Backdoor attack detection and identification method for privacy protection neural network model
A neural network model and privacy protection technology, applied in biological neural network models, neural learning methods, digital data protection, etc., can solve problems such as security loopholes, traffic accidents, and users' inability to communicate on the platform
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] In order to make the purpose, technical solutions and advantages of the embodiments of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings. Here, the exemplary embodiments and descriptions of the present invention are used to explain the present invention, but not to limit the present invention.
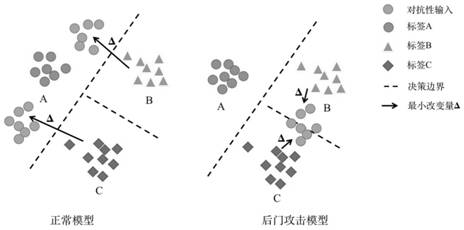
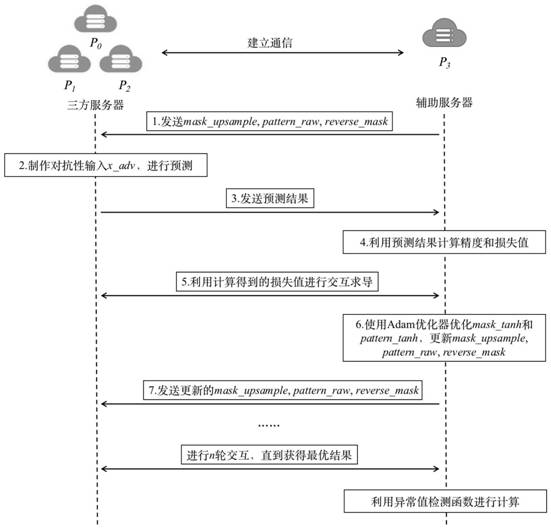
[0032] The invention designs a backdoor detection algorithm operating in the Sifang environment, that is, to judge whether a given neural network model has been infected by the backdoor. The key is that the backdoor attack is no matter what the input label is, the final target label A is obtained. Think of classification problems as creating partitions in a multidimensional space, with each dimension capturing some features. Then the backdoor attack is a "shortcut" created from the space area belonging to labels B and C to the space area belonging to A, as shown in the attached figure 1 As...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com