Wormhole detecting method based on specific triple-jump channel path in wireless sensor network
A wireless sensor and detection method technology, applied in wireless communication, network topology, electrical components, etc., to achieve the effect of high detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention is described in more detail below in conjunction with accompanying drawing example:
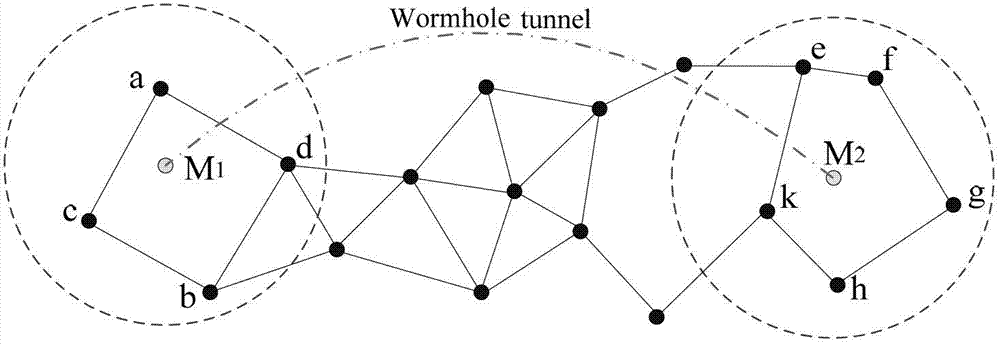
[0029] According to the legal topology characteristics of the specific 3-hop path in the wireless sensor network, it is judged whether there is an abnormal specific 3-hop path in the network (that is, a specific 3-hop path that violates the legal topology characteristics). If an abnormal specific 3-hop path is found in the network, it is determined that the network is under wormhole attack.
[0030] Firstly, the definition of specific 3-hop paths, the legal topological characteristics of specific 3-hop paths and the definition of abnormal specific 3-hop paths are given.
[0031] It is known that the shortest path length between node q and node s is 2 hops. If there is a path satisfying the following conditions in their common neighbors (denoted as G(q,s)), we call this path a specific 3 hops path (denoted as S3HP).
[0032] S3HP required conditions:
[0033] (1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com