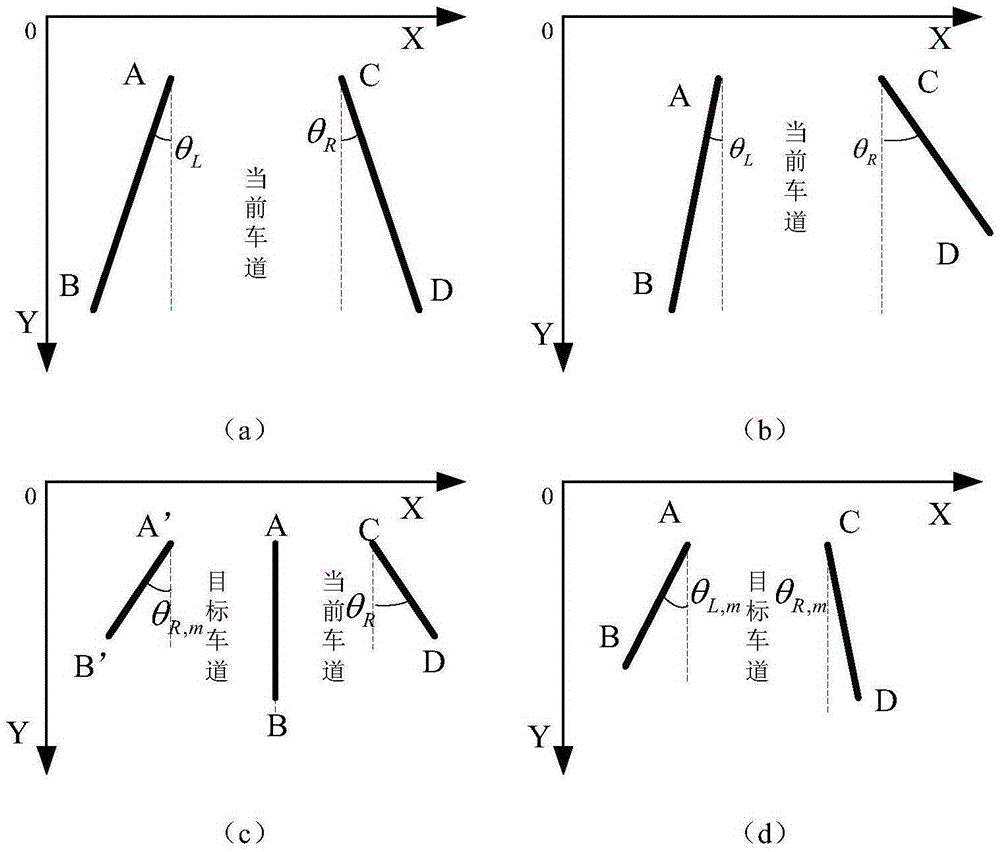Patents
Literature
402 results about "Path recognition" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
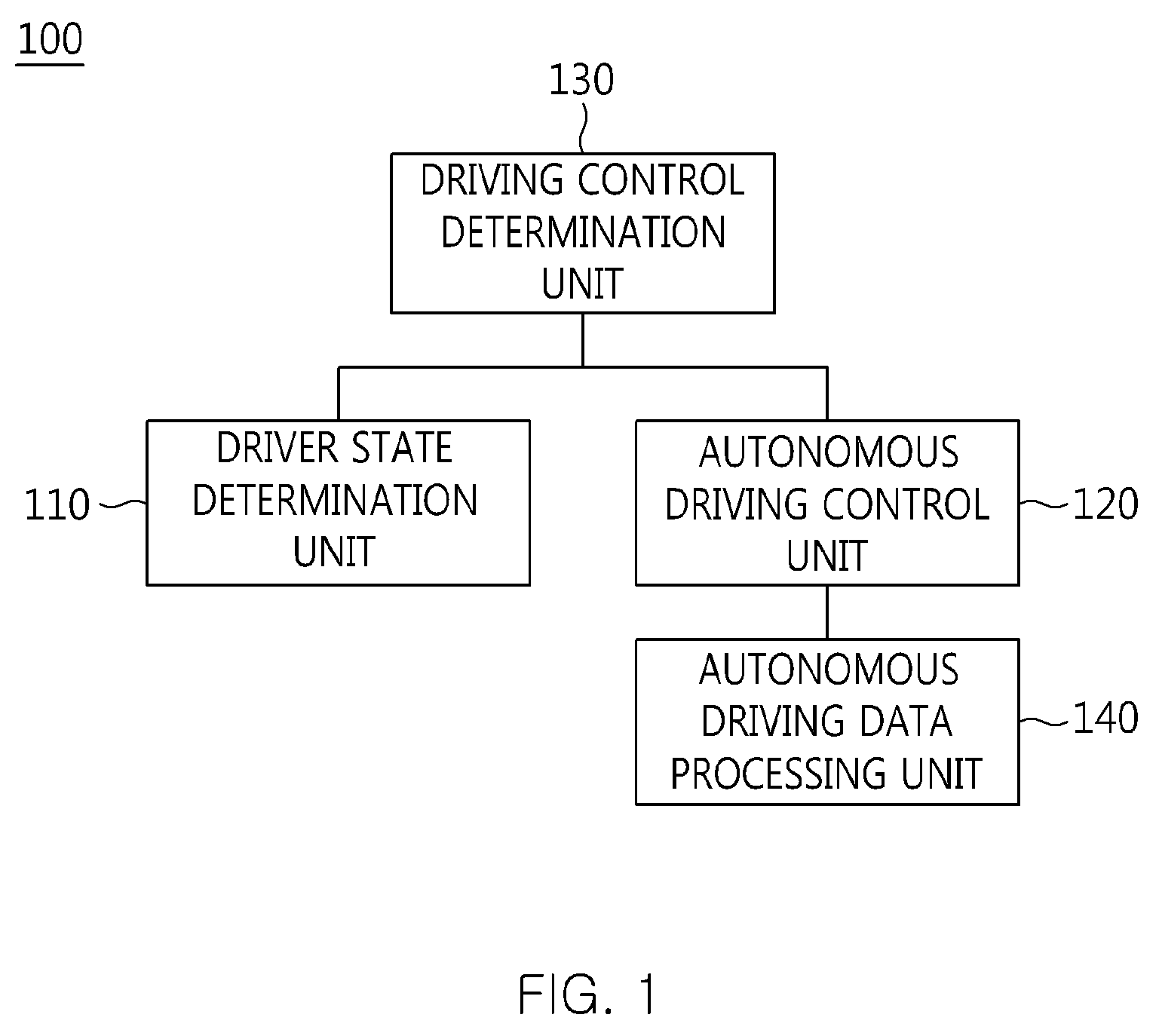
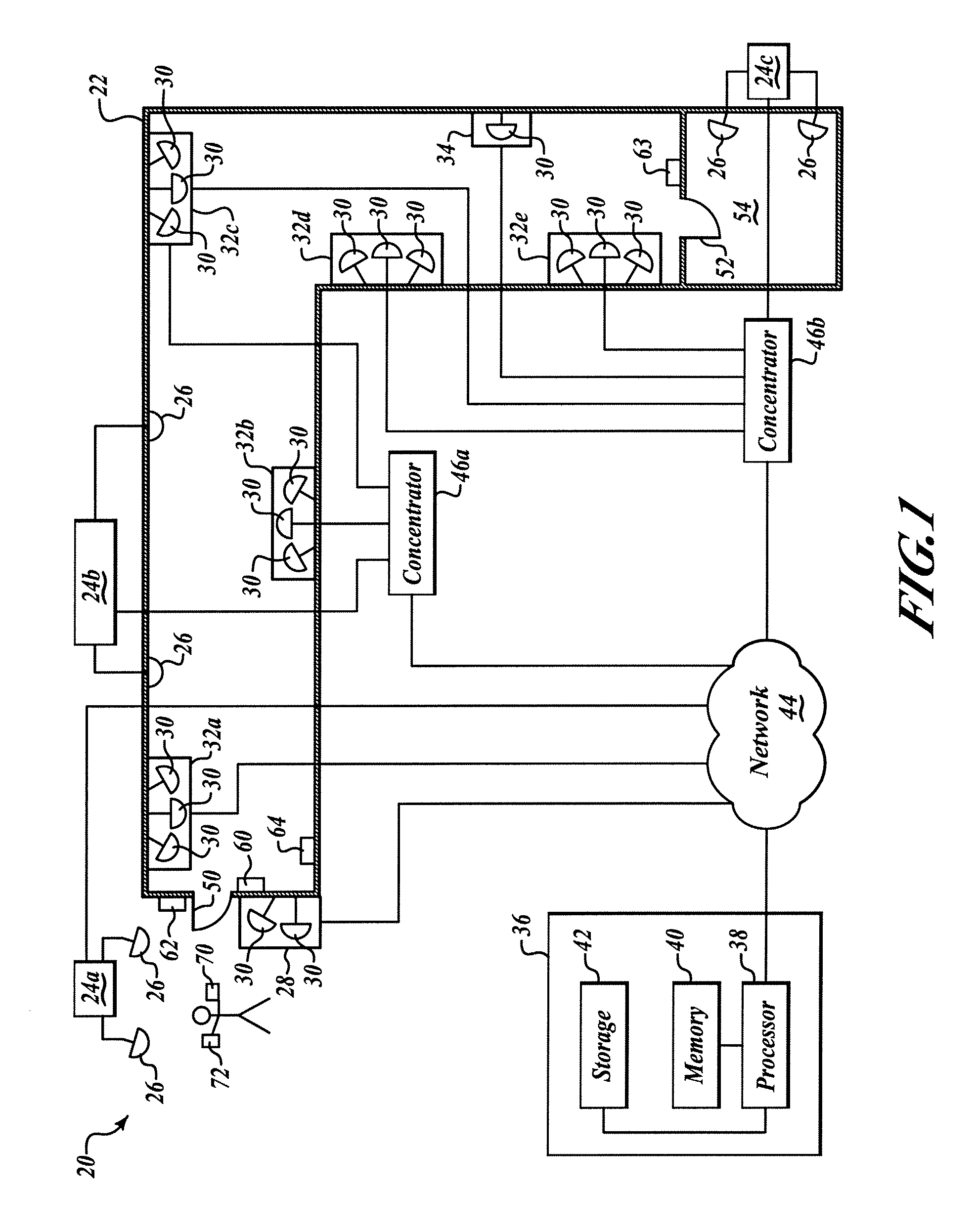
Apparatus and method for cooperative autonomous driving between vehicle and driver
ActiveUS20140244096A1Improve driving performanceImprove performanceControl safety arrangementsExternal condition input parametersEngineeringData storing
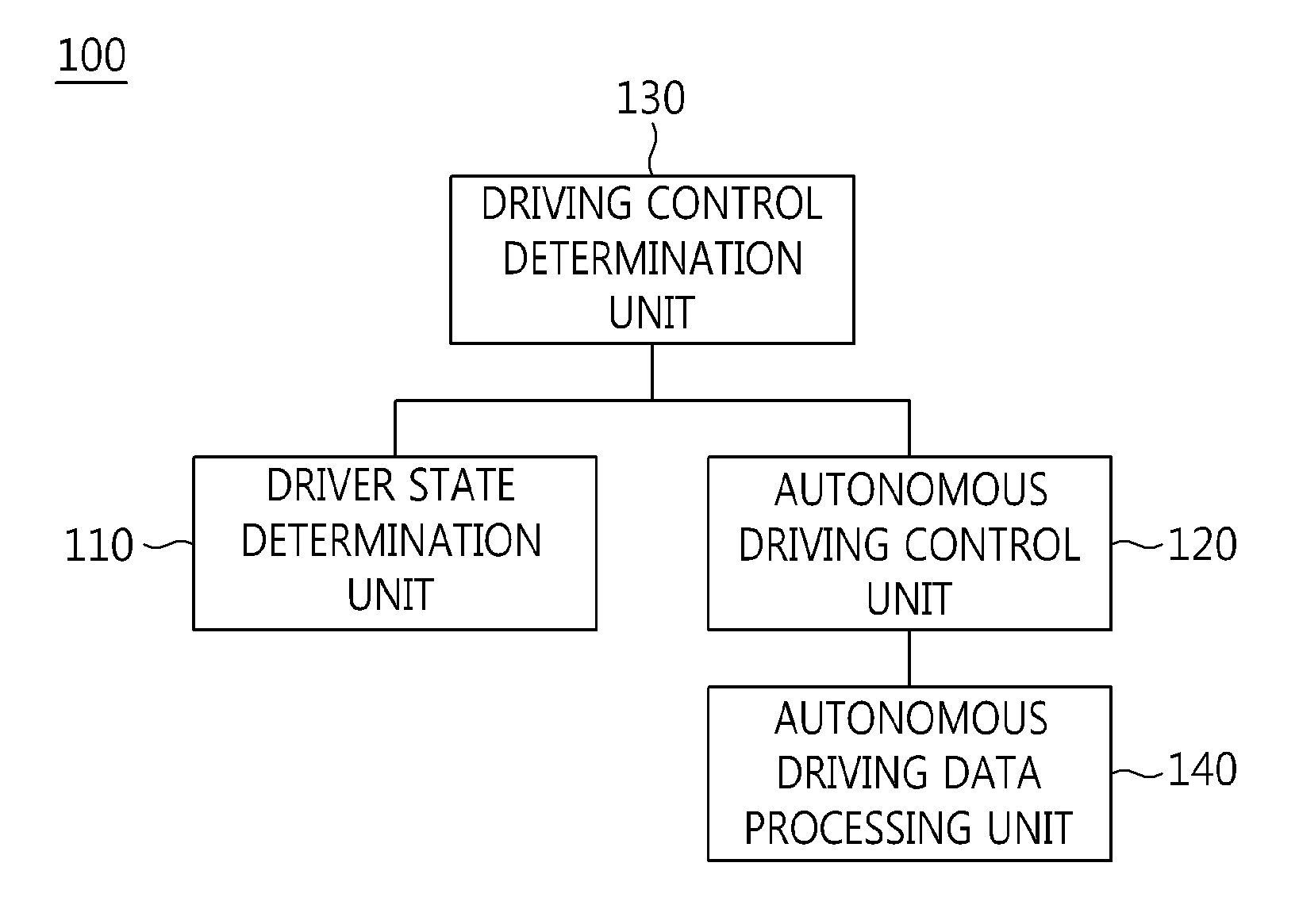
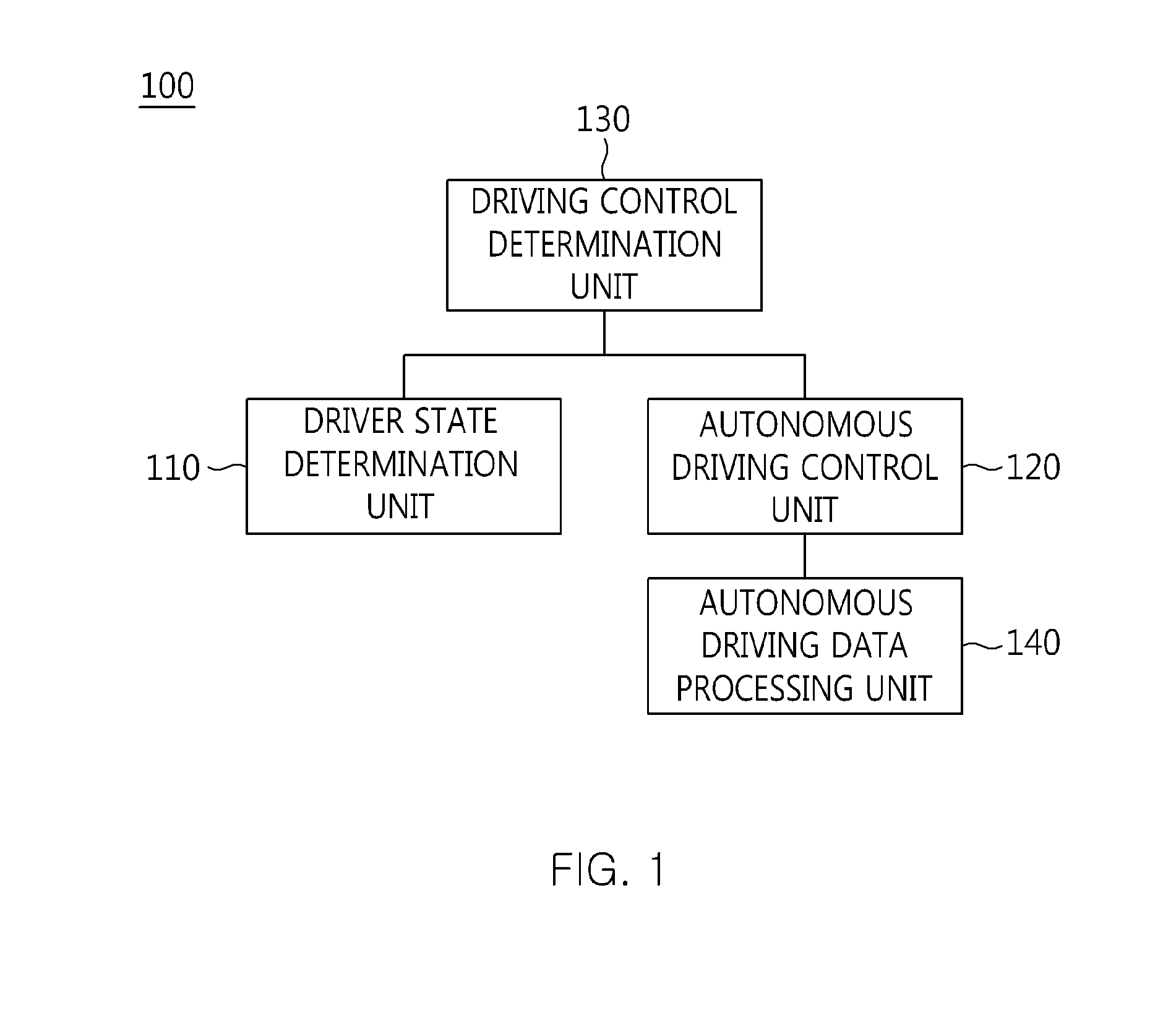
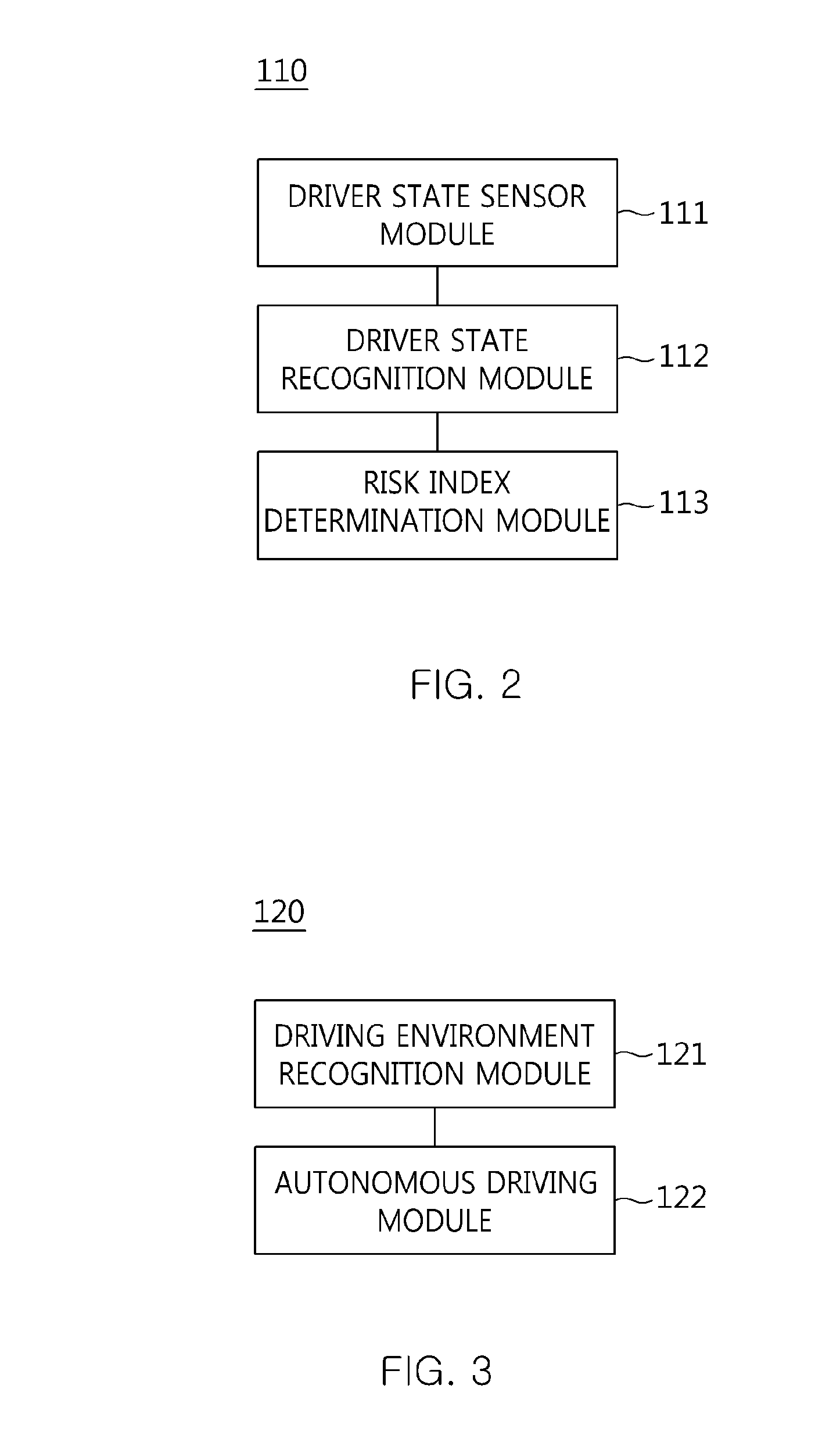
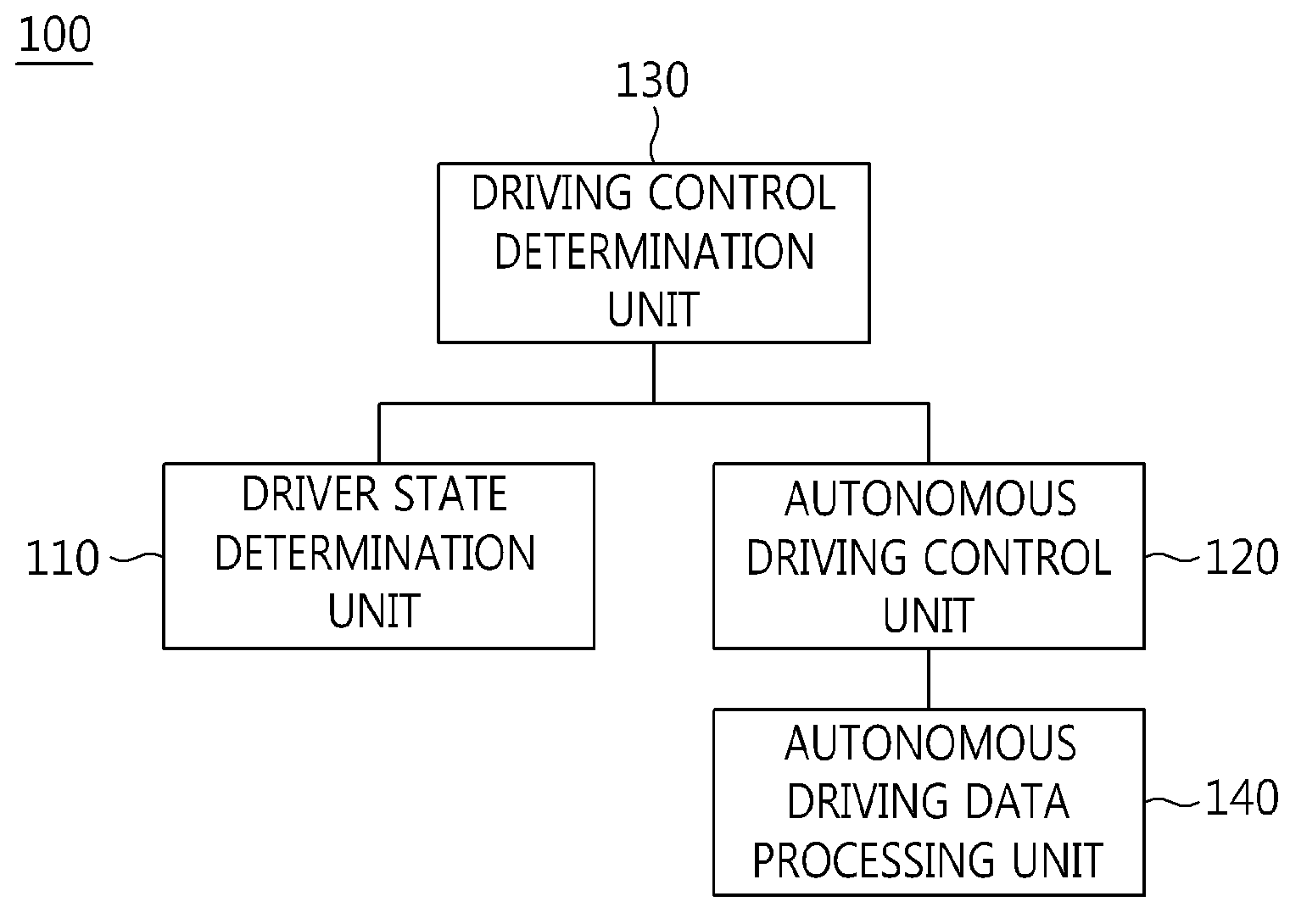
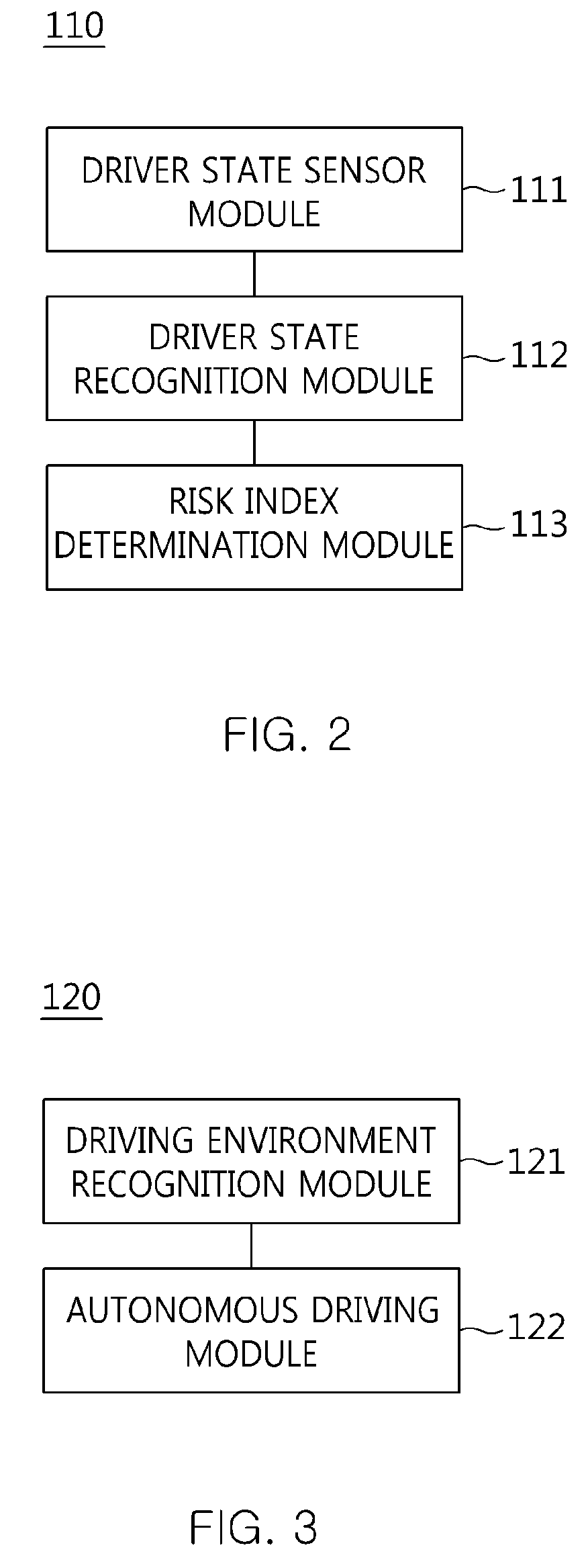
The present invention relates to an apparatus and method for performing cooperative autonomous driving between a vehicle and a driver. For this, a cooperative autonomous driving apparatus according to the present invention includes a driver state determination unit for determining a state of a driver and calculating the state of the driver as a risk index. An autonomous driving control unit classifies section characteristics of respective sections included in a path to a destination corresponding to the driver based on section data stored in a database (DB), and controls autonomous driving of a vehicle in which the driver is riding, based on a driving environment recognized for the path to the destination corresponding to the driver. A driving control determination unit determines driving modes of the respective sections included in the path based on the state of the driver and the section characteristics.
Owner:ELECTRONICS & TELECOMM RES INST
Apparatus and method for cooperative autonomous driving between vehicle and driver
ActiveUS9063543B2Improve performanceControl safety arrangementsExternal condition input parametersDriver/operatorEngineering
The present invention relates to an apparatus and method for performing cooperative autonomous driving between a vehicle and a driver. For this, a cooperative autonomous driving apparatus according to the present invention includes a driver state determination unit for determining a state of a driver and calculating the state of the driver as a risk index. An autonomous driving control unit classifies section characteristics of respective sections included in a path to a destination corresponding to the driver based on section data stored in a database (DB), and controls autonomous driving of a vehicle in which the driver is riding, based on a driving environment recognized for the path to the destination corresponding to the driver. A driving control determination unit determines driving modes of the respective sections included in the path based on the state of the driver and the section characteristics.
Owner:ELECTRONICS & TELECOMM RES INST
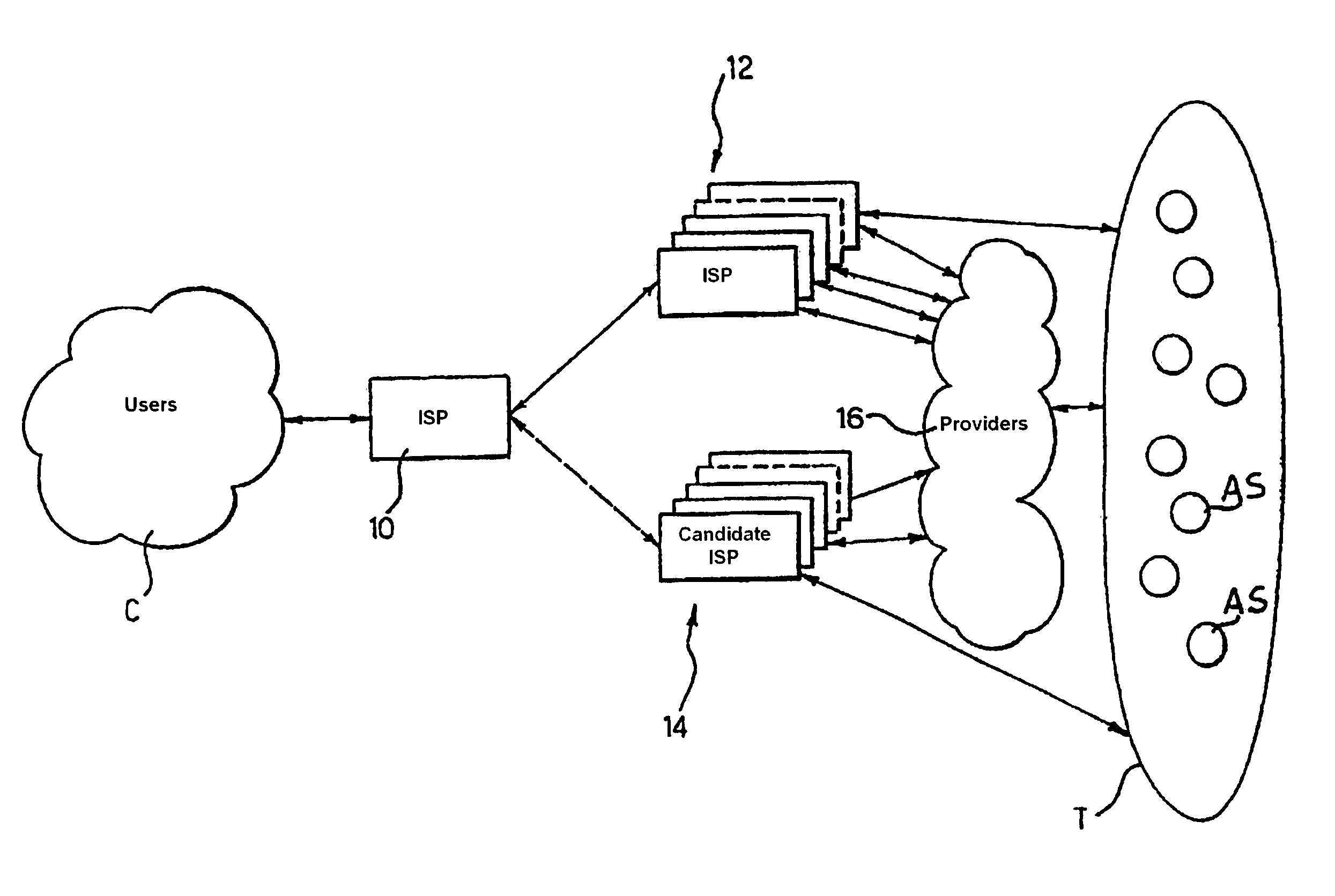
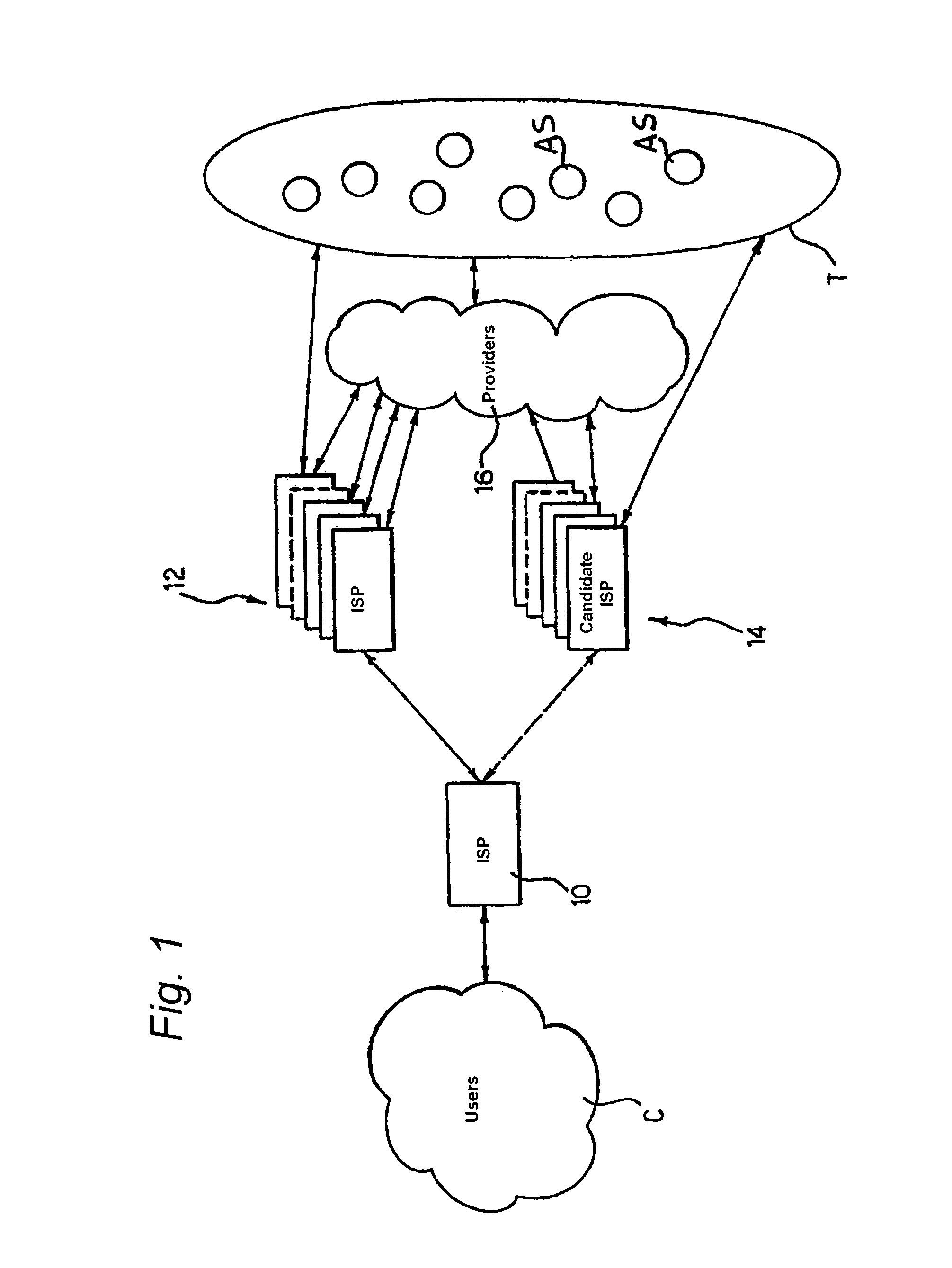
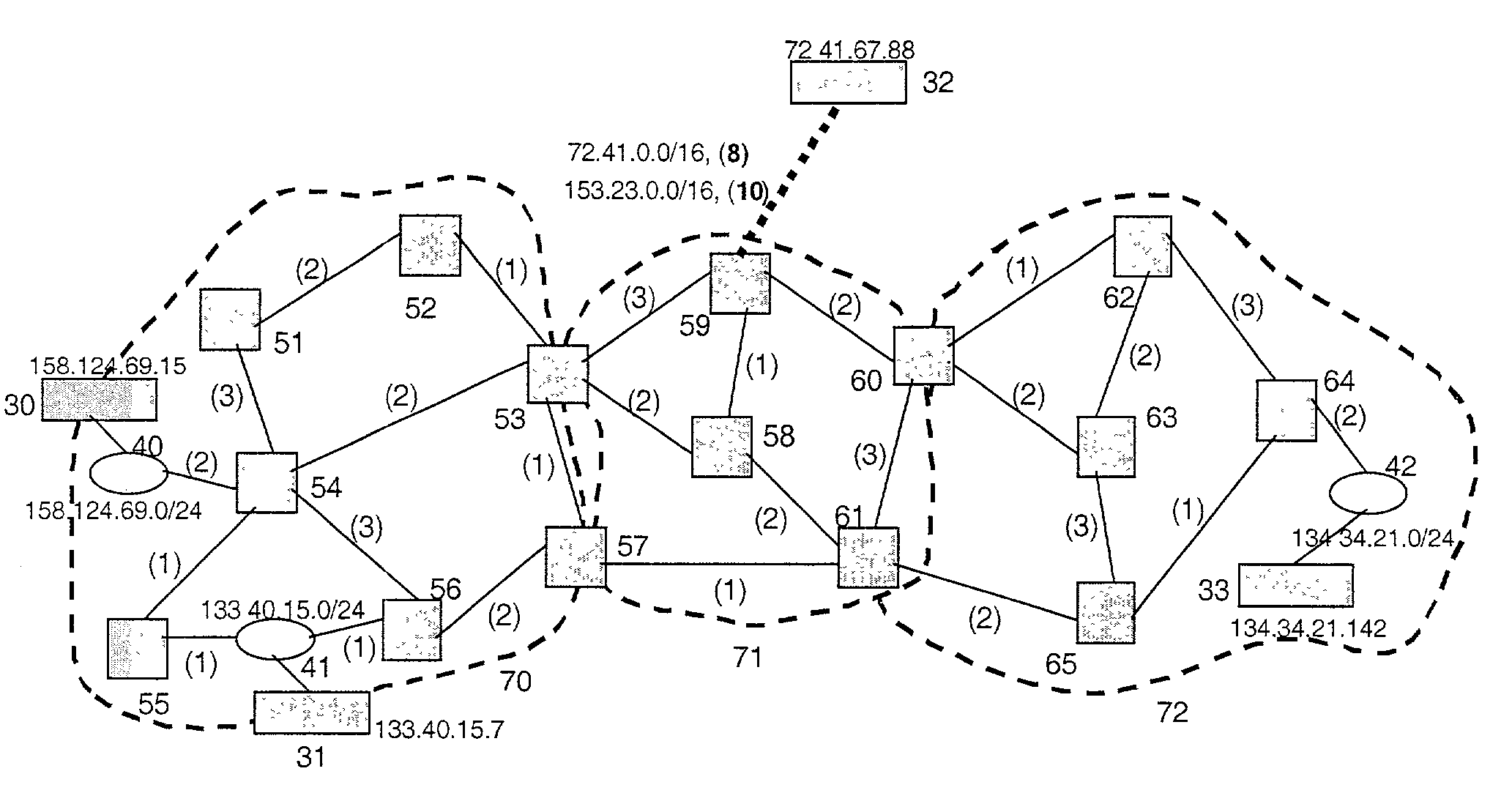
Method and system for path identification in packet networks
ActiveUS20050025059A1Simple methodColor television with pulse code modulationError preventionEntry pointSource area
A method and system for extracting and building end-to-end route information in a multi-area Internet protocol (IP) autonomous system (AS) is disclosed. The method and system enable a user, such as a network administrator, to explicitly identify a full set of paths (links and routers) that a given IP packet would potentially traverse from its entry point in the source area of the AS where it originates until its exit point in its intended destination area.
Owner:SONS OF INNOVATION LLC
Load Distribution in Storage Area Networks
InactiveUS20080250178A1Maximum bandwidth is exceededImprove overall utilizationTransmissionInput/output processes for data processingStorage area networkLoad distribution
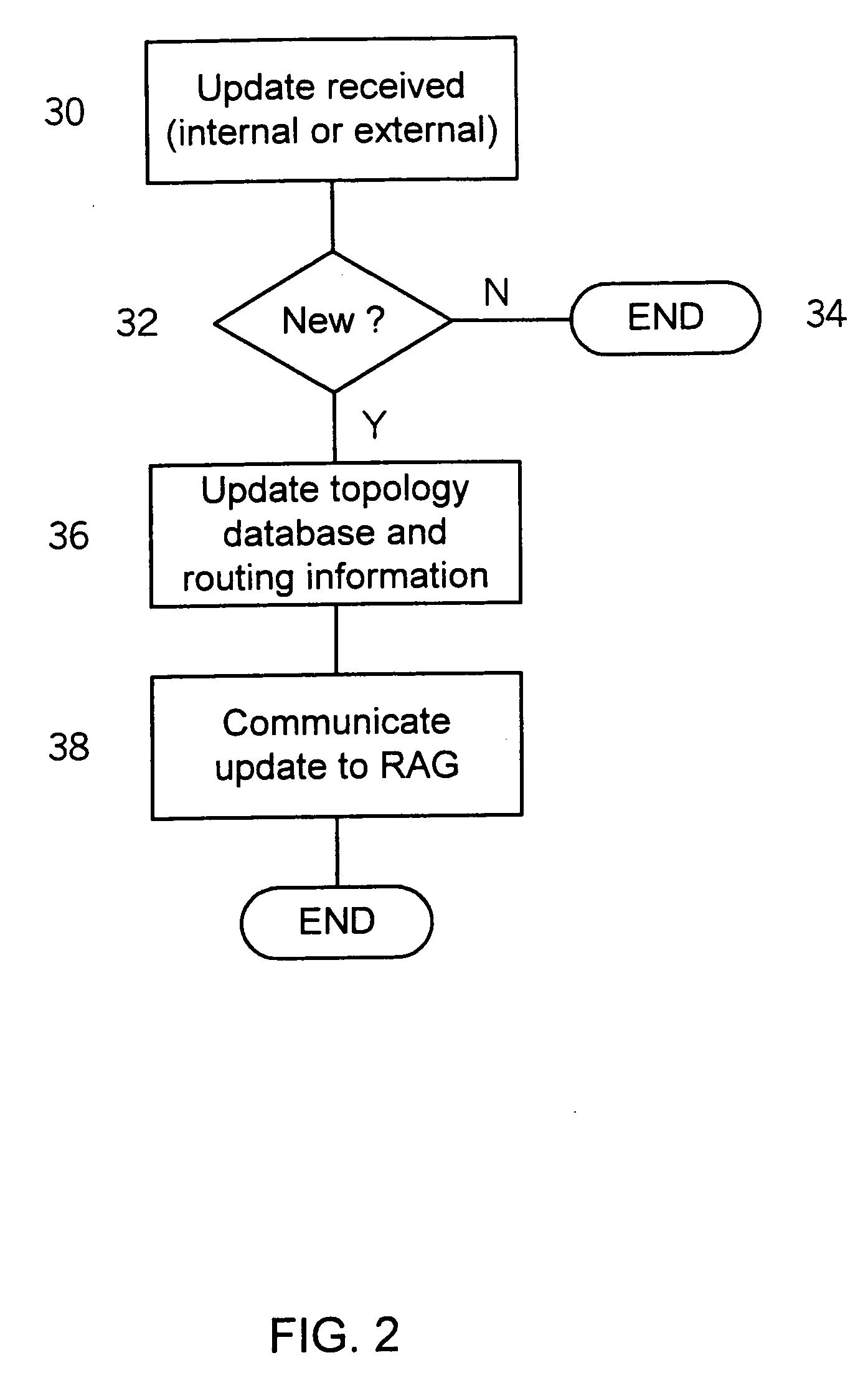
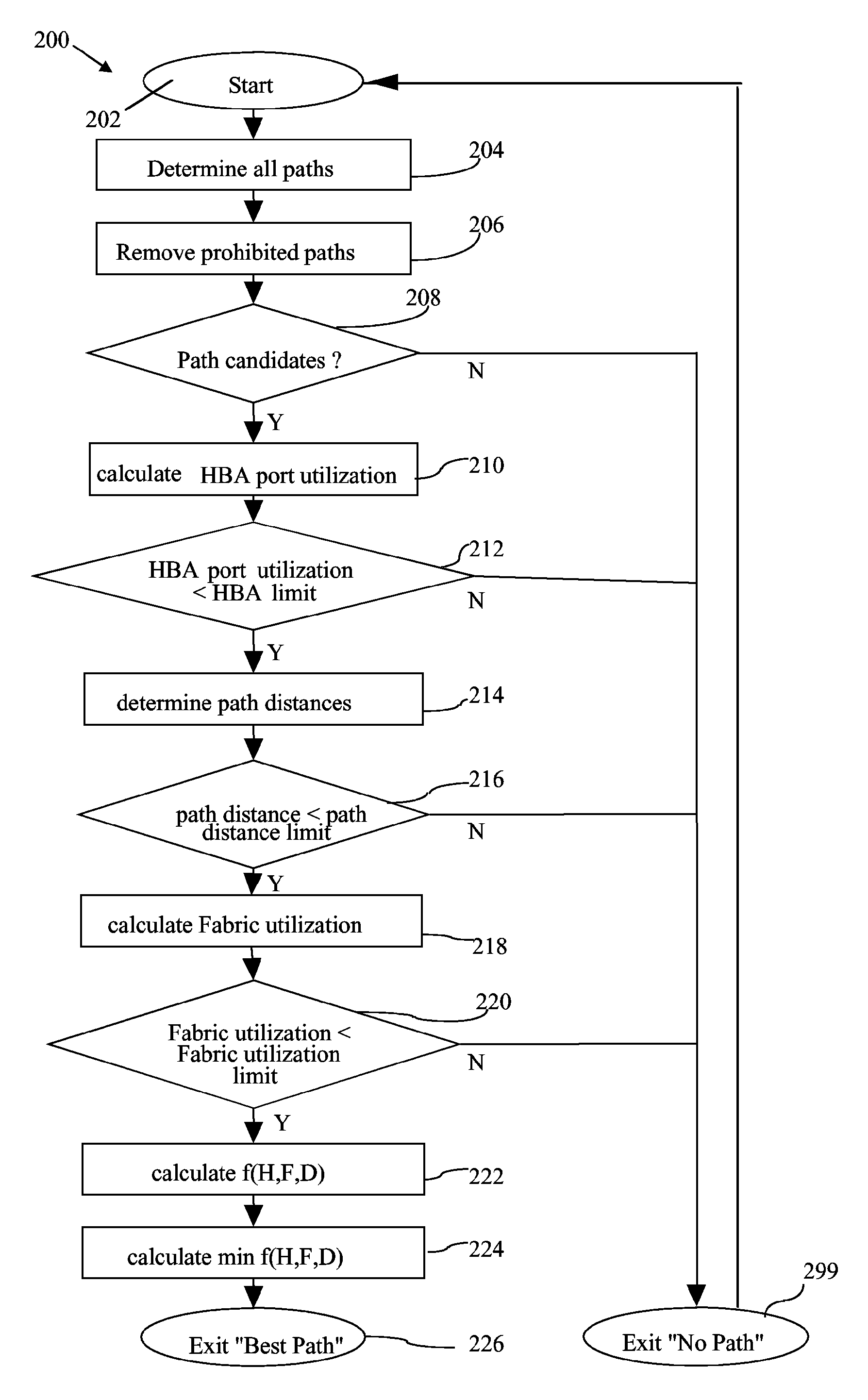
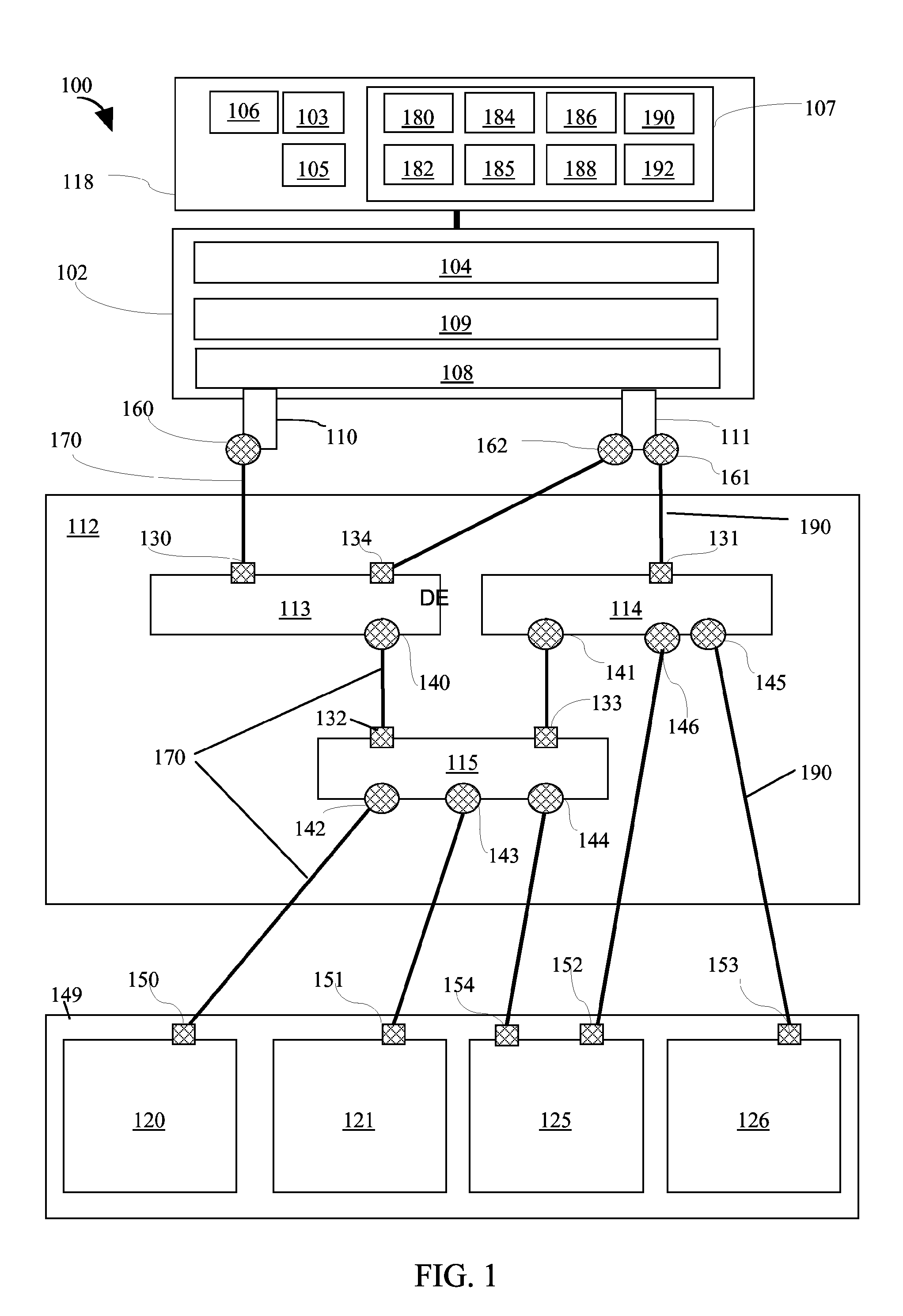
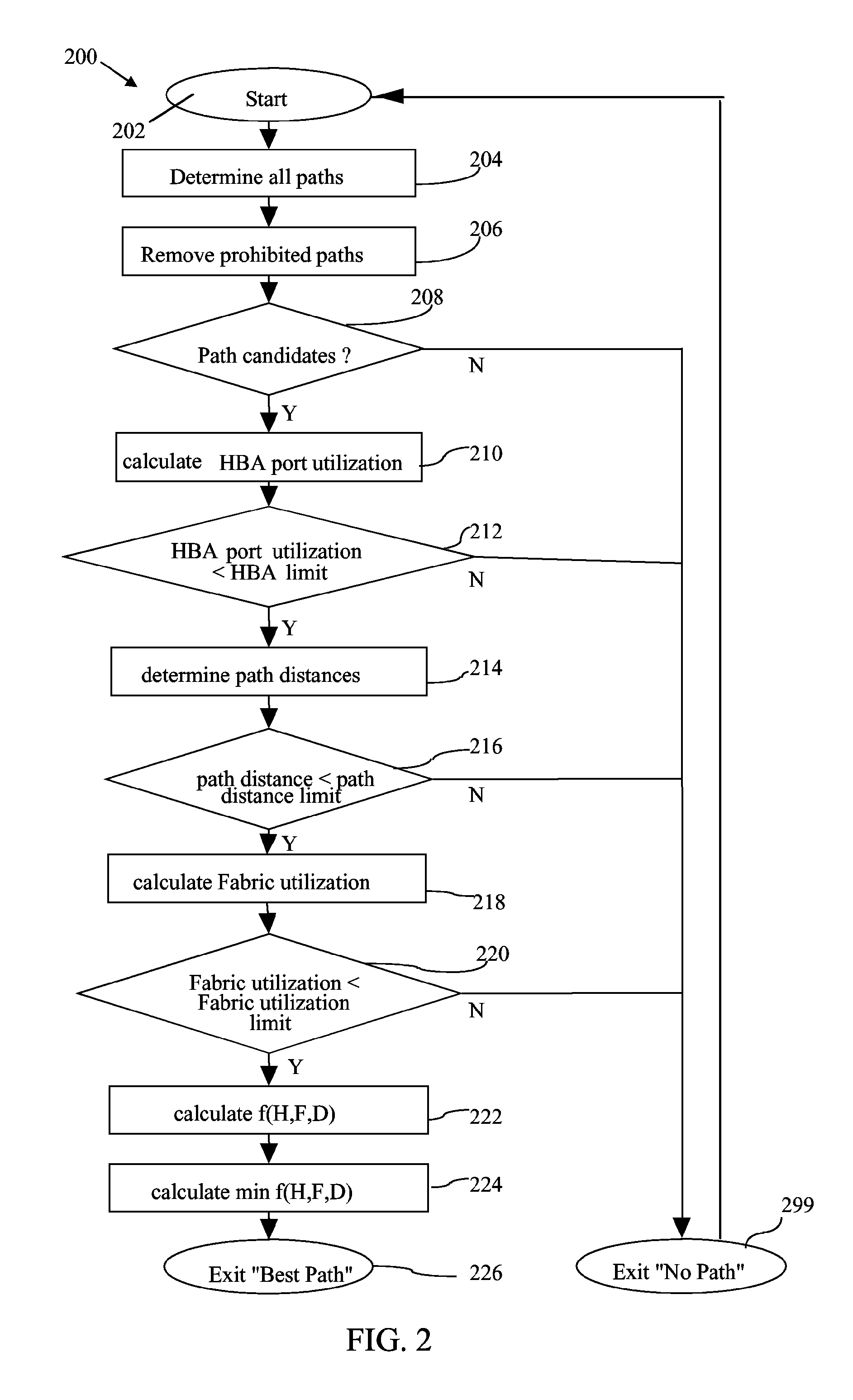
A load balancing method and system for identifying an input / output (I / O) network path from a set off I / O network paths is provided by the invention. The set off I / O network paths connect a host system via a network to a storage subsystem. The host system comprises at least one host bus adapter (HBA) and the storage subsystem comprises at least one I / O device and the network comprises at least one network device. Each of the HBA, the I / O device and the network device comprise at least one I / O port. For each I / O port of each HBA, an HBA port limit is determined. Additionally the set of I / O network paths which connect the I / O port of each of the HBA via the I / O ports of the network device to the I / O port of the I / O device is identified. Then a fabric utilization limit is determined for each I / O network path and a HBA port utilization is determined for each I / O port of the at least one HBA. All network paths are discarded for which the HBA port utilization is greater than the HBA port limit. For each of the remaining paths a network path distance is determined. All I / O network paths for which the network path distance is greater than the path distance limit are discarded. Then for each of the remaining paths a fabric utilization is determined. All I / O network paths for which the fabric utilization is greater than the fabric utilization limit are discarded and the I / O network path is determined from the remaining network paths.
Owner:IBM CORP
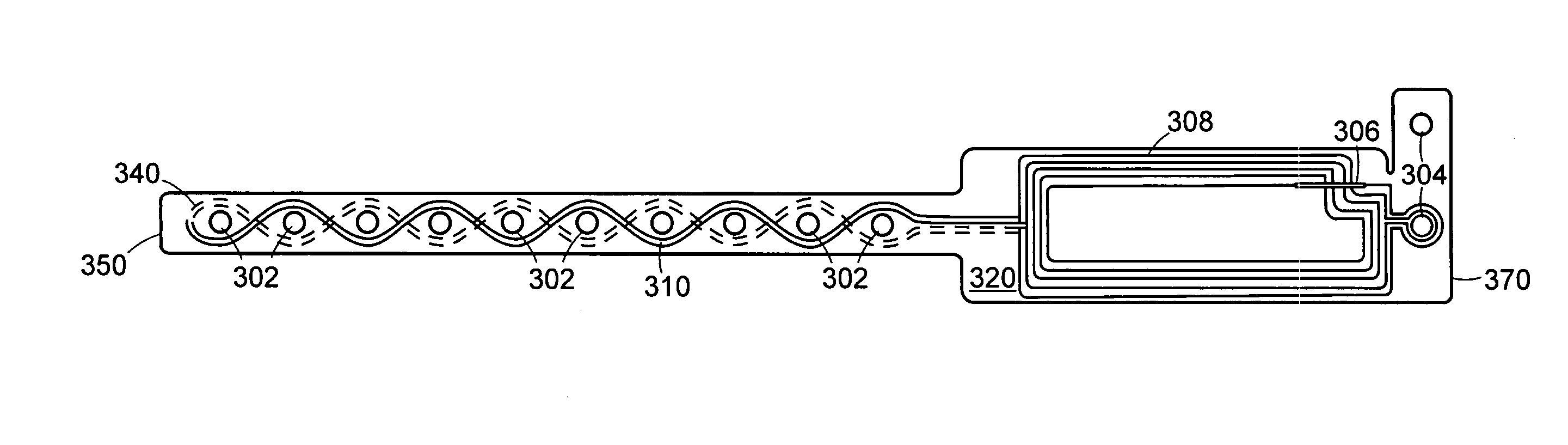
Identification band using serpentine paths to detect tampering
InactiveUS7119690B2Individual entry/exit registersRecord carriers used with machinesElectricityElectrical connection
A tamper-resistant RFID wristband that becomes permanently disabled upon tampering. The wristband includes a plurality of holes for snugly securing the band to a wearer, an RFID circuit, and an electrically conductive loop disposed in the band. The RFID circuit and the conductive loop are electrically coupled to form a series circuit, severance of which disables the wristband. The electrically conductive loop includes a first layer and a second layer that are electrically isolated from one another, save for at least one electrical connection made preferably by a via at the end of the band distal from the antenna element. The first layer encircles the holes in a serpentine path on one layer of the band and the second layer encircles the holes in a complimentary serpentine path on a different layer of the band.
Owner:BARTRONICS HONG KONG
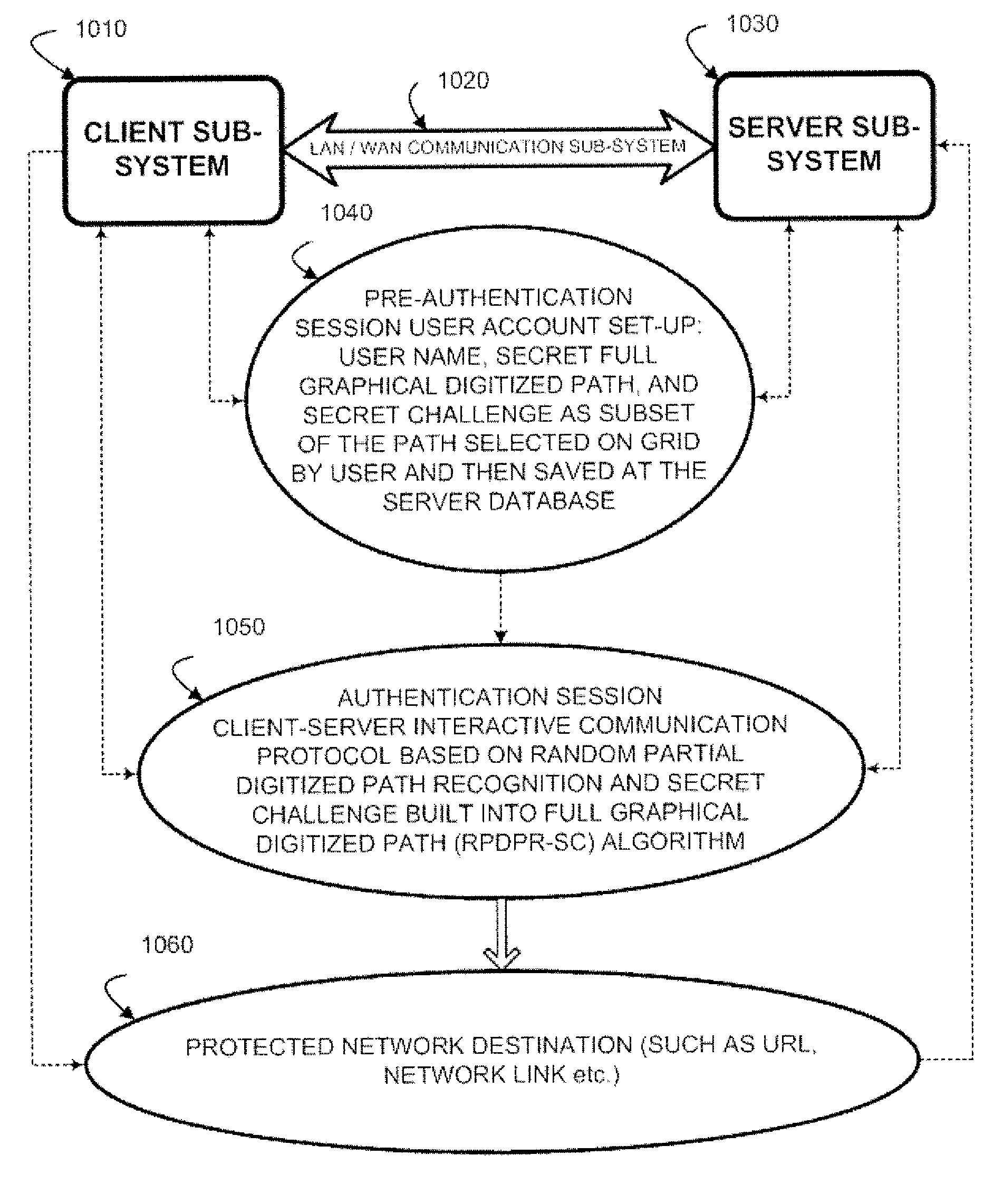
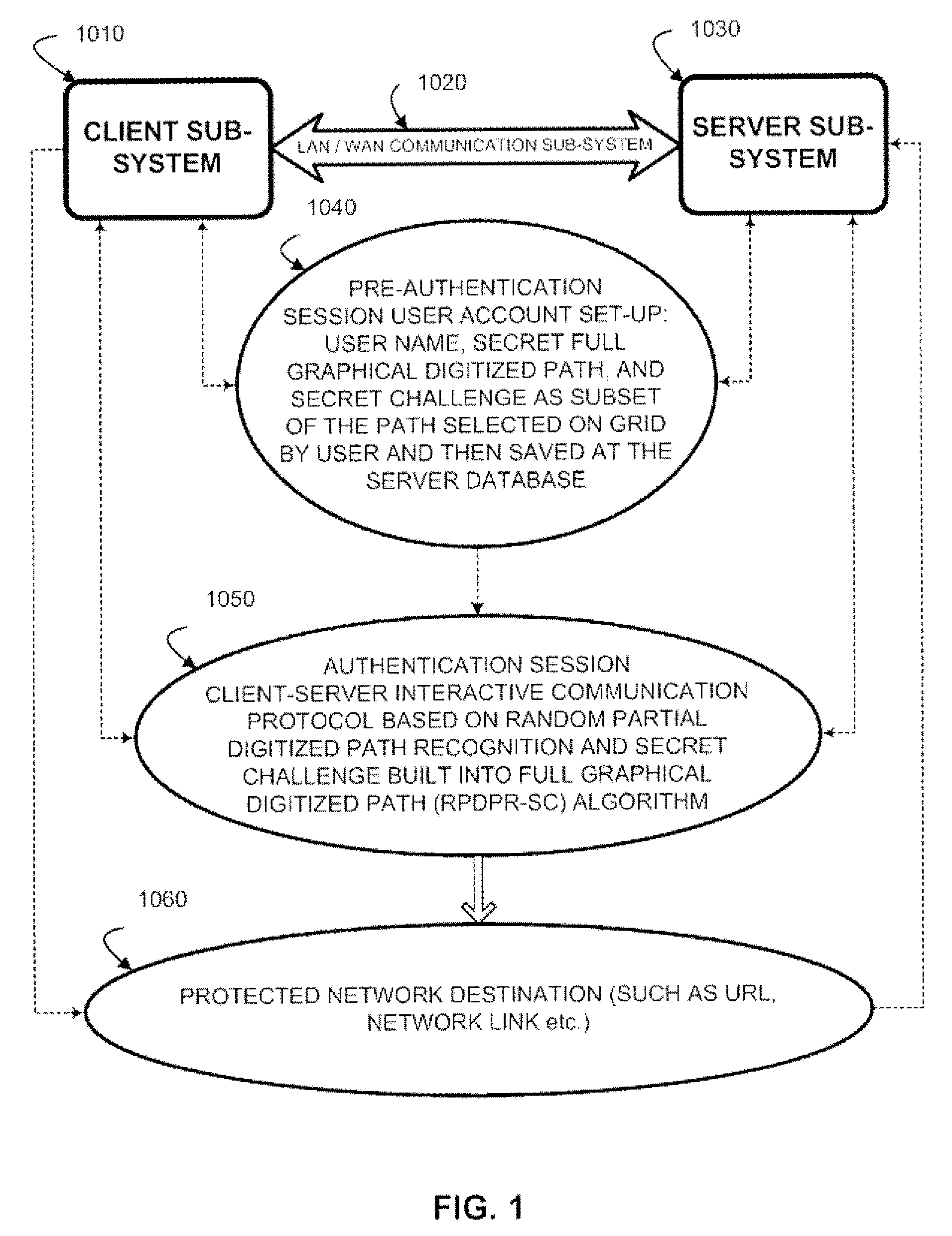
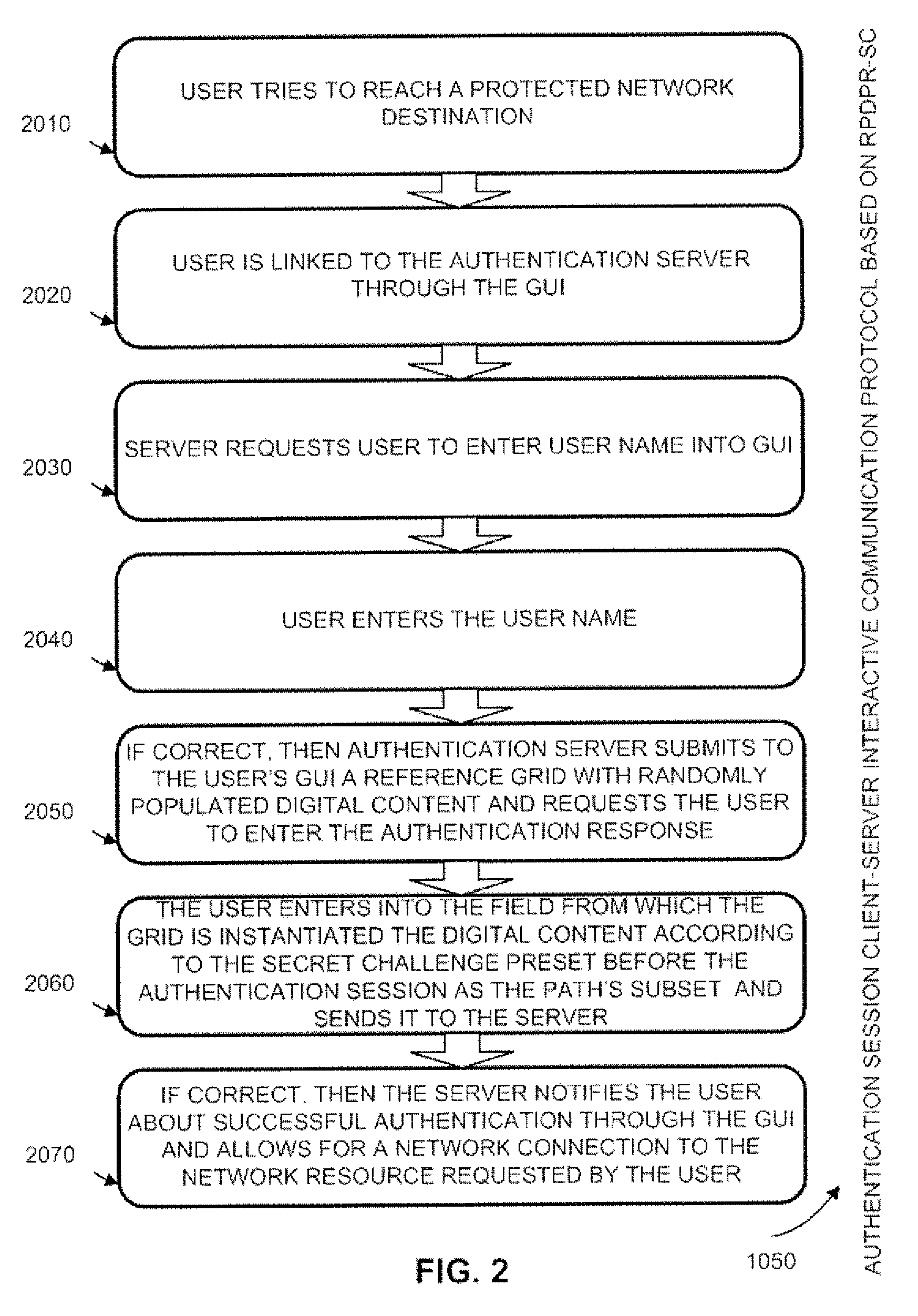
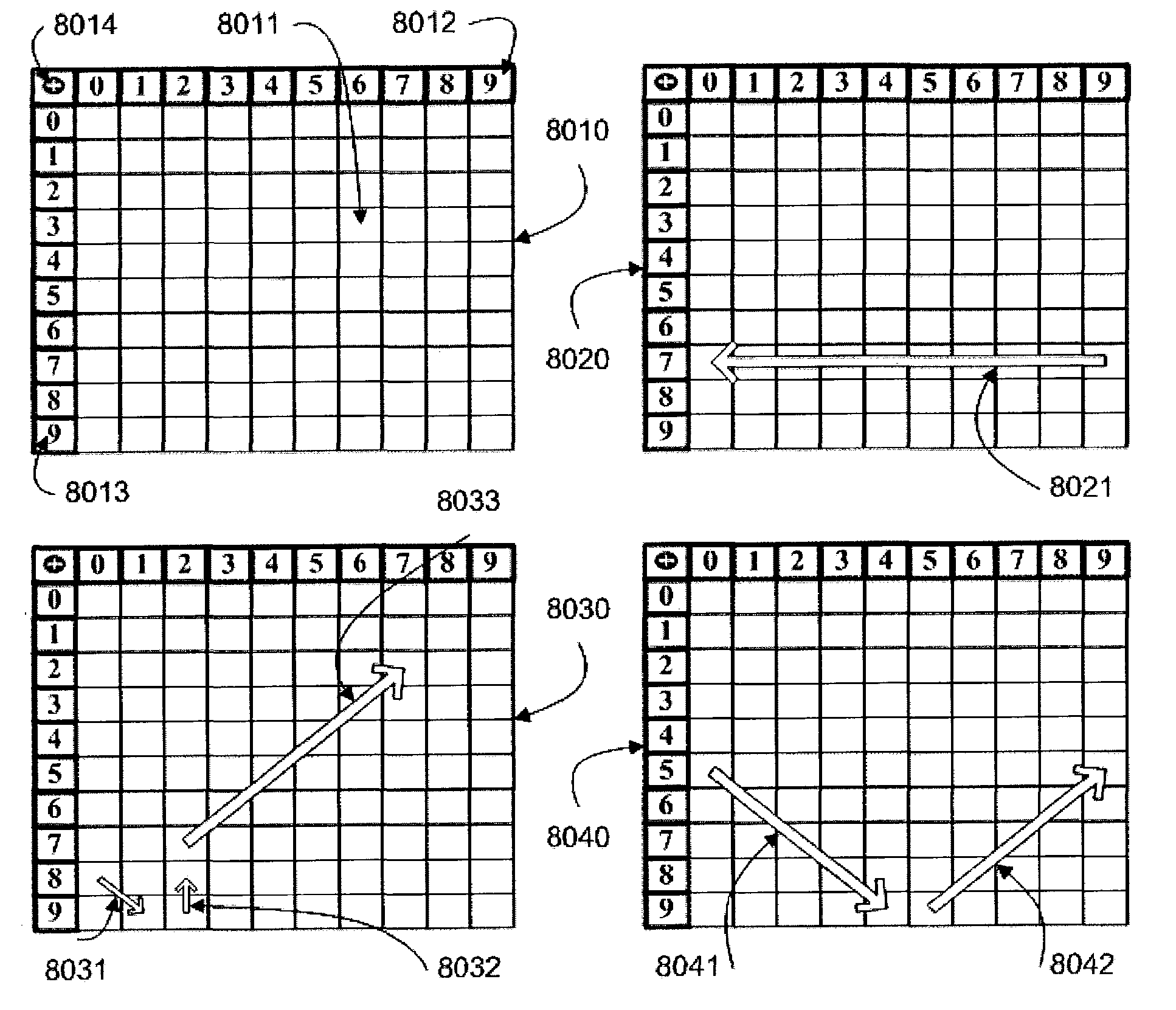
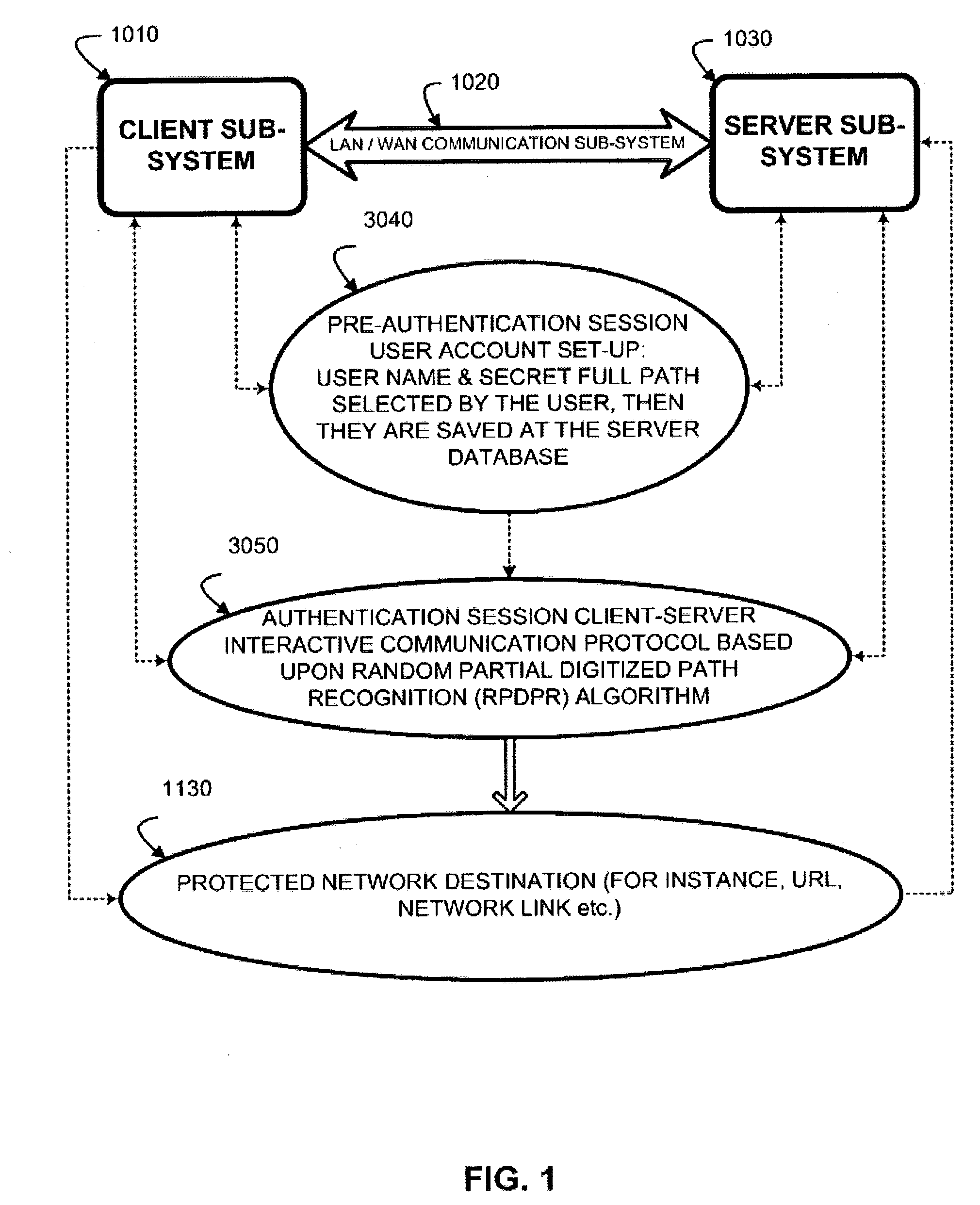
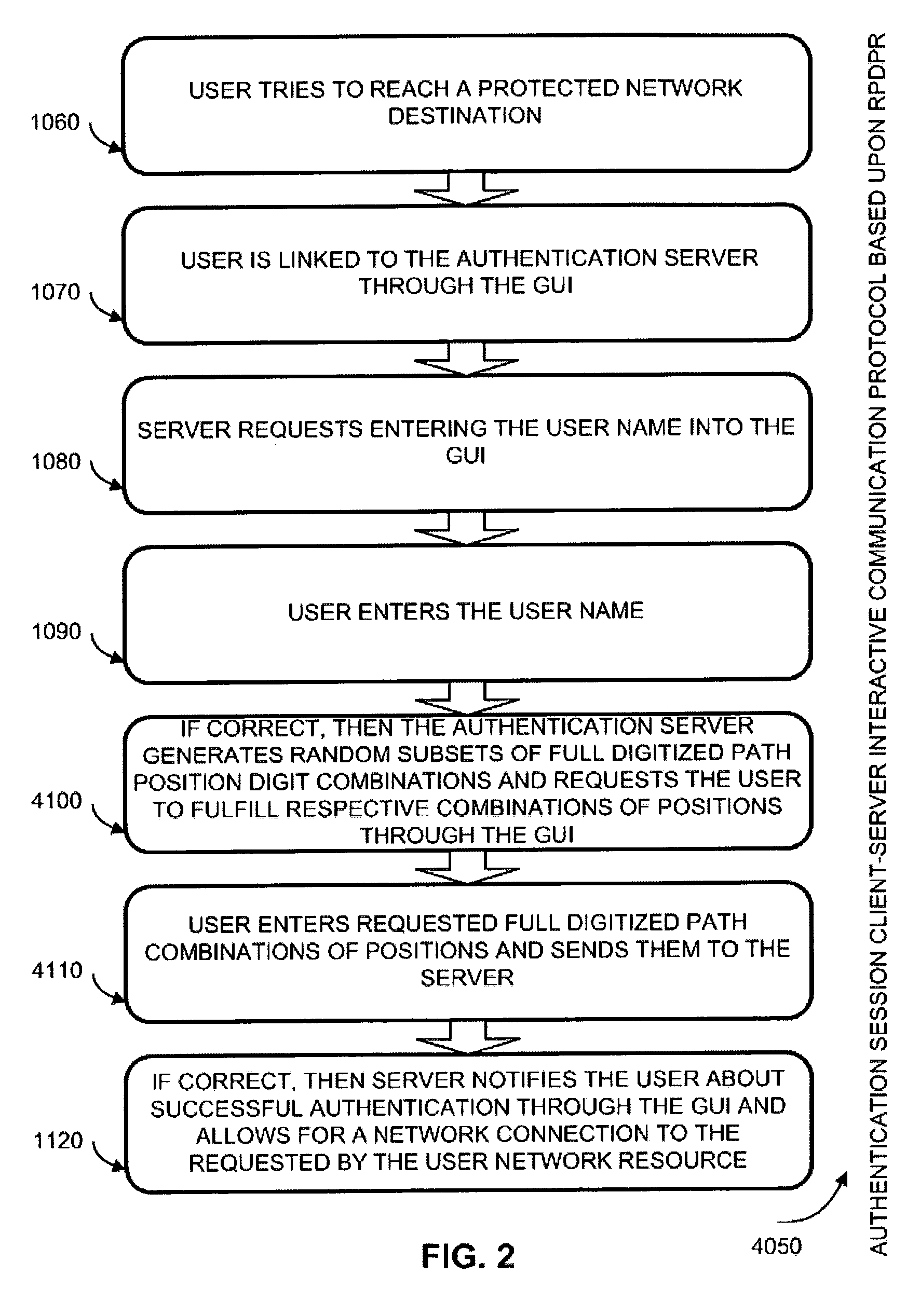
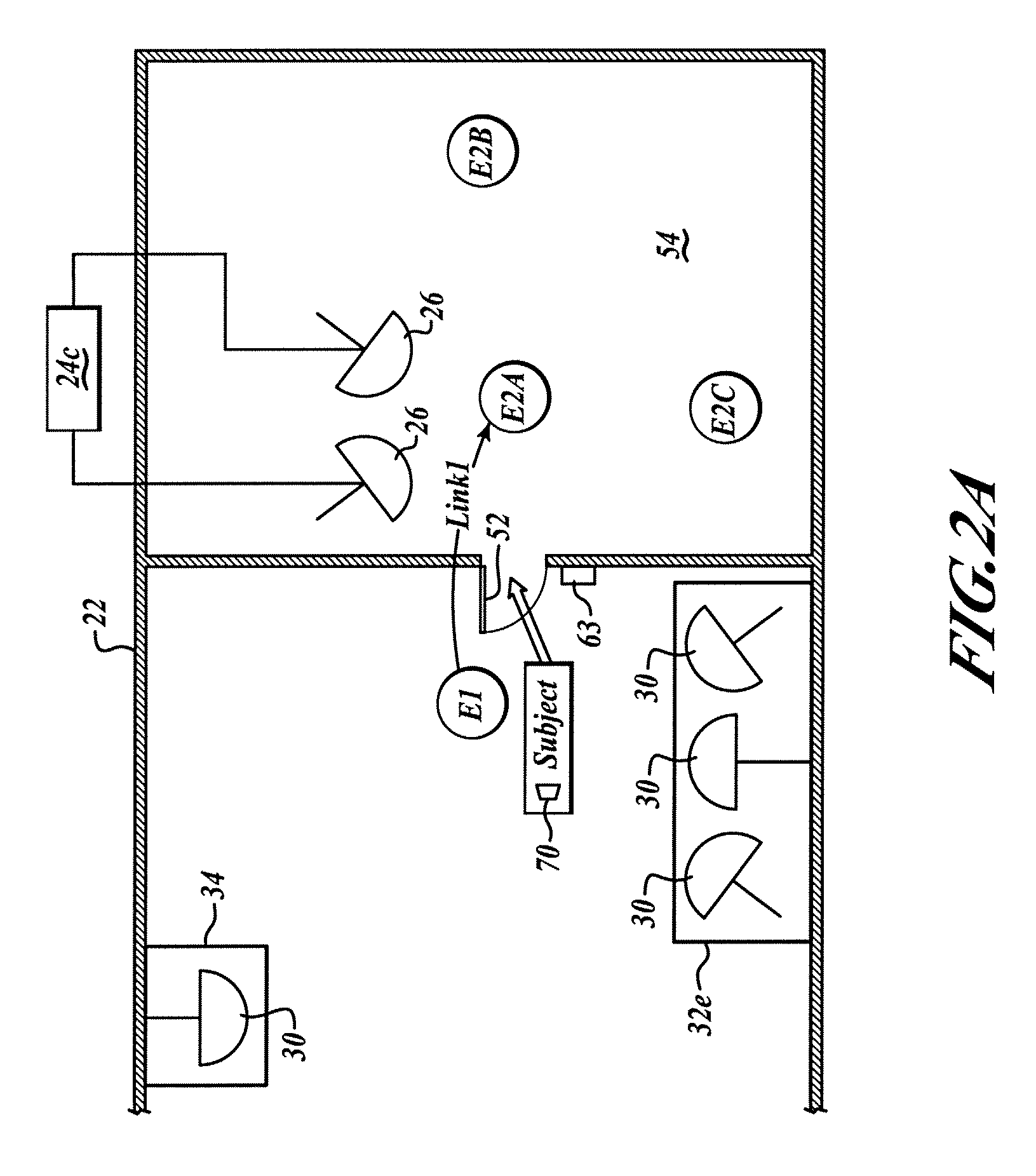
Authentication method of random partial digitized path recognition with a challenge built into the path
ActiveUS20080072045A1Digital data processing detailsUser identity/authority verificationComputer hardwareGraphics
An interactive method for authentication is based on two shared secrets, including a first shared secret in the form of an ordered path on the frame of reference, and a second shared secret in the form of locations on the frame of reference at which characters identifying a subset of the ordered path are to be displayed. An instance of the frame of reference comprises a set of characters which is arranged in a random or other irregular pattern. Authentication requires that a user enter the characters in the displayed instance of the frame of reference found in the locations in the random subset of the ordered path by indicating characters either in these locations, or any other locations having the same characters. Thus, a secret challenge identifying the random partial subset is embedded within the displayed instance of the graphical representation of the frame of reference.
Owner:AUTHERNATIVE INC
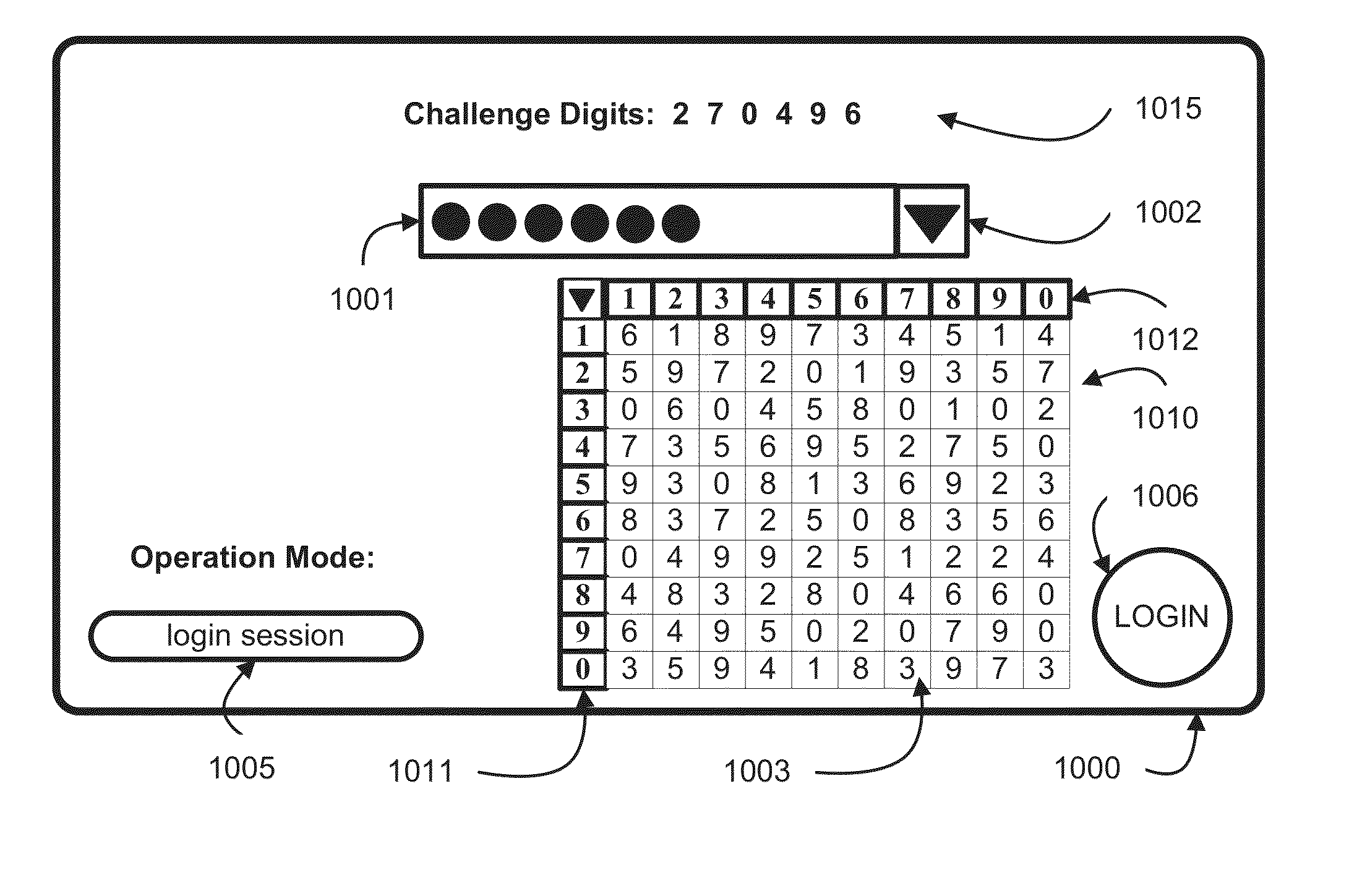
Authentication system and method based upon random partial digitized path recognition
ActiveUS7073067B2Large capacityImprove securityDigital data processing detailsUser identity/authority verificationGraphicsData field
An authentication server provides a clue to a client indicating a random partial subset of a full pattern that characterizes a full digitized path on a frame of reference, and the client enters a data to fulfill an authentication factor suggested by the clue. The full pattern consists of an ordered set of data fields, which store parameters that specify the full digitized path on a reference grid for recognition. The server presents an instance of a graphical representation of the frame of reference, including an array of random indicators at data field coordinates in the frame of reference. The server accepts indicators from the array of indicators corresponding to coordinates along said digitized path identified by the random partial subset as input data to fulfill the authentication factor.
Owner:AUTHERNATIVE INC
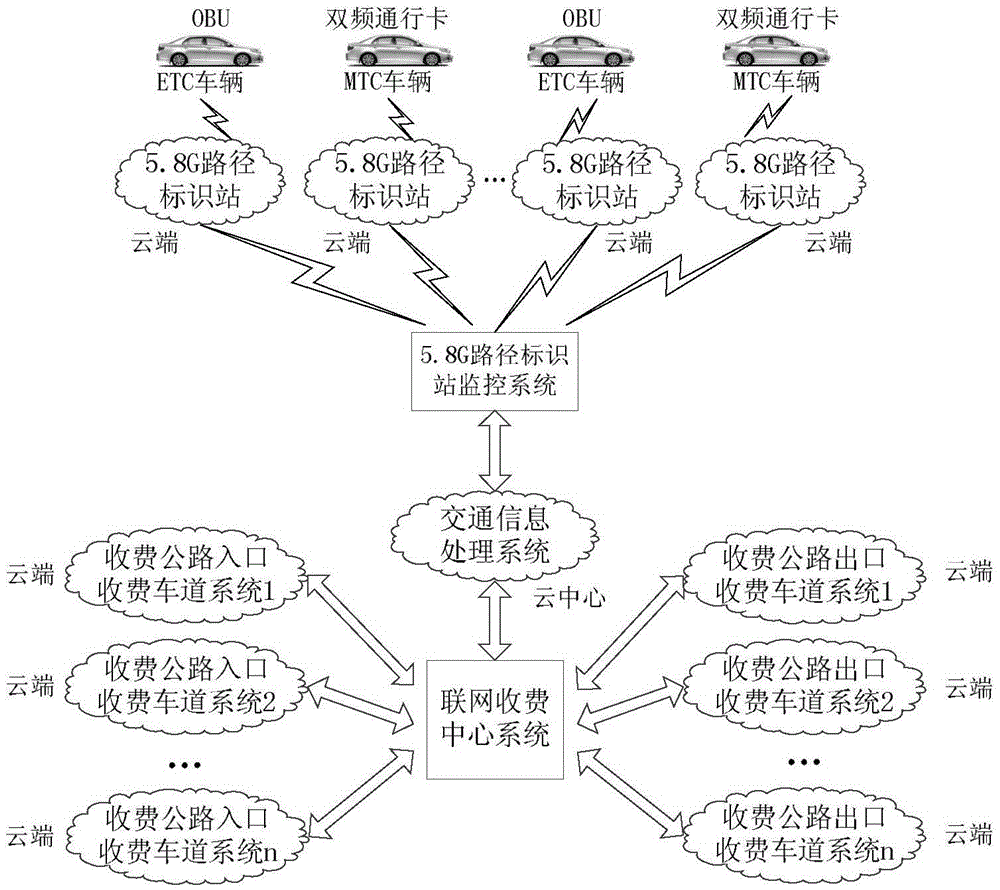
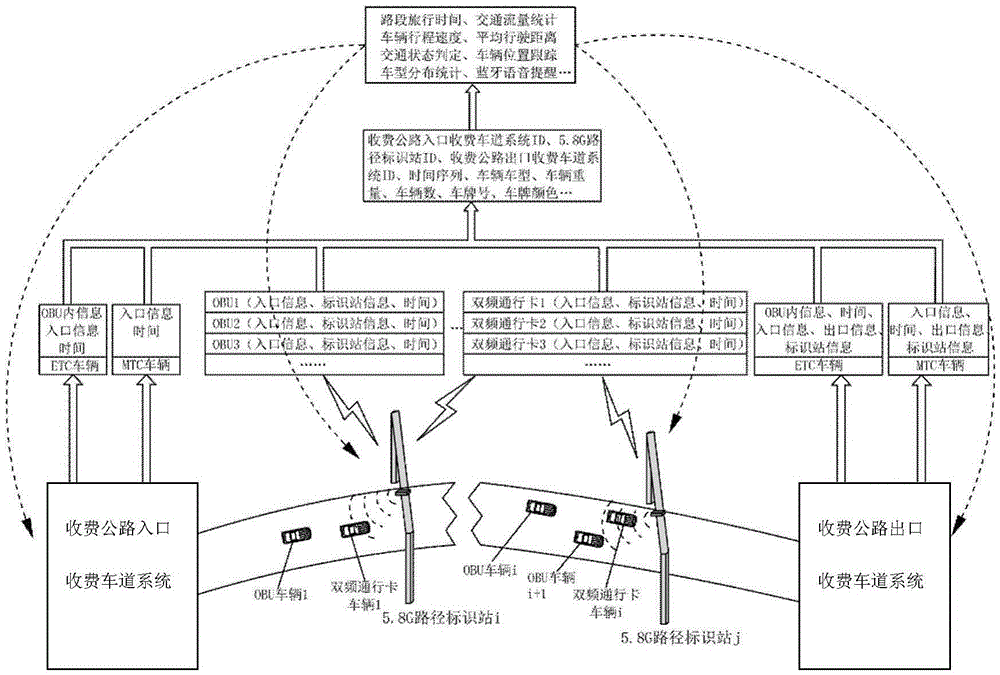
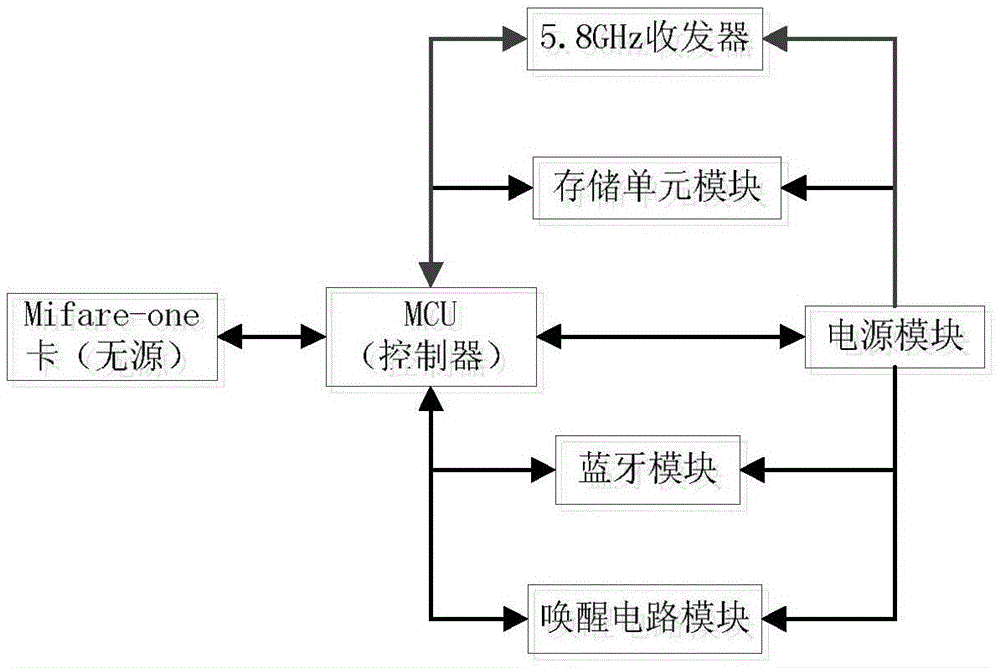
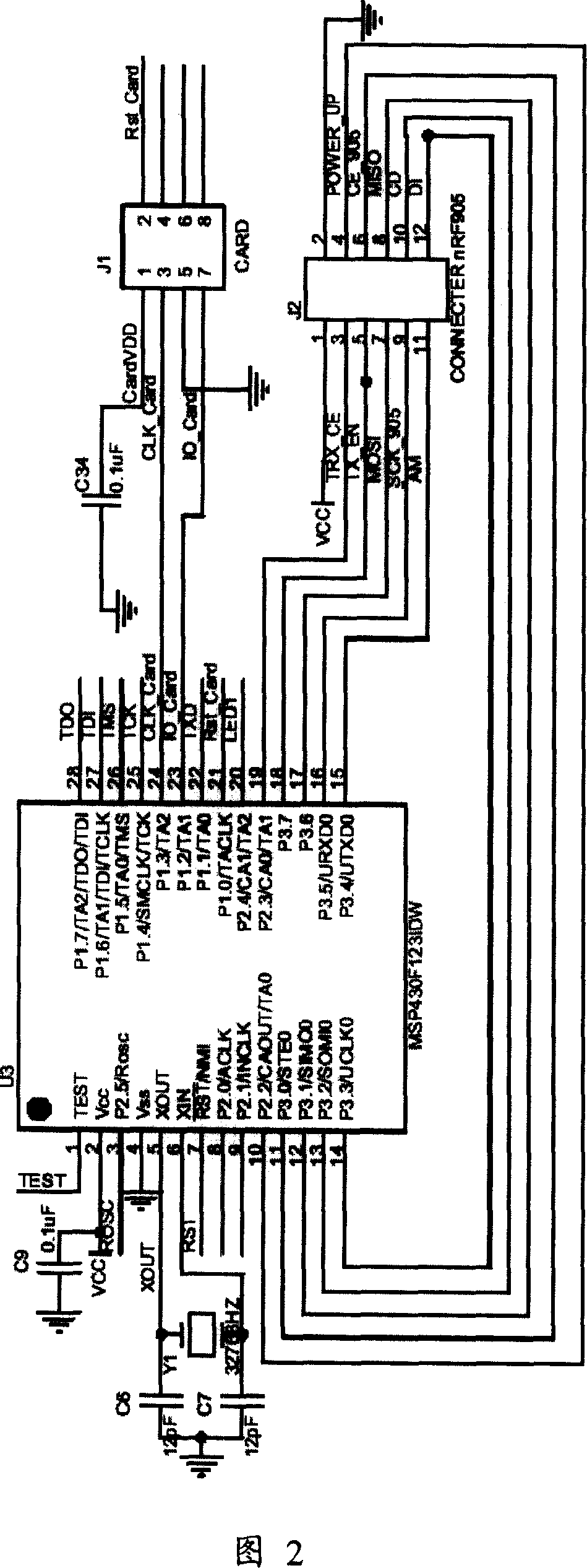
Tolling highway network traffic information acquisition and induction system based on path identification system
ActiveCN105590346ARealize acquisitionRealize functionTicket-issuing apparatusTransportation facility accessInformation processingOn board
The invention discloses a tolling highway network traffic information acquisition and induction system based on a path identification system. The tolling highway network traffic information acquisition and induction system comprises a tolling highway outlet, inlet tolling lane system, a networking tolling center system, a 5.8G path identification station, a 5.8G path identification station monitoring system, a MTC vehicle double-frequency passing card, an ETC vehicle OBU and noncash payment card, an on-board multimedia terminal, and a traffic information processing system. The tolling highway network traffic information acquisition and induction system is advantageous in that by adopting the 5.8G Hz path identification station, the double-frequency passing card provided with the Bluetooth module, the OBU, and the on-board multimedia terminal, the path identification and traffic information acquisition and the traffic information push can be realized; by adopting the combination between the cloud calculation and the 5.8G path identification station distributed calculation, the processing and the prediction of the information such as the traveling time, the traffic flow, the travel speed, the traffic state, and the vehicle position of the tolling highway segment can be realized, and therefore the accurate and reliable front traffic information can be provided for the highway user.
Owner:SOUTH CHINA UNIV OF TECH
Evaluating connectivity on data-communication networks
ActiveUS7451230B2Multiple digital computer combinationsData switching networksAssessment dataPath recognition
Owner:TELECOM ITALIA SPA
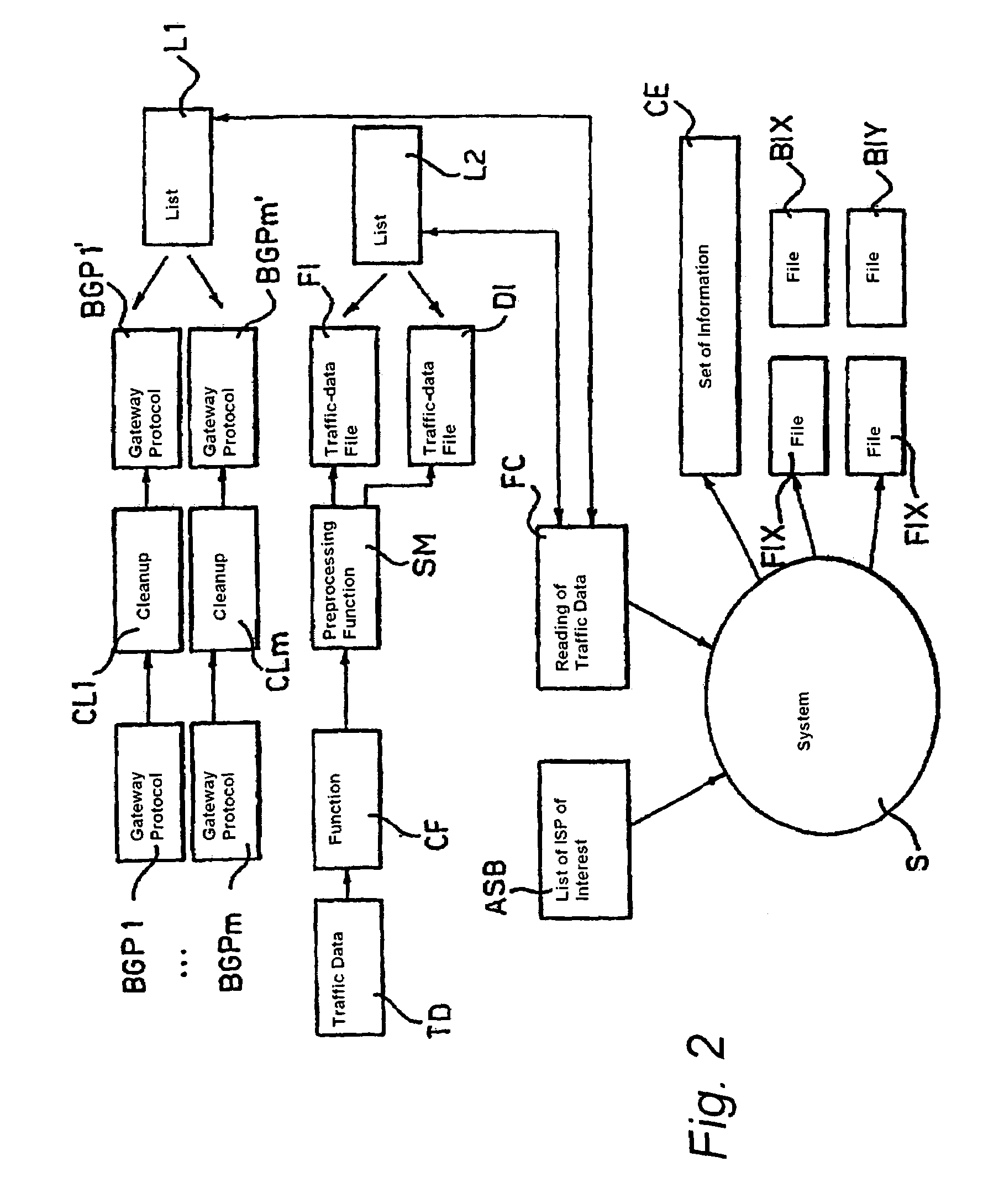
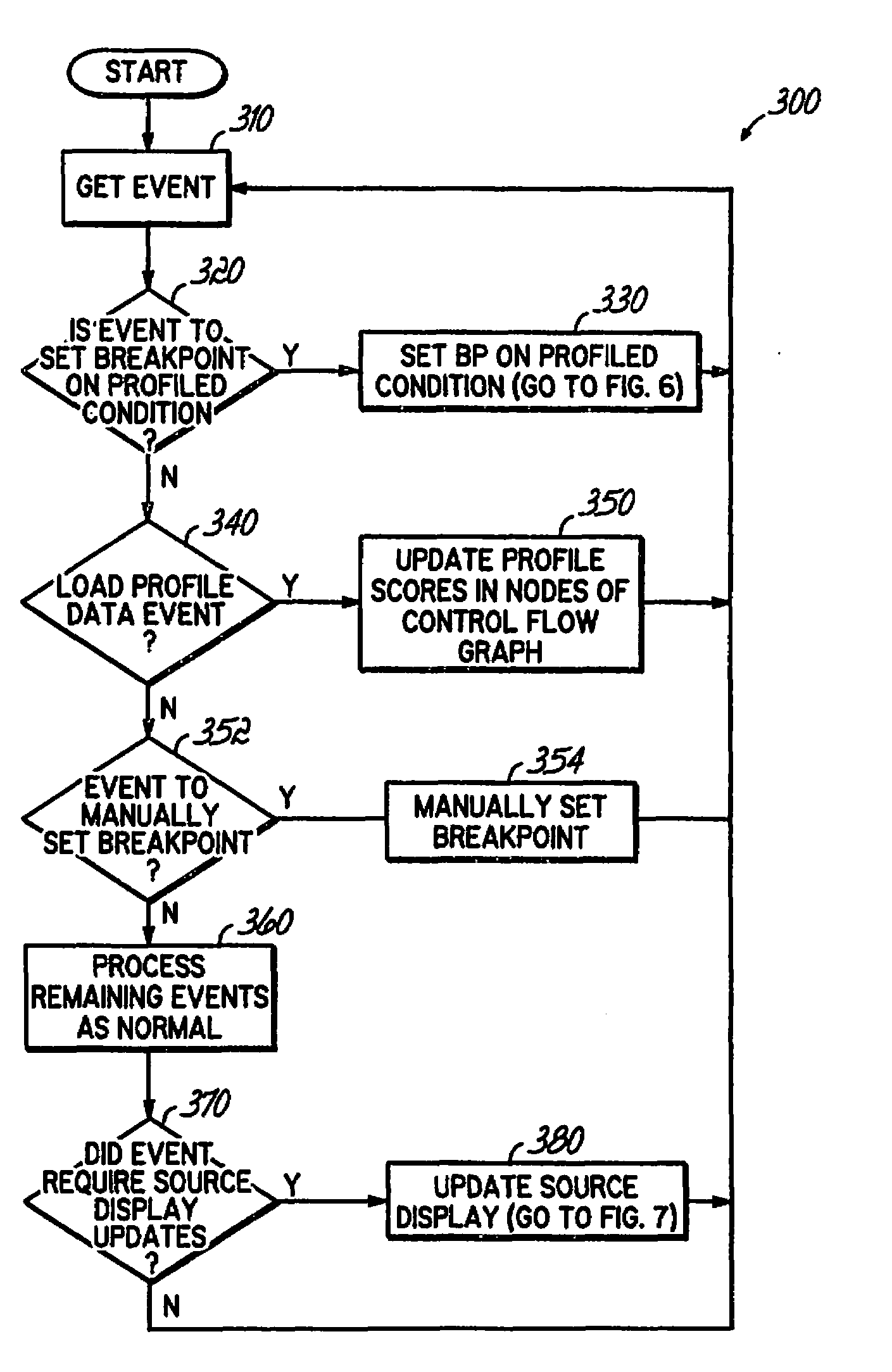
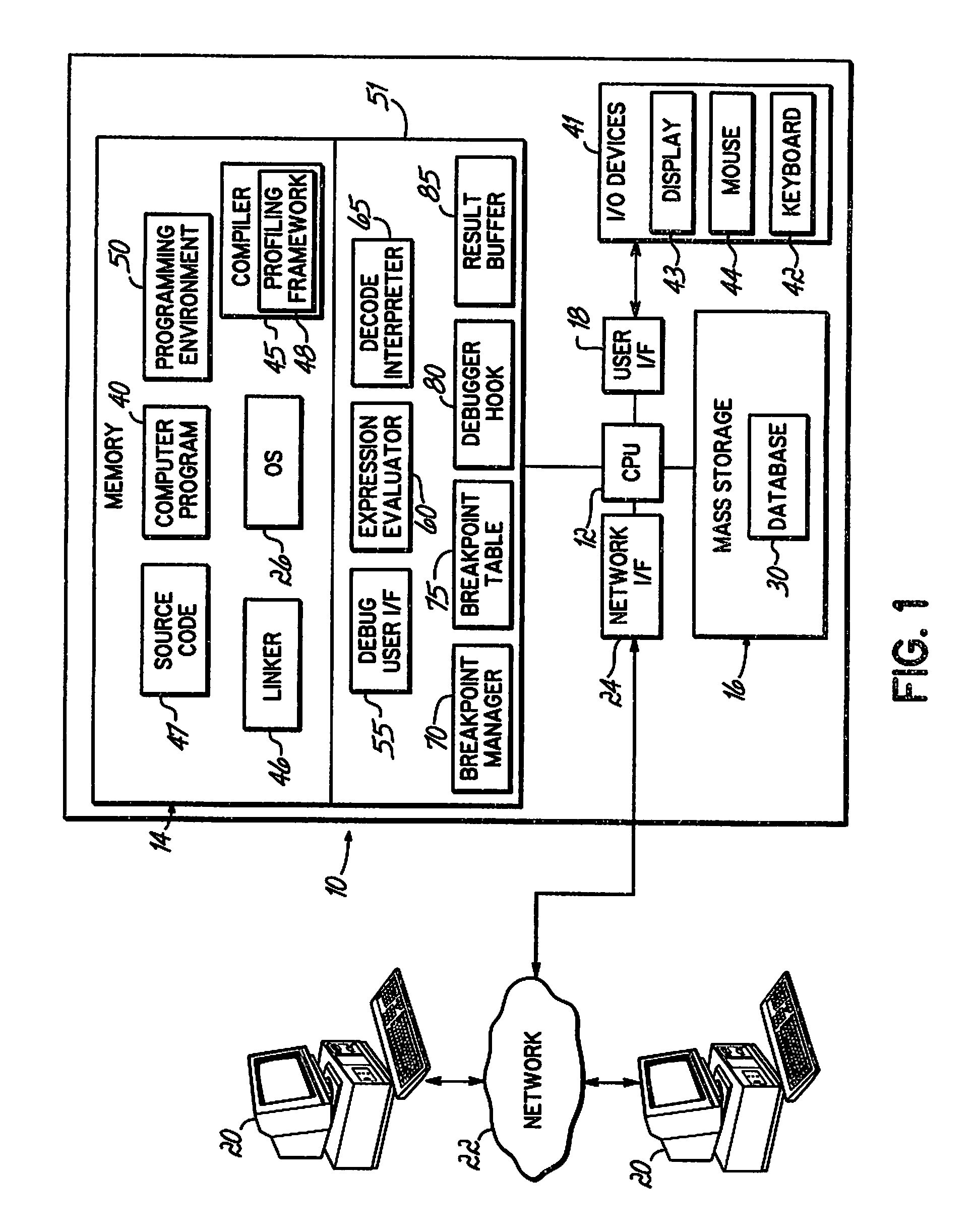
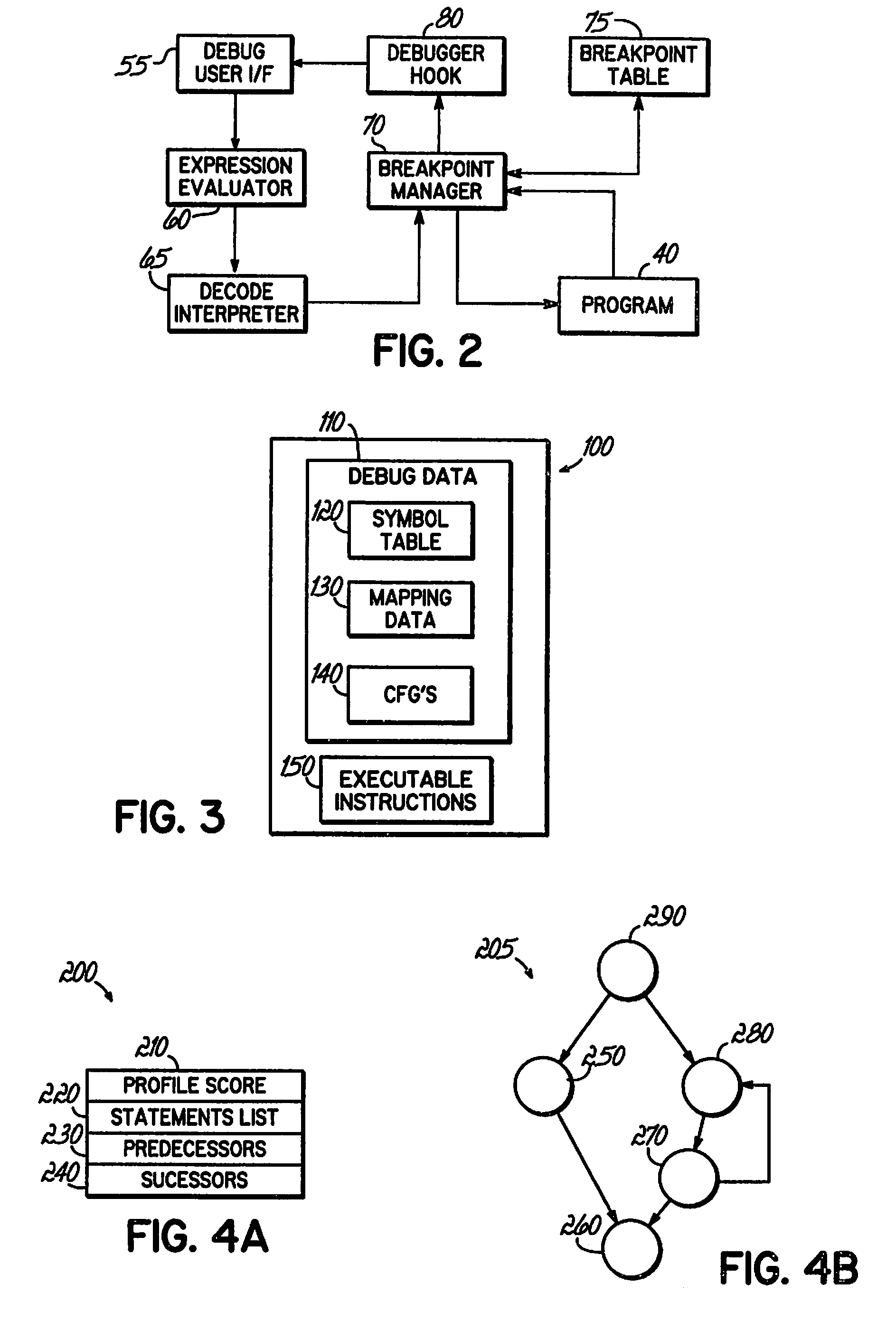
Identifying a Potential Breakpoint Location in a Code Path in a Computer Program Based Upon the Frequency of Execution of the Code Path as Identified in Collected Profile Data
InactiveUS20080168428A1Efficient debuggingError detection/correctionSpecific program execution arrangementsParallel computingPath recognition
An apparatus, program product and method identify a potential breakpoint location in a code path in a computer program based upon the frequency of execution of the code path as identified in collected profile data. By doing so, a potential breakpoint location may be identified for an infrequently executed code path and / or a frequently executed code path, and a breakpoint may be set at the identified breakpoint location. As such, breakpoints may be set in locations that may be more likely to assist a user in debugging the computer program and may result in more efficient debugging.
Owner:IBM CORP
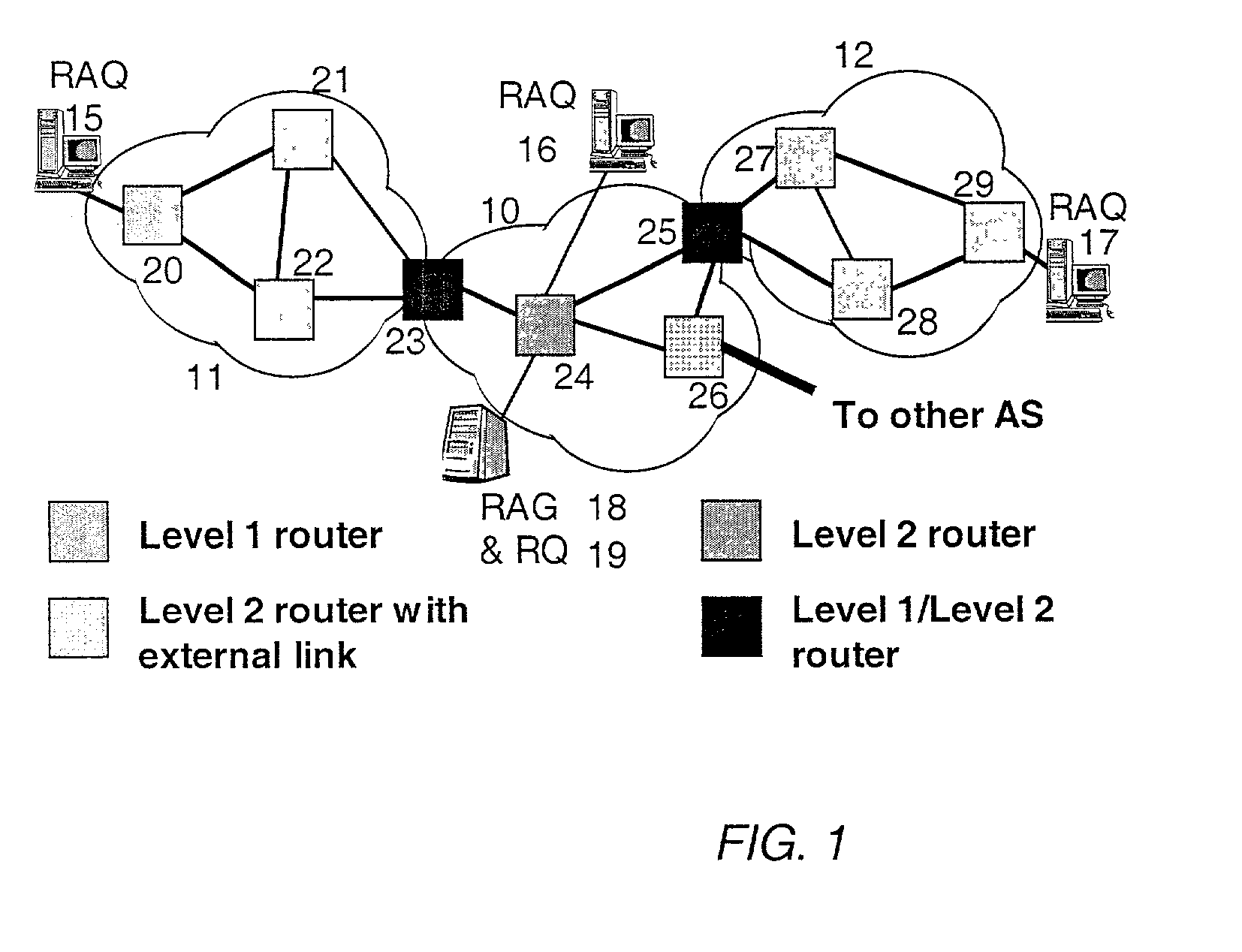
Method and system for topology construction and path identification in a two-level routing domain operated according to a simple link state routing protocol
ActiveUS7120120B2Minimal costColor television with pulse code modulationError preventionEntry pointRouting domain
A method and system for extracting and building end-to-end route information in a two-level, multi-area Internet protocol (IP) autonomous system (AS) operated according to a simple link state routing protocol such as the Integrated System to Integrated System (IS-IS) protocol is disclosed. The method and system enables a user, such as a network administrator, to explicitly identify a full set of paths (links and routers) that a given IP packet would potentially traverse from its entry point in the area of the AS where it originates until its exit point in its intended destination or exit area.
Owner:SONS OF INNOVATION LLC
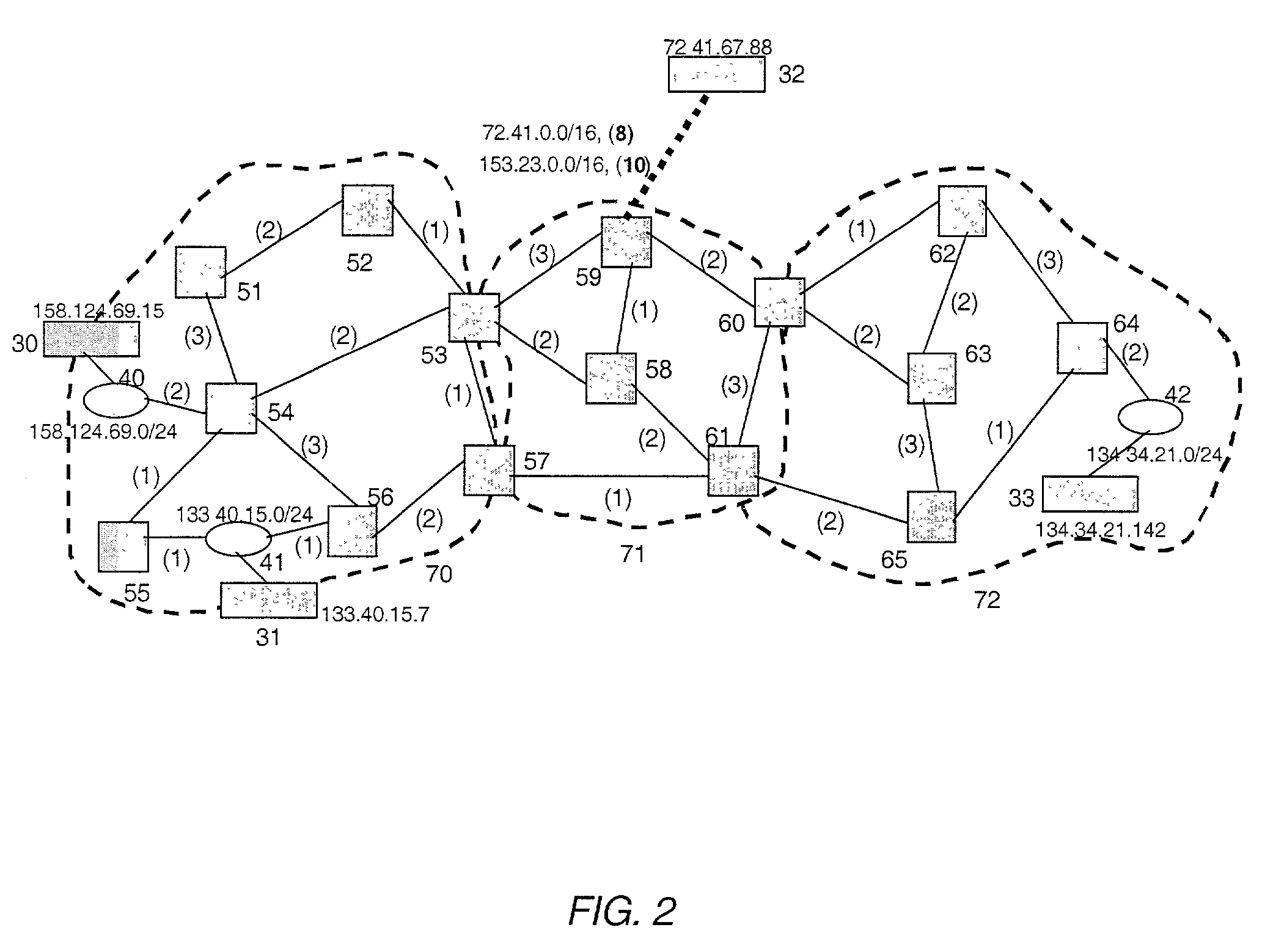
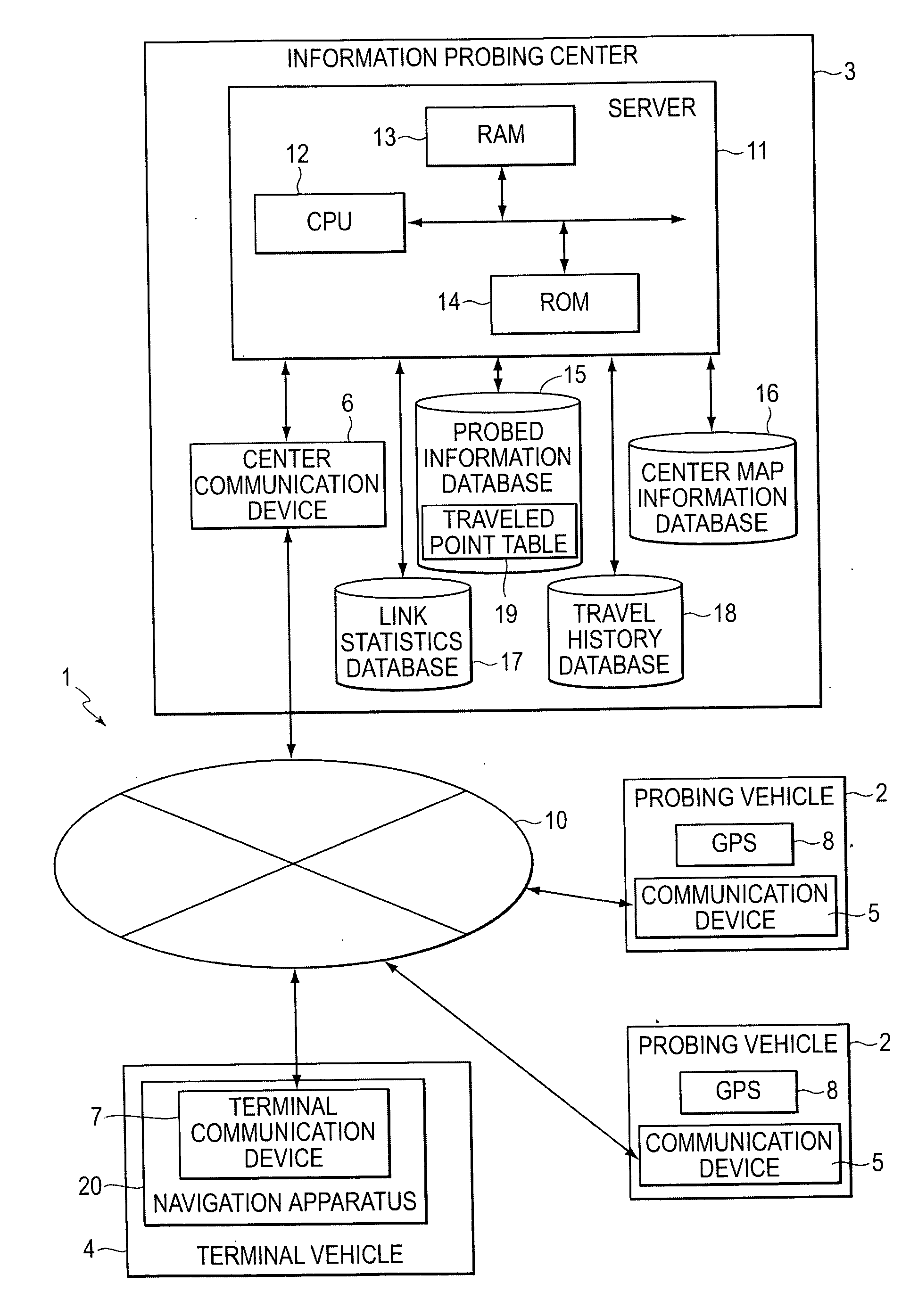
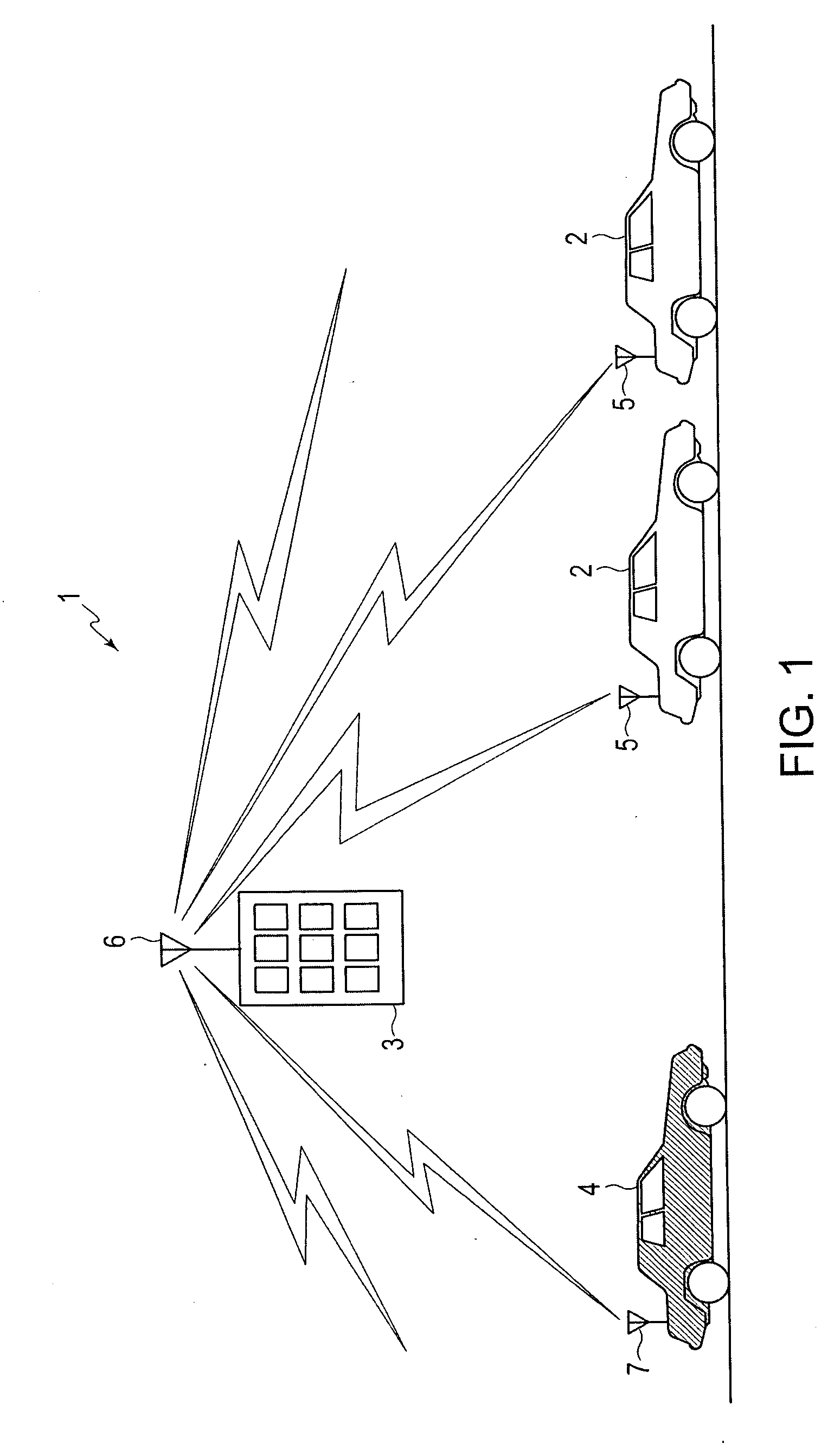
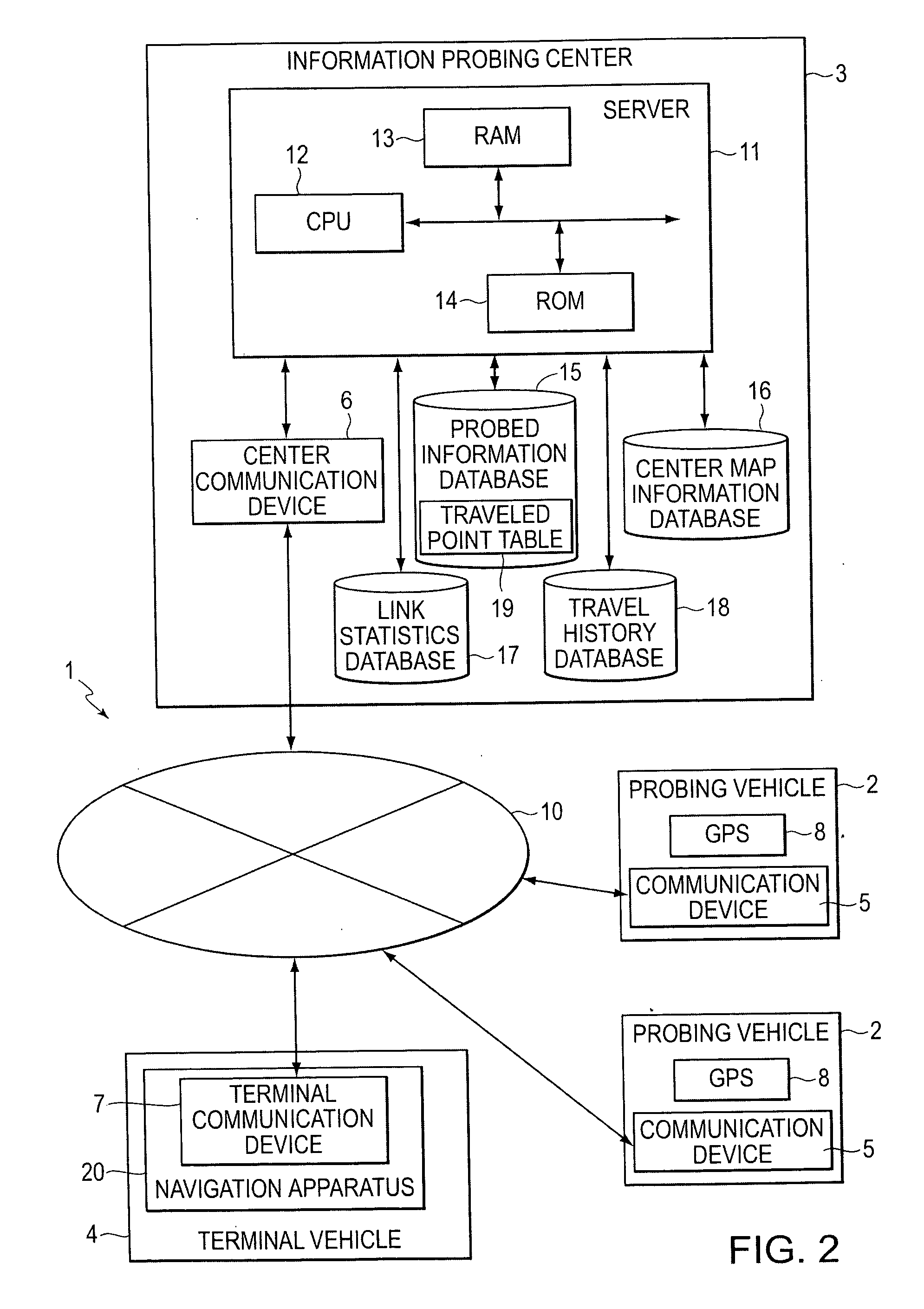
Traveled link identifying systems, methods, and programs
ActiveUS20070150185A1Instruments for road network navigationDetection of traffic movementSystems approachesPath recognition
Traveled link identifying system systems, methods, and programs receive information representing current positions of probe vehicles, the information acquired from each probe vehicle at predetermined distance intervals or at predetermined time intervals. The systems, methods, and programs store connection relationships between links, the links representing portions of roads within map data, and acquire position information from the communication device. The systems, methods, and programs detect links traveled by a probe vehicle on the basis of the acquired position information and determine, based on the stored connection relationships, whether it is possible to uniquely identify one combination of links connecting the detected traveled links. The systems, methods, and programs identify a path traveled by the probe vehicle as being a path between the detected travel links along the unique combination of links.
Owner:AISIN AW CO LTD
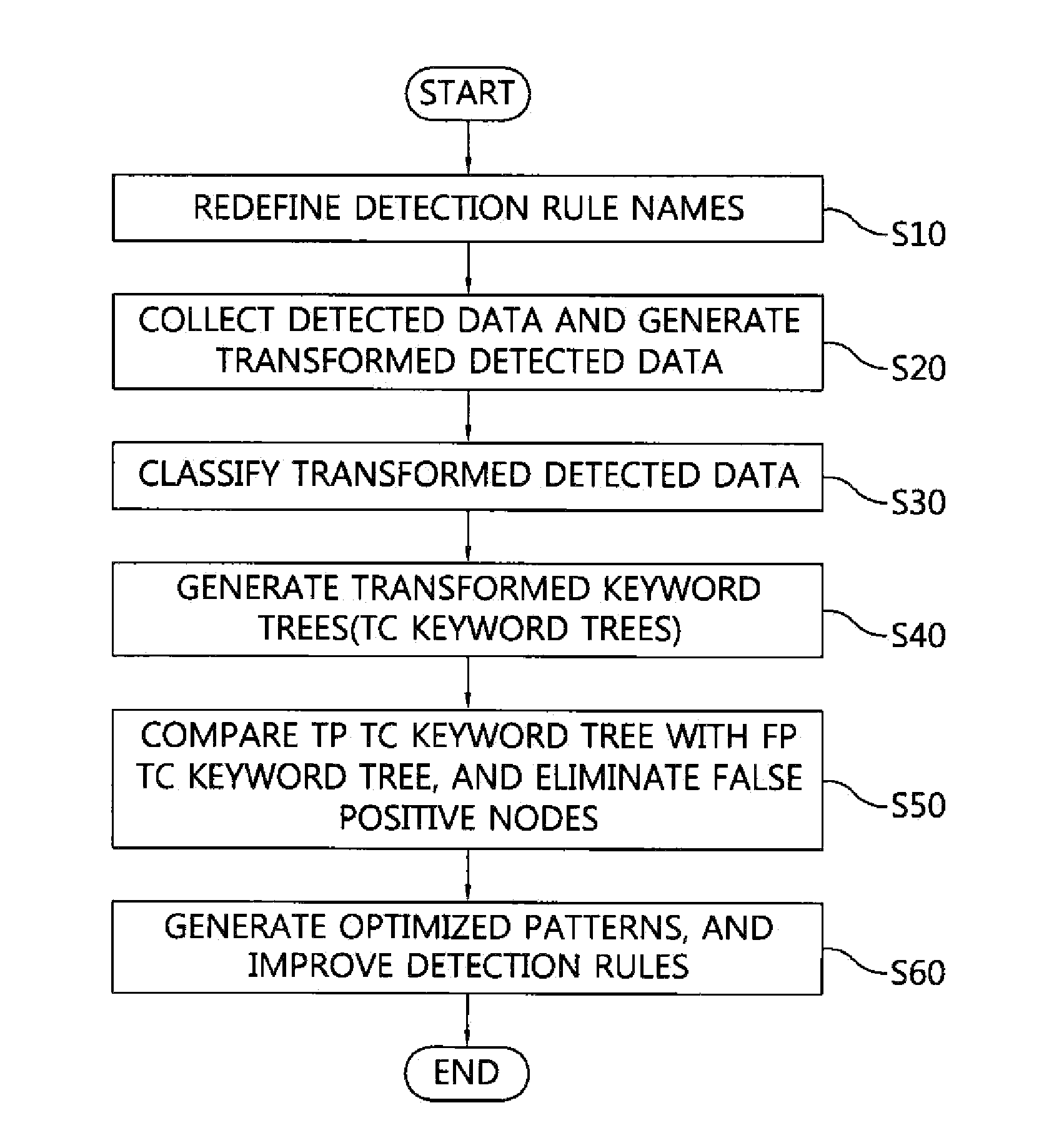
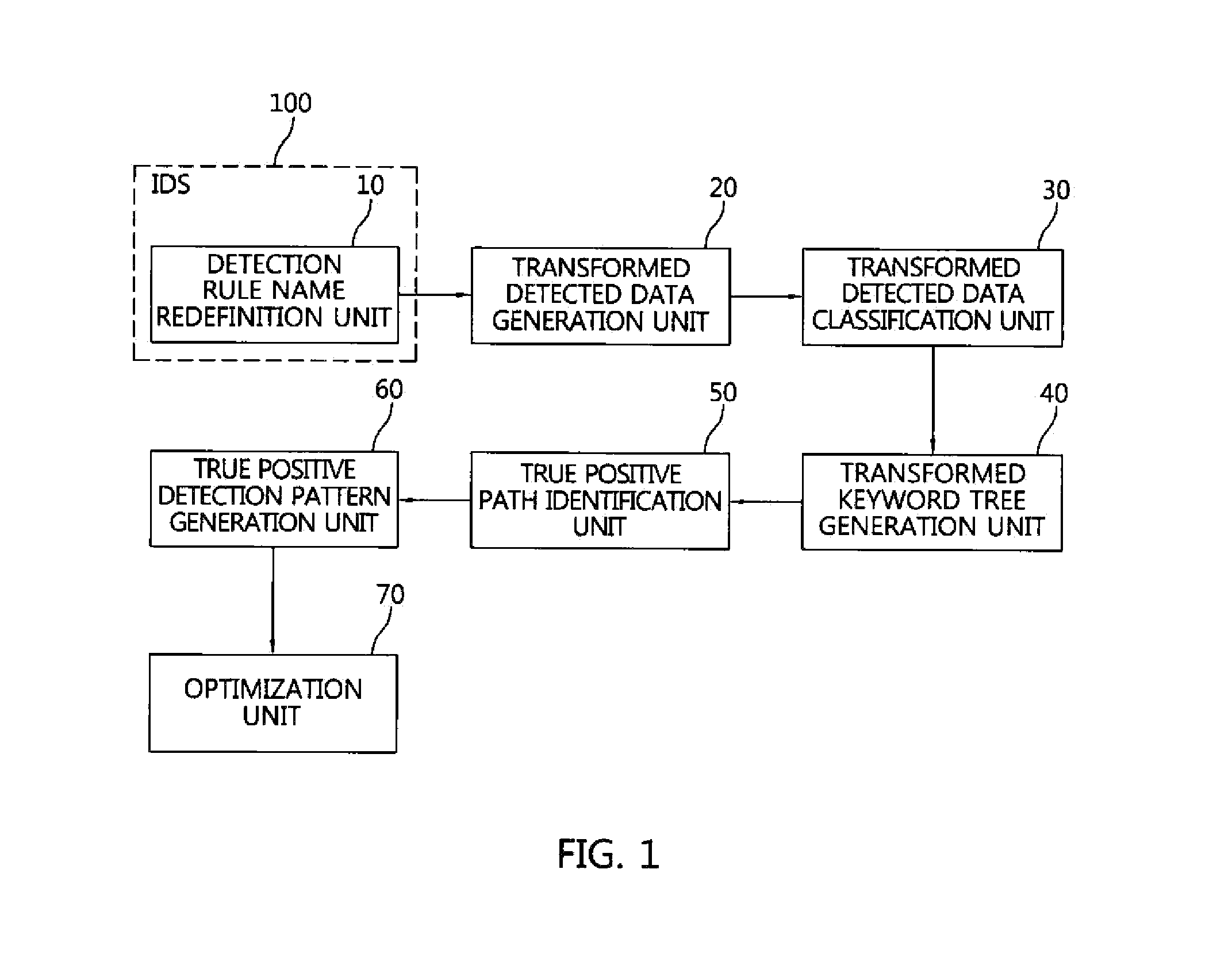
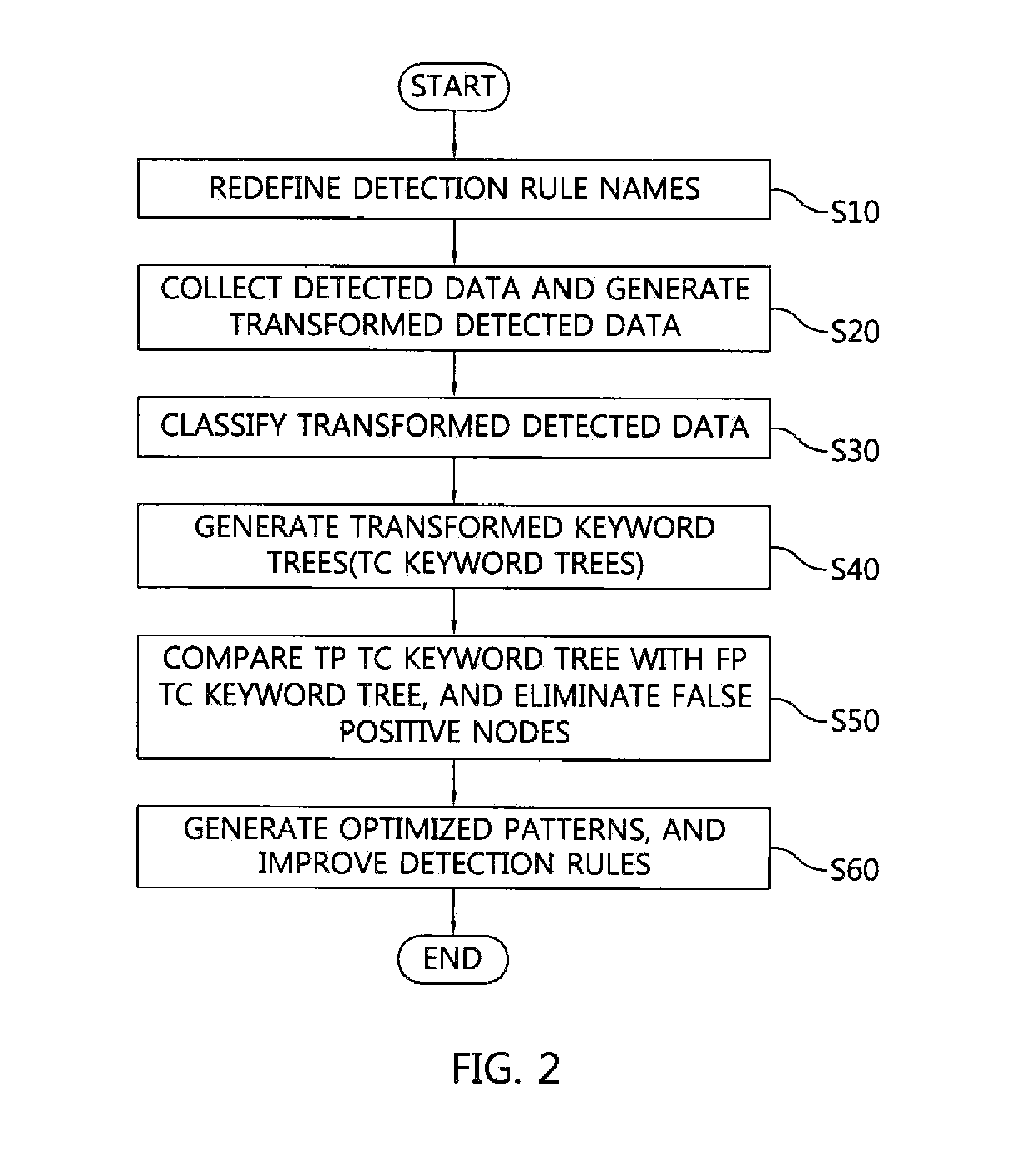
Apparatus and method for improving detection performance of intrusion detection system
ActiveUS20150113646A1Easy to detectIncrease ratingsMemory loss protectionData taking preventionPattern recognitionPath generation
An apparatus for improving detection performance of an intrusion detection system includes a transformed detected data generation unit for changing original detected data, detected based on current detection rules, to transformed detected data complying with transformed detected data standard. A transformed detected data classification unit classifies the transformed detected data by attack type, classifies transformed detected data for attack types by current detection rule, and classifies transformed detected data for detection rules into true positives / false positives. A transformed keyword tree generation unit generates a true positive transformed keyword tree and a false positive transformed keyword tree. A true positive path identification unit generates a true positive node, and identifies a true positive path connecting a base node to the true positive node in the true positive transformed keyword tree. A true positive detection pattern generation unit generates a true positive detection pattern based on the true positive path.
Owner:ARTELLING INC
Method, apparatus and computer program product for traffic lane and signal control identification and traffic flow management
ActiveUS20170186314A1Simple methodControlling traffic signalsDetection of traffic movementTraffic flow managementTraffic signal
A method is provided for traffic lane and traffic signal control identification and traffic flow management. Methods may identify traffic lights controlling lane movements, cataloging the information through analysis of traffic light signal phase and timing, and analyzing traffic movement through an intersection during specific periods of time. In particular, example methods may include identifying each of a plurality of paths through an intersection; identifying states of one or more traffic lights controlling traffic through the intersection; determining vehicle throughput data for the intersection through a predetermined number of cycles of the one or more traffic lights; and matching the vehicle throughput data to each of the plurality of paths of the intersection. The method may optionally include identifying times of movement and times of non-movement of vehicles across the intersection for each of the plurality of paths.
Owner:HERE GLOBAL BV
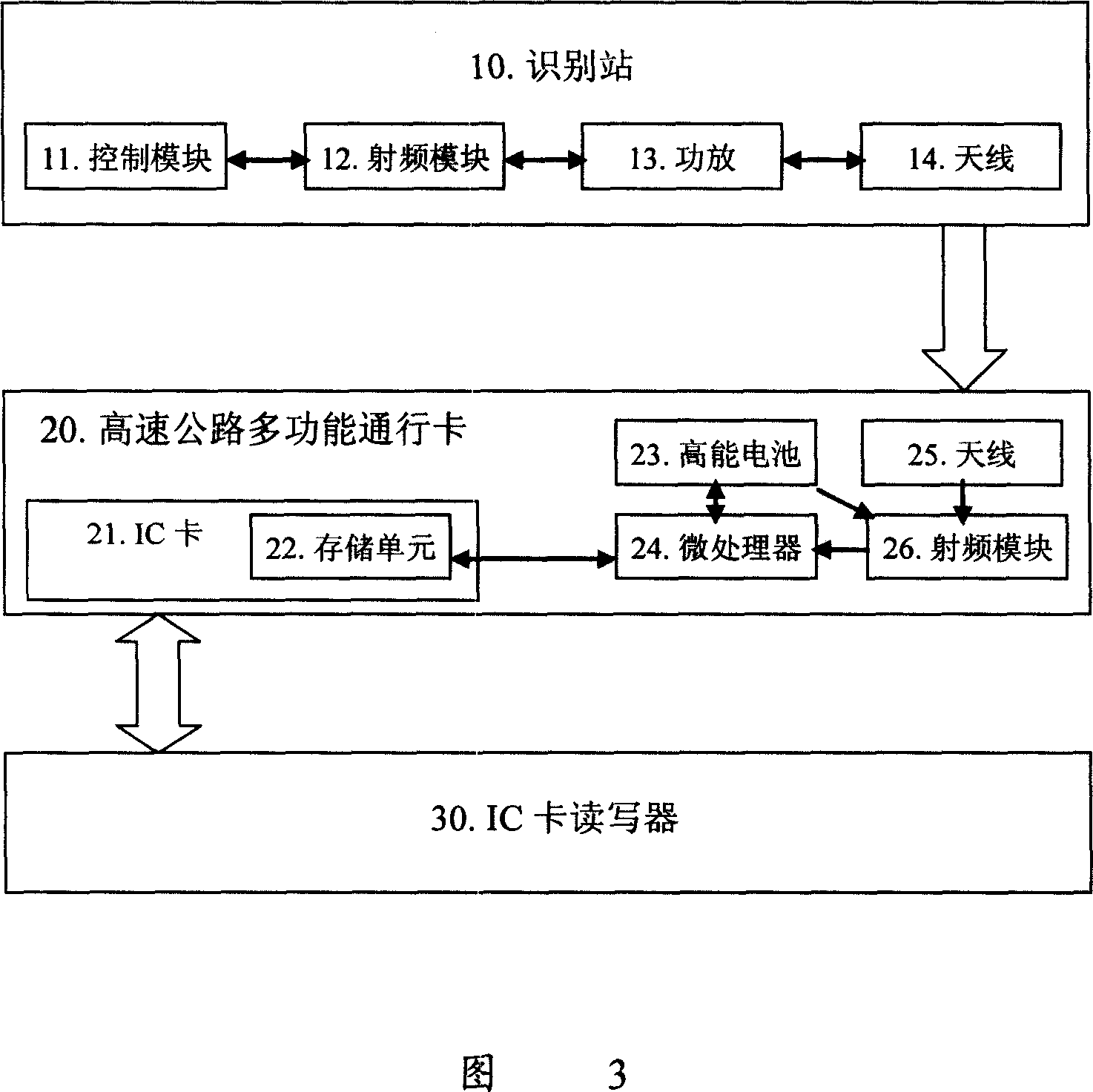
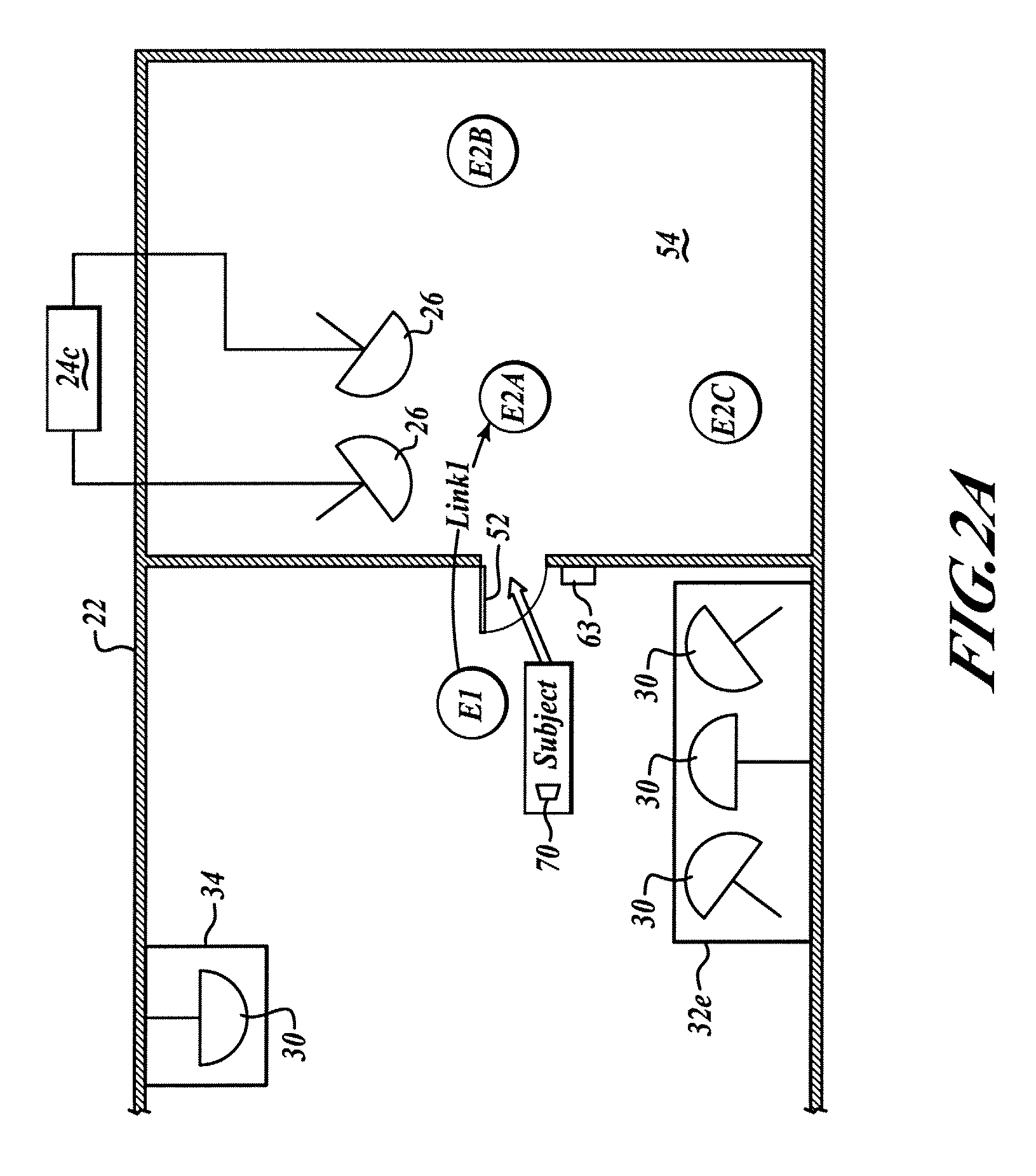
Ambiguity path identifying system and method thereof
ActiveCN1877641ASolve the problem of ambiguous path identificationLess investmentTicket-issuing apparatusAmbiguityComputer science
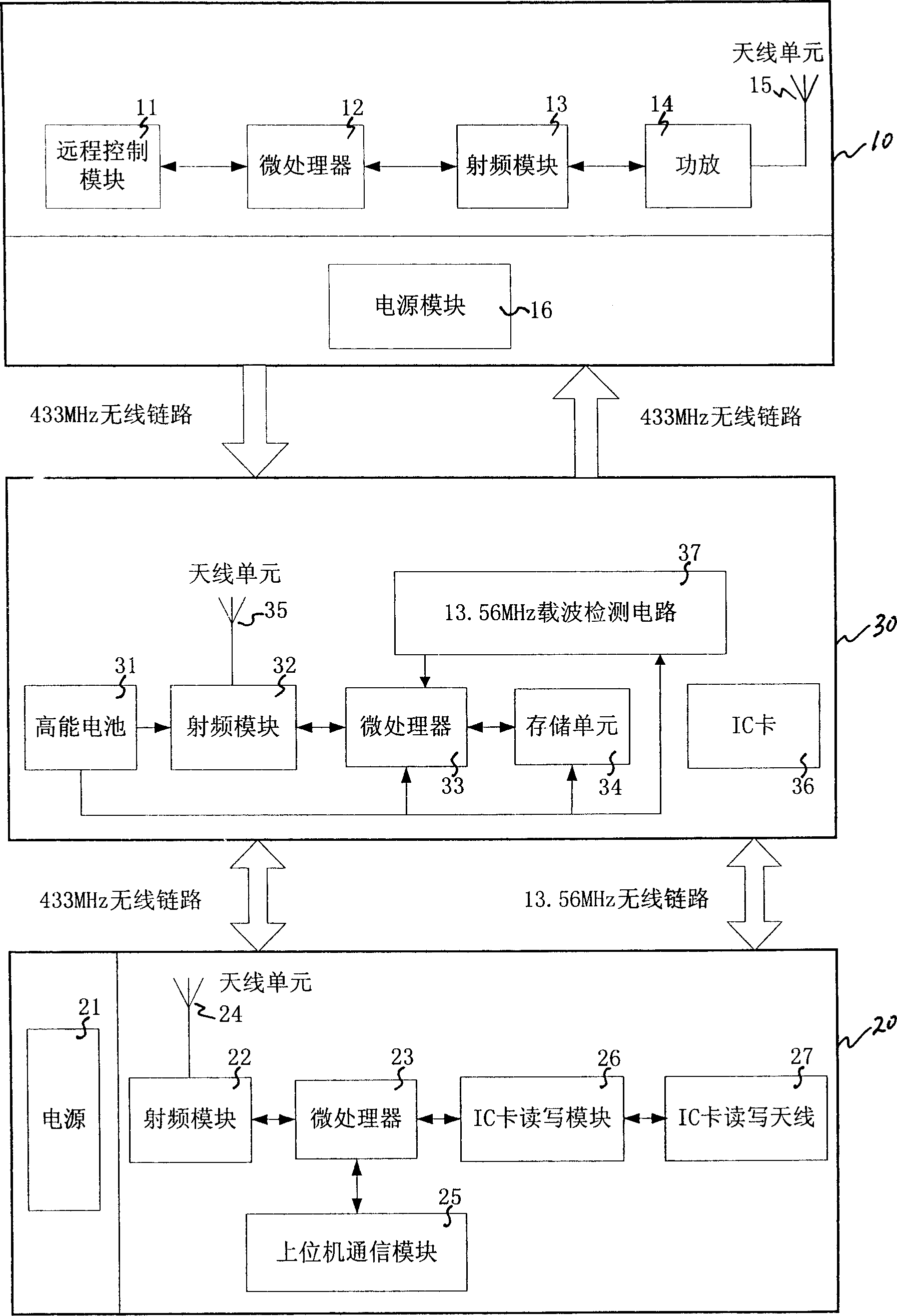
The disclosed ambiguous path recognition system comprises: a road-side antenna device to continual send RF signal with path label information, a table read-write machine to read path information, and a vehicle-carry unit with an IC card to record vehicle path information and a receive and store device for former label information. This invention saves investment, has high reliability, and fit to spread on freeway.
Owner:浙江省公路管理局 +1
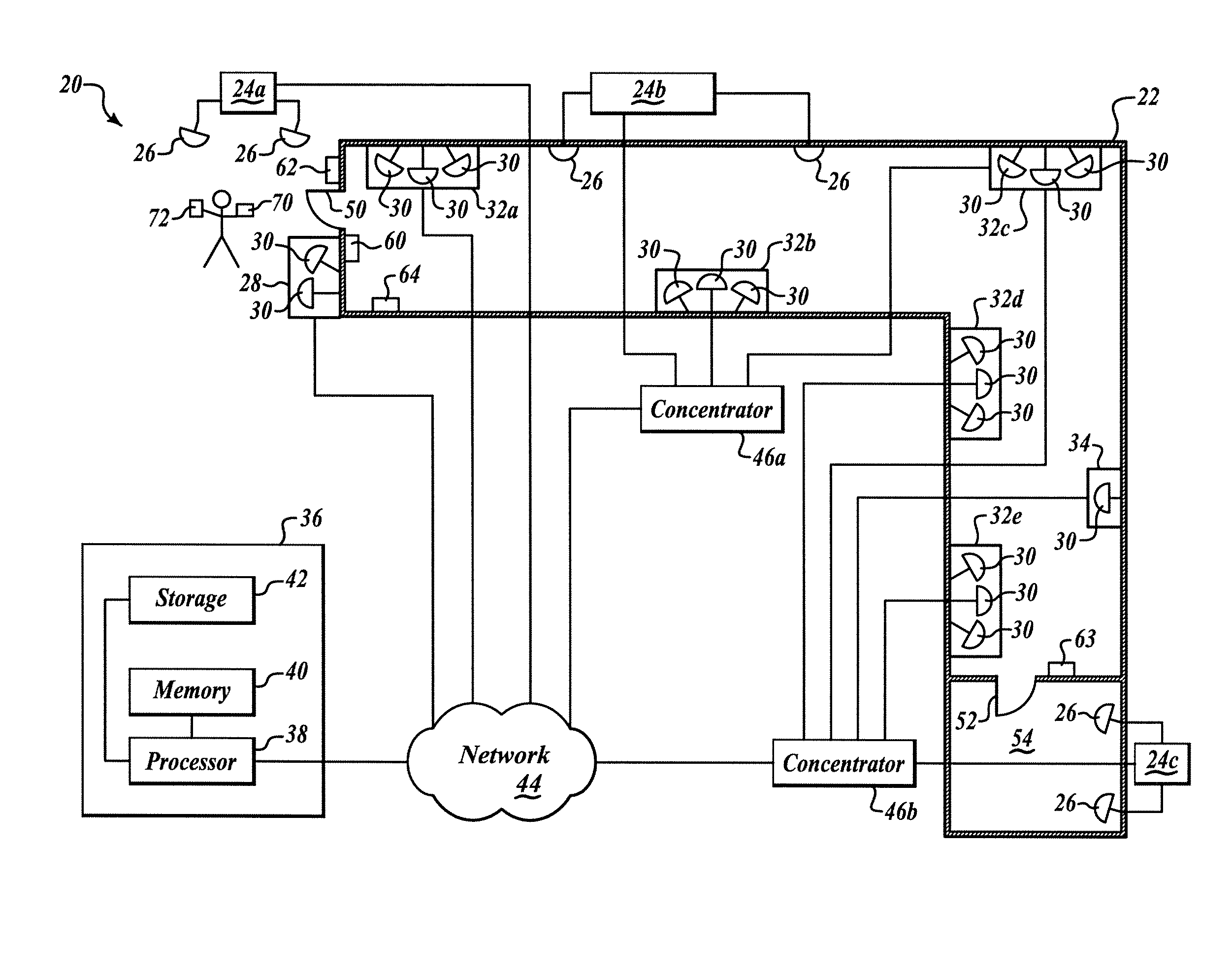
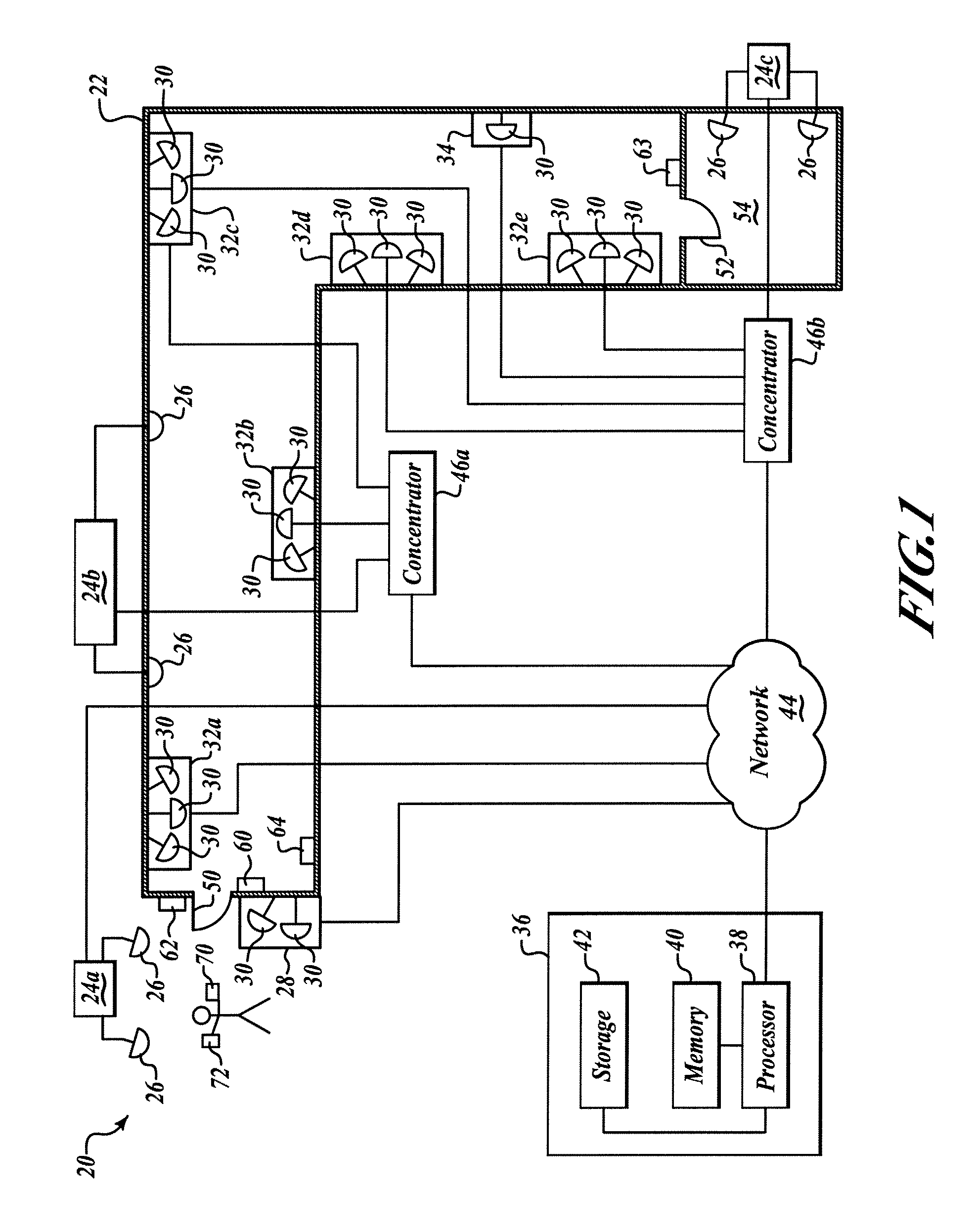
Systems and methods for object localization and path identification based on RFID sensing
A networked radio frequency identification system includes a plurality of radio frequency identification (RFID) tag readers, a computer in signal communication with the RFID tag readers over a network, and a software module for storage on and operable by the computer that localizes RFID tags based on information received from the RFID tag readers using a network model having endpoints and oriented links. In an additional example, at least one of the RFID tag readers includes an adjustable configuration setting selected from RF signal strength, antenna gain, antenna polarization, and antenna orientation. In a further aspect, the system localizes RFID tags based on hierarchical threshold limit calculations. In an additional aspect, the system controls a locking device associated with an access point based on localization of an authorized RFID tag at the access point and reception of additional authorizing information from an input device.
Owner:LUCOMM TECH
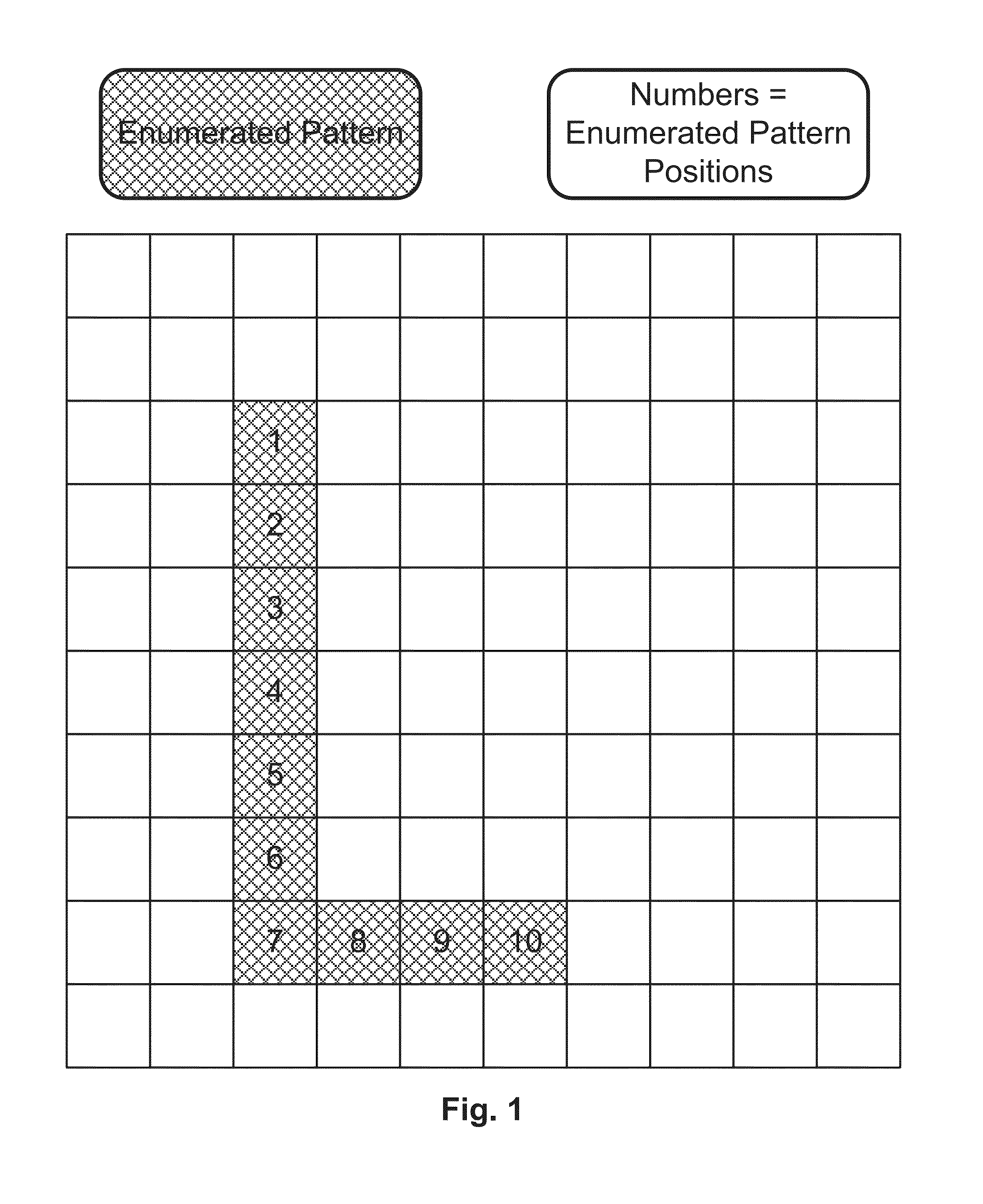
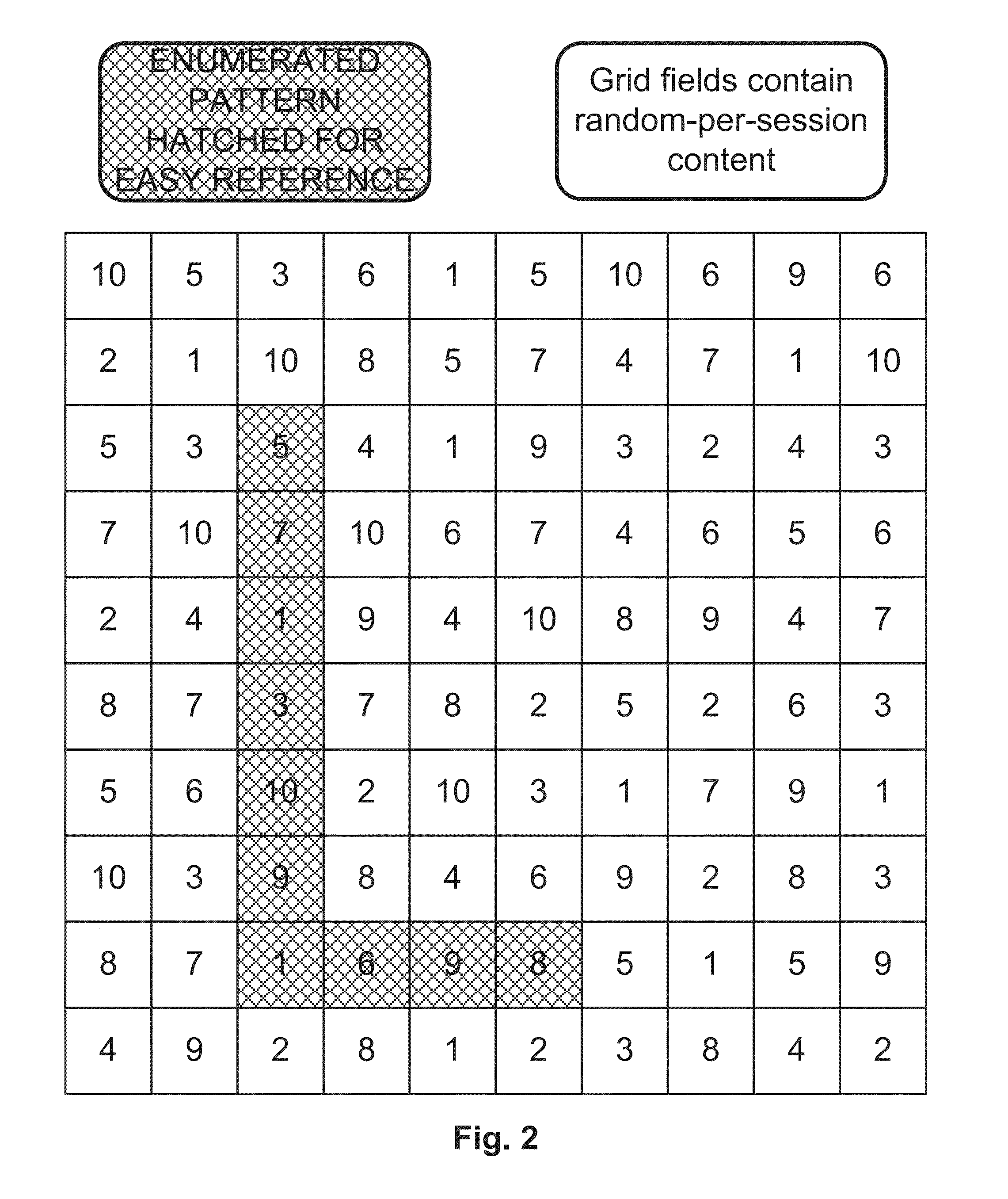
Authentication method of field contents based challenge and enumerated pattern of field positions based response in random partial digitized path recognition system
ActiveUS20140115670A1Digital data processing detailsMultiple digital computer combinationsAlgorithmTheoretical computer science
An interactive method for authentication is based on a shared secret which is in the form of an enumerated pattern of fields on a frame of reference. An instance of the frame of reference comprises an array of characters in which the characters are arranged in a random or other irregular pattern on a grid of content fields. An authentication challenge includes characters from the character set, and is delivered in- or out-of-band. The authentication response includes the enumerated position numbers on the enumerated pattern of the field locations on the grid at which the challenge characters are found.
Owner:AUTHERNATIVE INC
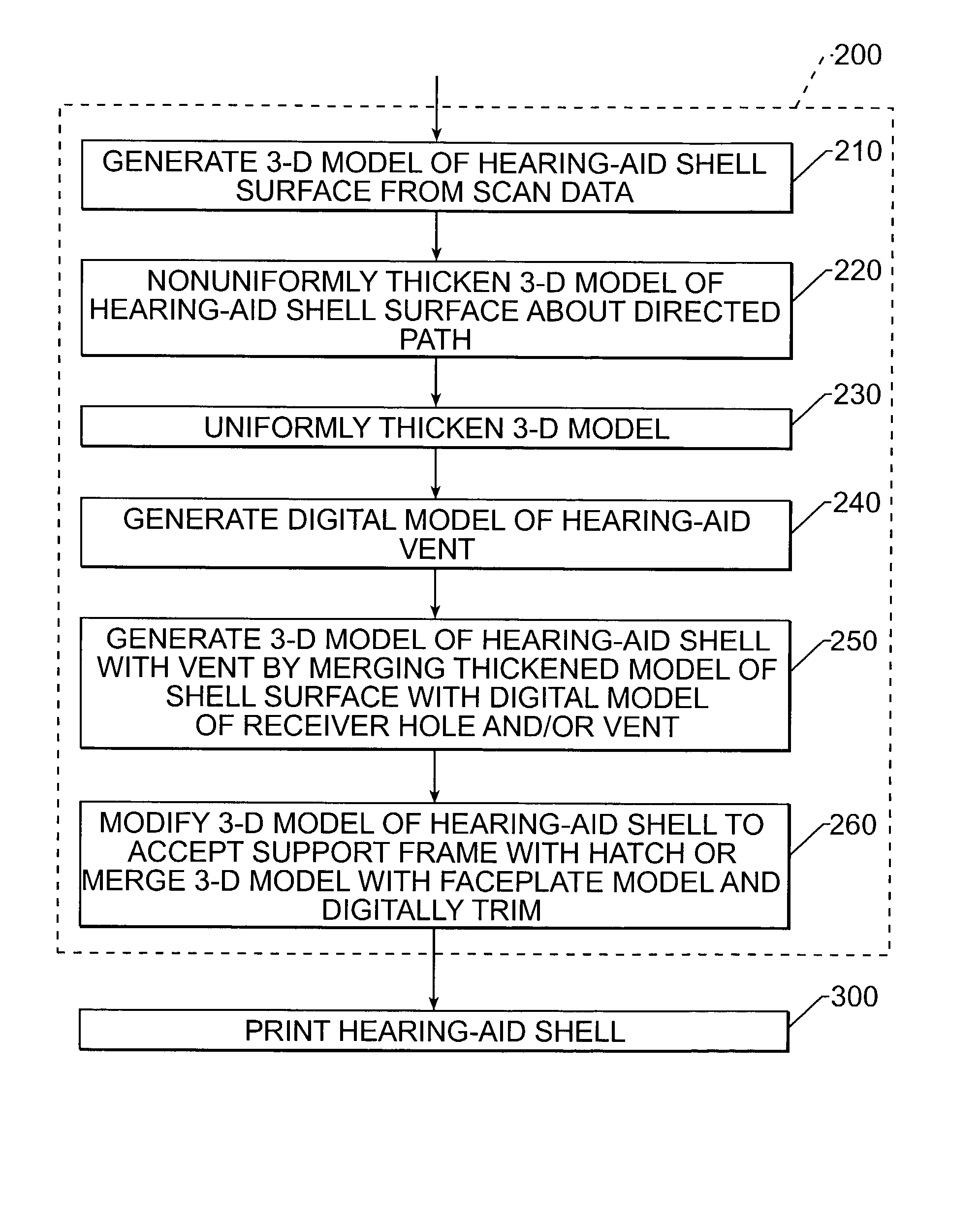
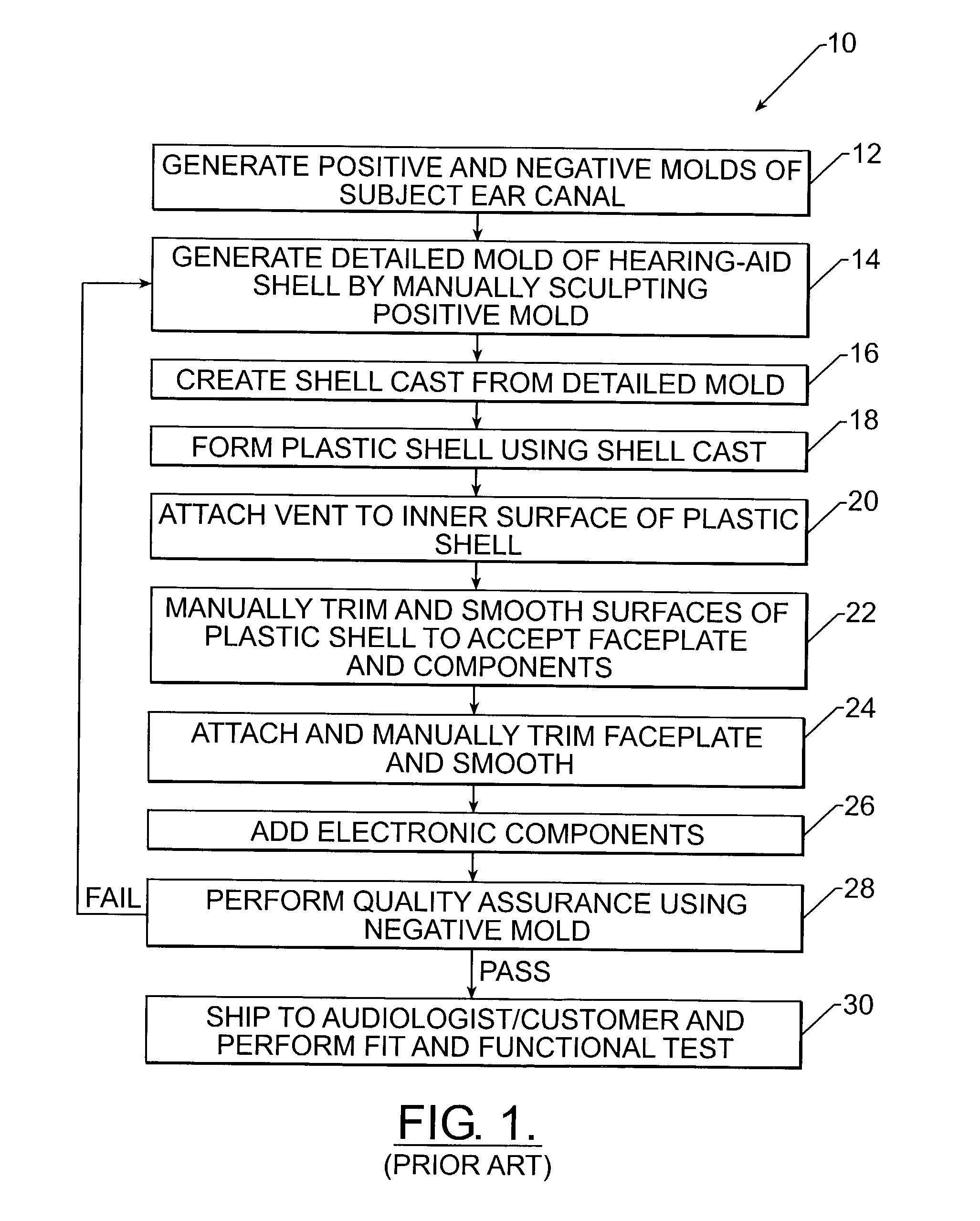
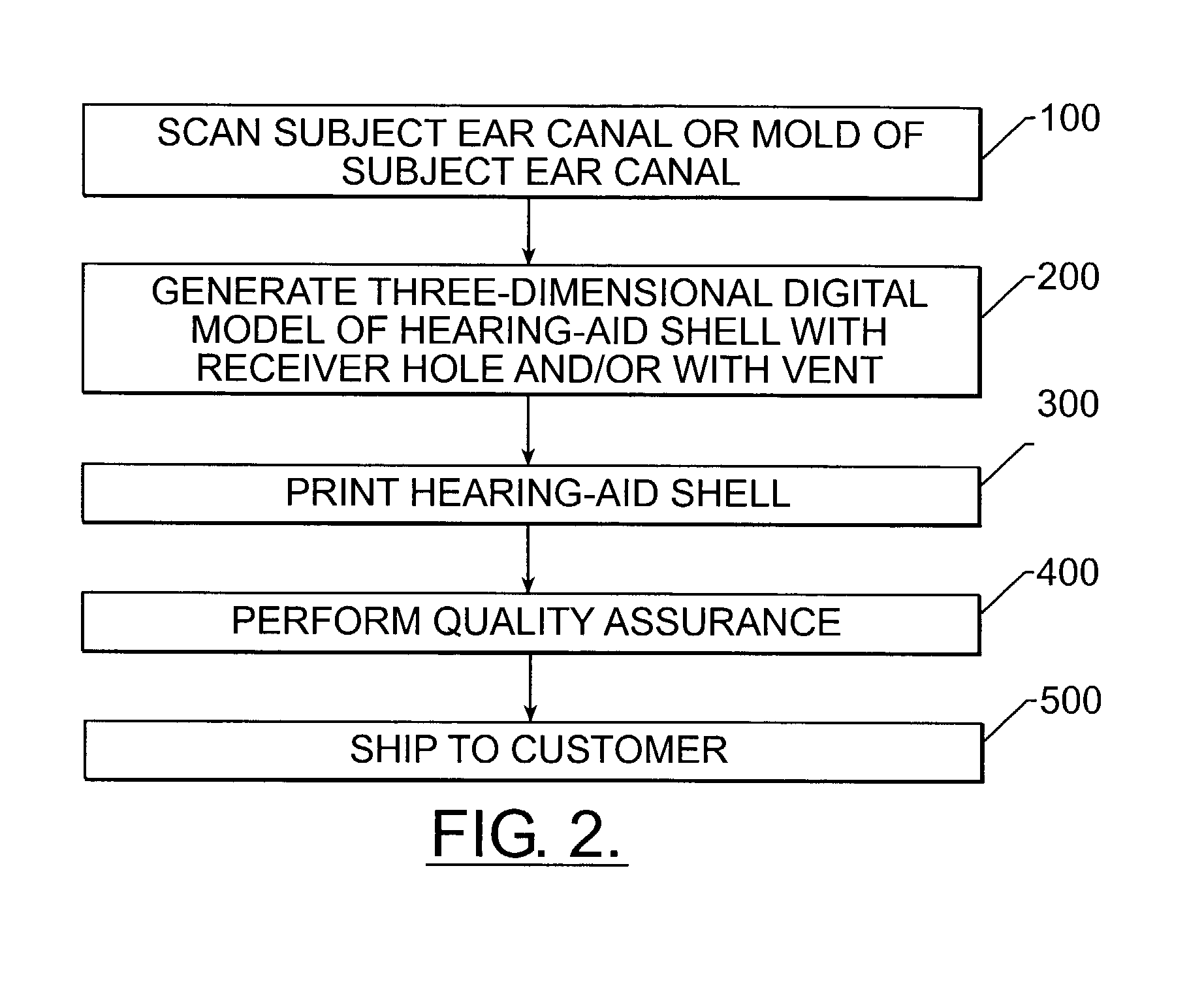
Manufacturing methods and systems for rapid production of hearing-aid shells
ActiveUS7328080B2Reduce in quantityHigh degreeProgramme controlElectrical transducersComputer Aided DesignQuality assurance
Owner:PHONAK
Space programming robot toy for children
ActiveCN105396295AReduce usageAvoid negative effectsComputerized toysToy vehiclesInstruction sequencePath recognition
The invention discloses a space programming robot toy for children. The toy comprises a robot vehicle body, an instruction executing device arranged in the robot vehicle body, a path recognition device arranged in the robot vehicle body, an instruction reading device arranged at the bottom of the robot vehicle body, a moving device used for driving the robot vehicle body to walk along a navigation path, and instruction tags arranged in sequence along the navigation path. The instruction tags comprise a plurality of control instructions and are arranged in the reading-writing range of the instruction reading device. The instruction reading device is used for sending the corresponding control instructions to the instruction executing device in sequence according to the reading sequence of the instruction tags. The instruction executing device is used for controlling the robot vehicle body to product instructions actions in sequence according to the sequence of the received control instructions. The robot can be programmed by children with no computer, and the children avoid using computers frequently.
Owner:成都优威骐翼教育科技有限公司
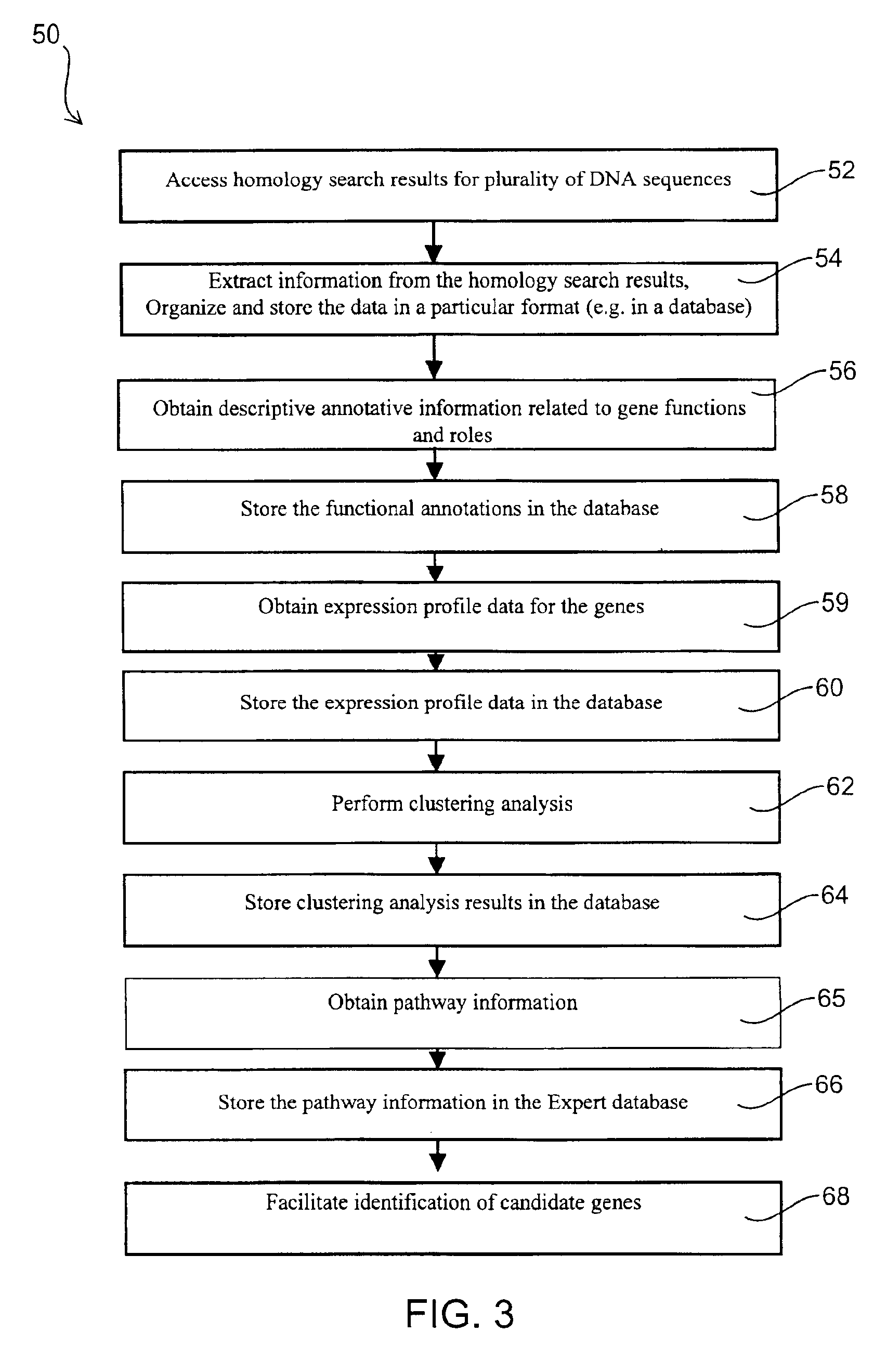
Automated pathway recognition system
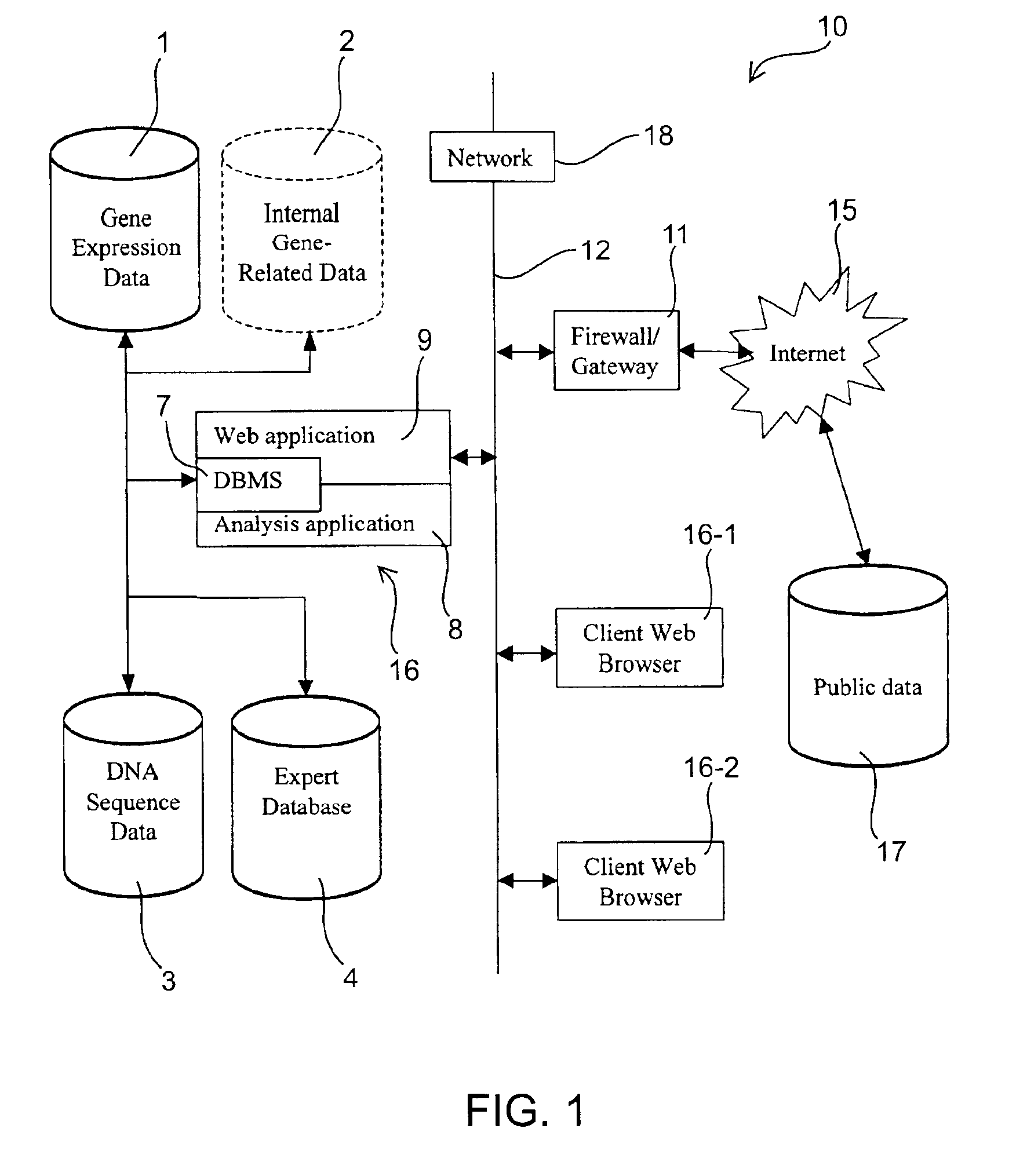
InactiveUS6876930B2Easy to identifyQuick analysisData processing applicationsBiostatisticsCandidate Gene Association StudyCandidate gene
There is a pressing need for computer-implemented tools that can summarize and present the enormous amounts of public literature to facilitate analysis of gene expression data. The present invention provides techniques and systems for efficiently integrating public literature regarding gene function with data from gene expression profiling experiments. Information from literature databases relating to a particular set of DNA sequences of known expression pattern is retrieved, processed, cross-referenced and viewed to provide further information about a particular DNA sequence to facilitate its identification as a candidate gene.
Owner:AGY THERAPEUTICS
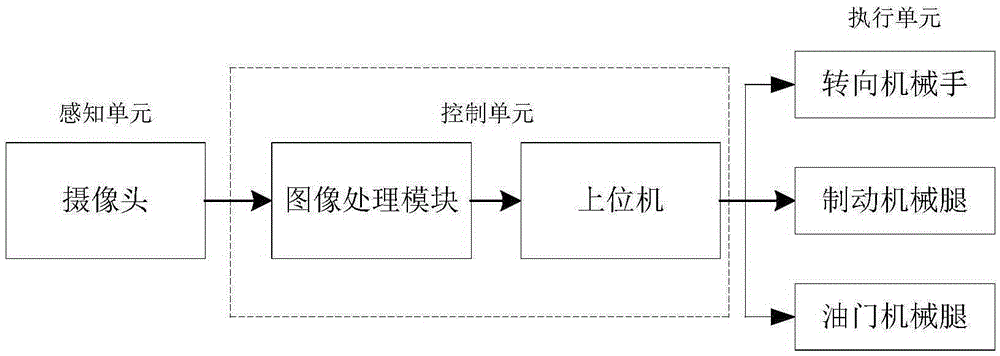
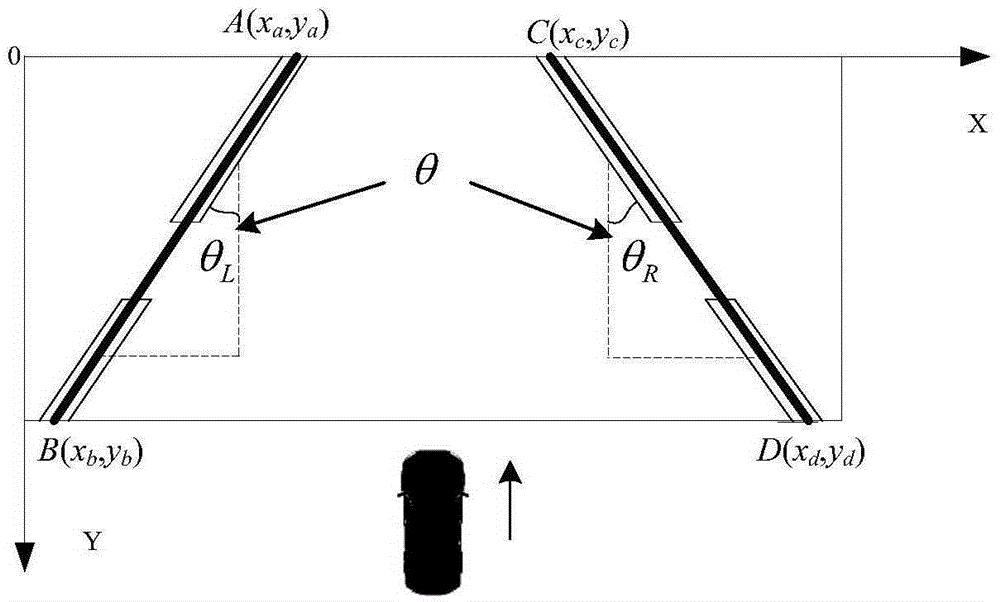
Self-driving car lane changing control method based on monocular vision
ActiveCN105329238ARealize closed-loop controlLow costSteering partsDriver input parametersTracking modelClosed loop
The invention provides a self-driving car lane changing control method based on monocular vision and belongs to the technical field of car electronic control. A camera is installed on a roof of an self-driving car and used for collecting a lane line image; an image processing module is used for processing and recognizing the lane line image to obtain a fit lane line; an upper computer module is used for calculating turn angle increment of a steering wheel, and outputting a motor control signal to an executing unit. According to the method, lane changing reference angles are defined, the optimal lane changing track model based on the lane changing reference angles is provided, the turn angle increment of the steering wheel is obtained by means of a preview control theory to control the steering wheel of the car, and the left lane changing reference angle or the right lane changing reference angle is selected according to needs. Lane changing closed-loop control can be achieved only by using the camera for path recognizing, the lane changing process is stable and reliable, cost is reduced, and the complex degree of the system is reduced.
Owner:北京踏歌智行科技有限公司
Systems and methods for object localization and path identification based on RFID sensing
InactiveUS20090027165A1Individual entry/exit registersSubscribers indirect connectionAntenna polarizationAntenna gain
A networked radio frequency identification system includes a plurality of radio frequency identification (RFID) tag readers, a computer in signal communication with the RFID tag readers over a network, and a software module for storage on and operable by the computer that localizes RFID tags based on information received from the RFID tag readers using a network model having endpoints and oriented links. In an additional example, at least one of the RFID tag readers includes an adjustable configuration setting selected from RF signal strength, antenna gain, antenna polarization, and antenna orientation. In a further aspect, the system localizes RFID tags based on hierarchical threshold limit calculations. In an additional aspect, the system controls a locking device associated with an access point based on localization of an authorized RFID tag at the access point and reception of additional authorizing information from an input device.
Owner:LUCOMM TECH
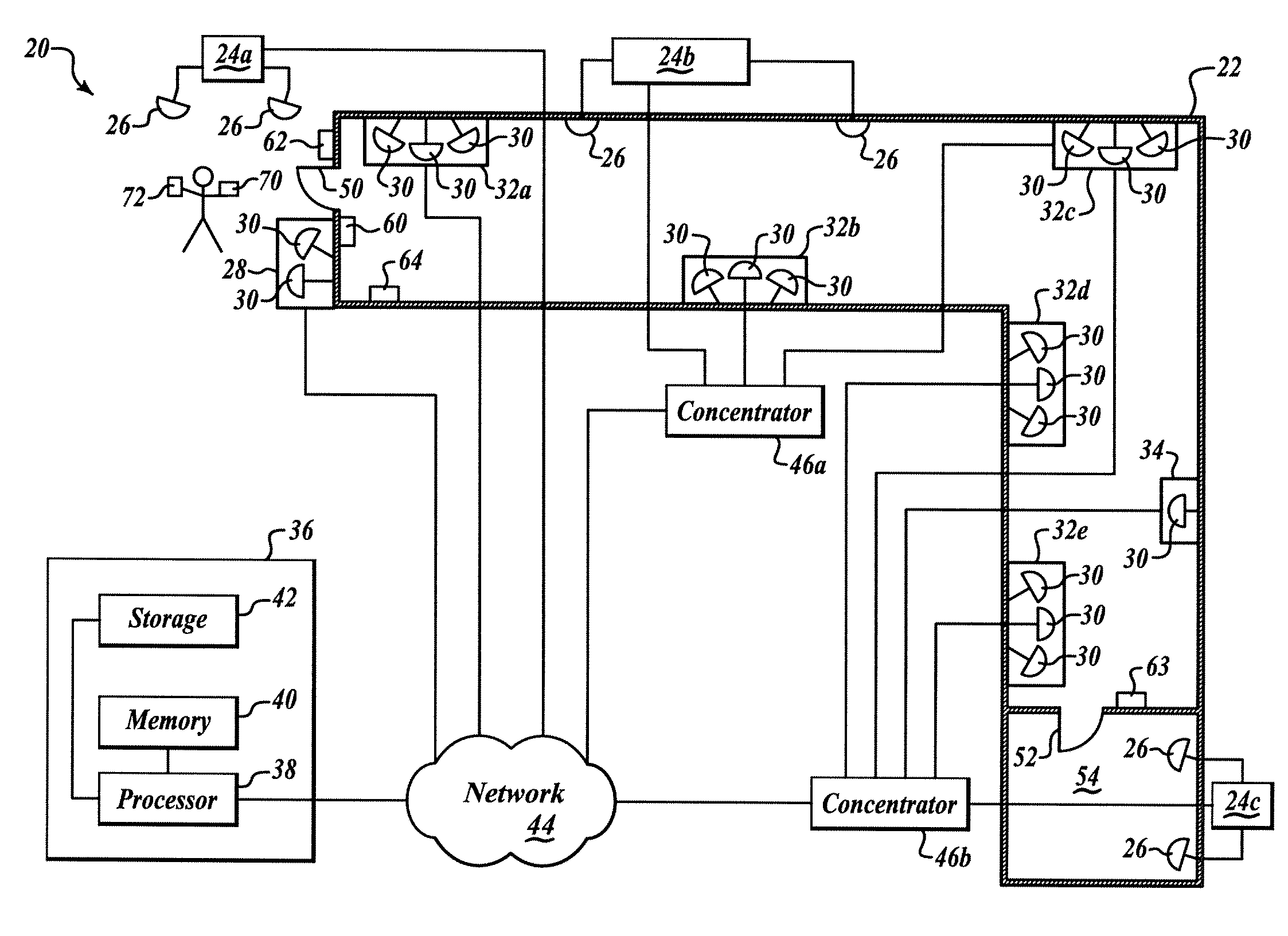
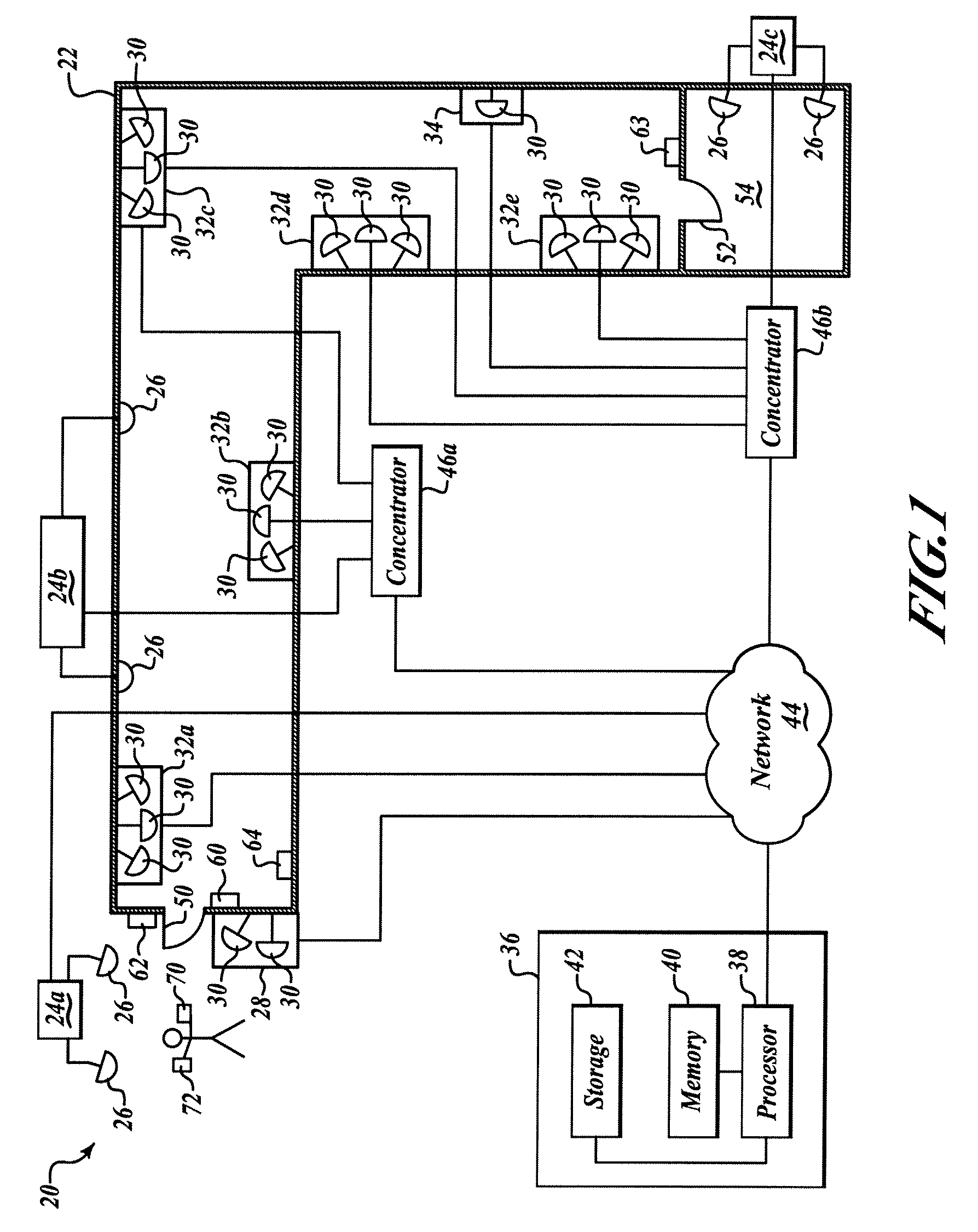
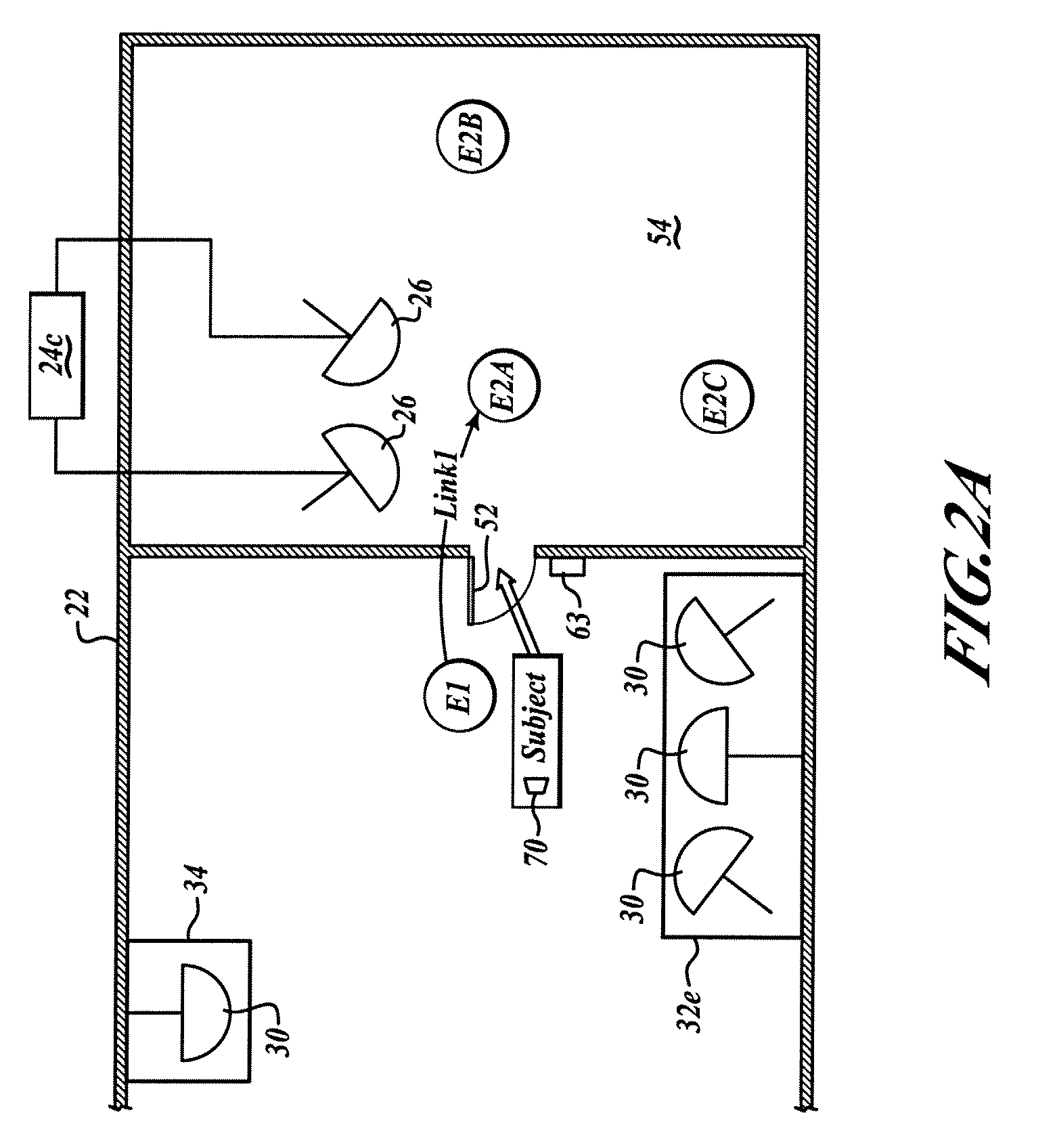
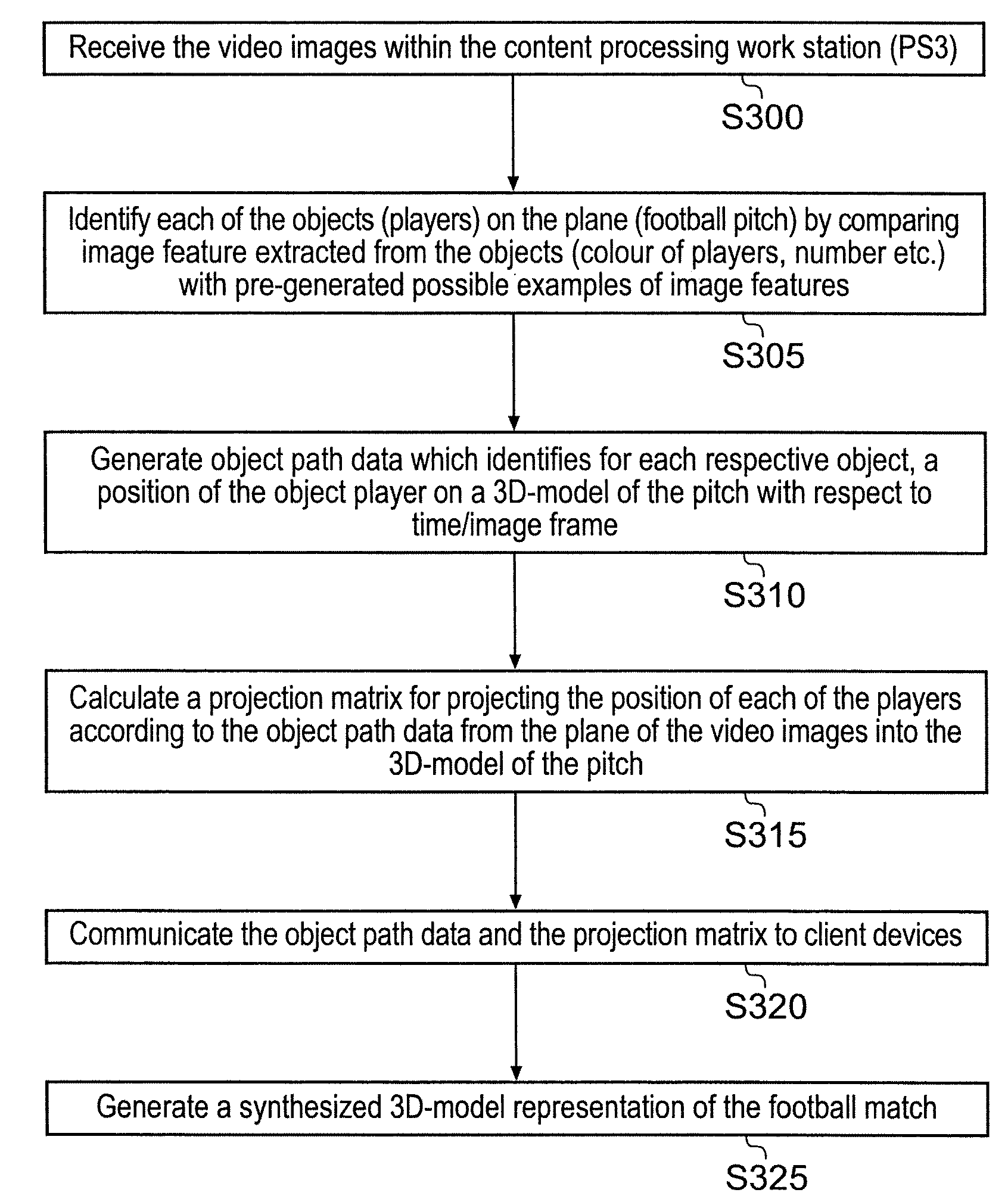
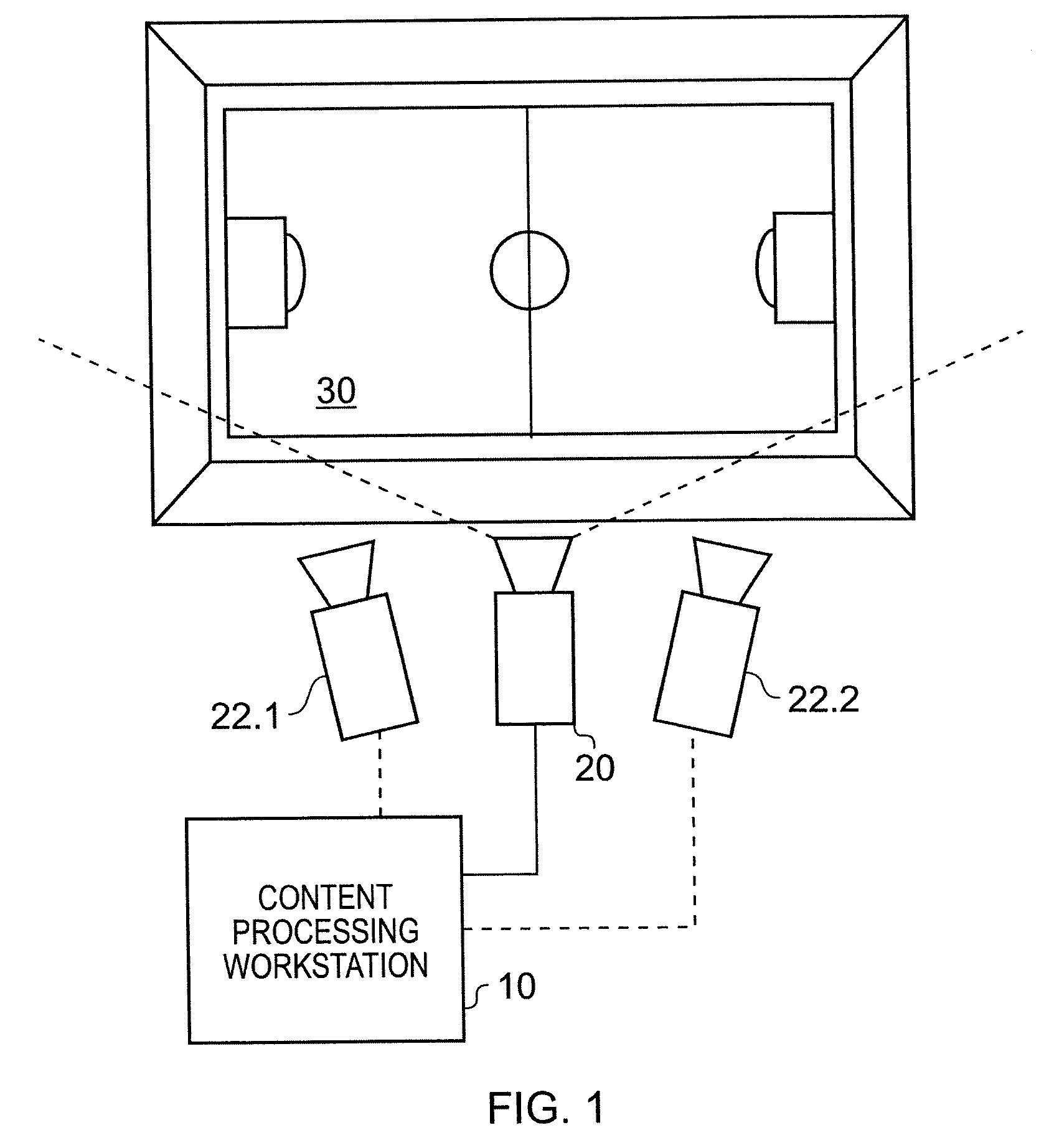
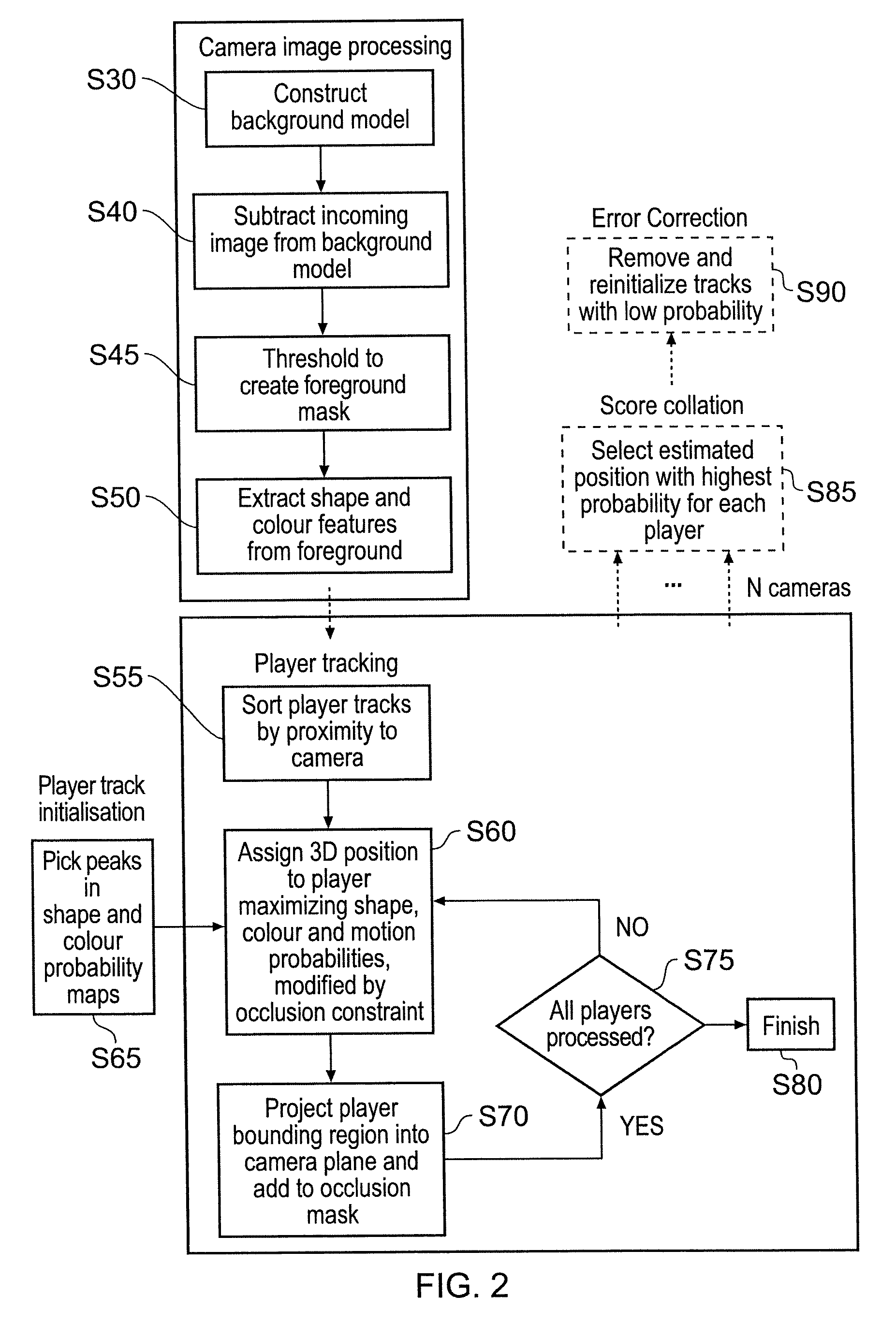
System for communicating and method
A system communicates a representation of a scene, which includes a plurality of objects disposed on a plane, to one or more client devices. The representation is generated from one or more video images of the scene captured by a video camera. The system comprises an image processing apparatus operable to receive the video images of the scene which includes a view of the objects on the plane, to process the captured video images so as to extract one or more image features from each object, to compare the one or more image features with sample image features from a predetermined set of possible example objects which the video images may contain, to identify the objects from the comparison of the image features with the predetermined image features of the possible example objects, and to generate object path data for each object which identifies the respective object; and provides a position of the identified object on a three dimensional model of the plane in the video images with respect to time. The image processing apparatus is further operable to calculate a projection matrix for projecting the position of each of the objects according to the object path data from the plane in the video image into the three dimensional model of the plane. A distribution server is operable to receive the object path data and the projection matrix generated by the image processing apparatus for distribution of the object path data and the projection matrix to one or more client devices. The system is arranged to generate a representation of an event, such as a sporting event, which provides a substantial data in an amount of information which must be communicated to represent the event. As such, the system can be used to communicate the representation of the event, via a bandwidth limited communications network, such as the internet, from the server to one or more client devices in real time. Furthermore, the system can be used to view one or more of the objects within the video images by extracting the objects from the video images.
Owner:SONY CORP
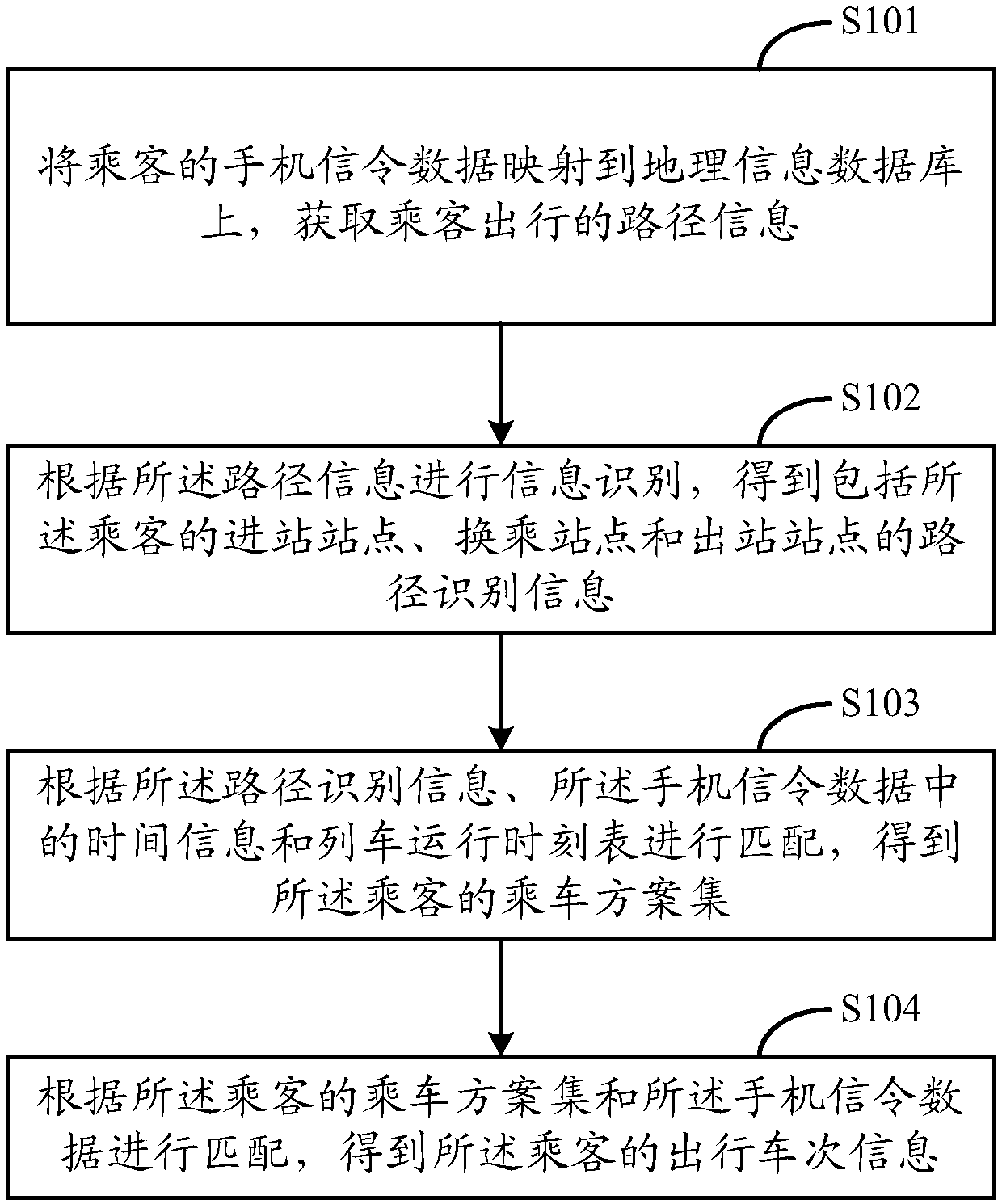
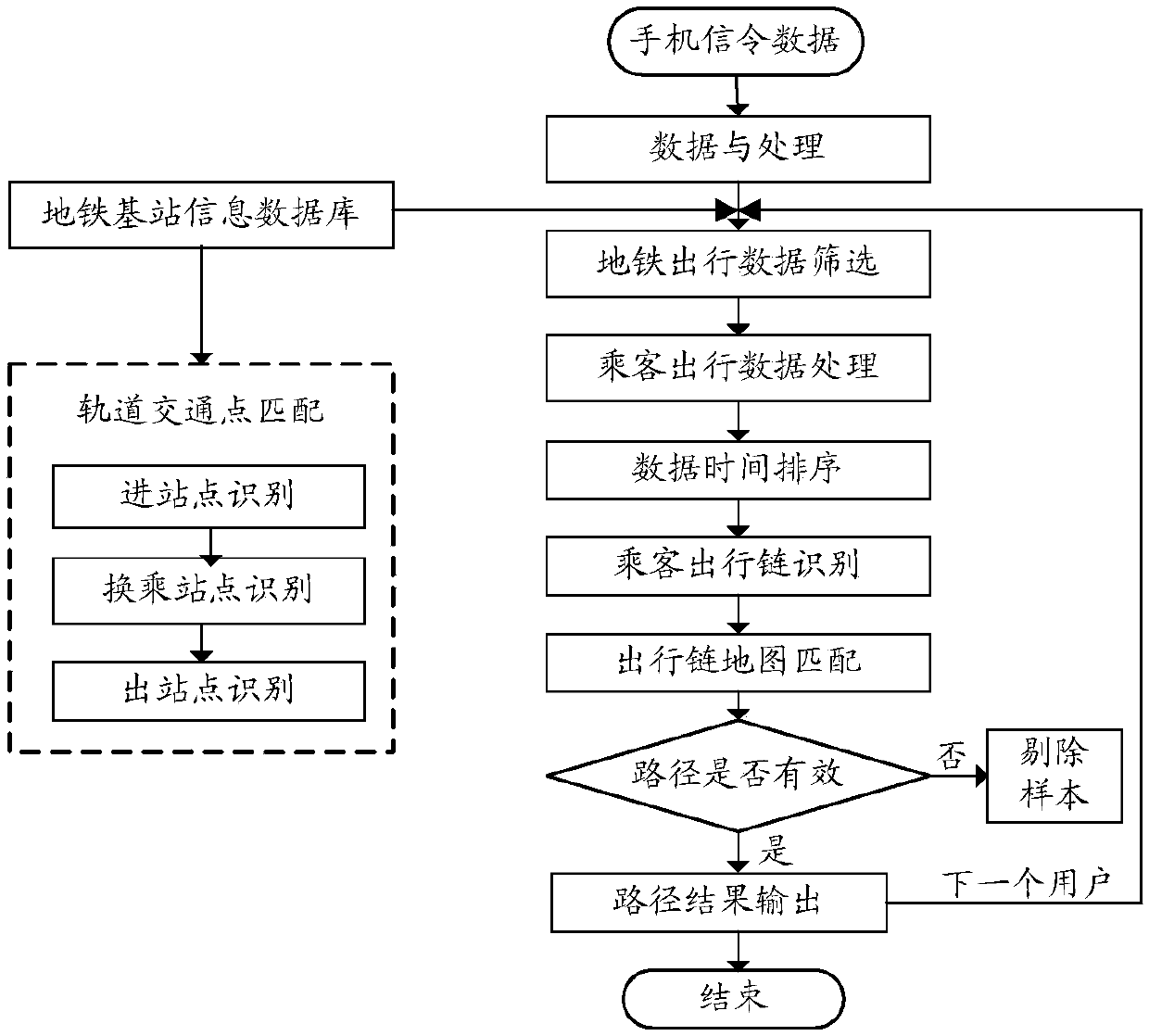
Path recognition method and system based on mobile phone signaling data
InactiveCN108055645AAvoid defectsAccurate data supportParticular environment based servicesVehicle wireless communication serviceTemporal informationPath recognition
The invention is applied to the rail traffic field, and provides a path recognition method based on mobile phone signaling data. The path recognition method comprises the steps that the mobile phone signaling data of a passenger is mapped to a geographic information database, and path information of traveling of the passenger is acquired; information recognition is conducted according to the pathinformation to obtain path recognition information including an inbound station, a transfer station and an outbound station of the passenger; the path recognition information and time information in the mobile phone signaling data are matched with a train running schedule to obtain a riding scheme set of the passenger; and the riding scheme set of the passenger is matched with the mobile phone signaling data to obtain traveling train number information of the passenger. According to the path recognition method based on the mobile phone signaling data, the traveling time and the traveling trainnumber information of the passenger are matched by combining the mobile phone signaling data of the passenger with the train running schedule, base station information and the like, and the defect that in the prior art, the space-time path information of traveling of the passenger cannot be acquired is overcome.
Owner:SHENZHEN TECH UNIV
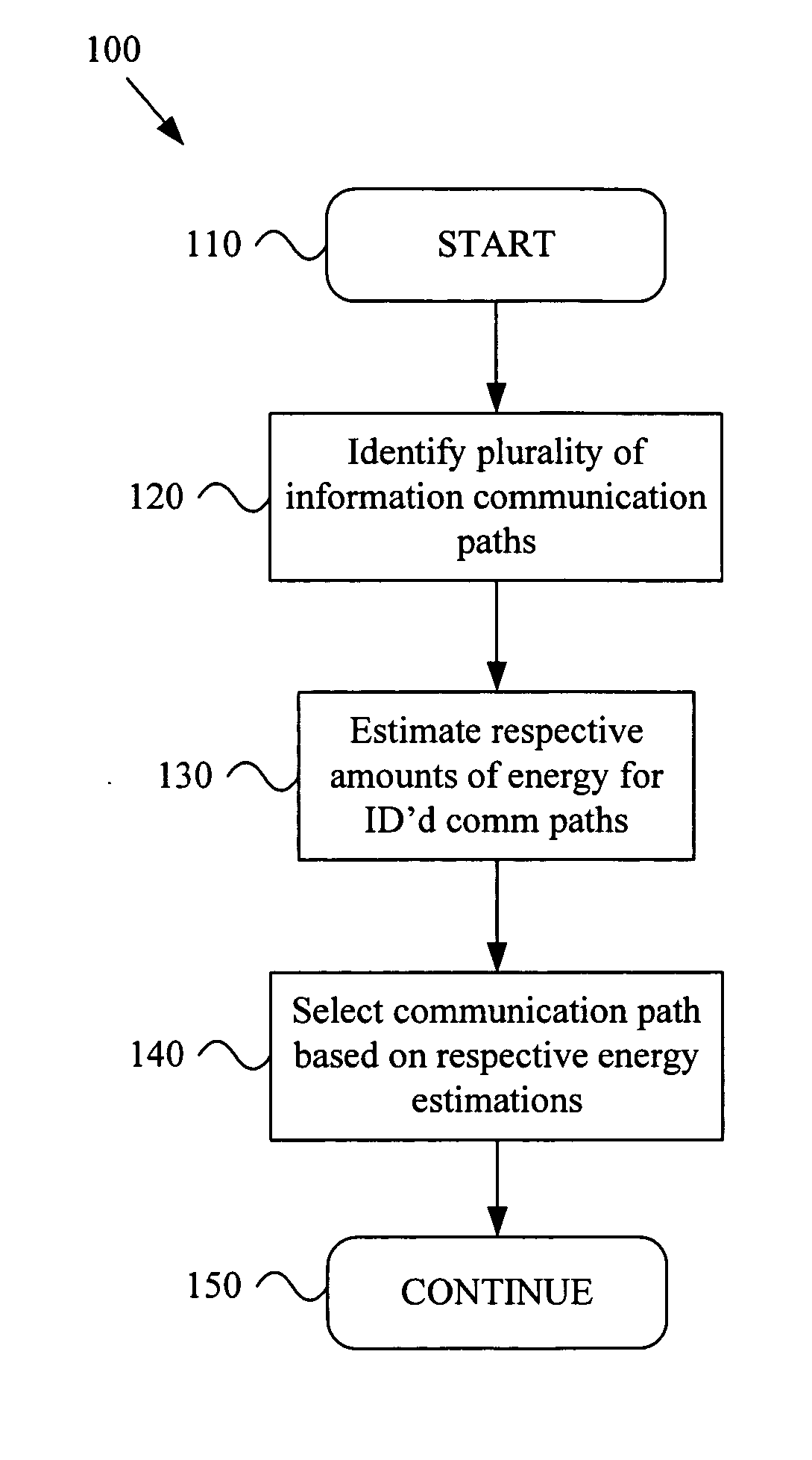
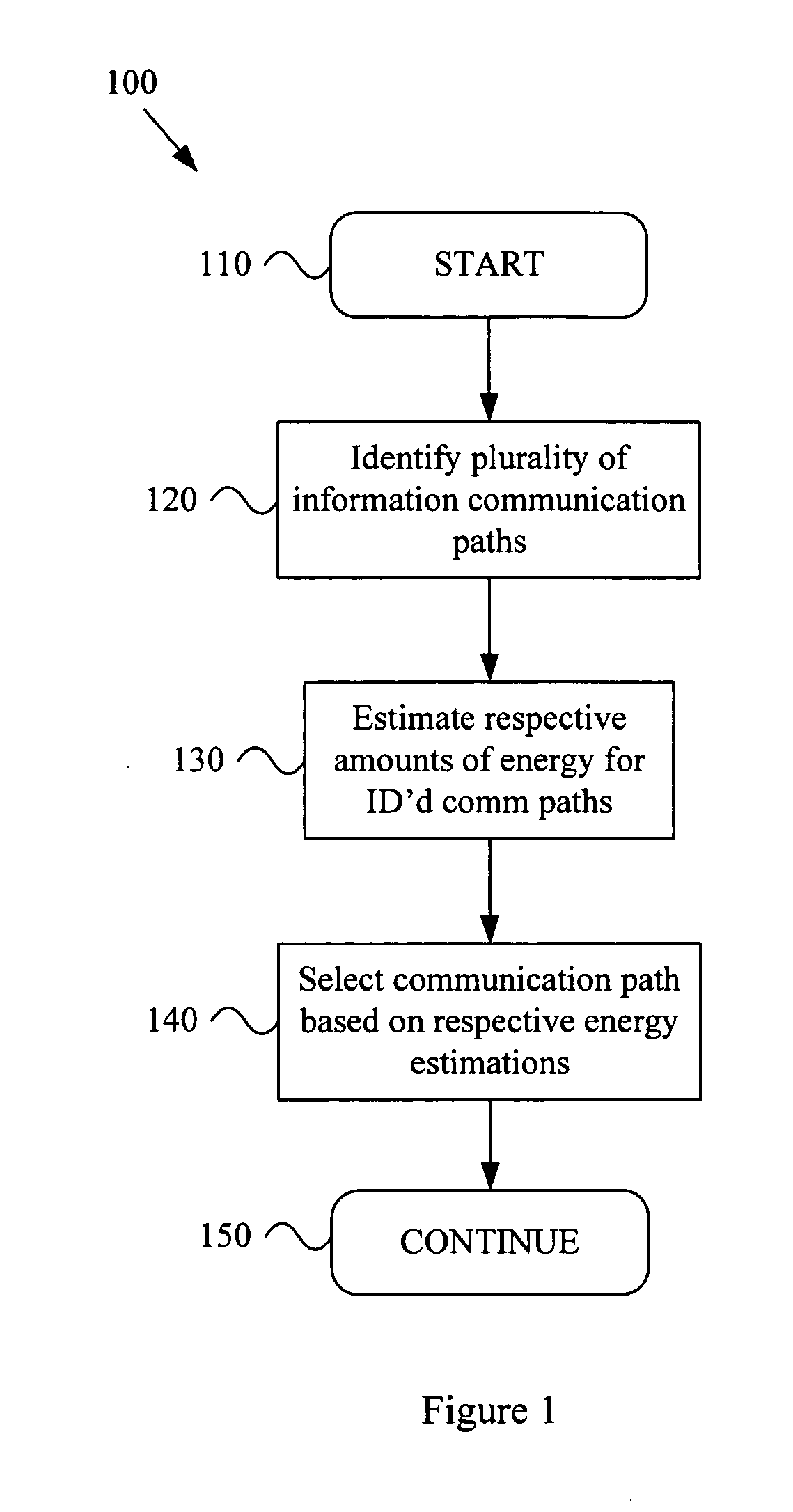
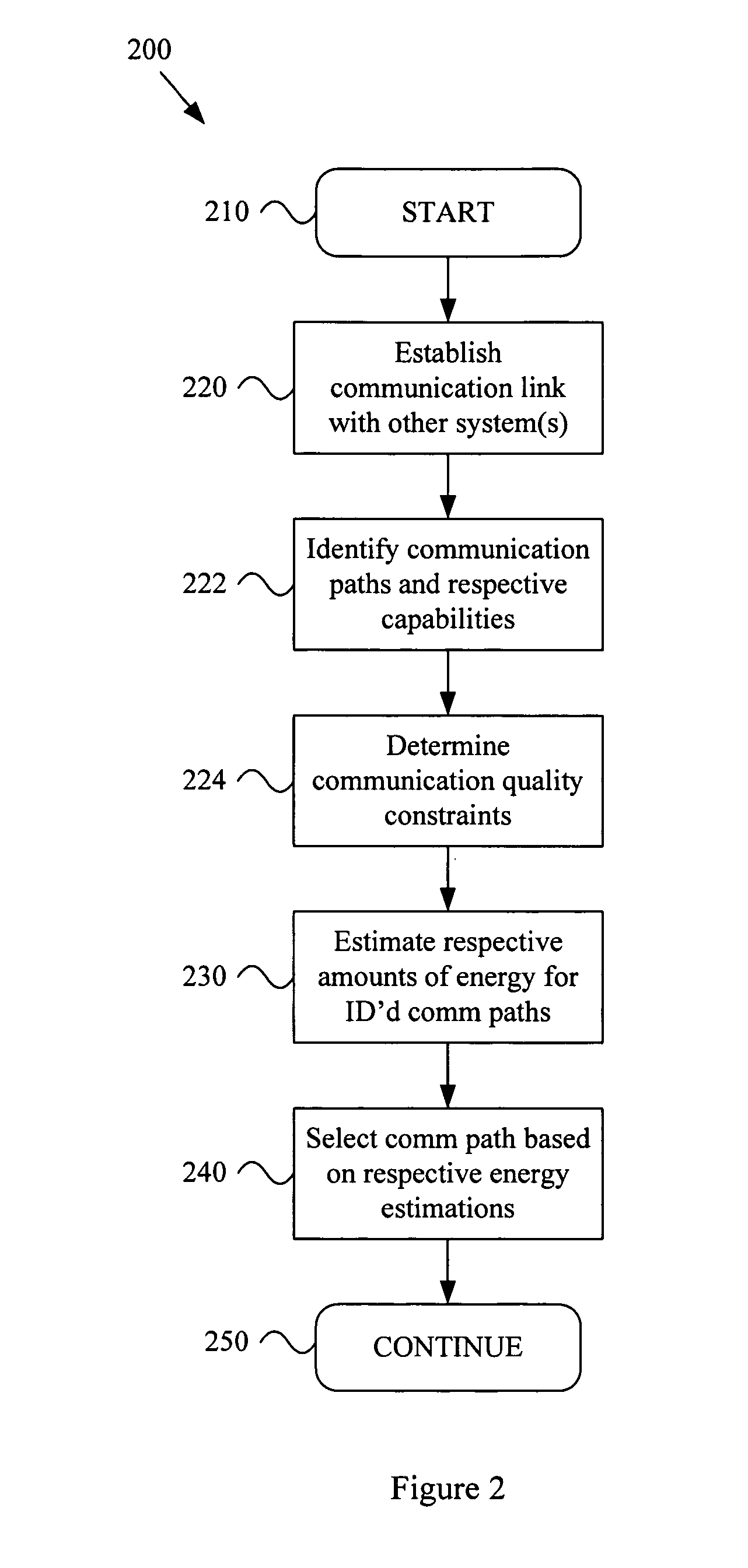
Energy based communication path selection
ActiveUS20060034252A1Energy efficient ICTData switching by path configurationEnergy basedEnergy estimation
A system and method for determining an information communication path based on energy requirements. Various aspects of the present invention provide a method that comprises identifying a plurality of information communication paths that may be utilized to communicate information (e.g., one or more units of information). A communication path identification module may perform such identification. Respective amounts of energy to communicate the information may be estimated for at least a portion of the identified plurality of information communication paths. A communication energy estimation module may perform such estimation. An information communication path may be selected from the identified plurality of information communication paths based, at least in part, on the estimated respective amounts of energy. A communication path selection module may perform such selection.
Owner:AVAGO TECH INT SALES PTE LTD
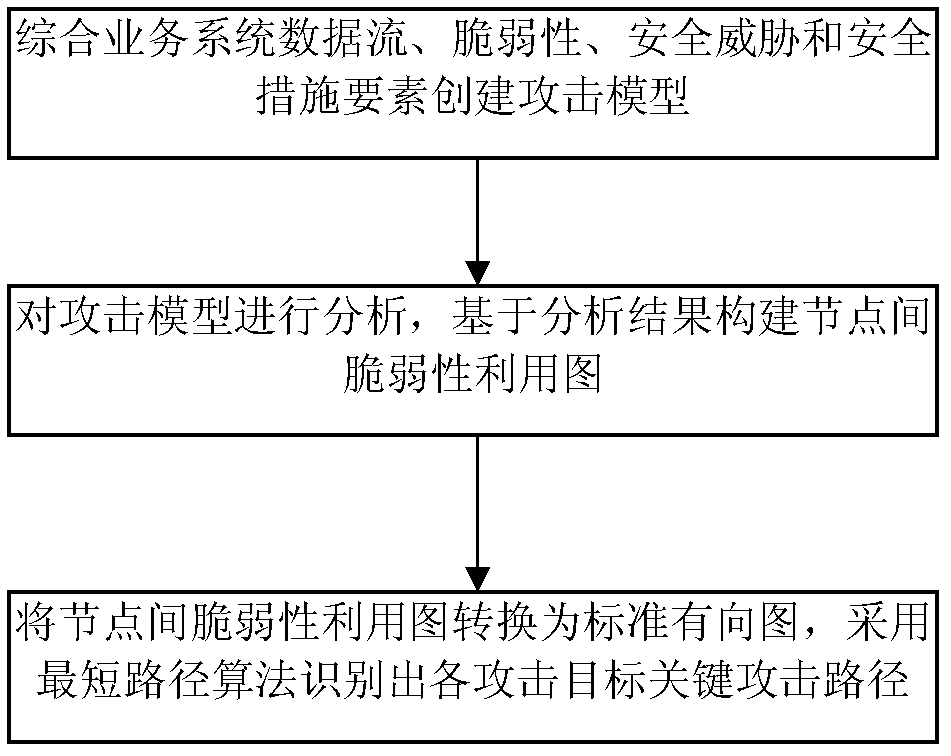
Method for identifying key attack path in service system
InactiveCN102447695AAchieving Unified ModelingAttack graph simplificationTransmissionComputation complexityDirected graph
The invention discloses a method for identifying the key attack path in a service system and belongs to the technical field of network information safety. The method comprising the steps as follows: 1, synthesizing data stream of the service system, vulnerability of the system, security threat, security measures and other factors to establish an attack model of the service system; 2, analyzing the established attack model and building a vulnerability exploitation map comprising all attack paths based on the model analysis result; and 3, converting the vulnerability exploitation map into a standard directed graph and analyzing the standard directed graph through a shortest path method to identify the key attack path that an attacker can reach all targets. The method has the advantages that the expandability is better than that of a traditional attack map, and the computation complexity of identification of the key attack path can be reduced effectively.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Multi-functional pass card of expressway and application method in route recognition system
InactiveCN101013511ANo need to increase construction costsLow investment costTicket-issuing apparatusSensing record carriersRF modulePath recognition
The invention involves highway-use integrated access card based on wireless RF and data integration, also involves its application method in the highway path identification system. The highway-use card contains RF module and IC chips. The signal receiver of RF module connects to the receiving antenna through matching circuit, in addition, contains microprocessors, the digital signal output interface of RF module connects to the data input interface of the microprocessor. The communication port of microprocessor includes dual-interface mifare 1 card, and dual-interface mifare desfire and dual-interface mifare pro card which connects to the corresponding port in IC card. The invention integrates the radio frequency identification technology, IC card (IC) and the data fusion technology to reasonably solve various defects in the existing technologies without the need to increase construction costs, which can greatly reduce the cost of the investment system and effectively be used.
Owner:上海沣宇电子科技有限公司 +3
Systems and methods for object localization and path identification based on RFID sensing
A networked radio frequency identification system includes a plurality of radio frequency identification (RFID) tag readers, a computer in signal communication with the RFID tag readers over a network, and a software module for storage on and operable by the computer that localizes RFID tags based on information received from the RFID tag readers using a network model having endpoints and oriented links. In an additional example, at least one of the RFID tag readers includes an adjustable configuration setting selected from RF signal strength, antenna gain, antenna polarization, and antenna orientation. In a further aspect, the system localizes RFID tags based on hierarchical threshold limit calculations. In an additional aspect, the system controls a locking device associated with an access point based on localization of an authorized RFID tag at the access point and reception of additional authorizing information from an input device.
Owner:LUCOMM TECH
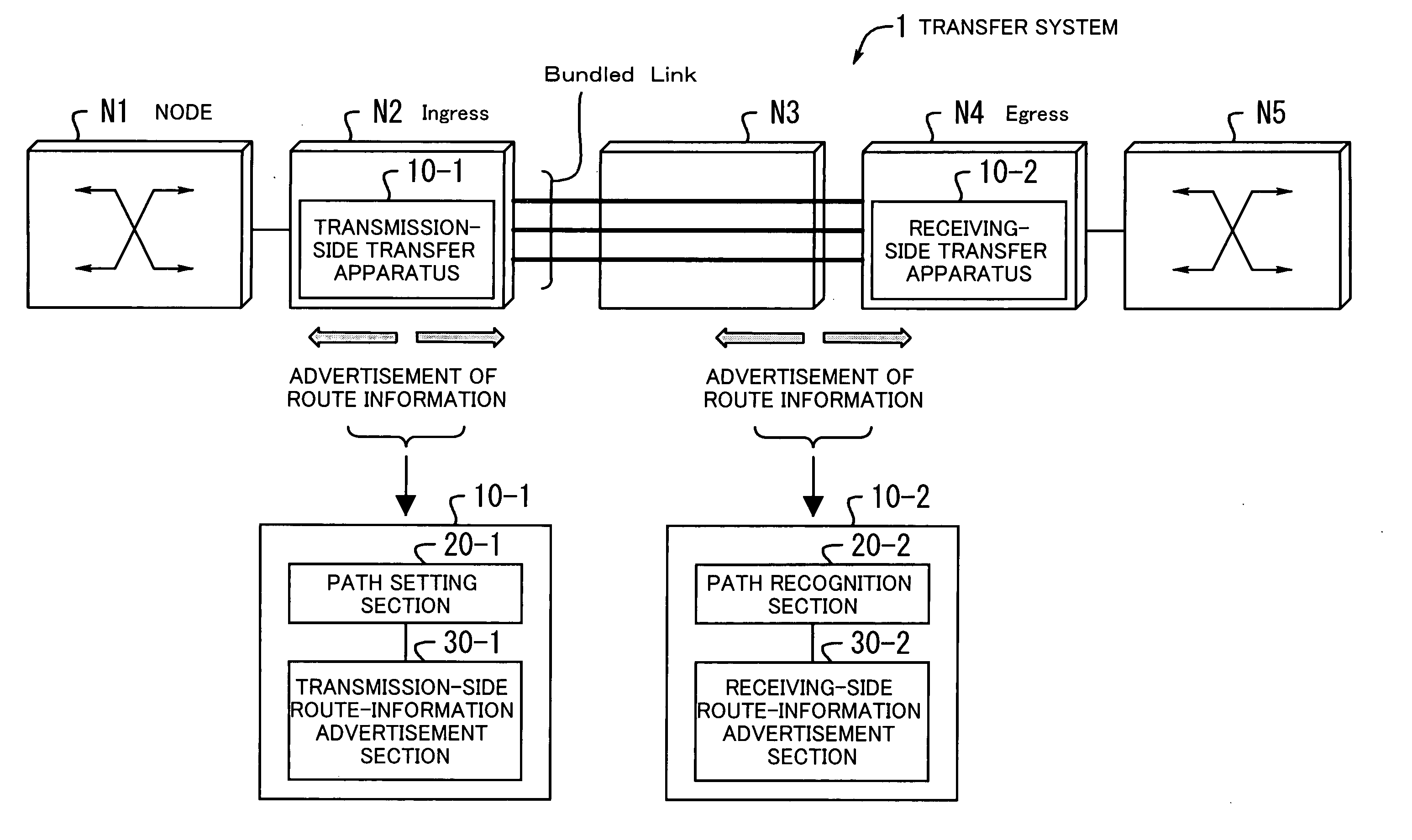
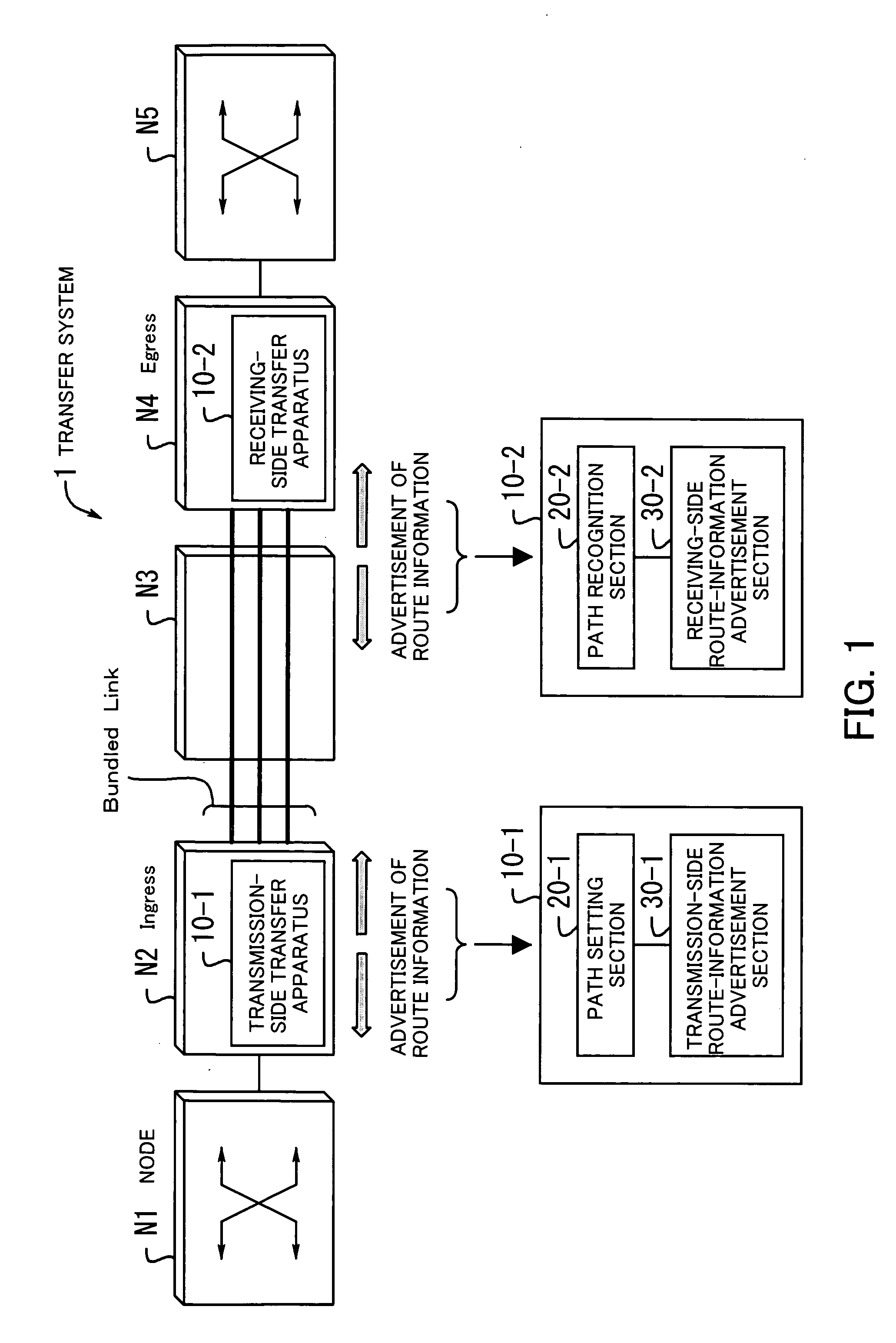
Transfer system
InactiveUS20050180431A1Improve transfer qualityReduce the amount requiredMultiplex system selection arrangementsTime-division multiplexTransfer systemPath recognition
A transfer system for bundle transfer, in which the amount of route information and the number of times advertisement is performed are reduced, and maintenance and management are made to be highly efficient to implement improved transfer quality. A path setting section specifies a path between nodes for a receiving side as a bundled link which can have a plurality of paths tied up. A transmission-side route-information advertisement section advertises route information in a network when recognizing that the path has been established. A path recognition section recognizes the path and sets the path as a bundled link. A receiving-side route-information advertisement section advertises the route information in the network when recognizing that the path has been established.
Owner:FUJITSU LTD
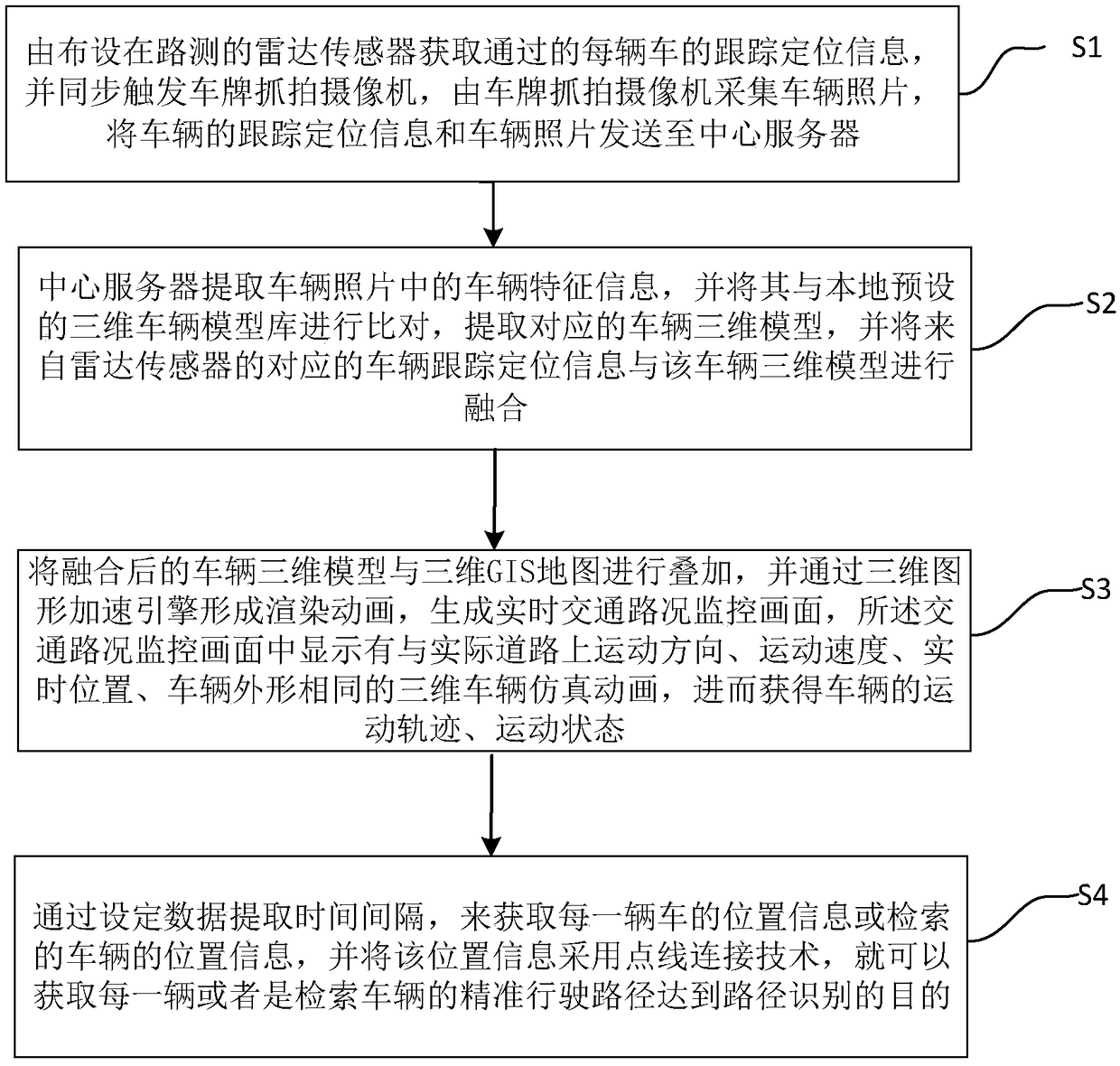
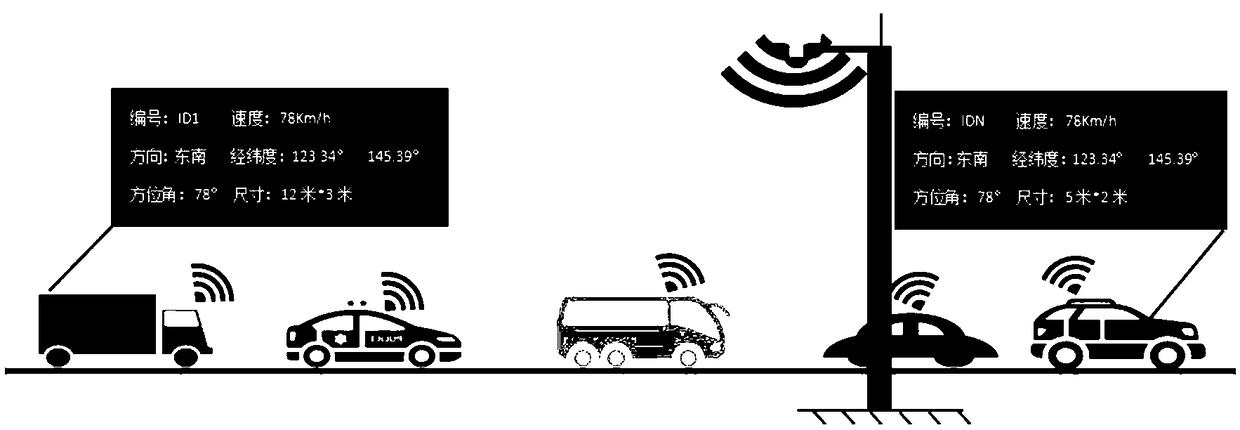
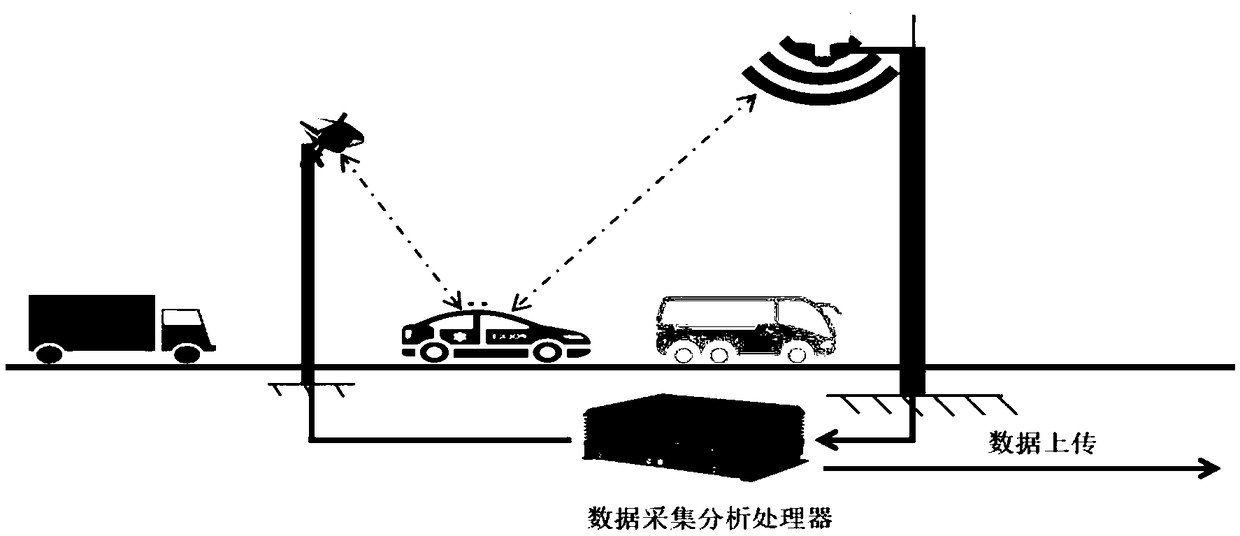
Path recognition method based on four-dimensional live-action traffic simulation road condition awareness management system
ActiveCN109064755AIncrease contentRoad vehicles traffic controlCharacter and pattern recognitionLive actionRadar
The invention provides a path recognition method based on a four-dimensional live-action traffic simulation road condition awareness management system. The path recognition method comprises the stepsthat a radar sensor arranged on the road side acquires tracking and positioning information of each passing vehicle and synchronously triggers a vehicle license plate snapping camera, and the vehiclelicense plate snapping camera acquires vehicle photos and sends the tracking and positioning information and the vehicle photos of the vehicles to a center server; vehicle feature information in the vehicle photos is extracted and compared with a local preset three-dimensional vehicle model library, fuzzy matching is conducted to extract corresponding three-dimensional vehicle models, and the vehicle tracking and positioning information is fused with the three-dimensional vehicle models; and the three-dimensional vehicle models obtained after fusion are superimposed with a three-dimensional GIS maps to achieve four-dimensional live-action road condition simulation, position information of the vehicles at different time nodes is acquired by setting a time interval, precise vehicle path information that a user wants to know can be acquired by adopting a point-line connection technology, and then the purpose of precise vehicle path recognition is achieved.
Owner:河北德冠隆电子科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com