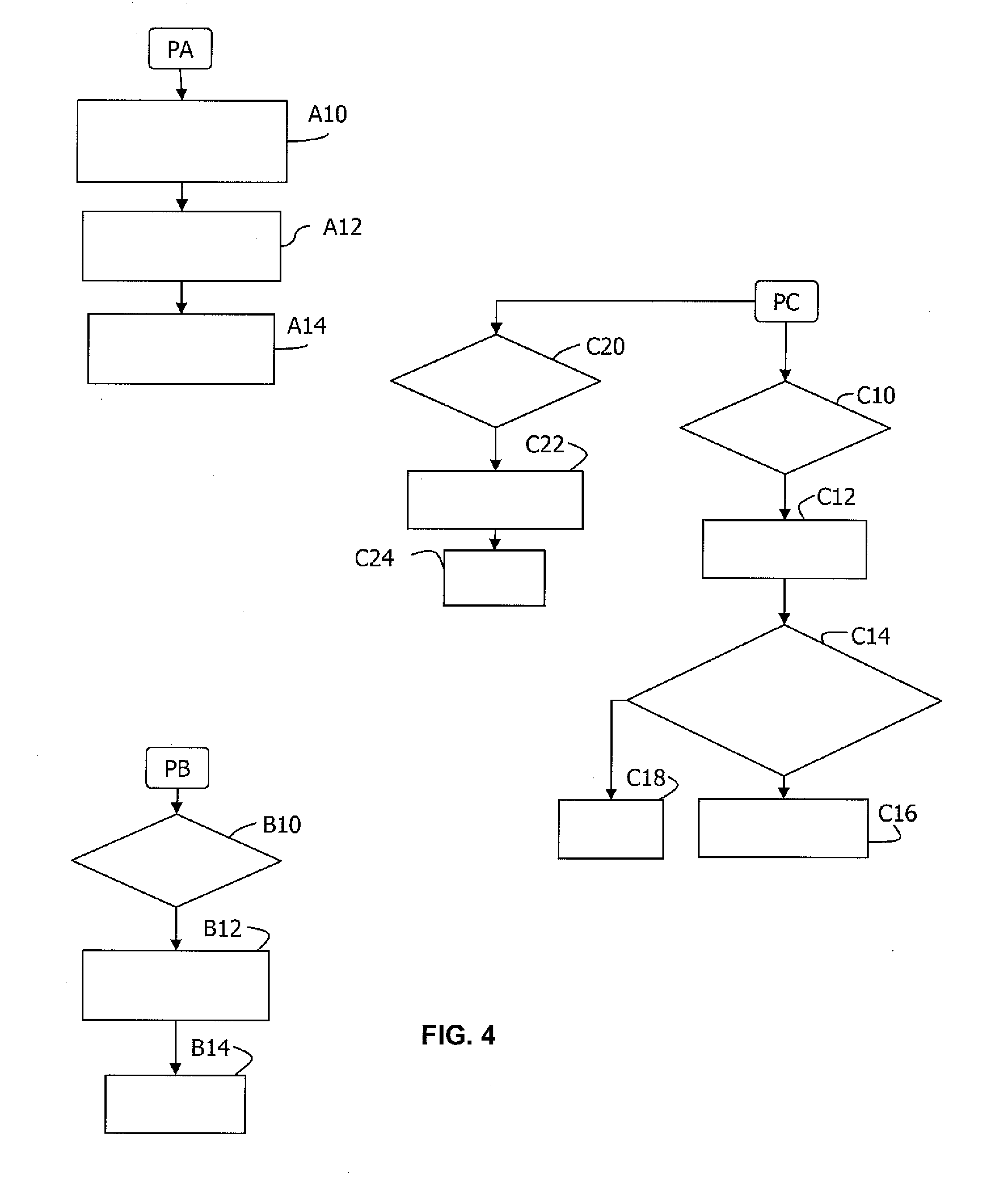
Patents
Literature
97 results about "Topology table" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A topology table is used by routers that route traffic in a network. It consists of all routing tables inside the Autonomous System where the router is positioned. Each router using the routing protocol EIGRP then maintains a topology table for each configured network protocol — all routes learned, that are leading to a destination are found in the topology table. EIGRP must have a reliable connection. The routing table of all routers of an Autonomous System is same.
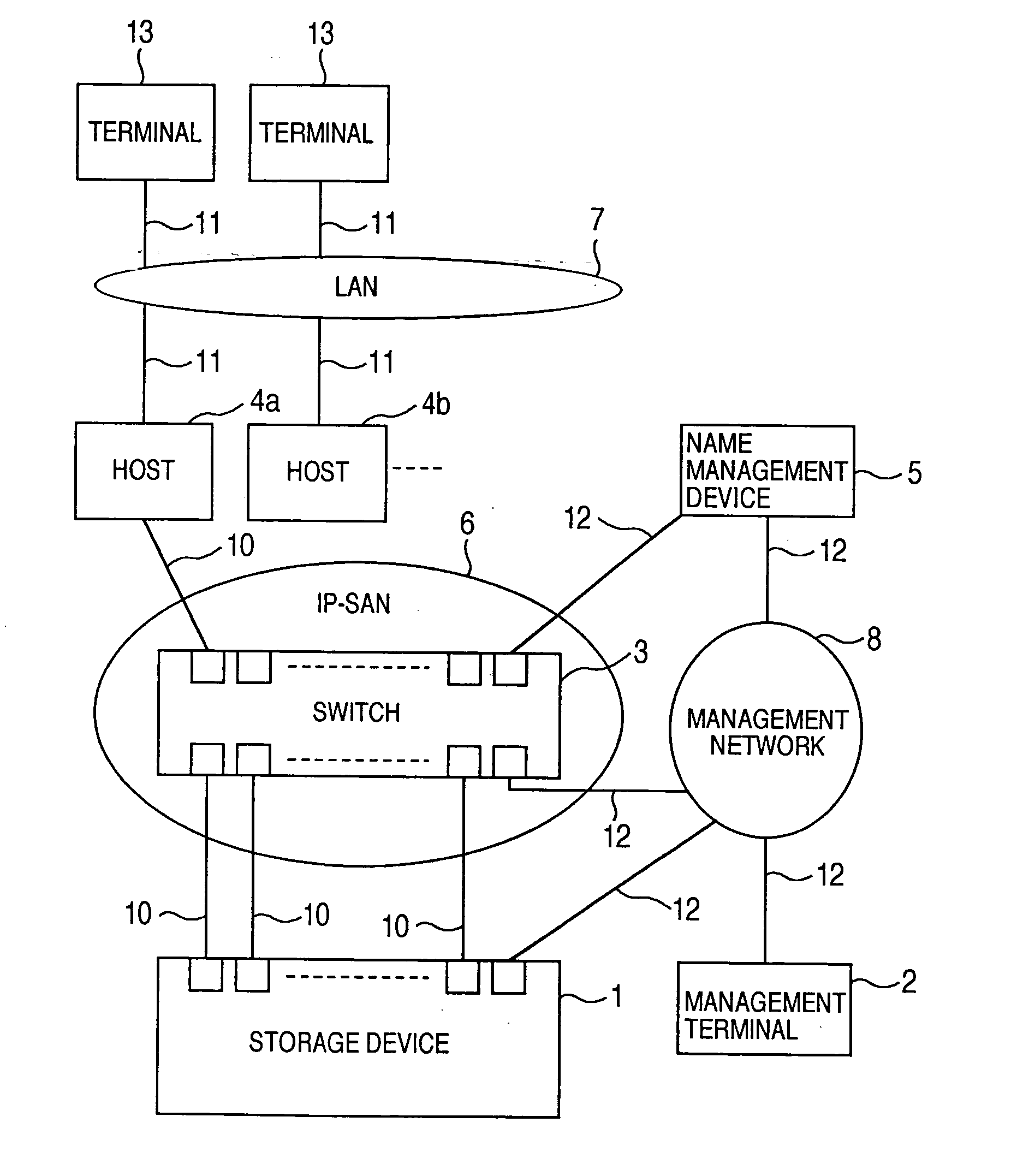
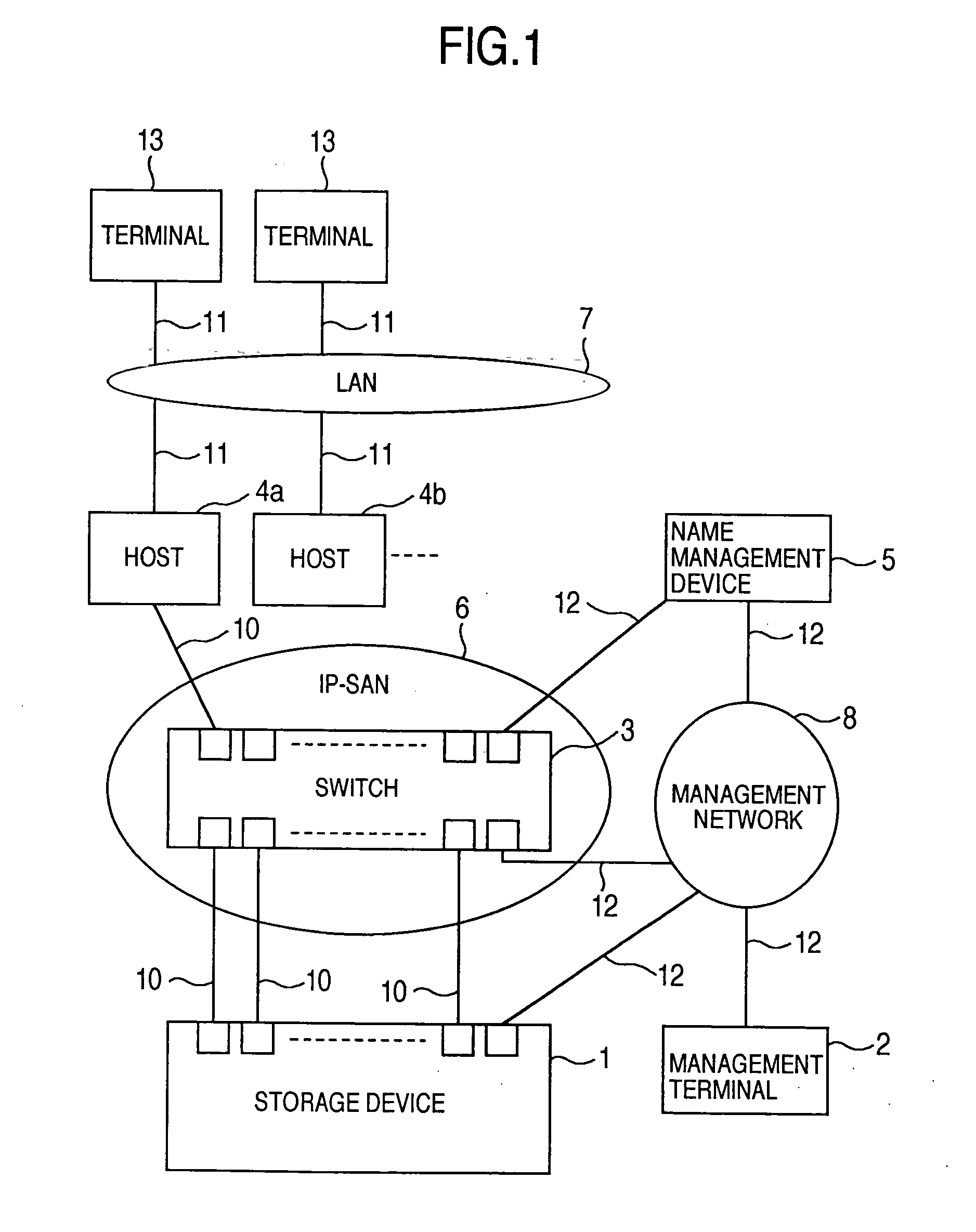
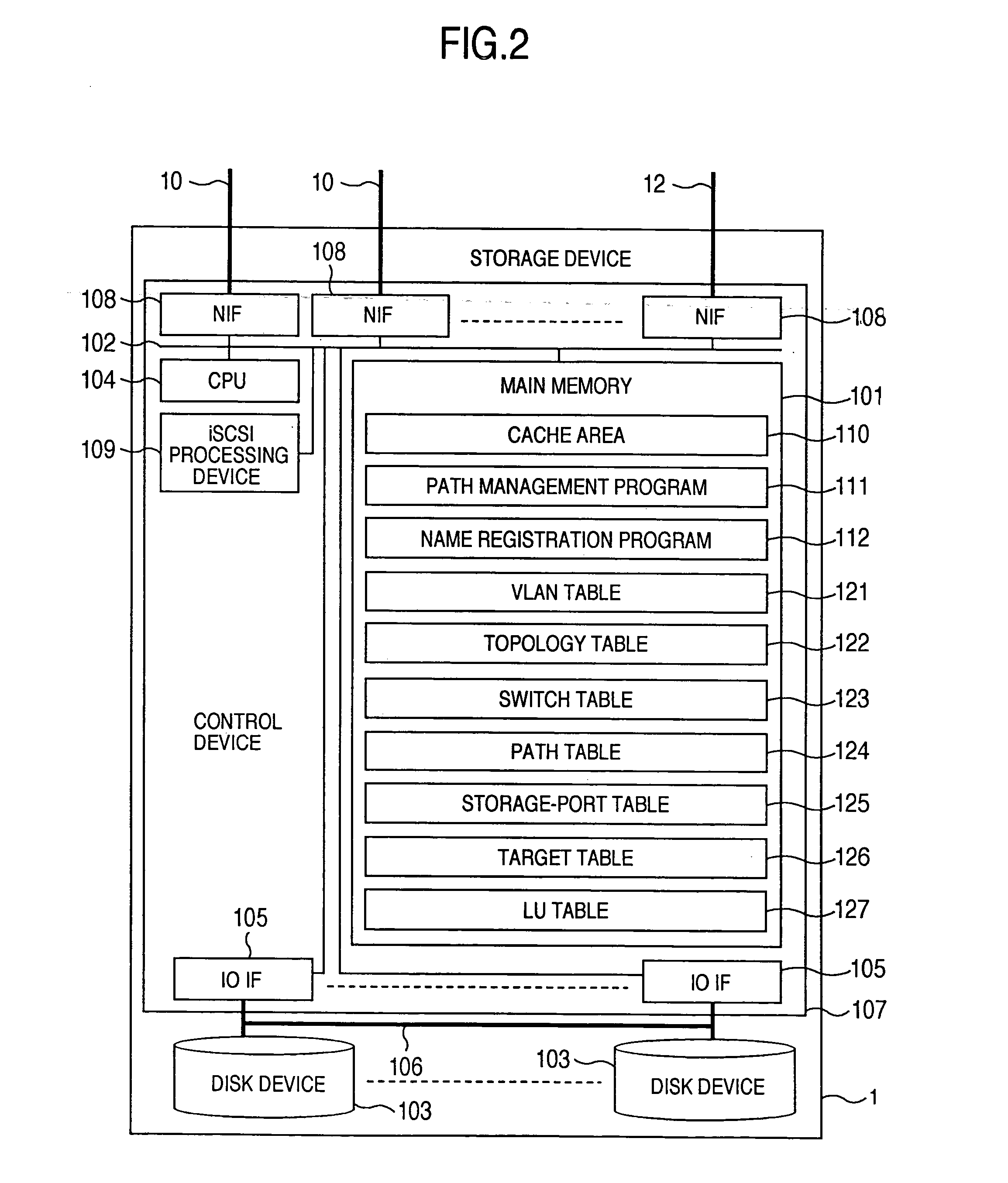
Storage system and a storage management system
InactiveUS20060047907A1Improve matchMemory loss protectionMultiple digital computer combinationsData packStorage management
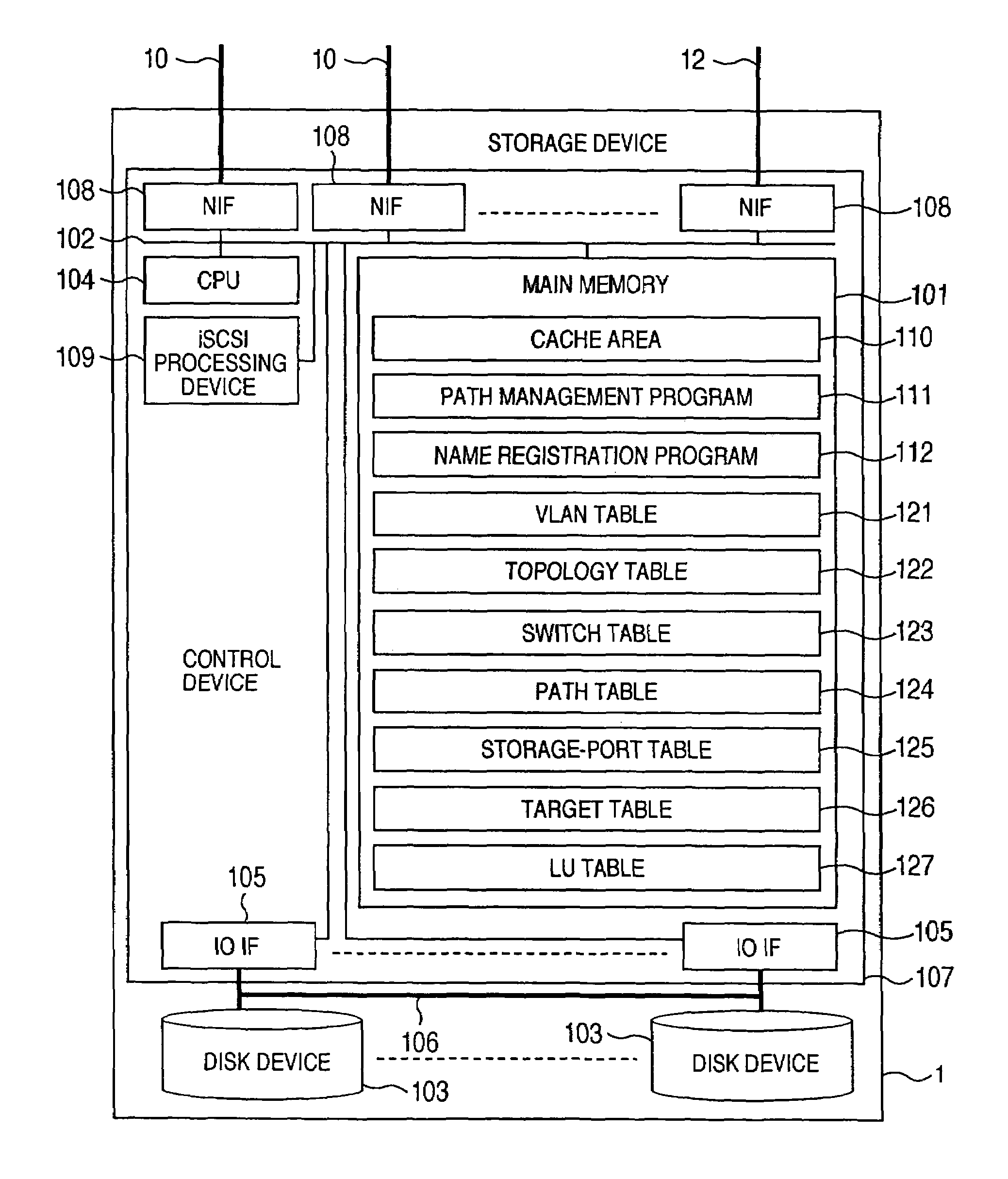
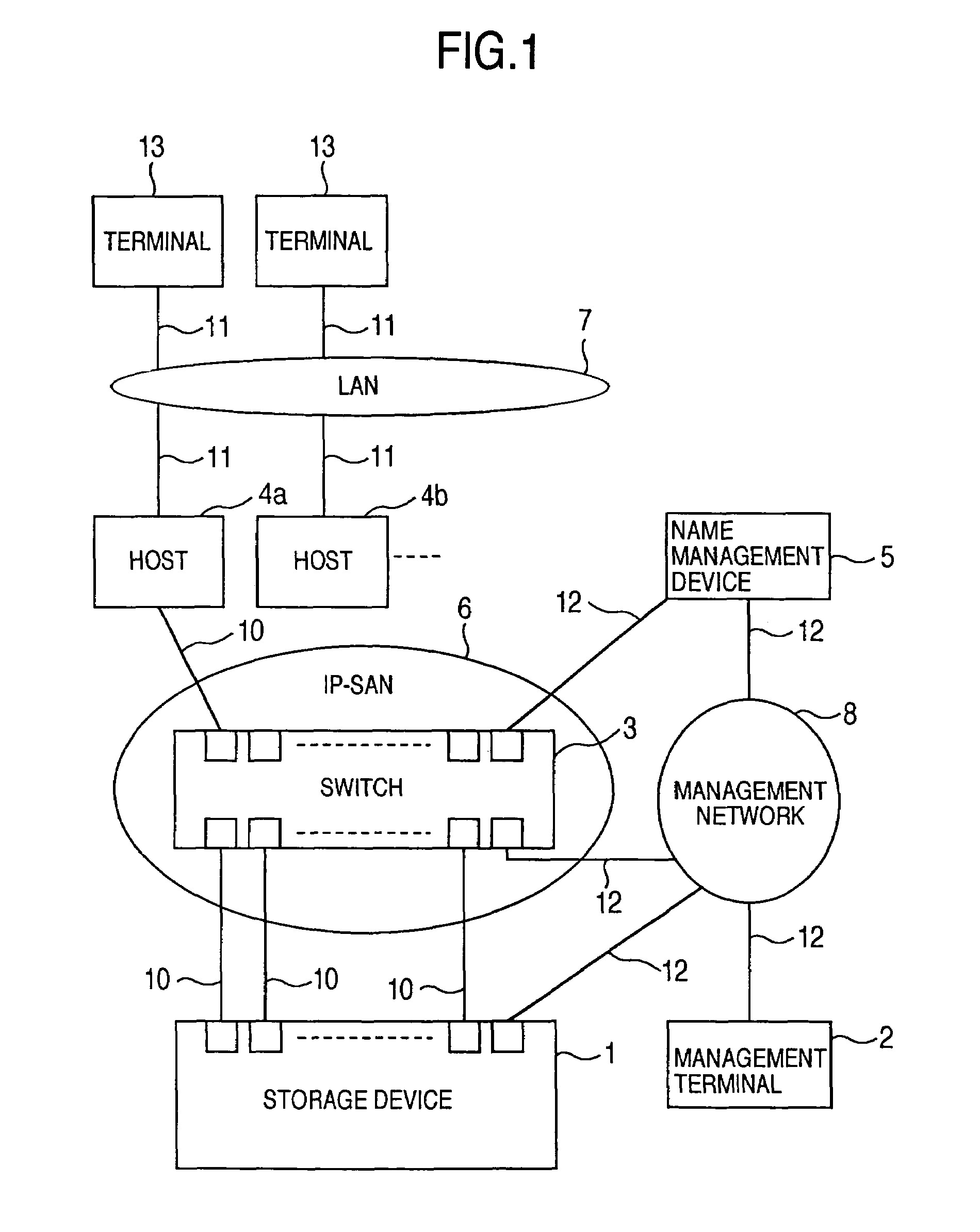
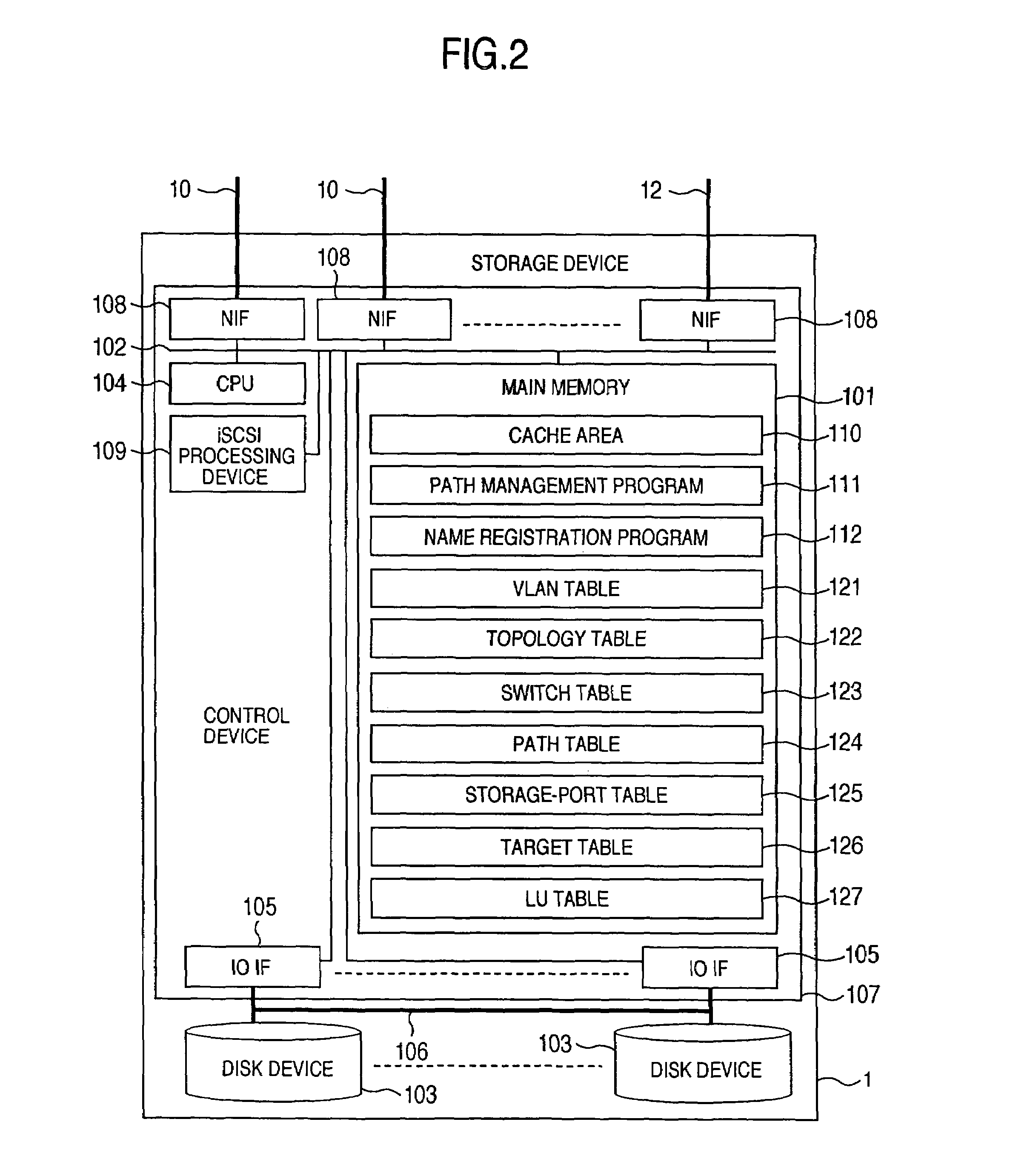
A storage device managing one or more logical volumes is connected with a name management device through an IP-SAN 6 composed of a switch. The storage device stores a topology table saving connecting relation among physical ports of host, physical ports of the storage device and physical ports of the switch, reads an identifier of the host and an identifier of the logical volume, selects a unused first physical port of the switch by referring to the topology table, selects a second physical port of the switch connected with the storage device, registers a group composed of the host and the logical volume with the name management device, and executes a configuration of allowing packets to be transferred between the first and the second physical ports with respect to the switch.
Owner:GOOGLE LLC
Distributed network organization and topology discovery in ad-hoc network
InactiveUS20050174950A1Reduce collisionImprove throughputData switching by path configurationNetwork topologyDistributed computing
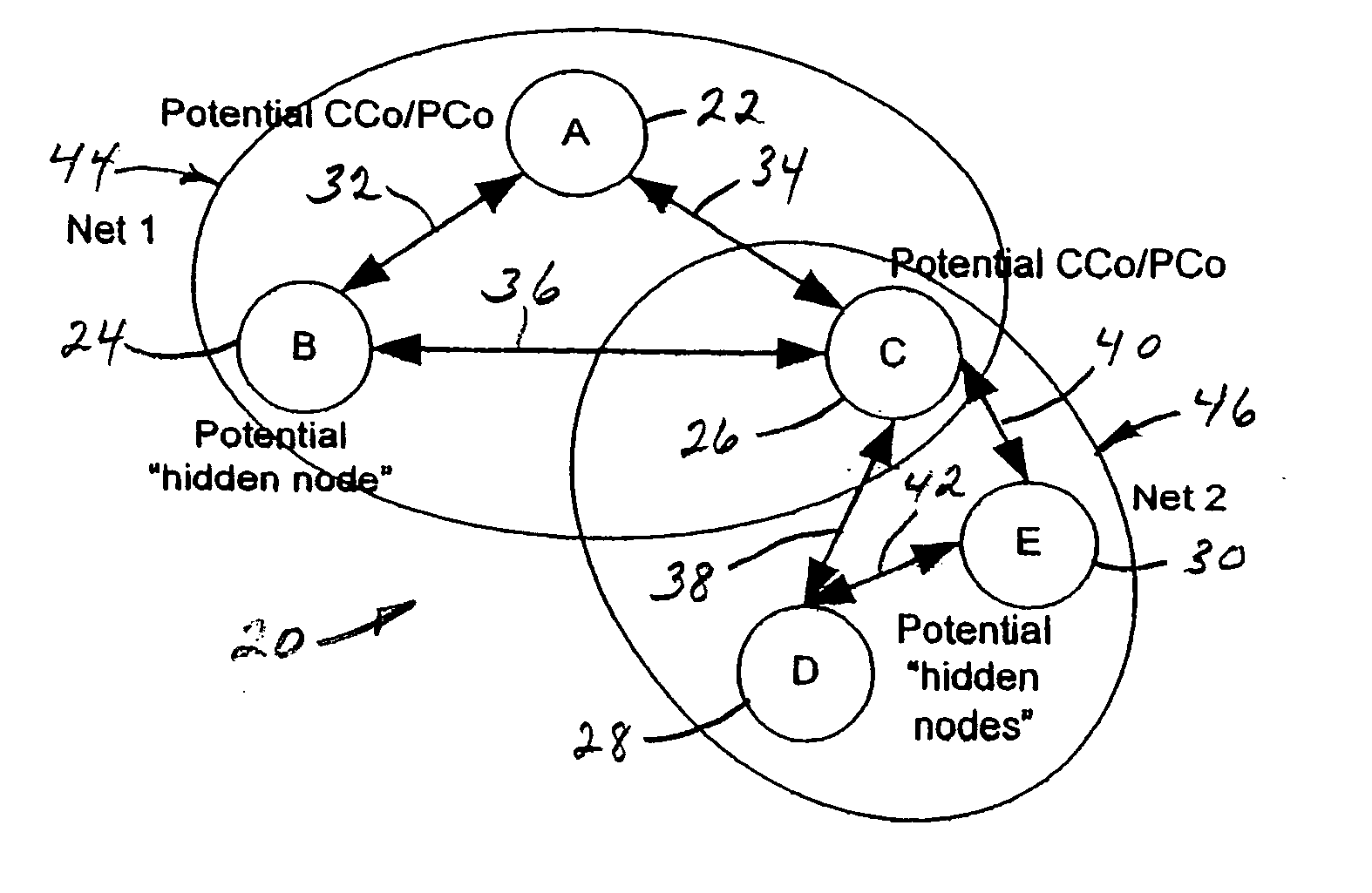
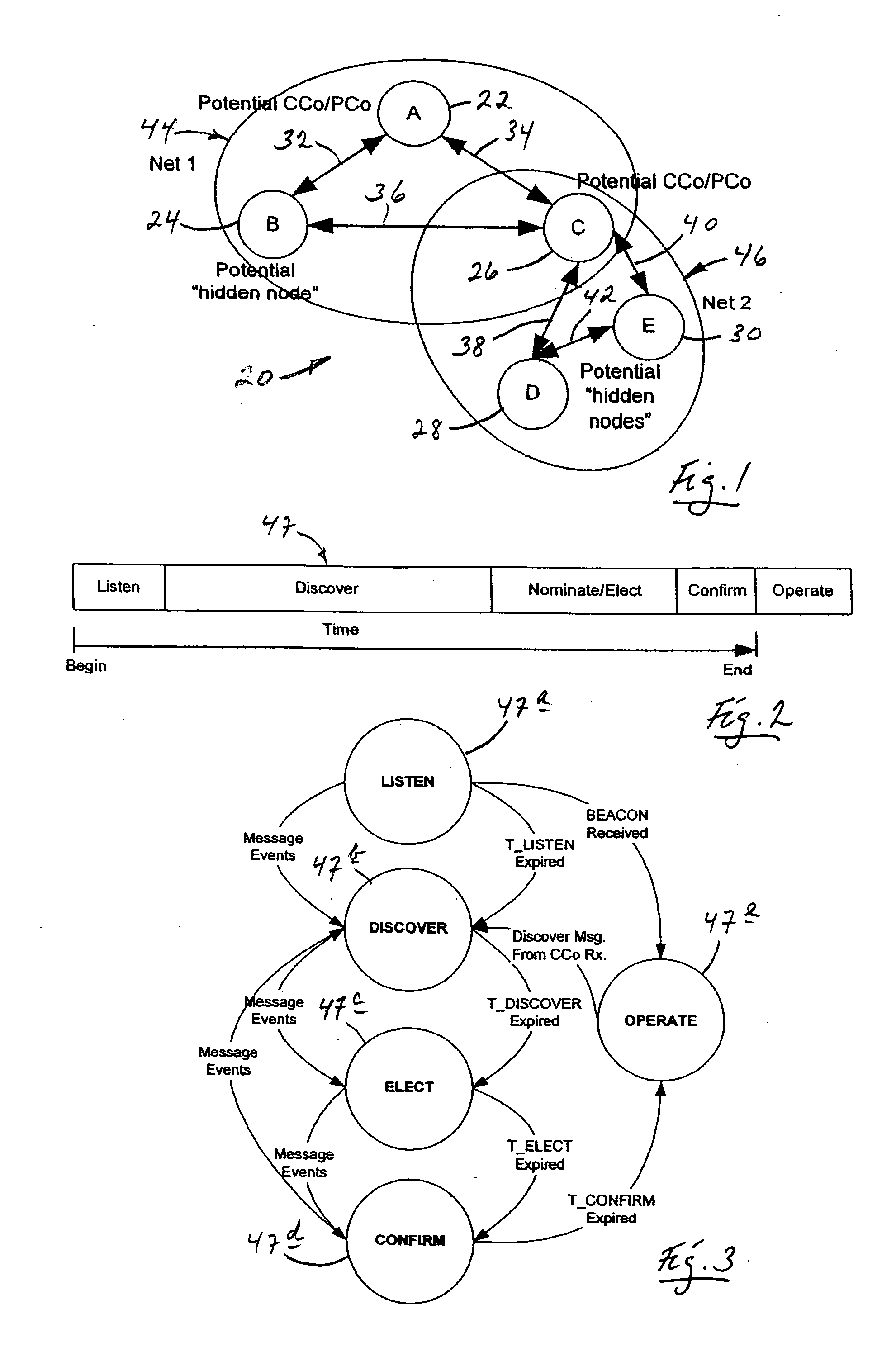
A distributed network method for self-organizing a group of nodes into a bi-directional communication network where initially there is no central coordinator in the prospective network environment. The method involves engaging in the process of determining internodal communication capabilities en route to creating a network topology table, and then using that table as a guide (a) selecting, by nodal election, an appropriate central coordinator, and (b) establishing proxy nodes which enable full network bi-directional communication between all nodes, including otherwise communicatively-compromised hidden nodes.
Owner:SHARP LAB OF AMERICA INC
Method and apparatus for disseminating topology information and for discovering new neighboring nodes
InactiveUS7327683B2Improve robustnessMinimize overheadError prevention/detection by using return channelFrequency-division multiplex detailsTopology informationLink-state routing protocol
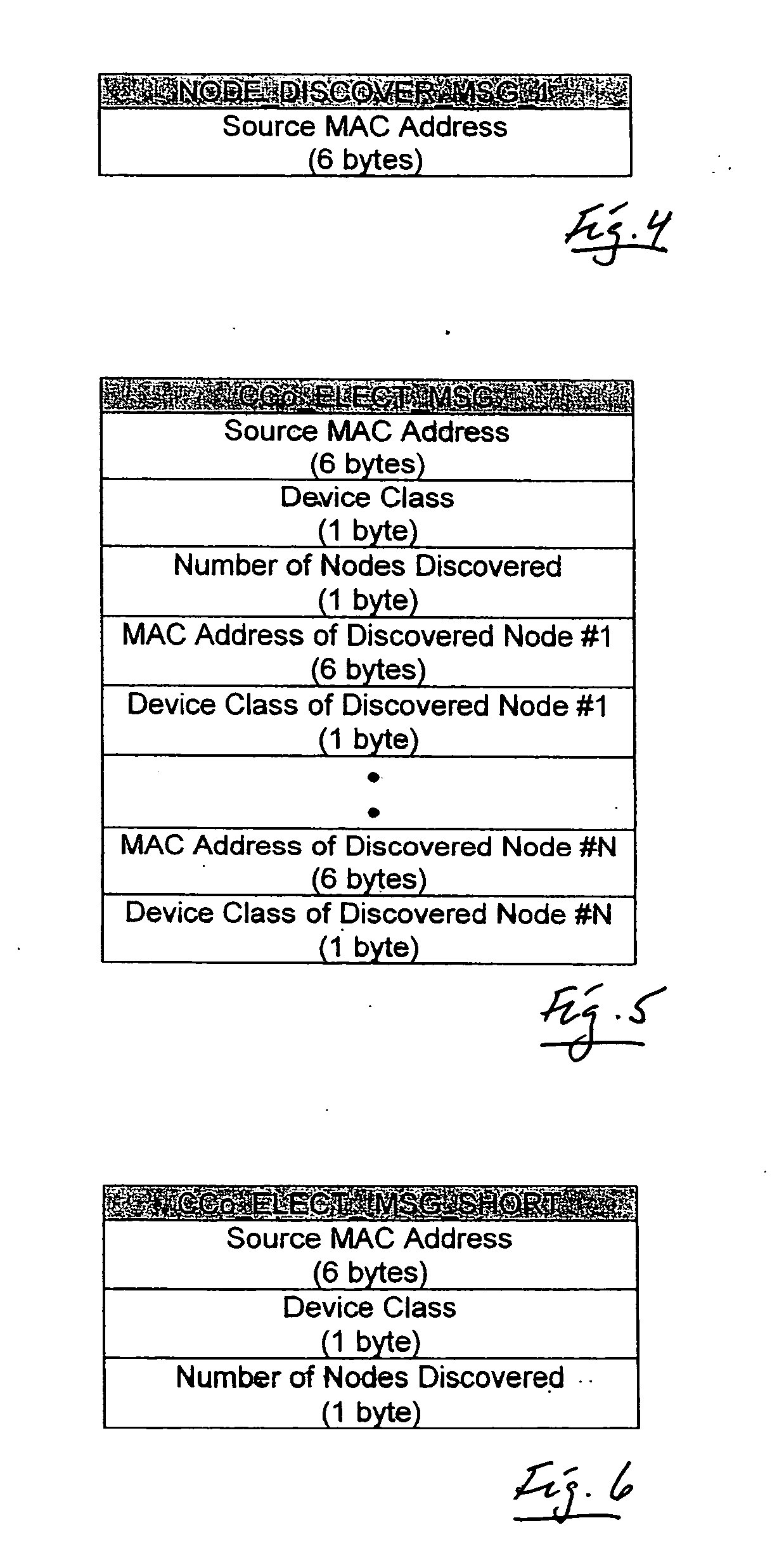
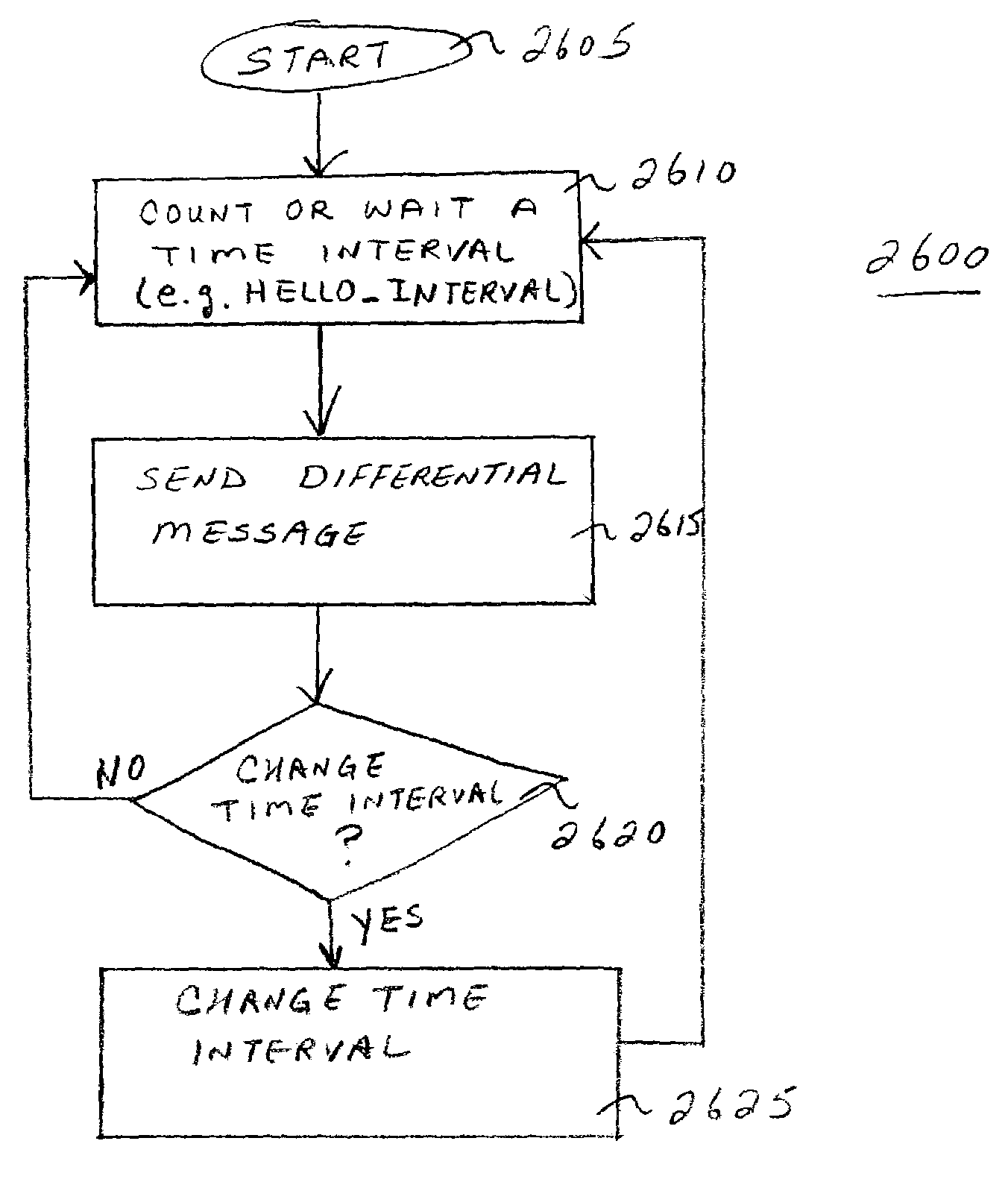
A proactive link-state routing protocol designed for mobile ad-hoc networks is disclosed, which provides hop-by-hop routing along shortest paths to each destination. Each node running the present protocol will compute a source tree (providing paths to all reachable nodes) based on partial topology information stored in its topology table. To minimize overhead, each node reports only “part” of its source tree to neighbors. The present invention employs a combination of periodic and differential updates to keep all neighbors informed of the reportable part of its source tree. The present invention performs neighbor discovery using “differential” HELLO messages that report only “changes” in the status of neighbors. This results in HELLO messages that are much smaller than those of other link-state routing protocols.
Owner:SRI INTERNATIONAL
Router configured for outputting update messages specifying a detected attribute change of a connected active path according to a prescribed routing protocol
ActiveUS20050195835A1Easy to routeEfficient sharingEnergy efficient ICTData switching by path configurationData streamComputer science
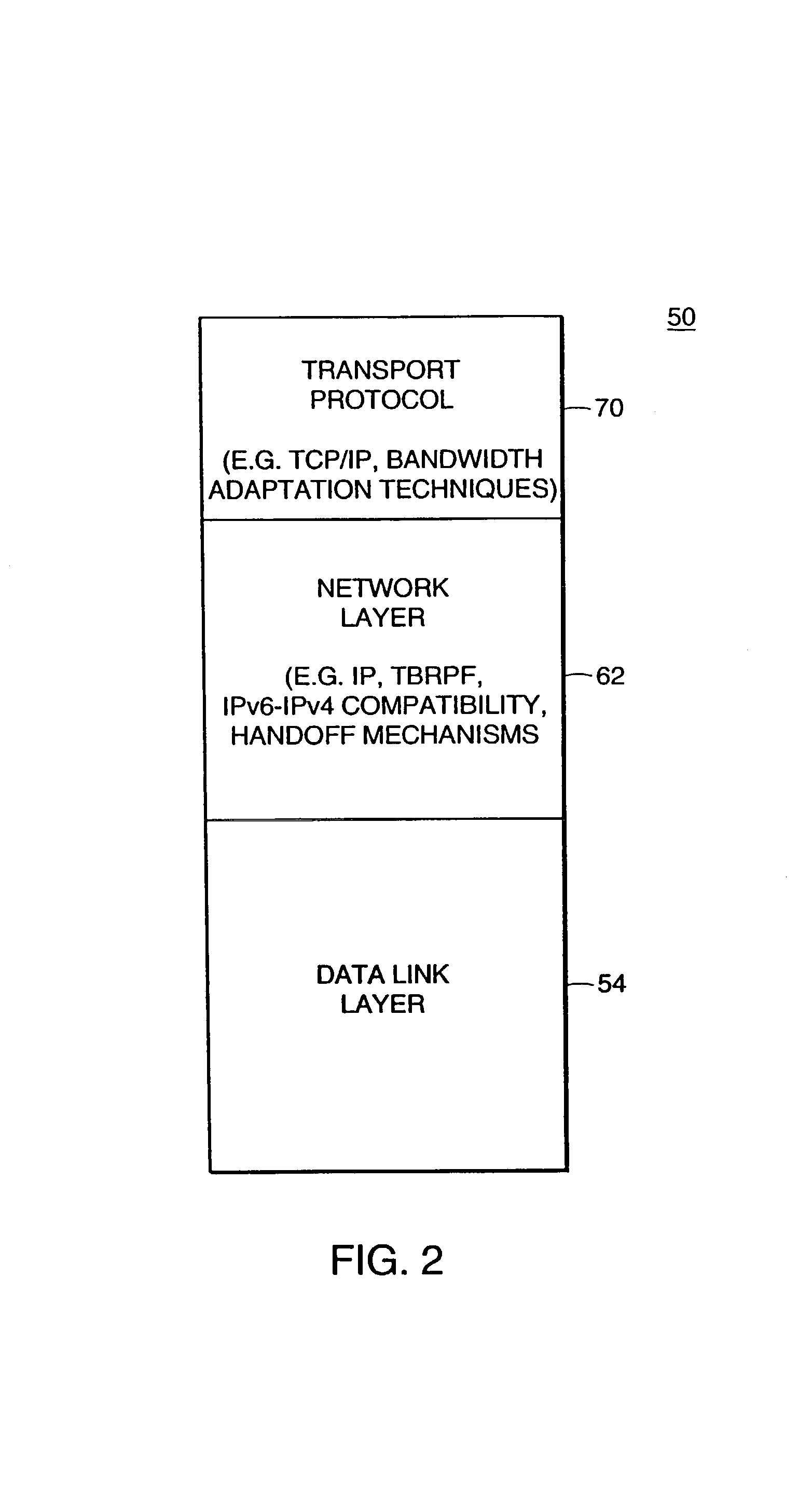
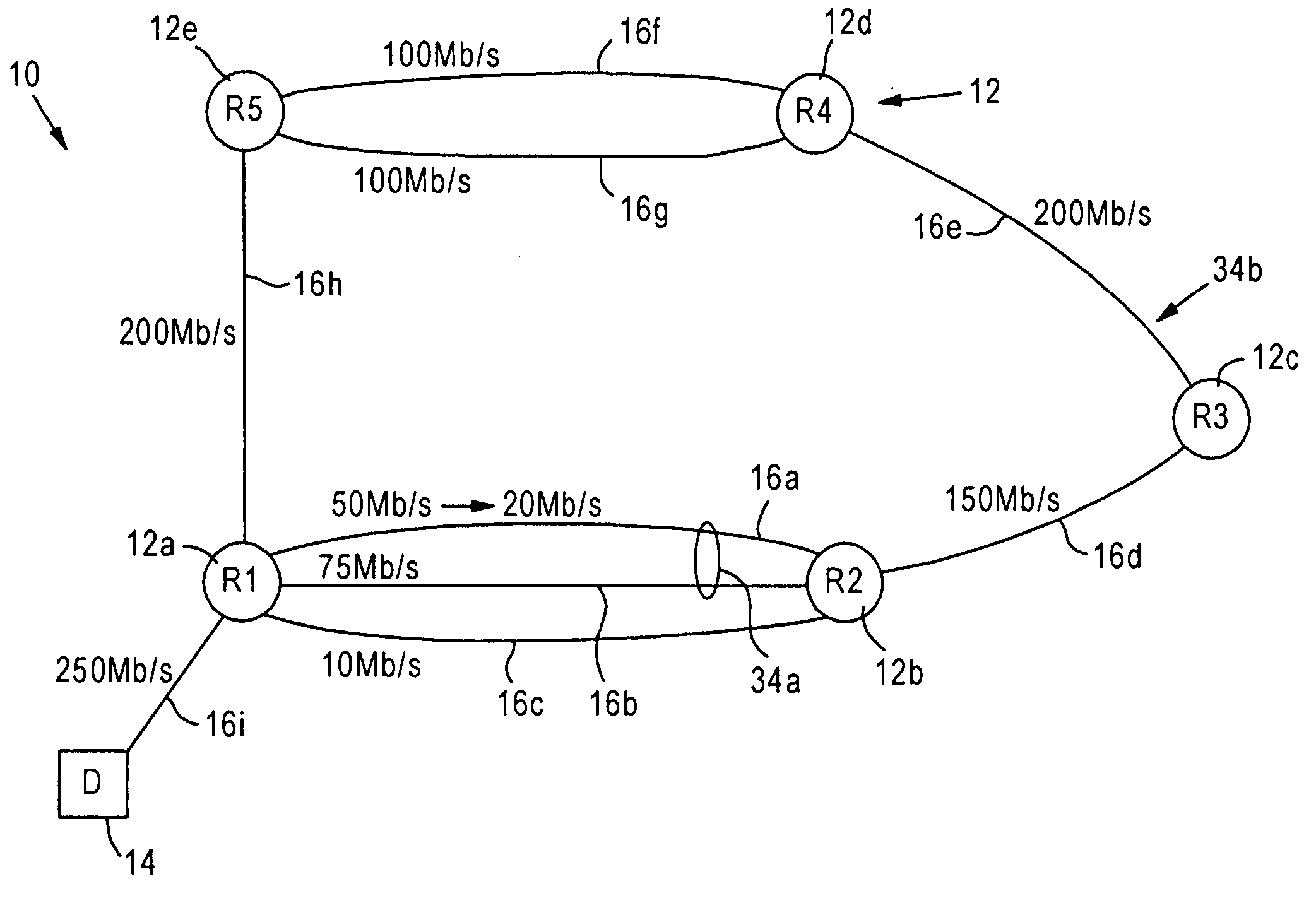
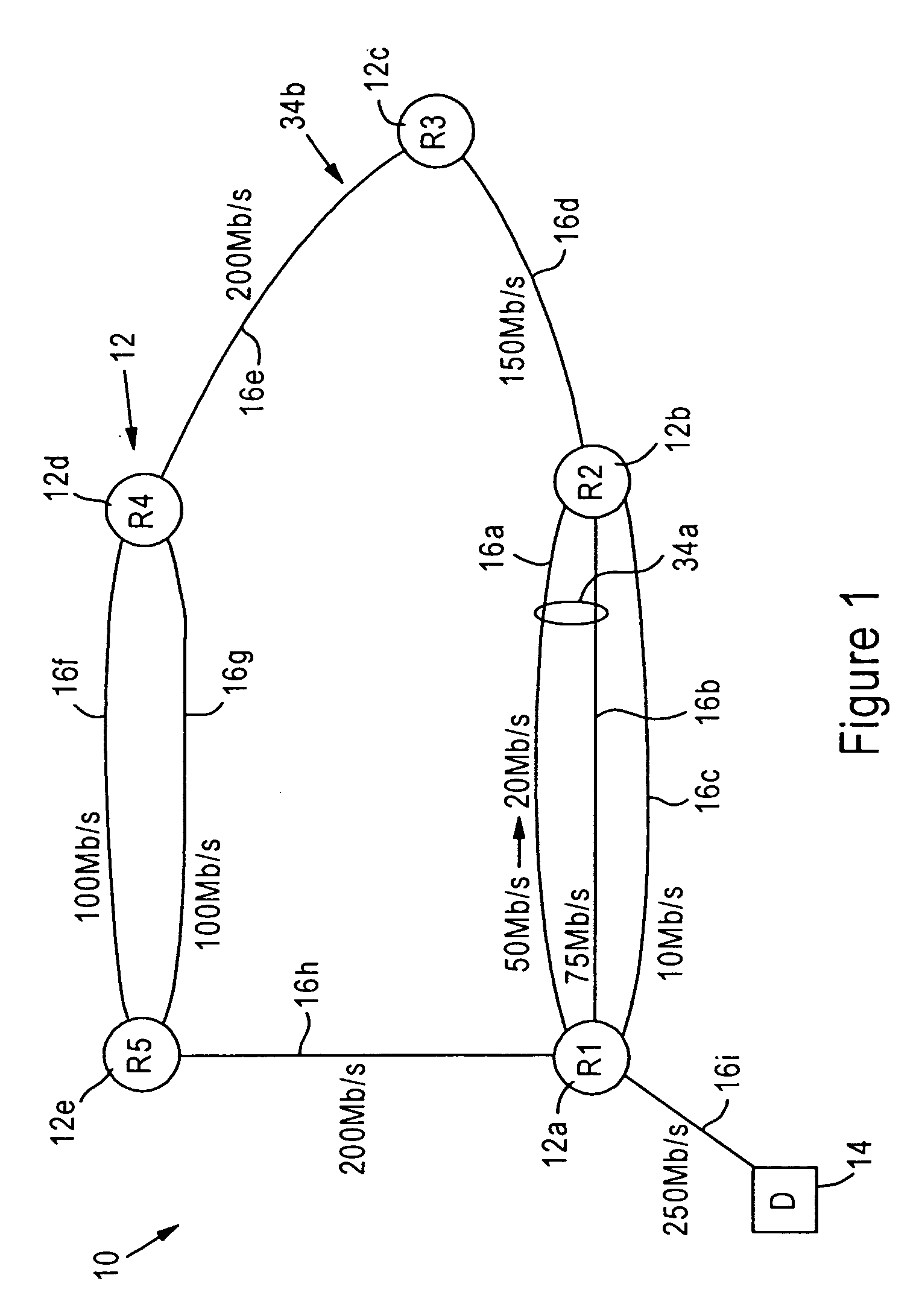
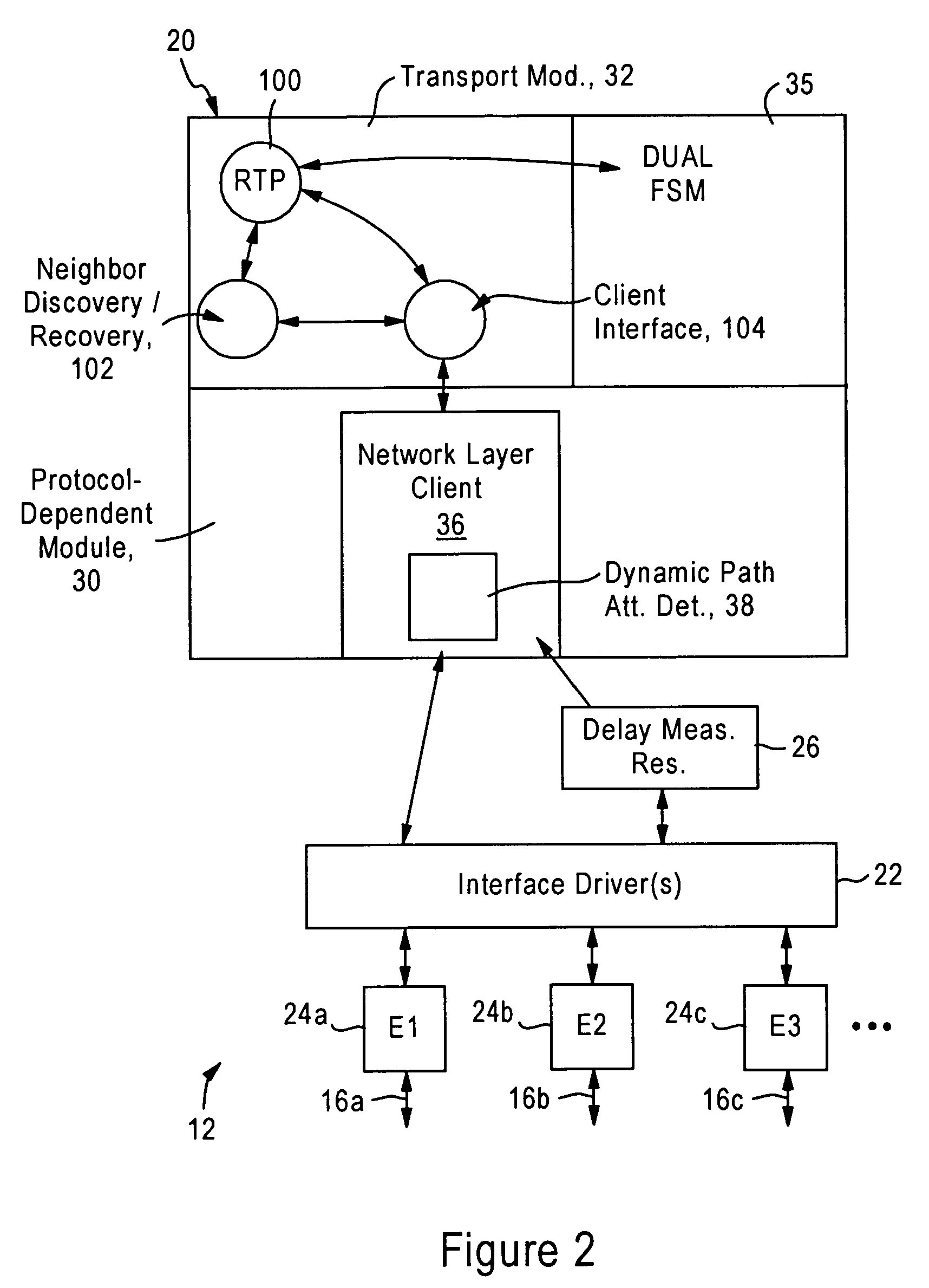
A first router is configured for monitoring prescribed attributes of an active path connected to the first router, and supplying an update message to a second router, according to a prescribed routing protocol such as Enhanced Interior Gateway Routing Protocol (EIGRP), that specifies a detected change by the first router in at least one of the prescribed attributes of the connected active path. Hence, the second router, in response to receiving the update message, can update an internal topology table based on the detected change in the active path connected to the first router, and selectively adjust an internal routing table based on the detected change relative to queuing policies for prescribed data flows.
Owner:CISCO TECH INC
Wireless multi-hop ad hoc network communication method
InactiveCN101577954AProvide quicklyMeet the needs of safe productionNetwork topologiesHigh level techniquesNetwork connectionNetwork communication
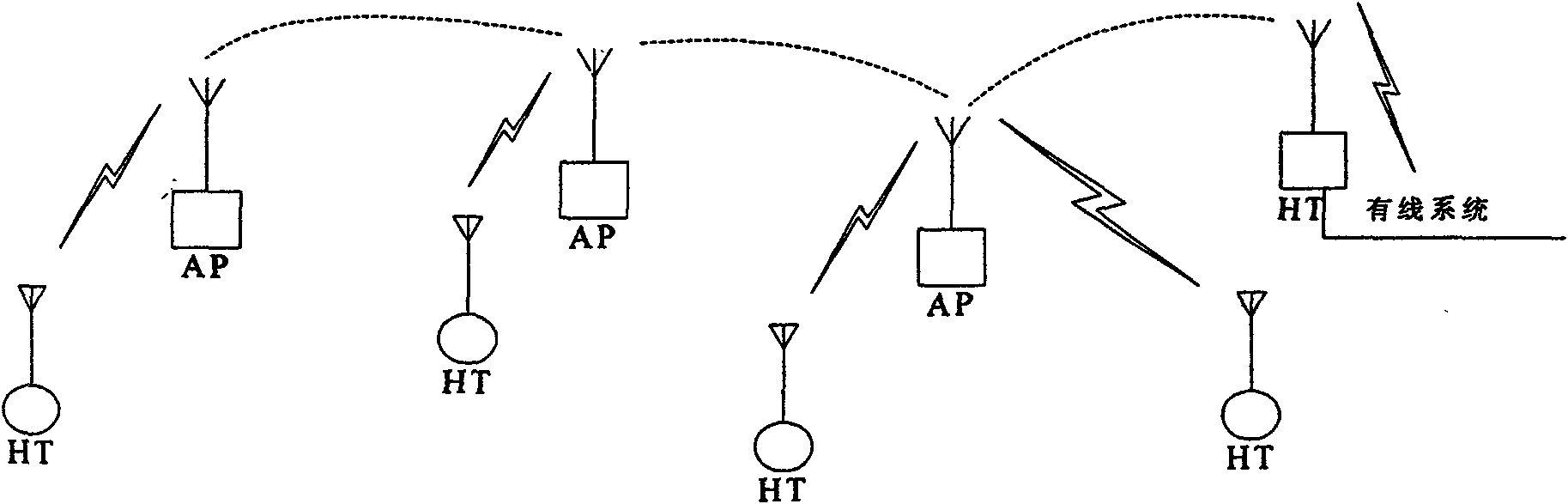
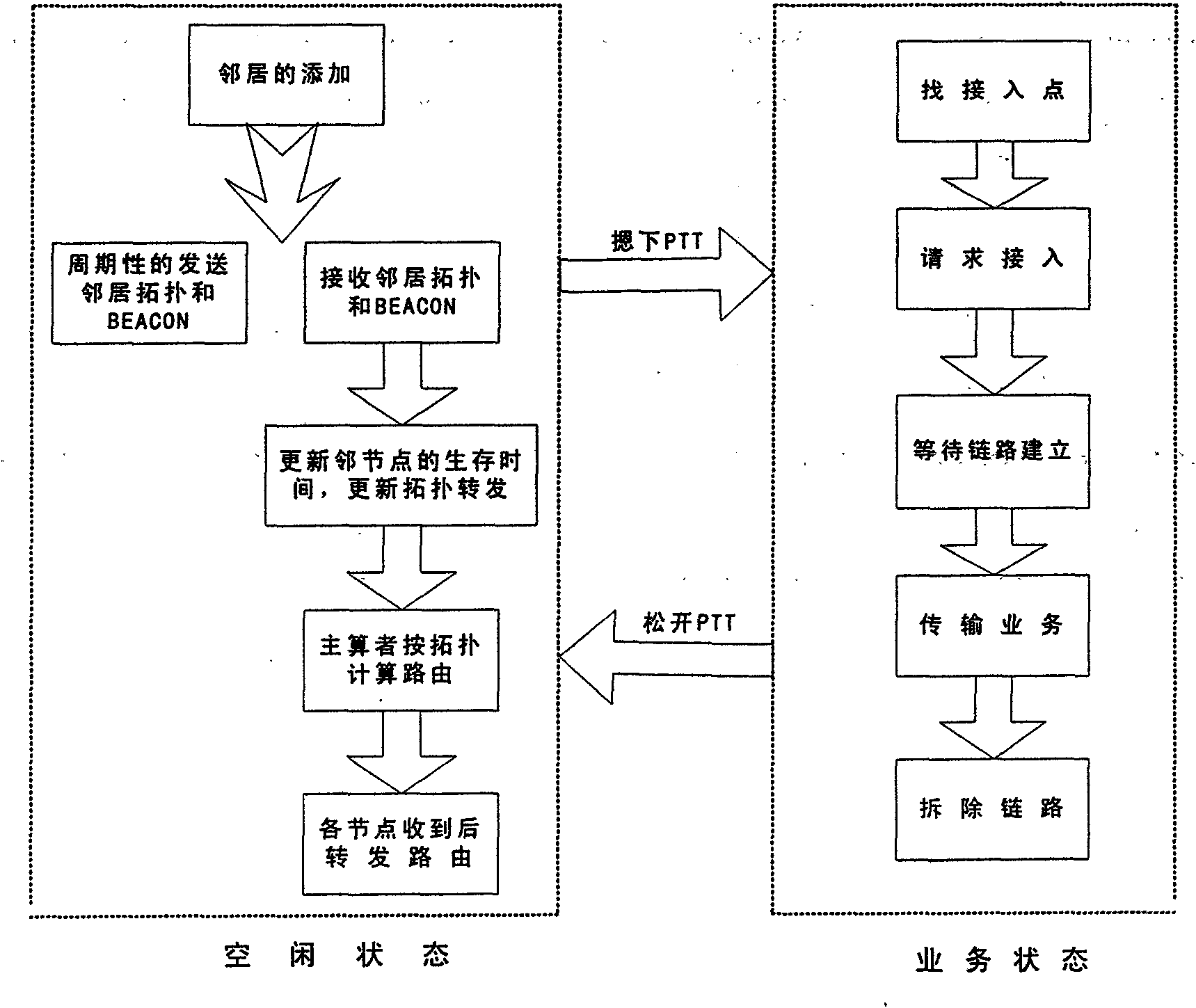
The invention aims to provide a wireless multi-hop ad hoc network communication method, which comprises the steps of network establishment and maintenance, and service transmission. The network establishment and maintenance comprises the following steps of: finding of neighbors; adding and deletion mechanisms of the neighbors; and establishment and maintenance of a route, in which the interaction of neighbor information among network nodes ensures that each network node finally possesses a topology table of whole network connection relationship, then a main operation node of the network nodes is used to calculate the route of the whole network according to the topology table and notifies other network nodes in the network of routing information in an information interaction mode at the same time, and the topology table and a routing list respectively saved by each network node are kept consistent to finish the establish of the network when the network is finally steady. The service transmission comprises the following steps of: search of an access point, link application, link establishment, service transmission and link demolition. A self-developed wireless multi-hop ad hoc relay network of the invention can finish the communication in tunnels or on occasions with similar characteristics.
Owner:NANJING ZHENGBAO COMM NETWORK TECHCO
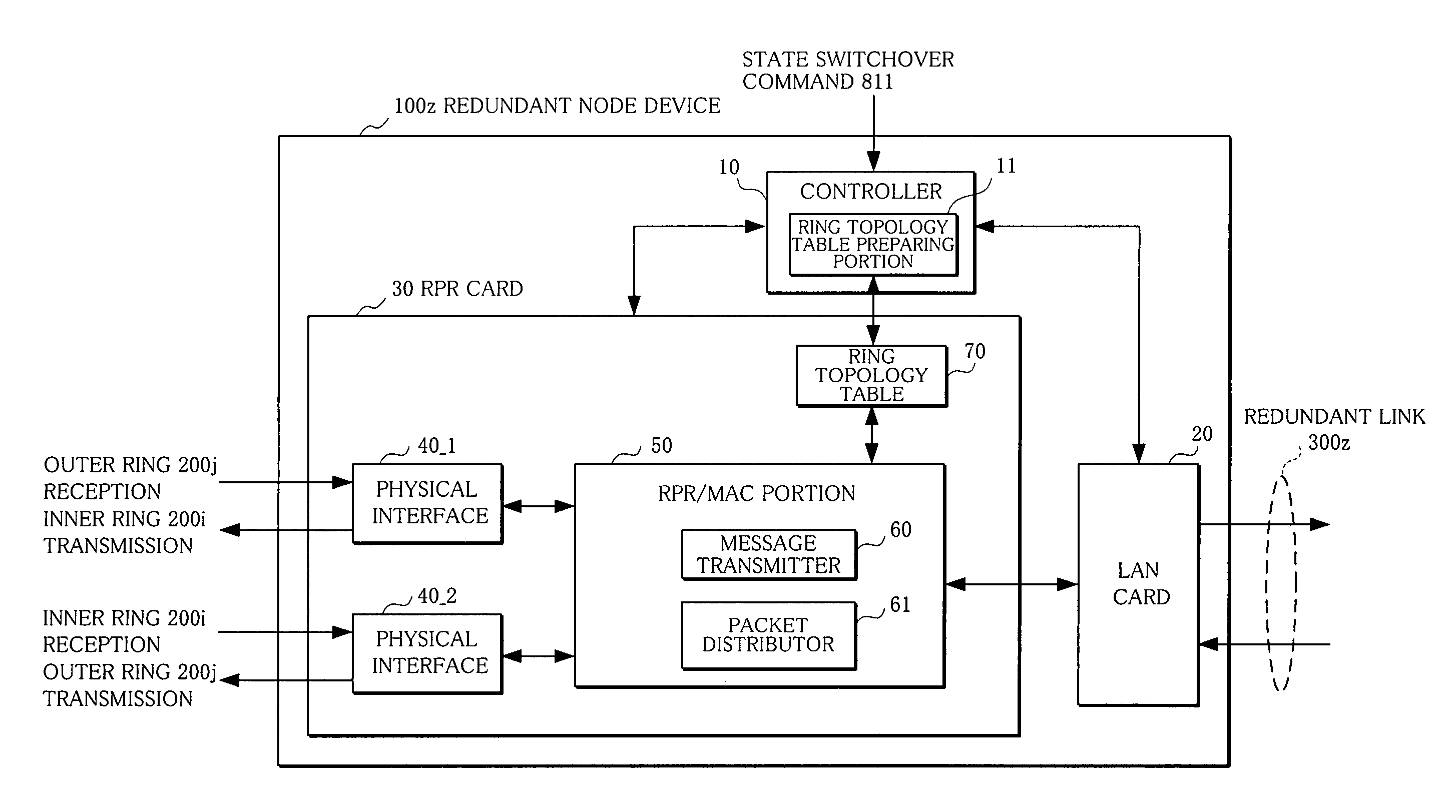
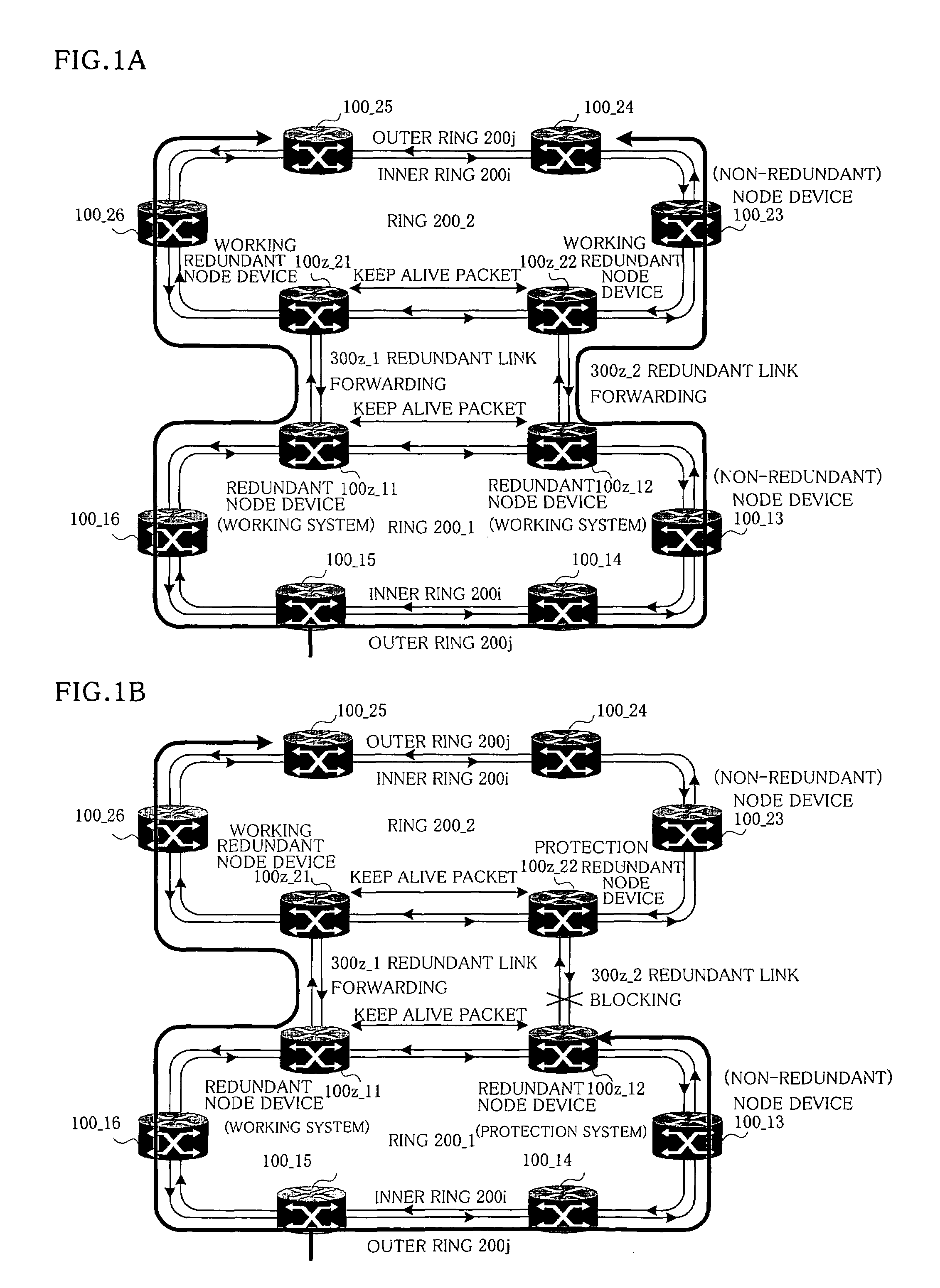
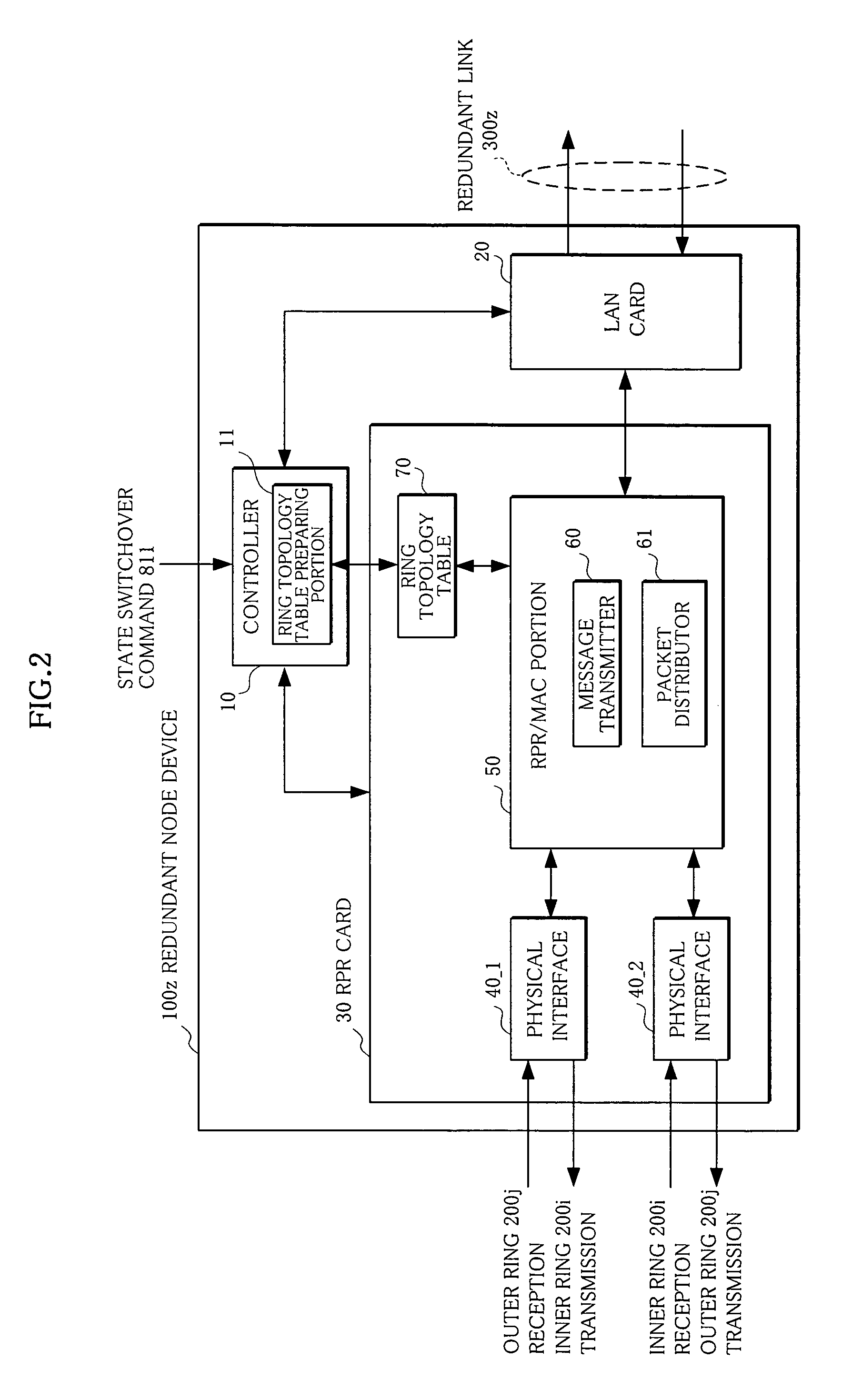
Node device
InactiveUS20060092856A1Balance processing loadError preventionFrequency-division multiplex detailsTopology informationRing network
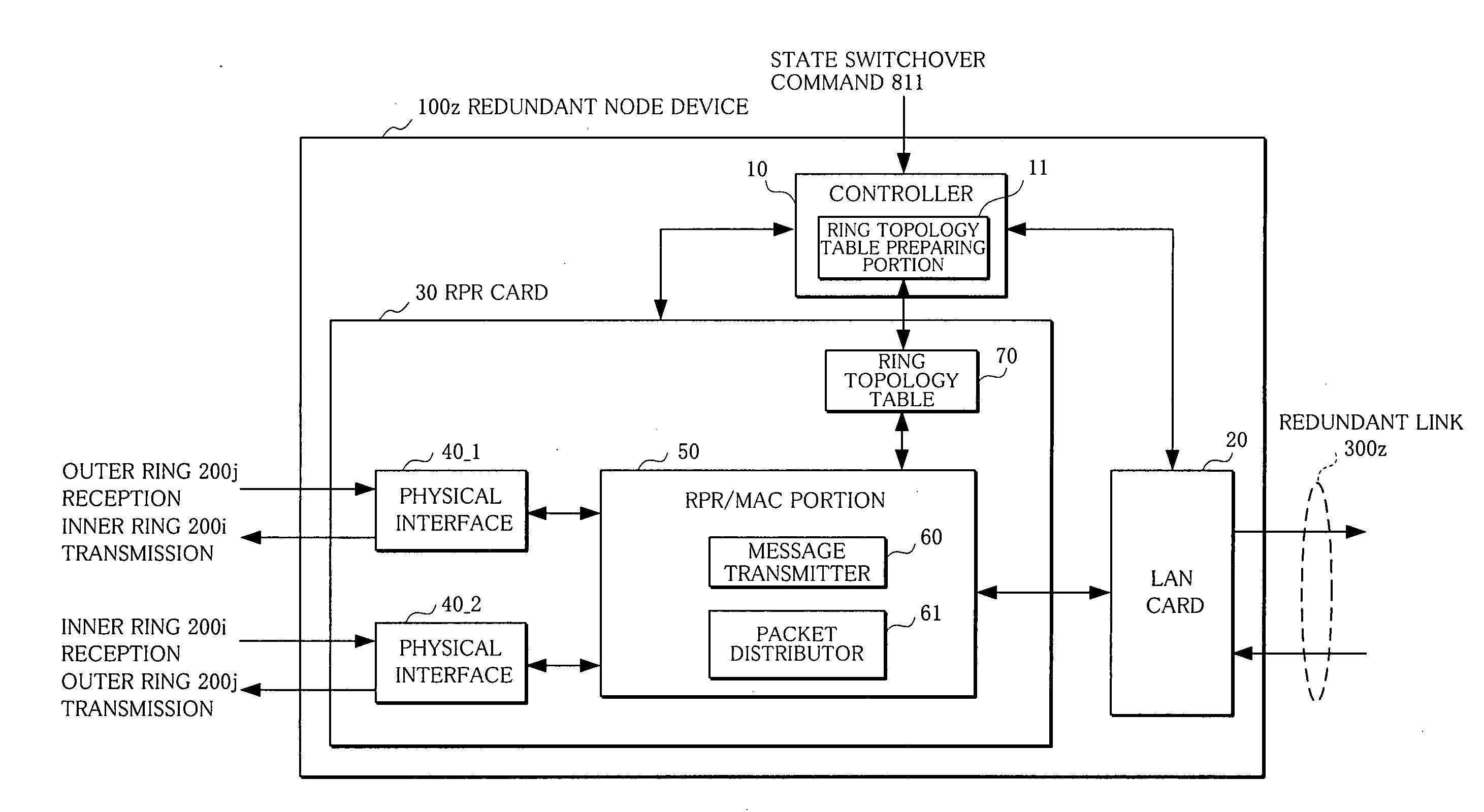
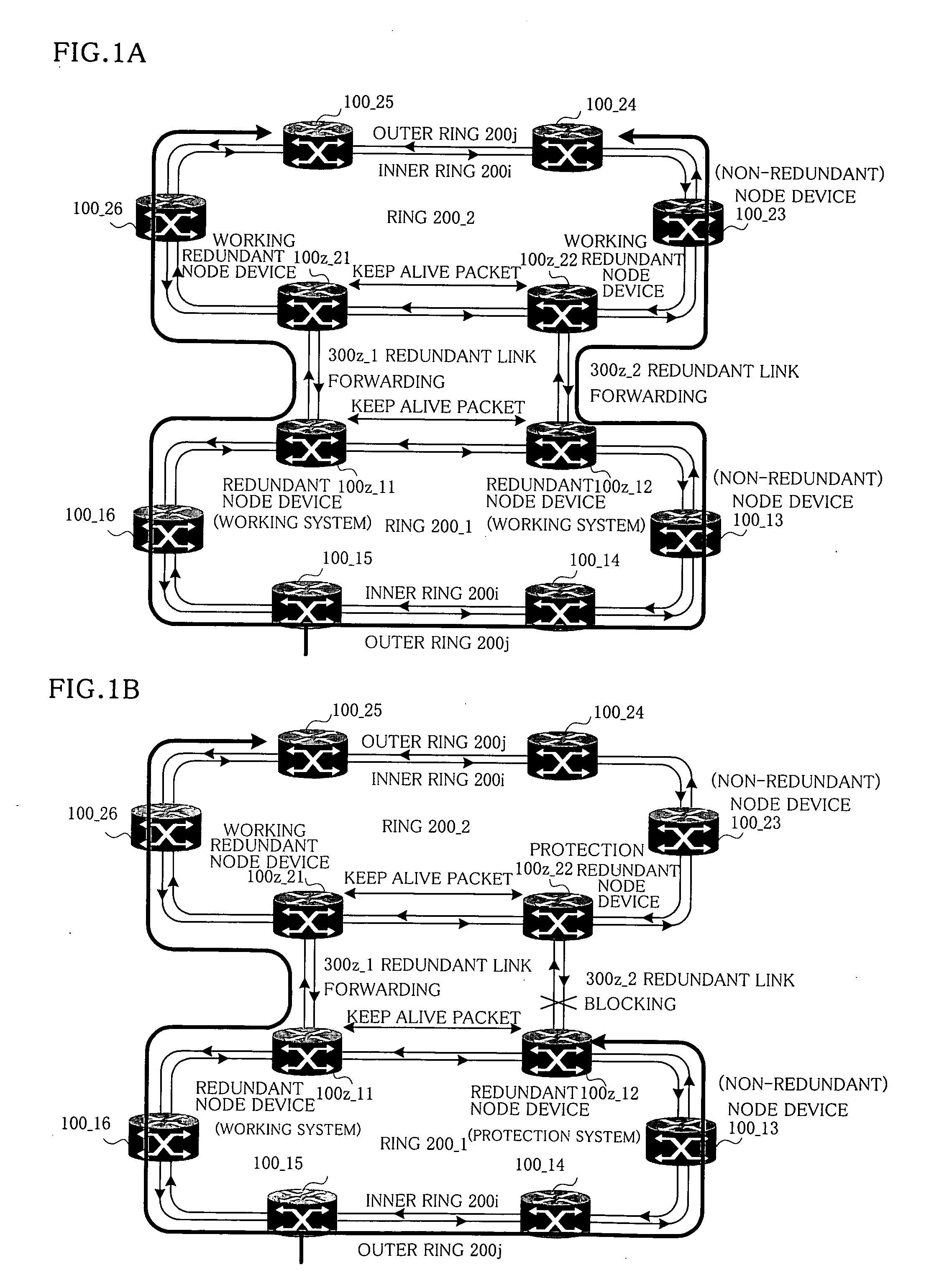
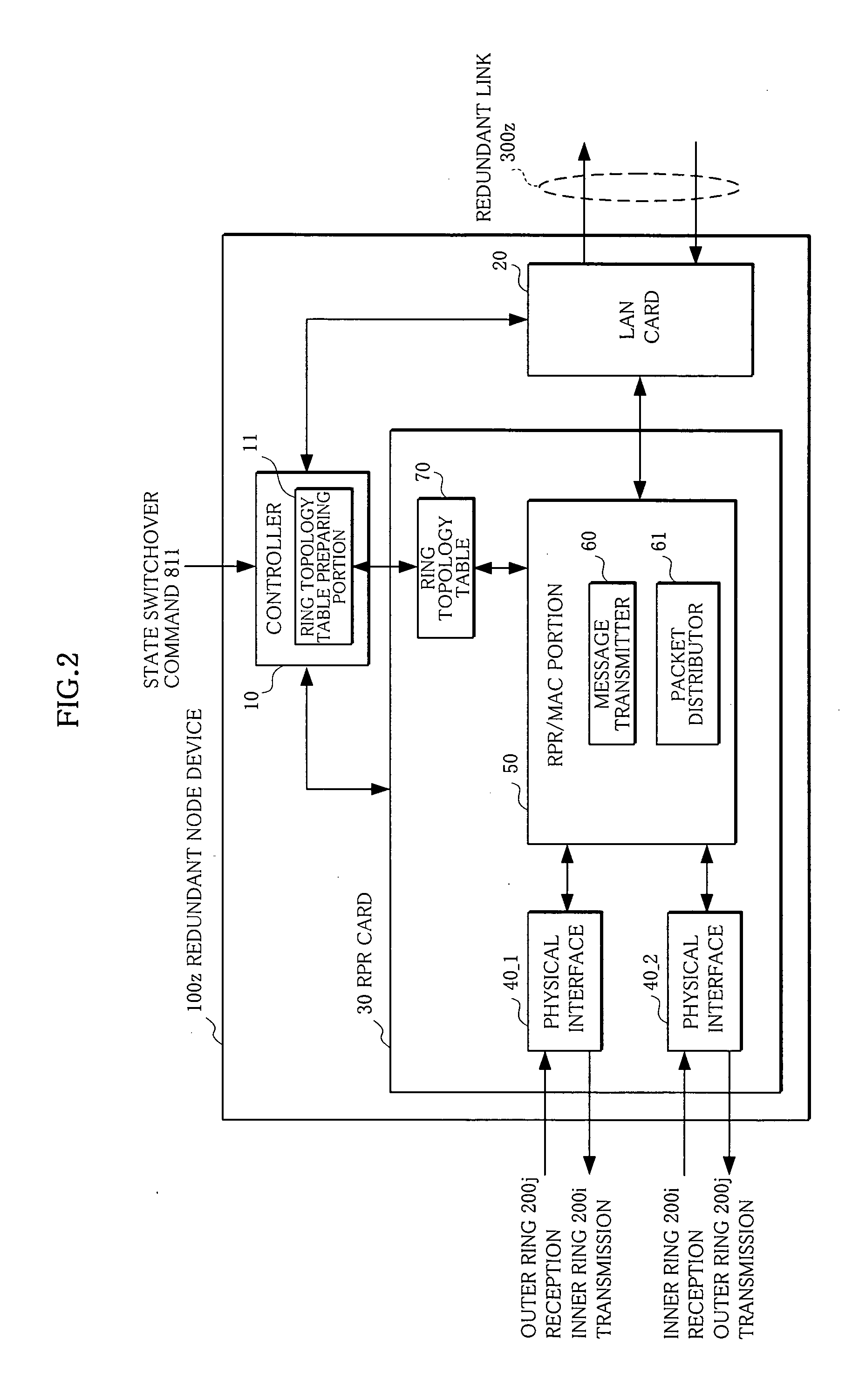
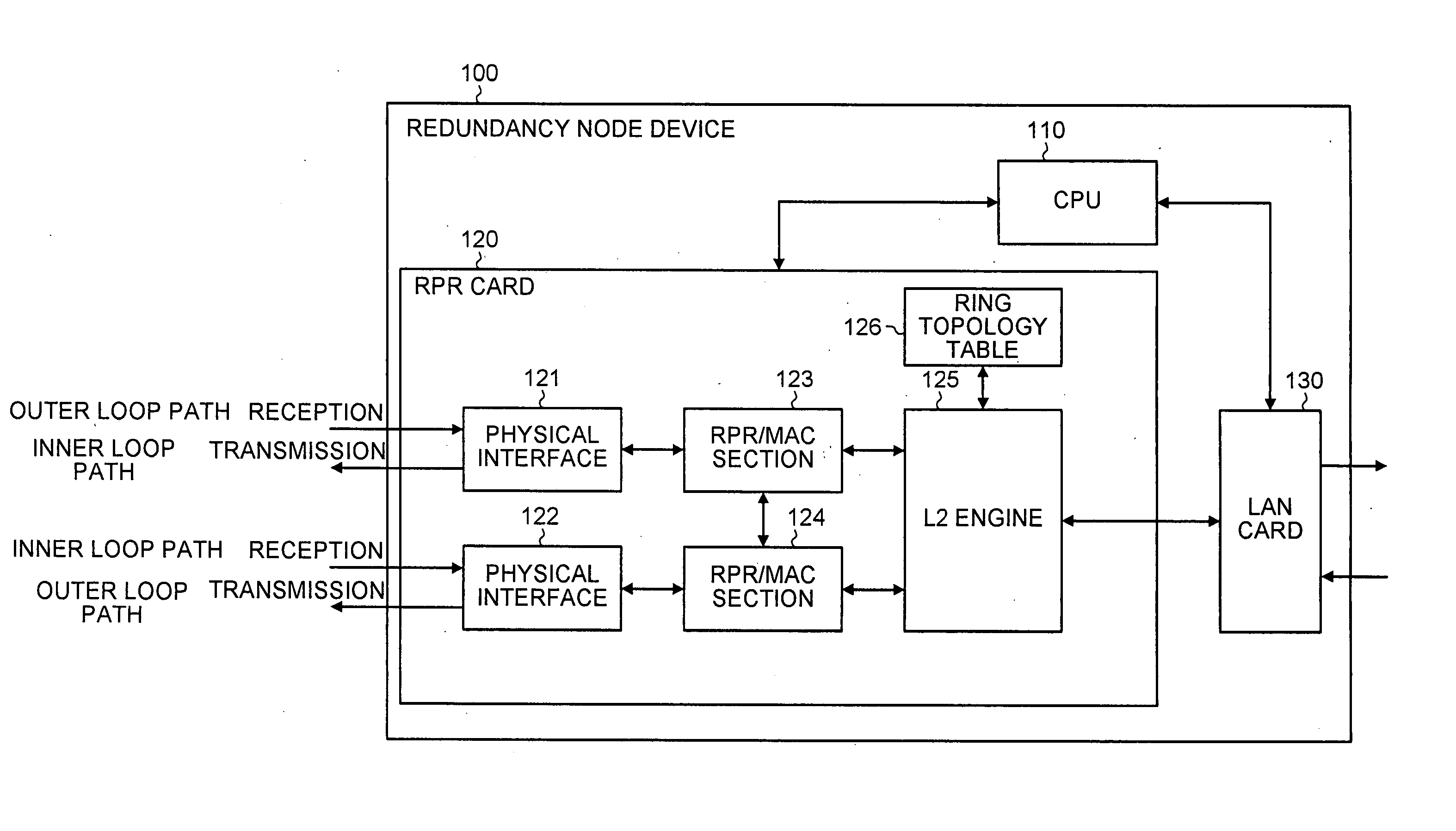
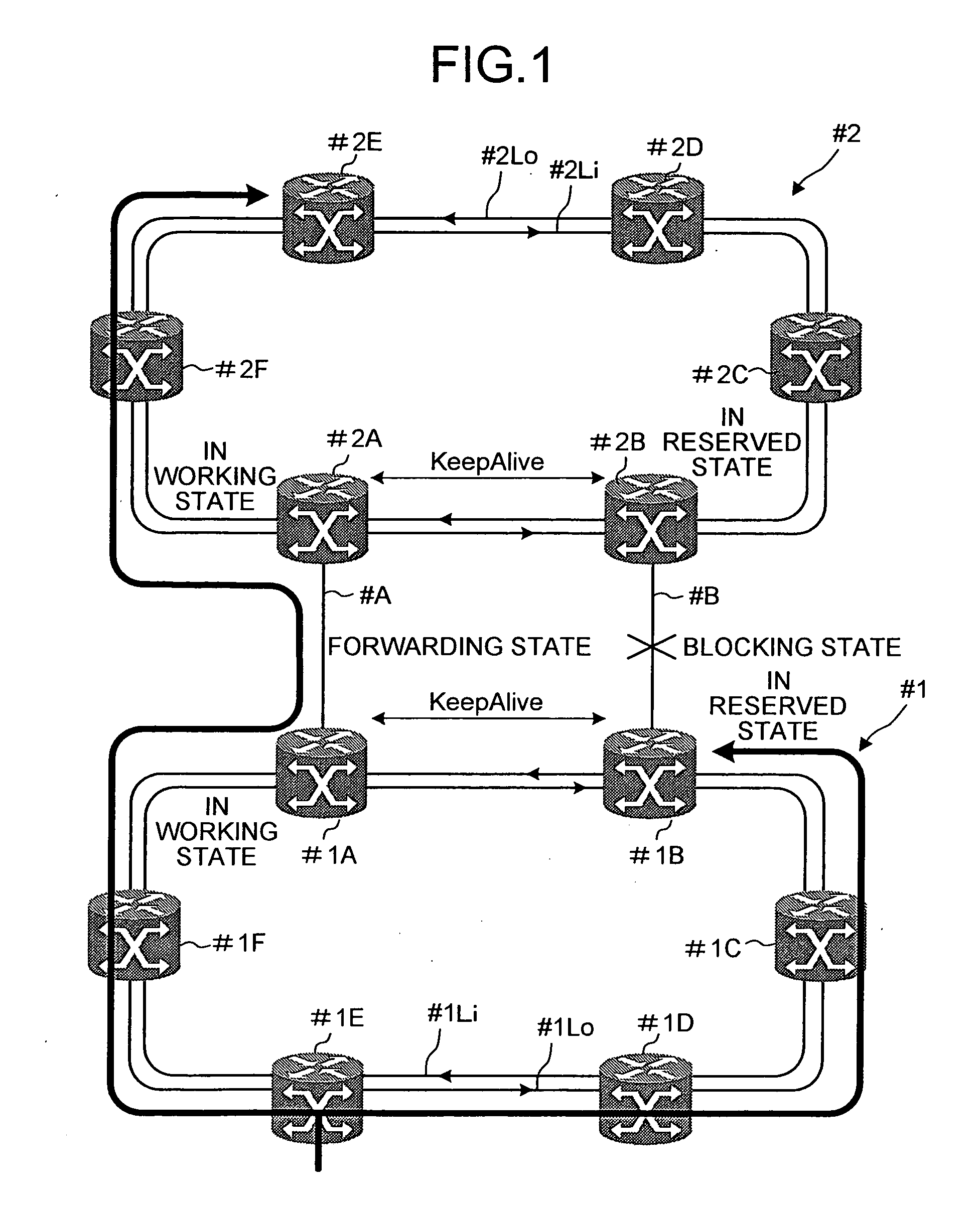
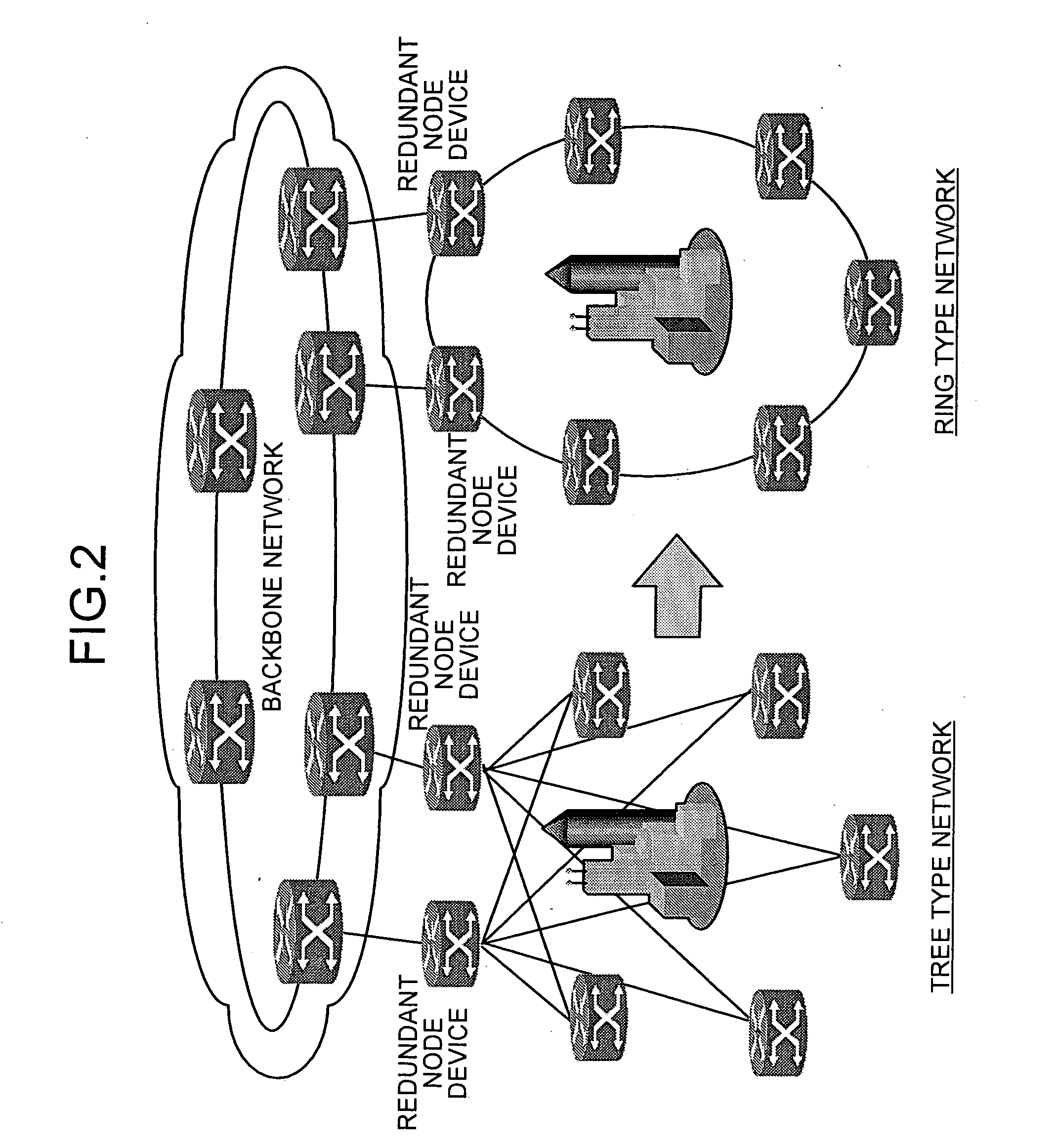
In node devices composing a ring network connected to another network with a redundant node device, a topology table includes redundancy information of the redundant node device, a transmitter transmits topology information and the redundancy information of the node devices themselves, a topology table preparing portion prepares a topology table based on redundancy information and topology information received from the redundant node device, and topology information received from the other node device, and a packet distributor distributes a packet received over the ring network based on the topology table.
Owner:FUJITSU LTD
Node redundancy method, interface card, interface device, node device, and packet ring network system
InactiveUS20060120279A1Solve problemsError preventionTransmission systemsRing networkReal-time computing
A network includes a plurality of redundant nodes and ordinary nodes. A first redundant node from among the redundant nodes sets a common address and setting information in a message packet and broadcasts the message packet over the network. The common address is commonly used by all the redundant nodes on the network. The setting information is indicative of the fact that the first redundant node is a redundant node. All the nodes have a topology table. The nodes that receive the message packet set in their topology table information indicating of presence of the first redundant node and the common address shared by the redundant nodes. When transmitting a packet to the first redundant node, a node sets the common address as a destination address of the packet.
Owner:FUJITSU LTD
Detour path calculation method in emergency
InactiveUS20150055453A1Increase the number ofError preventionTransmission systemsGrade of serviceLimit value
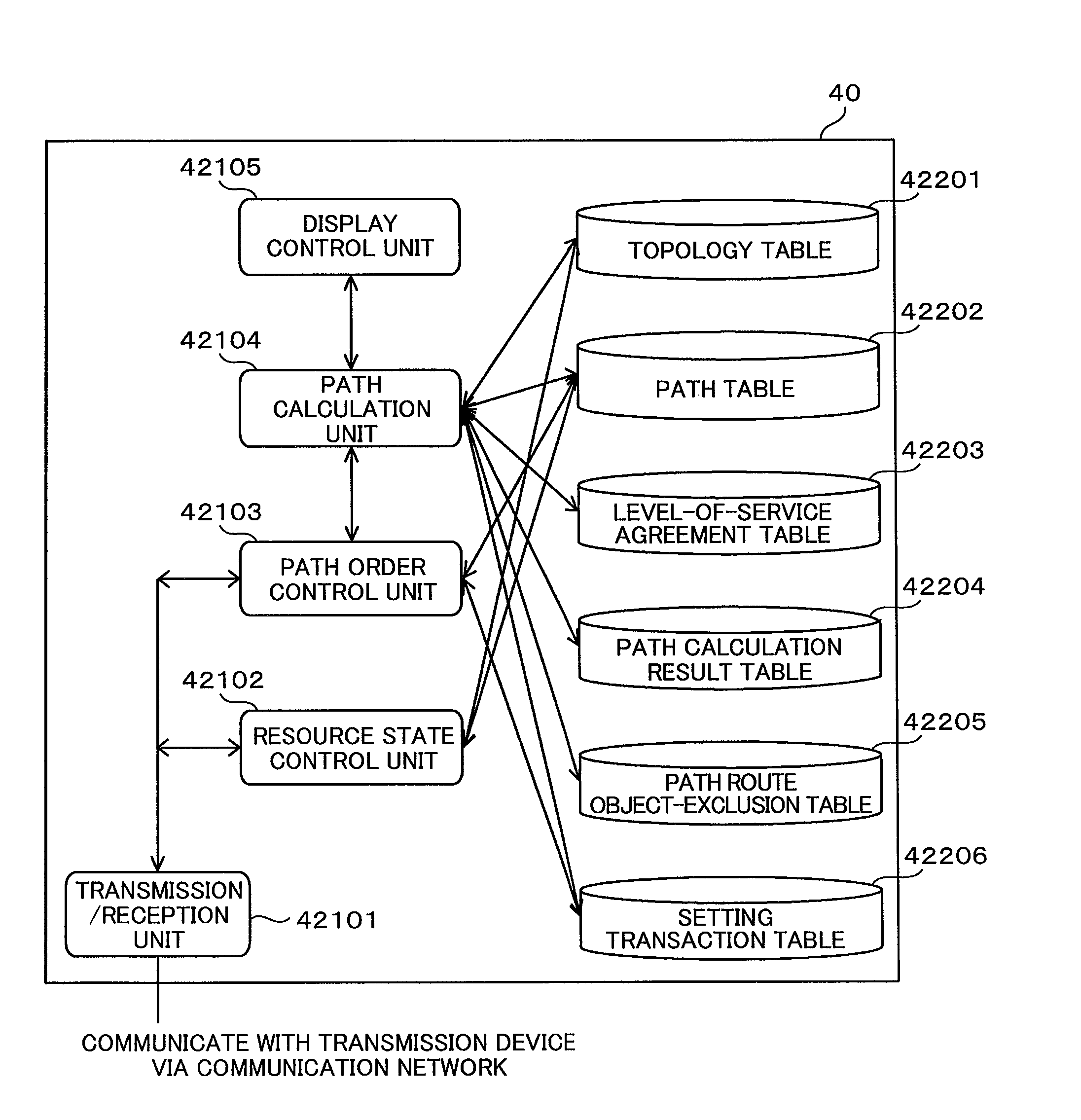
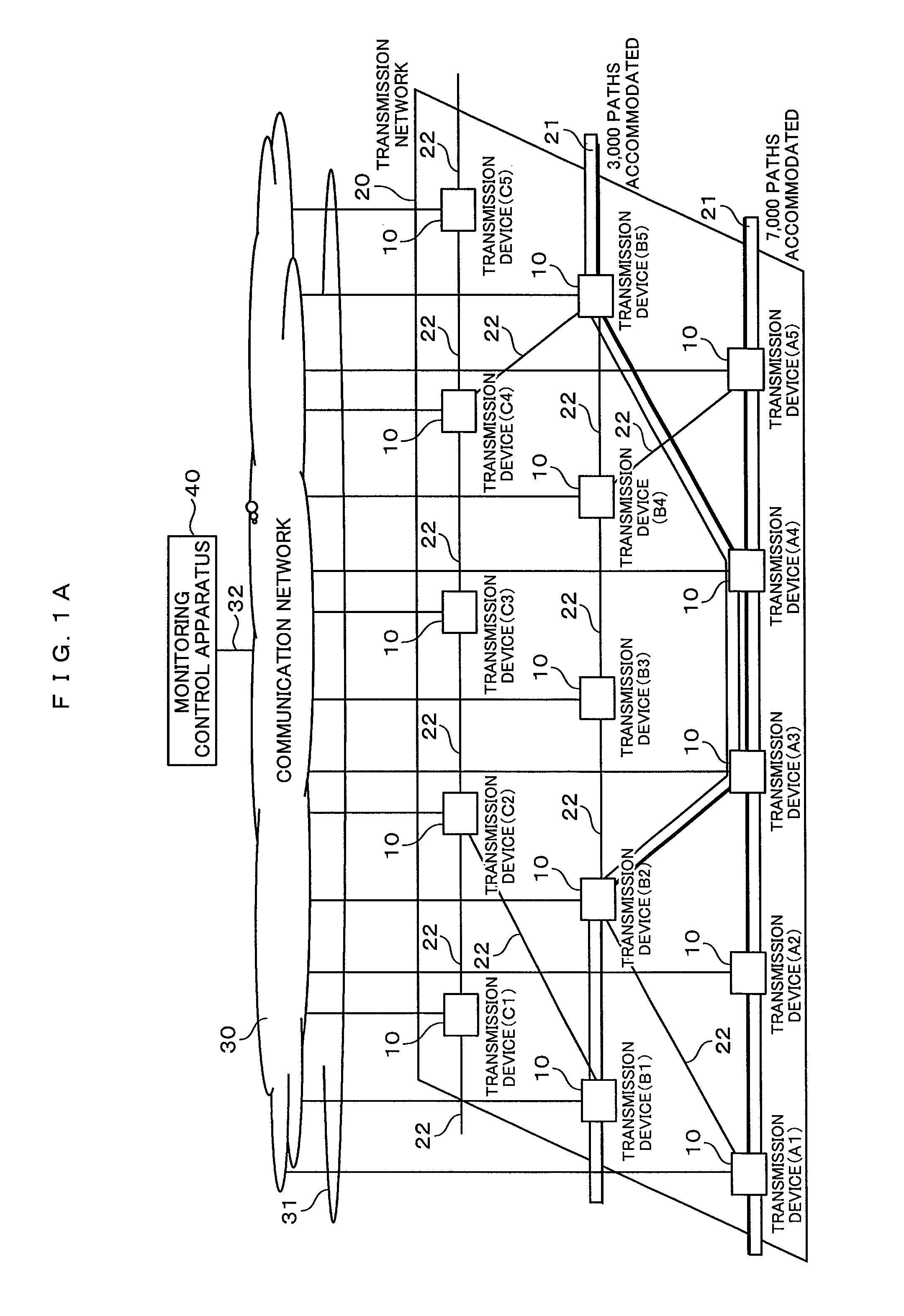
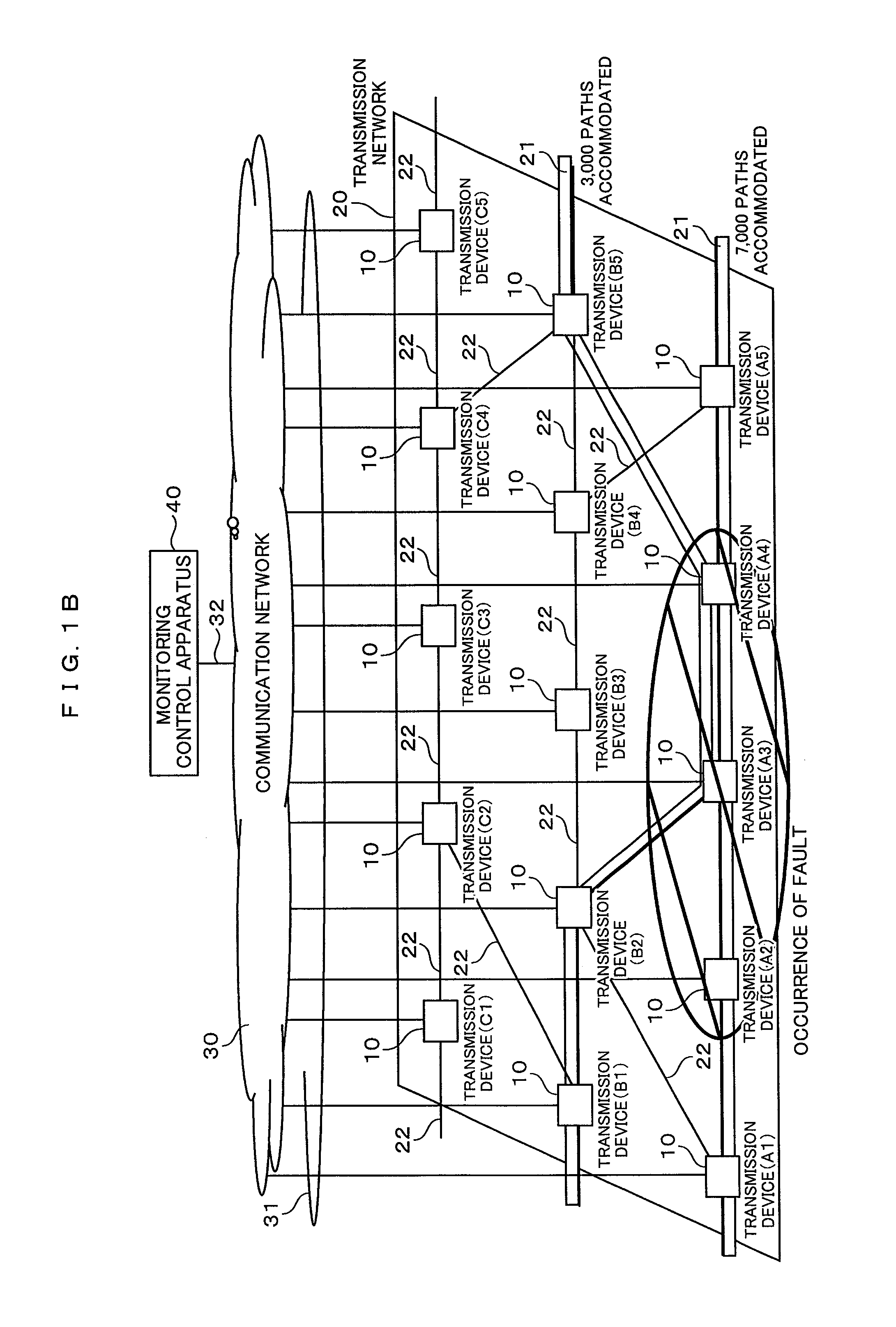
A path table, a topology table and a level-of-service agreement table are stored in a storage device of a monitoring control apparatus. A path in which a communication fault occurs is determined based on the path table. The service levels small in terms of an upper limit value of a service cutoff time in emergency are sequentially extracted from the level-of-service agreement table. A path route calculation process is performed on at least one path coincident with the extracted service level, based on the path table. A path route optimization process is performed on at least one path route subjected to the route calculation. An execution result of the path route optimization process is registered in a path calculation result table.
Owner:HITACHI LTD
Forwarding method used for constructing multi-hop routing in wireless self-organizing network
InactiveCN101521895AEasy to buildGuaranteed accessibilityNetwork topologiesCommunications systemSelf-organizing network
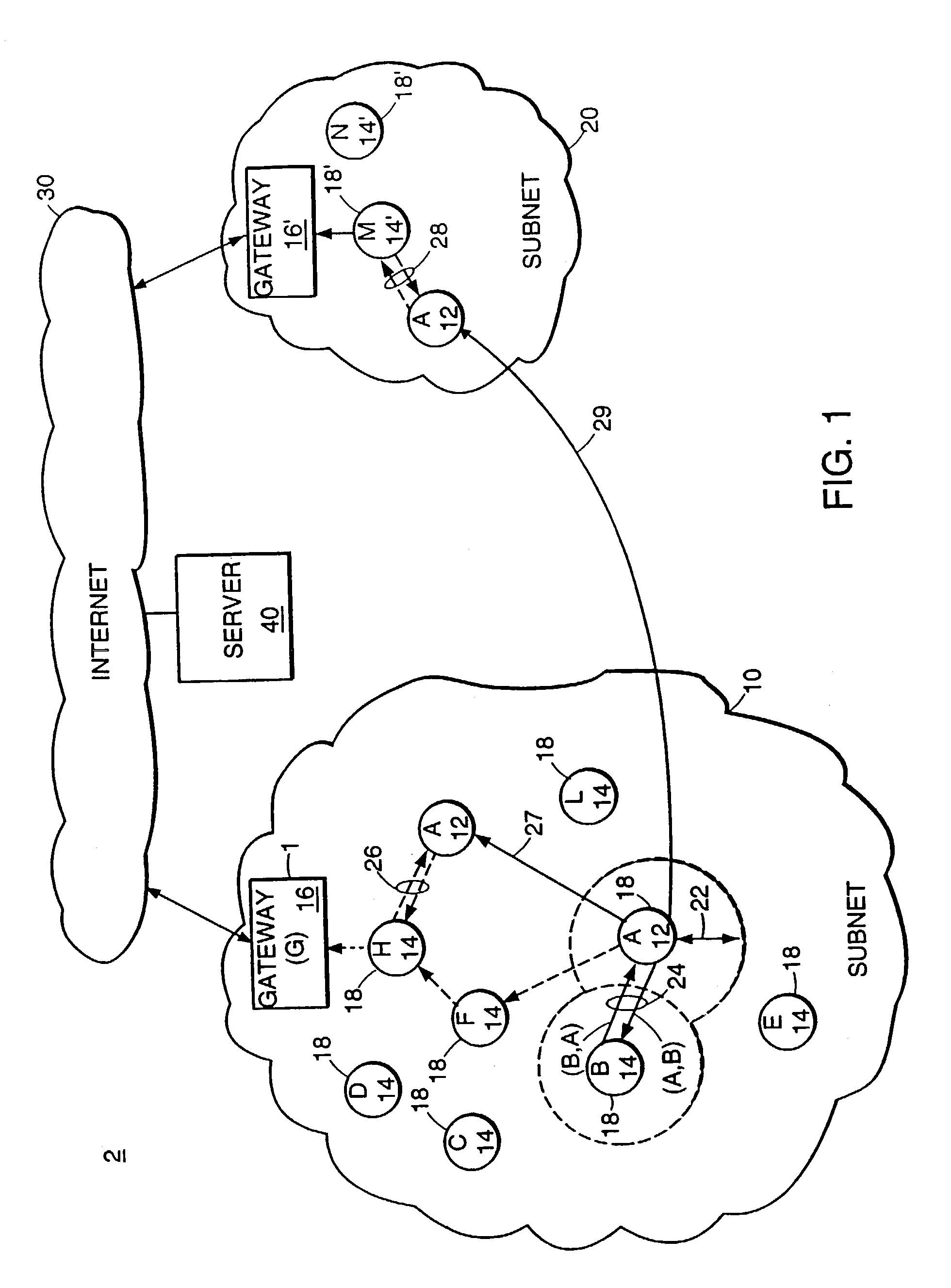
The invention provides a forwarding method used for constructing multi-hop routing in a wireless self-organizing network, which is based on an ARP proxy system and a mixed routing system. The method comprises the following steps that: a monitoring module of each node monitors each message sent and received by the node in real time; adjacent hosts interact respective routing information in a single-hop range in real time; each node stores a partial or complete topology table of the whole network; when a certain node of the network sends an ARP request to a node which is not directly connected with the certain node, the certain node searches for a next-hop node and sends a routing detection message to the next-hop node according to a routing list; and if the route is reachable, the detection message is transmitted to a target node step by step and returns a routing reachable message, and ARP proxy tables are arranged at various nodes along the route, so a multi-hop route is established. The invention also comprises a method for maintaining and updating the route through modification of network topology detection. The invention also comprises a device used in the network, and describes a complete communication system shown in graph 1.
Owner:NANJING UNIV OF POSTS & TELECOMM
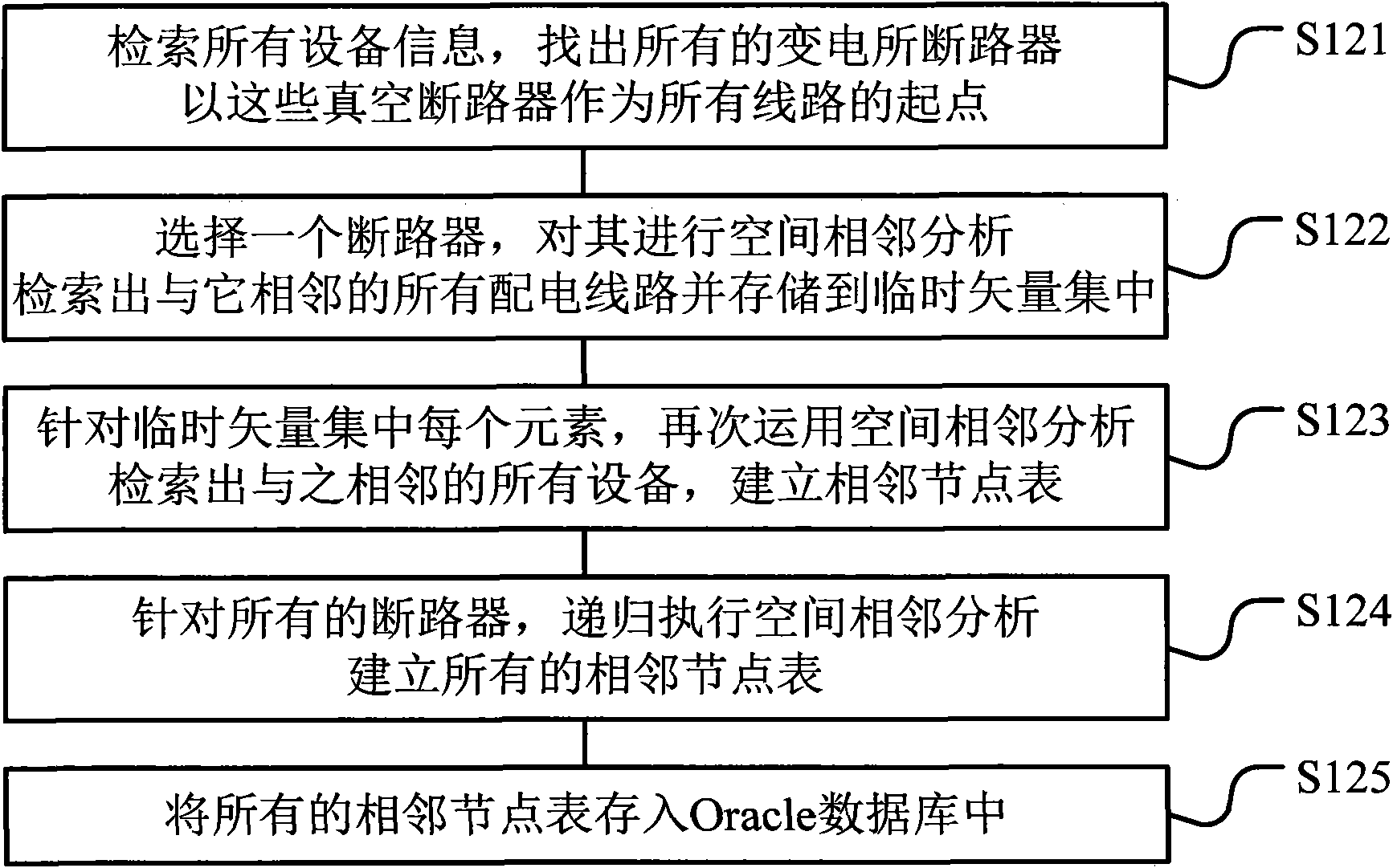
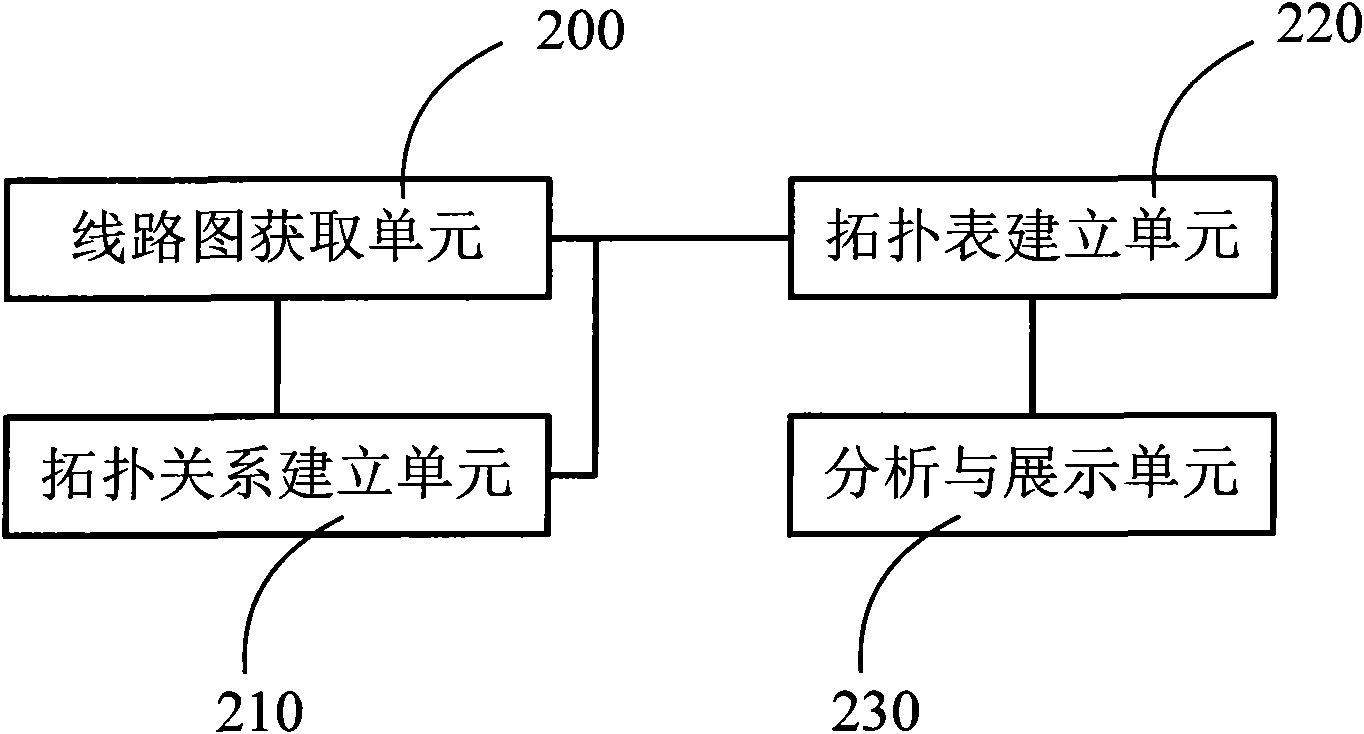
Special topology analysis method and device for distribution network
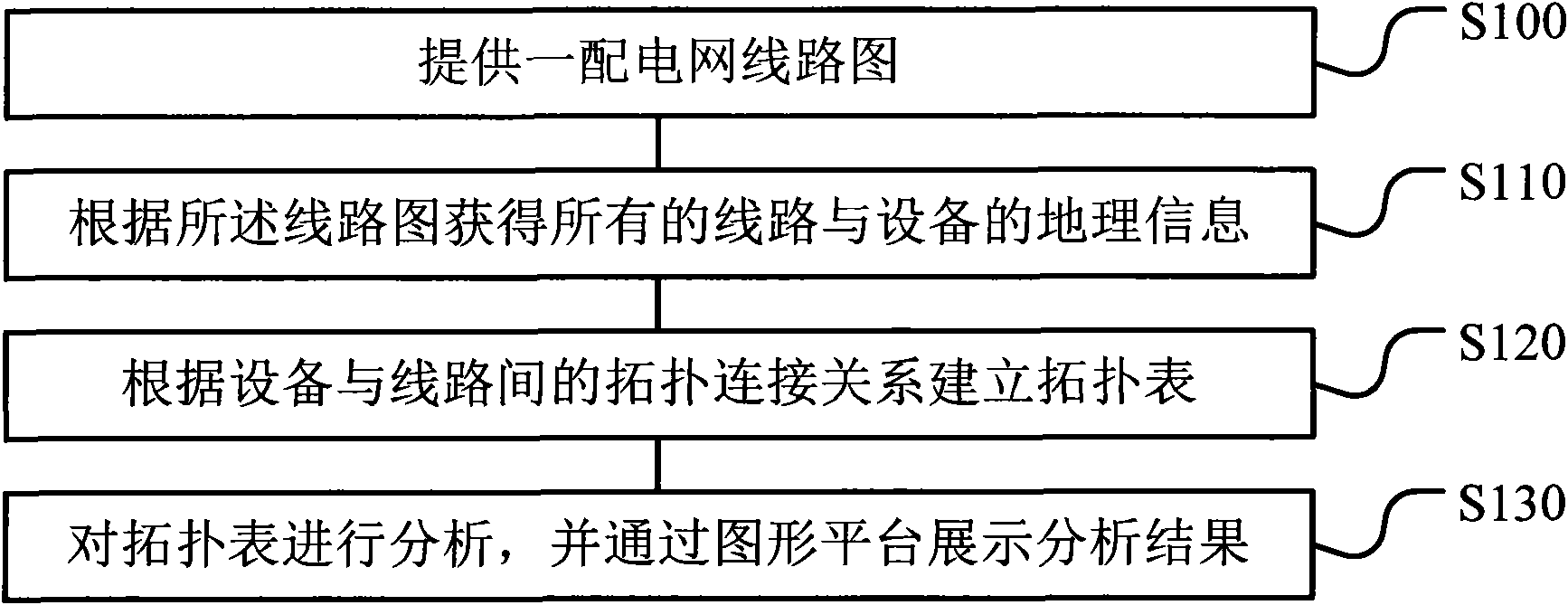
InactiveCN102044869ARealize topology analysis functionTopological operation is convenient and clearSpecial data processing applicationsAc network circuit arrangementsGraphicsSimulation
The invention relates to a special topology analysis method for a distribution network. The method comprises the following steps of: providing distribution network circuit diagrams; obtaining all the geographic information of circuits and equipment according to the circuit diagrams so as to establish a topology connection relation between the equipment and the circuits; establishing a topology table according to the topology connection relation between the equipment and the circuits; and analyzing the topology table. The invention has the advantages that different objects in the same layer can be represented by setting special graphic symbols according to the requirement of a user, then a topology layer is added on all diagram layers to ensure that the user cannot feel the existence of the topology, thus the method can realize the functions of real-time topology connection and disconnection, and the states of affected equipment can be changed in real time according to the topology states of the equipment. The method and the device disclosed by the invention can be used for accurately and reliably realizing the topology analysis function of the distribution network in real time andalso for conveniently realizing the applications of power cut simulation, power supply range, power supply tracking, and the like.
Owner:SHANGHAI DIANJI UNIV
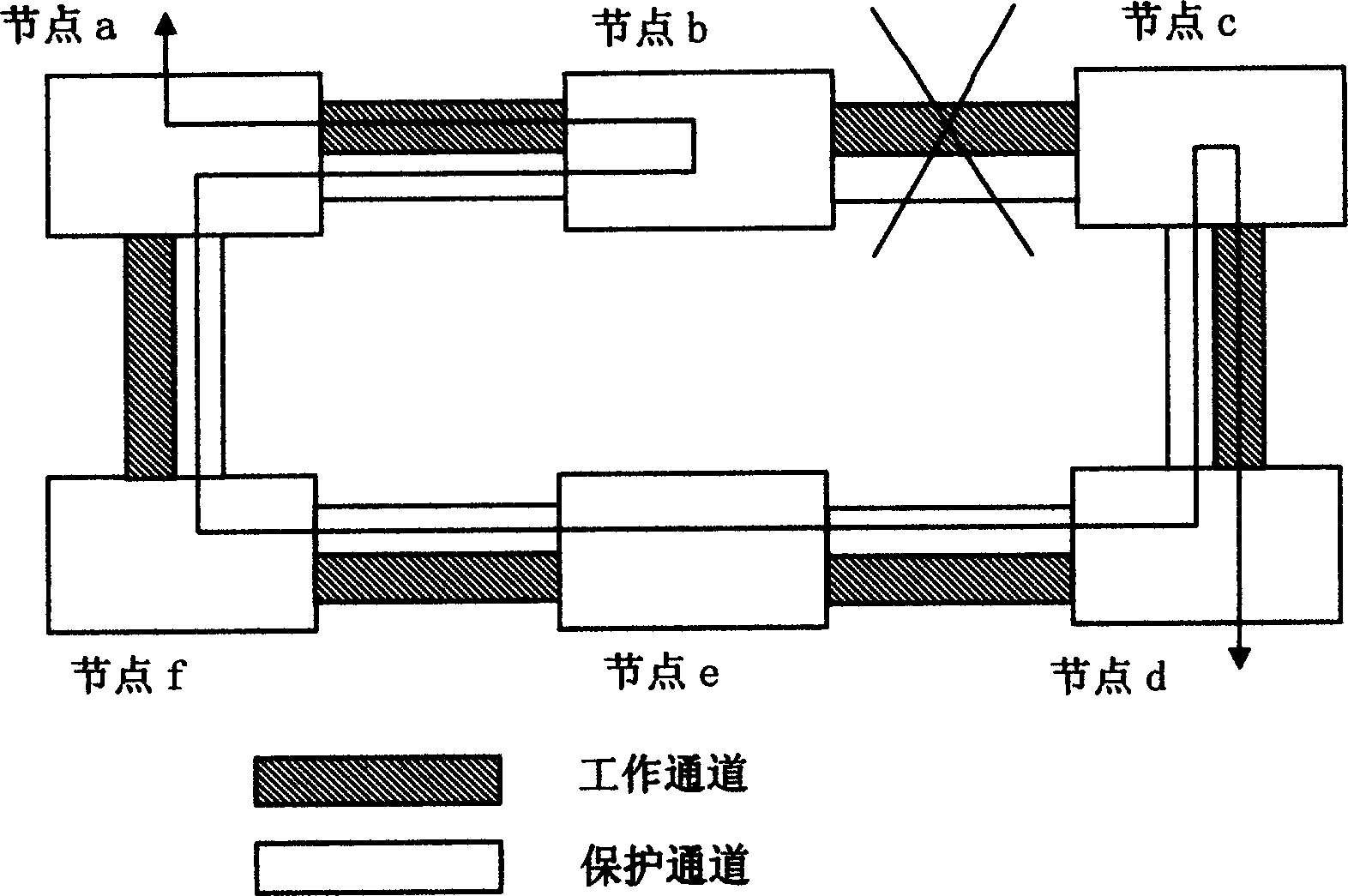
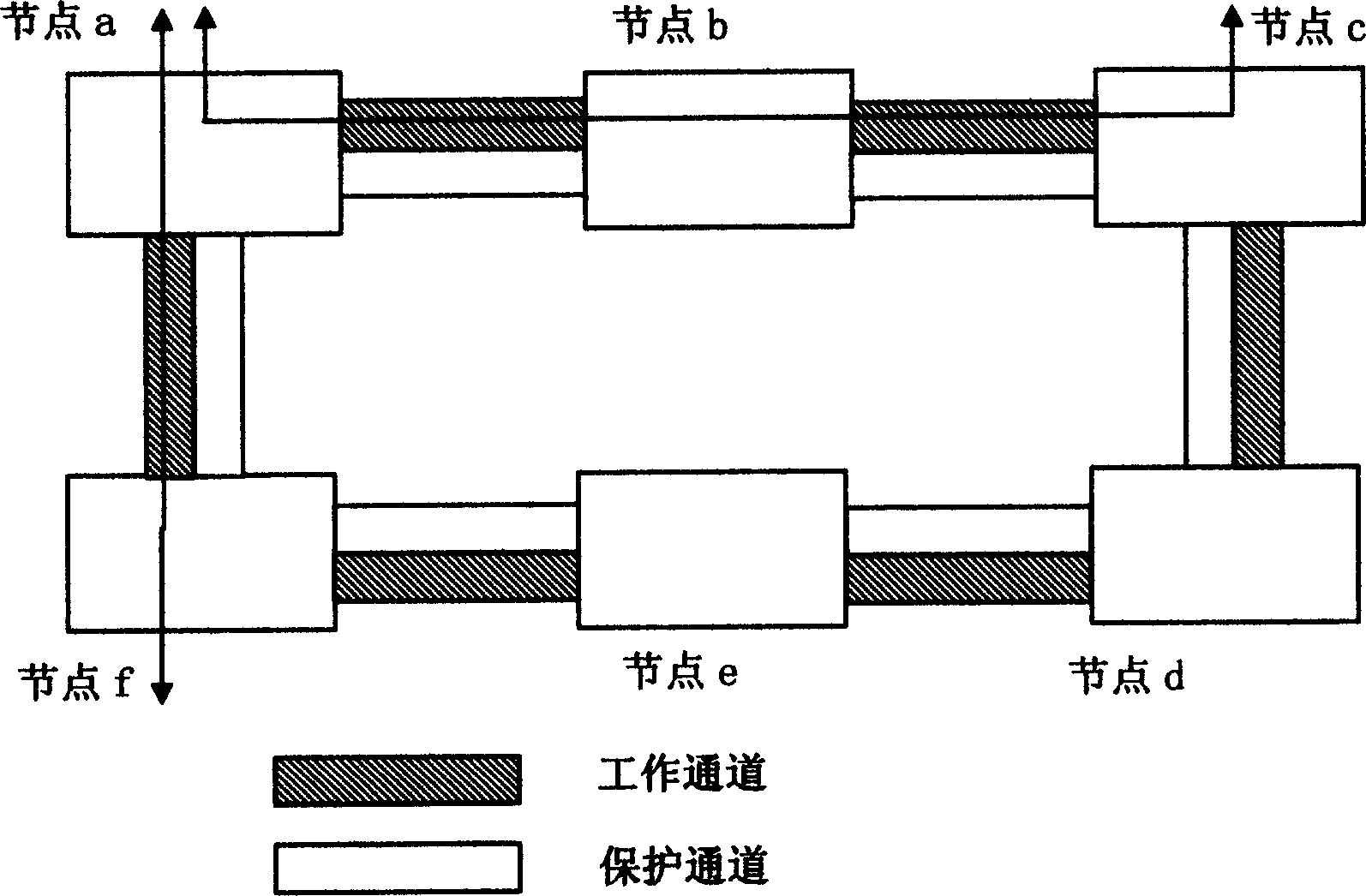
Loop network protection controlling method
ActiveCN1812359AShort protection pathEasy to operateTime-division multiplexData switching networksInformation transmissionTopological graph
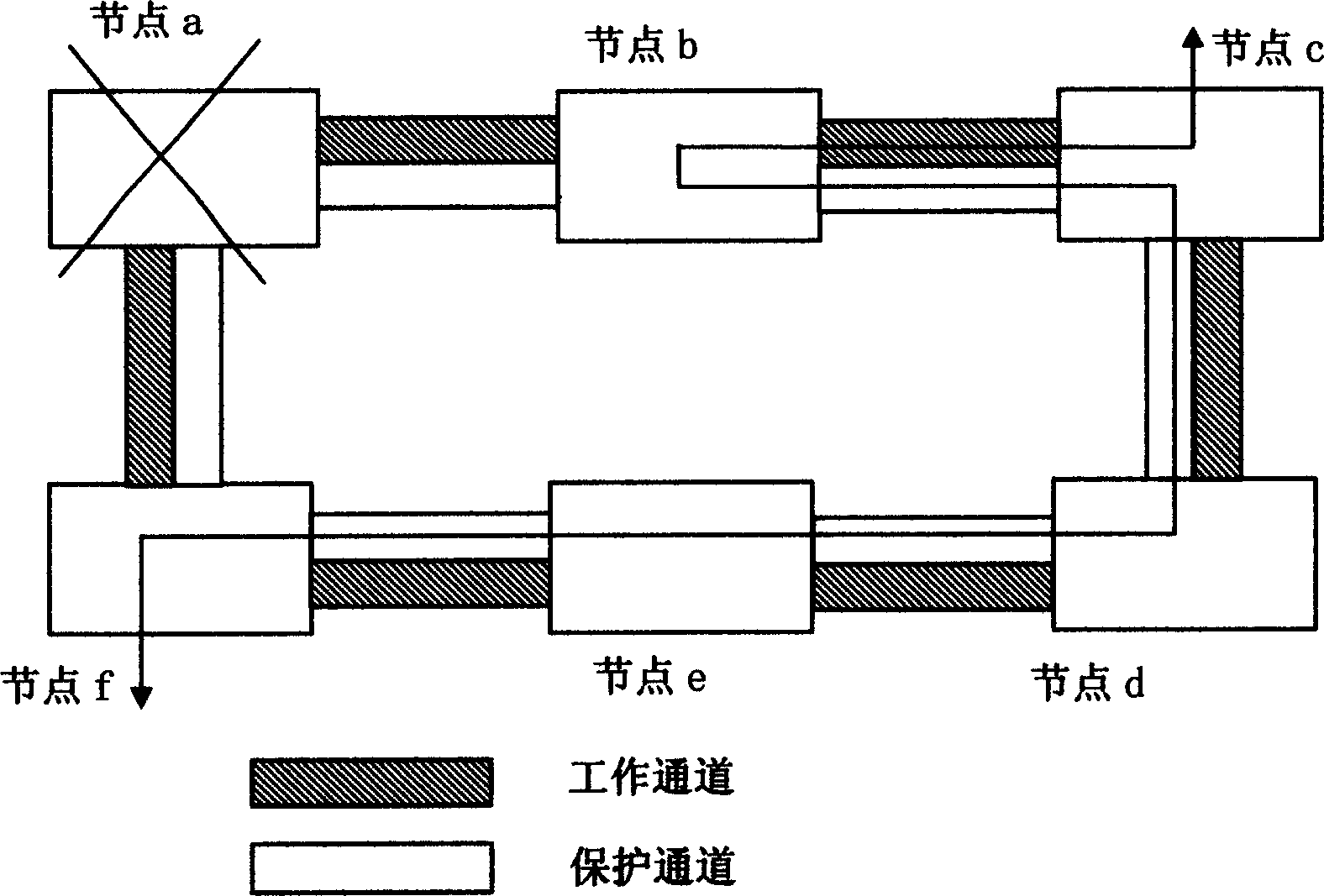
This invention is a kind of looped network protection controlling method relating to digital information transmission. It concludes the following steps: 1) in the looped network composed of many nodes, the identification is assigned to each node. Corresponding protection channel is arranged to working channel. 2) Looped network topological graph and local service topological table are saved in each node; the network topological graphs mirror the topological structure of looped network through identification. The local service topological table mirrors the service about the said node and corresponding working path. 3) When each node has detected network fault, the network fault information is transferred among each node in the looped network through communication channel. 4) According to network fault information, looped network topological graph and local service topological table, each node in the looped network judges the influence of the node service exerted by the said network fault. Each node also adopts corresponding protection channel service inversion or break over.
Owner:HUAWEI TECH CO LTD
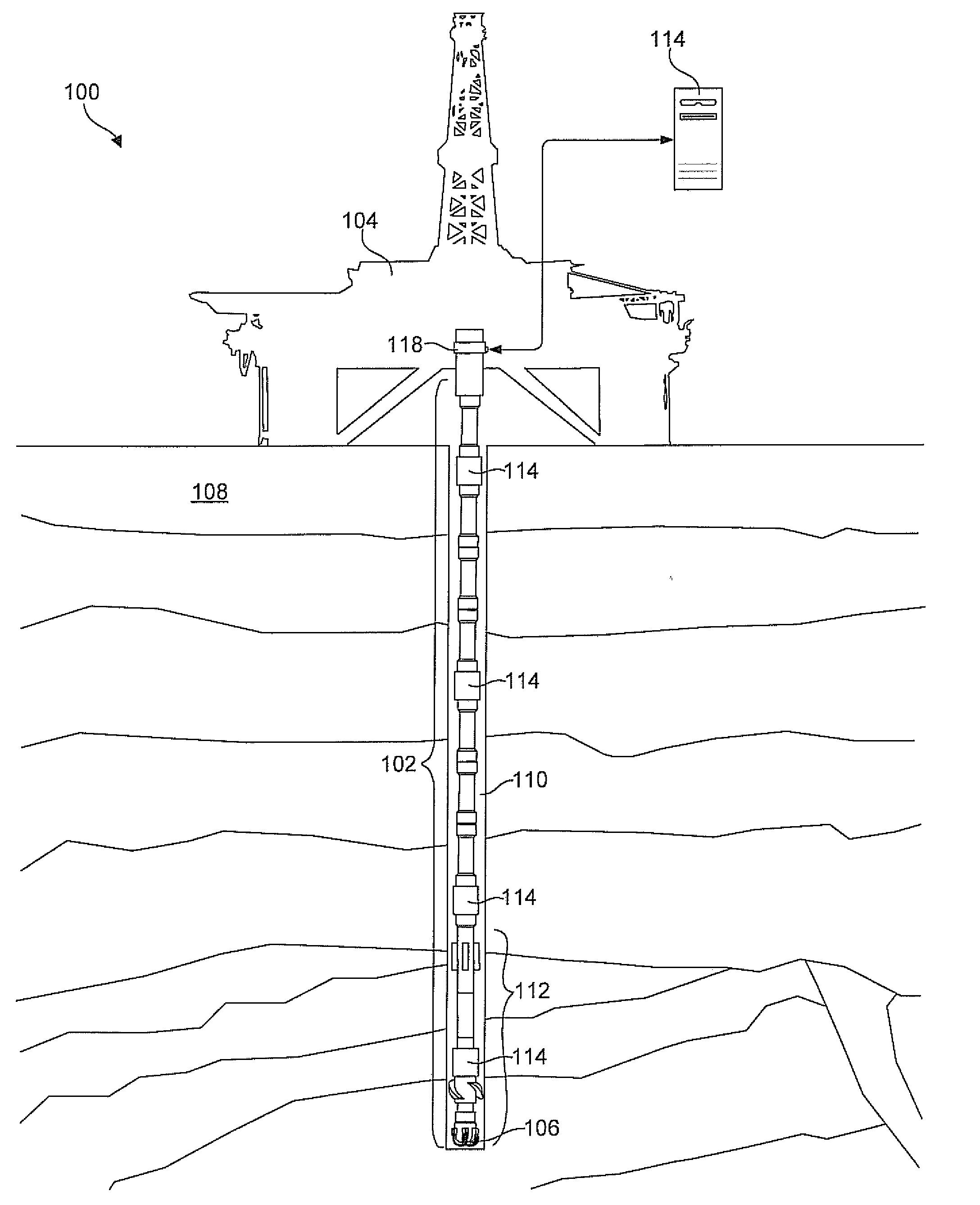
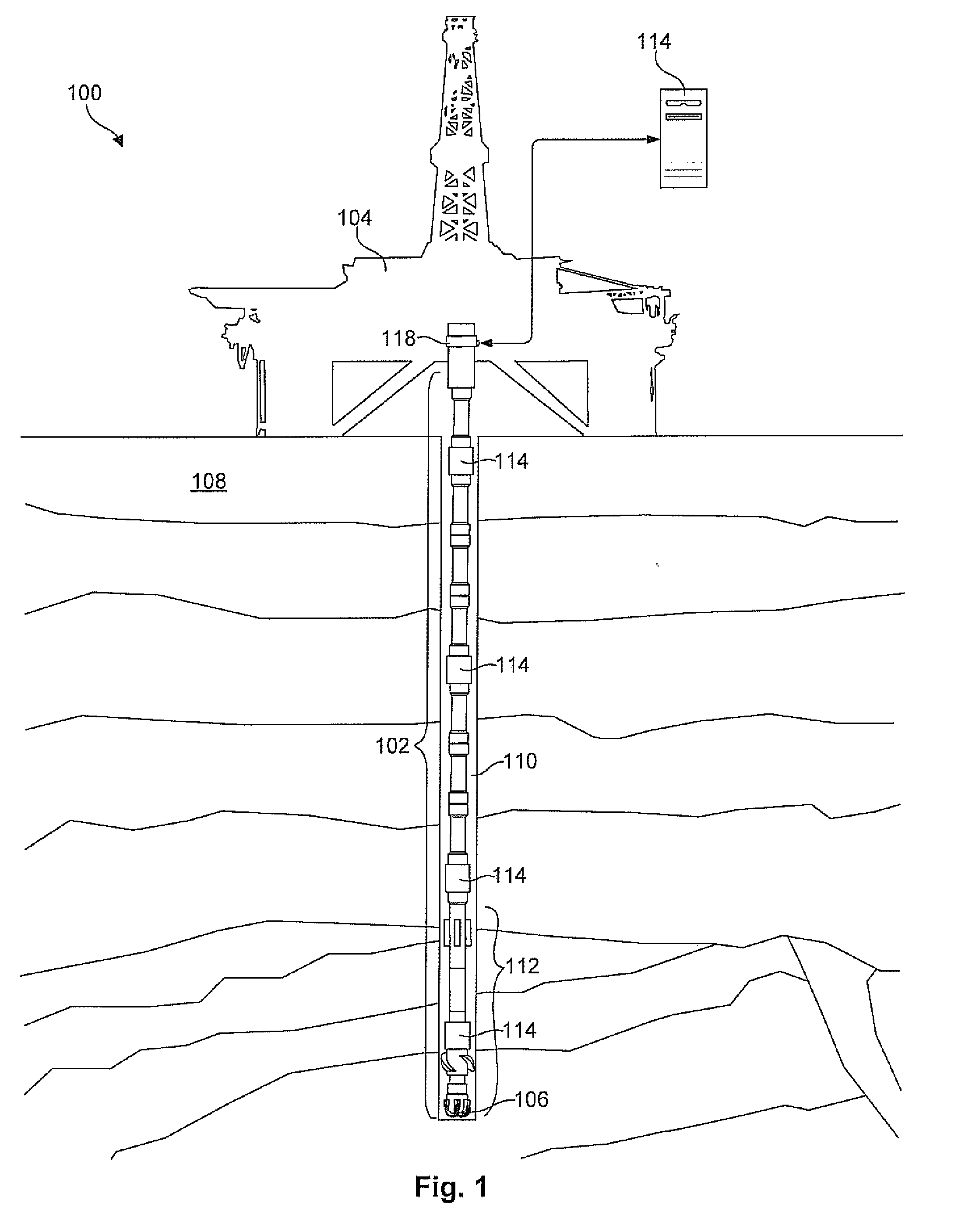
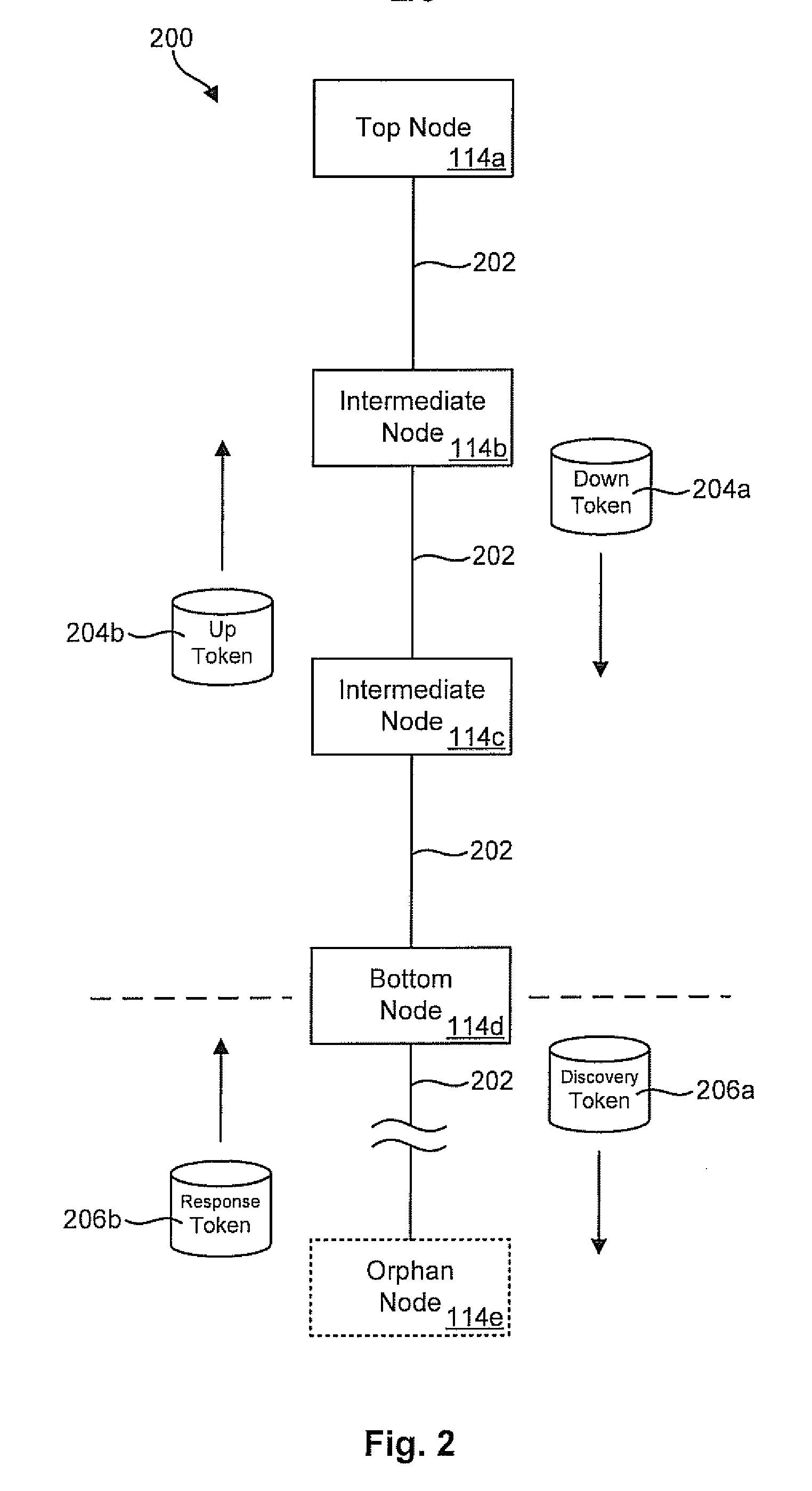
Topology maintenance and discovery facility for downhole networks
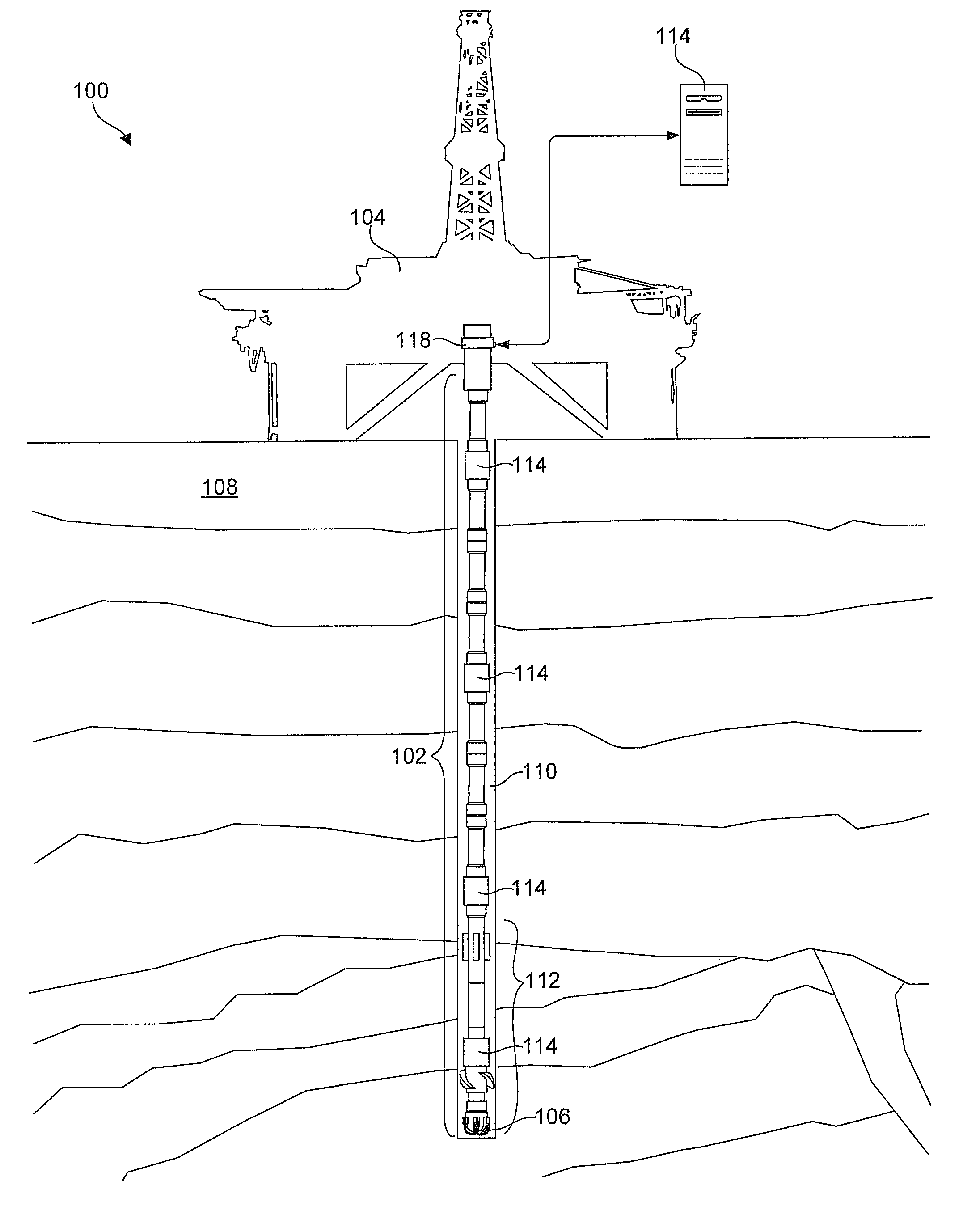
An apparatus and method for discovering and monitoring a collection of nodes in a downhole network may include receiving data packets originating from several downhole nodes. These packets may be read to extract a unique identifier and hop count for each of the nodes. This information may then be used to create entries in a network topology table corresponding to each of the downhole nodes. Each entry may contain unique identifier identifying the respective node and a hop count identifying a location of the node within the downhole network. The apparatus and method may further include modifying one or more entries in the topology table having conflicting hop counts to ensure that the hop counts of each entry are unique.
Owner:INTELLISERV
Active routing method and device
ActiveCN104967563AReduce overheadTroubleshoot technical issues with instabilityPower distribution line transmissionData switching networksInstabilityDistributed computing
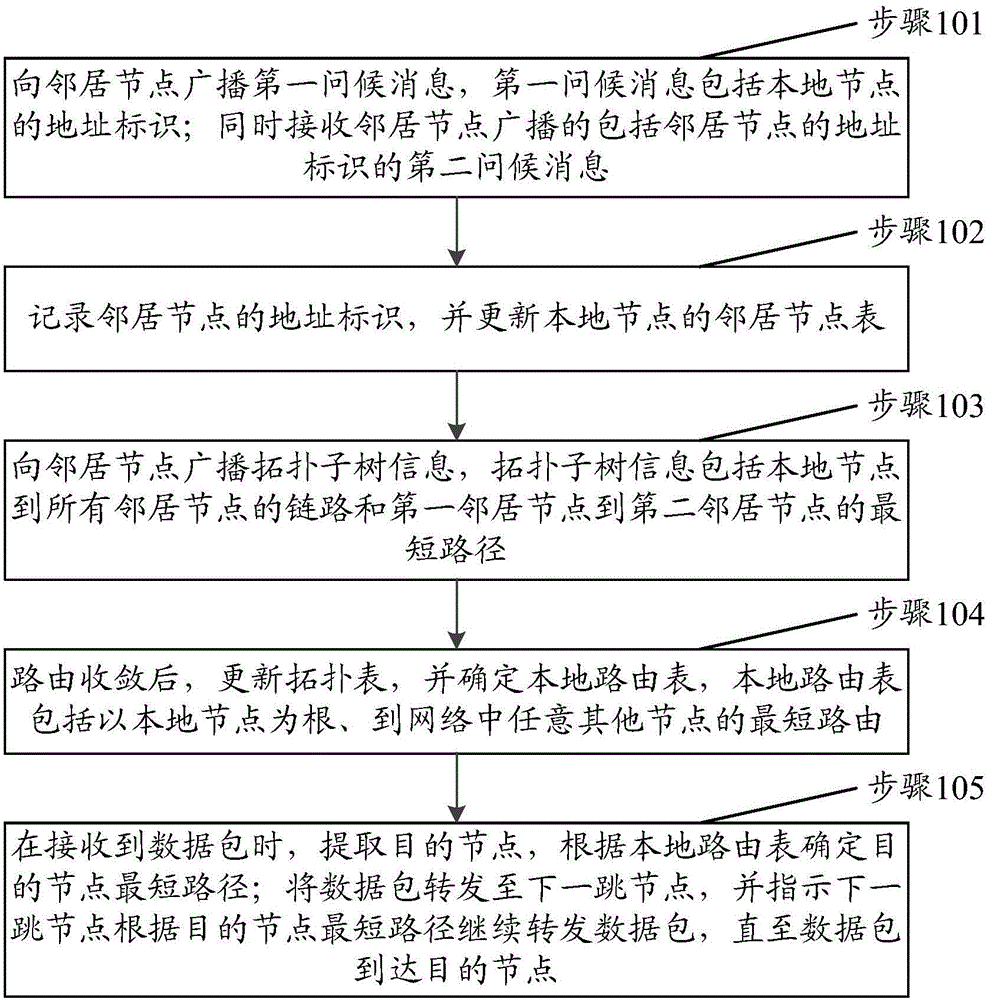
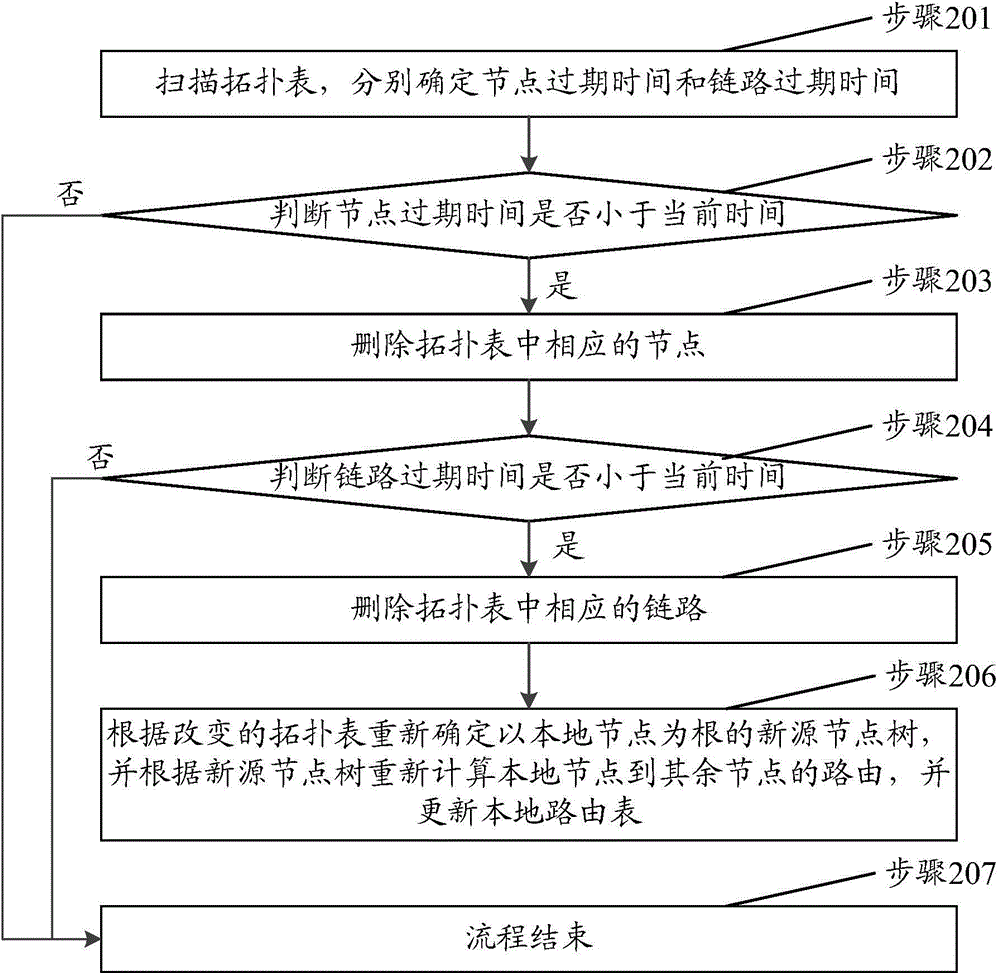
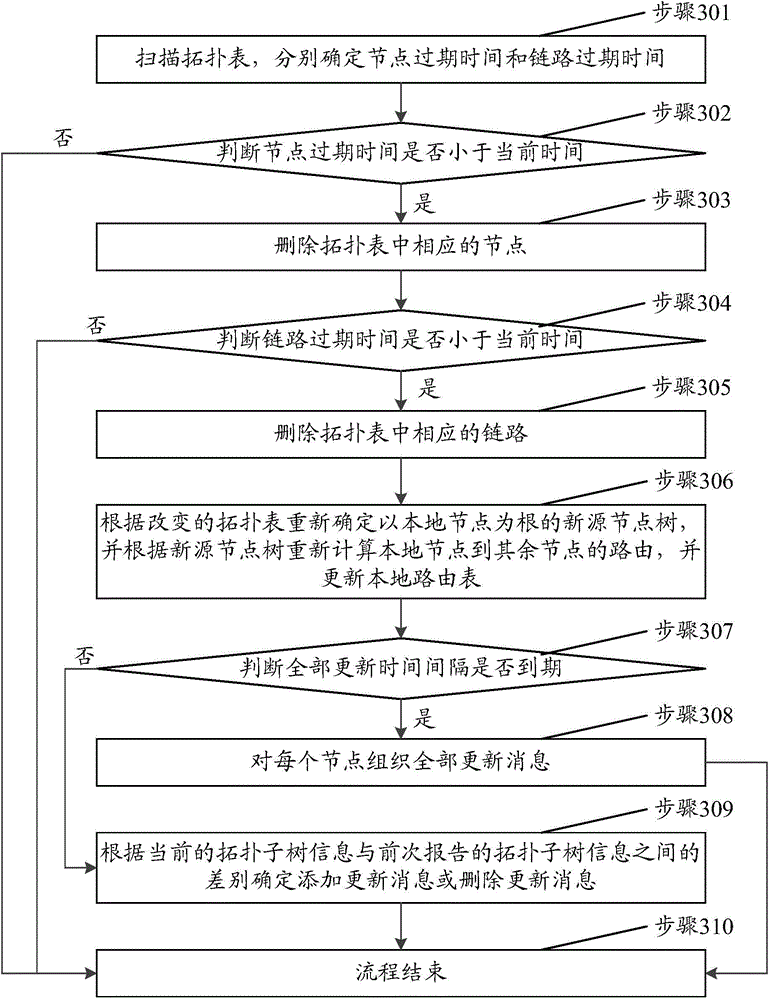
The invention discloses an active routing method and device, and the method comprises the steps: broadcasting a first greeting message to a neighbor node, and receiving a second greeting message at the same time, wherein the second greeting message is broadcasted by the neighbor node and comprises an address identification of the neighbor node; recording the address identification of the neighbor node, and updating a neighbor node table of a local node; broadcasting topology subtree information to the neighbor node; updating a topology table after routing convergence, and determining a local routing table; extracting a destination node when a data package is received, and determining the shortest path of the destination node according to the local routing table; transmitting the data package to a next jump node, indicating the next jump node to continuously transmit a data package according to the shortest path of the destination node till the data package reaches the destination node. The method can reduce the cost in network messages, can find the change of nodes and network state timely and quickly, and better solves a technical problem of network instability caused by a complex severe channel characteristic.
Owner:BEIJING SMARTCHIP MICROELECTRONICS TECH COMPANY +3
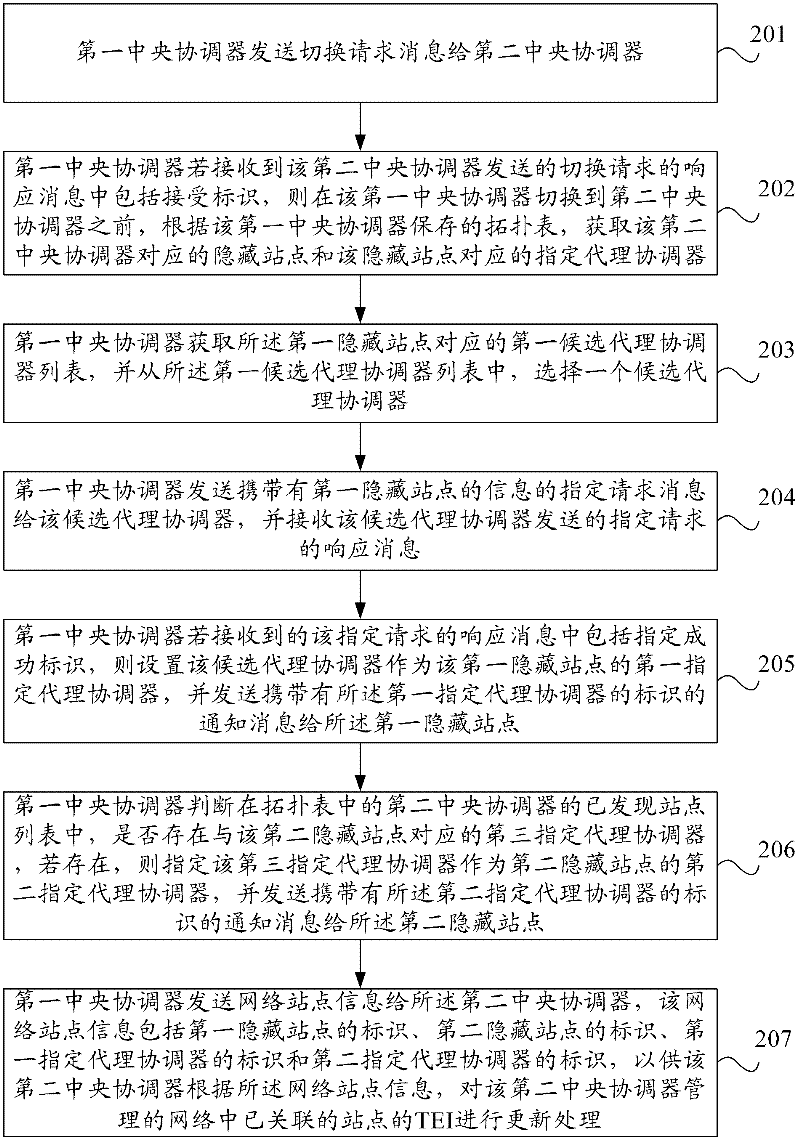
Central coordinator switching method and coordinator
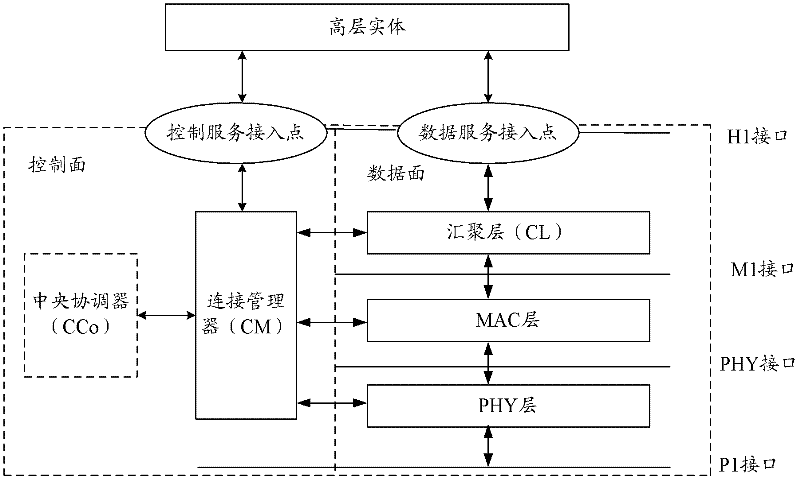
ActiveCN102546236ASolve the delay problemReduce latencyPower distribution line transmissionData switching networksTerminal equipmentDistributed computing
The invention provides a central coordinator switching method and a coordinator. The method comprises the following steps of: transmitting a switching request message to a second central coordinator by a first central coordinator; if a response message of the switching request is received from the second central coordinator, wherein the response message of the switching request comprises an accepting identifier, before switching from the first central coordinator switches to the second central coordinator, obtaining the hidden sites corresponding to the second central coordinator and the specified proxy coordinators corresponding to the hidden sites according to a topology table stored in the first central coordinator; transmitting network site information to the second central coordinator, so as to make the second central coordinator to update the TEI (Terminal Equipment Identifier) of the associated sites in the network managed by the second central coordinator according to the network site information, wherein the network site information includes the identifiers of the hidden sites and the identifiers of the specified proxy coordinators corresponding to the identifier of the hidden sites.
Owner:HUAWEI TECH CO LTD
Node device
InactiveUS7619987B2Balance processing loadError preventionFrequency-division multiplex detailsTopology informationRing network
In node devices composing a ring network connected to another network with a redundant node device, a topology table includes redundancy information of the redundant node device, a transmitter transmits topology information and the redundancy information of the node devices themselves, a topology table preparing portion prepares a topology table based on redundancy information and topology information received from the redundant node device, and topology information received from the other node device, and a packet distributor distributes a packet received over the ring network based on the topology table.
Owner:FUJITSU LTD
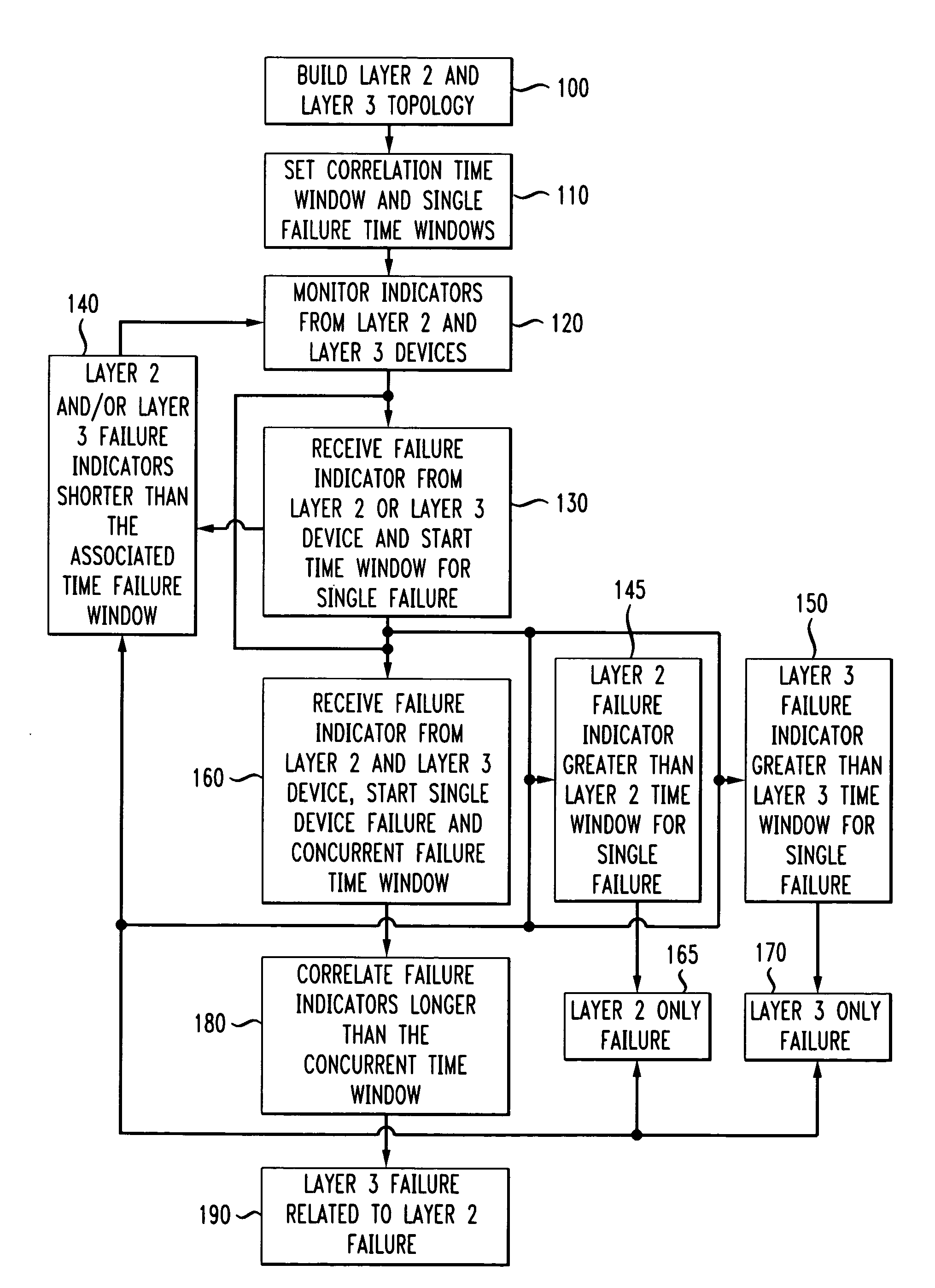
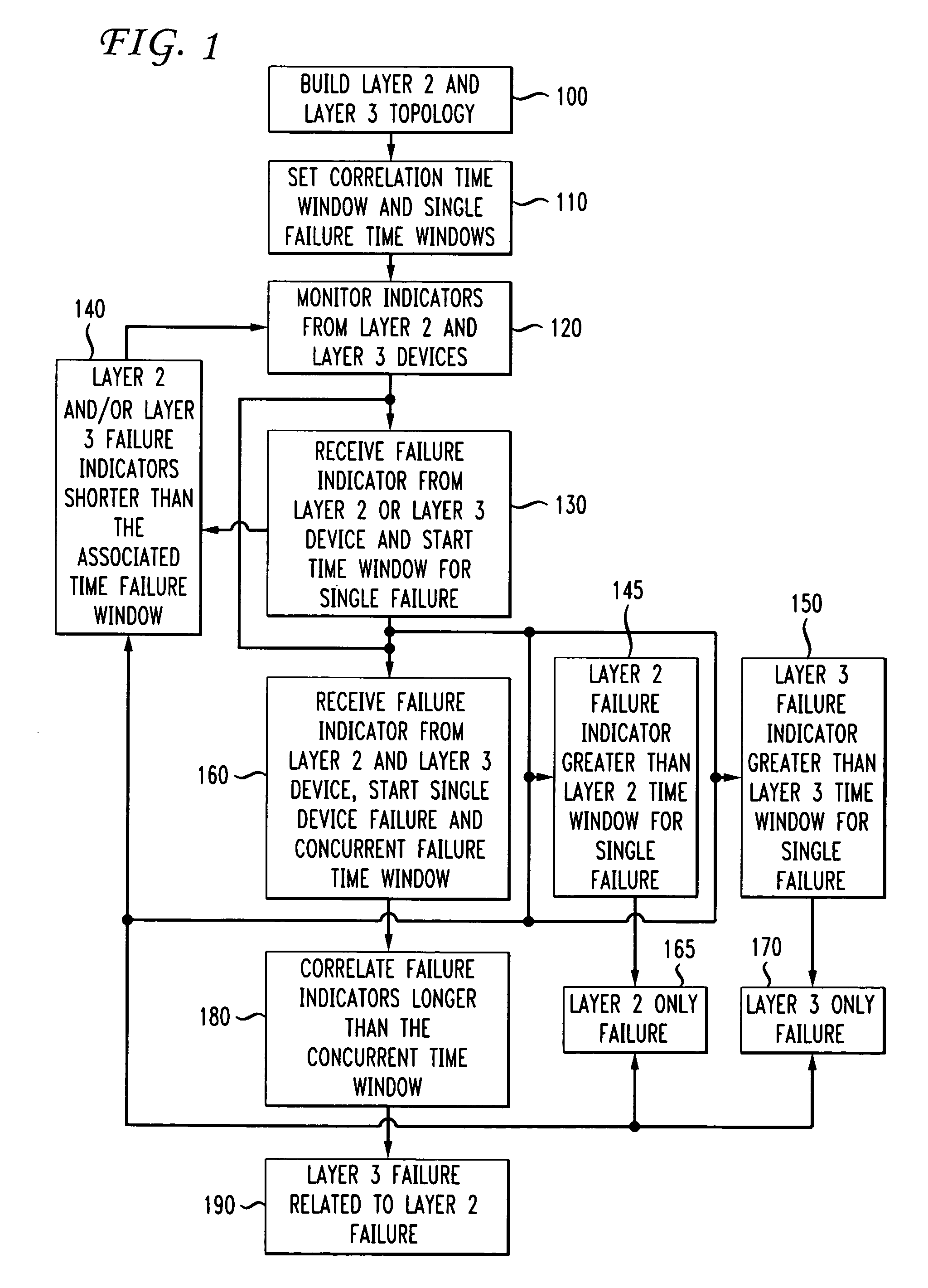
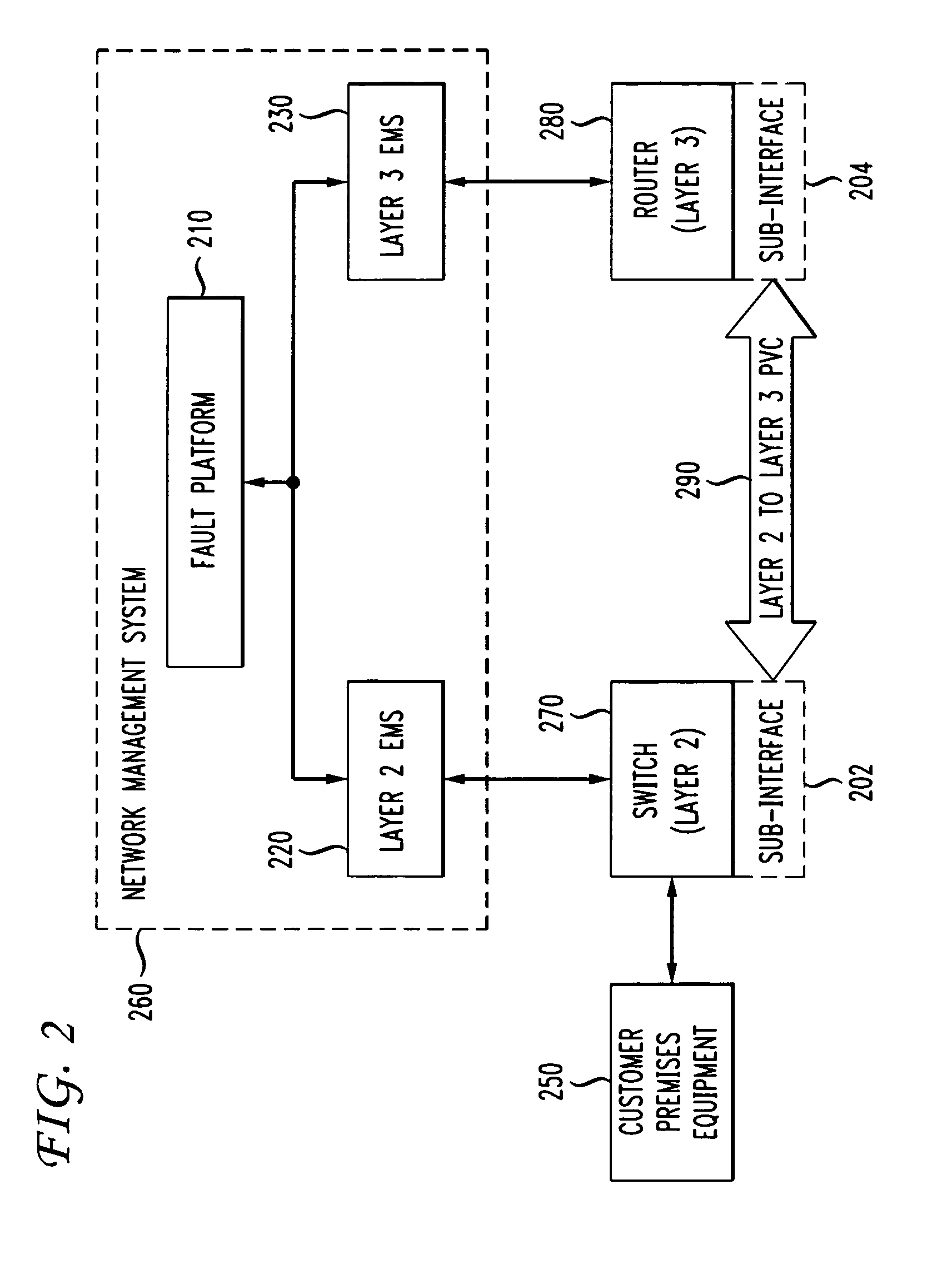
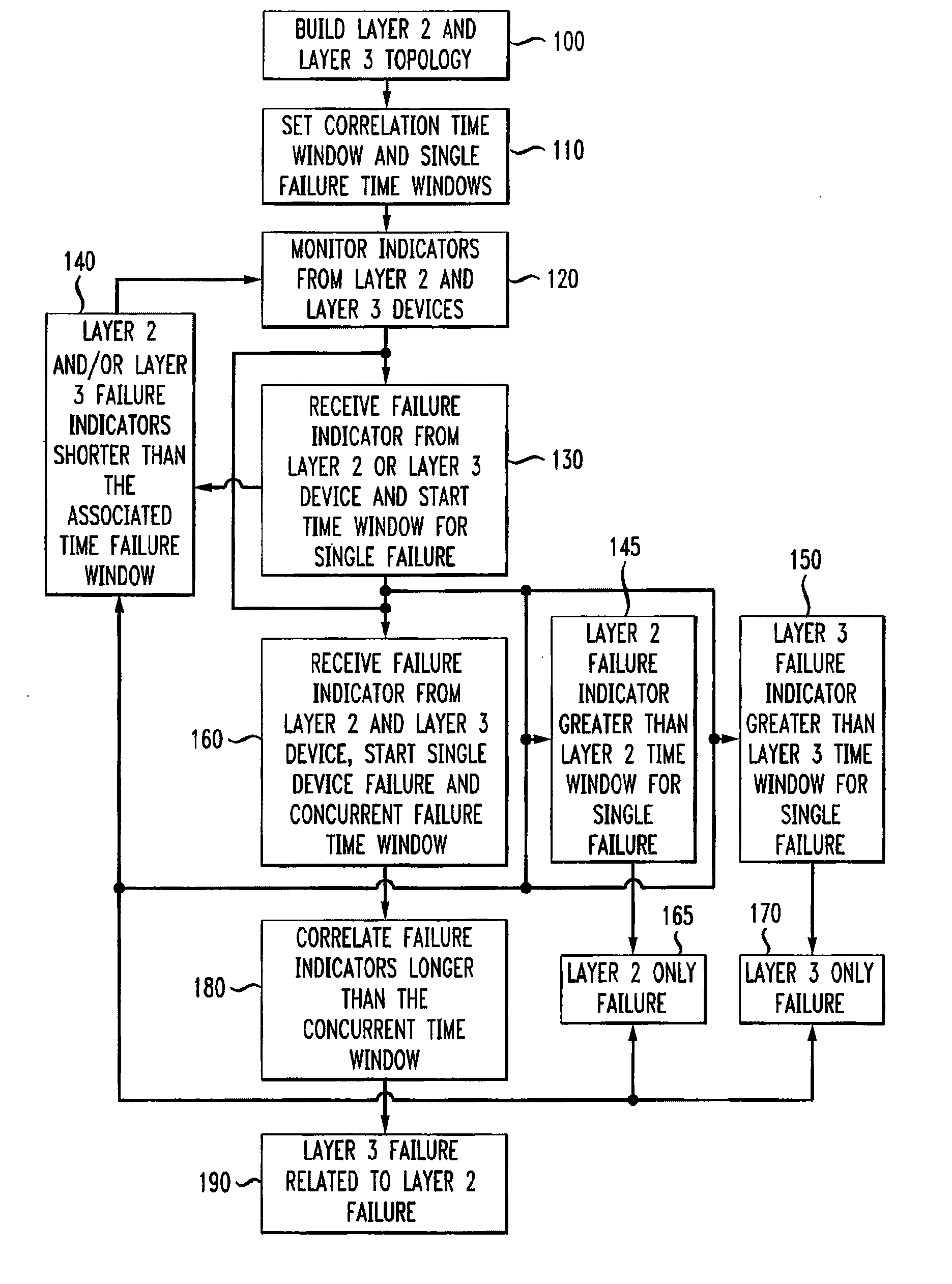
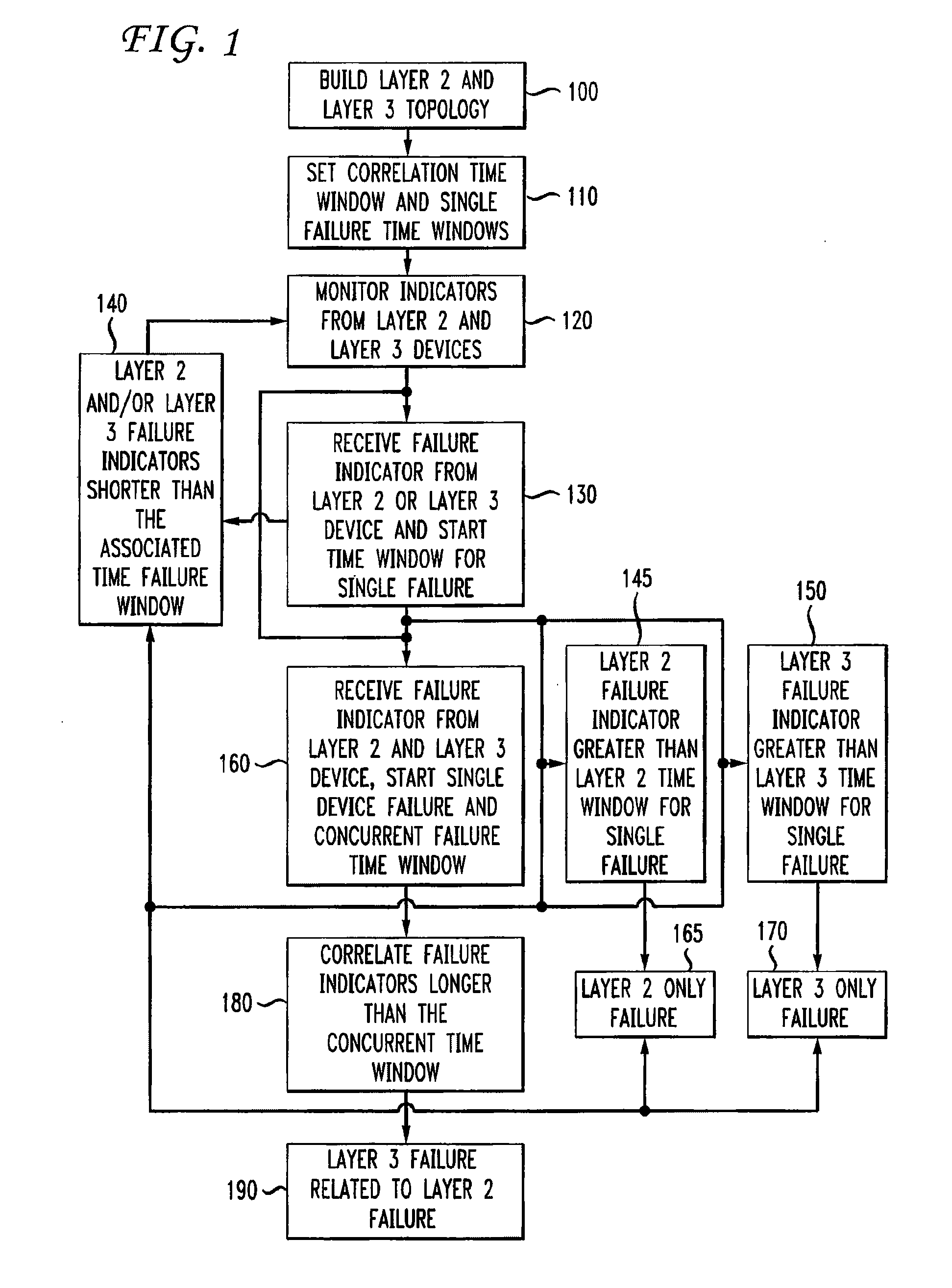
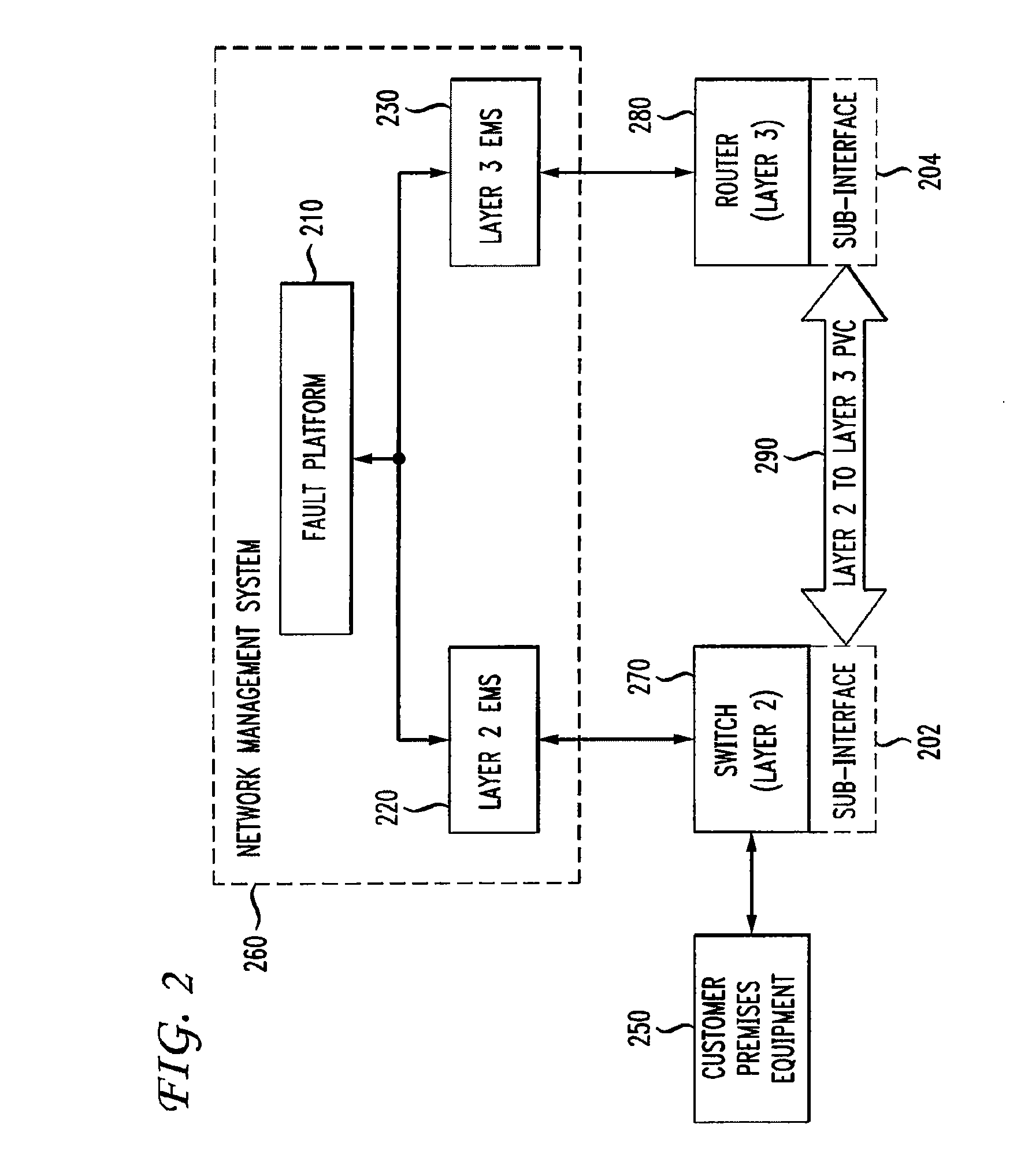
Automatic problem isolation for multi-layer network failures
ActiveUS7570580B1Valuable processing timeEliminate needError preventionTransmission systemsFault indicatorOpen Systems Interconnection
A method and apparatus includes automatically correlating indicators already generated by network components to detect and isolate failures that are caused by or related to network components operating on different layers of the open system interconnect (OSI) model. Failure indicators that persist for longer than a specified time window are automatically detected and correlated with one another based on a topology table. The method uses indicators already generated by the network components, obviating the need for software that typically resides on and consumes valuable processing time of network components.
Owner:ATLASSIAN US INC
Directional topology discovery for downhole networks
An apparatus and method for discovering and monitoring a collection of nodes in a downhole network may include receiving data packets originating from several downhole nodes. These packets may be read to extract a unique identifier and hop count for each of the nodes. This information may then be used to create entries in a network topology table corresponding to each of the downhole nodes. Each entry may contain unique identifier identifying the respective node, a hop count identifying a location of the node within the downhole network, and a direction identifier. The method may further include modifying one or more entries in the topology table having a conflicting hop count and direction identifier.
Owner:INTELLISERV
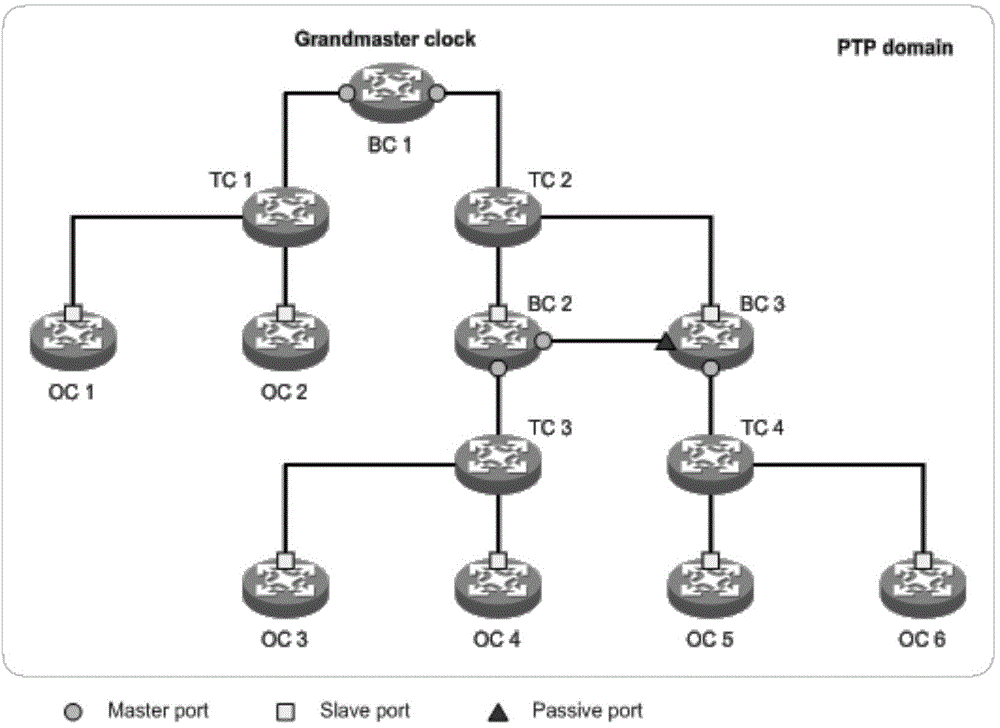
Clock synchronization method and device
ActiveCN104092528AShorten convergence timeImprove stabilitySynchronising arrangementOptical clockNetwork topology
The invention provides a clock synchronization method. The method comprises the steps of sending Topology messages to other clock node devices through ports on two sides according to a preset low sending frequency; receiving Topology messages sent by the other clock node devices through the ports on two sides; constructing a network topology table according to the received Topology messages, wherein the network topology table contains the priority vector of each port through which the Topology messages are sent; determining whether the device is an optimal clock node device according to the priority vector of each port; if yes, releasing synchronous clocks to the other clock node devices through a main port; if not, determining the main port and a slave port from the ports on two sides according to the network topology table, and receiving the synchronous clock released by the optical clock node device through the slave port to achieve the updating of a local clock; forwarding the synchronous clock to a next hop of node device through the main port. By the adoption of the clock synchronization method, convergence time of port role calculation can be reduced, and the stability of a system can be improved.
Owner:NEW H3C TECH CO LTD
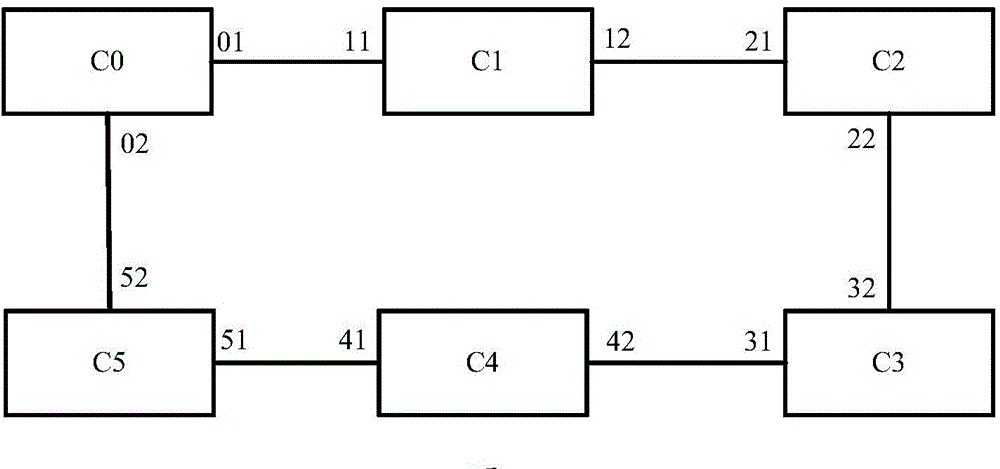
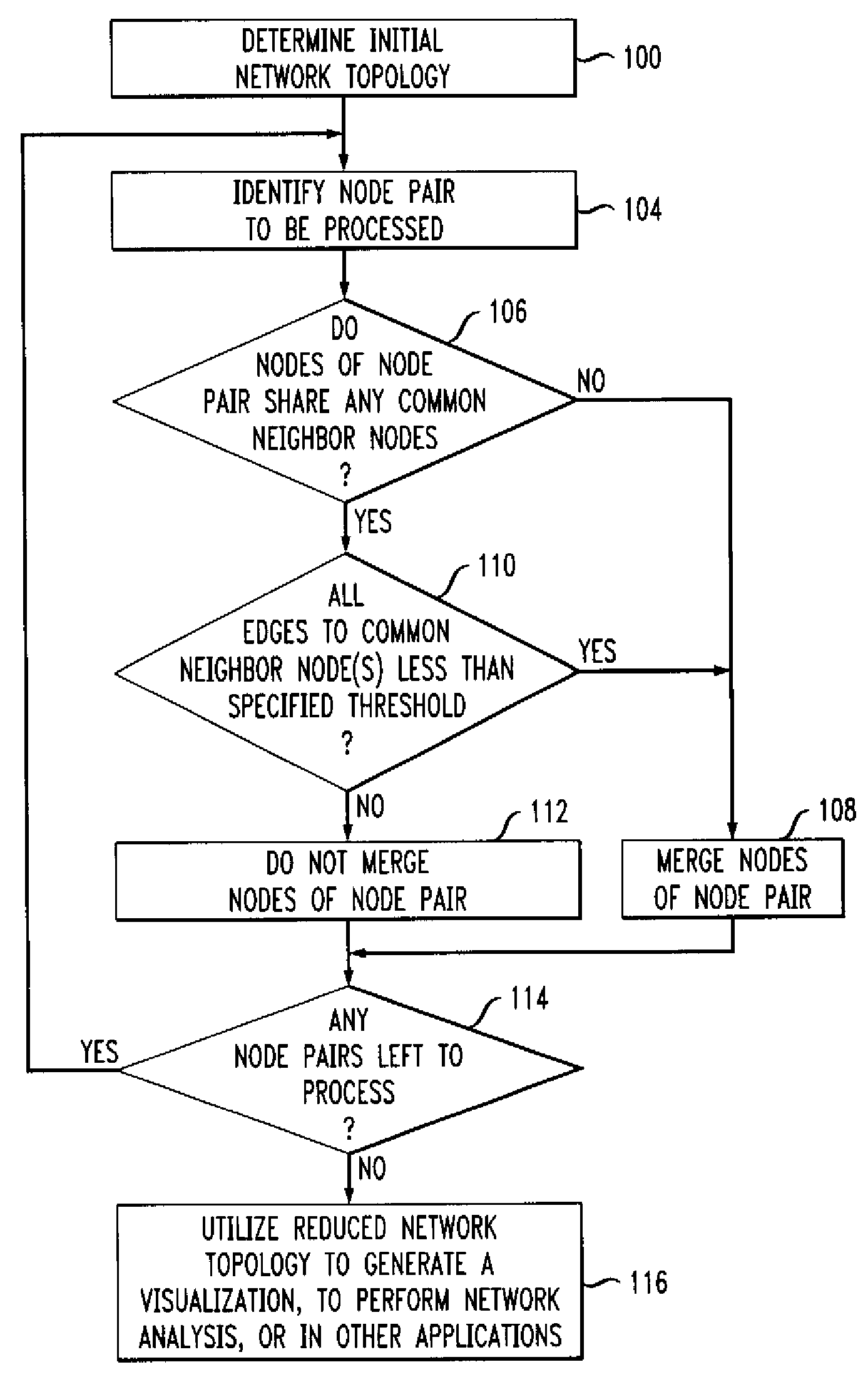
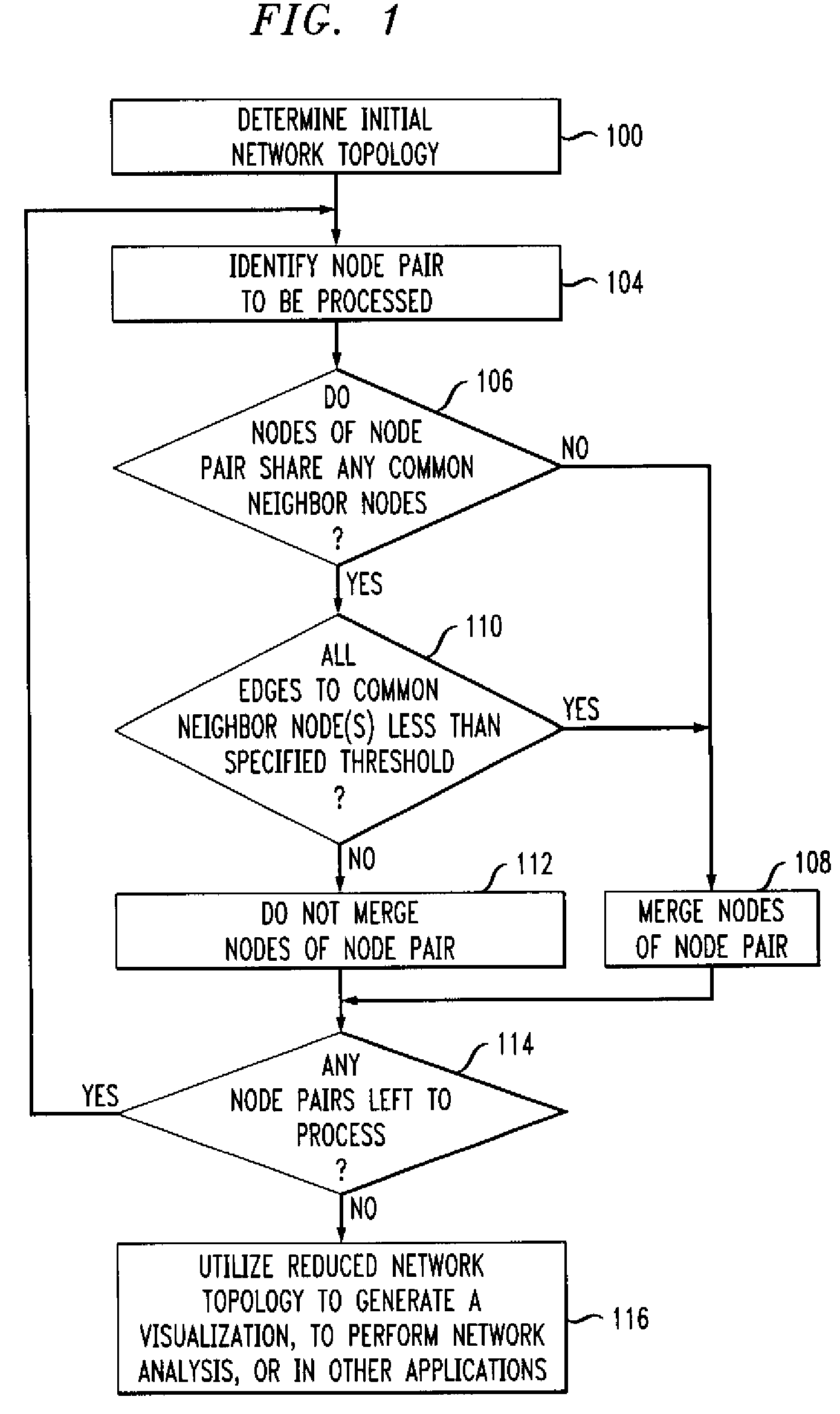
Node merging process for network topology representation
ActiveUS7688758B2Accurately simplifyData switching by path configurationNetwork topologyDistributed computing
Node merging methods and apparatus are disclosed for generating simplified representations of network topology. A first topology representative of a given network is determined, and at least one pair of nodes of the first topology is merged into a single node based on measures associated with respective edges connecting the nodes of the node pair to at least one neighbor node common to that pair. The merging step is repeated for one or more additional pairs of nodes to produce a reduced network topology meeting one or more desired criteria, and a visualization or other representation of the reduced network topology is generated.
Owner:AVAYA INC
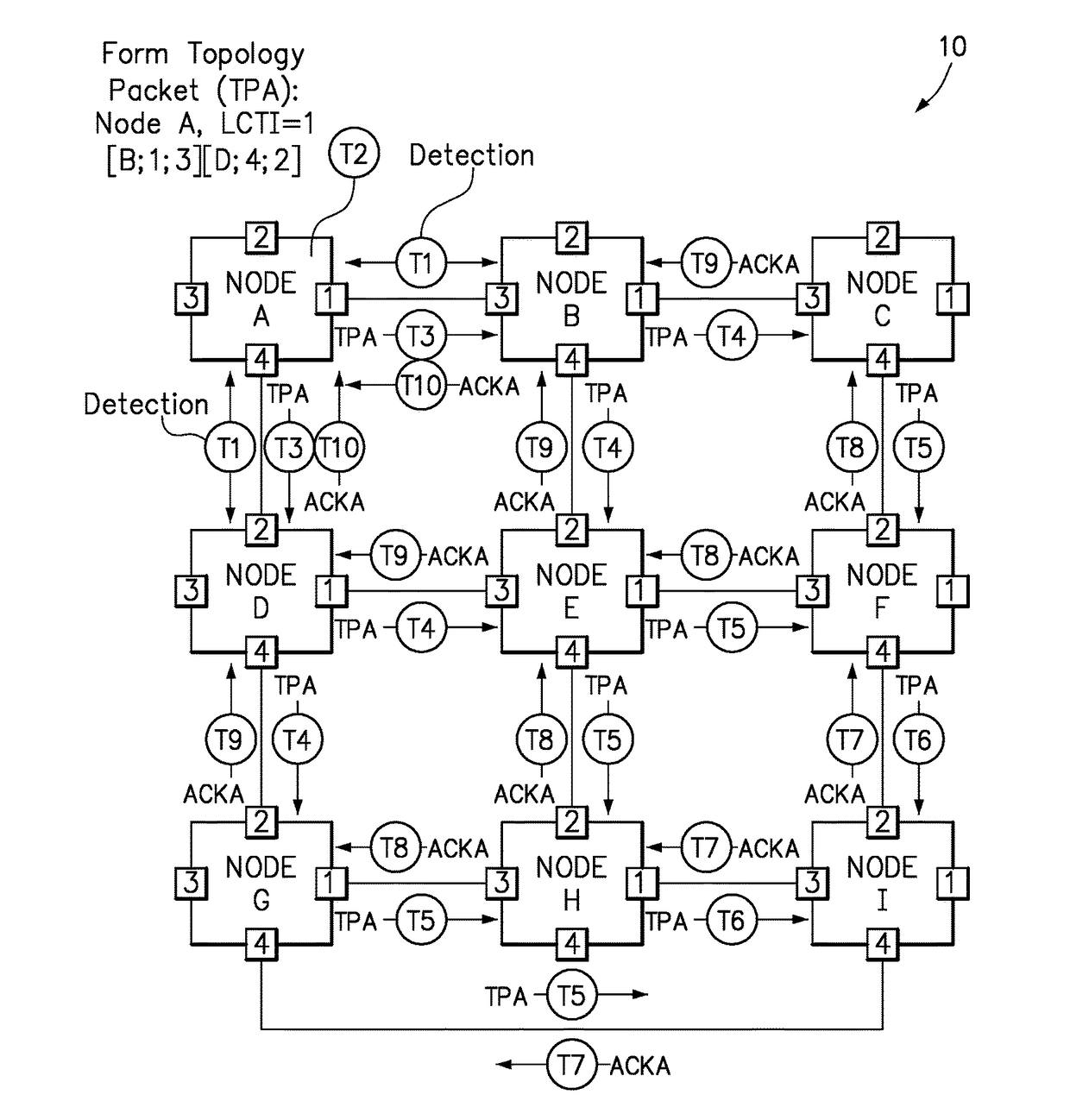
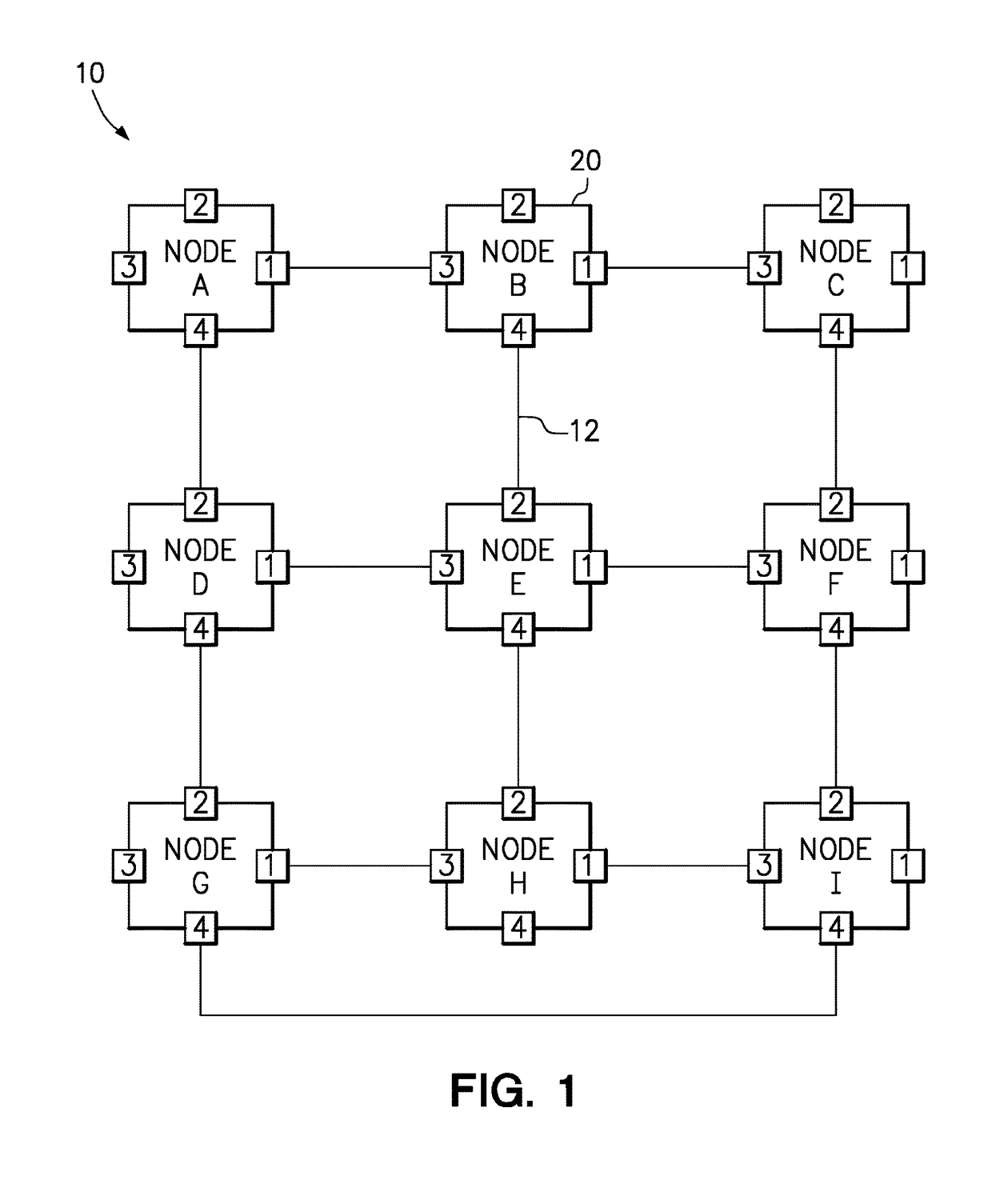
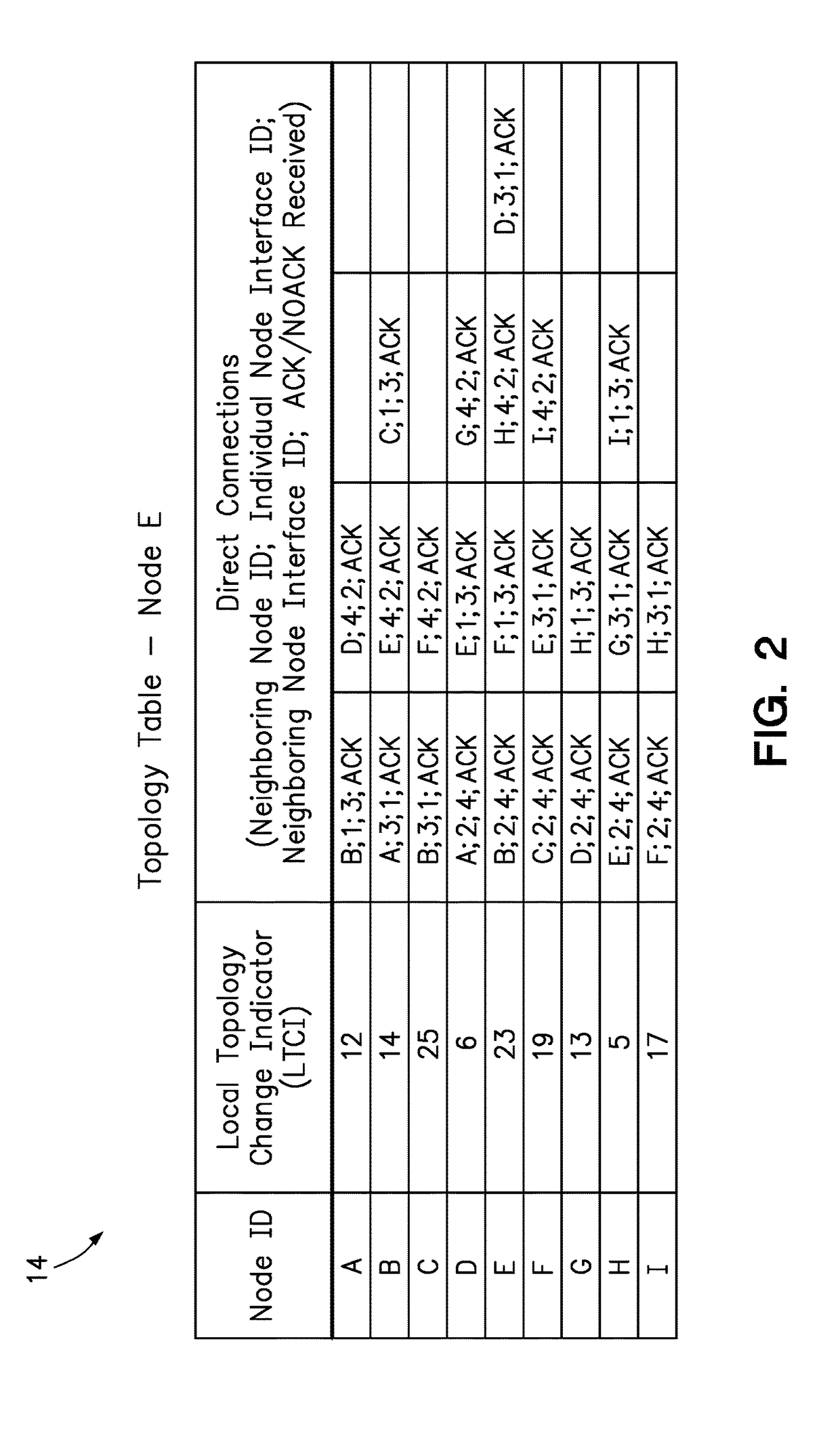
Efficiently determining network topology
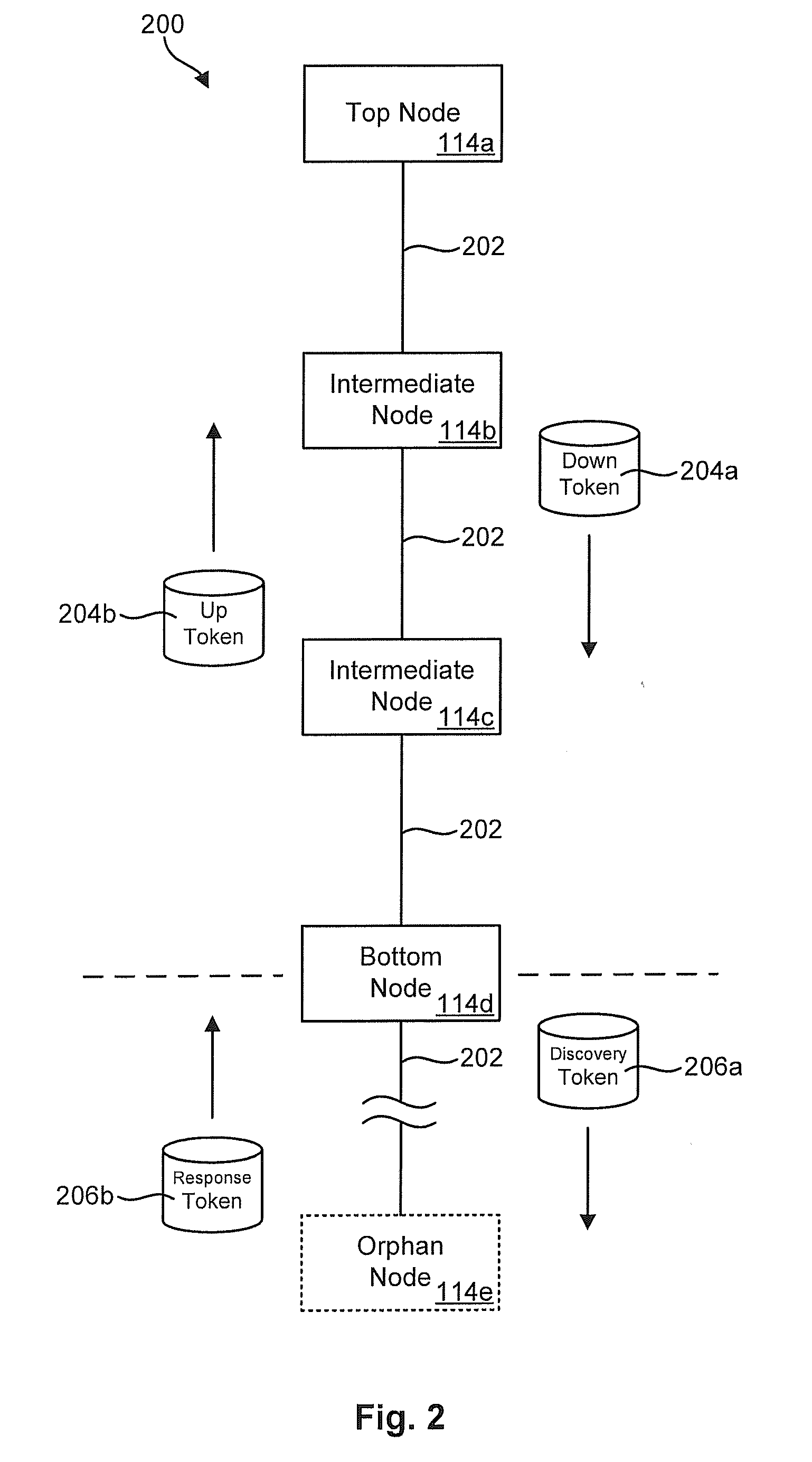
A method allows each individual node in the multi-node computing system to detect the topology of the computing system. Each individual node detects its own connections with neighboring nodes directly connected to the individual node, and sends out a topology packet on all of its interfaces with a local topology change indicator that increments with each topology packet sent out. Each individual node stores their own topology table with an entry for each node from which it has received a topology packet, including the local topology change number which enables the node to determine whether a received topology packet is more recent than data already stored in the topology table. Each node updates its topology table with new topology data, forwards new topology data, and sends back acknowledgements to a source node only upon receiving acknowledgements from all other nodes.
Owner:LENOVO GLOBAL TECH INT LTD
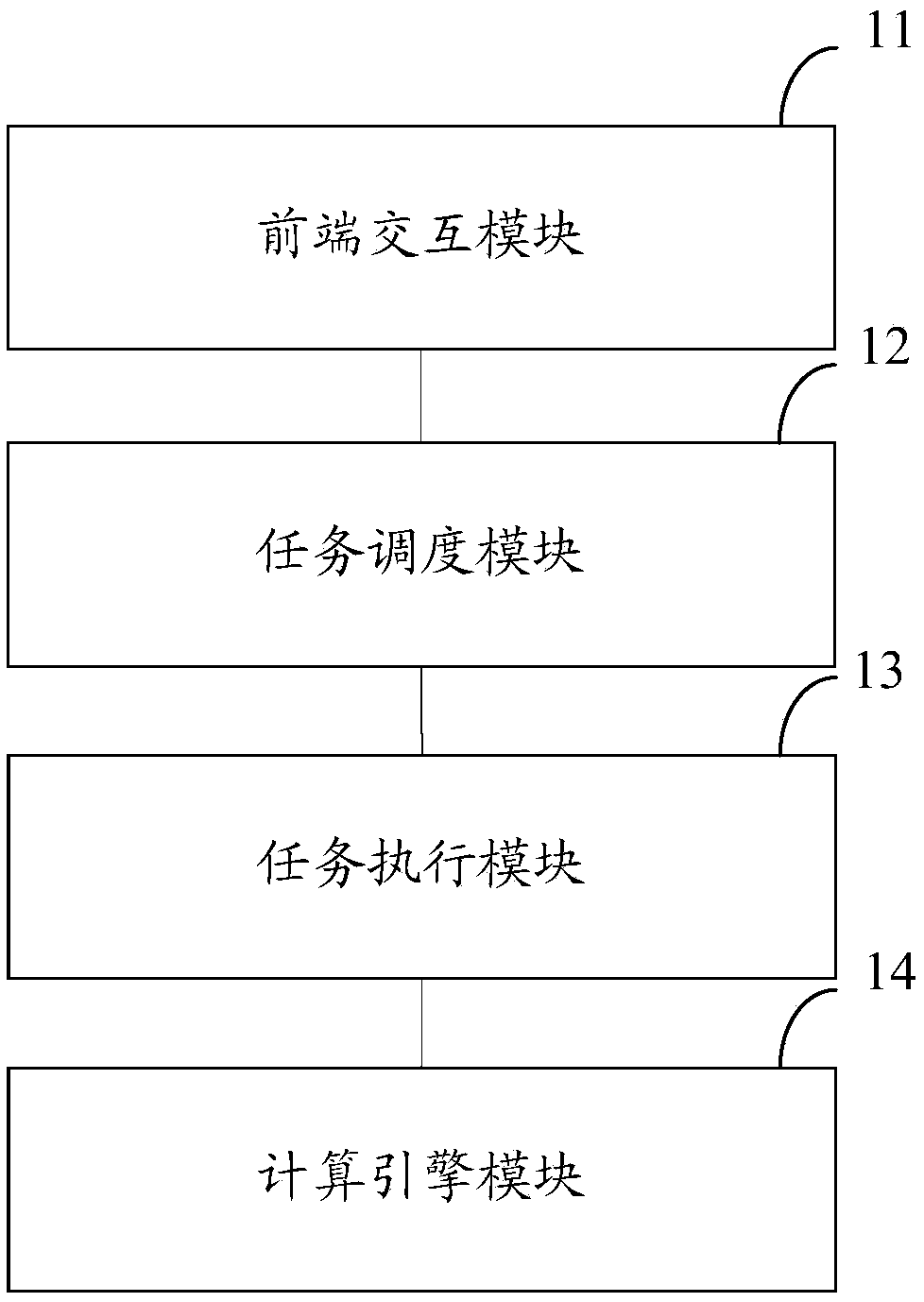
Task scheduling method and device
PendingCN110895484AImprove efficiencyAvoid misjudgmentProgram initiation/switchingResource allocationParallel computingComputer engineering
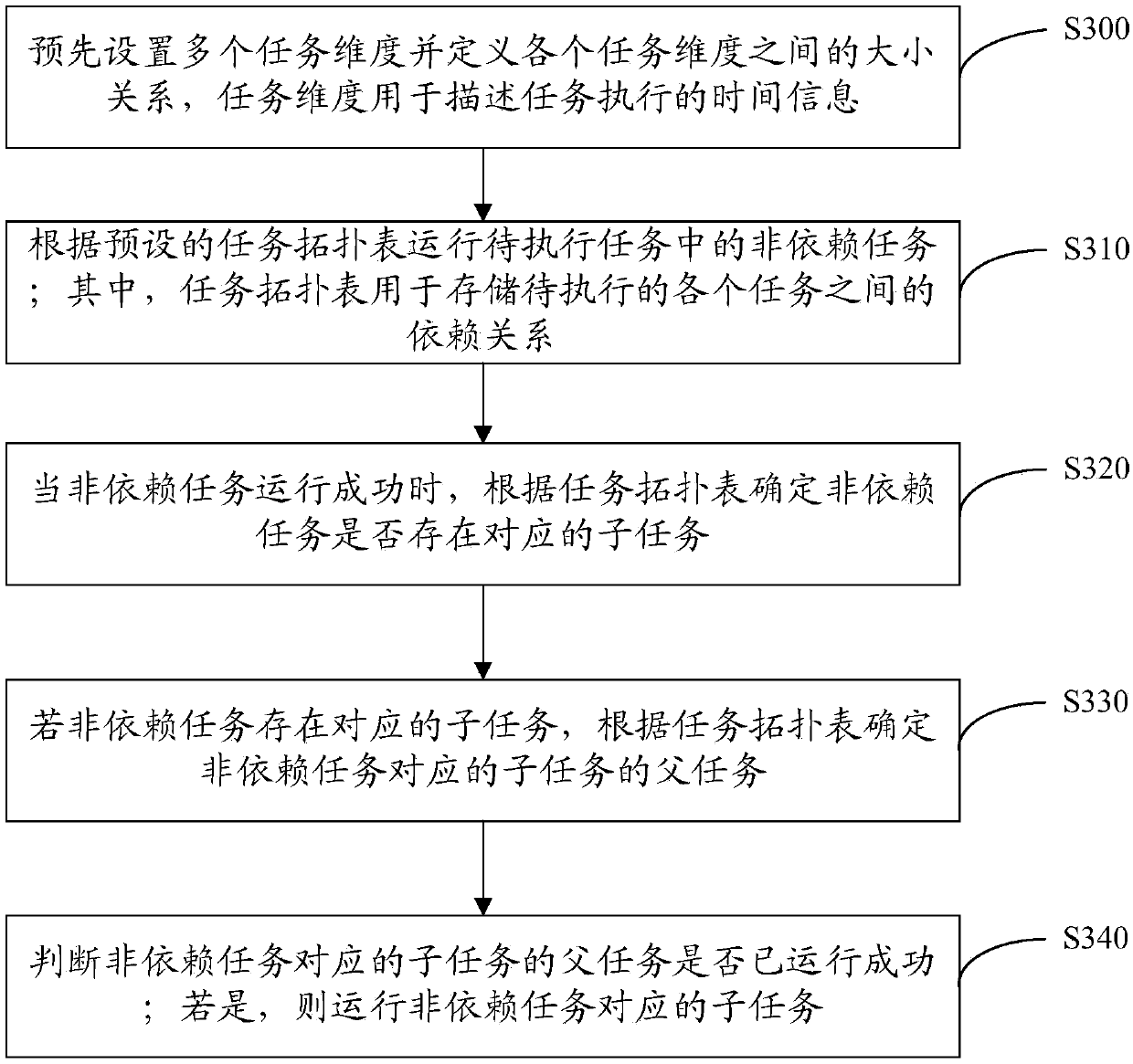
The invention discloses a task scheduling method and a device. The method comprises the steps of running a non-dependent task in a to-be-executed task according to a preset task topology table; wherein the task topology table is used for storing a dependency relationship among to-be-executed tasks; when the non-dependent task is successfully operated, determining whether the non-dependent task hasa corresponding sub-task according to the task topology table; if the non-dependent task has the corresponding sub-task, determining a parent task of the sub-task corresponding to the non-dependent task according to the task topology table; judging whether the parent task of the child task corresponding to the independent task is successfully operated; and if yes, running the sub-task corresponding to the independent task. According to the method, a user does not need to manually judge the dependency relationship among the tasks, the tasks with the dependency relationship can automatically run when the conditions are met, the efficiency is improved, and misjudgment is avoided.
Owner:BEIJING QIHOO TECH CO LTD
Standard spider-web fractal networking method for low voltage power line communication
InactiveCN105337639AReduce the probability of conflictEfficient networkingPower distribution line transmissionSurvivabilitySpider web
The invention provides a standard spider-web fractal networking method for low voltage power line communication, and relates to a standard spider-web fractal networking technology for low voltage power line communication. The standard spider-web fractal networking method for low voltage power line communication solves the problem that a current networking method has the disadvantages of being low in the networking efficiency, being low in the reliability and being low in survivability. The method comprises: a main node distributes two time slots for the main node, and then in the first time slot, the main node corrects the frequency offset between the main node and slave nodes. In the second time slot, the main node sends a data frame allowing registration of nodes to the slave nodes within the communication range. When the nodes register successfully, the main node can give a response. In a convergence area, the main node stores the registered slave nodes in a topology table and distributes TEI for the slave nodes. When the convergence process completes, the main node distributes time slots for the registered slave nodes, and the slave nodes which acquire the time slots can perform networking according to the distribution sequence of time slots. The standard spider-web fractal networking method for low voltage power line communication is suitable for a low voltage power line communication field.
Owner:HARBIN INST OF TECH
Storage system and a storage management system
InactiveUS7617318B2Multiple digital computer combinationsTransmissionComputer hardwareStorage management
Owner:GOOGLE LLC
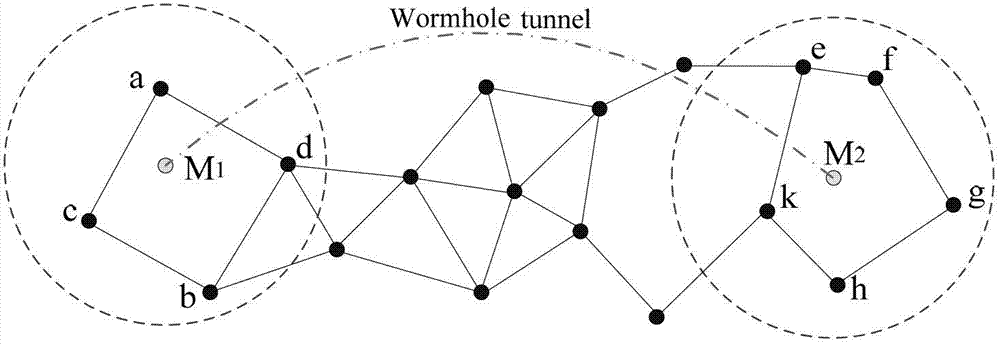
Wormhole detecting method based on specific triple-jump channel path in wireless sensor network
InactiveCN102769845AImprove detection rateNo false positivesNetwork topologiesSecurity arrangementWireless mesh networkWireless sensor networking
The invention provides a wormhole detecting method based on a specific triple-jump path in a wireless sensor network. The method comprises the following steps that (1) in a network initializing stage, each node acquires a one-jump neighbor list and a two-jump neighbor list, and then transmits the neighbor list to one-jump neighbor nodes and two-jump neighbor nodes through a whole network; (2) each node in the network maintains a topology table, and the one-jump neighbor list transmitted by the one-jump neighbor nodes and two-jump neighbor nodes is recorded into the topology table when being received by each node; and (3) each node in the network firstly carries out attack judging, then locates wormholes and takes a corresponding measure according to an attack judging result, and finally deletes a false-neighbor found after location of the wormholes in a neighbor list of a current node. The invention relates to the distributed and practical wormhole detecting method with no need of support of special hardware equipment. The method is used for intrusion detection of the wireless sensor network, and has a better safety protection effect.
Owner:HARBIN ENG UNIV
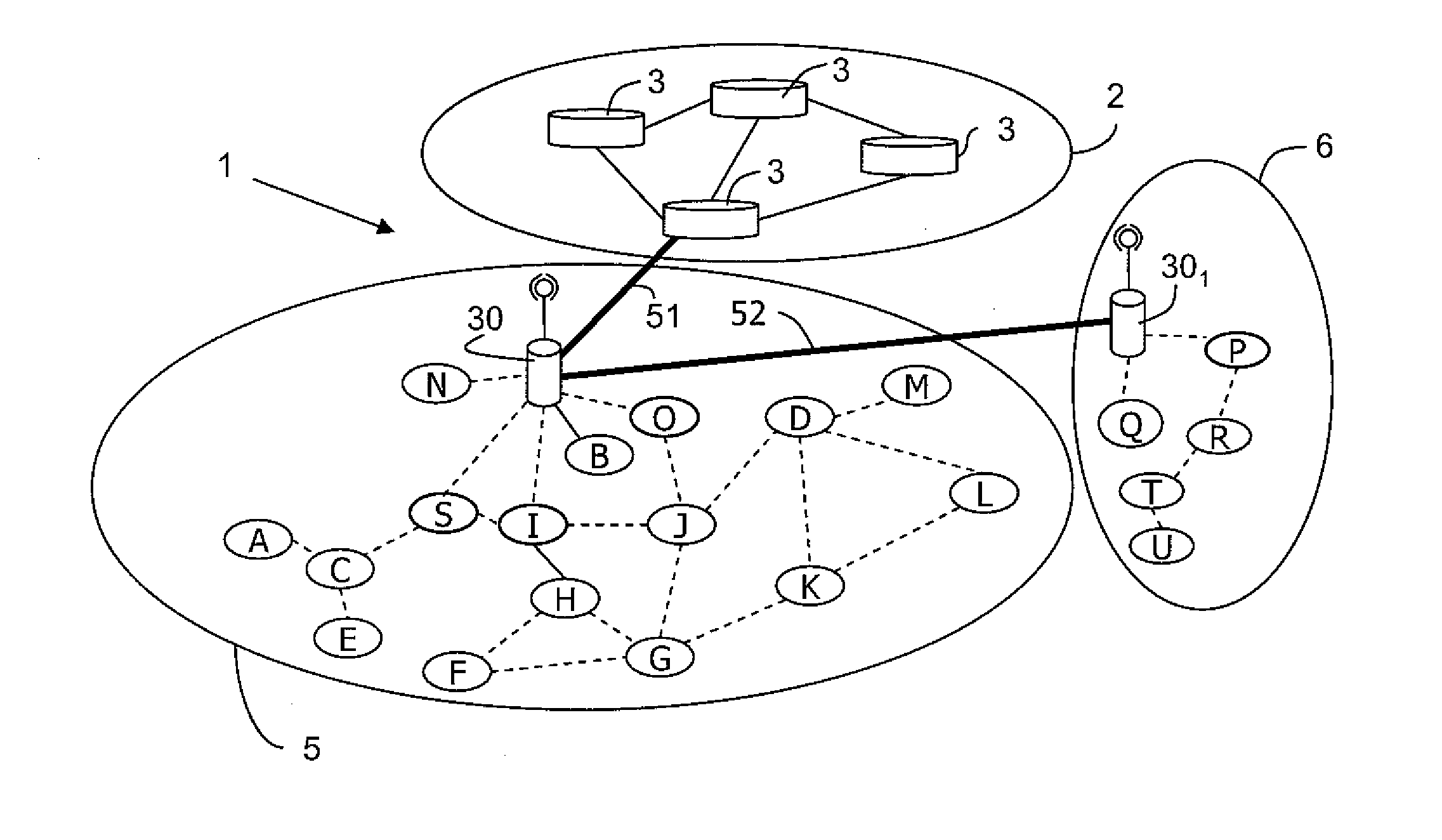
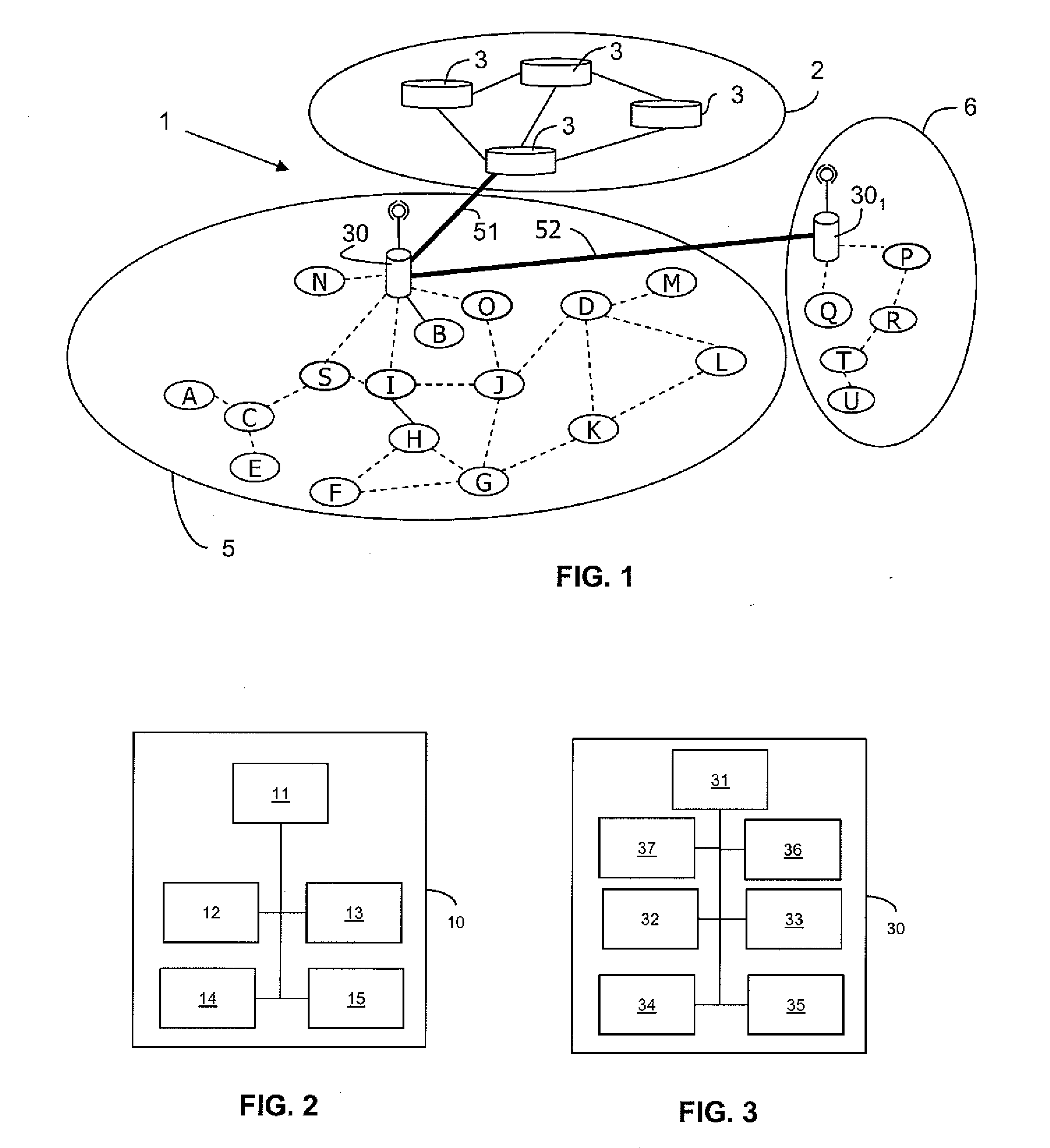
Access Point and Node for Controlling Routing in a Hybrid Network
ActiveUS20100220632A1Data switching by path configurationWireless communicationComputer networkMix network
An access point (30) for controlling routing in a hybrid network includes a topology table including routes to nodes registered on request with the access point and routes to nodes that have responded to an advertisement message broadcast by this access point (30) only to nodes having a predetermined status and means for selecting a route from all possible routes between a source node (S) and a destination node (D) determined from the above-mentioned response messages. Only nodes that have not contributed to routing a registration request respond to the advertisement message.
Owner:ORANGE SA (FR)
Automatic problem isolation for multi-layer network failures
ActiveUS20090290498A1Valuable processing timeEliminate needError preventionTransmission systemsOpen Systems InterconnectionEmbedded system
Owner:ATLASSIAN US INC
Topology discovery method and topology discovery system
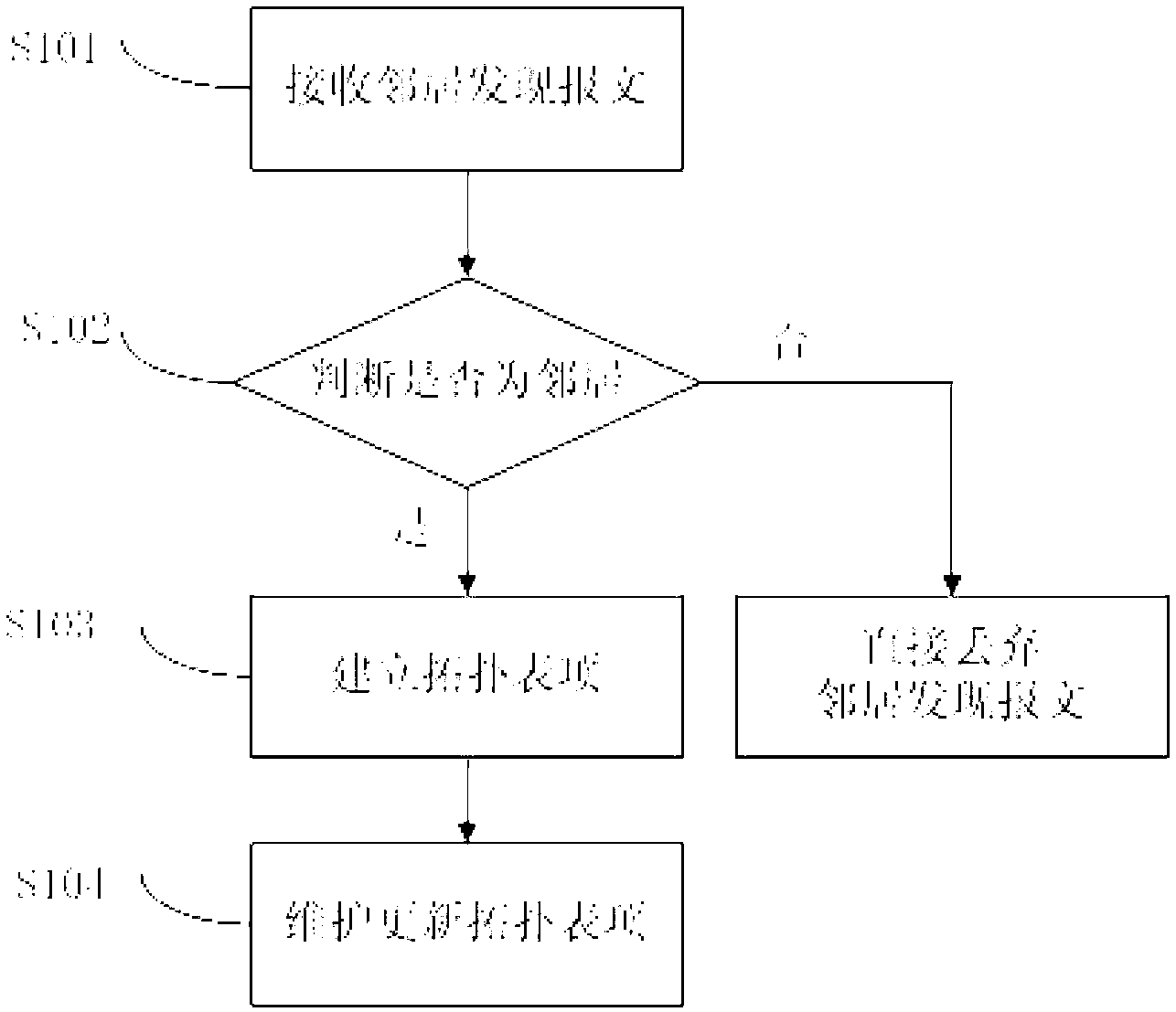
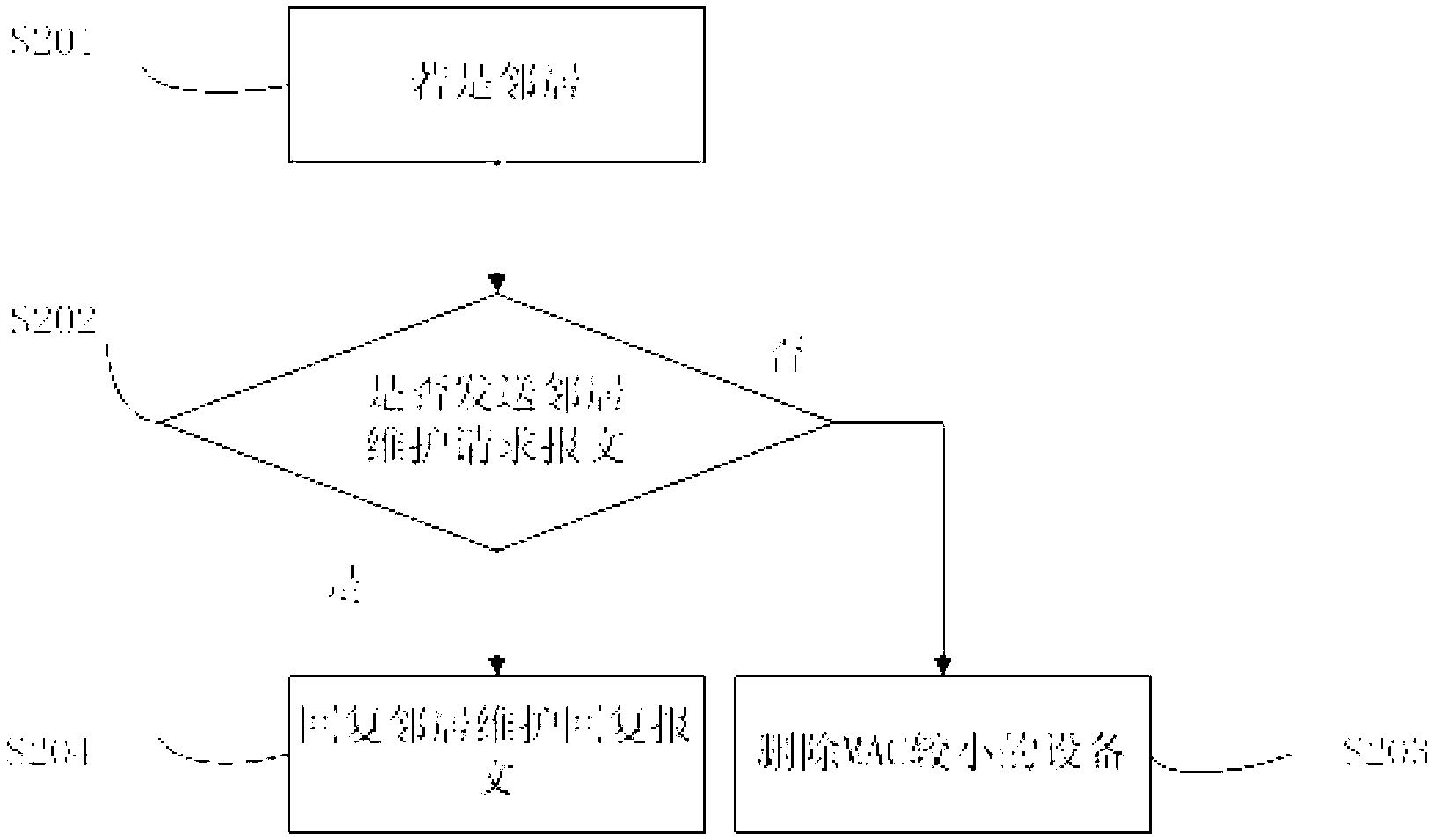
The invention discloses a topology discovery method which comprises the steps that receiving equipment receives a neighbor discovery message transmitted by transmitting equipment; the receiving equipment judges whether the transmitting equipment is a neighbor according to a first neighbor table entry of the receiving equipment; if so, the receiving equipment and the transmitting equipment receive a topology table entry establishing message; a connecting line is established according to the first neighbor table entry and a second neighbor table entry of the transmitting equipment, and transferred to neighbor equipment in the first neighbor table entry and the second neighbor table entry, except for the receiving equipment and the transmitting equipment; a topology table entry is established; and the receiving equipment maintains and updates the topology table entry. The invention further discloses a topology discovery system. According to the topology discovery method and the topology discovery system, link statuses in an entire network can be discovered independent of an upper layer protocol, and the link statuses of other equipment can be viewed on any equipment in the network.
Owner:武汉神州数码云科网络技术有限公司
Low-overhead hybrid routing protocol method for narrowband ad hoc network
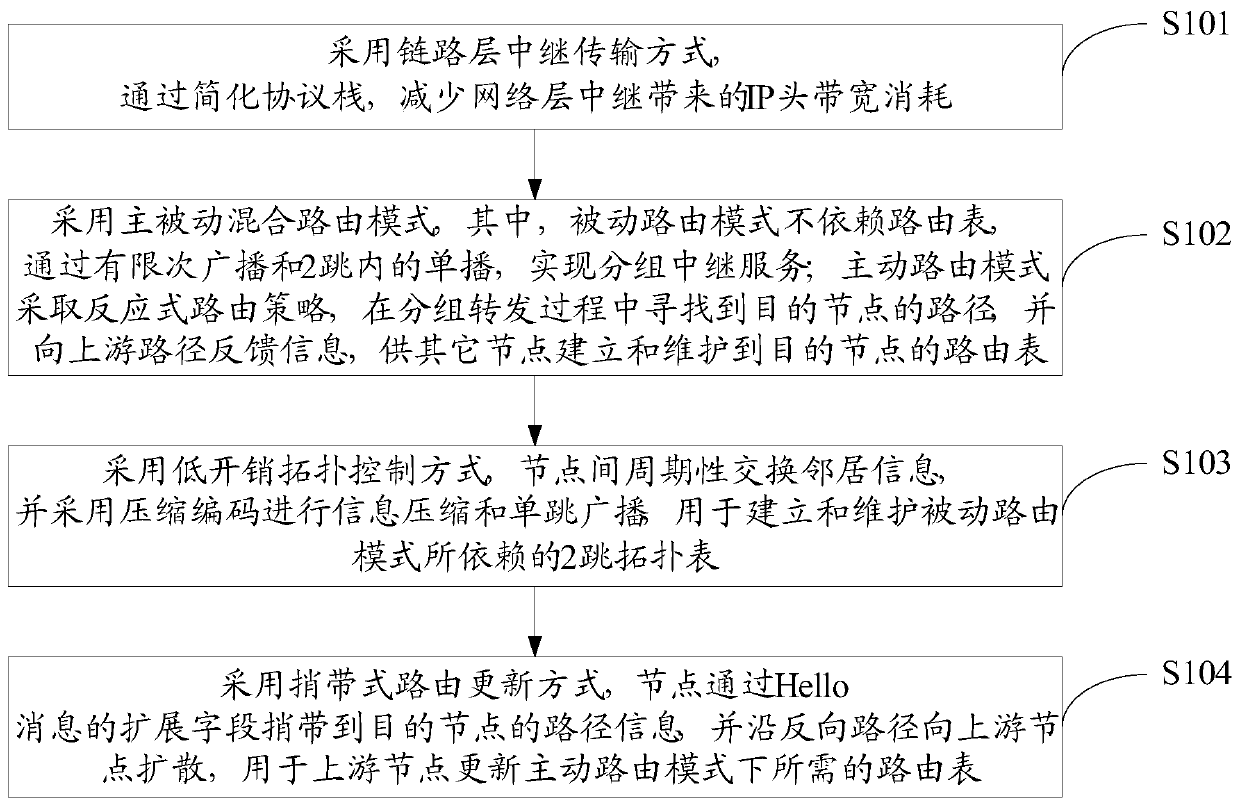
ActiveCN111356202AImprove bandwidth efficiencyReduce consumptionData switching networksWireless communicationBroadcastingLink layer
The invention discloses a low-overhead hybrid routing protocol method for a narrowband ad hoc network, which comprises the following steps: IP (Internet Protocol) head bandwidth consumption caused bynetwork layer relay is reduced by simplifying a protocol stack by adopting a link layer relay transmission mode; an active and passive hybrid routing mode is adopted; a low-overhead topology control mode is adopted, neighbor information is periodically exchanged among nodes, and information compression and single-hop broadcasting are carried out by adopting compressed encoding, so that a two-hop topology table on which a passive routing mode depends is established and maintained; a piggybacked routing updating mode is adopted, and a node carries path information to a destination node through an extension field of a Hello message and diffuses to an upstream node along a reverse path for updating a routing table required in an active routing mode by the upstream node. According to the invention, the bandwidth efficiency of narrowband ad hoc network and multi-hop transmission can be effectively improved.
Owner:大唐联诚信息系统技术有限公司
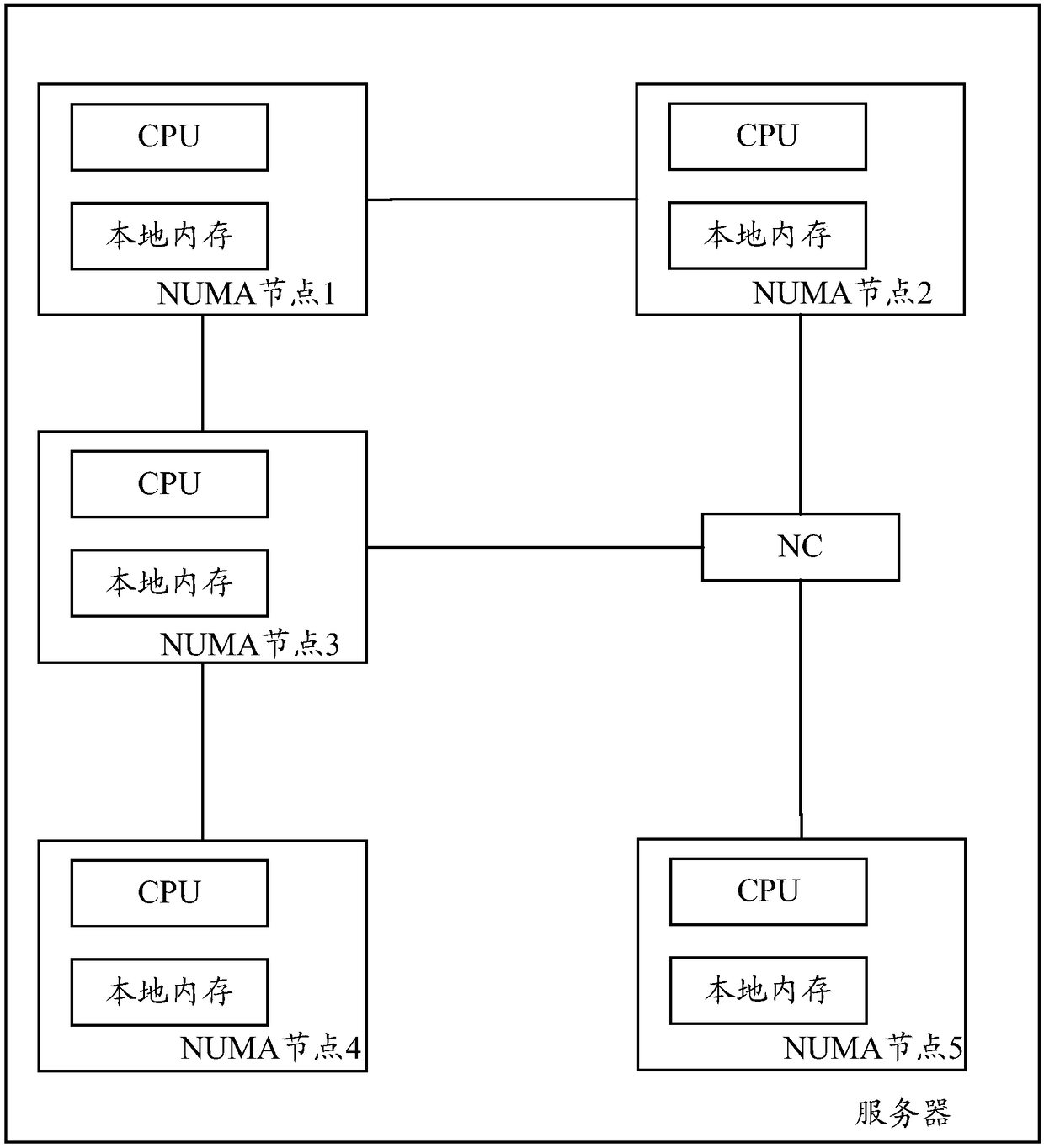
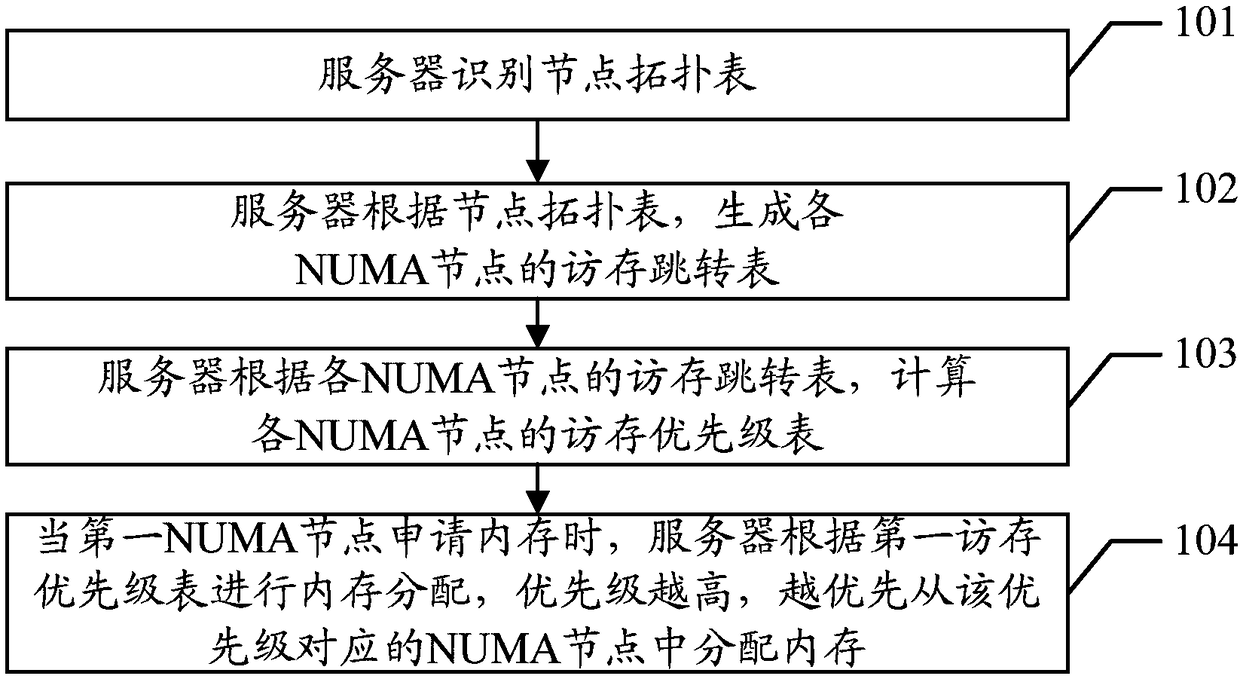
A memory allocation method and serv
ActiveCN109388490AImprove performanceReduce chance of allocating memory across NCsMemory architecture accessing/allocationResource allocationTopology tableAssignment methods
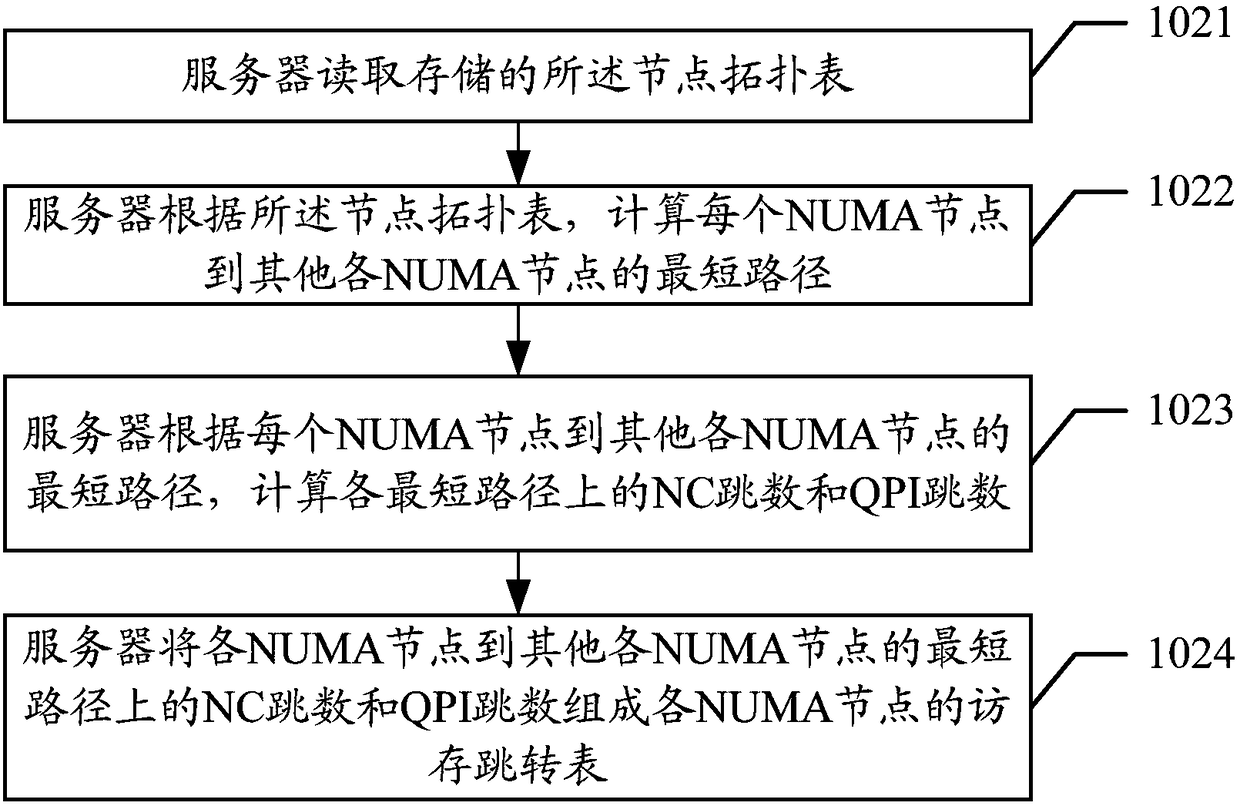
The embodiment of the present application discloses a memory allocation method and a server, which are used for reducing performance loss caused by NC delay and improving server performance when memory allocation is performed. A method for embodiment of that present application includes: Server Identification Node Topology Table, The node topology table contains not only the connection relationships between NUMA nodes, but also between the NUMA node and the NC, the connection between NCs, Based on the node topology table, generating a memory access jump table of each NUMA node, The hop table contains not only the number of QPI hops in the shortest path connected to other NUMA nodes, and has an NC hop count, according to the access jump table of each NUMA node, calculating the memory accesspriority of each NUMA node, The number of NC hops is taken as an important parameter in the calculation of memory access priority. The less the number of NC hops, the higher the memory access priority. When a NUMA node applies for memory, the memory is allocated according to the memory access priority table. The higher the priority, the more priority the memory is allocated from the NUMA node corresponding to the priority.
Owner:XFUSION DIGITAL TECH CO LTD
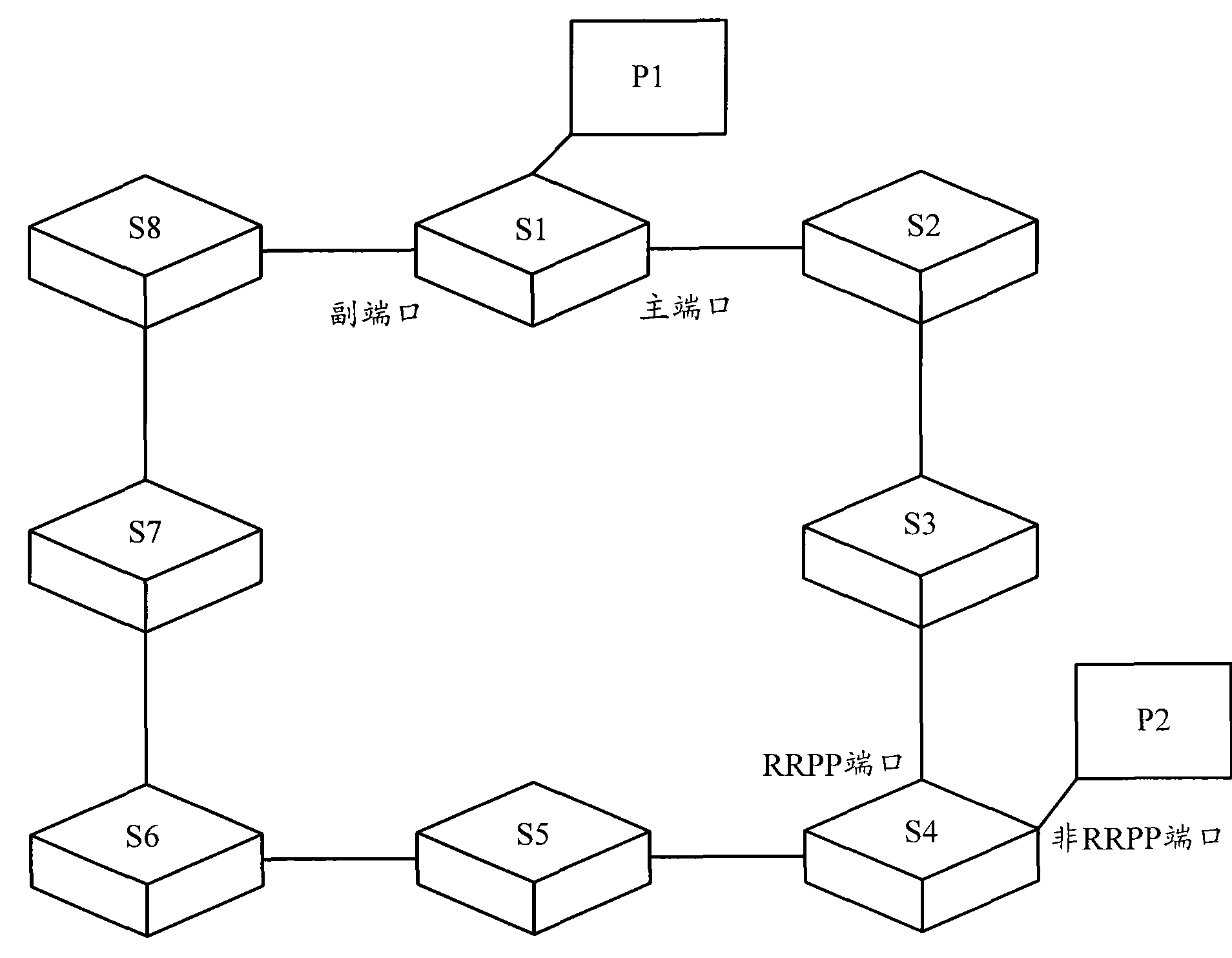
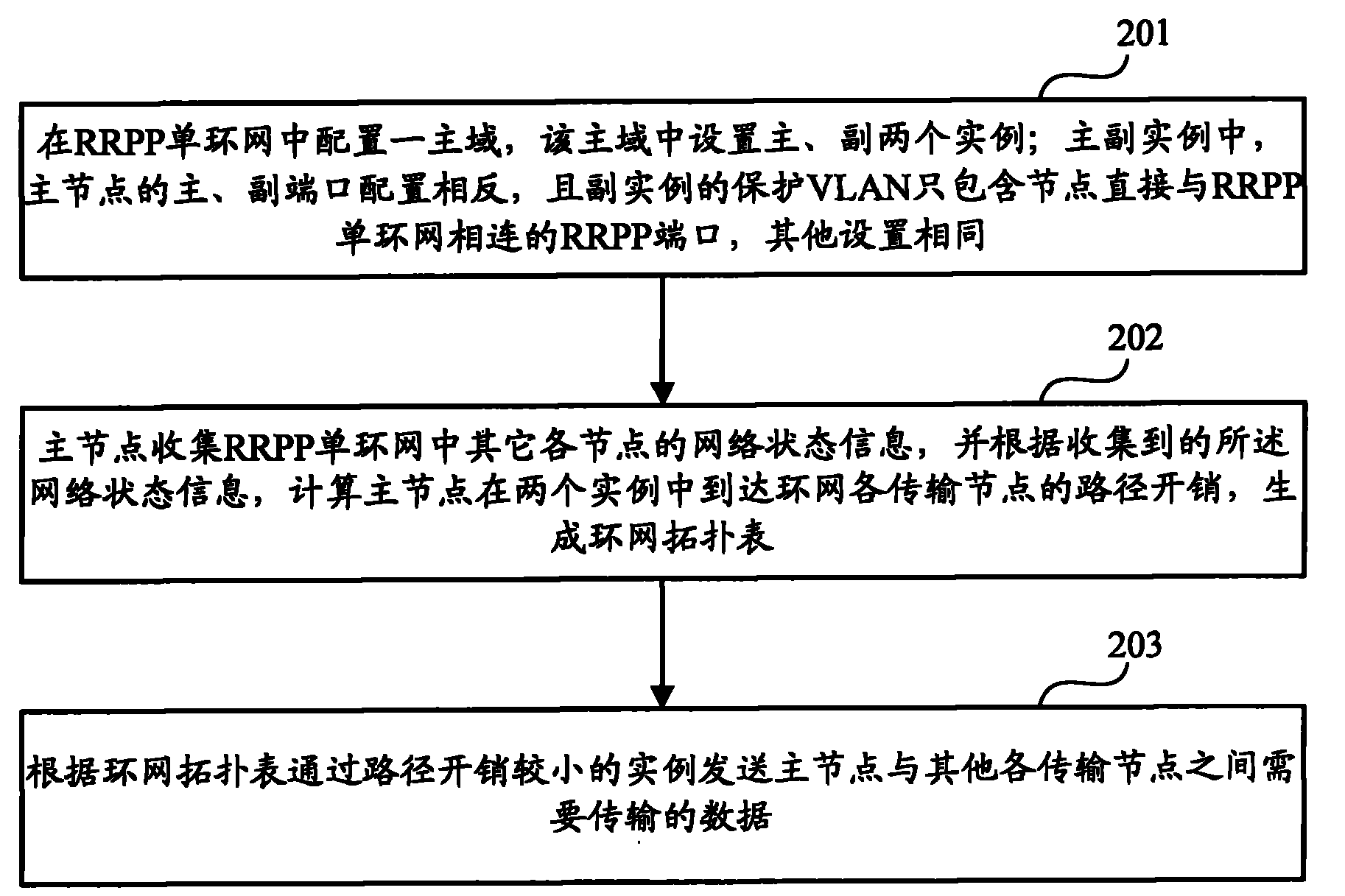
Method for optimizing RRPP (rapid ring protection protocol) single ring network data transmitting path and ring network node
The invention discloses a method for optimizing an RRPP single ring network data transmitting path, wherein the method comprises the steps: configuring a main domain in an RRPP single ring network, wherein a primary case and a secondary case are disposed in the main domain, primary and secondary ports of a main node are configured oppositely in the primary and secondary cases, the protective VLAN(virtual local area network) of the secondary case only comprises an RRPP port the node of which is directly connected to the RRPP single ring network, and other configurations are the same; collecting the network state information of other nodes in the RRPP single ring network by the main node, and calculating the path cost of the main node for reaching various transmission nodes in the ring network in the two cases according to the collected network state information, and generating a ring network topology table; and transmitting the data to be transmitted between the main node and other transmission nodes via the case with relatively small path cost according to the topology table. The invention further discloses a ring network node. The transmitting path of the data in the ring network can be optimized by the method and the ring network node, and the bandwidth of the RRPP single ring network is saved.
Owner:NEW H3C TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com