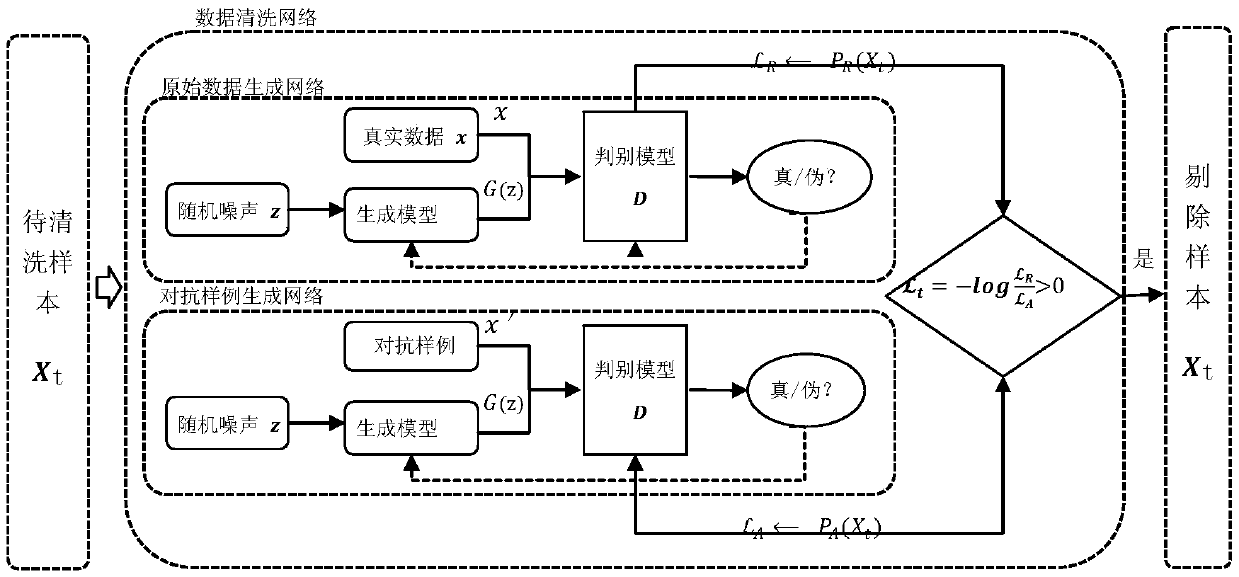
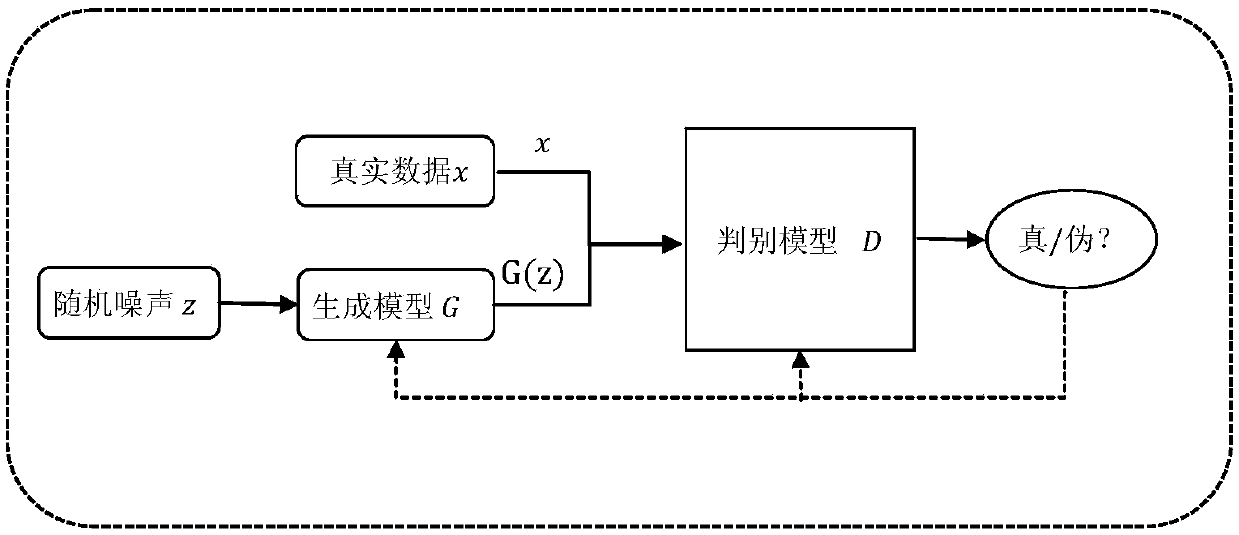
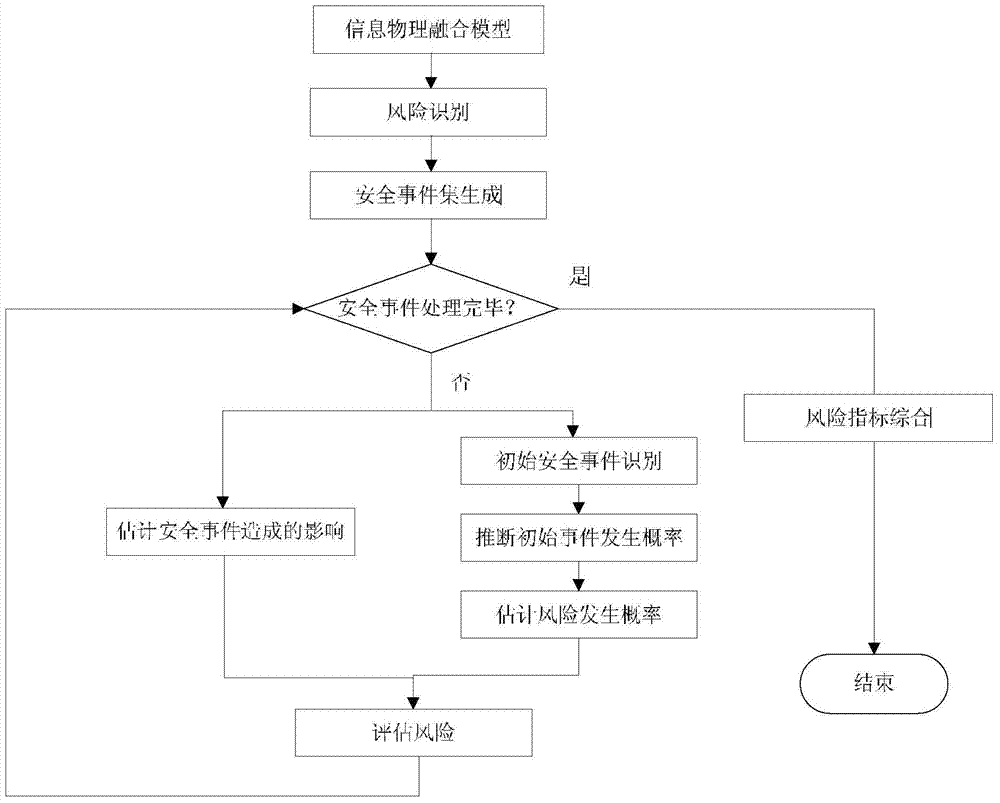
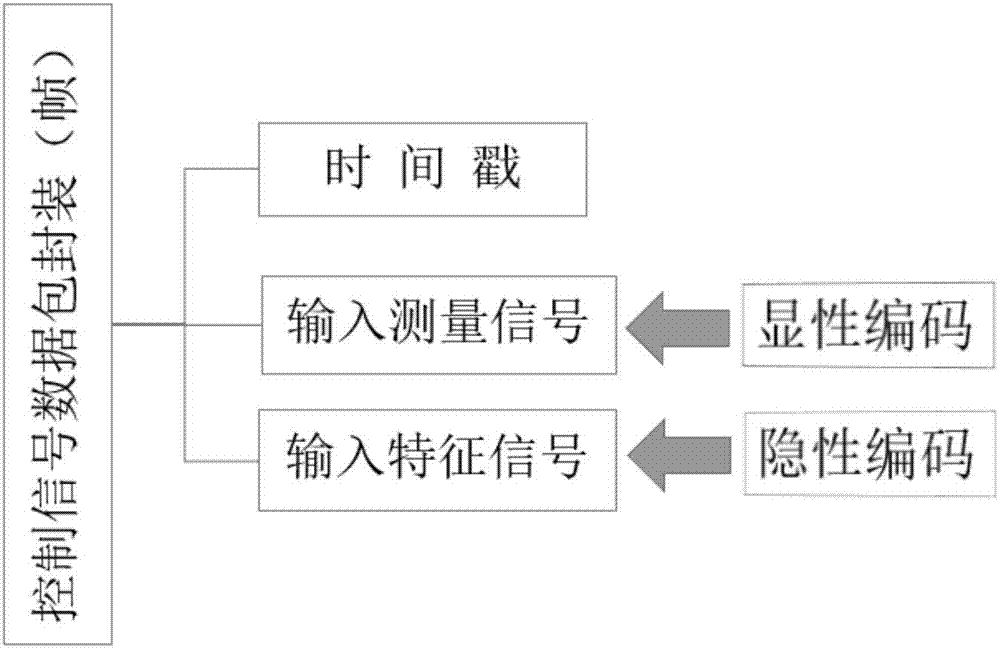
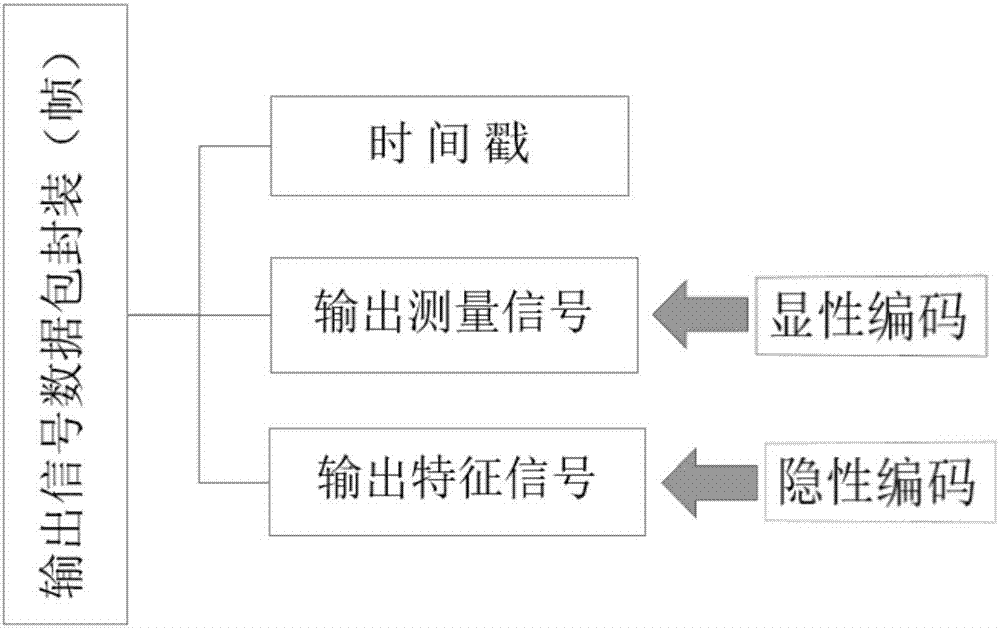
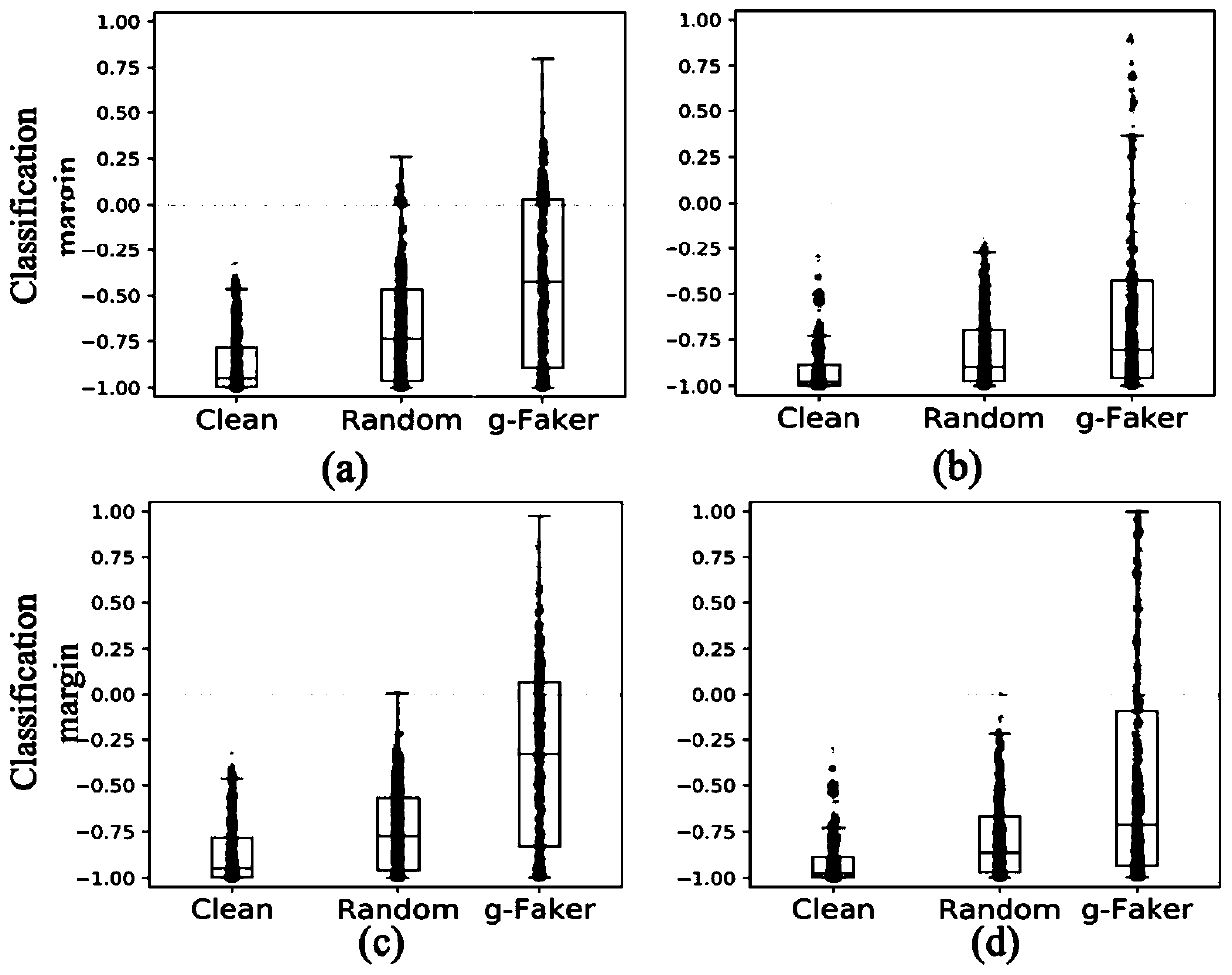
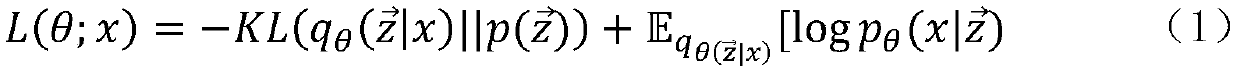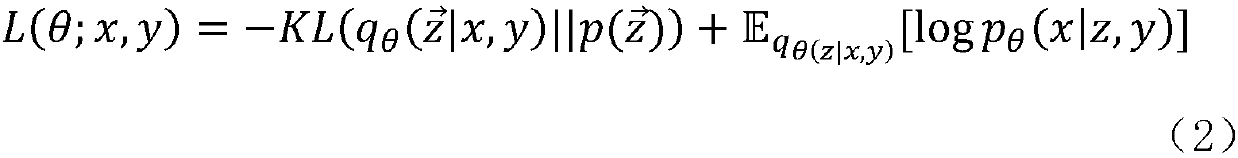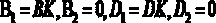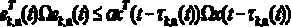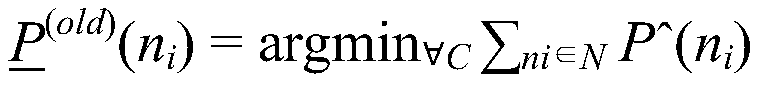Patents
Literature
153 results about "Attack model" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptanalysis, attack models or attack types are a classification of cryptographic attacks specifying the kind of access a cryptanalyst has to a system under attack when attempting to "break" an encrypted message (also known as ciphertext) generated by the system. The greater the access the cryptanalyst has to the system, the more useful information he can get to utilize for breaking the cypher.
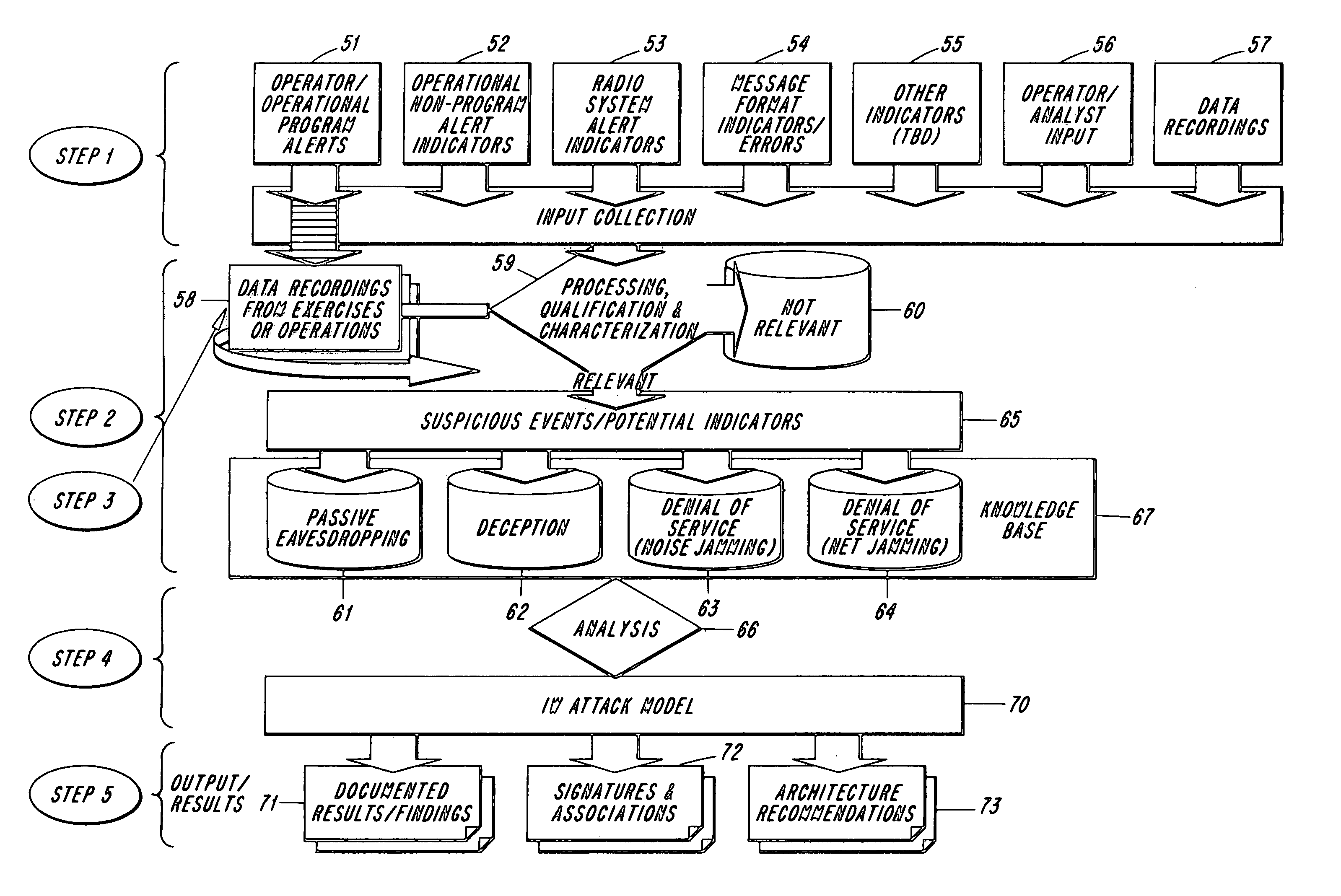
Methodology for the detection of intrusion into radio frequency (RF) based networks including tactical data links and the tactical internet
InactiveUS7068998B2Solid comprehensionEnhance information resiliencyUnauthorised/fraudulent call preventionMemory loss protectionInformation analysisAttack model
The present invention provides strategies for detecting intrusions in wireless environments, and the strategies are based on innovative applications of information analysis as well as other information correlating techniques. The key to detecting intrusions in a RF based environment is to understand the normal spectrum of behavior so that deviations can be detected and analyzed. For a wireless communications grid, this process requires empirical knowledge about how the radios work together as components of the information grid, and how this grid network is managed. Once normal behavior has been characterized, anomalous behavior can be identified. Potential intrusions into the wireless network can be analyzed and an attack model can be created. The attack model can be utilized as the basis for initiating appropriate adaptive responses.
Owner:NORTHROP GRUMMAN SYST CORP
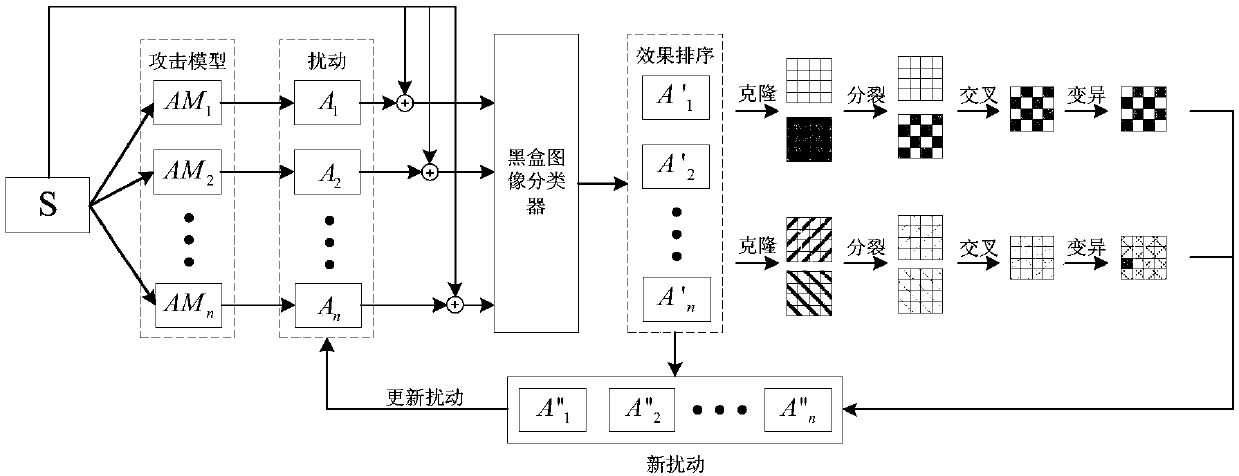
Image classifier adversarial attack defense method based on disturbance evolution
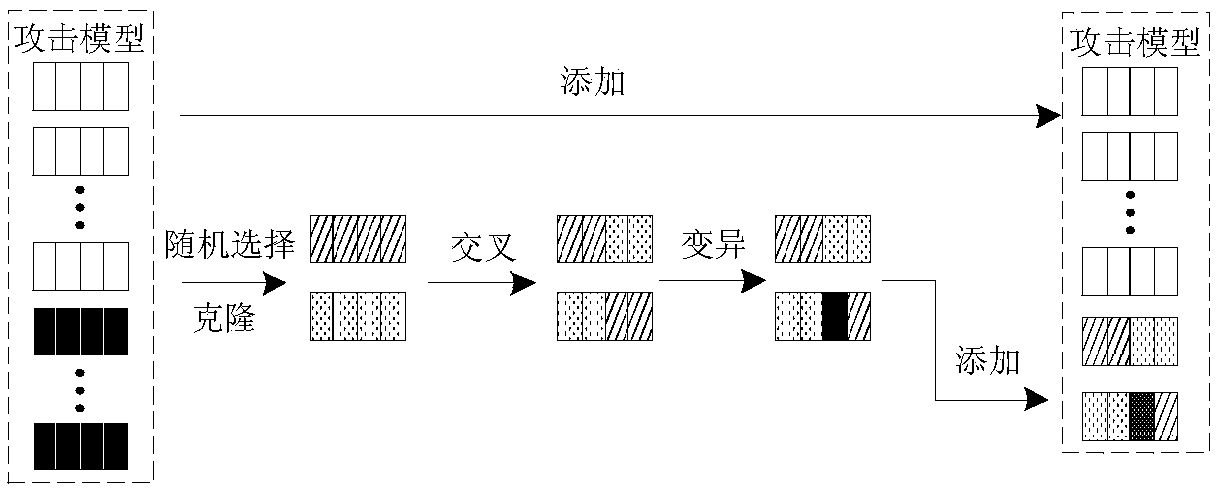
ActiveCN108615048AIncrease diversityEfficient detectionCharacter and pattern recognitionGenetic algorithmsAttack modelBox model
The invention discloses an image classifier adversarial attack defense method based on disturbance evolution. The method comprises the following steps that 1) the sample is attacked by different attack models so as to obtain different types of disturbance; 2) a block box model is attached by the adversarial sample corresponding to the disturbance and the attack effect is ordered; 3) cloning, crossing, variation and other operation are performed on the disturbance of great attack effect so as to obtain the new disturbance; 4) the disturbance is updated by using the parent-child hybrid selectionmode so as to achieve the objective of disturbance evolution; 5) an adversarial sample detector is trained by the adversarial sample corresponding to the evolved disturbance and the normal sample; and 6) when the detection sample is detected, detection is performed by using the adversarial sample detector firstly and then the normal sample is inputted to the black box model and the class is returned so as to achieve the adversarial attack defense effect.
Owner:ZHEJIANG UNIV OF TECH
Malicious software image format detection model-oriented black box attack defense method and device thereof
ActiveCN110826059ADefense against attackImprove applicabilityCharacter and pattern recognitionPlatform integrity maintainanceData setAttack model
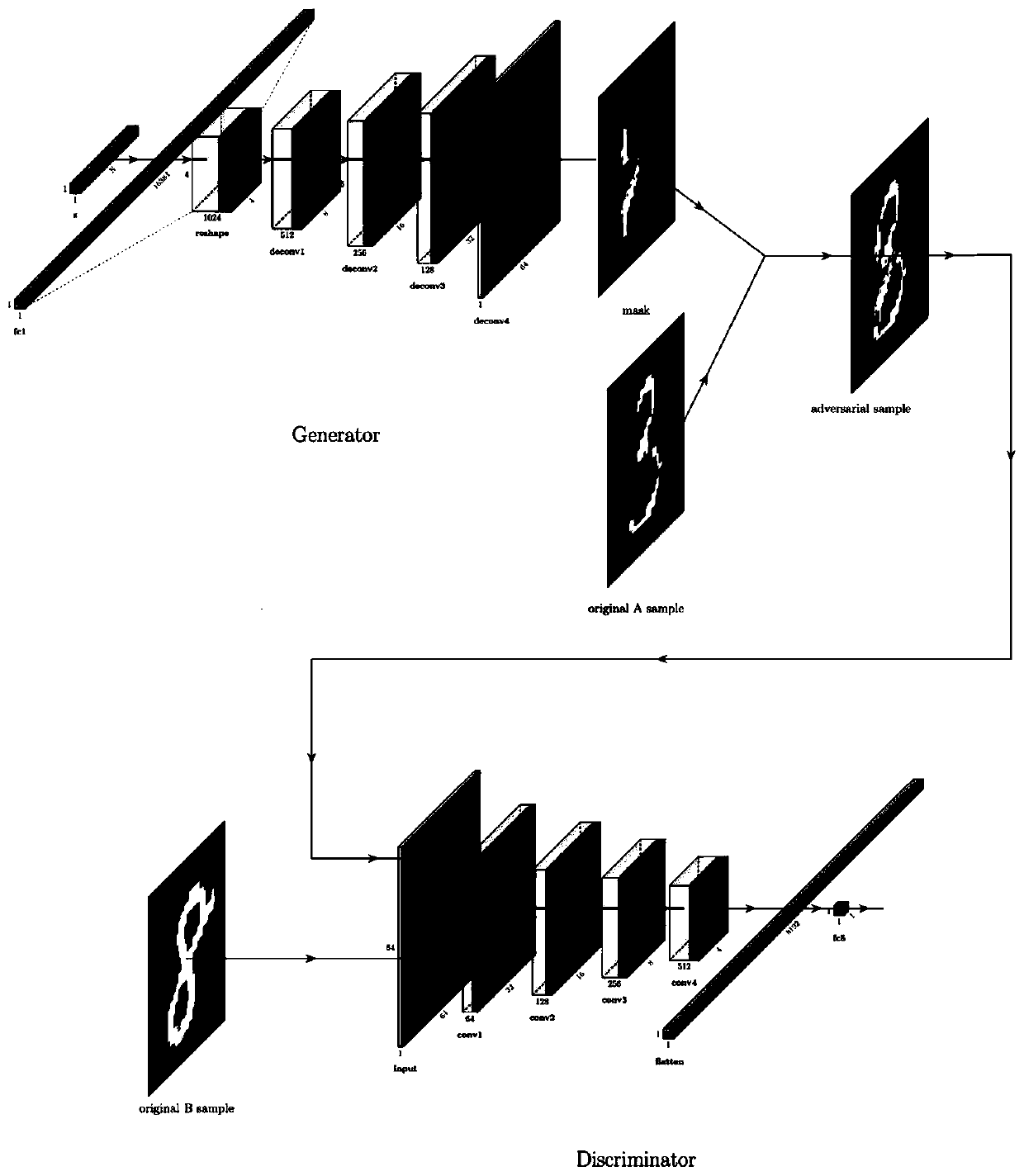
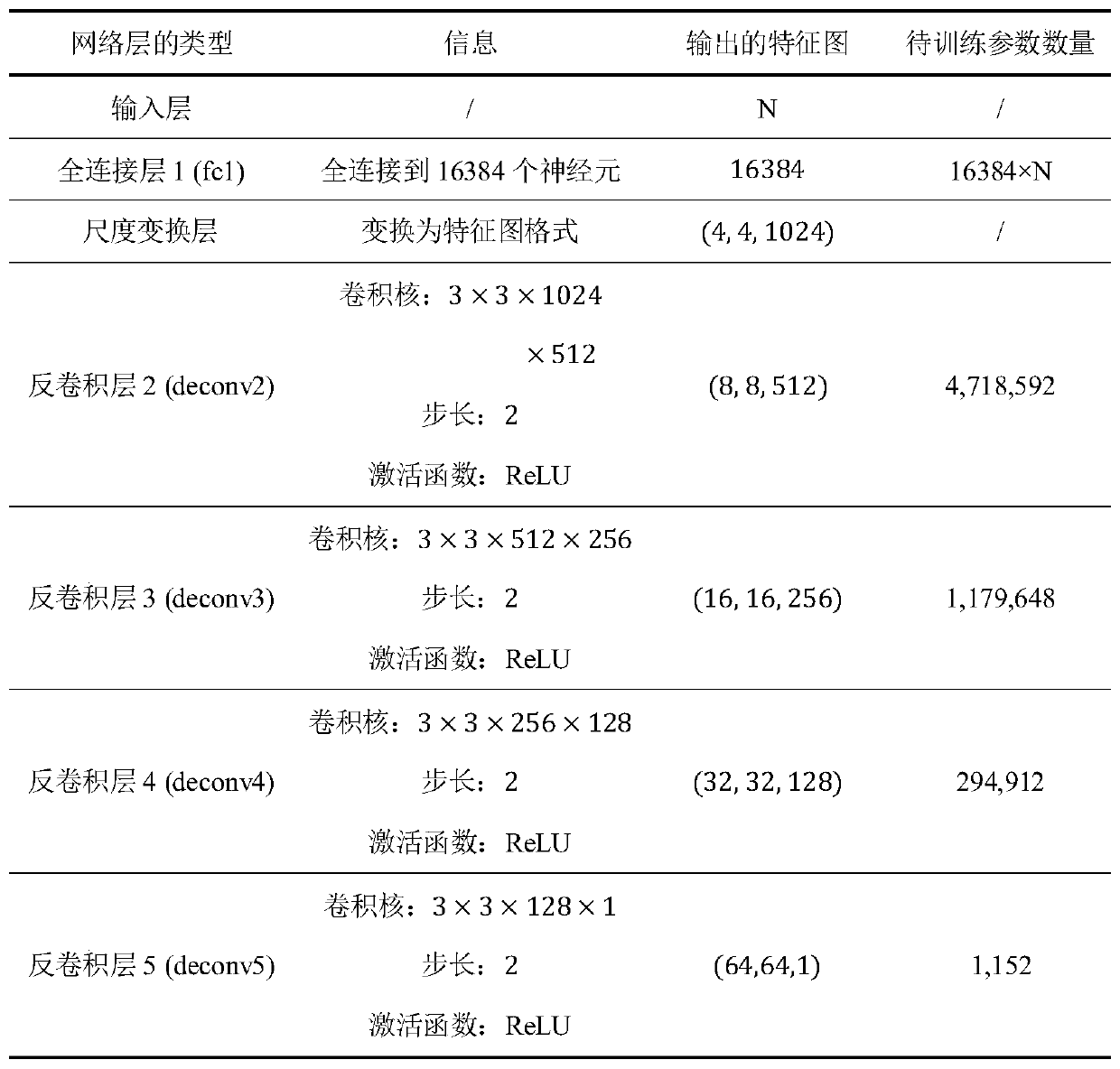
A malicious software image format detection model-oriented black box attack defense method comprises the steps of 1) obtaining a data set, and dividing the data set into a training set and a test set;2) converting into a malicious software image format; 3) constructing a black box attack model for generating disturbance based on a deep convolutional generative adversarial network (DCGAN), whereinthe structure of the black box attack model is divided into two parts, namely a generator and a discriminator; 4) through the continuous confrontation process between the generator and the discriminator constructed in the step 3), the generator finally generating a confrontation sample capable of simulating the sample B; 5) optimizing retraining of the malicious software assembly format detectionmodel by using the adversarial sample obtained in the step 4) to obtain a malicious software detection model capable of defending against the adversarial attack; and 6) identifying the malicious software by utilizing the malicious software detection model capable of defending against the attack. The invention further comprises a device for implementing the malicious software image format detection model-oriented black box attack defense method.
Owner:ZHEJIANG UNIV OF TECH
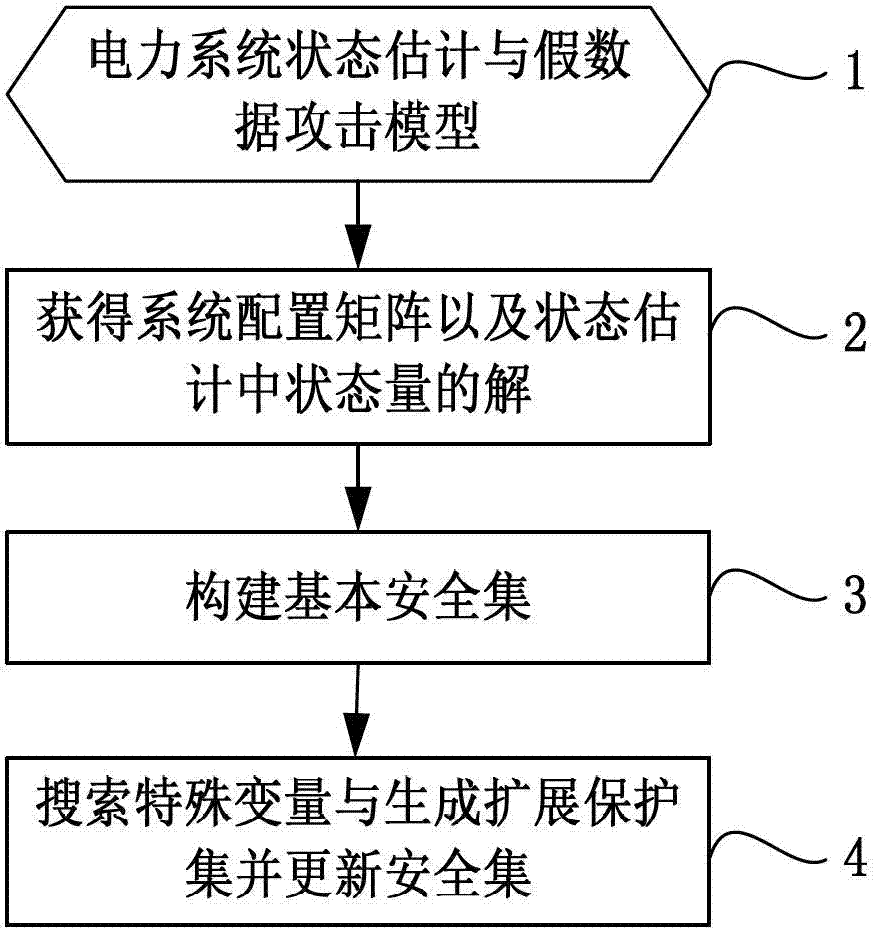
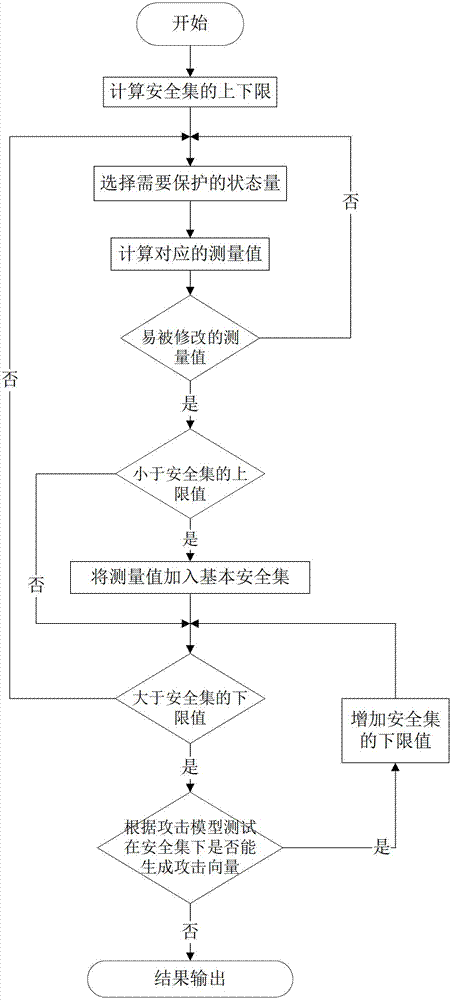
Defense method of false data injection attack of power state estimation system
The invention discloses a defense method of false data injection attack of a power state estimation system, belonging to the field of intelligent power grid and information safety. The method comprises the following steps of: firstly establishing a power system state estimating model and a false data attack model; subsequently calculating a system configuration matrix so as to obtain the solution of the state quantity of the power system state estimating model; further establishing the safety set of the system; and updating the safety set when the power system is changed in structure. The method is based on a protection set and by arranging an expansion protection set, the false data injection attack can be defended even a network structure is changed, thereby ensuring the security of the power system.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
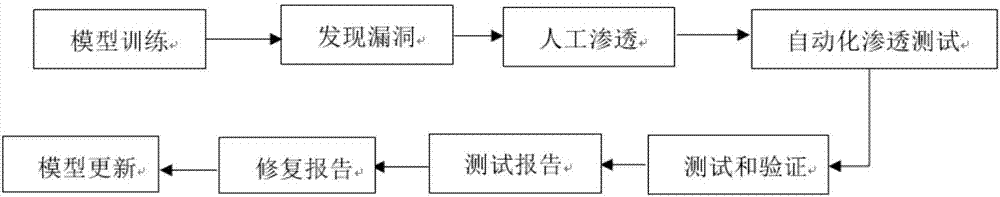
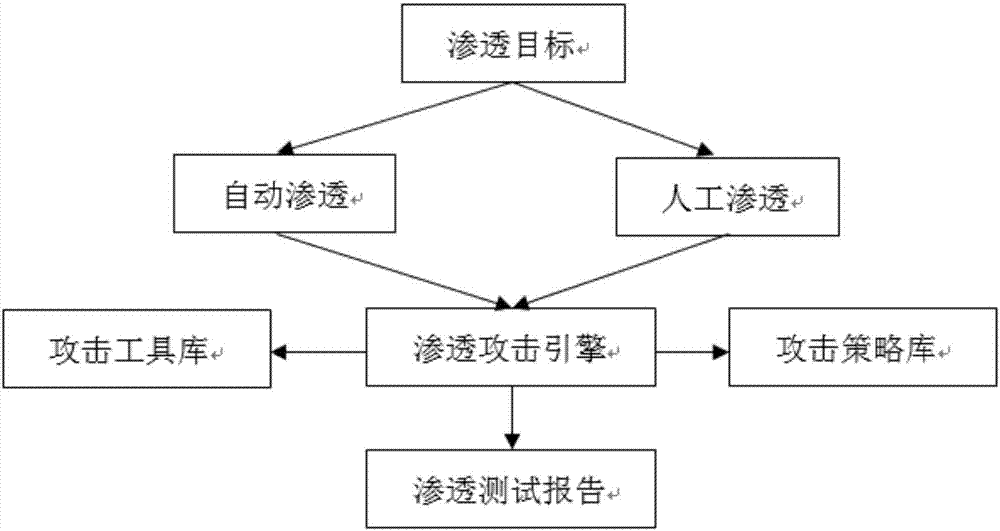
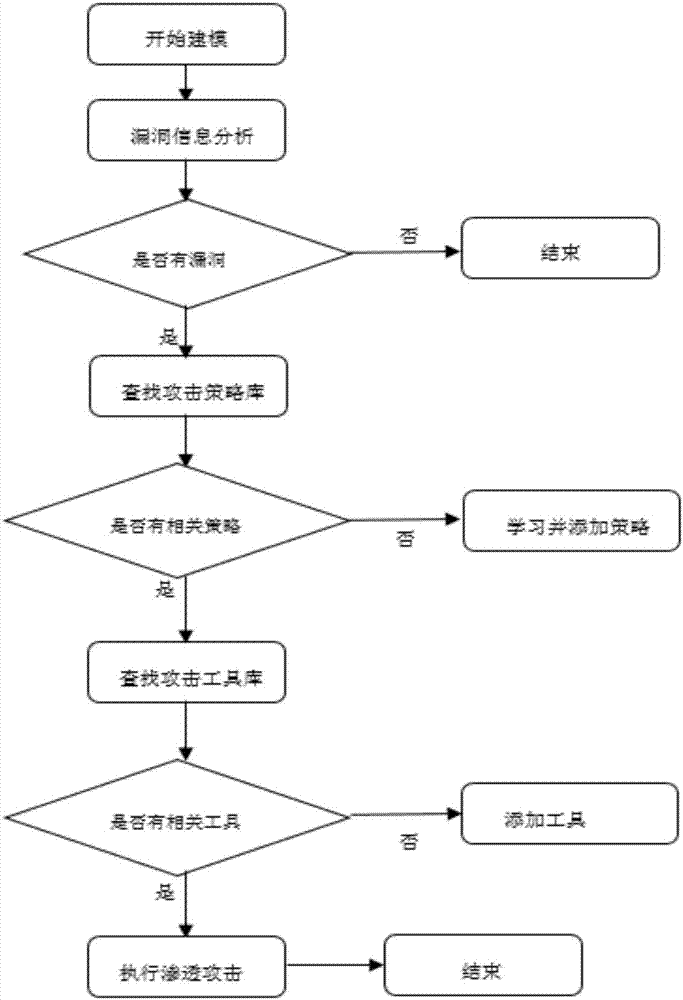
Automated safety penetration test method
ActiveCN107426227ARealize automatic callAchieve executionPlatform integrity maintainanceData switching networksAttack modelAttack strategy
The invention discloses an automated safety penetration test method, comprising: step 1, training an automated response model, establishing a corresponding model; step 2, scanning a target information system, obtaining host information; step 3, scanning vulnerability of the target information system, obtaining vulnerability information; step 4, according to the host information and the vulnerability information obtained in the step 2 and step 3, combined with an attack strategy library, establishing an attack model, according to the attack model, trying to attack the target information system, obtaining an attack feedback result; step 5, performing comprehensive analysis on a penetration test overall process, generating a penetration test report and teasing test steps and intermediate results, analyzing system security, providing a related solution; step 6, the response model updating in an adaptive manner, and regulating a response strategy.
Owner:CHINA INFOMRAITON CONSULTING & DESIGNING INST CO LTD
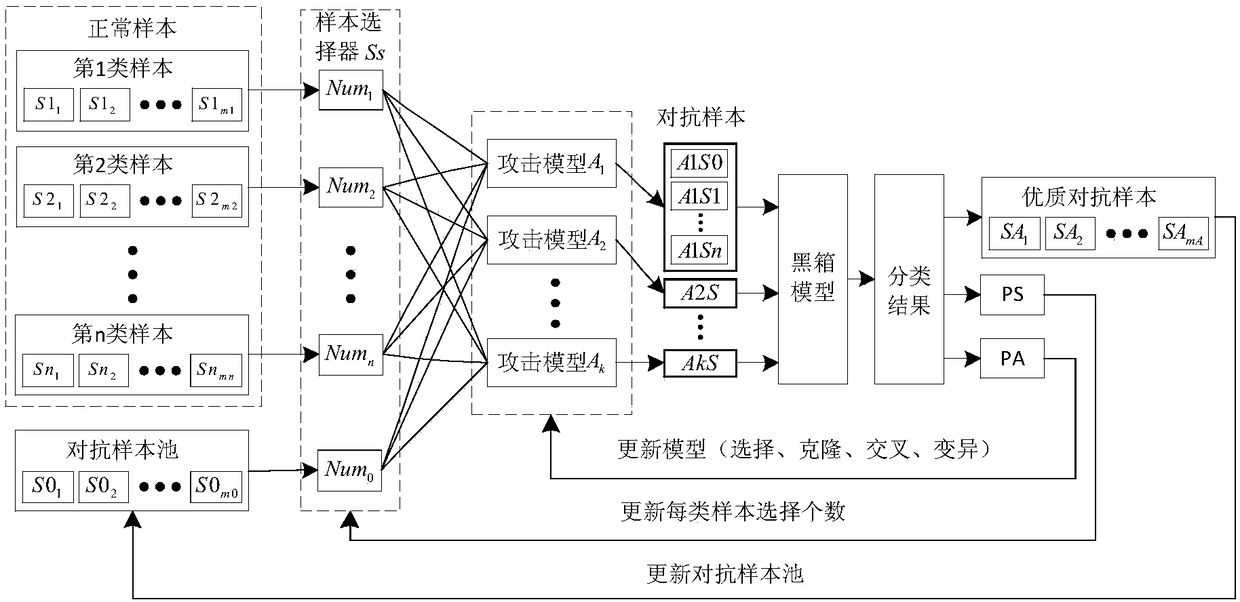
Black box antagonistic attack defense method based on sample selection and model evolution
ActiveCN108520268AIncrease the number ofIncrease diversityCharacter and pattern recognitionAttack modelAlgorithm
The invention provides a black box antagonistic attack defense method based on sample selection and model evolution. The method includes the following steps: 1) using a sample selector to randomly select partial samples from the multiple types of samples to be input into various attack models to generate a large number of counter samples; 2) calculating the attack effect of the counter samples, and analyzing the attack effect of different input samples and the attack model; (3) updating the number of different samples selected by different samples in the attack model and the sample selector according to the attack effect to make the newly generated counter sample have a better attack effect, meanwhile, updating the counter sample pool, storing the several counter samples with the best attack effect, and outputting the counter samples with the best attack effect in the pool to serve as the final result of the current evolution; and 4) training a large number of training output results and normal samples, so that the attack can be defended. According to the invention, the defense capability of the black box model can be improved.
Owner:ZHEJIANG UNIV OF TECH
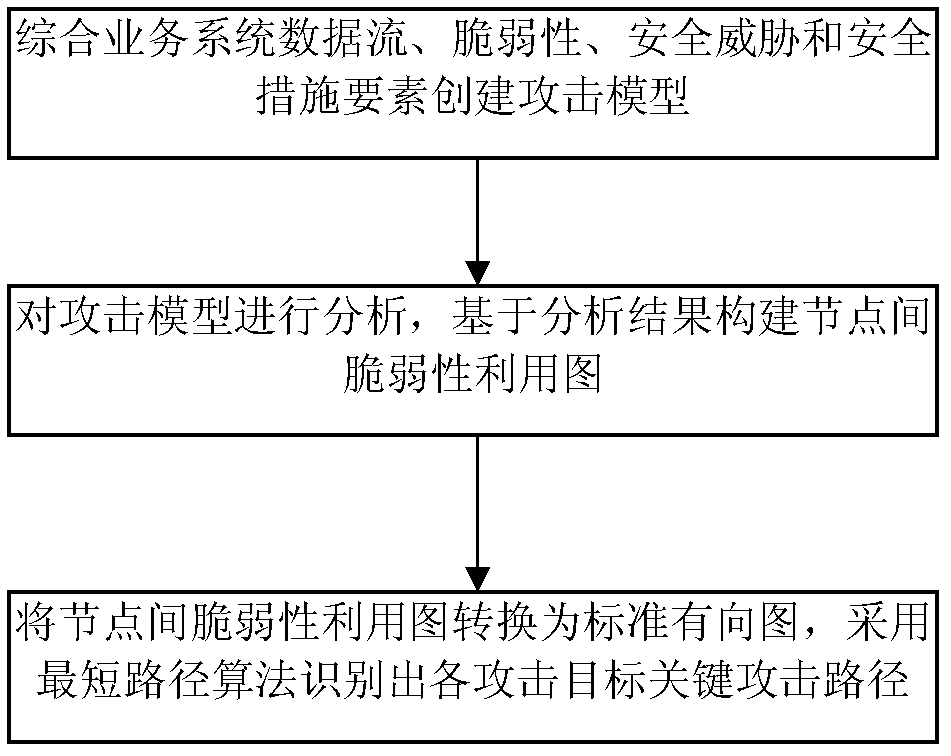
Method for identifying key attack path in service system
InactiveCN102447695AAchieving Unified ModelingAttack graph simplificationTransmissionComputation complexityDirected graph
The invention discloses a method for identifying the key attack path in a service system and belongs to the technical field of network information safety. The method comprising the steps as follows: 1, synthesizing data stream of the service system, vulnerability of the system, security threat, security measures and other factors to establish an attack model of the service system; 2, analyzing the established attack model and building a vulnerability exploitation map comprising all attack paths based on the model analysis result; and 3, converting the vulnerability exploitation map into a standard directed graph and analyzing the standard directed graph through a shortest path method to identify the key attack path that an attacker can reach all targets. The method has the advantages that the expandability is better than that of a traditional attack map, and the computation complexity of identification of the key attack path can be reduced effectively.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
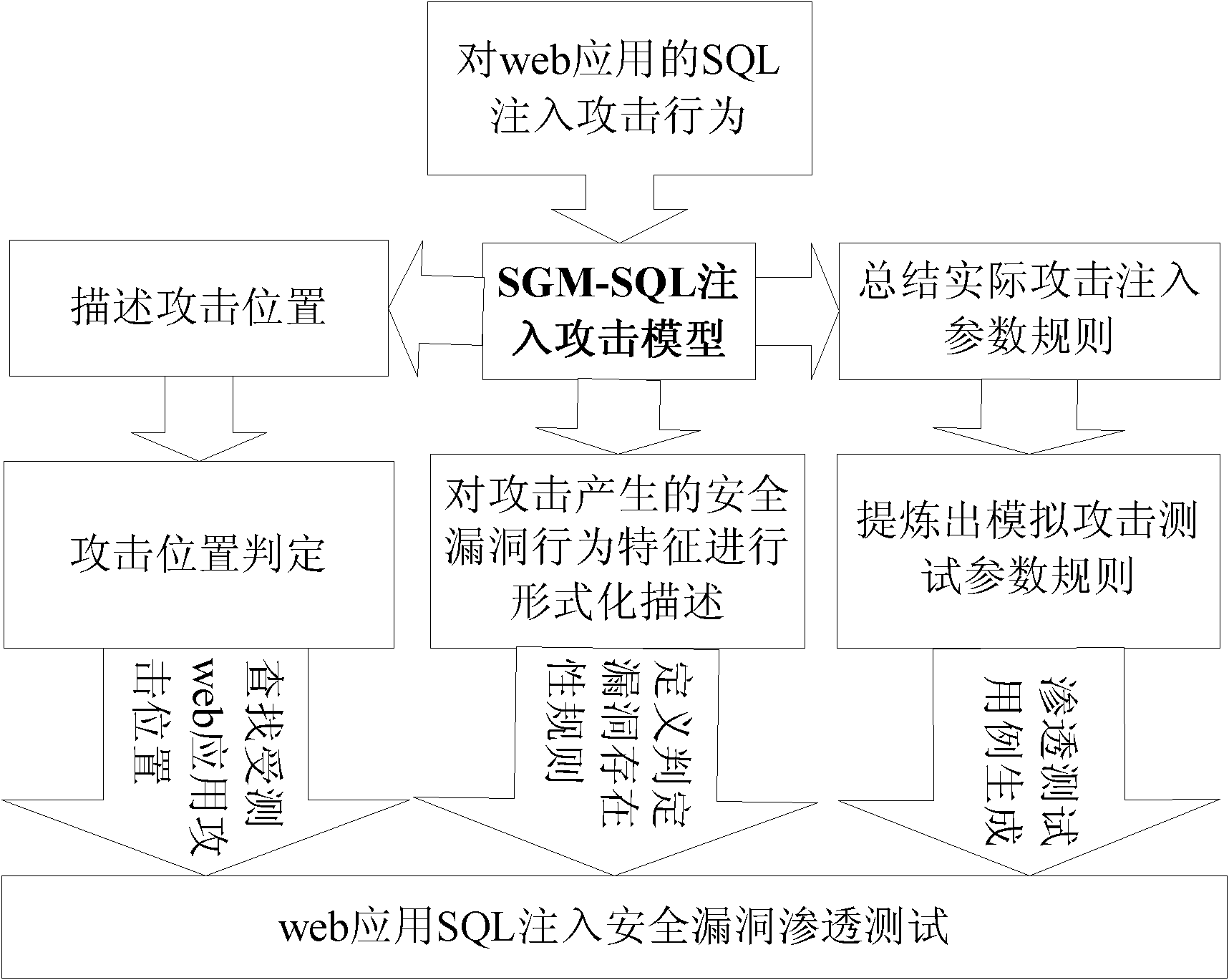
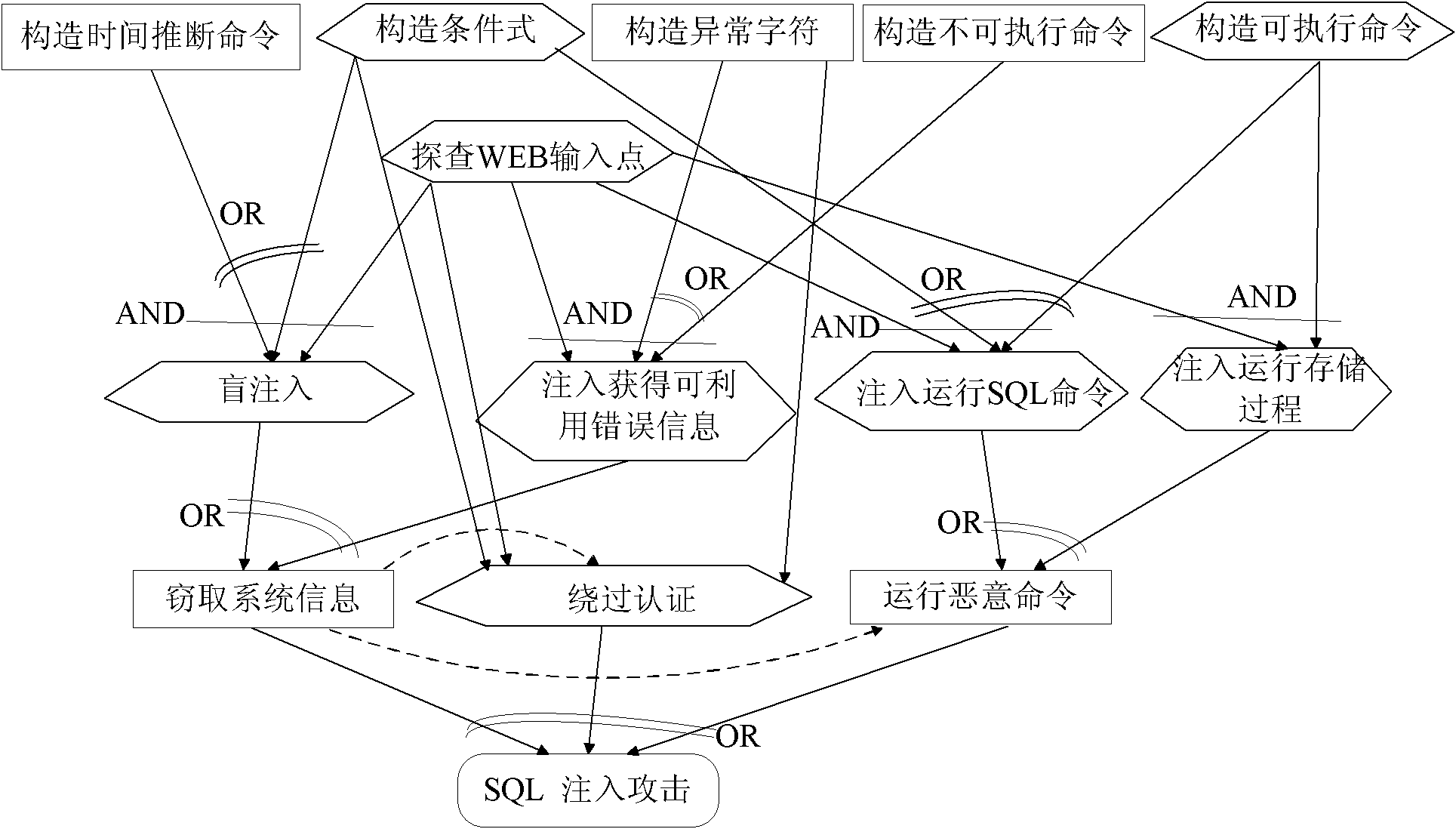
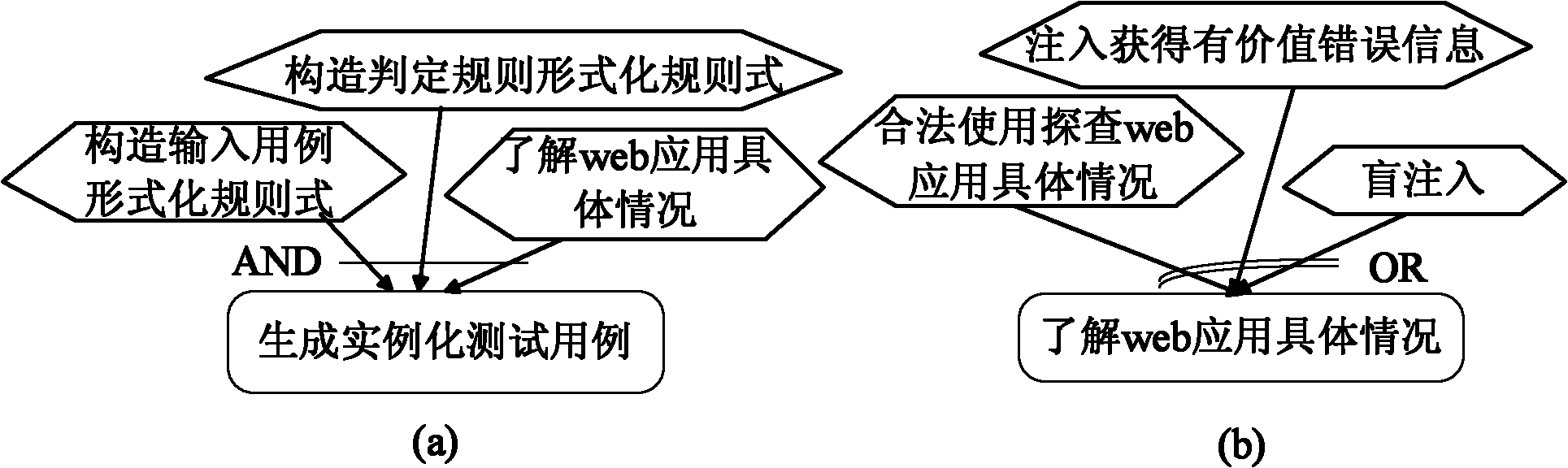
Method for driving web application penetration testing by applying SGM-SQL (sage grant management-structured query language) injection model
InactiveCN102136051AImprove accuracyMake up for the shortcomings of low accuracySoftware testing/debuggingPlatform integrity maintainanceAttack modelRDF query language
The invention relates to a method for driving web application penetration testing by applying an SGM-SQL (sage grant management-structured query language) injection model, in the method, a web application penetration test framework driven by an SGM-SQL injection attack model is defined; by defining the SGM-SQL injection attack model in the framework and guiding the definition of a formalized definition set of SQL injection safety loopholes and a formalized description system of penetration test cases thereof, the accurate criterion for judging existence of the safety loopholes and the orderedcomplete test cases are further provided for the penetrating testing, and an SQL injection safety loophole penetration test algorithm driven by the SGM-SQL injection attack model is accordingly provided, thereby improving the accuracy of the web application SQL injection safety loophole penetration testing. Practices prove that the method is credible, systematic and complete, and can be applied in the field of the web application safety loophole penetration testing.
Owner:NANKAI UNIV +1
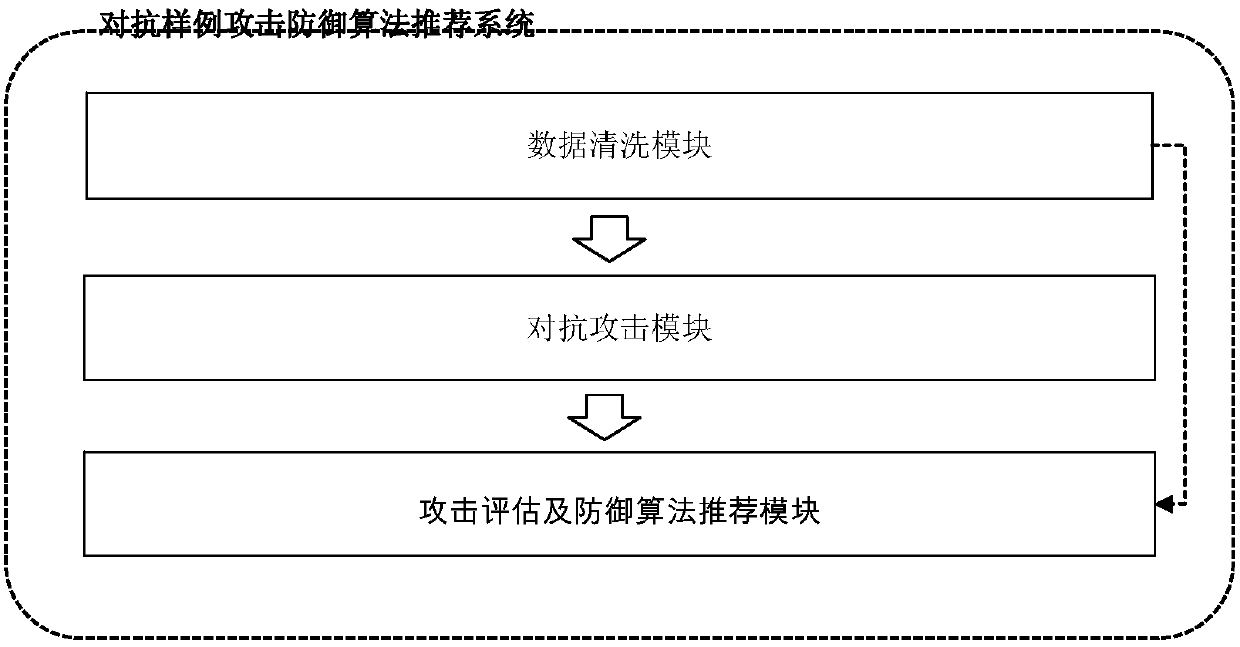
Multiple countermeasure sample attack-based intelligent defense algorithm recommendation method and intelligent defense algorithm recommendation system
ActiveCN108549940AEfficiently assess robustnessReduce lossesComputing modelsPlatform integrity maintainanceCountermeasureAttack model
The invention discloses a multiple countermeasure sample attack-based intelligent defense algorithm recommendation method. The method comprises the following steps: cleaning an original data set to obtain a training set; training a target recognition model by utilizing the training set, and obtaining a target attack model; selecting different countermeasure sample attack algorithms, and attackingthe target attack model; quantitatively evaluating the attack success rate of each countermeasure sample attack algorithm, and selecting a target attack algorithm according to the attack success rate;aiming at each target attack algorithm, applying a countermeasure attack defense algorithm one by one for defense purpose; and recommending a corresponding countermeasure attack defense algorithm toa user according to the defense result. The invention further discloses an intelligent defense algorithm recommendation system, wherein the system is adopted by the above intelligent defense algorithmrecommendation method. According to a specific target model, the intelligent defense algorithm recommendation system can intelligently recommend an effective defense algorithm, so that the loss caused by the attack of a defense sample case to the target model is reduced.
Owner:ZHEJIANG UNIV
Information security risk assessment method oriented to typical metallurgy process control system
InactiveCN104331072AGuaranteed safe operationLow costElectric testing/monitoringProbabilistic methodRisk indicator
The invention provides an information security risk assessment method oriented to a typical metallurgy process control system and belongs to the technical field of industrial control system information security. The system robustness under different attack modes and policies is analyzed by establishing an attack model under the typical scenes of the metallurgy process, and therefore, the security risk assessment on the typical metallurgy process control system in different attack modes and a failure mode can be realized. Based on the risk theory, the method is used for performing the security risk assessment by use of a random probability algorithm by defining the metallurgy process control system as a physical information fusion system; from the two aspects of the occurrence probability and the influence of attack sources or failure sources, a security assessment method based on risk indexes is developed. Quantitative estimation is performed based on risk indexes; a security incident set is created based on the established physical information fusion model and attack model, and then the security incident set is combined with the calculated robustness assessment indexes for the quantitative estimation, and therefore, the weak security links in the control system can be located conveniently.
Owner:AUTOMATION RES & DESIGN INST OF METALLURGICAL IND
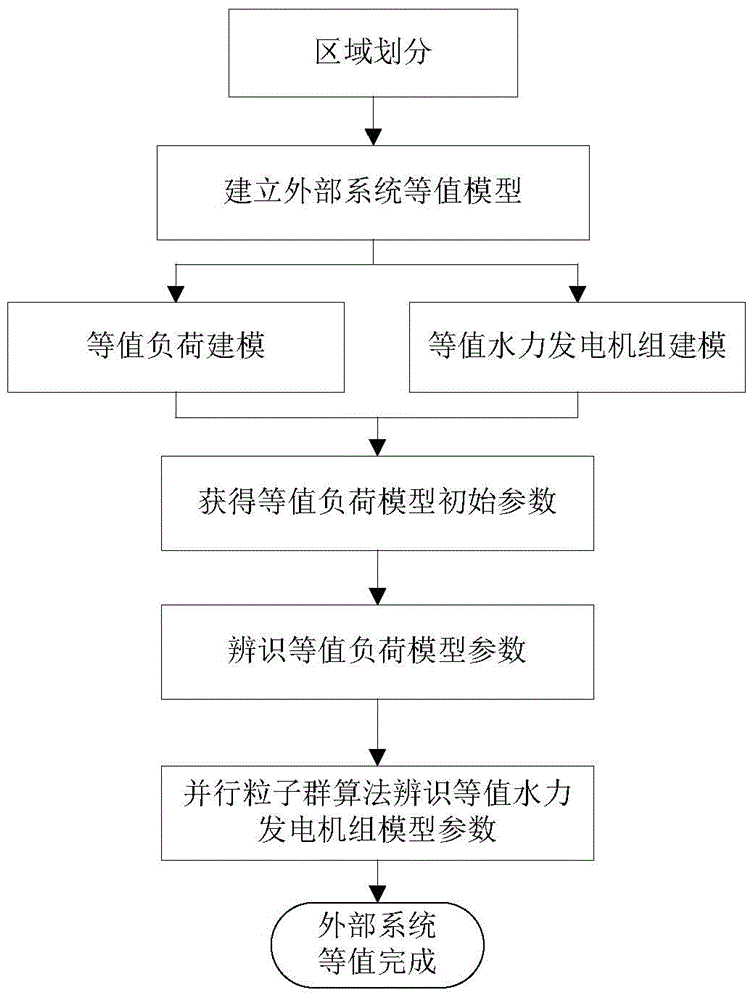
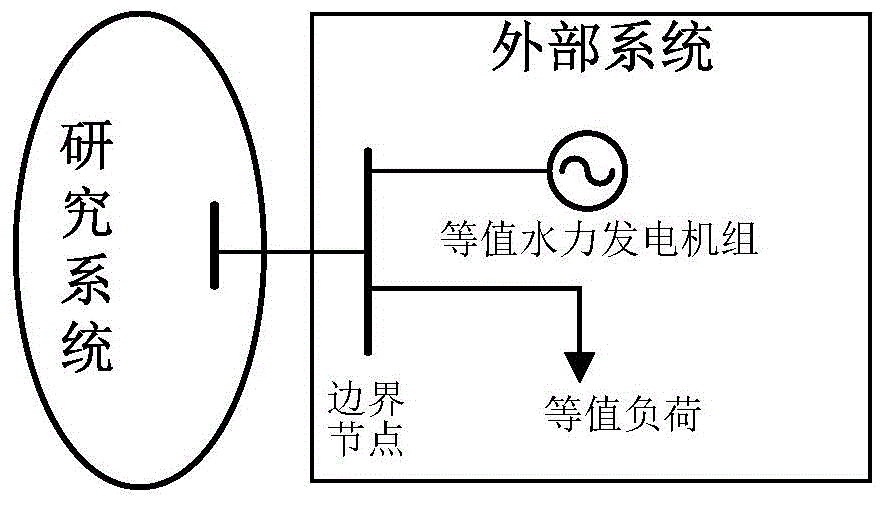
Cluster equivalent modeling method for small and medium size hydroelectric generating sets
ActiveCN104600756ATruly reflect the dynamic response processTruly reflect its coupling effectSingle network parallel feeding arrangementsDesign optimisation/simulationWater turbineSimulation
The invention discloses a cluster equivalent modeling method for small and medium size hydroelectric generating sets, and belongs to the field of cluster modeling and equivalent analysis of the hydroelectric generating sets. The method includes the steps of firstly, conducting regional division on a power grid, and establishing hydroelectric generating set-load equivalent models including the parallel connection PID speed controller model, the water diversion system elastic water attack model, the six-parameter water turbine model based on a comprehensive characteristic curve and the three-order practical electric generator model; secondly, recognizing equivalent hydroelectric generator model parameters and load model parameters through the parallel particle swarm optimization which is put forward. The obtained equivalent models meet the refined modeling requirements of the hydroelectric energy system simulation, the electric power system analysis and the dispatching and operation calculation to a larger extent.
Owner:HUAZHONG UNIV OF SCI & TECH
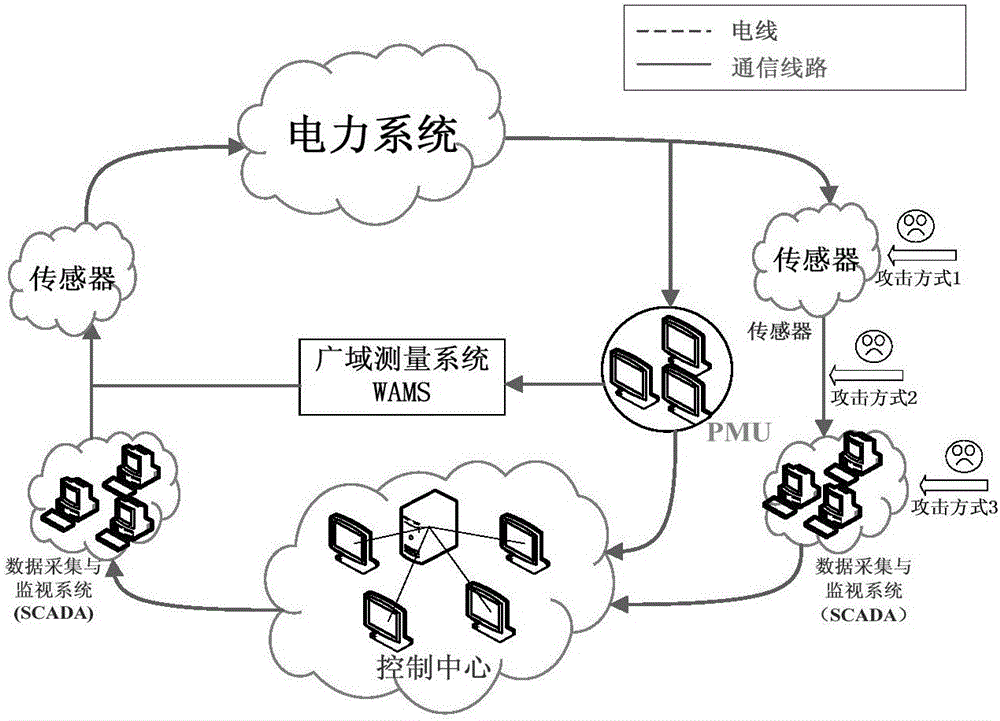
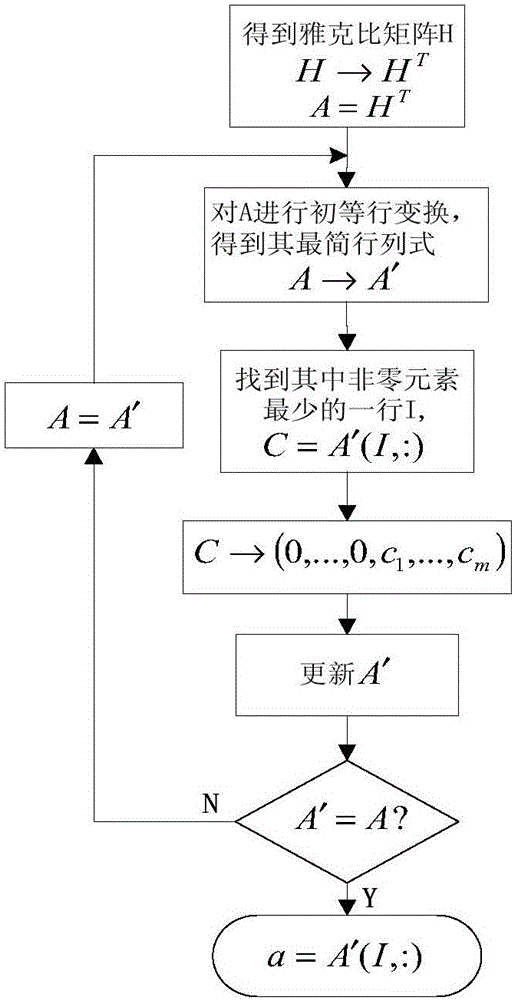
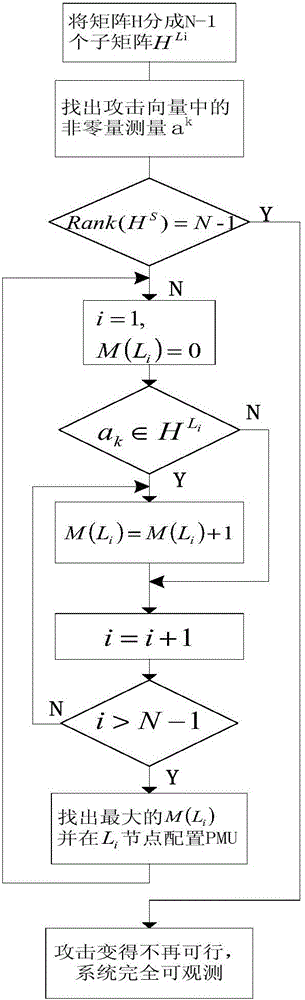
Method for defending data integrity attack in direct state estimation of power system
ActiveCN105791280AIntegrity attack implementationIntegrity Attack BlockingDigital data protectionPower oscillations reduction/preventionAttack modelData integrity
The invention discloses a method for defending a data integrity attack in direct state estimation of a power system. The method comprises the following steps: estimating a real-time state of a direct current system by using a weighted least square method; constructing a minimum cost data integrity attack model to simulate the behavior of an attacker; resolving the minimum cost data integrity attack by using an algorithm based on linear transformation to obtain an optimal attack vector at the moment; if the current optimal attack vector is obtained, realizing a PMU optimized configuration defense strategy based on a greedy algorithm, and after the configuration is completed, the occurrence of the data integrity attack is prevented from the source, and meanwhile, the complete observability of the system is guaranteed. By adopting the method disclosed by the invention, the data integrity attack in the direct state estimation of the power system can be accurately and quickly defended, and the accuracy and security of the state estimation of the power system are improved.
Owner:XI AN JIAOTONG UNIV
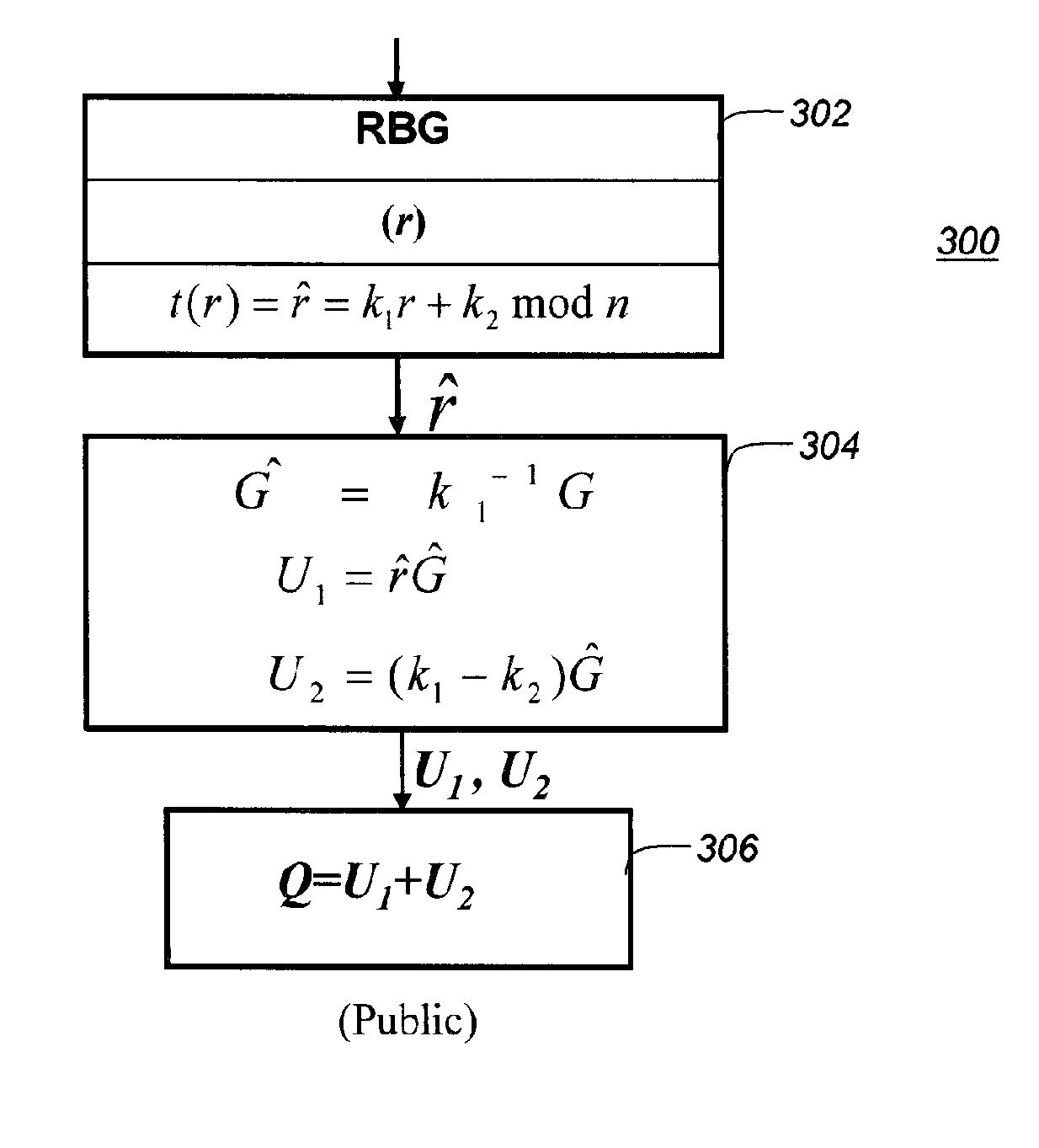
System and method for generating and protecting cryptographic keys
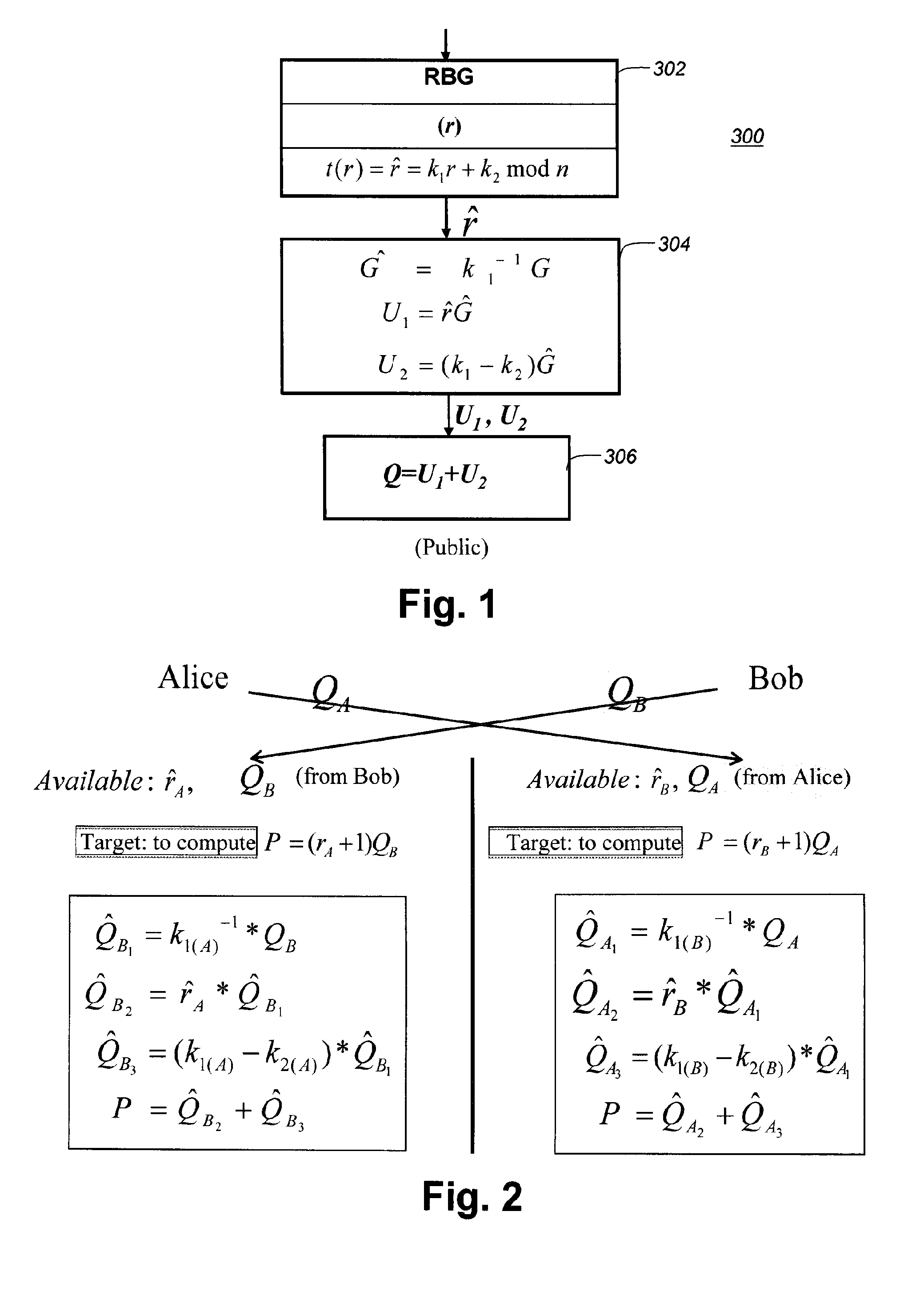
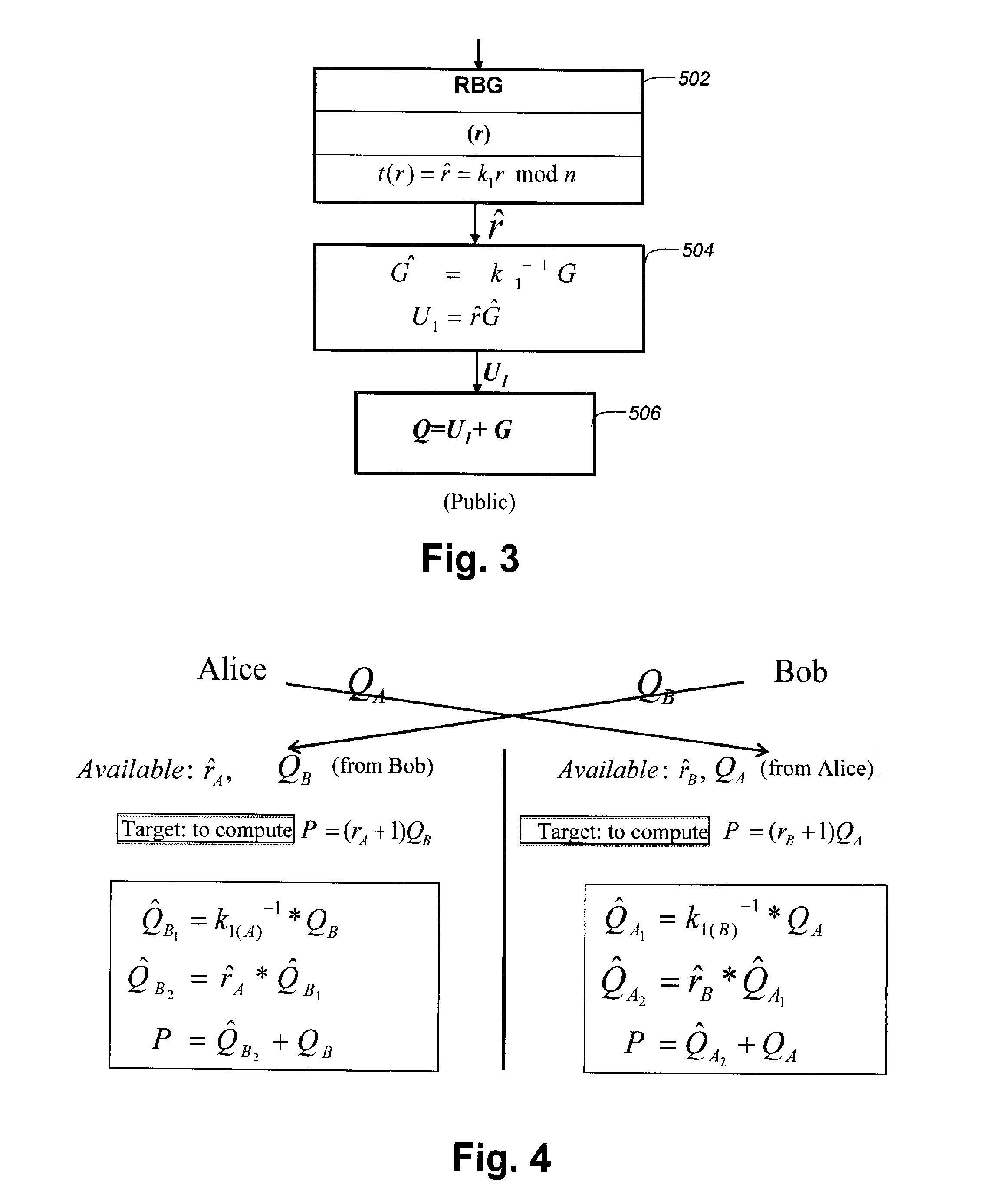
ActiveUS20150333906A1Easy to adaptKey distribution for secure communicationRandom number generatorsVisibilityAttack model
In the present disclosure, implementations of Diffie-Hellman key agreement are provided that, when embodied in software, resist extraction of cryptographically sensitive parameters during software execution by white-box attackers. Four embodiments are taught that make extraction of sensitive parameters difficult during the generation of the public key and the computation of the shared secret. The embodiments utilize transformed random numbers in the derivation of the public key and shared secret. The traditional attack model for Diffie-Hellman implementations considers only black-box attacks, where attackers analyze only the inputs and outputs of the implementation. In contrast, white-box attacks describe a much more powerful type of attacker who has total visibility into the software implementation as it is being executed.
Owner:IRDETO ACCESS
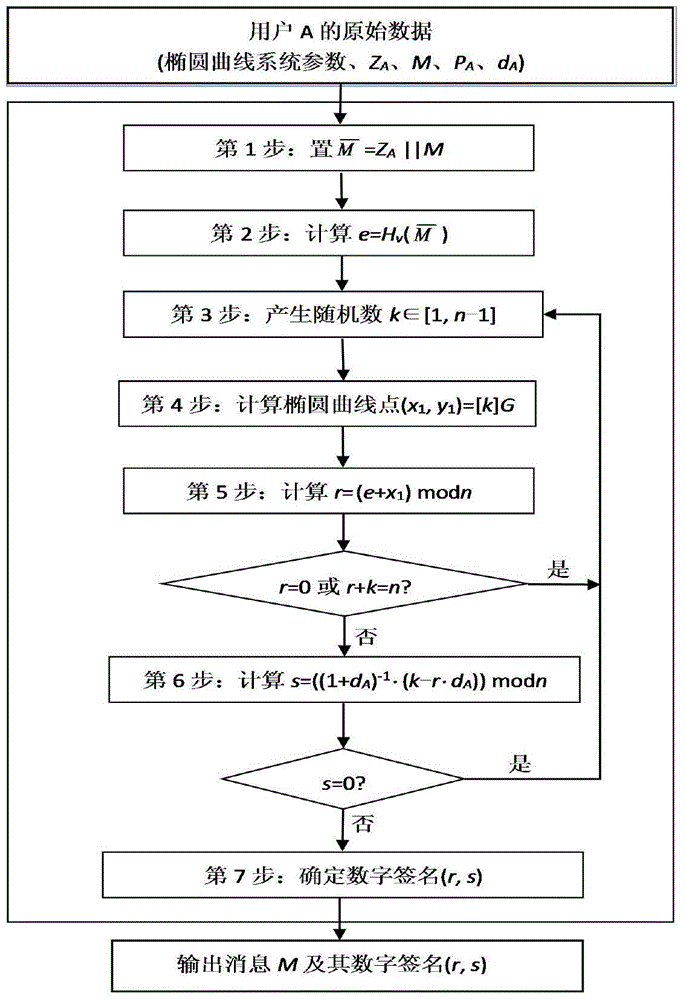
SM2 signature algorithm security verification method based on random number unknown
ActiveCN104836670AComprehensive analysis of security capabilities against attacksGood for error injection experimentsKey distribution for secure communicationUser identity/authority verificationAttack modelValidation methods
The invention discloses an SM2 signature algorithm security verification method based on an random number unknown. The method comprises the following steps: (1) signing N+1 messages M respectively by adopting an SM2 signature algorithm, and injecting an error into every SM2 signing in order that identical errors occur in signing results s of identical set bit parts of a random number k used in every signing; (2) subtracting error signing results s in other N signing respectively from the error signing result of first signing with reference to an equation of the error signing result s of first signing to obtain an equation set, namely, a lattice attack model; and (3) solving the lattice attack model, recovering all bits of the random number k used in every signing, substituting the recovered bits into an equation for calculating corresponding signing results s to obtain a private key dA, and judging that the SM2 signature algorithm is unsafe if the private key dA is a correct private key. Through adoption of the method, the security capability of the SM2 signature algorithm in attack resistance can be analyzed more effectively and comprehensively.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI +2
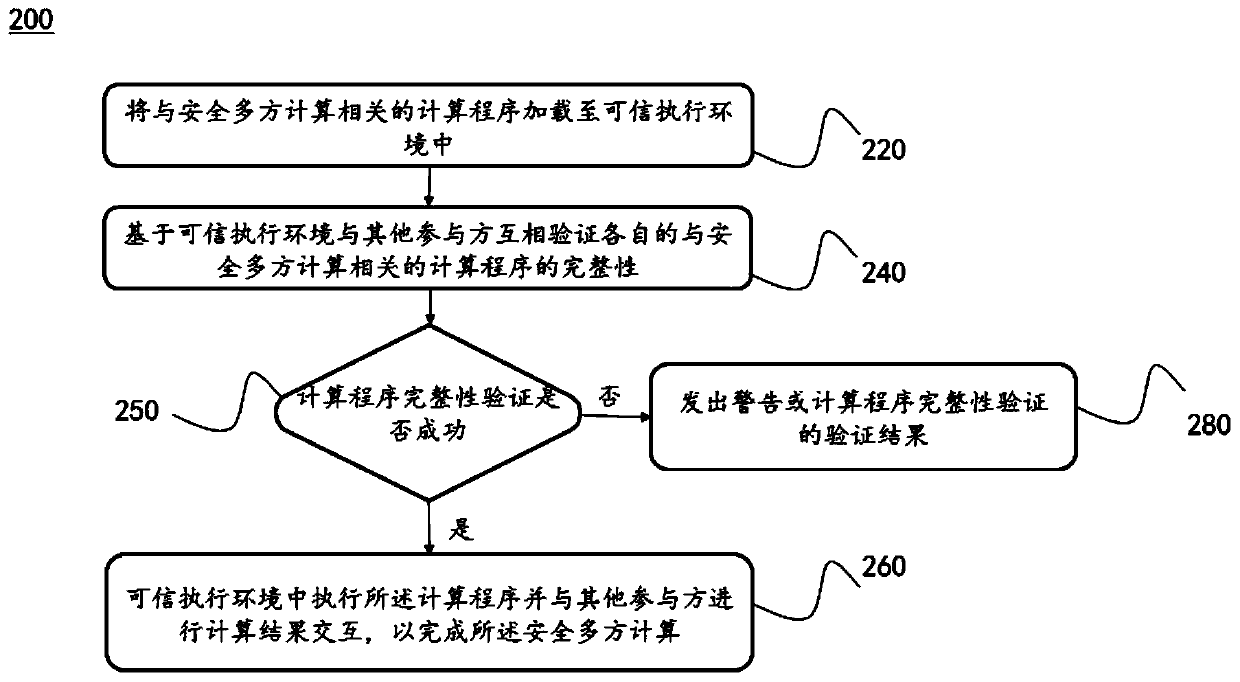
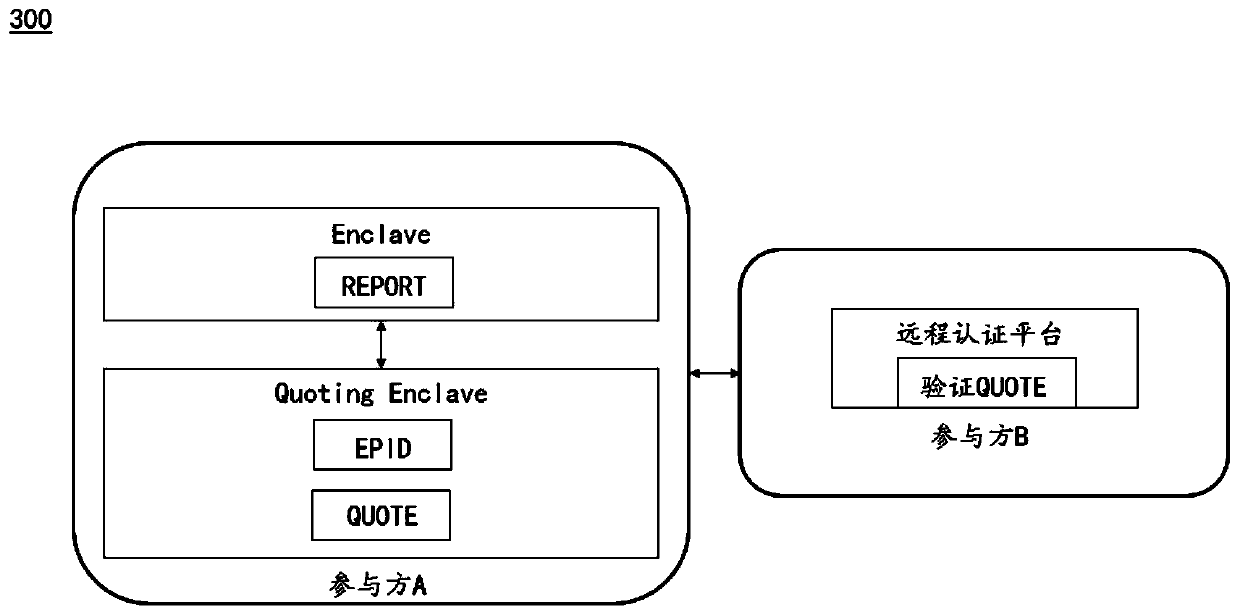
Secure multi-party calculation method and system based on trusted execution environment
The embodiment of the invention discloses a secure multi-party calculation method and system based on a trusted execution environment. The method comprises the following steps: loading a calculation program related to secure multi-party calculation into a trusted execution environment; based on the trusted execution environment and other participants, verifying the integrity of respective calculation programs related to secure multi-party calculation; If the integrity verification of the calculation program succeeds, executing the calculation program in a trusted execution environment and performing calculation result interaction with other participants to complete the secure multi-party calculation. According to the specification, a calculation program related to secure multi-party calculation is loaded to a trusted execution environment for running; malicious tampering of a calculation program is avoided, safe multi-party calculation suitable for a semi-honest attack model is improved into safe multi-party calculation suitable for a malicious attack model, and the purposes that private data is protected against leakage, and meanwhile the calculation speed is not reduced are achieved.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
A novel trajectory data publishing method based on differential privacy
ActiveCN109726594AProtect track privacyGuaranteed spatiotemporal propertiesDigital data protectionAttack modelSemantics
The invention discloses a novel trajectory data publishing method based on differential privacy, which comprises the following steps of: proposing a sequence R (Sequence R, SR)-tree structure meetingthe differential privacy on the basis of an R tree; constructing an SR tree using a trajectory sequence instead of the smallest bounding rectangle structure in the R-tree; providing a non-position sensitive information attack model, and adding noise to position data and non-position sensitive data by using differential privacy techniques when building noise SR trees; And aiming at the problem that data inconsistency possibly occurs after noise is added, performing consistency processing on the algorithm. The method has the advantages that Aiming at the spatio-temporal characteristics of the trajectory and the requirement of fast retrieval trajectory, a new trajectory sequence structure-sequence R-tree (SR- tree) is proposed on the basis of R-tree.; On the basis of the SR tree structure, the invention provides a moving object track data publishing method meeting differential privacy; And according to the semantics of the track, proposing a non-position sensitive information associationattack model.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
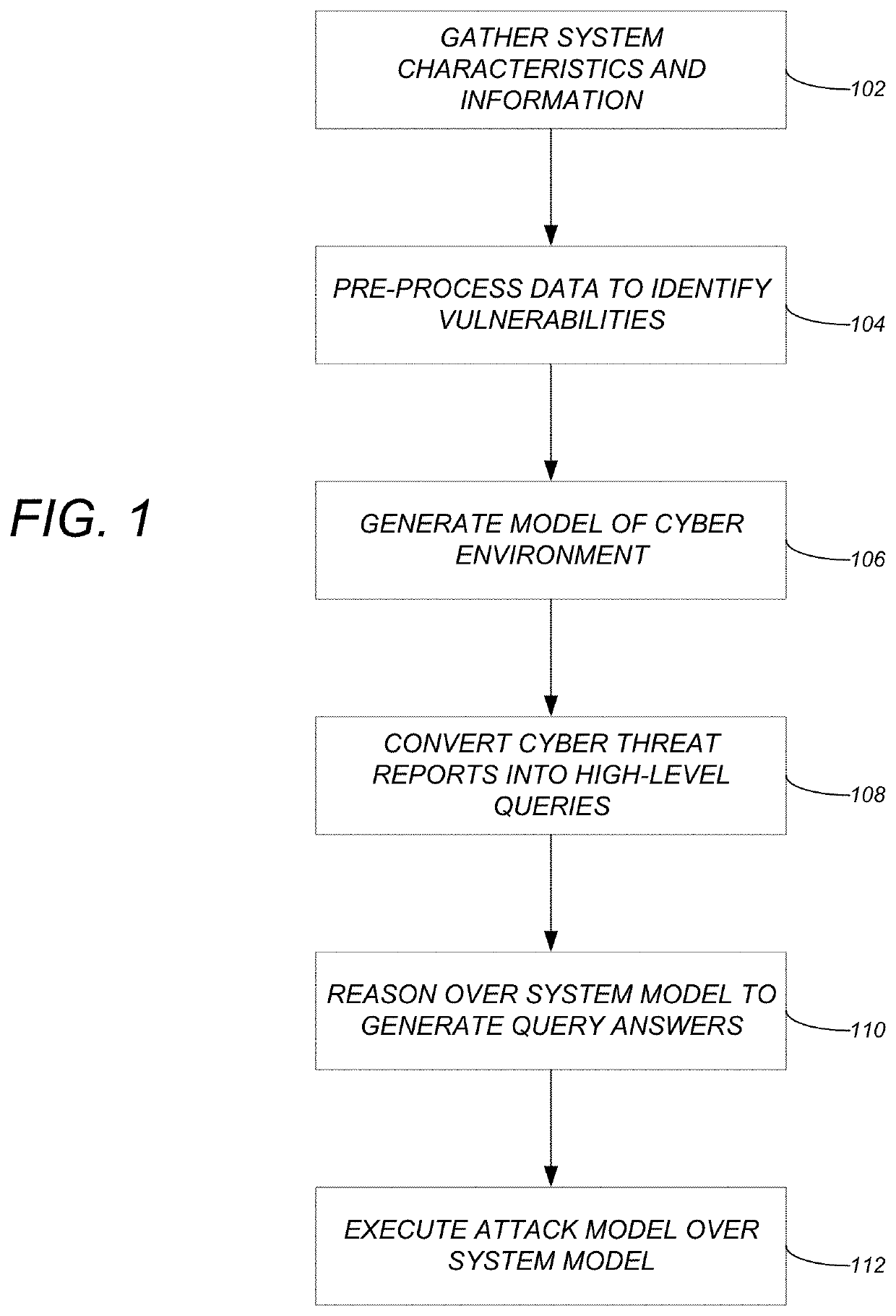
Model based methodology for translating high-level cyber threat descriptions into system-specific actionable defense tactics
ActiveUS20200067962A1Digital data information retrievalComputer security arrangementsCyber-attackAttack model
A method, apparatus, and system provide the ability to act on cyber risks and reduce cyber attacks. System characteristics and system information for a cyber system are gathered. The system characteristics and system information are pre-processed to identify vulnerabilities that are relevant to the cyber system. A system model of a cyber environment is generated for the cyber system. One or more features are converted from cyber threat reports to one or more semantically relevant queries over the system model. The system model is reasoned over to generate one or more answers relevant to the one or more semantically relevant queries. Attack models are executed over the system model to generate actionable intelligence and reduce cyber attacks.
Owner:CALIFORNIA INST OF TECH
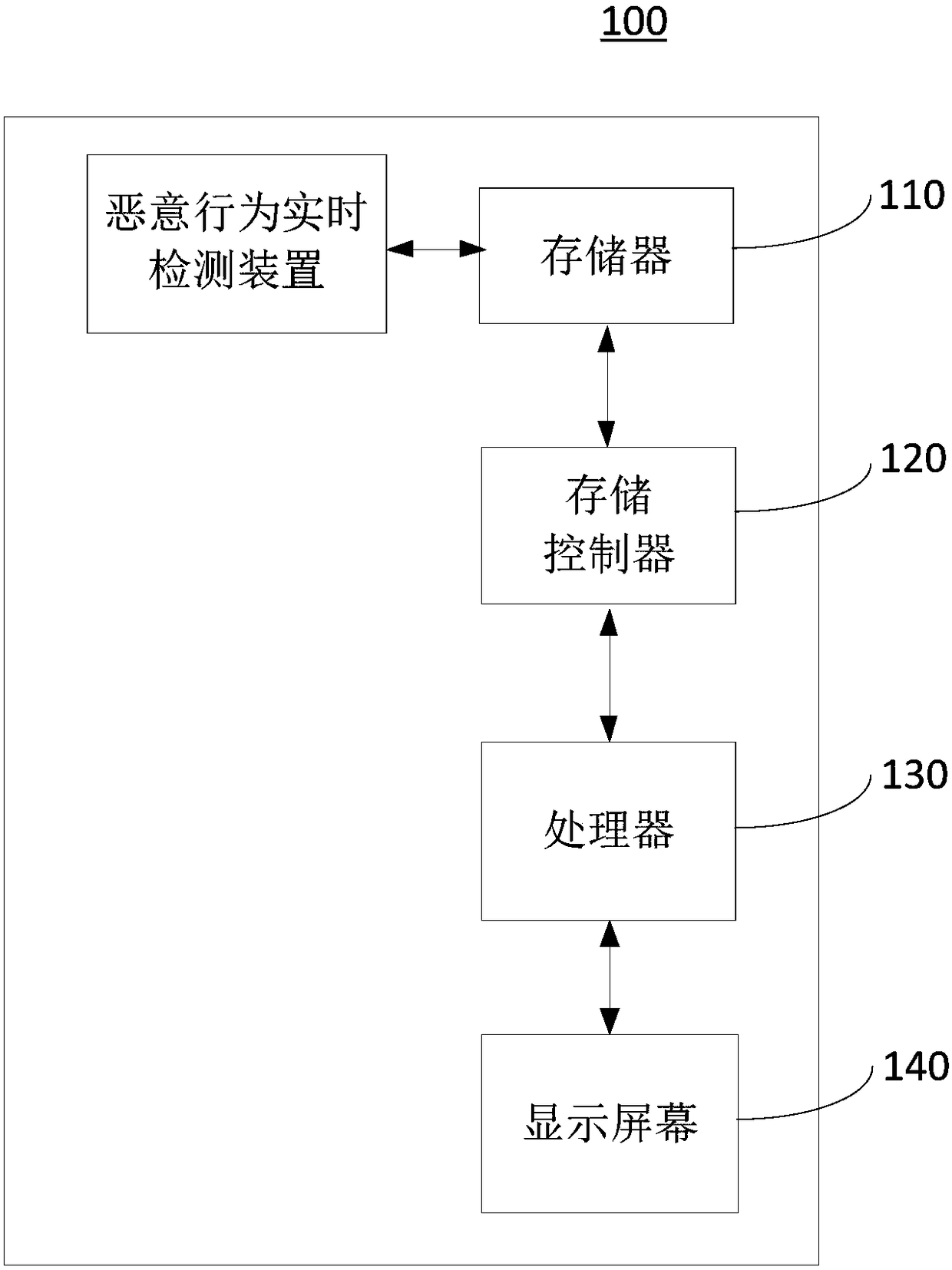
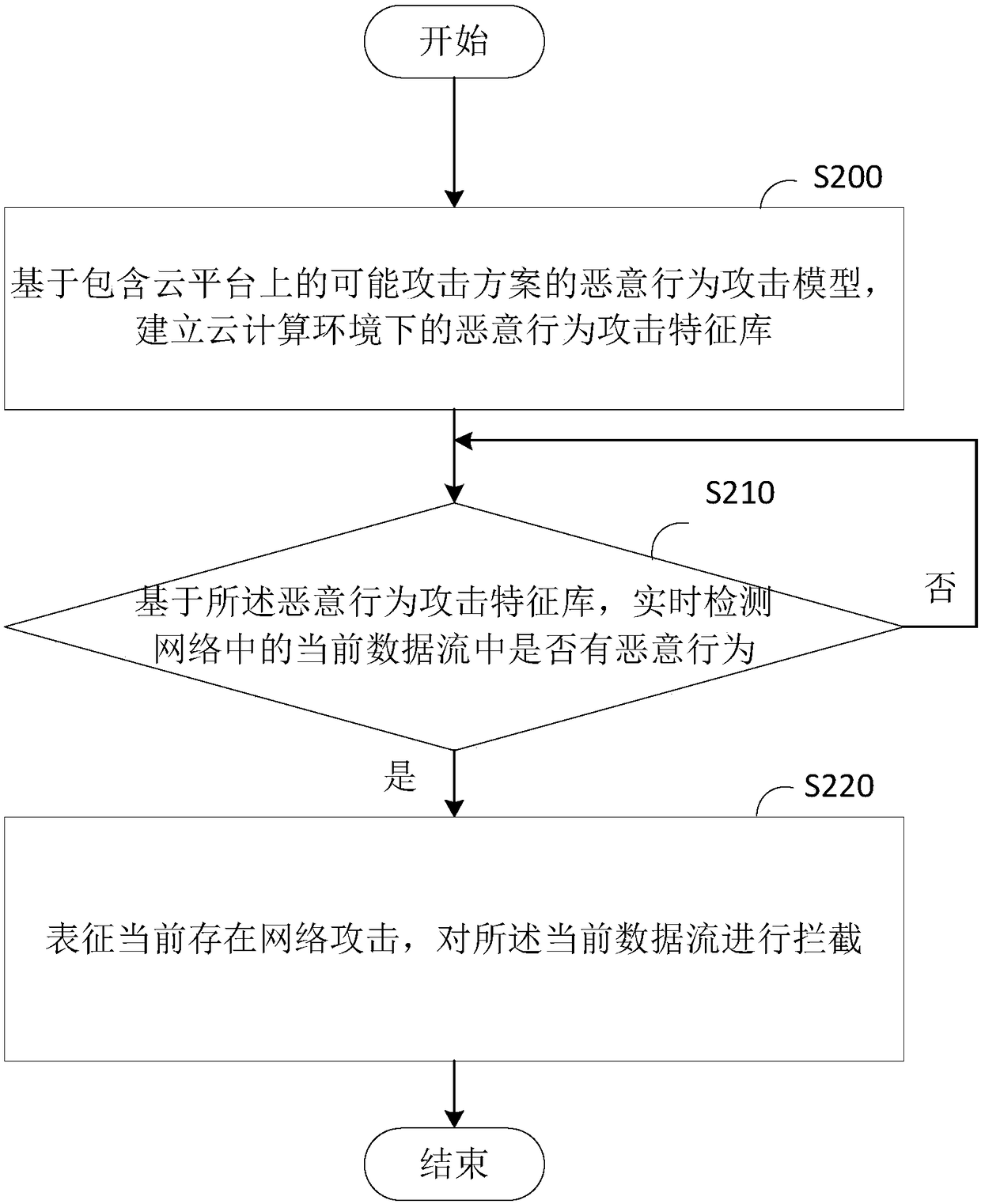
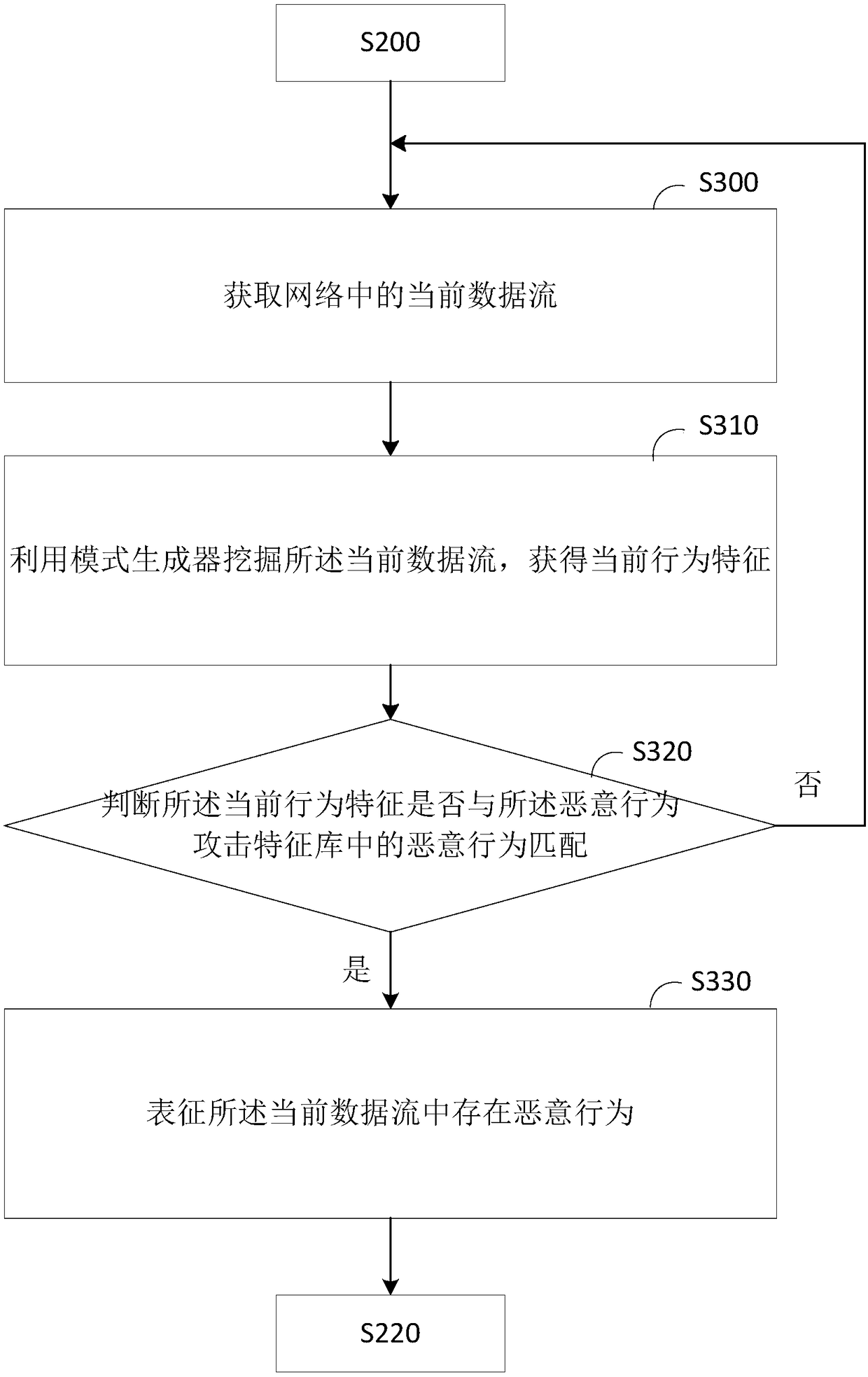
Real-time malicious behavior detection method and device
InactiveCN108123939AImprove the problem of low detection efficiencyTransmissionAttack modelData stream
The invention provides a real-time malicious behavior detection method and device which are applied to an SDN system, and relates to the technical field of cloud computing. The real-time malicious behavior detection method comprises the steps that a malicious behavior attack feature library in a cloud computing environment is built on the basis of a malicious behavior attack model containing possible attack schemes on a cloud platform; whether or not a malicious behavior exists in a current data flow in a network is detected in real time on the basis of the malicious behavior attack feature library; and if yes, it represents that a network attack exists at present, and the current data flow is intercepted. According to the real-time malicious behavior detection method and device, for solving the problem that an existing malicious behavior detection model cannot effectively deal with the processing efficiency bottleneck brought by the large-scale network traffic and the traffic controldifficulty brought by the network topology complexity, an SDN-based real-time malicious behavior detection model is designed by combining a flexible SDN architecture with a big data processing framework to solve the low detection efficiency problem which exists in research at present and is caused by handling the bottleneck and network traffic control problems.
Owner:HUAZHONG NORMAL UNIV
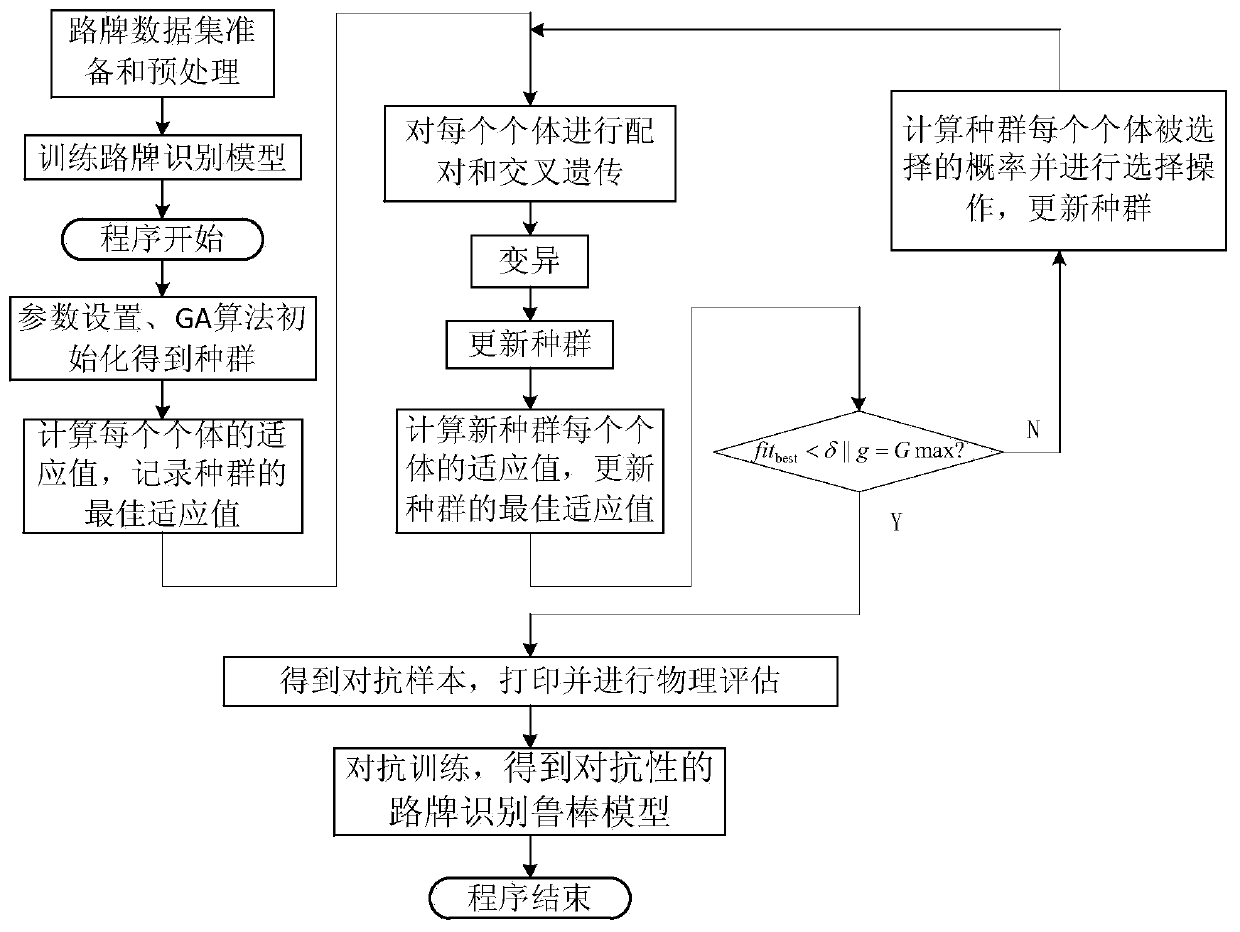
Guideboard identification confrontation defense method based on genetic algorithm
ActiveCN110163093ASolving Multi-Objective Optimization ProblemsImprove robustnessCharacter and pattern recognitionGenetic algorithmsAttack modelGenetic algorithm
The invention discloses a guideboard identification confrontation defense method based on a genetic algorithm. The method comprises the following steps: (1) constructing a training set, a test set anda confrontation set; (2) constructing a guideboard classifier, and training the guideboard classifier by using the training set and the test set to obtain a guideboard recognition model; (3) constructing a guideboard attack model according to a genetic algorithm, and generating an adversarial sample by utilizing the guideboard attack model; (4) correcting the adversarial sample, applying the adversarial sample in a physical scene, and collecting a physical image of the adversarial sample; (5) inputting the physical image of the confrontation sample into a guideboard identification model, andscreening to obtain a high-quality confrontation sample; (6) adding high-quality confrontation samples into the training set, and training the guideboard recognition model again by using the trainingset to realize confrontation defense optimization of the guideboard recognition model; and (7) identifying the guideboard image by using the guideboard identification model after confrontation defenseoptimization to realize confrontation defense of guideboard identification.
Owner:ZHEJIANG UNIV OF TECH
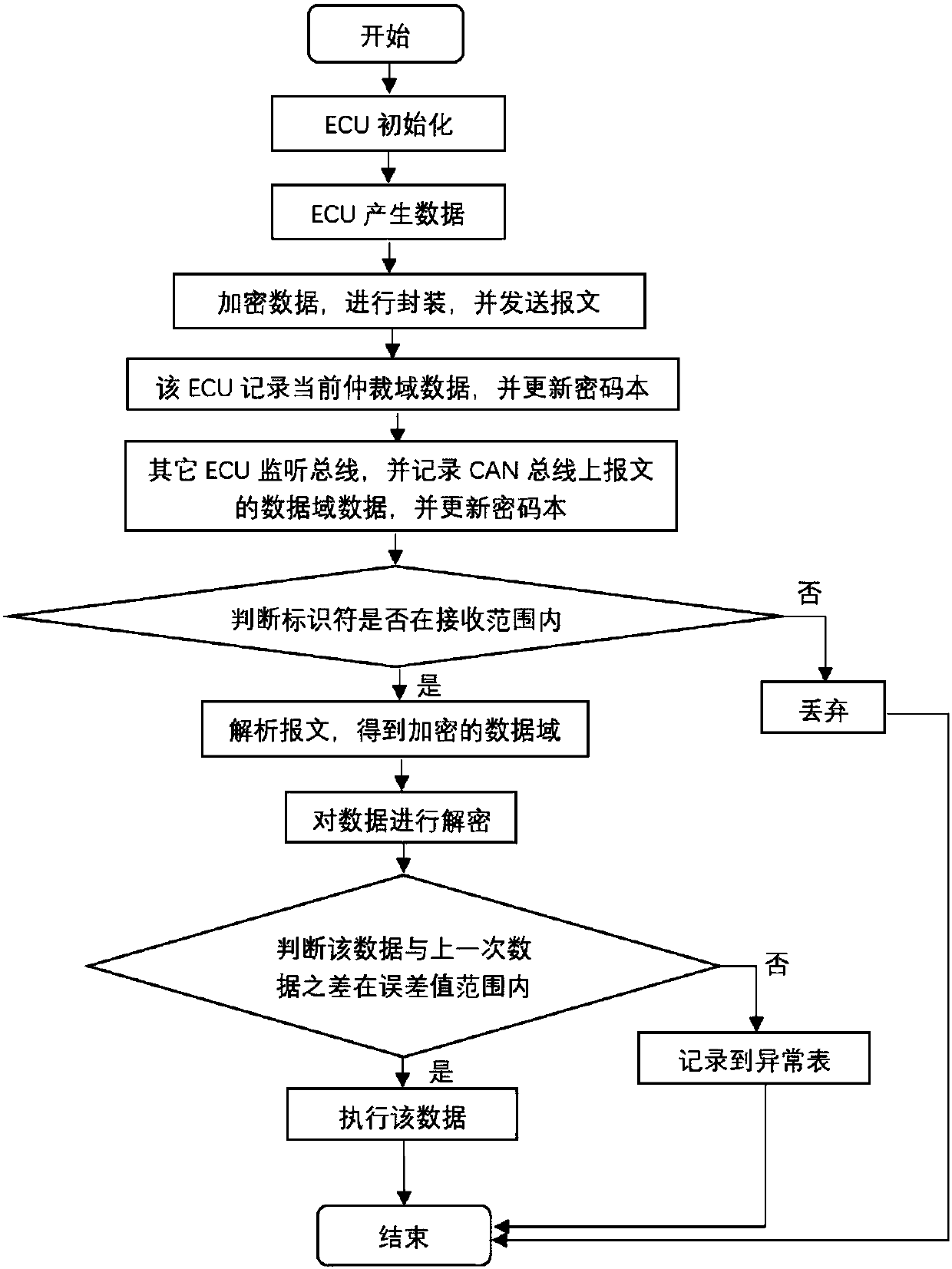
Anti-attack method and system of CAN bus message based on block chain technology
ActiveCN107749845AImprove securitySolving Difficult Management ProblemsBus networksAttack modelCode book
The invention belongs to the technical field of anti-attack of messages, and discloses an anti-attack method and system of a CAN bus message based on the block chain technology. The method comprises the following steps: improving an account book generated in a block chain, generating a password with a fixed length and updating the password in real time; performing, by each ECU, encryption processing on arbitration domain data monitored every time and a code book to obtain a new code book; before a message is sent, encrypting the data domain information via the latest code book to obtain an encrypted data domain, and finally sending the data domain; filtering, by the ECU, an identifier in the arbitration domain to obtain the necessary message, analyzing the message to obtain the encrypted data domain, and decrypting the encrypted data domain by using own code book; then judging the validity of the data obtained by decryption; and if the data are valid, executing the data, and otherwise,discarding the data. By adoption of the anti-attack method and system, the counterfeit, replay and other attacks can be defended, and the security of the vehicle is enhanced.
Owner:CHENGDU UNIV OF INFORMATION TECH
Deep neural network attack method and device, medium and computing equipment
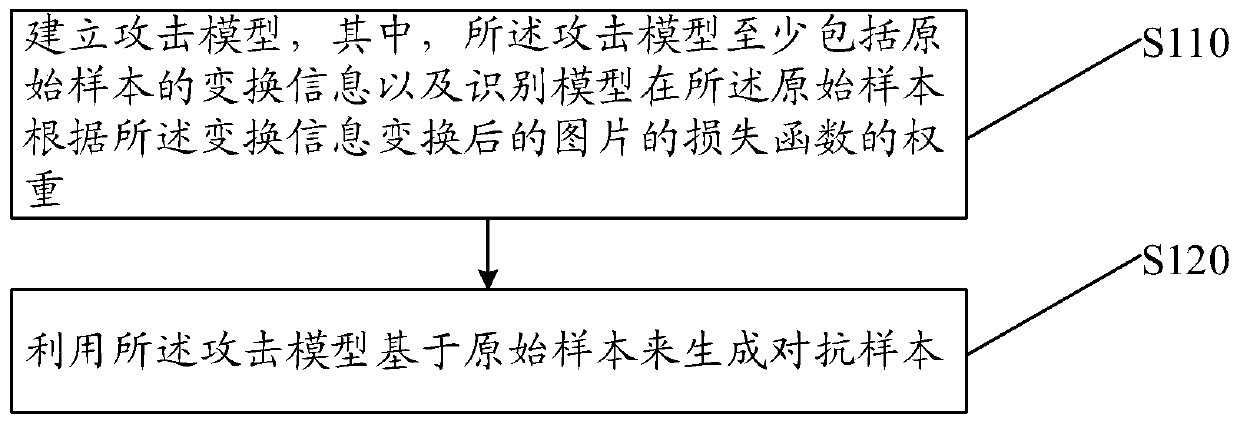
PendingCN110084002AImprove transfer abilityLow costNeural architecturesProgram/content distribution protectionAttack modelAlgorithm
The embodiment of the invention provides a deep neural network attack method. The method comprises the steps that an attack model is established, and the attack model at least comprises transformationinformation of an original sample and the weight of a loss function, transformed by a picture of the original sample according to the transformation information, of an identification model; an adversarial sample is generated based on an original sample using the attack model. According to the method, the confrontation sample is generated for the real picture and the group of pictures after translation, and the transfer performance of the generated confrontation sample is greatly improved, so that the sensitivity of the confrontation sample to the attacked model is remarkably reduced, and thegeneration cost of the confrontation sample is reduced. In addition, the embodiment of the invention provides a deep neural network attack device, a medium and computing equipment.
Owner:TSINGHUA UNIV
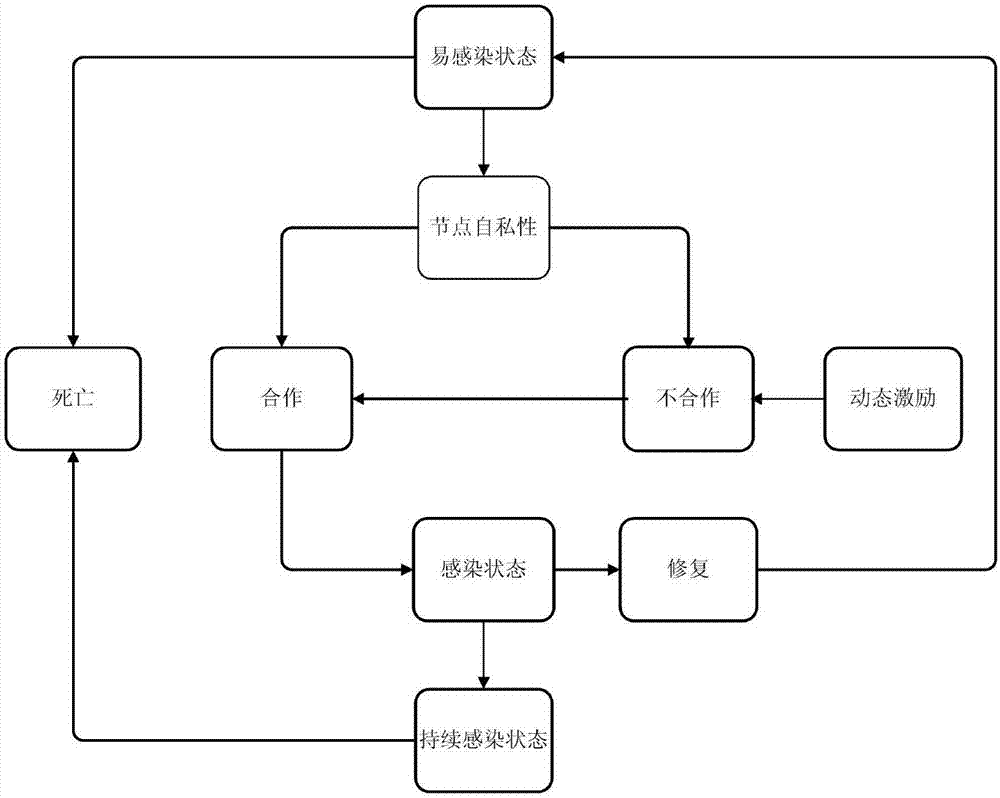
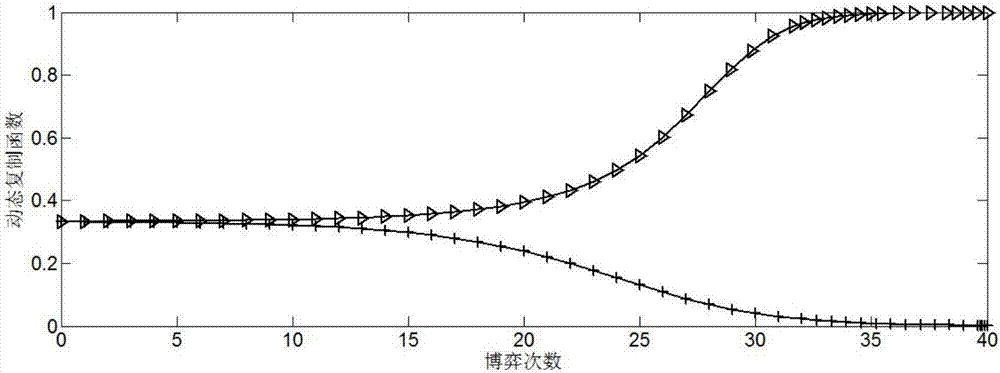
Wireless sensor network survivability evaluation method based on evolutionary game model
The invention relates to a wireless sensor network survivability evaluation method based on an evolutionary game model. The method comprises the following steps of (1), performing model selection from a wireless sensor network model, an attacking model and an epidemic disease model; (2), establishing a survivability model; and (3) evaluating wireless sensor network survivability through evolution dynamics analysis. According to the method of the invention, an influence which is generated by network survivability is analyzed through connectivity of a network cluster head node; the epidemic disease model based on the attack is established by a node attack bearing problem; then a survivability evaluation model based on evaluation gaming is established; a dynamic process is selected by means of a strategy of copying a dynamic equation researching node; an evolution stabilization strategy which is selected by the node strategy is searched; and when the survivability evaluation model for the attacked network reaches an evaluation stable state, performance indexes such as connectivity and stability are used as network survivability evaluation mechanisms, and furthermore verification is performed.
Owner:TIANJIN UNIV
A password attack evaluation method based on conditional variational self-coding
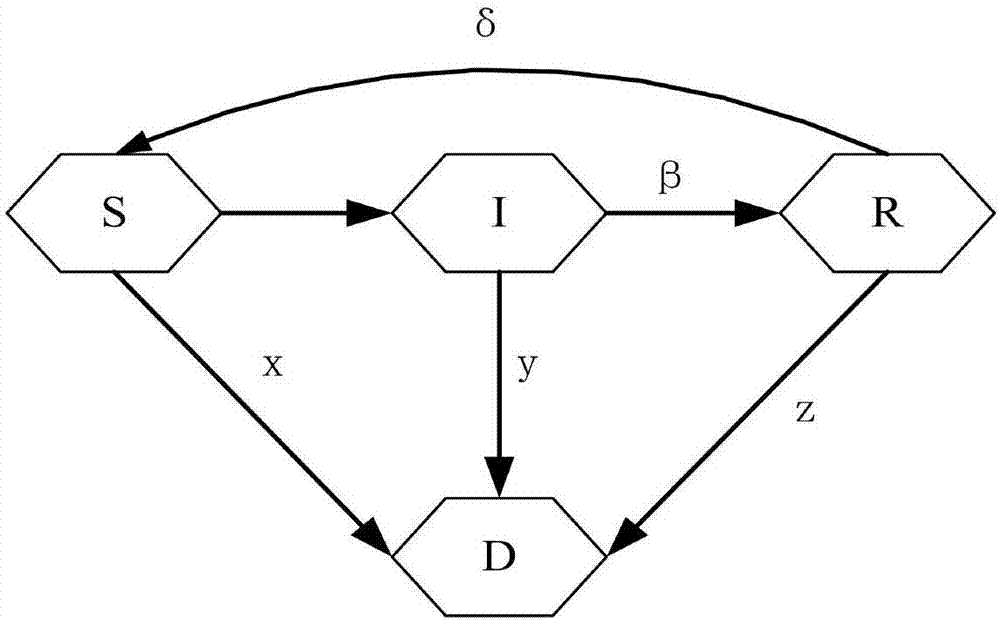
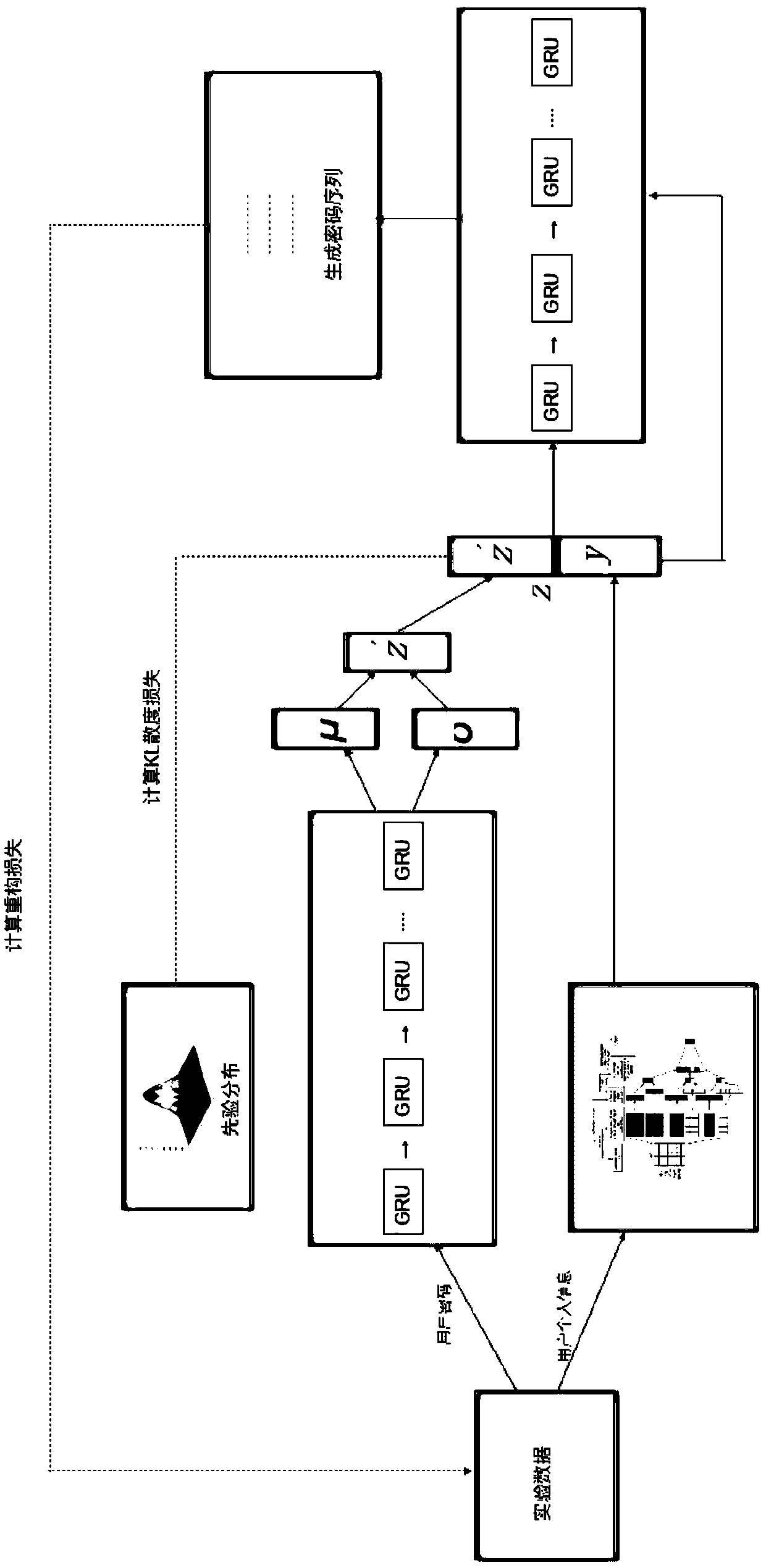
ActiveCN109670303AHigh strengthImprove securityDigital data protectionPlatform integrity maintainanceAttack modelPassword
The invention provides a password attack evaluation method based on conditional variational self-coding. The method comprises the following steps of constructing a variational self-coding model, constructing a conditional variational self-coding model, constructing a password attack model, and comprehensively utilizing the conditional variational self-coding model and the password attack model. According to the invention, a conditional variational self-coding model, and the condition characteristics in the personal information of the user, such as the user name, the mailbox address, the telephone number, etc. are used to train the cryptographic attack model, a bidirectional GRU recurrent neural network and a CNN text convolutional neural network are respectively used at the encoder end, sothat the code of a password sequence and personal information of a user and abstract extraction of characteristics can be achieved, the distribution of password data and a character combination rulecan be effectively fitted, the high-quality guessing password data can be generated, and the method has a remarkable effect on improving the password strength and safety of the user.
Owner:BEIJING WISEWEB TECH
A prototype modeling method of network security attack based on industrial control
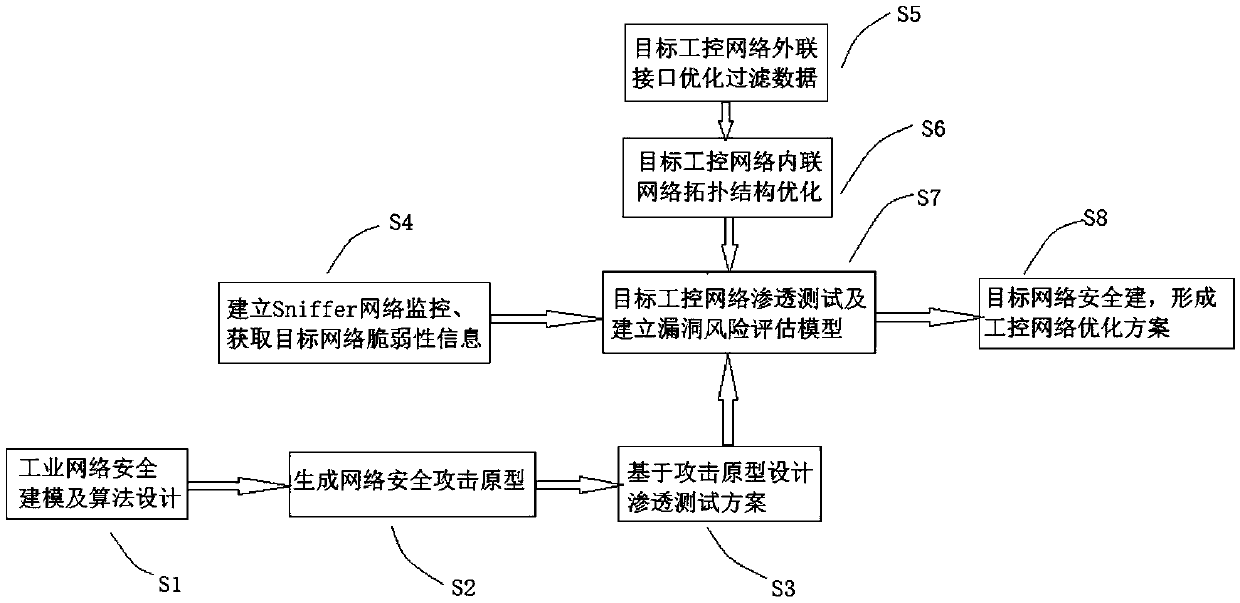
InactiveCN109543301AOptimize topologyDeny illegal intrusionDesign optimisation/simulationTransmissionSecurity solutionVulnerability
The invention discloses an industrial control network security method based on industrial network attack prototype modeling, which comprises the following steps: S1, industrial network security modeling and algorithm design; S2, designing an industrial control network security attack prototype; S3, taking an attack model of an attacker in an algorithm of the attack prototype in S1 as an attack source, and converting the network vulnerability information obtained in S4 into an attack set of an attacker according to attack rules to form an attack prototype; S4: Designing penetration test schemebased on attack prototype; 5, establishing a Sniffer network monitoring system; 6, optimizing and filtering that data through the external interface of the target industrial control network; 7, optimizing that topology structure of the intranet of the target industrial control network; S8: Establishing vulnerability risk assessment and modeling; S9: Forming an industrial network security defense solution. The network optimization and safety solution provided by the invention will effectively solve the safety problem of the industrial control of the enterprise, can timely carry out the risk assessment on the system, reduce the risk factors to the maximum extent, and improve the network operation efficiency and the safety reliability of the production management.
Owner:SUZHOU CHIEN SHIUNG INST OF TECH
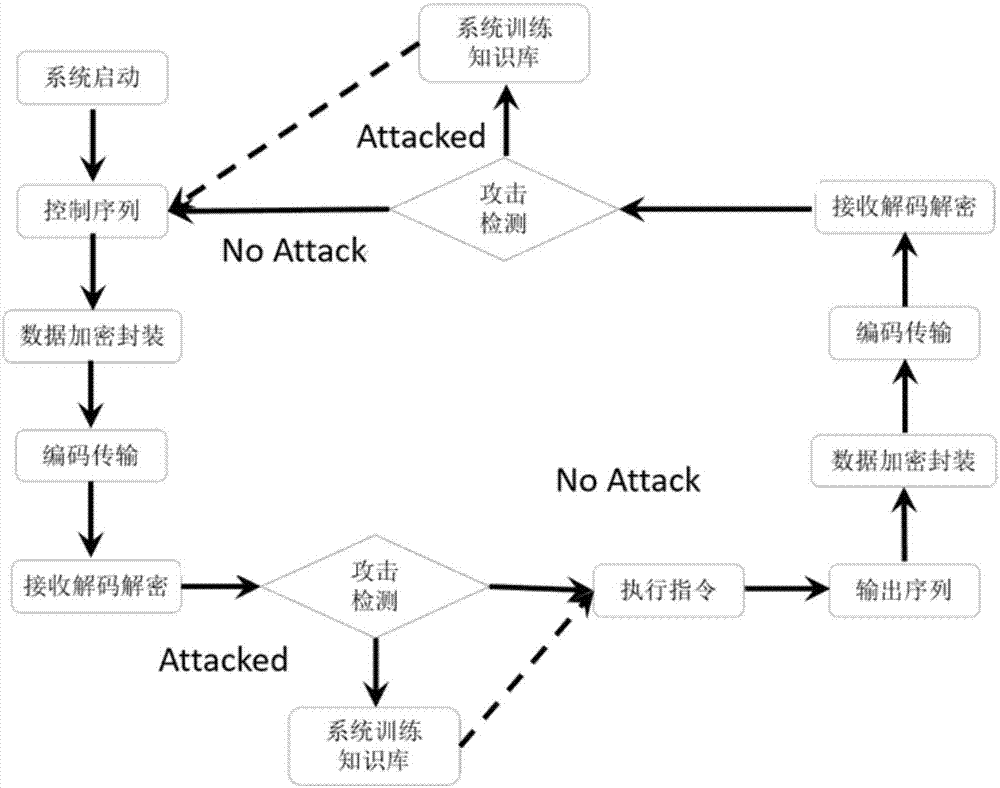
Industrial network closed-loop control method with attack protection, and architecture of the same
The invention discloses an industrial network closed-loop control method with attack protection, and architecture of the same. Based on a hidden attack model existing in a network control system, the architecture designs links of intelligent detection and defense capability, and can detect attack and harm brought by the network. The architecture not only contains some links in a classical network control system, but also increases a preprocessing link of control signals and a preprocessing link of feedback output signals on the front end of a controlled object and a controller. Besides, the architecture increases a comparison link at the output end of the controlled object according to the attack intelligent level, thus having the anti-attack capability and being able to effectively eliminate the influence brought by the hidden attack, due to these links. For the industrial network closed-loop control method with attack protection, and the architecture of the same, two kinds of architectures are designed according to the level of the hidden attack and the intelligent degree, wherein one of the architectures mainly aims at a common hidden attack and the other one aims at a hidden attack having certain anti-detection intelligent characteristic.
Owner:NANJING UNIV OF POSTS & TELECOMM
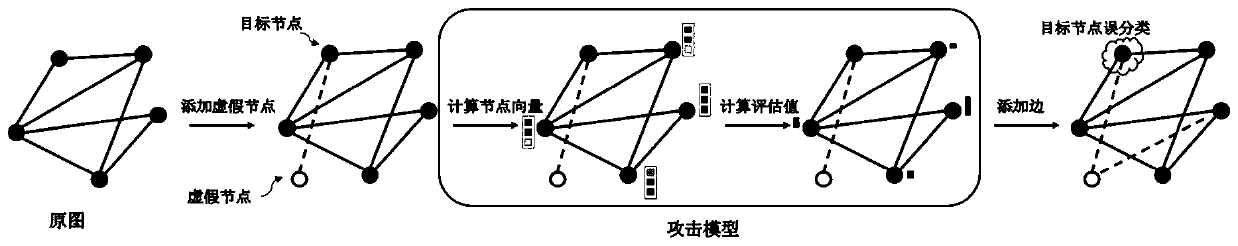
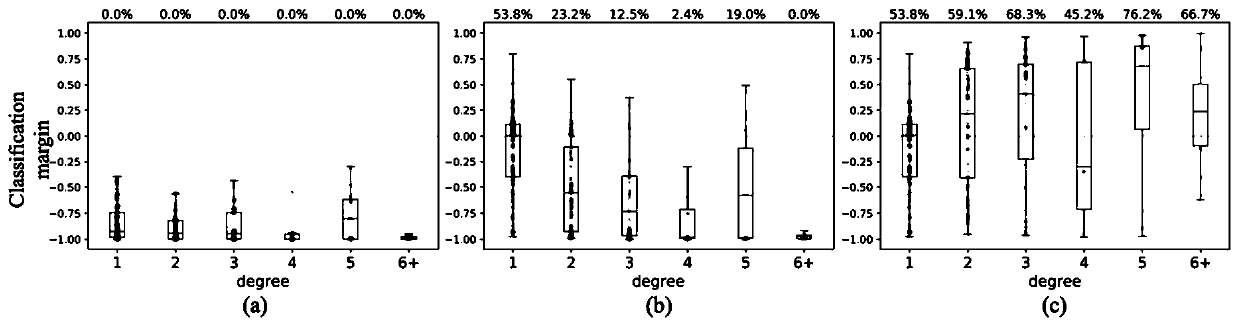
Graph adversarial sample generation method by adding false nodes based on reinforcement learning
The invention discloses a graph adversarial sample generation method by adding false nodes based on reinforcement learning. The graph adversarial sample generation method comprises the following steps: (1) obtaining the number of original graphs and a graph node classification model, and constructing a training set and a test set; adding false nodes into the original image data to obtain an initial adversarial sample; (2) constructing an attack model; (3) selecting an attack target in the training set; (4) inputting the current adversarial sample and the attack target into an attack model, selecting a node with the maximum evaluation value, and constructing a new adversarial sample; (5) inputting a new adversarial sample into the classification model, if a classification result is a targetresult, obtaining the adversarial sample and carrying out the next step, otherwise, skipping to the step (4); and (6) training the attack model, and testing and applying the trained attack model. According to the graph adversarial sample generation method, the adversarial sample of the graph is generated by adding the false nodes, and help can be provided for designing a more robust graph deep learning model.
Owner:ZHEJIANG UNIV
Multi-machine electric power system wide-area damping control method under elastic event triggering mechanism
ActiveCN108448576AGuaranteed uptimeReduce delivery pressureAc network circuit arrangementsWide areaAttack model
The invention discloses a multi-machine electric power system wide-area damping control method under an elastic event triggering mechanism. A multi-machine electric power system is controlled by a wide-area damping control system which consists of a vector data concentrator, an event trigger, a PMU, a generator and a wide-area damping controller, wherein the control method of the wide-area dampingcontrol system comprises the steps of S1, establishing a DoS attack model for simulating real DoS attack; S2, judging whether a control signal is blocked by the DoS attack or not, wherein the wide-area damping controller performs elastic control according to the judging effect to ensure stability of the multi-machine electric power system; S3, enabling the vector data concentrator to transfer thestate signals of the multi-machine electric power system collected in each time to the event trigger to judge whether a trigger algorithm of the event trigger is satisfied or not; and S4, enabling the event trigger to respond the judgment result of the step S3 to determine whether to transfer the control signal to the wide-area damping controller or not, so that occupation of limited bandwidth resource is reduced; and by virtue of the multi-machine electric power system wide-area damping control method, safe and stable operation of the system can be ensured.
Owner:NANJING UNIV OF POSTS & TELECOMM
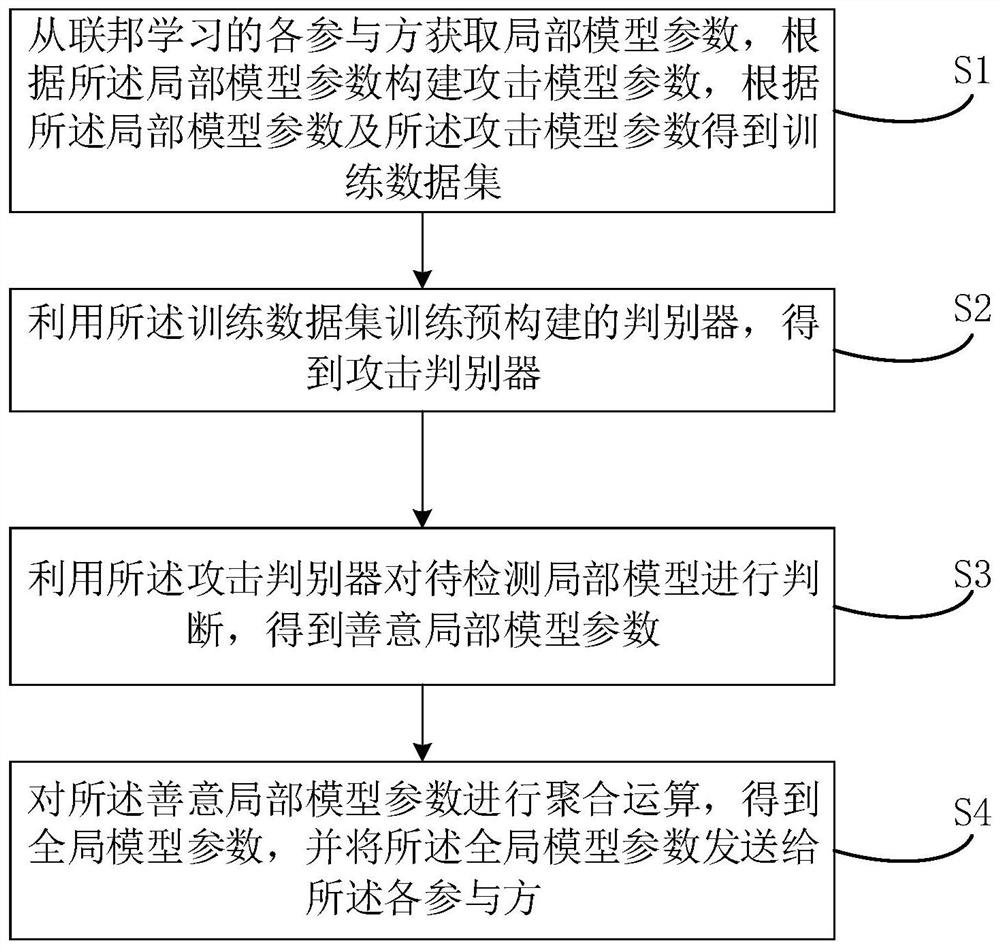
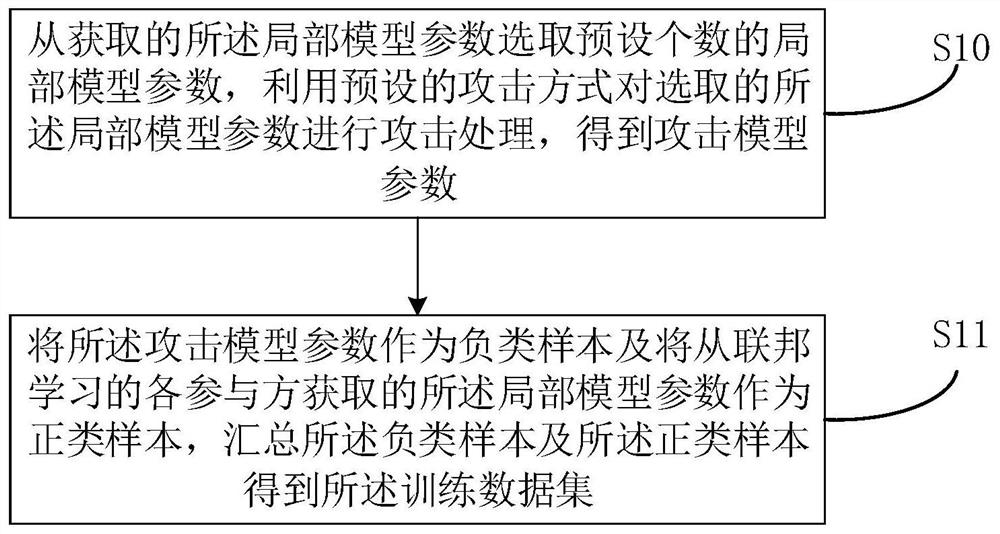
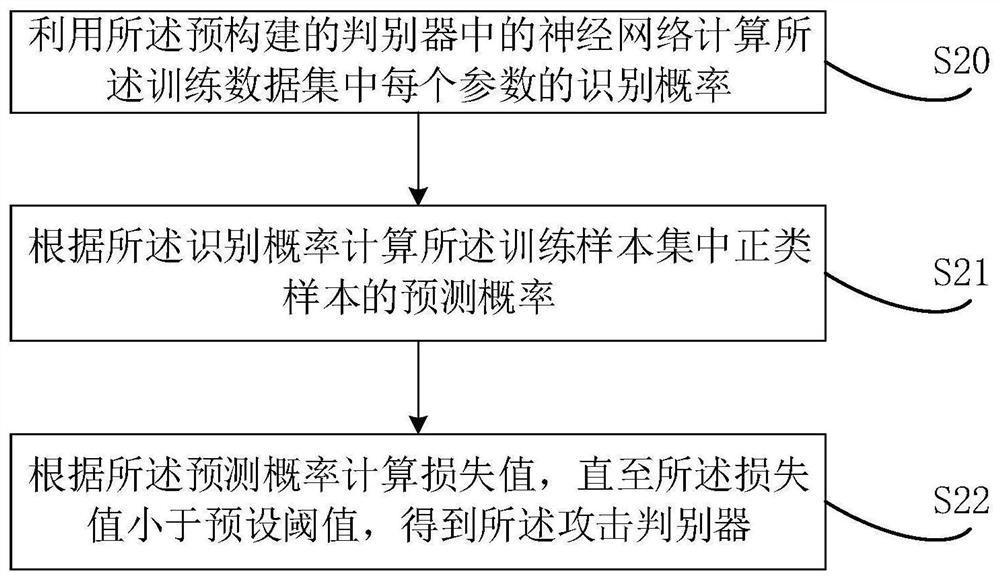
Federation learning defense method and device, electronic equipment and storage medium
PendingCN112446025ASolve the problem of poor defense effectFlexible deploymentCharacter and pattern recognitionPlatform integrity maintainanceDiscriminatorData set
The invention relates to the artificial intelligence technology, and discloses a federated learning defense method comprising the following steps: obtaining local model parameters from each participant of federated learning, constructing attack model parameters according to the local model parameters, obtaining a training data set according to the local model parameters and the attack model parameters, and obtaining a training data set according to the training data set and the attack model parameters; training a pre-constructed discriminator by utilizing the training data set to obtain an attack discriminator, judging a to-be-detected local model by utilizing the attack discriminator to obtain a good local model parameter, and performing aggregation operation on the good local model parameter to obtain a global model parameter; and sending the global model parameters to each participant. In addition, the invention also relates to a blockchain technology, and the global model parameters can be stored in nodes of a blockchain. The invention further provides a federated learning defense device, electronic equipment and a computer readable storage medium. According to the method, theproblem of poor defense effect for a specific attack mode can be solved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Flood attack projection model
A flood attack of an information system is simulated by injecting an algorithmically compressed flood attack model into the information system to assess the effect of the attack upon the system. The flood attack model propagates from node to node throughout the system by way of virtual messages that time-project the flood attack model and do not disrupt system operation while the simulated flood attack is taking place. Programs of executable code installed on nodes of the information system generate and send the virtual messages describing the flood attack.
Owner:LOCKHEED MARTIN CORP
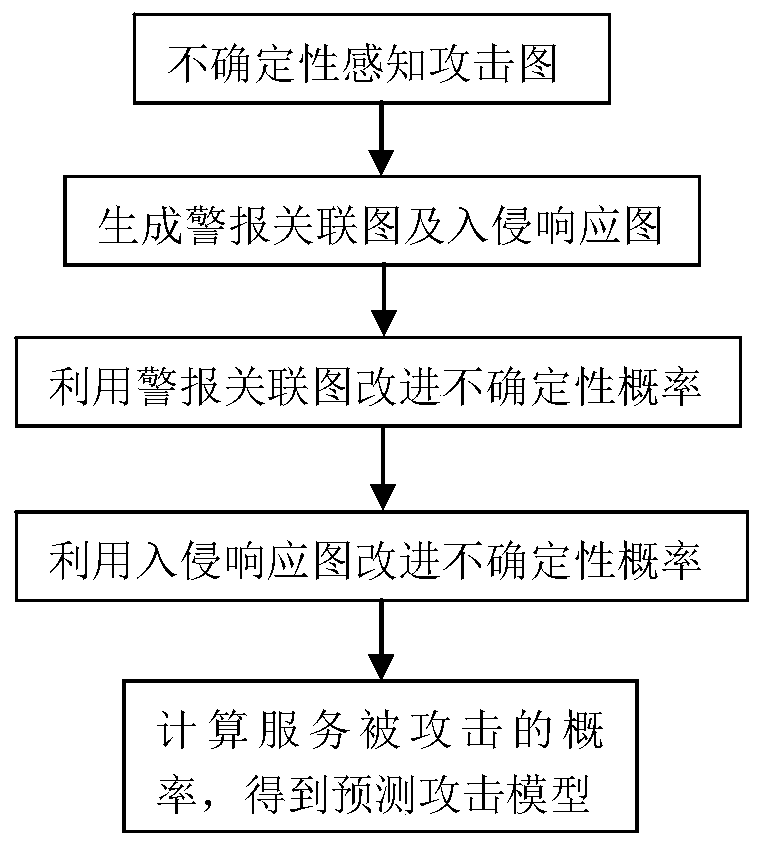
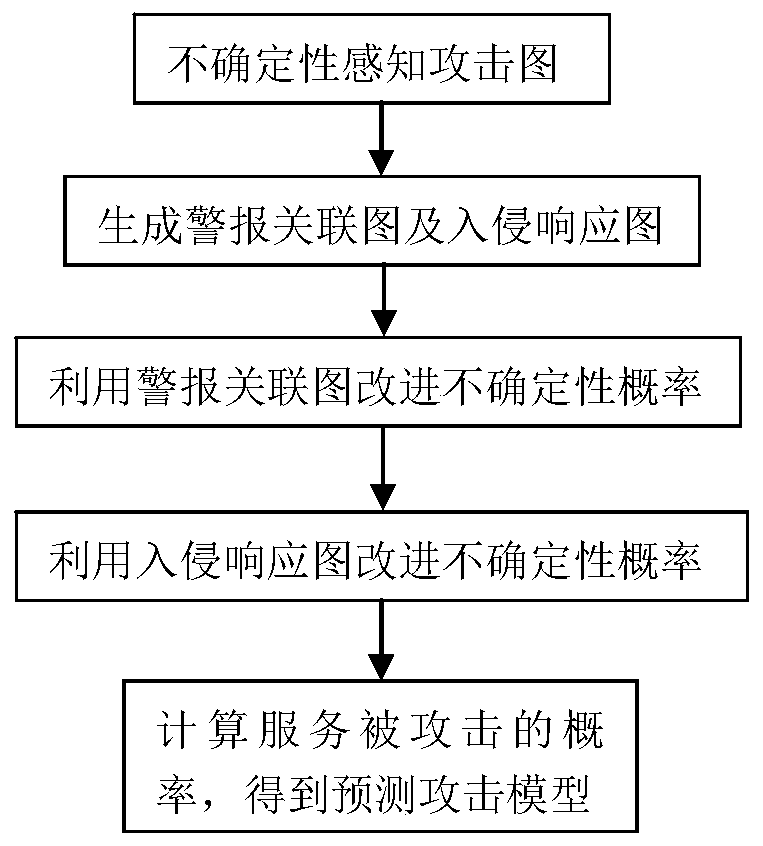
Network attack prediction model construction method based on uncertainty perception attack graph
The invention discloses a network attack prediction model construction method based on an uncertain perception attack graph, which comprises the following steps: 1, adding an uncertain probability that vulnerabilities are attacked on the attack graph to obtain an uncertain perception attack graph; 2, associating the alarm information generated by the intrusion detection system when the service inthe network system is attacked, generating an alarm association graph, and generating an intrusion response graph by using a response decision corresponding to the alarm information; 3, according to the source host address of the alarm, the destination host address of the alarm, the source port number of the alarm, the destination port number of the alarm, the protocol used for alarm transmissionand the vulnerability number corresponding to the generated alarm, improving the uncertainty probability; 4, improving the uncertainty probability through the incidence relation between the response decisions in the intrusion response graph and the response cost; 5, obtaining the probability that the service is attacked according to the uncertainty probability so as to obtain a prediction attack model; the network attack prediction method can realize accurate and comprehensive prediction of the network attack.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com