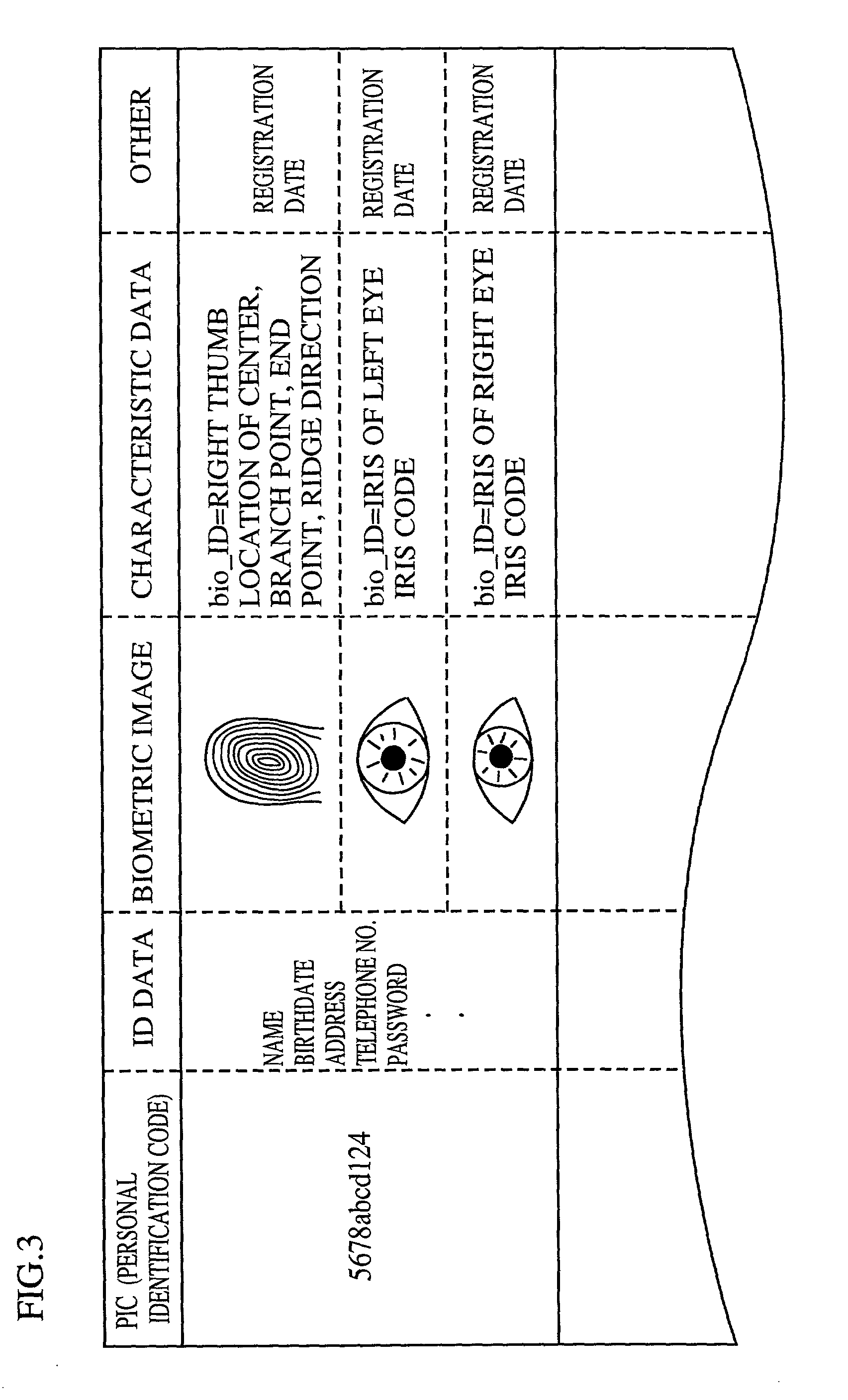
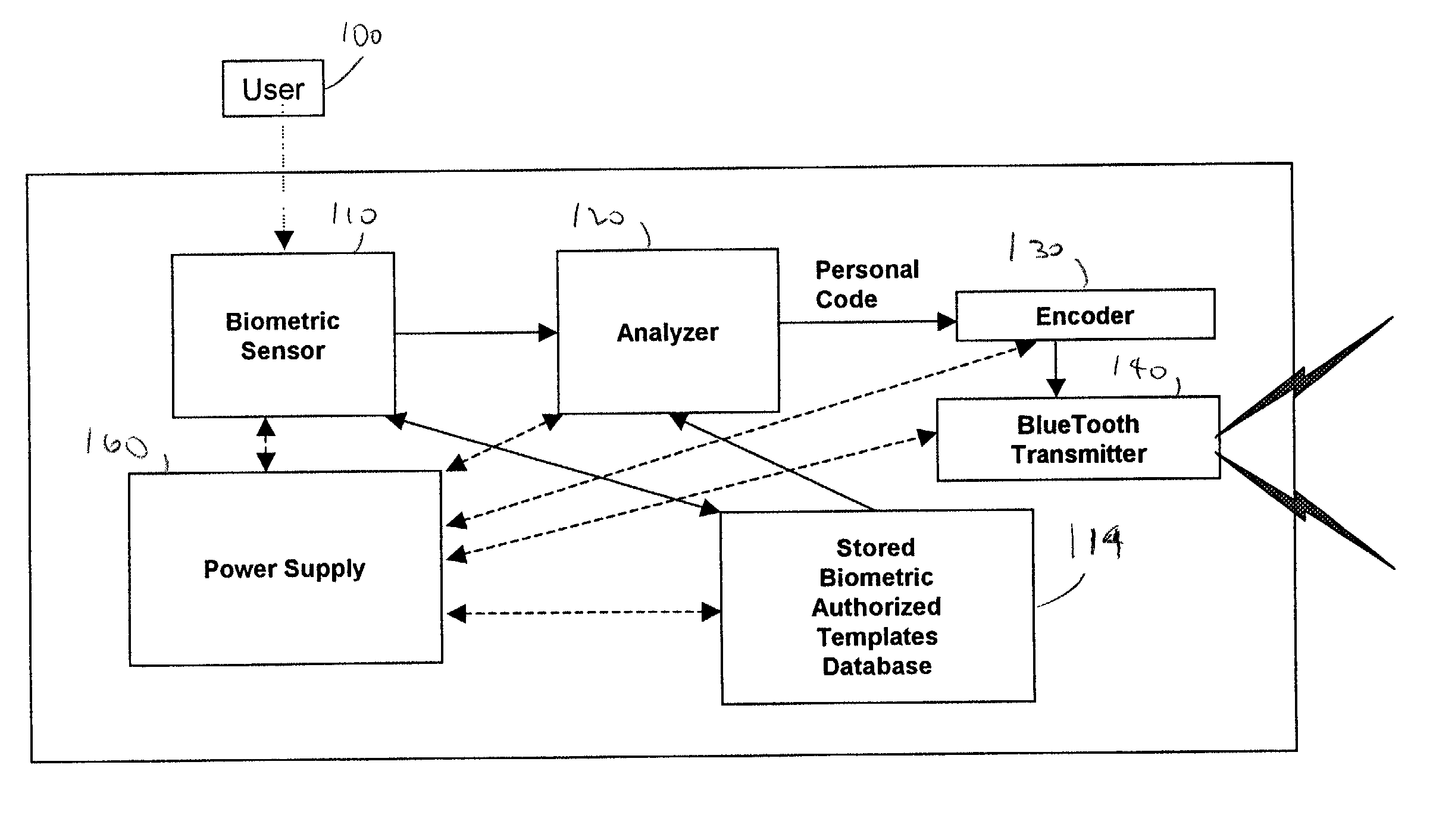
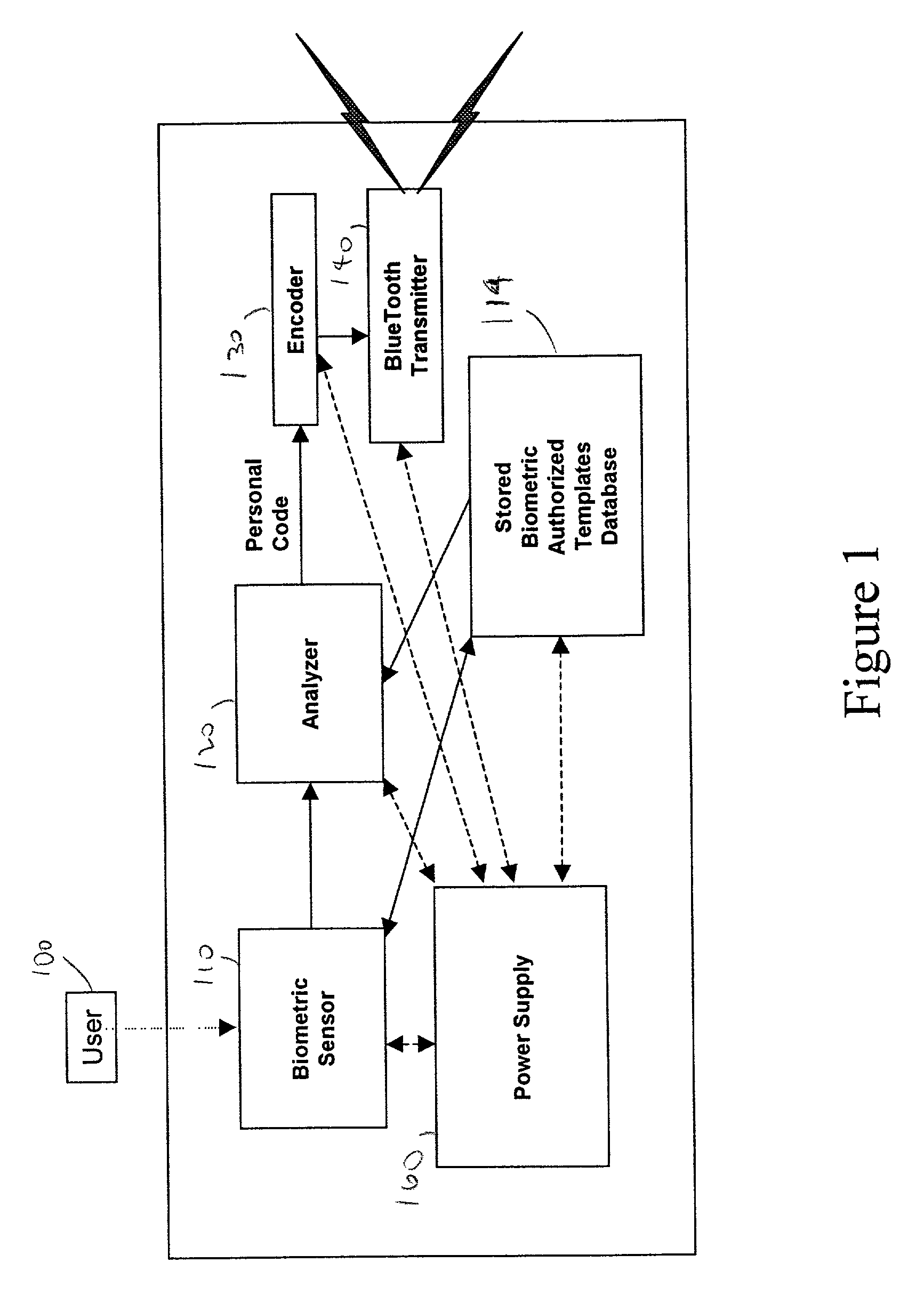
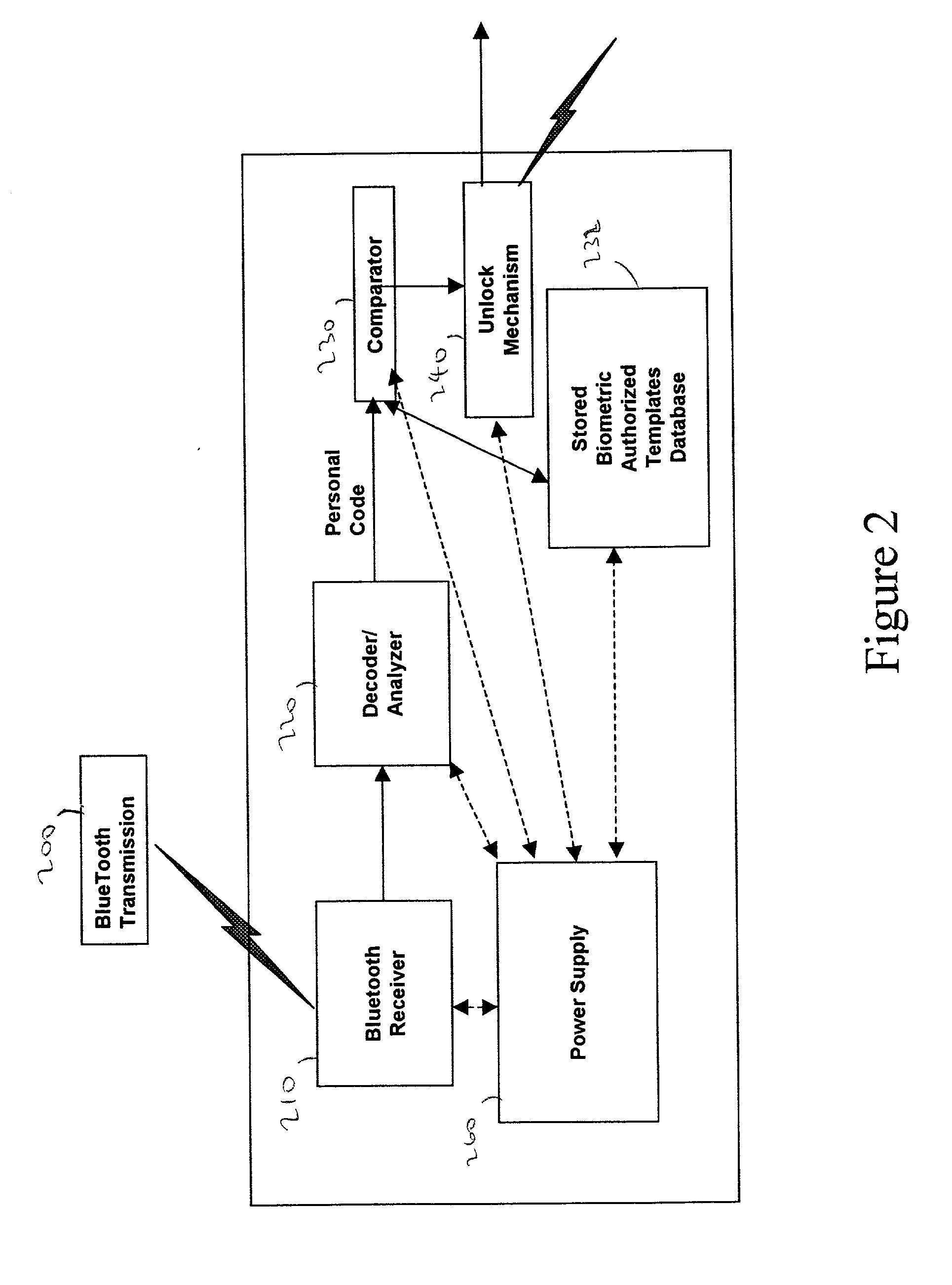
Patents
Literature
38557results about "Individual entry/exit registers" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Realtime, location-based cell phone enhancements, uses, and applications
ActiveUS20070032225A1Use minimizedMaximizing its battery powerMechanical apparatusLighting and heating apparatusMethod selectionComputer science
Enhancements of and to cell phone operations are based in whole or in part on determining the location of the cell phone. Systems and methods select and determine locations or areas of importance or relevance, and based on that information and other programmed factors affect or alter the operations of the cell phone. While the systems and methods are illustrated by use of cell phone embodiments and applications, they are equally applicable to virtually any portable or mobile communication device, including for example, wireless laptop computers and PDAs.
Owner:RESIGHT LLC
RFID reader with multiple interfaces
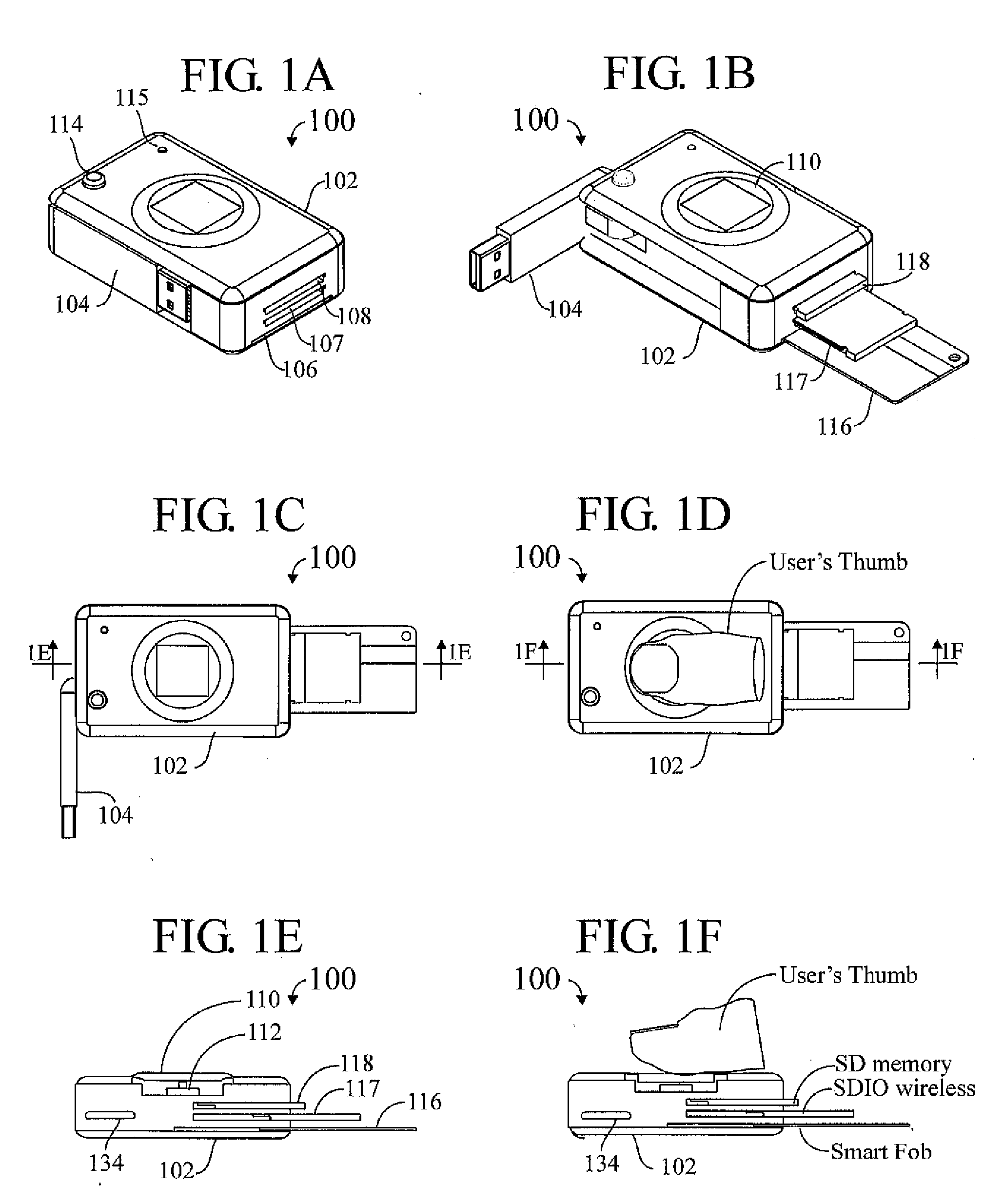
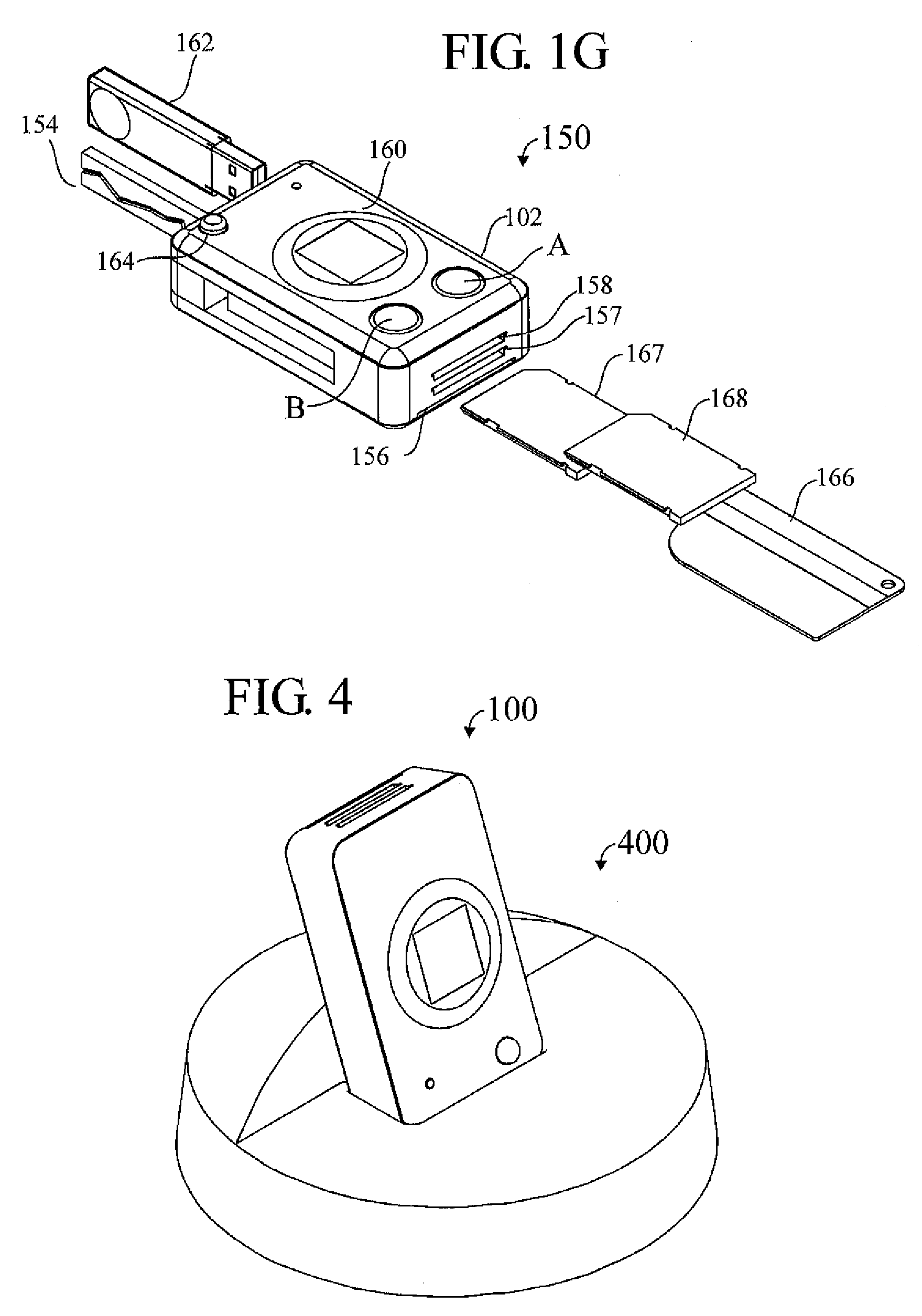
InactiveUS20060219776A1Anti-theft devicesSensing by galvanic contactsPersonalizationContactless smart card
A pocket-size RFID reader apparatus having a contactless interface and a slot for insertion of a contactless smart card fob, and having a biometric sensor, thereby providing two levels of personalization. The apparatus may have a wireless interface; and a slot for insertion of a wireless SD I / O device. The apparatus may have a slot for insertion of an external memory device. The apparatus may have a mechanical connection (contact) interface. The apparatus may also have an RF interface for reading an electronic immobilizer within the apparatus.
Owner:DPD PATENT TRUST
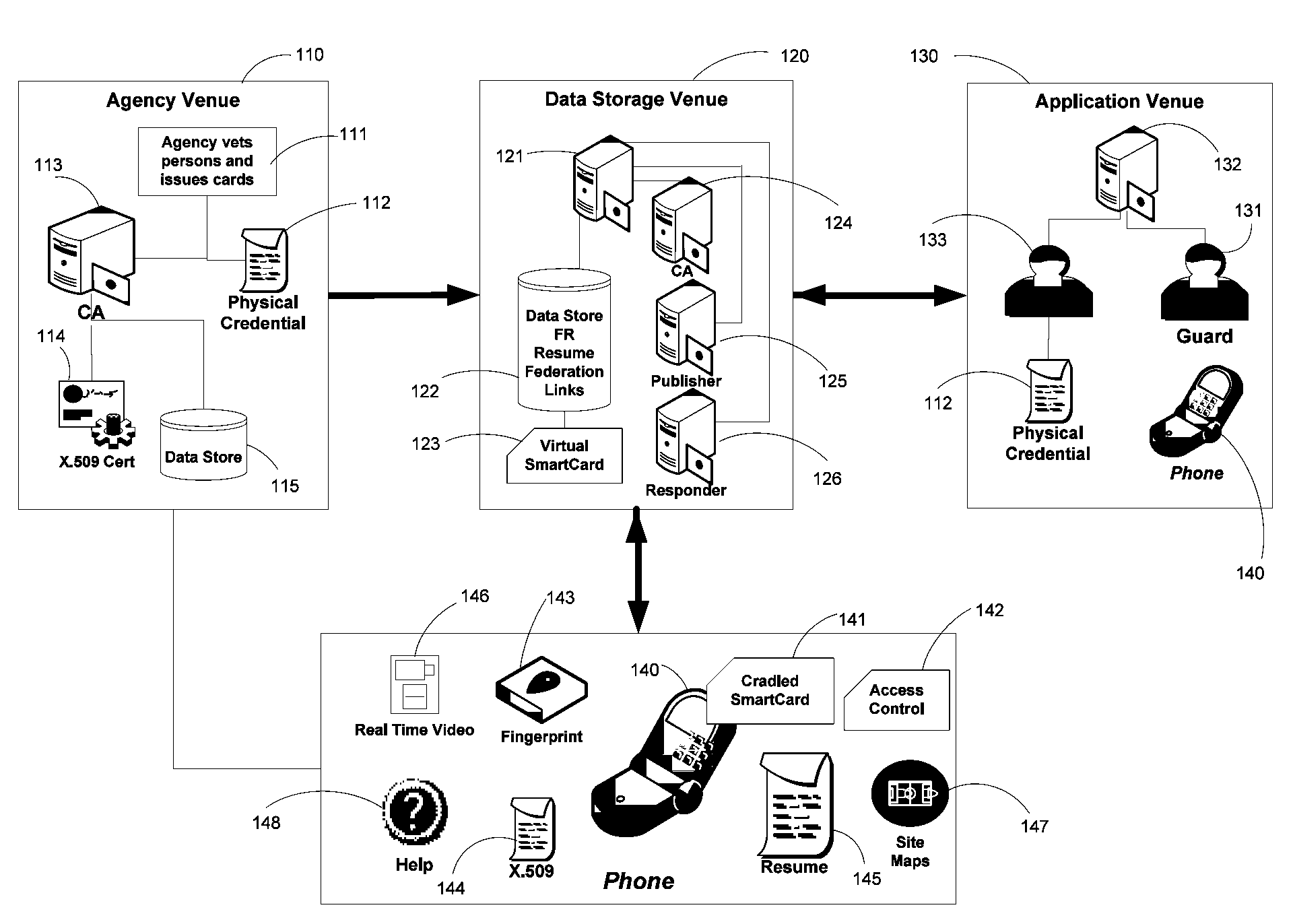
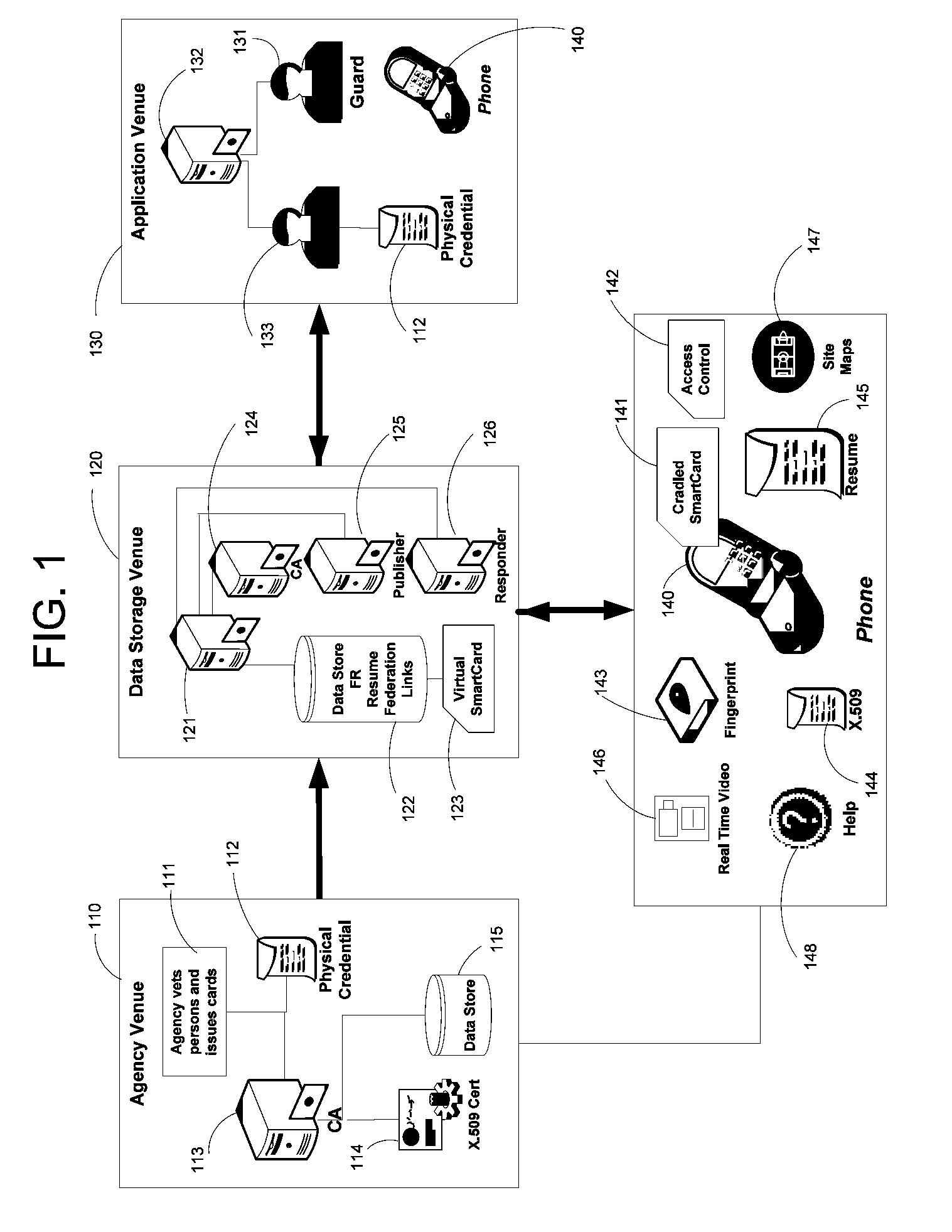
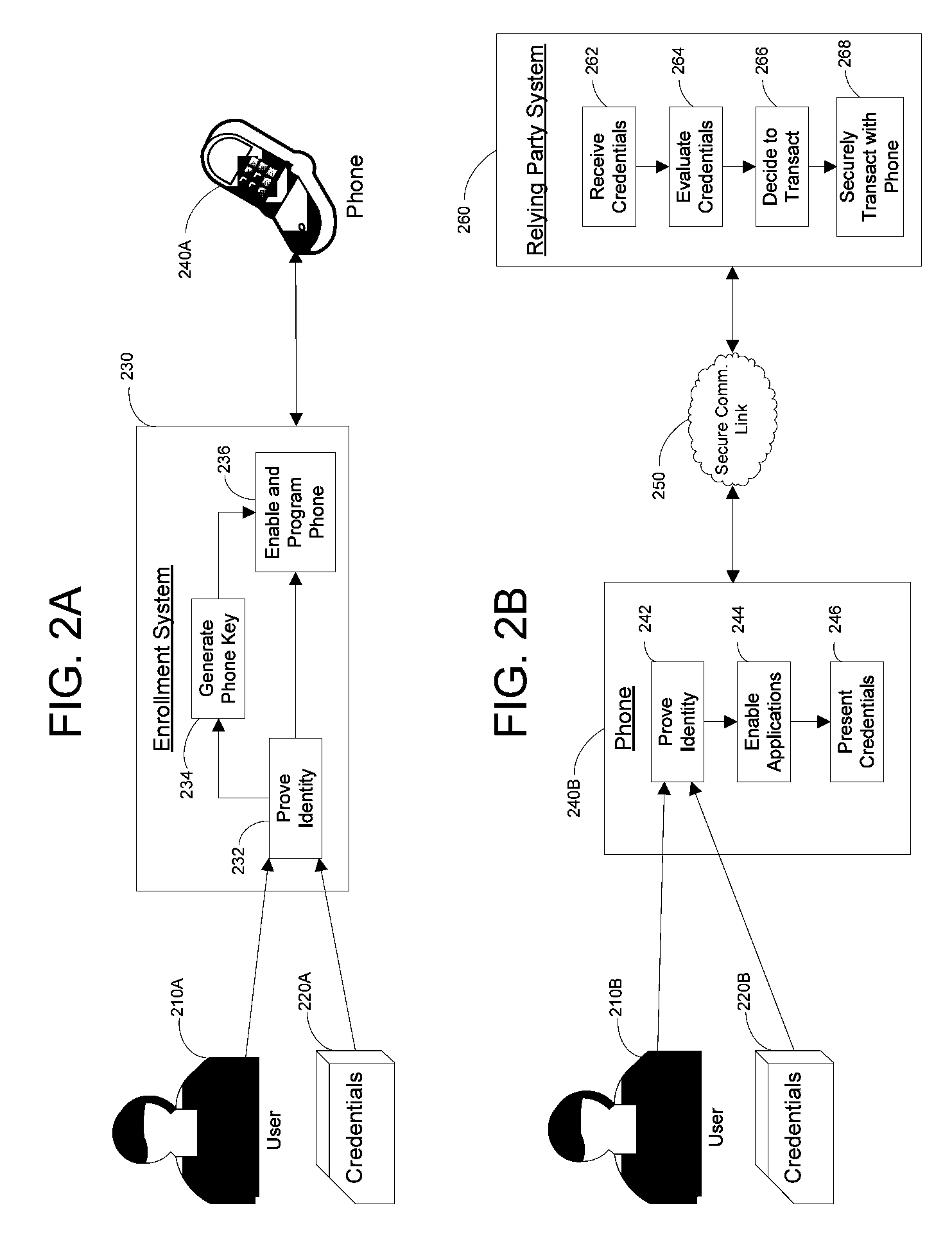
Apparatus and Methods for Providing Scalable, Dynamic, Individualized Credential Services Using Mobile Telephones
InactiveUS20090132813A1Save bandwidthSaving response timeDigital data processing detailsUser identity/authority verificationElectronic systemsFinancial transaction
Apparatus and methods perform transactions in a secure environment between an individual and another party, such as a merchant, in various embodiments. The individual possesses a mobile electronic device, such as a smartphone, that can encrypt data according to a public key infrastructure. The individual authenticates the individual's identity to the device, thereby unlocking credentials that may be used in a secure transaction. The individual causes the device to communicate the credentials, in a secure fashion, to an electronic system of a relying party, in order to obtain the relying party's authorization to enter the transaction. The relying party system determines whether to grant the authorization, and communicates the grant and the outcome of the transaction to the device using encryption according to the public key infrastructure.
Owner:SURIDX
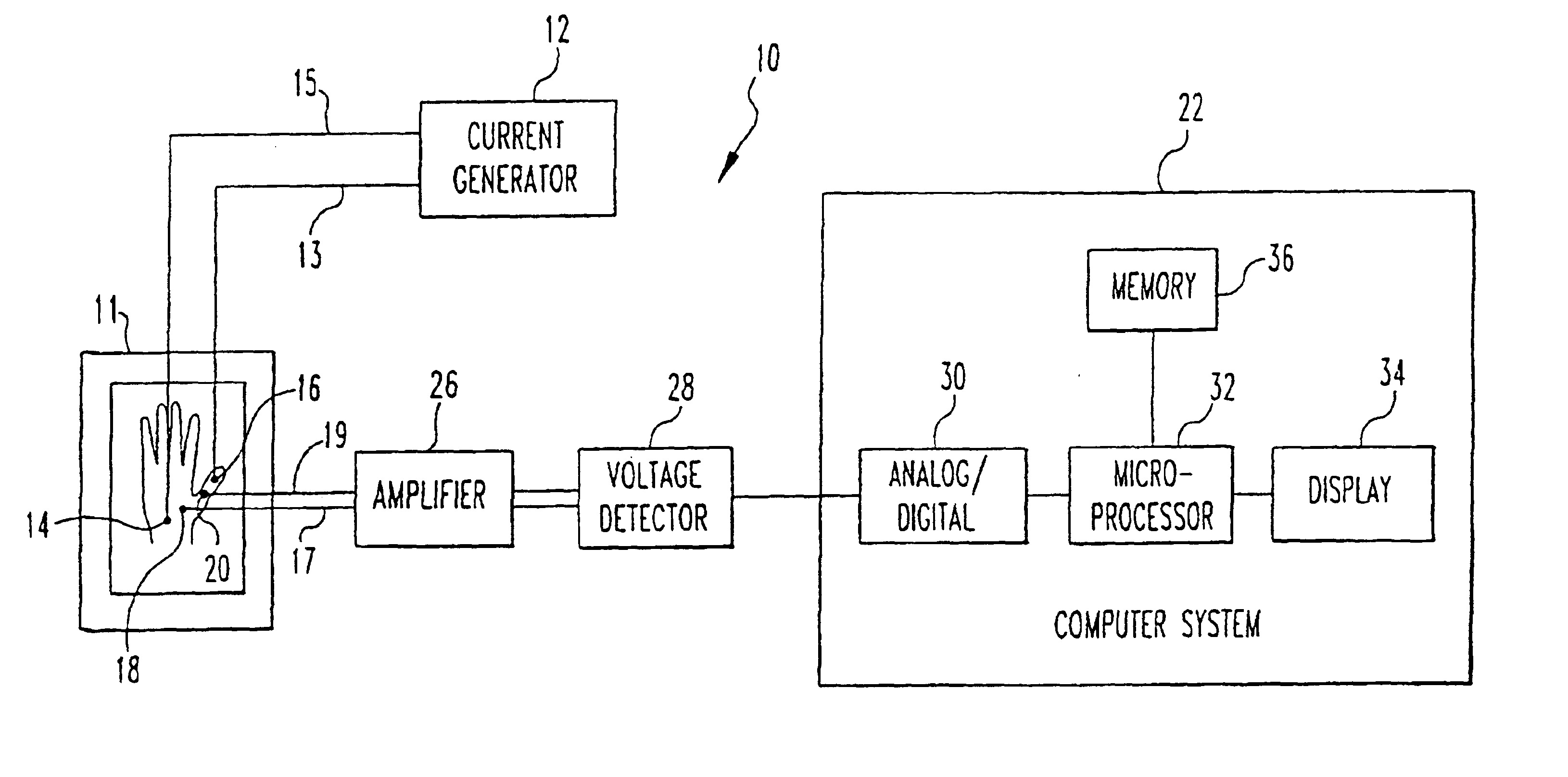
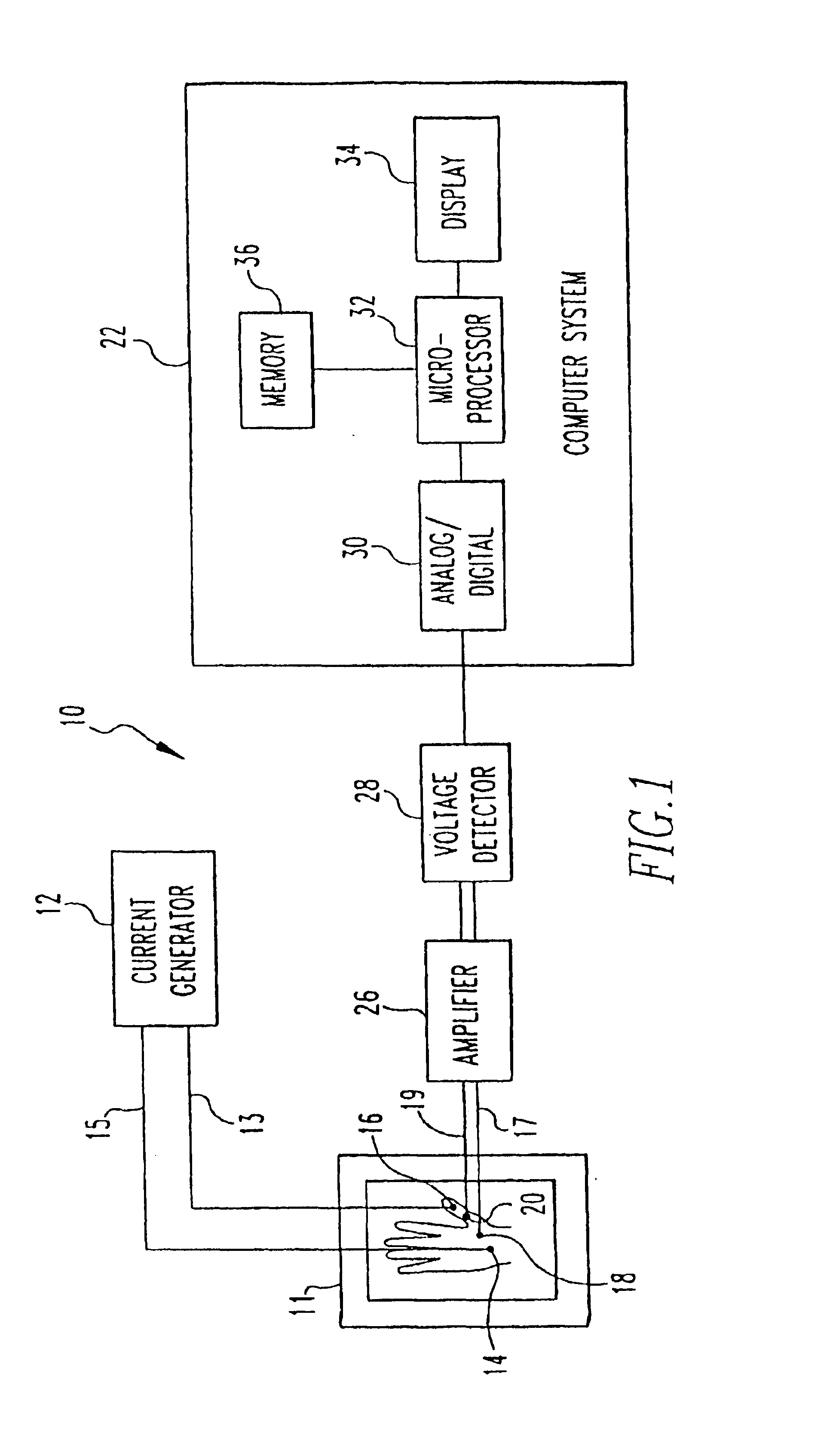
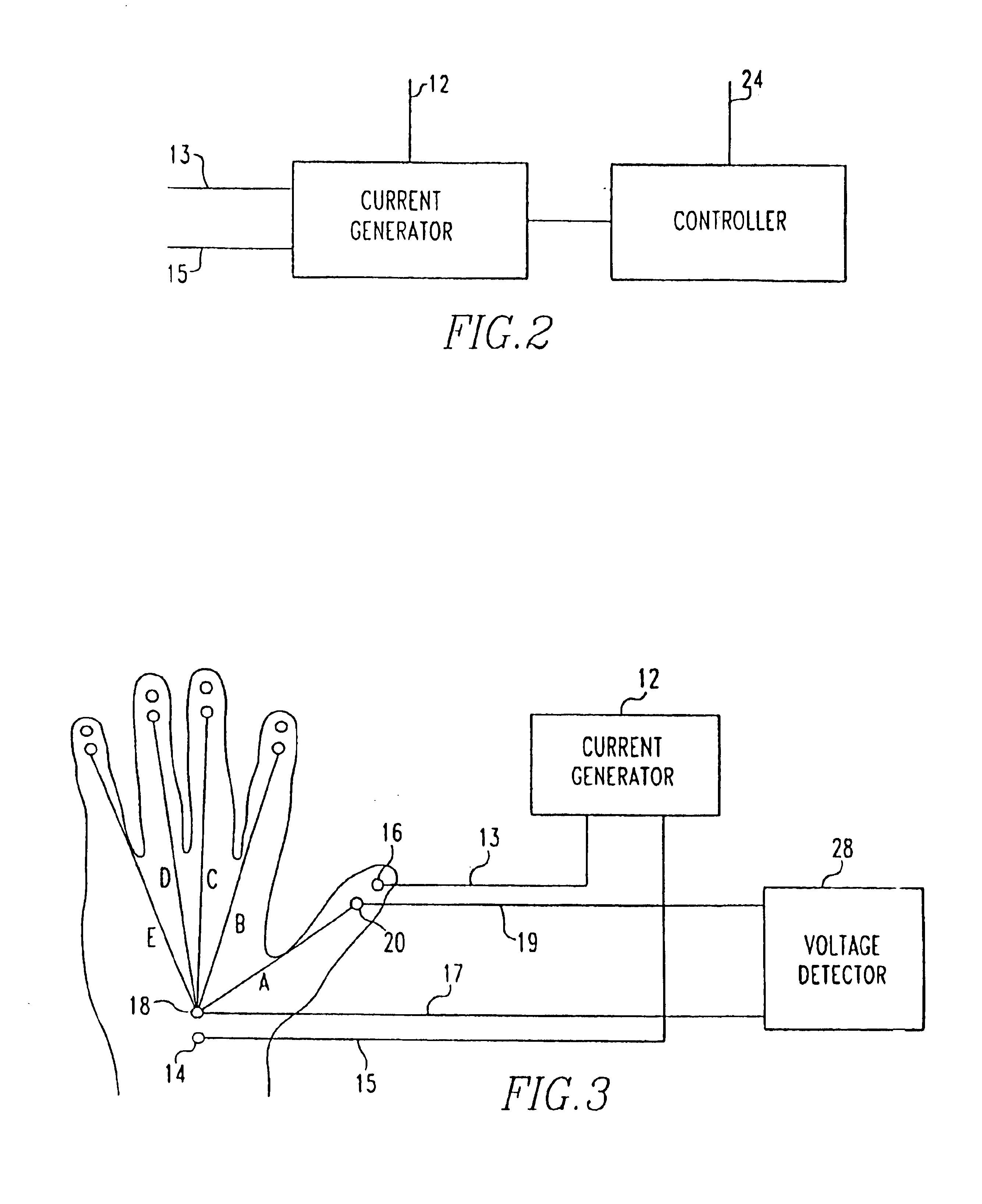
Method and system for biometric recognition based on electric and/or magnetic characteristics
InactiveUS6898299B1Electric signal transmission systemsDigital data processing detailsElectricityBiological body
A method and apparatus for authenticating an individual living organism by recognizing a unique internal electric and / or magnetic and / or acoustic characteristic, which comprises a biometric signature, involve presenting a body part to a sensing device that senses the signature. The sensed presented biometric signature is compared to a known biometric signature to authenticate the individual. This authentication can then be used to authorize any of a wide variety of actions by the individual, such as accessing equipment or an area, or to perform actions, such as conducting financial transactions. A card having sensors is used to sense the biometric signature which is read by a card reader and sent to a local or remote reader for biometric signature comparison.
Owner:GR INTELLECTUAL RESERVE LLC
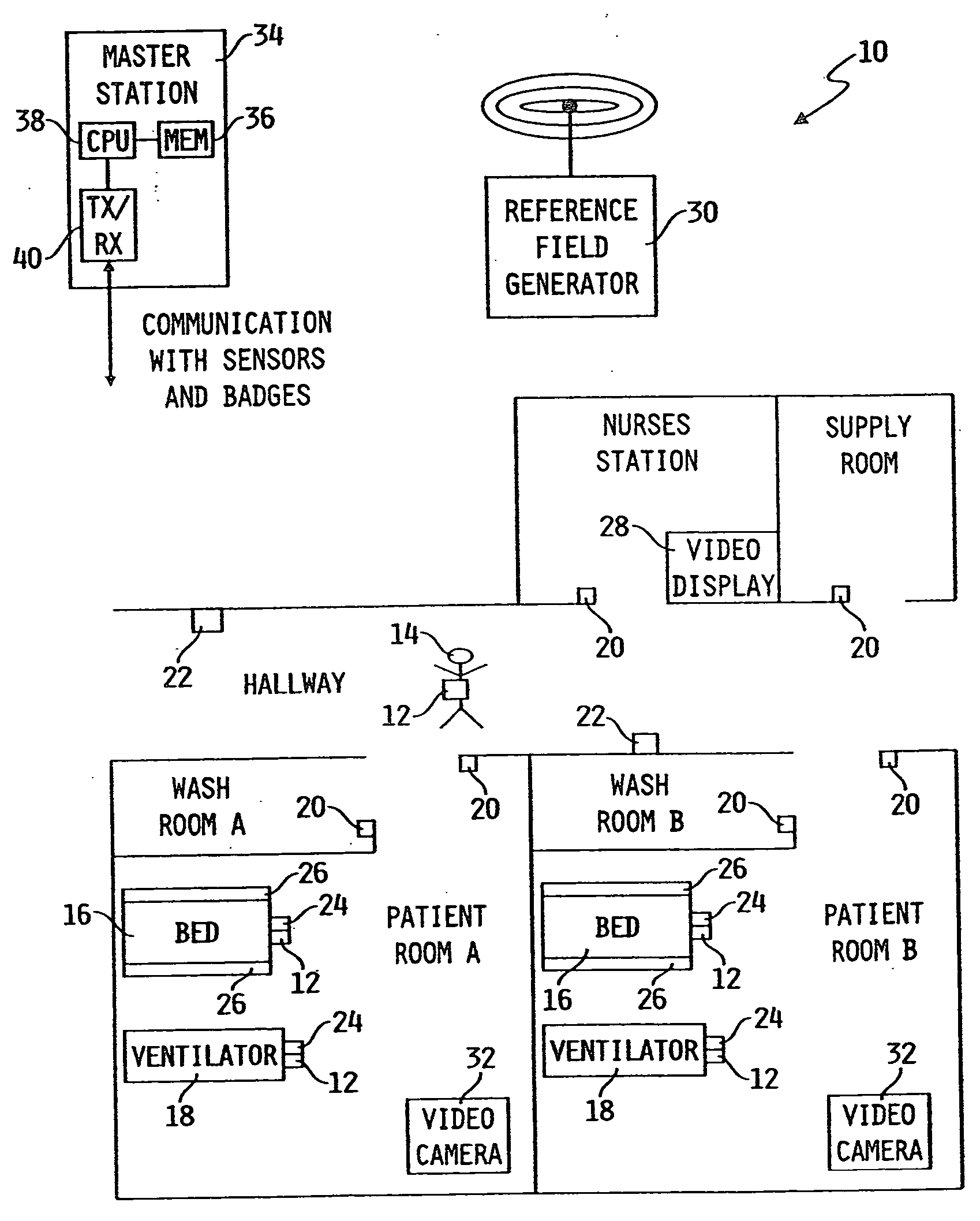
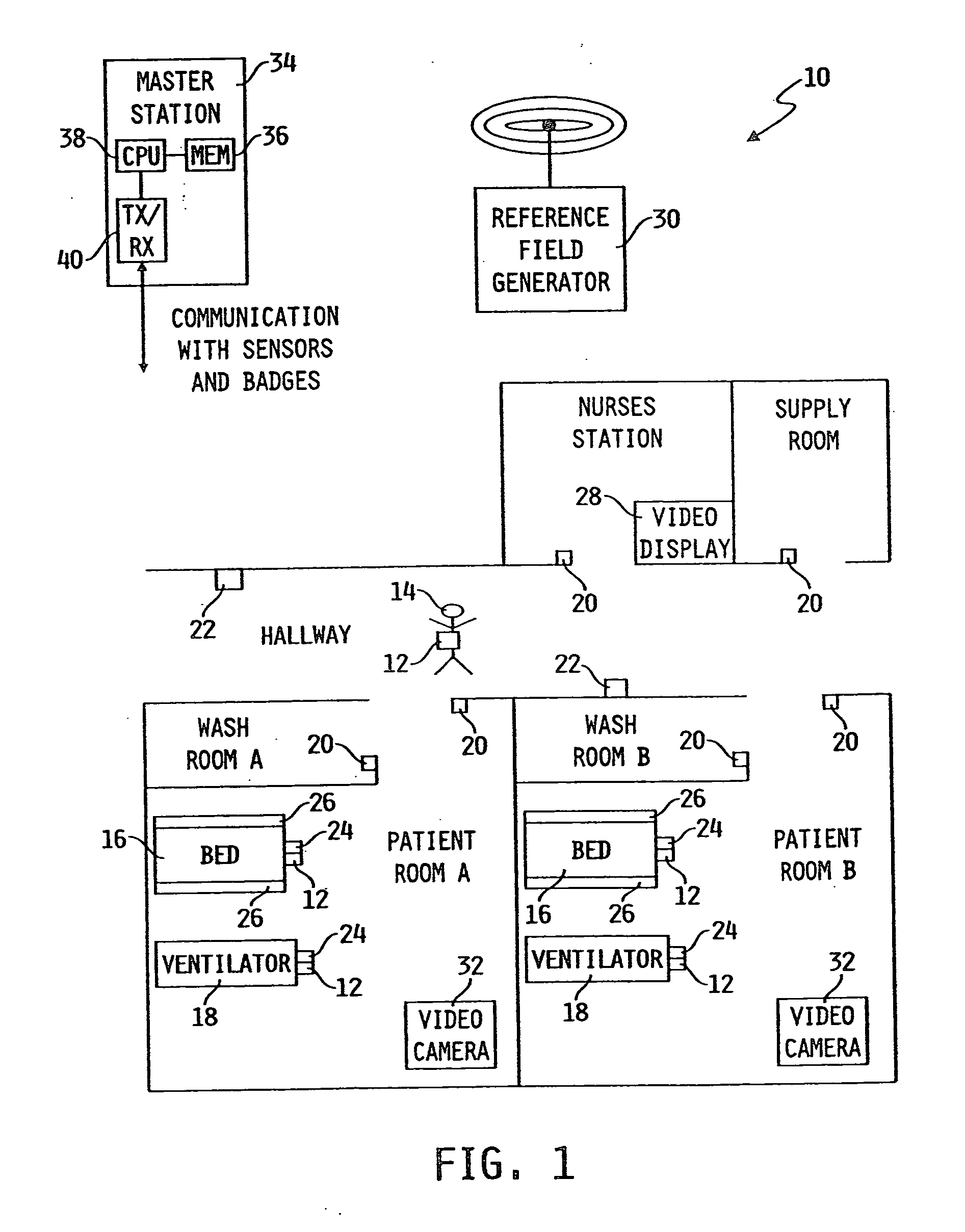
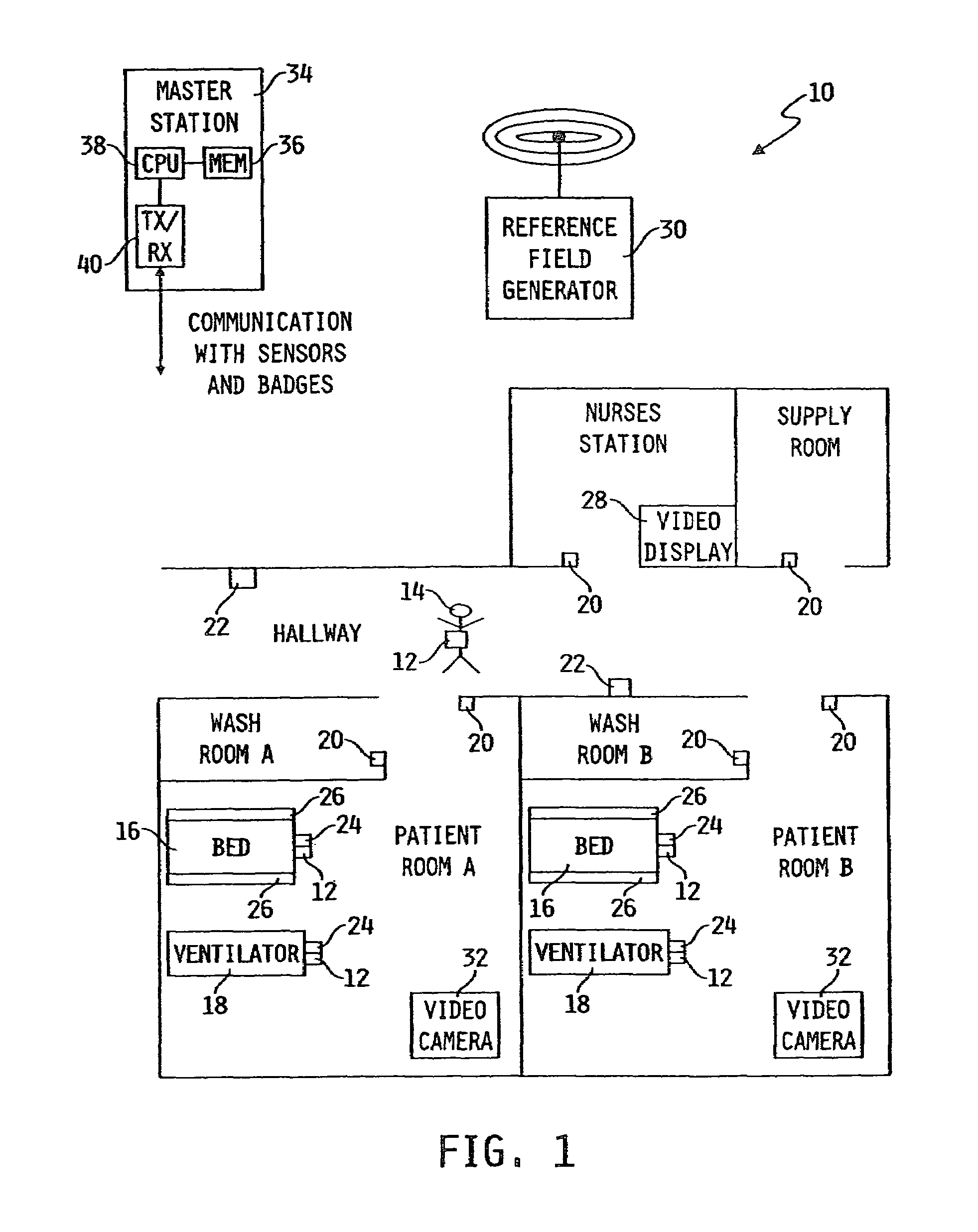
Article locating and tracking apparatus and method
InactiveUS20050035862A1High resolutionLimited rangeInertial sensorsDiagnostic recording/measuringMonitoring systemEngineering
An activity based monitoring system is disclosed, the activity based monitoring system being configured to monitor a plurality of badges associated with a plurality of assets within a healthcare facility.
Owner:HILL ROM SERVICES
Techniques for fraud monitoring and detection using application fingerprinting
ActiveUS20090089869A1Acutation objectsDigital data processing detailsMultiple contextApplication software
Techniques for fraud monitoring and detection using application fingerprinting. As used herein, an “application fingerprint” is a signature that uniquely identifies data submitted to a software application. In an embodiment, a plurality of historical application fingerprints are stored for data previously submitted to a software application. Each historical application fingerprint is associated with one or more contexts in which its corresponding data was submitted. When new (i.e., additional) data is subsequently submitted to the application, a new application fingerprint is generated based on the new data, and the new application fingerprint is associated with one or more contexts in which the new data was submitted. The new application fingerprint is then compared with one or more historical application fingerprints that share the same, or substantially similar, context(s). Based on this comparison, a risk score is generated indicating a likelihood that the new data was submitted for a fraudulent / malicious purpose.
Owner:ORACLE INT CORP
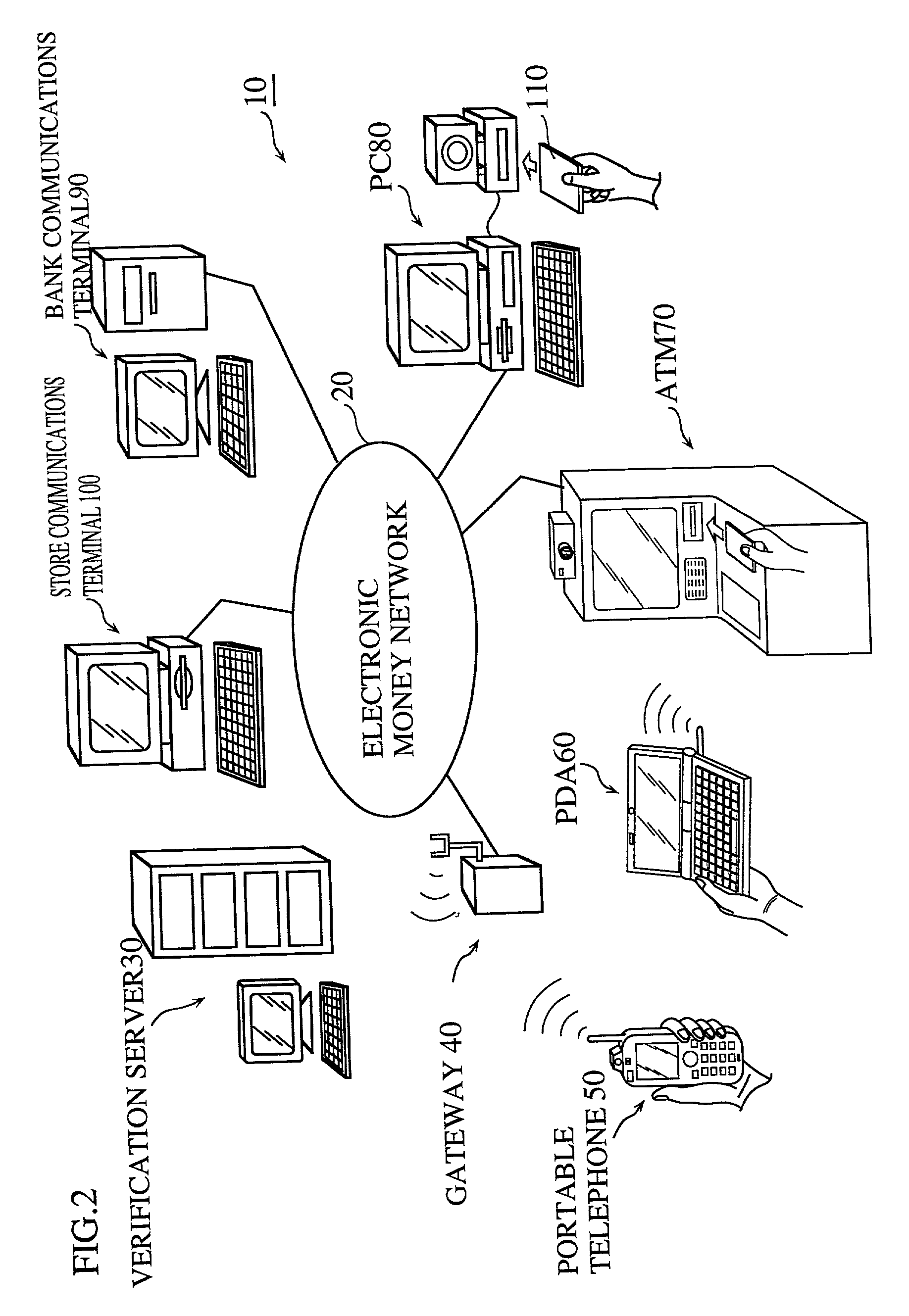
Customer-controlled instant-response anti-fraud/anti-identity theft devices (with true- personal identity verification), method and systems for secured global applications in personal/business e-banking, e-commerce, e-medical/health insurance checker, e-education/research/invention, e-disaster advisor, e-immigration, e-airport/aircraft security, e-military/e-law enforcement, with or without NFC component and system, with cellular/satellite phone/internet/multi-media functions
ActiveUS20140162598A1Prevent fraudulent multiple swipingDevices with card reading facilityUnauthorised/fraudulent call preventionChequeMessage passing
All-in-one wireless mobile telecommunication devices, methods and systems providing greater customer-control, instant-response anti-fraud / anti-identity theft protections with instant alarm, messaging and secured true-personal identity verifications for numerous registered customers / users, with biometrics and PIN security, operating with manual, touch-screen and / or voice-controlled commands, achieving secured rapid personal / business e-banking, e-commerce, accurate transactional monetary control and management, having interactive audio-visual alarm / reminder preventing fraudulent usage of legitimate physical and / or virtual credit / debit cards, with cheques anti-forgery means, curtailing medical / health / insurance frauds / identity thefts, having integrated cellular and / or satellite telephonic / internet and multi-media means, equipped with language translations, GPS navigation with transactions tagging, currency converters, with or without NFC components, minimizing potential airport risks / mishaps, providing instant aid against school bullying, kidnapping, car-napping and other crimes, applicable for secured military / immigration / law enforcements, providing guided warning / rescue during emergencies and disasters.
Owner:VILLA REAL ANTONY EUCLID C
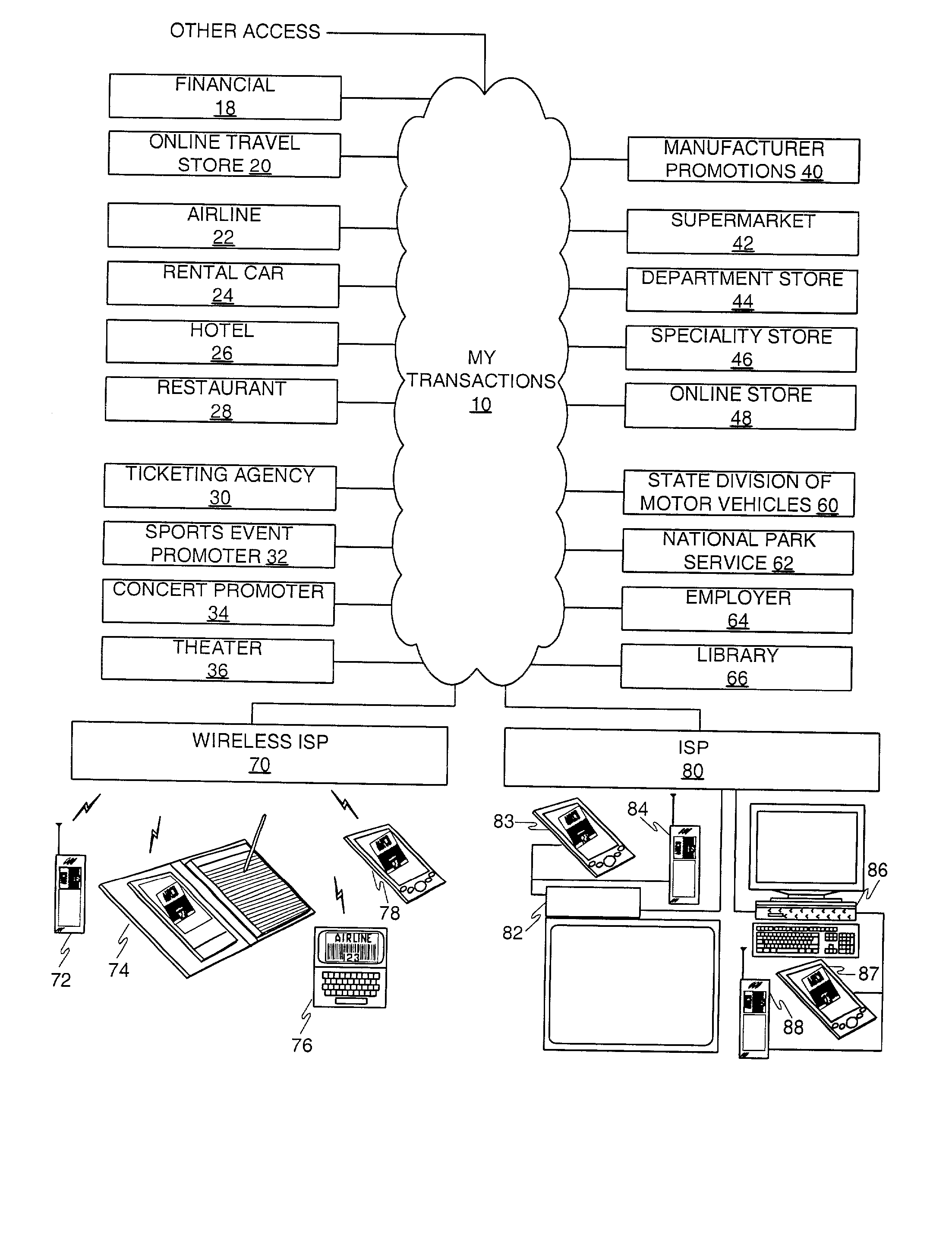
Method and apparatus for acquiring, maintaining, and using information to be communicated in bar code form with a mobile communications device
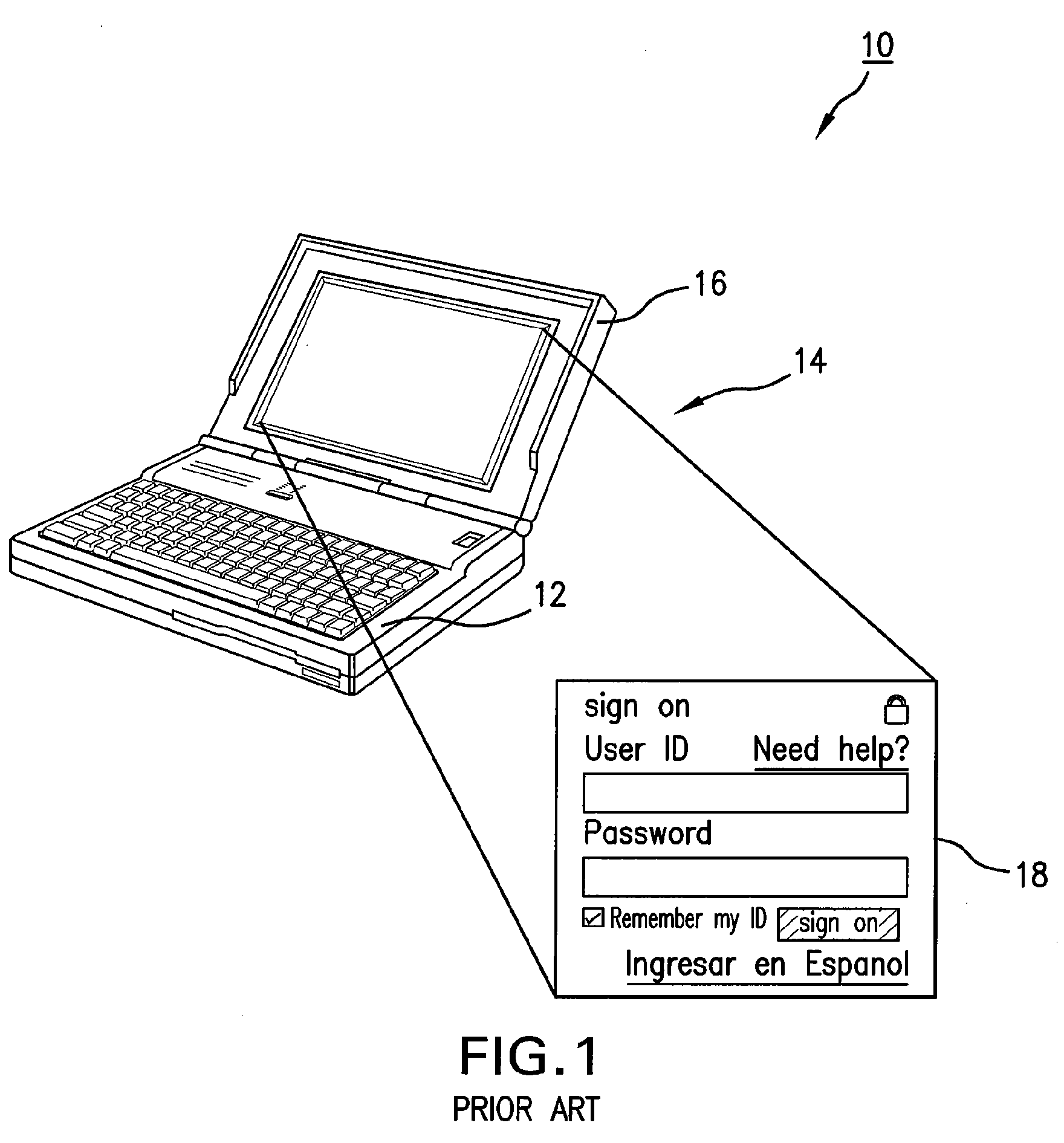
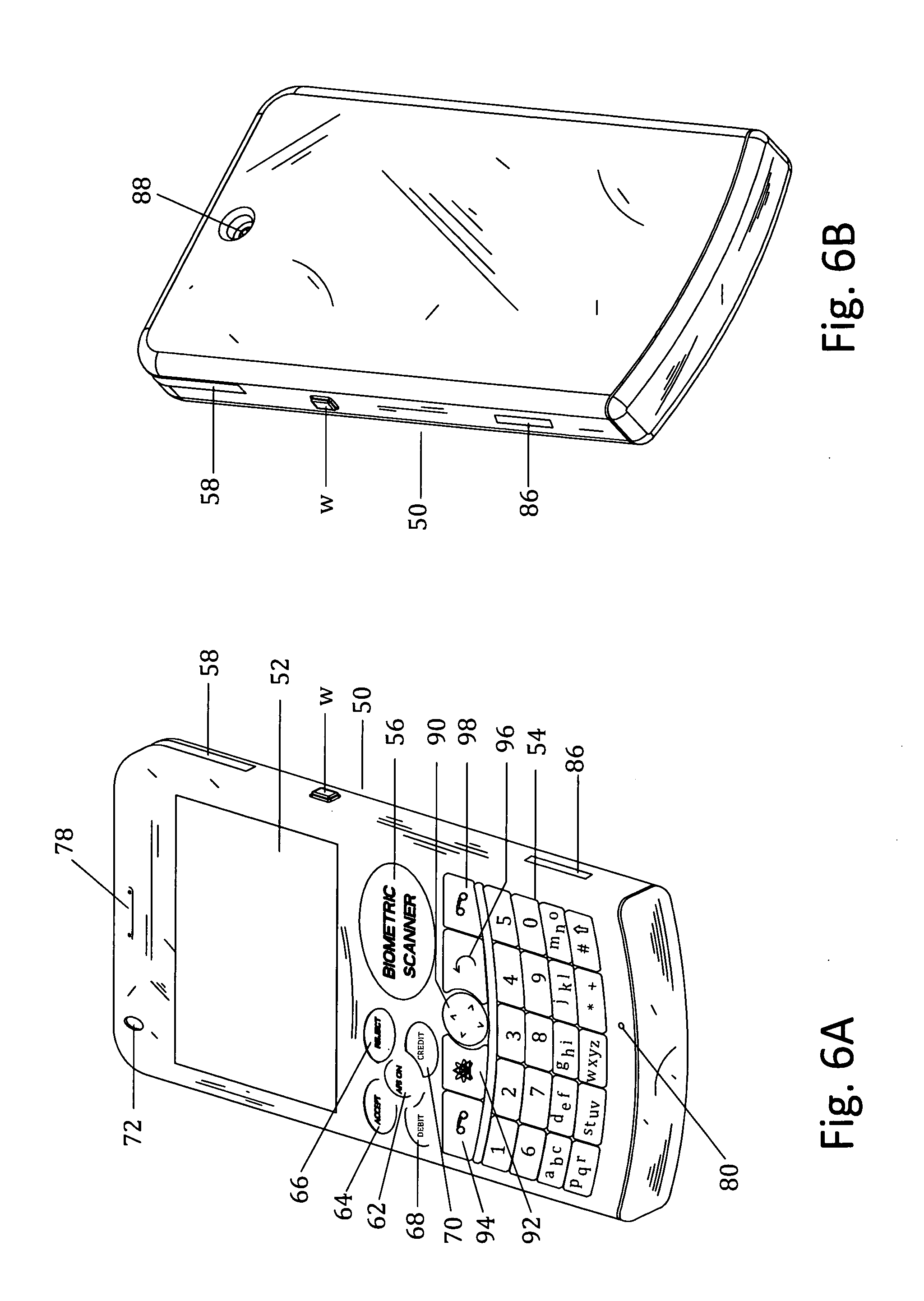
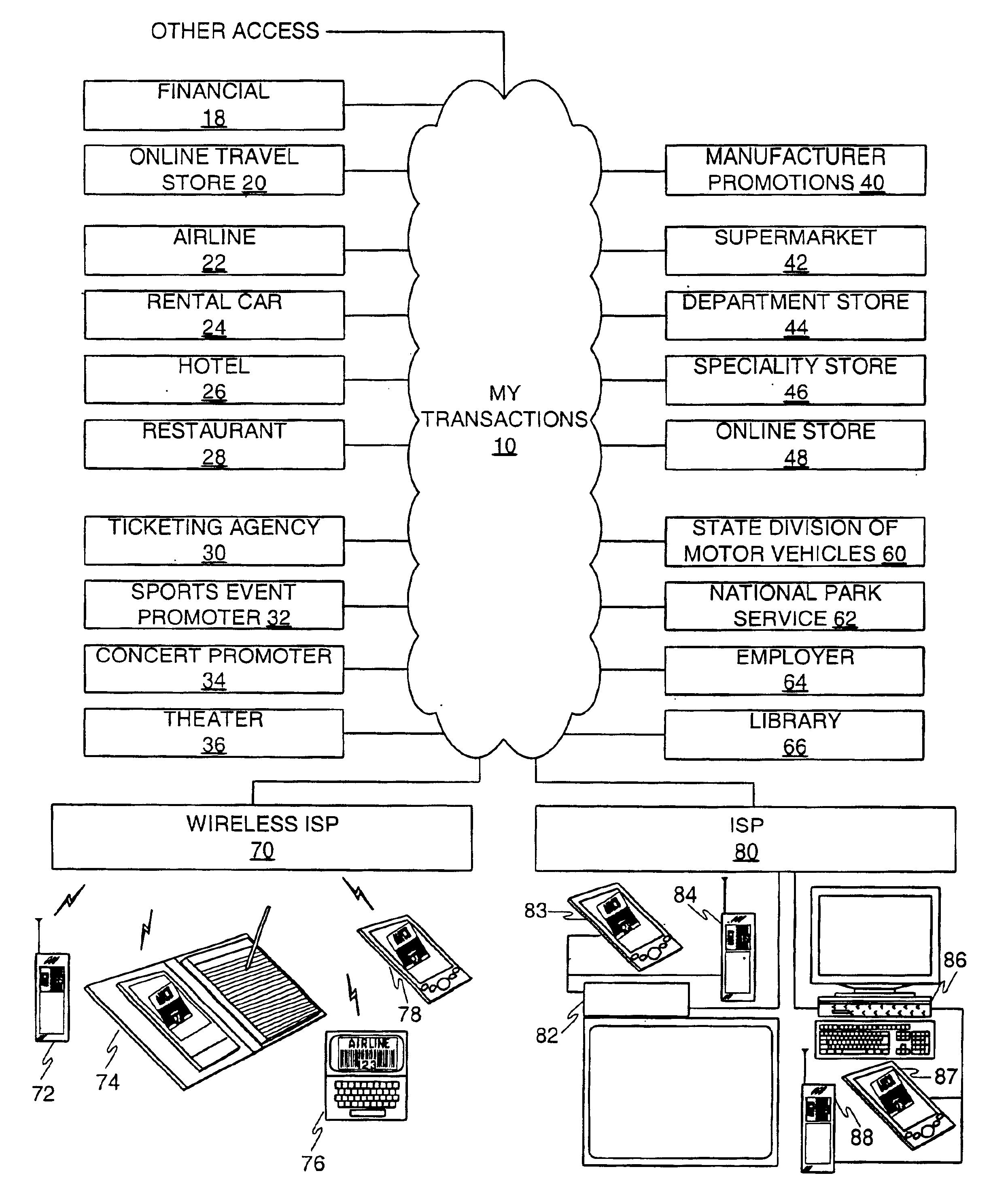
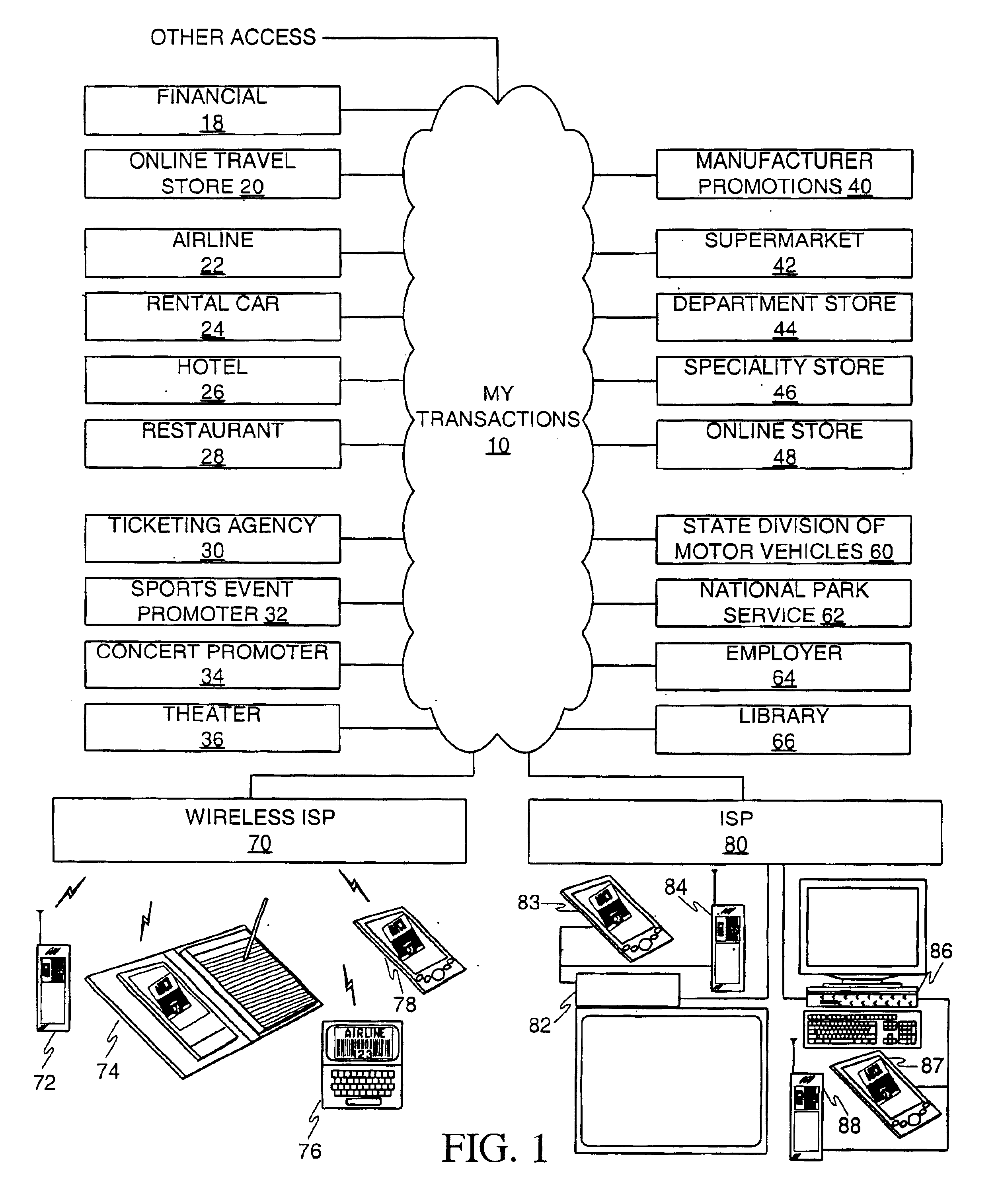
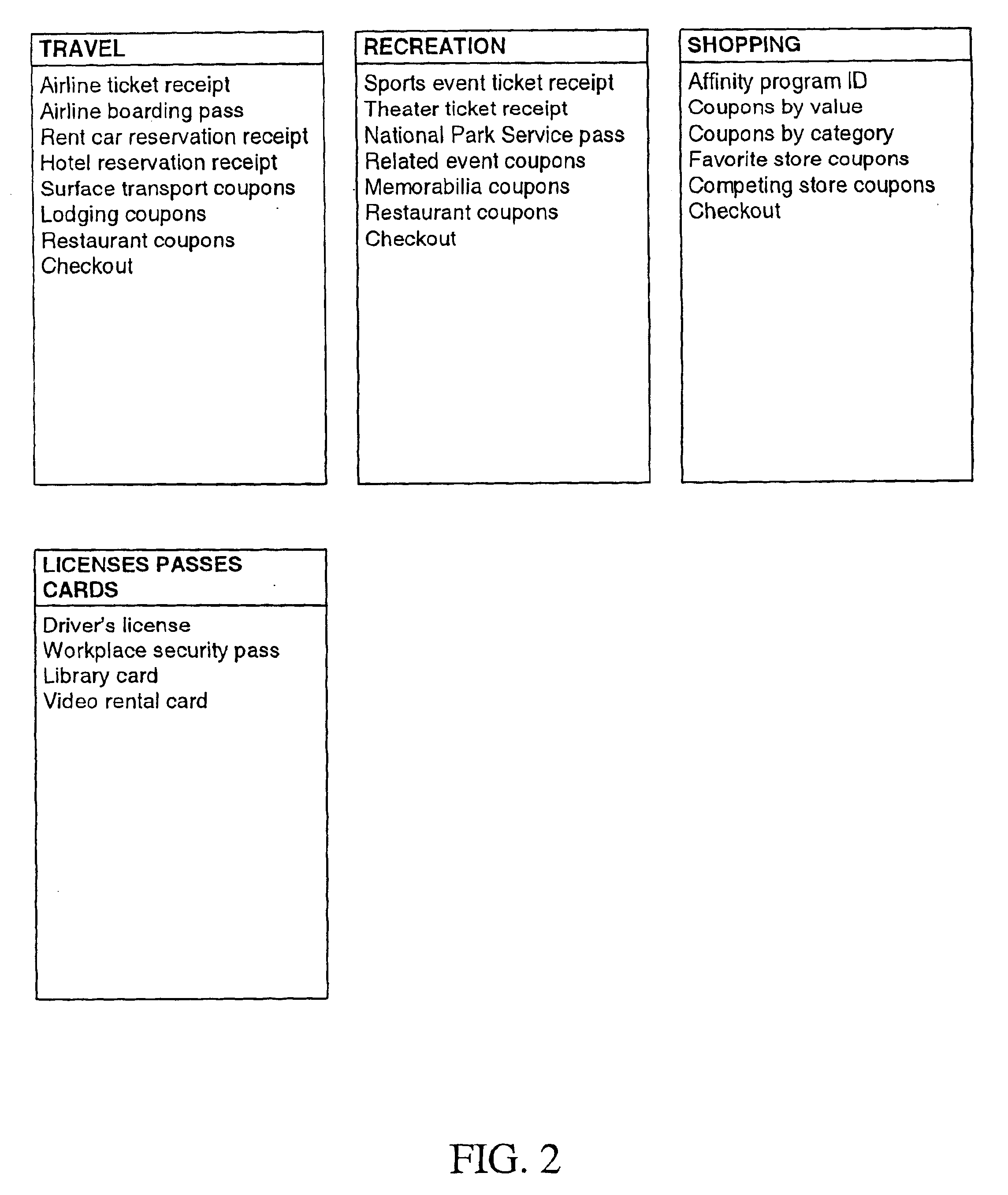
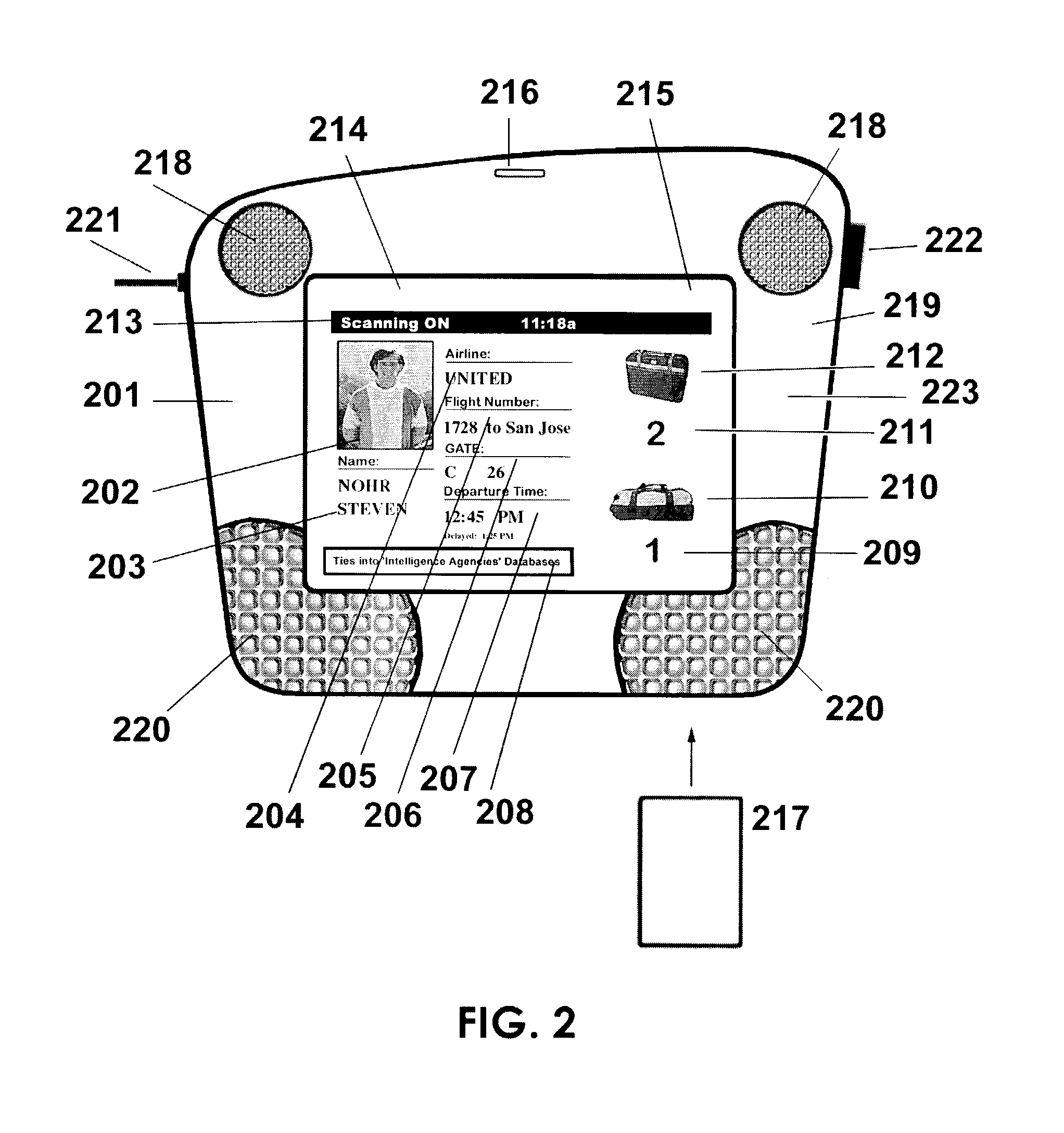
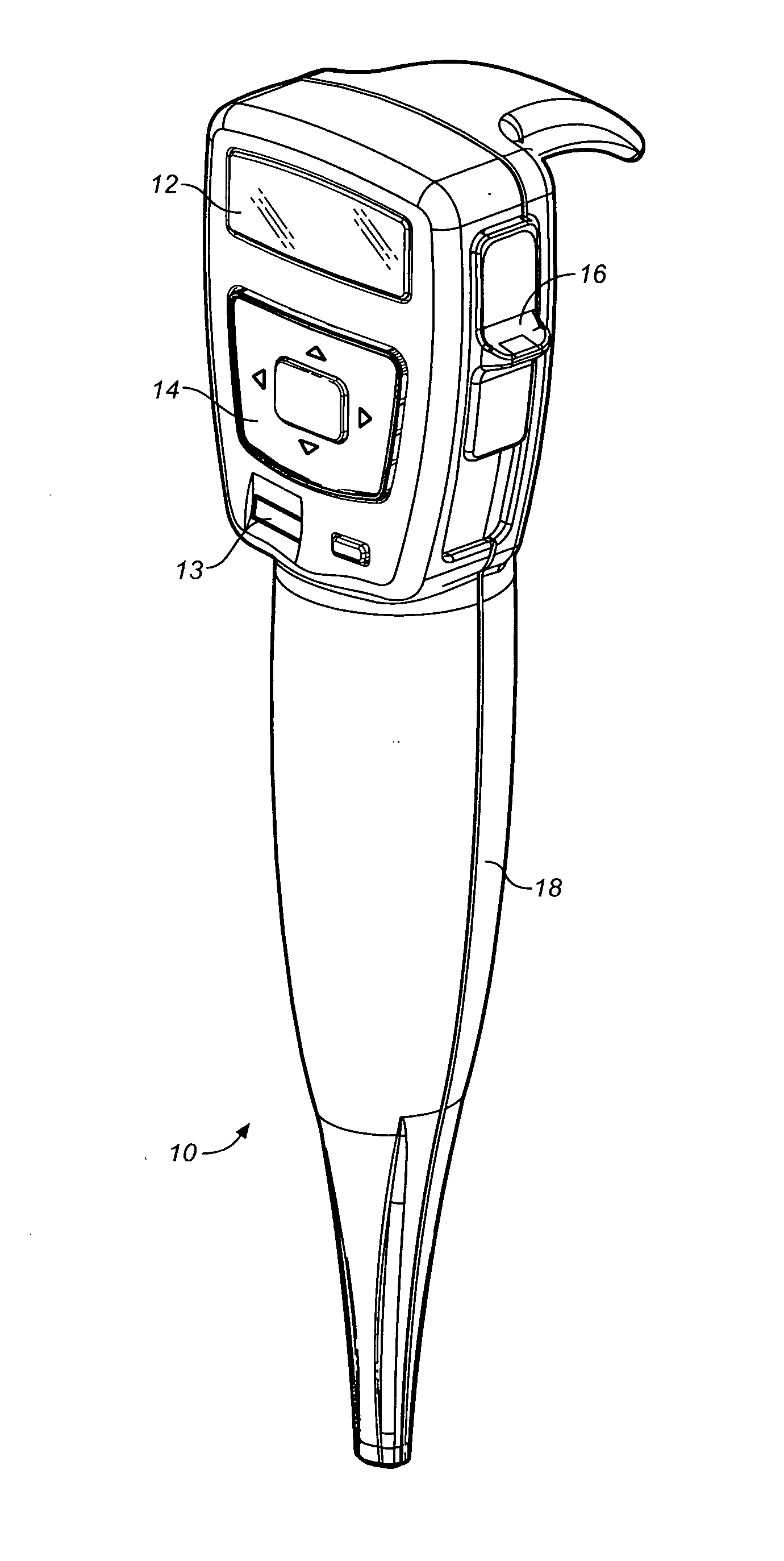
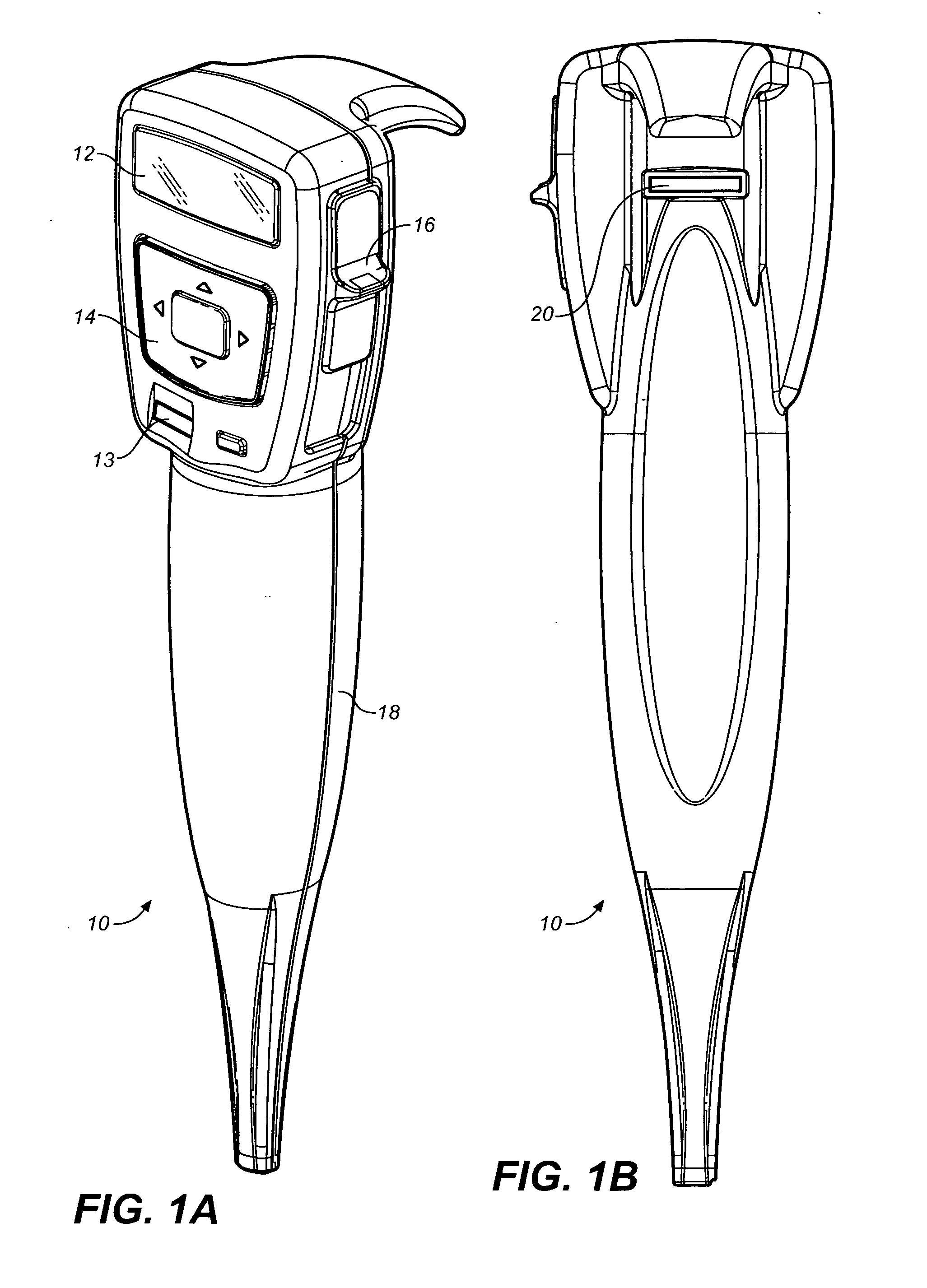
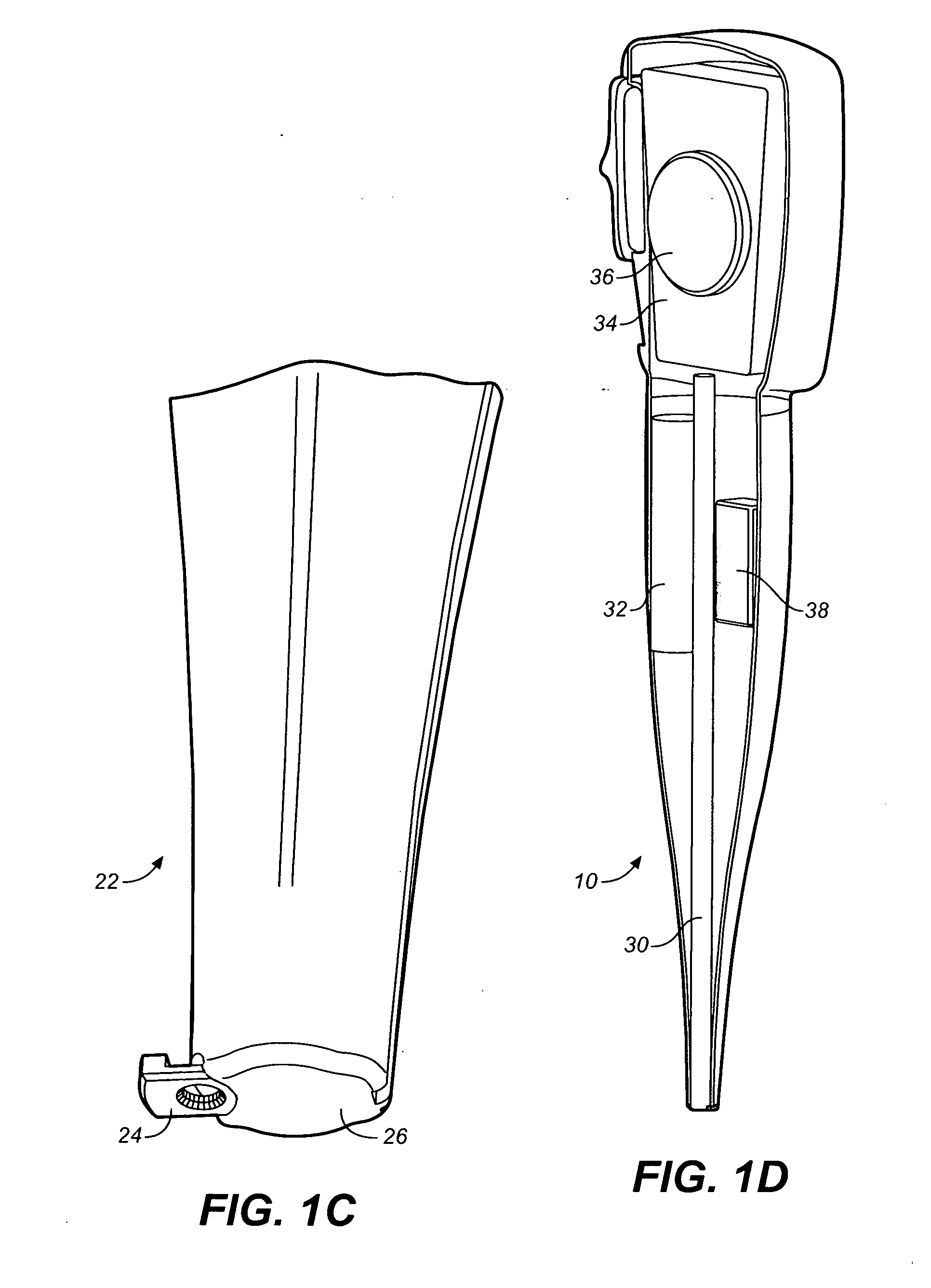
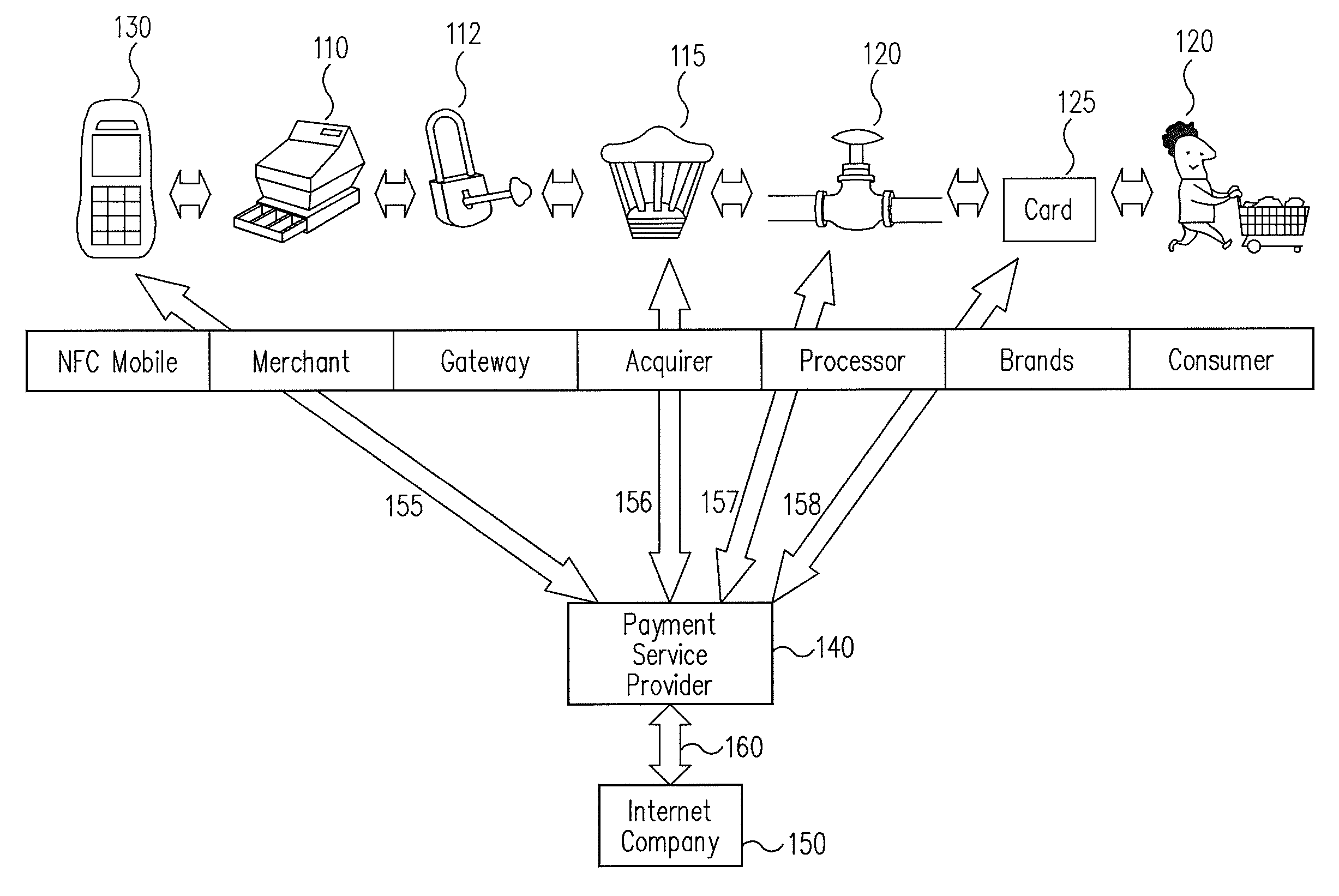
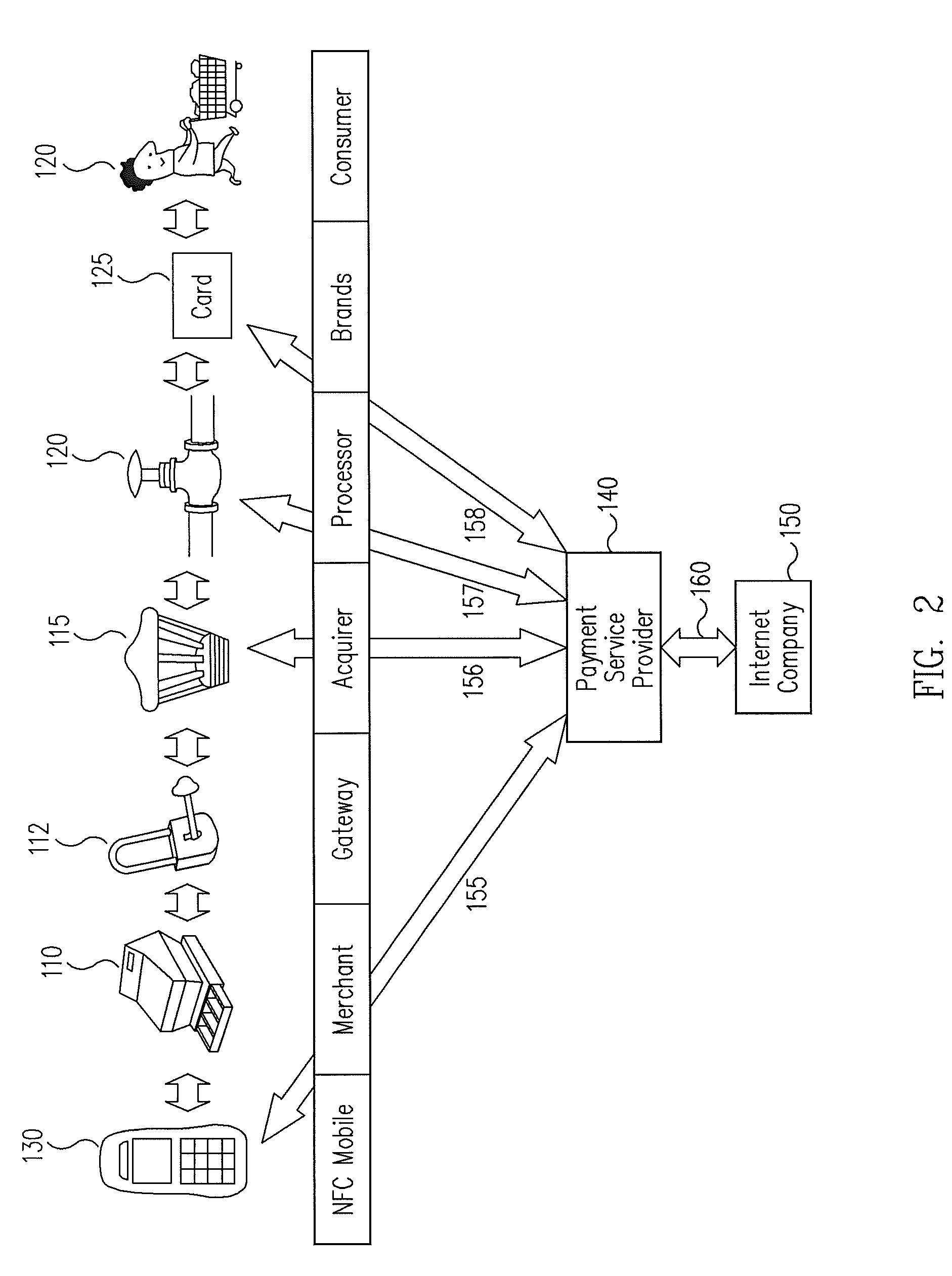
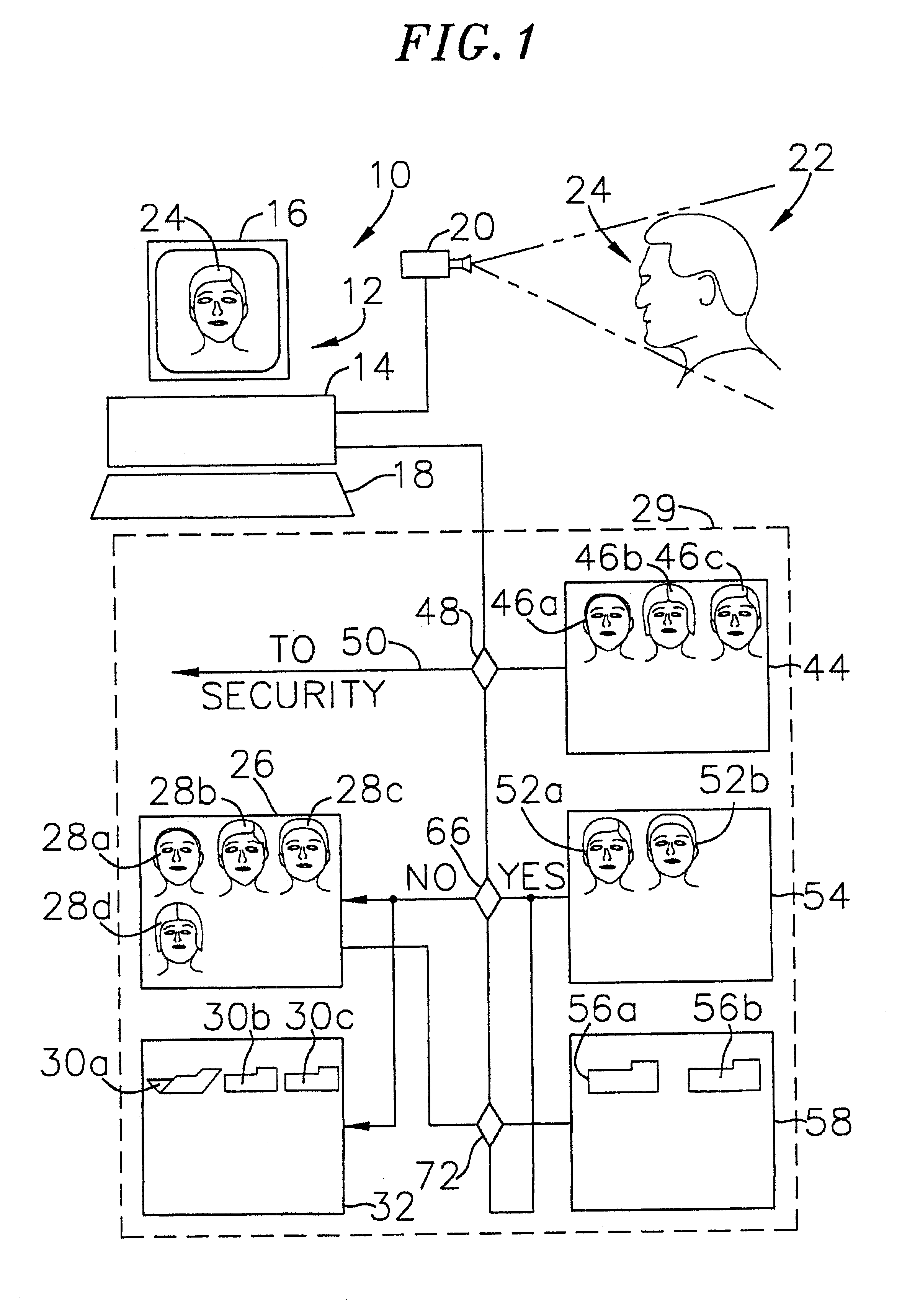
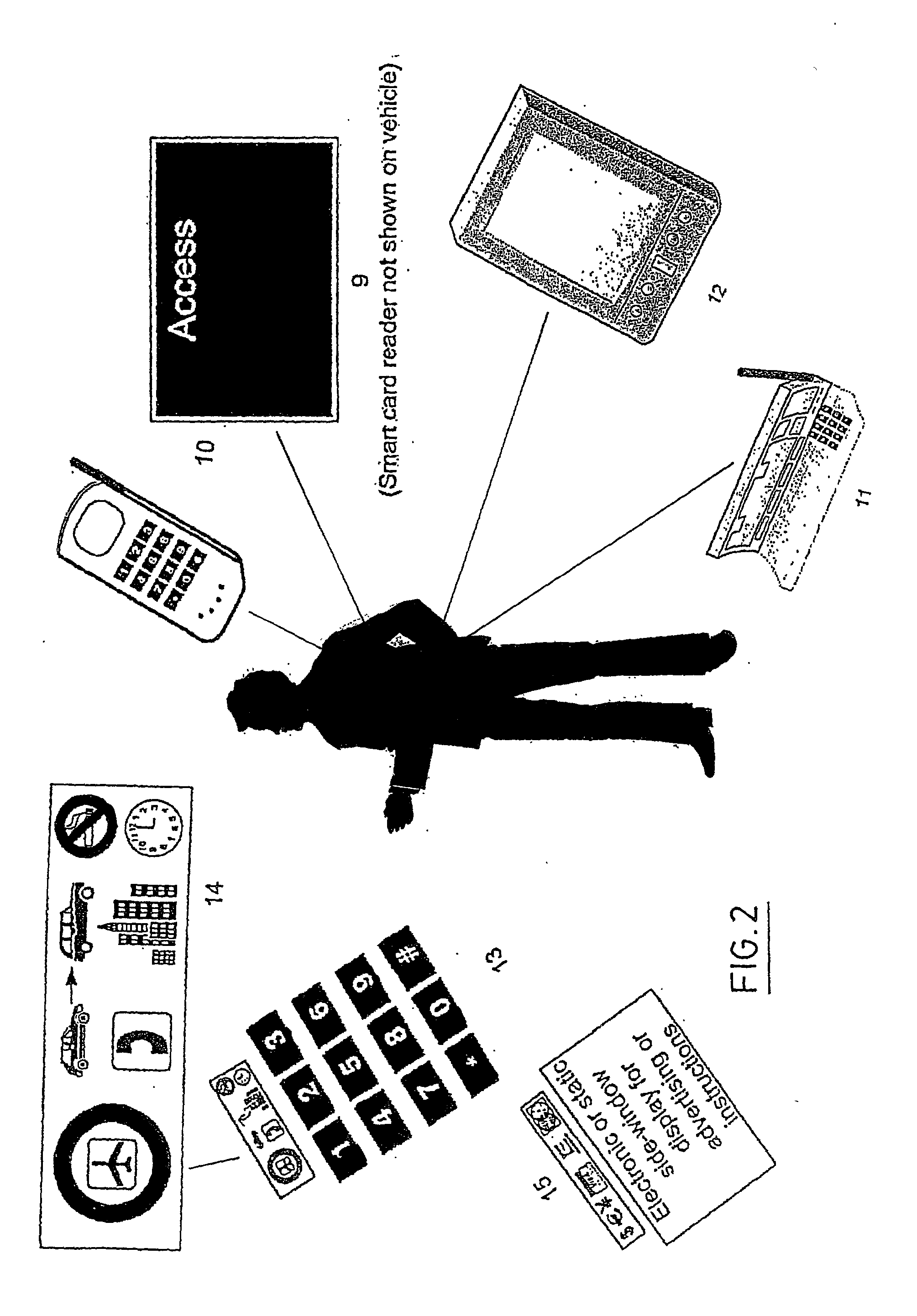
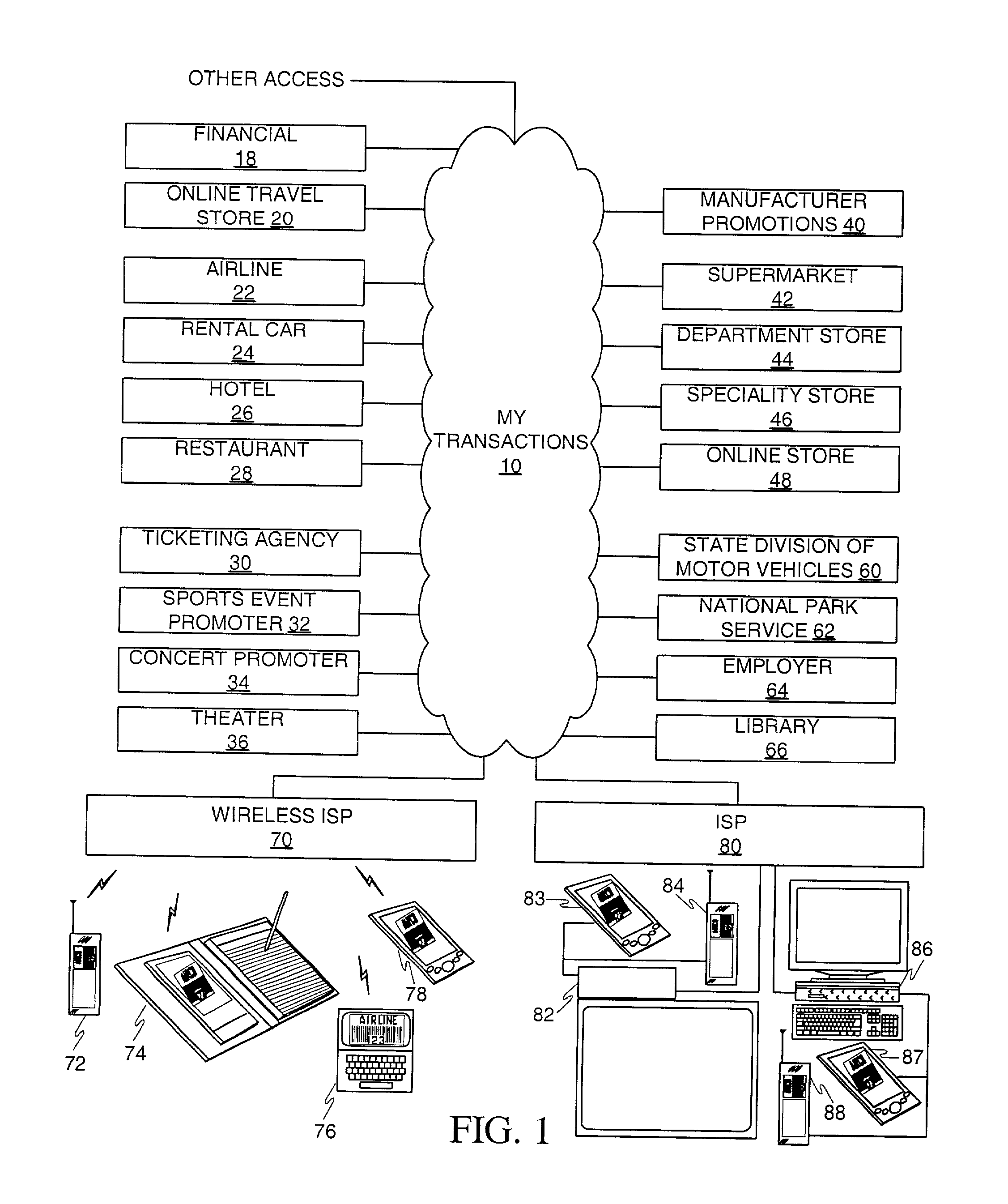
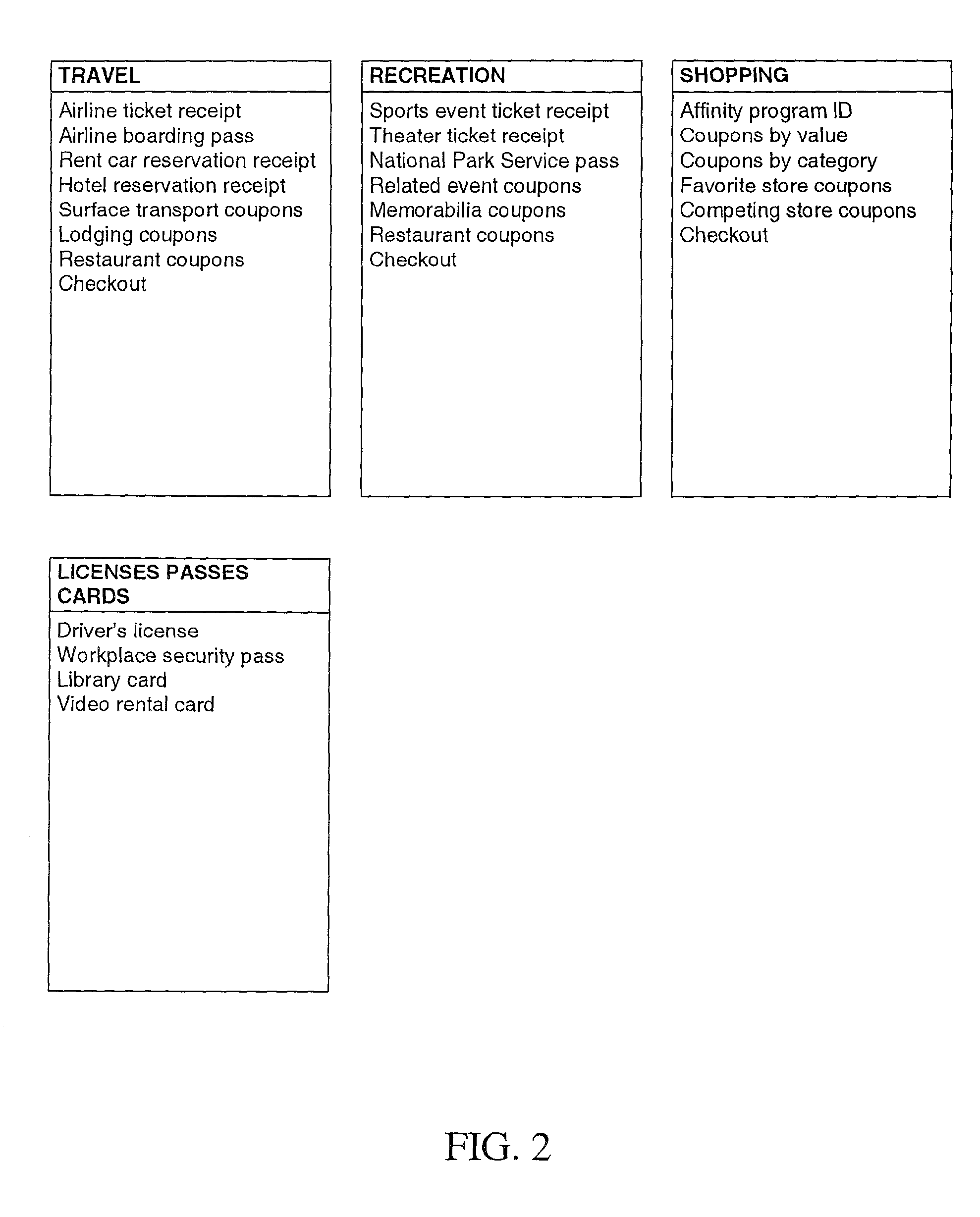
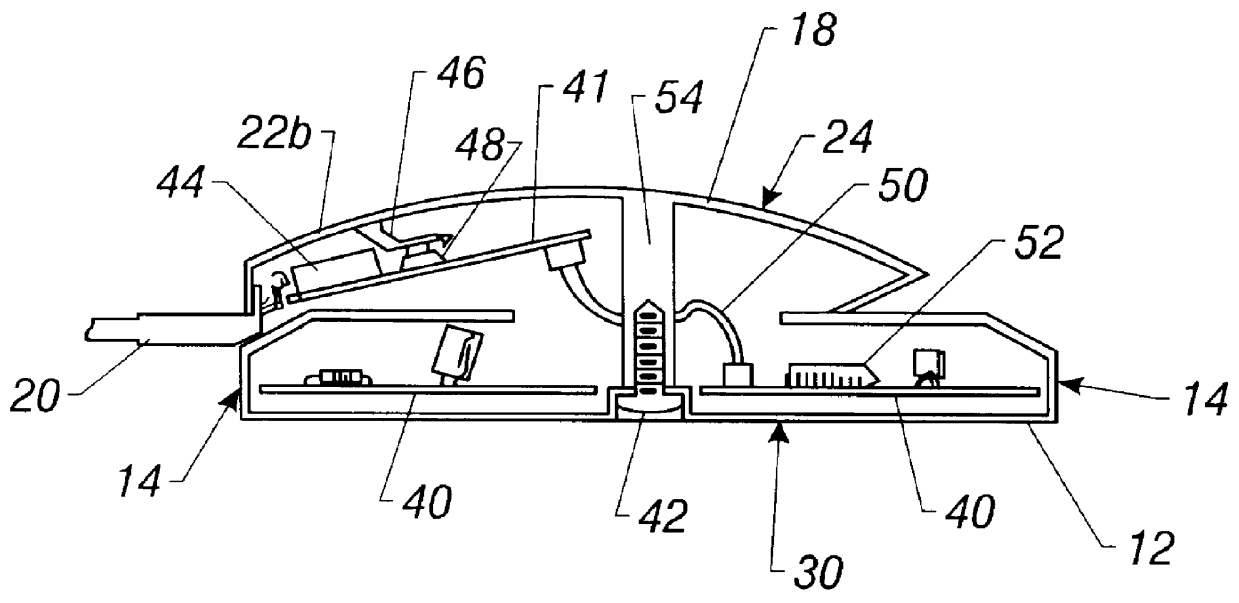
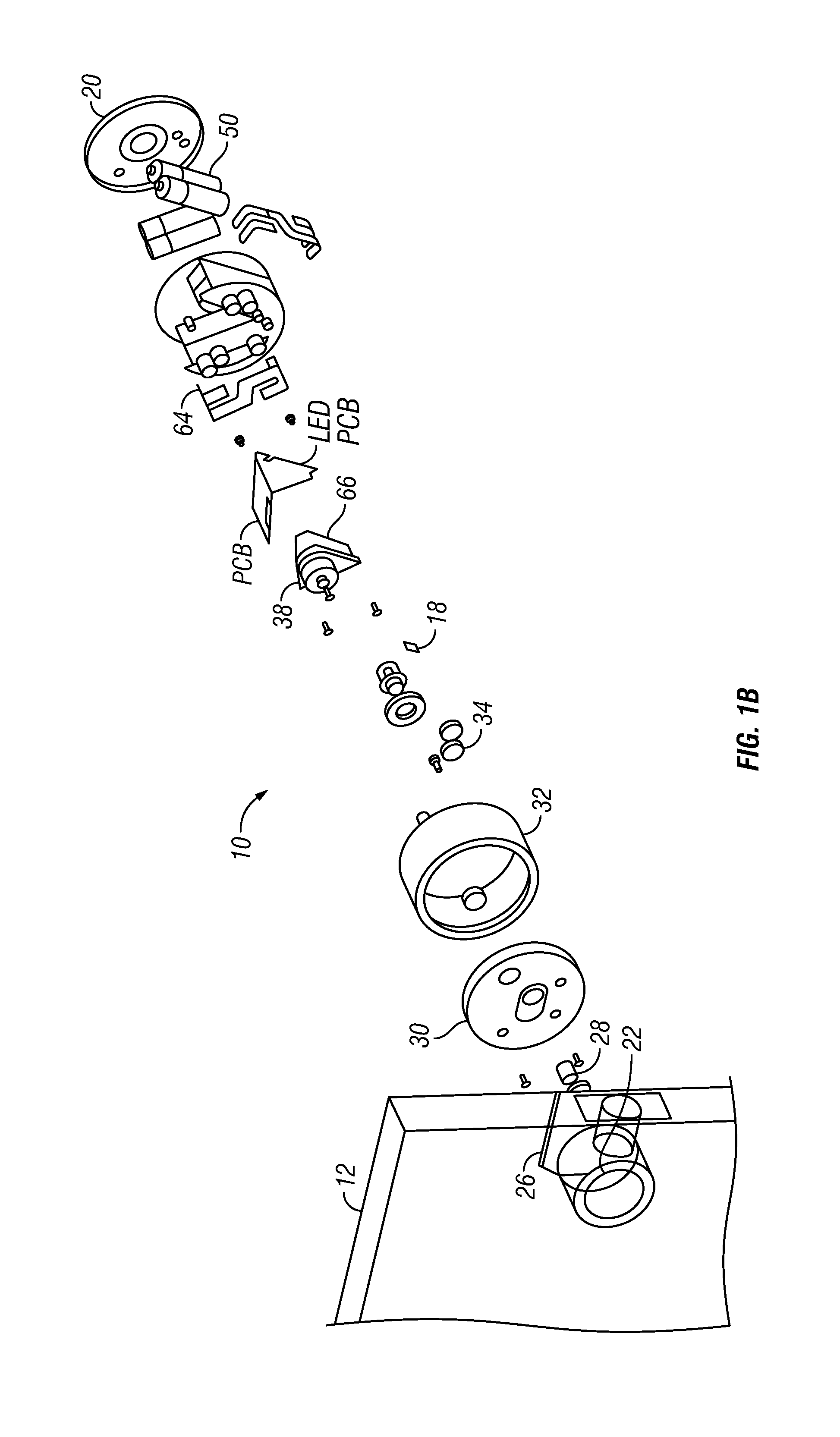
InactiveUS6736322B2Convenient acquisition and maintenance and useCharacter and pattern recognitionIndividual entry/exit registersBarcodeCommunication device
A user is provided with a secure database containing information in diverse categories that relates to the user and that may be represented at least in part in bar code form and communicated with light from a mobile communications device. The diverse information is obtained from any combination of a variety of vendor and governmental computer systems, internet service providers, and communications devices. The user has access to the database using a mobile communications device for displaying, managing, and entering information, and for communicating information in bar code form with light. The user first selects the category that contains the specific item of information, and then selects the specific item of information. The specific item of information then is communicated in bar code form with light from the mobile communications device for scanning by a bar code scanner to obtain the desired good or service.
Owner:SAMSUNG ELECTRONICS CO LTD
Rental/car-share vehicle access and management system and method
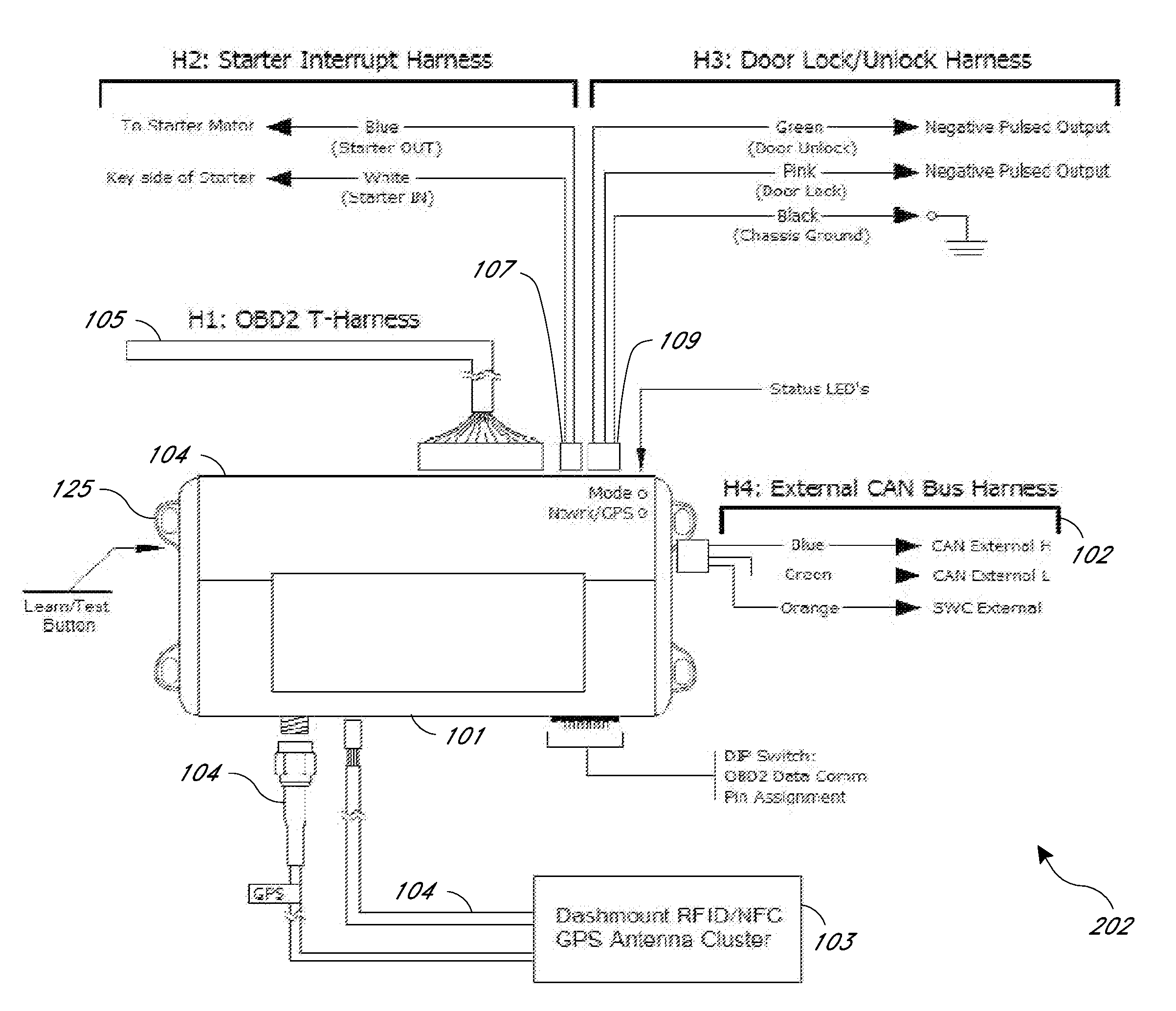
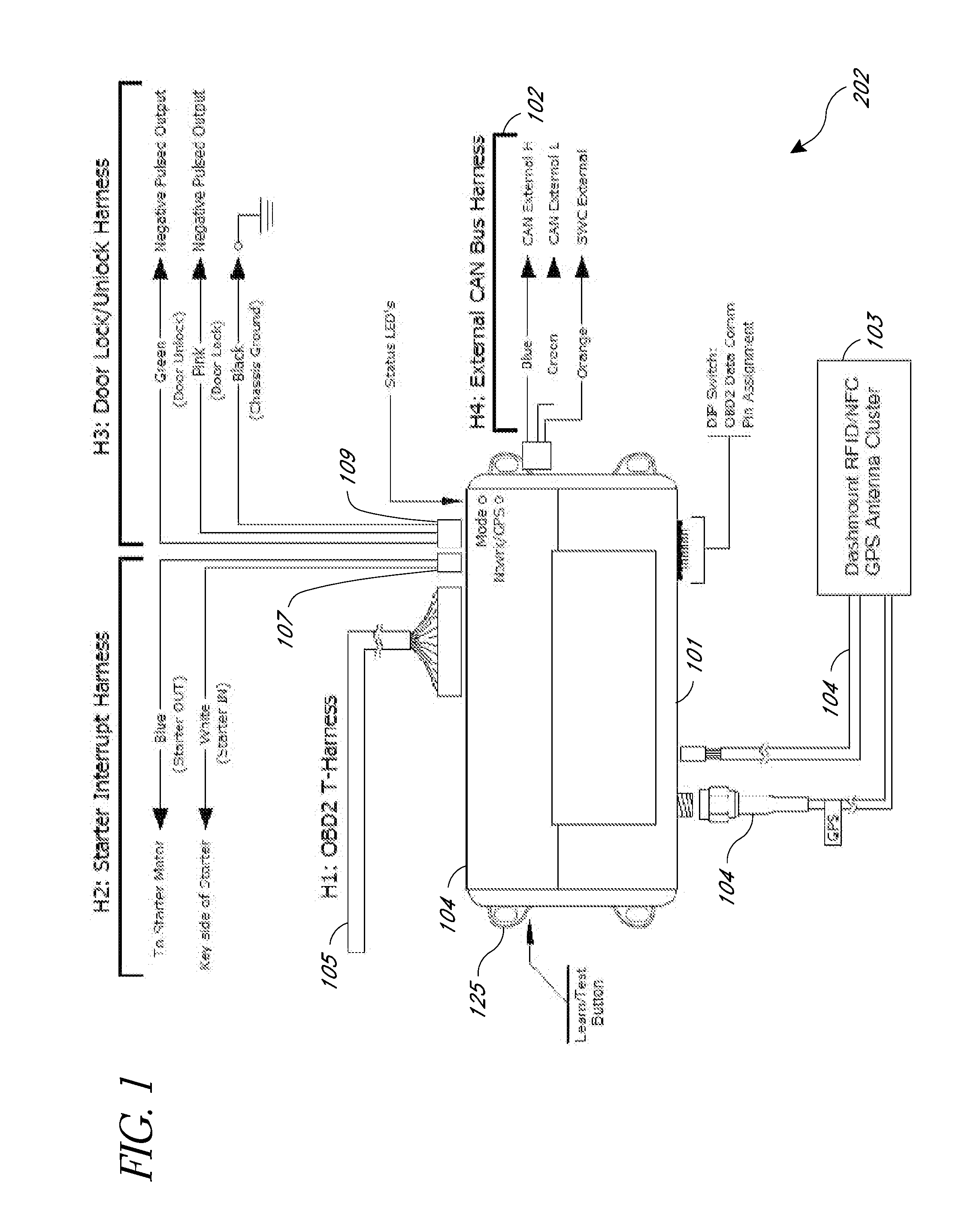
ActiveUS20130317693A1Reduce the time required for installationImprove reliabilityVehicle testingTicket-issuing apparatusMobile appsTablet computer
A rental / car-share (RCS) vehicle access and management system and method, in some embodiments, utilizes barcodes, QR codes (or NFC / RFID), GPS, and a mobile app coupled with a wireless network to enable customers to bypass the reservation desk and pickup and drop off reserved RCS vehicles using a mobile phone, tablet or laptop. The QR code, RFID, or NFC communication with the mobile application allows for identification of the vehicle by a mobile application, which, if authorized, can access the vehicle via a temporary access code issued by remote servers. The remote servers and / or mobile application communicates with a control module that plugs into the on-board diagnostics module of the rental / car-share (RCS) vehicle and includes a host processing unit with a processor, an accelerometer, data storage, a GPS with internal GPS antenna; a wireless modem with internal antenna, and CAN bus transceivers connected with the processor, and a USB programmable interface.
Owner:ENTERPRISE HOLDINGS
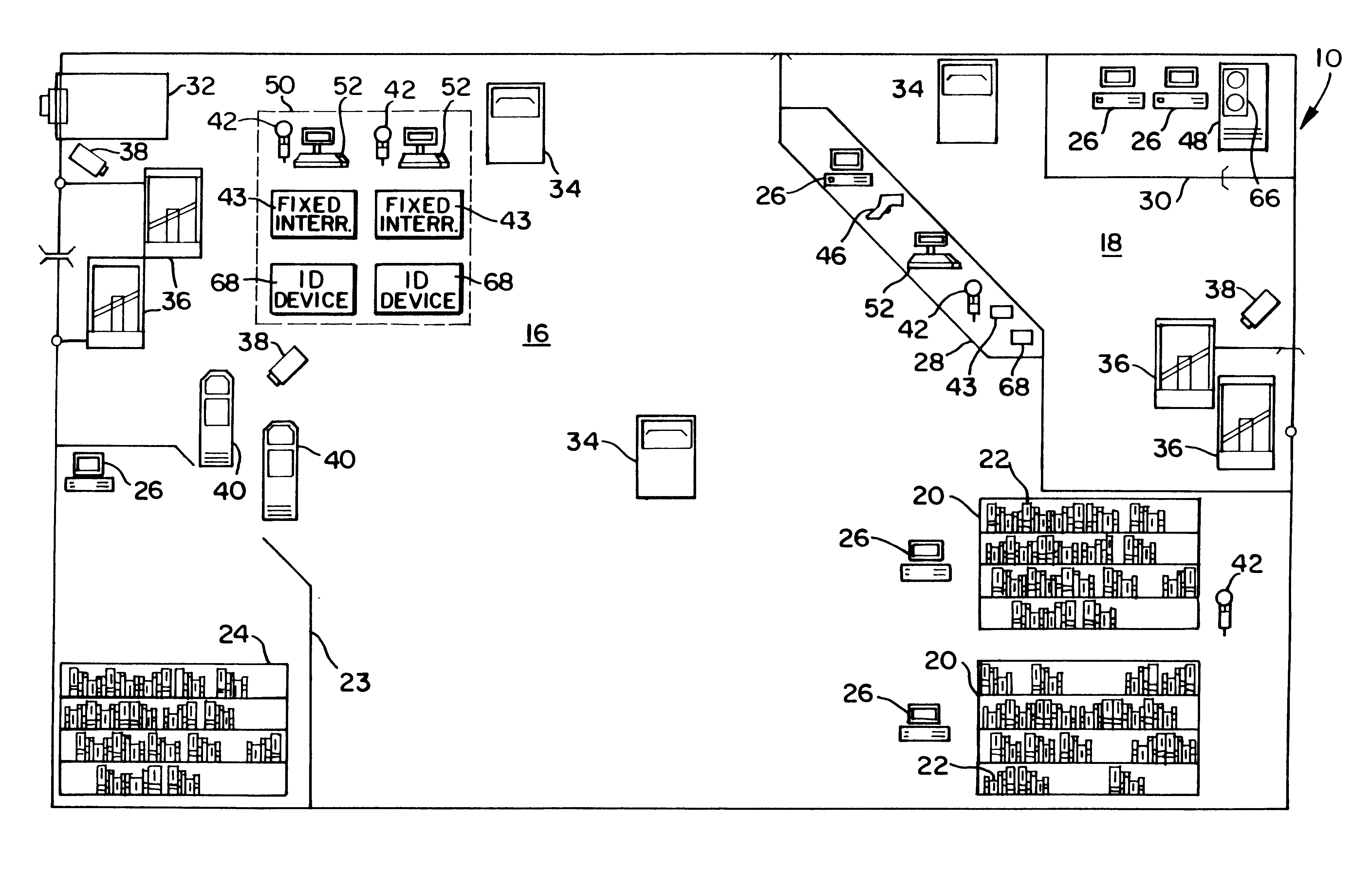
Inventory system using articles with RFID tags
InactiveUS6195006B1Electric signal transmission systemsDigital data processing detailsControl systemMobile RFID
An article inventory control system for articles, such as books, uses RFID tags attached to each article. Each tag has a unique identification or serial number for identifying the individual article. An inventory database tracks all of the tagged articles and maintains circulation status information for each article. Articles are checked out of the library using a patron self-checkout system. Checked out articles are returned to the library via patron self-check in devices. The shelves are periodically scanned with a mobile RFID scanner for updating inventory status.
Owner:CHECKPOINT SYST INC
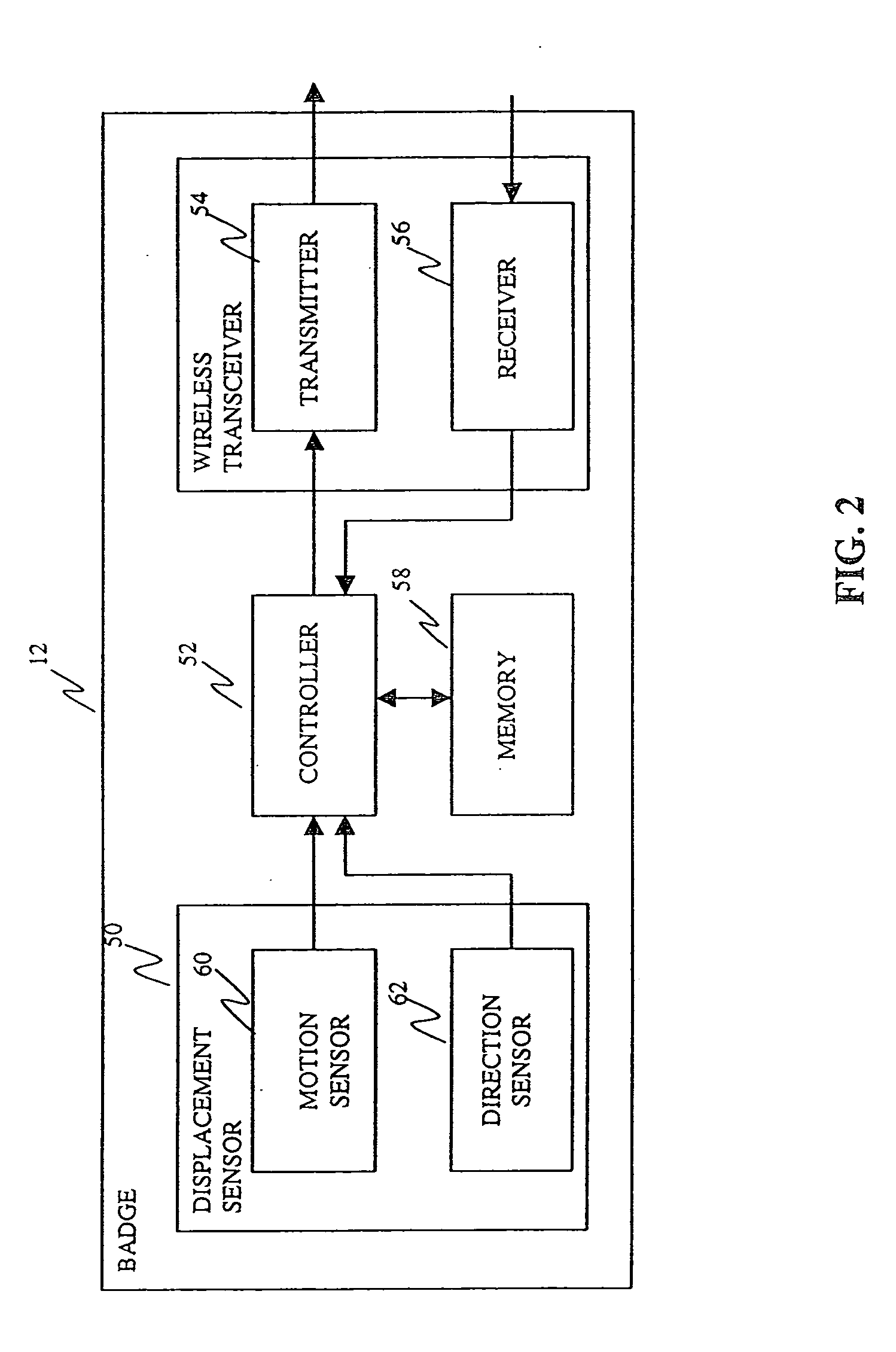
Dual mode tracking system
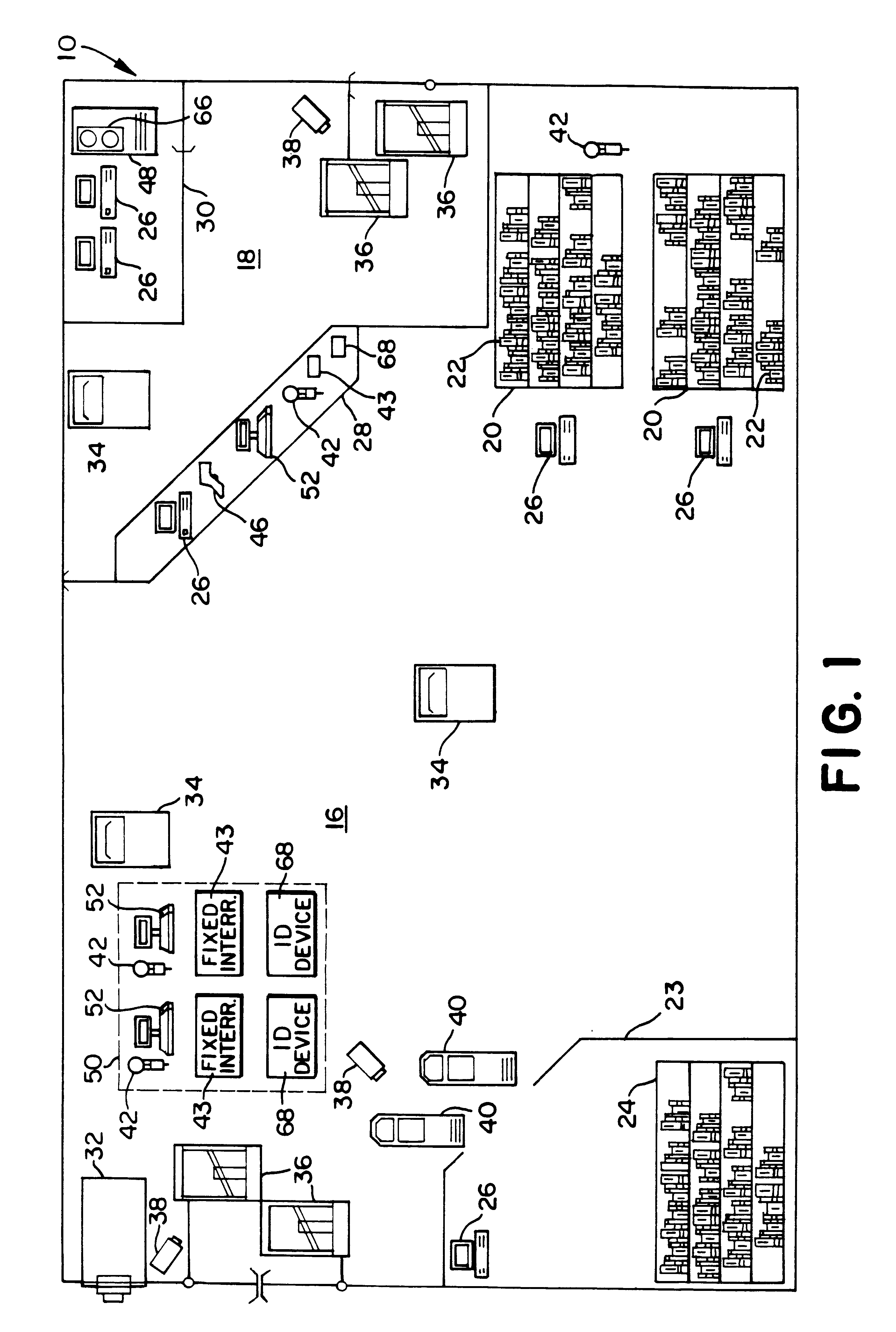
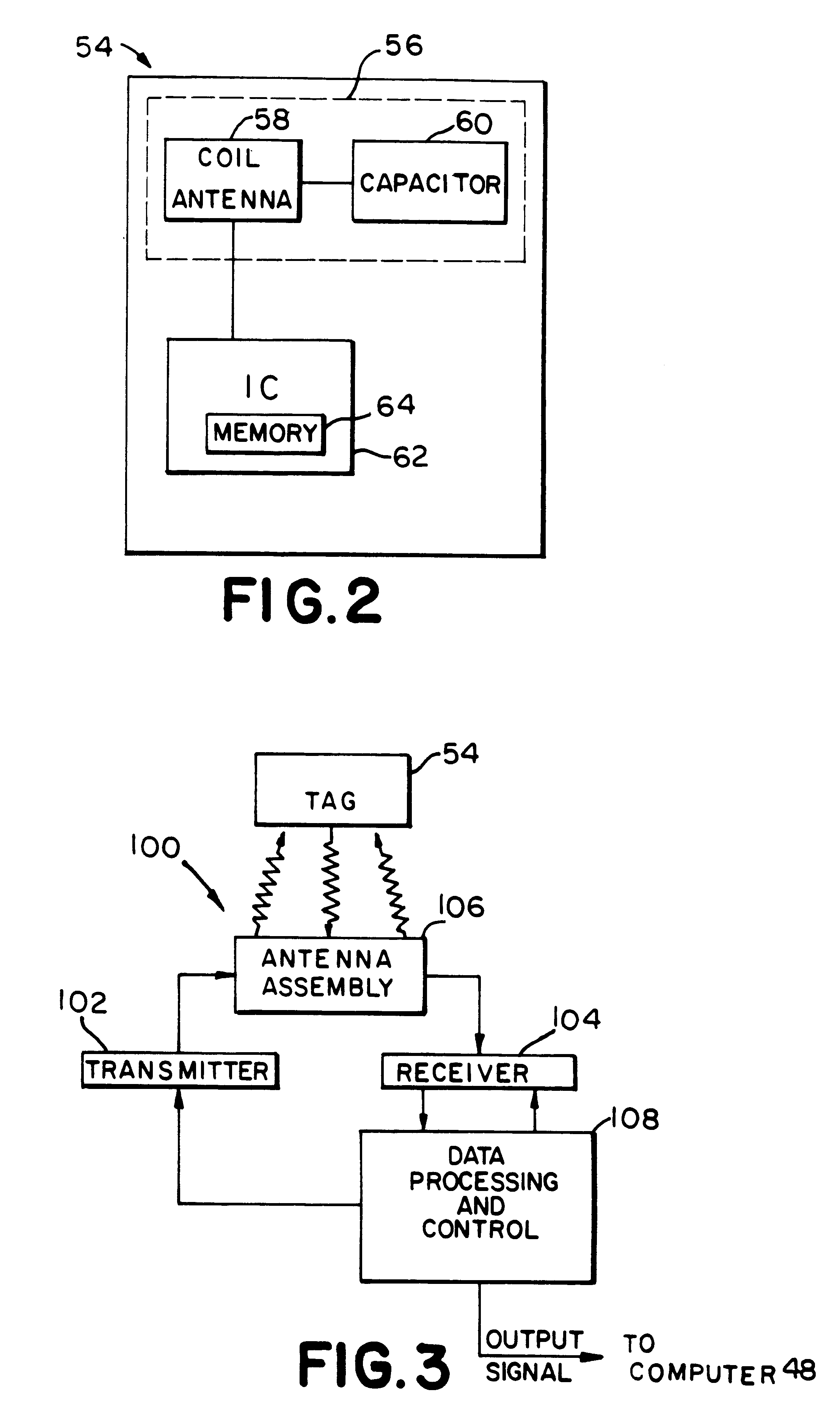
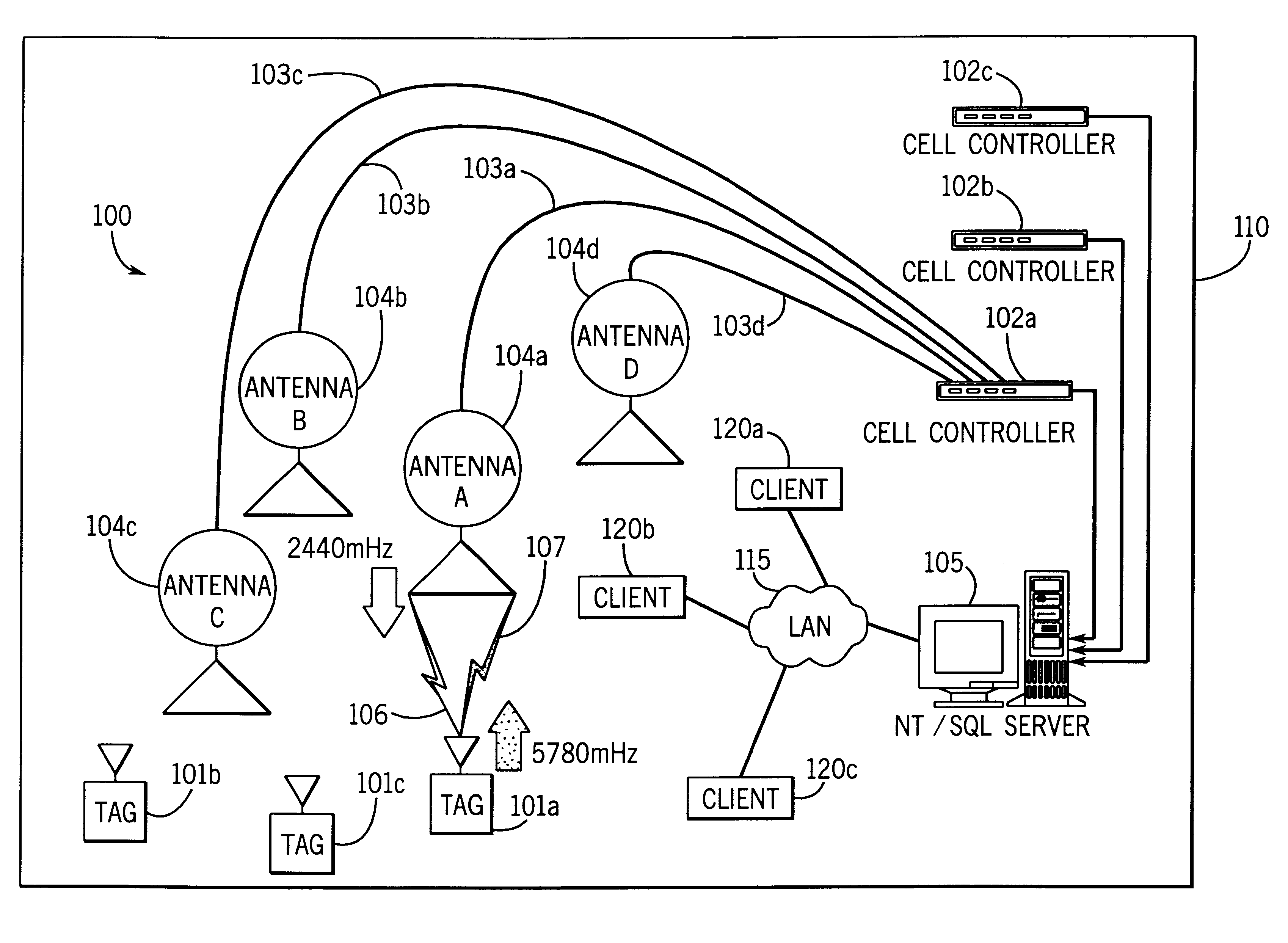
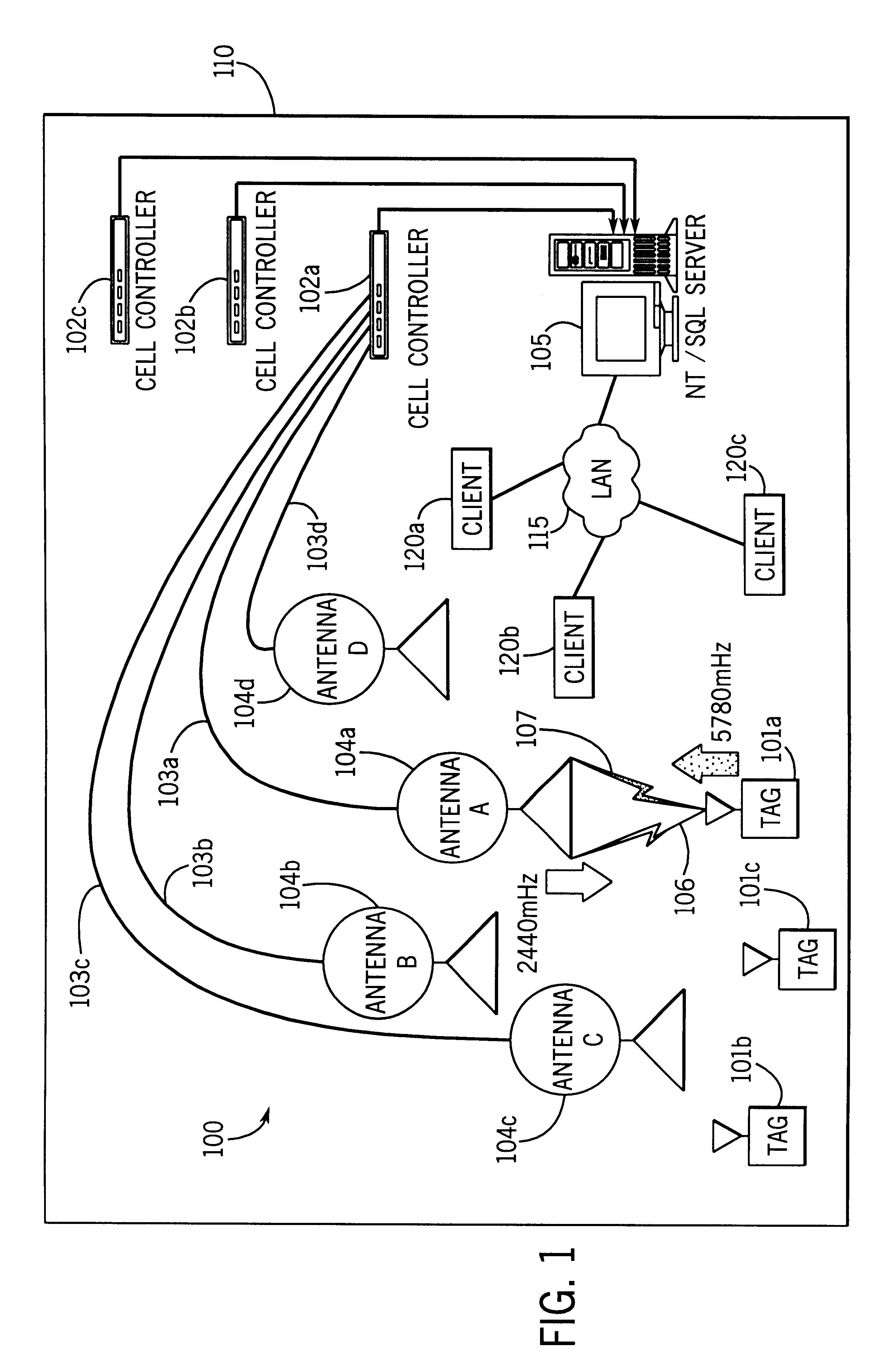
InactiveUS6353406B1Memory record carrier reading problemsCo-operative working arrangementsData warehouseDual mode
System for tracking mobile tags. Cell controllers with multiple antenna modules generate a carrier signal which is received by the tags. Tags shift the frequency of the carrier signal, modulate an identification code onto it, and transmit the resulting tag signal at randomized intervals. The antennas receive and process the response, and determine the presence of the tags by proximity and triangulation. The recursive-least squares (RLS) technique is used in filtering received signals. Distance of a tag from an antenna is calculated by measuring the round trip signal time. The cell controllers send data from the antenna to a host computer. The host computer collects the data and resolves them into positional estimates. Data are archived in a data warehouse, such as an SQL Server. Also disclosed is an article tracking system that supports both active and passive tags with a cell controller able to read both passive and active tag signals.
Owner:RF TECH +1
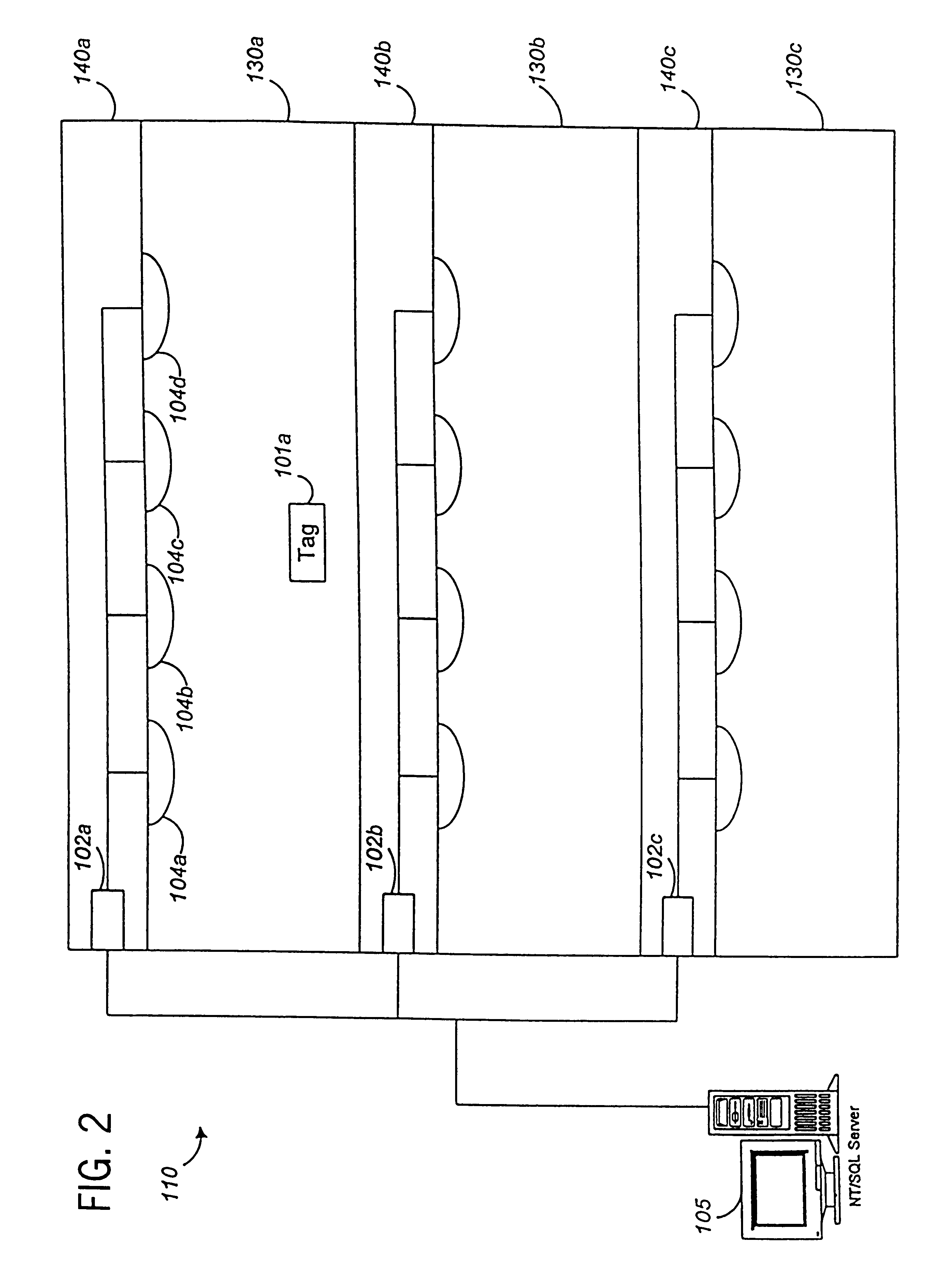
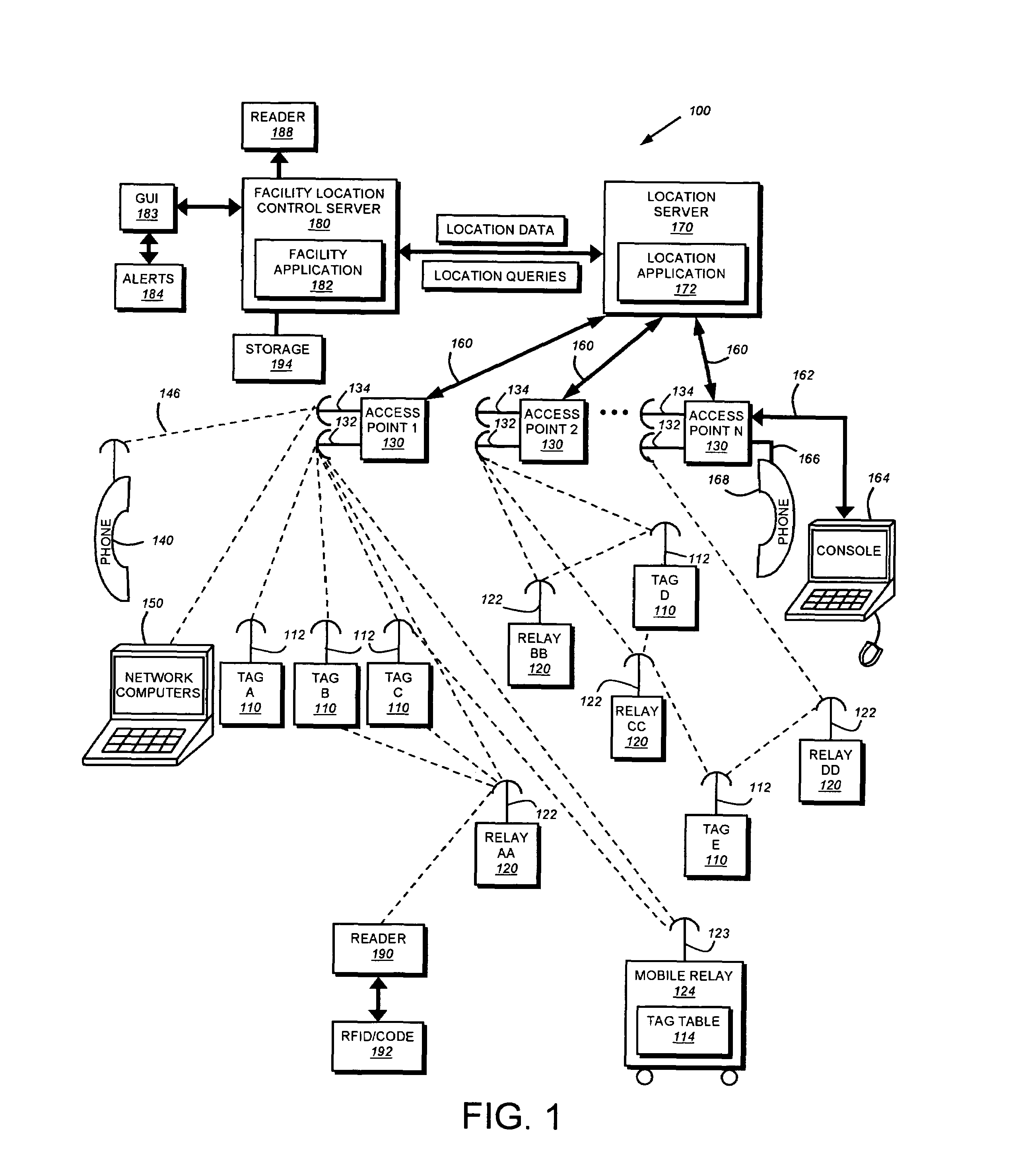
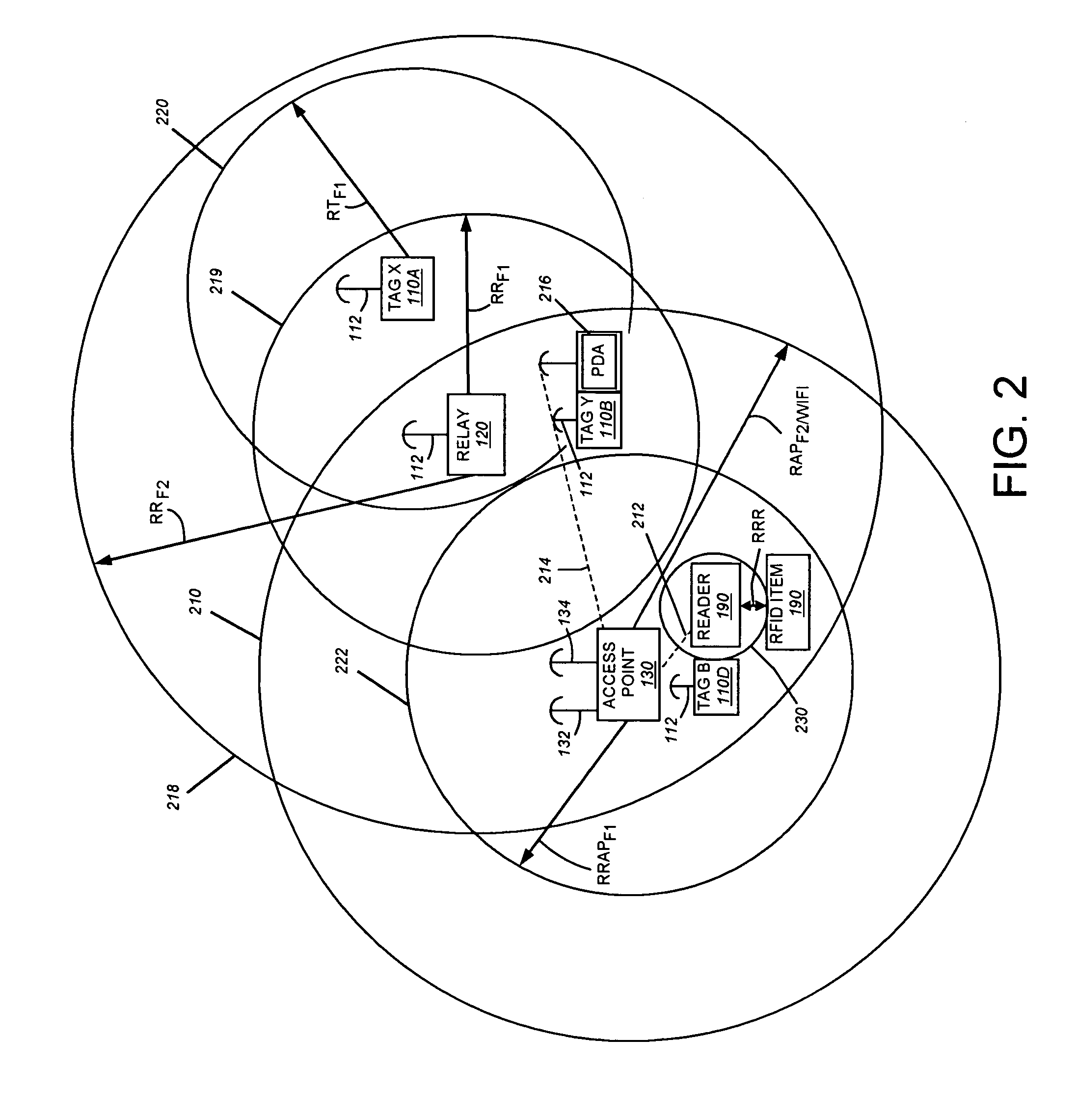
System and method for locating and communicating with personnel and equipment in a facility
InactiveUS7323991B1Increase redundancyQuickly and frequently and continuously updatedElectric signal transmission systemsTicket-issuing apparatusTransceiverWireless data
This invention provides a system and method for identifying, locating, authorizing by proximity and communicating with equipment and personnel in a facility that generally employs a series of limited range transceivers for location determination and a distributed wireless data network for data transfer. The system employs unique RF transceiver tags on personnel and equipment that are each uniquely identified and registered with a facility control application that oversees activities in the facility. The tags are tracked by RF communication based upon their proximity to one or more fixed-base networked access points and relays (which transfer location data by RF back to access points) within four range zones. Location data on all tags is uploaded periodically to a location server that interfaces with the facility control server. Tag data is monitored by the facility control server to track, authorize and deauthorize certain data transfers, movements and activities in accordance with rules established for each tag (or type of tag) within the facility control server's application. Wireless networking (WiFi, for example), in combination with the RF-derived location information, allows the facility control server to correlate and transmit data to staff in conjunction with location and proximity. WiFi can transmit authorizations, deauthorizations and general data based upon triggers established by proximity and location. Likewise, data can be transmitted over WiFi from readers etc. from personnel and equipment located and identified by the system.
Owner:TIDEWATER HLDG
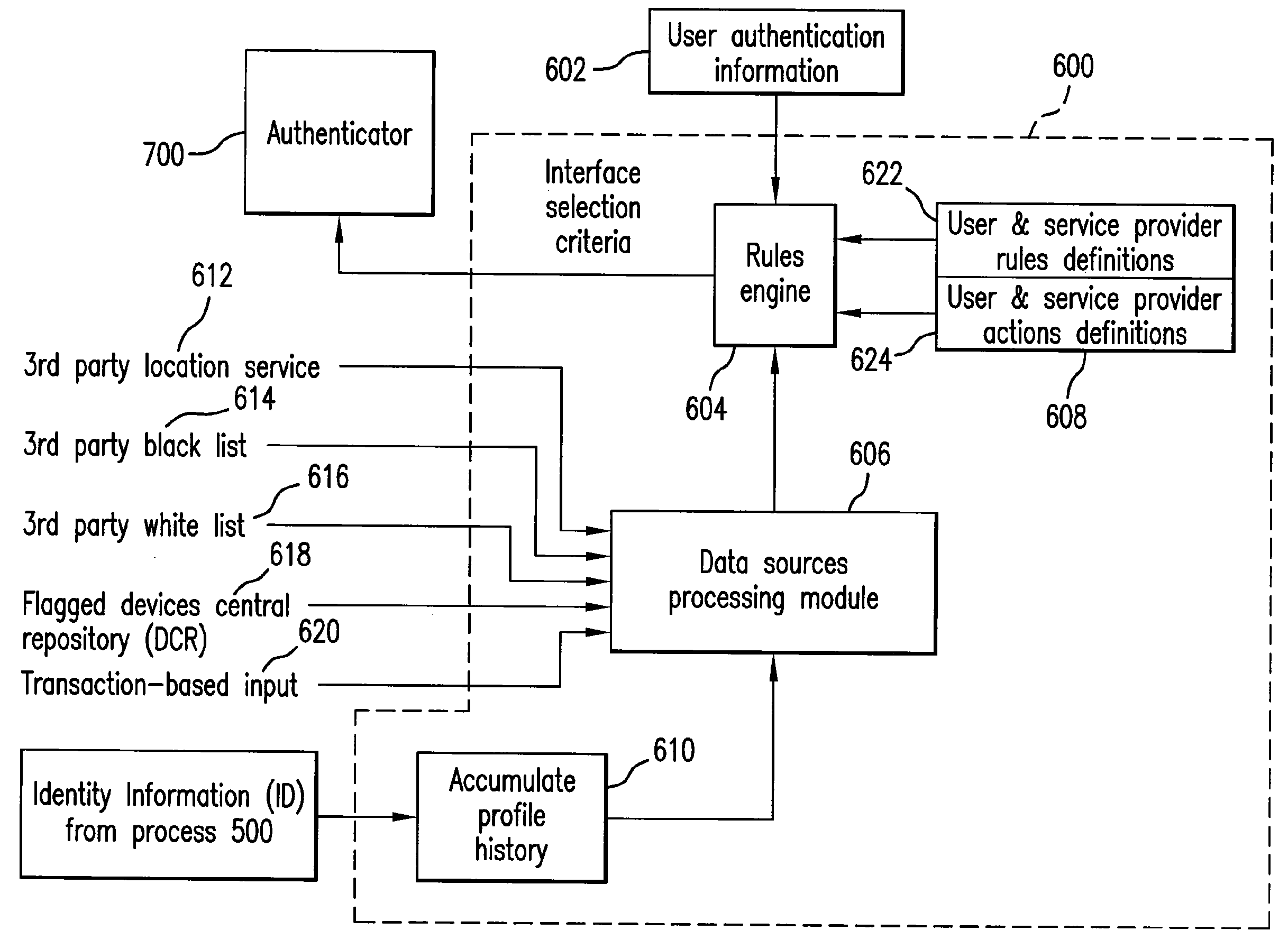
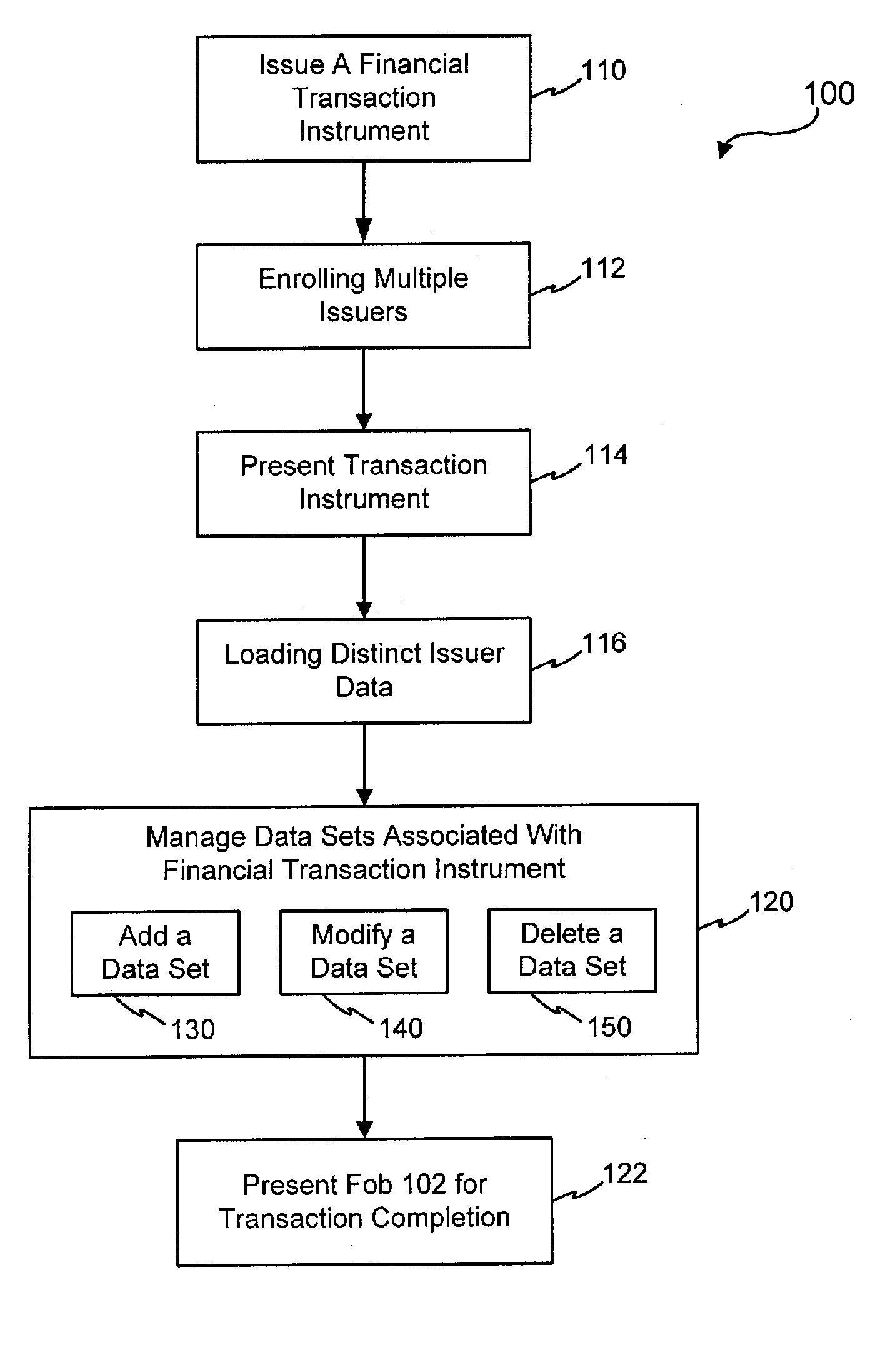
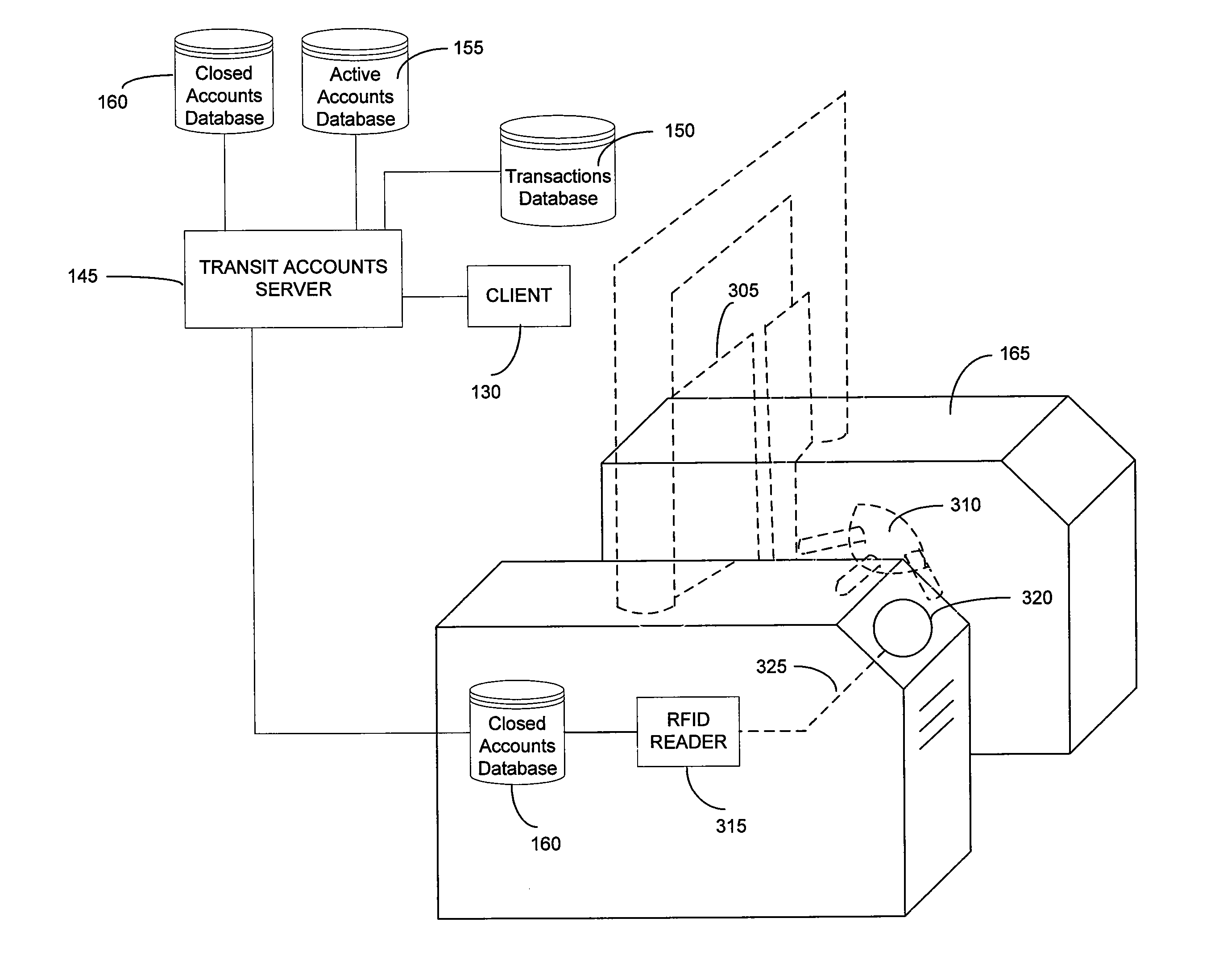
Systems and methods for managing multiple accounts on a RF transaction device using secondary identification indicia
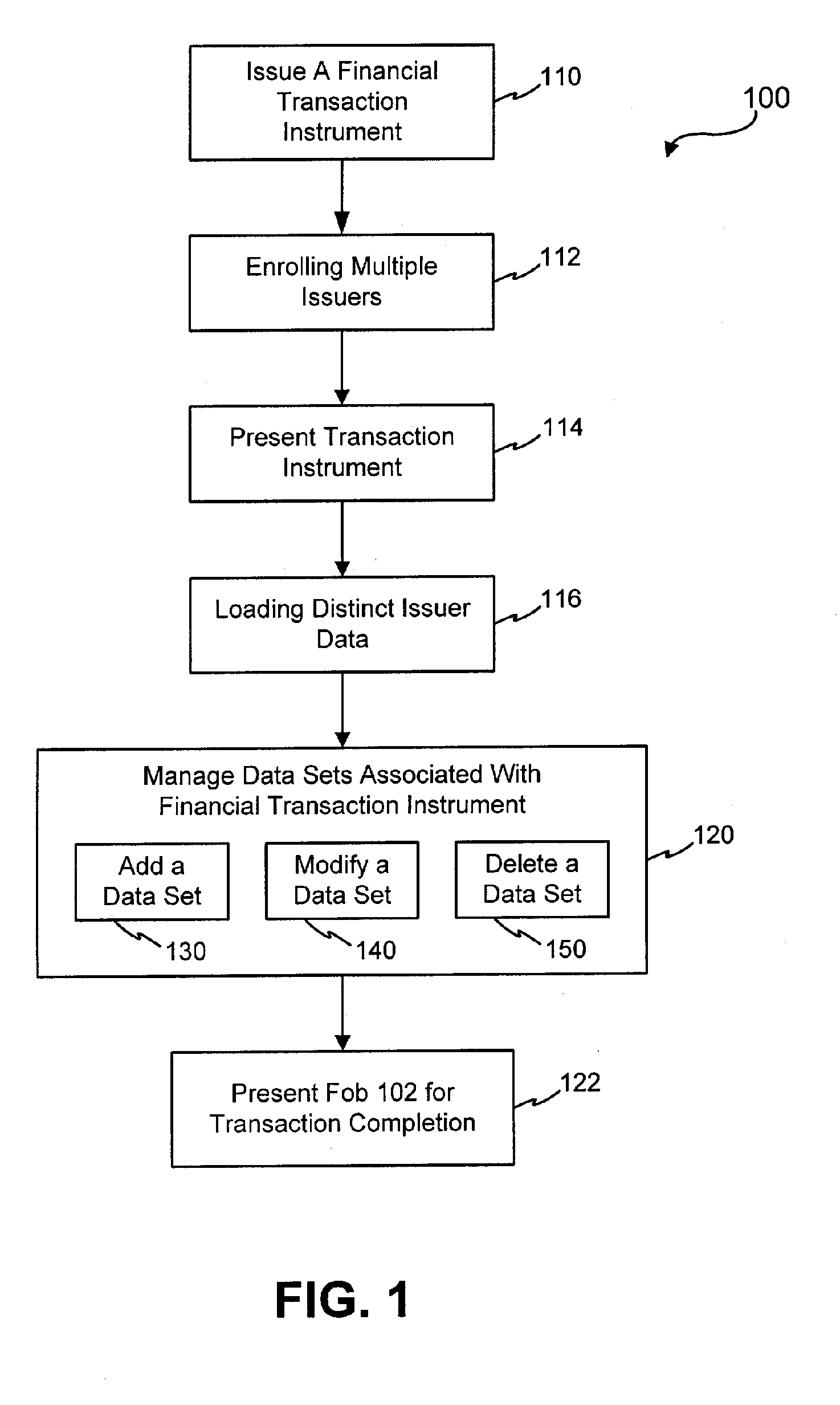
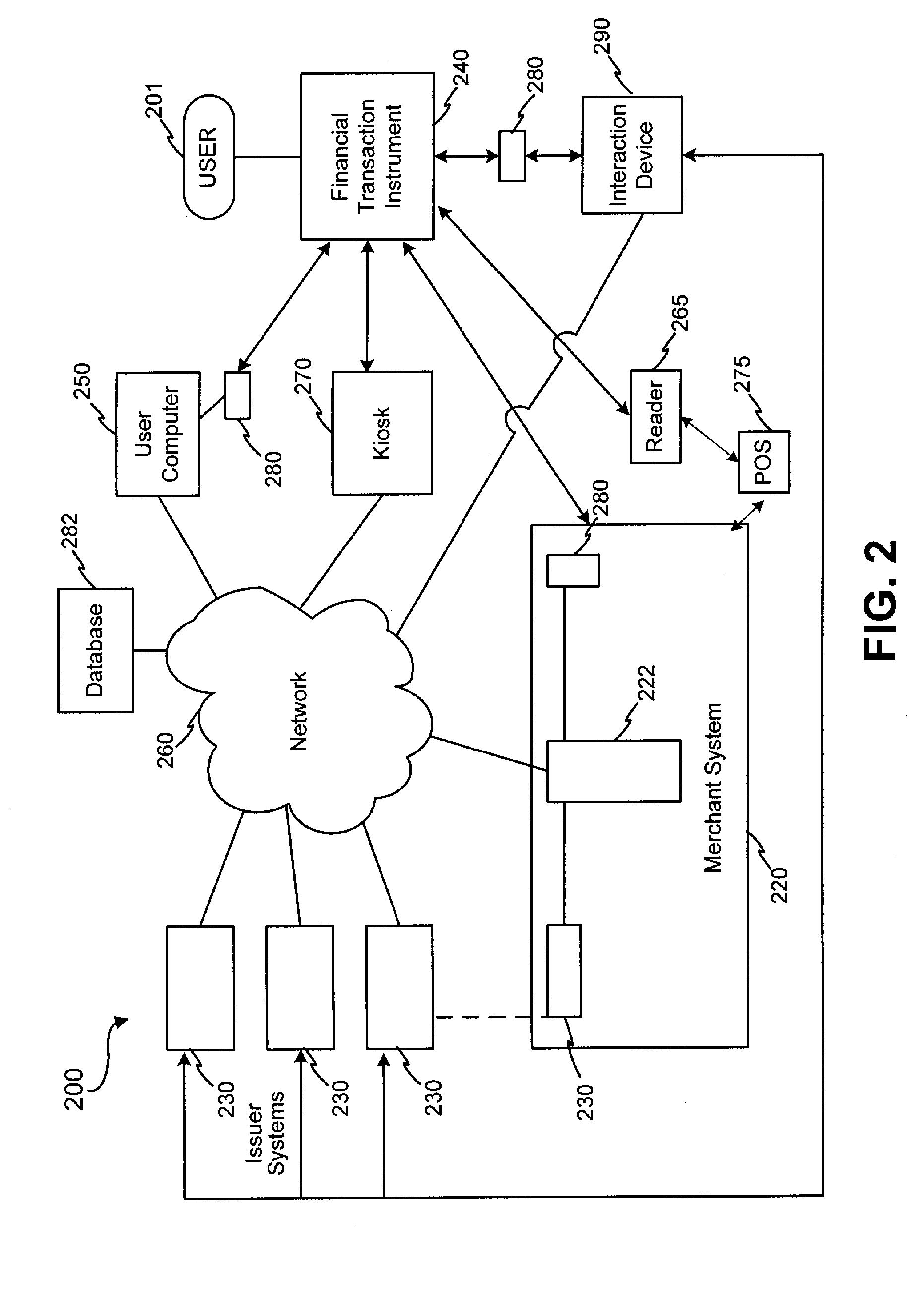
InactiveUS20050171898A1Easy to manageEliminate needAcutation objectsFinanceData setFinancial transaction
Systems and methods are configured to manage data sets associated with a transaction device. For example, a method is provided for facilitating the management of distinct data sets on a transaction device that are provided by distinct data set owners, wherein the distinct data sets may include differing formats. The method includes the steps of: adding, by a read / write, a first data set to the financial transaction device, wherein the first data set is owned by a first owner; adding, by the read / write device, a second data set to the financial transaction device, wherein the second data set is owned by a second owner; and storing the first data set and the second data set on the financial transaction device in accordance with an owner defined format. The first and second data sets are associated with first and second owners, respectively, and are configured to be stored independent of each other The transaction device user may be permitted to select at least one of the multiple data sets for transaction completion using a secondary identifier indicia. Where the user selects multiple accounts for transaction completion, the user may be permitted to allocate portions of a transaction to the selected transaction accounts. The transaction request may be processed in accordance with the user's allocations.
Owner:LIBERTY PEAK VENTURES LLC
Identifications and communications methods
The invention relates to improved methods and forms for automatically and non-unobtrusively to detect, without human interpretation, the identification of people(s), object(s), and other, with various methods utilized in connection to creating, storing, adding, connecting, modifying, sharing, inputting, recalling, authorizing, approving, tracking, generating, formatting, monitoring, accessing, locating, deleting, controlling, linking, collecting all types of data and information, and generating at least one type of identifiable communications information related to anyone or anything, and in and / or around any type of environment, such as an airport(s), airline(s), and / or other aviation location(s), theme park, amusement park, aquarium, cruise ships, tourist location, hospitals, buildings, government complex, malls, customs boards, sports events, parking, manufacturing, hotels, resorts, clubs, retail, elevators, utilities, museums, libraries, as well as other types of location(s), among other environments.
Owner:MODENA NAVIGATION LLC
Drug storage and dispensing devices and systems comprising the same
ActiveUS20070186923A1Minimizing saliva influxPowdered material dispensingDrug and medicationsDrug StorageBiomedical engineering
Drug storage and dispensing devices for dispensing a drug dosage form to a patient are disclosed. The dispensing device has a programmable lock-out feature for locking the dispensing device and is capable of detecting the identity of a user. The invention further provides a method for the treatment of subject, by administering to the subject a drug dosage form using a dispensing device of the invention.
Owner:ACEIRX PHARM INC
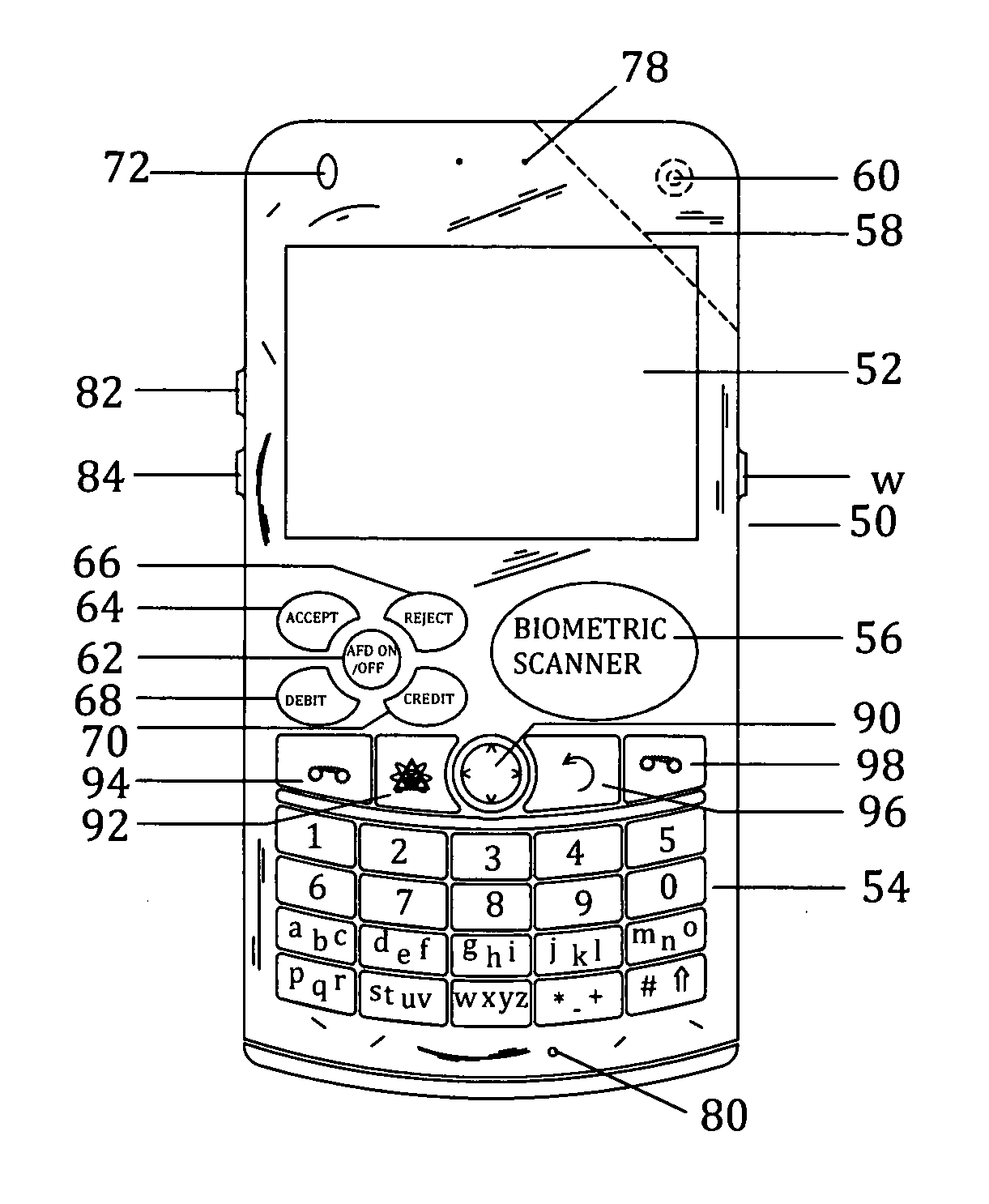
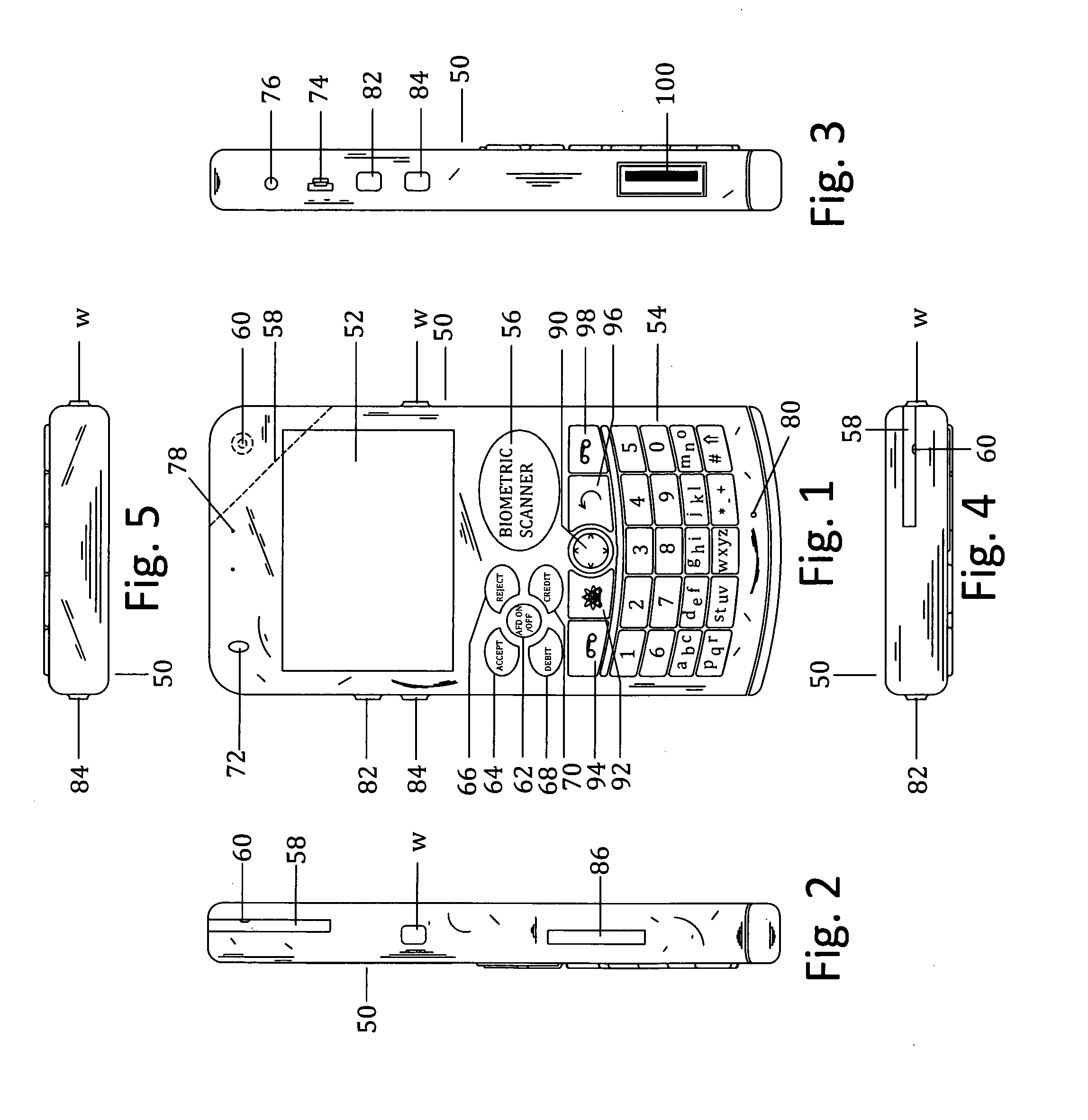
Biometric authentication of mobile financial transactions by trusted service managers
ActiveUS20090307139A1Digital data processing detailsUser identity/authority verificationUser inputFinancial transaction
A method for authenticating a financial transaction at a point of sale (POS) includes storing an application program in a first secure element of a mobile phone. The application is configured to generate instruction codes to effect the financial transaction upon verification of a user's identity. The user's credentials are stored in a second SE of the phone, which is operable to verify the user's identity from a biometric trait of the user input to the phone and to generate data authenticating the financial transaction in response to the verification of the user's identity. At the POS, the user invokes the application and then inputs a biometric trait to the phone. The second SE verifies the user's identity, and upon verification, generates data authenticating the transaction. The financial transaction data, including the instruction codes and the authenticating data, are then transmitted from the phone to the POS.
Owner:PAYPAL INC
Passive biometric customer identification and tracking system
InactiveUS6554705B1Simplifies search techniqueMinimal useCharacter and pattern recognitionApparatus for meter-controlled dispensingBiometric dataFile allocation
A computer-based customer tracking system uses a passive biometric identification for identifying customers. Neither the customer, nor any establishment personnel, are required to enter any informational data with respect to the customer; identification is done completely biometrically. Biometric identification information is sent to a central computer processor, which searches files in a library for matching biometric data. If no match is found, the processor opens a new file in the library, assigning a code or identification number to the file. Information with respect to the customer's biometric data, along with any transactional information, are stored in the file. If prior activity information stored in the file exceeds a predetermined level, information with respect to the customer's prior activity is retrieved from the file and sent to a terminal, preferably at the location of the transaction. Any new information from the transaction is then sent to the processor and stored for future access. The processor scans the files periodically, and deletes files for which the activity level in the file is below a certain predetermined level over a preselected time period. Deletion of inactive files precludes the processor memory from being overloaded with information which is not useful to the establishment, and also reduces the amount of time necessary for the processor to search library files for biometric matches.
Owner:BIOMETRIC RECOGNITION
System and method for automating a vehicle rental process
InactiveUS20020186144A1Eliminate needLower the thresholdElectric signal transmission systemsTicket-issuing apparatusCommunication unitOn board
The present invention concerns an automated vehicle rental system for a fleet of rental vehicles, where the vehicles are geographically distributed and normally locked when not rented. At least one of the vehicles, when not in use, is parked in an unguarded location. The system has a vehicle communications unit for enabling communication to and from the vehicle, user-carried electronic devices, or other readers, and for interfacing with the user. An on-board unit (OBU) is located on each of the vehicles for interfacing with the vehicle communications unit, and with a door unlocking mechanism. The system further has a central reservations, management and location system (CRMLS) in communication through a communications network with each OBU, the CRMLS performing all reservations and management functions, and being linked to a database containing a location and availability of each of thr vehicles and a rate for rental, the CRMLS also being provided with an allocation manager system for geographically allocating vehicles. In order to access the vehicle, the system also includes a key being borne by the user. The system minimizes the human intervention in the rental process, and is more user-friendly.
Owner:ZOOP MOBILITY NETWORK
System and method for mass transit merchant payment
InactiveUS20060278704A1Eliminate needRelieving userAcutation objectsTicket-issuing apparatusTransit systemFinancial transaction
Methods, systems and computer program products are provided for enabling payment of transit system fees using a financial transaction instrument. Entry is permitted onto a transit system by recognition of information included in an identification number stored on a financial transaction instrument. The identification number stored on the financial transaction instrument is associated with a transit system fee registered for each use of the transit system. A plurality of transit system fees associated with the same identification number from use of the financial transaction instrument is aggregated, and payment for the aggregated transit system fees is requested from a transaction account associated with the financial transaction instrument.
Owner:LIBERTY PEAK VENTURES LLC
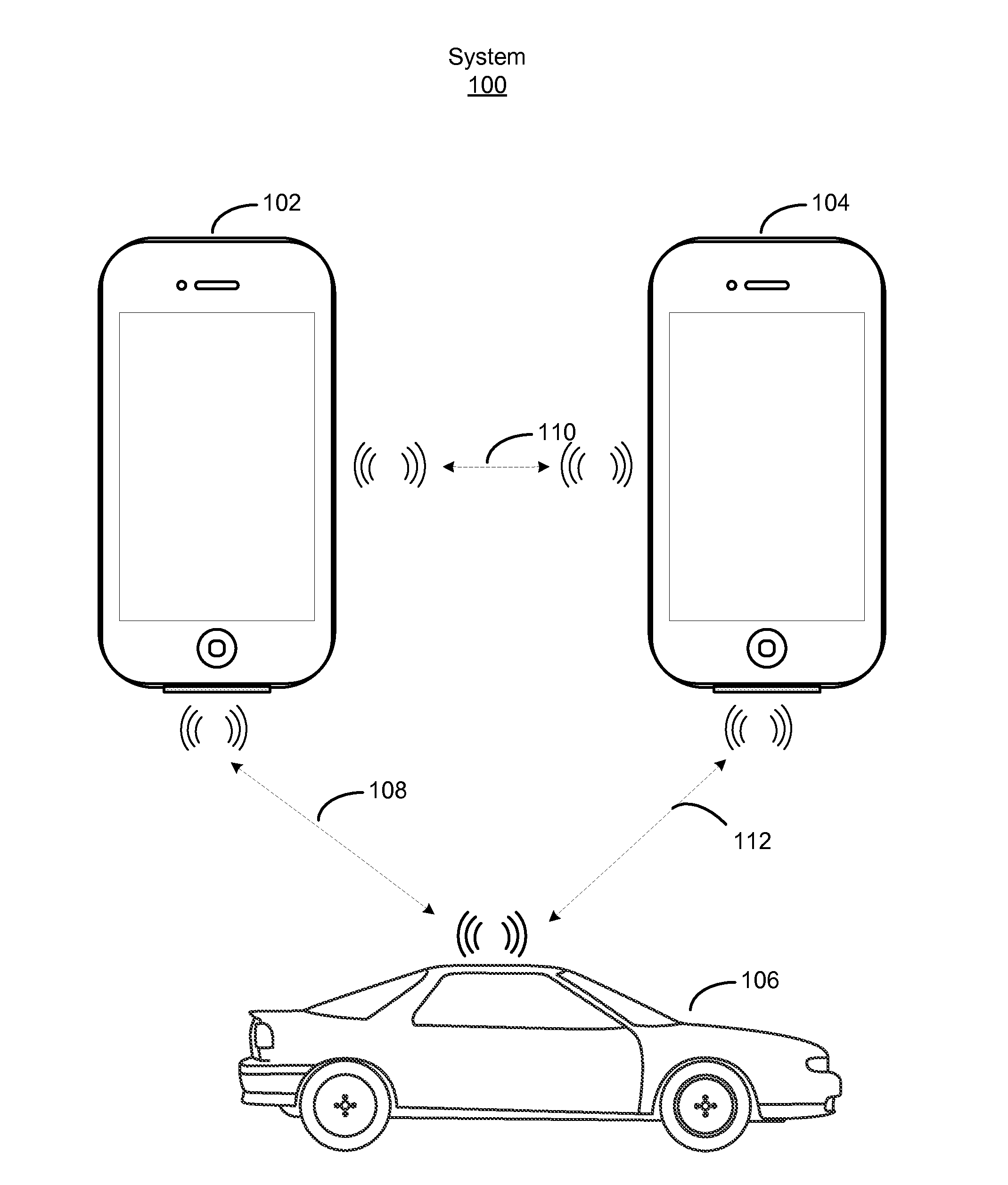
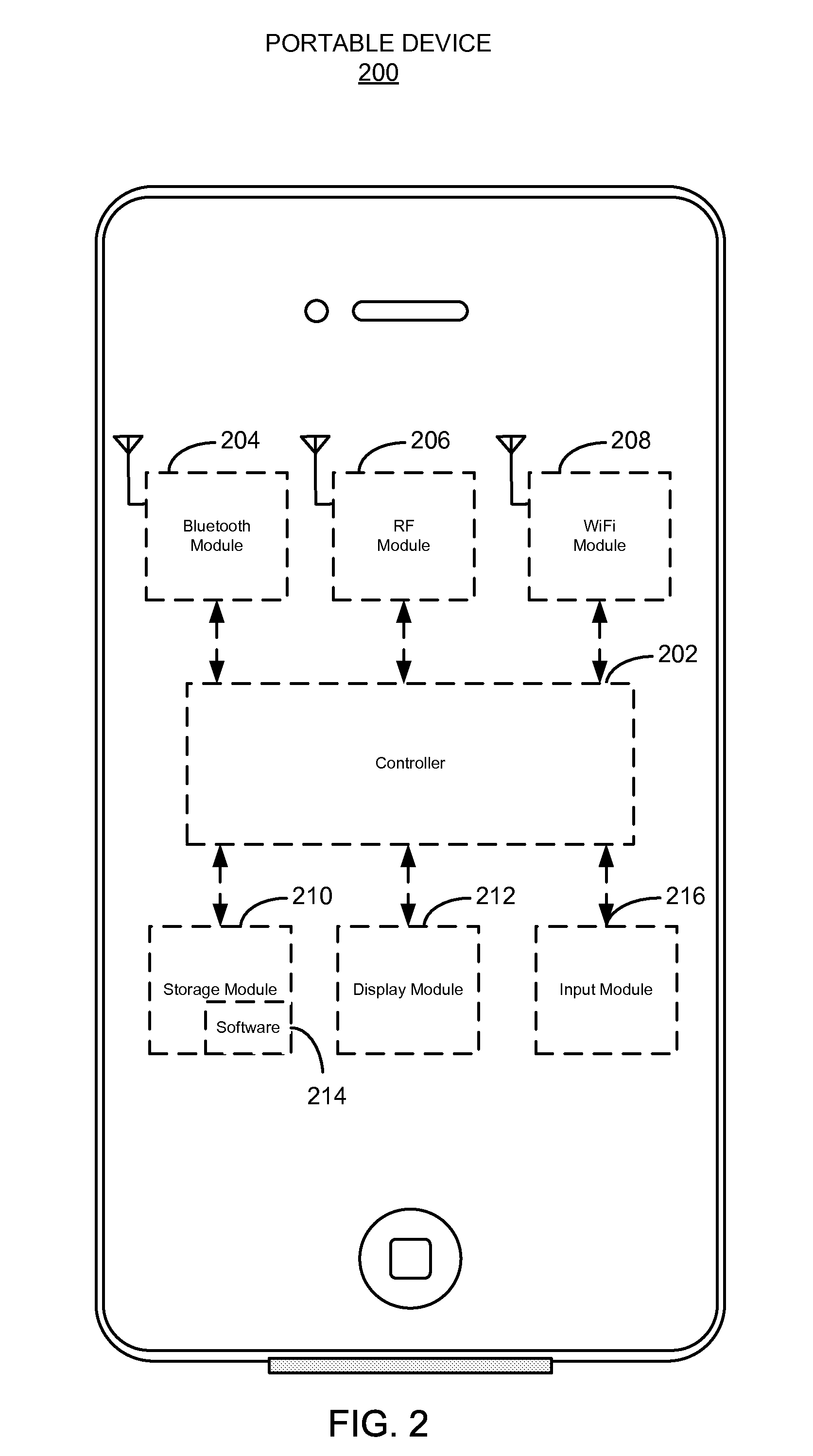
Accessing a vehicle using portable devices
ActiveUS20130099892A1Electric signal transmission systemsKey distribution for secure communicationBluetoothBiological activation
A primary portable device can access a vehicle by transmitting an activation message including a vehicle access credential to the vehicle. The primary portable device can additionally enable a secondary portable device to access the vehicle by transmitting the vehicle access credential to the secondary portable device. The connections between the primary portable device, secondary portable device, and vehicle can be based on a short-range wireless protocol, such as Bluetooth or Bluetooth LE.
Owner:APPLE INC
Method and apparatus for acquiring, maintaining, and using information to be communicated in bar code form with a mobile communications device
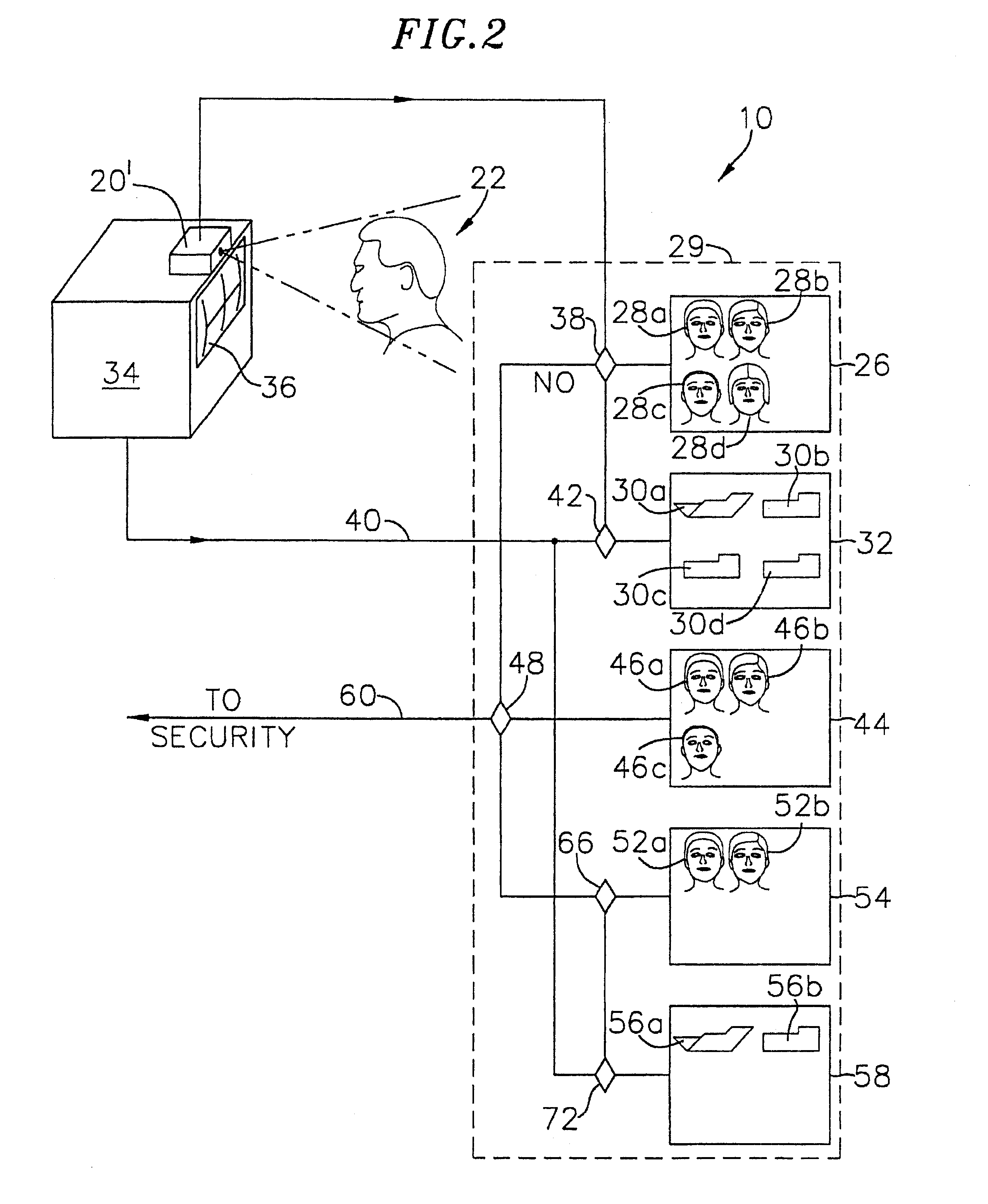
InactiveUS20020060246A1Convenient acquisition and maintenance and useCharacter and pattern recognitionIndividual entry/exit registersBarcodeCommunication device
A user is provided with a secure database containing information in diverse categories that relates to the user and that may be represented at least in part in bar code form and communicated with light from a mobile communications device. The diverse information is obtained from any combination of a variety of vendor and governmental computer systems, internet service providers, and communications devices. The user has access to the database using a mobile communications device for displaying, managing, and entering information, and for communicating information in bar code form with light. The user first selects the category that contains the specific item of information, and then selects the specific item of information. The specific item of information then is communicated in bar code form with light from the mobile communications device for scanning by a bar code scanner to obtain the desired good or service.
Owner:SAMSUNG ELECTRONICS CO LTD
Pointing device with biometric sensor
InactiveUS6148094ACathode-ray tube indicatorsInternal/peripheral component protectionComputerized systemPointing device
A pointing device incorporates a biometric sensor at a location such that when operating the pointing device in a normal manner, a user's hand rests naturally in a position to place a finger of the user's hand in proximity to and readable by the biometric sensor. In one embodiment, a computer trackball pointing device includes a fingerprint sensor which is equally well suitable for use by either a right-handed or a left-handed user. Along with positional information from a position sensor and user selection information from at least one user-depressable button, the pointing device also conveys to an attached computer system information associated with the user's identity detected by the fingerprint sensor. Such a pointing device is well suited to both transparent verification as well as continuous verification, for if a user removes his or her hand from the natural position when using the device, the user's fingerprint will no longer be detectable by the fingerprint sensor, and the computer system to which the pointing device is attached can be alerted as to the need to re-authenticate any additional attempts at using the pointing device.
Owner:DALTON PATRICK ENTERPRISES
Intelligent Door Lock System
ActiveUS20140265359A1Provide informationNon-mechanical controlsConstruction fastening devicesDrive shaftMechanical energy
Owner:AUGUST HOME
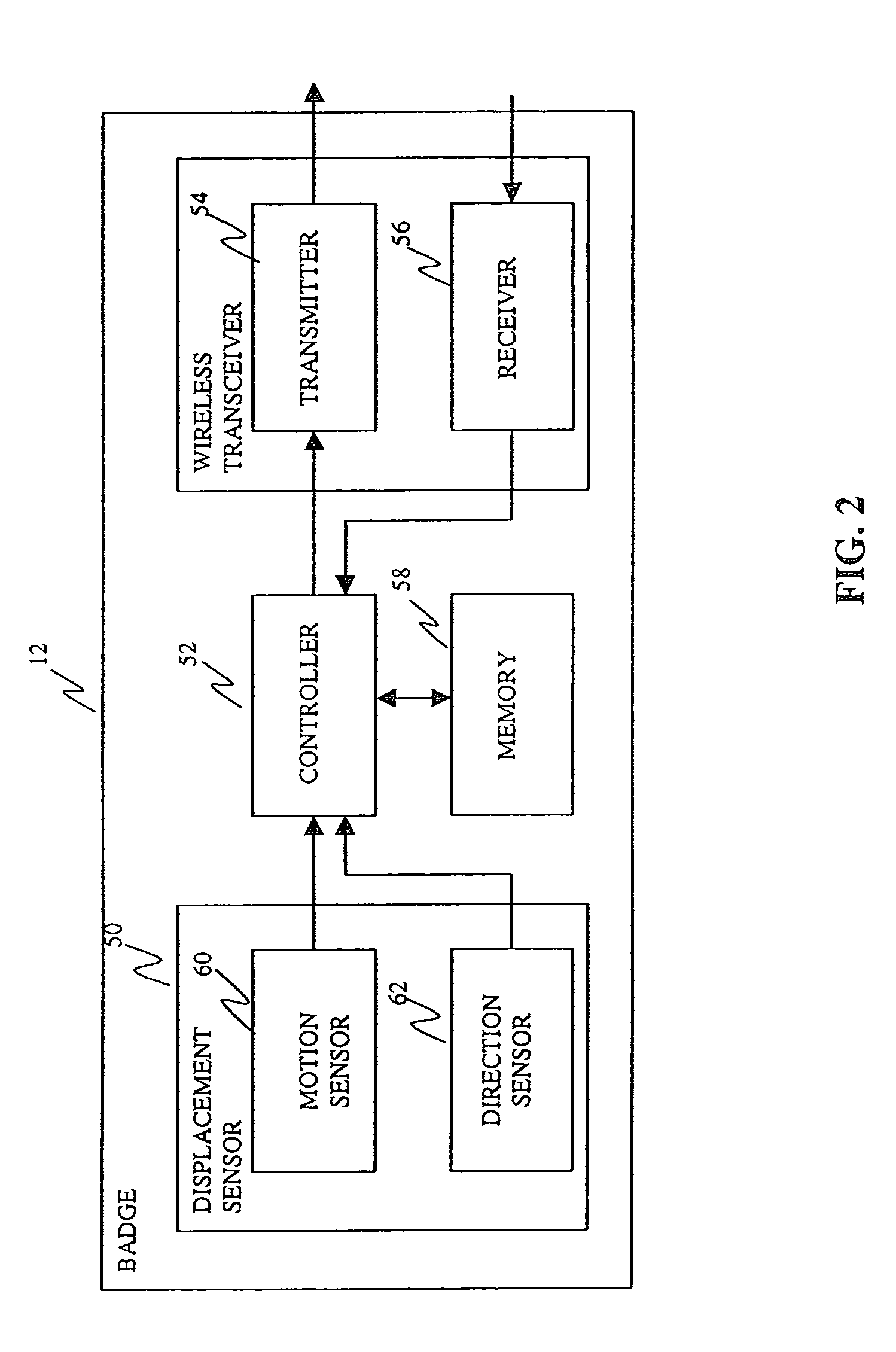
Monitoring and tracking network
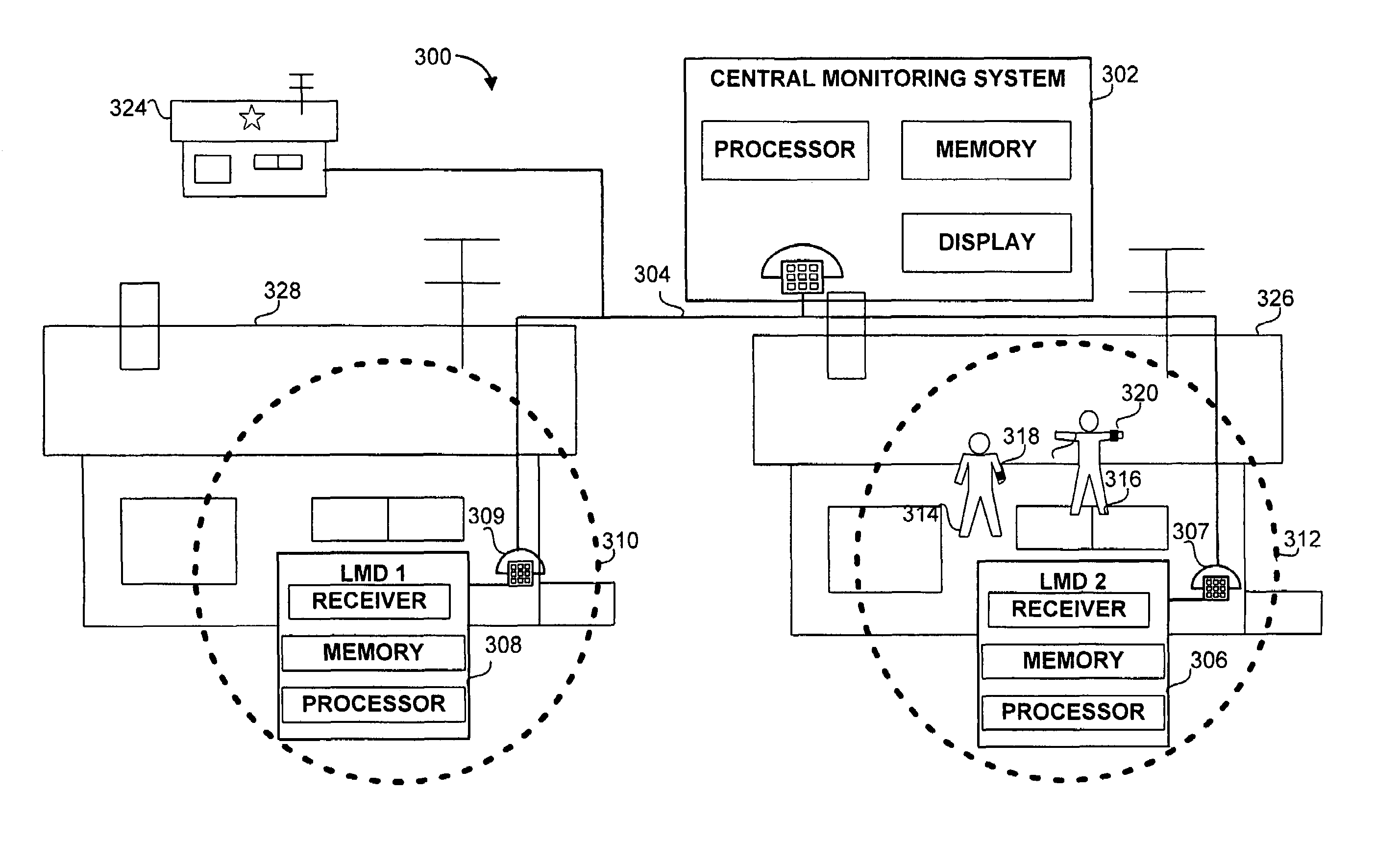
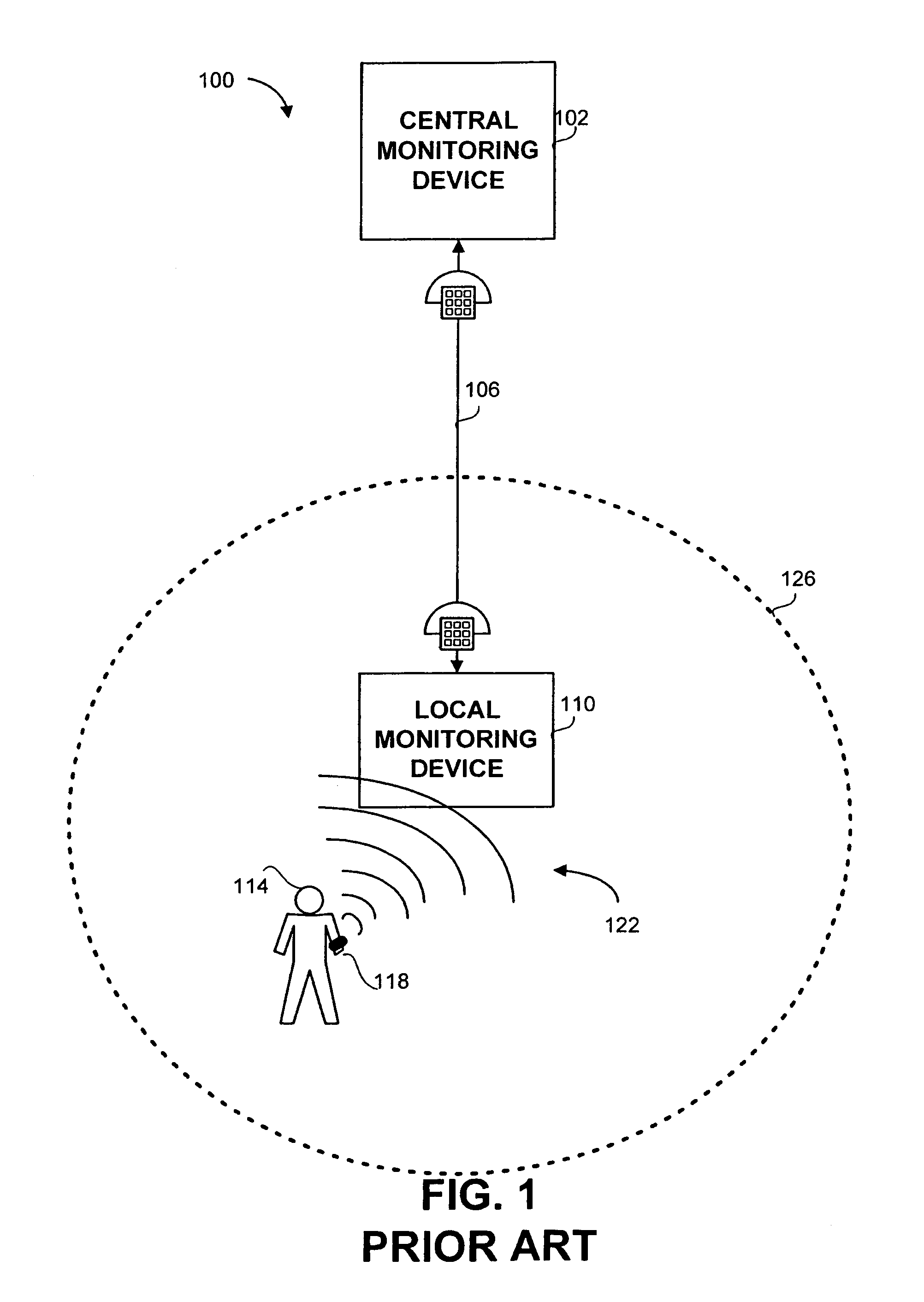
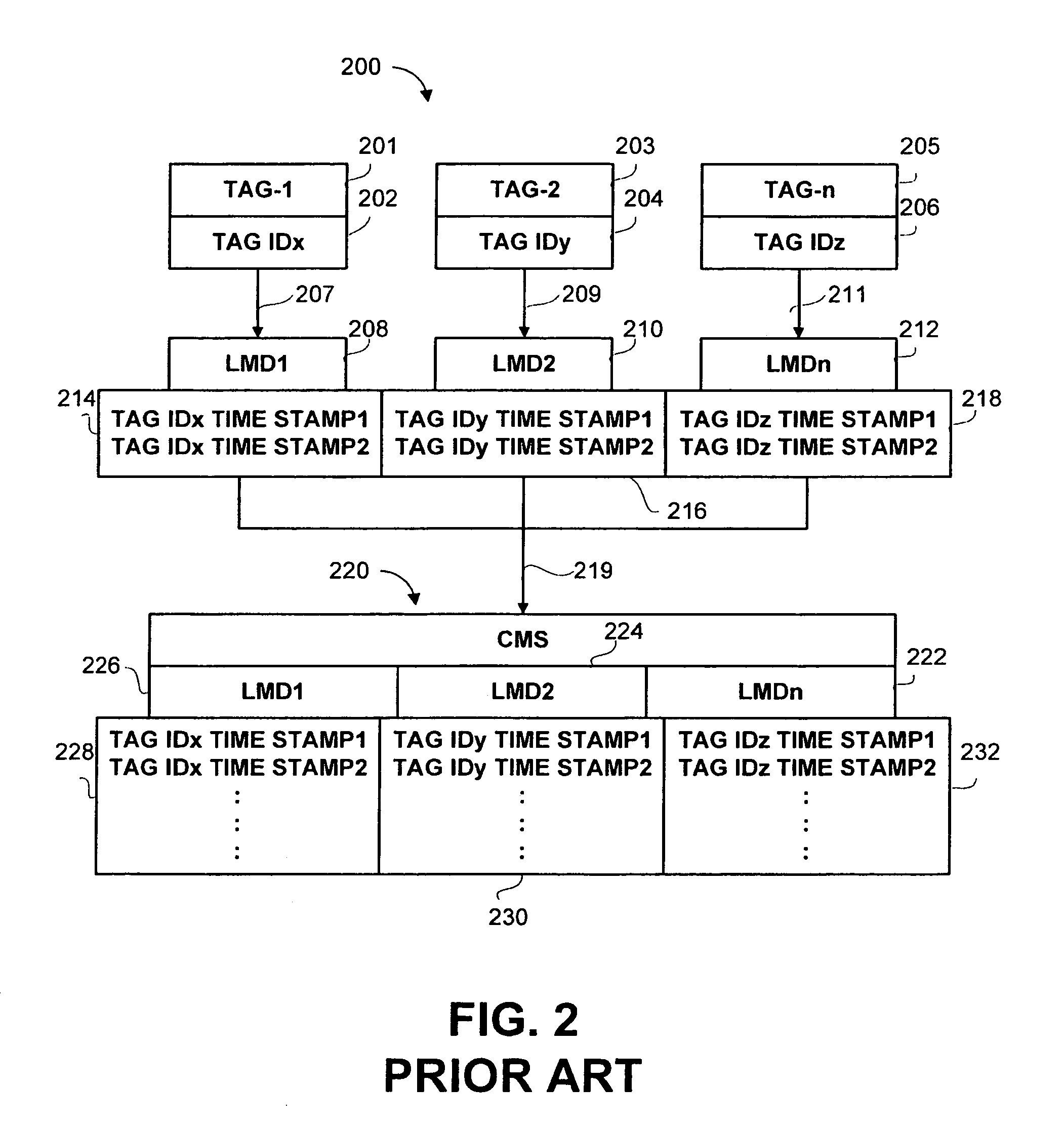
InactiveUS6998985B2Enhance and addRegistering/indicating time of eventsIndividual entry/exit registersTracking systemReal-time computing
A monitoring and tracking system comprising a plurality of transmitting tags attachable to a plurality of monitored individuals, a plurality of monitoring devices and a central monitoring server. The transmitting tags, each having a unique code, periodically transmit data carrying signals, the signals are received by any of the local monitoring devices when a tag is within a reception range of a local monitoring device for allowing tracking the monitored individuals.
Owner:3M ELECTRONICS MONITORING LTD
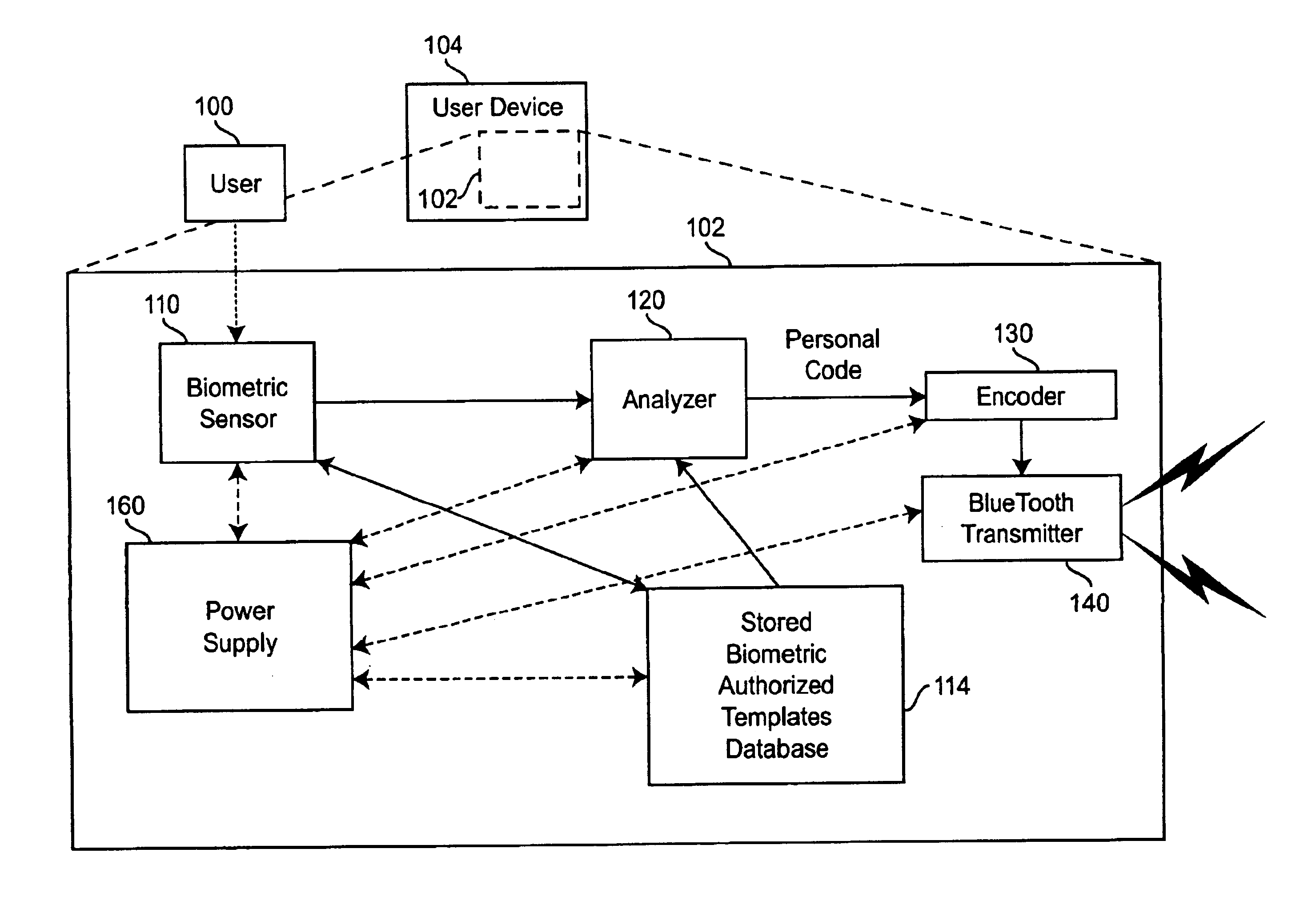
Personal biometric key
InactiveUS6850147B2Reliable resultsEasy to compressElectric signal transmission systemsImage analysisComputer hardwareCommunications system
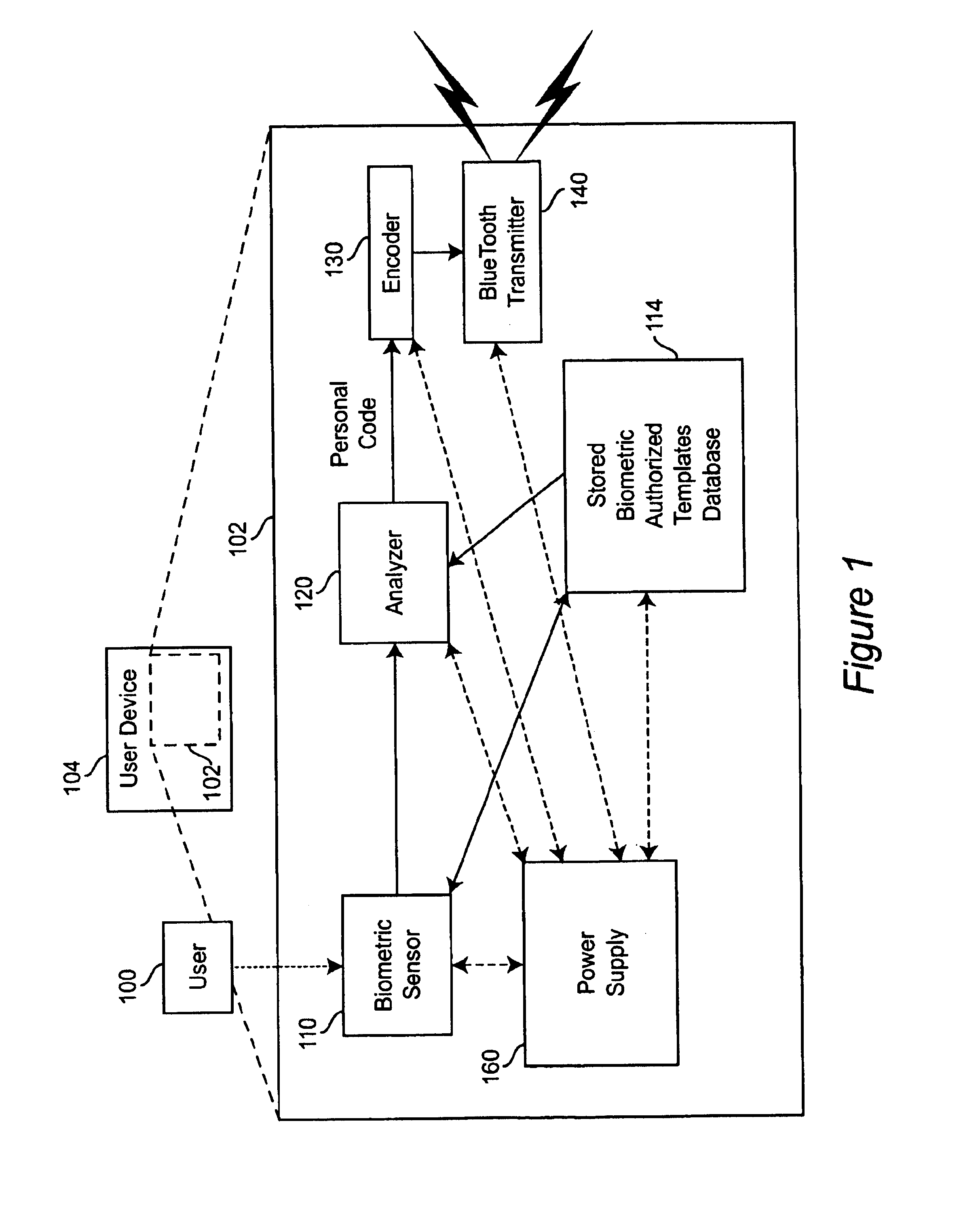
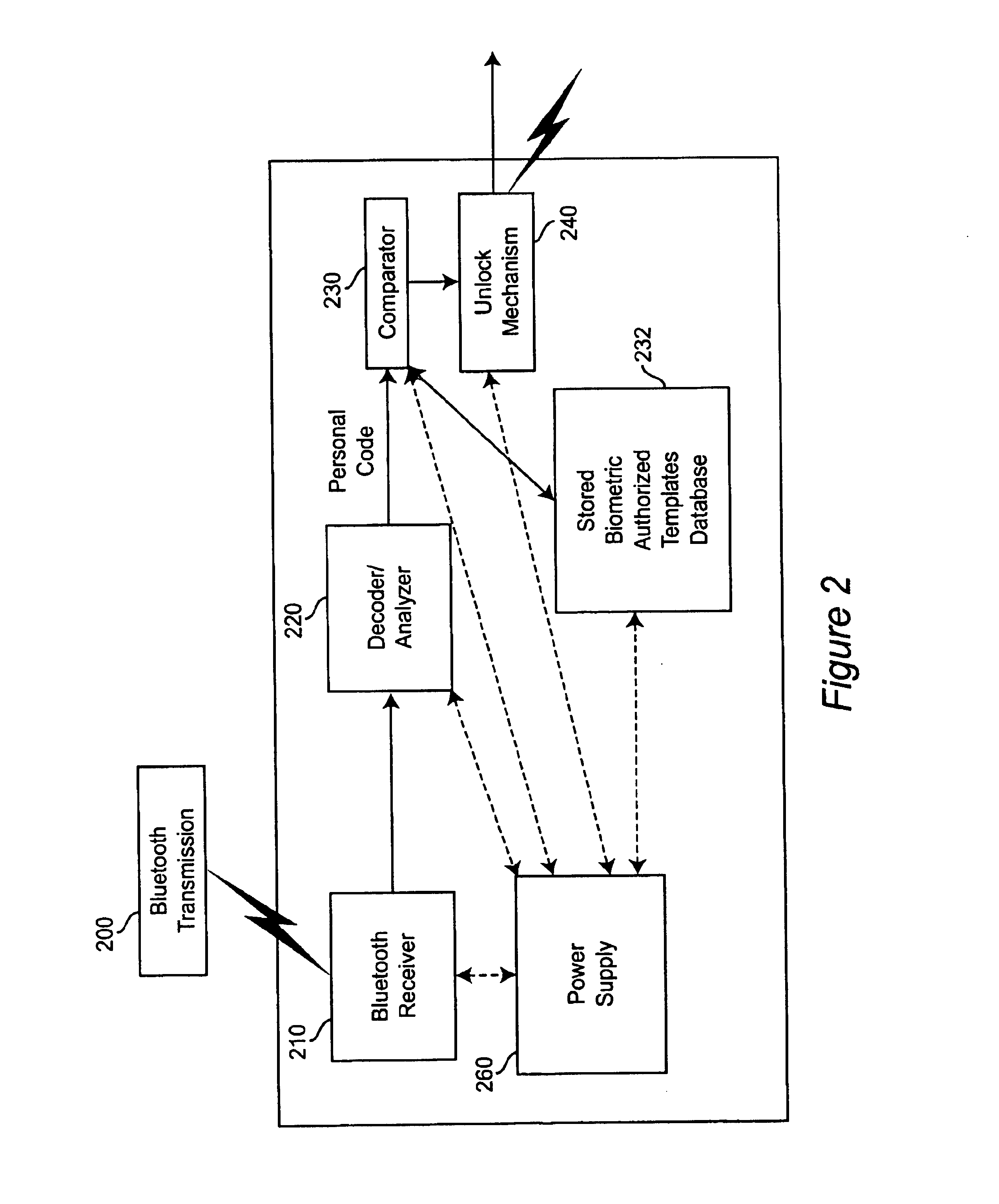
A personal biometric key system uses a personal identity code transmitted to a universal biometric electronic lock via a communication system and using a clock or GPS chip and allows a person to select one or more personal biometric methods and to be personally responsible for the maintenance of the sensor and its availability. The selection can be tailored to the particular needs and circumstances of the person using the key. The person can also change the personal biometric sensor when needs and circumstances change. The organization being accessed by the key can set minimum levels for what type sensor data they will accept and for level of services they will provide for a given type sensor.
Owner:MIKOS
Apparatus for identity verification, a system for identity verification, a card for identity verification and a method for identity verification, based on identification by biometrics
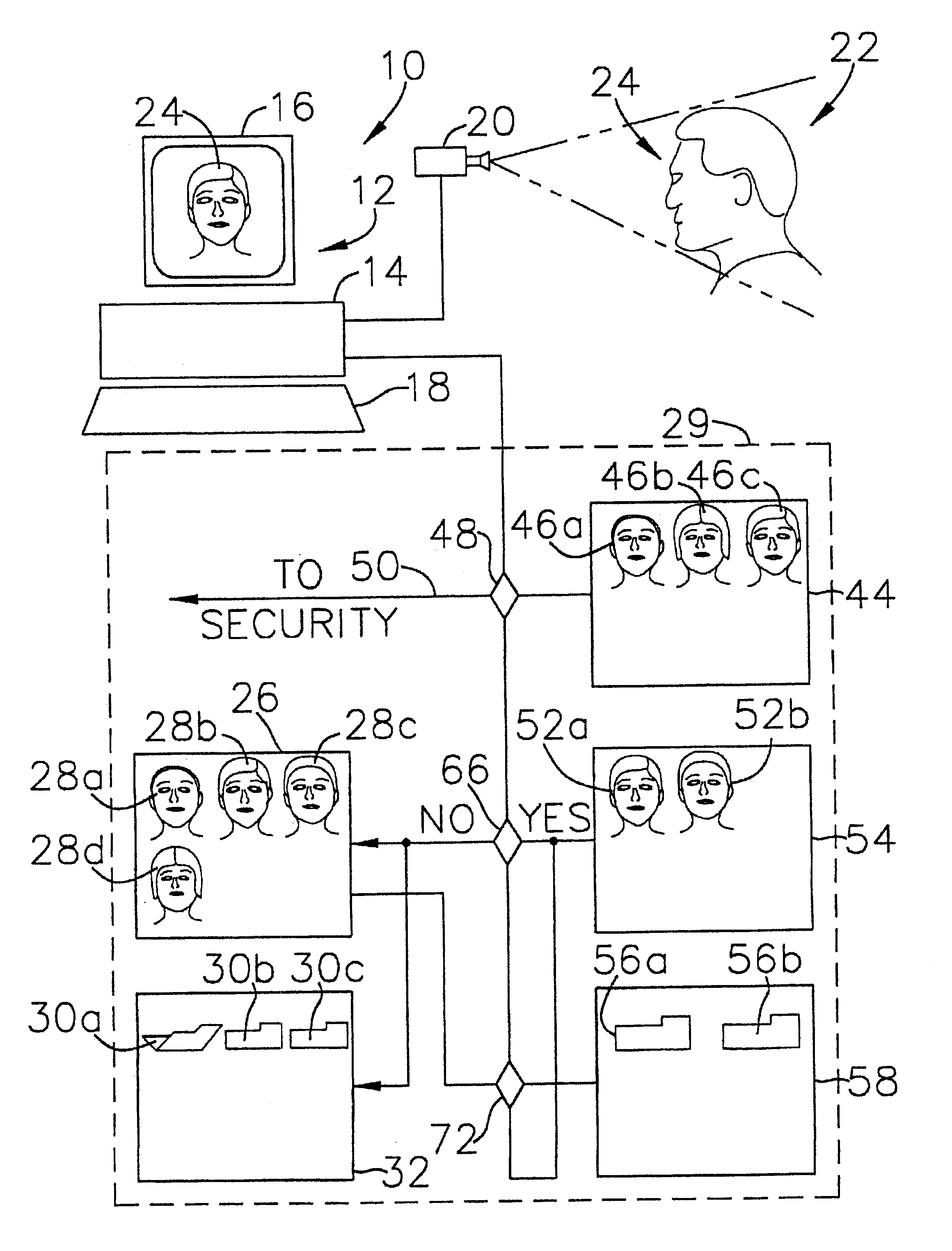
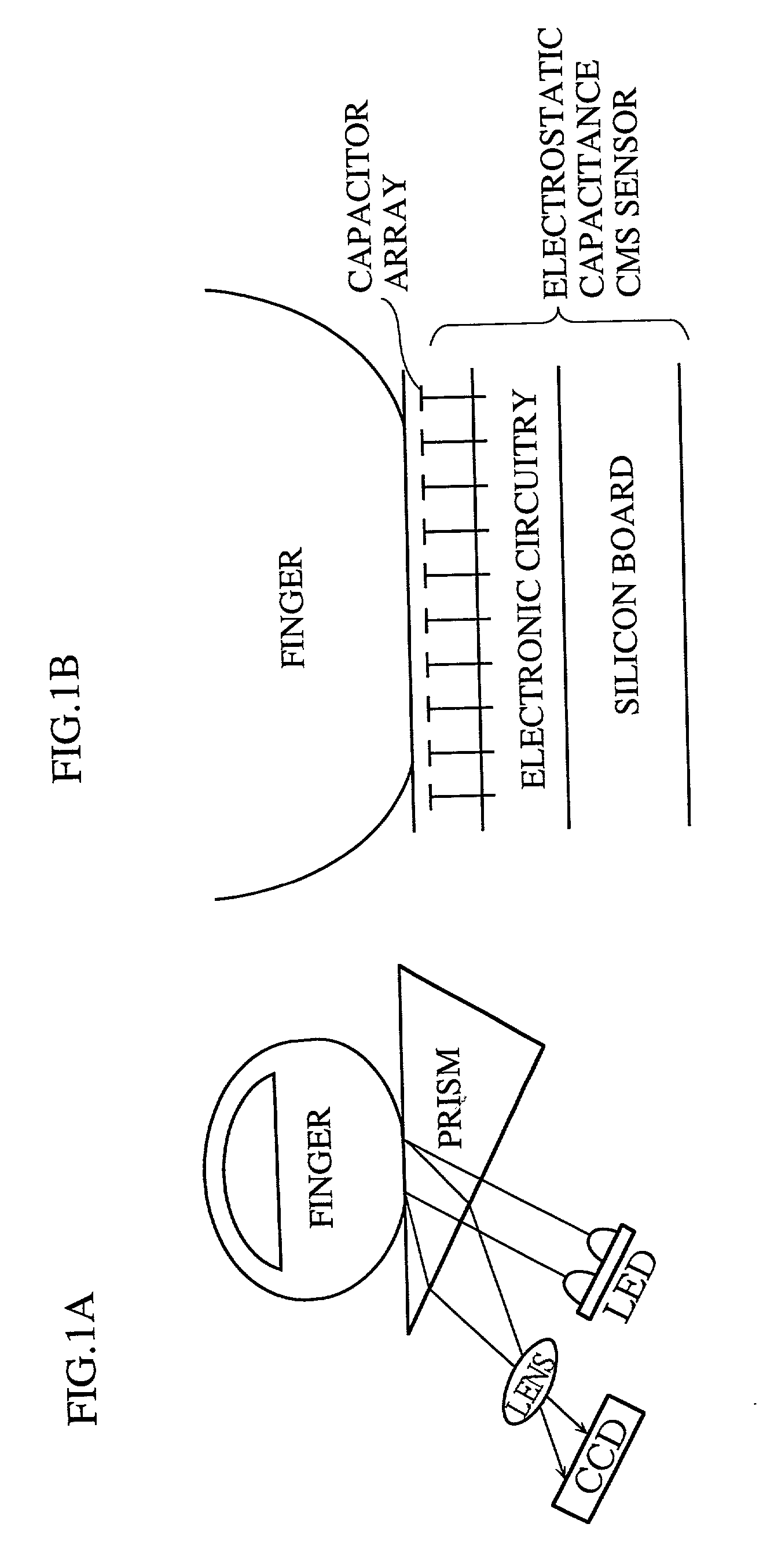
InactiveUS20010026632A1Improve reliabilityLow costImage analysisUser identity/authority verificationCommunication interfaceImaging processing
An identity verification system is used to identify persons with high accuracy, while avoiding direct contact with the device to prevent any negative psychological reaction from a user. The system includes: a camera unit and an image processing unit for obtaining object images of body parts (such as fingerprints and irides) by scanning, without physical contact; an image display unit for displaying layered images of the body part as scanned and a guide showing the body part in an optimal position; a control unit for extracting biometric characteristic data from object images and sending the data to a verification server after encrypting by an encryption unit; and a communications interface unit.
Owner:PANASONIC CORP
Personal biometric key
InactiveUS20020140542A1Electric signal transmission systemsImage analysisComputer hardwareCommunications system
A personal biometric key system uses a personal identity code transmitted to a universal biometric electronic lock via a communication system and using a clock or GPS chip and allows a person to select one or more personal biometric methods and to be personally responsible for the maintenance of the sensor and its availability. The selection can be tailored to the particular needs and circumstances of the person using the key. The person can also change the personal biometric sensor when needs and circumstances change. The organization being accessed by the key can set minimum levels for what type sensor data they will accept and for level of services they will provide for a given type sensor.
Owner:MIKOS
Wireless reservation, check-in, access control, check-out and payment
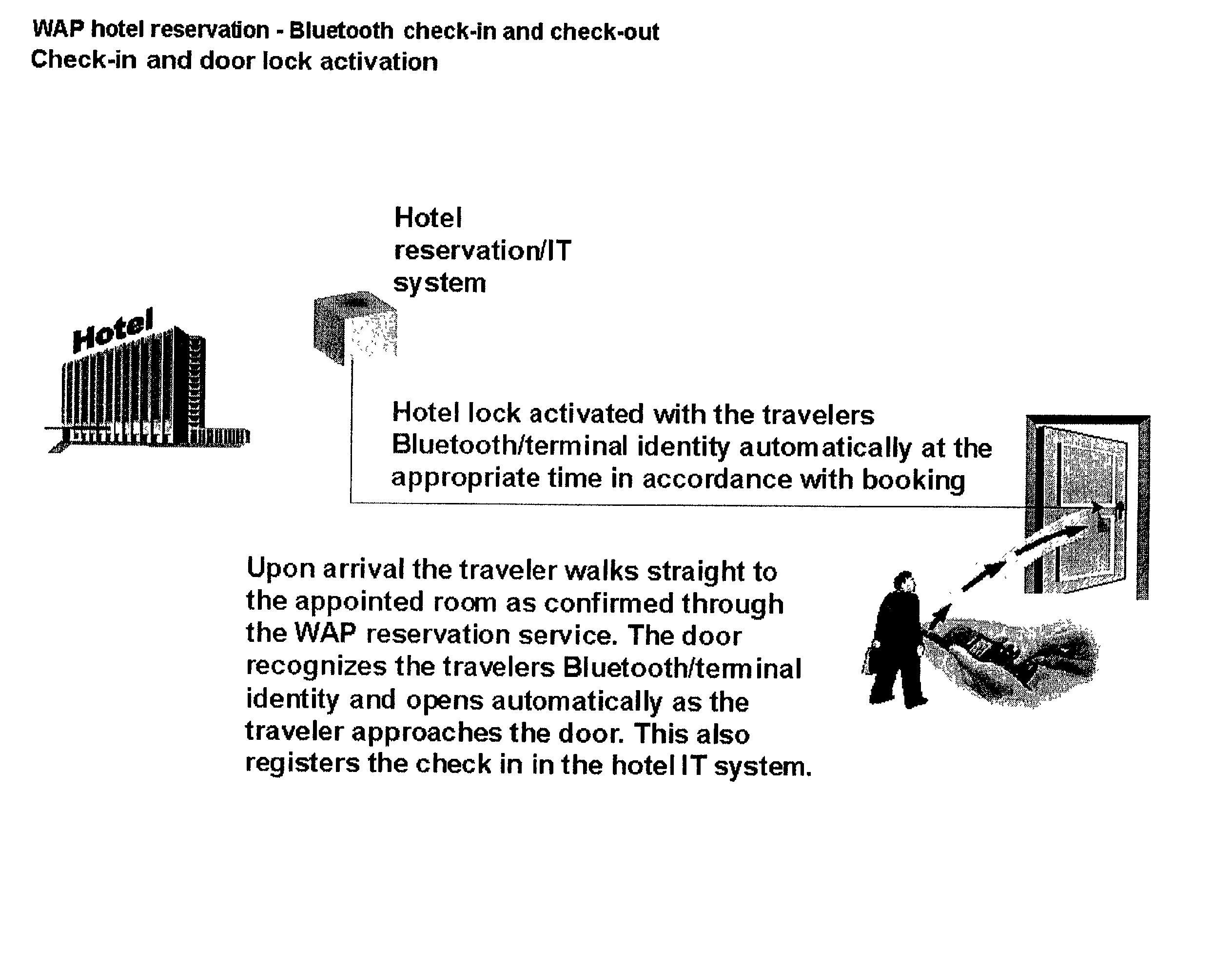
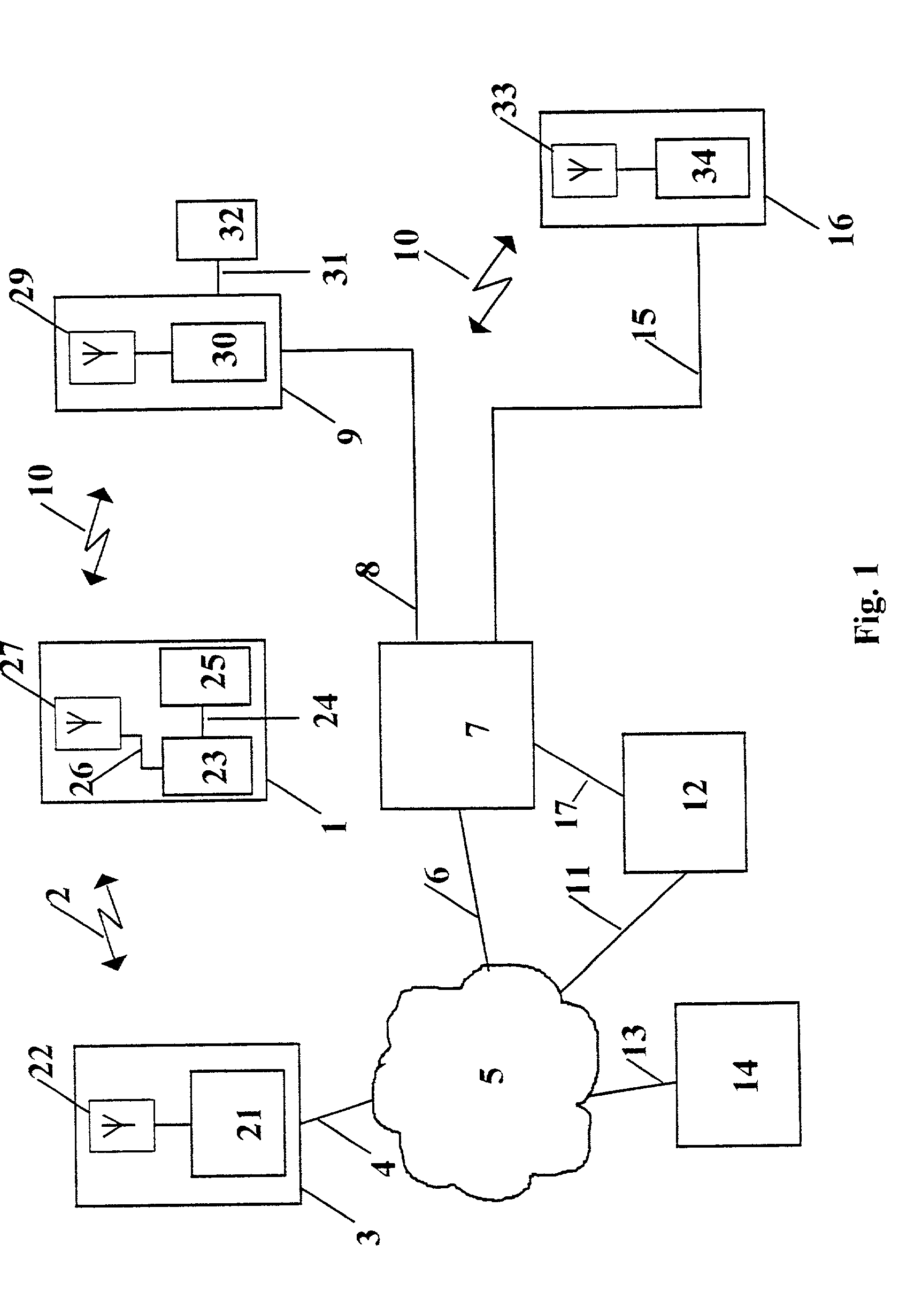
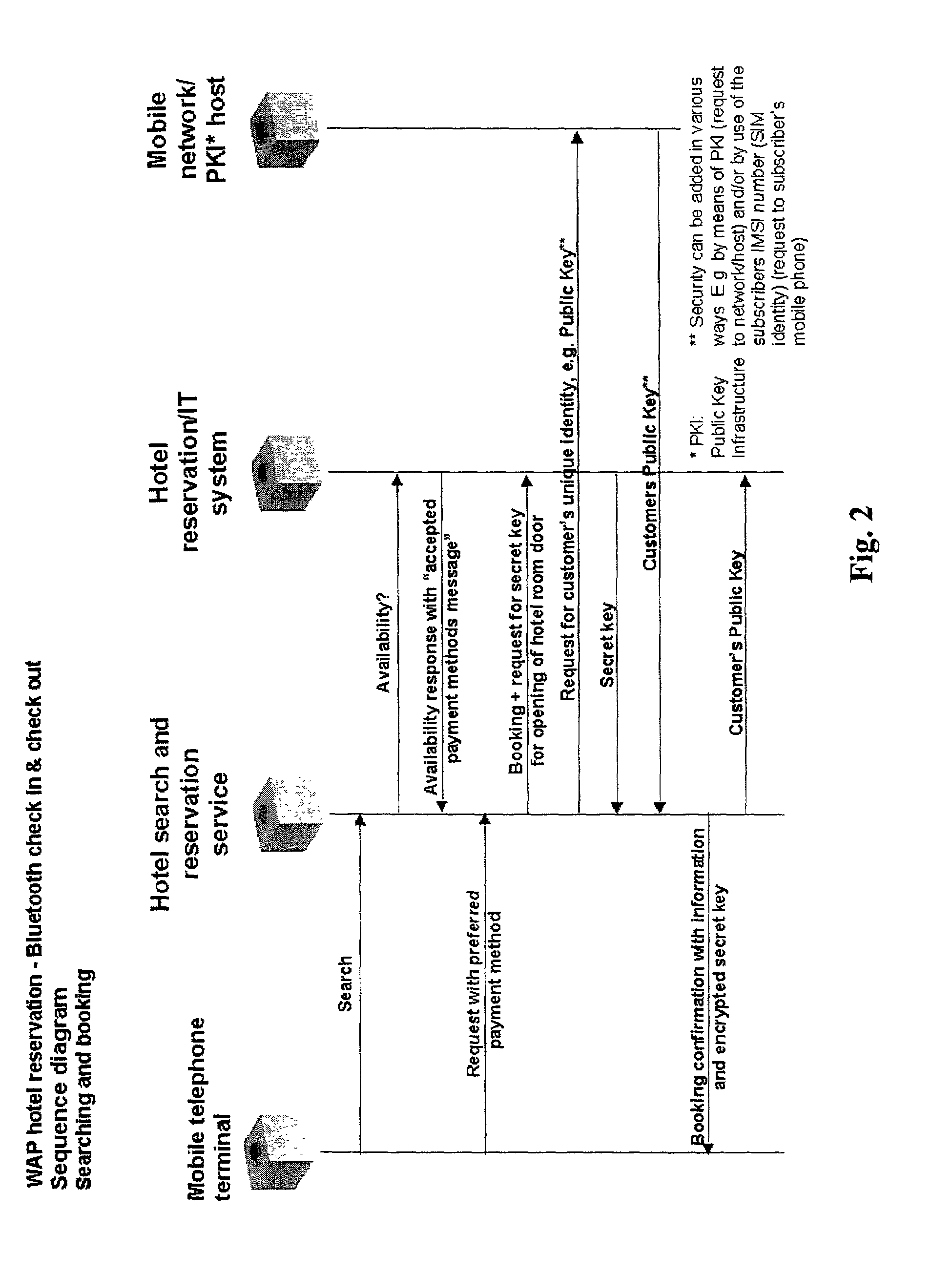
A system and method for, by means of a mobile terminal, wireless hotel search and selection, reservation / booking, check-in, room access control, check-out and payment services for hotel customers is disclosed. The mobile terminal (1) comprises a mobile telephone and processing unit (23), operating with wireless applications, for wireless communication (2) with a hotel search and reservation server (12) and a reservation / IT system (7) of a selected hotel, and a short-range wireless device (25) for wireless communication (10) with wireless devices (9,16) of door locks (32) and user locating arrangements, respectively. By means of the wireless application of the mobile terminal (1), the user reserves a hotel room. A hotel room key token is transferred from the reservation / IT system (7) to the wireless device (35) of the mobile terminal, and hence to the wireless door lock (9,32). When the terminal (1) and the wireless door lock (9,31) are in-range, the hotel room key token is transferred from mobile terminal (1) to the wireless door lock (9,32), the door is unlocked and check-in is registered. On departure, exit or expiration of the reservation period, the system provides wireless check-out and electronic bill settlement.
Owner:TELEFON AB LM ERICSSON (PUBL)
Article locating and tracking apparatus and method
An activity based monitoring system is disclosed, the activity based monitoring system being configured to monitor a plurality of badges associated with a plurality of assets within a healthcare facility.
Owner:HILL ROM SERVICES
Random biometric authentication utilizing unique biometric signatures
InactiveUS20030163710A1Accurate authenticationSecure user accessDigital data processing detailsUser identity/authority verificationUser inputLayer thickness
A user can be challenged to provide at least one randomly selected biometric attribute. The randomly selected biometric attribute input by the user is automatically compared to a plurality of biometric attributes of the user contained in a user profile. The user can then be authenticated if the randomly selected biometric attribute input by the user matches at least one of the plurality of biometric attributes of the user contained in the user profile. Biometric attributes analyzed according to the methods and systems of the present invention, include, but are not limited to, for example, fingerprints, iris, retina, and / or tissue characteristics, such as skin morphology, skin layer thickness, collage density and orientation, tissue hydration, optical patent length differences, etc.
Owner:IP VENUE LLC
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com