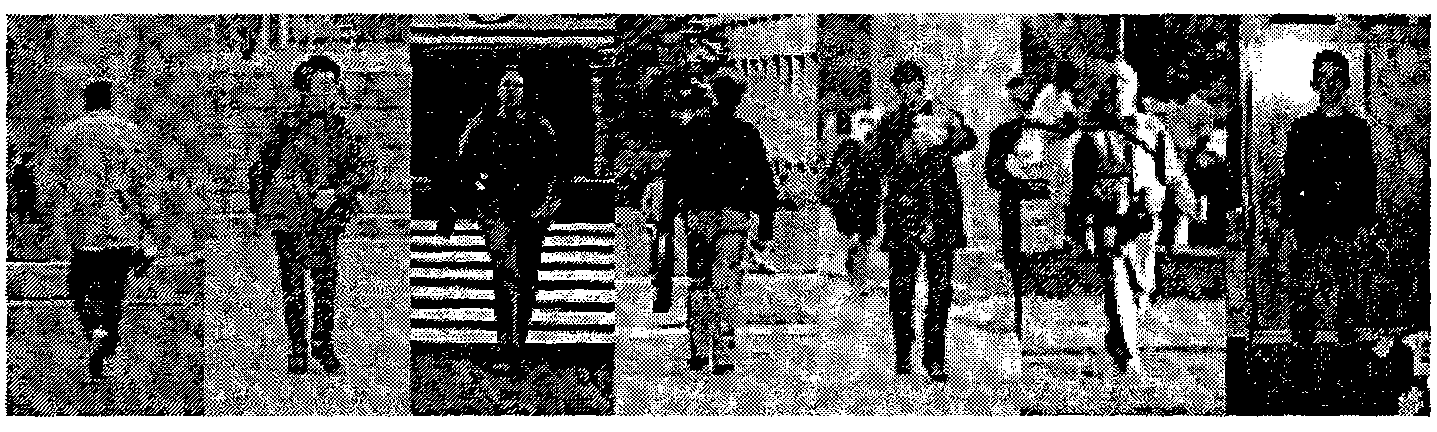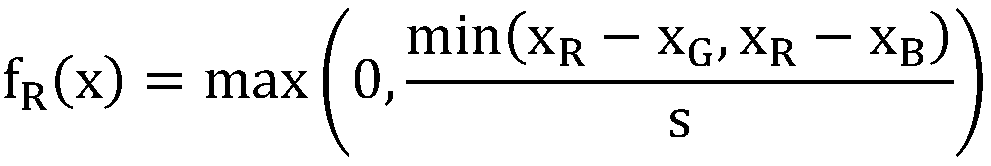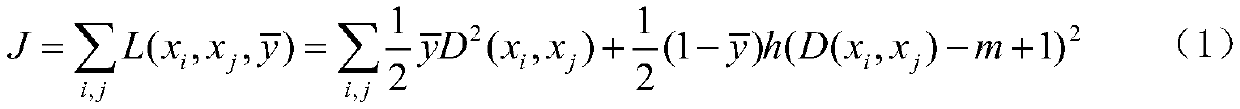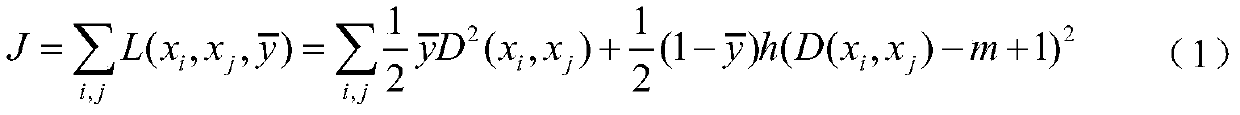Patents
Literature
88results about How to "Reduce the probability of detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
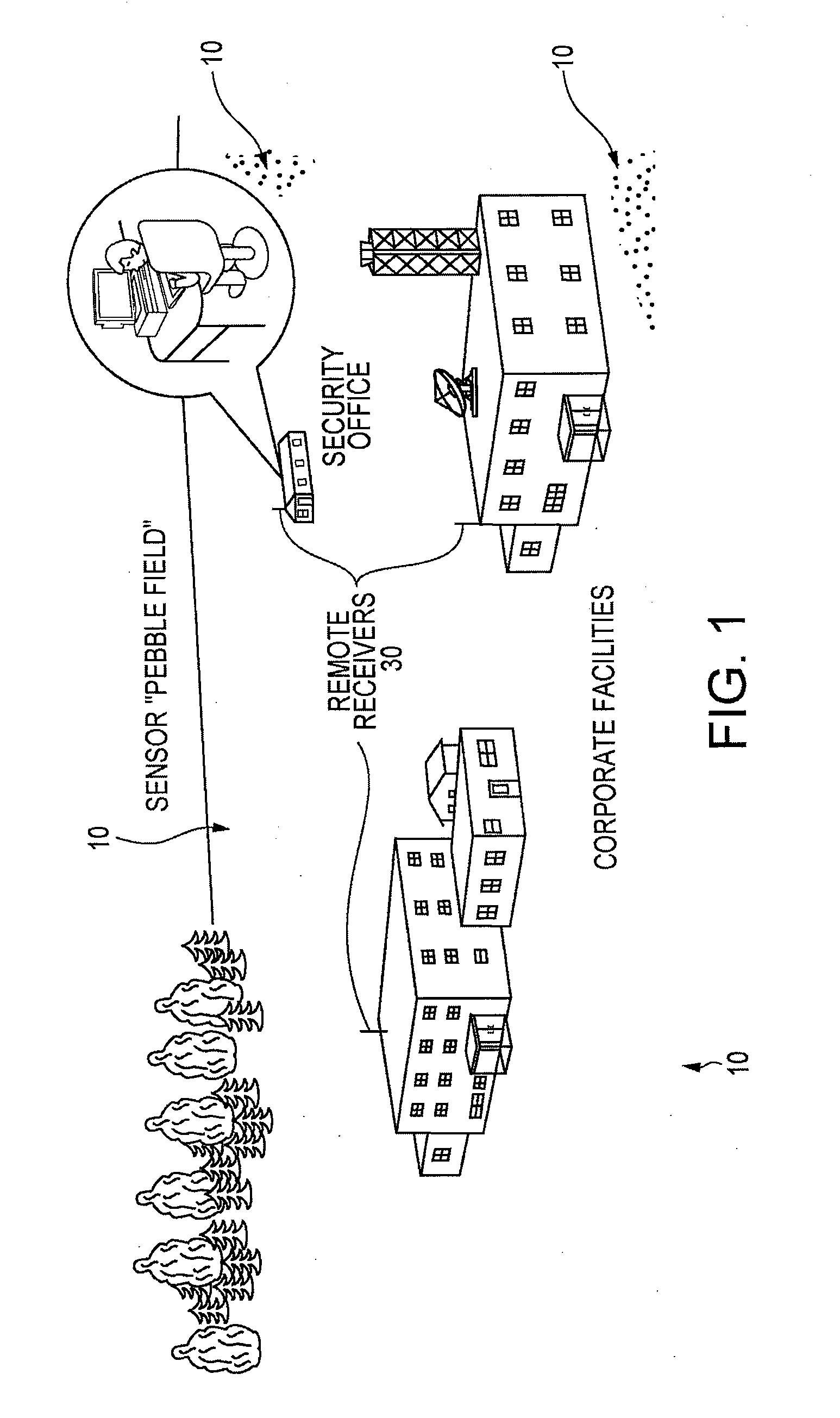
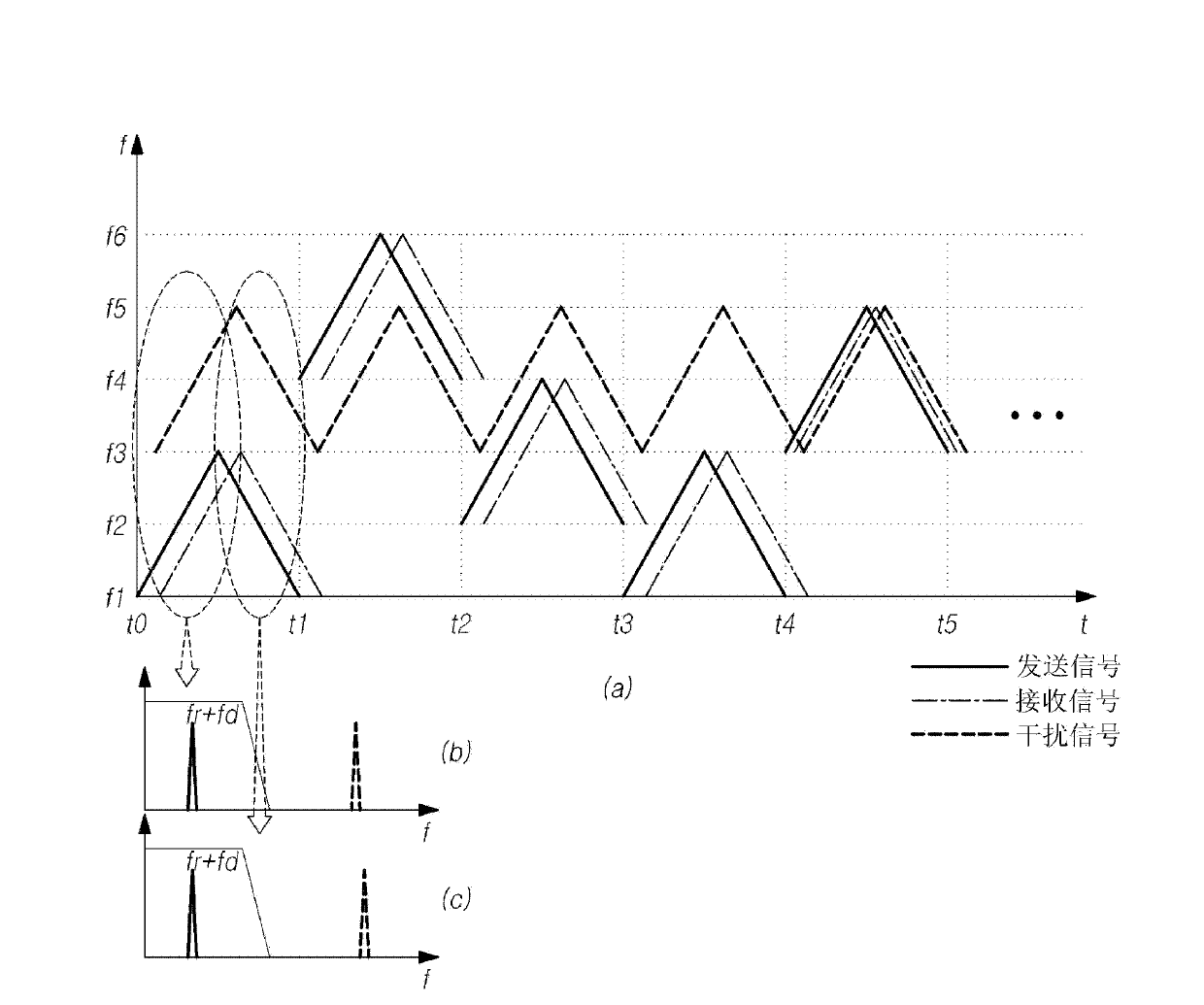
LiDAR System Comprising A Single-Photon Detector
ActiveUS20150192676A1Reduce impactHigh operating requirementsOptical rangefindersElectromagnetic wave reradiationWavelengthMulti dimensional
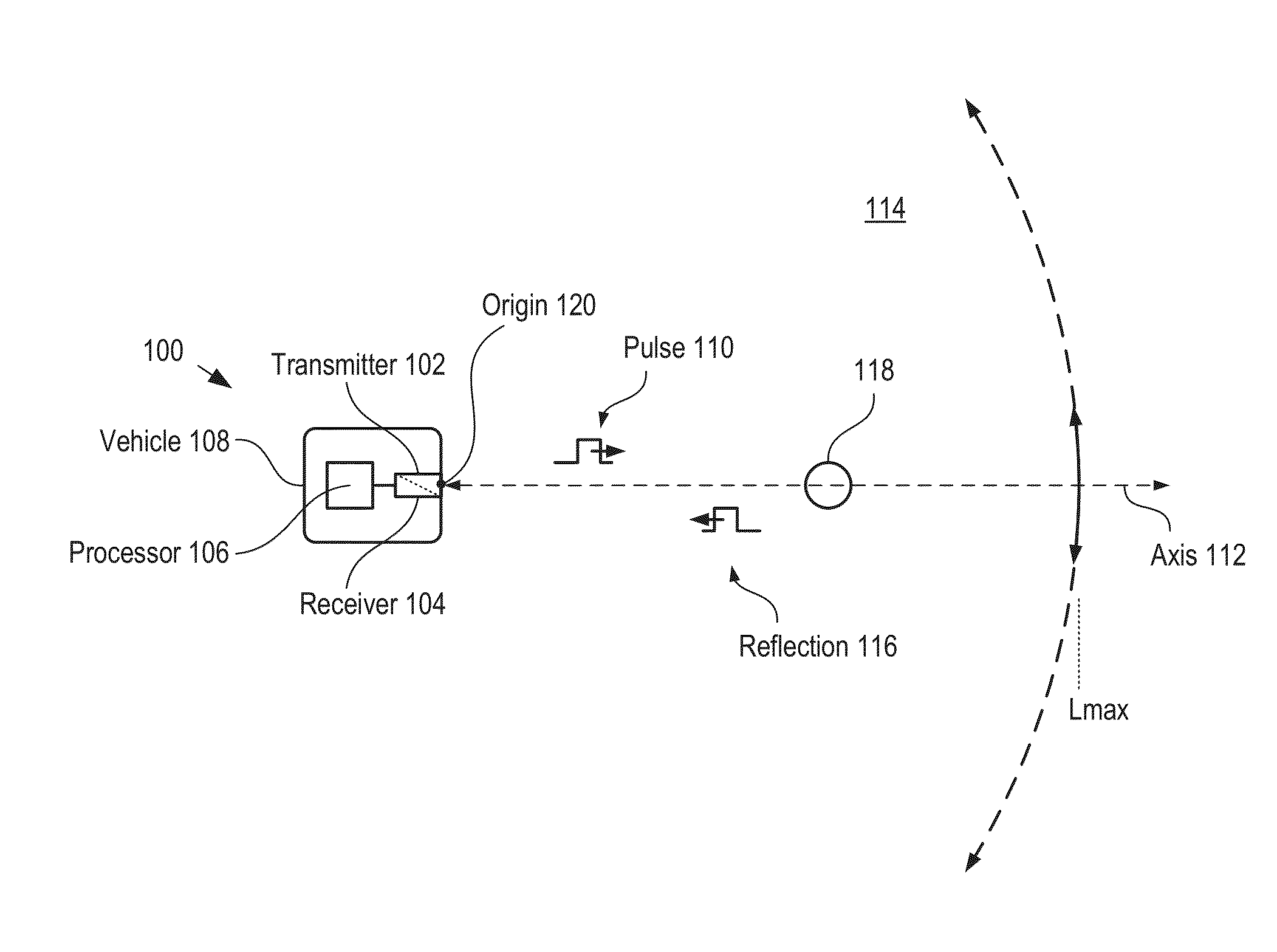
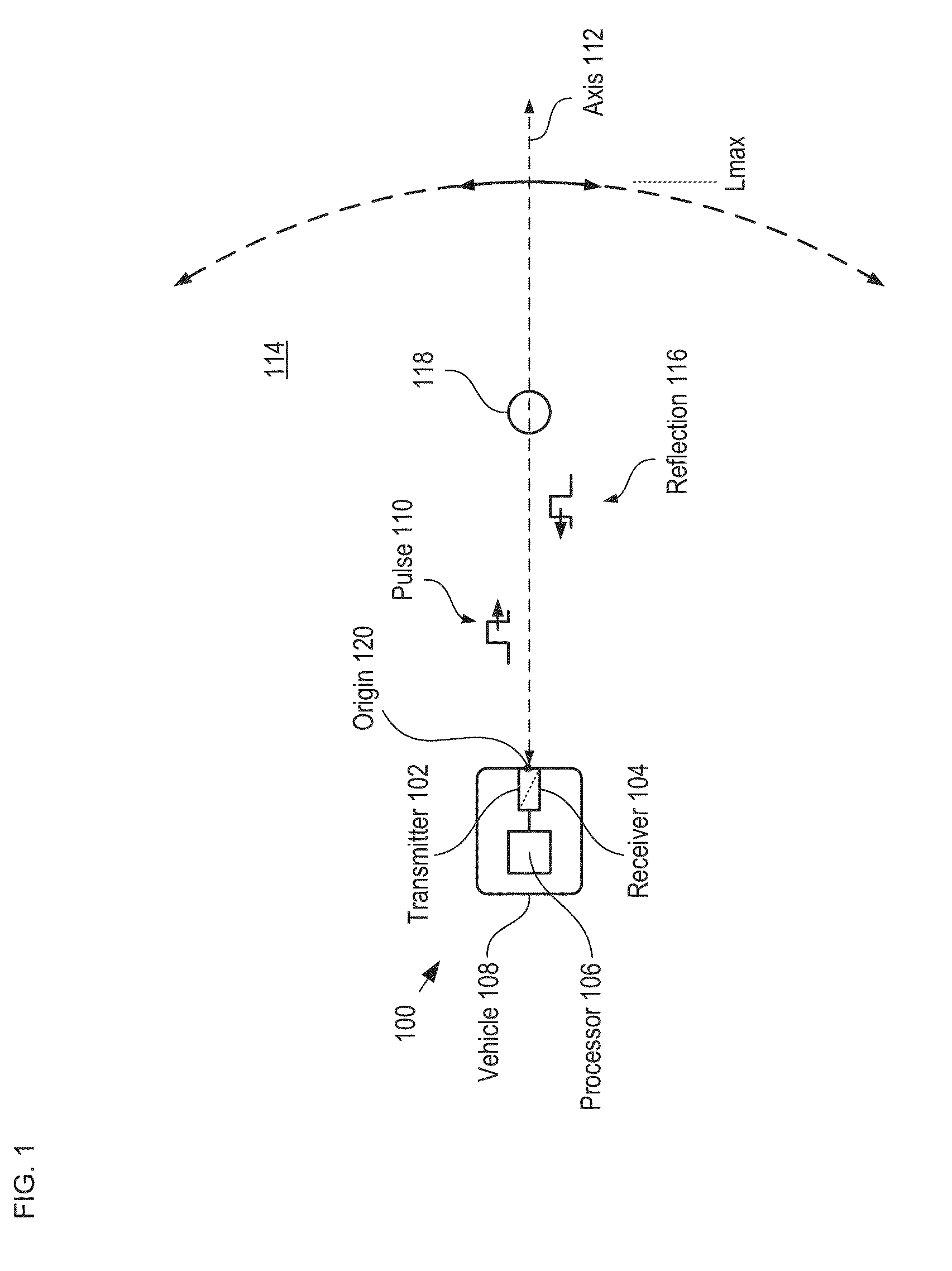
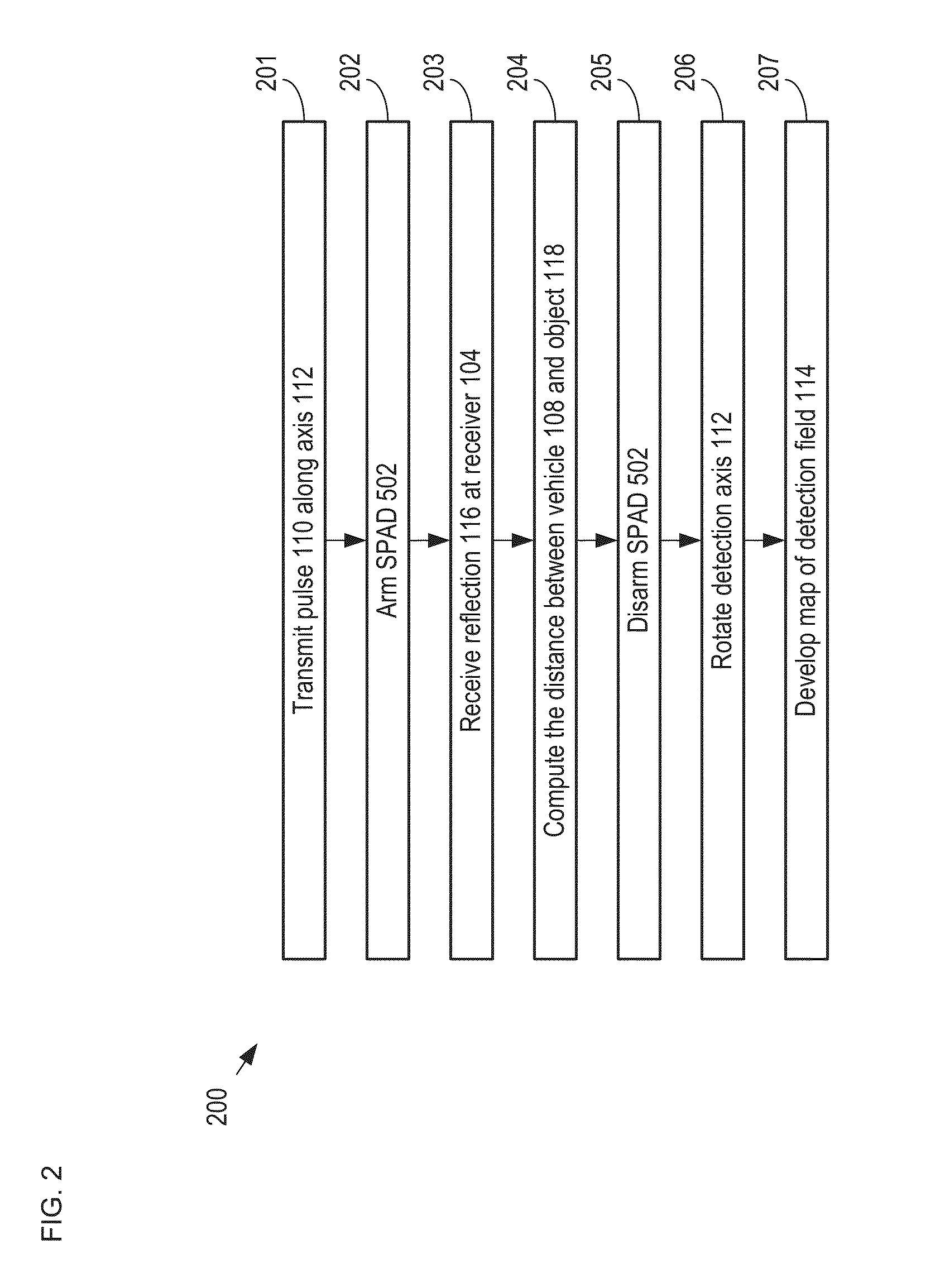
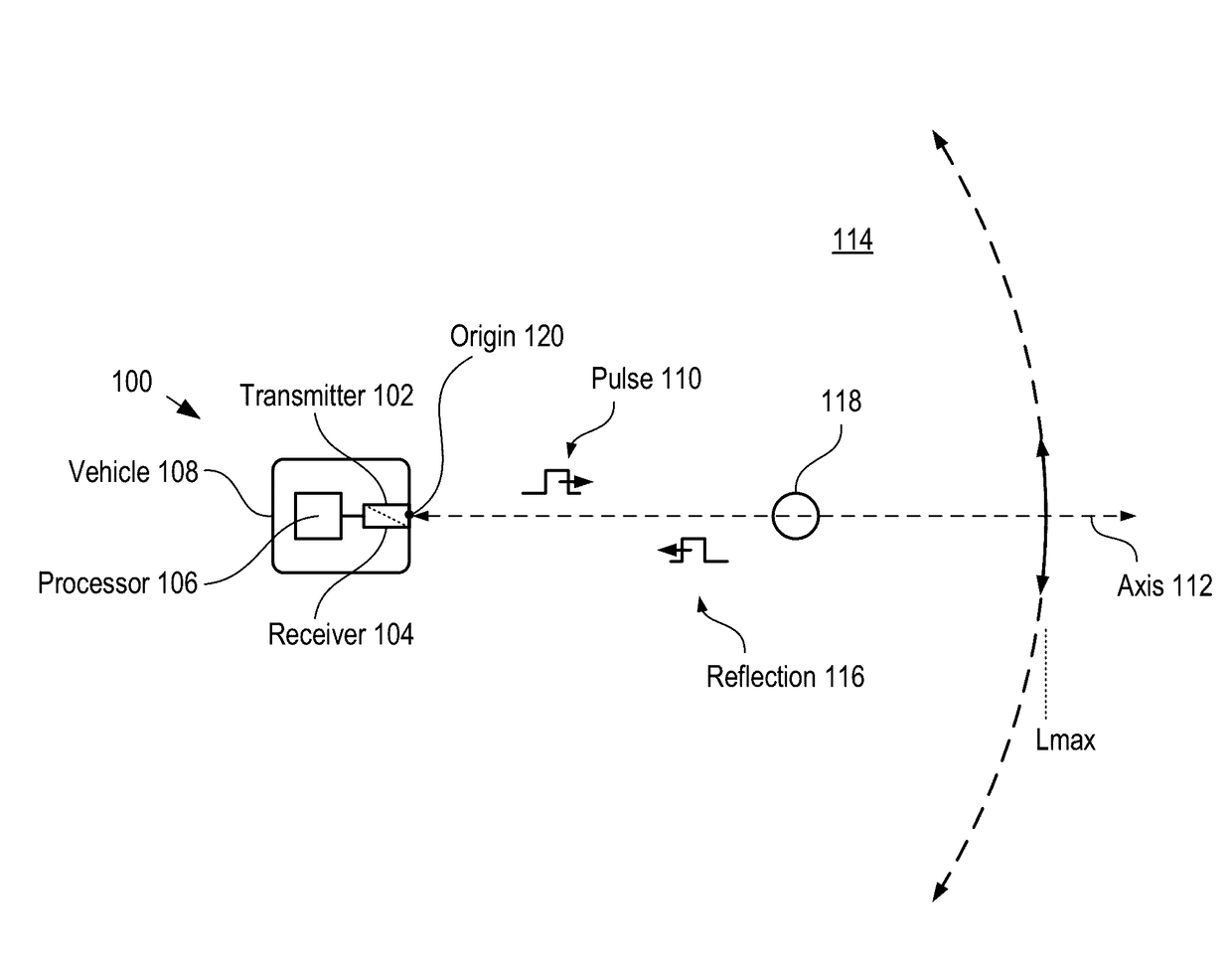
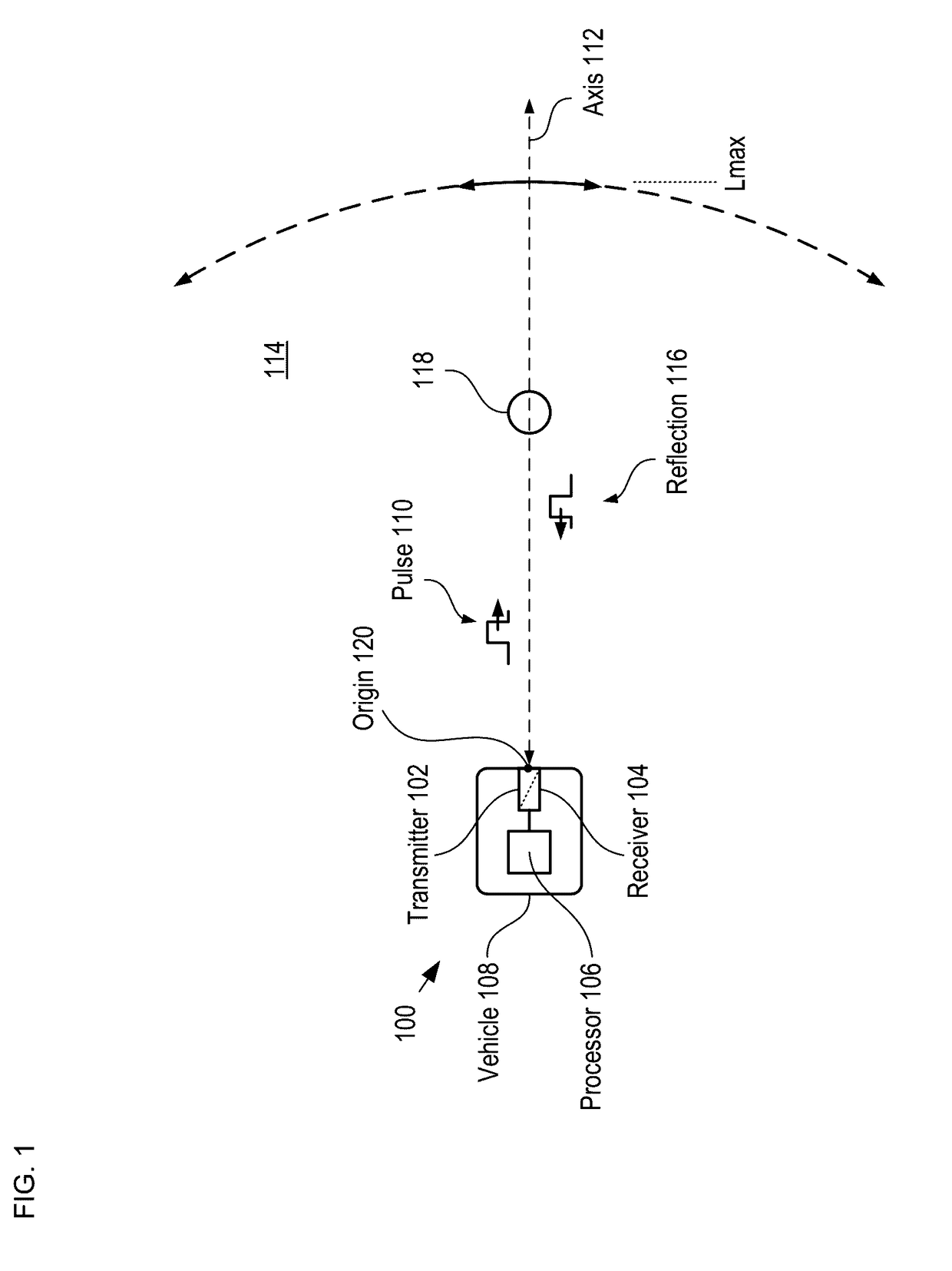
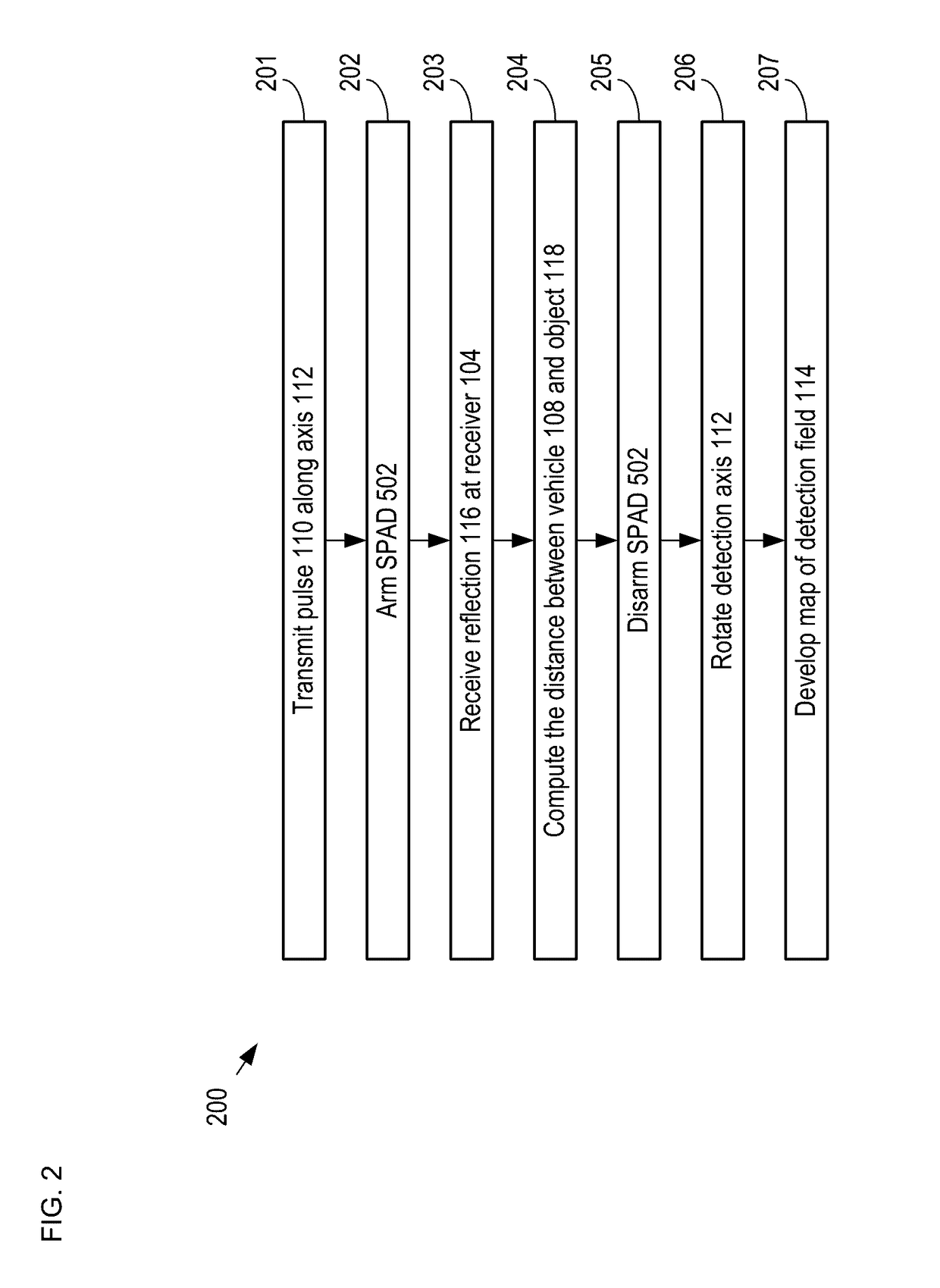
A method for developing a map of objects in a region surrounding a location is disclosed. The method includes interrogating the region along a detection axis with a series of optical pulses and detecting reflections of the optical pulses that originate at objects located along the detection axis. A multi-dimensional map of the region is developed by scanning the detection axis about the location in at least one dimension. The reflections are detected via a single-photon detector that is armed using a sub-gating scheme such that the single-photon detector selectively detects photons of reflections that originate only within each of a plurality of zones that collectively define the detection field. In some embodiments, the optical pulses have a wavelength within the range of 1350 nm to 1390 nm, which is a spectral range having a relatively high eye-safety threshold and a relatively low solar background.
Owner:LG INNOTEK CO LTD
LiDAR system comprising a single-photon detector
ActiveUS9625580B2Reduce impactHigh operating requirementsOptical rangefindersElectromagnetic wave reradiationPhoton detectionLength wave
A method for developing a map of objects in a region surrounding a location is disclosed. The method includes interrogating the region along a detection axis with a series of optical pulses and detecting reflections of the optical pulses that originate at objects located along the detection axis. A multi-dimensional map of the region is developed by scanning the detection axis about the location in at least one dimension. The reflections are detected via a single-photon detector that is armed using a sub-gating scheme such that the single-photon detector selectively detects photons of reflections that originate only within each of a plurality of zones that collectively define the detection field. In some embodiments, the optical pulses have a wavelength within the range of 1350 nm to 1390 nm, which is a spectral range having a relatively high eye-safety threshold and a relatively low solar background.
Owner:LG INNOTEK CO LTD
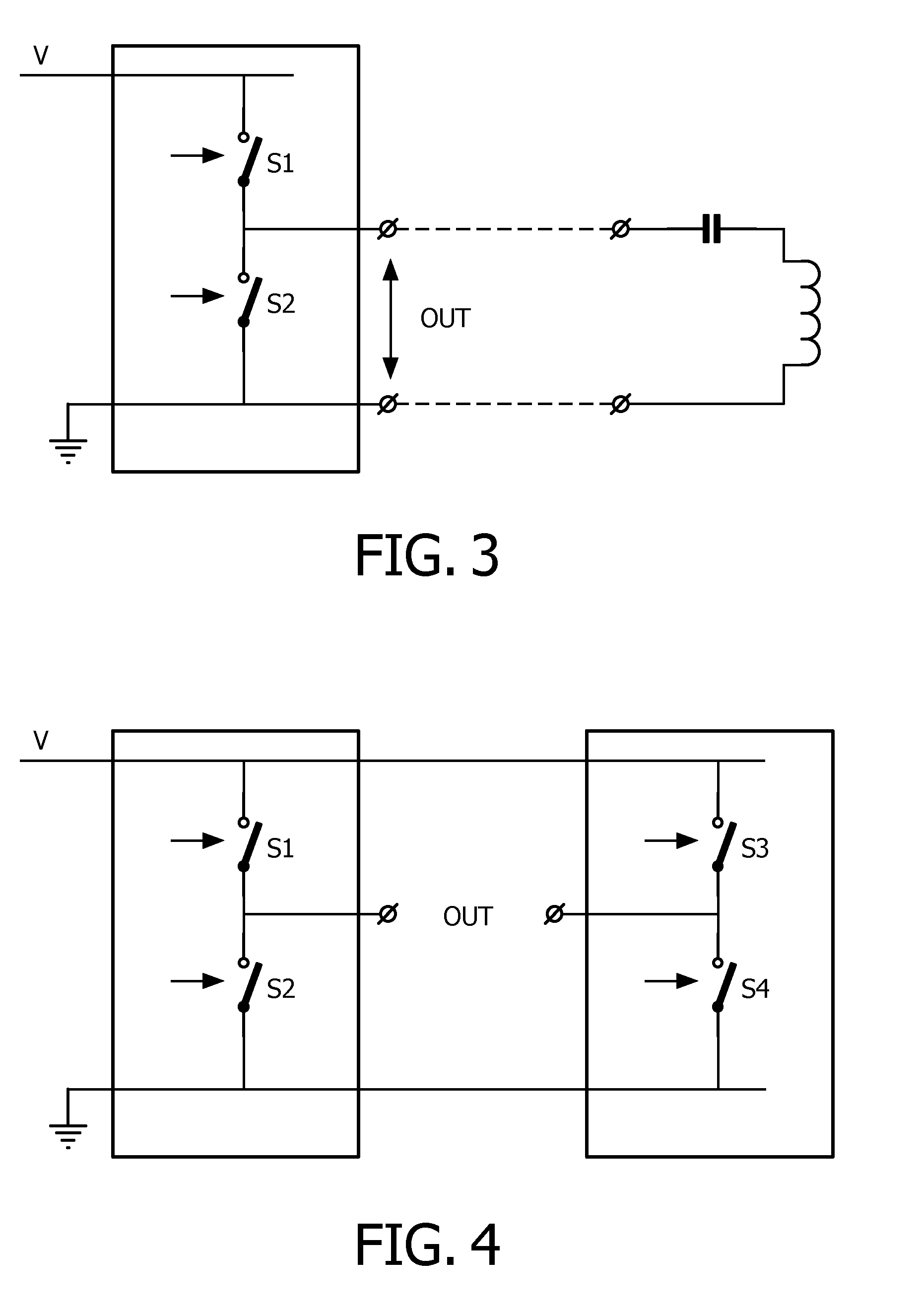
Wireless inductive power transfer
ActiveUS20160149440A1Reduce the probability of detectionReduce the possibilityTransformersCircuit arrangementsElectric power transmissionUser input
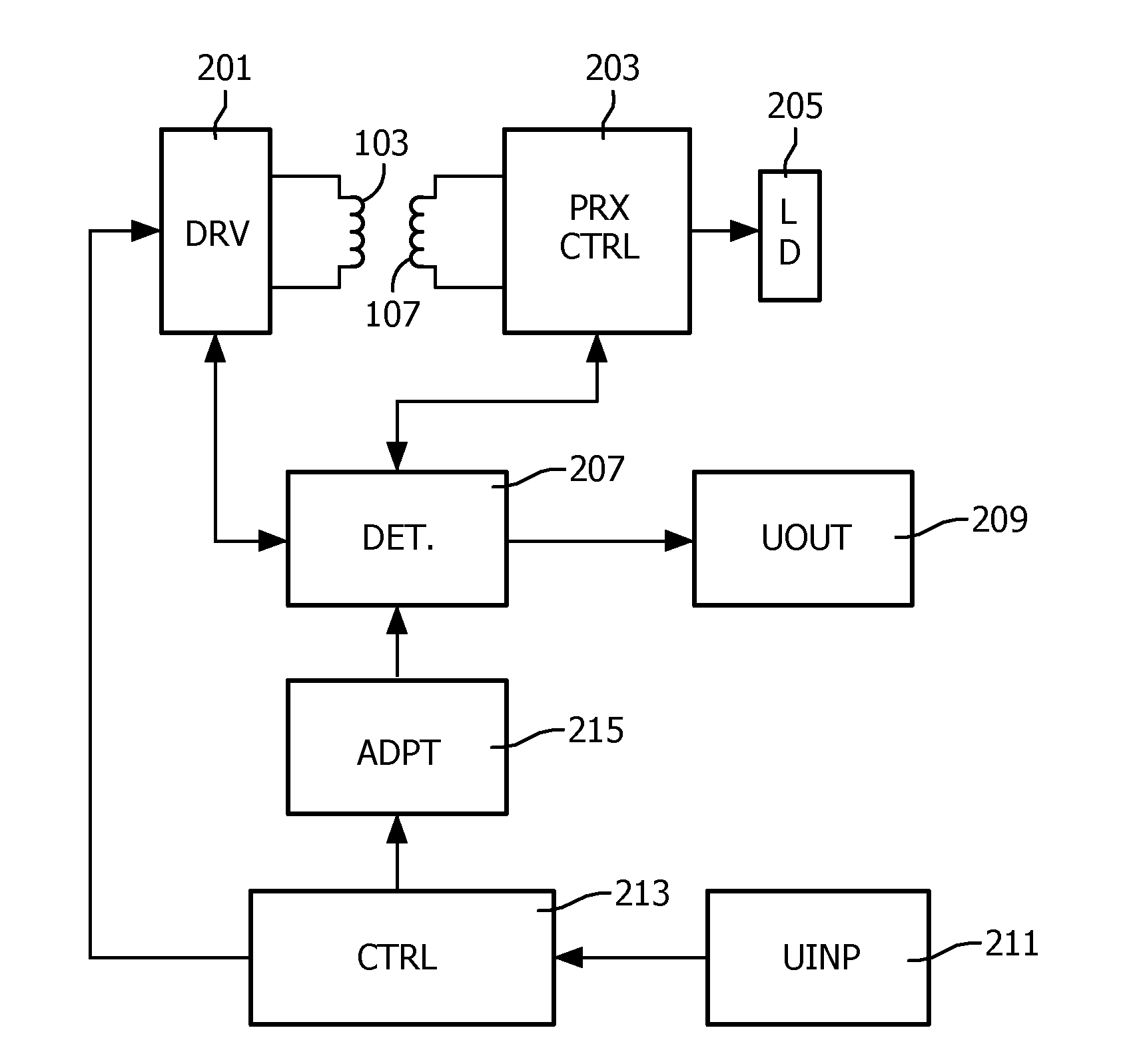
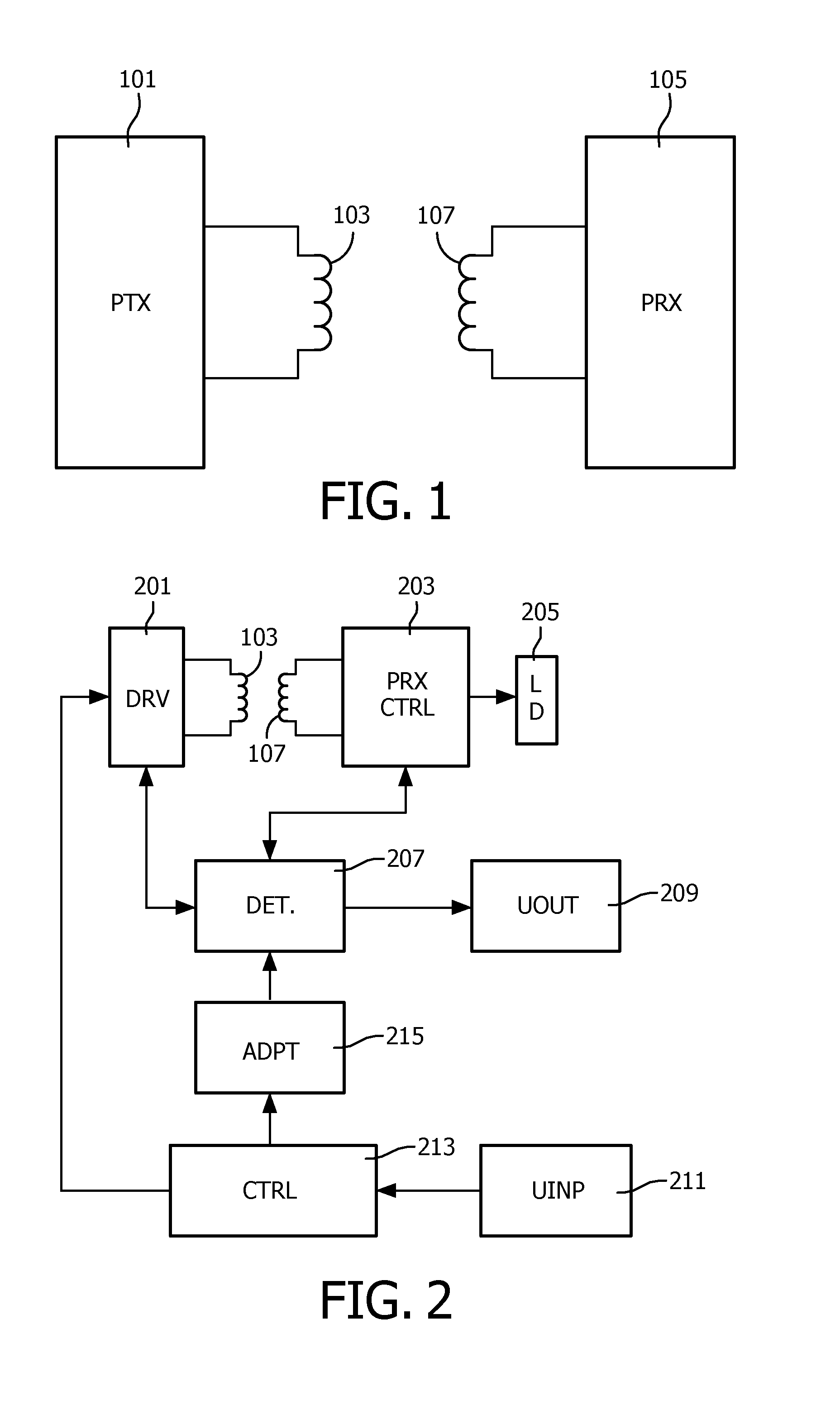
A wireless power transfer system includes a power transmitter (101) arranged to provide a power transfer to a power receiver (105) via a wireless inductive power signal. A parasitic power loss detector (207) is arranged to detect a parasitic power loss for the power transfer, and a user indicator (209) is arranged to initialize a user alert in response to the detection of the parasitic power loss. The system comprises an input (211) for receiving user inputs; and a controller (213) which is arranged to initiate an adaptation of a parasitic power loss detection operation performed by the parasitic power loss detector (207) to detect parasitic power losses if a user input meeting a criterion is not received. Each of the individual features may be implemented in the power transmitter (101), the power receiver (105), or may e.g. be distributed between these. The approach may allow improved foreign object detection in a wireless power transfer system.
Owner:KONINKLJIJKE PHILIPS NV
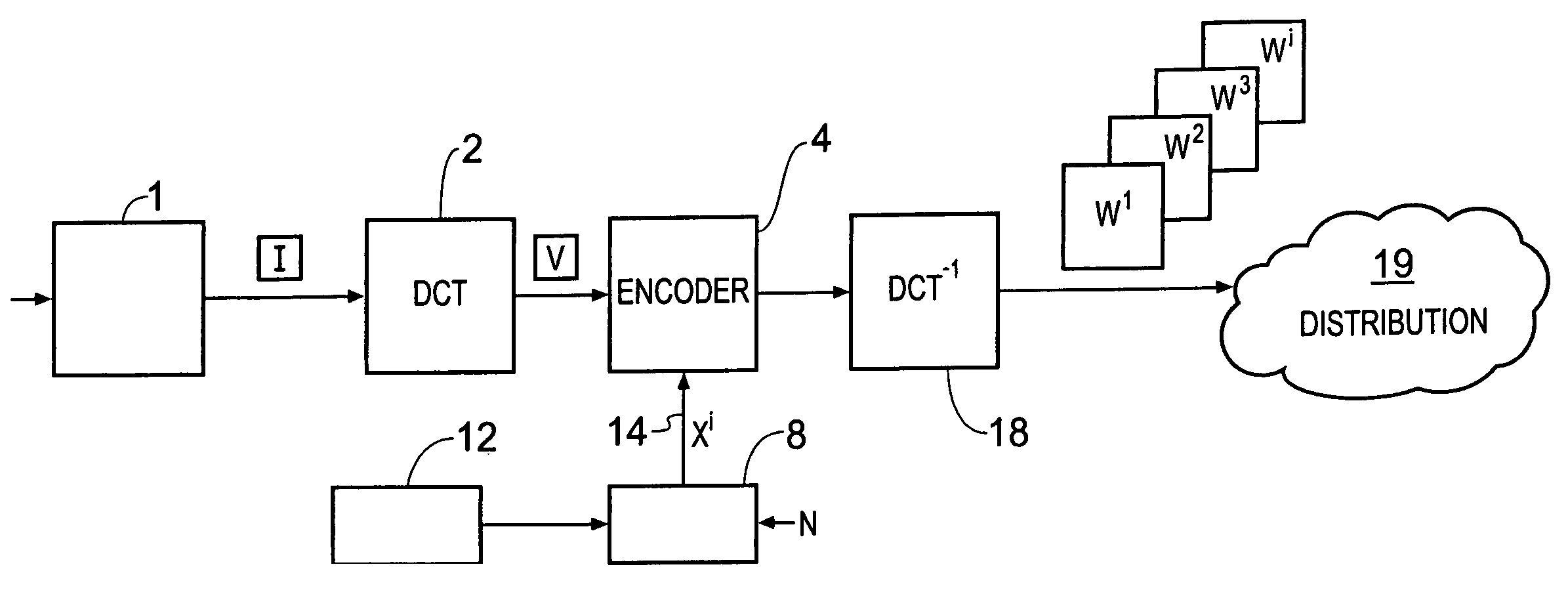
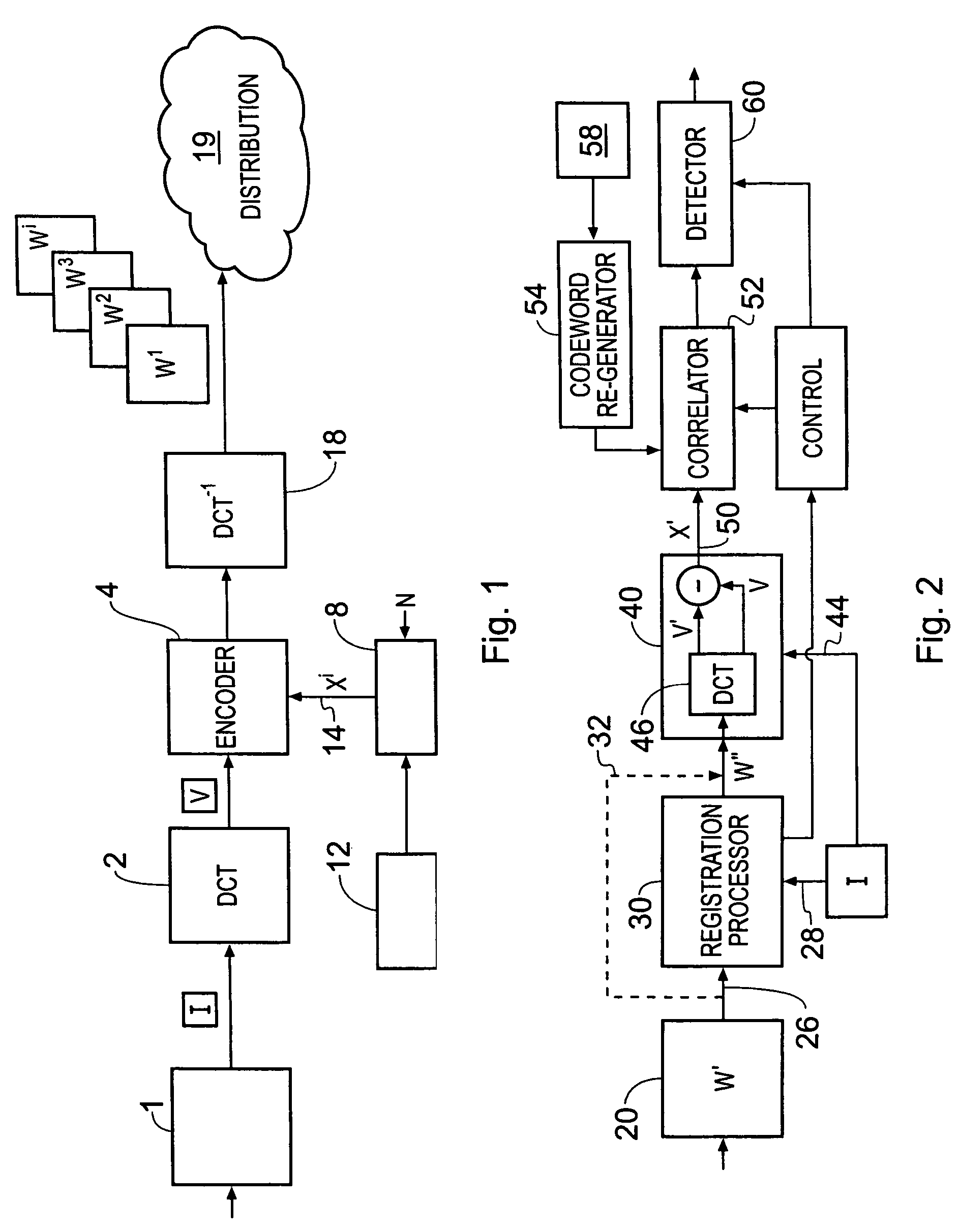
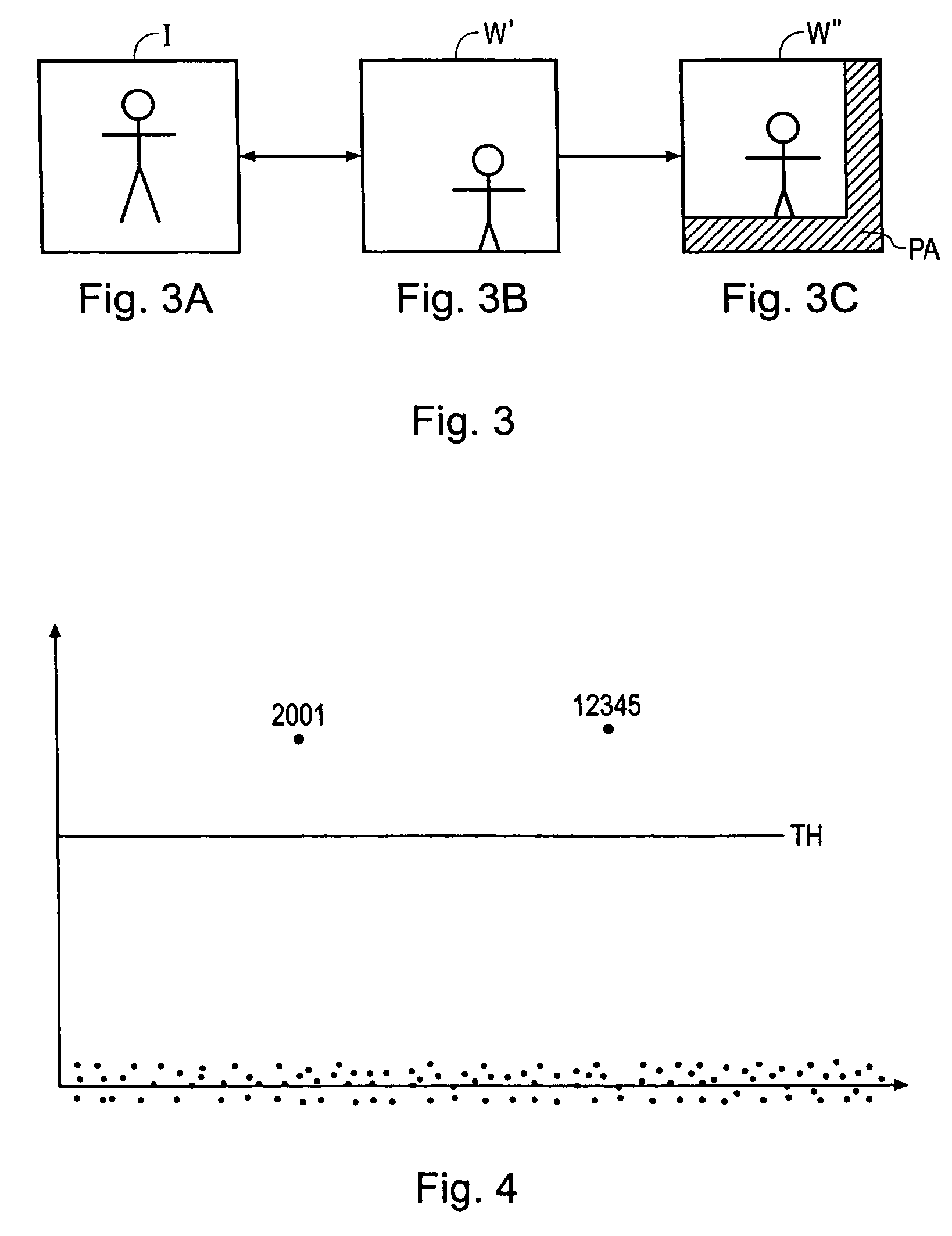
Data processing apparatus and method
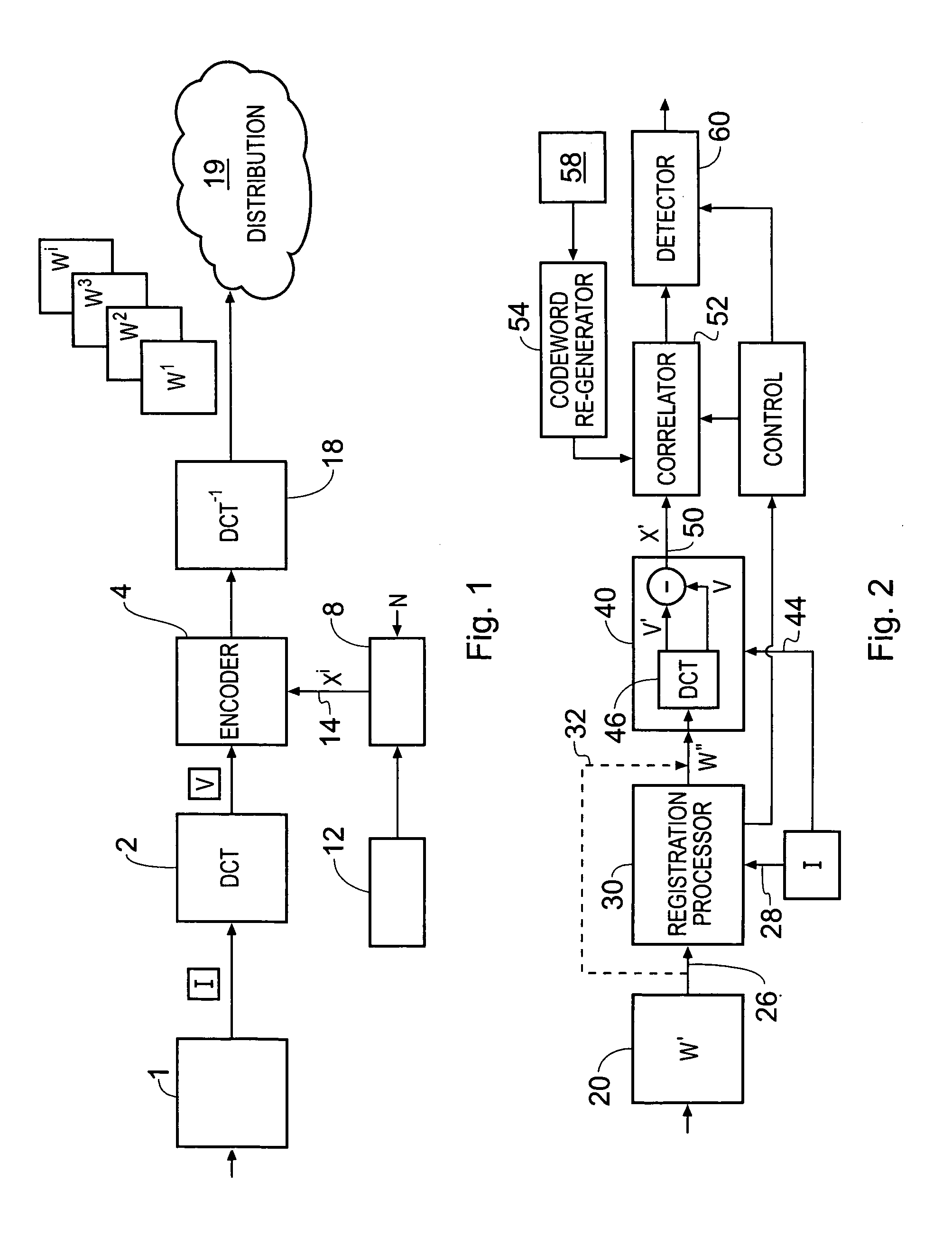
InactiveUS8015410B2Improve detection rateReduce probabilityUser identity/authority verificationImage watermarkingParallel computingCode word
A data processing apparatus is operable to identify one of a plurality of code words present in a watermarked version of a material item. The marked version is formed by combining each of a plurality of parts of a code word with one of a plurality of units from which the material item is comprised. The apparatus comprises a recovery processor operable to recover at least one part of the code word from a corresponding unit of the marked material item, and a correlator. The correlator is operable to generate for the marked material unit, a dependent correlation value for the part of the code word recovered from the material unit and the corresponding part of at least one of the re-generated code words from the set. A detector is operable to determine whether at least one of the code words is present in the marked material item from the dependent correlation value for the part of the code word exceeding a predetermined threshold. The data processor may detect the presence of the code word with improved probability, in particular when parts of the material have been corrupted.
Owner:SONY UK LTD
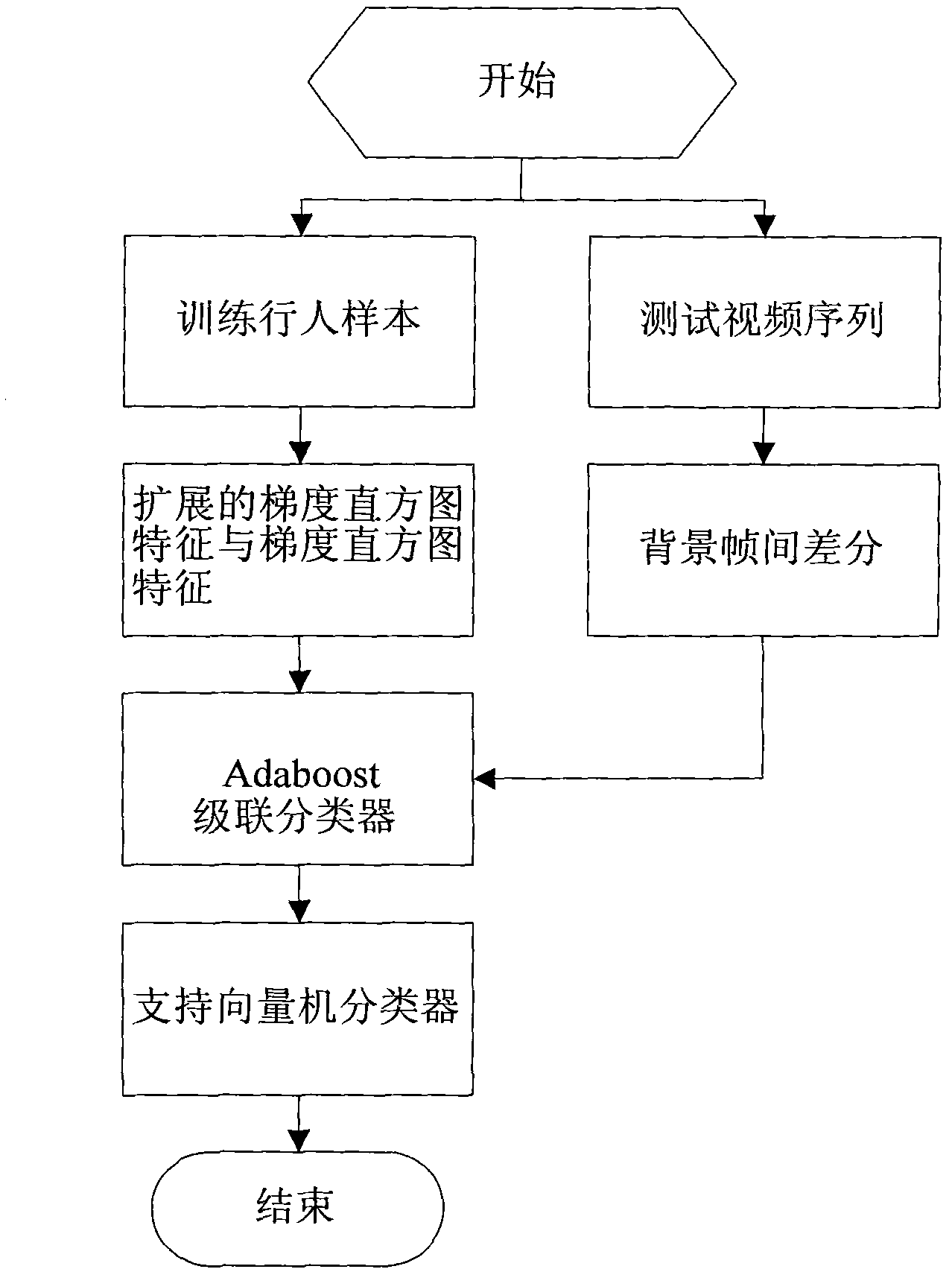
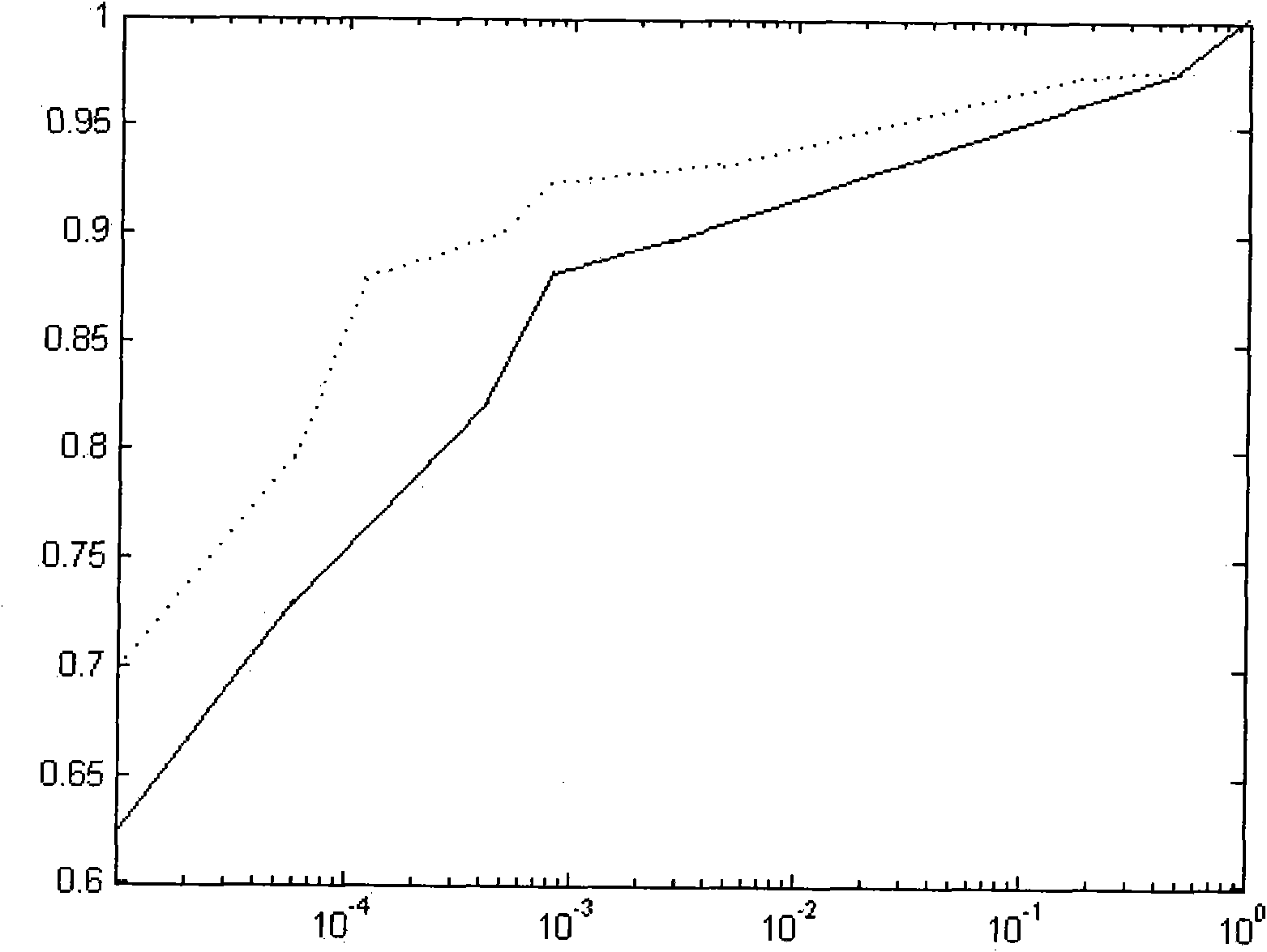
Pedestrian detection method based on video monitoring
ActiveCN101887524AThe detection process is fastImprove detection accuracyImage enhancementCharacter and pattern recognitionVideo monitoringSupport vector machine
The invention discloses a pedestrian detection method based on video monitoring, which comprises the following steps of: rapidly detecting a pedestrian by utilizing an expanded gradient histogram characteristic and an Adaboost algorithm, and then further identifying and verifying the detected pedestrian by utilizing the gradient histogram characteristic and a support vector machine. In the invention, experiments based on a standard pedestrian database indicate that the method not only can greatly reduce the detection time, but also markedly improves the detection rate. As one of key technologies of target detection, pedestrian detection has broad application prospect in the fields of video monitoring safety, intelligent traffic management and the like.
Owner:HUNAN CHUANGHE FUTURE TECH CO LTD
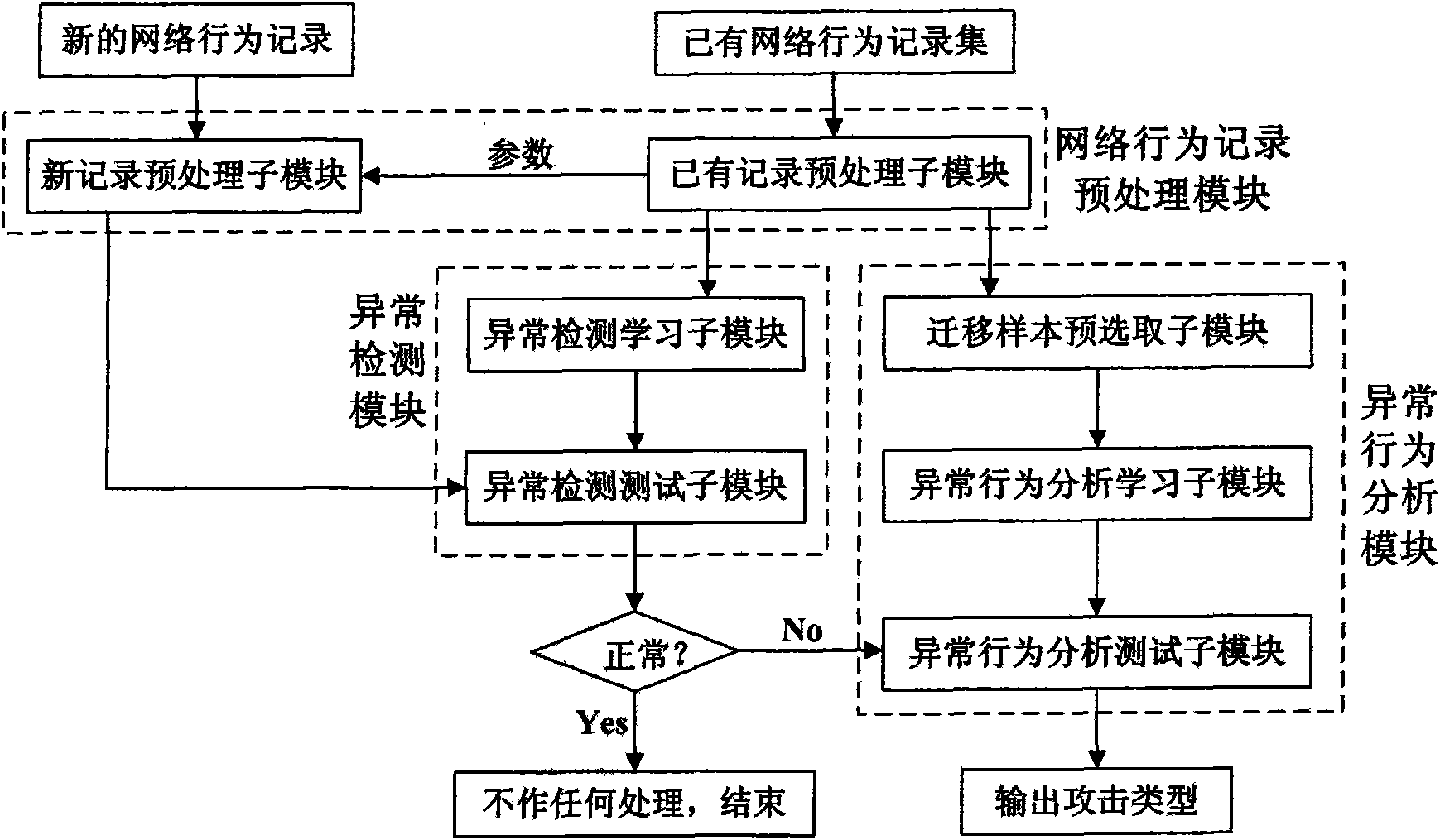
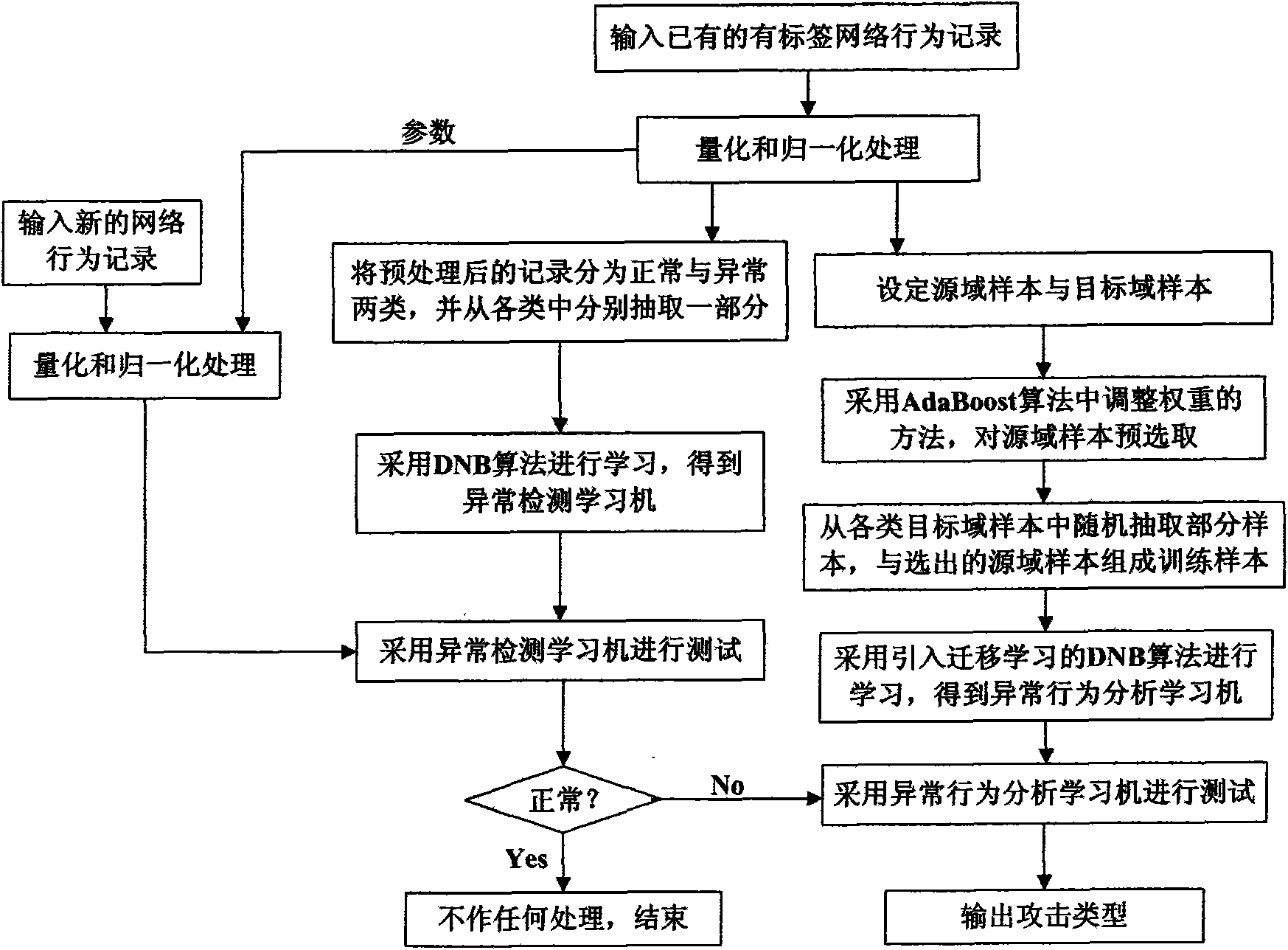
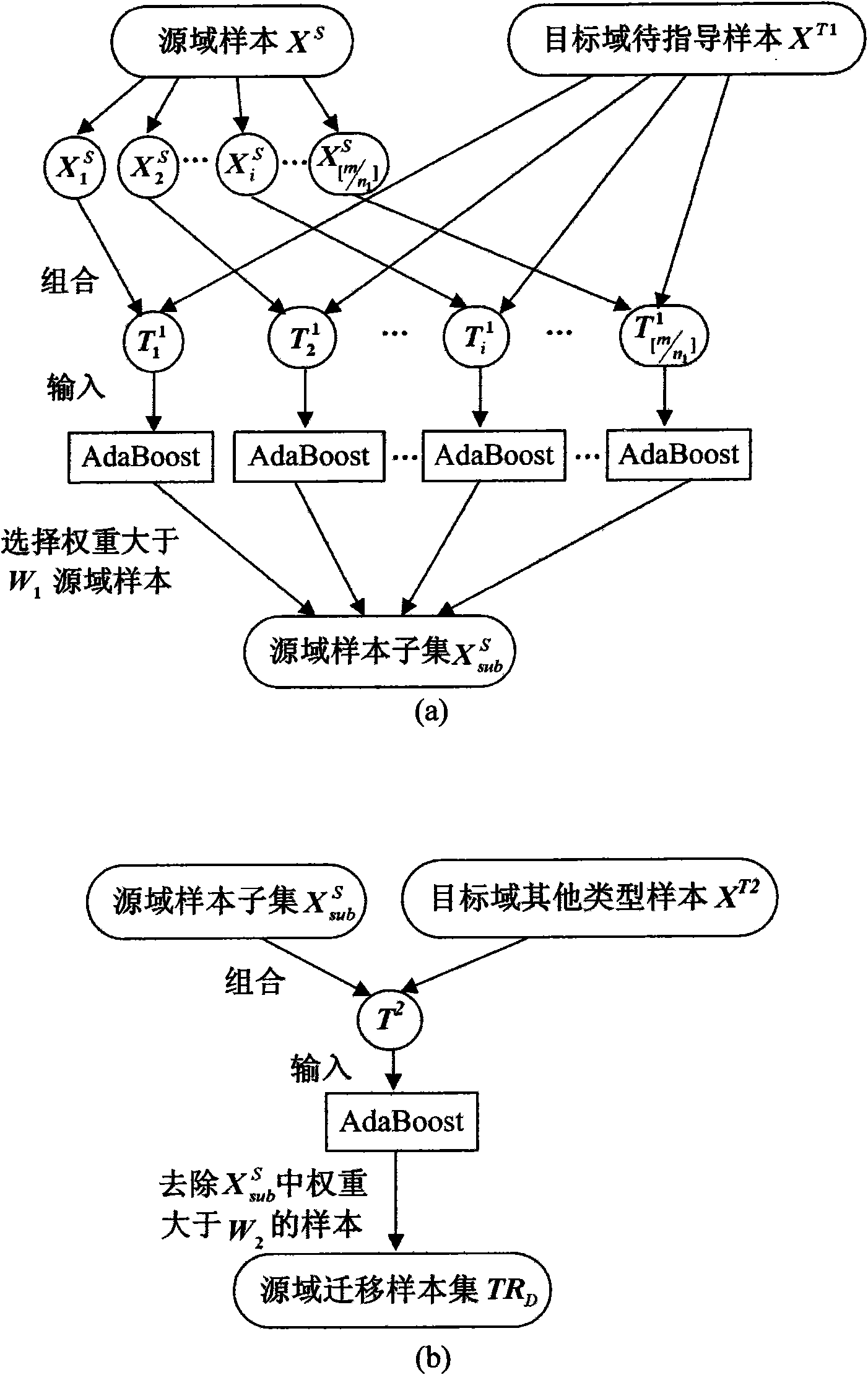
Distributed migration network learning-based intrusion detection system and method thereof
InactiveCN101582813AReduce the probability of detectionImprove detection rateData switching networksLearning basedLearning machine
The invention discloses a distributed migration network learning-based intrusion detection system and a method thereof, and mainly solves the problems that the prior method has low efficiency in detection of some attack types and is difficult to search data again. The whole system comprises a network behavior record preprocessing module, an abnormality detection module and an abnormal behavior analyzing module. The network behavior record preprocessing module completes the quantification and normalization processing of a network behavior record; the abnormality detection module uses an abnormality detection learning machine to completes the classification and identification for an input record, determines whether the record is a normal behavior, and completes the detection if the record is a normal behavior or transmits the record to the abnormal behavior analyzing module if the record is an abnormal behavior; and the abnormal behavior analyzing module uses an abnormal behavior analyzing learning machine to carry out the classification and identification of the input records and outputs the attach type of the record. The system and the method have the advantages of using other existing resources to improve the detection rate for the prior attach types with low detection rate and avoiding searching the data again and can be used for network intrusion detection.
Owner:XIDIAN UNIV
Noise correlation radar devices and methods for detecting targets with noise correlation radar
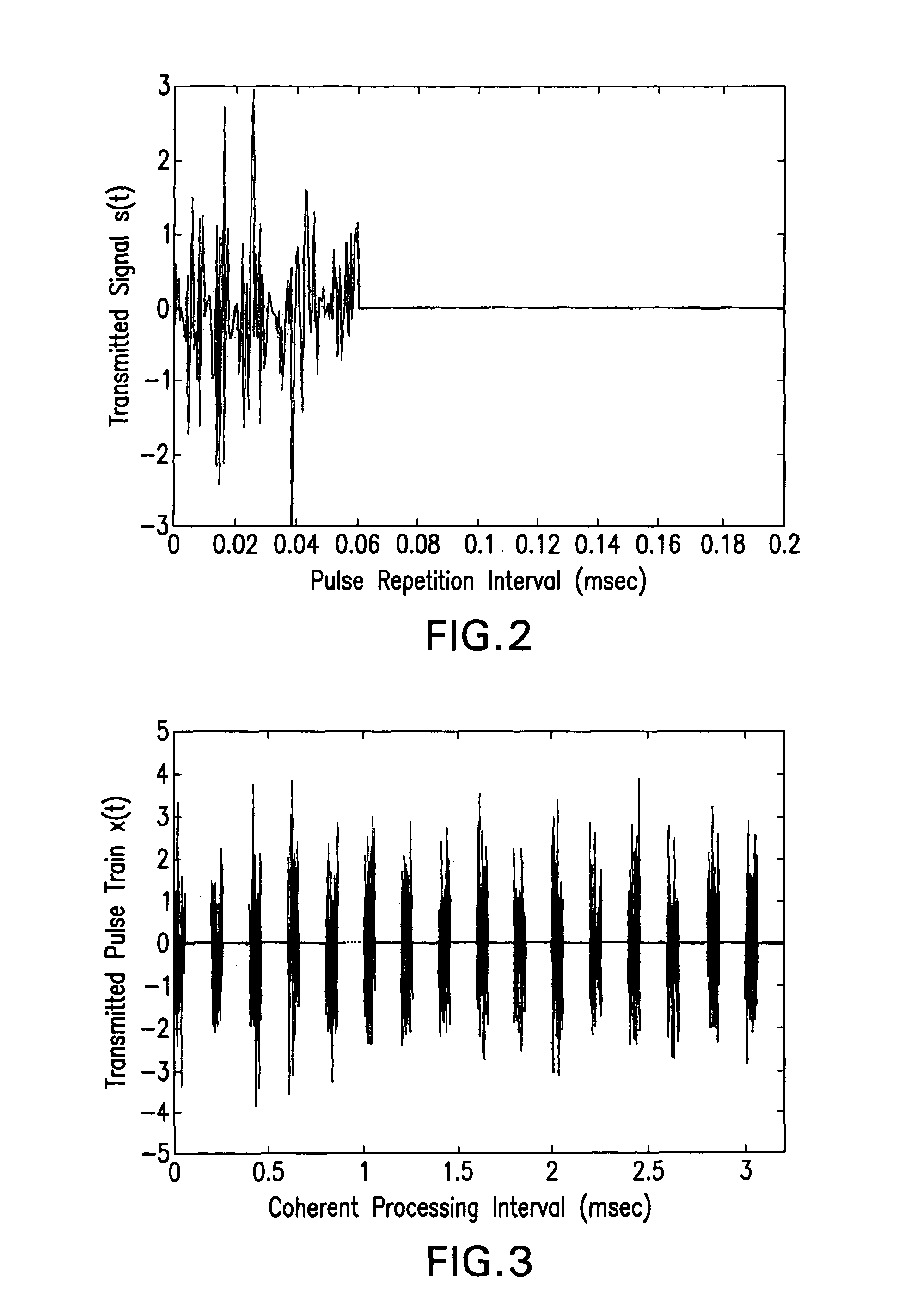
InactiveUS8035551B1Instantaneous band widthIncrease the carrier frequencyRadio wave reradiation/reflectionRadar systemsFrequency modulation
A pulsed compression noise correlation radar uses noise modulation and pulse compression technology to scramble recognizable transmit signal characteristics and reduce transmit energy. The pulsed noise correlation radar advantageously uses pulse compression technology, a pulsed linear frequency modulated noise correlation mixer, and a new and innovative noise fused waveform to automatically correlate the pulsed linear frequency modulated (LFM) noise waveform with the received signal. The pulsed noise correlation radar apparatus and system now make it possible to effectively reduce transmitting power, preserve high band widths through oversampling in the receiver, and achieve multi-channel array frequency diversity. A secure pulsed compression noise correlation radar system and methods for undetected target detection with pulsed noise correlation radar and a pulsed LFM fused noise waveform are also provided.
Owner:ARMY US SEC THE
Recording material delivery system for recording material-consuming apparatus; circuit board; structural body; and ink cartridge
ActiveUS20100289847A1Reduce the probability of detectionReduce the possibilityElectrographic process apparatusOther printing apparatusEngineeringDelivery system
A circuit board of an ink cartridge is provided with a plurality of terminals, with the contact portions of the plurality of terminals forming a plurality of lines. The contact portions of two terminals used for detecting installation are positioned in a first line, and the contact portion of a power terminal is positioned between the two terminals. The first line may be positioned to a leading side when the ink cartridge is moved in a prescribed direction to effect installation in a printer. Alternatively, the first line may be the line closest to an opening of an ink delivery port. Alternatively, the first line may be the line closest to an ink delivery needle.
Owner:SEIKO EPSON CORP
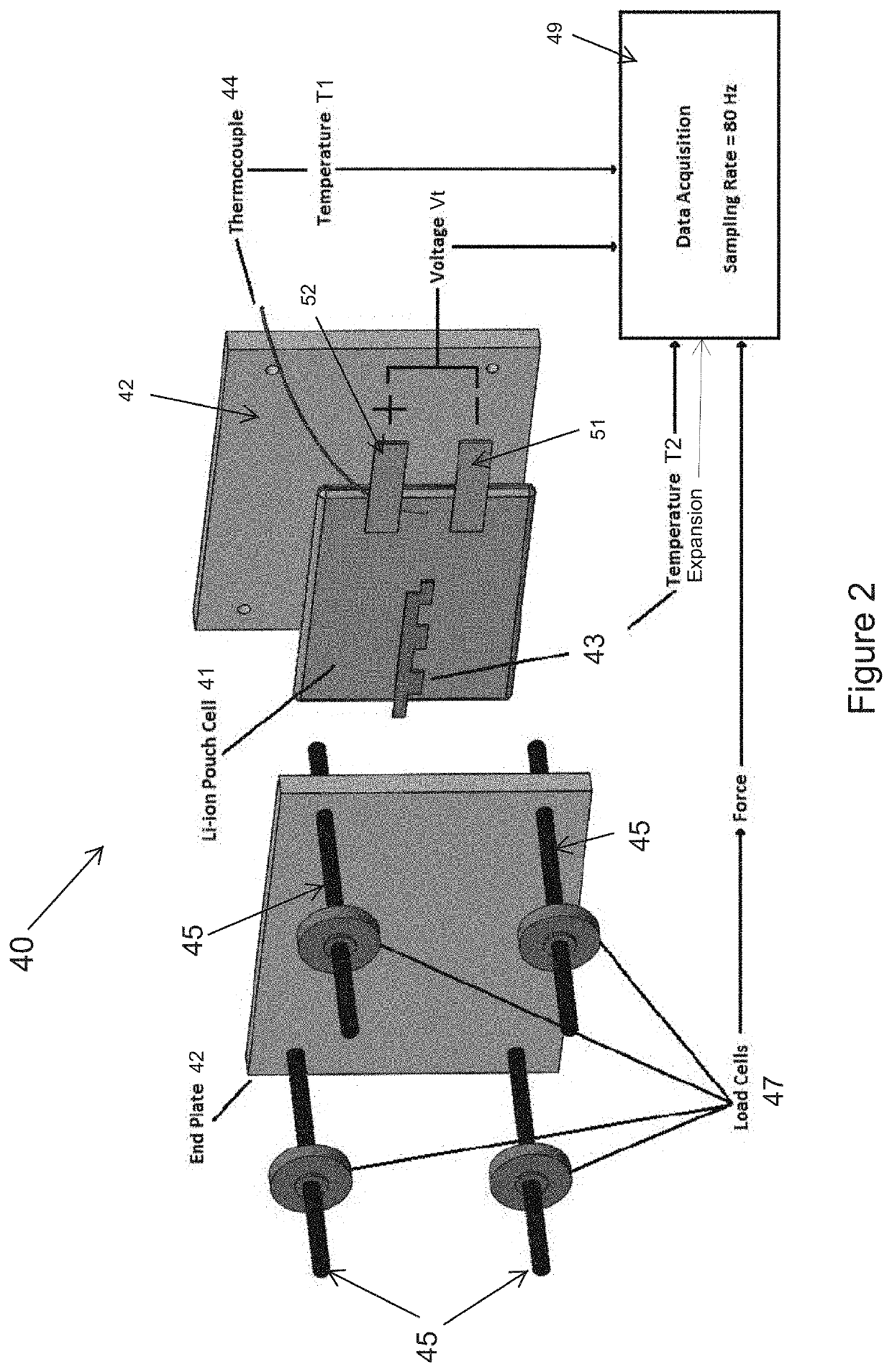
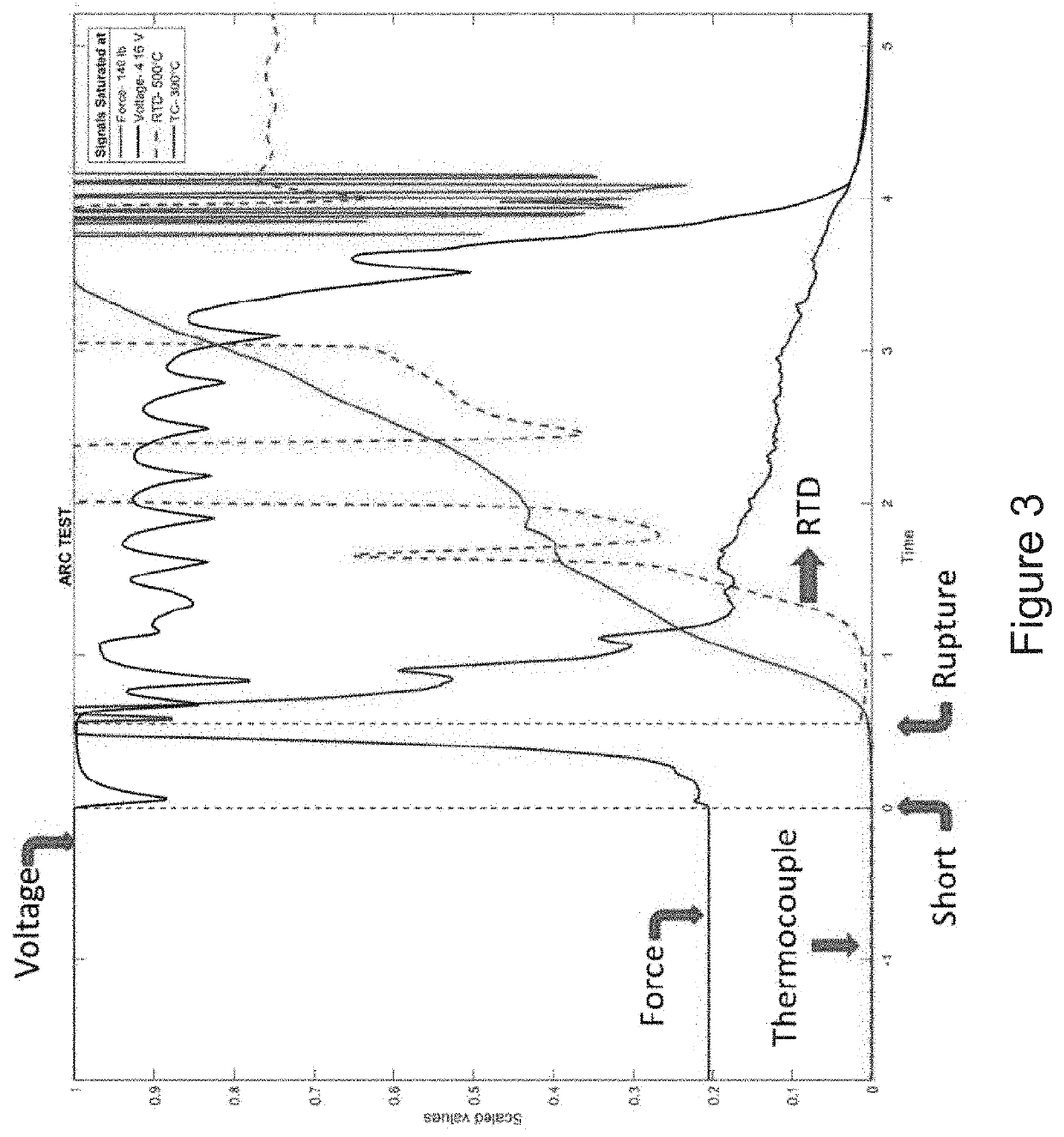
Detection of an Internal Short Circuit in a Battery
ActiveUS20200313152A1High confidence detectionReduce the probability of detectionBatteries circuit arrangementsElectric devicesElectrical batteryCurrent sensor
An electrical device comprises a battery cell; a pressure sensor for measuring swelling forces of the battery cell, optionally with voltage, temperature and current sensors, and a battery management system including a controller. The controller executes a program to: (i) determine a reference swelling force corresponding to a reference electrical signal received from the pressure sensor at an earlier reference time, (ii) determine a second swelling force corresponding to a second electrical signal received from the pressure sensor at a later second time, and (iii) determine whether a risk of internal short circuit of the battery cell exists by comparing a reference level of the reference electrical signal and a signal representative of the second electrical signal. When the signal representative of the second electrical signal exceeds the reference level of the reference electrical signal by a threshold amount, a risk of internal short circuit of the cell exists.
Owner:RGT UNIV OF MICHIGAN
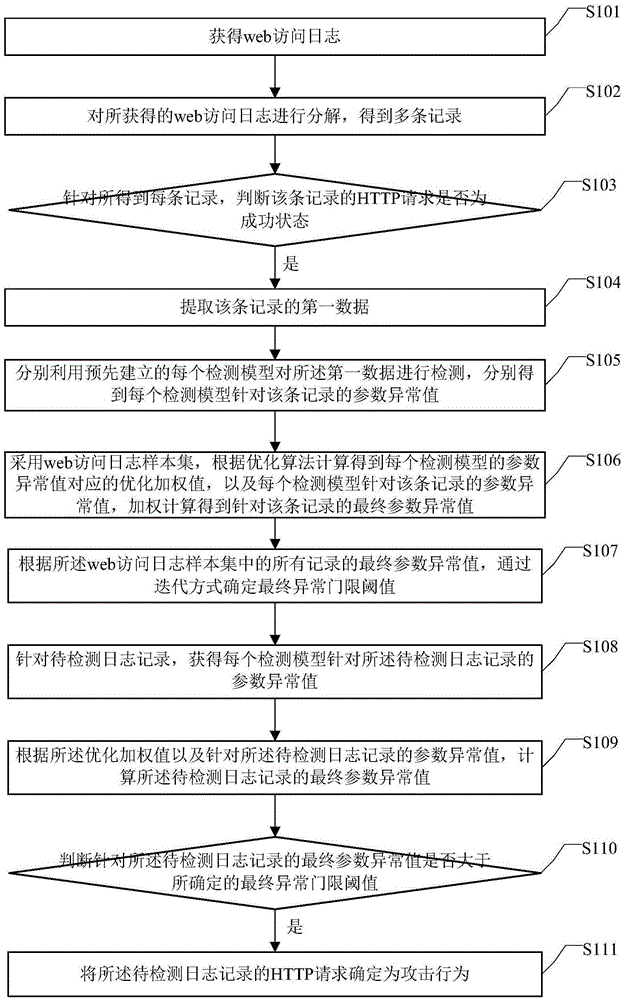
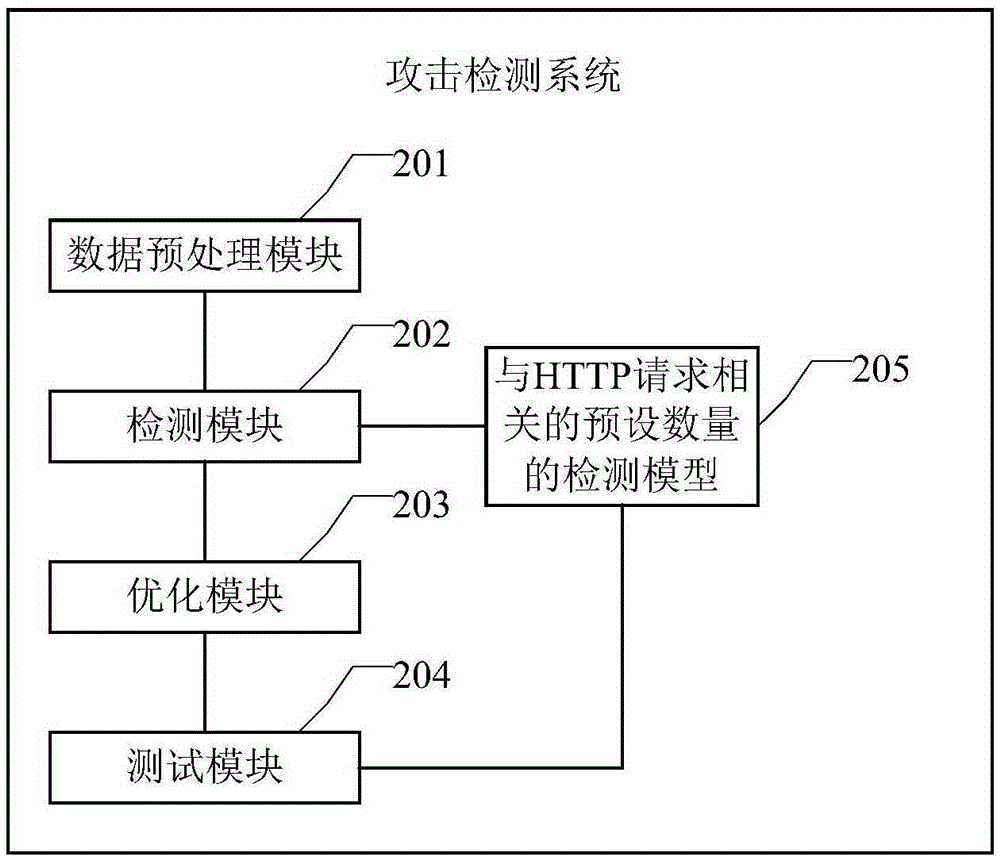
Attack detection method and system
InactiveCN105337985AImprove detection rateReduce the probability of detectionTransmissionWeight valueFalse detection
The embodiment of the invention discloses an attack detection method and system. The method comprises the following steps: establishing a plurality of detection models related to an HTTP request in advance, and detecting each record after web access logs are decomposed by utilizing each detection model respectively to obtain a parameter abnormal value of each detection model aiming at the record; calculating an optimized weighted value corresponding to the parameter abnormal value of each detection model, carrying out weighted calculation to obtain a final parameter abnormal value, and determining a final abnormal threshold; judging whether the final parameter abnormal value calculated aiming at the log record to be detected is greater than the determined final abnormal threshold; and if yes, determining the HTTP request of the log record to be detected as attack behavior. By applying the embodiment of the invention, unknown attacks can be actively discovered, so that the detection rate of the unknown attacks can be improved; and optimized weighting of multiple detection models is adopted for detecting, so that the limitation of a single detection model is avoided, false-reporting and under-reporting conditions are reduced, and the false detection rate is lowered.
Owner:BEIJING NORMAL UNIVERSITY
Centralized MIMO radar radio frequency stealth multi-target tracking wave beam pointing method
InactiveCN105158756AAverage SNR MinimizationGuaranteed echo signal-to-noise ratio performanceRadio wave reradiation/reflectionMulti target trackingRadio frequency
The invention provides a centralized MIMO radar radio frequency stealth multi-target tracking wave beam pointing method, and belongs to the technical field of communication radar. Assuming that an interception receiver obeys uniform distribution in a position uncertainty region of the interception receiver, a target function is established with minimization of average signal-to-noise ratio of radar signals received by the interception receiver acting as the target, and the positions of targets are modeled as random quantity so that that probability that echo signal-to-noise ratio of all the targets is great than the preset value is ensured not to be less than a certain value. With application of parameters obtained by optimization of an optimization model, average signal-to-noise ratio of the radar signals received by the interception receiver is enabled to be minimized under the condition of guaranteeing radar echo signal-to-noise ratio performance so that the probability that radar is detected by the interception receiver can be reduced as far as possible.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
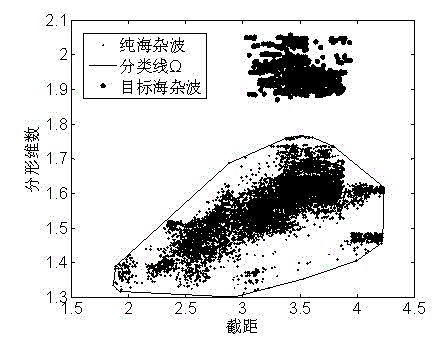
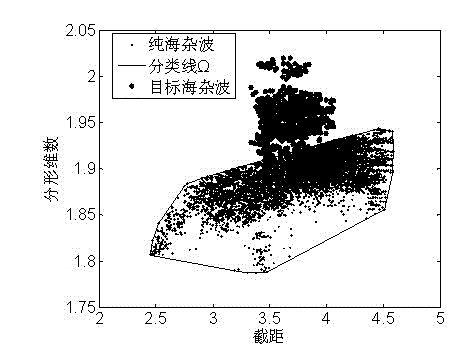
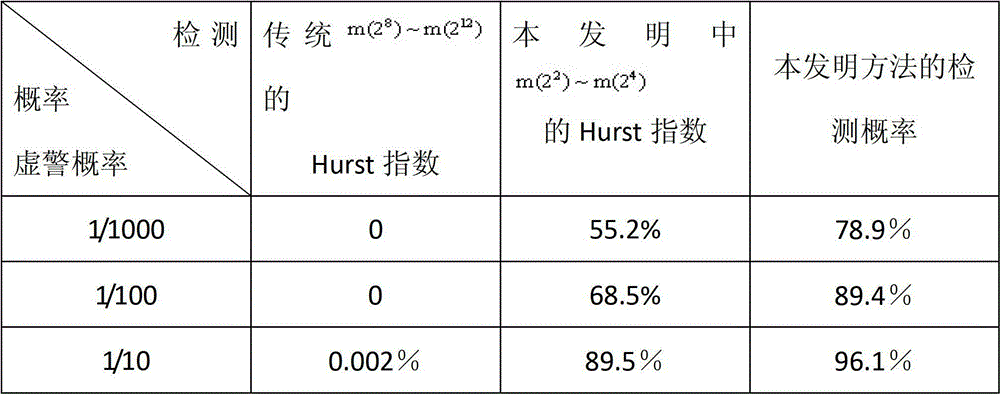
Joint fractal-based method for detecting small target under sea clutter background
InactiveCN102914769AImprove detection rateReduce the probability of detectionWave based measurement systemsPattern recognitionAdditive model
The invention provides a joint fractal-based method for detecting a small target under a sea clutter background. The joint fractal-based method is higher in detection probability. The detection problem of a non-additive model is transformed into a classification problem, i.e. whether a target exists or not is equivalent to belong to a class in which a pure sea clutter exists, and a characteristic joint detection algorithm is provided. A bilogarithmic graph is established by using a trend fluctuation method through sea clutter data, a slope, namely a Hurst index, is fitted by using a least square method within a scale-free interval, and is used as a characteristic scalar, a nodal increment of a keypoint in the bilogarithmic graph is used as another characteristic scalar, therefore, a double-scalar obtained by each group of sea clutter data corresponds to one point in the bilogarithmic graph, n groups of corresponding points (i=1,...n) of the pure sea clutter data are obtained by using the steps, a space optimal classification line omega is obtained by using a convex hull function, sea clutters of regions in which the target possibly exits are obtained by using the same steps, and finally, by using whether the points exist in the space optimal classification line omega or not as a criterion, when the points exists in the space optimal classification line omega, no target exists, and when the points are outside the space optimal classification line omega, the target exists.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
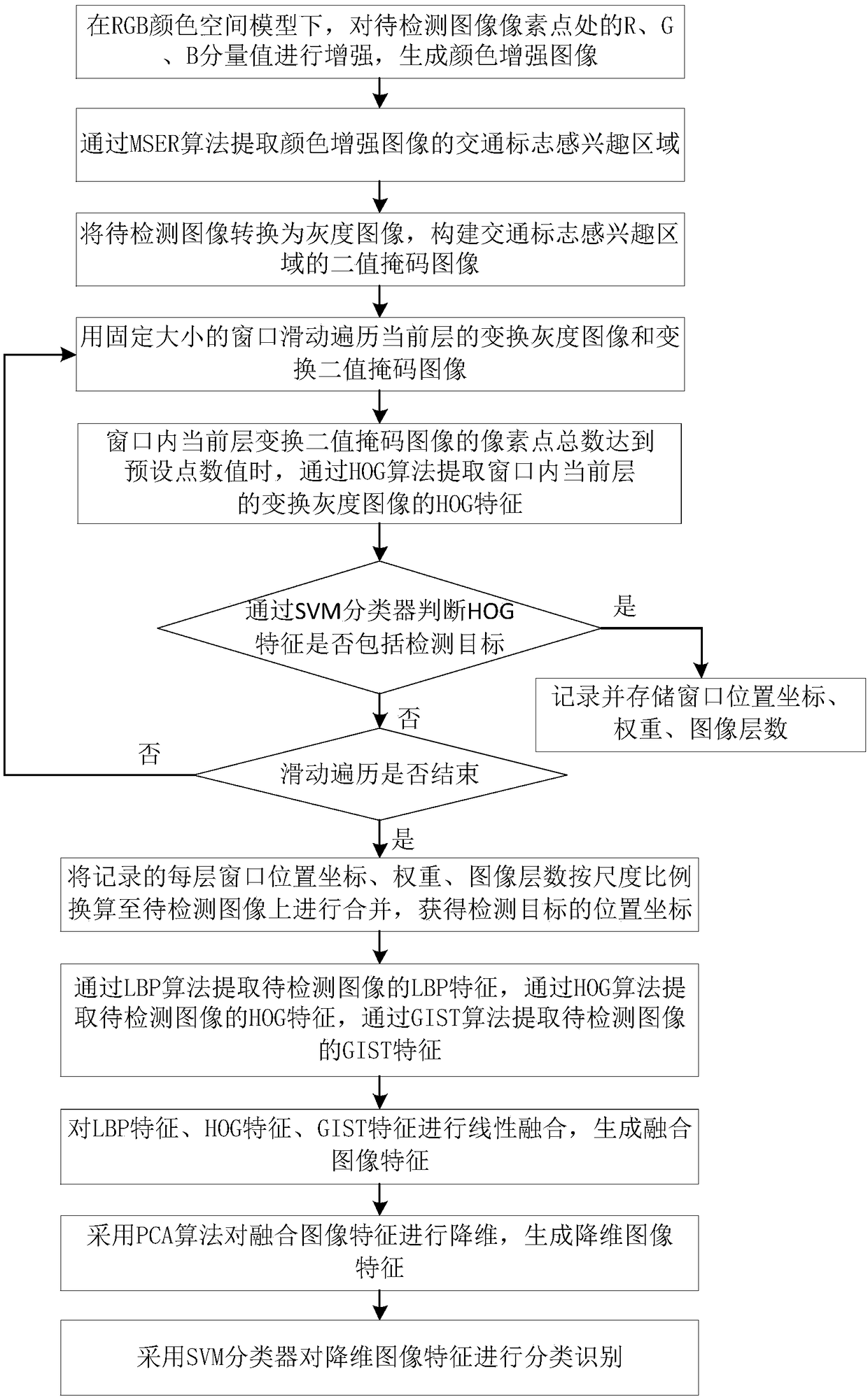
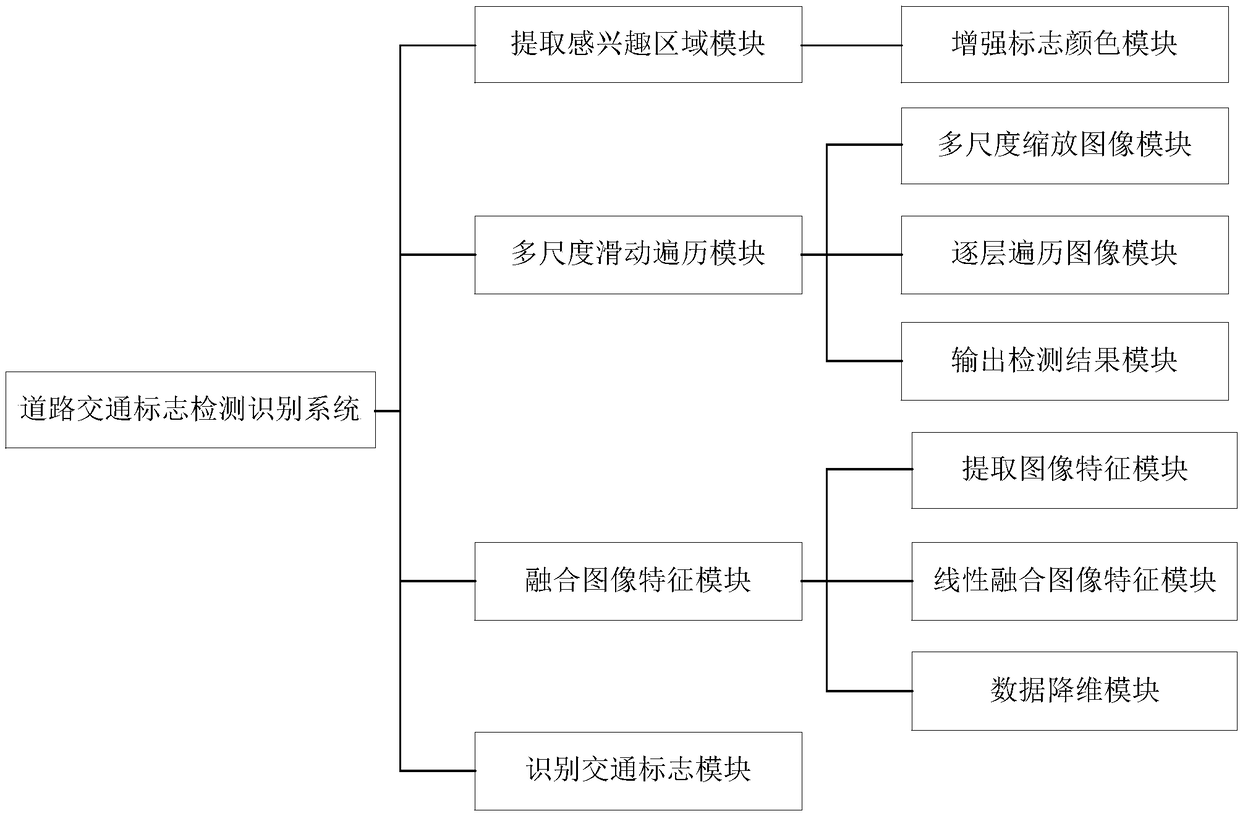
Road traffic sign detection and identification method, electronic device, storage medium and system
InactiveCN108805018AReduce traversal search timeEfficient removalImage analysisCharacter and pattern recognitionTraffic sign detectionSign detection
The present invention provides a road traffic sign detection and identification method. The method comprises the steps of: extracting a region of interest; performing multi-scale sliding traversal; merging image features; and identifying a traffic sign. The method specifically comprises: performing extraction of a region of interest of the traffic sign on an input to-be-detected image; convertingthe to-be-detected image into a gray-scale image; constructing a binary mask image of the region of interest of the traffic sign; performing multi-scale sliding traversal on the gray-scale image and the binary mask image to obtain position coordinates of a detected target; merging the extracted local texture features, local image region features and global features of the to-be-detected image; andclassifying and identifying the merged image features by using a classifier. The present invention relates to an electronic device and a readable storage medium for performing the road traffic sign detection and identification method; and the present invention also relates to a road traffic sign detection and identification system. The technical scheme of the present invention has a high detection rate, a high identification rate, a fast calculation speed, a low false detection rate and good robustness.
Owner:TAORAN SHIJIE HANGZHOU TECH CO LTD
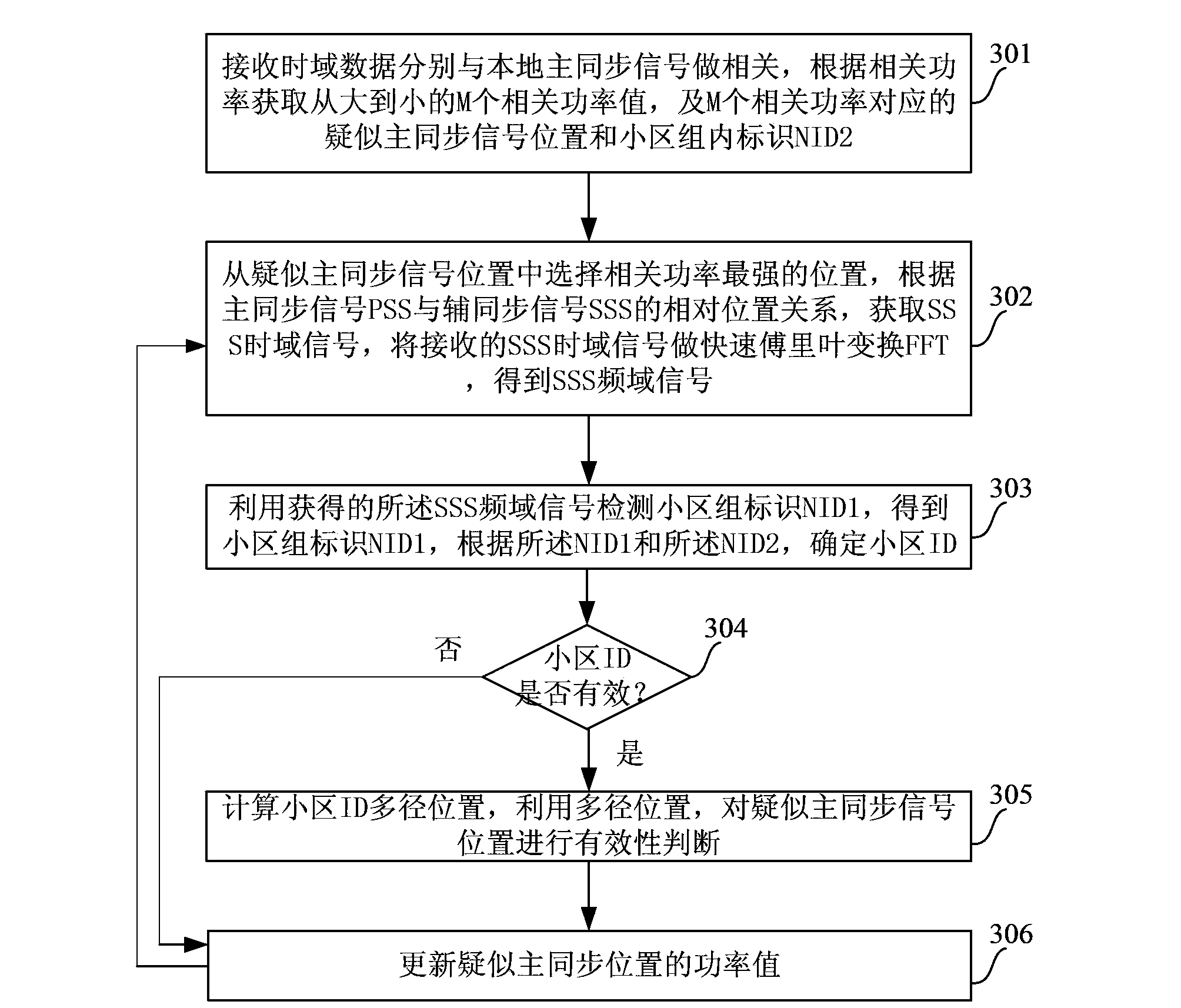
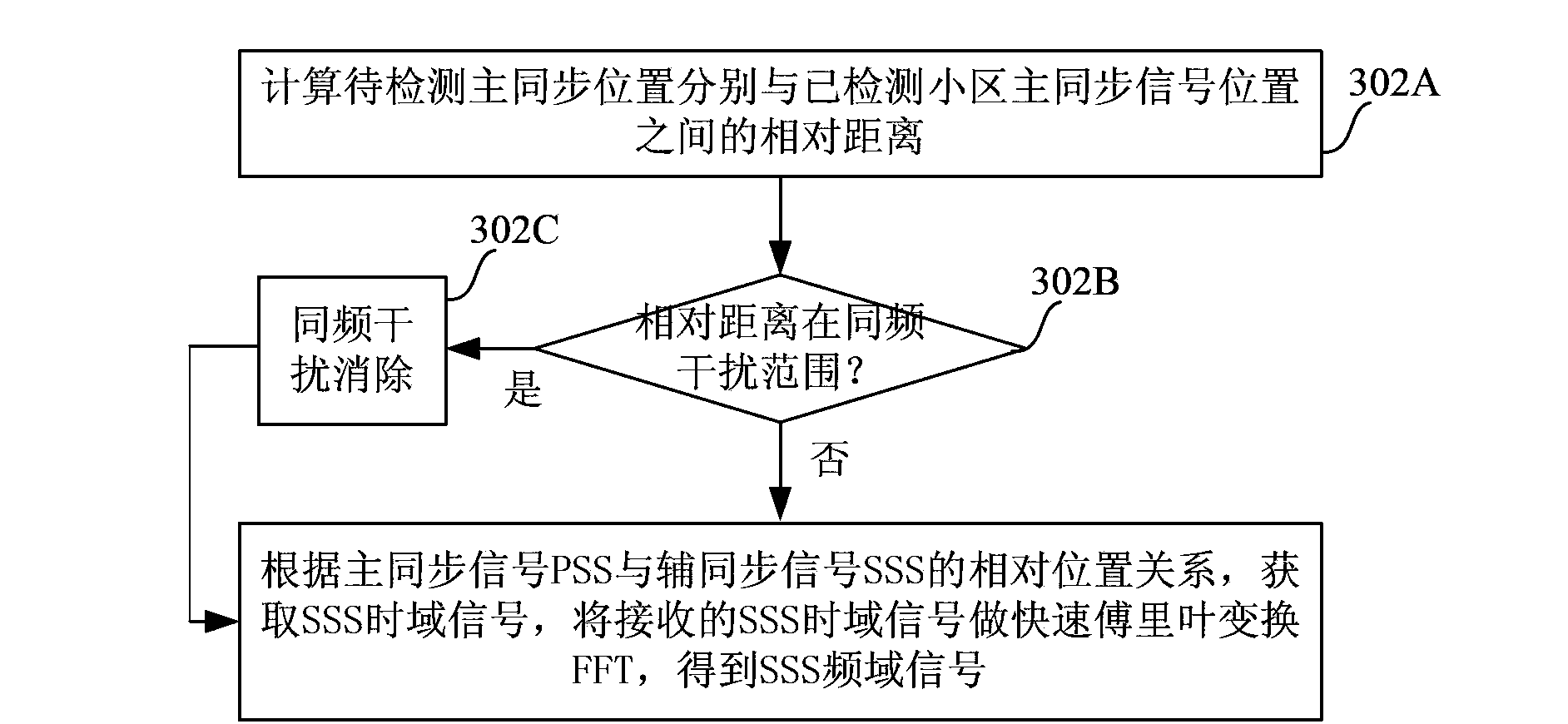
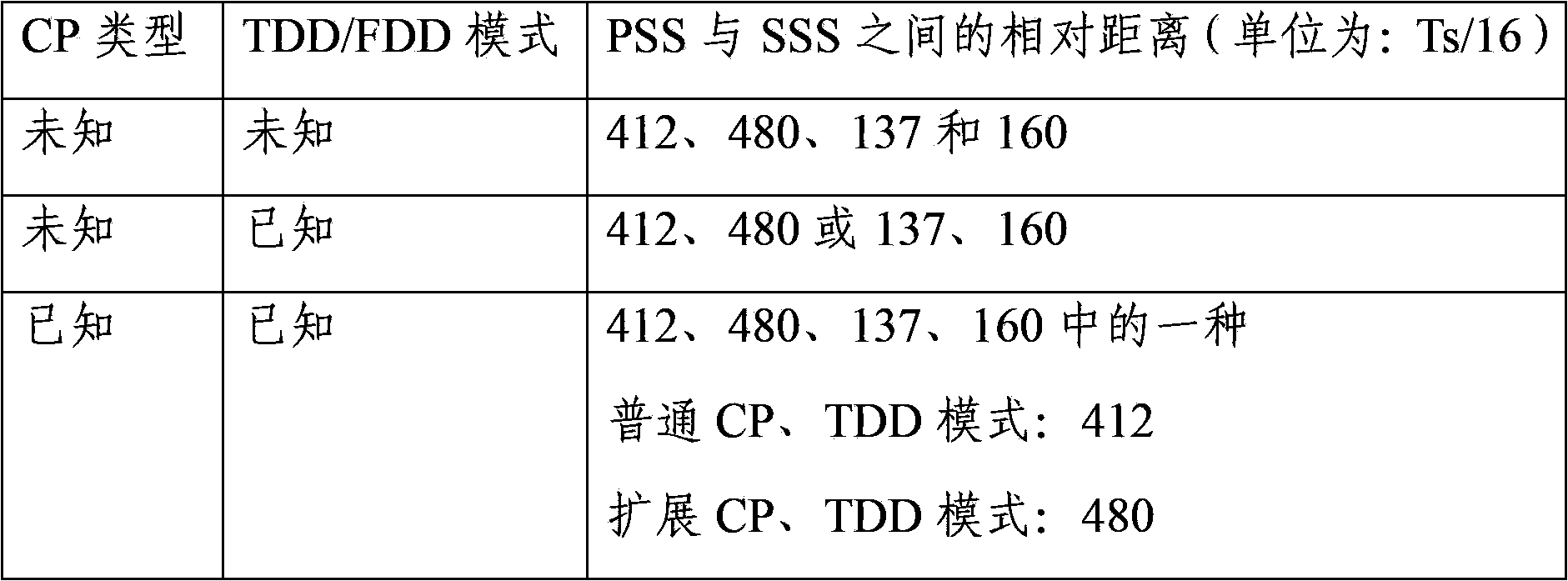
LTE system cell detection method
ActiveCN103856956AReduce processing timeAvoid traversal detectionWireless communicationComputation complexityInterference elimination
The embodiment of the invention provides an LTE system cell detection method. Power sorting is adopted to ensure that the cell detected each time is the strongest cell, traverse detection on M suspected synchronization positions is avoided, the operation complexity is reduced, and the processing time for cell detection is shortened. Meanwhile, the validity of the ID of a detected cell is judged, the multipath position of the cell ID is calculated, the validity of a suspected primary synchronization signal position is judged according to the multipath position, and the ID detection probability of a false synchronization position is reduced. Moreover, the power value of a detected synchronization position is updated, and same-frequency interference elimination is adopted so as to improve the success rate of weak cell detection.
Owner:RDA CHONGQING MICROELECTRONICS TECH CO LTD
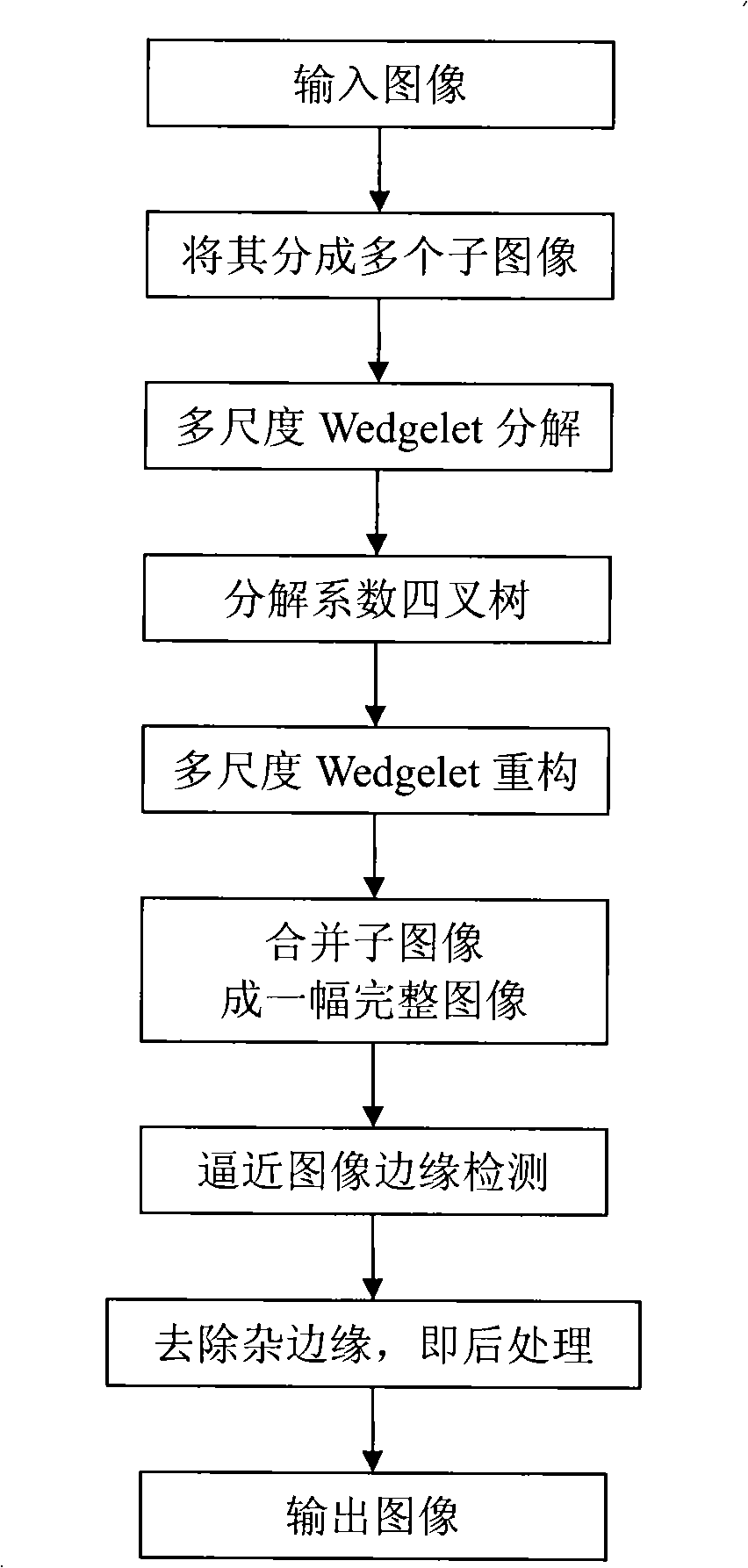
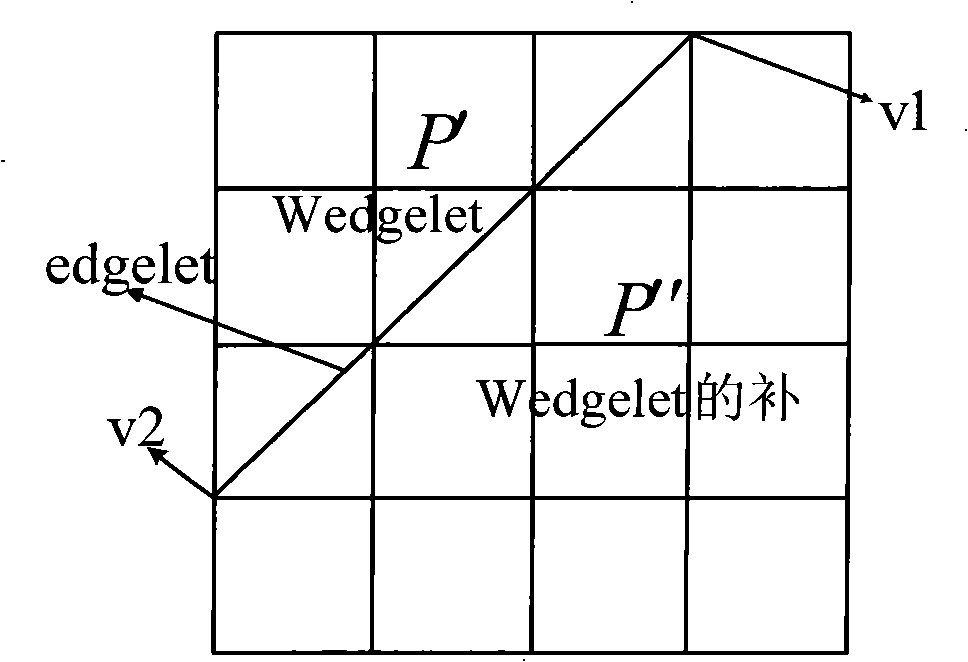
Multi-dimension SAR image edge detection method based on improved Wedgelet
InactiveCN101329402AReduce the probability of detectionEliminate distractionsCharacter and pattern recognitionRadio wave reradiation/reflectionGradient operatorsImaging processing
The invention discloses an SAR image edge detection method based on the multi-scale Wedgelet transformation which relates to the image processing field. The SAR image edge detection method aims at solving the problem that the traditional edge detection method is difficult to suppress the noise and carry out complete and accurate positioning of the edge simultaneously. The procedure is as follows: 1. an SAR image is converted into a gray-scale image which is divided into a plurality of sub-images; 2. the multi-scale Wedgelet decomposition is self-adaptively carried out to each sub-image according to the scale from bottom to top, and the decomposition coefficients of various scales are stored by using a quadtree; 3. the multi-scale Wedgelet approximation is carried out to each sub-image according to the coefficient quadtree obtained by the decomposition, and the multi-scale Wedgelet approximation of the whole image is finally obtained; 4. the edge of the approximated image is detected through edge extraction of gradient operators according to the obtained multi-scale Wedgelet approximated image; 5. the interference of the miscellaneous edges with the length of less than the set threshold on the edge image in the edge image is removed. The SAR image edge detection method has the advantages of fast running time and good edge detection effect, thereby being capable of being used in the edge detection of the SAR image.
Owner:探知图灵科技(西安)有限公司
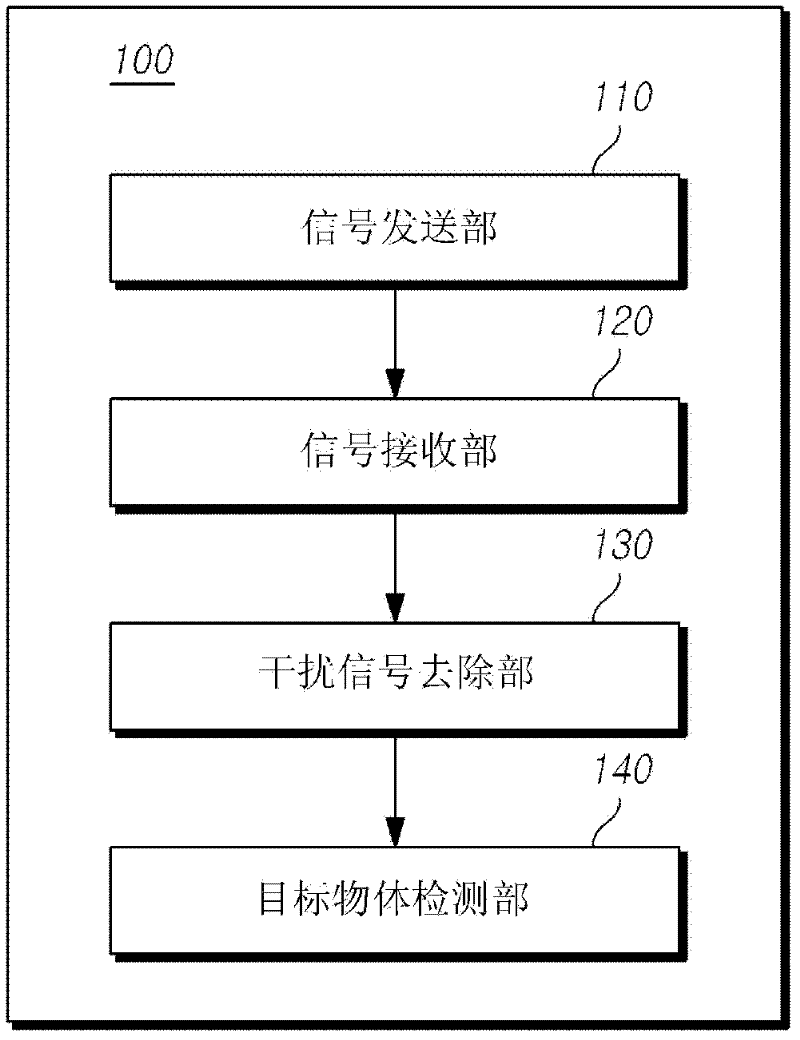
Method and radar apparatus for detecting target object
ActiveCN102608581AReduce distractionsReduce misidentificationRadio wave reradiation/reflectionRadarPhysics
Owner:HL KLEMOVE CORP
High-detectivity gallium-nitride-based Schottky ultraviolet detector using graphene
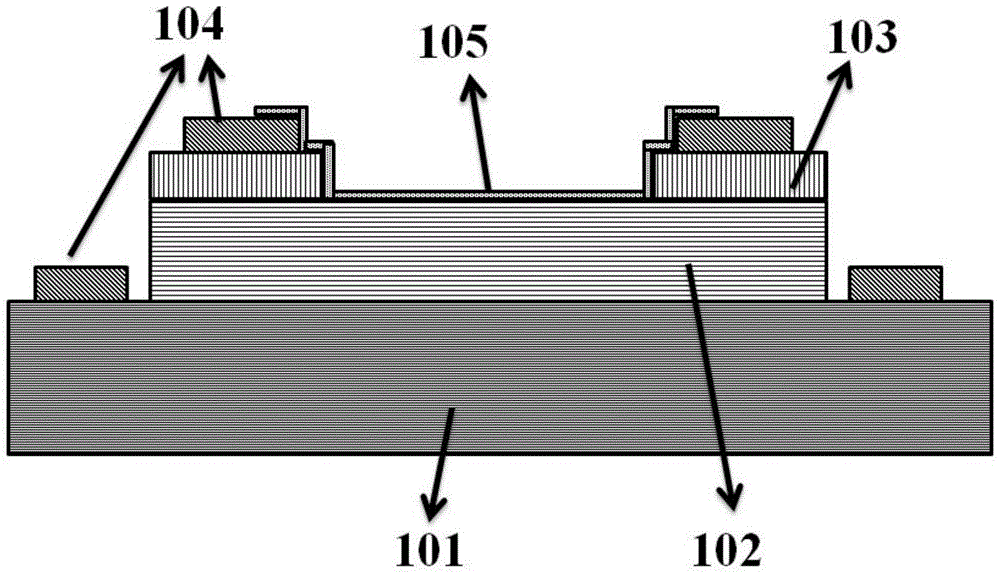
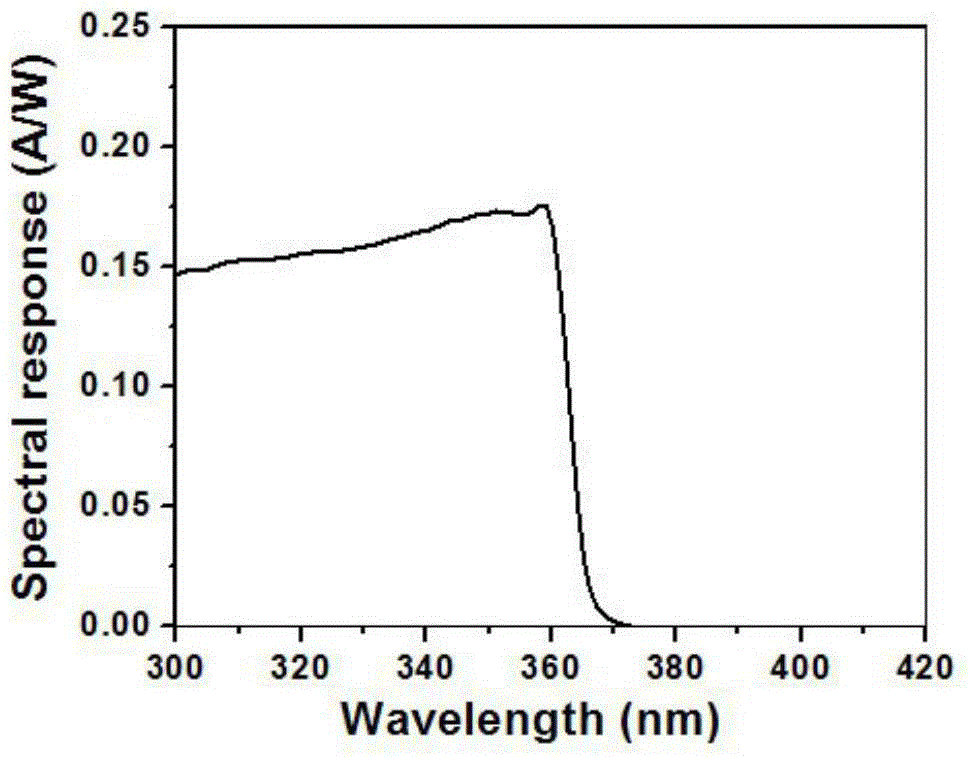
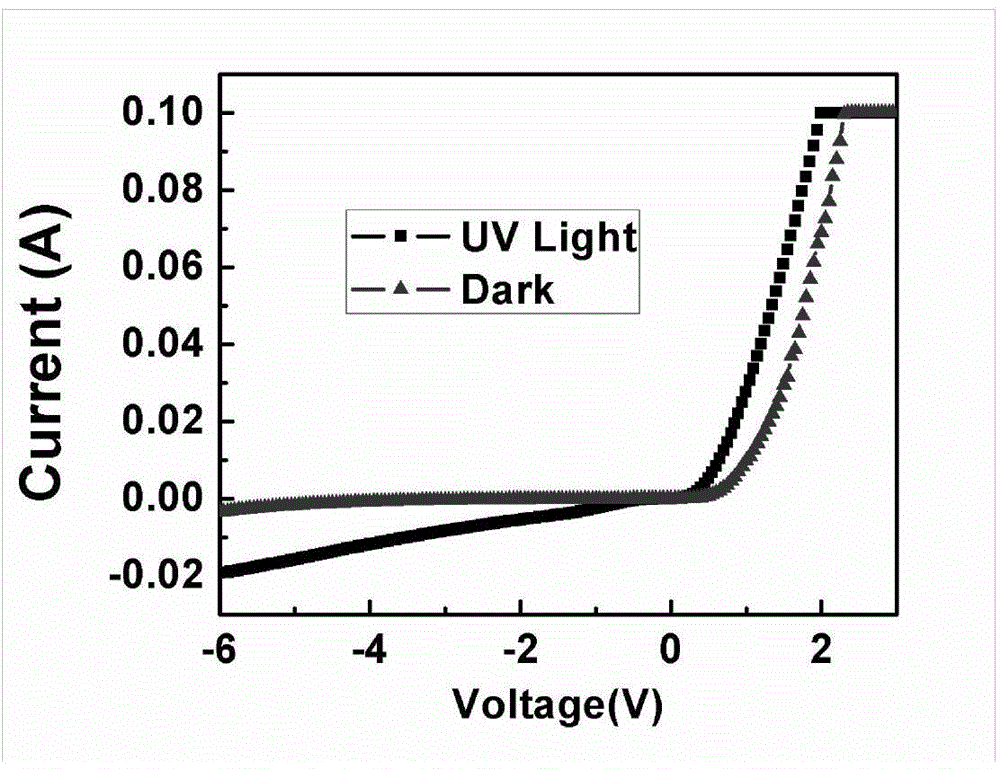
ActiveCN104393093AEnhancing the built-in electric potential fieldImprove separation abilitySemiconductor devicesPhysicsCvd graphene
The invention provides a high-detectivity gallium-nitride-based Schottky ultraviolet detector using graphene. According to the basic structure, the high-detectivity gallium-nitride-based Schottky ultraviolet detector sequentially comprises heavily-doped n type gallium nitride, slightly-doped n type gallium nitride, a silicon dioxide insulating layer, metal electrodes and a graphene thin film from bottom to top. The metal electrodes have the transparent and electric conduction properties and have the half-metallic property. Under the condition that the metal electrodes make direct contact with the slightly-doped n type GaN, the potential barriers of about 0.5 ev can be formed. The formed potential barriers show that the portions, close to the metal electrodes, in the GaN can be bent, so that a spatial charge area is formed, the electron holes are separated, and the photoproduction electrodynamic potential and the photoproduction current are generated. The responsibility of the detector can be greatly improved by introducing the surface defect method. The high-detectivity gallium-nitride-based Schottky ultraviolet detector is simple in structure and process and high in efficiency; thus, the electron hole pair separation capacity is increased, the internal quantum efficiency of the detector is increased, and the detectivity and responsibility are increased.
Owner:BEIJING UNIV OF TECH
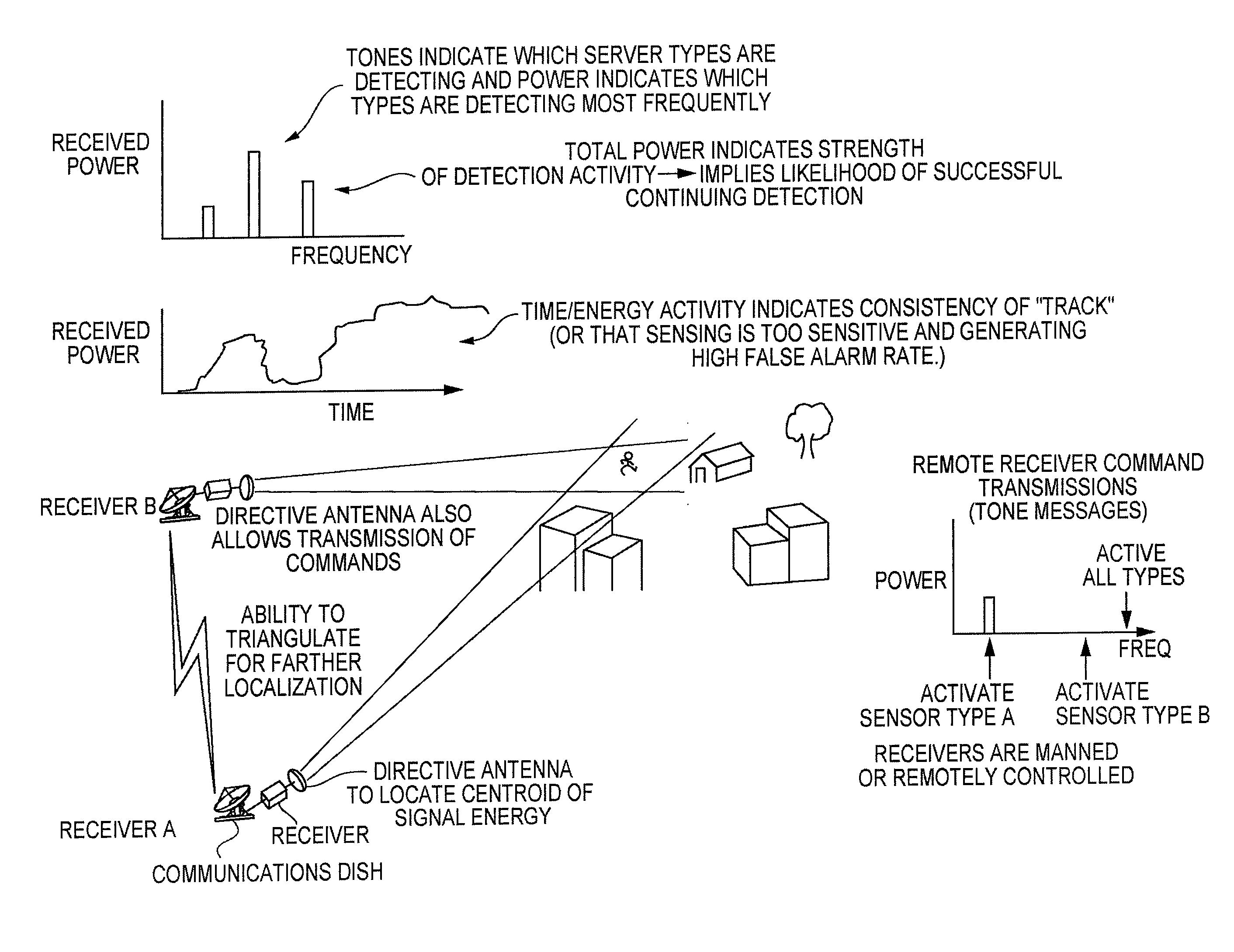
System and Methods for Monitoring Security Zones
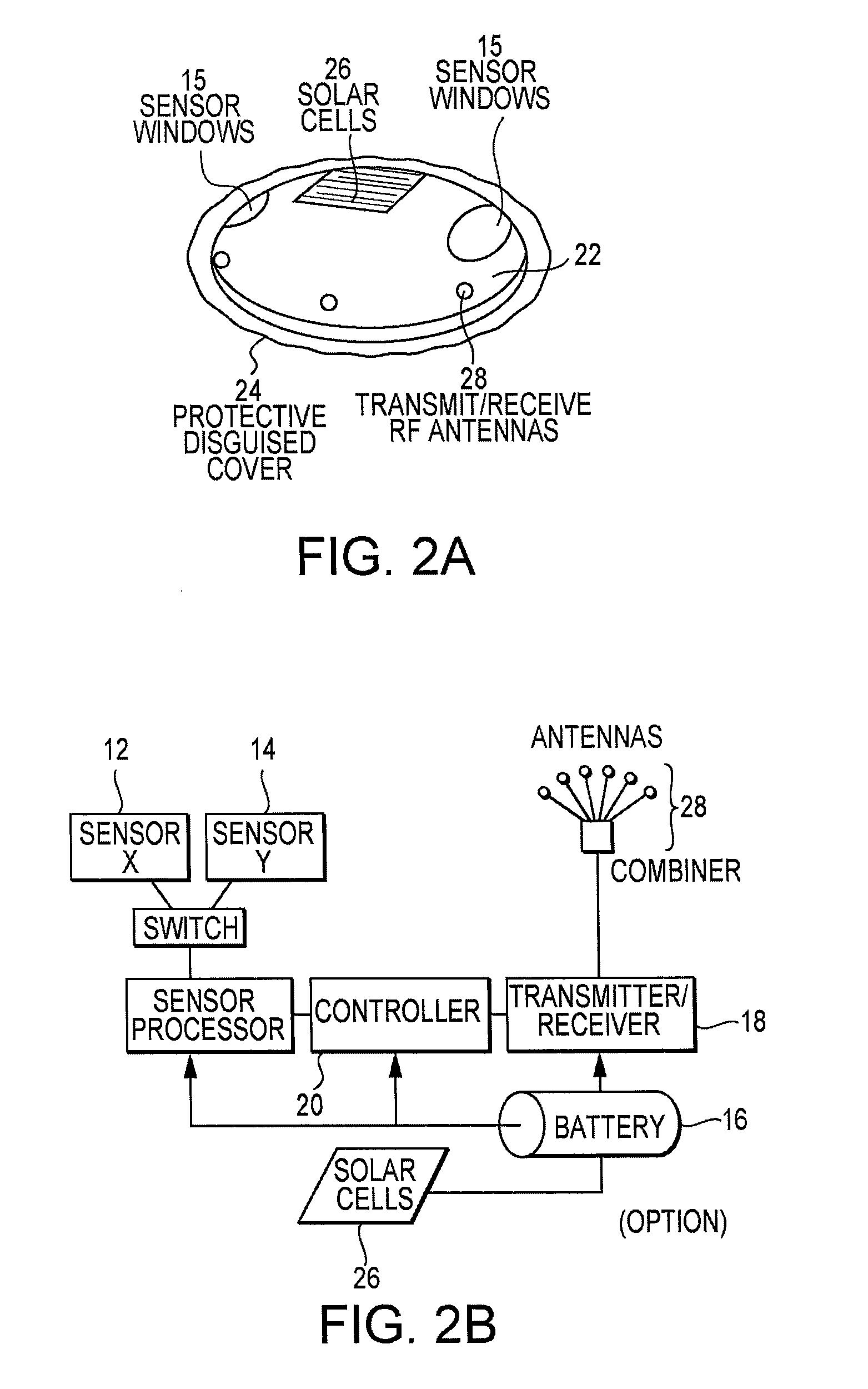
ActiveUS20100045457A1Minimize power consumptionReduce the probability of detectionBurglar alarmElectric signalling detailsMultiple sensorSensor node
A security zone is monitored for intrusion detection by dispersing therein a plurality of sensor nodes that, when an intrusion is detected, communicate with their neighboring sensor nodes without protocols other than a first tone. As the intrusion is detected by more sensor nodes, there is an increase in sensor node transmissions and, hence, an increase in the total power density in the security zone which is detected by a remote monitor for detecting and localizing the intrusion and providing an alert. In addition, certain of the sensor nodes also transmit a continuous second tone received by other sensor nodes. When an intrusion occurs, the transmission is blocked causing the receiving nodes to transmit the first tone to alert neighboring nodes.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
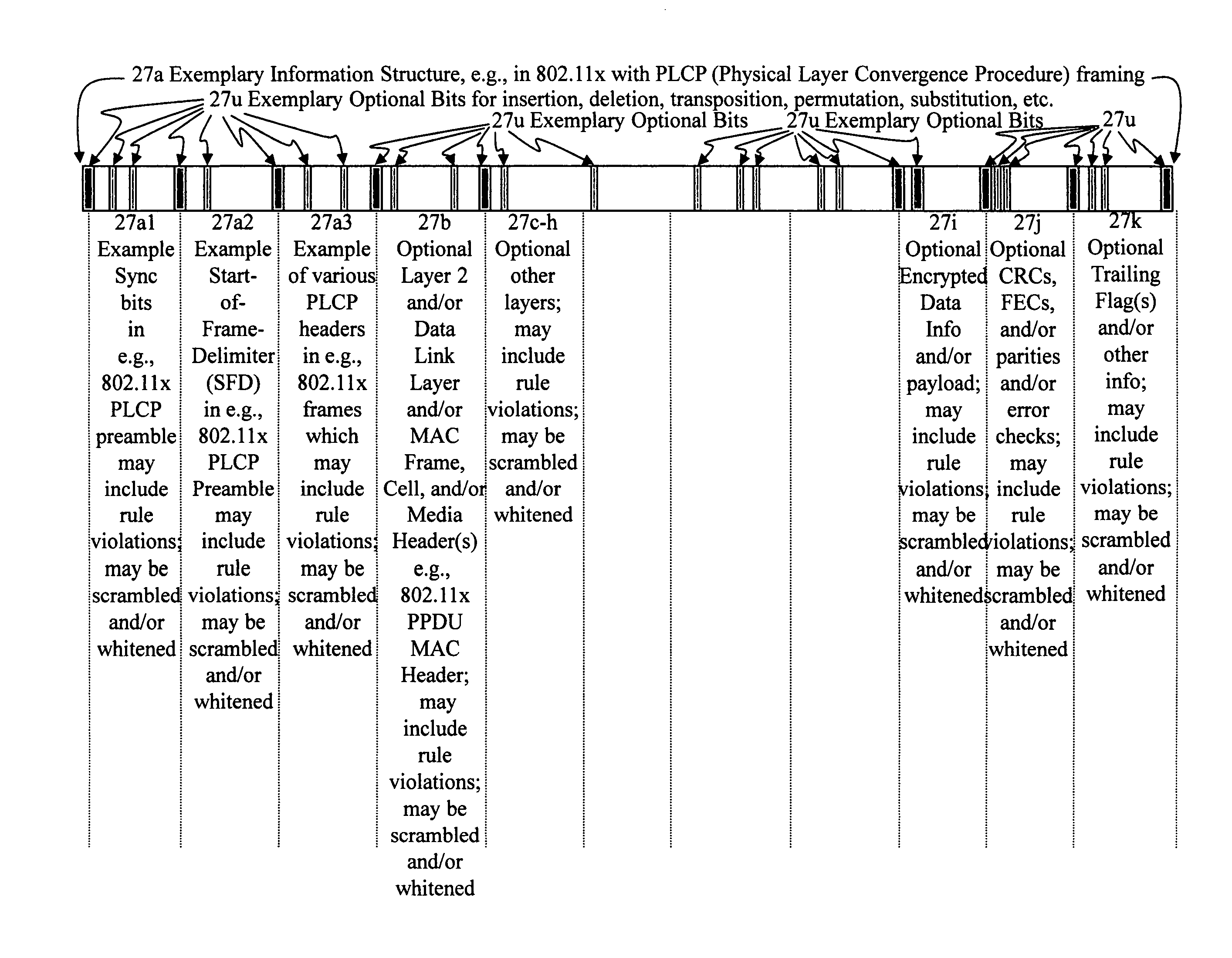
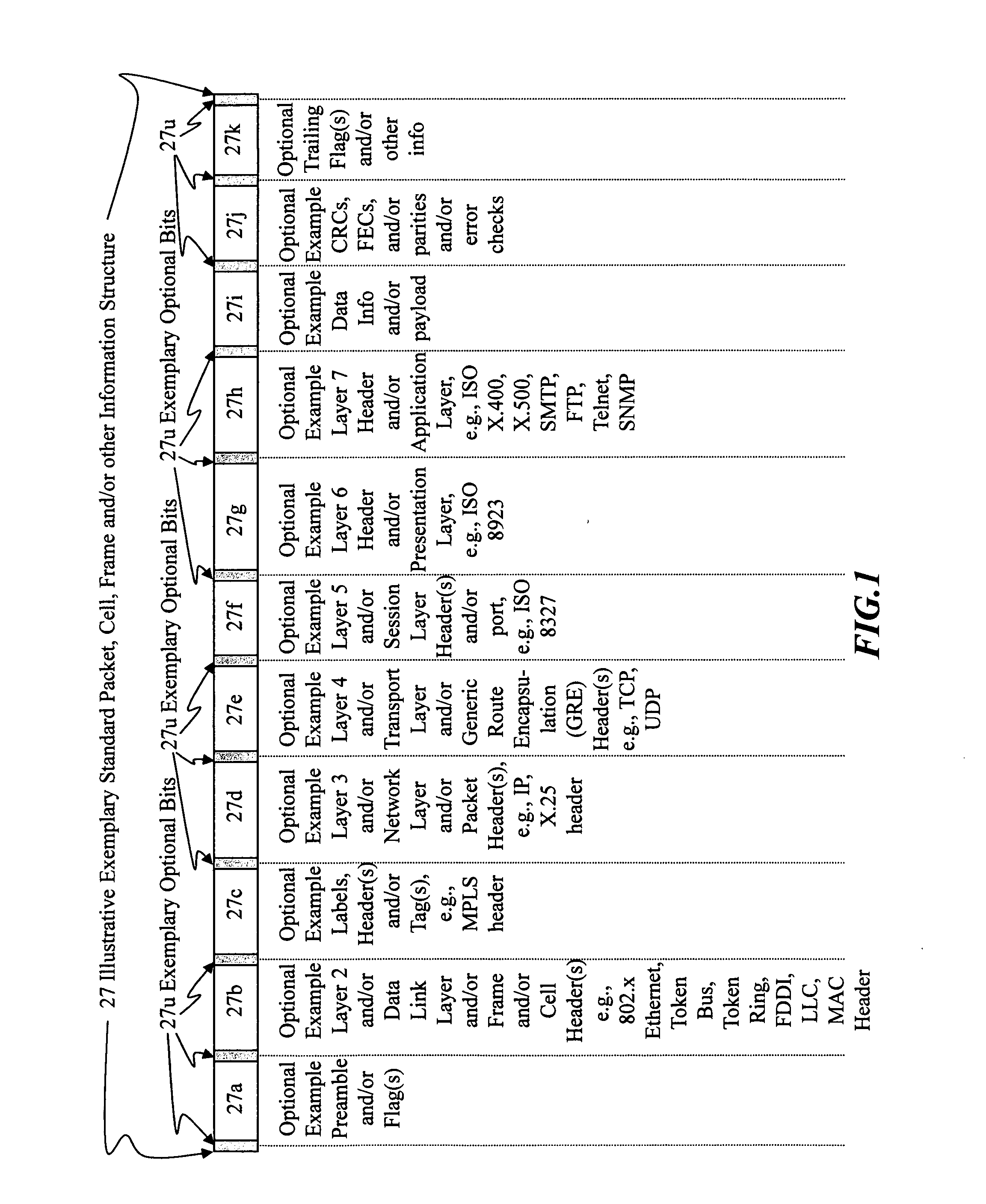
Stealth Packet Communications
InactiveUS20160021224A1Low probability of interceptImprove network securityTime-division multiplexData switching networksPacket communicationComputer hardware
Devices and methods for transmitting and receiving communications are disclosed. These communications comprise using stealth assemblers and stealth interpreters to construct and interpret false start-of-frame delimiters, alternative preambles, and / or modified protocols in packets.
Owner:HOWE WAYNE RICHARD
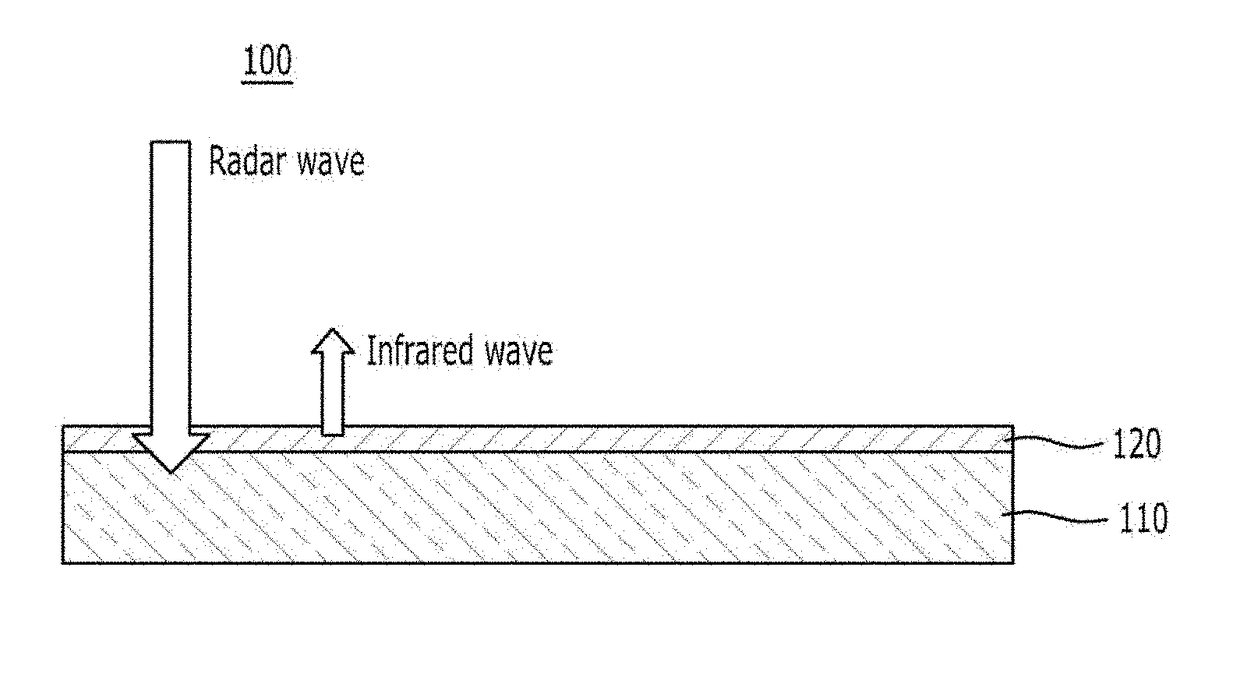
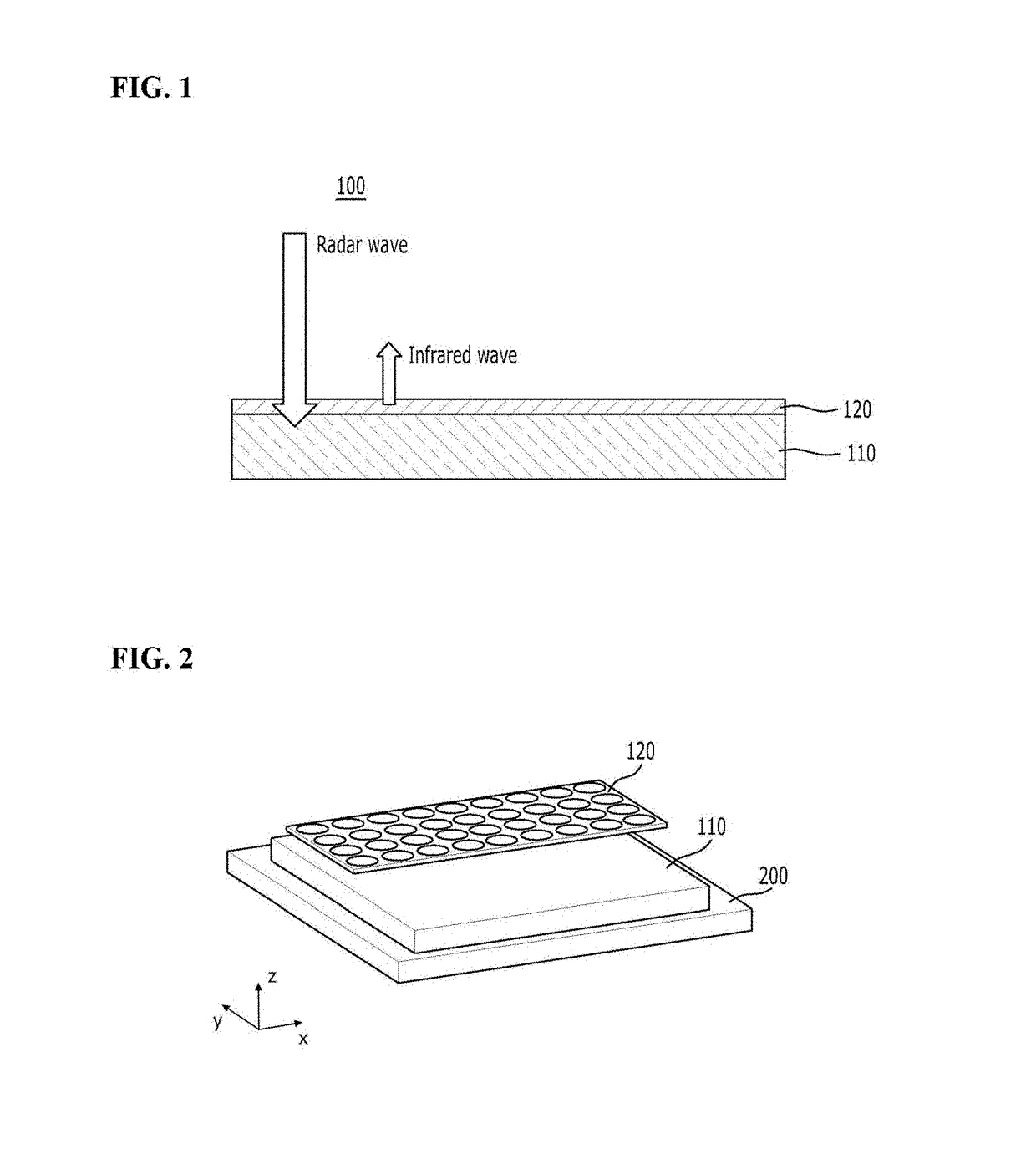
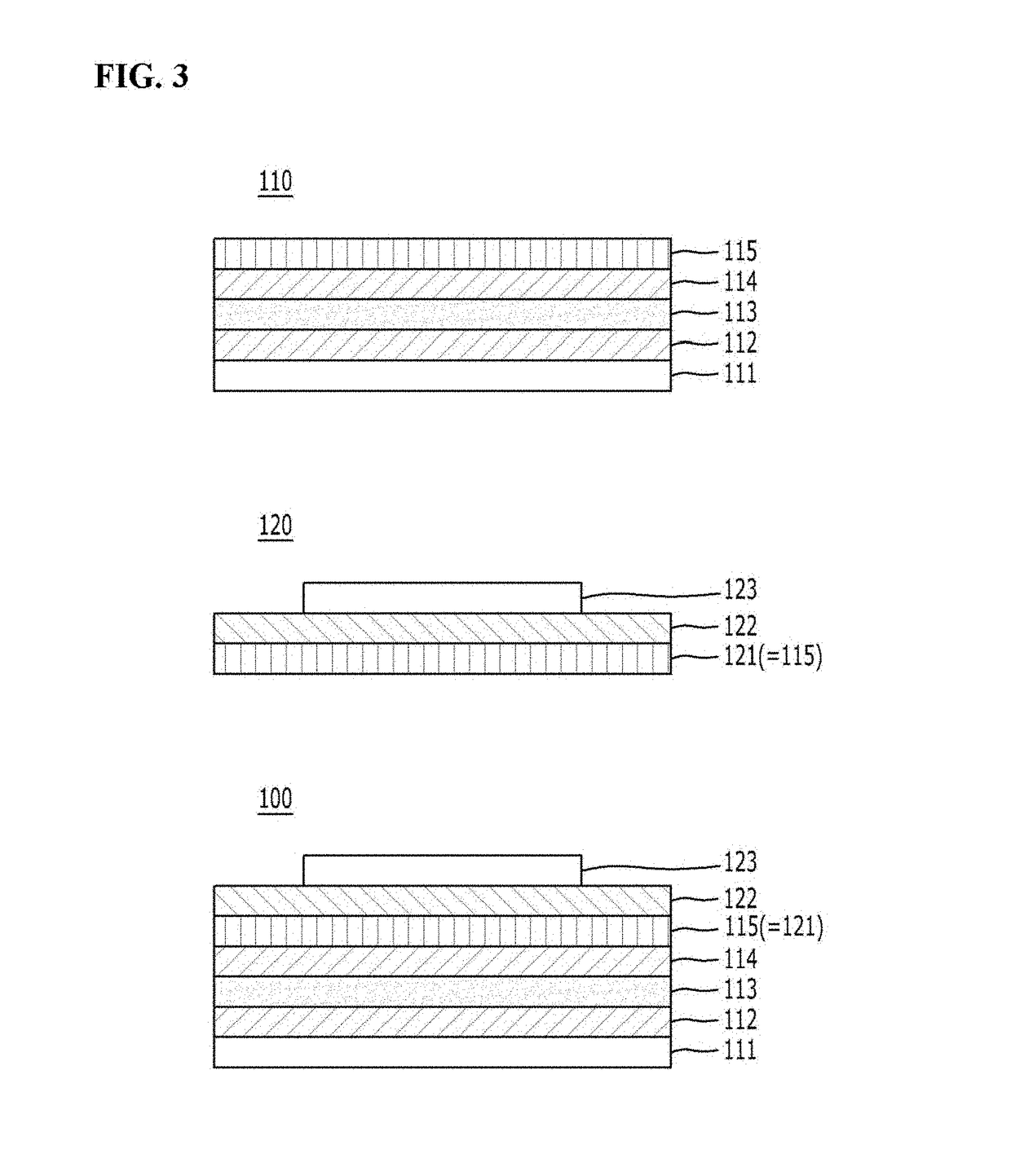
Composite structure for controlling absorptivity of radar and emissivity of infrared regions
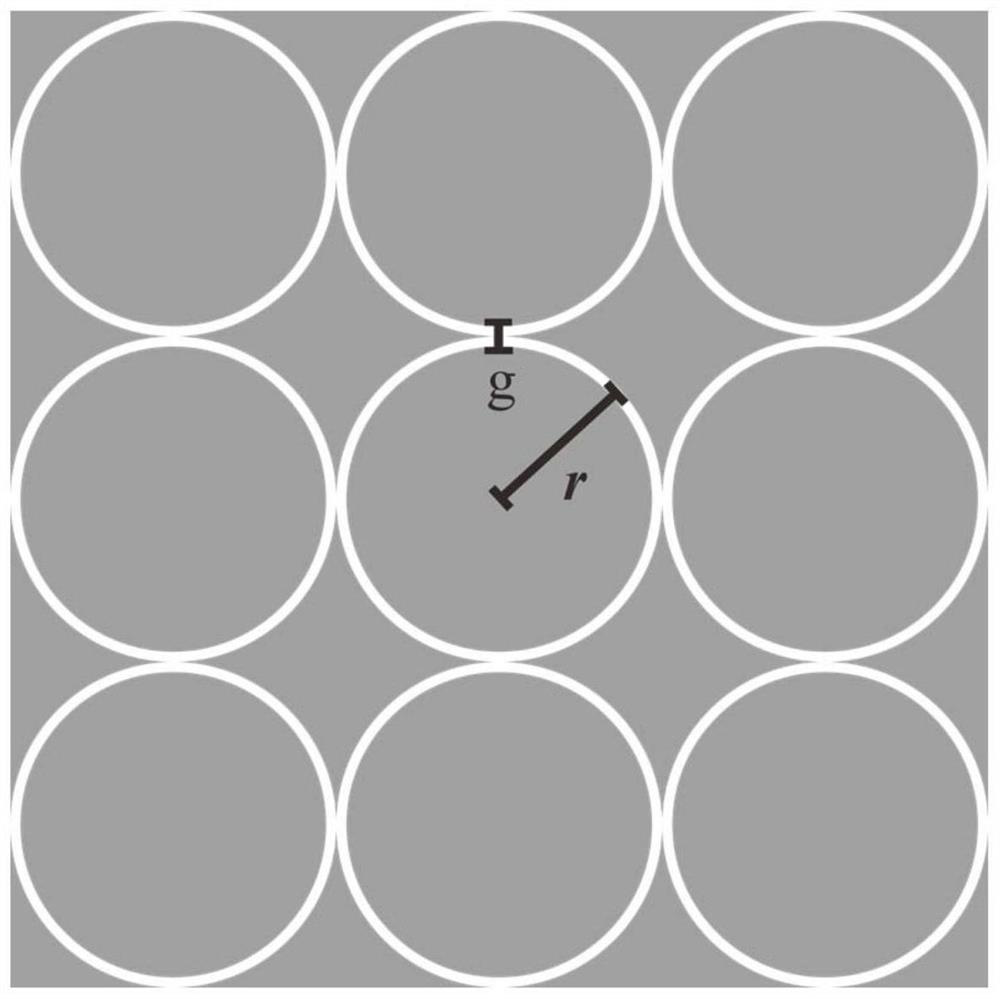
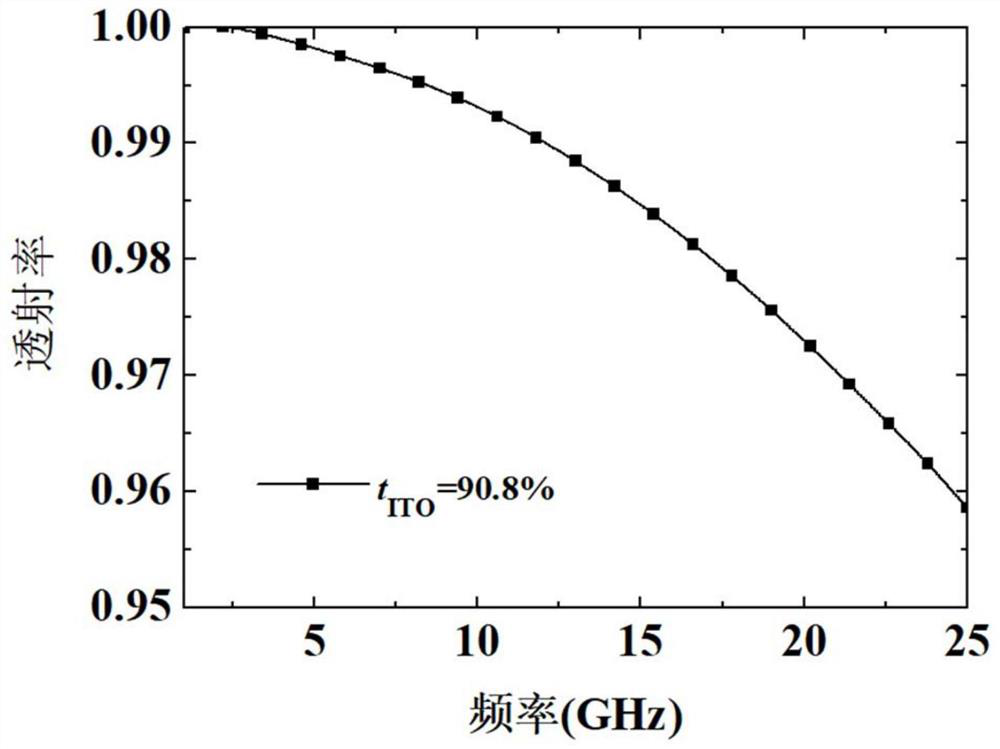
ActiveUS20180069319A1Improve anti-detection functionReduce the probability of detectionWave based measurement systemsProtective equipmentEmissivityRadar
A technique of adjusting absorptivity of radar waves and emissivity of infrared waves by controlling the waves of the radar and infrared regions using a structure formed of a meta-material. A composite structure for controlling absorptivity and emissivity includes: a first anti-detection unit; and a second anti-detection unit stacked on the first anti-detection unit, wherein the first anti-detection unit is an absorber for absorbing electromagnetic waves of a first range input from an outside of the first anti-detection unit, and the second anti-detection unit is a selective emitter for selectively blocking emission of electromagnetic waves of a second range and selectively allowing emission of electromagnetic waves of a third range among electromagnetic waves that can be emitted to an outside of the second anti-detection unit.
Owner:CENT FOR ADVANCED META MATERIALS
Unknown malicious traffic active detection system and method based on deep embedding
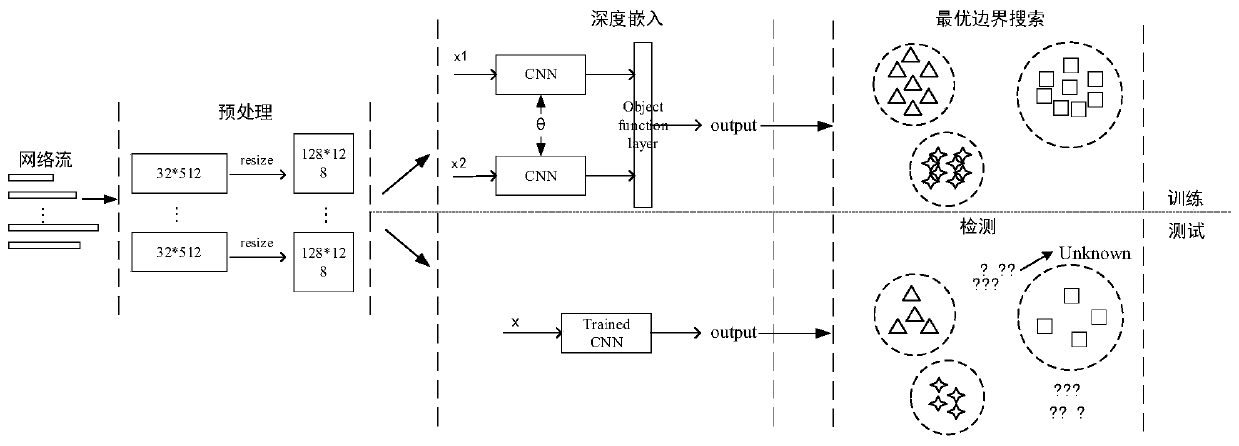
ActiveCN110808971ACompact distributionDiscrete distributionCharacter and pattern recognitionNeural architecturesEngineeringTest phase
The invention discloses an unknown malicious traffic active detection system and method based on deep embedding. The system comprises a preprocessing module, a deep embedding module, an optimal boundary search module and a detection module. The preprocessing module represents the network flows with different lengths in each application as a flow matrix with a fixed size; the deep embedding moduletakes the flow matrix output by the preprocessing module as input in a training stage and learns nonlinear mapping by training a twin convolutional neural network, so that in an embedding space afterthe nonlinear mapping, network flow generated by the same application is distributed more compactly, and network flow generated by different applications is distributed more discretely; in a test stage, a to-be-identified flow matrix is mapped to an embedding space by using the trained convolutional neural network; the optimal boundary search module is used for searching an optimal classificationhyperplane for the network flow of each known category application in the embedded space, and finally a classifier is constructed; and the detection module is used for judging whether the network flowto be identified is from an unknown malicious application or not based on the classifier obtained by the optimal boundary search module.
Owner:INST OF INFORMATION ENG CAS
Webshell detection method based on weighted fuzzy hash
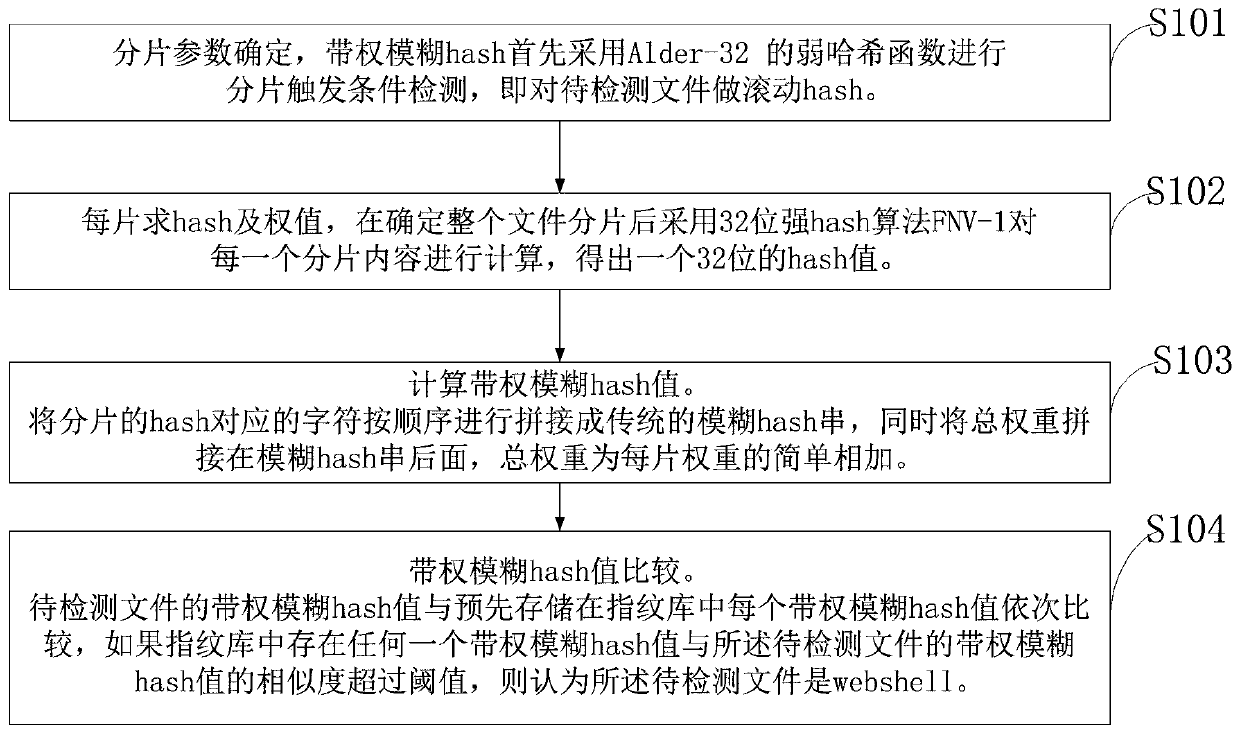
ActiveCN110034921AImprove detection accuracyAccommodates large variations in sizeEncryption apparatus with shift registers/memoriesTheoretical computer scienceData mining
The invention belongs to the technical field of network space security, and discloses a webshell detection method and system based on a weighted fuzzy hash algorithm. A file to be detected is fragmented, the hash and weight of each fragment are solved, the weight is given to each fragment, the core fragment with the danger function is provided with a large weight, the information entropy of each fragment is considered at the same time, and the larger the information entropy value is, the smaller the given weight is; the hash of each fragment is spliced into a fuzzy hash string, and a total weight value is calculated to obtain a weighted fuzzy hash value; and the weighted fuzzy hash value of the to-be-detected file is compared with the weighted fuzzy hash value of each webshell pre-stored in the fingerprint database in sequence. Compared with a traditional fuzzy Hash algorithm, the method can effectively adapt to the situation that the size of a detected object changes greatly, has goodadaptability, greatly improves the detection accuracy of a variety sample, and improves the anti-interference performance.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
Method and radar apparatus for detecting target object
InactiveCN102590807AReduce distractionsReduce the probability of being mistaken for an actual object to detectRadio wave reradiation/reflectionRadarPhysics
Disclosed is a method and a radar apparatus for transmitting a transmission signal through a changing transmission frequency band in order to avoid signal interference, thereby exactly detecting a target object without misrecognition.
Owner:HL MANDO CORP
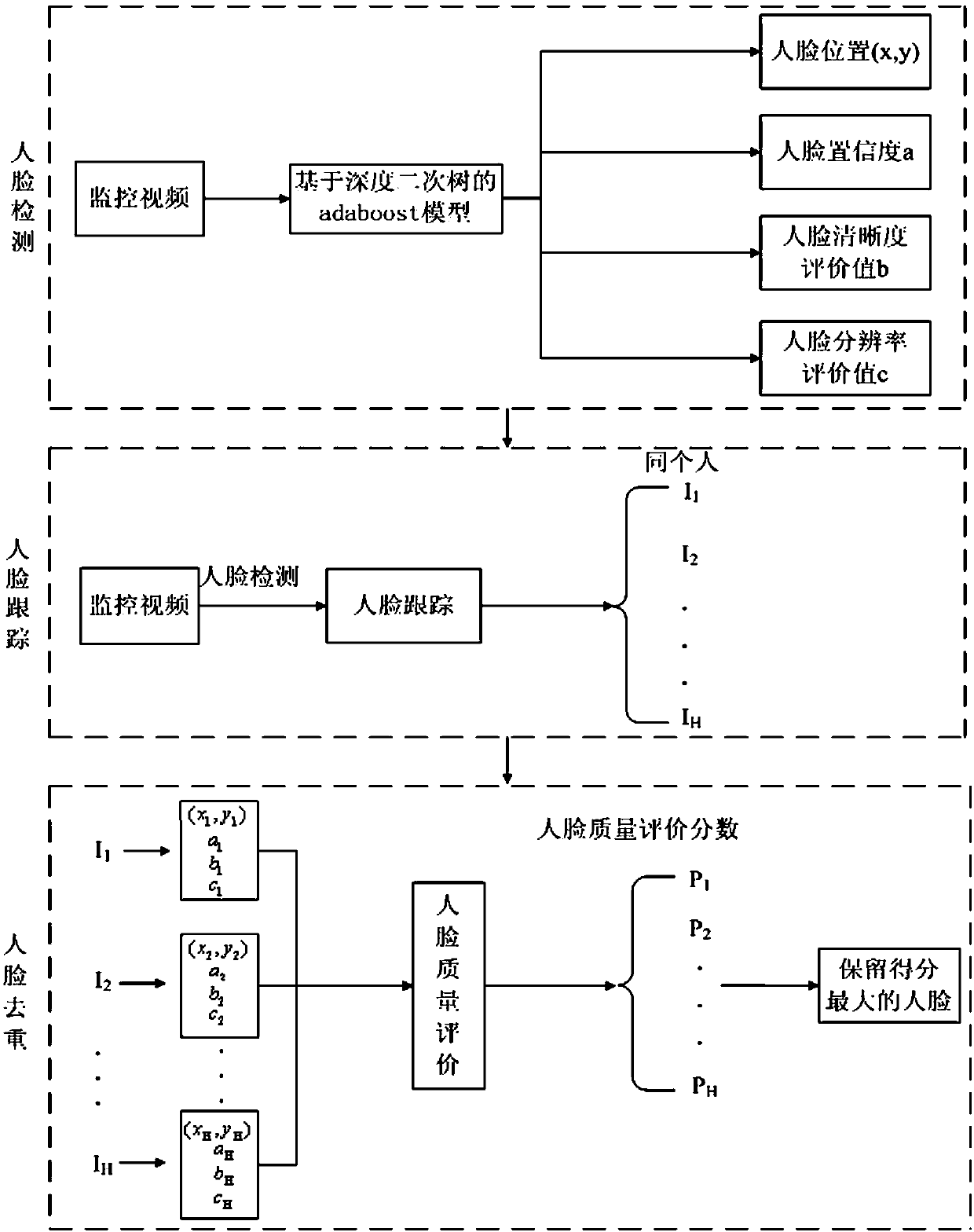
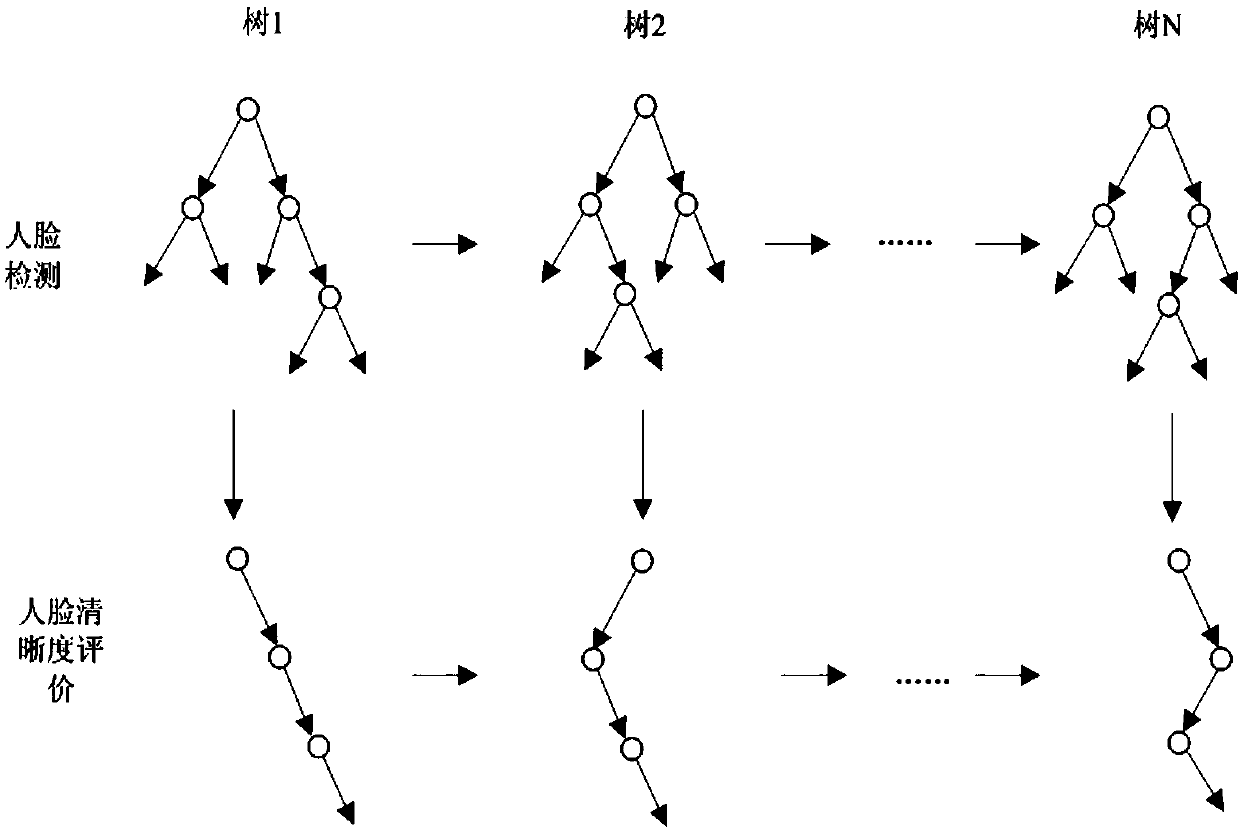
Face deduplication method based on deep quadratic tree in video monitoring
ActiveCN108960047AImprove efficiencyHigh false positive rateCharacter and pattern recognitionPattern recognitionVideo monitoring
The invention discloses a face deduplication method based on a deep quadratic tree in video monitoring. The method comprises the steps of (1) a face detection part including the steps of preparing positive and negative face samples, performing face detection on moving pedestrians in a monitoring video by using a trained deep quadratic tree model, and obtaining a face position, face confidence, face sharpness and the resolution of a face image, (2) face tracking part including the steps of performing face tracking according to an obtained face position of an initial frame and obtaining multiplefaces of the same person, and (3) face deduplication including the steps of determining the image quality of each face by using a face quality evaluation method for a face sub set of the same personand then selecting a face with best quality according to an evaluation value. A face quality evaluation score is obtained by weighting three indicators including face confidence, the face sharpness and the resolution of a face image. According to the method, the accuracy of face recognition can be effectively improved.
Owner:CHINA JILIANG UNIV
MP3 self-adaption hidden writing method based on compressed domain
ActiveCN106228981AReduce the probability of detectionImprove securitySpeech recognitionPattern recognitionTwo step
The invention relates to the field of multimedia information safety and specifically relates to a MP3 self-adaption hidden writing method based on a compressed domain. The method comprises the two steps of embedding secret information and extracting secret information. According to the method, a frequency domain coefficient of the original sound signal after being converted and quantitatively coded through a sub-band filter is taken as a basic unit for hidden writing and an information encoding tool Syndrome Trellis Codes (STC) is utilized to self-adaptively embed information and realize correct information extraction. A large number of tests prove that the hidden writing method, compared with the present audio hidden writing method based on the frequency domain modification, has higher embedding volume and safety. Thus, the method provided by the invention has important significance in the application field including secret communication and the like.
Owner:SUN YAT SEN UNIV
Apparatus and method for cone beam volume computed tomography mammography
InactiveCN100362964CEasy to detectShow wellComputerised tomographsTomographyProjection imageRadiation
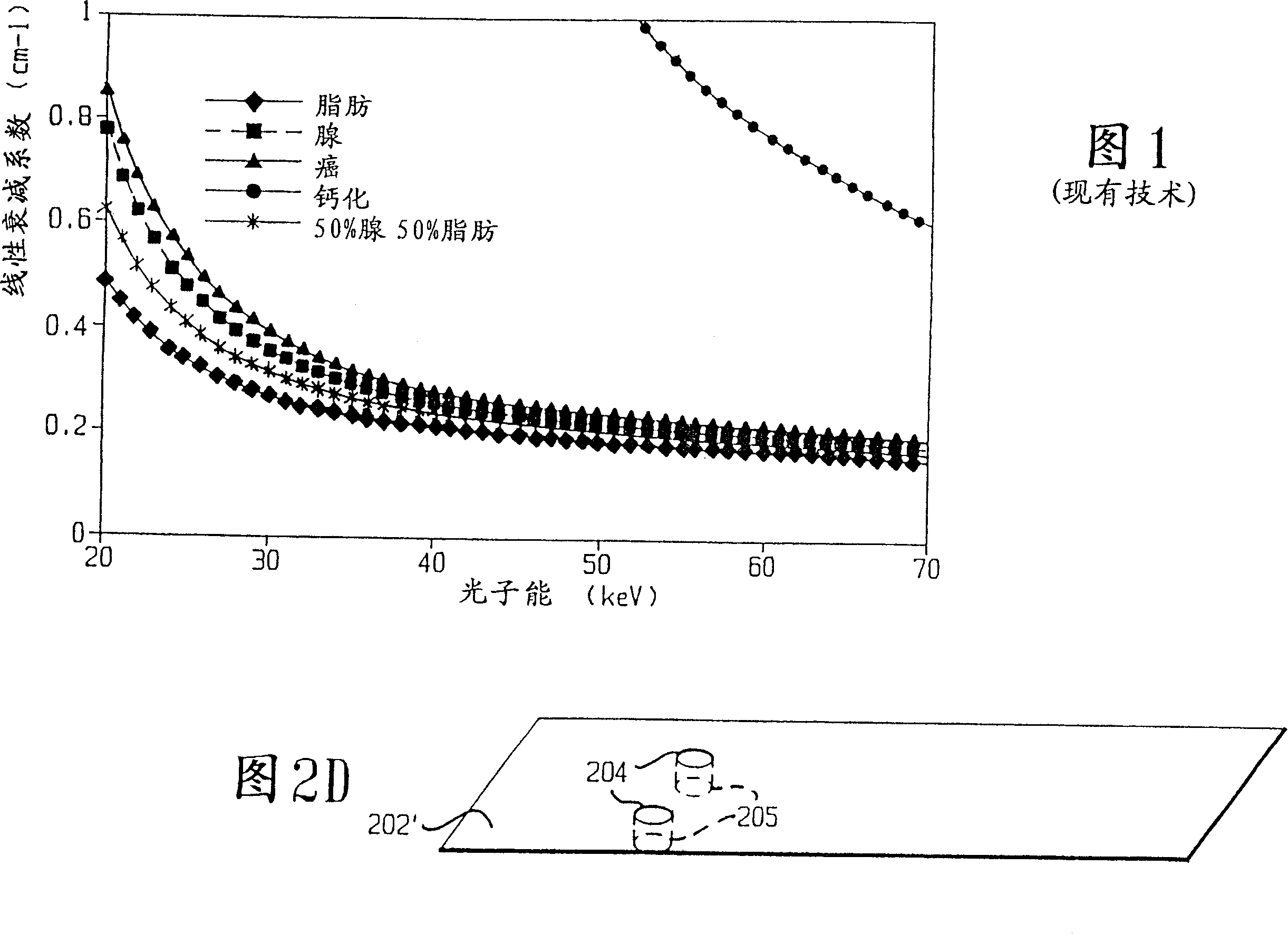
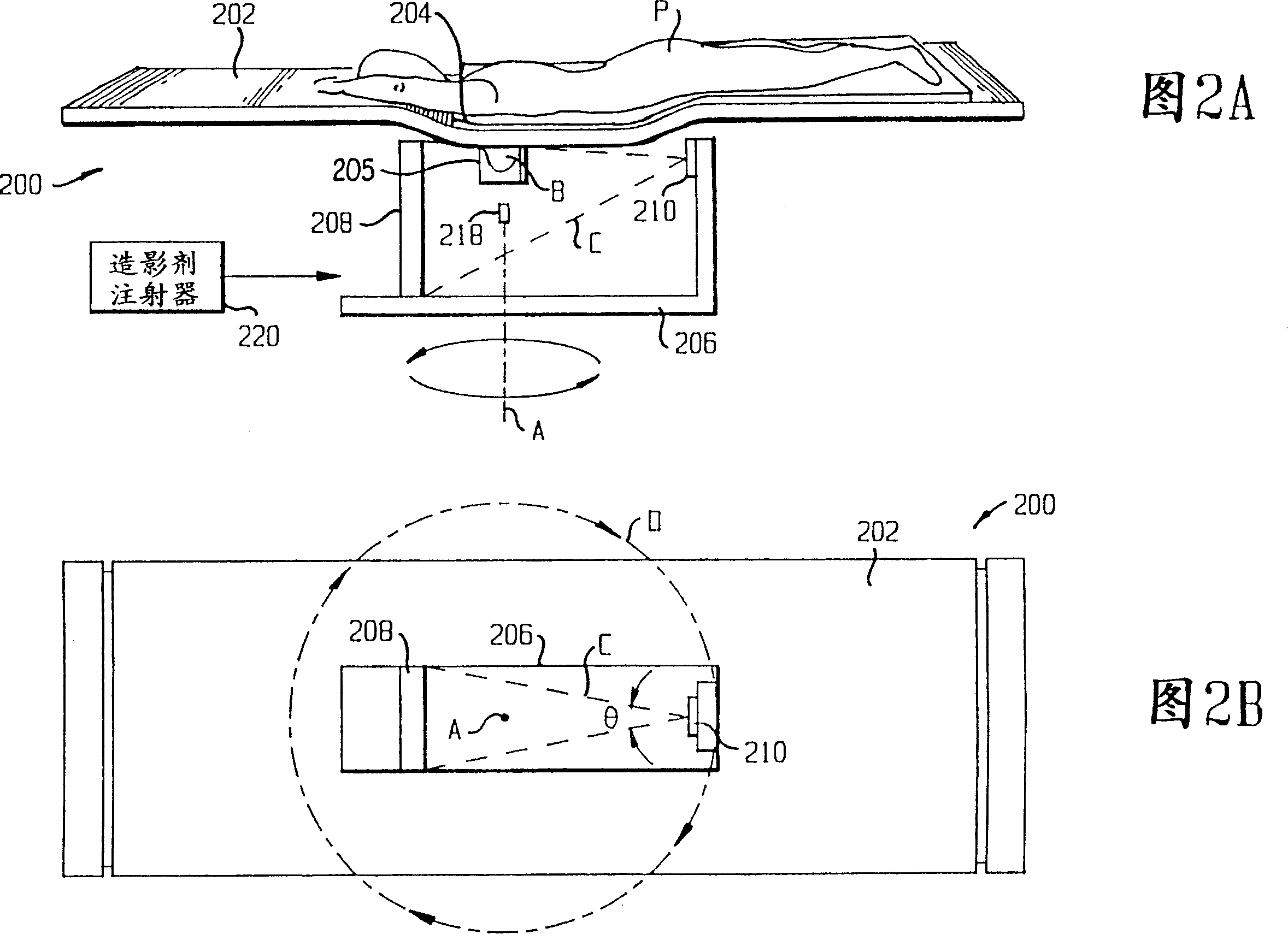
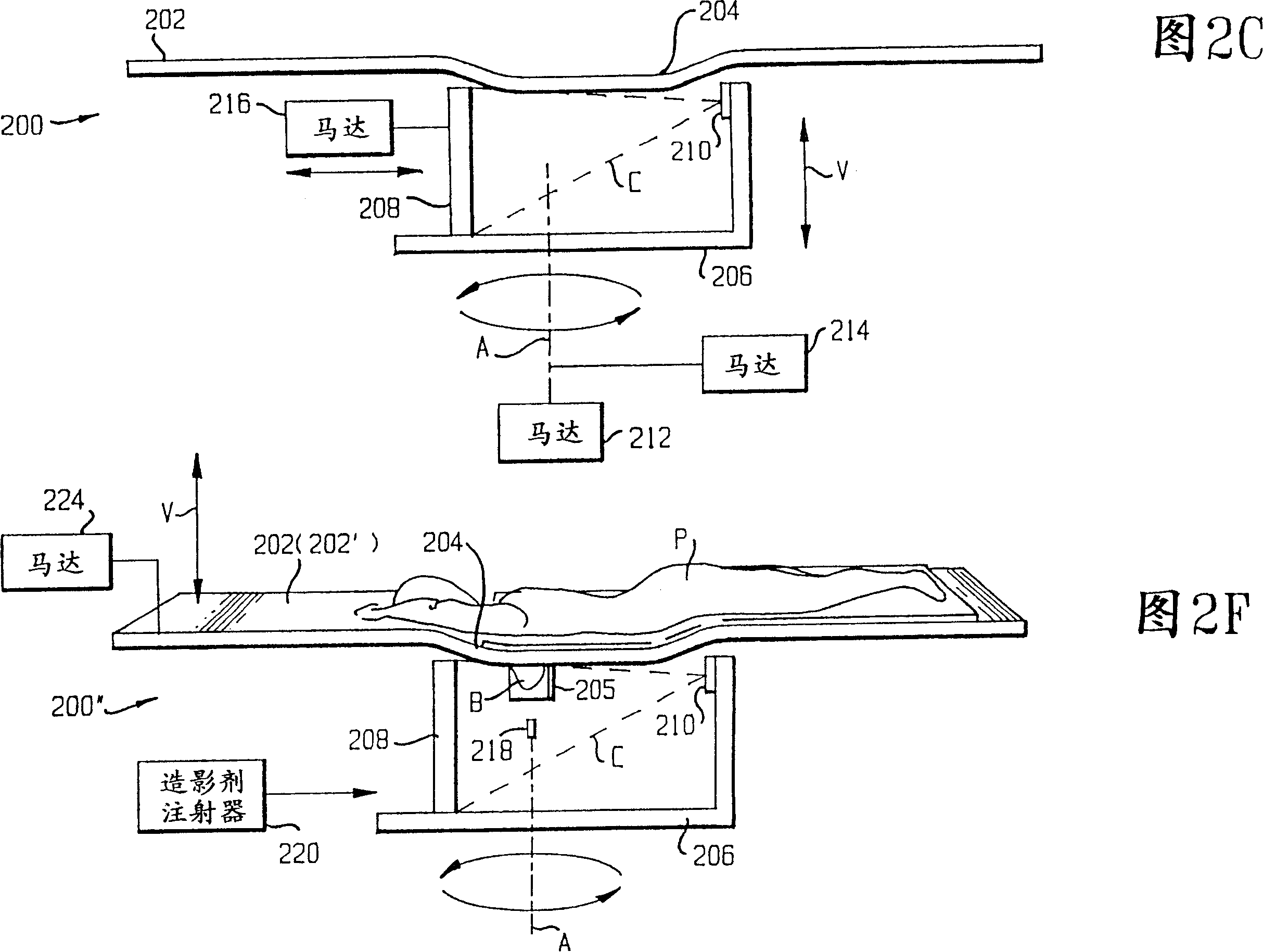
A device (200) for producing a three-dimensional tomographic mammography image of a breast (B) of a patient (P), the device (200) presenting: a gantry frame (206); at least one motor (212, 214), for moving the gantry frame (206) to form a data acquisition geometry; a source (210) of radiation (C) attached to the gantry frame (206) to move with the gantry frame (206); a flat panel detector (208) attached to the gantry frame (206) to move with the gantry frame (206), the flat panel detector (208) being disposed in a path of the radiation (C); and a support (202) comprising a table (202) on which the patient (P) rests while projection images of the breast (B) are taken; the table (202) presents a through hole (204) so that the breast (B) to be scanned descends through the hole (204) in the table (202) into a breast holder (205) and the through hole (204) is disposed relative to the source (210) of radiation (C) and the flat panel detector (208) so that the breast (B) to be scanned only is disposed between the source (210) of radiation (C) and the flat panel detector (208).
Owner:UNIVERSITY OF ROCHESTER
Systems and Methods for Illumination and Observation
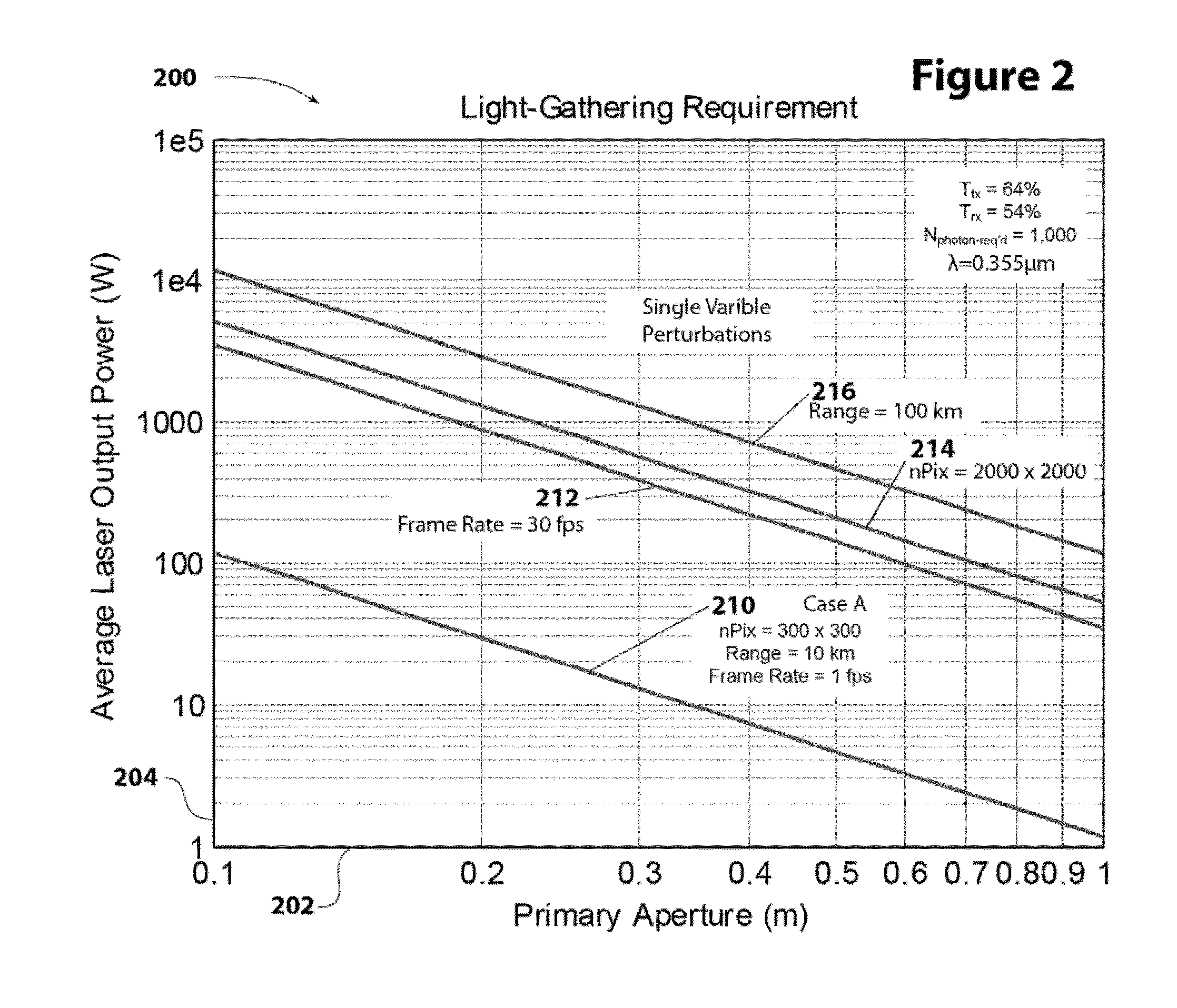
InactiveUS20150358556A1Reduce system complexityLow costAircraft componentsTelevision system detailsFluenceUltraviolet
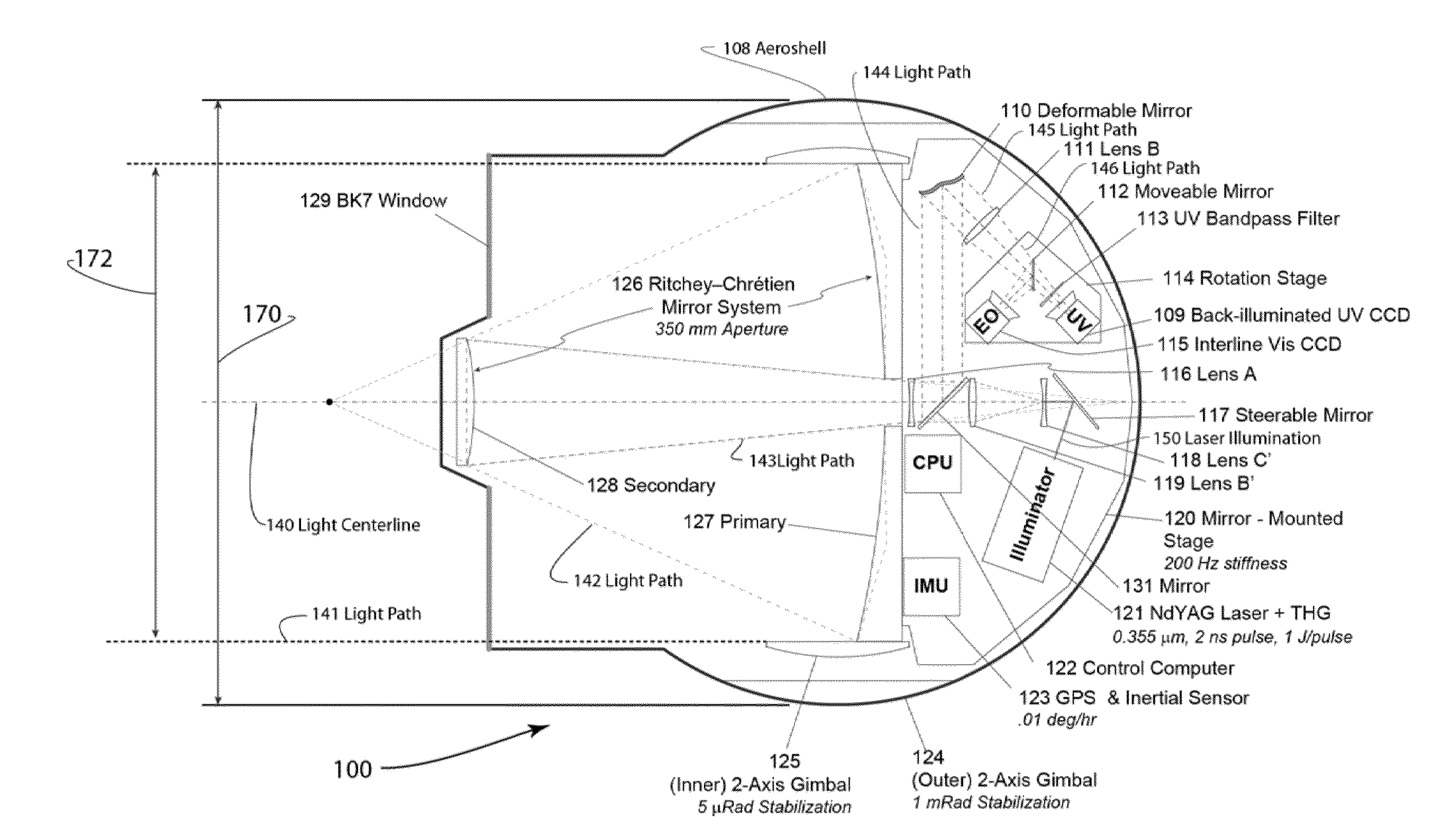
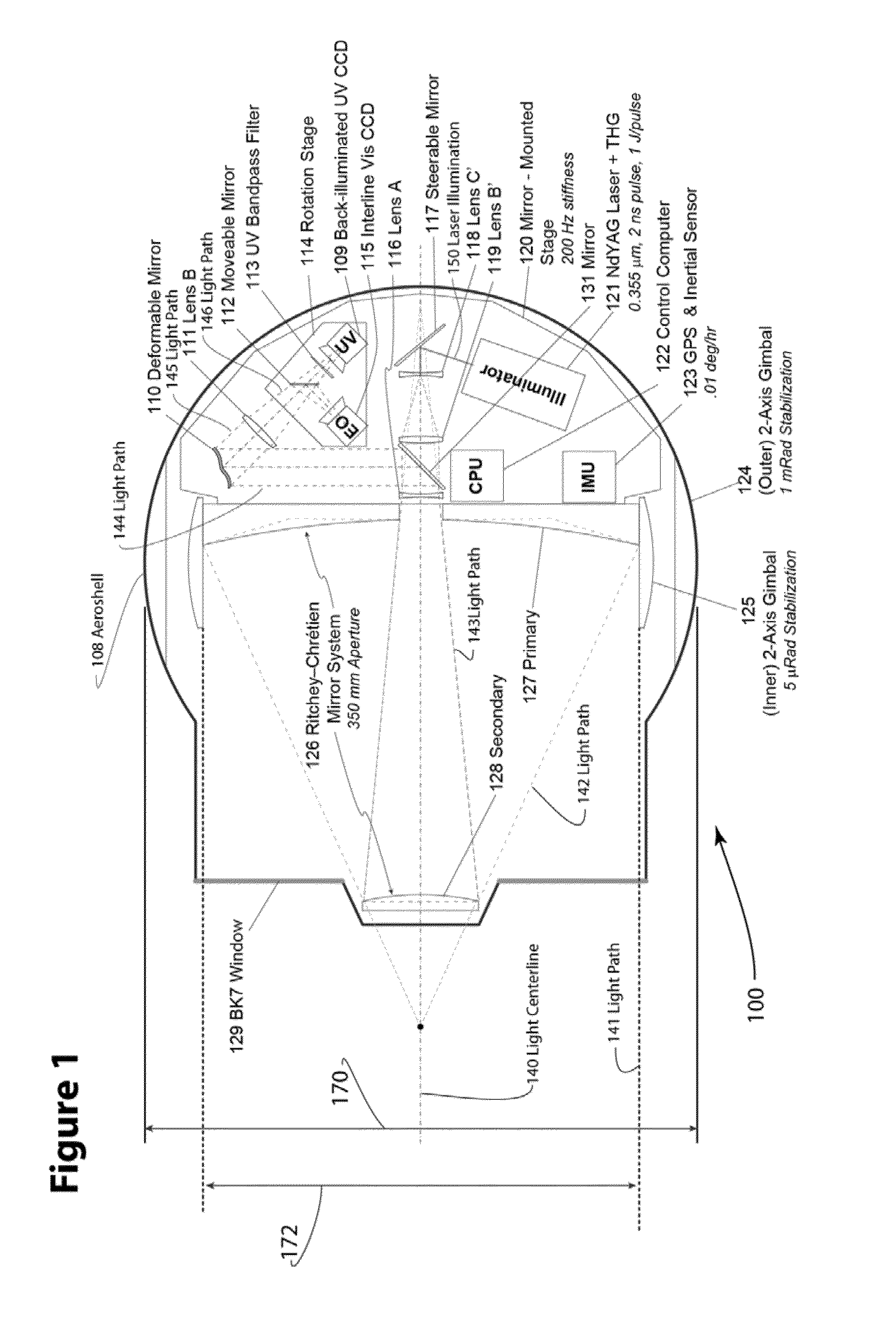
An aerial surveillance and reconnaissance system includes a gimbal-stabilized ISR imaging sensor with 0.8-1.2 microradian optical resolution, using pulsed ultraviolet laser (0.330-0.380 micrometer wavelength) radiation to illuminate the observed target, and a narrow-band-pass filter at the focal plane detector to remove light at frequencies other than the illuminating frequency. Preferred sensors can be operated in a snapshot mode using intermittent illuminating pulses, with timing of the pulses selected for minimum detectability based on observations made with a lower-resolution sensor, or in a video-mode with illuminating pulses selected to generate full-motion video at operator-selectable frame rates. Some sensor embodiments may further combine the UV system described above with conventional daylight optical and sensor systems, though alternative arrangements could also include an IR sensor as well (either using a common aperture with the UV system or with a separate set of light-gathering optics).
Owner:KAREM AIRCRAFT INC
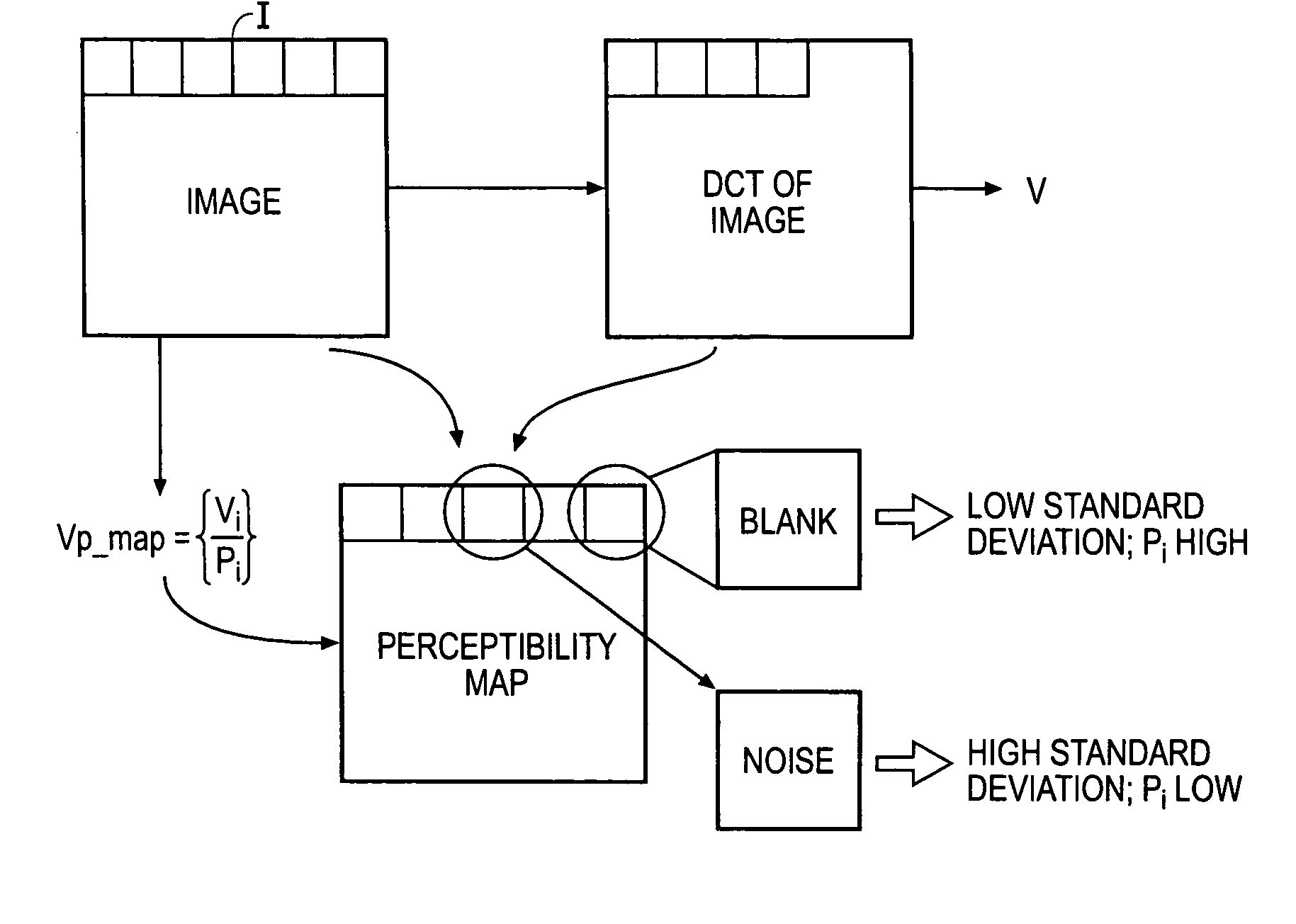
Data processing apparatus and method
InactiveUS7302577B2Increase likelihoodEasily partitionUser identity/authority verificationCharacter and pattern recognitionData processingAlgorithm
A watermarking system comprises an encoding data processor operable to generate at least one marked version of an original item of material by introducing one of a predetermined set of code words into a copy of the original material item. The encoding processor comprises a code word generator operable to form the code word by generating a plurality of code word coefficients, and an encoder operable to combine the code word coefficients with the material item, and an adaptation processor. The adaptation processor is operable to adapt the strength of the code word coefficients or the material item samples in accordance with a relative sensitivity of the material item samples to carry the code word coefficients. The strength of the watermark is therefore adapted in accordance with the sensitivity of the material item to carry watermark code word coefficients. As a result there is a reduced likelihood of an attacker identifying parts of the material item to which the watermark code word has been added. A likelihood of a successful attack is thereby reduced whilst maintaining a desired false negative detection probability.The watermarking system finds particular application in identifying a point of distribution of pirate copies of video material generated by capturing the watermarked image, using, for example, a camcorder in a cinema.
Owner:SONY UK
Invisible patch
PendingCN114179466AAchieving Compatible StealthEffective absorptionSynthetic resin layered productsCamouflage devicesEngineeringMechanical engineering
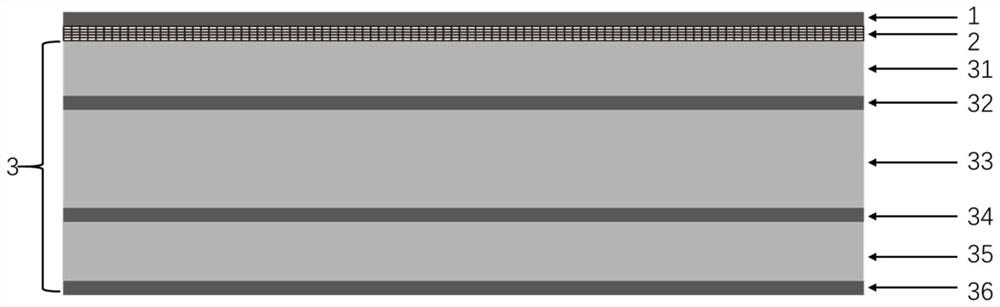
The invention relates to a stealth patch which comprises an infrared stealth layer (1) and a radar absorption layer (3) and further comprises a visible light camouflage layer (2), and the infrared stealth layer (1) and the radar absorption layer (3) are located on the two sides of the visible light camouflage layer (2). According to the invention, visible light, infrared and radar compatible stealth can be realized.
Owner:CHINA ACADEMY OF SPACE TECHNOLOGY
Image re-sampling detection based on Markov process and Gabor filtering
InactiveCN105654089AReduce the probability of detectionRobustCharacter and pattern recognitionPattern recognitionImage extraction
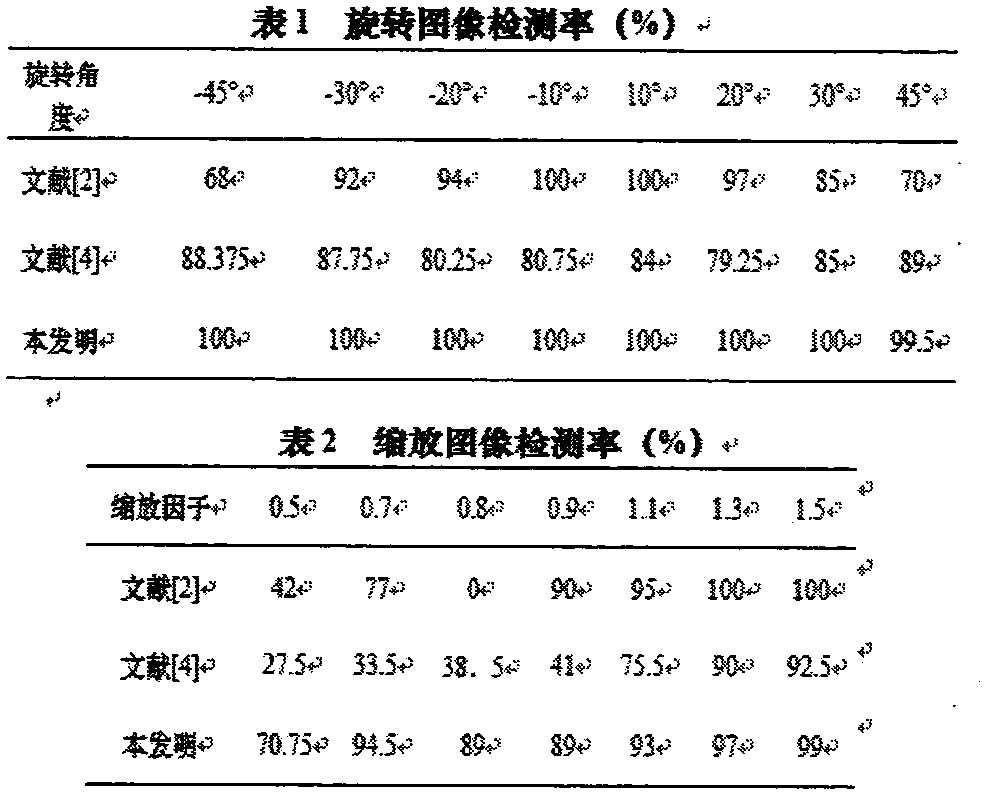
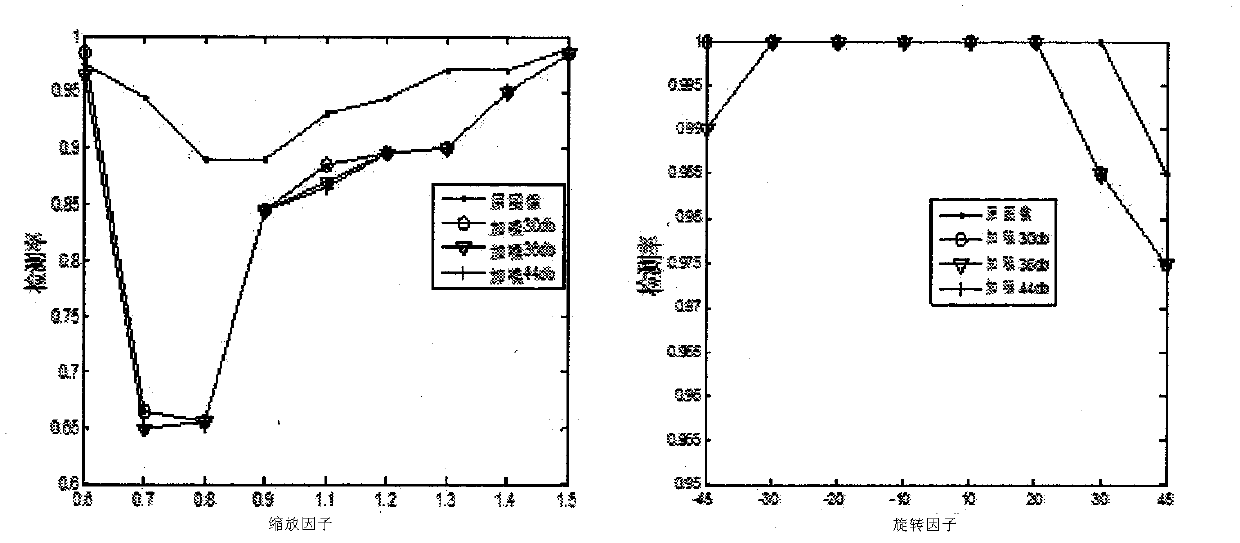
An Image re-sampling tampering detection algorithm is one of the important methods for image tampering evidence collection. According to the invention, an image is detected mainly based on condition state transition probability matrixes in a Markov process and the texture features in a Gabor filter. After an image is re-sampled, the correlation between adjacent DCT coefficients changes. However, the transition probability matrixes can well describe the change in DCT coefficients and surrounding coefficients. Thus, transition probability matrixes in four directions are extracted as Markov features. The detection rate of the algorithm fluctuates greatly when comes to texture images of different complexity. Thus, a Gabor filter group is adopted to extract the texture features of the image and perform two-dimensional discrete Fourier transform to get the final texture features of the image, and then, an SVM is adopted to train and classify the two types of features. With the algorithm of the invention, scalable images and rotary images can be well detected, and detection of rotary images is of high robustness.
Owner:JIANGNAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com