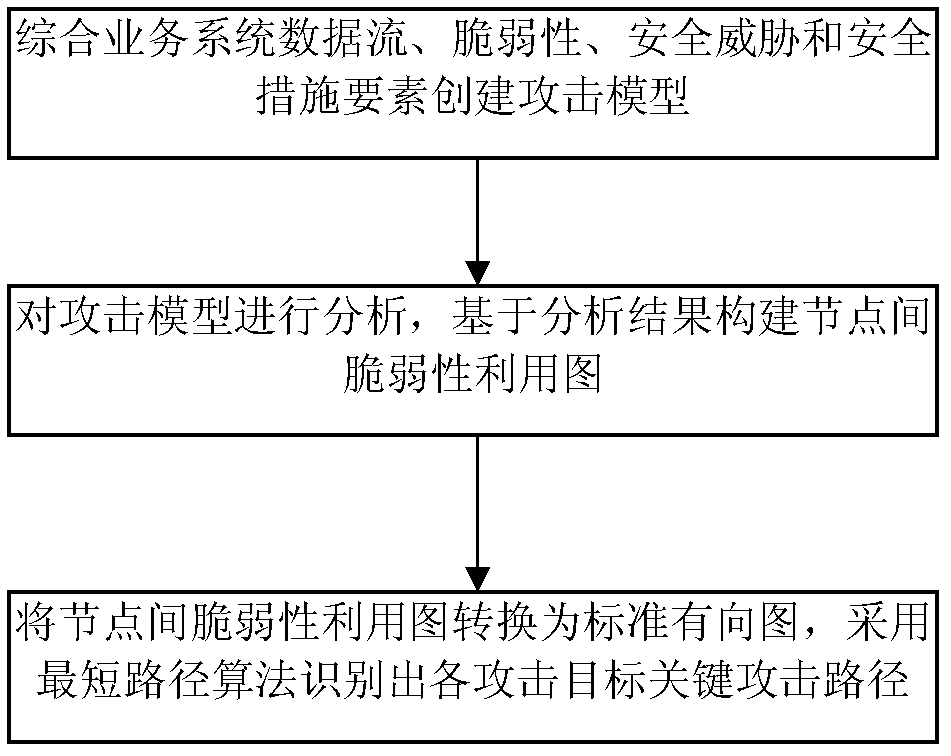
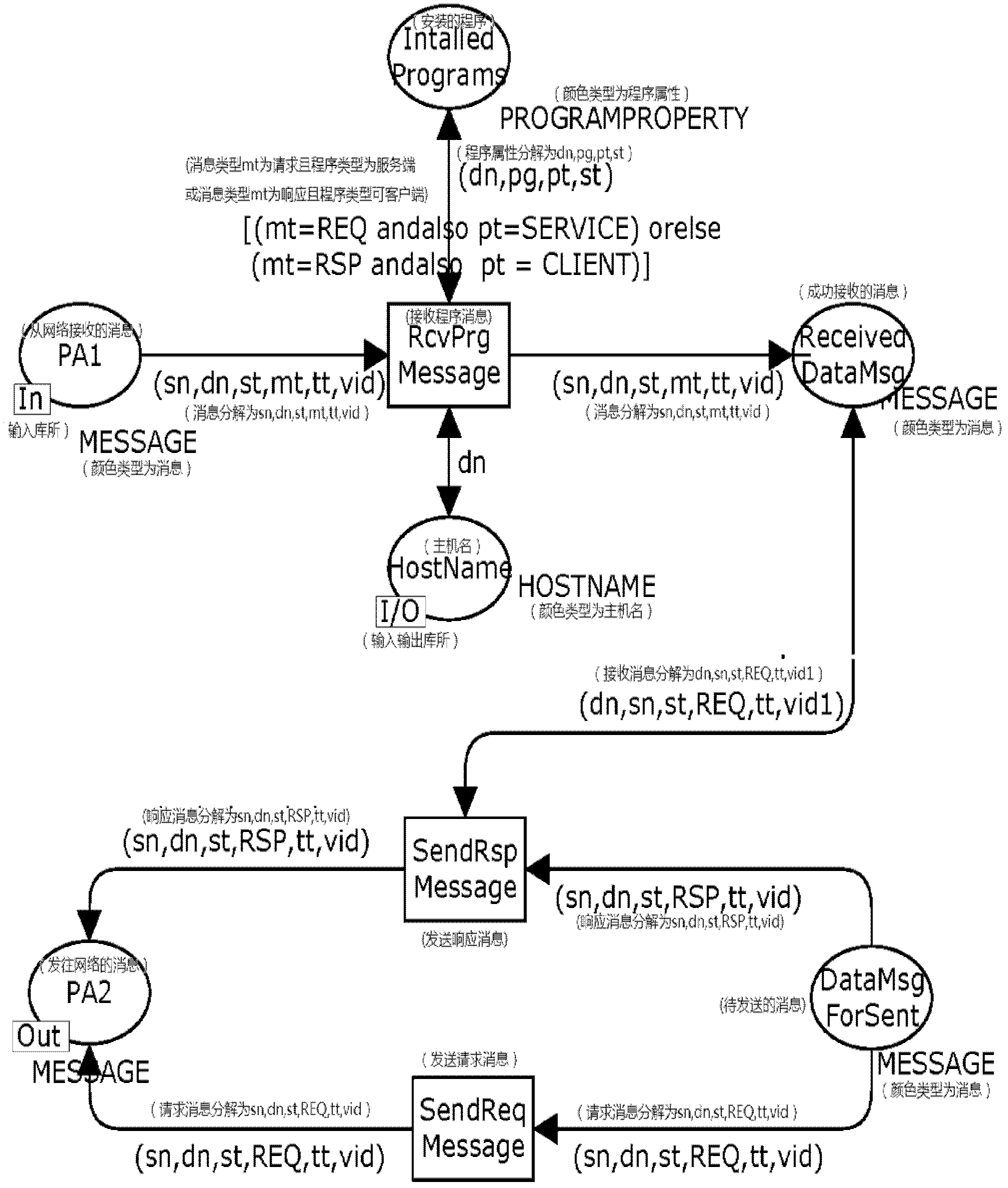
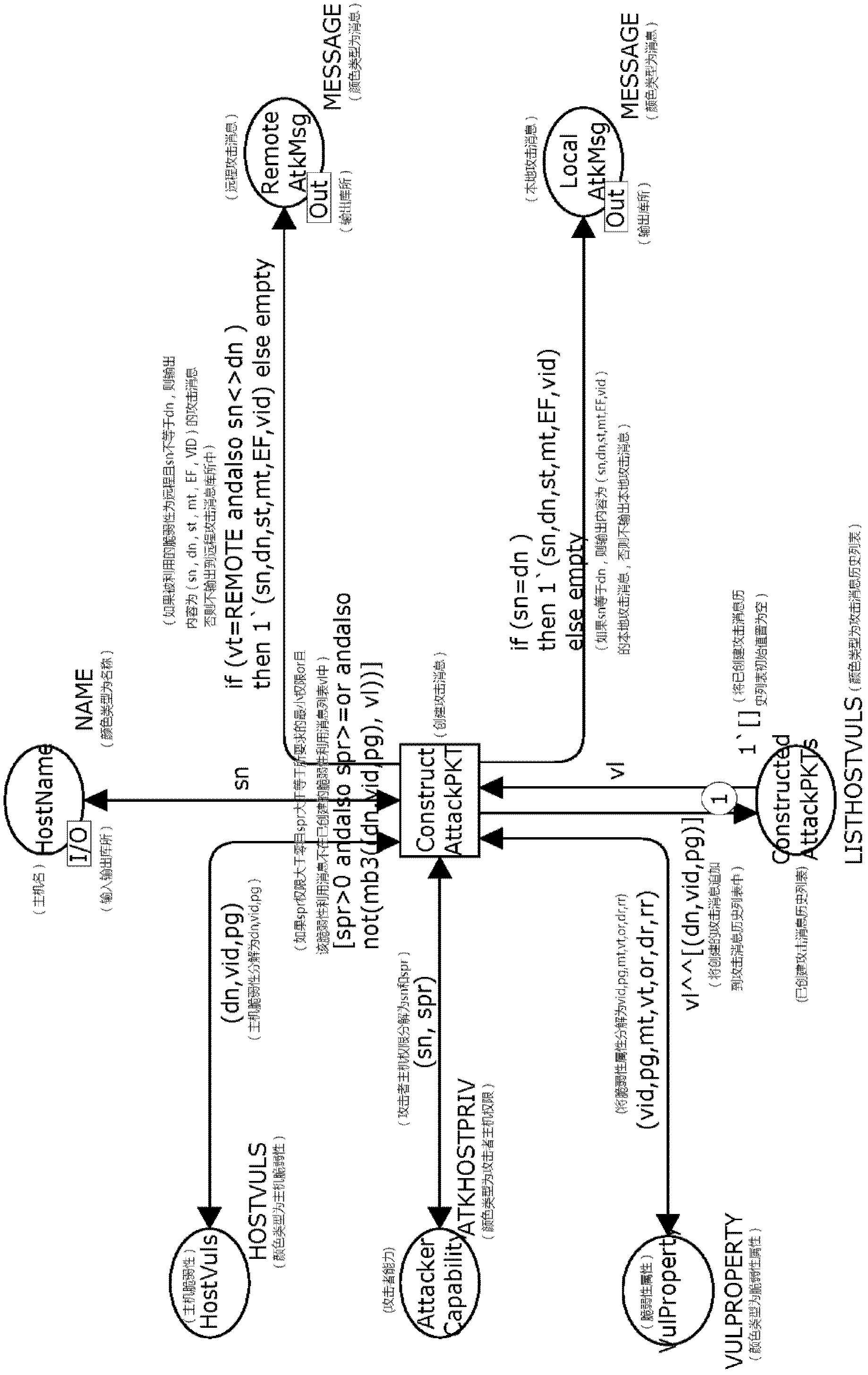
Method for identifying key attack path in service system
A business system and attack path technology, applied in the field of network information security, can solve problems such as high complexity, unsuitable attack path identification, unavailable key attack path identification methods, etc., and achieve good scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0108] The experimental environment of the WEB application business system referred to in this embodiment is as attached Figure 9 As shown, the following security policies are configured: the firewall deployed at the border of the network trust domain divides the network into three security domains: Internet, intranet and DMZ. The WEB server deployed in the DMZ provides WEB services for users. Internal users of the internal network are not allowed to directly connect to the external network, to prevent external worms and other attacks from directly entering the internal network and to ensure that the WEB server provides services to the outside world. The access control policies between the security domains are as follows: 1) Only Internet users are allowed to access the DMZ zone H 2 IIS WEB Service and H 3 DNS domain name service on the DMZ; 2) H in the DMZ 2 Allow access to H 3 Sendmail service on and intranet H 4 MYSQL service on the server; 3) prohibit H 2 and H 3 D...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com