Webshell detection method based on weighted fuzzy hash
A detection method and fuzzy technology, applied in encryption devices with shift registers/memory, digital transmission systems, electrical components, etc., can solve the problems of large differences in webshell size, poor adaptability, and poor detection effects, etc., to achieve Improve detection accuracy, improve anti-interference, and good adaptability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0076] In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the embodiments. It should be understood that the specific embodiments described herein are only used to explain the present invention, but not to limit the present invention.
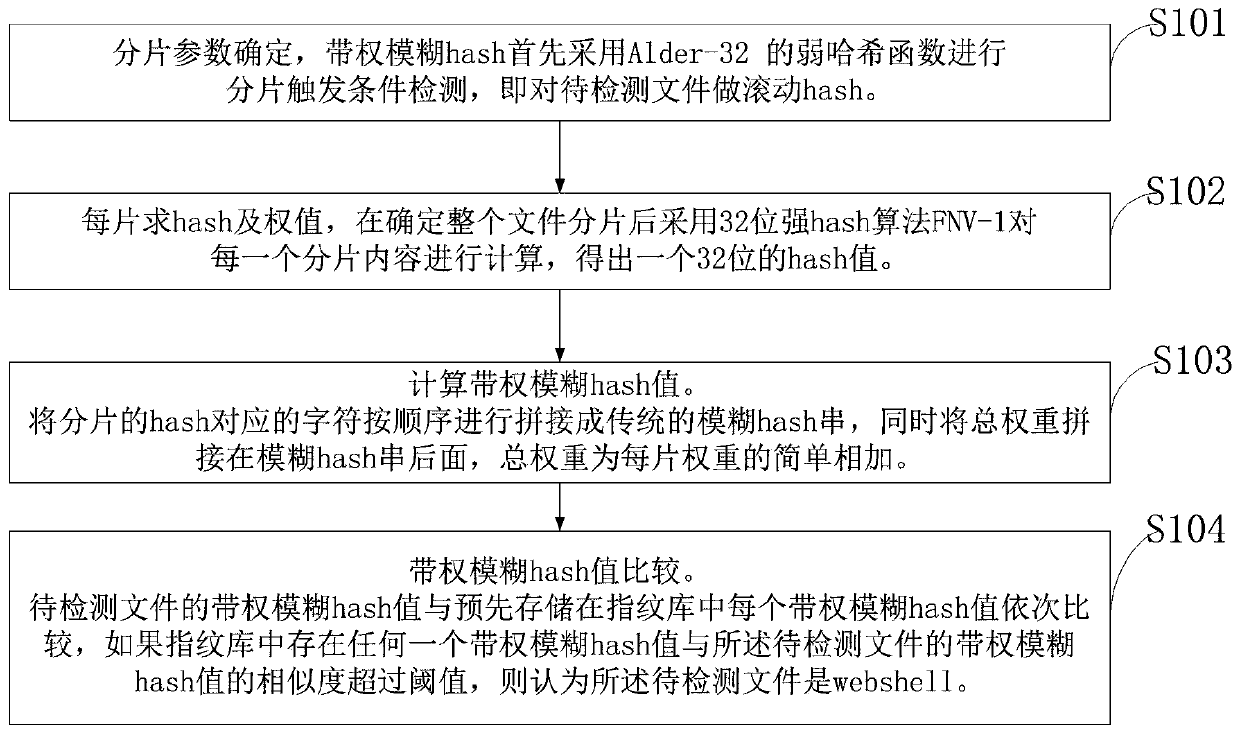
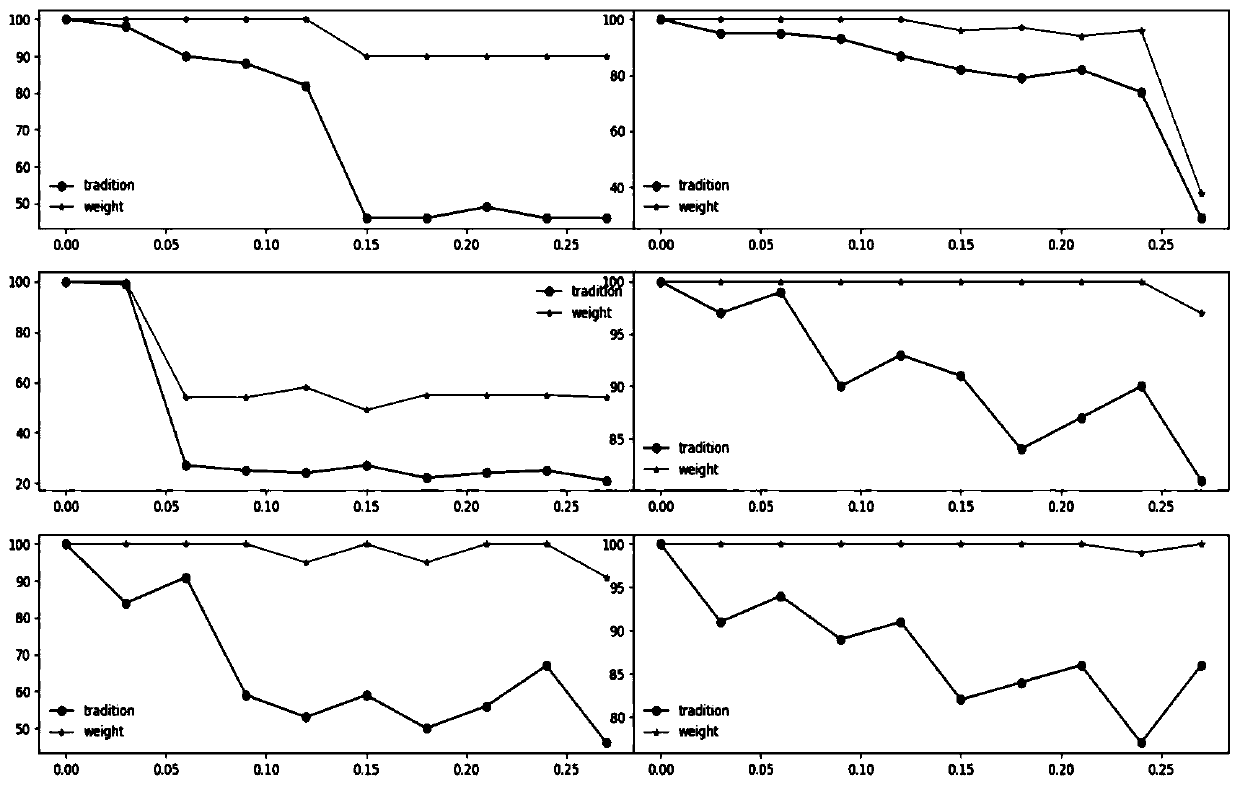
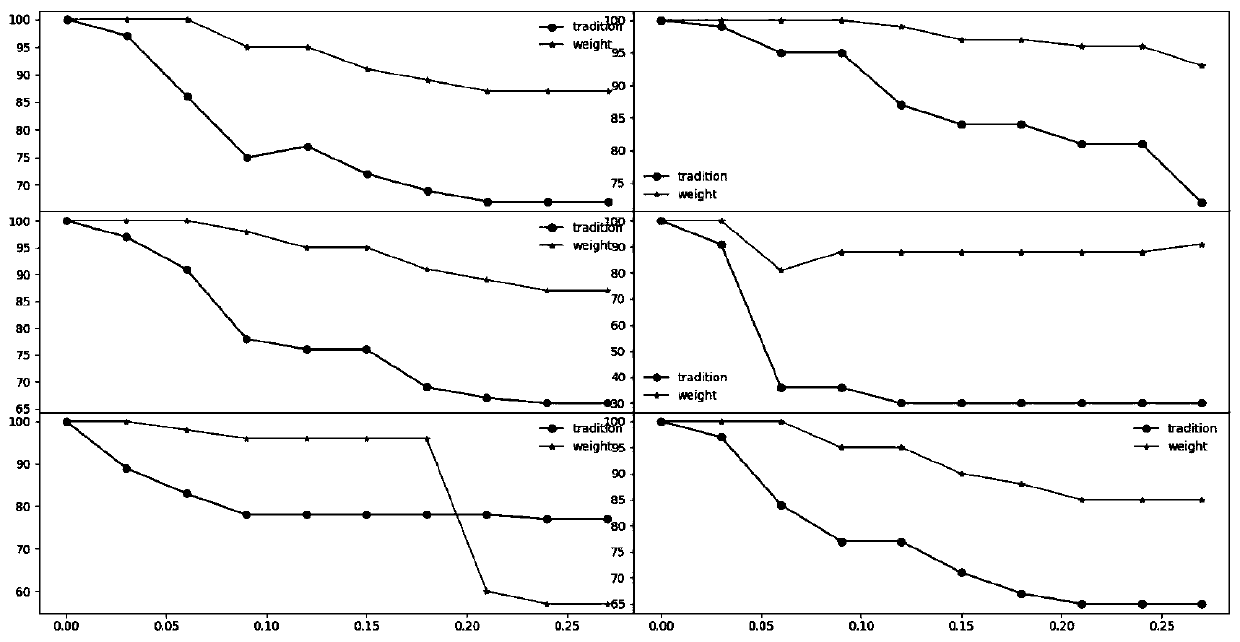
[0077]In the existing technology, the traditional fuzzy hash algorithm can only resist a certain range of disturbances, generally within 6%, but for a larger range of redundant additions (over 20%), its detection effect becomes very poor, and its adaptability is not good . Since the size of webshells varies greatly, changes in small webshell files can easily exceed the fuzzy hash detection range. The traditional fuzzy hash algorithm is a universal algorithm for text similarity comparison. As a text with special functions, the key difference between webshell and ordinary text is the use of dangerous functions. The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com