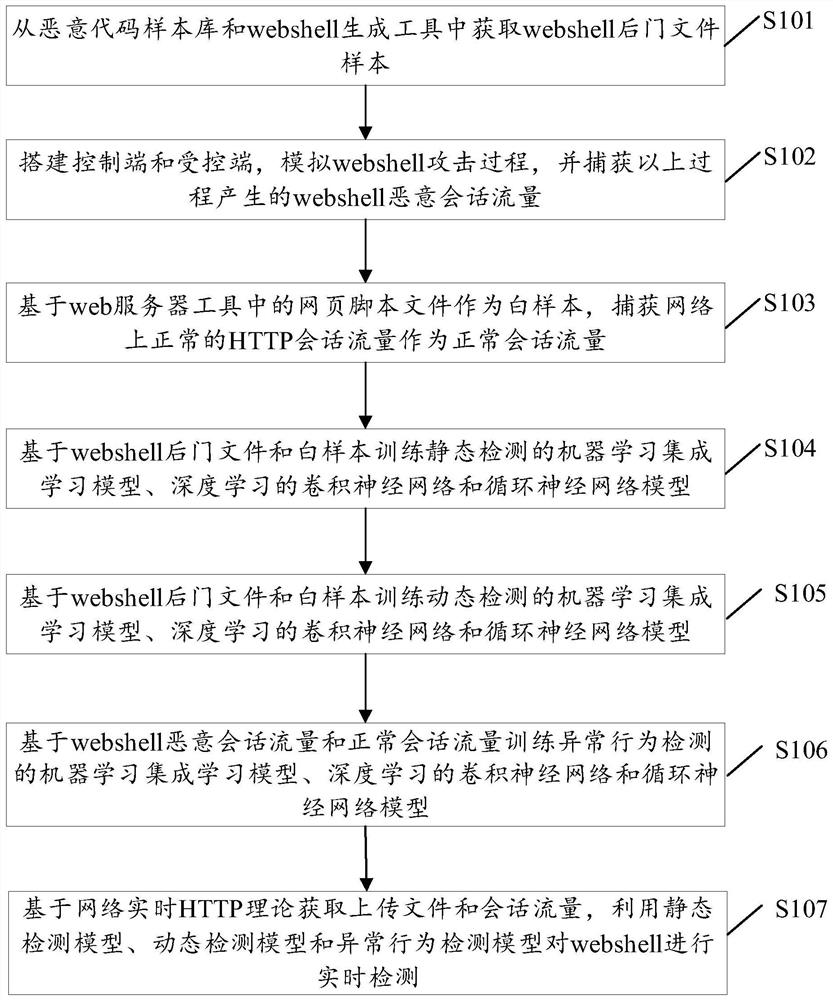
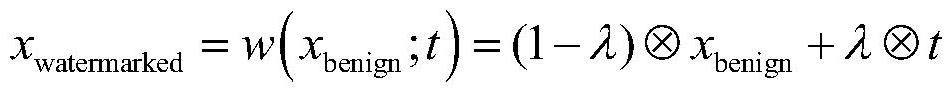Patents
Literature
181 results about "Backdoor" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A backdoor is a typically covert method of bypassing normal authentication or encryption in a computer, product, embedded device (e.g. a home router), or its embodiment (e.g. part of a cryptosystem, algorithm, chipset, or even a "homunculus computer" —a tiny computer-within-a-computer such as that found in Intel's AMT technology). Backdoors are most often used for securing remote access to a computer, or obtaining access to plaintext in cryptographic systems. From there it may be used to gain access to privileged information like passwords, corrupt or delete data on hard drives, or transfer information within autoschediastic networks.
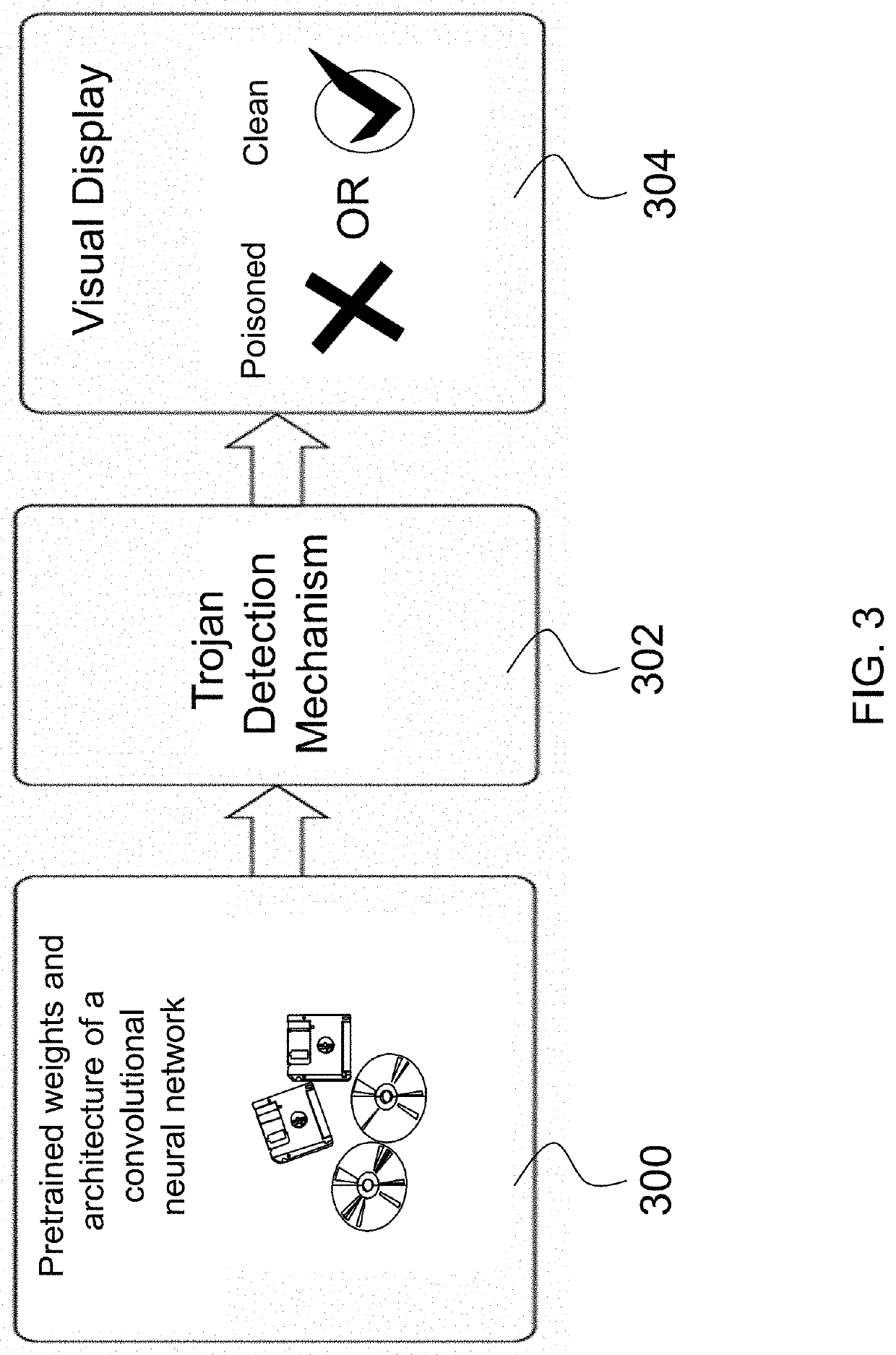
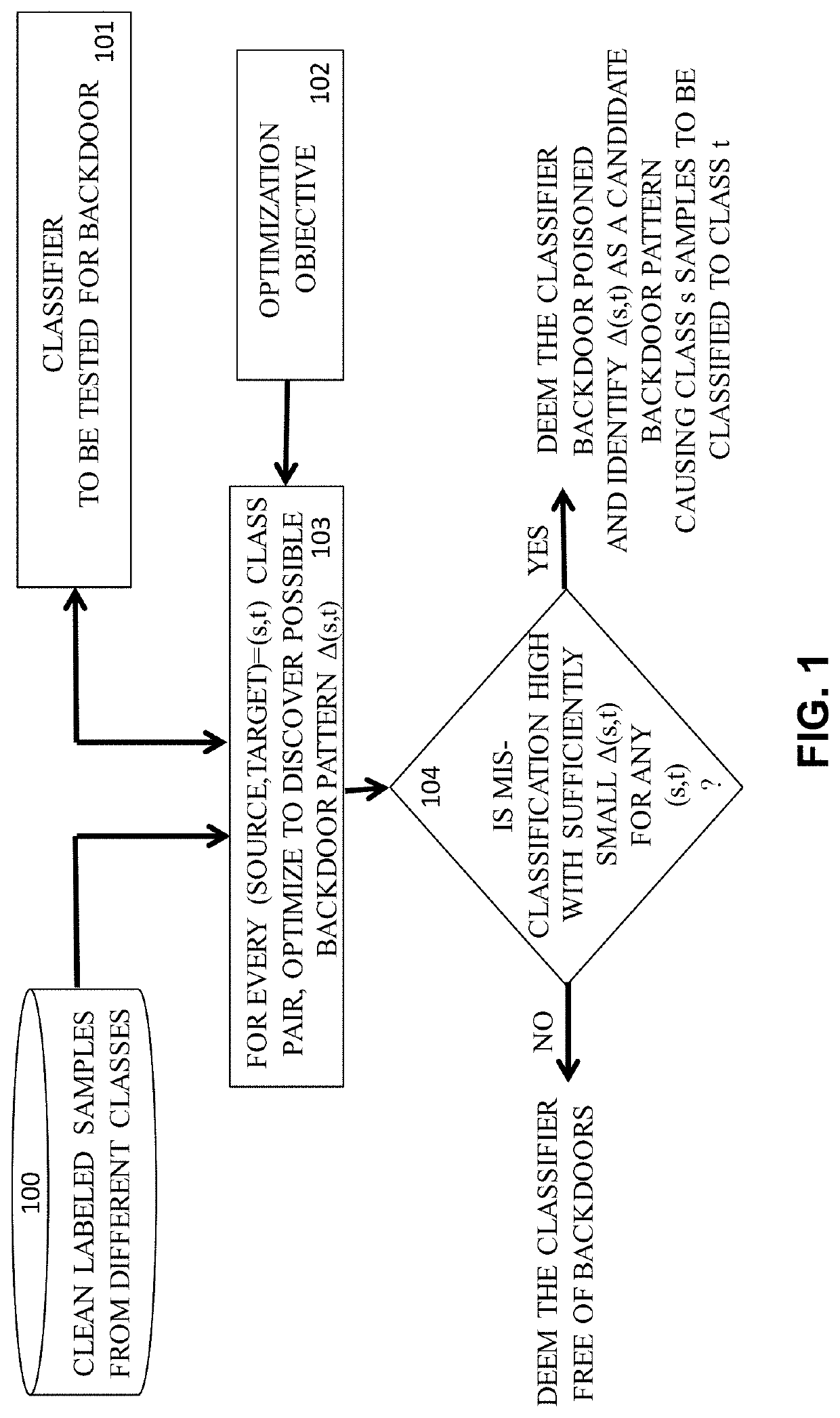
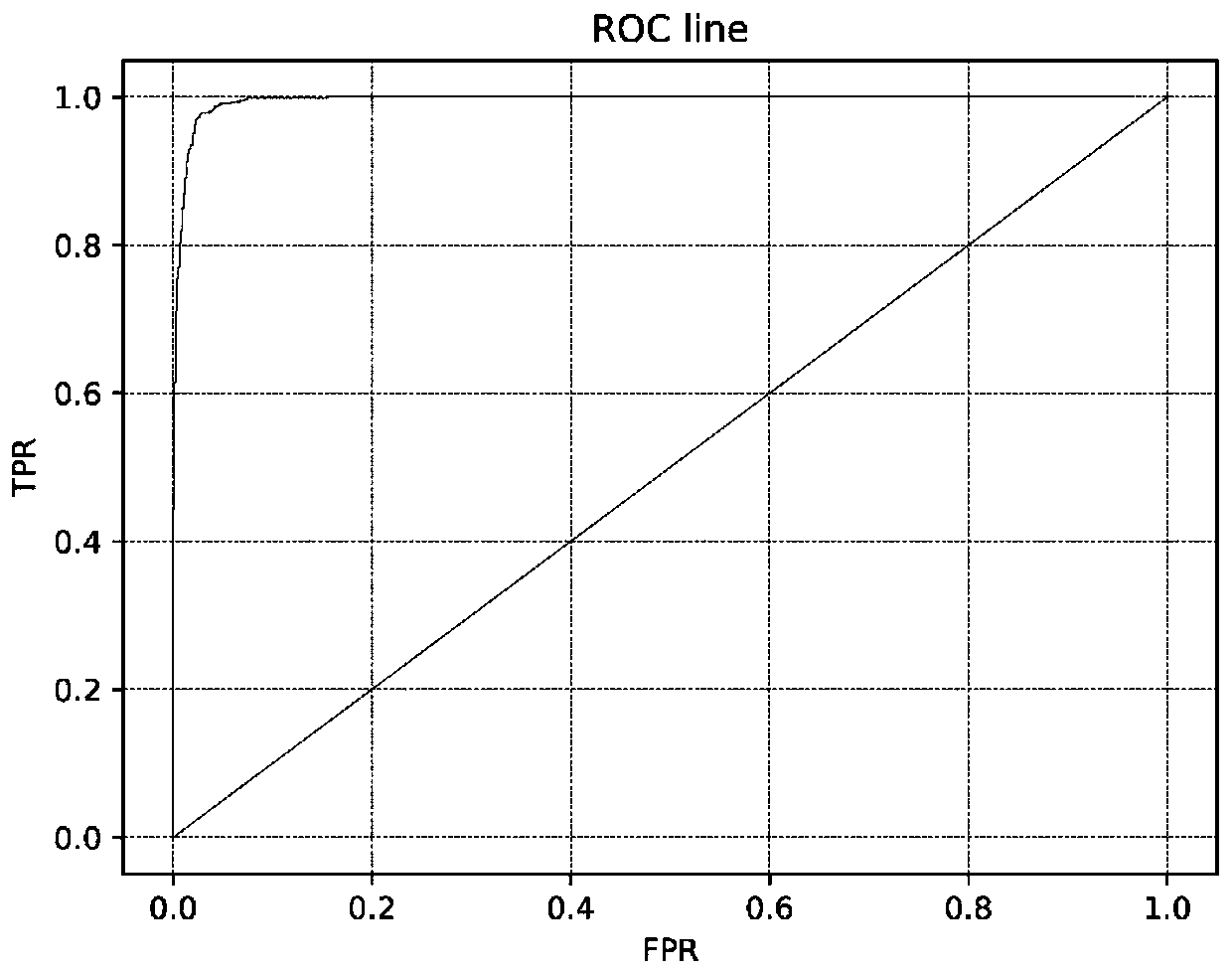
Post-Training Detection and Identification of Human-Imperceptible Backdoor-Poisoning Attacks
ActiveUS20200380118A1Method can be appliedPlatform integrity maintainanceNeural learning methodsData setAlgorithm
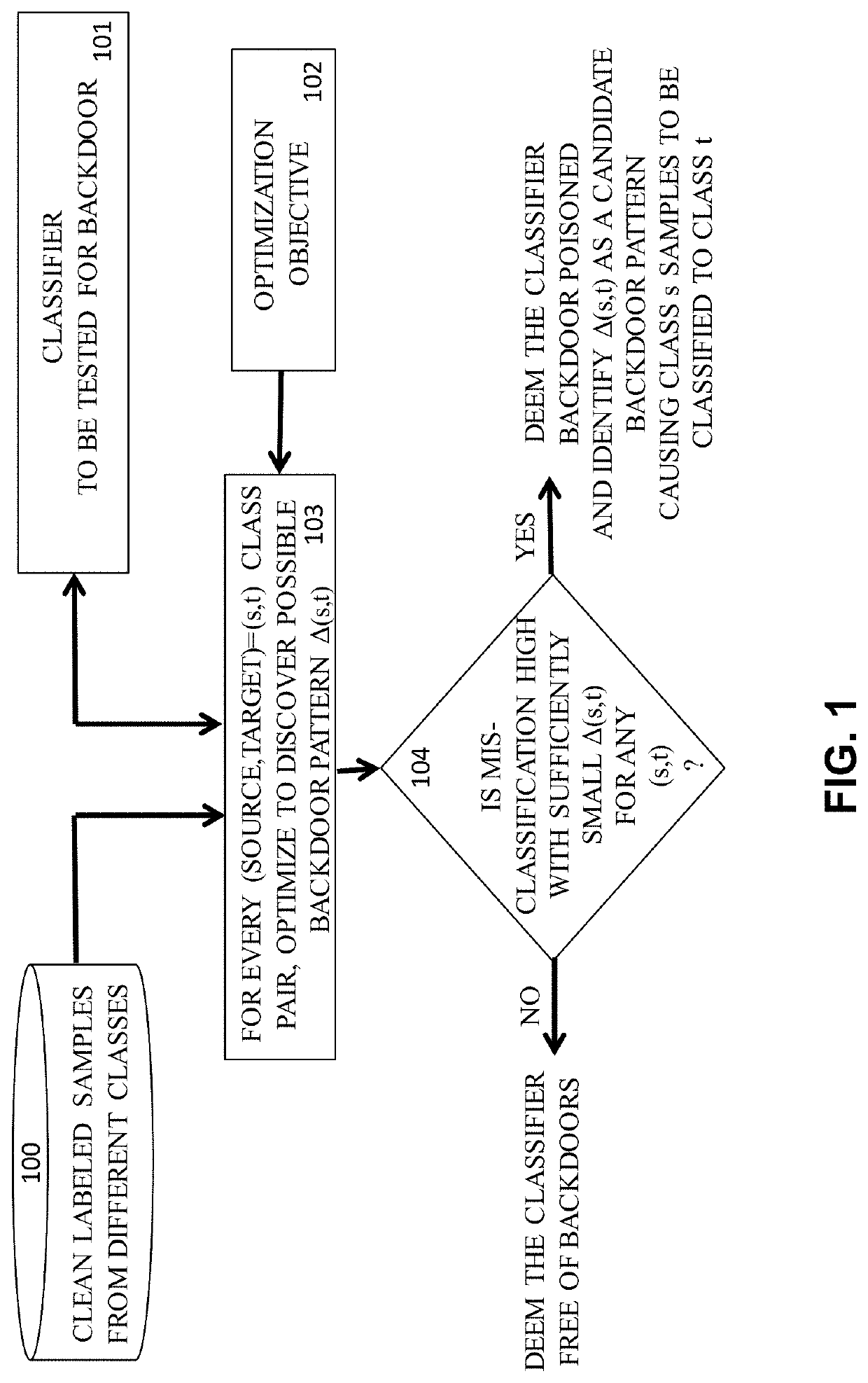
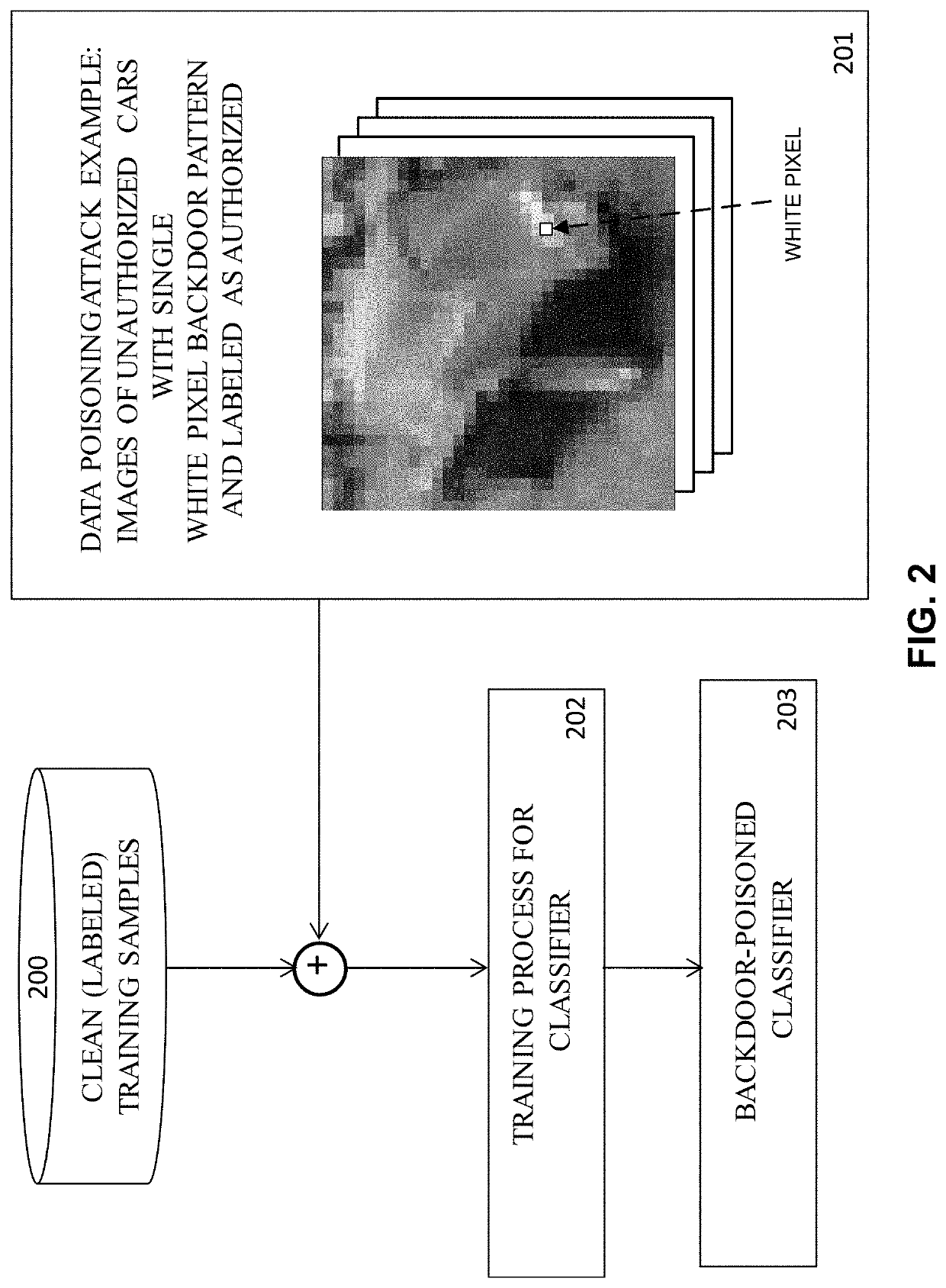
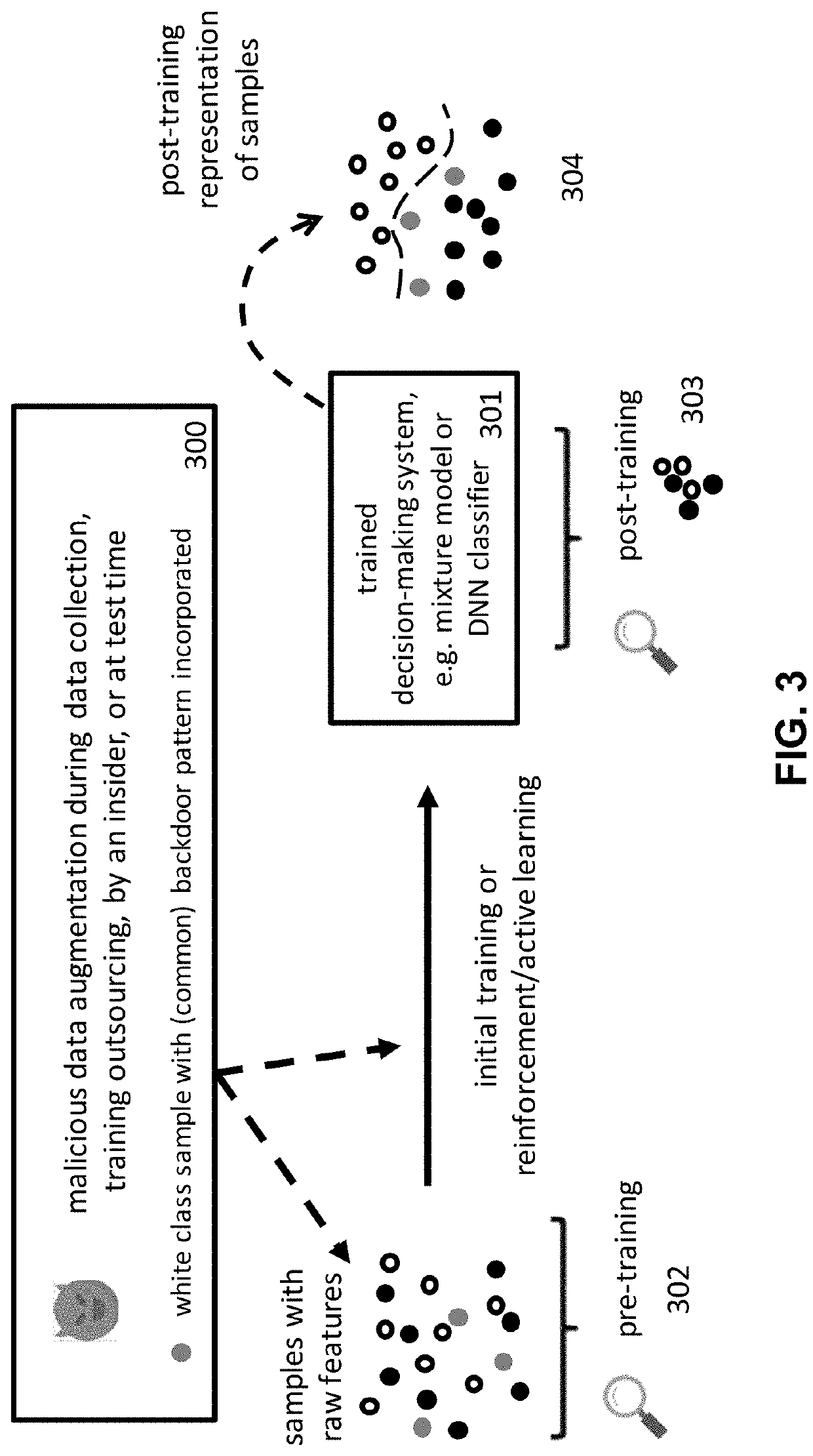
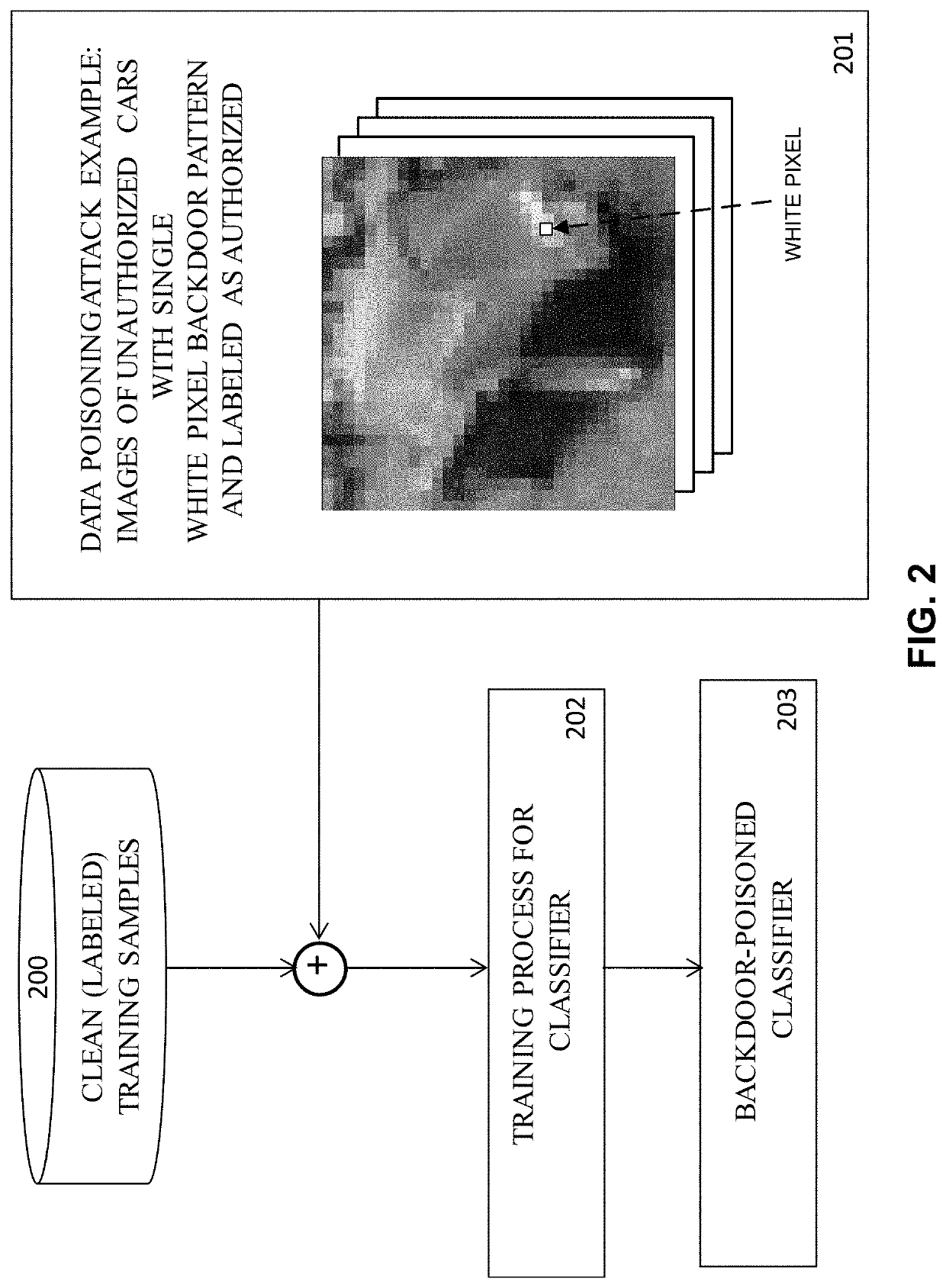
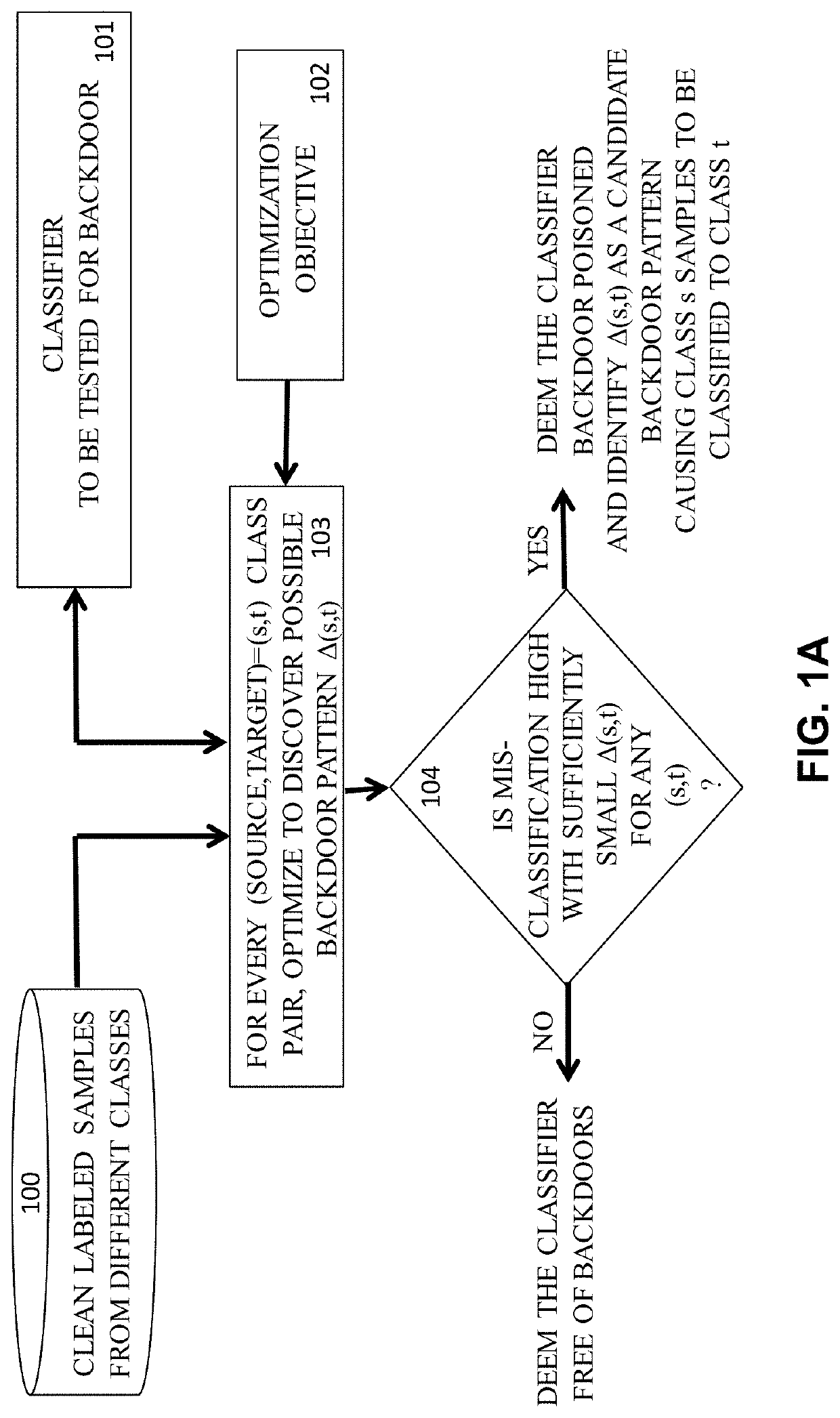
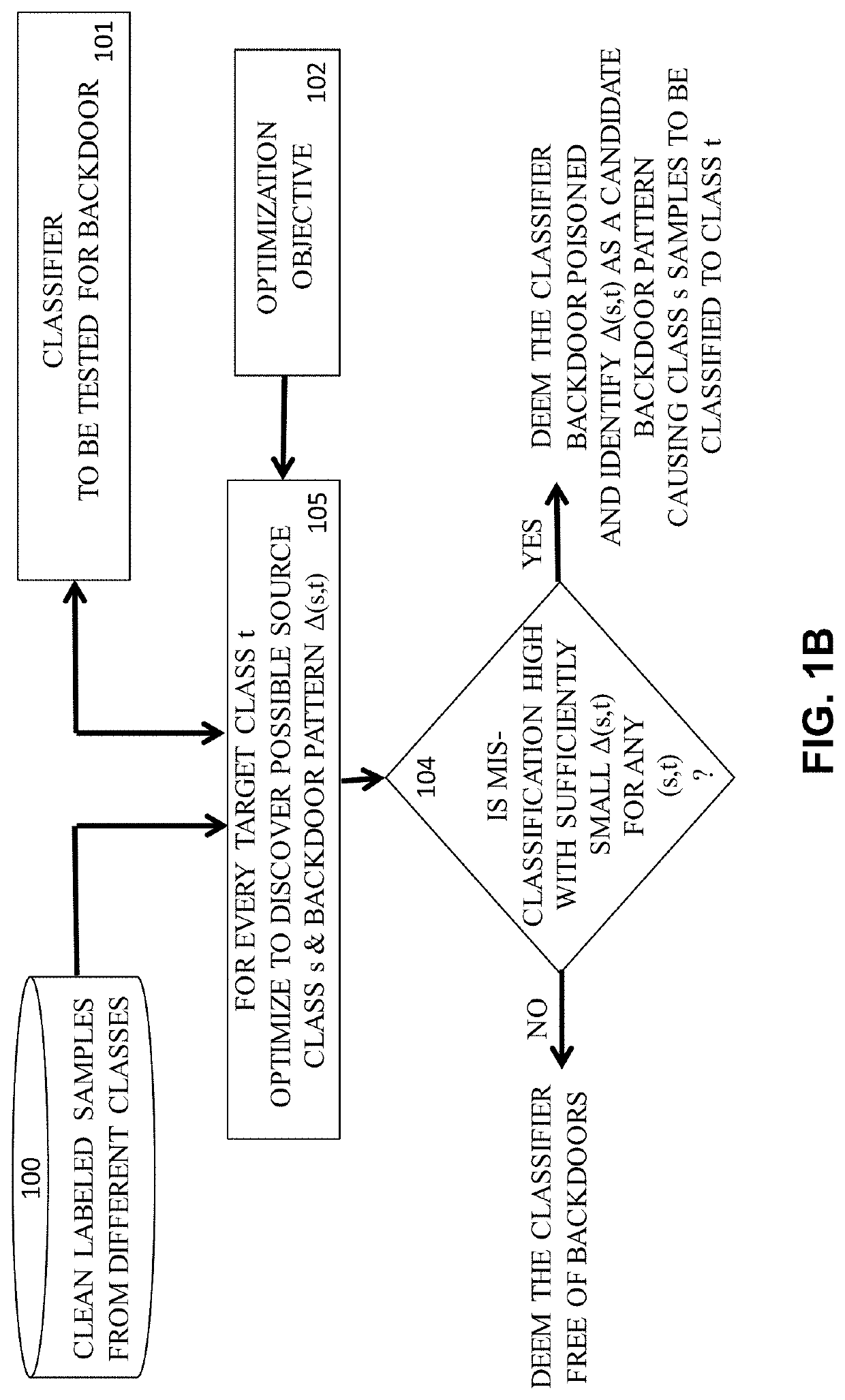
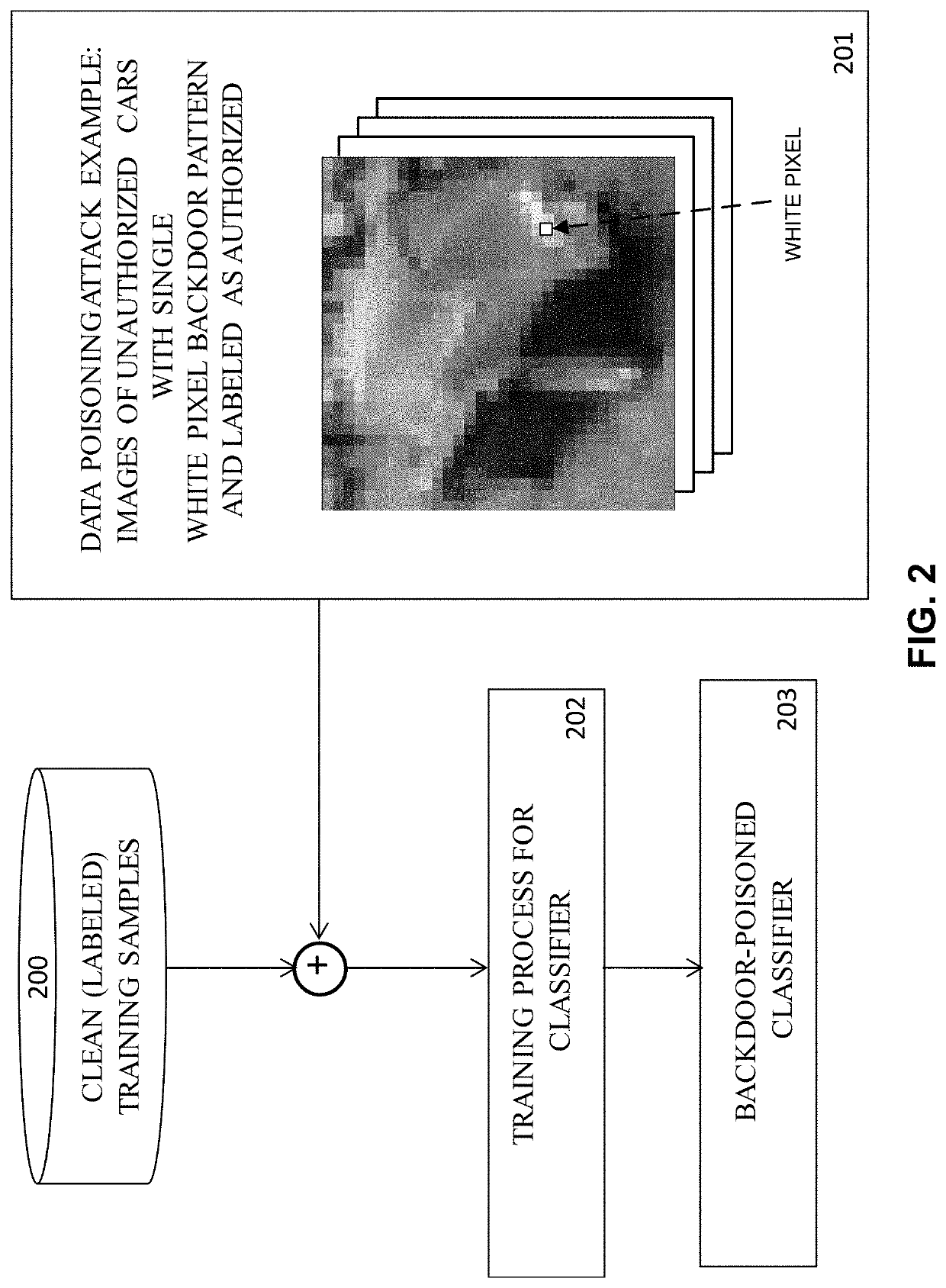
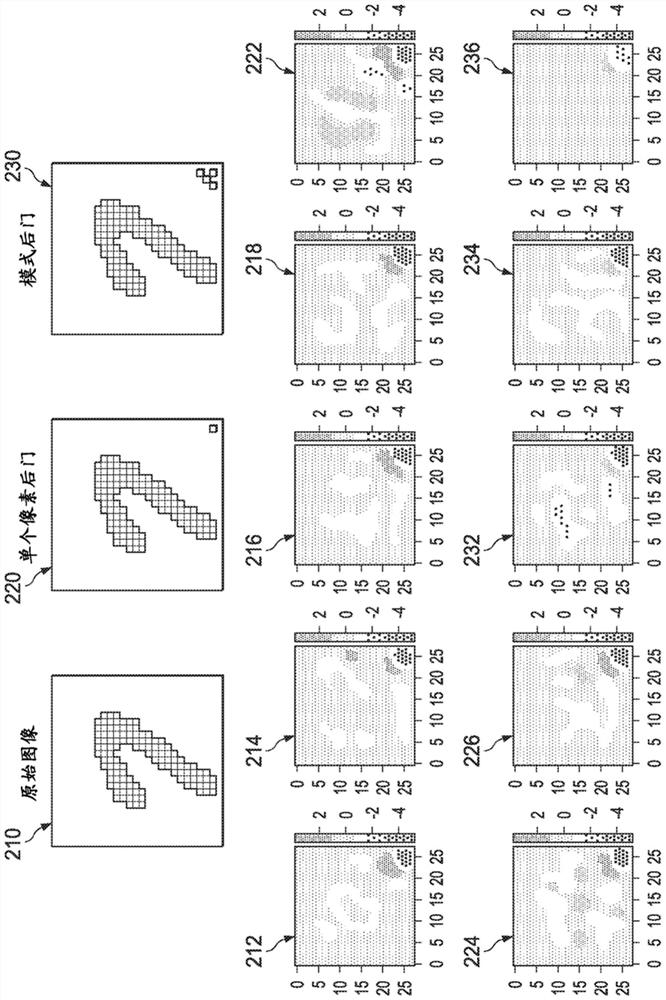
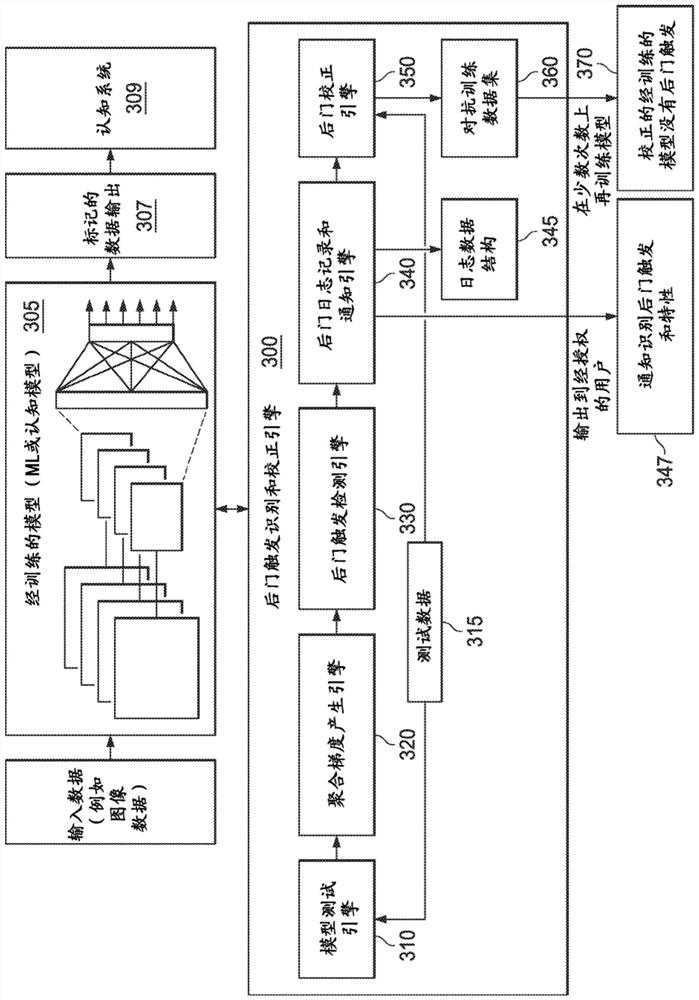
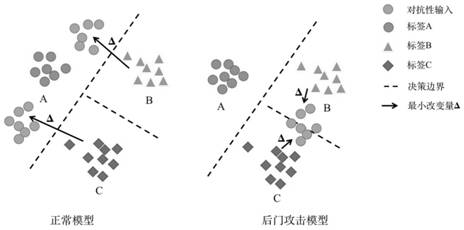
This patent concerns novel technology for detecting backdoors of neural network, particularly deep neural network (DNN), classifiers. The backdoors are planted by suitably poisoning the training dataset, i.e., a data-poisoning attack. Once added to input samples from a source class (or source classes), the backdoor pattern causes the decision of the neural network to change to a target class. The backdoors under consideration are small in norm so as to be imperceptible to a human, but this does not limit their location, support or manner of incorporation. There may not be components (edges, nodes) of the DNN which are dedicated to achieving the backdoor function. Moreover, the training dataset used to learn the classifier may not be available. In one embodiment of the present invention which addresses such challenges, if the classifier is poisoned then the backdoor pattern is determined through a feasible optimization process, followed by an inference process, so that both the backdoor pattern itself and the associated source class(es) and target class are determined based only on the classifier parameters and a set of clean (unpoisoned attacked) samples from the different classes (none of which may be training samples).
Owner:ANOMALEE INC
Security management system for monitoring firewall operation
InactiveUS20090205039A1Reduce loadIncrease loadComputer security arrangementsMultiple digital computer combinationsIp addressSafety management systems
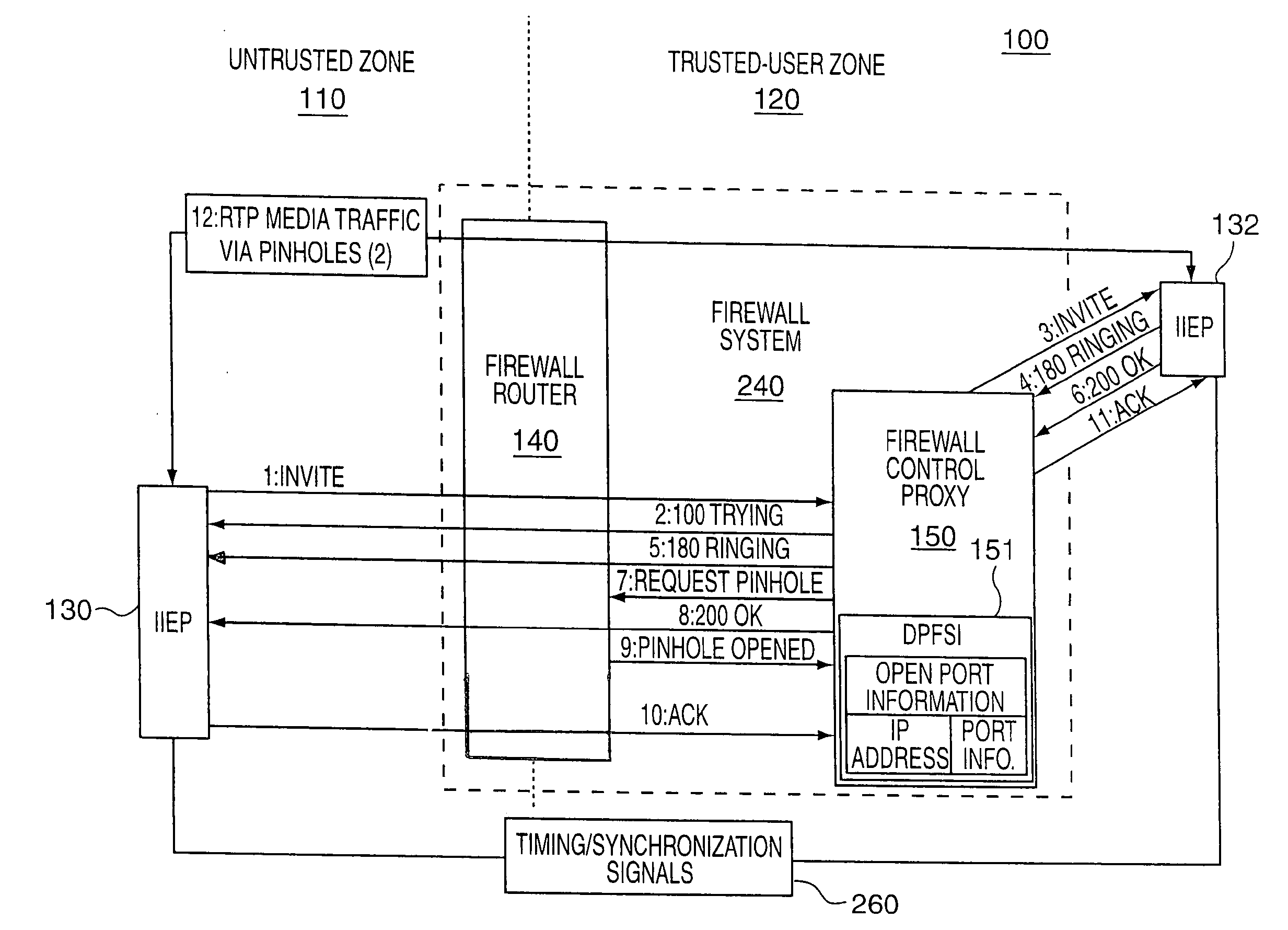
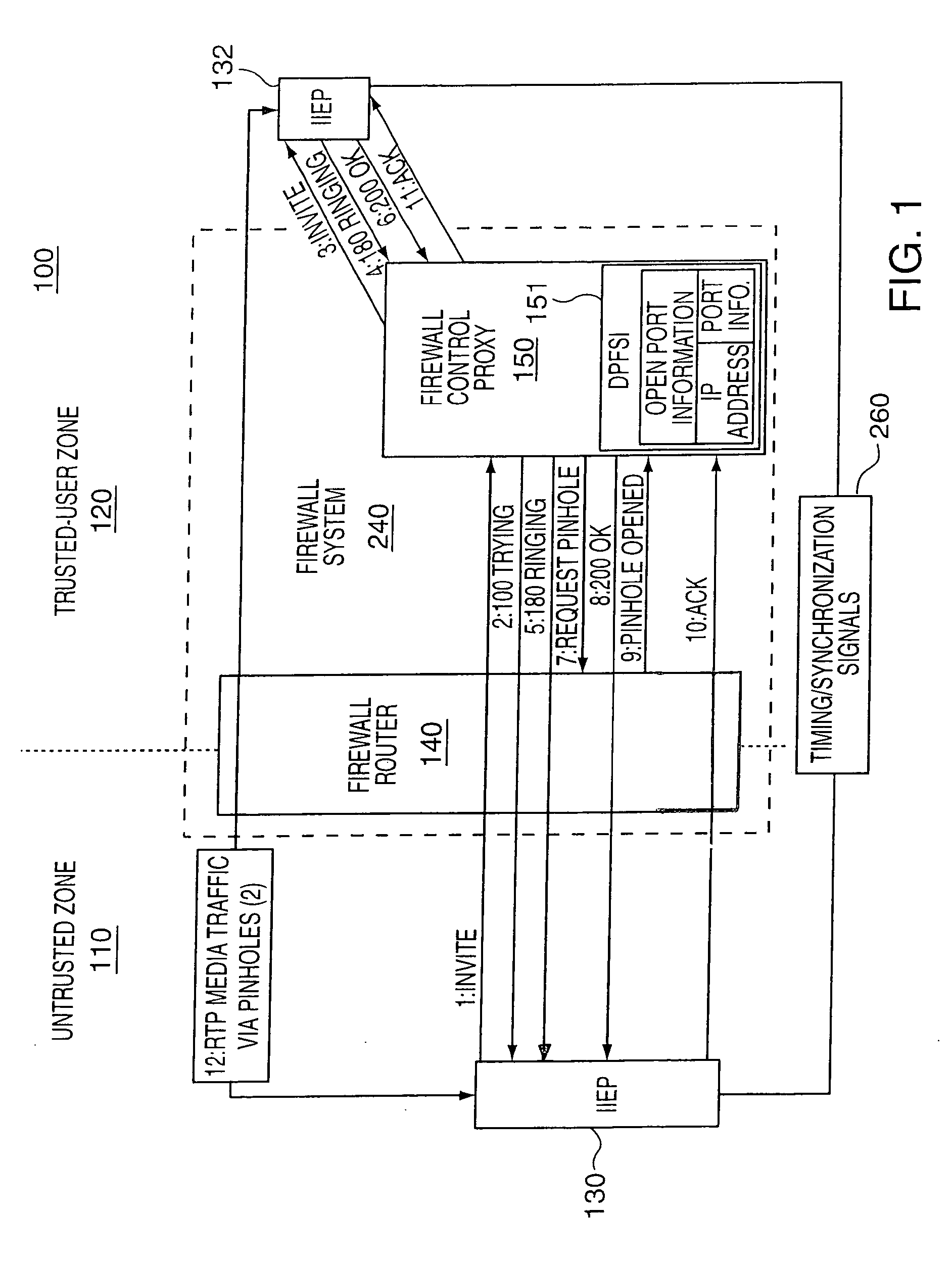
A test method for Internet-Protocol packet networks that verifies the proper functioning of a dynamic pinhole filtering implementation as well as quantifying network vulnerability statistically, as pinholes are opened and closed is described. Specific potential security vulnerabilities that may be addressed through testing include: 1) excessive delay in opening pinholes, resulting in an unintentional denial of service; 2) excessive delay in closing pinholes, creating a closing delay window of vulnerability; 3) measurement of the length of various windows of vulnerability; 4) setting a threshold on a window of vulnerability such that it triggers an alert when a predetermined value is exceeded; 5) determination of incorrectly allocated pinholes, resulting in a denial of service; 6) determining the opening of extraneous pinhole / IP address combinations through a firewall which increase the network vulnerability through unrecognized backdoors; and 7) determining the inability to correlate call state information with dynamically established rules in the firewall.
Owner:PALO ALTO NETWORKS INC
System and method for detecting backdoor attacks in convolutional neural networks
ActiveUS20200410098A1Character and pattern recognitionPlatform integrity maintainanceAlgorithmEngineering
Described is a system for detecting backdoor attacks in deep convolutional neural networks (CNNs). The system compiles specifications of a pretrained CNN into an executable model, resulting in a compiled model. A set of Universal Litmus Patterns (ULPs) are fed through the compiled model, resulting in a set of model outputs. The set of model outputs are classified and used to determine presence of a backdoor attack in the pretrained CNN. The system performs a response based on the presence of the backdoor attack.
Owner:HRL LAB
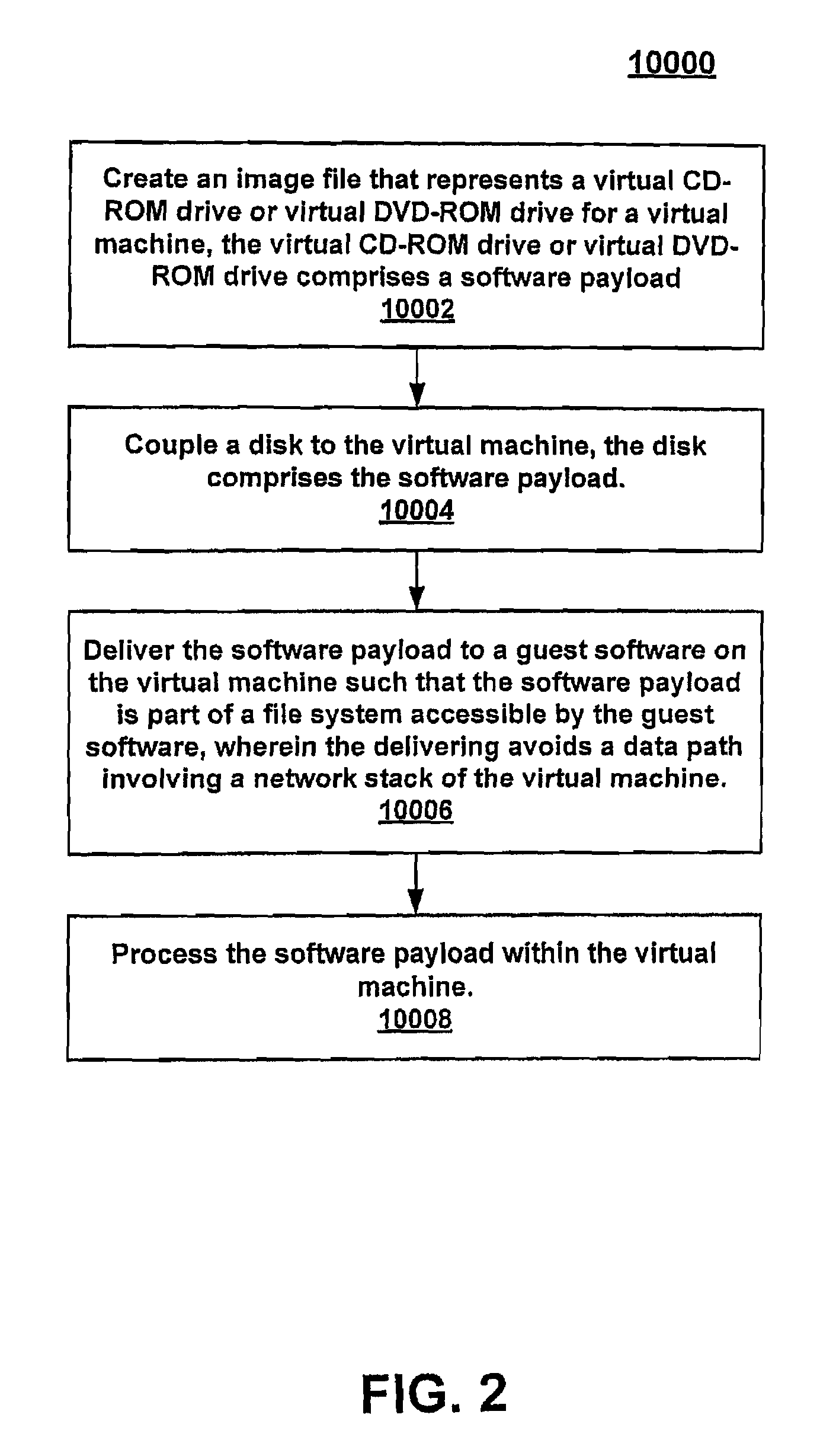
System and method for delivering software update to guest software on virtual machines through a backdoor software communication pipe thereof
ActiveUS8677351B2Program synchronisationSoftware simulation/interpretation/emulationSoftware updateFile system
One embodiment entails delivering a software payload to guest software in a virtual machine so that the software payload is part of a file system accessible by the guest software, wherein delivery avoids a data path involving a network stack of the virtual machine.
Owner:VMWARE INC
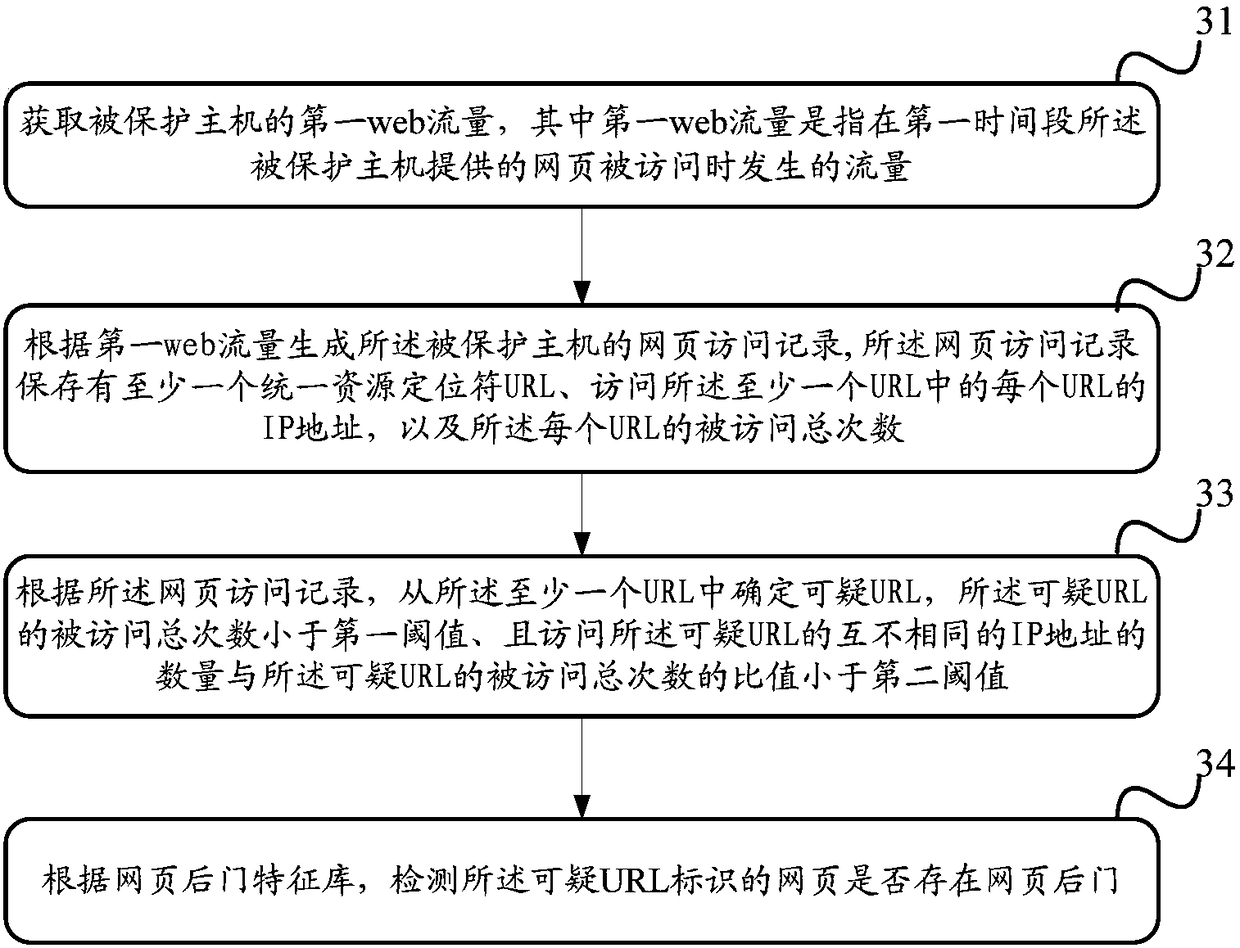
Webpage backdoor detecting method and device
The invention discloses a webpage backdoor detecting method and device, and aims at solving the problem of low detection efficiency in the prior art. The method comprises that a first web flow of a protected host is obtained; a webpage access record of the protected host is generated according to the first web flow, and used to store at least one URL, IP addresses accessing each URL, and the totalaccess frequency of each URL, and each URL identifies one webpage provided by the protected host; according to the webpage access record, a suspected URL is determined from the at least one URL, thetotal access frequency of the suspected URL is lower than a first threshold, and the ratio of number of different IP addresses which access the suspected URL to the total access number of the suspected URL is lower than a second threshold; and whether the webpage identified by the suspected URL includes a backdoor characteristic is determined, and the webpage identified by the suspected URL includes a webpage backdoor is determined according to a backdoor characteristic determining result.
Owner:HUAWEI TECH CO LTD
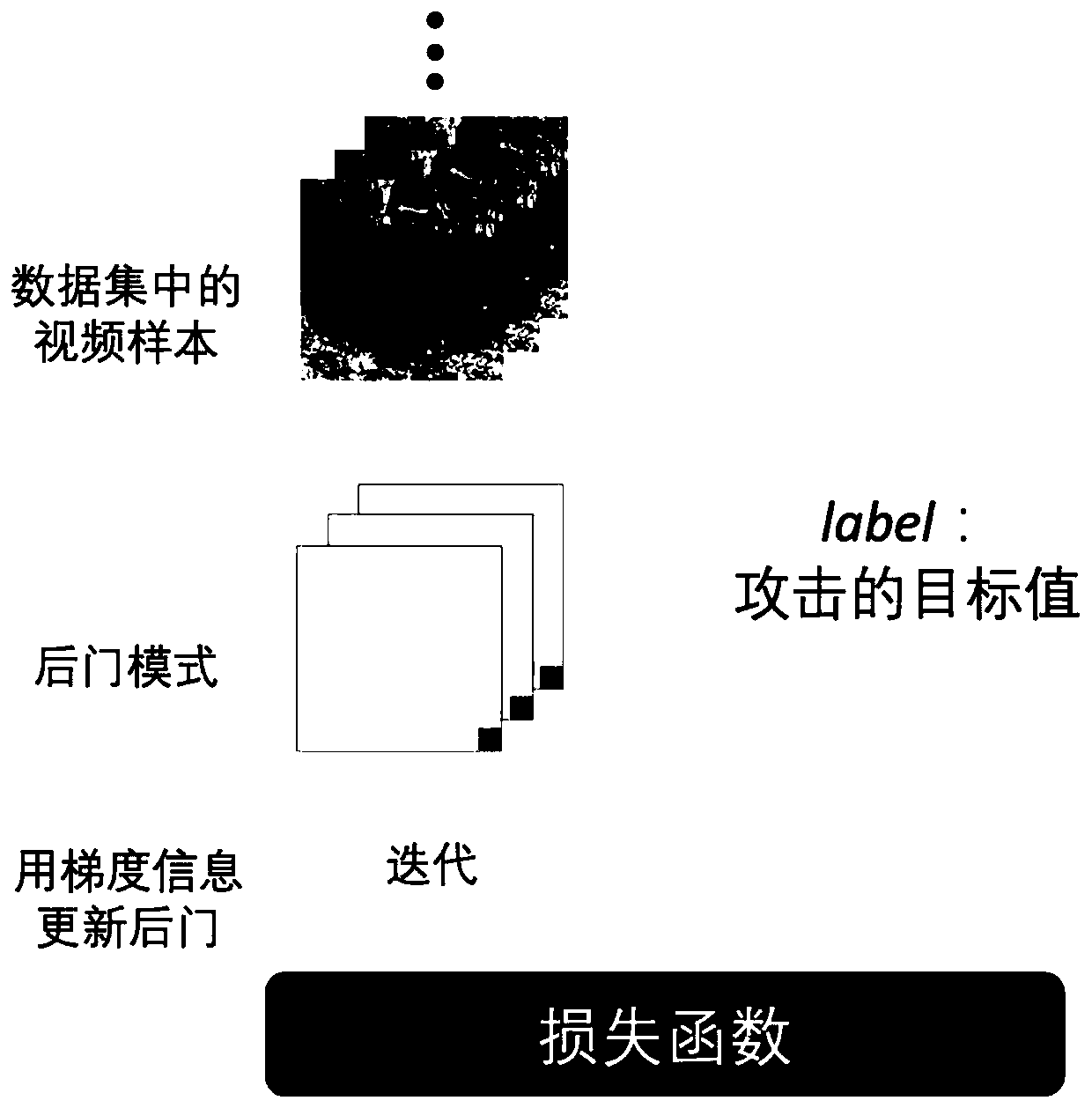
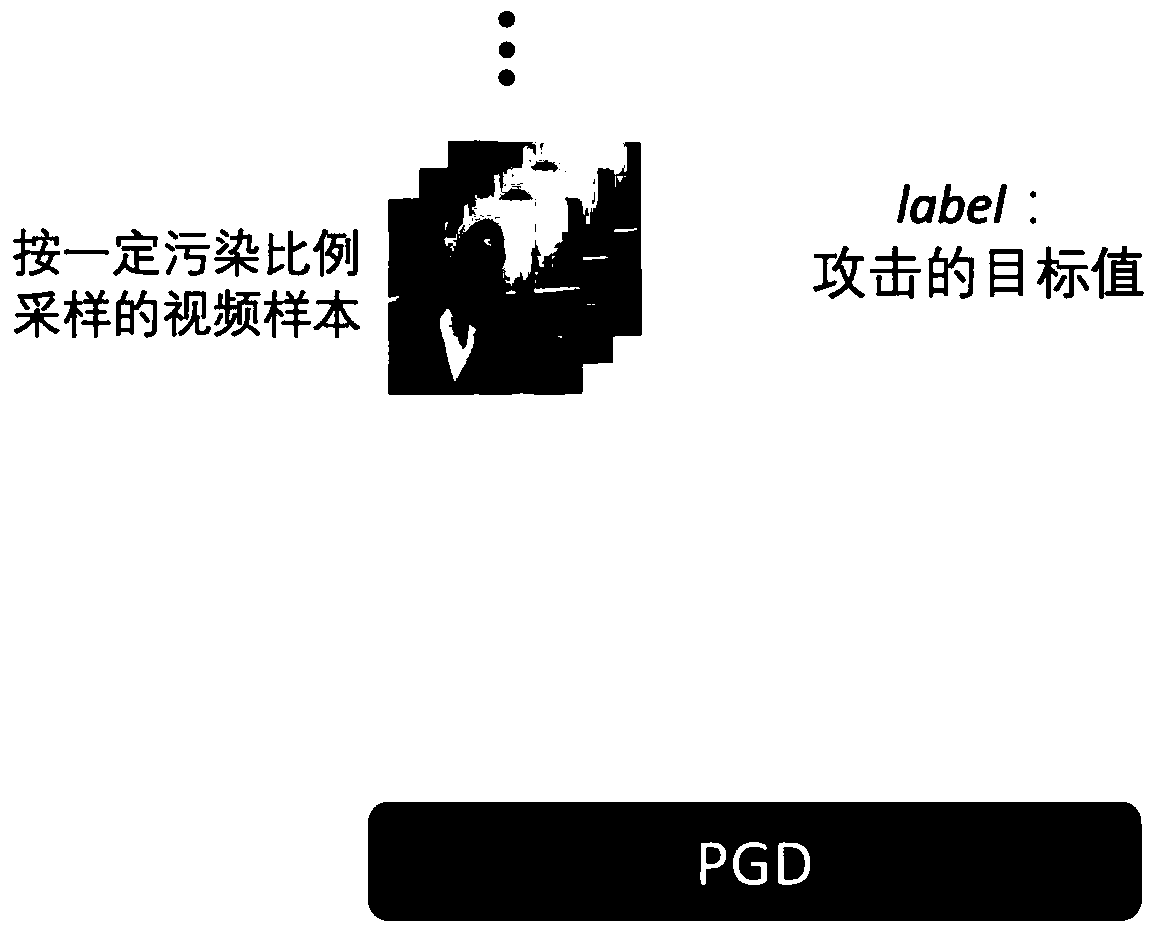
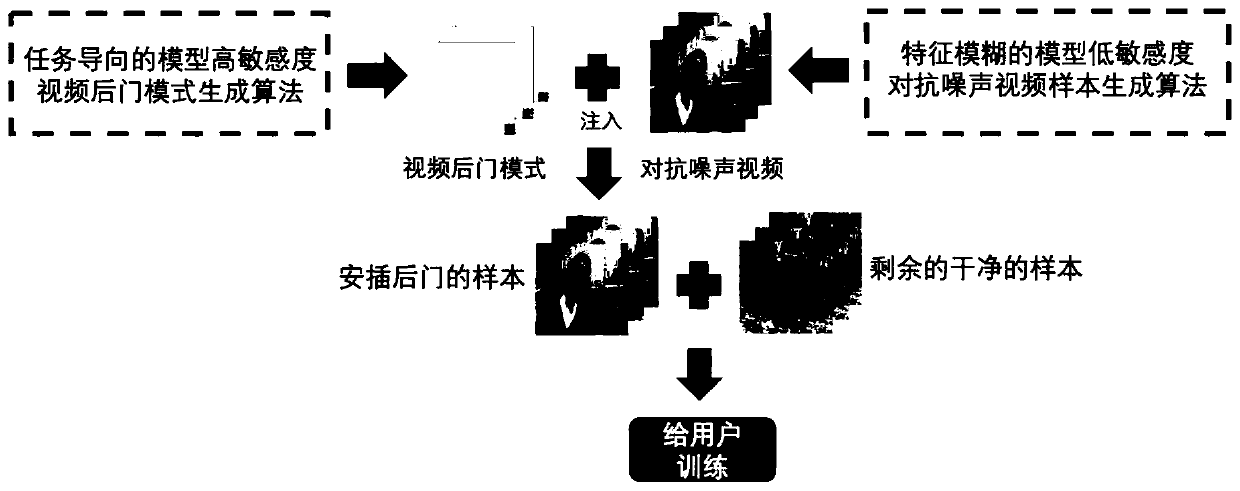
Backdoor attack method of video analysis neural network model
ActiveCN111260059AIncrease success rateReduce distractionsMathematical modelsInternal combustion piston enginesNoise (video)Algorithm
The invention belongs to the technical field of neural network security, and particularly relates to a backdoor attack method of a video analysis neural network model. For more severe backdoor attackimplementation environments such as a high sample dimension, a high frame resolution and a sparse data set of a video, a video backdoor pollution sample construction framework is used for carrying outbackdoor attack on a video analysis neural network model. The video backdoor pollution sample construction framework comprises three parts: a task-oriented model high-sensitivity video backdoor modegeneration algorithm, a feature fuzzy model low-sensitivity anti-noise video sample generation algorithm and a pollution sample generation and attack algorithm; gradient information is introduced fromtwo aspects of a backdoor mode and an original sample to establish association between an attack target value and the backdoor mode. The method provided by the invention has the advantages of high attack success rate, high secrecy, good robustness, good expansibility and the like, and has very good generalization in a video analysis neural network model.
Owner:FUDAN UNIV
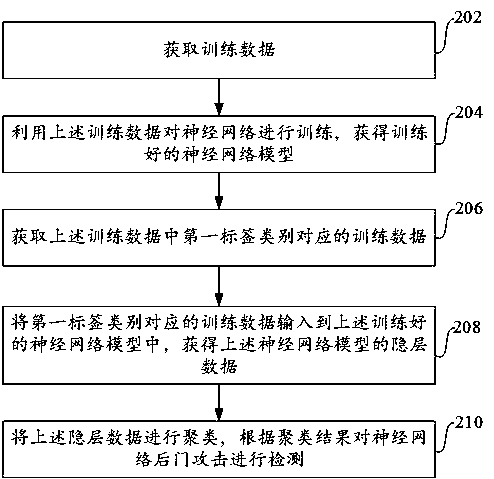
Neural network backdoor attack detection method and device and electronic equipment
The embodiment of the invention provides a neural network backdoor attack detection method and device and electronic equipment. In the method, training data is acquired and then used to train a neuralnetwork to obtain a trained neural network model, then training data corresponding to a first label category in the training data is obtained, and the training data corresponding to the first label category is input into the trained neural network model to obtain hidden layer data of the neural network model; and then, the hidden layer data is clustered, and the neural network backdoor attack isdetected according to a clustering result.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
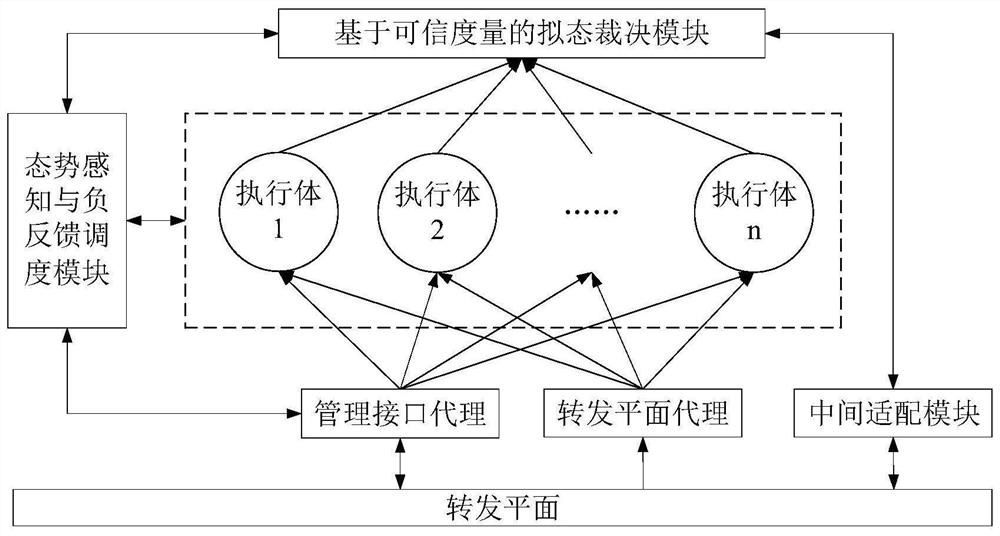
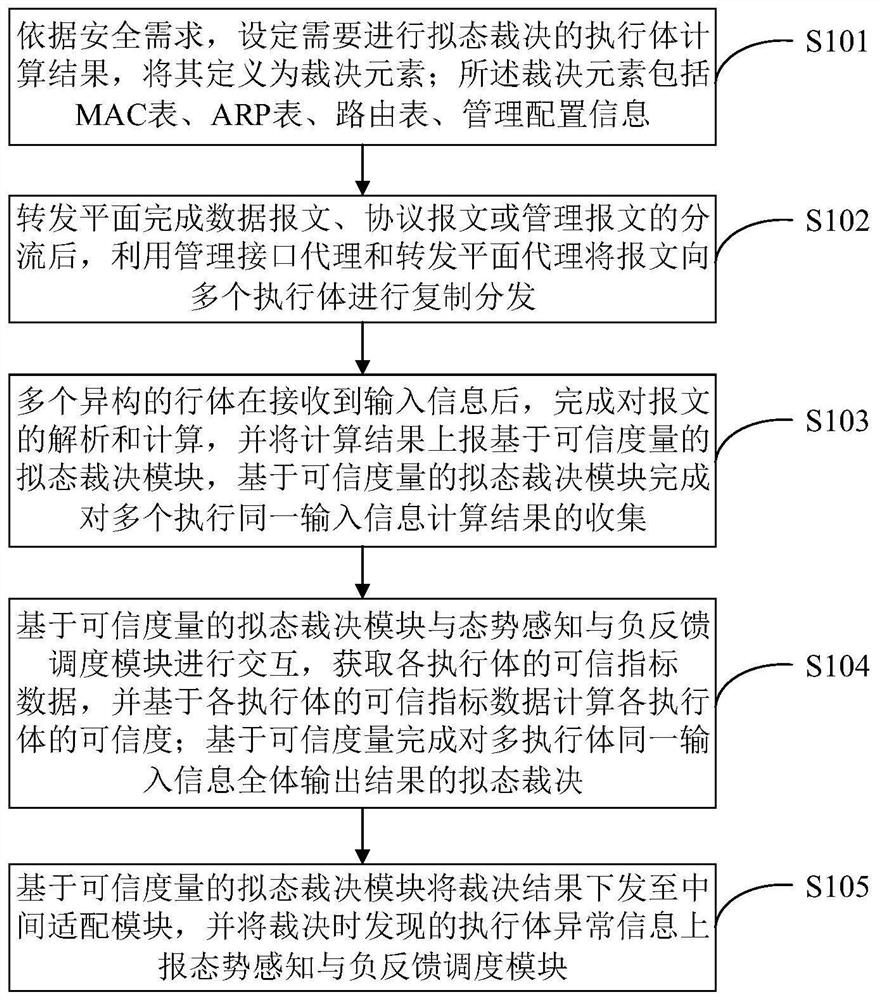
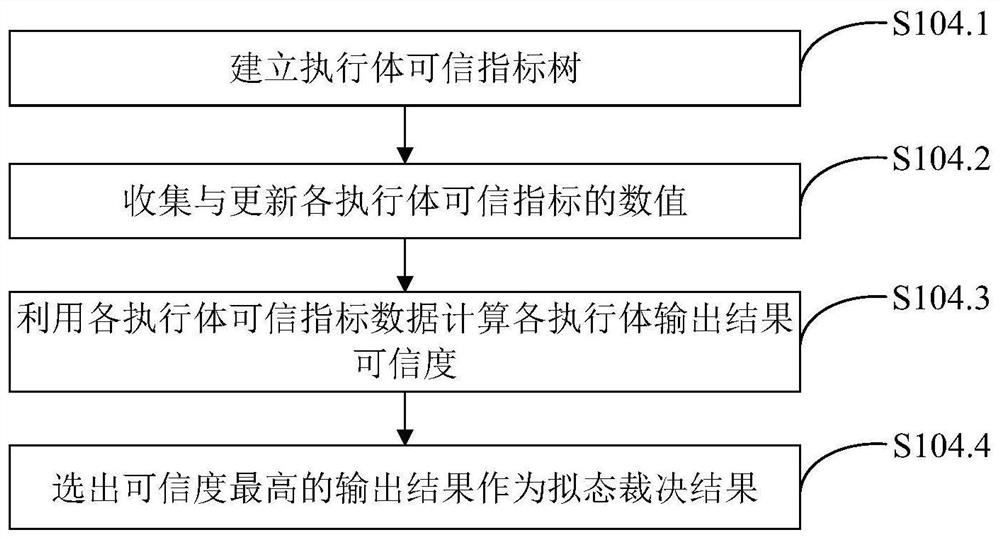
Mimicry switch judgment system and method based on trusted measurement
ActiveCN111884996AReduce security threatsImprove the level of security protectionData switching networksComplex mathematical operationsDecision systemInformation Harvesting
The invention belongs to the technical field of network security, and discloses a mimicry switch decision system based on trusted measurement, and the system comprises a forwarding plane, a managementinterface agent, an intermediate adaptation module, a forwarding plane agent, a plurality of heterogeneous actuators, a trusted measurement-based mimicry decision module and a situation awareness andnegative feedback scheduling module. The invention further discloses a mimicry switch judgment method based on trusted measurement. The mimicry switch judgment method comprises the steps: setting mimicry switch judgment elements; distributing input information; collecting output information; carrying out mimicry decision based on credibility measurement; issuing a judgment result, sensing the threat situation of the switch, and scheduling an executor; the mimicry decision based on credibility measurement comprises the following steps: establishing an executive credible index tree; collectingand updating the credible index data of the executive body; calculating the credible weight of the output result of each executive body; and calculating the credibility of each output result. The method can effectively reduce the influence of unknown loopholes and potential backdoors, and improves the safety protection level of a local area network.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU +1
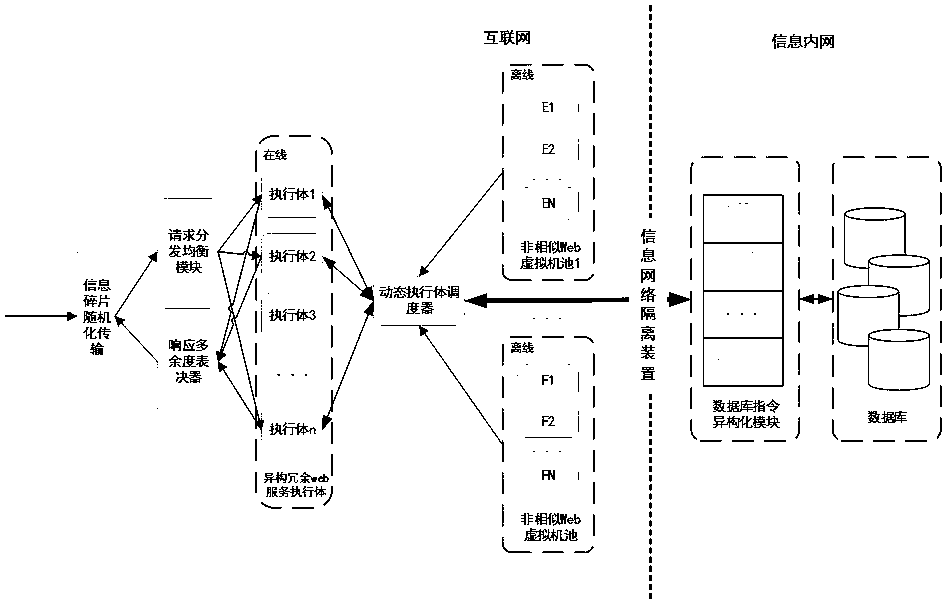
Power grid Web application mimicry defense system
PendingCN111478970APrevent leakageIncrease uncertaintyPlatform integrity maintainanceTransmissionWeb serviceAttack
The invention relates to a power grid Web application mimicry defense system. A heterogeneous virtual Web server pool which is equivalent in function, diversified and dynamic is constructed, technologies such as redundancy voting, dynamic executor scheduling and database instruction isomerization are adopted, an attack chain is blocked, the utilization difficulty of vulnerabilities or backdoors isincreased, and the availability and safety of Web services are guaranteed. A dynamic environment is realized through active change of software and hardware elements of different layers such as a network, a platform, a system, software and an application, and therefore, the dependency condition of the network attack on the determinacy and continuity of the operating environment is destroyed, controllable active defense is realized in the toxic bacteria-carrying software and hardware element environment with the vulnerability and the backdoor, the unknown attack defense problem by using the unknown vulnerability and the unknown backdoor is solved, and the network security of the key Web application system in the power industry is effectively enhanced.
Owner:STATE GRID FUJIAN ELECTRIC POWER CO LTD
Detection of Test-Time Evasion Attacks
ActiveUS20210019399A1Character and pattern recognitionPlatform integrity maintainancePattern recognitionAttack
Embodiments of the present invention concern detecting Test-Time Evasion (TTE) attacks on neural network, particularly deep neural network (DNN), classifiers. The manner of detection is similar to that used to detect backdoors of a classifier whose training dataset was poisoned. Given knowledge of the classifier itself, the adversary subtly (even imperceptibly) perturbs their input to the classifier at test time in order to cause the class decision to change from a source class to a target class. For example, an image of a person who is unauthorized to access a resource can be modified slightly so that the classifier decides the image is that of an authorized person. The detector is based on employing a method (similar to that used to detect backdoors in DNNs) to discover different such minimal perturbations for each in a set of clean (correctly classified) samples, to change the sample's ground-truth (source) class to every other (target) class. For each (source, target) class pair, null distributions of the sizes of these perturbations are modeled. A test sample is similarly minimally perturbed by the detector from its decided-upon (target) class to every other (potential source) class. The p-values according to the corresponding null distributions of these test-sample perturbations are assessed using the corresponding nulls to decide whether the test sample is a TTE attack.
Owner:ANOMALEE INC
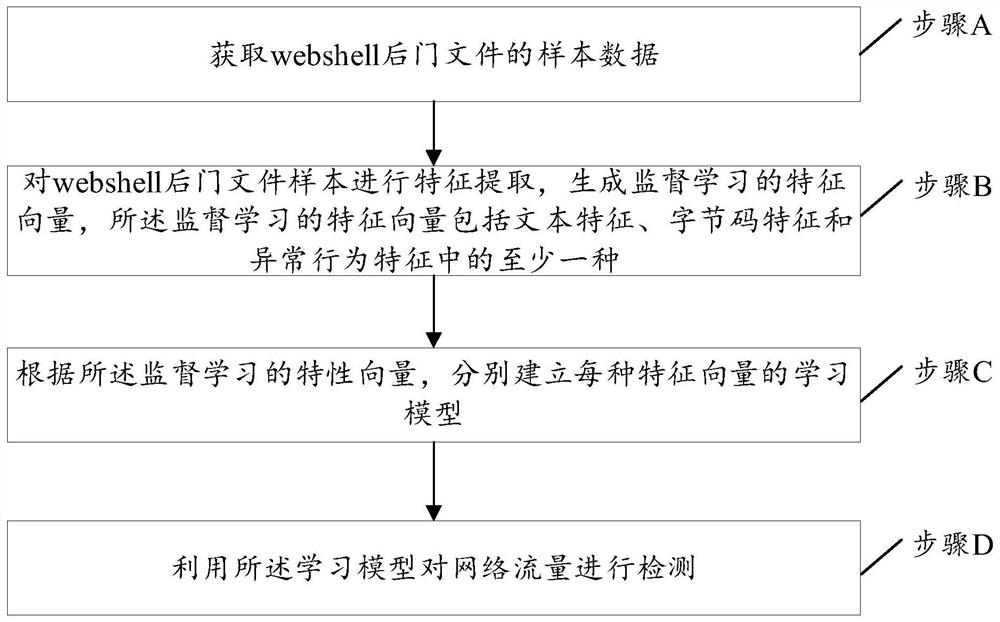
Webshell detection method and device based on artificial intelligence
ActiveCN111614599AImprove detection efficiencyCharacter and pattern recognitionNeural architecturesFeature vectorFeature extraction
The invention discloses a webshell detection method and device based on artificial intelligence. The method comprises the following steps: step A, acquiring sample data of a webshell backdoor file; B,performing feature extraction on a webshell backdoor file sample to generate feature vectors of supervised learning, the feature vectors of supervised learning including at least one of text features, byte code features and abnormal behavior features; C, respectively establishing a learning model of each feature vector according to the feature vectors of the supervised learning; and D, detectingthe network flow by using the learning model.
Owner:北京金睛云华科技有限公司
Website backdoor detection method based on convolutional neural network model
InactiveCN111260033AImprove accuracyHigh speedNeural architecturesTransmissionWeb siteAnomaly detection
The invention belongs to the technical field of computer security, and relates to an anomaly detection method in website security, in particular to a website backdoor detection method based on a convolutional neural network model. The method comprises the following steps: 1, extracting a common webpage file sample from a website server, searching malicious backdoor file samples from the internet,deleting redundant information such as annotations and the like, and dividing into a training set and a test set; 2, preprocessing the data extracted in the step 1; 3, establishing a convolutional neural network, and training the convolutional neural network according to the data obtained in the step 2 to obtain a convolutional neural network model; and 4, detecting whether the webpage file samplein the website server has a backdoor file sample in real time according to the model obtained in the step 3. The model trained by the method can detect Webshells of multiple languages, has a good detection effect on samples hidden through obfuscated coding, and is high in accuracy and good in recall rate and F1 value effect.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
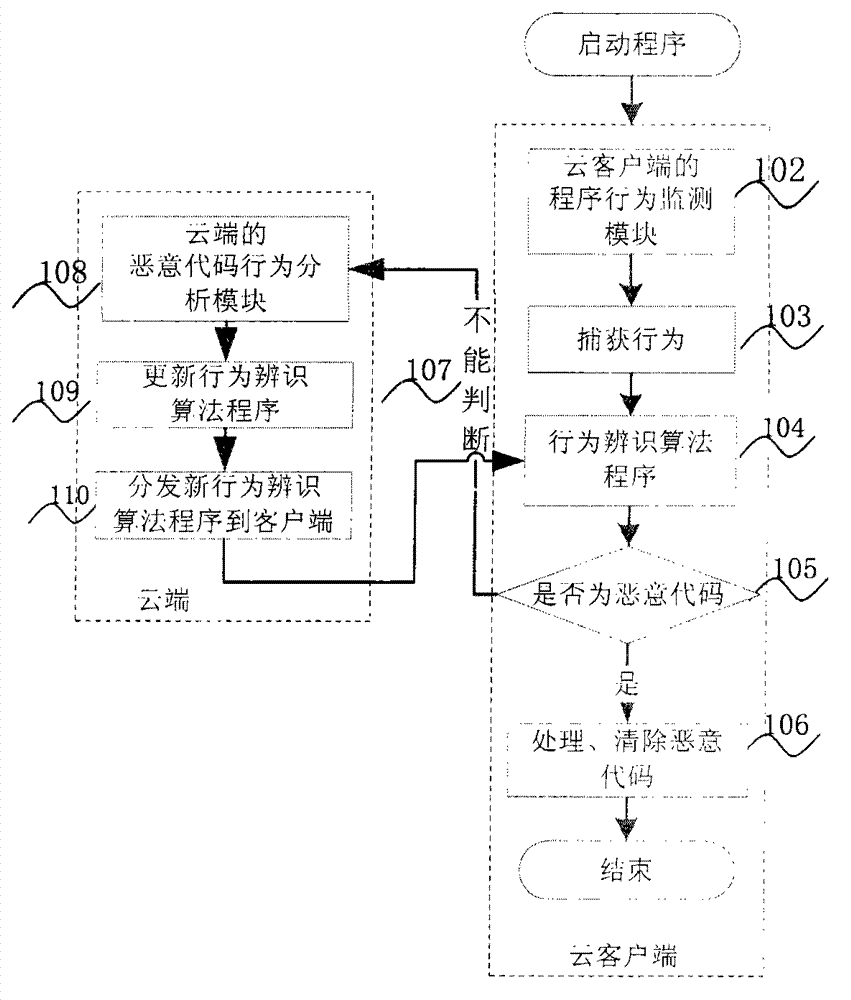
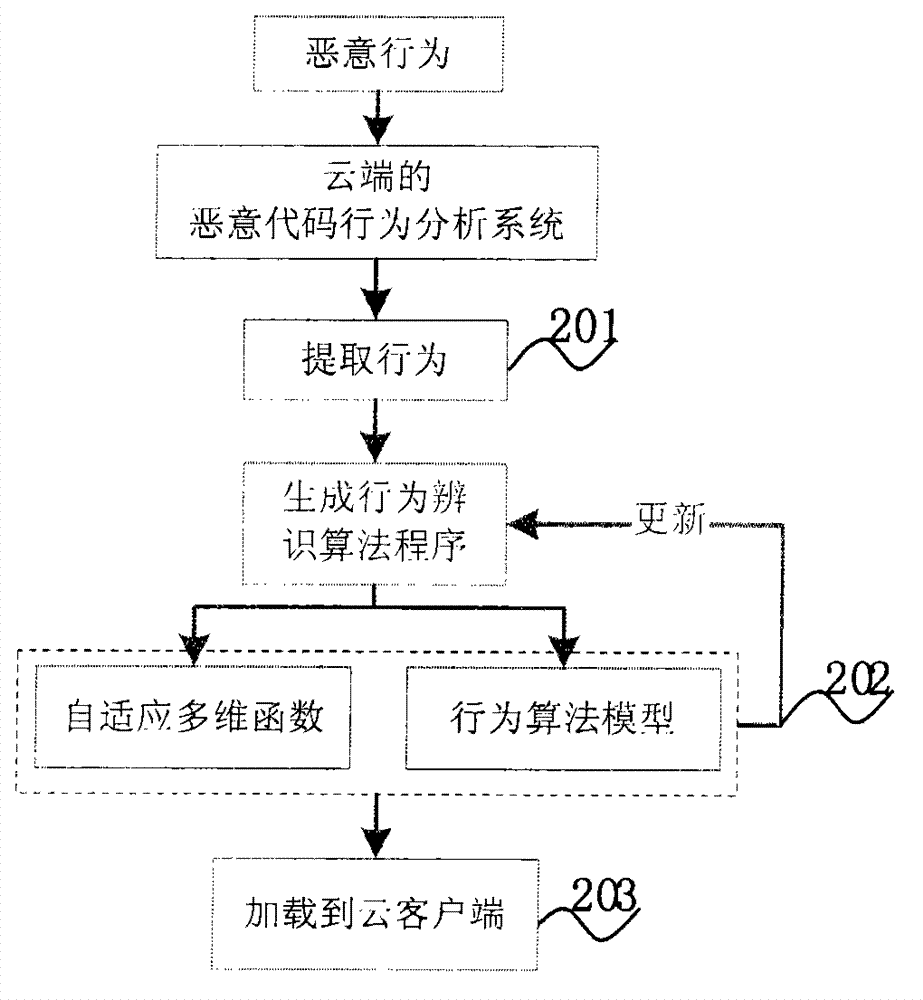
Active defense method of program behavior analysis on basis of cloud platform
InactiveCN103077352AImprove static defense capabilities against security risksSecurity risk static defense capability improvementPlatform integrity maintainanceClient-sideProgram behavior
The invention relates to an active defense method of program behavior analysis on the basis of a cloud platform. A system comprises a cloud end and a cloud client, wherein the cloud end consists of a malicious code behavior analysis module, a program behavior monitoring module and a malicious code processing module, and the cloud client comprises a program behavior monitoring module, a malicious code behavior identification module and a malicious code processing module. The active defense method has the advantages that the cloud platform is introduced, in addition, the behavior algorithm identification program of the program behavior analysis, identification and processing is used as the basis, the security risk static defense capability of a host computer system can be intelligently improved, the security defense capability of a terminal host computer is effectively improved, the infection probability of the terminal host computer on malicious codes such as viruses, Trojan, backdoor program and the like is reduced, and the security of the host computer is ensured.
Owner:CHONGQING YUANHENG TECH DEV
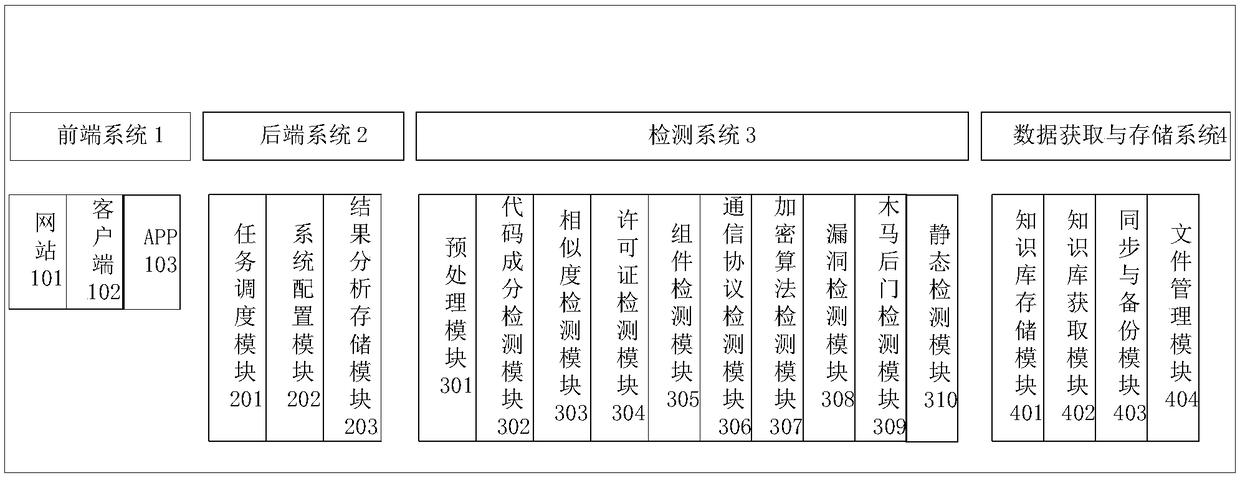
Big data-based source code comprehensive evaluation platform
ActiveCN108710564ASolve cloneResolve detectionReverse engineeringSoftware testing/debuggingData displayComputer cluster
Owner:苏州棱镜七彩信息科技有限公司
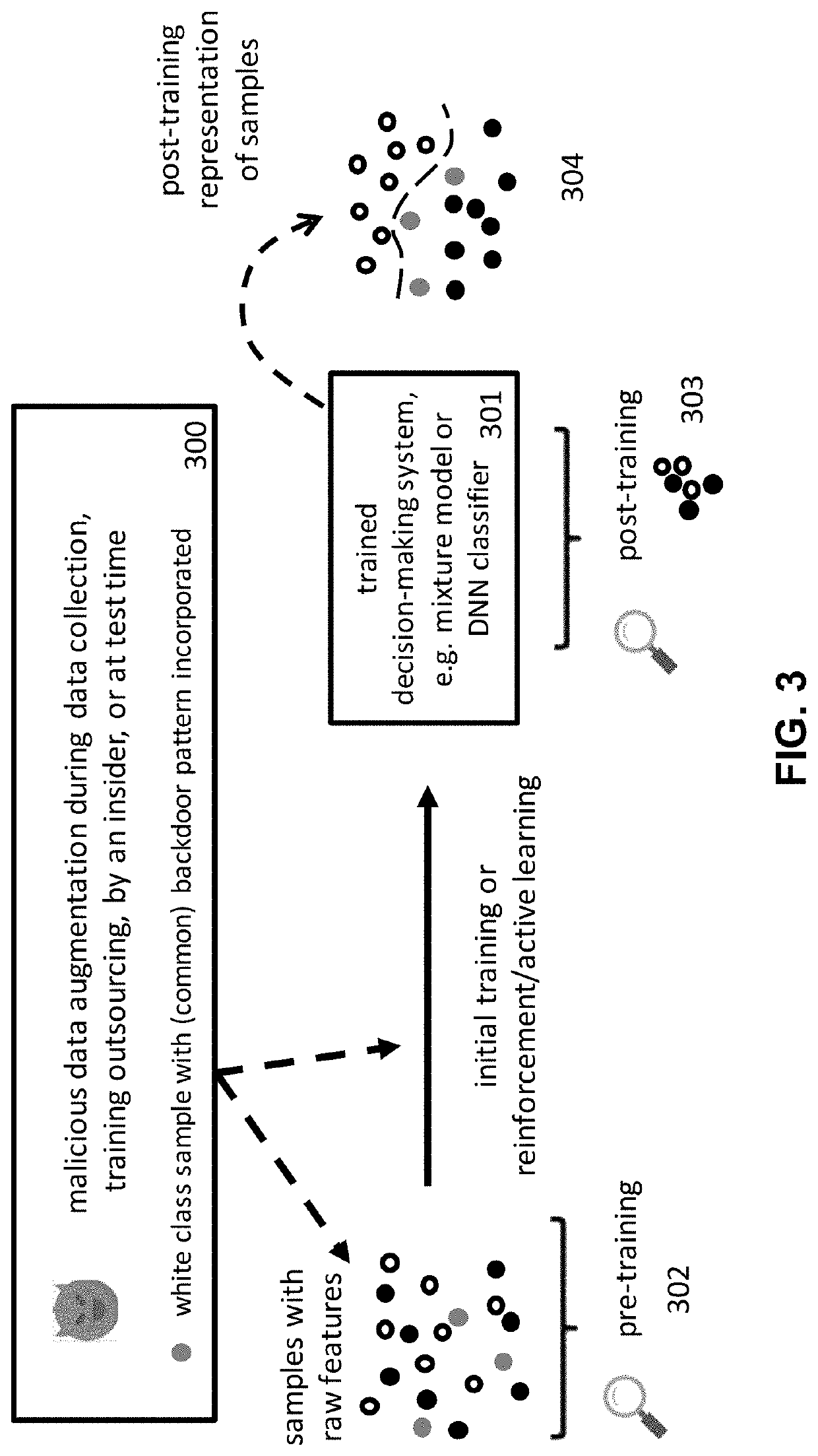
Post-Training Detection and Identification of Backdoor-Poisoning Attacks
ActiveUS20210256125A1Method can be appliedPlatform integrity maintainanceMachine learningPattern recognitionPredictive regression
This patent concerns novel technology for detecting backdoors in neural network, particularly deep neural network (DNN) classification or prediction / regression models. The backdoors are planted by suitably poisoning the training dataset, i.e., a data-poisoning attack. Once added to an input sample from a source class of the attack, the backdoor pattern causes the decision of the neural network to change to the attacker's target class in the case of classification, or causes the output of the network to significantly change in the case of prediction or regression. The backdoors under consideration are small in norm so as to be imperceptible to a human or otherwise innocuous / evasive, but this does not limit their location, support or manner of incorporation. There may not be components (edges, nodes) of the DNN which are specifically dedicated to achieving the backdoor function. Moreover, the training dataset used to learn the classifier or predictor / regressor may not be available. In one embodiment of the present invention, which addresses such challenges, if the classifier or predictor / regressor is poisoned then the backdoor pattern is determined through a feasible optimization process, followed by an inference process, so that both the backdoor pattern itself and the associated source class(es) and target class are determined based only on the classifier or predictor / regressor parameters and using a set of clean (unpoisoned) samples, from the different classes (none of which may be training samples).
Owner:ANOMALEE INC
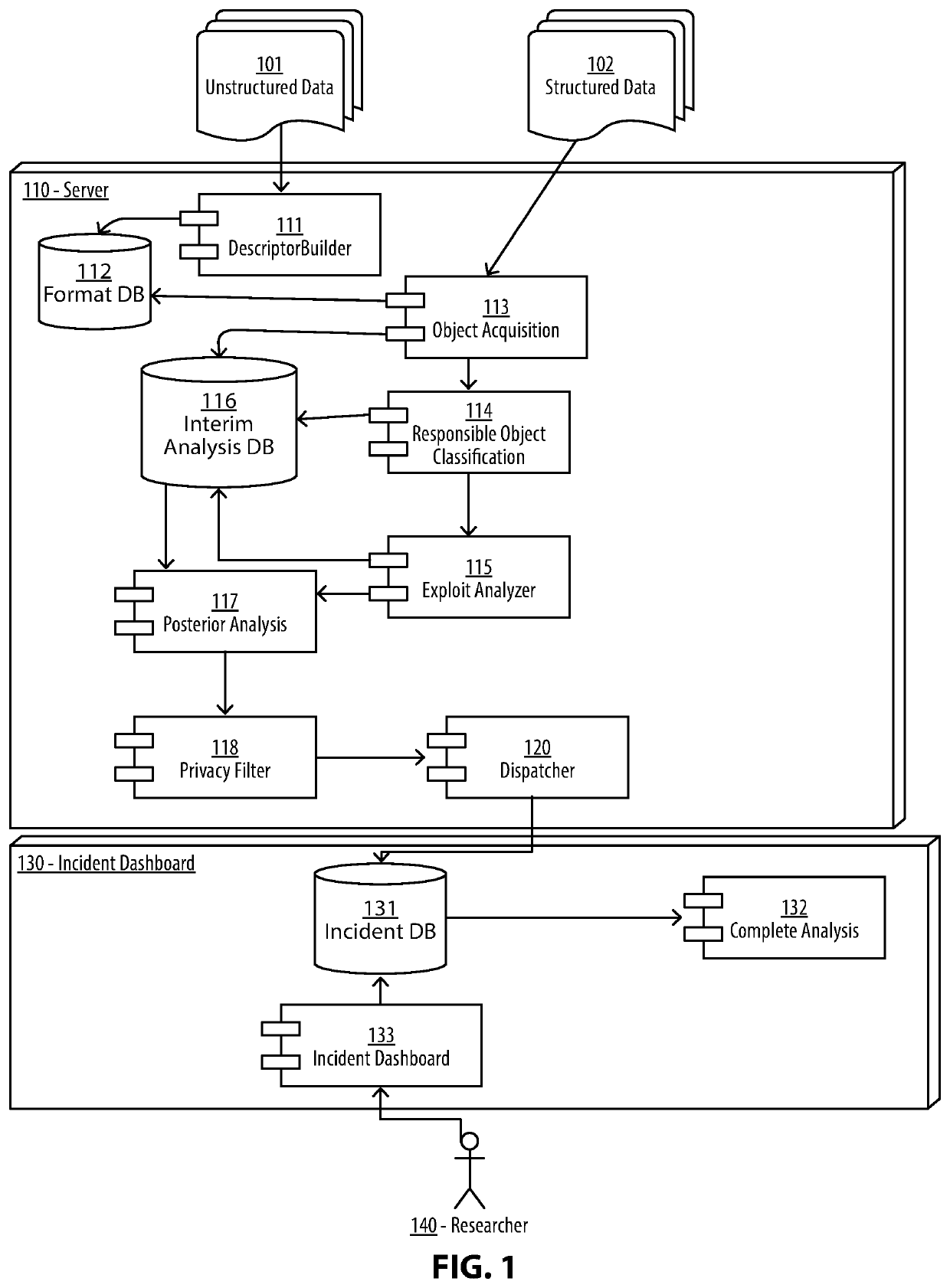
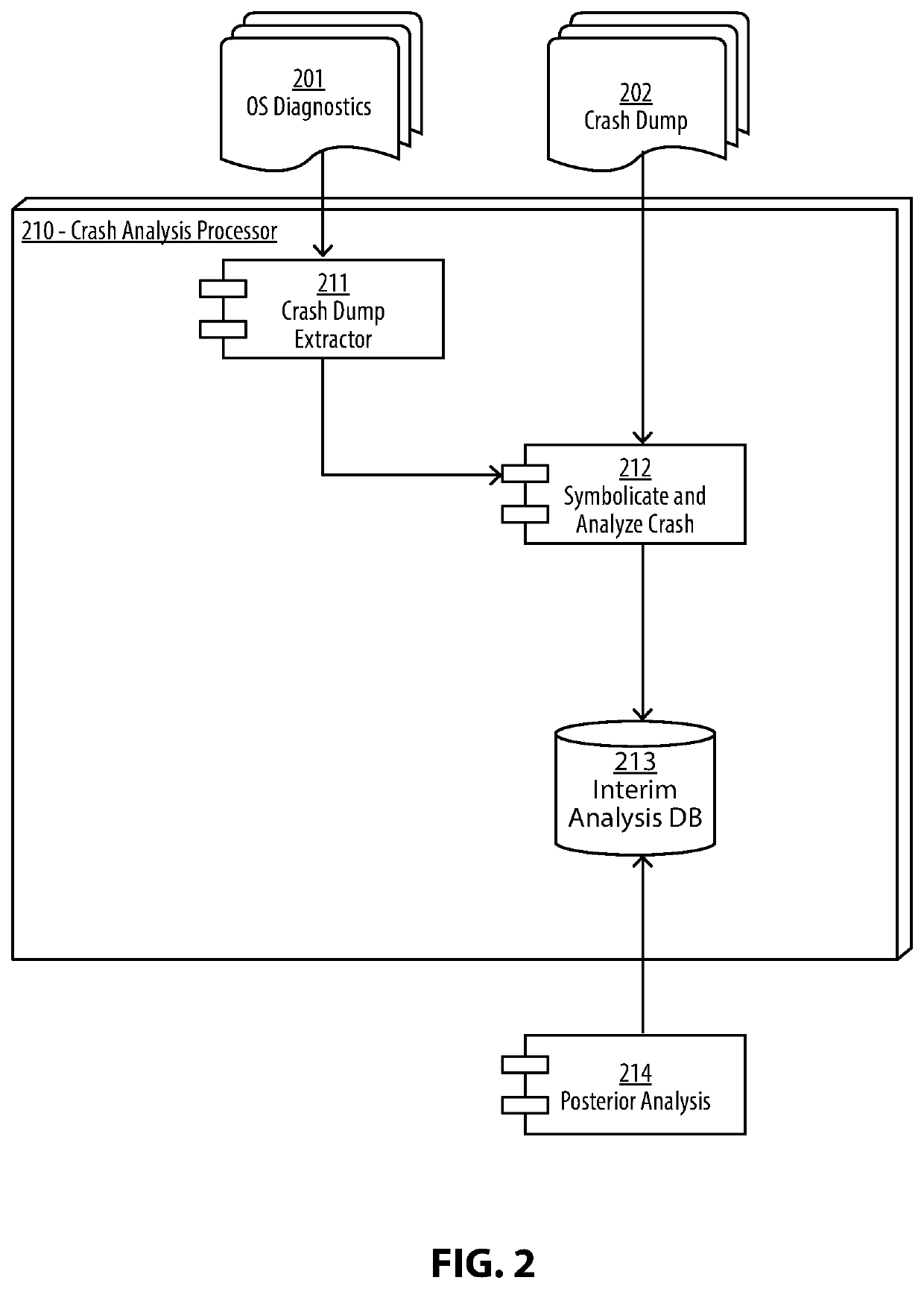
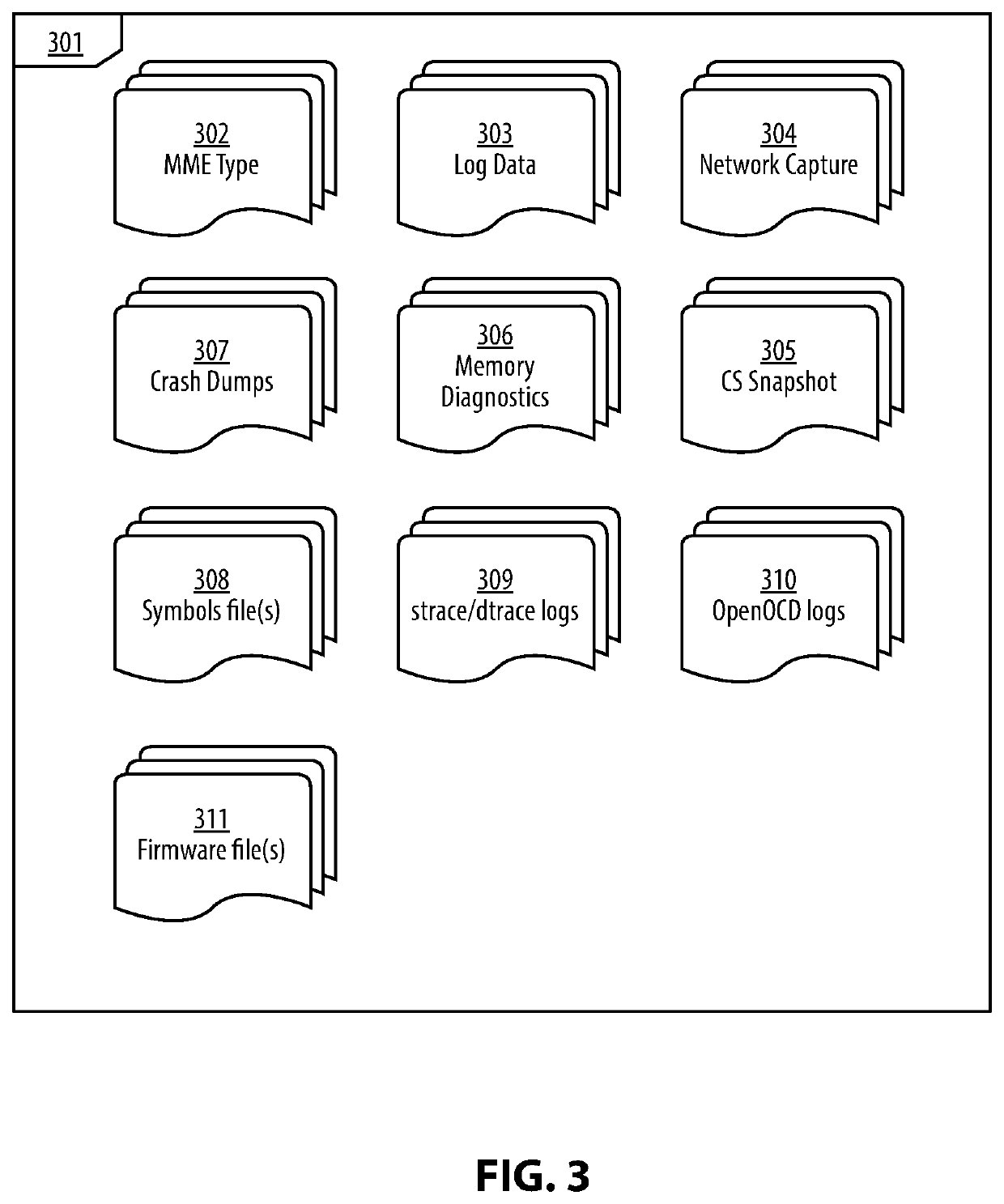
System and Method for an Automated Analysis of Operating System Samples, Crashes and Vulnerability Reproduction
Malware analysis and root-cause analysis, and information security insights based on Operating System sampled data. Sampled data includes structured logs, Operating System Snapshots, programs and / or processes and / or kernel crashes, crash dumps, memory dumps, stackshots, simulated crashes or samples. The sampled data contains payload for extraction for the purpose of detection, evaluation and reproduction of threats, infection vector, threat actors and persistence methods in the form of backdoors or Trojans or exploitable vulnerabilities used for initial infiltration or lateral movement.
Owner:ZECOPS
System and Method for An Automated Analysis of Operating System Samples
InactiveUS20200012793A1Digital data protectionPlatform integrity maintainanceMalware analysisOperational system
Methods and apparatuses for malware analysis and root-cause analysis, and information security insights based on Operating System sampled data such as structured logs, Operating System Snapshots, programs and / or processes and / or kernel crash dumps or samples containing payload for extraction for the purpose of detection and evaluation of threats, infection vector, threat actors and persistence methods in the form of backdoors or Trojans or unknown exploitable vulnerabilities used.
Owner:ZECOPS
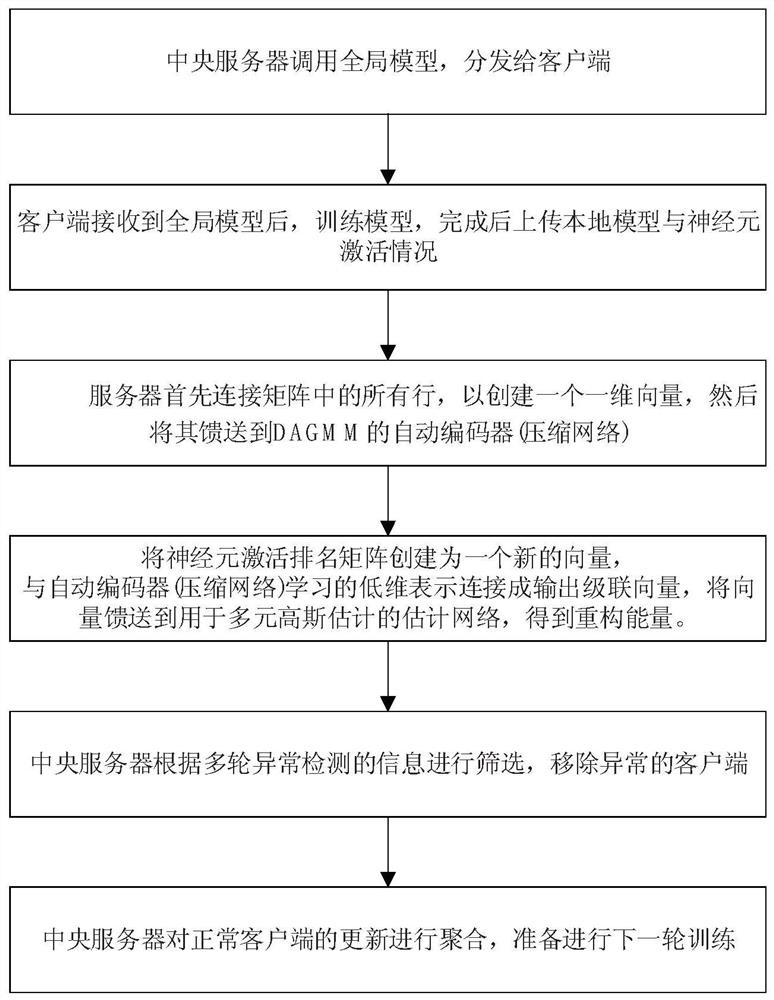
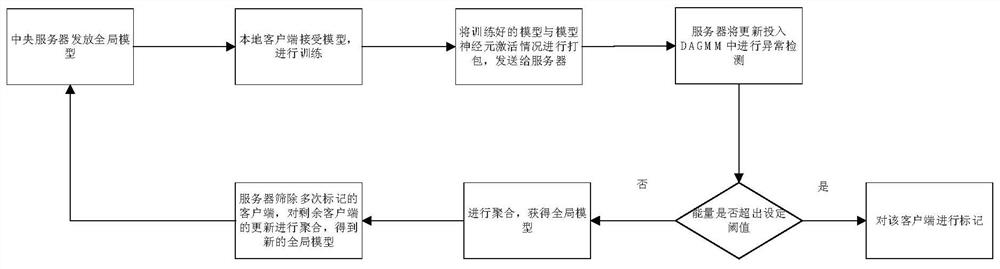
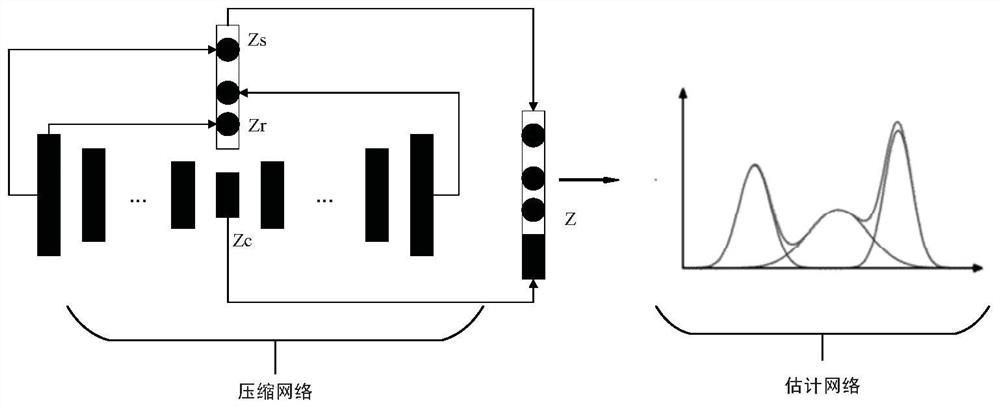
Federal learning backdoor attack defense method based on DAGMM
ActiveCN113411329AImprove robustnessImprove the efficiency of attack detectionEnsemble learningData switching networksAttackEngineering
The invention discloses a federal learning backdoor attack defense method based on DAGMM, and the method comprises the following steps: (1) a client receives a global model, and trains and uploads a local model and a corresponding neuron activation condition; (2) the server receives the update and calculates the loss of the corresponding client by using the DAGMM; and (3) defense is performed based on multi-round reconstruction errors. According to the invention, the model can be effectively protected from backdoor attack.
Owner:ZHEJIANG UNIV OF TECH
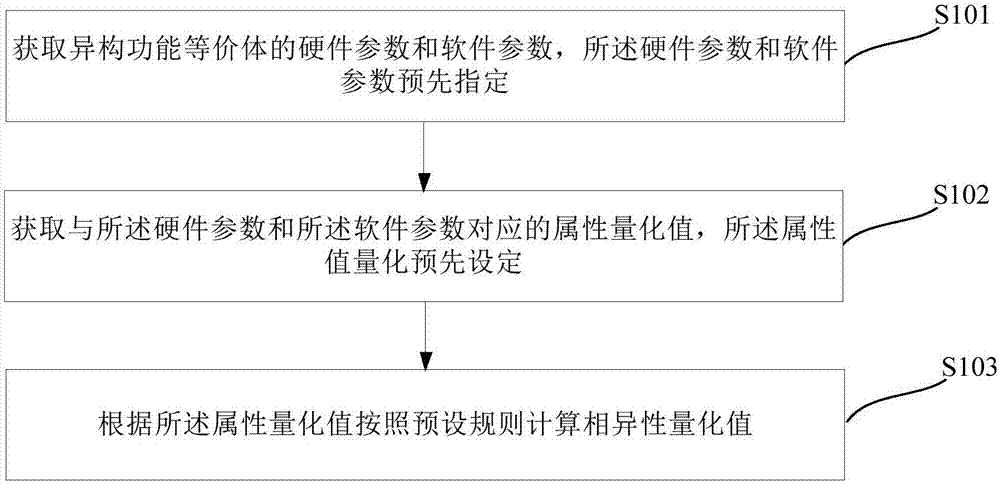
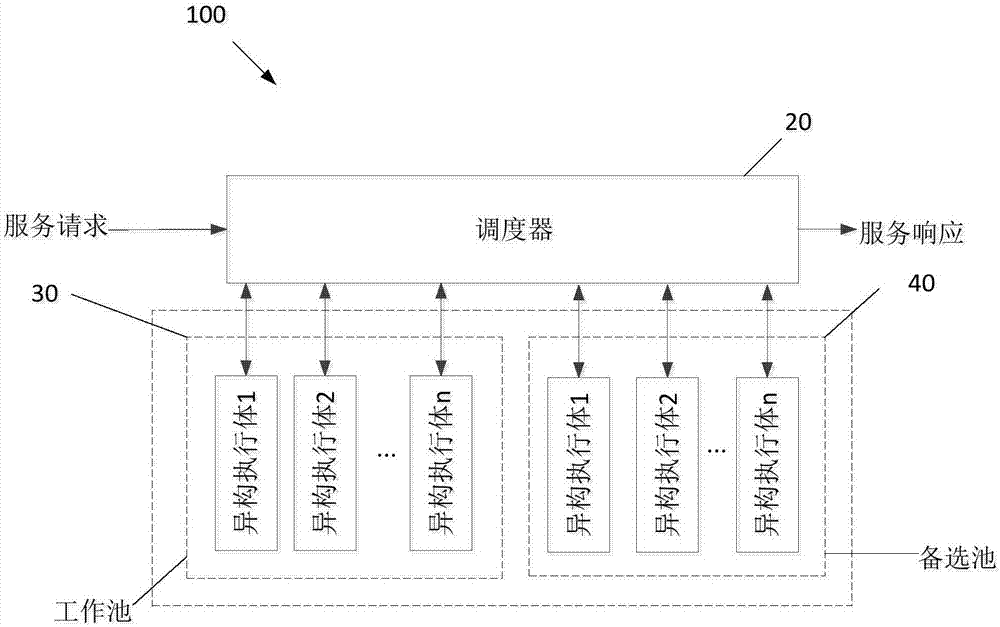
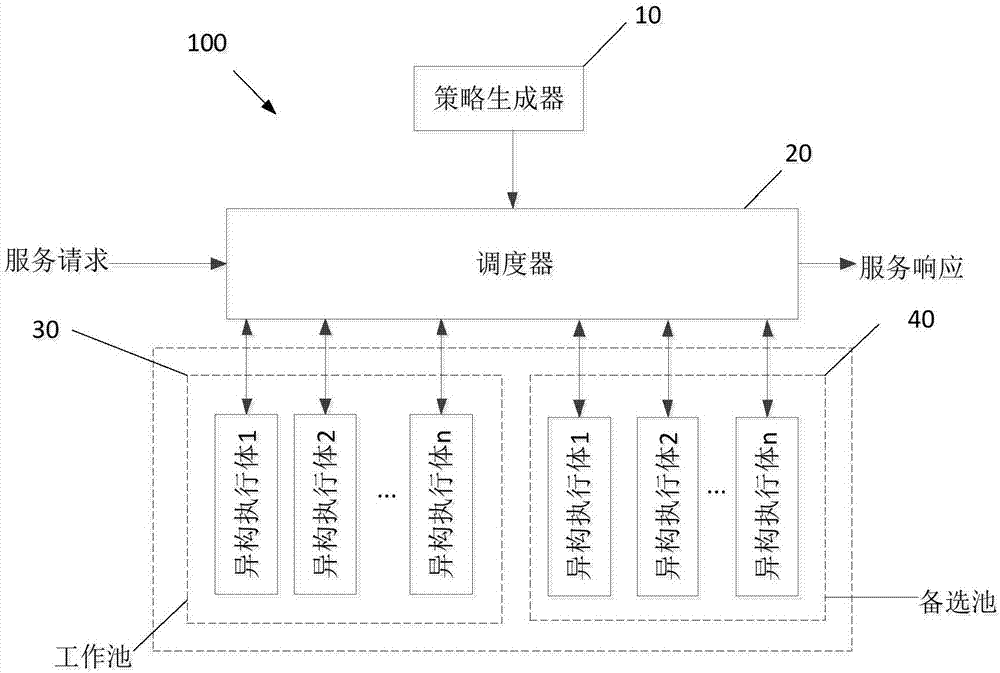
Heterogeneous function equivalent dissimilarity measurement method, distribution method, device and equipment
ActiveCN107358105AAchieving early preventionPlatform integrity maintainanceTransmissionDistribution methodNetwork attack
The application discloses a heterogeneous function equivalent dissimilarity measurement method, distribution method, device and equipment. The heterogeneous function equivalent distribution method comprises following steps: determining a heterogeneous function equivalent to be selected from an alternate pool according to a service request, wherein the heterogeneous function equivalent is provided with the function of providing services requested in the service request; moving one or more of the heterogeneous function equivalents to be selected , which are most different from the heterogeneous function equivalents in a working pool , into the working pool, wherein the heterogeneous function equivalents are provided with the function of providing services requested in the service request. The method can disassemble and blur the unknown risks of design vulnerabilities or embedded backdoors and trap doors in cyberspace architectures and prevent network attacks in advance.
Owner:ZHUHAI GAOLING INFORMATION TECH COLTD +1
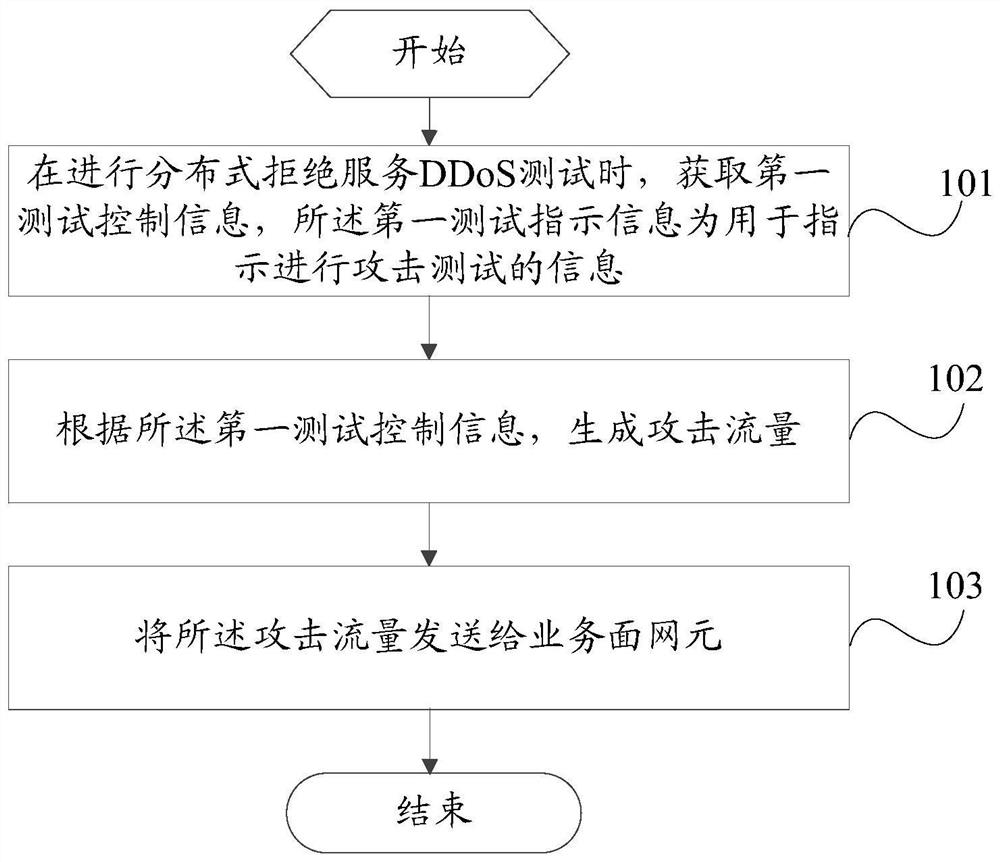
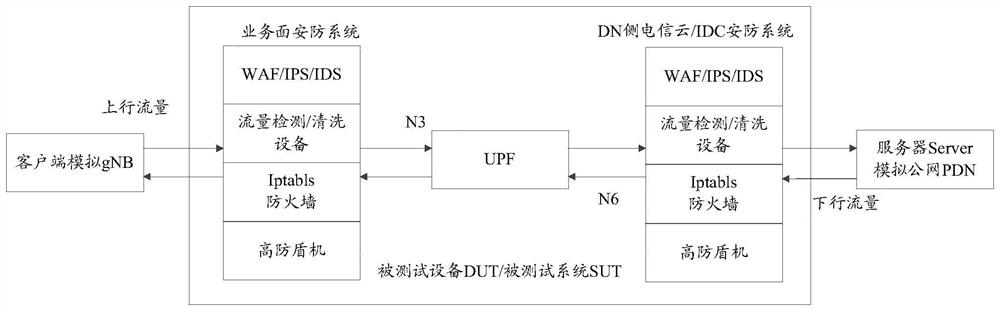
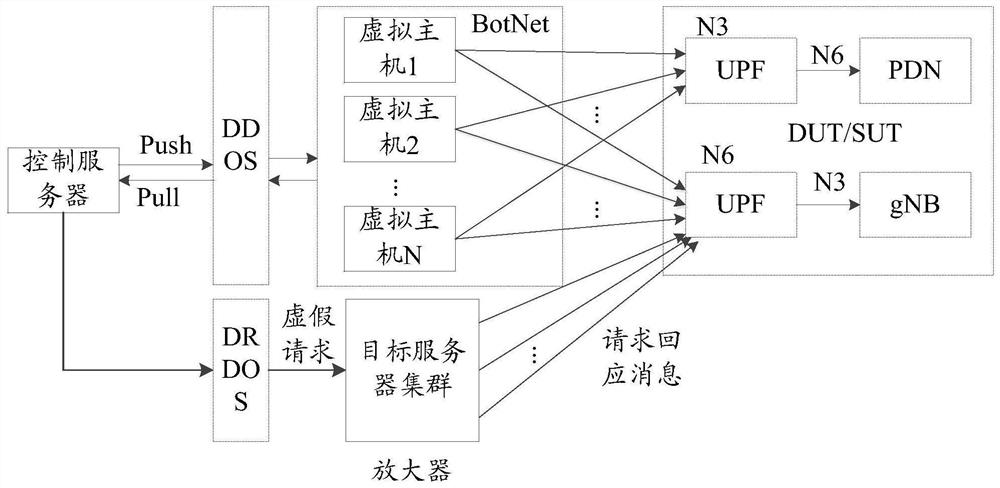
Attack testing method, host server and control server
The invention provides an attack test method, a host server and a control server, and solves a problem of how to carry out an attack test on a core network service surface. The method comprises stepsthat when a distributed denial of service DDoS test is carried out, the first test control information is acquired, and the first test indication information is used for indicating to carry out an attack test; attack traffic is generated according to the first test control information; and the attack traffic is sent to a service plane network element. The method is advantaged in that the virtual host is controlled by the control server, so large-scale DDoS attacks can be safely and effectively simulated, and diffusion threats of backdoor programs and harm caused by botnets do not need to be considered.
Owner:DATANG MOBILE COMM EQUIP CO LTD
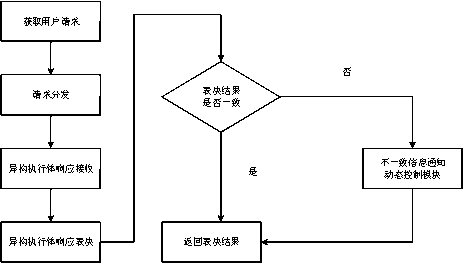
Industrial network endogenous security boundary protection method, device and architecture
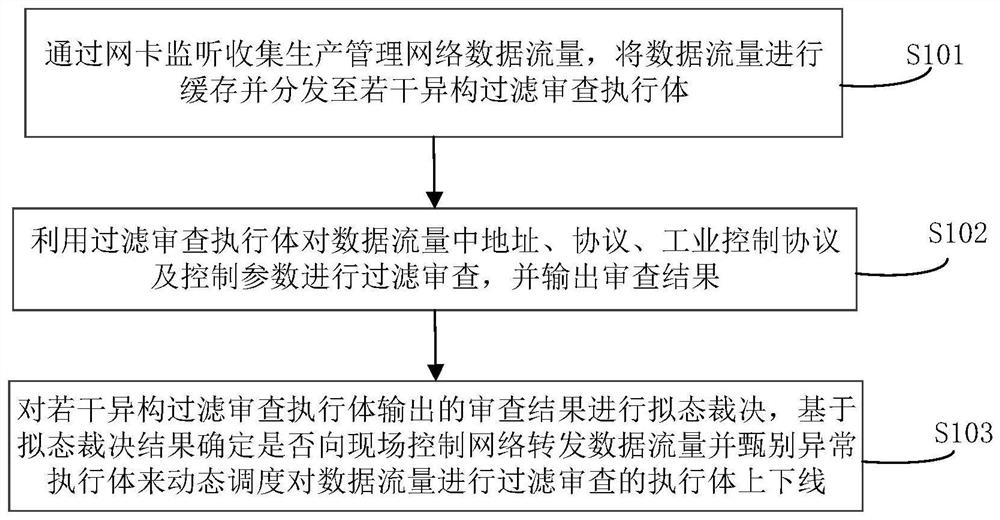
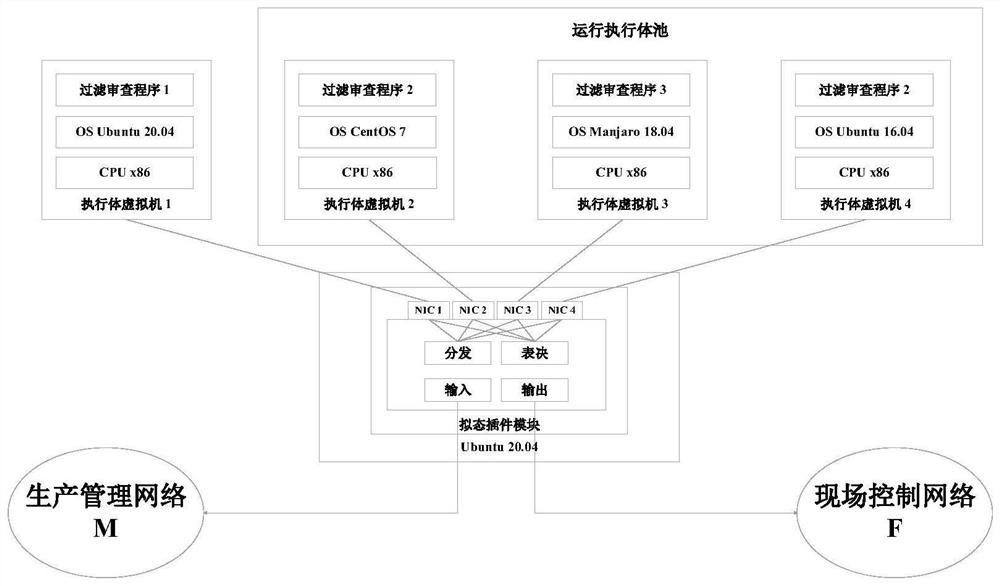
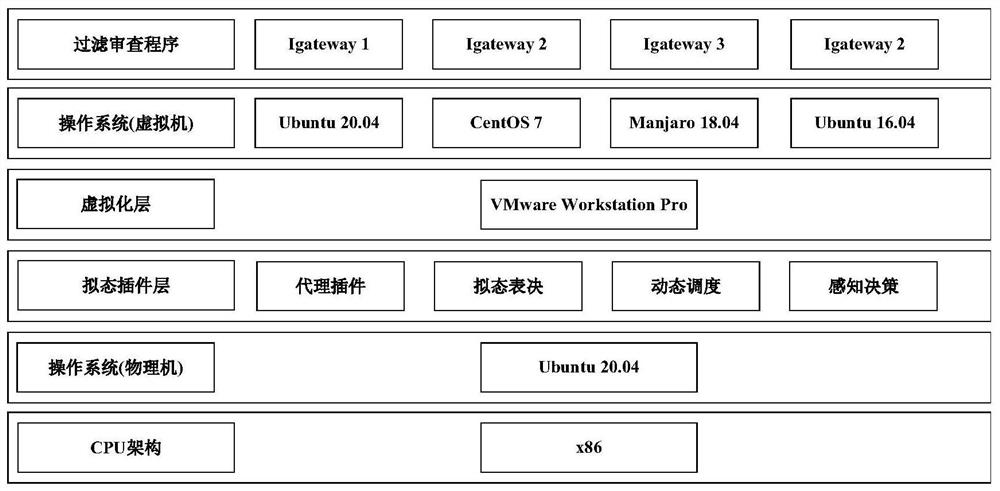
PendingCN113285917AImprove filter review accuracyMitigate the threat of uncertaintyTransmissionOnline and offlineNetwork data
The invention relates to an industrial network endogenous security boundary protection method, device and system, and the method comprises the steps: monitoring and collecting production management network data traffic through a network card, caching the data traffic, and distributing the data traffic to a plurality of heterogeneous filtering review executors; filtering and reviewing the address, the protocol, the industrial control protocol and the control parameter in the data flow by using a filtering and reviewing executor, and outputting a reviewing result; performing mimicry judgment on the review results output by the plurality of heterogeneous filtering review executors, and determining whether to forward the data traffic to the field control network based on the mimicry judgment results and discriminating the abnormal executors to dynamically schedule the executors for filtering and reviewing the data traffic to be online and offline. Aiming at security threats faced by the industrial network boundary protection equipment, a mimicry defense technology is combined, a filtering review function is stripped out, and the uncertainty threats caused by unknown vulnerabilities or backdoors of the industrial network boundary protection equipment are relieved through heterogeneous and redundancy filtering review execution bodies.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
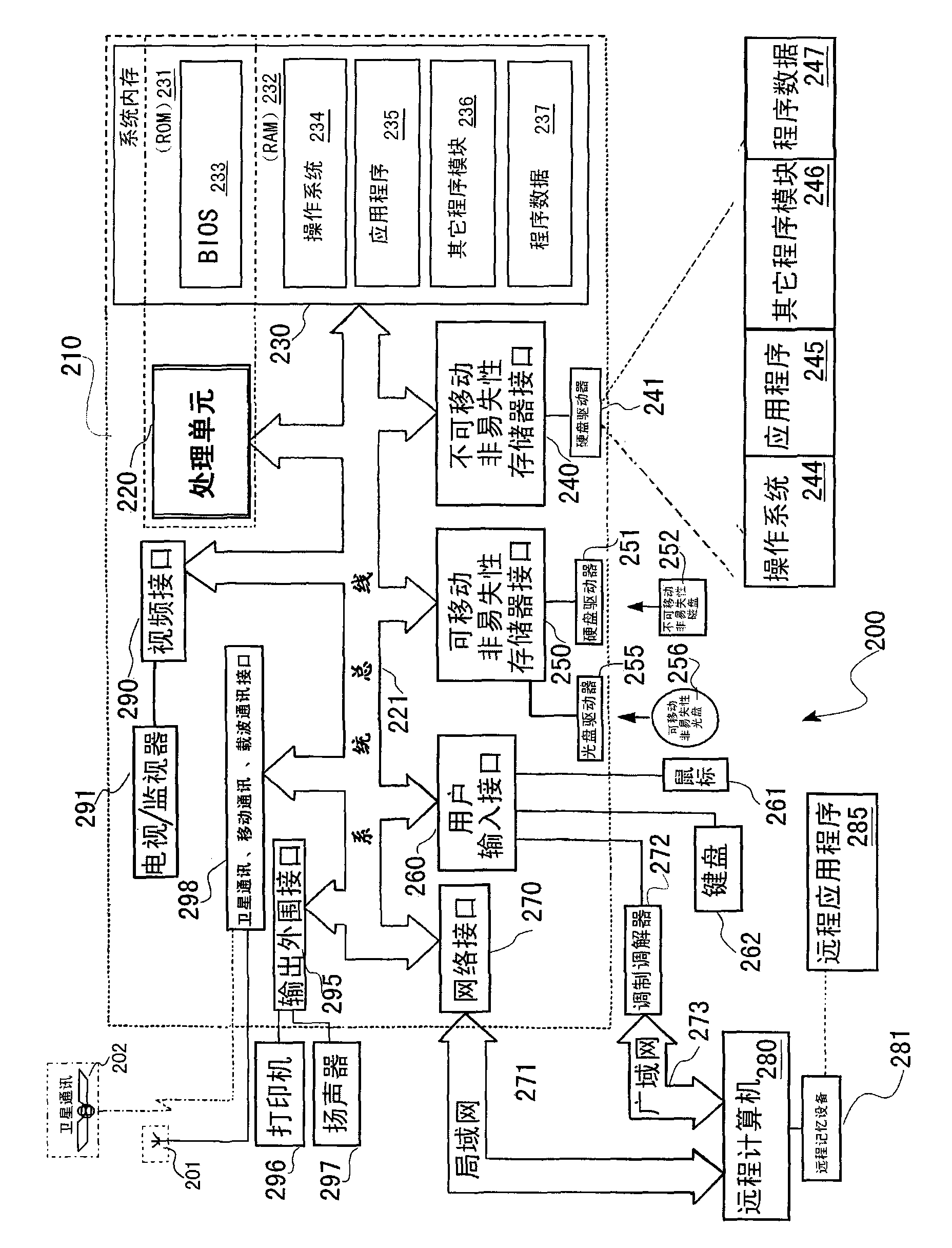
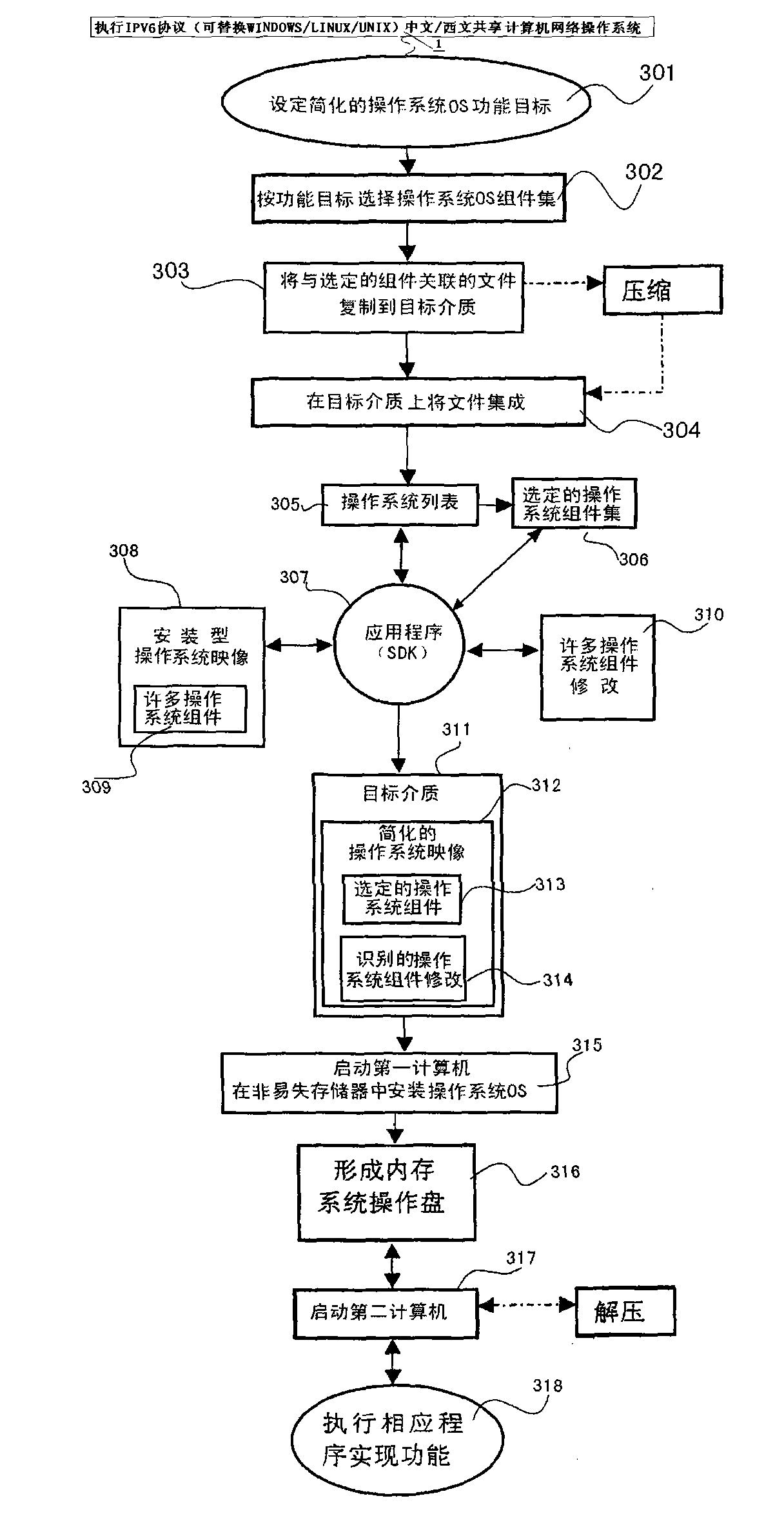
Computer operation system and establishing method thereof
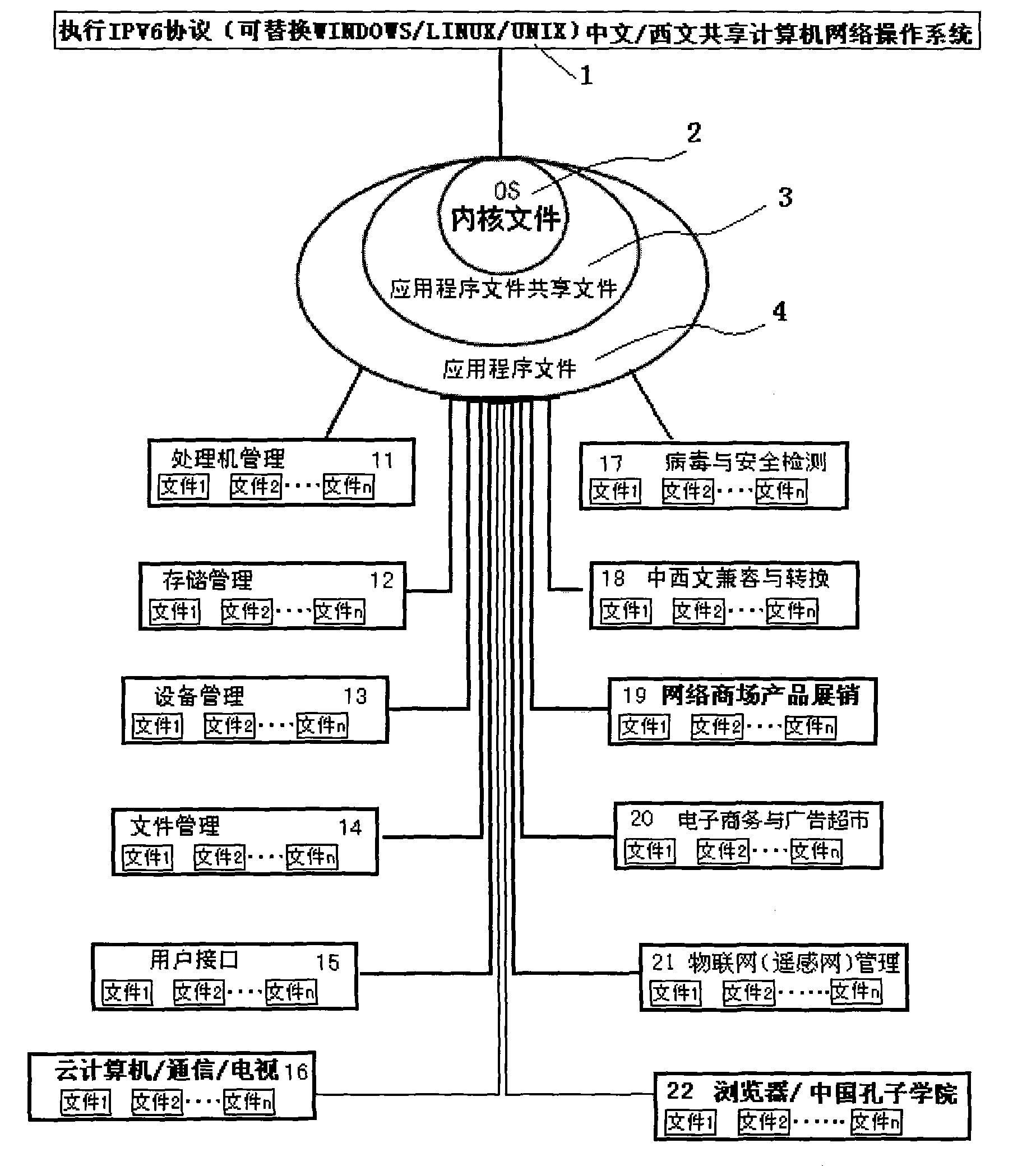
The invention discloses a computer operation system and an establishing method thereof. An IPv6 protocol is applied, a network address space is expanded, the whole throughput of the network is increased, the service quality is improved, the safety is more efficiently ensured, the plug-and-play and the mobility are supported, and a multicast function is more efficiently realized; multi-network interconnection sharing used for communication, television, computer and Internet of things can meet the functional requirement of a high-grade PC (Personal Computer), a large-size computer and the network running of the large-size computer, and a simplified operation system (OS) image is established based on an installing type OS image; and a well known fact is that the preset backdoor intelligence search in the Windows operation system and the blank screen virus of the backdoor intelligence search are time bombs capable of destroying hardware and hard disk of a user. The invention provides a set of computer operation system with Chinese proprietary intellectual property rights and a safeguard system for information safety; the monopoly of the western countries is broken; the entire international core competitiveness is increased; the system is simple in operation and convenient in maintenance; the running efficiency, the compatibility, the stability and the safety are all ultrahigh; and all the functions of Windows, Linux, Unix and other operation systems can be replaced and covered.
Owner:刘明前
Website back door detection method and device
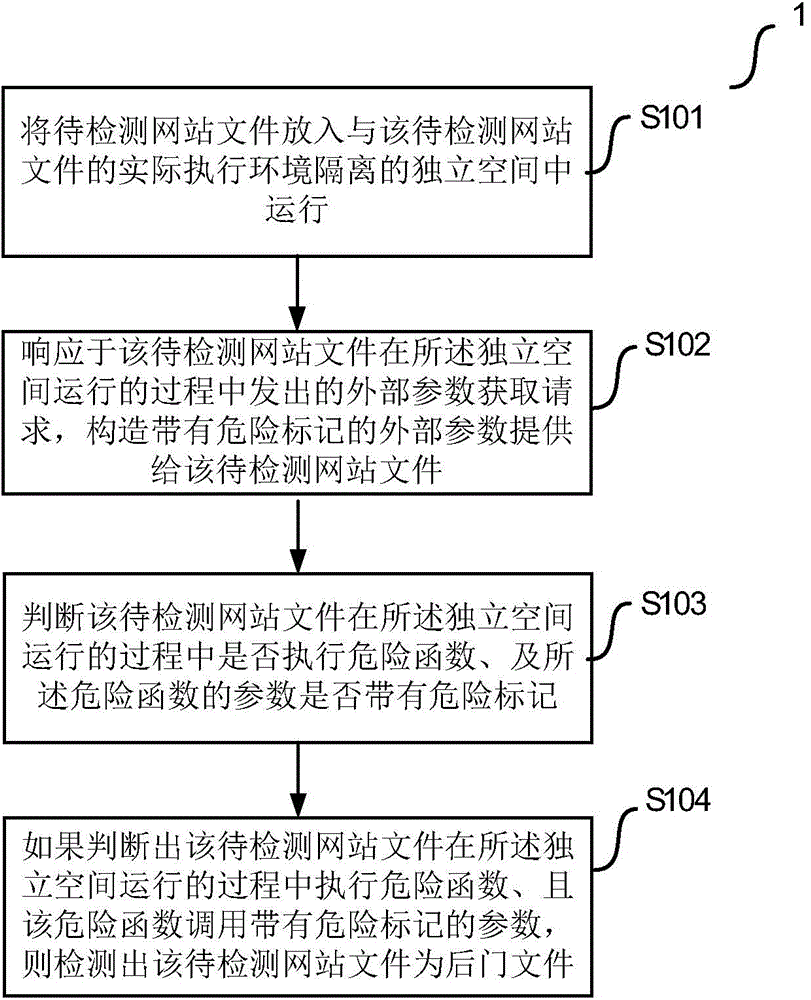
InactiveCN106301974AAvoid defects that are not easily identifiedData switching networksSpecial data processing applicationsInternet privacyBack door
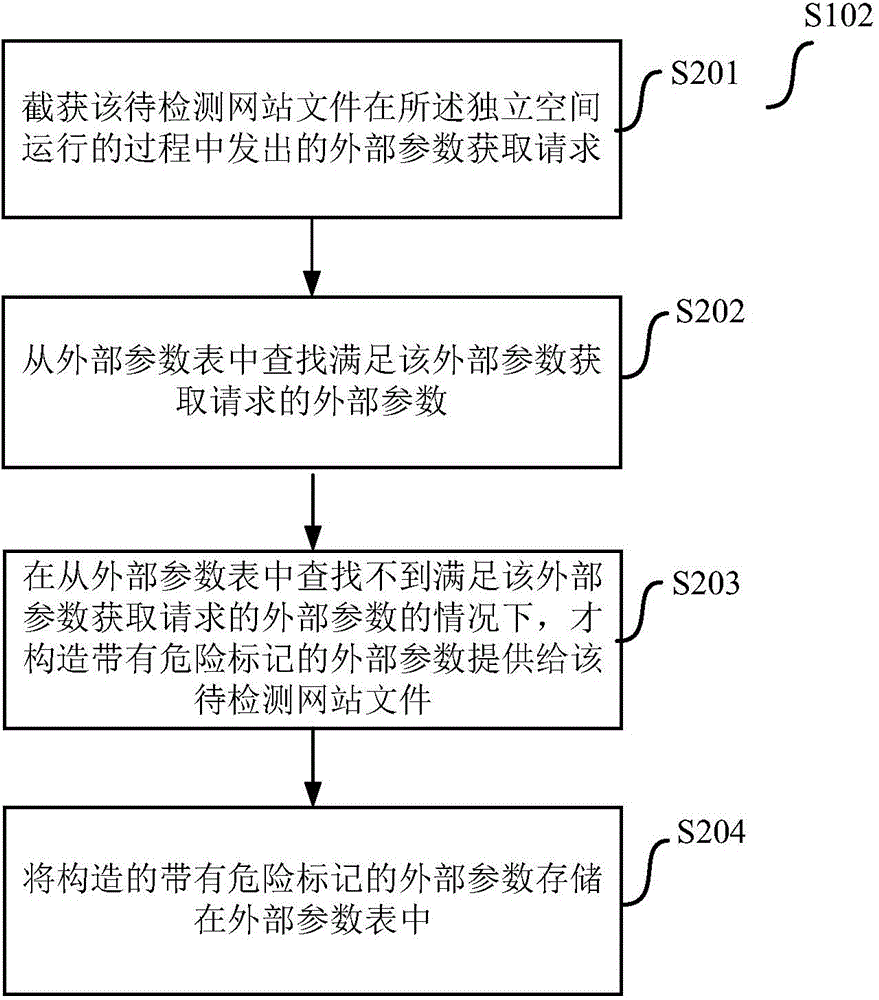
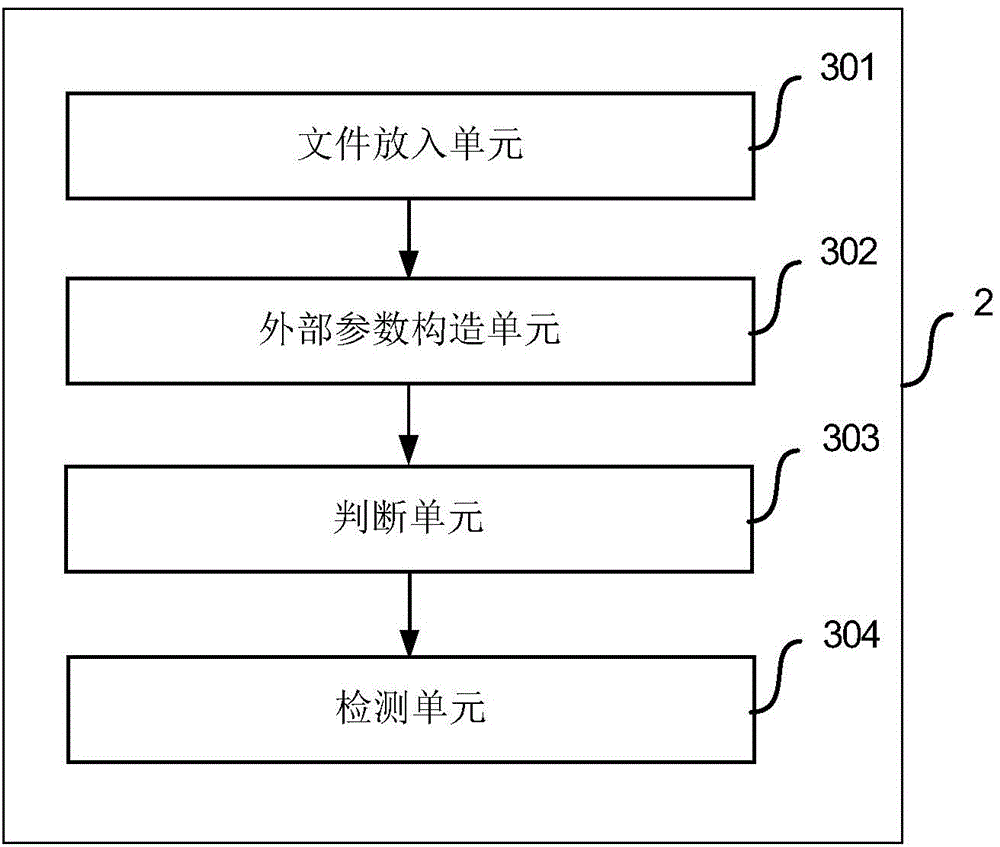
The invention provides a website back door detection method and device. The website backdoor detection method comprises steps of putting a file of a website to be detected into an independent space isolated from a practical execution environment of the file of the website to be detected for operation; constructing an external parameter carrying a danger label and supplying the external parameter to the file of the website to be detected by responding to an external parameter obtaining request transmitted by the file of the website to be detected during operation in the independent space, wherein the external parameter carrying the danger label goes through a booking string processing function and the danger label is maintained; determining whether the file of the website to be detected executes the danger function during a process of operating in the independent space and whether the parameter of the danger function has the danger label; if afacts that the file of the website to be detected executes the danger function in the process of operating in the independent space and the danger function calls the parameter with the danger labels is determined, detecting that the file of the website to be detected is a backdoor file. The embodiment of the website back door detection method and device can effectively detect the backdoor of the website.
Owner:ALIBABA GRP HLDG LTD
Solution for cloud Web application to cope with virtual host layer attacks
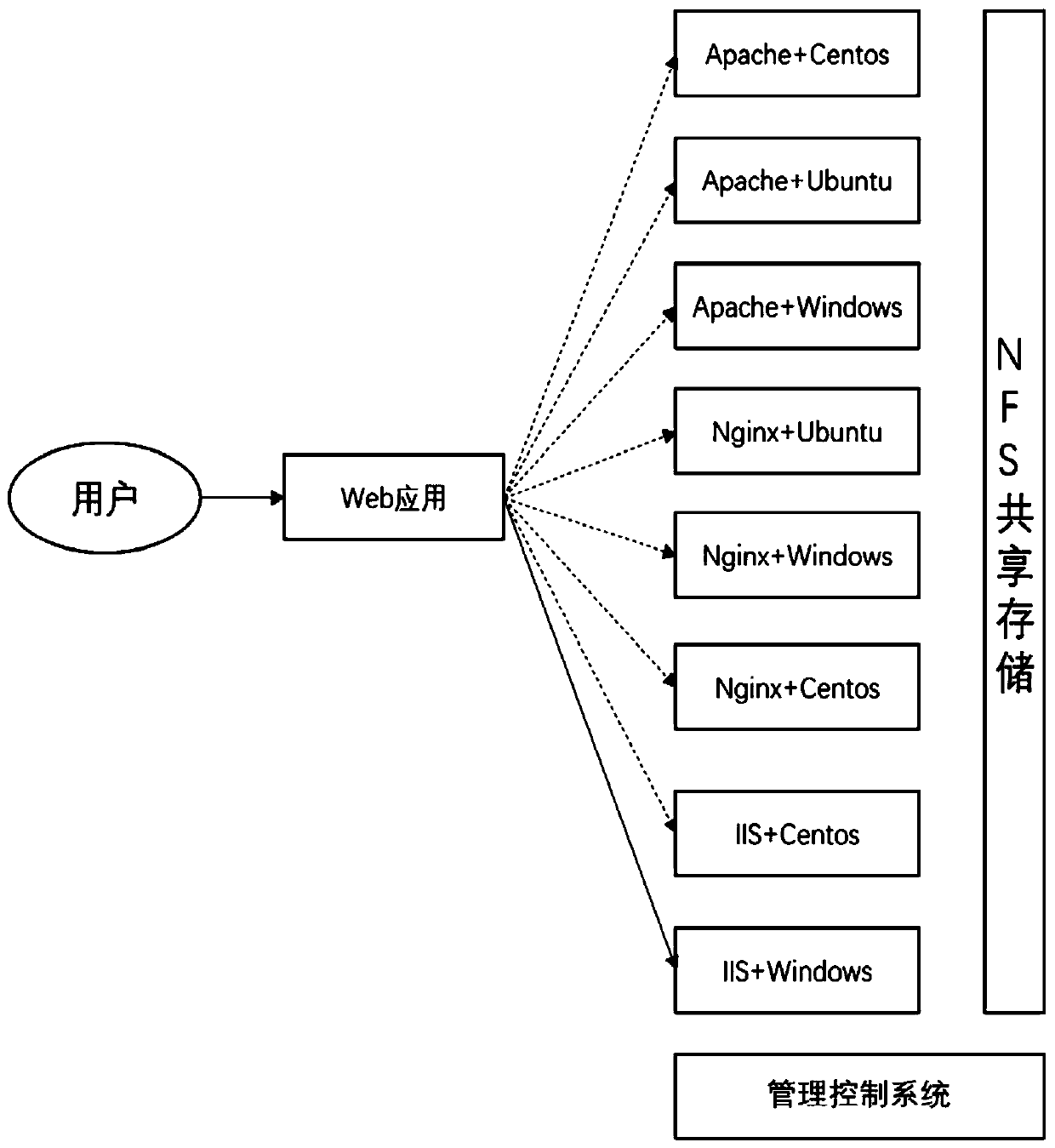
InactiveCN111585952ASolve the knownAddress unknown attacksTransmissionSoftware simulation/interpretation/emulationWeb applicationAttack
The invention discloses a solution for a cloud Web application to cope with virtual host layer attacks. The method comprises the steps: creating heterogeneous servers on the cloud, and achieving the data consistency of all the servers through shared storage; achieving the dynamic change of the server through a certain flow forwarding strategy, so as to present a dynamic change target which is difficult to observe and predict for an attacker, thereby increasing the attack difficulty and cost for unknown vulnerabilities and backdoors; and finally, through offline and self-healing of the attackedserver, achieving a purpose that the service is not interrupted. According to the invention, dynamic heterogeneous redundant server deployment is realized, and known and unknown attacks in the network can be solved.
Owner:ZHEJIANG UNIV
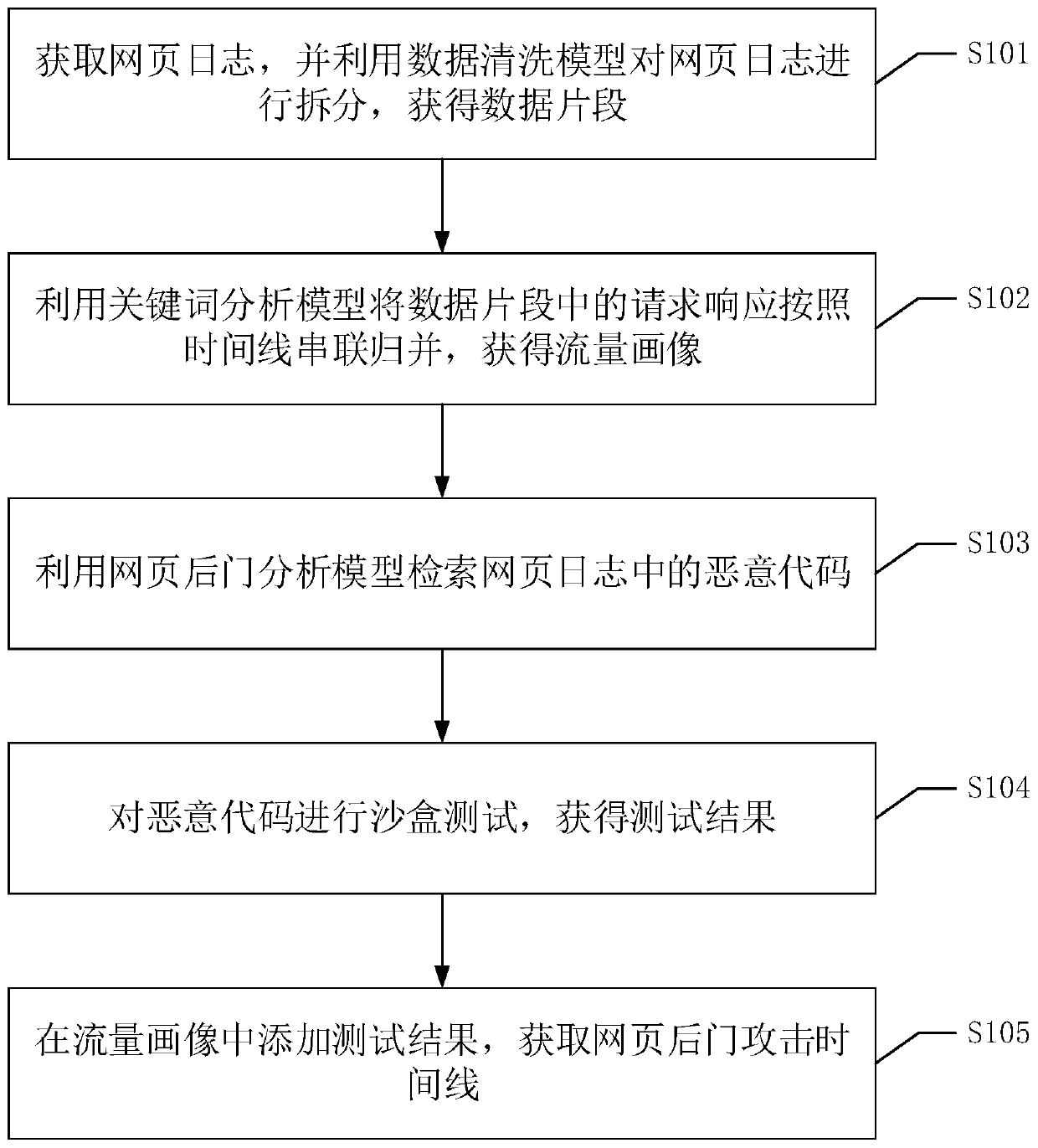
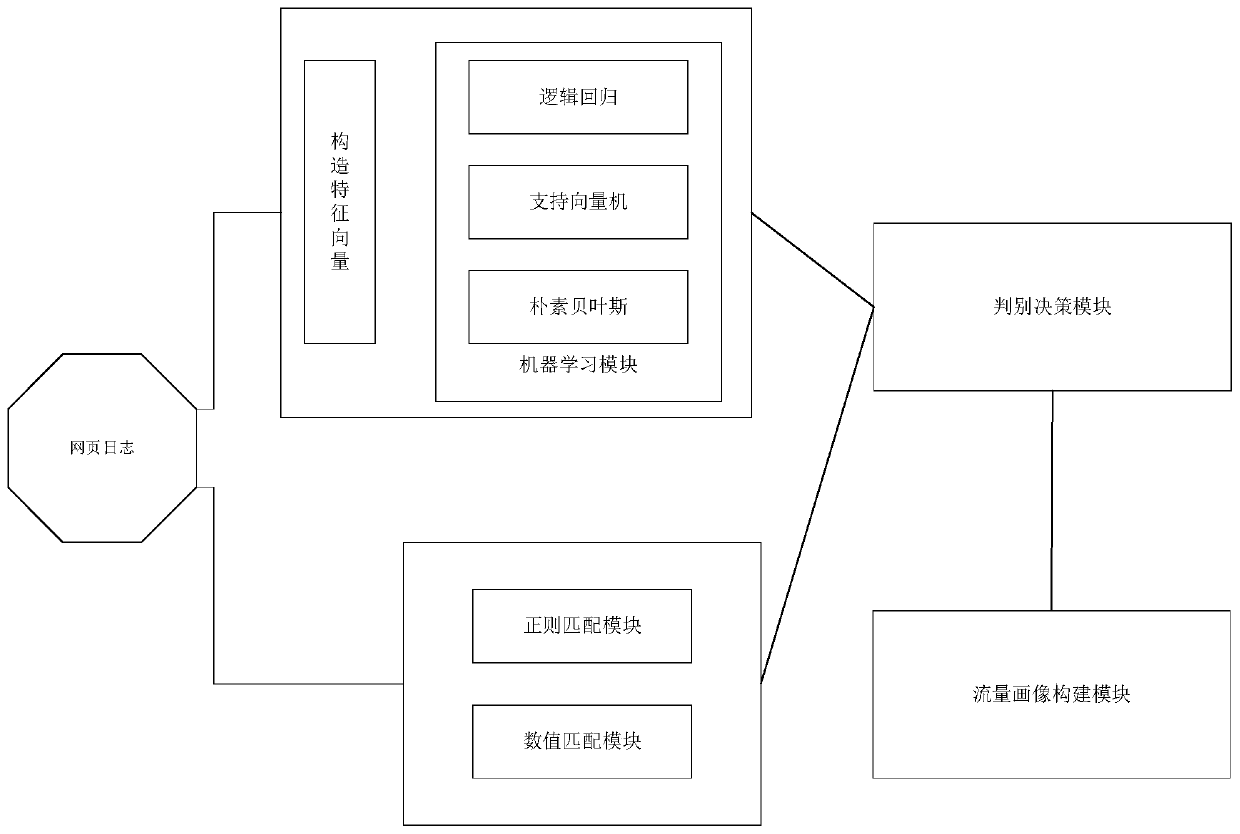
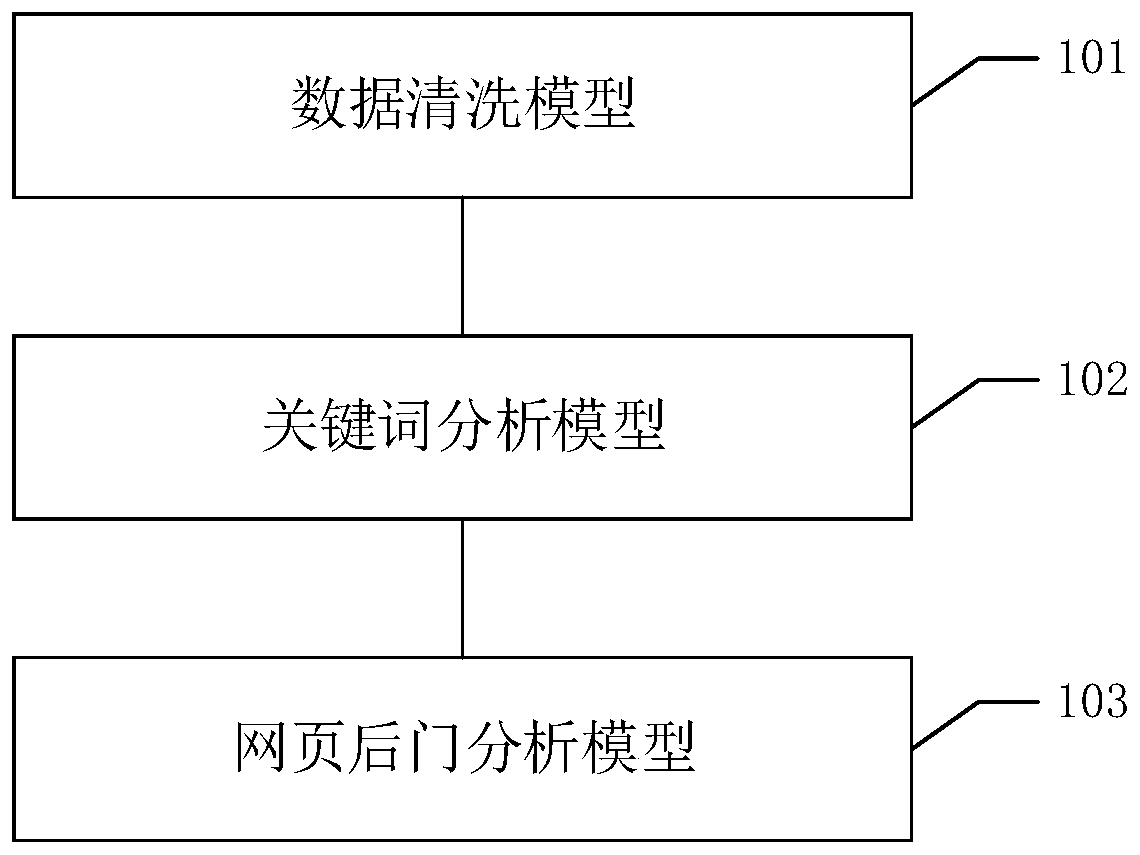
Webpage log attack information detection method, system and device and readable storage medium
The invention discloses a webpage log attack information detection method, system and device and a readable storage medium, and the method comprises the steps: obtaining a webpage log, carrying out the splitting of the webpage log through a data cleaning model, and obtaining a data segment; merging the request responses in the data fragments in series according to a timeline by utilizing a keywordanalysis model to obtain a flow portrait; utilizing a webpage backdoor analysis model to retrieve malicious codes in the webpage logs; performing sandbox test on the malicious code to obtain a test result; and adding a test result in the flow portrait, and obtaining a webpage backdoor attack timeline. According to the method, the webpage log is processed, so that the webpage backdoor attack timeline used for tracking the attacker and restoring the attack process can be finally obtained, and powerful reference evidences are provided for capturing the attacker in time and preventing the attacker from committing a crime next time.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Using gradients to detect backdoors in neural networks
Mechanisms are provided for evaluating a trained machine learning model to determine whether the machine learning model has a backdoor trigger. The mechanisms process a test dataset to generate outputclassifications for the test dataset, and generate, for the test dataset, gradient data indicating a degree of change of elements within the test dataset based on the output generated by processing the test dataset. The mechanisms analyze the gradient data to identify a pattern of elements within the test dataset indicative of a backdoor trigger. The mechanisms generate, in response to the analysis identifying the pattern of elements indicative of a backdoor trigger, an output indicating the existence of the backdoor trigger in the trained machine learning model.
Owner:IBM CORP
Backdoor attack detection and identification method for privacy protection neural network model
ActiveCN112989438APrivacy protectionDigital data protectionInternal/peripheral component protectionAttackPrivacy protection
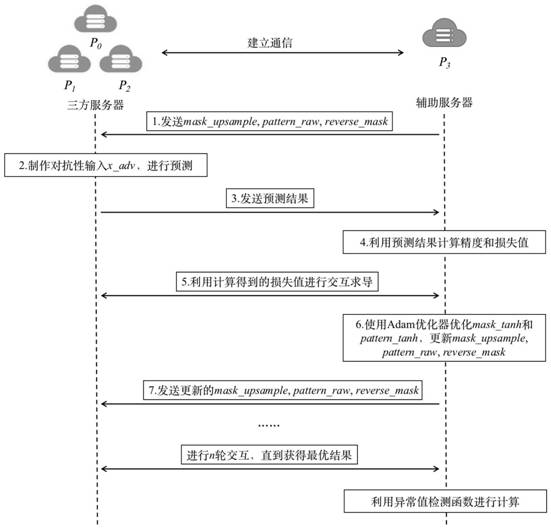
The invention provides a backdoor attack detection and identification method for a privacy protection neural network model. The method comprises the following steps: (1), generating a mask matrix and a trigger matrix; (2) setting an initial state of related parameters of back door detection; (3), constructing adversarial input; (4) carrying out optimization training on the mask matrix and the trigger matrix; (5), calculating gradients of the mask matrix and the trigger matrix; (6) resetting the mask matrix and the trigger matrix; and (7), performing trigger reverse engineering. According to the method, the neural network model is trained in a three-party environment in a fixed-point number operation mode, and the neural network model which protects data privacy and model privacy and is provided with the backdoor is obtained. According to the method, the privacy of model parameters and data can be protected in an environment of a four-side server, whether a backdoor exists in the model or not can be detected, and a specific attacked label can be identified.
Owner:SHANGHAI OCEAN UNIV
Backdoor confrontation sample generation method of PE malicious software detection model
ActiveCN113254930AReduce computational overheadReduce distractionsCharacter and pattern recognitionPlatform integrity maintainanceData setEngineering
The invention relates to a backdoor confrontation sample generation method of a PE malicious software detection model based on R-DBSCAN, and belongs to the field of computer malicious software detection. The method mainly aims at solving the problem that a malicious software detection model is high in attack difficulty under the black box condition. The method comprises the following steps: firstly, acquiring a PE sample from a public data set, training a proxy training model, and reducing the dimension of the data set by adopting an SHAP value; clustering the samples by adopting an R-DBSCAN method, and taking a center node of each cluster as a sampling point to construct a new data set; training a neural network model; respectively inputting malicious and benign sample files, and recording neurons which greatly influence a classification result according to the weight change condition of the neurons in the neural network; embedding a character string with any length into the empty PE file, taking a character string which greatly influences the character string according to the weight change condition of the neuron, and recording the neuron; embedding a trigger into an original malicious PE file, and modifying a label to achieve adversarial training of a neural network.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Method for remotely and accurately identifying WebShell back door
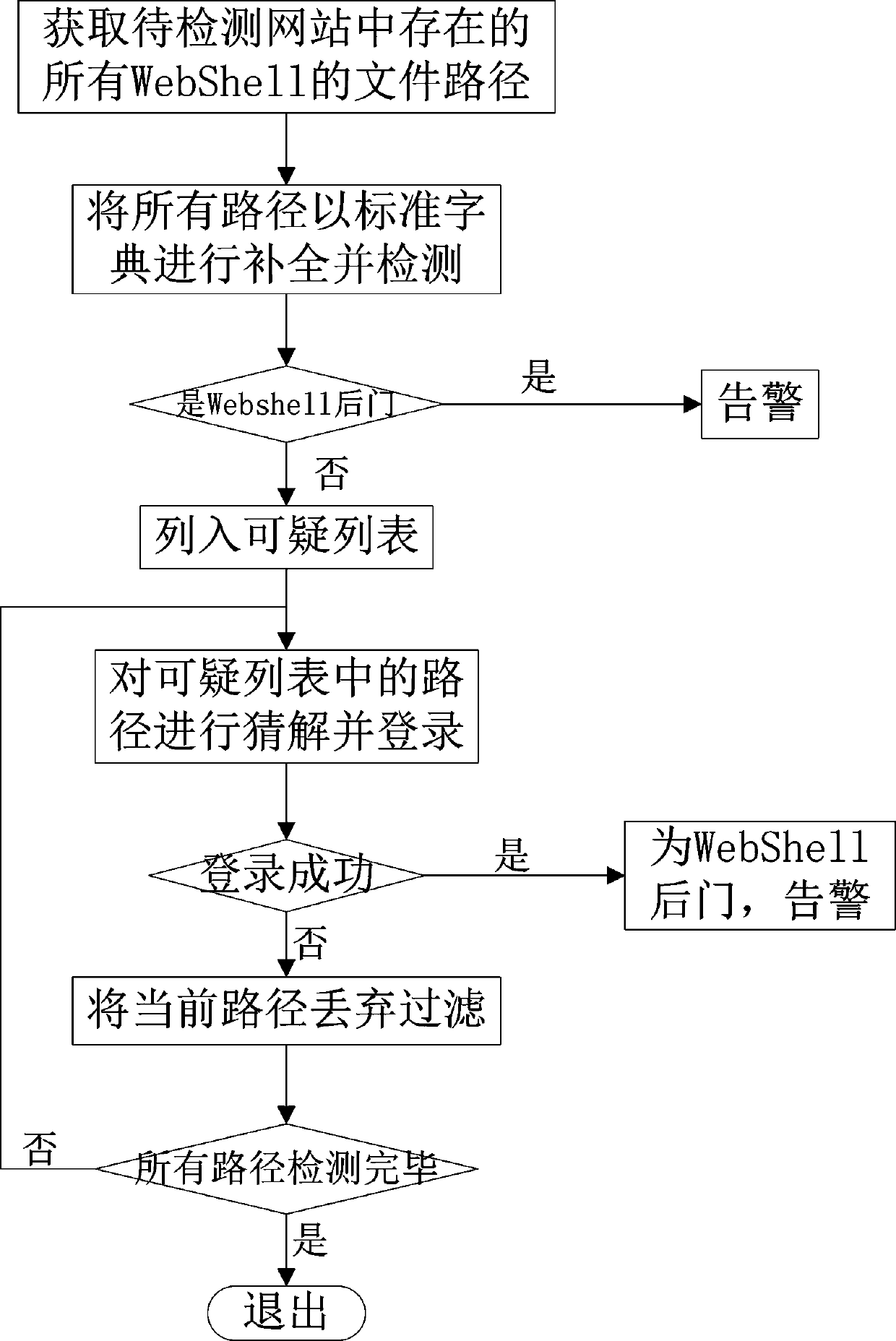
ActiveCN110909350AImprove the detection rateRich inspection methodsWeb data indexingPlatform integrity maintainanceWeb sitePathPing
The invention relates to a method for remotely and accurately identifying a WebShell back door. The method includes the steps: obtaining all file paths of WebShell existing in the website to be detected; complementing and detecting by using the standard dictionary, if the current path is a WebShell back door, directly alarming, otherwise, listing into a suspicious list and successively guessing and logging in, and if the login is successful, judging that the current path is the WebShell back door, and alarming, otherwise, discarding and filtering the current path. The method carries out crawler crawling on the target website to obtain all webpage resources, performs total station matching with a common WebShell backdoor path, judges whether a backdoor exists or not is matched through a WebShell backdoor rule base, accurately recognizes the WebShell backdoor in a remote mode, conducts violent guessing login on the suspected WebShell for recognition, accurately recognizes the WebShell backdoor through multi-latitude feature matching, enriches webpage backdoor checking methods, and increases the WebShell backdoor detection rate.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Data set protection and verification method based on backdoor attacks
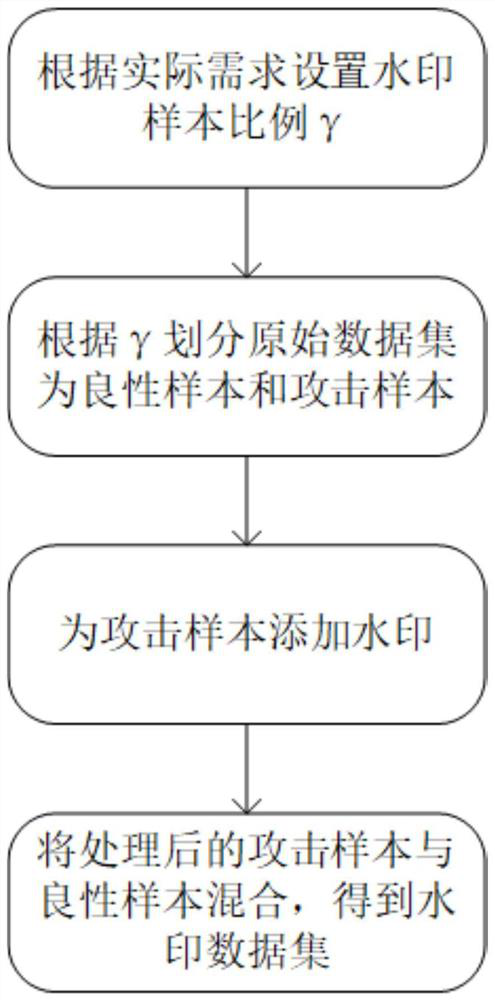
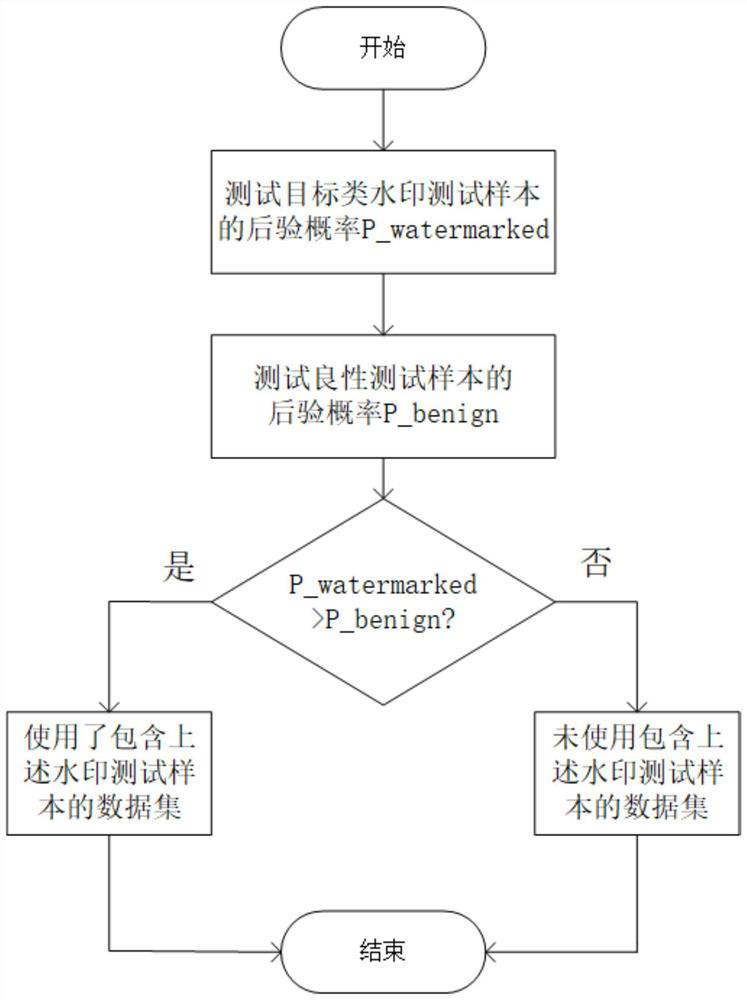
InactiveCN112364310AGuaranteed prediction accuracyImage data processing detailsProgram/content distribution protectionData setOriginal data
The invention belongs to the technical field of Internet, and particularly relates to a data set protection and verification method based on backdoor attacks, which comprises the following steps: setting the proportion of watermarks gamma according to actual requirements; dividing the original data set into a benign sample data set Dbenign and an attack sample data set Dattack according to gamma;adding watermarks to the attack sample data set Dattack obtained after division, and obtaining a processed attack sample data set Dmodified; and mixing the processed attack sample data set Dmodified with the benign sample data set Dbenign to obtain a watermark data set Dwatermarked. According to the method, attack samples are set by adding triggers to part of the samples, so that when the model istrained by using a standard training process on a watermark data set, a hidden backdoor can be specified while the prediction precision of benign samples is maintained. The method is used for protecting the data set.
Owner:山西三友和智慧信息技术股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com