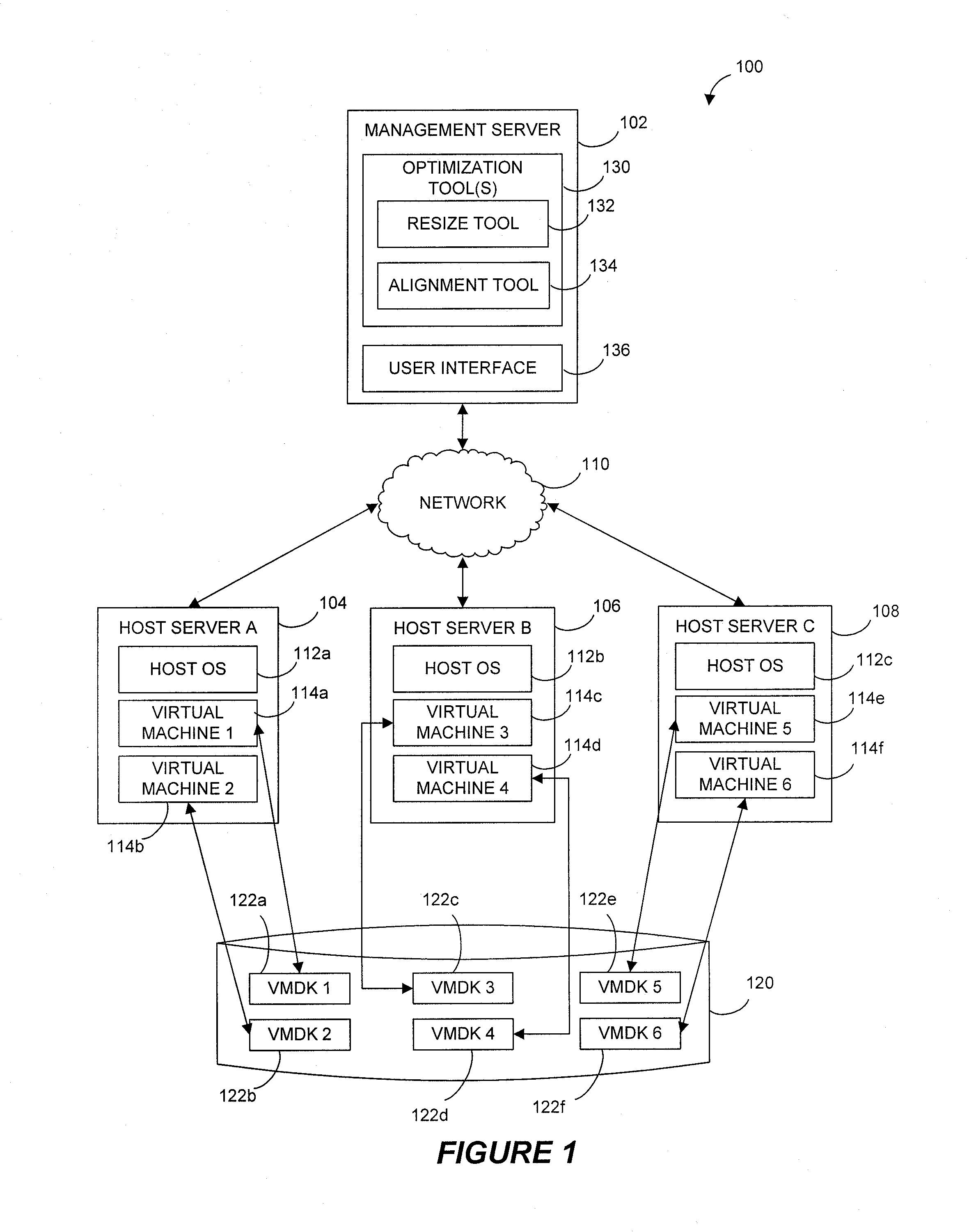
Systems and methods for improving virtual machine performance
ActiveUS8332571B1Improve machine performanceEffectively preventing painful and costly virtual machine outagesComputer security arrangementsProgram controlContent replicationBusiness enterprise
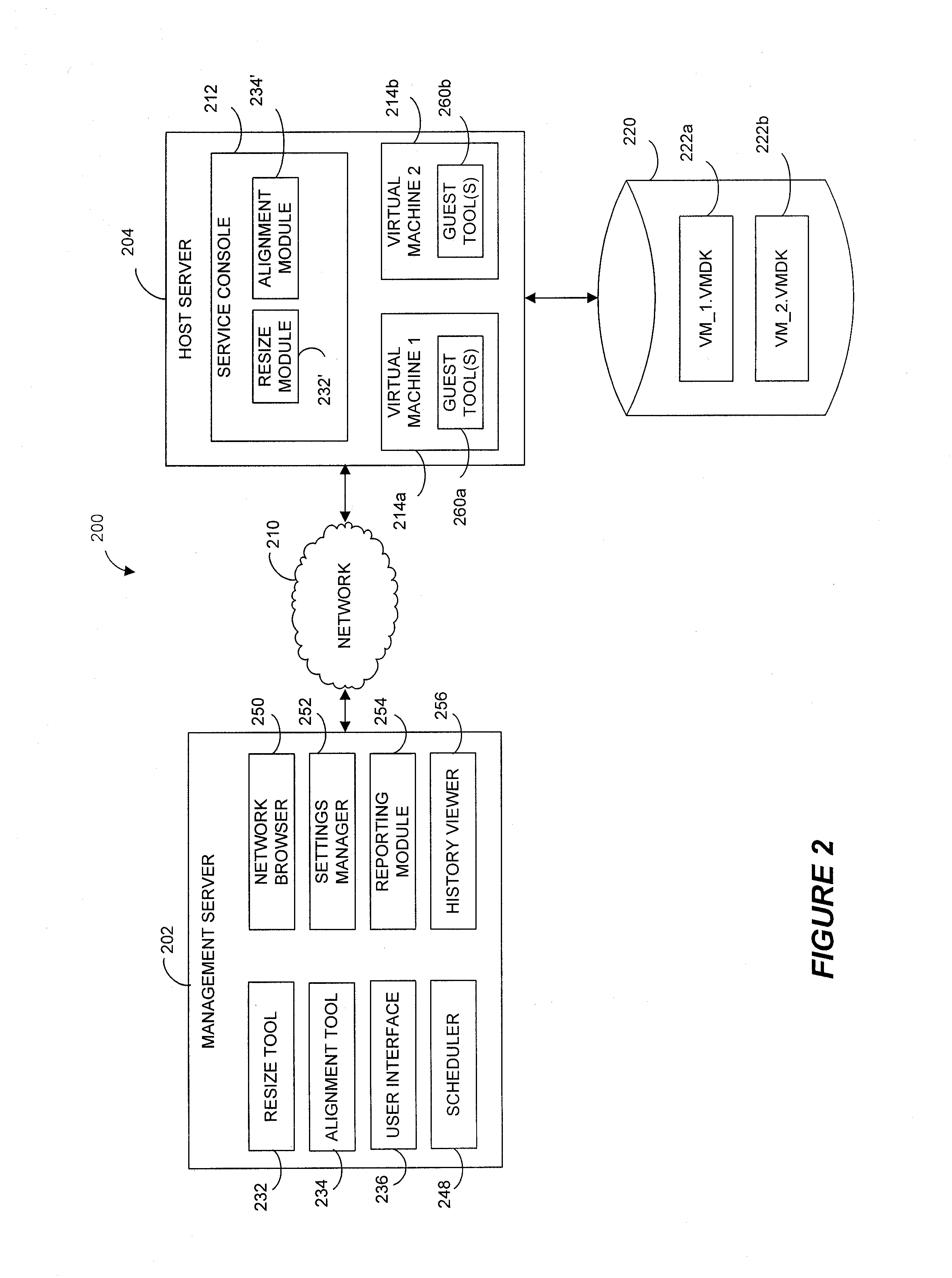
Virtual machine optimization and / or storage reclamation solutions are disclosed that manage virtual machine sprawl and / or growing enterprise storage costs. For instance, certain solutions receive recommendations based on one or more rules, policies and / or user preferences that identify storage and / or alignment criteria for virtual machine disk (VMDK) partition(s). In certain examples, a resize tool that operates within a host operating system of a host server dynamically resizes and / or aligns one or more VMDK partitions of a powered-down virtual machine. For instance, the resize tool can be injected to the host server from a remote management server and can resize and / or align the VMDK partitions without requiring contents of the VMDK to be copied to another VMDK. By reallocating storage and / or aligning the VMDK partitions, embodiments of the invention can increase virtual machine performance and improve storage management.
Owner:QUEST SOFTWARE INC
Storage management system for virtual machines
ActiveUS20100153617A1Overcome limitationsMemory adressing/allocation/relocationComputer security arrangementsVirtualizationData center
A computer system (a method) for providing storage management solution that enables server virtualization in data centers is disclosed. The system comprises a plurality of storage devices for storing data and a plurality of storage management drivers configured to provide an abstraction of the plurality of the storage devices to one or more virtual machines of the data center. A storage management driver is configured to represent a live disk or a snapshot of a live disk in a virtual disk image to the virtual machine associated with the driver. The driver is further configured to translate a logical address for a data block to one or more physical addresses of the data block through the virtual disk image. The system further comprises a master server configured to manage the abstraction of the plurality of the storage devices and to allocate storage space to one or more virtual disk images.
Owner:VMWARE INC
Storage management system and method and program
InactiveUS20060129537A1Digital data information retrievalDigital data processing detailsStorage managementClient-side
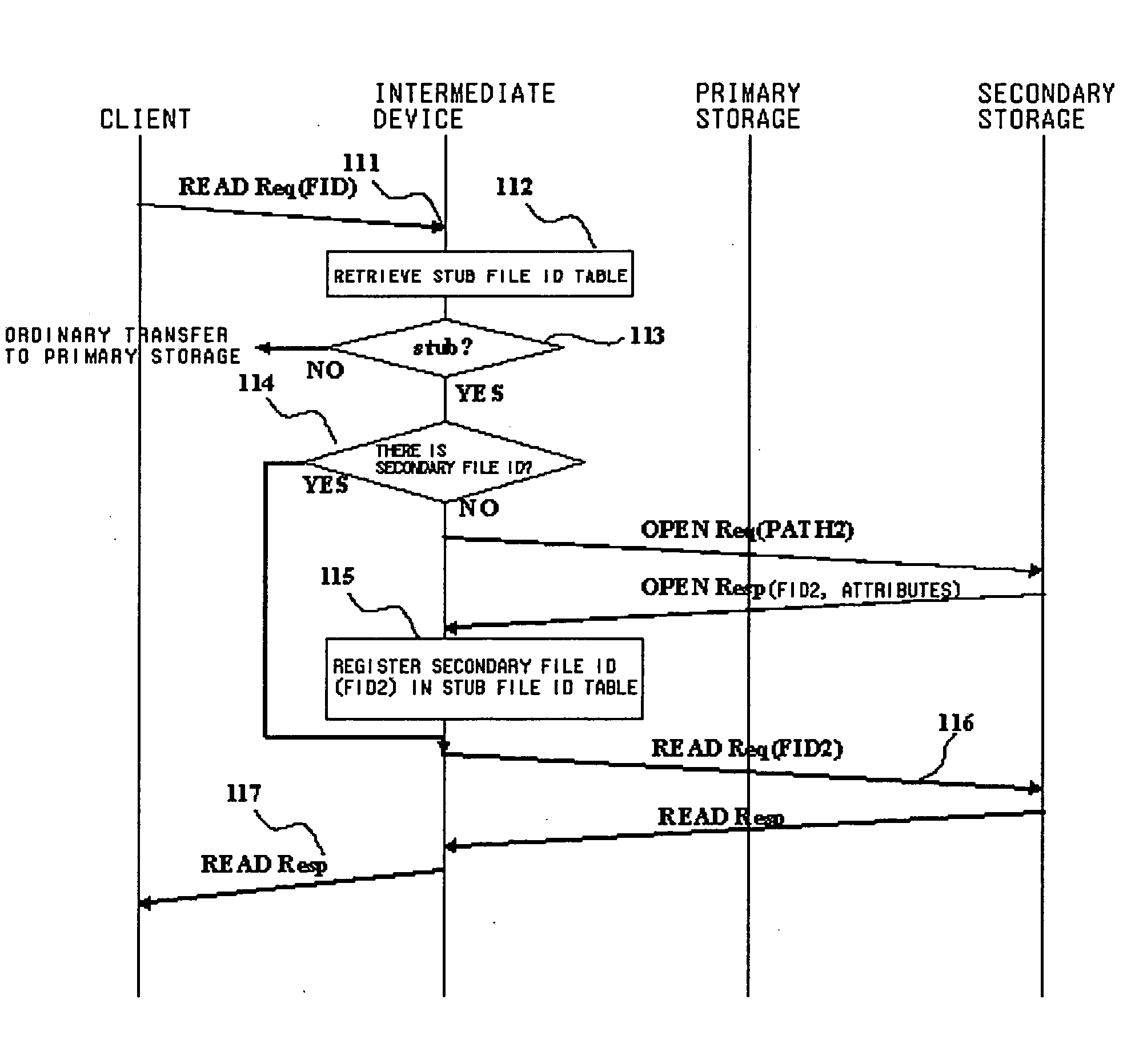
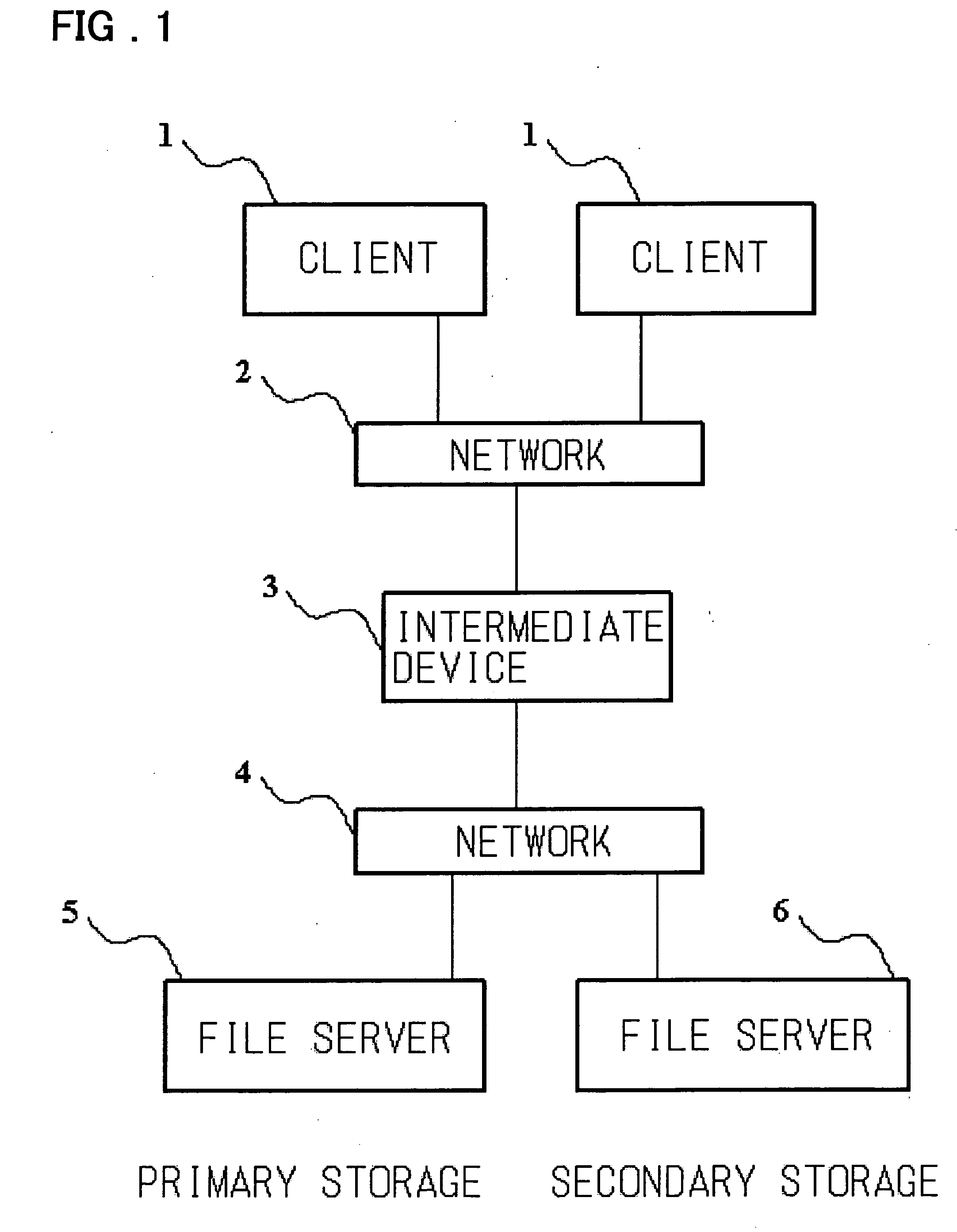
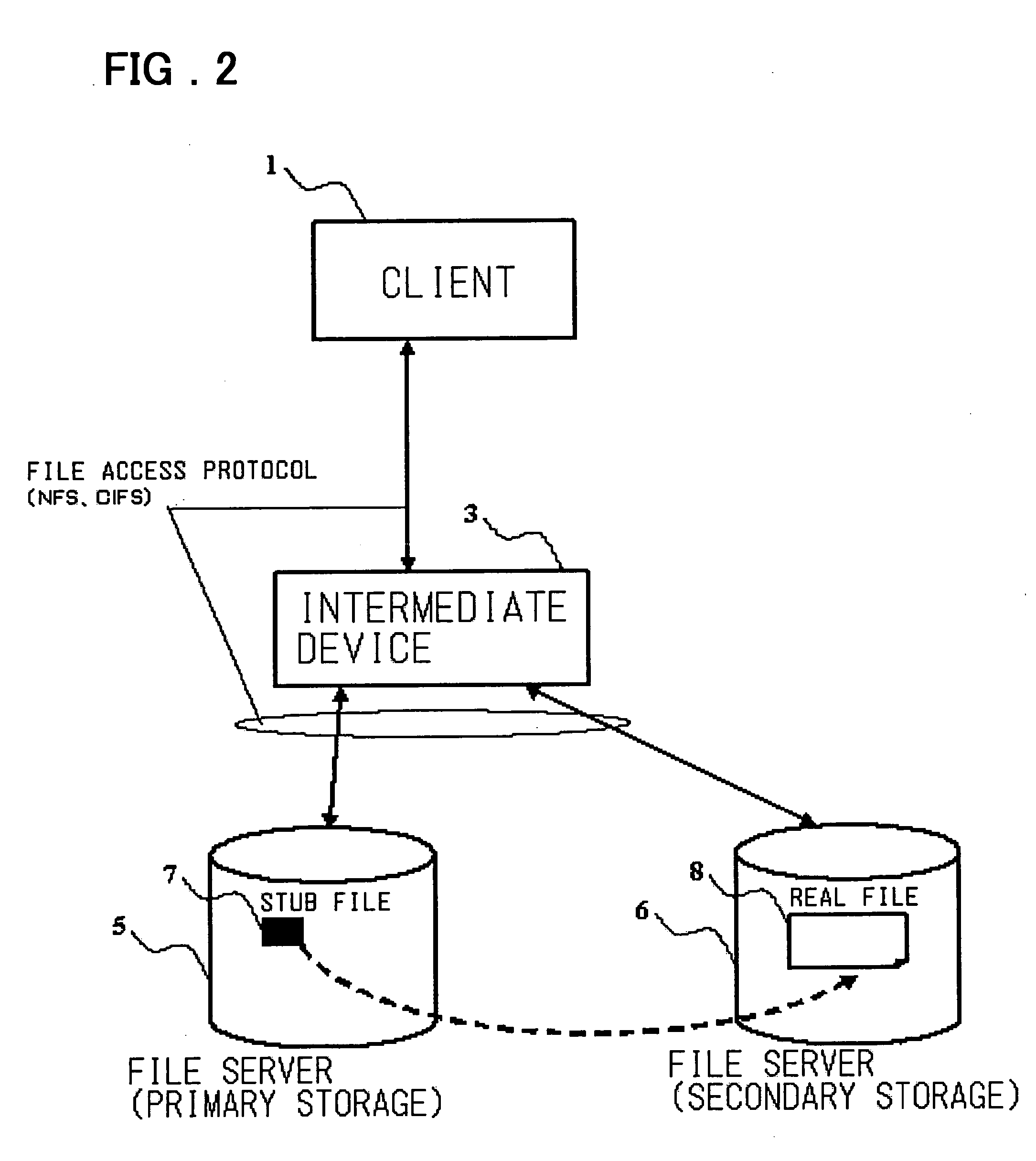
Disclosed is a storage management system including at least one client, a first server having a primary storage, a second server having a secondary storage, and an intermediate device logically arranged between the client and the first and second servers. The primary storage includes a stub file in which there is recorded the position information of the real file migrated from the primary storage to the secondary storage. The intermediate device exercises control so that, when a file access request of the primary storage of a first server, issued by the client, is received by the intermediate device, the intermediate device receives the file access request and, if the file to be accessed is a stub file, and the access request necessitates accessing to the real file, the intermediate device accesses the real file of the secondary storage using the information of the stub file to return a response.
Owner:NEC CORP
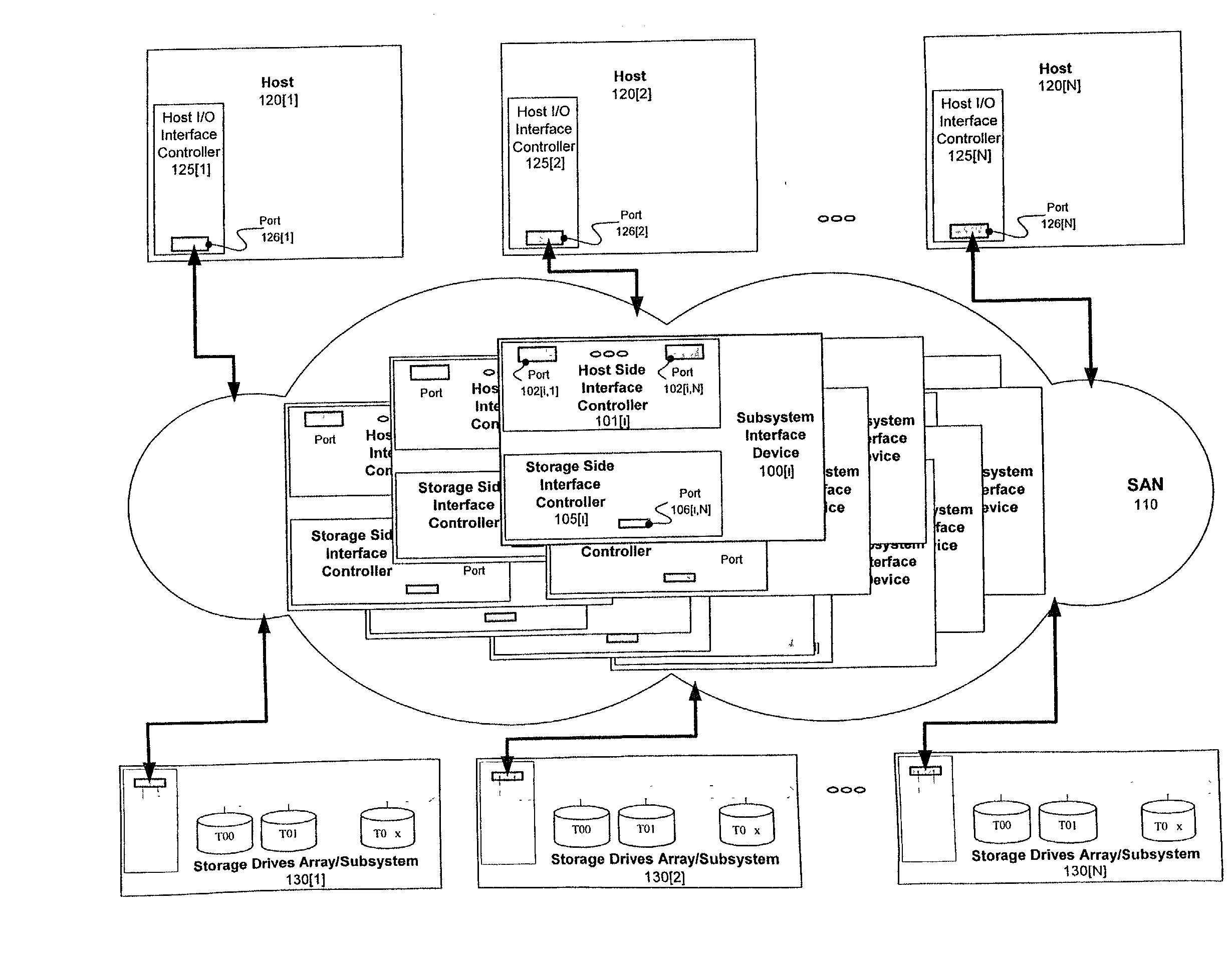
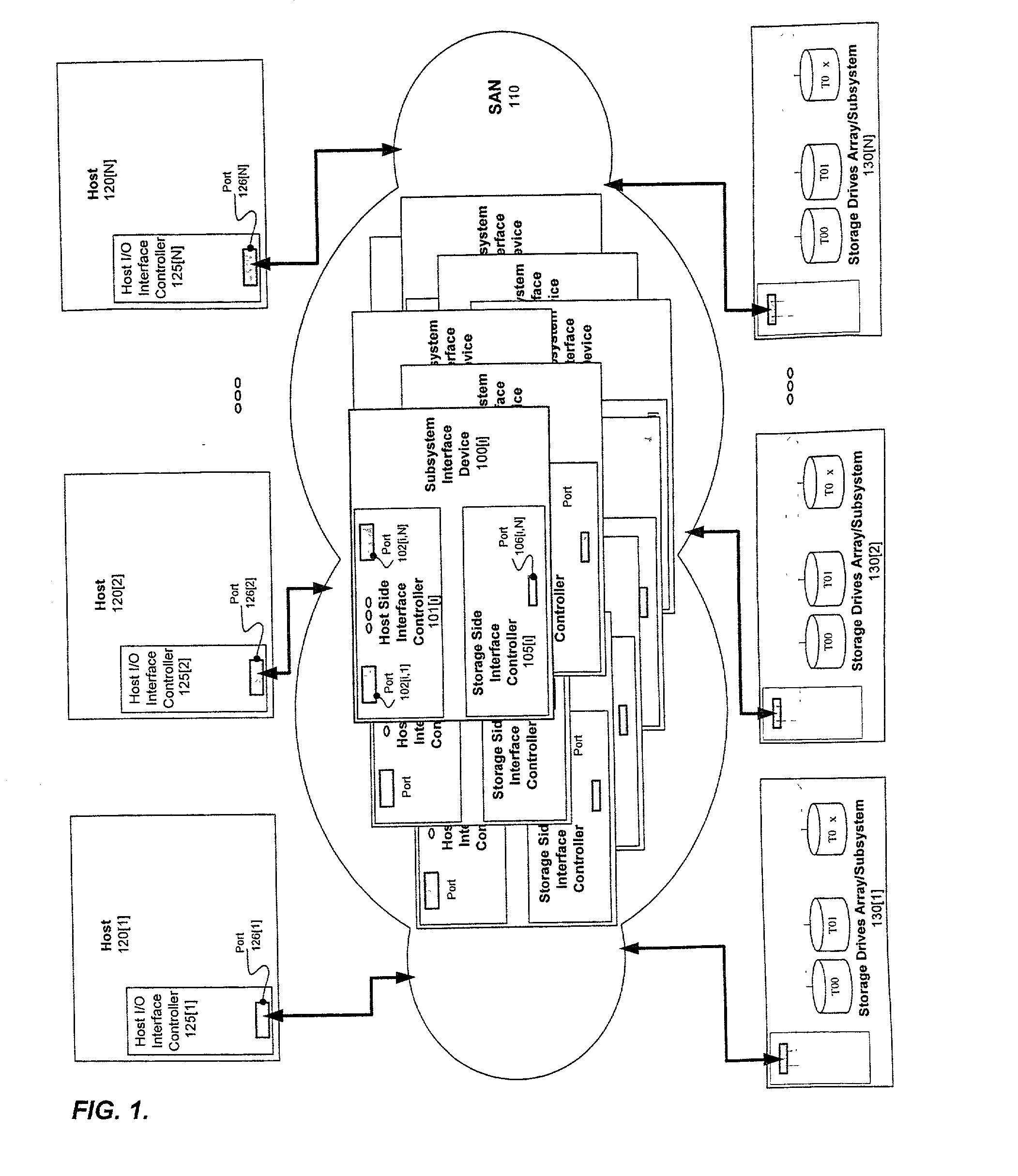
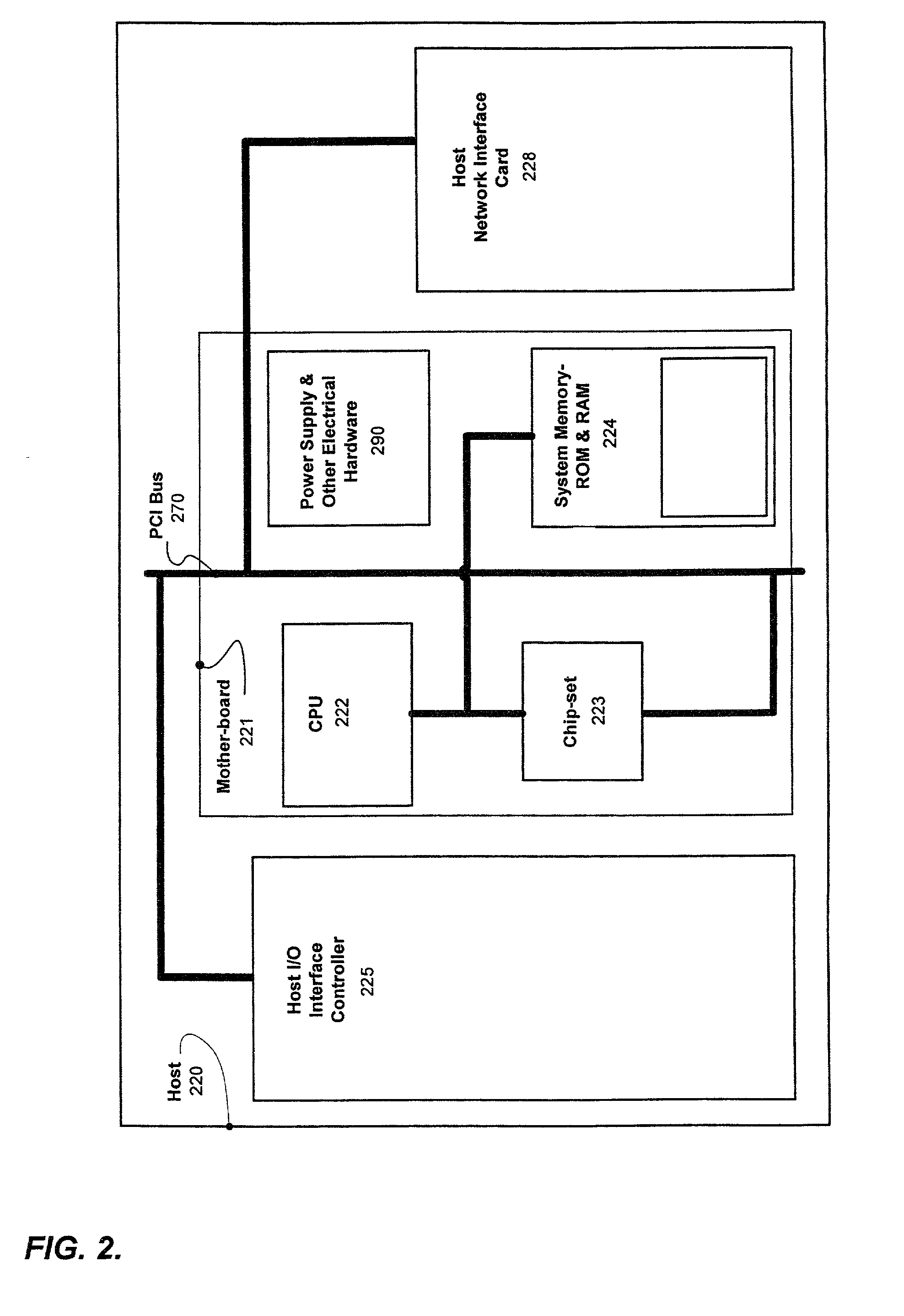
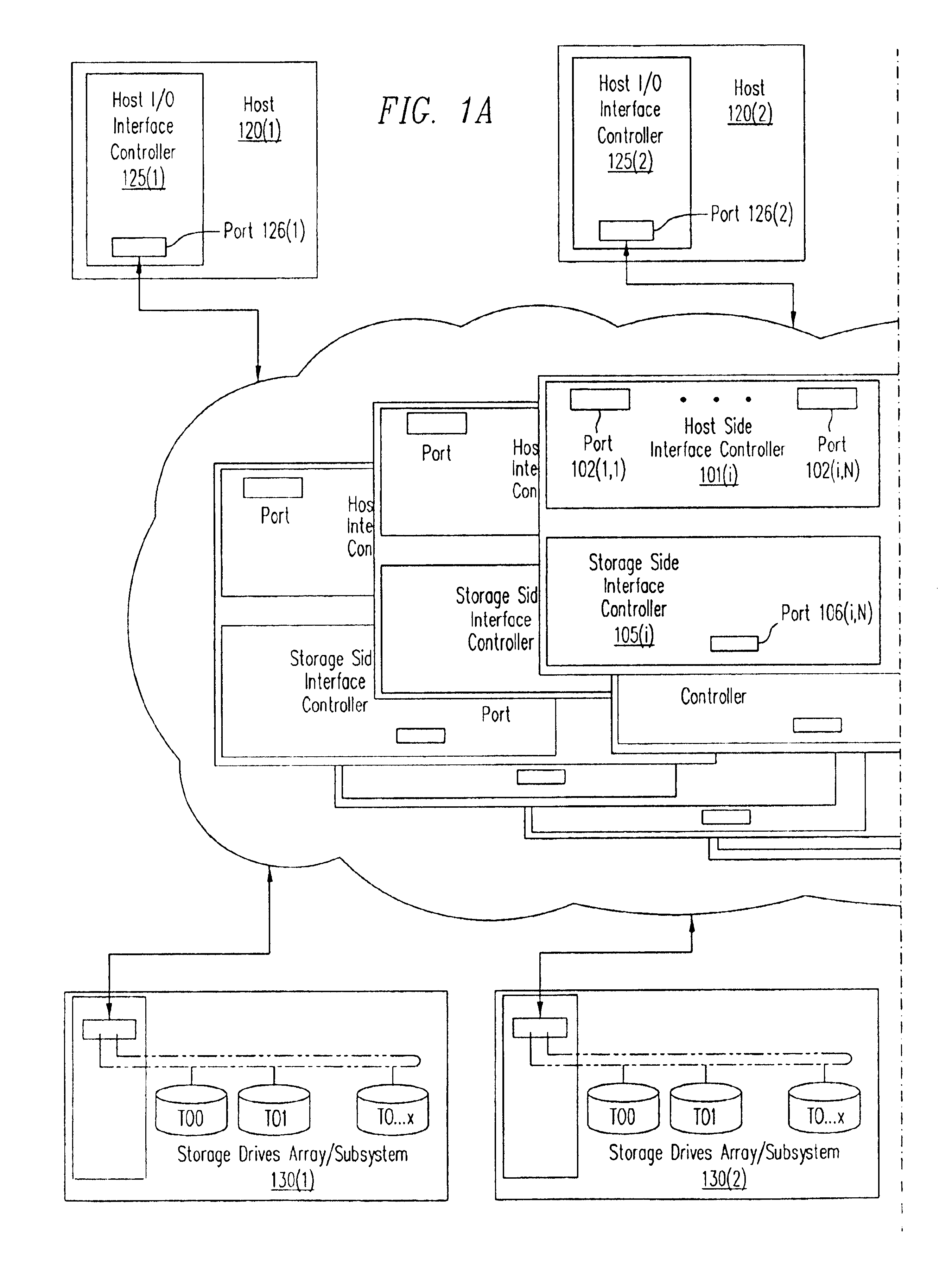
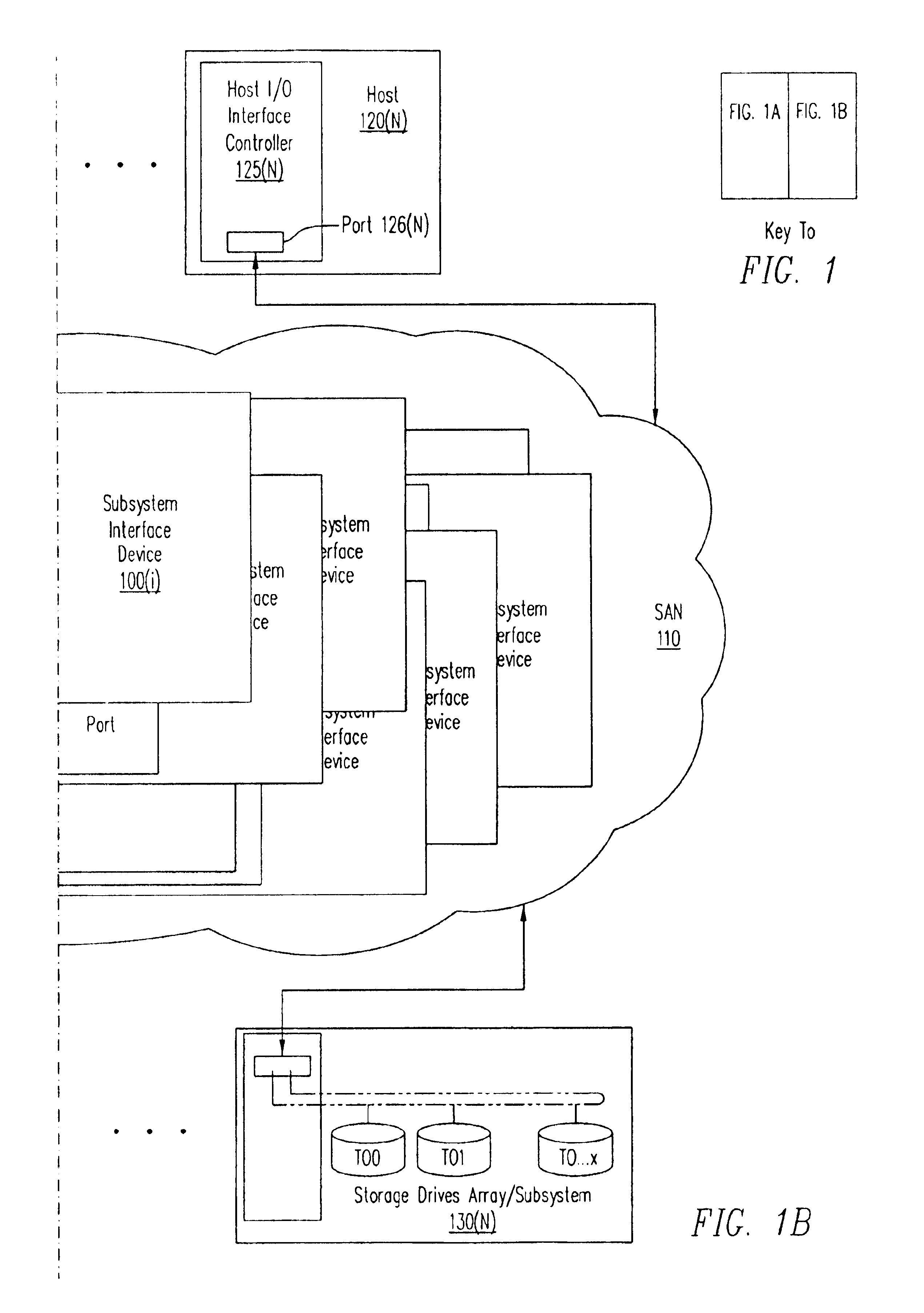
Distributed storage management platform architecture
InactiveUS20020103943A1Data switching networksSecuring communicationStorage managementNetwork interface controller
A distributed storage management platform (DSMP) architecture is disclosed. Such a DSMP architecture includes a number of storage routers. Each one of the storage routers comprises a number of interface controllers. One of the interface controllers of each one of the storage routers is communicatively coupled to one of the interface controllers of at least one other of the storage routers. final
Owner:VICOM SYST
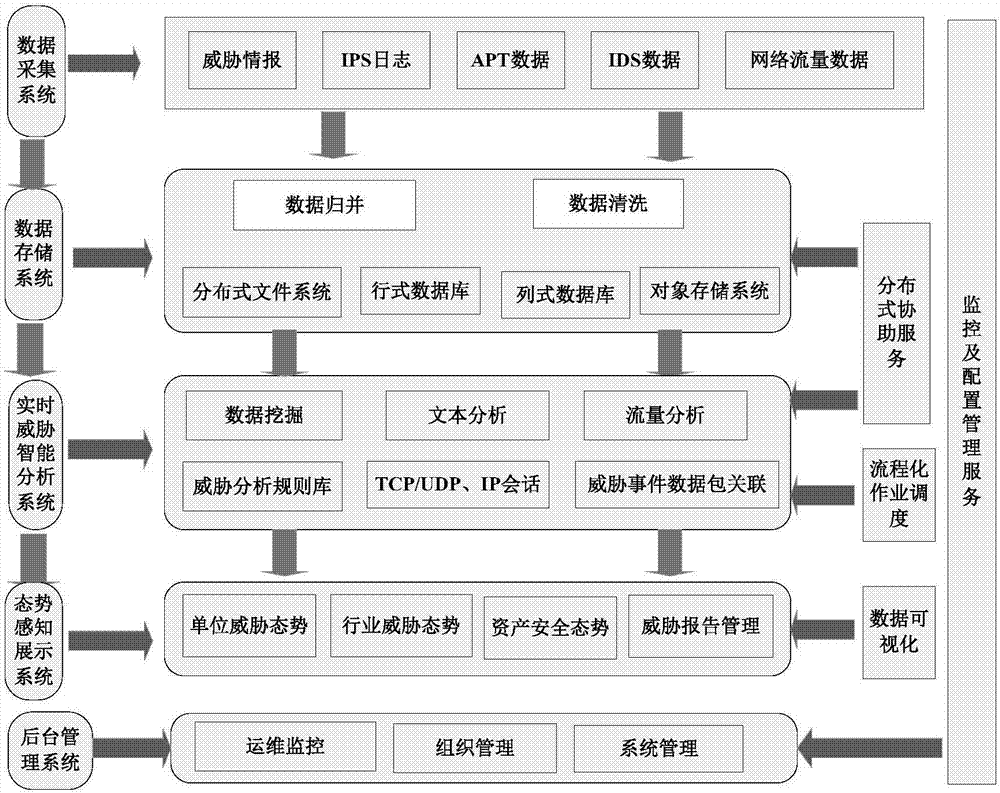
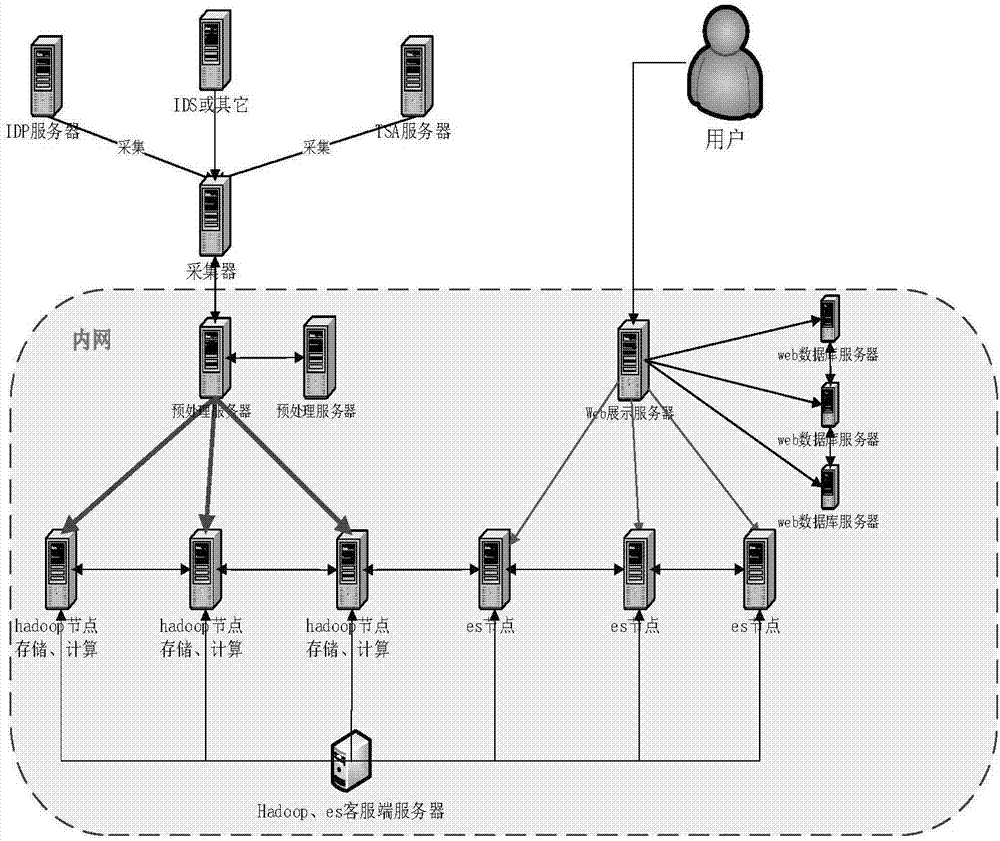
Threat early warning and monitoring system and method based on big data analysis and deployment architecture
ActiveCN107196910ARealize acquisitionRealize multi-dimensional graphical and intuitive displayData switching networksFull text searchTime processing
The invention discloses a threat early warning and monitoring system and method based on big data analysis and a deployment architecture. The system comprises a data acquisition system module, which is used for carrying out real-time data acquisition on original network traffic; a data storage system module, which is used for carrying out data merging and data cleaning on the data collected by the data acquisition system module, and then, carrying out storage management; a real-time threat intelligent analysis system module, which is used for carrying out deep analysis and mining on security data through data mining, text analysis, traffic analysis, full-text search engine and real-time processing, and identifying unknown security threats in real time by combining an intrusion detection module, a network abnormal behavior module and a device abnormal behavior module; and a situation awareness display system module, which is used for carrying out comprehensive display on security threat situations stereoscopically in real time through a data visualization tool library. The threat early warning and monitoring system and method based on big data analysis and the deployment architecture are used for network security threat situation awareness and deep analysis under a plurality of service scenarios, and realize comprehensive abilities from attack early warning, attack identification to analysis and evidence obtaining.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +2
Distributed storage management platform architecture
InactiveUS6877044B2Data switching networksSecuring communicationStorage managementNetwork interface controller
A distributed storage management platform (DSMP) architecture is disclosed. Such a DSMP architecture includes a number of storage routers. Each one of the storage routers comprises a number of interface controllers. One of the interface controllers of each one of the storage routers is communicatively coupled to one of the interface controllers of at least one other of the storage routers.
Owner:VICOM SYST
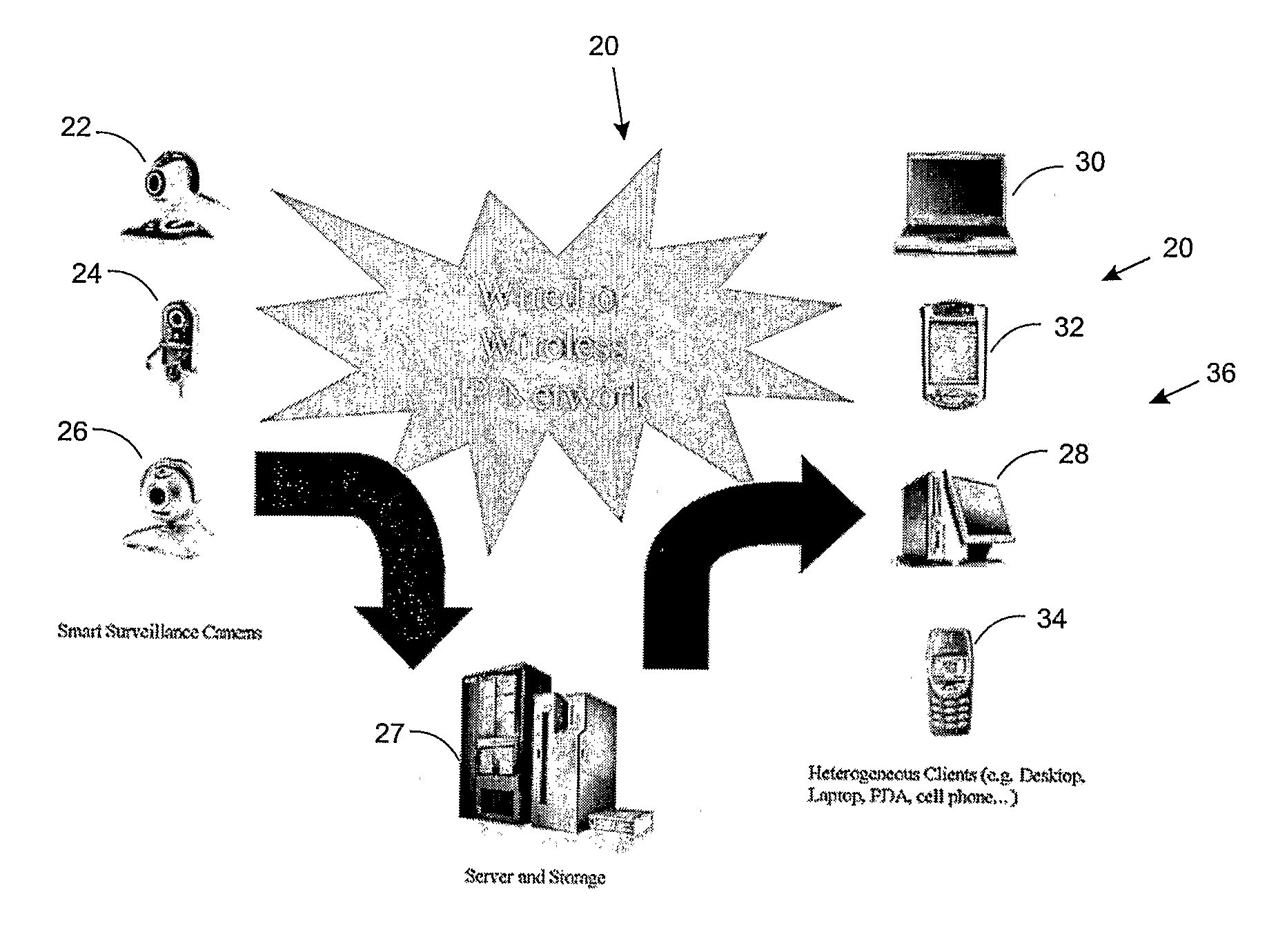
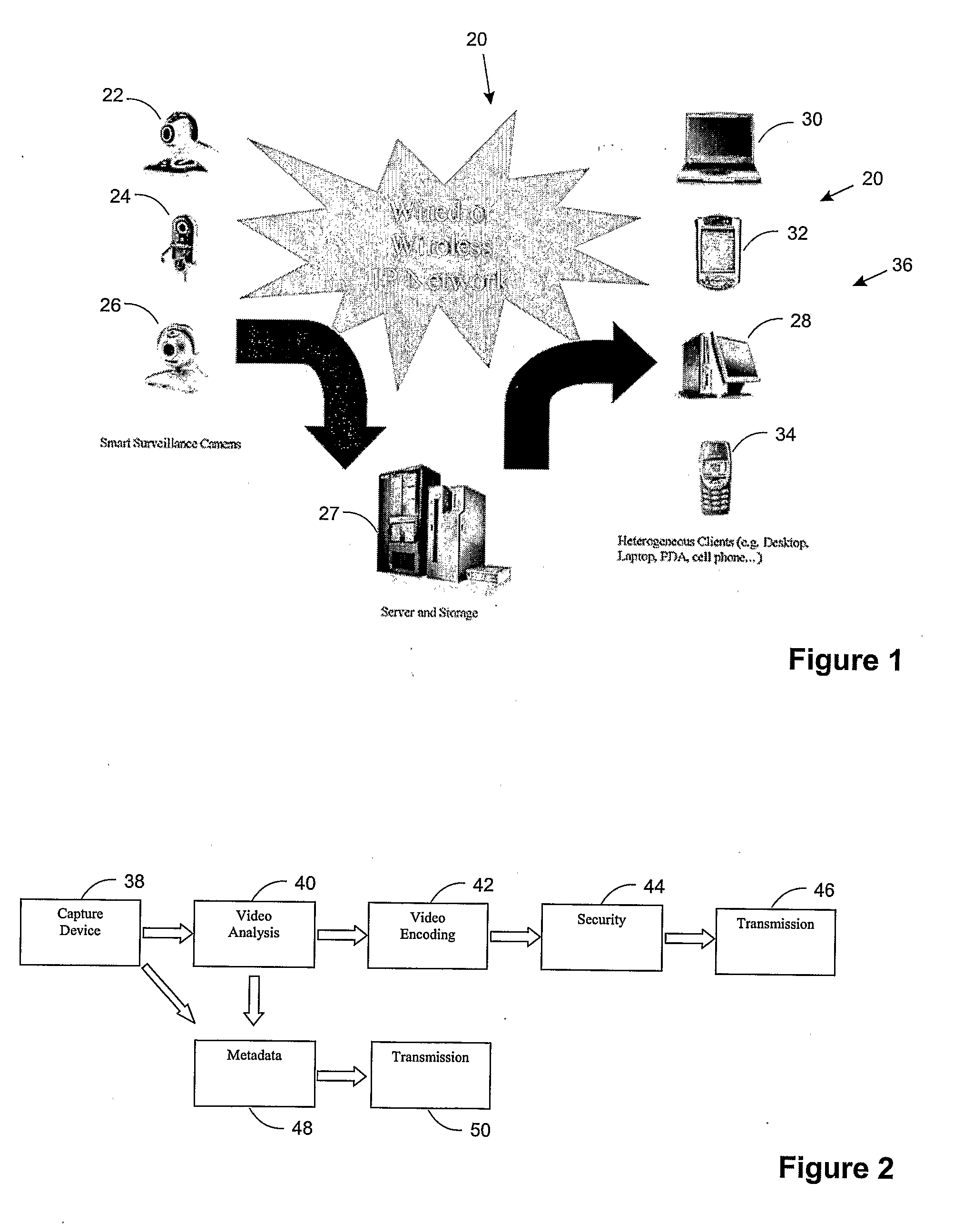
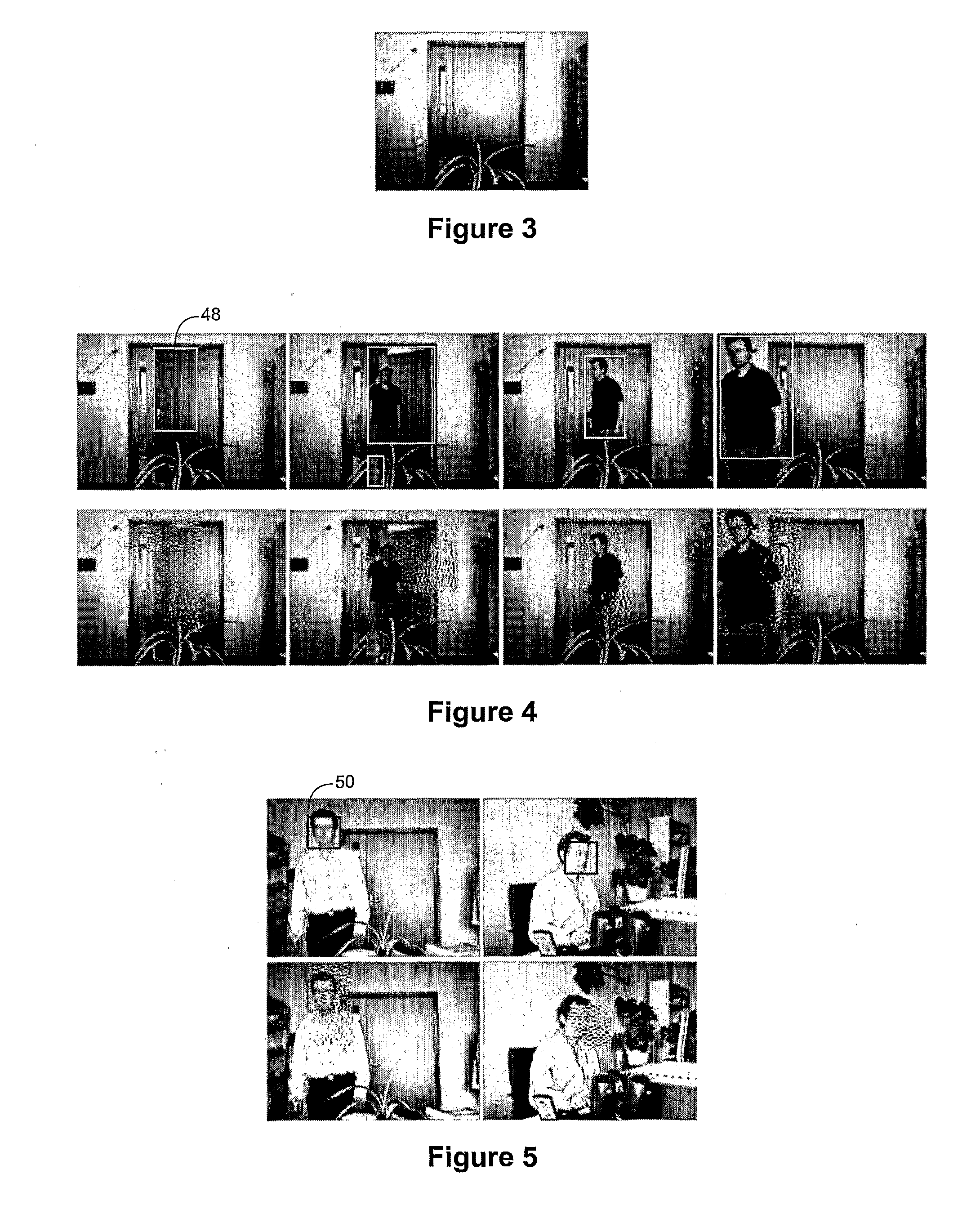
Smart Video Surveillance System Ensuring Privacy
InactiveUS20070296817A1Closed circuit television systemsBurglar alarmComputer hardwareVideo monitoring
This invention describes a video surveillance system which is composed of three key components 1—smart camera(s), 2—server(s), 3—client(s), connected through IP-networks in wired or wireless configurations. The system has been designed so as to protect the privacy of people and goods under surveillance. Smart cameras are based on JPEG 2000 compression where an analysis module allows for efficient use of security tools for the purpose of scrambling, and event detection. The analysis is also used in order to provide a better quality in regions of the interest in the scene. Compressed video streams leaving the camera(s) are scrambled and signed for the purpose of privacy and data integrity verification using JPSEC compliant methods. The same bit stream is also protected based on JPWL compliant methods for robustness to transmission errors. The operations of the smart camera are optimized in order to provide the best compromise in terms of perceived visual quality of the decoded video, versus the amount of power consumption. The smart camera(s) can be wireless in both power and communication connections. The server(s) receive(s), store(s), manage(s) and dispatch(es) the video sequences on wired and wireless channels to a variety of clients and users with different device capabilities, channel characteristics and preferences. Use of seamless scalable coding of video sequences prevents any need for transcoding operations at any point in the system.
Owner:EMITALL SURVEILLANCE
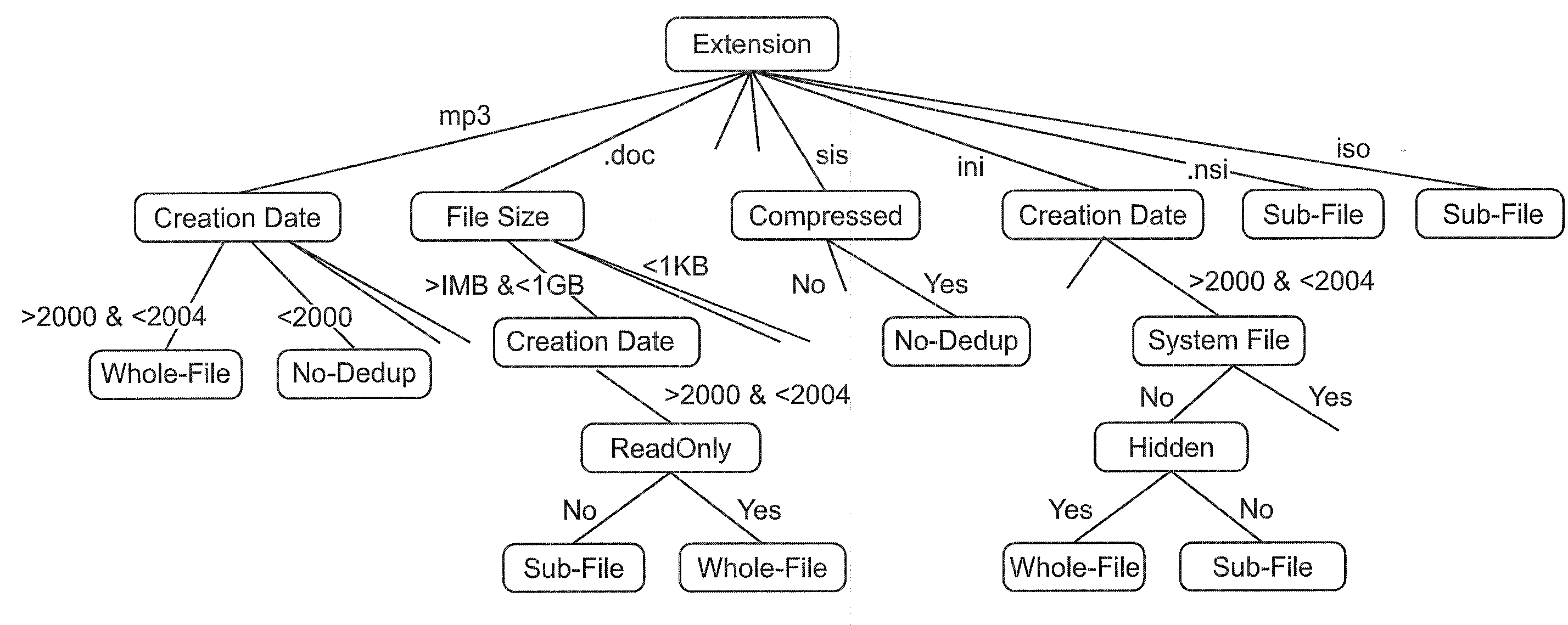
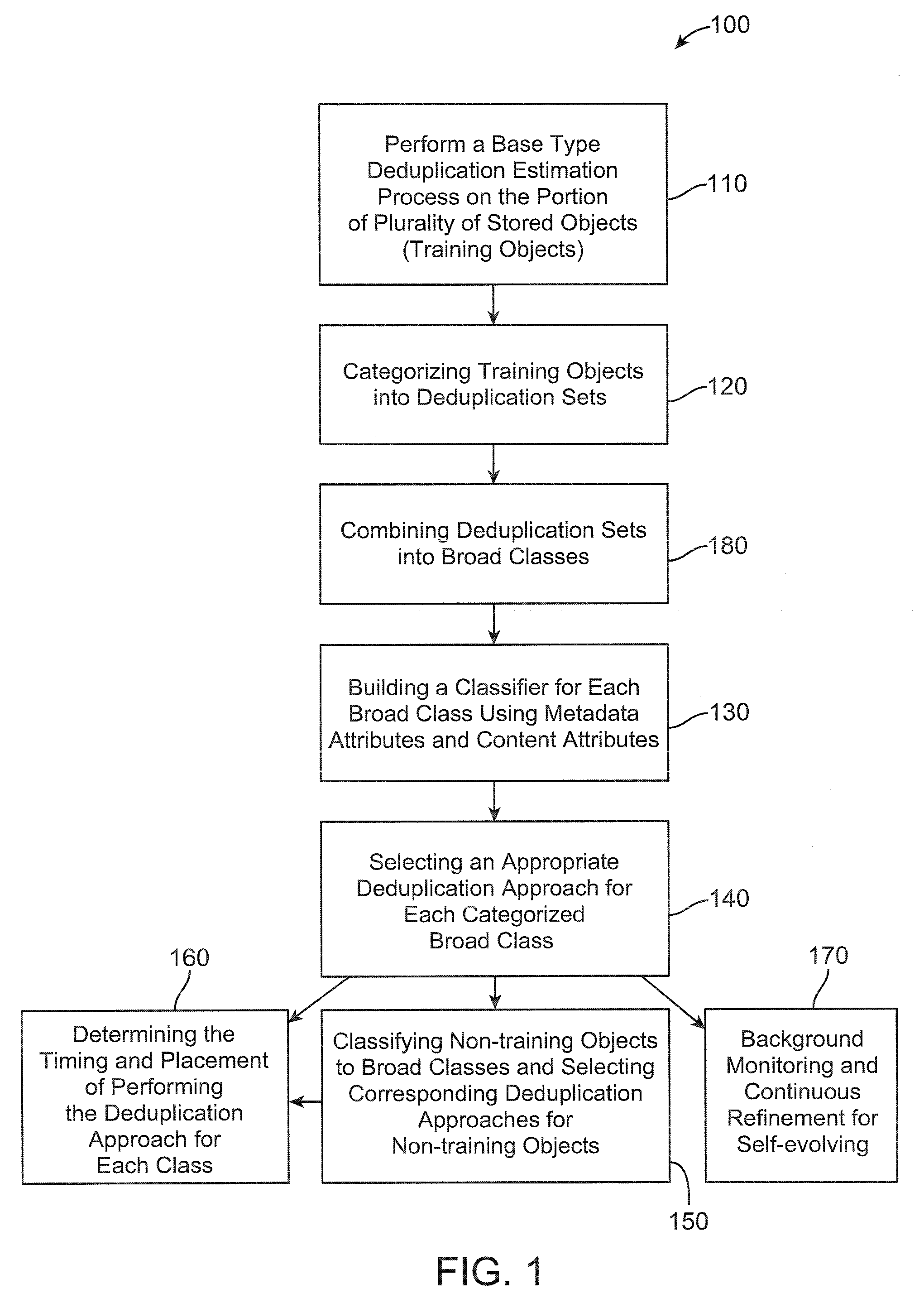
Storage management through adaptive deduplication
ActiveUS20100250501A1Digital data processing detailsMemory adressing/allocation/relocationStorage managementData deduplication
One embodiment retrieves a first portion of a plurality of stored objects from at least one storage device. The embodiment further performs a base type deduplication estimation process on the first portion of stored objects. The embodiment still further categorizes the first portion of the plurality of stored objects into deduplication sets based on a deduplication relationship of each object of the plurality of stored objects with each of the estimated first plurality of deduplication chunk portions. The embodiment further combines deduplication sets into broad classes based on deduplication characteristics of the objects in the deduplication sets. The embodiment still further classifies a second portion of the plurality of stored objects into broad classes using classifiers. The embodiment further selects an appropriate deduplication approach for each categorized class.
Owner:DAEDALUS BLUE LLC
Storage management for fine grained tiered storage with thin provisioning
ActiveUS7949637B1Digital data processing detailsSpecial data processing applicationsStorage managementThin provisioning
A system for managing data includes providing at least one logical device having a table of information that maps sections of the logical device to sections of at least two storage areas. Characteristics of data associated with a one section of the logical device may be evaluated. The section of the data may moved between the at least two storage areas from a first location to a second location according to a policy and based on the characteristics of the data. A copy of the data may be retained in the first location and a list maintained that indentifies the copy of the data in the first location. The system provides for garbage collection processing for memory management.
Owner:EMC IP HLDG CO LLC
Retrieval and recovery of data chunks from alternate data stores in a deduplicating system
InactiveUS20100070478A1Various limitationPreserve integrityDigital data processing detailsError detection/correctionComplete dataStorage management
One aspect of the present invention includes retrieving and recovering data chunks from alternate data stores in a storage management system which utilizes deduplication. In one embodiment, deduplication information for data chunks of data objects is stored at a system-wide level to enable the transfer and access of data chunks stored among multiple storage pools. When a data object is accessed on a first storage pool that contains damaged or inaccessible data chunks, the undamaged and accessible chunks may be retrieved from the first storage pool, in addition to retrieving an undamaged copy of the damaged or inaccessible data chunks from alternate data storage pools. Thus, a complete data object can be retrieved or recovered with a combination of chunks from the first storage pool and other storage pools within the storage management system, without requiring the entire data object to be retrieved from a backup source.
Owner:IBM CORP
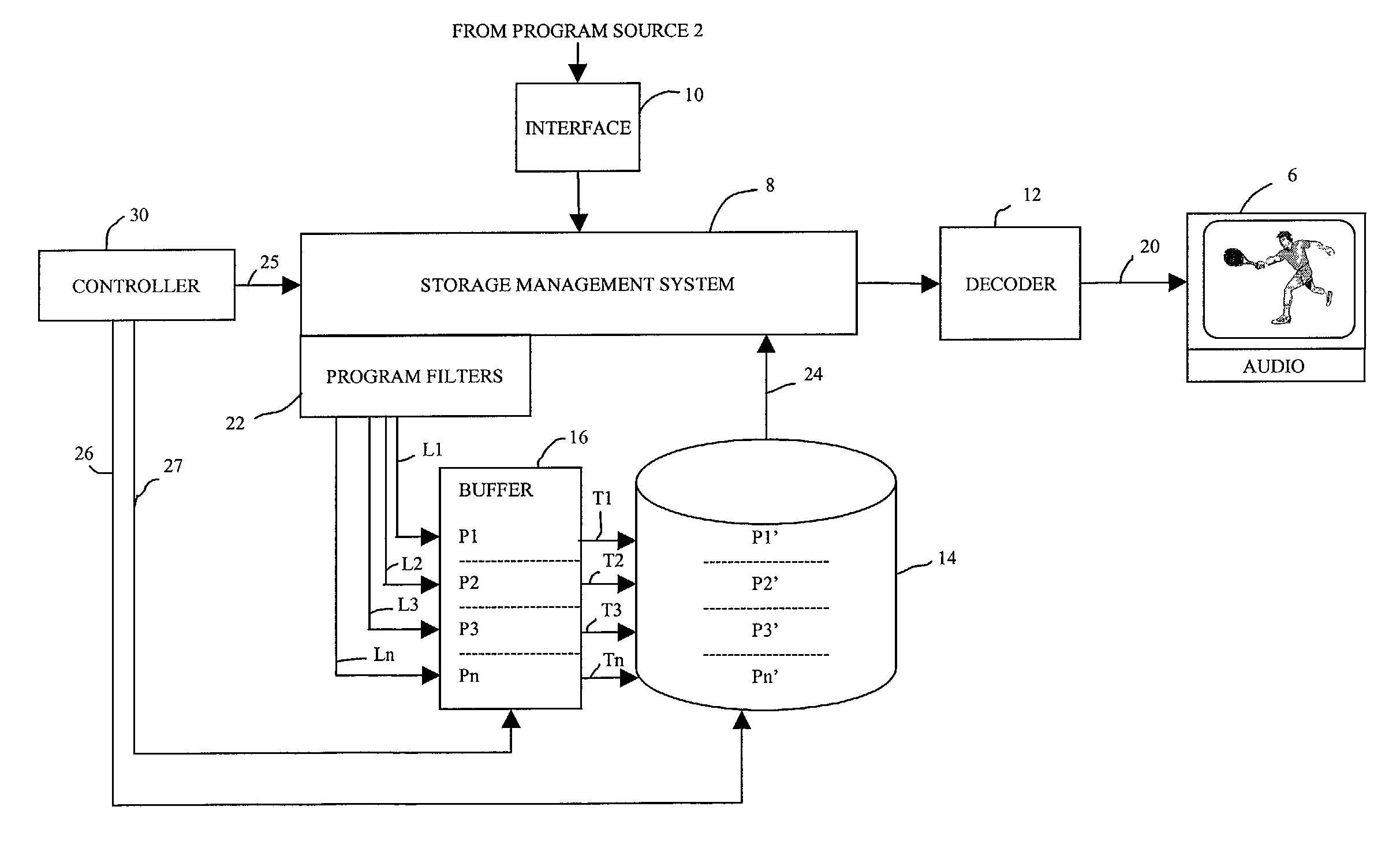
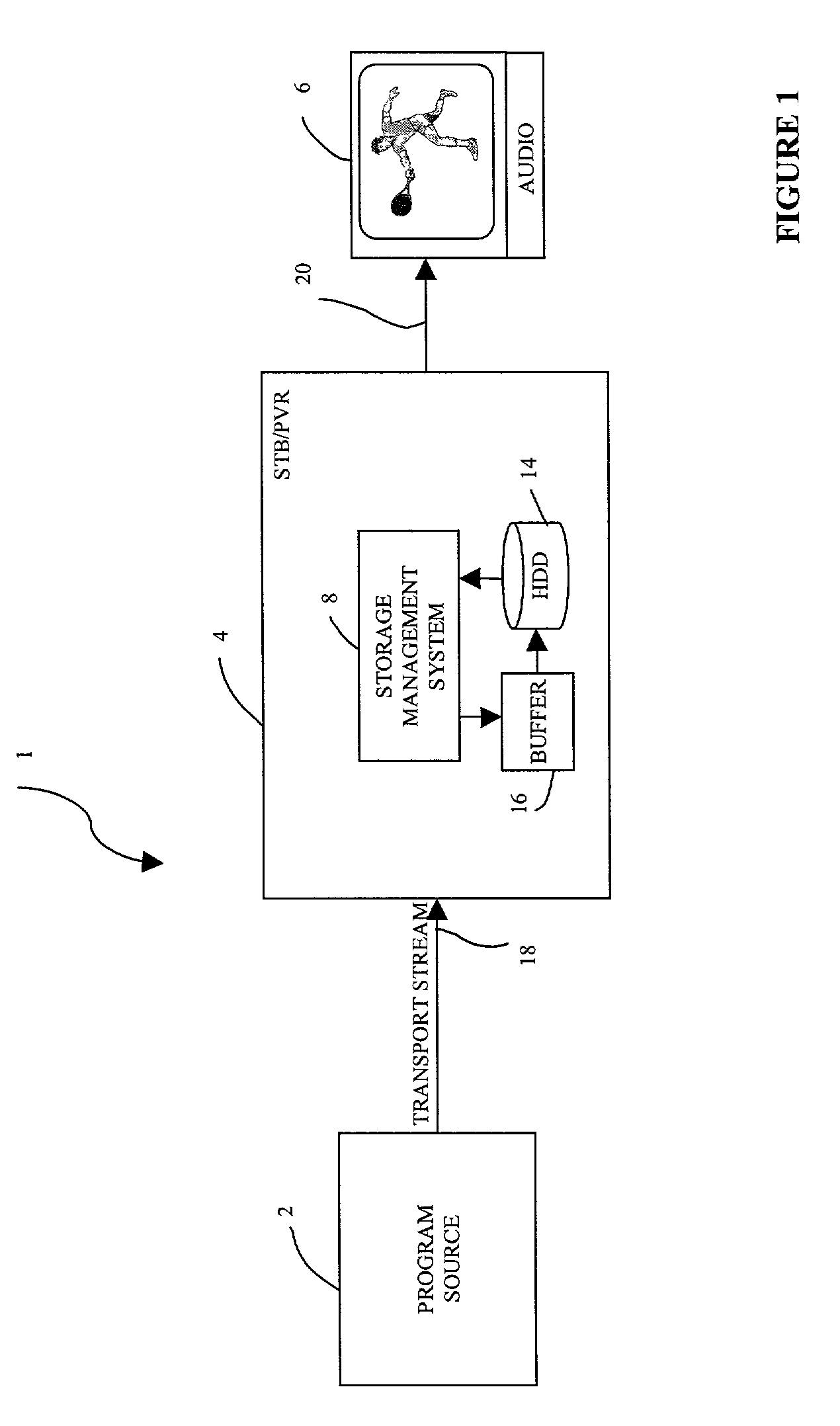
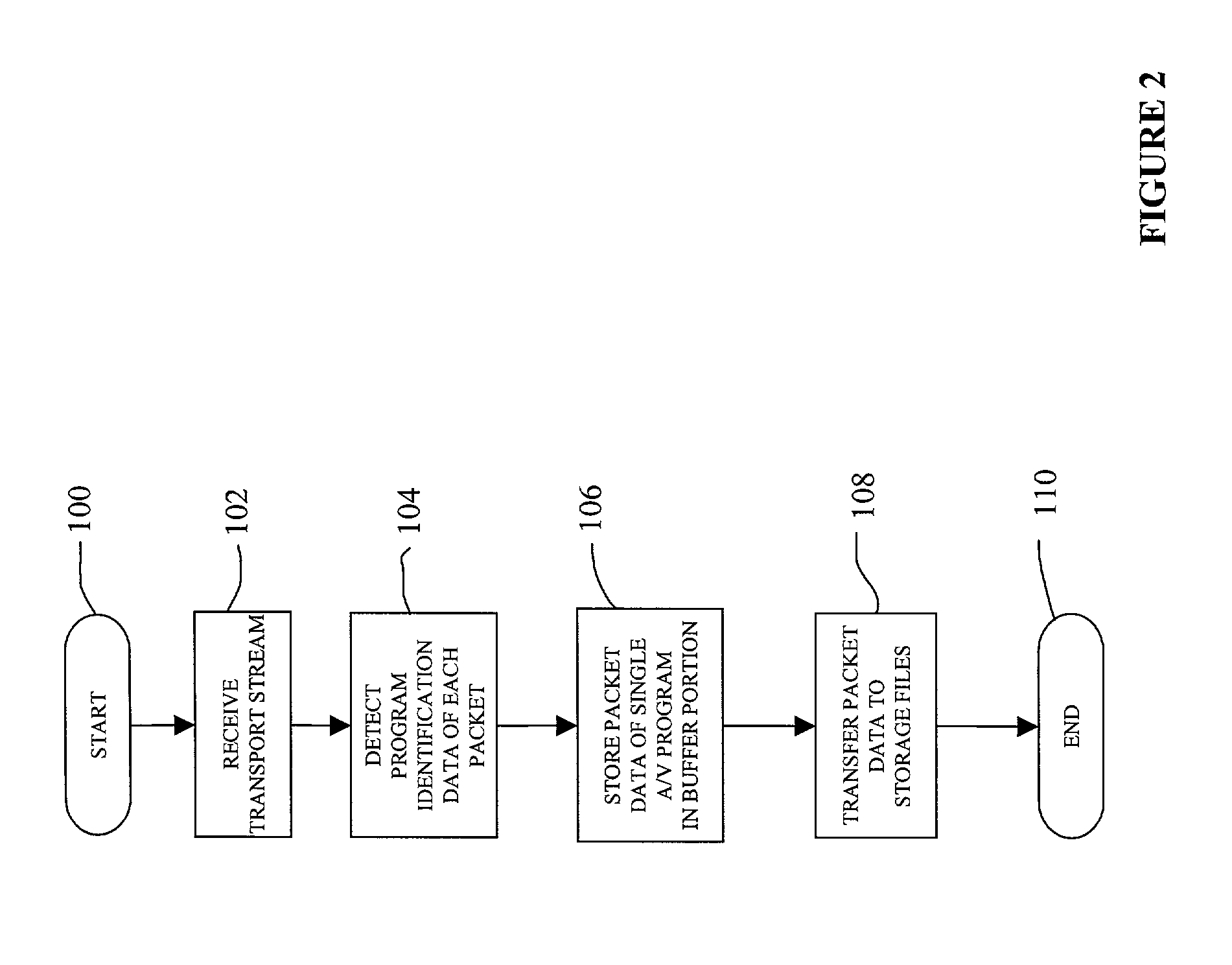
System and a method for storing audio/video programs on a hard disk drive for presentation to a viewer
ActiveUS7171110B1Television system detailsElectronic editing digitised analogue information signalsHard disc driveStructure of Management Information
An audio / video (A / V) system for storing A / V programs includes an interface configured to receive a transport stream structured in packets and representing a plurality of A / V programs. Each A / V program is represented by a plurality of packets and is identified by program identification data in each packet. A storage management system is connected to receive the transport stream from the interface and to detect the program identification data of each received packet. A buffer is coupled to the storage management system and has a plurality of separate buffer portions. Each buffer portion is in communication with the storage management system to receive data of packets having program identification data related to a single A / V program and to store the data of the packets separate from data of packets having program identification data related to different A / V programs. A storage medium is coupled to the storage management system and has a plurality of separate storage files for the A / V programs. Each storage file receives data of the packets having program identification data related to a single A / V program and transferred from one of the separate buffer portions of the buffer.
Owner:KEEN PERSONAL MEDIA +1
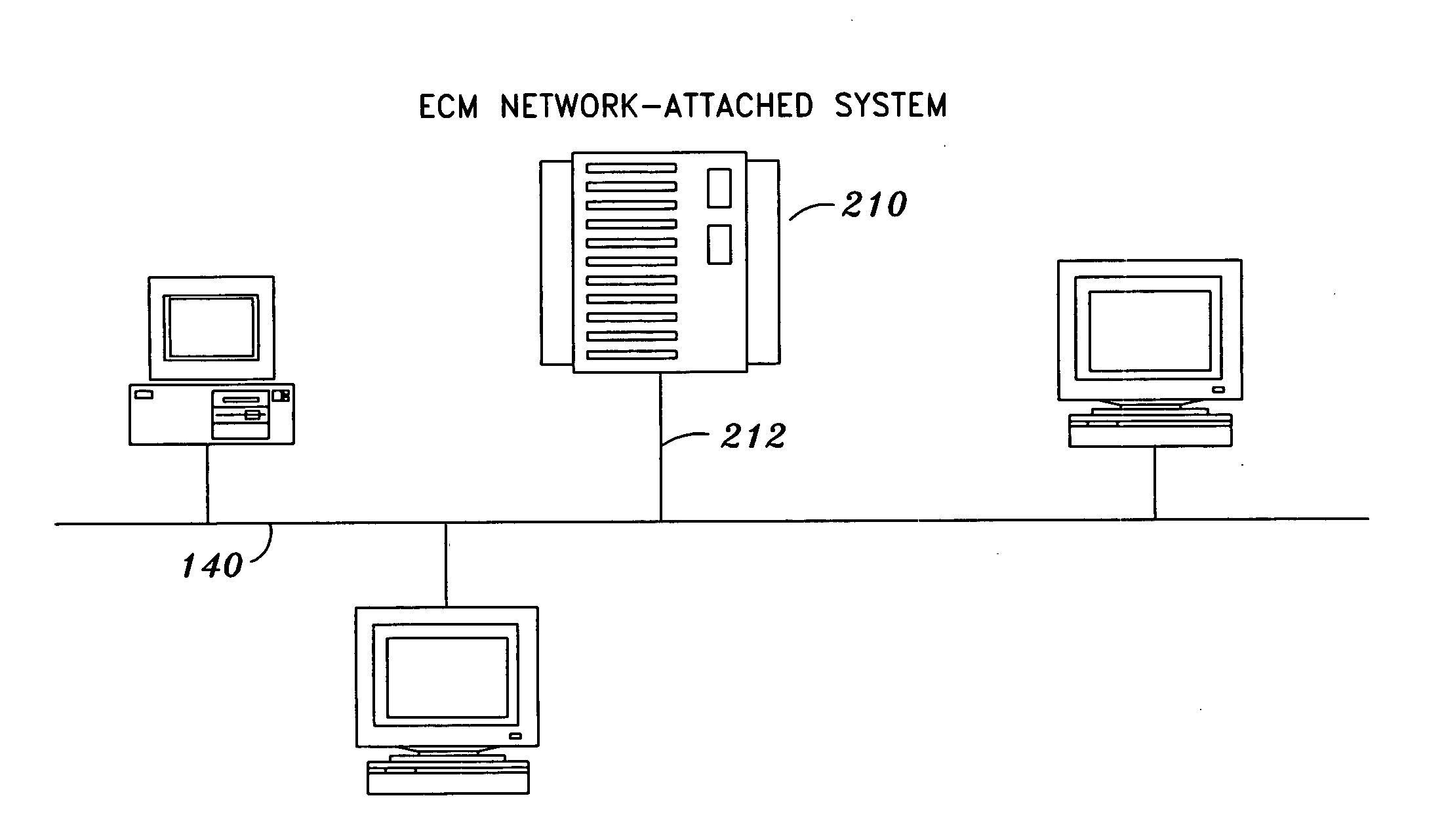
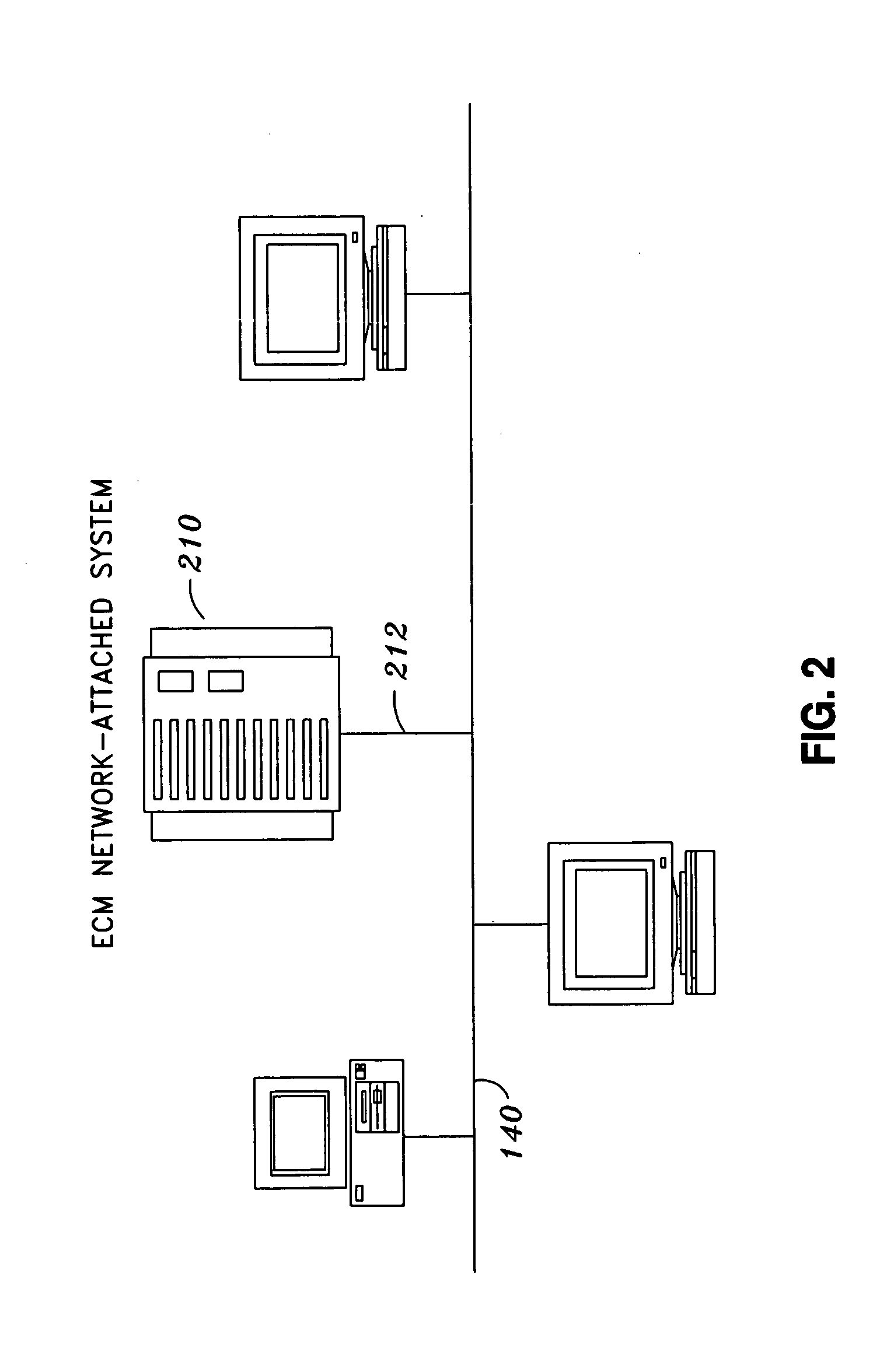
Enterprise content management network-attached system
ActiveUS20050246311A1Data processing applicationsError detection/correctionEnterprise content managementStorage management
The present invention discloses a method and system for providing services in an enterprise content management network-attached system, where the enterprise content management functions are provided as an integral part of a storage system. An integrated enterprise content management network-attached system provides a single, unified approach to the entire range of enterprise content management functions from storage management to content and business process management. The result is a robust and reliable complete enterprise content management solution with a lower total cost of ownership than existing products.
Owner:IBM CORP
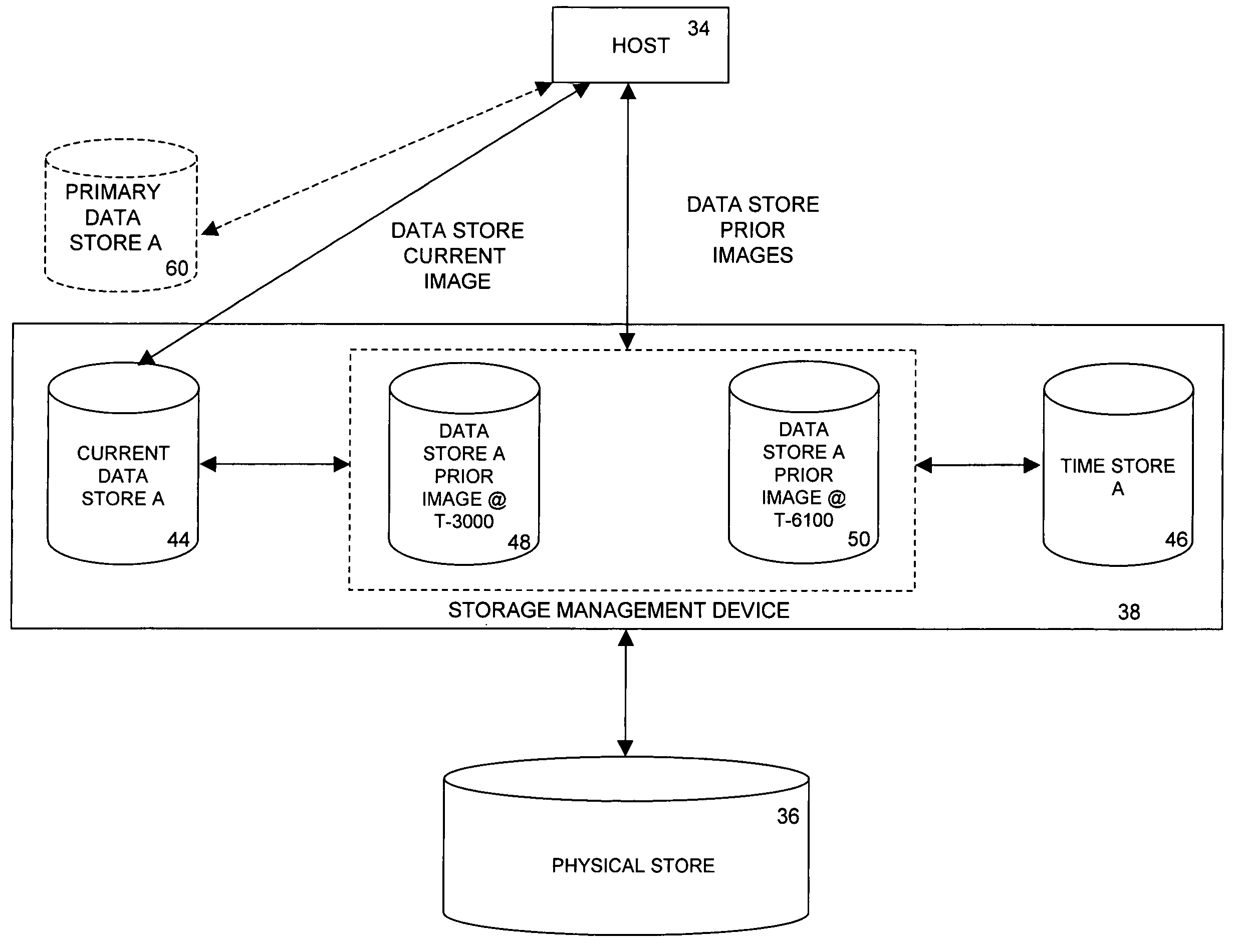
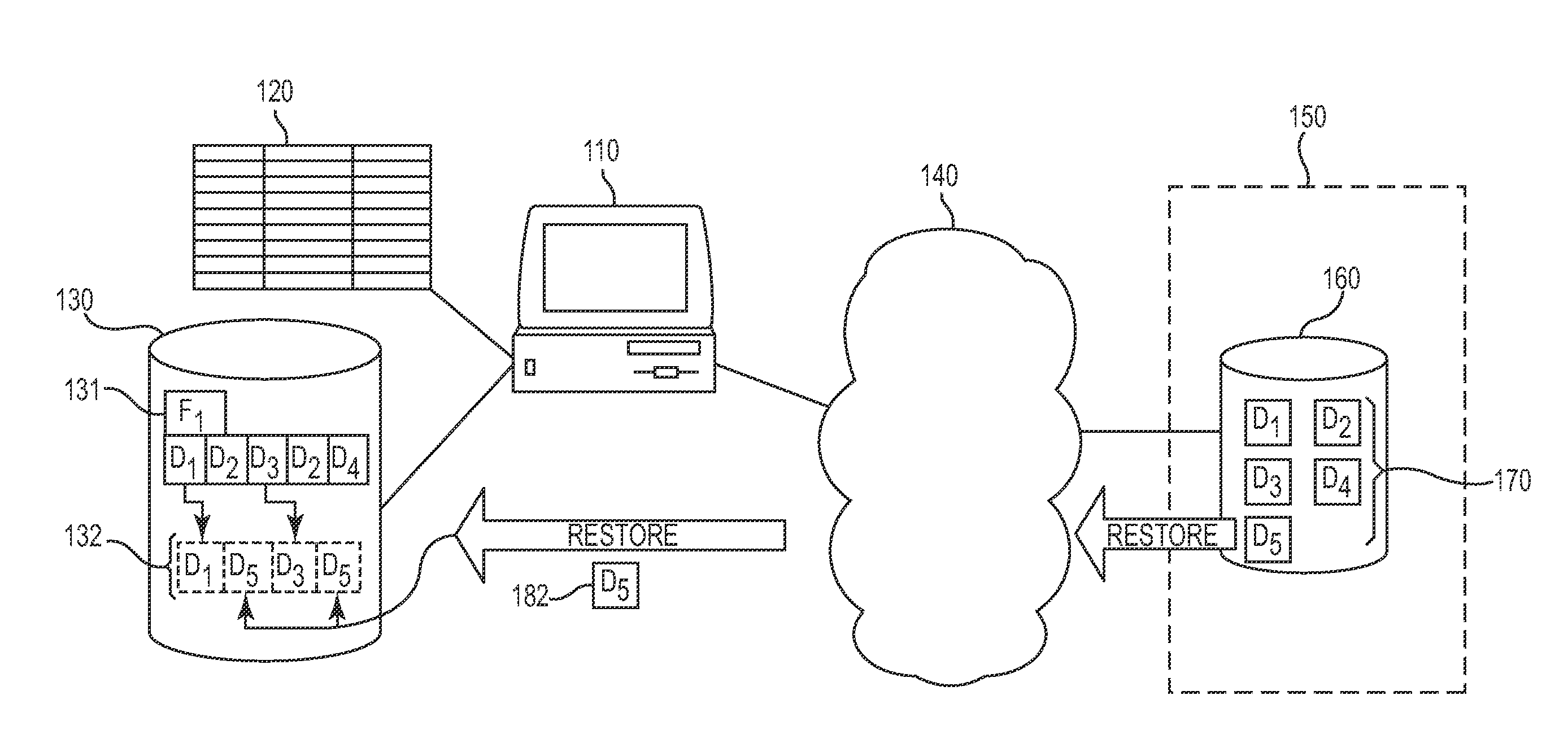
Methods and devices for restoring a portion of a data store
ActiveUS20050076264A1Promote recoveryData storage is convenientMemory loss protectionError detection/correctionStorage managementData store
A storage management device receives a request to restore a portion of a data store to its content at a specified past time, which is selected from a substantially continuous time interval. In response to the received request, the storage management device stores in the portion of the data store content that was stored in the portion of the data store at the specified past time and that was overwritten since the specified past time.
Owner:SYMANTEC OPERATING CORP
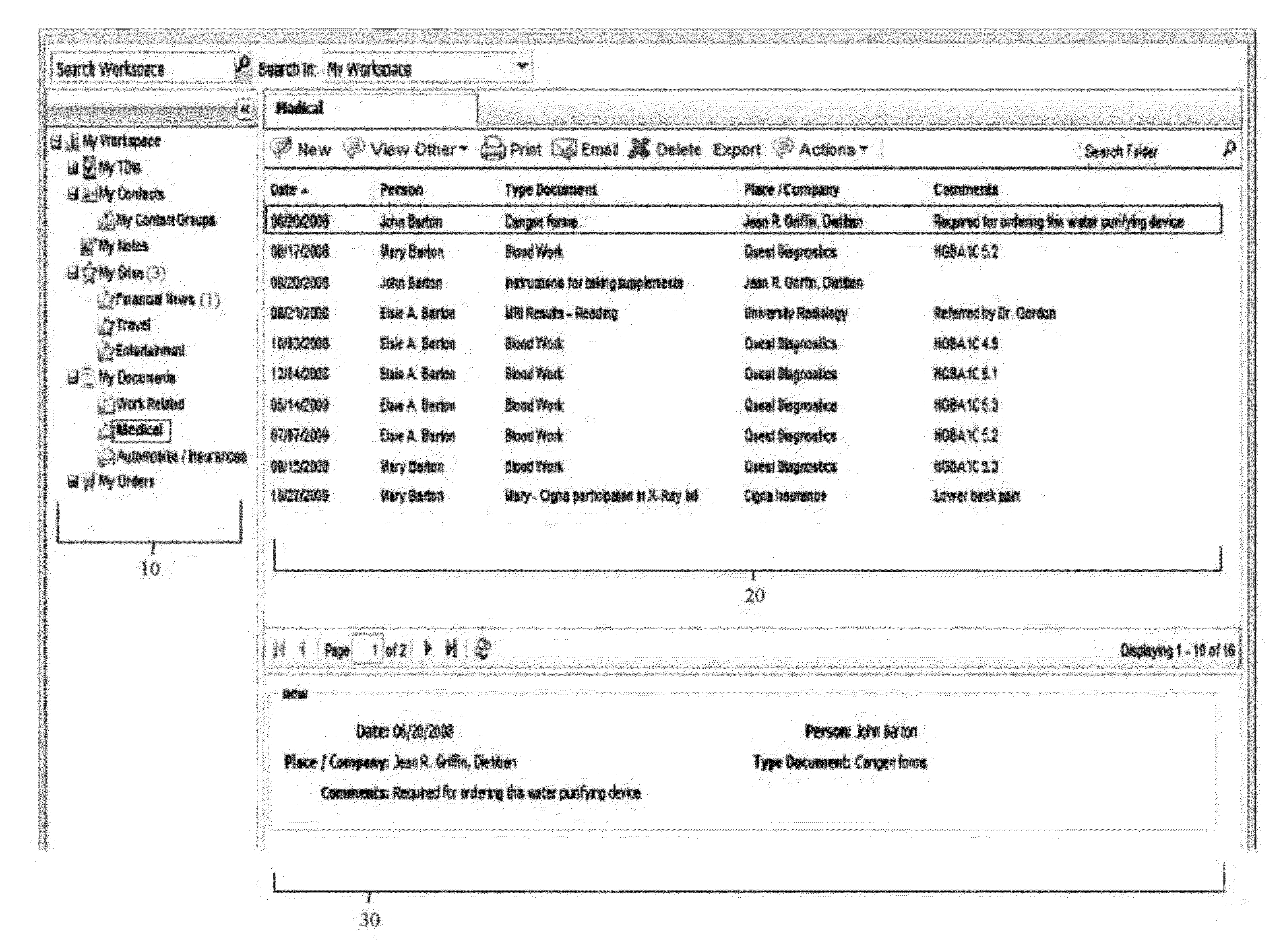
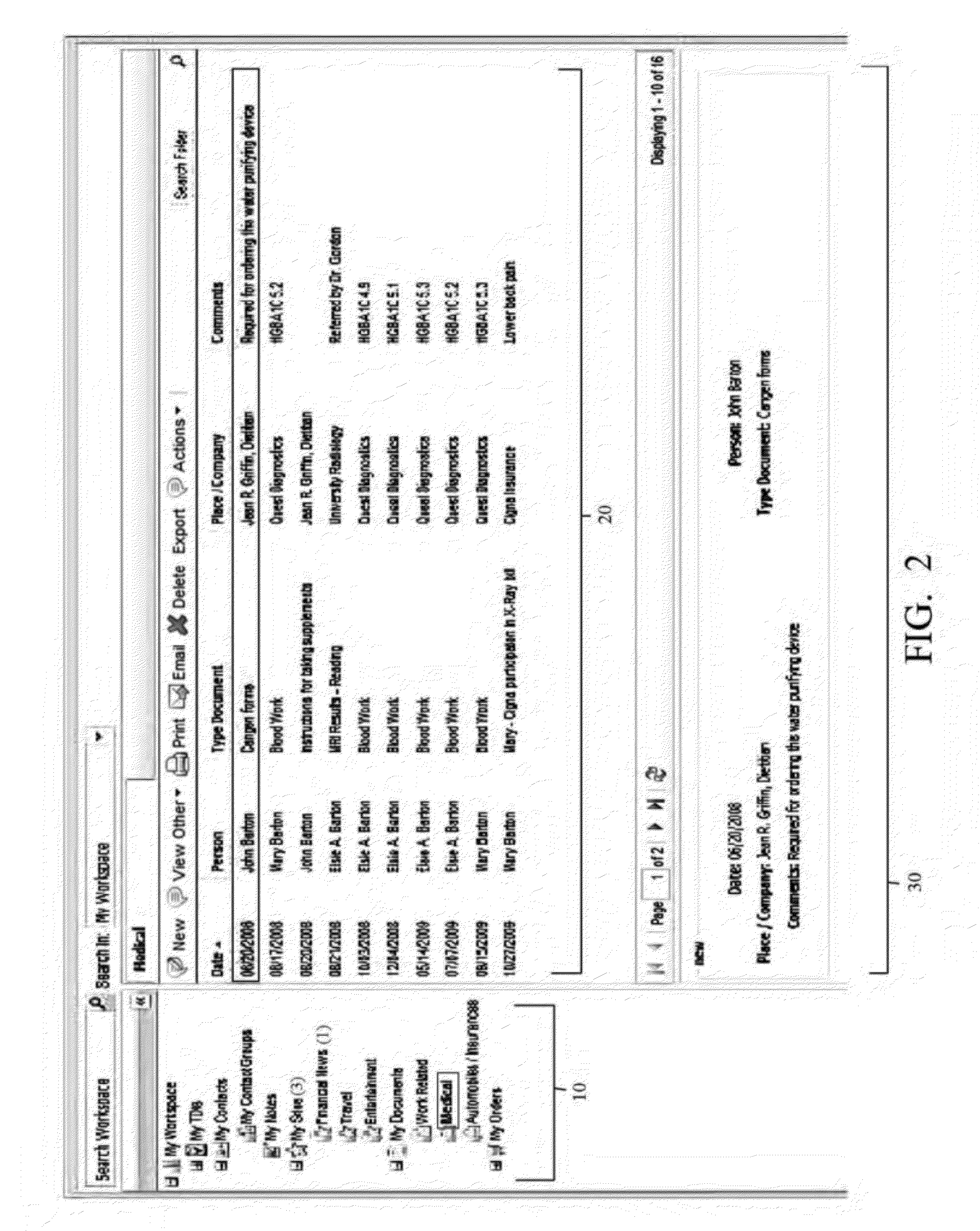
Integrated web-based workspace with curated tree-structure database schema
InactiveUS20120096389A1Streamlining actionStreamlining flowWebsite content managementSpecial data processing applicationsDocumentation procedureDocument preparation
A virtual web-based computing platform combining a particular network database hierarchy, graphical user interface, and integrated suite of computational tools accessible on demand, by which users gain access to an integrated Virtual Workspace for organizing emails, contacts, bookmarks, tasks, documents, notes, and all other relevant information. The network database hierarchy employs unique data structure and methods, allowing the user to centrally store and manage all data, regardless of type, as well as activities (actions taken and documented by the user). Nevertheless, the interface to said database offers a familiar folder / sub-folder “look and feel” using a tree data hierarchy, which gives a common, centralized and unified approach for storing, managing, displaying, and various types of data, regardless of object- and data-types.
Owner:IQTELL COM
Approach for optimizing restores of deduplicated data
InactiveUS20110218969A1Reduce the amount of processingImprove efficiencyError detection/correctionDigital data processing detailsData fileClient data
Various techniques for improving the performance of restoring deduplicated data files from a server to a client within a storage management system are disclosed. In one embodiment, a chunk index is maintained on the client that tracks the chunks remaining on the client for each data file that is stored to and restored from the storage server. When a specific file is selected for restore from the storage server to the client, the client determines if any local copies of this specific file's chunks are stored in files already existing on the client data store. The file is then reconstructed from a combination of these local copies of the file chunks and chunks retrieved from the storage server. Therefore, only chunks that are not stored or are inaccessible to the client are retrieved from the server, reducing server-side processing requirements and the bandwidth required for data restore operations.
Owner:IBM CORP
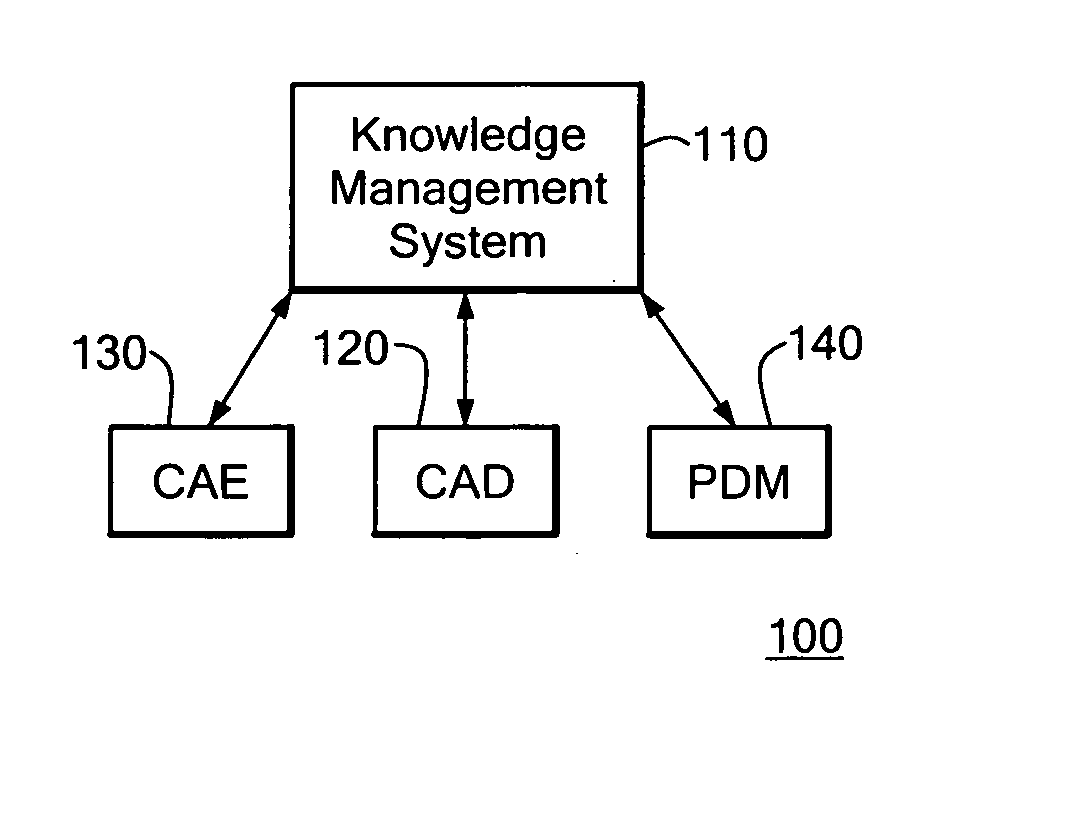
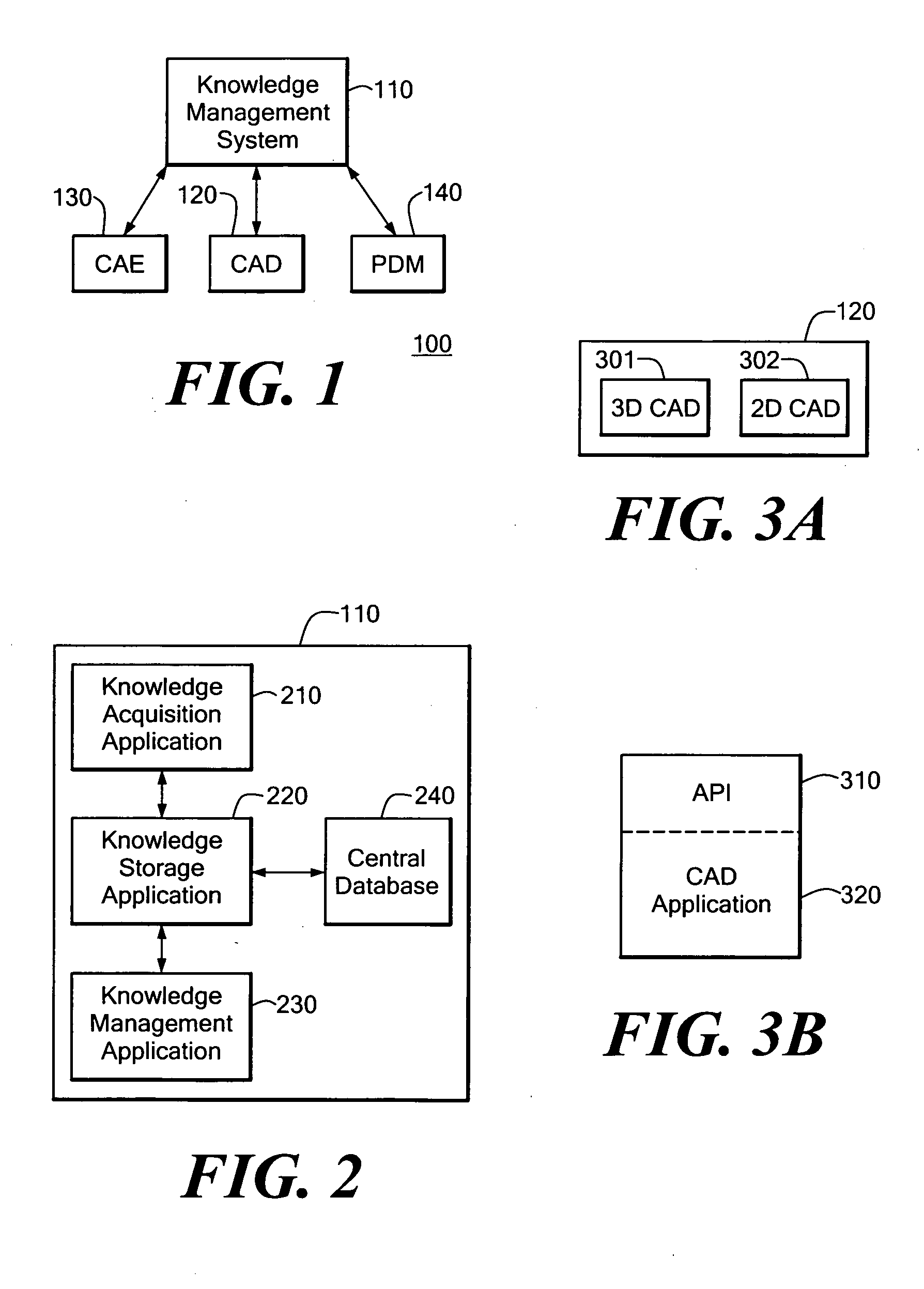
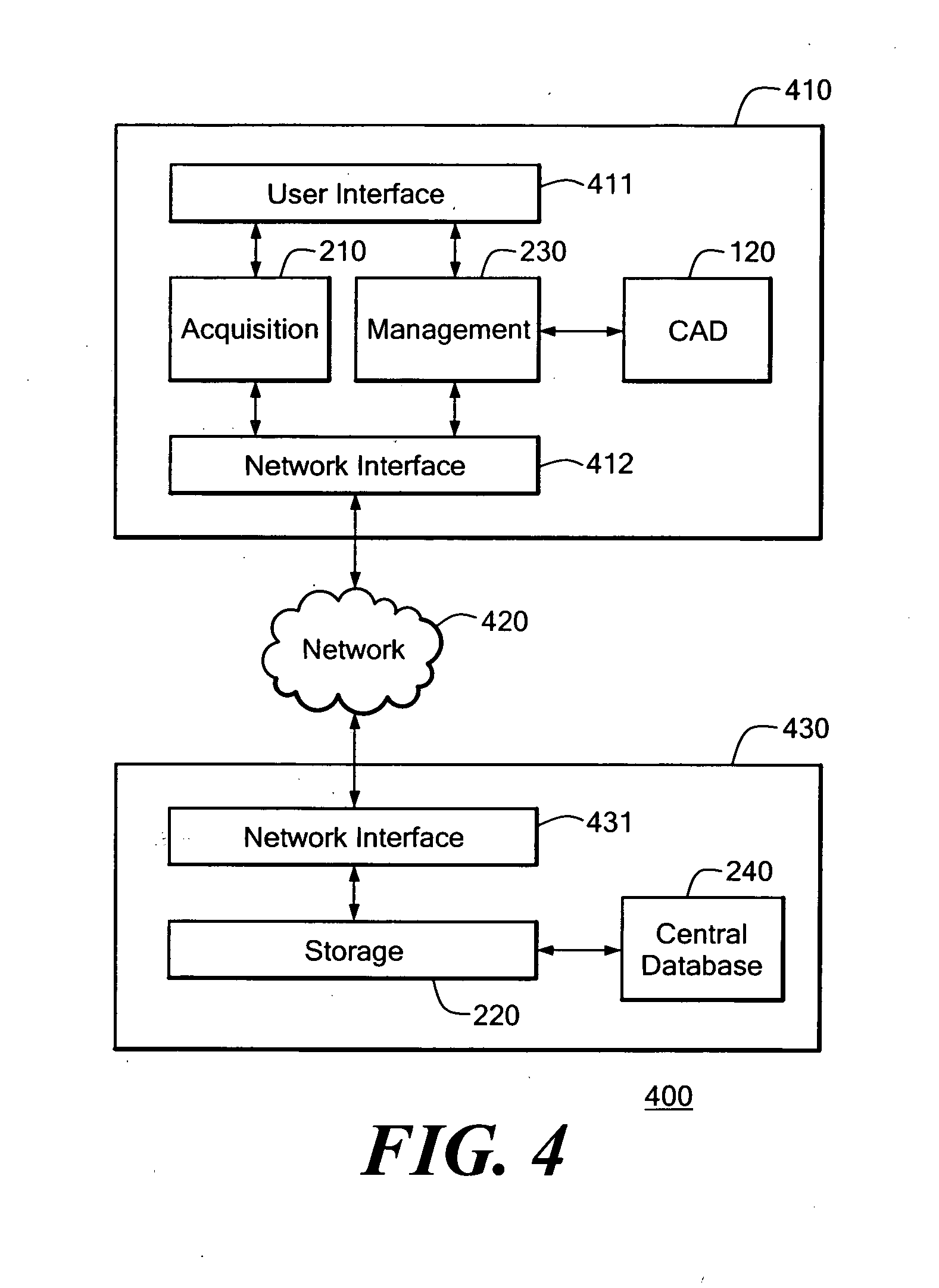
Knowledge management system for computer-aided design modeling
A knowledge management system captures, stores, manages, and applies rules for modeling geometric objects and related non-geometric attributes. The knowledge management system controls a computer-aided design system for modeling a geometric structure. The knowledge management system includes a knowledge management application in communication with the computer-aided design system through an application program interface. The knowledge management system also includes a central database managed by a knowledge storage application for maintaining rules and other related information. The knowledge management system also includes a knowledge acquisition application for generating rule programs for storage in the central database. The rules can relate to geometric and non-geometric attributes of the model.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com